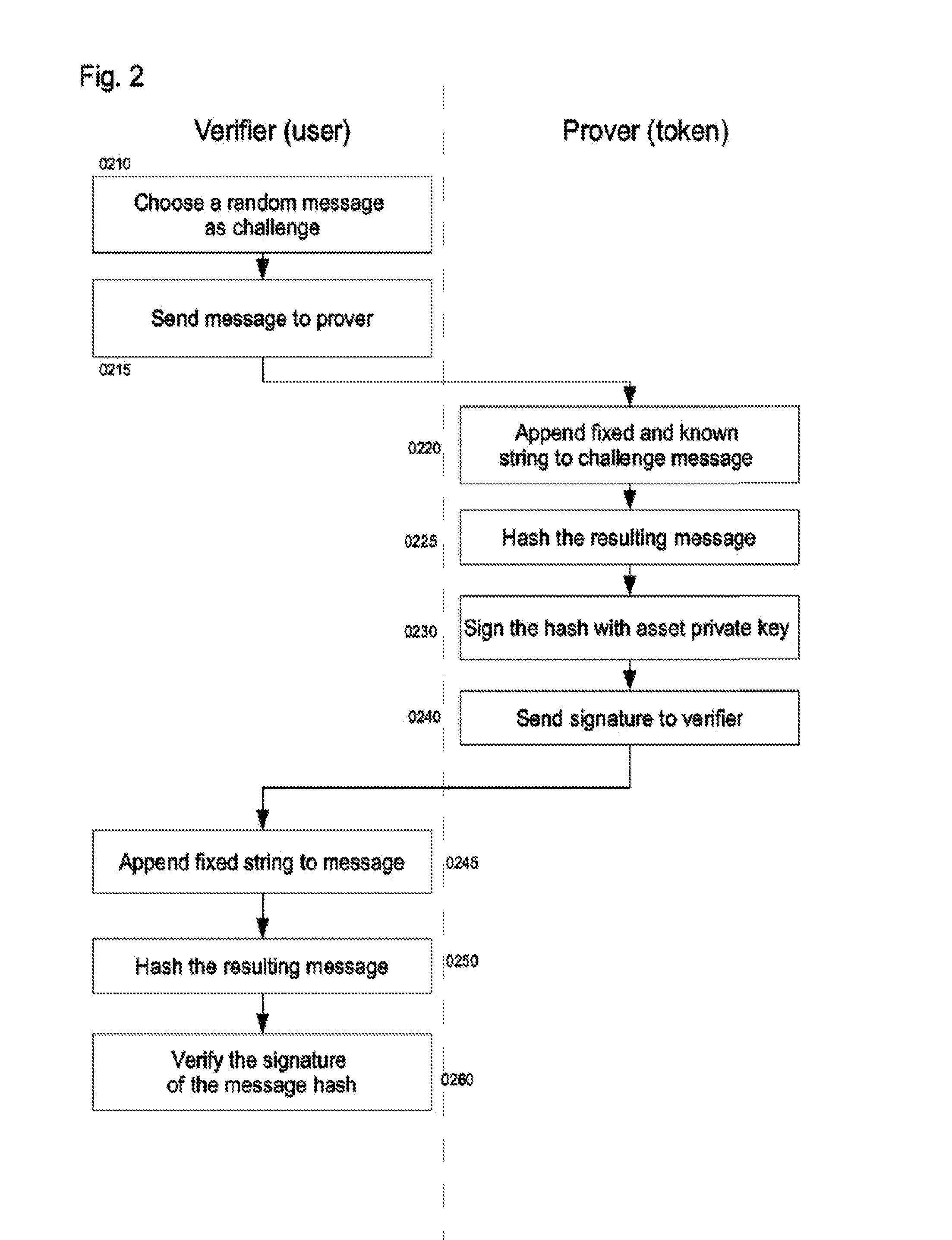
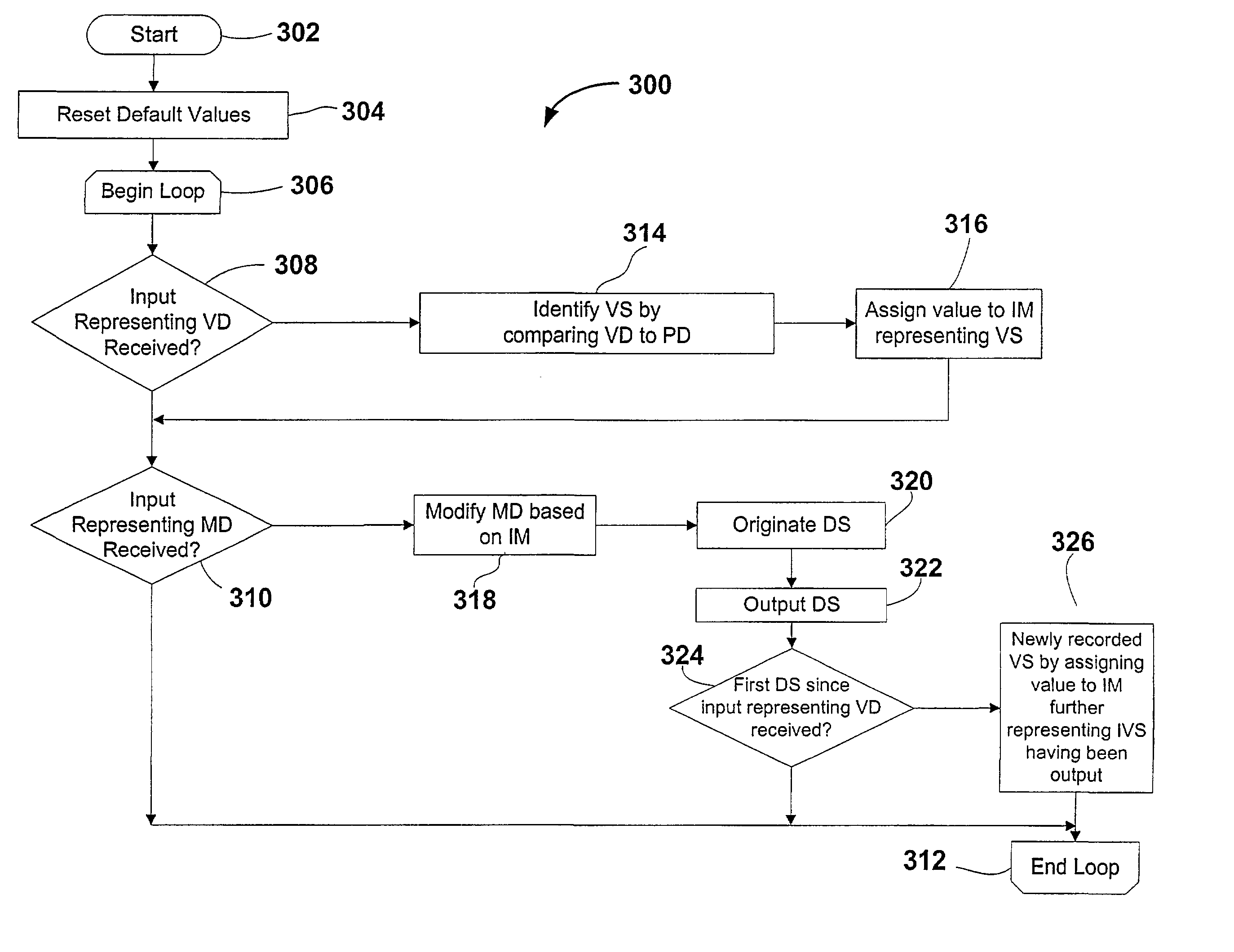
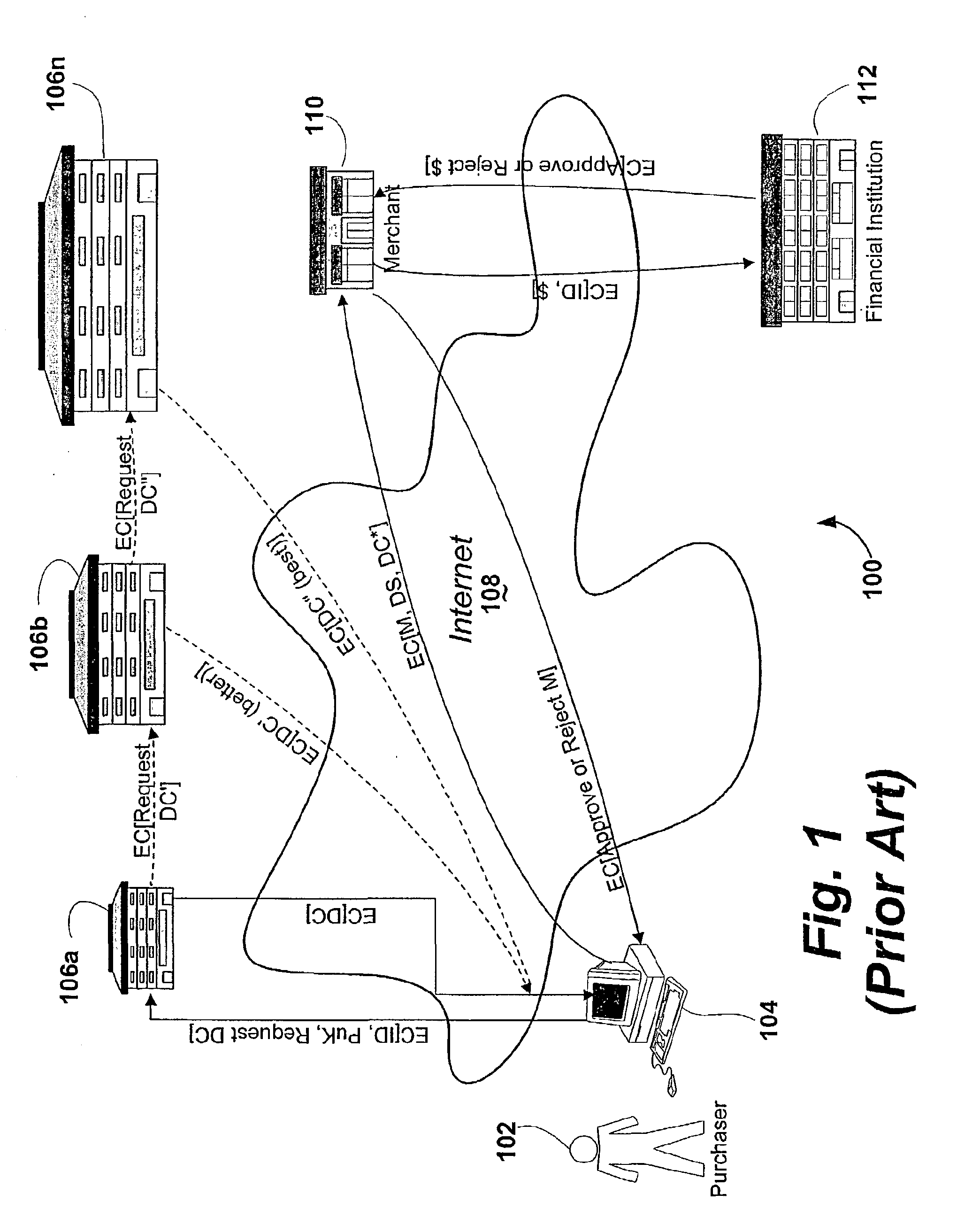
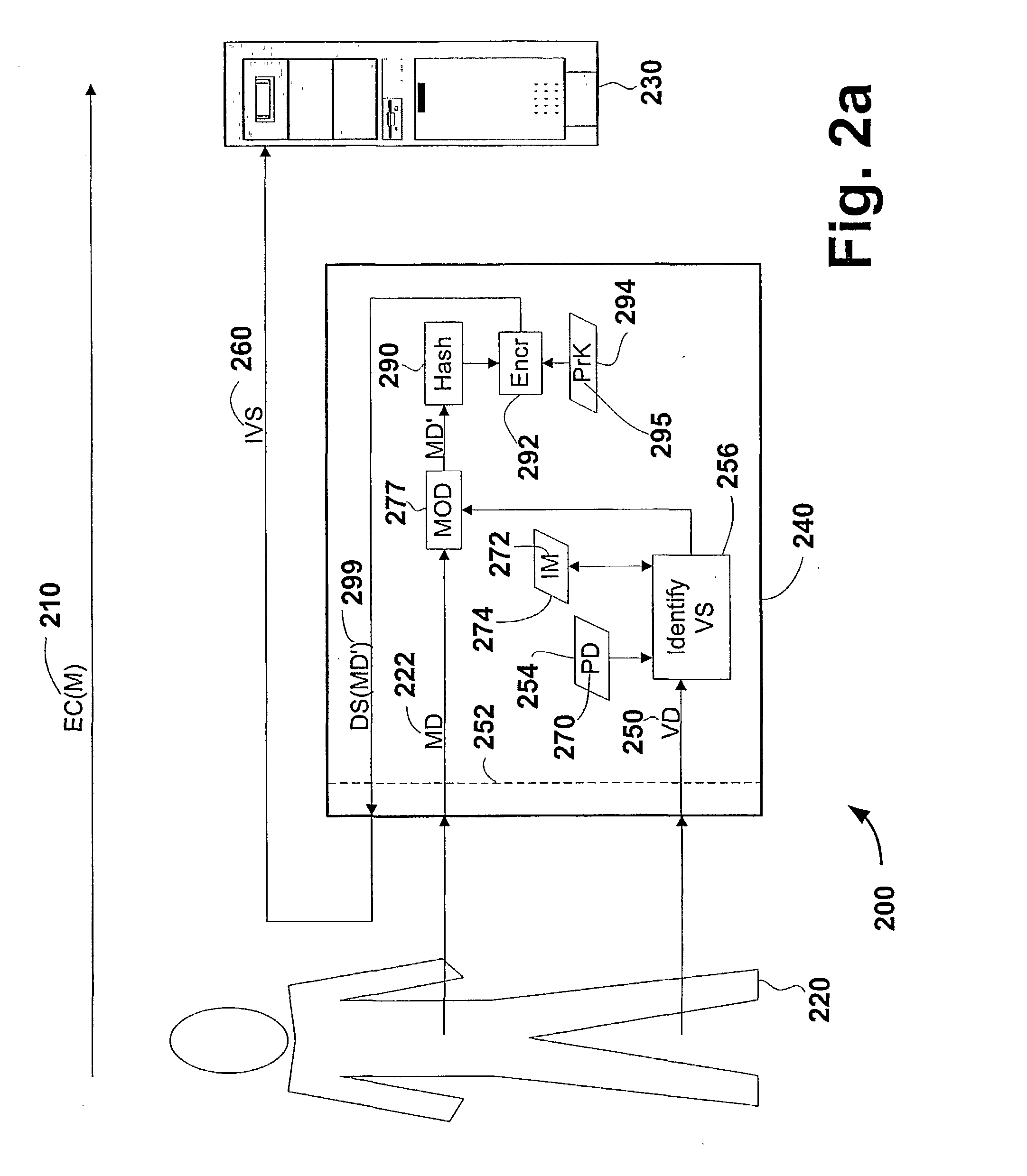
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5857 results about "Digital signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
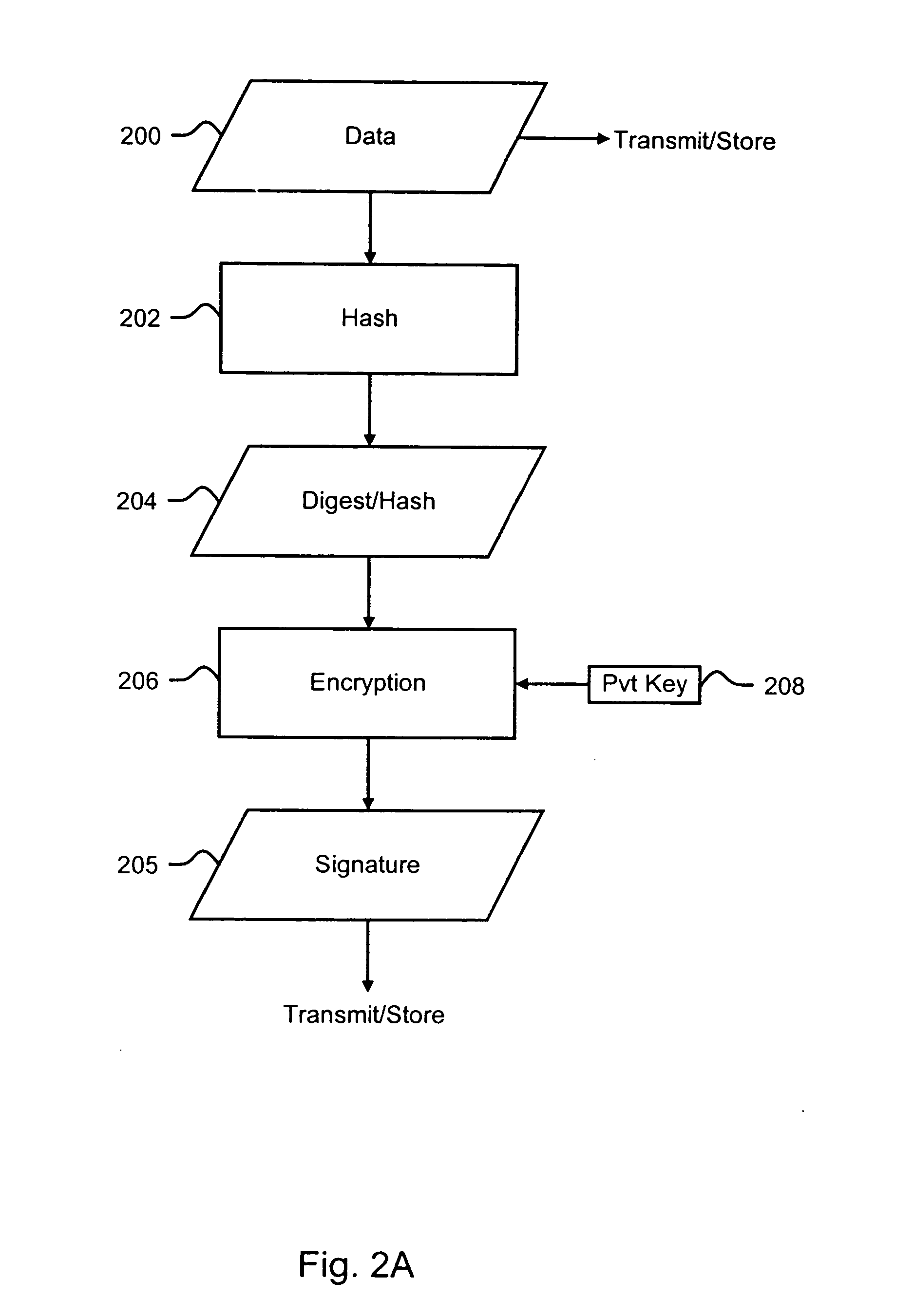
A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents. A valid digital signature, where the prerequisites are satisfied, gives a recipient very strong reason to believe that the message was created by a known sender (authentication), and that the message was not altered in transit (integrity).
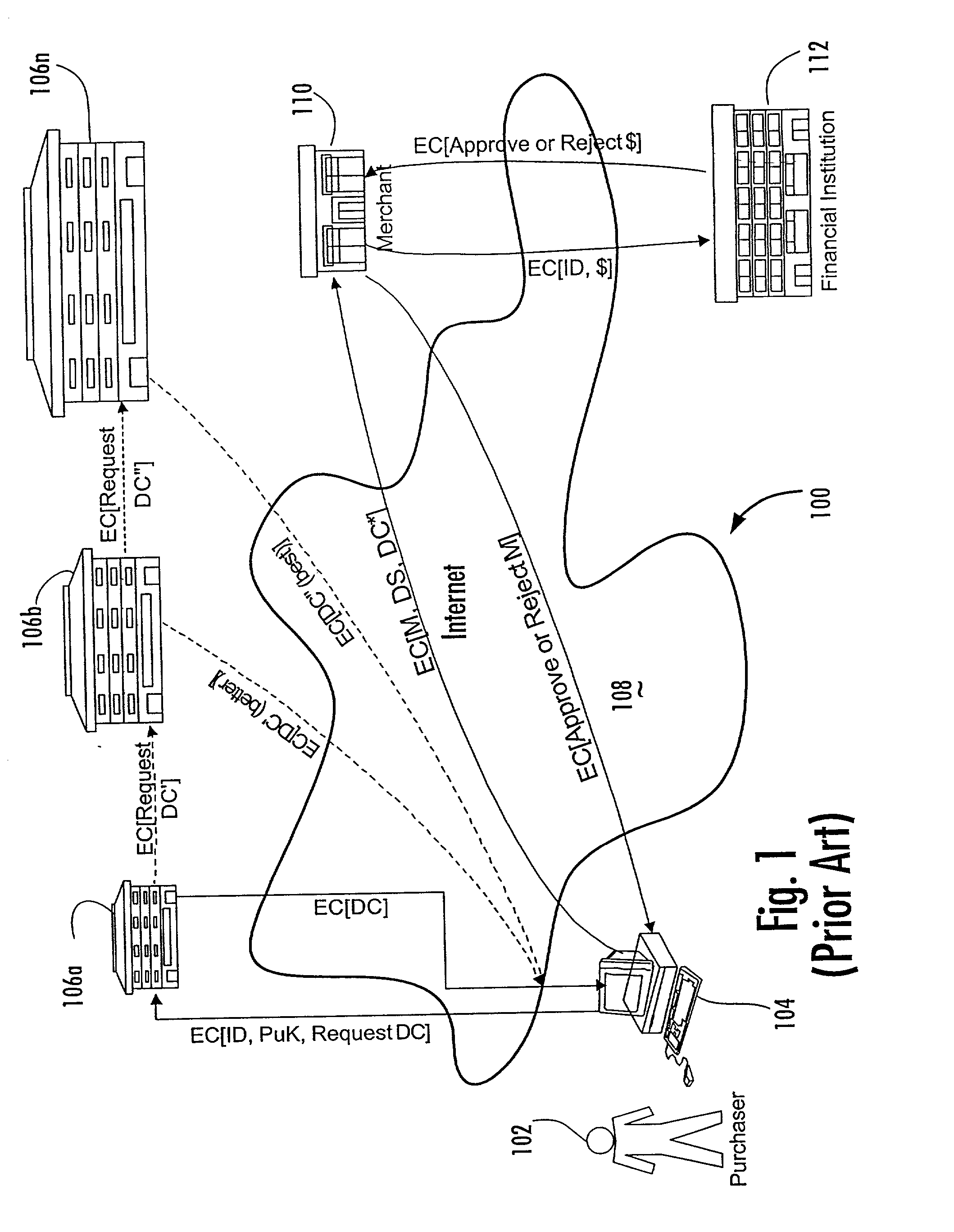
Electronic menu document creator in a virtual financial environment
The disclosure provides for creating a finalized document relating to a transaction. A buyer selects documents associated with a proposed transaction and indicates trade terms of an agreement relating to the documents selected. The trade terms are presented to a seller on an electronic form via an electronic document platform. The electronic form includes a combined purchase order proforma invoice, a transportation document, and a shipping document. The seller can amend the trade terms on the form, and each amendment creates a new version of the form. Negotiations of the trade terms between the buyer and the seller are conducted electronically and the negotiated fonn detailing the negotiation of the trade terms is generated and displayed electronically, also. A compliance check is performed and is triggered in response to a digital signature of the form. Payment is initiated to the seller after a verification of credit of the buyer.
Owner:ACCENTURE GLOBAL SERVICES LTD
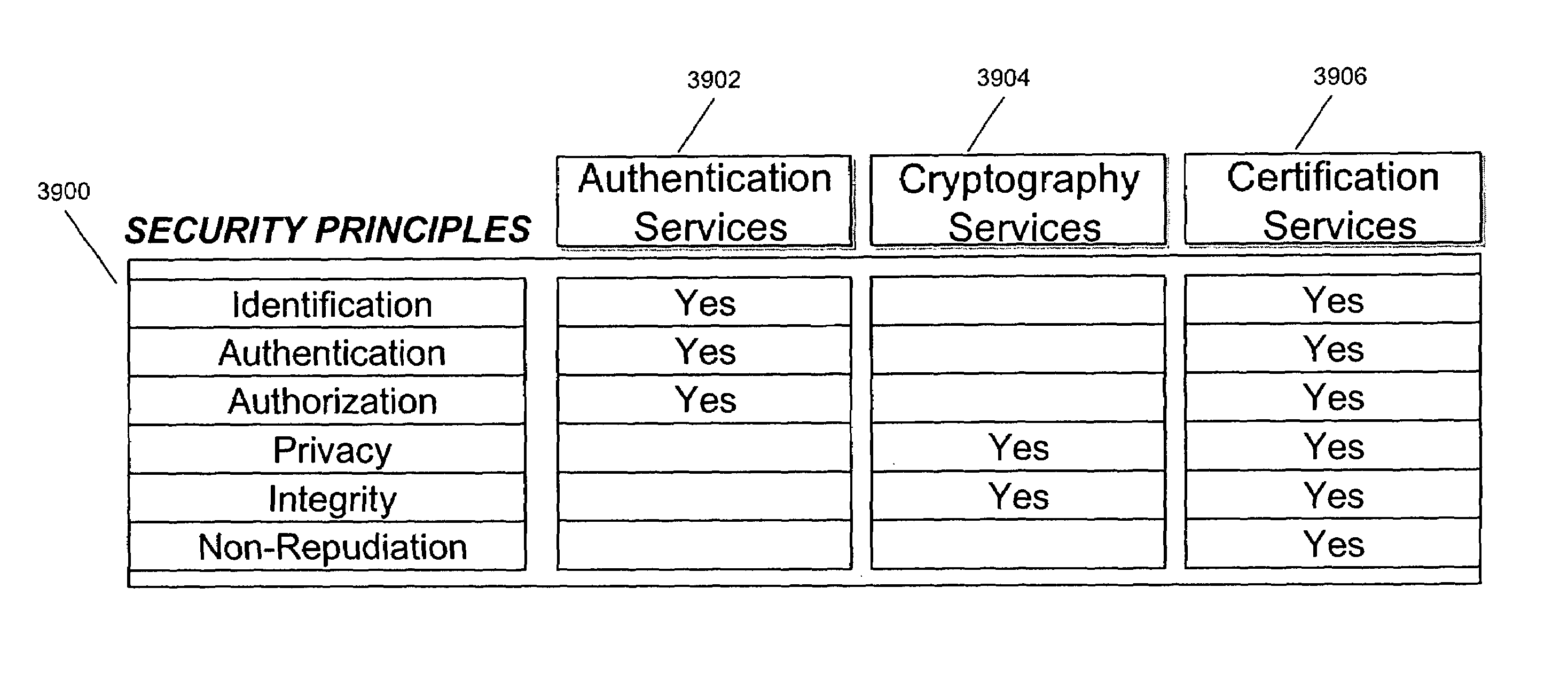
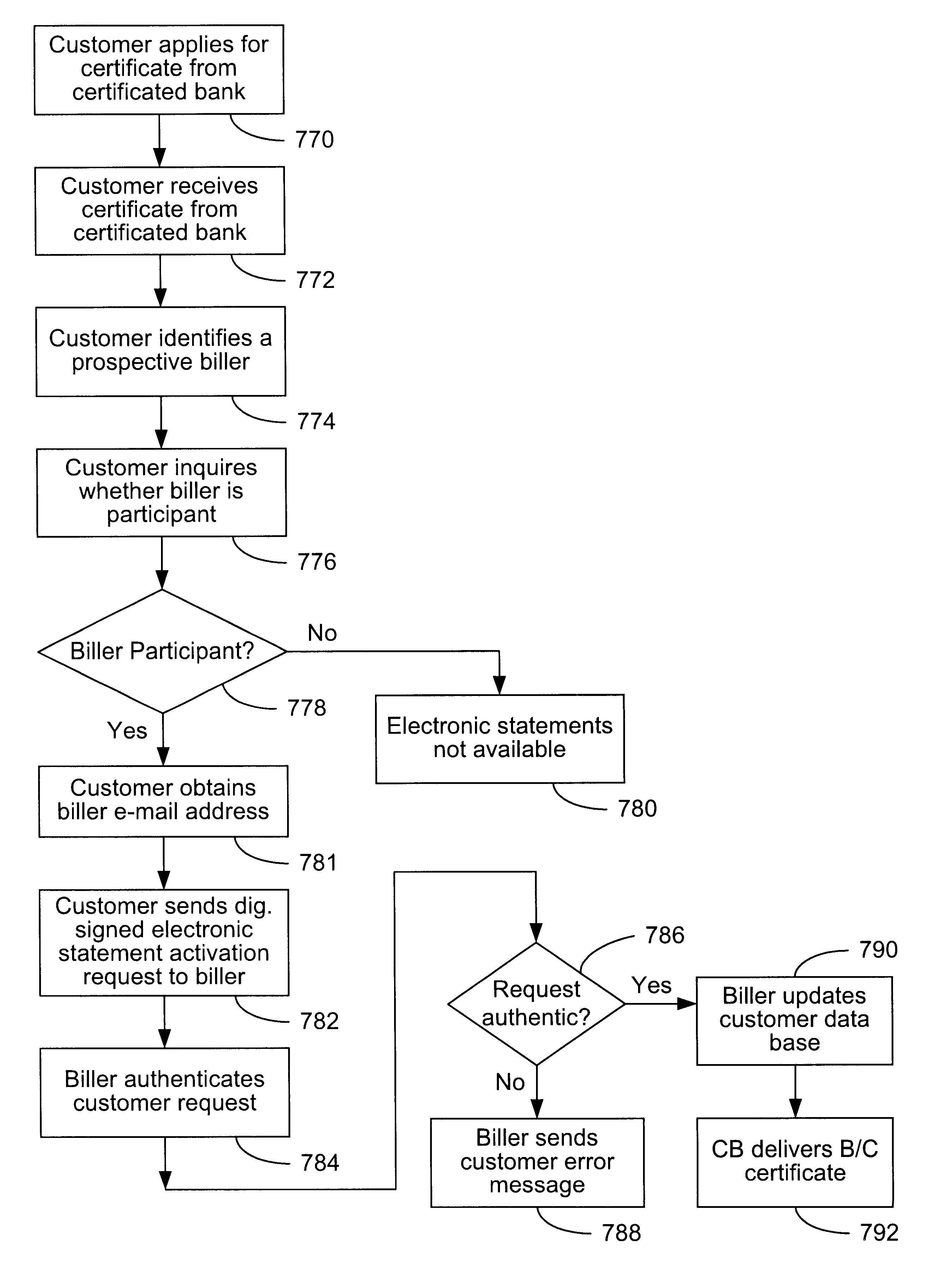
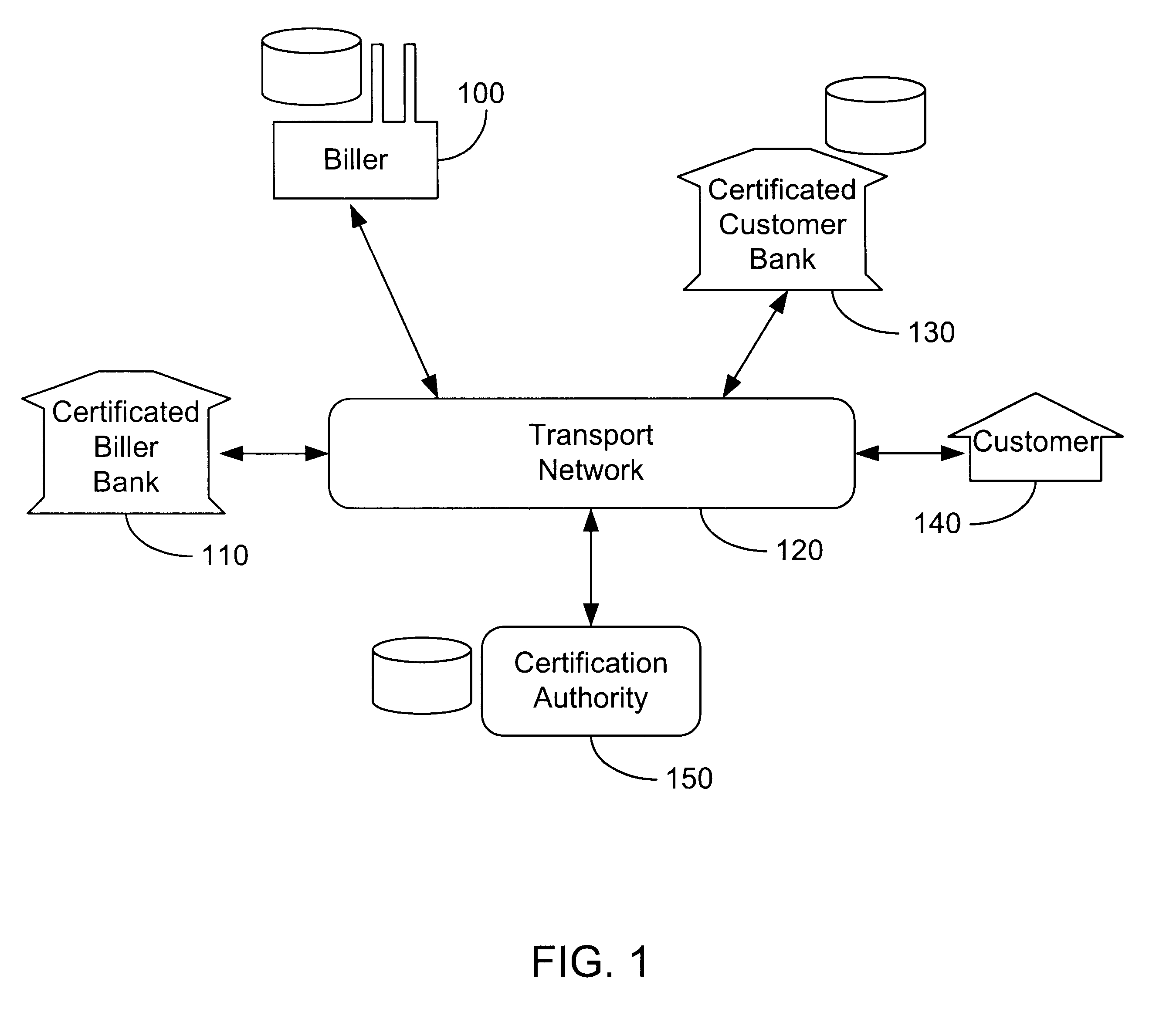
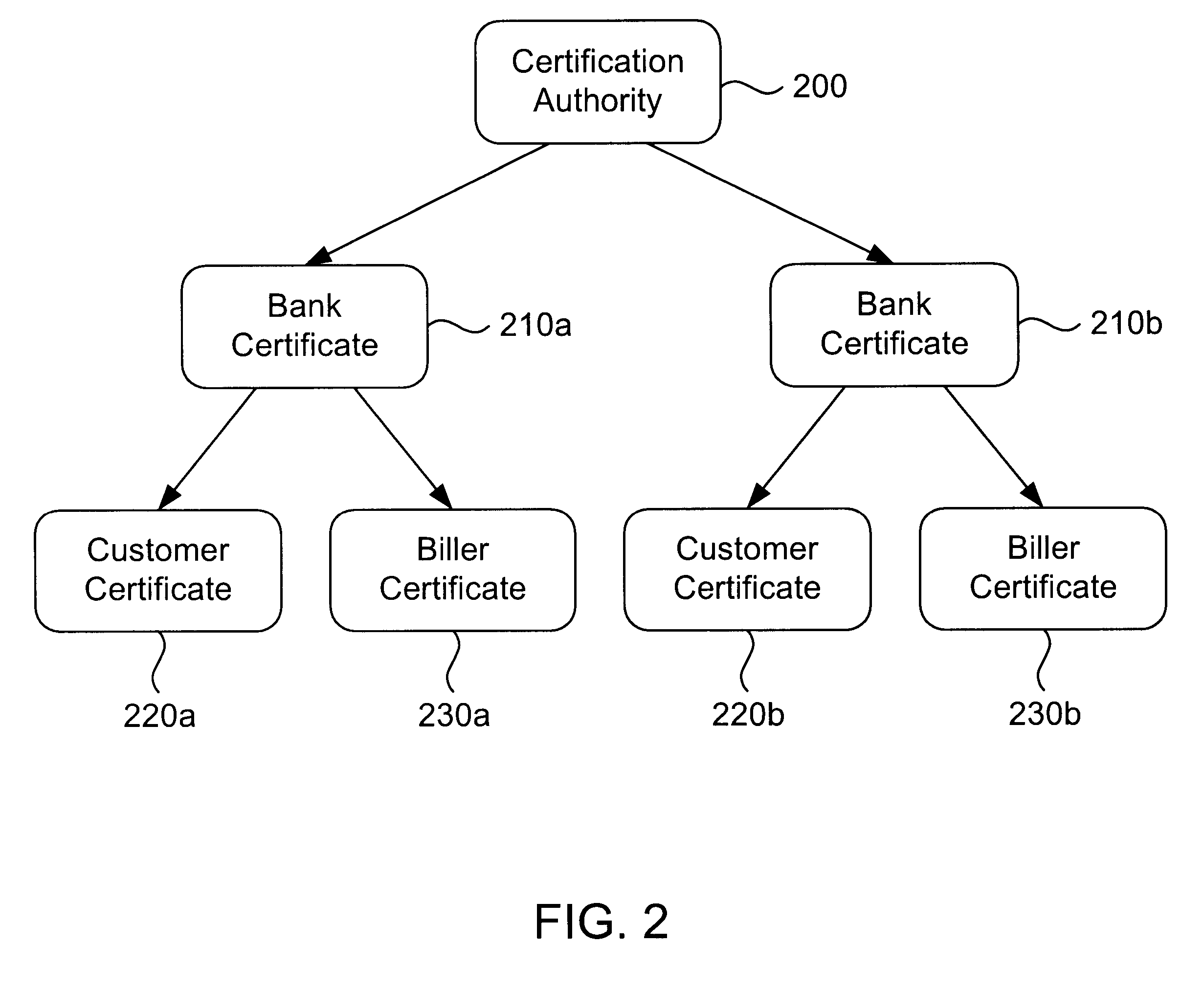
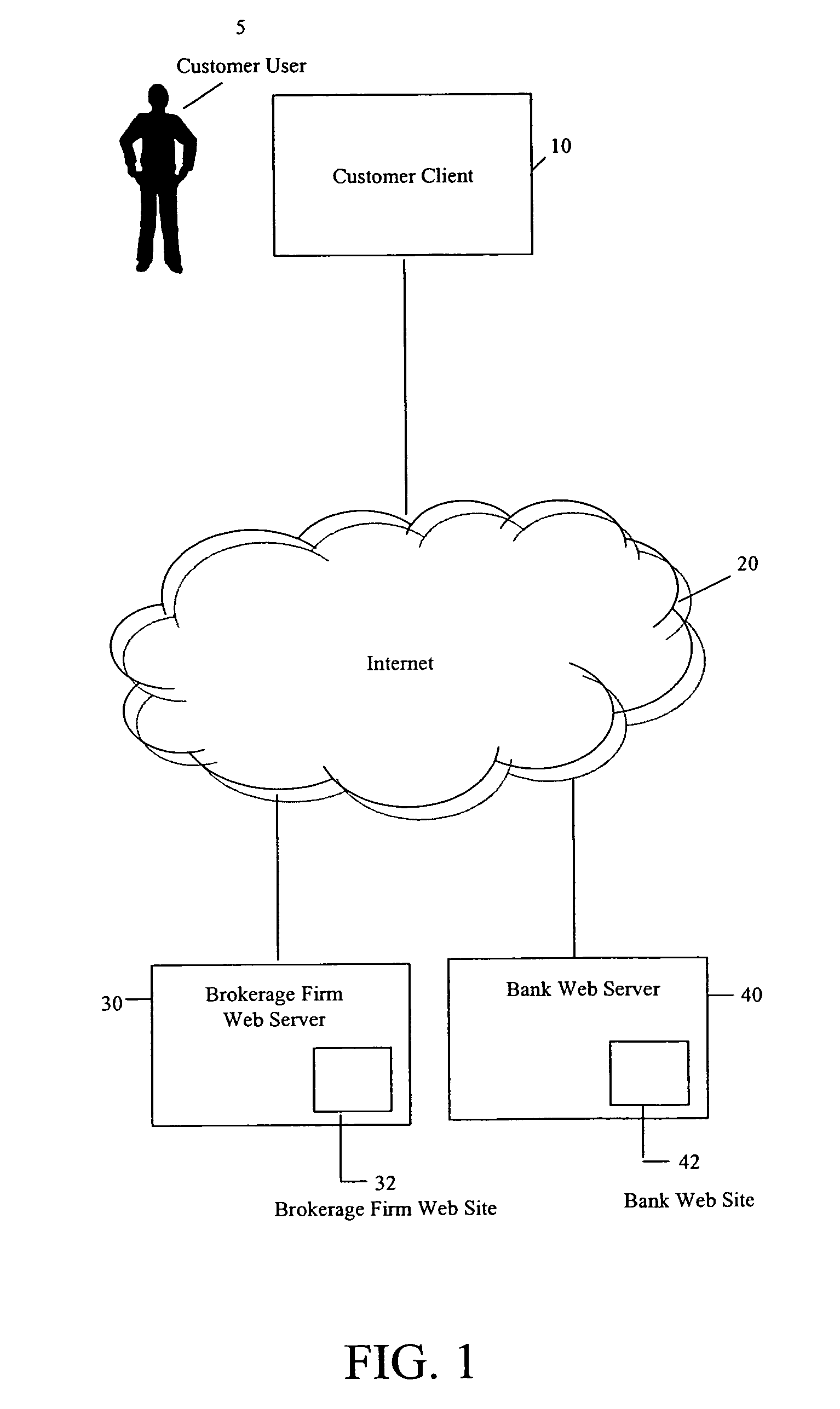
Secure interactive electronic account statement delivery system
InactiveUS6285991B1Good flexibilityBilling is thereby complicatedFinanceUser identity/authority verificationDigital dataNetwork communication
The present invention consists of a secure interactive electronic account statement delivery system suitable for use over open networks such as the Internet. The invention utilizes a certification hierarchy to insure that electronic bills, invoices, and other account statements can be securely sent over open networks. The participants in the system are a certification authority, certificated banks, billers, and customers. The certification authority grants digital certificates to the certificated banks, which in turn grant digital certificates to billers and customers. Digital certificates form the basis for encryption and authentication of network communications, using public and private keys. The certificates associate a customer and biller with a certificated bank and with the electronic billing system, much like payment cards associate a customer with a payment card issuer and a particular payment card system. Digital signatures are used for authentication and non-repudiation. The certificates may be stored as digital data on storage media of a customer's or biller's computer system, or may be contained in integrated circuit or chip cards physically issued to billers and customers. The electronic bill itself may be a simple text message containing the equivalent of summary information for the bill, or may be more elaborate. In one embodiment of the invention, the electronic bill contains a number of embedded links, for example an embedded URL of a biller's world wide web server that allows the customer to interactively bring up detailed billing information by activating the link. The e-mail message may also include links to third party websites.
Owner:VISA INT SERVICE ASSOC
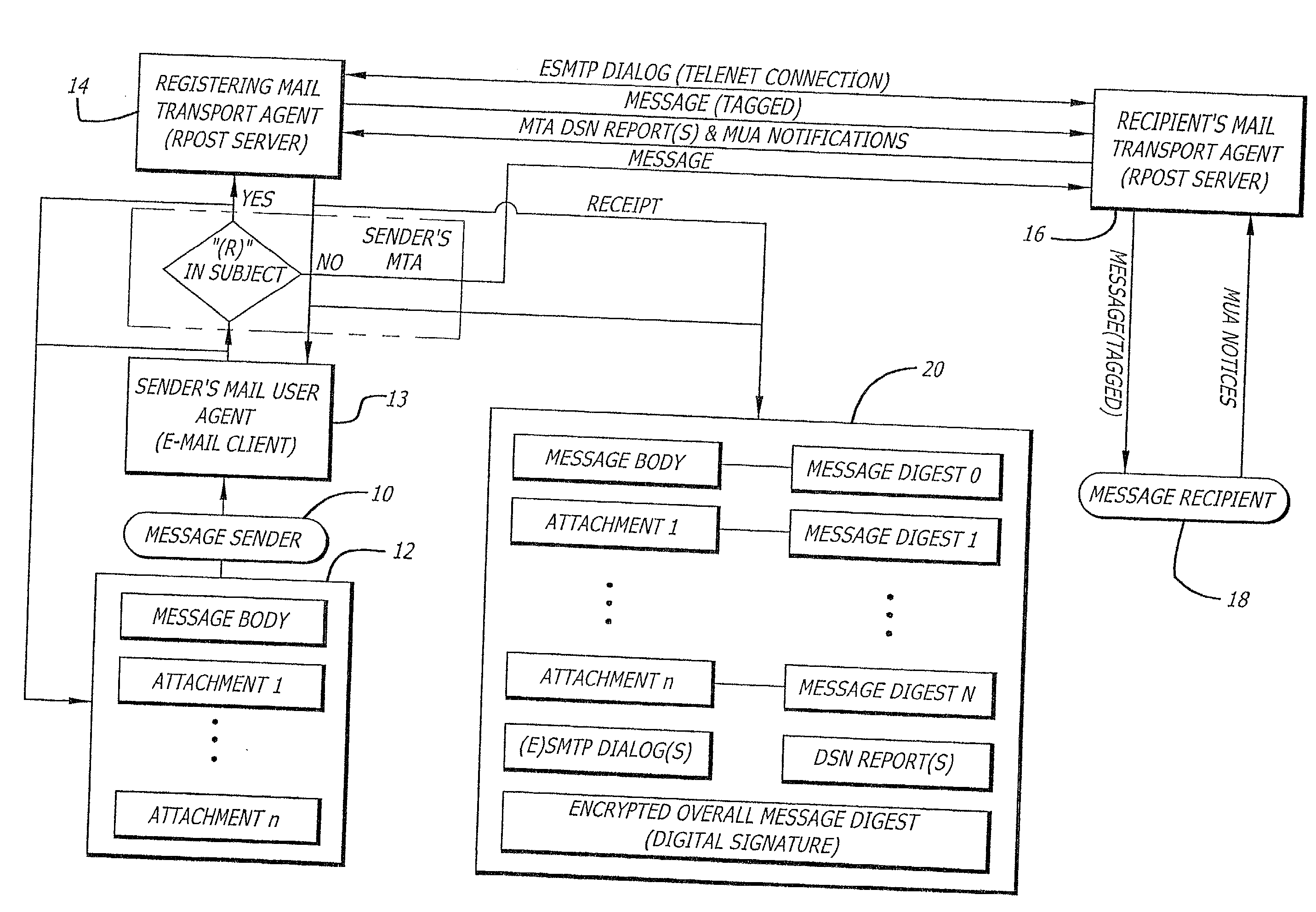
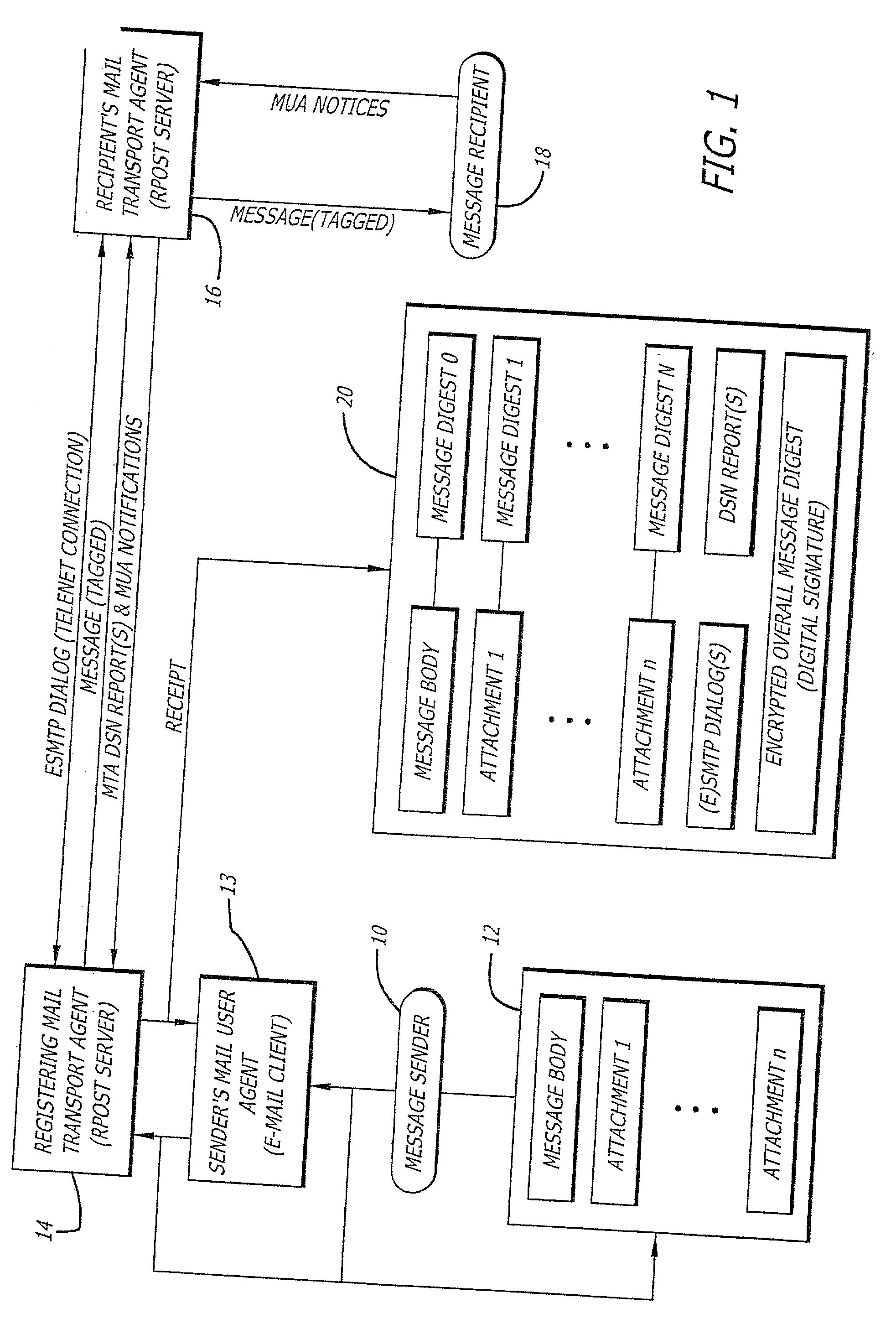
System and method for verifying delivery and integrity of electronic messages
InactiveUS20020144154A1Key distribution for secure communicationDigital data processing detailsDigital signatureThe Internet
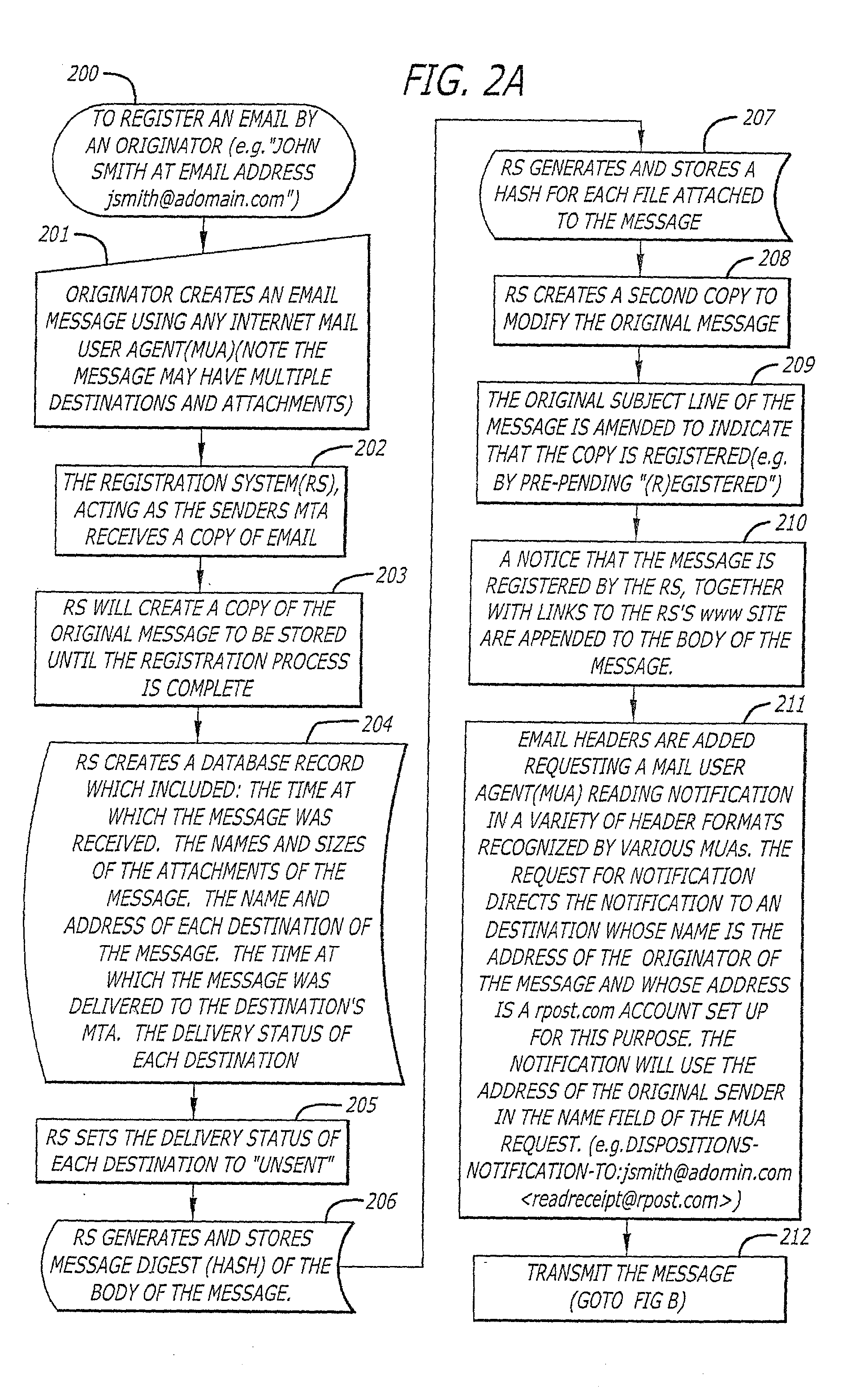
A server receives a message from a sender and transmits the message through the Internet to a recipient. The server normally transmits the message in a first path through the Internet to the recipient. When the sender indicates at a particular position in the message that the message is registered, the server transmits the message in a second path through the Internet to the recipient. The sender can also provide additional indications in the message to have the server handle the message in other special ways not normally provided by the server. After learning from the receipt or the recipient's agent through the Internet that the message was successfully received, the server creates, and forwards to the sender, an electronic receipt. The receipt includes at least one, and preferably all: the message and any attachments, a delivery success / failure table listing the receipts, and the receipt times, of the message by the recipient's specific agents, and the failure of other agents of the recipient to receive the message and a digital signature of the message and attachments subsequently. By verifying that the digital signature on the sender's receipt matches the digital receipt at the server, the server can verify, without retaining the message, that the receipt is genuine and that the message is accurate.
Owner:RPOST COMM
Blockchain identity management system based on public identities ledger
ActiveUS9635000B1Effectively prevents unauthorized sharingMultiple keys/algorithms usagePublic key for secure communicationSystems managementIdentity management system
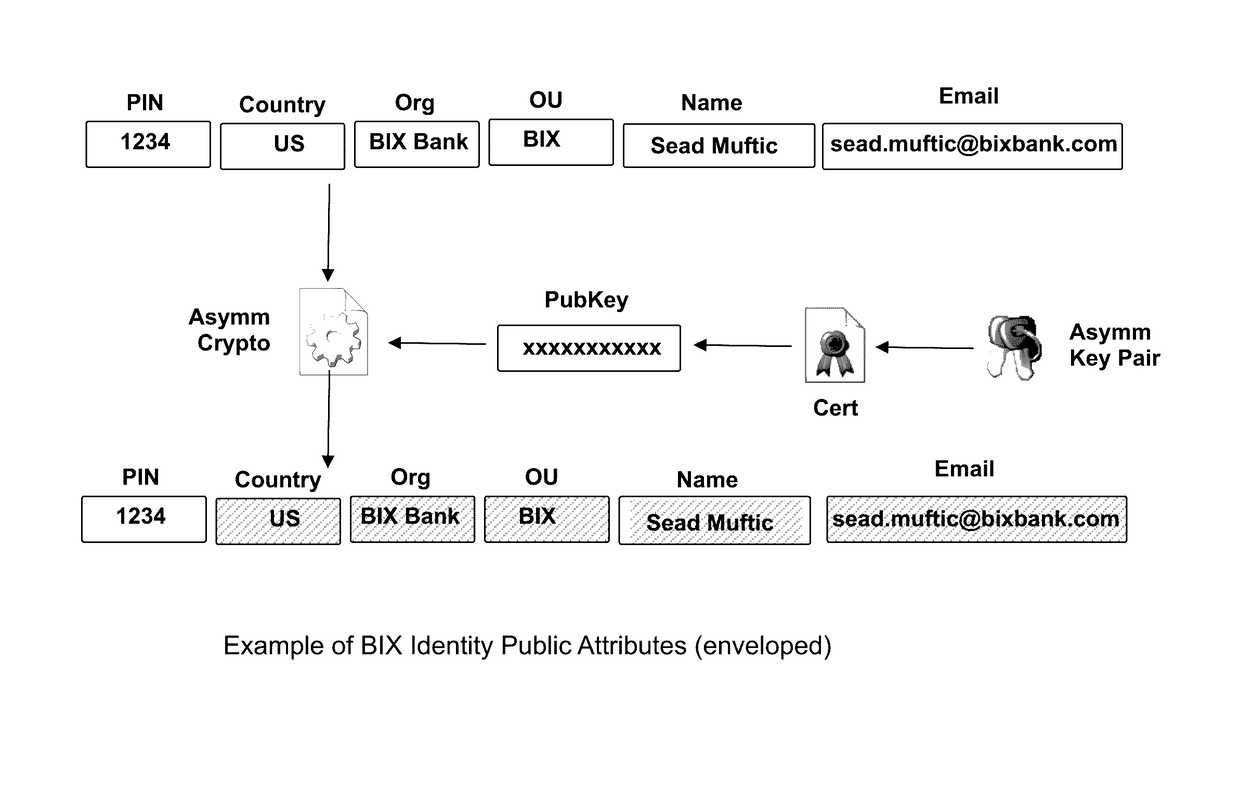
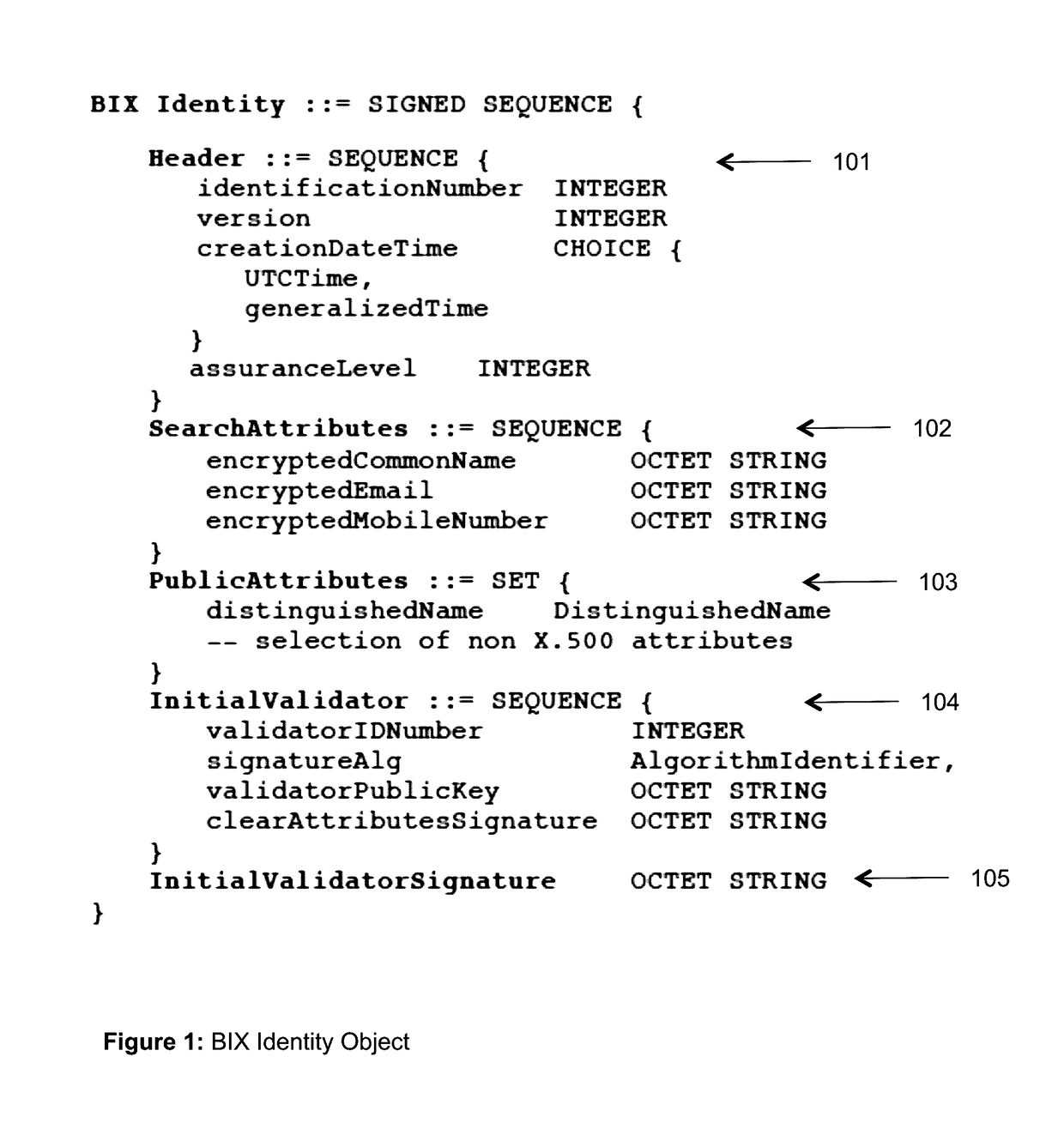
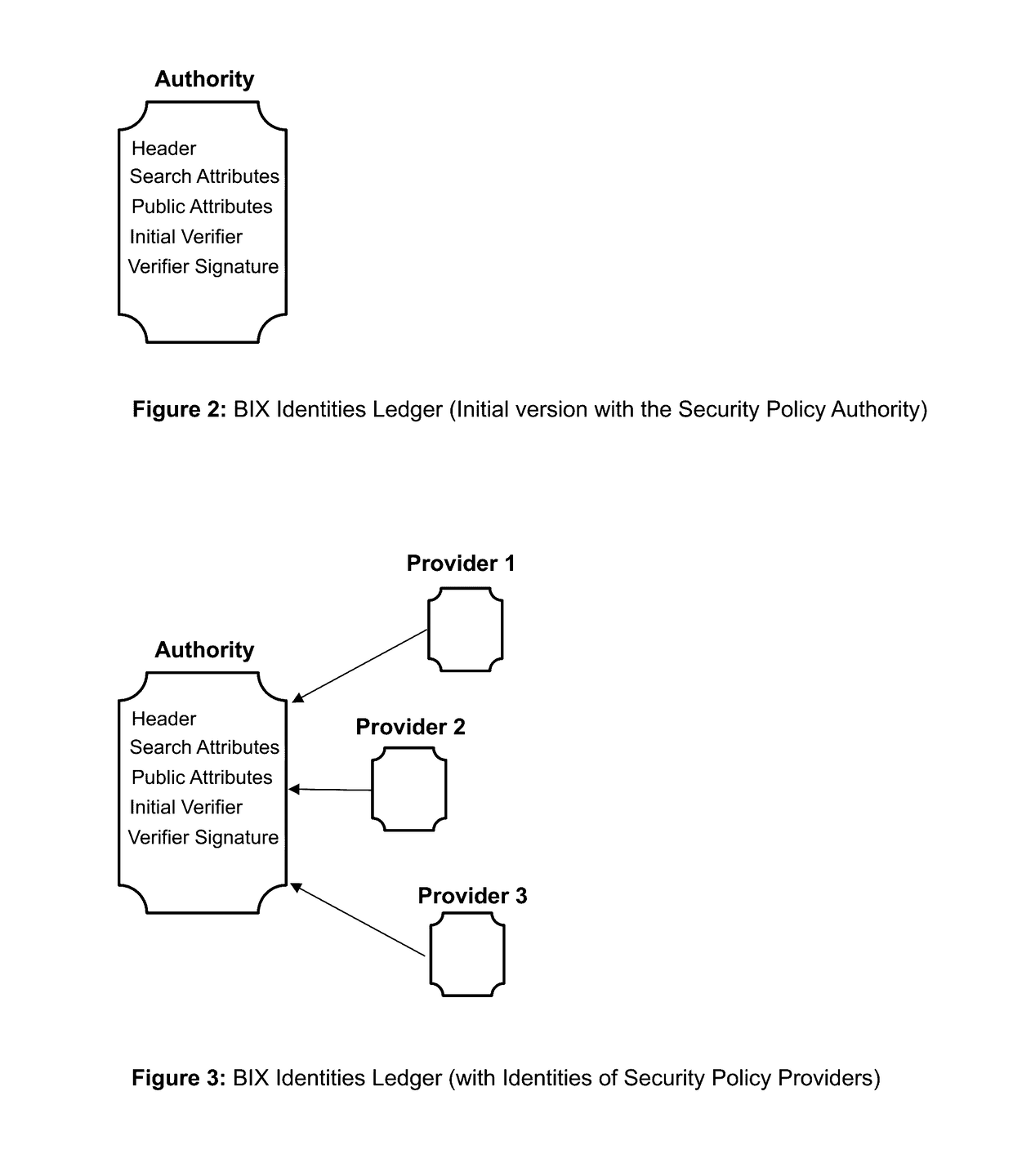
The invention describes an identity management system (IDMS) based on the concept of peer-to-peer protocols and the public identities ledger. The system manages digital identities, which are digital objects that contain attributes used for the identification of persons and other entities in an IT system and for making identity claims. The identity objects are encoded and cryptographically encapsulated. Identity management protocols include the creation of identities, the validation of their binding to real-world entities, and their secure and reliable storage, protection, distribution, verification, updates, and use. The identities are included in a specially constructed global, distributed, append-only public identities ledger. They are forward- and backward-linked using the mechanism of digital signatures. The linking of objects and their chaining in the ledger is based on and reflect their mutual validation relationships. The identities of individual members are organized in the form of linked structures called the personal identities chains. Identities of groups of users that validated identities of other users in a group are organized in community identities chains. The ledger and its chains support accurate and reliable validation of identities by other members of the system and by application services providers without the assistance of third parties. The ledger designed in this invention may be either permissioned or unpermissioned. Permissioned ledgers have special entities, called BIX Security Policy Providers, which validate the binding of digital identities to real-world entities based on the rules of a given security policy. In unpermissioned ledgers, community members mutually validate their identities. The identity management system provides security, privacy, and anonymity for digital identities and satisfies the requirements for decentralized, anonymous identities management systems.
Owner:MUFTIC SEAD
Account-based digital signature (ABDS) system
InactiveUS20020026575A1Key distribution for secure communicationFinanceDigital signatureElectronic communication
A method of authenticating an entity by a receiving party with respect to an electronic communication that is received by the receiving party and that includes both a unique identifier associated with an account maintained by the receiving party and a digital signature for a message regarding the account, consists of the steps of, before receipt of the electronic communication, first associating by the receiving party a public key of a public-private key pair with the unique identifier and, thereafter, only conducting message authentication using the digital signature received by the receiving party in the electronic communication and the public key associated with the account identifier.
Owner:FIRST DATA
Network message generation for automated authentication
ActiveUS8819253B2Avoids presentationImprove user experienceDigital data processing detailsUser identity/authority verificationUser deviceNetwork generation
A message generation mechanism for a network interface is provided. The message generation mechanism is operable to generate a message which includes data for signing and authentication procedure instructions. The message is for conveying information to a user device for presentation to a user via a user interface of the user device. The data is arranged in the message in a manner which permits the user device to utilize the data in an automated signing procedure. The automated signing procedure may be a digital signing procedure. The data for signing may be random data, pseudo-random data or secure random data and may be arranged in the message in a manner which avoids presentation to the user.
Owner:ORACLE INT CORP
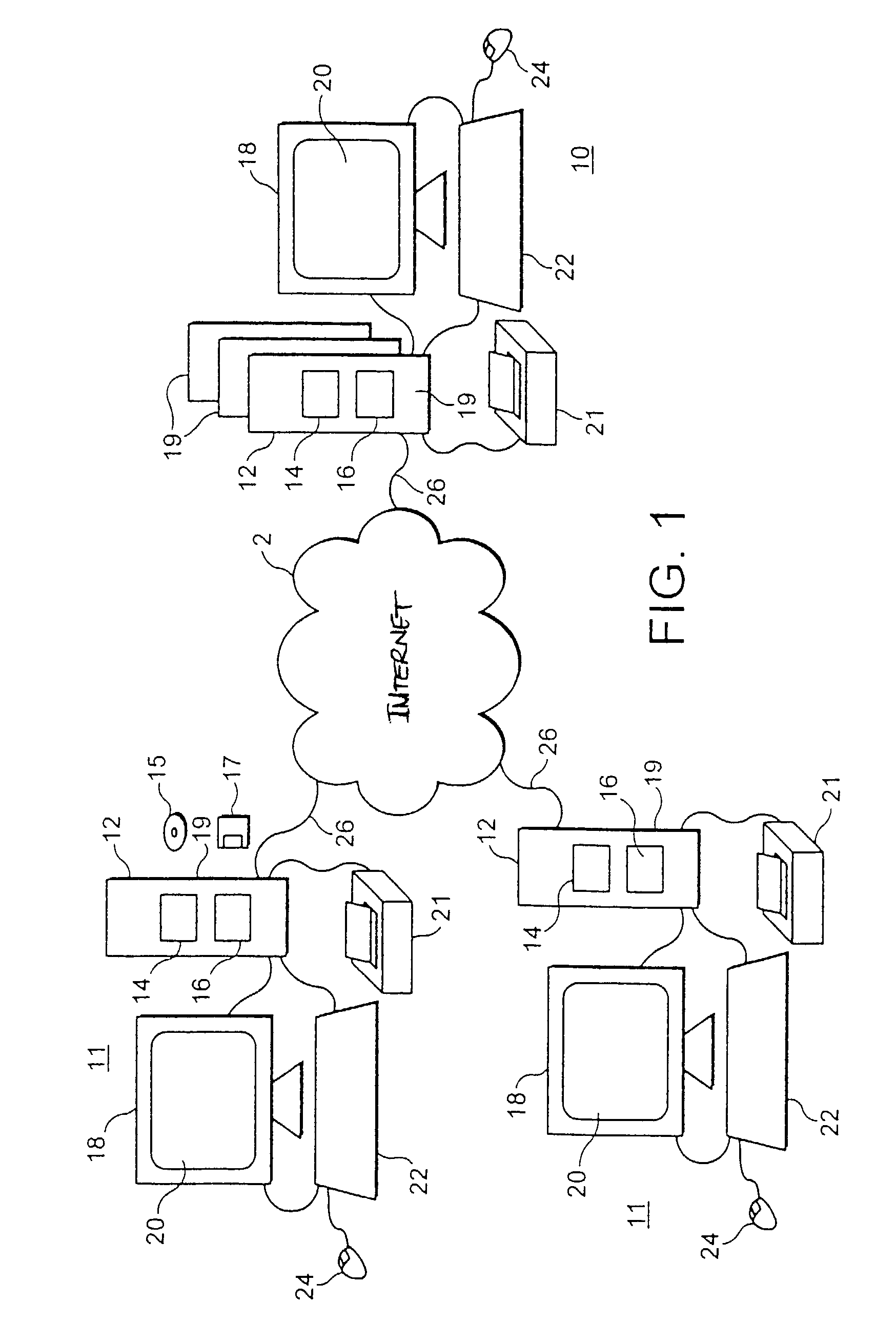
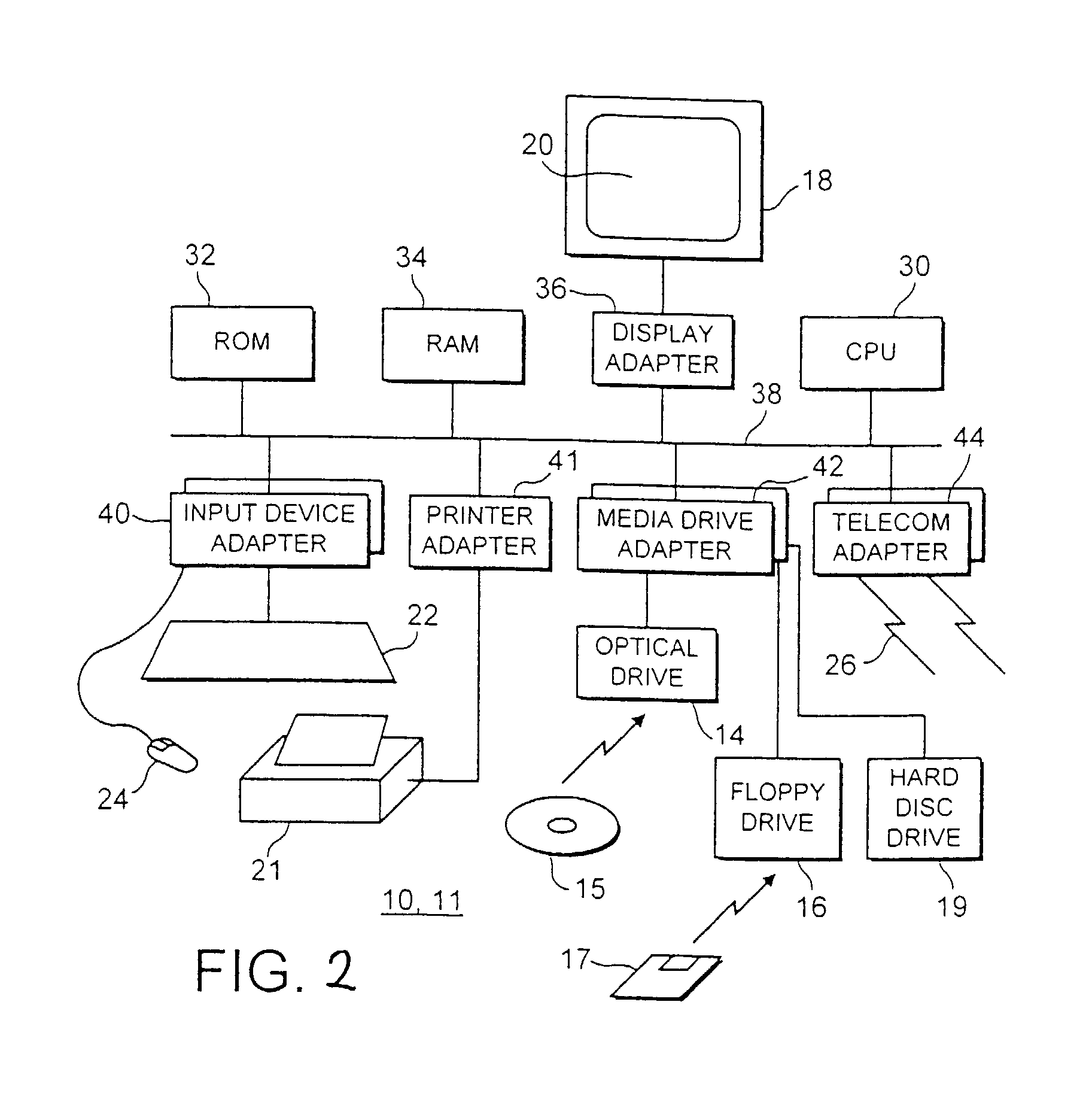
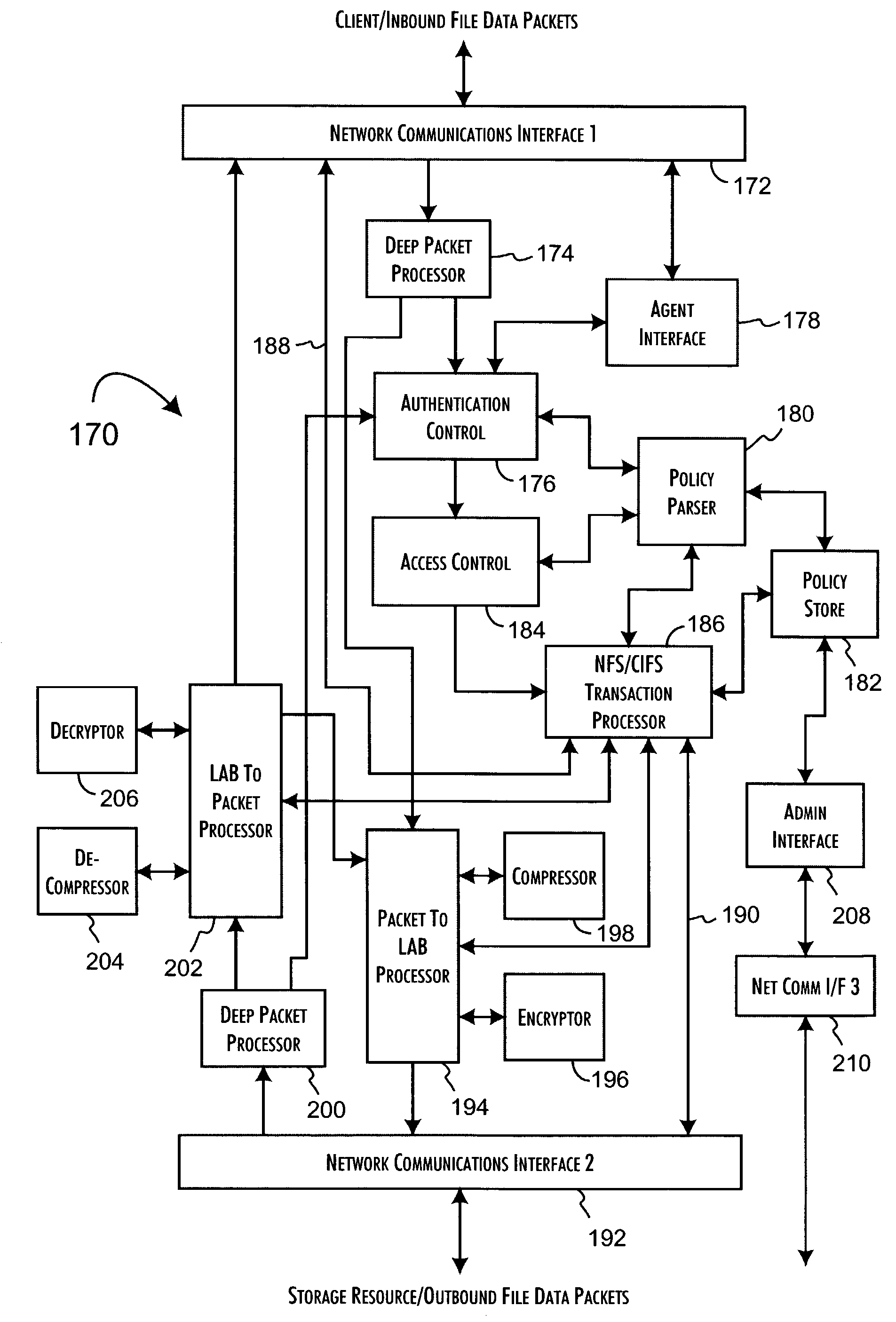
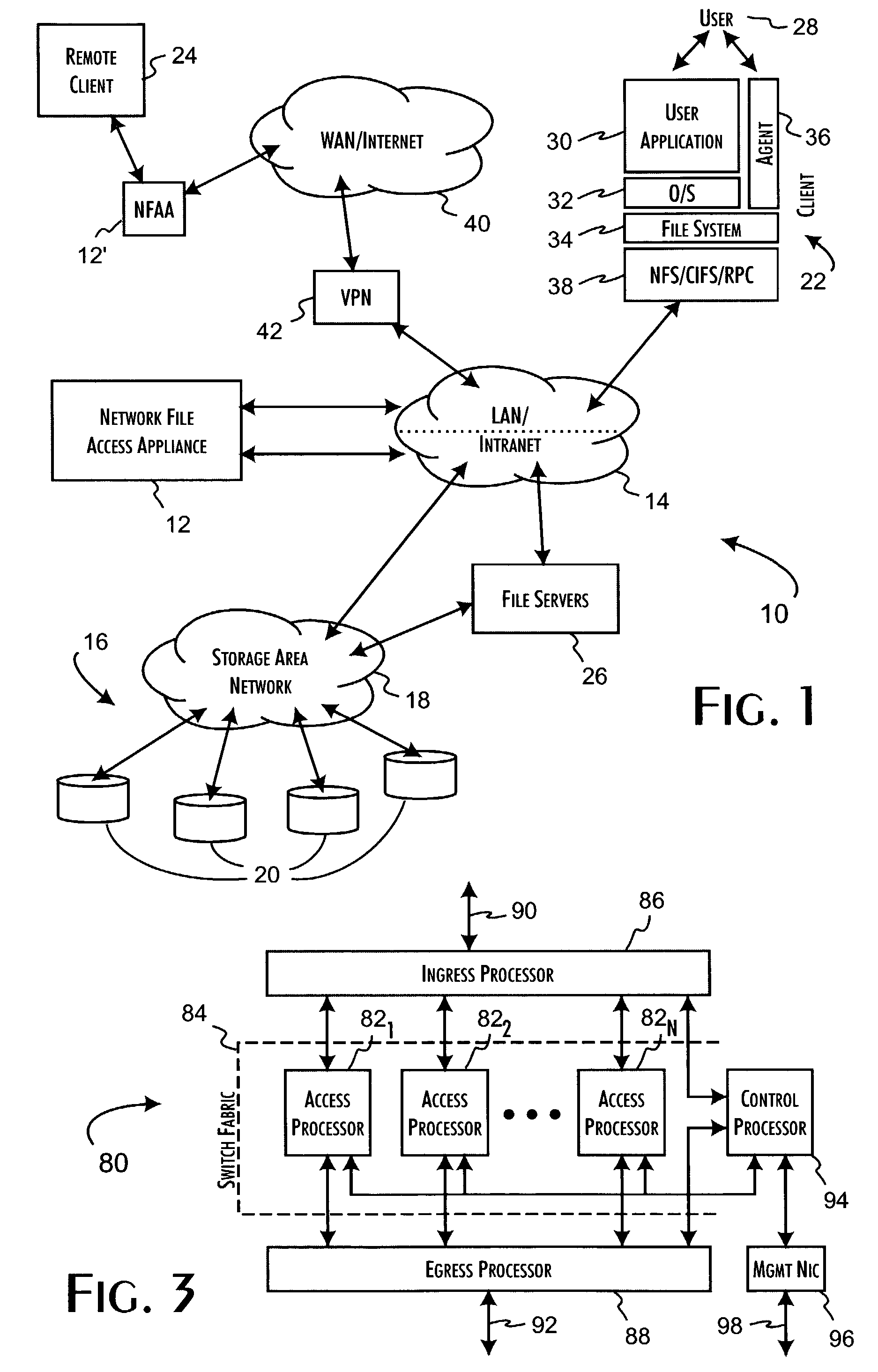
Logical access block processing protocol for transparent secure file storage
InactiveUS7334124B2Ensure integritySafe storageDigital data processing detailsUser identity/authority verificationComputer hardwareDigital signature
Network data files are secure through the operation of an infrastructure gateway-based network file access appliance. Network file data, corresponding to network pocket payload data, are further reduced to a sequence of data blocks that are secured through any combination of block encryption, compression, and digital signatures. File meta-data, including encryption, compression and block-level digital signatures are persistently stored with the file data, either in-band in the file as stored or out-of-band key as a separately stored file or file policy record. File meta-data is recovered with accesses of the file data to support bidirectional encryption and compression and to detect tampering with the file data by comparison against block-level digital signatures.
Owner:THALES ESECURITY INC
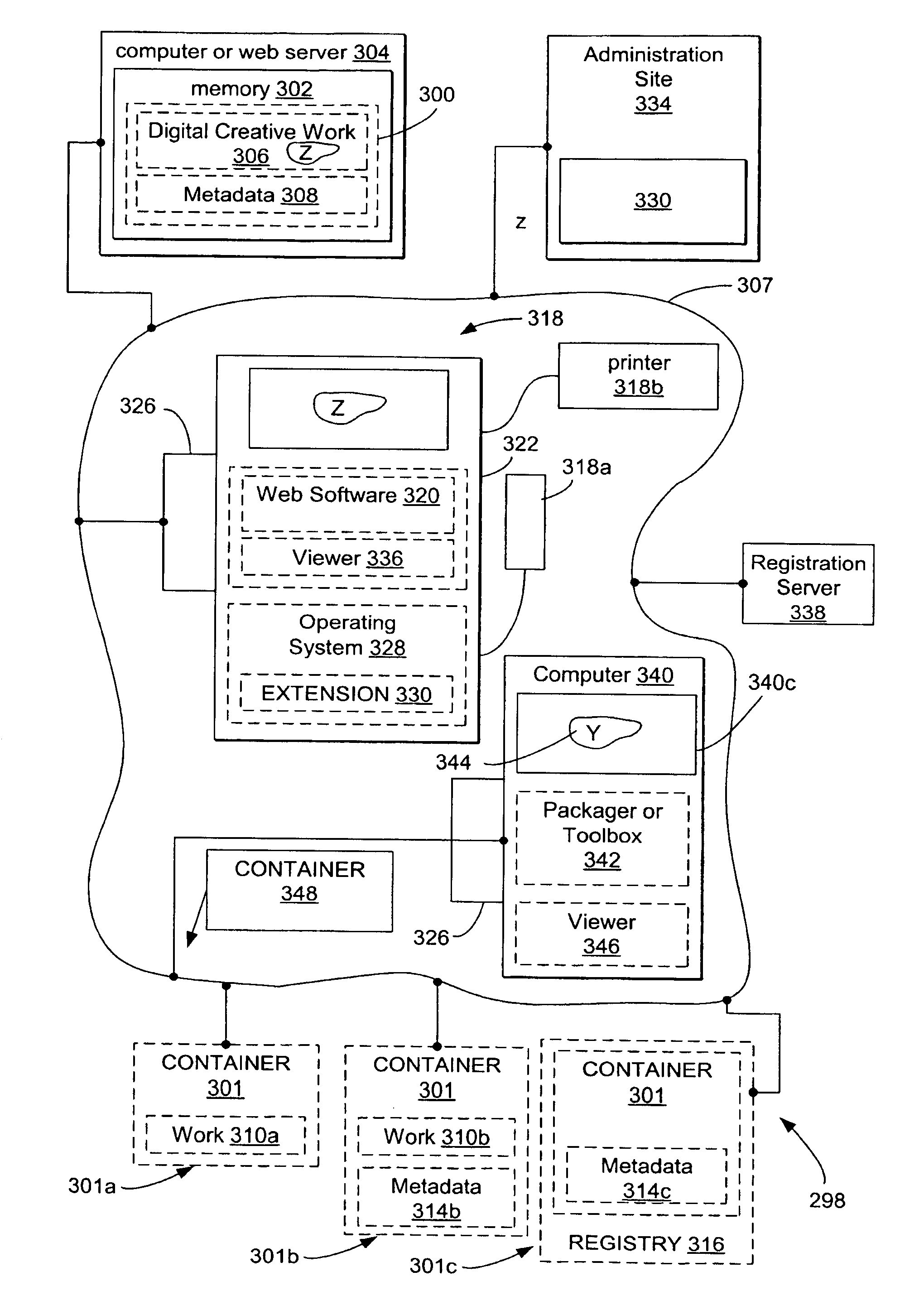
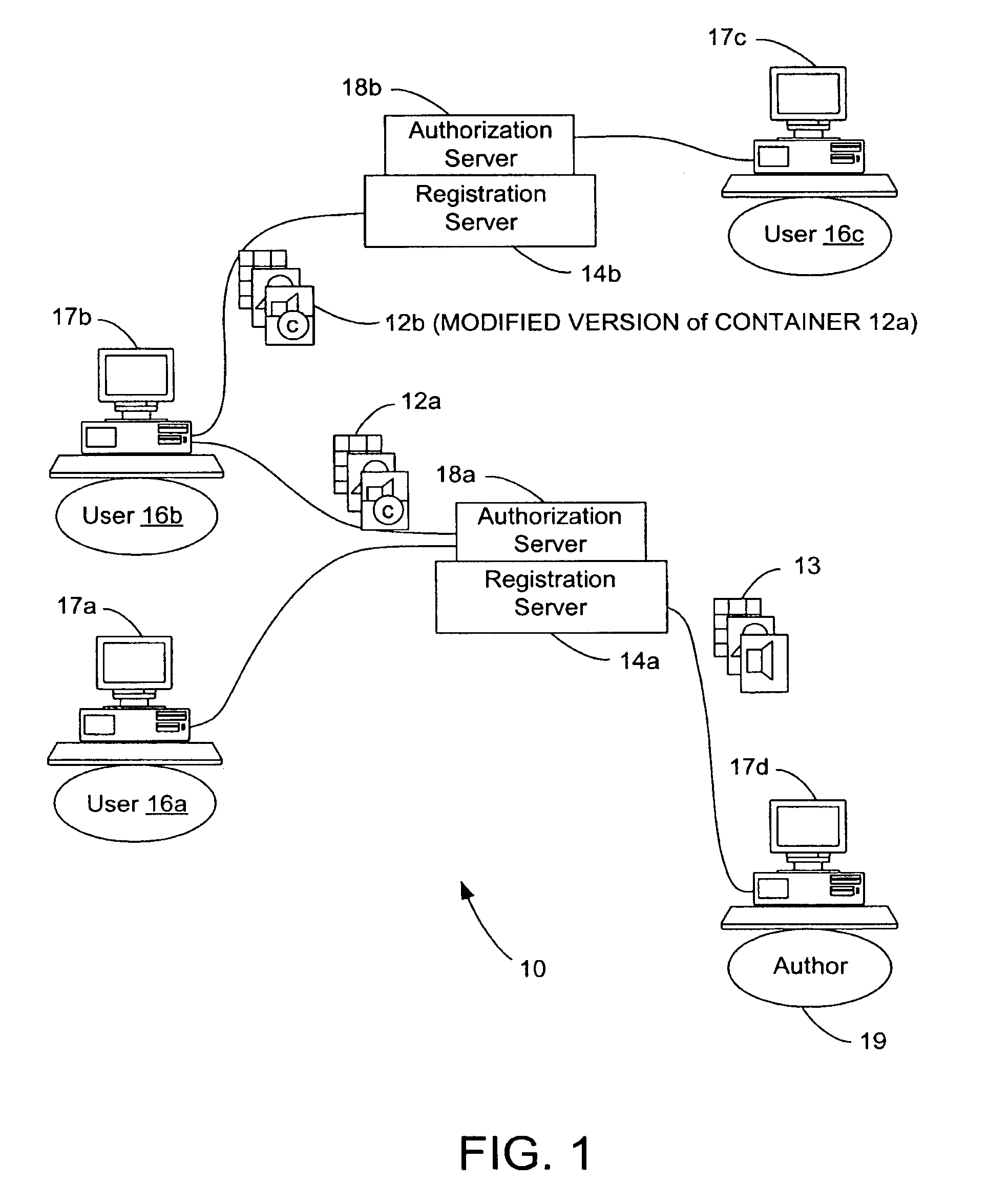
System and methods for managing digital creative works
InactiveUS7047241B1Improve network efficiencyEliminate needKey distribution for secure communicationData processing applicationsData setDigital signature
Digital Creative Works such as copyrighted electronic media are packaged in a secure electronic format, or CONTAINER, and registered on associated registration server, which serves to provide on-line licensing and copyright management for that Work. Users are connected to the registration server through a computer network or the Internet to enable data transfers and to transact licenses to utilize the media. Packaged electronic media are typically created by an author or derivative user of the work. Once the packaged media is registered on the server, the media is made available for limited use and possible license through an authorization server. This limited use is specified within the minimum permissions data set assigned to each packaged media. Without a license, users are typically permitted to view the packaged media—through a system which unpackages the media—but cannot save, print or otherwise transfer the media without obtaining auxiliary permissions to do so from the authorization server. The electronic media is authenticated through digital signatures and optional encryption.
Owner:DIGIMARC CORP
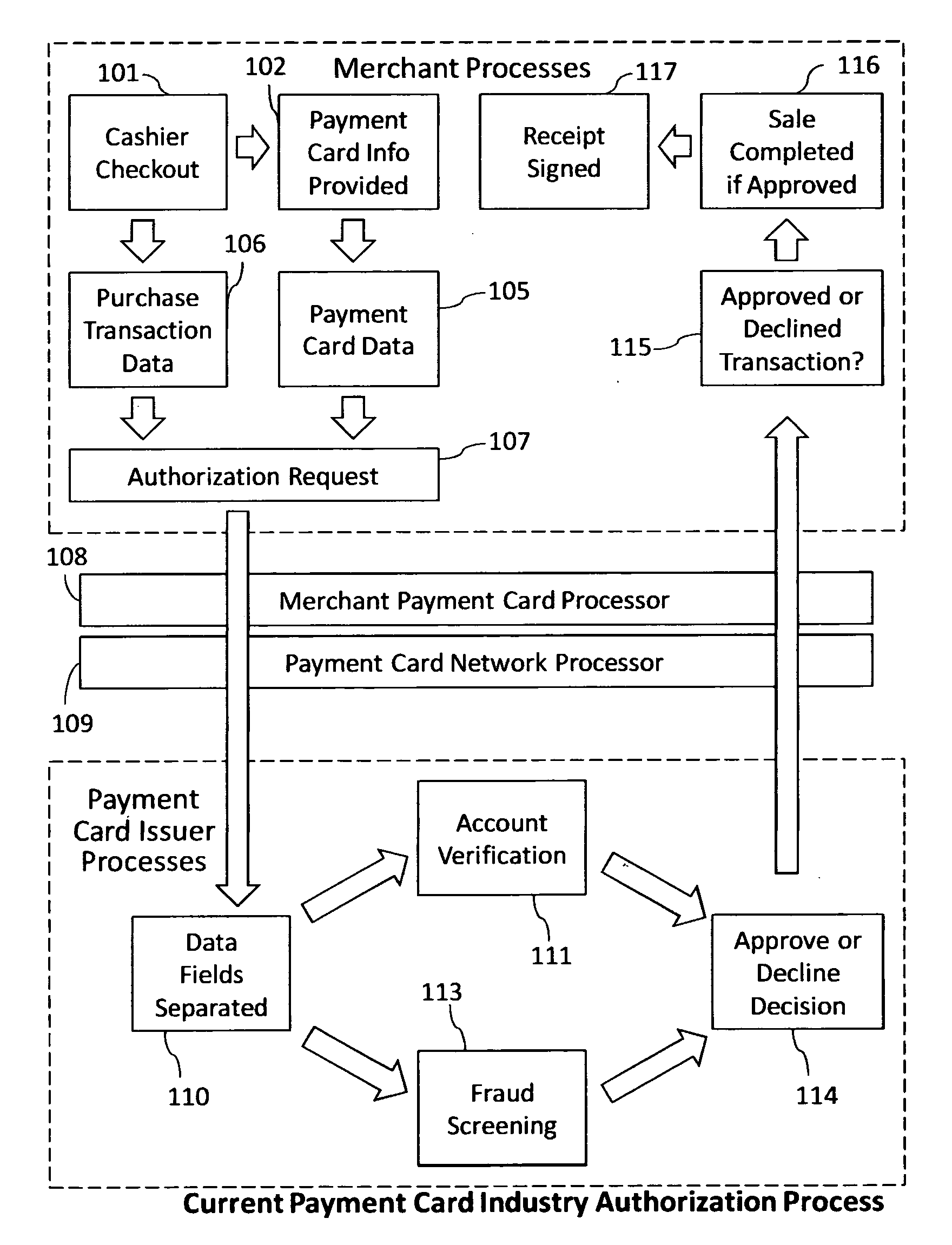
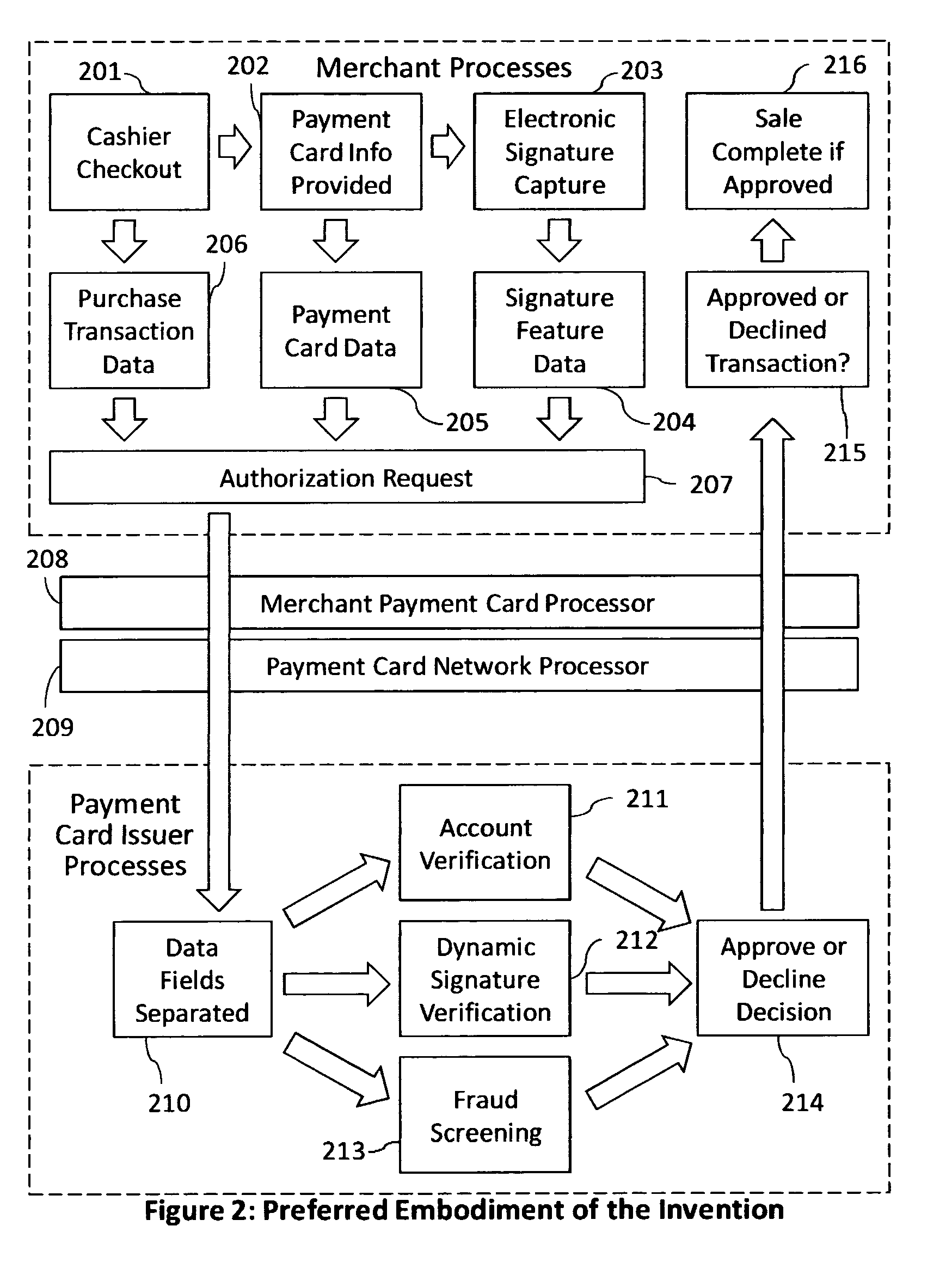
Reduction of transaction fraud through the use of automatic centralized signature/sign verification combined with credit and fraud scoring during real-time payment card authorization processes
InactiveUS20110238510A1Reduce payment card industry fraud lossReduce the amount of dataFinanceCharacter and pattern recognitionDigital signatureIdentity theft
A dynamic signature / sign biometric verification system for detecting and preventing fraudulent transactions is described. The system comprises remote digital signature / sign input devices, a means to extract spatial and temporal features from the signature, a means to transmit the signature / sign features along with customer identifier information to a centralized signature / sign verification authority, a means for combining signature / sign feature verification with other forms of fraud detection technology, and a means for transmitting the results of a signature / sign verification back to the remote location where the signature / sign was captured. The system was primarily developed for use in payment card industries (e.g. credit cards, debit cards) but has applicability to other centralized signature / sign verification applications such as Automated Teller Machine authorizations and other identity theft detection and monitoring services.
Owner:BIOCRYPT ACCESS LLC
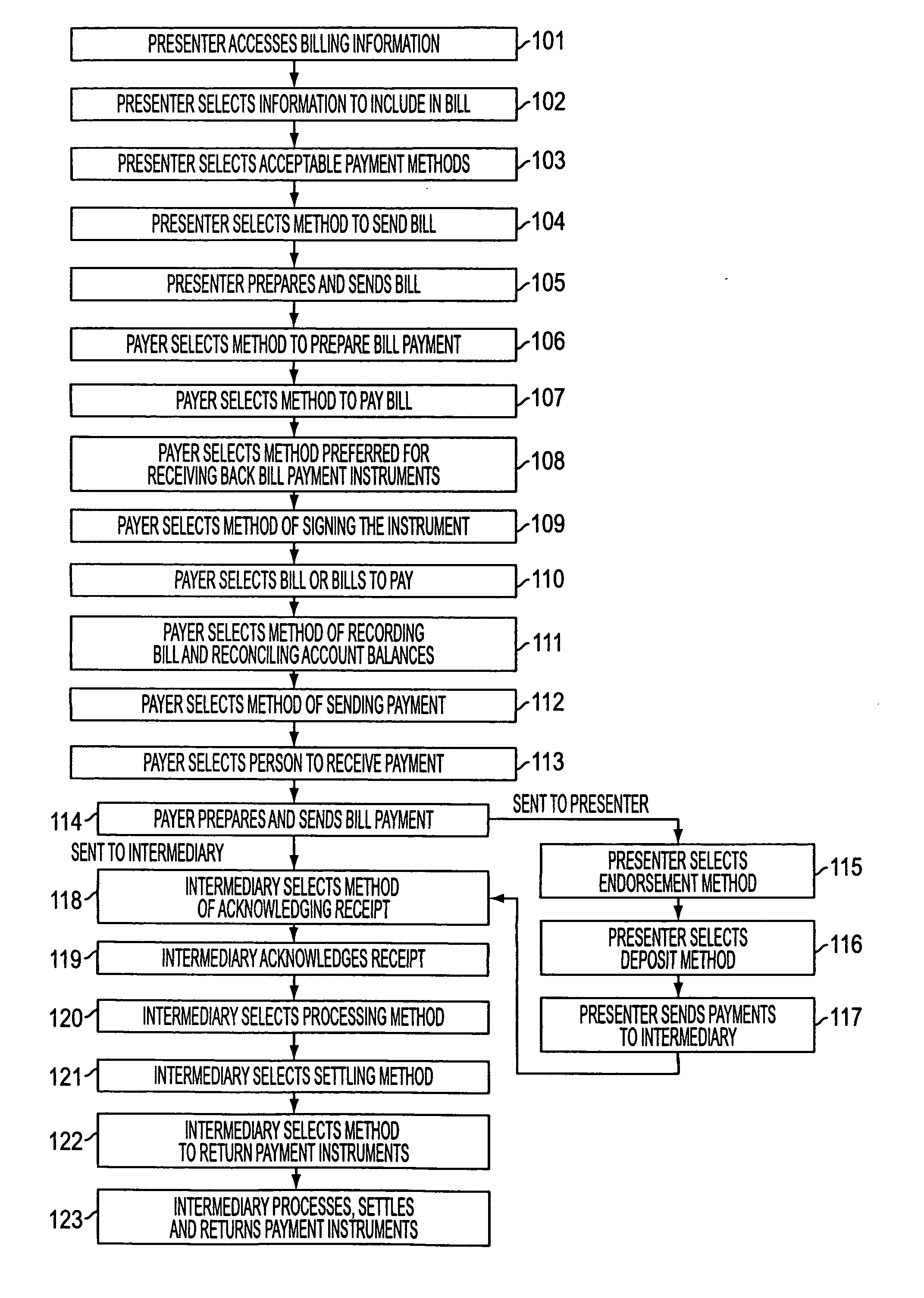
System and method for digital bill presentment and payment
InactiveUS20050033690A1Reduce complexityEnhanced interactionFinancePayment architectureCredit cardDigital data
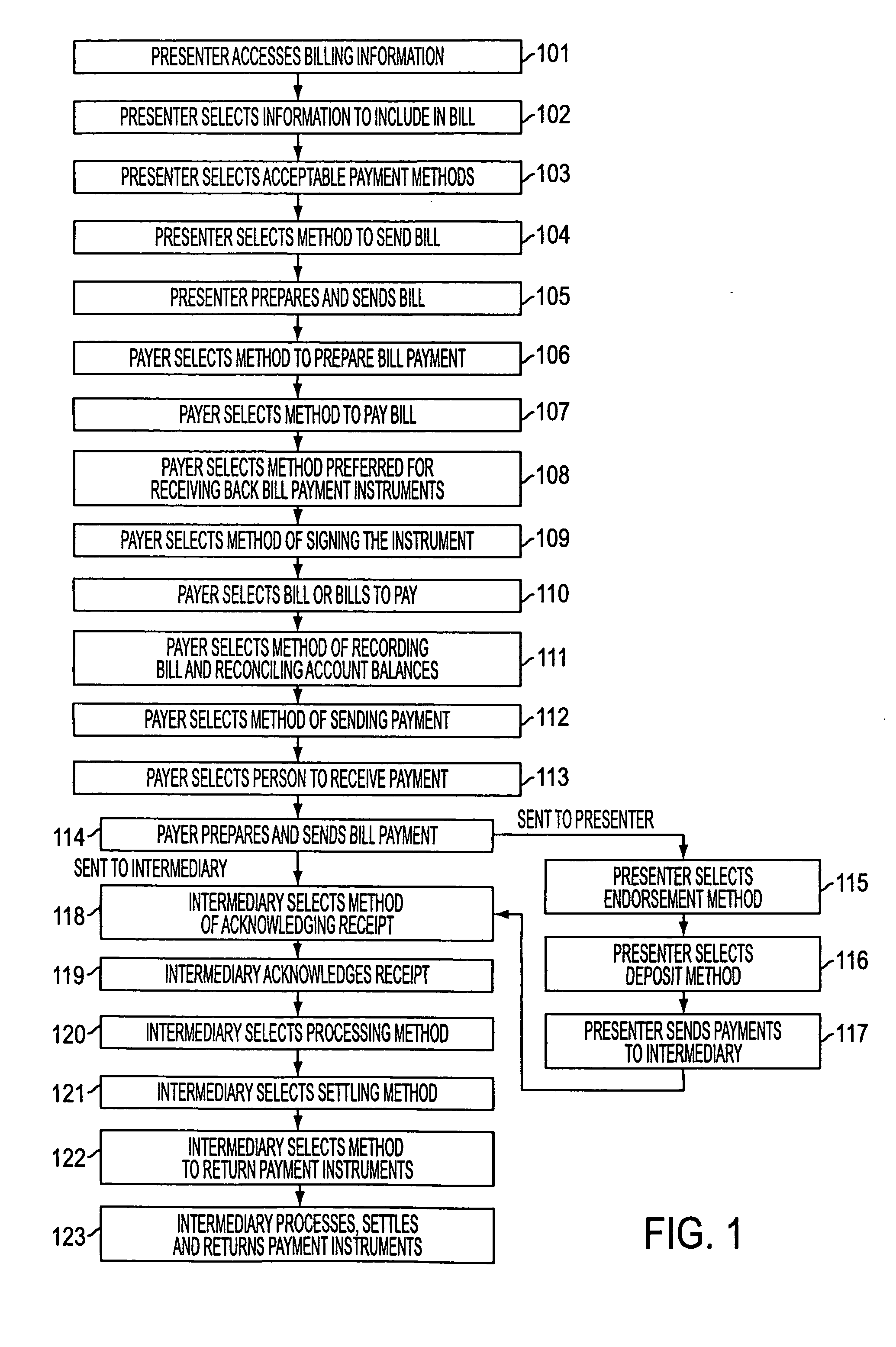
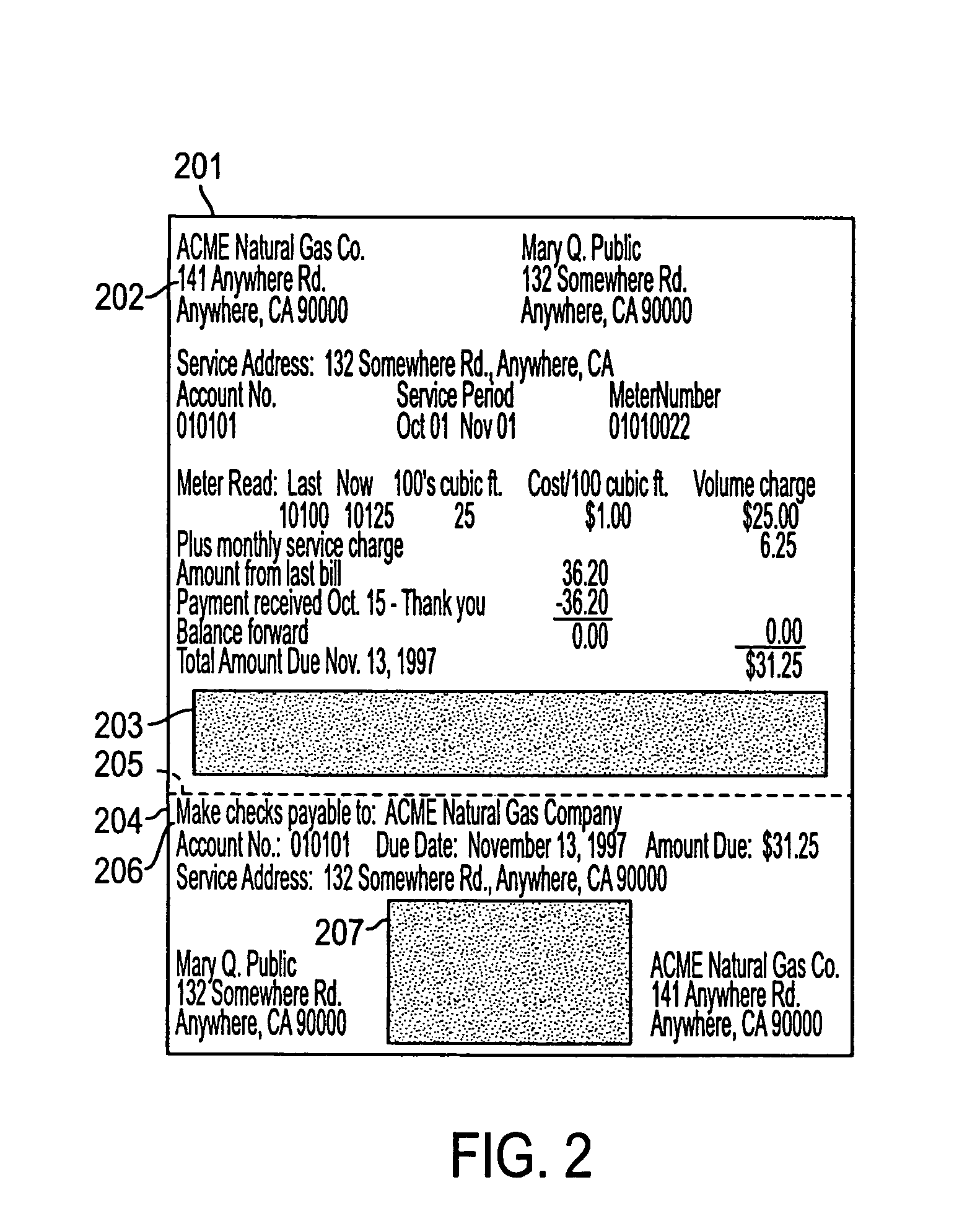
A system of bill presentment and bill payment. The parties to the process, which typically include the bill presenter, bill payer, and bank, credit card company or other intermediary, select from a number of choices in the selection of information to include in the bill, preparation of the bill, acceptable payment methods, means to send the bill and bill payment instrument, means of signing the bill, bill payment instrument, receipt acknowledging deposit and payment, method of recording and reconciling payments, and further actions. An accumulation of choices by the involved parties can include digital information in each step that represents all of the significant data accumulated up to and including that step. That digital data preferably includes digital signatures of each party at each step so as to provide an audit trail in purely digital form. Where digital data is chosen for each step, the digital data can be electronic or, using machine readable code, printed on paper, regardless of the form chosen in prior or later steps.
Owner:ANTOGNINI WALTER GERARD +1
Secure Storing and Offline Transferring of Digitally Transferable Assets
InactiveUS20160085955A1Digital data processing detailsUnauthorized memory use protectionDigital signatureData memory
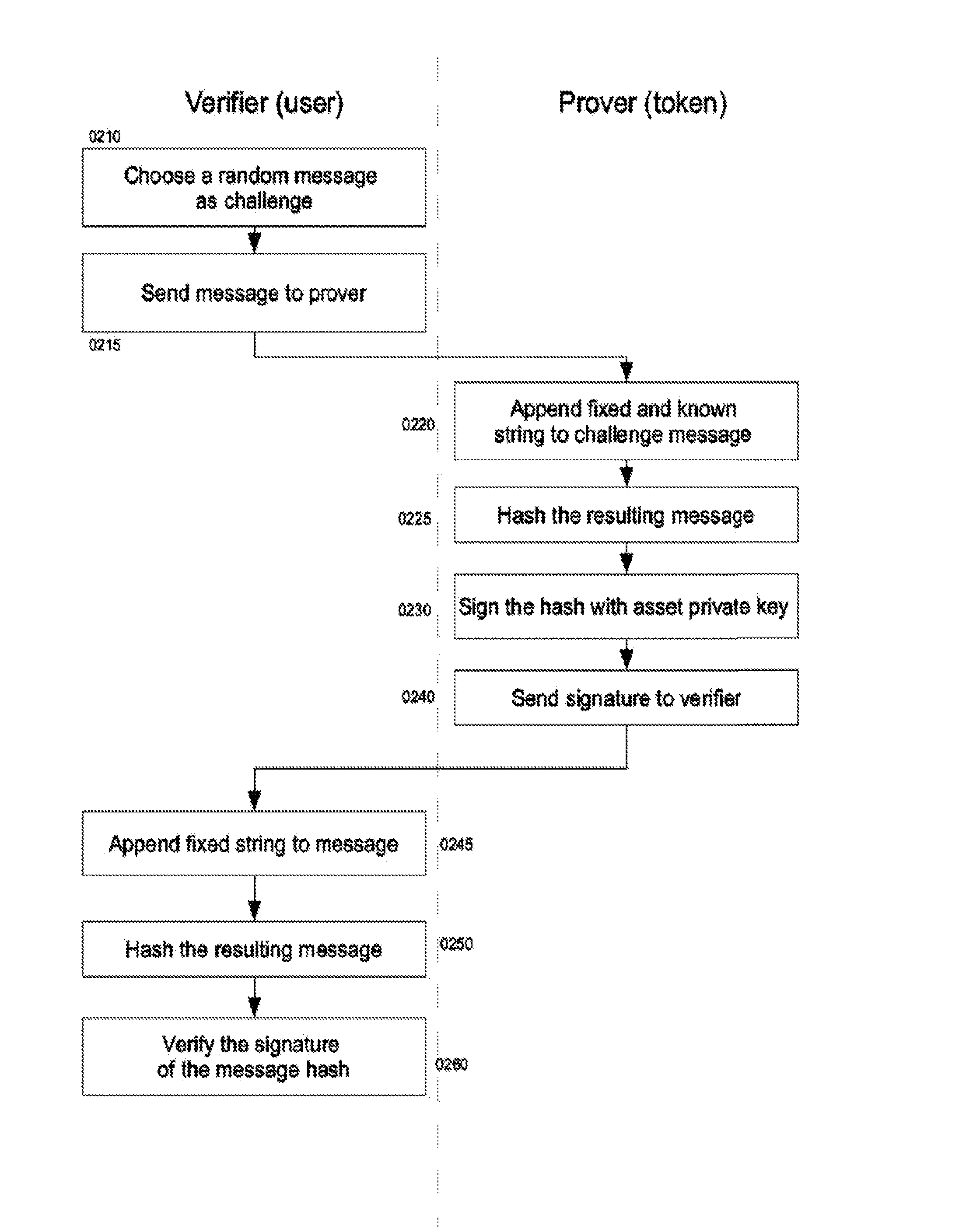
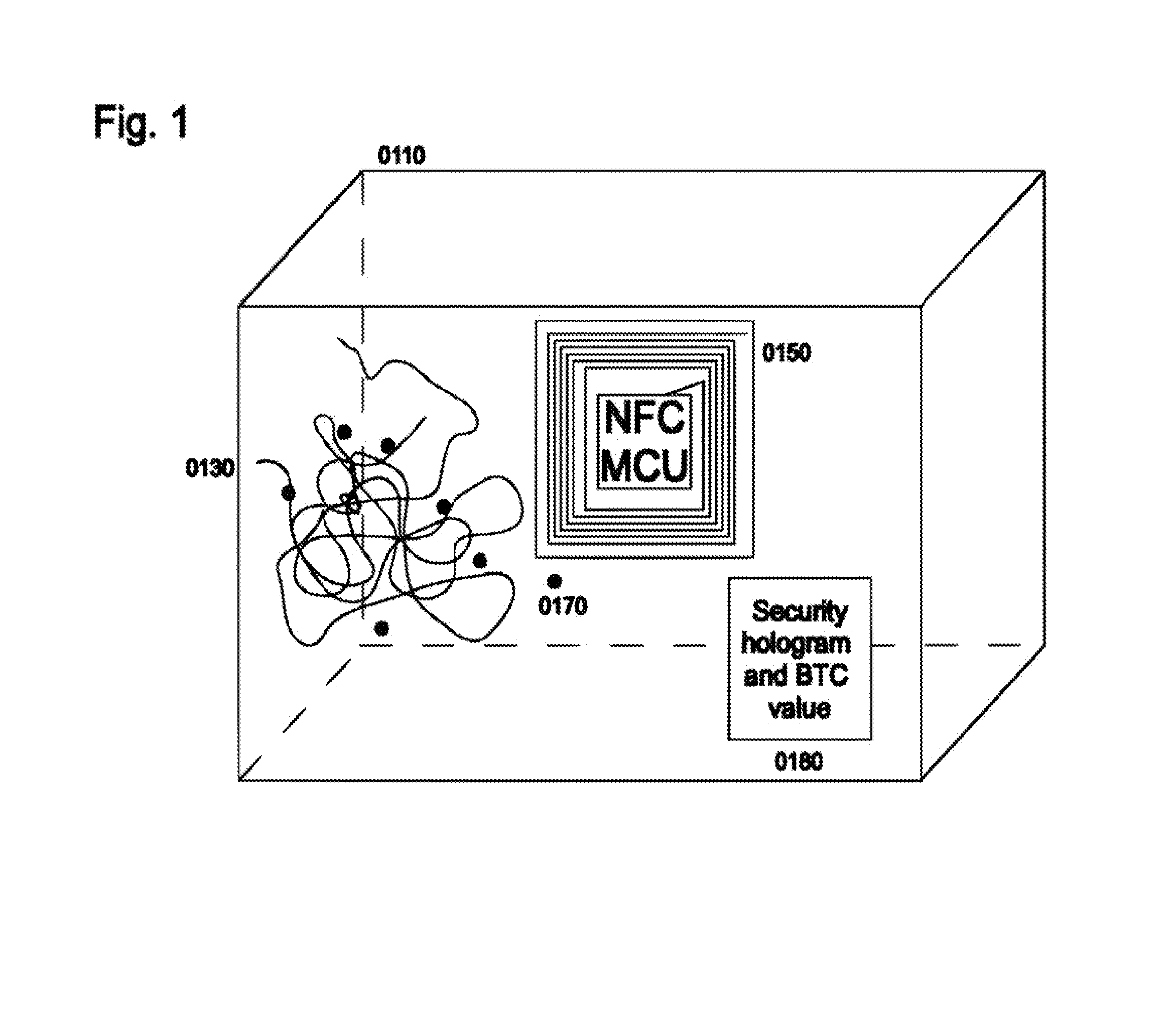
A handheld electronic device enables securely transferring control of a valuable asset associated with a code. The device includes a processor, non-transitory data storage, and a communication component configured to transmit data external to the device. A case houses the components, and is mechanically tamper evident. Software stores within the data storage at least one code, prevents transmission of any code through the communication component without authorization by the user, invalidates the association of a particular code with respect to a particular asset when the software carries out at least one of (i) authorizing transmission of the particular code, and (ii) authenticating a valid transaction using the particular code and authorizing transmission of the digital signature through the communication component.
Owner:DOOSRA
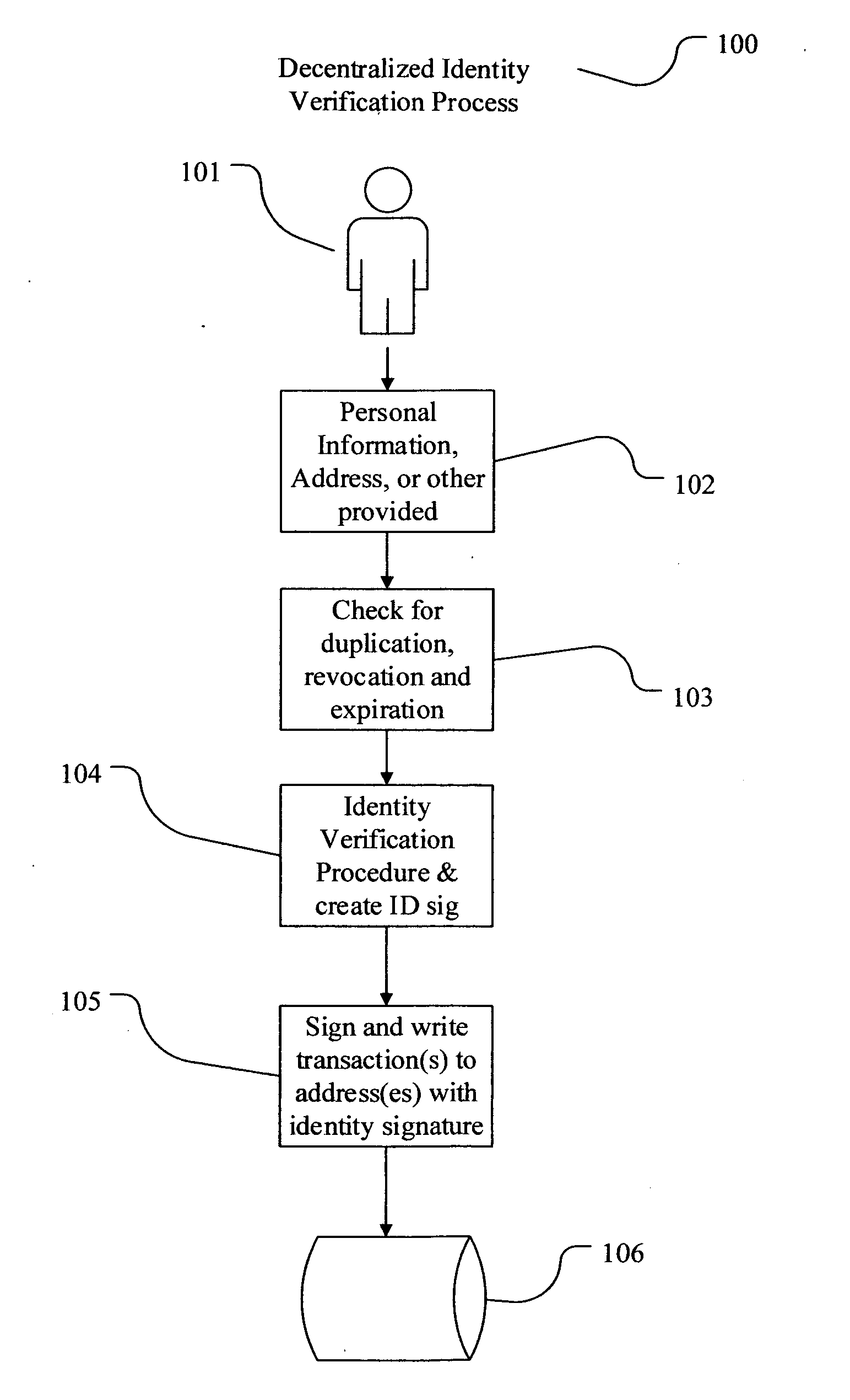
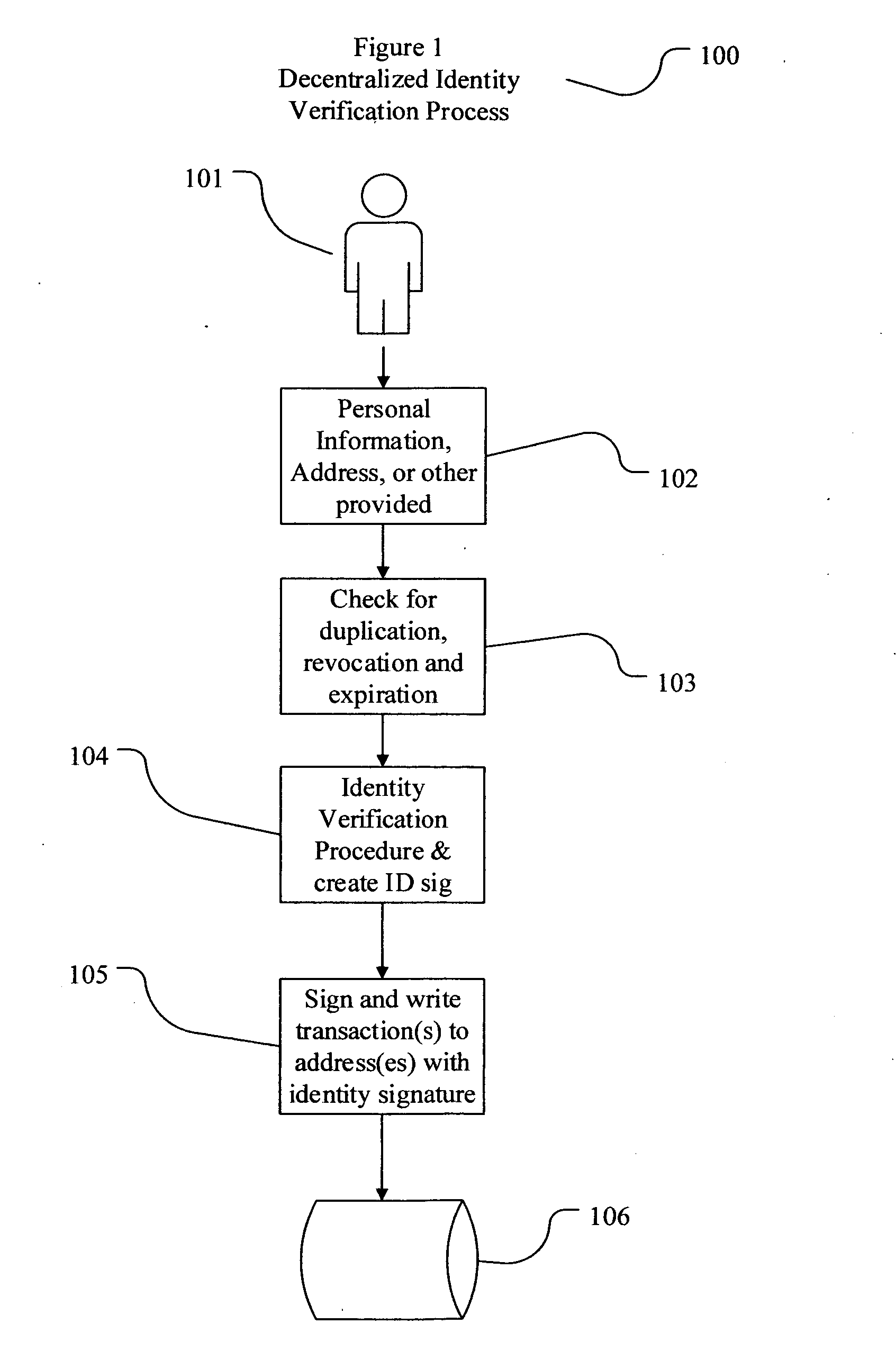
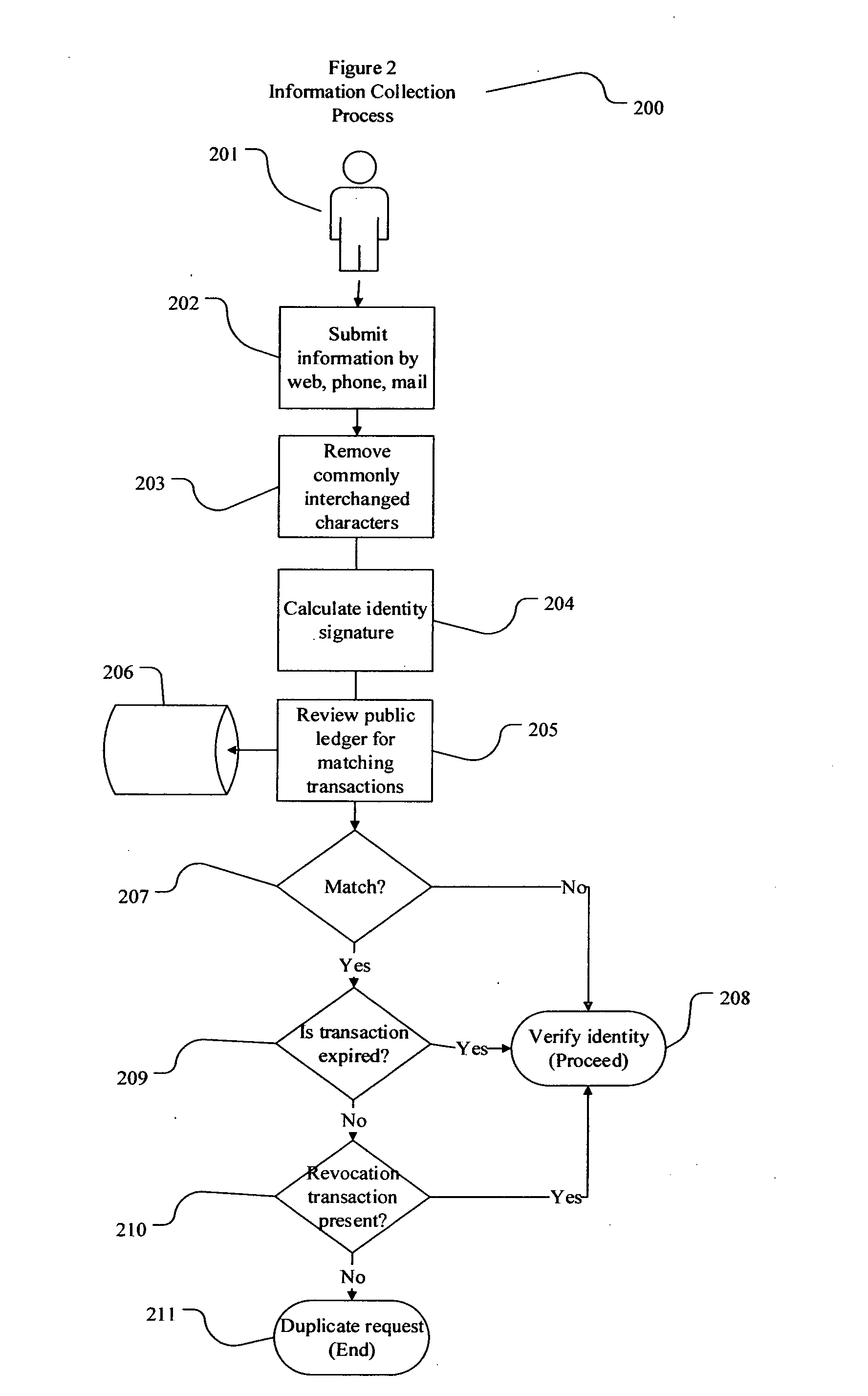
Decentralized identity verification systems and methods
InactiveUS20150356523A1Cryptography processingUser identity/authority verificationRegulatory authorityFinancial transaction
The present invention involves systems and methods that allow participants in cryptocurrency networks to exchange cryptocurrency for traditional currency legally and safely without requiring the use of a traditional exchange or online brokerage as a fiduciary. The invention accomplishes this through the use of a decentralized identity verification protocol that allows a service provider to verify the identity of a participant and then publish an identity signature on the participant's cryptocurrency address or addresses. The invention enables full compliance with Country specific customer identification program and anti-money laundering requirements, and maintains the ability to independently satisfy requests for information or data retention requirements if requested by legally authorized parties, but does not require that the participant store the private keys or access controls to their cryptocurrency on an exchange or brokerage service.The invention serves to verify a participant's identity in full compliance with US Bank Secrecy and Patriot Act provisions or similar regulations where identification may be achieved through non-documentary or documentary identity verification procedures. After passing the applicable verification procedure, the service provider stamps the participant's cryptocurrency address with a transaction containing an identity signature. This identity signature within the transaction consists of a public indicator of the participant's Country and subdivision, a compliance level code, an ID type indicator, and an identity hash. The identity hash is created from the digests of cryptographic hash functions where the participant's personal information is used as an input. The service provider signs the transaction with their authorized private key that corresponds to their publicly accessible public key. This serves as a publicly verifiable confirmation that the identity associated with the address in question was validated by the service provider authorized to act on behalf of the regulatory authority.The participant may then purchase and sell cryptographic currency from and to a third party exchange or brokerage service legally and safely when using their verified cryptocurrency address. This is because the third party is able to confirm compliance by openly referencing and verifying the identity verification transaction present on the address. Subsequent transactions where the third party sells or purchases cryptocurrency for the verified participant are similarly stamped with a transaction conforming to the identity verification protocol. This allows the third party interacting with the verified participant's address to observe any regulations limiting the amount or frequency of transactions over a variable period of time. It follows that this address could be used with any third party or participant in the cryptocurrency network that observes the decentralized identity verification protocol, all without requiring the third party or participant to collect and verify personal information redundantly. The ability to verify an identity remotely also eliminates the need for the third party to act as a fiduciary holding the private keys or access controls to the verified address. Lawful requests for information by authorized authorities are served to the service provider as digitally signed transactions that may then be linked to the participant's identity and transactions, allowing the protocol to observe subpoenas or similar lawful requests for information. The encrypted personal information may be held in escrow by the service provider indexed to the verified cryptocurrency address for such purposes. An alternate embodiment would store the encrypted personal information in a decentralized network of other participants, with the information accessible for retrieval using the public key of the verified cryptocurrency address and decryption using the corresponding private key, decentralizing the process entirely except for the identity verification step.
Owner:CHAINID
Digital Signatures for Communications Using Text-Independent Speaker Verification
ActiveUS20120296649A1Improve speech recognition performanceSpeech recognitionTransmissionText independentDigital signature
A speaker-verification digital signature system is disclosed that provides greater confidence in communications having digital signatures because a signing party may be prompted to speak a text-phrase that may be different for each digital signature, thus making it difficult for anyone other than the legitimate signing party to provide a valid signature.
Owner:NUANCE COMM INC
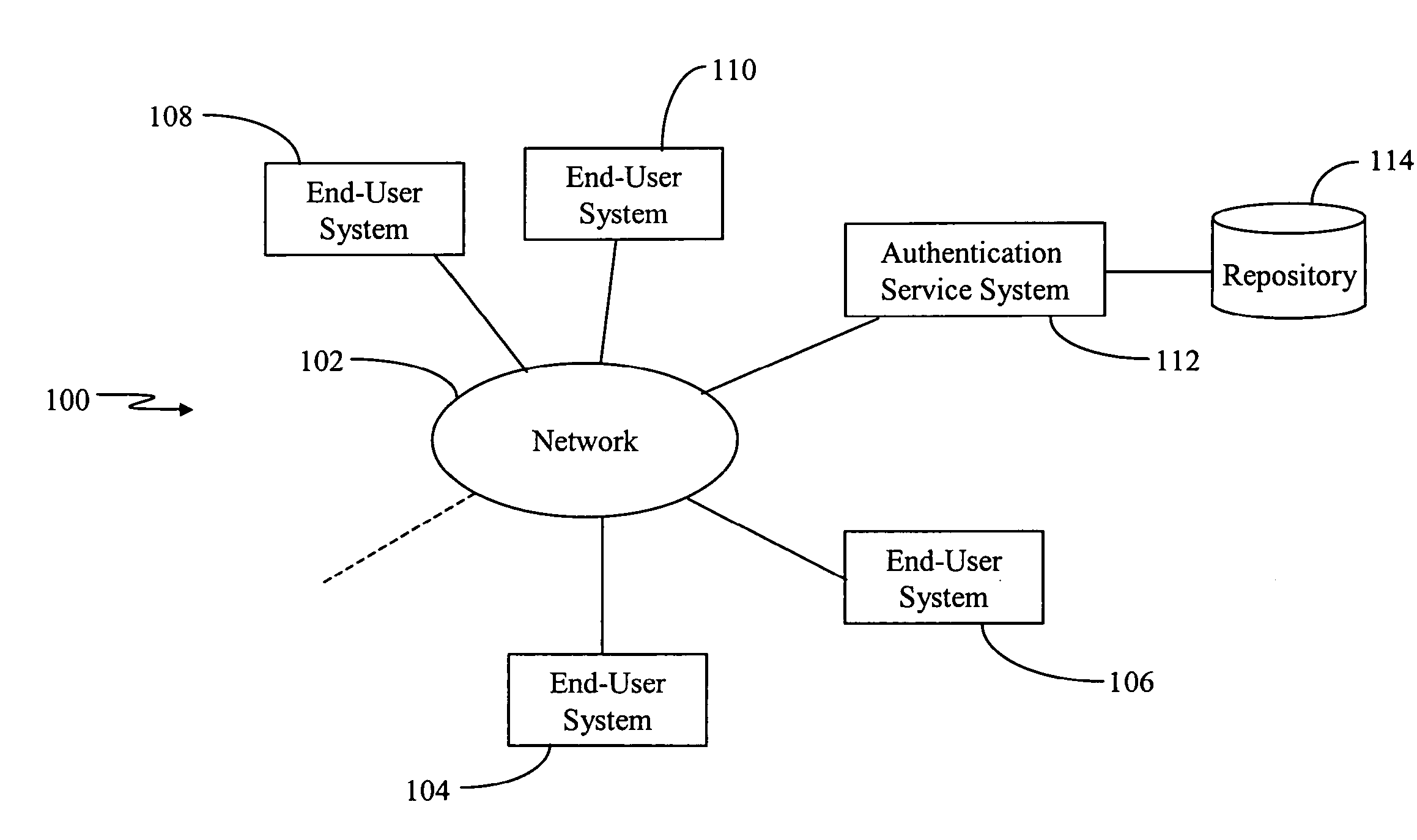
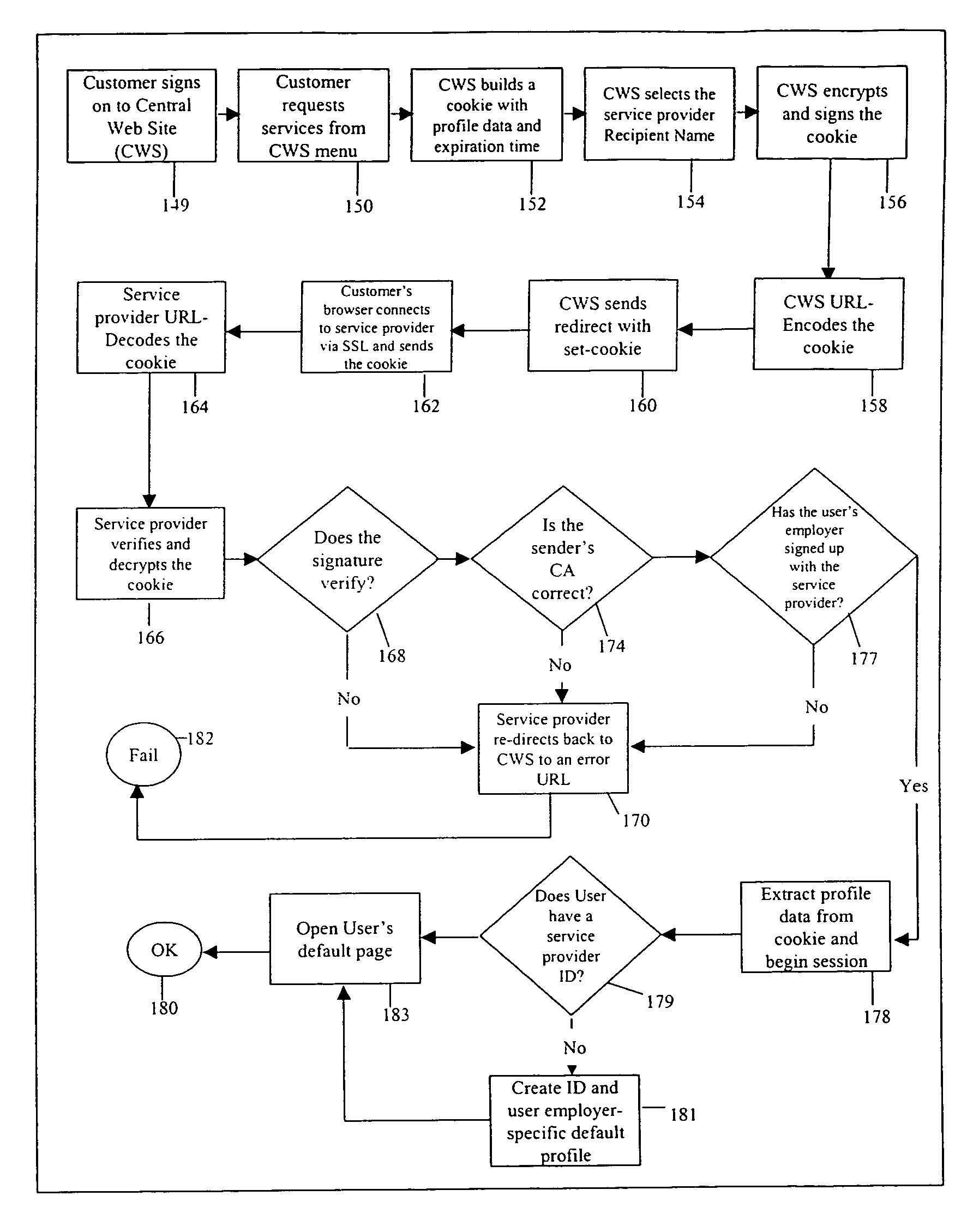
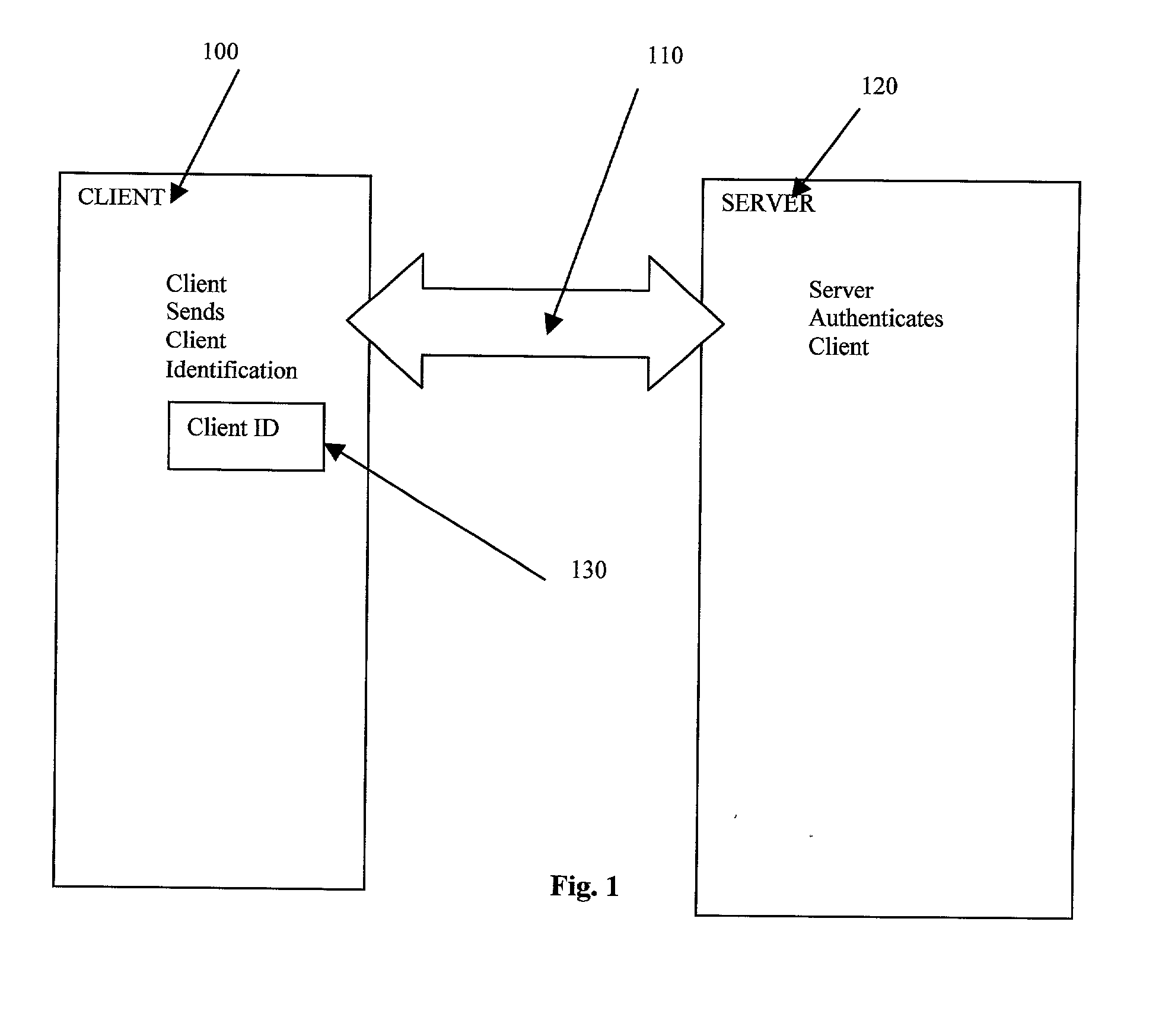
Method and system for single sign-on user access to multiple web servers
InactiveUS7137006B1User identity/authority verificationDigital data authenticationExpiration TimeHyperlink
Methods and systems for single sign-on user access to multiple web servers are provided. A user is authenticated at a first web server (e.g., by user name and password). The first web server provides a web page to the user having a service selector (e.g., a hyperlink comprising the URL of a second web server offering the service indicated by the selector). When the user activates the service selector, the first web server constructs and transmits an encrypted authentication token (e.g., a cookie) from the first web server to a second web server via the user client. The first and second web servers share a sub-domain. The authentication token comprises an expiration time and is digitally signed by the first web server and is authenticated at the second web server. Upon authentication, the second web server allows the user to conduct a session at the second web server.
Owner:CITICORP CREDIT SERVICES INC (USA)
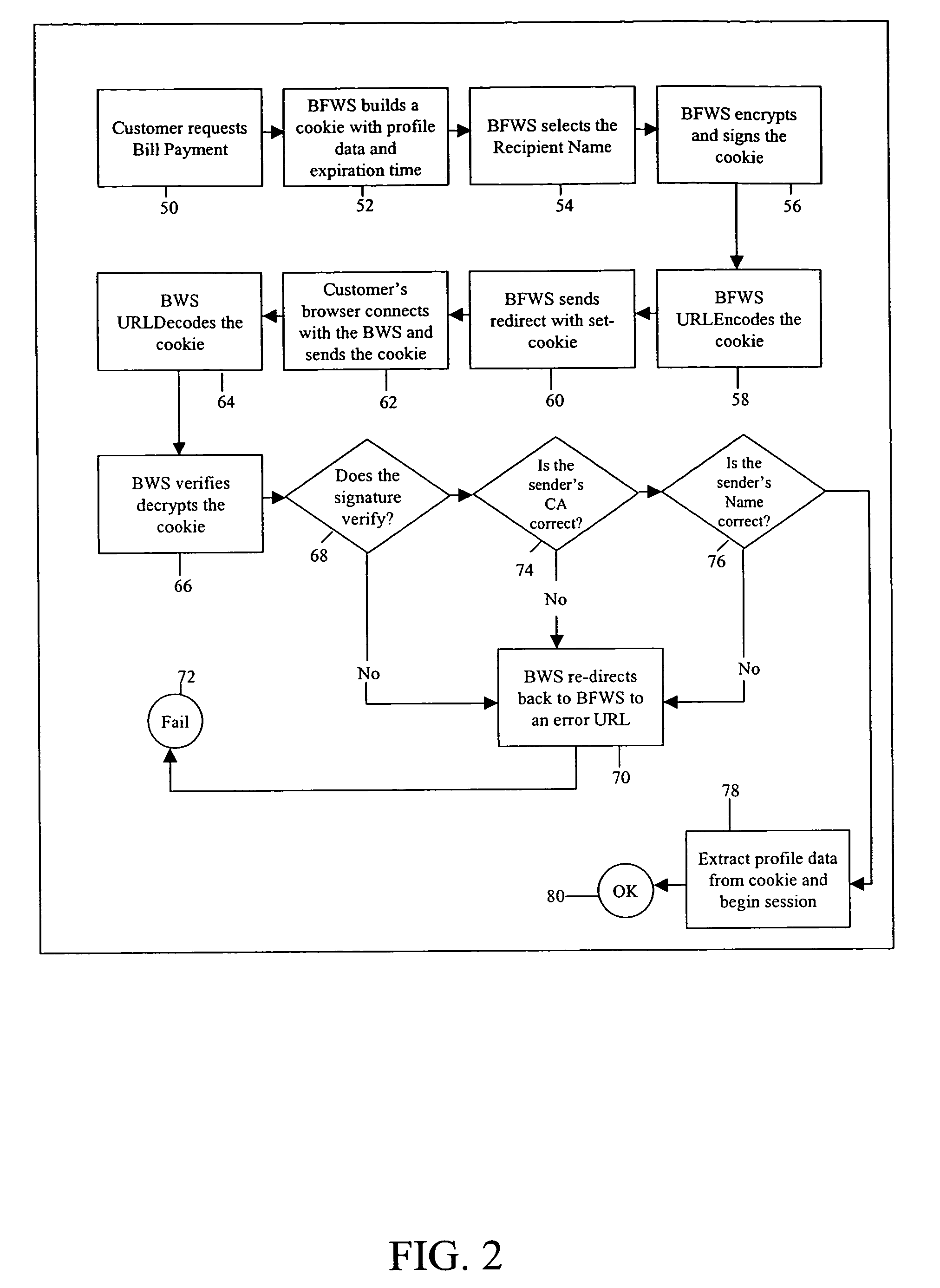
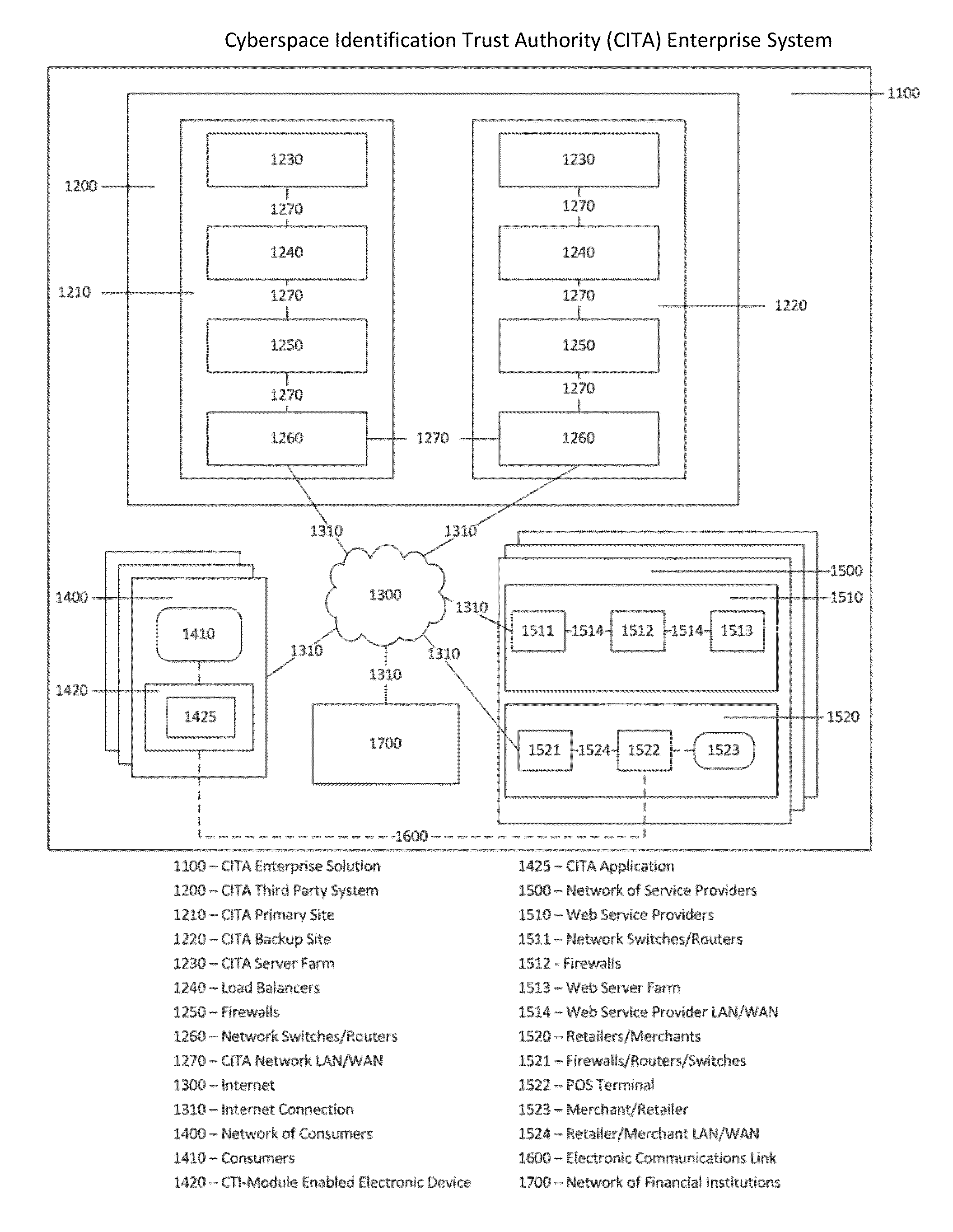
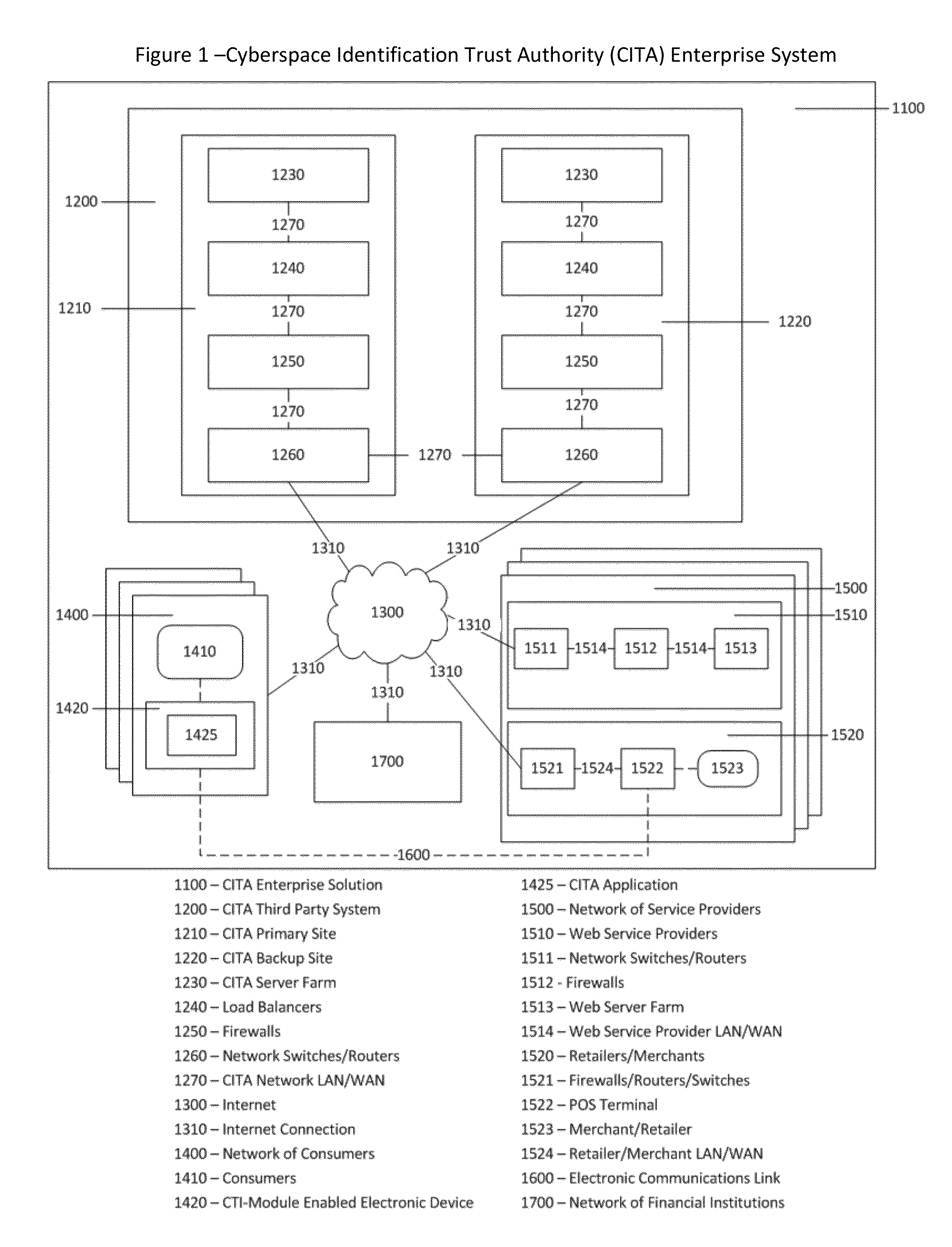
Cyberspace Identification Trust Authority (CITA) System and Method
InactiveUS20130226813A1Eliminate chanceSecure transmissionFinanceProtocol authorisationTrusted authorityPayment
When two parties of a cyberspace transaction register their identity attributes under a CITA system each party is assigned a unique, encrypted and digitally signed identity token. When the consuming party seeks access too, or payment for, cyberspace services, the providing party submits their identity token to the consuming party. The consuming party creates a request token, containing both the consumers' and the providers' identity tokens, and the transaction related information, to the CITA system. The CITA system validates the identity tokens and either creates a payment confirmation token by processing the payment request, or creates an access confirmation token by dynamically defining the minimal consumer identity attributes required to gain access to the provider's service. The confirmation token is encrypted and digitally signed and returned to the consumer, and then forwarded to the provider to complete the transaction without either party openly exchanging personal identity attributes.
Owner:VOLTZ ROBERT MATTHEW
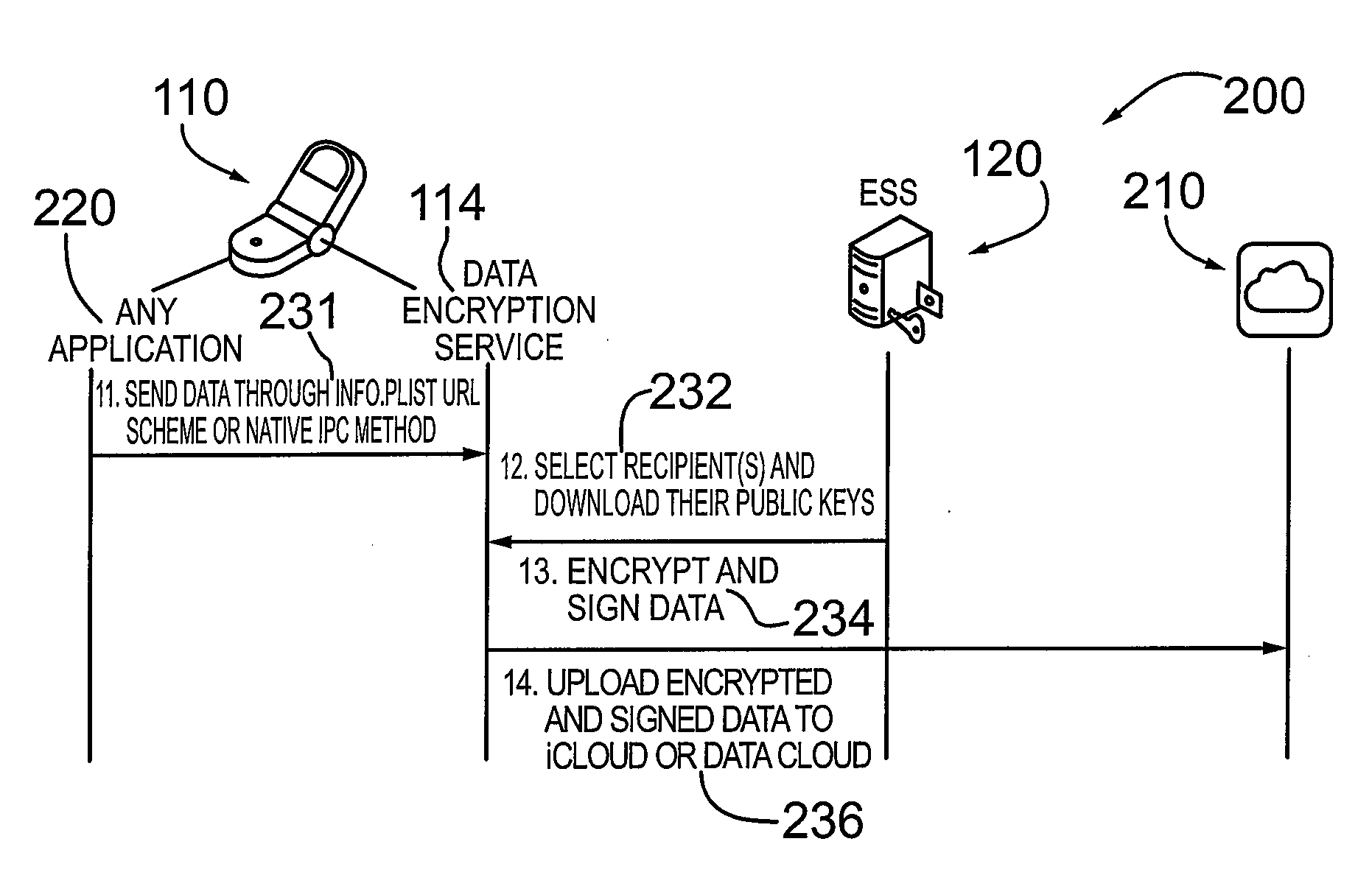
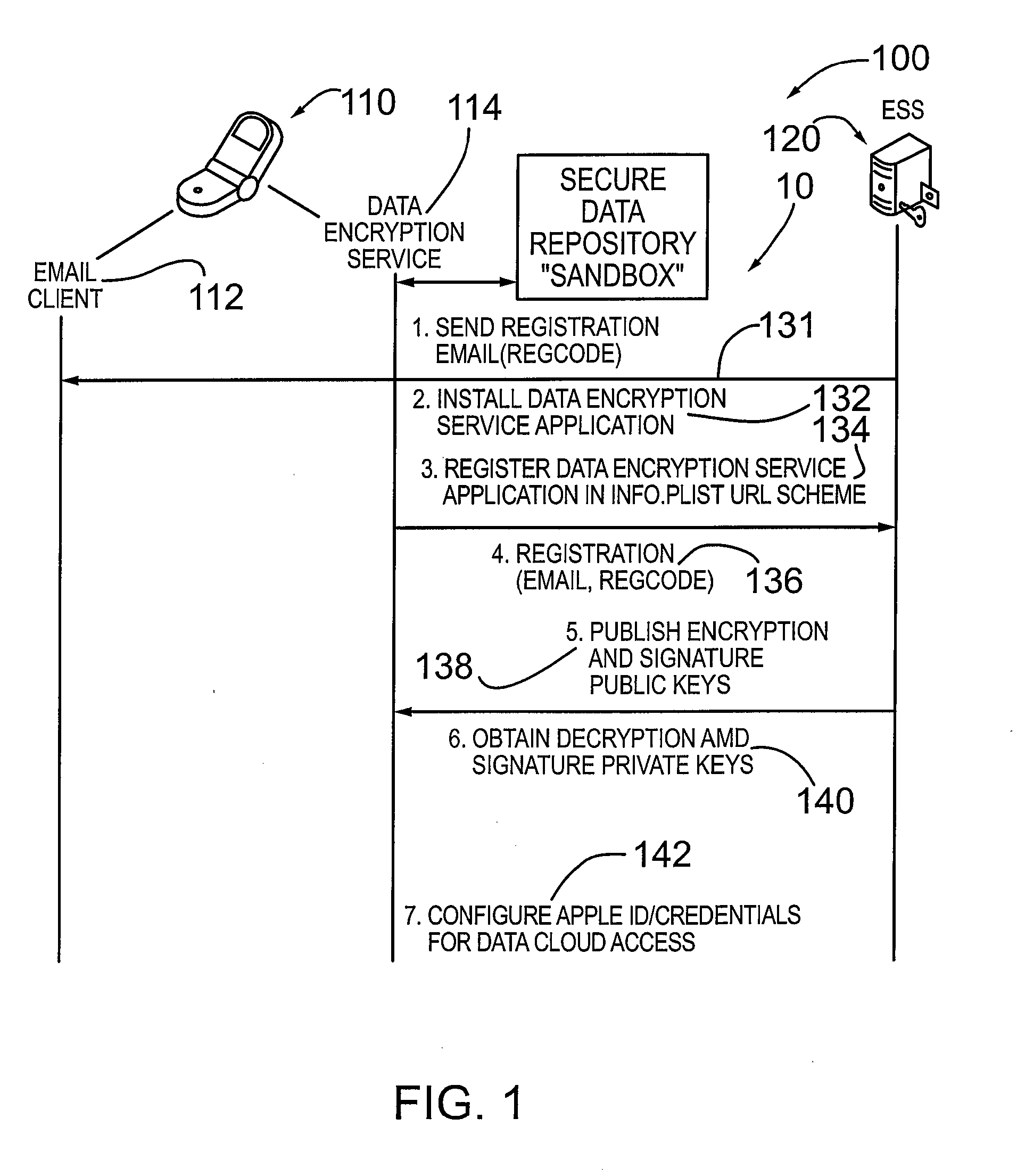
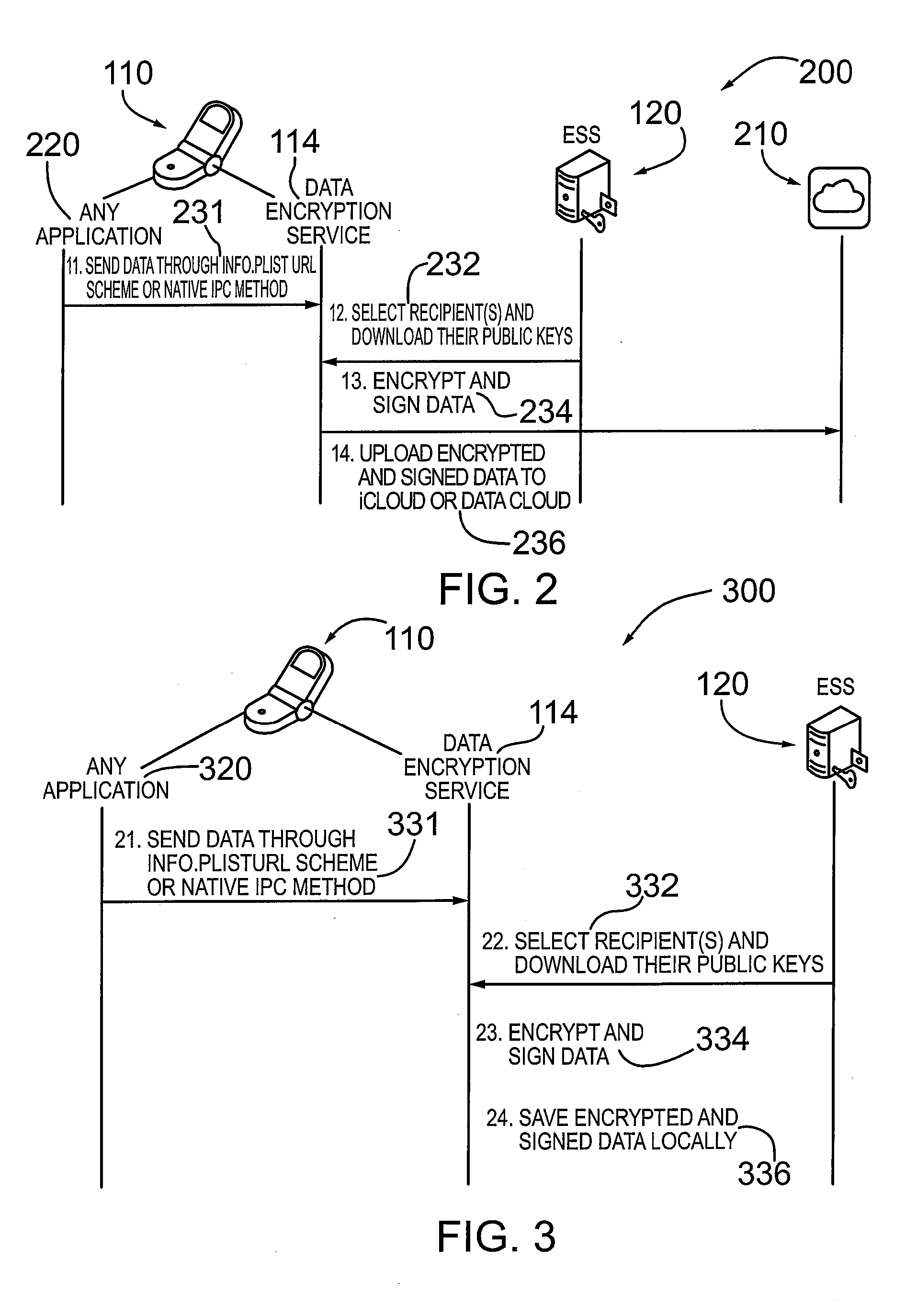
METHOD AND SYSTEM FOR CREDENTIAL MANAGEMENT AND DATA ENCRYPTION FOR iOS BASED DEVICES
InactiveUS20130067232A1User identity/authority verificationComputer security arrangementsOperational systemDigital signature
A mechanism and method for managing credentials on an electronic device and providing encryption and decryption services for the electronic device comprising a mobile communication device, smart phone or other computing device. According to an embodiment the device is configured with an iOS based operating system. The device is configured with a data encryption service application and an associated secure data repository. According to an embodiment, the electronic device is configured to download and / or cache credentials from a credential management system operatively coupled to the device, comprising public-private key pairs in a PKI system. According to an embodiment, the electronic device is configured with or stores a digital verification signature. The data encryption service application is configured to encrypt / decrypt data (e.g. files, documents) and optionally digitally sign the encrypted file. The encrypted (and digitally signed data) is contained in the sandbox associated with the data encryption service application.
Owner:ECHOWORX CORP
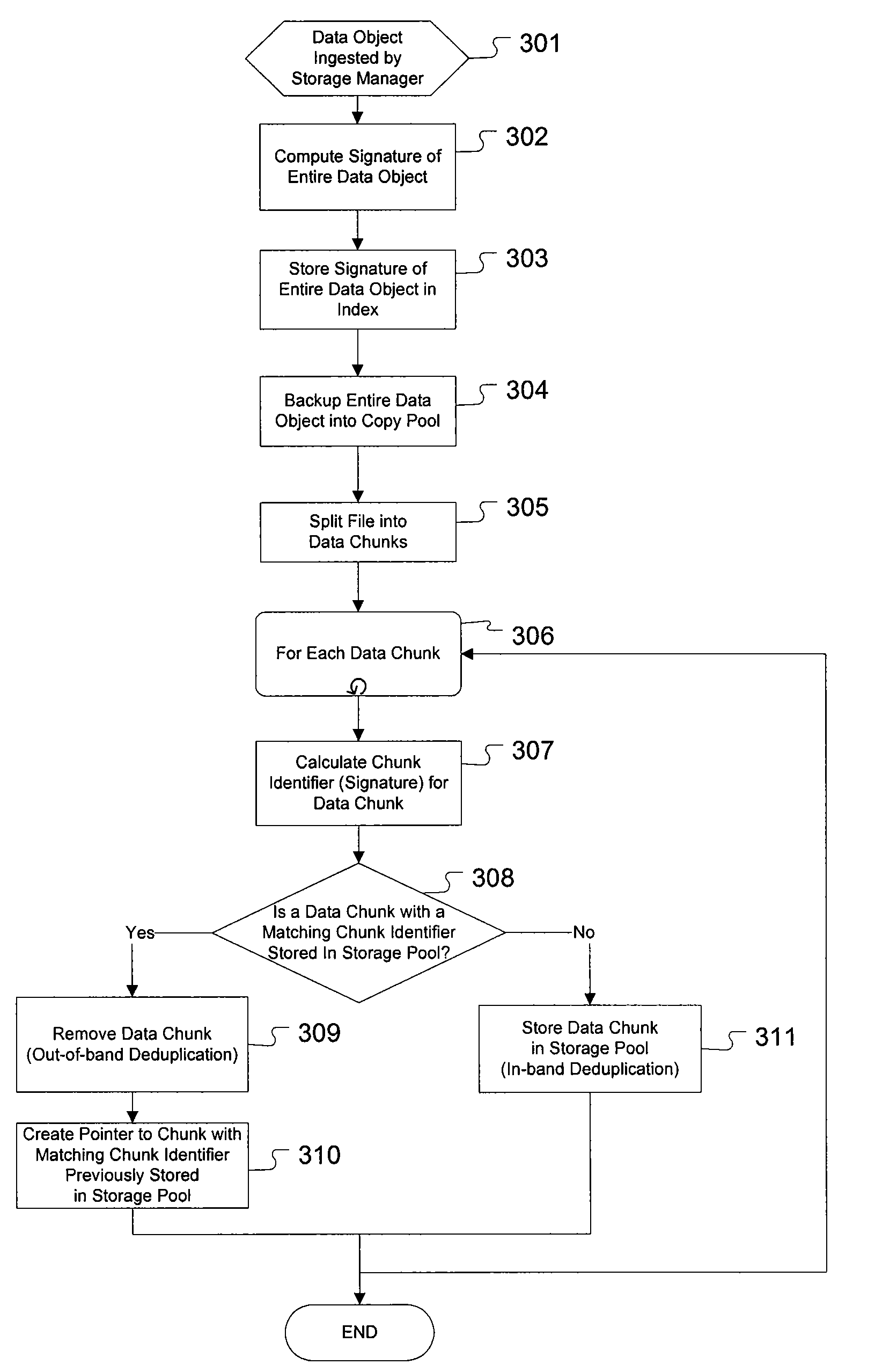
Enhanced method and system for assuring integrity of deduplicated data
ActiveUS20090271454A1Access latencyDigital data information retrievalDigital data processing detailsHash functionDigital signature
The present invention provides for an enhanced method and system for assuring integrity of deduplicated data objects stored within a storage system. A digital signature of the data object is generated to determine if the data object reassembled from a deduplicated state is identical to its pre-deduplication state. In one embodiment, generating the object signature of a data object before deduplication comprises generating an object signature from intermediate hash values computed from a hash function operating on each data chunk within the data object, the hash function also used to determine duplicate data chunks. In an alternative embodiment, generating the object signature of a data object before deduplication comprises generating an object signature on a portion of each data chunk of the data object.
Owner:DROPBOX
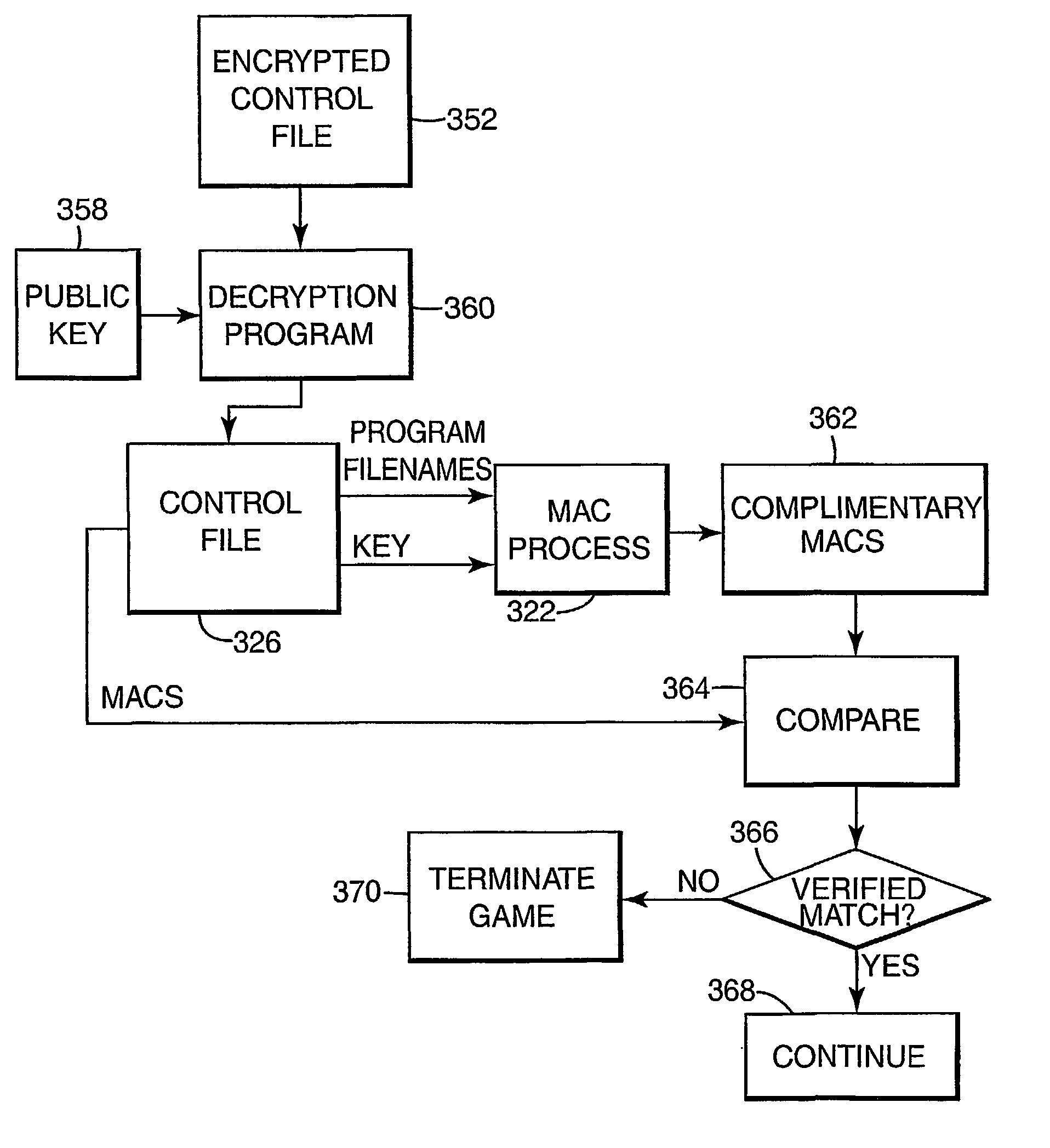
Encryption in a secure computerized gaming system
InactiveUS7043641B1Straightforward and easy to manageUser identity/authority verificationUnauthorized memory use protectionHash functionDigital signature
An architecture and method for a gaming-specific platform are disclosed that features secure storage and verification of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. These and other functions make use of encryption, including digital signatures and hash functions as well as other encryption methods.
Owner:IGT
Token verification using limited use certificates
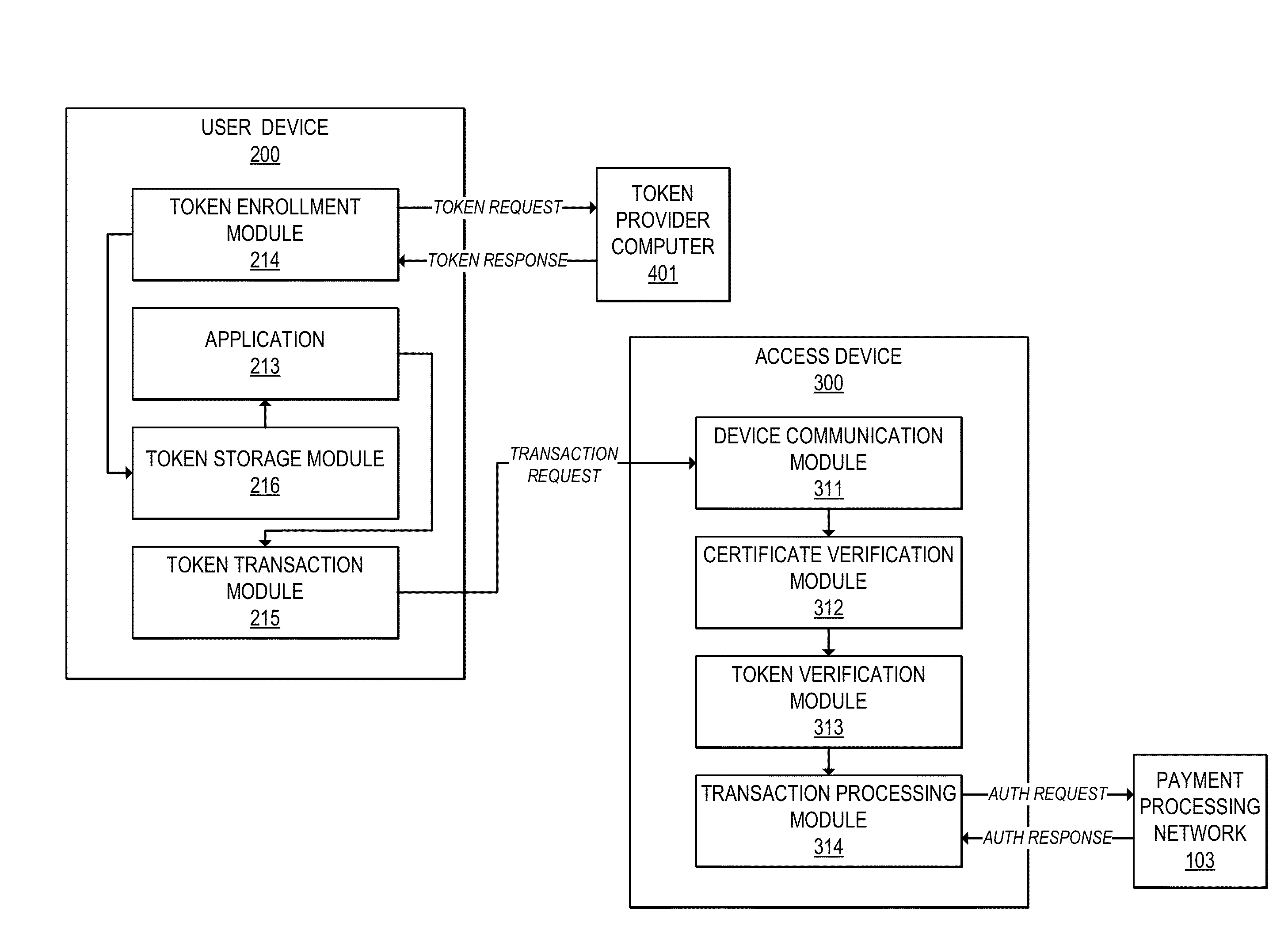
InactiveUS20150220917A1User identity/authority verificationPayment protocolsUser deviceDigital signature
Methods, devices, and systems are provided for verifying tokens using limited-use certificates. For example, a user device can send a token request to a token provider computer, and receive in response a token and a token certificate associated with the token. The token certificate may include, for example, a hash of the token and a digital signature by the token provider computer or another trusted entity. The user device can provide the token and the token certificate to an access device. The access device can verify the token using the token certificate, and verify the token certificate using a digital signature. In some cases, the token and token certificate may be verified offline. The access device can then conduct a transaction using the token.
Owner:VISA INT SERVICE ASSOC
Method and apparatus for image authentication
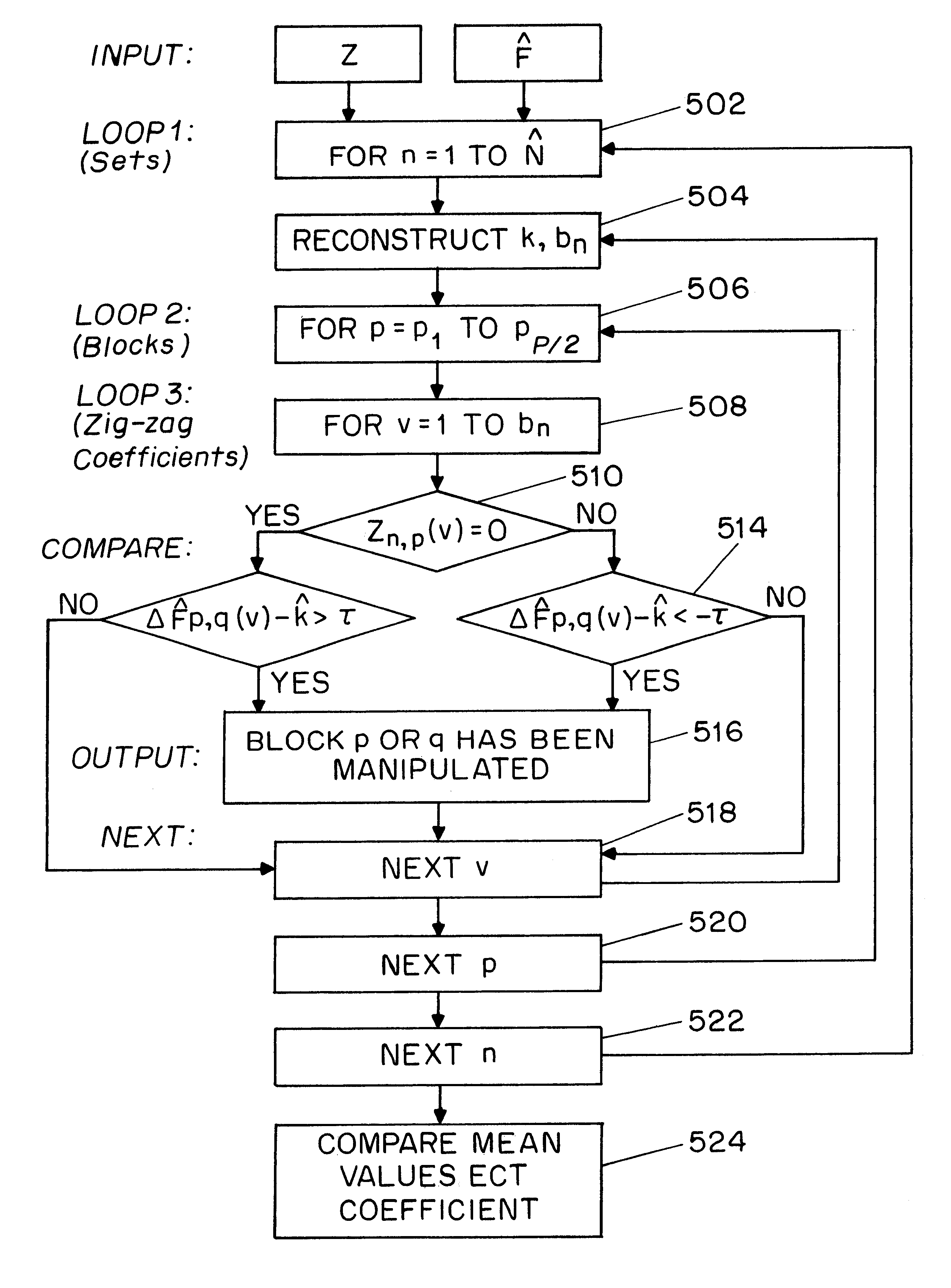
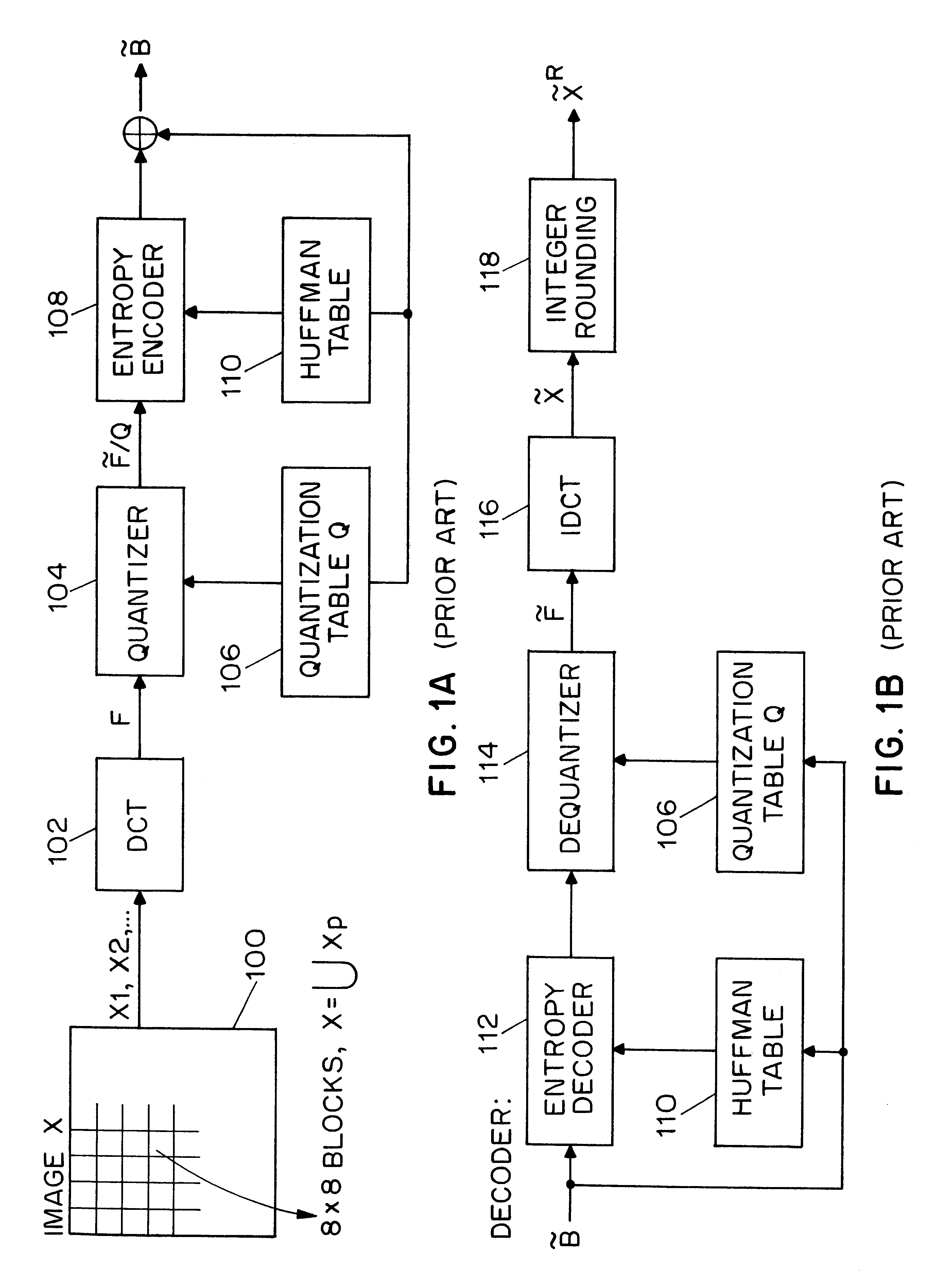
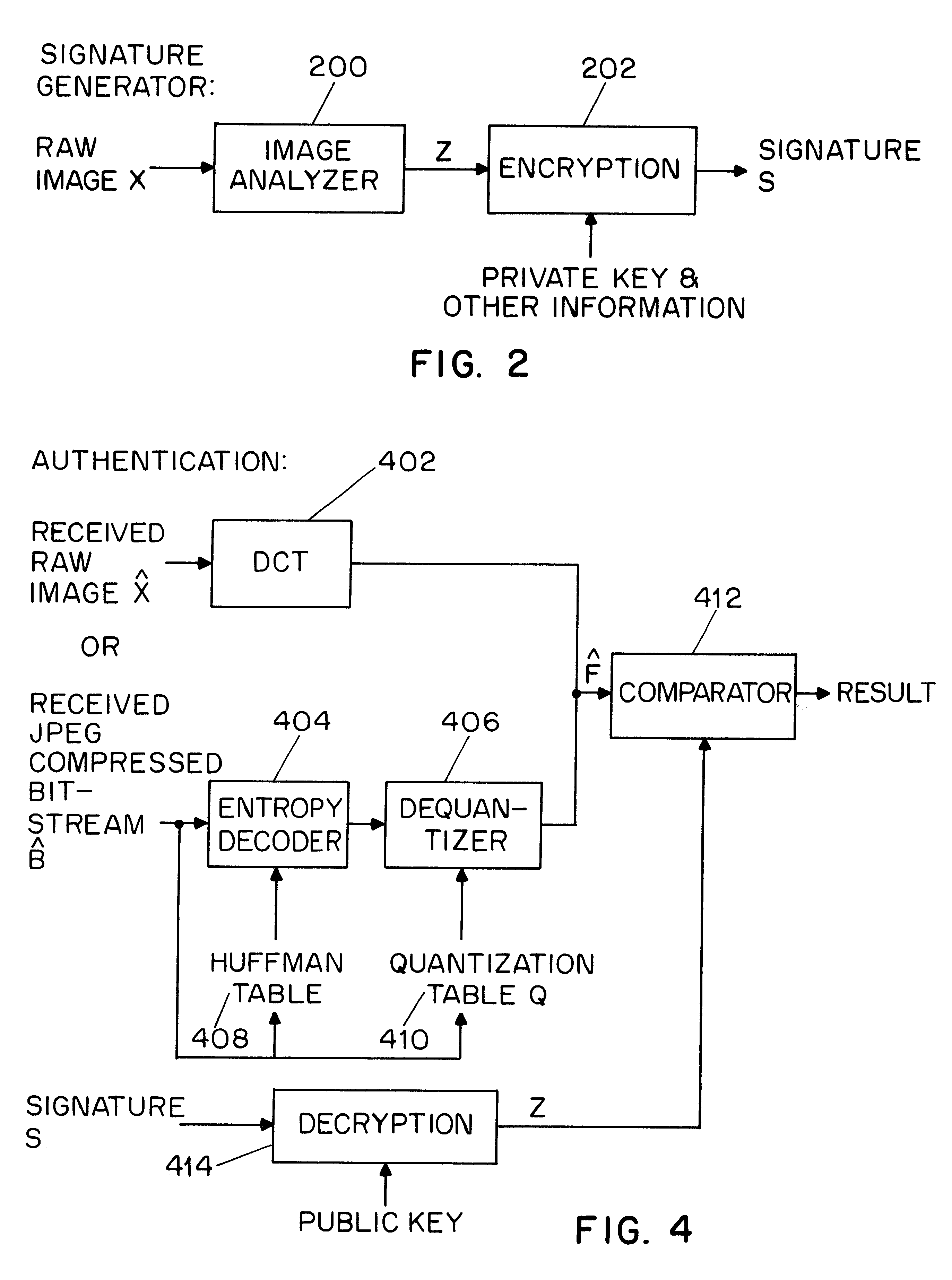
InactiveUS6532541B1User identity/authority verificationImage watermarkingDigital signatureDiscrete cosine transform
A system for authentication of a digital image includes a signature generator for creating a robust digital signature for an original image based on instrument features of the image. An authentication processor extracts a set of invariant features for the original image from the digital signature, generates a corresponding set of invariant features for the present image to be authenticated and compares the two sets of invariant features to determine whether the image has been subjected to malicious manipulation. The invariant features include the polarity and magnitude of the difference between discrete cosine transform coefficients at corresponding coefficient locations in selected image block pairs. The intensity of the original image is also authenticated by comparing a mean value of coefficient of the original image to the mean value of the coefficient of the present image.
Owner:NAT SCI FOUND NSF
Policies for secure software execution
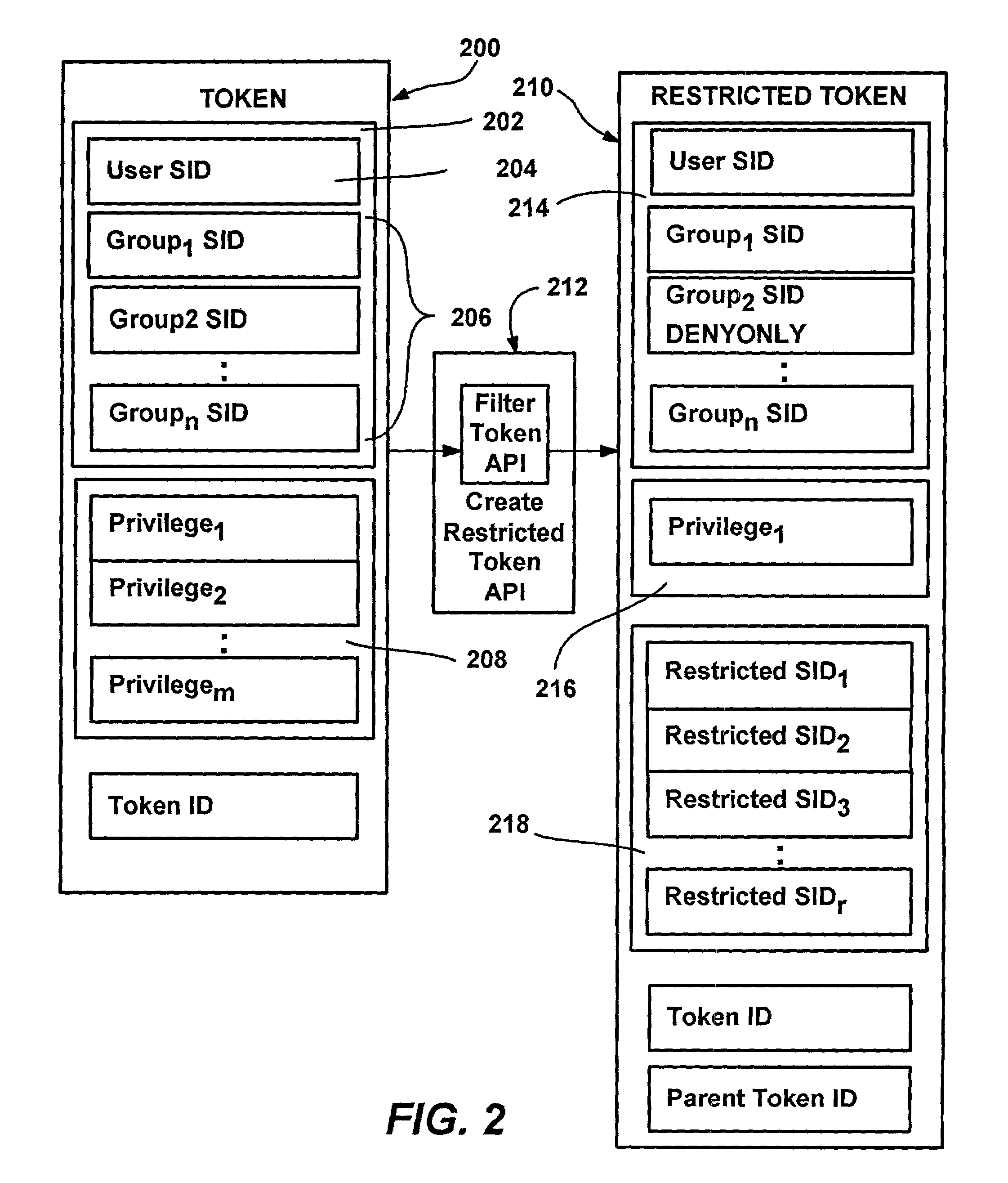
InactiveUS7350204B2Efficiently constrain (or prevent from running) everything on a machineDigital data processing detailsUnauthorized memory use protectionFile systemDigital signature
A system and method that automatically, transparently and securely controls software execution by identifying and classifying software, and locating a rule and associated security level for executing executable software. The security level may disallow the software's execution, restrict the execution to some extent, or allow unrestricted execution. To restrict software, a restricted access token may be computed that reduces software's access to resources, and / or removes privileges, relative to a user's normal access token. The rules that control execution for a given machine or user may be maintained in a restriction policy, e.g., locally maintained and / or in a group policy object distributable over a network. Software may be identified / classified by a hash of its content, by a digital signature, by its file system or network path, and / or by its URL zone. For software having multiple classifications, a precedence mechanism is provided to establish the applicable rule / security level.
Owner:MICROSOFT TECH LICENSING LLC
Digital License Sharing System and Method
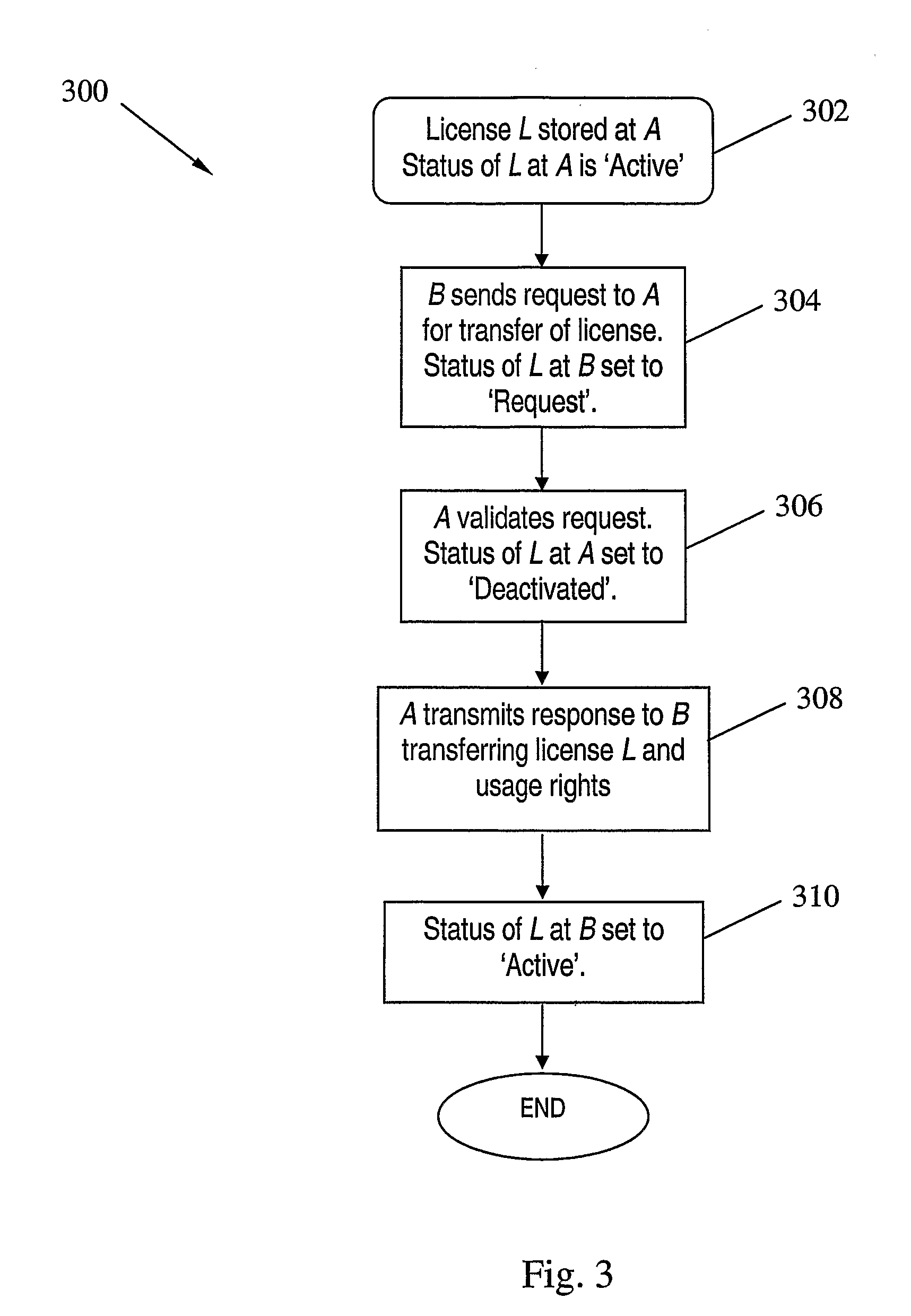
InactiveUS20070219917A1Fail can be robustAvoid trackingUser identity/authority verificationComputer security arrangementsInternet privacyDigital rights management system
A digital license sharing method, system and apparatus is provided for use in a digital rights management system. Usage rights in respect of digital content are transferred between content player devices or applications by associating with each player a status indication. Transfer is carried out by transmitting a request to obtain the usage rights from a player requiring usage rights to a player currently holding the rights. The transferring player sets a first status indication to indicate that it is no longer entitled to exercise the rights, and transmits a response to the requesting player to transfer the usage rights. The requesting player then sets a second status indication to indicate that it is henceforth entitled to exercise the rights. Methods and apparatus for creating transferable licenses are also provided that employ a sharable license format including a validated portion and an unvalidated portion. The validated portion, which may be, for example, digitally signed by a license issuing authority, includes characteristic information of a digital content decryption key required to access the digital content controlled by the license. The unvalidated portion includes the digital content key itself, encrypted using an encryption key associated with a player entitled to use the license.
Owner:SMART INTERNET TECH CRC
Secure anonymous information exchange in a network
InactiveUS6061789AMinimize additional effort and expenditureUser identity/authority verificationDigital data protectionSystems designData set
PCT No. PCT / IB96 / 00025 Sec. 371 Date Jul. 2, 1998 Sec. 102(e) Date Jul. 2, 1998 PCT Filed Jan. 12, 1996 PCT Pub. No. WO97 / 25801 PCT Pub. Date Jul. 17, 1997Computer network management for electronic commerce requires technical implementations of business processes. The process addressed here is a technical method for a communication in which two or more parties legitimately want to communicate anonymously, often before discussing a deal or closing a business, e.g. for anonymous bidding or auctioning in electronic commerce. Essentially, the invention is a method, described by a protocol, for safely exchanging data in a network that provides a public key infrastructure and an anonymous communication possibility between network users. It consists of a sequence of steps in which both sender (e.g. customer) and addressee (e.g. merchant) compose data sets (i.e., requests and replies) that are based on received data and / or prior knowledge. The data sets are enciphered to provide anonymity, and digitally signed to provide proof of the partner. The invention is also a system designed to implement the invented method.
Owner:GOOGLE LLC
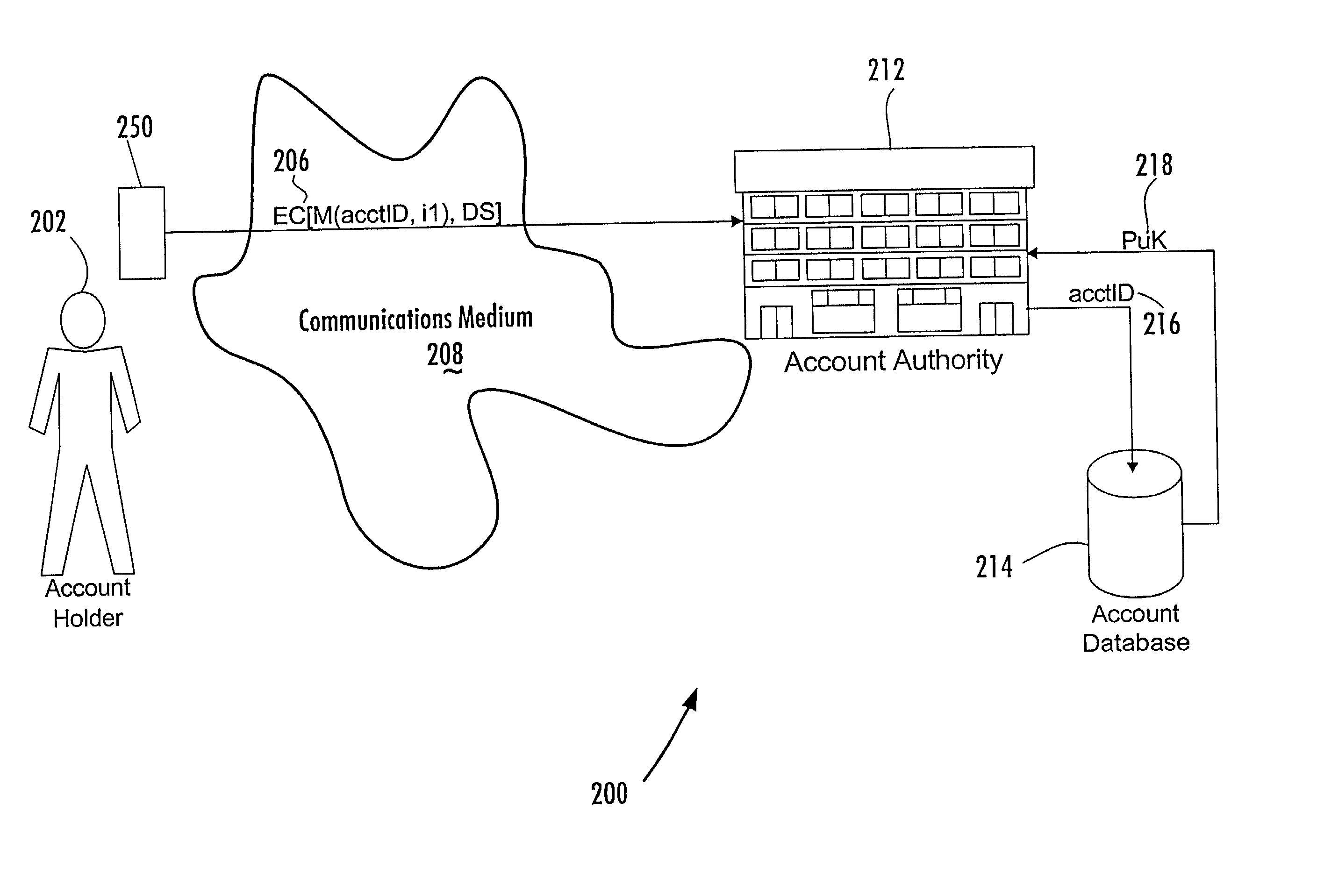
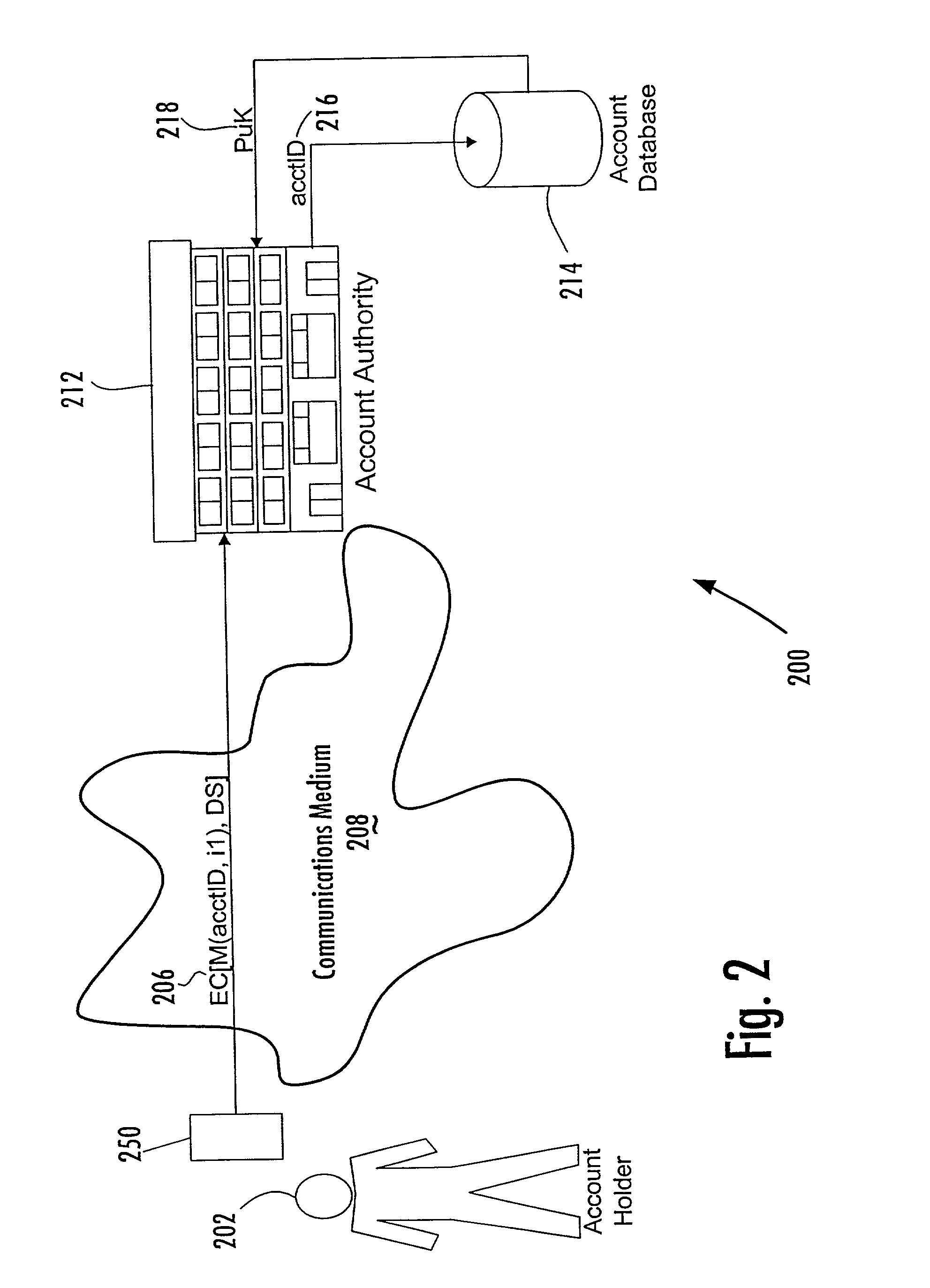
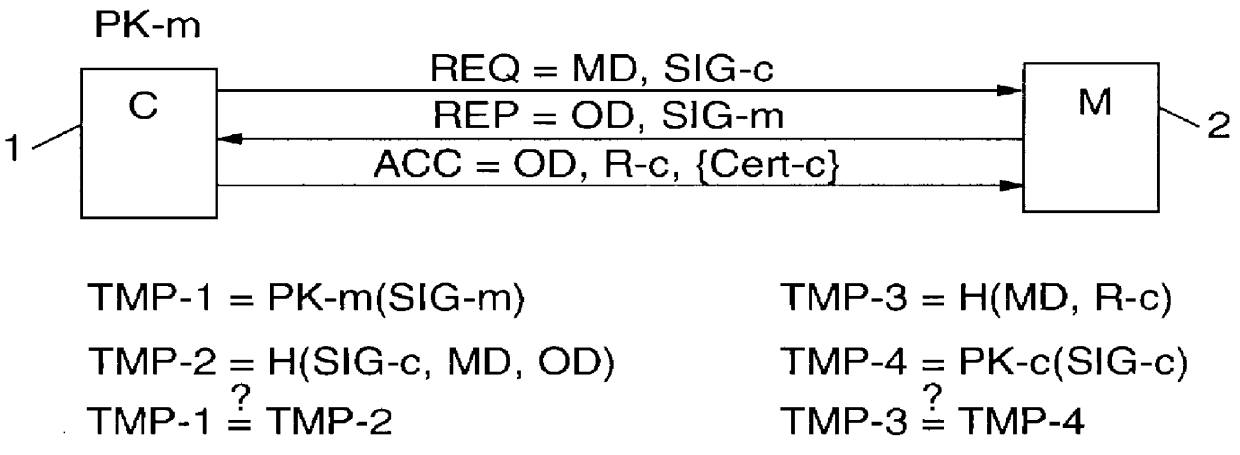
Trusted authentication digital signature (tads) system
Trusted entity authentication includes creating a public-private pair in a secure environment; storing the private key within a device during its manufacture in the secure environment; linking the public key with other information in the secure environment, receiving input within the device comprising verification data of an entity, identifying within the device a verification status based on the verification data and data prestored within the device; independent of the verification status identified, generating a digital signature for a message including an indication of the identified verification status using the private key; outputting the digital signature for transmission with an EC; identifying upon receipt of the EC the information linked with the public key by authenticating the message with the public key, and considering the identified information and the indicated verification status. The linked information includes device security aspects and the verification status regards entity authentication performed by the device.
Owner:FIRST DATA
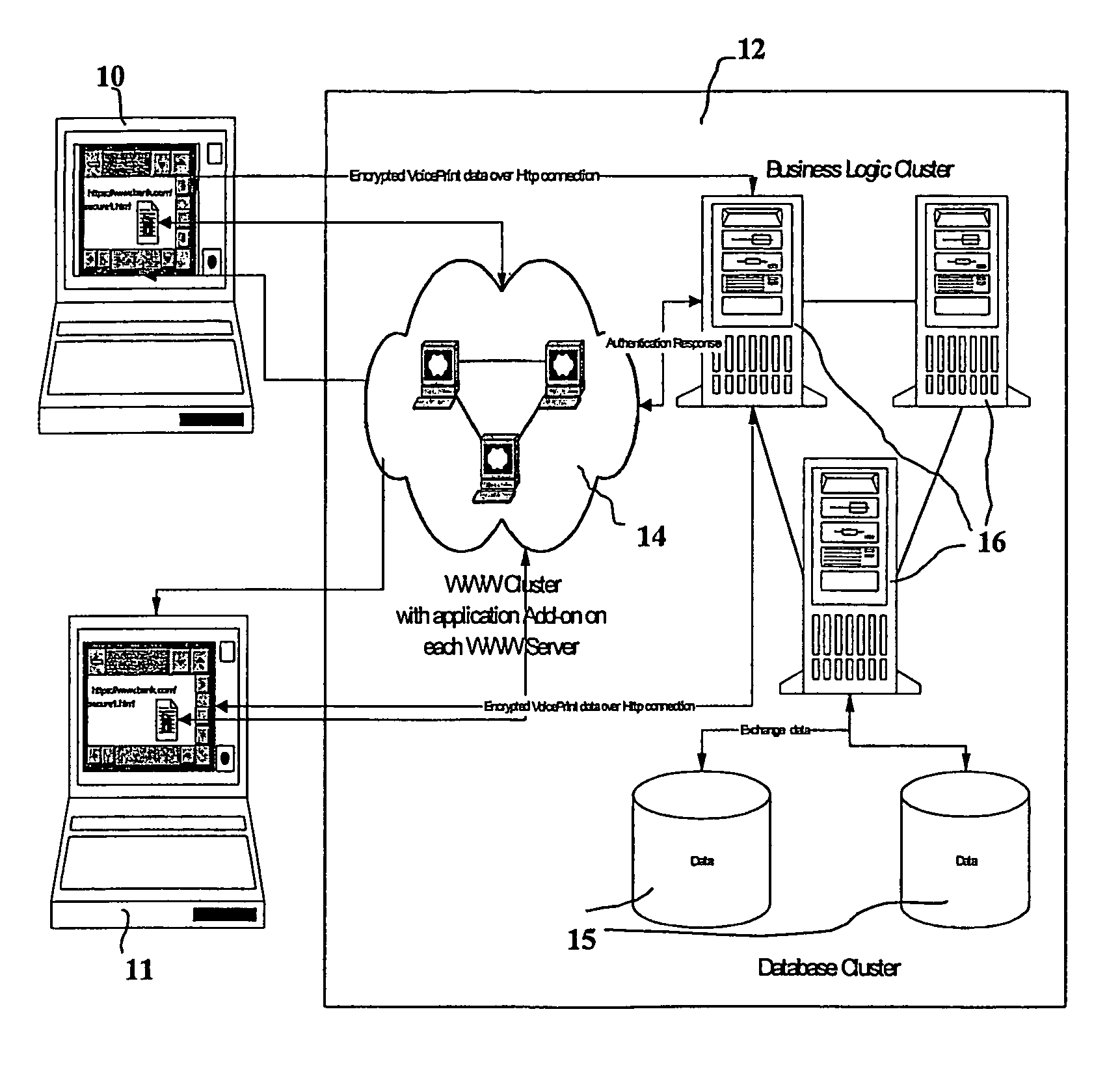
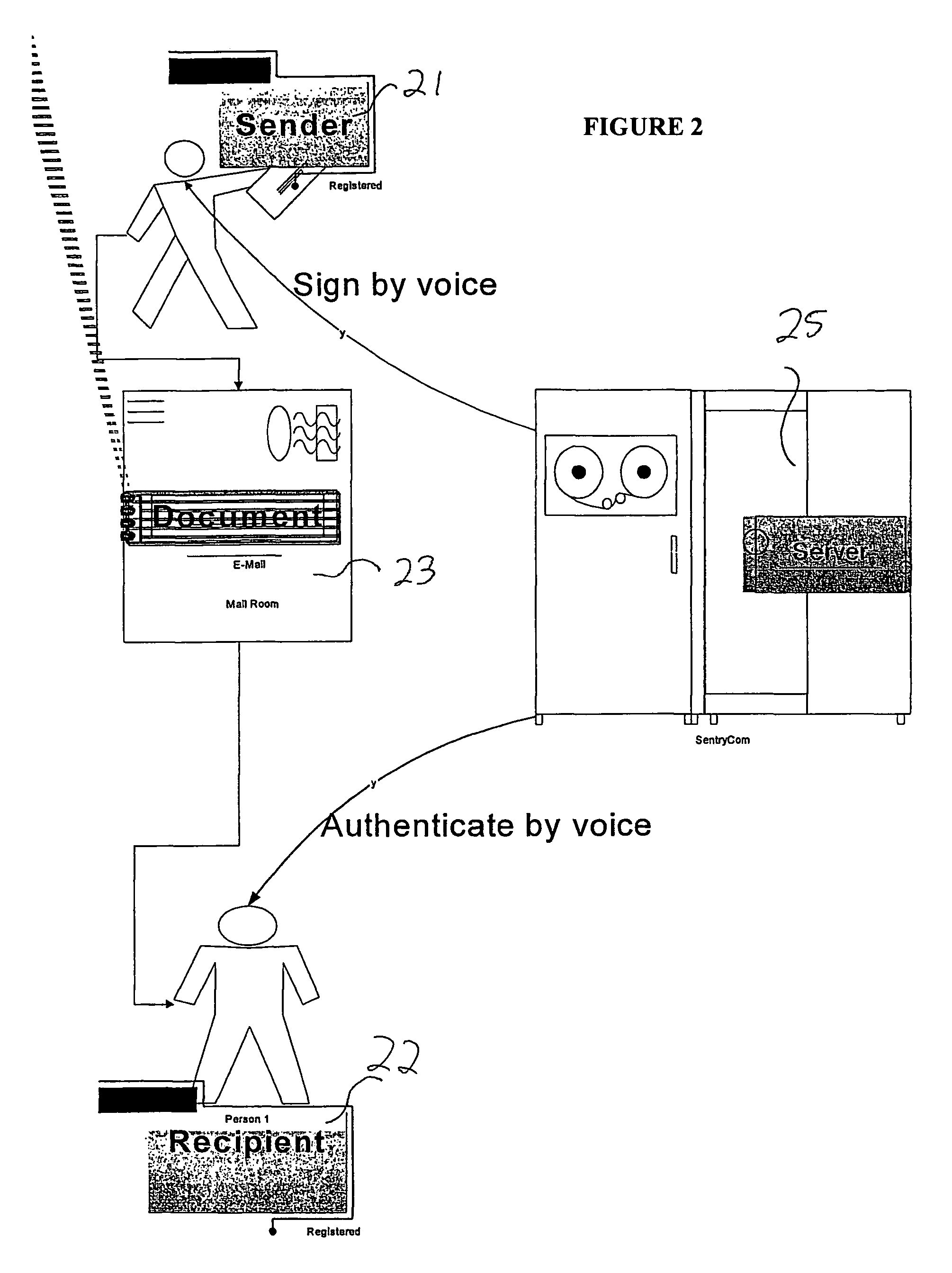
Biometric-based system and method for enabling authentication of electronic messages sent over a network
InactiveUS7689832B2Digital data processing detailsUser identity/authority verificationReal time validationData authenticity
A network based mechanism for real time verification and authentication of data and user identities. The present invention enables a method whereby biometric elements, such as voice prints, are utilized to enhance the Public Key Infrastructure as a means to decrypt data and verify data authenticity, such that the user's private key is authenticated remotely on a one-time basis. The present invention comprises an authentication server (25) with various software modules that enable authentication of user identity, secure user access to data, digital signatures, secure messaging and secure online transactions.
Owner:SENTRYCOM
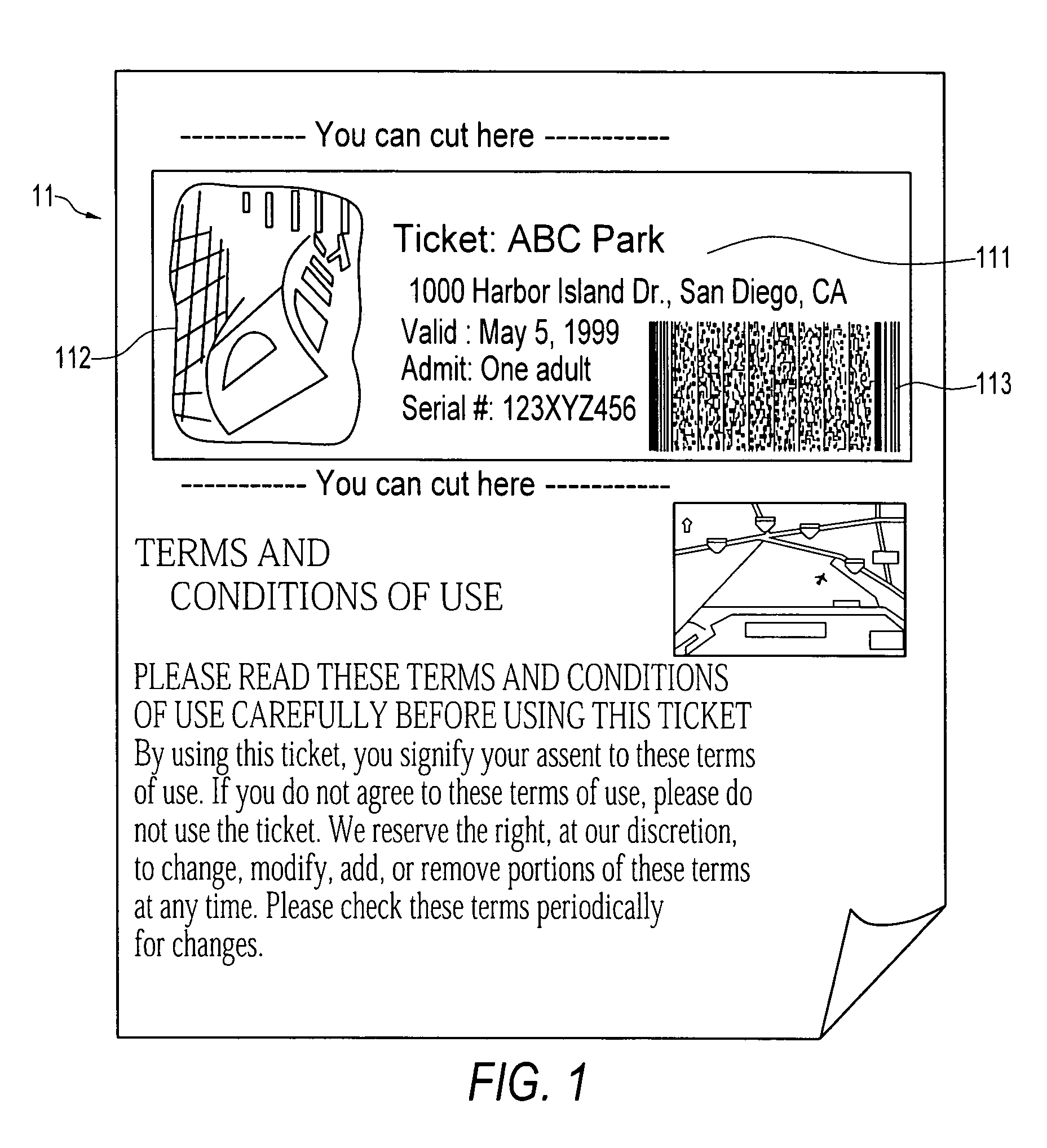
System and method for delivering and examining digital tickets
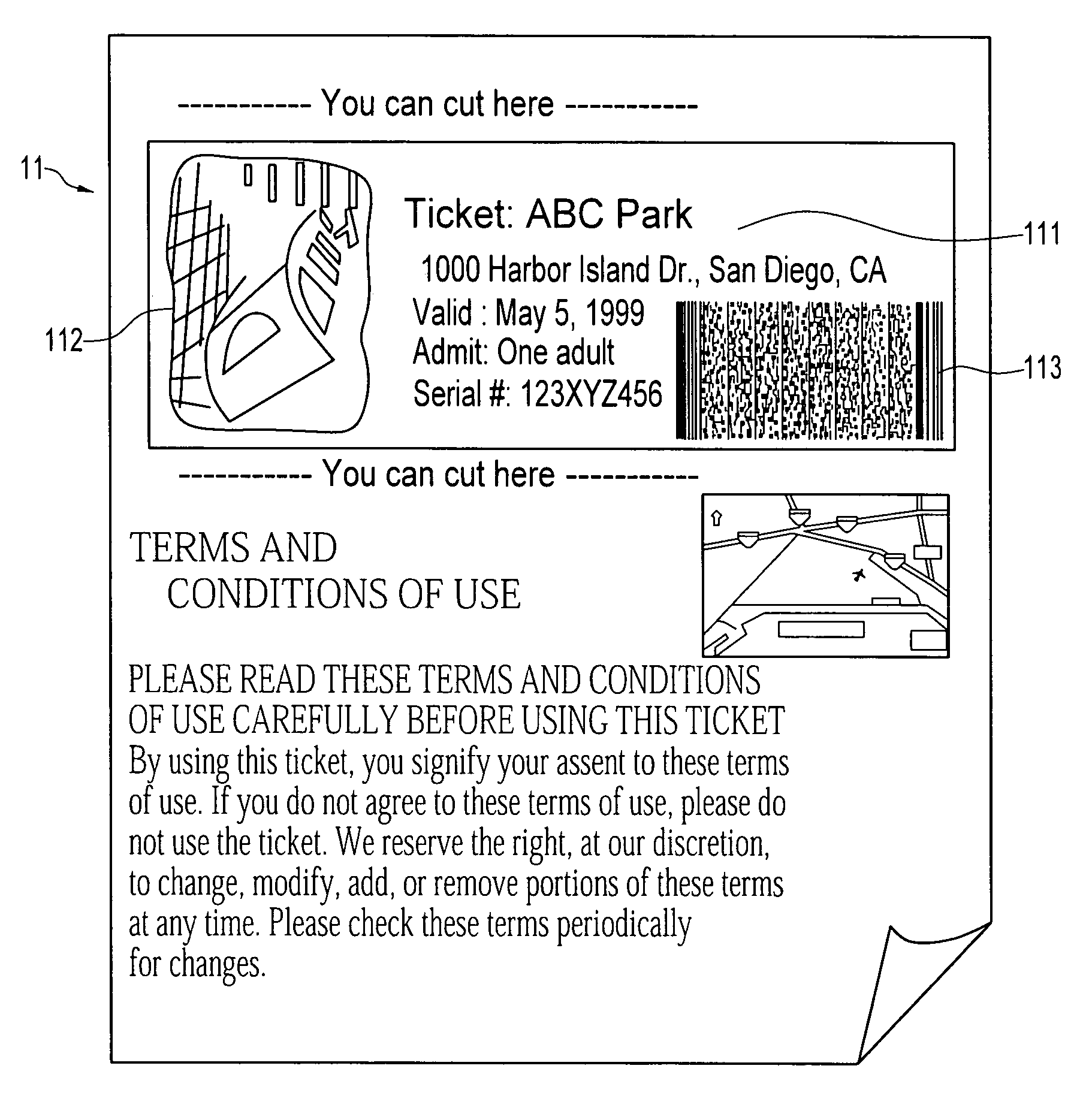
InactiveUS7093130B1Cost effectiveModest appearanceTicket-issuing apparatusUser identity/authority verificationTicketThe Internet
A digital ticket is procured by a client ticket consumer upon, preferably, the Internet from and by staged interaction with a ticket provider server. The digital ticket becomes embodied in a tangible transportable data storage medium, normally a 2-D bar code printed on paper by the consumer, or on the consumer's flexible disk or smart card, containing Sign(s,I||hash(R))||R where (1) R is a number having its origin in the computer of the ticket consumer, which number R is appended to (2) a number Sign(s,I||hash(R)). This number Sign(s,I||hash(R)) was earlier computed in the computer of the ticket provider as a digital signature using signature key s of a number hash(R) combined with event information I, and was subsequently communicated across the communications network to the computer of the ticket consumer. The number hash(R) was itself even earlier computed in the computer of the ticket consumer as a one-way function of random number R, which computed one-way function was subsequently communicated to the computer of the ticket provider. The number R is private to the ticket consumer and not public; the digital signature key s is private to the ticket provider.The digital ticket is redeemed by (1) transporting the transportable storage medium within which the Sign(s,I||hash(R))||R is written to the particular selected event; (2) tendering the digital ticket for verification and for admission; (3) reading the Sign(s,I||hash(R))||R to an event computer and extracting the number R; (4) decrypting the remaining Sign(s, I||hash(R)) with verification key v of the ticket producer to get hash(R) and I; (5) re-calculating from R, with the same one-way function previously used, a re-calculated hash(R); then, having this recalculated hash(R) to hand; (6) comparing the re-calculated hash(R) to the extracted hash(R). The (4) decrypting will work, producing a proper I for the selected event, and the (6) comparing will be equal, only for a legitimate ticket.
Owner:RGT UNIV OF CALIFORNIA
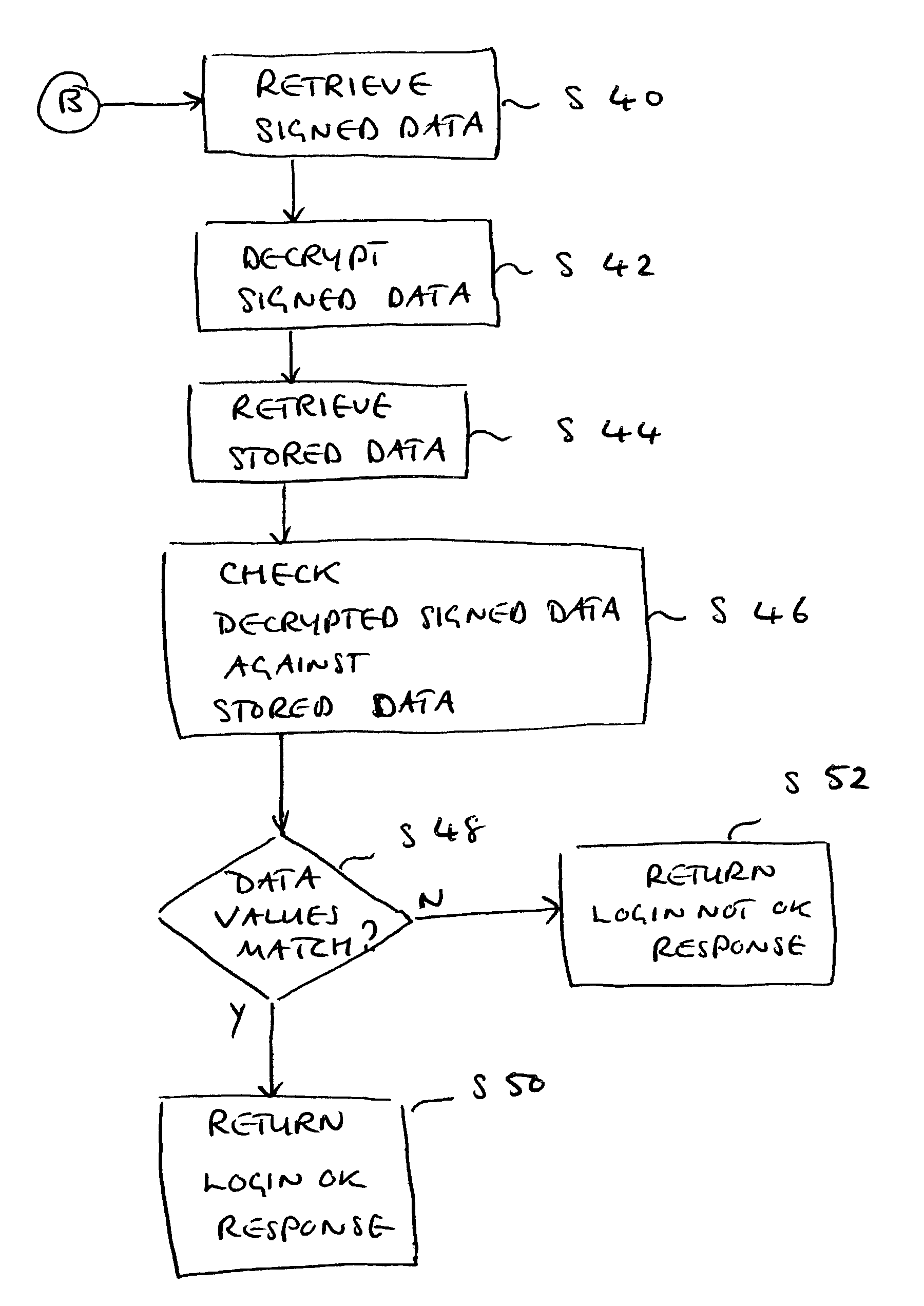
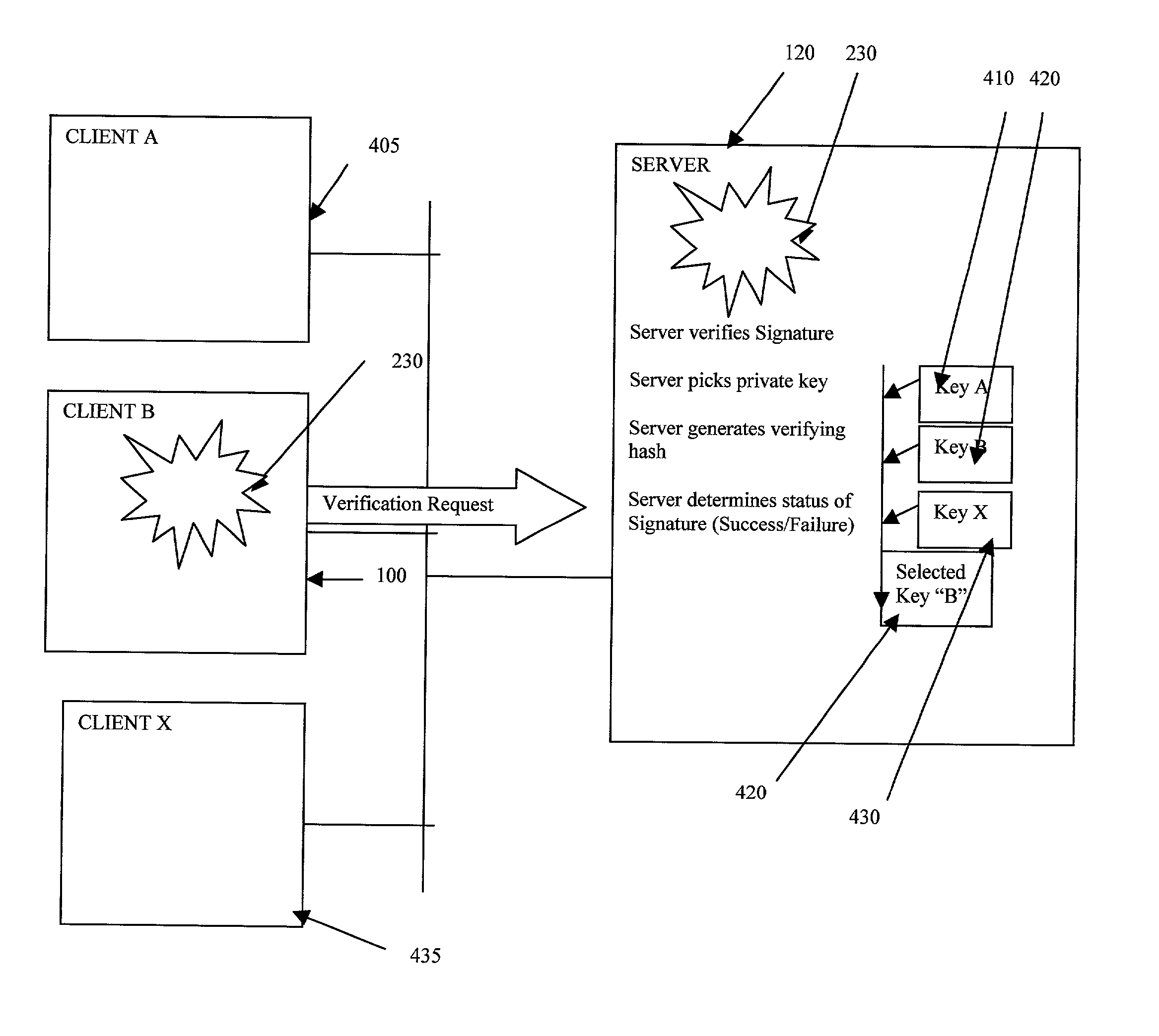
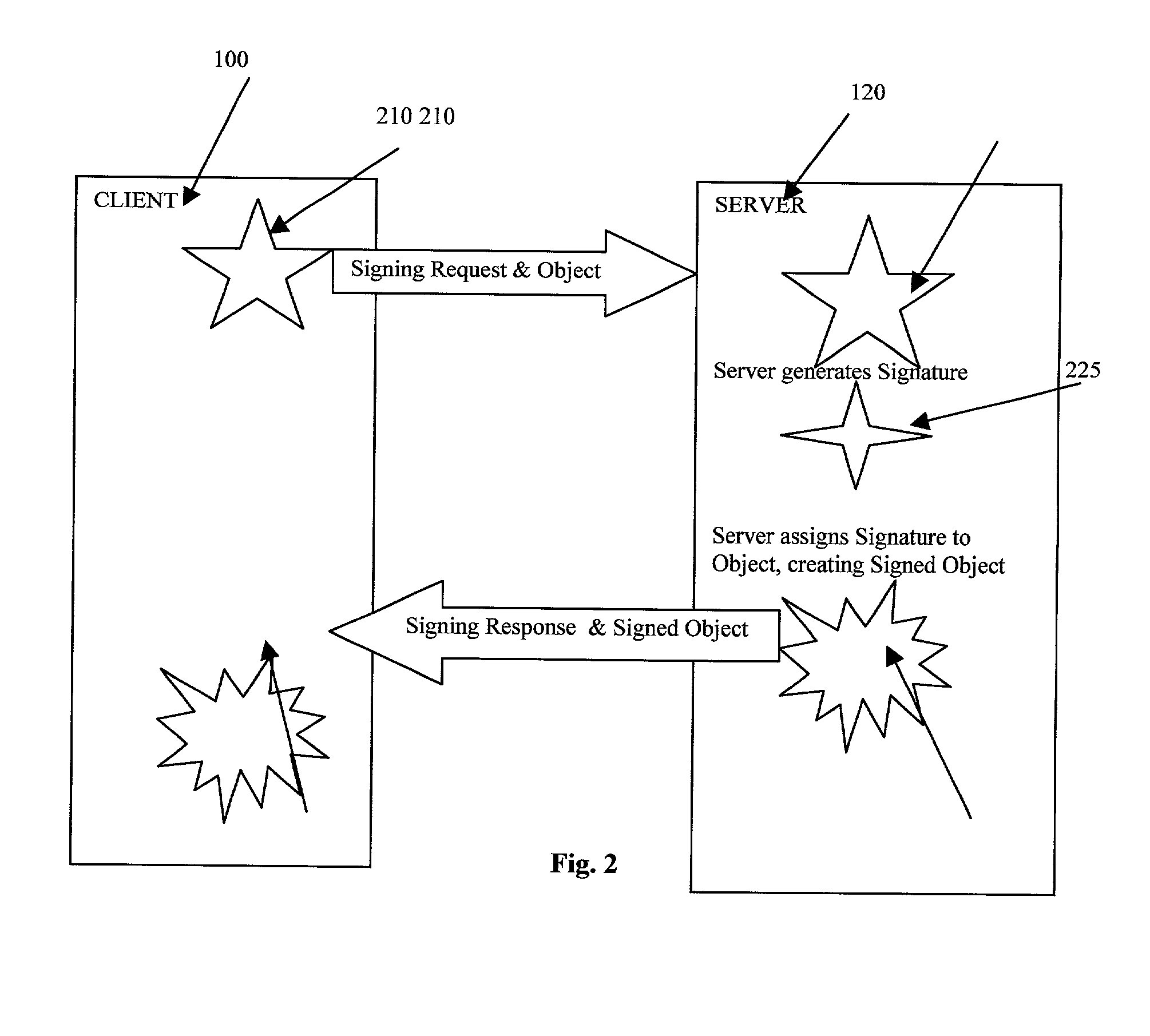
Server-side digital signature system
A digital signature system is provided on a server for use by remote clients, such as by using a browser. The server generates and maintains all of the users' keys used for producing a digital signature. A user sends a data object to the server, and the server generates a digital signature for the data object using the private key stored at the server. The server then sends the digital signature to the client. A client can, at a later time, send the signature back to the server for verification.
Owner:ZOLERA SYST
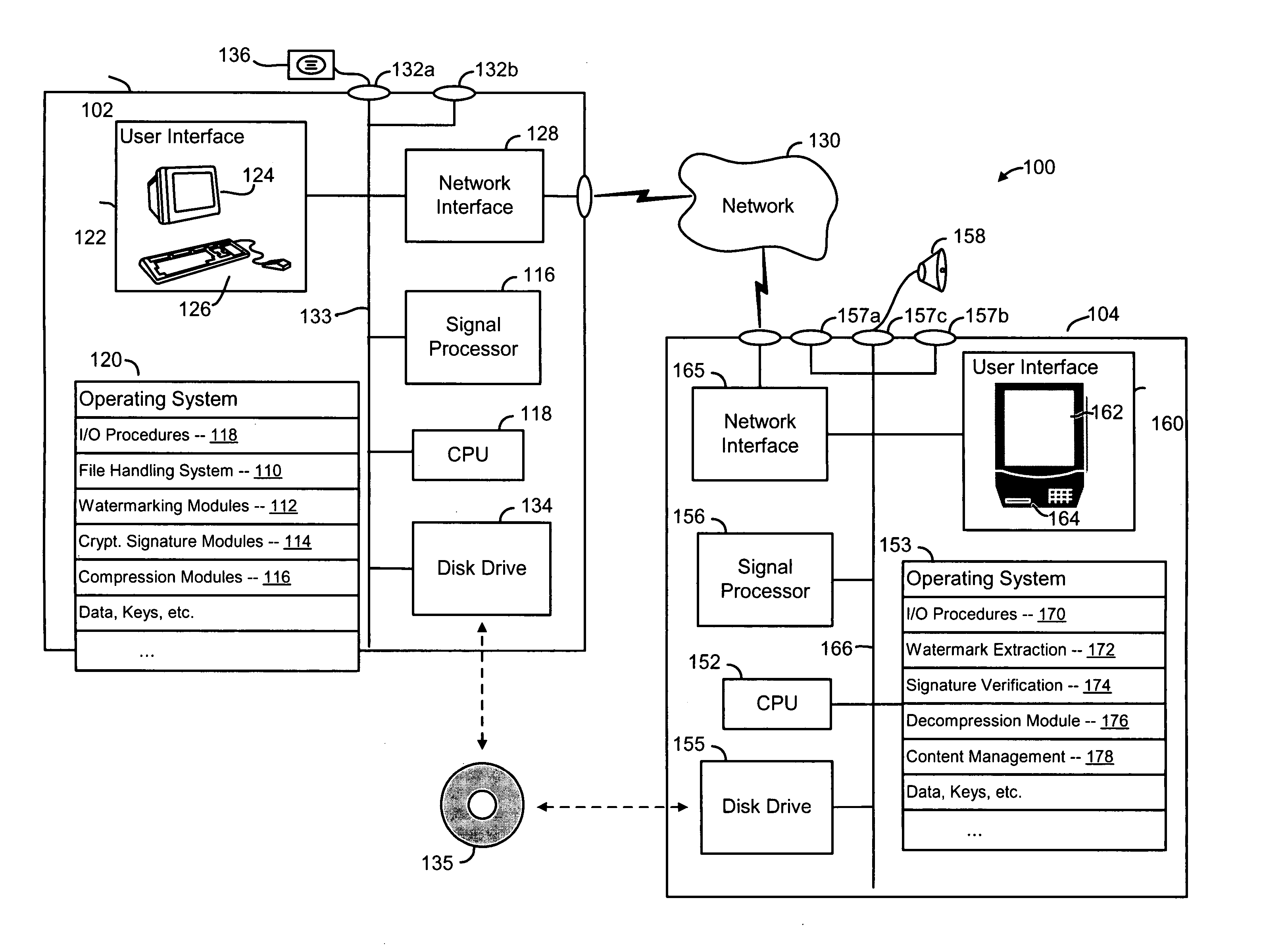
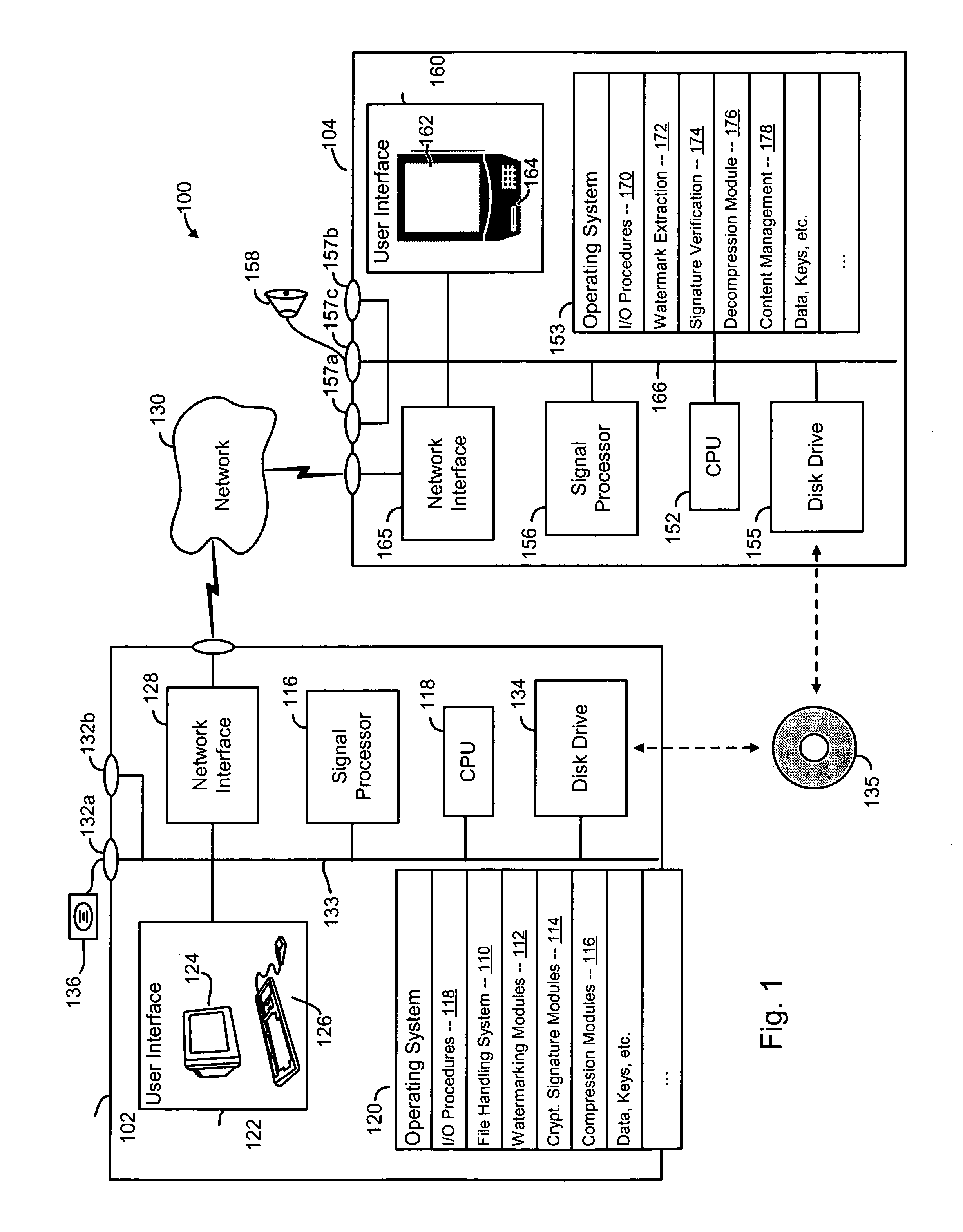
Methods and systems for encoding and protecting data using digital signature and watermarking techniques
InactiveUS20050050332A1Verify authenticityTelevision system detailsUser identity/authority verificationCompact discDigital signature
Systems and methods are provided for protecting and managing electronic data signals that are registered in accordance with a predefined encoding scheme, while allowing access to unregistered data signals. In one embodiment a relatively hard-to-remove, easy-to-detect, strong watermark is inserted in a data signal. The data signal is divided into a sequence of blocks, and a digital signature for each block is embedded in the signal via a watermark. The data signal is then stored and distributed on, e.g., a compact disc, a DVD, or the like. When a user attempts to access or use a portion of the data signal, the signal is checked for the presence of a watermark containing the digital signature for the desired portion of the signal. If the watermark is found, the digital signature is extracted and used to verify the authenticity of the desired portion of the signal. If the signature-containing watermark is not found, the signal is checked for the presence of the strong watermark. If the strong watermark is found, further use of the signal is inhibited, as the presence of the strong watermark, in combination with the absence or corruption of the signature-containing watermark, provides evidence that the signal has been improperly modified. If, on the other hand, the strong mark is not found, further use of the data signal can be allowed, as the absence of the strong mark indicates that the data signal was never registered with the signature-containing watermark.
Owner:INTERTRUST TECH CORP
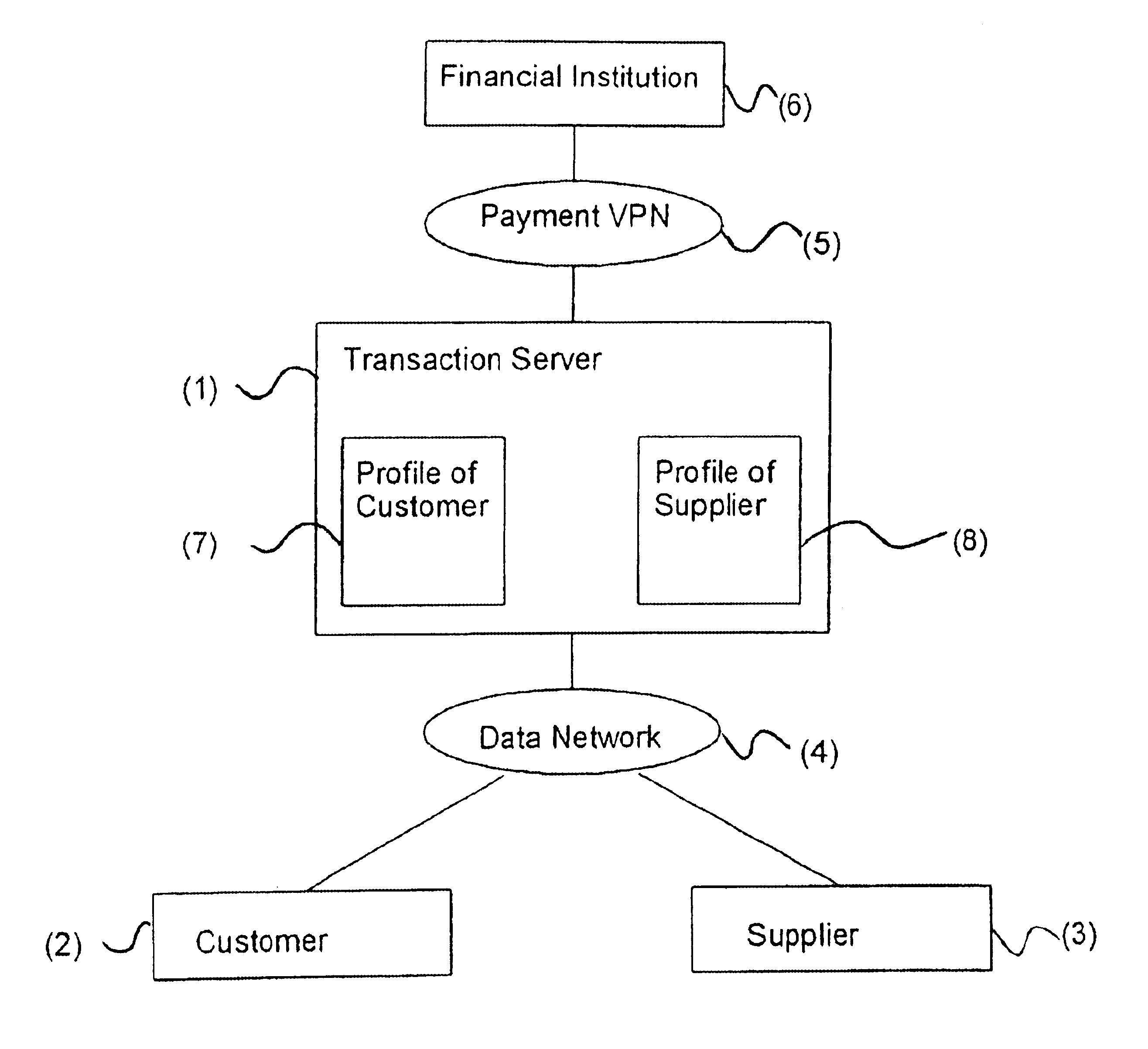
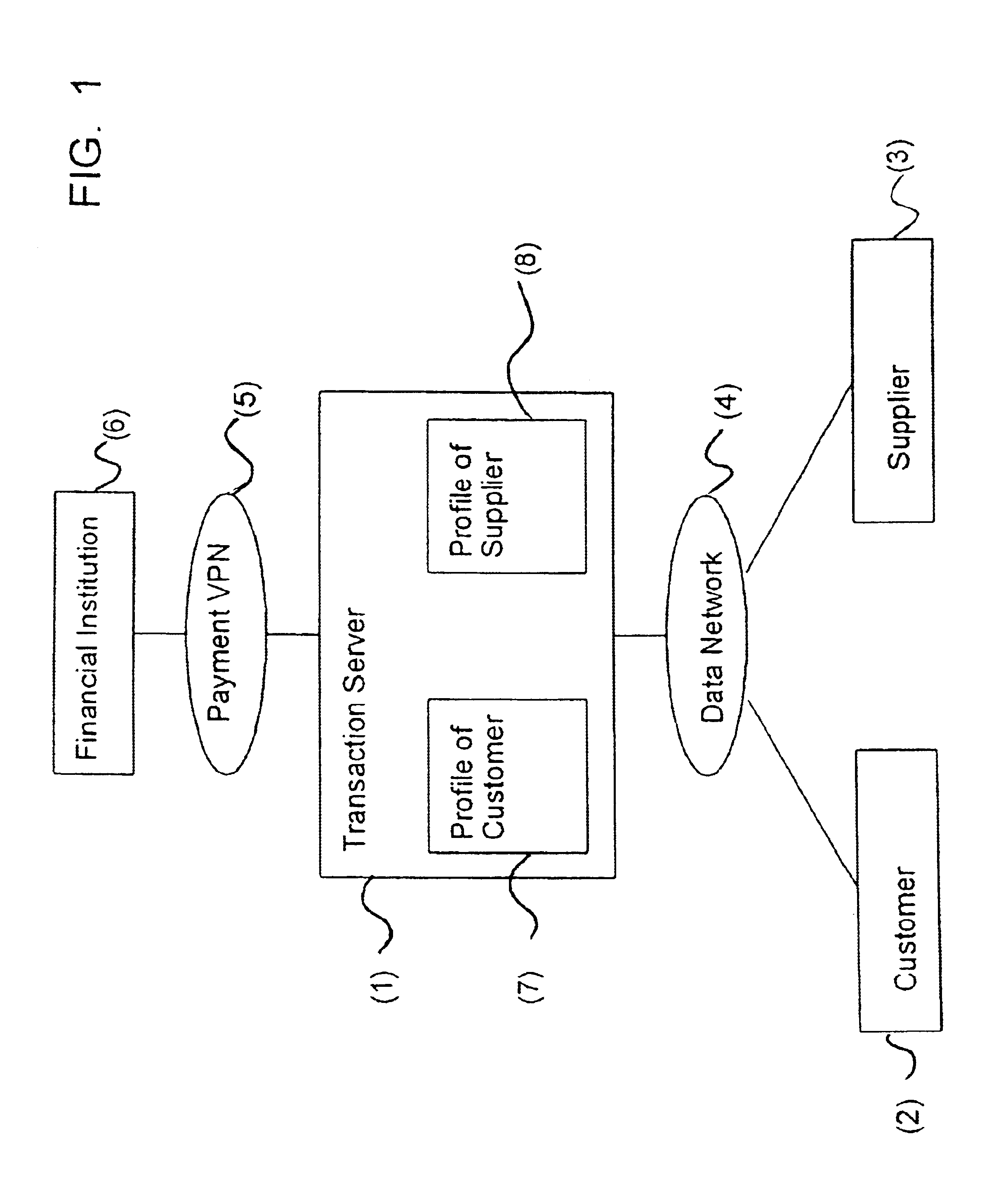
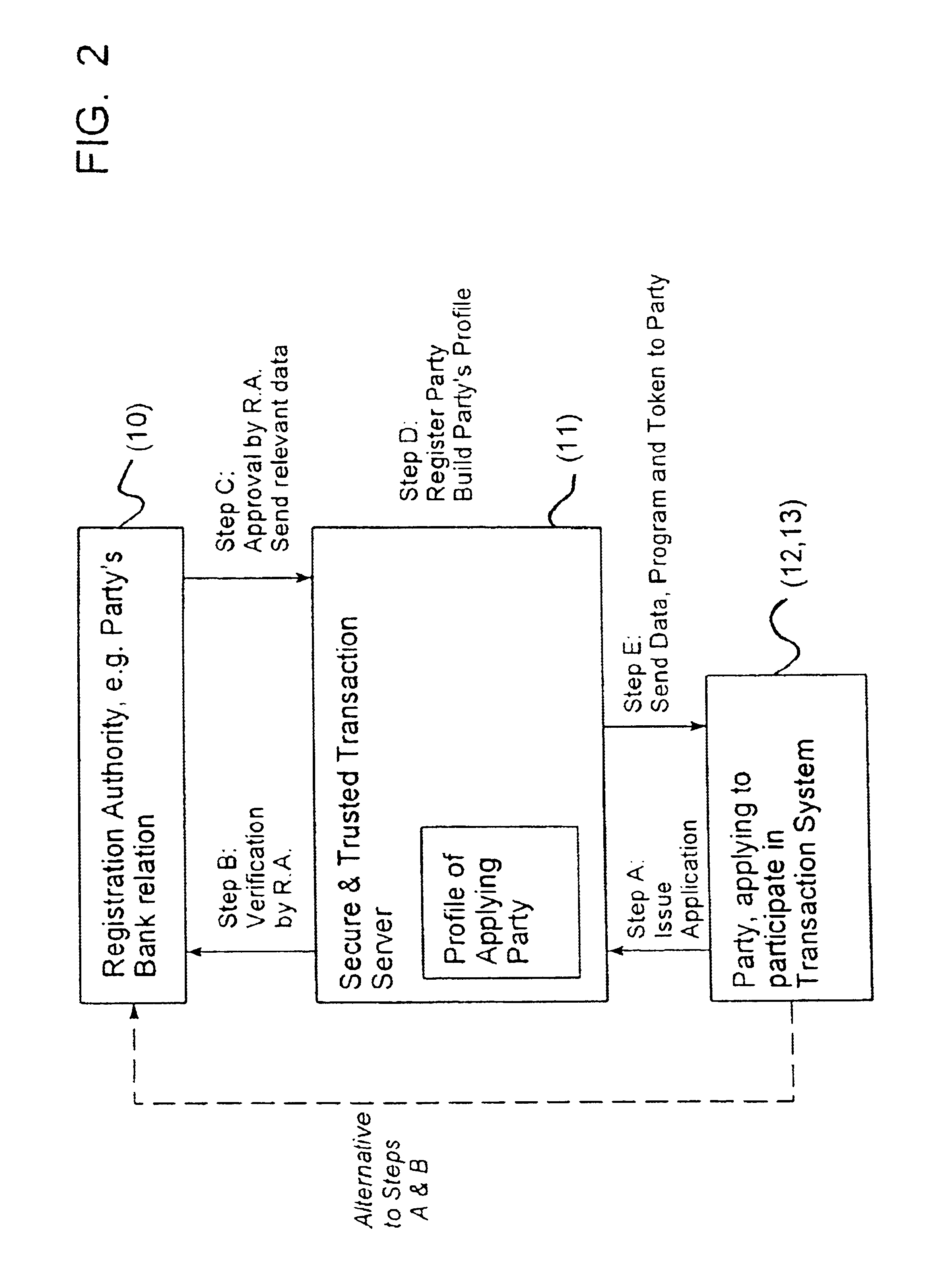
Transaction method and system for data networks, like internet
InactiveUS6889325B1Easy to implementEliminate needUser identity/authority verificationMultiple digital computer combinationsTransaction serviceDigital signature
A method and a system for performing a transaction between at least one first party and at least one second party are disclosed. A data network connects data input / output terminals of the parties. In the data network, a secure and trusted transaction server is provided, in which a profile of the parties is registered, having a party identifier identifying a particular party, and authentication data for authenticating the party and data sent by the party. The parties communicate with each other through the transaction server by means of various transaction messages, which are digitally signed using a table of random numbers and a hashing operation, wherein the table of random numbers is generated by reading a token.
Owner:UNICATE
Encryption in a secure computerized gaming system
InactiveUS7203841B2Straightforward and easy to manageUser identity/authority verificationUnauthorized memory use protectionComputer hardwareHash function
The present invention provides an architecture and method for a gaming-specific platform that features secure storage (354) and verification (366) of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments of the invention provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. The invention provides these and other functions by use of encryption (216), including digital signatures (220) and hash functions (210) as well as other encryption methods.
Owner:IGT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com