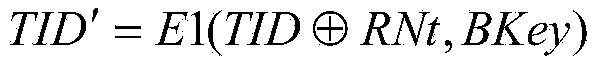Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
286results about How to "Avoid tracking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
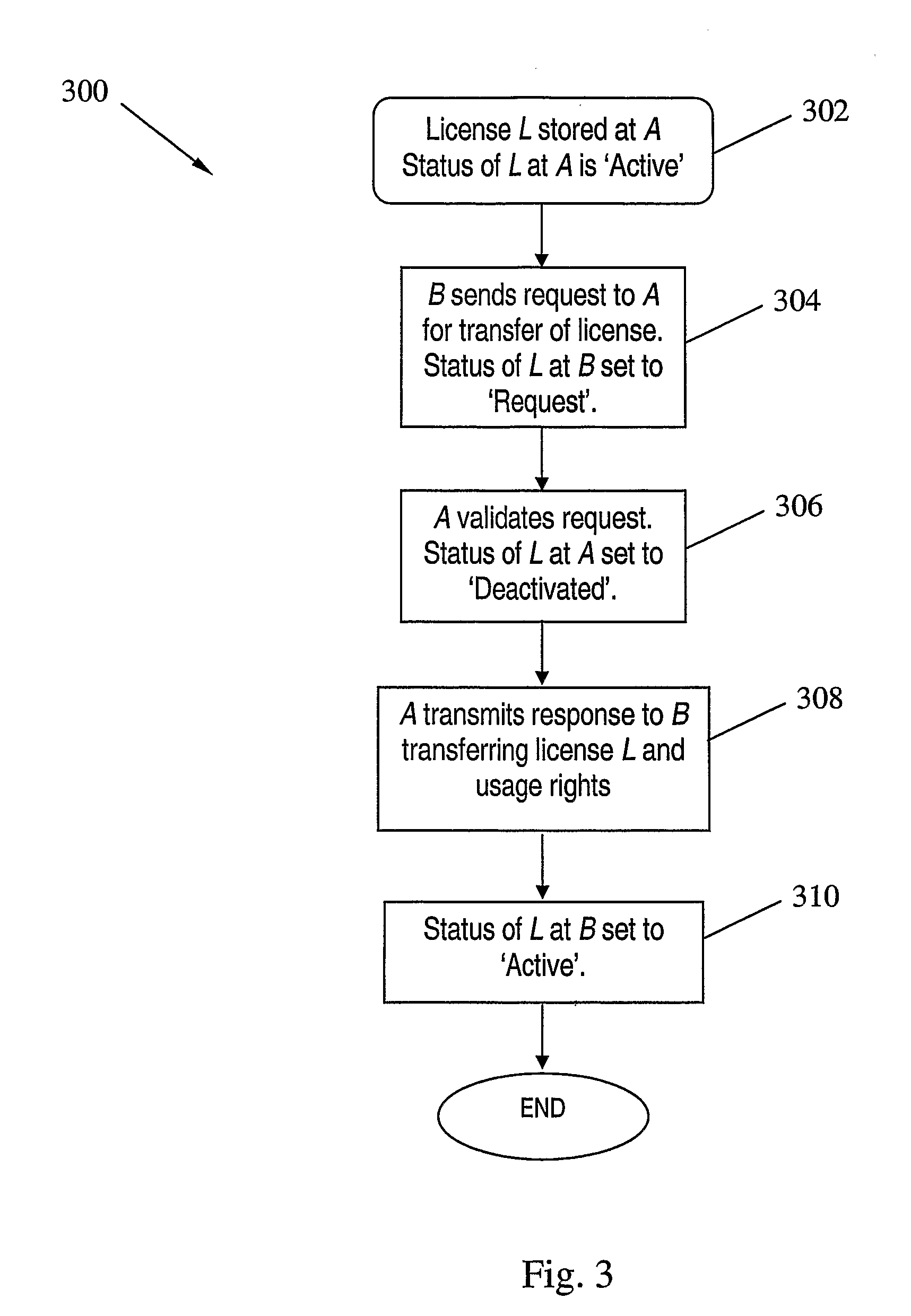
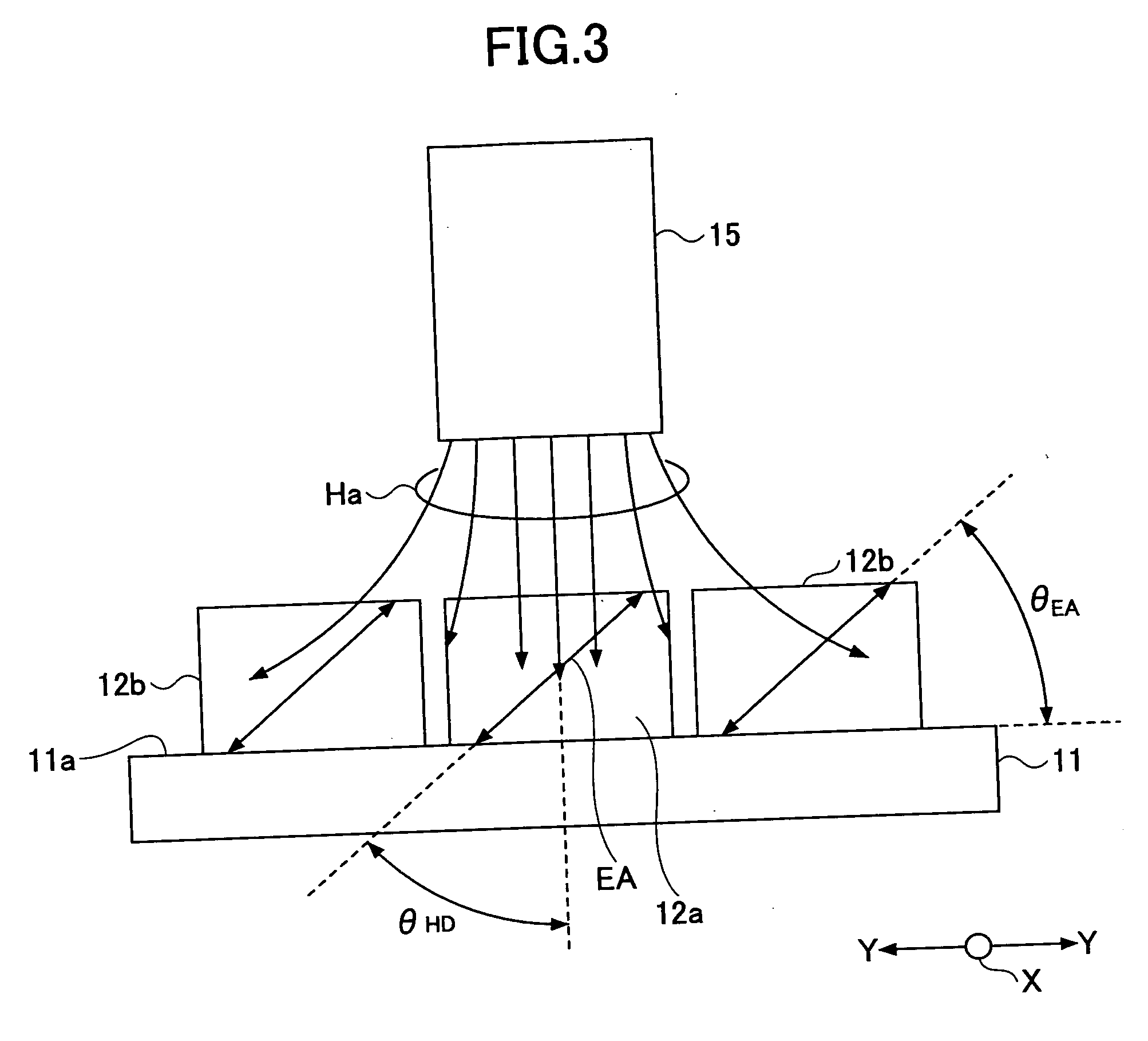
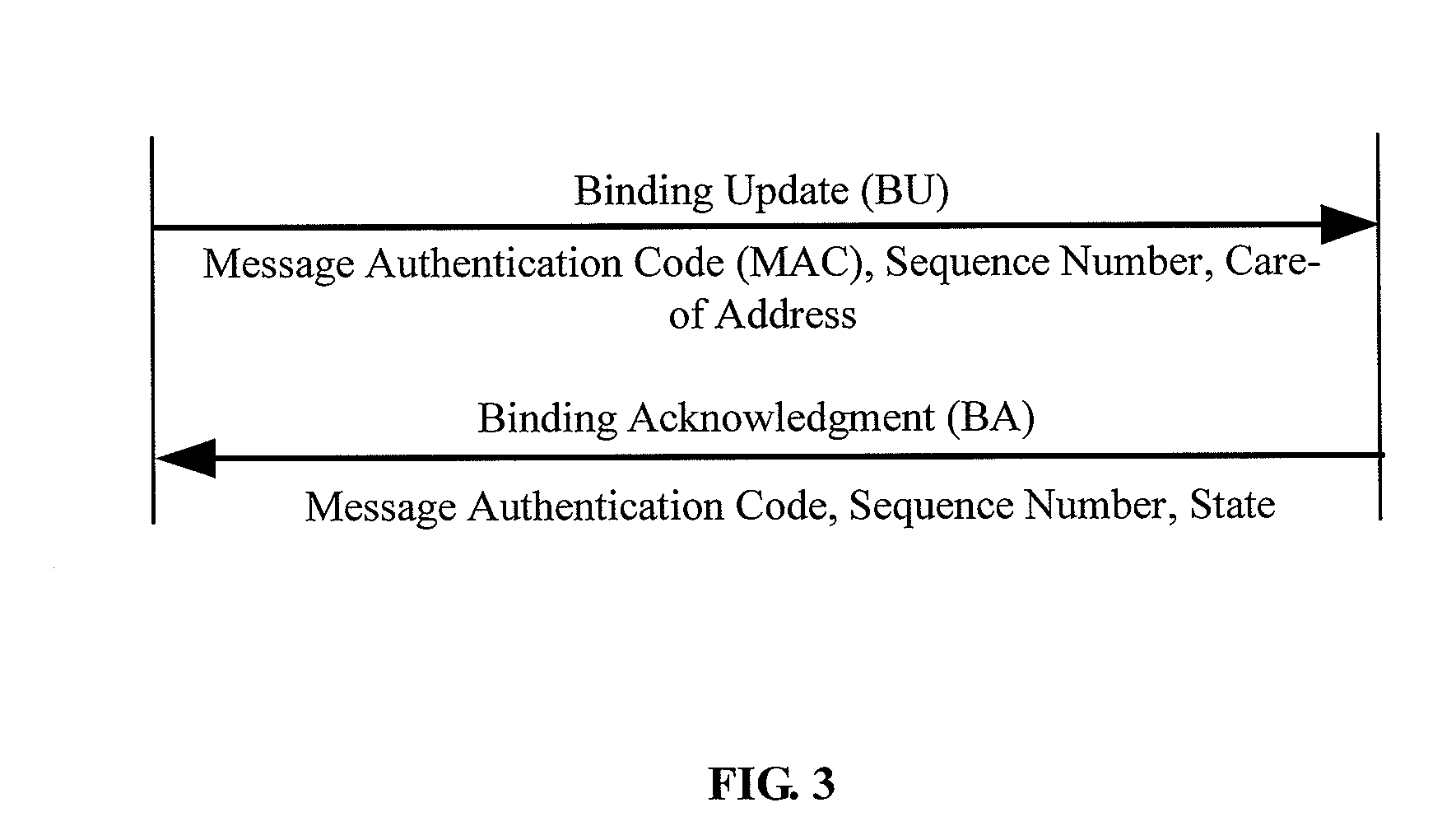
Digital License Sharing System and Method
InactiveUS20070219917A1Fail can be robustAvoid trackingUser identity/authority verificationComputer security arrangementsInternet privacyDigital rights management system
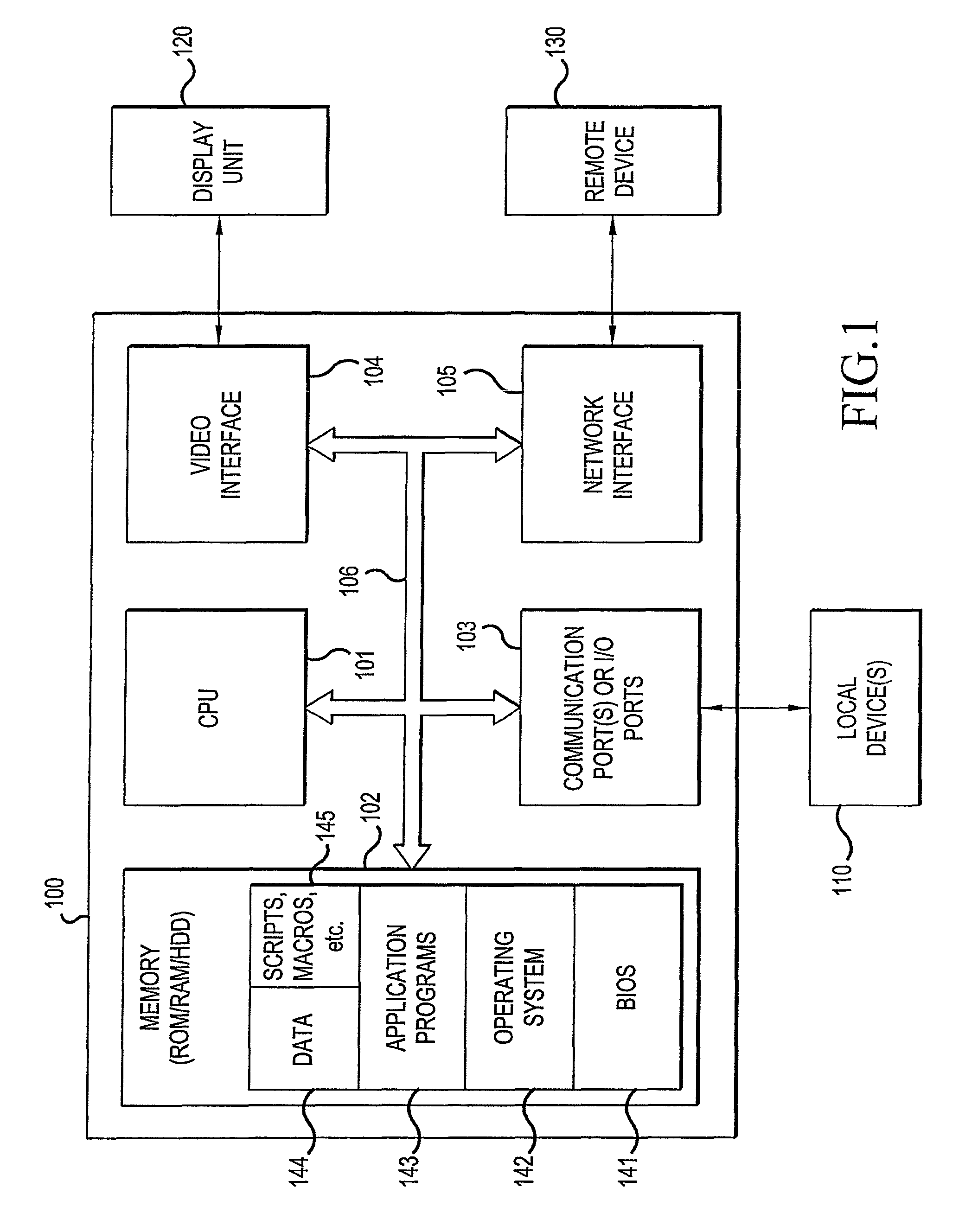
A digital license sharing method, system and apparatus is provided for use in a digital rights management system. Usage rights in respect of digital content are transferred between content player devices or applications by associating with each player a status indication. Transfer is carried out by transmitting a request to obtain the usage rights from a player requiring usage rights to a player currently holding the rights. The transferring player sets a first status indication to indicate that it is no longer entitled to exercise the rights, and transmits a response to the requesting player to transfer the usage rights. The requesting player then sets a second status indication to indicate that it is henceforth entitled to exercise the rights. Methods and apparatus for creating transferable licenses are also provided that employ a sharable license format including a validated portion and an unvalidated portion. The validated portion, which may be, for example, digitally signed by a license issuing authority, includes characteristic information of a digital content decryption key required to access the digital content controlled by the license. The unvalidated portion includes the digital content key itself, encrypted using an encryption key associated with a player entitled to use the license.
Owner:SMART INTERNET TECH CRC
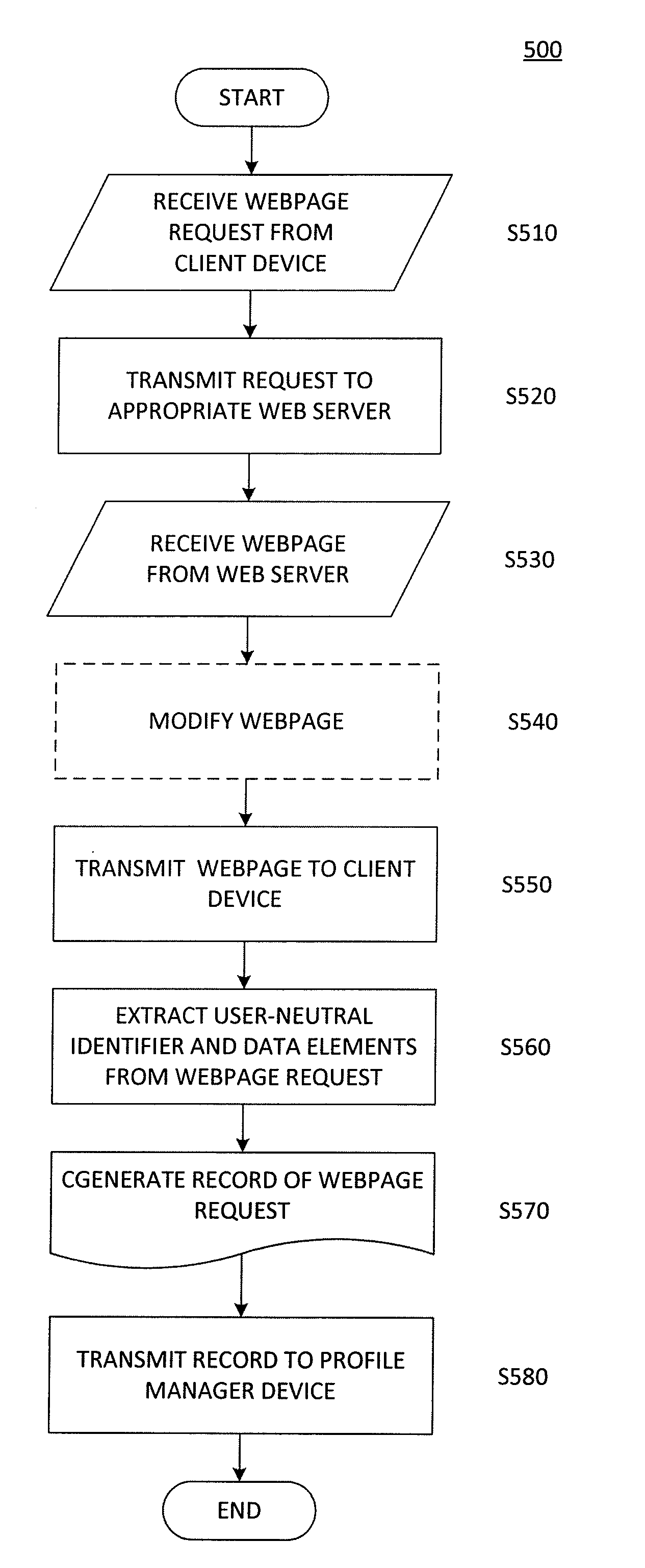
Server side mobile audience intelligence creation
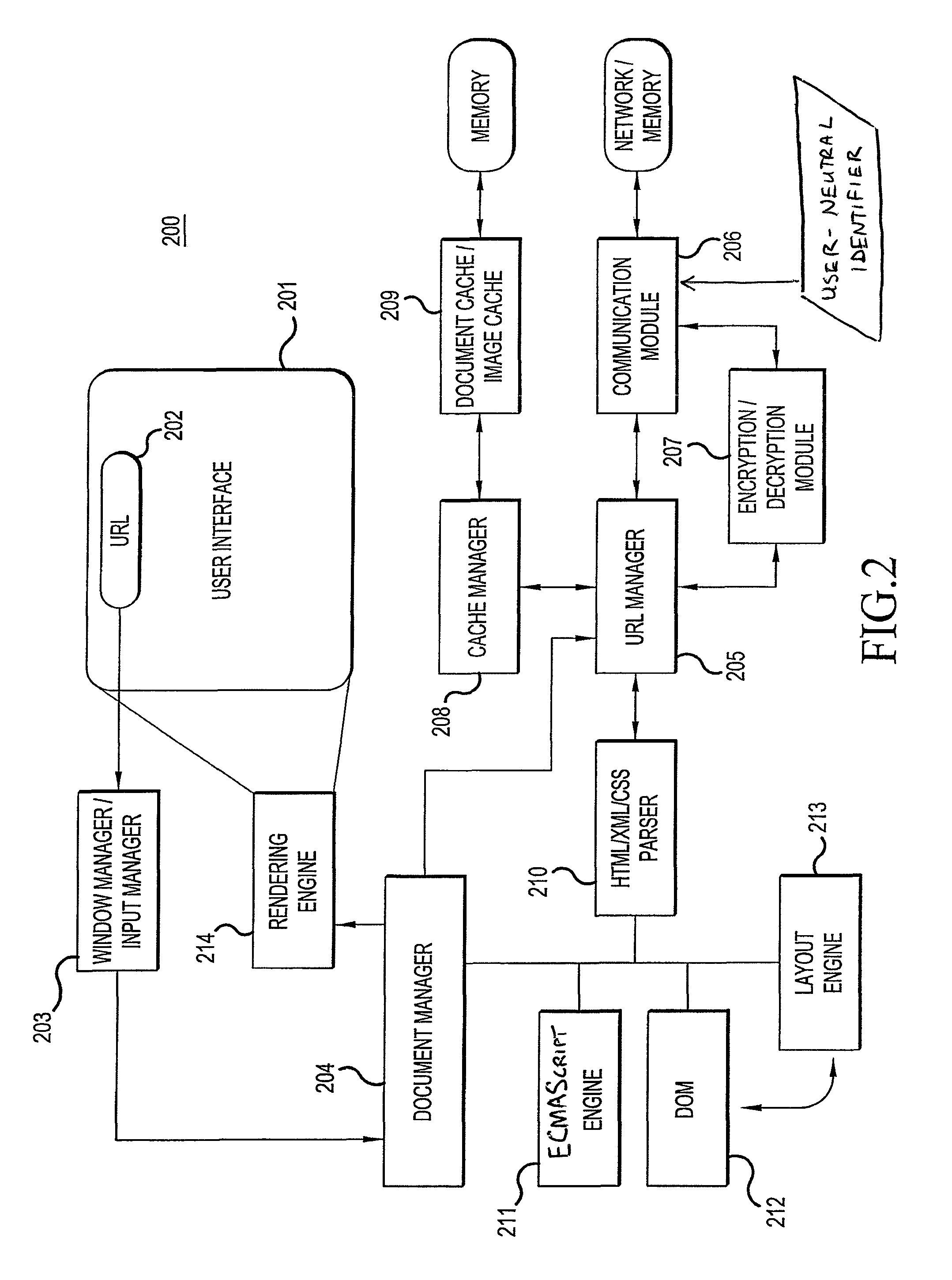
ActiveUS20130080498A1Improve browsing experienceAvoid trackingAdvertisementsMultiple digital computer combinationsWeb siteWeb browser
The present invention is directed toward a method and system for tracking webpage requests from web browsers without invading the privacy of the corresponding users. A server receives the webpage requests, and extracts from each of them a user-neutral identifier and URL. The server creates records of these webpage requests, and these records are used to create and update profiles for the corresponding user-neutral identifiers. Since the user-neutral identifiers are not tied to user-specific information, the profiles are made anonymous and user privacy can be protected. However, since each user-neutral identifier is tied to a particular web browser, useful information regarding individual browsing behavior can be obtained. Furthermore, the requested URL's can be categorized before being used to update the profiles, thus eliminating concerns that a user's browsing activity might be tracked from website to website.
Owner:OPERA SOFTVEAR AS
Magnetic head for perpendicular magnetic recording having a main pole and a shield
ActiveUS8295008B1Prevention of adjacent track eraseImprovement of write characteristicRecord information storageHeads for perpendicular magnetisationsElectrical and Electronics engineeringNon magnetic
Owner:HEADWAY TECH INC +1
High-precision maximum power point tracing method
ActiveCN101651436AOvercoming misjudgmentReduce energy lossPV power plantsPhotovoltaic energy generationObservation methodMppt algorithm
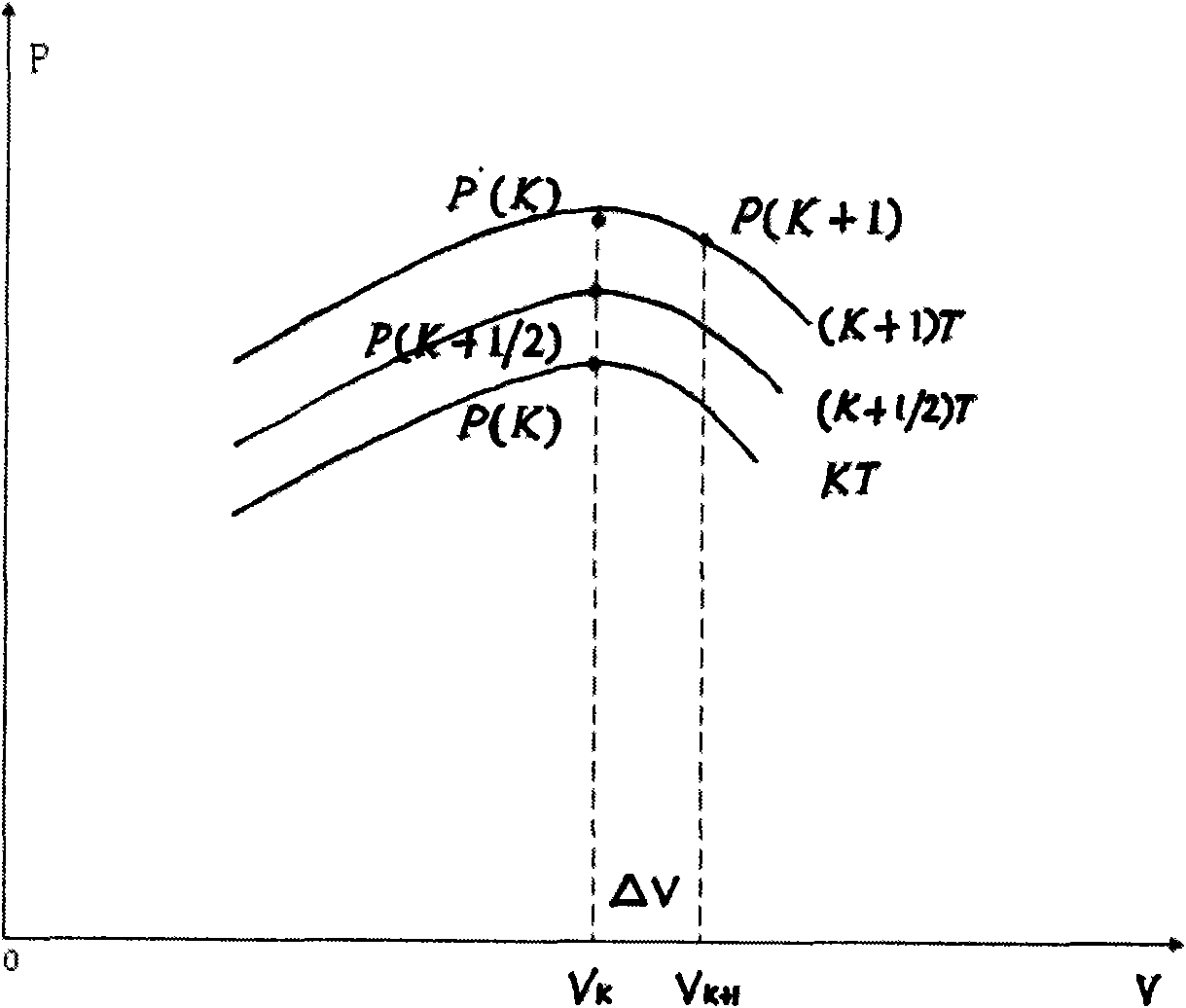
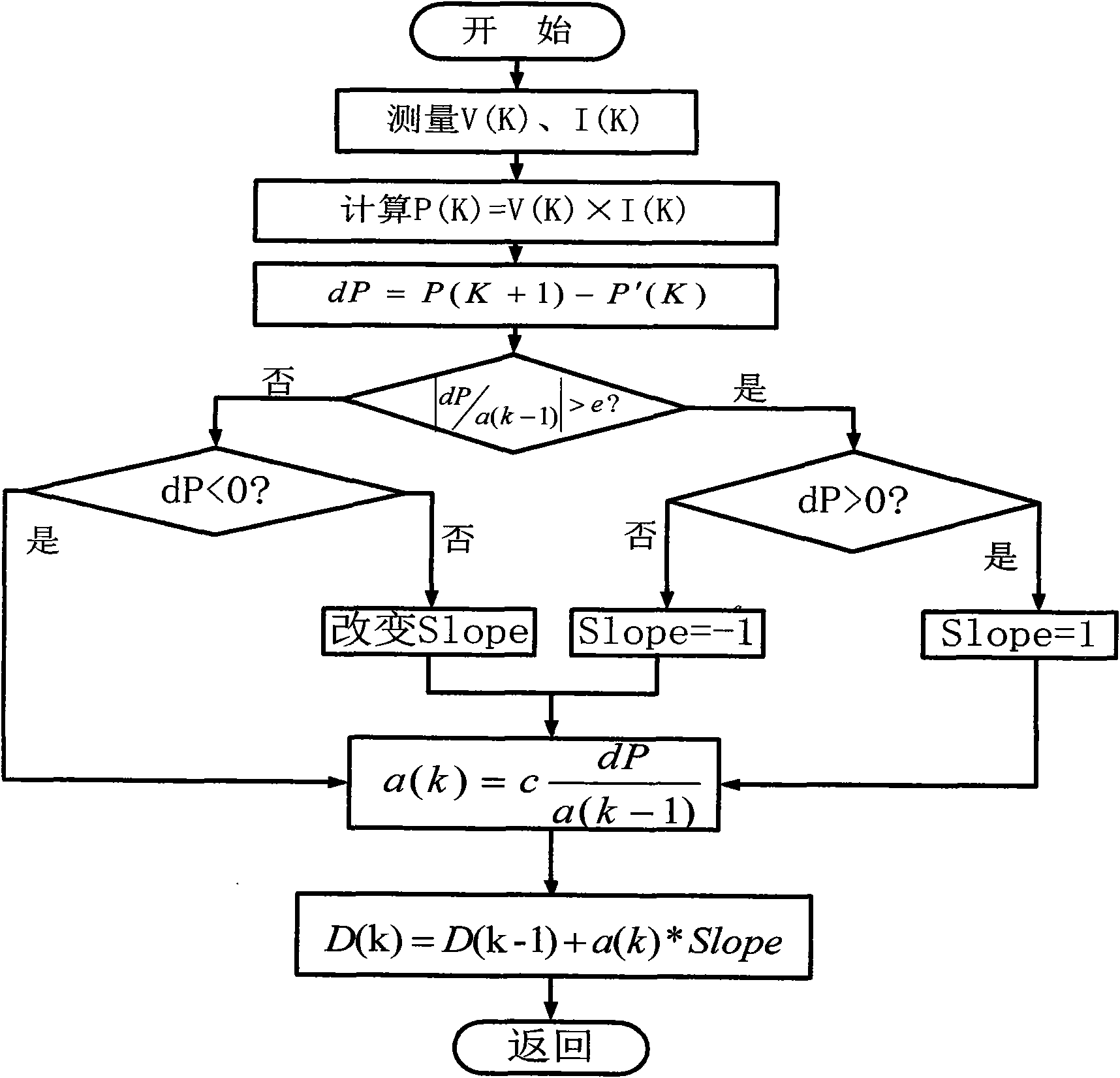
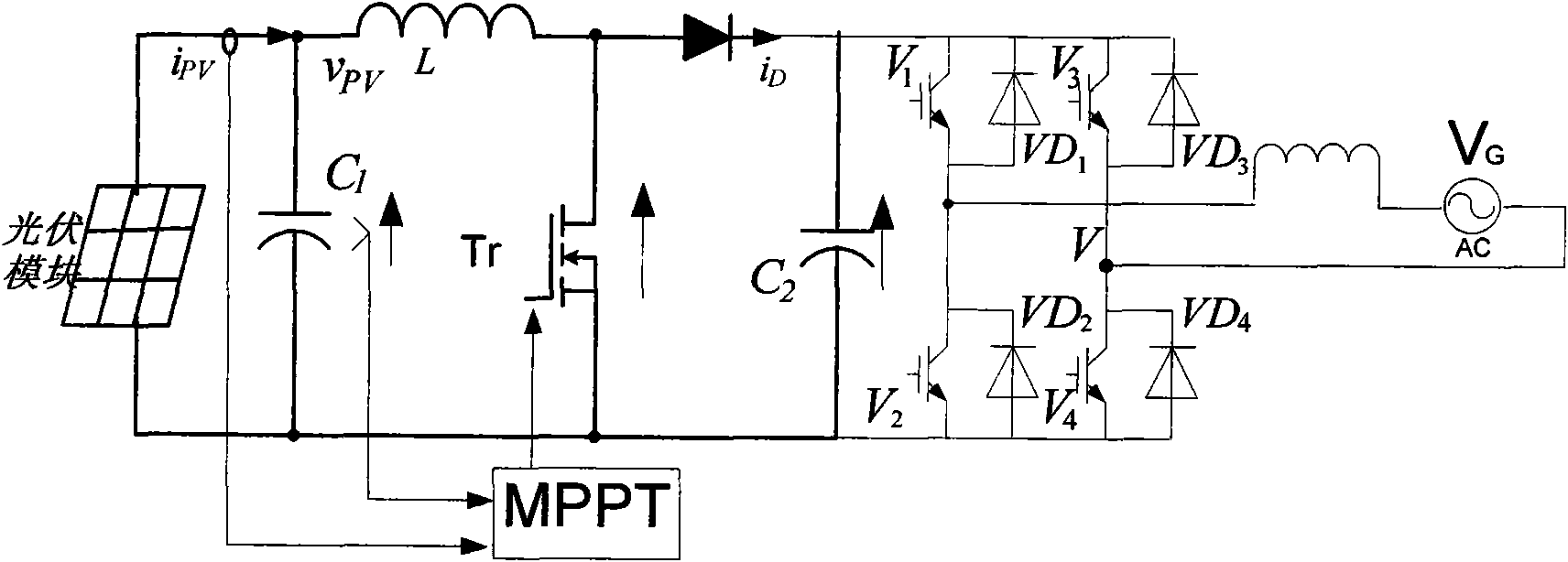
The invention relates to a high-precision maximum power point tracing method, which is an MPPT algorithm combining variable step-size optimization and a disturbance observation method based on power prediction, i.e. a variable step-size disturbance observation method based on the power prediction. The high-precision maximum power point tracing method can overcome the defects of the conventional disturbance observation method, the variable step-size disturbance observation method, and the like, solve the problems of failure judgment, local maximum power, and the like and quickly and precisely trace a maximum power point.
Owner:SUNGROW POWER SUPPLY CO LTD
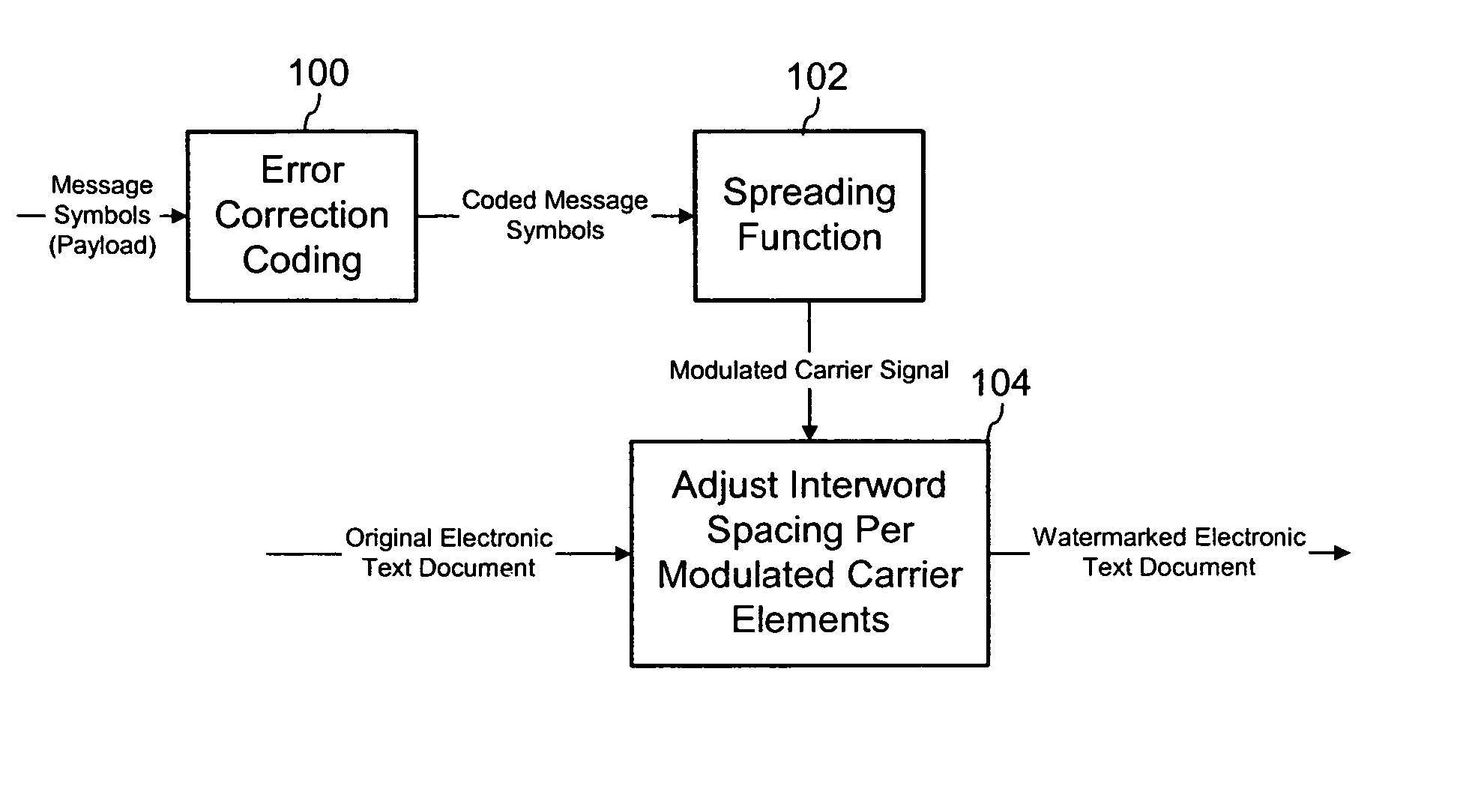
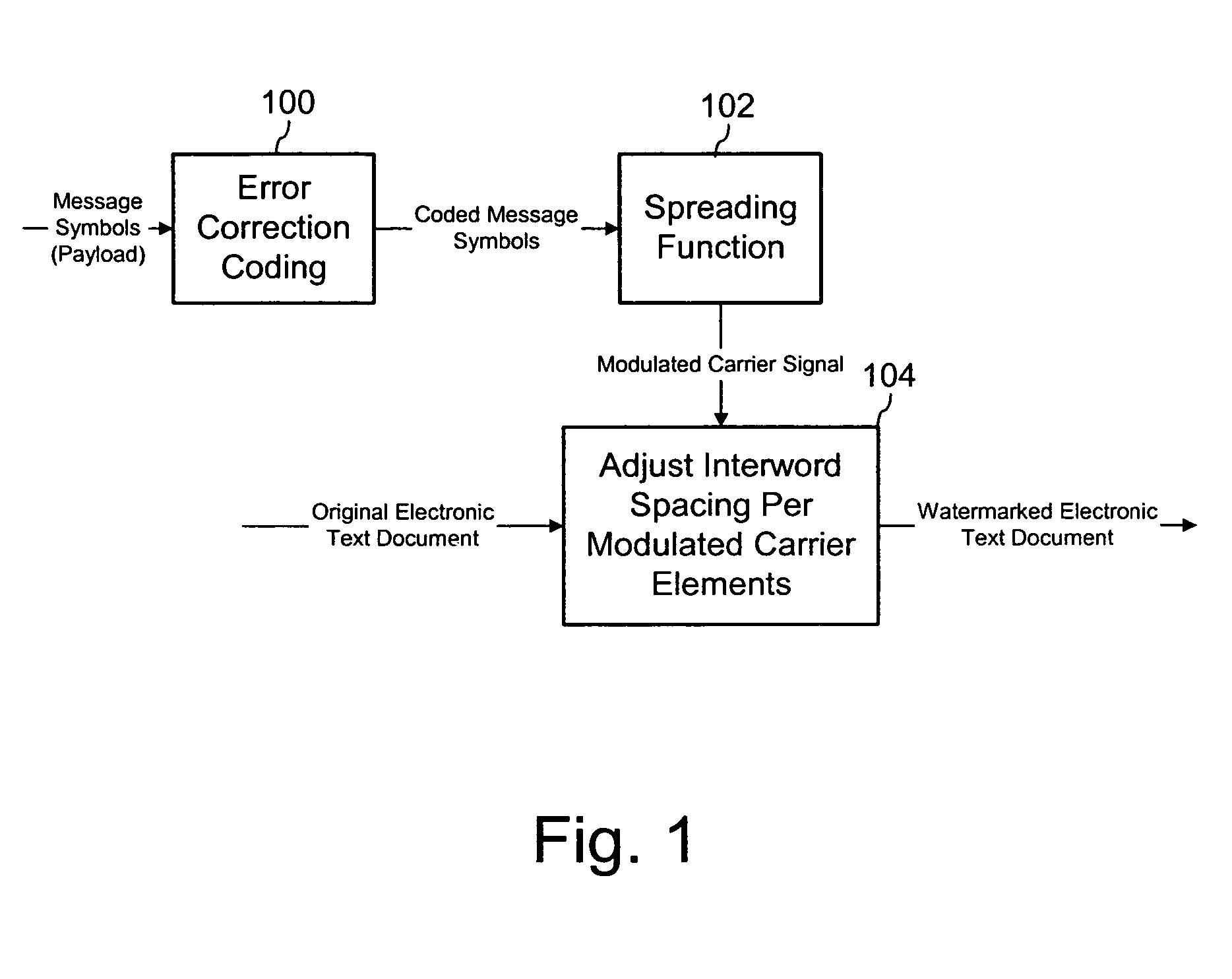
Watermarking electronic text documents
ActiveUS20050039021A1Limited accessAvoid trackingUser identity/authority verificationCharacter and pattern recognitionCarrier signalPaper document
A text watermarking method embeds an auxiliary message in an original electronic text document to form a watermarked text document. The method applies a spreading function to message symbols to spread the symbols over a carrier, which forms a modulated carrier. It maps elements of the modulated carrier to corresponding inter-word spaces in the electronic text document, and applies an embedding function to modify the corresponding inter-word spaces according to elements of the modulated carrier signal such that the modified inter-word spaces hide the modulated carrier signal in the watermarked text document. The message symbols are automatically decodable from the watermarked document without the original electronic text document. A compatible decoder extracts the auxiliary message from a printed or electronic watermarked text document. The decoder automatically measures inter-word spaces in the watermarked text document. It estimates elements of a modulated carrier signal embedded in the inter-word spaces to form an estimated modulated carrier signal, and applies a de-spreading function to the estimated modulated carrier signal to extract message symbols.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
Dual-Loop Dynamic Fast-Tracking MPPT Control Method, Device, and System
ActiveUS20110175454A1Improve response dynamic and overall recovered powerFast dynamic responseDc network circuit arrangementsAc-dc network circuit arrangementsDual loopFast tracking
A converter unit to improve the response dynamics and overall recovered power in a photovoltaic array configuration. Each photovoltaic panel in the photovoltaic array may be coupled to a respective converter unit, which may include a controller to sense an output voltage and output current produced by the solar panel, and control operation of a power converter to output modified voltage and current corresponding to the solar panel onto a bus coupling the converter units. The controller may operate as an analog or (digital) firmware control system to regulate the input voltage of each power converter unit under indirect guidance of a Maximum Power Point Tracking (MPPT) controller to optimize and regulate the resultant power, and achieve very fast dynamic response to environmental transients. Input voltage and output voltage management may be achieved by way of a fast inner control loop and a corresponding MPPT control system configured as an outer guidance loop providing a reference signal to the inner control loop.
Owner:BLUED ACQUISITION CORP
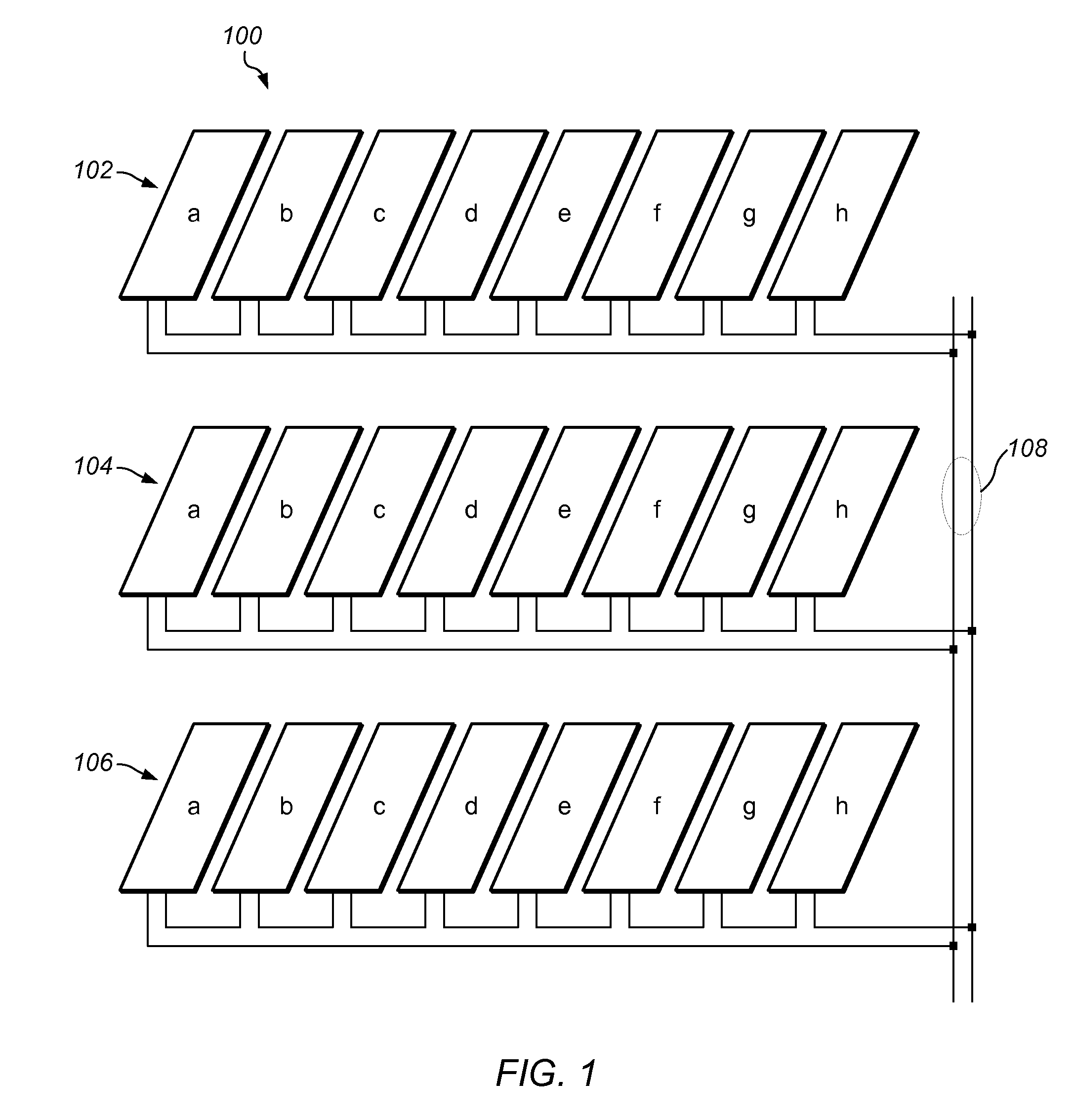
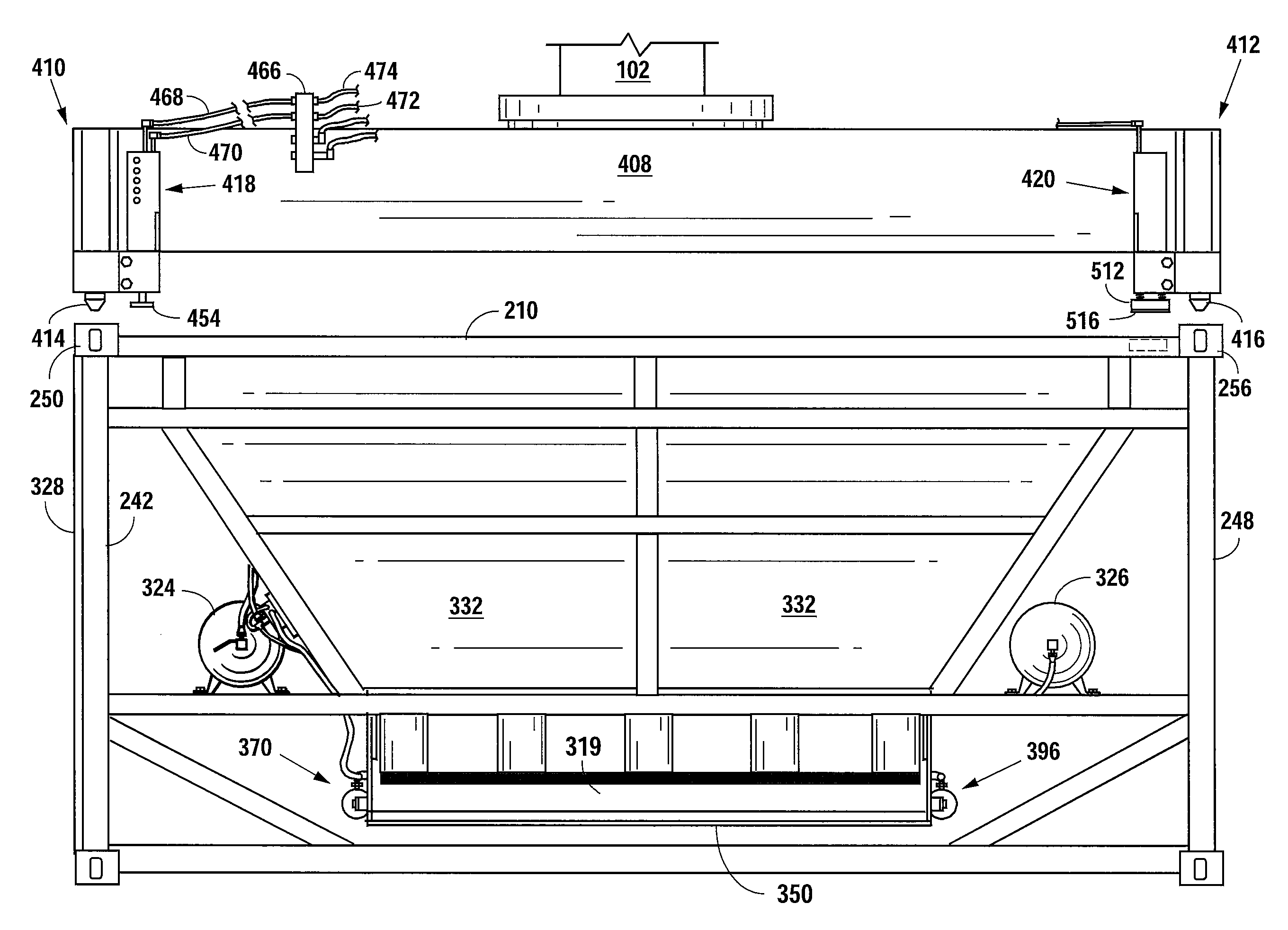
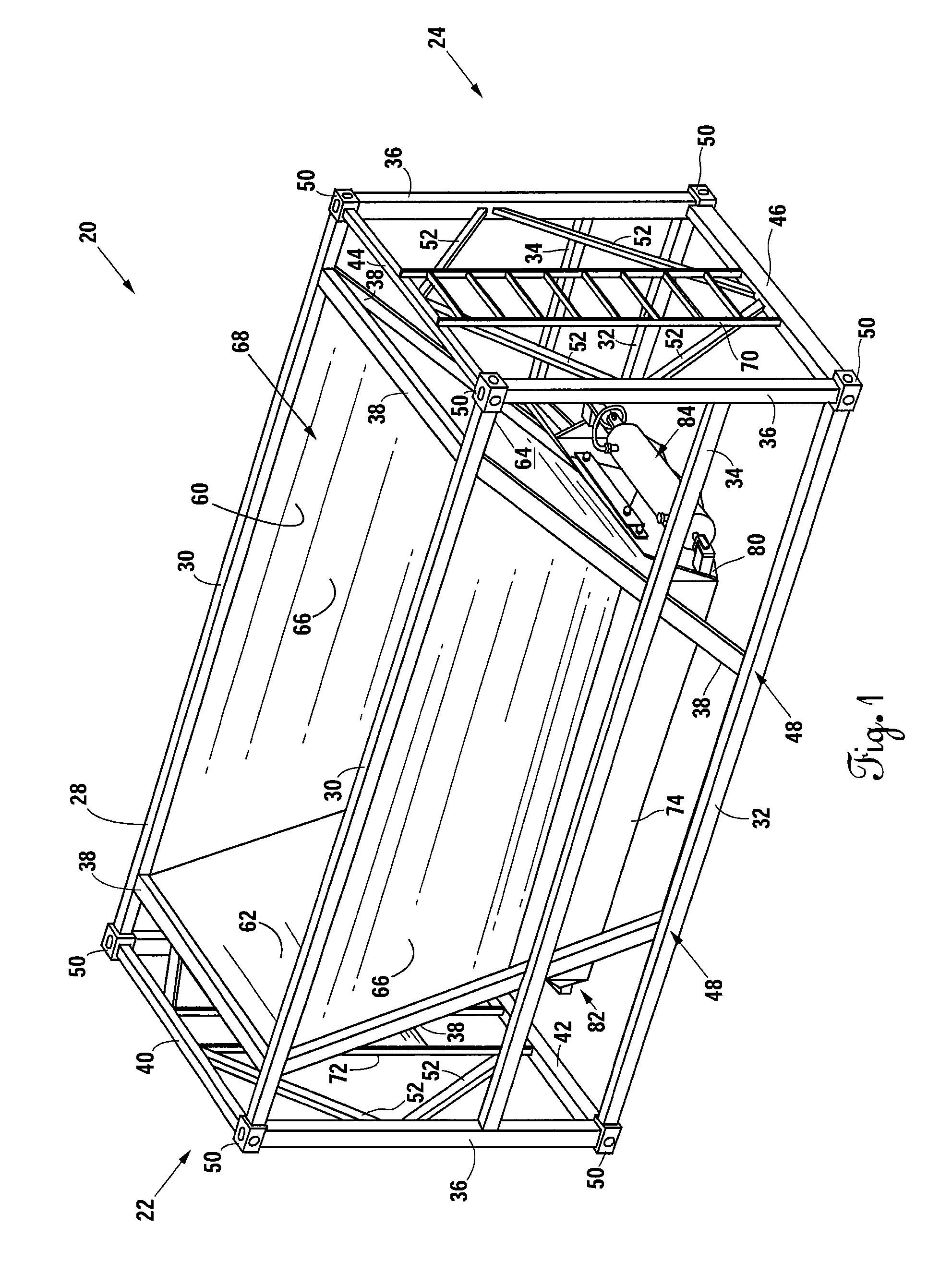
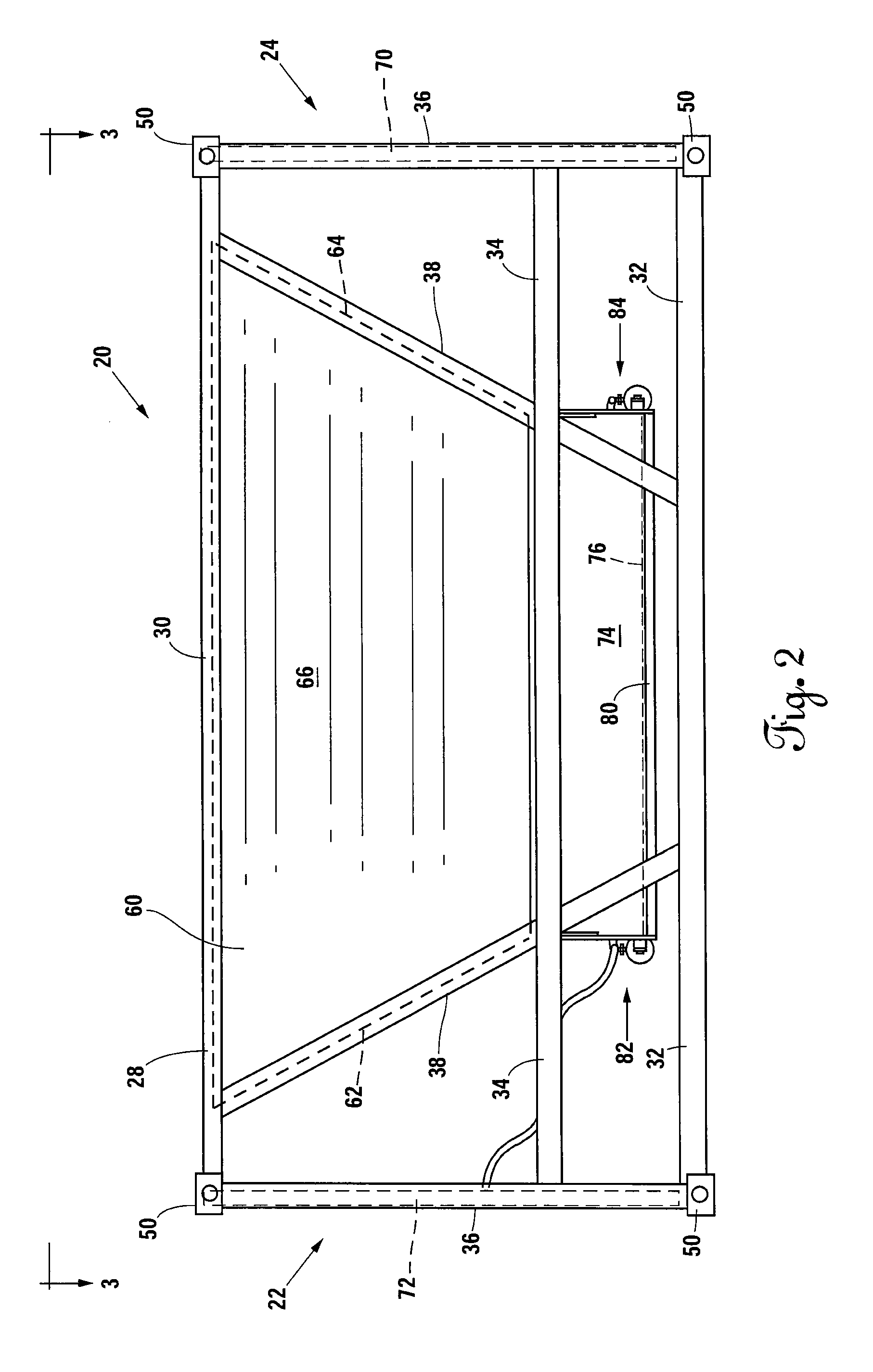
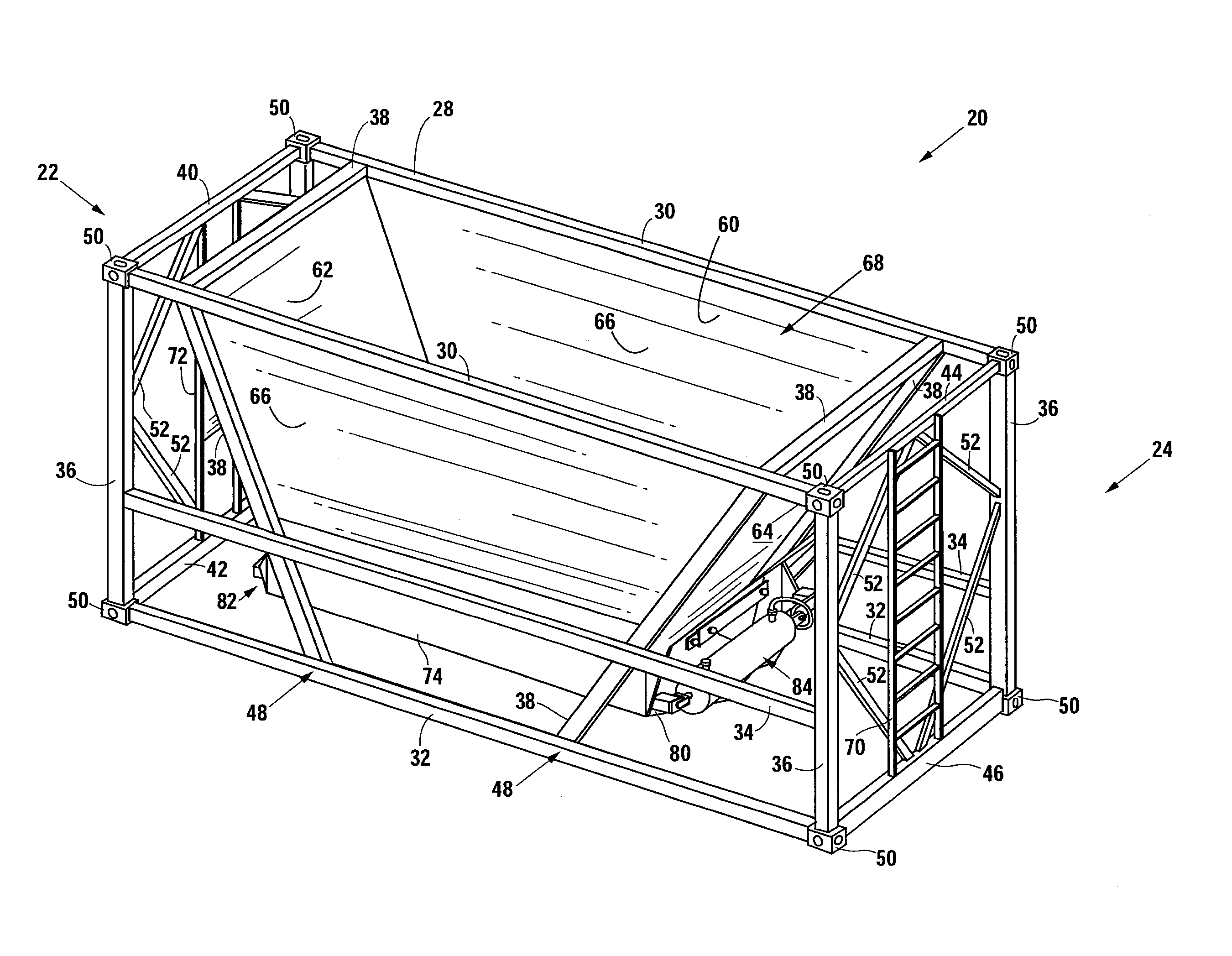
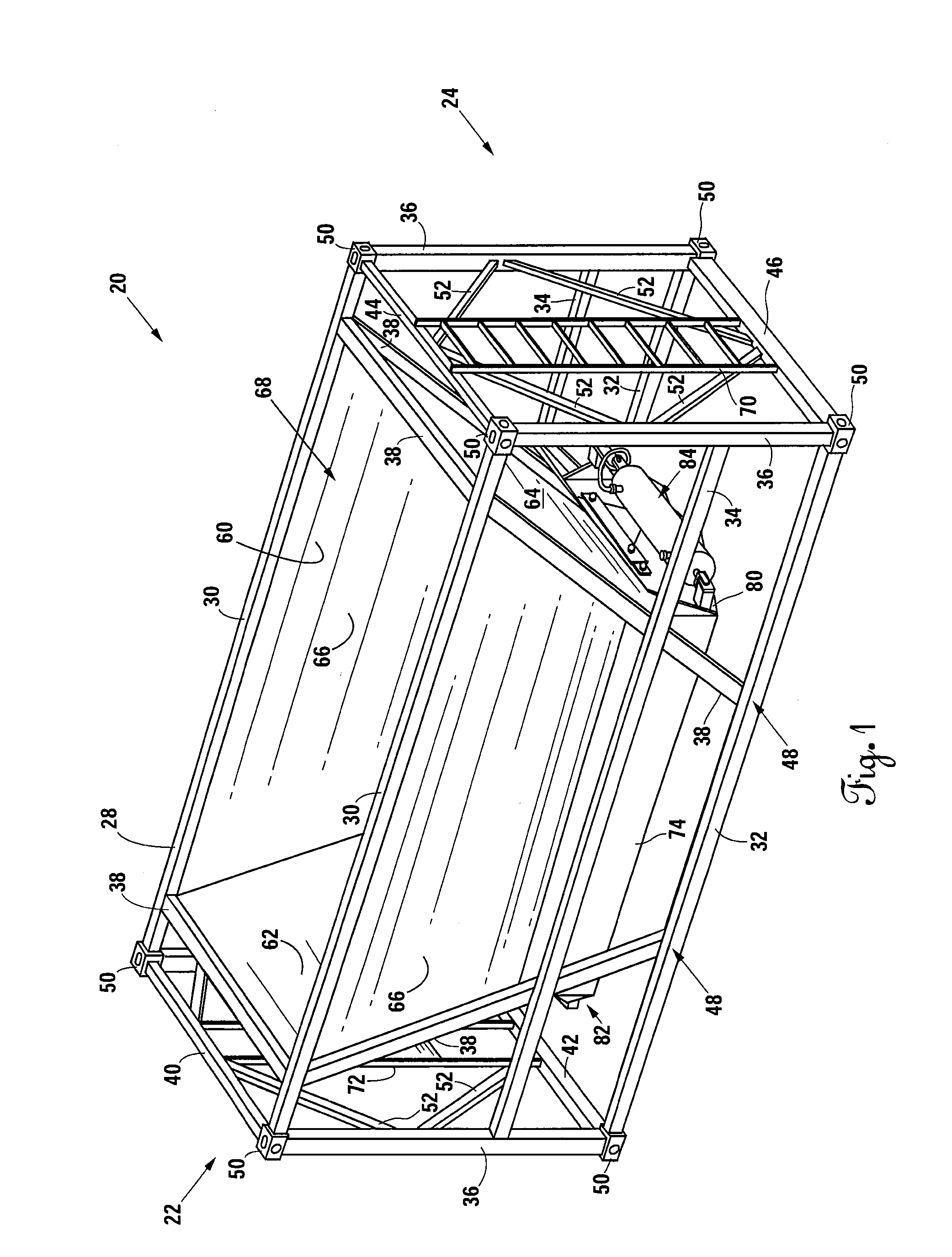
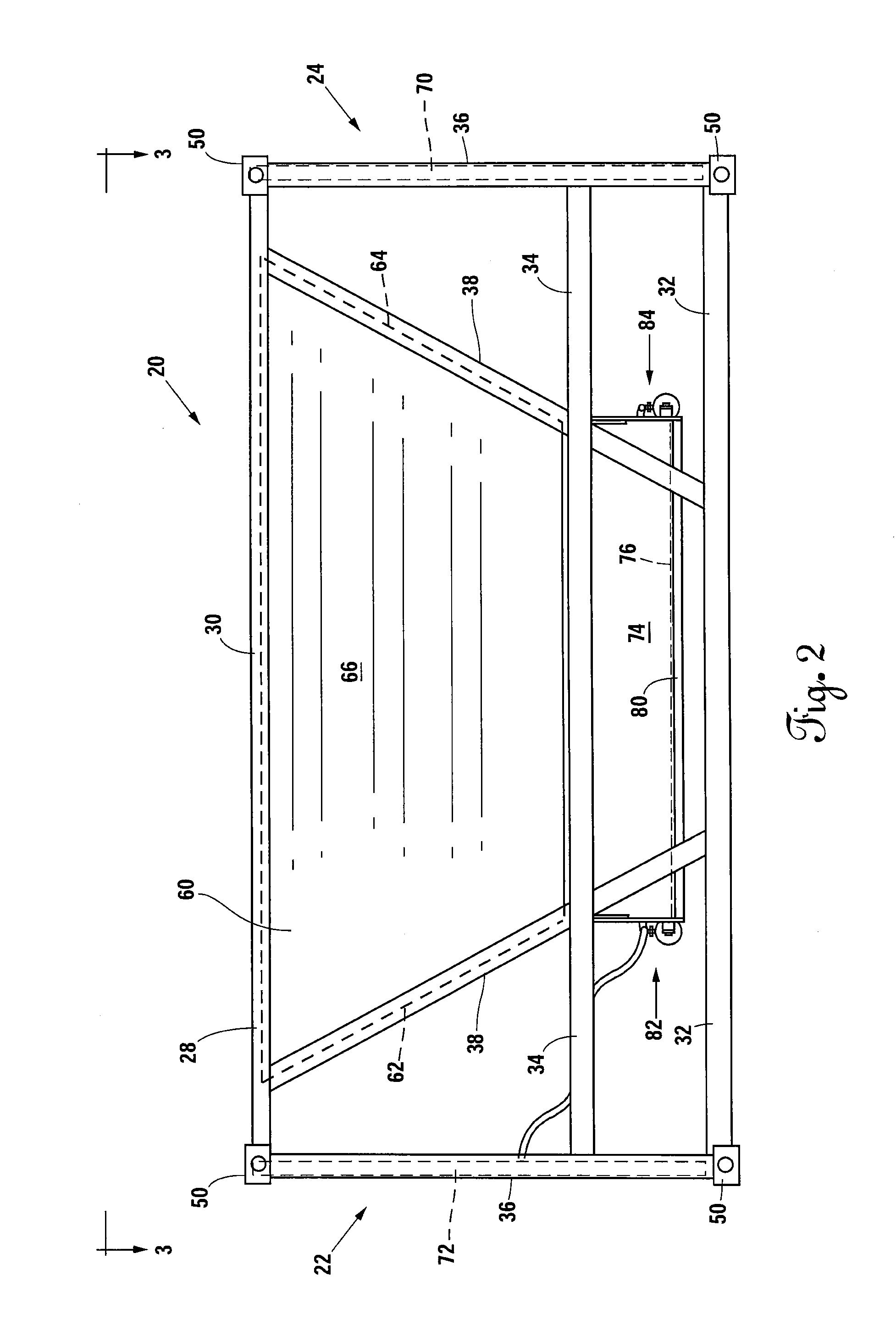
Belly-dump intermodal cargo container
ActiveUS9309064B2Efficient unloadingMinimize chargesLarge containersLoading/unloadingTerrainTransfer system
A container comprising a frame conforming to ISO intermodal container dimensions, a hopper attached within the frame; the hopper defining a chute having a first opening and a second opening, at least one door pivotally attached to the hopper proximal to the second opening; at least one gate assembly attached to the at least one door; a connector apparatus panel mounted to the frame; and at least one actuating fluid or electrical line connected between the at least one gate and the connector apparatus panel. An alternative embodiment includes at least one air tank connected to the container and filled through an air transfer system and a plunger system to cause actuation of container doors for releasing of materials into a second receptacle and where the air transfer and plunger systems reside partially on a rough terrain container handler vehicle.
Owner:LOGICHAUL LOGISTICS LLC
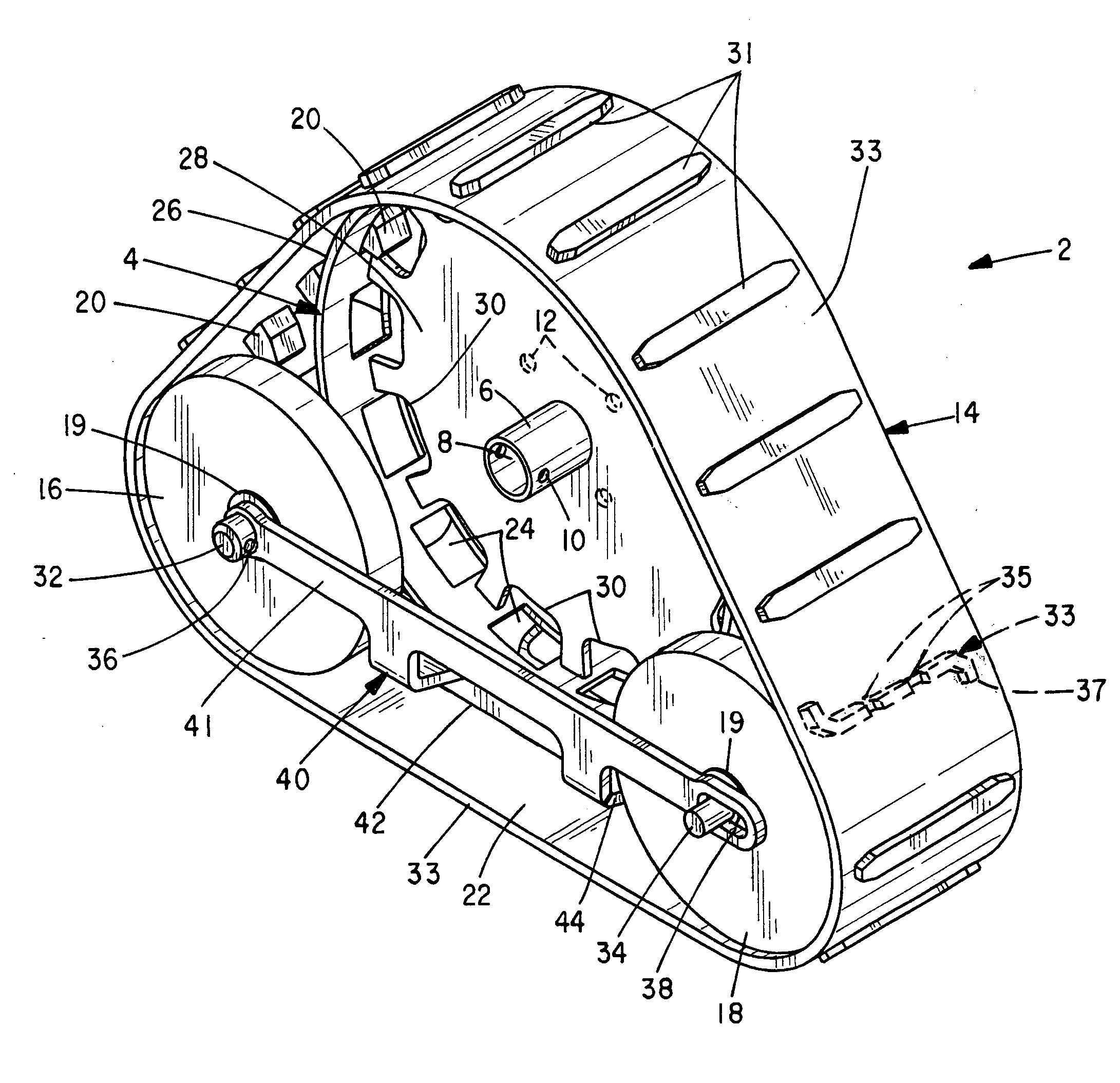
Frameless track assembly
ActiveUS20120161511A1Prevent collection of abrasive materialAvoid trackingPortable liftingEndless track vehiclesSprocketEngineering
A track assembly comprising an endless track trained about a sprocket and forward and aft sets of idler wheels. A plurality of apertures at the sprocket engage drive lugs that project from an interior track surface. Longitudinal stabilizer arms restrain the idler wheel axles, idler wheels, sprocket support rollers, sprocket and track against lateral movement and tension the track. Overlapping seals are formed at the idler wheels and / or sprocket support rollers. Alternative sprockets having cutouts or pockets that capture different drive lug configurations are also disclosed along with several alternative track tensioning assemblies that rotate in an eccentric fashion to tension the track.
Owner:BRAZIER GLEN
Belly-Dump Intermodal Cargo Container
ActiveUS20150368052A1Reduce in quantitySave a lot of costLarge containersArticle unpackingTerrainTransfer system
A container comprising a frame conforming to ISO intermodal container dimensions, a hopper attached within the frame; the hopper defining a chute having a first opening and a second opening, at least one door pivotally attached to the hopper proximal to the second opening; at least one gate assembly attached to the at least one door; a connector apparatus panel mounted to the frame; and at least one actuating fluid or electrical line connected between the at least one gate and the connector apparatus panel. An alternative embodiment includes at least one air tank connected to the container and filled through an air transfer system and a plunger system to cause actuation of container doors for releasing of materials into a second receptacle and where the air transfer and plunger systems reside partially on a rough terrain container handler vehicle.
Owner:LOGICHAUL LOGISTICS LLC
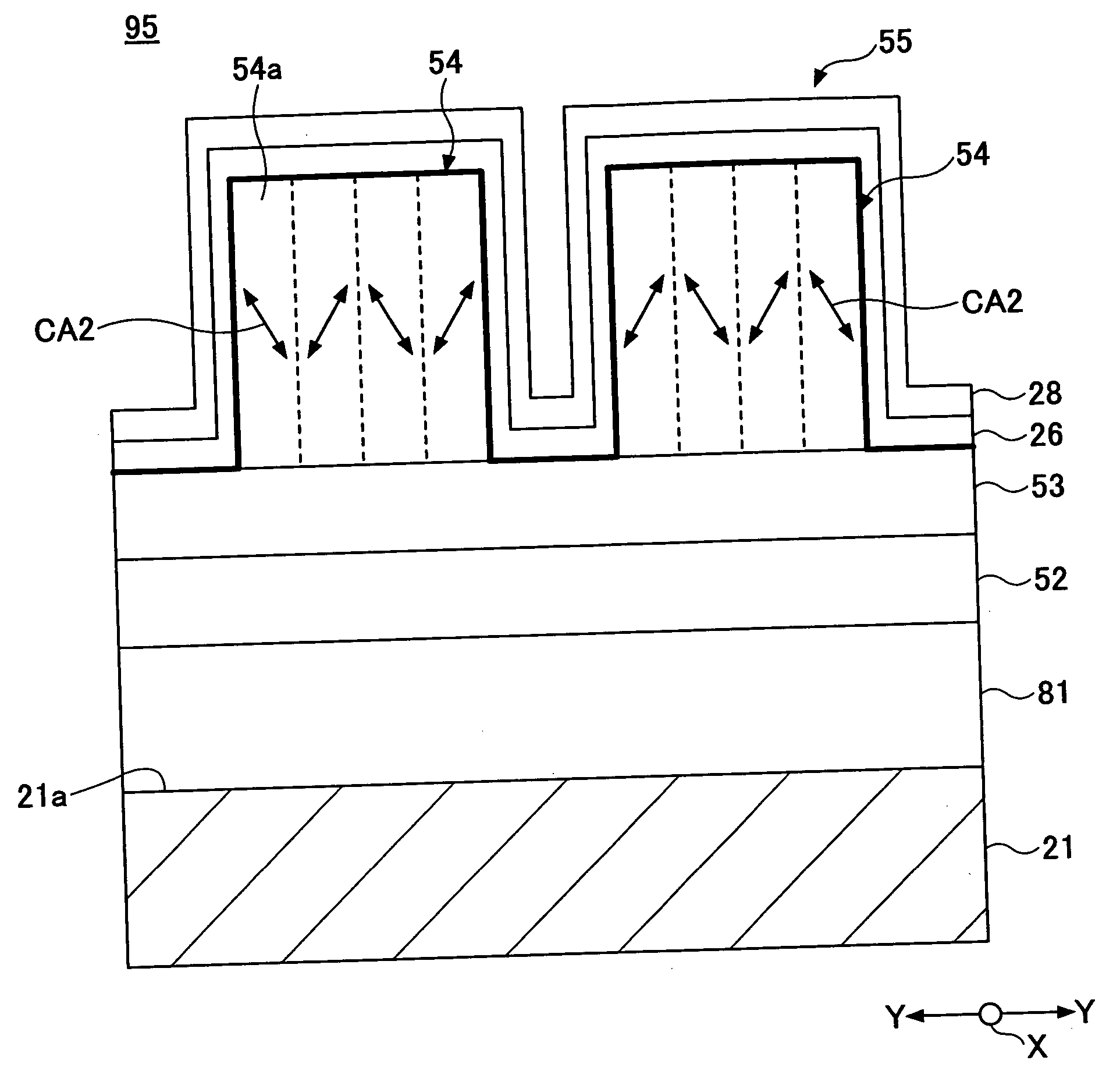
Magnetic recording medium and magnetic storage apparatus
InactiveUS20060222896A1Reduce noiseGood ease in recordingRecord information storageCoating part of support with magnetic layerMagnetic storageRecording layer
A magnetic recording medium includes a plurality of recording cells separated from each other on a substrate in a recording direction and a track width direction perpendicular to the recording direction. The recording cell includes a recording layer. The recording layer has a magnetic easy axis inclining in a designated oblique direction against a surface of the substrate.
Owner:FUJITSU LTD
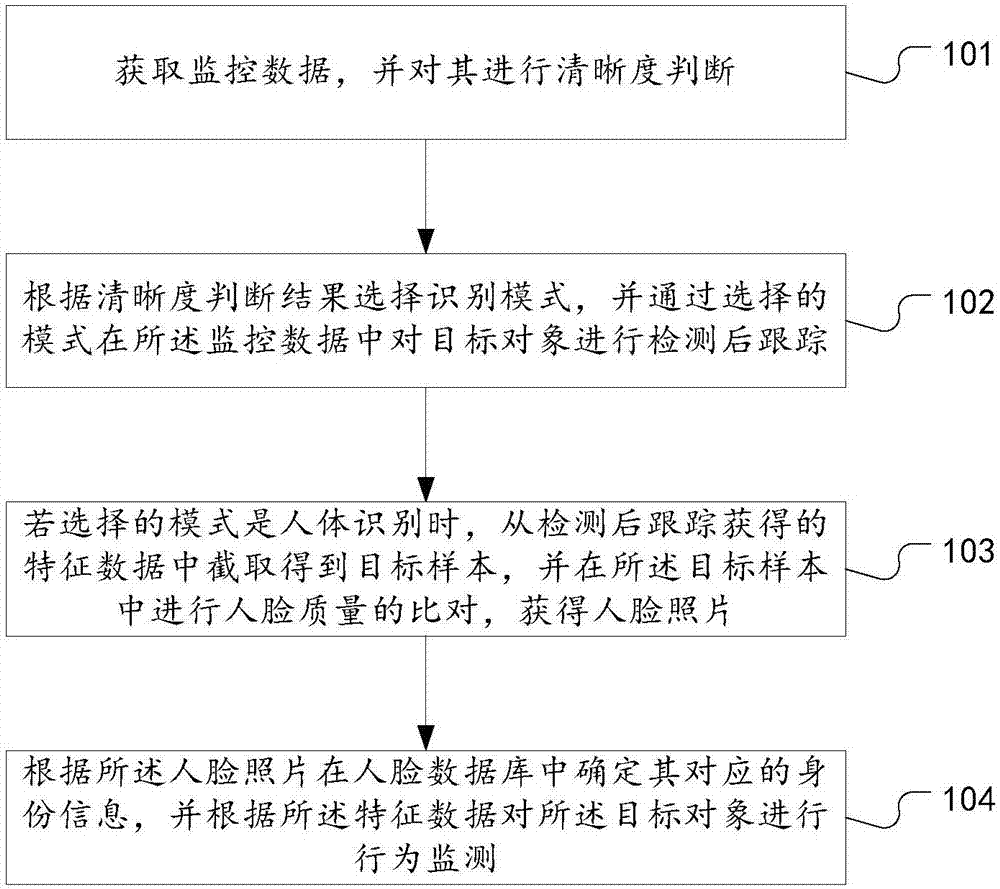
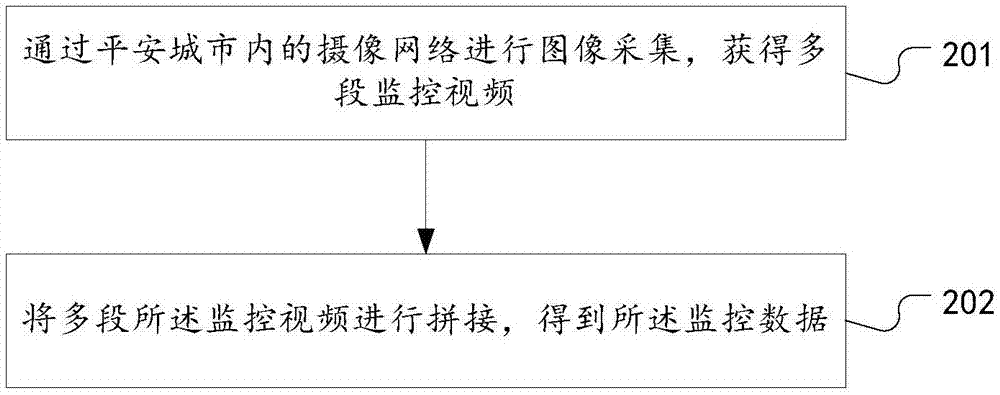
People searching method and system based on face and human body identification
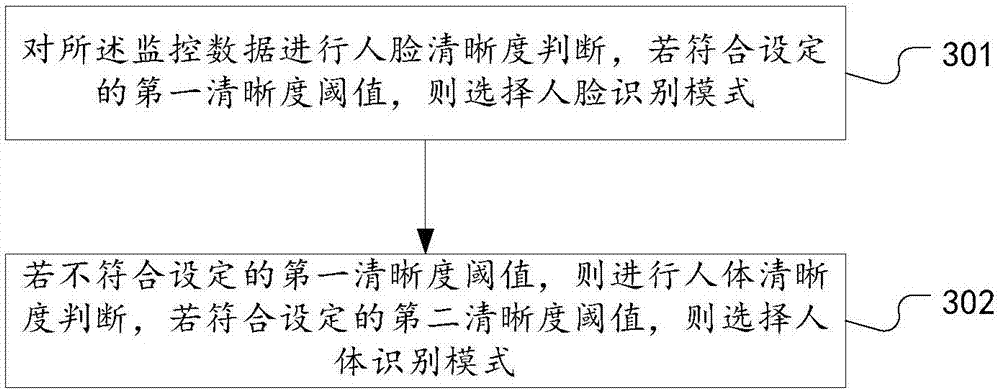
InactiveCN107292240AAvoid detectionAvoid trackingBiometric pattern recognitionHuman bodyFace detection
The invention discloses a people searching method and system based on face and human body identification; the method selects an identification mode from two identification modes through sharpness determinations, thus providing options for the identification modes, and effectively improving the identification performance; the method uses a human body identification mode to carry out after-detection tracking, thus preventing face identification failure caused by an unclear face, realizing face detection and tracking of a target person, improving the city safety level without changing hardware, and saving modification costs; the method uses the human body identification to realize ID authentication and behavior monitoring, thus reducing ID authentication and monitoring failure probability, and improving post-event tracing back capability; the searching system comprises a data determination unit, a mode selection unit, and a human body identification unit; the human body identification unit also comprises a face obtaining module and a behavior detection module; beneficial effects of the method and system are realized.
Owner:深圳市深网视界科技有限公司
Peer-to-peer network and node of a peer-to-peer network
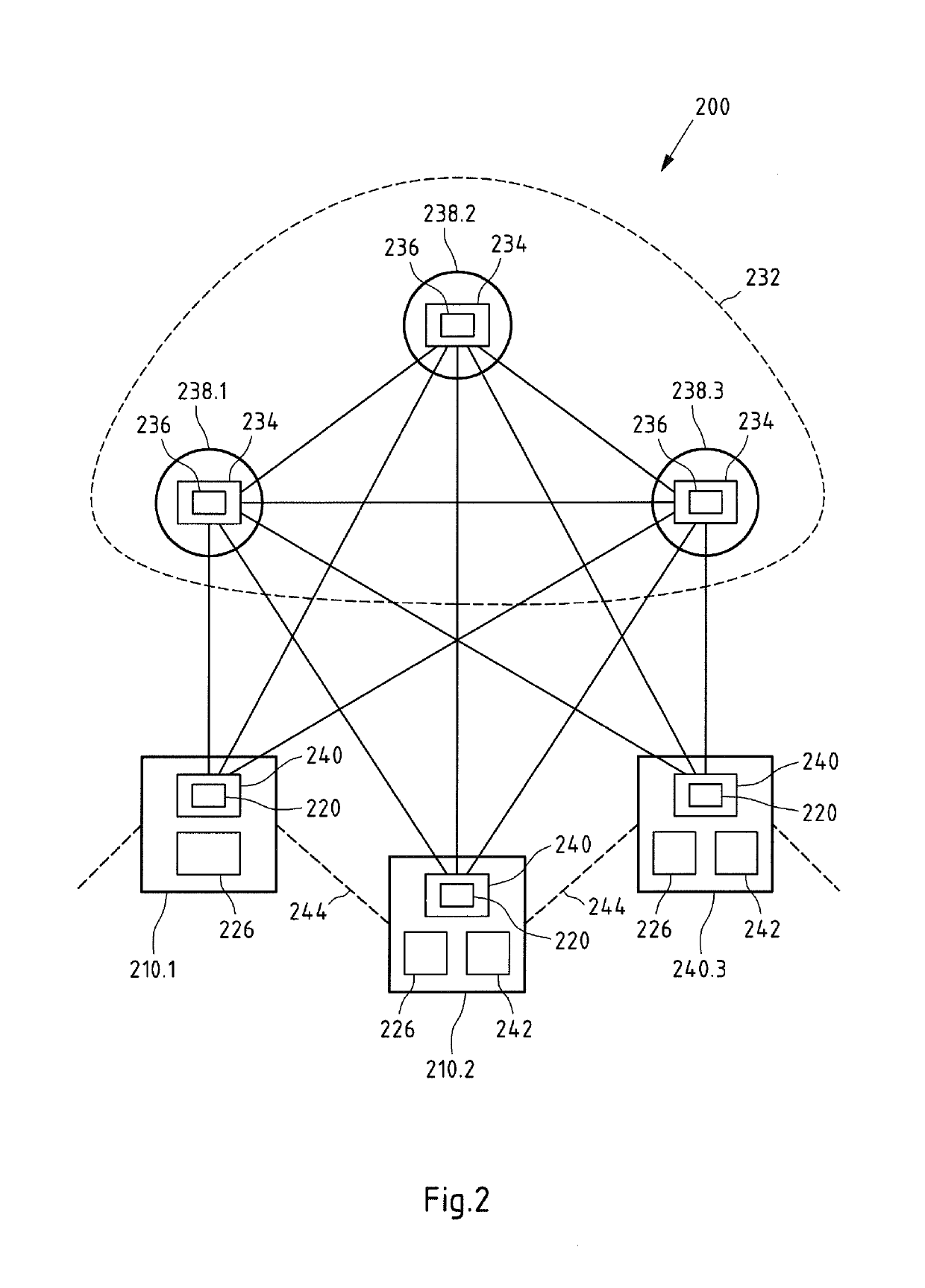
ActiveUS20190089716A1Simple processImprove tamper resistanceSynchronisation receiversTime-division multiplexDistributed computingPeer-to-peer
The invention relates to a peer-to-peer network having at least one first node with a first clock module and part of a peer-to-peer application. Also included is at least one second node with a second clock module and part of the peer-to-peer application. At least one communication connection between the first node and the second node is establishable. The first node comprises at least one first synchronization clock module. The second node comprises at least one second synchronization clock module. At least the first synchronization clock module is configured to transmit at least one first synchronization clock message to the second synchronization clock module via the communication connection, the second synchronization clock module is configured to synchronize the clock signal of the second clock module to the clock signal of the first clock module based on synchronization information included in the first synchronization clock message.
Owner:INNOGY INNOVATION GMBH
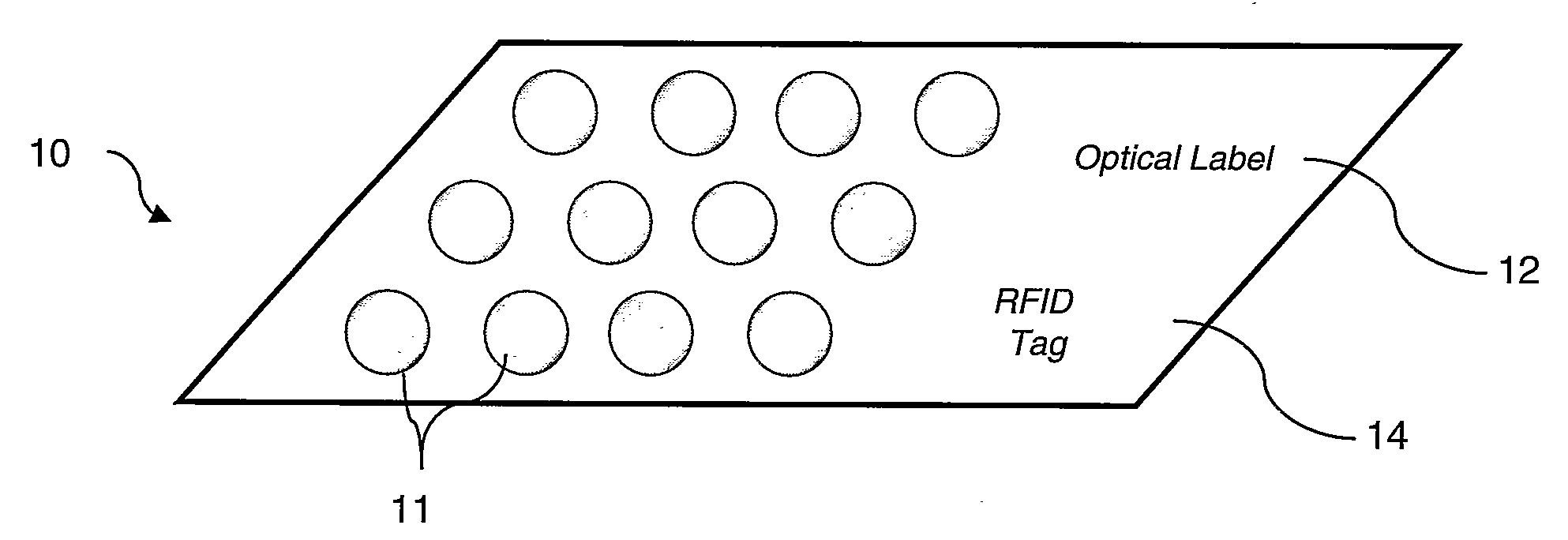
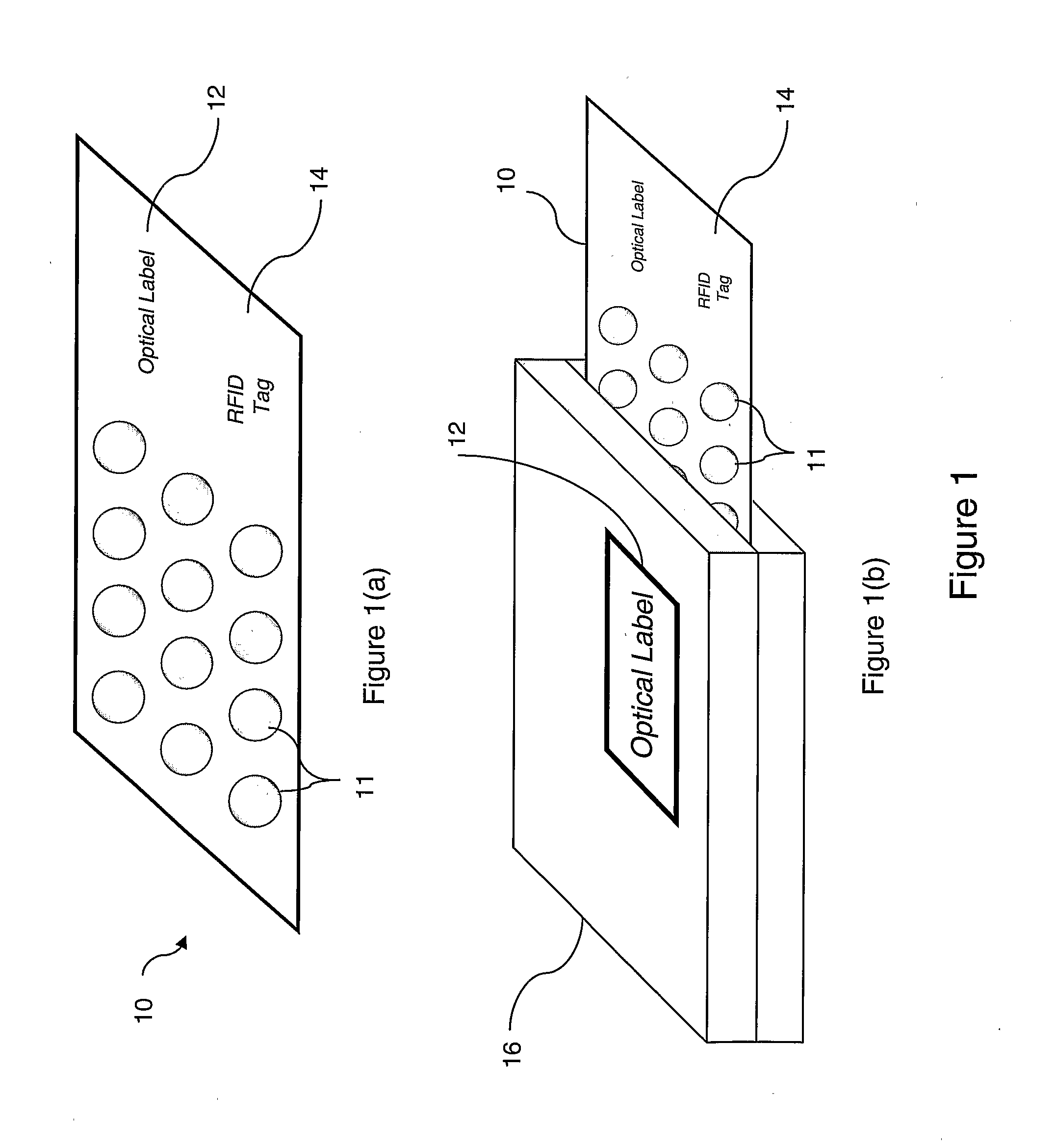
Method and device for obtaining item information using RFID tags
ActiveUS20090273451A1Avoid it happening againGuaranteed successCo-operative working arrangementsSubscribers indirect connectionIdentification deviceComputer science
Methods and devices for enabling a user to obtain item information relating to an item (10), the item having associated therewith an item identification means (12) and an RFID response means (14) arranged to provide a predetermined response on being subjected to a currently applicable trigger signal; the method comprising steps of: establishing from the item identification means (12) item identification information; using the item identification information to determine from an item information source (30) a currently applicable trigger signal for the RFID response means (14); subjecting the RFID response means (14) to the currently applicable trigger signal; receiving a predetermined response from the RFID response means (14); and using the predetermined response to obtain item information from the item information source (30); wherein the RFID response means (14) is arranged to generate a new currently applicable trigger signal and a new predetermined response associated therewith following subjecting of the RFID response means (14) to the currently applicable trigger signal.
Owner:BRITISH TELECOMM PLC
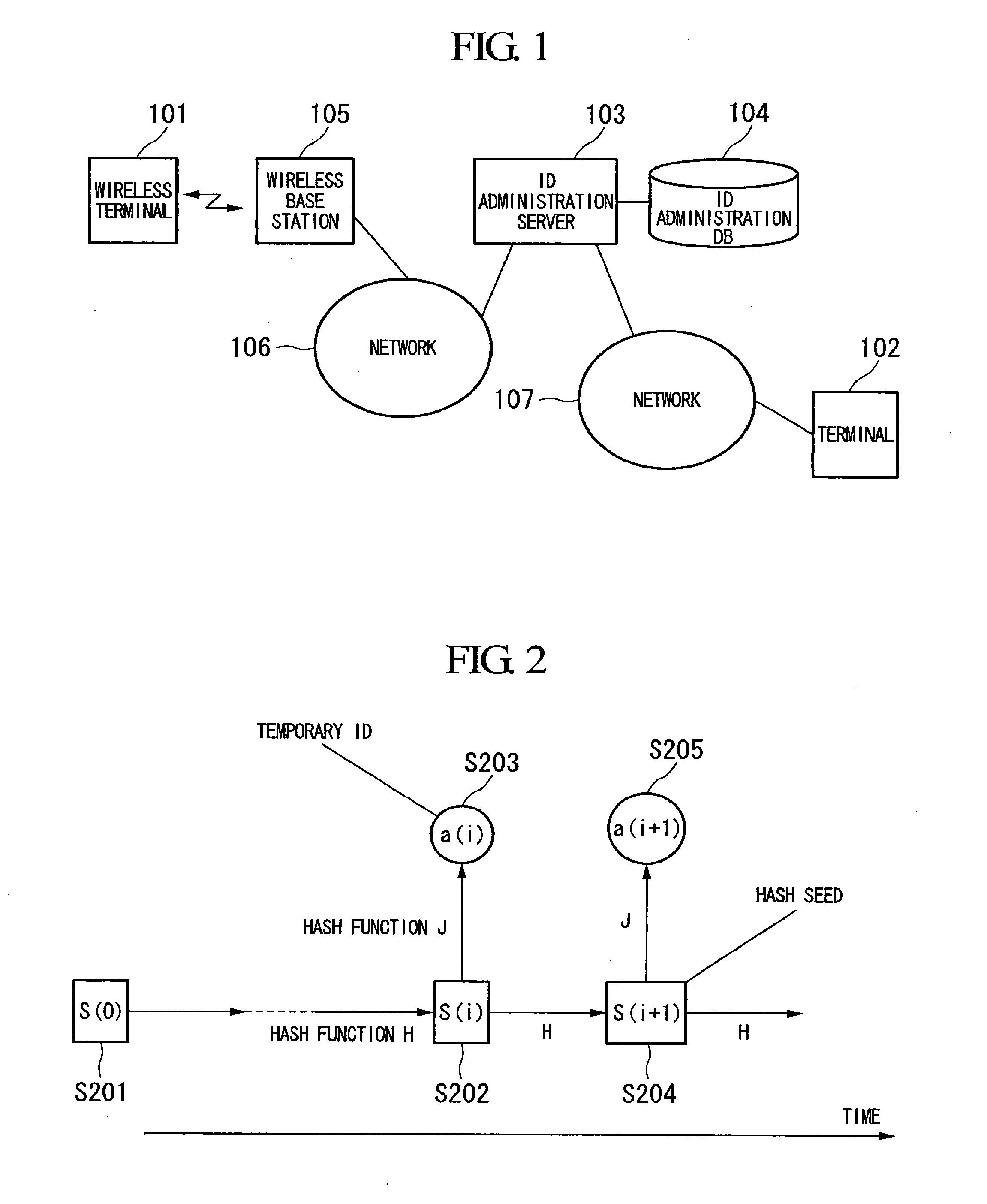
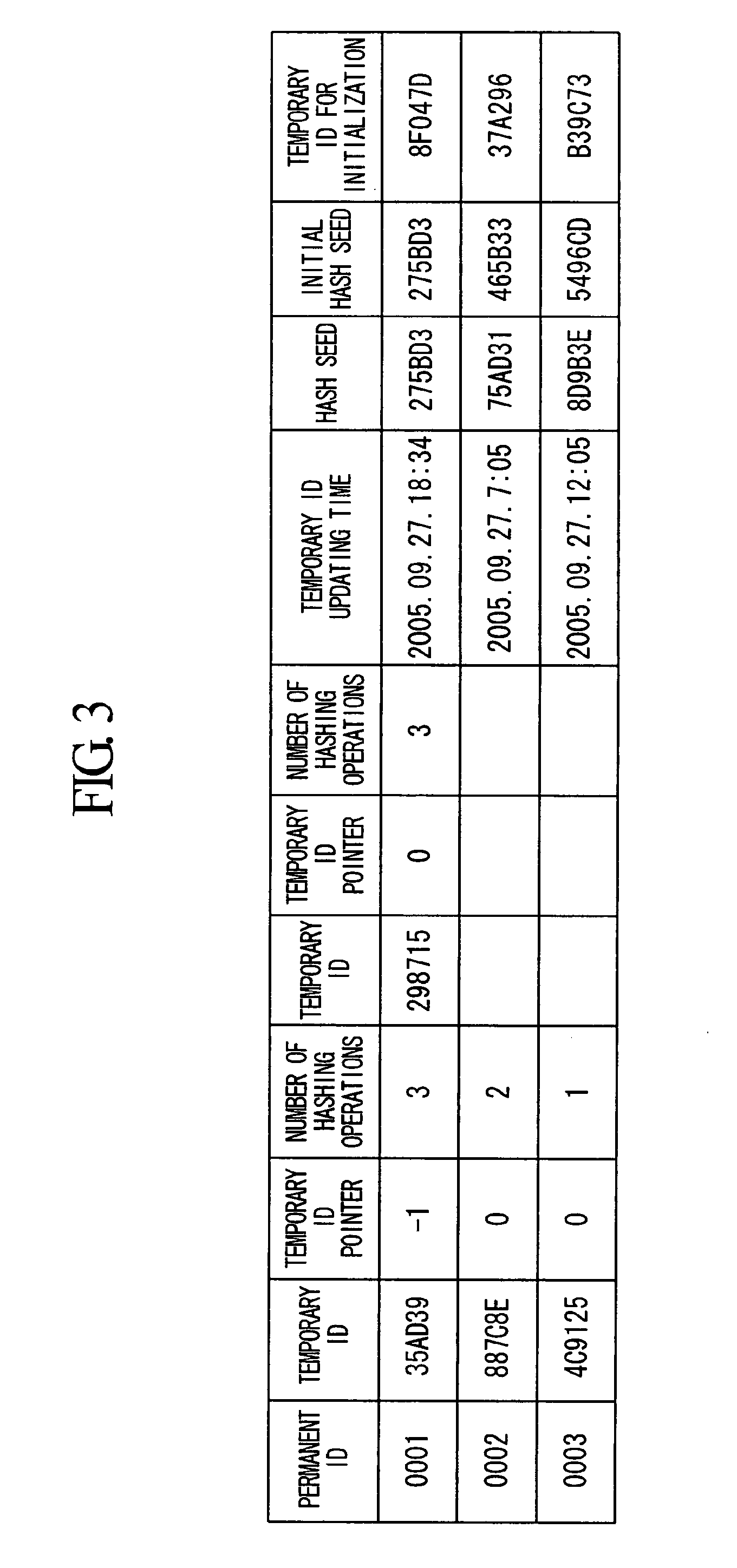
Terminal Identification Method, Authentication Method, Authentication System, Server, Terminal, Wireless Base Station, Program, and Recording Medium
ActiveUS20110072121A1Ensuring protection of privacyAvoid trackingEnergy efficient ICTDigital computer detailsHash functionComputer terminal
A terminal identification method is provided which enables two-way communications between terminals and a network while identifying terminal IDs and protecting privacy. Also, authentication method and system are provided which require no complicated calculating process, less steps and smaller amount for wireless communications, and less power consumption. A server and terminal share a hash function and an initial value determined for each terminal, calculate the same temporary ID by hashing the initial value the same number of times with the hash function, and identify the terminal using the calculated temporary ID. The server and the terminal also hold a common hash function and authentication information, acquire an authenticating communication parameter from communication parameters temporarily common during communication, and generate an authentication key using the authentication information, the authenticating communication parameter, and the hash function. Then at least one of the server and terminal performs authentication using the generated authentication key.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
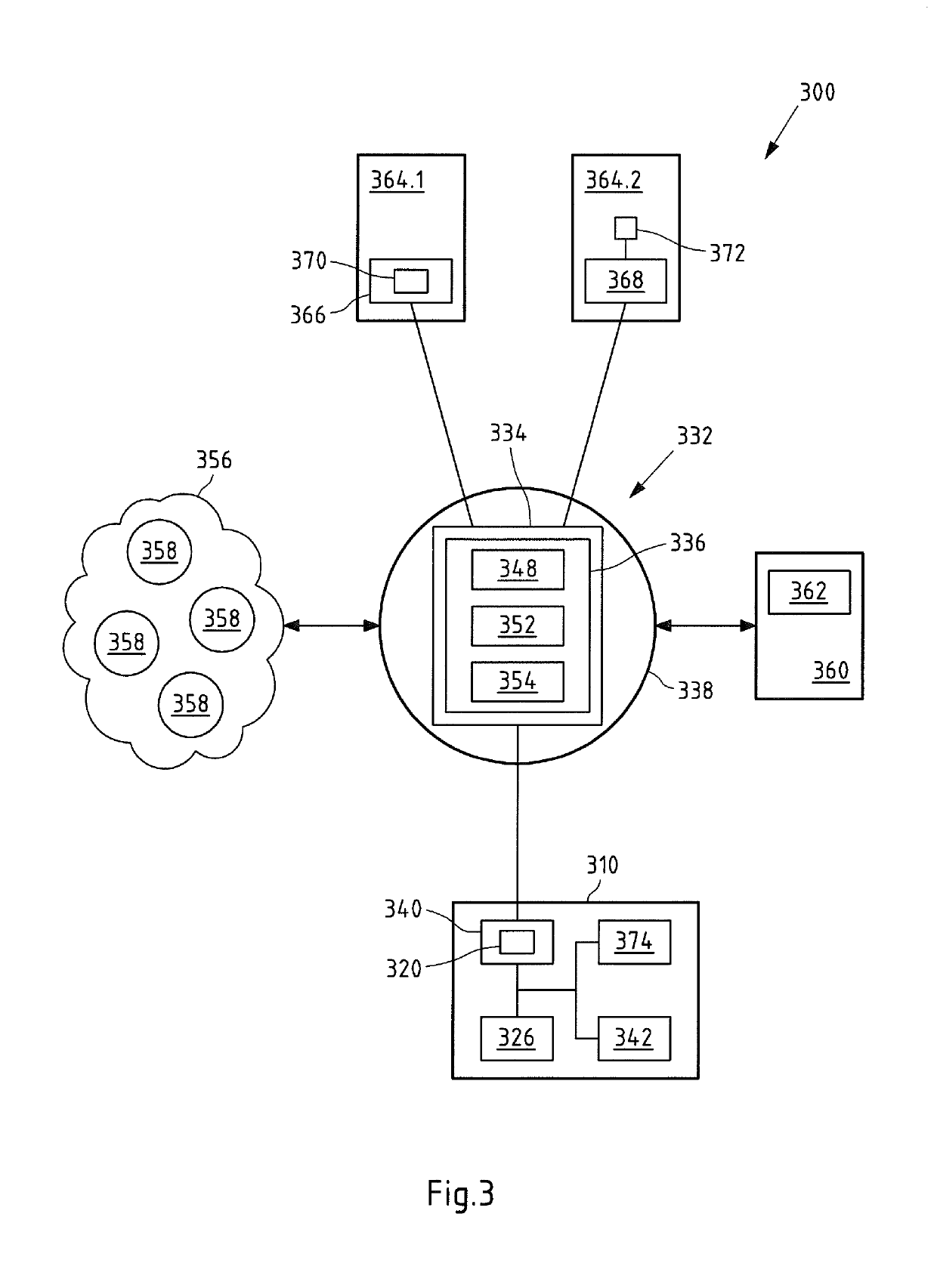
Software defined networking system
ActiveUS20190149429A1Reduce amountImprove scalabilityData switching networksSoftware-defined networkingSoftware
The invention relates to a Communications system, in particular, a software defined networking communications system, comprising at least one network device comprising at least one data forwarding unit configured to forward at least one data packet, wherein the network device comprises at least one first peer-to-peer module, wherein the first peer-to-peer module is configured to communicate with at least one peer-to-peer application of at least one peer-to-peer network, wherein the peer-to-peer application comprises at least one controlling means configured to manage at least the network device.
Owner:INNOGY INNOVATION GMBH
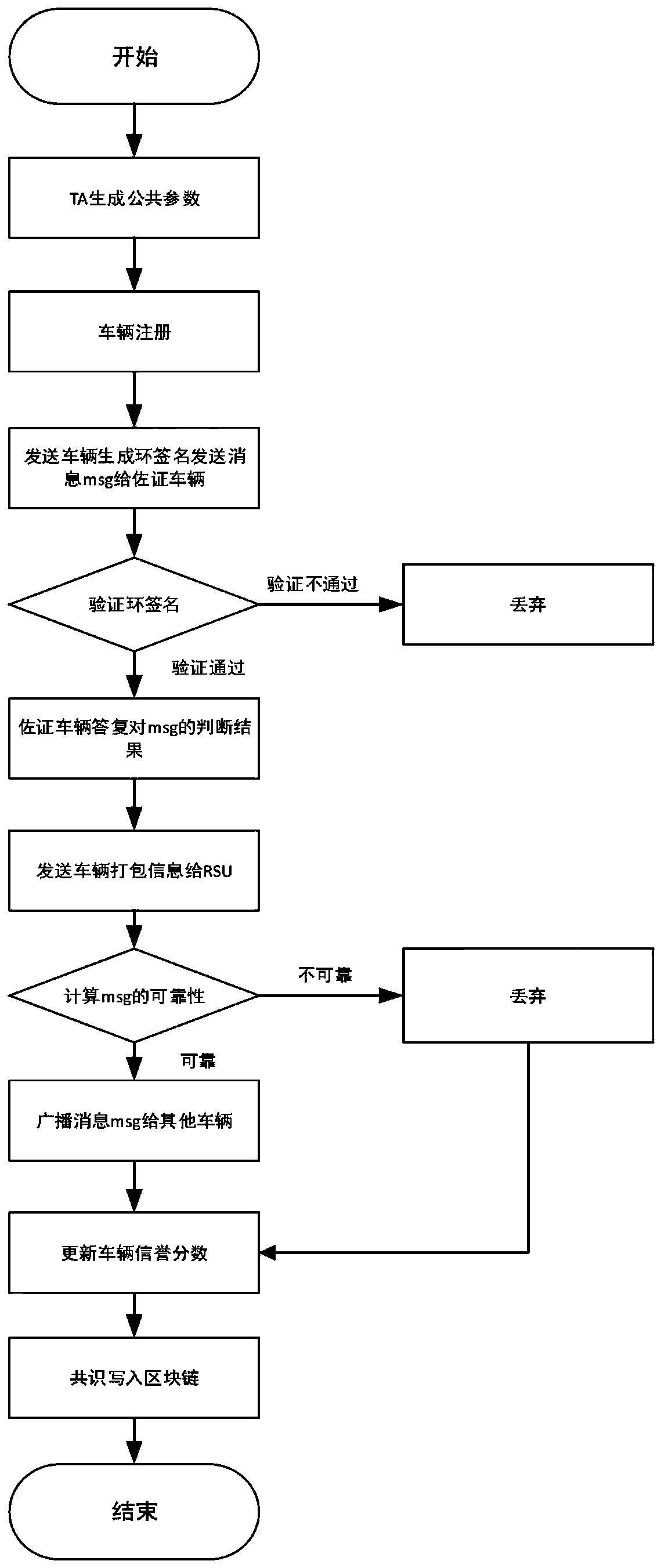
Internet of Vehicles privacy protection trust model based on block chain
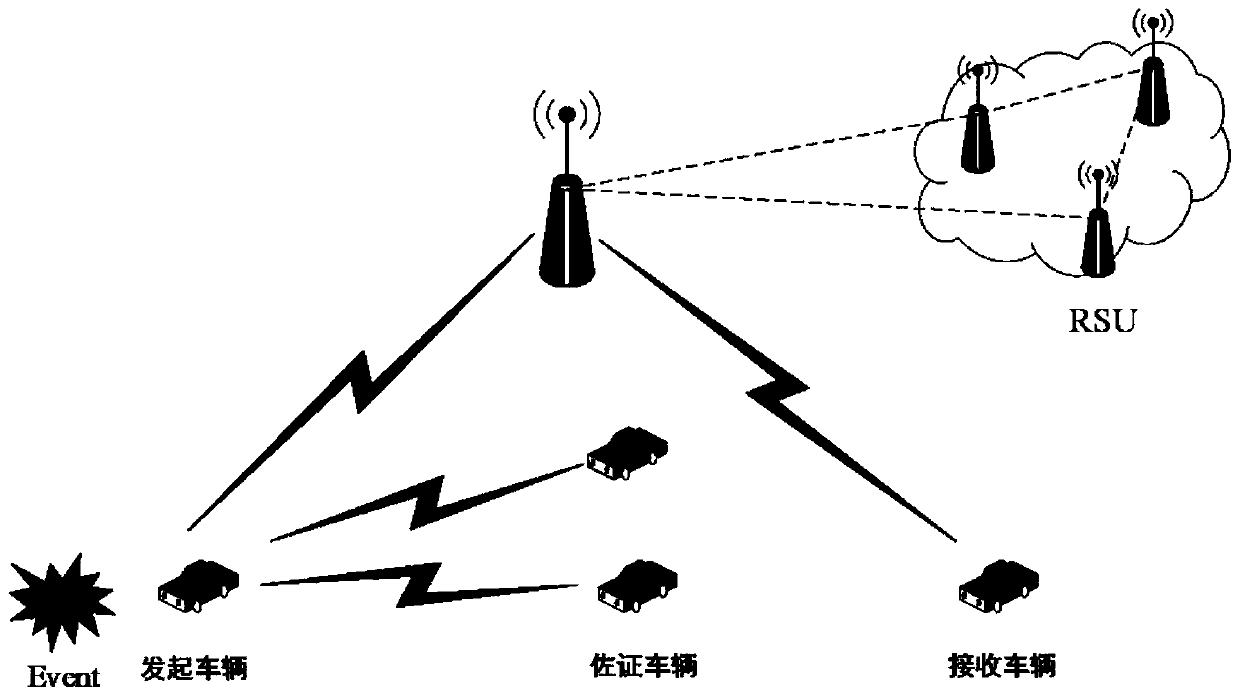
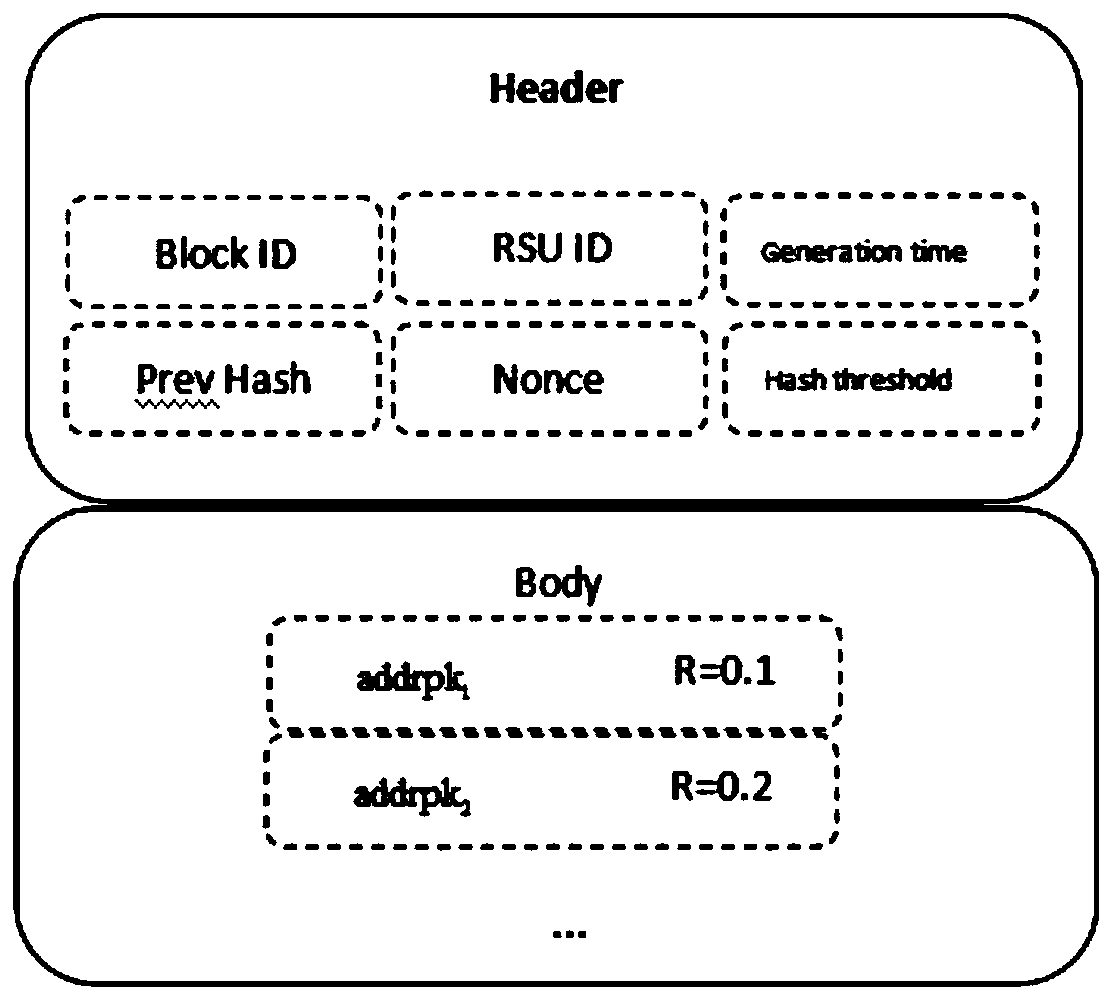
ActiveCN110300107AAddress privacy concernsResolve trust issuesUser identity/authority verificationRing signaturePrivacy protection
The invention provides an Internet of Vehicles privacy protection trust model based on a block chain. Vehicles on the road generate and broadcast messages through the vehicle-mounted ad hoc network toshare surrounding traffic information so as to improve the traffic efficiency and safety. However, due to the untrusted network environment of the vehicle-mounted ad hoc network, the privacy of the vehicle is easy to expose, and whether the received message is reliable cannot be judged. The message is anonymously sent by the vehicle through the ring signature technology, so that the vehicle is prevented from being tracked by a malicious vehicle. Messages sent by the vehicle are evaluated and screened through a reputation evaluation mechanism based on the block chain technology, and forged information in the messages is filtered. Based on the characteristics of the block chain, it is guaranteed that the vehicle reputation is not maliciously tampered, real-time synchronous updating of the vehicle reputation is achieved, and the safety and usability of the vehicle-mounted ad hoc network are further improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Magnetic head for perpendicular magnetic recording with shield around main magnetic pole
ActiveUS8289649B2Avoid it happening againEasy to shapeElectrical transducersManufacture head surfaceMagnetic polesEngineering
Owner:HEADWAY TECH INC
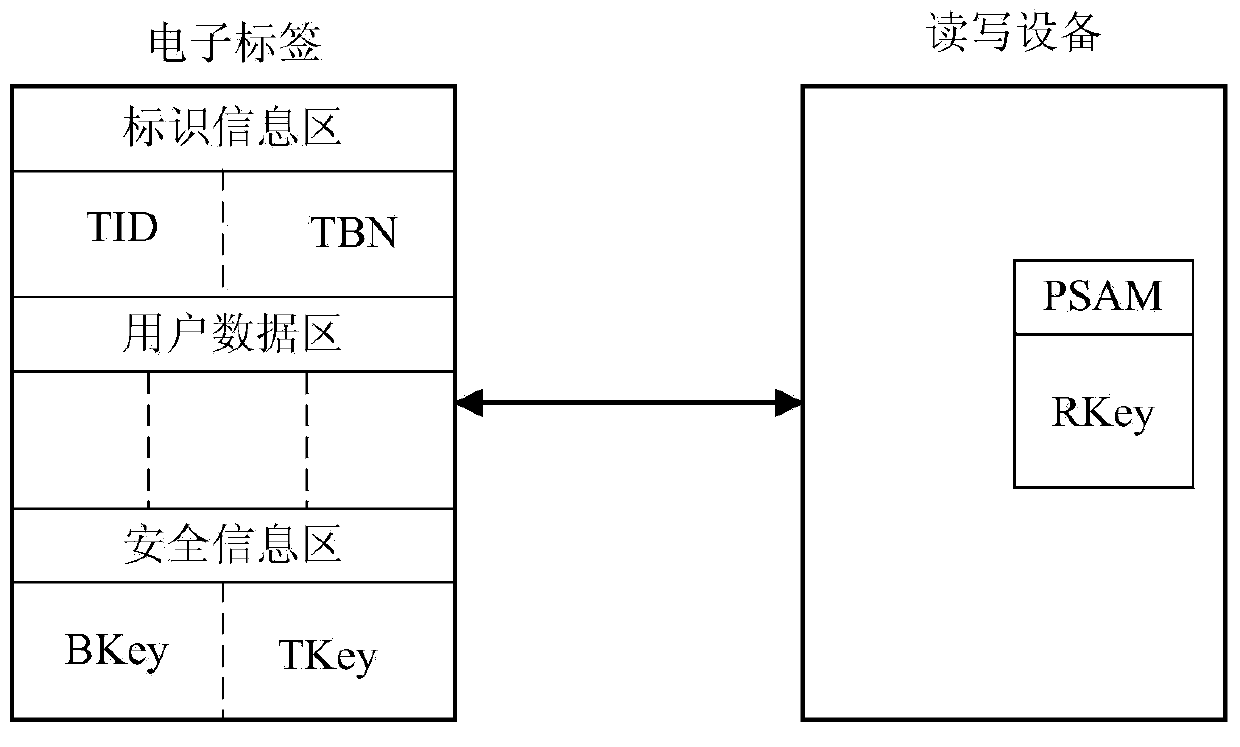
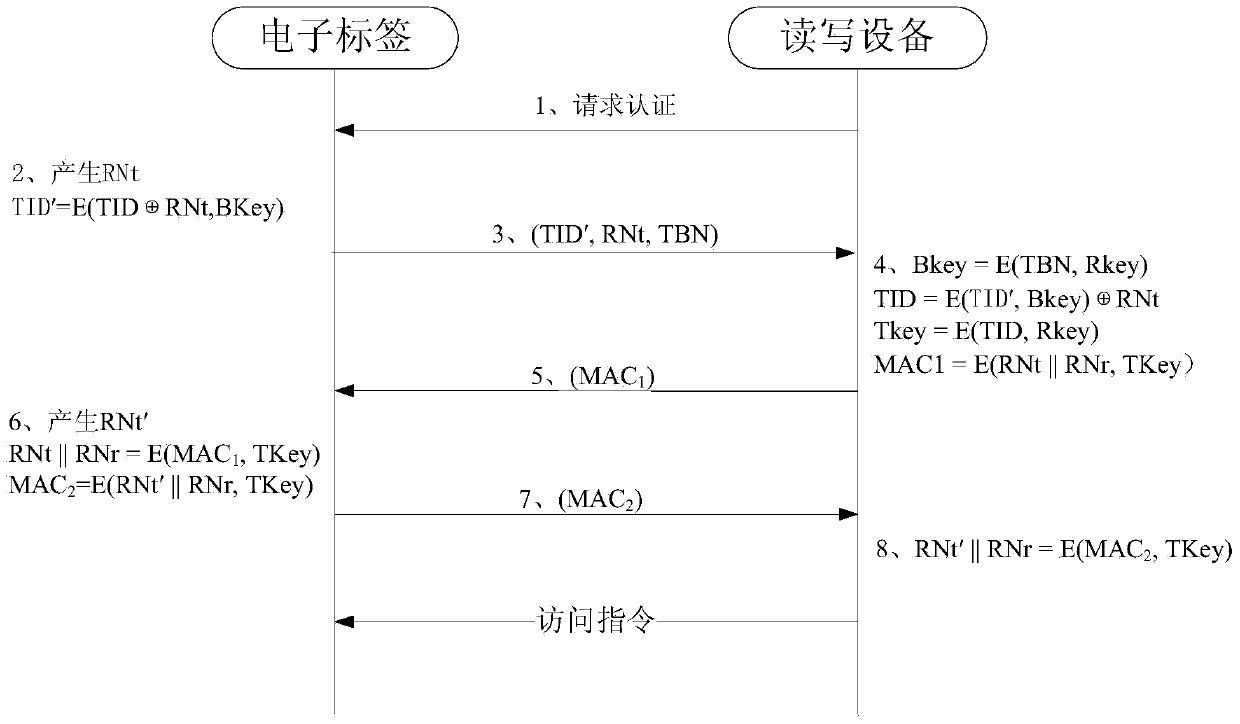
Safety authentication method for hiding ultrahigh-frequency electronic tag identifier (TID)
ActiveCN104217230AImprove the protective effectThe installation certification method has obvious advantagesCo-operative working arrangementsSensing record carriersCiphertextSecure authentication
Owner:TRAFFIC MANAGEMENT RES INST OF THE MIN OF PUBLIC SECURITY
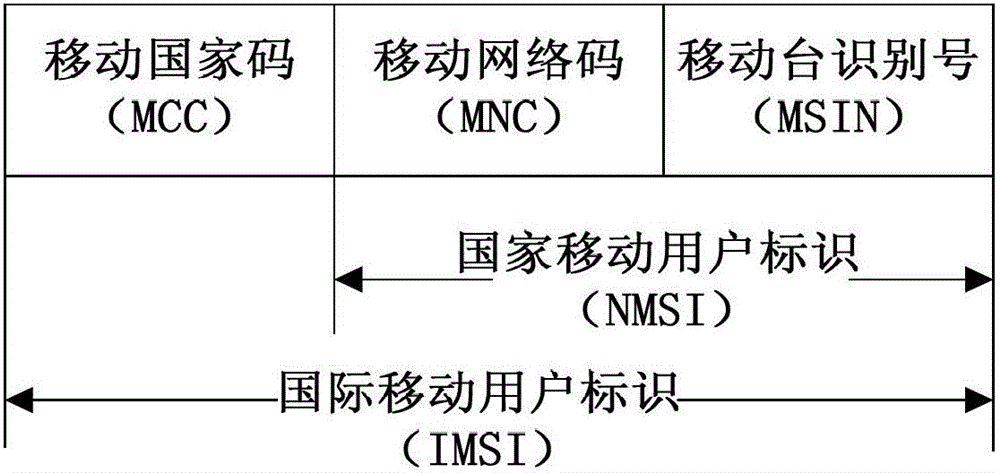
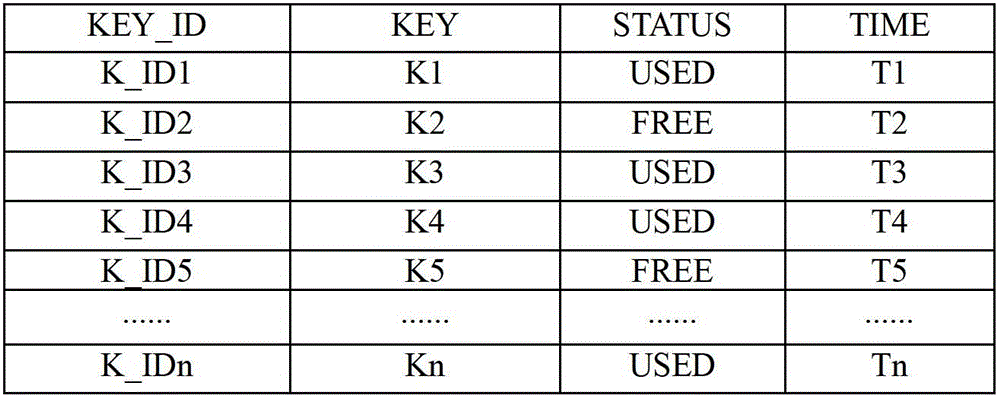
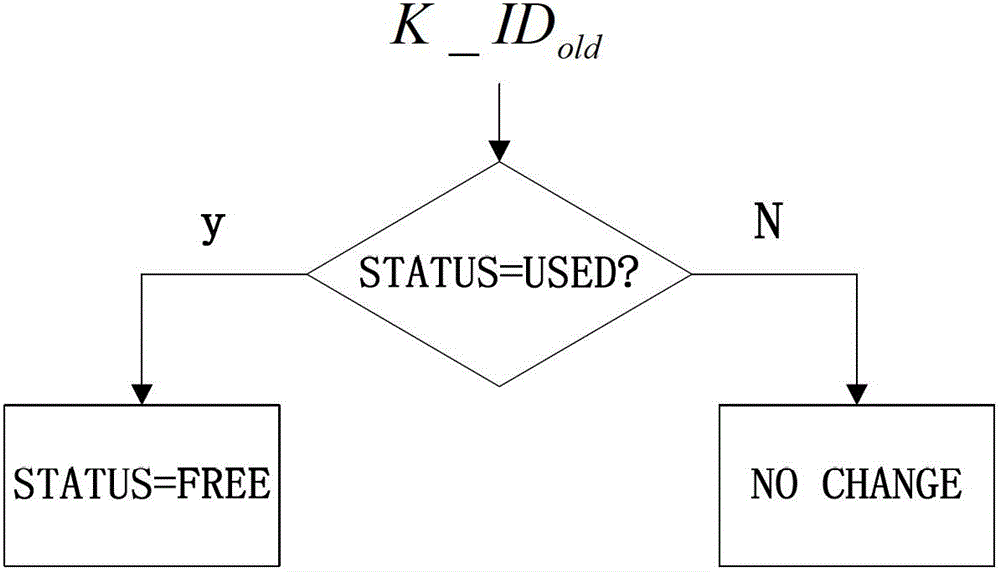
3G accessed IMSI (international mobile subscriber identity) privacy protection method
The invention discloses a 3G accessed IMSI (international mobile subscriber identity) privacy protection method. The method comprises the following steps that a VLR (visitor location register) sends a subscriber identity request, an MS (mobile subscriber) replies the subscriber identity response; the VLR / SGSN (serving GPRS supported node) sends an authentication data request to an HLR (home location register), and the HLR replies the authentication data response; and when the MS is authorized, the VLR / SGSN sends a subscriber authorization request to the MS, and the MS replies the subscriber authorization response. Through the method, the confidentiality of the IMSI is protected by means of key identifiers and key groups; and after the user transmitted IMSI information is encrypted, the information is transmitted by means of cipher texts, so that the IMSI is avoided from being leaked. At the same time, when the HLR generates an authentication vector for the user, an encryption key which is updated in real time is distributed, so that the representation forms are different after the user encrypts the IMSI information for each time, and the user can be avoided from being tracked.
Owner:SOUTHEAST UNIV
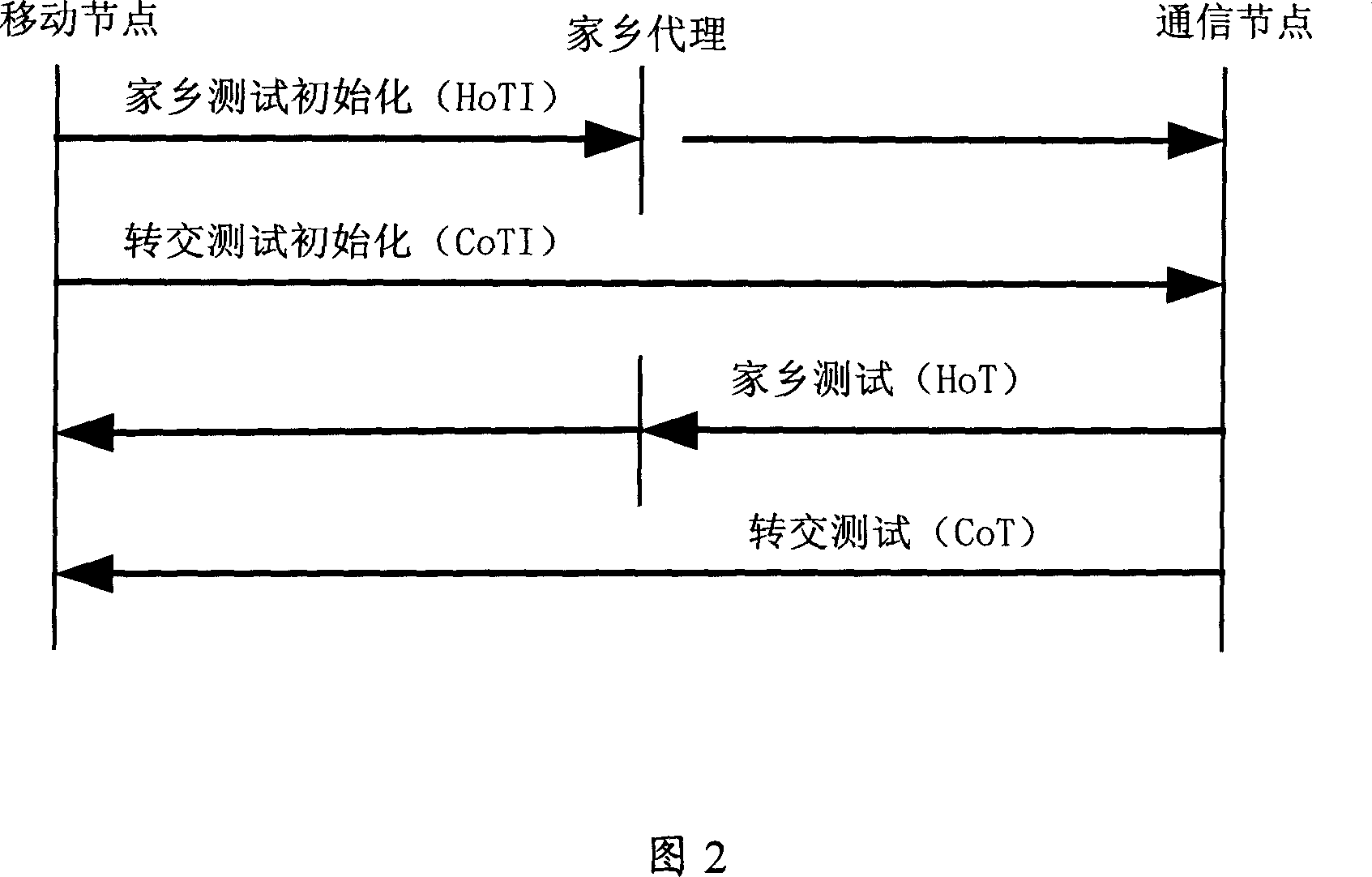
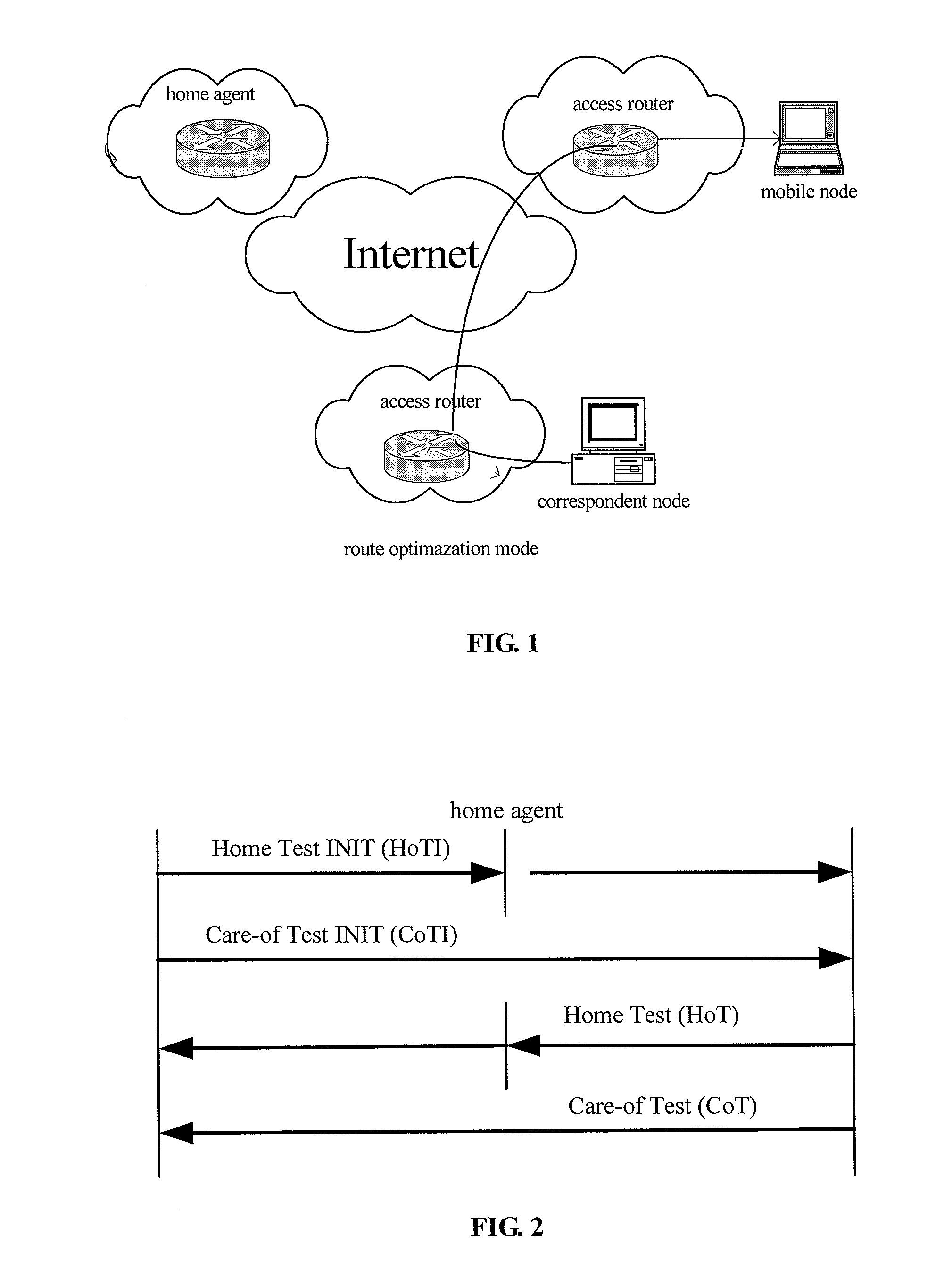
Communication method of MIPv6 moving node
InactiveCN101001261AAvoid trackingRandomWireless network protocolsData switching networksAccess networkIPv6 address
Owner:HUAWEI TECH CO LTD +1
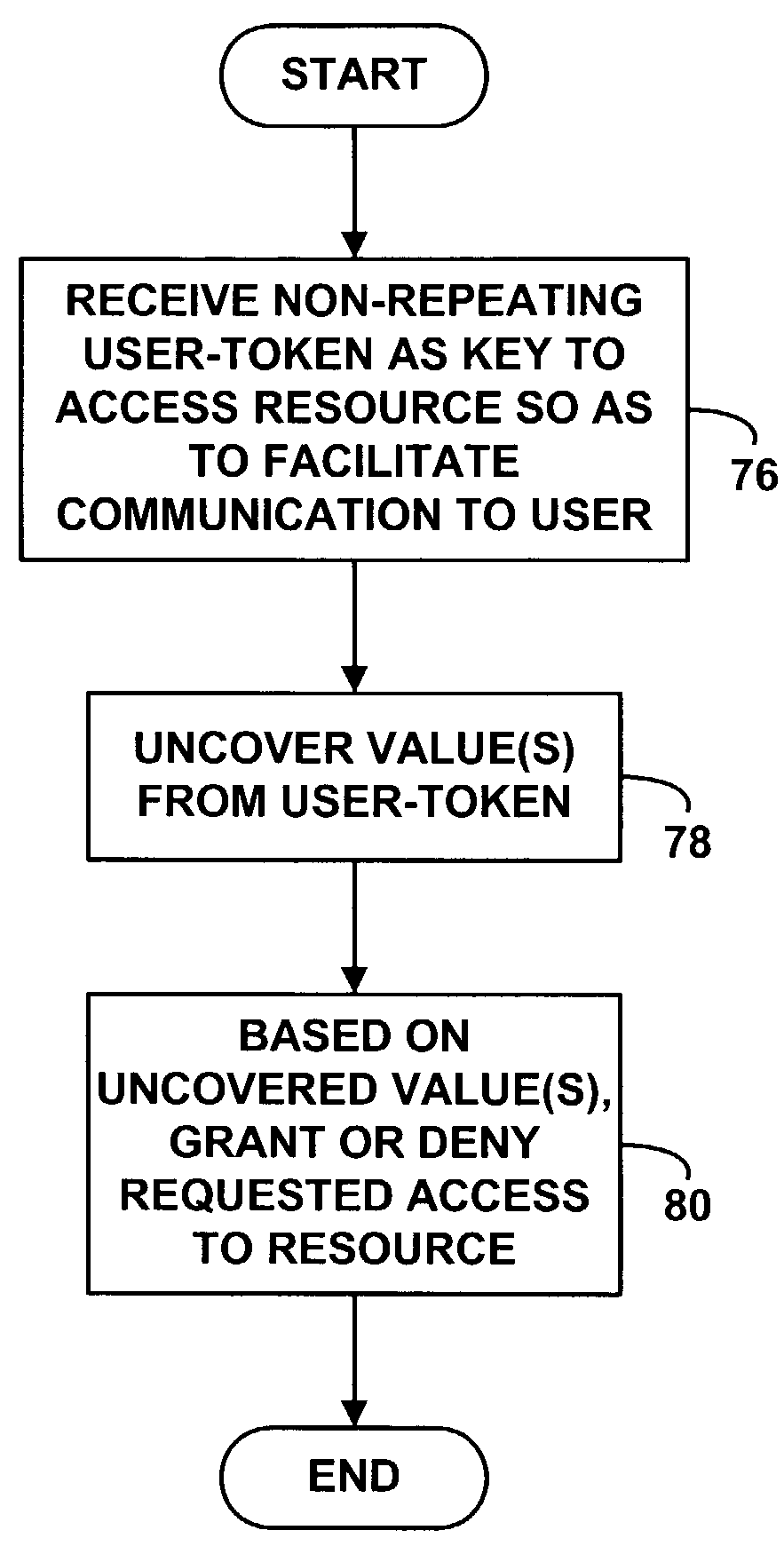
Method and system for non-repeating user identification in a communication system
ActiveUS7900245B1Facilitate communicationAvoid trackingDigital data processing detailsUser identity/authority verificationCommunications systemInternet privacy
A method and system operative to preclude content providers from tracking users, while still allowing content providers to communicate to users. An intermediary, such as an access channel provider for instance, gives content providers non-repeating user-identification-tokens, each of which a content provider can use as a key to access an intermediary resource that facilitates a communication to the user, without revealing the user's identity to the content provider.
Owner:SPRINT SPECTRUM LLC
METHOD FOR COMMUNICATION OF MIPv6 MOBILE NODES
InactiveUS20080291885A1Prevent malicious attacksAvoid trackingWireless network protocolsSecret communicationComputer networkIPv6 address
A method for communication of MIPv6 mobile nodes, comprising: the mobile node accesses network at access location and obtains care of address, calculating a privacy identifier PID using the care of address etc. the mobile node replaces its home address by the PID, and sends the PID and the care of address together as binding update message to the home agent and correspondent node, the home agent and correspondent node recover the home address for the mobile node using the PID after they have received the binding update message. The method for communication of MIPv6 mobile nodes according to the present invention uses that a configuring replaced identifier replacing the home address is sent, thereby hiding Ipv6 address. By setting PID and its algorithm, we improve the sequence number in the binding update messages enabling the sequence number has randomness, and prevent the intercepting person continue tracking the mobile node through the home address.
Owner:HUAWEI TECH CO LTD +1
OFDM-MFSK underwater acoustic communication broadband Doppler estimation and compensation method of known sub-carrier frequency
ActiveCN107547143AAvoid SNR LossImprove real-time performanceMulti-frequency code systemsCarrier signalBroadband
The invention discloses an OFDM-MFSK underwater acoustic communication broadband Doppler estimation and compensation method of known sub-carrier frequency, and belongs to the field of the underwater acoustic communication. The content disclosed by the invention is specifically as follows: a transmitting end adds a plurality of sub-carries and inserts a pulse pair signal into each OFDM-MFSK data symbol; a receiving end intercepts the pulse pair signal and data, and performs coarse estimation on the Doppler factor, and determines the Doppler frequency deviation search range of each known frequency sub-carrier; performing over-sampling processing on each OFDM-MFSK data block, and computing a mean Doppler factor of the current data block; and then computing new locations of all sub-carriers ofthe whole data block after being influenced by the Doppler, and finishing the broadband Doppler compensation by extracting the corresponding data. By using the method disclosed by the invention, theaccurate estimation and compensation of the broadband Doppler in the underwater OFDM-MFSK communication system can be realized only through once data over-sampling, the process of resampling the datain the traditional Doppler estimation and compensation method is avoided, and the computing efficiency is improved.
Owner:HARBIN ENG UNIV
Constraint Weighted Regulation of DC/DC Converters
ActiveUS20110187198A1Improve response dynamicImprove recovery powerApparatus without intermediate ac conversionDc source parallel operationOperating pointTransverter
A converter unit to improve overall recovered power in a photovoltaic array configuration. Each photovoltaic panel in the photovoltaic array may be coupled to a respective converter unit, which may include a controller to sense an output voltage and output current produced by the solar panel, and manage the output voltage of a corresponding power converter to optimize and regulate the resultant bus voltage to a point which reduces overall system losses, maintains a low loss condition, and removes series-string non-idealities when the panels are series connected. The controller may also adapt to output condition constraints. Instead of single-port regulation, a combination of input voltage and output voltage management and regulation may be performed within the converter. The source voltage and current characteristic may be shaped to correspond to an optimized power curve at the desired bus voltage to allow MPPT tracking according to the DC voltage bus. The optimized power curve may be tracked to hold the DC-bus voltage at the desired operating point.
Owner:BLUED ACQUISITION CORP
Server side mobile audience intelligence creation
ActiveUS9106709B2Improve browsing experienceAvoid trackingAdvertisementsMultiple digital computer combinationsWeb siteWeb browser
The present invention is directed toward a method and system for tracking webpage requests from web browsers without invading the privacy of the corresponding users. A server receives the webpage requests, and extracts from each of them a user-neutral identifier and URL. The server creates records of these webpage requests, and these records are used to create and update profiles for the corresponding user-neutral identifiers. Since the user-neutral identifiers are not tied to user-specific information, the profiles are made anonymous and user privacy can be protected. However, since each user-neutral identifier is tied to a particular web browser, useful information regarding individual browsing behavior can be obtained. Furthermore, the requested URL's can be categorized before being used to update the profiles, thus eliminating concerns that a user's browsing activity might be tracked from website to website.
Owner:OPERA SOFTVEAR AS
Traffic management system and method
InactiveCN102147974AGet driving statusImplement queryControlling traffic signalsTraffic signalEngineering
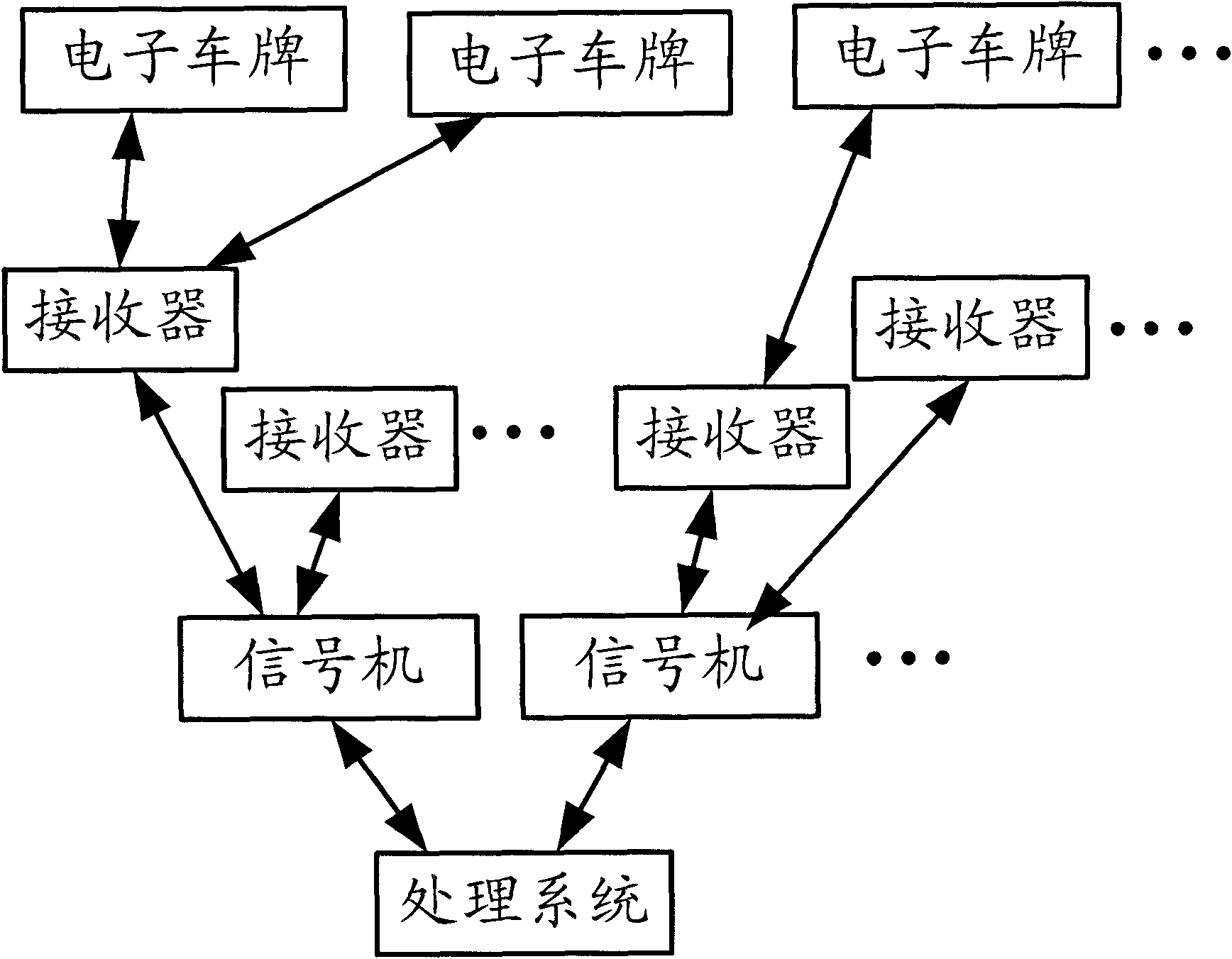
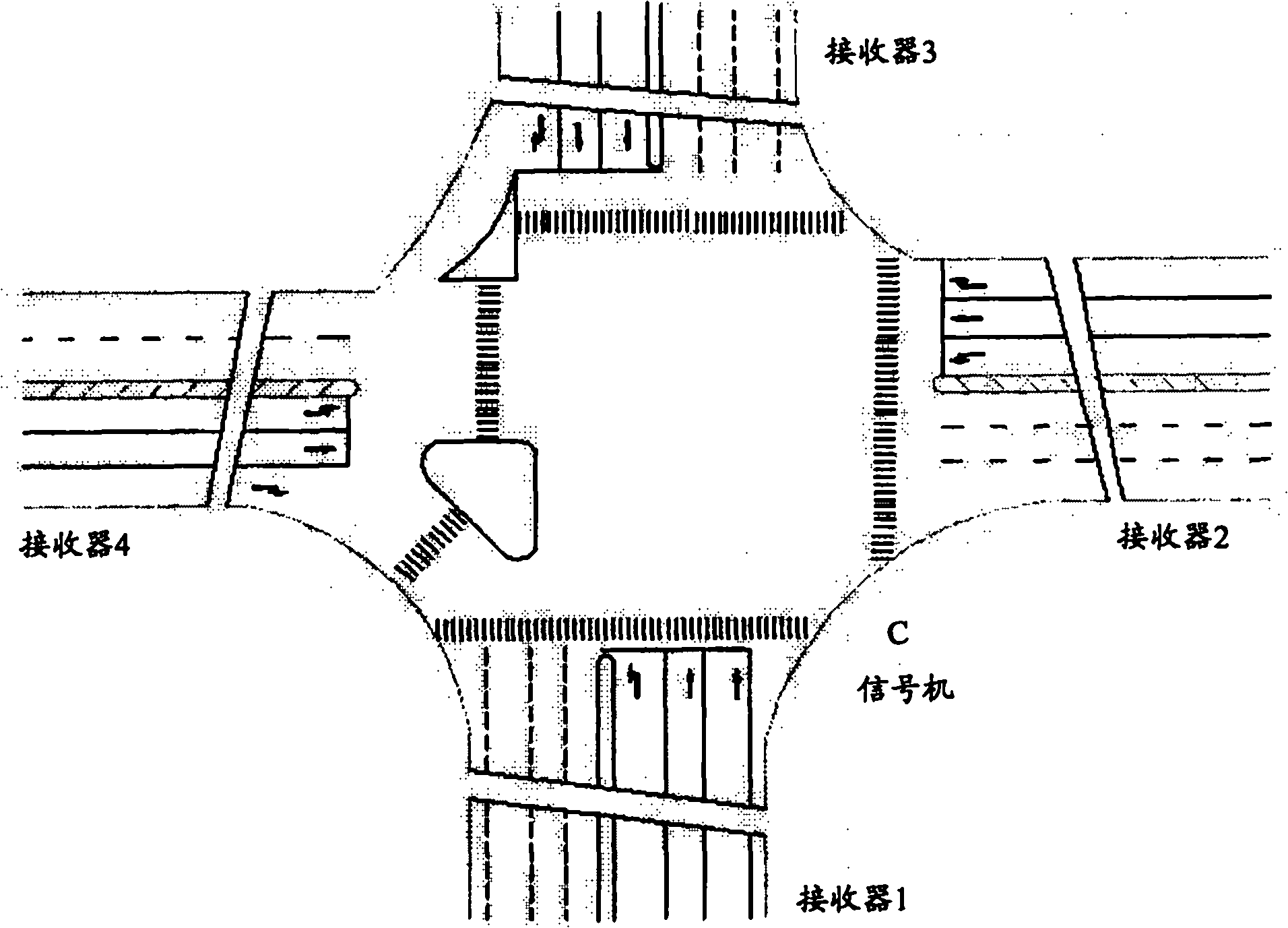
The invention discloses traffic management system and method, wherein the traffic management system comprises at least one receiver, at least one annunciator and a processing system, wherein the receivers are used for receiving vehicle information from a nearby electronic license plate and reporting the received vehicle information; the annunciators are used for receiving the vehicle information reported by the receivers, inducing the reported vehicle information and sending inducing results, wherein the inducing results are used for indicating the driving conditions of vehicles carried with electronic license plates; and the processing system is used for receiving the inducing results sent by the annunciators, generating traffic management commands according to the inducing results and sending the traffic management commands to the annunciator. The traffic management system and method disclosed by the invention can be used for accurately acquiring the driving conditions of the vehicles on roads, thereby contributing to the reasonable optimization of traffic signal control; and the invention can realize the search of passing places of specific vehicles, thereby being convenient for tracking and survey.
Owner:李丽
Vacuum suction apparatus
InactiveUS20130082475A1Avoid product qualityCurb consumptionGripping headsSemiconductor/solid-state device manufacturingEngineeringMechanical engineering
Owner:SMC CORP
Deployment system
InactiveUS20130126670A1Avoid skewAvoid trackingAircraft stabilisationWithout power ampliicationBraking systemAerospace engineering
Owner:AIRBUS OPERATIONS LTD
Automatic focusing apparatus and control method therefor
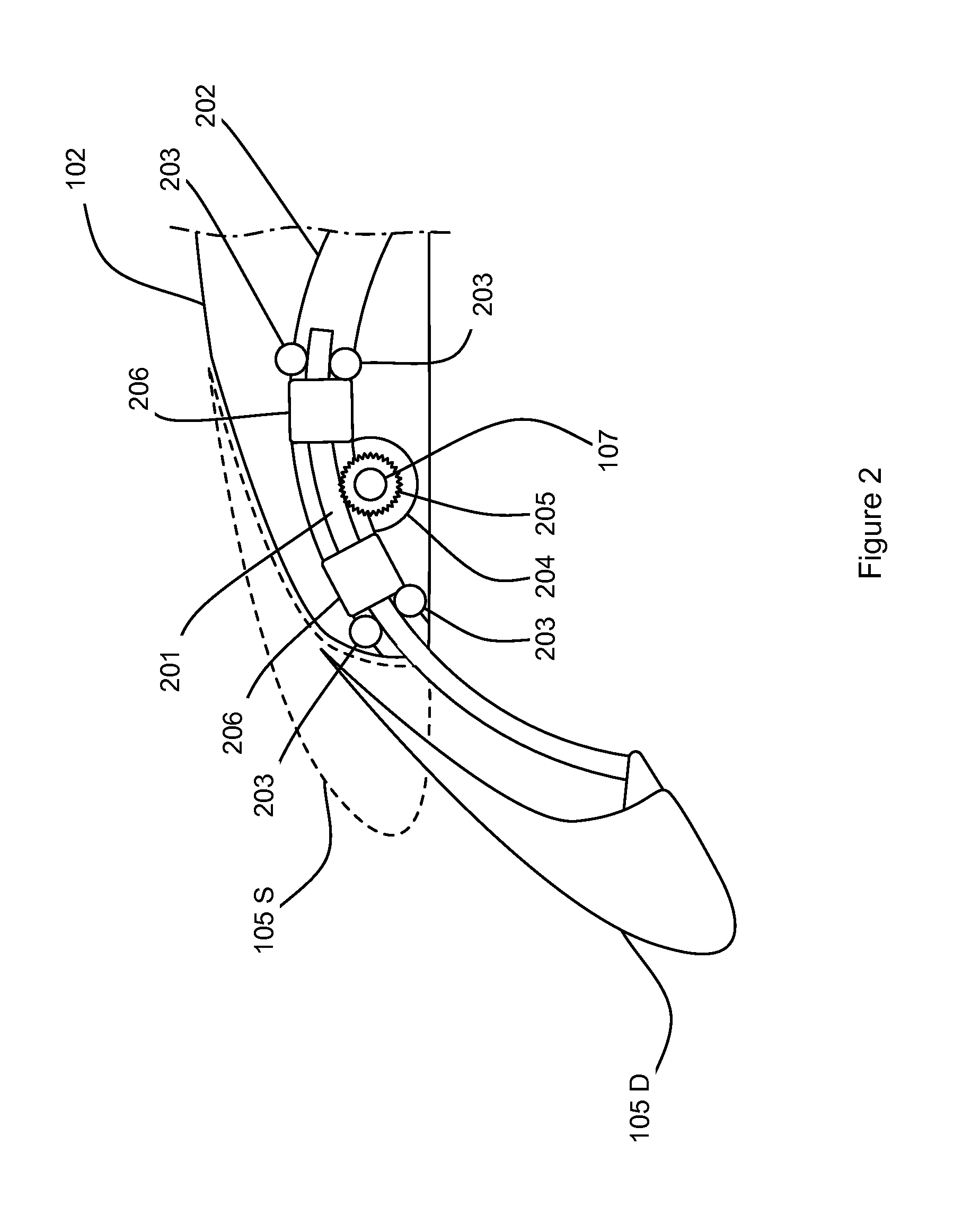
InactiveUS20100067891A1Preventing tracking abilityAvoid trackingTelevision system detailsProjector focusing arrangementCamera lensSimulation
An automatic focusing apparatus detects presence or absence of change in a distance between an object and the automatic focusing apparatus while operating in an operation mode to continuously perform an adjustment of the position of a focus lens to focus on the object, and stops a movement of the focus lens if a change in the distance is not detected.
Owner:CANON KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com