Internet of Vehicles privacy protection trust model based on block chain
A privacy protection and trust model technology, applied in secure communication devices, user identity/authority verification, digital transmission systems, etc., can solve problems such as RSU malicious attacks, reduce malicious influence, strengthen message integrity, and prevent tampering. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings of the specification.
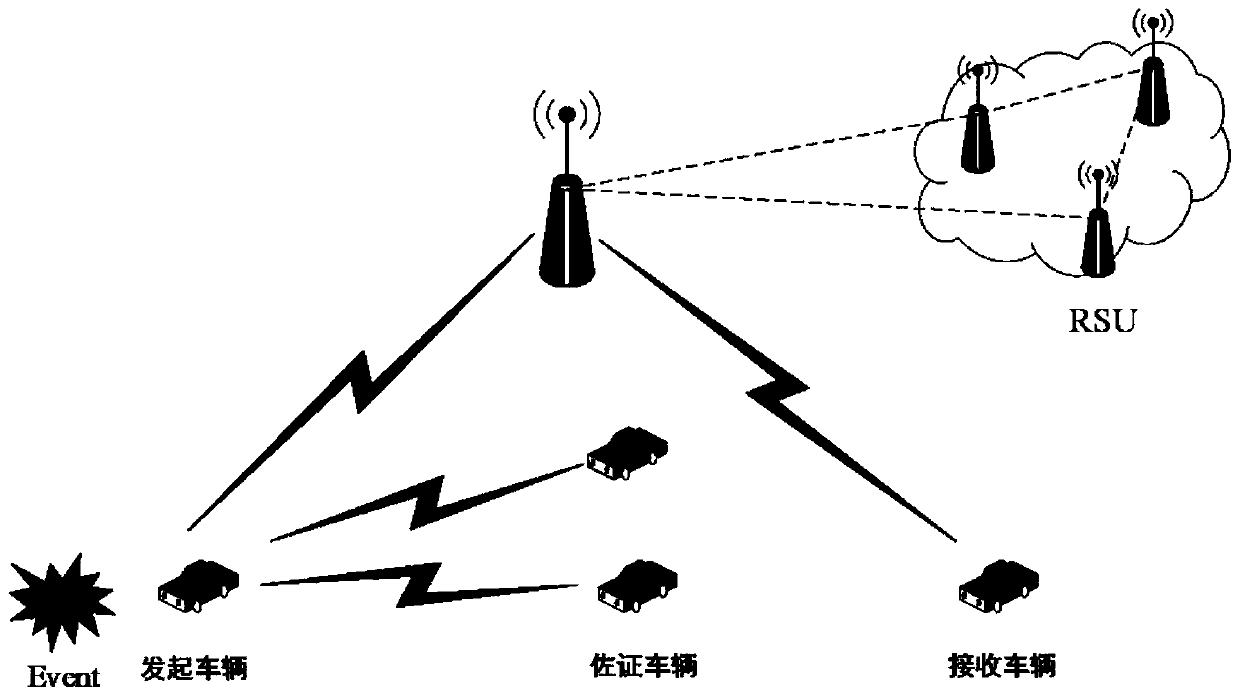
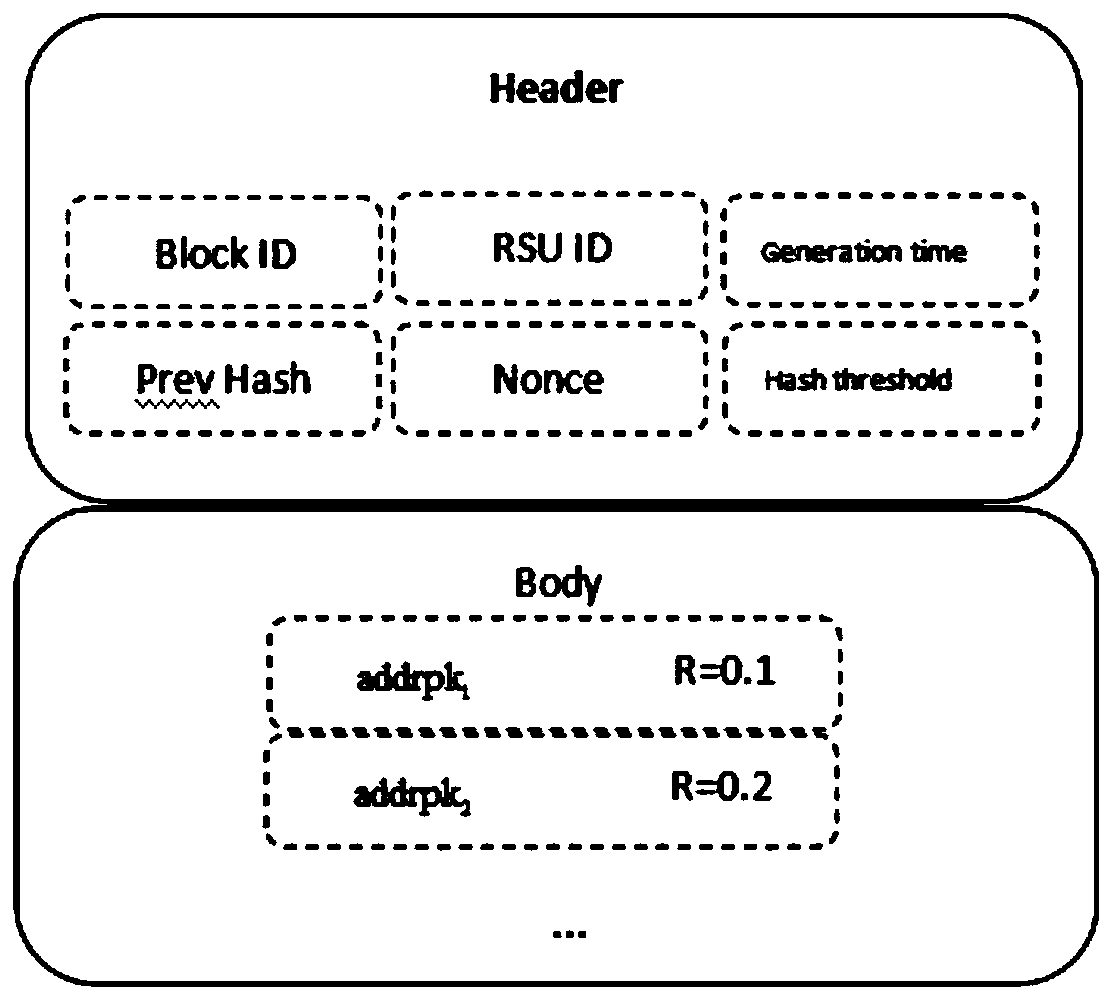
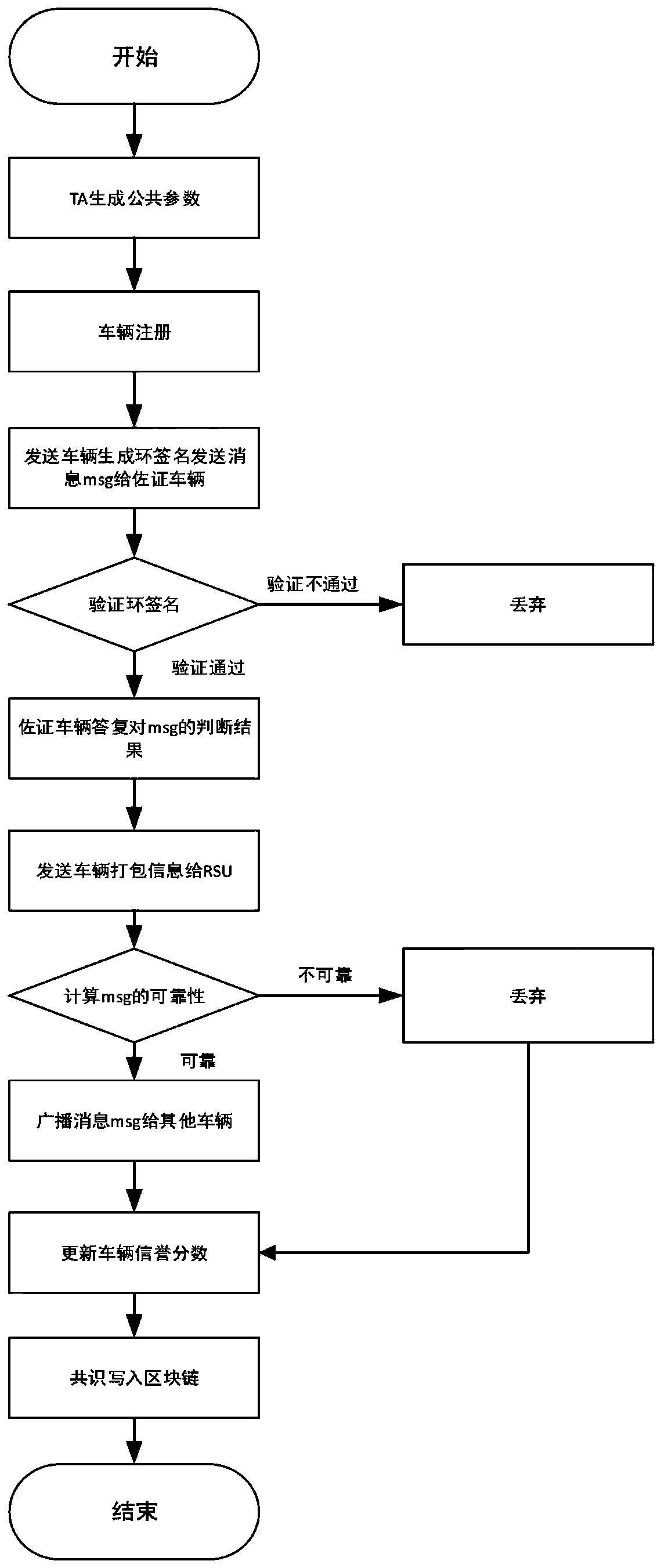
[0071] A blockchain-based privacy protection trust model for the Internet of Vehicles includes the following steps:
[0072] Step 1. The trusted authority center TA chooses E k (x) is a symmetric encryption protocol that uses a key k to encrypt x. The public key and private key of the symmetric encryption protocol are the same key, and the following public parameters or objects are selected or generated at the same time:
[0073] Step 1-1, select G as the additive group whose point is on the elliptic curve, q is the order of G, and g is the generator of G.
[0074] Step 1-2, choose H as the hash function, H: {0,1}*→{0,1} n , That is, map a 0,1 data set with any length to a 0,1 data set with a length of n.
[0075] Step 1-3, generate Means from (Set of integers of arbitrary length with order q) Assign any element in the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com