Radio frequency identification transponder security
A technology of radio frequency identification and transponder, which is applied in the field of RFID and can solve problems such as recoding
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
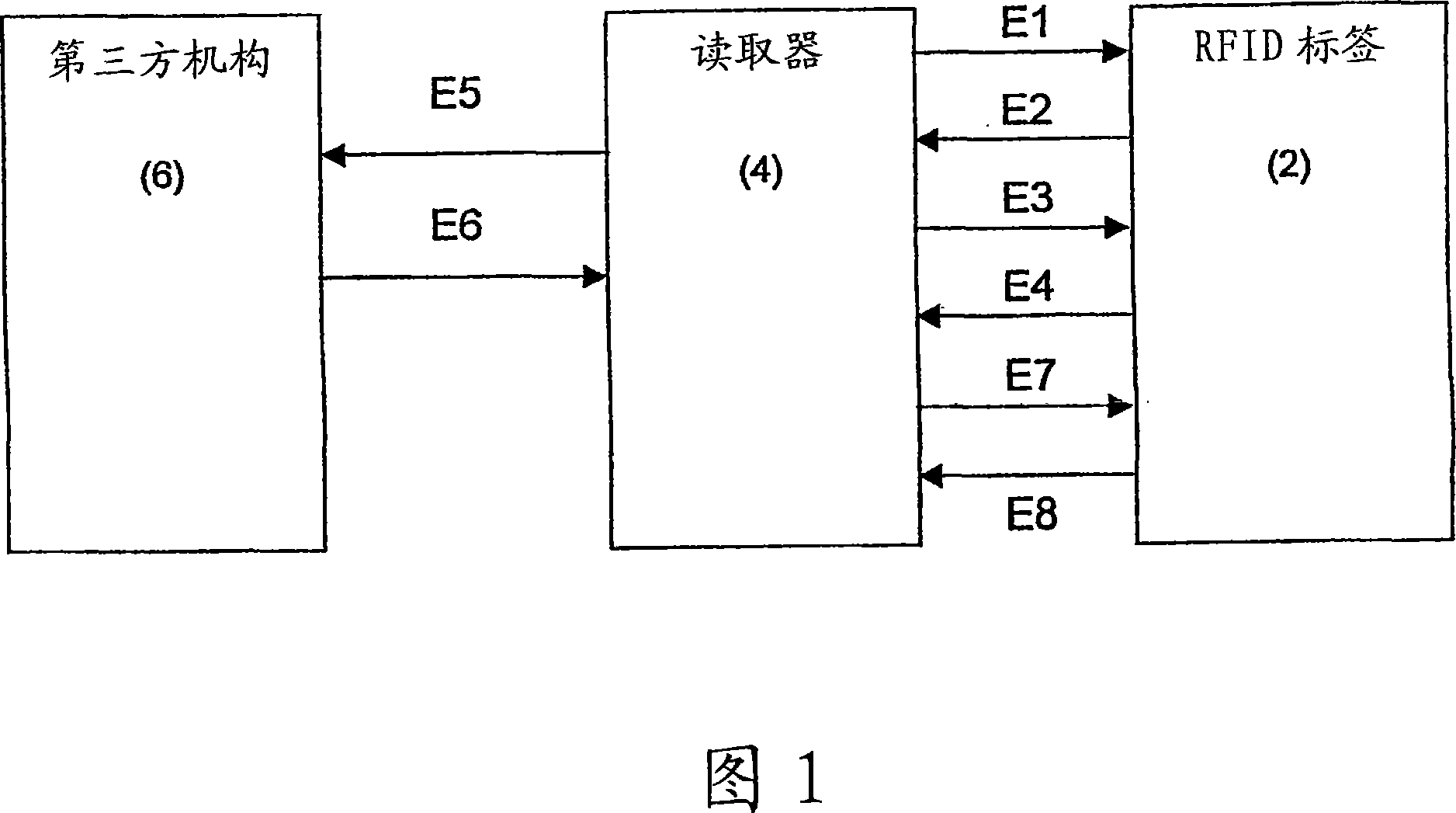
[0044] Figure 1 is a schematic overview of an embodiment of the invention showing the relationship and communication between the three main components of an RFID system according to the invention. Several exchanges E1 to E5 occur during the event between the tag, the reader and the third party.
[0045] Figure 2 is a flowchart describing the steps of a typical read and access session.
[0046] Embodiments of the present invention will now be discussed in conjunction with FIGS. 1 and 2 .
[0047] In step S1 of Figure 2, the reader (4) establishes initial contact with the tag (2) by scanning the tag (2) with appropriate radio frequency radiation. This is depicted by the arrow labeled E1 in Figure 1 .
[0048] In step S2, the tag responds by sending an output E2 to the reader comprising the "pseudo-name".
[0049] In step S3, the reader receives the pseudonym (output E2). If the reader has within itself the information that allows it to "decode" the pseudonym ("yes"), there i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com