Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
20193results about How to "Integrity guaranteed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
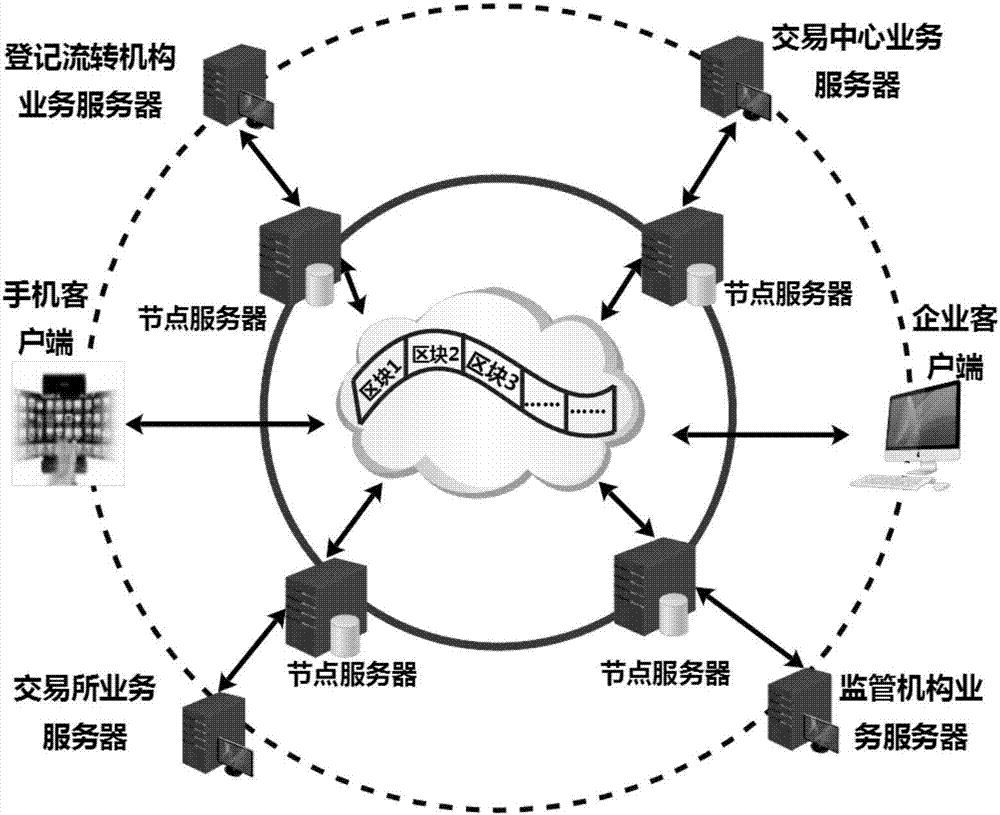
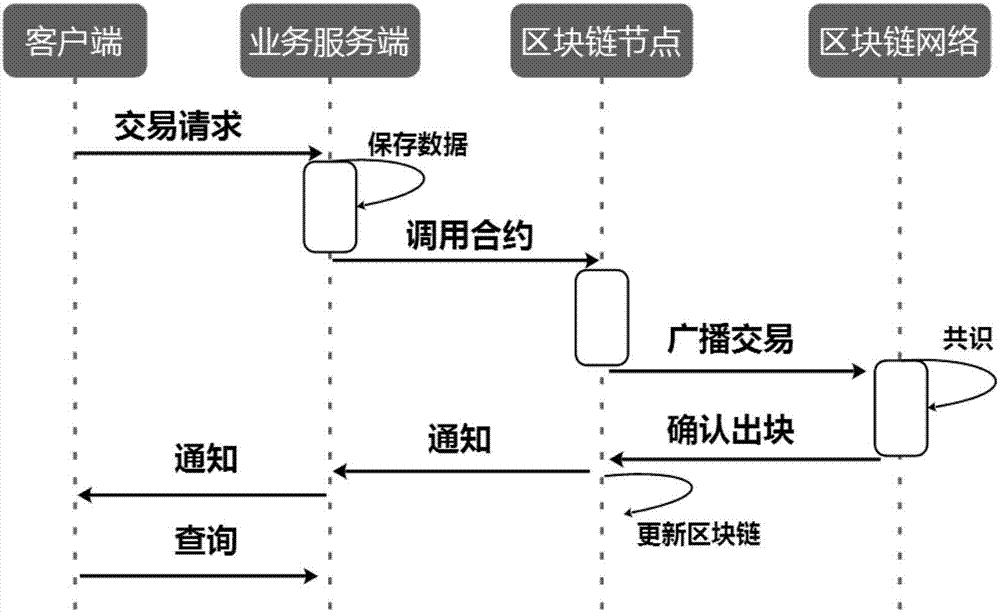
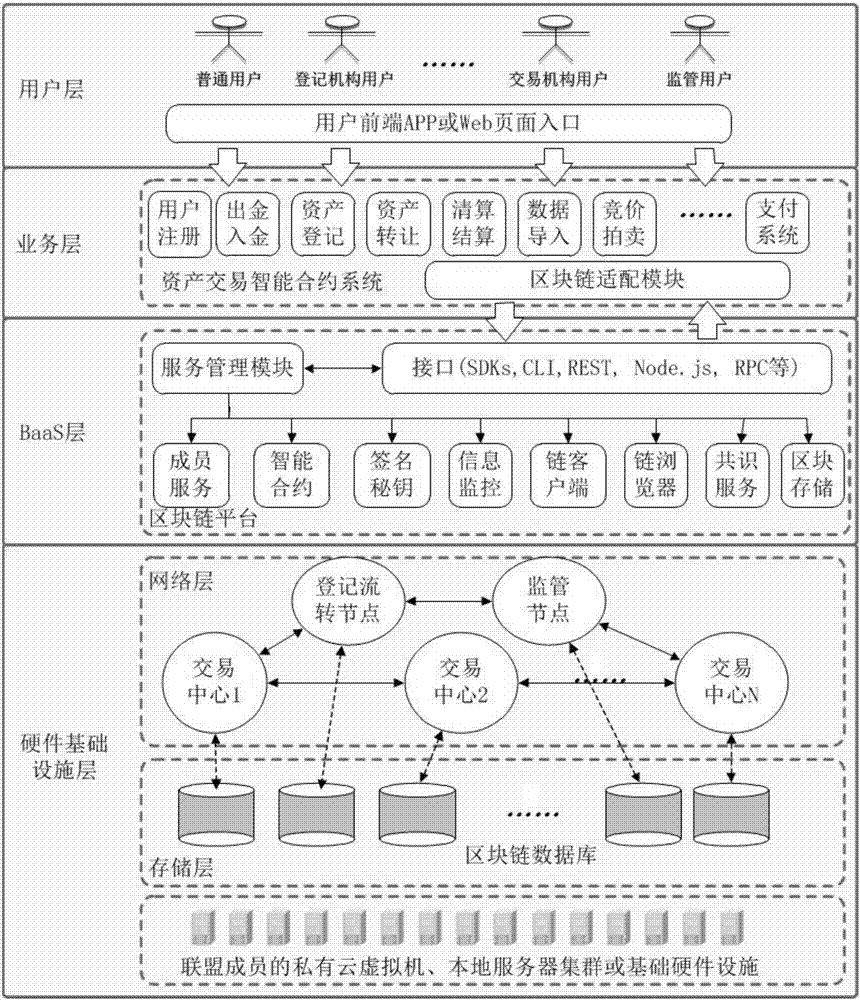
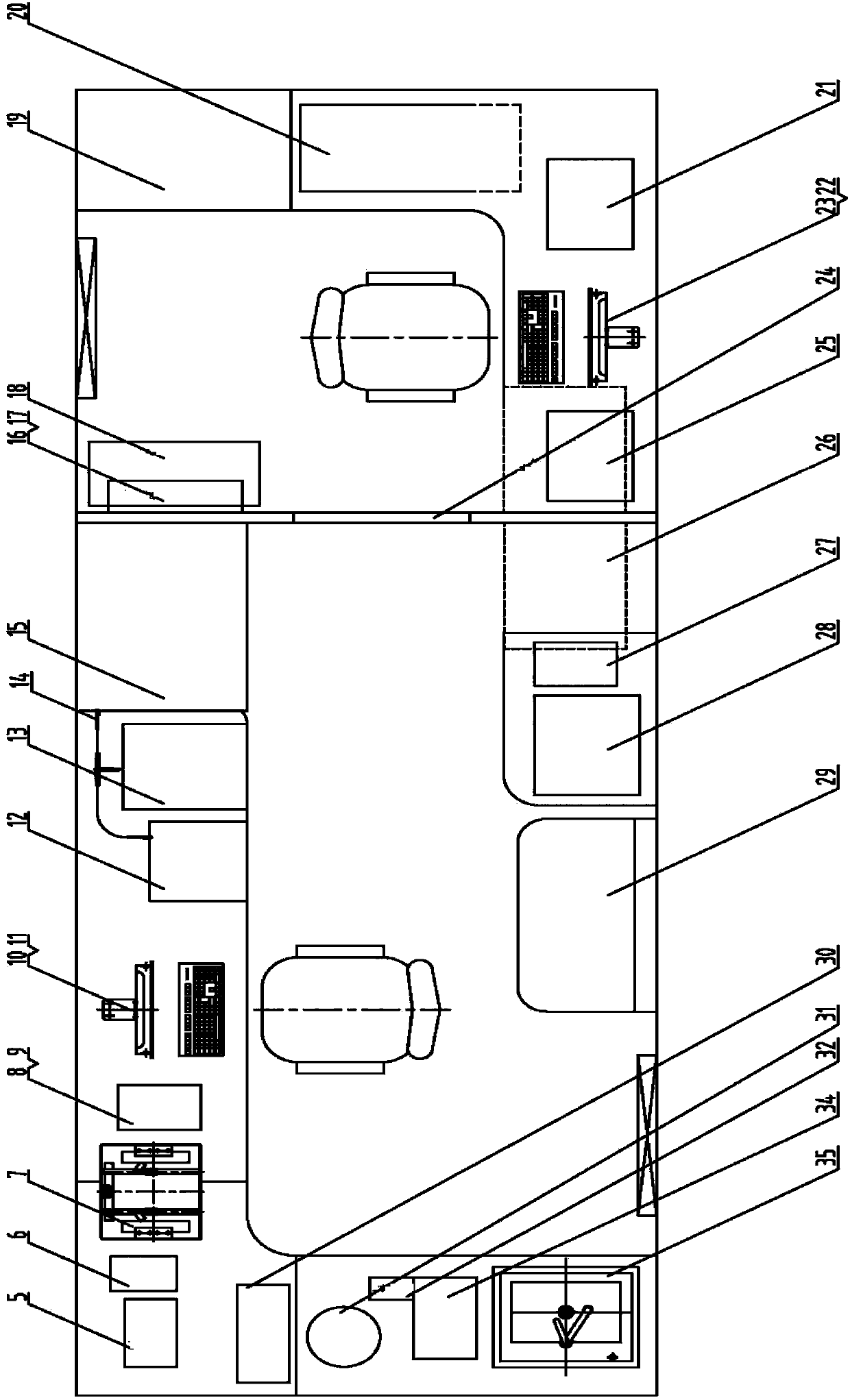
Method for constructing financial asset trading system based on alliance chain
InactiveCN107025602AProtect interestsReduce credit riskFinanceElectronic credentialsData miningComputer science
The invention discloses a method for constructing a financial asset trading system based on an alliance chain. With an alliance chain as a technical support, a novel financial asset digital unique certificate is provided based on the existing laws and regulations. The system uses a distributed technology architecture. All participants jointly maintain the ledger of financial asset trading. It is ensured that the trading of financial assets is open, transparent, real and credible. The credit risk of trading is reduced. The cross-platform and cross-region flow of financial assets is promoted. Tedious manual account checking work between platforms is omitted. In addition, the block chain technology is applied to the field of financial asset trading for the first time. A unified and standardized financial asset trading platform is established. Digital management of financial assets is realized. The credit risk of trading can be prevented effectively. The efficiency of trading and supervising is improved. The trading cost is reduced.
Owner:HANGZHOU YUNXIANG NETWORK TECH
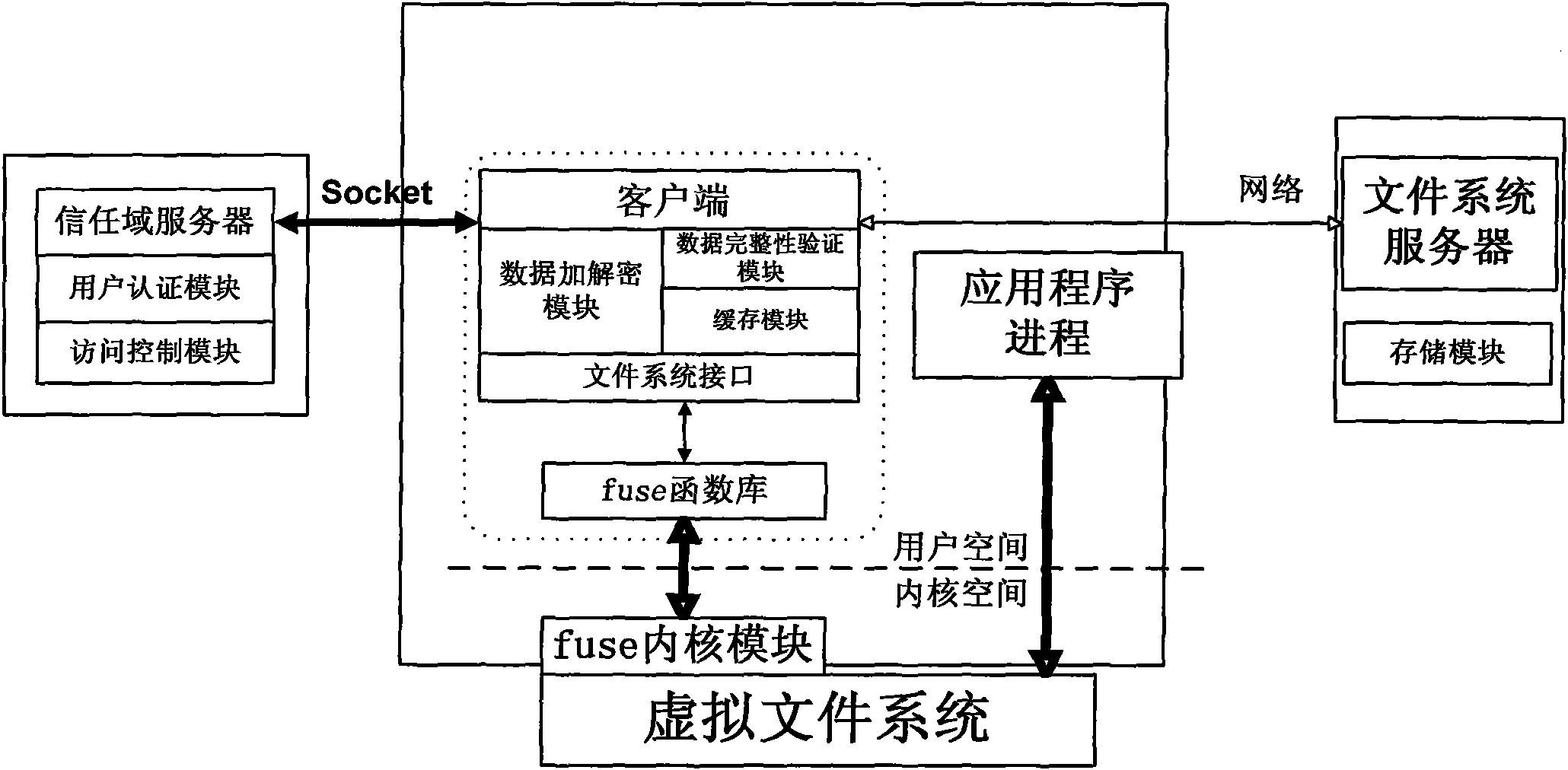
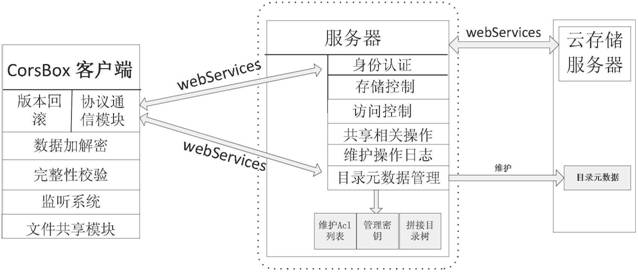
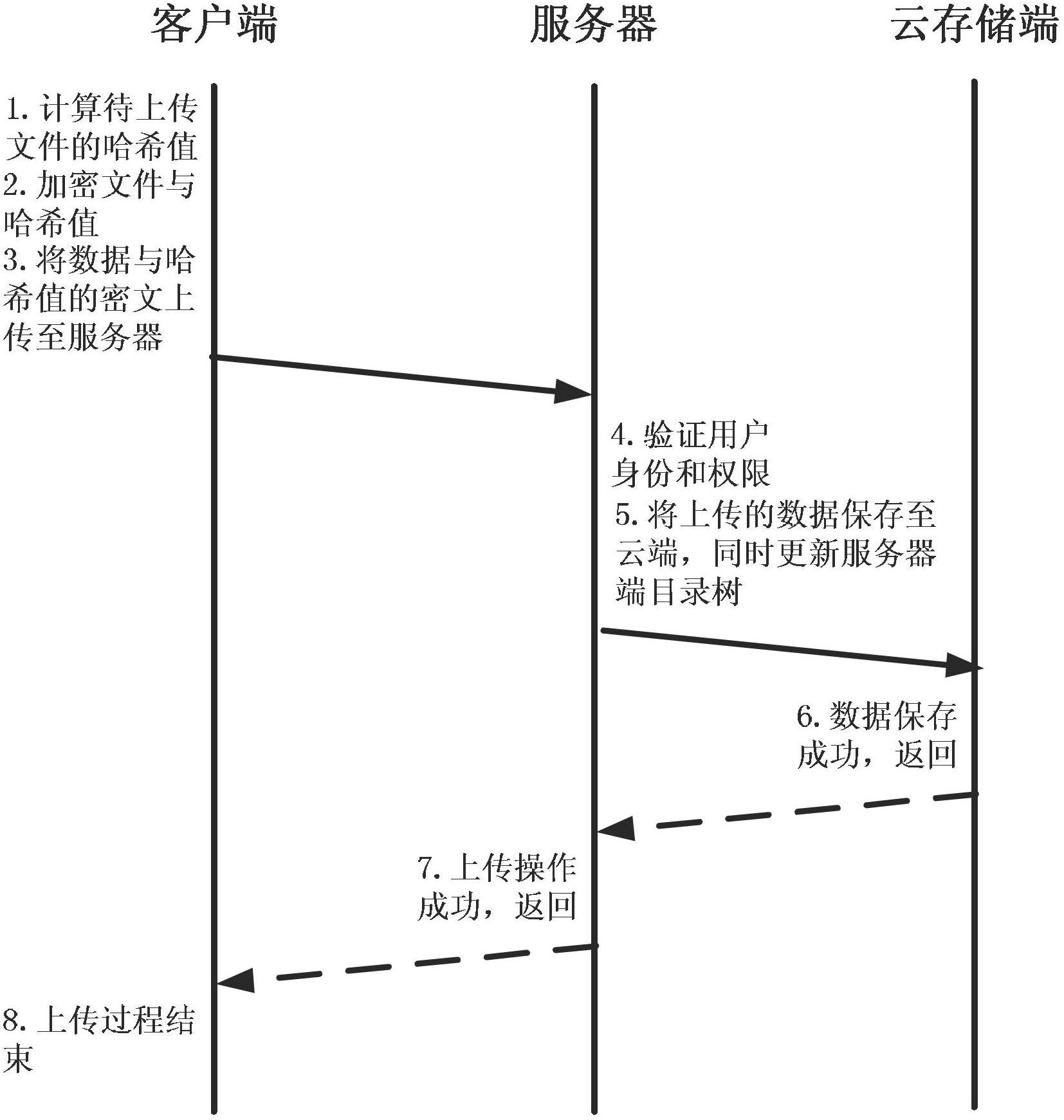
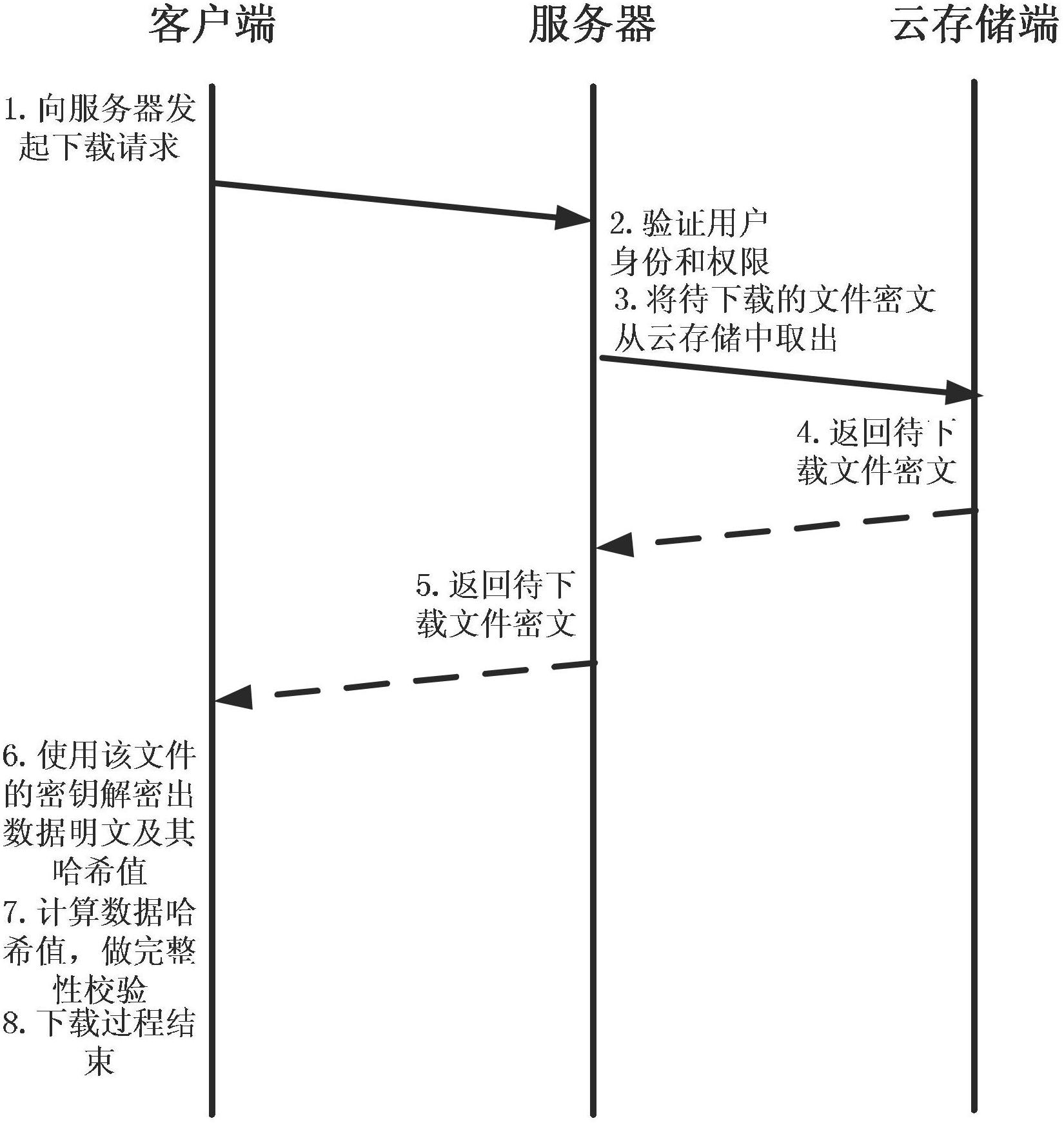
Method for implementing safe storage system in cloud storage environment
ActiveCN102014133AGuaranteed confidentialityTimely detection of damage, etc.TransmissionConfidentialityCiphertext
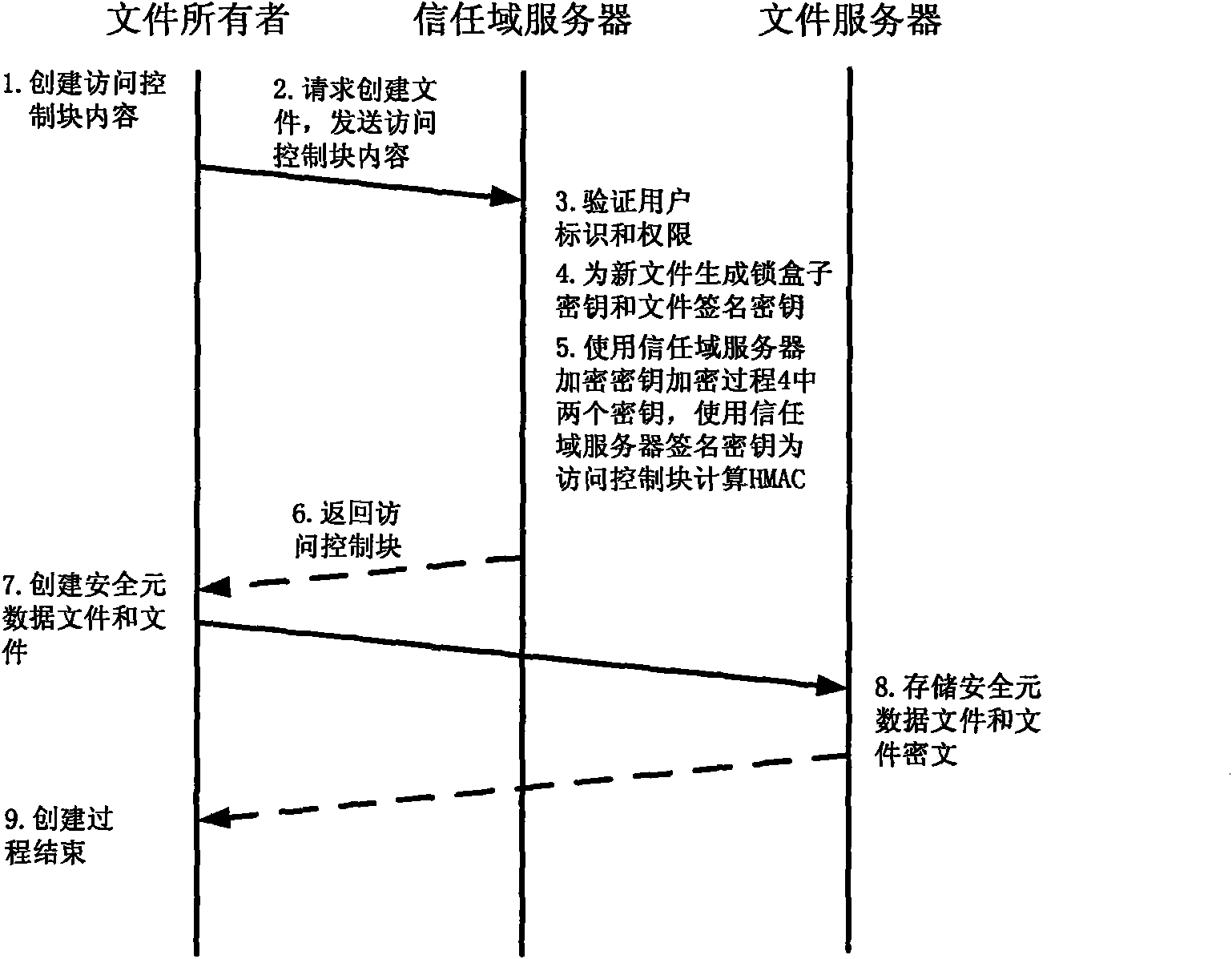
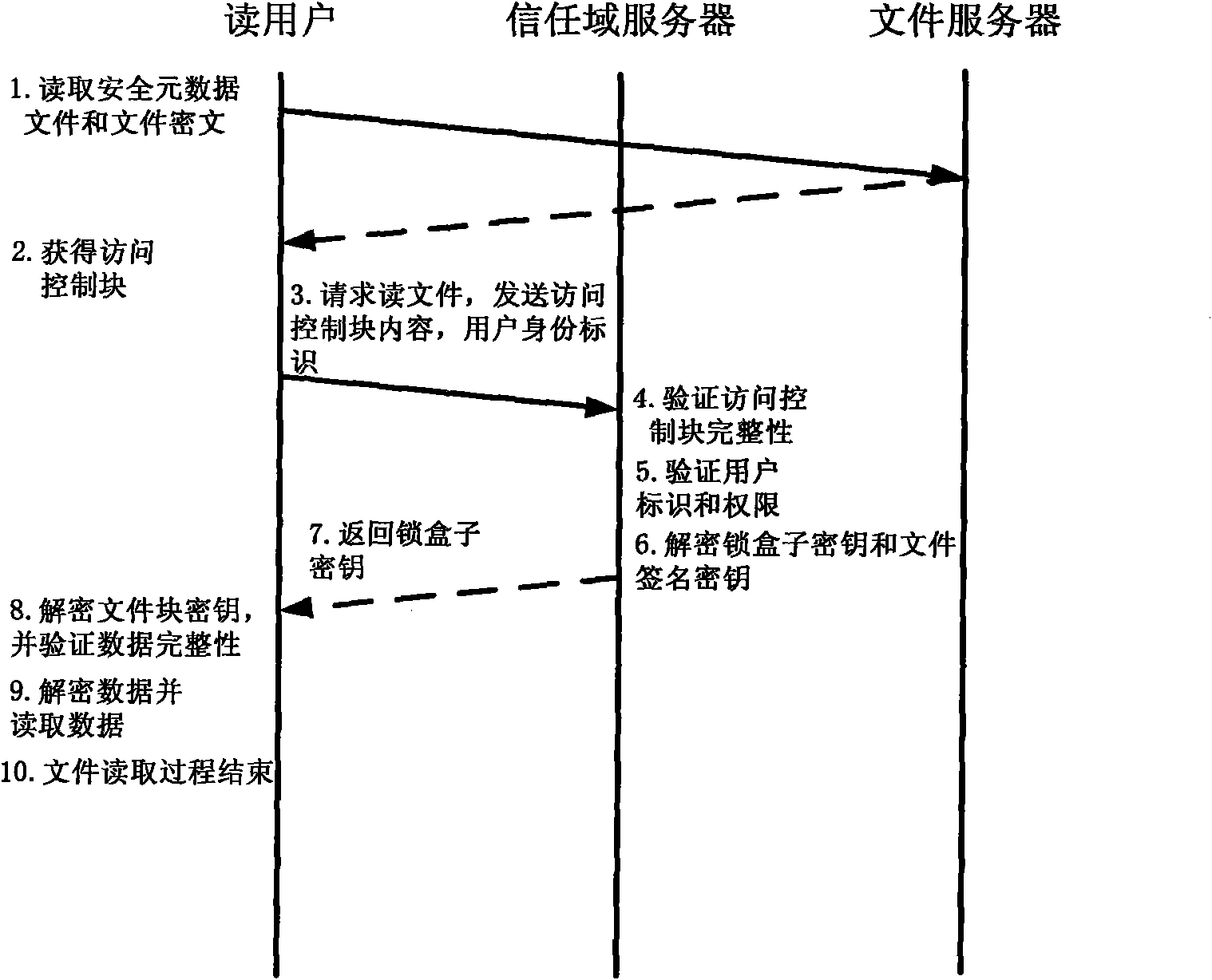
The invention relates to a method for implementing a safe storage system in a cloud storage environment and belongs to the technical field of storage safety. The method is characterized in that a trust domain is established in a server according to the requirements of a user; in the trust domain, identity authentication is performed by using an public key infrastructure (PKI); the independence between the storage system and a bottom layer system is realized by utilizing a filesystem in user space (FUSE); a hash value of a file is calculated by utilizing a secure hash algorithm (SHA1) and taking a block as a unit, a file block is encrypted by utilizing a key and an advanced encryption standard (AES) algorithm of a symmetric encipherment algorithm and taking a block as a unit, and a file cipher text is uploaded to a file server in a cloud storage area so as to guarantee the confidentiality and integrity of the file; a filer owner postpones encrypting the file again when permission is revoked by designating a user with the permission of accessing the file and the permissions thereof in an access control list; and only when the user modifies the content of the file, the user encrypts the file block in which the modified content is positioned again and the system implements three layers of key management, namely a file block key, a safe metadata file key and a trust domain server key so that not only the safety of the file is guaranteed when the permission is revoked, but also the management load of the system is not increased.
Owner:TSINGHUA UNIV
Method for realizing secure network backup system under cloud storage environment
ActiveCN102685148AGuaranteed confidentialityIntegrity guaranteedTransmissionPublic key infrastructureRevision control
The invention relates to a method for realizing a secure network backup system under a cloud storage environment, belonging to the technical field of storage security. The method is characterized in that a system architecture is invented in a trust network of a network backup system under the cloud storage environment, a trust domain is established in a server according to a user requirement, and then identity authentication is performed by using a public key infrastructure (PKI), so that the non-deceptiveness and non-repudiation of a user are guaranteed; a Hash algorithm is used to calculate a Hash value of a file, a key and an advanced encryption standard (AES) algorithm are used for data encryption, and then the ciphertext of the file is uploaded to a file server in a cloud storage area, so that the confidentiality and the completeness of data are guaranteed; a synchronization manner based on a directory tree is used to increase the synchronization efficiency and the confidentiality of the system; a hierarchical key management manner is used to reduce the management burden of the system while guaranteeing data security; a version control function is provided to guarantee the continuity of the version of the file; and encryption key selection manners of many levels of granularity are provided to increase the flexibility of the system.
Owner:TSINGHUA UNIV
Display panel and electronic equipment
ActiveCN107610635AAchieve full screen display effectGuaranteed continuityStatic indicating devicesElectricityComputer graphics (images)
The invention relates to the technical field of display, and discloses a display panel and electronic equipment. The display panel comprises display regions and a non-display region. The display regions include a first display region and a second display region. The first display region is provided with a plurality of first pixels. Pixel electrodes of the first pixels are transparent. The non-display region is provided with a plurality of first pixel circuits for providing display signals to the first pixels. In the display panel, the first display region can be used for displaying frames andcan transmit light rays; the first display region can serve as a functional region to correspondingly arrange functional elements of the electronic equipment; the first display region does not damagethe regular shape of a display area, so that continuity and completeness of display frames can be guaranteed, and real full-screen display effect of the electronic equipment can be realized. By the display panel, full-screen display of the electronic equipment can be realized, and continuous and complete full-screen display effect can be provided.
Owner:WUHAN TIANMA MICRO ELECTRONICS CO LTD
Package system and method
InactiveUS6875486B2Effective maintenanceIntegrity guaranteedEnvelopes/bags making machineryHeat storage plantsRadiant barrierElectrical and Electronics engineering
Owner:MILLER DRAYTON +1
Electronic document safe sharing system and method thereof
InactiveCN101989984AGuarantee authenticitySafe storagePublic key for secure communicationUser identity/authority verificationClient-sideSafe storage
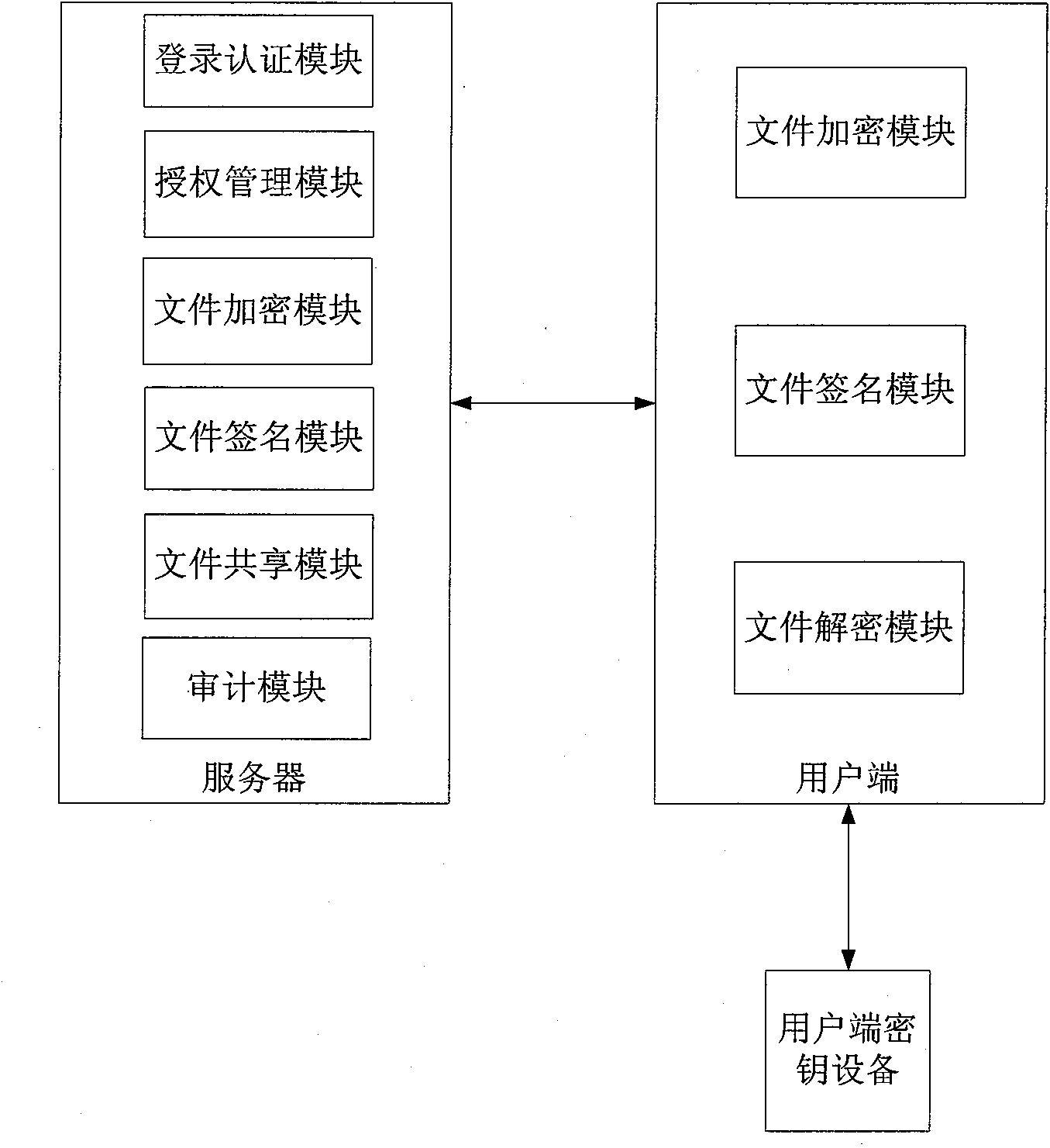
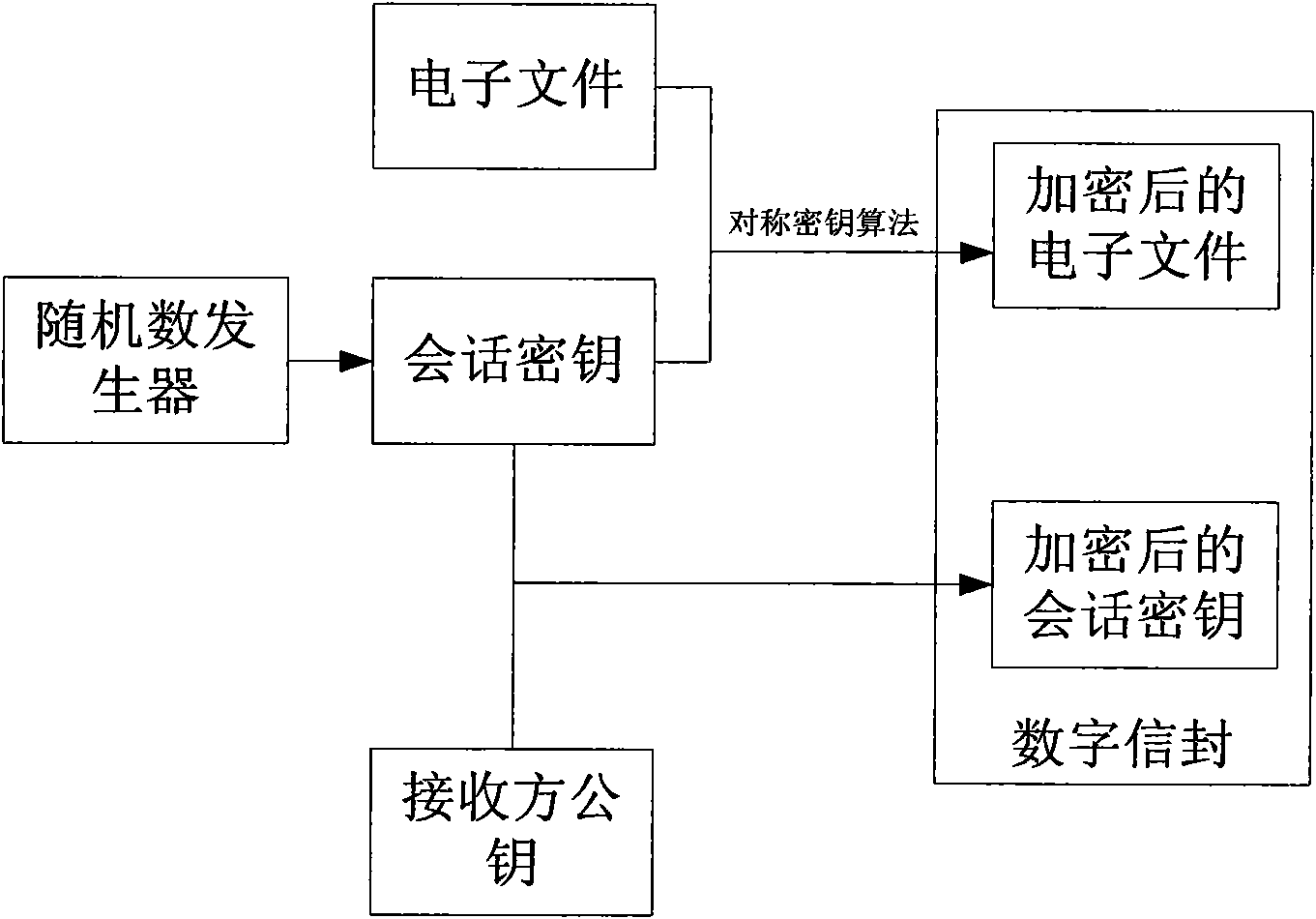
The invention discloses an electronic document safe sharing system which can realize safe storage and fully sharing of secret document. The electronic document safe sharing system comprises a document encrypting module and a document decrypting module; wherein the document encrypting module utilizes a session key to symmetrically encrypt electronic document data, receiver identification (public key) is utilized to asymmetrically encrypt the session key, and finally the encrypted symmetric key and encrypted electronic document data are packed into a digital envelop; and the document decrypting module utilizes an own private key to decrypt the digital envelop. The electronic document safe sharing method of the invention takes CPK combined public key or CPK compound public key technology as the basis, flexible digital signature and secret key exchange capacity thereof are utilized, and a confidential document management system which is from a server to a client, contains information storage and transmission to each use link and is integrated with document data encryption, access control, authorization management, dynamic key exchange and process audit trail into a whole is constructed.
Owner:BEIJING E HENXEN AUTHENTICATION TECH +1
Firmware upgrading and encapsulating method and device based on digital signing
InactiveCN101436141AIntegrity guaranteedPrevent tamperingProgram loading/initiatingProgram/content distribution protectionDigital signatureXML
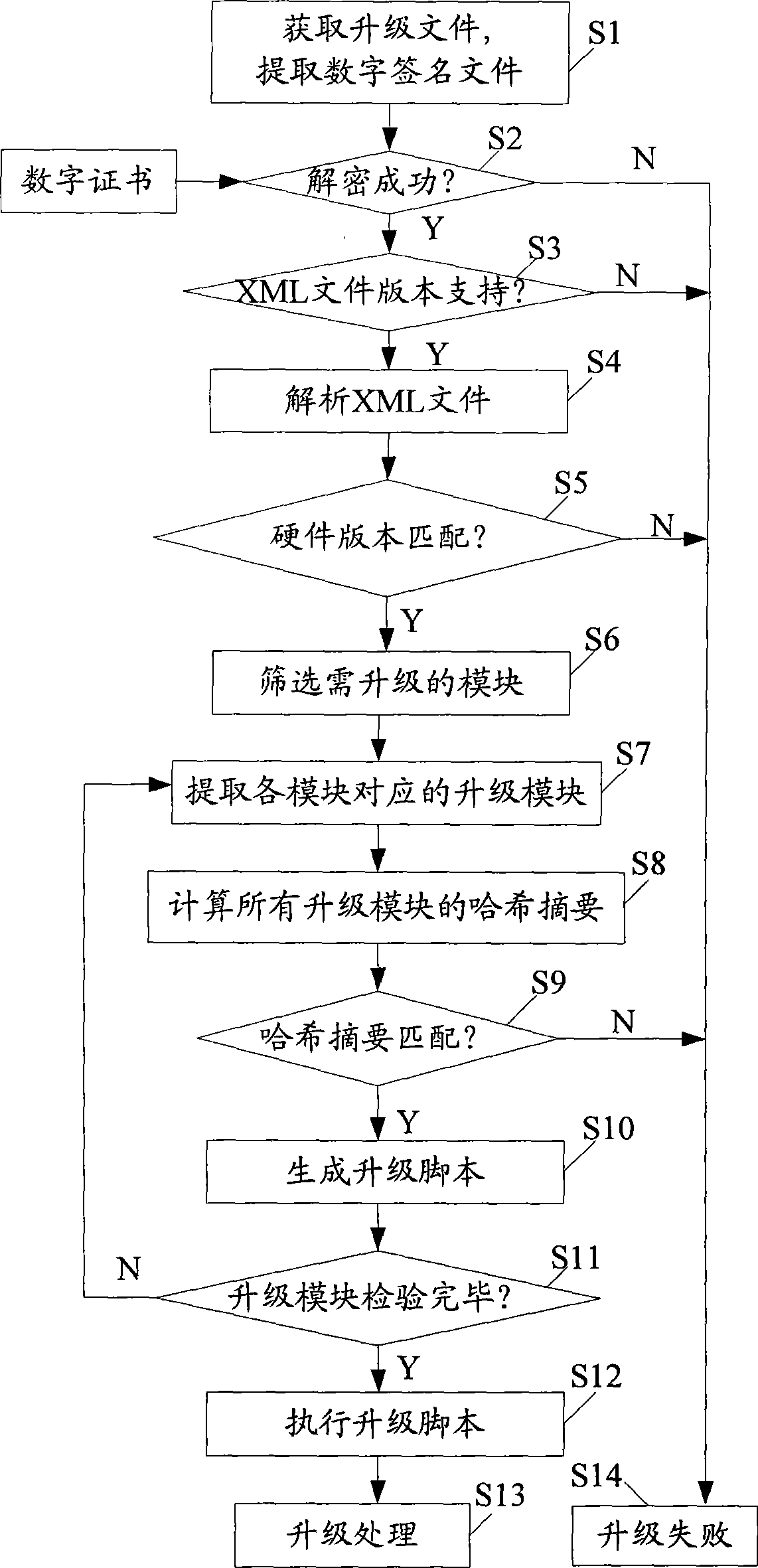
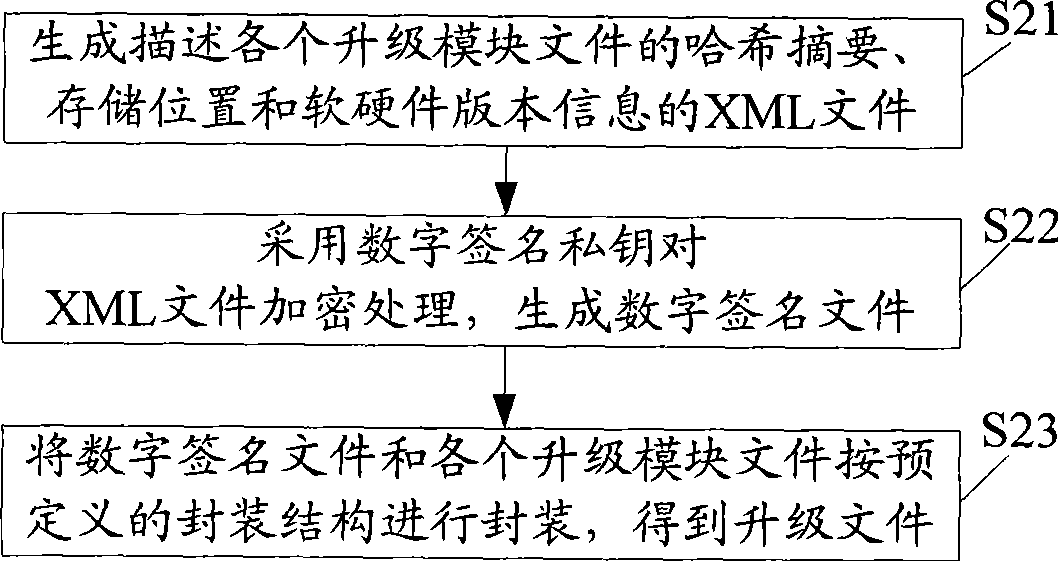
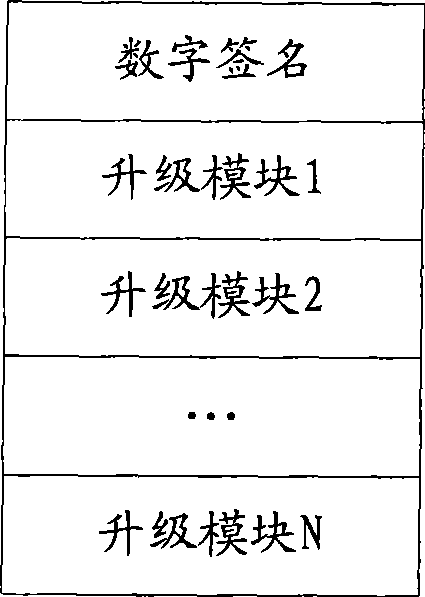
The invention discloses a firmware upgrading method based on digital signatures, and a device thereof, wherein the upgrading method comprises the following steps: encapsulation is performed according to a predefined encapsulation structure so as to generate an upgrading file based on a digital signature; a product needing firmware upgrading obtains the upgrading file; a digital signature file is extracted from the upgrading file and decrypted, so as to obtain an XML file; the XML file is analyzed so as to screen out upgrading module files needing to be upgraded; the legitimacy and integrity of every upgrading module file needing to be upgraded are verified respectively, so as to generate an upgrading script for upgrading all the upgrading module files which pass verification; and the upgrading script is executed so as to upgrade the firmware. The invention discloses a firmware encapsulating method based on digital signatures, and a device thereof. The invention verifies the integrity and legitimacy of every upgrading module file in the upgrading file through the digital signature file, and generates the upgrading script to finish upgrading firmware, thereby improving the security and convenience of firmware upgrading.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
Authenticated and distributed transaction processing
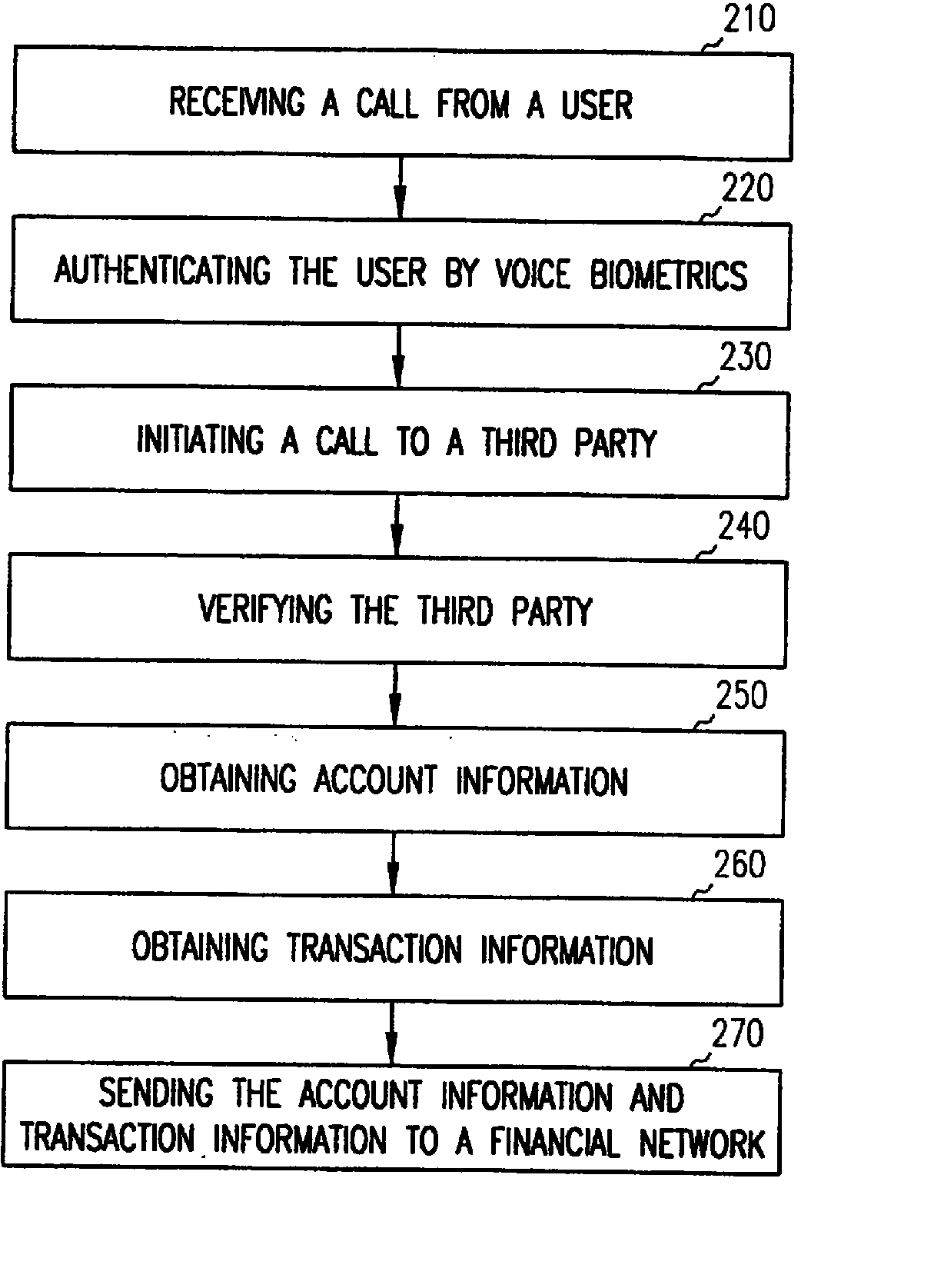
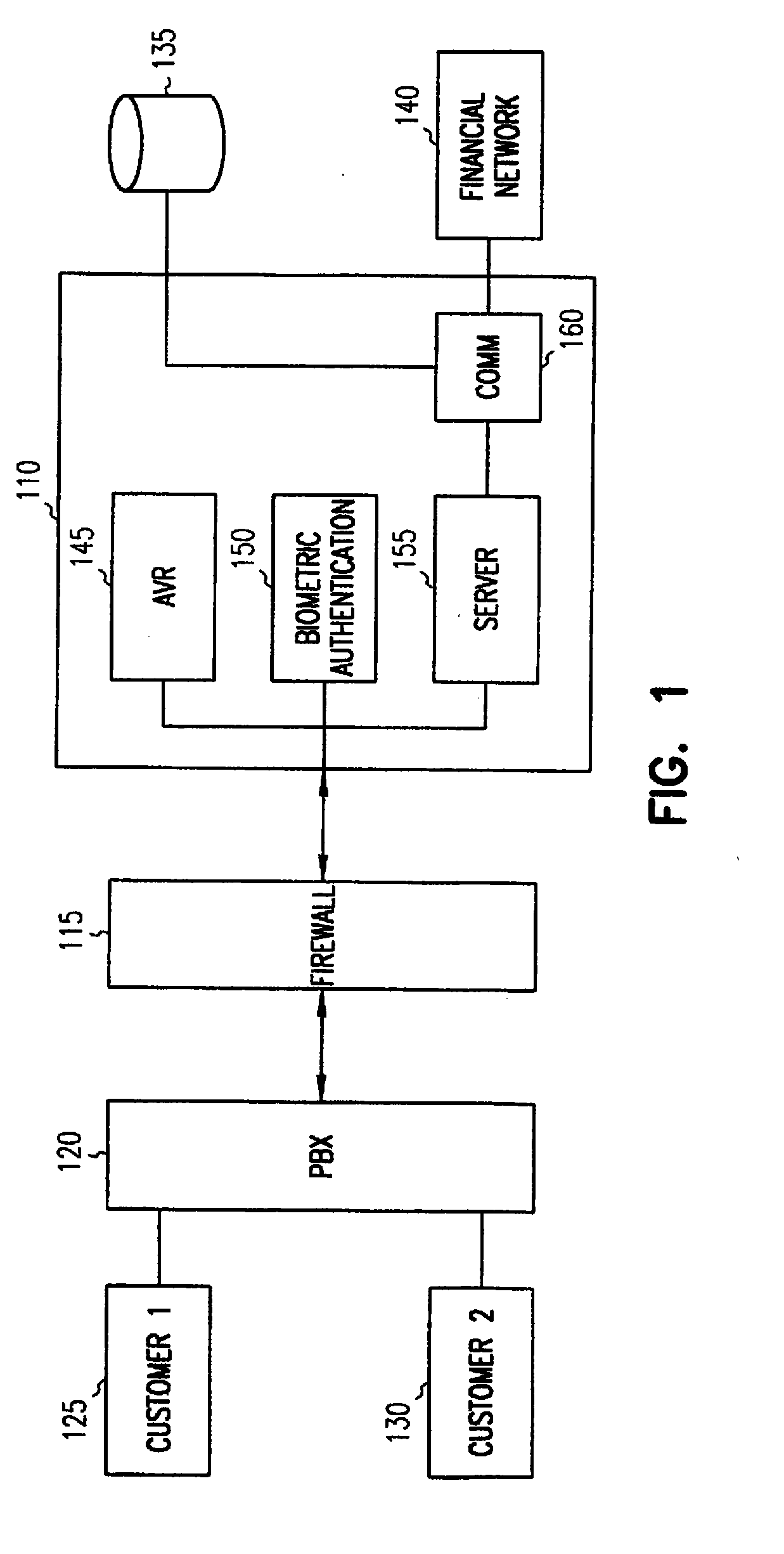
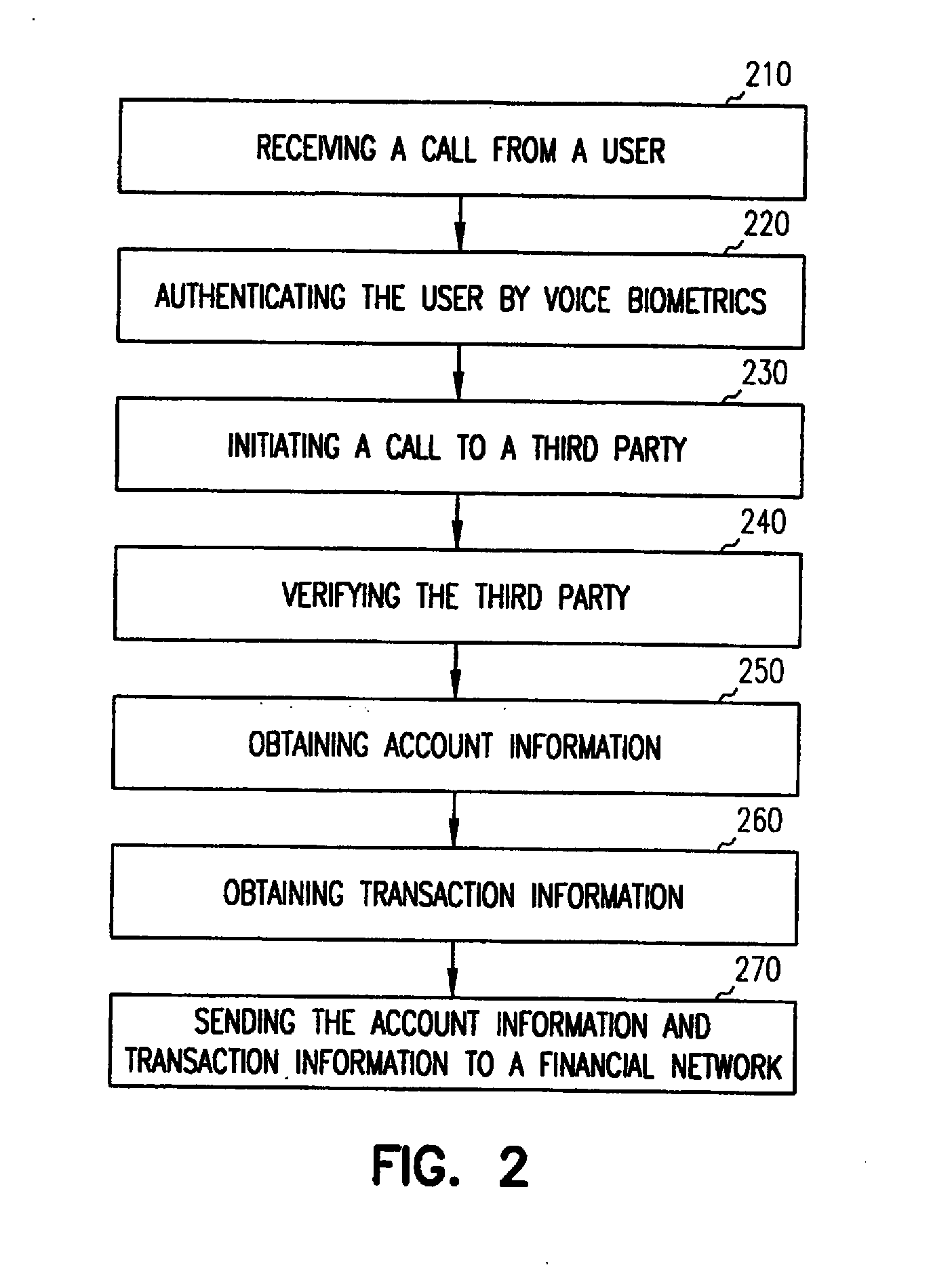
InactiveUS20070174186A1Prevent leakageIntegrity guaranteedFinanceUser identity/authority verificationThird partyDistributed transaction processing
An integrity network is used to authorize electronic transfer of funds between two entities such as a caller or user and a third party. The network is accessed by a user via an electronic device that is capable of transmitting voice, such as a telephone. The network uses voice recognition functions, and optionally other information to uniquely identify the user and hence guarantee the integrity of transactions. In one embodiment, a user's phone number, a cellular phone serial number, or other code can be used as a security token. A person called via the network can further validate the identity of the user. Once validated, the user becomes a trusted member of the integrity network. Financial product can be provided to the trusted member with guarantees to the network of the identity of the trusted member.
Owner:HOKLAND SEAN
Online fracturing test vehicle
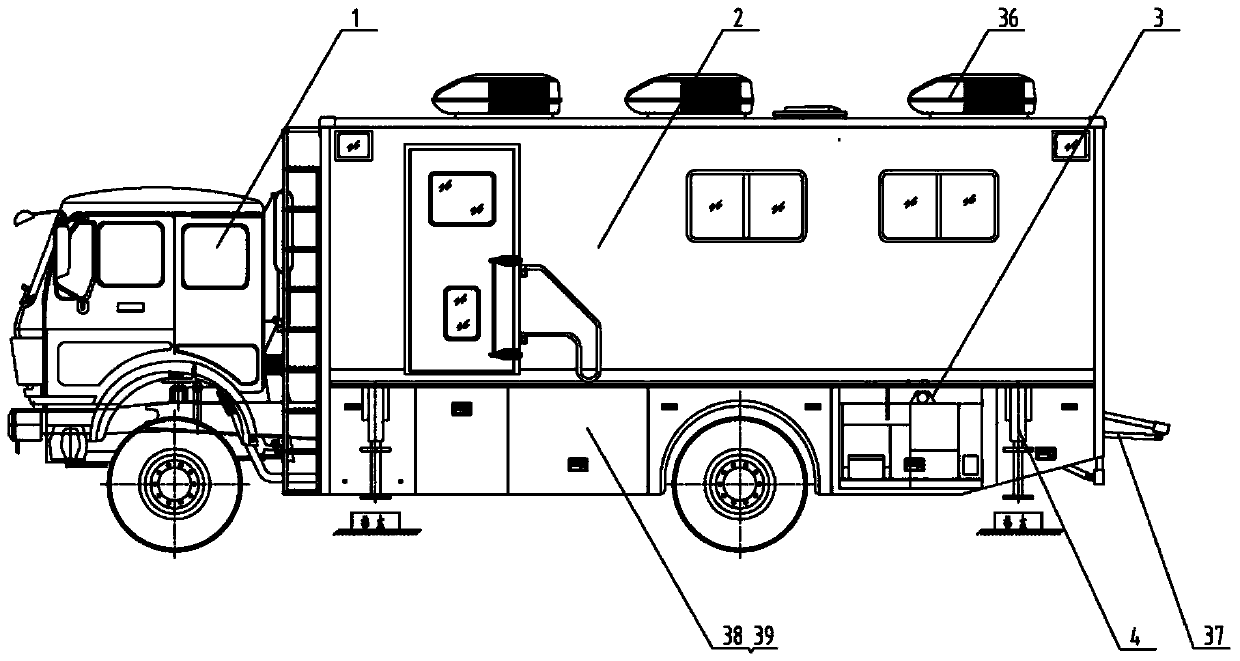
ActiveCN104369687AGuaranteed shock absorptionEasy to useFluid removalItem transportation vehiclesOnline testFracturing fluid
The invention relates to an online fracturing test vehicle. The online fracturing test vehicle comprises a chassis, a shelter, a back protection device, a skirt edge box, a heating system and an automatic leveling device, wherein the shelter is mounted at the upper part of the chassis; the back protection device is mounted at the back end of the chassis; the skirt edge box and a generator are mounted at the side of the chassis; the automatic leveling device is mounted at four corners of the bottom of the chassis; the heating system is mounted at the top of the chassis; the shelter is integrated with an experiment instrument for a fracturing fluid test and a support agent analysis evaluation test; and the experiment instrument for the fracturing fluid test and the support agent analysis evaluation test is mounted on the chassis provided with the shelter, so that the online test can be performed on spot, the detecting accuracy and preciseness can be improved, and the detecting efficiency is improved.
Owner:YANTAI JEREH PETROLEUM EQUIP & TECH CO LTD
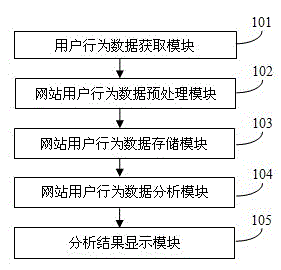
System and method for analyzing network user behavior information
InactiveCN102946319AGet goodIntegrity guaranteedData switching networksData conversionInformation analysis
The invention discloses a system and a method for analyzing network user behavior information. The system comprises a network user behavior data obtaining module, a network user behavior data preprocessing module, a network user behavior data storage module, a network user behavior data analyzing module and an analysis result display module, which are connected with each other in sequence; and the method comprises the steps of data collection, data preprocessing, data conversion, data analysis, data displaying and so on. According to the invention, the network user behavior information can be conveniently and rapidly obtained, and integrity, continuity and effectiveness of the user behavior information are guaranteed.
Owner:FOCUS TECH +1
Method for quick-speed preparing aerogel by hydro-thermal synthesis at low cost
InactiveCN101456569AReduce surface tensionIntegrity guaranteedSilicaAlkali metal silicatesReaction temperatureHydrothermal synthesis
The invention discloses a method for preparing aerogel materials by combining hydrothermal synthesis technology and sol-gel technology. The prepared aerogel comprises one or more of alumina aerogel, silica aerogel, zirconia aerogel and titania aerogel. The method comprises the following steps: mixing a reactant and a structure-directing agent according to certain proportion, and adding a pH value control agent to adjust the pH value; sealing hydrothermal reaction equipment, heating the mixture to be between 50 and 280 DEG C, making the mixture stand for 0 to 72 hours, raising the temperature to be between 60 and 300 DEG C, and continuously reacting for 0.1 to 72 hours; and cooling gel, taking out the gel, drying the gel and obtaining the aerogel. Compared with the prior art, the method has low reaction temperature and pressure, small equipment investment and simple and controllable technology, reduces potential safety hazards, greatly improves the preparation speed of the aerogel, saves the production cost, and is favorable to realize commercial mass production.
Owner:纳诺科技有限公司 +1
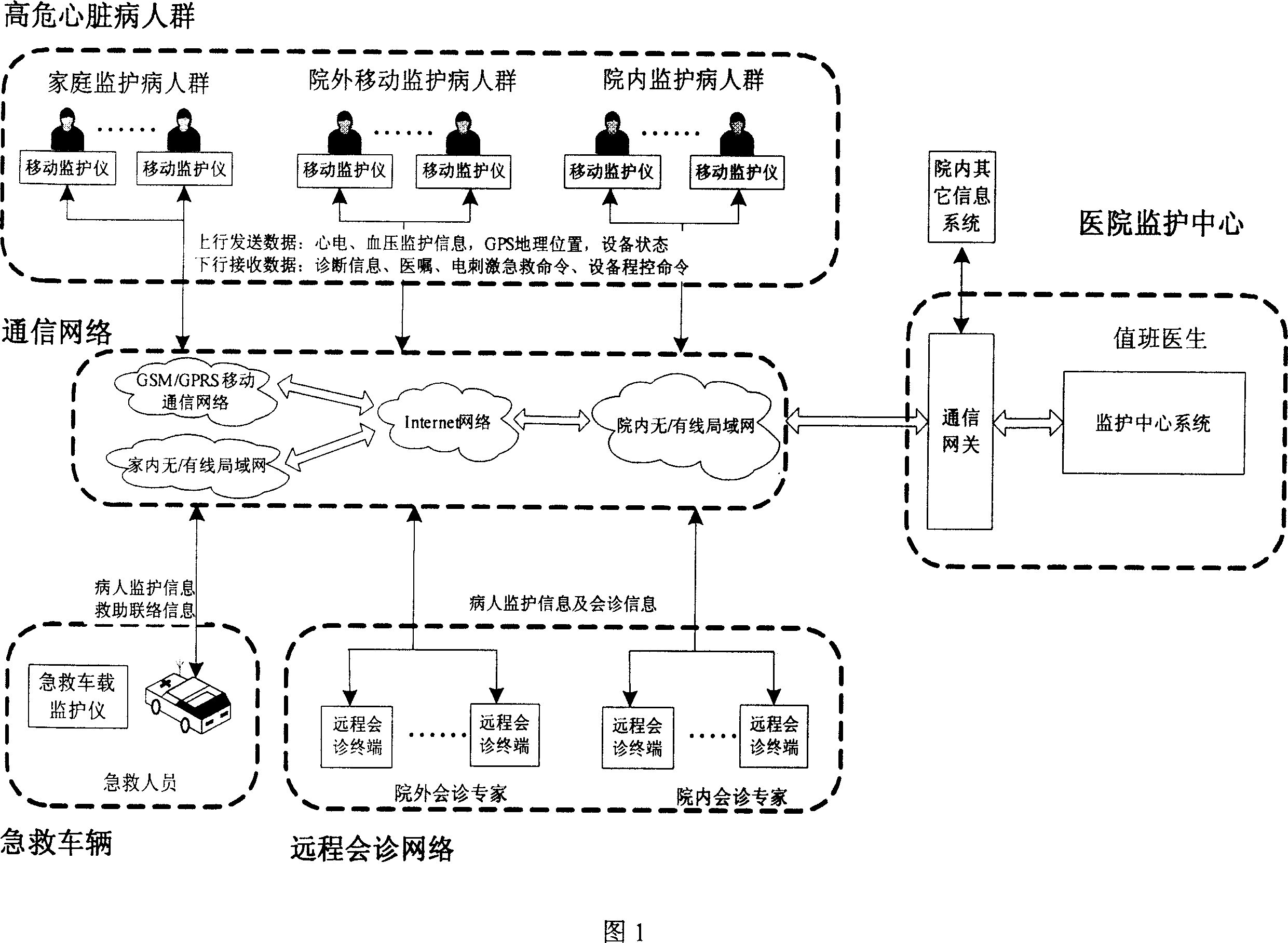
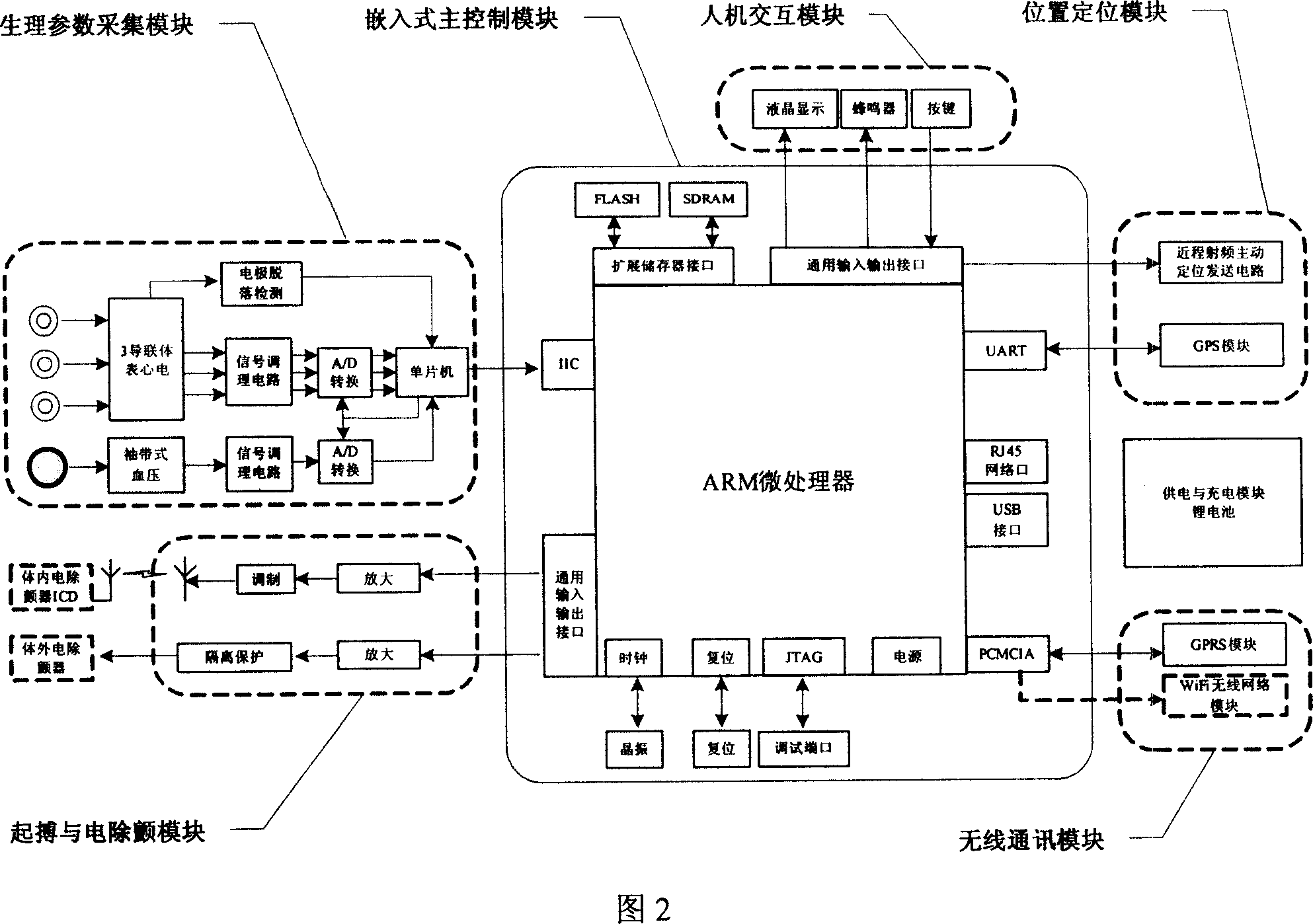
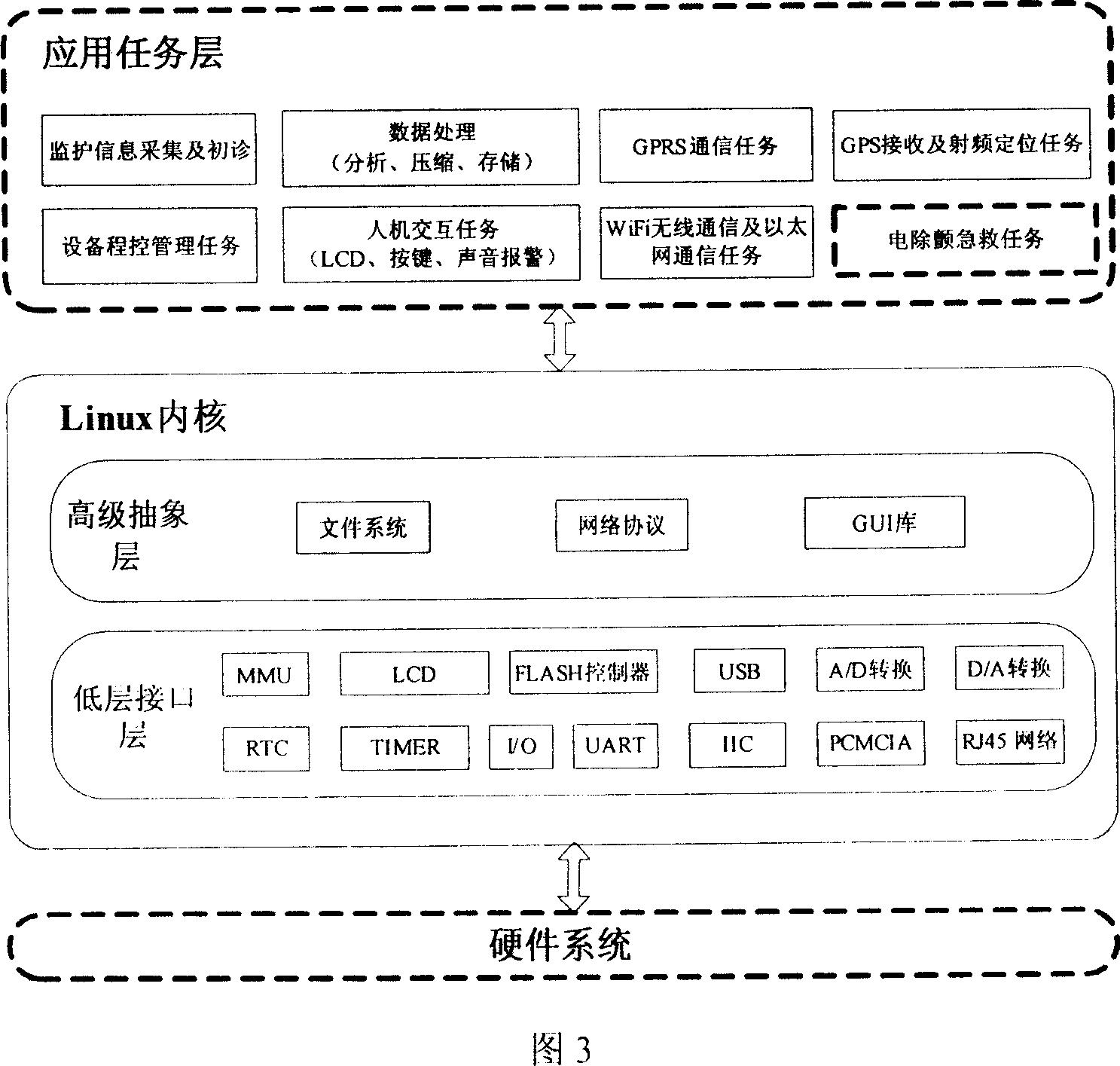
Realtime remote monitoring system for high risk heart disease crowd and integrated control type continuous monitoring method
InactiveCN1943505ARealize centralized continuous monitoringMeet clinical monitoringSurgeryVaccination/ovulation diagnosticsFar distanceCrowds
The invention belongs to supervisory technical field for distance treatment, particularly for applying far distance patient monitor system and centralized continuously monitoring process to high-risk people of heart disease. Said system comprising portable monitor carried by patients, hospital central monitor center, doctors' far distance group consultation terminal, ambulance monitor, communication net system, etc. The monitor process is, through communication network such as mobile , local, wireless and internet communication, making hospital central monitor center and portable monitor in and out of the hospital , ambulance carrying monitor and far distance group consultation real-time connecting, exchanging and transmitting information such as real-time ECG, blood pressure, etc., patient geographical location, doctor group consultation and advice, and far distance equipment remote measurement & program controlled in each terminal, realizing continuously monitor to high-risk people of heart disease, applying central remote measurements and program control of far distance mobile terminal, prior to coming on of heat disease early period proper diagnosis given and applying real-time treatment to serious patient, etc.
Owner:方祖祥 +2
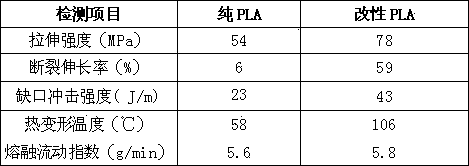
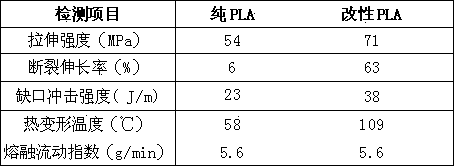
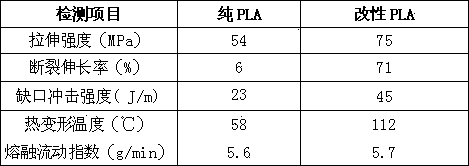
3D printing modified polylactic acid material and preparation method thereof
InactiveCN103467950AIncrease profitSelf-performance has not declinedMonocomponent polyesters artificial filamentArtifical filament manufactureHeat deflection temperaturePolymer science
A 3D printing modified polylactic acid material comprises, by weight, 70-85 parts of polylactic acid, 1-5 parts of chain extenders, 1-5 parts of cross-linking agents, 0.5-1 part of nucleating agents, 5-10 parts of polymers with low molecular weights, 5-10 parts of flexibilizers, 1-5 parts of fortifiers and 0.3-0.8 part of antioxidants. According to the 3D printing modified polylactic acid material, a low-temperature smashing hybrid reaction technology is utilized, modified processing is carried out on polylactic acid, toughness, impact strength and the heat distortion temperature for the polylactic acid are improved to a large extent, and the polylactic acid can have wider application prospects in 3D printing materials.
Owner:佛山市斯太克科技有限公司
Method for integrating and exchanging data on basis of unique identification
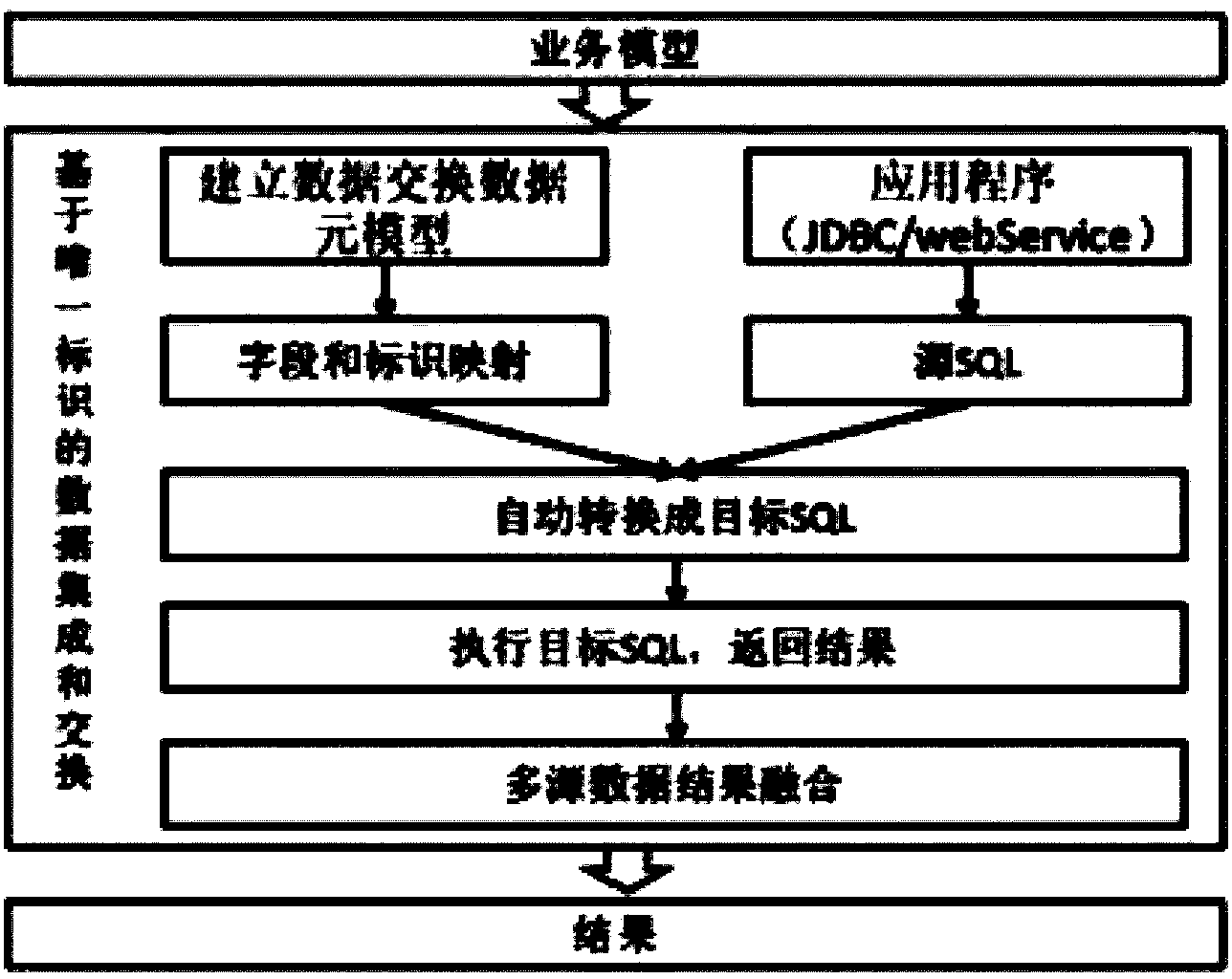
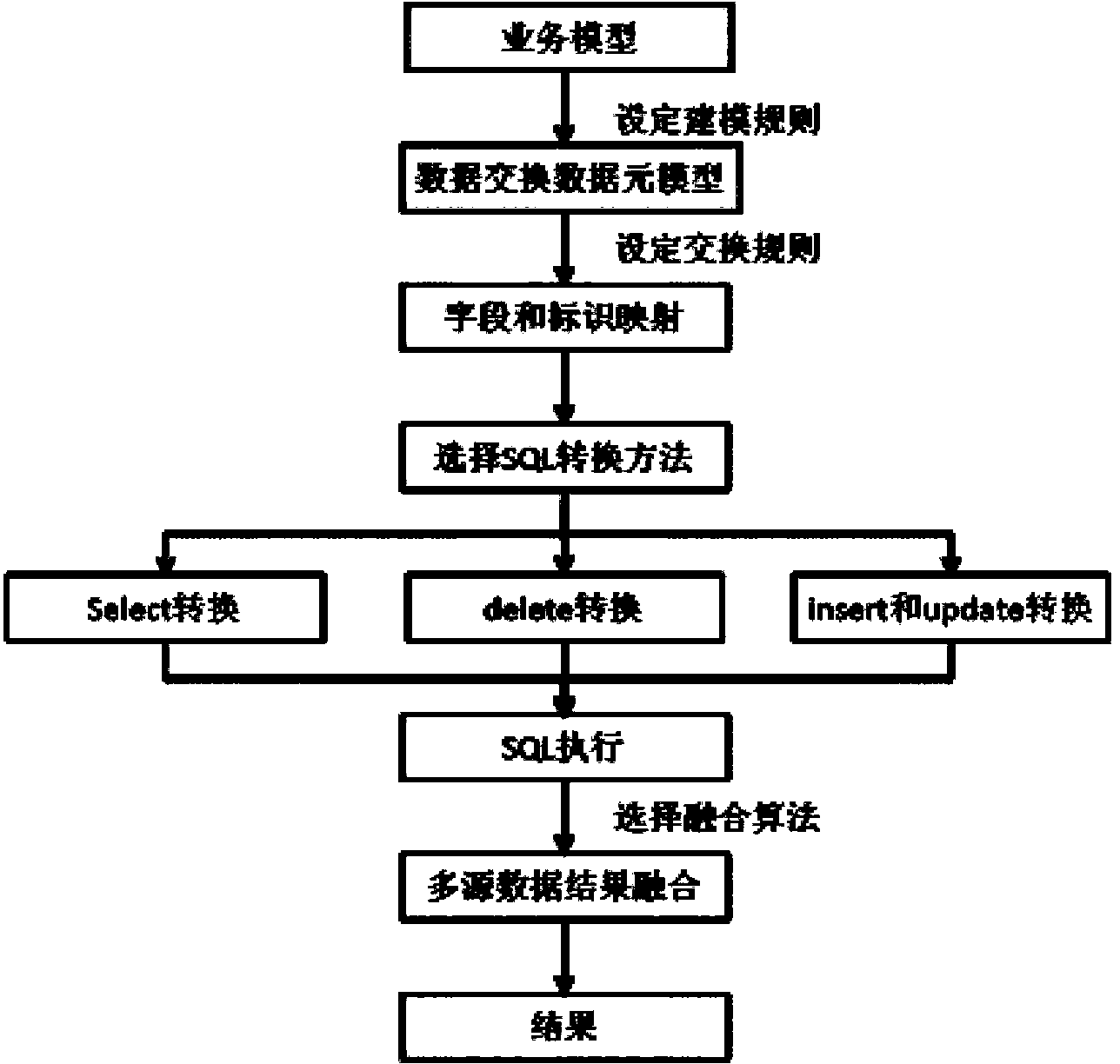
ActiveCN104346377ARealize unified and centralized managementAccurate extractionDatabase management systemsSpecial data processing applicationsData sourceResult set
The invention relates to the technical field of information, and particularly discloses a method for integrating and exchanging data on the basis of unique identification. The method includes building data element management models for business required to be integrated, exchanged and shared, and uniquely identifying each data item in each data element management model; mapping the identification in the data element management models with fields of multi-source heterogeneous databases; generating corresponding target SQL (structured query language) statements according to the fields corresponding to the identification; accessing the multi-source heterogeneous databases, executing the target SQL statements and returning result sets; fusing and processing the result sets by the aid of fusion algorithms. The method has the advantages that conflict examples in heterogeneous data sources can be effectively recognized and fused by the aid of the method, and accordingly data integration / data fusion effects can be improved on high level; the data exchange and integration accuracy can be effectively improved, and the data integration and exchange efficiency can be greatly enhanced.
Owner:KARAMAY HONGYOU SOFTWARE
Map update data supplying apparatus, version table, map data updating system, and map update data supplying method
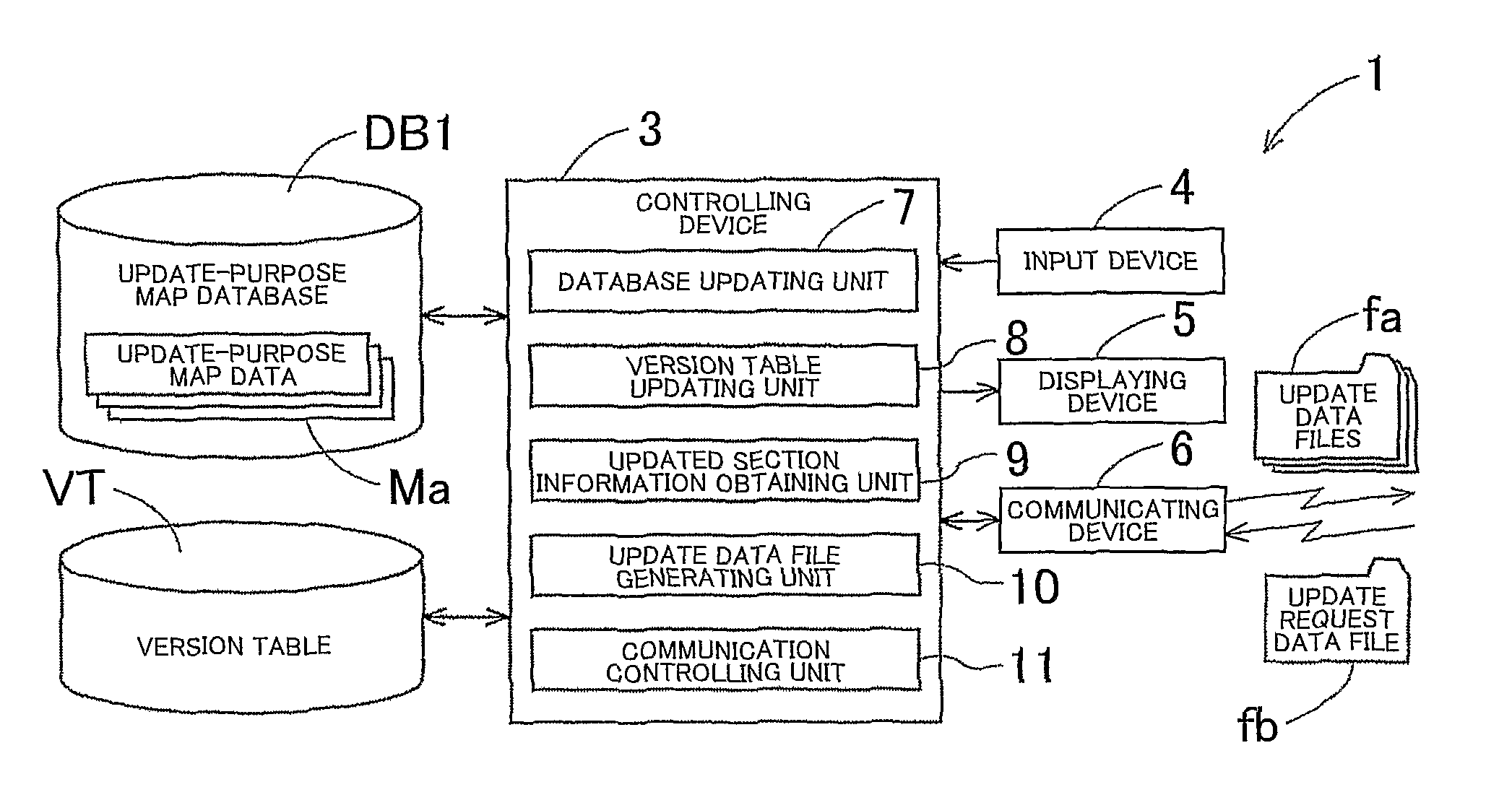
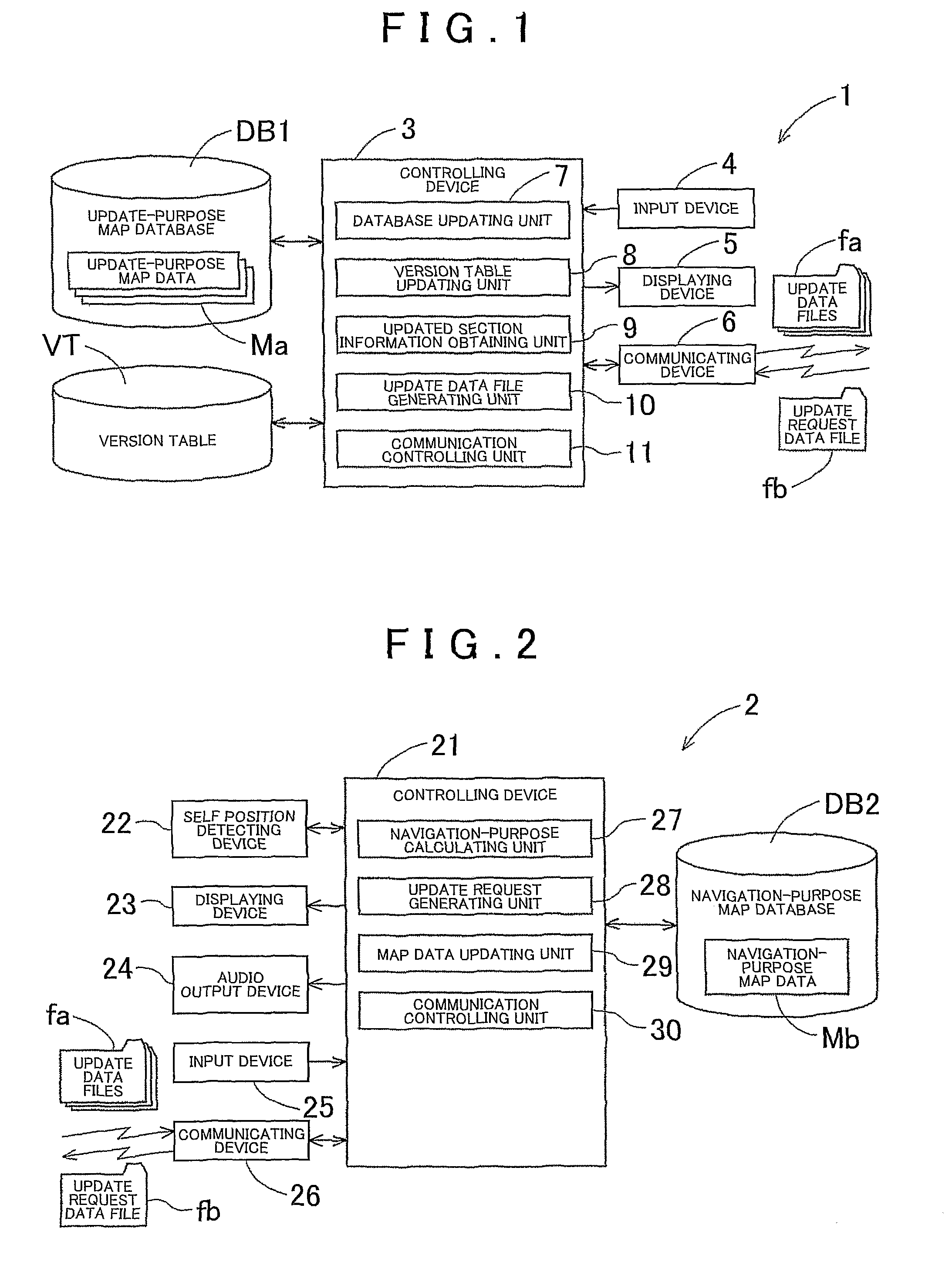
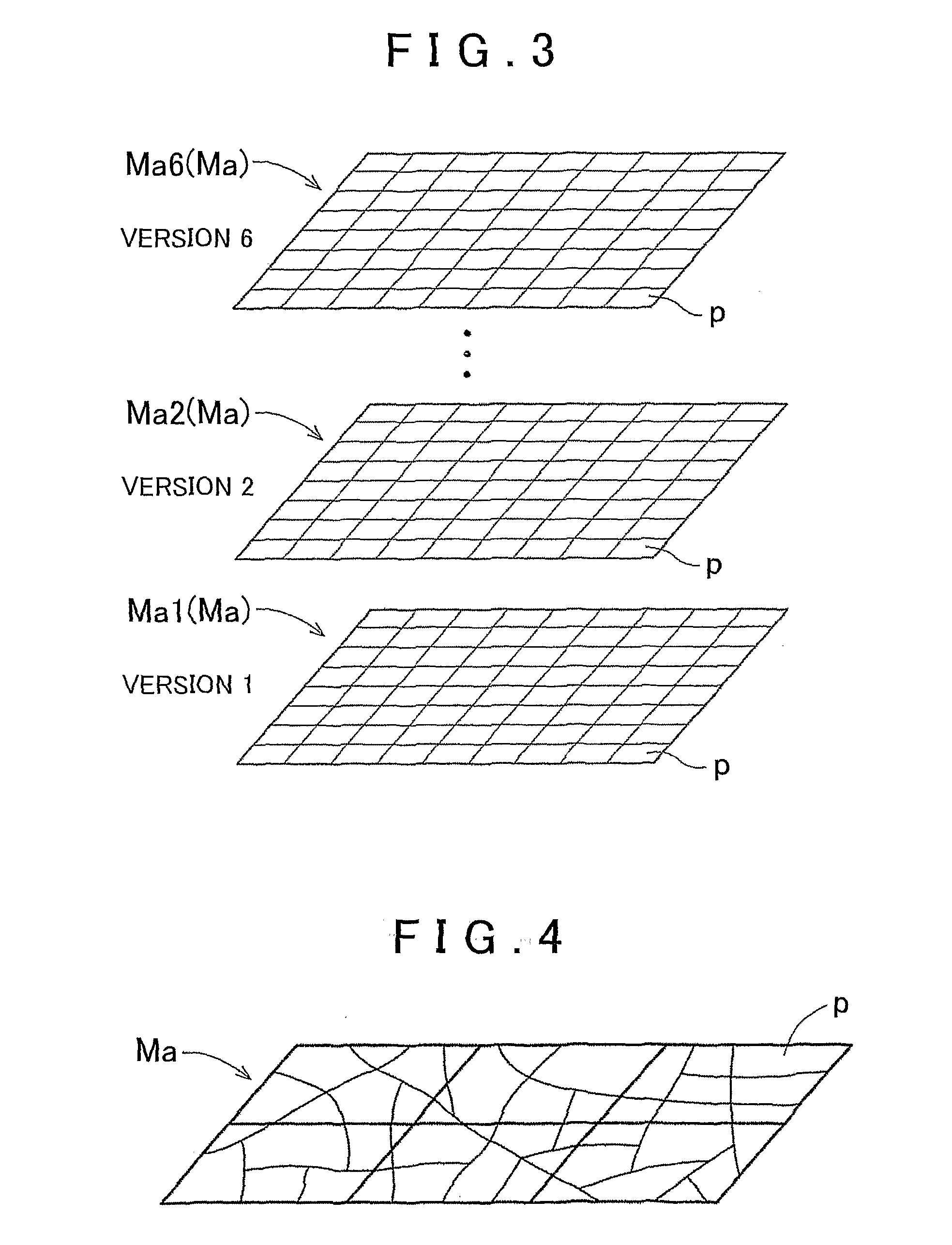
ActiveUS20090248758A1Integrity guaranteedInstruments for road network navigationMaps/plans/chartsData fileComputer science
Map updating systems, methods, and programs that extract update requiring sections with respect to an update requesting section that is one of the sections being a target of an update request requesting that the target map data should be updated, obtain the information related to the guaranty versions respectively corresponding to the extracted update requiring sections by referring to the version table, the update requiring sections each being one of the sections that needs to be updated in order to guarantee integrity between the sections that are positioned adjacent to each other after the update requesting section has been updated, and generate, based on the update-purpose map database, one of the update data files regarding the update requesting section as well as other ones of the update data files regarding the update requiring sections and having the update versions indicated as the guaranty versions.
Owner:AISIN AW CO LTD +1
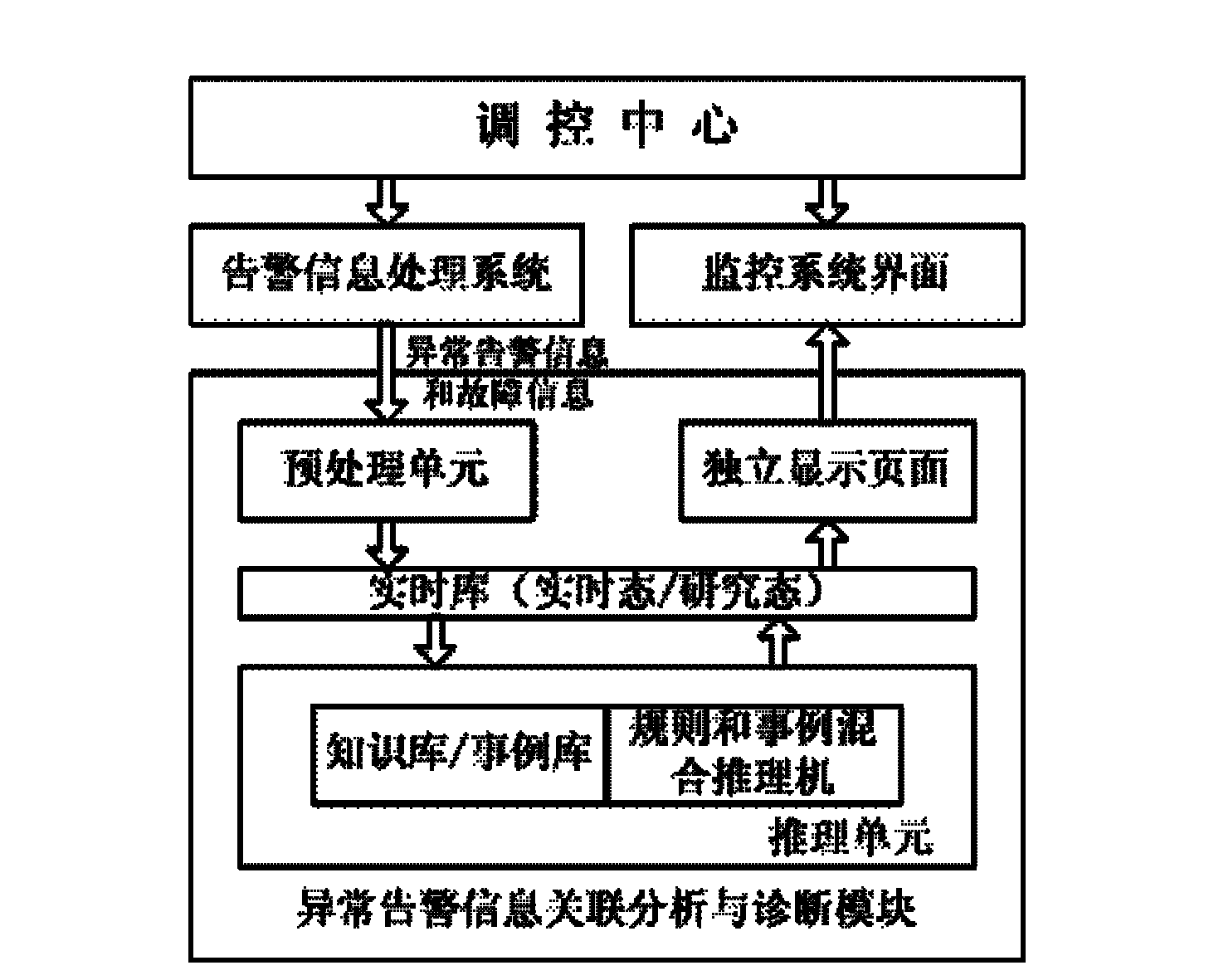
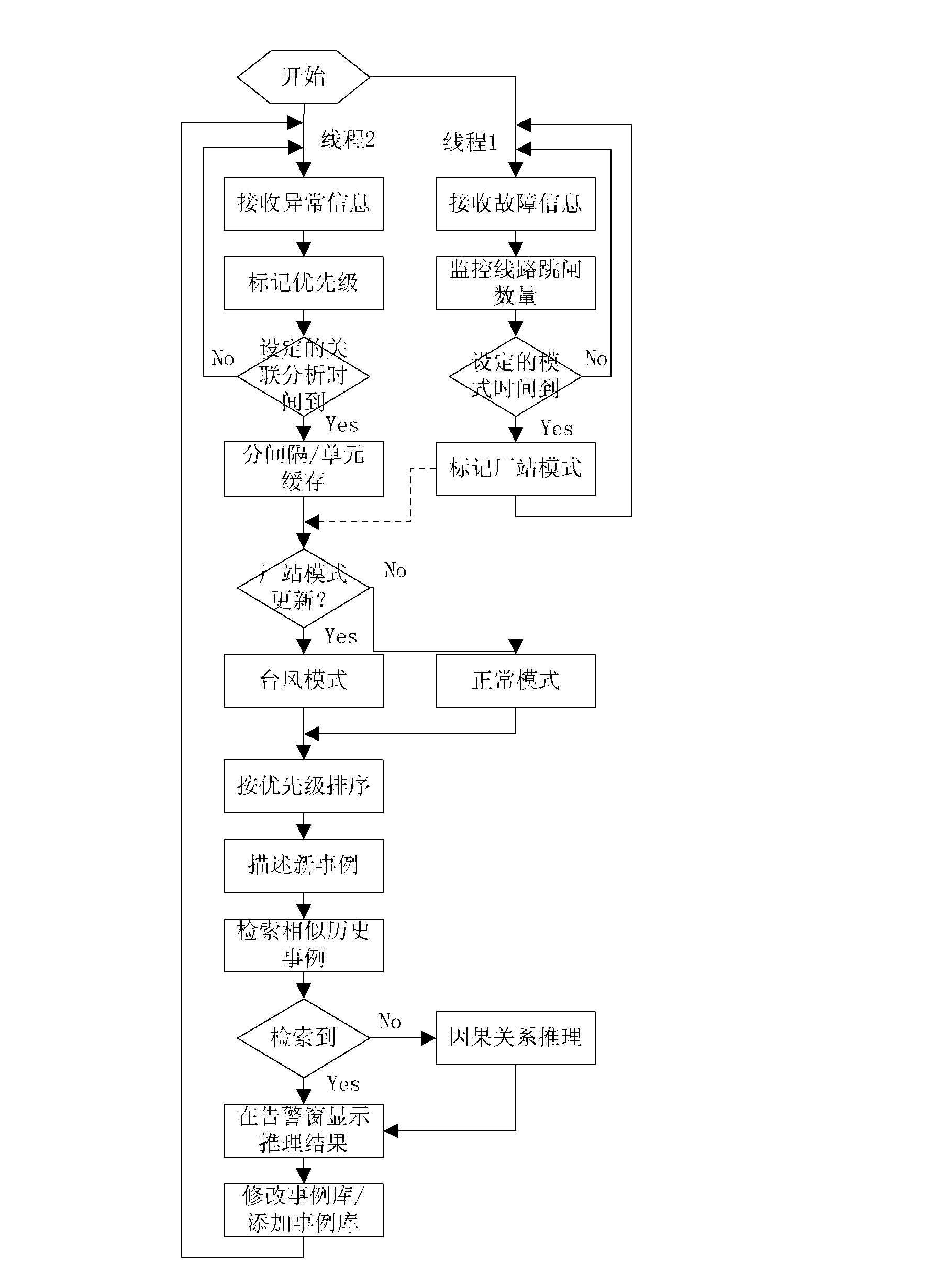
District power network equipment abnormal alarm signal association analysis and diagnosis method
InactiveCN102638100AIntegrity guaranteedGuarantee authenticityCircuit arrangementsInformation processingPower system scheduling
The invention discloses a district power network equipment abnormal alarm signal association analysis and diagnosis method in the field of automation of scheduling of electric power systems. According to the method disclosed by the invention, the weather situation of a plant station region at which abnormal alarm information is located can be automatically identified so as to determine the information processing mode. The method disclosed by the invention has the beneficial effects that by realizing intelligent association analysis and auxiliary decision making of the equipment abnormal alarm information under the real-time state, and performing playback on historical alarm information and performing real-time treatment on manual set information under the research state, the abnormal treatment time is greatly reduced, the incidence of accidents is reduced, a real-time, rich and intelligent auxiliary decision-making support is provided for regulation and control staff, and the safe, high-quality, economical and stable operation of an electric fence is further ensured.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
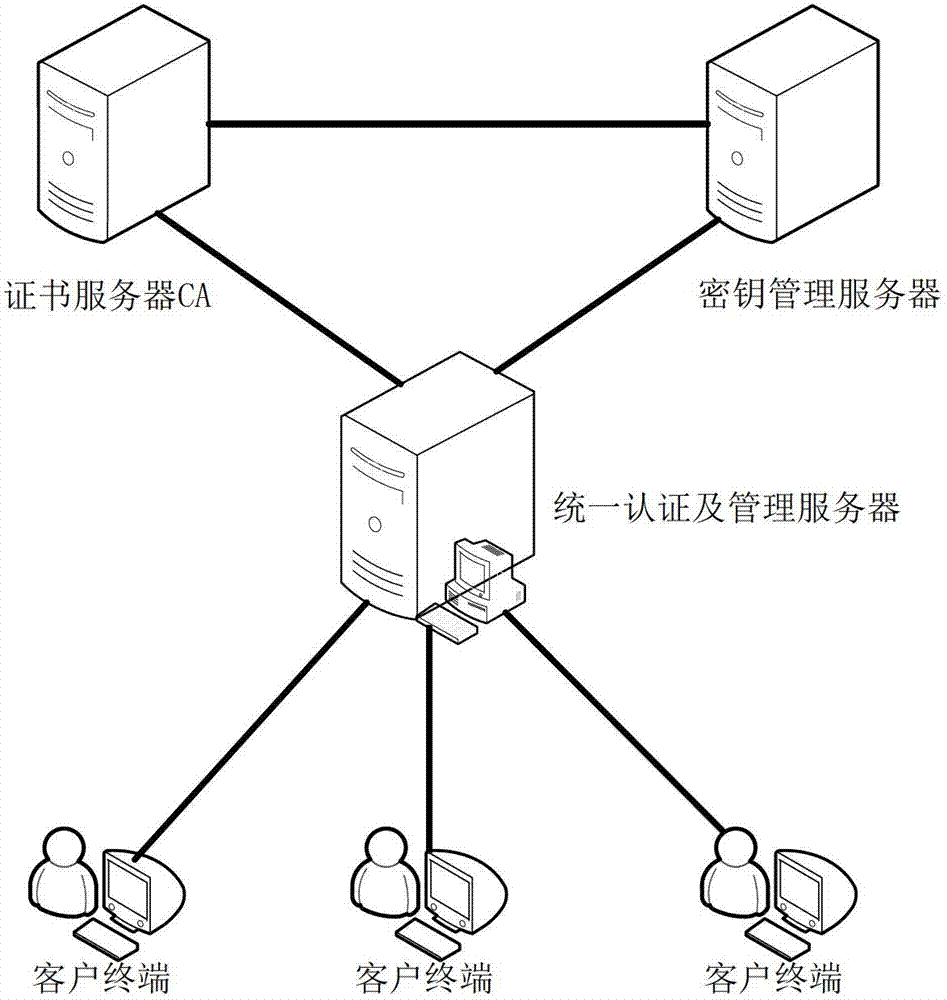
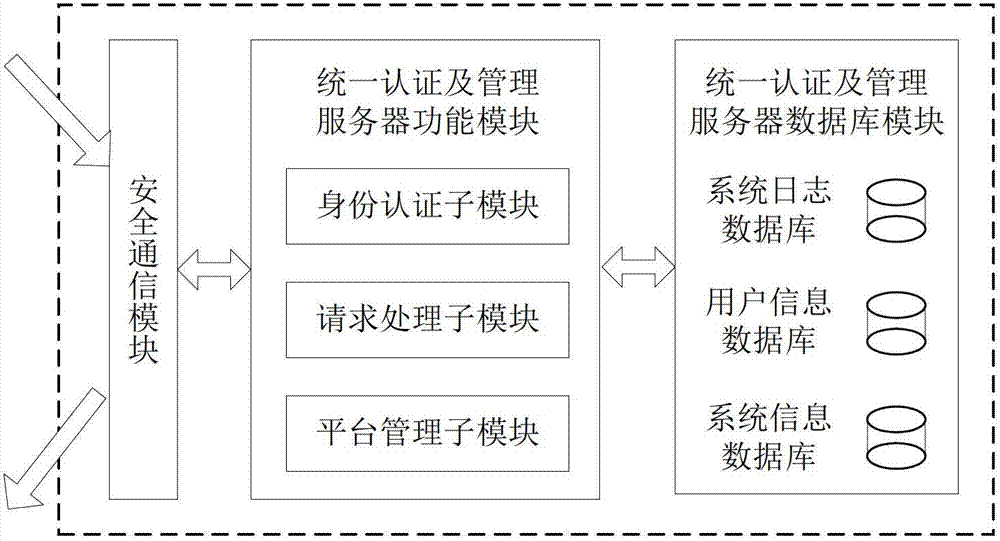
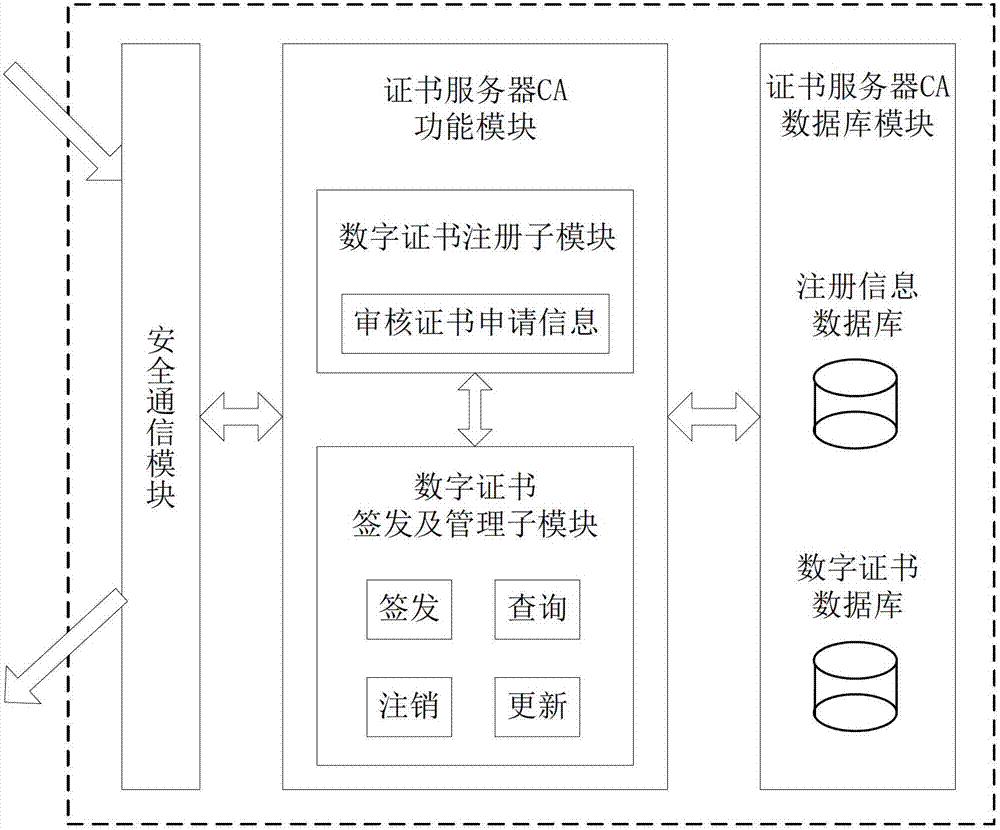
File safe protection system and method thereof
ActiveCN102970299ASimple structureEasy to buildKey distribution for secure communicationUser identity/authority verificationConfidentialityComputer terminal
The invention discloses a file safe protection system and a method, which mainly solves the problems of network illegal invasion, information stealing and tamping, impersonation and weak deny resistance in the conventional information system. The file safe protection system consists of a unified authentication and management server, a certificate server CA, a secret key management server and a client terminal; the unified authentication and management server is used as a middle node and is used for processing or transmitting a service request sent by the client terminal; the certificate server CA processes a certificate service request of the client terminal and provides basic support for identification; and the secret key management server processes the secrete key service requests of the client terminal and the certificate server CA, and is used for encrypting and decrypting a file for the client terminal and providing parameter support for a digital certificate signed by the certificate server CA. With the adoption of the file safe protection system and method provided by the invention, identification, confidentiality, integration and non-repudiation services can be provided; and the file can be safely protected in transmission, storage, sharing and access processes.
Owner:XIDIAN UNIV
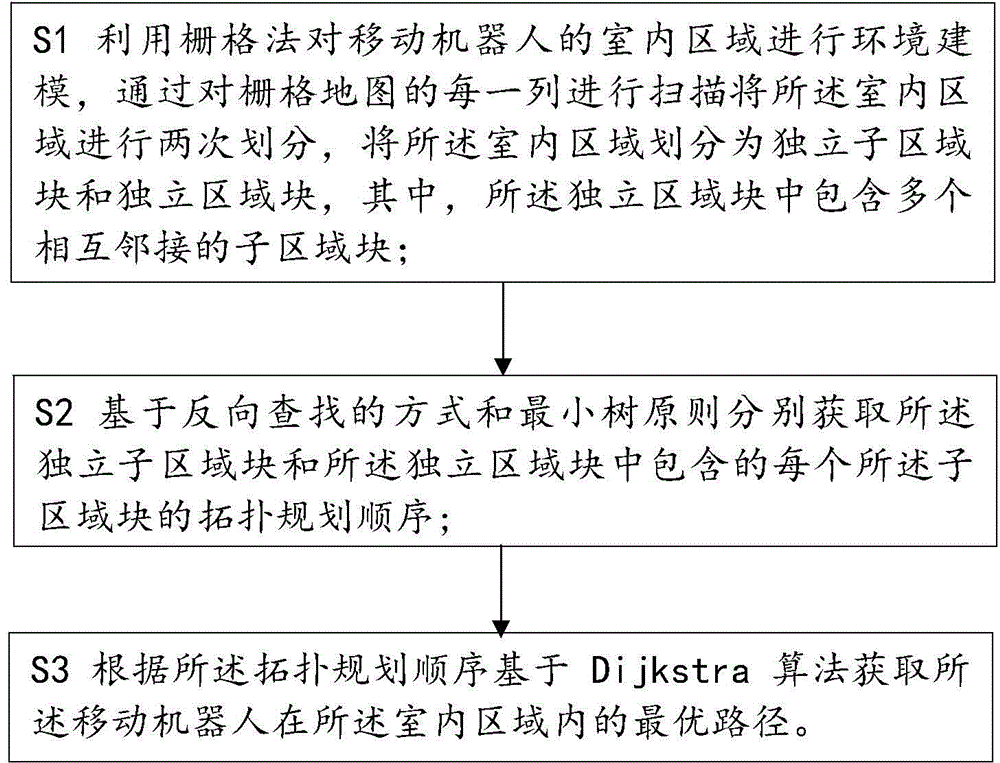
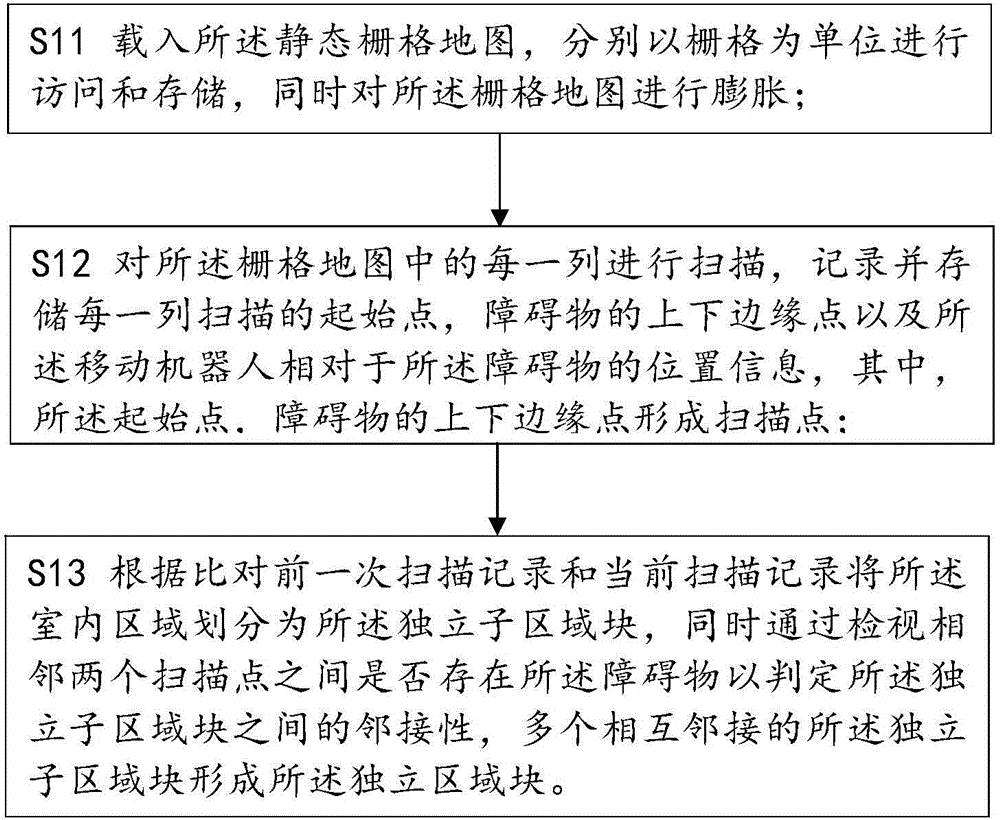
Dynamic indoor region coverage division method and device for mobile robot
ActiveCN104615138AConform to thinkingEasy to operatePosition/course control in two dimensionsCognitionComputer science
The invention discloses a dynamic indoor region coverage division method and device for a mobile robot. The dynamic indoor region coverage division method at least includes that scanning each row of a raster map to divide the indoor region for two times, dividing the indoor region into an independent sub-region block and an independent region block, wherein the independent region block comprises a plurality of adjacent independent sub-region blocks; acquiring the topology planning sequence of the independent sub-region block and the topology planning sequence of each independent sub-region block of the independent region block based on a reverse searching mode and a minimum tree principle; acquiring the optimal route of the mobile robot in the indoor region based on a Dijkstra algorithm according to the topology planning sequences. The dynamic indoor region coverage division method and device for the mobile robot start from the environment cognition habits of the human to divide the indoor environment for two times, the completeness of the region with a certain function in the environment is guaranteed, and meanwhile, the region with a certain function is divided into the independent sub-regions where the mobile robot can walk; the dynamic indoor region coverage division method and device for the mobile robot conform to the robot thought.
Owner:山东越浩自动化设备有限公司
Cove elements and floor coatings and methods for installing
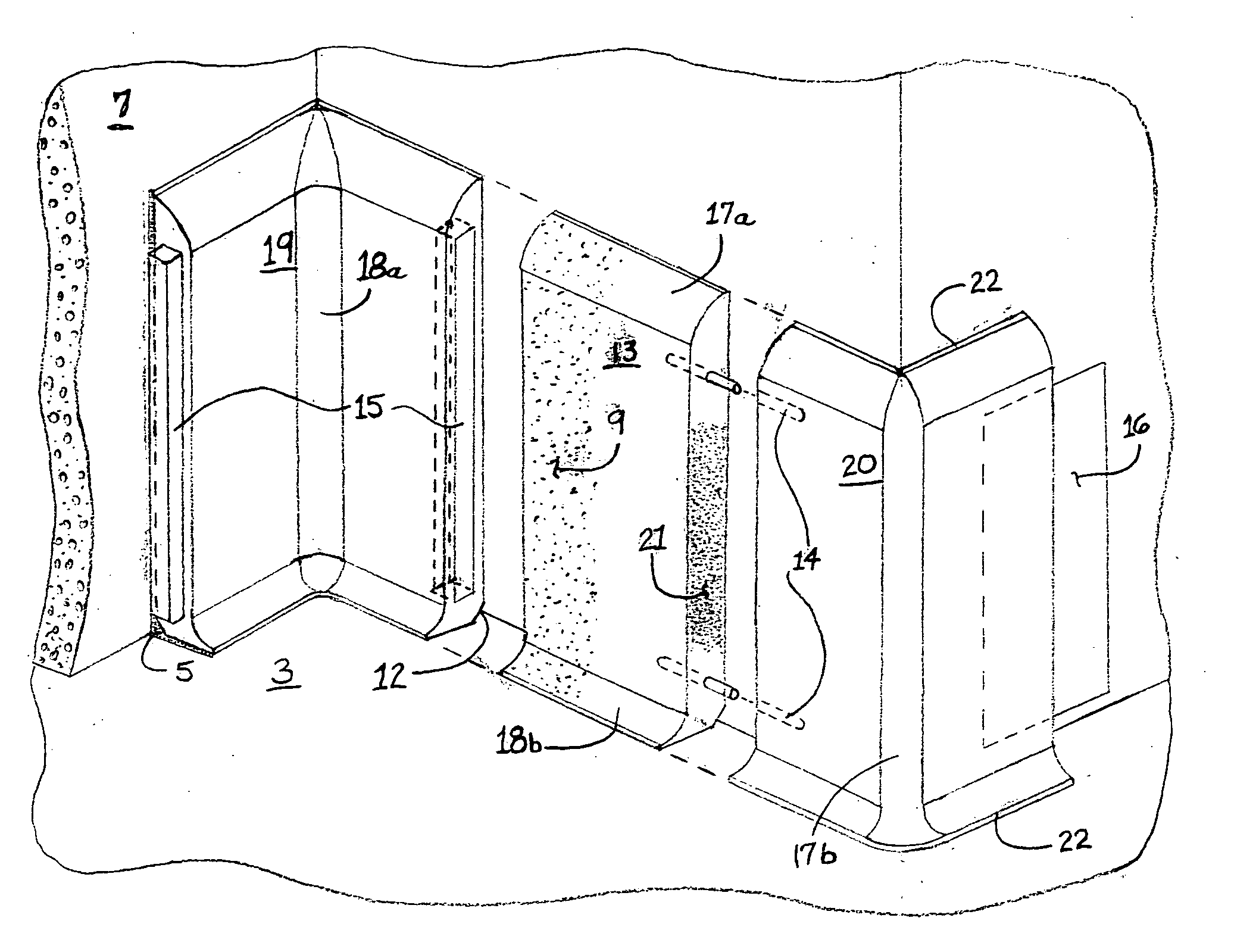
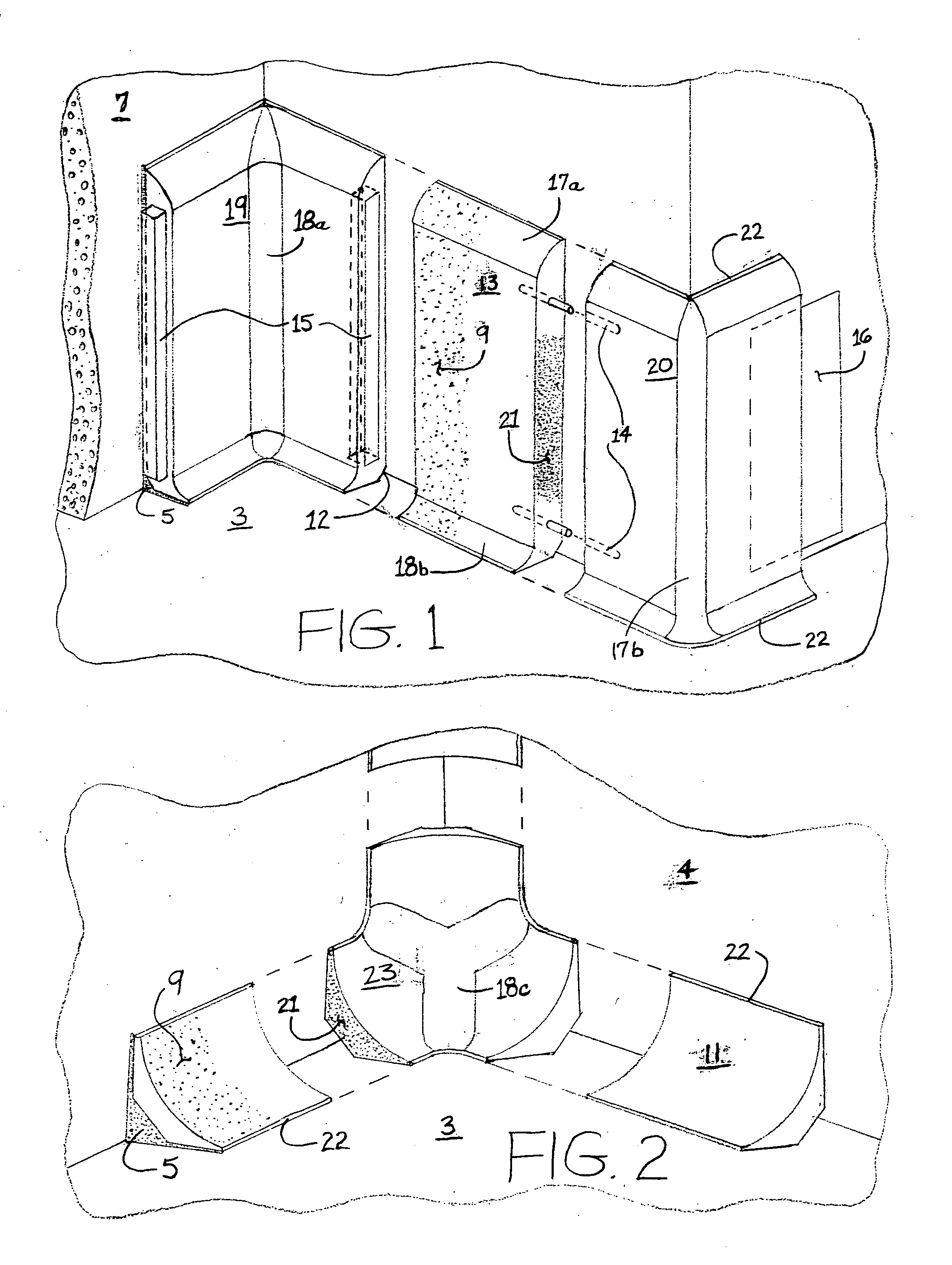
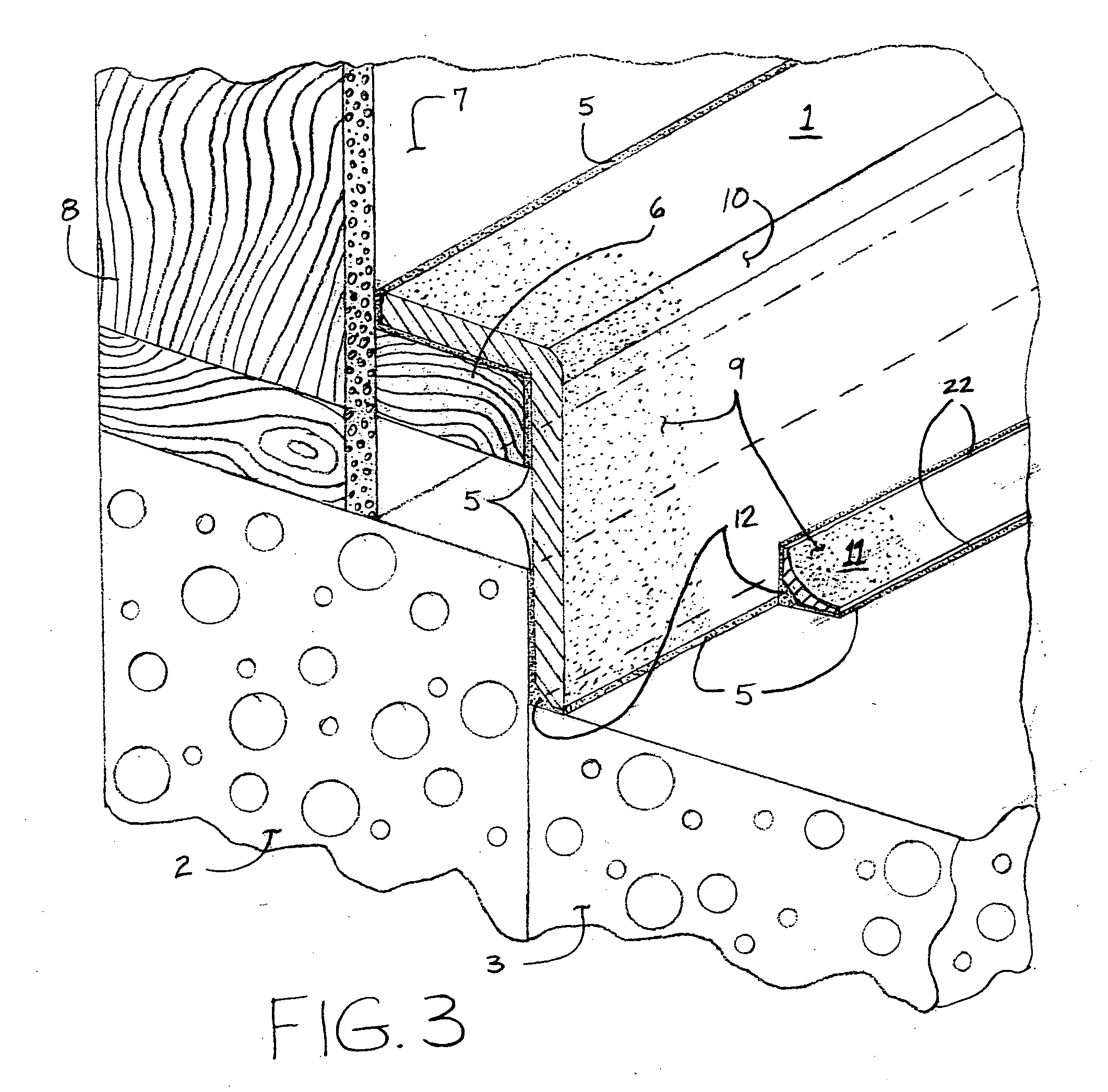
InactiveUS20050011159A1Less-expensive to installSuitable for mass productionWallsMouldsEngineeringShape formation
Described herein is a monolithic flooring system that includes cove elements that are shaped to provide a transition between floor and wall such that a floor coating may be installed over the cove elements and sub-flooring to create a unitary floor-cove covering making for a surface that is more sanitary and easier to clean. Also described are various shaped cove elements that enable creation of a good transition between wall and floor. The cove elements are preferably made of material similar to the sub-floor, for instance a cementitious material. The floor coating is preferably a resinous material.
Owner:STANDAL DOUGLAS J +1
High-quality transfer method of graphene prepared by chemical vapor deposition method
The invention relates to a high-quality transfer method of graphene prepared by a chemical vapor deposition method. The method comprises the following steps: a, spinning a polymethylmethacrylate (PMMA) thin layer having even thickness on the surface of graphene prepared on a copper foil substrate with the chemical vapor deposition method; b, dissolving the copper foil; c, laminating; and d, and removing PMMA. By using the method provided by the invention, graphene can be stably, reliably and high-quality transferred, and the impurities in graphene are less, thereby ensuring the completeness and good property of prepared graphene not to be damaged and meeting the requirement of researching and applying graphene. After the method provided by the invention is adopted, complete and less-impurity-containing graphene can be stably, reliably and high-quality transferred, and thus a reliable guarantee for representation, research and application of graphene is provided.
Owner:SOUTHEAST UNIV
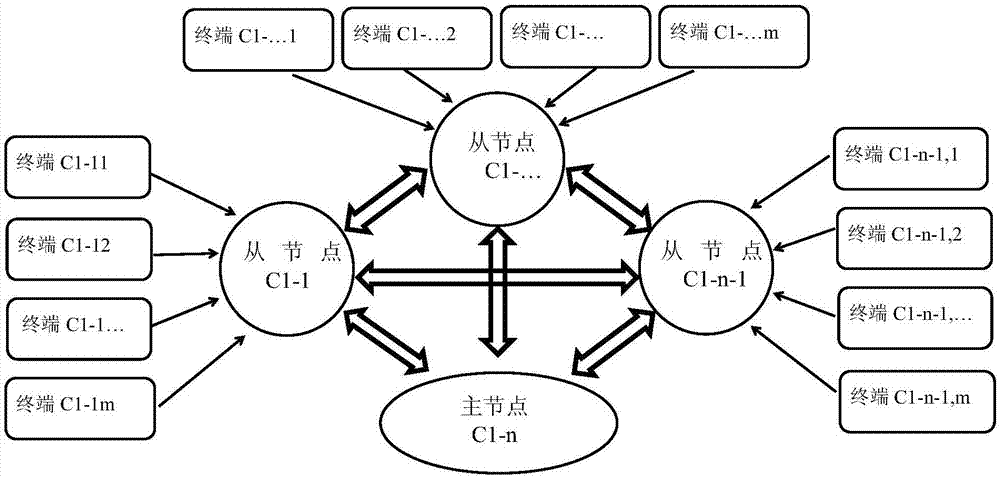
Data management system and method based on composite blockchain network
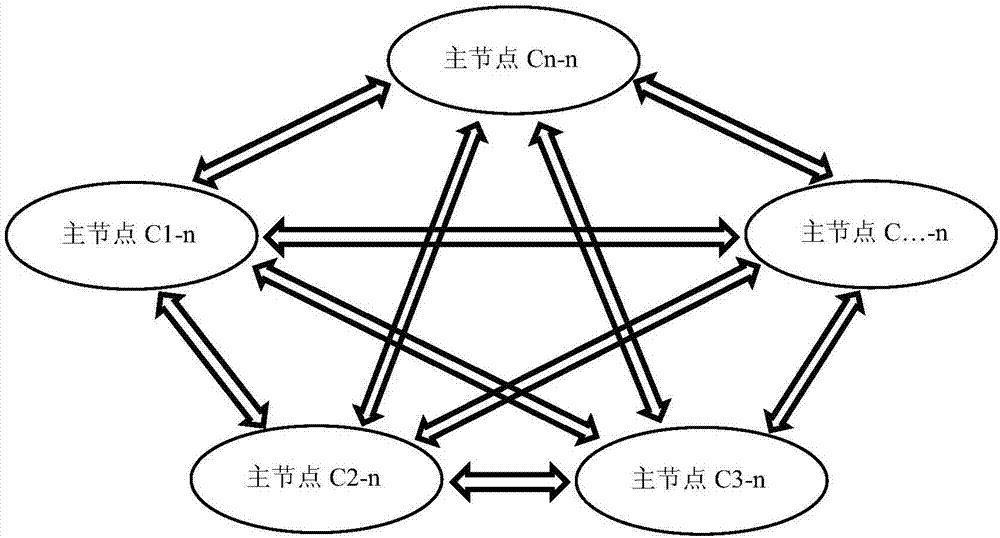
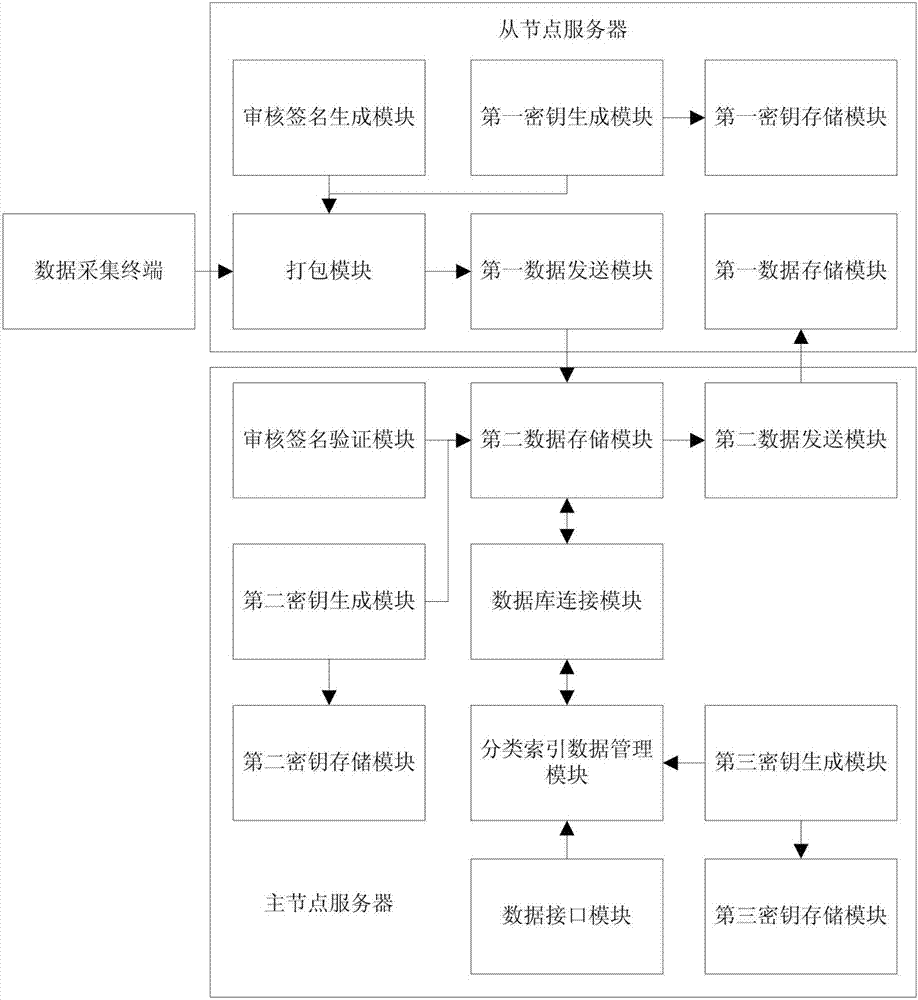
InactiveCN107222482AIntegrity guaranteedGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationAuthorization ModeStructure of Management Information
The invention relates to a data management system and method based on a composite blockchain network, wherein the system comprises a first-level blockchain network and at least one second-level blockchain network; the second-level blockchain network comprises multiple mutually connected slave node servers; the second-level blockchain network sets a master node server in all the slave node servers; and the master node servers in all the second-level blockchain networks are mutually connected, so that the first-level blockchain network is formed. By means of the data management system and method disclosed by the invention, the integrity, the authenticity and the standardization of data can be ensured through audit signature verification of the composite multi-level blockchain network; the security of the data is ensured in a hierarchical encryption and multiple authorization mode; structural design of hierarchical storage of detailed data and classified index data is carried out through a blockchain technology and the composite multi-level network; therefore, the data is relatively smooth to interconnect, intercommunicate and exchange; furthermore, audit tracing can be realized; and the data retrieving, applying and sharing efficiency can be increased.
Owner:黑龙江卓亚科技有限公司
Security reinforcement method for credible container based on Docker
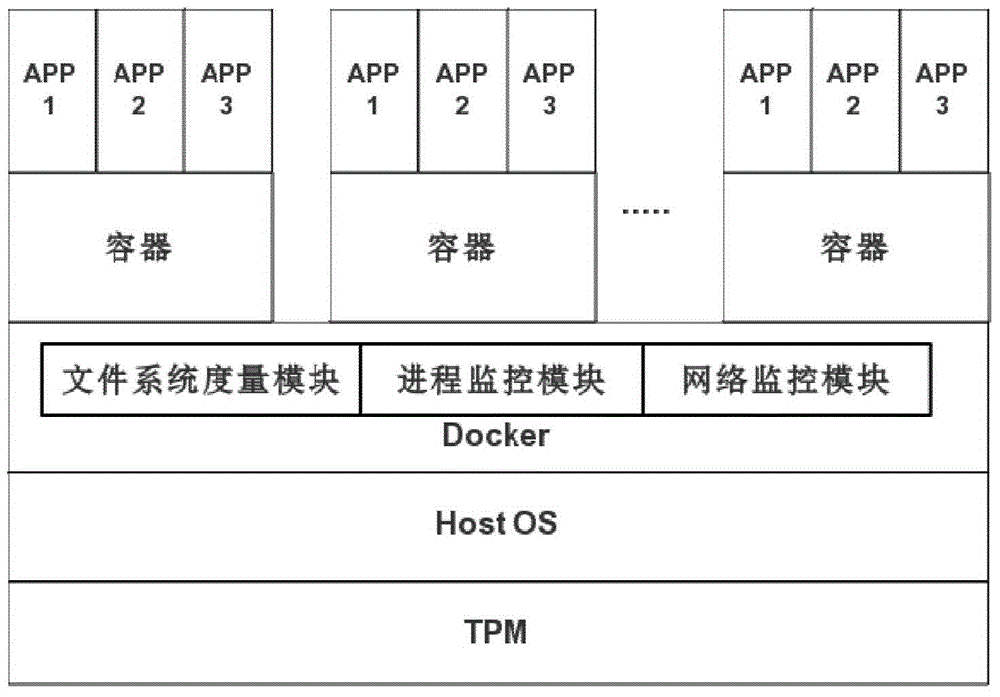
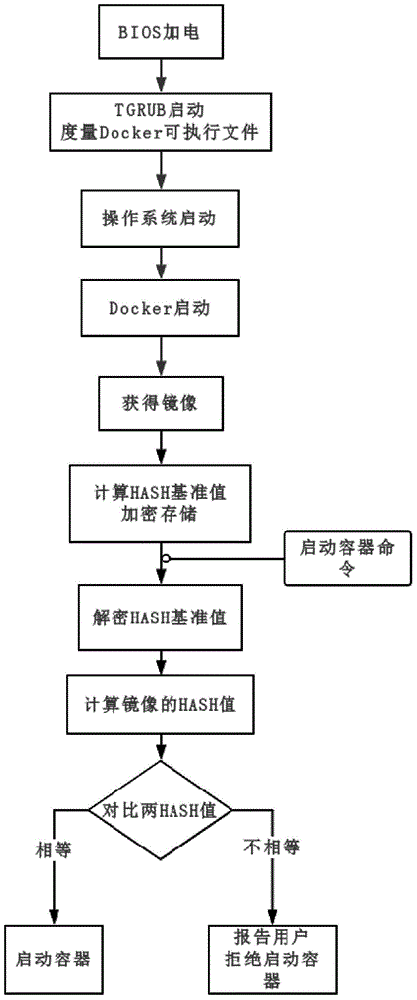
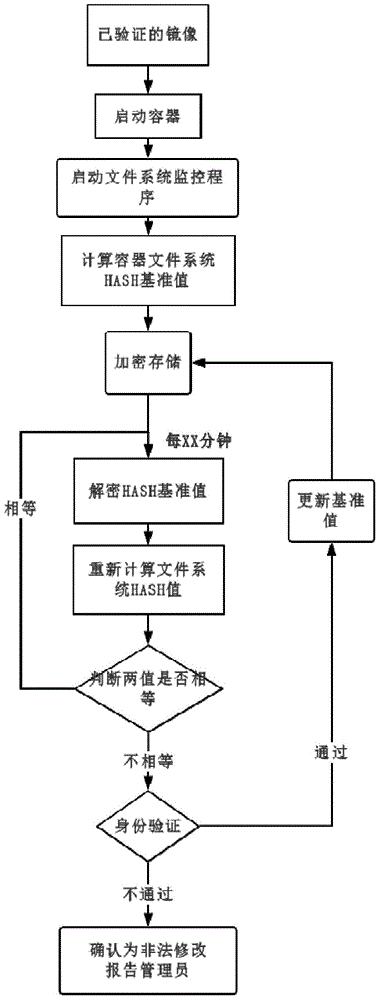
ActiveCN105069353ATrusted bootGuaranteed normal startupPlatform integrity maintainanceNetwork communicationMirror image
The invention discloses a security reinforcement method for a credible container based on Docker used for performing security reinforcement on a Docker container system, and realizes the credible container based on the Docker, as well is applied to a server cluster based on the Docker. The credible container based on the Docker comprises a container program Docker, a container credible measurement module, a progress monitoring module and a network communication monitoring module, wherein the container credible measurement module comprises a credible booting sub-module and a file measurement sub-module. The reinforcement method focuses on the credibility of the Docker container; a credible computing and integrity measurement technology is matched with a real-time monitoring module to reinforce the container system based on the Docker, so that the container and a mirror image are prevented from tampering; and meanwhile, a network communication behavior of the container is limited, and an inner progress of the container is monitored, so as to realize the security reinforced credible container.
Owner:WUHAN UNIV
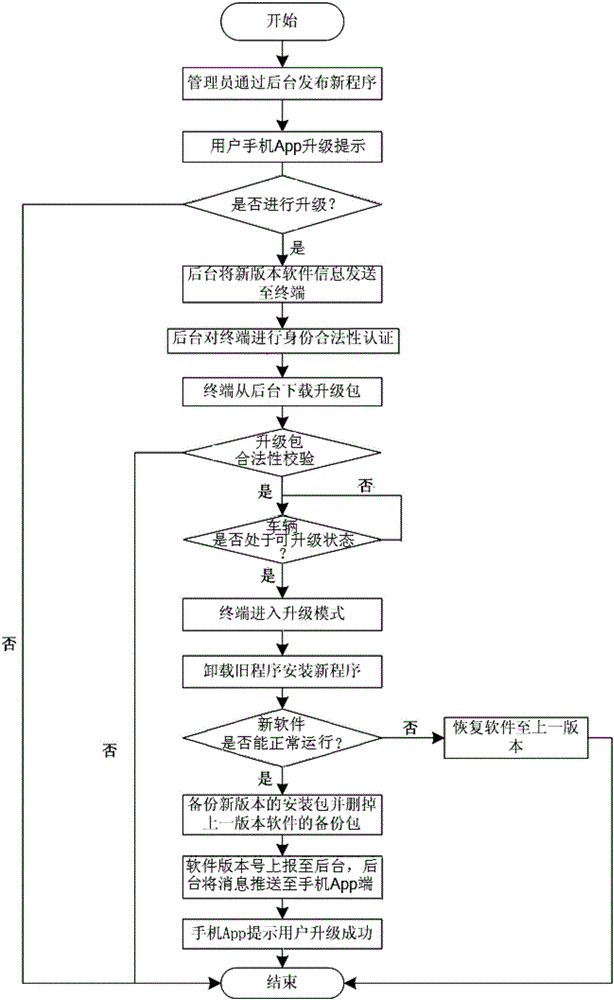
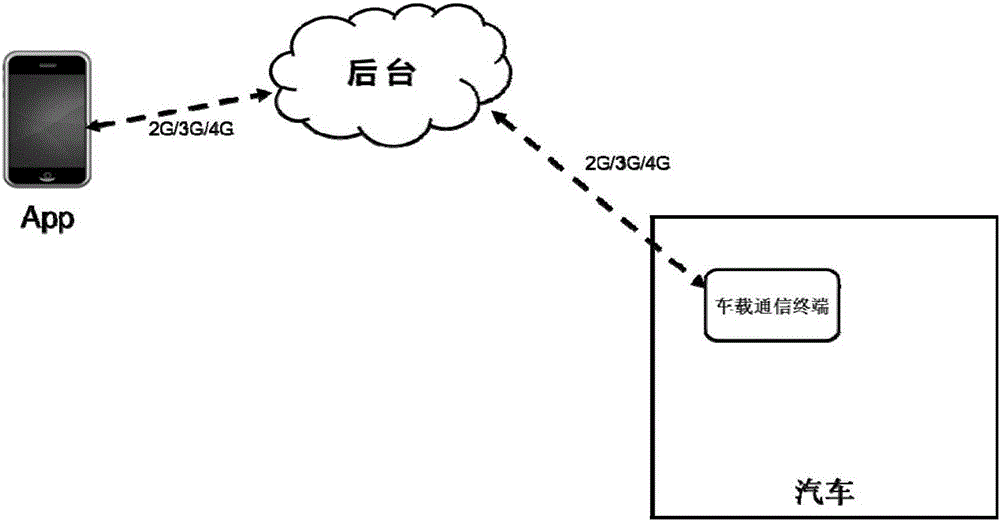
Remote upgrading method for vehicle-mounted communication terminal
InactiveCN105978921AImprove safety and reliabilityInformation transparencySoftware maintainance/managementTransmissionMobile phoneSoftware
The invention relates to a remote upgrading method for a vehicle-mounted communication terminal. The method comprises the following steps that 1, a background server issues a new version of a terminal; 2, the background server sends an upgrading inform to a mobile phone App end; 3, the mobile phone App end receives an upgrading selection sent by a user; 4, the background server sends new version software information to the terminal; 5 the background server authenticates the identity legality of the terminal; 6, the terminal downloads an upgrading patch; 7,upgrading patch legality and integrity are checked; 8, whether a vehicle has the upgrading condition or not is judged; 9, the terminal is remotely upgraded; 10, a new version program is installed for the terminal; 11, the terminal judges whether operation of new version software is normal or not is judged; 12, an original version program back-up patch is deleted, and the new version program is backed up; 13, the number of the new version software is reported to the background server; 14, the mobile phone App end prompts the user to upgrade information. The safety problems in the upgrading process in the prior art are solved.
Owner:CHONGQING CHANGAN AUTOMOBILE CO LTD
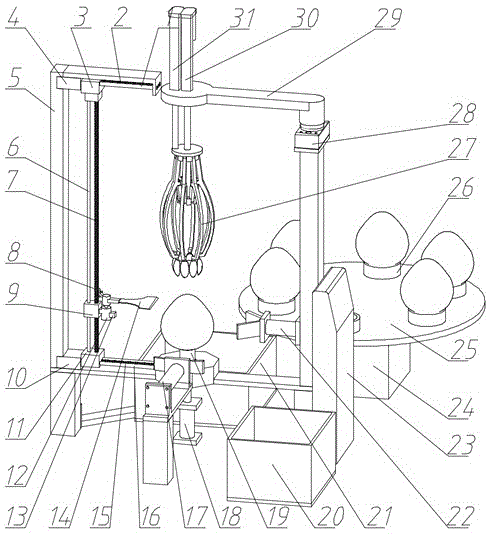
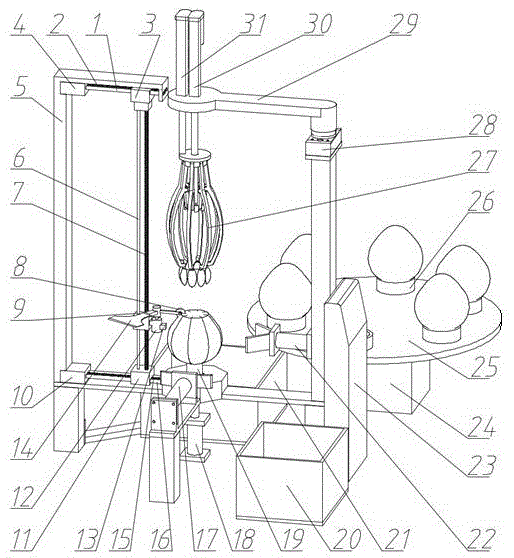
Automatic pomelo peel-flesh separating device and method
The invention discloses an automatic pomelo peel-flesh separating device and an automatic pomelo peel-flesh separating method. The method comprises the following steps: first, clamping and placing a pomelo on a fixing needle which is in the center of a working bench by cooperatively controlling a vertical electric push rod and an unfolding electric push rod, and operating a peeling mechanical claw; then, measuring the size of the profile of the pomelo by utilizing a laser distance sensor, performing data analysis processing on the data of the profile size of the pomelo and determining subsequent actions by a power supply and a control cabinet, and respectively cutting off the top cover of the pomelo and dividing the peel of the pomelo into eight pieces equally by cooperatively controlling the actions of an upper horizontal stepping motor, a lower horizontal stepping motor and a vertical stepping motor, and utilizing a top removal cutting knife and a peel scratching hobbing knife; finally, cooperatively controlling the vertical electric push rod and the unfolding electric push rod to move, and enabling the peeling mechanical claw to move along the trajectory in the peel of the pomelo to peel the peel of the pomelo, clamp the flesh of the pomelo and separate the flesh from the peel. According to the device and the method, the pomelo can be charged and discharged automatically; after the top of the pomelo is removed and the peel is scratched, all pieces of the peel are peeled precisely simultaneously without hurting the flesh.
Owner:JIANGSU UNIV
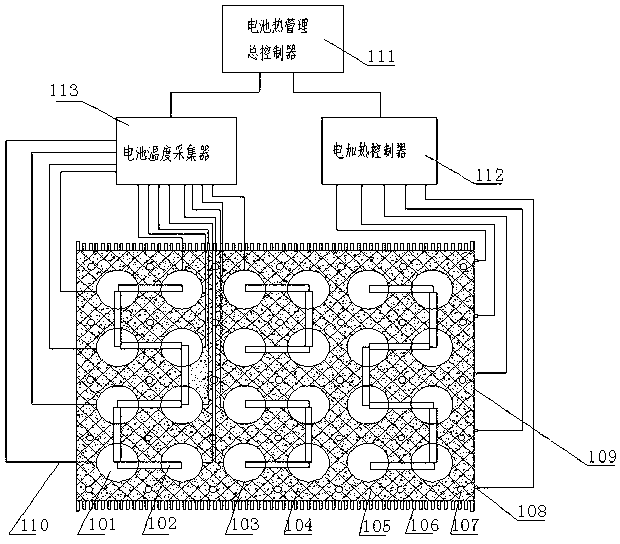
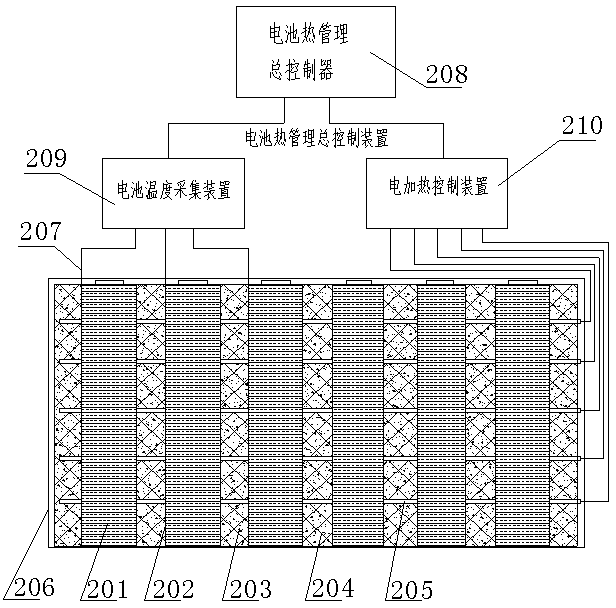
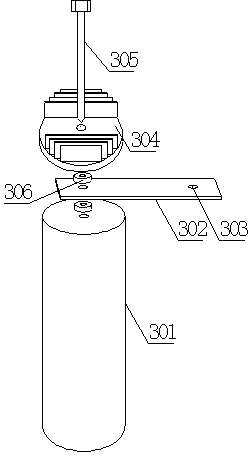
Battery heat management equipment with efficient balanced radiating function and electric heating function
The invention discloses battery heat management equipment with an efficient balanced radiating function and an electric heating function. The battery heat management equipment comprises a radiating cooling device, an electric heating device and a temperature acquisition device, wherein a battery radiating device comprises a plurality of battery monomers, battery connecting pole pieces, insulating high heat conduction battery protection shells, a composite phase change material, a framework structure material for improving heat transfer and strength, heat pipes, a battery module box and heat pipe radiating fins; a battery electric heating device comprises the electric heating device and an electric heating controller; the electric heating device is embedded into the phase change material and connected with the electric heating controller; the temperature acquisition device comprises a thermocouple and a temperature acquirer; the thermocouple is arranged in a composite phase change material cooling module and transfers a sensed signal to the temperature acquirer; the temperature acquirer transfers the signal to a battery heat management equipment master controller; and the battery heat management equipment master controller is connected with the electric heating controller. According to the battery heat management equipment, a power battery is high in working performance, high in safety and long in cycle life.
Owner:GUANGDONG UNIV OF TECH
Multifunctional remote medical care system based on multi-network fusion
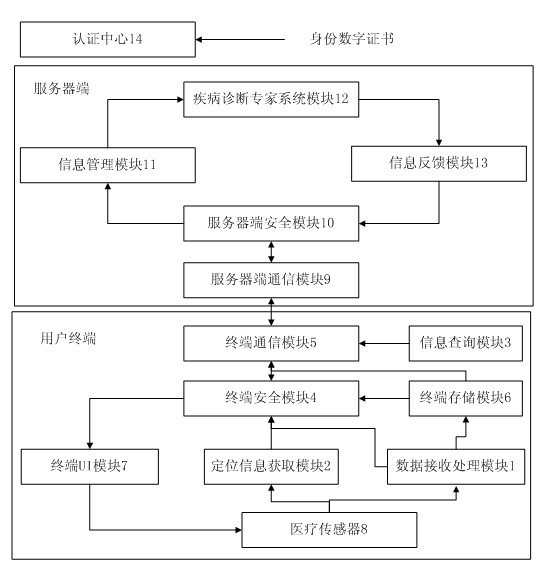
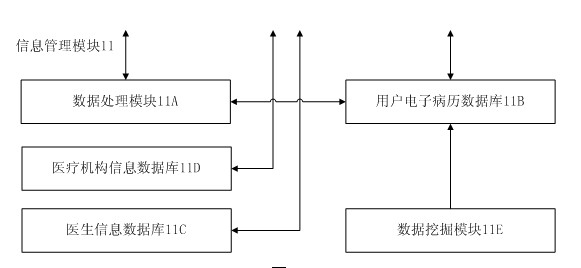
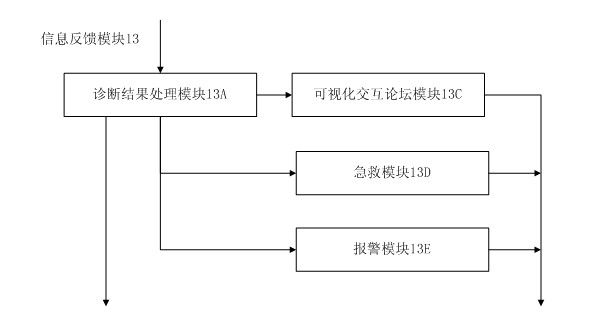
InactiveCN102085116AConvenient treatmentTimely treatmentSurgeryDiagnostic recording/measuringMedical recordFunctional expansion
The invention discloses a multifunctional remote medical care system based on multi-network fusion. The system involves the processes of registration from an entity to an authentication center, establishment of electronic medical record, data acquisition, remote diagnosis and information feedback; and a user terminal comprises a smart phone and a medical sensor. The smart phone comprises a data receiving processing module, a location-information acquisition module, an information querying processing module, a terminal safety module, a terminal communication module, a terminal storage module and a terminal UI (User Interface) module, wherein the medical sensor is provided with a wireless network interface and can be placed on a third medical sensor placed on the body of a user, a system server side comprises a server communication module, an information management module, a server-side safety module, a disease diagnostician system module, an information feedback module and an authentication center. The multifunctional remote medical care system based on multi-network fusion has the characteristics of rapid response, capability of detecting pathological changes in time, convenience and rapidness and the like, is easy for functional expansion, and has a greater upgrading function.
Owner:HUAZHONG UNIV OF SCI & TECH
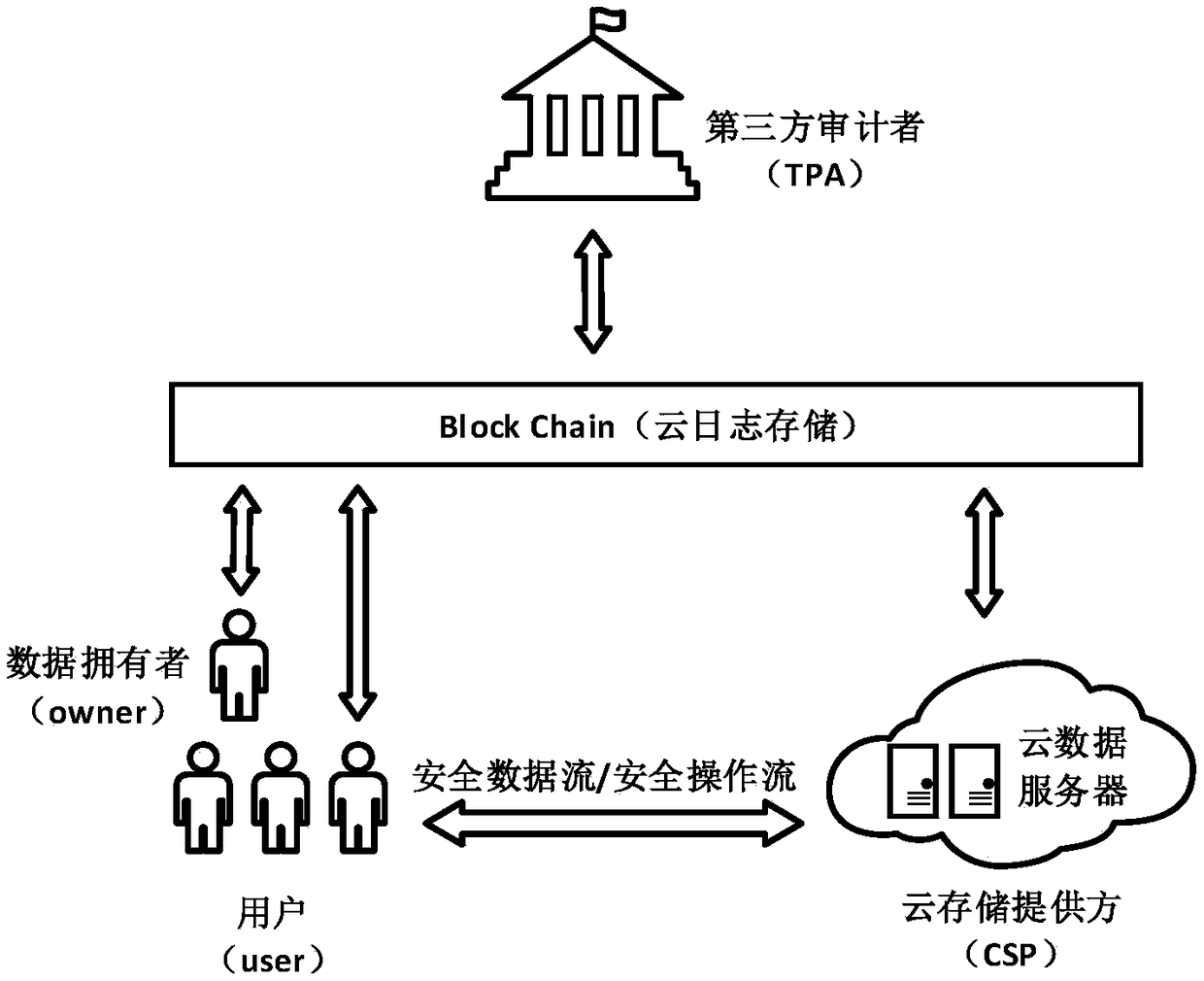
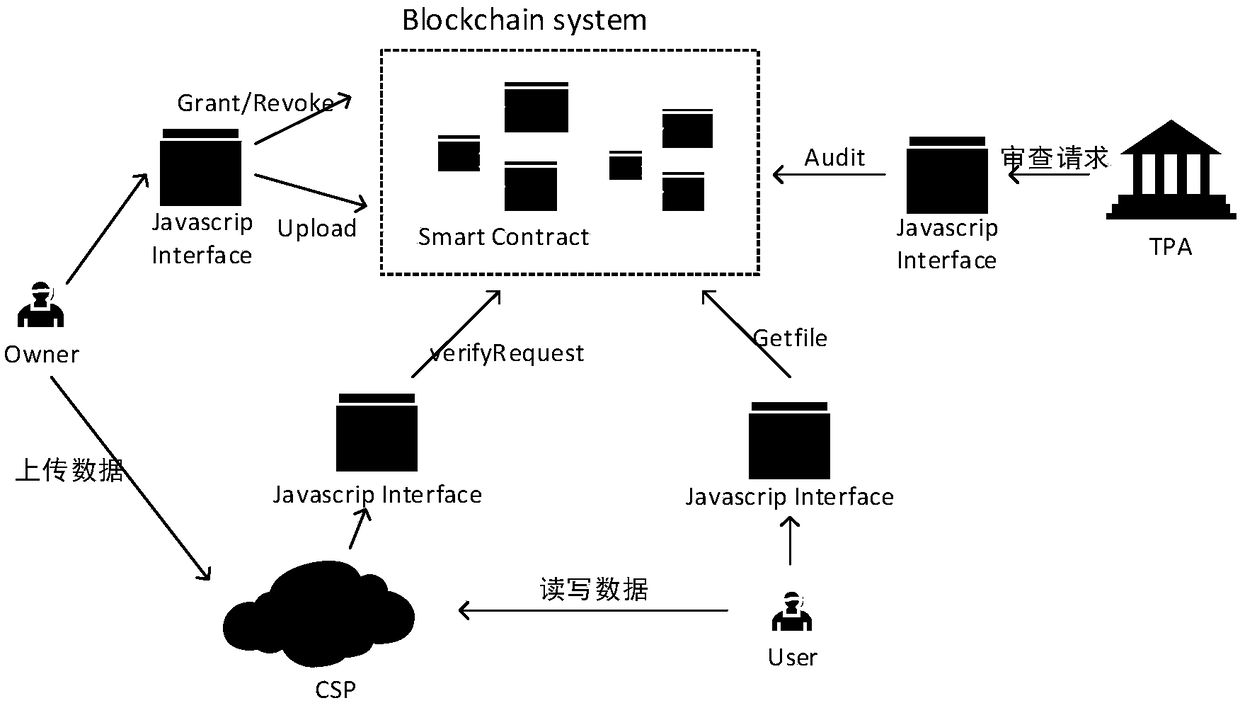
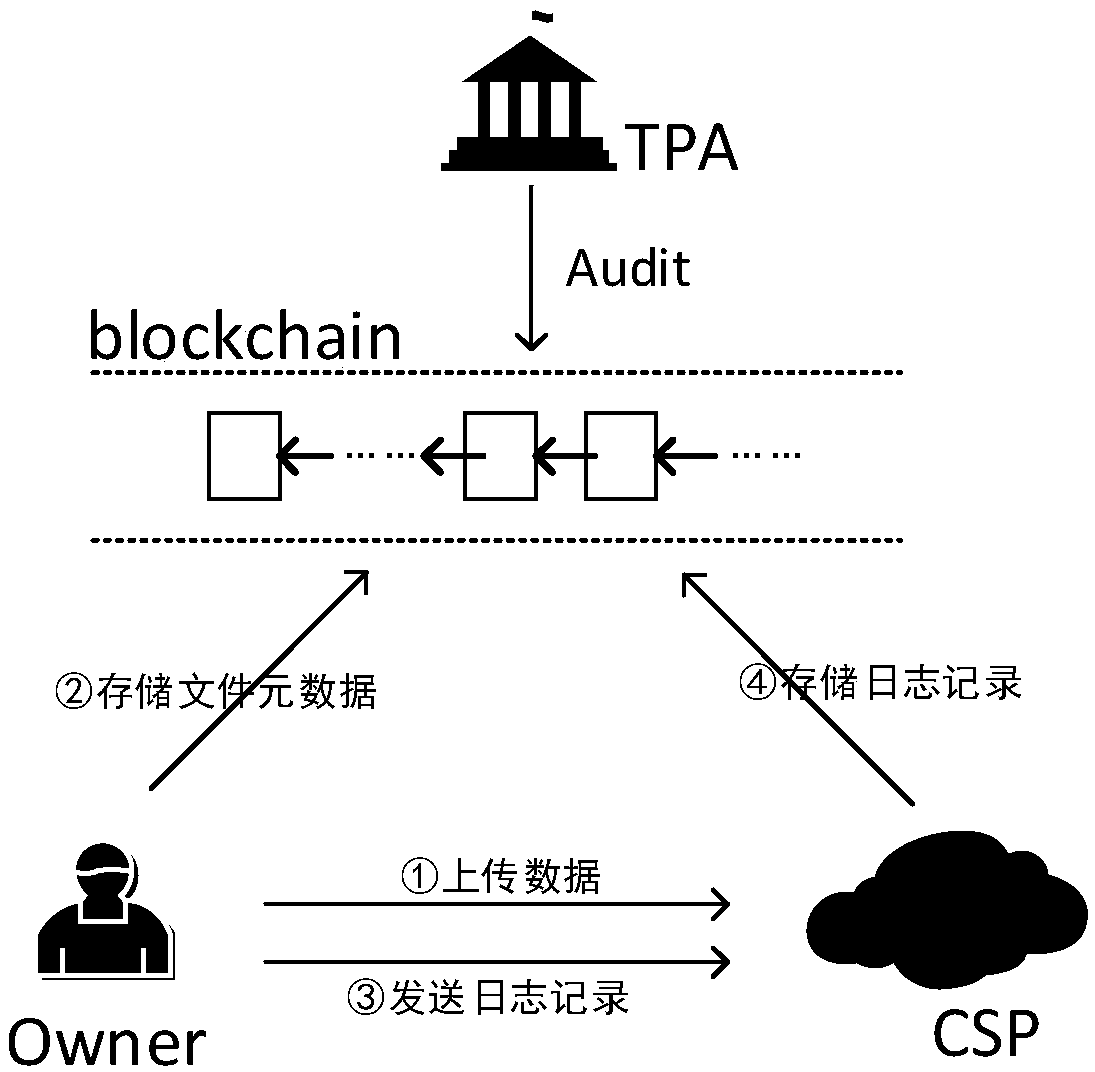
A log behavior audit method based on a block chain in cloud storage environment
The invention discloses a log behavior audit method based on a block chain in a cloud storage environment. Each interface required in the flow of the method is compiled by an intelligent contract, which ensures that both sides cannot deny the behavior of the log behavior, so that the log record in the block chain network is completely trusted. The audit interface of the intelligent contract is called when there is an audit requirement, and the log records are reviewed by the intelligent contract and the results are returned to the requesting user. By transferring the cloud log storage from thecloud storage provider to the block chain, the invention ensures the safety and integrity of the log data by utilizing the characteristics of decentralization, decentralization and high reliability of the block chain. The intelligent contract is used to make the block chain network provide the log read-write interface and audit structure, and the data access process is designed for the interaction between users and cloud service providers, which can ensure that users and cloud storage parties can record the log completely on the block chain network, and the log record cannot be denied and tampered with.
Owner:HUAZHONG UNIV OF SCI & TECH
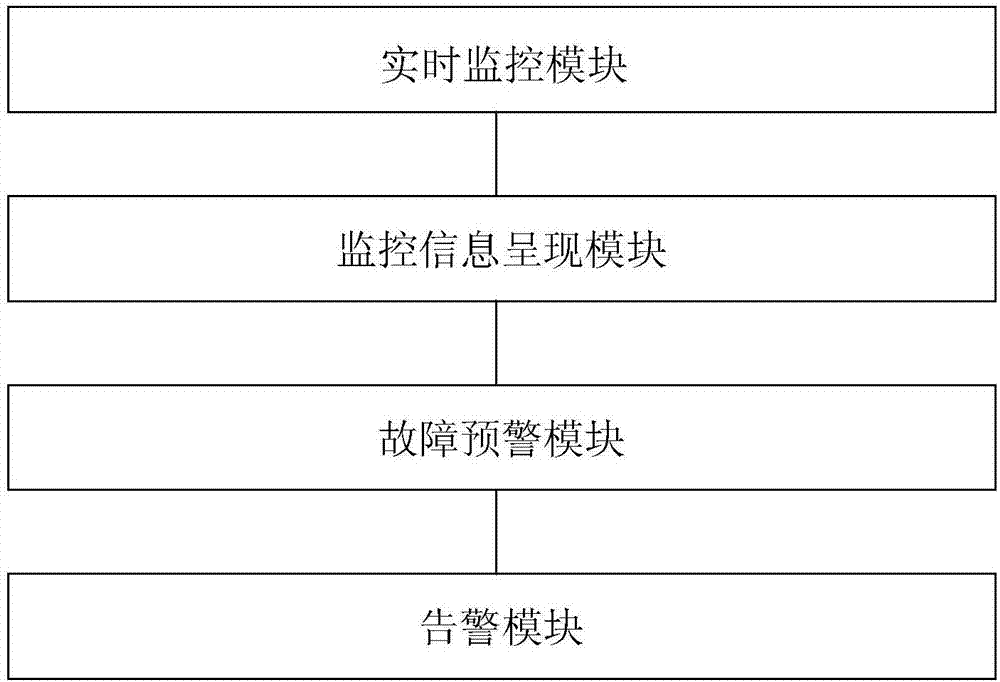
Device detection and fault early warning system and method in cloud computing environment
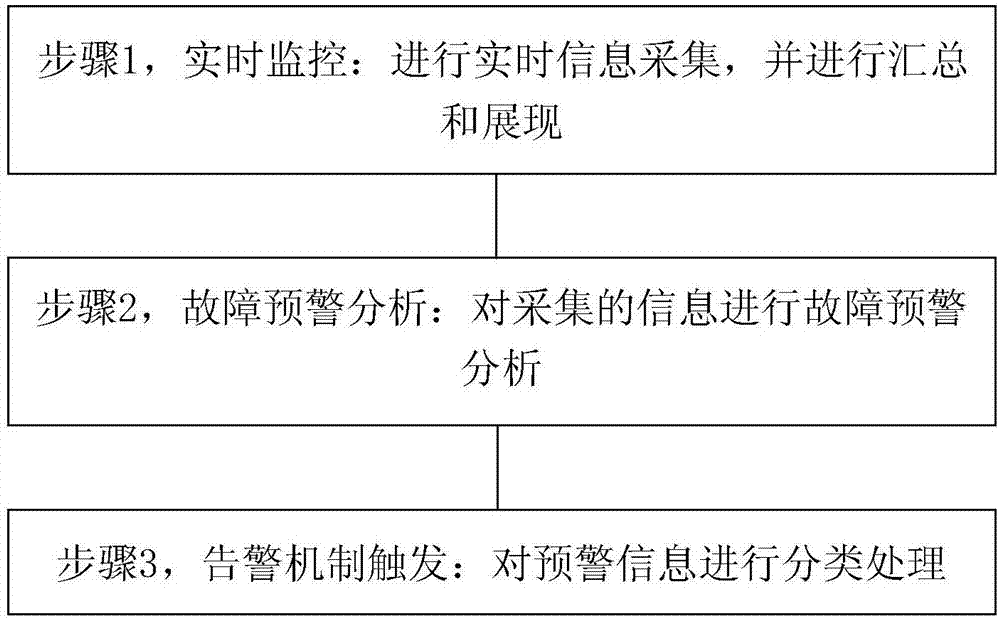
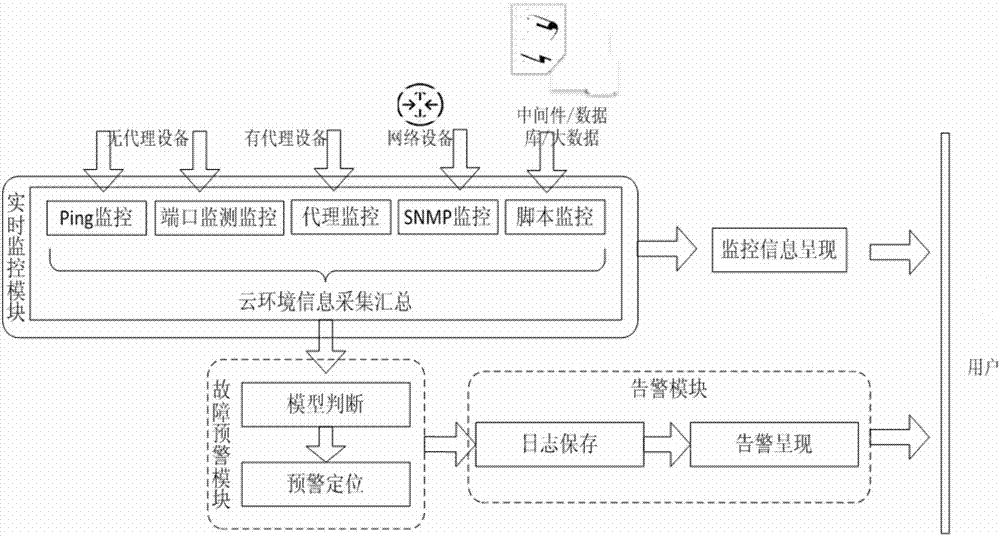
InactiveCN107491375AReduce in quantityImprove the efficiency of fault warningHardware monitoringData switching networksTime informationDevice type
The invention discloses a device detection and early fault warning system and method in a cloud computing environment. The system comprises a real-time monitoring module, a monitoring information presentation module, an early fault warning module and a warning module. The method comprises the following steps that firstly, real-time monitoring is conducted, wherein real-time information collection is conducted, and the real-time information is aggregated and presented; secondly, early fault warning analysis is conducted, wherein the collected information is subjected to early fault warning analysis; thirdly, a warning mechanism is triggered, wherein early warning information is classified. The device detection and early fault warning system and method can support protocols, autonomously and controllably select detecting indexes, adapt to different monitoring modes, customizing warning triggering conditions, extending the number of monitoring devices on a large scale and the like according to the types and the number of devices in a cloud computing data center, collection, monitoring, warning and fault positioning can be intensively conducted in a unified system, and the operation and maintenance efficiency is effectively improved.
Owner:INFORMATION COMM COMPANY STATE GRID SHANDONG ELECTRIC POWER +1
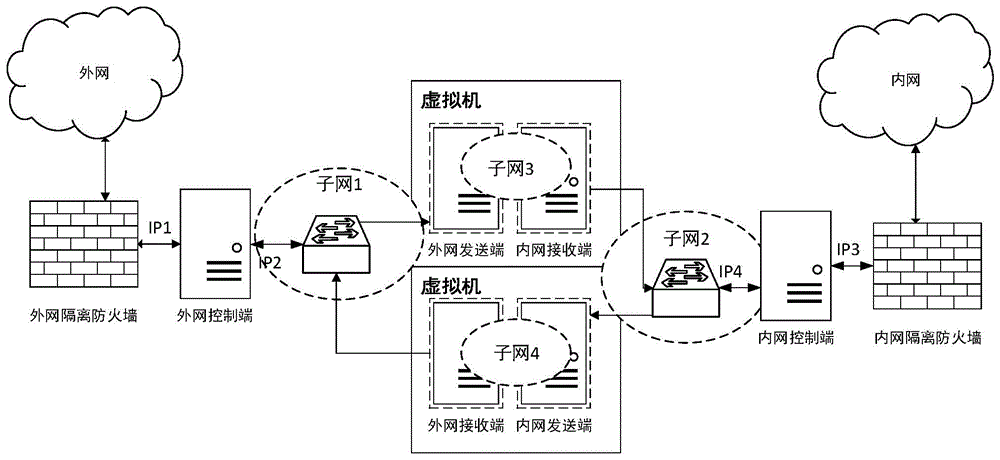
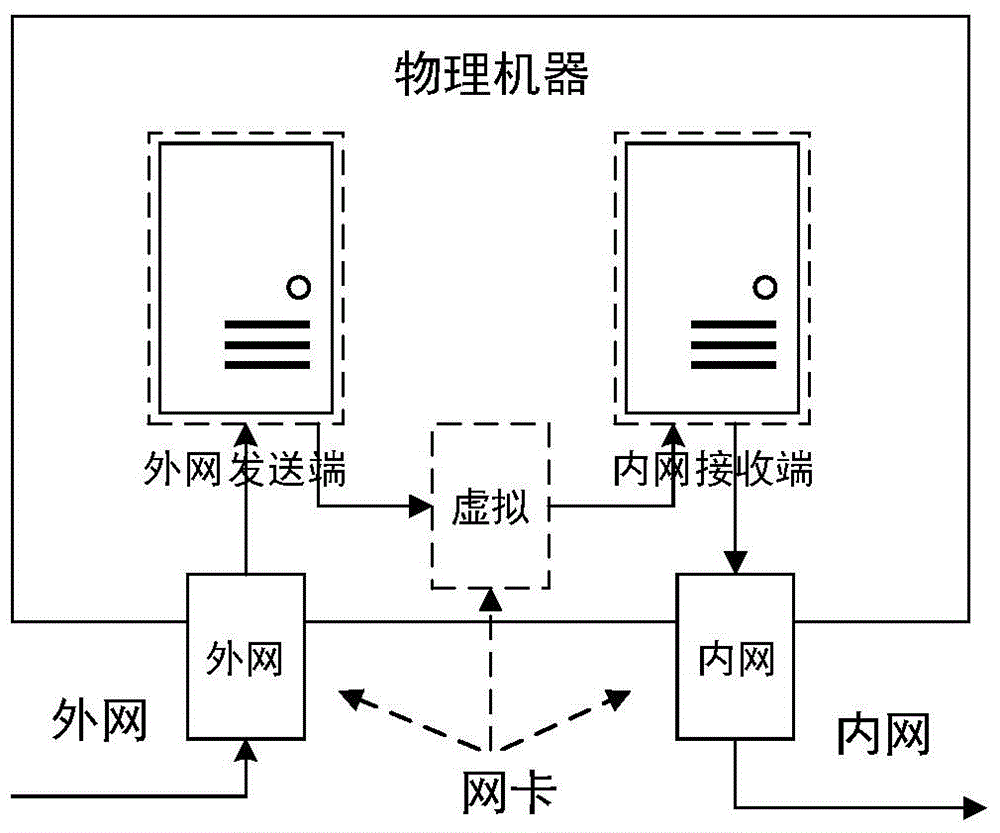
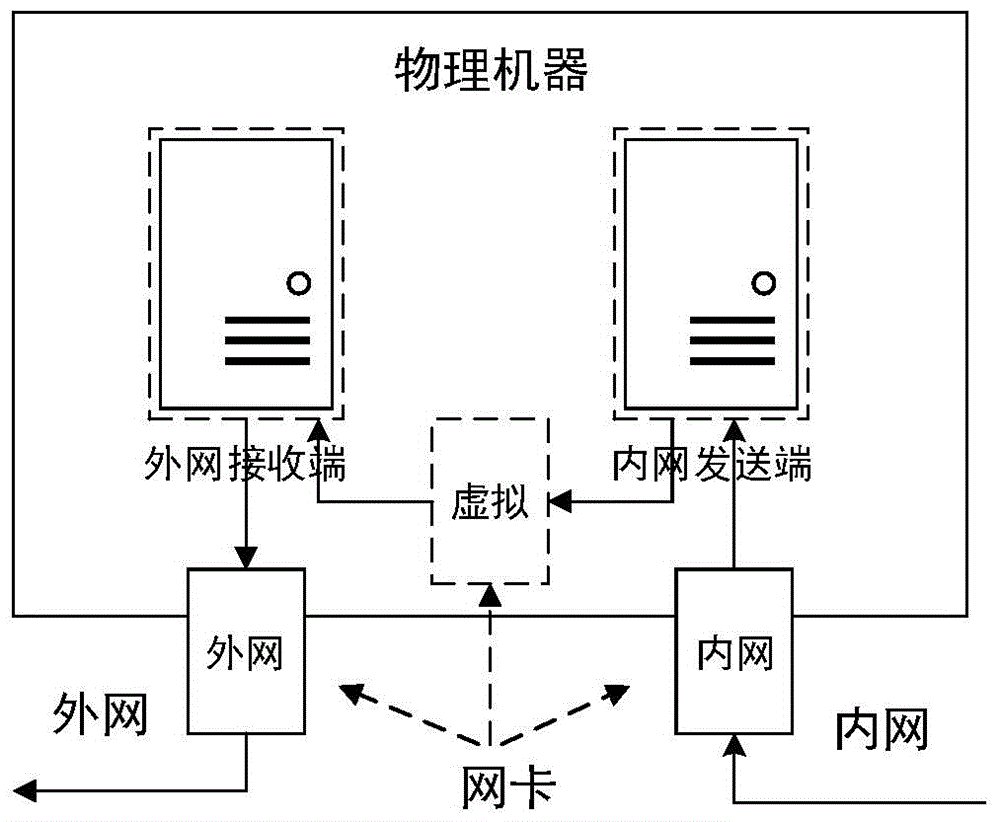
Network safety isolation file transmission control method
InactiveCN104363221AEnsure safetyKeep Content SafeSecuring communicationComputer hardwareConfidentiality
The invention relates to a safety isolation file transmission control method, in particular to a file transmission control method between taxation network safety isolation systems. A transmission control system comprises an external network isolation firewall, an external network control end, an external network transmitting end, an external network receiving end, an internal network transmitting end, an internal network receiving end, an internal network control end and an internal network isolation firewall. A computer system, a virtual machine system and the isolation firewalls are combined to achieved a relatively universal safety data transmission manner, safe and reliable bidirectional data transmission is achieved by the control method with a special safety protocol, confidentiality, completeness and non-repudiation during information transmission are achieved by safety techniques such as data encryption, digital signatures and information authentication codes, data exchanging performance is increased while safety of internal and external network systems is guaranteed, and the whole system can work reliably and stably.
Owner:QINGDAO WEIZHIHUI INFORMATION
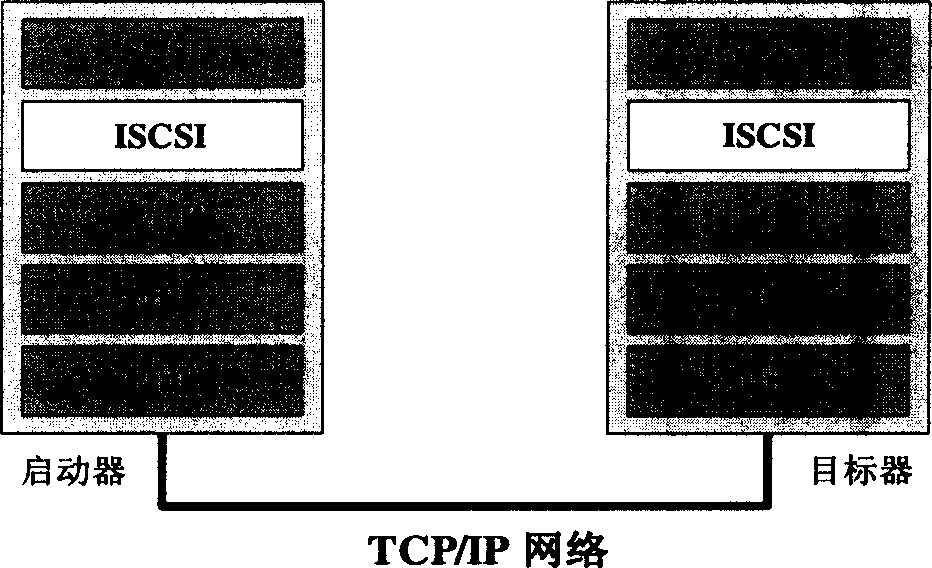
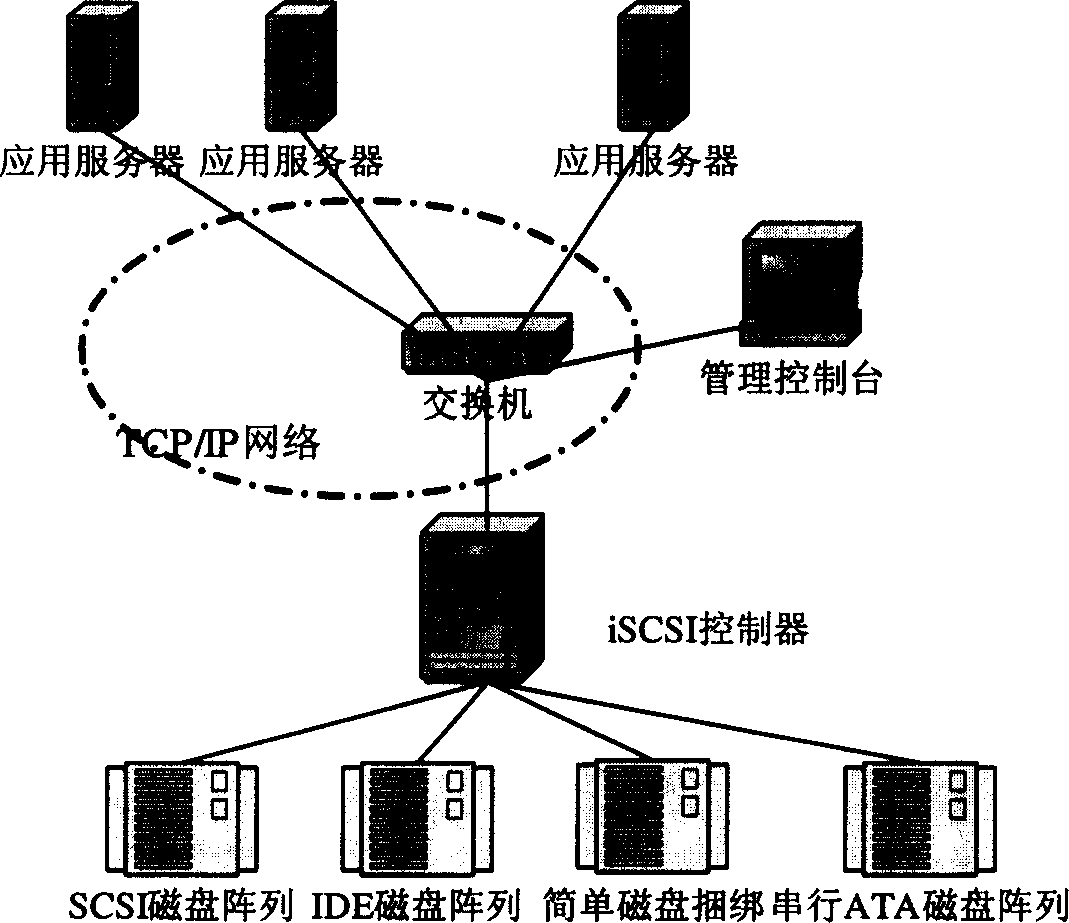
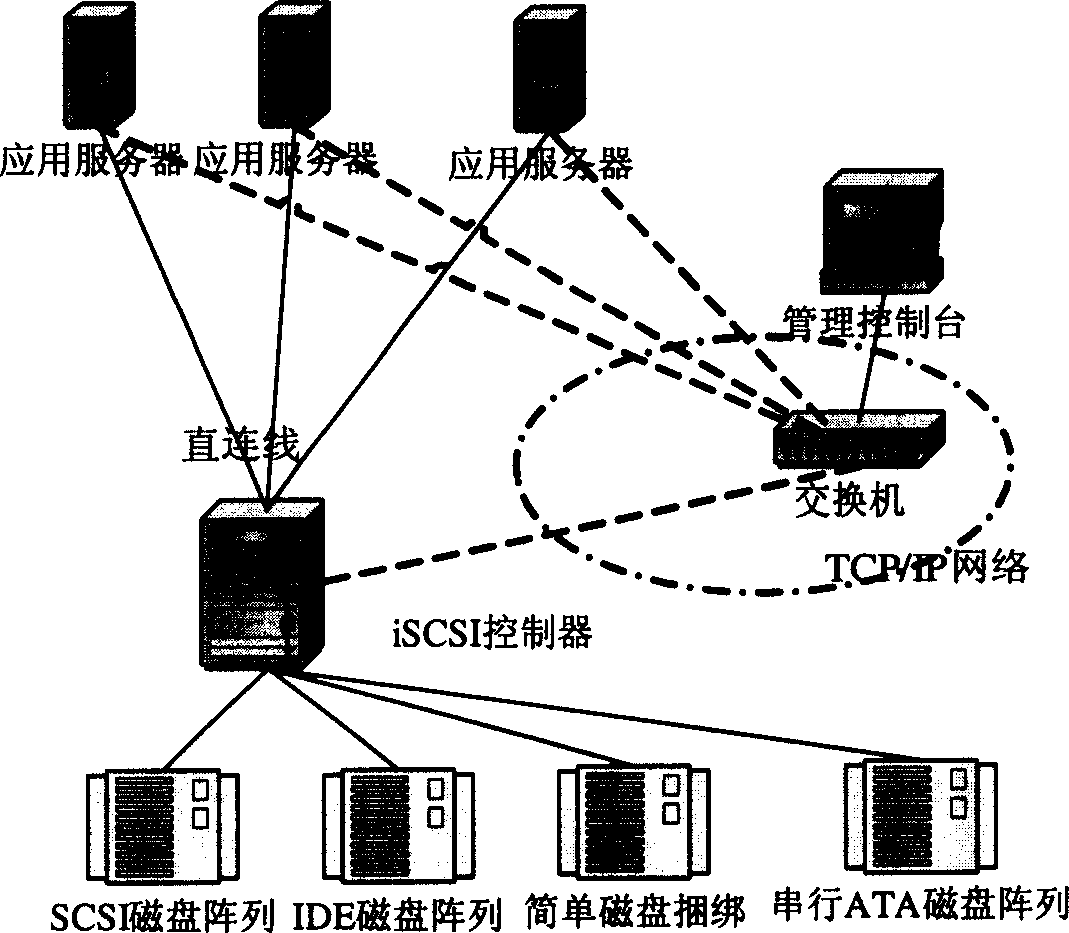
A method for implementing iSCSI memory system
A realization method for ISCSI storage system characterizes in realizing ISCSI protocol on ISCSI controller including a net card binding module realizing different load balances, a storage device management module providing fixed virtual device identifier and the heat plug function, an adaptive IQ load control program controlling parallel IQ load of low end storage device and a multi-path module for IQ requiring controlling different storage array channels. Storage device image module controlling the access limitation of a starter to the storage device, a block device support module realizing the transformation of SCSI order and soft device IQ and a software RAID module are added if necessary.
Owner:TSINGHUA UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com