Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1050 results about "Safe storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
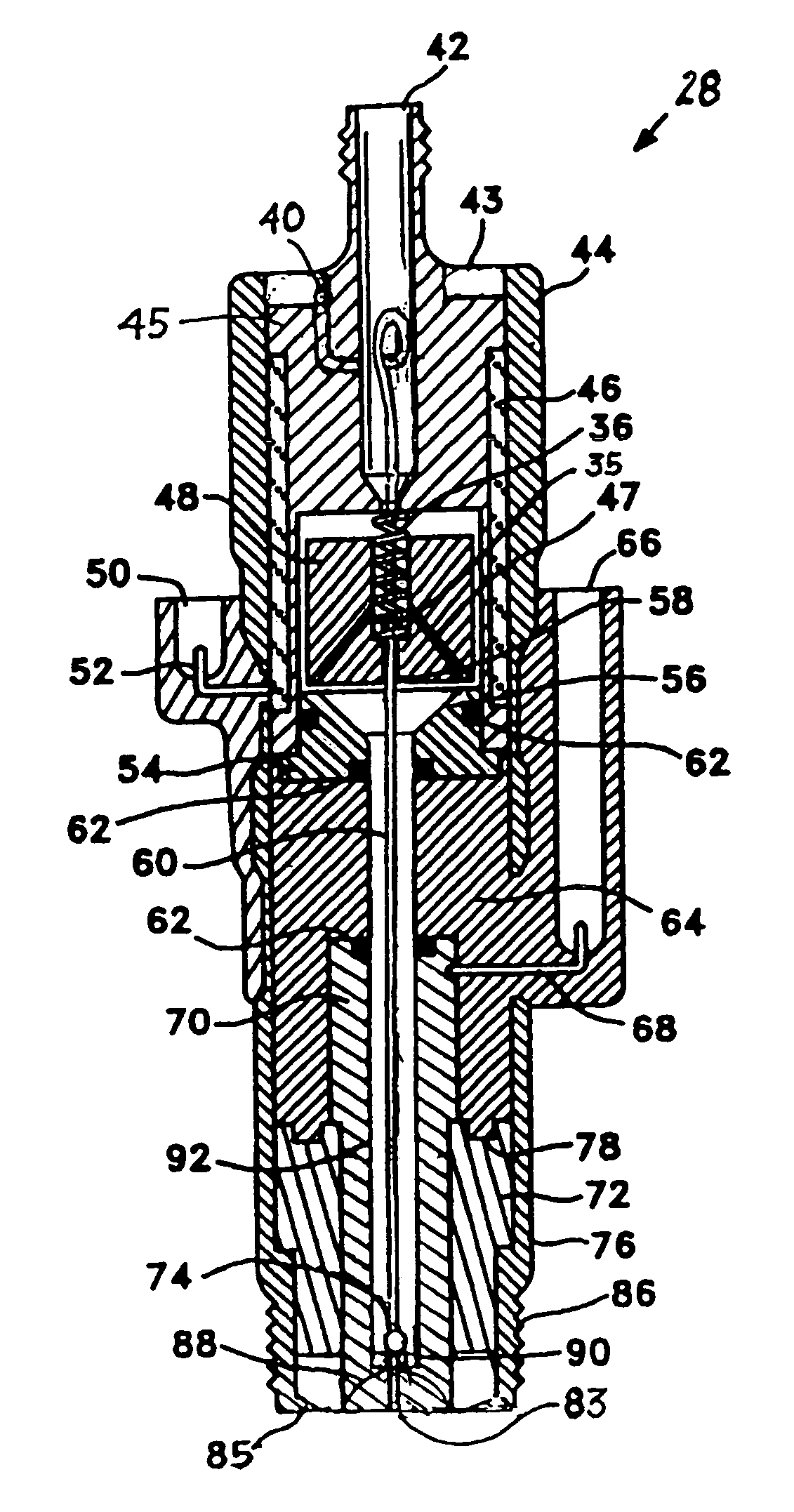
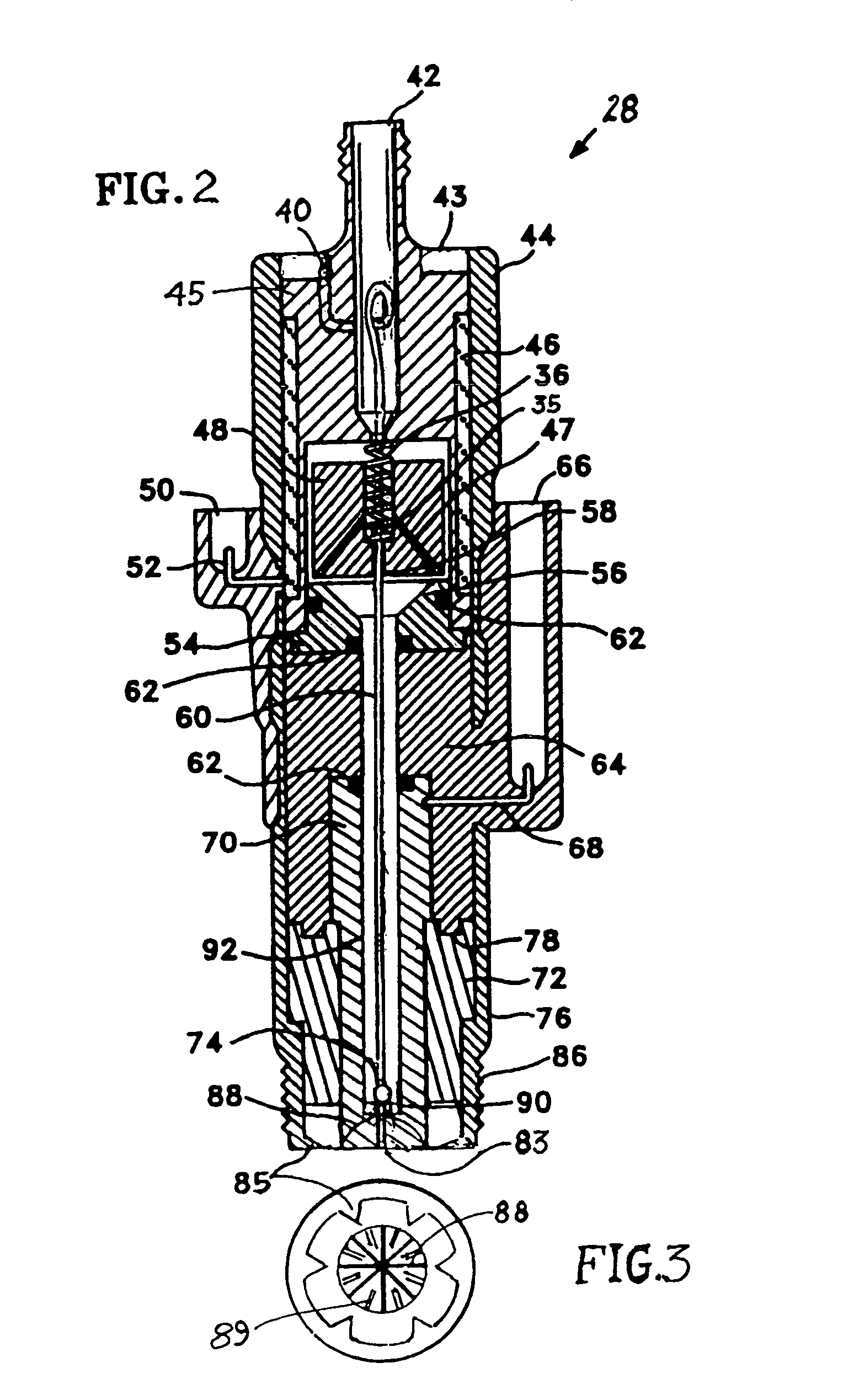
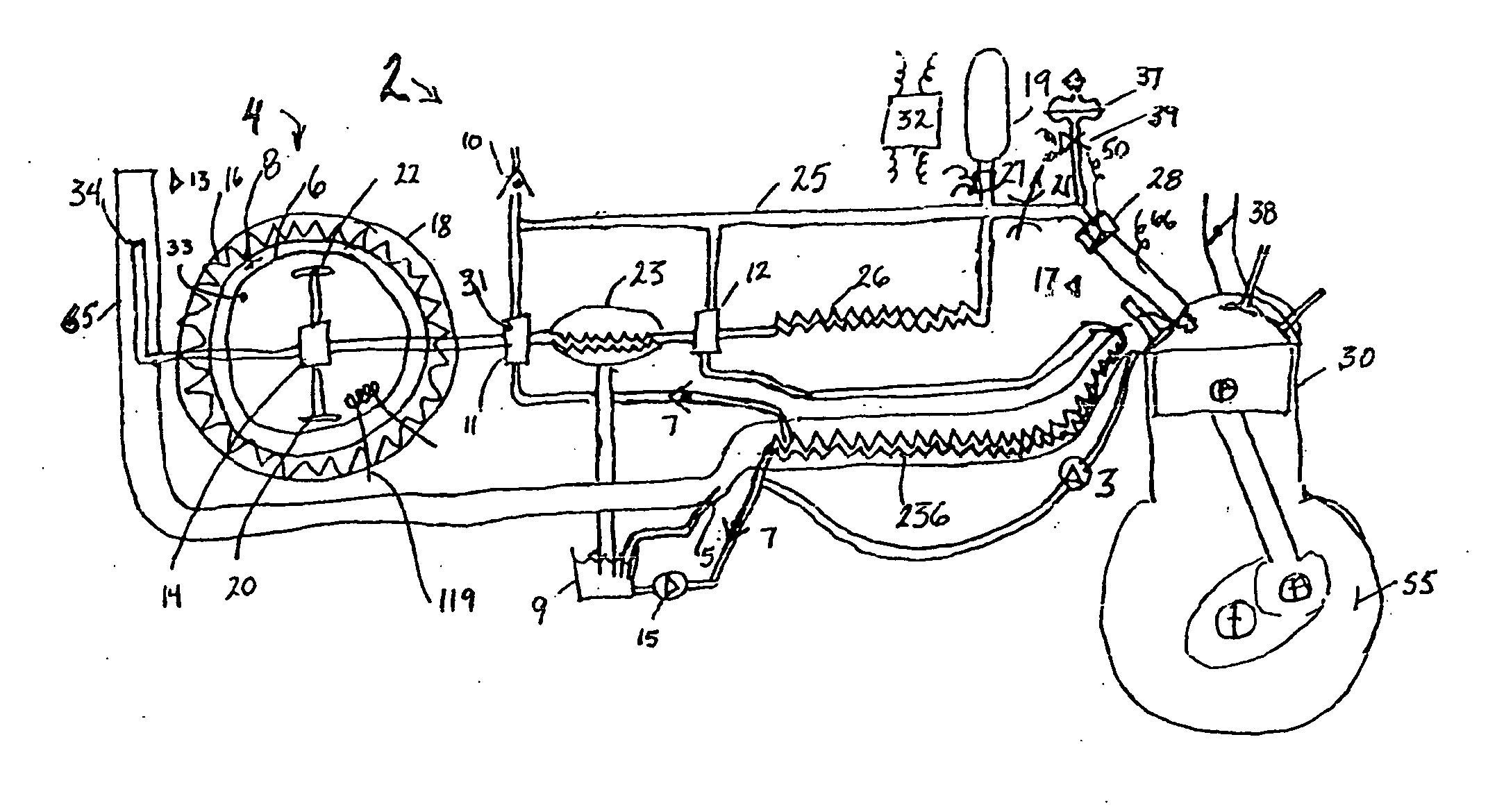
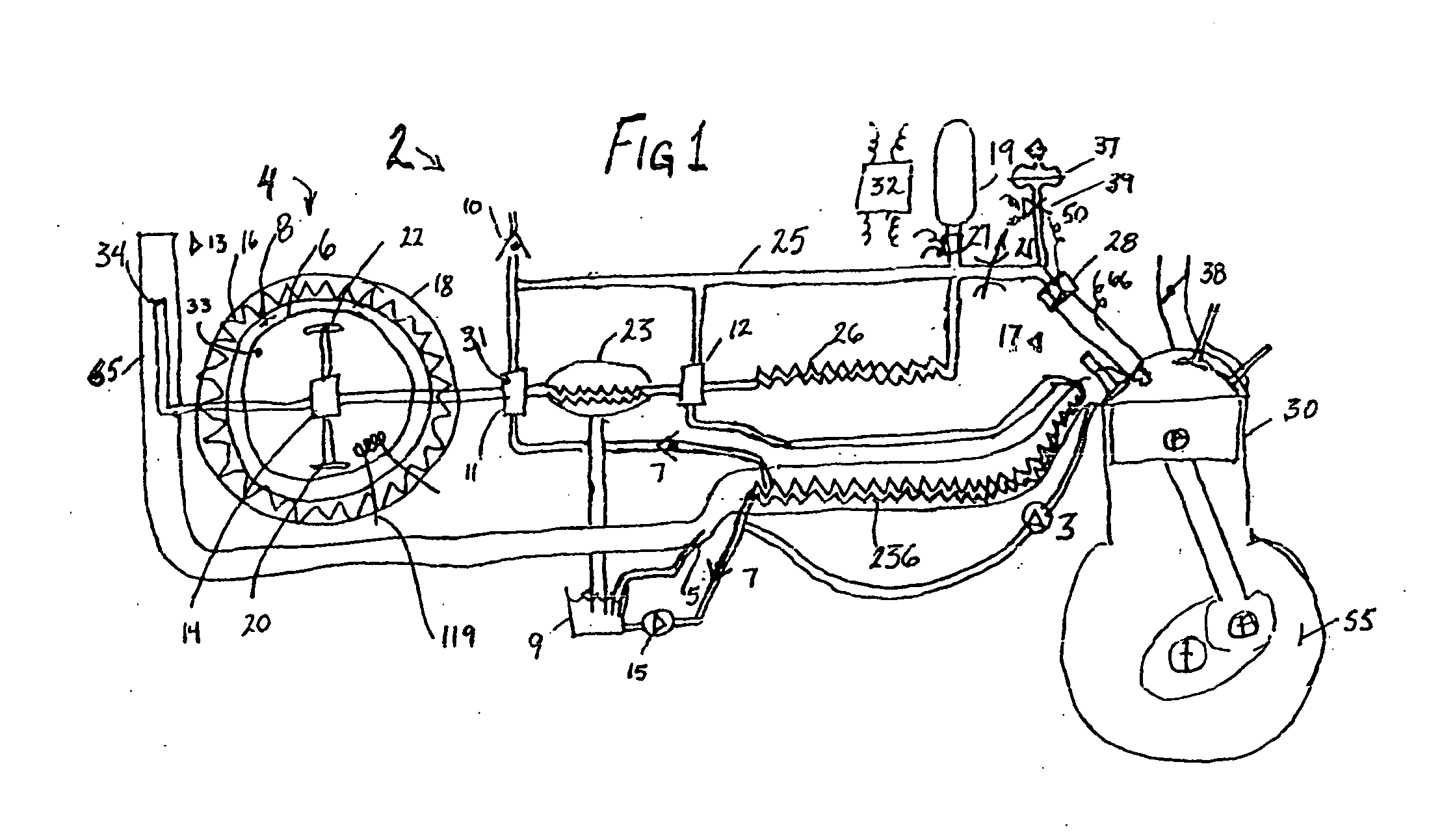
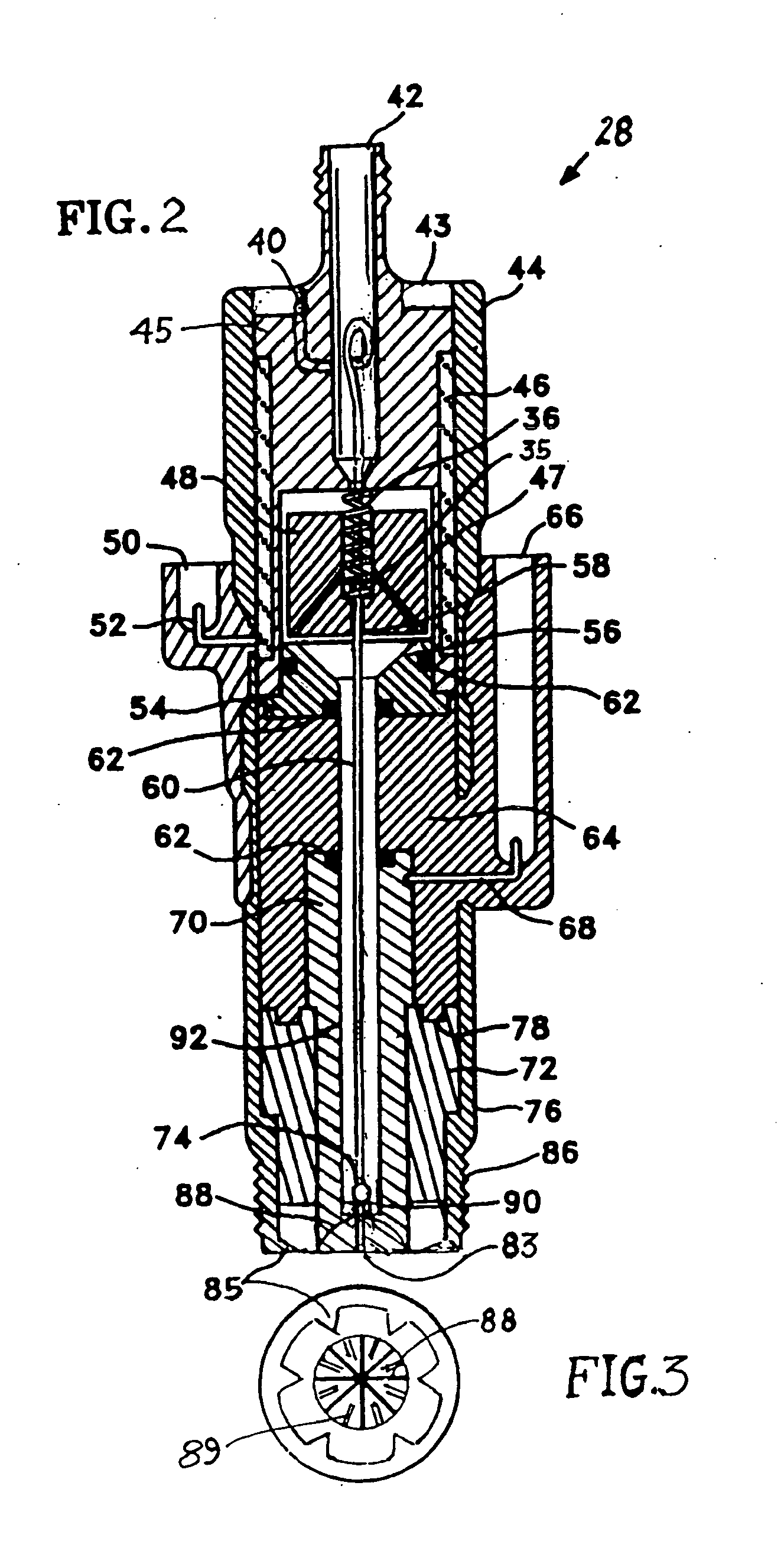
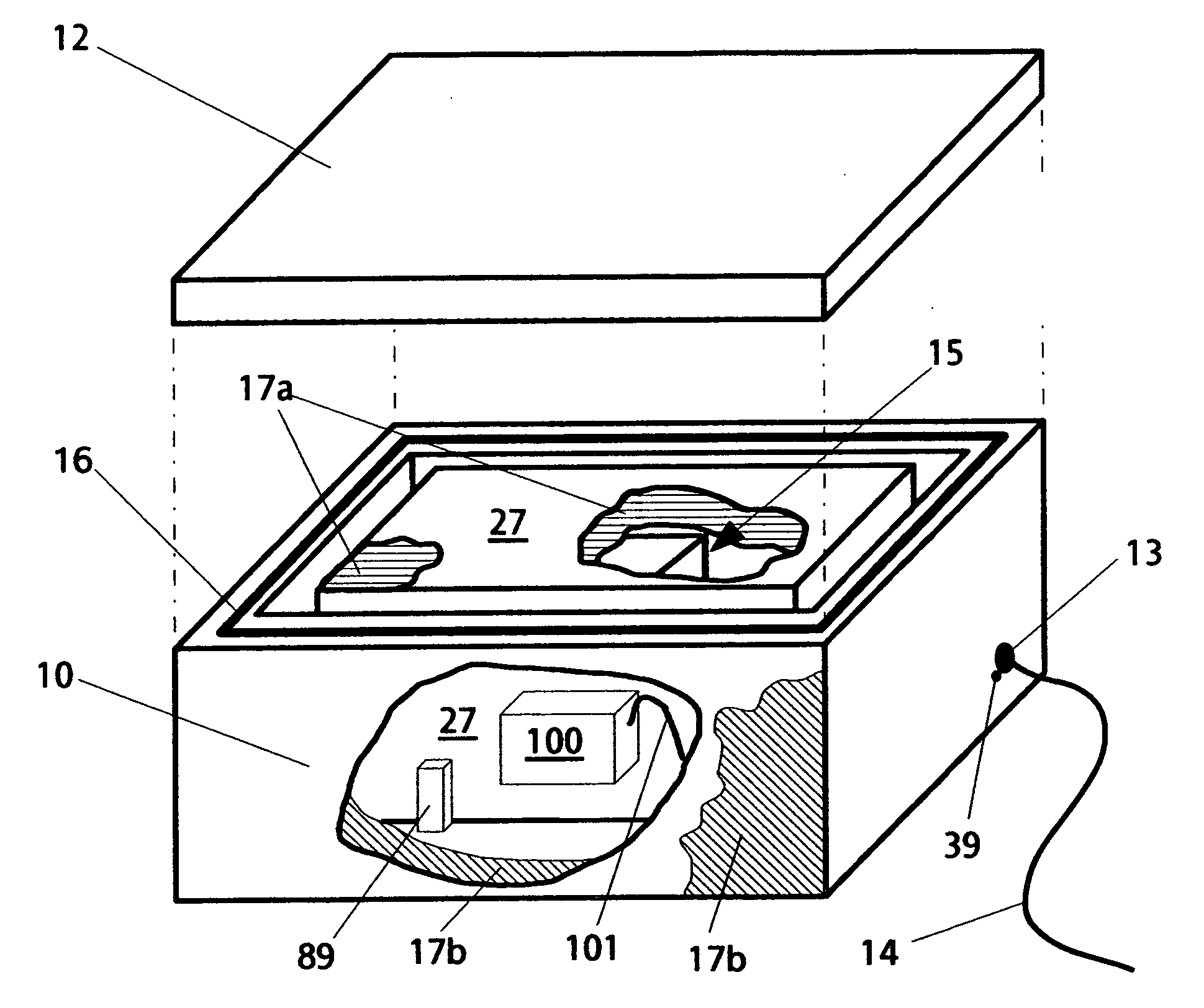
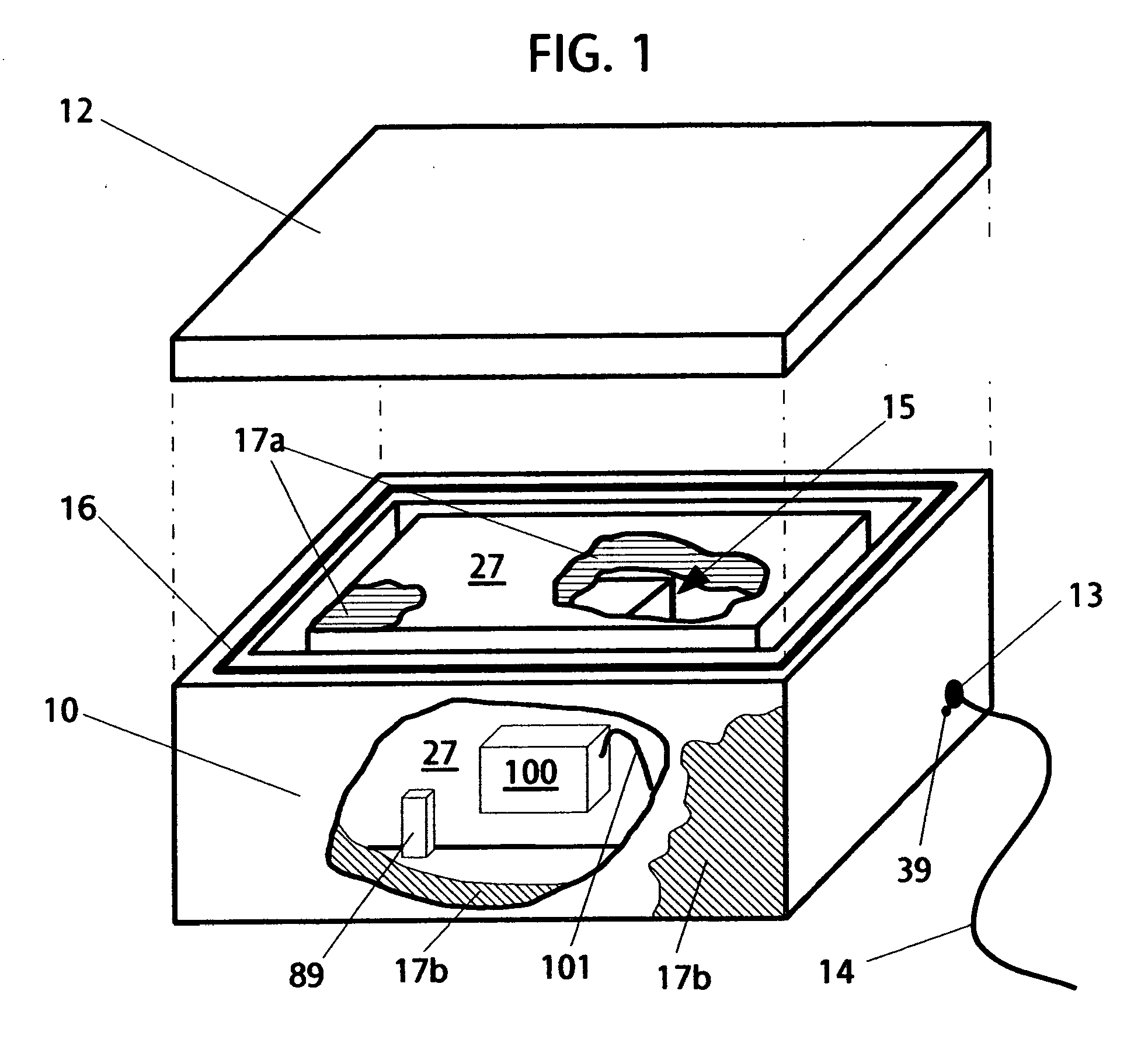
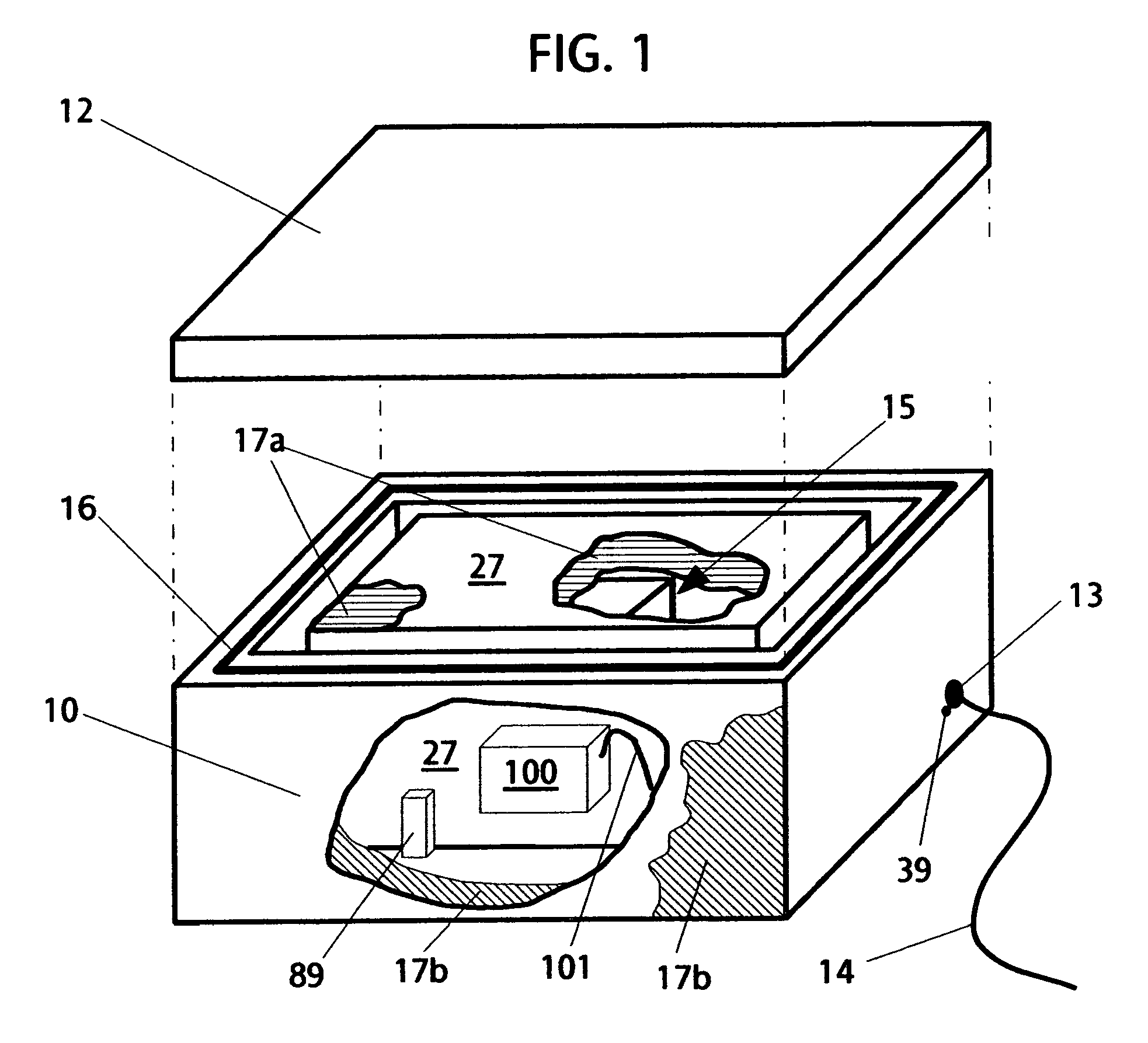
Multifuel storage, metering and ignition system
A system for safe storage and efficient utilization of a variety of fuel selections that range in composition and phase from cryogenic mixtures of solids and liquids to elevated temperature gases is provided for unique applications with various types of heat engines and fuel cells including hybridized combinations.
Owner:ADVANCED GREEN INNOVATIONS LLC +1
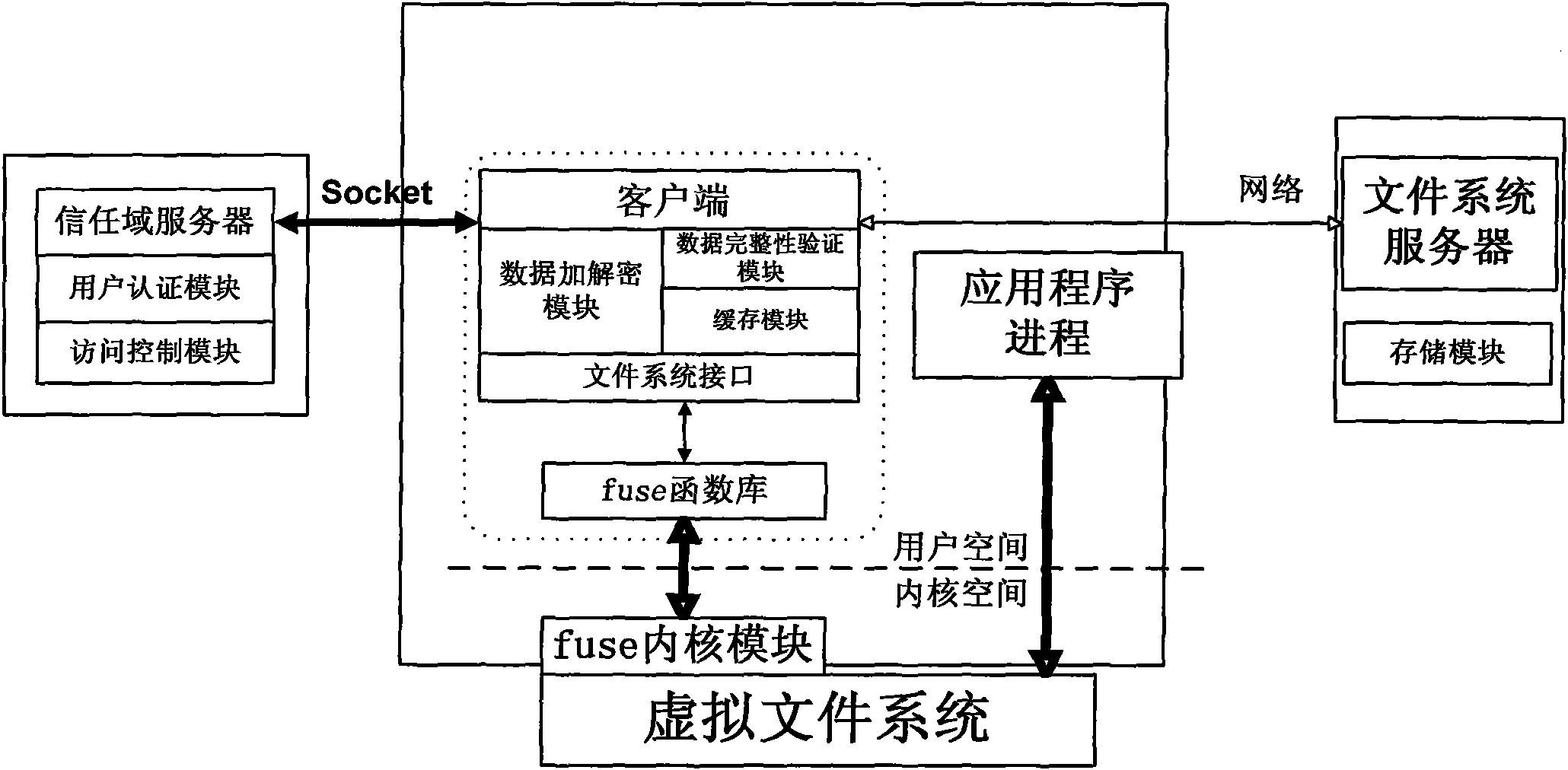
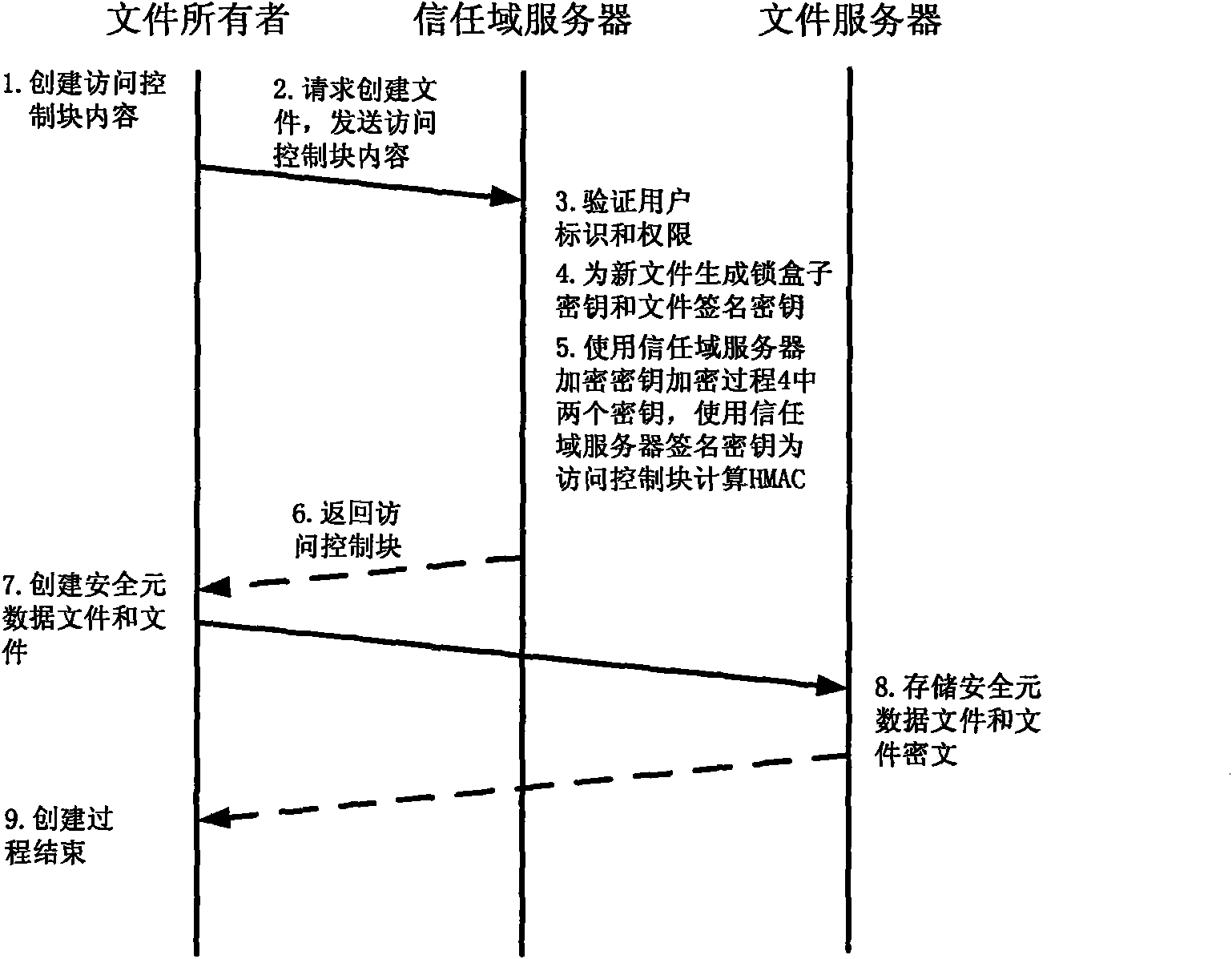
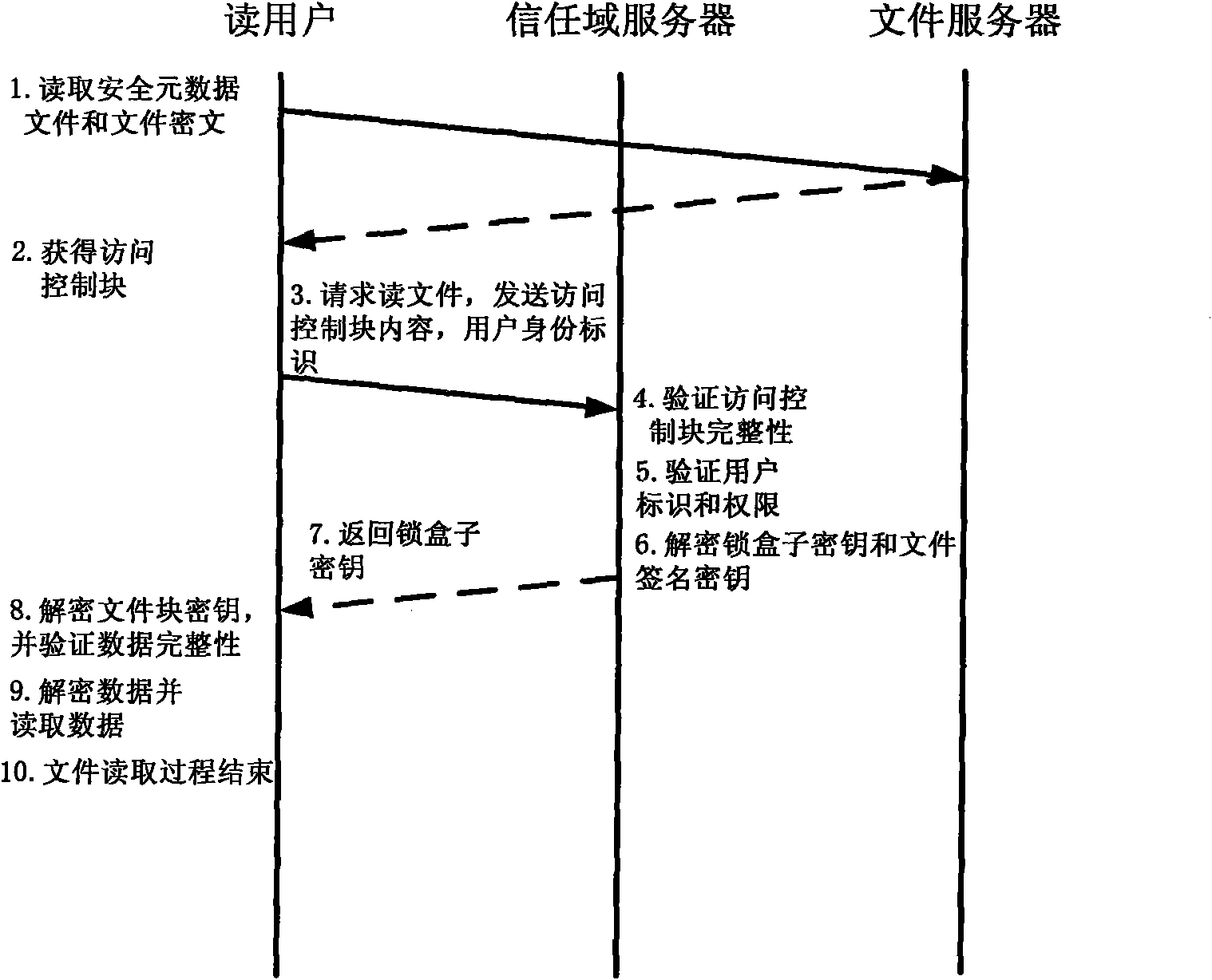
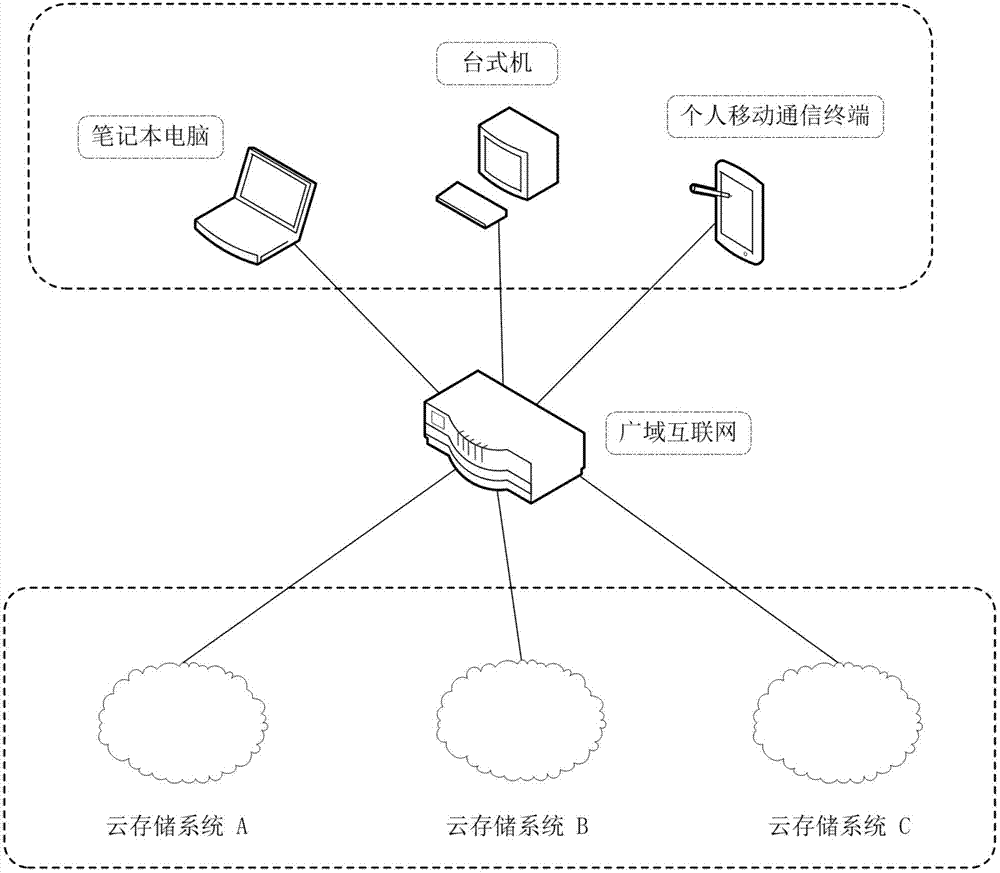
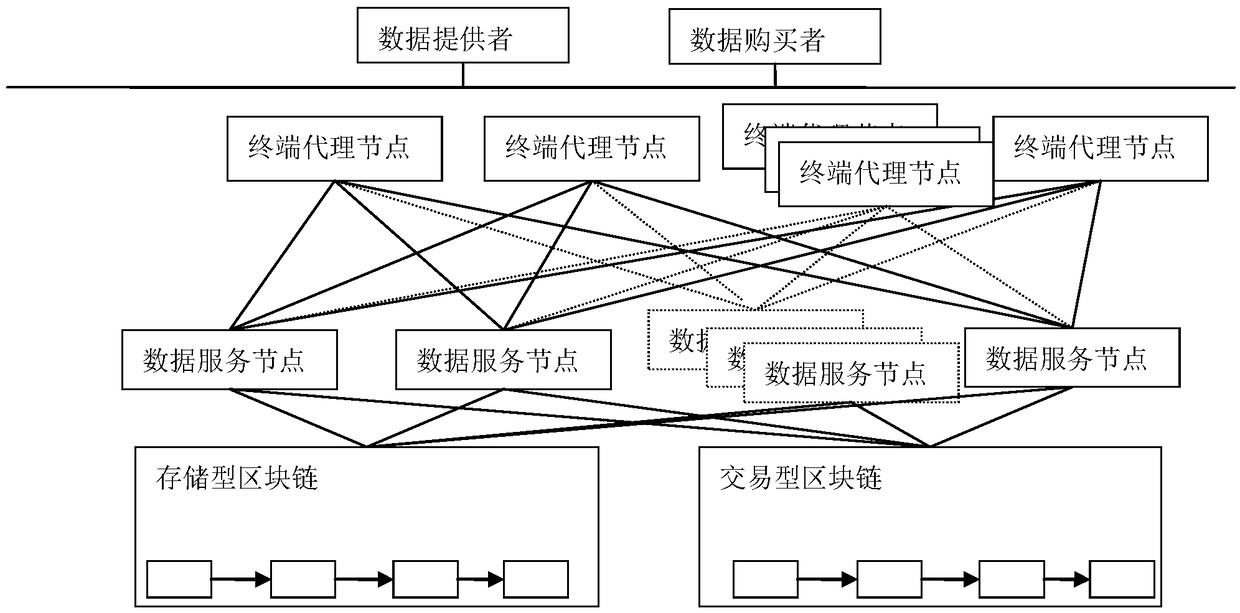
Method for implementing safe storage system in cloud storage environment
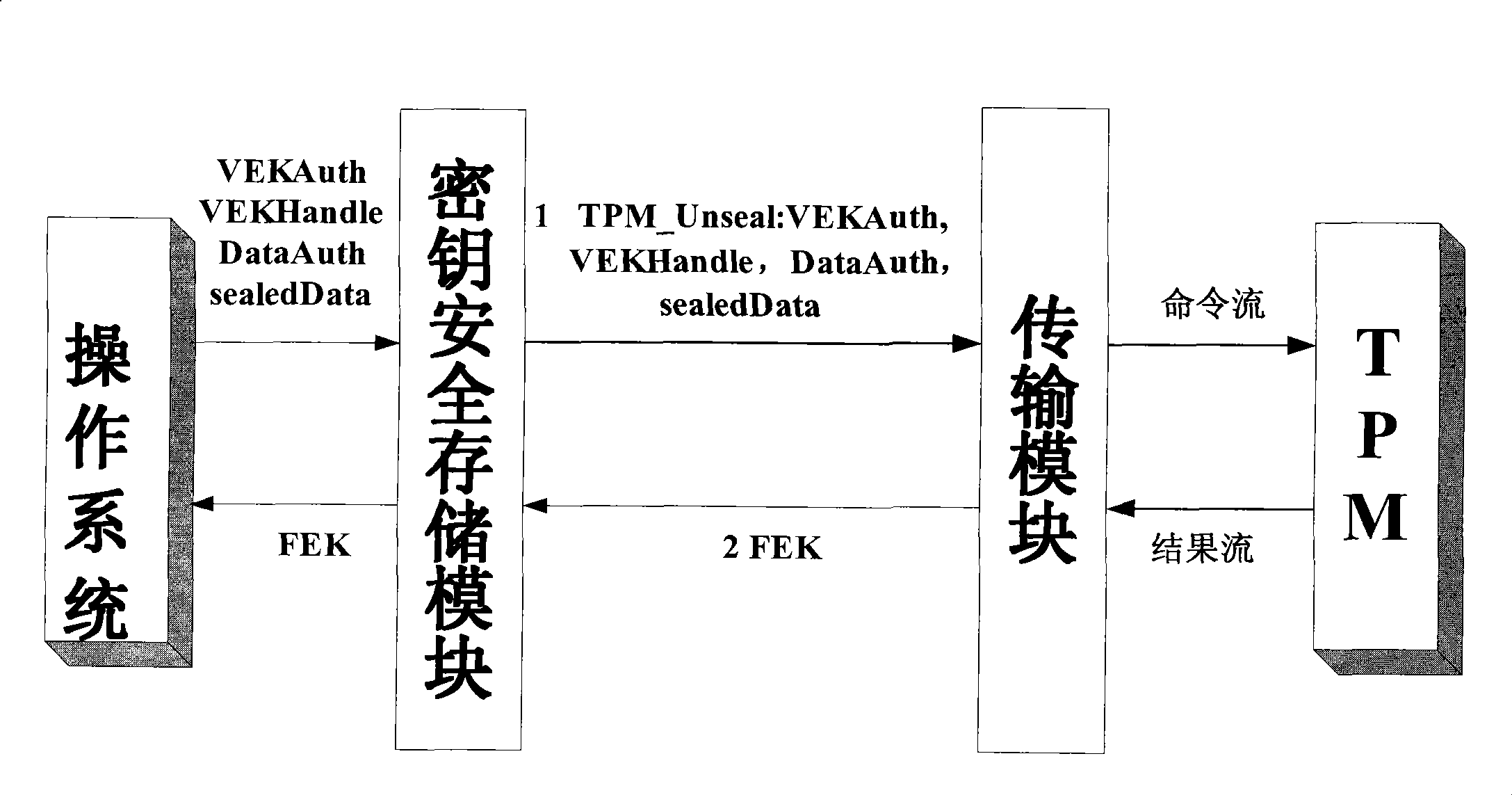
ActiveCN102014133AGuaranteed confidentialityTimely detection of damage, etc.TransmissionConfidentialityCiphertext
The invention relates to a method for implementing a safe storage system in a cloud storage environment and belongs to the technical field of storage safety. The method is characterized in that a trust domain is established in a server according to the requirements of a user; in the trust domain, identity authentication is performed by using an public key infrastructure (PKI); the independence between the storage system and a bottom layer system is realized by utilizing a filesystem in user space (FUSE); a hash value of a file is calculated by utilizing a secure hash algorithm (SHA1) and taking a block as a unit, a file block is encrypted by utilizing a key and an advanced encryption standard (AES) algorithm of a symmetric encipherment algorithm and taking a block as a unit, and a file cipher text is uploaded to a file server in a cloud storage area so as to guarantee the confidentiality and integrity of the file; a filer owner postpones encrypting the file again when permission is revoked by designating a user with the permission of accessing the file and the permissions thereof in an access control list; and only when the user modifies the content of the file, the user encrypts the file block in which the modified content is positioned again and the system implements three layers of key management, namely a file block key, a safe metadata file key and a trust domain server key so that not only the safety of the file is guaranteed when the permission is revoked, but also the management load of the system is not increased.
Owner:TSINGHUA UNIV
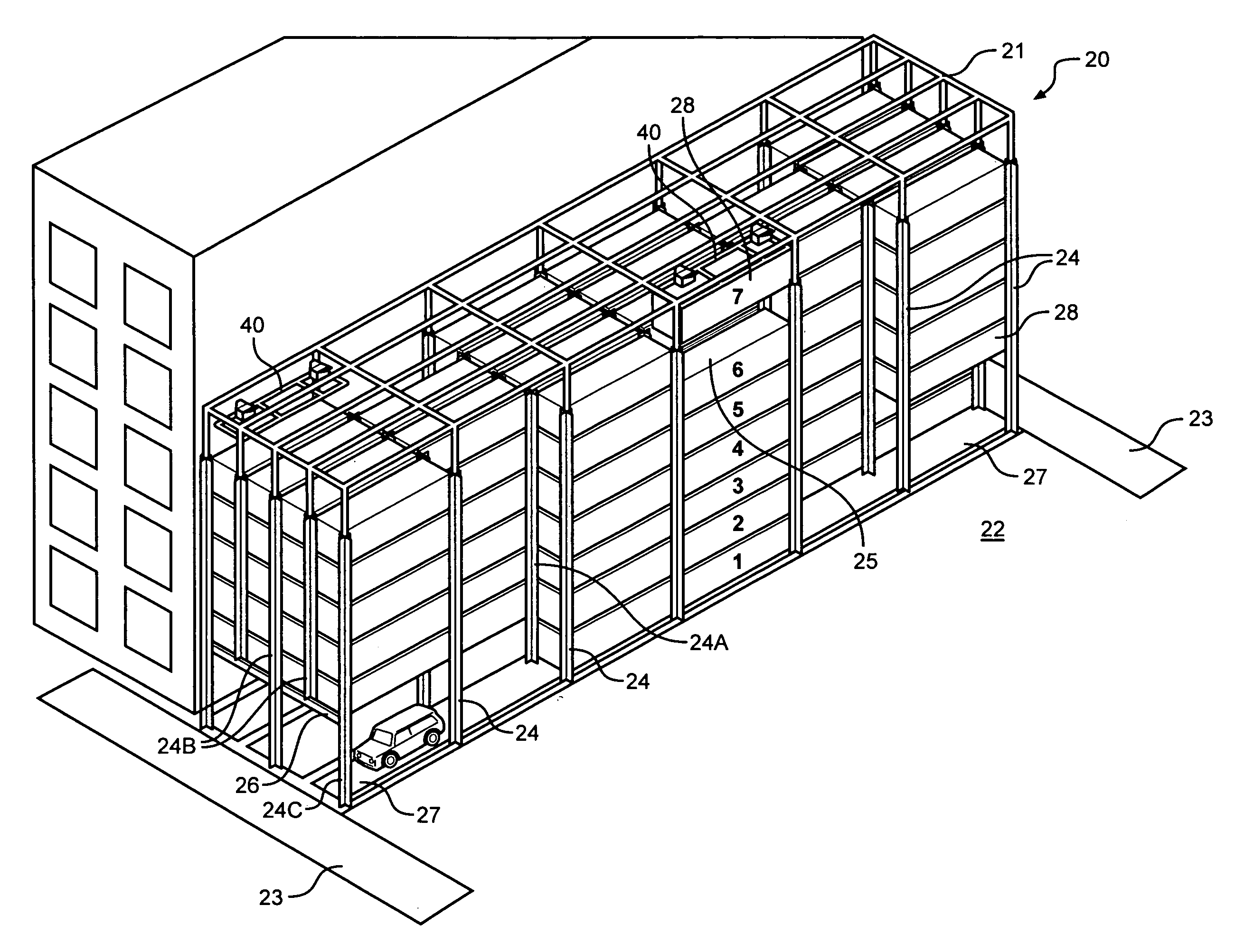
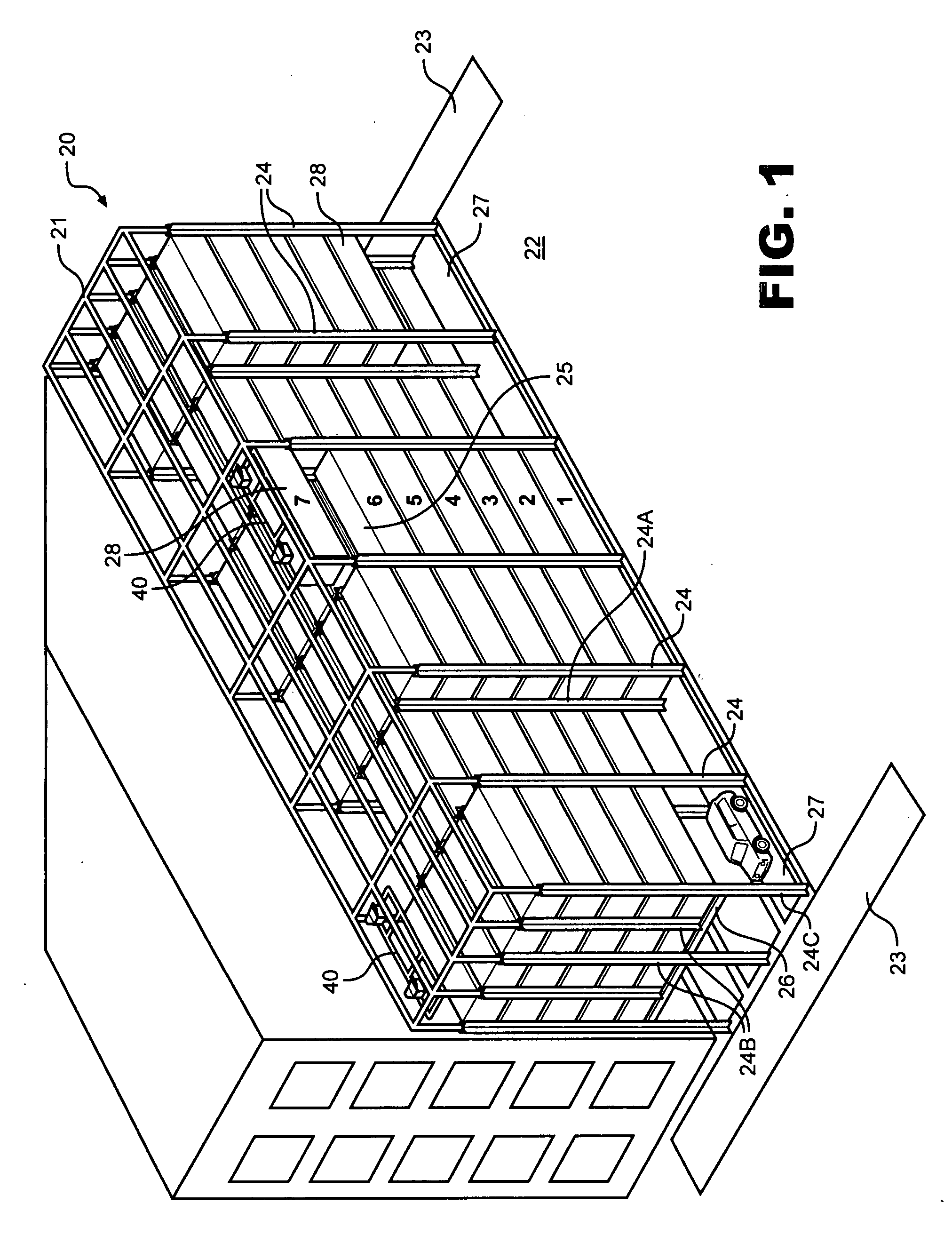
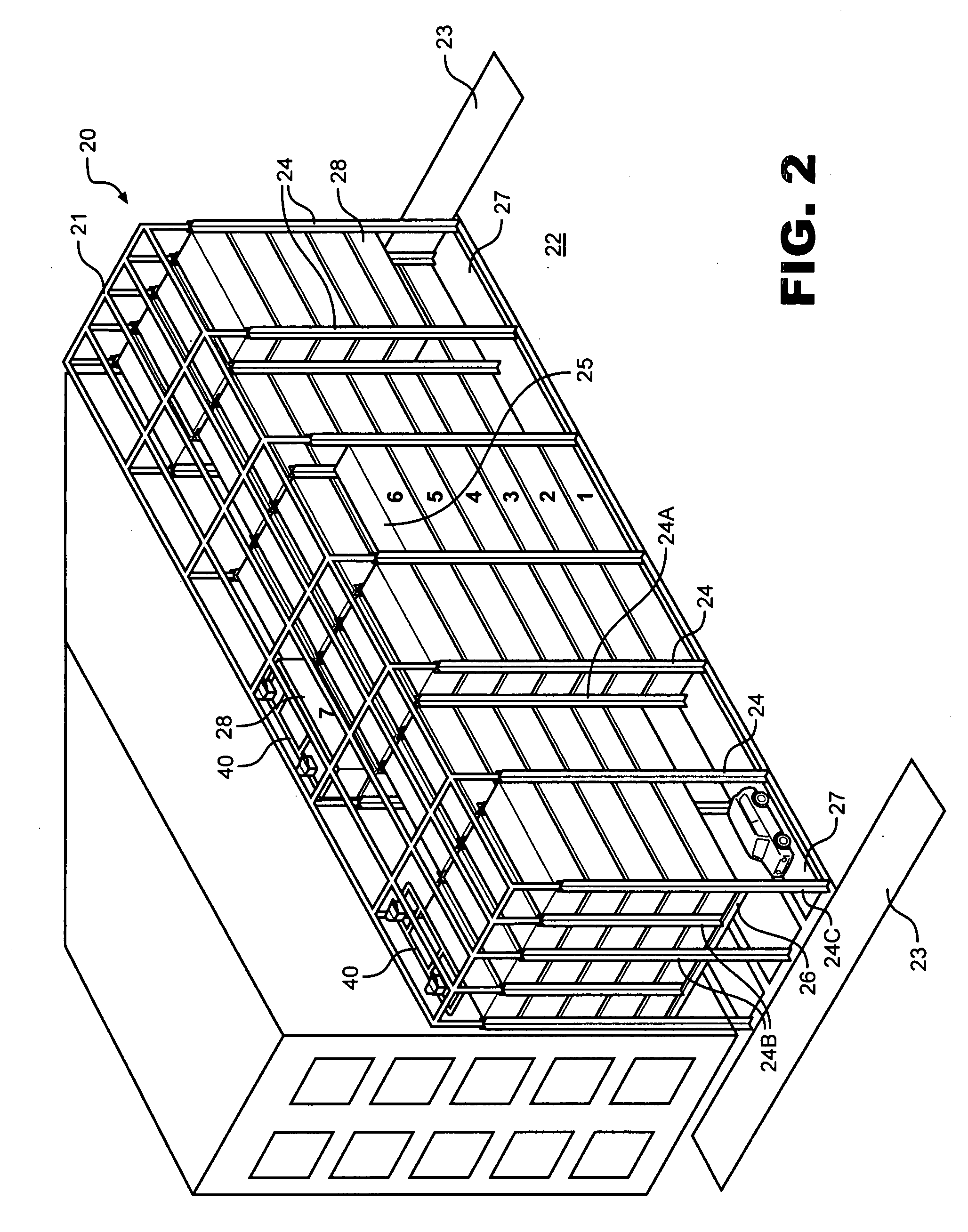
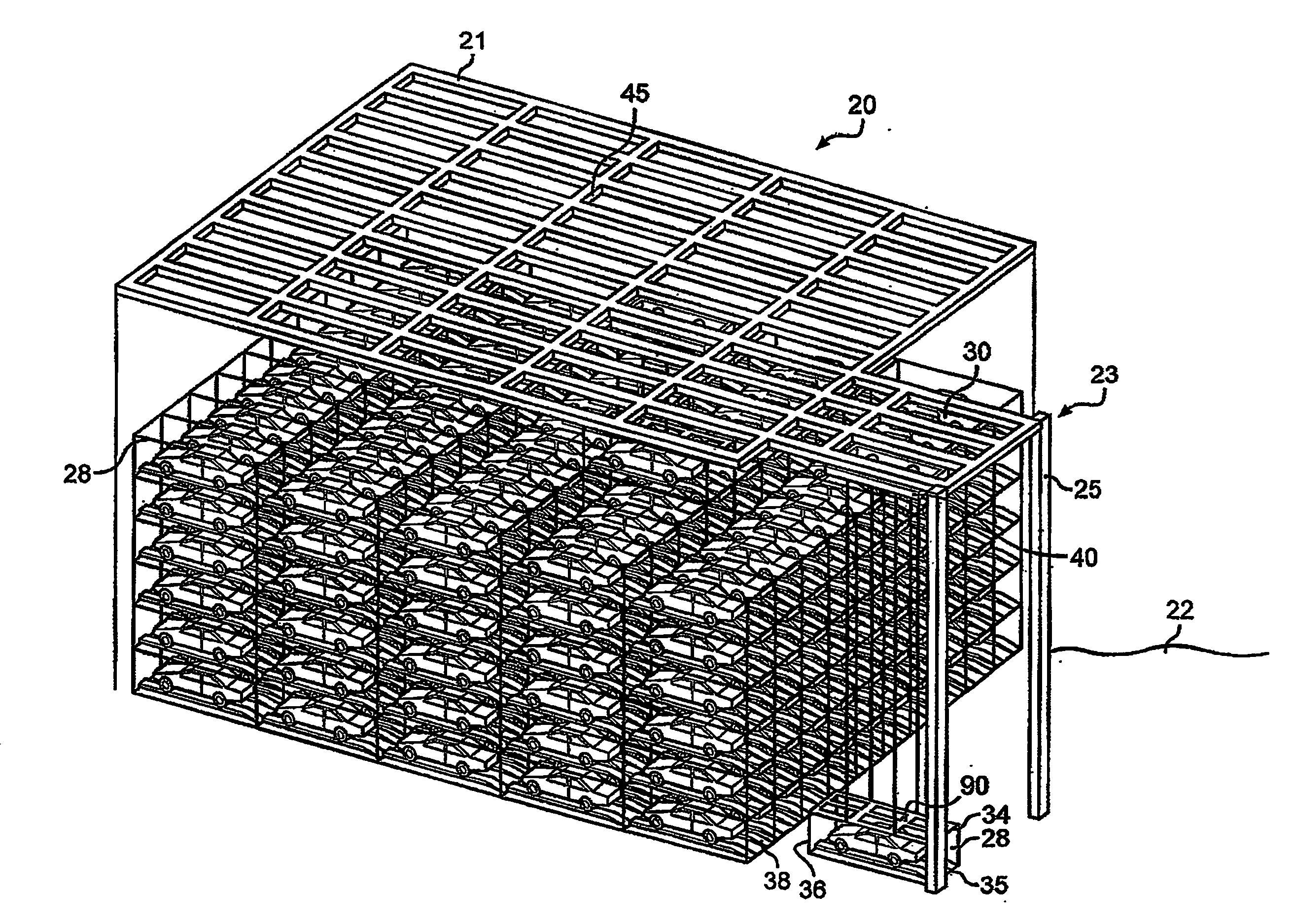
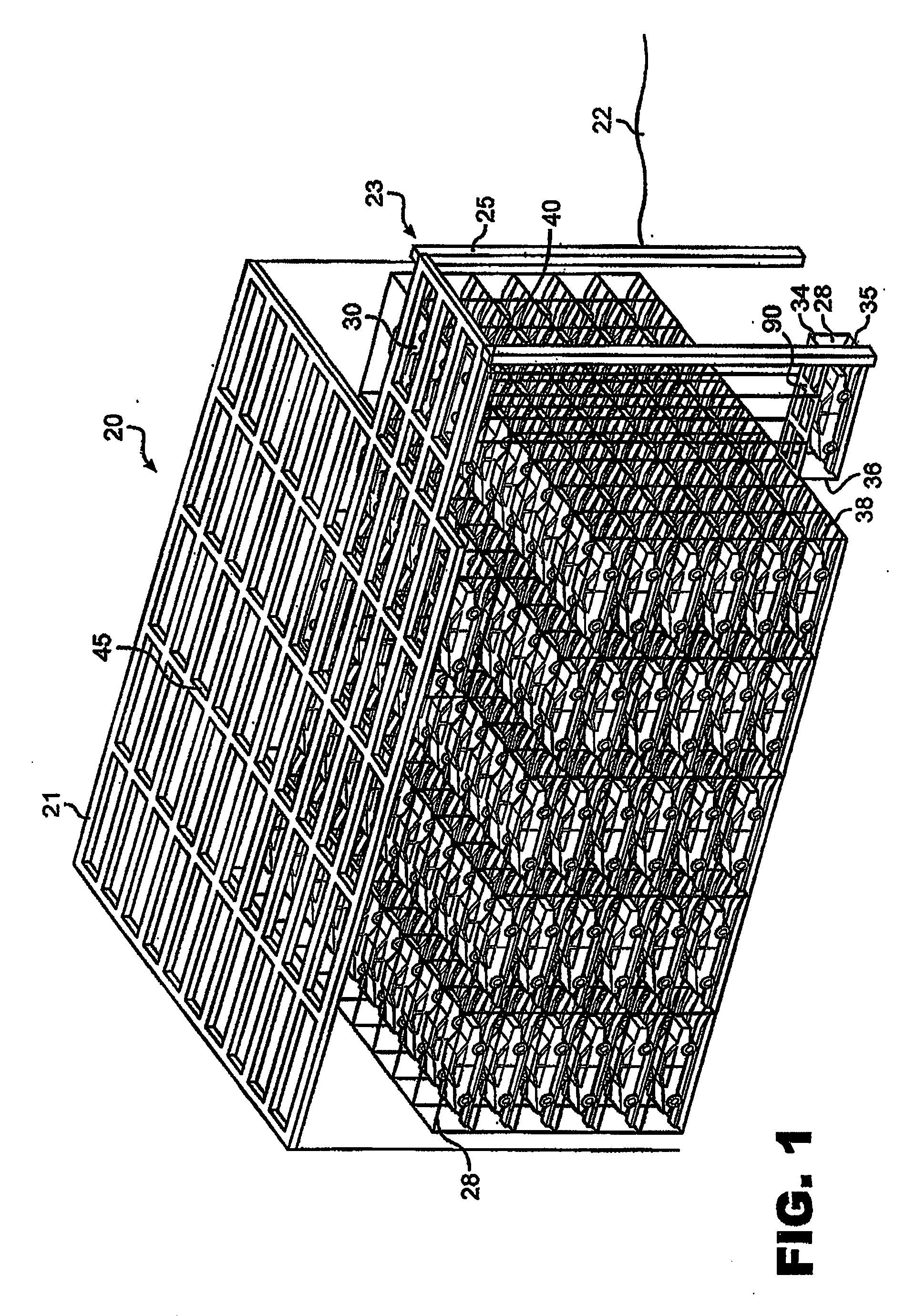
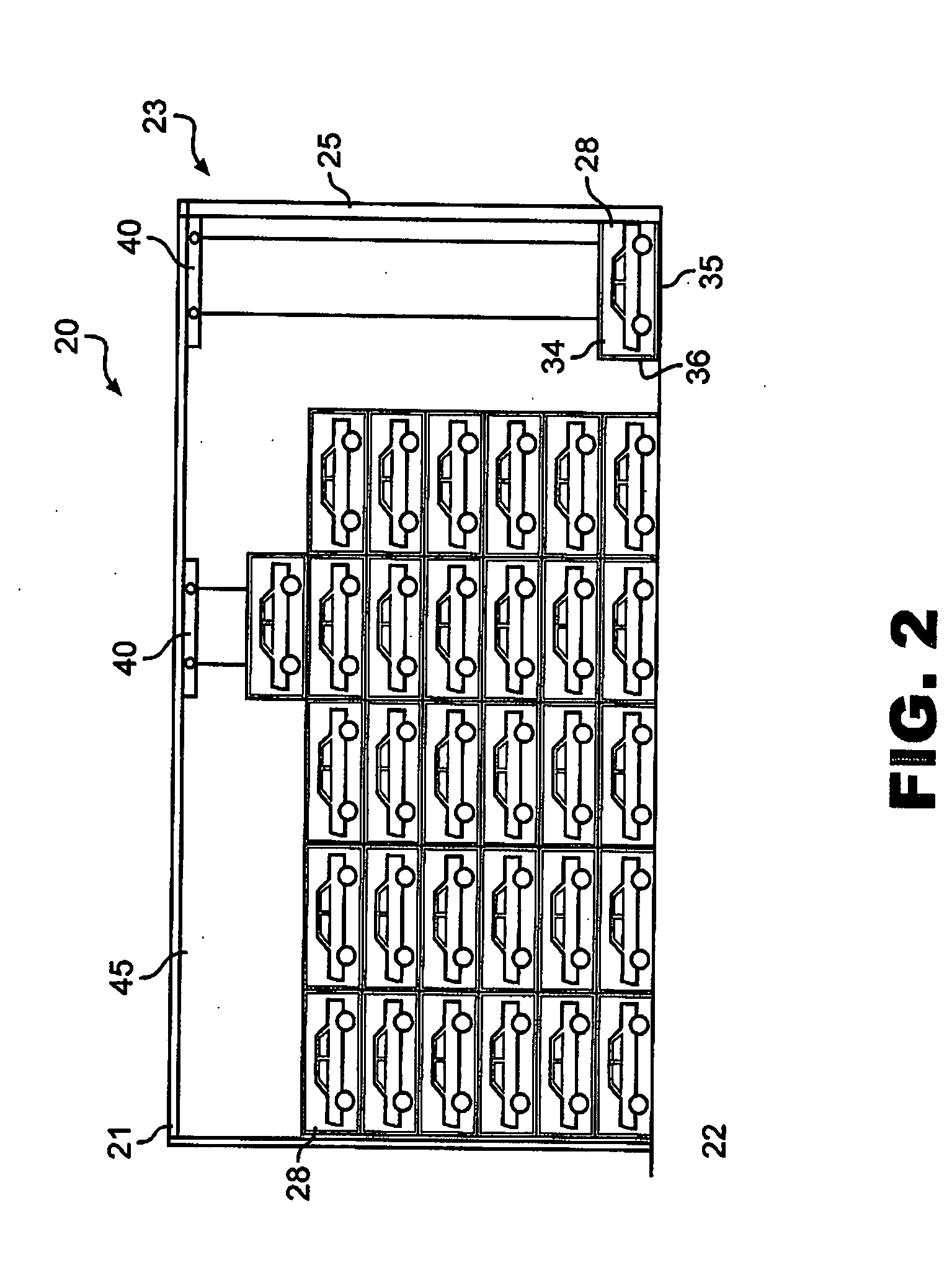
Warehouse storage system
ActiveUS20080075569A1Maximize storage spaceReduce areaTravelling cranesLoading/unloadingEngineeringStorage cell
A system and method for the safe storage of items wherein a storage structure is provided having a first section in which storage units are stored in vertically oriented cells with each storage unit being stacked one upon another and wherein at least one transfer vehicle is provided for selectively engaging and conveying the storage units along an overhead grid track system between the first section and a second section wherein the at least one transfer vehicle may be used to either lift or lower a storage unit and move the storage unit to and from a storage position in one of the vertical storage cells of the first section of the storage structure.
Owner:GEBRR BECKER
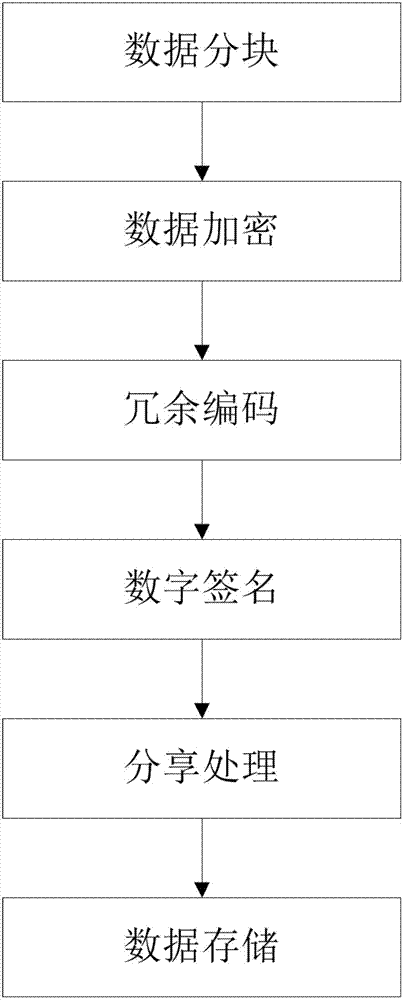
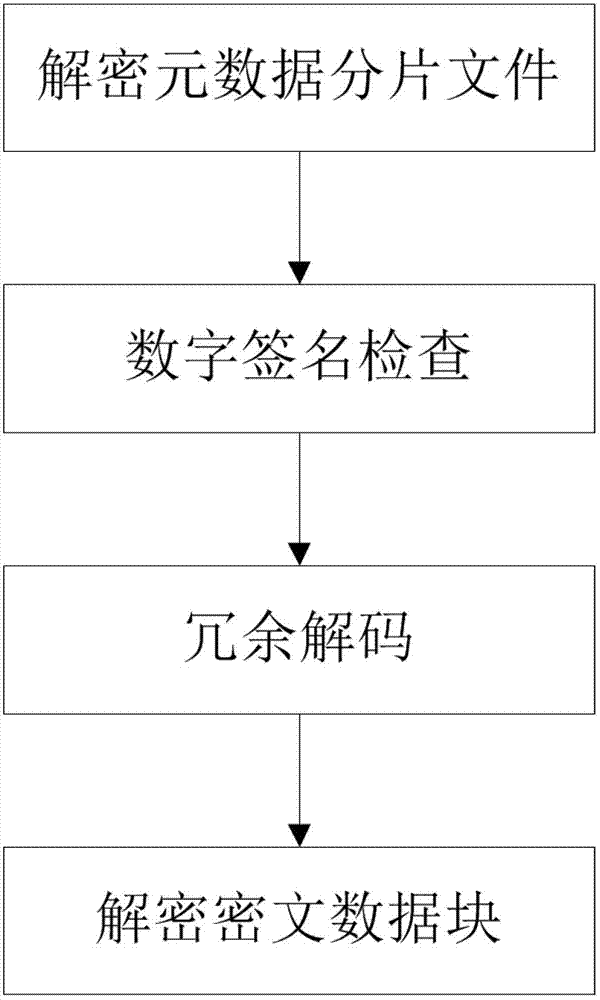
Safe storage method based on a plurality of cloud storage systems and system thereof
InactiveCN103118089AImprove fault toleranceAvoid inaccessibilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCode moduleCiphertext
The invention belongs to the technical field of computer storage, and provides a safe storage method based on a plurality of cloud storage systems and a system thereof. The method and the system can achieve the purpose that in the plurality of existing cloud storage systems, safety of data and metadata can be guaranteed at the same time. The safe storage method comprises a step of data writing operation and a step of data reading operation, wherein the step of data writing operation comprises the sub-steps of data partitioning, data encryption, redundancy encoding, digital signature, sharing processing, and data storage. The step of data reading operation comprises the sub-steps of metadata partition file decryption, digital signature inspection, redundancy decoding and cipher text data block decryption. The safe storage system comprises an encryption and decryption coding module, a redundancy encoding module, a secret sharing module and a digital signature module. By means of the method and the system, metadata privacy and high availability can be guaranteed, and meanwhile, a user does not need to store any metadata information for indexing and data query.
Owner:HUAZHONG UNIV OF SCI & TECH
Overhead vehicle storage system
ActiveUS20080075566A1Easy retrievalThe process is convenient and fastStorage devicesParkingsCOMPONENT IISafe storage
A system and method for the safe storage of vehicles wherein a storage structure is provided having a first section in which vehicles are stored in vertically oriented cells with each vehicle being carried within a vehicle storage unit such that the units may be stacked one upon another and wherein at least one transfer vehicle is provided for selectively engaging and conveying the vehicle storage units along an overhead grid track system between the first section and a second section wherein the grid track system is at least partially oriented over a roadway such that the at least one transfer vehicle may be used to either lift or lower a vehicle contained within a vehicle storage unit relative to the roadway and move the vehicle storage unit to and from a storage position in one of the vertical storage cells of the first section of the storage structure.
Owner:GEBRR BECKER
Gas-target neutron generation and applications
InactiveUS6922455B2Improve performanceMaximize productionNuclear energy generationX-ray tube electrodesHigh resistanceNeutron emission
Described herein are integrated systems for generating neutrons to perform a variety of tasks including: on-line analysis of bulk material and industrial process control (as shown in FIG. 1), security interrogation (as shown in FIG. 2), soil and environmental analysis, and medical diagnostic treatment. These systems are based on novel gas-target neutron generation which embodies the beneficial characteristics of replenishable fusible gas targets for very long lifetime, stability and continuous operation, combined with the advantageous features common to conventional accelerator neutron tubes including: on / off operation, hermetically sealed operation, and safe storage and transport. Innovative electron management techniques provide gas-target neutron production efficiencies that are comparable or surpass existing sources. The high-pressure high-resistance gaseous discharge is presented as a favorable gas-target neutron generator embodiment, combining ion source regions, accelerator regions, gas-target regions and electron management components within a single simple cost-effective device that is adaptable to various geometric configurations that provide specific neutron emission profiles for greater analysis capacity.
Owner:STARFIRE INDS MANAGEMENT
Remote Aerodrome for UAVs
InactiveUS20170158353A1Reduce riskMaximize free airspaceCharging stationsShutters/ movable grillesAerodromeUncrewed vehicle
An Aerodrome providing safe storage for Unmanned Aerial Vehicles (UAVs) that includes an enclosure to protect UAVs from the elements (weather). The Aerodrome includes an enclosure, a foldable flight deck, a service interface, and a telescoping video and audio feed unit. The aerodrome can be remotely operated, and can be mounted on a roof of a structure or vehicle, allowing a completely automated service of the UAV without the need of a person being physically present in the vicinity of the UAV.
Owner:SCHMICK MARK
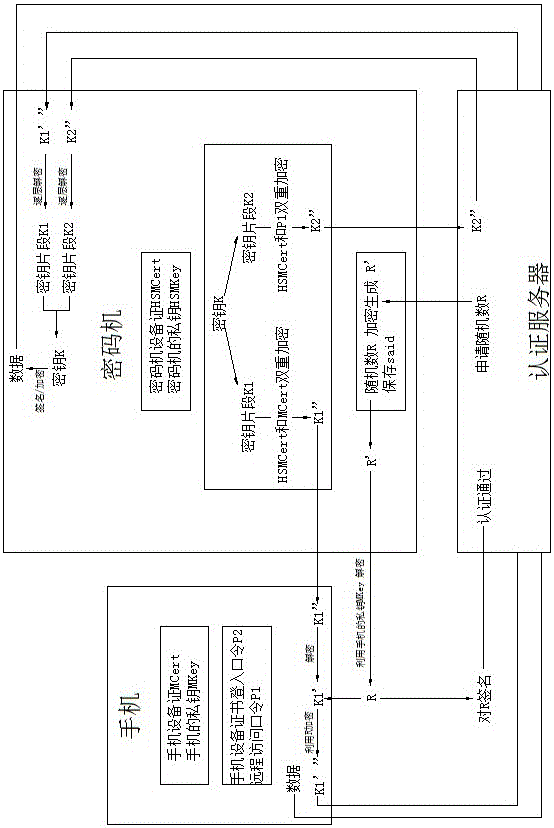
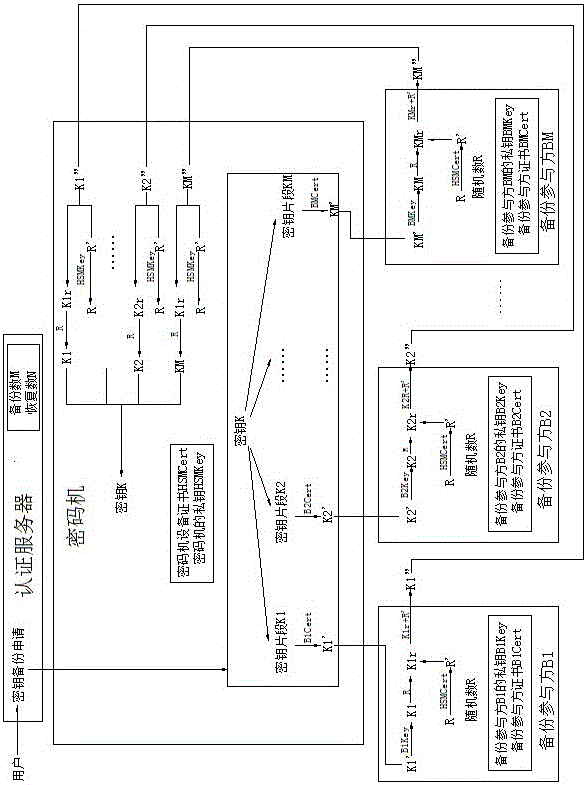
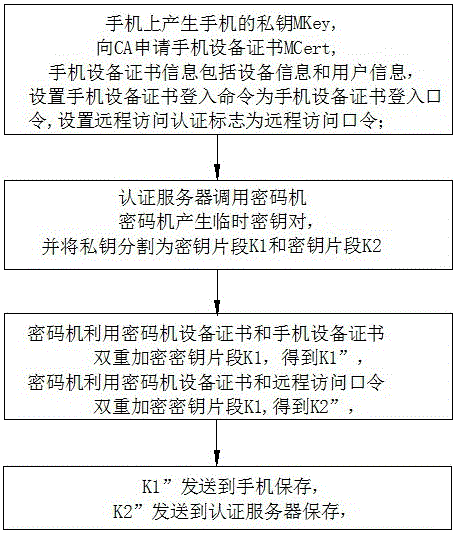
Method and system for realizing block chain private key protection based on key segmentation
ActiveCN106548345AImprove securityAvoid Permission RisksKey distribution for secure communicationPayment protocolsPasswordStructure of Management Information
The invention discloses a method and a system for realizing block chain private key protection based on key segmentation, and aims to solve a technical problem that a private key of a block chain is lack of security and cannot be retrieved. The method for realizing block chain private key protection based on key segmentation comprises that hard encryption for a block chain private key supporting mobile phone equipment certificate authentication and password authentication is realized by taking a mobile phone as a terminal carrier and using a cipher machine and an authentication server of the cloud; and the block chain private key is segmented by using a threshold algorithm, and multi-party participating key backup and key recovery / retrieval is realized. The method comprises (1) a registration procedure, (2) a private key utilization procedure, (3) a private key backup procedure, and (4) a private key recovery / retrieval procedure. The system structurally comprises a cipher machine and an authentication server of the cloud and a mobile phone acting as the terminal carrier. The method and the system disclosed by the invention can realize safe storage, safe utilization, multi-party participating backup and multi-party participating retrieval of the block chain private key.
Owner:北京信任度科技有限公司
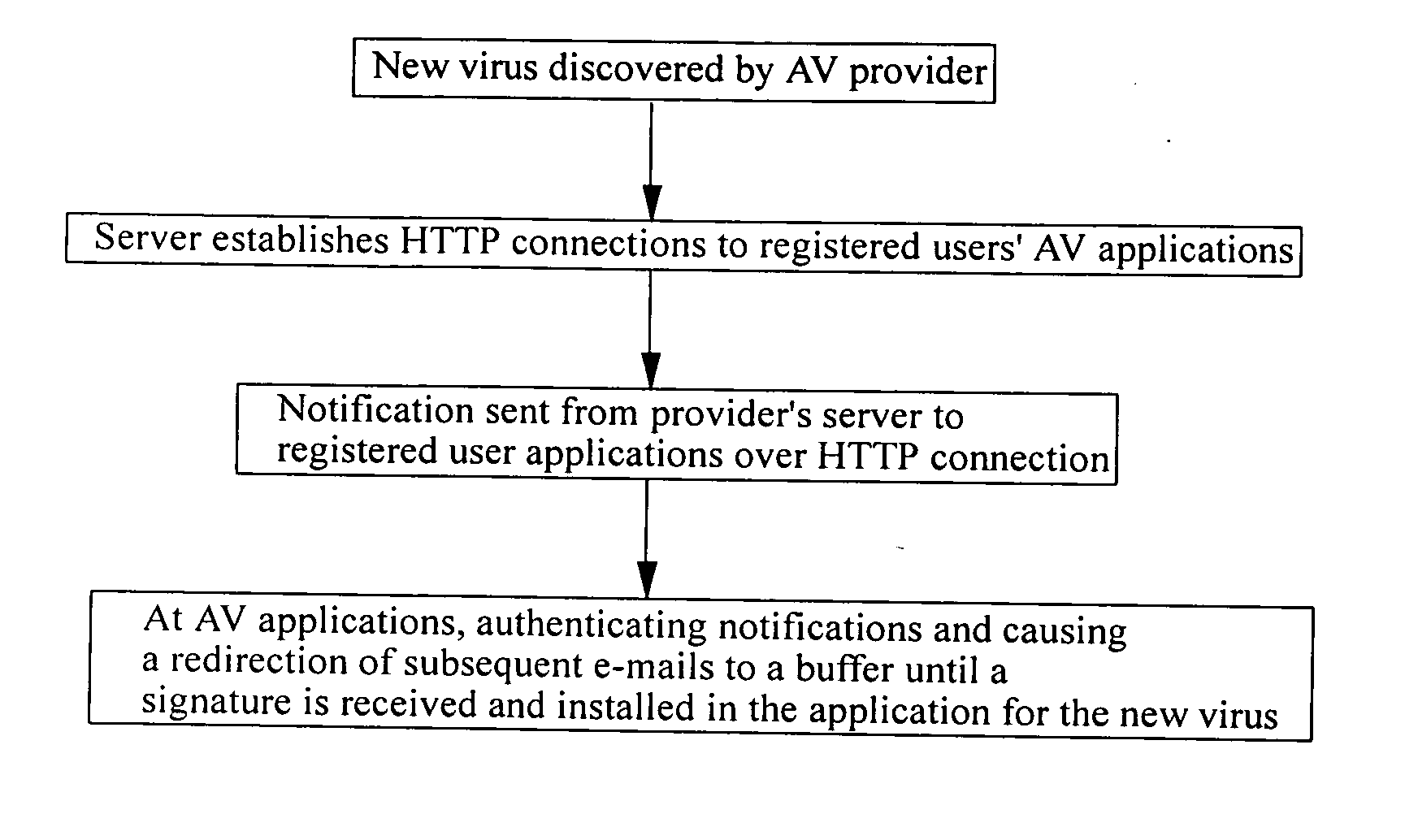
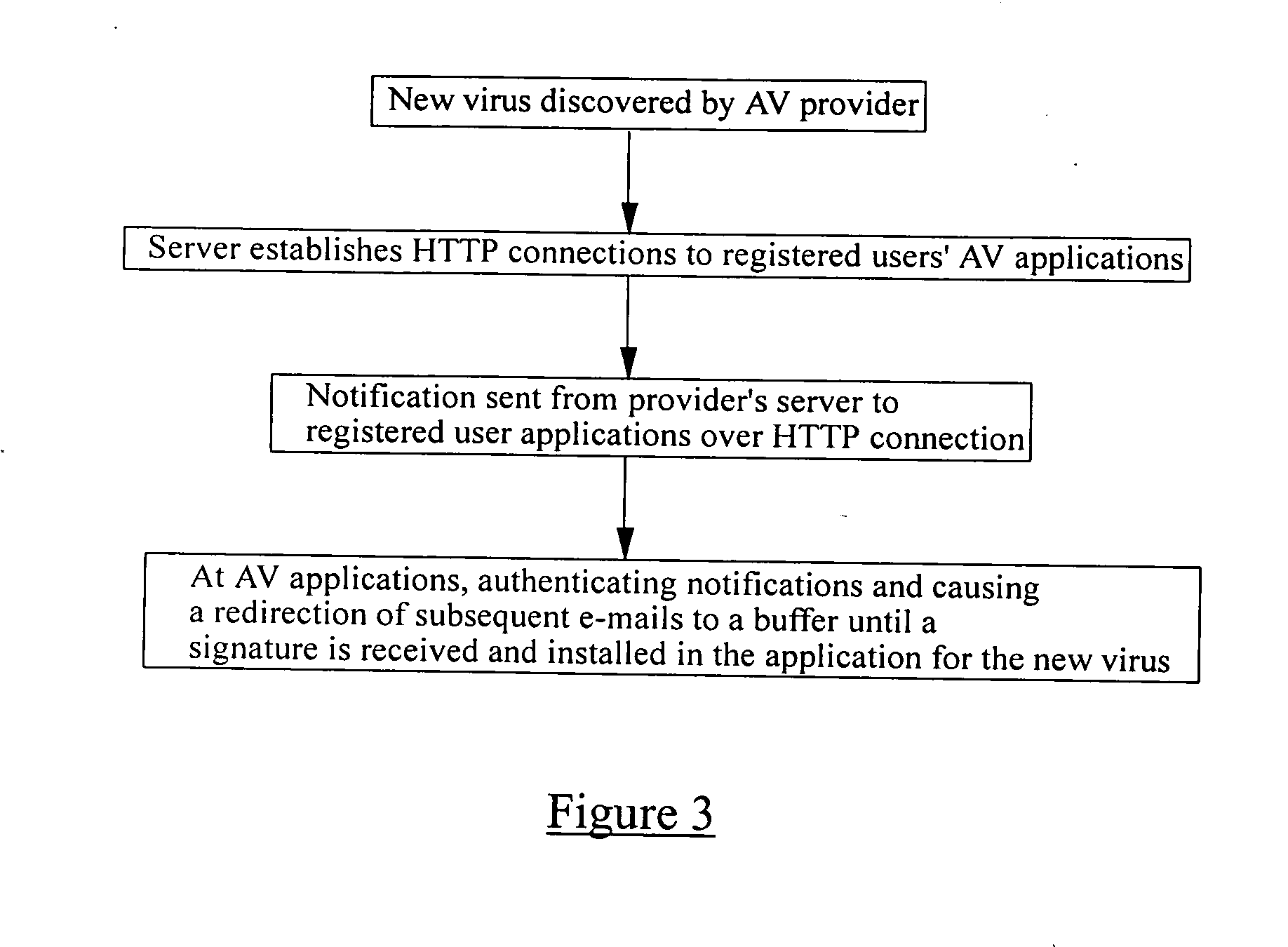
Anti-virus protection at a network gateway
InactiveUS20050120229A1Minimize exposureMemory loss protectionDigital data processing detailsAnti virusVirus
A method of preventing the infection of a computer network 1 by a computer virus, where that virus can be spread by e-mail traffic. The method comprises installing at an e-mail gateway 7 of the network an anti-virus application 12, which application scans at least incoming e-mail traffic for known viruses. In the event that a new virus is detected by the provider of the anti-virus application 12, a notification of this event is sent from the provider to the anti-virus-application 12. At the anti-virus application 12, receipt of said notification results in the diversion of incoming e-mails or their attachments to a buffer 13 for safe storage.
Owner:F SECURE CORP
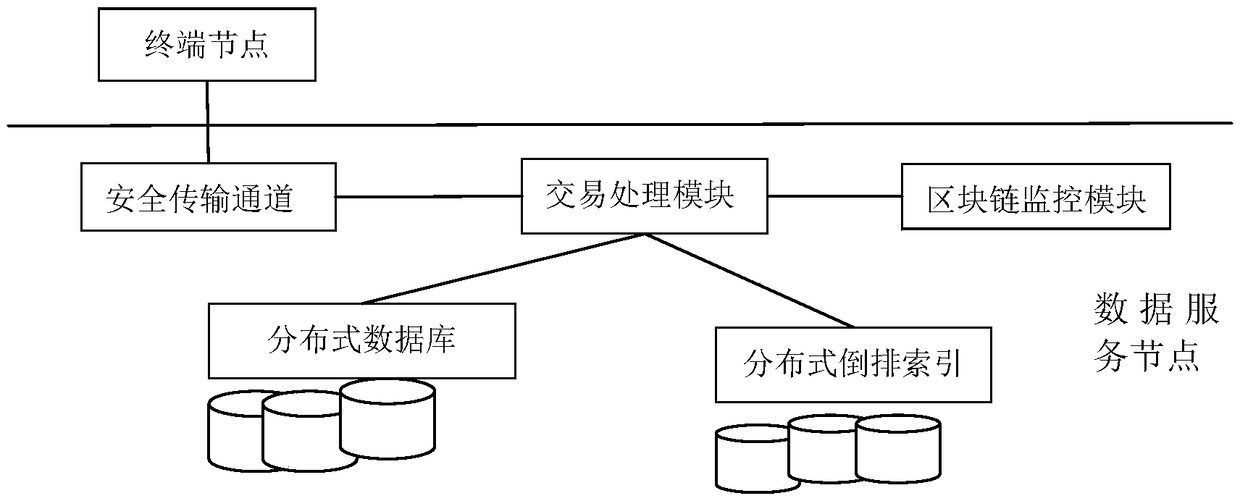
System and method for implementing high-efficiency security memory
ActiveCN101488104AImprove reliabilityImprove storage efficiencyRedundant operation error correctionData storeRaw data
The invention discloses a system for realizing efficient safe storage and a method thereof. The invention comprises the steps as follows: a storage server, a protocol server, a coding server, a decoding server and a metadata server are arranged; during writing operation, the protocol server writes initial data for writing into the storage server and at the same time indicates the coding server to encode the data for writing, the coding server encodes the data to generate redundant data and assigns the redundant data to the appointed storage server, and after writing is finished, basic information of the written file data is stored in the metadata server; during reading operation, the protocol server accesses the metadata server to obtain the storage position of the initial data for reading and obtains the data from the storage position of the data to be combined into the file data; when the initial data can not be read normally, the metadata server is accessed, the storage position of the redundant data is obtained, and the redundant data is read into the decoding server. The invention can effectively improve the efficiency and the reliability of data storage.
Owner:BEIJING 21VIANET DATA CENT
Lightweight back-up and efficient restoration method of health block chain data encryption keys
InactiveCN105812126AReduce management complexityAvoid heavy burdenKey distribution for secure communicationBody area networkRestoration method
The invention provides a lightweight back-up and efficient restoration method of health block chain data encryption keys.Body area networks achieve physiological parameters acquisition of healthy body health, health block chains are produced by a group of credible IT devices appointed by multiple health institutions and used for receiving and storing health data of the body area networks, the health block chain data encryption keys are produced by utilizing a fuzzy technology fuzzy vault and physiological signals acquired by the body area networks, human physiological data acquired in different time periods is encrypted by utilizing different data encryption keys and then is saved in the block chains of the IT devices without storage of historical data encryption keys; historical secret keys are restored by utilizing the health data acquired by the body area networks in real time.The lightweight back-up and efficient restoration method integrates the body area networks with the health block chains, avoids huge burden brought by secret key splitting related in a traditional secret key restoration method and safe storage and retrieval of shadow secret keys and greatly reduces management complexity of the health block chain data encryption keys.
Owner:QILU UNIV OF TECH
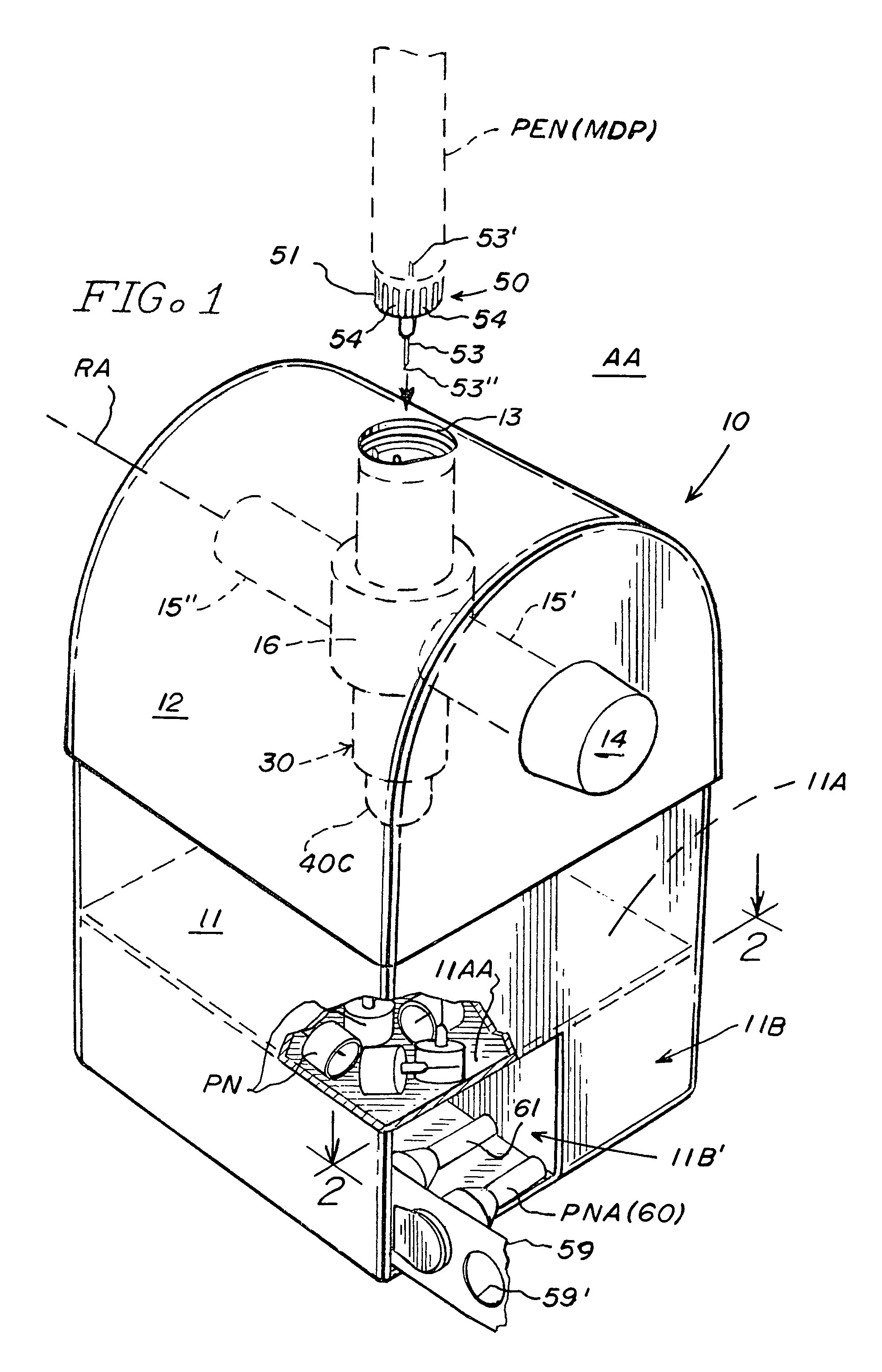
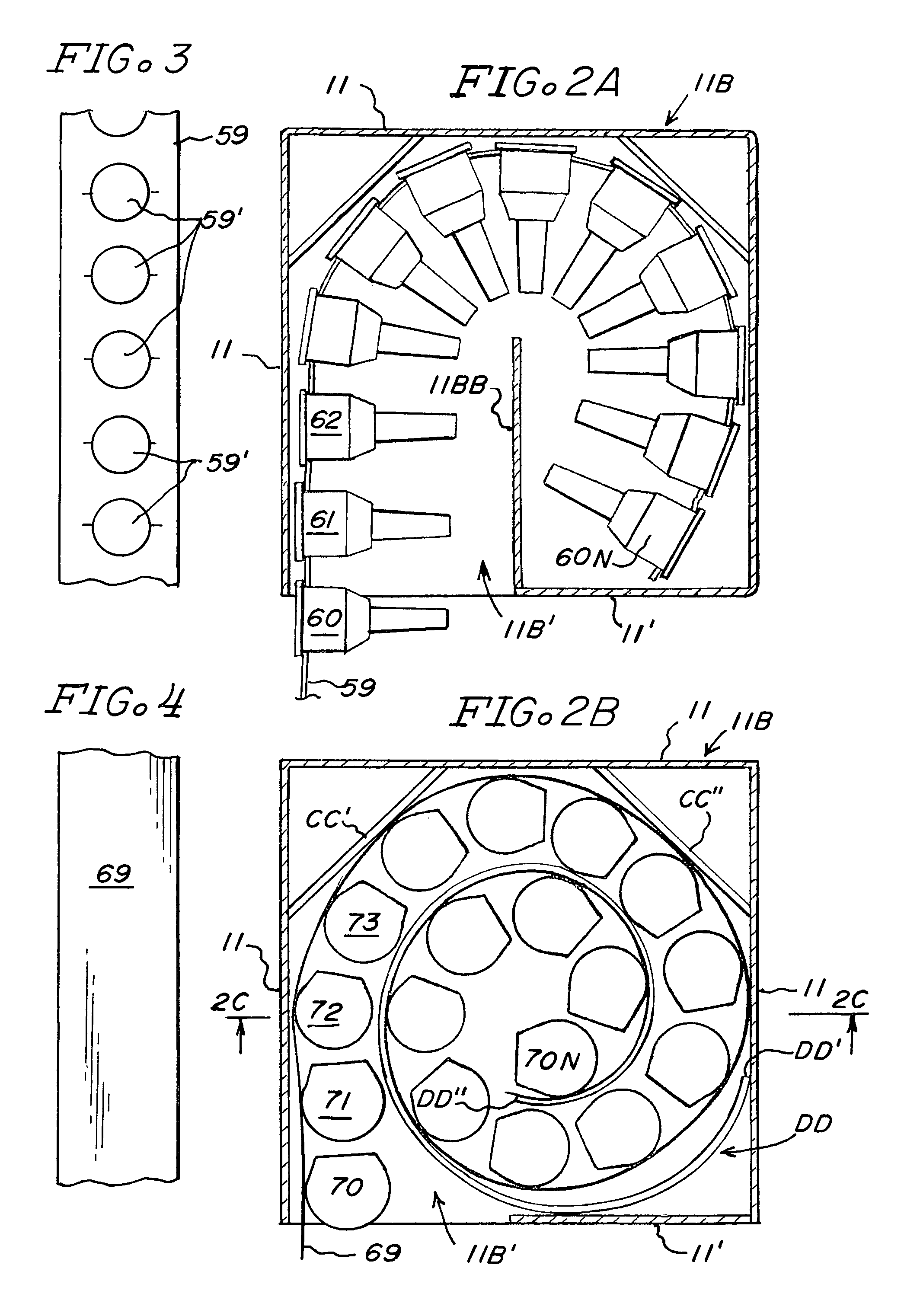
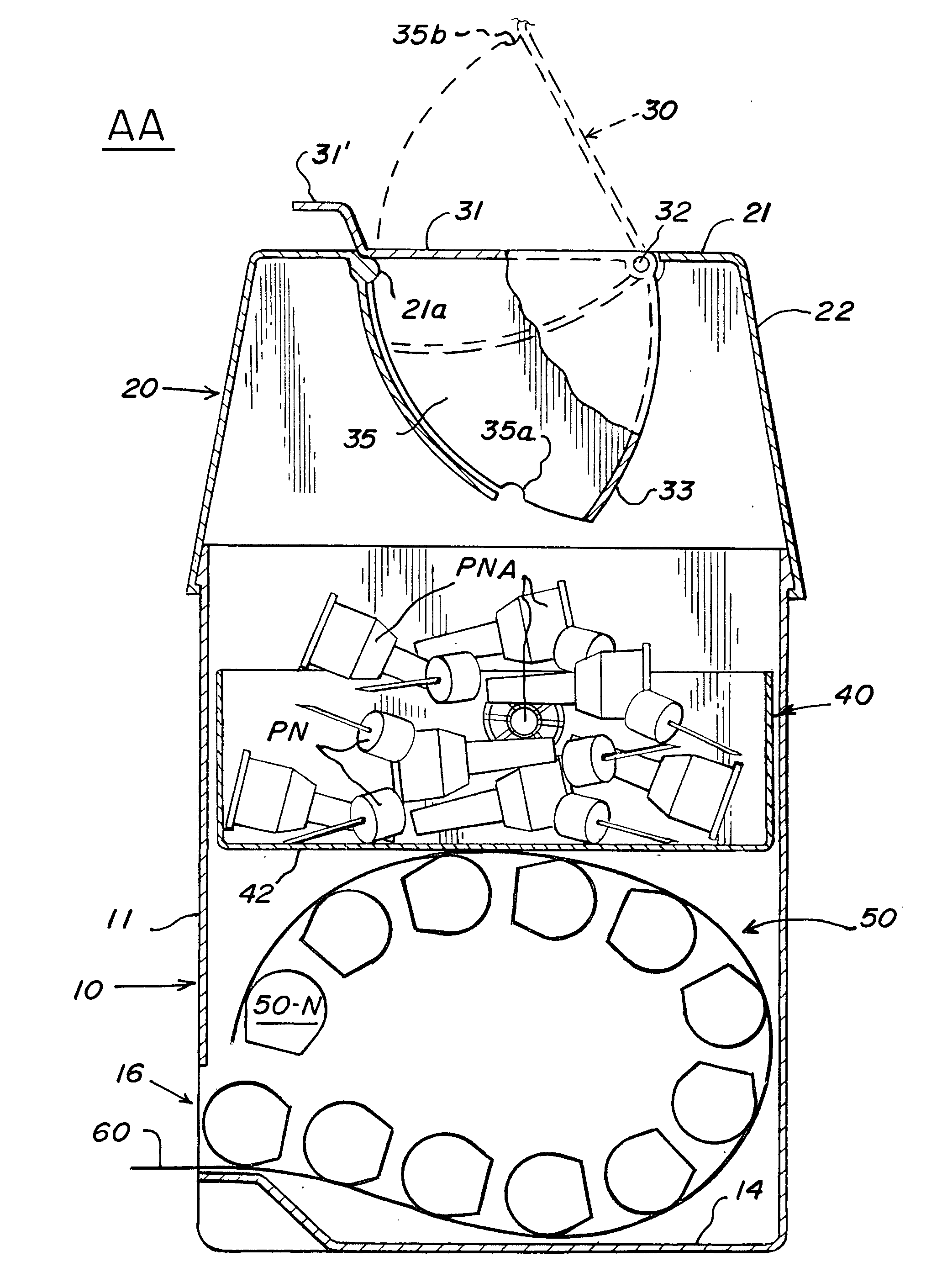
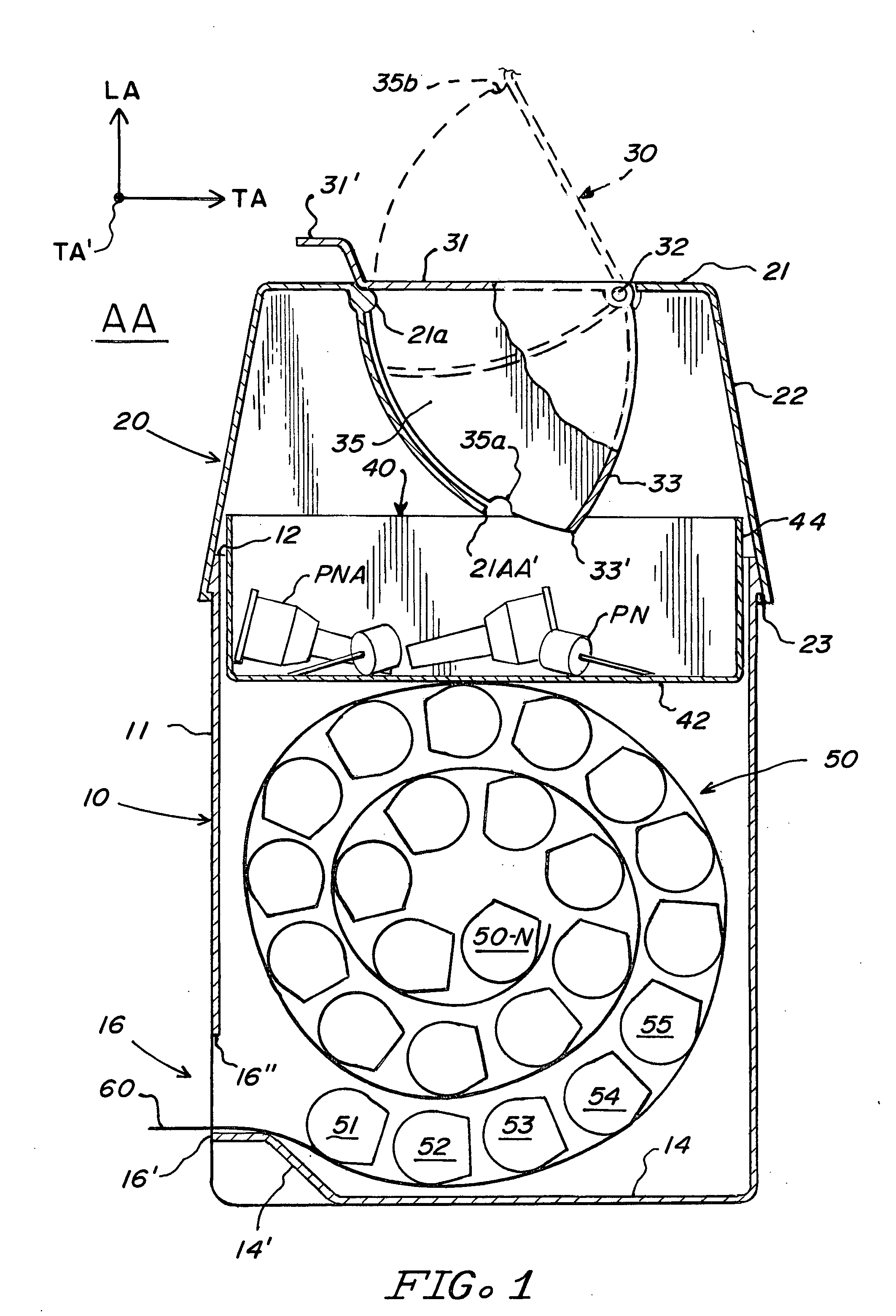
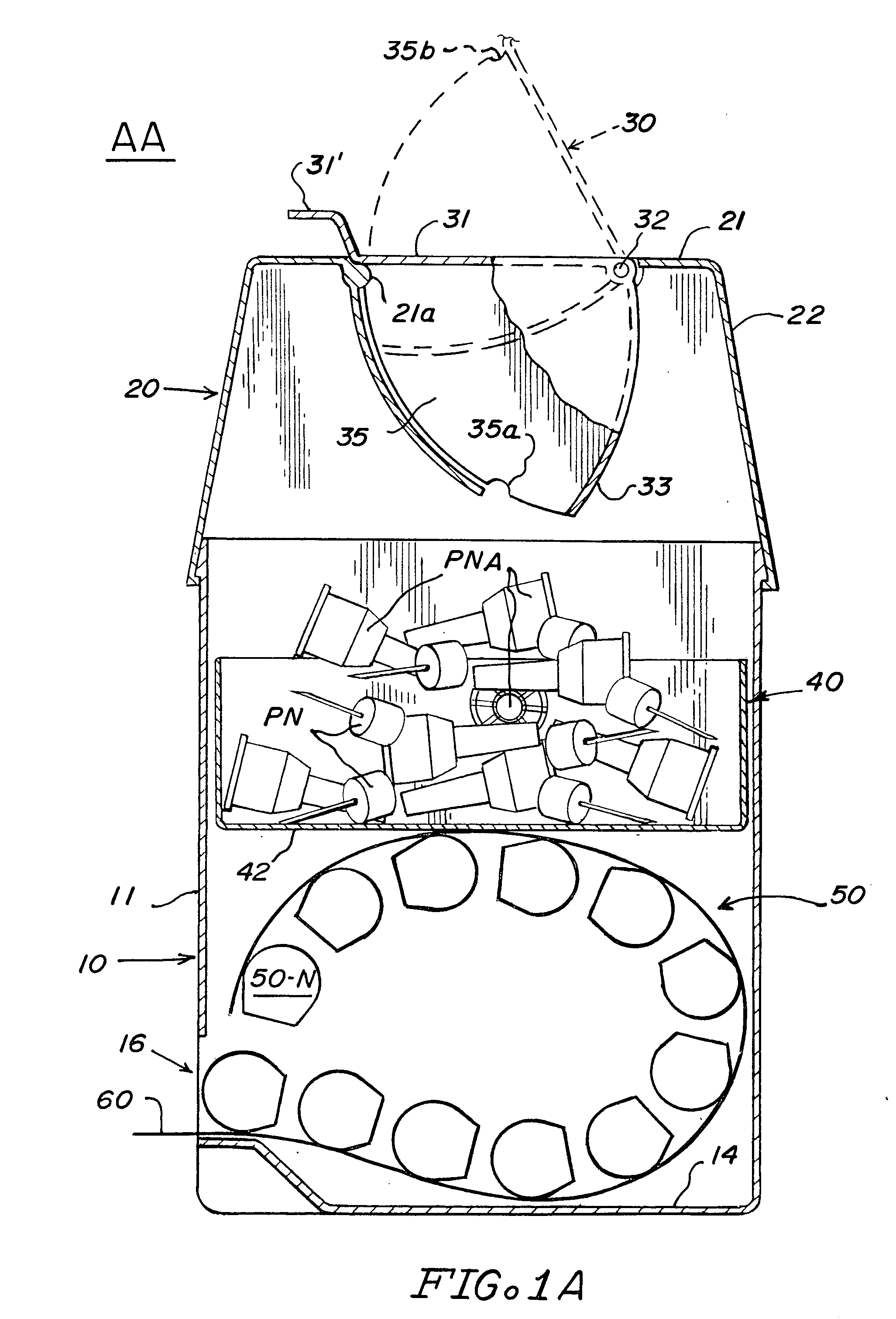
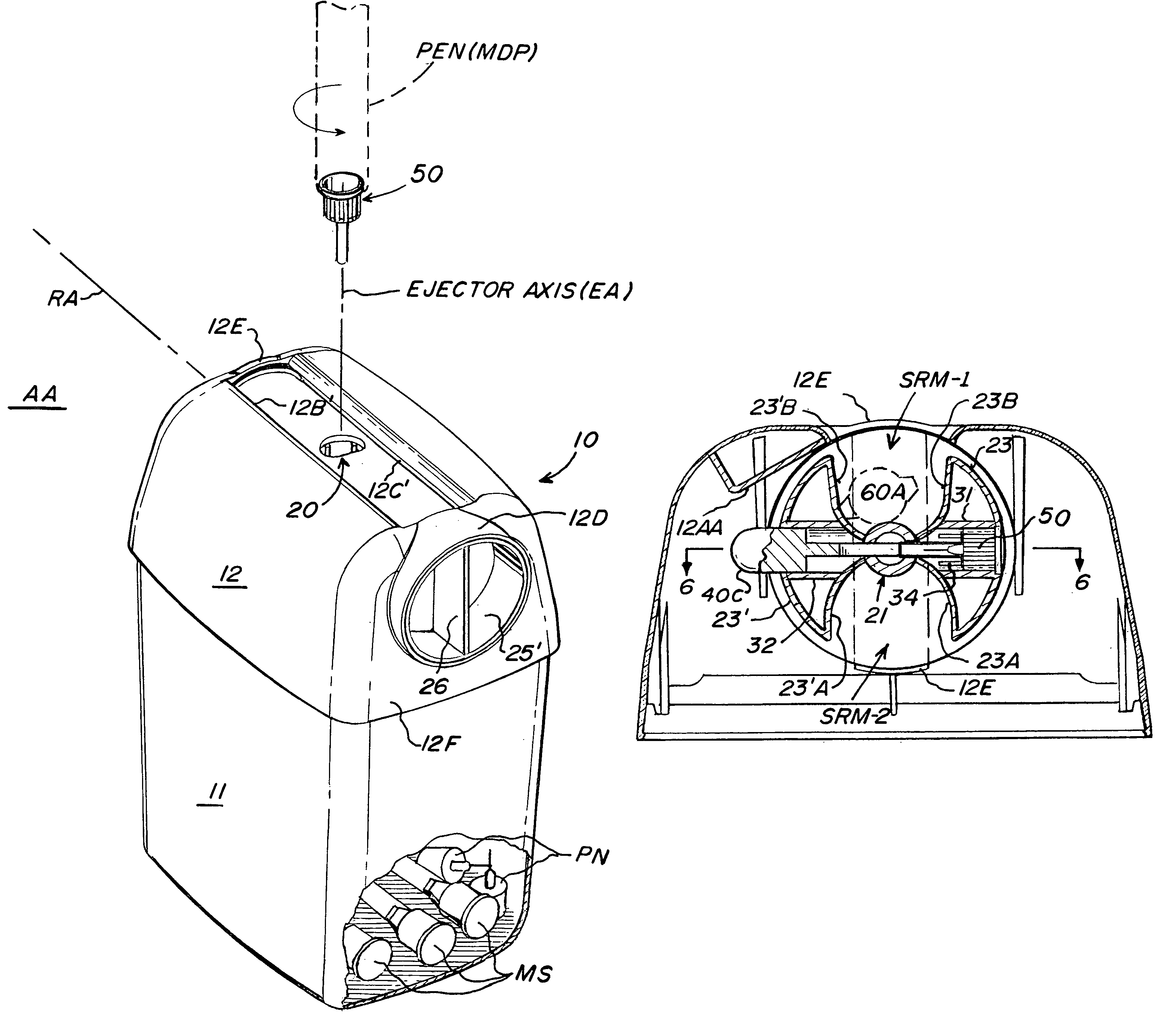
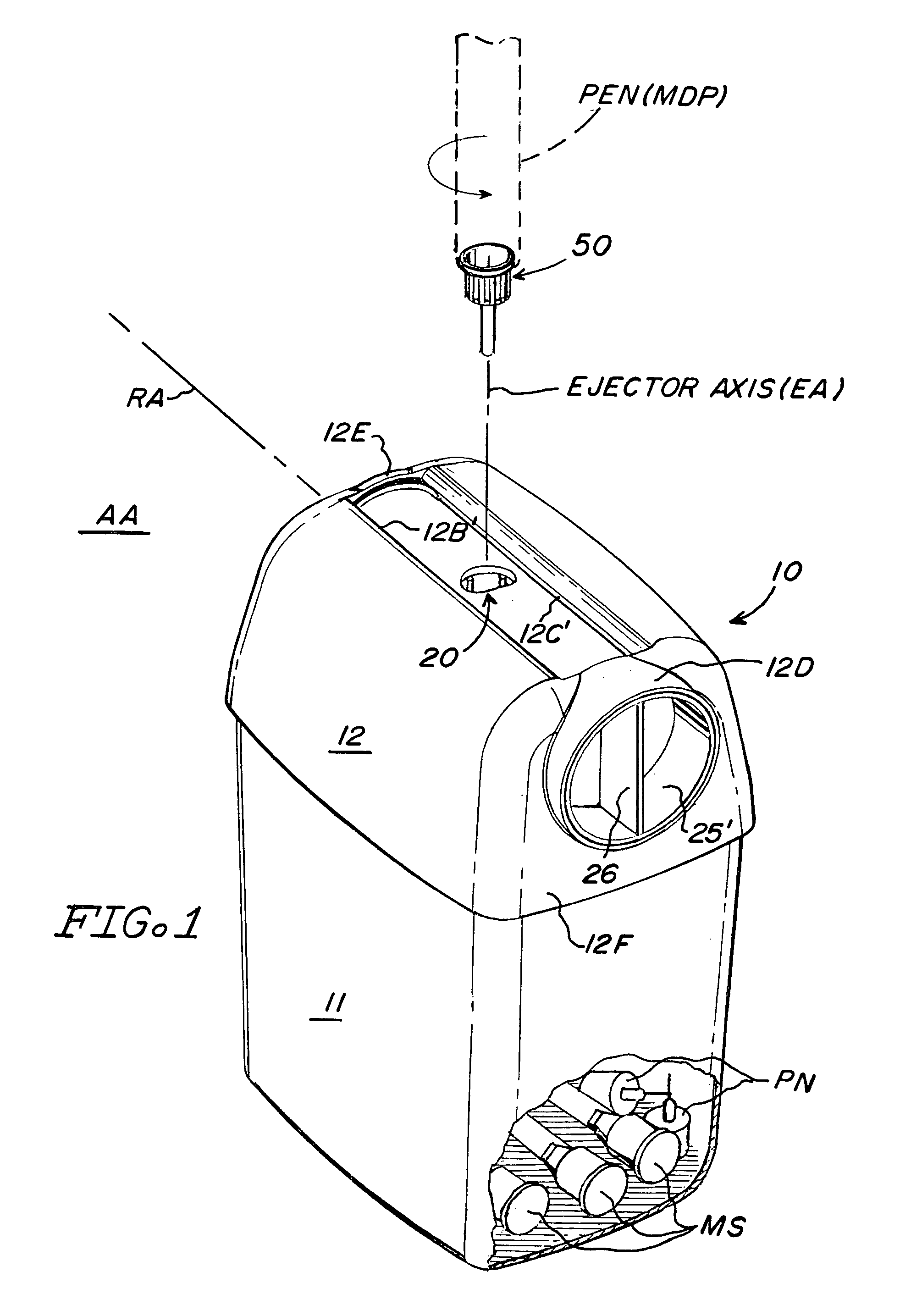
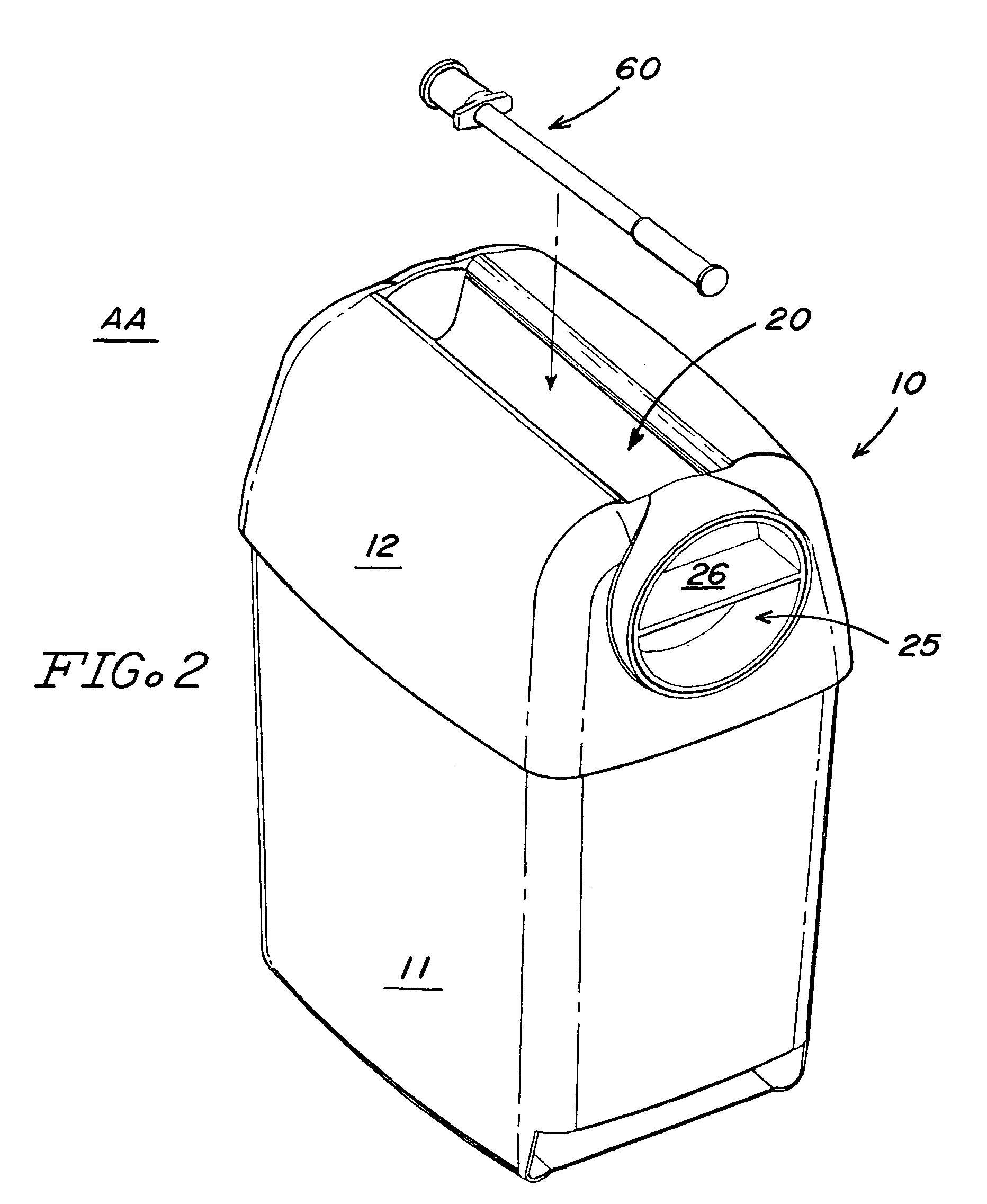
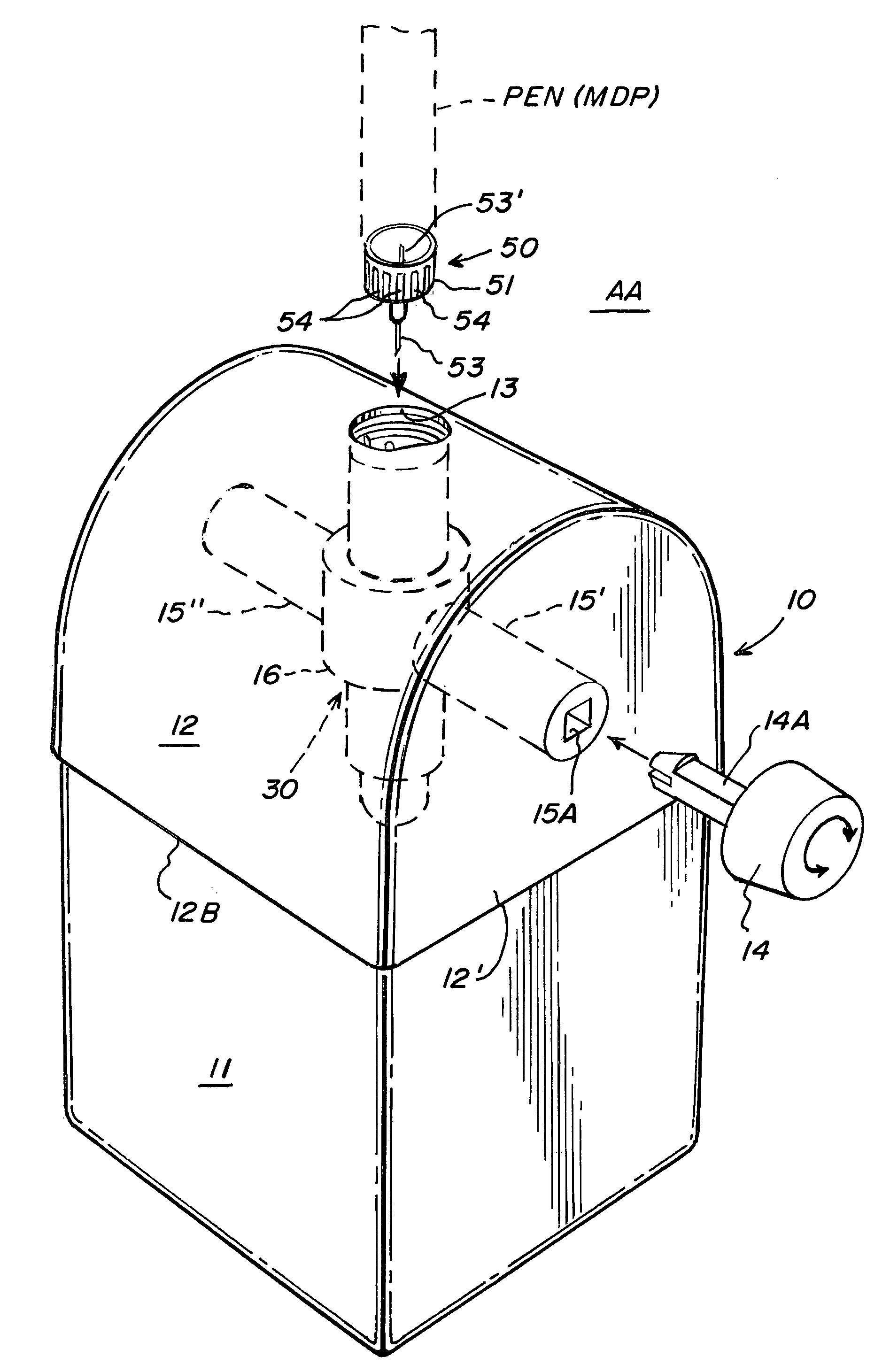
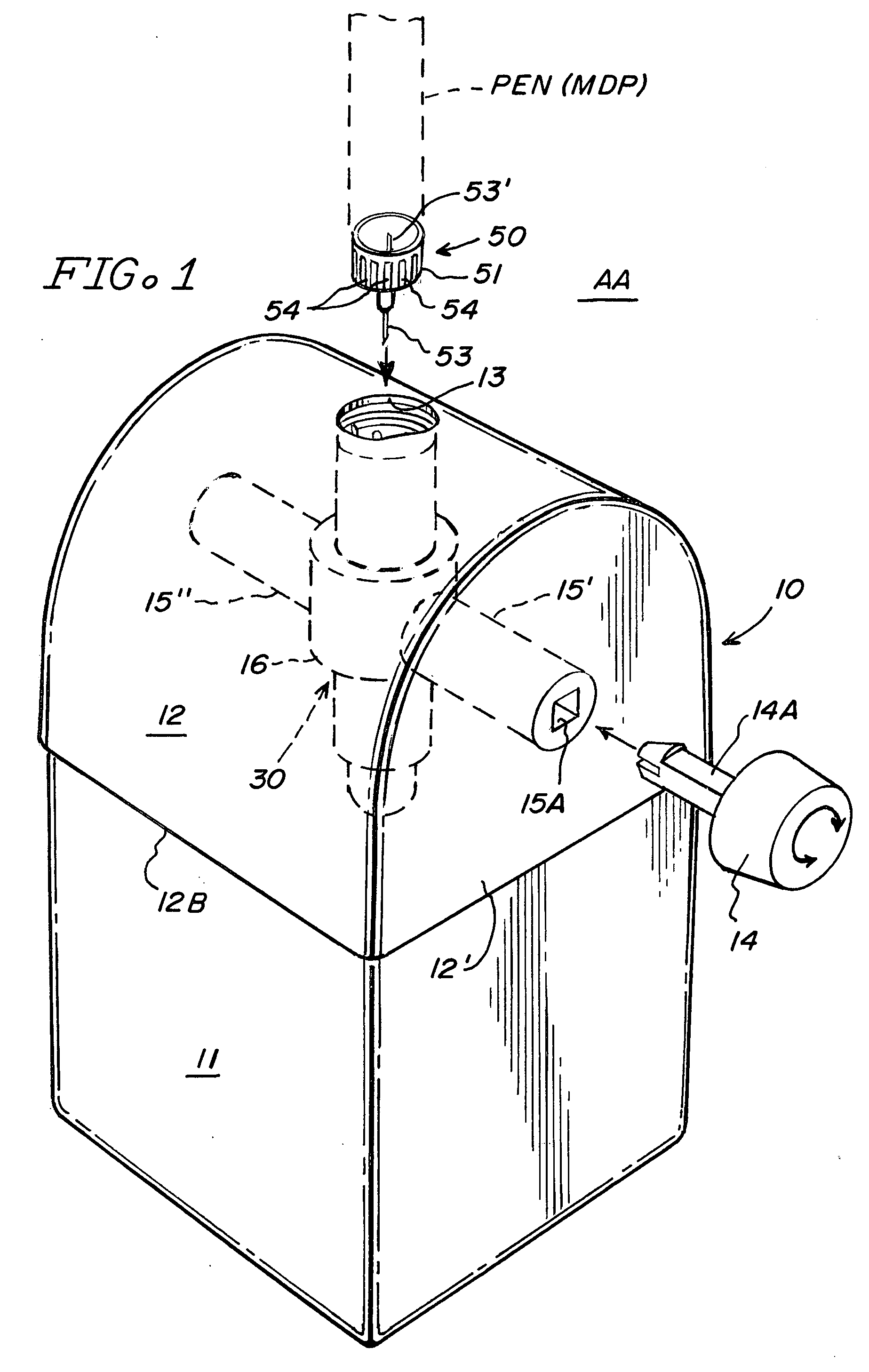
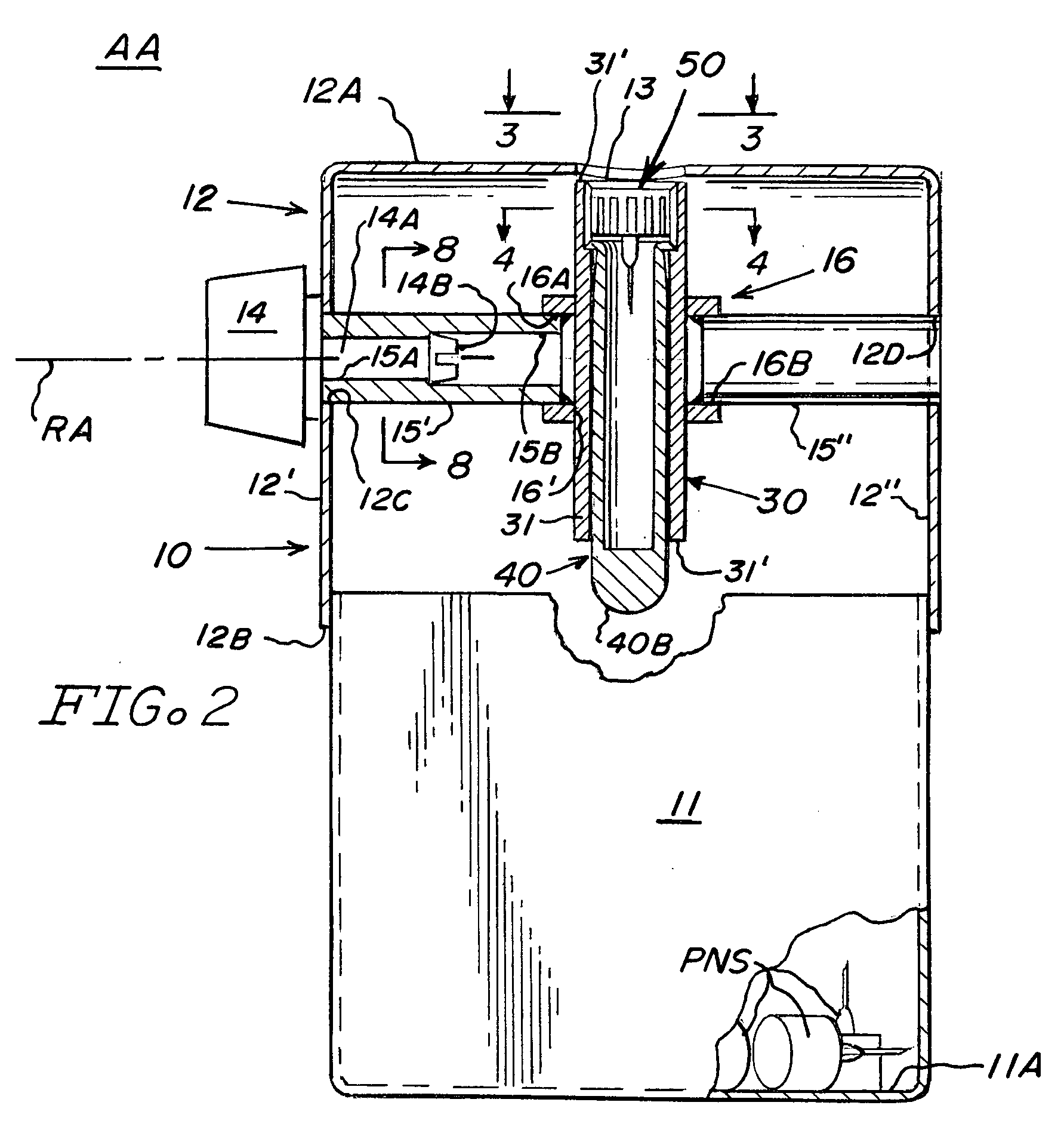
Sharps container for safe transportation and dispensing of unused pen needle assemblies and for sequential safe storage of used pen needles
ActiveUS6923319B1Easy to storeIncrease supplyRod article dispensingOther accessoriesCamSyringe needle
A sharps container for (i) the safe storage and dispensing of unused pen needle assemblies and (ii) a safe means for receiving used pen needles and ejecting same into the container. The container comprises a housing within which is rotatably mounted a used pen needle receiving and ejecting means. Used pen needles are inserted into the receiving means. The receiving and ejecting means is rotated and, during the rotation, cam follower means connected to the ejecting means engages cam means within the housing to cause the ejection of the used pen needle into the housing. The housing also has a separate storage space for unused pen needle assemblies. Alternate structures provide for withdrawal of unused pen needle assemblies for dispensing. The dispensing can be done on a serial basis where the pen needle assemblies which are attached to a flexible tape for serial withdrawal from the housing through an exit opening. The dispensing can also be done on a bulk basis where a plurality of unused pen needle assemblies are transferred through the exit opening at the same time.
Owner:ULTIMED INC
Rotating-type grain distributor and granary provided with grain distributor
InactiveCN104709729AGuaranteed safe storageReduce accumulationLoading/unloadingTangential forceEngineering
The invention discloses a rotating-type grain distributor and a granary provided with the grain distributor, and belongs to the technical field of granaries. The rotating-type grain distributor comprises a grain collecting barrel. The grain collecting barrel comprises a barrel wall and a barrel bottom. The outer side of the barrel wall of the grain collecting barrel is provided with two downward-inclined grain sliding pipes. The bottom face and one side face of each grain sliding pipe are curved surfaces which are of an integral structure. When the rotating-type grain distributor is used, the rotating-type grain distributor is arranged at a grain inlet of the granary, after grain enters the grain collecting barrel, the grain flows into the grain sliding pipes, and when the rotating-type grain distributor rotates, the grain sliding pipes rotate along with the rotating-type grain distributor. Due to the fact that the bottom face and one side face of each grain sliding pipe are curved surfaces which are of the integral structure, when the rotating-type grain distributor rotates, under the effect of centrifugal force and tangential force generated by the curved surfaces, the grain is scattered and flows out of the grain sliding pipes, and the grain falls onto a circular cross section of the granary. According to the rotating-type grain distributor, the impurity accumulation caused by automatic grading formed by concentrated falling of the grain is alleviated, and the safe storage of the grain is guaranteed.
Owner:BEIJING U PRECISION TECH
Thermal-insulating external-wall coating of nano-composite water and its production
InactiveCN101029206AImprove insulation performanceGood weather resistanceFireproof paintsEmulsion paintsRefractive indexSlurry
A water nan-composite thermal-insulating coating for external wall and its production are disclosed. The coating consists of water, polymer emulsion, high-refractive index pigment, filler, nano-tin-antimony oxide slurry, nano-SiO2, wet dispersant, filming accessory, pH adjuster, thickener, de-foaming agent, anti-freezing agent and mildew-proof bactericide. It's cheap and simple, has excellent wash and weather resistances, better thermal-insulating performance, safe storage and no environmental pollution. It can be used for apparatus surface and architecture external wall.
Owner:SOUTH CHINA UNIV OF TECH +1
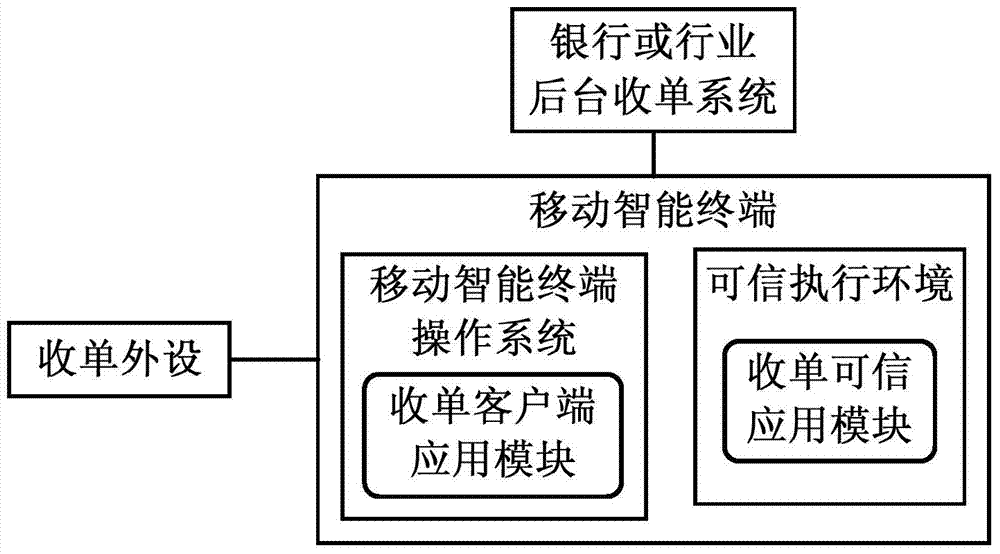
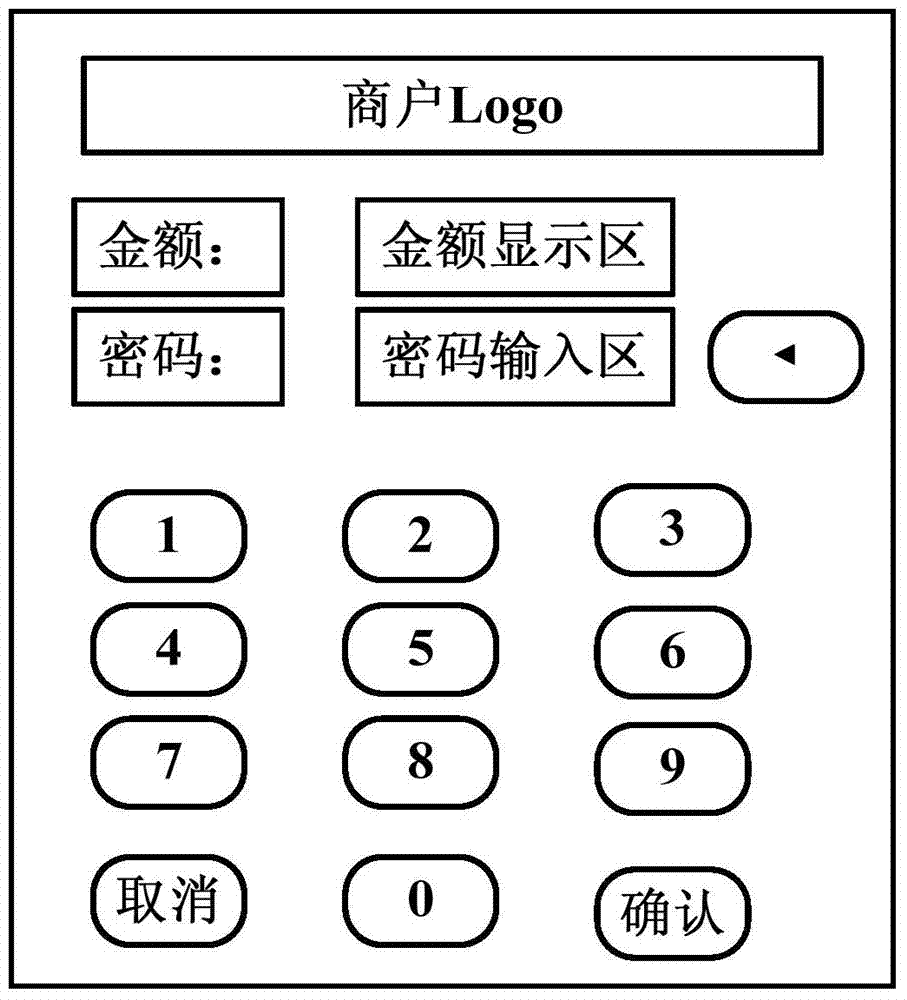
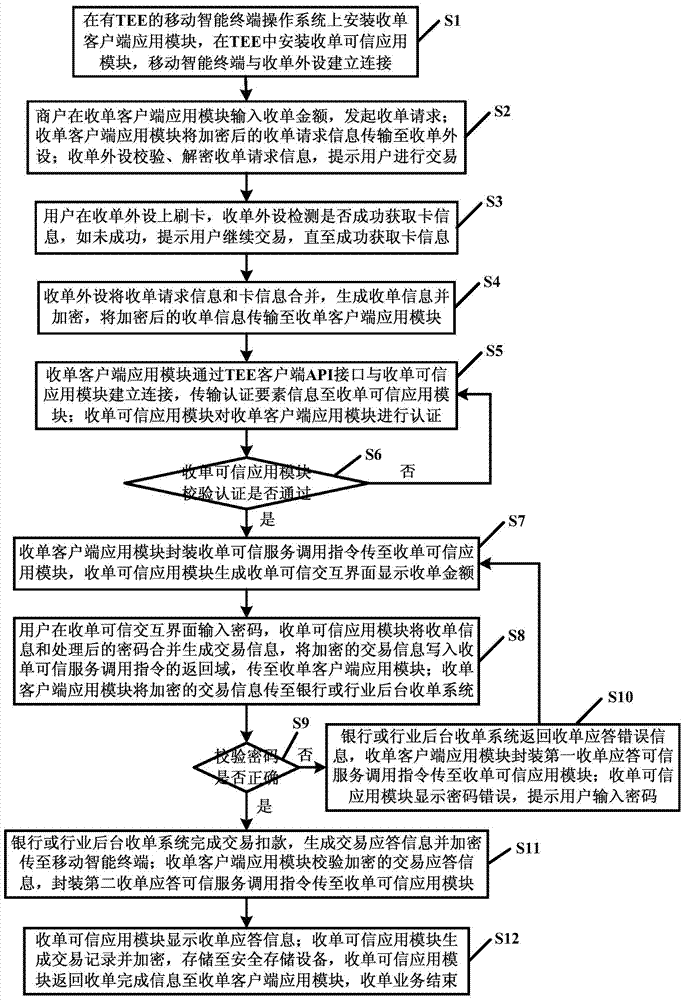
Mobile intelligent terminal acquirer system and method suitable for bank cards and business cards
ActiveCN103793815ABest security statusOvercome the pricePayment architecturePersonalizationOperational system
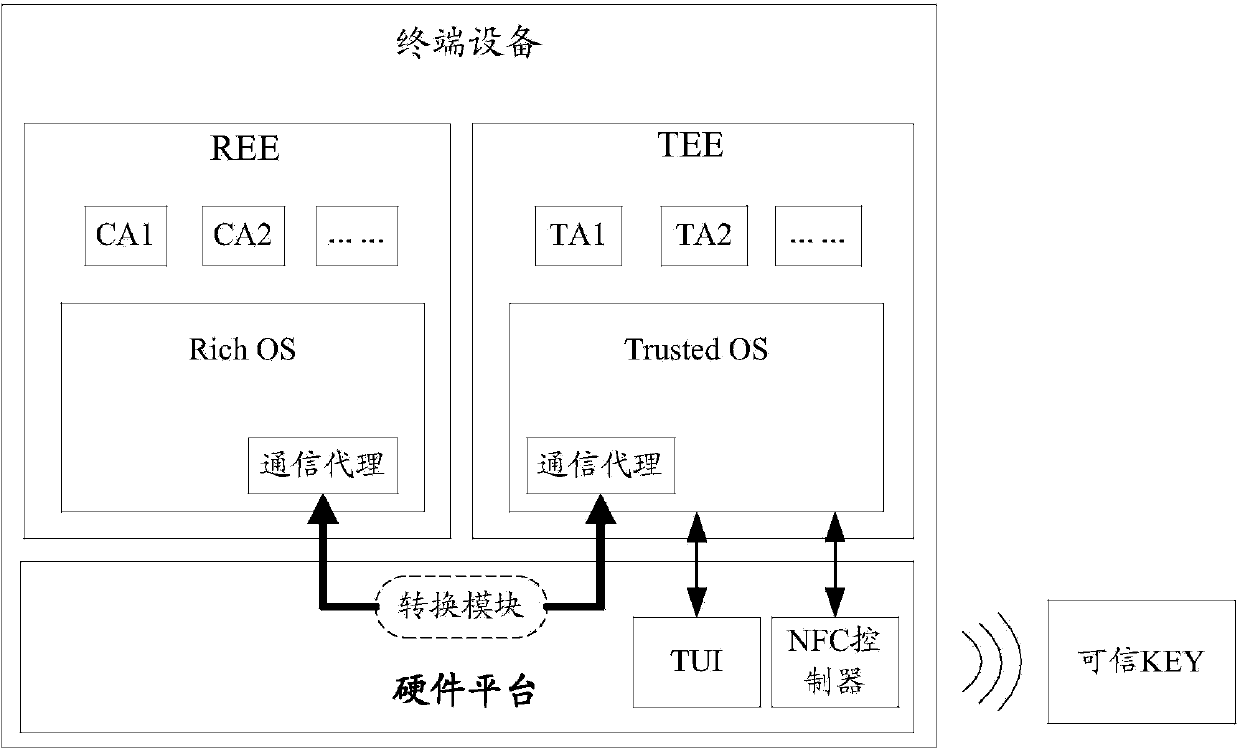
The invention discloses a mobile intelligent terminal acquirer system and method suitable for bank cards and business cards and relates to the field of mobile intelligent terminals. The system comprises a bank or business backstage acquirer system, a mobile intelligent terminal and an acquirer peripheral. The mobile intelligent terminal comprises a mobile intelligent terminal operation system and a trustworthy execution environment (TEE) insulated with the operation system. The mobile intelligent terminal operation system comprises an acquirer client-side application module. The TEE comprises an acquirer trustworthy application module. The TEE provides a trustworthy interaction interface, a code calculation environment and a safe storage environment. Downloading, upgrading, personalization and deletion of the acquirer trustworthy application module are realized through the TSM technology in a remote mode. The acquirer trustworthy module provides an acquirer trustworthy interaction interface. According to the system and method, the TEE provided by the mobile intelligent terminal is used for providing the safe user interaction interface and the code calculation operation environment for acquiring business, so that the safe input and encryption processing of codes and reliable display of messages in the acquiring business process are realized.
Owner:WUHAN TIANYU INFORMATION IND
Sharps container for safe transportation and dispensing of unused pen needle assemblies and for safe storage of used pen needle assemblies
ActiveUS20050269227A1Easy to useSafe storageDispensing apparatusOther accessoriesEngineeringSafe storage
A sharps container for (i) safe transportation and dispensing of a large number of unused pen needle assemblies, and (ii) safe storage of used pen needle assemblies. The unused pen needle assemblies may be connected to a flexible tape and are removed from a storage receptacle via an exit opening in the receptacle.
Owner:ULTIMED INC
Multifuel storage, metering and ignition system
A system for safe storage and efficient utilization of a variety of fuel selections that range in composition and phase from cryogenic mixtures of solids and liquids to elevated temperature gases is provided for unique applications with various types of heat engines and fuel cells including hybridized combinations.
Owner:ADVANCED GREEN INNOVATIONS LLC +1
Robotic harvesting of solids from fluids
InactiveUS6417007B1Solve the real problemPolycrystalline material growthFrom normal temperature solutionsPipetteRobotic arm
The present invention is directed to the method and apparatus for the robotic harvesting of solids from liquids as exemplified by harvesting protein crystals. Further, the present invention is directed to a fluid / solid management system in a chamber that automates the task of solid harvesting. The fluid / solid management system includes two supporting structures for at least one pipette on one structure and a second pipette on the other structure, the two pipettes in tip-to-tip alignment. The pipettes each having a drop of liquid at the end thereof are moved apart to form a liquid bridge in which the solid crystal is isolated. A robotic arm has a device on the end thereof for the harvesting of the solid at the working point between the tips of the pipettes. The system has a flash freezing system in the chamber for the safe storage of the harvested solid.
Owner:OCEANEERING INTERNATIONAL +2
Sharps container for safe storage of used pen needles and used medical syringes
A sharps container for safe reception and storage of used pen needles and used medical syringes comprises a housing which supports a manually rotatable member. A used pen needle receiving and ejecting apparatus is connected to the rotatable member. Used pen needles are inserted into the receiving apparatus. As the receiving and ejecting apparatus is rotated, a cam follower connected to the ejecting apparatus engages a cam within the housing to cause the ejection of the used pen needle from the receiving apparatus into the housing. The rotatable member also has an elongated recess sized to receive a medical syringe. Manual rotation of the rotatable member rotates the elongated recess to drop the medical syringe into the housing.
Owner:ULTIMED INC
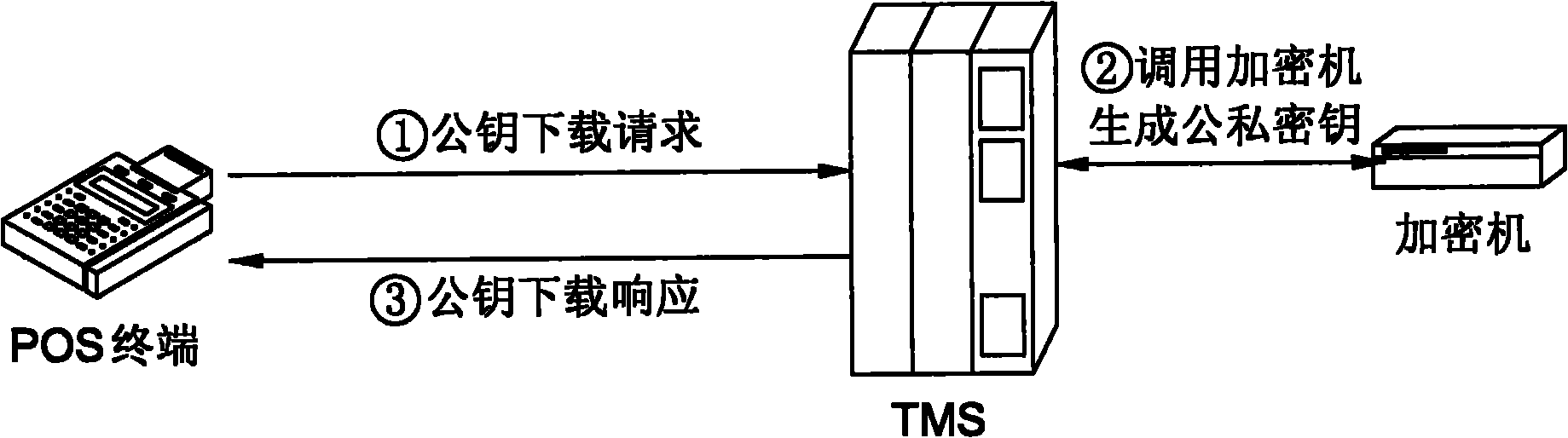
Method for safely downloading master key automatically in bank card payment system and system thereof
ActiveCN101930644AAvoid security breachesImprove securityCash registersTransmissionPlaintextCiphertext
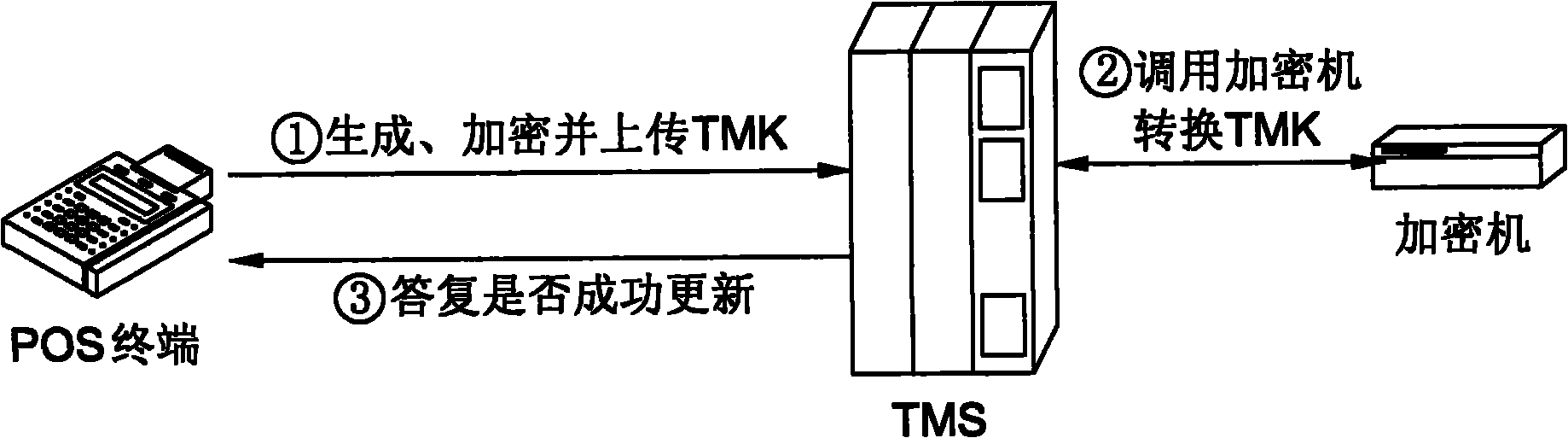
The invention discloses a method for safely automatically downloading a terminal master key TMK in a bank card payment system and a system thereof. The bank card payment system comprises a point of sales (POS) terminal, a terminal management system (TMS), a password keyboard and a hardware security machine. The method comprises that: the TMS calls the security machine to generate a pair of public and private keys; the POS terminal calls the password keyboard to randomly generate the terminal master key TMK, and encrypts the TMK by using the public key of the TMS and uploads the encrypted TMK to the TMS; and the TMS calls the security machine and decrypts the TMK by using the private key and stores the decrypted TMK. The TMK is randomly generated, the transmission process is closed, a TMK plaintext cannot appear outside safe storage equipment and is encrypted by the public key in the transmission process, and a TMK ciphertext can only be decrypted in the security machine of the TMS, so that the method and the system have high safety.
Owner:CHINA UNIONPAY
Container for an automatic injector
InactiveUS20080289984A1Open fastSafe storageDispensing apparatusContainer filling methodsSyringe needleSafe storage
A container for an automatic injector provides safe, quick, and easy access to an automatic injector stored therein. The container includes tactile features that allow a user to easily determine the orientation of the container by feel alone. A hinged cap with an automatic spring assist feature allows a user to single-handedly open the container quickly and easily to remove the injector from the container without interference from the cap. The container is structured to receive the automatic injector needle end first and has a puncture resistant bottom to prevent the needle of the injector from piercing through the body wall of the container. The container also provides safe storage of a discharged automatic injector, with the hinged cap spring assist feature automatically closing the cap enough to prevent the discharged injector from falling out of the container.
Owner:MERIDIAN MEDICAL TECH
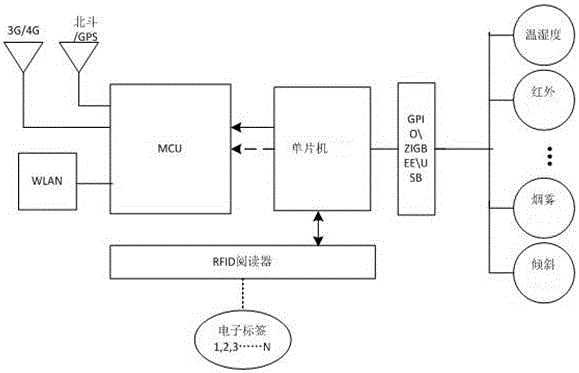
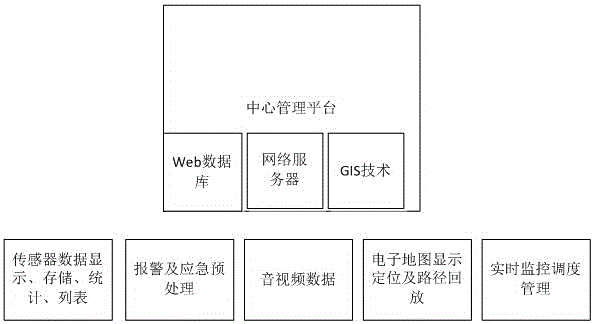
Dangerous chemical raw material logistics storage management system and dangerous chemical raw material logistics storage management method based on Internet-of-things
InactiveCN106228332AAchieve real-time trackingGuaranteed safe storageLogisticsVideo monitoringData information
The invention provides a dangerous chemical raw material logistics storage management system and a dangerous chemical raw material logistics storage management method based on Internet-of-things. The dangerous chemical raw material logistics storage management system comprises a storage information monitoring system, a data information transmission system, an information management system and a dangerous accident pretreatment system, wherein the storage information monitoring system is connected with the data information transmission system, the data information transmission system is connected with the information management system, and the information management system is connected with the dangerous accident pretreatment system. In storage, electronic label marking is performed on the dangerous chemical raw material, and furthermore real-time monitoring is performed according to a preset value through various kinds of intelligent sensors and cameras in a warehouse. In cargo delivering, stock information can be automatically updated and real-time tracking can be performed; video monitoring equipment and alarming equipment are arranged at important positions; through a Beidou positioning system which is installed on a transportation vehicle, real-time displaying of a driving route on a monitoring system can be realized. Furthermore, sensors such as a temperature / humidity sensor, a pressure sensor, a vibration sensor, an inclination angle sensor and a harmful gas sensor and a camera are mounted on the transportation vehicle, thereby performing real-time monitoring on the transportation cargo. Real-time monitoring and management, full-course information tracking, full-course monitoring of the transportation vehicle, information integration of a transportation system and a storage system, and automatic real-time system alarming in the whole logistics chain of the dangerous chemical raw material can be realized, thereby ensuring safe storage and safe transportation of the dangerous chemical raw material.
Owner:FOURTH RES INST OF TELECOMM TECH
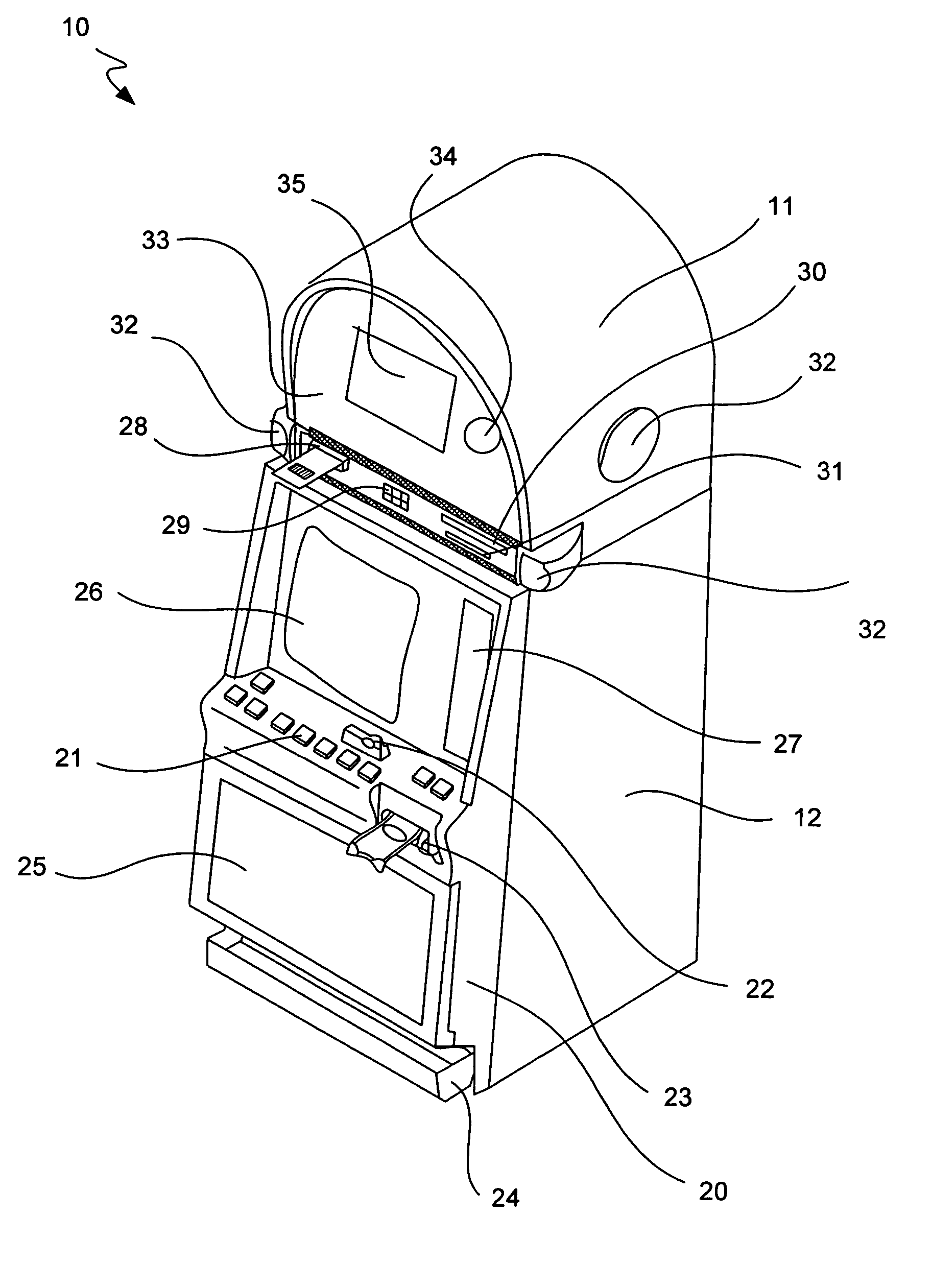
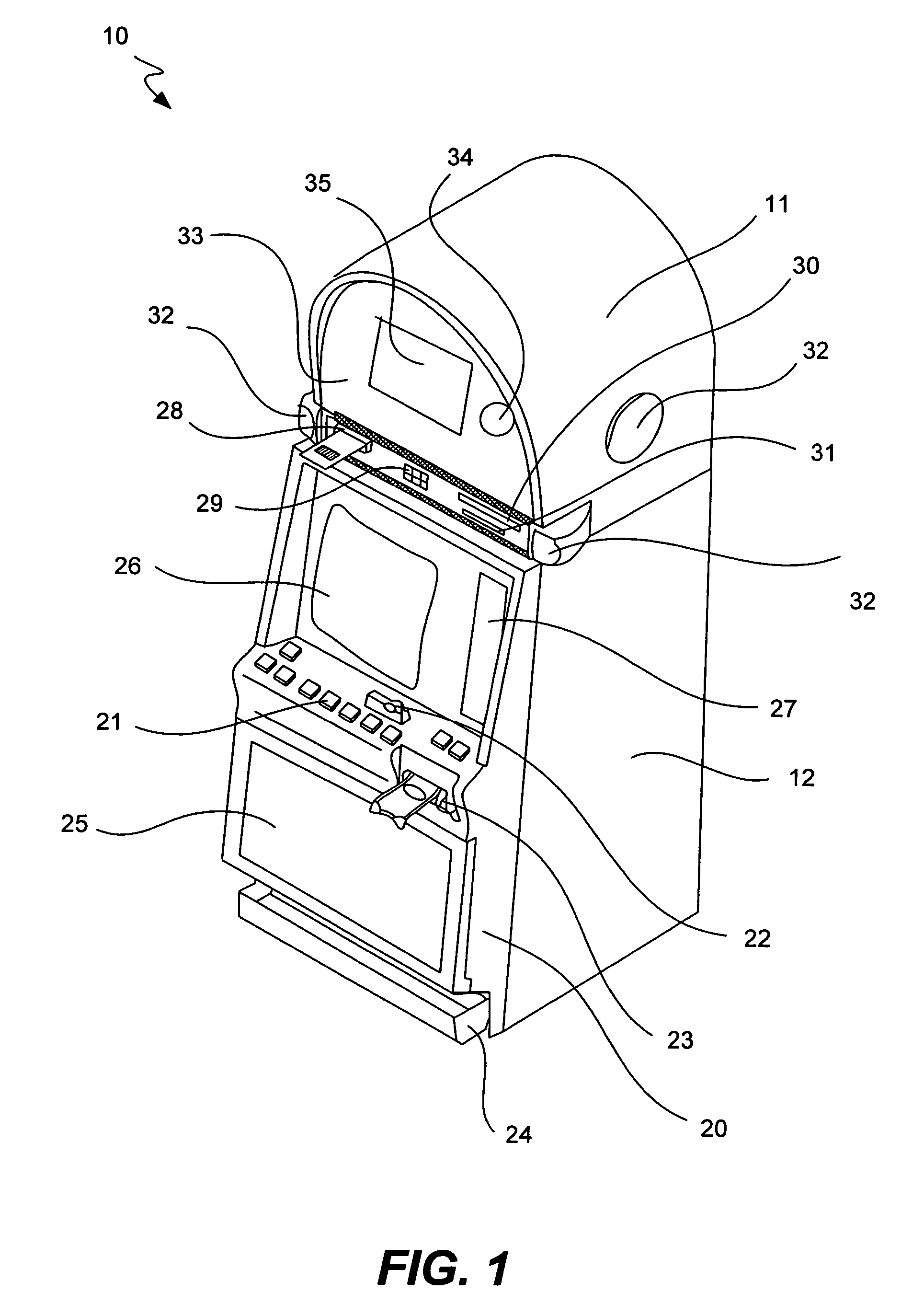
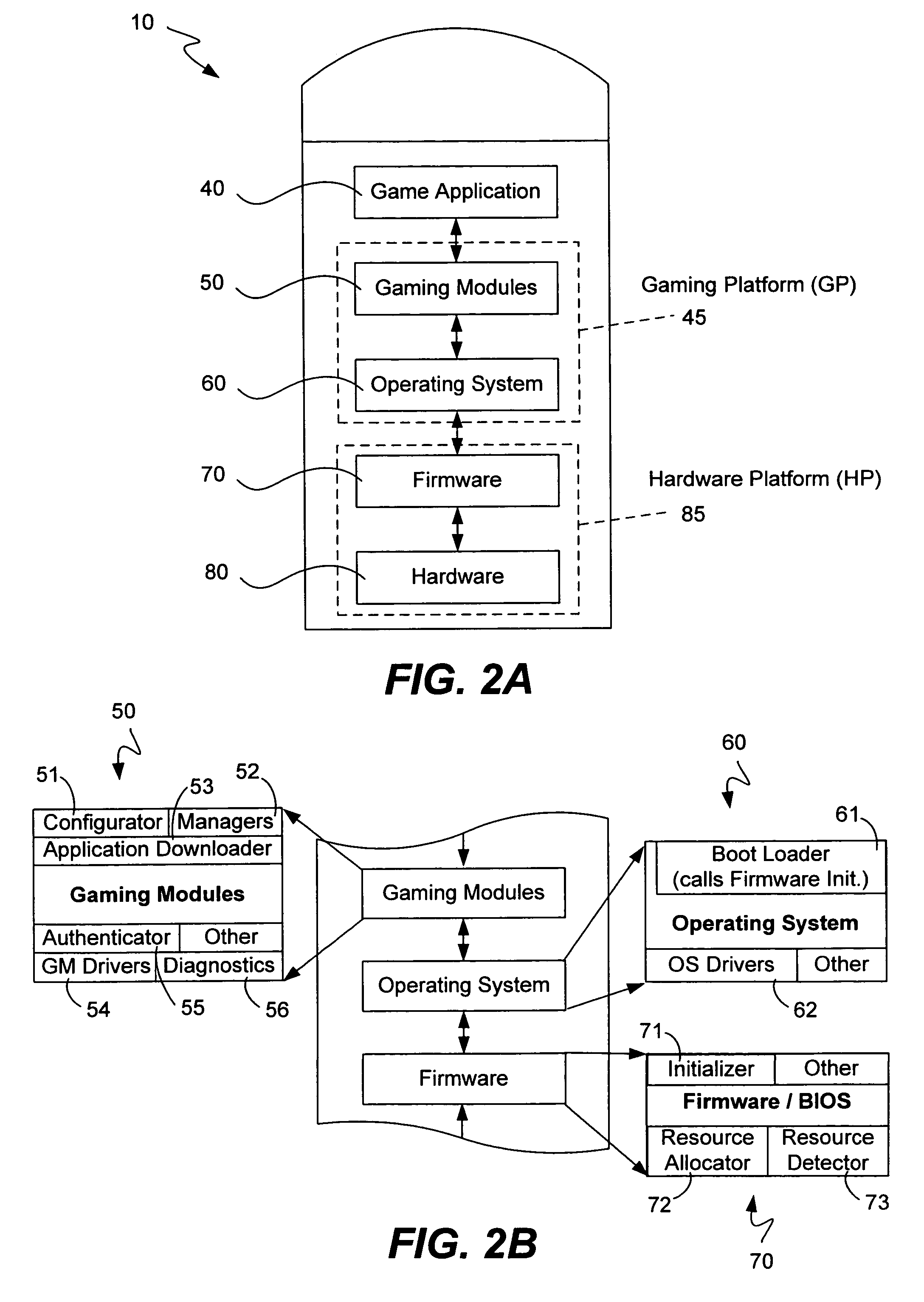
Universal operating system to hardware platform interface for gaming machines
ActiveUS7966485B2Large levelFaster and more streamlined boot processDigital computer detailsApparatus for meter-controlled dispensingOperational systemComputer module
Gaming machines and systems having a universal interface layer linking a gaming platform to a hardware platform are disclosed. In particular, the universal interface layer is configured such that the gaming platform is hardware platform independent and such that the hardware platform is gaming platform independent. Platform independence can facilitate the interchangeability of one platform without a corresponding need to modify the other platform. The gaming platform can include various gaming modules and an operating system, while the universal interface layer can include firmware, various additional gaming modules, hardware specific drivers and various APIs to facilitate communication between the gaming platform and other universal interface layer components. A safe storage manager can be included to utilize a non-volatile storage component to store data regarding a gaming machine state, with the state being recoverable after a substantial interruption to the machine.
Owner:IGT
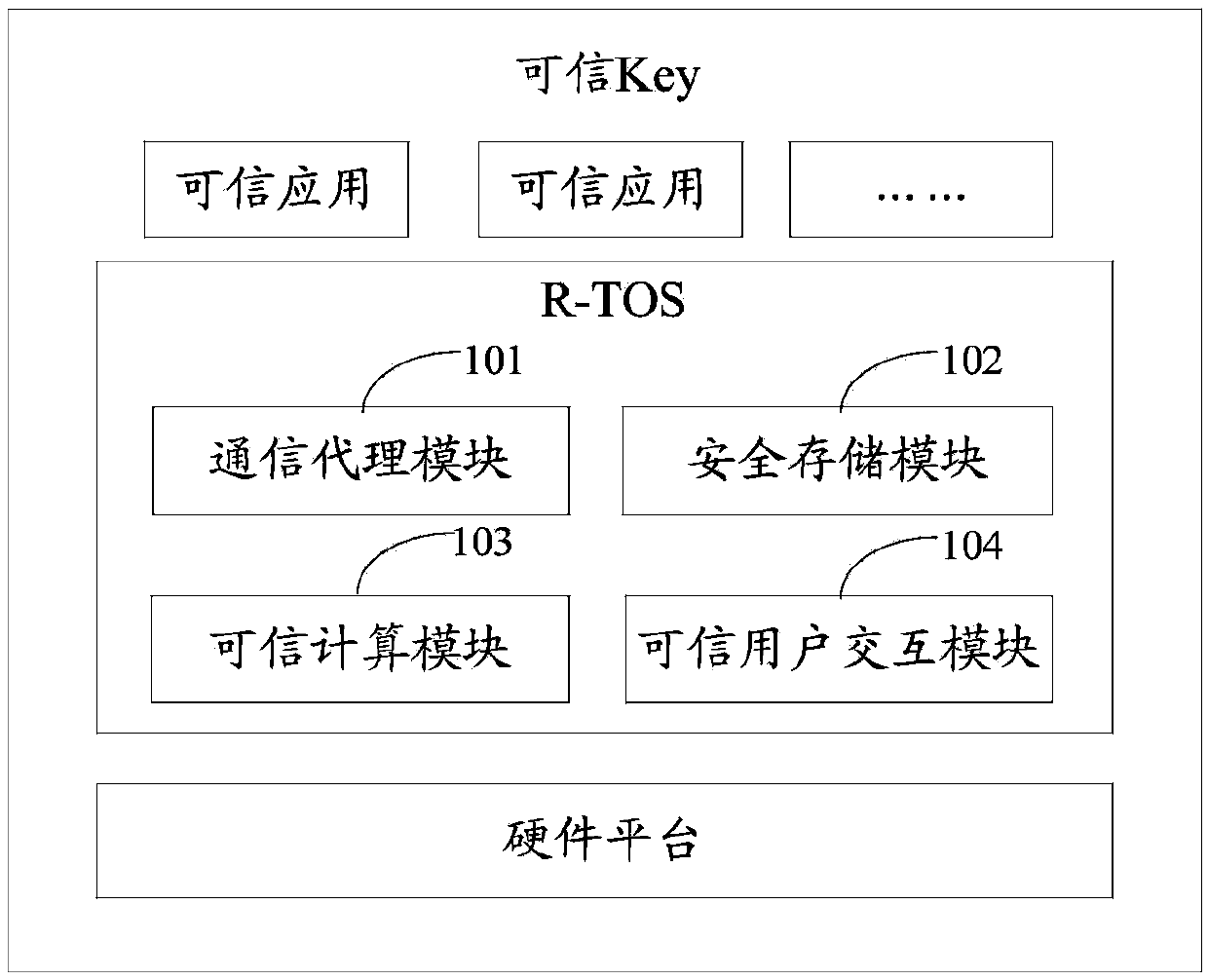
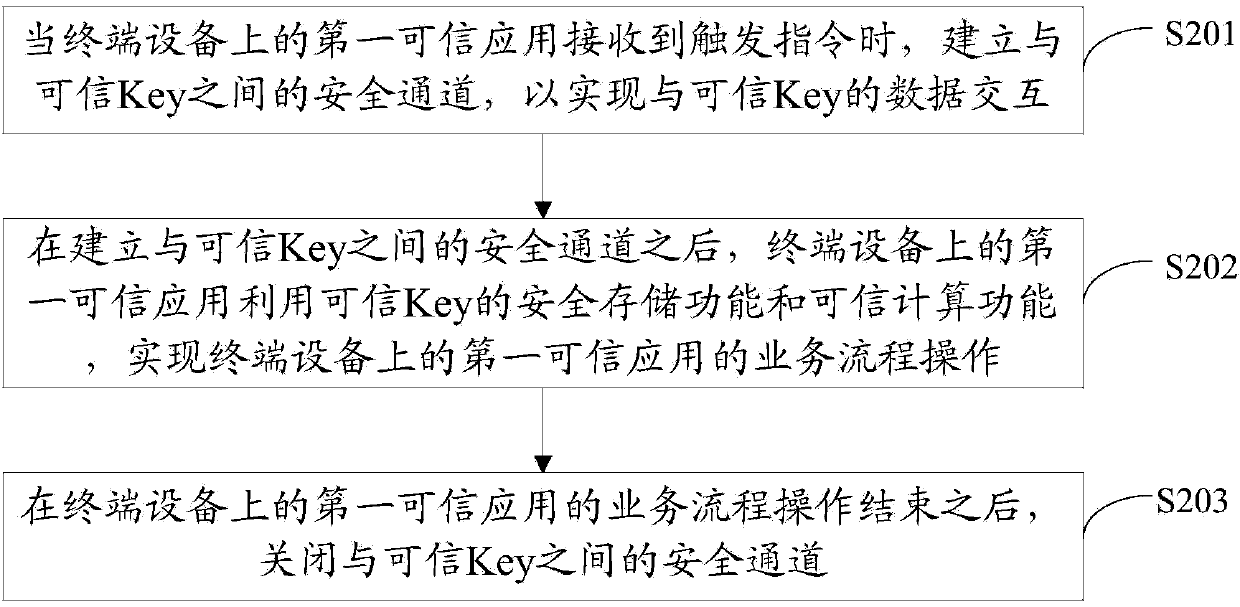
Credible Key and safe operation method thereof
InactiveCN103745155ASimple designEasy to operatePayment architectureDigital data authenticationPaymentOperational system
The invention provides a credible key and a safe operation method thereof. The credible Key comprises a communication agent module, a safe storage module, a credible computation module and a credible interaction module, wherein the communication agent module is used for establishing a safe channel between the credible Key and a credible operating system of terminal equipment; the safe storage module is used for providing a safe storage API (Application Program Interface) for developing a credible application, and providing a safe storage function for the credible Key; the credible computation module is used for providing a credible computation API for the credible application, and providing a credible computation function for the terminal equipment; the credible interaction module is used for transmitting an interaction command to the credible operating system of the terminal equipment through the communication agent module on the basis of user operation. The credible KEY can be used together with a credible running environment on the terminal equipment, thereby realizing credible services such as remote payment, online transfer, safe storage and credible computation.
Owner:EASTCOMPEACE TECH
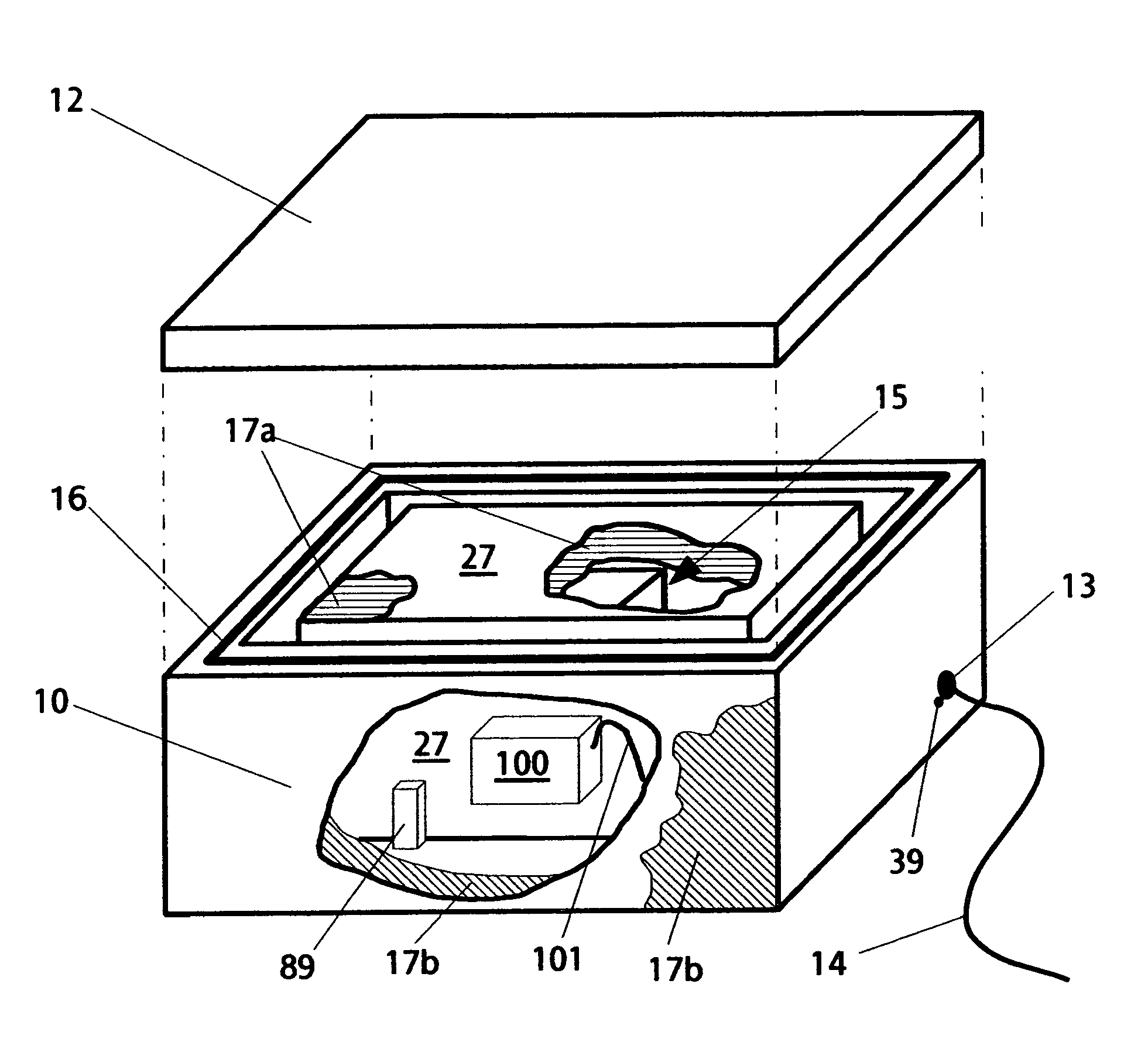
Method and apparatus for the enhanced disaster survivability of a networked computer server
InactiveUS20070061598A1Reducing temperature influence on carrierDigital data processing detailsSurvivabilityData store
An apparatus for protecting a digital electronic data processor or stored digital data from damage includes a digital data unit comprising a data storage medium, a protective housing having side, top, and bottom walls defining a closed compartment which contains the digital data unit to shield the digital data therein from environmental damage. Active and passive protection from overheating and data encryption provides further data protection. The housing has at least one access port for supplying electrical power or for information transfer to or from the data unit therein. The port is sealed to prevent the introduction of environmental substances into the housing in the event of potential damage from an environmental disaster or other cause. The invention thus makes possible the safe storage of digital information in a computer data storage system which therefore has substantially increased capacity to survive disasters such as fires, floods, earthquakes, and theft, as well as more common computer problems such as disk drive failures. The invention can employ multiple computer network data access mechanisms that store digital data, including but not limited to Microsoft Windows File Sharing, Common Internet File Systems (CIFS), Network File Systems (NFS), Novell Netware File Systems, iSCSI, Storage Area Network Protocol, and Network SQL Database Mechanism or other data processing units.
Owner:BITTON YOSEF +2
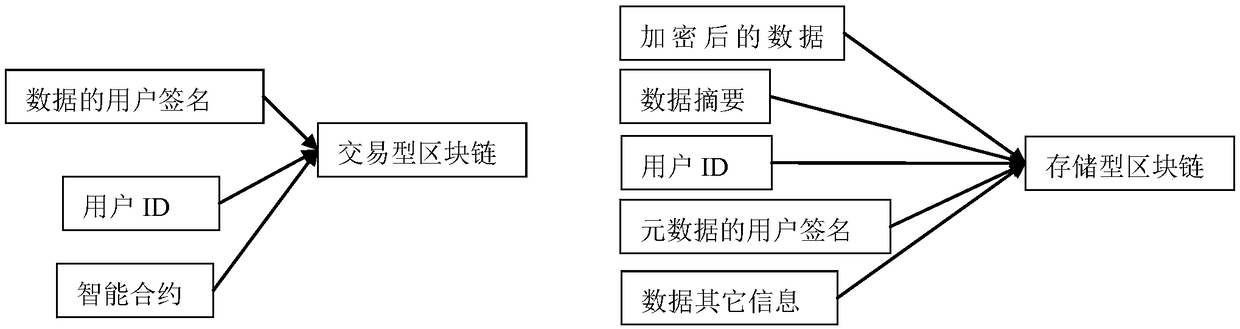
A secure storage and retrieval method based on block chain
ActiveCN109299217AImprove performanceEnsure safetyDigital data protectionText database indexingTransaction serviceTransfer procedure
The invention discloses a safe storage and retrieval method based on a block chain, belonging to the technical field of computer software, comprising four steps of initializing a public key and a private key, writing a data document, data retrieval and data scoring, which can improve safety and usability by using a plurality of technologies while providing data transaction service. Secure tunnel transmission technology is adopted to ensure the information security in the transmission process. Using block chain technology and distributed system to ensure the stability, reliability, security andavailability of the system, using block chain technology to ensure the information security, disclosure, availability and high performance of the system.
Owner:符安文
Method and apparatus for the enhanced disaster survivability of a networked computer server
InactiveUS7916487B2Reducing temperature influence on carrierDigital data processing detailsDigital dataArea network
An apparatus for protecting a digital electronic data processor or stored digital data from damage includes a digital data unit comprising a data storage medium, a protective housing having side, top, and bottom walls defining a closed compartment which contains the digital data unit to shield the digital data therein from environmental damage. Active and passive protection from overheating and data encryption provides further data protection. The housing has at least one access port for supplying electrical power or for information transfer to or from the data unit therein. The port is sealed to prevent the introduction of environmental substances into the housing in the event of potential damage from an environmental disaster or other cause. The invention thus makes possible the safe storage of digital information in a computer data storage system which therefore has substantially increased capacity to survive disasters such as fires, floods, earthquakes, and theft, as well as more common computer problems such as disk drive failures. The invention can employ multiple computer network data access mechanisms that store digital data, including but not limited to Microsoft Windows File Sharing, Common Internet File Systems (CIFS), Network File Systems (NFS), Novell Netware File Systems, iSCSI, Storage Area Network Protocol, and Network SQL Database Mechanism or other data processing units.
Owner:BITTON YOSEF +2
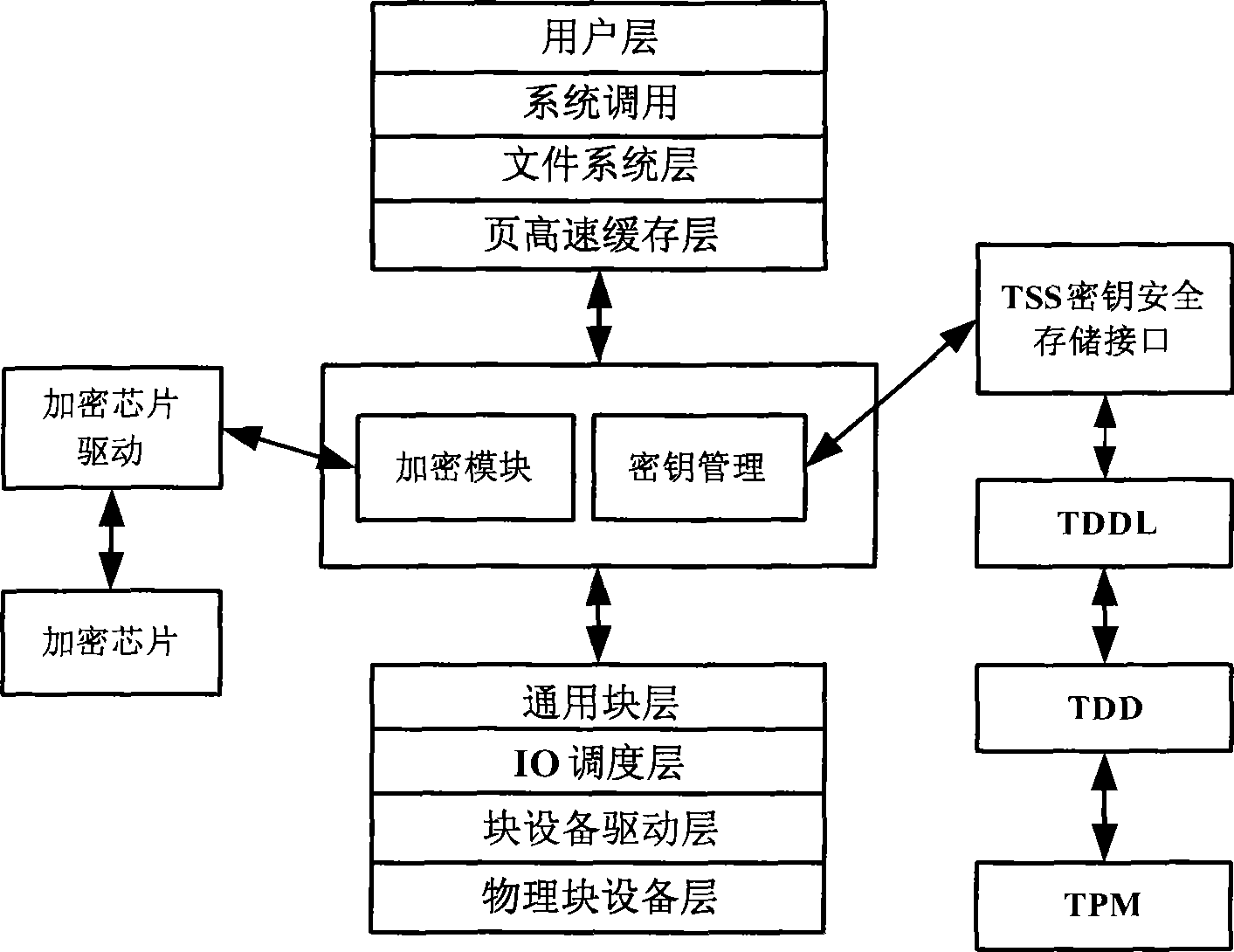
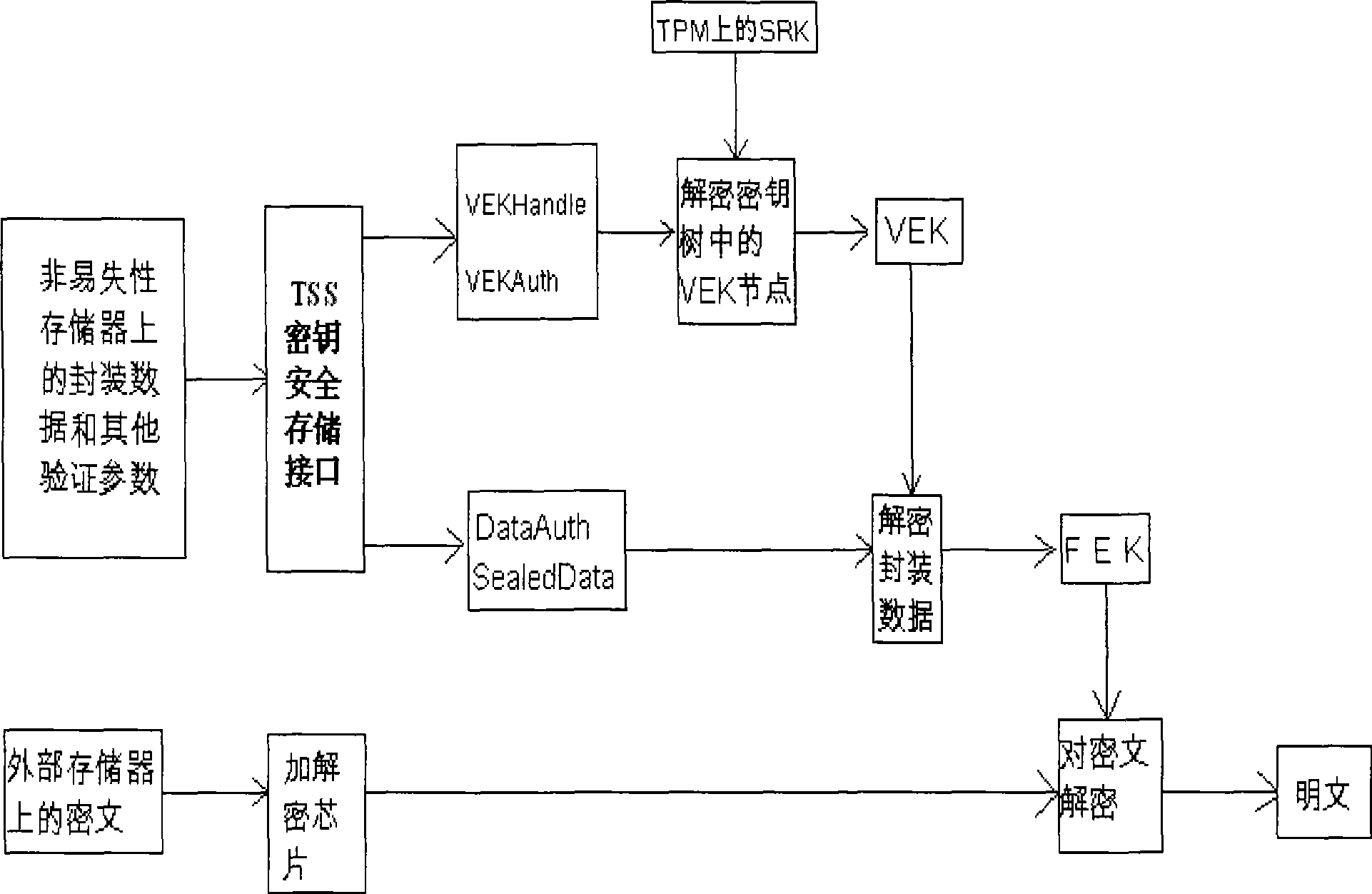
Movable equipment based on credible embedded platform and its security storage method
InactiveCN101430747AImprove securityImprove security strengthDigital data protectionMobile deviceEmbedded system
The invention provides a mobile device based on a trustable embedded platform and a safe storage method thereof. The mobile device comprises an embedded platform, an encrypt / decrypt chip and a TPM module, wherein, the embedded platform, the TPM module and the encrypt / decrypt chip are connected with a high speed bus. In the device and the storage method, according to the characteristics of an embedded system, the embedded platform, the TPM trustable platform module and the hardware encrypt / decrypt chip together are combined, thereby effectively solving the problem of key safe storage, breaking through bottleneck of transmission speed of an embedded system and an encryption engine, and ensuring a reliable environment for encrypt / decrypt operation.
Owner:WUHAN UNIV
Digital copyright management method and system
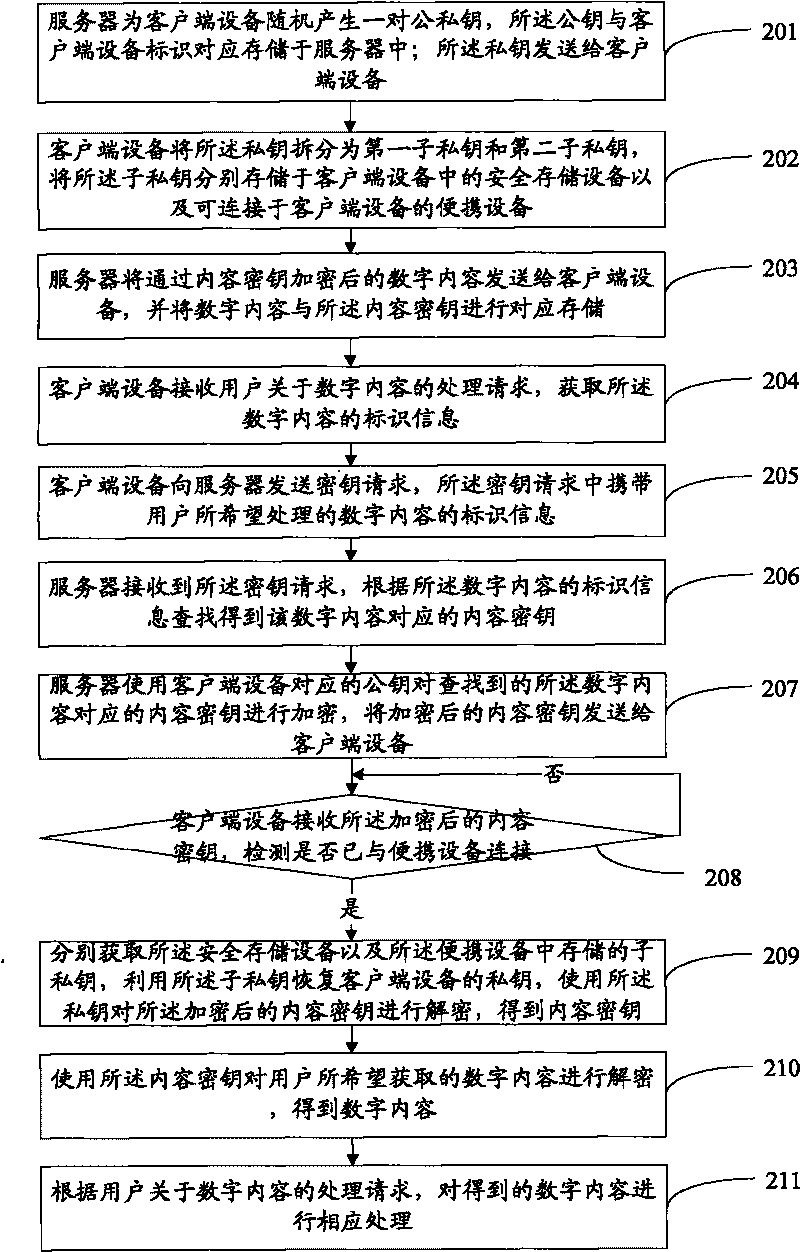
ActiveCN101719205AIncrease the difficultyImprove controlProgram/content distribution protectionDigital contentTerminal equipment
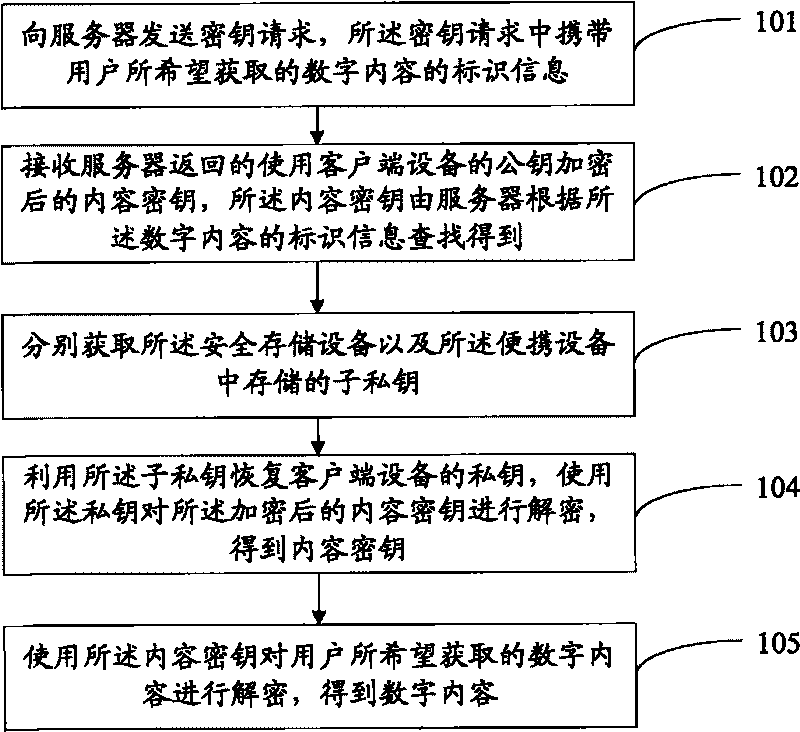
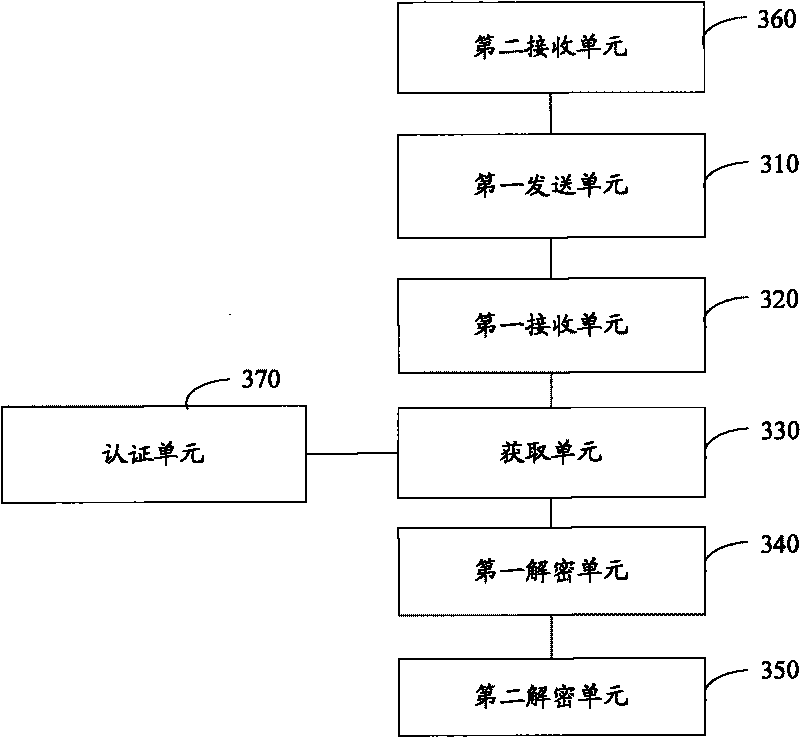
The invention discloses digital copyright management method and system. In the method, a private key of client terminal equipment is divided into a first assistant private key and a second assistant private key, and the first assistant private key and the second assistant private key are respectively stored in safe storage equipment in the client terminal equipment and portable equipment which can be connected to the client terminal equipment; when an encrypted content key is received, the assistant private keys stored in the safe storage equipment and the portable equipment are respectively obtained; and the assistant private keys are utilized to recover the private key of the client terminal equipment, the private key is used for obtaining the content key by decryption, and the content key is used for obtaining a digital content by decryption, so that a user can obtain the digital content. The method and the system can better control the copyright of the digital content.
Owner:中央宣传部电影数字节目管理中心
Sharps container for "no-touch," sequential safe storage of used pen needles
A sharps container for safe storage of used pen needles comprises a housing within which is rotatably mounted a used pen needle receiving and ejecting means. Used pen needles are inserted into the receiving means. The receiving and ejecting means is rotated; during the rotation, cam follower means connected to the ejecting means engages cam means within the housing to cause the ejection of the used pen needle into the housing.
Owner:ULTIMED INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com