Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
75results about How to "Avoid inaccessibility" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Safe storage method based on a plurality of cloud storage systems and system thereof
InactiveCN103118089AImprove fault toleranceAvoid inaccessibilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCode moduleCiphertext
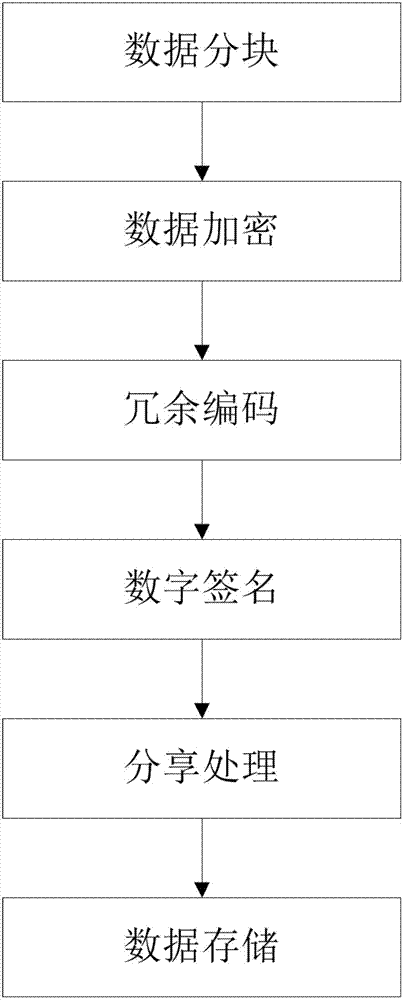
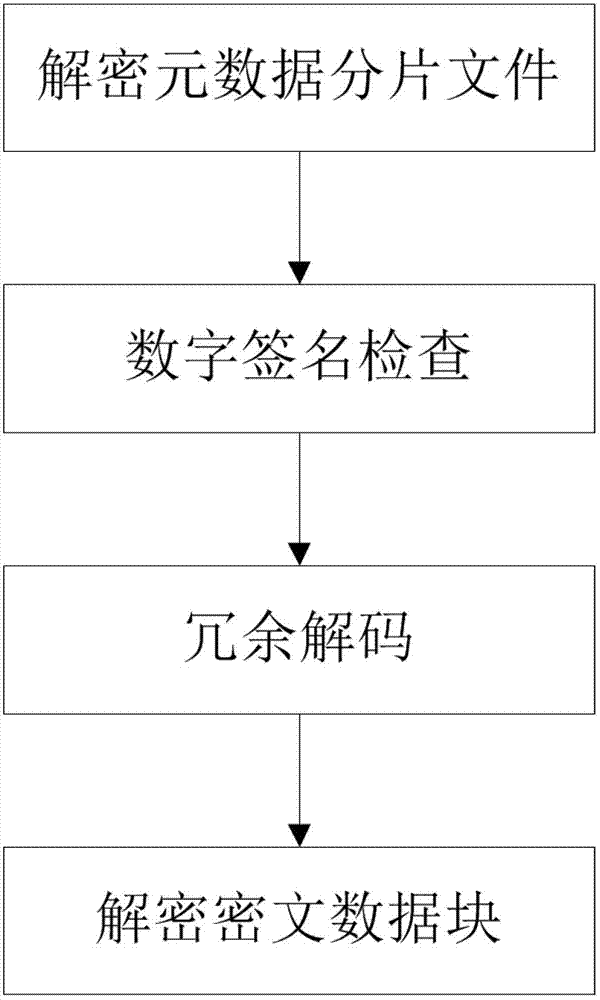
The invention belongs to the technical field of computer storage, and provides a safe storage method based on a plurality of cloud storage systems and a system thereof. The method and the system can achieve the purpose that in the plurality of existing cloud storage systems, safety of data and metadata can be guaranteed at the same time. The safe storage method comprises a step of data writing operation and a step of data reading operation, wherein the step of data writing operation comprises the sub-steps of data partitioning, data encryption, redundancy encoding, digital signature, sharing processing, and data storage. The step of data reading operation comprises the sub-steps of metadata partition file decryption, digital signature inspection, redundancy decoding and cipher text data block decryption. The safe storage system comprises an encryption and decryption coding module, a redundancy encoding module, a secret sharing module and a digital signature module. By means of the method and the system, metadata privacy and high availability can be guaranteed, and meanwhile, a user does not need to store any metadata information for indexing and data query.
Owner:HUAZHONG UNIV OF SCI & TECH
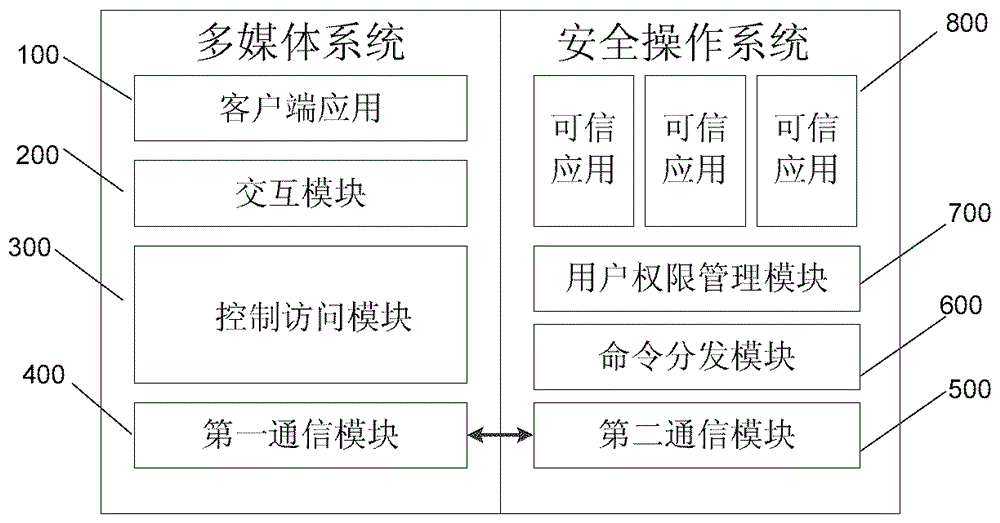
TEE access control method and mobile terminal for achieving same
ActiveCN105809036AAvoid inaccessibilityImprove usabilityInternal/peripheral component protectionDigital data authenticationOperational systemComputer terminal
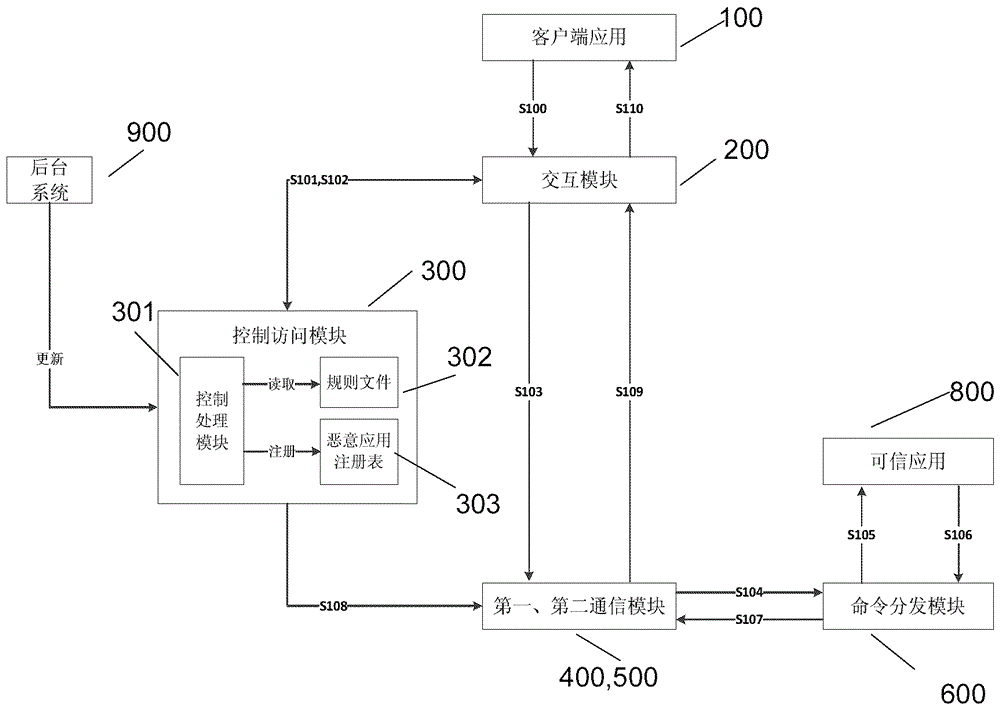
The invention relates to an access control method of a multimedia system on a secure operating system and a mobile terminal for achieving the method.The method comprises the steps that an application access request for selecting dependable applications is initiated for the secure operating system from client side applications of the multimedia system; whether the current client applications initiating calling are vicious applications or not is judged, if not, the next step continues, and if yes, the information that selection fails is returned to the client side applications, and processing is interrupted; the application access request is sent to the secure operating system from the multimedia system; the dependable applications are obtained in the secure operating system according to the application access request and returned to the multimedia system.According to the method, vicious access initiated by the vicious applications to the dependable applications in the secure operating system can be prevented under the condition of not switching the systems, and the problem that access to the dependable applications cannot be achieved due to vicious access can be avoided.
Owner:CHINA UNIONPAY
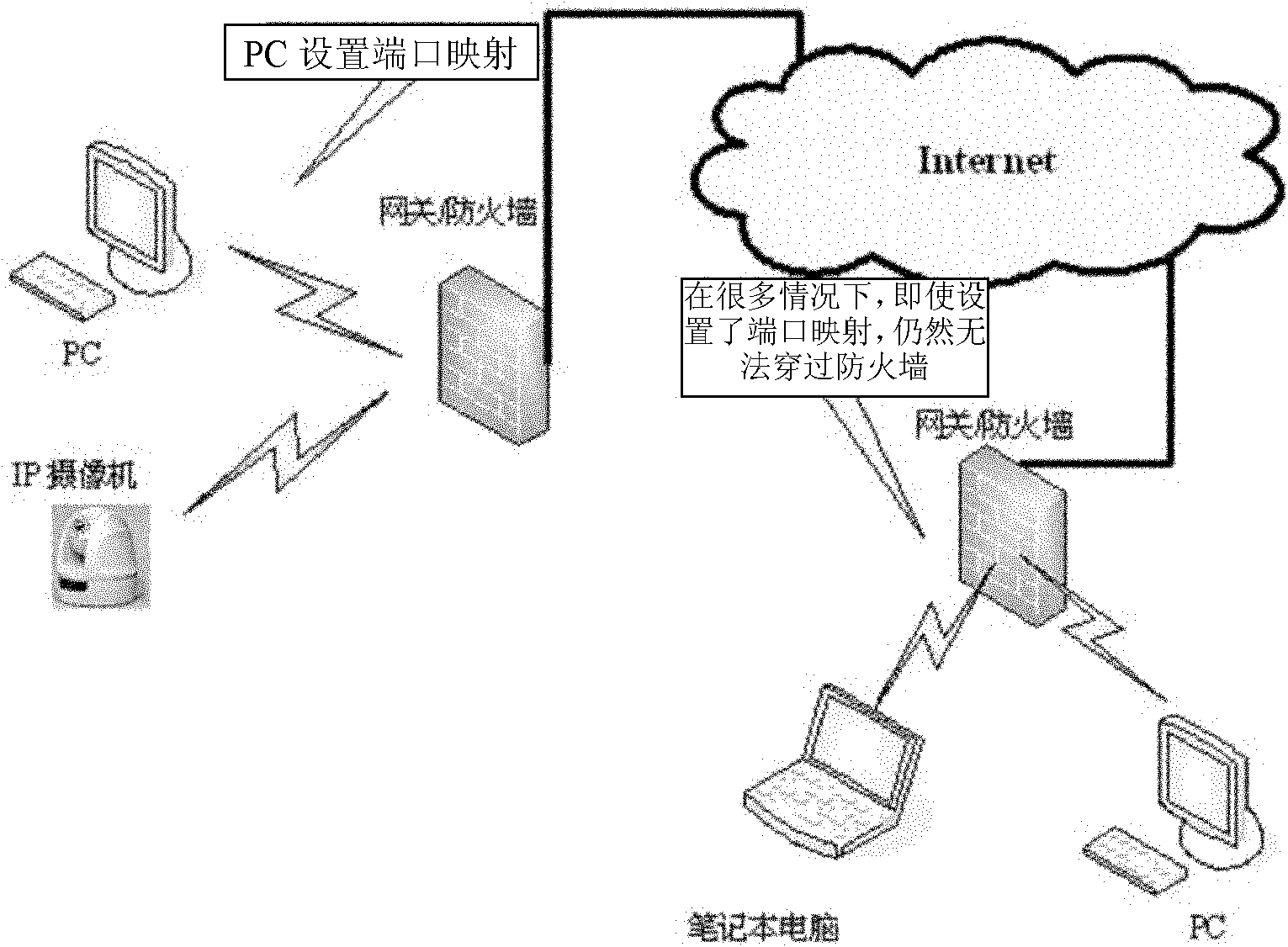
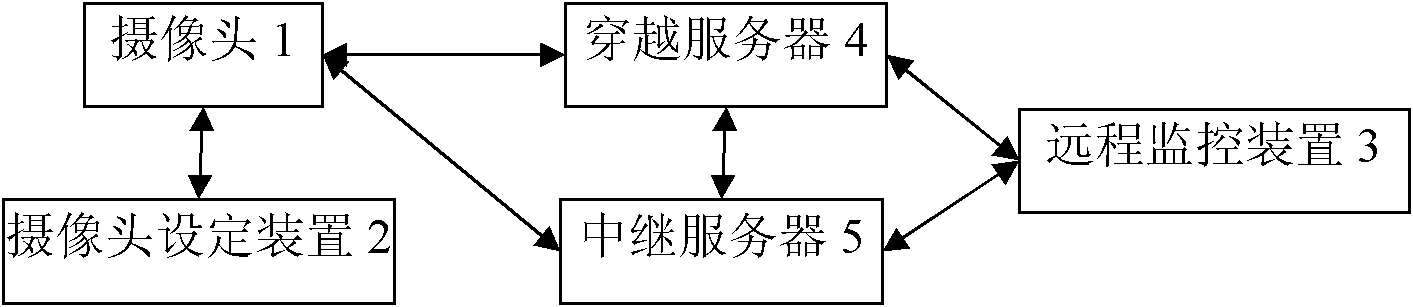
Network camera system
InactiveCN102647550AEasy to set upEasy accessTelevision system detailsColor television detailsPrivacy preservingNetwork camera
The invention relates to a network camera system, which comprises a web camera, a web camera setting device, a remote monitoring device and a penetrating server, wherein the penetrating server causes the web camera and the remote monitoring device to carry out point-to-point connection and is respectively connected with the web camera and the remote monitoring device; and the web camera is connected with the camera setting device. The network camera system disclosed by the invention is simple in setting and is convenient to access, the privacy can be protected, and the defects that the original network camera system is complex in setting and can not be accessed, and the privacy can not be protected are avoided.
Owner:SHENZHEN GOSPELL SMARTHOME ELECTRONICS
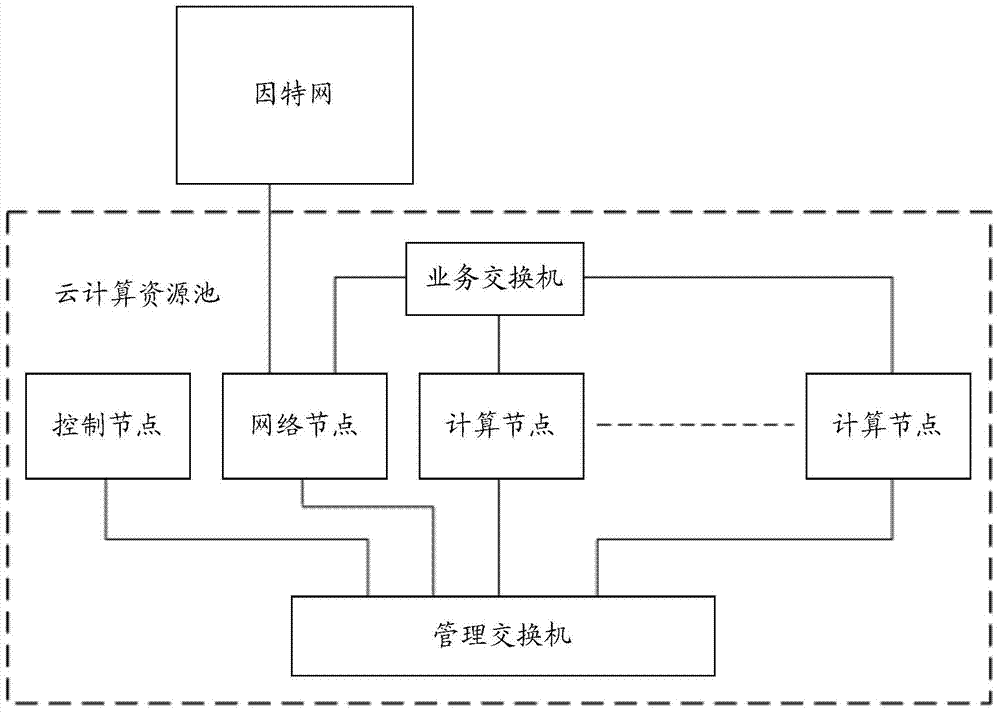
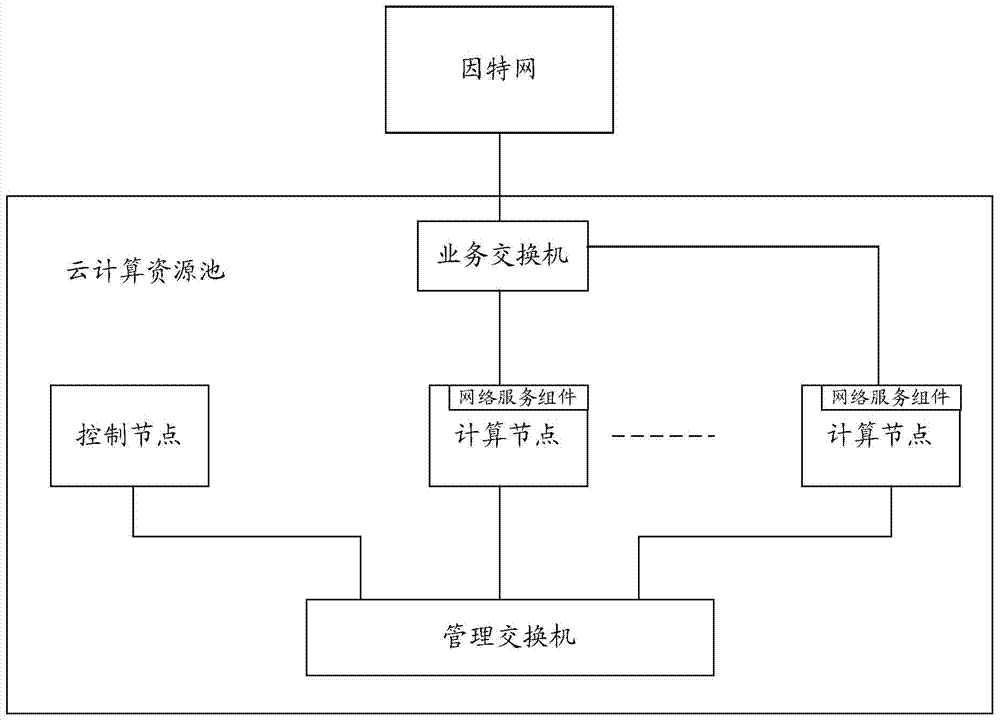
Cloud computing resource pool system and implement method thereof
ActiveCN103581324AAvoid inaccessibilityImprove bandwidth utilizationTransmissionResource poolNetwork management
The invention discloses a cloud computing resource pool system and an implement method of the cloud computing resource pool system. The method includes the step that network service components are deployed for all computing nodes respectively, wherein the network service components are used for achieving network management functions of virtual machines in the corresponding computing nodes, such as IP address management and VLAN id allocation. Because network node functions of a traditional cloud computing resource pool are distributed to all the computing nodes respectively, if the network service component in a single computing node breaks down, network interruption of the virtual machine in only the computing node is caused while the other computing nodes in the resource pool will not be affected, and accordingly the problem that services of the whole resource pool can not be accessed due to faults of a single node is solved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
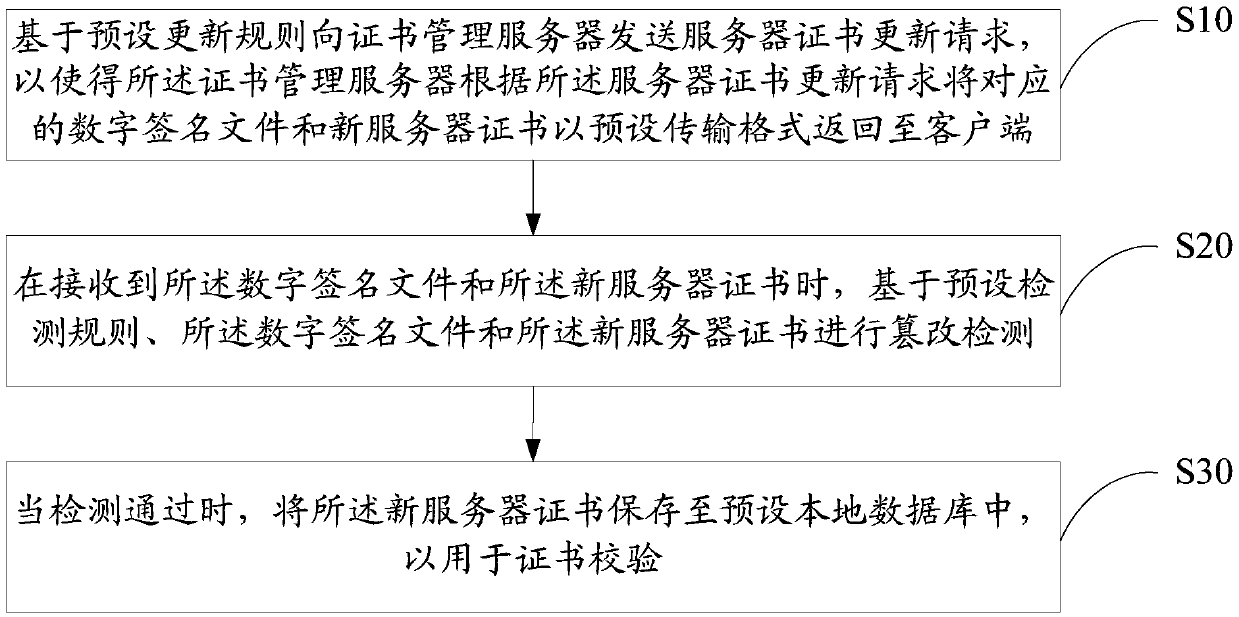
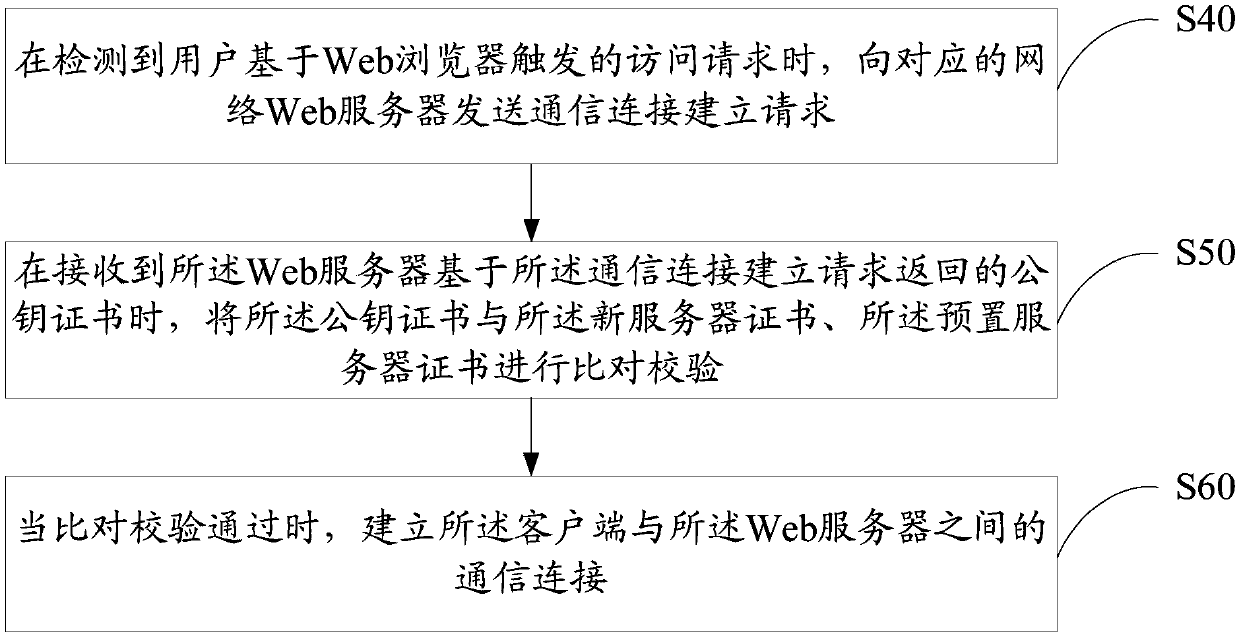
Server certificate updating method and device, equipment and computer-readable storage medium
ActiveCN109639661AImplement automatic updatesEnsure normal communicationEncryption apparatus with shift registers/memoriesUser identity/authority verificationWeb serviceDigital signature
The invention discloses a server certificate updating method. The server certificate updating method includes: sending a server certificate updating request to a certificate management server on the basis of a preset updating rule to enable the certificate management server to return a corresponding digital signature file and a new server certificate to a client in a preset transmission format according to the server certificate updating request; carrying out tampering detection on the basis of a preset detection rule, the digital signature file and the new server certificate when the digitalsignature file and the new server certificate are received; and when detection is successful, saving the new server certificate into a preset local database to use the same for certificate verification. The invention also discloses a server certificate updating device, equipment and a computer-readable storage medium. The method can realize automatic updating of the server certificate to ensure normal communication between the client and a Web server.
Owner:WEBANK (CHINA)
Chain balancing method based on domain name system (DNS)
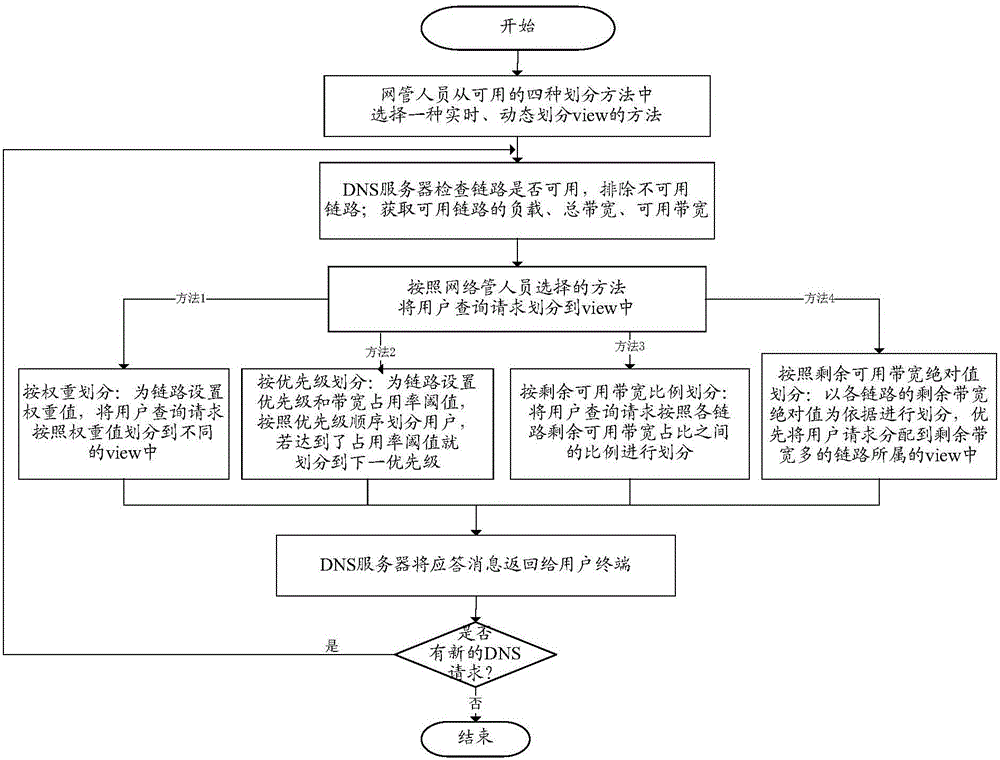
ActiveCN105872079ASolve the problem of unbalanced load usageAvoid inaccessibilityData switching networksDomain nameIp address
The invention discloses a chain balancing method based on a domain name system (DNS). The method includes the steps that when a network is provided with two or more outlet links, a load including links and network service or a usability state is to serve as balance factors of the links, user query requests are dynamically divided into different views to achieve load balance of the links according to a weight or priority or residual available bandwidth ratio or residual available bandwidth absolute value method. The problem that in the prior art, link bandwidth utilization is imbalanced as a fixed IP address range is adopted to divide user view is effectively solved, a fault-tolerant mechanism is provided, and it is avoided that when the links or a server has faults, follow-up flow continues to be guided into the failed links or server. Only a view dividing mode is changed in the DNS server without additionally arranging hardware, and the operation is visible for a network user; the client side is not changed, and normal operation and behaviors of existing users are not interfered. Therefore, popularizing prospects are good.
Owner:BEIJING WANGRUIDA TECH CO LTD
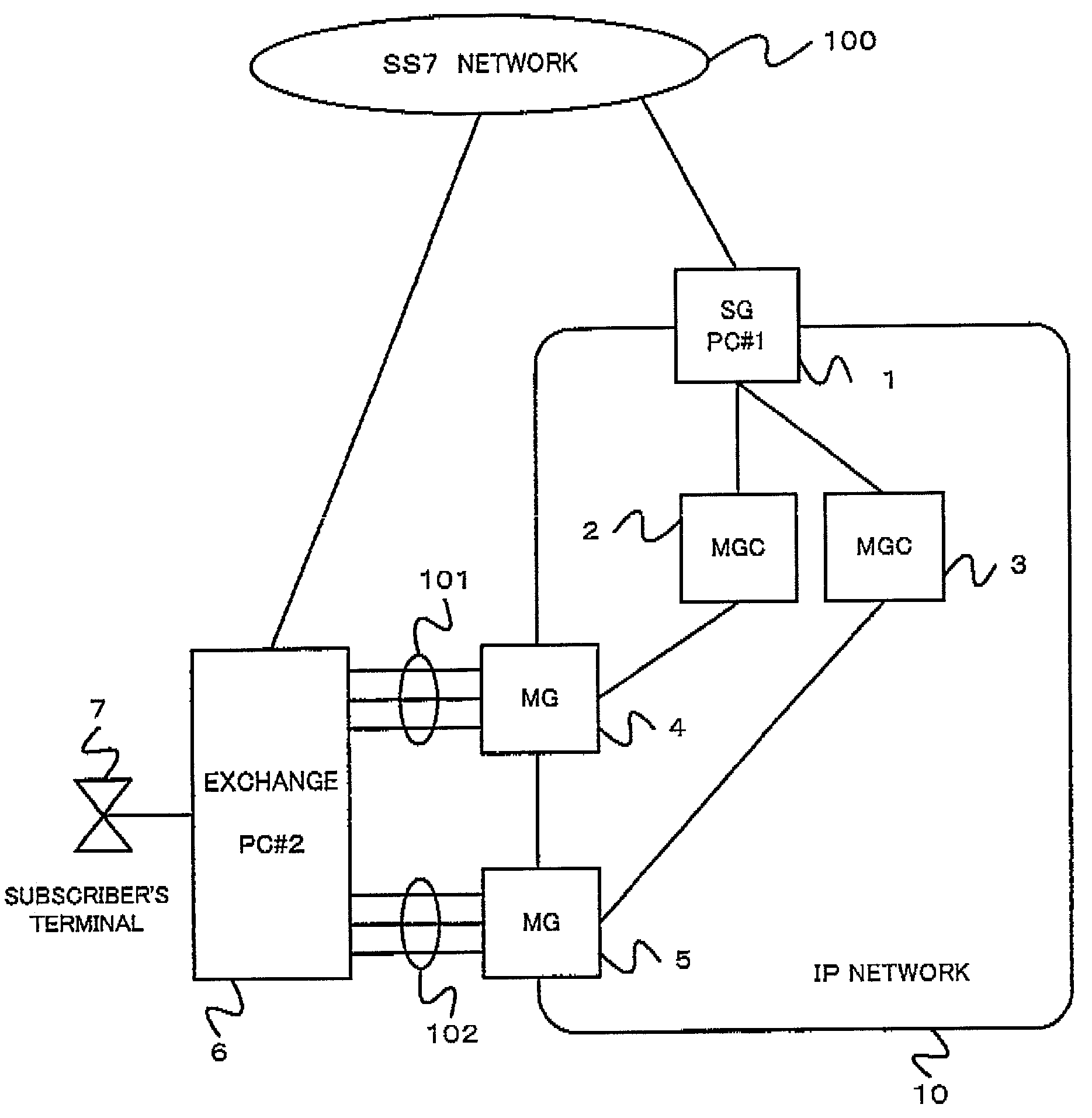
Gateway system and fault management method
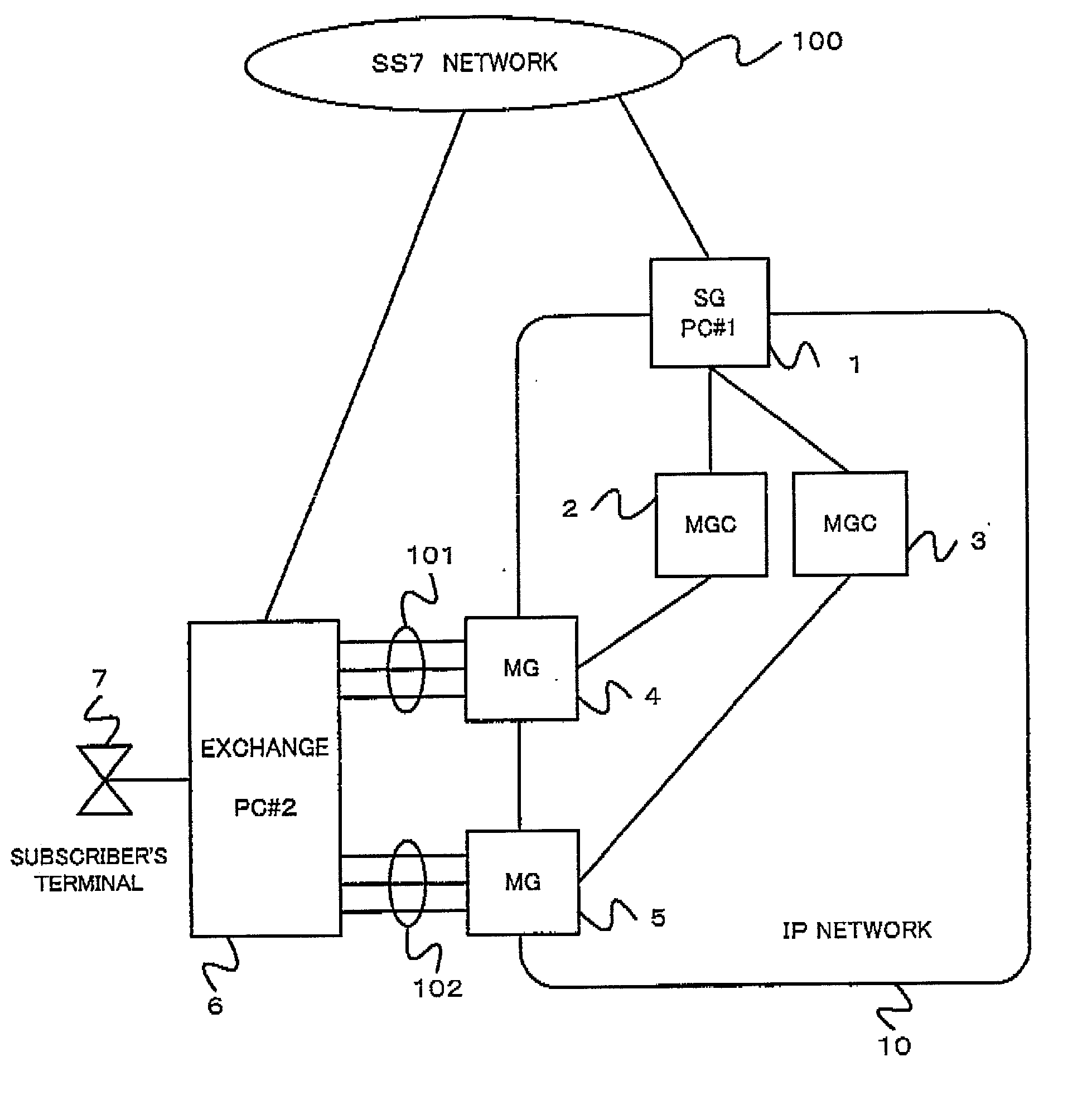
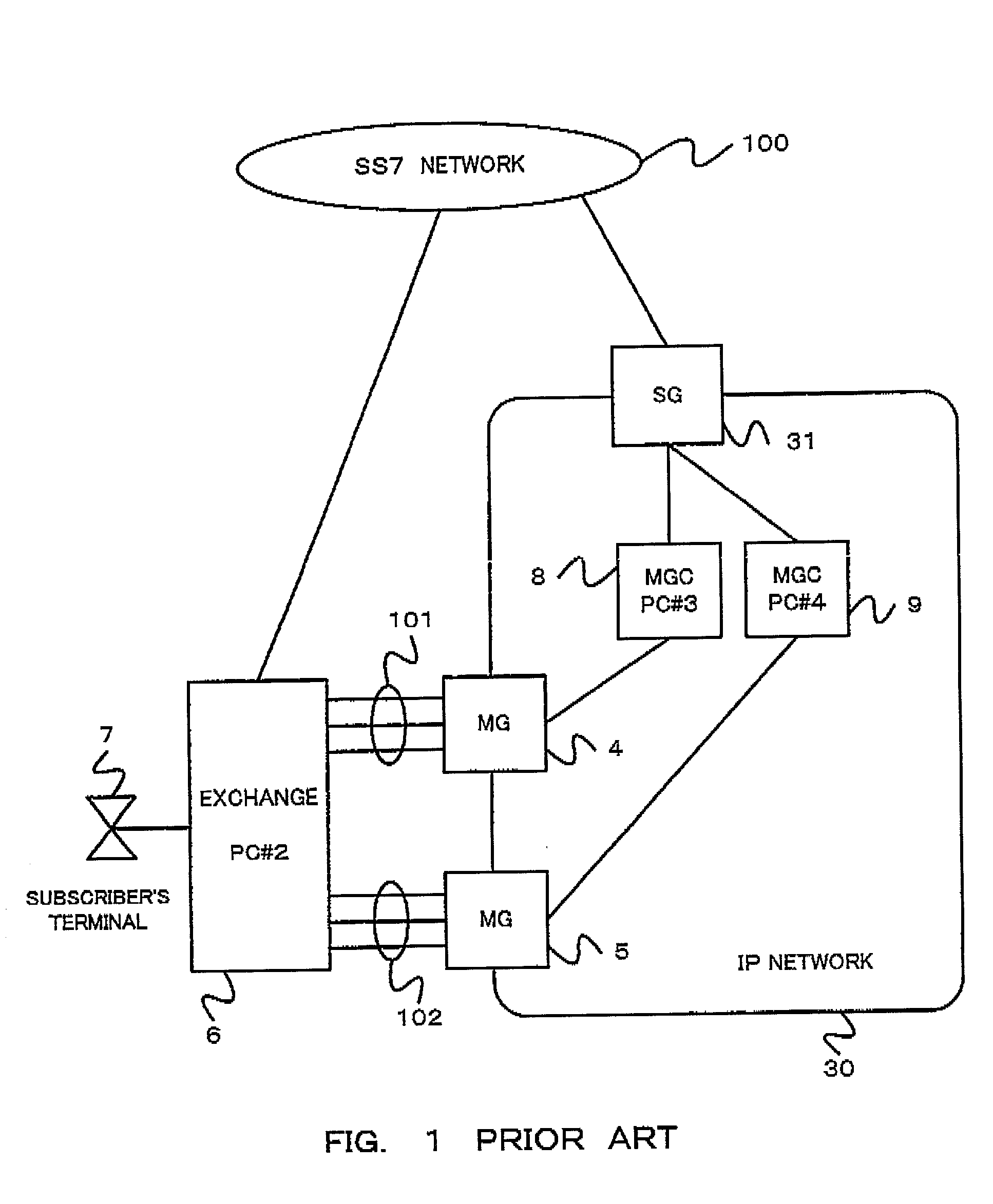
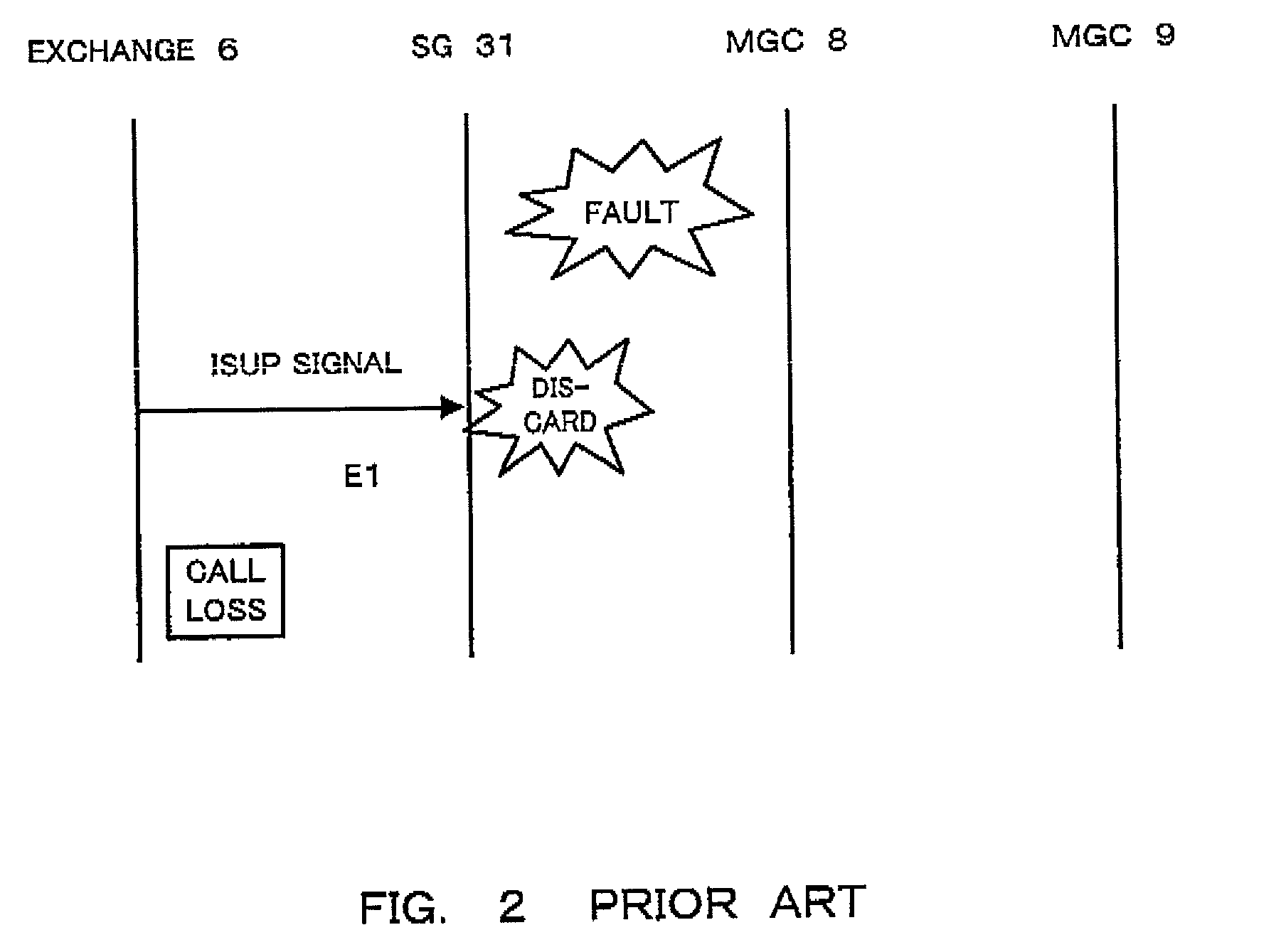
InactiveUS20020141562A1Avoid it happening againEfficient use ofError preventionFrequency-division multiplex detailsEngineeringFault management
A gateway system prevent an occurrence of a call loss and an inaccessibility of the SG and can effectively utilize communication lines, even if a fault occurs on the MGC side. In the gateway system, a PC is supplied to an SG connected to a plurality of MGCs, and an occurrence of a call loss and an inaccessibility of the SC can be prevented by incorporating to the SG a function that requires line close operation for an opposed node of the SCN when a fault occurs on the MGC which is structured to have no PC.
Owner:NEC CORP
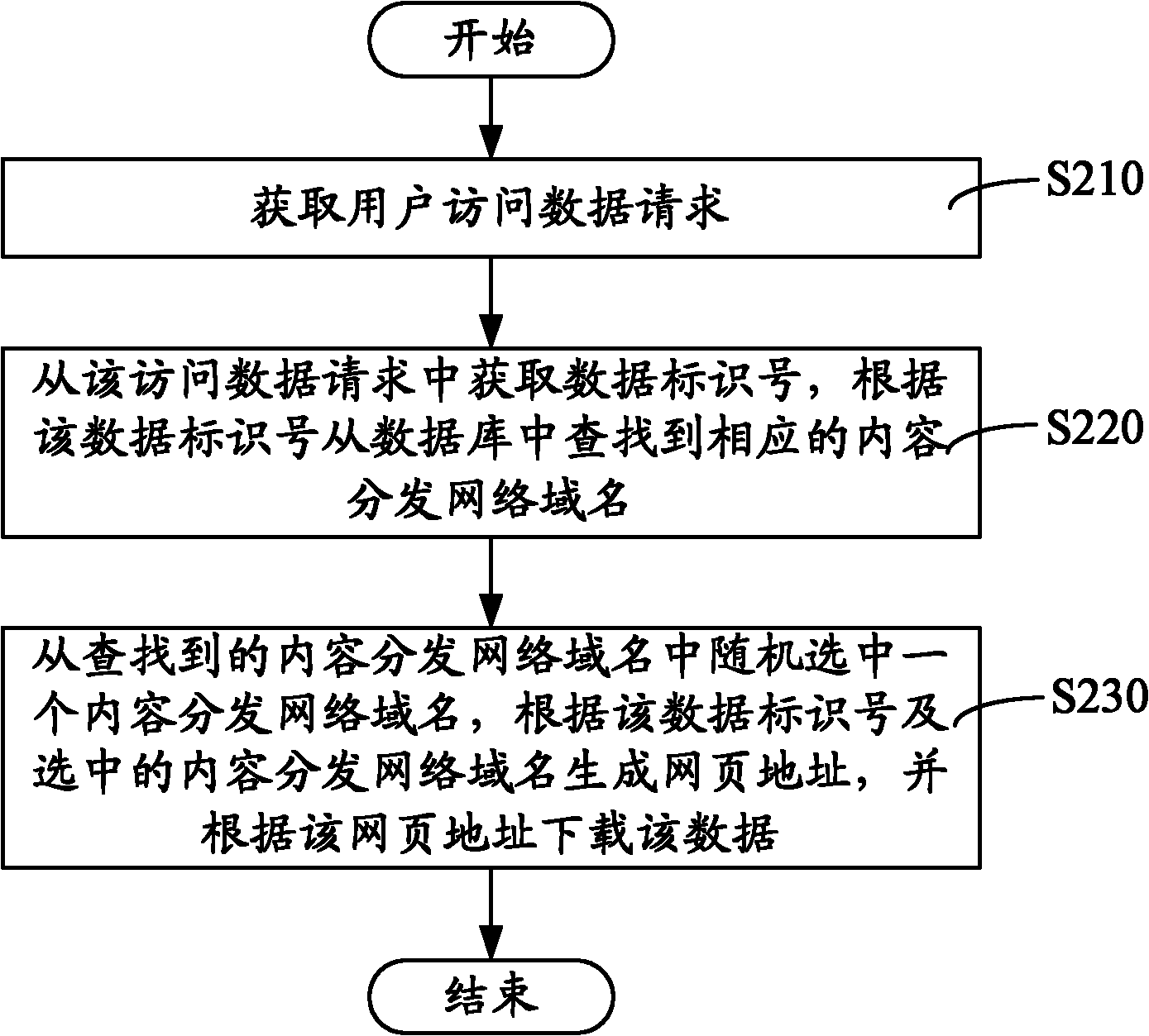
Method and system for dynamically adjusting data flow
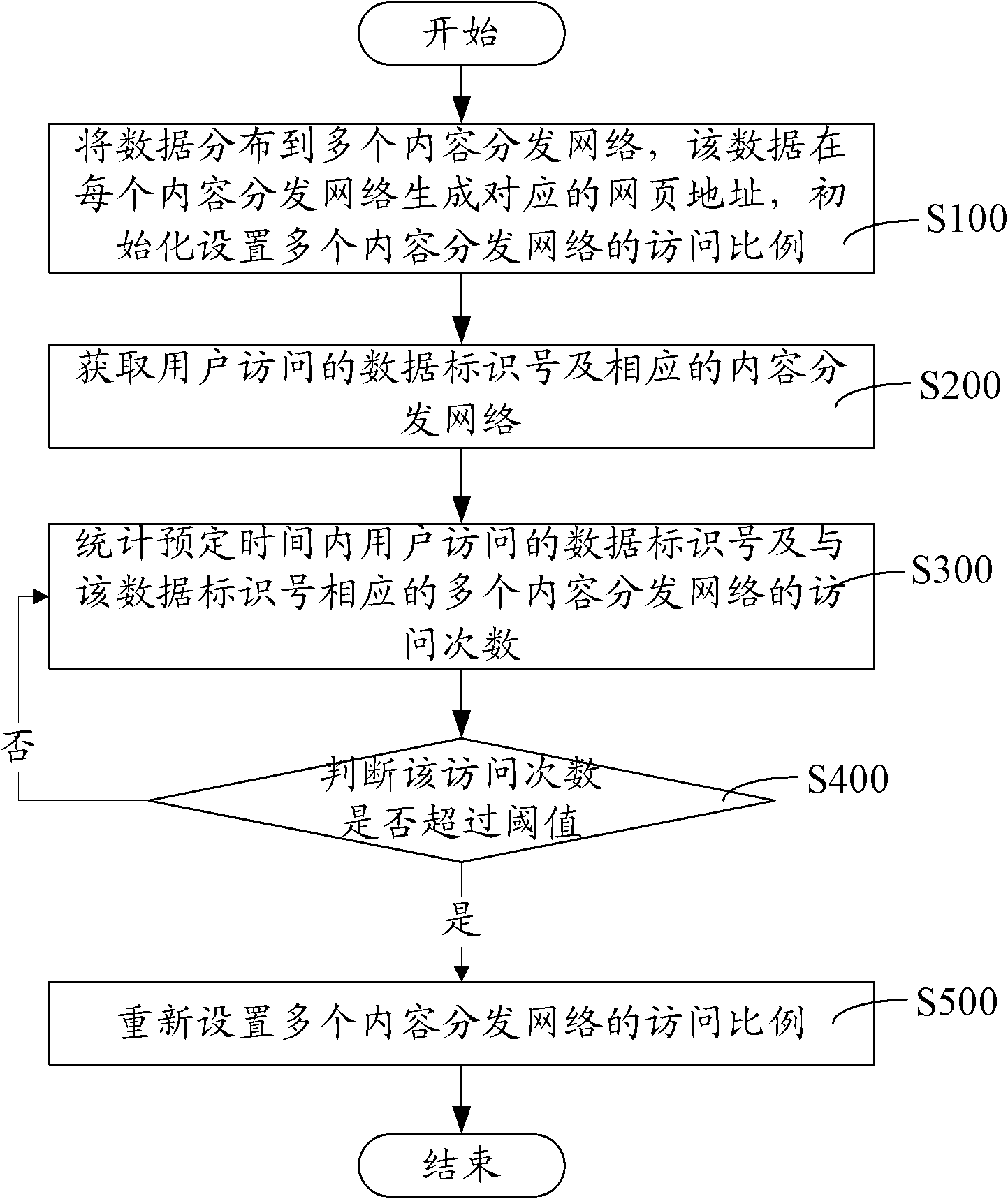
The invention relates to a method and a system for dynamically adjusting data flow. The method includes the steps: distributing data to multiple content distribution networks, enabling webpage addresses corresponding to the data to be generated in each content distribution network, and initializing and setting the access proportion of the content distribution networks; acquiring user access data identification numbers and corresponding content distribution networks; counting user access data identification numbers and access times of the content distribution networks corresponding to the data identification numbers within preset time; and judging whether the access times exceeds a threshold or not, if yes, resetting the access proportion of the content distribution networks, and otherwise, returning to the step of counting user access data identification numbers and access times of the content distribution networks corresponding to the data identification numbers within preset time. By the method and the system for dynamically adjusting data flow, failure in user access due to massive accesses within short time is avoided, user access is facilitated, and utilization rate of bandwidth resources is increased.
Owner:TENCENT TECH (SHENZHEN) CO LTD
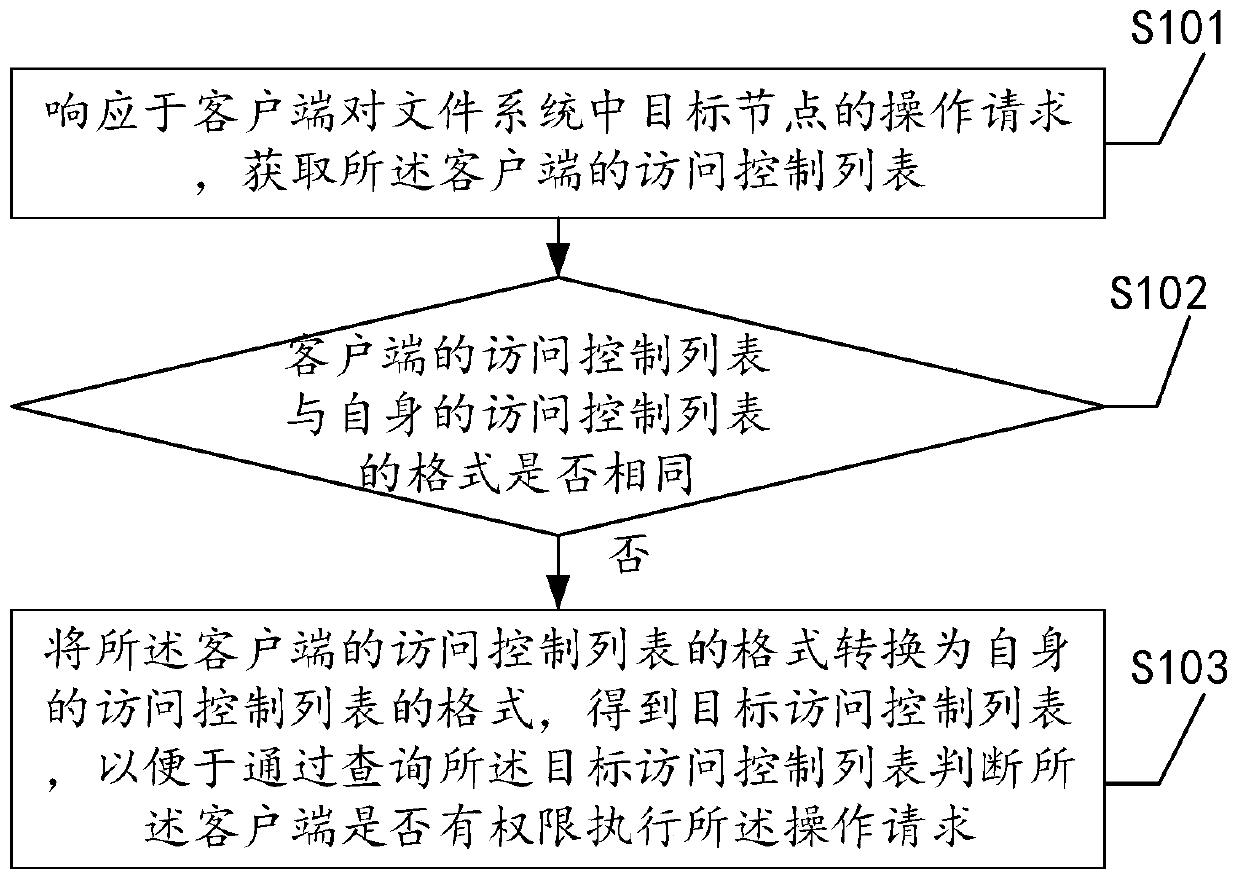
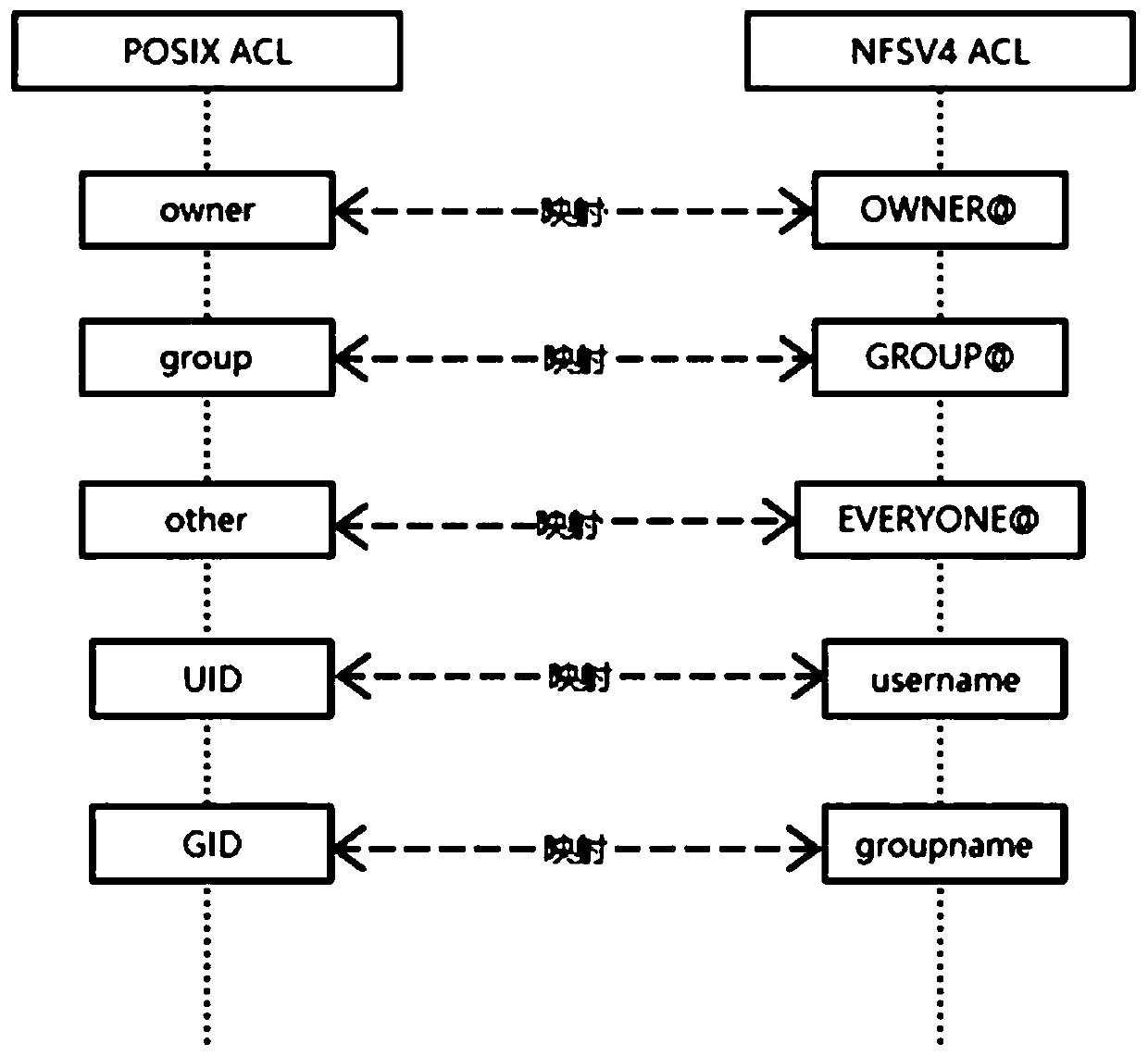
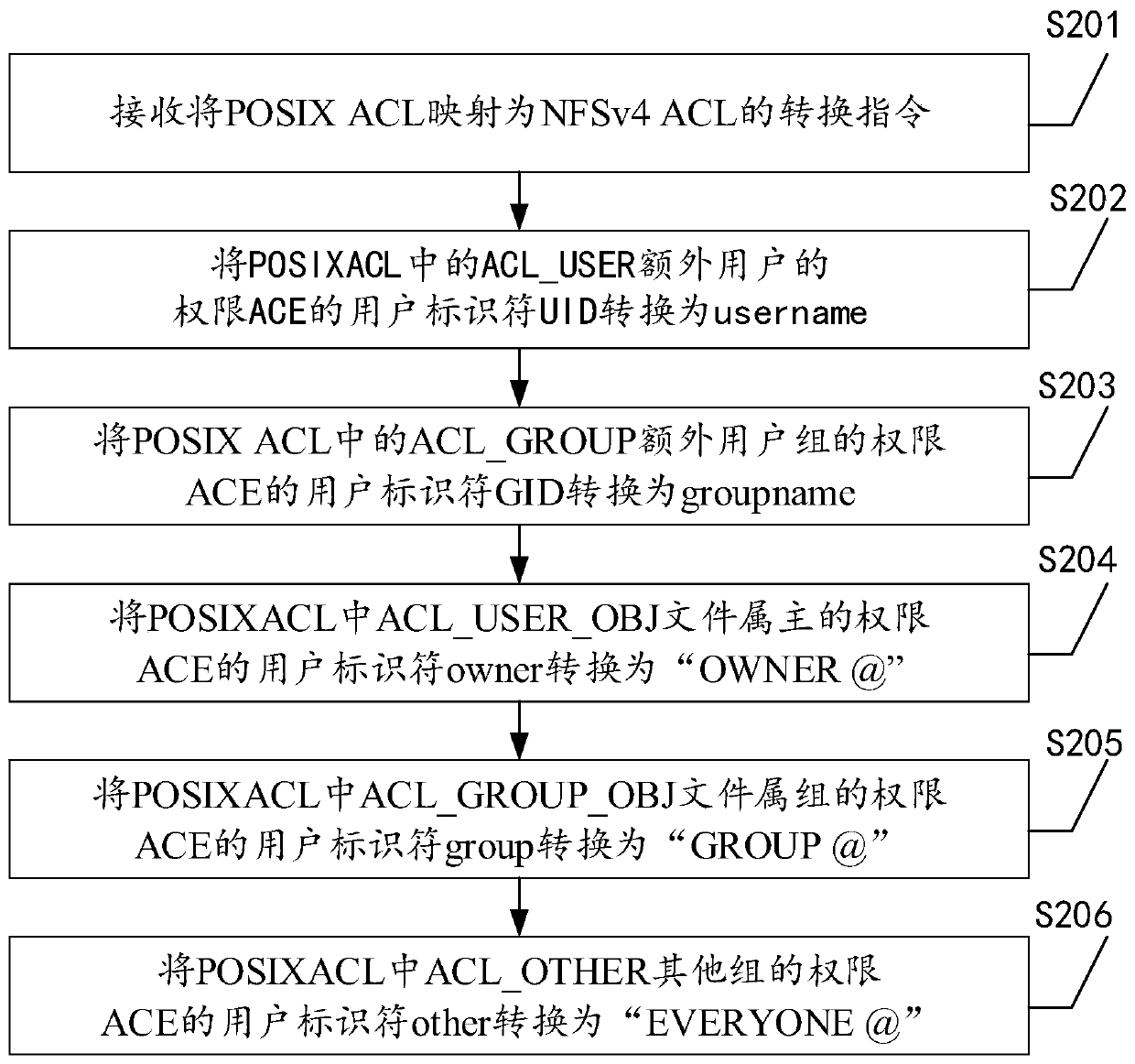
A mapping method of a file system access control list
InactiveCN109740367ASolve the problem of not being able to access normallyImprove scene adaptabilityDigital data protectionFile systemClient-side
The invention discloses a mapping method of a file system access control list and is applied to file server. An operation request of a client for a target node in the file system can be responded; anaccess control list of the client can be obtained, whether the format of the access control list of the client is the same as that of the access control list of the client or not is judged; and if not, the format of the access control list of the client is converted into the format of the access control list of the client to obtain a target access control list, so as to judge whether the client has permission to execute the operation request by inquiring the target access control list. Therefore, according to the method, when the client initiates the operation request, the format of the access control list is unified, the problem that access cannot be achieved is avoided, and the scene adaptability of the file server is improved. In addition, the invention further provides a mapping device of the file system access control list, a file server and a storage system, and the effects of the mapping device, the file server and the storage system correspond to those of the method.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
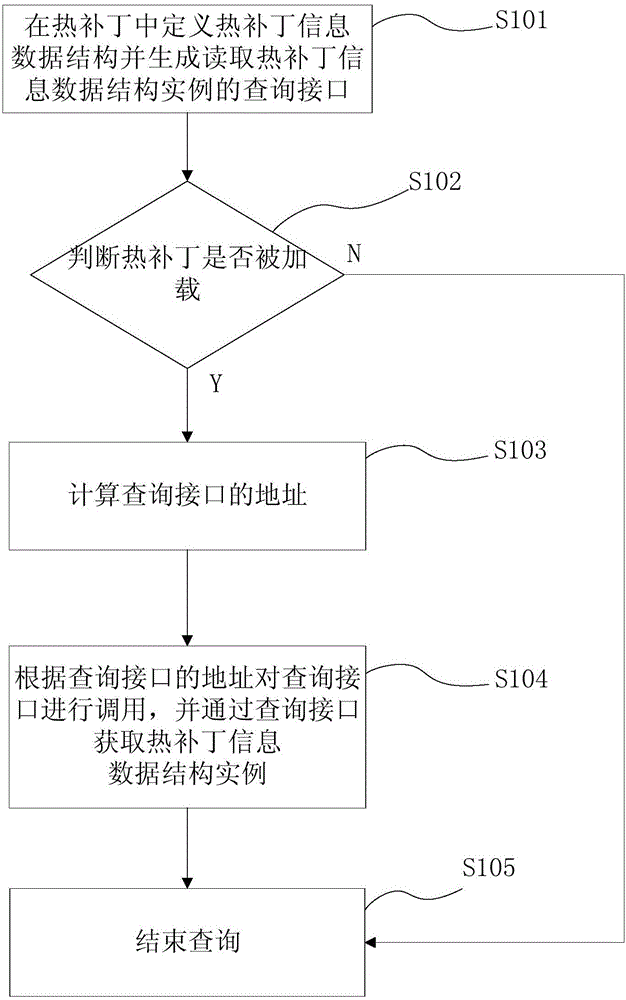
Hot patch information inquiring method and device
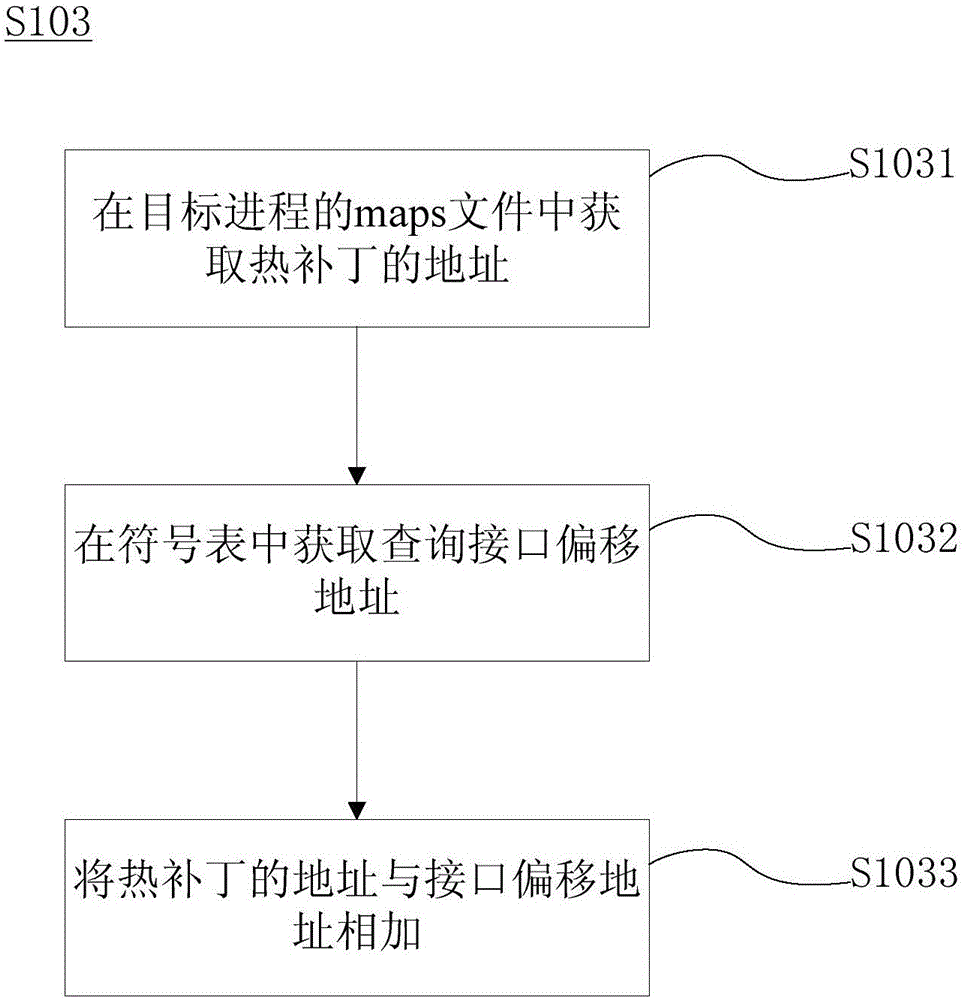
ActiveCN106610857AGuaranteed stabilityIt will not happen that the hot patch information cannot be queriedSoftware engineeringComputer security arrangementsSoftware engineeringComputer science
The invention provides a hot patch information inquiring method and device. The hot patch information inquiring method comprises the steps that step S101: when a hot patch is pre-generated, the hot patch information data structure is defined in the hot patch, and an inquiring interface for reading the hot patch information data structure instance is generated in the hot patch; step S102: whether the hot patch is loaded is judged, the step S103 is performed if the judgment result is yes, or hot patch information inquiring is ended; step S103: the address of the inquiring interface is computed; and step S104: the inquiring interface is called according to the address of the inquiring interface, and the hot patch information data structure instance is acquired through the inquiring interface so as to acquire the hot patch information. The hot patch information data structure is defined in the hot patch and the inquiring interface is generated, and the inquiring interface is called to read the hot patch information data structure instance so as to acquire the hot patch information without additional arrangement of configuration files.
Owner:UCLOUD TECH CO LTD
Method and device for processing service
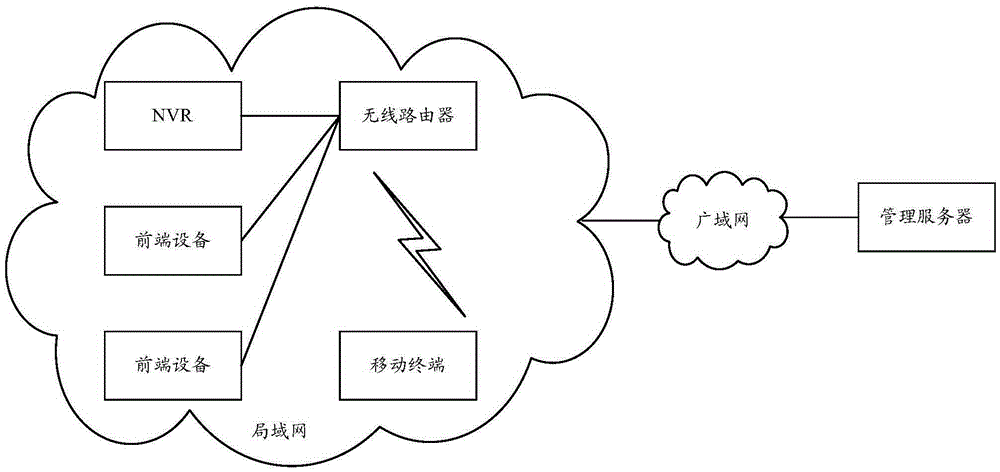
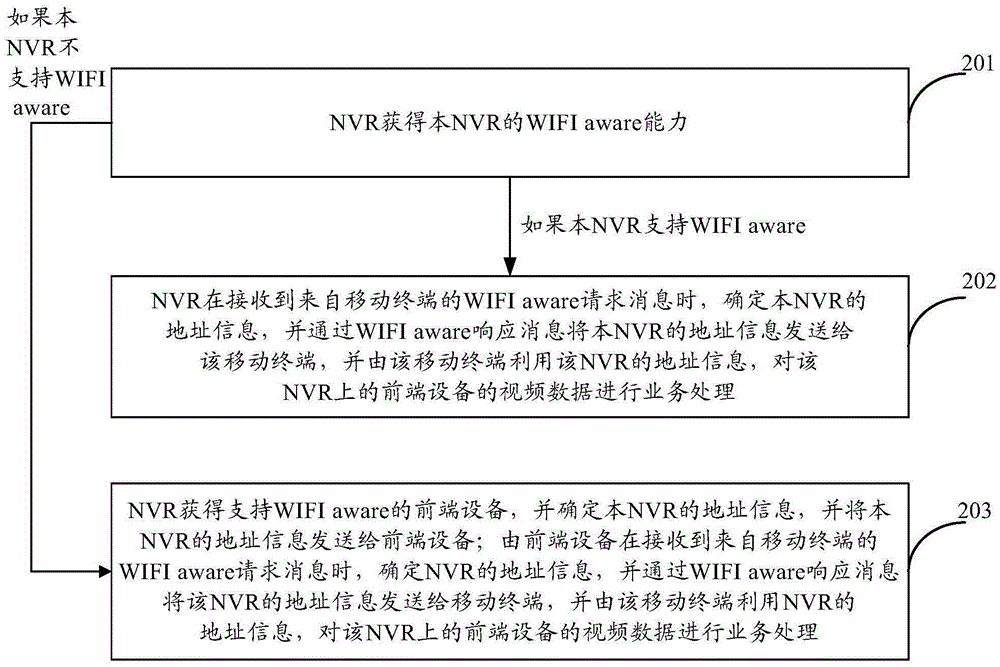
ActiveCN105391979ARelieve stressAvoid inaccessibilityClosed circuit television systemsTransmissionWireless routerWide area network
The present invention provides a method and a device for processing service. The method comprises the steps as follows: an NVR obtains a WIFI aware ability of the NVR; if the NVR does not support the WIFI aware, the NVR obtains front-end equipment supporting the WIFI aware, and determines address information of the NVR, and transmits the address information of the NVR to the front-end equipment; the front-end equipment determines the address information of the NVR when receiving a WIFI aware request message from a mobile terminal, and transmits the address information of the NVR to the mobile terminal through a WIFI aware response message, the mobile terminal utilizes the address information of the NVR to perform service processing on video data of the front-end equipment on the NVR. According to the technical solution of the present invention, when a wide area network between the mobile terminal and a management server does not work and the mobile terminal and the management server cannot be connected, the mobile terminal can obtain the address information of the NVR and can access the NVR through a wireless router in a local area network.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
Large-view-field photoelectric auto-collimator for secondary imaging
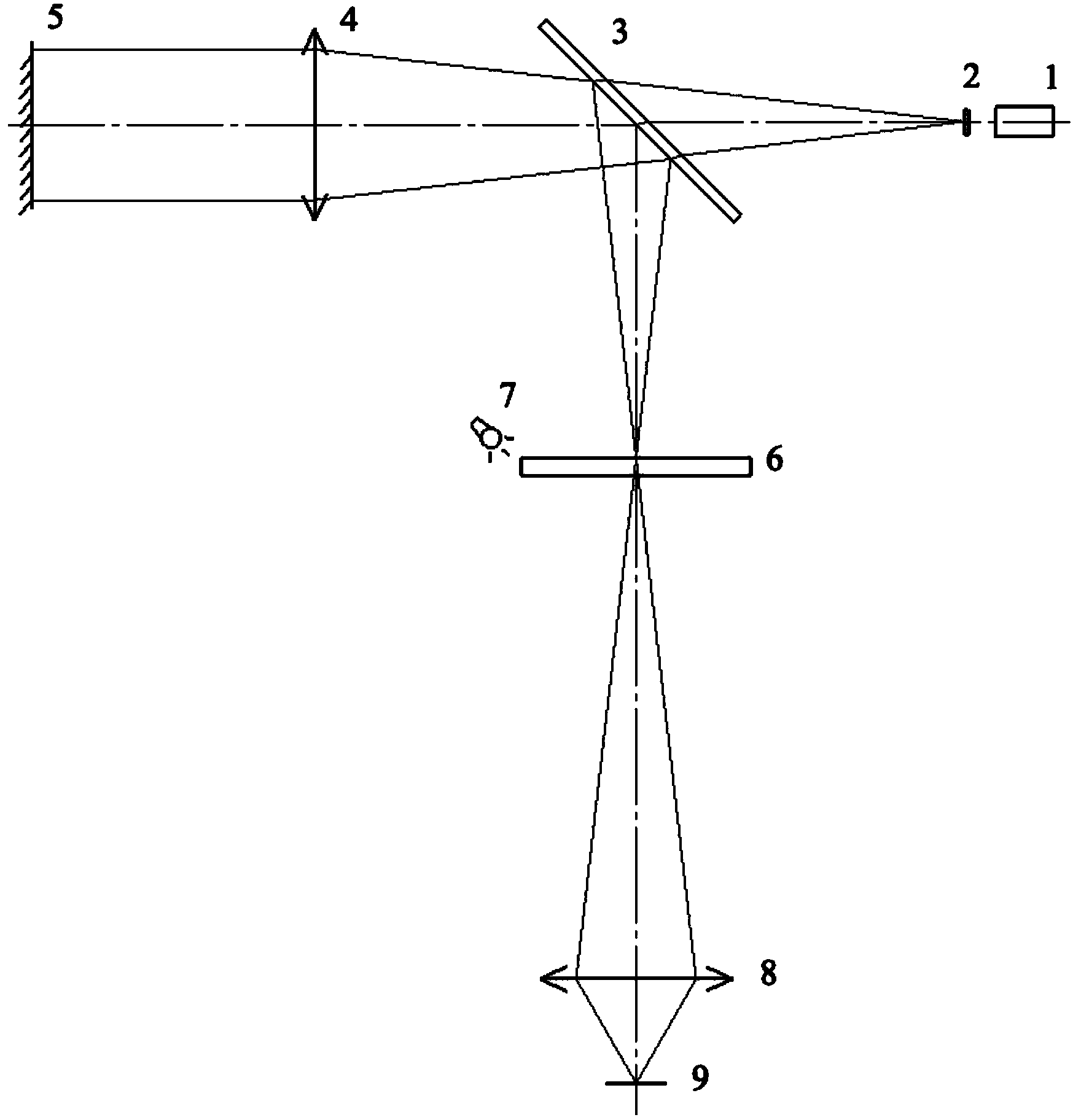
InactiveCN104075671AAvoid inaccessibilityEliminate the effect of interference diffraction fringesUsing optical meansOptical elementsHigh definitionLight source
The invention discloses a large-view-field photoelectric auto-collimator for secondary imaging. The large-view-field photoelectric auto-collimator comprises a semiconductor laser unit, an illumination reticle, a spectroscope, a collimator objective lens set, a measurement reticle, a CCD imaging objective lens and a CCD. The number of pixels of the CCD is 4 million so that high-definition image measurement can be provided, and the accuracy can meet requirements. The view field of collimator objective lenses is not smaller than 8.5 degrees, and the caliber of the collimator objective lenses is not smaller than 90 mm. After passing through the collimator objective lenses and the spectroscope, light beams reflected back by a reflecting mirror are reflected and form images on ground glass. The CCD is utilized for measuring secondary imaging of light spots on the ground glass. For achieving the system calibration convenience, a ground glass reticle is engraved with two pairs of lines with a fixed interval. For measuring and observing the engraved lines on the ground glass, white-light LED light sources are adopted around for illumination. The ground glass is adopted as the reticles, and therefore the phenomenon that the inclined light beams in the auto-collimator can not enter the CCD can be avoided, the influence that a system interferes with diffraction fringes is eliminated, and the system error is small.
Owner:HUAZHONG AGRICULTURAL UNIVERSITY
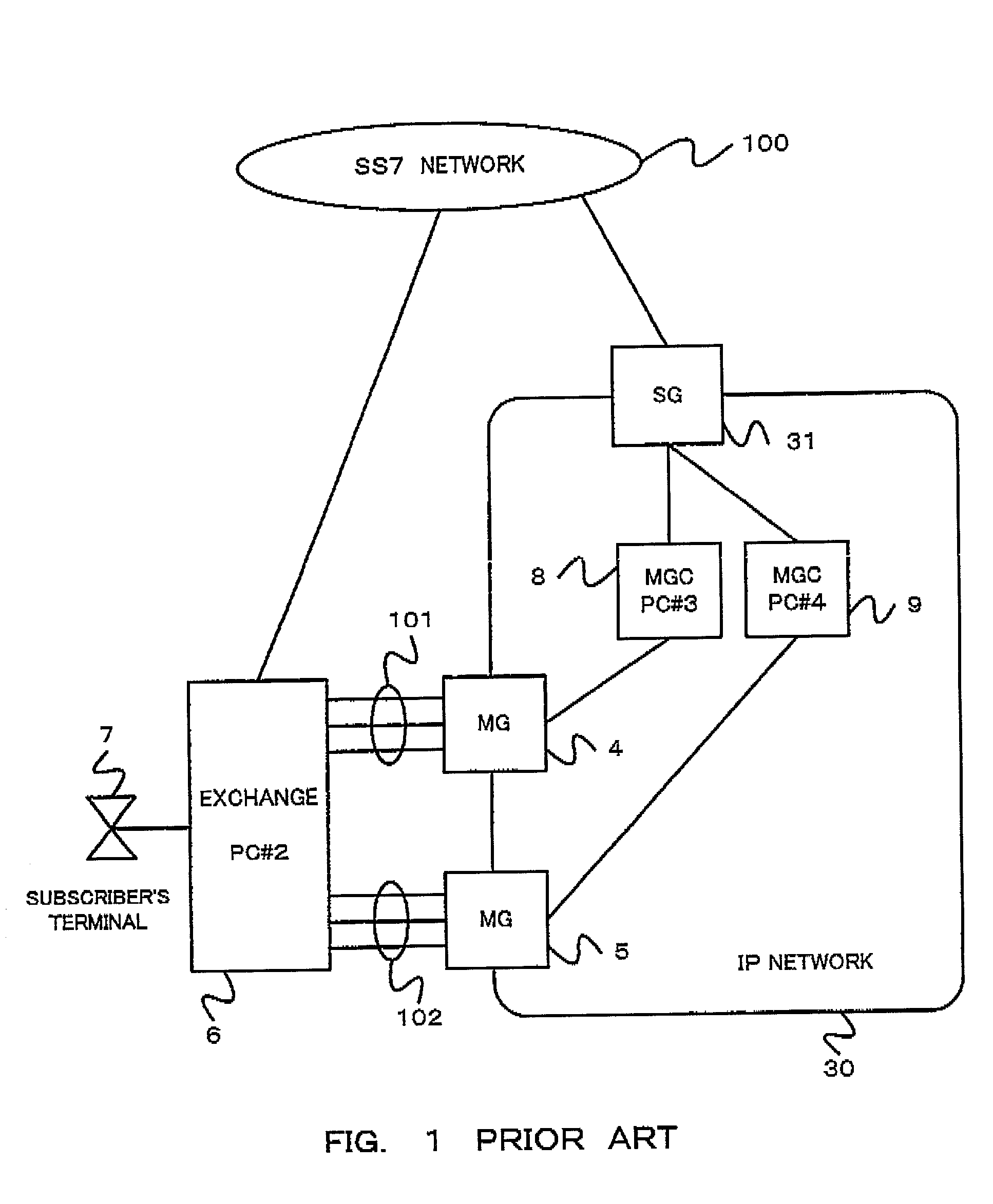
Gateway system and fault management method
InactiveUS7046684B2Avoid it happening againEffectively utilize communication linesError preventionFrequency-division multiplex detailsEngineeringFault management
A gateway system prevent an occurrence of a call loss and an inaccessibility of the SG and can effectively utilize communication lines, even if a fault occurs on the MGC side. In the gateway system, a PC is supplied to an SG connected to a plurality of MGCs, and an occurrence of a call loss and an inaccessibility of the SC can be prevented by incorporating to the SG a function that requires line close operation for an opposed node of the SCN when a fault occurs on the MGC which is structured to have no PC.
Owner:NEC CORP
Request scheduling method, system, device and electronic equipment
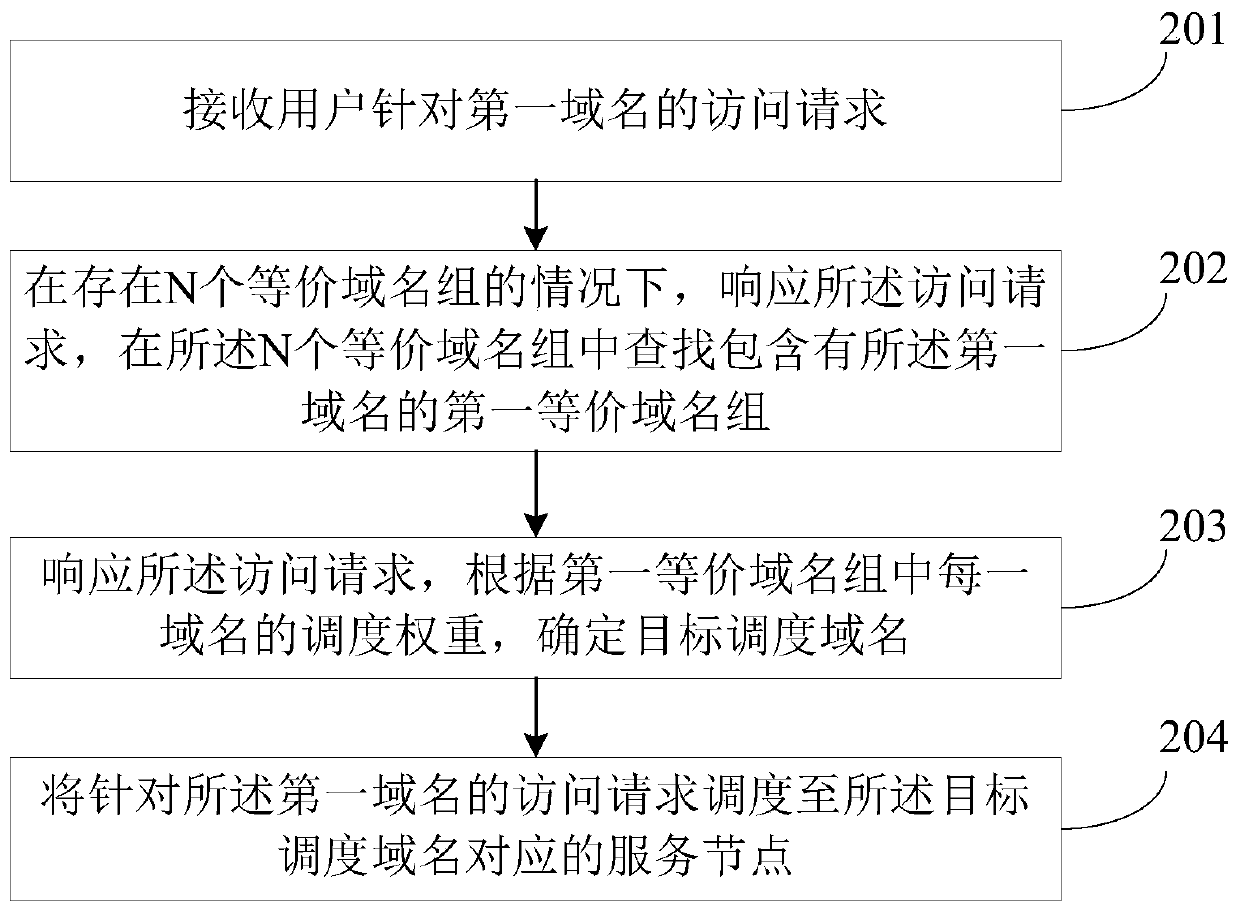
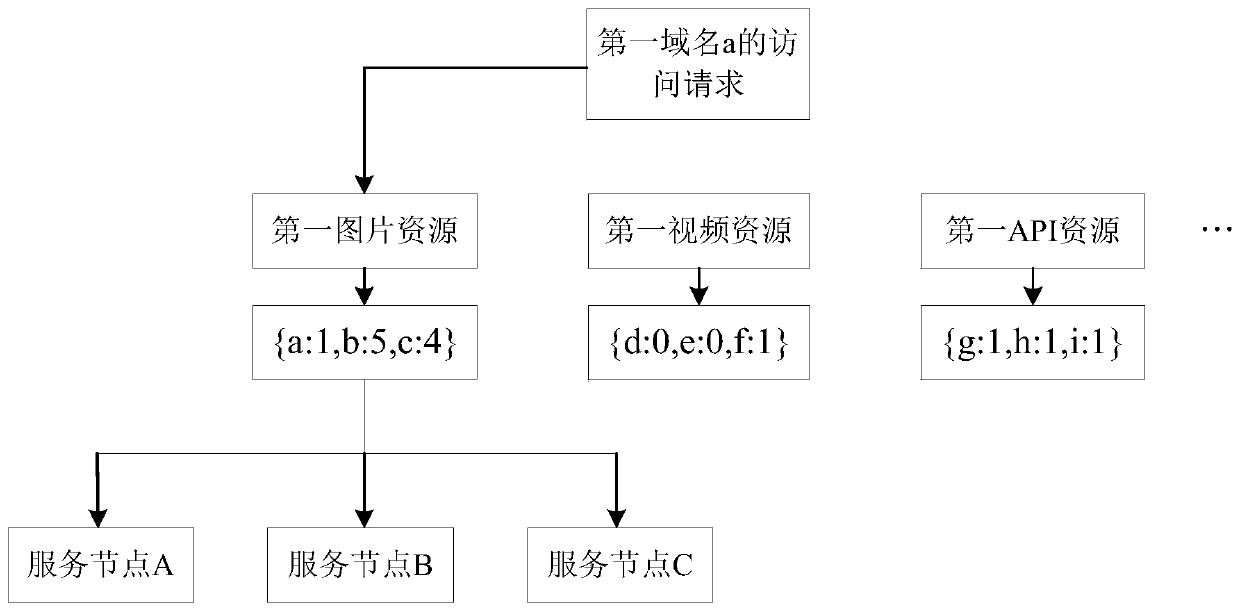
InactiveCN111556135AImprove disaster toleranceAvoid inaccessibilityTransmissionDomain nameComputer network
The embodiment of the invention provides a request scheduling method, a system, a device and electronic equipment, and the method comprises the steps: receiving an access request of a user for a firstdomain name; in response to the access request, determining a target scheduling domain name according to the scheduling weight of each domain name in a first equivalent domain name group, and each domain name in the first equivalent domain name group can provide service provided by the first domain name; and scheduling an access request for the first domain name to a service node corresponding tothe target scheduling domain name. According to the method, the target scheduling node is determined according to the scheduling weight of each domain name in the equivalent domain name group, and the service state of the service node corresponding to each domain name is considered, so that the accuracy of request scheduling is improved, the problem that resource services cannot be accessed due to faults of a single service node can be avoided, and the disaster tolerance of a request scheduling system is improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Method and device for network address translation
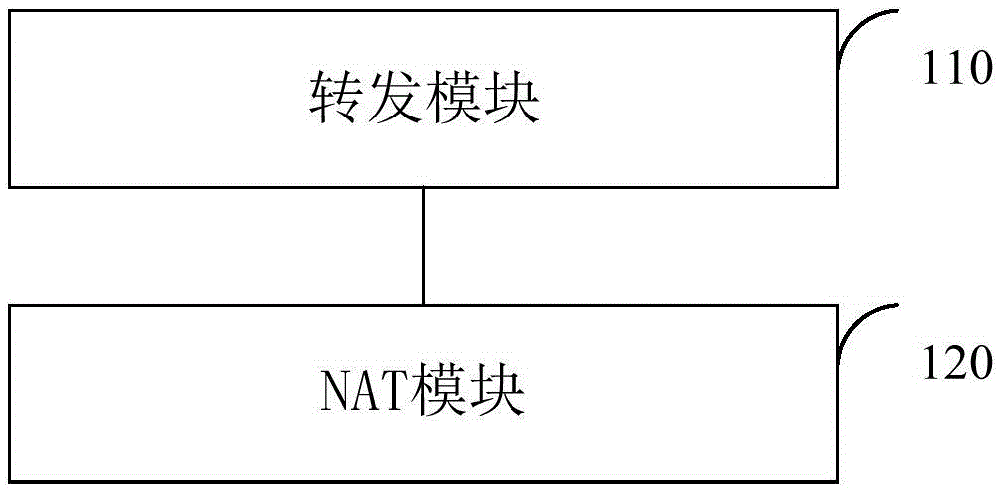
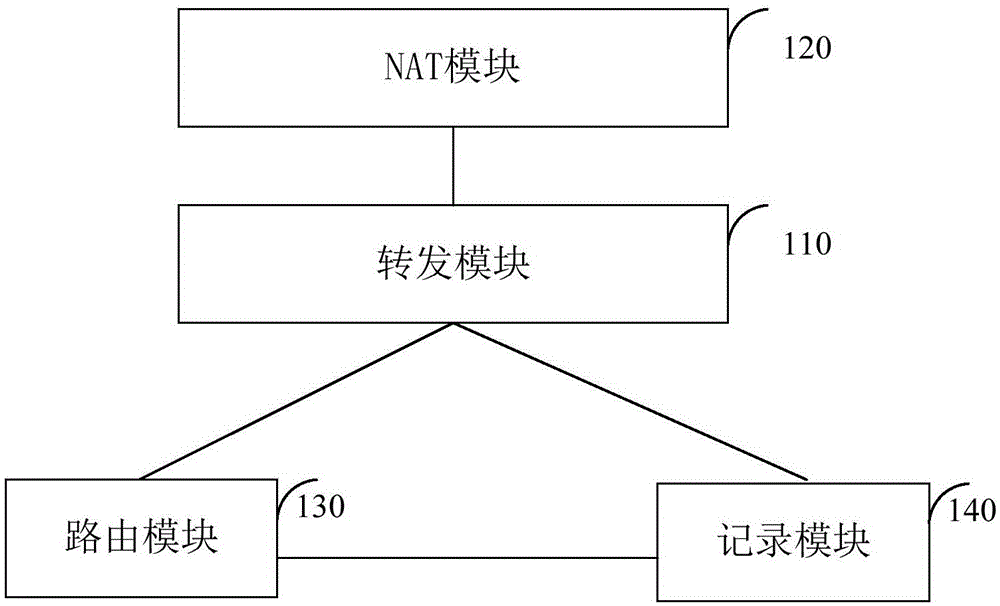
ActiveCN105100300AAvoid CatonAvoid inaccessibilityTransmissionNetwork address translationData connection
The invention relates to the technical field of communications and discloses a method and a device for network address translation. The method comprises the steps as follows: receiving a message in a data connection; judging whether a message exit in the data connection is changed or not; performing address translation to the received message according to the addresses before and after translating in translation information while the message exit in the data connection is not changed; performing rule matching to the received message while the message exit in the data connection is changed and re-determining the translated address of the message, and performing the address translation to the received message by using the determined translated address and transmitting the message whose address is translated. The method and the device of the invention could ensure the address used by the message is the address provided by an operator corresponding to a forwarding exit so as to ensure that the message will not be discarded because the message does not pass test of an original address of an operator server to solve the problem that the message is blocked or unable to access because the message is discarded.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Distributed file system and data access method
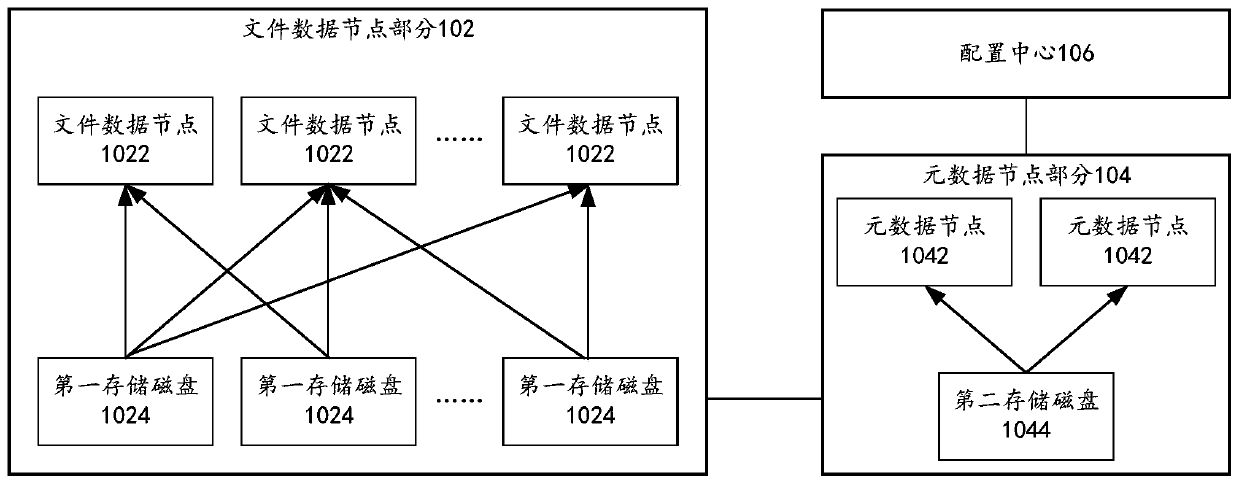
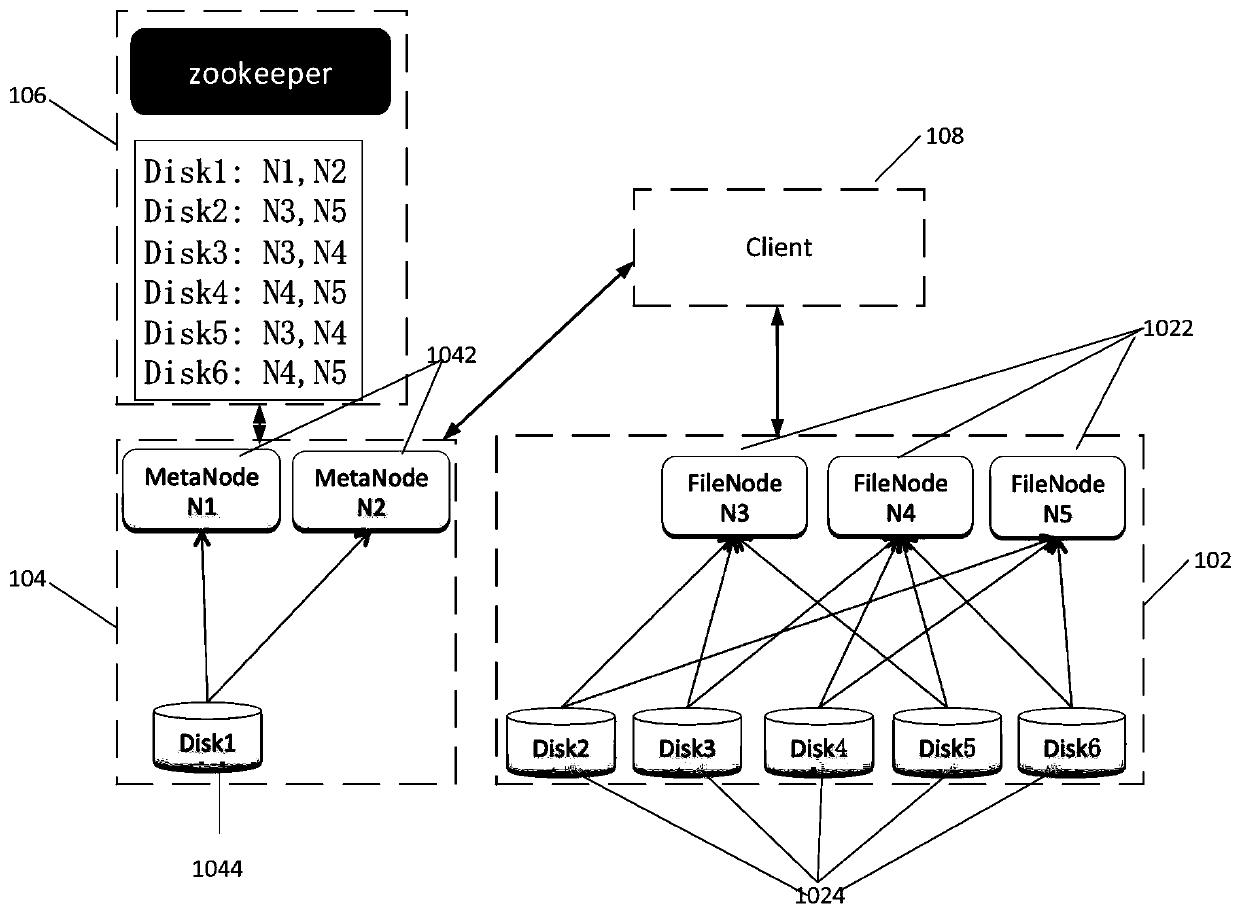
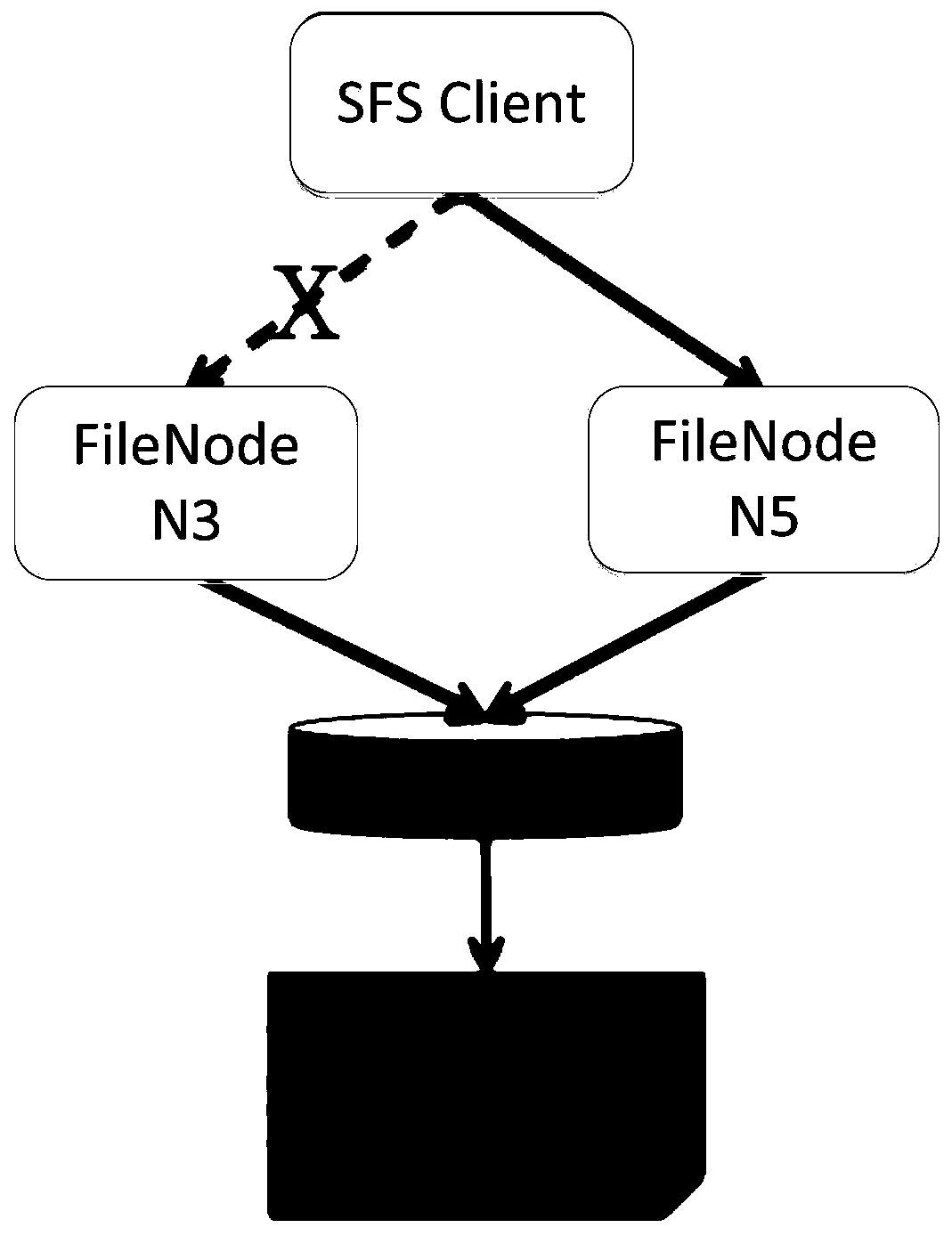
ActiveCN111444157AAvoid inaccessibilityAvoid redundancyFile access structuresSpecial data processing applicationsDistributed File SystemFile system
The embodiment of the invention provides a distributed file system and a data access method, and the distributed file system comprises a file data node, a first storage disk mounted on the file data node, a metadata node, a second storage disk mounted on the metadata node, and a configuration center. The number of the file data nodes and the number of the first storage disks are multiple, each file data node mounts at least one first storage disk, each first storage disk mounts at least two file data nodes, and file data is stored in the first storage disks; the configuration center is used for storing a mounting relationship between the first storage disk and the file data node; the metadata node is used for receiving a file operation request of a client, obtaining metadata of the file from mounted second storage disk or sending the information of the file data node matched with the file operation request obtained from the configuration center to the client, so that the client accesses the first storage disk to perform file operation requested by the file operation request through the first storage disk.
Owner:ALIBABA GRP HLDG LTD
Intelligent device finding method based on feature information
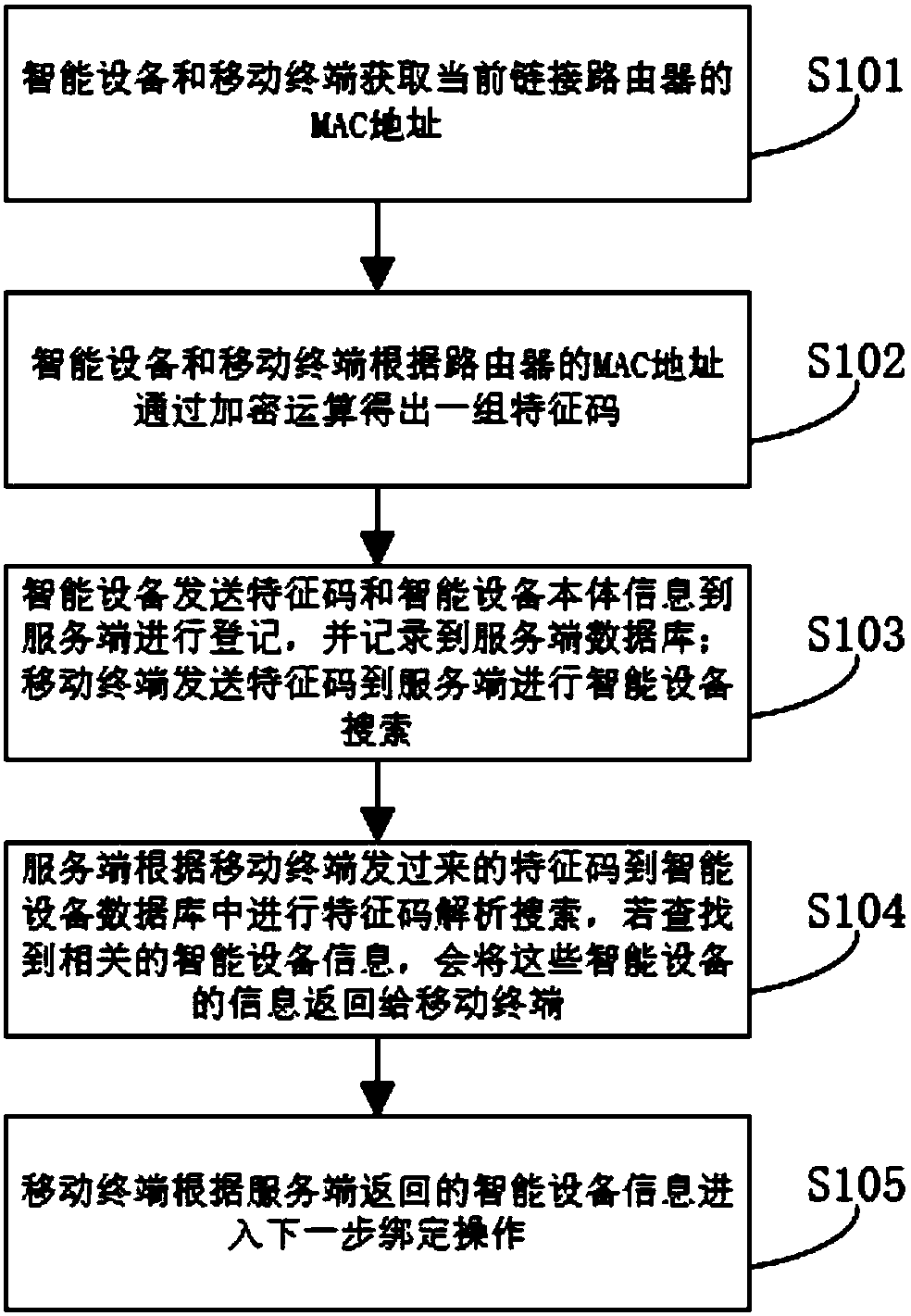
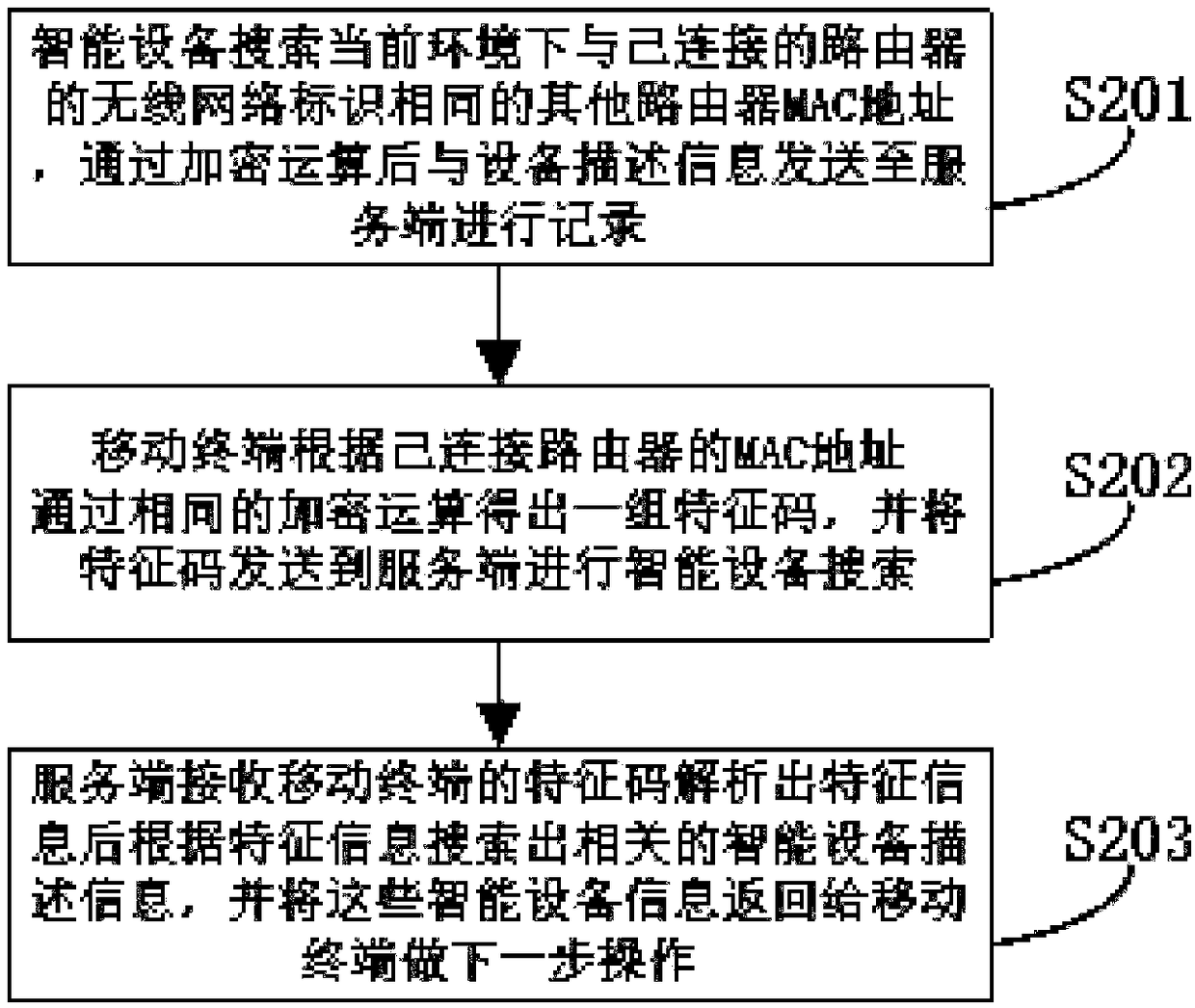
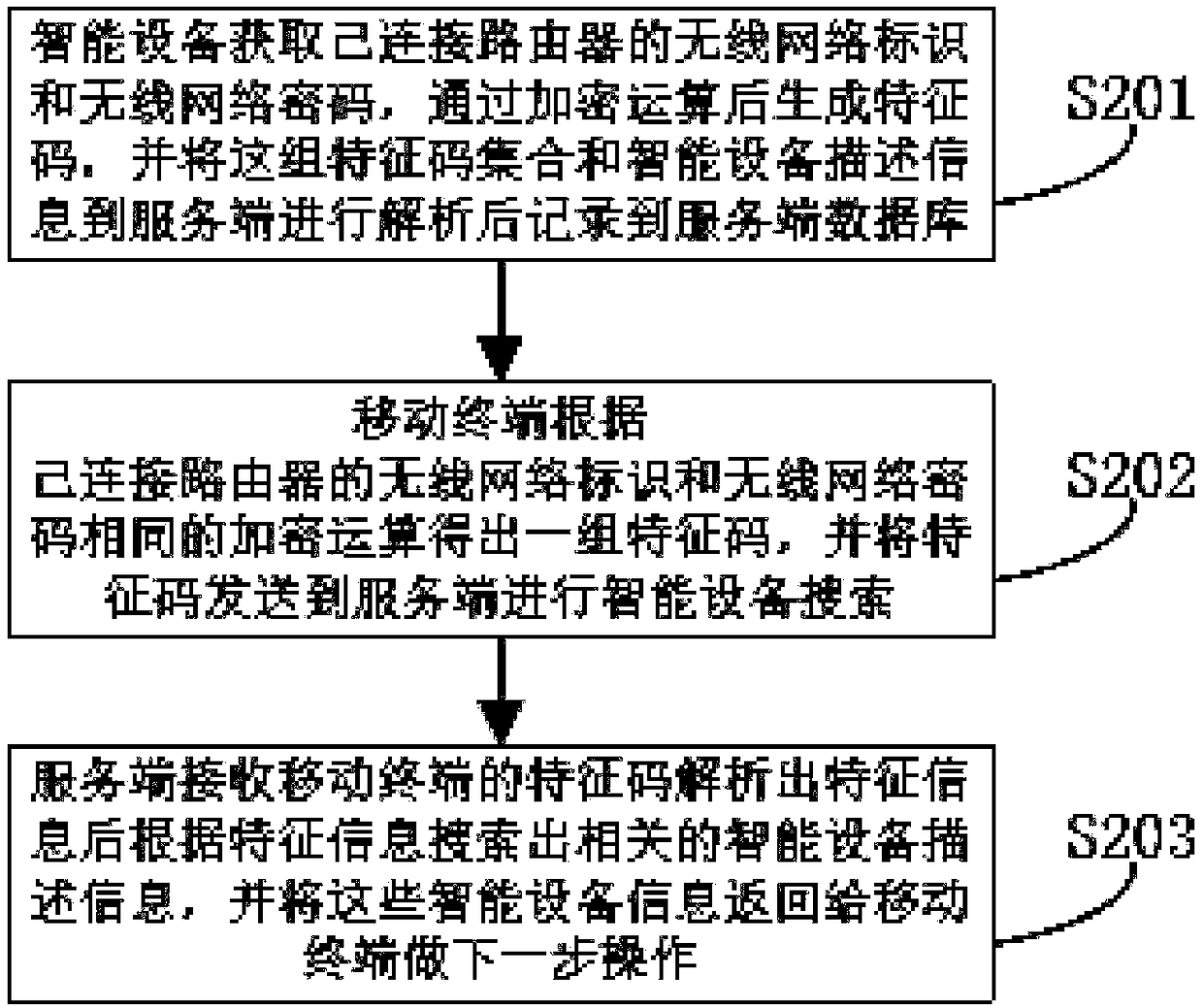
ActiveCN108093390AAvoiding Security Access IssuesAvoid inaccessibilityData switching networksSecurity arrangementThe InternetComputer terminal
The technical scheme of the invention comprises an intelligent device finding method. The method comprises the steps that an intelligent device and a mobile terminal are disposed in the same local area network; the intelligent device sends the device description information and the feature information of the local area network to the database of the service terminal for storage; the mobile terminal sends the the feature information of the local area network to the database of the service terminal for storage; the service terminal searches the intelligent device information consistent with thedevice description information and the feature information of the local area network, which are sent by the intelligent device in the database of the service terminal, and returns the intelligent device information to the mobile terminal; the mobile terminal is connected to the intelligent device. The invention is advantageous in that after the intelligent device is successfully connected to the Internet, the intelligent device determines that it is in the same local area network with the mobile terminal through the feature information of the local area network, so that the safety access problem before the intelligent device is bound can be avoided; by means of HTTP network protocol, the initial access problem of the intelligent device of the local area network can be simplified, and the problem that the intelligent device cannot be accessed due to the limit of a router can be avoided.
Owner:珠海多士科技有限公司
Construction waste crushing device
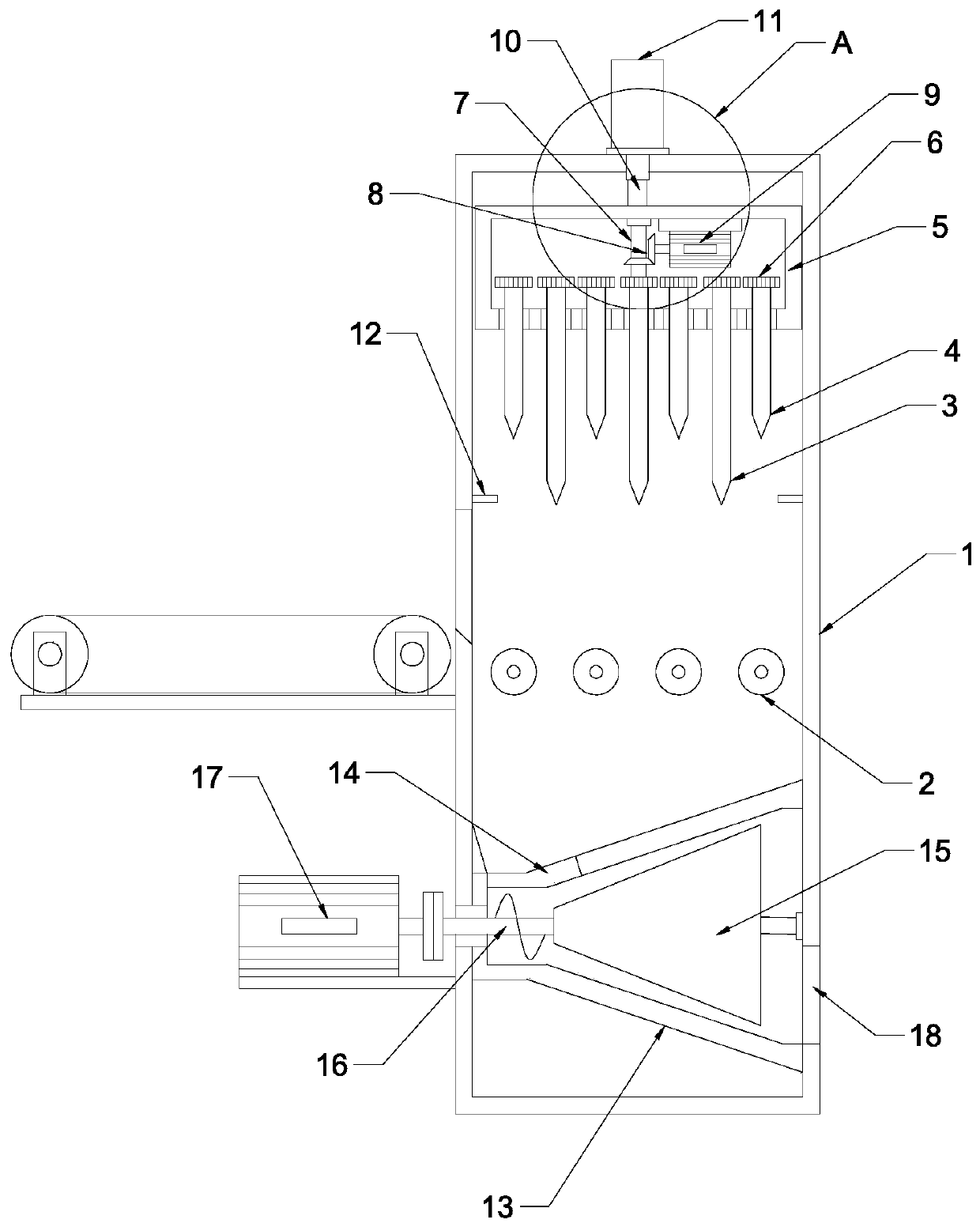
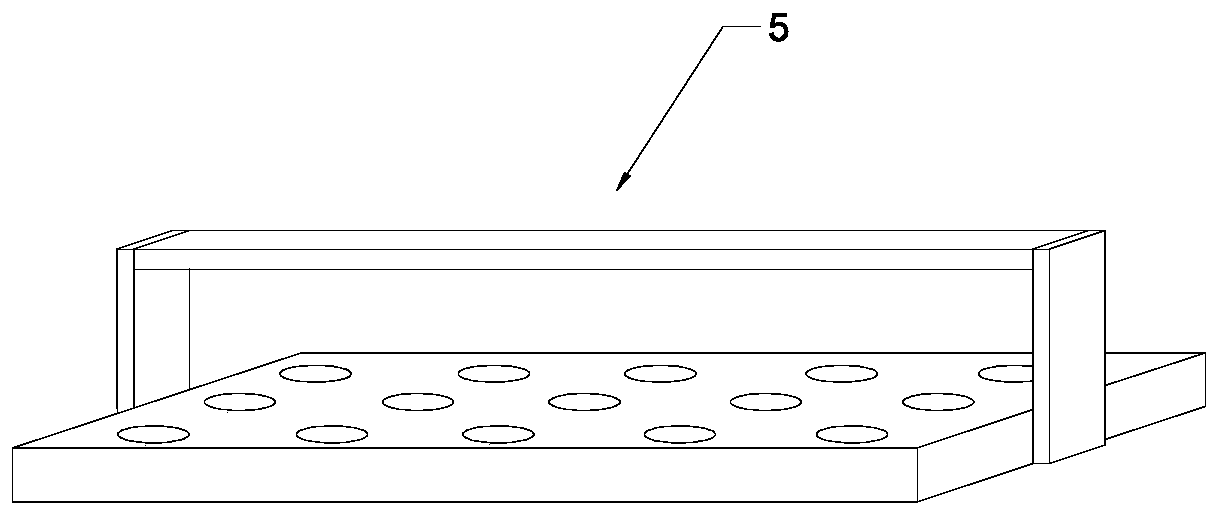
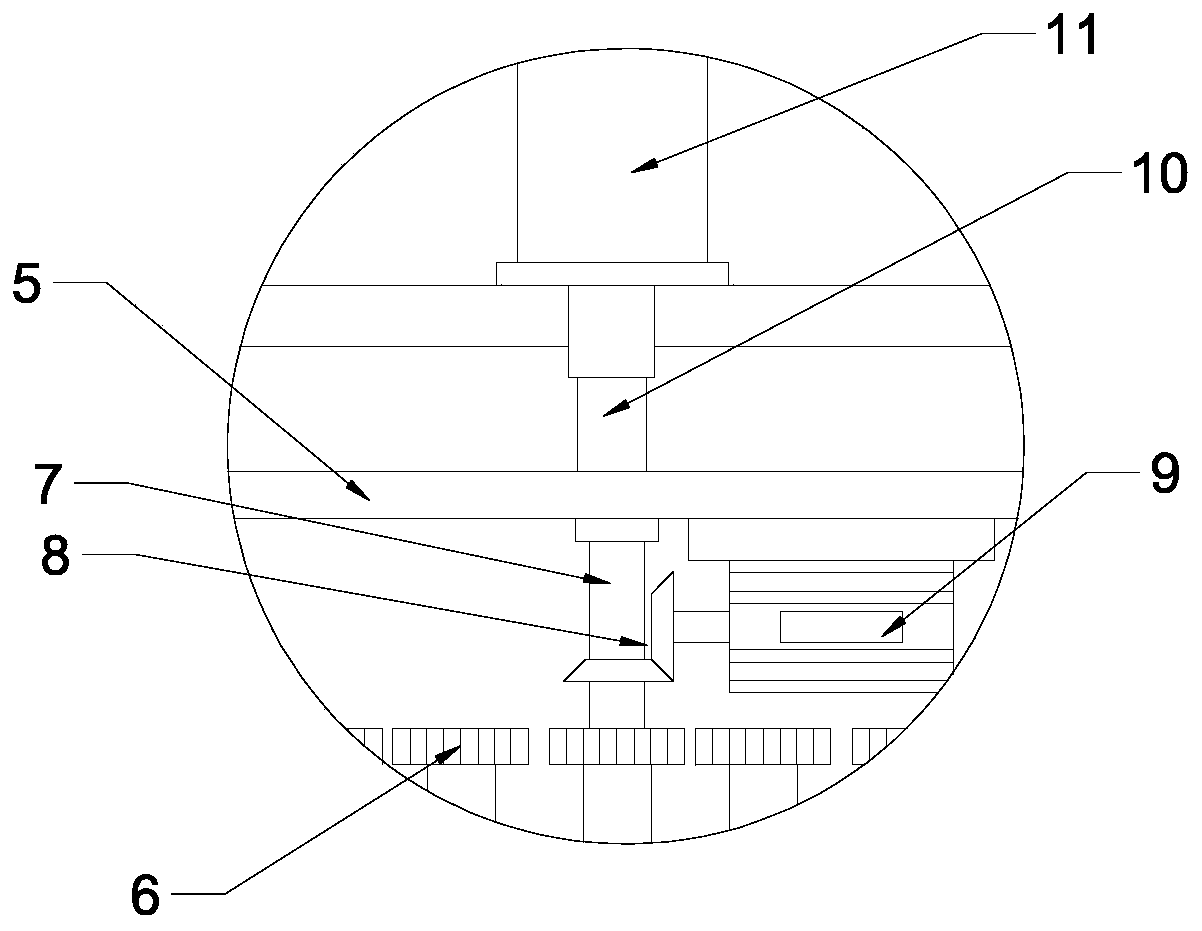
InactiveCN110340108APromote fragmentationAvoid inaccessibilityConstruction waste recoverySolid waste disposalStructural engineeringDrill pipe
The invention discloses a construction waste crushing device. The device comprises a crushing box, wherein a plurality of groups of crushing rollers which are longitudinally arranged at equal intervals are arranged in the crushing box, short drill rods and long drill rods which are uniformly distributed are arranged above the crushing rollers, and the short drill rods and the long drill rods are distributed at intervals. According to the device, the short drill rods, the long drill rods, transmission teeth and a sliding frame are arranged, the short drill rods and the long drill rods can moveup and down while rotating, concrete blocks are drilled and crushed, the problem that the concrete blocks cannot enter into the spaces between the crushing rollers is avoided while accelerating concrete crushing, so that the crushing efficiency is improved; and a grinding cone and a grinding cylinder are arranged, so that the concrete blocks are further granulated, and the subsequent recycling isfacilitated.
Owner:李星来
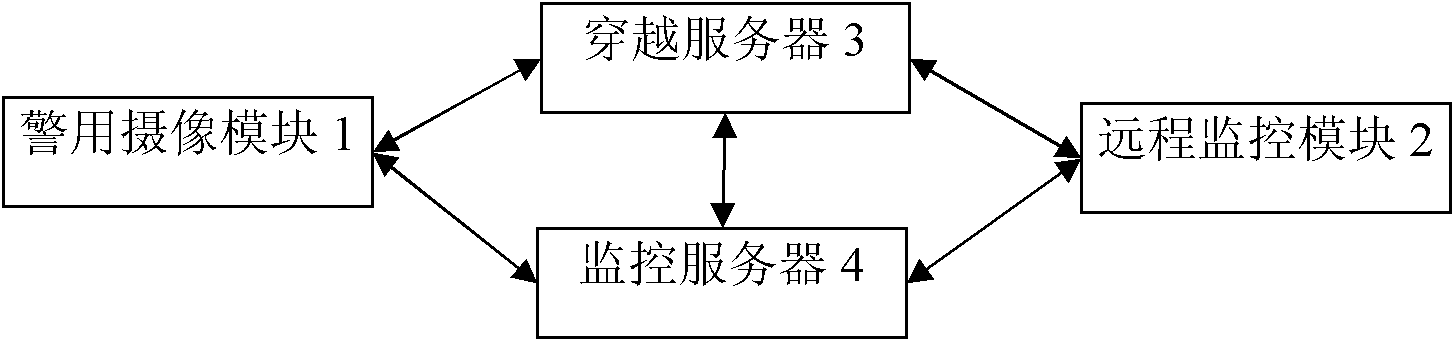
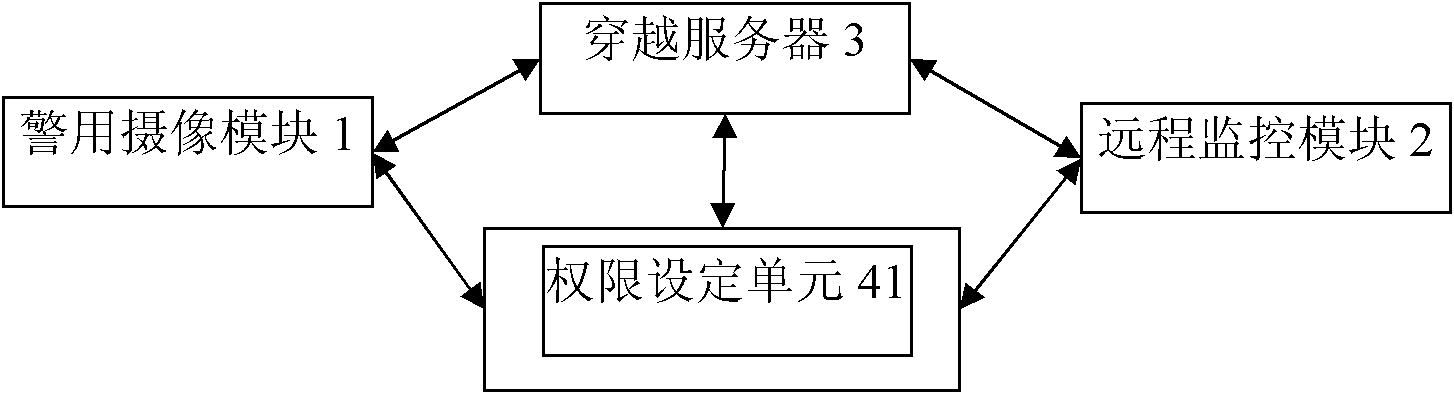
Police network monitoring system
ActiveCN102647435AImprove utilization efficiencyEfficient use ofClosed circuit television systemsTransmissionPrivacy protectionCamera module
The invention relates to a police network monitoring system, which comprises a police camera module and a remote monitoring module, wherein the police network monitoring system also comprises a traversal server, which is respectively connected with the police camera module and the remote monitoring module, and the police camera module is connected with the remote monitoring module in a peer-to-peer manner. The police network monitoring system integrates the P2P (Peer to Peer) technology with the network police recorder, and is easy to set and convenient to access, meanwhile, privacy can be protected, the system can effectively utilize network resources, increase the network utilization efficiency, save social resources and overcome the defects of the conventional network police recorder, i.e. complex setting, inaccessibility and no privacy protection.
Owner:SHENZHEN GOSPELL SMARTHOME ELECTRONICS
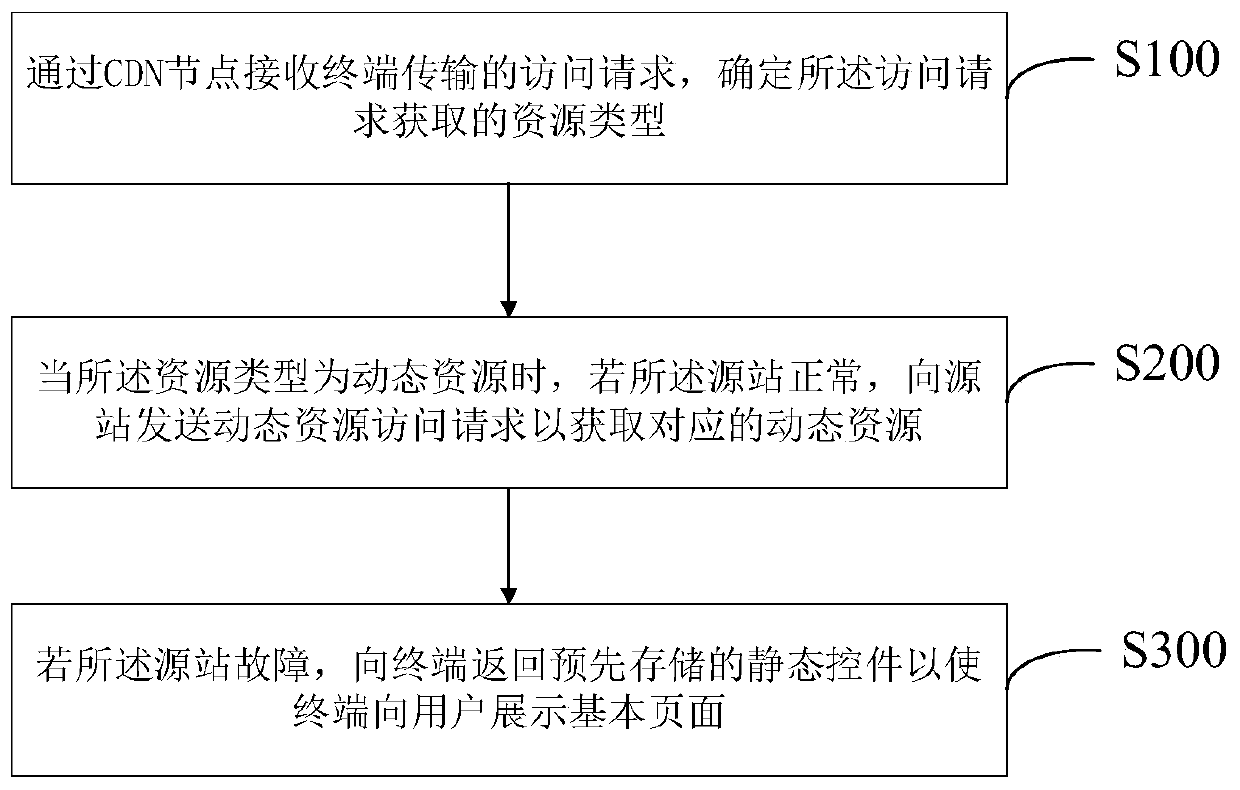
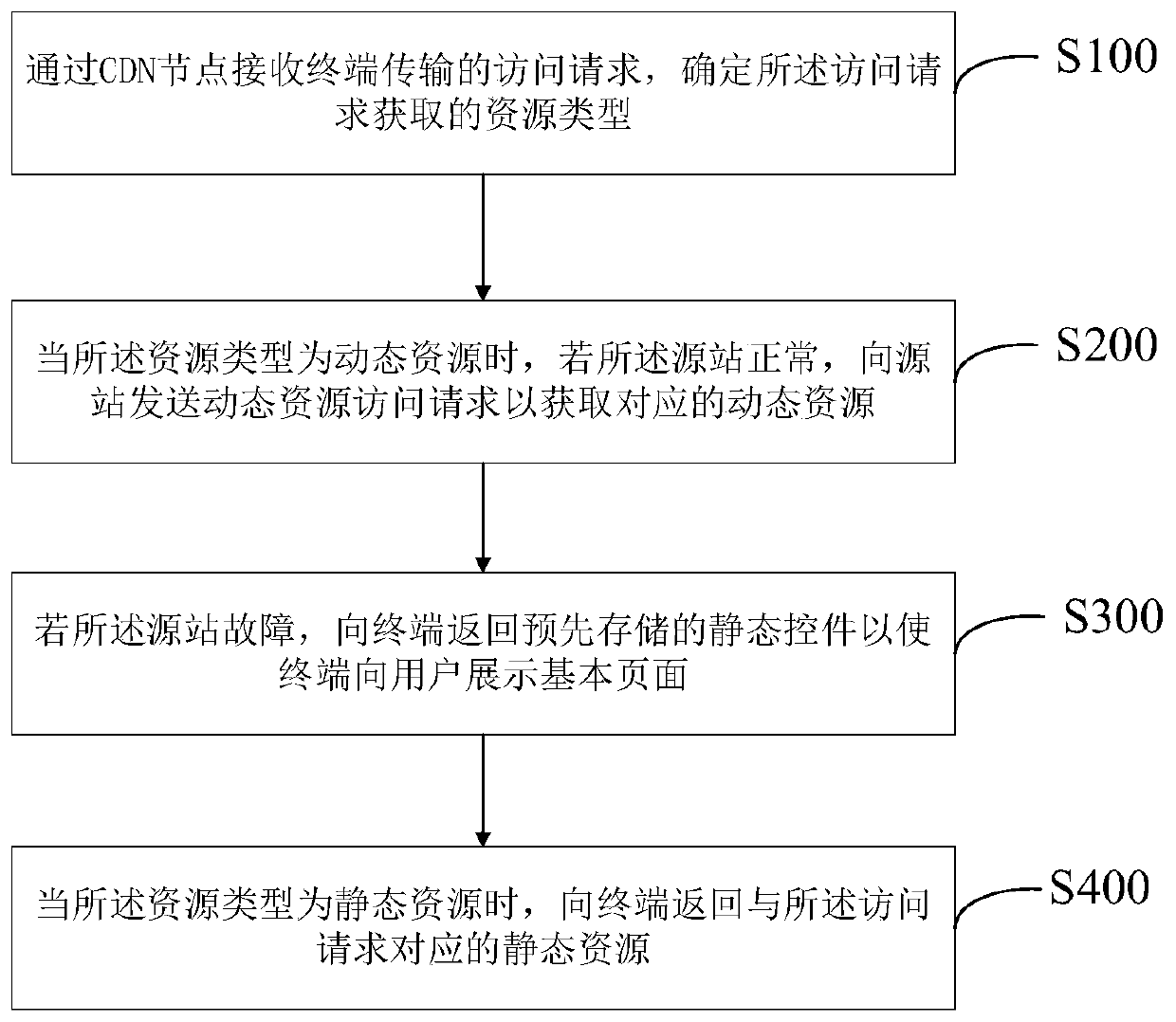
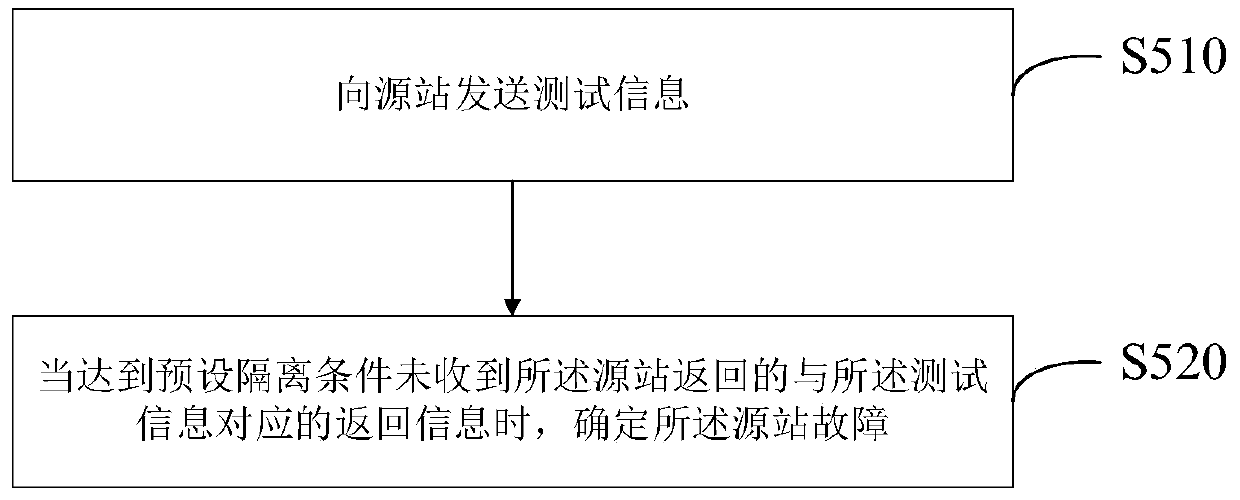
CDN node emergency processing method and system for source station fault
PendingCN111355612AReduce experience impactAvoid inaccessibilityData switching networksComputer networkTelecommunications
The invention provides a CDN node emergency processing method and system for a source station fault, and the method comprises the steps: receiving an access request transmitted by a terminal through aCDN node, and determining a resource type obtained by the access request; when the resource type is a dynamic resource, if the source station is normal, sending a dynamic resource access request to the source station to obtain the corresponding dynamic resource; and if the source station fails, returning a pre-stored static control to the terminal to enable the terminal to display a basic page toa user. The invention can provide an automatic detection takeover and recovery strategy of the CDN node when the source station fails, effectively control the service influence range and improve thecustomer experience.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Content output apparatus, content playback system, content output method, and program
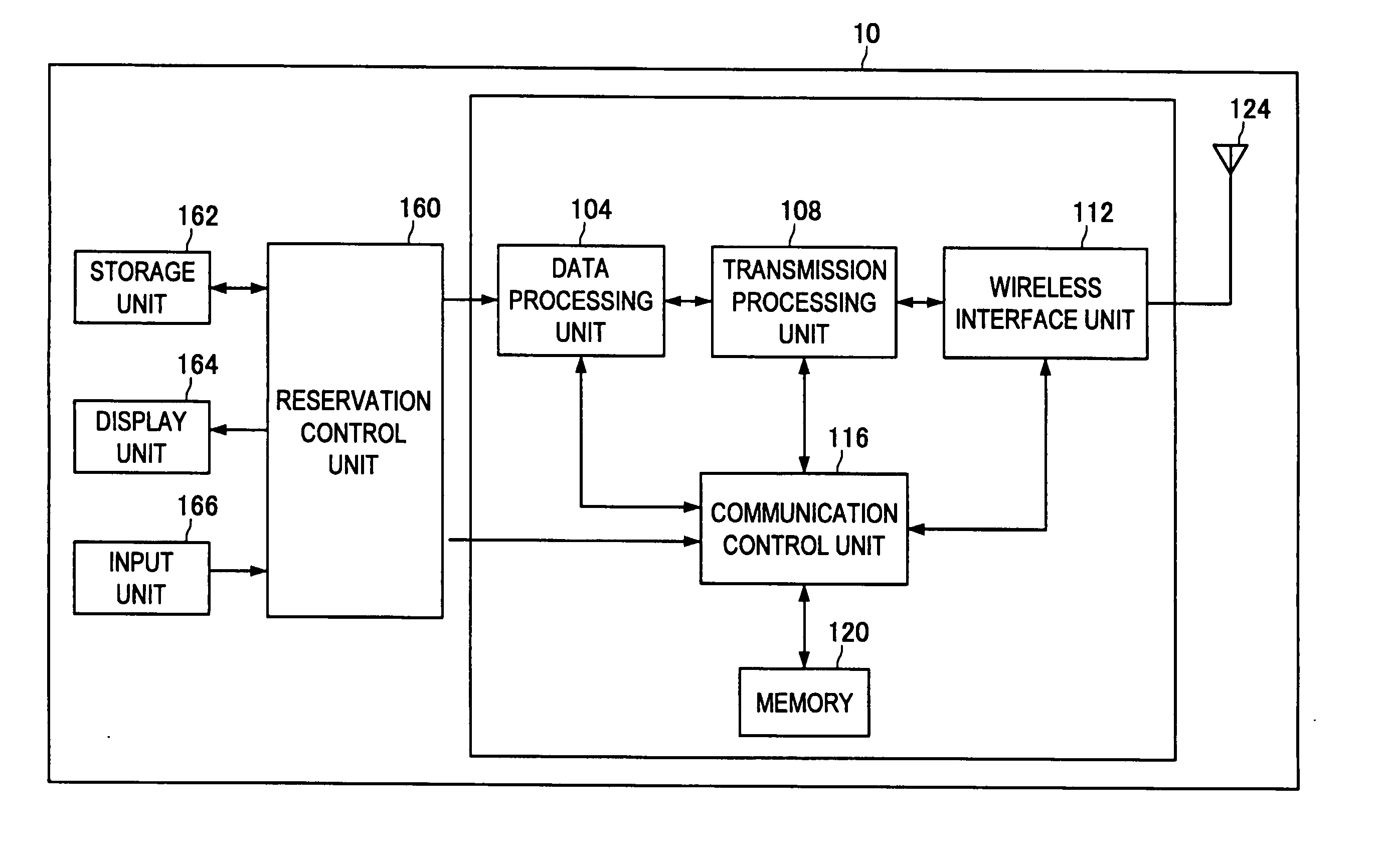
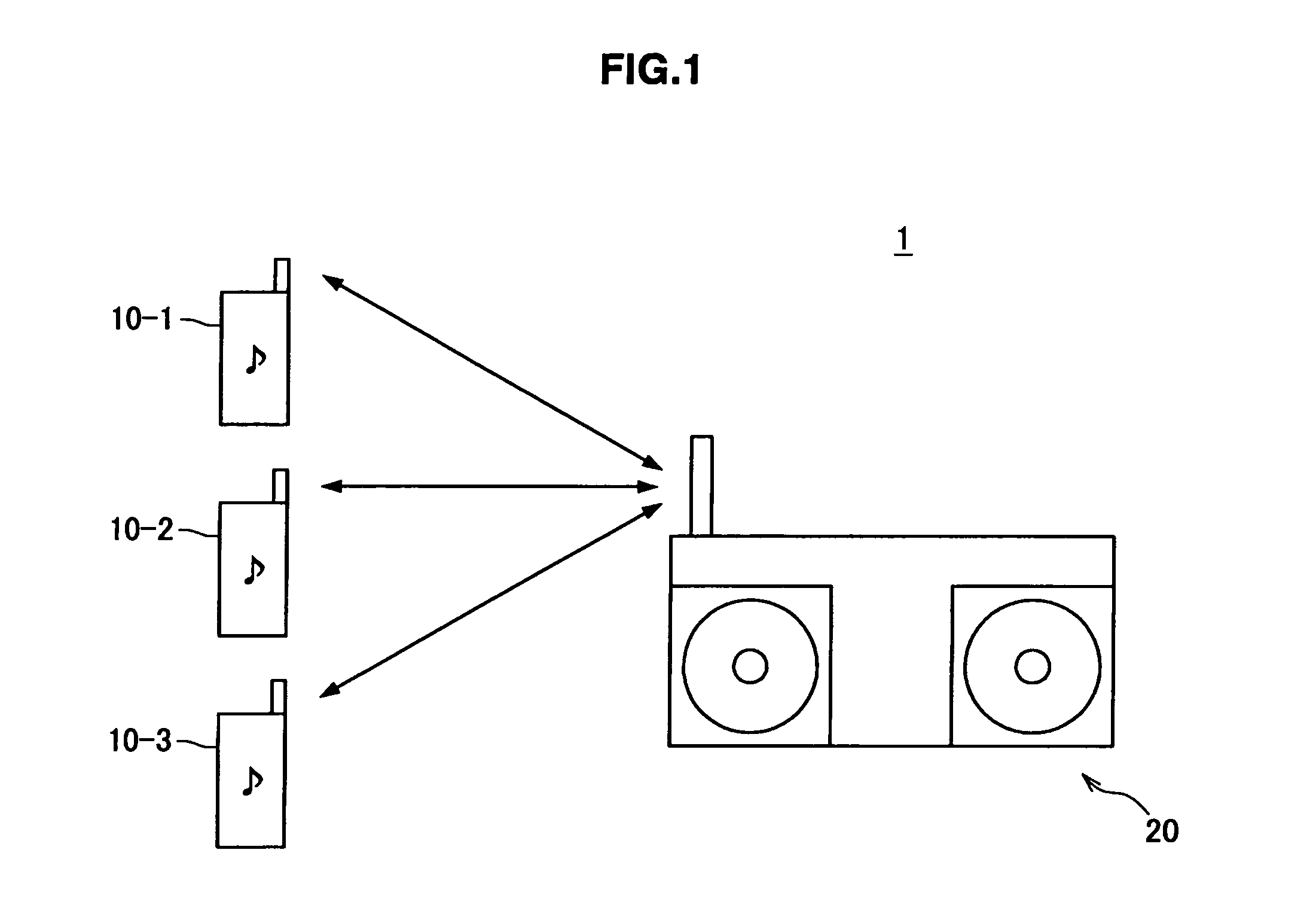
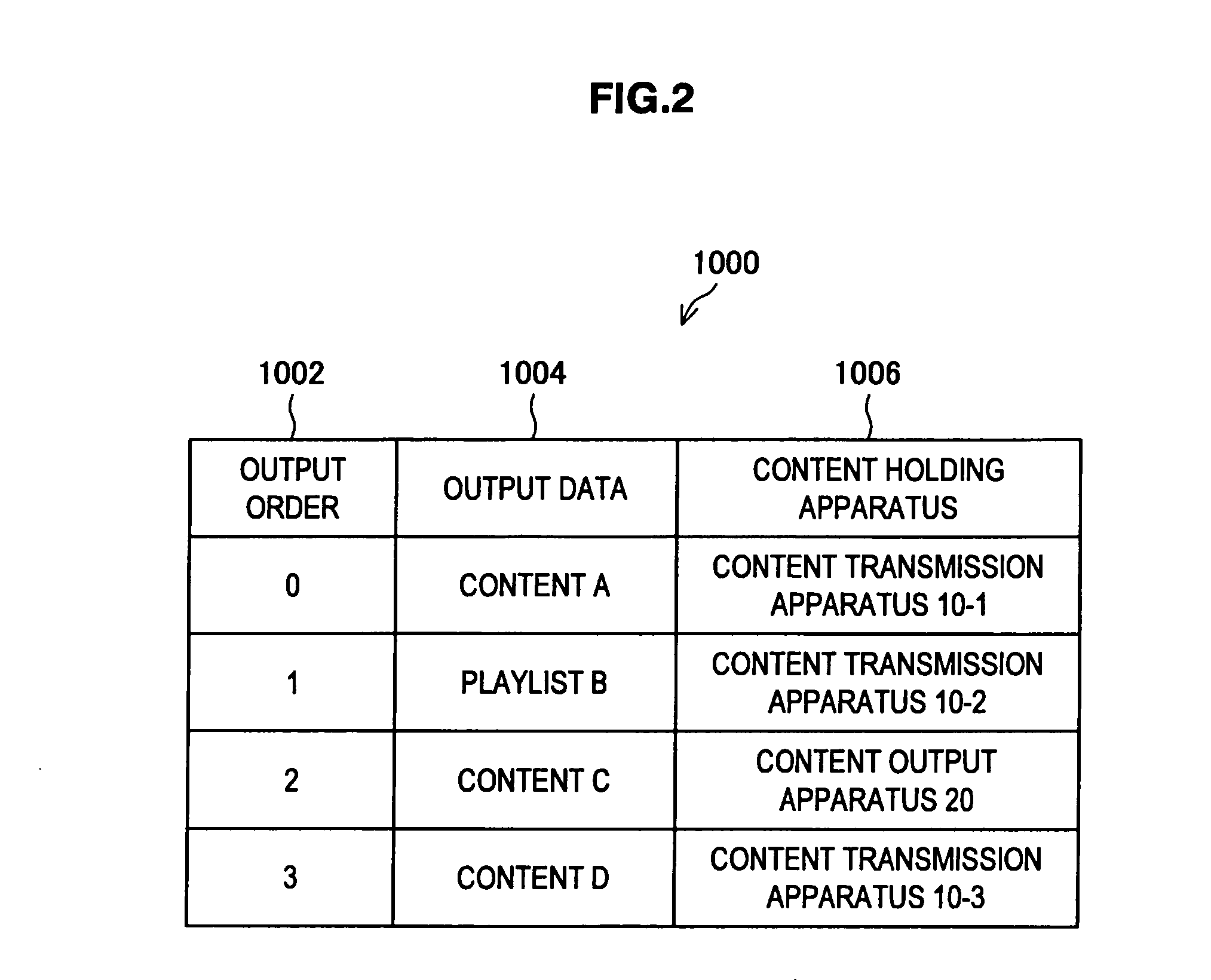
InactiveUS20110222474A1Avoid inaccessibilityAvoid playingDigital data information retrievalWireless commuication servicesCommunication unitCommunication control
There is provided a content output apparatus including a wireless communication unit for transmitting an acquisition request for content data based on a position of the content data in an output order, a communication control unit for investigating whether or not acquisition of the content data is possible, before transmitting the acquisition request, and an output control unit for rearranging the output order according to a result of the investigation.
Owner:SONY CORP
Security analysis method for firmware of embedded equipment
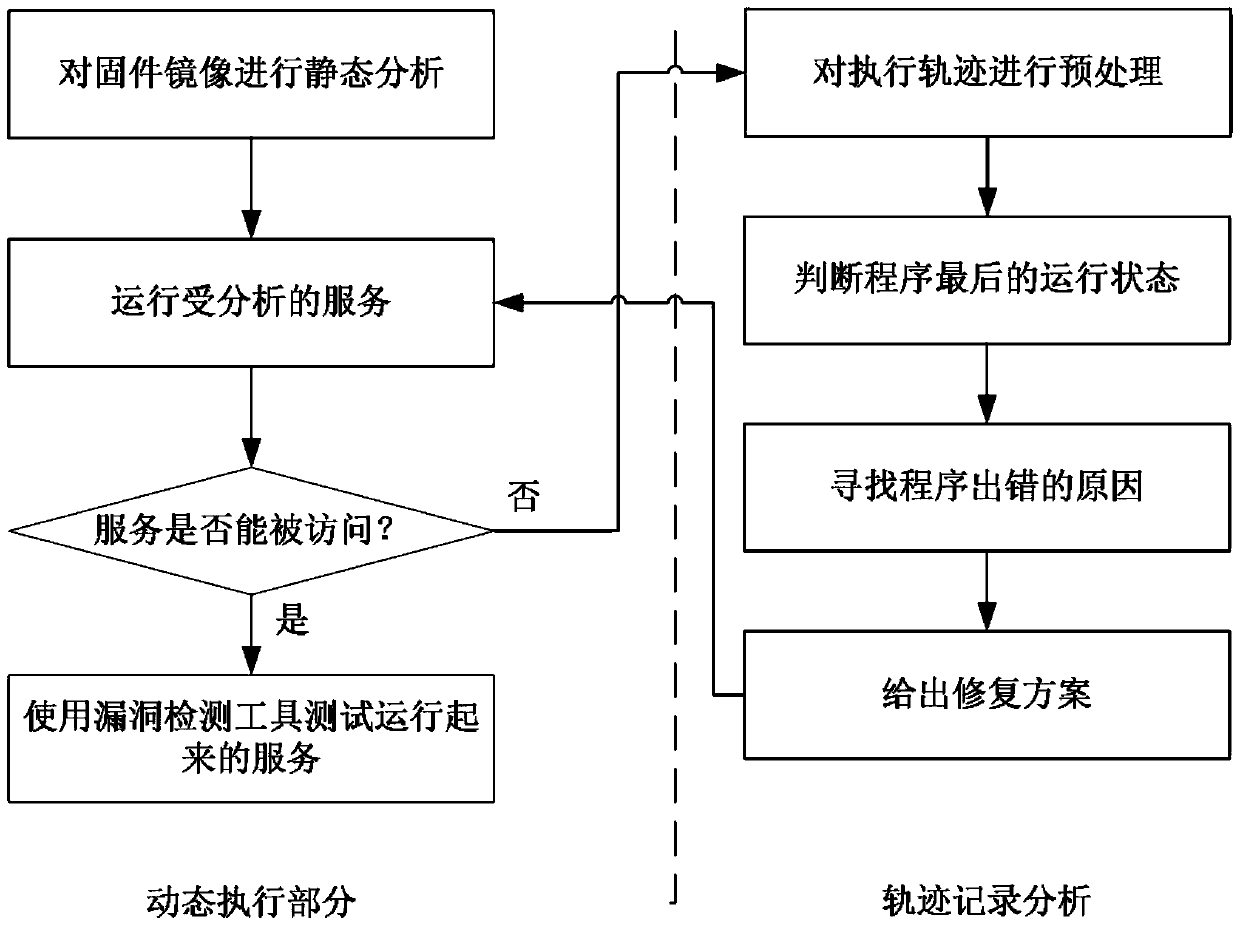
ActiveCN111428233AAvoid inaccessibilityPromote repairPlatform integrity maintainanceFile systemEngineering
The invention discloses a security analysis method for firmware of embedded equipment, which comprises the following steps: 1, carrying out static analysis on a file system of the firmware of the embedded equipment, searching parameters and configuration files used for starting a service daemon, and packaging the file system of the firmware of the embedded equipment into a disk mirror image of a virtual machine; 2, starting a service daemon by utilizing the searched parameters and the configuration file, and recording an execution track of the service daemon; if yes, executing the step 5, otherwise, executing the step 3; 3, searching for a reason why the service daemon cannot be started according to the recorded execution track of the service daemon; 4, repairing the service daemon according to the searched reason why the service daemon cannot be started, and executing the step 2 after repairing; and 5, testing the started network service. According to the method, more types of embedded equipment firmware are supported, and various pieces of operation semantic information in the firmware program running process are obtained for safety analysis.
Owner:XIDIAN UNIV
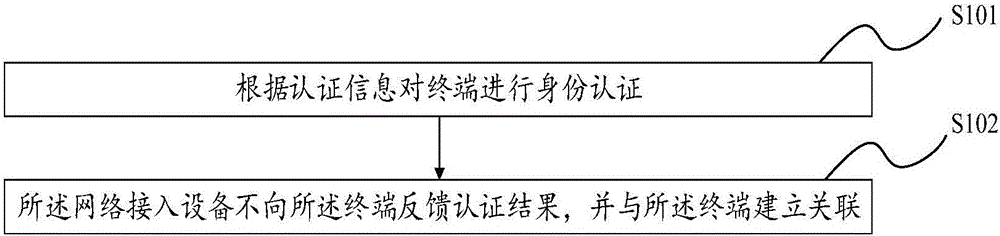
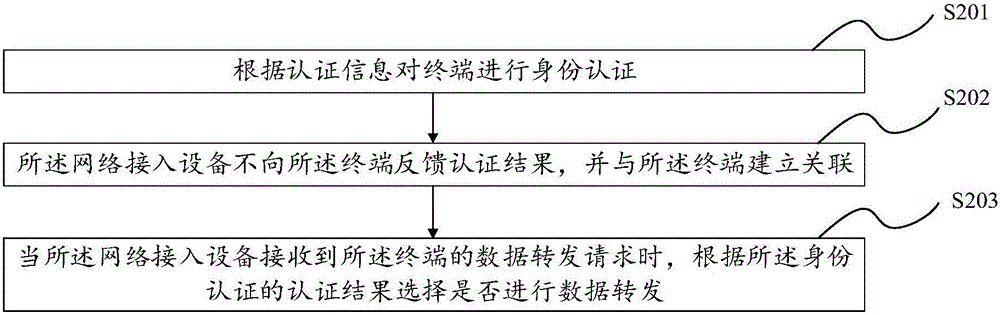
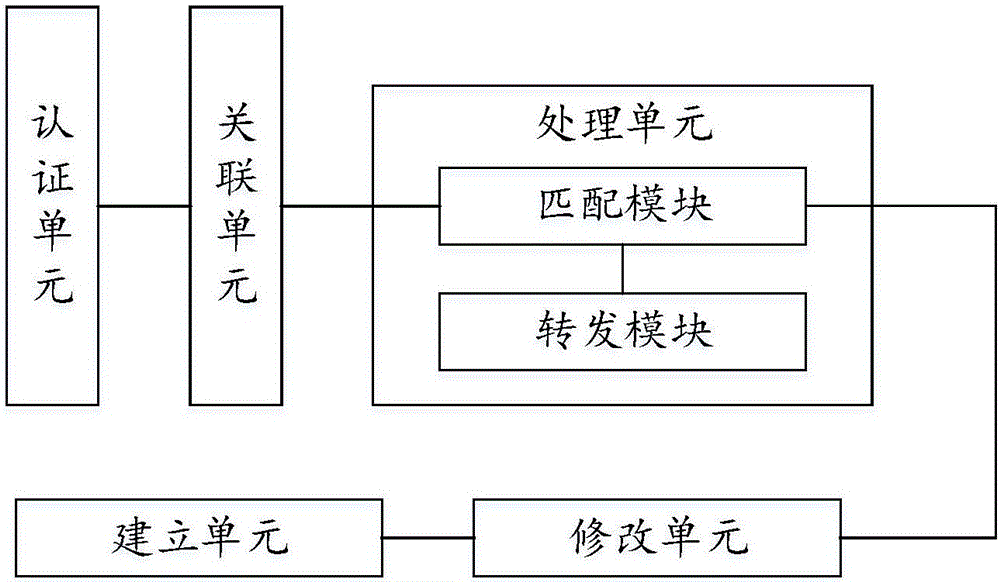
Network authentication method, access control method and network access equipment
The invention discloses a network authentication method, an access control method and network access equipment for implementing the network authentication method. The network authentication method comprises: after identity authentication is performed on a terminal according to authentication information, the network access equipment does not feed back an authentication result to the terminal, but is associated with the terminal. Through the network authentication method, the access control method and the network access equipment, after the authentication information of the terminal is accomplished, the network access equipment does not feed back the corresponding authentication result, but is directly associated with the terminal, so that a connected user does not know whether the access succeeds or not, an invalid user cannot confirm whether an accurate password is decrypted or not, and then the invalid user can be prevented from sending various combined passwords to the network access equipment to continue verification and finally decrypt the password.
Owner:云账户数字科技(天津)有限公司
Method for expanding server load balancing network card device
ActiveCN107046469APrecise positioningReduce maintenance costsData switching detailsBalancing networkNetwork interface controller
The invention discloses a method for expanding a server load balancing network card device. The identification rule of a network card is adjusted to guide the operation and maintenance personnel to accurately locate the network card device and quickly add a new network card device to the load balancing configuration when the network card is expanded, therefore the maintenance cost of the enterprise IT is reduced, the situations that the server system is faulty and the service system cannot be accessed after the network card is added, and that the network bandwidth is reduced and the like can be avoided, the operation and maintenance risks of the enterprise IT system are reduced, the network card bandwidth of the server can be effectively increased, and the pause maintenance time of the server is shortened, thereby reducing the pause maintenance time of the enterprise IT system.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
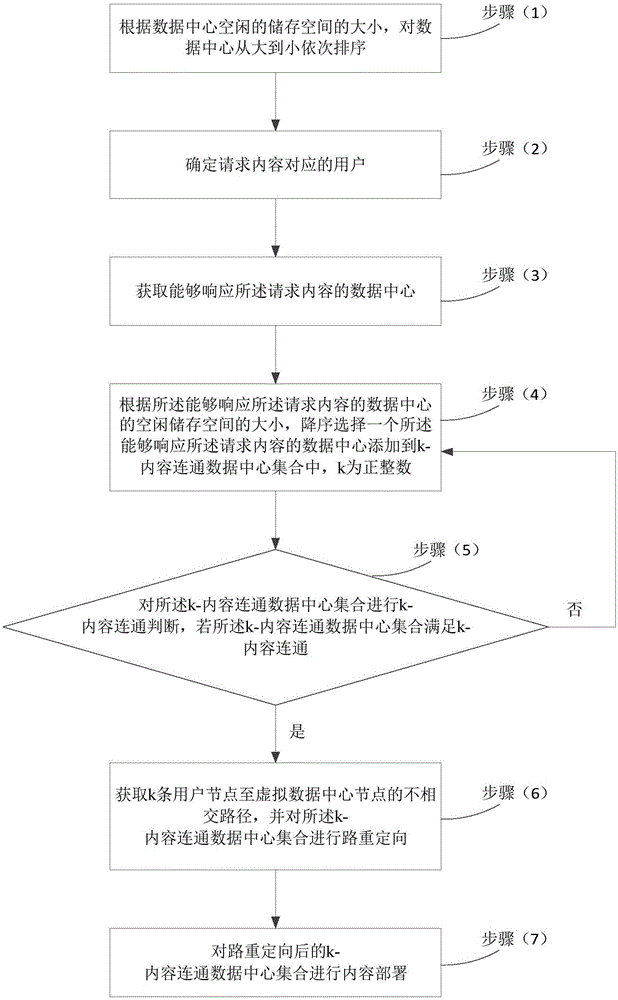
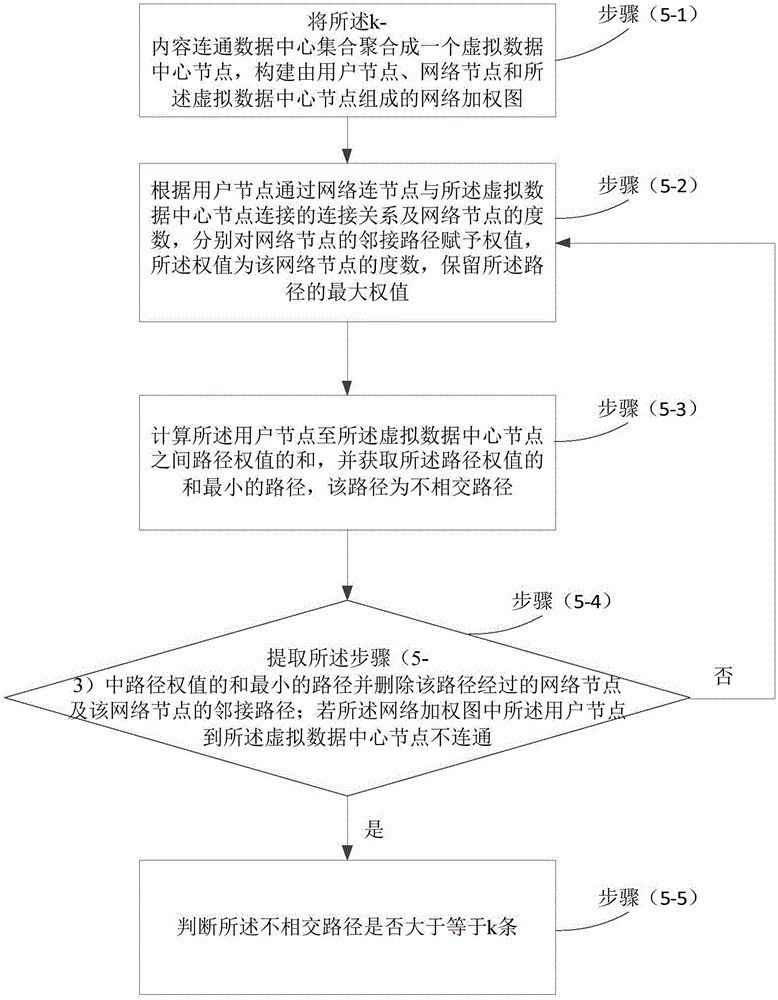
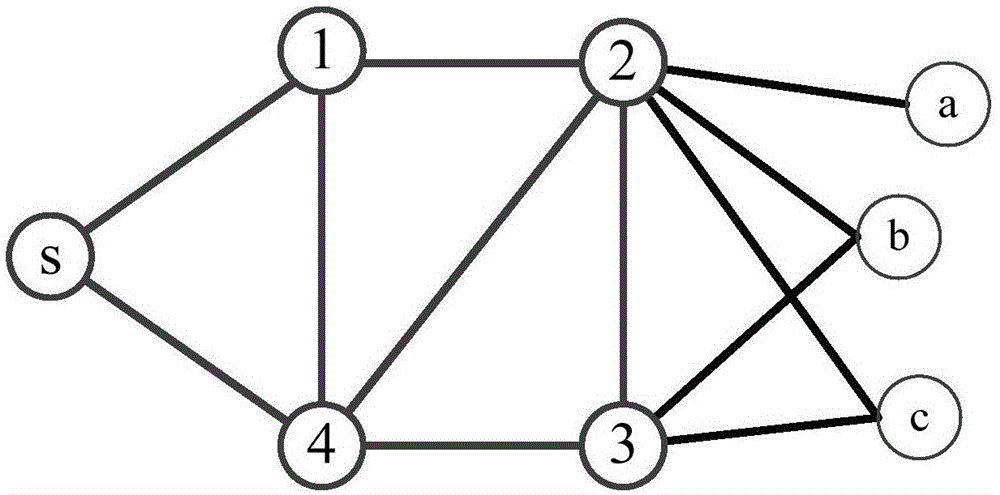
Realization method for content connection in data center network
The invention relates to a realization method for content connection in a data center network. The method comprises the steps of determining users corresponding to request contents; obtaining data centers capable of responding to the request contents; selecting one data center capable of responding to the request contents in a descending mode, according to sizes of idle storage spaces of the data centers capable of responding to the request contents, adding the selected data center to a k-content connection data center set, wherein the k is a positive integer; carrying out k-content connection judgment on the k-content connection data center set; obtaining k non-intersected paths according to the k-content connection data center set and carrying out path redirection on the k-content connection data center set; and carrying out content deployment on the k-content connection data center set. According to the method provided by the invention, the data center is reasonably selected for content deployment according to the k non-intersected paths from point to point and the request contents of the user, and the connection from the users to the contents is ensured under the multi-fault condition.
Owner:CHINA ELECTRIC POWER RES INST +1
Access service processing method and device, storage medium and electronic equipment
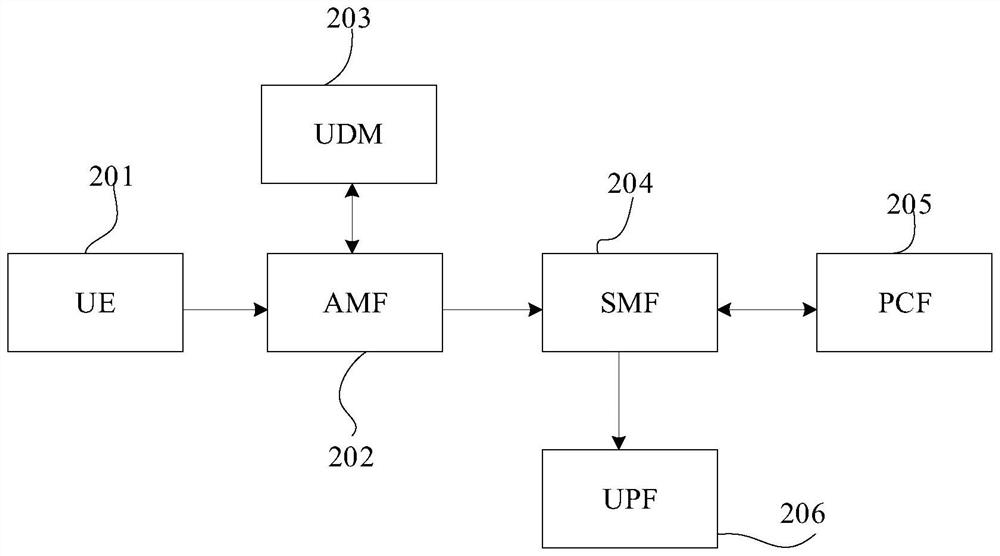
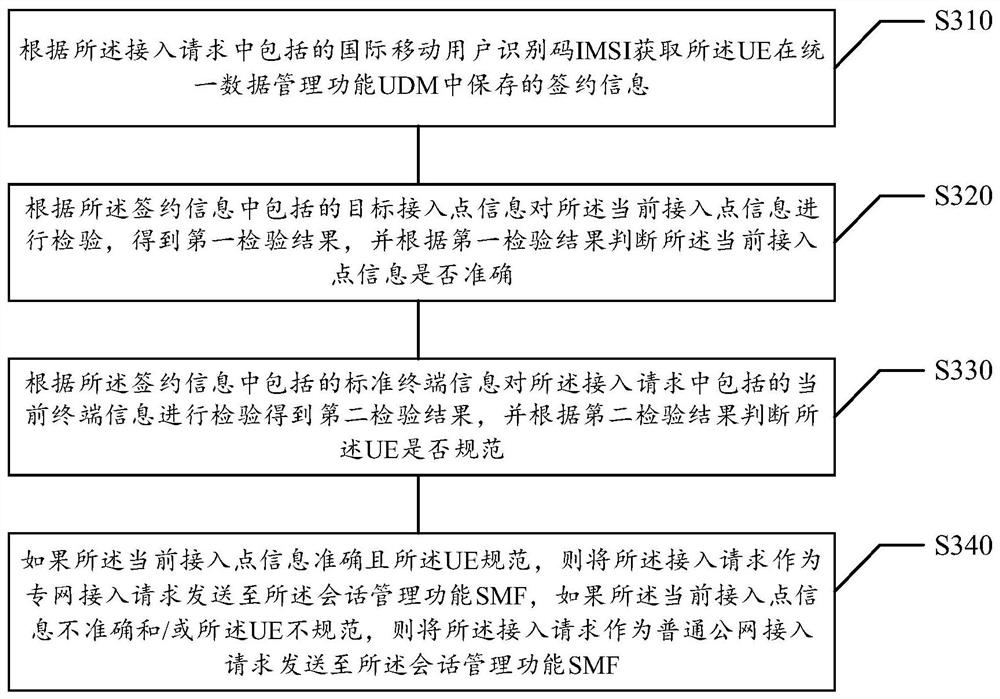
ActiveCN113473417AImprove experienceRealize multi-network access functionService provisioningNetwork data managementInformation repositoryUser equipment
The invention relates to an access service processing method and device, a storage medium and electronic equipment, and relates to the technical field of 5G communication, and the method comprises the steps that an AMF receives an access request sent by user equipment UE, and forwards the access request to an SMF; the SMF generates a policy acquisition request according to current access point information and an international mobile subscriber identity (IMSI) included in the access request, and sends the policy acquisition request to the PCF; the PCF queries a preset MDN and policy binding online information base according to current access point information and IMSI included in the policy acquisition request to obtain an access policy of the UE, and sends the access policy to the SMF; and the SMF matches an access rule for the UE according to the access strategy and sends the access rule and the access request to the UPF, and the UPF processes an access service included in the access request according to the access rule. The security of the user information is improved.
Owner:CHINA TELECOM CORP LTD
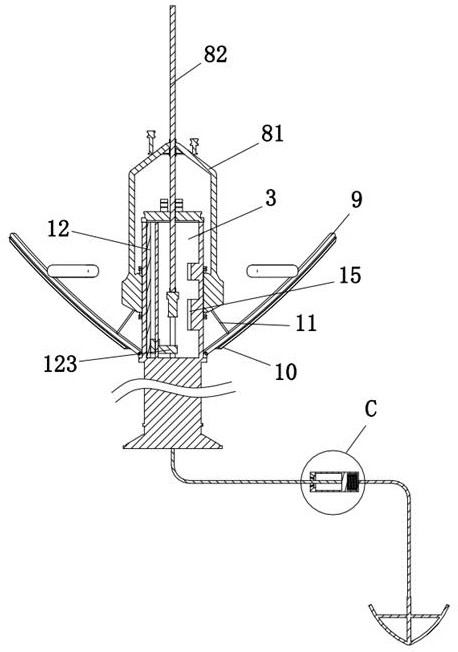
Marine environmental monitoring buoy mechanism
The invention discloses a buoy mechanism for marine environment monitoring, relates to the technical field of buoys, and includes a buoy body and a monitoring mechanism. An installation chamber is arranged inside the buoy body, a power generation component is arranged in the installation chamber, and an electric storage structure is arranged at the lower end of the buoy body. The lower end of the power storage structure is provided with a fixed rope, the lower end of the fixed rope is provided with a fixed anchor, the outside of the buoy body is provided with a floating block, the power generation component and the floating block are provided with a connecting assembly, and the lower end of the buoy body is provided with an anti-collision assembly , the anti-collision components include anti-collision strips, the side of the anti-collision strips away from the buoy body is provided with elastic floating strips, elastic ropes are provided between each anti-collision strip and the floating block, and recovery auxiliary components are provided in the installation cavity, fixed A buffer component is arranged on the rope. The invention can effectively improve the anti-collision effect of the buoy, and the retractable setting of the anti-collision component will not affect the recovery work of the buoy.
Owner:海域海岛环境科学研究院(烟台)有限公司 +3
IPV6 network address management method and system
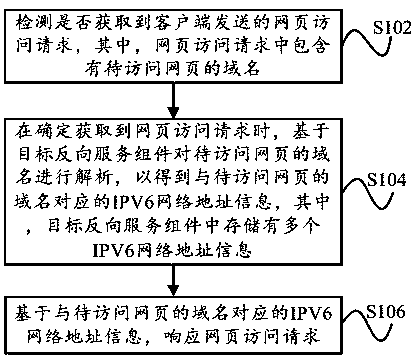
PendingCN110191205AAvoid inaccessibilityImprove access efficiencyTransmissionDomain nameNetwork addressing
The invention provides an IPV6 network address management method and system, and the method comprises the steps: detecting whether a webpage access request sent by a client is obtained, and enabling the webpage access request to comprise the domain name of a to-be-accessed webpage; when it is determined that the webpage access request is obtained, analyzing the domain name of the webpage to be accessed based on a target reverse service component to obtain IPV6 network address information corresponding to the domain name of the webpage to be accessed, and storing multiple pieces of IPV6 networkaddress information in the target reverse service component; and responding to the webpage access request based on the IPV6 network address information corresponding to the domain name of the webpageto be accessed. Through the technical scheme of the invention, the resolution speed of the IPV6 network domain name is ensured, the IPV6 network access efficiency of a user is improved, and the use experience of the user is improved.
Owner:ZHENGZHOU GLACIER NETWORK TECH CO LTD
Computer web page management system
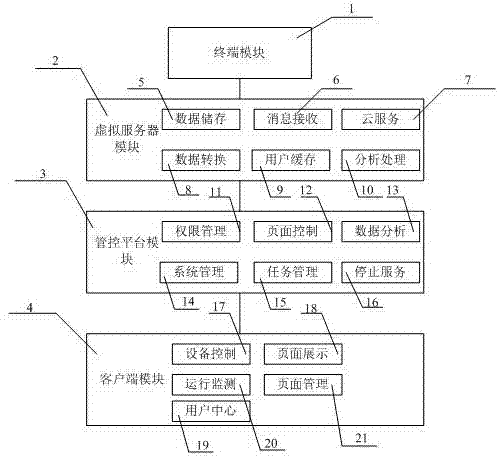
InactiveCN107483266ASolve management difficultiesImprove system managementWebsite content managementData switching networksSystems managementComputer terminal
The invention discloses a computer web page management system, comprising a terminal module, a virtual server module, a control platform module and a client module, wherein the terminal module is connected with the virtual server module, the virtual server module is connected with the control platform module, and the control platform module is connected with the client module; the virtual server module includes data storage, message reception, cloud services, data conversion, user caching and analysis processing; the control platform module includes authority management, page control, data analysis, system management, task management and stop services; and the client module includes equipment control, page display, user centers, operation monitoring and page management. According to the web page management system disclosed by the invention, the management of web pages can be implemented through a control platform, the problem of difficult web page management can be effectively solved, the functions of system management, page control and the like can be increased, the web pages can be timely repaired in case of failures, and the problem that the web pages cannot be accessed can be avoided.
Owner:苏州千阙传媒有限公司
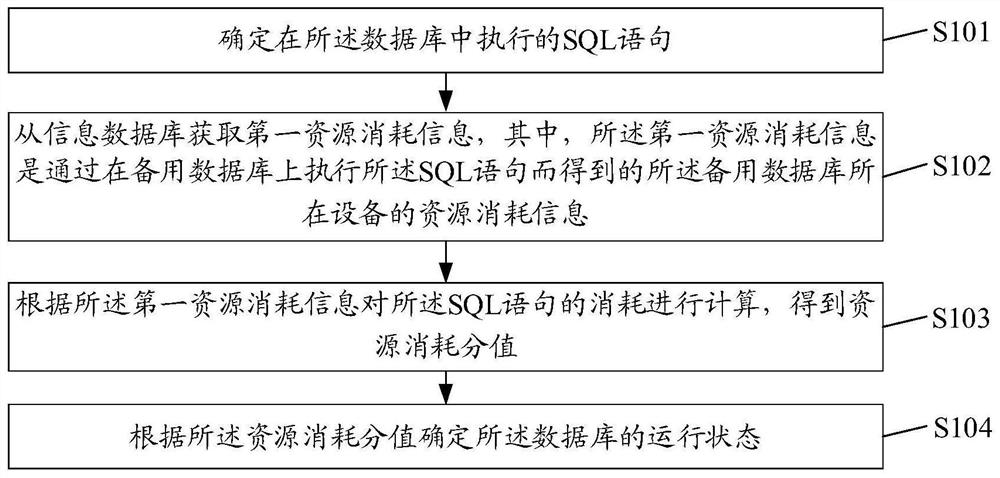
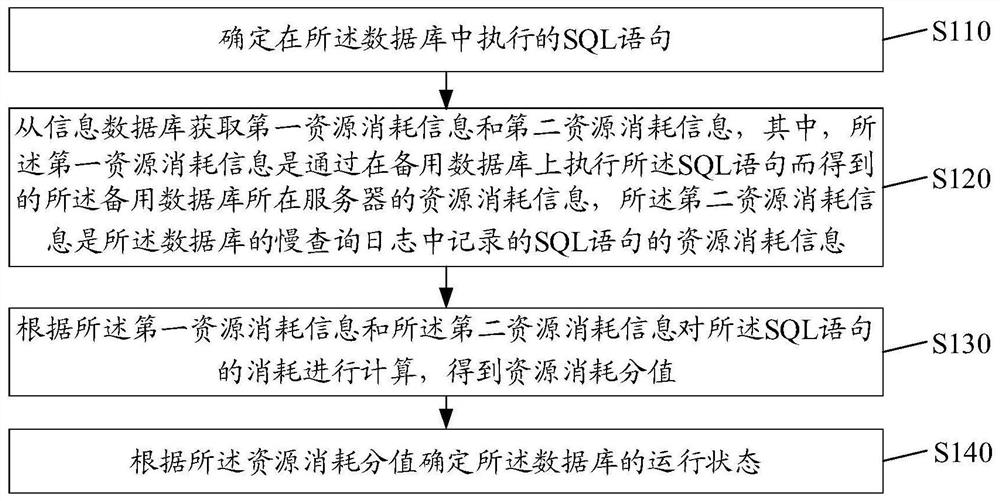
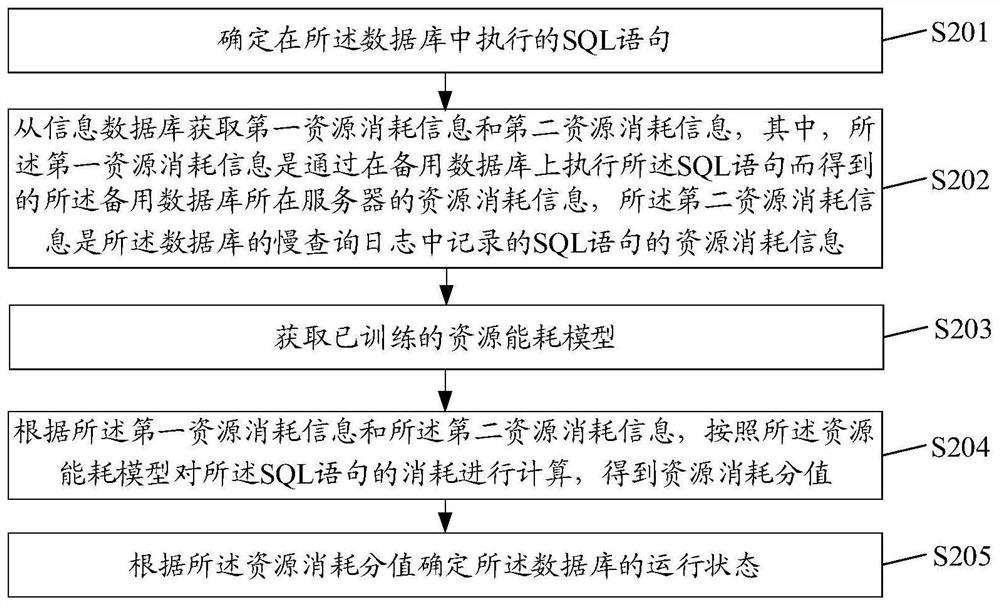
Database state determination method and device, equipment and storage medium
ActiveCN112181840AAvoid detecting inaccurate situationsGuaranteed uptimeDigital data information retrievalHardware monitoringData miningIndustrial engineering
The embodiment of the invention discloses a database state determination method and device, equipment and a storage medium. The method comprises the steps: determining an SQL statement executed in a database; obtaining first resource consumption information from an information database, wherein the first resource consumption information is resource consumption information of a device where a backup database is located obtained by executing the SQL statement on the backup database; calculating the consumption of the SQL statement according to the first resource consumption information to obtaina resource consumption score; and determining the running state of the database according to the resource consumption score.
Owner:WEBANK (CHINA)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com