Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
423 results about "Privacy preserving" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
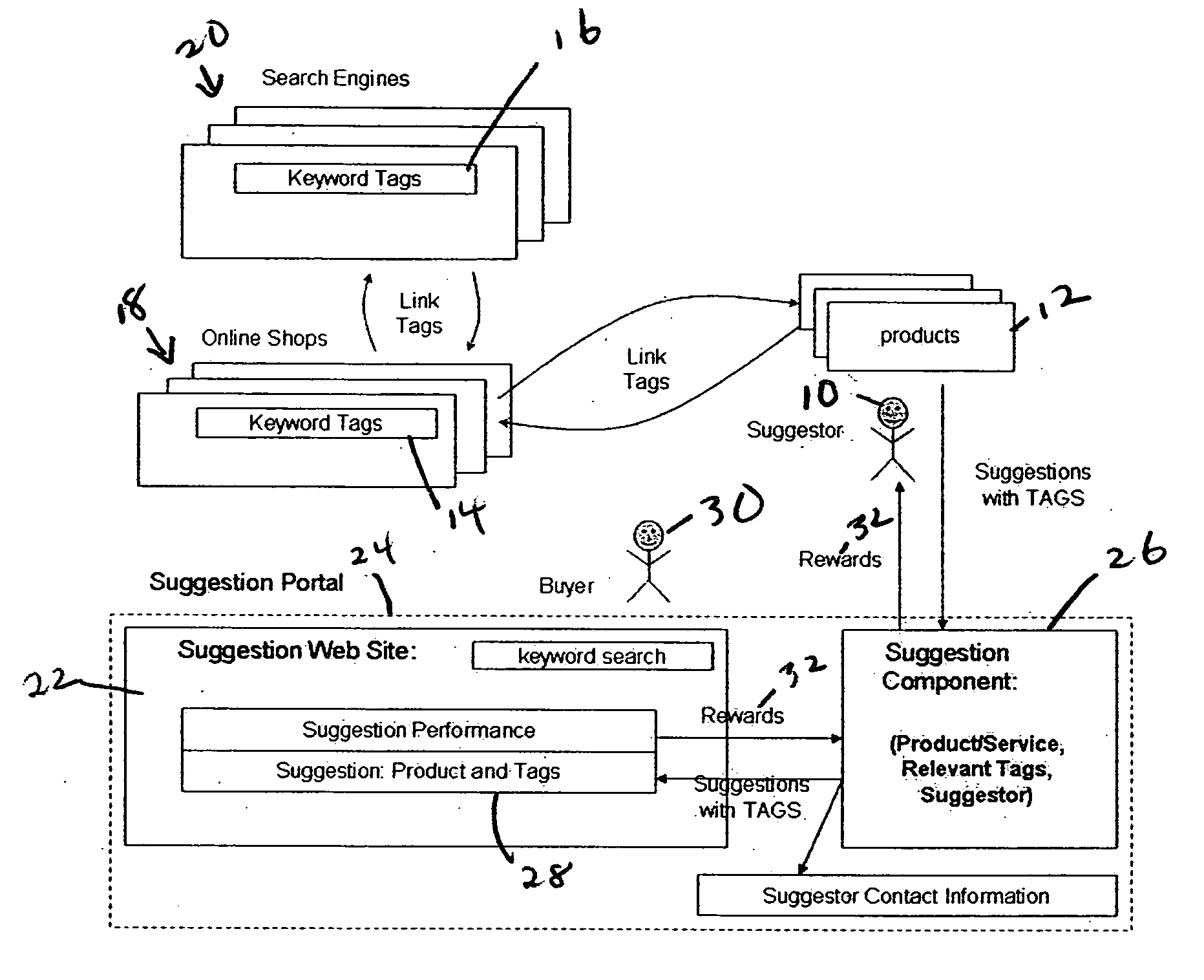
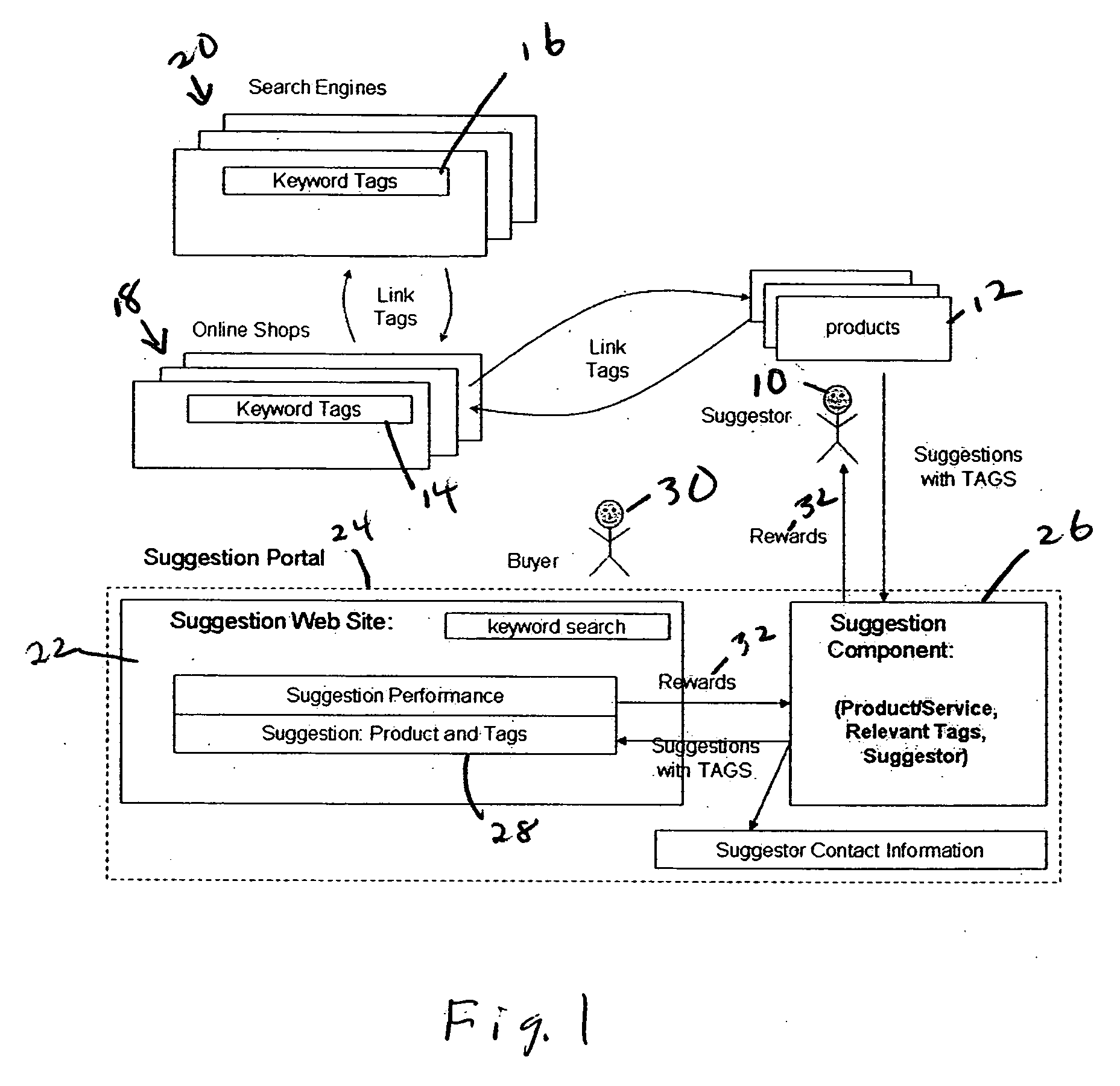
Reward driven online system utilizing user-generated tags as a bridge to suggested links
InactiveUS20070043583A1Increase conversionsHigh trafficWeb data indexingMarketingWeb sitePrivacy preserving
A web site for user suggestions of products, services or other information. The Suggestor also submits tags with those suggestions. To the extent subsequent users use the same tags to access or purchase the user suggestion, the suggesting user will be rewarded. The present invention also provides mechanisms for disbursing rewards for “finding-and-buying-thru-tags”, ranking suggestions, enabling various privacy preserving communications and deal validation mechanisms among shoppers, Suggestors and their social networks.
Owner:ARIZONA STATE UNIVERSITY
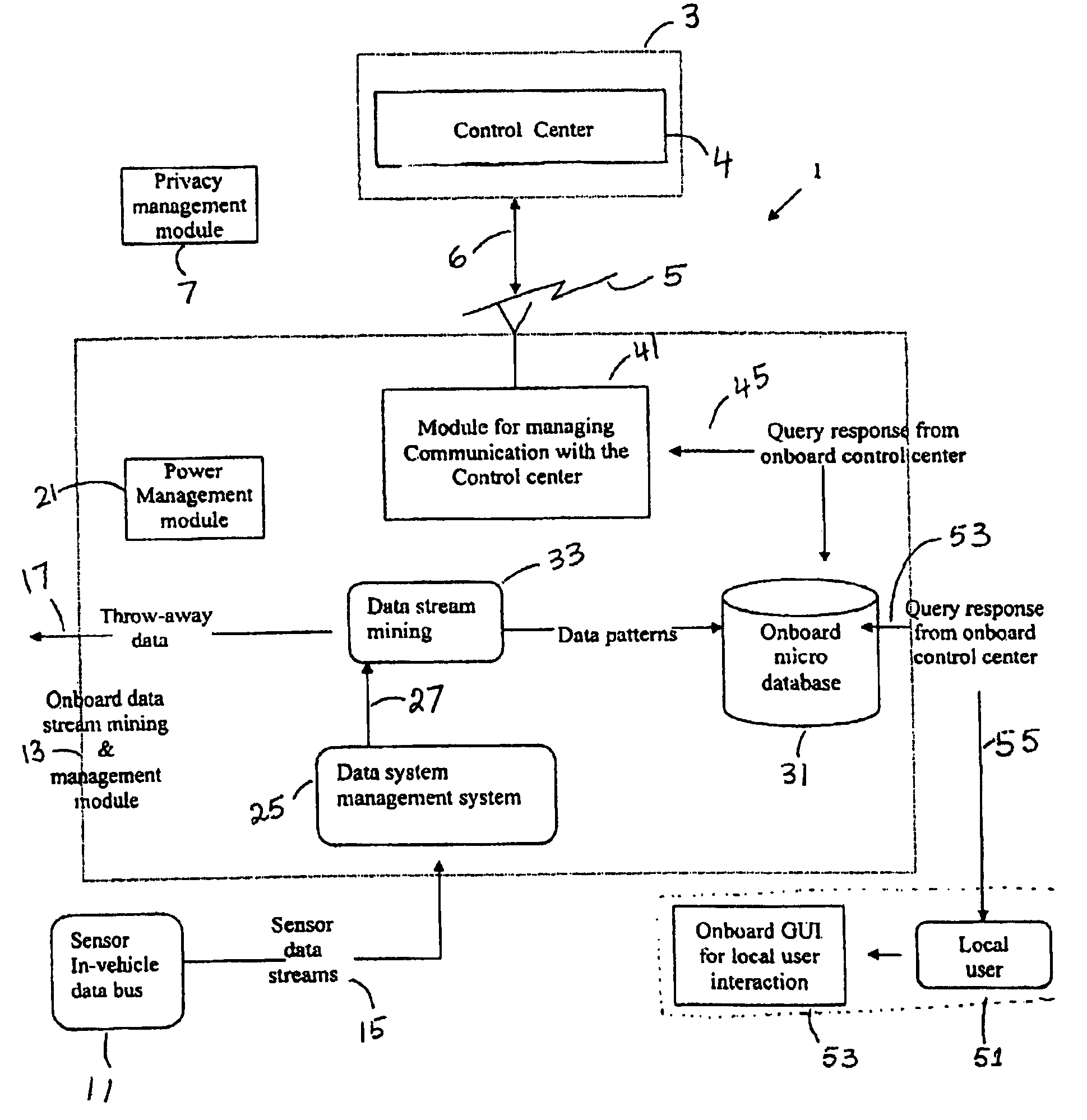
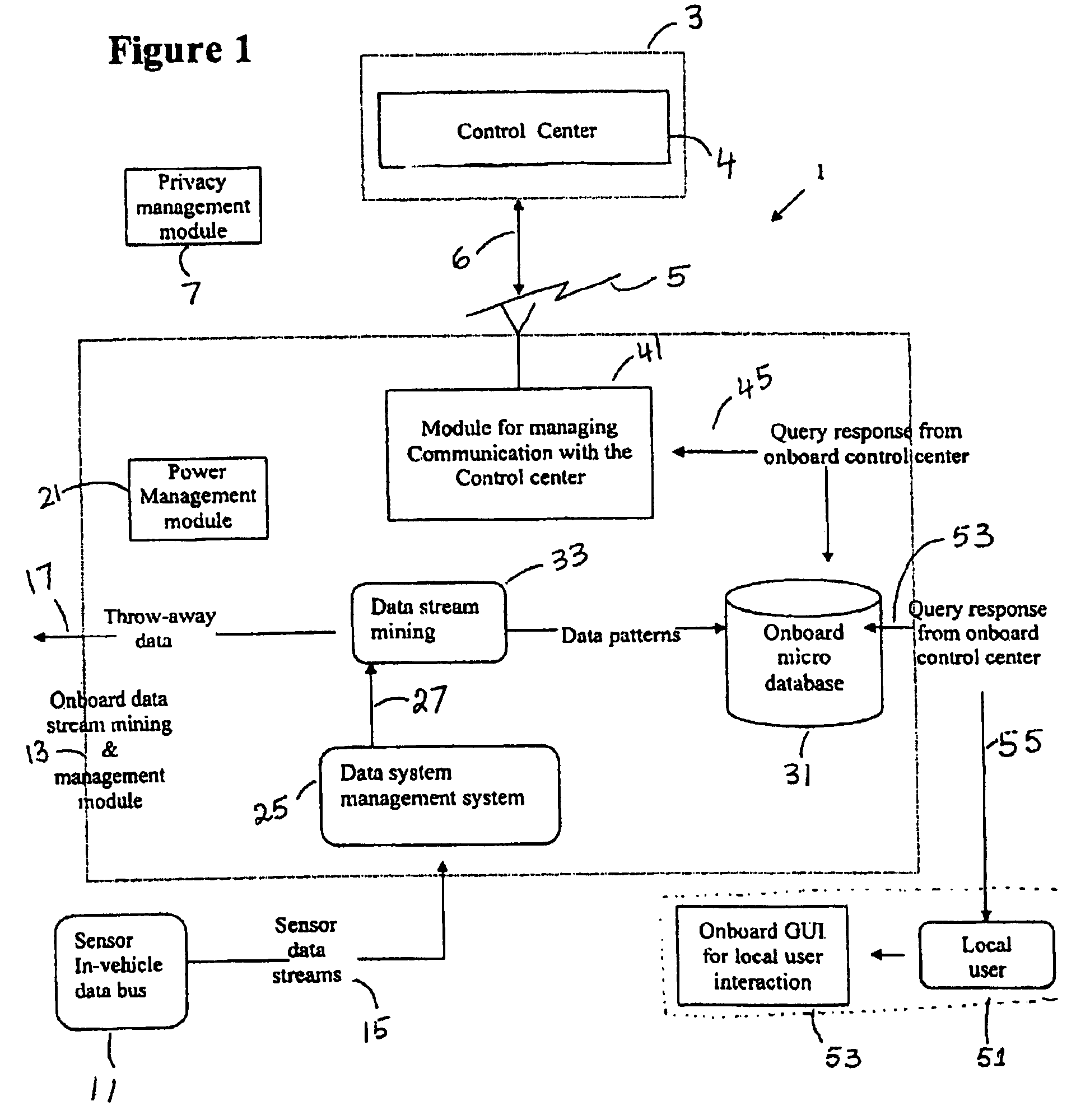
Onboard driver, vehicle and fleet data mining
ActiveUS7715961B1Avoid expensiveReduce operating costsVehicle testingCoupling device connectionsSystem usagePrivacy preserving
The method and system use onboard data stream mining for extracting data patterns from data continuously generated by different components of a vehicle. The system stores the data patterns in an onboard micro database and discards the data. The system uses a resource-constrained, small, lightweight onboard data stream management processor, with onboard data stream mining, an onboard micro database, and a privacy-preserving communication module, which periodically and upon request communicates stored data patterns to a remote control center. The control center uses the data patterns to characterize the typical and unusual vehicle health, driving and fleet behavior.
Owner:AGNIK
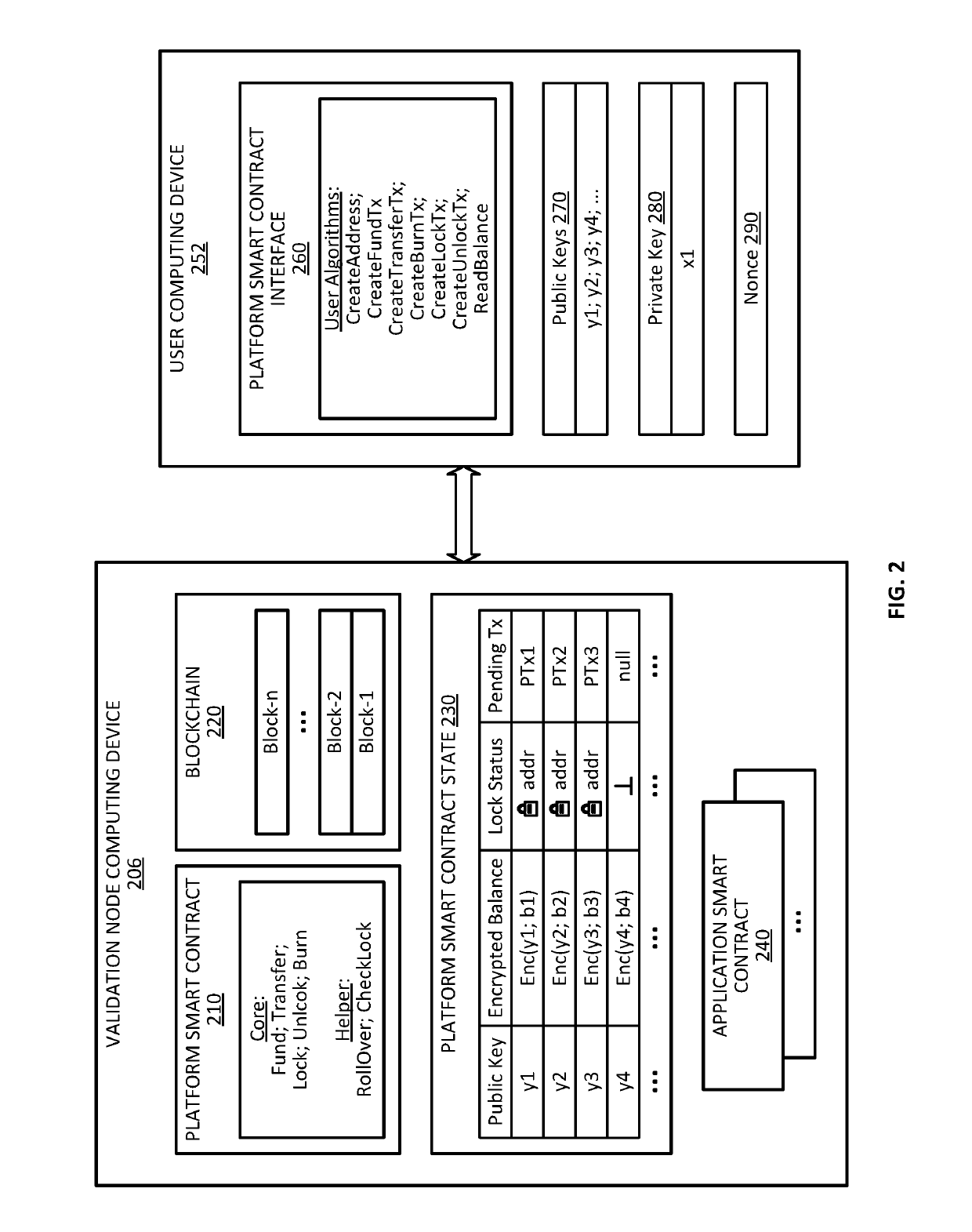
Blockchain system for confidential and anonymous smart contracts
ActiveUS20190164153A1Improve confidentialityEnhanced anonymityEncryption apparatus with shift registers/memoriesCryptography processingInternet privacyPrivacy preserving
Blockchain-based, smart contract platforms have great promise to remove trust and add transparency to distributed applications. However, this benefit often comes at the cost of greatly reduced privacy. Techniques for implementing a privacy-preserving smart contract is described. The system can keep accounts private while not losing functionality and with only a limited performance overhead. This is achieved by building a confidential and anonymous token on top of a cryptocurrency. Multiple complex applications can also be built using the smart contract system.
Owner:VISA INT SERVICE ASSOC +1
Privacy preserving method for summarizing user data
Owner:J D POWER
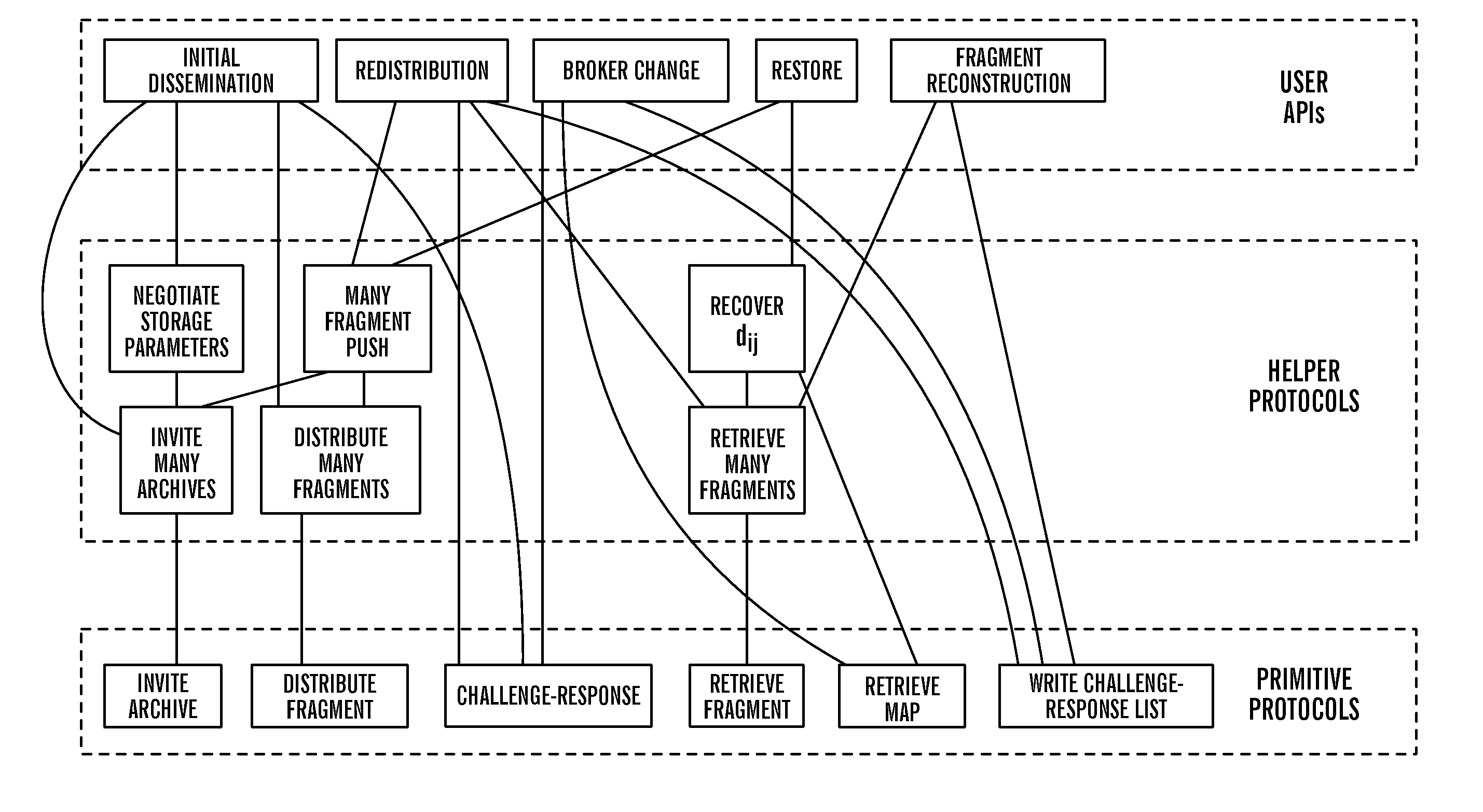
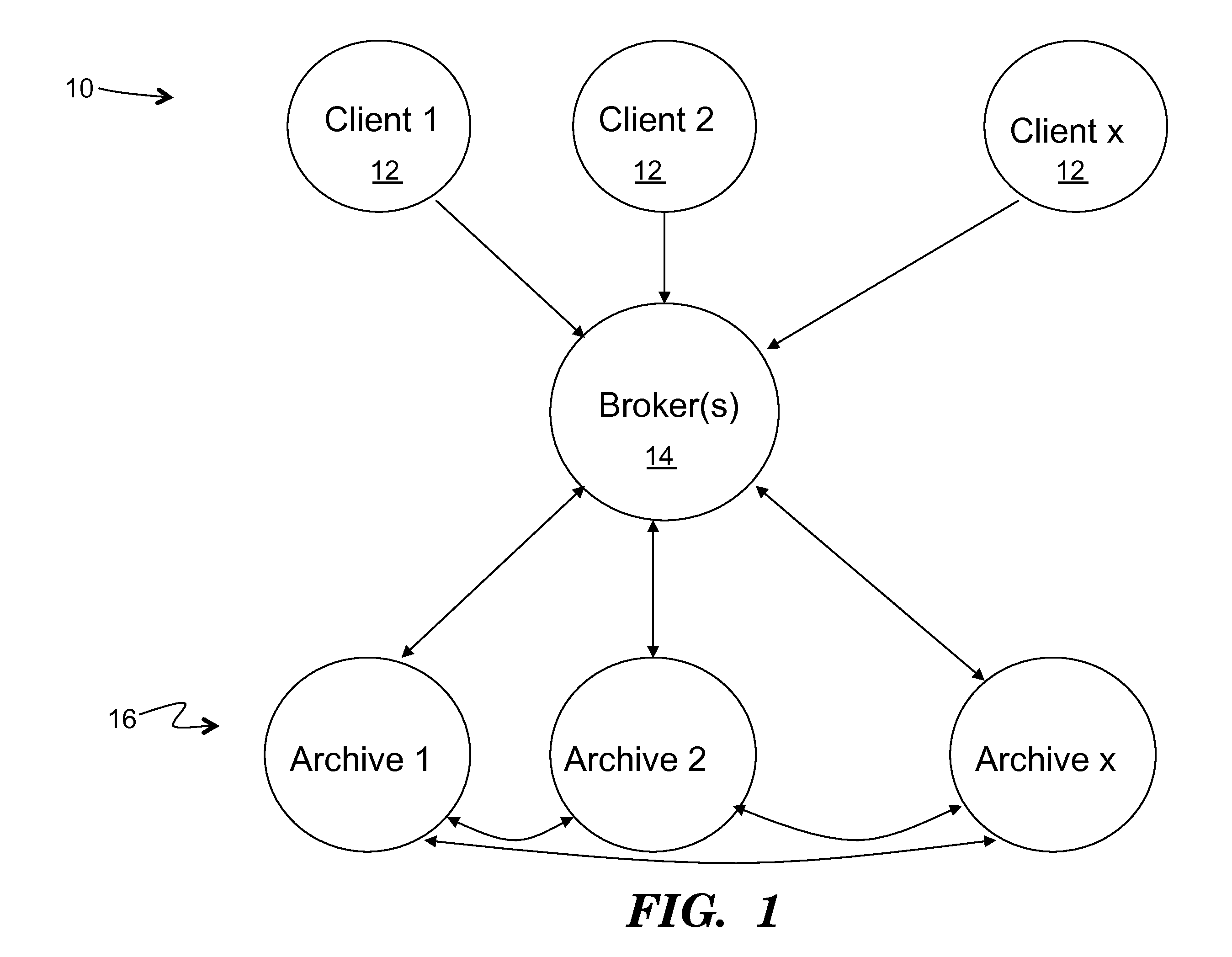
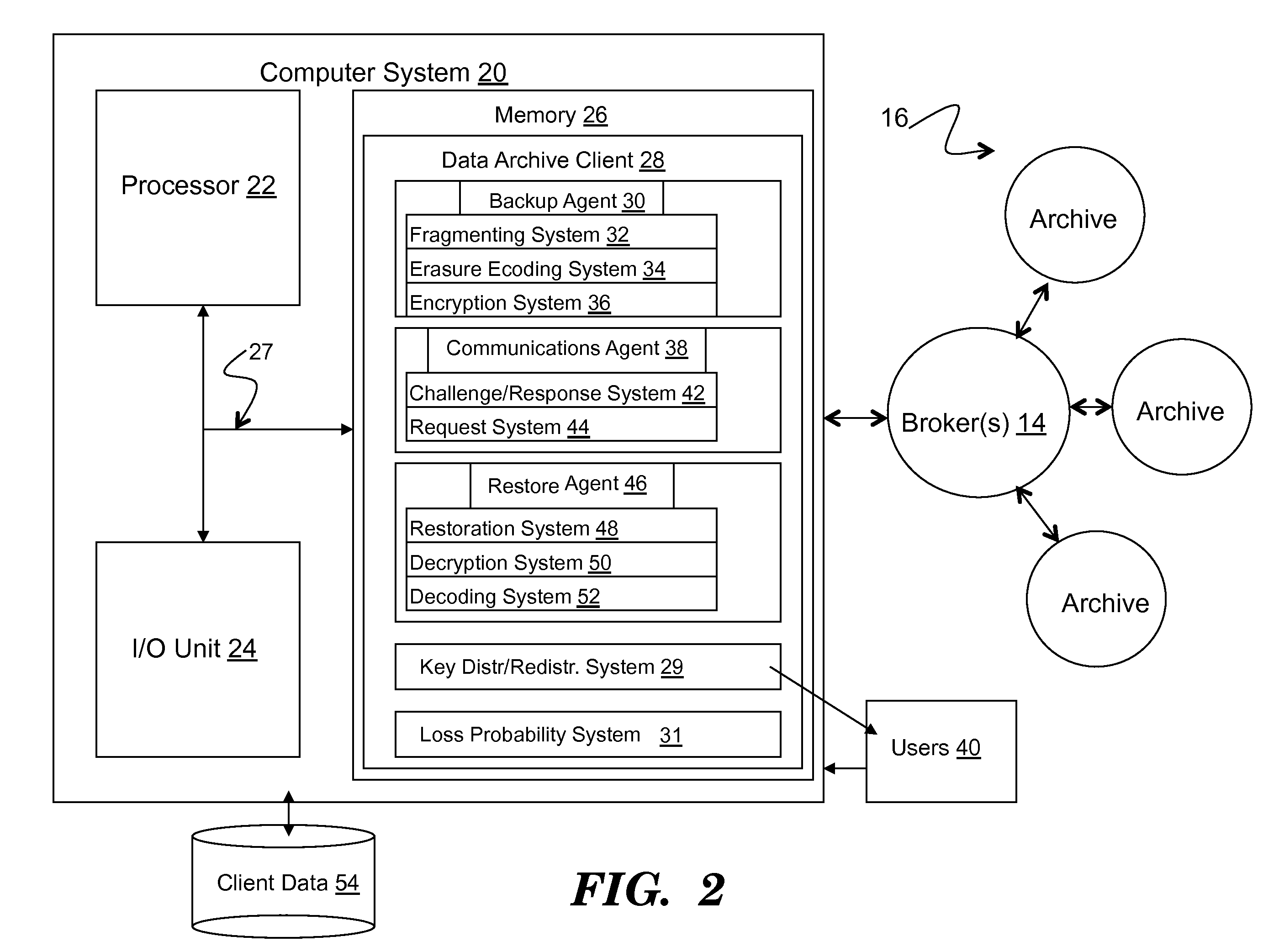
Method to support privacy preserving secure data management in archival systems
InactiveUS20100037056A1Digital data information retrievalUser identity/authority verificationInternet privacyPrivacy preserving
An infrastructure for archiving data among a client, a broker, and a plurality of archives, wherein the client comprises: a backup agent configured to fragment and erasure encode the data to create a set of erasure encoded data fragments; a communications agent configured to communicate the erasure encoded data fragments to the broker, issue a challenge for a challenge / response protocol to the broker, and to request data from the archives; and a restore agent configured to combine the data fragments obtained from the broker upon a data restore request.
Owner:ALTAVAULT
Method and apparatus for efficient and flexible surveillance visualization with context sensitive privacy preserving and power lens data mining
InactiveUS20080198159A1Overcome problemsQuickly explore potential abnormalitiesBurglar alarm3D modellingGraphicsData dredging
The surveillance visualization system extracts information from plural cameras to generate a graphical representation of a scene, with stationary entities such as buildings and trees represented by graphical model and with moving entities such as cars and people represented by separate dynamic objects that can be coded to selectively reveal or block the identity of the entity for privacy protection. A power lens tool allows users to specify and retrieve results of data mining operations applied to a metadata store linked with objects in the scene. A distributed model is presented where a grid or matrix is used to define data mining conditions and to present the results in a variety of different formats. The system supports use by multiple persons who can share metadata and data mining queries with one another.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
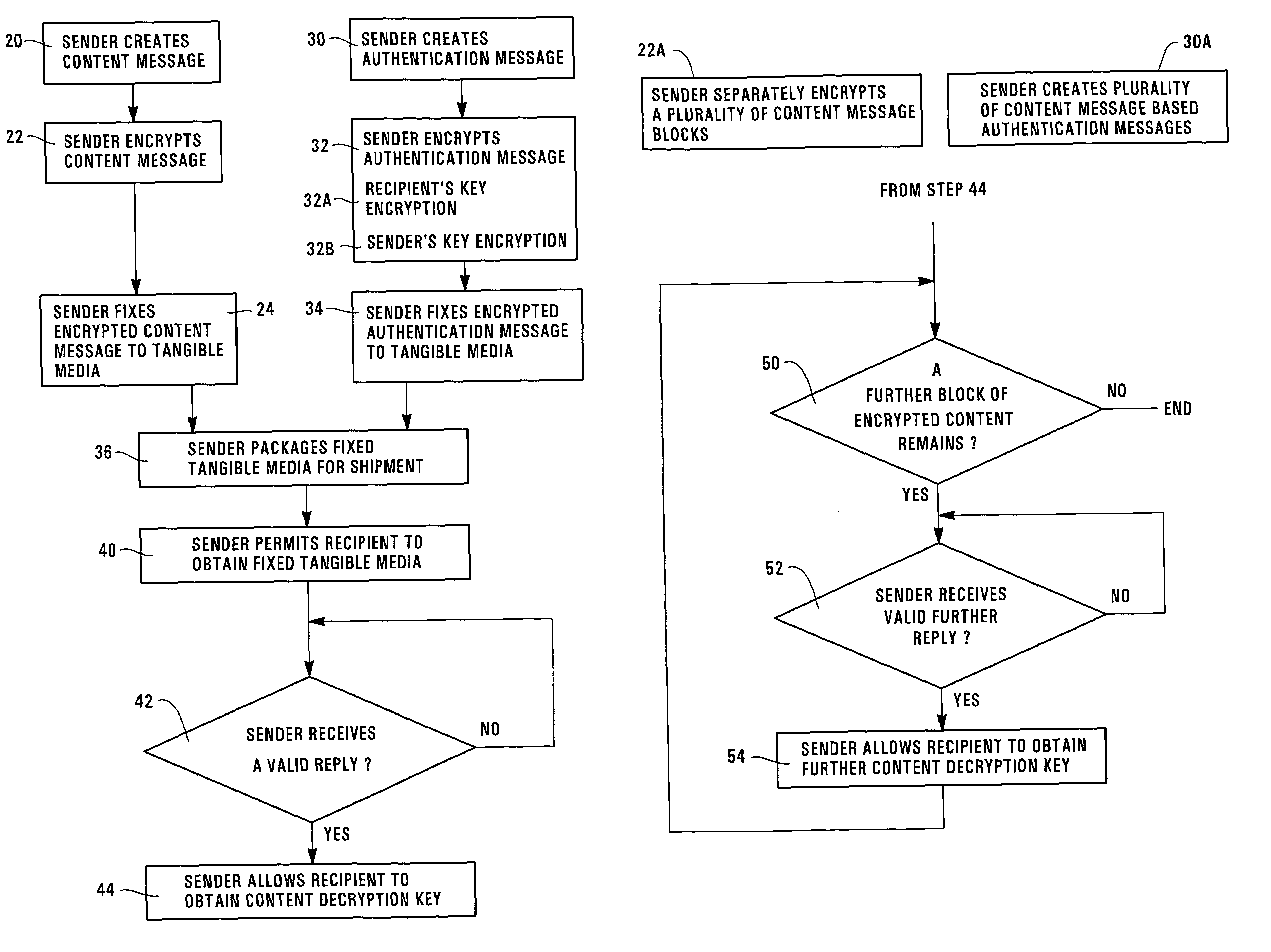
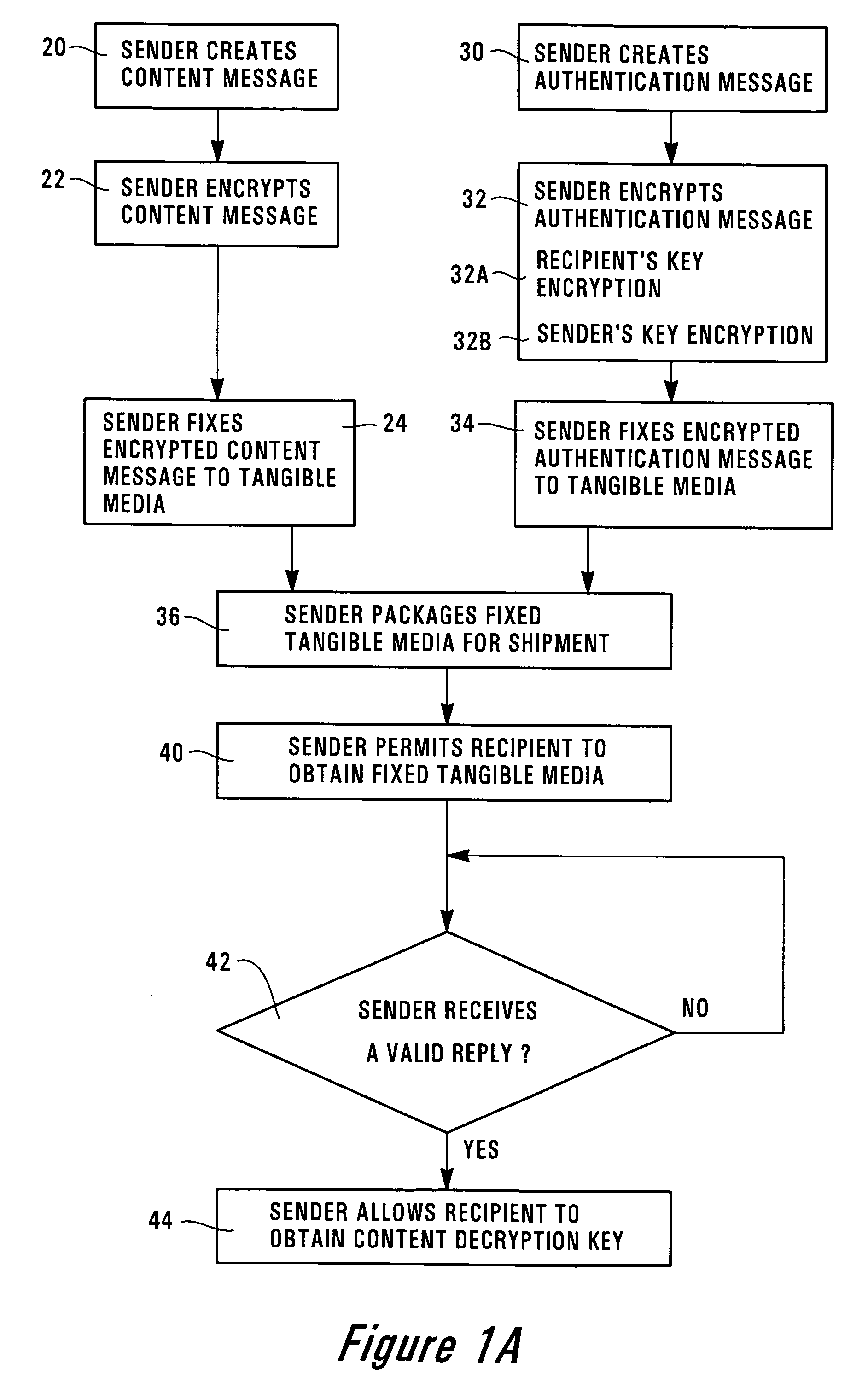
Digital signatures for tangible medium delivery
InactiveUS7165268B1Inhibitory contentDigital data processing detailsUser identity/authority verificationDigital signatureS/KEY
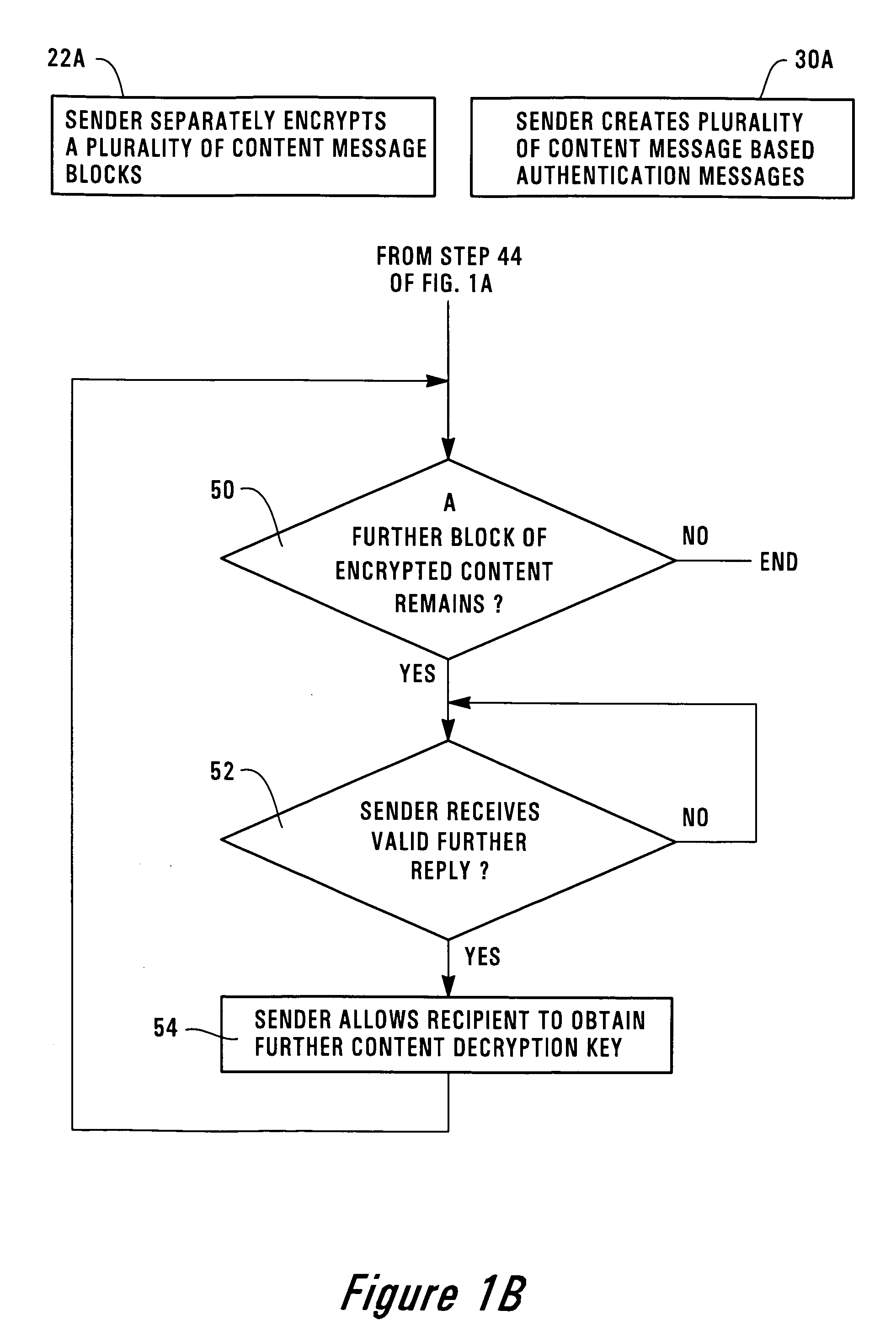
The invention provides a method for a sender to send a message on a tangible medium and ensure that it is privacy protected until verification that the medium has been received by the authorized recipient. The invention provides a method in which a sender creates an encrypted content message that may be decrypted using a content decryption key that is unknown to the authorized recipient. The sender creates an encrypted authentication message that may be decrypted using a recipient's key that is known to the authorized recipient but is unknown to others, except perhaps to the sender. The sender fixes the encrypted content message and the encrypted authentication message onto a tangible medium and then permits the authorized recipient to obtain the tangible medium. The authorized recipient uses the recipient's key to decrypt the encrypted authentication message and then creates a valid reply that is based upon or which uses the decrypted authentication message. The authorized recipient sends the valid reply to the sender and upon verification that the reply is valid the sender allows the authorized recipient to obtain the content decryption key. With the content decryption key, the authorized recipient is able to decrypt the encrypted content message. The invention also includes an article of manufacture for sending an encrypted message from a sender to an authorized recipient using a method, of the invention.
Owner:HEWLETT PACKARD DEV CO LP
Targeting Ads to Subscribers based on Privacy Protected Subscriber Profiles
InactiveUS20070233571A1Maintain privacyBroadcast information switching/replacementAnalogue secracy/subscription systemsTelevision systemPrivacy preserving
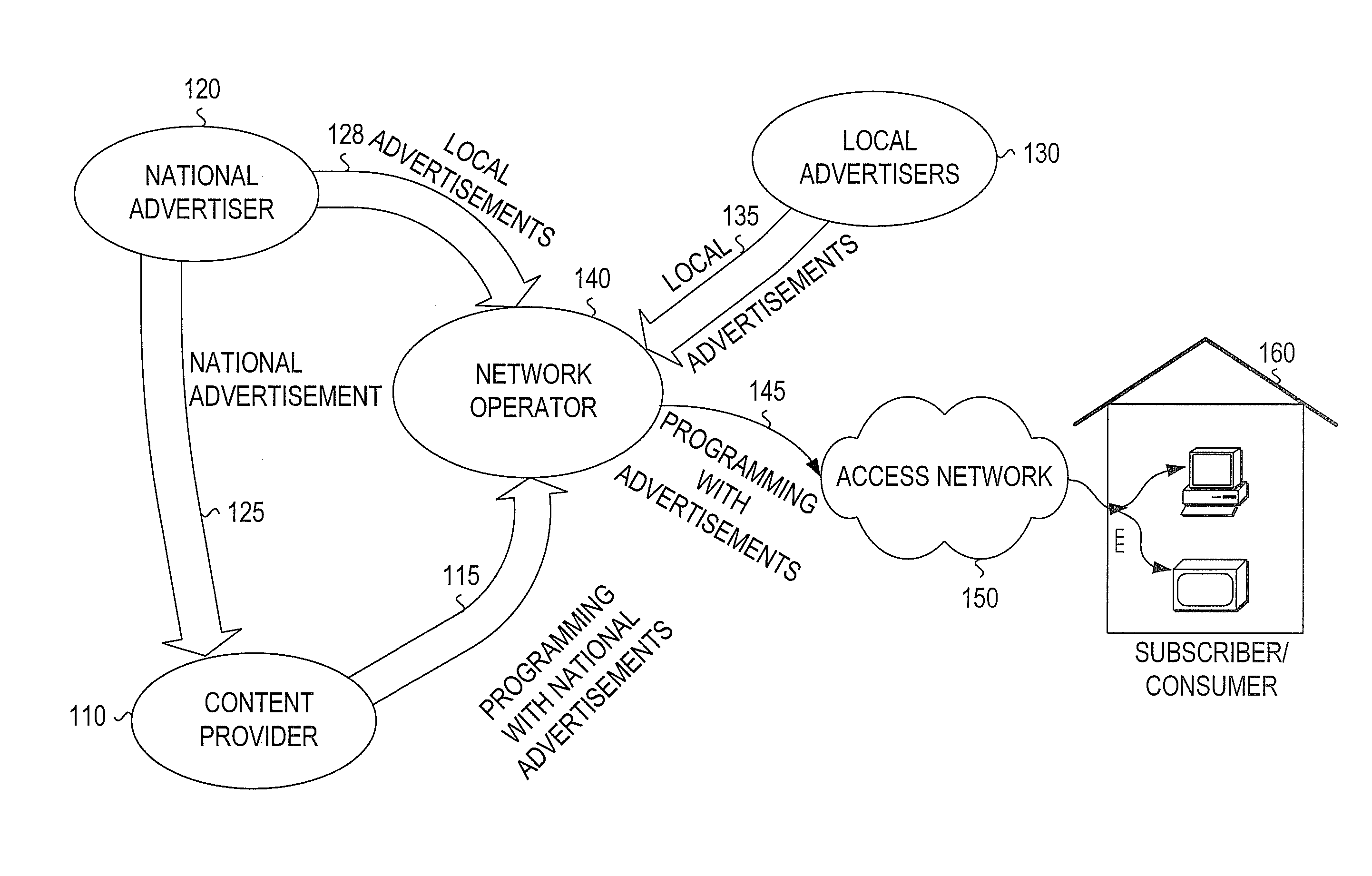
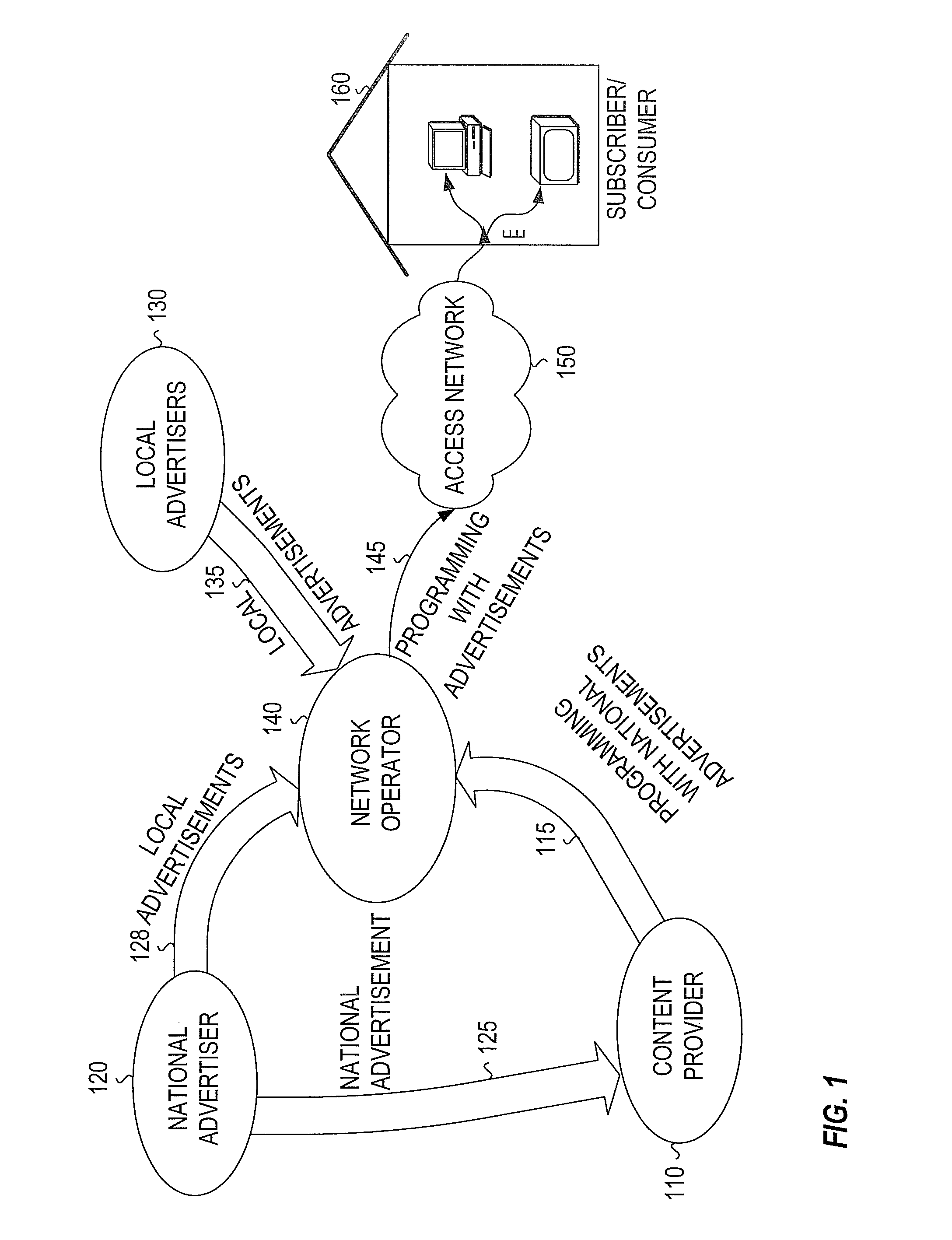
Monitoring subscriber viewing interactions, such as television viewing interactions, and generating viewing characteristics therefrom. Generating at least one type of subscriber profile from at least some subset of subscriber characteristics including viewing, purchasing, transactions, statistical, deterministic, and demographic. The subscriber characteristics may be generated, gathered from at least one source, or a combination thereof. Forming groups of subscribers by correlating at least one type of subscriber profile. The subscriber groups may correlate to elements of a content delivery system (such as head-ends, nodes, branches, or set top boxes (STBs) within a cable TV system). Correlating ad profiles to subscriber / subscriber group profiles and selecting targeted advertisements for the subscribers / subscriber groups based on the correlation. Inserting the targeted ads in place of default ads in program streams somewhere within the content delivery system (head-end, node, or STB). Presenting the targeted ads to the subscriber / subscriber group via a television.
Owner:PRIME RES ALLIANCE E LLC
System and method for authenticated and privacy preserving biometric identification systems
InactiveUS7711152B1Opportunities decreaseElectric signal transmission systemsImage analysisOnline modelControl system
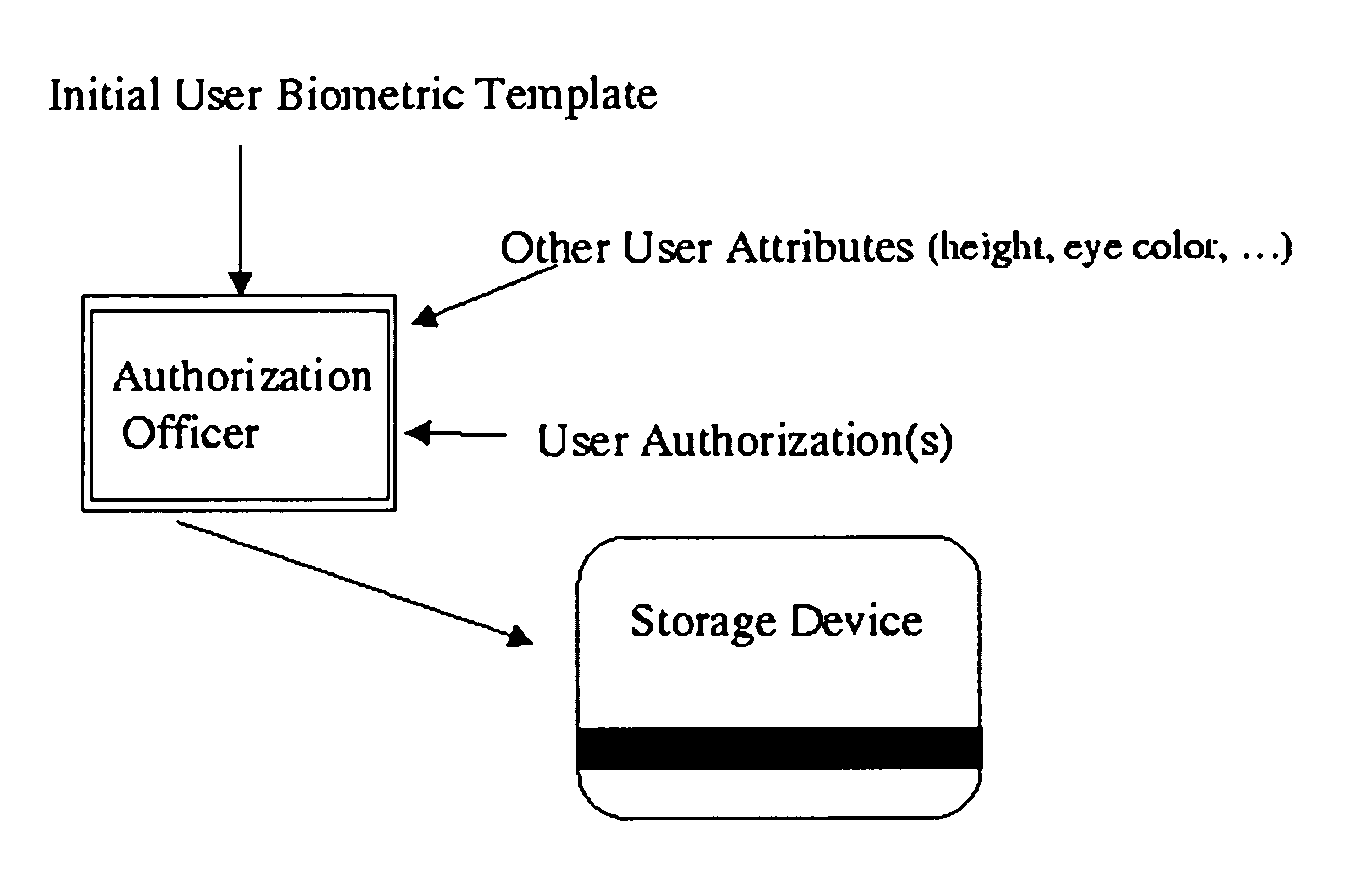
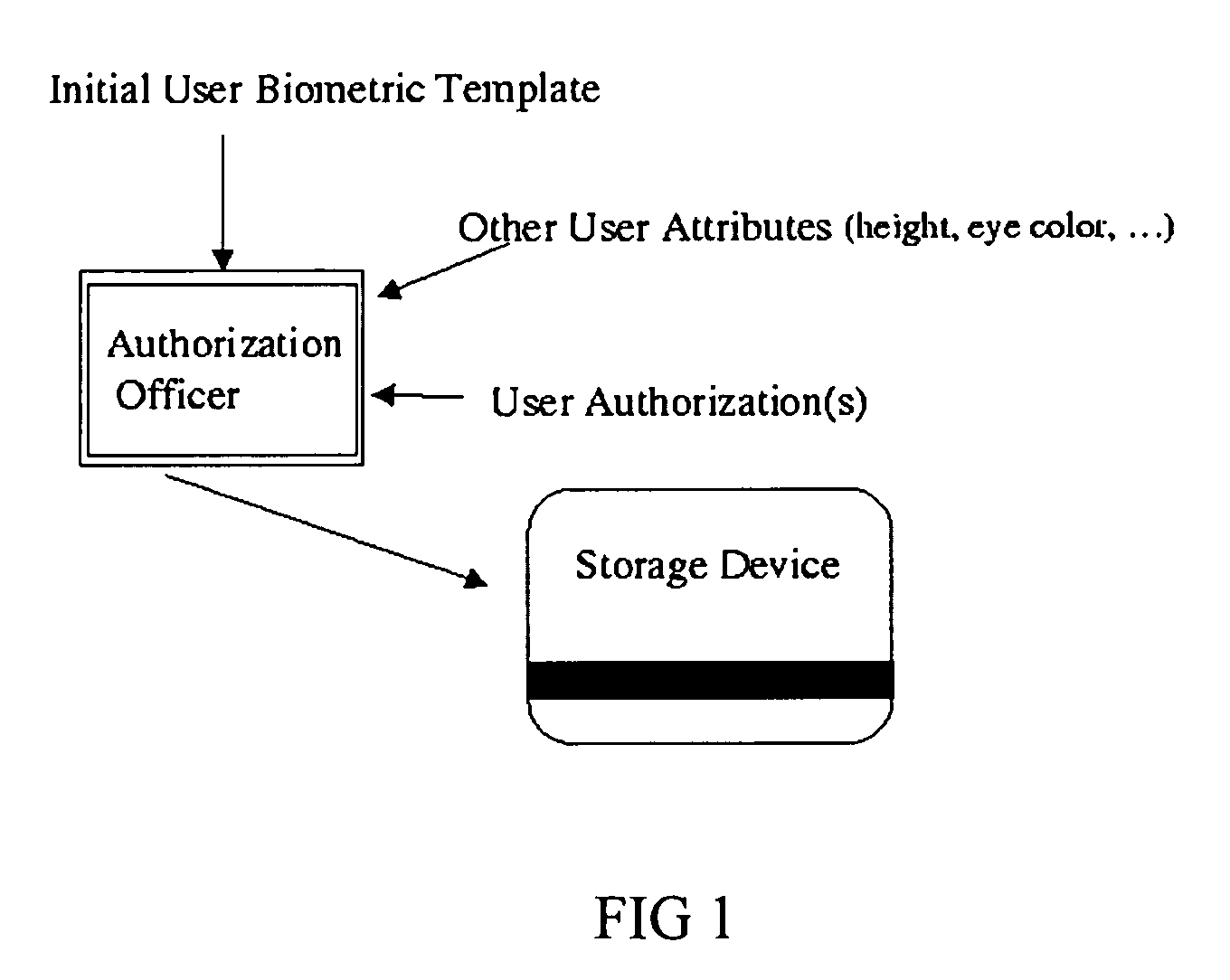
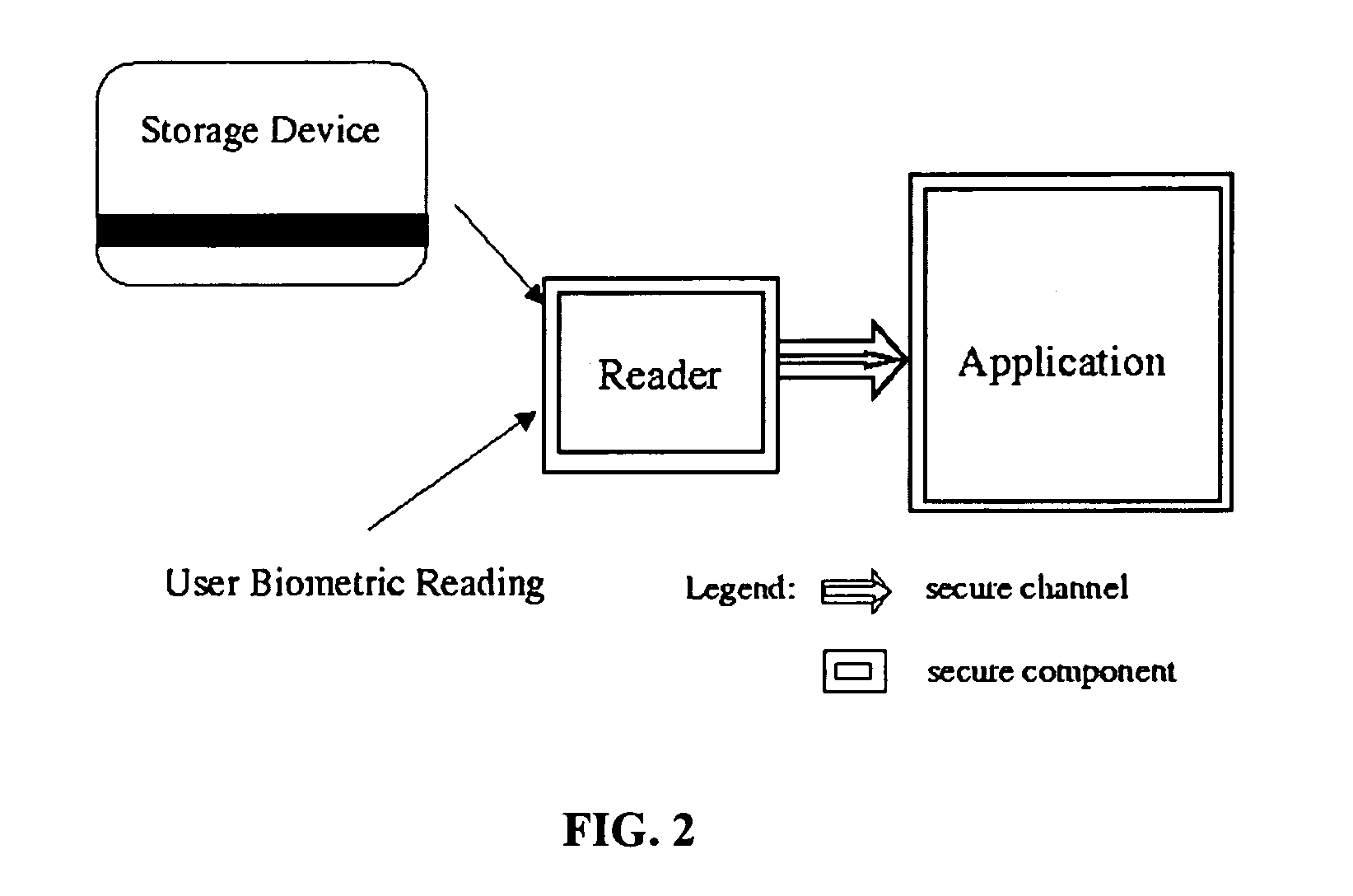
A system and method for the identification of users and objects using biometric techniques is disclosed. This invention describes a biometric based identification and authorization systems which do not require the incorporation of an on-line database of stored complete biometrics for the security infrastructure. In order to remove the connectivity requirements, an off-line biometric system is achieved by incorporating an identity verification template (IVT) on a storage device / token (e.g., magnetic strip or smart-card) during the user's registration which provides for a reliable storage medium; however, there are no security requirements required of the token even to protect the privacy of the stored biometric. The IVT does not contain complete information of the user's biometric but allows for the verification of the user when that user later provides a biometric reading. To deal with errors that may be introduced into later scans of the biometric (for example at the time of verification) error correcting techniques, well known in the art of communication and error control systems, are incorporated into the system. The system is also usable in the online model. Moreover, it may also be used to enable cryptographic operations by being used to partially compose or encrypt private keys for cryptographic operation.
Owner:GIDIPO LLC
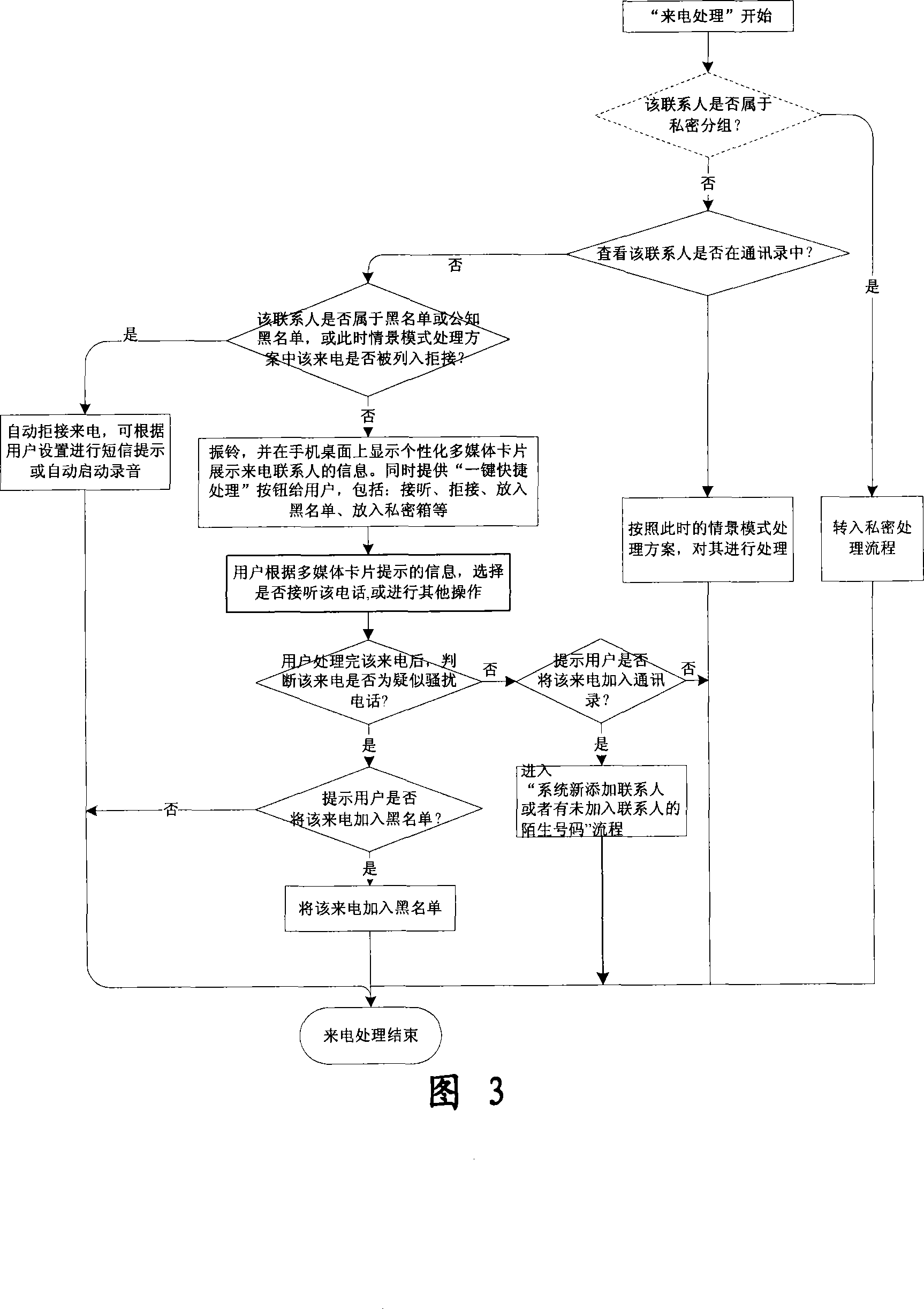
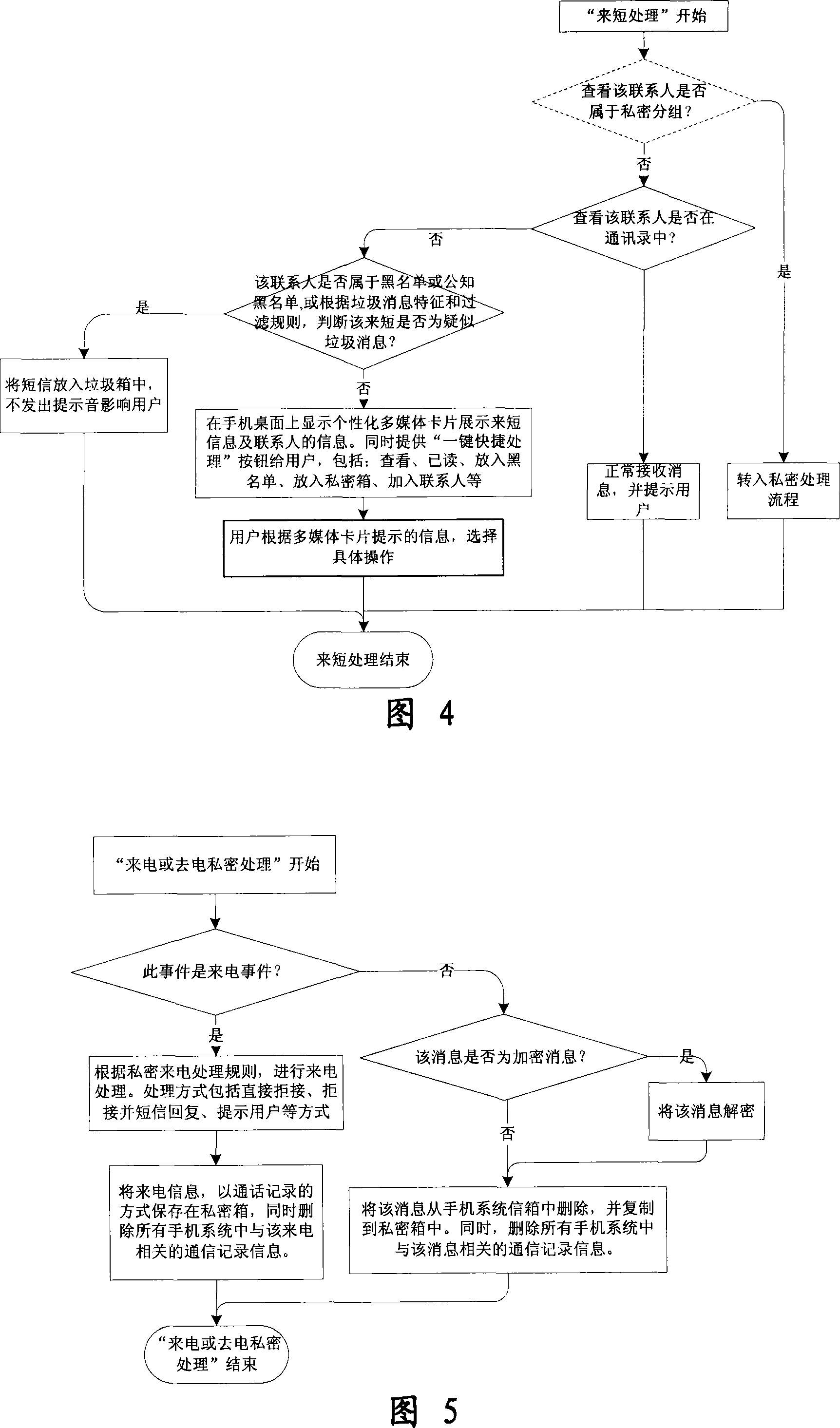
Mobile phone telephone and message anti-disturbance and private communication method and system
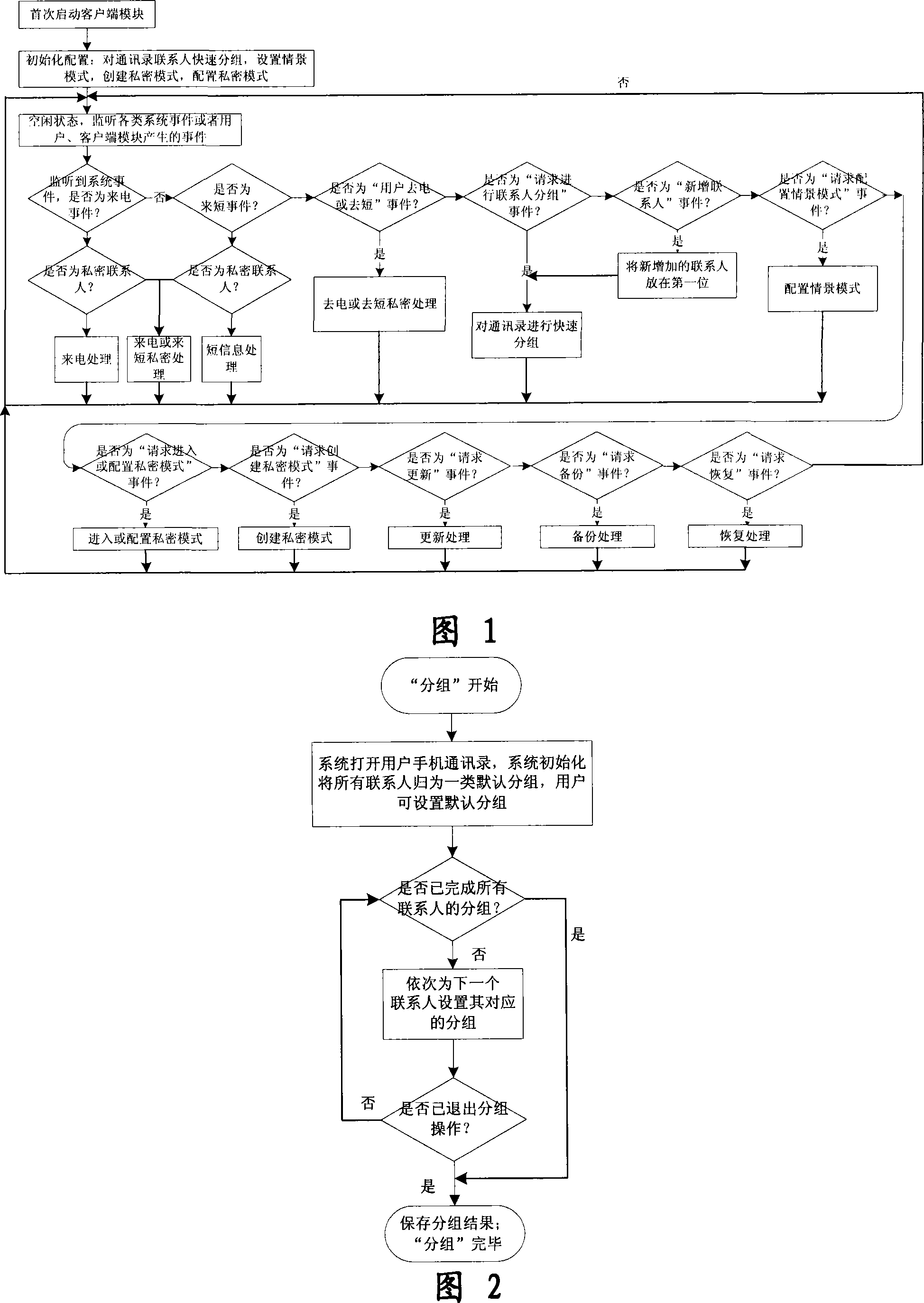
InactiveCN101184264AImprove filtering effectOptimize the effect of anti-harassmentRadio/inductive link selection arrangementsSubstation equipmentPrivate communicationSocial statistics
The invention relates to a processing method and the system of anti-harassment of mobile phone calls and messages and private communication, which is as follow: when grouping the contacts in the mobile phone address list according to different classes, a private group of private communicating contacts is added, and different scene modes of the user are set; when receiving a mobile phone call or a message (text message, multimedia message), depending on the grouping sort of the contact of the incoming call or the message or the multimedia message, and the current scene of the user, together with the behavior characteristics of the harassing call and the spam message with the database information of the public harassing message issued by the authoritative institution or obtained from social statistics, the corresponding process to the call, the message and the multimedia message of the mobile phone is executed to reduce harassment; meanwhile the communication records of incoming, dialed calls and message, multimedia message with the contacts in the private grouping are encrypted and preserved to protect the personal privacy of the user. The invention has the advantages of adopting the operating steps of uniform process, and resolving synthetically the harassment of calls, messages and multimedia messages for the mobile phone and the private protection.
Owner:BEIJING NETQIN TECH
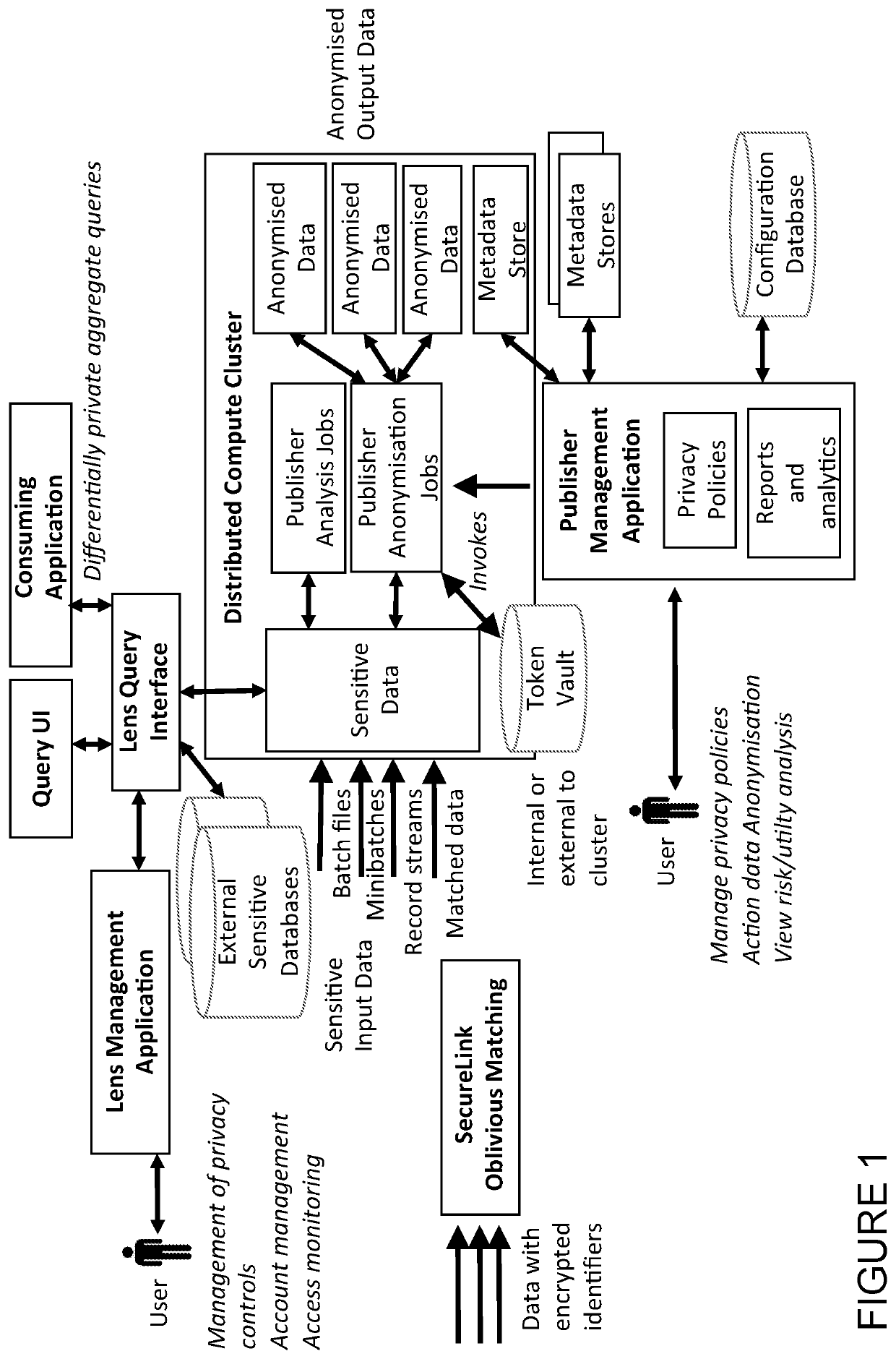
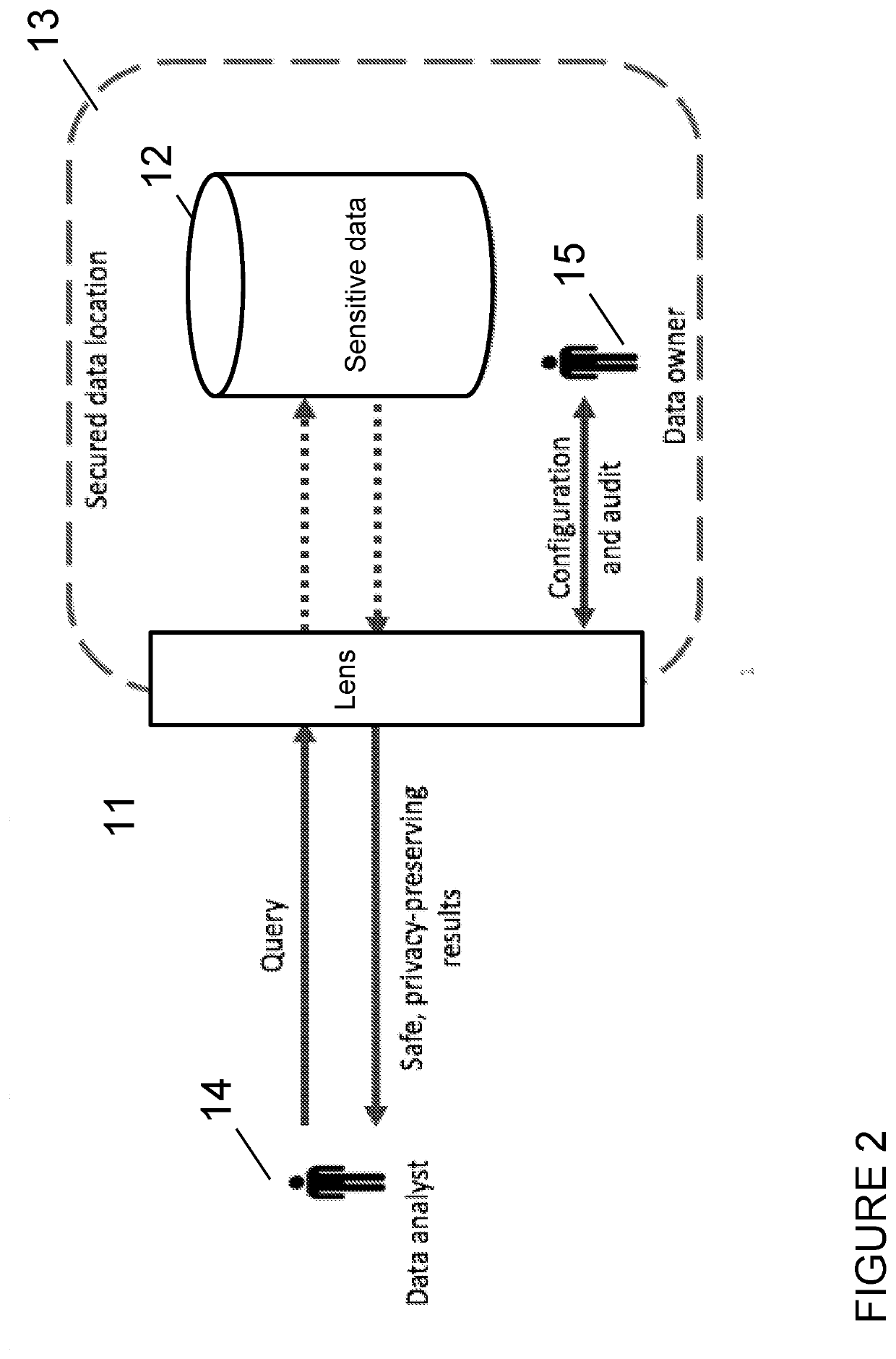
Computer-implemented privacy engineering system and method
ActiveUS20200327252A1Avoid problemsReduce prevent riskKey distribution for secure communicationUser identity/authority verificationData setEngineering
A system allows the identification and protection of sensitive data in a multiple ways, which can be combined for different workflows, data situations or use cases. The system scans datasets to identify sensitive data or identifying datasets, and to enable the anonymisation of sensitive or identifying datasets by processing that data to produce a safe copy. Furthermore, the system prevents access to a raw dataset. The system enables privacy preserving aggregate queries and computations. The system uses differentially private algorithms to reduce or prevent the risk of identification or disclosure of sensitive information. The system scales to big data and is implemented in a way that supports parallel execution on a distributed compute cluster.
Owner:PRIVITAR LTD
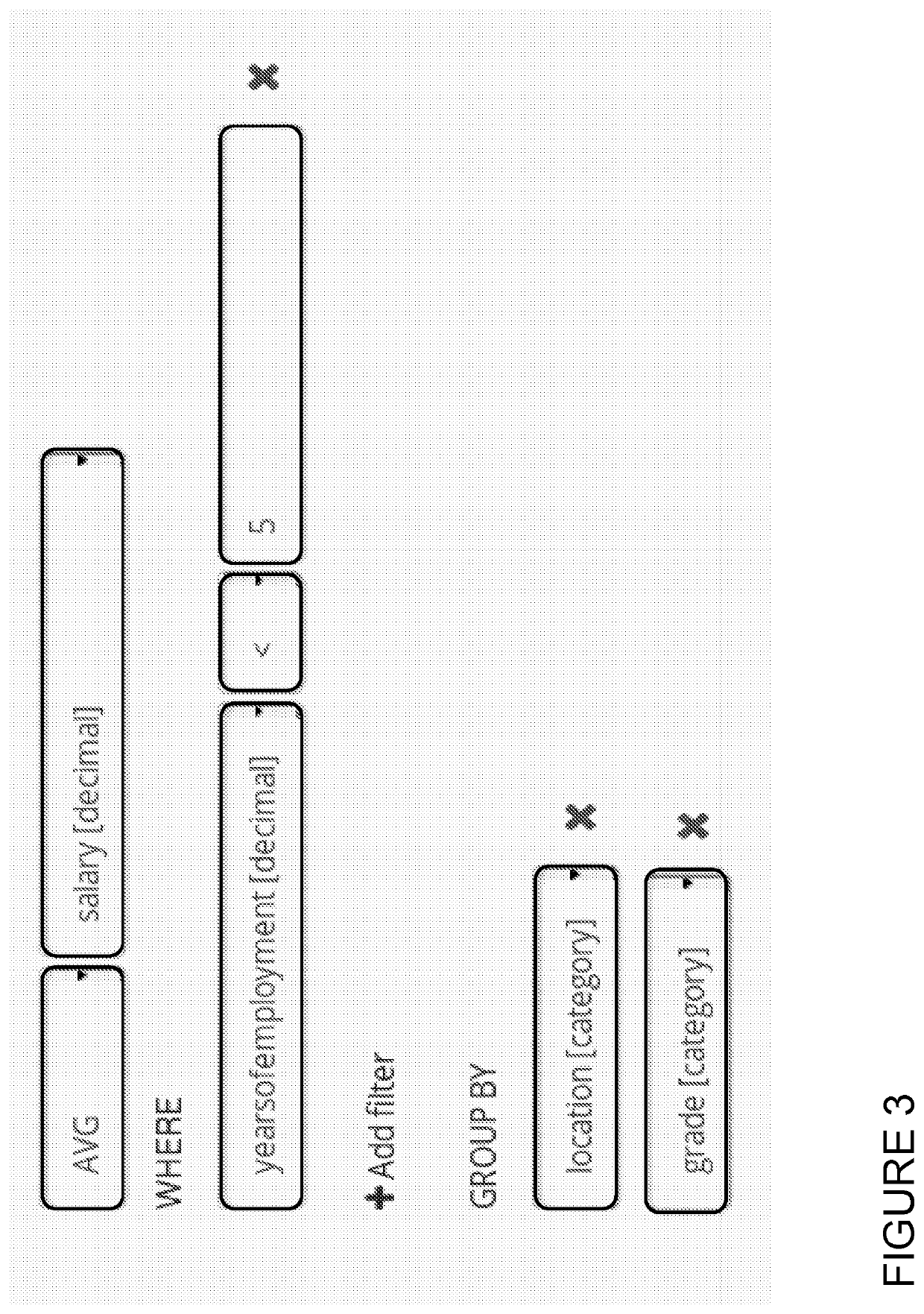
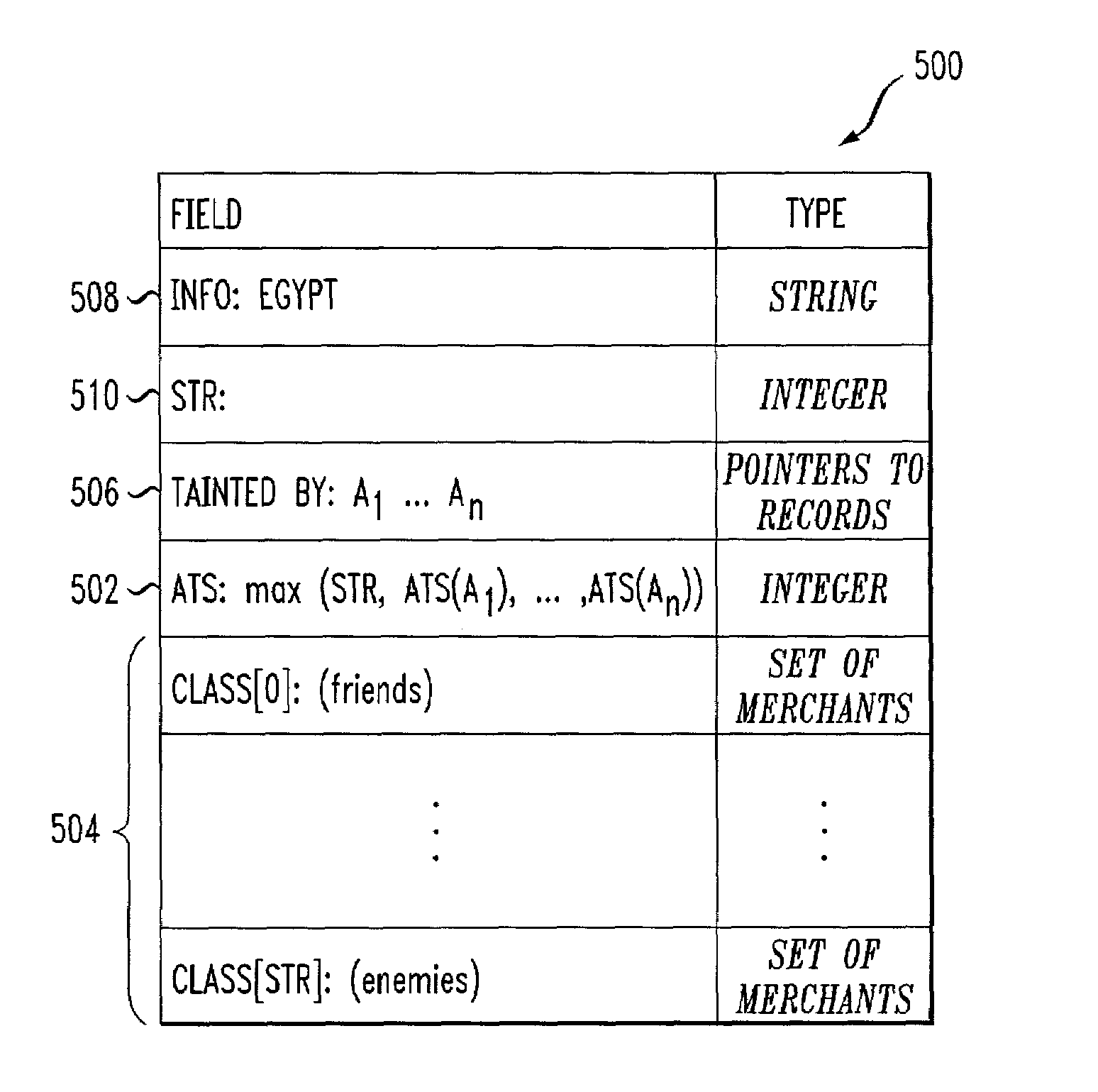
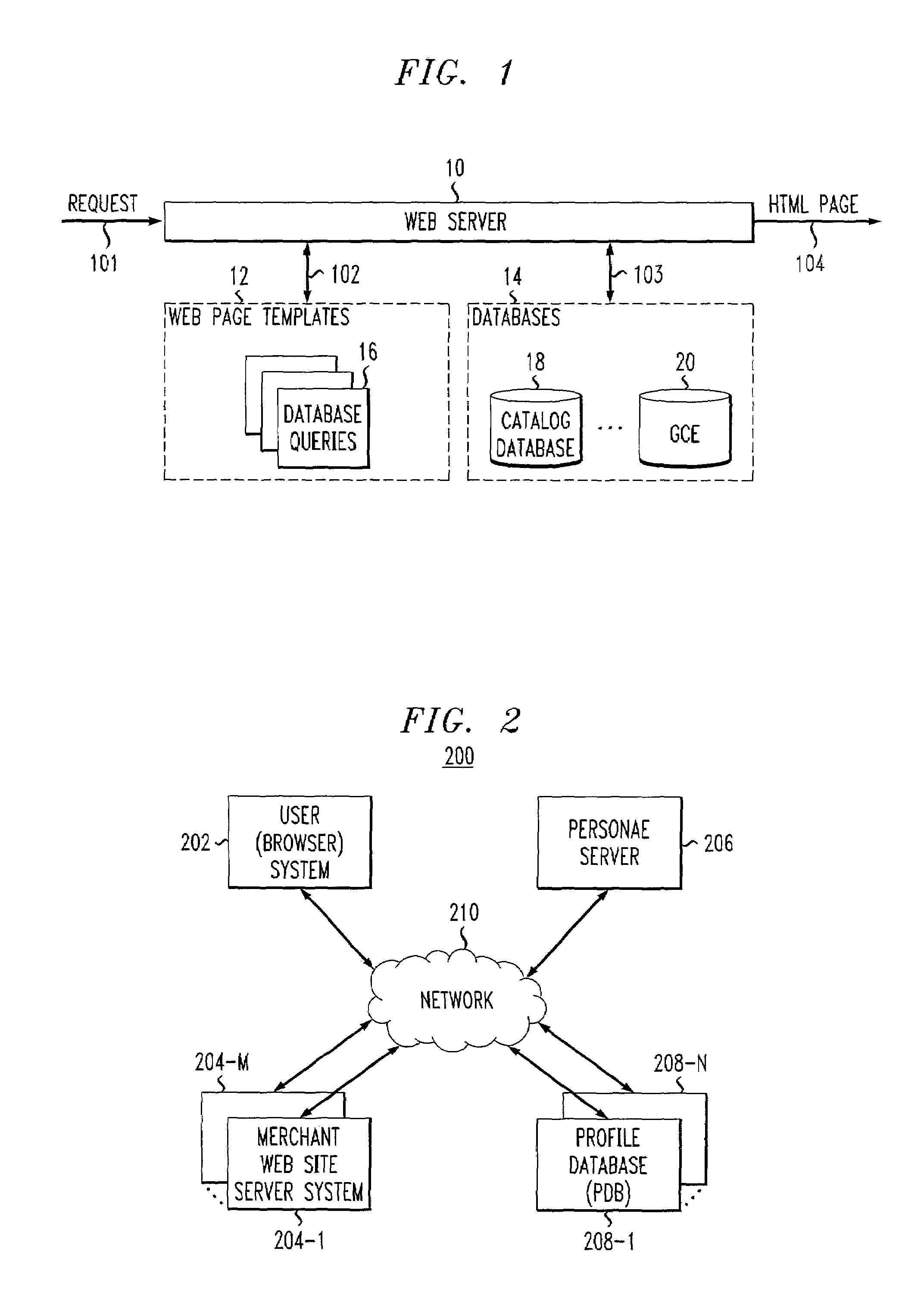
Methods and apparatus for providing privacy-preserving global customization
InactiveUS7107269B2Privacy protectionComputer security arrangementsMultiple digital computer combinationsPrivacy preservingUser control
Techniques and infrastructure are provided for supporting global customization. The invention enables persona profiles of user information to be maintained, and such persona profiles to be accessed by merchants. Via the persona abstraction, users control what information is grouped into a persona profile, and can selectively enable a merchant to read one of these profiles. The infrastructure of the invention employs a persona server that assists users in managing their personae. The infrastructure of the invention separates this from the profile databases at which persona profile information is stored, to eliminate any single point at which different persona profiles can be tied to the same user. Since merchants also have privacy concerns, the infrastructure of the invention provides a data protection model based on tainting, by which merchants can limit how the information they contribute can be exposed.
Owner:SOUND VIEW INNOVATIONS
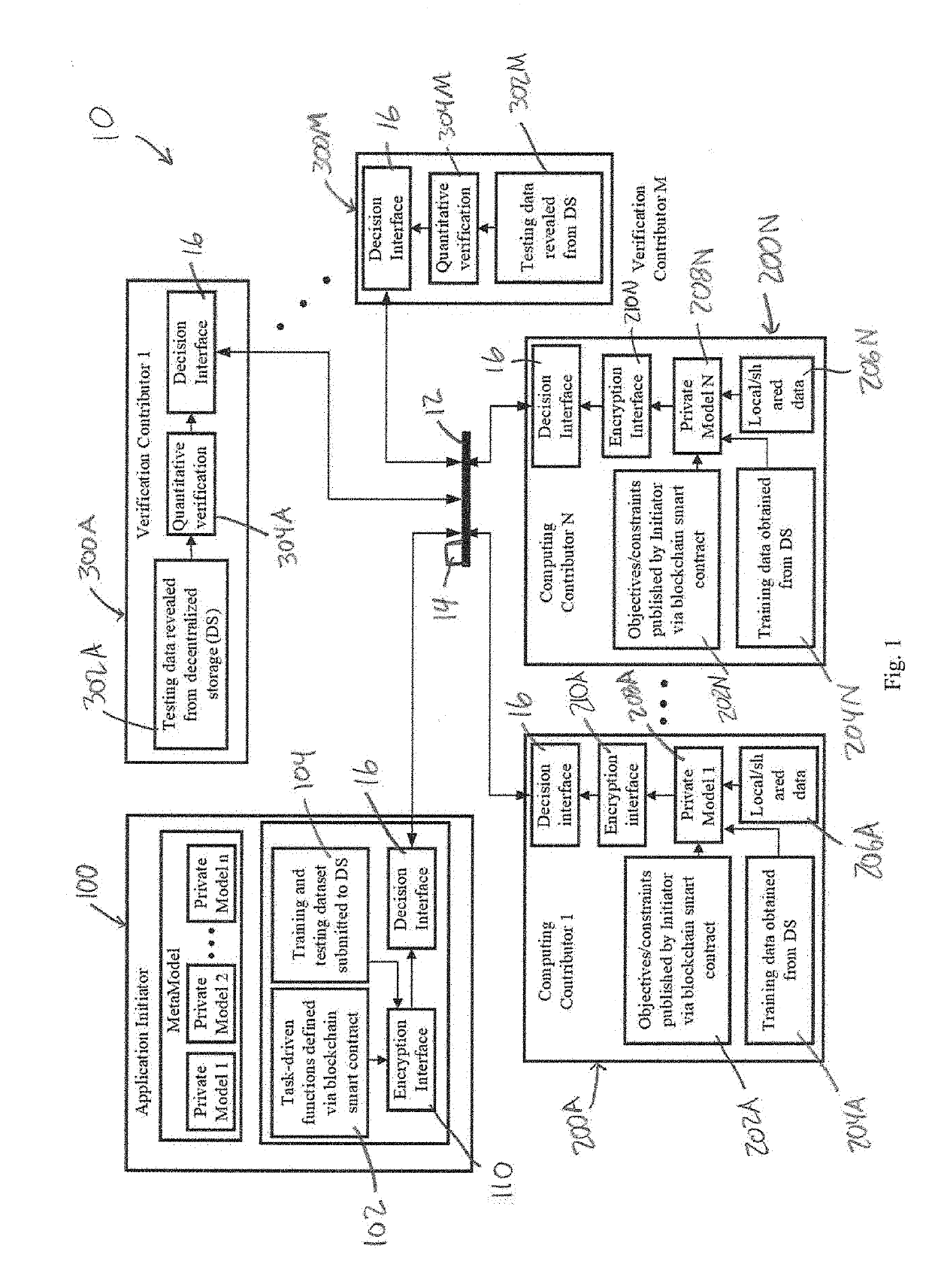
Blockchain-empowered crowdsourced computing system
ActiveUS20190334716A1User identity/authority verificationMachine learningInterface designPrivacy preserving
In various embodiments, the present invention is directed to a decentralized and secure method for developing machine learning models using homomorphic encryption and blockchain smart contracts technology to realize a secure, decentralized system and privacy-preserving computing system incentivizes the sharing of private data or at least the sharing of resultant machine learning models from the analysis of private data. In various embodiments, the method uses a homomorphic encryption (HE)-based encryption interface designed to ensure the security and the privacy-preservation of the shared learning models, while minimizing the computation overhead for performing calculation on the encrypted domain and, at the same time, ensuring the accuracy of the quantitative verifications obtained by the verification contributors in the cipherspace.
Owner:THE UNIVERSITY OF AKRON
Privacy-preserving aggregation of time-series data
ActiveUS20120204026A1Key distribution for secure communicationUser identity/authority verificationData aggregatorPrivacy preserving
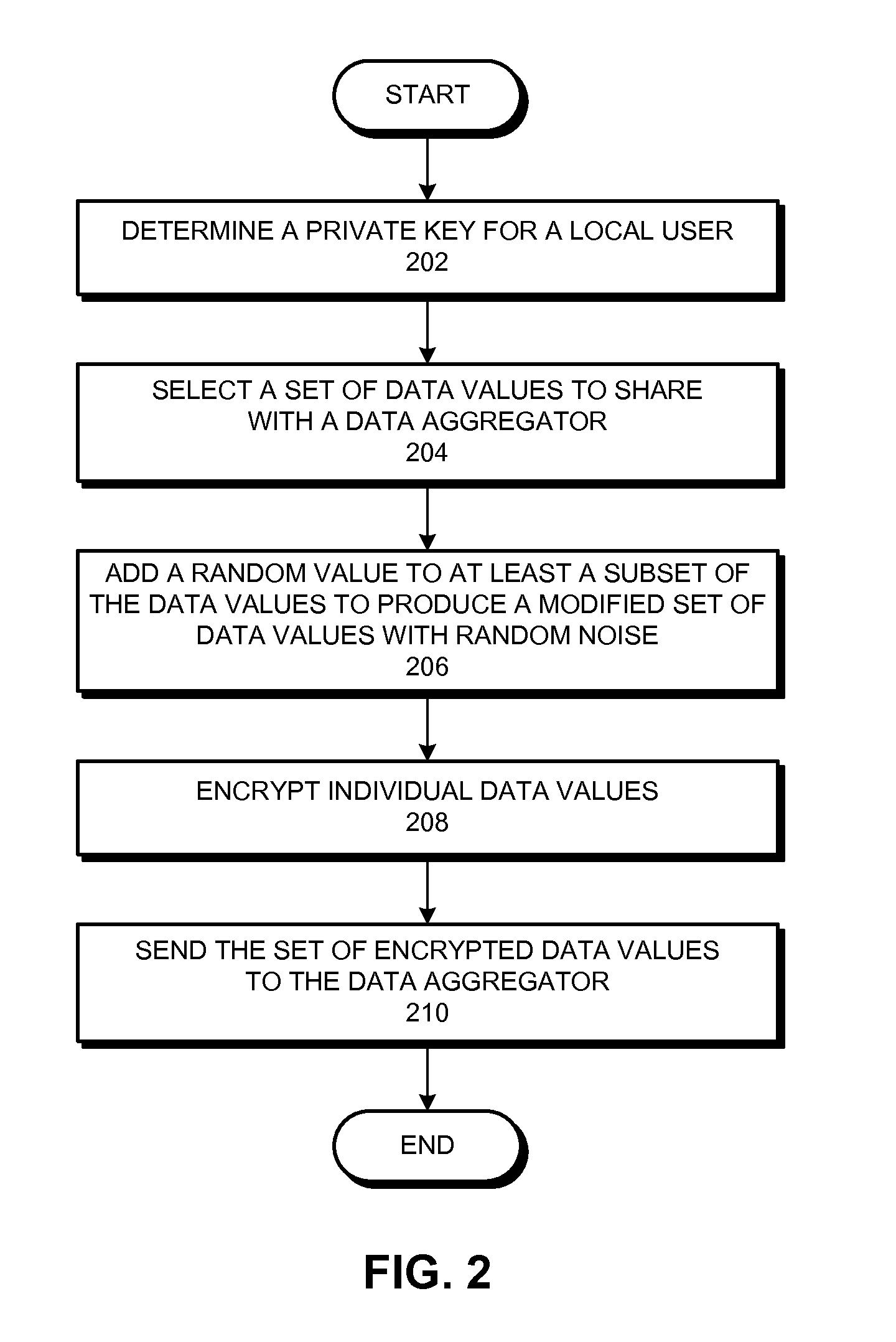
A private stream aggregation (PSA) system contributes a user's data to a data aggregator without compromising the user's privacy. The system can begin by determining a private key for a local user in a set of users, wherein the sum of the private keys associated with the set of users and the data aggregator is equal to zero. The system also selects a set of data values associated with the local user. Then, the system encrypts individual data values in the set based in part on the private key to produce a set of encrypted data values, thereby allowing the data aggregator to decrypt an aggregate value across the set of users without decrypting individual data values associated with the set of users, and without interacting with the set of users while decrypting the aggregate value. The system also sends the set of encrypted data values to the data aggregator.
Owner:XEROX CORP
Mining association rules over privacy preserving data
InactiveUS20050021488A1Digital data processing detailsComplex mathematical operationsPrivacy protectionData mining
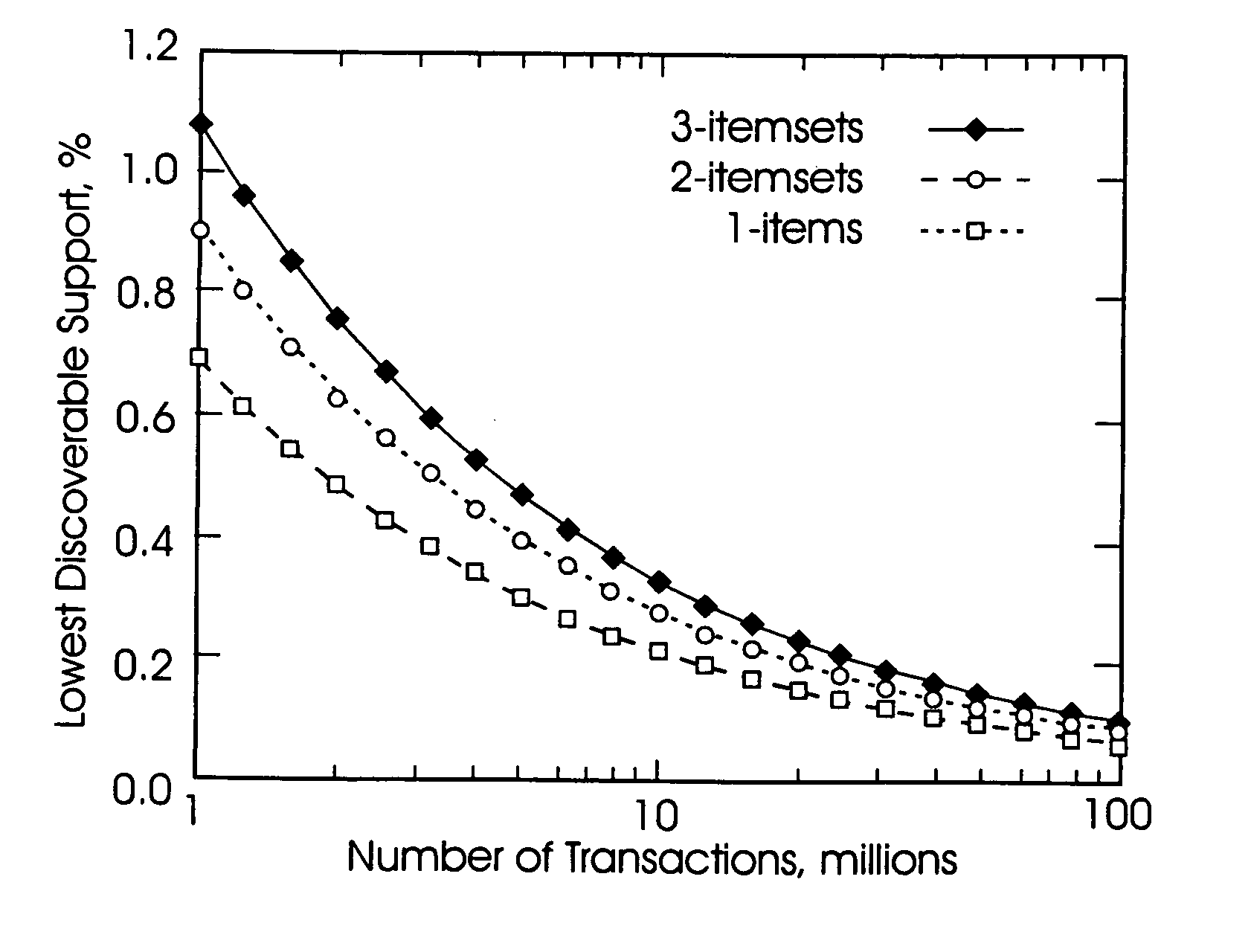
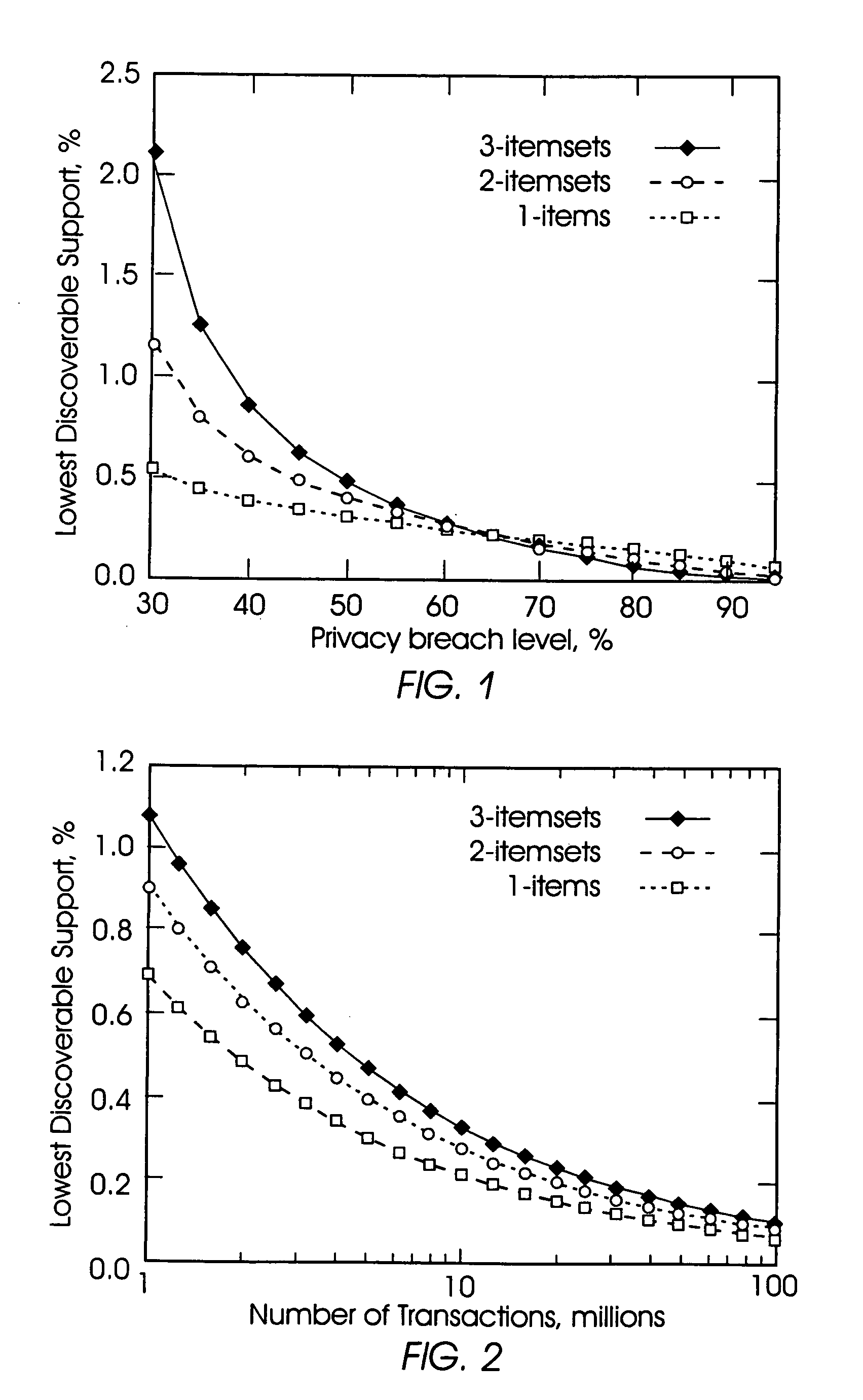
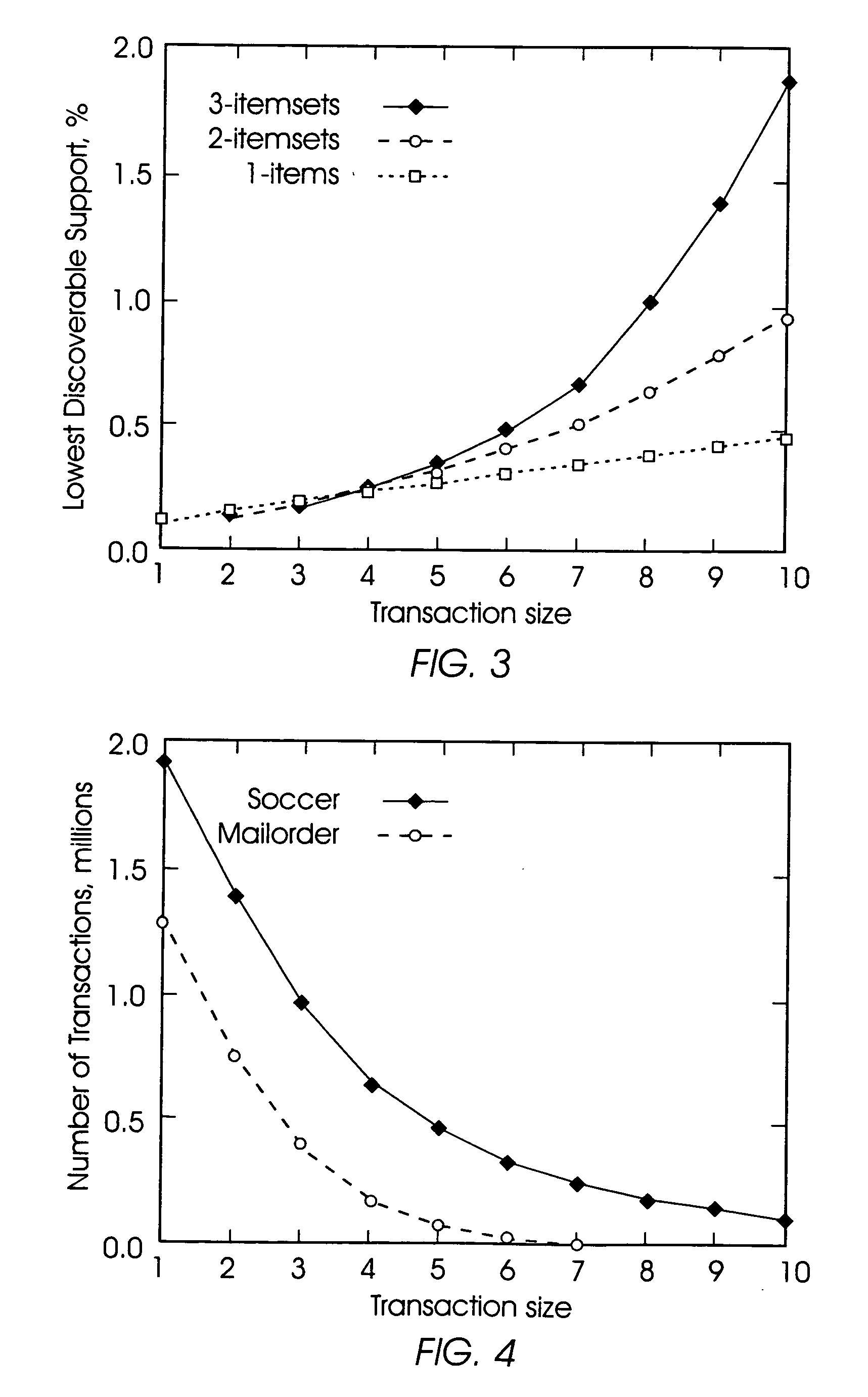
The following discloses a method of mining association rules from the databases while maintaining privacy of individual transactions within the databases through randomization. The invention randomly drops true items from transactions within a database and randomly inserts false items into the transactions. The invention mines the database for association rules after the dropping and inserting processes, and estimates the support of association rules in the original dataset based on their support in the randomized dataset. The dropping of the true items and the inserting of the false items is carried out to an extent such that the chance of finding a false itemset is sufficiently high relative to the chance of finding a true itemset in the database.
Owner:IBM CORP
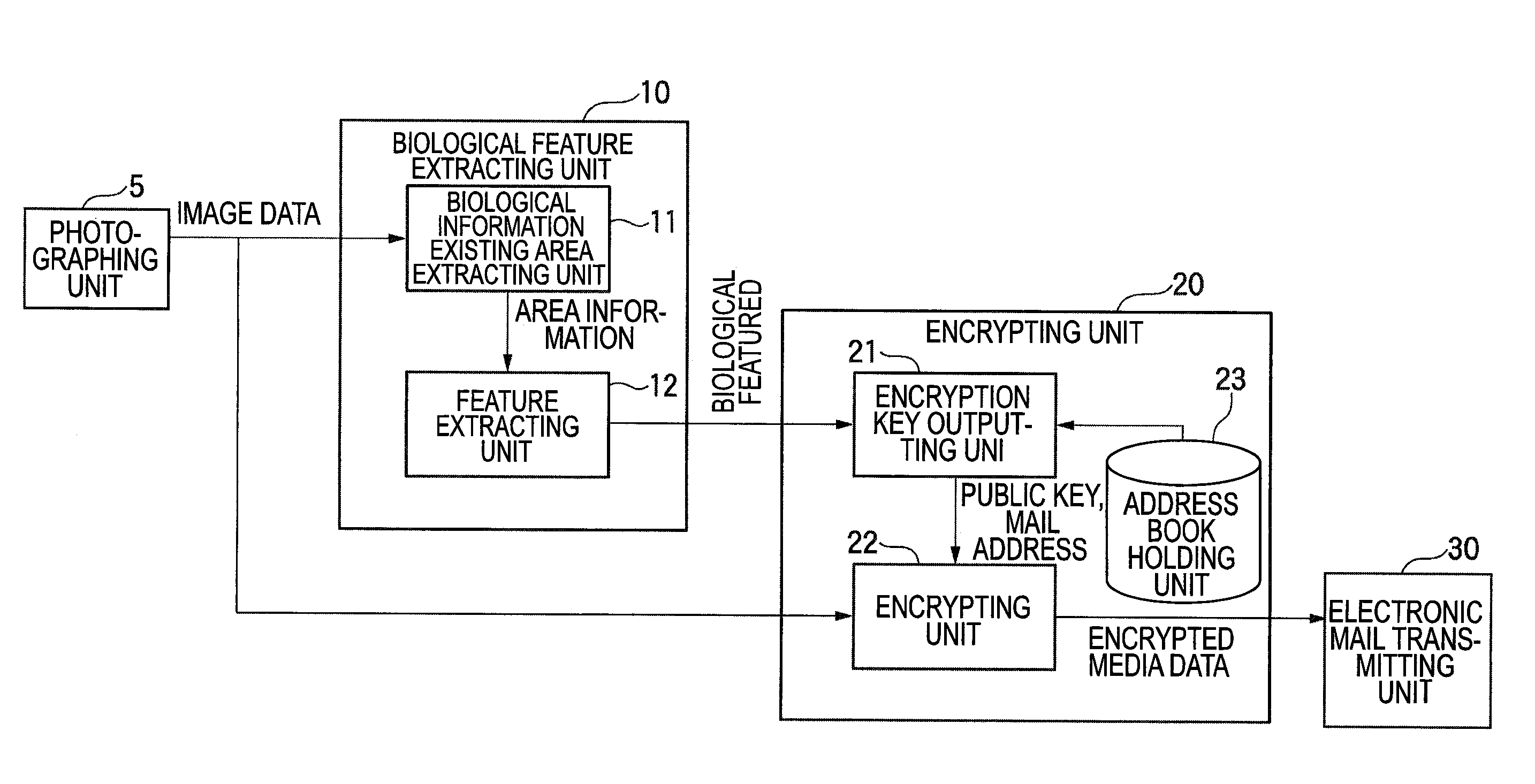
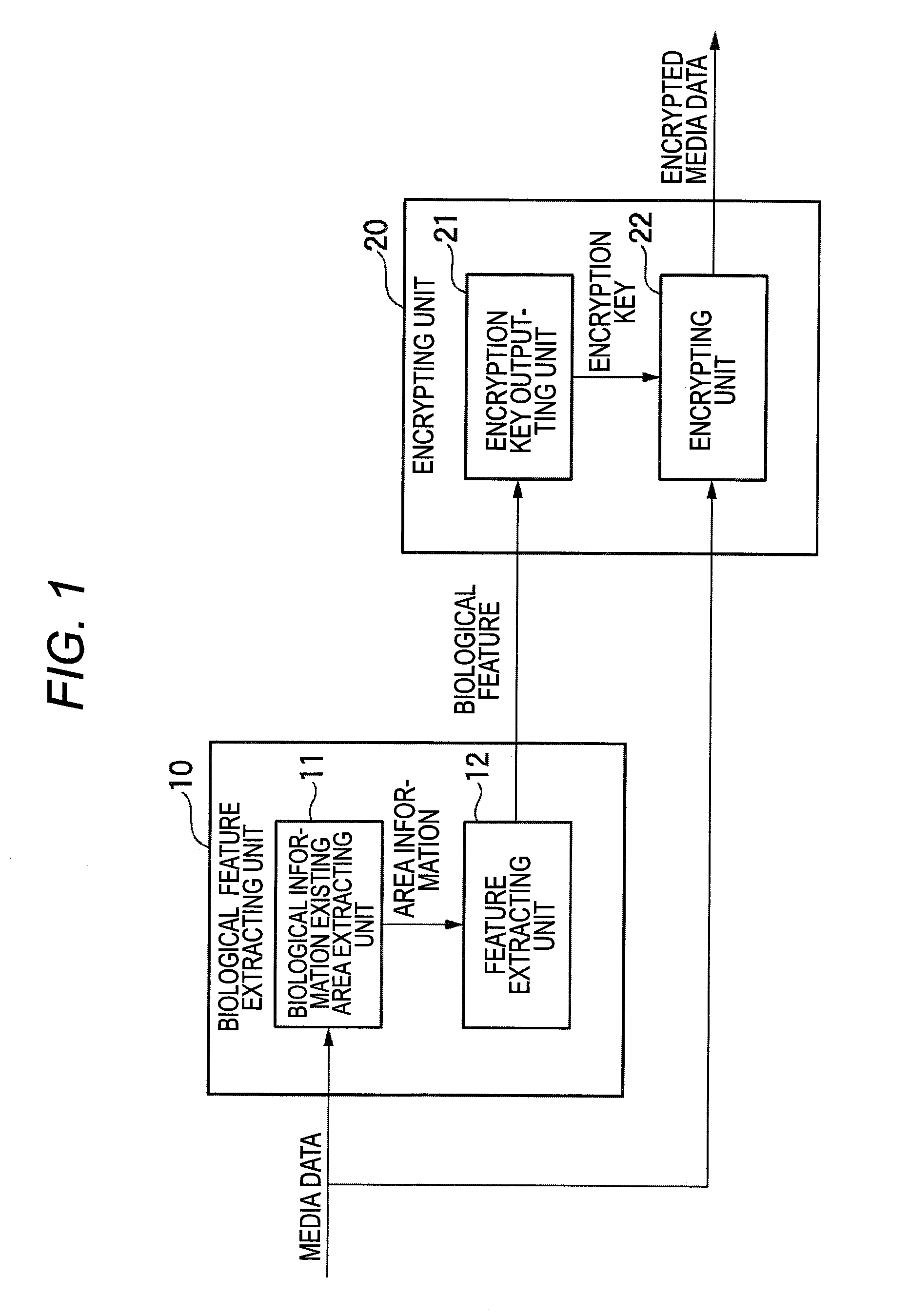
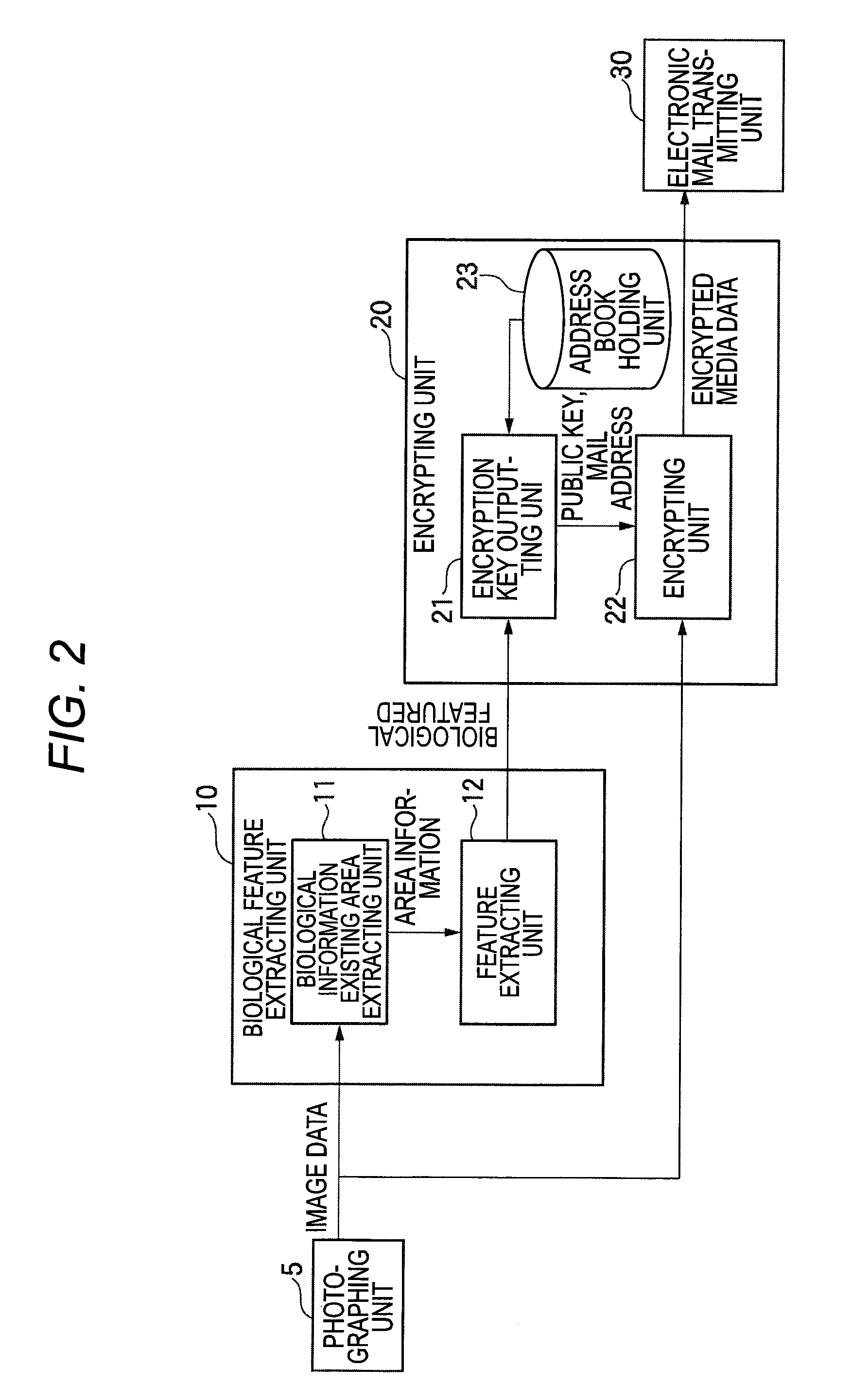
Media data processing apparatus and media data processing method
ActiveUS20090310819A1Increase management costsDeterioration of operability can be suppressedCharacter and pattern recognitionDigital data protectionPrivacy preservingOperability
In the case that media data containing image information of persons are managed, protection of privacy is realized, and an increase in management costs and a deterioration of operability are suppressed.In a media data processing apparatus into which media data containing at least one image information is inputted so as to produce encrypted media data, the media data processing apparatus is equipped with: biological feature extracting unit 10 for extracting a feature of biological information which is related to at least one person contained in said image information from the media data inputted thereinto; and encrypting process unit 20 for partially, or wholly encrypting the media data based upon the feature extracted by the biological feature extracting unit. A feature parameter of a face of the person contained in the media data is utilized.
Owner:SAMSUNG ELECTRONICS CO LTD
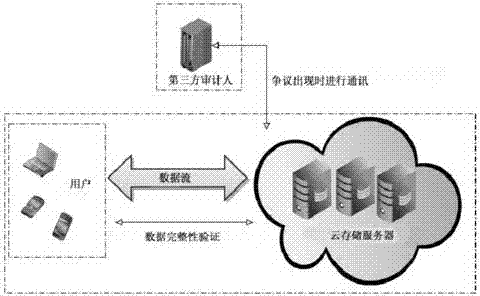
Remote data completeness verification method facing cloud storage
ActiveCN103699851AFlexible control over transparencyRealize protection controlDigital data protectionTransmissionThird partyData integrity
The invention provides a remote data completeness verification method facing cloud storage. According to the method, the aggregate signature and specified certifier signature technology is utilized, the verification function on the user data completeness by users and the third party auditors is realized, and meanwhile, the information of users for data completeness is enabled not to be leaked; the verification information transparency control is realized through the zero knowledge proving technology, and when the dispute exists between the users and a server, the third party auditors can generate the undeniable high-confidence-degree proving through the non-interactive zero knowledge proving technology. According to the method, under the condition that a cloud storage service provider is incredible, the accuracy of the cloud data completeness verification can also be ensured, and the method provided by the invention has the advantages that the realization is easy, the cost is low, the data protection performance is high, the third party audit is supported, the privacy protection mechanism is flexible, and the like.
Owner:HANGZHOU YUANTIAO TECH CO LTD
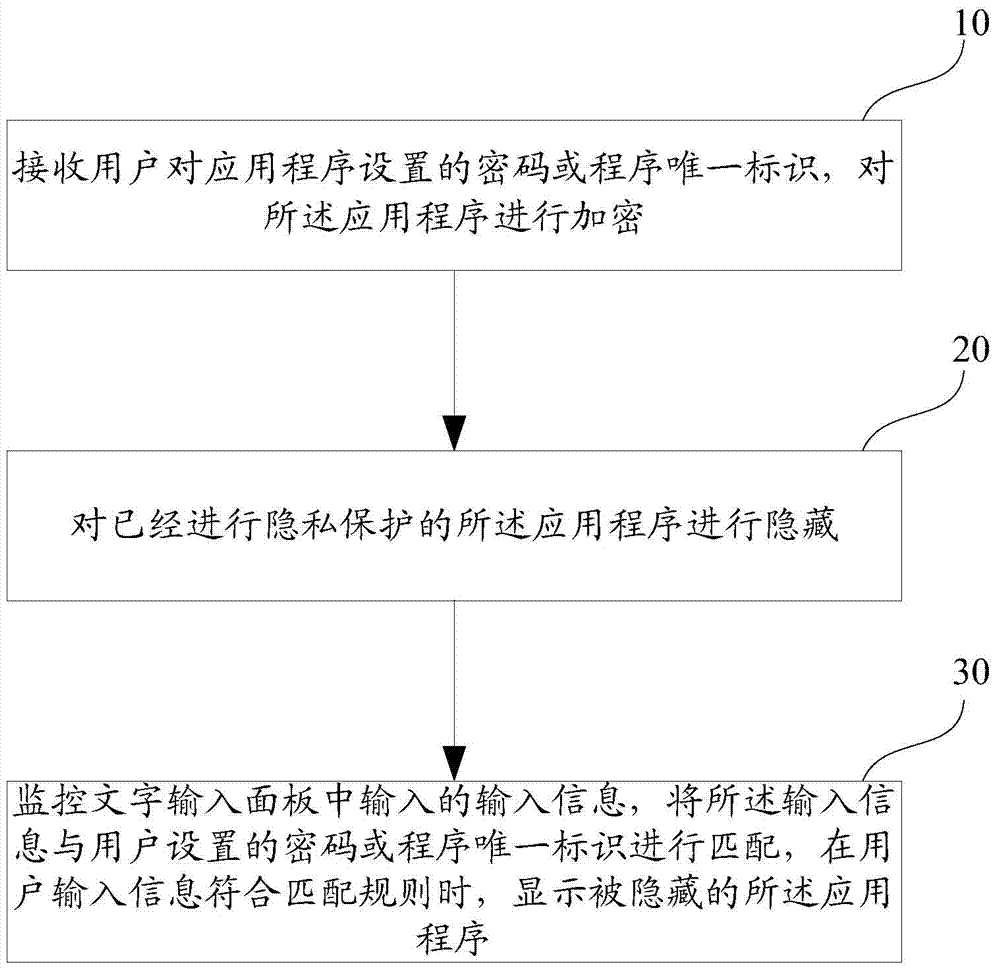
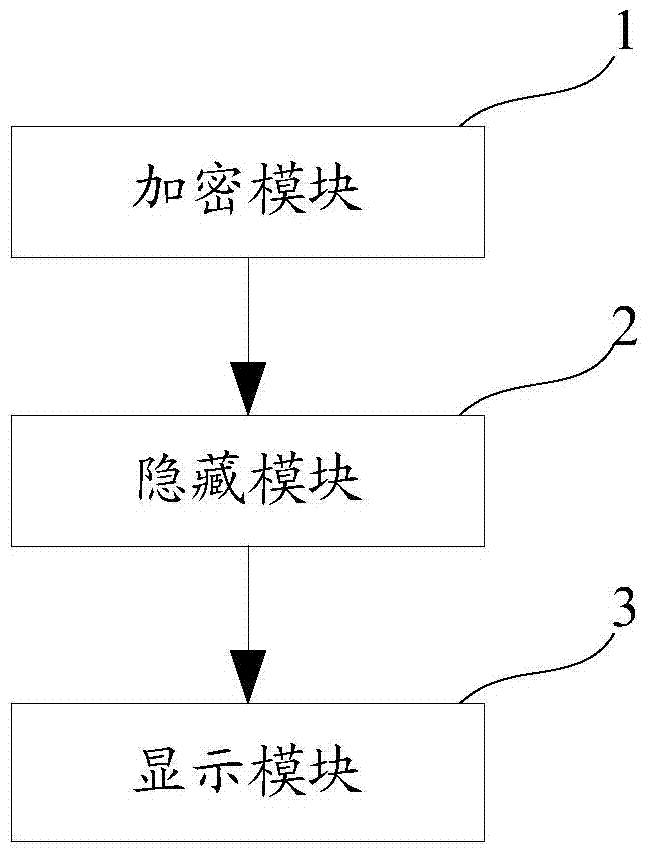
Privacy protection method and device
ActiveCN103617382AImprove concealmentReduce the risk of private content being discovered by othersDigital data authenticationUser inputPassword
The invention discloses a privacy protection method and device. The method includes: receiving a password or application unique identifier set for an application by a user, and encrypting the application; hiding the application encrypted; monitoring input information in a text input panel, matching the input information with the password or application unique identifier set by the user, and displaying the hidden application when the user-input information matches with password matching rules. Through the application of the privacy protection method and device, the private applications can be better hidden, and risk of others finding private contents is reduced.
Owner:BEIJING QIHOO TECH CO LTD
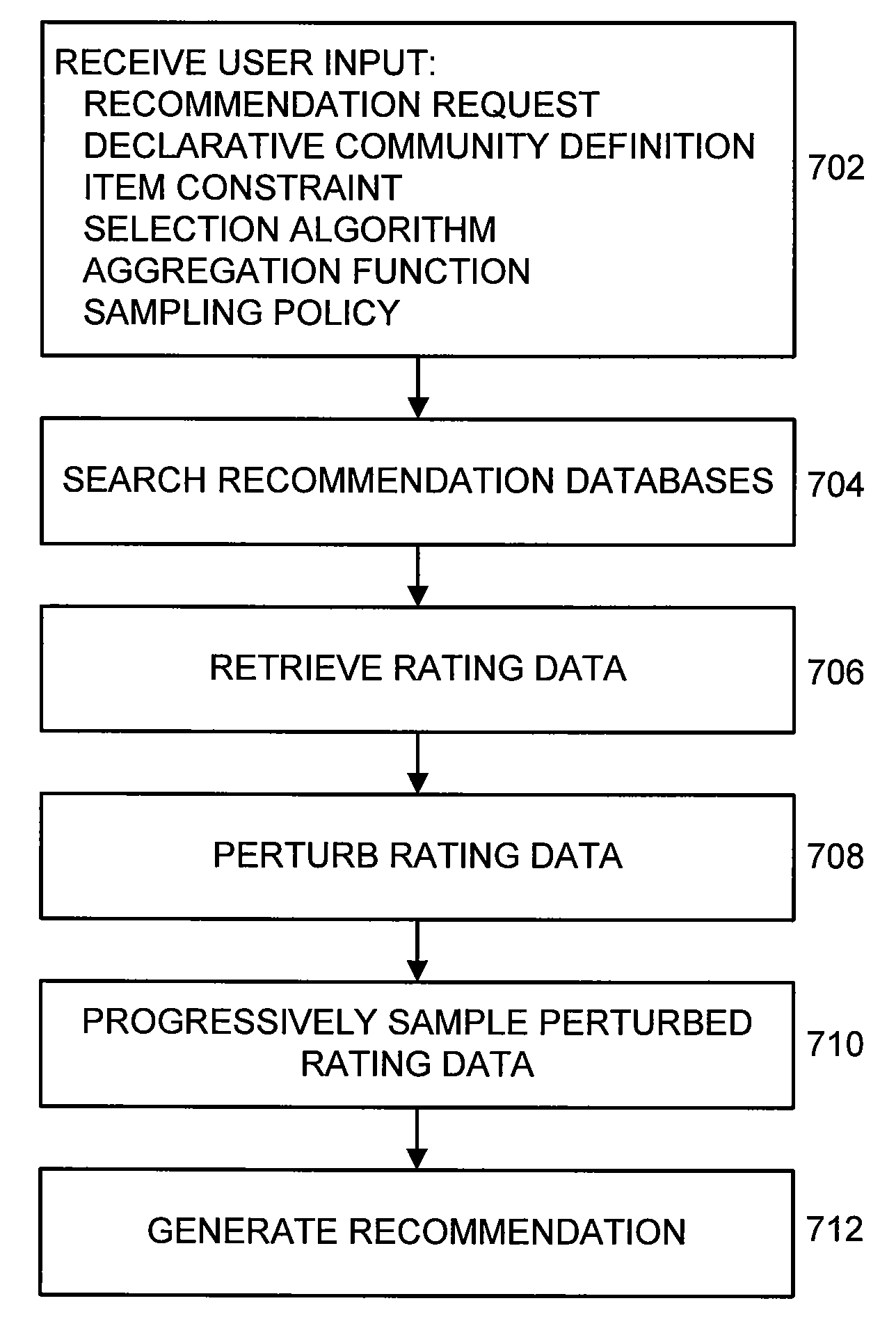
User-Powered Recommendation System
Recommendation systems are widely used in Internet applications. In current recommendation systems, users only play a passive role and have limited control over the recommendation generation process. As a result, there is often considerable mismatch between the recommendations made by these systems and the actual user interests, which are fine-grained and constantly evolving. With a user-powered distributed recommendation architecture, individual users can flexibly define fine-grained communities of interest in a declarative fashion and obtain recommendations accurately tailored to their interests by aggregating opinions of users in such communities. By combining a progressive sampling technique with data perturbation methods, the recommendation system is both scalable and privacy-preserving.
Owner:AT&T INTPROP I L P +1
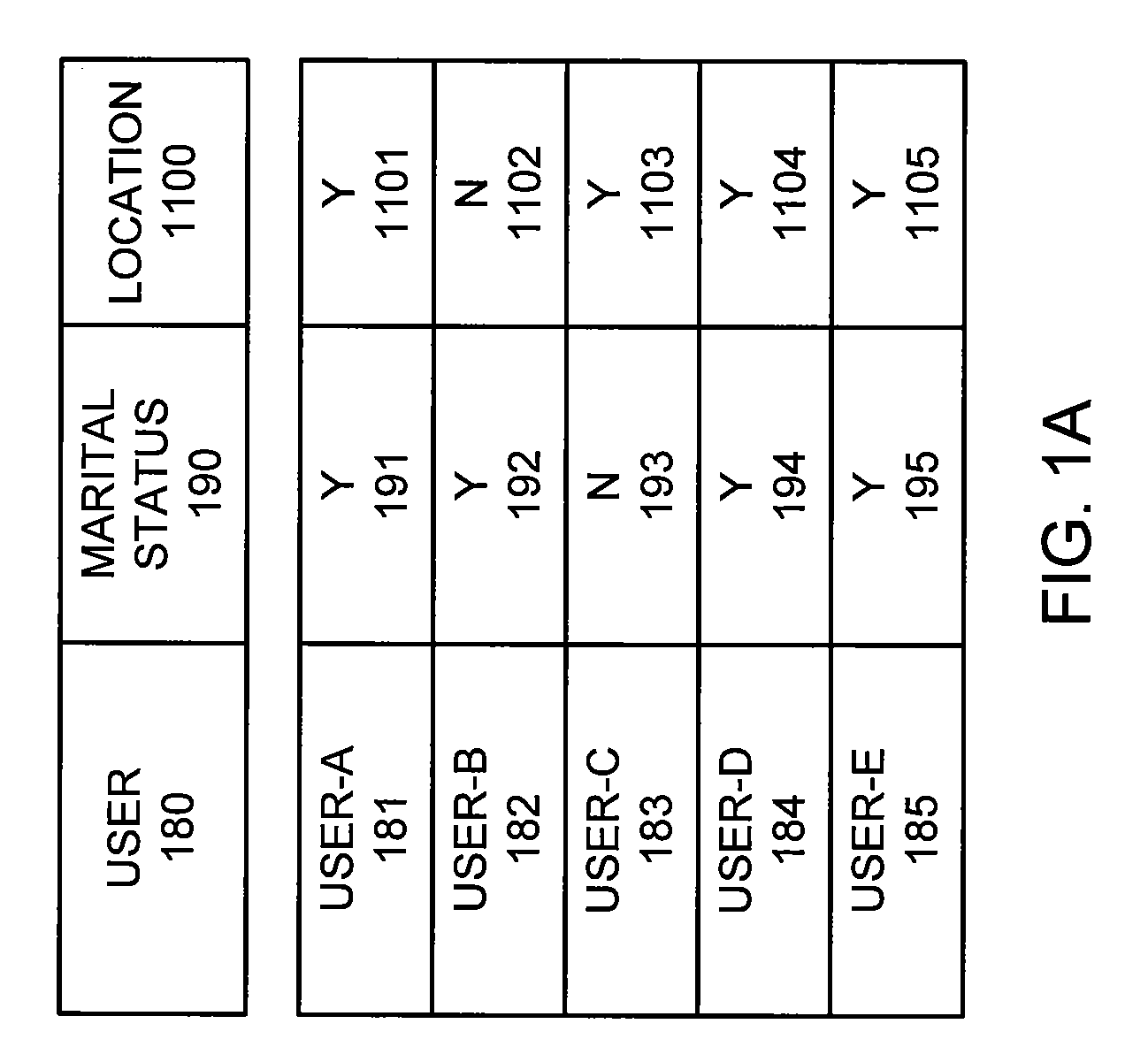
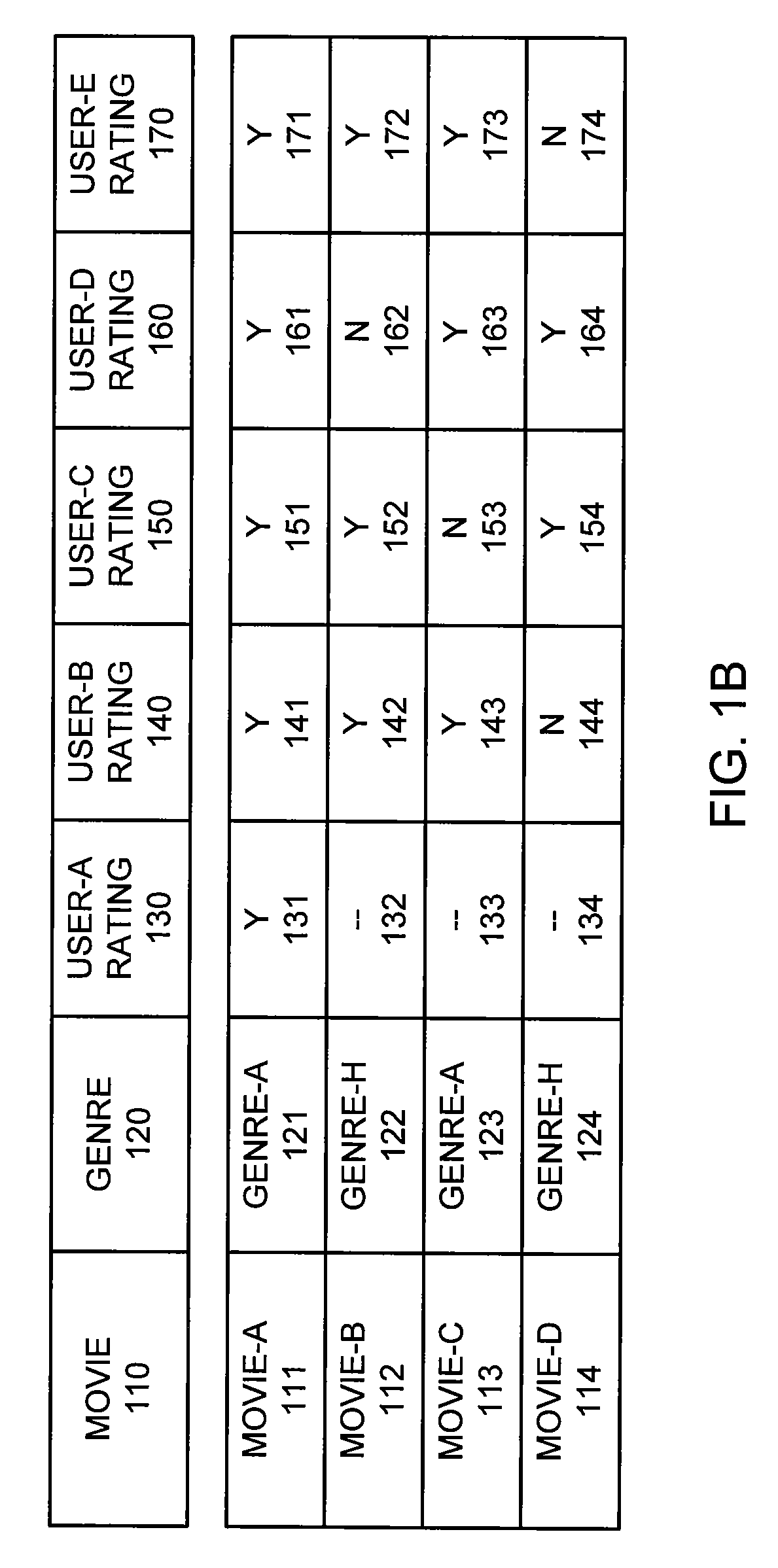
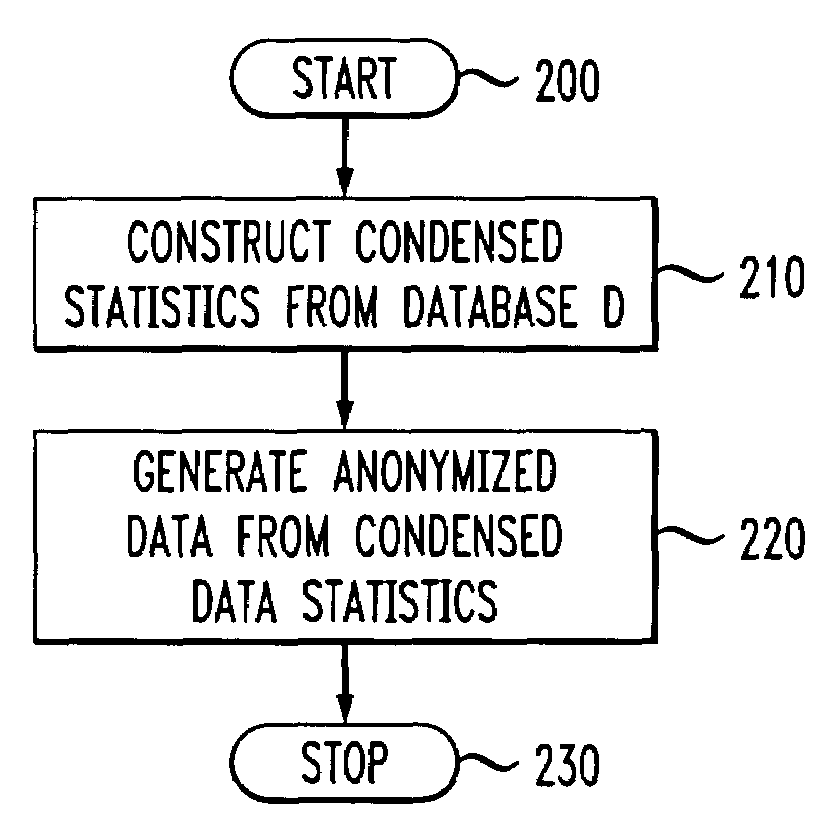
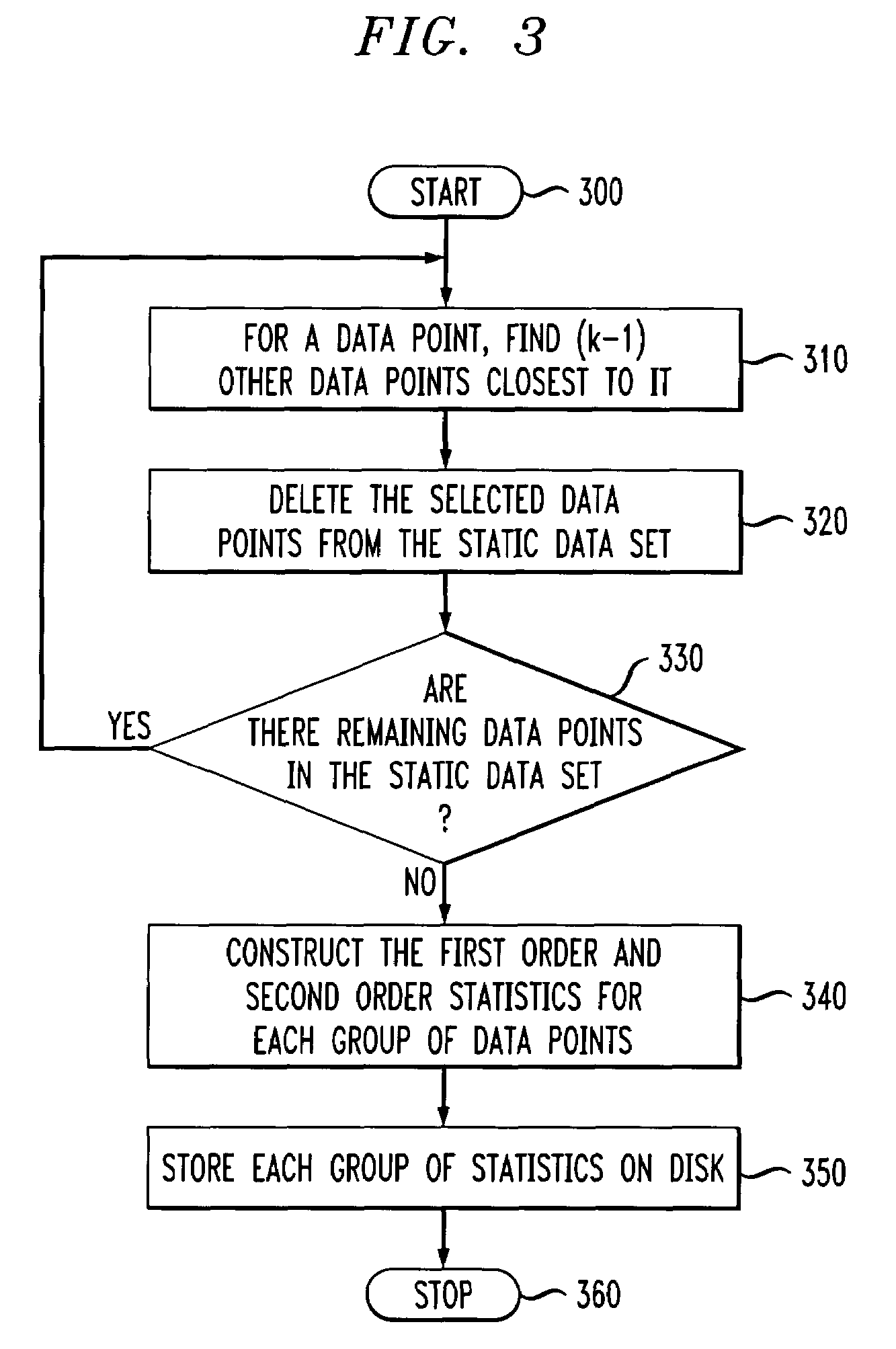
Methods and apparatus for privacy preserving data mining using statistical condensing approach
ActiveUS7302420B2Improve privacyImprove classification accuracyData processing applicationsDigital data processing detailsData setEngineering
Methods and apparatus for generating at least one output data set from at least one input data set for use in association with a data mining process are provided. First, data statistics are constructed from the at least one input data set. Then, an output data set is generated from the data statistics. The output data set differs from the input data set but maintains one or more correlations from within the input data set. The correlations may be the inherent correlations between different dimensions of a multidimensional input data set. A significant amount of information from the input data set may be hidden so that the privacy level of the data mining process may be increased.
Owner:IBM CORP
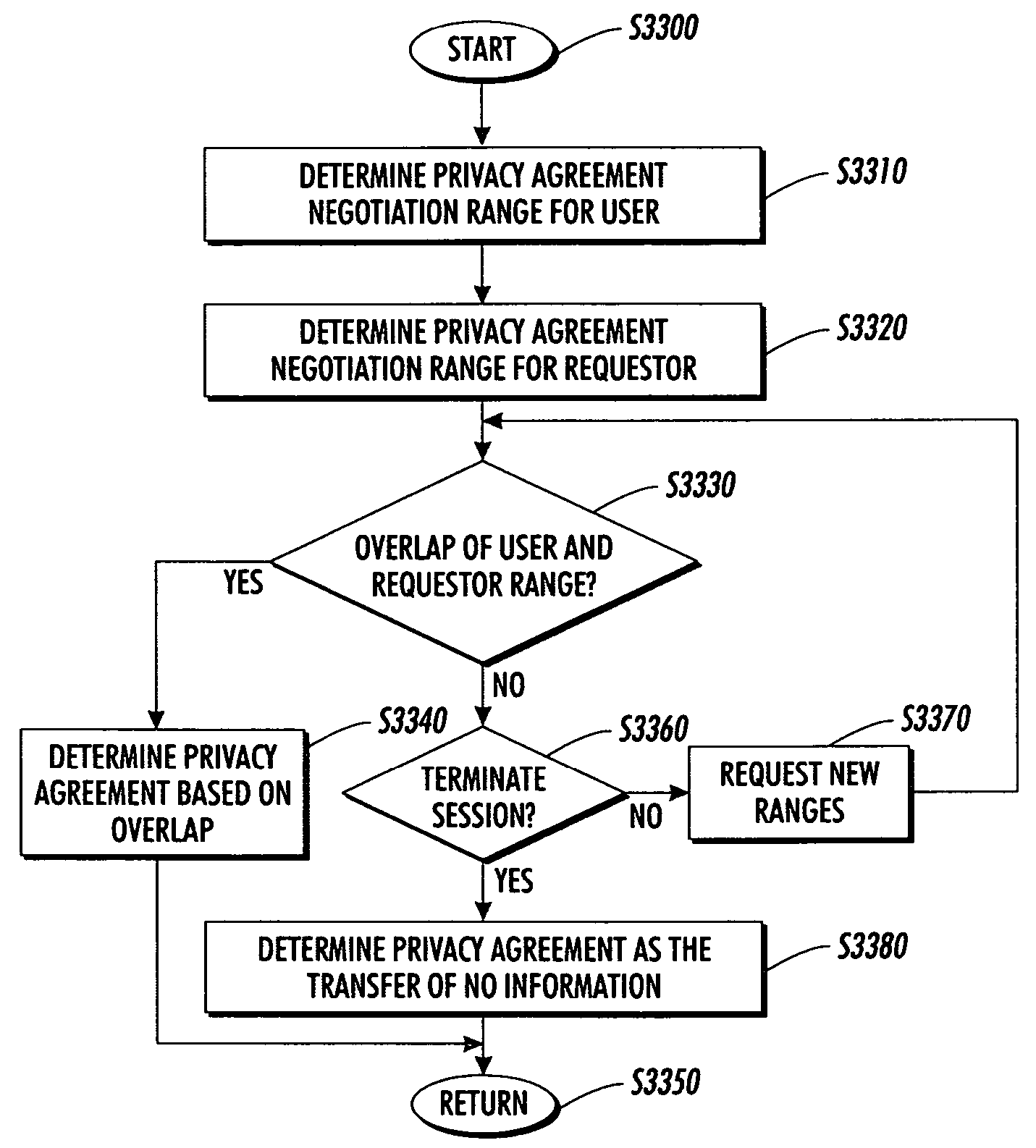
Systems and methods for protecting private information in a mobile environment
InactiveUS7707413B2Digital data processing detailsUser identity/authority verificationInternet privacyComputer compatibility
Techniques for protecting non-public information in a mobile environment are provided. A request for non-public information about users in a mobile environment is received. Privacy policies, non-public and optional public information about the users affected by the request are determined. An optional privacy impact indicator is determined based on how satisfying the request increases the current public information about the users. Crowds of users having similar attribute name / values are optionally determined. User and optional requestor privacy policies which associate threshold release criteria such minimum crowd size, minimum consideration with the non-public information are determined. A privacy agreement is reached for the disclosure of the requested non-public information based on the compatibility of the requester and user privacy policies. Privacy protecting transformations are optionally determined and applied to create crowds or groups associated with the requested attribute.
Owner:PALO ALTO RES CENT INC
Efficient Privacy-Preserving Ciphertext-Policy Attribute Based Encryption and Broadcast Encryption
InactiveUS20160241399A1Key distribution for secure communicationPublic key for secure communicationCommunications systemAttribute-based encryption
A new construction of CP-ABE, named Privacy Preserving Constant CP-ABE (PPC-CP-ABE) that significantly reduces the ciphertext to a constant size with any given number of attributes is disclosed. PPCCP-ABE leverages a hidden policy construction such that the recipients' privacy is preserved efficiently. A Privacy Preserving Attribute Based Broadcast Encryption (PP-AB-BE) scheme is disclosed. PP-AB-BE is flexible because a broadcasted message can be encrypted by an expressive hidden access policy, either with or without explicit specifying the receivers. PP-AB-BE significantly reduces the storage and communication overhead. Also, PP-AB-BE attains minimal bound on storage overhead for each user to cover all possible subgroups in the communication system.
Owner:ARIZONA STATE UNIVERSITY
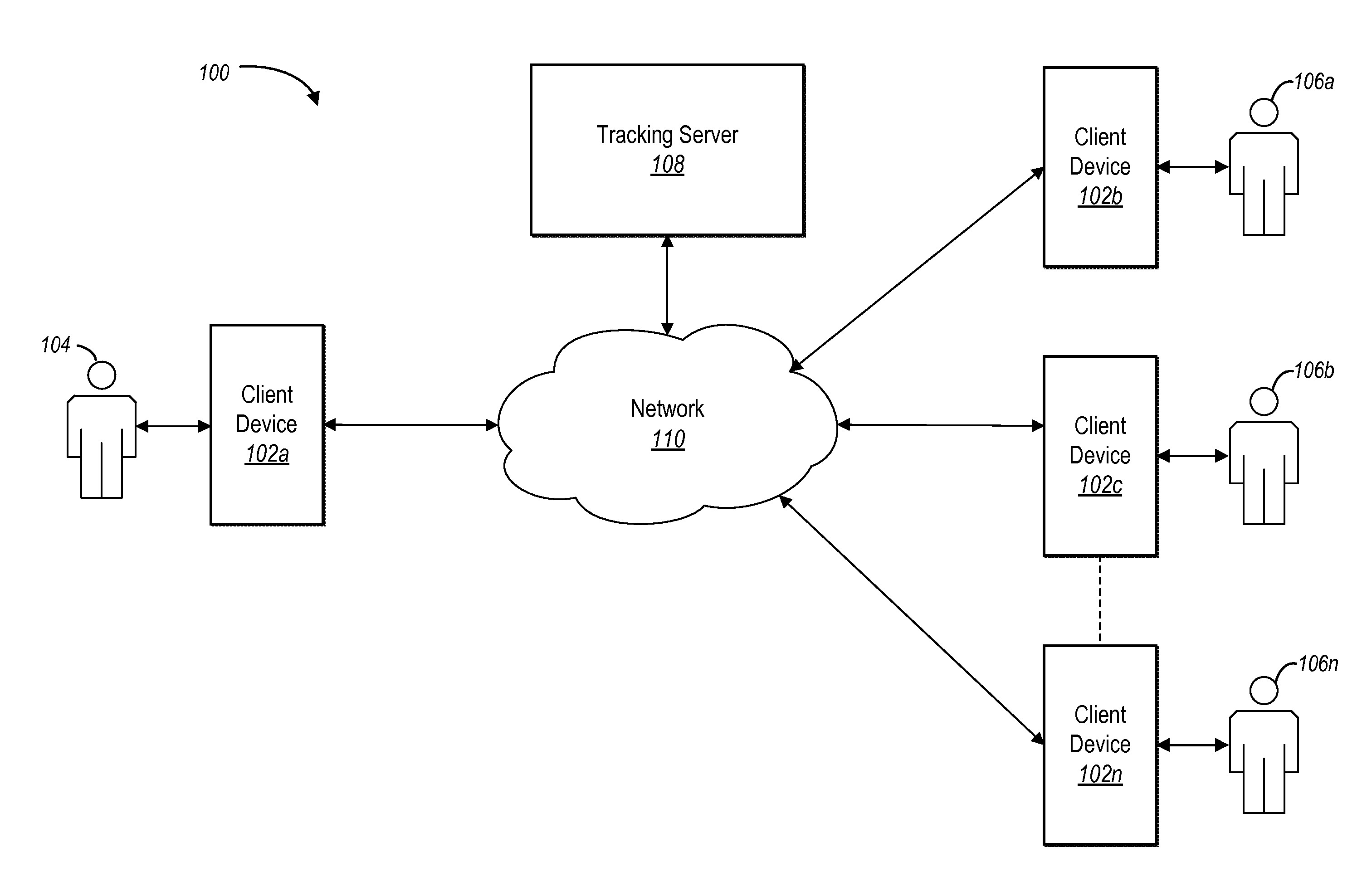
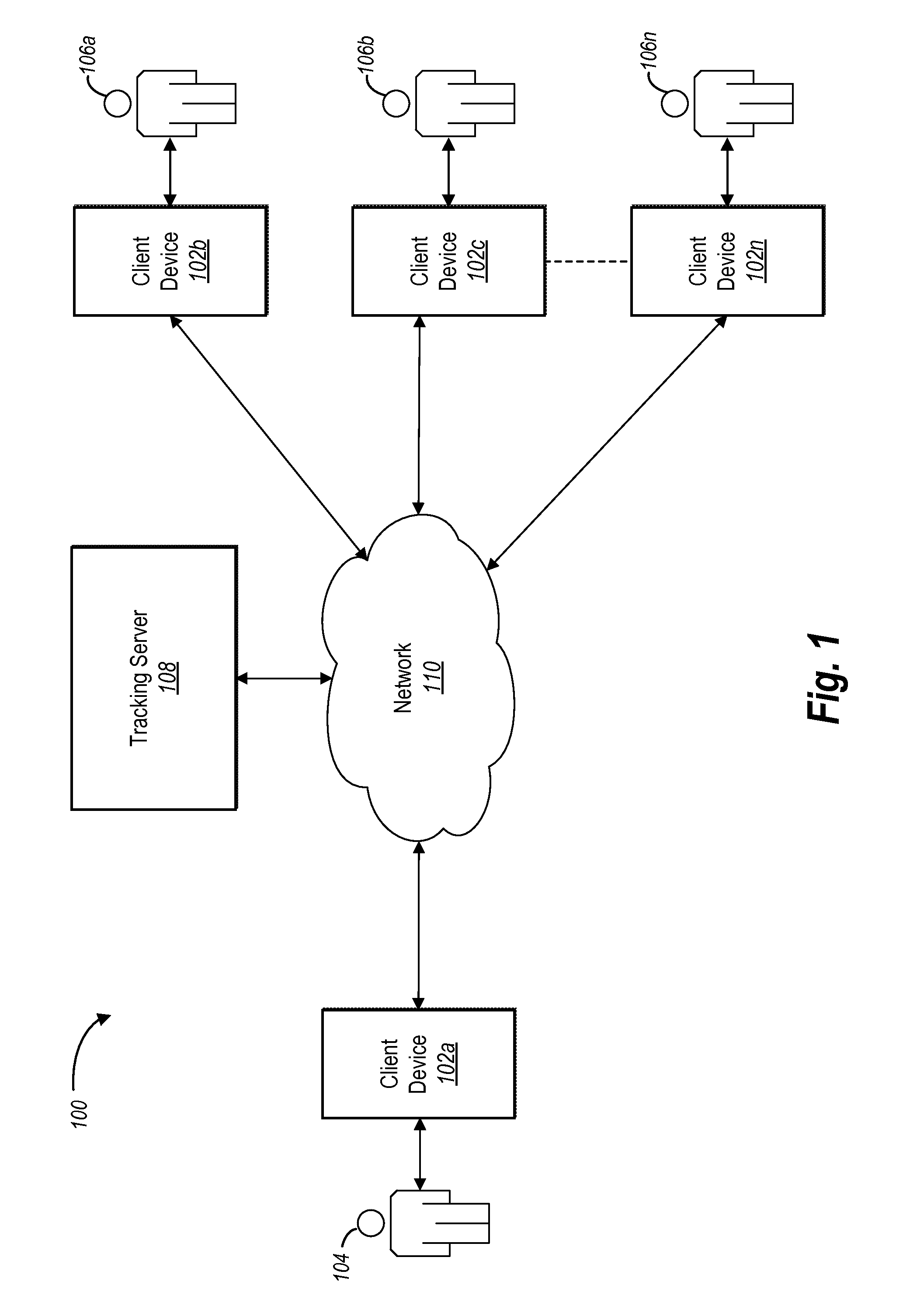
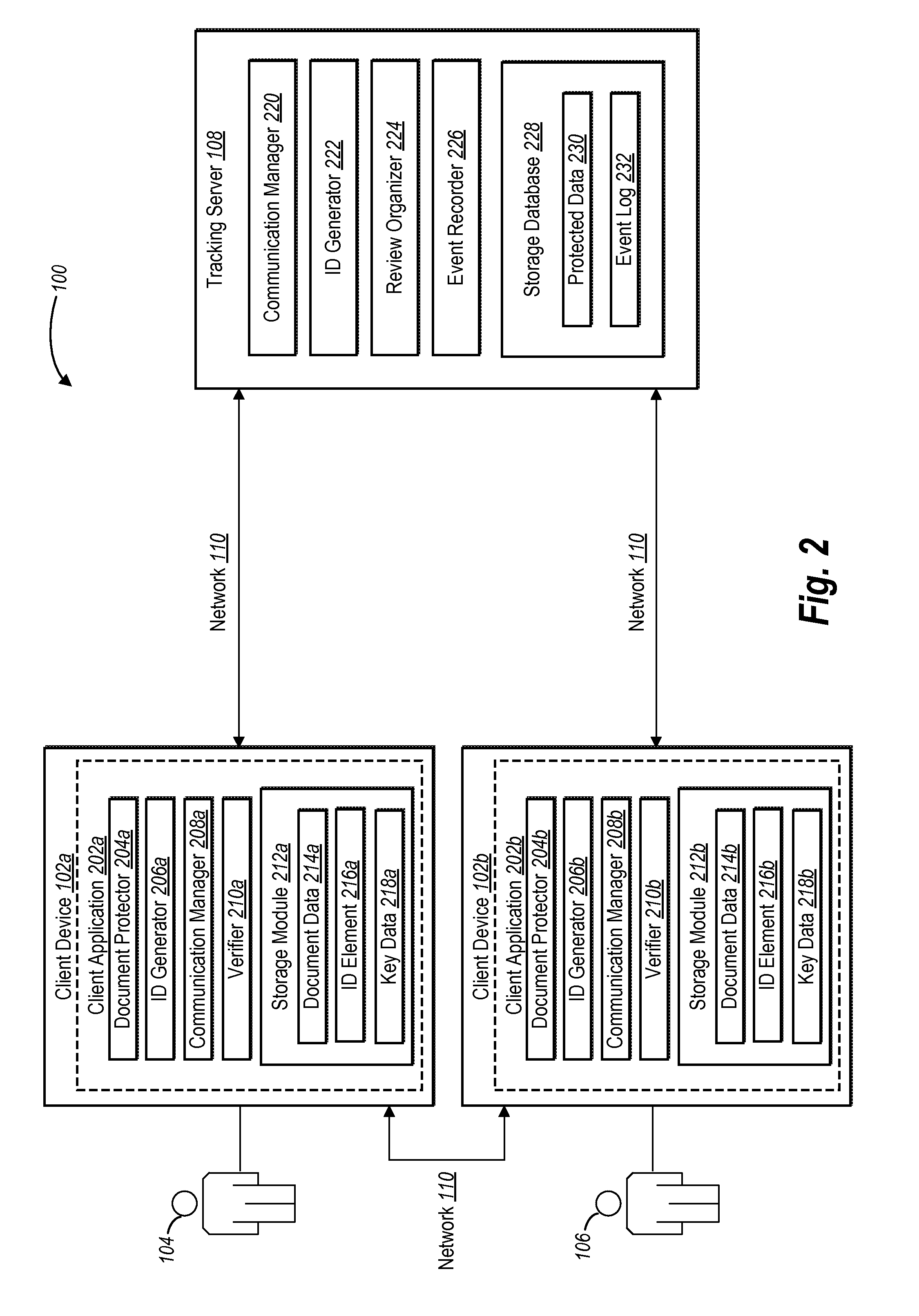
Privacy preserving electronic document signature service
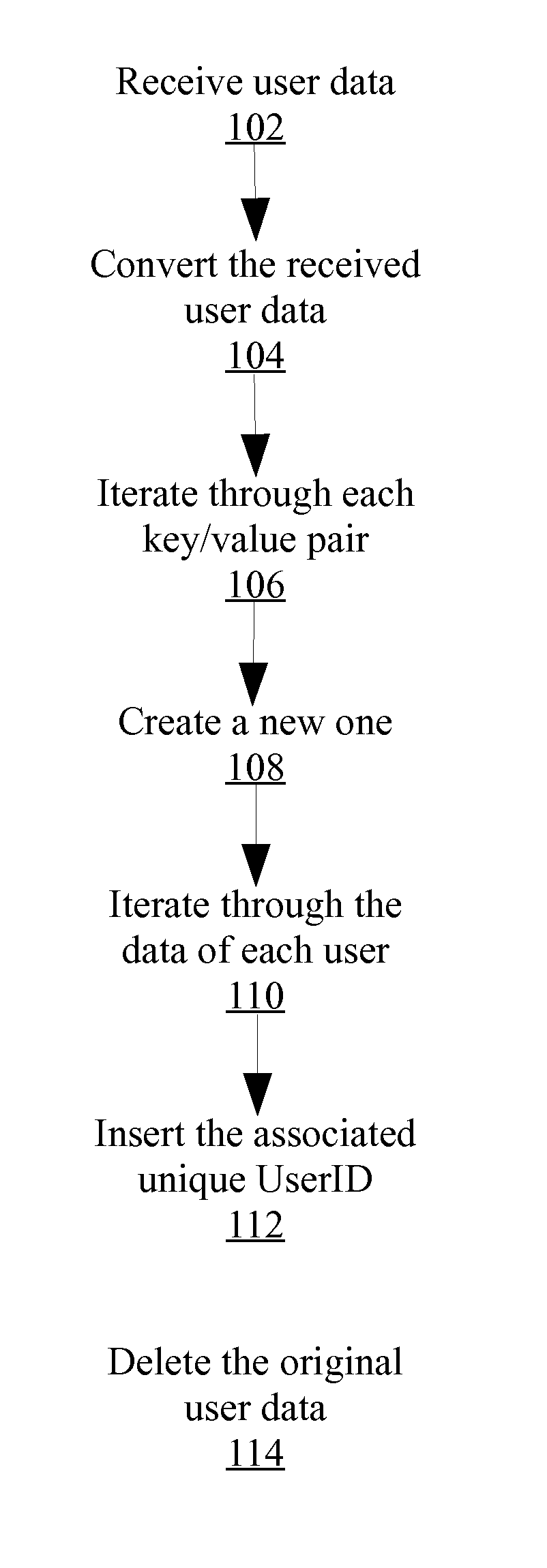
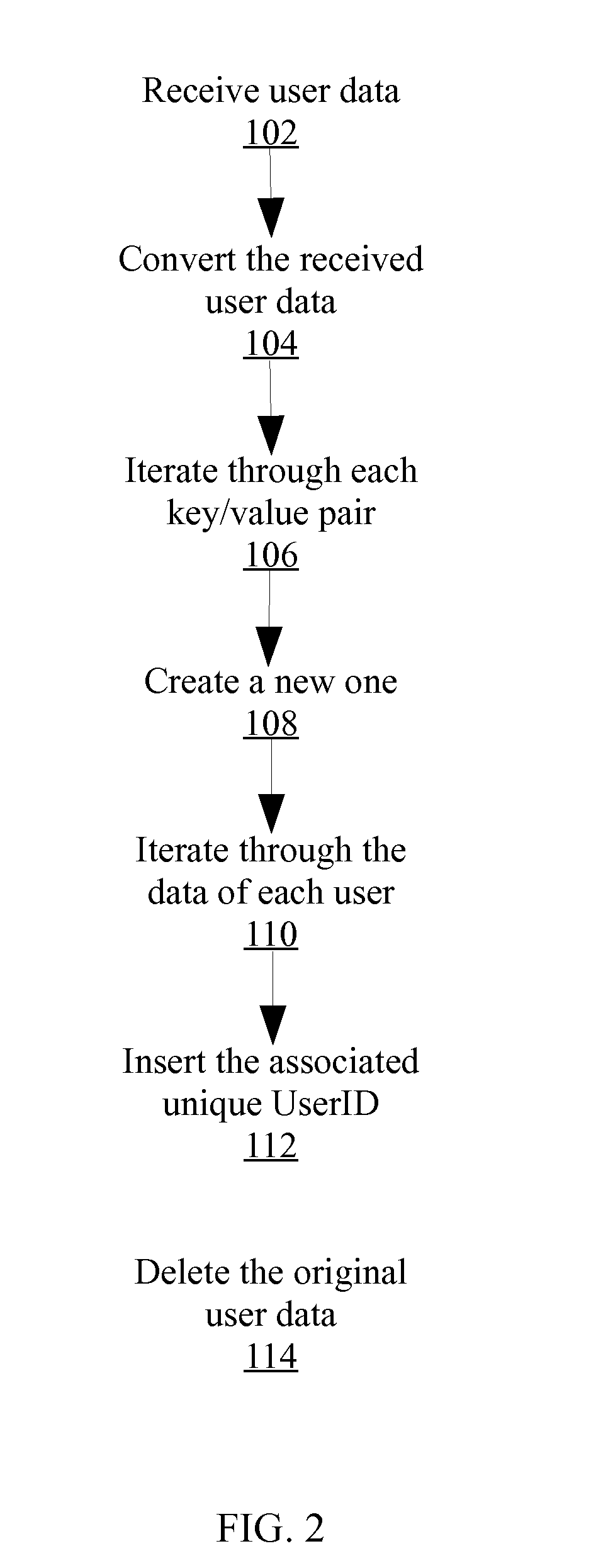
ActiveUS20150312227A1Easy to sign forEffective trackingUser identity/authority verificationDigital data authenticationElectronic documentPrivacy preserving
An electronic document signature system preserves the security of an electronic document while tracking a signature process corresponding to the electronic document. In particular, using a client application on a client device, an originating user can protect an electronic document and send the protected electronic document to a tracking server. The tracking server receives only a protected document such that the security the electronic document is preserved. Using a client applications on client devices, one or more participating users can subsequently receive the protected document from the tracking server, access the contents of the electronic document, and sign the electronic document. The tracking server can record events that occur with respect to the protected document to create an event log.
Owner:ADOBE INC
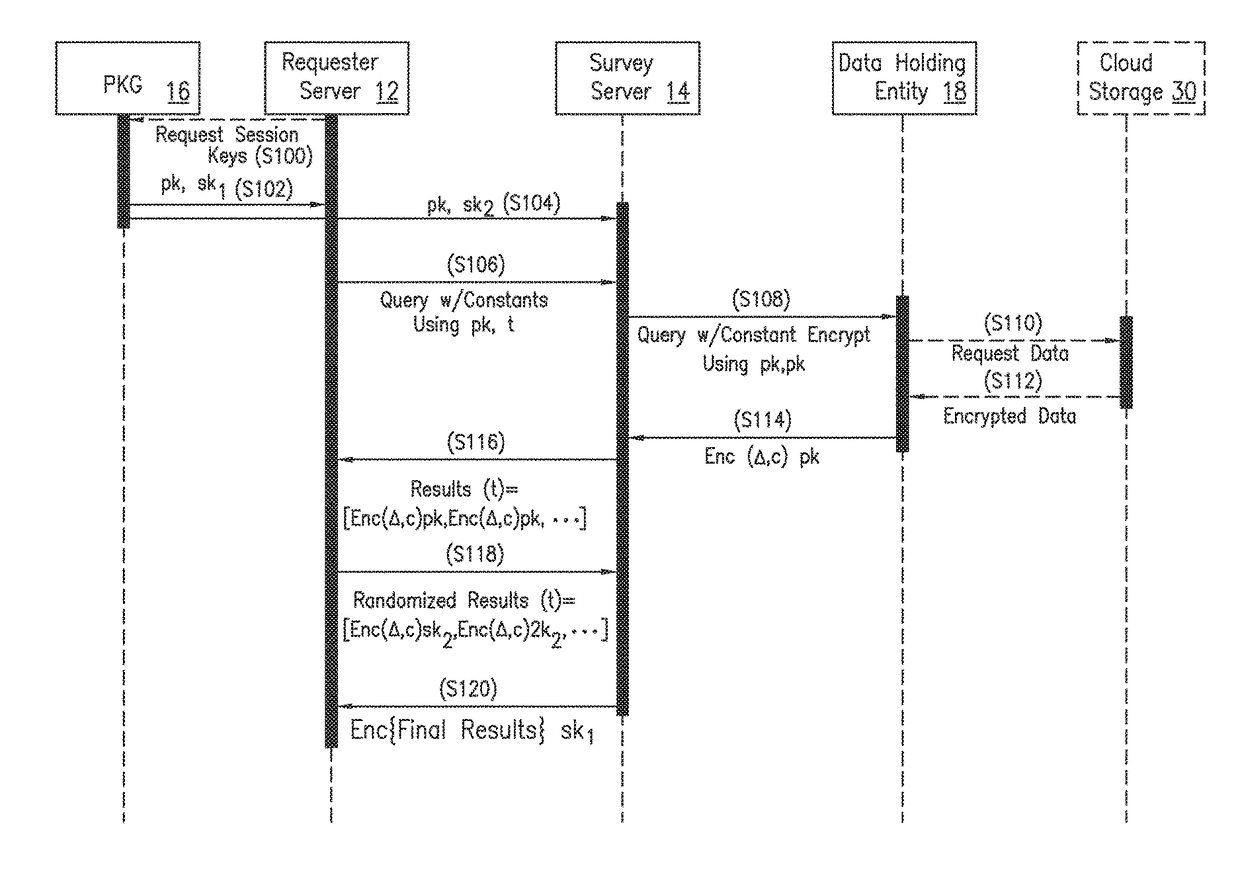
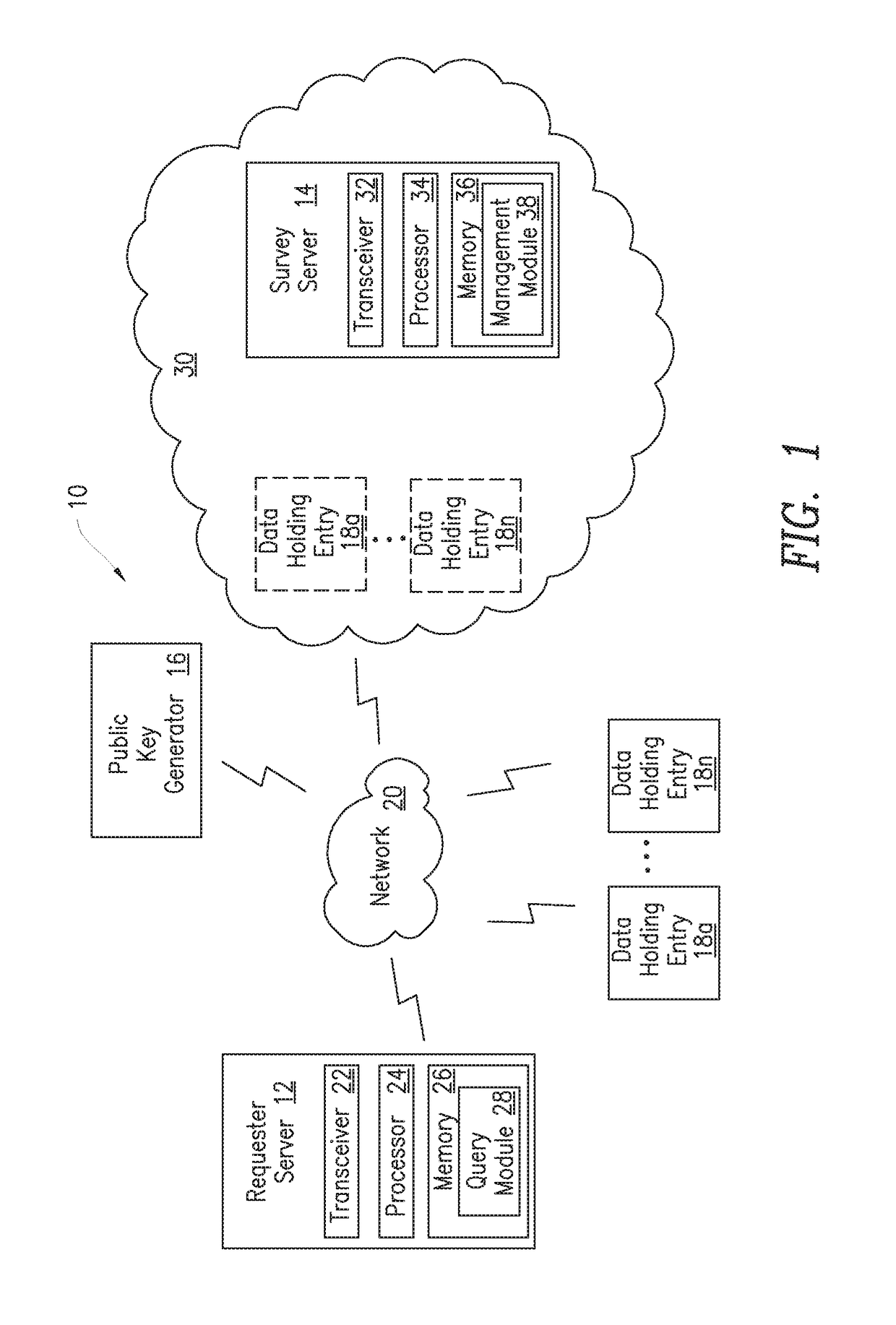
Privacy-preserving querying mechanism on privately encrypted data on semi-trusted cloud
ActiveUS20170124348A1Key distribution for secure communicationDigital data protectionPrivacy preservingProtocol for Carrying Authentication for Network Access
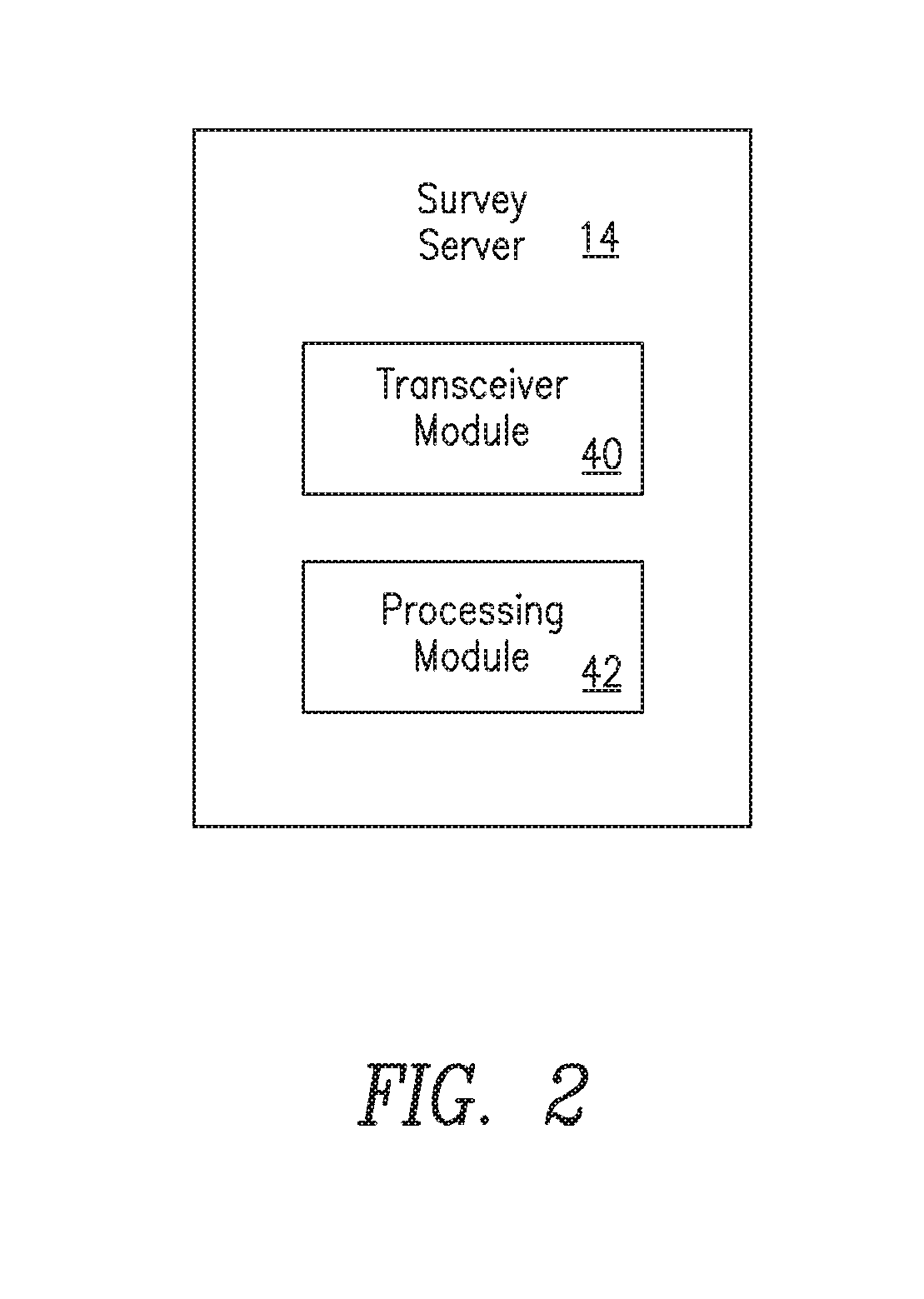
A method for a survey server for managing query communications between at least a requester server and at least one data holding entity is provided. The requester server holds a first share of a private key and the survey server holds a second share of the private key. An encrypted query is received and then forwarded to at least one data holding entity. A plurality of comparison responses is received. Each comparison response is generated by a private comparison protocol that compares the encrypted query with encrypted data. The encrypted data having been encrypted using the public key. Each comparison response having been partially decrypted with the first share of the private key and placed in the array in a randomized order. The array is decrypted using the second share of the private key. At least one result of the query is determined.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method for Querying Data in Privacy Preserving Manner Using Attributes
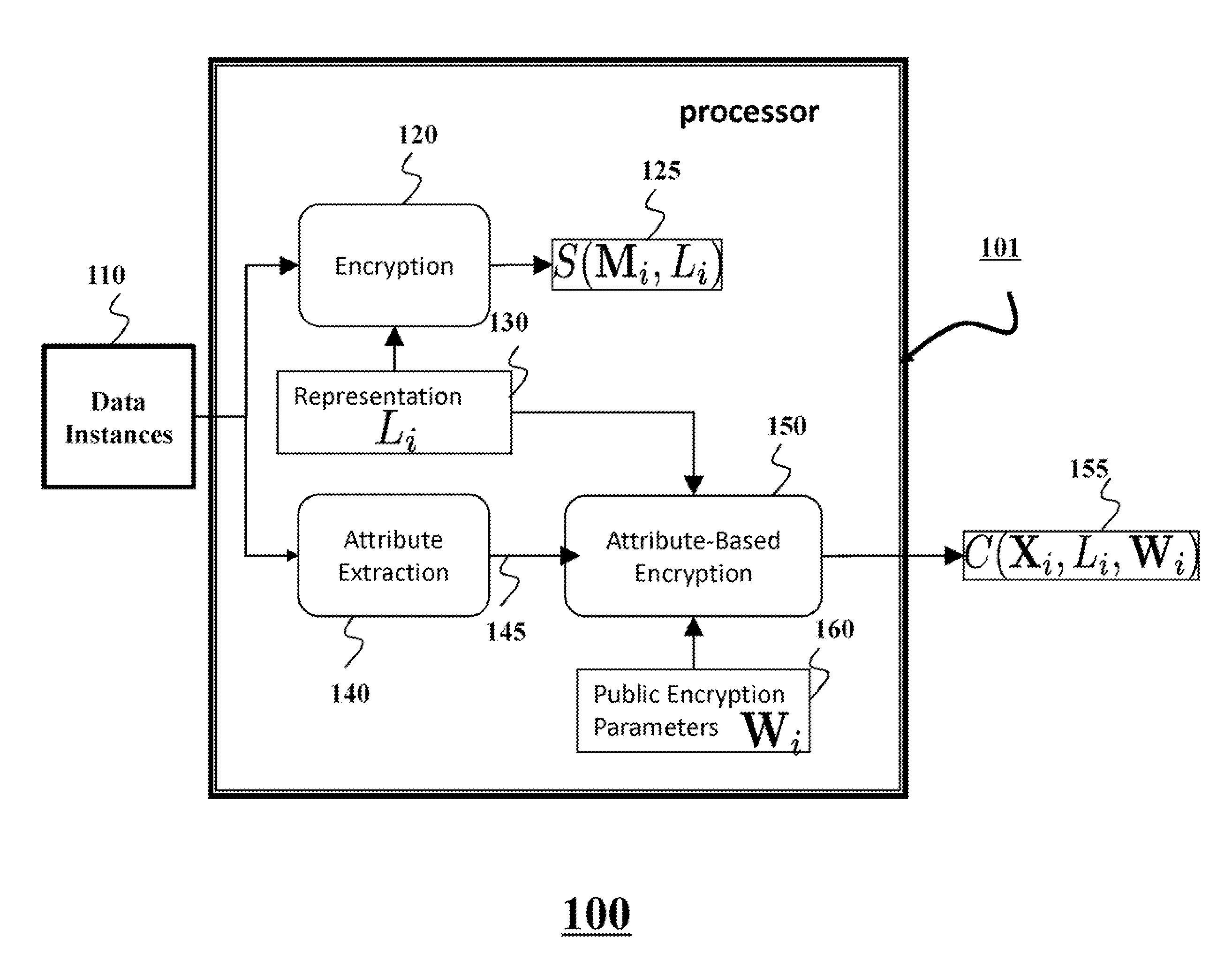
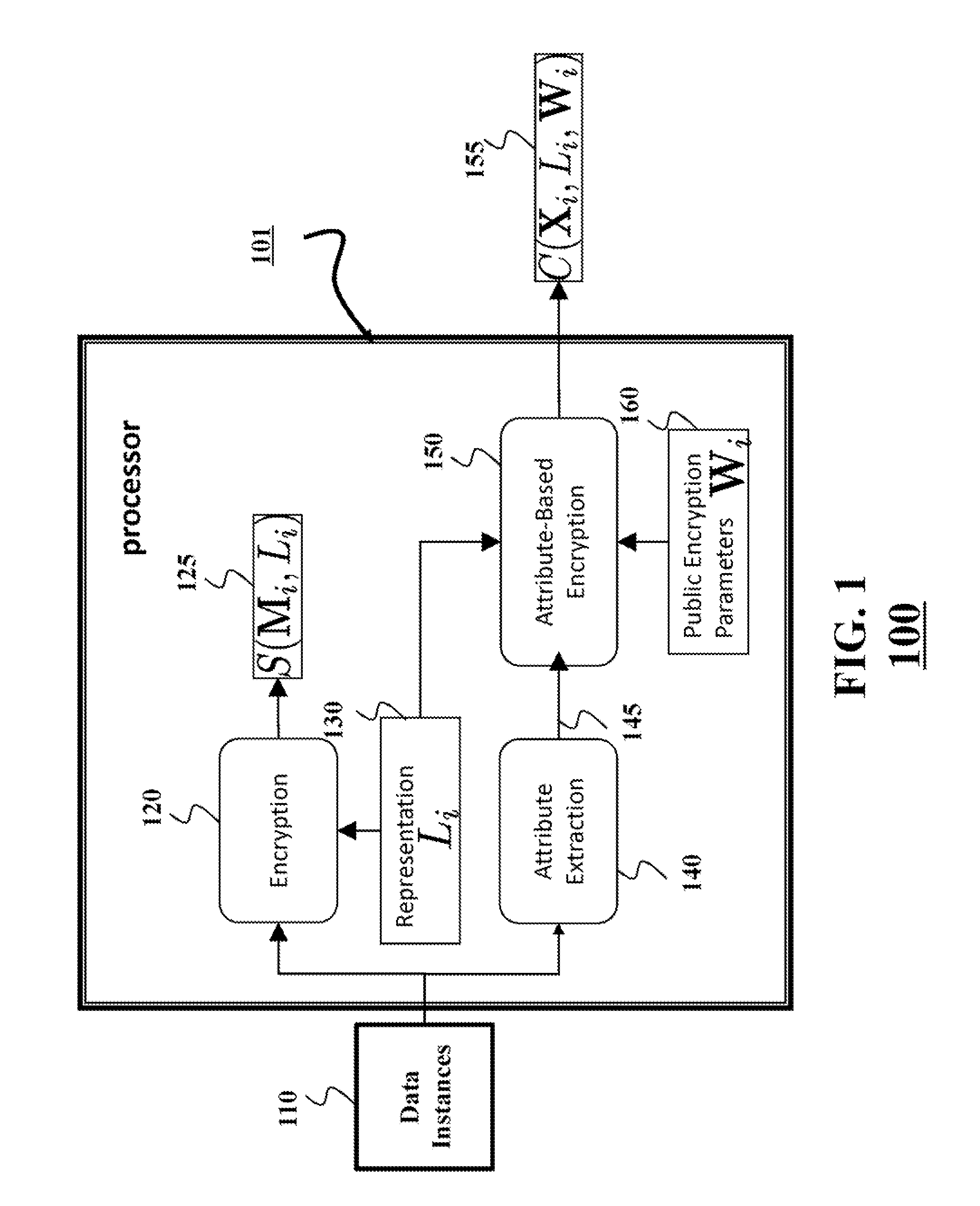
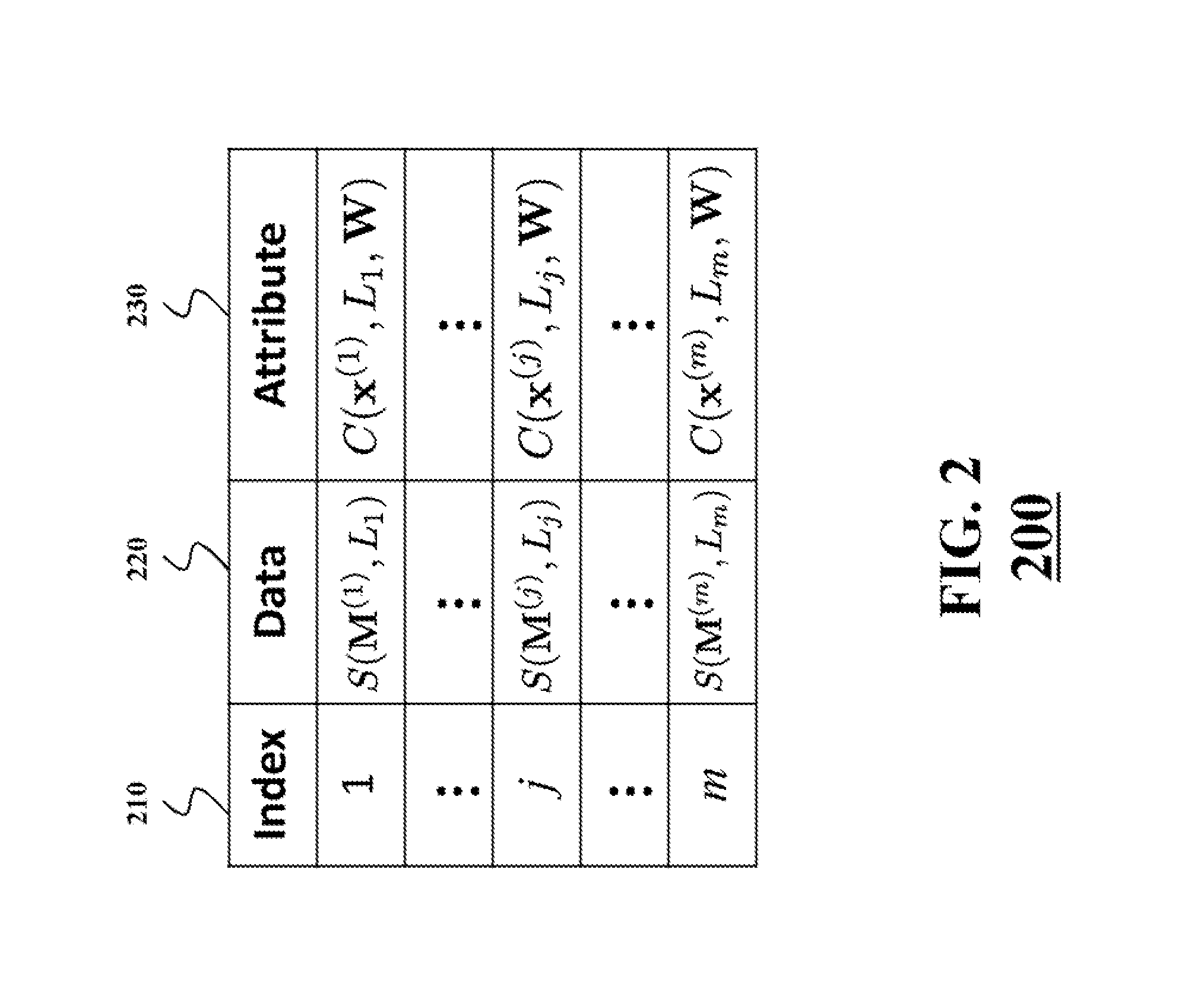
InactiveUS20130339751A1Unauthorized memory use protectionHardware monitoringCiphertextEncrypted function
A client queries a set of encrypted data instances located at a server with a query attribute of the client. The set of encrypted data instances is associated with a set of ciphertexts, wherein a ciphertext is an encrypted function of a representation of a corresponding data instance and a data instance attribute extracted from the corresponding data instance. The client decrypts the ciphertext from the set of ciphertexts based on a distance function of the query attribute and the data instance attribute to produce the representation, and accesses the corresponding data instance using the representation.
Owner:MITSUBISHI ELECTRIC RES LAB INC
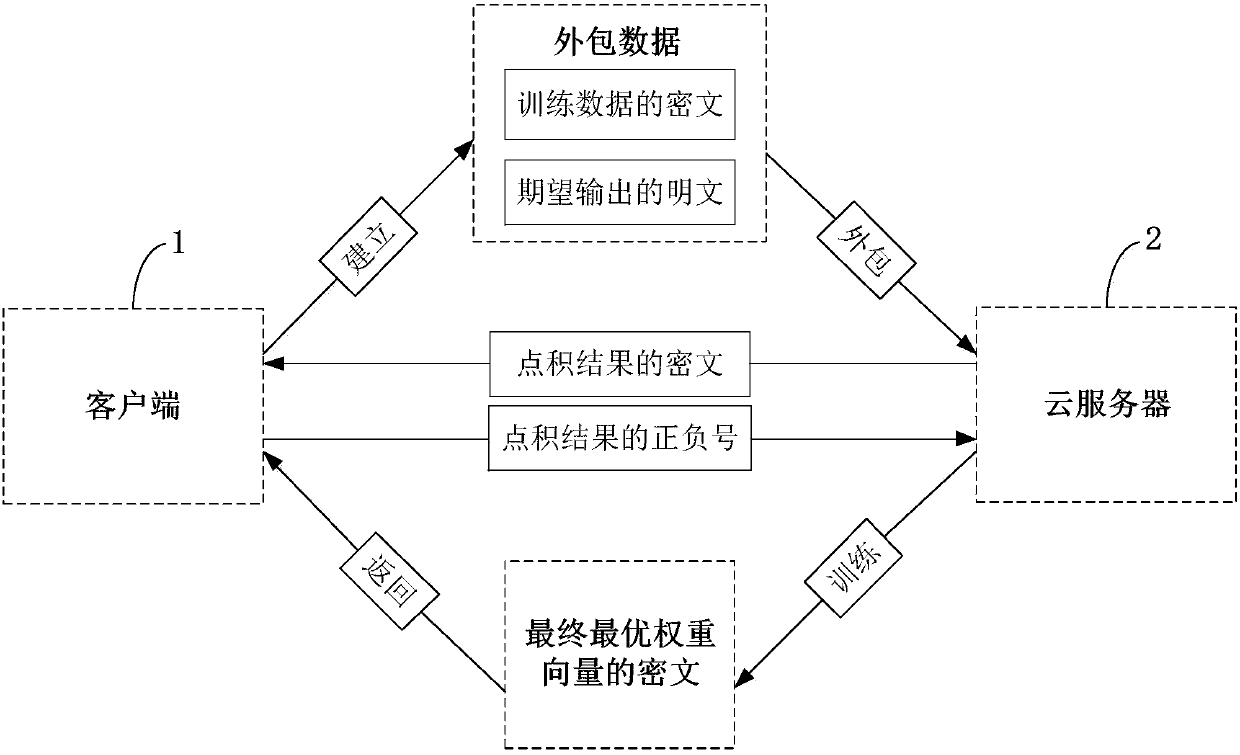
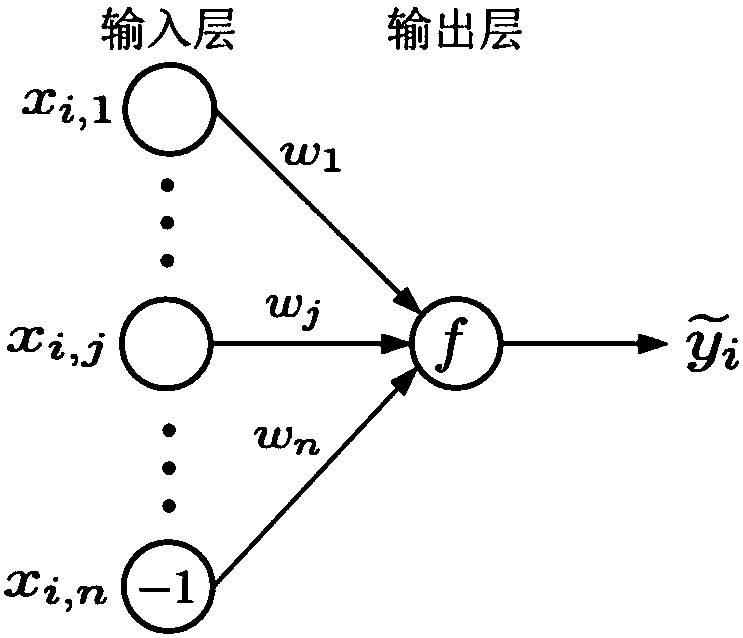
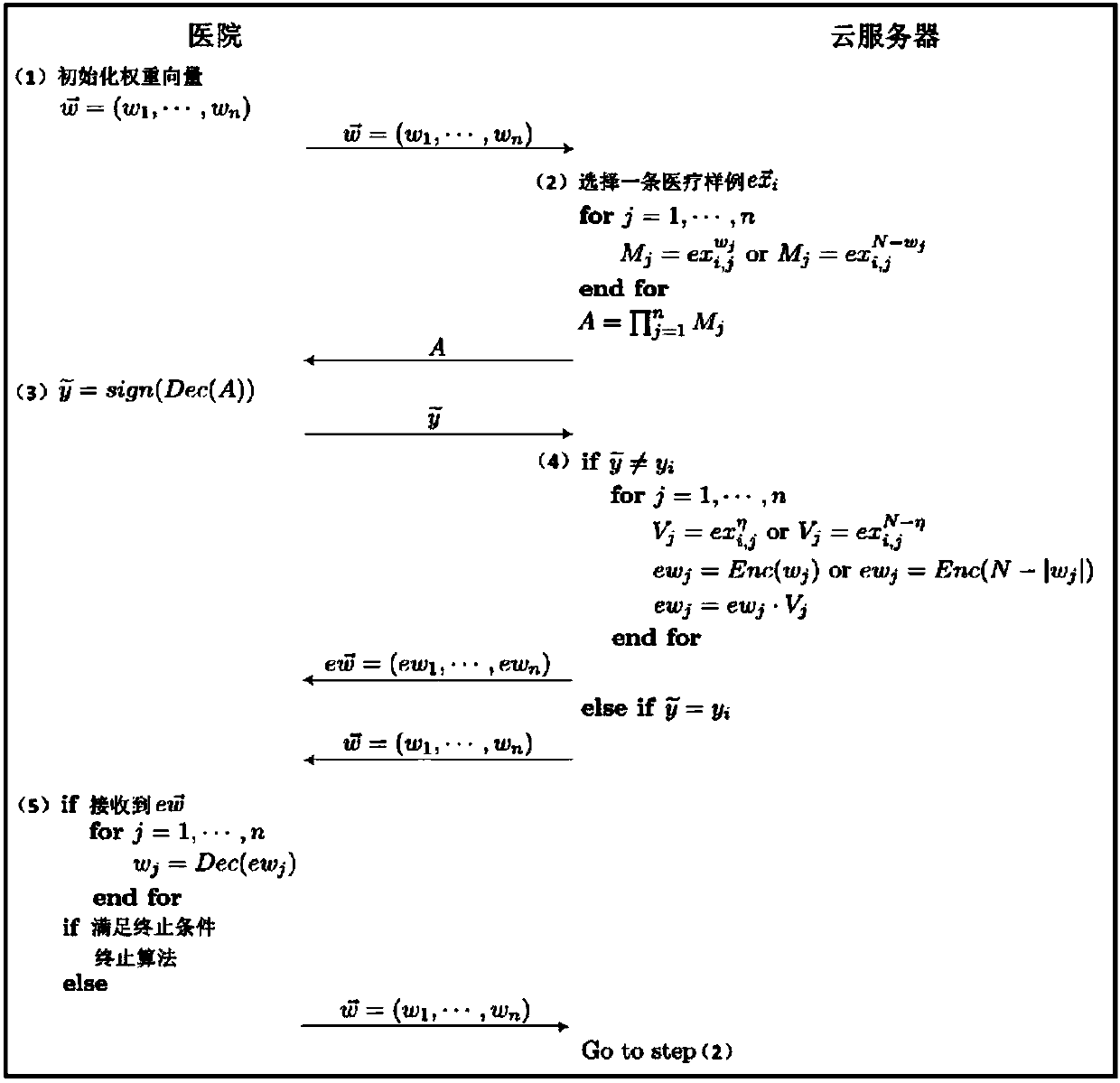
Efficient and privacy-preserving single-layer perceptron learning scheme in cloud computing environment
ActiveCN108259158APrivacy protectionComputationally efficientKey distribution for secure communicationCharacter and pattern recognitionCiphertextPrivacy preserving
The invention belongs to the technical field of cloud computing and discloses an efficient and privacy-preserving single-layer perceptron learning scheme in a cloud computing environment. The scheme comprises the steps that a client provides a security parameter, operates a key generation algorithm of a symmetric homomorphic encryption algorithm to calculate a public parameter and a key, then operates an encryption algorithm, encrypts training data through utilization of the key to obtain a corresponding ciphertext, and sends the ciphertext and related expectation to a cloud server, assists acloud server to judge a positive or negative characteristic of a dot product result in a training process, and decrypts the ciphertext of the received final optimum weight vector after a training taskis finished, thereby obtaining a single-layer perceptron prediction model; and the cloud server stores the training mode, trains a single-layer perceptron model and sends the ciphertext of the finaloptimum weight vector to the client after the training task is finished. The safety analysis shows that according to the scheme, in the training process, the privacy of the training data, an intermediate result and the optimum prediction model can be preserved, and the scheme is efficient in computing overhead and communication overhead aspects.
Owner:XIDIAN UNIV
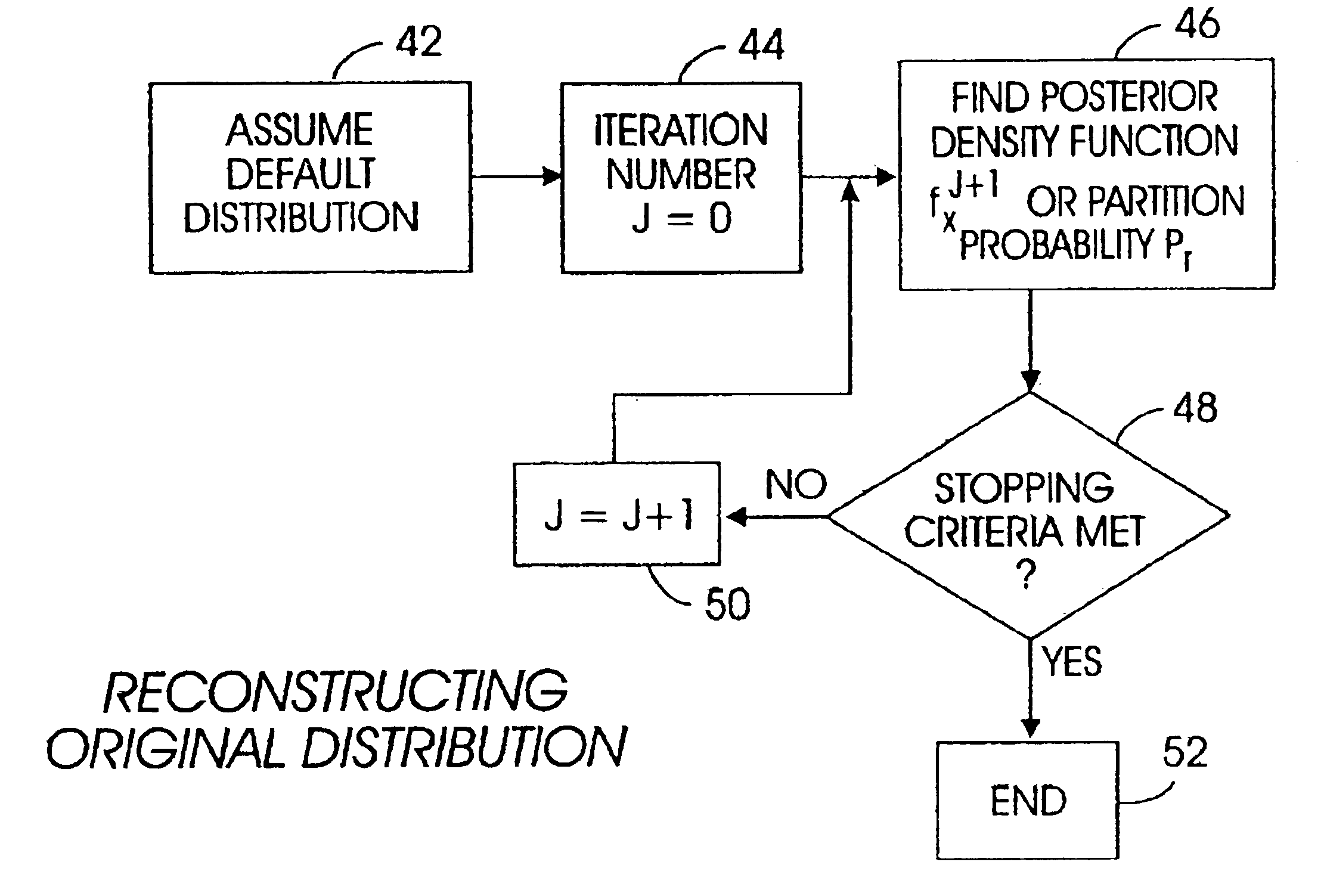
System and architecture for privacy-preserving data mining
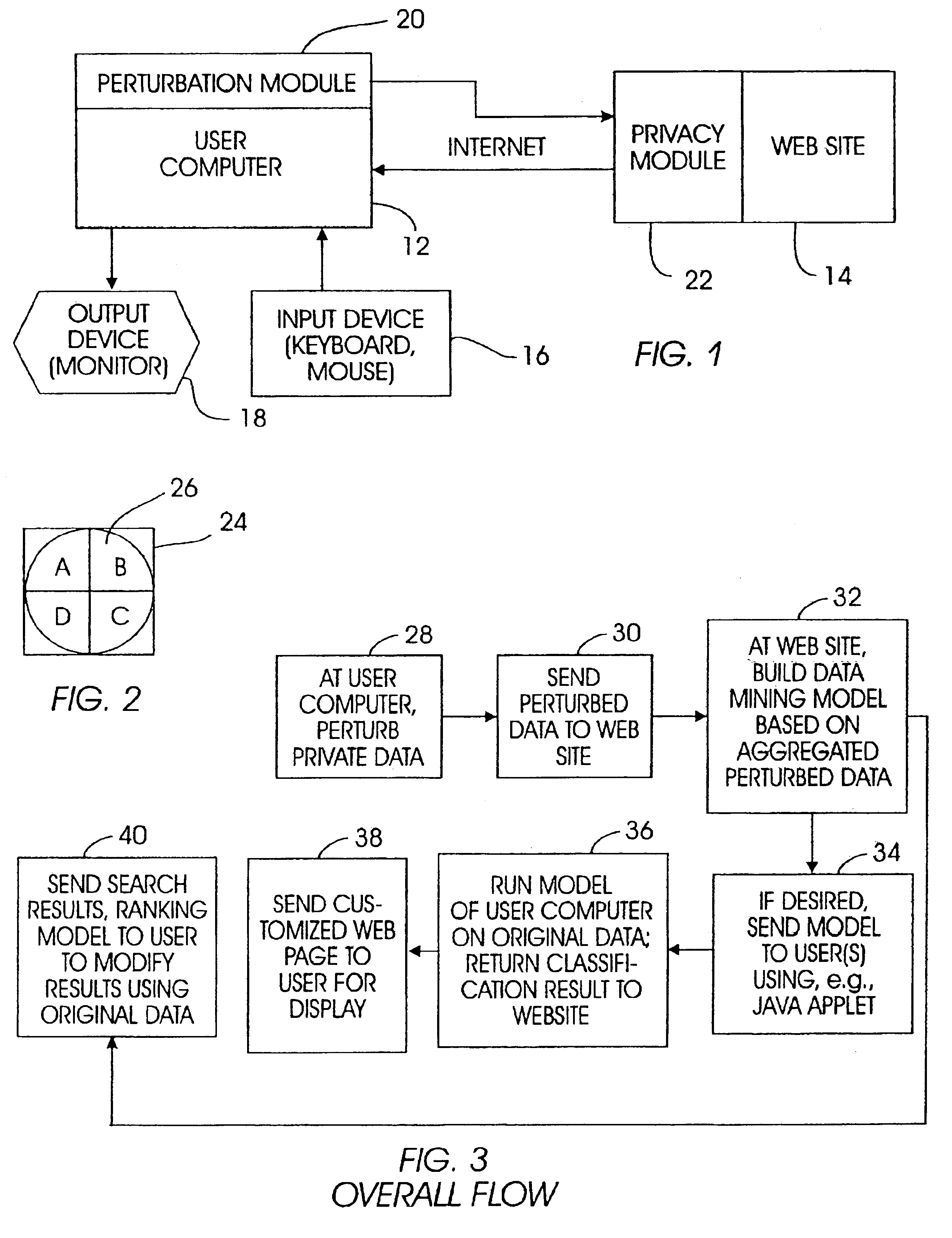
InactiveUS6931403B1Promote generationDigital data information retrievalDigital data processing detailsWeb siteRelevant information
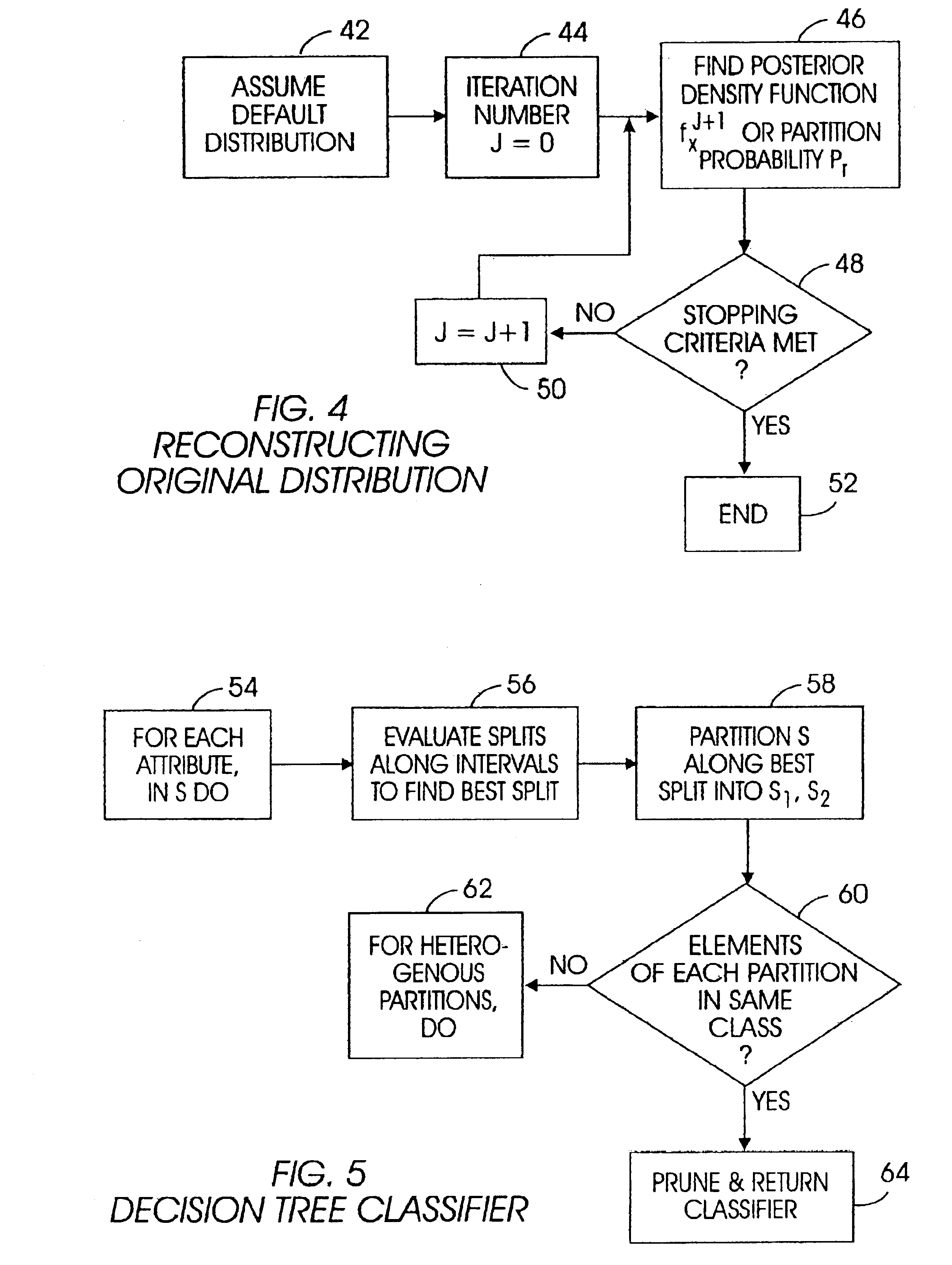
A system and method for mining data while preserving a user's privacy includes perturbing user-related information at the user's computer and sending the perturbed data to a Web site. At the Web site, perturbed data from many users is aggregated, and from the distribution of the perturbed data, the distribution of the original data is reconstructed, although individual records cannot be reconstructed. Based on the reconstructed distribution, a decision tree classification model or a Naive Bayes classification model is developed, with the model then being provided back to the users, who can use the model on their individual data to generate classifications that are then sent back to the Web site such that the Web site can display a page appropriately configured for the user's classification. Or, the classification model need not be provided to users, but the Web site can use the model to, e.g., send search results and a ranking model to a user, with the ranking model being used at the user computer to rank the search results based on the user's individual classification data.
Owner:IBM CORP
Storage, retrieval, analysis, pricing, and marketing of personal health care data using social networks, expert networks, and markets
InactiveUS20150154646A1Facilitate communicationMedical communicationMedical data miningFinancial transactionBiological data
Systems and processes are provided for securely storing, retrieving, sharing, and selling private data, such as genome wide sequences, sequence related metadata, electronic healthcare data, biological data, demographic data, medical data, and other biomedical data, which, in turn, may allow the usage of genomic variations at multiple scales and across multiple population strata. In some examples, users may be matched with healthcare experts based on a medical need or interest. In other examples, an information-based market for utilizing the available data in a privacy-preserving manner may be provided. In these examples, individual or group data may be tracked, compared, rated, analyzed, and priced to allow individuals to establish connections and / or carry out financial transactions using their data with other participants, healthcare practitioners, and businesses.
Owner:SEQSTER PDM INC +1
Method for Privacy Preserving Hashing of Signals with Binary Embeddings
ActiveUS20130114811A1Reduce complexityEfficiently determinedSecret communicationInternet privacyPrivacy preserving
A hash of signal is determining by dithering and scaling random projections of the signal. Then, the dithered and scaled random projections are quantized using a non-monotonic scalar quantizer to form the hash, and a privacy of the signal is preserved as long as parameters of the scaling, dithering and projections are only known by the determining and quantizing steps.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Privacy preserving computation protocol for data analytics
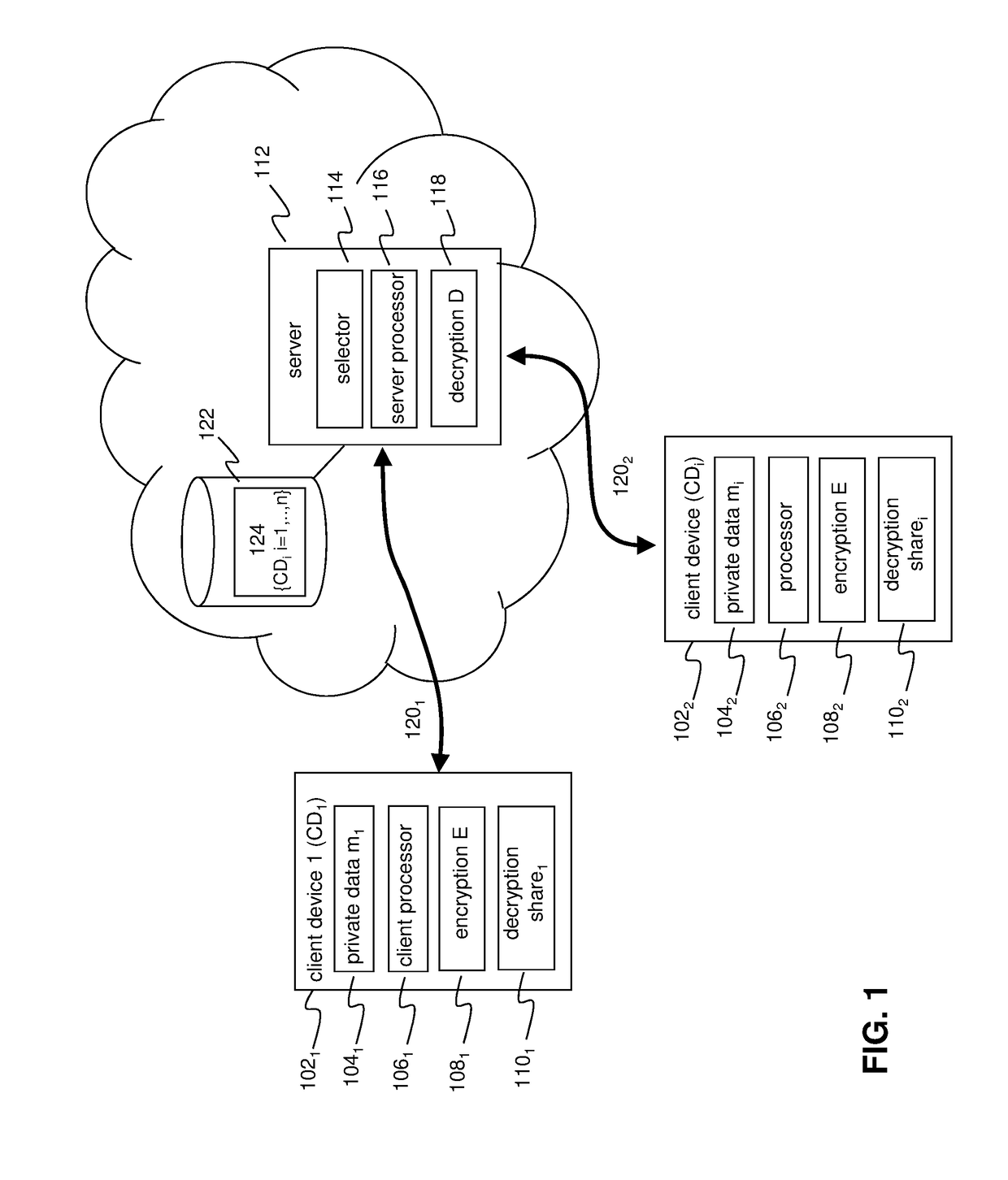
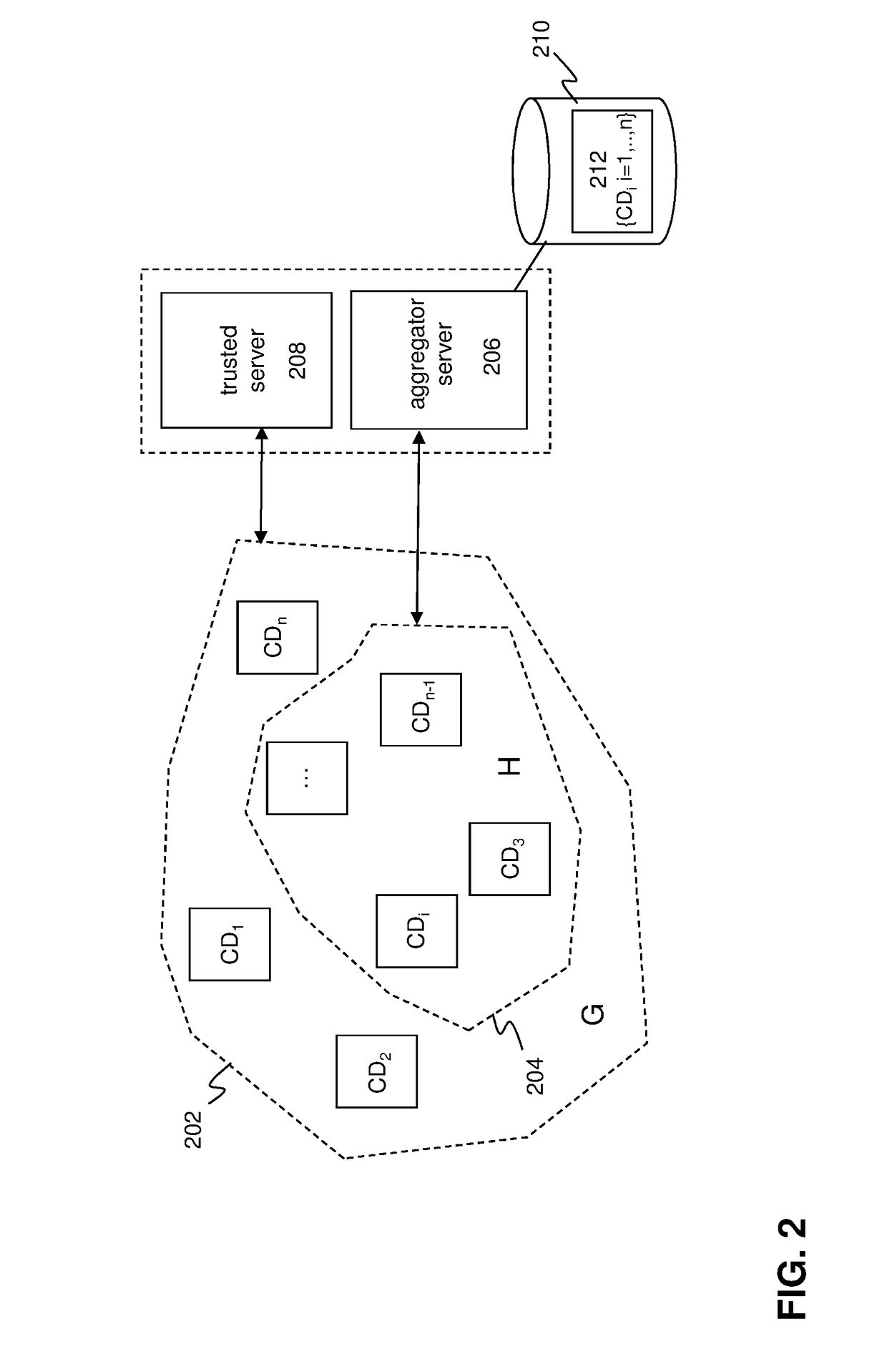
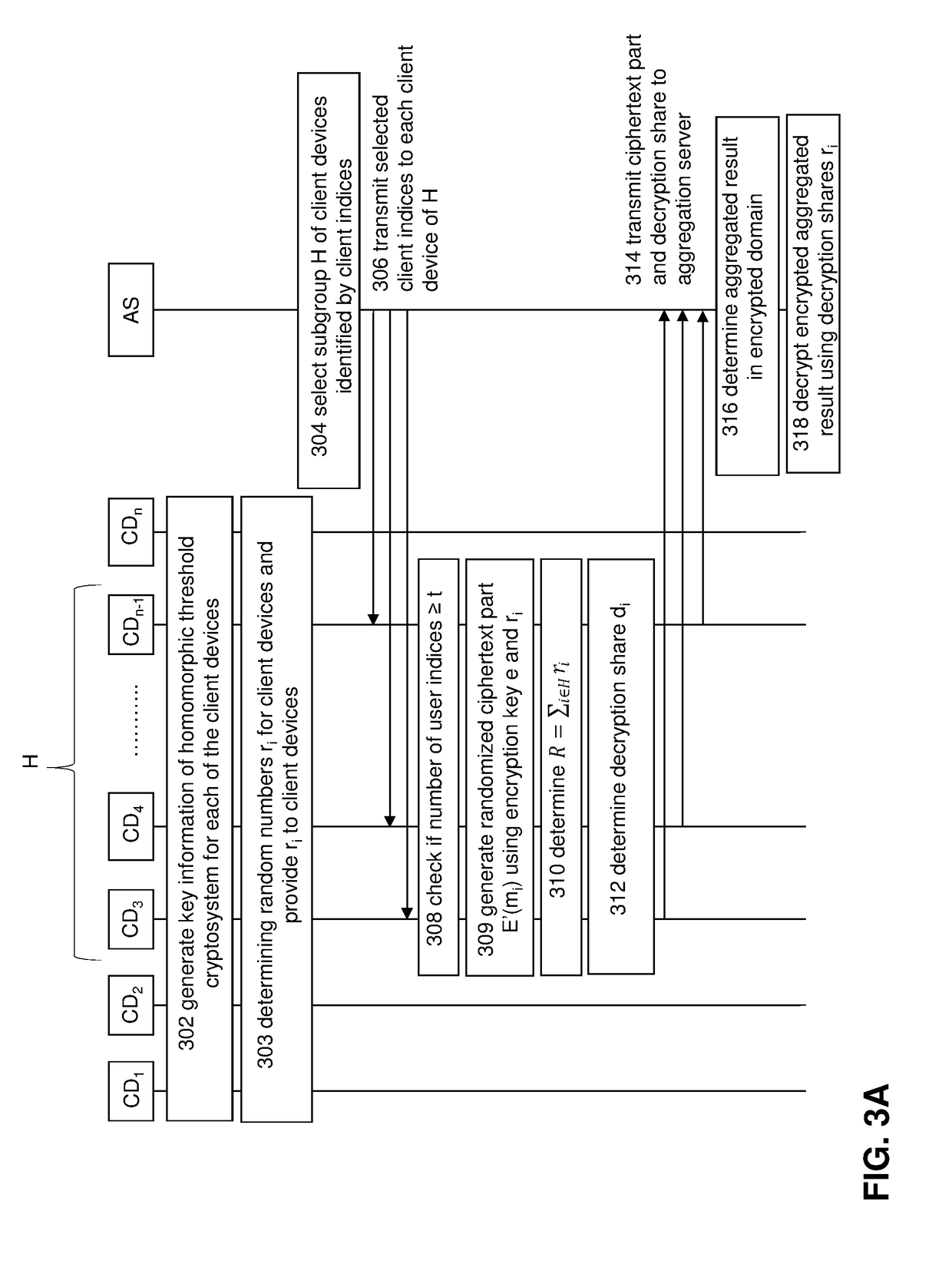
PendingUS20180373882A1Efficient privacy-preservingEfficient privacy-preserving protocolKey distribution for secure communicationMultiple keys/algorithms usagePlaintextEncrypted function
A privacy preserving computation protocol for data analytics is described. The protocol includes a method for privacy-preserving computation of aggregated private data of a group of client devices wherein the method comprises: a server selecting at least t client devices from the group of client devices, each client device in the group: being identifiable by client index i; comprising an encryption function; being provided with key information including an encryption key e and a decryption key of a homomorphic threshold cryptosystem; generating or being provided with an random value ri and having access to or being provided with the random values of the other client devices in the group; the server transmitting client information to each selected client device, the client information including client indices identifying the selected client devices, the client information signalling a client device that the server would like aggregate encrypted private data of each of the selected client devices; the server receiving randomized encrypted private data and an associated decryption share from each selected client device, the decryption shares being configured such that decryption key d can be reconstructed on the basis of t decryption shares; and, the server aggregating, preferably summing or adding, the received randomized encrypted private data of the selected client devices using the homomorphic properties of the cryptosystem and using the decryption shares for decrypting the aggregated randomized encrypted private data into cleartext.
Owner:FLYTXT MOBILE SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com