Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
234results about How to "Maintain privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
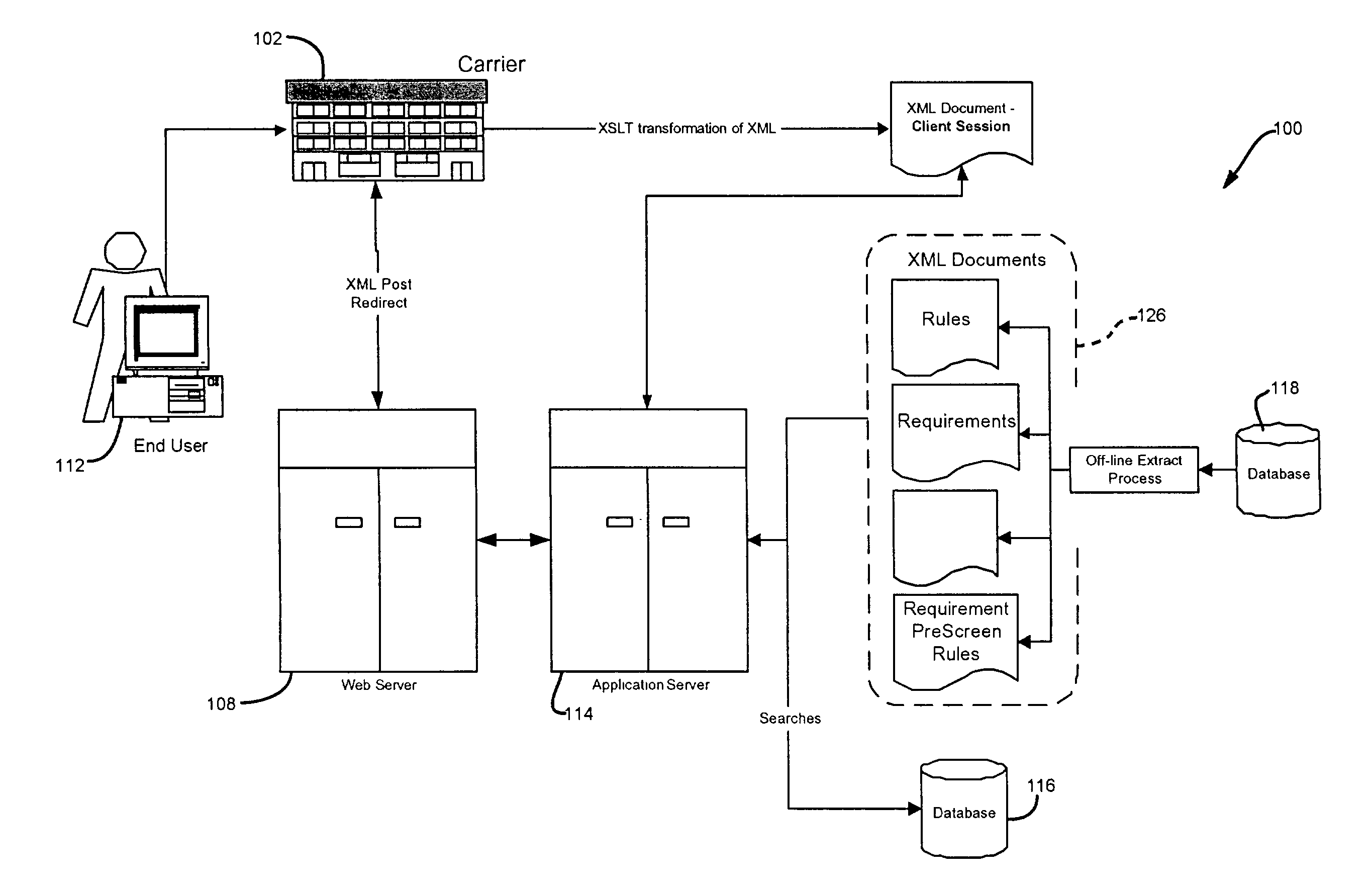
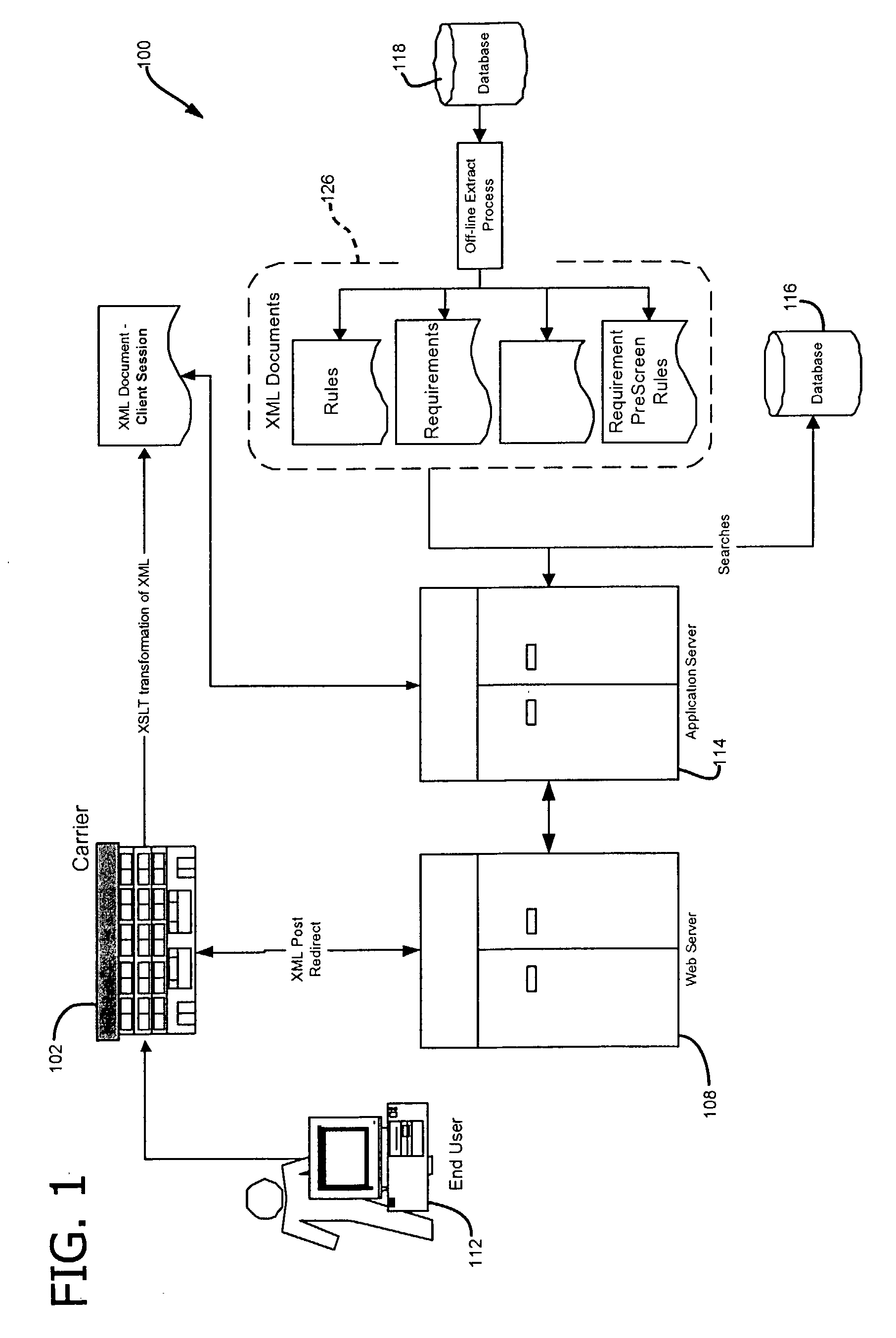
Methods, products, systems, and devices for processing reusable information
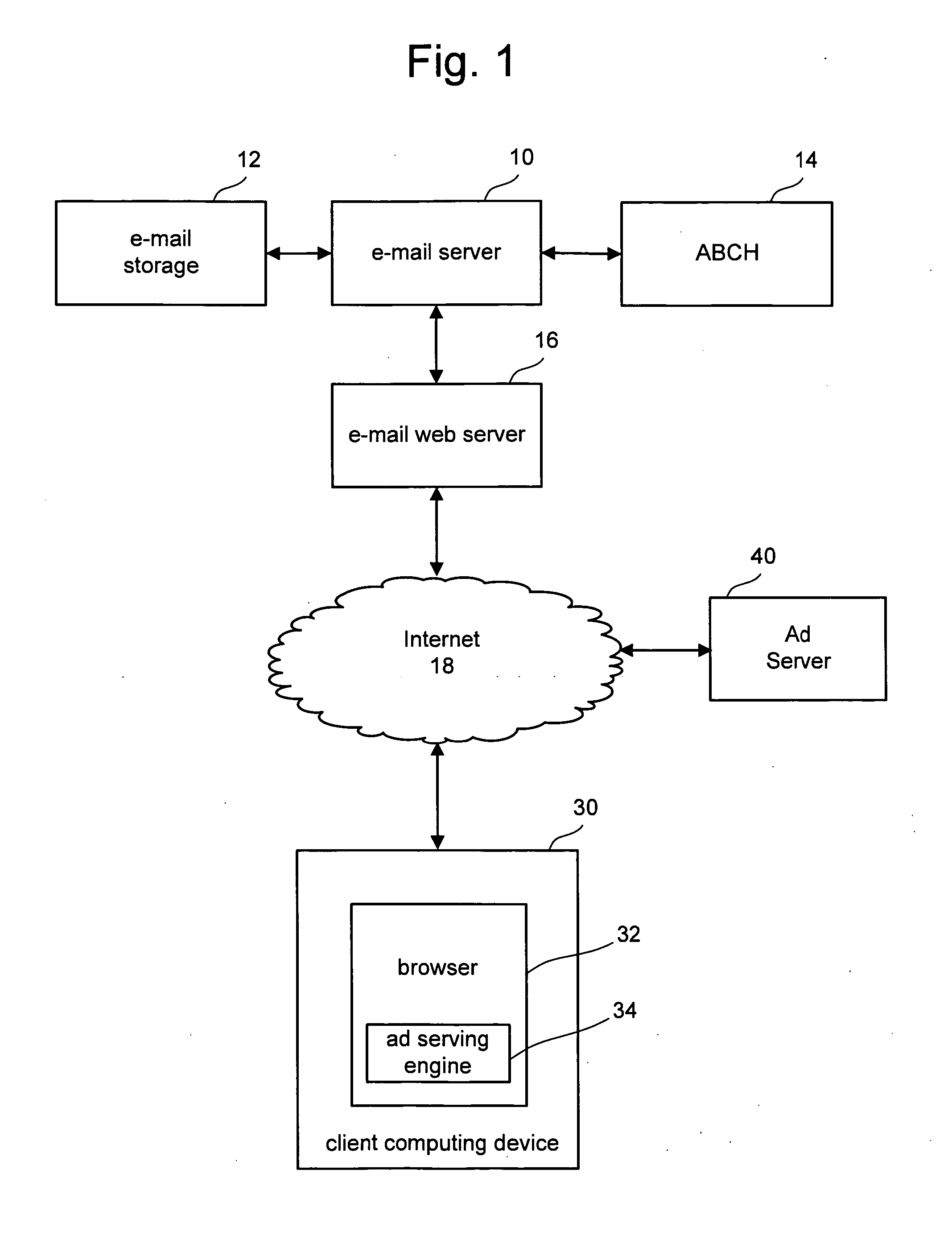
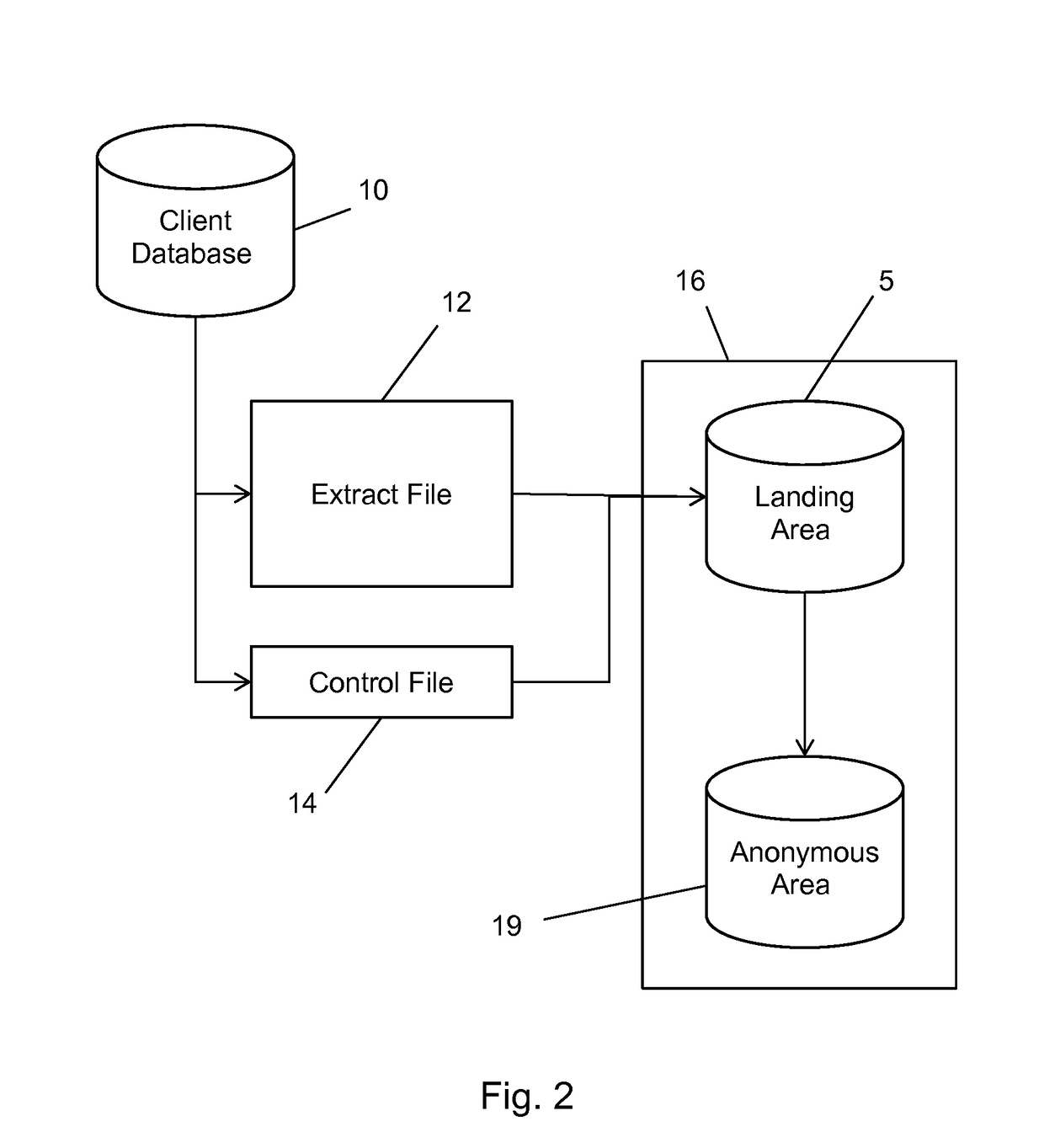
InactiveUS20080010365A1Increase subscription periodMinimize useData processing applicationsDigital computer detailsClient-sideTelecommunications link
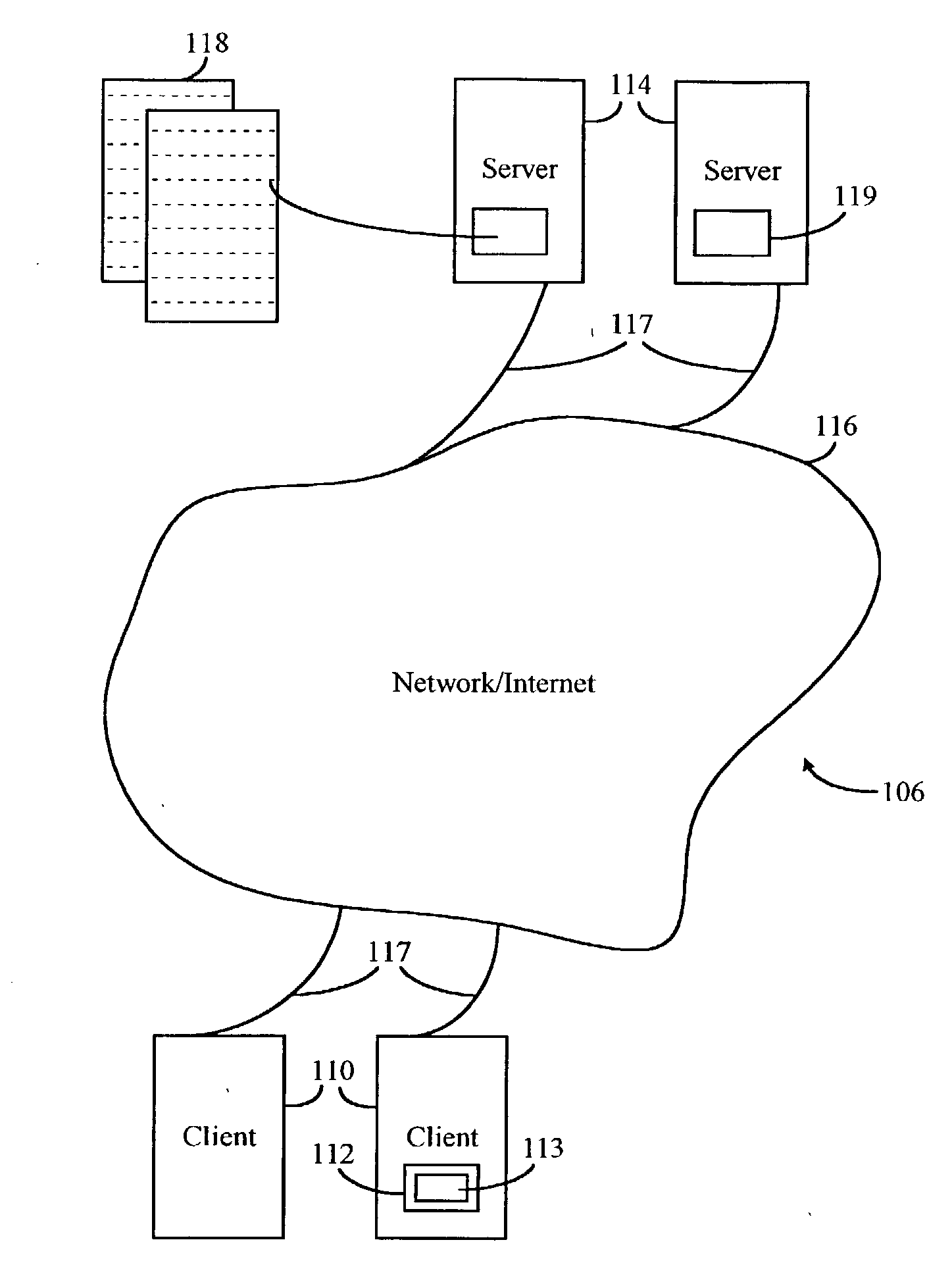
In a communication network having at least one communication link connecting at least one provider and a client, where the at least one provider is in communication with at least one database storing at least one identifier having variable ownership status, a method includes establishing that at least one identifier of significance to the client is unavailable for ownership by the client, communicating to the at least one provider at least one desired action the at least one provider is to take on behalf of the client to obtain an ownership interest in the at least one identifier of significance to the client, where the at least one identifier of significance to the client is unavailable for ownership by the client at the time of the communication, and determining whether to perform the at least one desired action without monitoring the ownership status of the at least one identifier of significance to the client.
Owner:MEC MANAGEMENT LLC +1
Late binding tokens
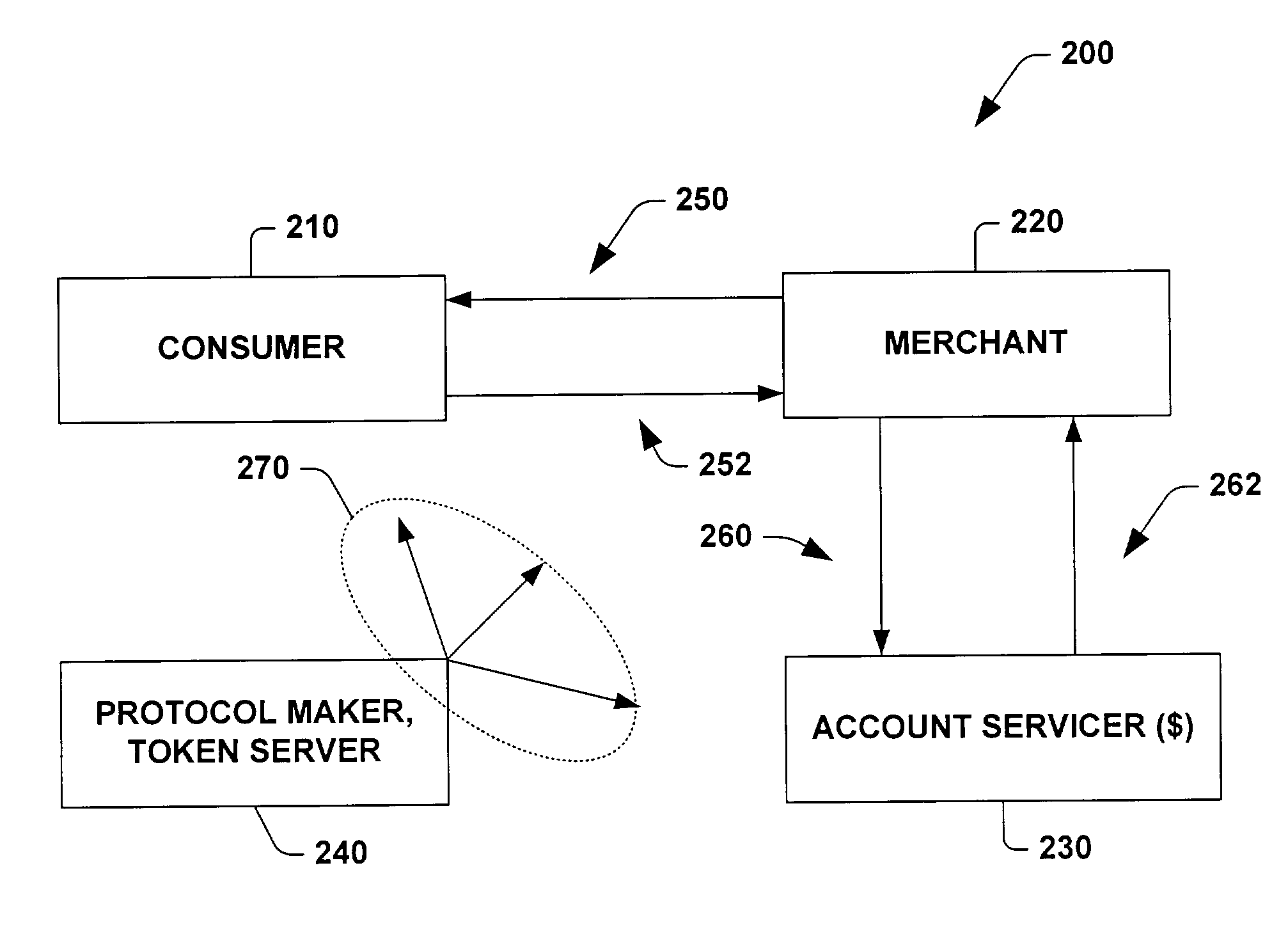
ActiveUS8060448B2Easy to createPrecise positioningFinanceMultiple digital computer combinationsClient-sideProtocol for Carrying Authentication for Network Access
A system for verifying intent in a card not present transaction is provided. The system includes a late binding token that is distributable to consumers without necessarily being bound to an account. The system also includes a client software that locates a token server configured to facilitate managing and communicating with the late binding token. The system also includes a protocol concerning how to build a verifiably secure structured proposal that carries an offer to the consumer through the client software.
Owner:JONES THOMAS C
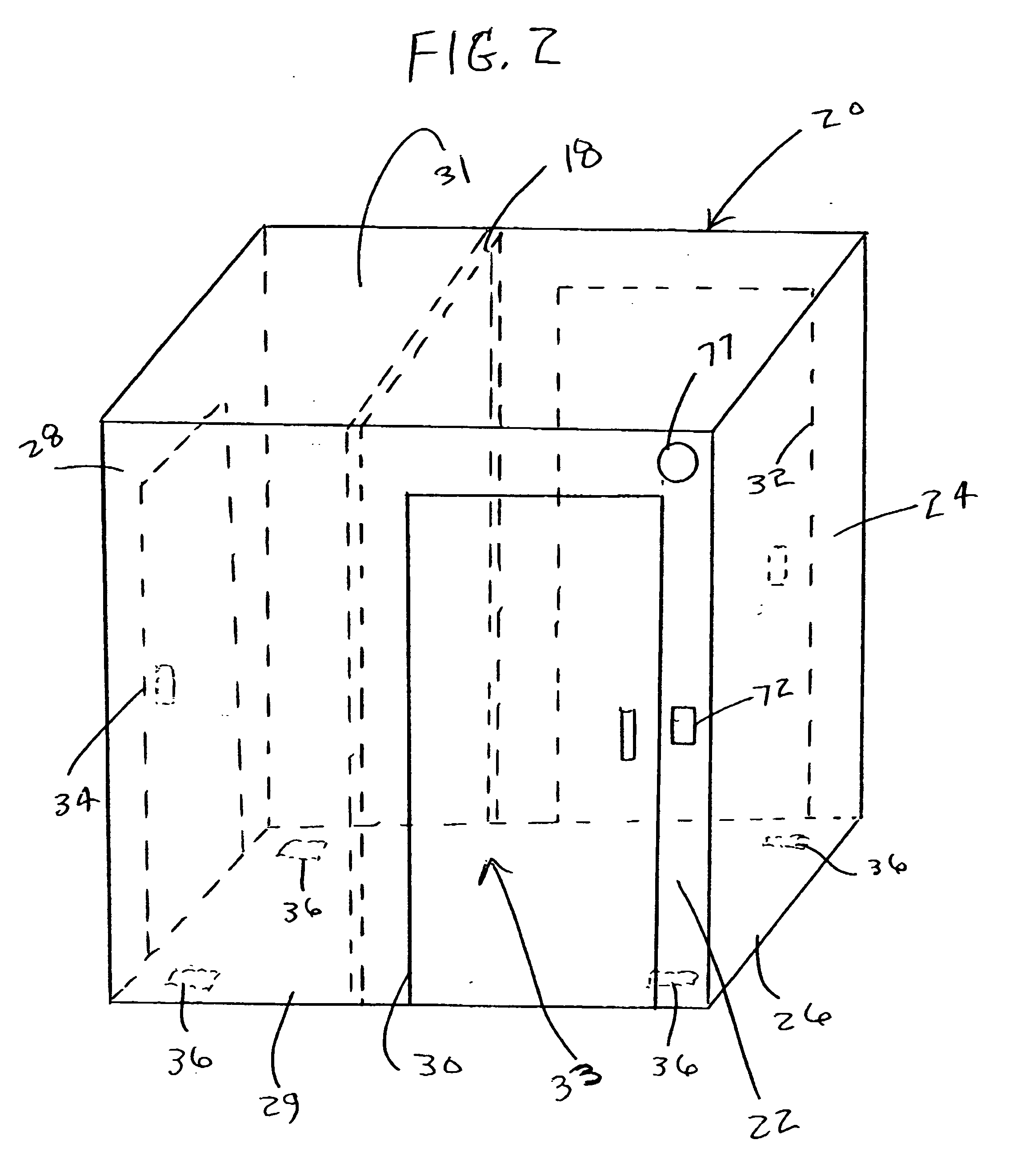
Electronic Window Shading System for Houses, Transport Vehicles and the Like
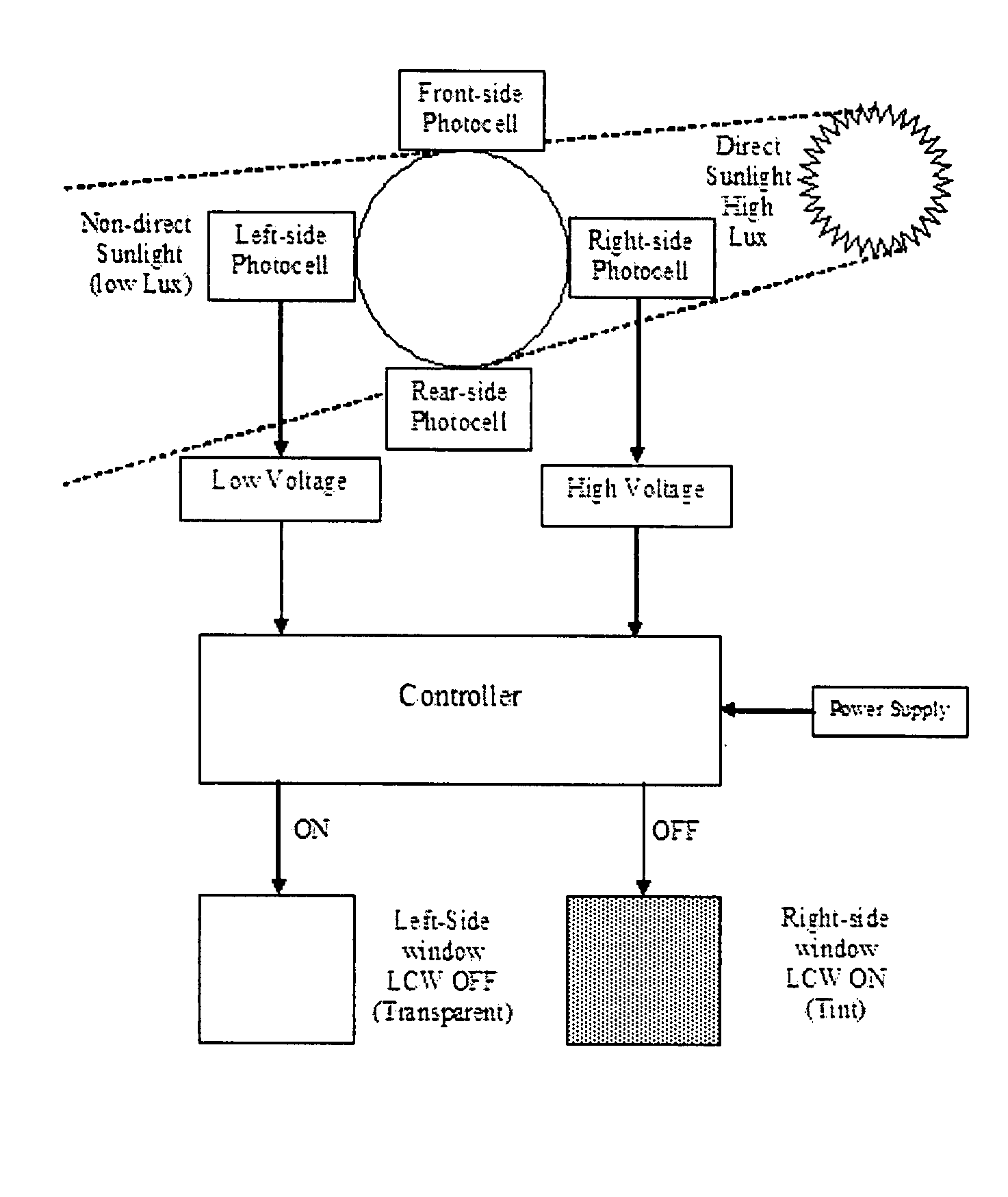
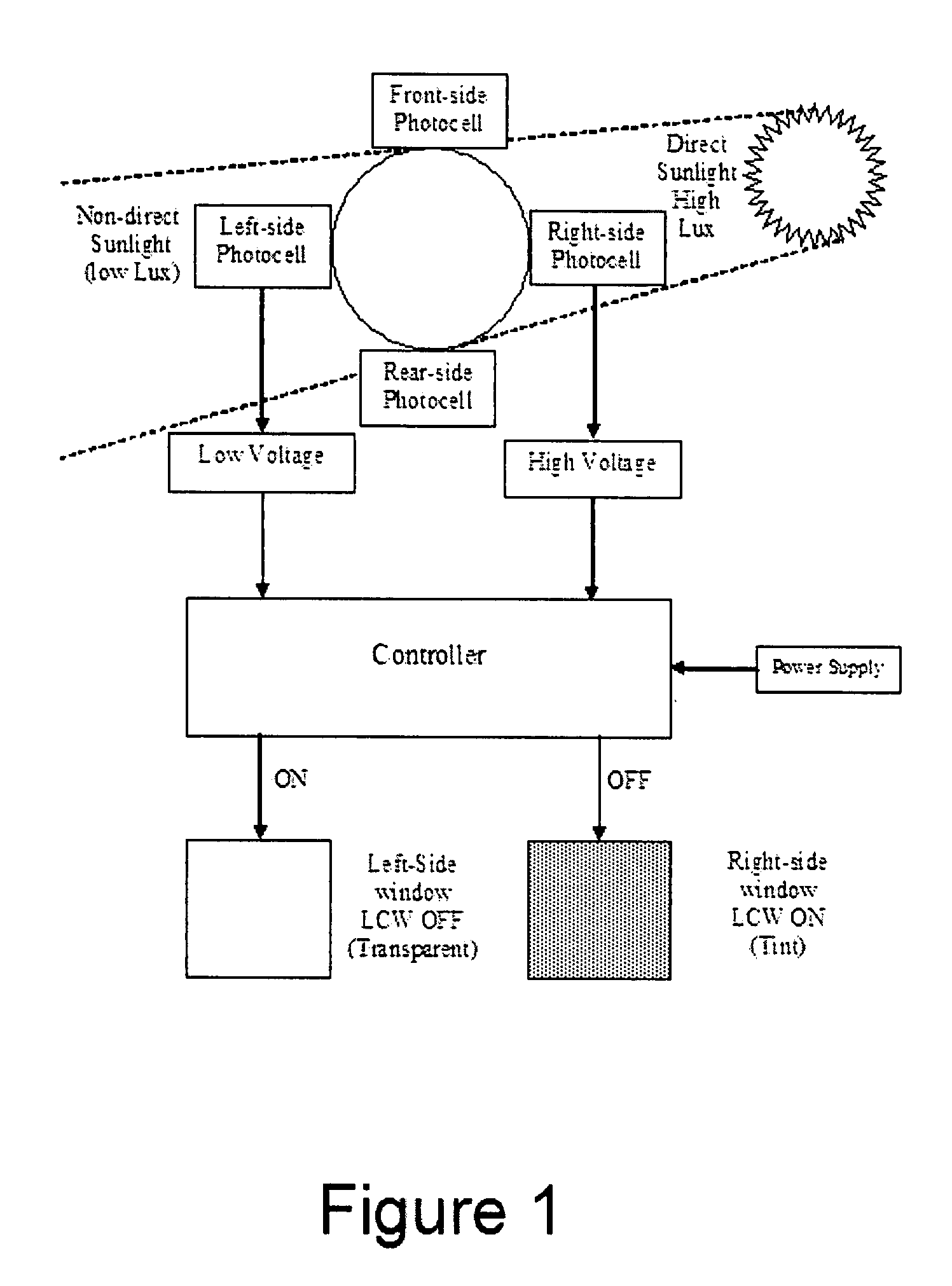
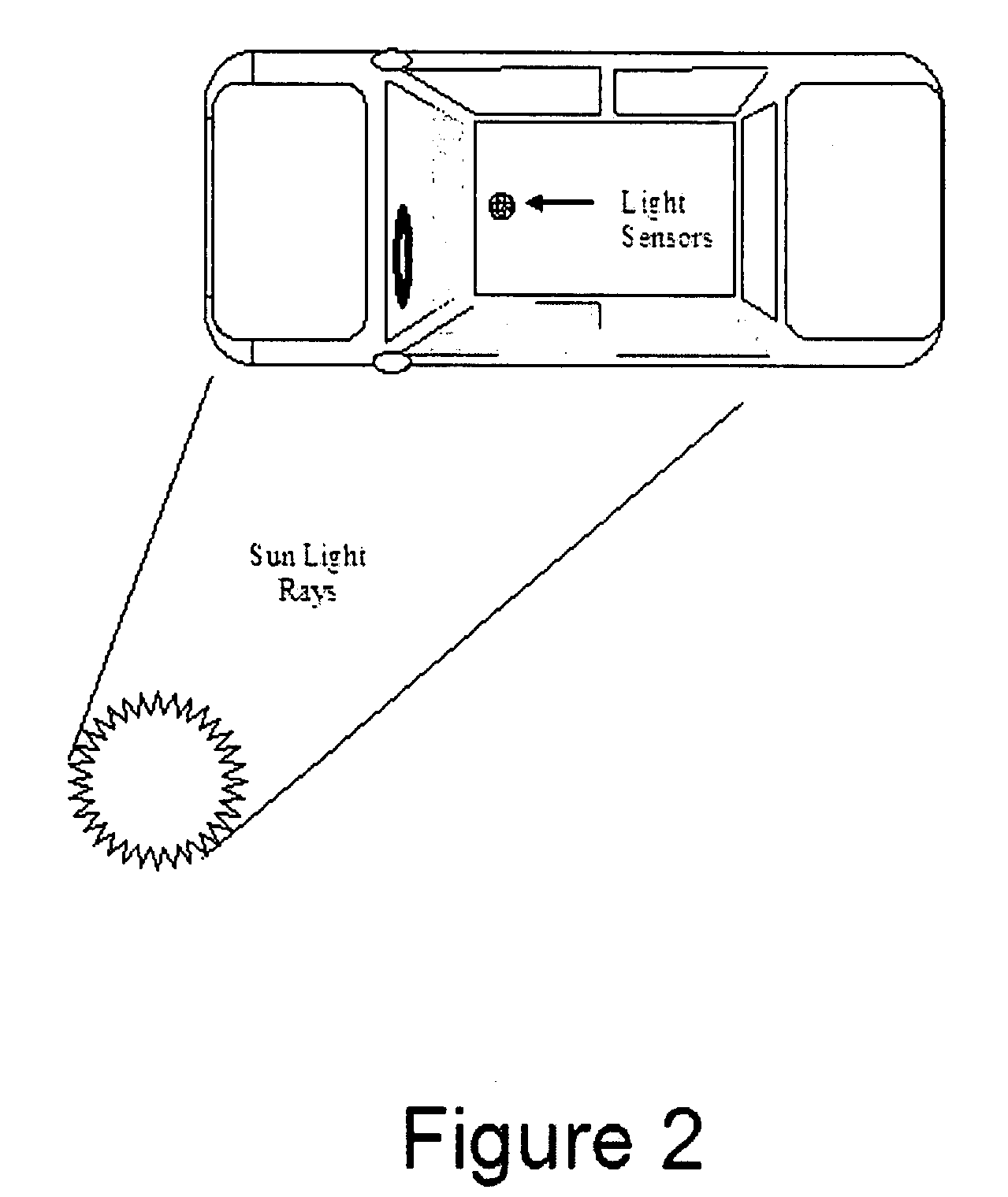
InactiveUS20090027759A1Reduce condensationConvenient lightingLight dependant control systemsAntiglare equipmentSuspended particlesTelecommunications
There is disclosed an automatic electronic window shading (tinting) system for houses and transport vehicles such as automobiles, RV's, trains, boats and the like, to provide shading for people to protect them from exposure to harmful direct sunlight, by providing the windows of said houses and transport vehicles with display elements and light (photocell / photovoltaic) sensors. The system comprises liquid crystal, electrochromic, suspended particle device (SPD), or NanoChromics display (NCD) element attached to a part of a transparent body (such as the windows) and a liquid crystal, electrochromic, suspended particle device (SPD), or NanoChromics display (NCD) controlling semiconductor element controlling the operation of the display element.
Owner:KUWAIT UNIV
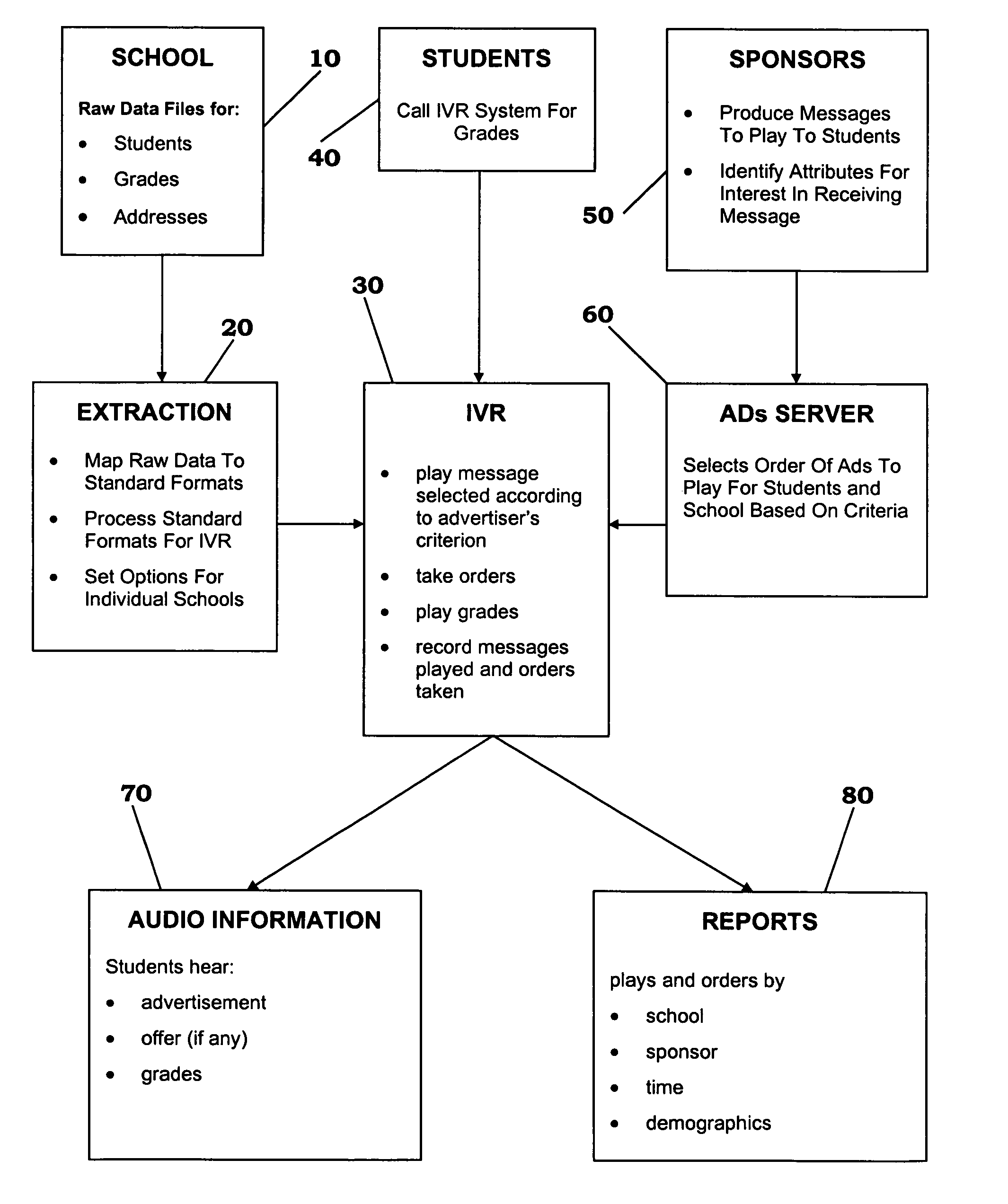
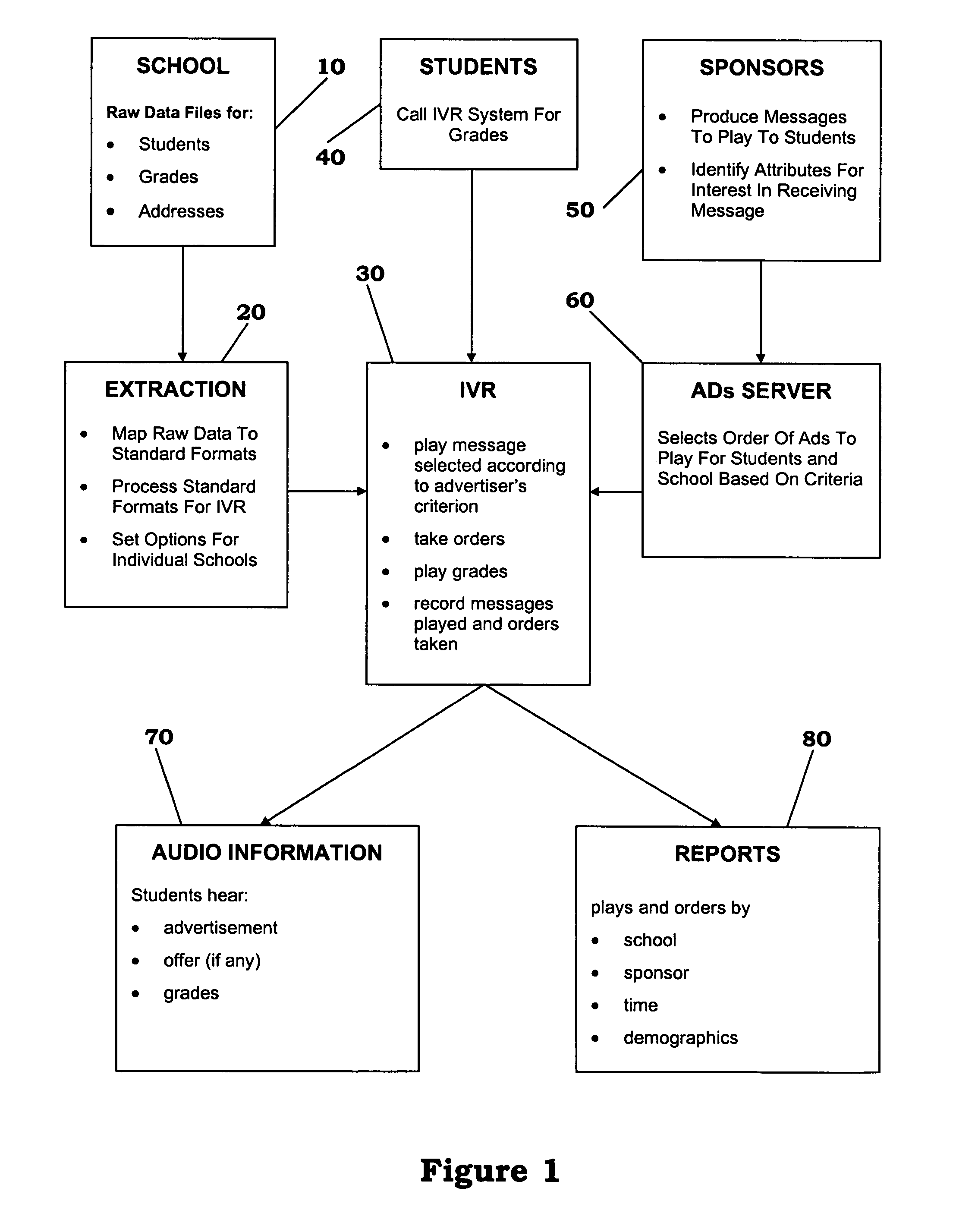
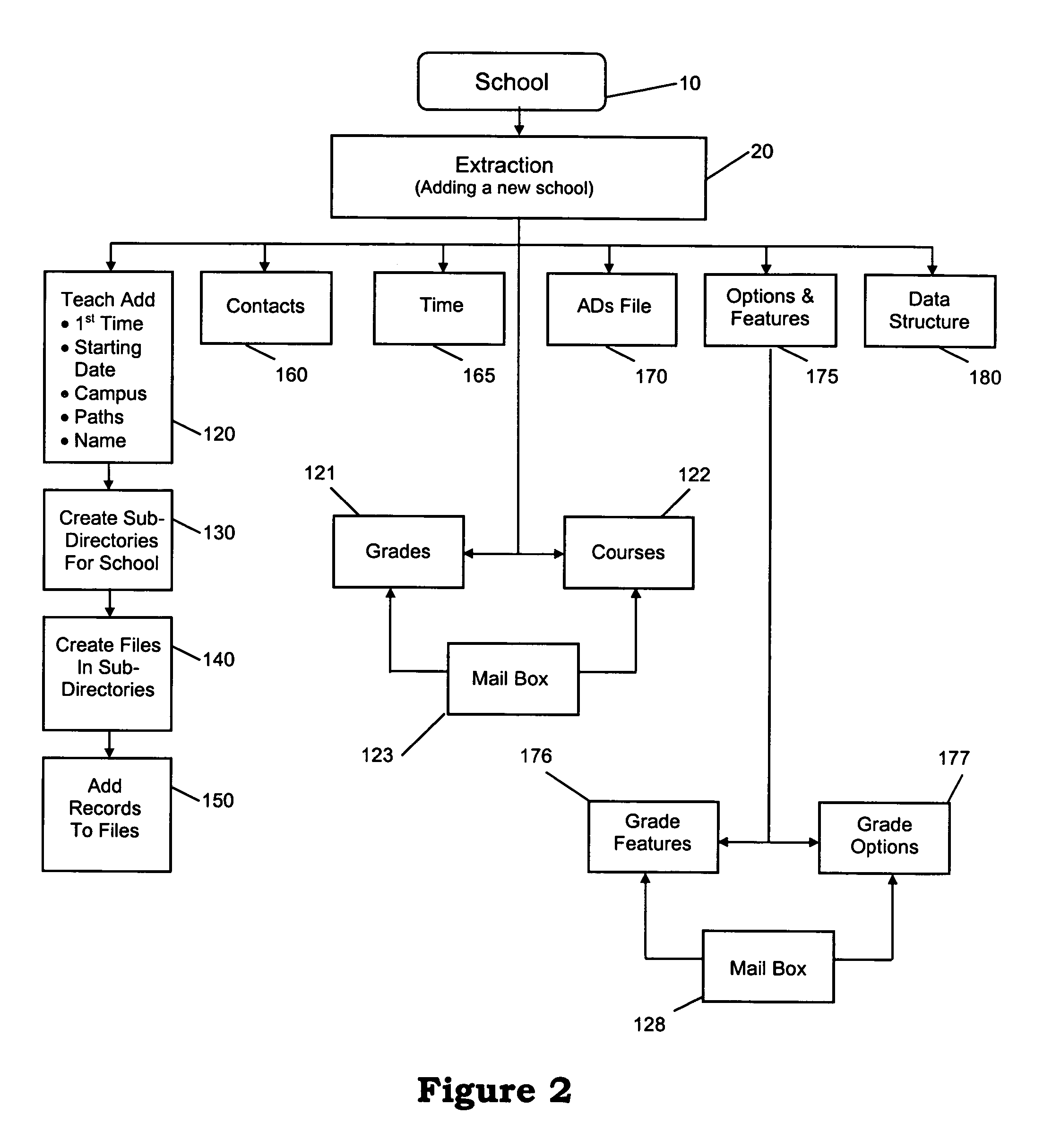
Sponsored information distribution method and apparatus
InactiveUS7006606B1Selected accurately and quicklyMaintain privacyAutomatic call-answering/message-recording/conversation-recordingManual exchangesWeb siteDistribution method
A database having information sought by a consumer, a database containing consumer attributes, and a database of advertising messages are made responsive to telephone calls placed to an interactive voice response (IVR) system. Alternatively, the databases can be linked to a web site responsive to consumer input. Either system can deliver the advertising messages to the consumer. The database of consumer attributes contains information already known about the consumer that can be used to decide on which advertising message to deliver. The consumer initiates activity by calling the interactive voice response system or accessing the web site. Software identifies the consumer via the consumer-inputted identification and delivers an advertising message likely appeal to the consumer. The advertising message can include an offer to purchase a product or service. The offer can be taken during the advertising period and recorded so as to be sent to a sponsor. The system then disseminates information sought by the customer, such as student grades. Alternatively, software resident at the Web site reads the identity of the customer who is accessing the Web site and recognizes and ascribes various attributes to the customer. The customer has the opportunity to either view the information or, preferably, interactively respond to the advertisement or offer by seeking additional advertisements or by placing an order for the products or services of the sponsoring vendor.
Owner:VOICE FX INT +1
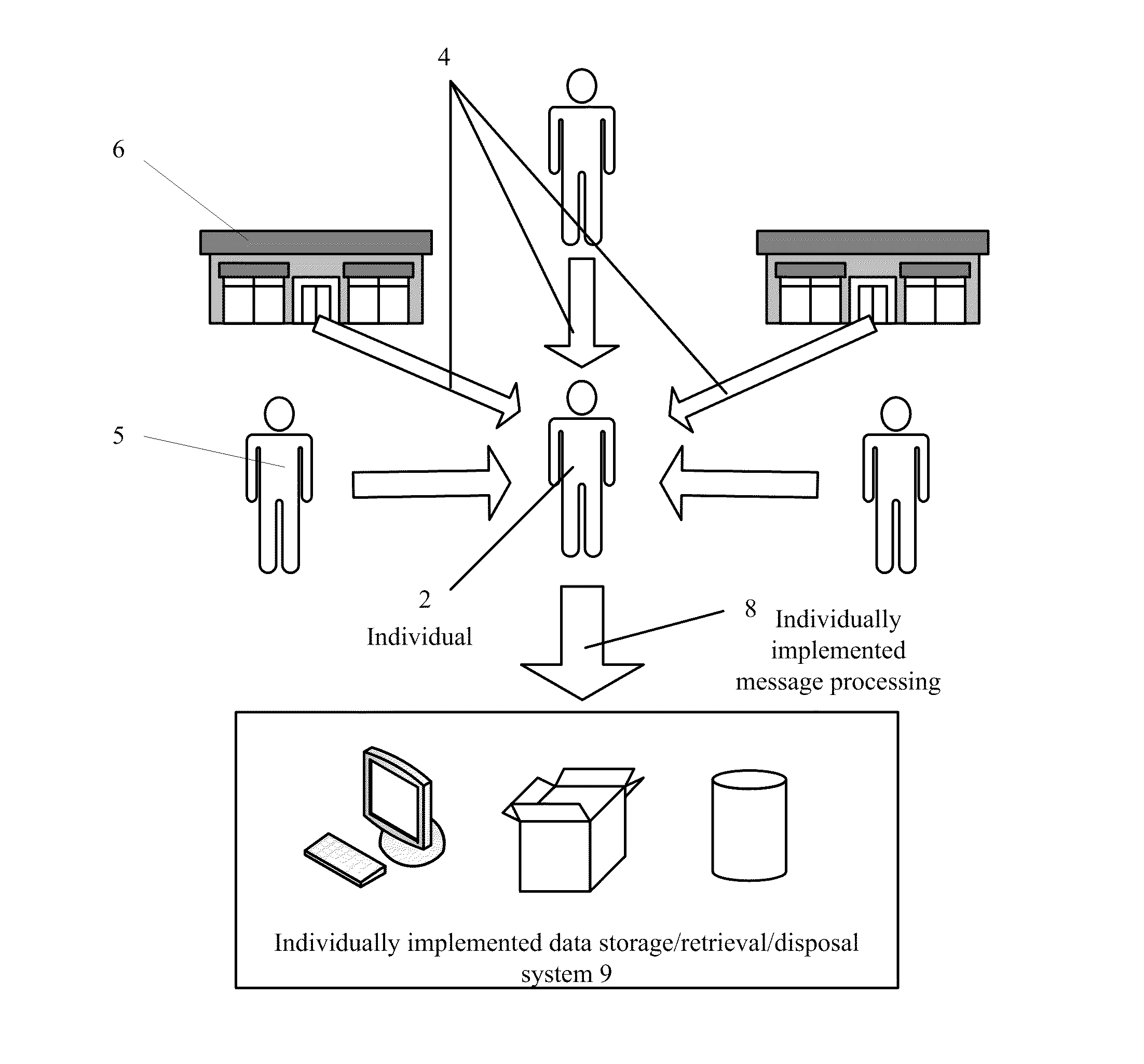
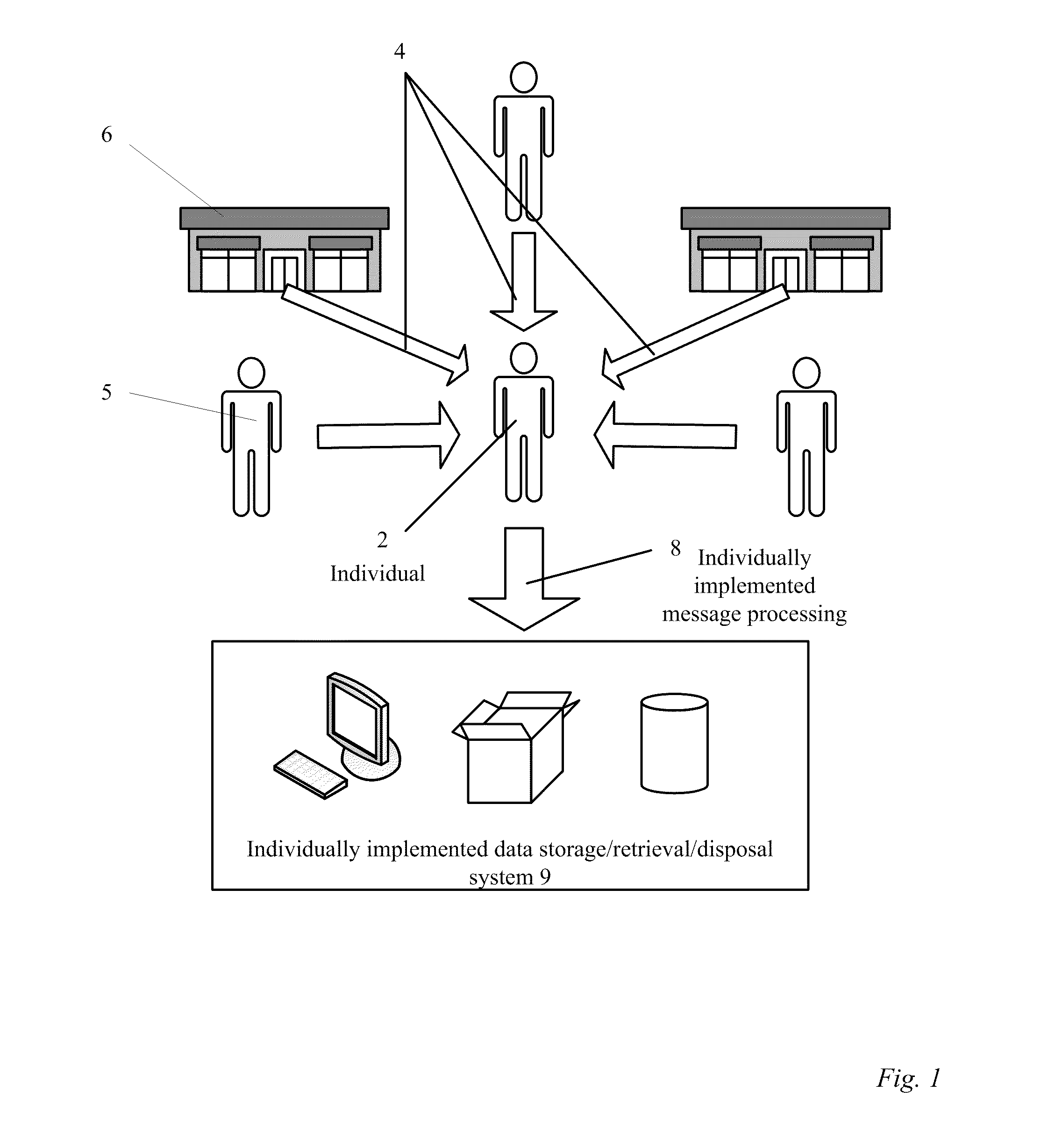
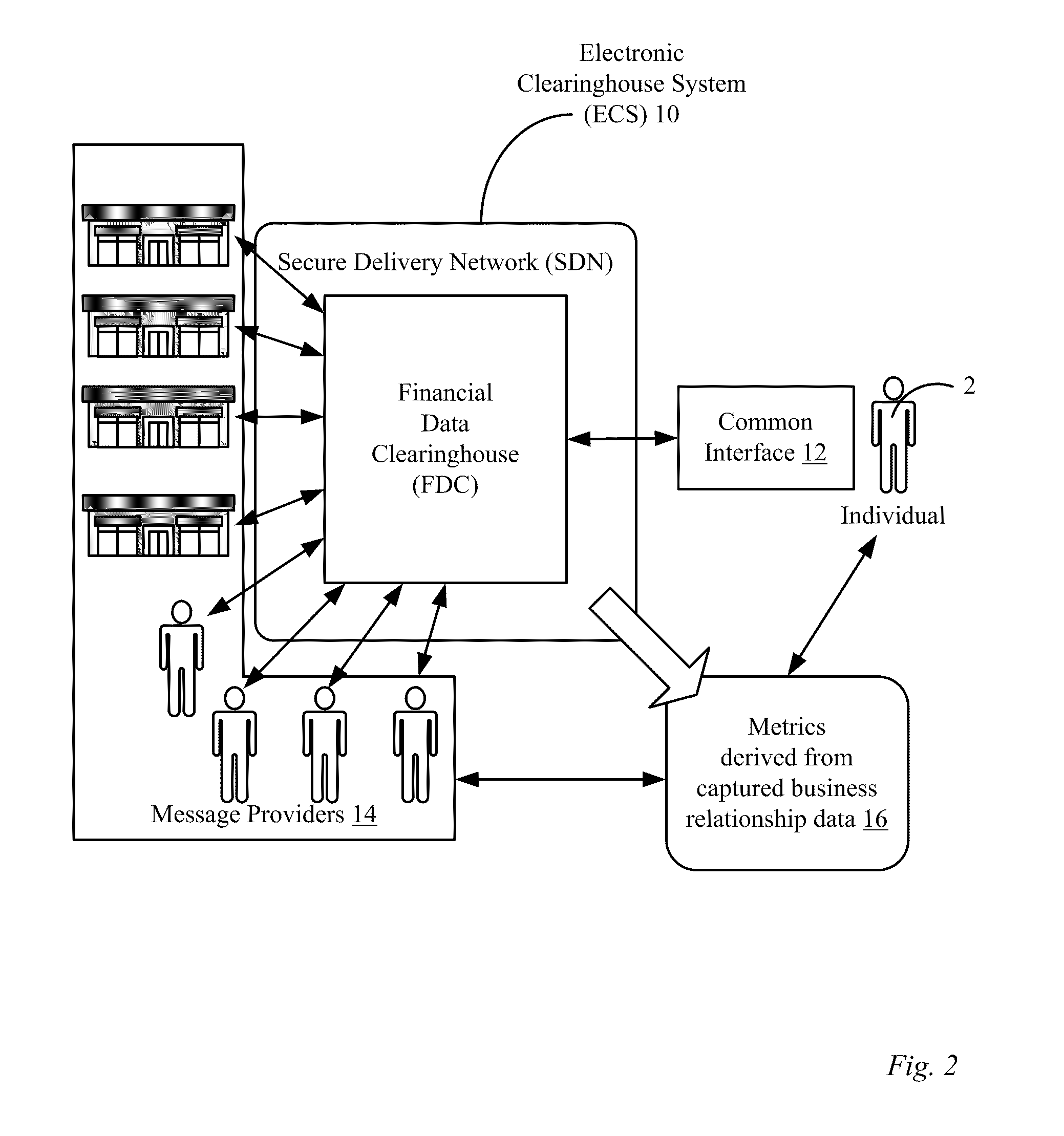
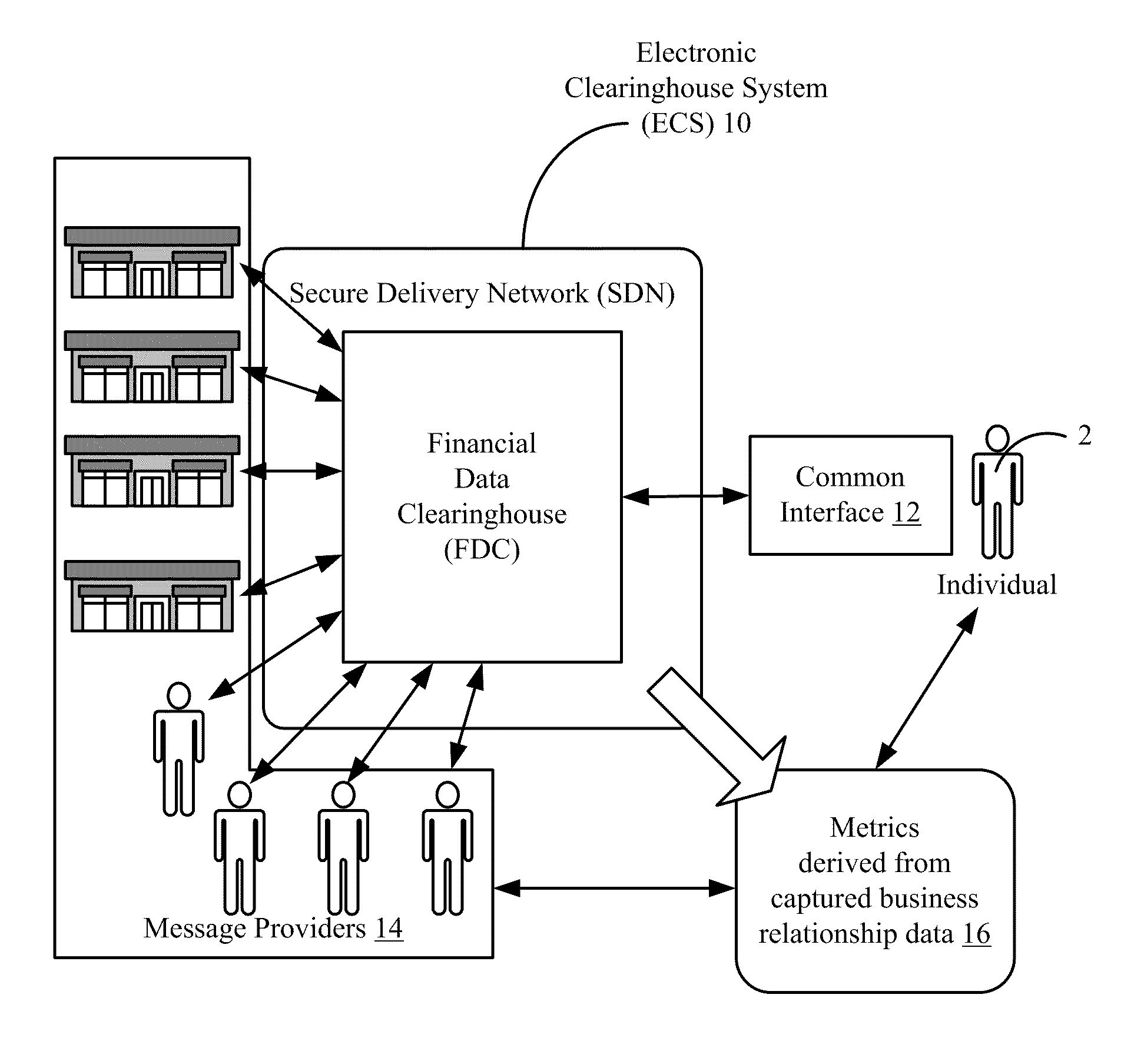
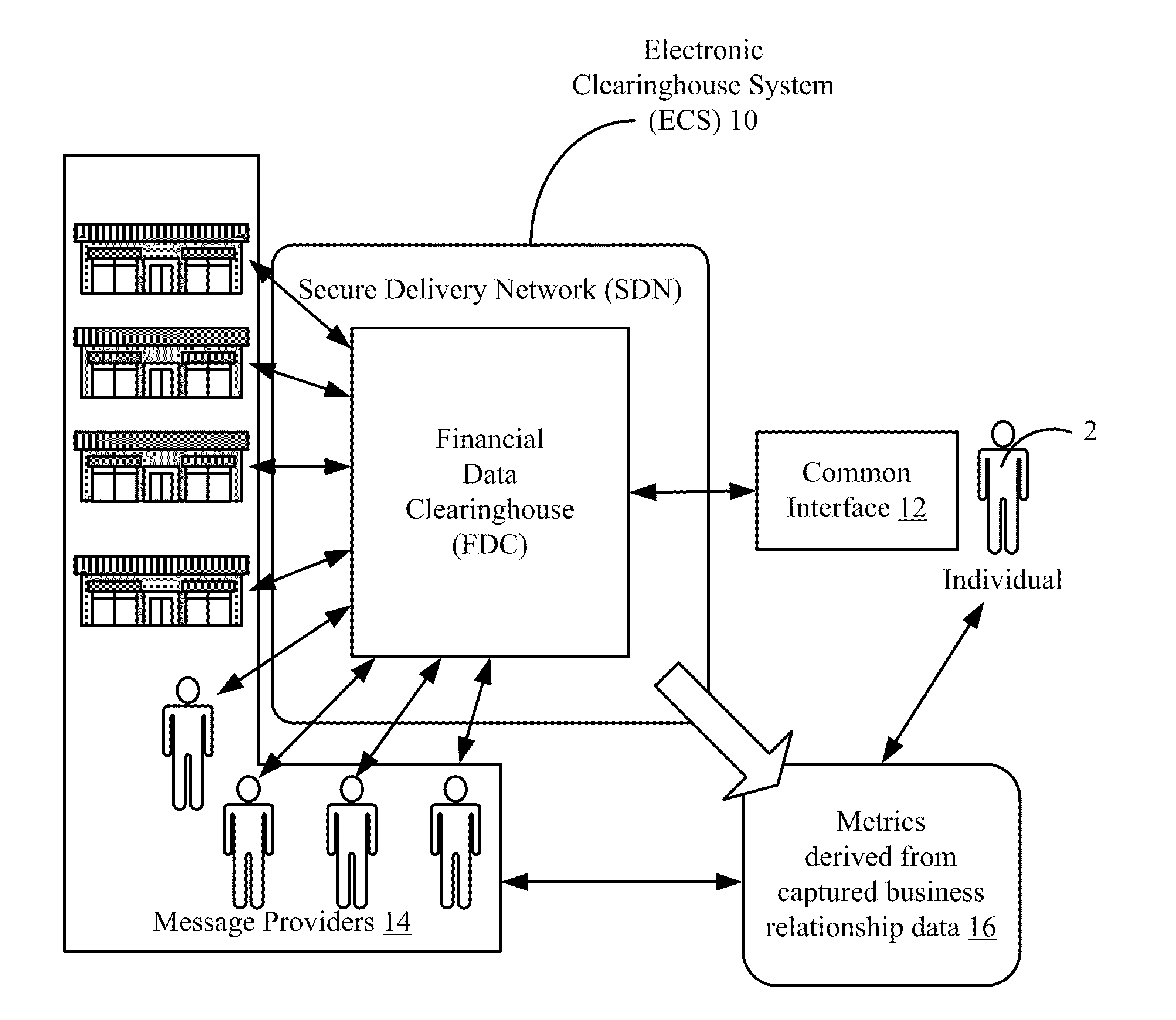
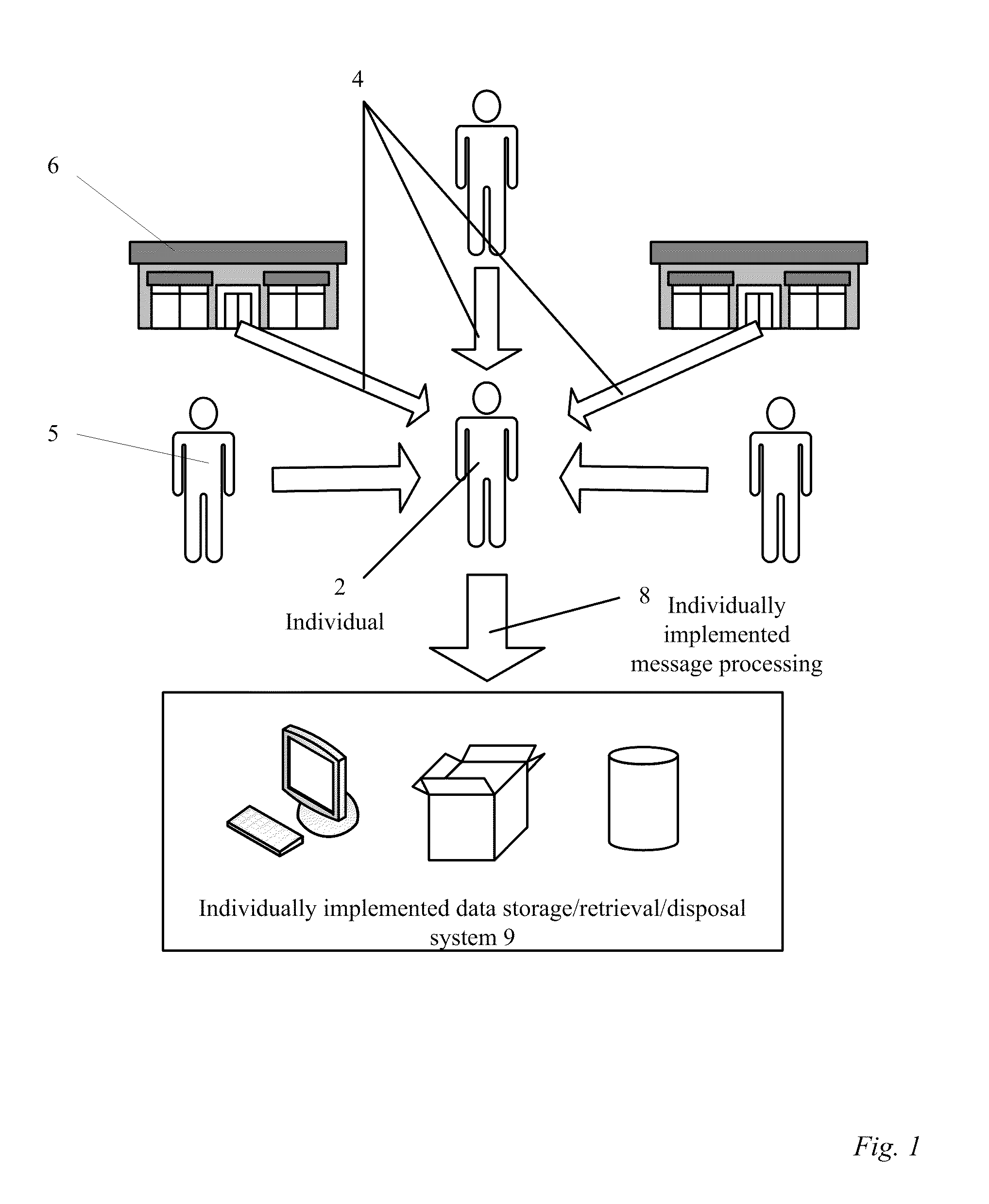
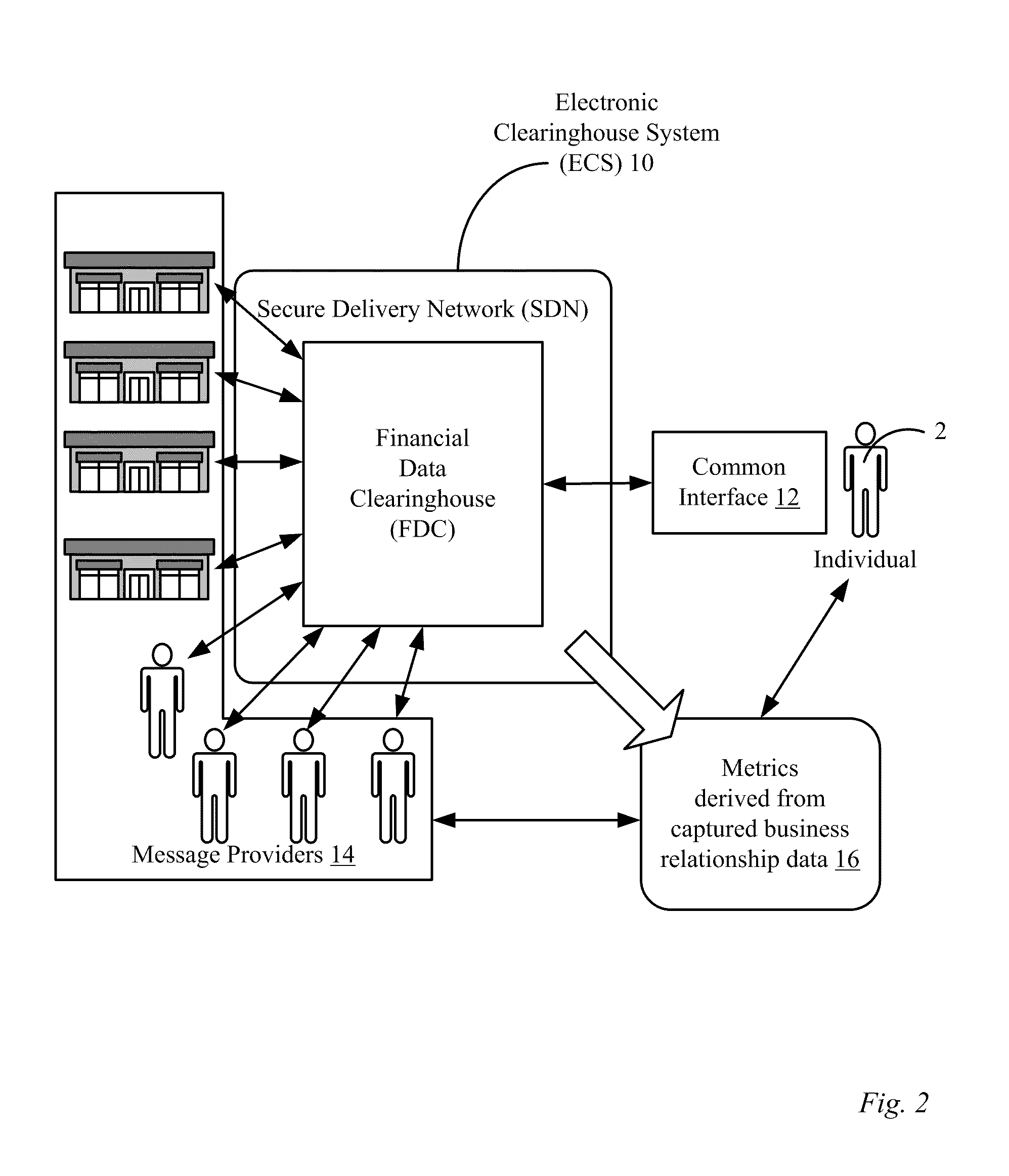
Methods and apparatus for a financial document clearinghouse and secure delivery network
InactiveUS20110270748A1Simplify opting outMaintain privacyFinancePayment architecturePaymentDocumentation procedure
An electronic clearinghouse system (ECS) for securely delivering, retrieving, authenticating, storing, generating and distributing messages, such as financial documents and / or records are described. For message providers, the ECS can provide a secure and trusted venue for delivering messages, such as messages including financial data to their clients that reduces their delivery costs. For users of the ECS, the ECS can provide a central location where each user can receive and consolidate their messages, such as financial documents and associated financial data from a number of different financial data providers. To facilitate these functions, the ECS can include an automated system for recording delivery status as well as evidence of delivery of messages, including whether a message has been viewed by a particular user. Further, the ECS can include components for scheduling events, such as monetary transfers and bill payments, and providing reminders for such events. Also, the ECS can provide utilities that allow a user to package and securely deliver messages to other users.
Owner:T CENT
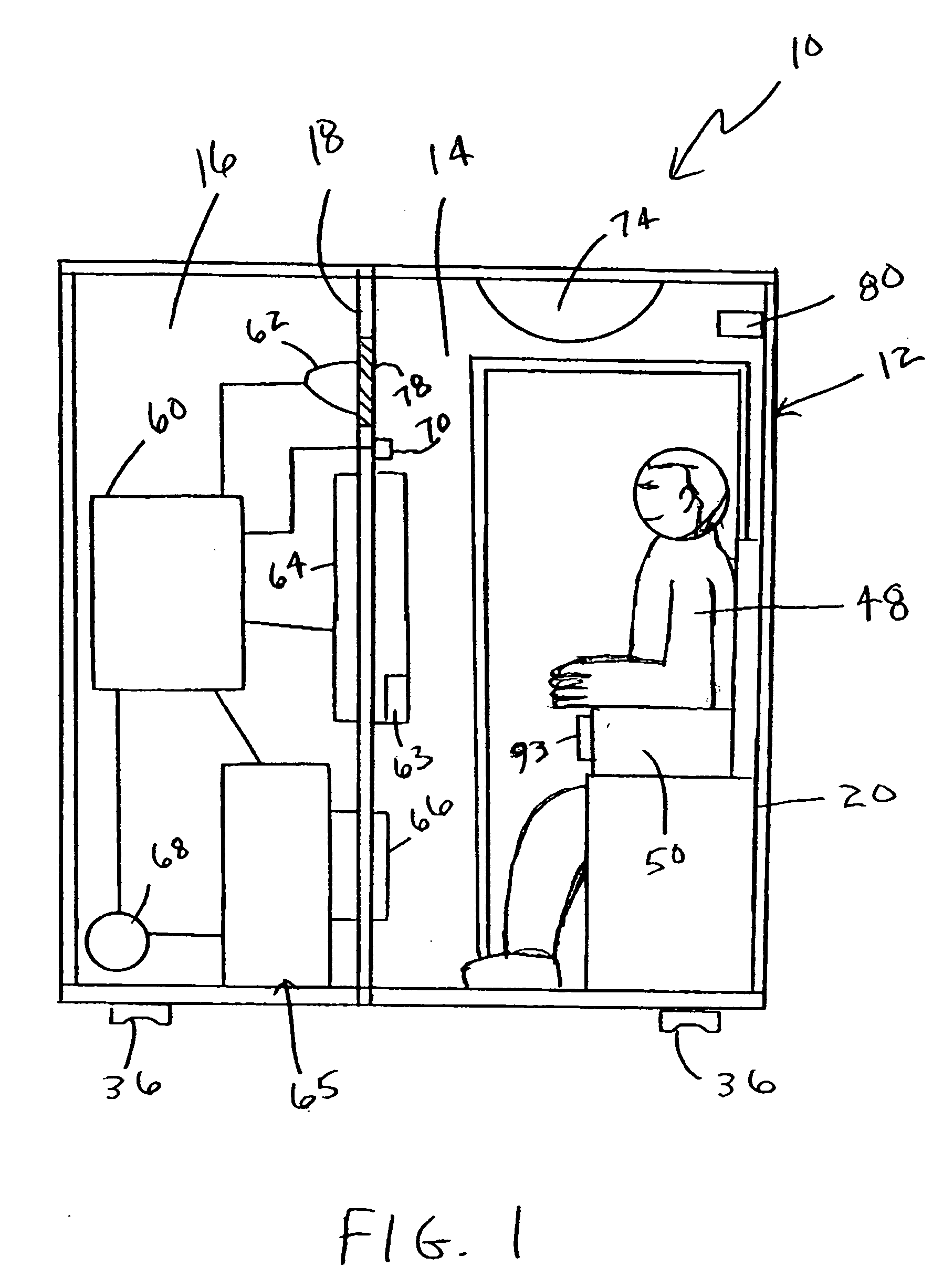
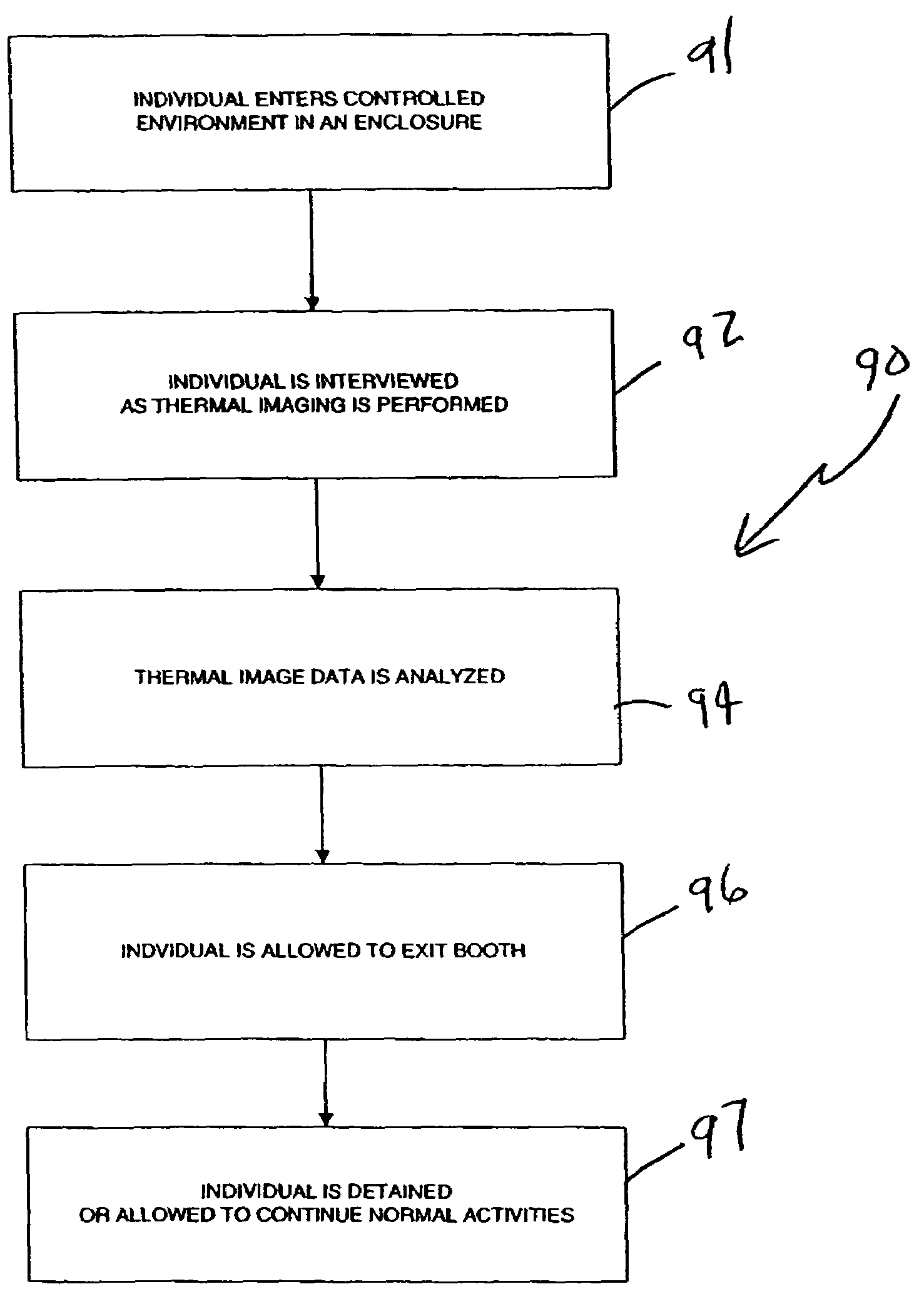
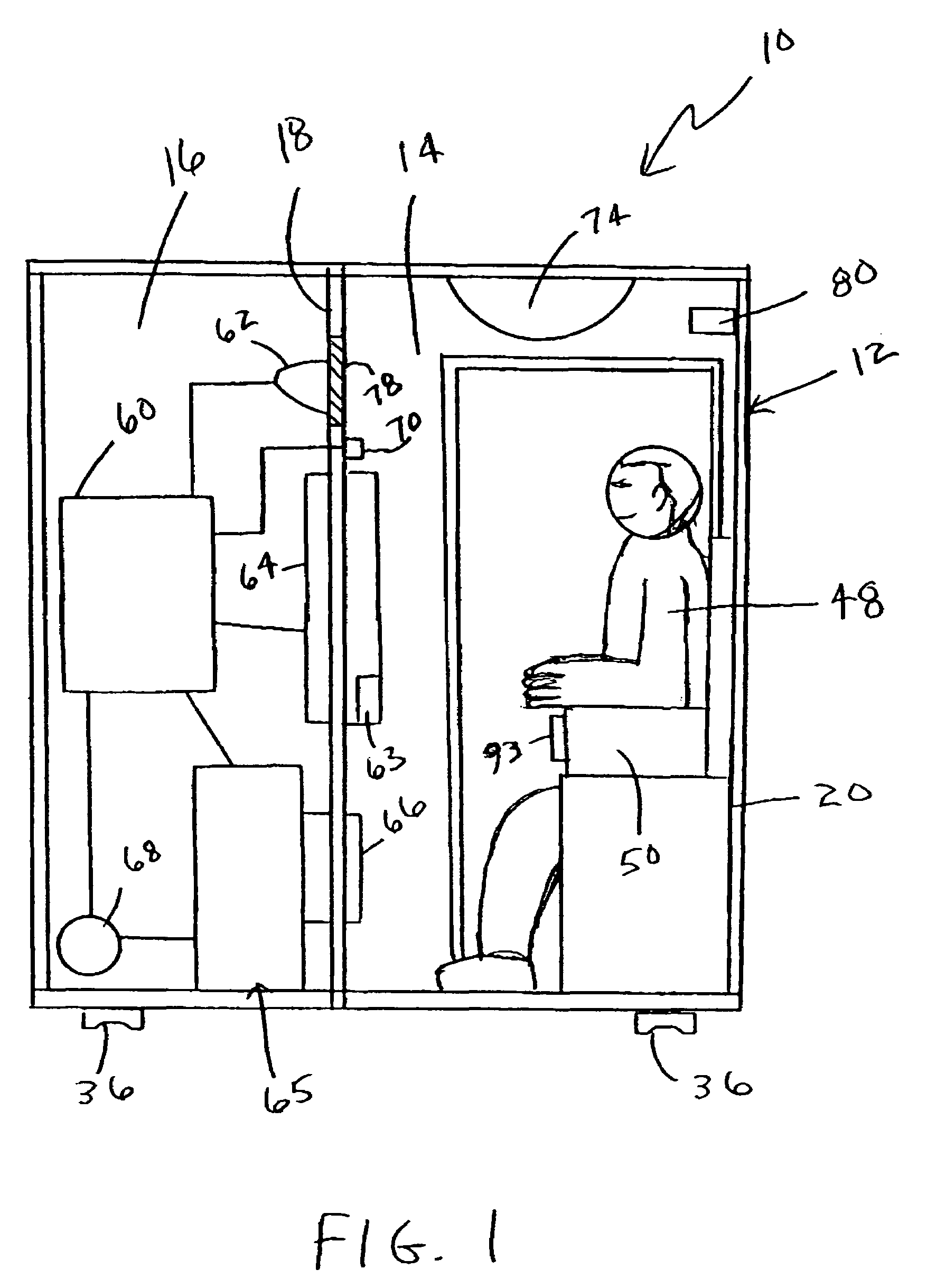
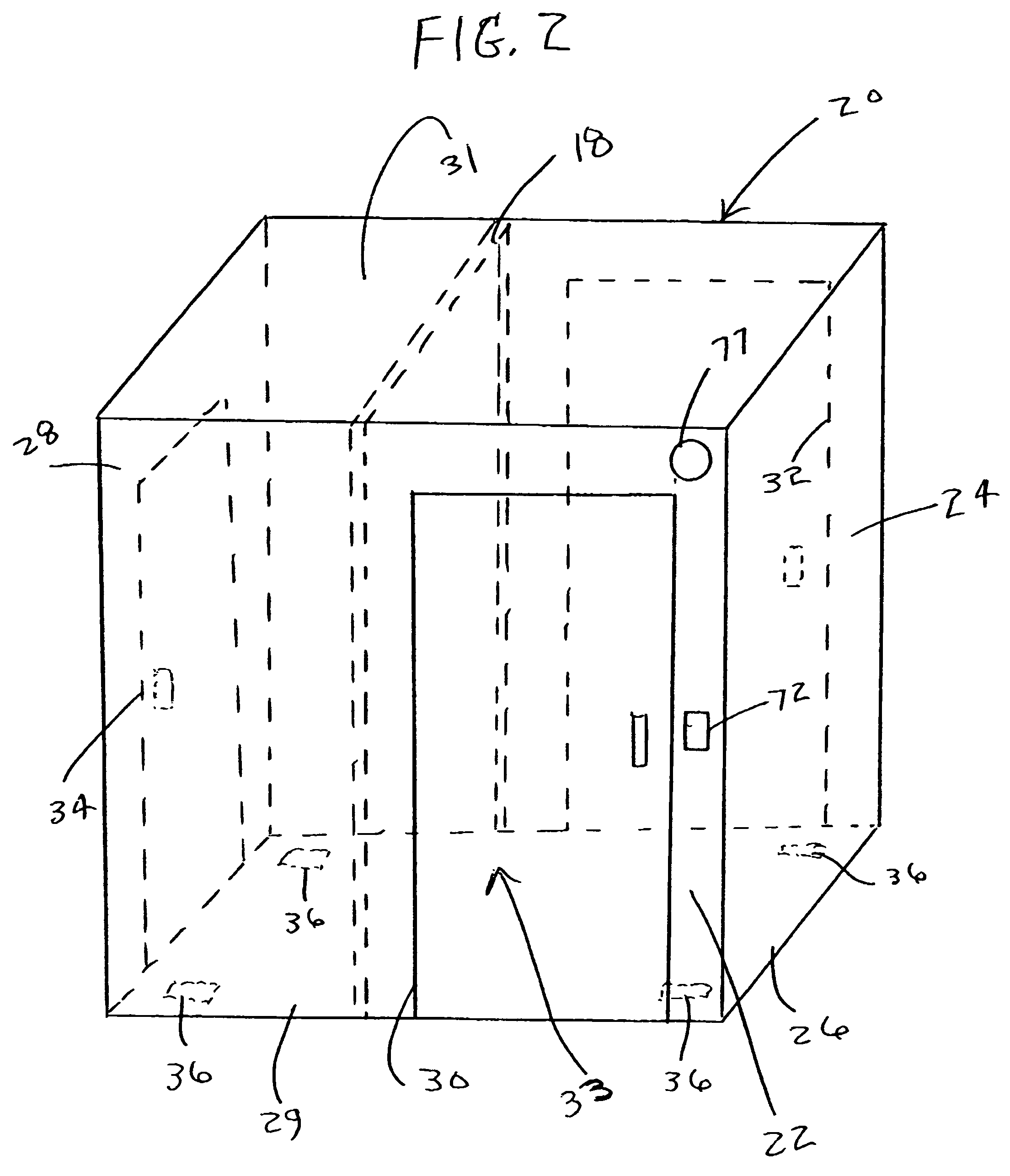
Controlled environment thermal image detection system and methods regarding same
InactiveUS20060116555A1Reduce noiseMaintain privacyElectric signal transmission systemsImage analysisImage detectionPhysical separation
Thermal infrared image data of at least a region of a face of a person in an enclosure is provided. The enclosure, for example, may include a first enclosed volume and a second enclosed volume physically separated from the first enclosed volume. The first enclosed volume may include an entrance door sized to allow a person to enter the first enclosed volume. The enclosure provides a controlled environment for performing measurements (e.g., capturing thermal infrared image data) for use in determining a physiological state of a person (e.g., anxiety, deception, etc.).
Owner:HONEYWELL INT INC
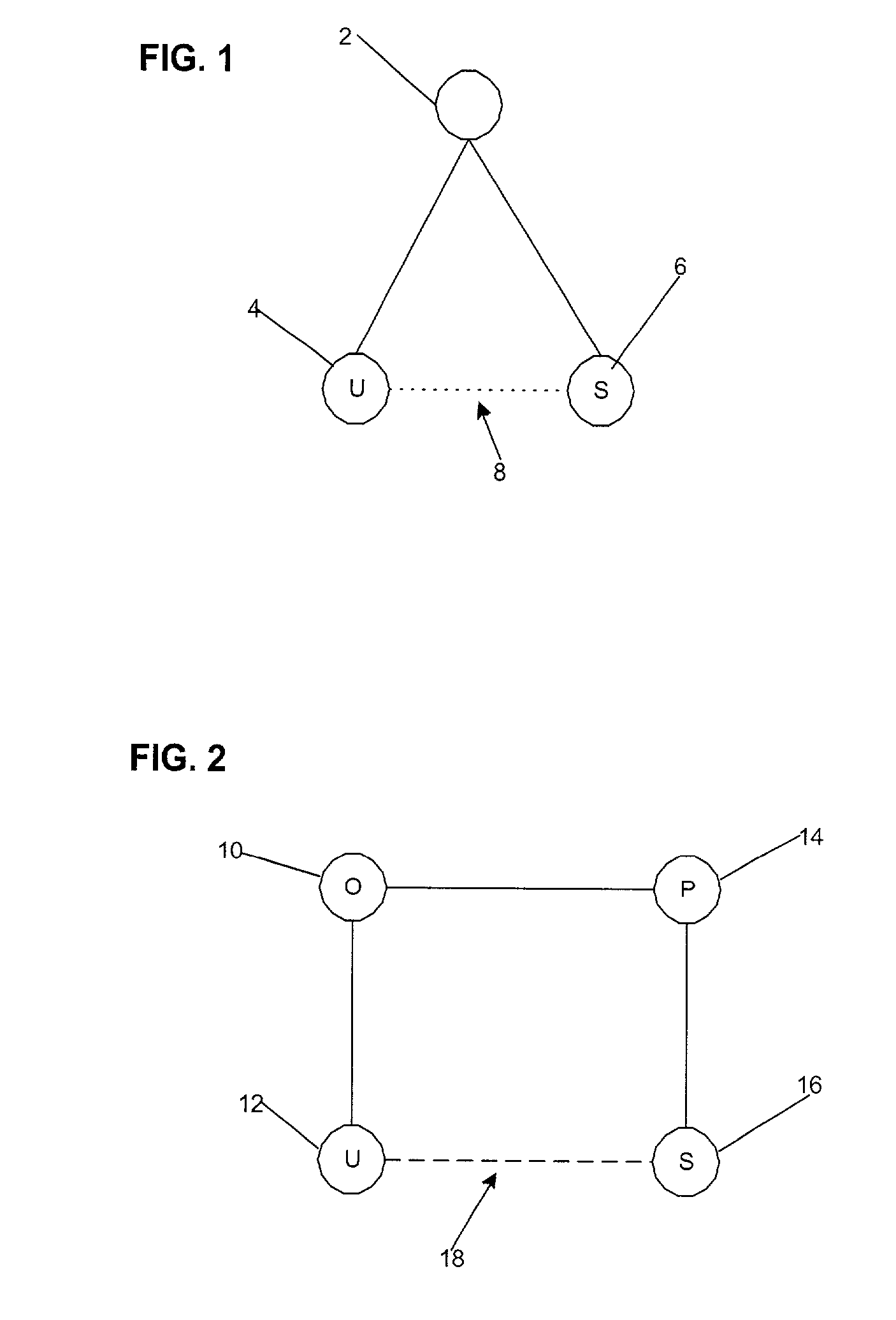
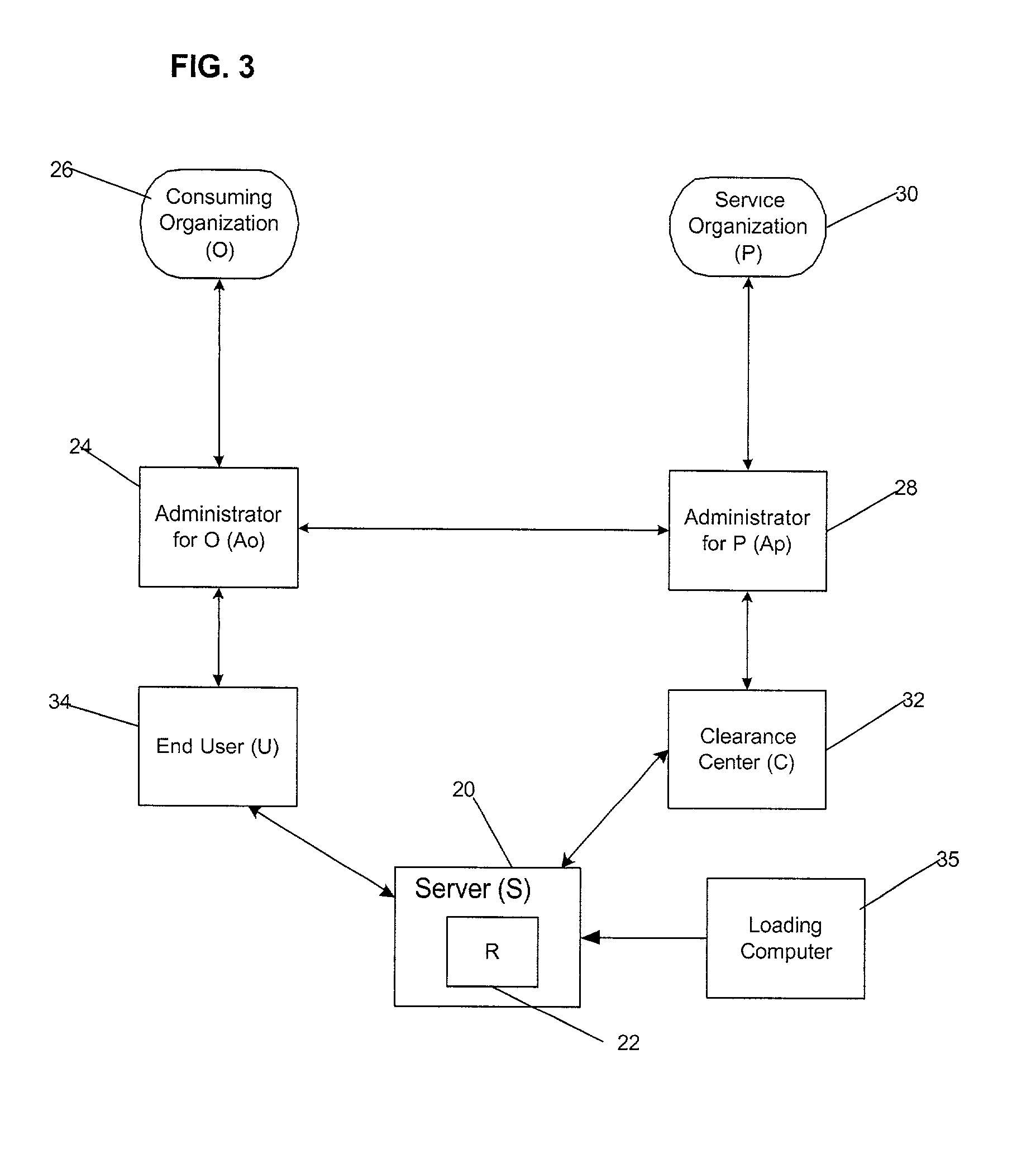
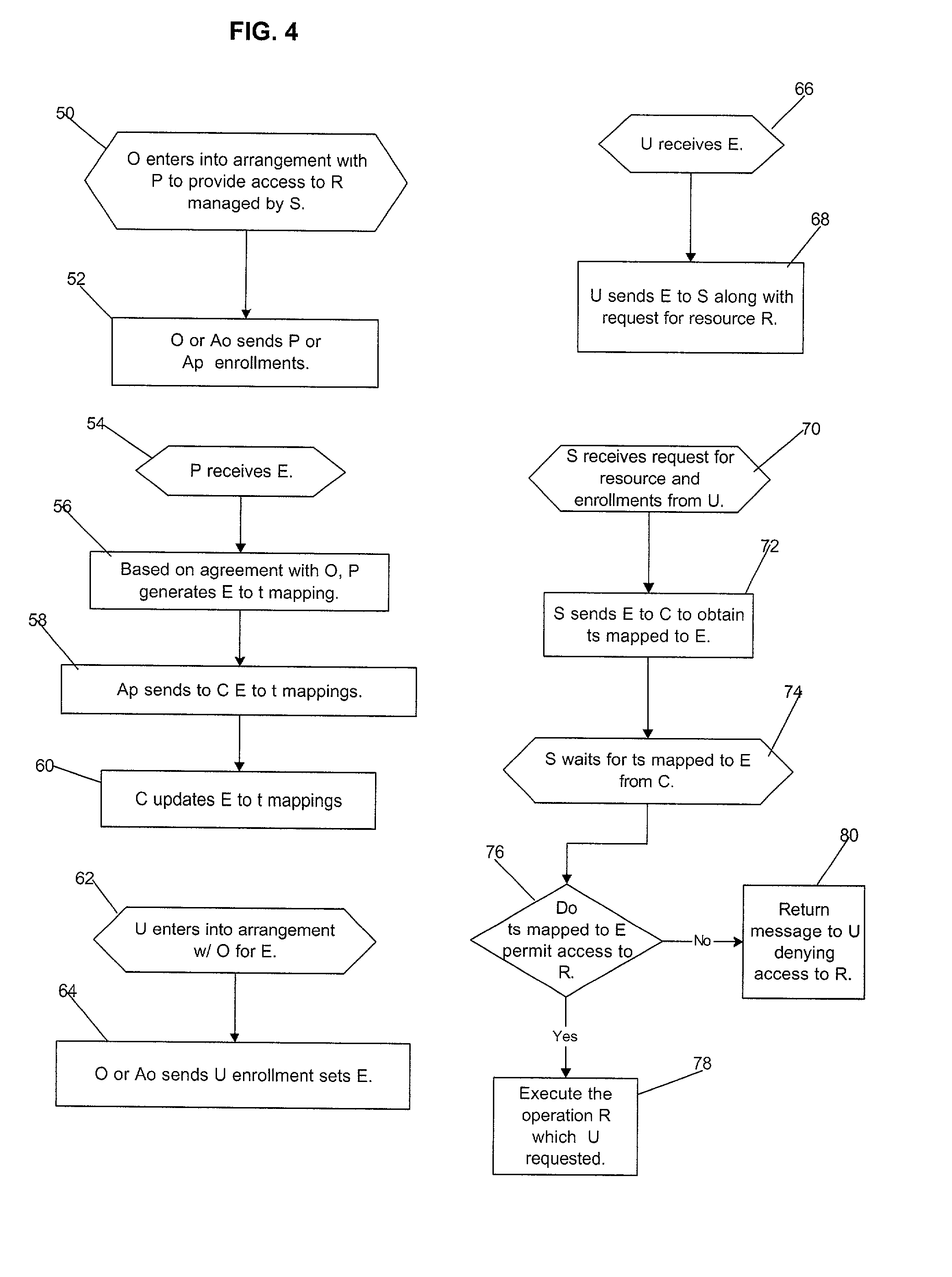
Umethod, system and program for managing relationships among entities to exchange encryption keys for use in providing access and authorization to resources
InactiveUS20010020228A1Strong level of assuranceMaintain privacyKey distribution for secure communicationUser identity/authority verificationAuthorizationComputer science
Provided is a method, system, and program for managing access to resources. Encryption keys are exchanged among a first entity, second entity, third entity, and a fourth entity. Each entity has one relationship with one other entity and the encryption keys are exchanged pursuant to the relationships. Electronic messages are encrypted with the encryption keys concerning digital enrollments to provide to the first entity. The digital enrollment is associated with at least one digital ticket that authorizes access to a resource managed by the fourth entity. Presentation of the digital enrollment causes the presentation of one digital ticket associated with the digital enrollment to authorize the first entity to access the resource.
Owner:IBM CORP
Mobile video teleconferencing authentication and management system and method
InactiveUS20070120965A1Properly balanceMaintain privacyTelevision conference systemsTwo-way working systemsManagement systemData bank
Owner:SANDBERG ROY BENJAMIN +1
Contextual ad processing on local machine
InactiveUS20060149677A1Privacy protectionMaintain privacyComputer security arrangementsData switching networksClient-sideData storing
A system is disclosed for serving advertisements to a user of a client device. A set of advertisements are downloaded to the client device. Based on data stored on the client device, or action taken on the client device, a subset of the advertisement are chosen for presentation to the user of the client device. In one embodiment, the choice of advertisement to present to the user is based on the content of one or more email messages. The scanning of the email message and the decision as to which advertisement(s) to present are made on the client machine in order to protect the privacy of the user. The chosen advertisements are then displayed with the one or more emails.
Owner:MICROSOFT TECH LICENSING LLC
Targeting Ads to Subscribers based on Privacy Protected Subscriber Profiles
InactiveUS20070233571A1Maintain privacyBroadcast information switching/replacementAnalogue secracy/subscription systemsTelevision systemPrivacy preserving
Monitoring subscriber viewing interactions, such as television viewing interactions, and generating viewing characteristics therefrom. Generating at least one type of subscriber profile from at least some subset of subscriber characteristics including viewing, purchasing, transactions, statistical, deterministic, and demographic. The subscriber characteristics may be generated, gathered from at least one source, or a combination thereof. Forming groups of subscribers by correlating at least one type of subscriber profile. The subscriber groups may correlate to elements of a content delivery system (such as head-ends, nodes, branches, or set top boxes (STBs) within a cable TV system). Correlating ad profiles to subscriber / subscriber group profiles and selecting targeted advertisements for the subscribers / subscriber groups based on the correlation. Inserting the targeted ads in place of default ads in program streams somewhere within the content delivery system (head-end, node, or STB). Presenting the targeted ads to the subscriber / subscriber group via a television.
Owner:PRIME RES ALLIANCE E LLC
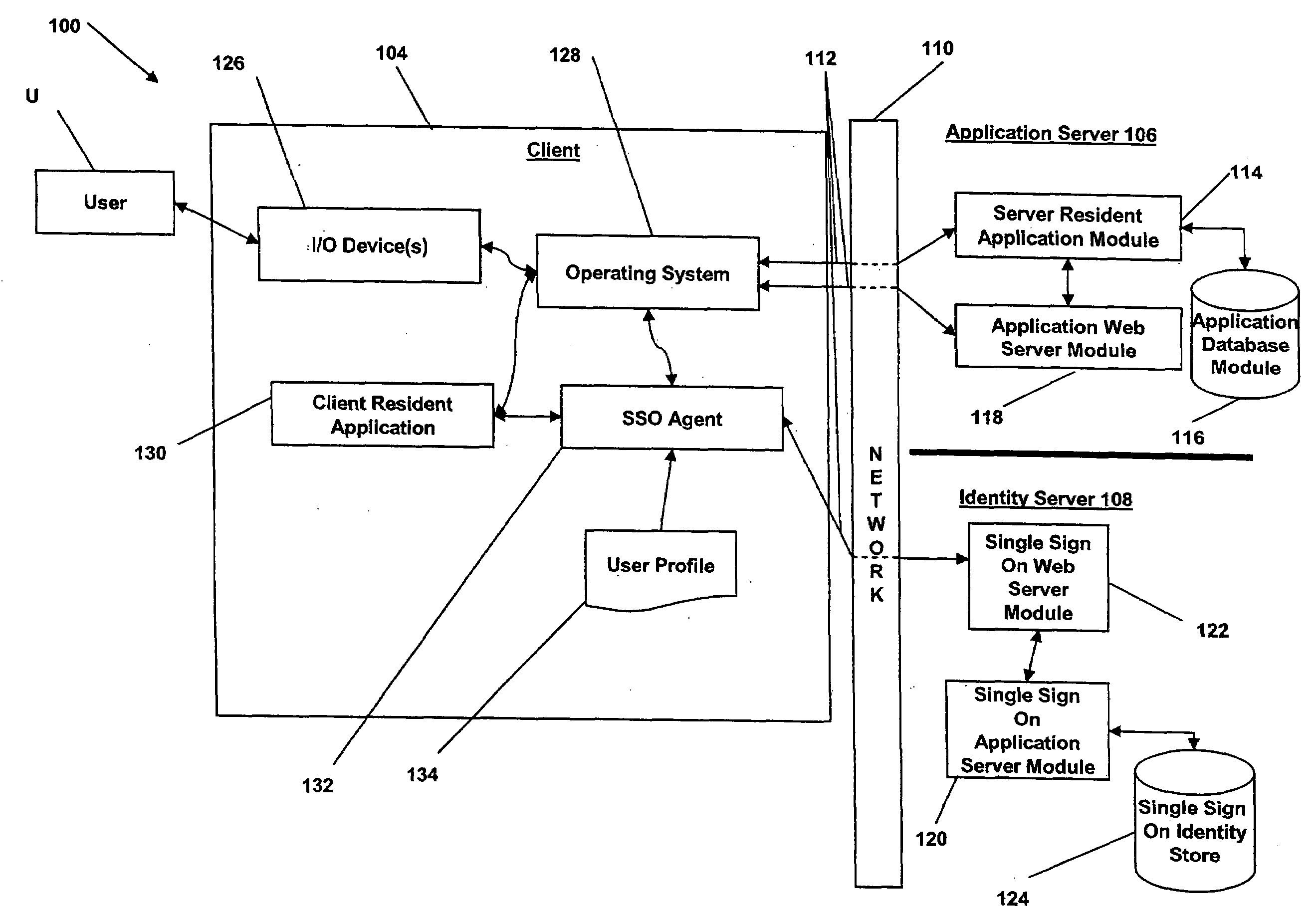
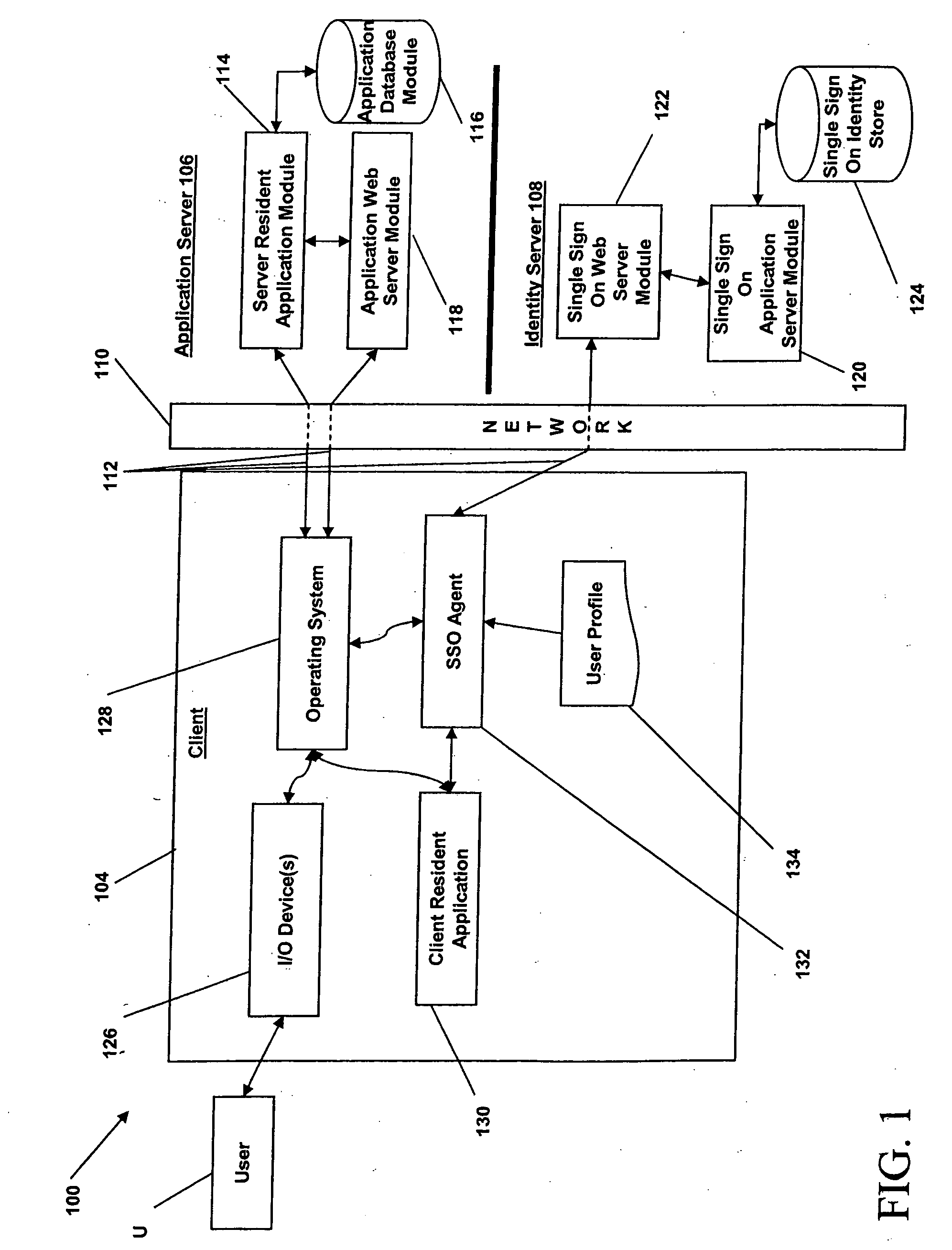
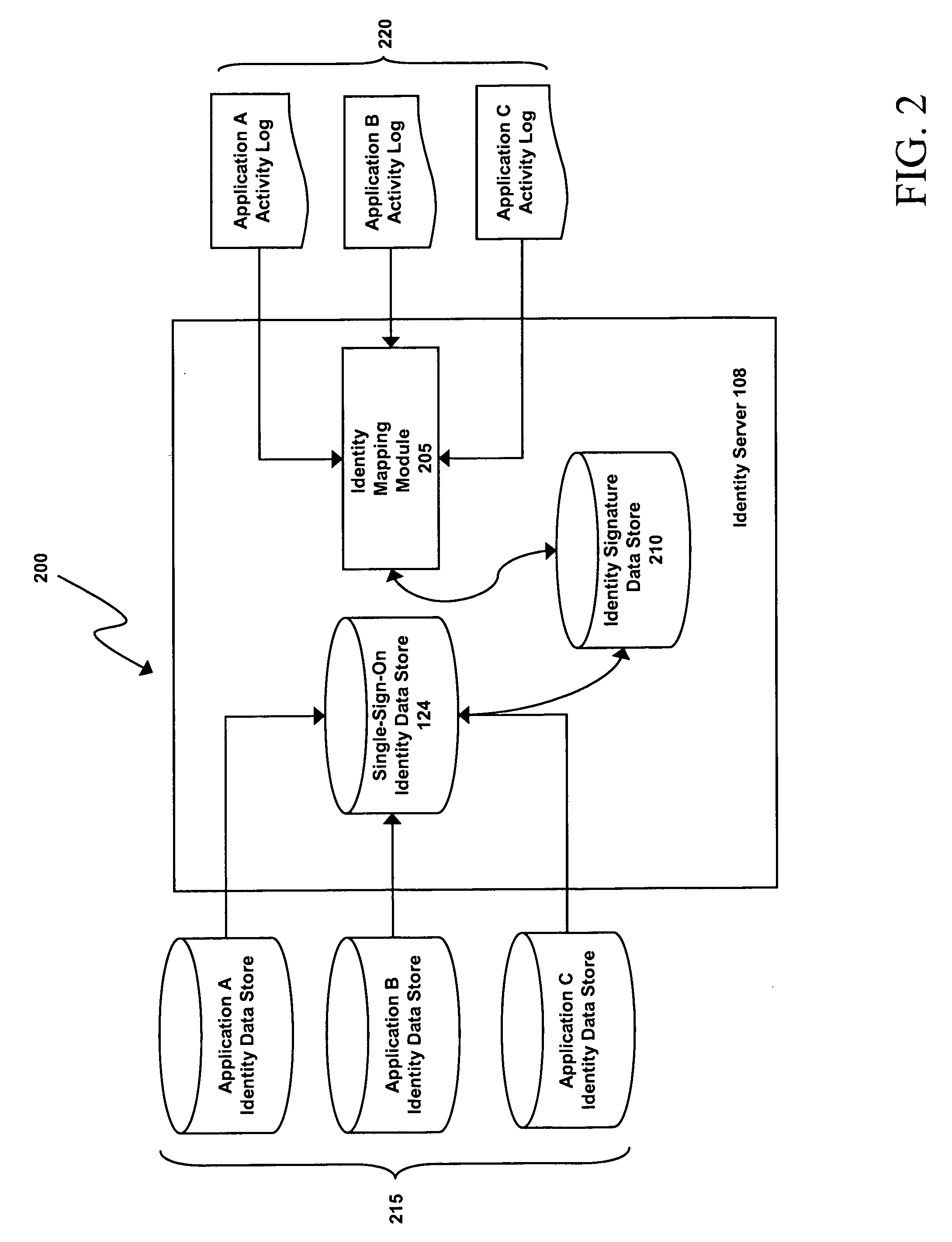
System and method for identity consolidation
ActiveUS20080184349A1Easy constructionEasy to integrateDigital data processing detailsUser identity/authority verificationUser authenticationSingle point
Application-specific and single-sign-on user-authentication credentials are analyzed and consolidated based on commonalities among the credentials and usage of the applications to which they are attributed.
Owner:IMPRIVATA
Method and system for sharing anonymous user information
ActiveUS7930252B2Enhanced anonymityIncreased ad rateComputer security arrangementsMultiple digital computer combinationsInternet privacyData source
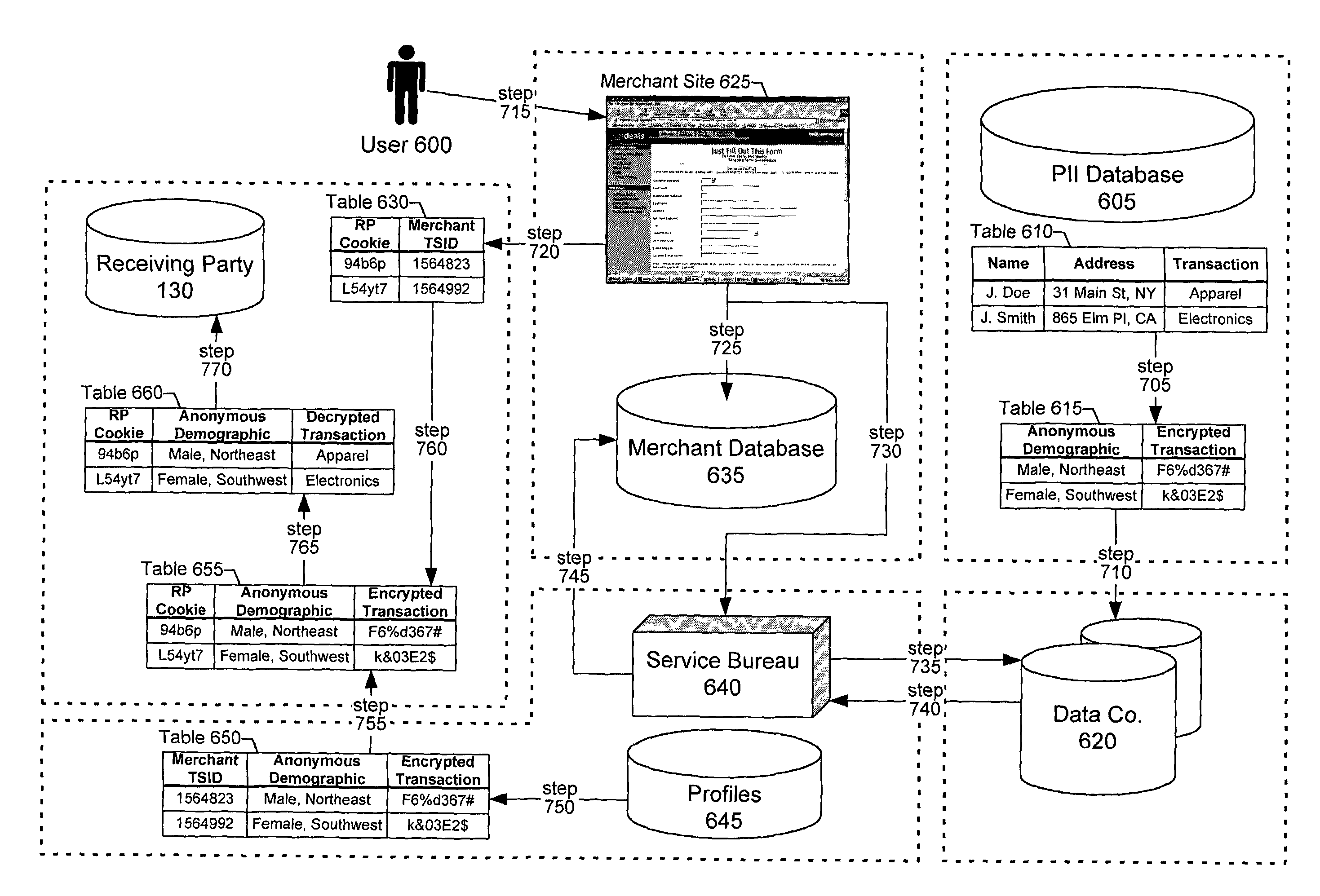
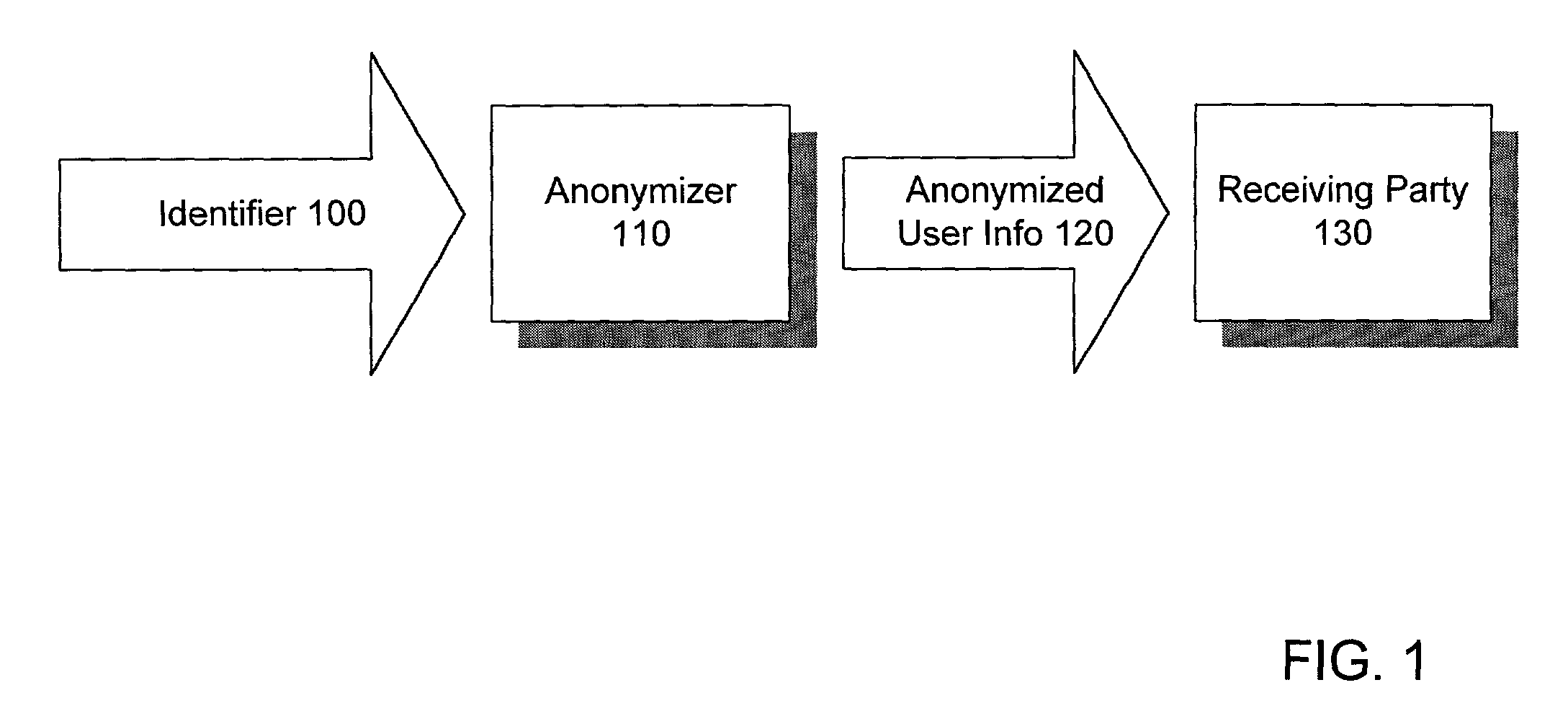
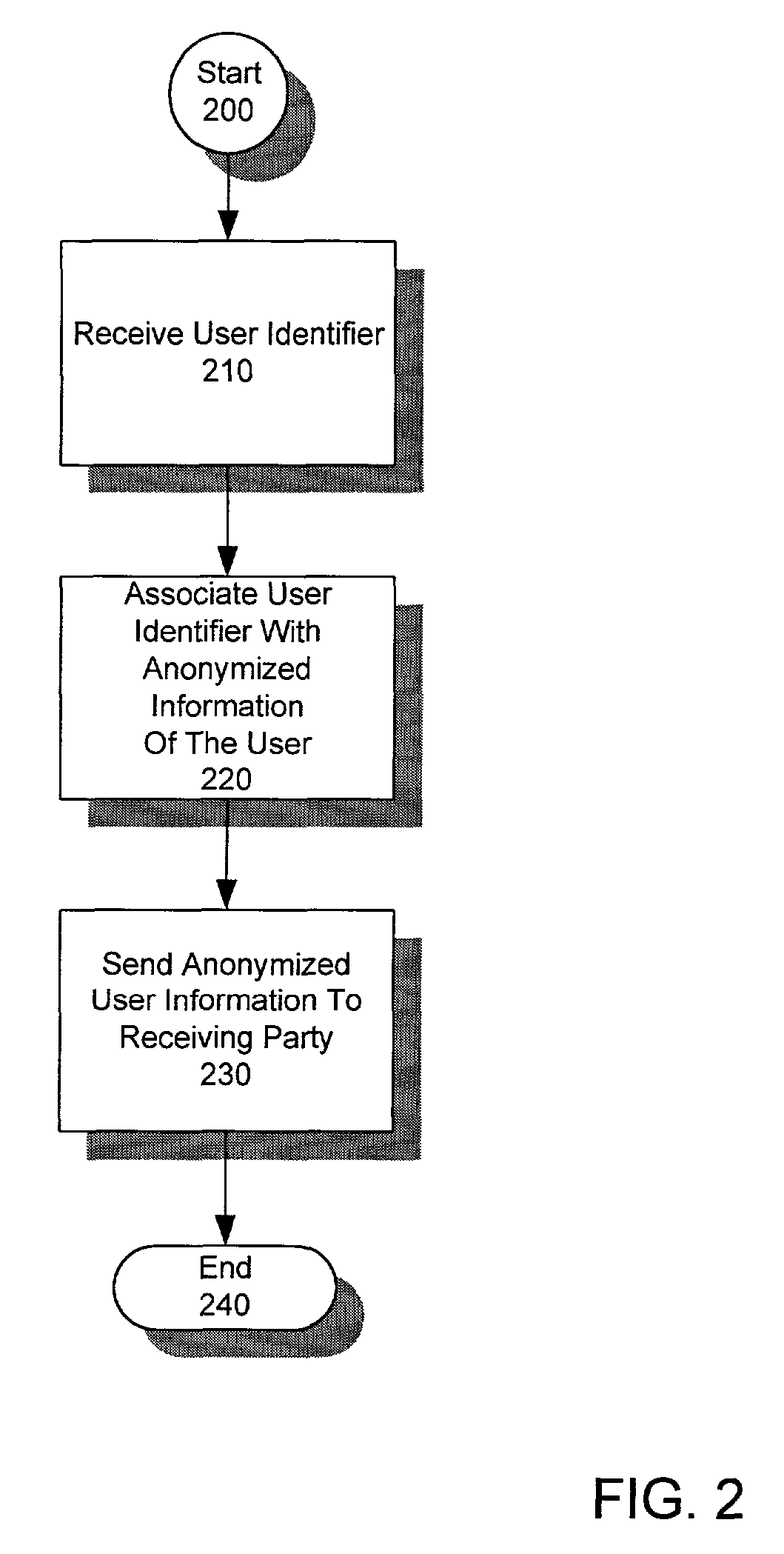
A method and system for sharing online user information in an anonymous manner. The system associates an identifier with anonymized information of the user, and sends the anonymized user information to a receiving party.In one embodiment, the system receives a temporary id with personally identifiable information from a Web site, uses the personally identifiable information as a key to obtain the anonymized information from a data source, and sends the temporary id with the anonymized information to the receiving party. The receiving party uses the temporary id, previously received by the Web site, as a key to obtain the anonymized information of the user.In another embodiment, the system receives a temporary id from a Web site with a cookie from the user, uses the cookie as a key to obtain the anonymized information from a data source, and sends the temporary id with the anonymized information to the receiving party. The receiving party uses the temporary id, previously received by the Web site, as a key to obtain the anonymized information of the user.
Owner:GOOGLE LLC
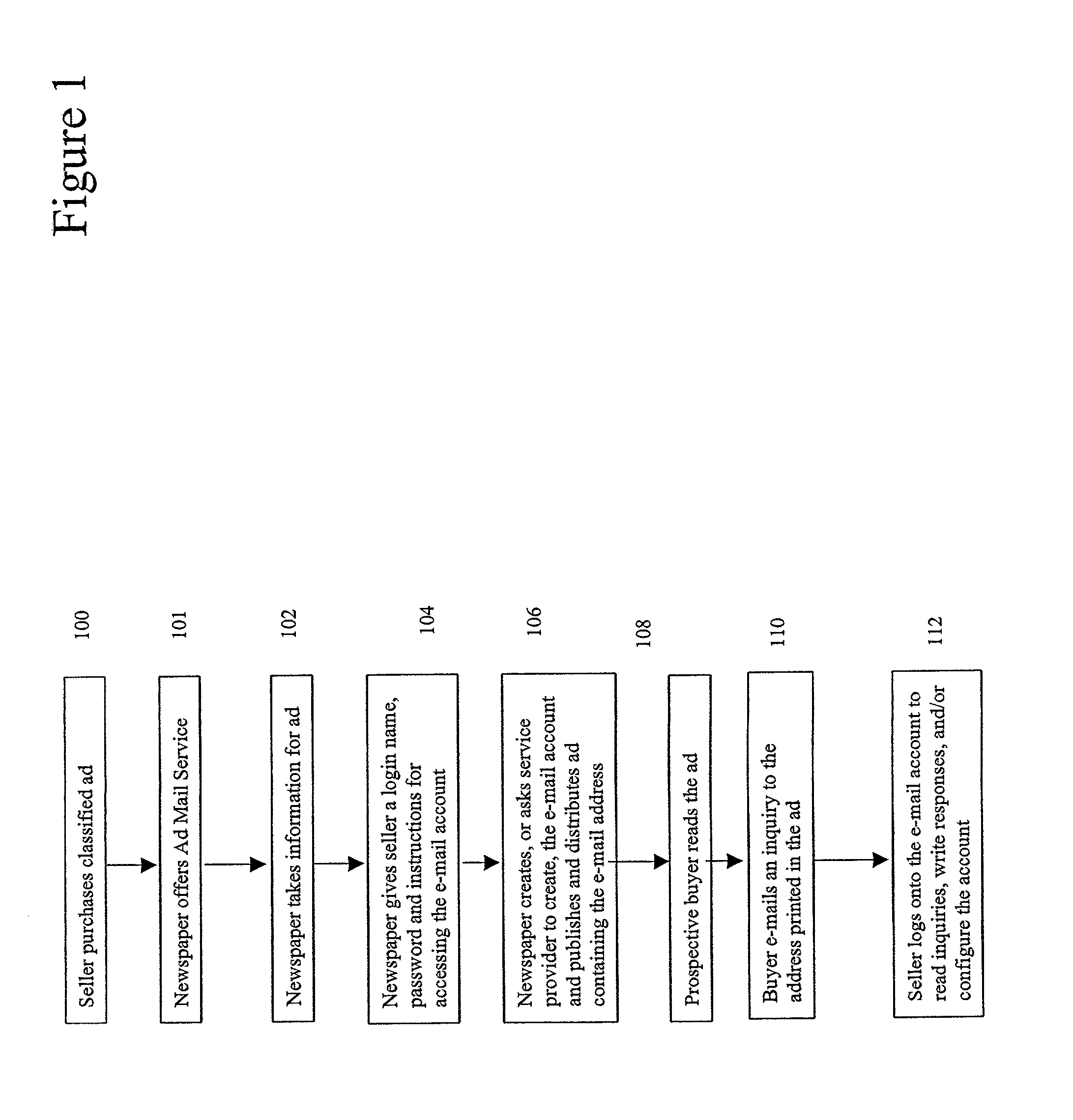
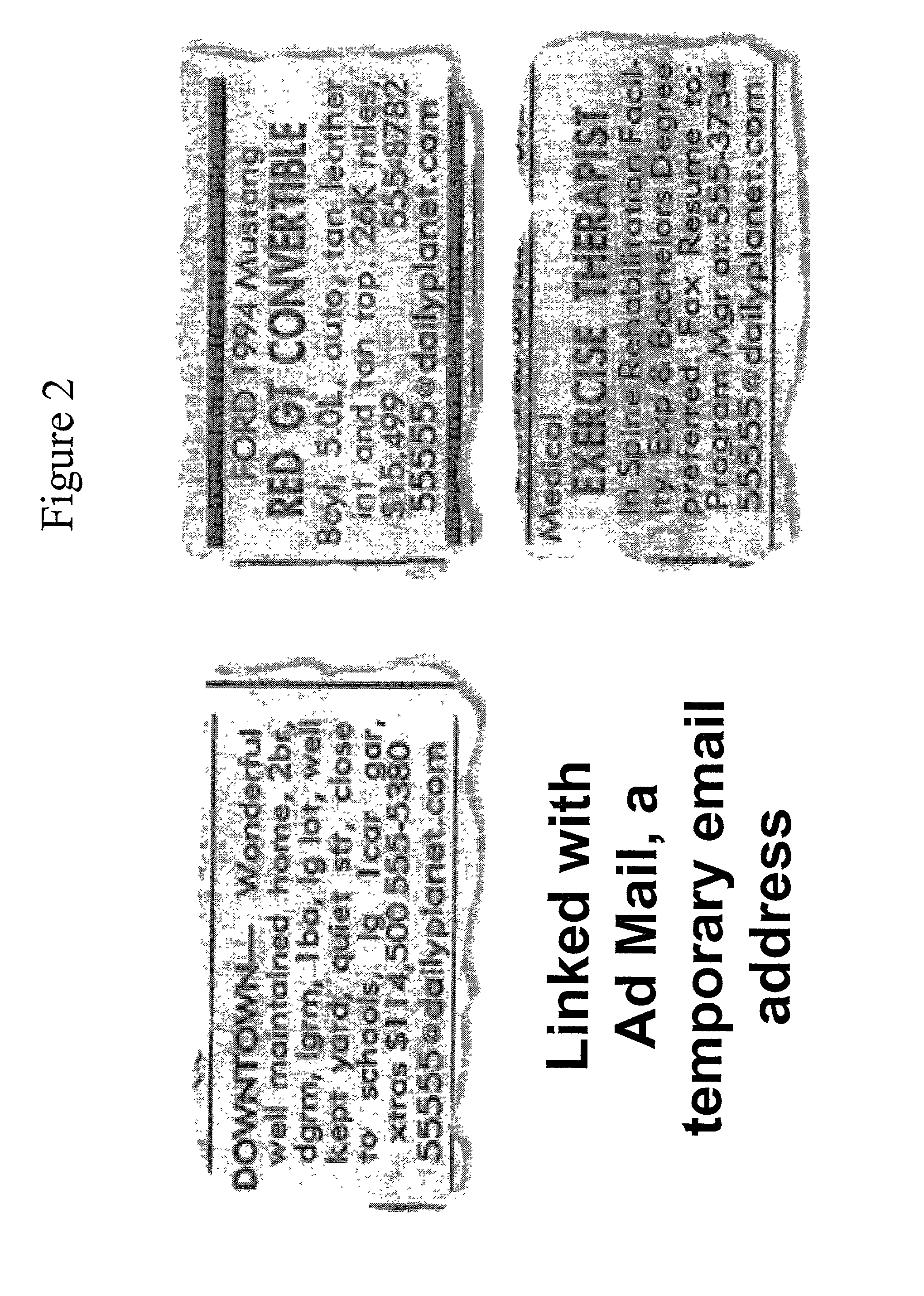
Electronic mail classified advertising system
InactiveUS20020016735A1Avoid necessityAvoid problemsMultiple digital computer combinationsOffice automationDocument handlingEmail classification
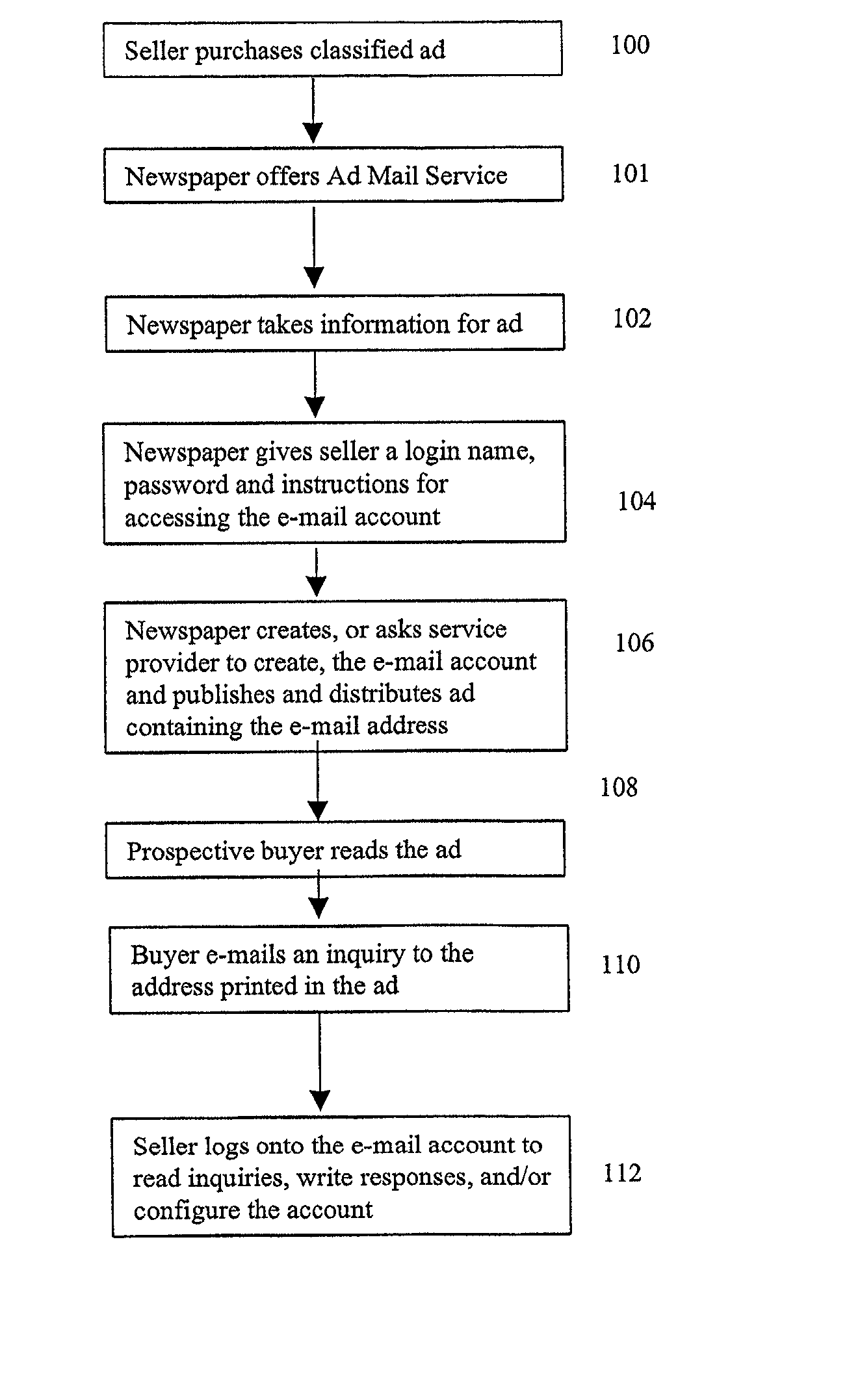
A system and method for establishing temporary electronic mail (e-mail) accounts is configured to operate with classified newspaper advertising. One of the aspects of the present invention is a file handling method that automates the process of establishing the e-mail accounts through interaction with a publisher's system for taking orders for classified advertisements. Typical newspaper classified advertising comprises two or three lines of text which provide only basic information about an item for sale. With the present invention, advertisers would be offered the option of creating a special e-mail account with a duration tied to the run of the advertisement. The e-mail accounts would be used to receive inquiries about the item for sale. The e-mail account could be also be configured to auto-respond to each incoming message with additional descriptive information about the item being offered for sale. Responders could learn more about the item, and thereby avoid the necessity of calling the seller. Sellers, in turn, can avoid the problem of repeated phone calls to request additional information, and may also remain anonymous while responding to multiple inquiries.
Owner:USA NET
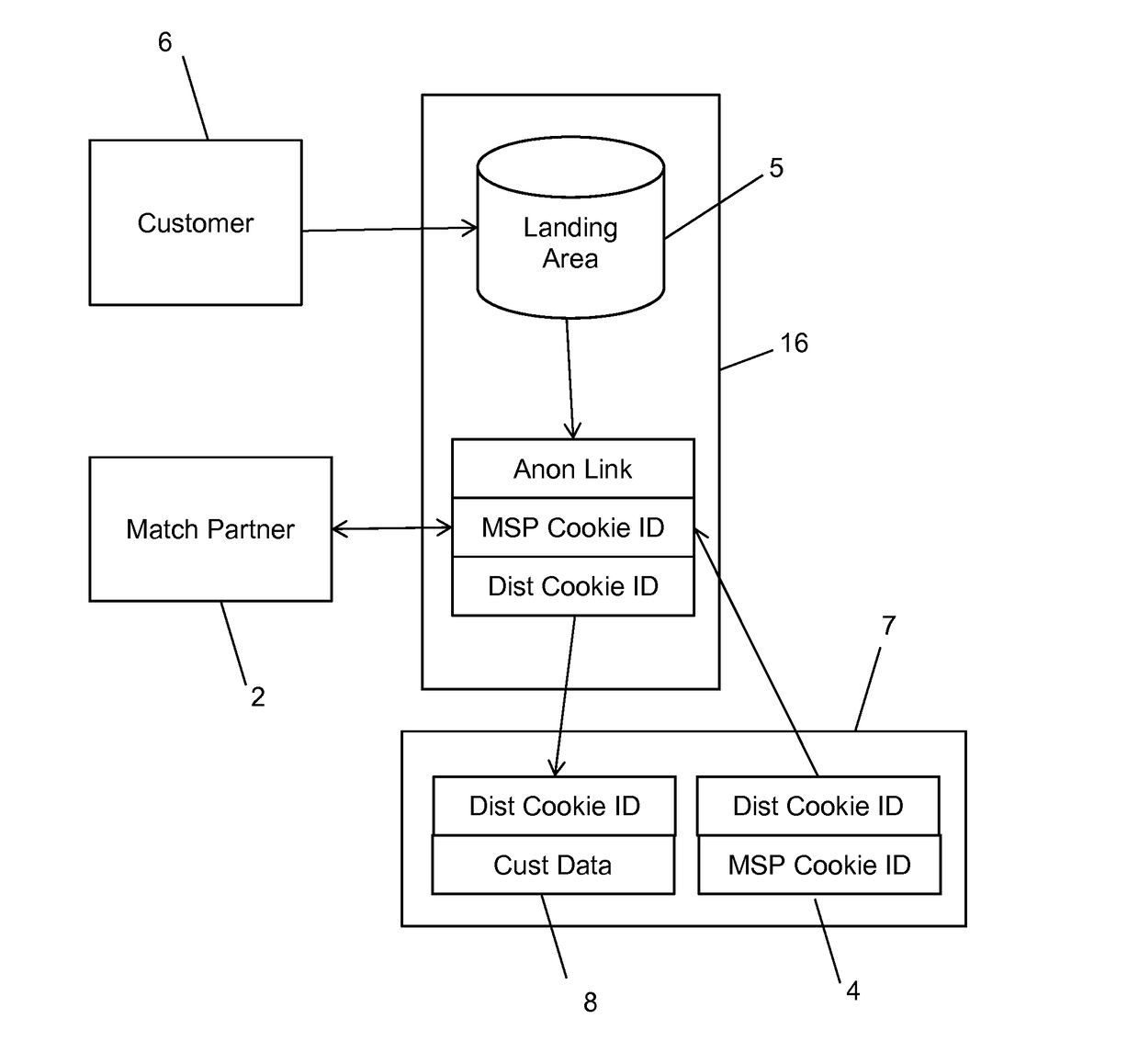
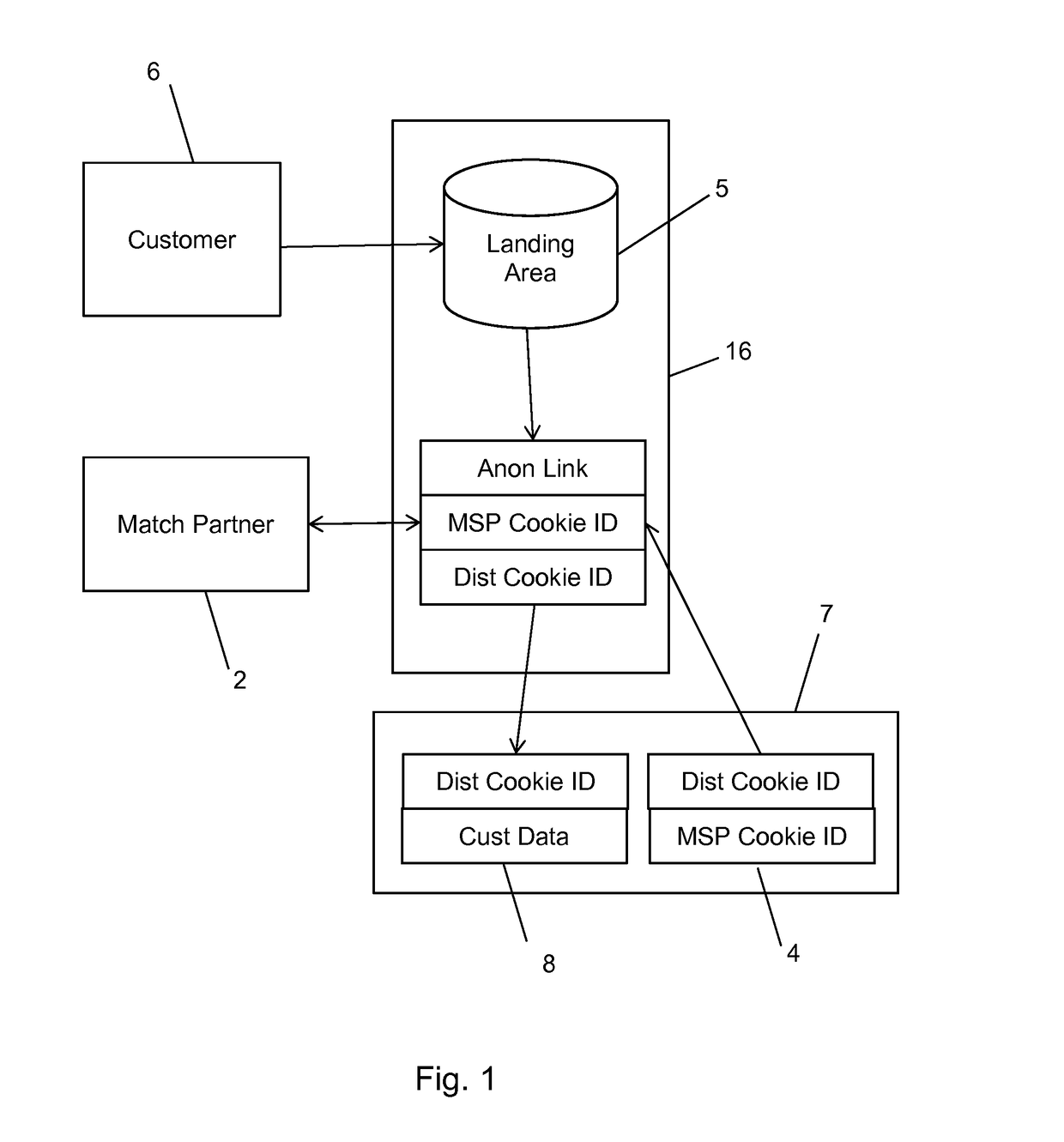
Apparatus and method for bringing offline data online while protecting consumer privacy
ActiveUS9665883B2Precise positioningIncreased marketingAdvertisementsComputer security arrangementsInternet privacyOnline and offline
A method and system for bringing together online and offline advertising uses anonymous links that are associated with consumer data. The anonymous links allow processing without personally identifiable information (PII) in a secure environment. Data is matched using the anonymous links, and further using identifiers that are encrypted for use in connection with individual match distribution partners. The method and system allows a marketer to utilize offline data to precisely target advertisements without the use of PII, and to perform analytics concerning the use of the online advertisements to more precisely determine the effectiveness of multichannel marketing efforts.
Owner:LIVERAMP
Method, system, and apparatus for maintaining user privacy in a knowledge interchange system
InactiveUS7730010B2Maintain privacyType is limitedDigital data processing detailsDigital computer detailsInternet privacyNoun phrase
A method, system, and apparatus are provided for maintaining user privacy in a knowledge interchange (“KI”) system. A user may provide privacy preferences relating to their participation in the KI system. The user may identify specific keywords, noun phrases, and contacts that should not be transmitted to a server computer. The user may also specify whether each keyword, noun phrase, or contact should be public or private. If a public keyword is identified during a search query as being associated with the user, the user's identity will be made available to a seeker If a private keyword is identified during a search query as being associated with the user, the user's identity will not be made available and a brokered communication process between the seeker and the user will be performed.
Owner:MICROSOFT TECH LICENSING LLC
Architecture for secure reverse mobile commerce
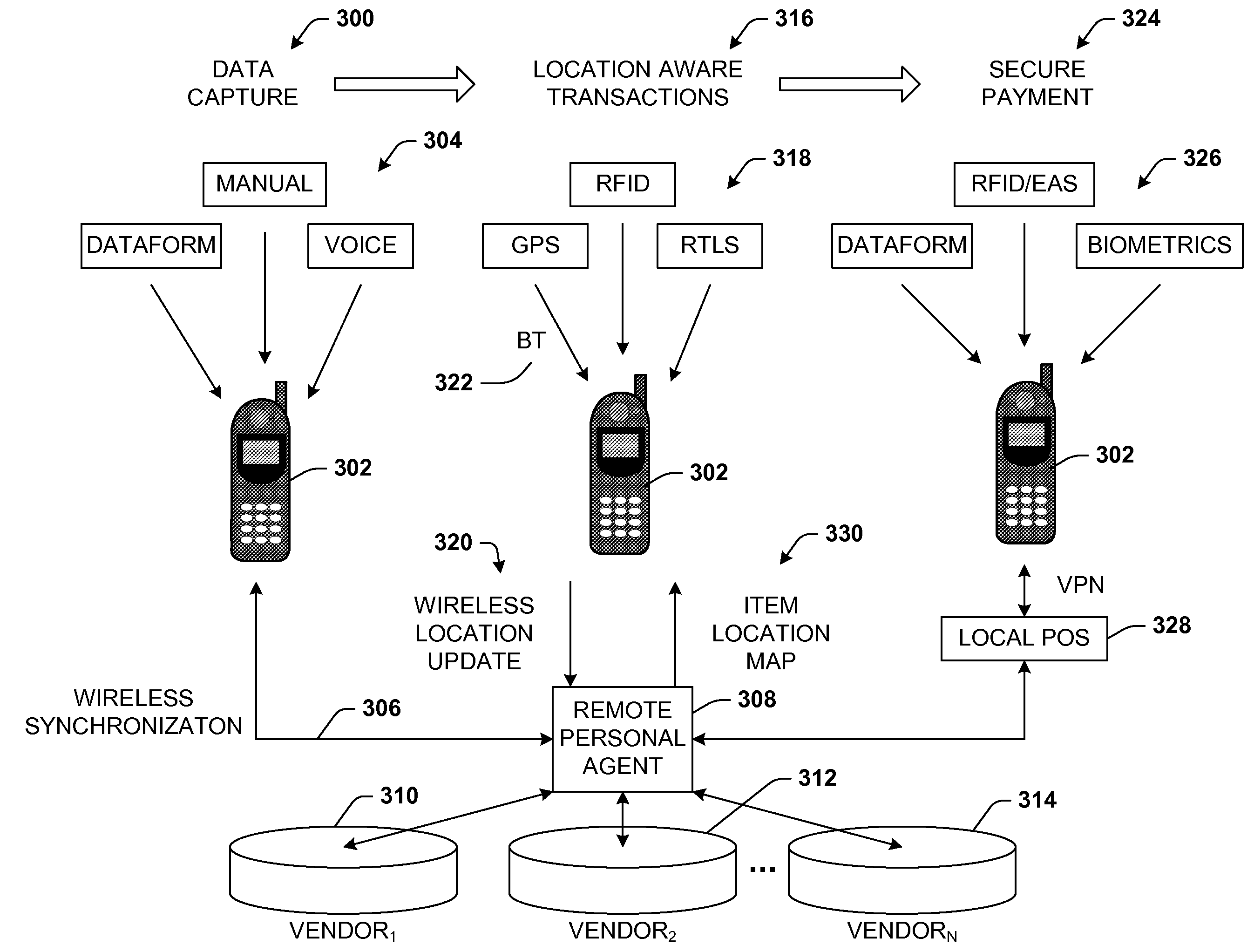
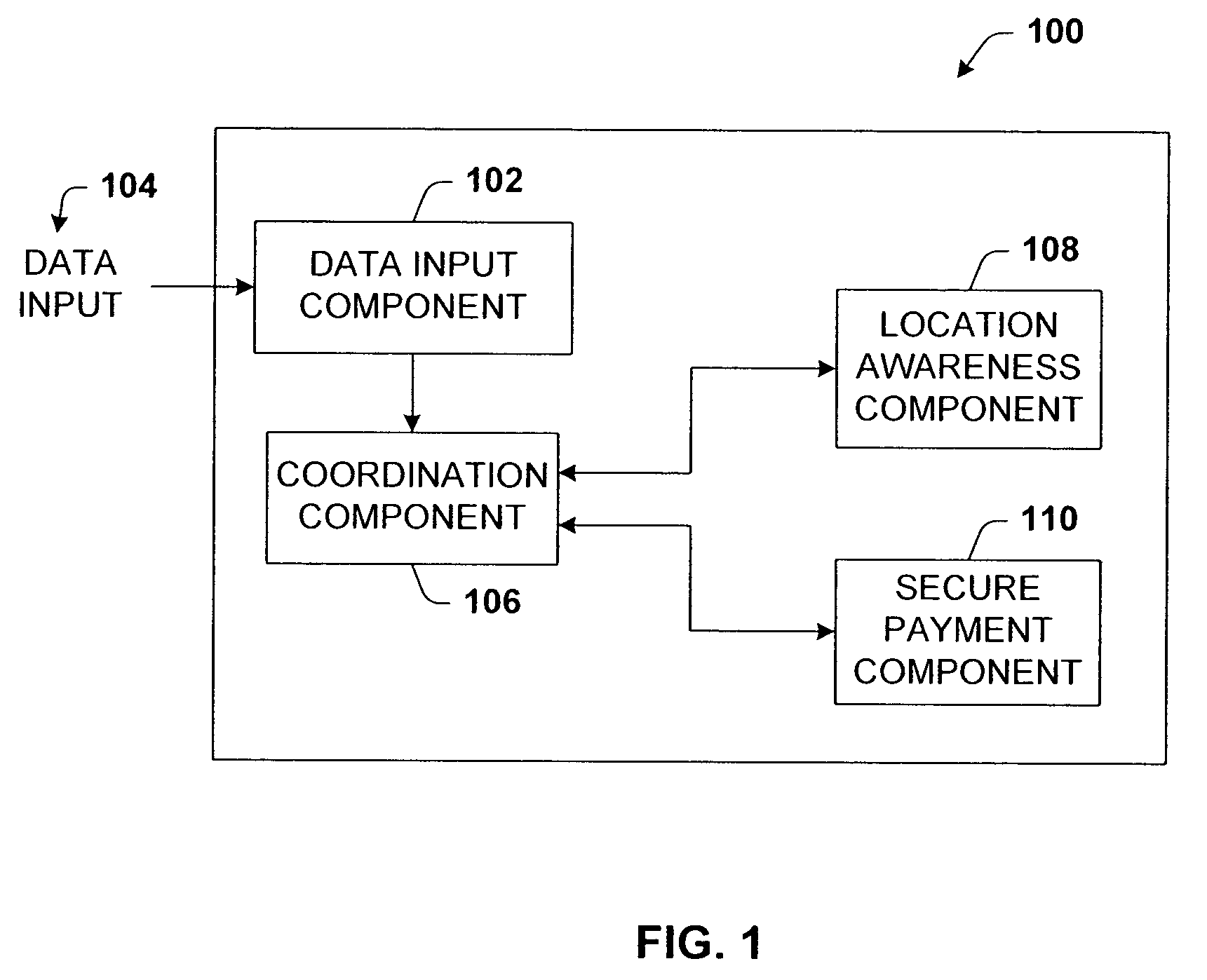
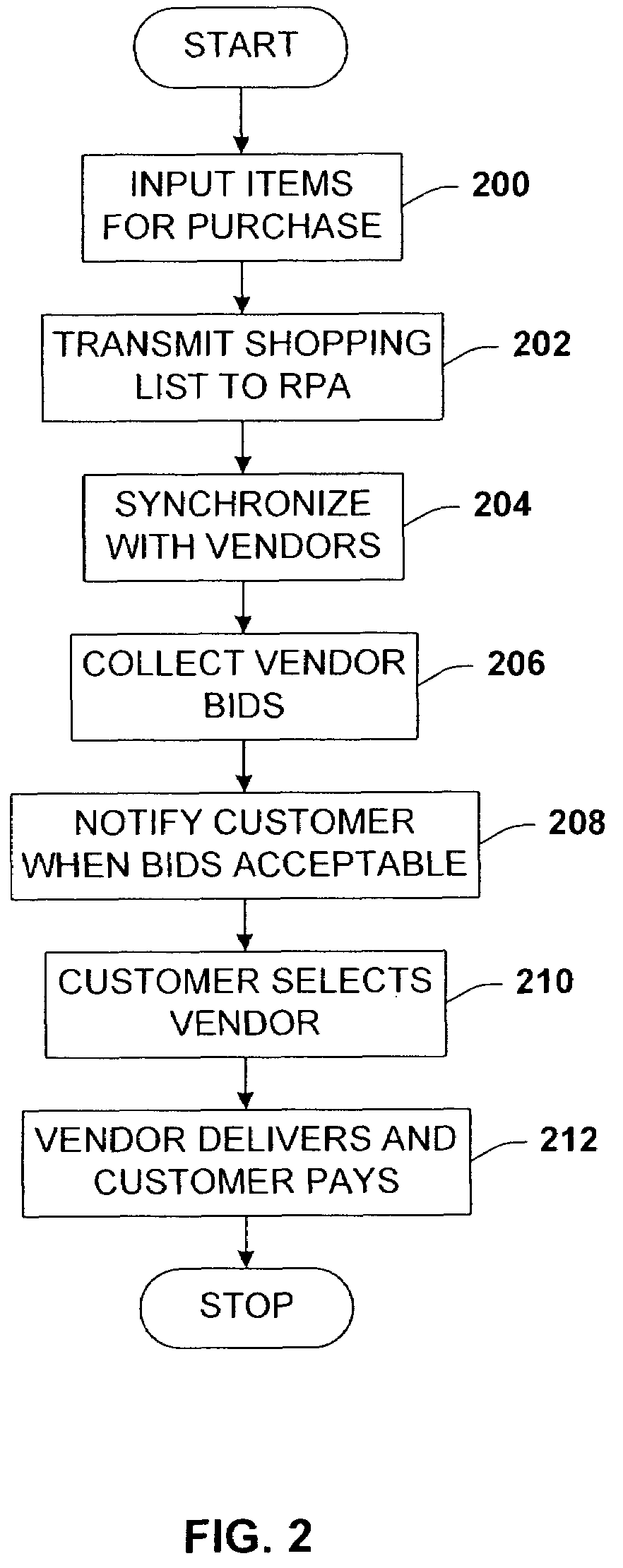
ActiveUS7668754B1Maintain privacyImprove accuracyFinanceBuying/selling/leasing transactionsPersonal agentComputer science
A secure m-commerce system and device. A consumer m-commerce device receives product data via a number of data input techniques. The product data is uploaded to a remote personal agent that requests bids from commercial partners to transact the list. When a bid is selected, the consumer transacts remotely to complete the purchase thereof. The system tracks geographically the device such that the consumer is alerted to a partner location, and may stop by the location for further information. The device may also output a store map to the consumer that locates all products on the shopping list.
Owner:SYMBOL TECH LLC
Methods and apparatus for a financial document clearinghouse and secure delivery network
InactiveUS20110276493A1Simplify opting outMaintain privacyFinanceComputer security arrangementsPaymentDocumentation procedure
An electronic clearinghouse system (ECS) for securely delivering, retrieving, authenticating, storing, generating and distributing messages, such as financial documents and / or records are described. For message providers, the ECS can provide a secure and trusted venue for delivering messages, such as messages including financial data to their clients that reduces their delivery costs. For users of the ECS, the ECS can provide a central location where each user can receive and consolidate their messages, such as financial documents and associated financial data from a number of different financial data providers. To facilitate these functions, the ECS can include an automated system for recording delivery status as well as evidence of delivery of messages, including whether a message has been viewed by a particular user. Further, the ECS can include components for scheduling events, such as monetary transfers and bill payments, and providing reminders for such events. Also, the ECS can provide utilities that allow a user to package and securely deliver messages to other users.
Owner:T CENT
Computerized system and method of performing insurability analysis
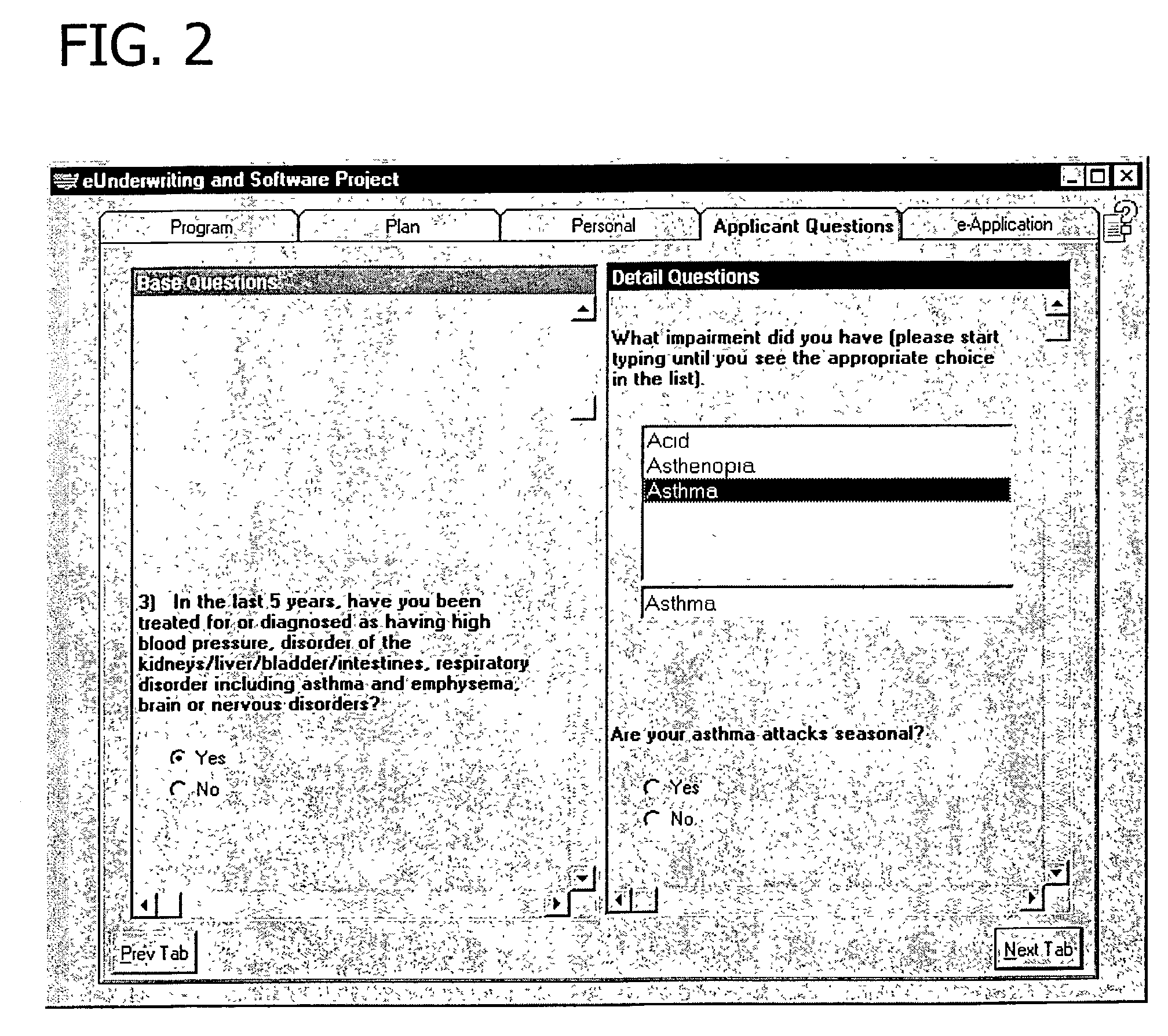
InactiveUS20030233260A1Ensure effective implementationQuickly and efficiently handlesFinanceOffice automationComputerized systemClient-side
A method and system for evaluating insurability of an applicant for insurance from a carrier. A server, receiving and responsive to communications from a client computer, renders a contemporaneous insurability decision. The communications from the client computer include responses to an interactive questionnaire presented via a browser. A database associated with the server stores a comprehensive set of questions for collecting underwriting information and the server executes processing rules to determine which questions to present in the questionnaire. The questionnaire includes base questions and detail questions. The detail questions are each related to at least one of the base questions for collecting further information related to the respective base question. The server renders the insurability decision and exports a summary file to the carrier. The summary file includes the questions and responses thereto as well as the insurability decision.
Owner:REINSURANCE GROUP OF AMERICA CORP +1
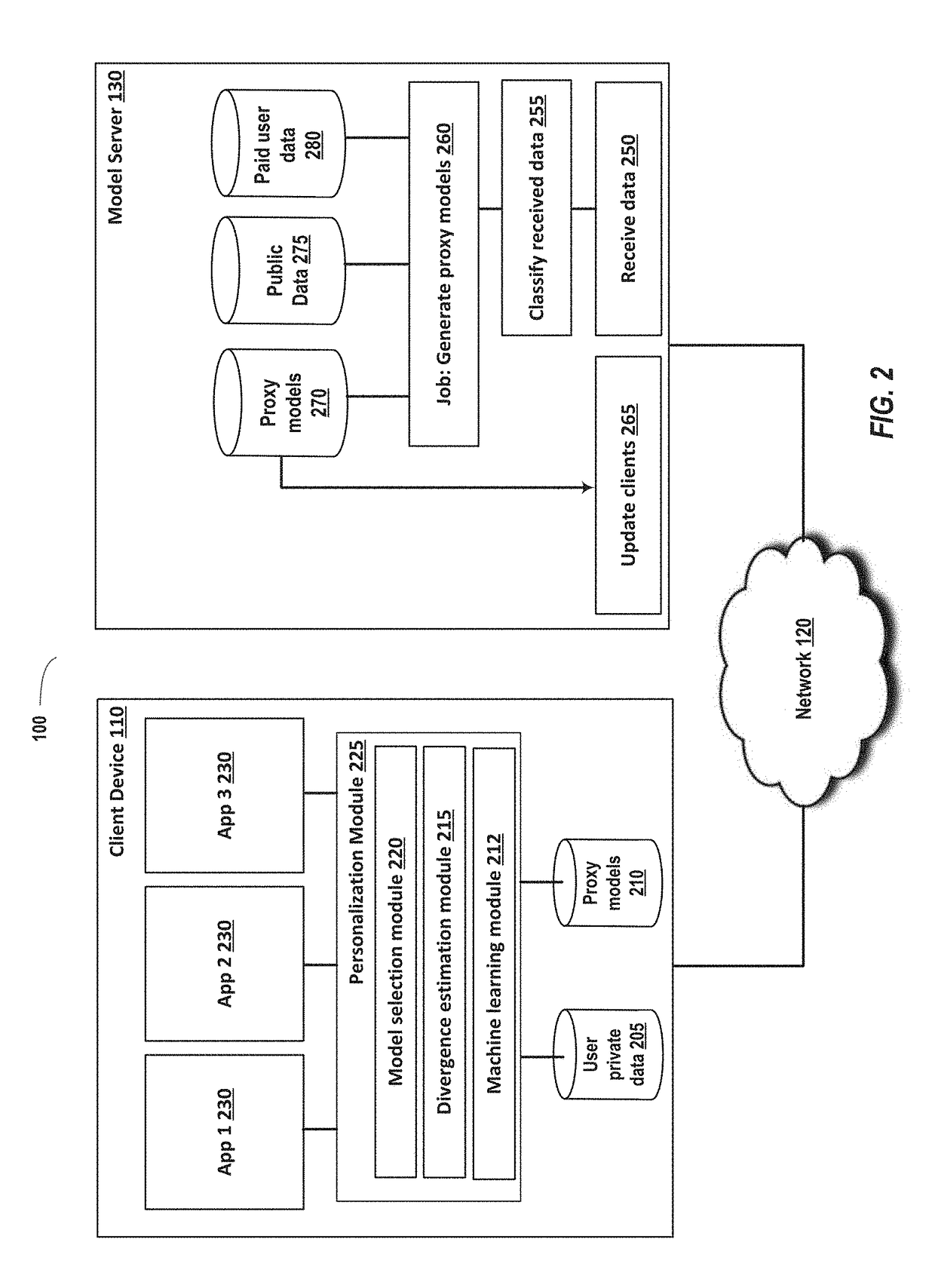
Using proxies to enable on-device machine learning
ActiveUS20180025287A1Improve experienceIncrease speedMachine learningInference methodsApplication softwareClient-side
Systems and methods are disclosed for a server generating a plurality of proxy prediction models for each of a plurality of applications for use by client devices. Providing a prediction model based on a data distribution that more closely matches the user private data of the actual user of the client device, as opposed to a generic model, can improve the accuracy of predictions and improve the benefits to the user of the client device. The plurality of prediction models are generated by a server and provided to a plurality of clients. For a particular application, a client device can use previously collected private user data to select one of the plurality of prediction models for the application as being a closest matching prediction model to use for a particular user.
Owner:APPLE INC
TLS tunneling
InactiveUS7529933B2Reduce interceptionProtect normal transmissionUser identity/authority verificationSecret communicationSecure communicationWireless mesh network
An authentication protocol can be used to establish a secure method of communication between two devices on a network. Once established, the secure communication can be used to authenticate a client through various authentication methods, providing security in environments where intermediate devices cannot be trusted, such as wireless networks, or foreign network access points. Additionally, the caching of session keys and other relevant information can enable the two securely communicating endpoints to quickly resume their communication despite interruptions, such as when one endpoint changes the access point through which it is connected to the network. Also, the secure communication between the two devices can enable users to roam off of their home network, providing a mechanism by which access through foreign networks can be granted, while allowing the foreign network to monitor and control the use of its bandwidth.
Owner:MICROSOFT TECH LICENSING LLC
Information Targeting Systems and Methods
ActiveUS20140025660A1Maintain privacyEffective matchingDigital data information retrievalDigital data processing detailsElectronic informationInternet privacy
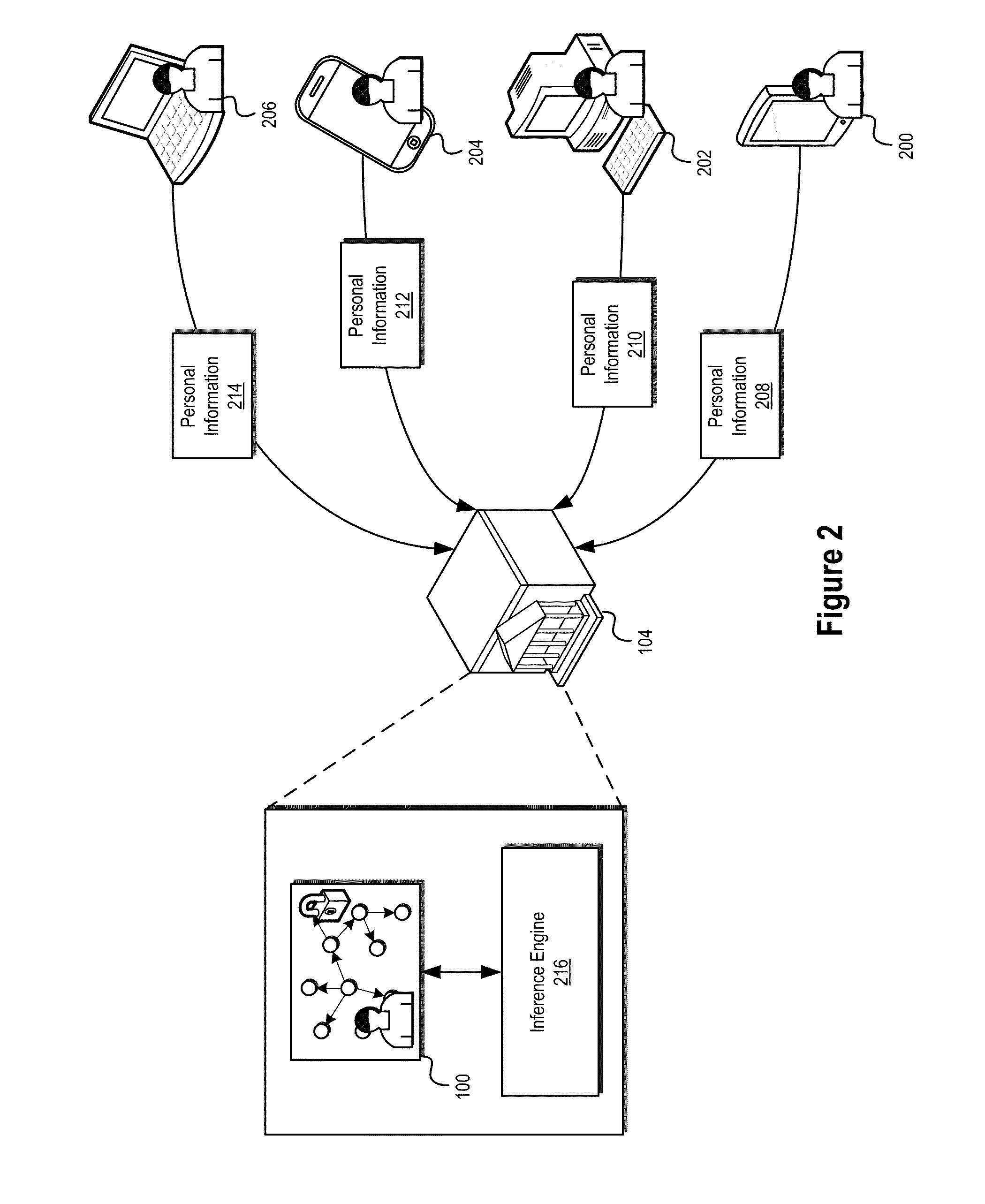
The present disclosure relates generally to systems and methods for the secure management of electronic information relating to a user. In certain embodiments, systems and methods disclosed herein may allow for personal information related to a user to be used in connection with information targeting systems and methods configured to match and / or target information for delivery to a user based on the user's interests. In some embodiments, personal information relating to a user may be stored and / or managed in a personal ontology graph or other data structure including, among other things, various inferred interests of the user derived from available personal information.
Owner:INTERTRUST TECH CORP
Safeguarding user data stored in mobile communications devices
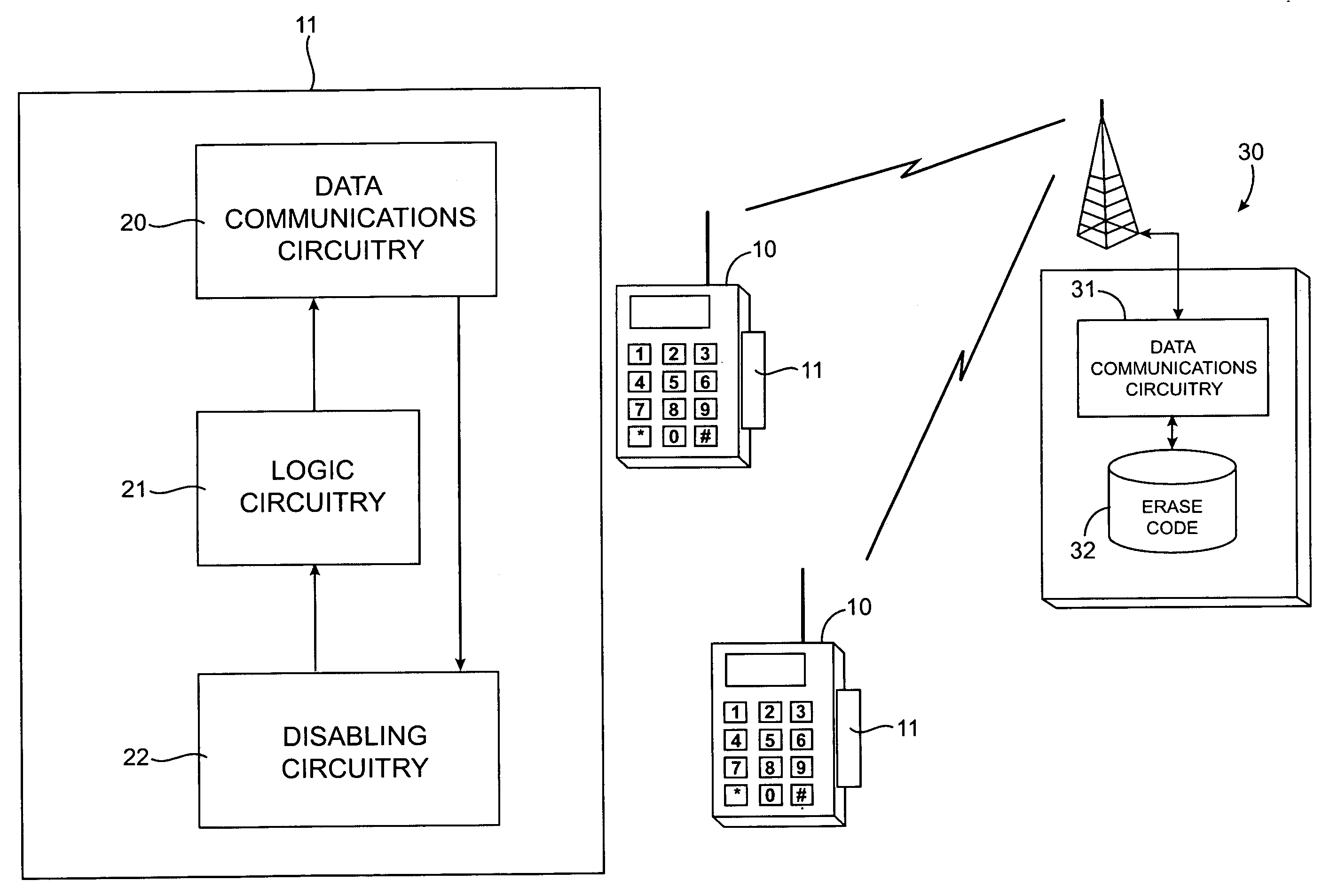
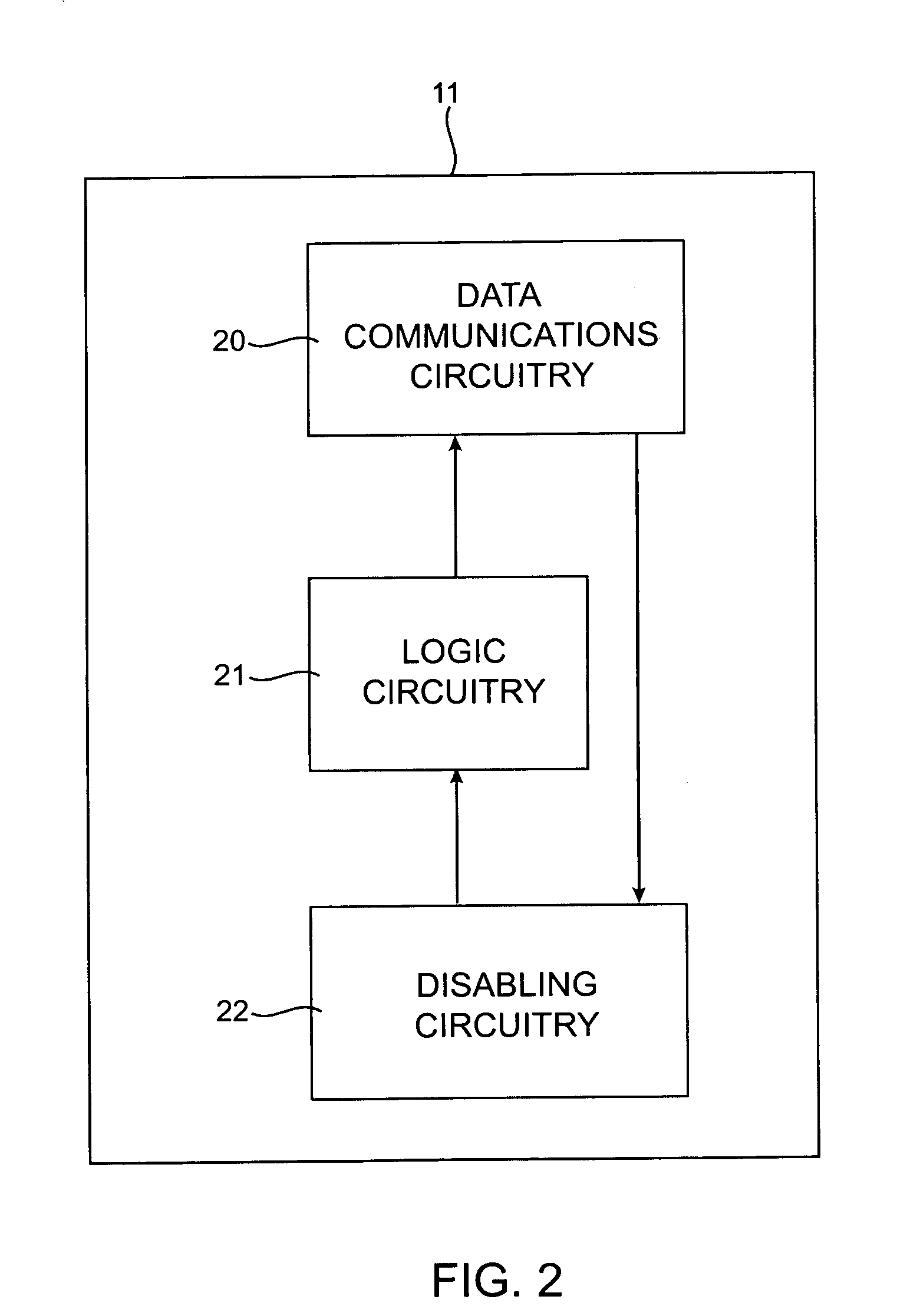
InactiveUS7054624B2Without disabling the telephone featuresMaintain privacyDevices with card reading facilityUnauthorised/fraudulent call preventionMemory chipData storing
The present invention permits safeguarding of private data entered into a memory chip of a cell phone by permitting the cell phone owner to erase the data in a lost or stolen phone, using an preset erase code and erase command in the cell phone or the network base station, and disabling or erasing circuitry on the memory chip, preferably an EEPROM chip.
Owner:X CYTE
Controlled environment thermal image detection system and methods regarding same
InactiveUS7138905B2Reduce noiseMaintain privacyElectric signal transmission systemsImage analysisImage detectionPhysical separation
Thermal infrared image data of at least a region of a face of a person in an enclosure is provided. The enclosure, for example, may include a first enclosed volume and a second enclosed volume physically separated from the first enclosed volume. The first enclosed volume may include an entrance door sized to allow a person to enter the first enclosed volume. The enclosure provides a controlled environment for performing measurements (e.g., capturing thermal infrared image data) for use in determining a physiological state of a person (e.g., anxiety, deception, etc.).
Owner:HONEYWELL INT INC
Methods and apparatus for a financial document clearinghouse and secure delivery network
InactiveUS20110270763A1Simplify opting outMaintain privacyFinancePayment architecturePaymentComputer science
An electronic clearinghouse system (ECS) for securely delivering, retrieving, authenticating, storing, generating and distributing messages, such as financial documents and / or records are described. For message providers, the ECS can provide a secure and trusted venue for delivering messages, such as messages including financial data to their clients that reduces their delivery costs. For users of the ECS, the ECS can provide a central location where each user can receive and consolidate their messages, such as financial documents and associated financial data from a number of different financial data providers. To facilitate these functions, the ECS can include an automated system for recording delivery status as well as evidence of delivery of messages, including whether a message has been viewed by a particular user. Further, the ECS can include components for scheduling events, such as monetary transfers and bill payments, and providing reminders for such events. Also, the ECS can provide utilities that allow a user to package and securely deliver messages to other users.
Owner:T CENT
Medical data storage server
InactiveUS20110161112A1Maintain privacyProtect privacyData processing applicationsMedical imagesAuthorizationMedical procedure
Provided is a method of documenting a medical procedure including receiving medical data captured during the medical procedure to be documented. Information indicative of an identity of at least one of a patient that is a subject of the medical procedure and a physician involved with the medical procedure is received. The medical data is stored in a non-transitory computer readable medium associated with the at least one of the patient and the physician. Access to the medical data stored on the computer readable medium is restricted, allowing the physician involved with the medical procedure to subsequently retrieve the medical data stored in the computer readable medium and view the medical data retrieved. Restricting access to the recorded medical data prevents another physician, who may not have been involved in the medical procedure, from viewing the medical data without first entering information indicative of authorization to view the medical data.
Owner:CODONICS
Privacy Preserving Statistical Analysis on Distributed Databases
ActiveUS20140281572A1Maintain privacyEnhance privacyUnauthorized memory use protectionHardware monitoringThird partyPrivacy preserving
Aggregate statistics are securely determined on private data by first sampling independent first and second data at one or more clients to obtain sampled data, wherein a sampling parameter substantially smaller than a length of the data. The sampled data are encrypted to obtain encrypted data, which are then combined. The combined encrypted data are randomized to obtain randomized data. At an authorized third-party processor, a joint distribution of the first and second data is estimated from the randomized encrypted data, such that a differential privacy requirement of the first and second is satisfied.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Computerized system and method of performing insurability analysis
InactiveUS20040181435A9Quickly and efficiently handlesFast and easy changeFinanceOffice automationComputerized systemClient-side
A method and system for evaluating insurability of an applicant for insurance from a carrier. A server, receiving and responsive to communications from a client computer, renders a contemporaneous insurability decision. The communications from the client computer include responses to an interactive questionnaire presented via a browser. A database associated with the server stores a comprehensive set of questions for collecting underwriting information and the server executes processing rules to determine which questions to present in the questionnaire. The questionnaire includes base questions and detail questions. The detail questions are each related to at least one of the base questions for collecting further information related to the respective base question. The server renders the insurability decision and exports a summary file to the carrier. The summary file includes the questions and responses thereto as well as the insurability decision.
Owner:REINSURANCE GROUP OF AMERICA CORP +1
Pressure responsive blowout latch
InactiveUS6866226B2Increase safetyIncreased strengthDoors/windowsAir-treatment apparatus arrangementsEngineeringSurface plate
Owner:HARTWELL
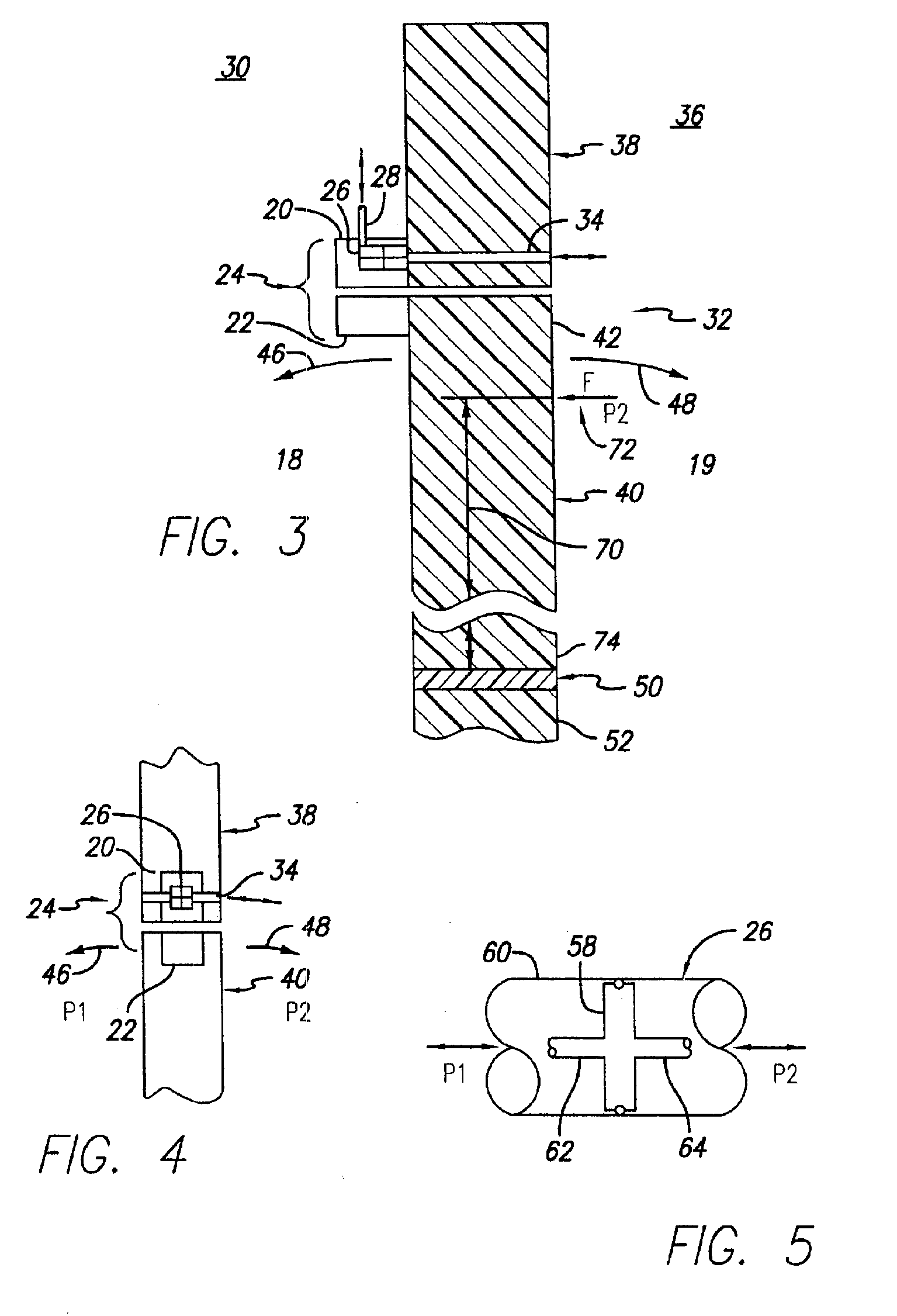
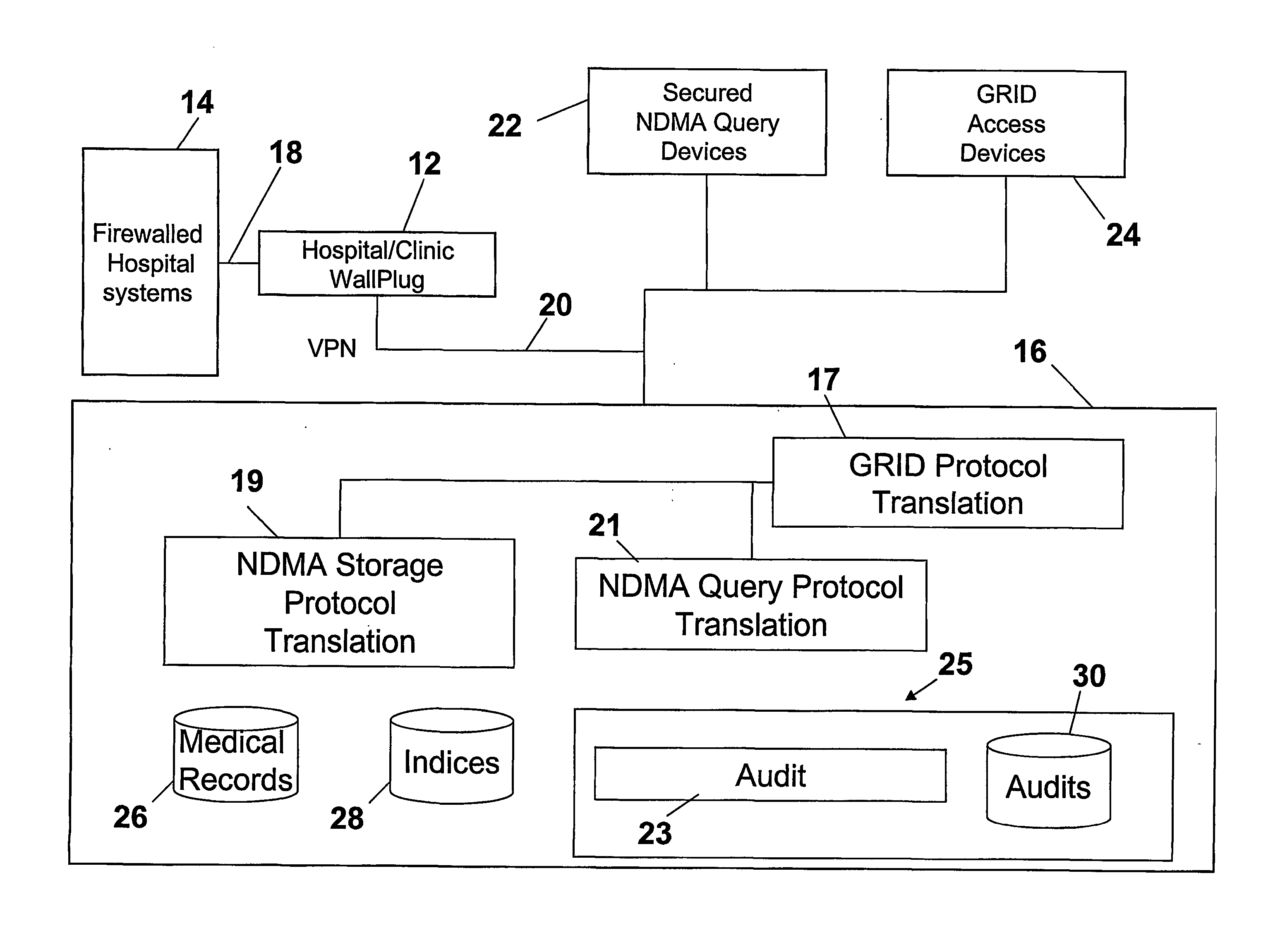
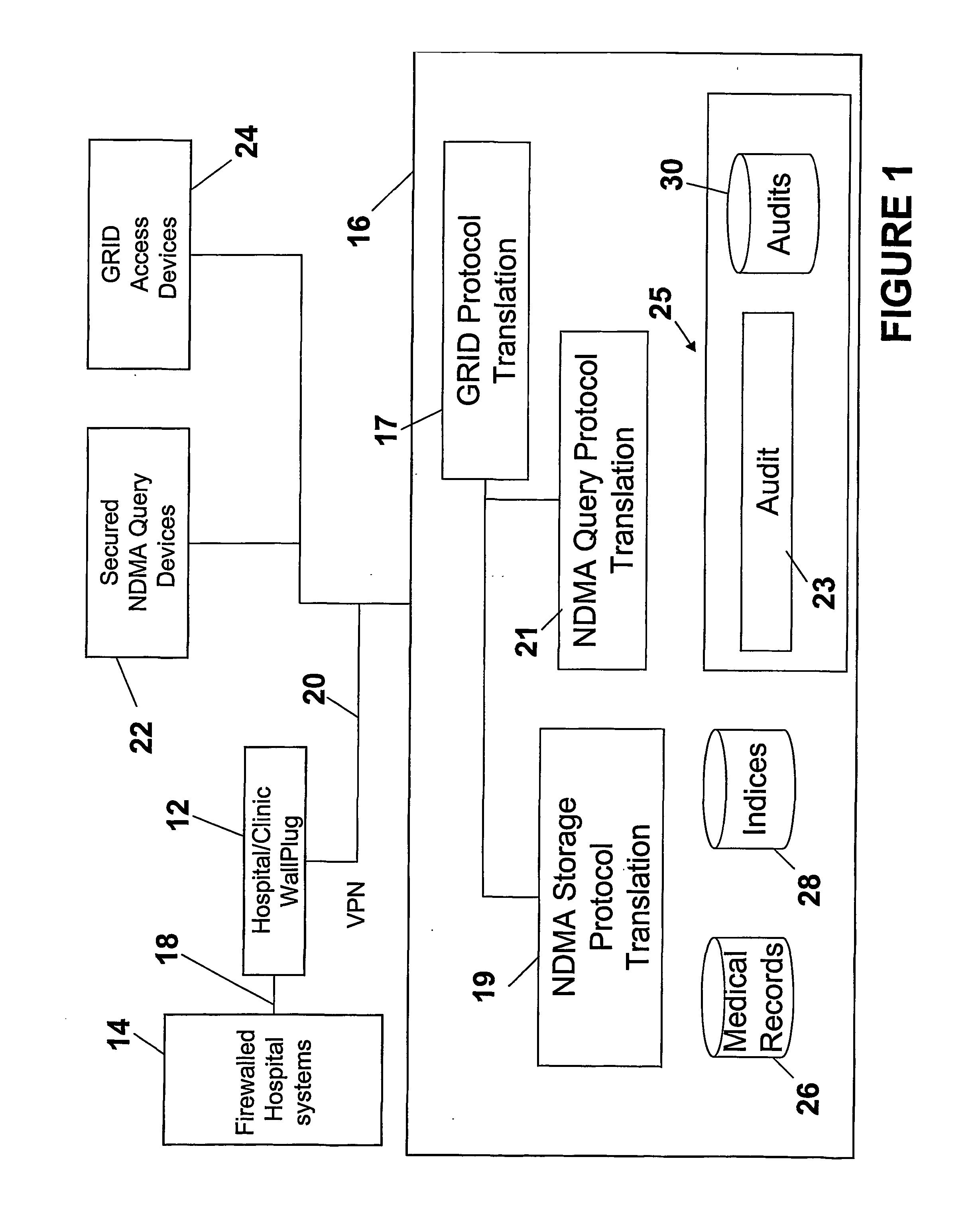
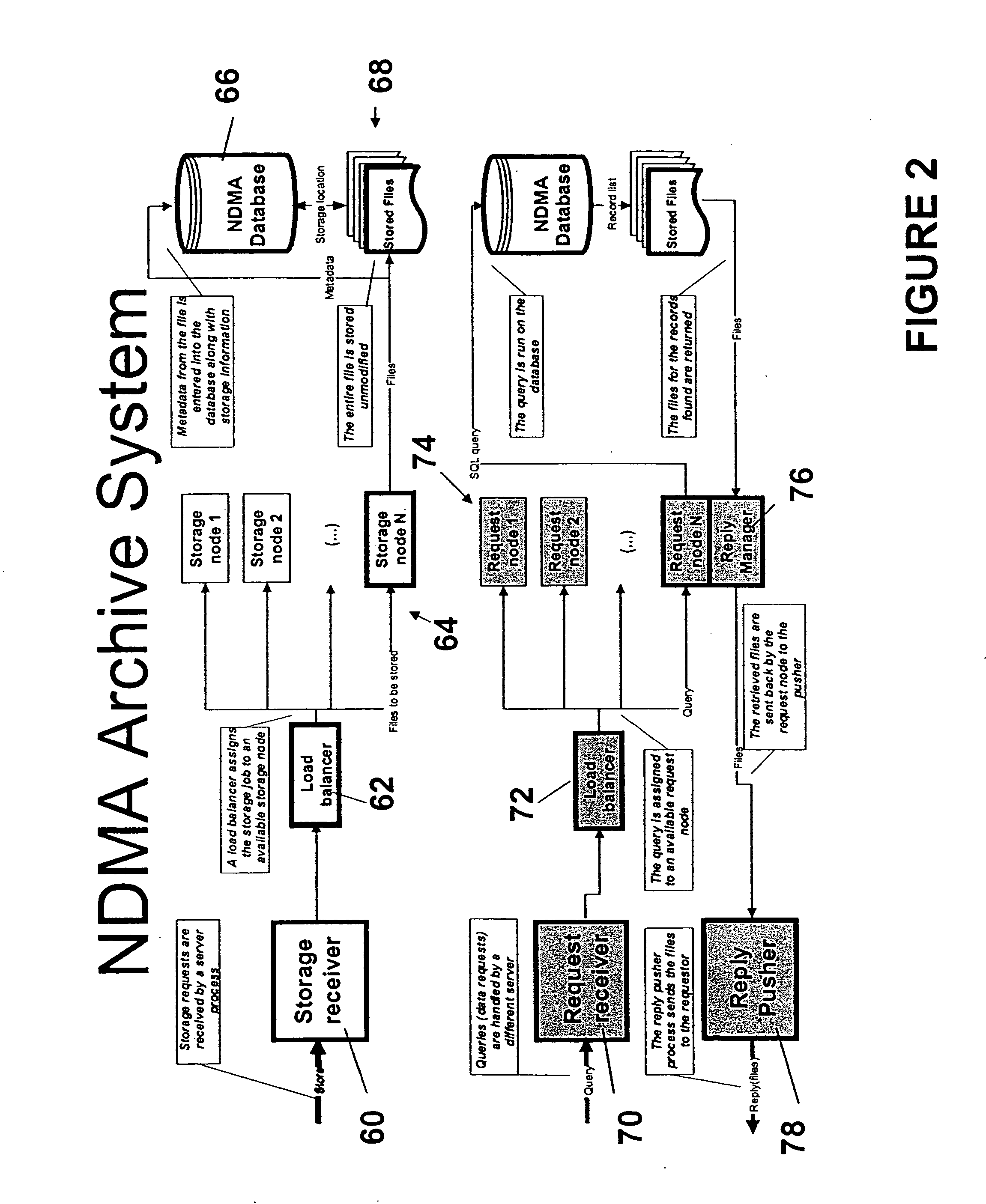
Ndma db schema, dicom to relational schema translation, and xml to sql query transformation
InactiveUS20060282447A1Efficiently handle transferMaintain privacyData processing applicationsDigital data information retrievalDICOMQuery transformation
A translation scheme translates DICOM content into a format compatible for storage in an NDMA relational database. The translation scheme employs a schema for indexing the DICOM content, and employs a mechanism for translating queries embedded in XML into SQL. The translation scheme translates DICOM compatible data into a tab delimited flat representation of the DICOM content. The flat representation is then translated into data compatible with a relational database format, such as SQL, and then into database insert commands. The schema enables capture of the DICOM information into relational tables. Methods are also provided to service XML formatted research and clinical queries, to translate XML queries to optimized SQL and to return query results to XML specified destinations with record de-identification where required. Methods are also provided to interface to NDMA WallPlugs, secured query devices, or GRID devices.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA
Virtual subnet controller and controlling method thereof
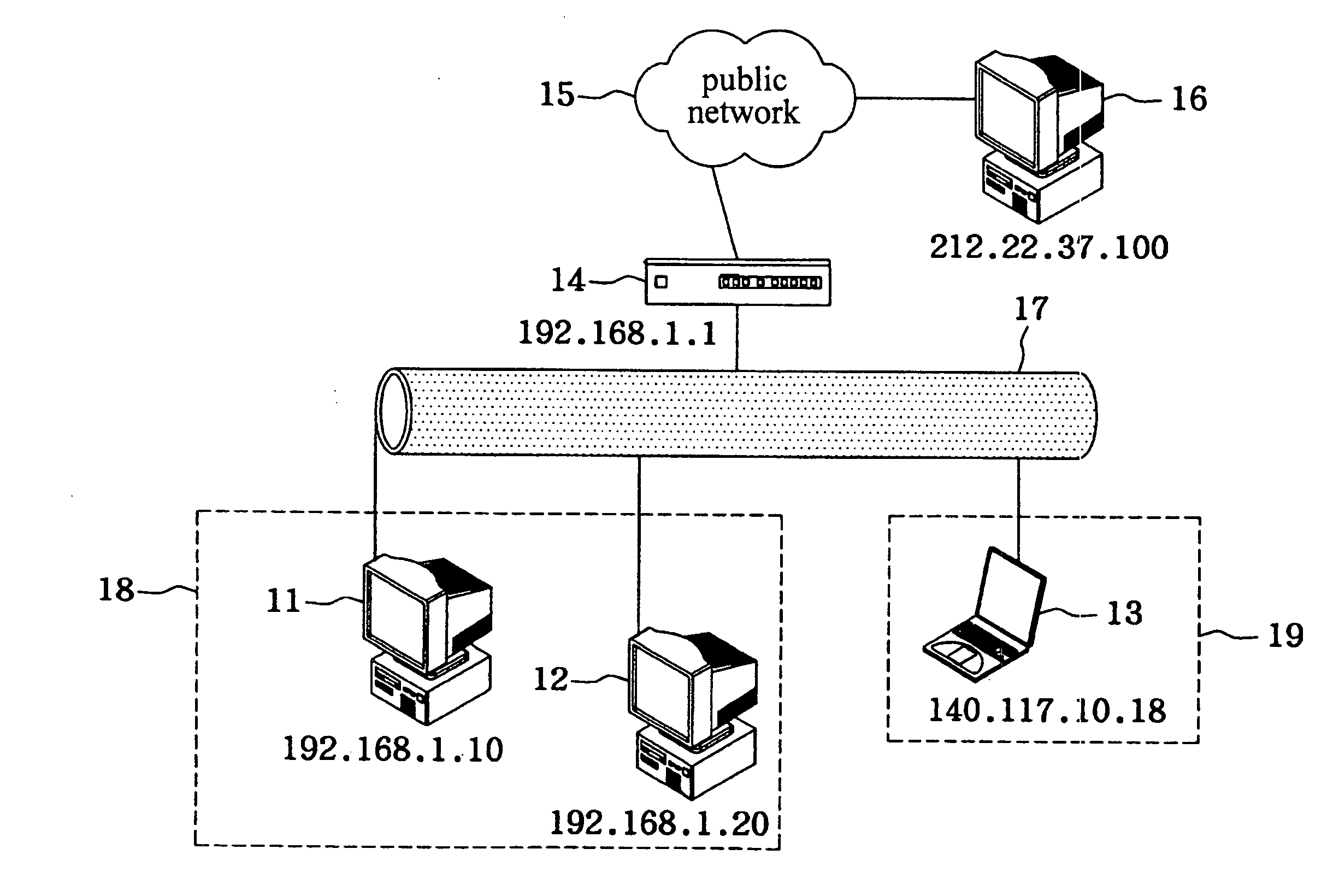
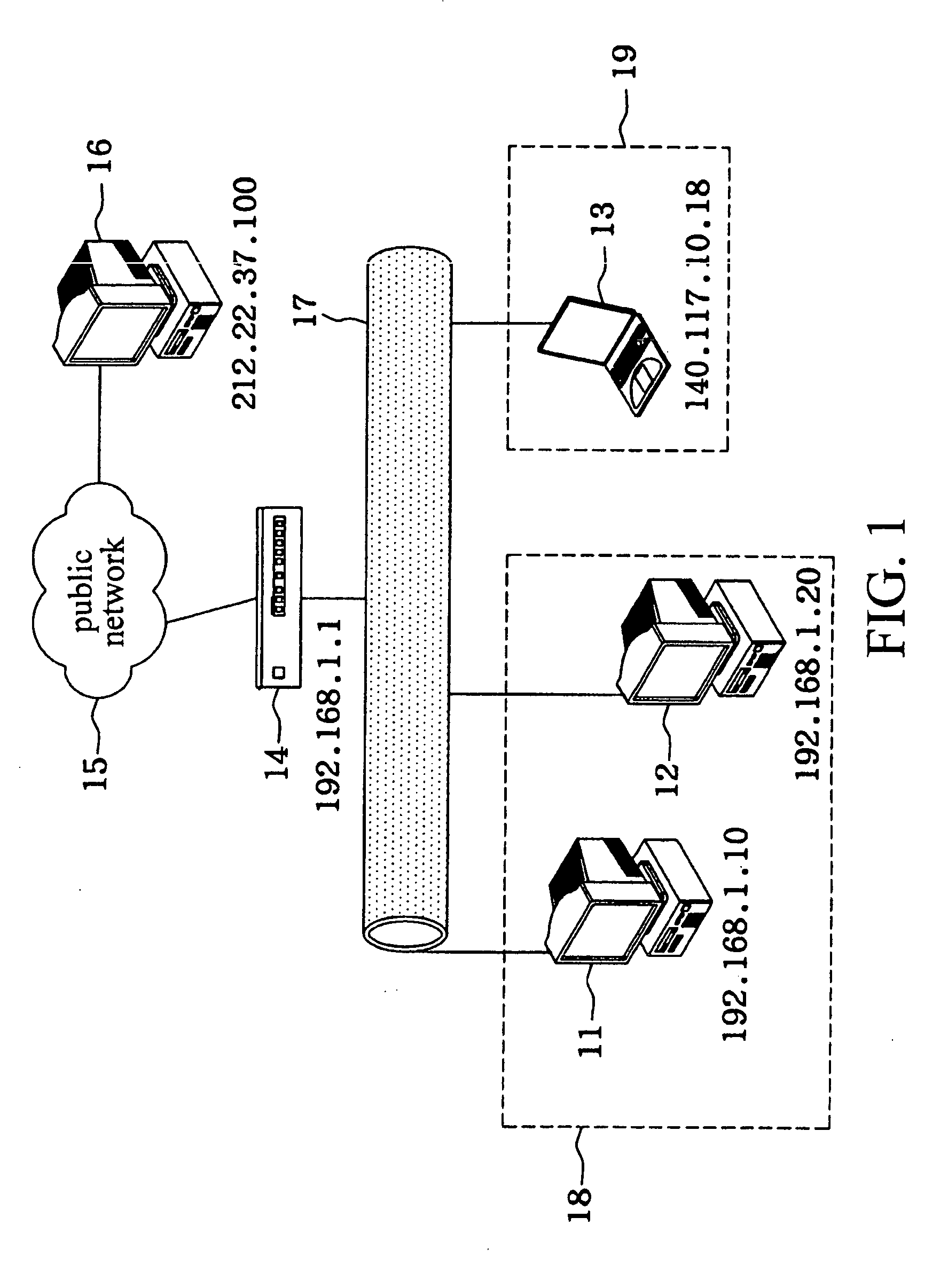
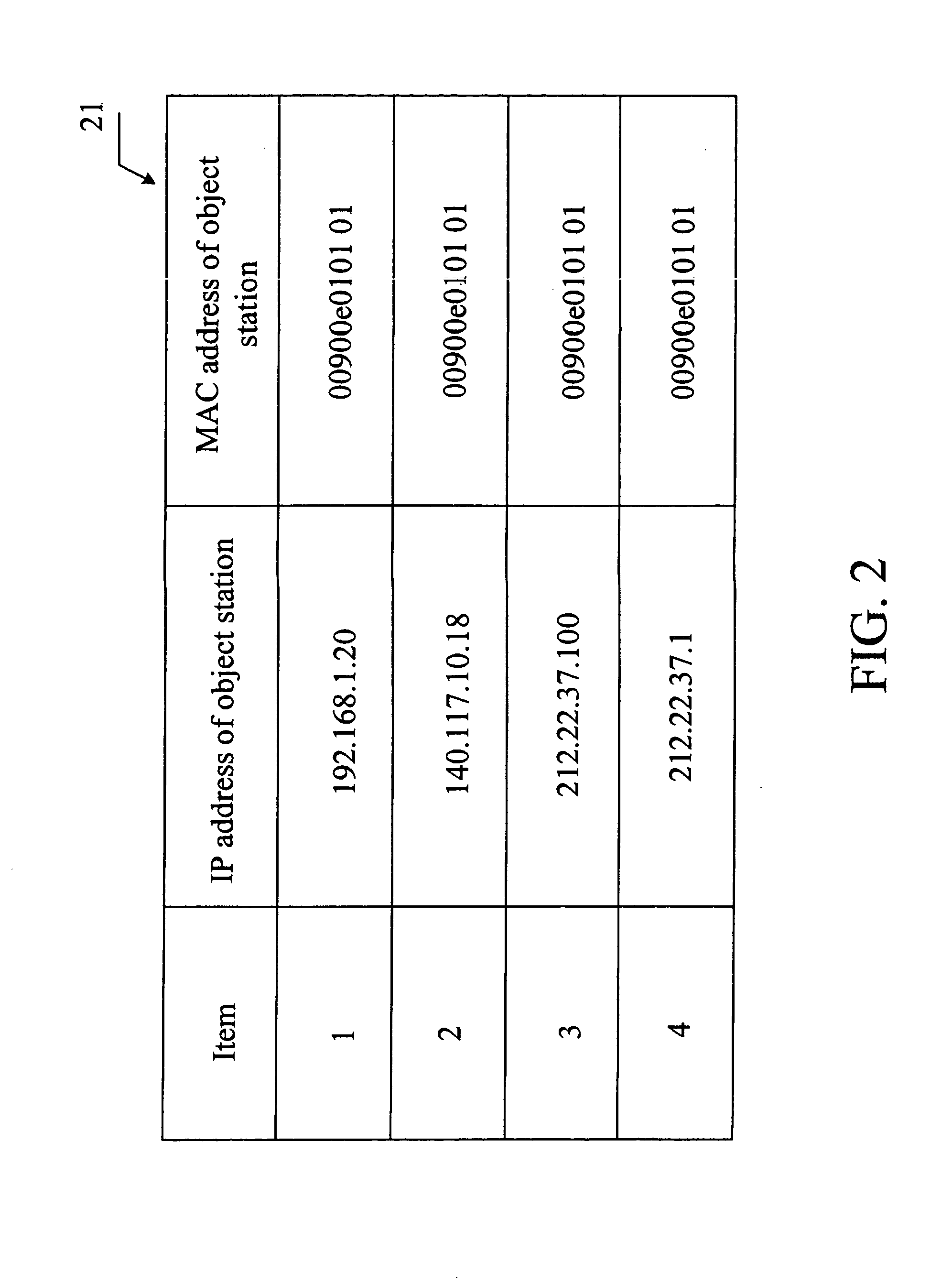
InactiveUS20040066788A1Maintain privacyTime-division multiplexData switching by path configurationIp addressPrivate network
A virtual subnet controller includes a subnet mapping table and a control unit. When the source and destination stations belong to a public network and a private network, respectively, the NAT protocol is used for converting the IP address of the data packet. After receiving the ARP request froma source station, the virtual subnet controller will respond with an ARP response, enabling the data packet transmitted from the source station.
Owner:HANDLINK TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com