Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
485 results about "Personally identifiable information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Personal data, also known as personal information, personally identifying information (PII), or sensitive personal information (SPI), is any information relating to identifying a person. The abbreviation PII is widely accepted in the United States, but the phrase it abbreviates has four common variants based on personal / personally, and identifiable / identifying. Not all are equivalent, and for legal purposes the effective definitions vary depending on the jurisdiction and the purposes for which the term is being used. Under European and other data protection regimes, which centre primarily around the General Data Protection Regulation, the term "personal data" is significantly broader, and determines the scope of the regulatory regime.
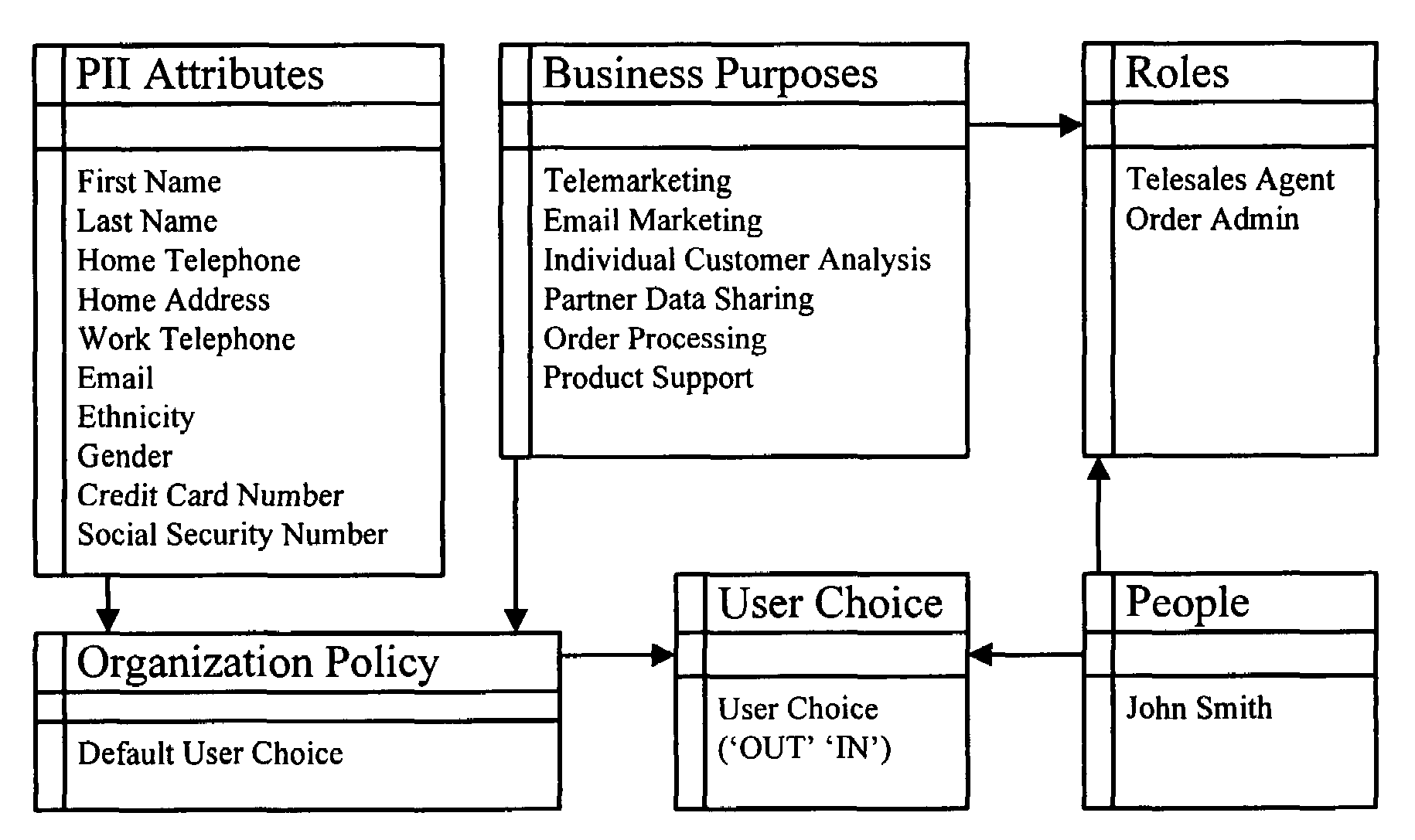
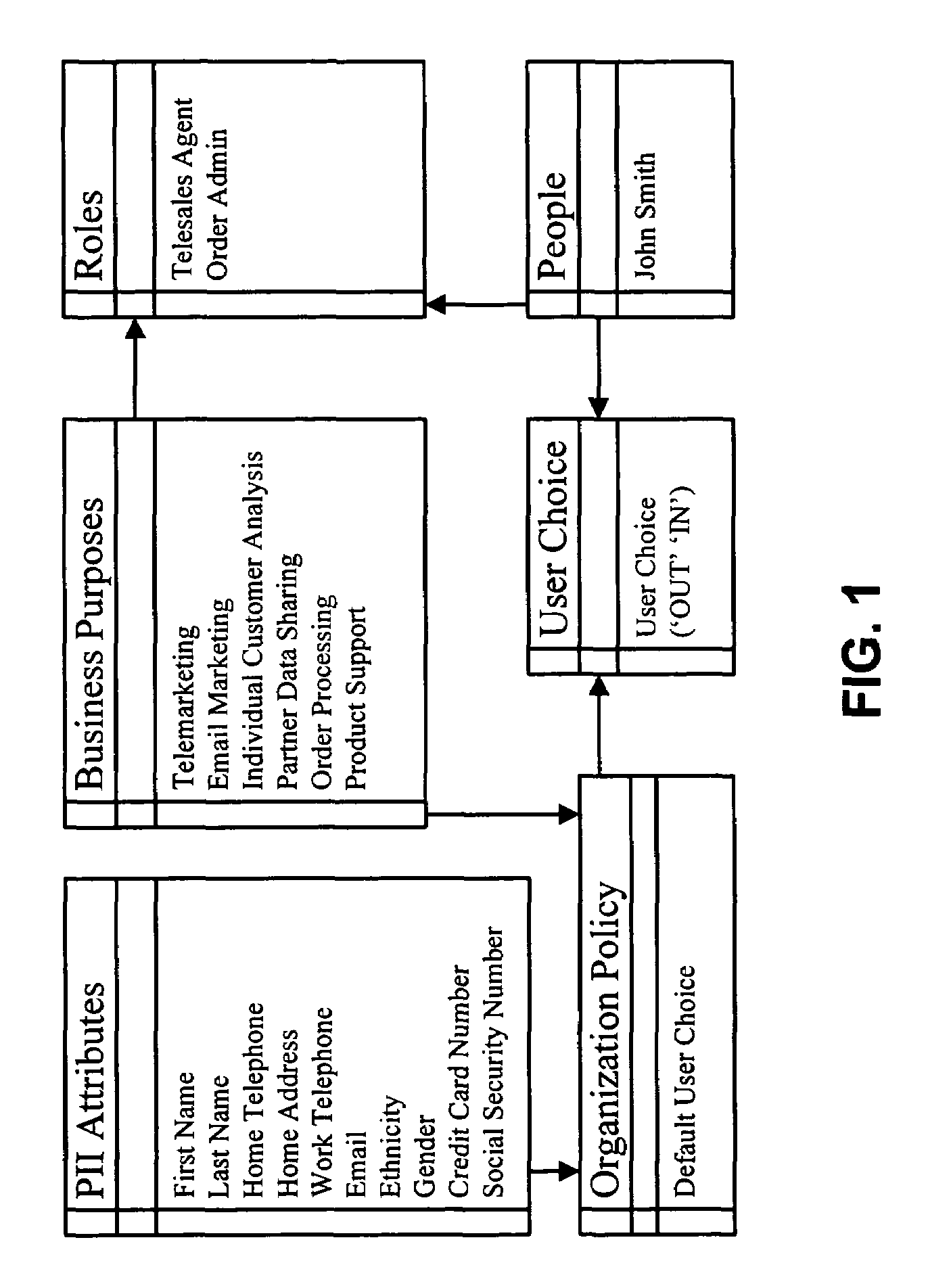
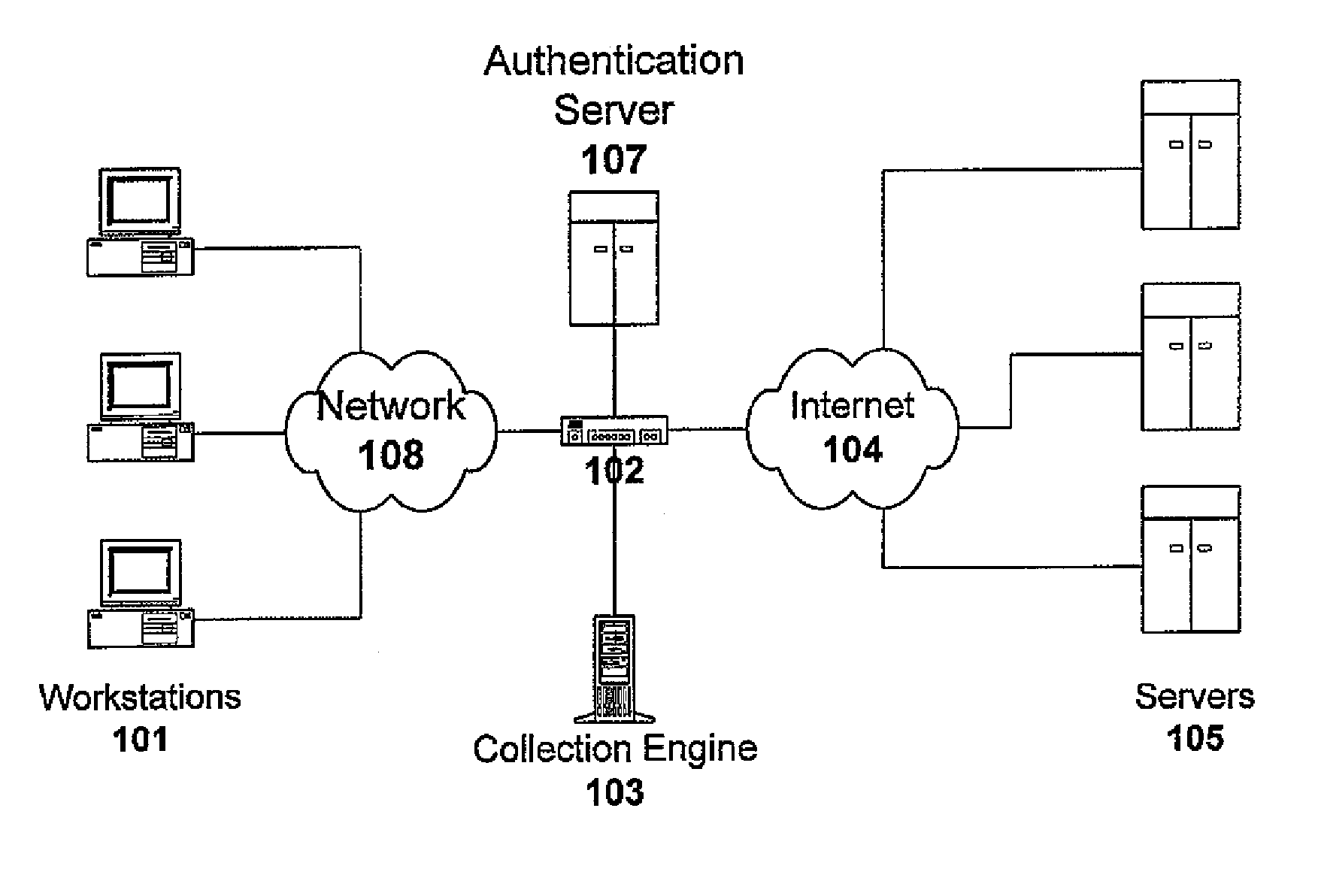
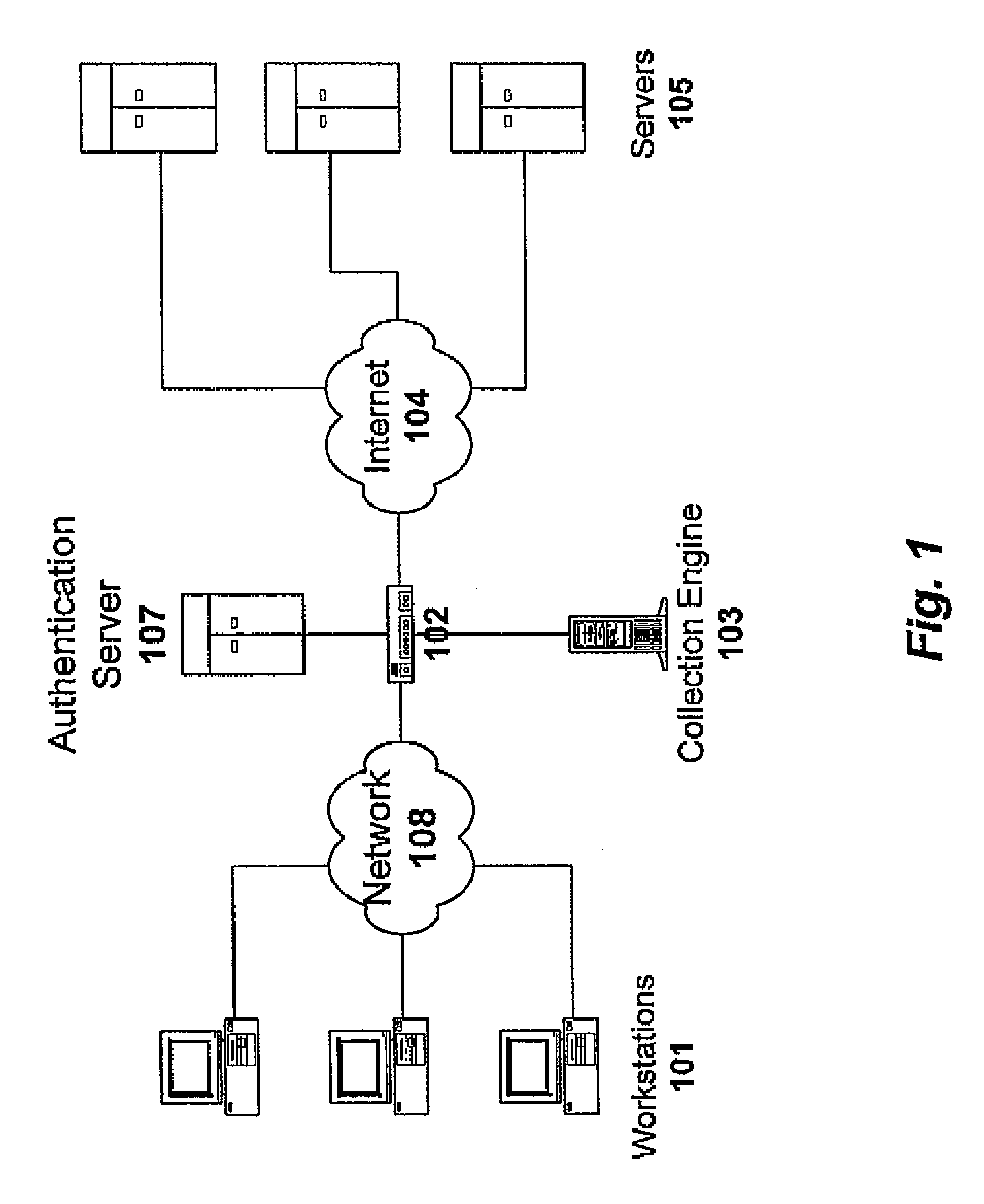
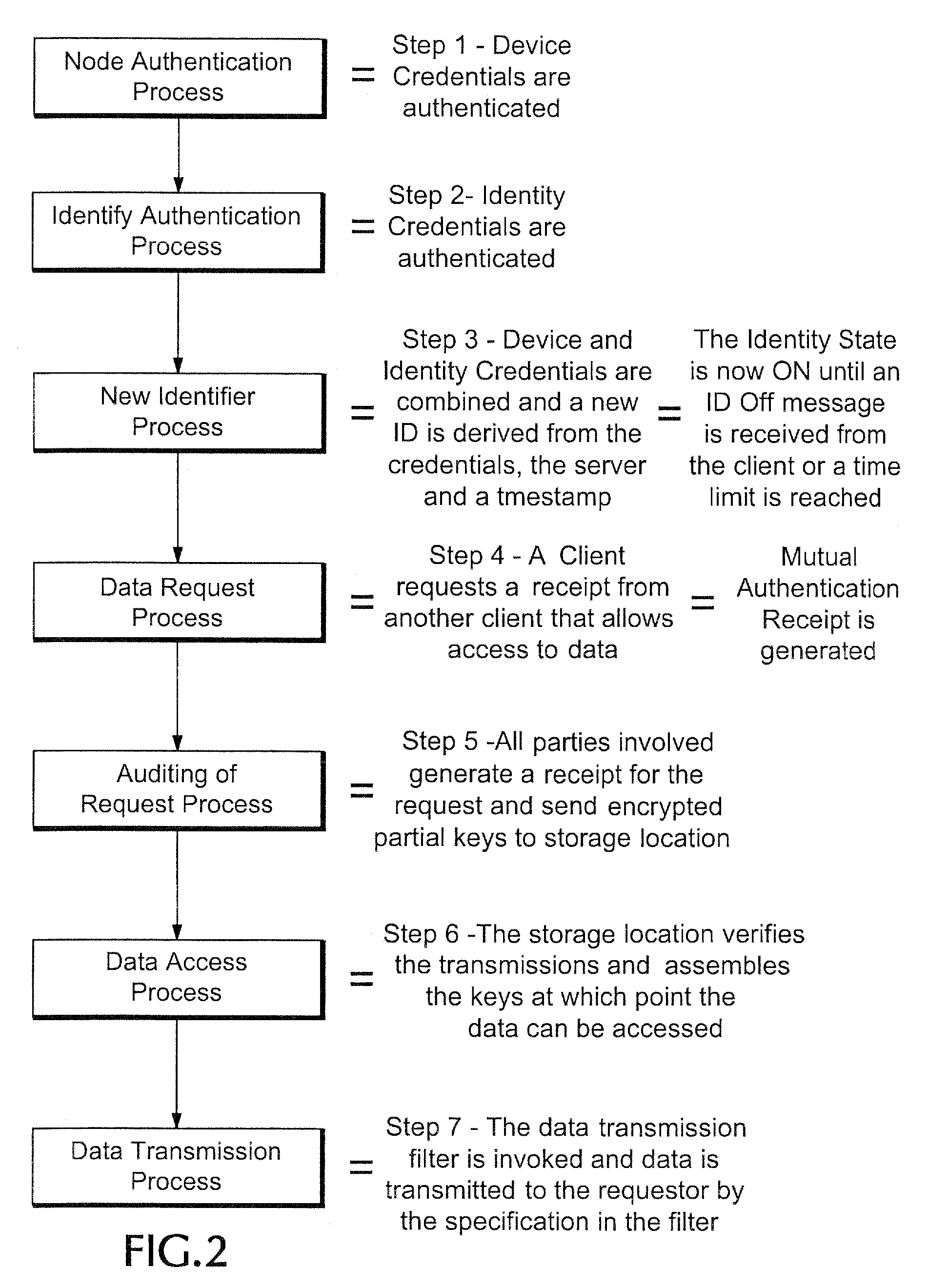
Method and apparatus for controlling access to personally identifiable information
ActiveUS7716242B2Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyApplication software
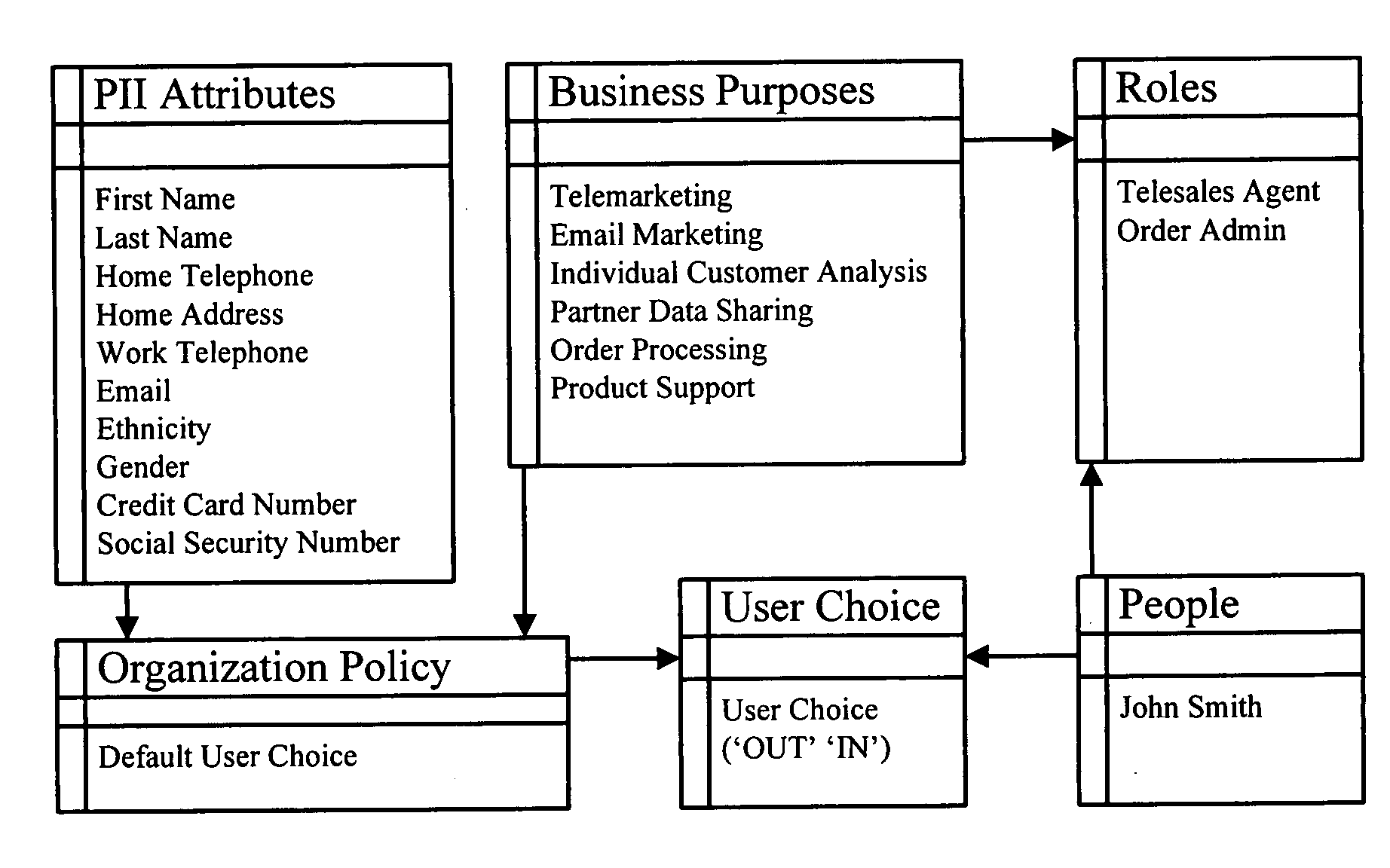
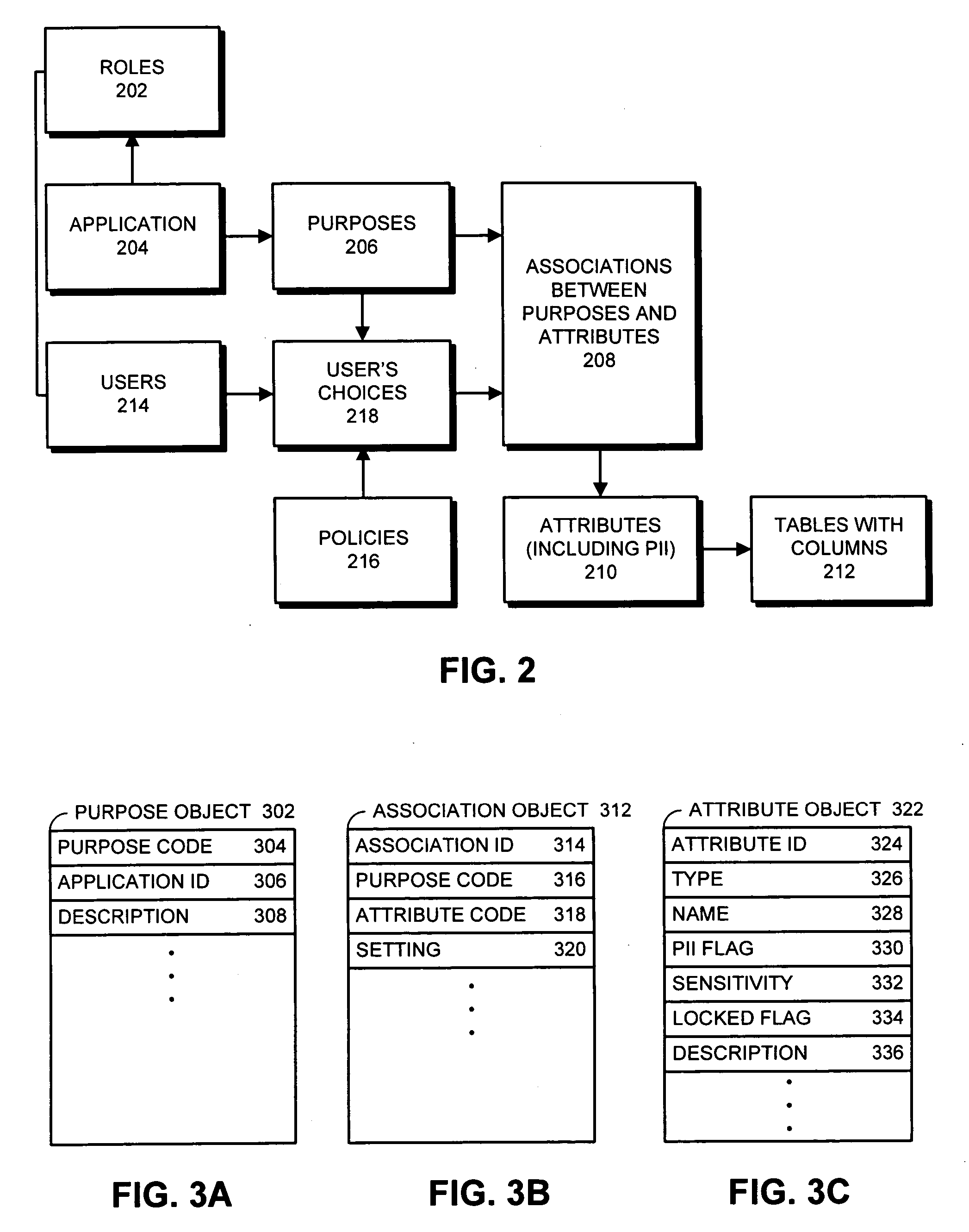
One embodiment of the present invention provides a system that controls access to personally identifiable information (PII) in a database system. During operation, the system receives a request from an application to perform a function which involves accessing information in the database system. In response to the request, the system identifies a purpose that the application has in making request to perform the function. Next, the system uses the purpose to identify a set of attributes in the database system, which are associated with the purpose. The system then determines if any of the identified attributes contain PII. If so, the system enforces access controls while accessing the identified attributes containing PII.
Owner:ORACLE INT CORP
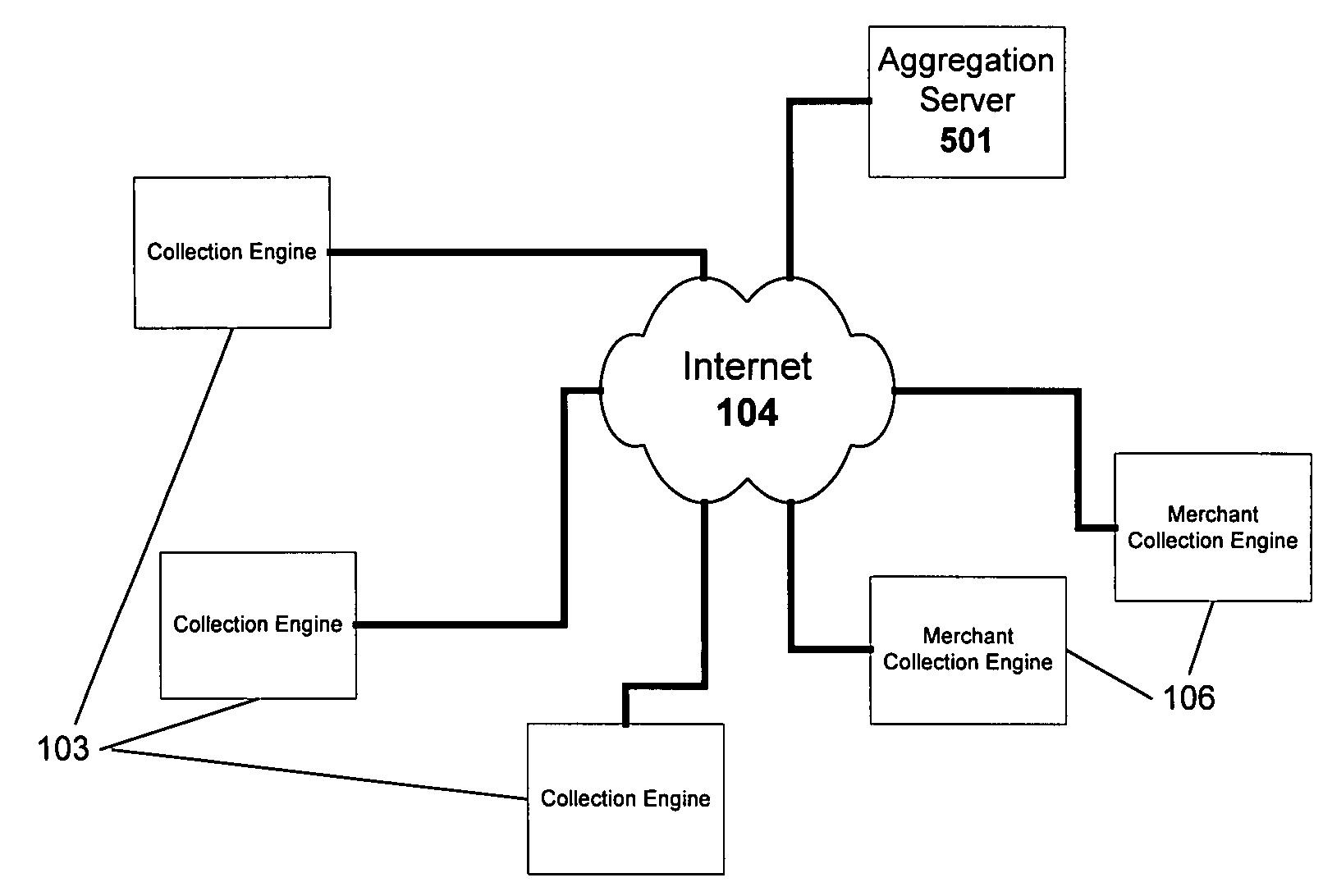
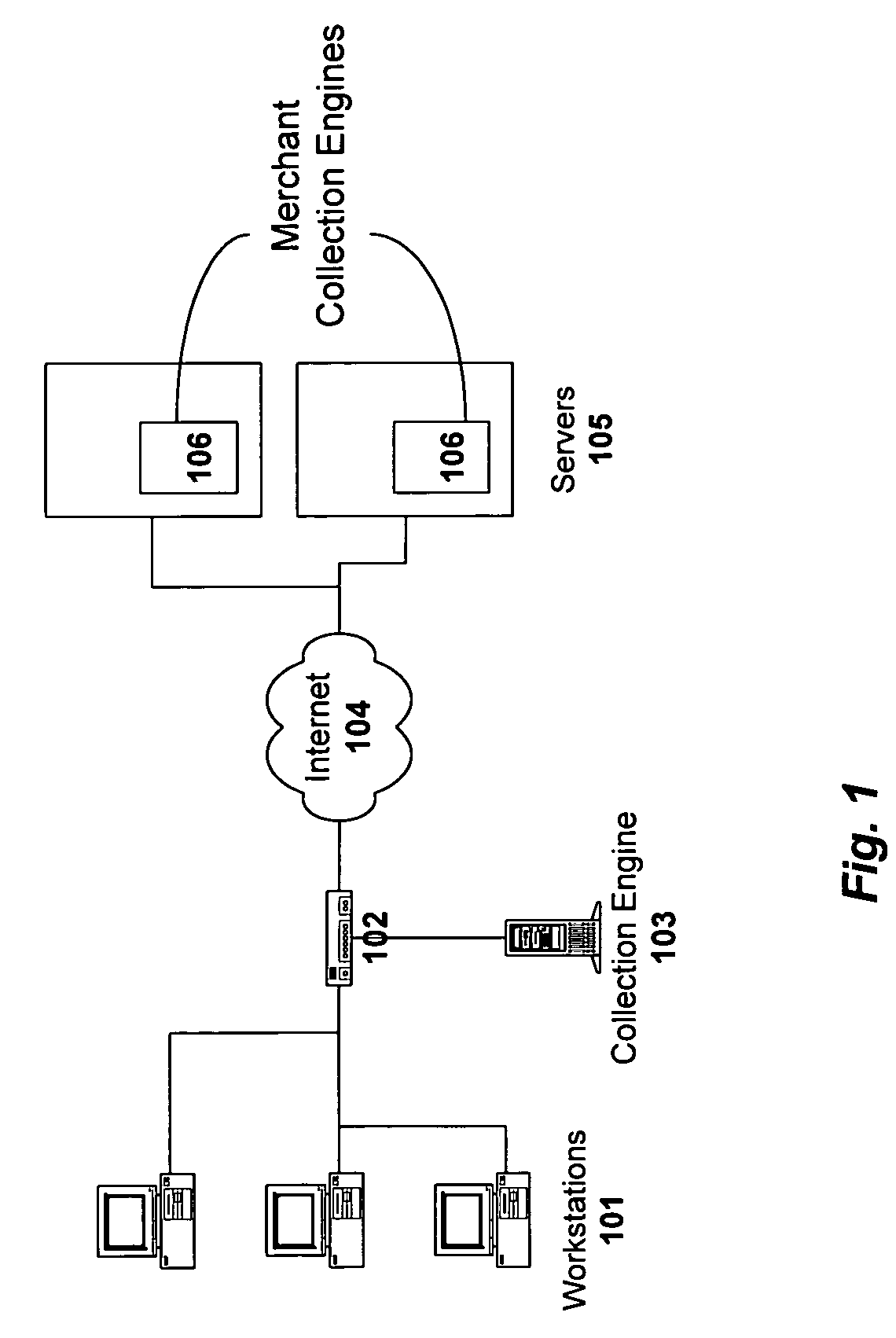
Method and system for monitoring online behavior at a remote site and creating online behavior profiles
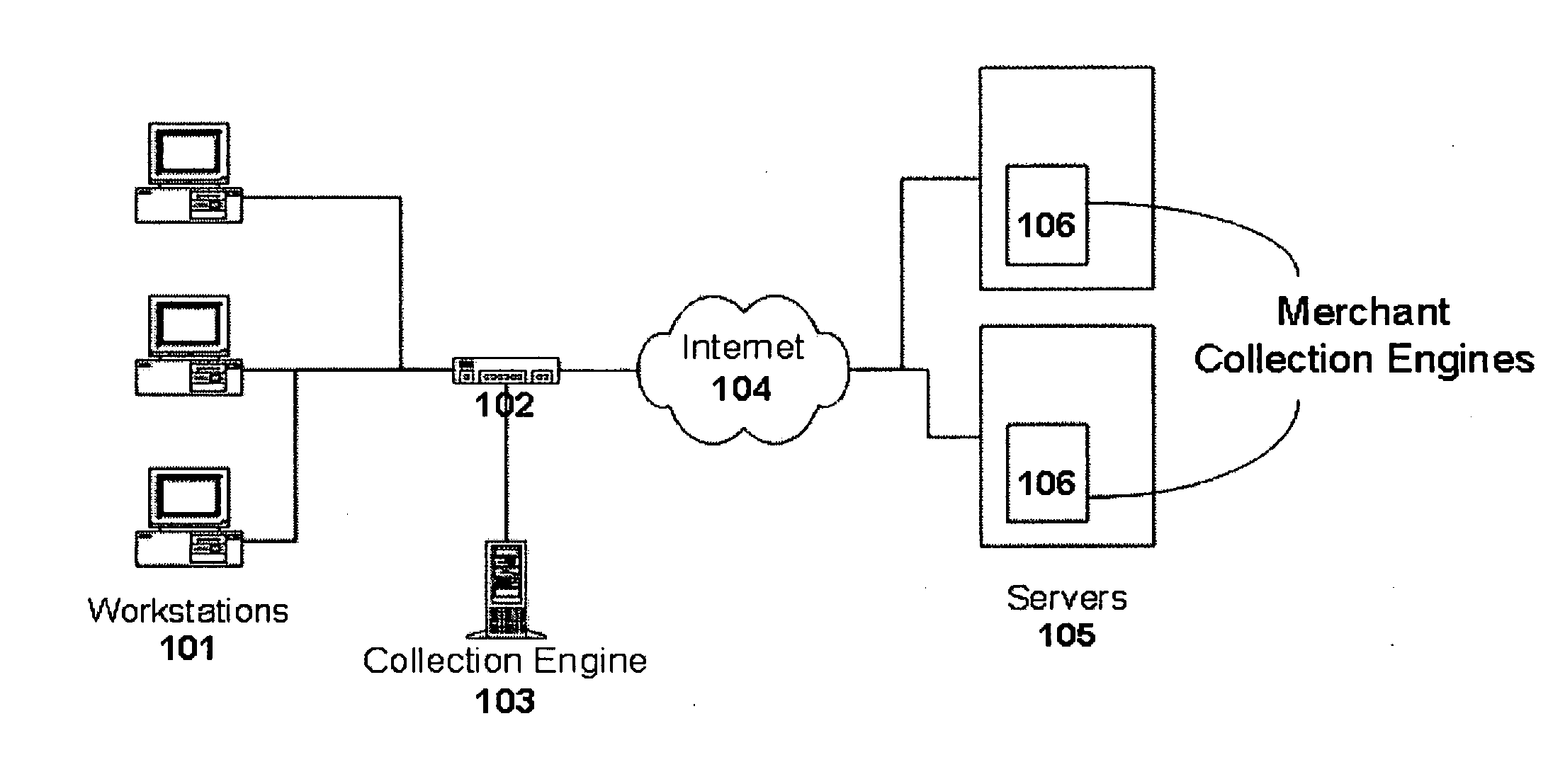
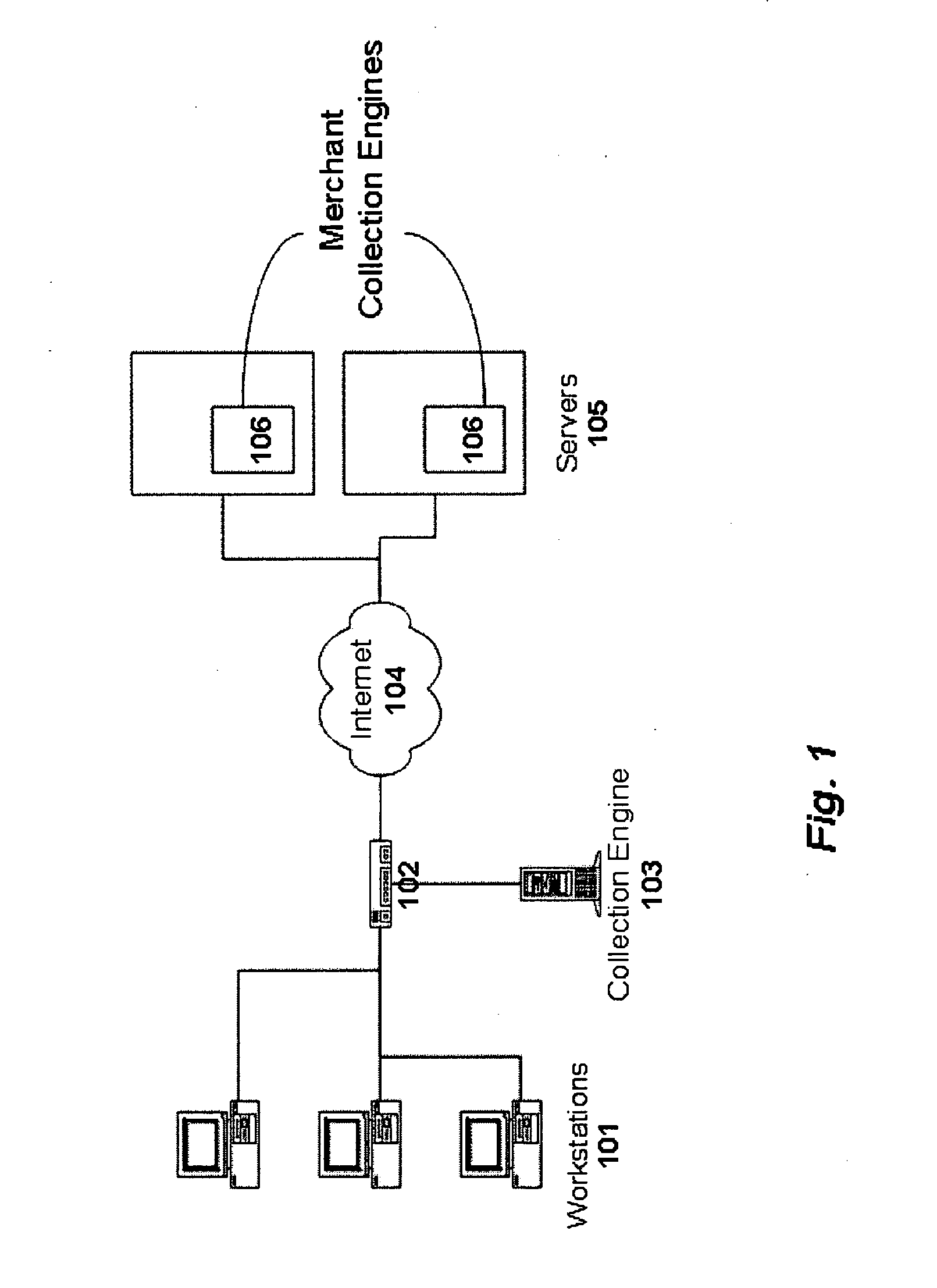
InactiveUS6983379B1Amount of timeHardware monitoringComputer security arrangementsInternet privacyTransaction data
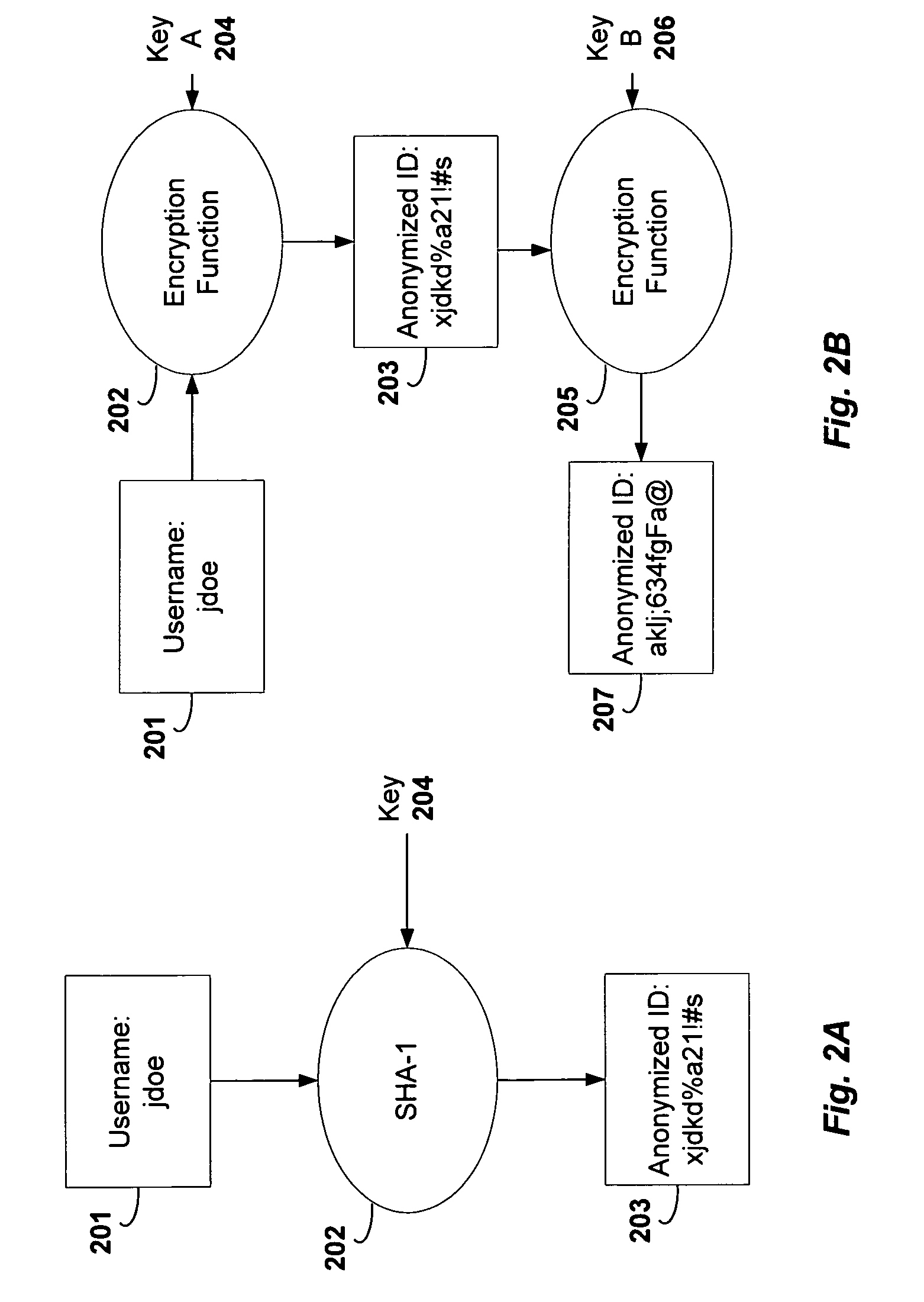
A method and system for monitoring users on one or more computer networks, disassociating personally identifiable information from the collected data, and storing it in a database so that the privacy of the users is protected. The system includes monitoring transactions at both a client and at a server, collecting network transaction data, and aggregating the data collected at the client and at the server. The system receives a user identifier and uses it to create an anonymized identifier. The anonymized identifier is then associated with one or more users' computer network transactions. The data is stored by a collection engine and then aggregated to a central database server across a computer network.
Owner:PLURIMUS CORP +1
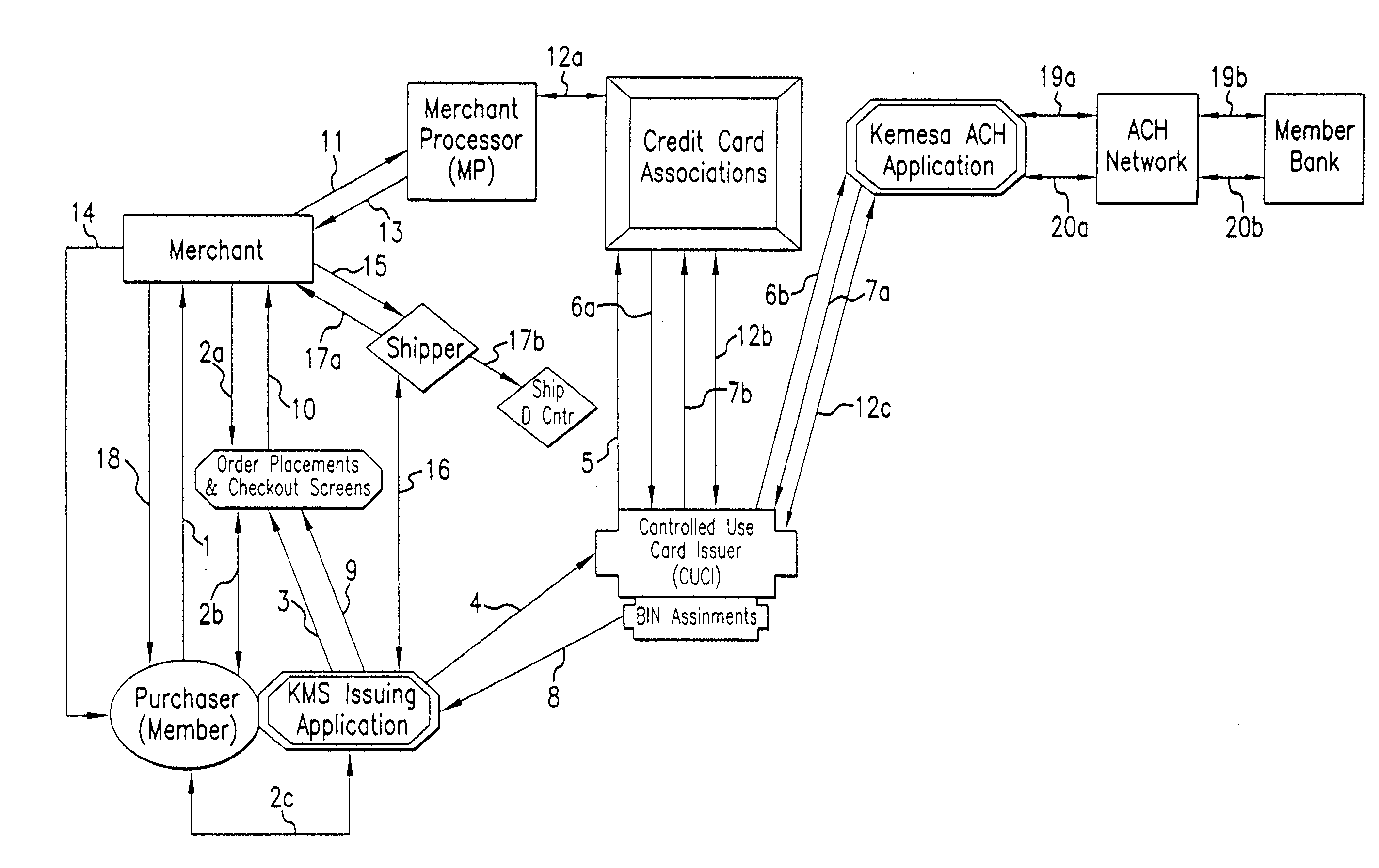
Identity theft and fraud protection system and method
ActiveUS20070083460A1Prevent theftMaximum anonymityFinanceDigital data protectionCredit cardEmail address
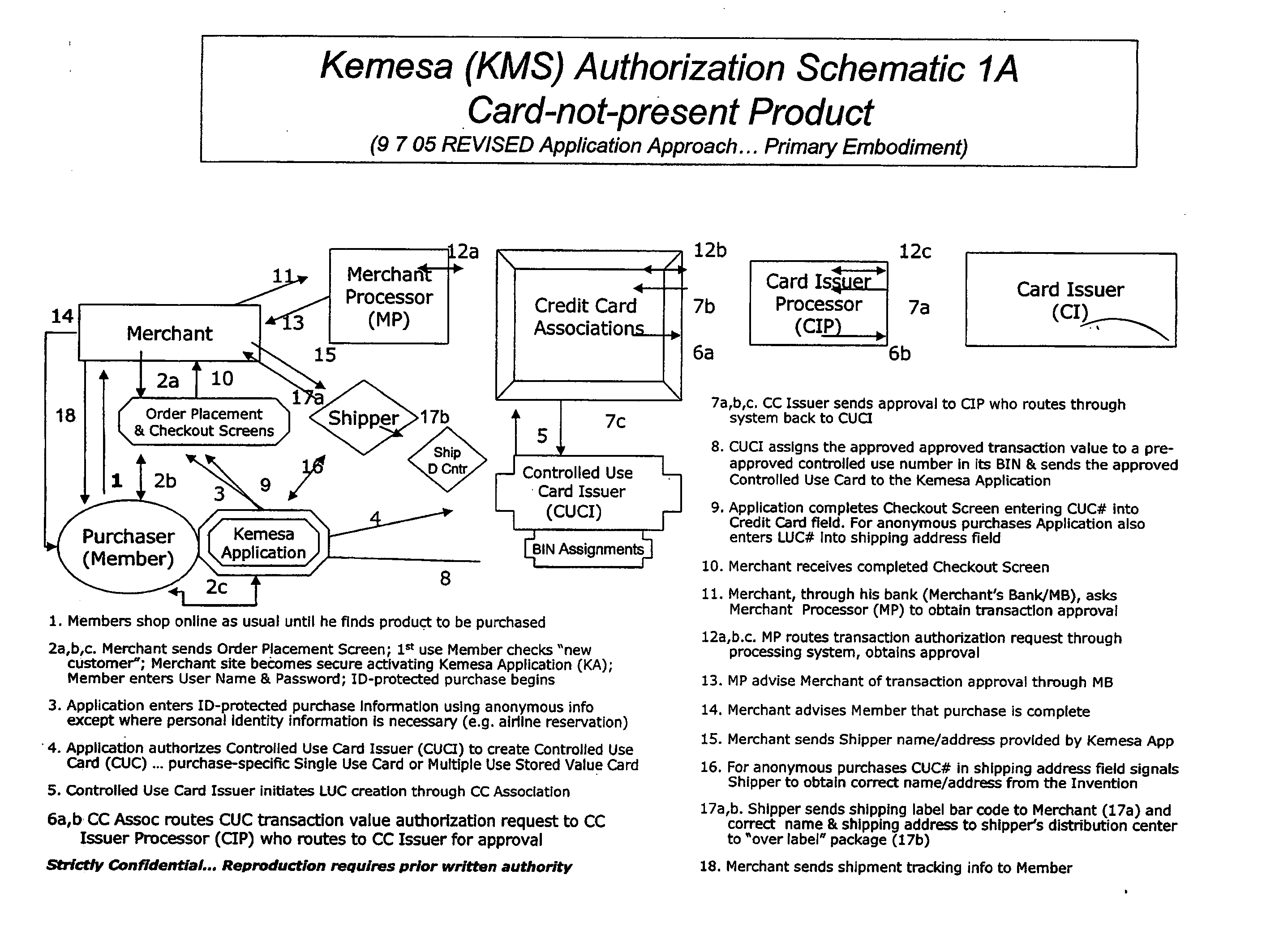
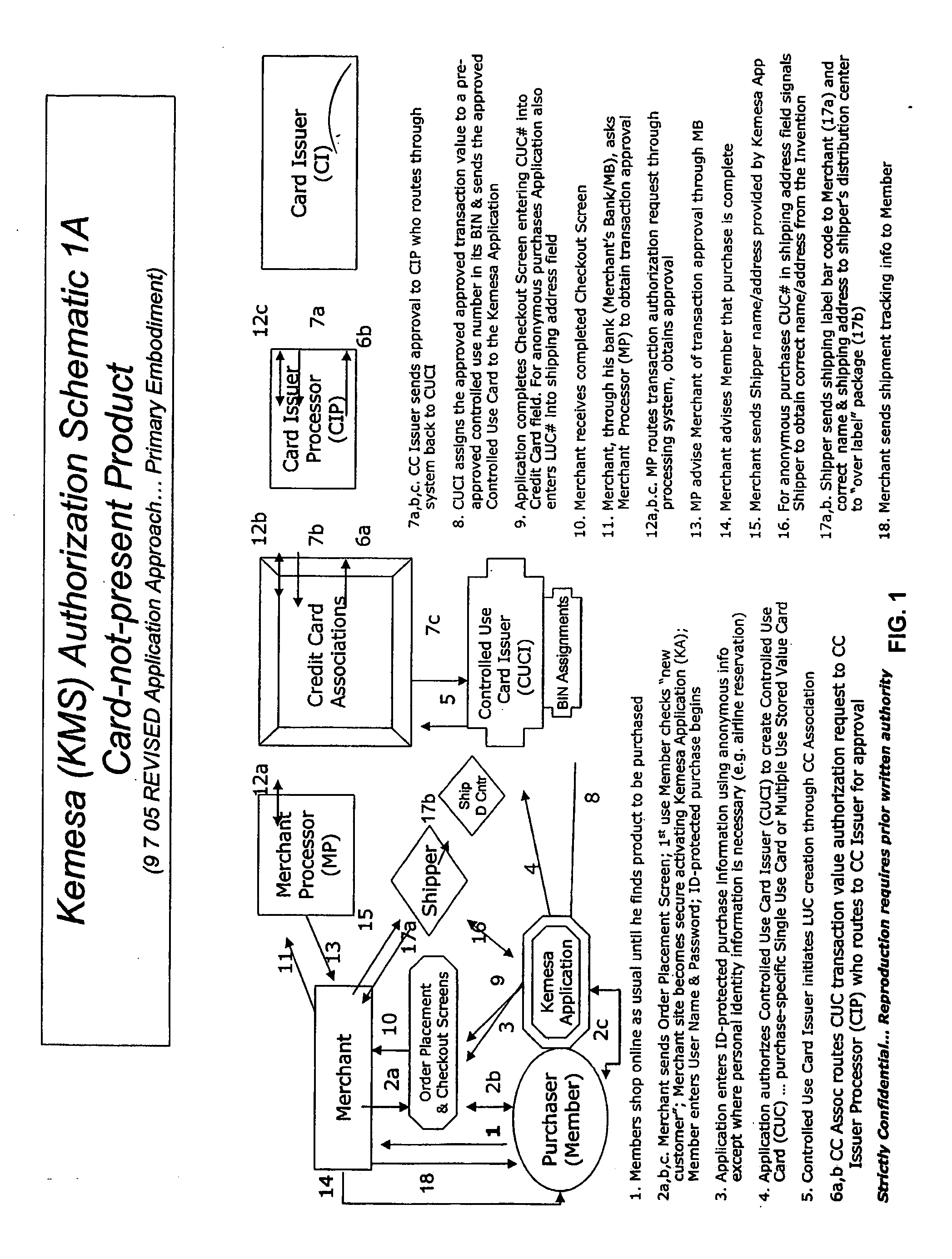
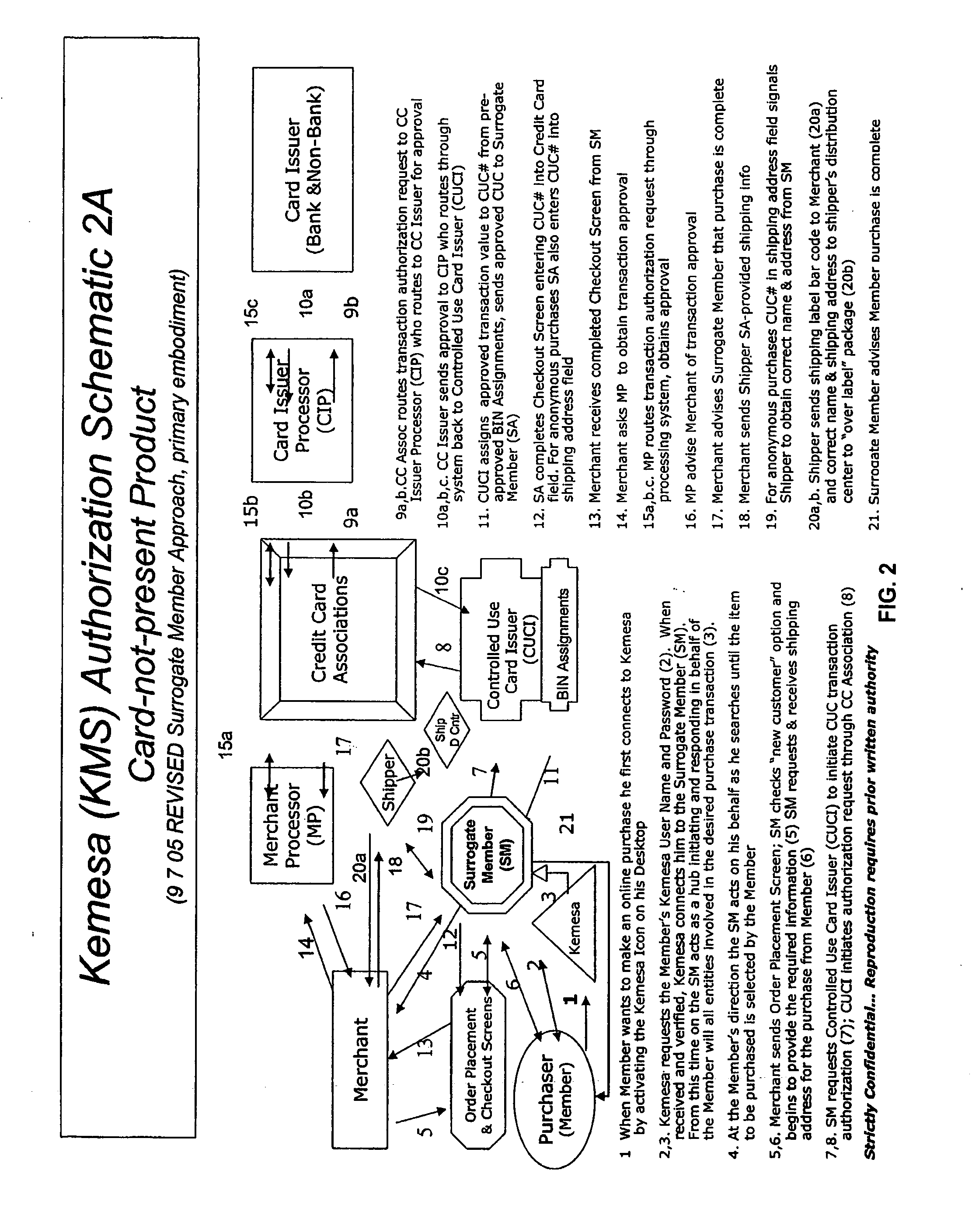
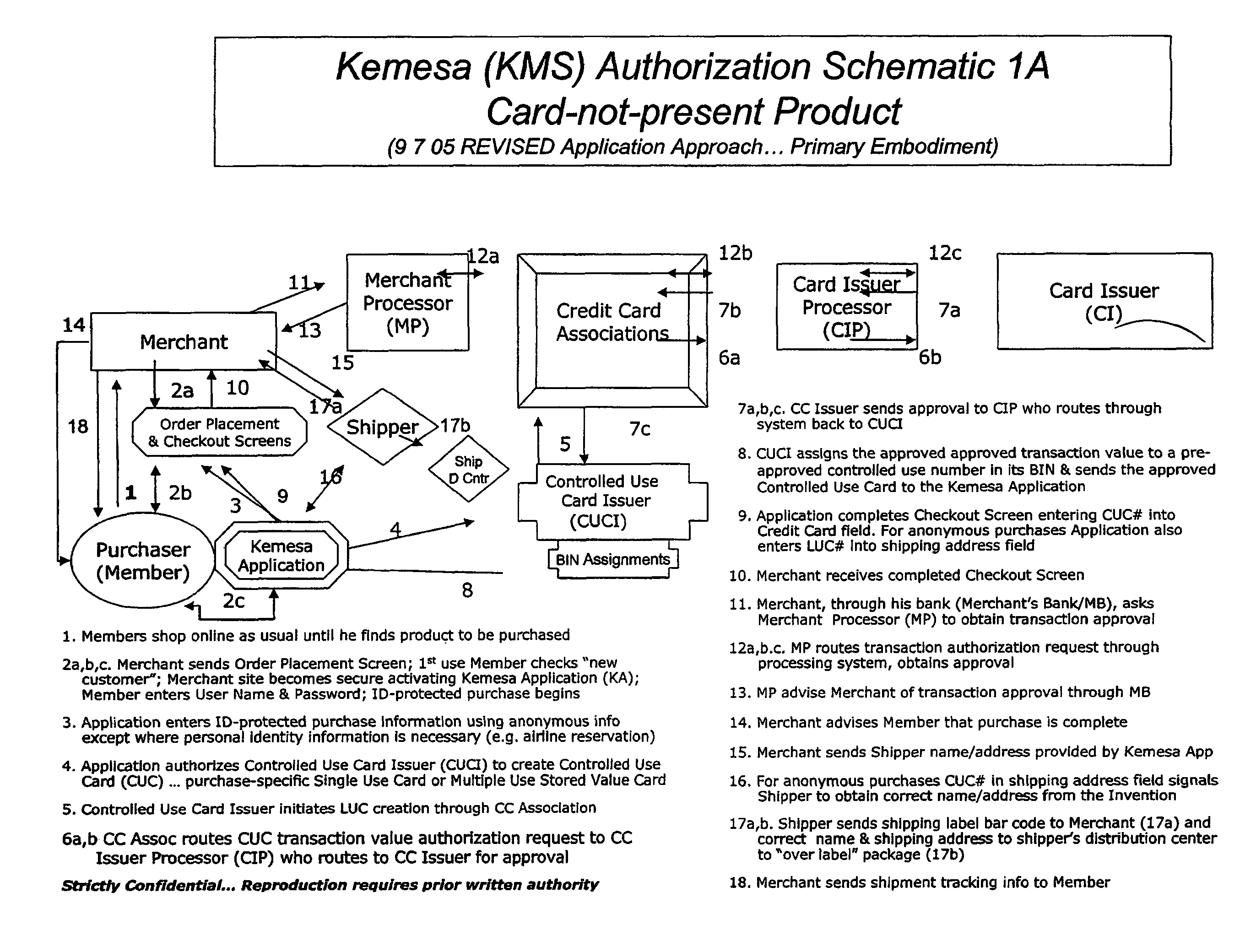
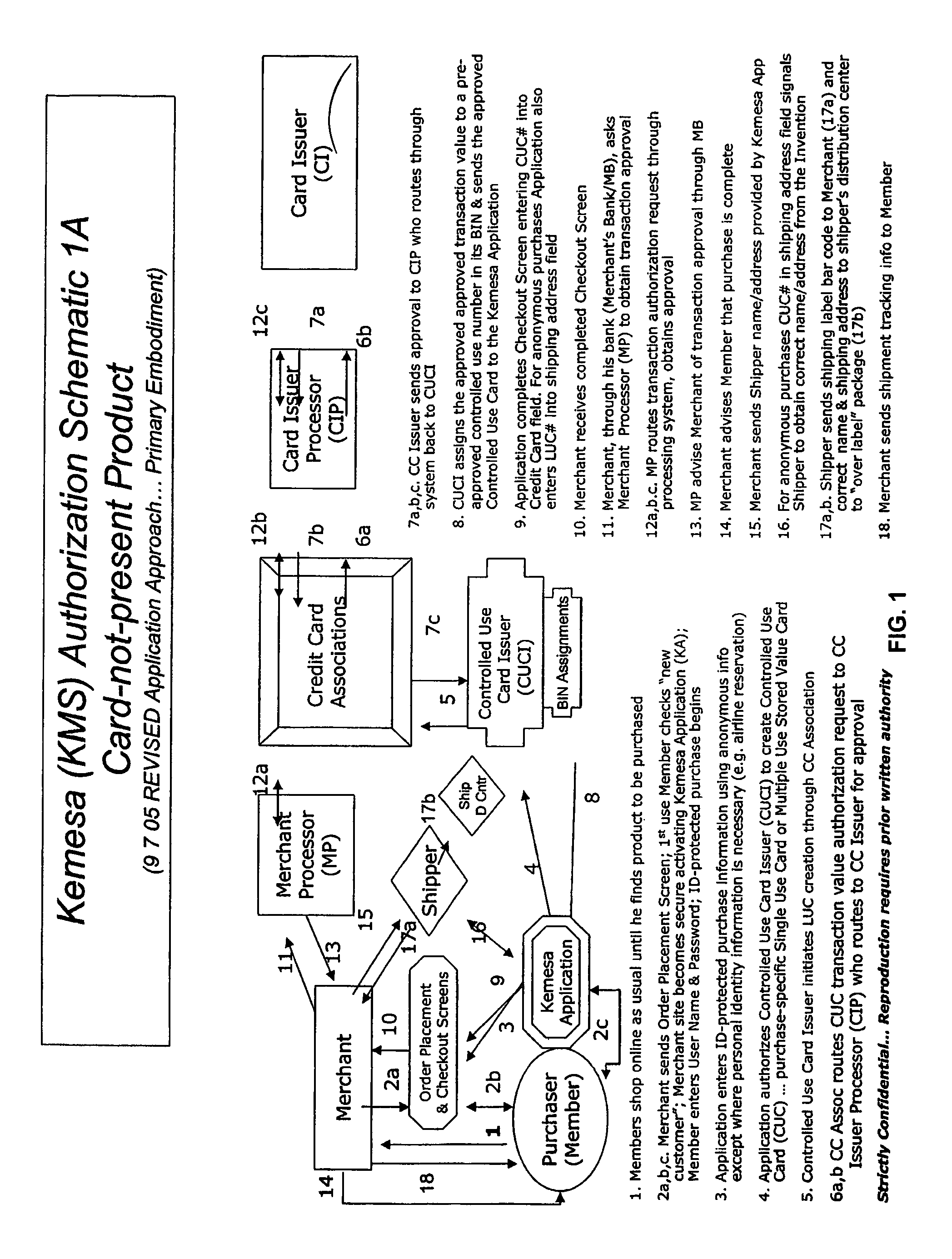
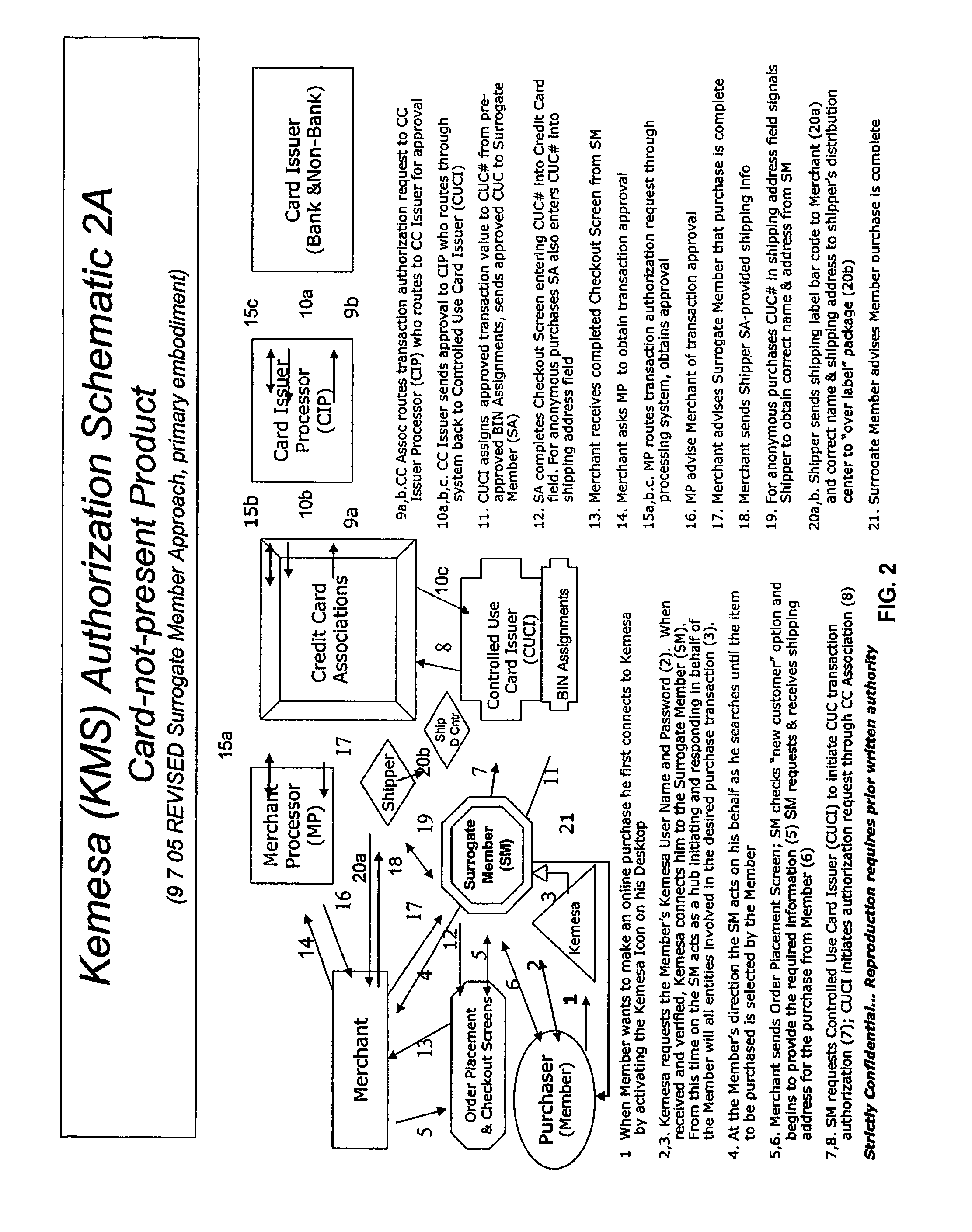
A system and method for preventing personal identity theft when making online and offline purchases requires a purchaser to first subscribe and become a member user by registering and providing relevant personal identity information. Once registered, the member is assigned a user name and a password. The subscribing member's personal identity information is then encrypted and stored at one or more highly secure locations. The ID protection system obtains a controlled use card (CUC) through a CUC issuer on behalf of the member for use to make each purchase transaction. The CUC is anonymous with respect to user (member) identity and may be a purchase-specific single-use card or a multiple-use stored value card with no traceable connection to any other financial account. When the member makes a secure online purchase, the system software enters anonymous information (i.e. not revealing the member's real name, email address, billing information, etc.) on the merchant's order placement screen, except in instances where the member's real identity information is required (e.g. airline tickets). The merchant receives the completed checkout screen, obtains credit approval through a credit card association, and sends the shipping information to a shipper which independently obtains the correct shipping name and address from the ID protection system prior to shipping the purchased product(s).
Owner:VIPR SYST +1
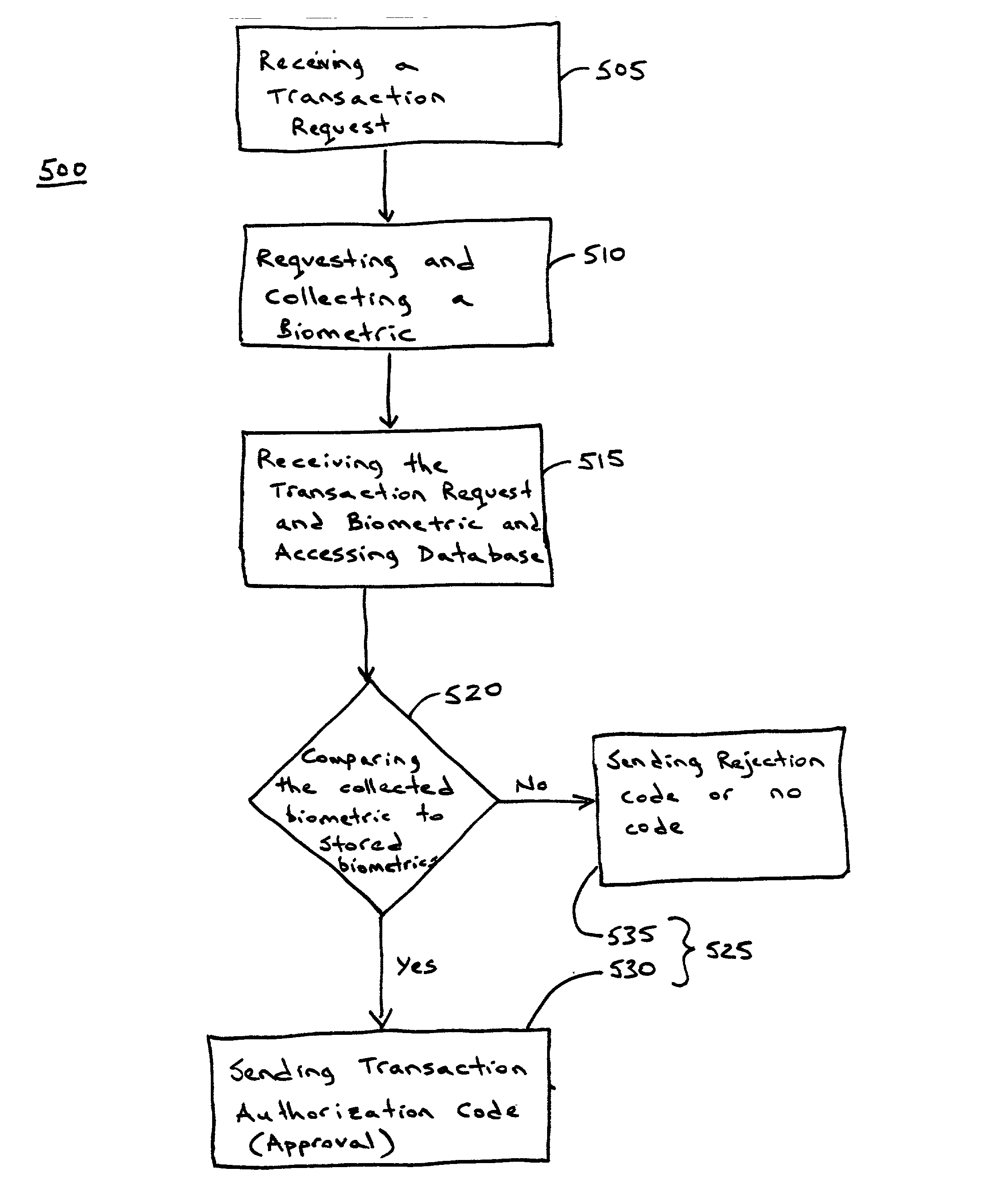
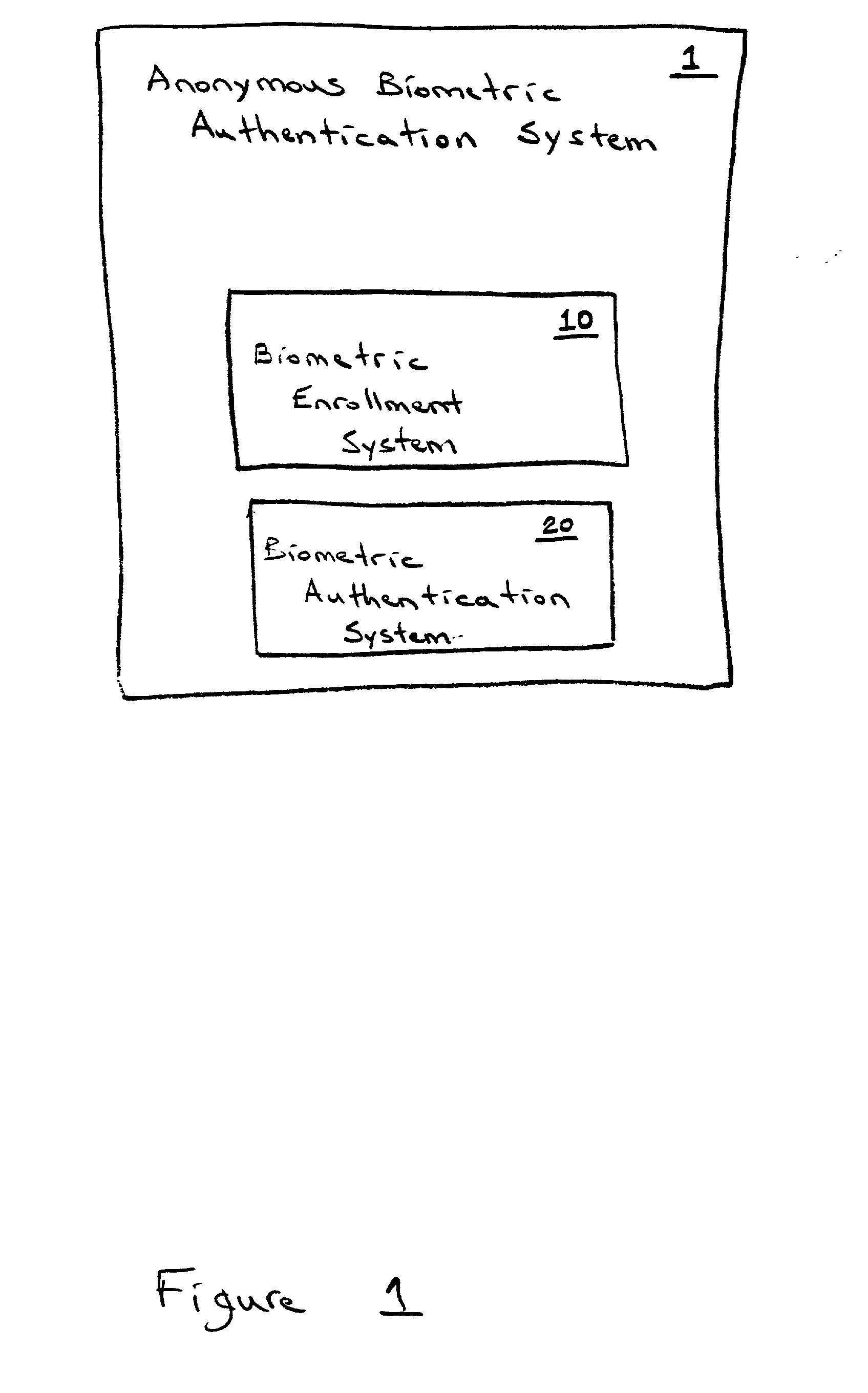
Anonymous biometric authentication
InactiveUS20020112177A1Digital data processing detailsUser identity/authority verificationInternet privacyAnonymous authentication
The use of an anonymous biometric authentication system and method that use biometrics to anonymously authenticate an individual and grant certain privileges based on the anonymous authentication is provided. The system and method permit enrollment of an individual by submission of a first biometric and associated identity documents or credentials to an enrollment authority. The enrollment authority verifies the identity of the identity of the individual submitting the biometric using the credentials which are then returned to the individual or discarded. The first biometric is stored in a database for later retrieval in anonymously authenticating an individual seeking to exercise certain privileges. No other personal identity information is stored along with the biometric during the enrollment process. When an individual later seeks to exercise certain privileges, they must submit a second biometric that is compared to the stored biometrics in the database in order to anonymously authenticate the identity of the individual as having access to such privileges. No other personal information is captured, collected, or solicited during the authentication process. Privileges are granted to an individual based on the comparison of the later captured biometric to the stored biometrics in the database. Alternatively, the anonymous biometric authentication system can be designed to avoid repeat offenders by capturing a biometric of an individual seeking to exercise a privilege and denying the privilege if the captured biometric is matched to a biometric stored in a database containing the biometrics of previous offenders. Preferably, the system and method include capture and storage of a powerful biometric identifier based on the iris of the eye which uniquely identifies the individual that has submitted the biometric. Anonymous biometric authentication allows verification of the identity of an individual seeking certain privileges while at the same time protecting the privacy of personal information about the individual.
Owner:IRIDIAN TECH
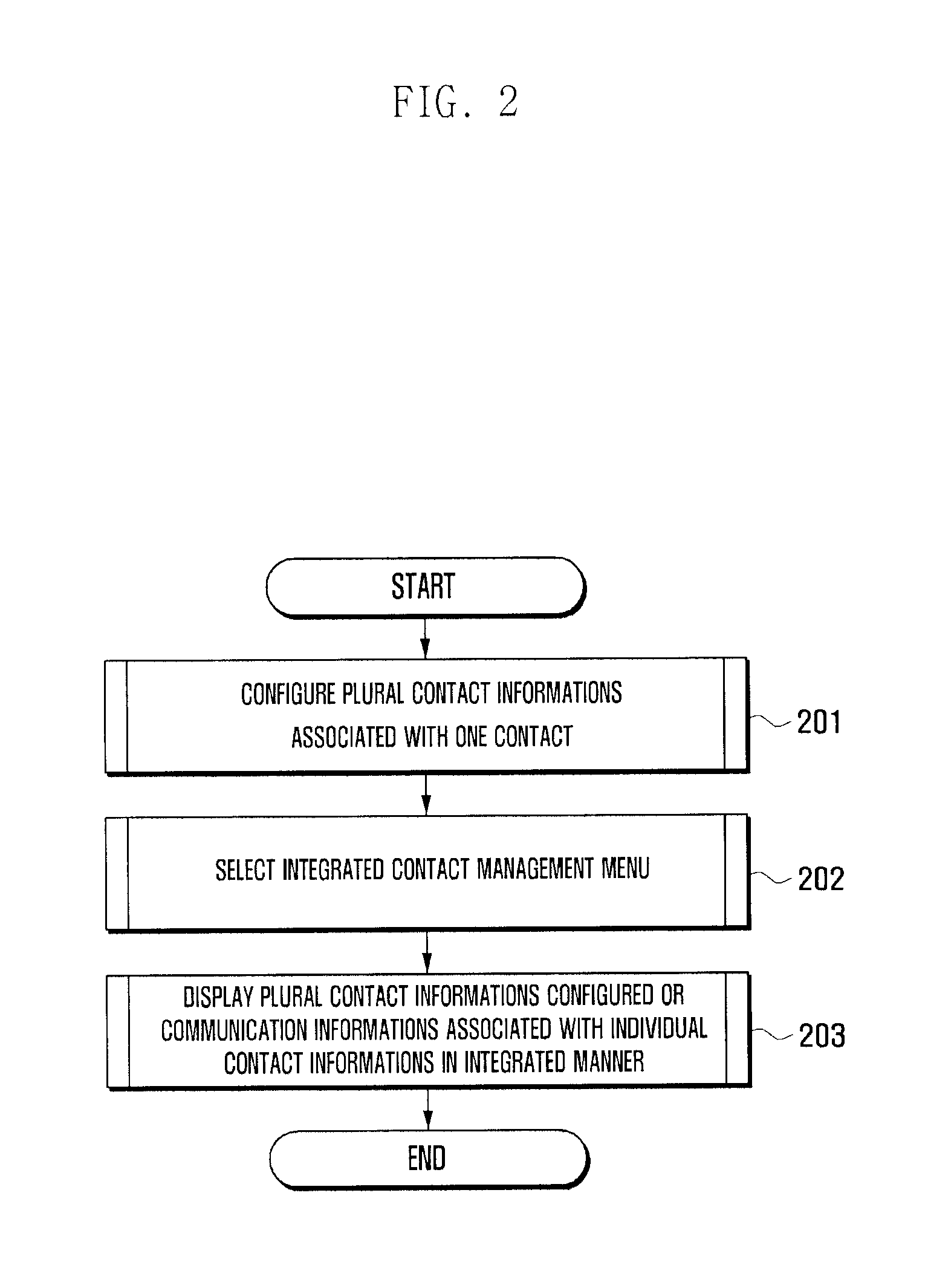
Method and apparatus for providing information in mobile terminal
ActiveUS20110197163A1Improve user convenienceServices signallingSubstation equipmentComputer networkPersonally identifiable information
An information provision method and apparatus of a mobile terminal is provided for managing and providing information items associated with a plurality of communication accounts of a user in an integrated manner. An information provision method for a mobile terminal includes configuring a plurality of identity informations associated with communications of a specific contact item; detecting an input for selecting an integrated contact management menu; and displaying the identity informations or communication informations associated with individual identity informations in an integrated manner.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for the protection and de-identification of health care data
ActiveUS20080147554A1Computer security arrangementsPatient personal data managementHash functionInternet privacy
A system for protecting and de-identifying healthcare data includes a storage device for storing the healthcare data and personally identifiable information for a person and a processor in communication with the database. The processor generates an anonymous linking code using a keyed hash function and a second hash function. The anonymous linking code is based at least in part on a portion of the personally identifiable information. The processor further appends the anonymous linking code to the healthcare data for the person.
Owner:IQVIA INC
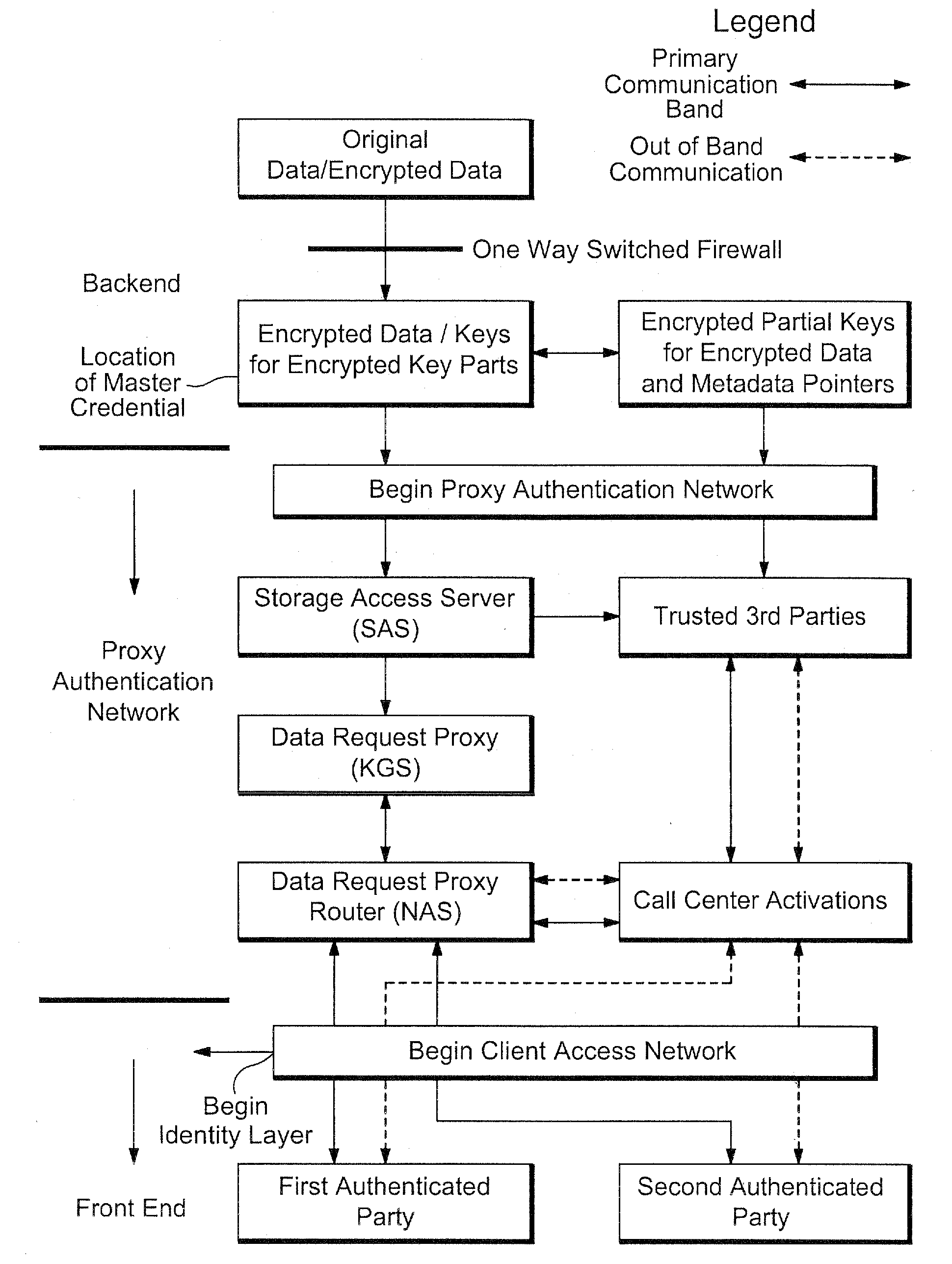
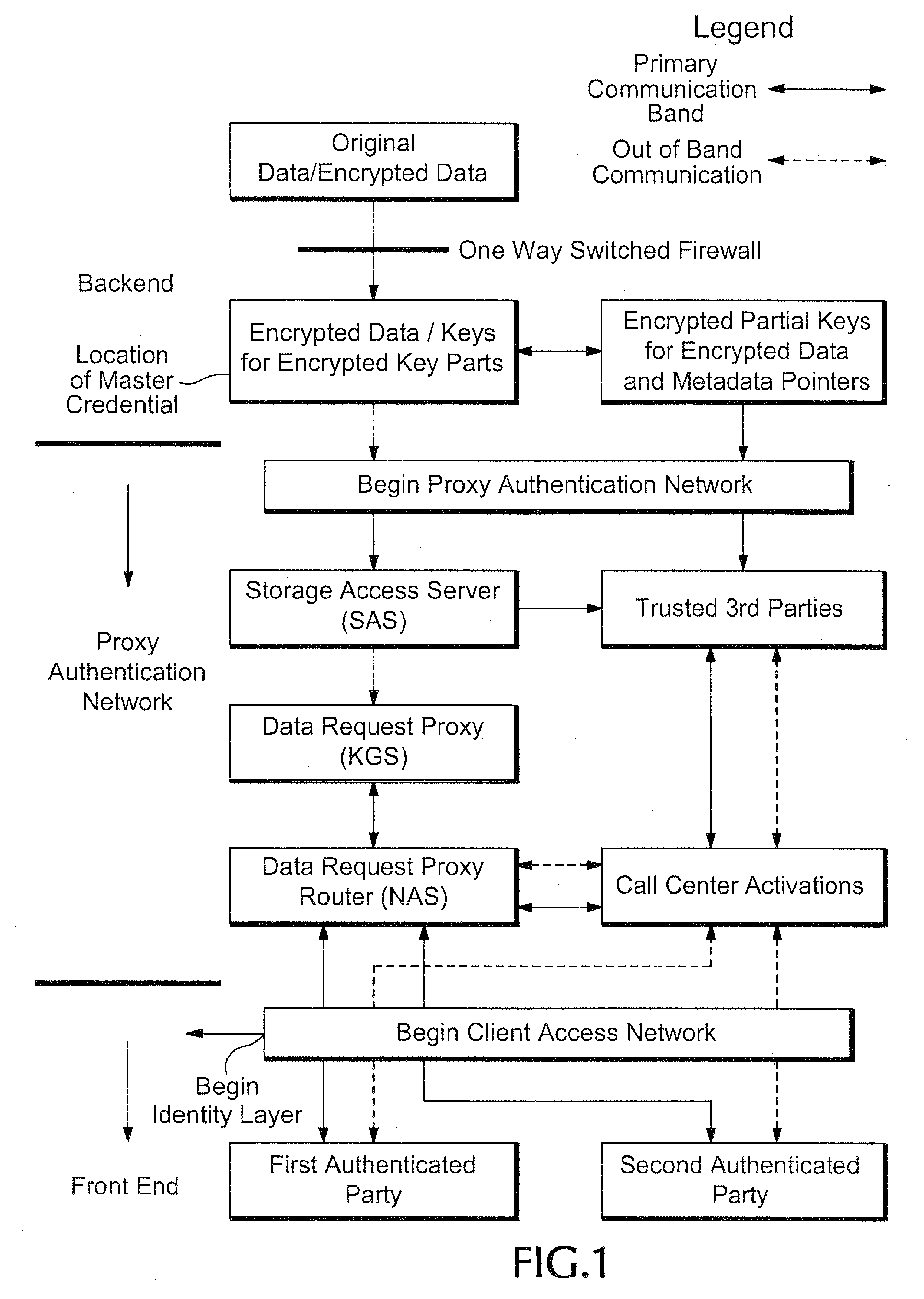
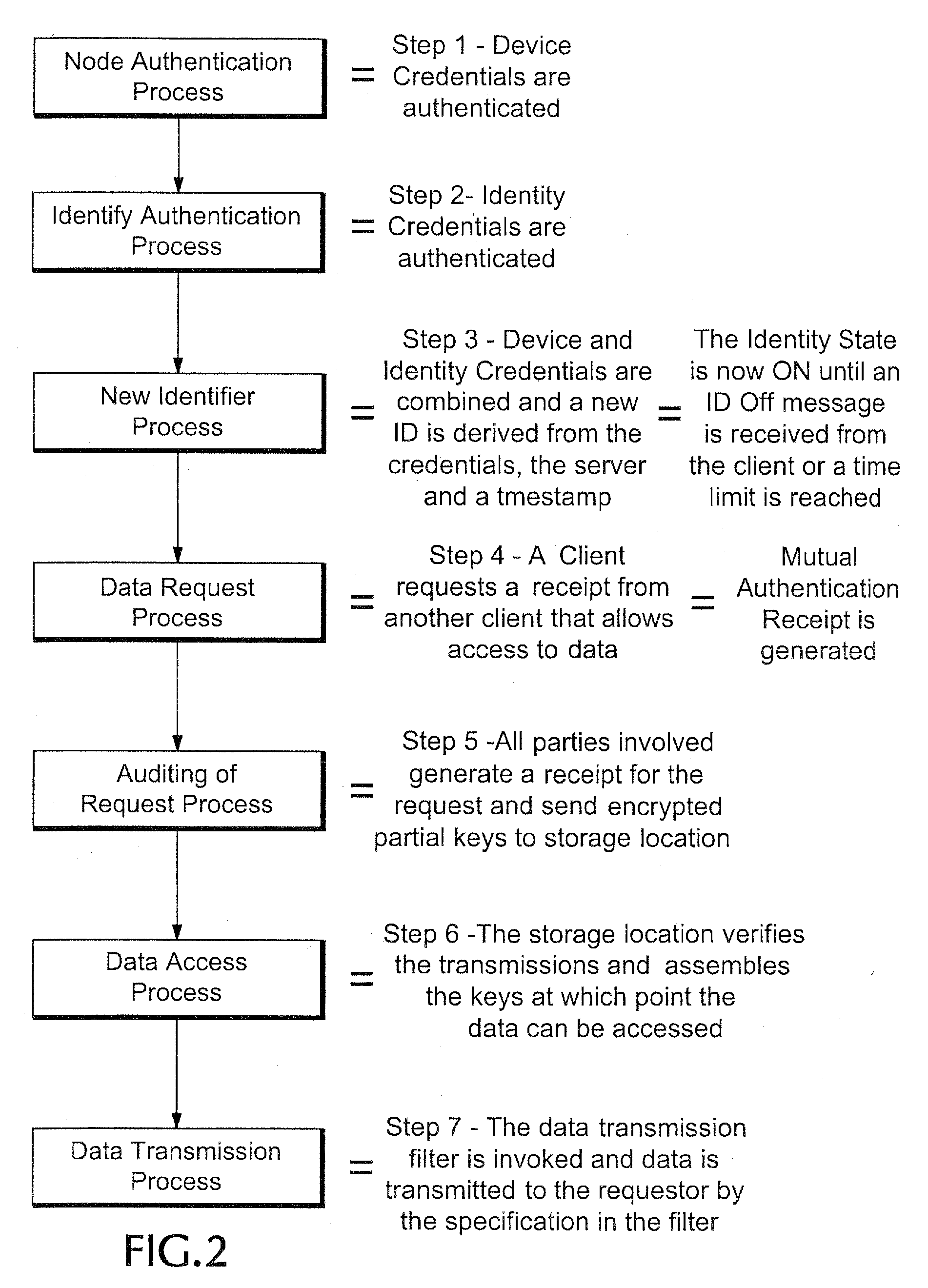
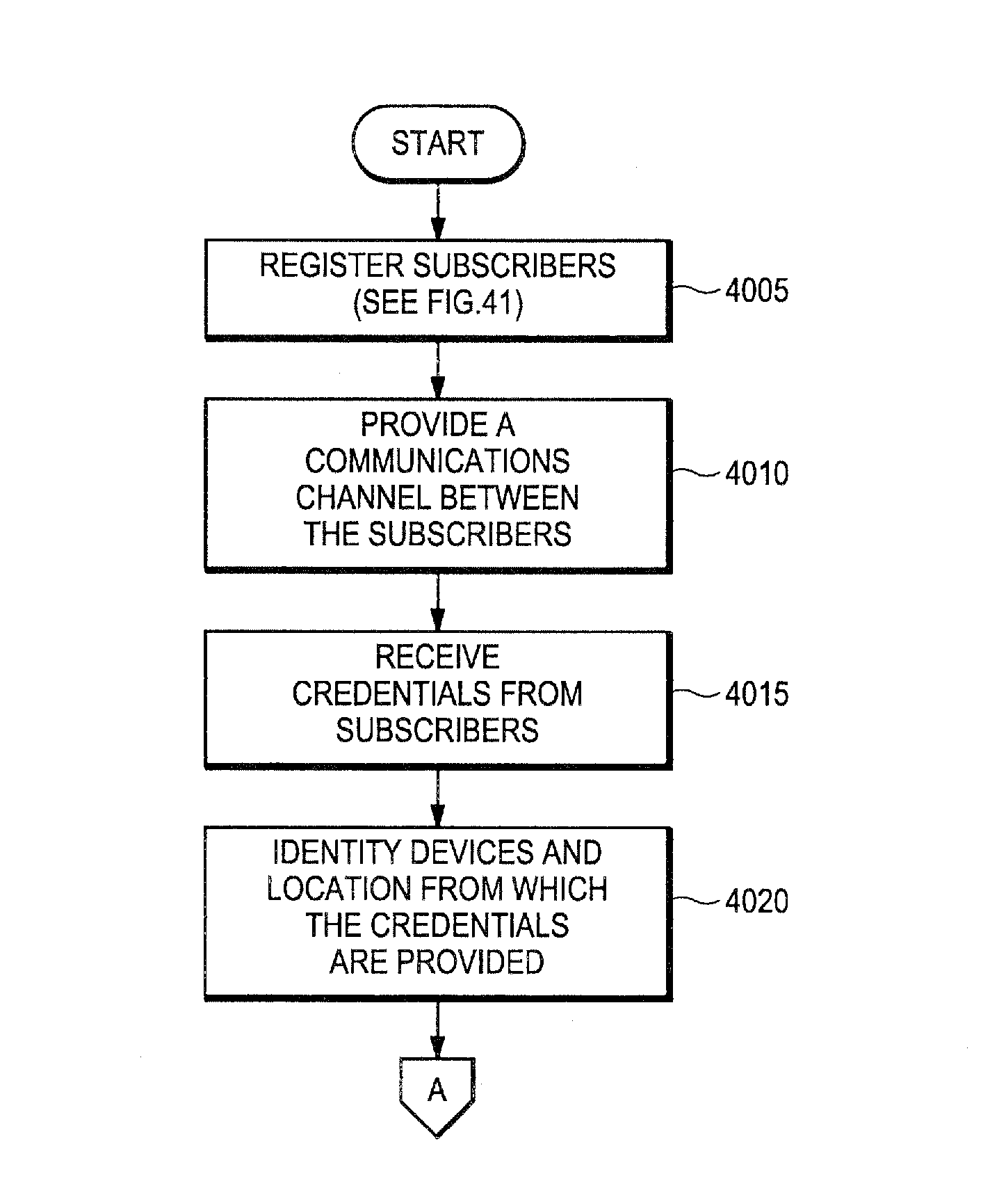
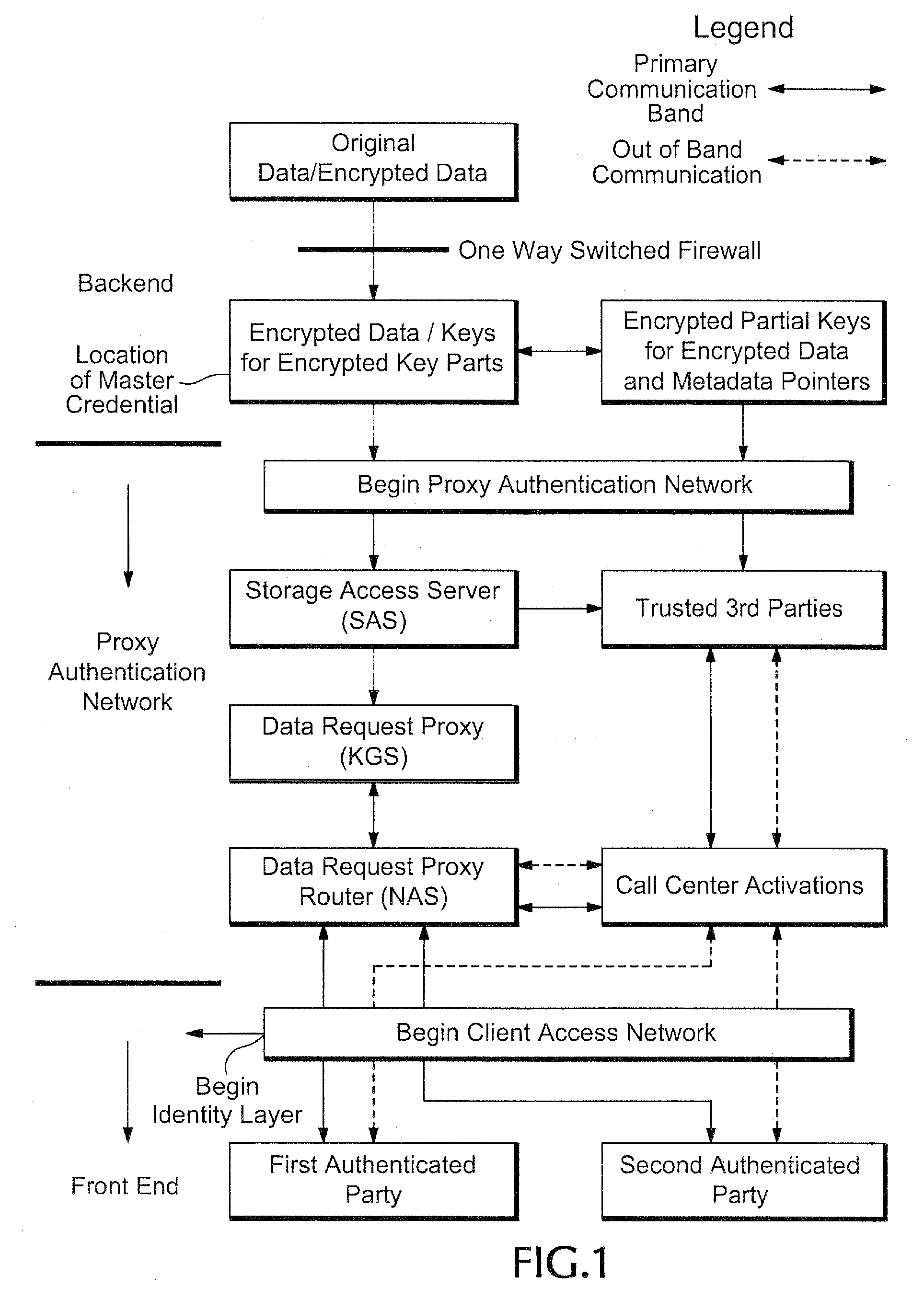
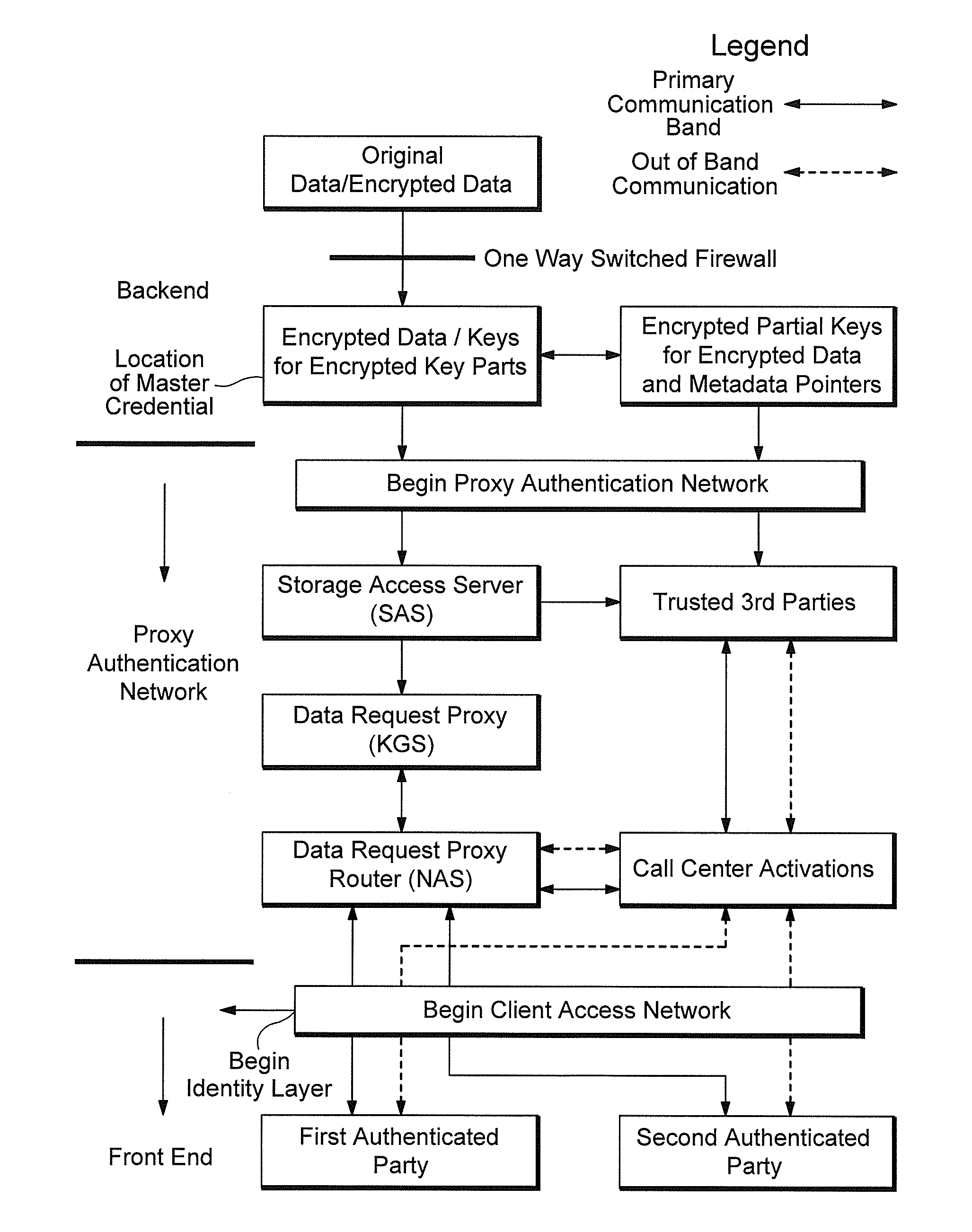
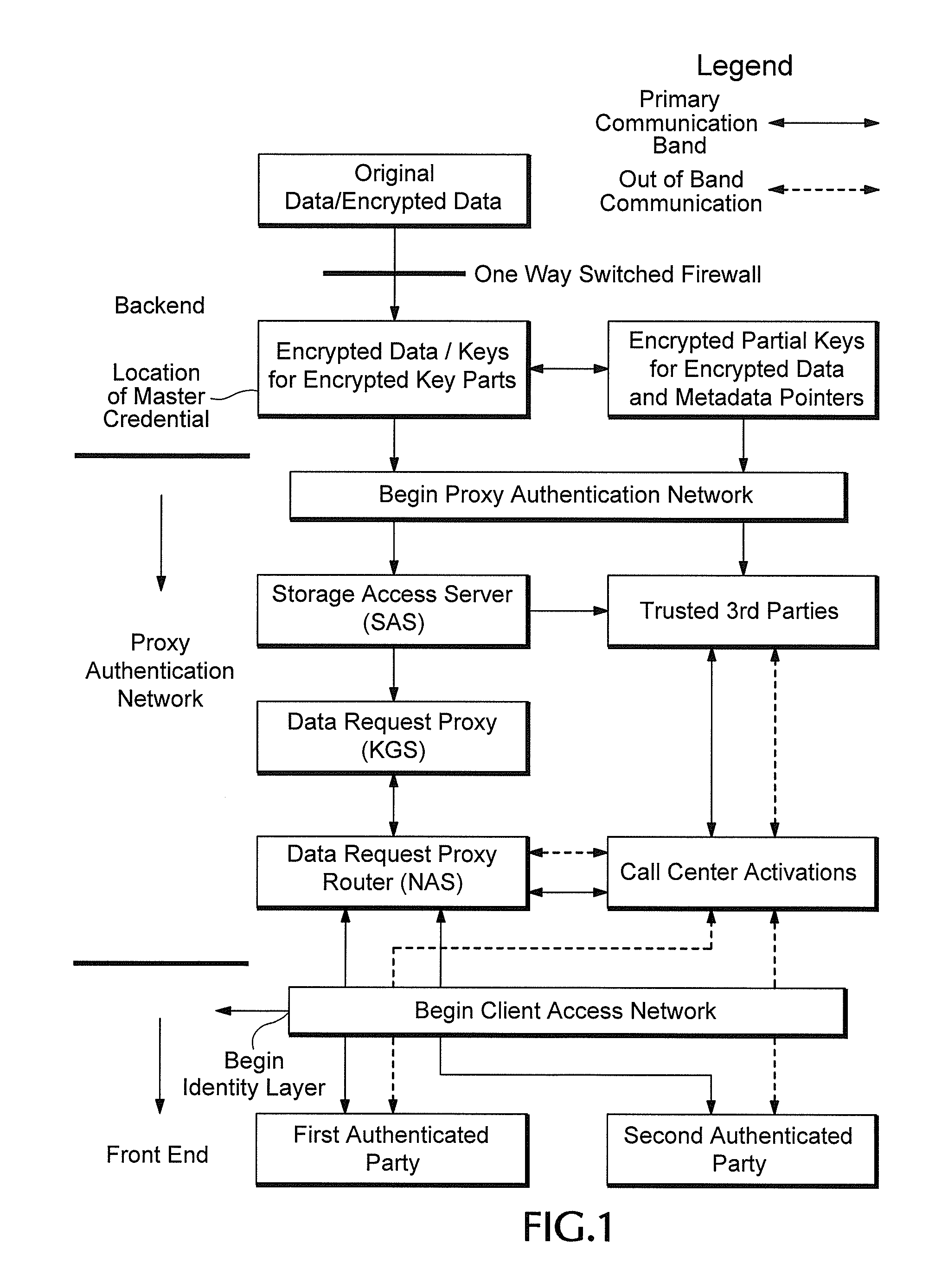
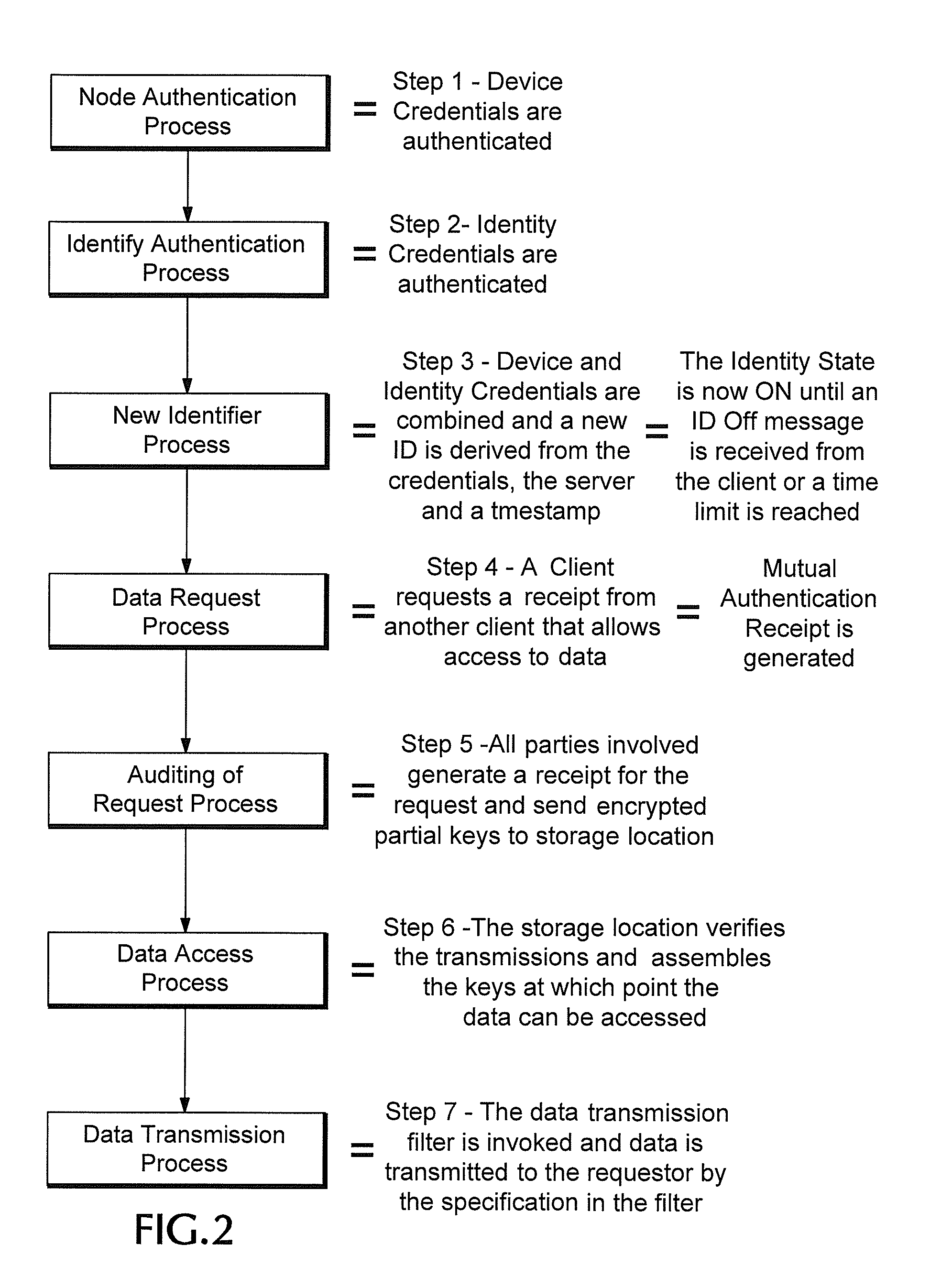
Proxy authentication network
InactiveUS20060282662A1Digital data processing detailsMultiple digital computer combinationsThird partyData storing
A Proxy Authentication Network includes a server that stores credentials for subscribers, along with combinations of devices and locations from which individual subscribers want to be authenticated. Data is stored in storage: the storage can be selected by the subscriber. The data stored in the storage, which can be personally identifiable information, can be stored in an encrypted form. The key used to encrypt such data can be divided between the storage and server. In addition, third parties can store portions of the encrypting key. Subscribers can be authenticated using their credentials from recognized device / location combinations; out-of-band authentication supports authenticating subscribers from other locations. Once authenticated, a party can request that the encrypted data be released. The portions of the key are then assembled at the storage. The storage then decrypts the data, generates a new key, and re-encrypts the data for transmission to the requester.
Owner:IAMSECUREONLINE
Method and system for monitoring online computer network behavior and creating online behavior profiles
InactiveUS7996912B2Digital data processing detailsAnalogue secracy/subscription systemsNetwork behaviorInternet privacy
Owner:CONNEXITY AUDIENCE INC
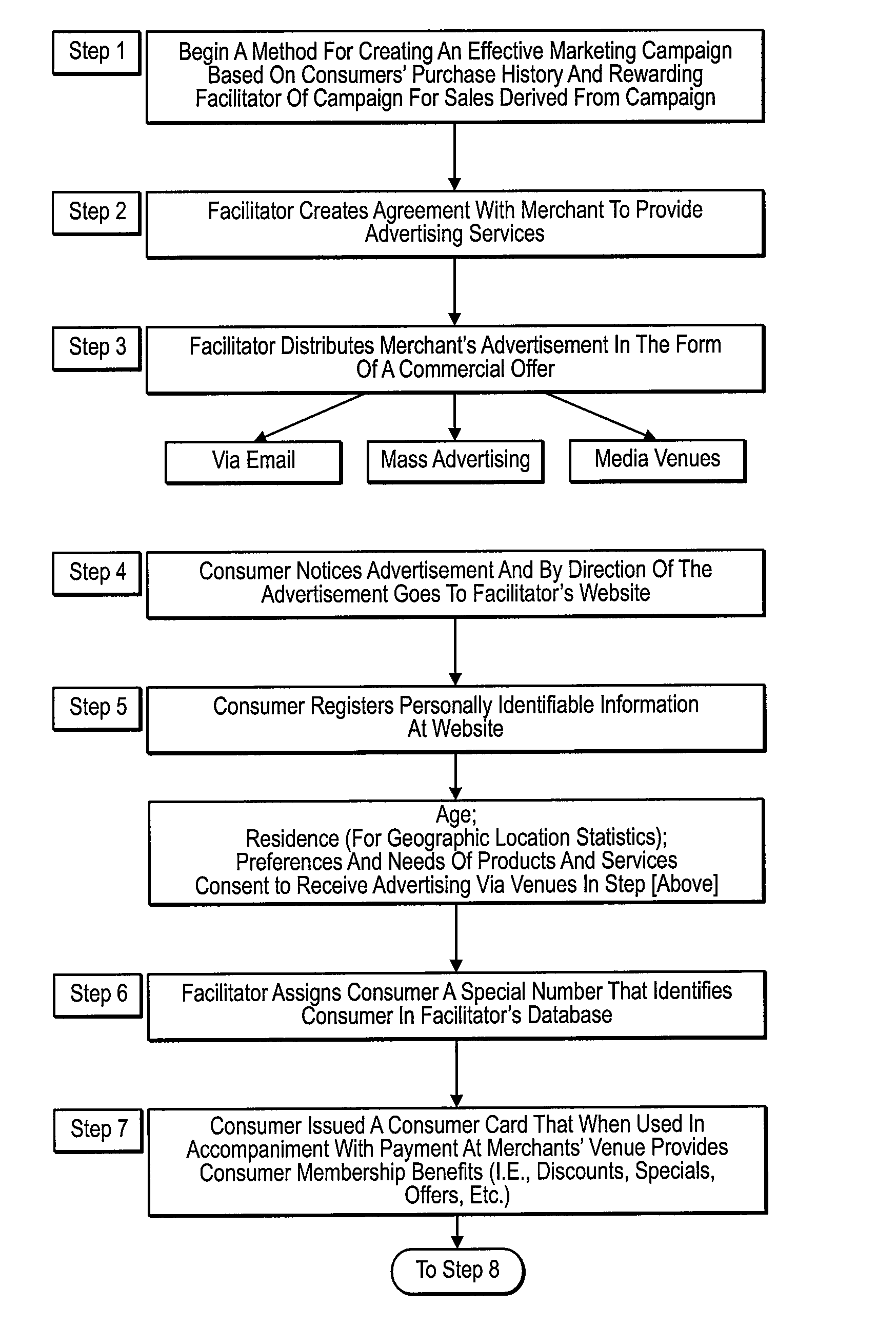
Method and System for Collecting, Tracking and Reporting Consumer Data to Improve Marketing Practices for Merchants and Banks
InactiveUS20070219865A1Redundant and inefficient advertisingSufficient informationAdvertisementsProgram planningPurchasing
A method and system for improving marketing practices for merchants and banks, the method and system comprising advertising via a commercial offer solicited to a consumer, wherein upon noticing the commercial offer, the consumer is directed to a website for a facilitator; collecting data from the consumer at a website, wherein the data contains the consumer's personally identifiable information and purchasing preferences and needs; using the data to enable the facilitator to formulate a focused marketing plan based on the consumer's needs and preferences; and compensating the facilitator based on purchases made by the consumer resulting from said facilitator's focused marketing plan.
Owner:LEINING ADAM C
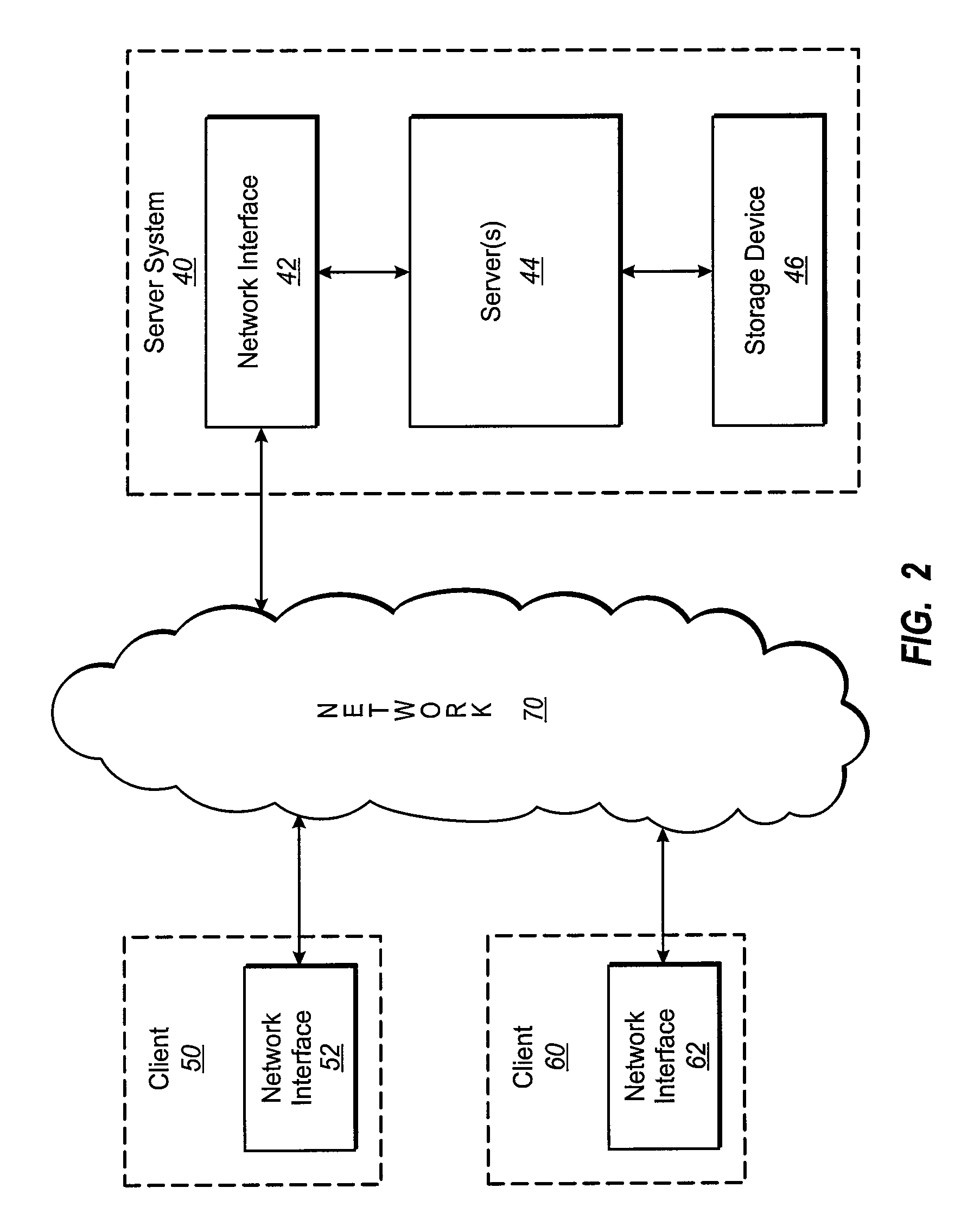
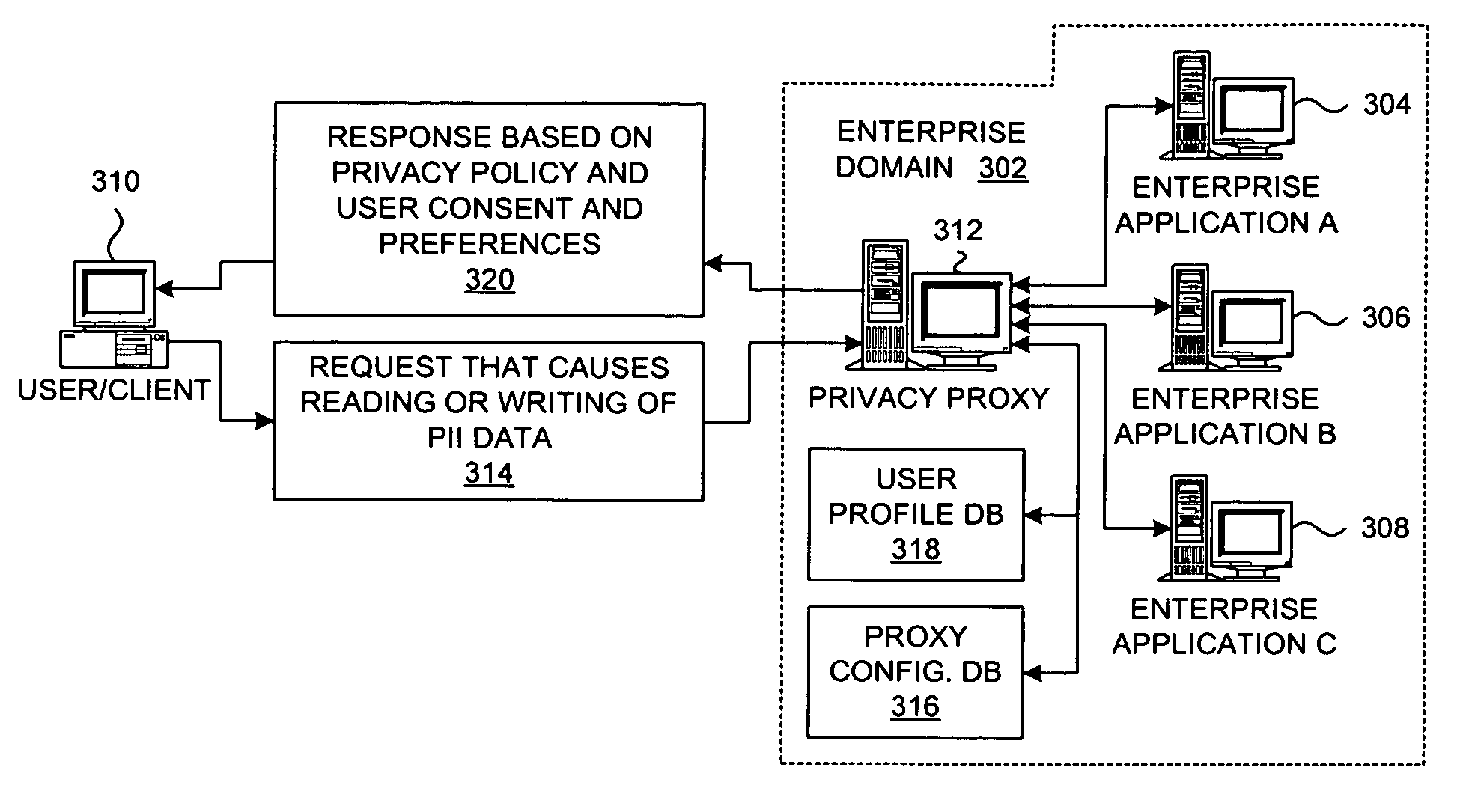
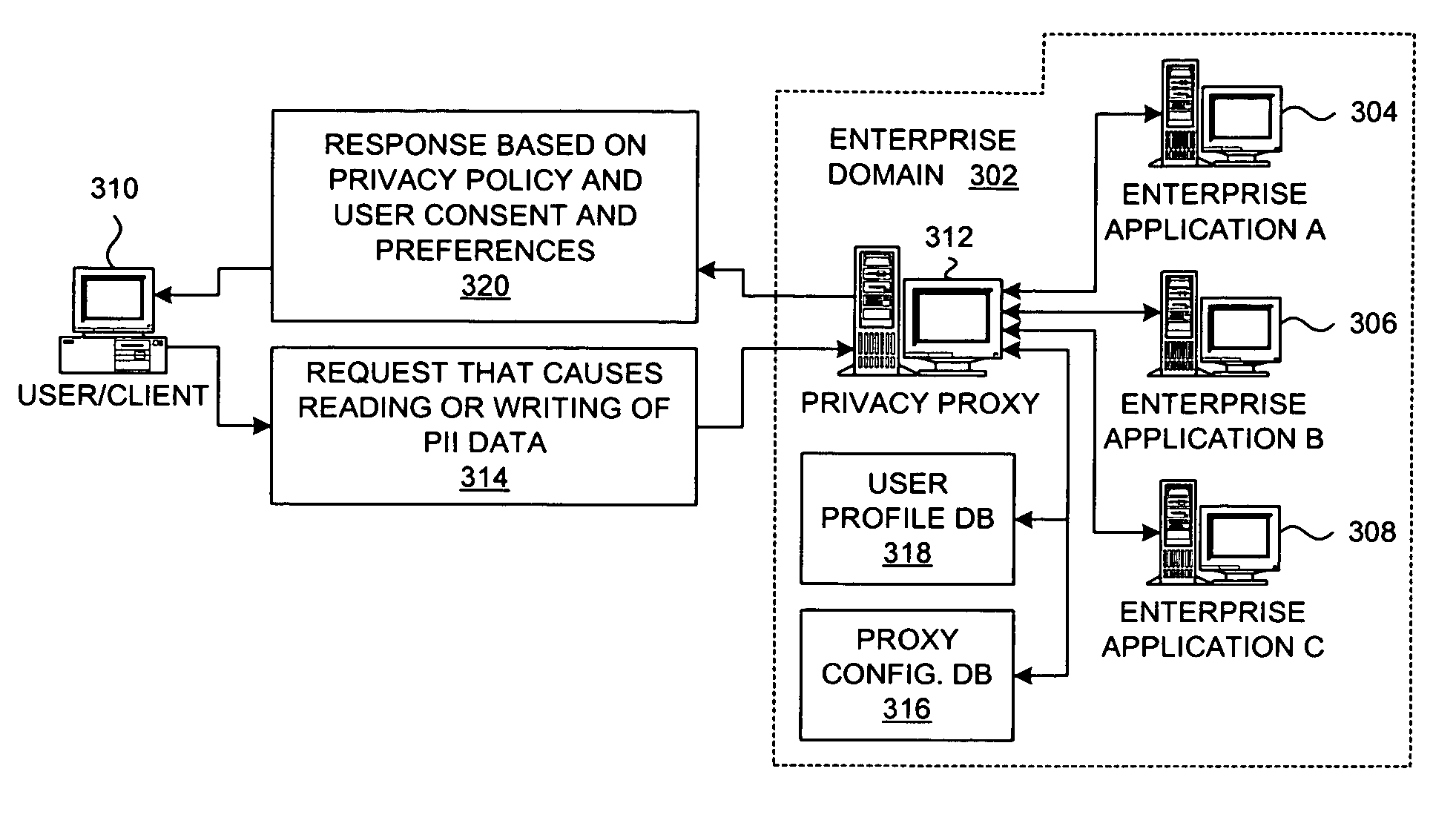
Method and system for implementing privacy notice, consent, and preference with a privacy proxy
ActiveUS8464311B2Digital data processing detailsUser identity/authority verificationData processing systemInternet privacy
A method is presented for processing data for a privacy policy concerning management of personally identifiable information. A proxy intercepts a first message from a server to a client and determines that the first message initiates collection of personally identifiable information from a user of the client. The proxy then sends a second message to the client that requests consent from the user to the privacy policy. If the user provides consent within a third message that is received by the proxy from the client, then the proxy sends the intercepted first message to the client. If the user does not provide consent, then the proxy sends a fourth message to the server that fails the collection of personally identifiable information from the client by the server. The proxy may also obtain user preferences for options concerning management of the personally identifiable information by a data processing system.
Owner:IBM CORP
Apparatus and method for bringing offline data online while protecting consumer privacy
ActiveUS9665883B2Precise positioningIncreased marketingAdvertisementsComputer security arrangementsInternet privacyOnline and offline
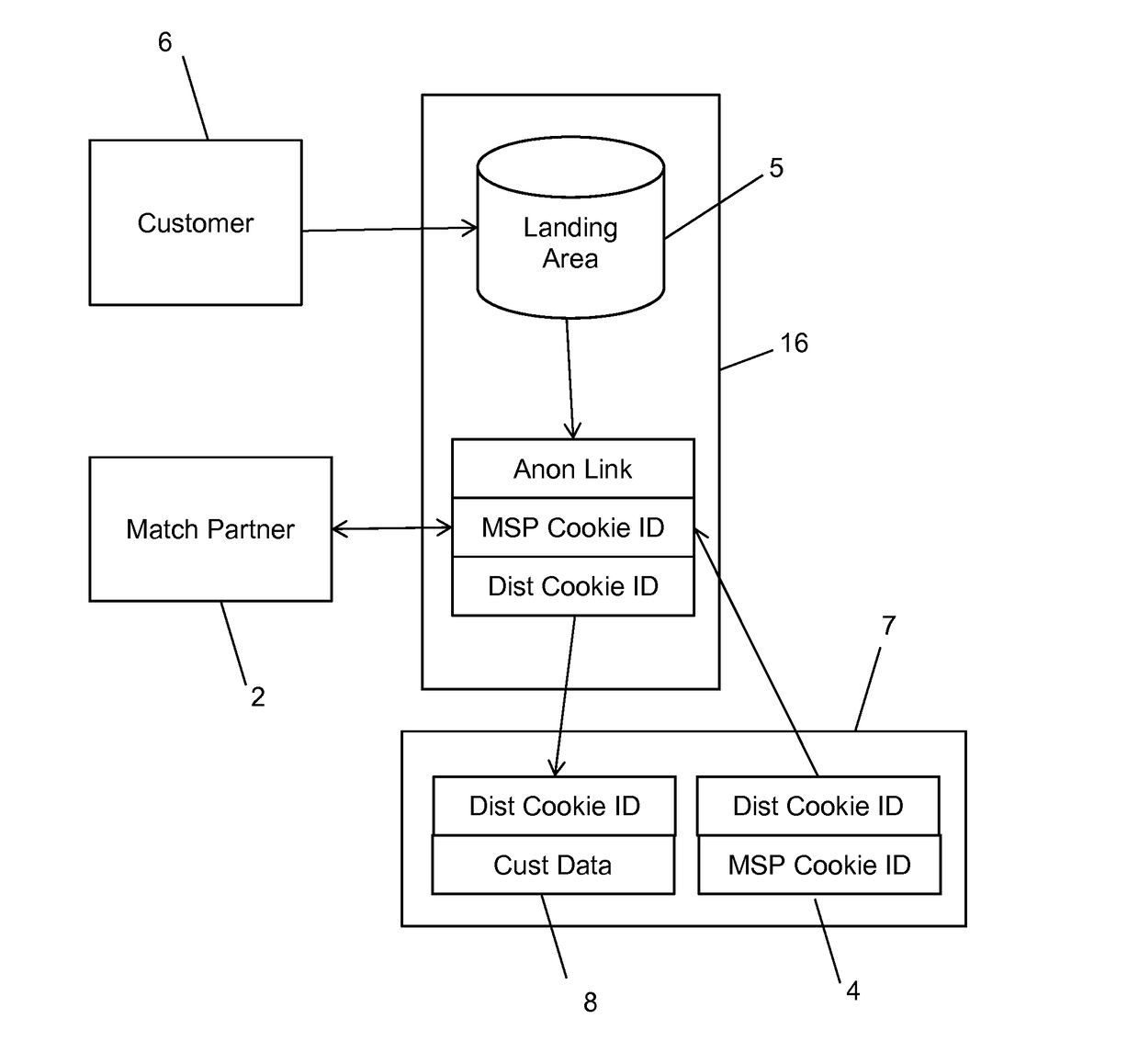
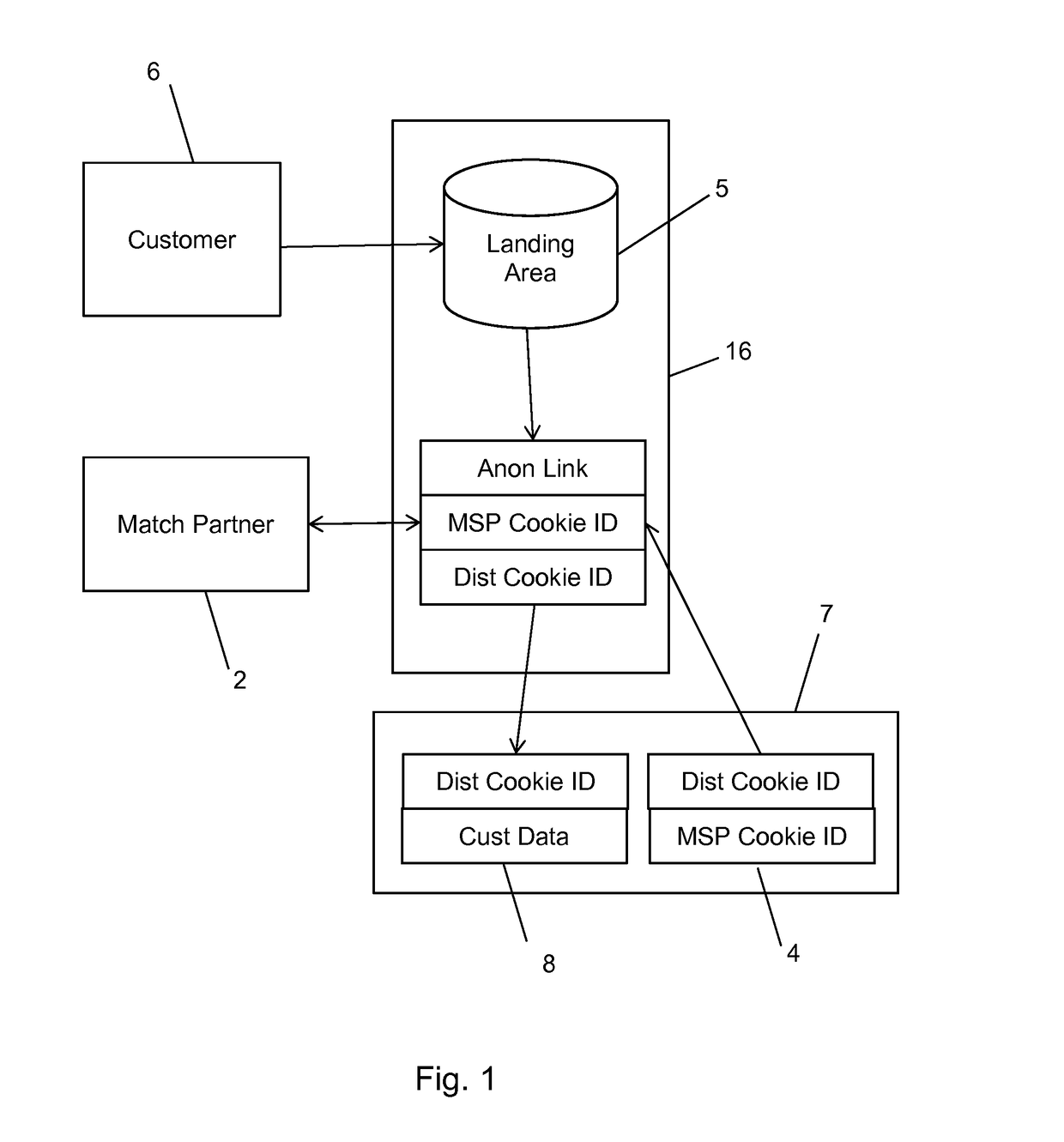
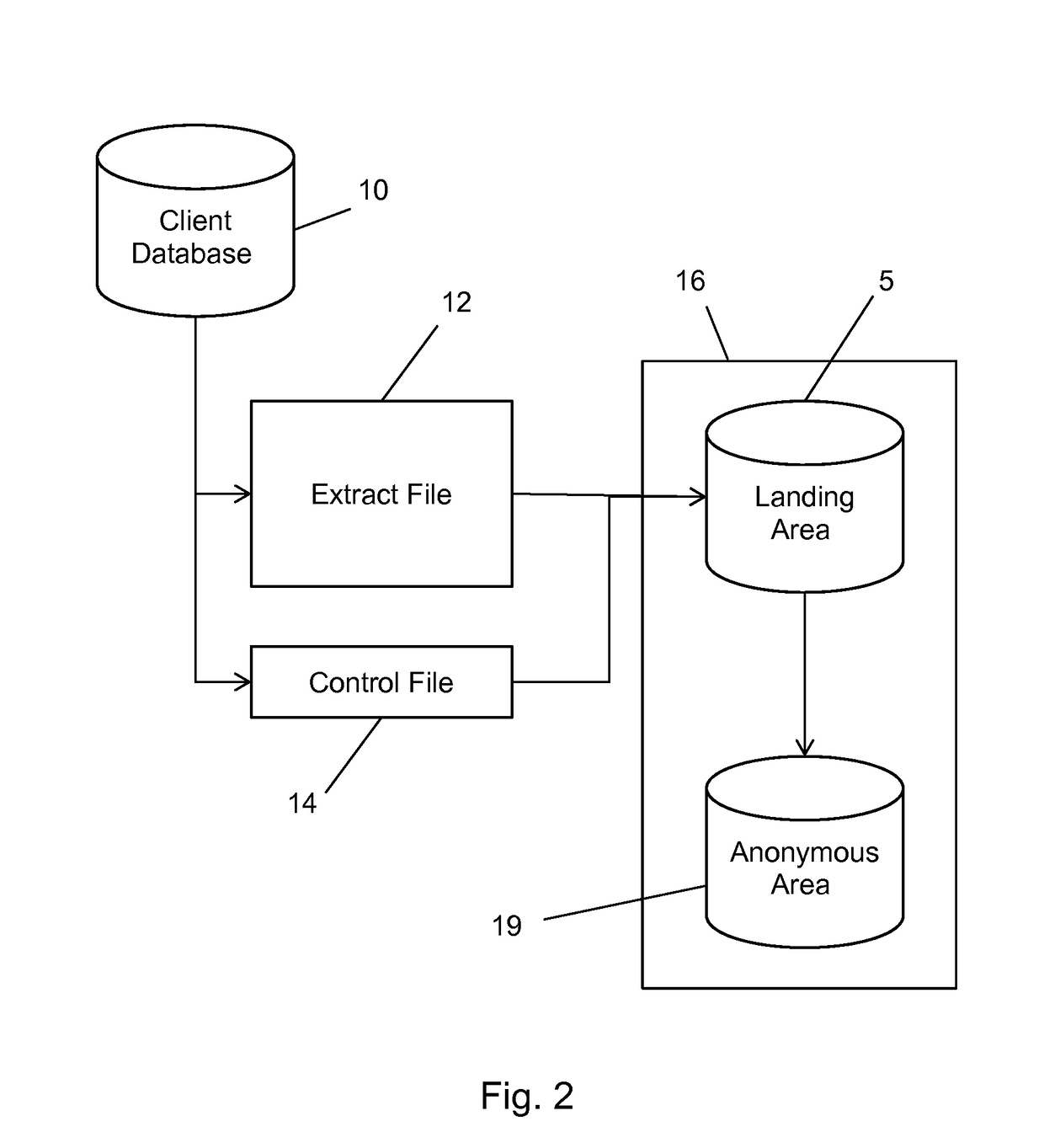
A method and system for bringing together online and offline advertising uses anonymous links that are associated with consumer data. The anonymous links allow processing without personally identifiable information (PII) in a secure environment. Data is matched using the anonymous links, and further using identifiers that are encrypted for use in connection with individual match distribution partners. The method and system allows a marketer to utilize offline data to precisely target advertisements without the use of PII, and to perform analytics concerning the use of the online advertisements to more precisely determine the effectiveness of multichannel marketing efforts.
Owner:LIVERAMP
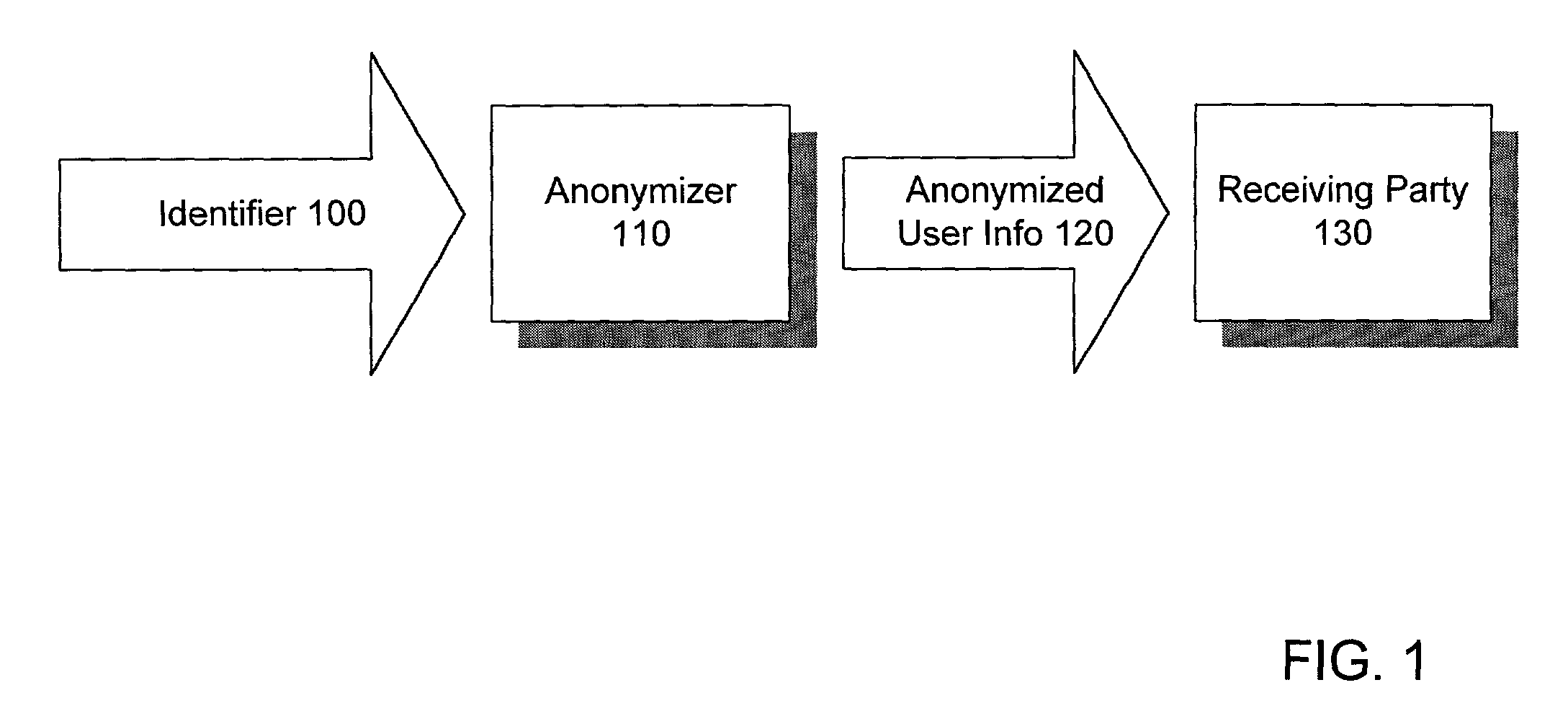
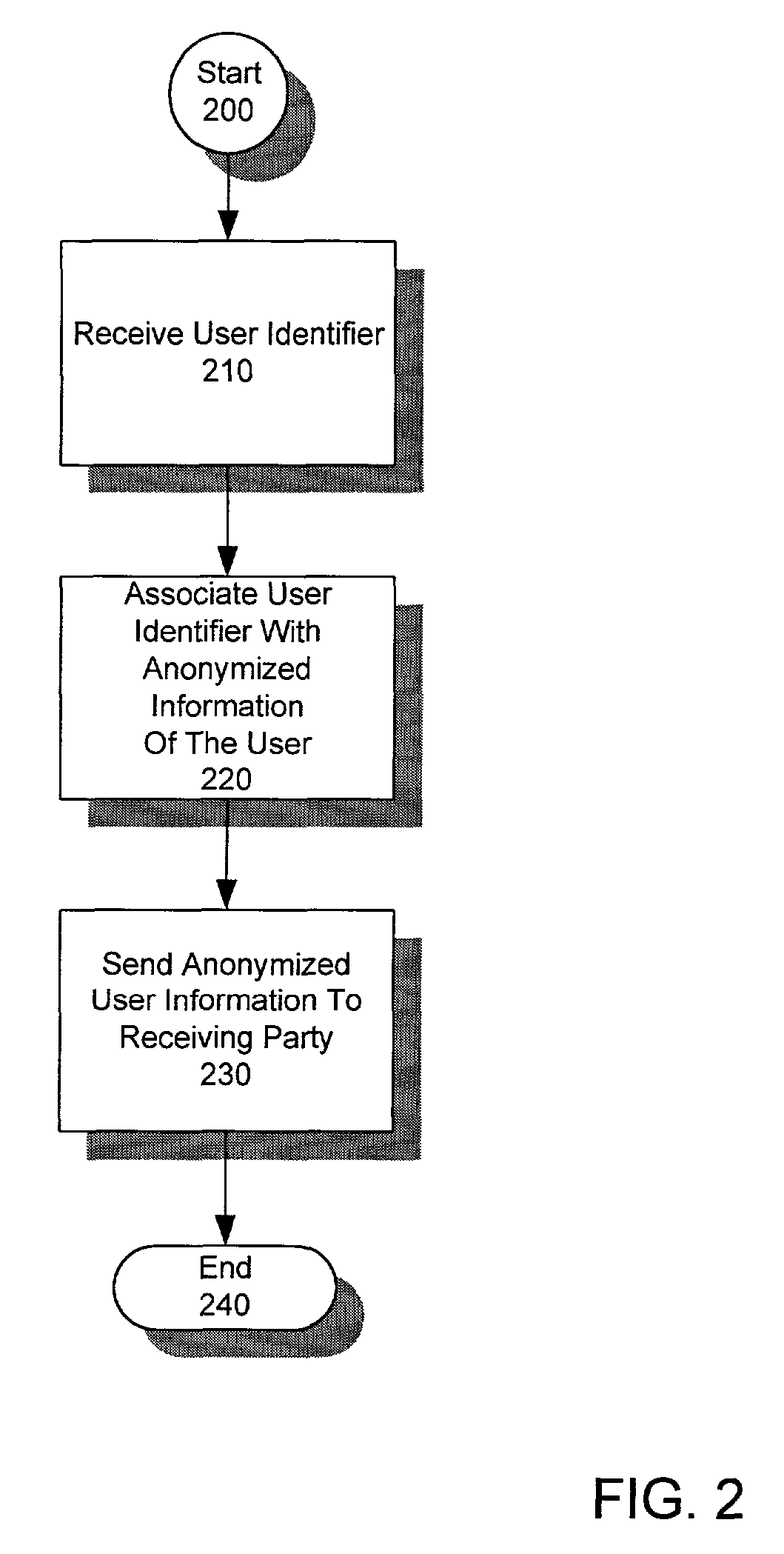
Method and system for sharing anonymous user information
ActiveUS7930252B2Enhanced anonymityIncreased ad rateComputer security arrangementsMultiple digital computer combinationsInternet privacyData source
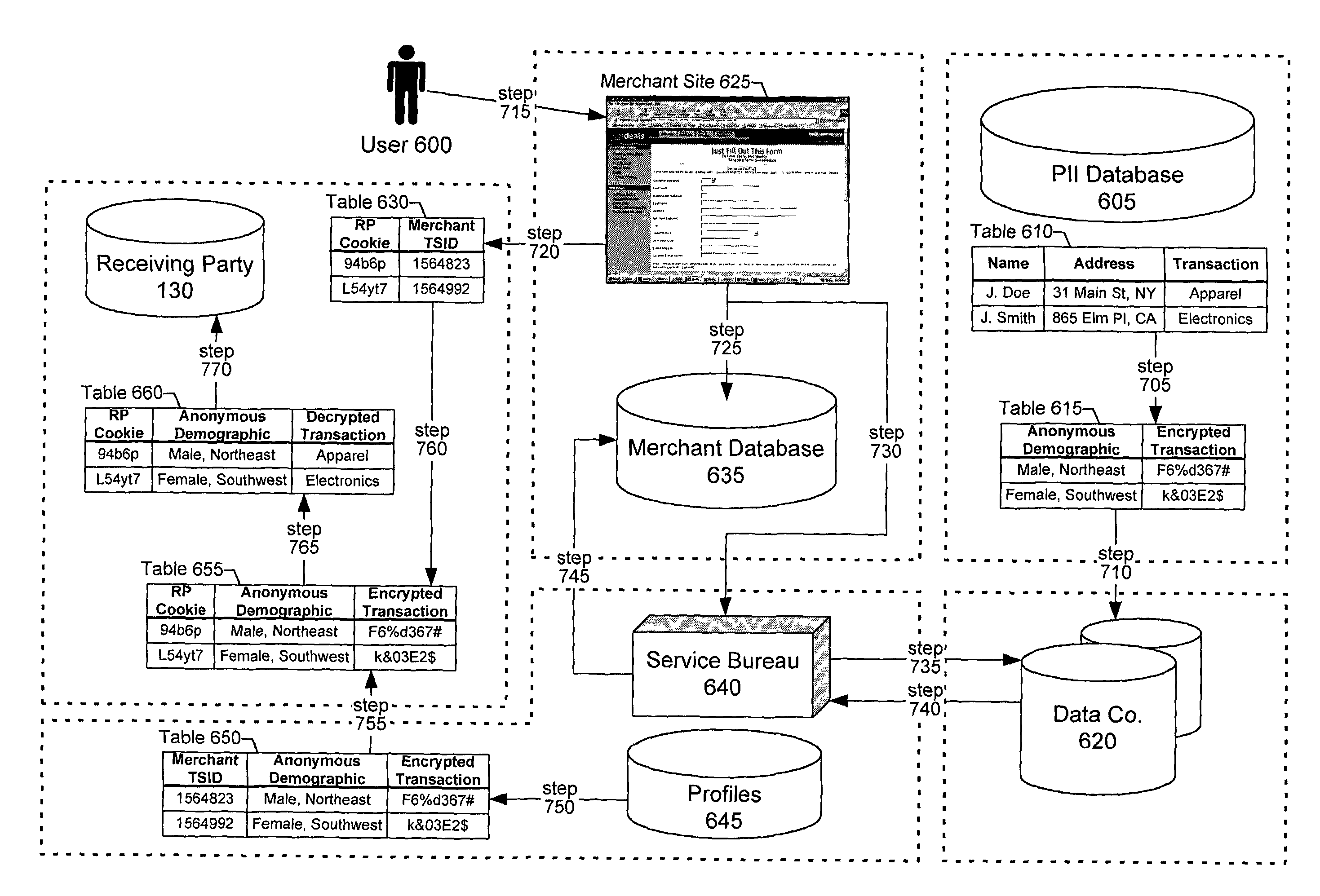
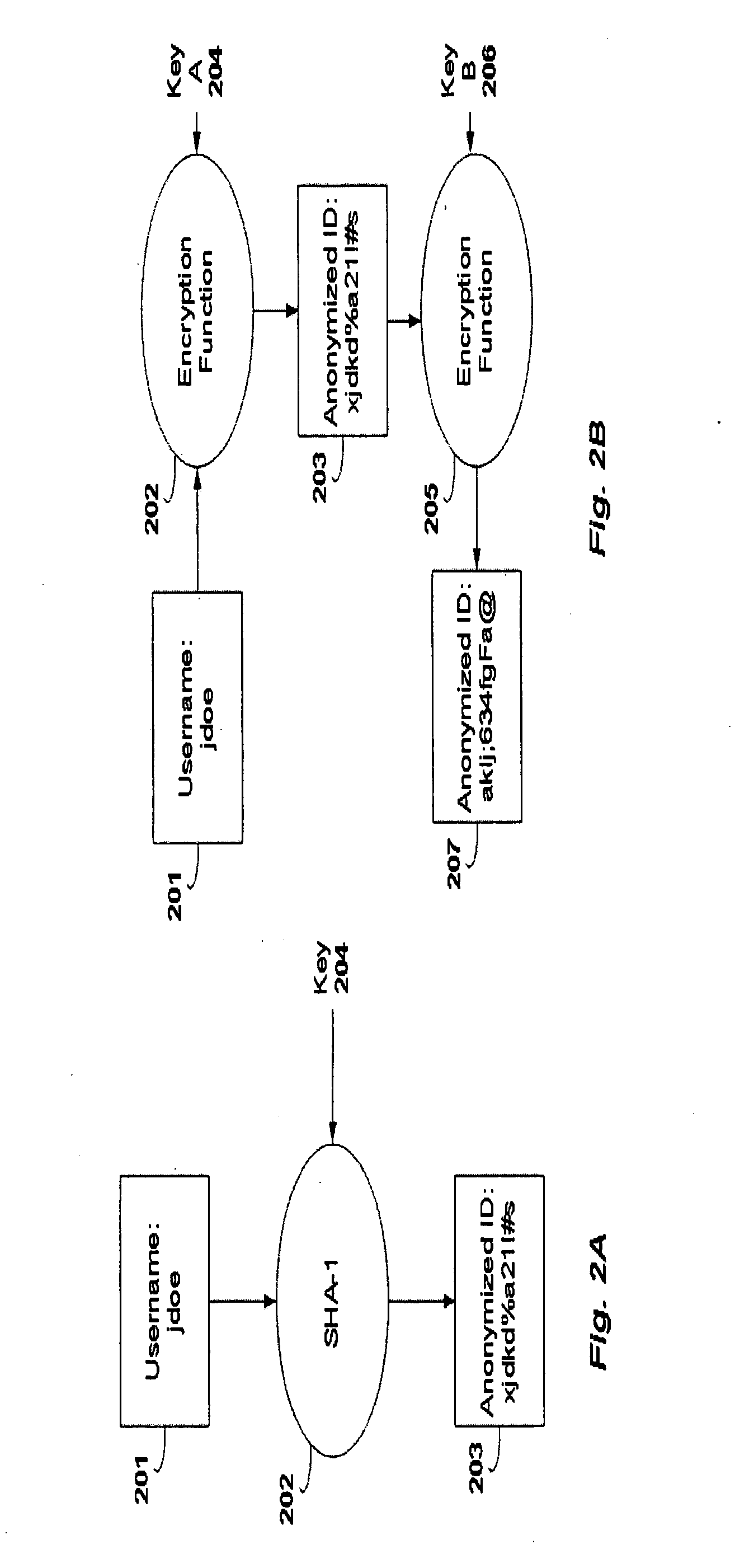
A method and system for sharing online user information in an anonymous manner. The system associates an identifier with anonymized information of the user, and sends the anonymized user information to a receiving party.In one embodiment, the system receives a temporary id with personally identifiable information from a Web site, uses the personally identifiable information as a key to obtain the anonymized information from a data source, and sends the temporary id with the anonymized information to the receiving party. The receiving party uses the temporary id, previously received by the Web site, as a key to obtain the anonymized information of the user.In another embodiment, the system receives a temporary id from a Web site with a cookie from the user, uses the cookie as a key to obtain the anonymized information from a data source, and sends the temporary id with the anonymized information to the receiving party. The receiving party uses the temporary id, previously received by the Web site, as a key to obtain the anonymized information of the user.
Owner:GOOGLE LLC
Proxy authentication network
InactiveUS8028329B2Digital data processing detailsMultiple digital computer combinationsThird partyData storing
A Proxy Authentication Network includes a server that stores credentials for subscribers, along with combinations of devices and locations from which individual subscribers want to be authenticated. Data is stored in storage: the storage can be selected by the subscriber. The data stored in the storage, which can be personally identifiable information, can be stored in an encrypted form. The key used to encrypt such data can be divided between the storage and server. In addition, third parties can store portions of the encrypting key. Subscribers can be authenticated using their credentials from recognized device / location combinations; out-of-band authentication supports authenticating subscribers from other locations. Once authenticated, a party can request that the encrypted data be released. The portions of the key are then assembled at the storage. The storage then decrypts the data, generates a new key, and re-encrypts the data for transmission to the requester.
Owner:IAMSECUREONLINE
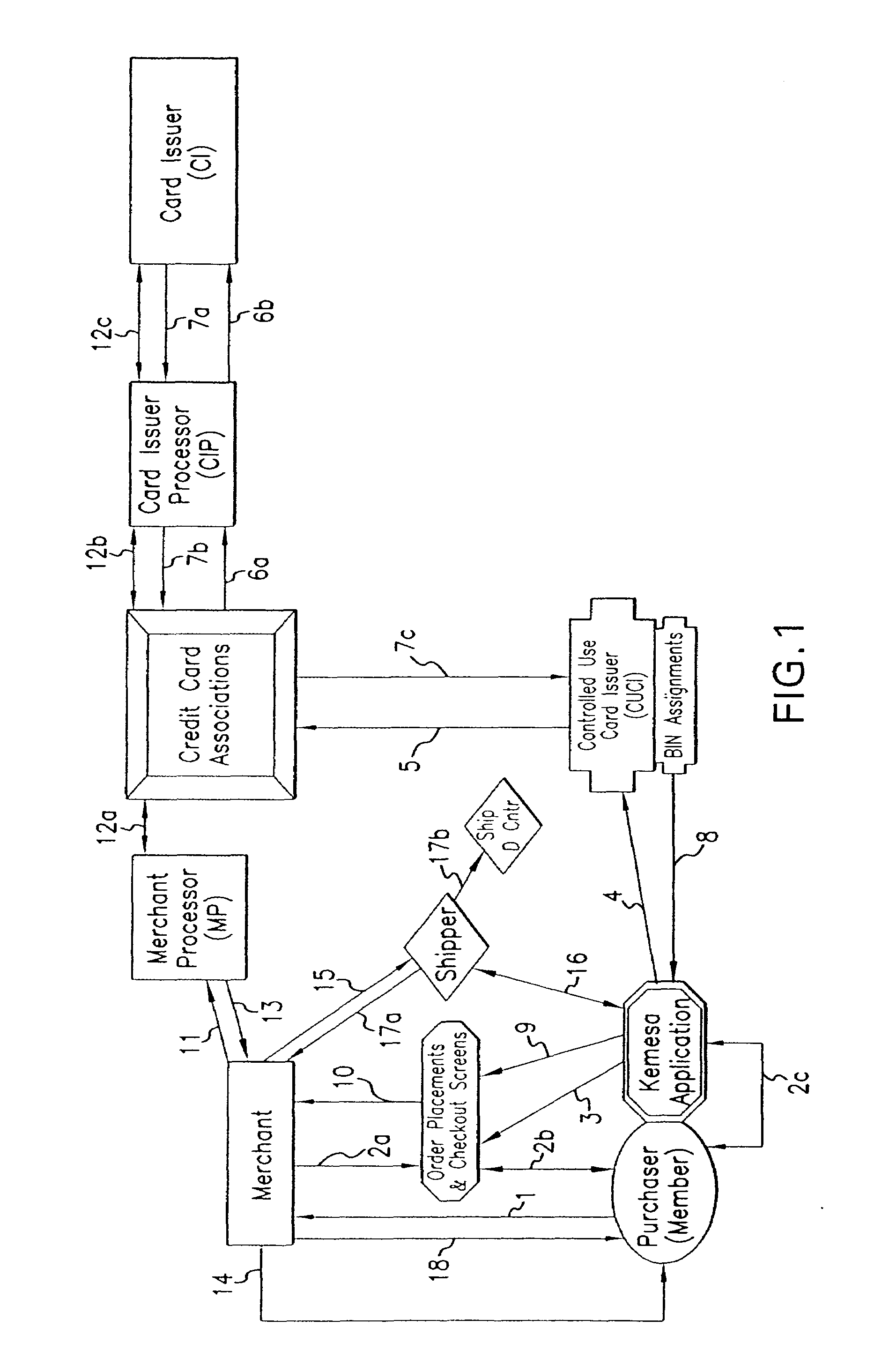
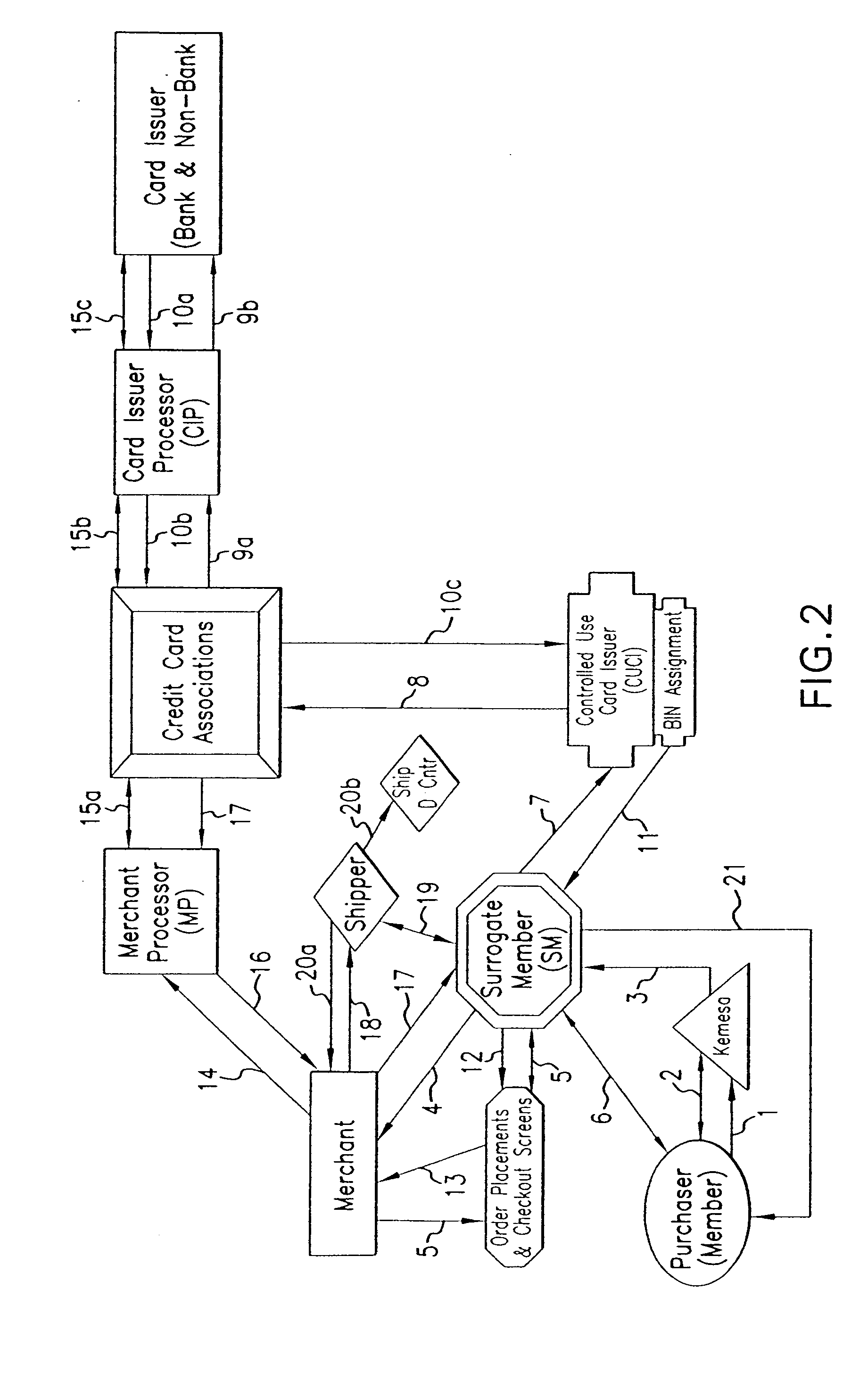
Identity Theft and Fraud Protection System and Method
A system and method for preventing personal identity theft when making online and offline purchases requires a Purchaser to first subscribe and become a Member user by registering, providing relevant personal identity information, and establishing two-way multi-factor authentication information for security purposes. The subscribing Member provides relevant information to any one or more financial sources (e.g. credit card accounts, bank accounts) that will be used to fund subsequent purchase transactions. Once registered, the Member is assigned a user name and a password. The subscribing Member's personal identity information is then encrypted and stored at one or more highly secure locations. The ID protection system obtains a controlled use card (CUC) through a CUC issuer on behalf of the Member for use in making each purchase transaction. The CUC is anonymous with respect to user (Member) identity and may be a purchase-specific single-use card or a multi-purpose card with no traceable connection to any other financial account. The CUC is funded by the Member's one or more financial sources, as selected by the Member. When the Member makes a secure purchase, the Merchant is presented with anonymous information (i.e. not revealing the Member's real name, email address, billing information, etc.), except in instances where the Member's real identity information is required (e.g. airline tickets). The Merchant obtains credit approval and sends the shipping information to a shipper which independently obtains the correct shipping name and address from the ID protection system prior to shipping the purchased product(s) to the ultimate destination selected by the purchasing Member.
Owner:AURA SUB LLC +1
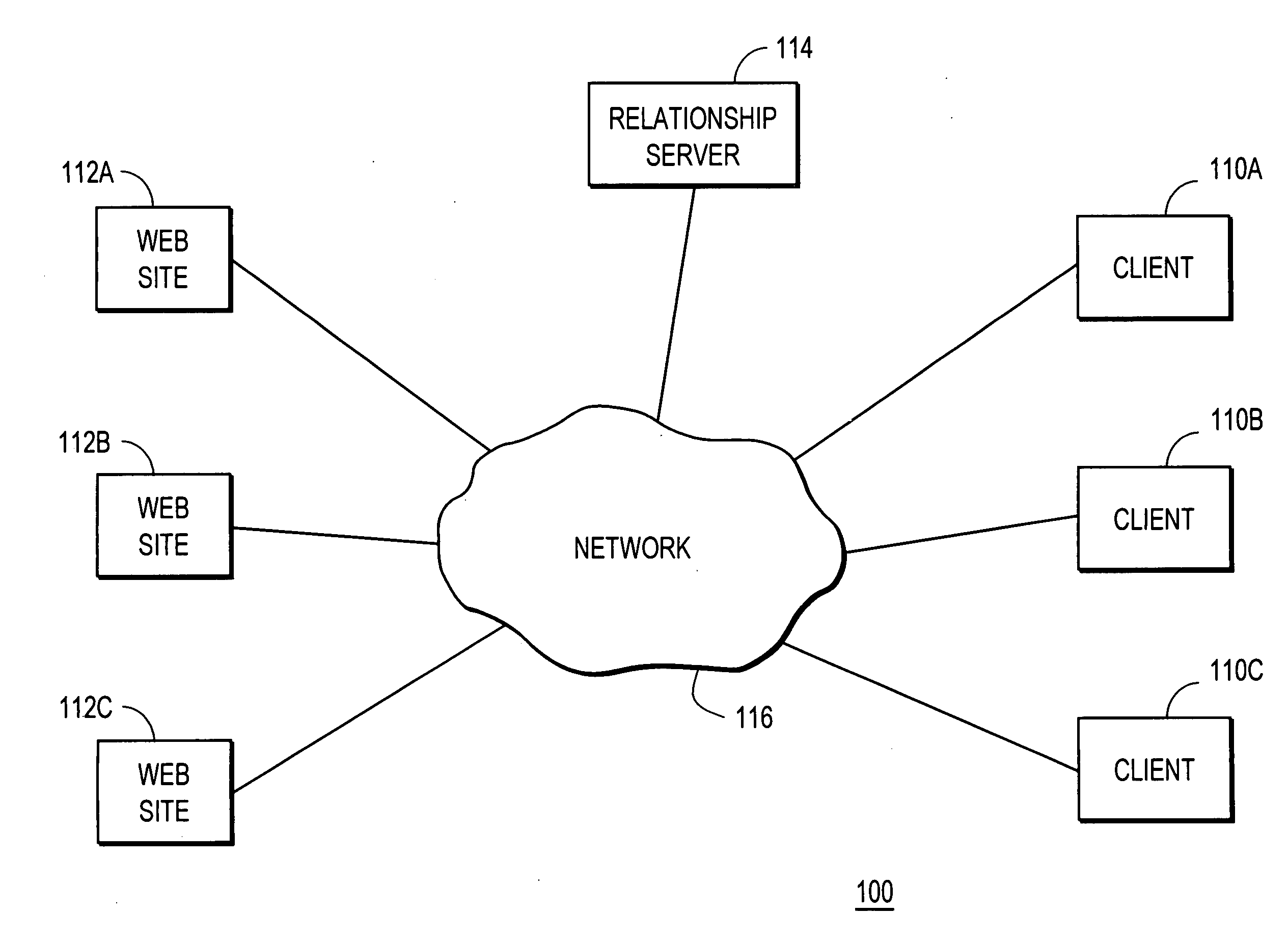
Using cross-site relationships to generate recommendations
A relationship server tracks end-user interactions across multiple web sites and generates recommendations. The web sites observe relationships established by end-user interactions. If end-users provide the same personally identifiable information to multiple web sites, the sites generate the same unique identifier for those end-users. The web sites send messages to the relationship server that reference the end-users using the identifiers and describe the relationships observed for the end-users. The relationship server receives messages from multiple web sites and canonicalizes them to produce an efficient representation of the relationships. Upon receiving a message requesting a recommendation based on an item, the relationship server performs collaborative filtering using the relationship data to identify a list of items to recommend. The relationship server sends the recommendations to the requesting entity and the recommendations are presented to the end-user.
Owner:AGGREGATE KNOWLEDGE LLC
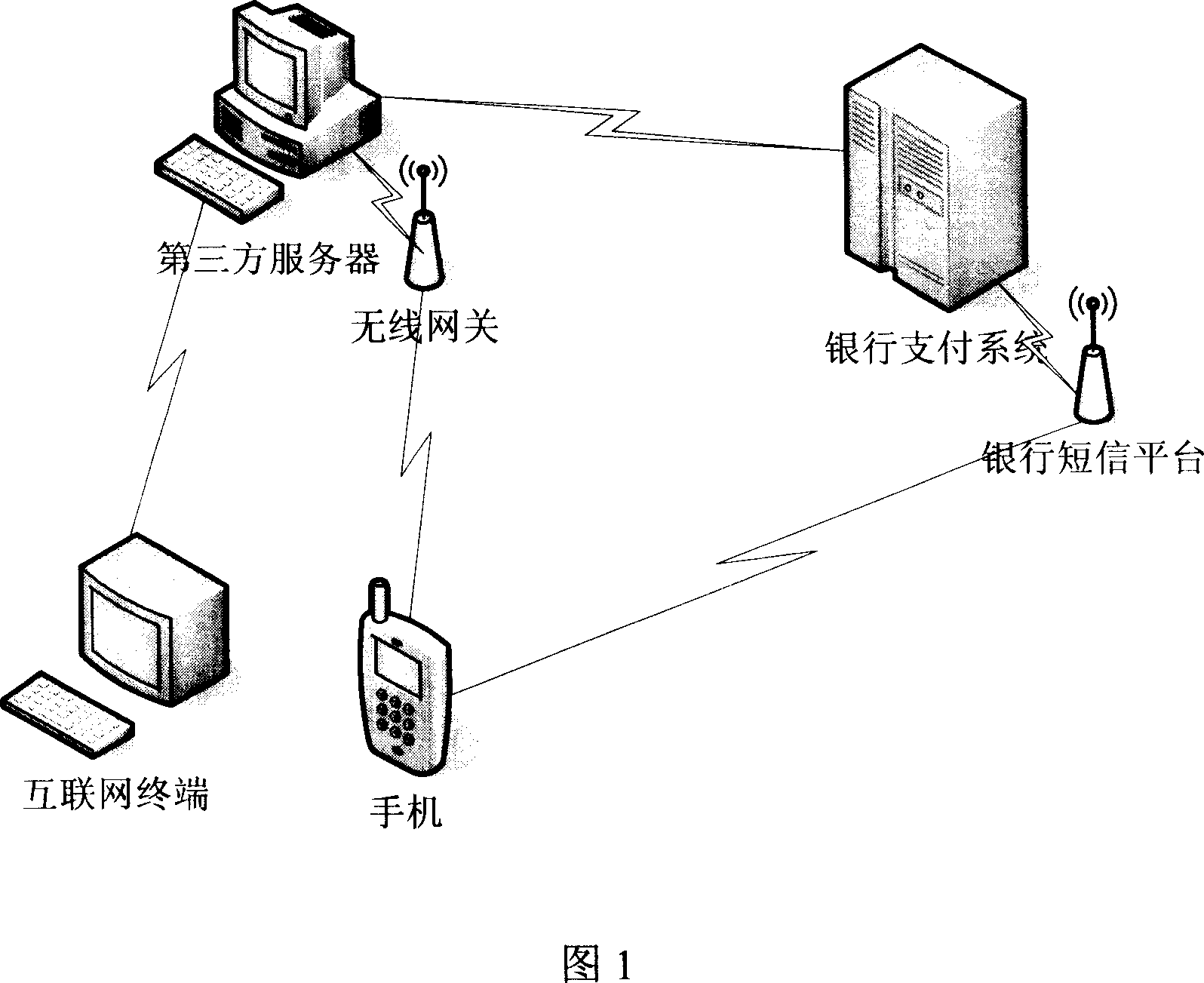
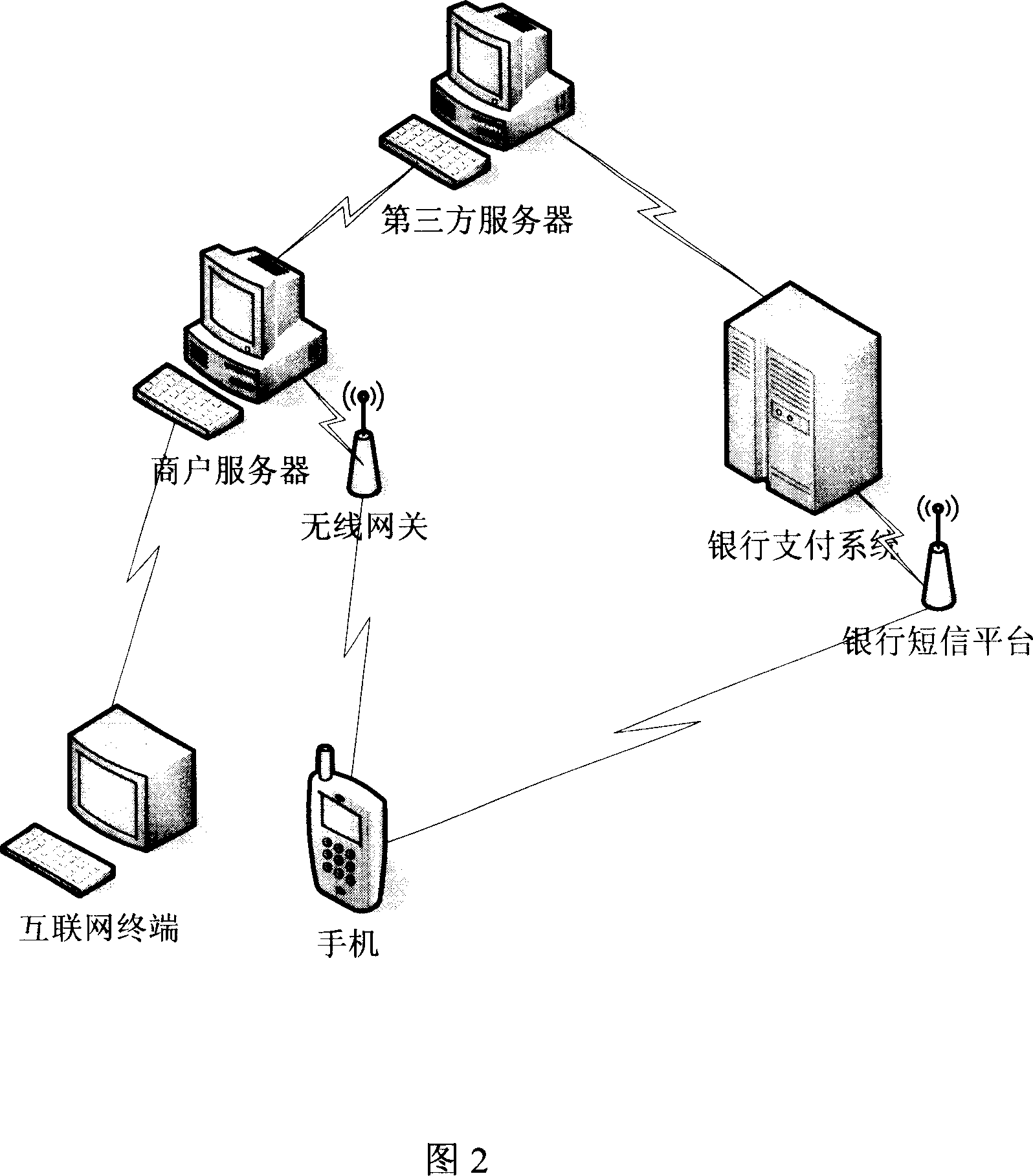
Method for safety verifying financial business information in electronic business
InactiveCN101051372AEliminate financial security concernsBroaden the fieldPayment protocolsCommerceThird partyBank account
The present invention relates to a method capable of making financial service information undergo the process of safety authentication in the electronic business. It is characterized by that it utilizes personal identity information stored and transferred to bank payment system by third party server and combines said personal identity information with user handset short-mail authorization and acknowledgement to implement safety authentication of bank payment service. Besides, said invention also provides the concrete steps of said method.
Owner:BEIJING YIFUJINCHUAN TECH
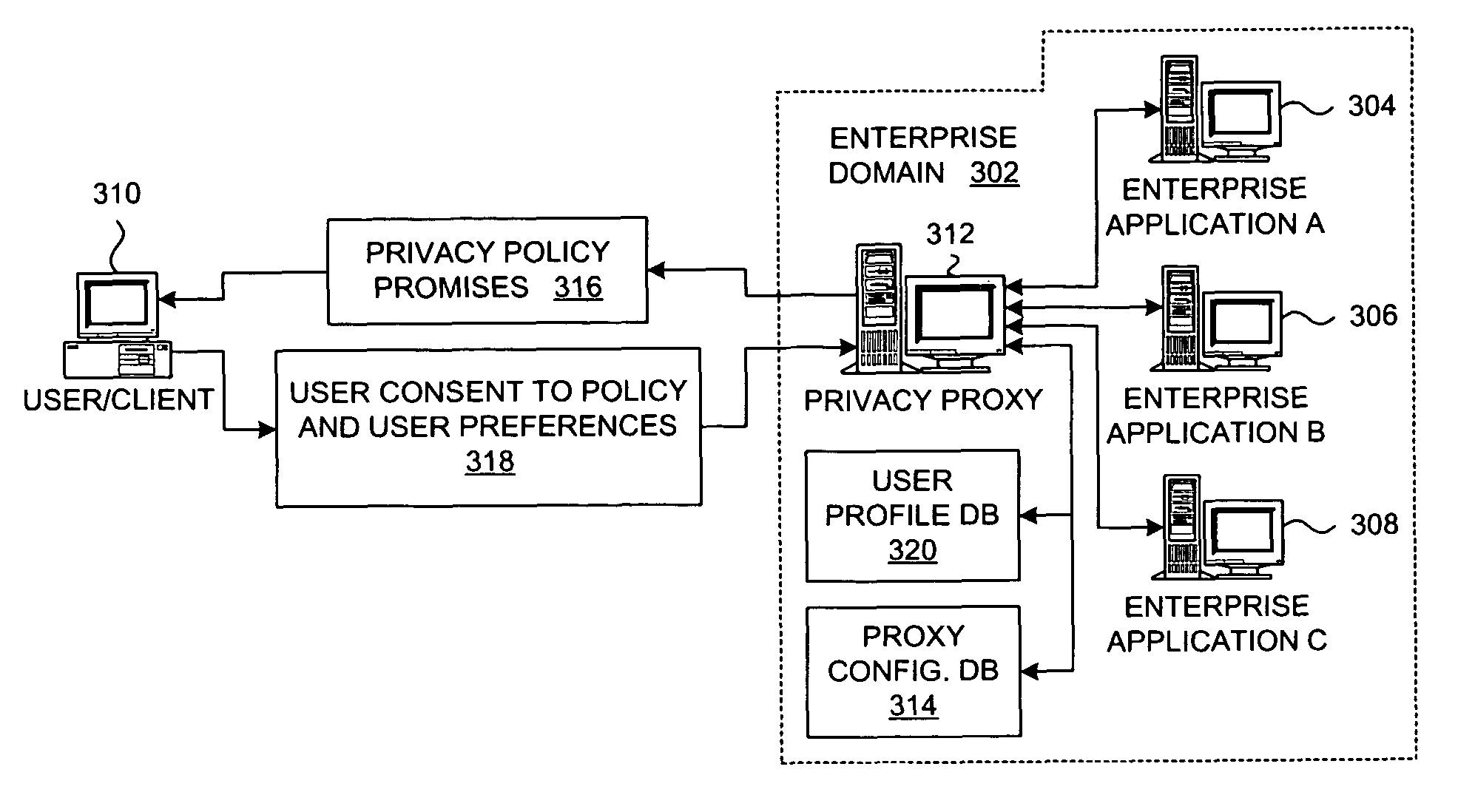
Method and system for implementing privacy policy enforcement with a privacy proxy
InactiveUS20060136985A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyUser privacy
A method is presented for enforcing a privacy policy concerning management of personally identifiable information in a centralized manner through a privacy proxy agent. A proxy intercepts a message from a first system to a second system, e.g., from a server to a client, and determines whether the message is associated with an operation on personally identifiable information; if not, then the proxy sends the message to the second system, but if so, then the proxy determines whether the operation on the personally identifiable information is compliant with a privacy policy and with user preference information with respect to the privacy policy for a user who is associated the personally identifiable information. If the message is compliant with the privacy policy and user preference data, then the proxy sends the first message to the second system; otherwise, an error indication is returned to the first system.
Owner:LINKEDIN
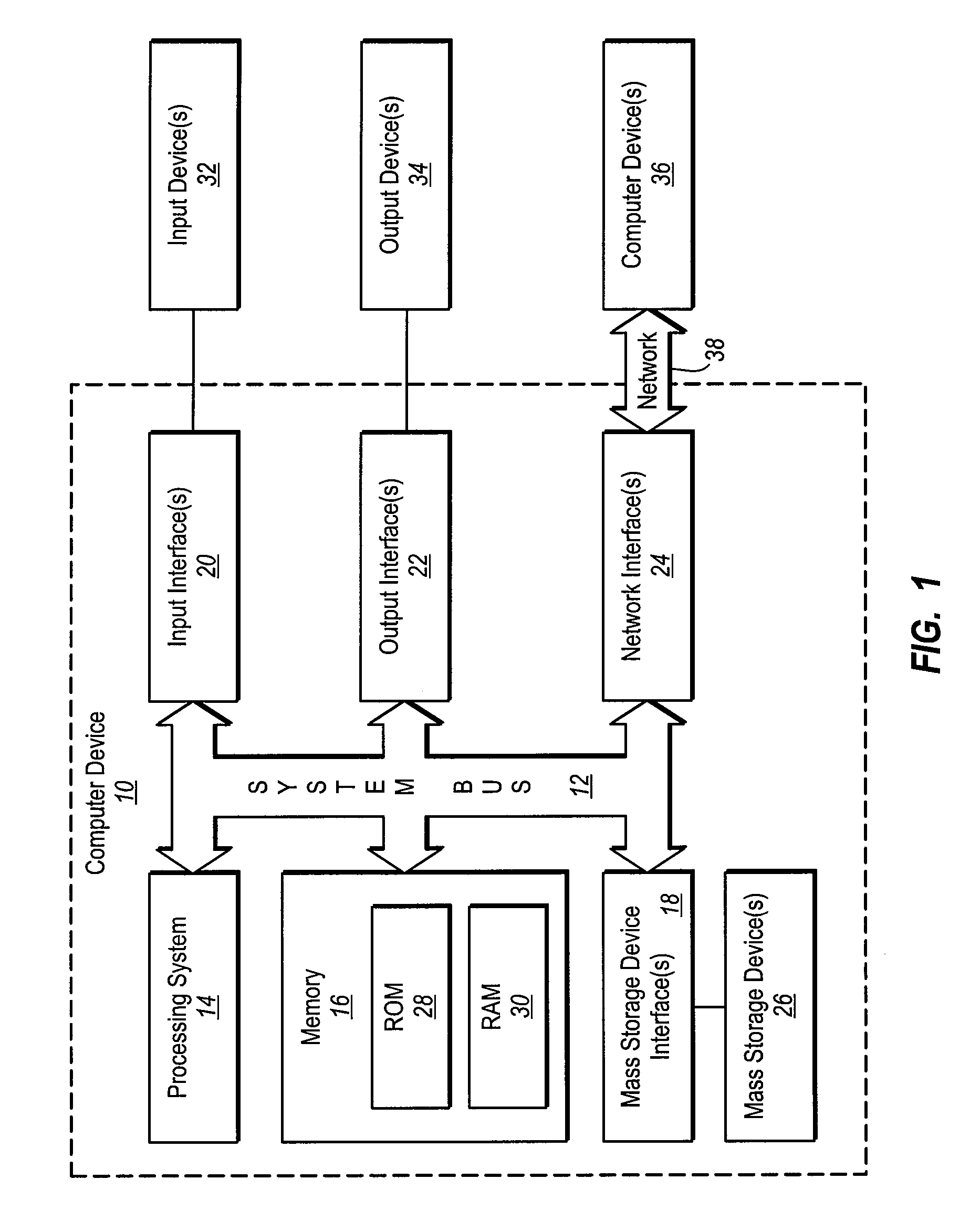
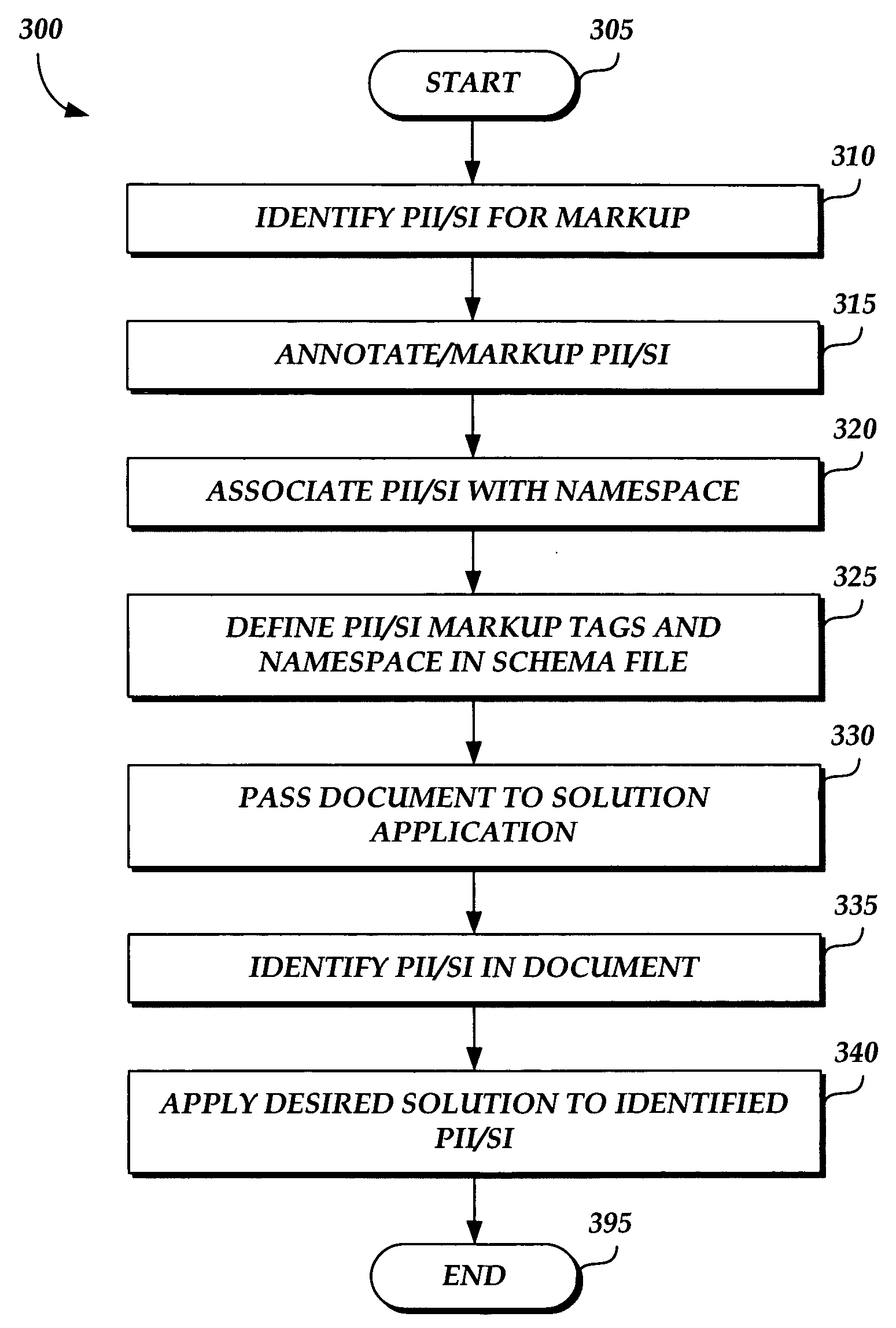
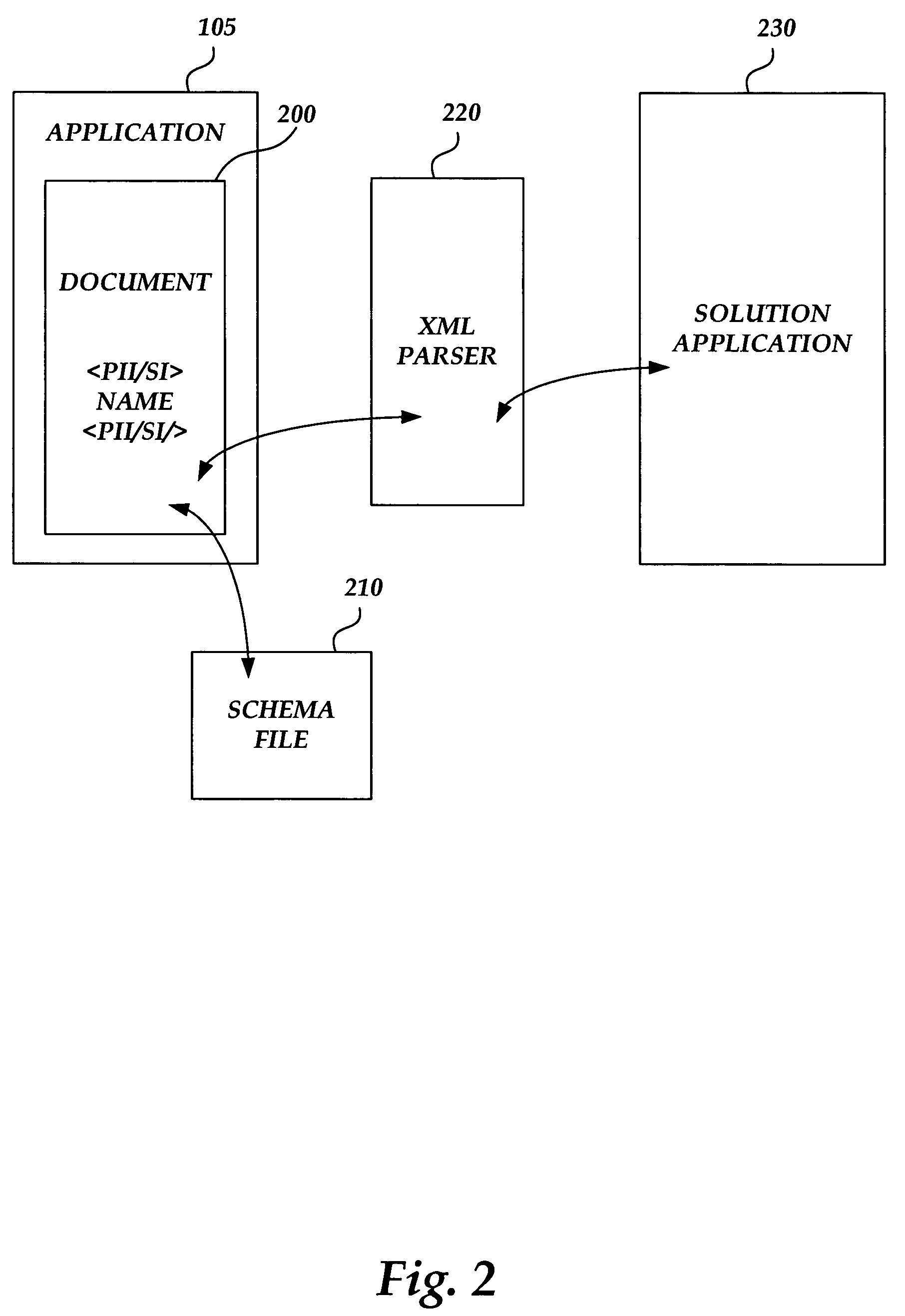
Method and system for managing personally identifiable information and sensitive information in an application-independent manner
InactiveUS20060143459A1User identity/authority verificationComputer security arrangementsXML namespacePaper document
Methods and systems are provided for managing personally identifiable and / or sensitive information (PII / SI) in a manner that is independent of a software application that is used for creating or editing a document containing the PII / SI. PII / SI in a document is marked or flagged in an application-independent manner so that a solution application programmed to discover and process marked PII / SI may readily discover the marked information for redacting the information, editing the information, or otherwise disposing of the information as desired. PII / SI in documents may be annotated according to the Extensible Markup Language (XML). A separate XML namespace may be used to distinguish the annotated PII / SI from other content in the document. An application-independent solution may be built for scanning a given document for all annotated information belonging to the namespace associated with the PII / SI. Once the annotated information is located in a given document, it may be redacted, edited, or otherwise processed or disposed of as desired.
Owner:MICROSOFT TECH LICENSING LLC
Proxy authentication network
InactiveUS20110289314A1User identity/authority verificationMultiple digital computer combinationsThird partyInternet privacy
A Proxy Authentication Network includes a server that stores credentials for subscribers, along with combinations of devices and locations from which individual subscribers want to be authenticated. Data is stored in storage: the storage can be selected by the subscriber. The data stored in the storage, which can be personally identifiable information, can be stored in an encrypted form. The key used to encrypt such data can be divided between the storage and server. In addition, third parties can store portions of the encrypting key. Subscribers can be authenticated using their credentials from recognized device / location combinations; out-of-band authentication supports authenticating subscribers from other locations. Once authenticated, a party can request that the encrypted data be released. The portions of the key are then assembled at the storage. The storage then decrypts the data, generates a new key, and re-encrypts the data for transmission to the requester.
Owner:IAMSECUREONLINE
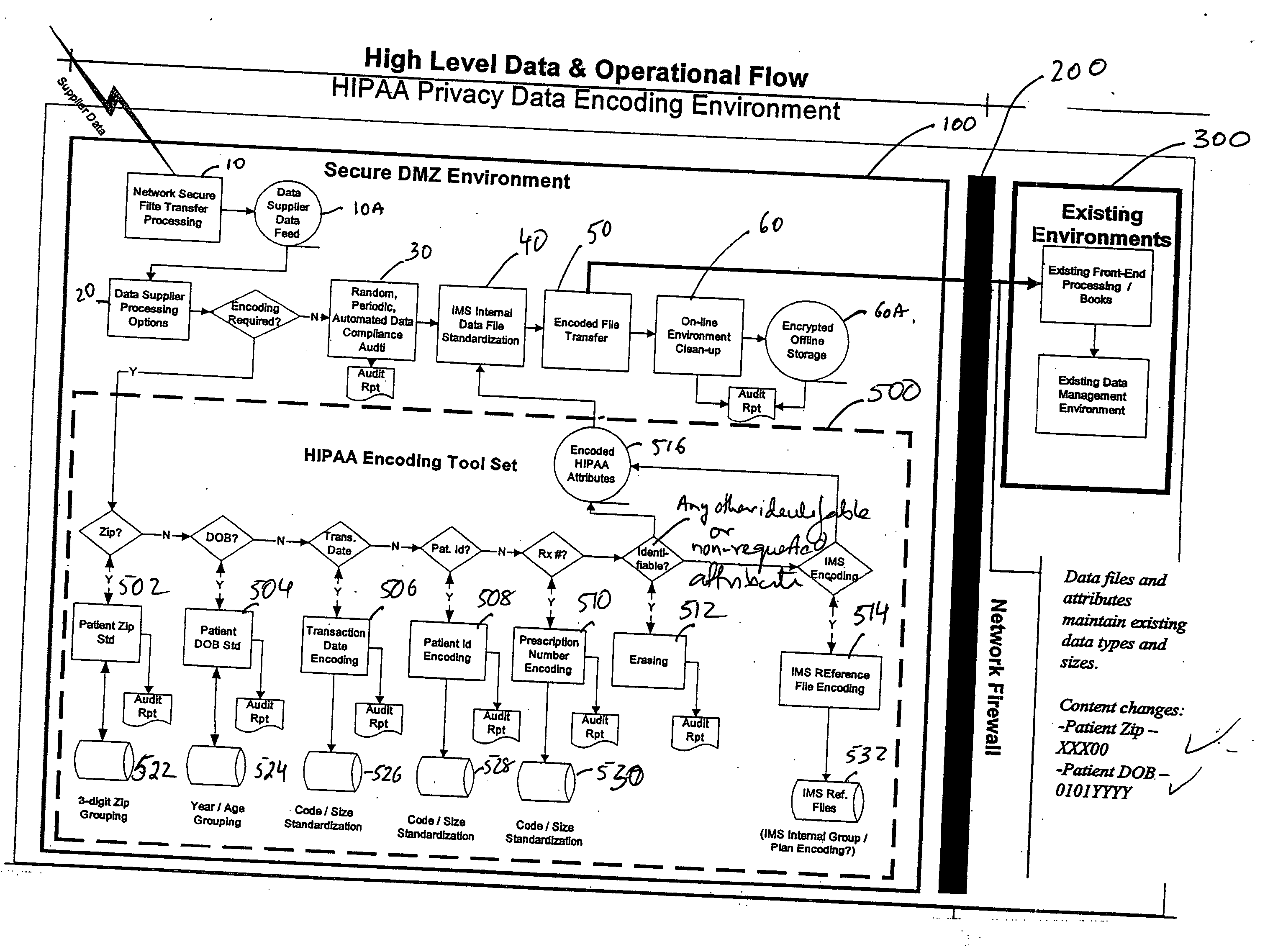
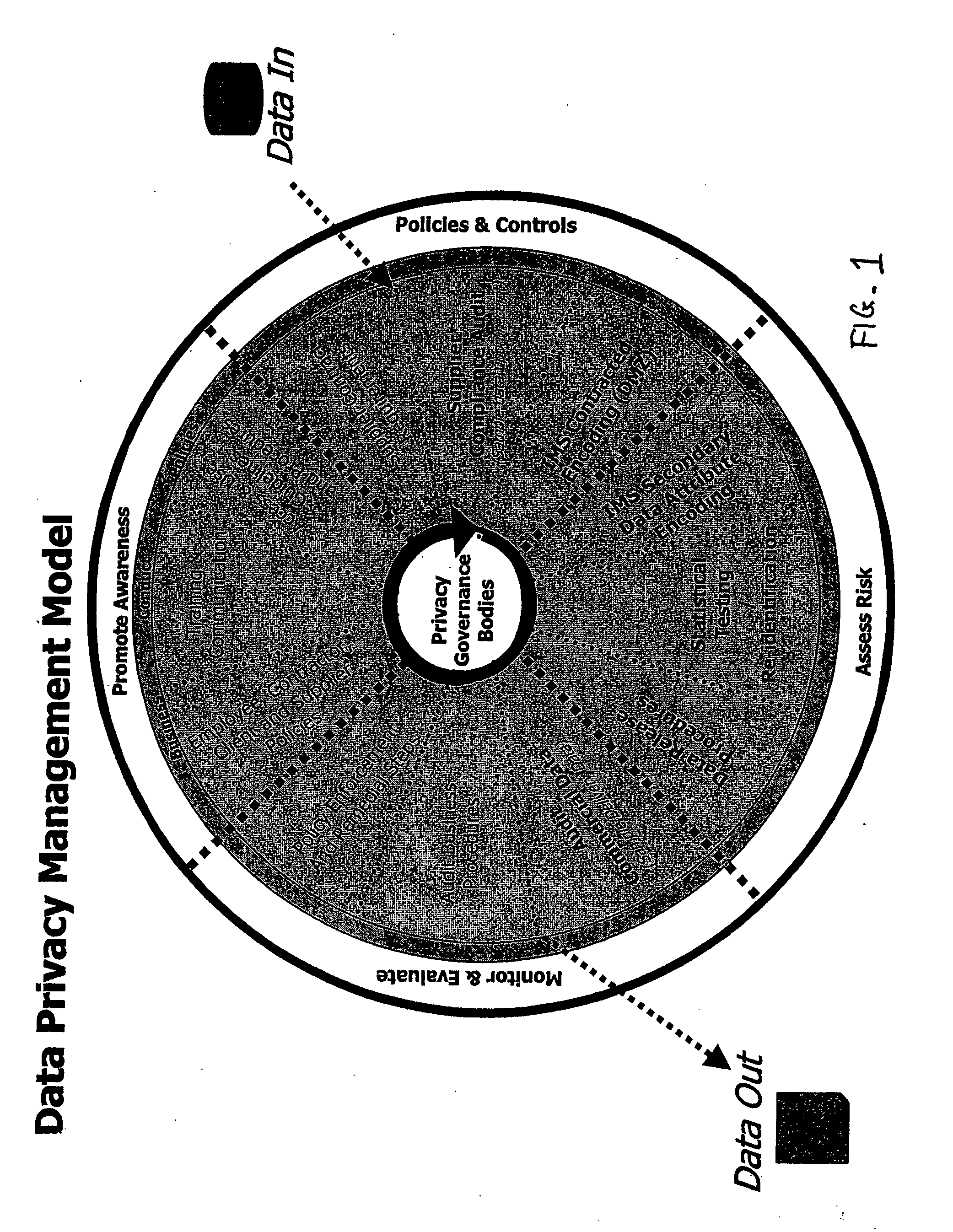
Data privacy management systems and methods
InactiveUS20050065824A1Ensure compliancePatient personal data managementOffice automationInternet privacyManagement process
Owner:IMS SOFTWARE SERVICES
Multi-tier transaction processing method and payment system in m- and e- commerce
A server executes a protocol that automates transactions involving a customer and a merchant agreeing to trade money in the customer's account for goods or services available from the merchant. The protocol protects personal identifying information of the customer from disclosure to the merchant, and protects all parties from repudiation of the specific transaction. The protocol defines a pre-authenticated form of the specific transaction; obtains authorization from the customer and the merchant to commit on their behalf to the pre-authenticated transaction; and obtains authorization from the bank to commit resources for settlement with the merchant. After obtaining authorizations, a transaction clearance code is generated completing a record of the pre-authenticated transaction for non-repudiation, for proof of a right to receive settlement from the third party and for proof of a right to receive the goods or services from the merchant.
Owner:AUTHERNATIVE INC
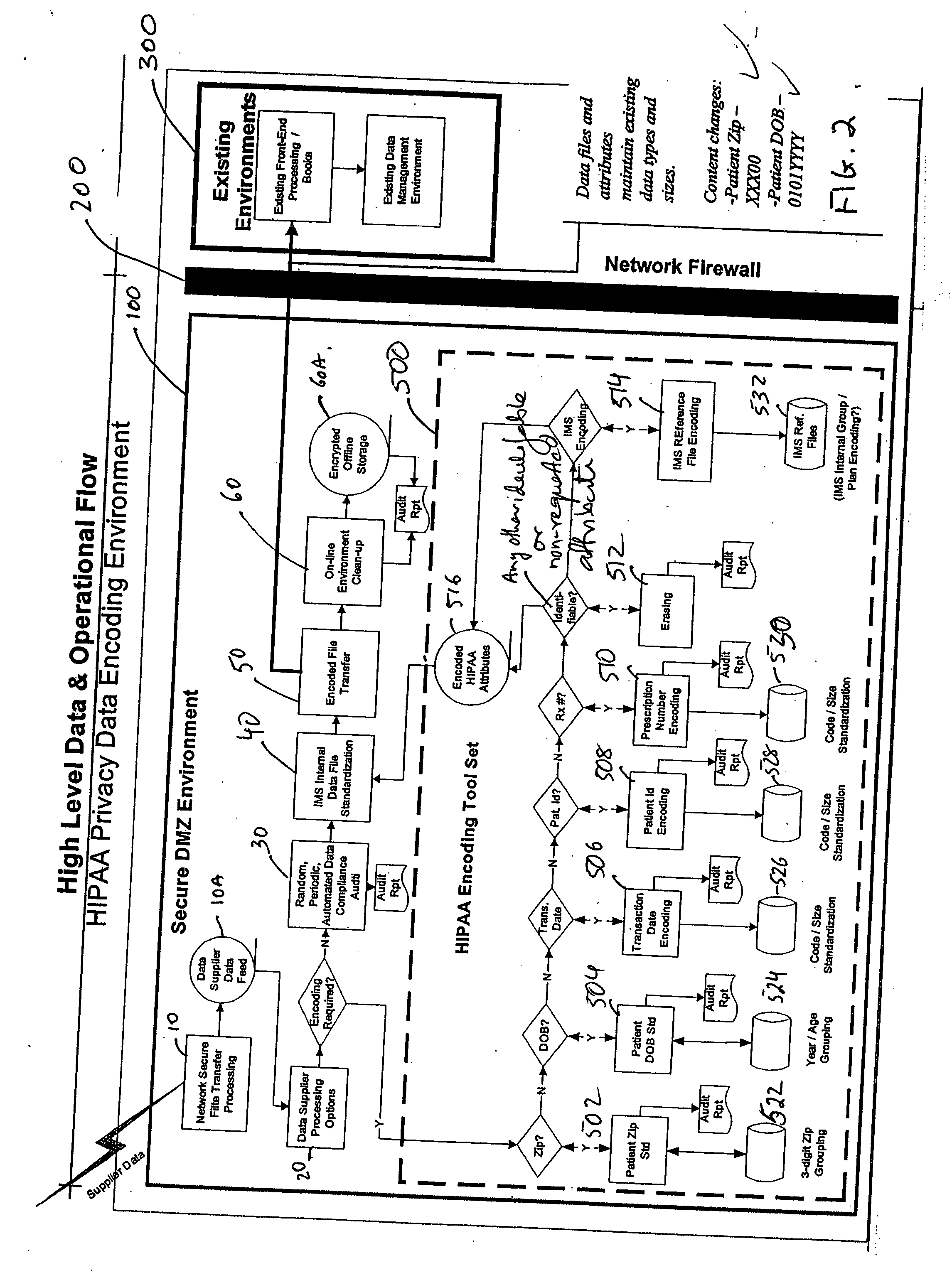
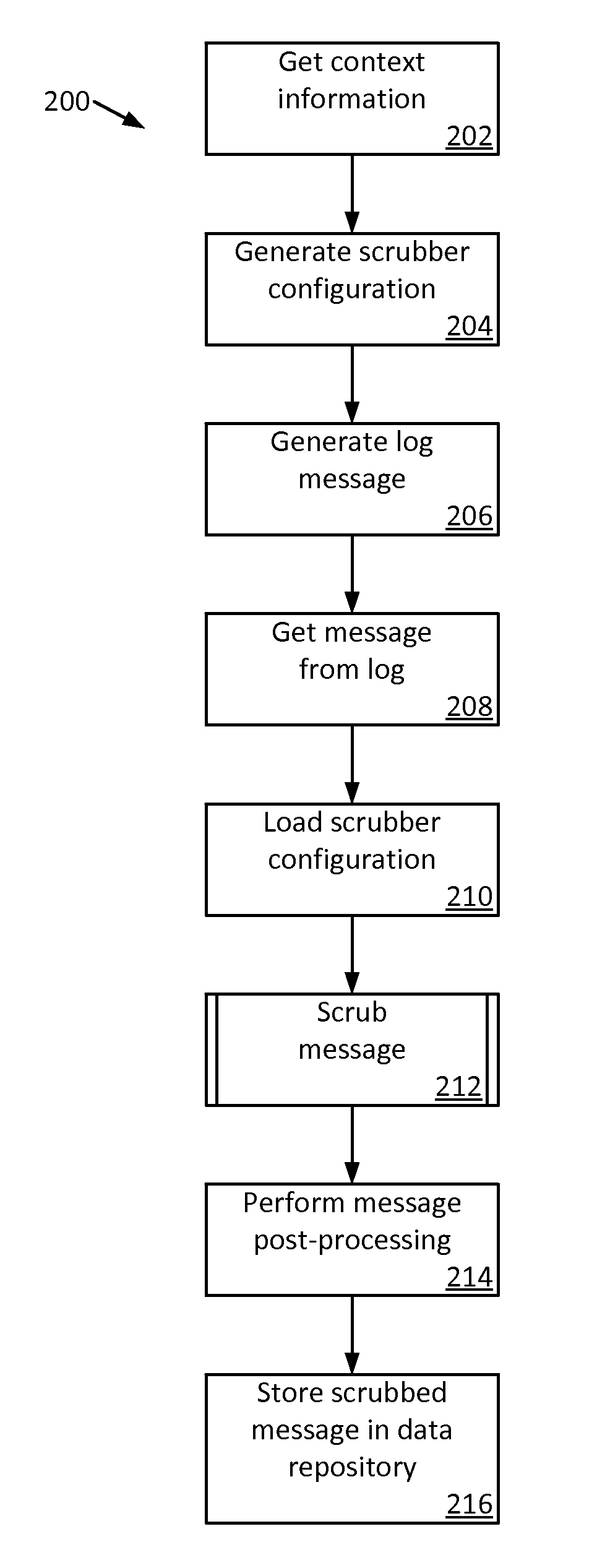
Scrubber to Remove Personally Identifiable Information
ActiveUS20150213288A1Quick and easy to createQuickly and easily and modifiedDigital data processing detailsAnalogue secracy/subscription systemsSurgical operationSurgical Scrubbing
A personally identifiable information (PII) scrubbing system. The PII scrubbing system surgically scrubs PII form a log based on a scrubber configuration corresponding to the log. The scrubber configuration includes context information about locations and types of PII in the log and rules specifying how to locate and protect the PII. Scrubber configurations are quickly and easily created or modified as scrubbing requirements change or new scenarios are encountered. The flexibility provided by the scrubber configurations allows only the PII to be scrubbed, even from unstructured data, without having to include surrounding data. Many consumers can use the scrubbed data without needed to expose the PII because less non-personal data is obscured. Surgical scrubbing also retains the usefulness of the underlying PII even while protecting the PII. Consumers can correlate the protected PII to locate specific information without having to expose additional PII.
Owner:MICROSOFT TECH LICENSING LLC
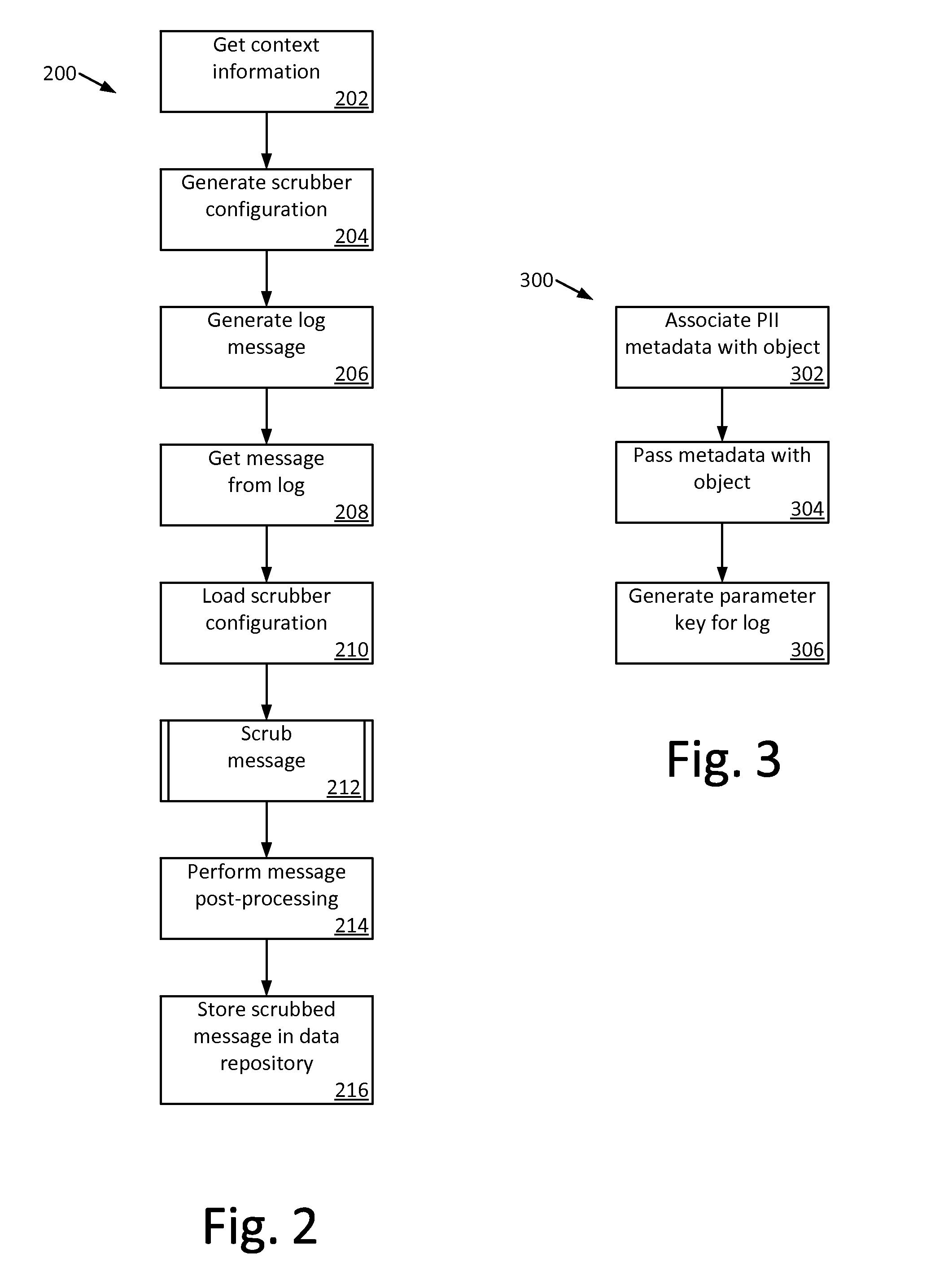
Method and system for protecting personally identifiable information
The present invention provides a way to protect PII (or, more generally, any user “sensitive” information) throughout its life cycle in an organization. The techniques described herein ensure that a user's PII is protecting during storage, access or transfer of the data. Preferably, this objective is accomplished by associating given metadata with a given piece of PII and then storing the PII and metadata in a “privacy protecting envelope.” The given metadata includes, without limitation, the privacy policy that applies to the PII, as well as a set of one more purpose usages for the PII that the system has collected from an end user's user agent (e.g., a web browser), preferably in an automated manner. Preferably, the PII data, the privacy policy, and the user preferences (the purpose usages) are formatted in a structured document, such as XML. The information in the XML document (as well as the document itself) is then protected against misuse during storage, access or transfer using one or more of the following techniques: encryption, digital signatures, and digital rights management.
Owner:IBM CORP
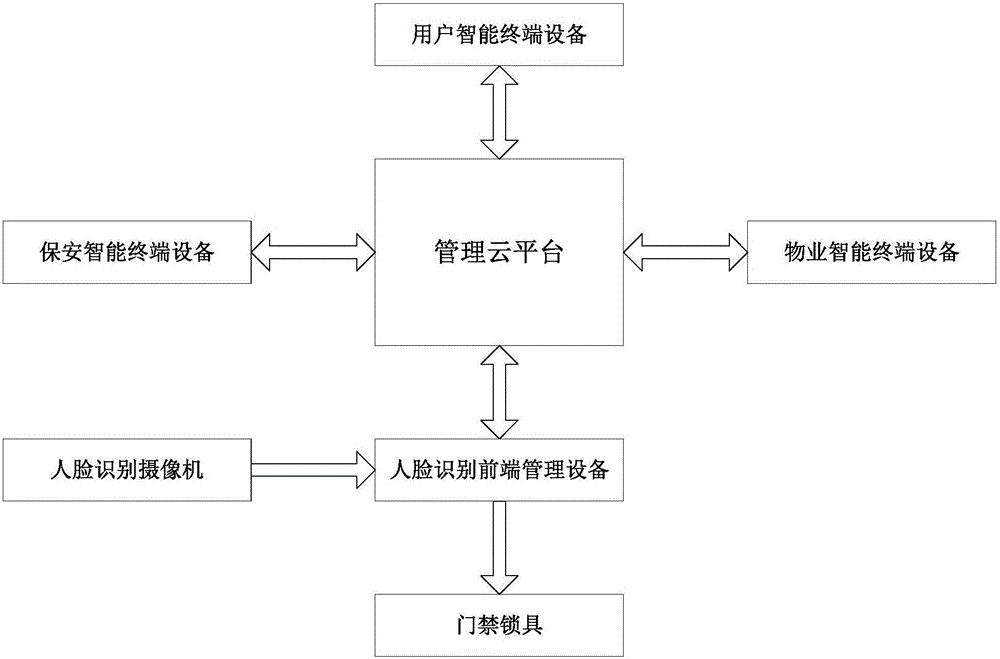
Access control cloud management system and method based on face recognition
ActiveCN105869248AHigh feasibilityImplement security managementCharacter and pattern recognitionIndividual entry/exit registersWorkloadPersonally identifiable information
The invention discloses an access control cloud management system and method based on face recognition. Through face recognition and a cloud technology thereof, a video real-time monitoring and alarming function is supplied to access control, integration of access control and video face recognition is achieved, and access control security and protection management is improved. According to the system and method, a user using threshold is low, operation is easy, the system and method can be used only by verifying personal identity information of a user, access control recognition is conducted by adopting face recognition, and therefore an access control system can easily, conveniently, rapidly and comprehensively record personnel entering and leaving information; entering and leaving of a person with the face which cannot be recognized can be forbidden, or alarming is conducted; entering and leaving information of a visitor also can be quickly generated and recorded, the security management effect can be effectively improved, and the workload of security personnel can be reduced.
Owner:CHENGDU QIANFAN TECH DEV
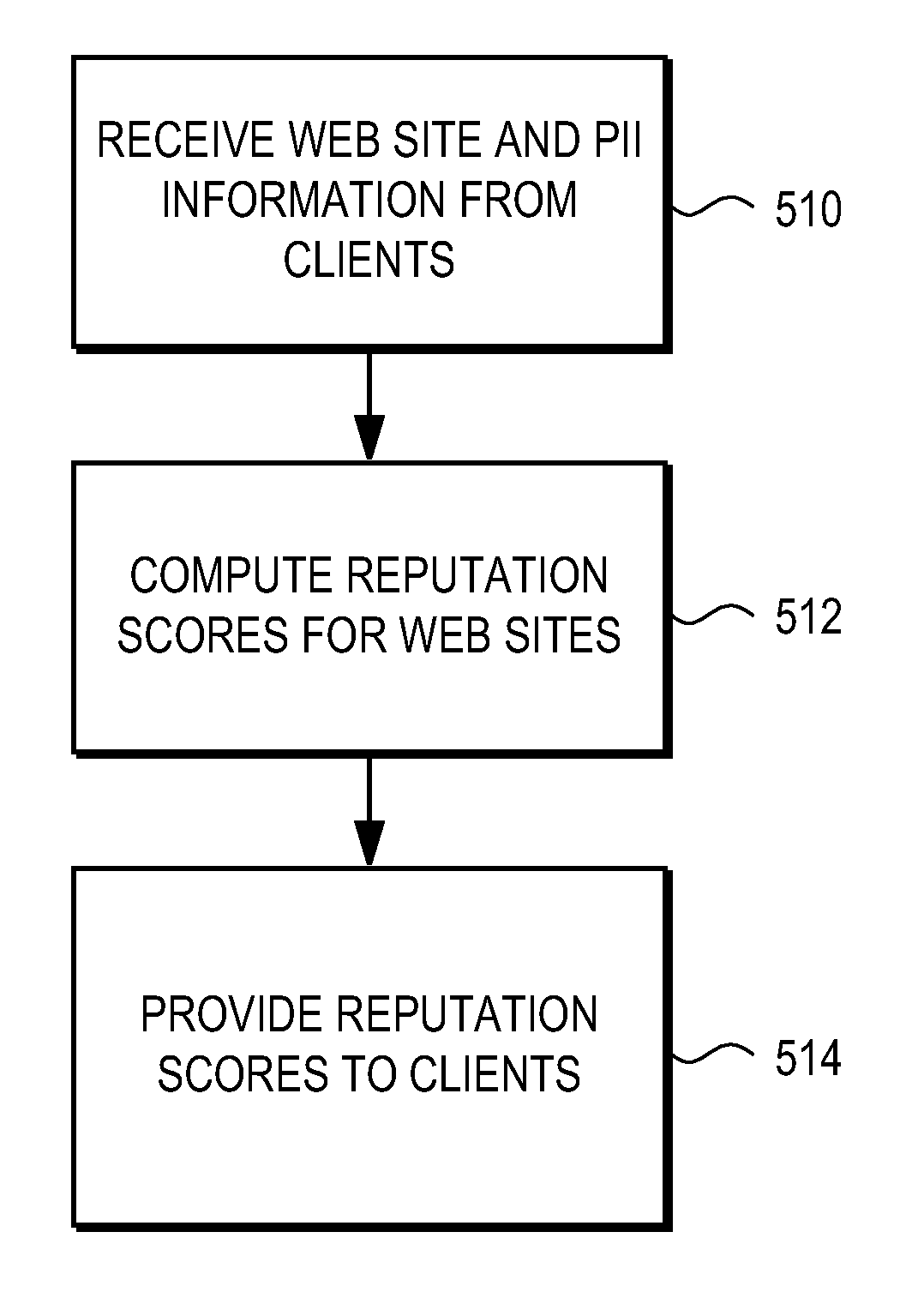
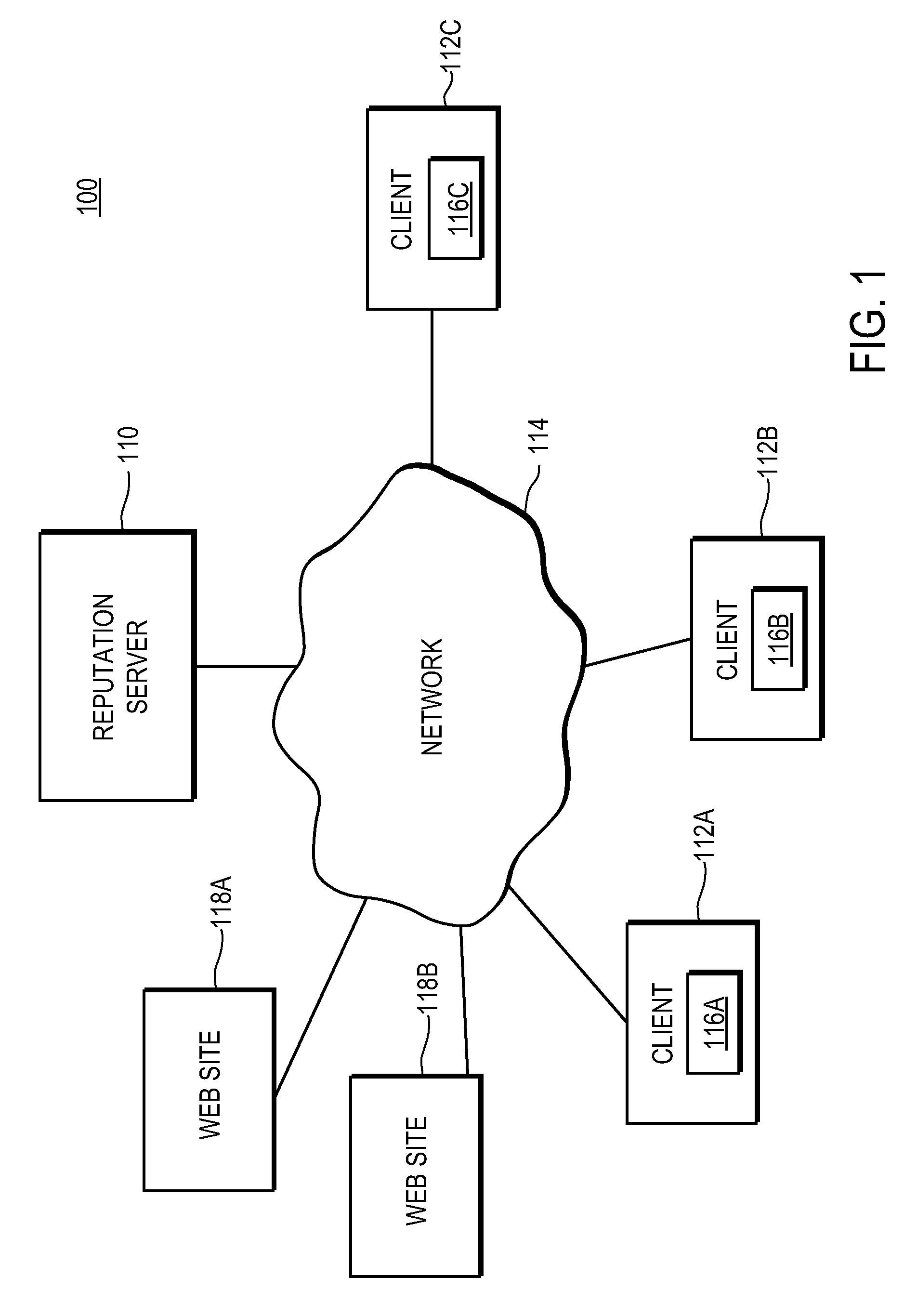
Deriving reputation scores for web sites that accept personally identifiable information
ActiveUS8019689B1Provide securityComputer security arrangementsPayment architectureWeb siteInternet privacy
A reputation server is coupled to multiple clients. Each client has a security module that detects submissions of personally identifiable information (PII) from the client to a web site. The security module reports the identity of the web site and the type of submitted PII to the reputation server. The reputation server computes a reputation score for the web site based on the number and type of PII submissions to it. The reputation score represents an assessment of whether the web site is trustworthy. The reputation server provides the reputation scores for the web site to a client. The security module at the client evaluates the reputation score of the web site and optionally generates an alert advising the user not to submit PII to the web site because the site is untrustworthy.
Owner:NORTONLIFELOCK INC
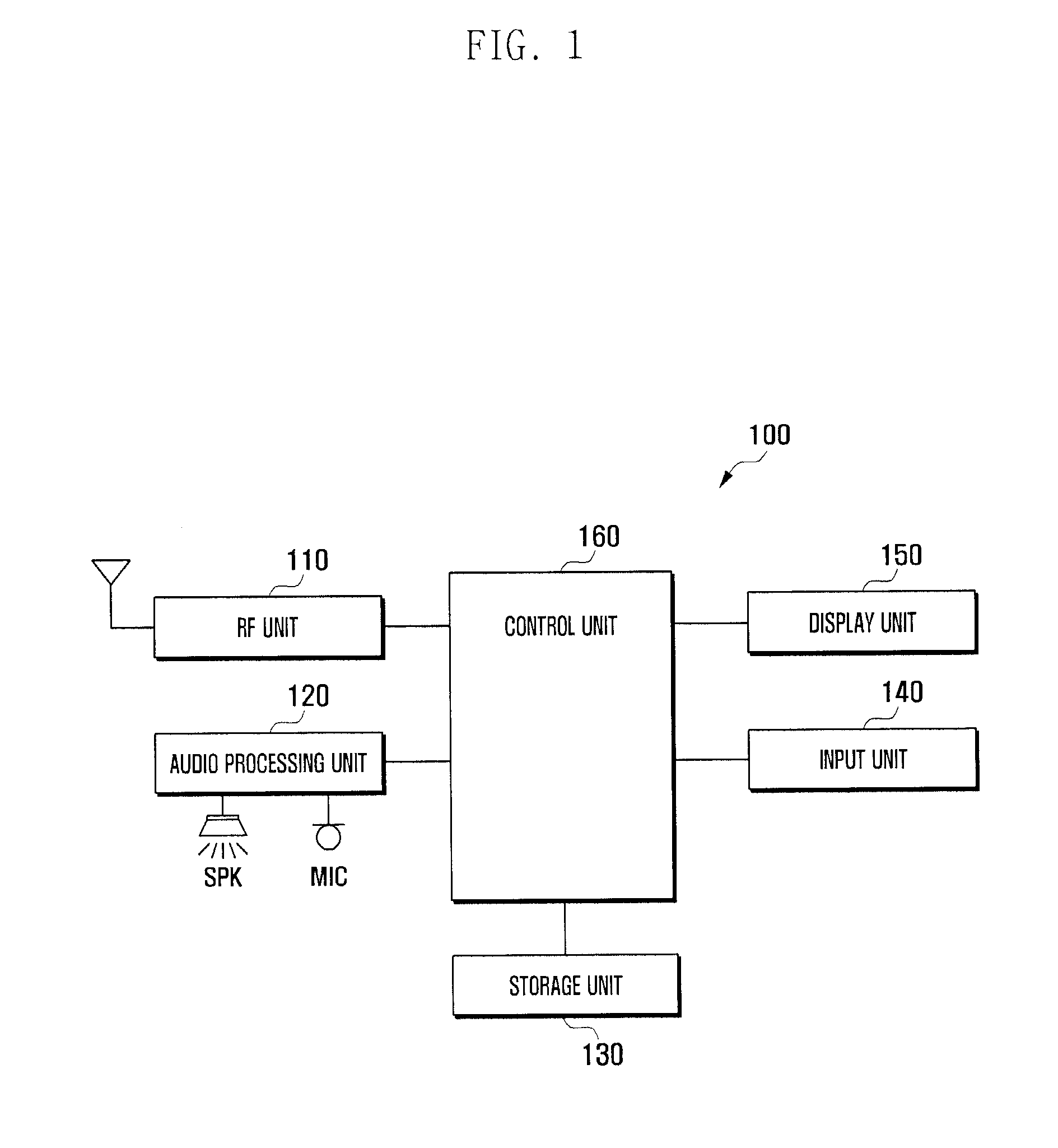
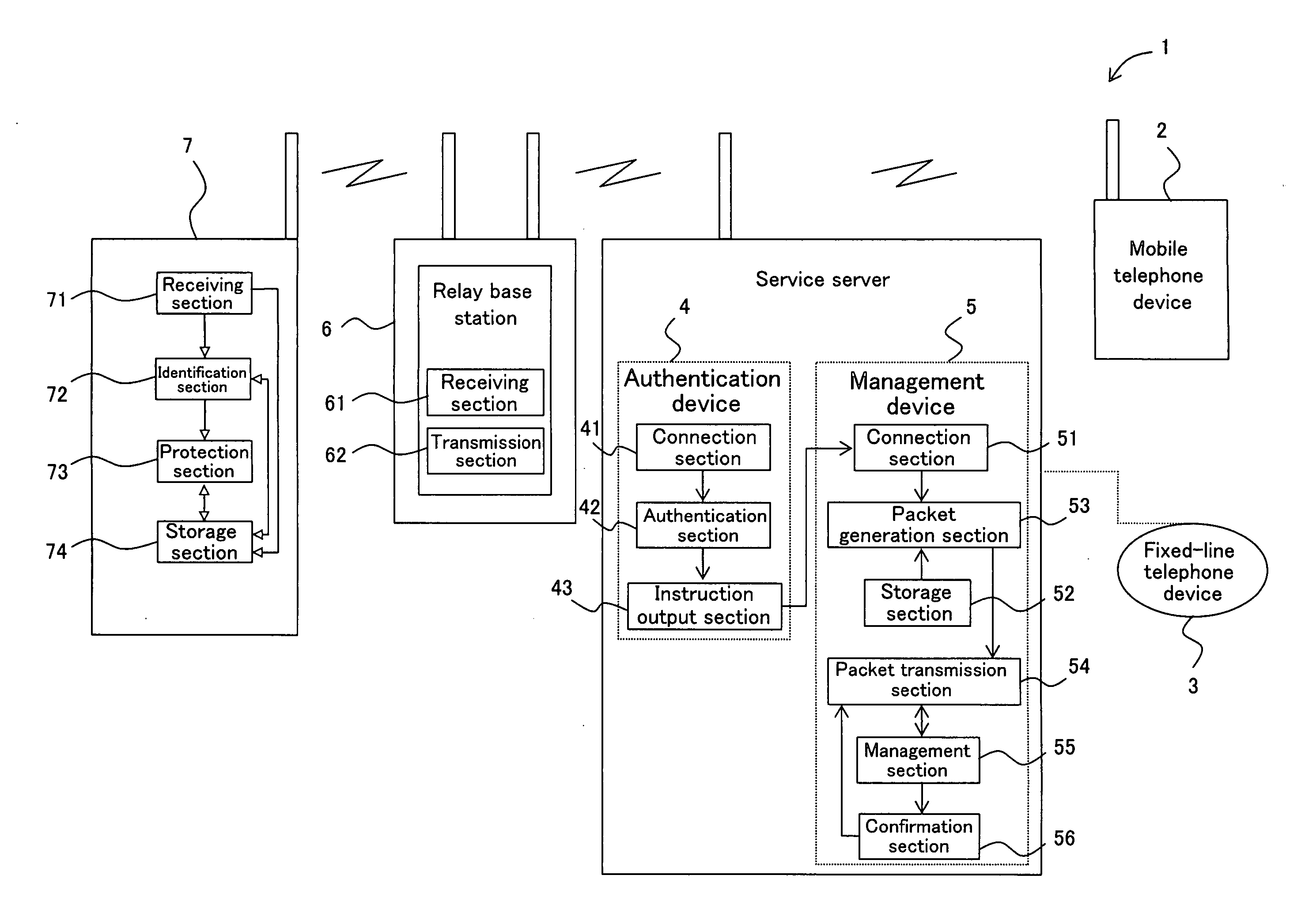
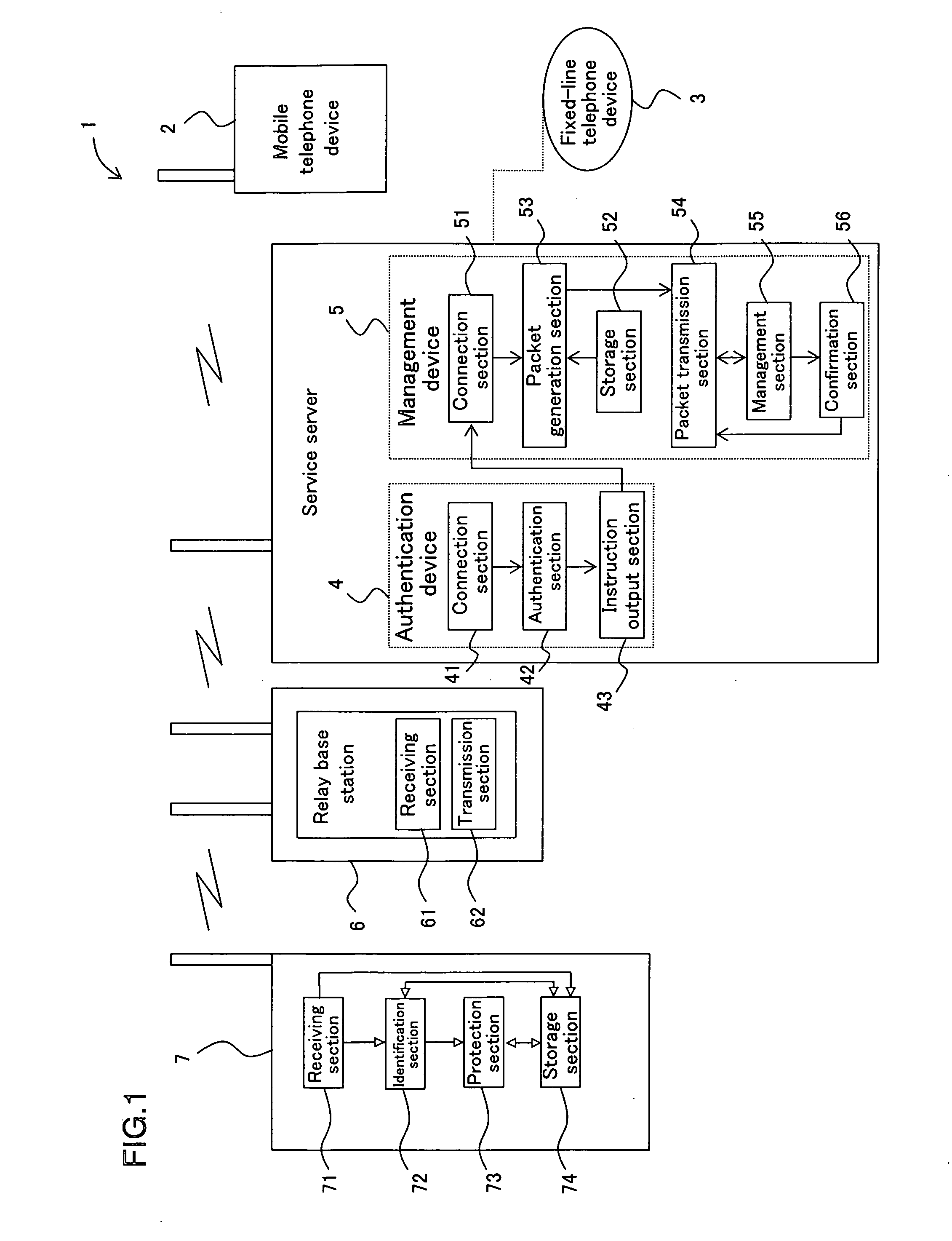
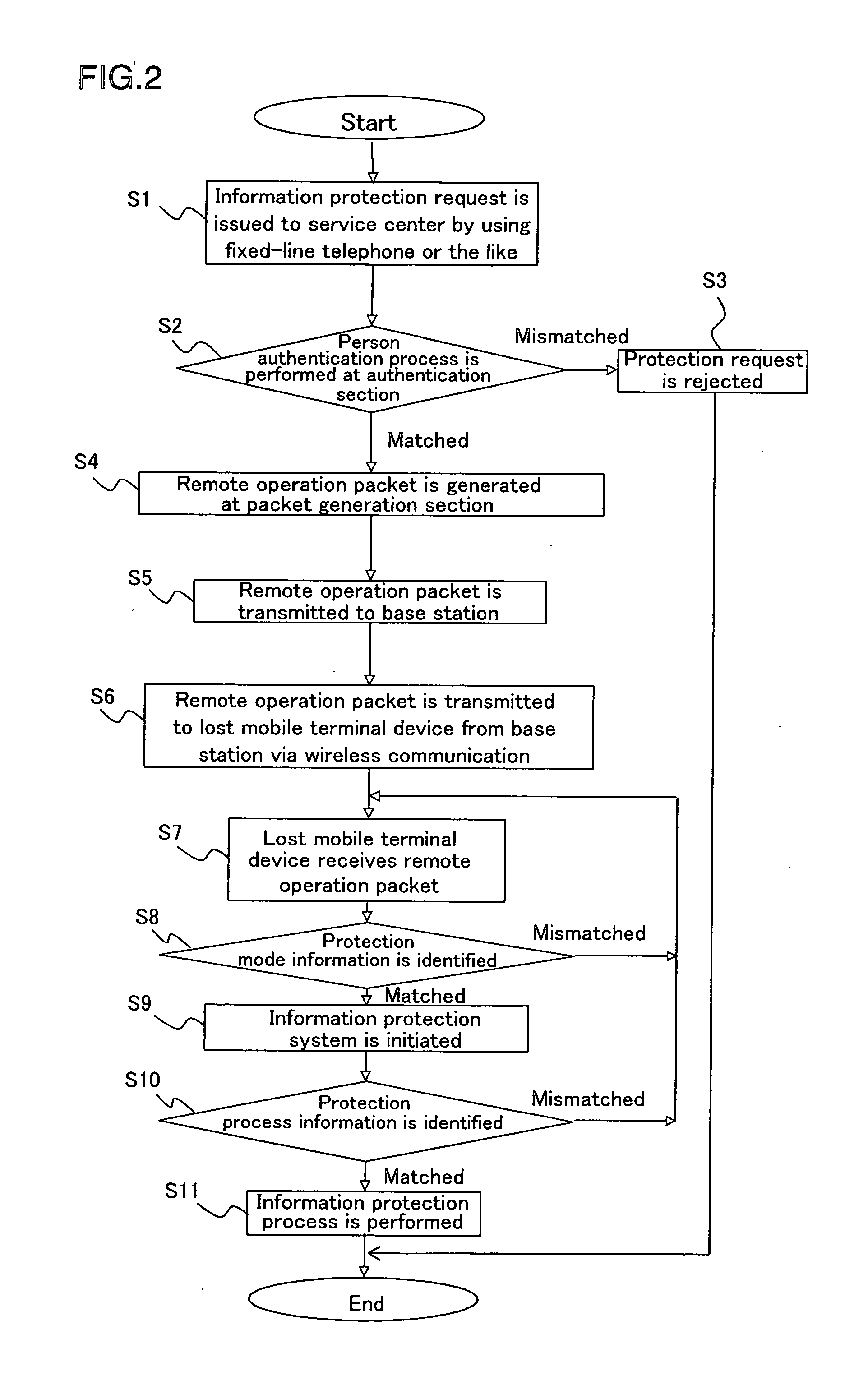
Information protection system for mobile terminal device, information protection method for mobile terminal device, control program, computer-readable medium and electronic information device
InactiveUS20060234679A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTerminal equipmentElectronic information
An information protection system for a mobile terminal device, the information protection system including: an authentication device for performing a person authentication process when an information protection request for the mobile terminal device is issued in order to identify whether any person being subjected to authentication is an owner of the mobile terminal device by using a personal identity information, the mobile terminal device being capable of performing a predetermined information protection process in accordance with a remote operation information; and a management device for generating the remote operation information in order to perform an information protection process for the mobile terminal device and for transmitting the remote operation information to the mobile terminal device when the person authentication process by the authentication process device matches the personal identity information.
Owner:SHARP KK
Method and system for monitoring online behavior at a remote site and creating online behavior profiles
InactiveUS20060070117A1Digital data processing detailsUser identity/authority verificationInternet privacyTransaction data
Owner:CONNEXITY AUDIENCE INC
Method and apparatus for controlling access to personally identifiable information
ActiveUS20060085443A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyApplication software
One embodiment of the present invention provides a system that controls access to personally identifiable information (PII) in a database system. During operation, the system receives a request from an application to perform a function which involves accessing information in the database system. In response to the request, the system identifies a purpose that the application has in making request to perform the function. Next, the system uses the purpose to identify a set of attributes in the database system, which are associated with the purpose. The system then determines if any of the identified attributes contain PII. If so, the system enforces access controls while accessing the identified attributes containing PII.
Owner:ORACLE INT CORP
Identity theft and fraud protection system and method
Owner:CF NEWCO INC +4
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com