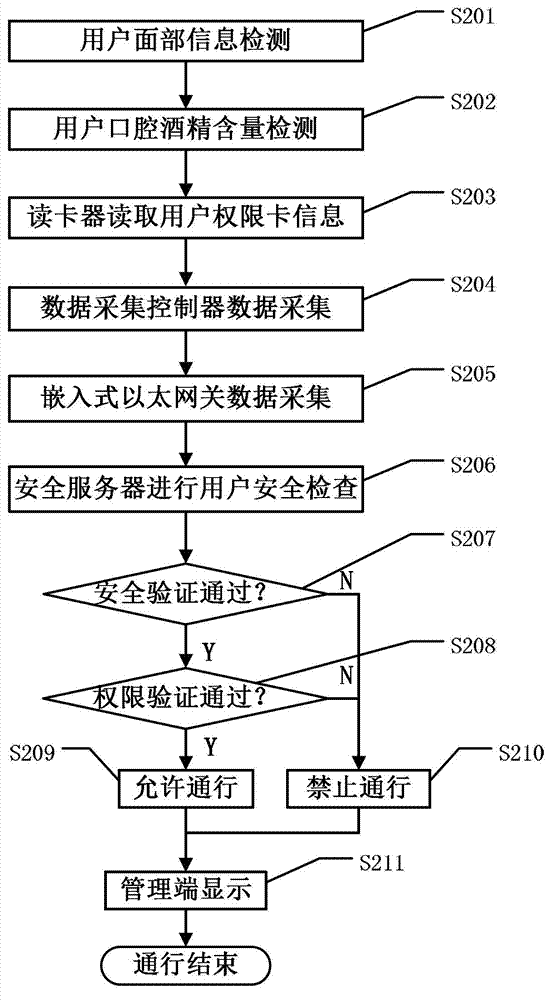
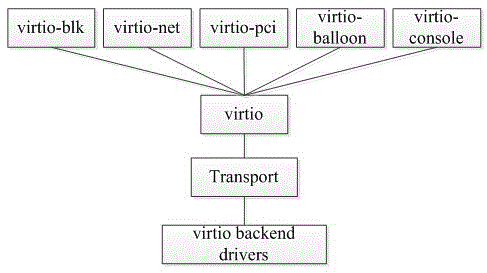
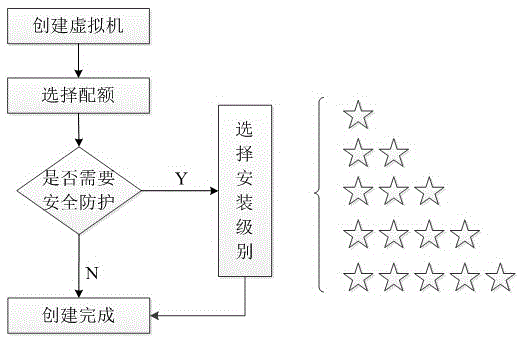
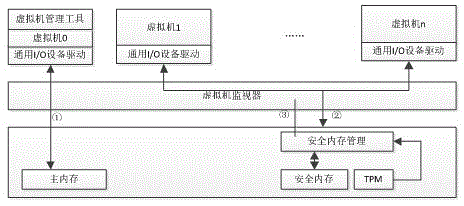
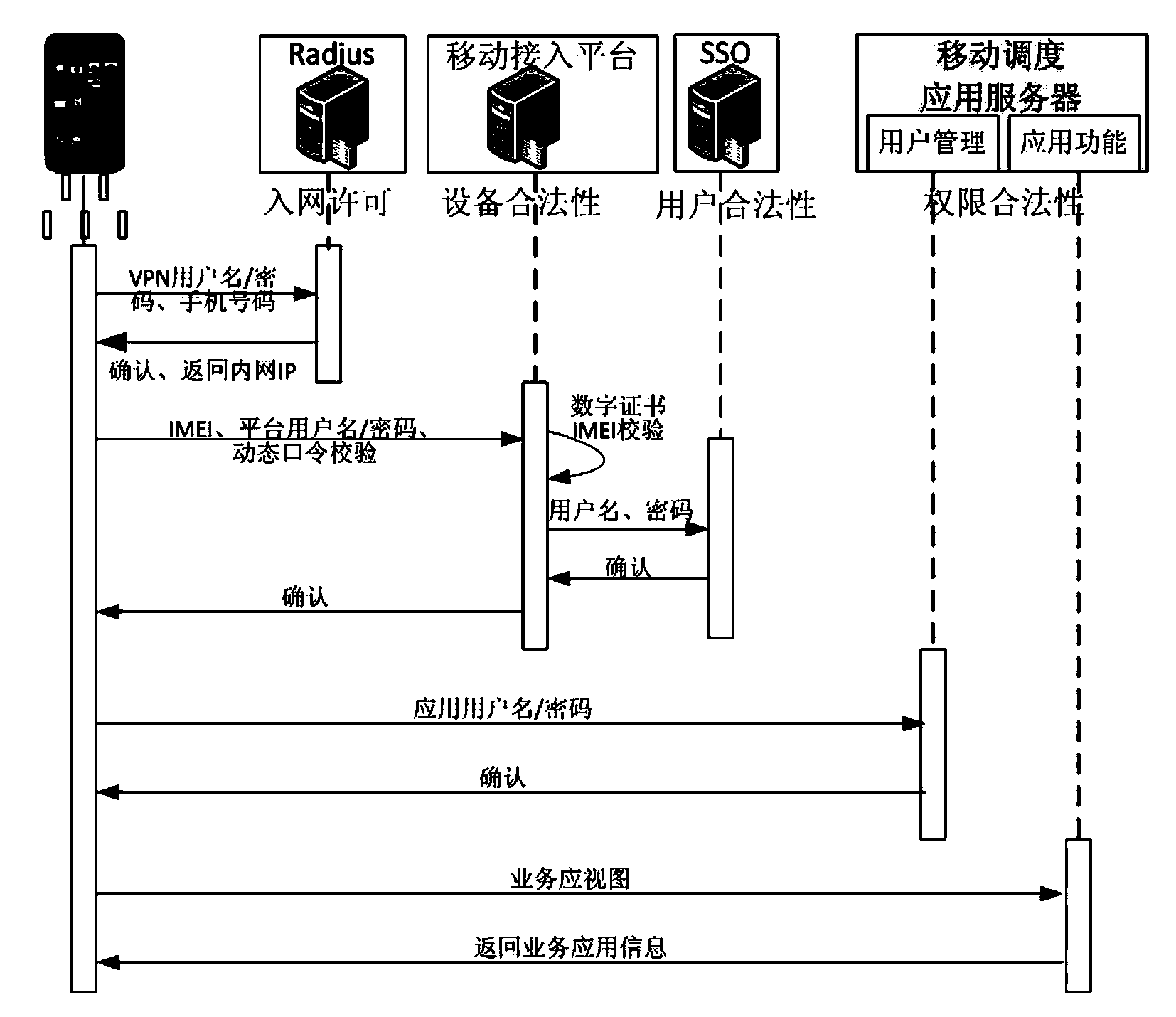
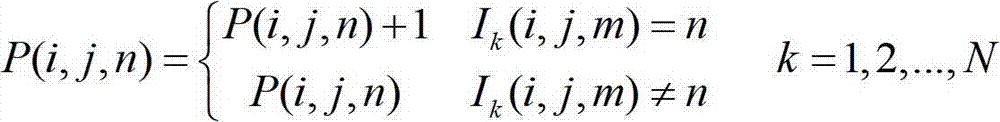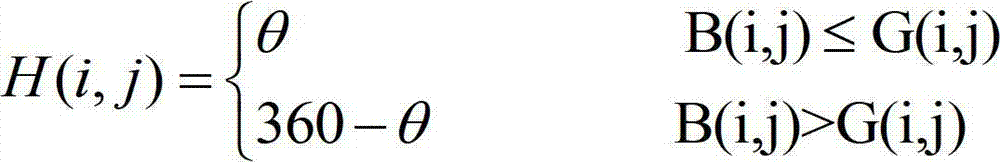Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
210results about How to "Implement security management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
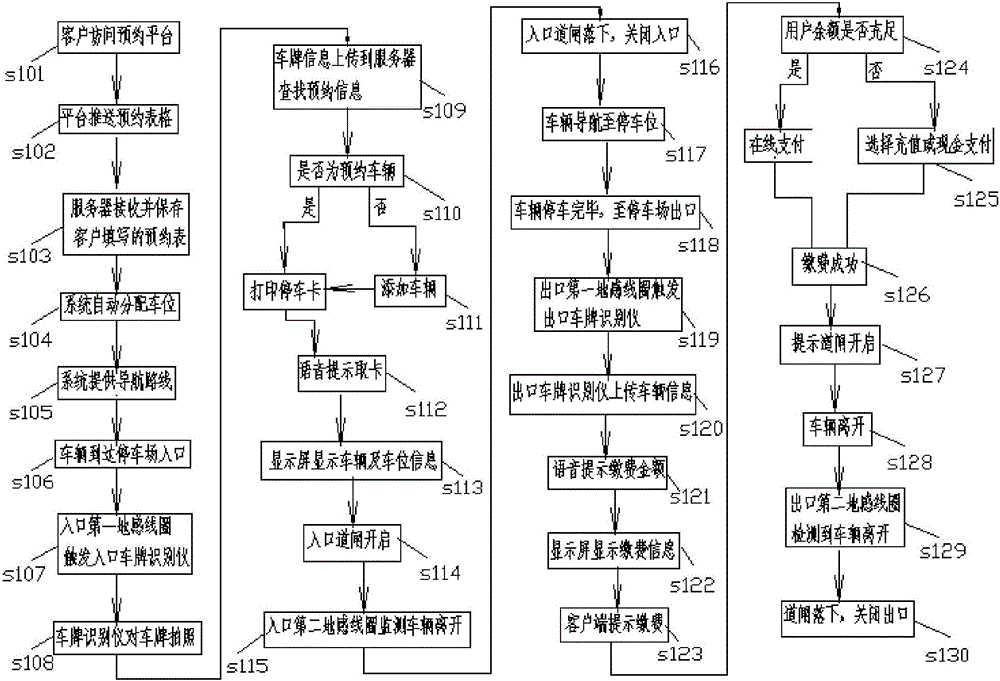
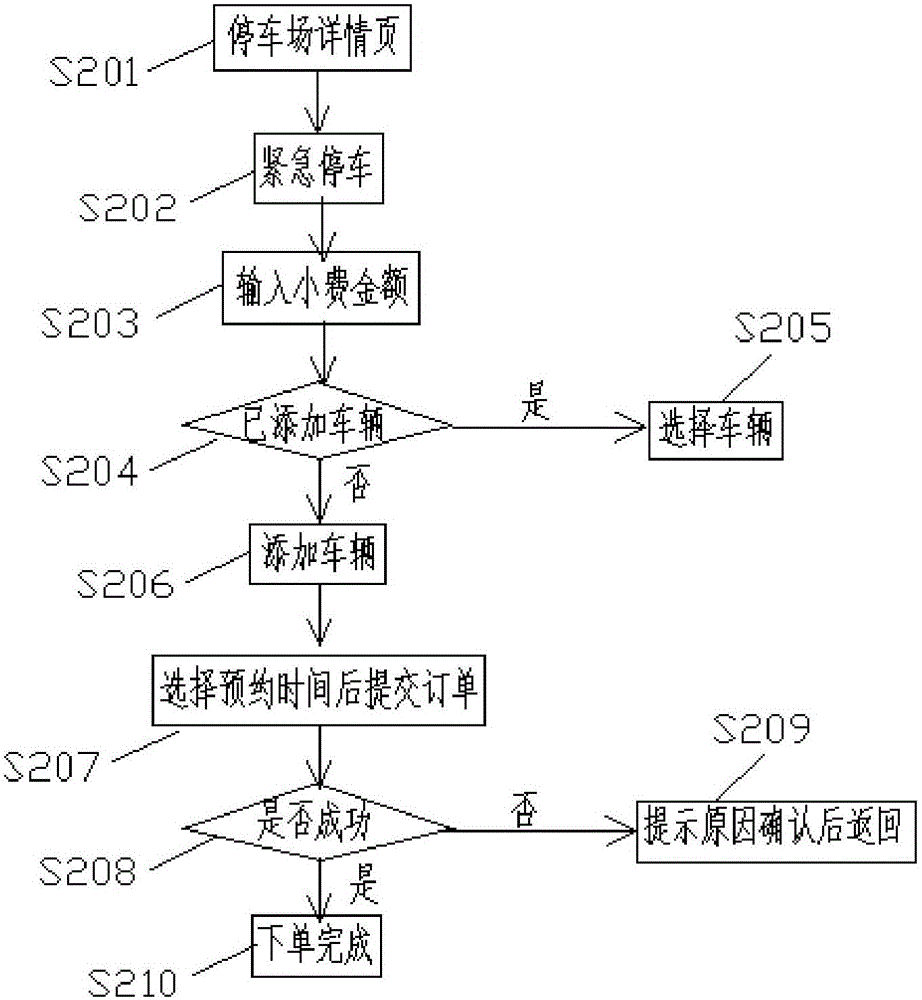
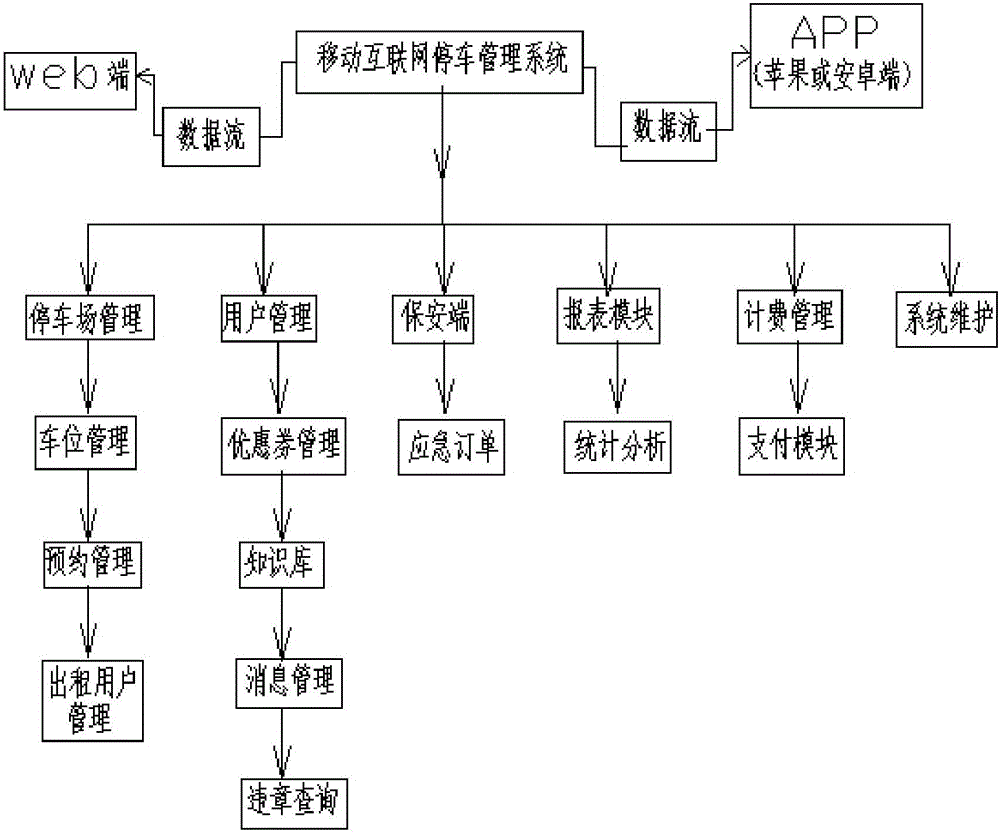
Mobile Internet parking management method and system
InactiveCN105825707AEasy dockingRealize data integration managementTicket-issuing apparatusReservationsPaymentSystem maintenance
The present invention relates to a mobile Internet parking management method and system. The mobile Internet parking management method includes the following steps that: a server receives a reservation parking request sent by a client and generates reservation information according to the reservation parking request and allocates a reserved parking space; when a reservation automobile arrives at the entrance of a parking lot according to a reservation, the server searches the reservation information according to automobile information uploaded by the entrance of the parking lot and instructs the entrance of the parking lot to carry out parking according to the reservation information; when the automobile leaves, the server calculates parking fees of the automobile and sends fee payment information to the client so as to prompt the user to pay the fees; and after the server receives online fee payment of the client, a current parking process is terminated. With the mobile Internet parking management system of the invention adopted, the user can carry out registration and make a reservation in advance, the registration and reservation are directly recorded through the system, an unoccupied parking space is reserved; and when an automobile is being parked, the system automatically identifies whether the automobile is a reservation automobile. With the mobile Internet parking management method and system adopted, a situation that a large number of parking space guidance and automobile searching devices are installed in a parking lot can be avoided, investment cost and system maintenance cost can be saved.
Owner:SINOFLEX OPTOELECTRONICS CHUZHOU
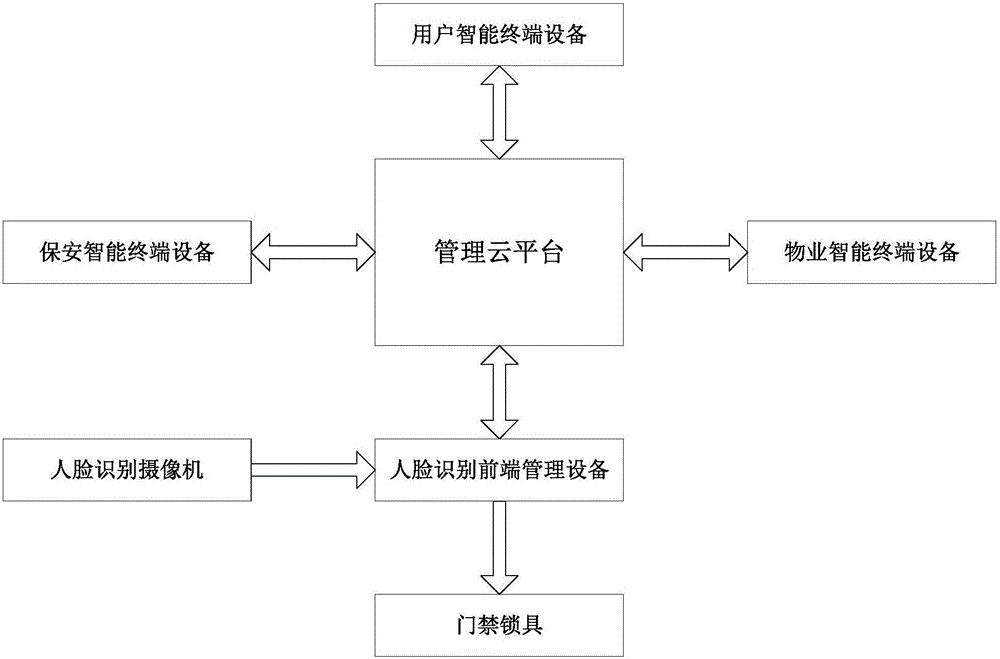
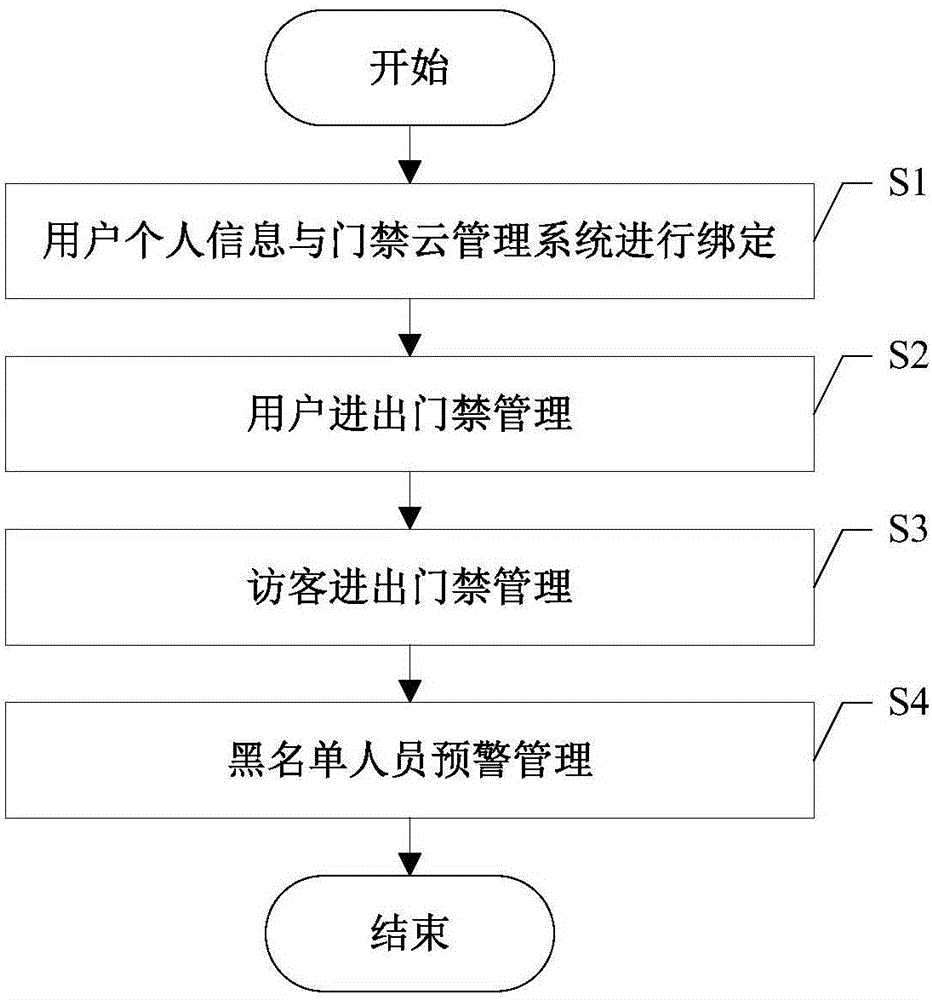
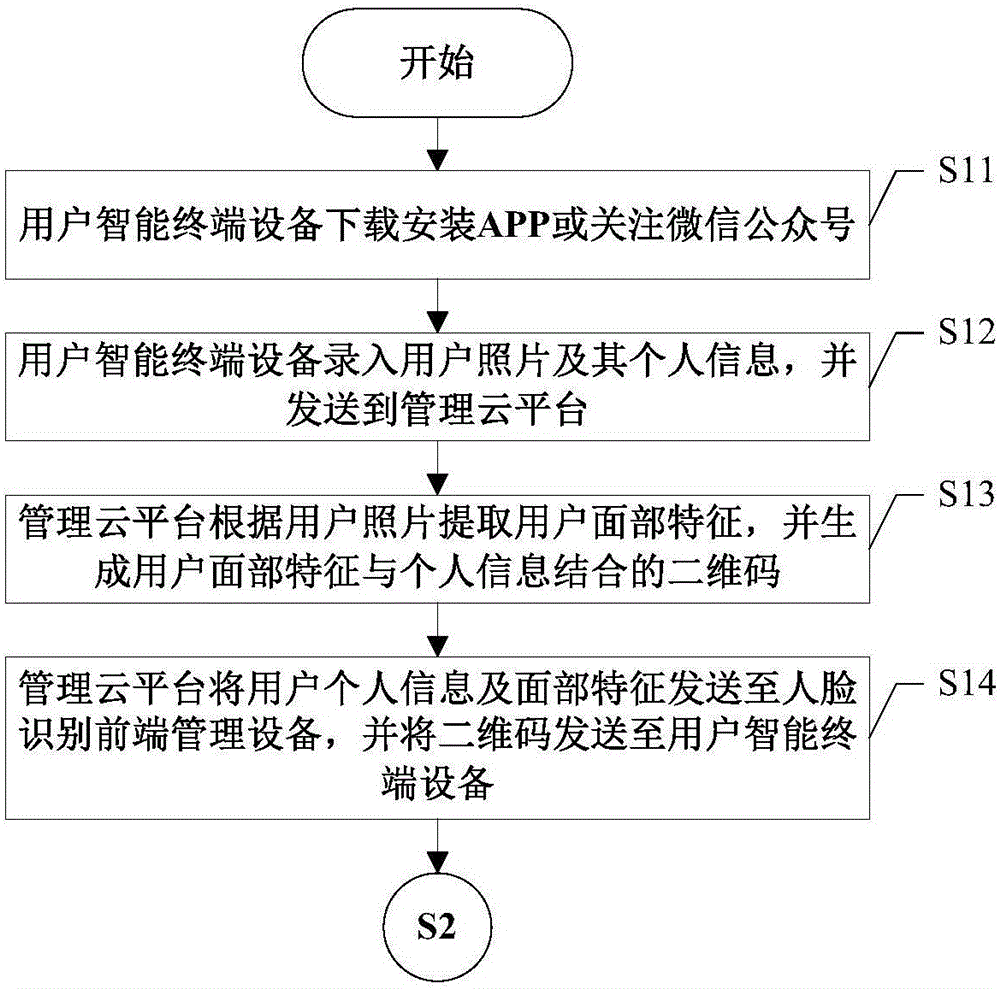
Access control cloud management system and method based on face recognition
ActiveCN105869248AHigh feasibilityImplement security managementCharacter and pattern recognitionIndividual entry/exit registersWorkloadPersonally identifiable information
The invention discloses an access control cloud management system and method based on face recognition. Through face recognition and a cloud technology thereof, a video real-time monitoring and alarming function is supplied to access control, integration of access control and video face recognition is achieved, and access control security and protection management is improved. According to the system and method, a user using threshold is low, operation is easy, the system and method can be used only by verifying personal identity information of a user, access control recognition is conducted by adopting face recognition, and therefore an access control system can easily, conveniently, rapidly and comprehensively record personnel entering and leaving information; entering and leaving of a person with the face which cannot be recognized can be forbidden, or alarming is conducted; entering and leaving information of a visitor also can be quickly generated and recorded, the security management effect can be effectively improved, and the workload of security personnel can be reduced.
Owner:CHENGDU QIANFAN TECH DEV
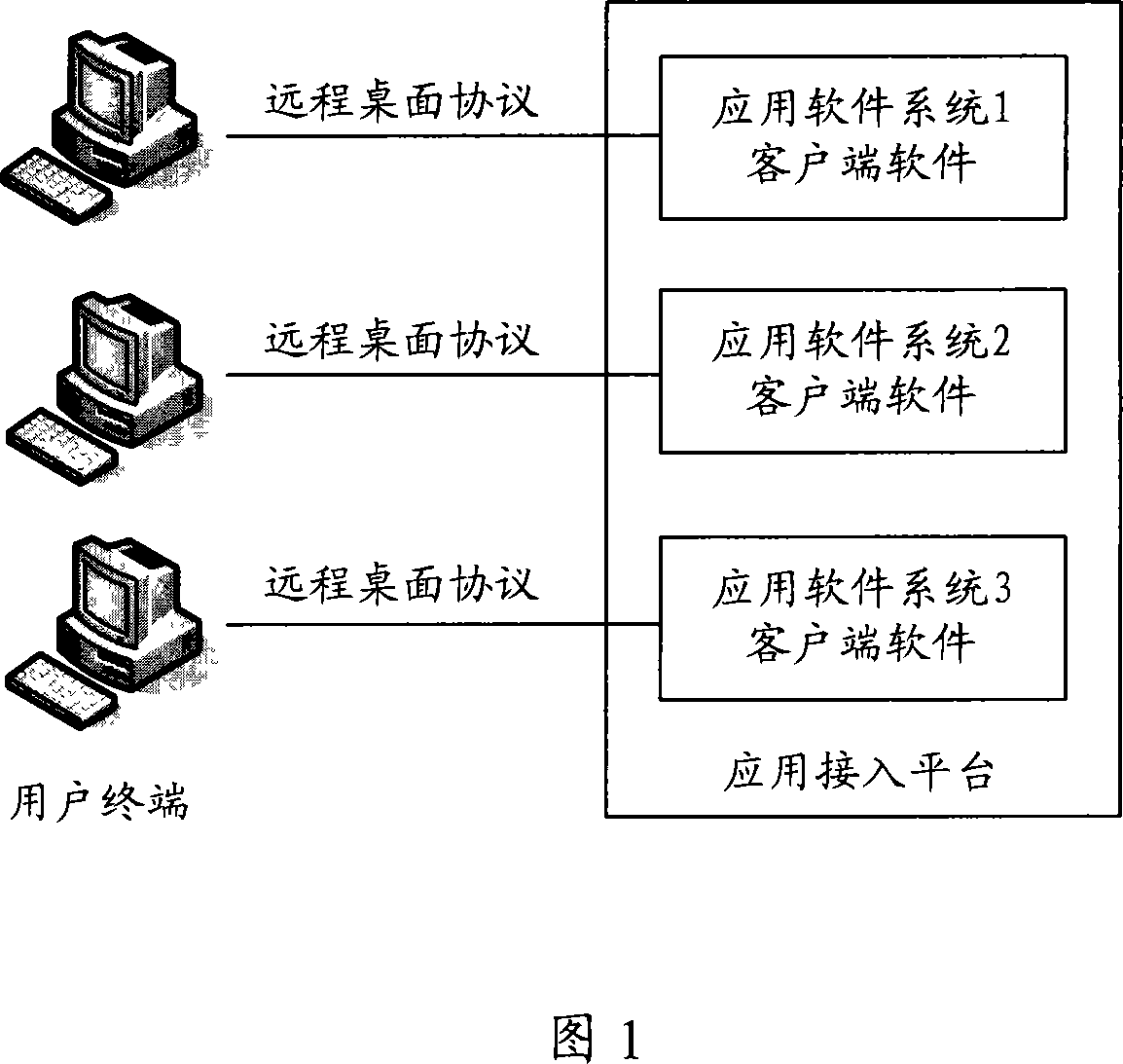
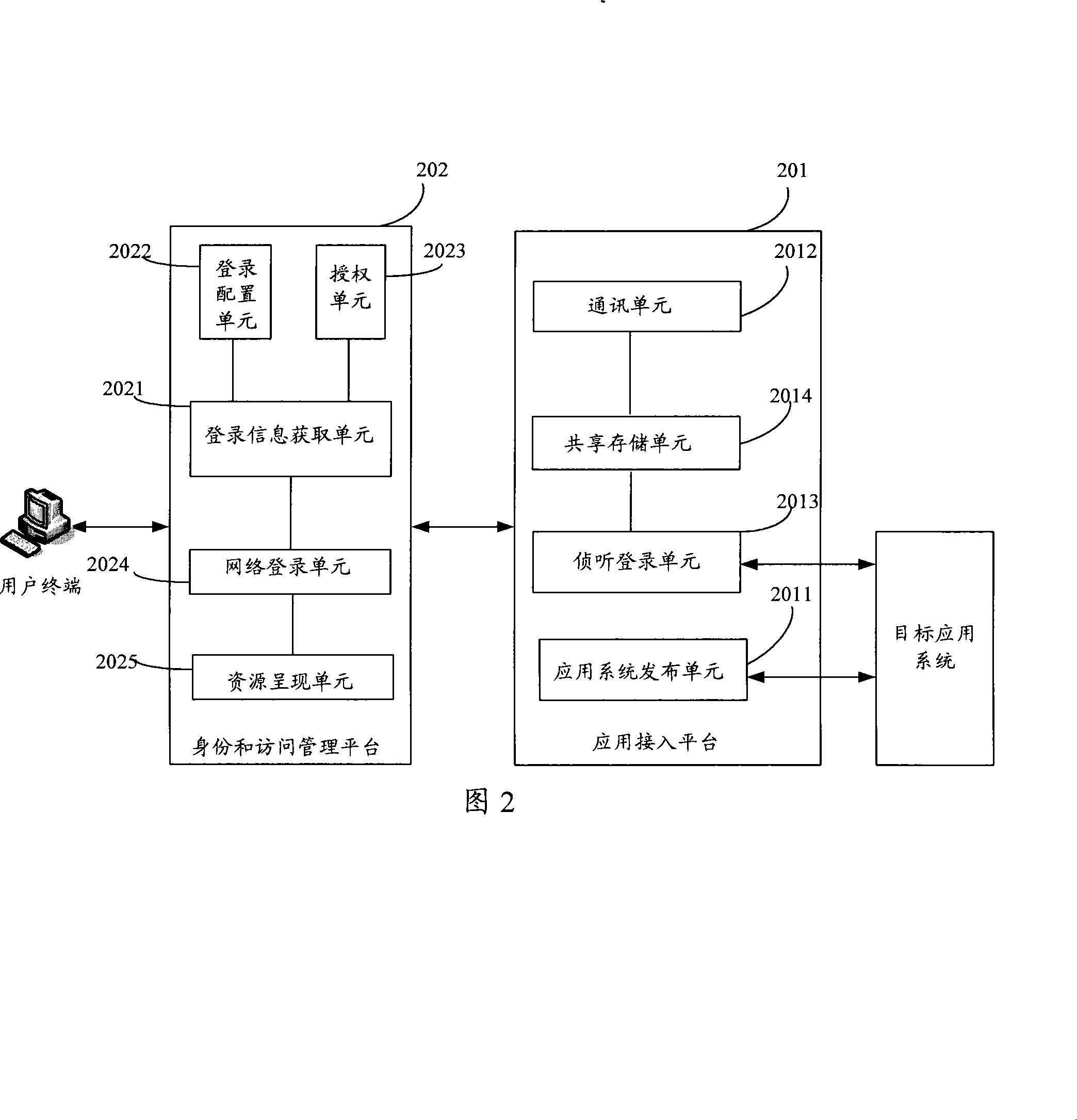
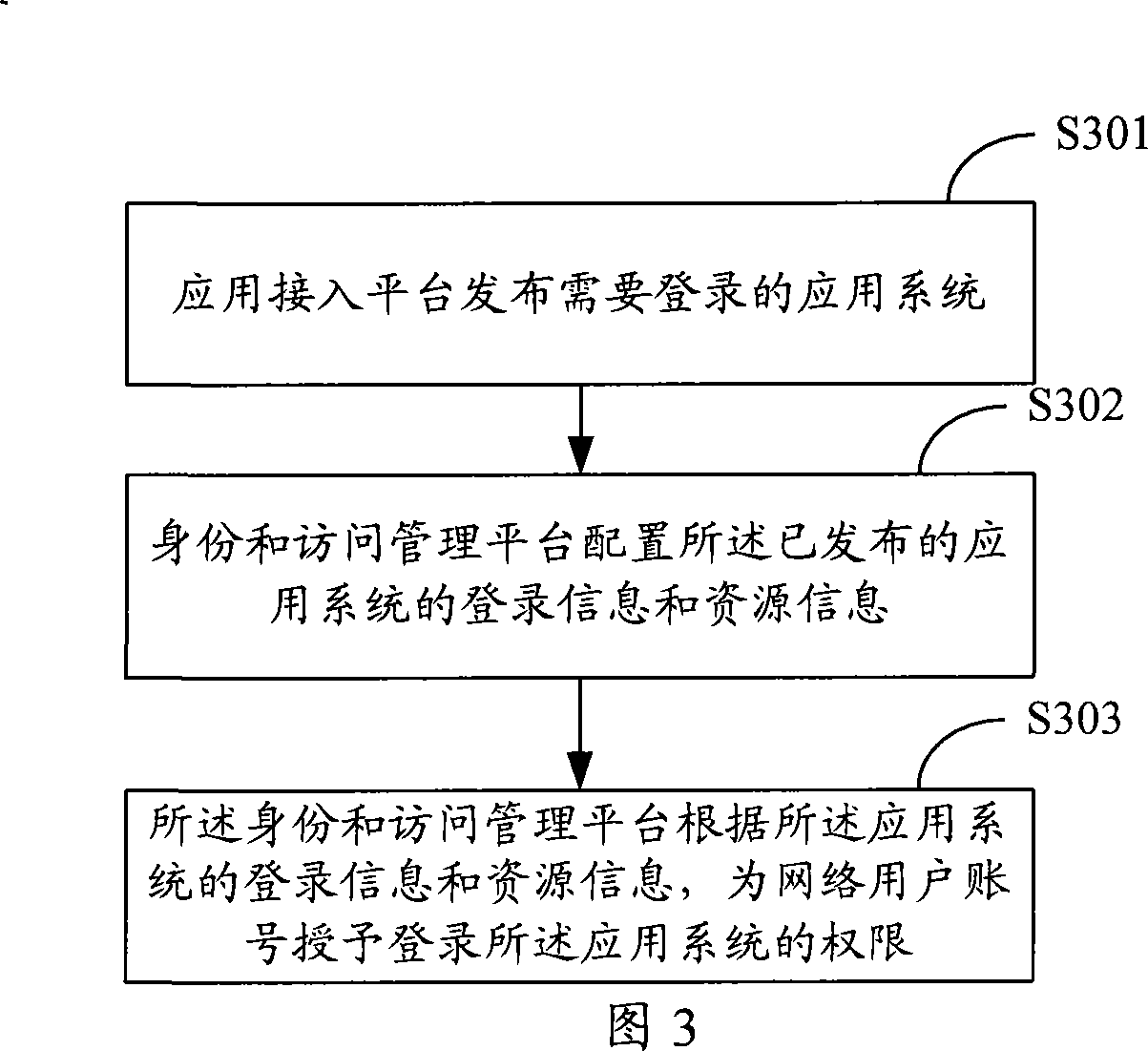
A network logging on system and the corresponding configuration method and methods for logging on the application system
InactiveCN101217368AImplement security managementSimplify login operationsUser identity/authority verificationDigital data authenticationRelevant informationResource information
The invention relates to the technical field of network security and discloses a login system which comprises an application access platform and an identity and access management platform; wherein, the application access platform is used for installing and issuing an application system so as to lead users to login the application access platform and realize the logging in the application system which can pre-arrange and store related information of the application system; the identity and access management platform is used for obtaining the logging information and resource information of the application system from the application access platform, arranging the relatively accessible resource content and corresponding relations of network users and the users logging the application system, receiving the logging and making authentication of the network users. After the network users login the identity and access management platform with the application of the system disclosed by the invention, the identity and access management platform accesses the resource of the application system as legal users of the application system without leading the users directly to access the application system and the invention is high in access security and simple in the login operation of users.
Owner:亿阳安全技术有限公司
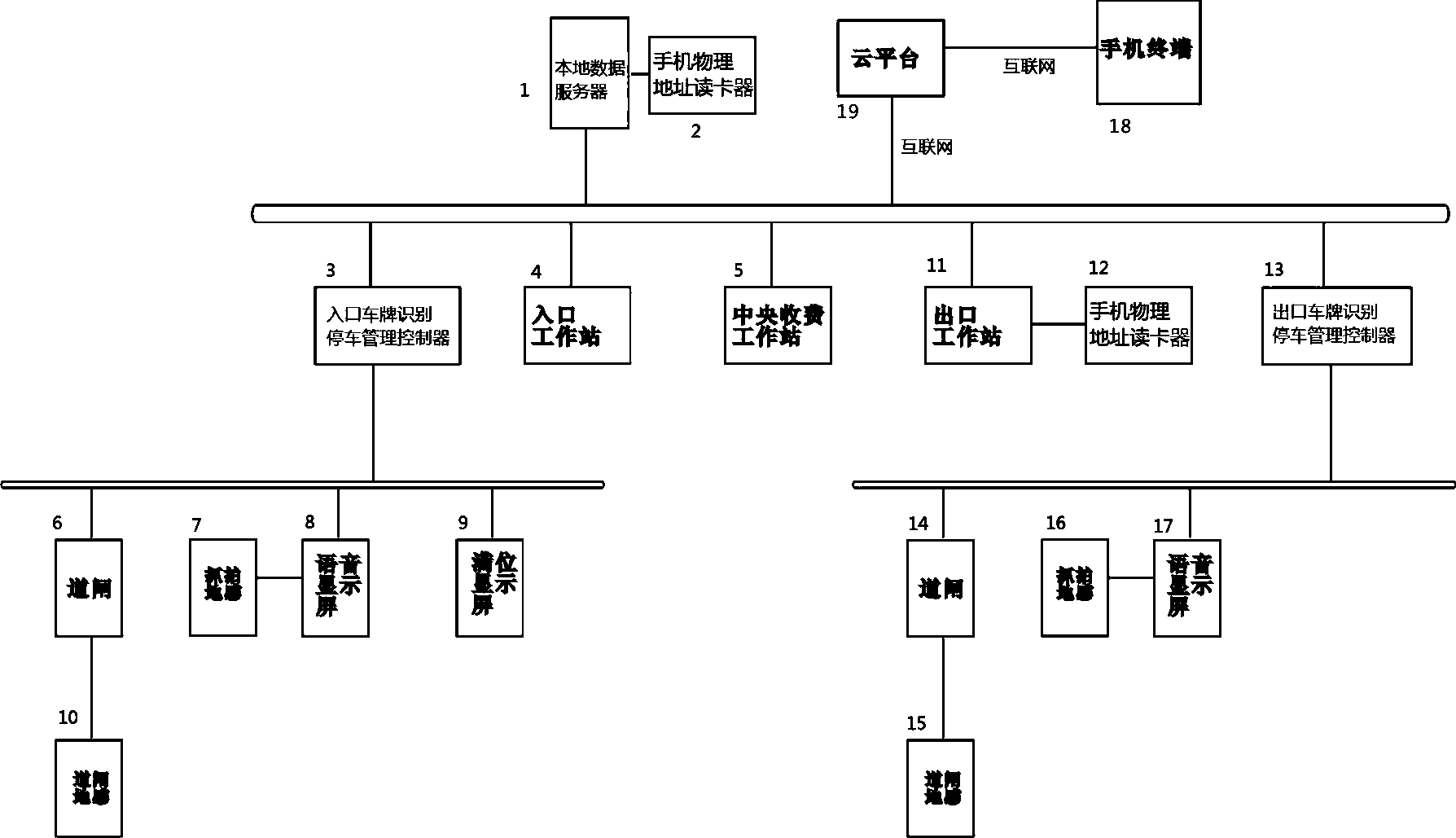
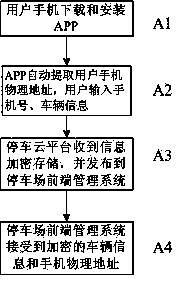
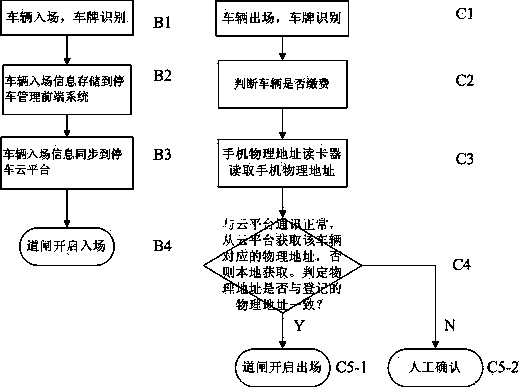
Cloud parking lot management system and vehicle anti-theft method based on intelligent terminal equipment
ActiveCN104240352AAdvantages of anti-theft methodsImplement security managementTicket-issuing apparatusIndication of parksing free spacesEmbedded systemManagement system
The invention discloses a cloud parking lot management system and a vehicle anti-theft method based on intelligent terminal equipment, such as cellphones. A cellphone physical address card reader is connected with a local data server; an entrance vehicle plate distinguishing and parking management controller and an exit vehicle plate distinguishing and parking management controller are connected with the local data server through the Internet, the cellphone physical address card reader is connected with an exit work station, and the terminal equipment is in data communication with the local data server through a cloud platform. The anti-theft method is not only suitable for vehicle plate distinguishing parking lots, but also suitable for all existing parking lots, and vehicle owner with the intelligent terminal equipment can use the anti-theft method. The anti-theft method is used for related anti-theft operation through a cellphone terminal, the use doorsill of users is low, the operation is simple, and the anti-theft function can be used so long as the physical address information of a vehicle and the physical address information of the intelligent terminal equipment need are verified.
Owner:CHENGDU QIANFAN TECH DEV
Method for authenticating identity and device for authenticating identity
InactiveCN104426884AImplement security managementStrong uniqueness and irreproducibilityTransmissionInternet privacyAuthorization
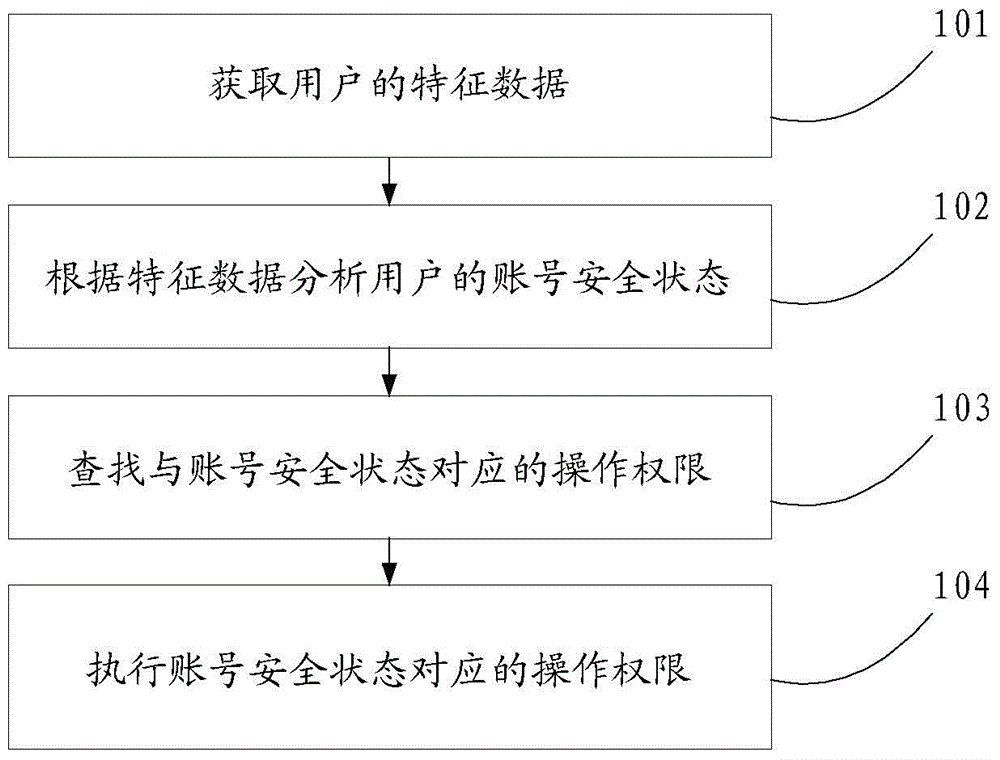
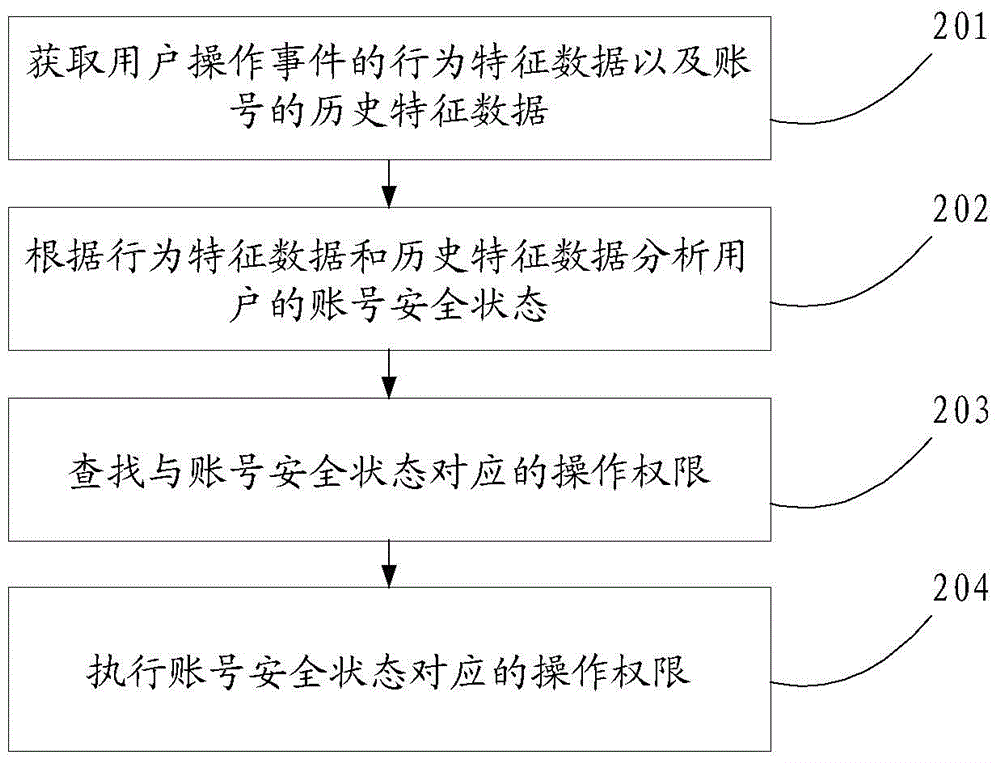
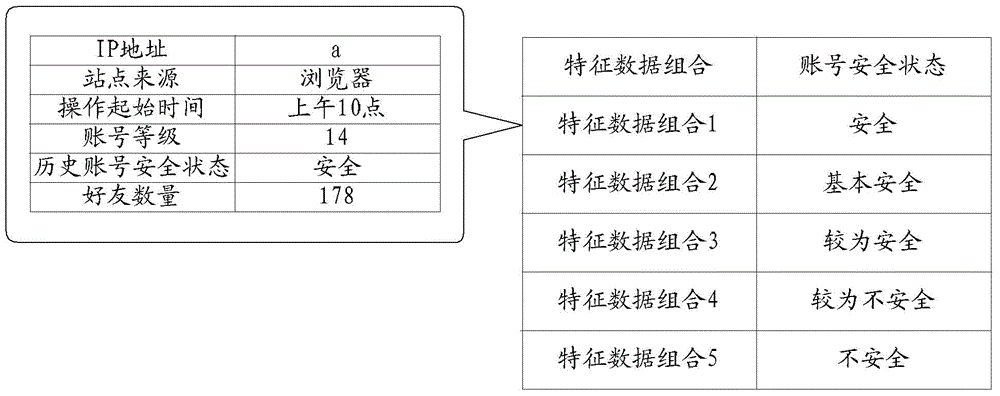
The invention discloses a method for authenticating an identity and a device for authenticating the identity, relates to the technical field of Internet, and can solve the problem that individual accounts in internet application can not be practically protected. The method disclosed by the invention comprises the following steps: obtaining characteristic data of a user; analyzing an account safety state of a user according to the characteristic data; finding an operating authorization corresponding to the account safety state; executing the operating authorization corresponding to the account safety state. The method and the device are mainly applied to an account safety detection process.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
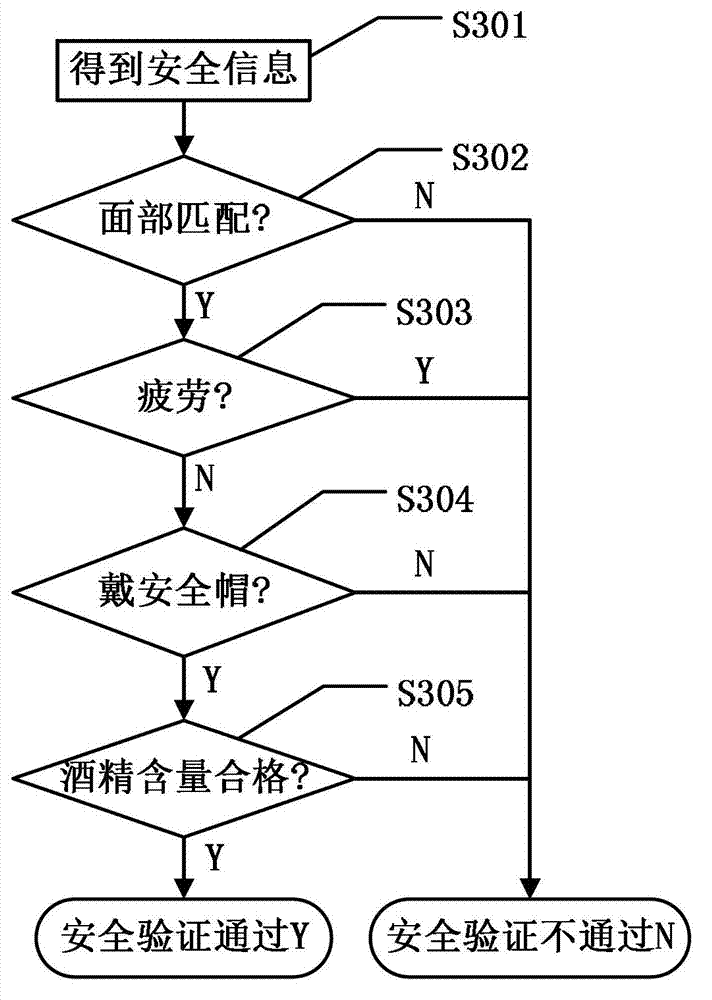
Personnel security management system and method in mining areas
InactiveCN103049949AAvoid dangerous workAudit flexibleIndividual entry/exit registersAlcohol contentData mining
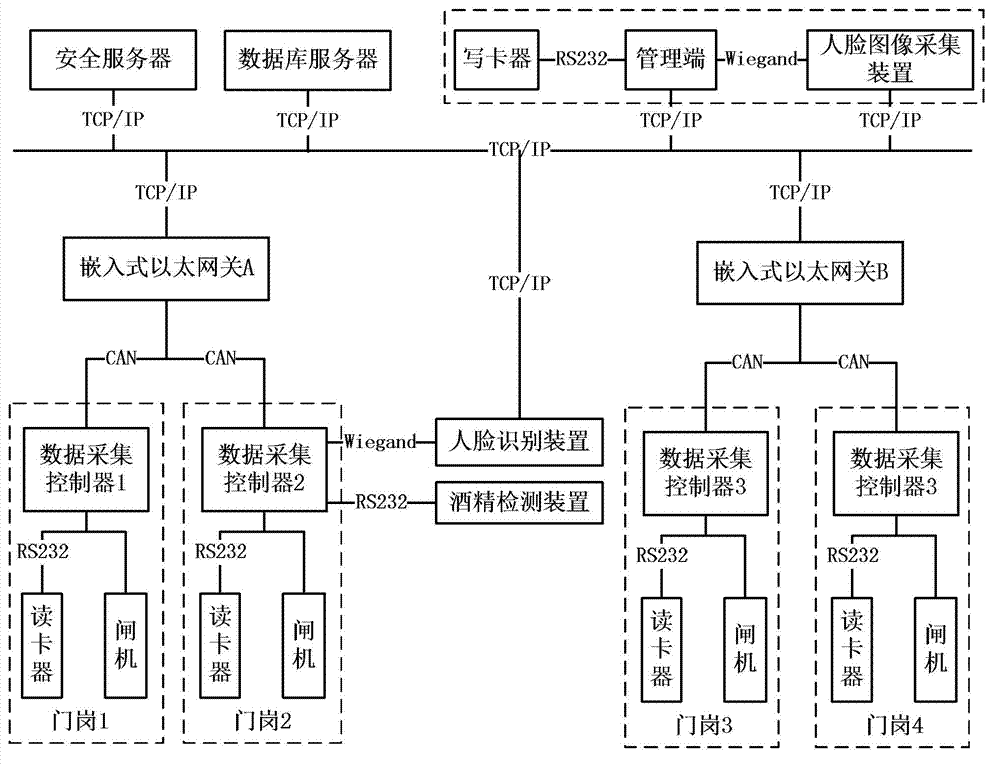
The invention discloses a personnel security management system and method in mining areas. According to special environments and conditions of the mining areas, security factors are detected. The system is internally provided with a face recognition device and alcohol detecting device, wherein the face recognition device is used for detecting whether face images are matched, whether security helmets are worn, and whether workers are fatigue; and the alcohol detecting device is used for detecting whether the alcohol content in oral cavities of the workers is qualified, thereby preventing dangerous operation of the workers in the mining areas; and multiple audit modes of holiday control, week control and time section control are adopted for user right verification. The personnel security management system of the mining areas can cover each gate entry and other important areas of the mining areas, improves the entry and working safety of the workers in the mining areas through security verification and right verification which are matched with each other, and is beneficial to safety production of the mining areas.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Hotel safety management method based on artificial intelligence
ActiveCN110443923AImprove concealmentImplement security managementReservationsCharacter and pattern recognitionFace detectionVideo monitoring
The invention discloses a hotel safety management system and method based on artificial intelligence. The safety management system at least comprises a hotel reservation system, an information collection system, a hotel management system, an intelligent entrance guard management control system, a face detection recognition system, a database storage system, and a center sever; various systems arecommunicated with the center server; furthermore, the system further comprises a visitor management system. The intelligent entrance guard is divided into public entrance guard systems at an elevator,the stair and like locations and a guest room entrance guard system; each of the public entrance guard systems and the guest room entrance guard system at least comprises a processing server and an embedded equipment terminal; the embedded equipment terminals are fixed beside the entrance guard and used for collecting the information and controlling the entrance guard to be on and off; and the processing servers are used for performing matching comparison recognition on a photo uploaded by the terminals. Through the method disclosed by the invention, the face information collection at the hotel entrance guard region and the intelligent video monitoring at the hotel public region are combined, and the method is aided by the visitor management system, thereby realizing the comprehensive artificial intelligence hotel safety management with high concealment.
Owner:LUMOUS INTELLIGENT TECH & SERVICE
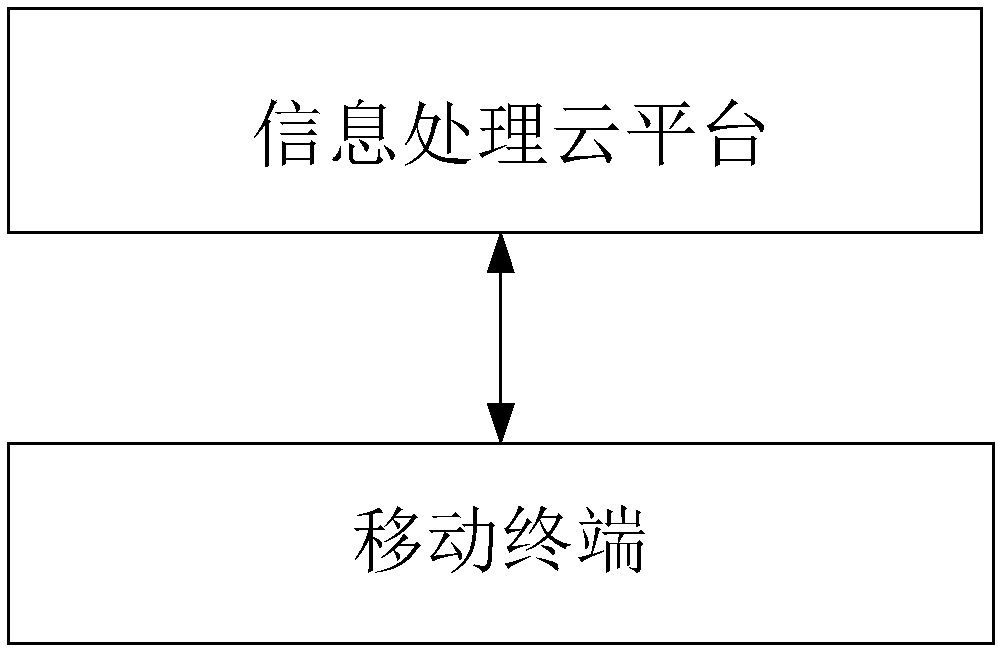
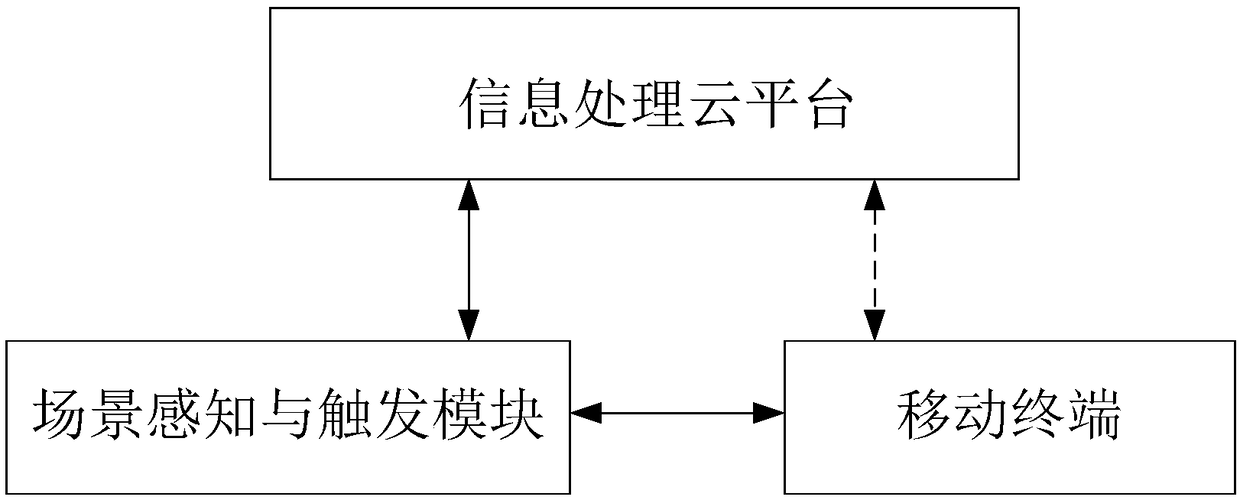
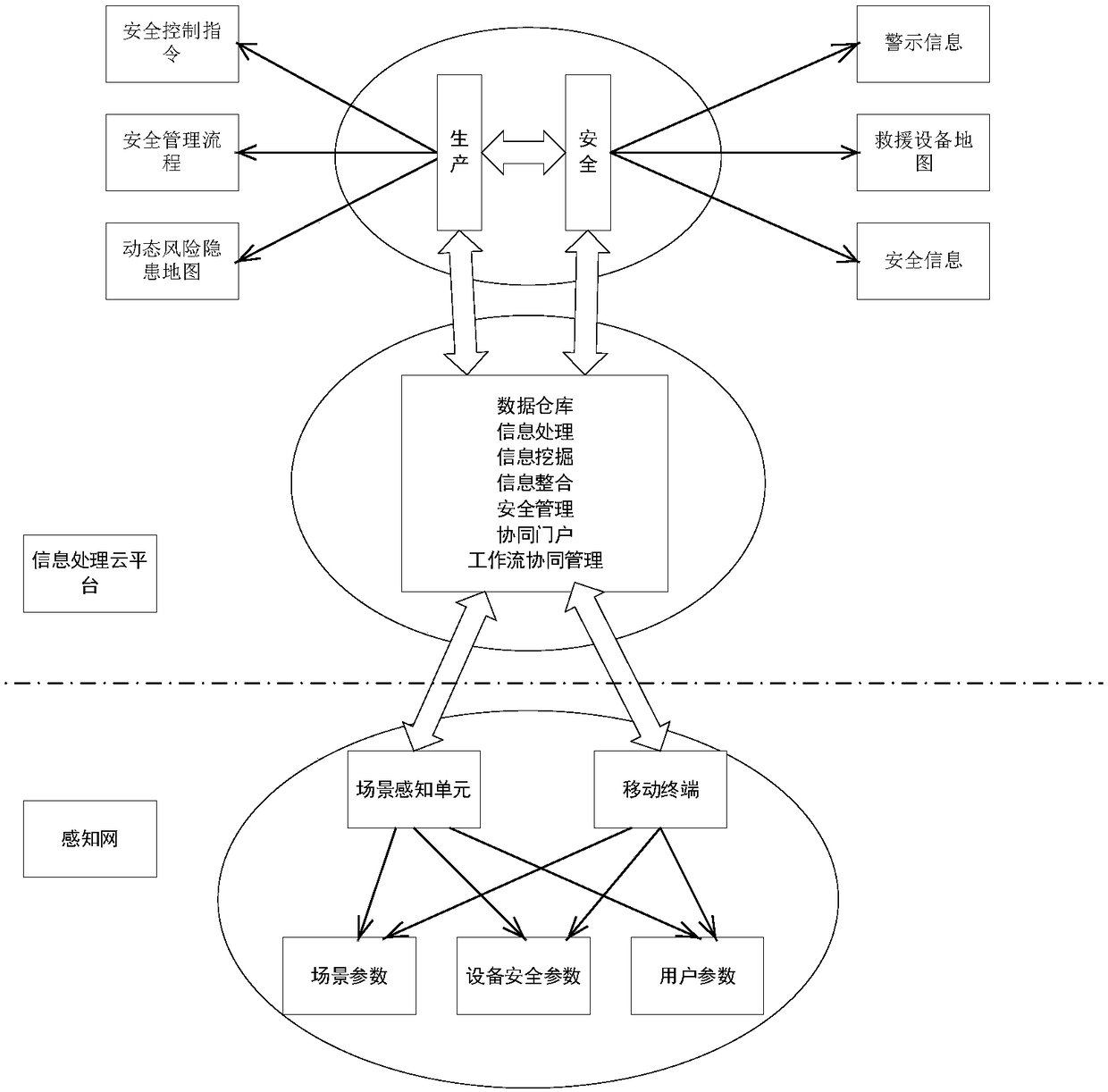
Security management system and method, equipment, storage medium, and information processing cloud platform
ActiveCN108319234AMaximize your subjective initiativeImplement security managementOffice automationTransmissionSafety management systemsEquipment Safety
The embodiment of the disclosure provides a security management system comprising an information processing cloud platform and at least one mobile terminal connected to the information processing cloud platform. The mobile terminal is used for sending scene description parameters to the information processing cloud platform, wherein the scene description parameters include a scene parameter, an equipment security parameter, and a user parameter corresponding to the mobile terminal. The information processing cloud platform is used for receiving the scene description parameters sent by the mobile terminal, determining the scene in which the mobile terminal is located and a corresponding security management process based on the scene parameter, evaluating safety states of equipment and / or the staff in the scene in which the mobile terminal is located according to the equipment security parameter and the scene parameter, determining a correlation degree between a user corresponding to themobile terminal and the scene in which the mobile terminal is located based on the user parameter, classifying the user corresponding to the mobile terminal into a work group of the scene in which the mobile terminal is located when the correlation degree is larger than a preset threshold, and sending the security management process to all mobile terminals of the work group.
Owner:分众共演(北京)科技有限公司
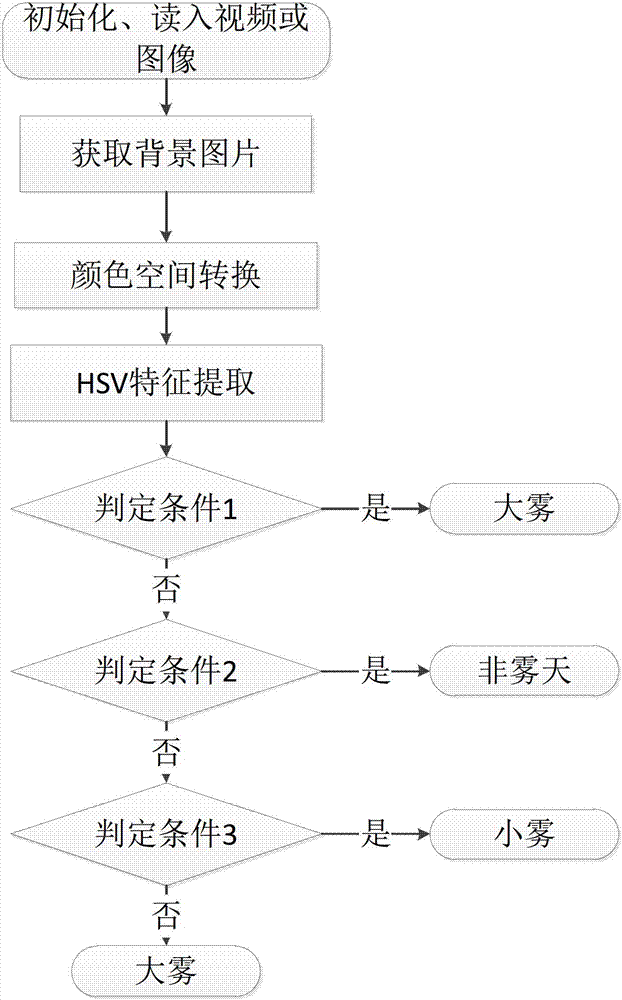
Foggy day detecting method based on image color spatial feature
InactiveCN102779349AImplement security managementAccurate divisionImage analysisPattern recognitionSingle image
The invention provides a foggy day detecting method based on an image color spatial feature. The method comprises the following steps of first step, obtaining a background picture through a video image or a single image; step 2, performing color space conversion for the background picture, and extracting the color space feature: firstly performing color space conversion for the background picture, converting from an RGB (red-green-blue) color space into an HSV (hue, saturation, value) color space, and extracting the features of various components of the HSV according to the information included image; and step 3, dividing the weather information included image into a non-foggy day, a little foggy day and a dense foggy day according to the identification conditions: at first, if the identification condition 1 is met, the weather is the dense foggy day, otherwise the identification is continued; secondly, if the identification condition 2 is met, the weather is the non-foggy day, otherwise, the identification is continued; and finally, if the identification condition 3 is met, the weather is the little foggy day, otherwise, the weather is the dense foggy day. The method provided by the invention is suitable for being used for monitoring the foggy day in expressways, particularly pre-warning the emergency of agglomerate fog in partial road segments, thus, the safe road driving can be ensured.
Owner:SOUTHEAST UNIV
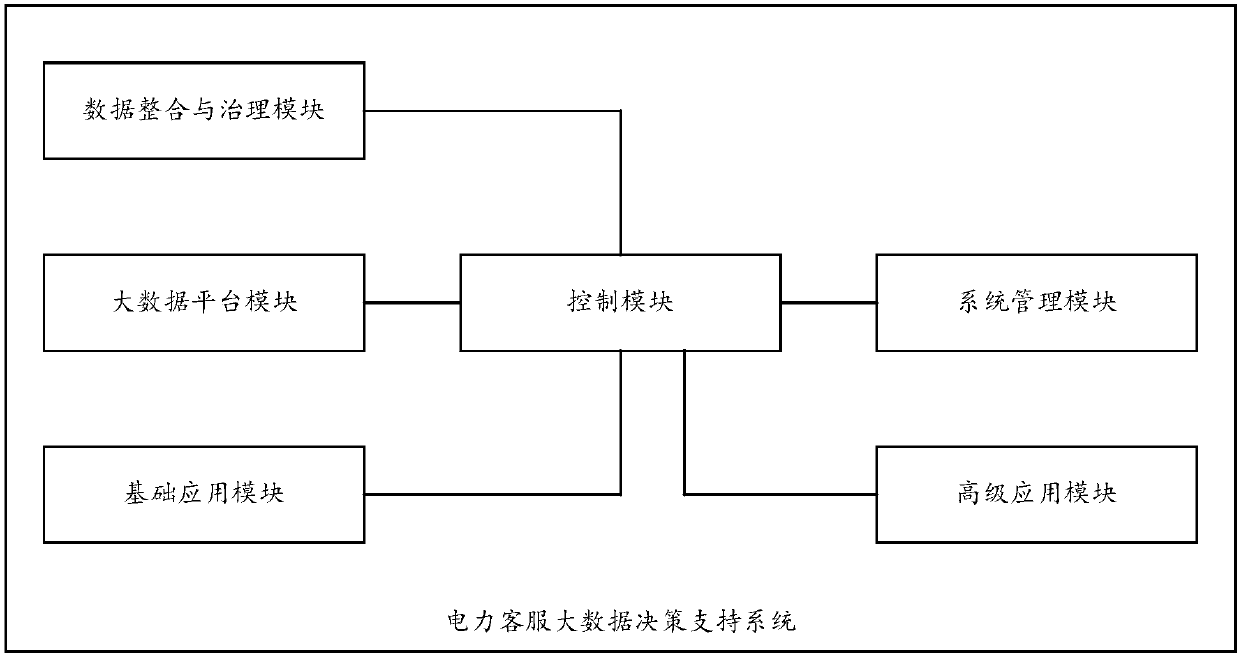
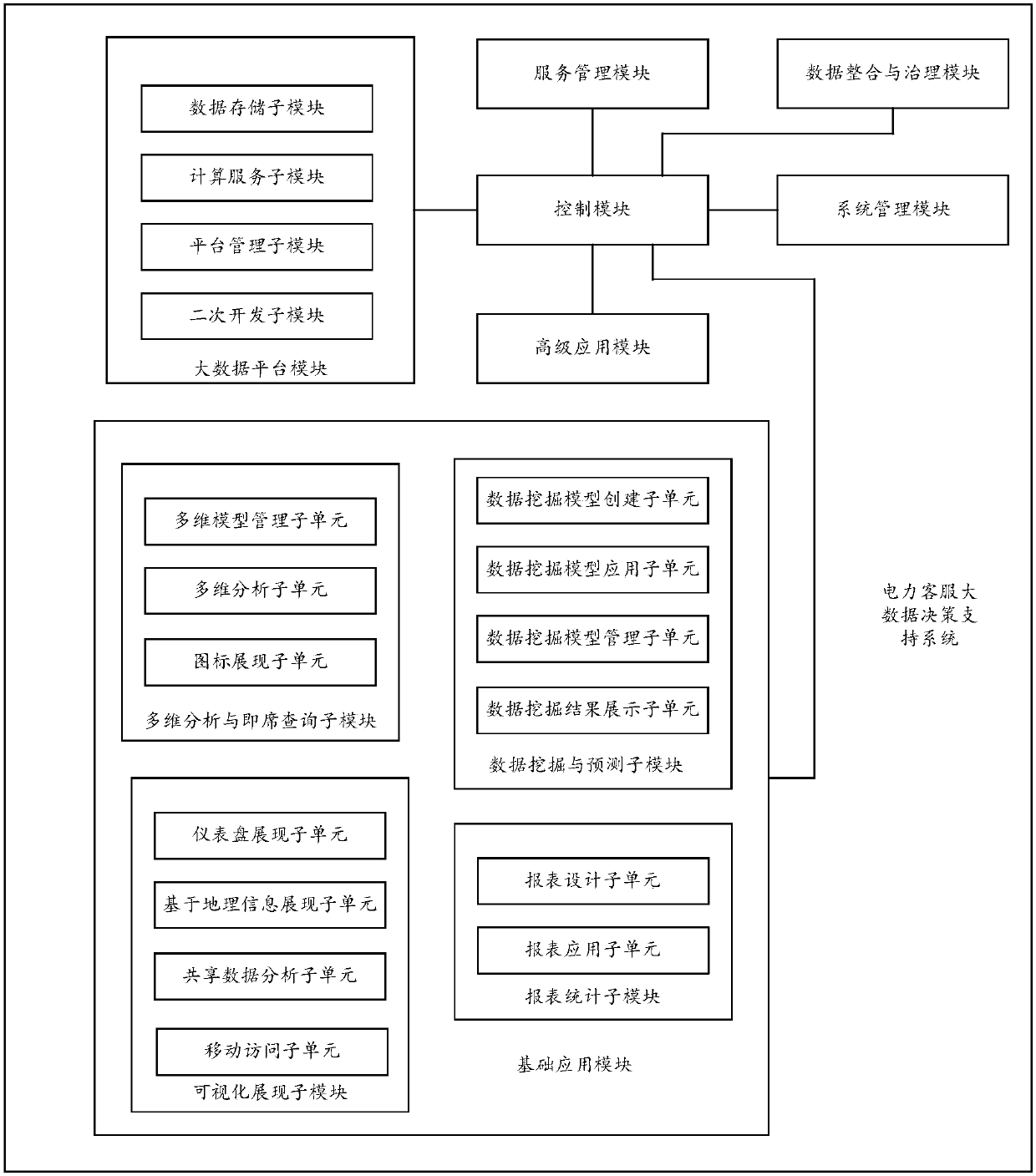
Electric power customer service big data decision support system
InactiveCN110163621ARealize the statistical report functionRealize functionCustomer relationshipSpecial data processing applicationsInformatizationData platform
The invention discloses an electric power customer service big data decision support system. The system comprises a control module, a big data platform module, a data integration and treatment module,a basic application module, a high-level application module and a system management module, and the control module is used for controlling the big data platform module, the data integration and treatment module, the basic application module, the high-level application module and the system management module to execute corresponding operation. Therefore, by implementing the embodiment of the invention, the electricity utilization rule and market behavior of a client can be discovered in vast quantities of power distribution and utilization data; and related business requirements of all-aroundcustomer service system support, fine decision of power grid operation, expansion of emerging business and reform support of the power market are met by combining power marketing management requirements, enterprise informatization management requirements and driving of power reform and new form of the power market.
Owner:GUANGZHOU POWER SUPPLY CO LTD
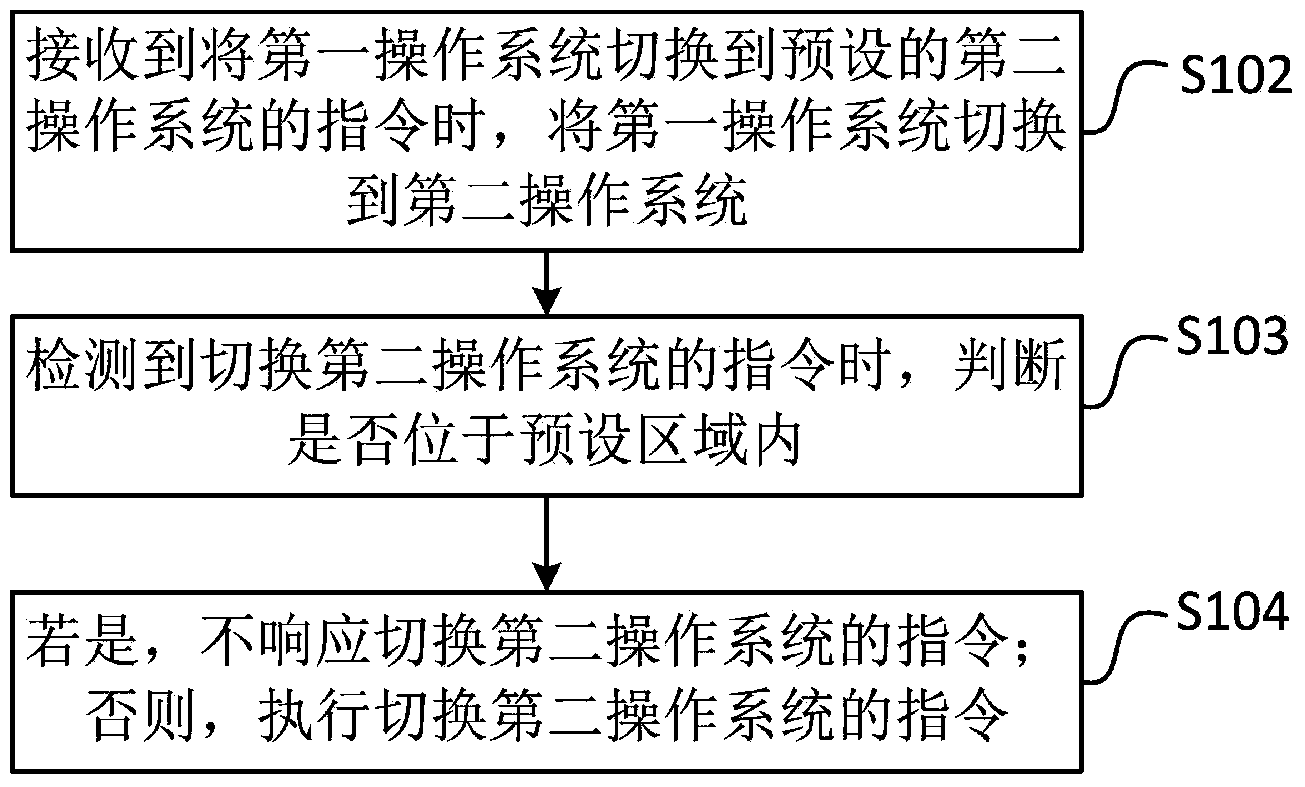
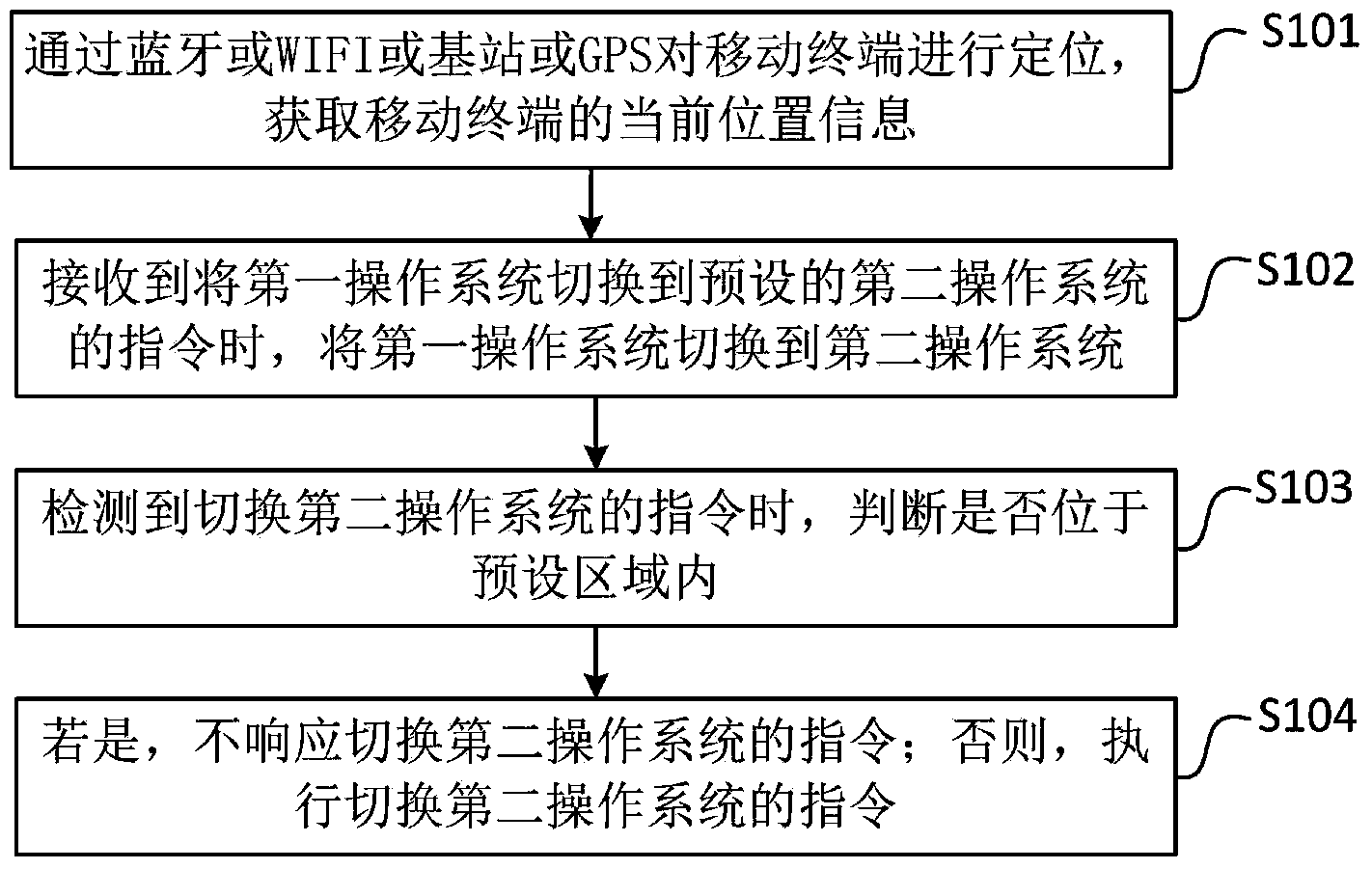
Mobile terminal as well as method and device for controlling switching of operation systems of mobile terminal
InactiveCN104239140AImplement security managementGuaranteed confidentialityProgram initiation/switchingComputer terminalInformation confidentiality
The invention discloses a mobile terminal as well as a method and a device for controlling switching of operation systems of the mobile terminal and belongs to the technical field of mobile terminals. The method comprises the following steps: when receiving an instruction of switching a first operation system to a preset second operation system, switching the first operation system to the second operation system; when detecting an instruction of switching to thse second operation system, judging whether the mobile terminal in positioned in a preset region; if yes, ensuring not to respond to the instruction of switching the second operation system; otherwise, executing the instruction of switching to the second operation system. By adopting the method, when the mobile terminal enters into a preset region which is required to keep confidential, controlling to switch the mobile terminal into the preset operation system, wherein the operation system is a safe operation system, applications or functions, such as photographing and sound recording, which possibly cause information leakage, are restricted, the operation system can not be switched from the preset operation system to another operation system in the preset region, united safety management for the mobile terminal is realized and the information confidentiality is ensured.
Owner:NUBIA TECHNOLOGY CO LTD
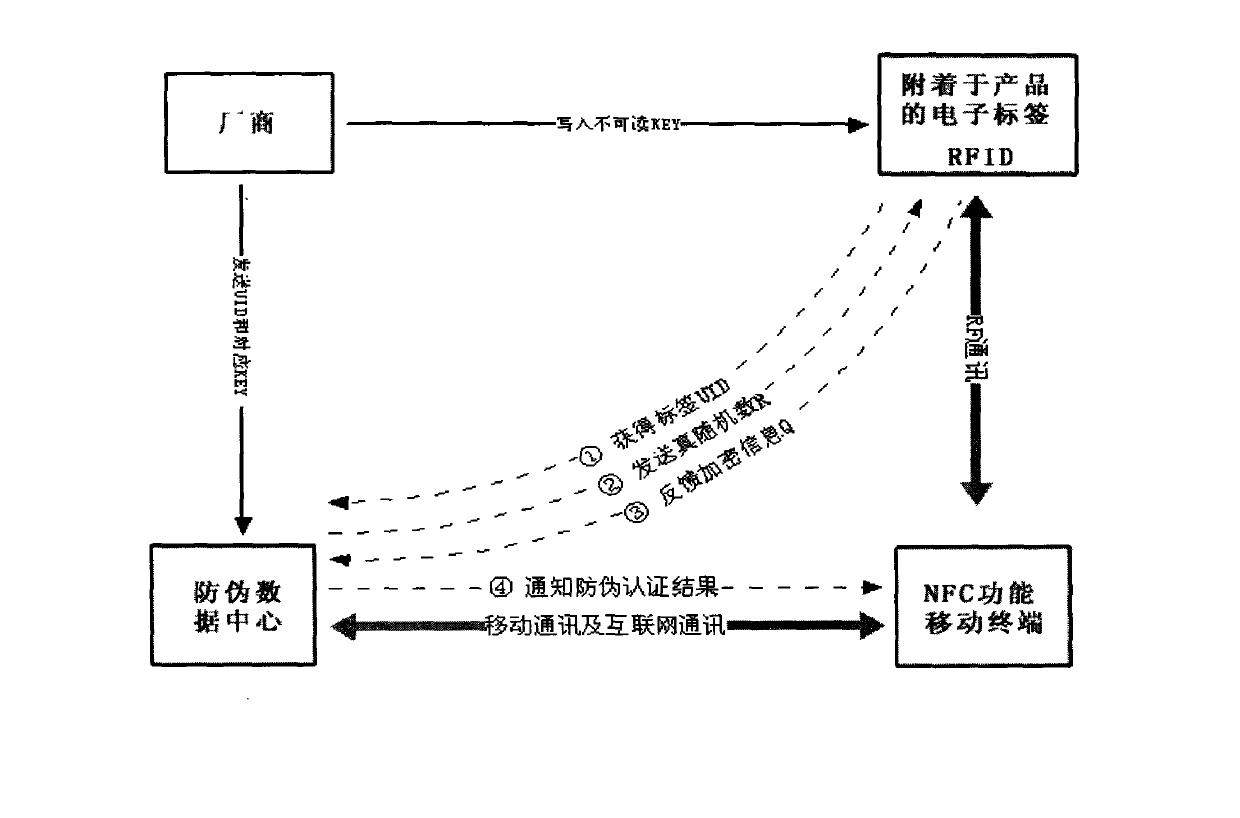
Radio frequency identification (RFID) anti-fake method
InactiveCN102629332APromote exchangeLower the thresholdKey distribution for secure communicationCo-operative working arrangementsEmbedded systemServer
The invention discloses a radio frequency identification (RFID) anti-fake method. A RFID chip which matches with the method is designed. Under the condition that high security can be guaranteed, an anti-fake query is performed through using a common NFC (near field communication) intelligent terminal to connect a remote server. According to the invention, the RFID chip with the high security is adopted. The common NFC intelligent terminal is connected to the remote server. And the remote server carries out anti-fake identification on a RFID tag. Therefore, a popularization threshold can be substantially reduced and simultaneously the high security can be maintained.
Owner:JIANGSU KILOWAY ELECTRONICS
Hazardous material management system and method
InactiveCN105574700AImplement security managementImprove management levelLogisticsManagement systemSecurity management
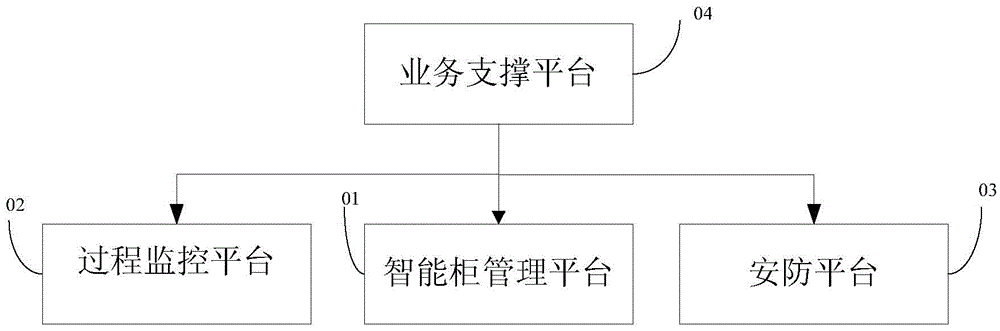
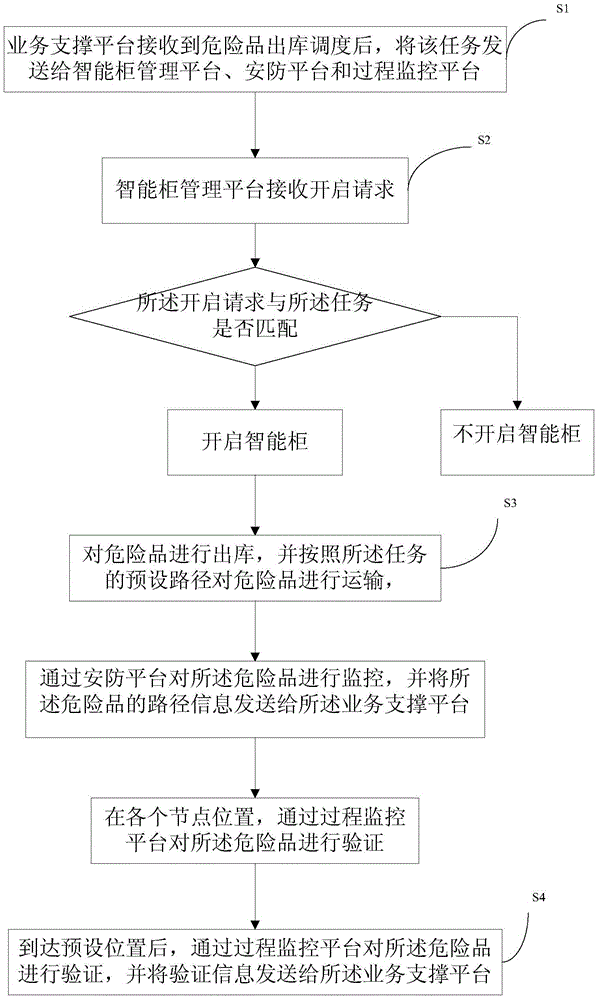
The invention provides a hazardous material management system and a method. The system comprises an intelligent cabinet management platform, a process monitoring platform, a security platform, and a business support platform, the intelligent cabinet management platform performs storage and storage management of the hazardous material, the security platform monitors the whole life cycle of the hazardous material, the hazardous material is verified in each important node via the process monitoring platform, and the business support platform receives data of the intelligent cabinet management platform, the process monitoring platform, and the security platform and manages the whole process of the hazardous material. According to the system and the method, the hazardous material is comprehensively managed in the whole life cycle, problems in any link can be monitored, the whole process of storage, usage, recycling, and management of the hazardous material in a plant area is effectively solved, comprehensive management is achieved, defects in the prior art are effectively overcome, and security management, process management, responsibility management, and tracking management of the hazardous material can be realized via an electronic monitoring method.
Owner:FOUNDER BROADBAND NETWORK SERVICE
Archive automatic management system based on radio frequency identification (RFID) electronic label
InactiveCN102903033AImplement security managementHelps with dynamic managementCo-operative working arrangementsResourcesDynamic managementData management
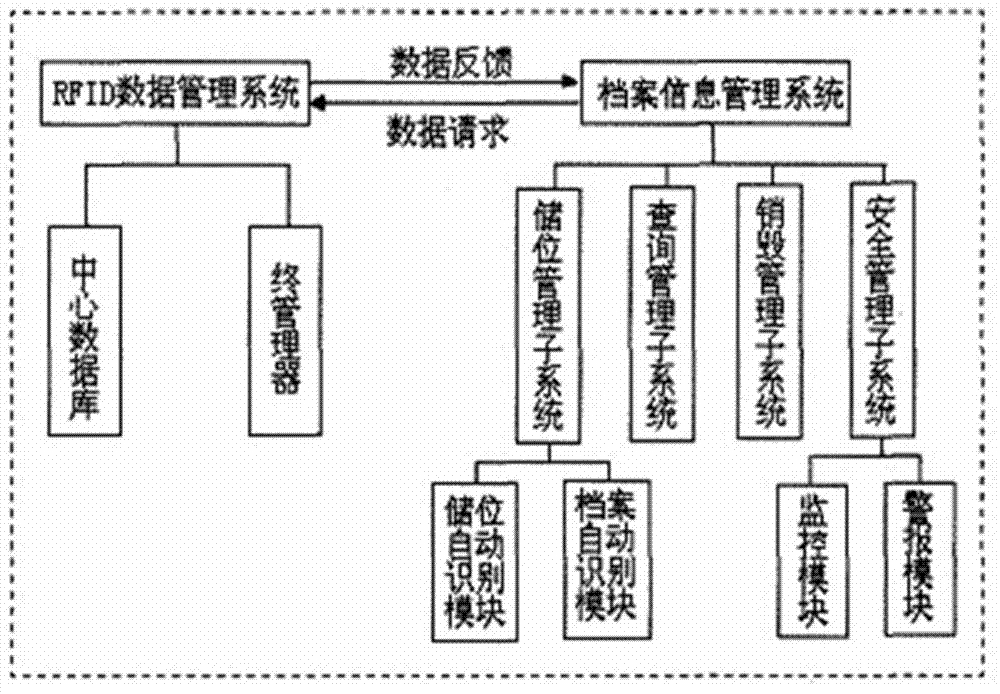
The invention discloses an archive automatic management system based on a radio frequency identification (RFID) electronic label. The archive automatic management system consists of an RFID data management system and an archive management information system, wherein the RFID data management system is butted with the archive management information system through a system interface; the RFID data management system performs acquisition, storage and electronic label reading and writing on archive data; and the archive management information system applies and manages archive information. The system is applied to archive management and has the characteristics of convenience in data reading and diversified management; by RFID, information of a plurality of chips can be read at the same time; a manager can conveniently execute dynamic management on inventory archives; labor intensity of a worker can be reduced; a working process is simplified; and the working efficiency is greatly improved.
Owner:广东凌康科技有限公司
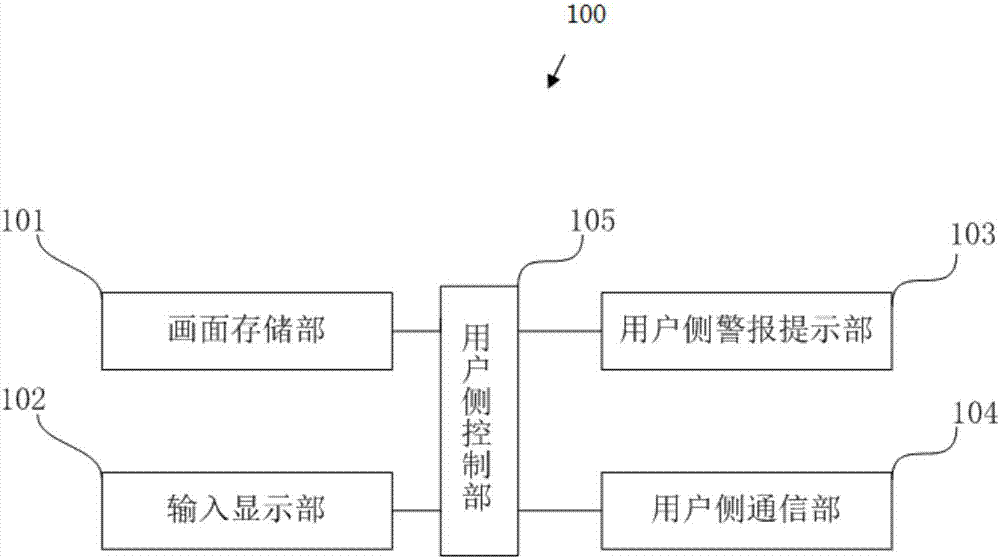
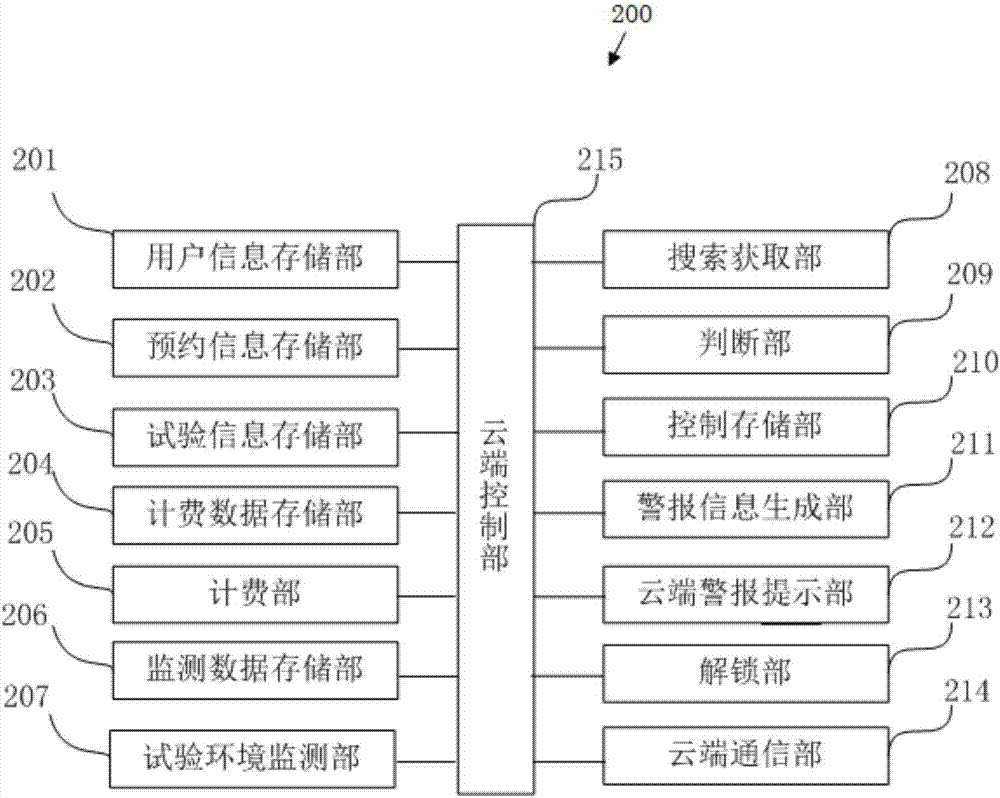
Laboratory management system
InactiveCN107016450AAchieve reasonable arrangementsEasy to arrangeMeasurement devicesReservationsSafety educationSecurity management
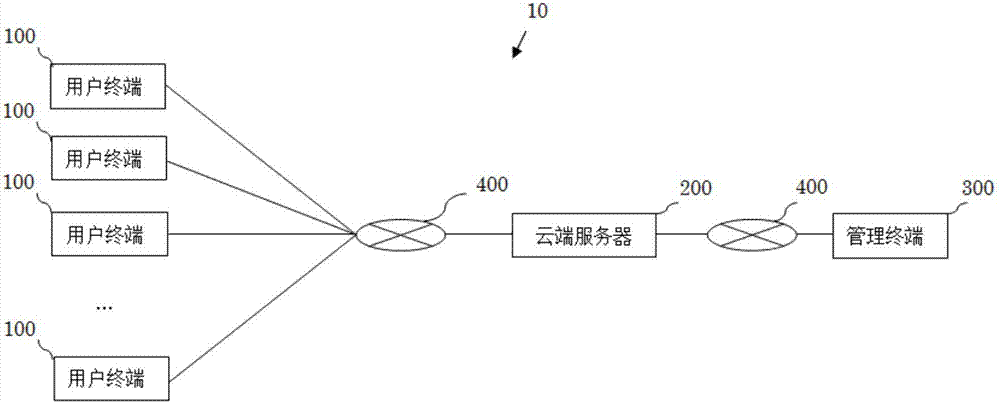
The invention relates to a laboratory management system, which comprises a plurality of user terminals, a management terminal and a cloud server, and is characterized in that the plurality of user terminals are held by a plurality of users respectively, the management terminal is held by a manager, and the cloud server performs communication connection with the user terminals and the management terminal through a communication network. The laboratory management system is used for performing management on user information, reservation information, test information, billing data and monitoring data, realizes safety management for registration and login accounts, laboratory access, instrument and equipment utilization and the like of users, realizes orderly, efficient and scientific reservation information management so as to facilitate the users to arrange tests reasonably, realizes safety education in tests, facilitates sharing of test experience of the users, realizes scientific and reasonable charge management, improves a circumstance that experimental resources are wasted and abused, realizes all-weather monitoring for the experiment environment so as to facilitate query for experiment environment data and be conducive to repeated operations of the tests, and realizes monitoring for emergency situations and notifies the concerned personnel to handle accidents.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
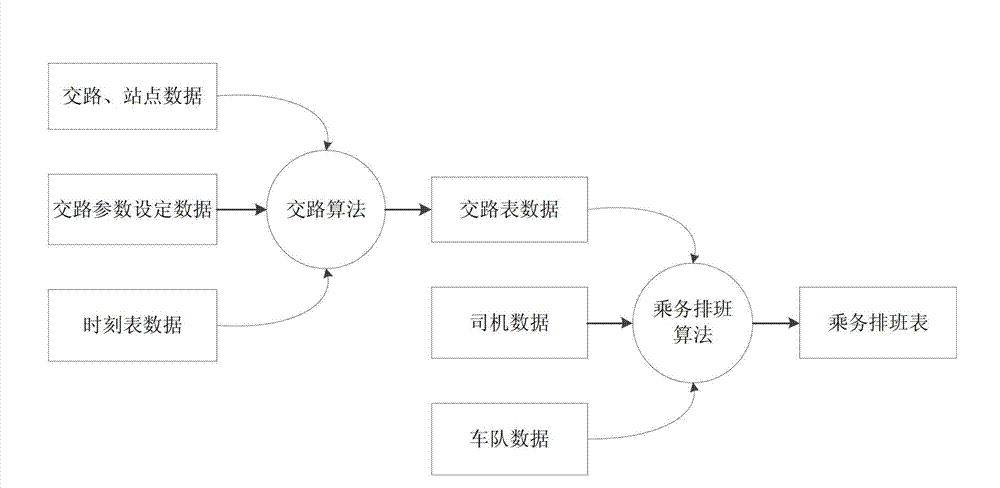
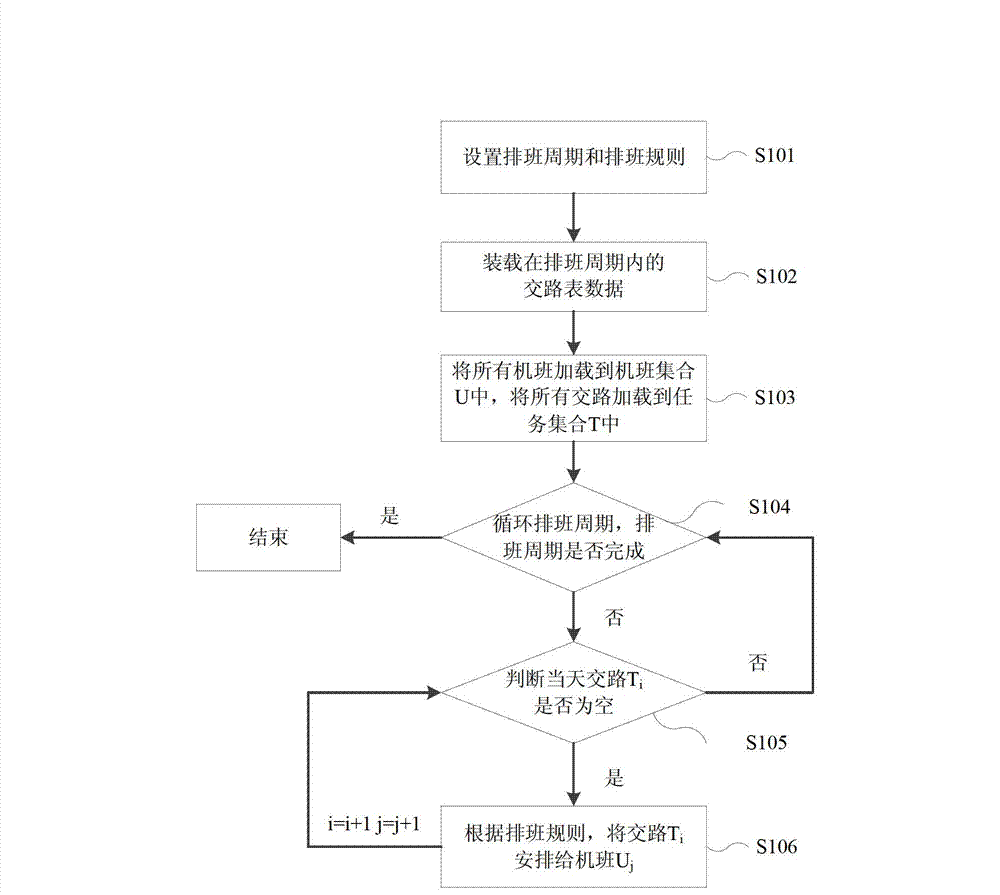
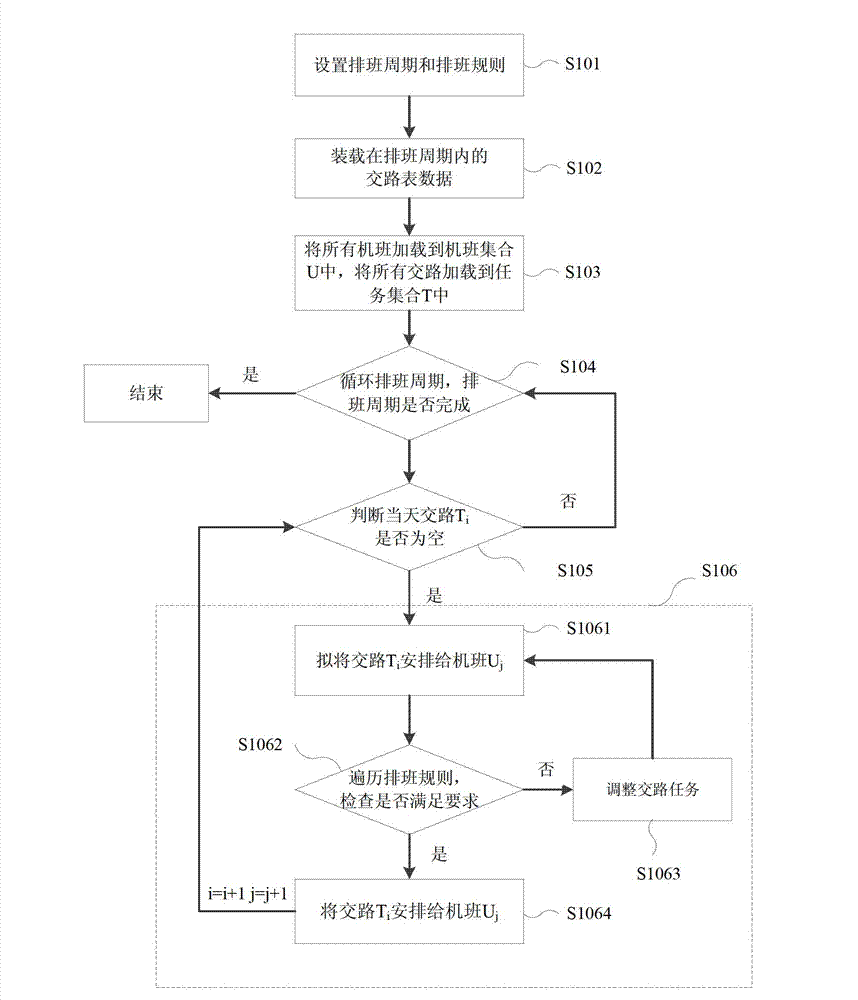
Scheduling method of subway attendant management system
InactiveCN102930399AImplement security managementSimple and fast operationMultiprogramming arrangementsResourcesRouting tableTime table
The invention discloses a scheduling method of a subway attendant management system. The scheduling method includes the following steps: step 101, arranging a scheduling cycle and a scheduling rule; step 102, adding routing table data in the scheduling cycle; step 103, adding all subway numbers in a subway number collection U and adding all routings in a task collection T; step 104, circulating the scheduling cycle and stopping the circulation if the scheduling cycle is completed; step 105, judging whether the routing Ti of the same day is empty and returning to the step 104 if the judged result is yes; step 106, arranging the routing Ti to a subway number Uj according to the scheduling rule, enabling i to be equal to i + 1 and j to be equal to j + 1, and returning to the step 105. According to the scheduling method of the subway attendant management system, attendant scheduling can be achieved by leading in a time table, operation is easy, errors cannot happen easily, and safe management of a subway is achieved.
Owner:深圳市地铁三号线投资有限公司
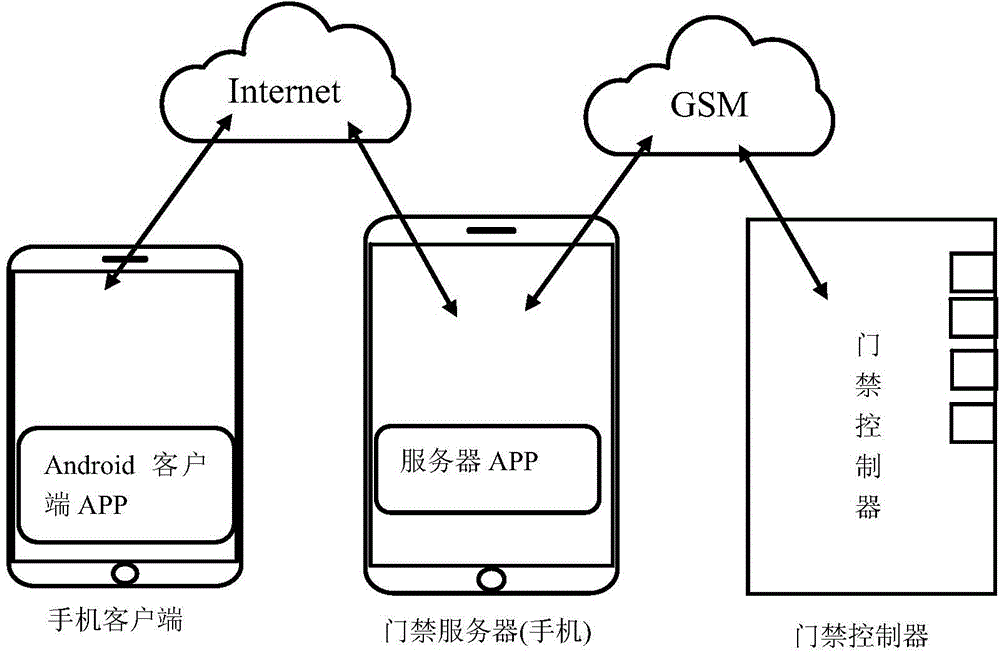
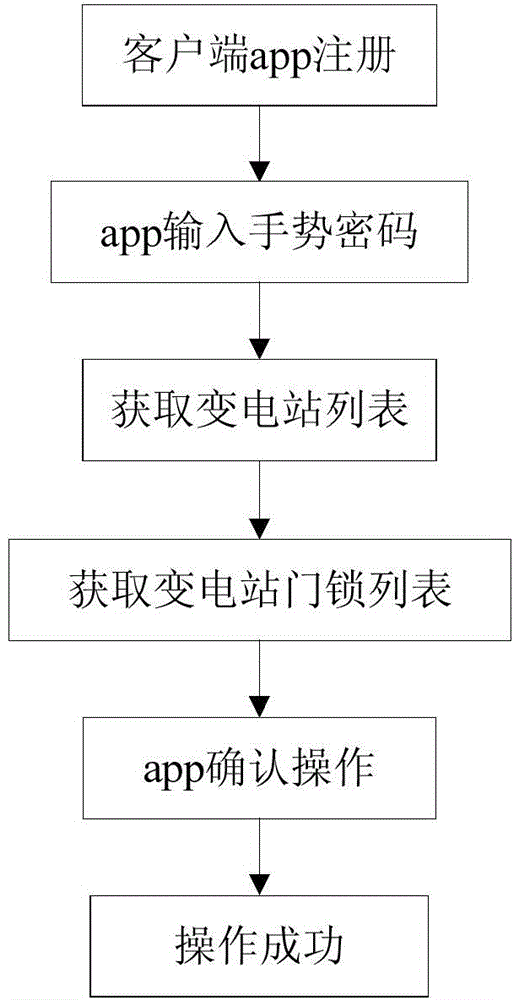
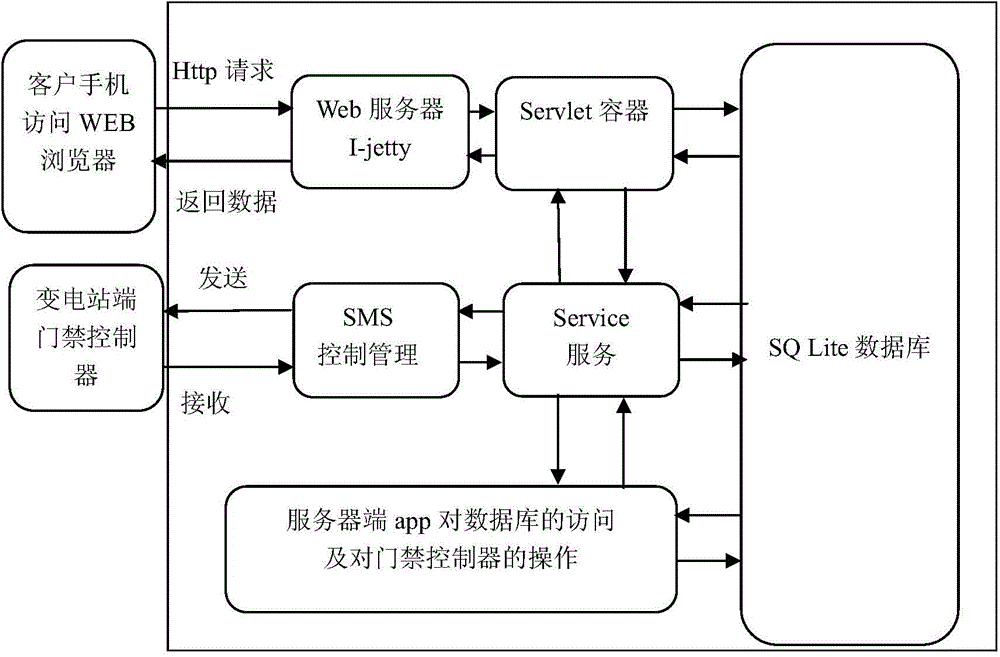
Unattended substation access control system and method based on intelligent mobile platform
The invention discloses an unattended substation access control system based on an intelligent mobile platform. The unattended substation access control system comprises a mobile phone client, an access control server and an access controller. An operation request is sent to the access control server through a wide area network by independence on app software of a smart phone, the access control server judges the operation request and then utilizes a mobile base station to send a GSM signal to the access controller at the front end of a substation, front-end equipment of the substation further controls to open a door, and a plurality of door locks of a plurality of substations in the same area can be controlled at the same time. Staffs can utilize smart phones to control the access and cardless door opening of the substations, so that the generated labor cost and vehicle cost are reduced, the substation entering efficiency is improved, and Internet of Things intelligence of the access control system is realized. The invention also discloses an unattended substation access control method based on the intelligent mobile platform.
Owner:江苏省电力公司太仓市供电公司
Big data safety management system
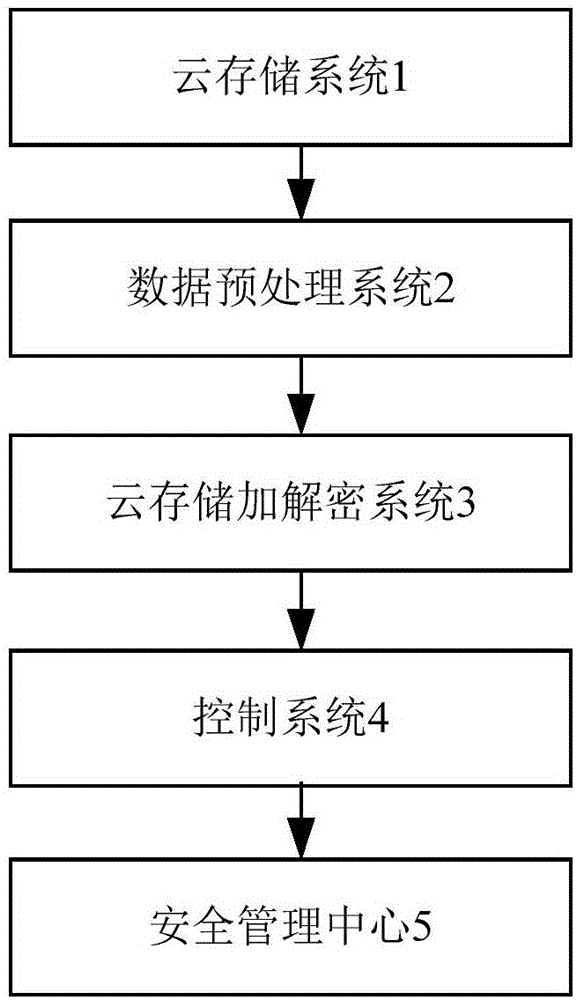
ActiveCN106203146AEasy to achieve unified managementEasy accessDigital data protectionControl systemSafety management systems
The invention provides a big data safety management system. The system comprises a cloud storage system, a data pre-processing system, a cloud storage encryption / decryption system, a control system and a safety management center. Through the brand-new module design, the data management level is improved, and the data security is enhanced.
Owner:GUANGDONG GANG XIN SCI & TECH
Method and platform for demonstrating multi-dimensional multi-industry information of two-dimensional codes
ActiveCN108229195AExpand the scope of application scenariosImplement security managementDigital data protectionSensing by electromagnetic radiationMulti dimensionalWorld Wide Web
Owner:高江涛
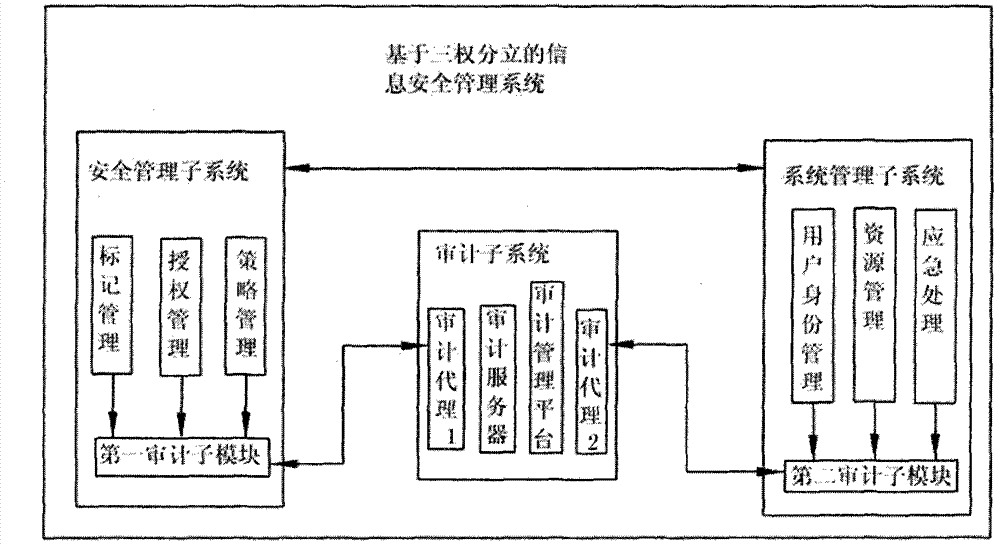
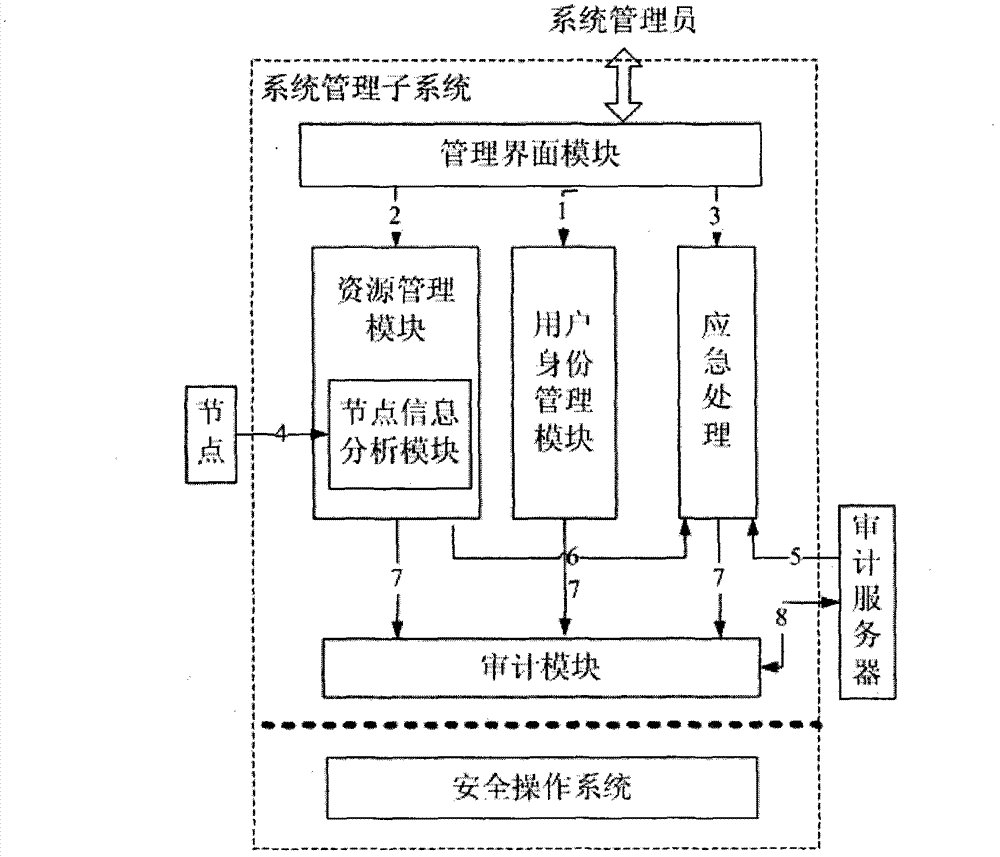
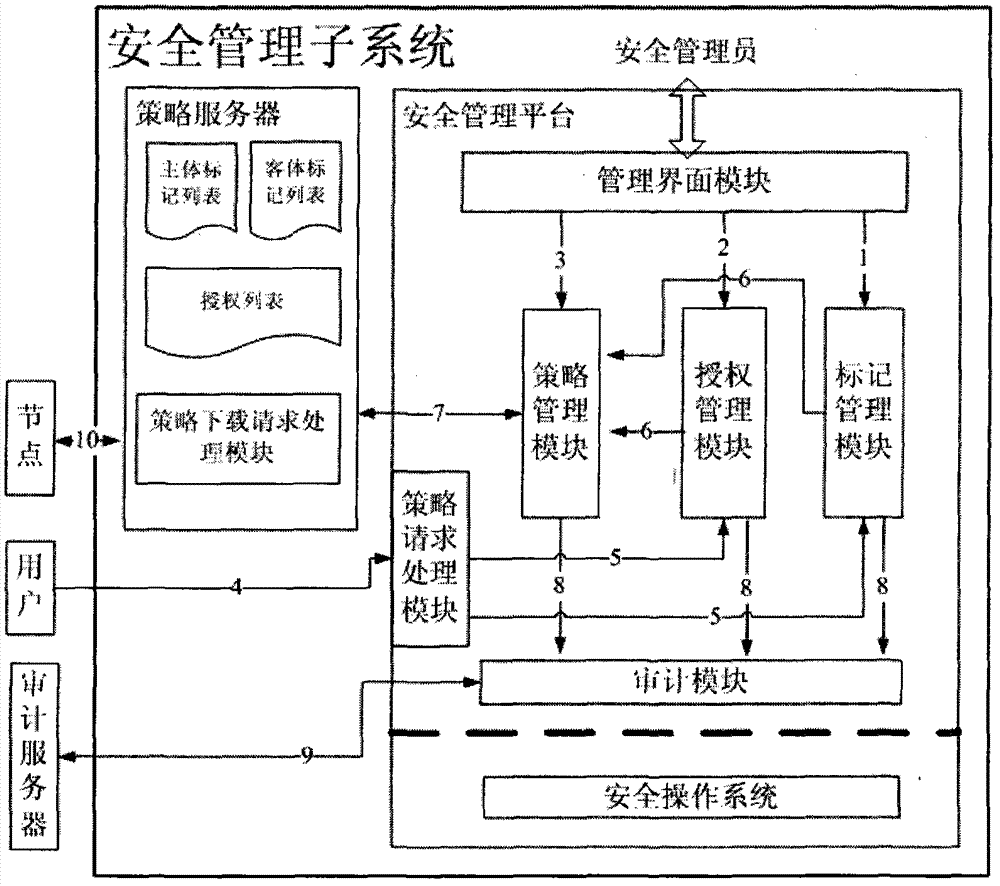
Three power separation-based information security management system and information security management method
ActiveCN102891840AImplement security managementRealize unified decentralized managementSecuring communicationSecurity policyManagement system
The invention discloses a three power separation-based information security management system which comprises a system management subsystem, a security management subsystem and an auditing management subsystem, wherein the system management subsystem manages system subject resources and system object resources to generate and send a first auditing record to the auditing management subsystem, the security management subsystem uniformly marks the system subject / object resources and authorizes the system subject and manages the security policy and distributive security mechanism of the system to generate and send a second auditing record to the auditing management subsystem, the auditing management subsystem centrally manages the security auditing policy and mechanism distributed in all components of the system, and the auditing management subsystem receives and manages the first and second auditing record and generates the system auditing record. Therefore, the information security management system is distinguished as the decentralized management of the three subsystems, the management authority of the subsystems is distributed, mutual authority restriction relationship is formed among the subsystems, and the information security and management reliability can be improved.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
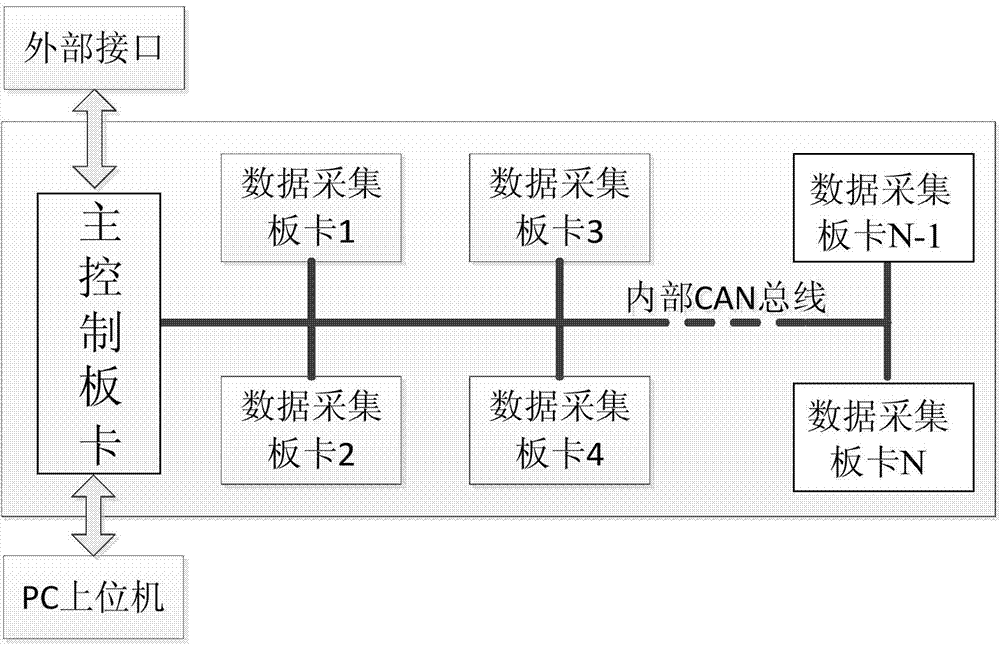
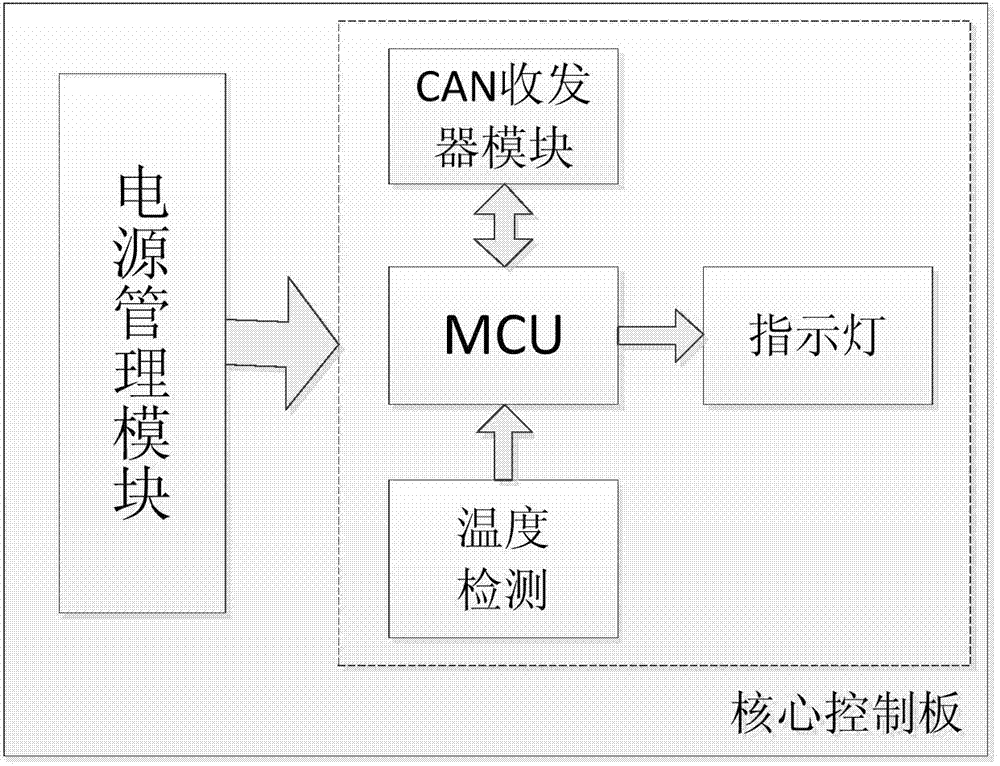
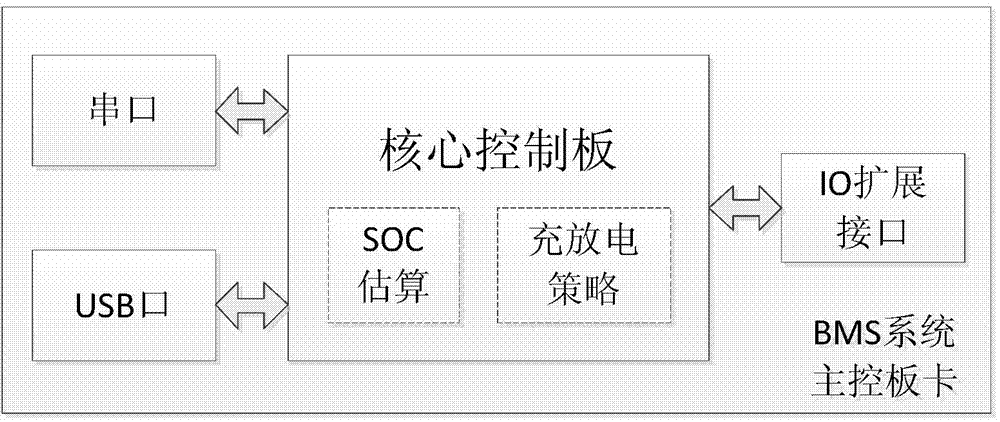
Lithium battery pack management system
InactiveCN104518530ARealize real-time monitoringReal-time monitoring of working statusCharge equalisation circuitIndicating/monitoring circuitsModularityEqualization
The invention relates to a lithium battery pack management system. The lithium battery pack management system comprises N sets of lithium batteries, N slave control panel cards, a main control board and a host computer. The system can monitor the voltage, the charging and discharging currents, the operating temperature and the environmental temperature of a single lithium battery in real time, equalization control can be performed on the single battery with a large state difference according to the detected voltage of the lithium battery and an equalization algorithm brought forward, and the consistency of the battery is improved. According to collected parameters, the main control board can give an SOC estimated value, provides a charging and discharging management strategy, and extends the service lifetime of the battery. The host computer displays the collected state information, control information, abnormality information and alarm information of a lithium battery pack and provides friendly man-computer interaction. Meanwhile, a similar modularization design scheme is brought forward for hardware development of the system, and the maintenance cost can be effectively reduced.
Owner:STATE GRID LIAONING ELECTRIC POWER CO LTD SHENYANG POWER +2
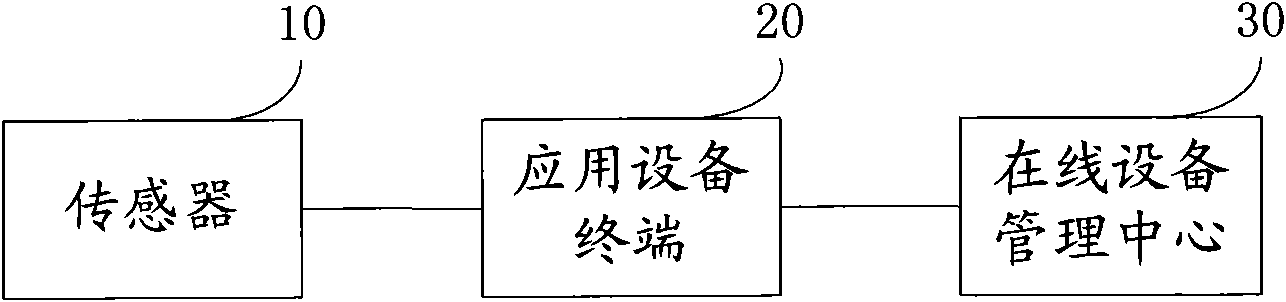
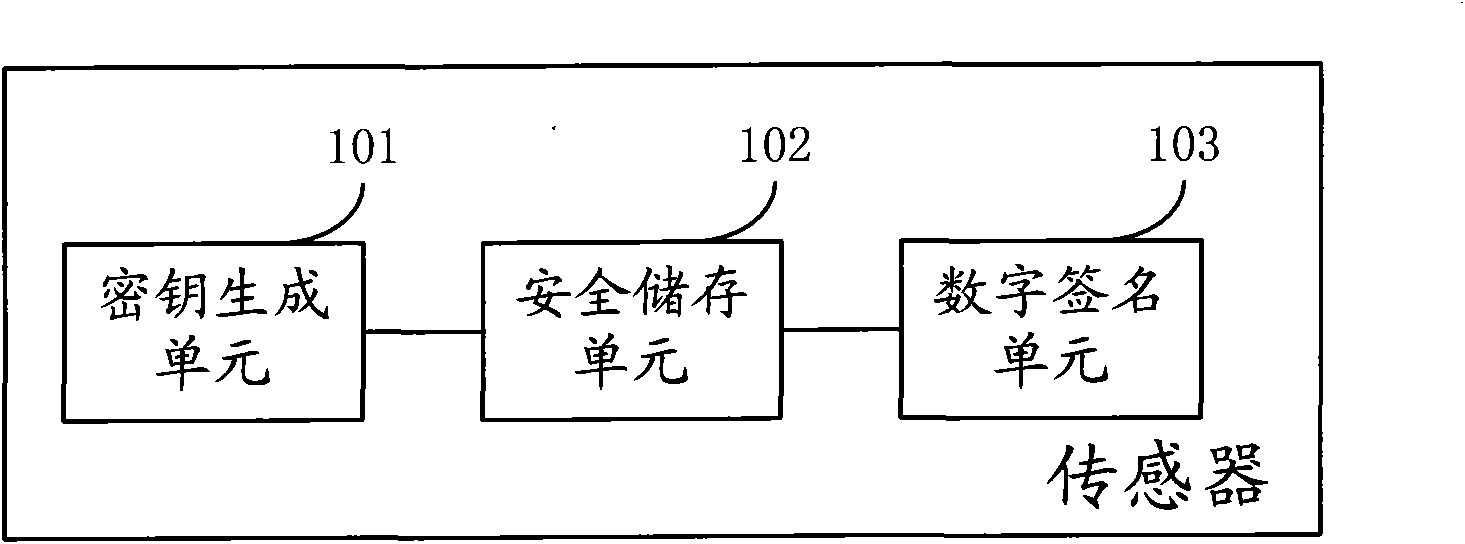
Safety authentication method of sensor, sensor and authentication system thereof
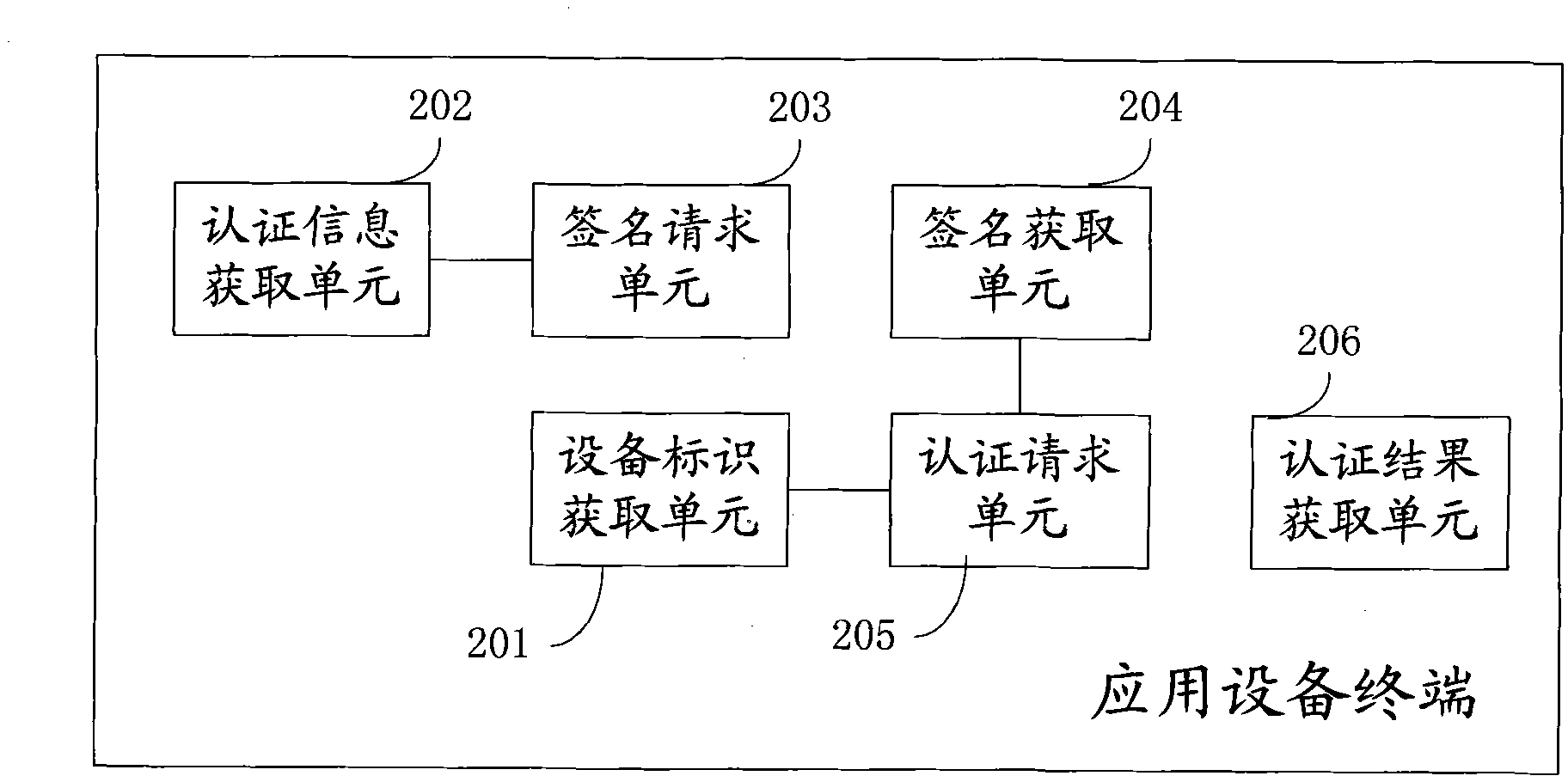
InactiveCN101778102AImplement security managementAvoid safety hazardsPublic key for secure communicationUser identity/authority verificationAuthentication systemTimestamp
The embodiment of the invention provides a safety authentication method of a sensor, comprising the following steps: acquiring authentication information from an on-line equipment management center, wherein the authentication information comprises a timestamp and a random number; acquiring a device identification of the sensor; sending the authentication information to the sensor so as to ask fora signature; acquiring an authentication information digitally signed by the sensor; uploading an authentication request to the on-line equipment management center, wherein the authentication requestcomprises the device identification, the authentication information and the authentication information digitally signed by the sensor; and acquiring an authentication result of the on-line equipment management center. The embodiment of the invention is correspondingly provided with a sensor and an authentication system thereof. By implementing the invention, the safety management of the sensor equipment is realized and the potential safety hazard brought by utilizing illegal sensor equipment is avoided.
Owner:卓望数码技术(深圳)有限公司
Lithium battery
PendingCN108511829AReal-time monitoring of deformationTimely reflection of work heat expansionSecondary cellsInternal pressureElectrochemical response
The invention provides a lithium battery. The lithium battery comprises an electrical core and a shell, wherein the electrical core is arranged in the shell, comprises a positive plate, a negative plate and a diaphragm, and is characterized in that a pressure transducer is arranged between the positive plate or / and negative plate and the diaphragm. Various pressure transducers for monitoring pressure changes are available; however, transducer for detecting the inner pressure of the battery should have a tiny size; and in measurement of high-fidelity transfer pressure, the pressure transducer is tightly pasted with the pole plates in the battery and has no influence on electrochemical reactions in the battery.
Owner:长沙聚能充新能源有限公司
Security reinforcement method for virtual machine in desktop cloud environment
ActiveCN105487916AEnsure safetyImplement security hardeningPlatform integrity maintainanceTransmissionOpen sourceKey factors
The invention discloses a security reinforcement method for a virtual machine in a desktop cloud environment. The method comprises: solving a security problem of a remote desktop protocol connection; solving a security problem of a host and a virtual machine running in the host; solving an on-demand distribution problem of security resources of desktop cloud; and solving a security protection problem of an open-source virtual machine manager. According to the method, various problems related to background security of the desktop cloud are studied; and by reducing the influence of key factors on virtual machine security and by assistance of resource scheduling specially for a desktop virtualization environment, the security reinforcement of the virtual machine and the security management of the virtual machine are realized and the virtual machine security of a user is ensured.
Owner:SHANGHAI JUNESH INFORMATION TECH CO LTD
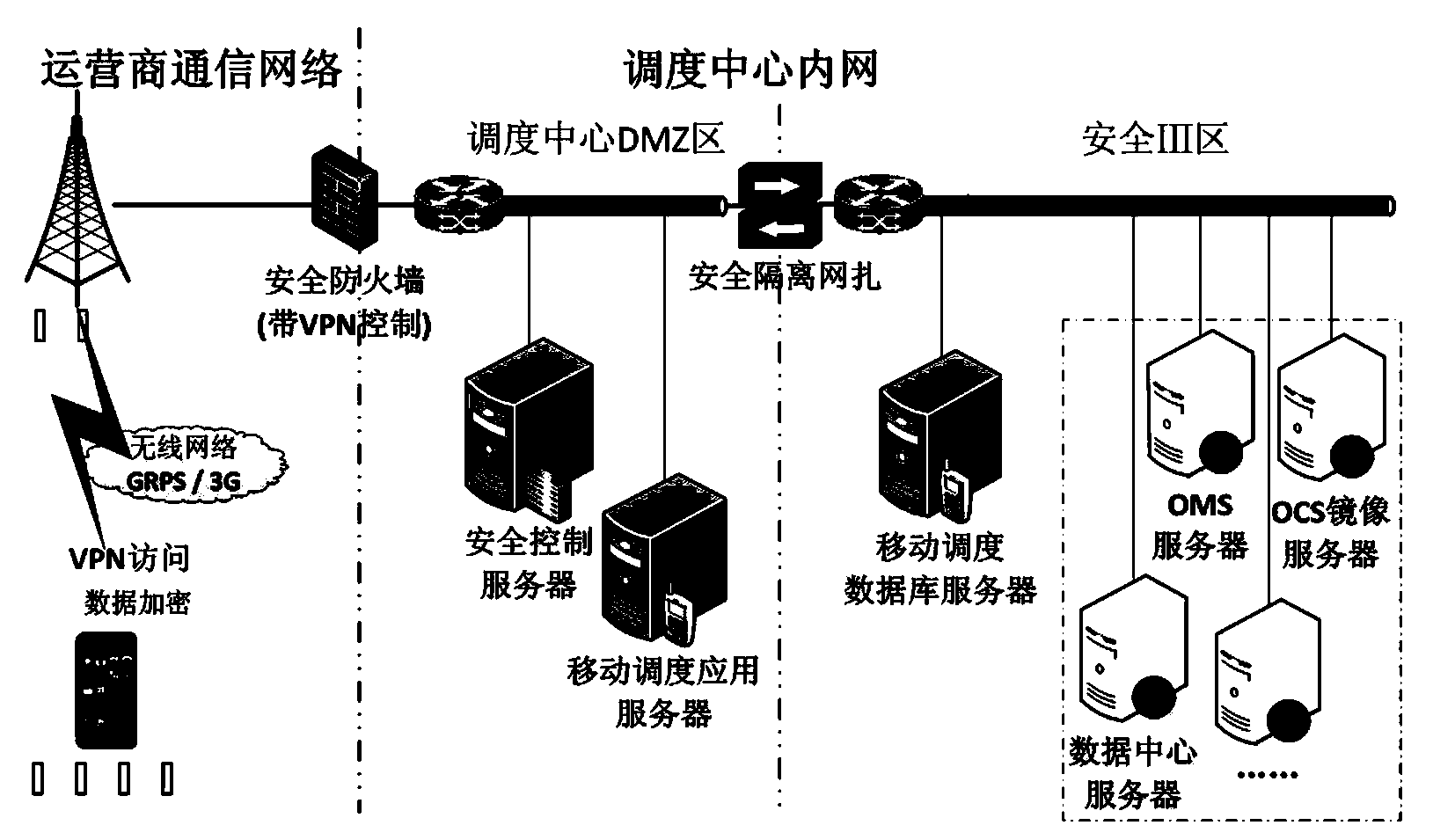
Power grid dispatching mobile platform safety guaranteeing and controlling method
InactiveCN104065485AImprove computing efficiencyImprove convenienceUser identity/authority verificationSystem safetyMobile end
Provided is a power grid dispatching mobile platform safety guaranteeing and controlling method. According to the method, safety control is carried out from the three aspects of equipment access, communication safety and data encryption, a full-process safety protection system is formed due to safety control from the three aspects, and safety of application and data at a mobile terminal can be effectively ensured. Aiming to solve the safety problems in the implementation of the power grid dispatching application on the intelligent mobile terminal, according to the relevant requirements of power grid secondary system safety protection, the safety guaranteeing and controlling method of the intelligent mobile terminal applied in the power grid dispatching is provided by carrying out research on safety technologies of the aspects such as access authentication, communication links and data of the intelligent mobile terminal, a high-standard safety control closed-loop process is formed, and therefore the safety and reliability of the intelligent mobile terminal applied in power grid dispatching management are improved.
Owner:CHINA SOUTHERN POWER GRID COMPANY +1
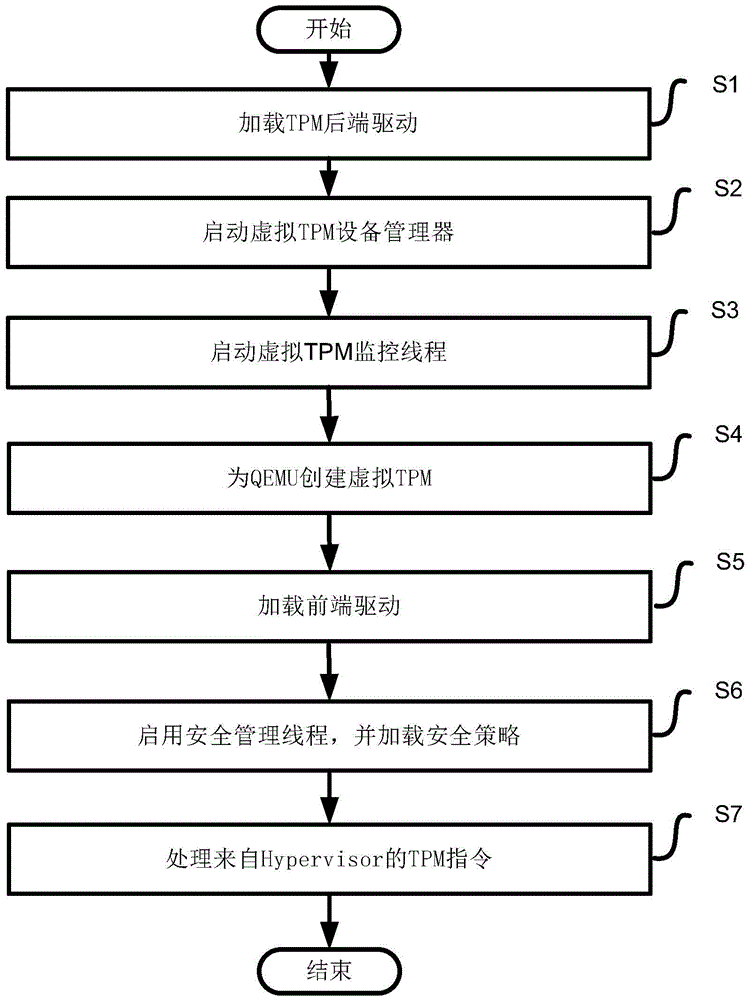
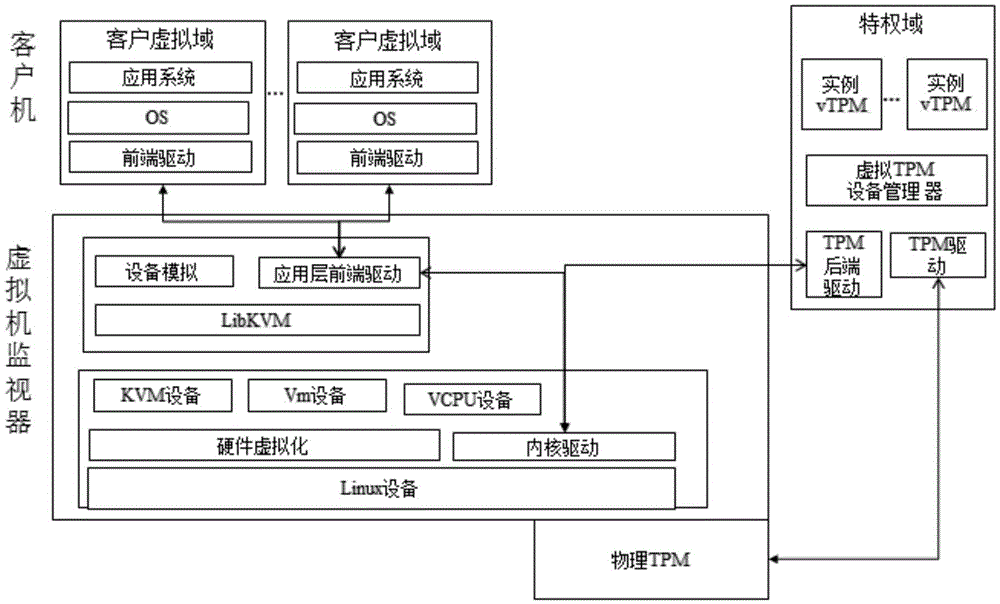
Security management method of virtual machine based on trust root
InactiveCN105574415AAbility to implement virtualizationImplement security managementPlatform integrity maintainanceSoftware simulation/interpretation/emulationSecurity policyProtocol Application
The invention provides a security management method of a virtual machine based on a trust root. The security management method comprises the following steps: S1, loading a back-end drive of an application layer to generate simulative equipment vTPM; S2, starting a virtualization monitor; S3, establishing a monitoring thread of a virtual TPM; S4, establishing the virtual TPM for a QEMU; S5, loading a front-end drive; S6, starting a security management thread, and loading a security strategy; and S7, processing a TPM instruction from a Hypervisor. The security management method of the virtual machine based on the trust root provided by the invention realizes the virtualization capability on the traditional TPM; integrity protection and isolation on a client machine are carried out over a virtualization system; and security management of the virtual machine is realized over the hypervisor.
Owner:CETC CHINACLOUD INFORMATION TECH CO LTD
Gas station calorgas safety linkage system and method
ActiveCN103985069ATo achieve the purpose of integrated linkageImprove securityData processing applicationsCo-operative working arrangementsGas cylinderComputer terminal
Provided are a gas station calorgas safety linkage system and method. The gas station calorgas safety linkage system comprises an instation service operational center, an entrance guard unit, an RFID collecting terminal, a touch screen, a license plate information collecting unit, a gas cylinder information collecting unit and a refilling card information collecting unit. The entrance guard unit, the RFID collecting terminal, the touch screen, the license plate information collecting unit, the gas cylinder information collecting unit and the refilling card information collecting unit are connected with the instation service operational center. A license plate, a gas cylinder, a refilling card, safety check information and other important information are collected to identify the safety of a vehicle, the gas cylinder, the refilling card and the like, the instation service operational center is informed of the identification result, the instation service operational center controls a refilling gun according to the identification result, and therefore the aim of the integrated linkage of the card, an engine, the vehicle and the cylinder is achieved.
Owner:WHALE CLOUD TECH CO LTD
Multifunctional three-phase electric power monitoring apparatus
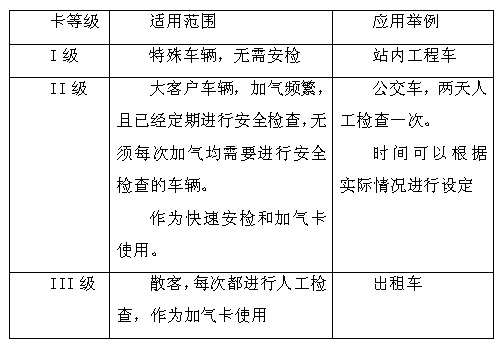
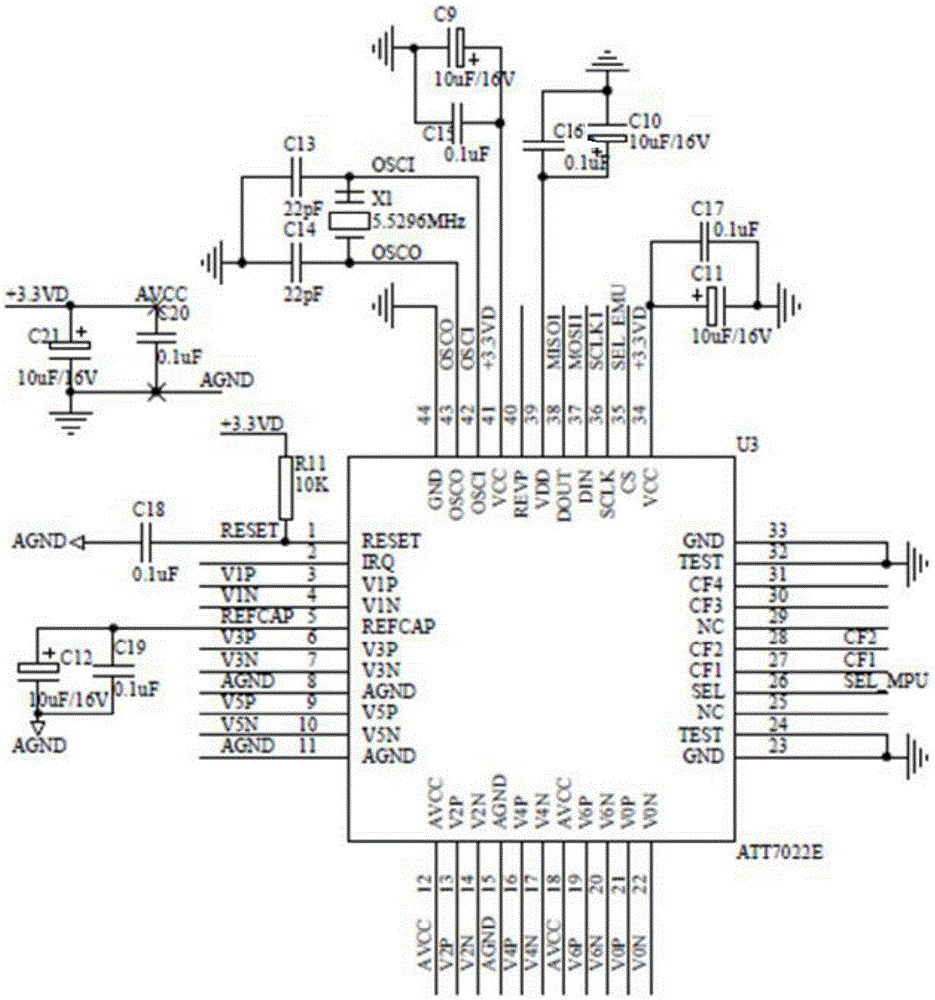
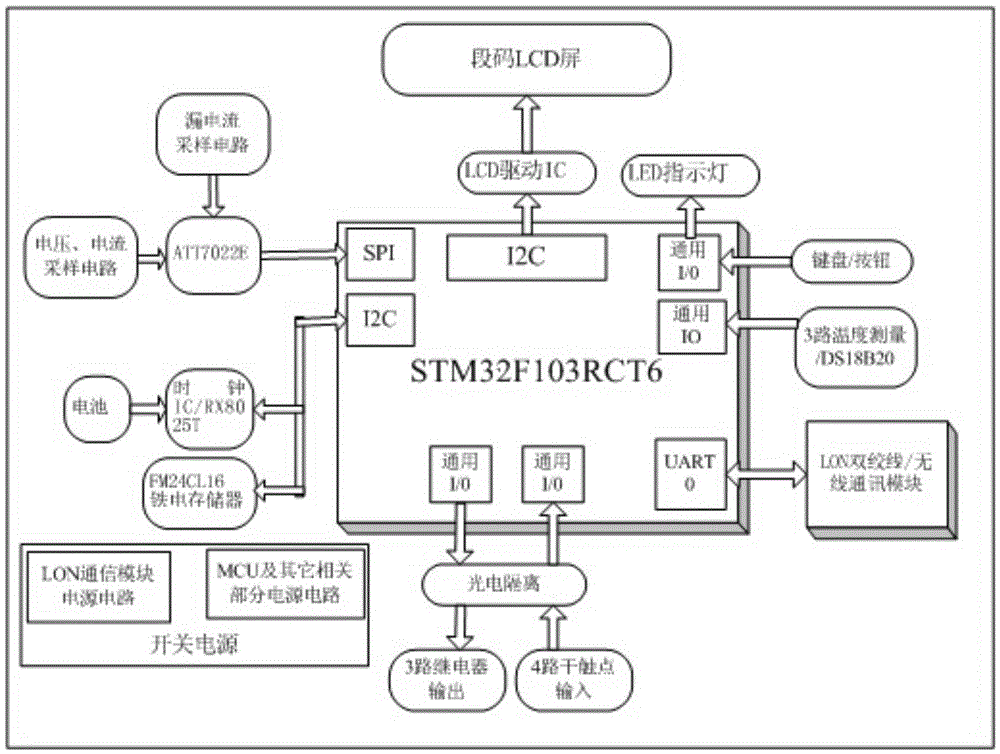
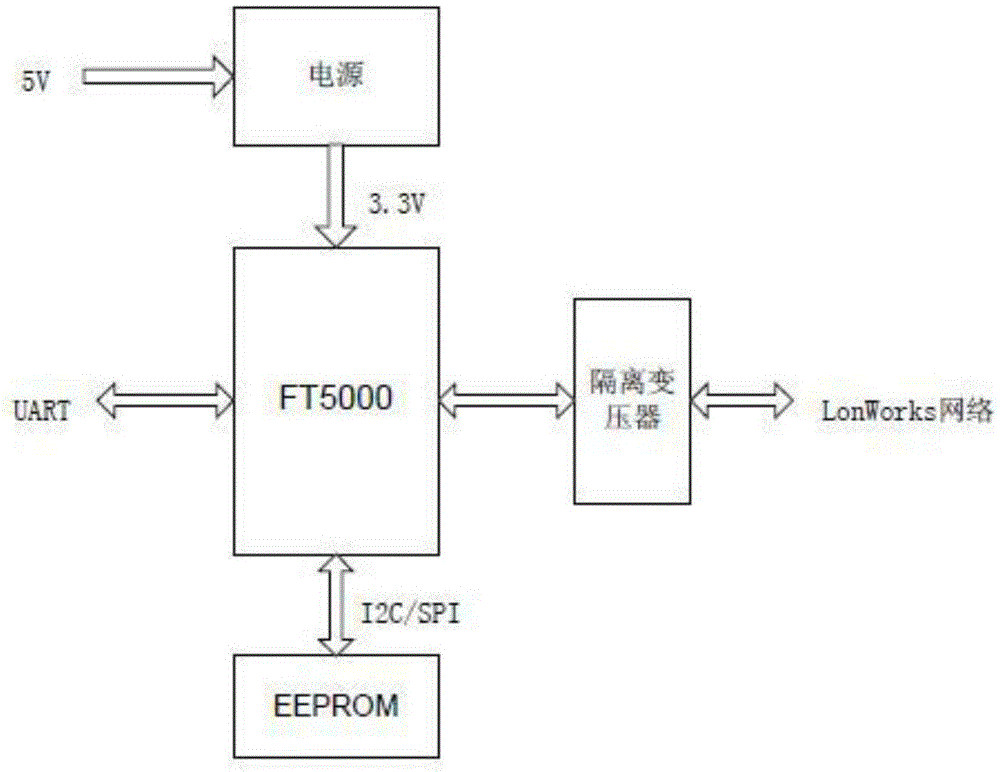
InactiveCN105634138ASolve the problem of insufficient comprehensive data collection and analysisEliminate potential safety hazardsCircuit arrangementsSustainable buildingsTransceiverLonWorks
The invention discloses a multifunctional three-phase electric power monitoring apparatus, and belongs to the technical field of power utilization safety and energy conservation. The multifunctional three-phase electric power monitoring apparatus comprises a micro-control unit, and a power supply unit, a Lonworks intelligent transceiver, a relay control module, a power utilization measurement chip, a cable temperature detection circuit, a data storage circuit and a high-precision real-time clock circuit that are connected with the micro-control unit separately. The multifunctional three-phase electric power monitoring apparatus has the functions of monitoring the voltage, current, power, power factors, leakage current, cable temperature, harmonic components and electric energy measurement, high-precision calendar clock, and the like; alarm threshold values can be set for all monitored parameters; an alarm can be sent out when parameter overrun occurs, and the system power supply can be configured to be switched off in case of alarms; various electric energy related parameter data is provided for performing evaluation and analysis for building electric energy quality; and in addition, automatic power supply or power off control can be carried out according to set time frames or remote instructions; and the energy conservation control for buildings satisfies the philosophy of green buildings.
Owner:江苏联宏智慧能源股份有限公司
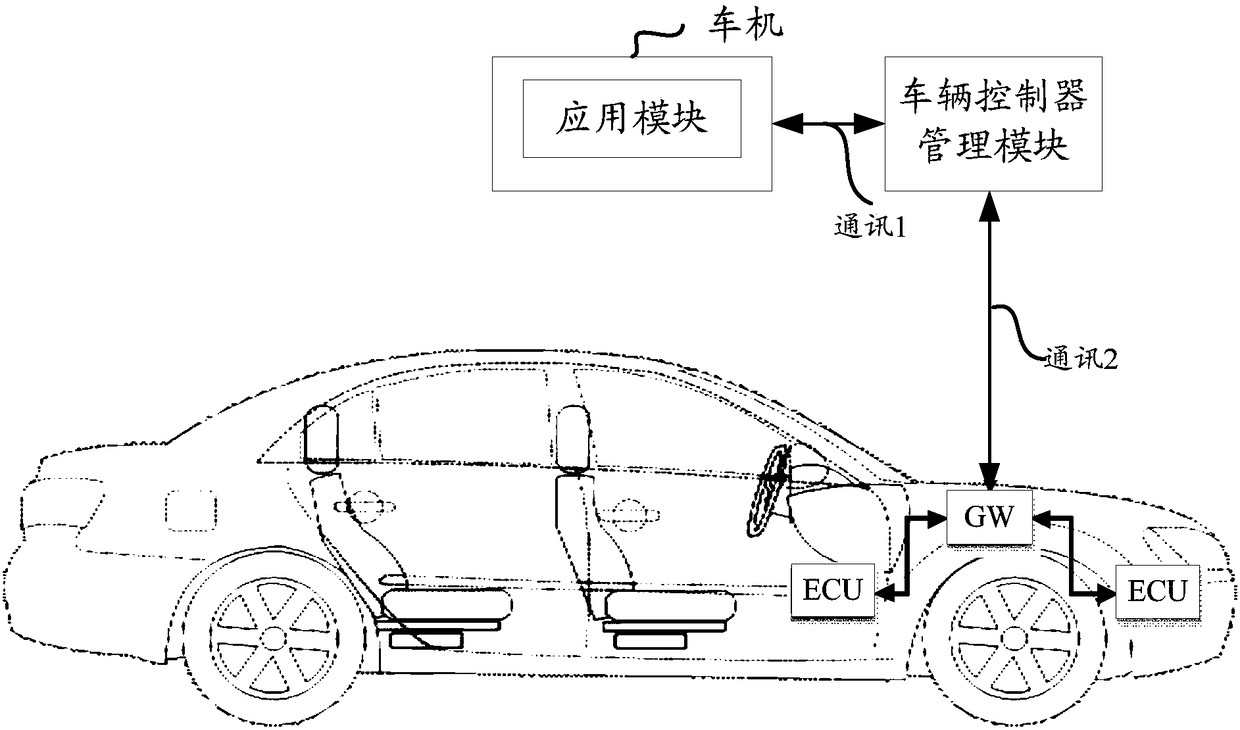
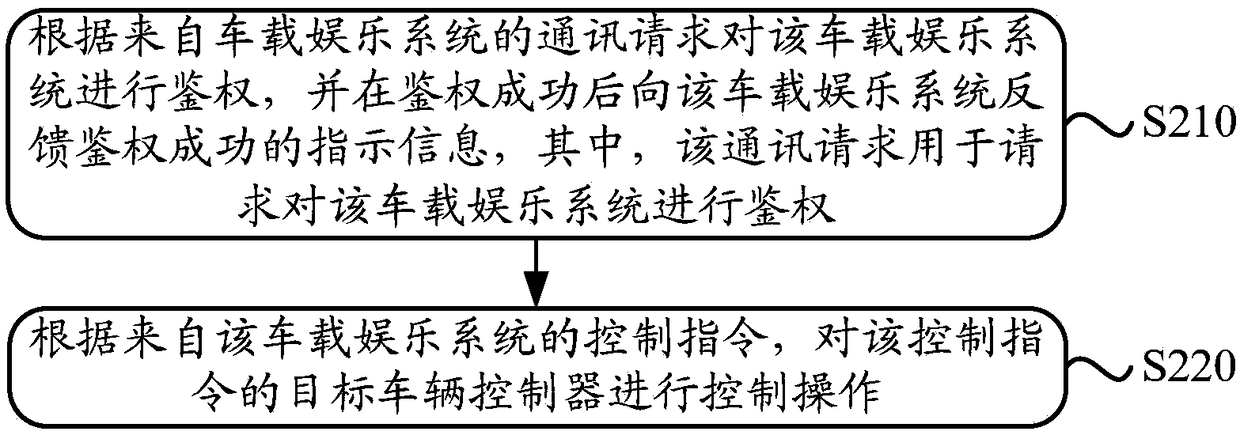
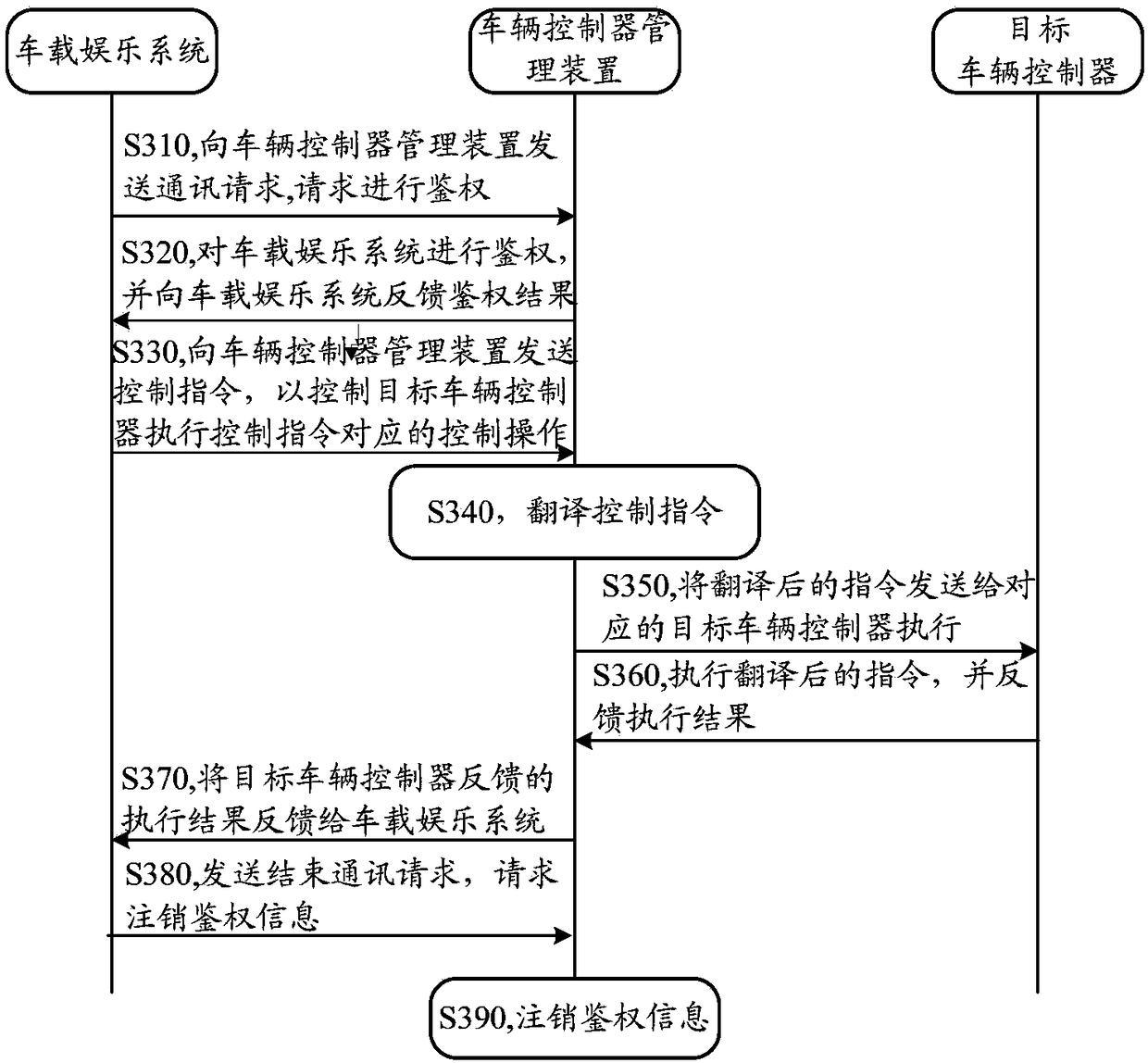
Vehicle controller management method and device, vehicle-mounted entertainment system and vehicle
InactiveCN108205272AImplement security managementImprove securityProgramme controlComputer controlAuthenticationReal-time computing
The invention discloses a vehicle controller management method and device, a vehicle-mounted entertainment system and a vehicle. The method comprises the steps of authenticating the vehicle-mounted entertainment system according to a communication request from the vehicle-mounted entertainment system; feeding back authentication success indication information to the vehicle-mounted entertainment system after the authentication is successful, wherein the communication request is used for requesting authentication of the vehicle-mounted entertainment system; and controlling the target vehicle controller of the control instruction according to a control instruction from the vehicle-mounted entertainment system. In the embodiment of the invention, the vehicle-mounted entertainment system is authenticated, and the target vehicle controller is controlled according to the control instruction of the vehicle-mounted entertainment system after the authentication is successful, so that the safetymanagement of the controller in the vehicle can be realized, and the safety of a vehicle system is improved.
Owner:FAFA AUTOMOBILE (CHINA) CO LTD
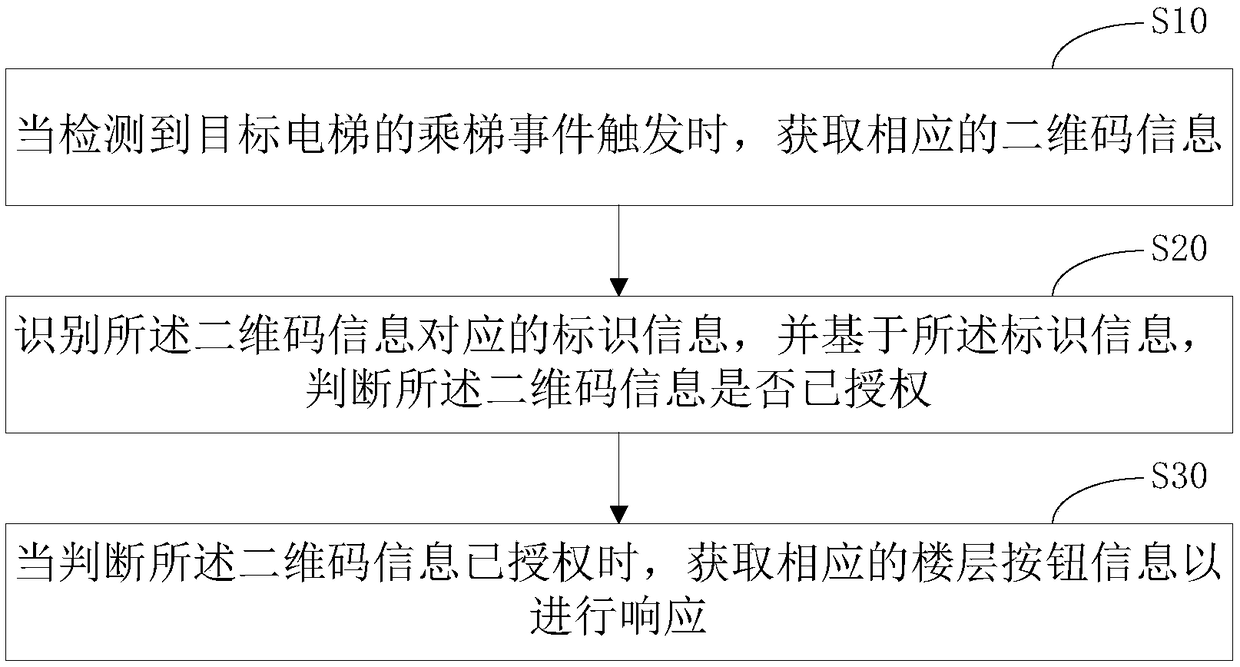
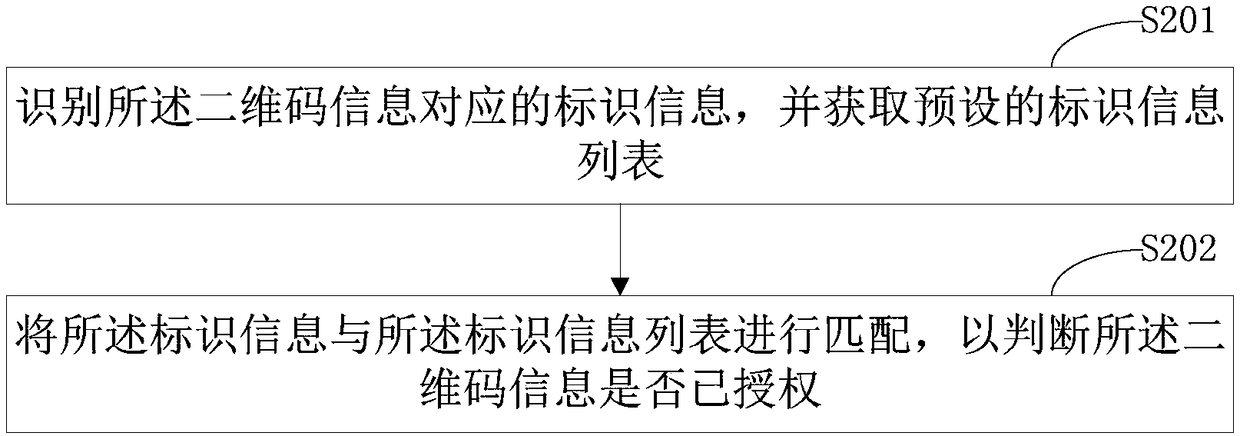
Control method and control device for elevator riding through two-dimensional code, and computer readable storage medium
InactiveCN108408513AImplement security managementReduce use costElevatorsSoftware engineeringFloor level
The invention discloses a control method for elevator riding through a two-dimensional code. The control method for elevator riding through the two-dimensional code comprises the following steps of when detecting that an elevator riding event of a target elevator is triggered, acquiring corresponding two-dimensional code information; recognizing identification information corresponding to the two-dimensional code information, and judging whether the two-dimensional code information is authorized or not based on the identification information; when judging that the two-dimensional code information is authorized, acquiring corresponding floor button information for responding. The invention further discloses a control device for elevator riding through the two-dimensional code, and a computer readable storage medium. According to the control method and the control device for elevator riding through the two-dimensional code, and the computer readable storage medium provided by the invention, during an elevator running process, whether a user can use the target elevator currently or not is judged through using the two-dimensional code information, so that the safety management of the elevator is effectively realized, and the use cost of elevator management is effectively reduced.
Owner:深圳市敢为特种设备物联网技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com