Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41140results about "Securing communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
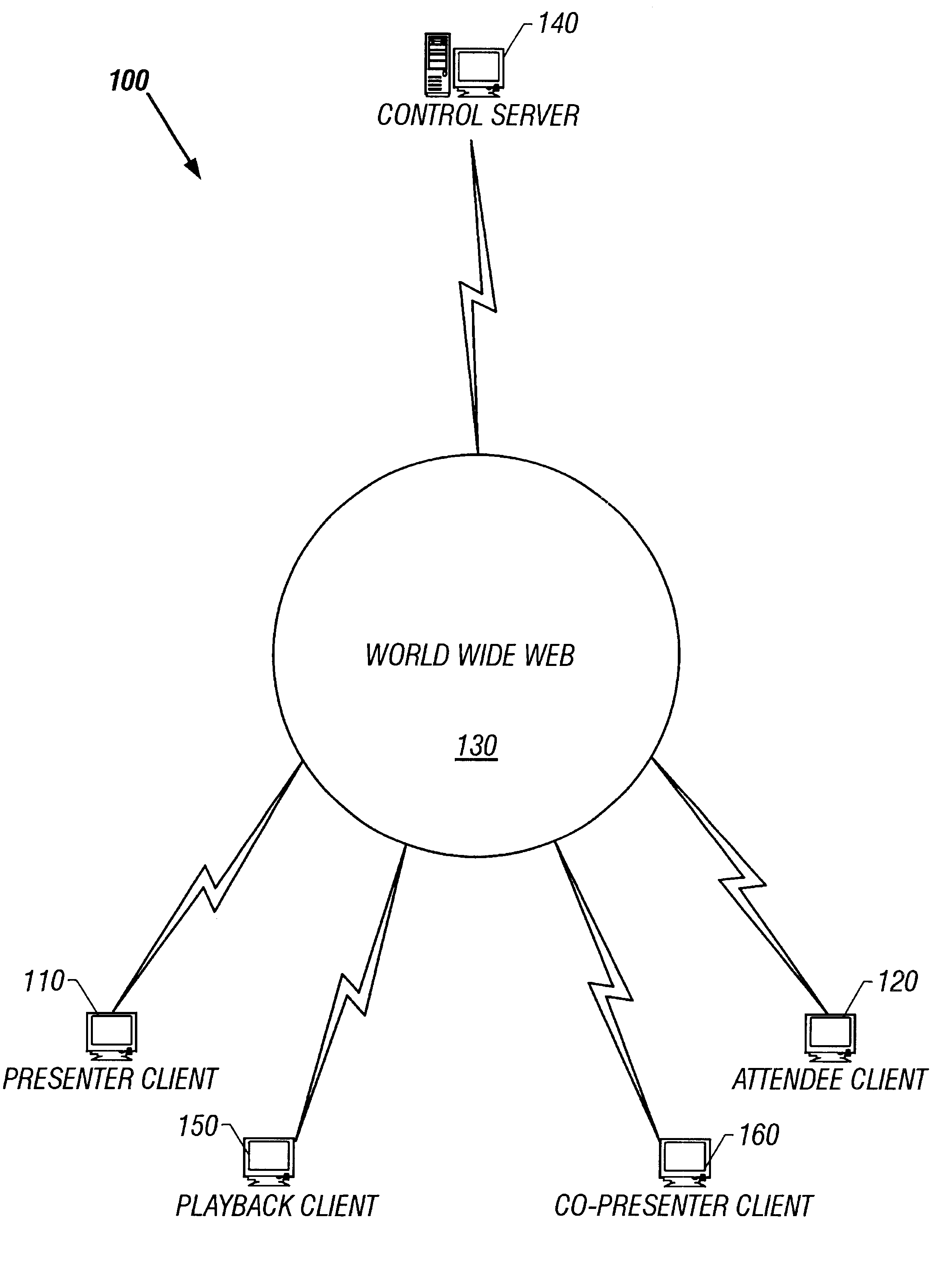
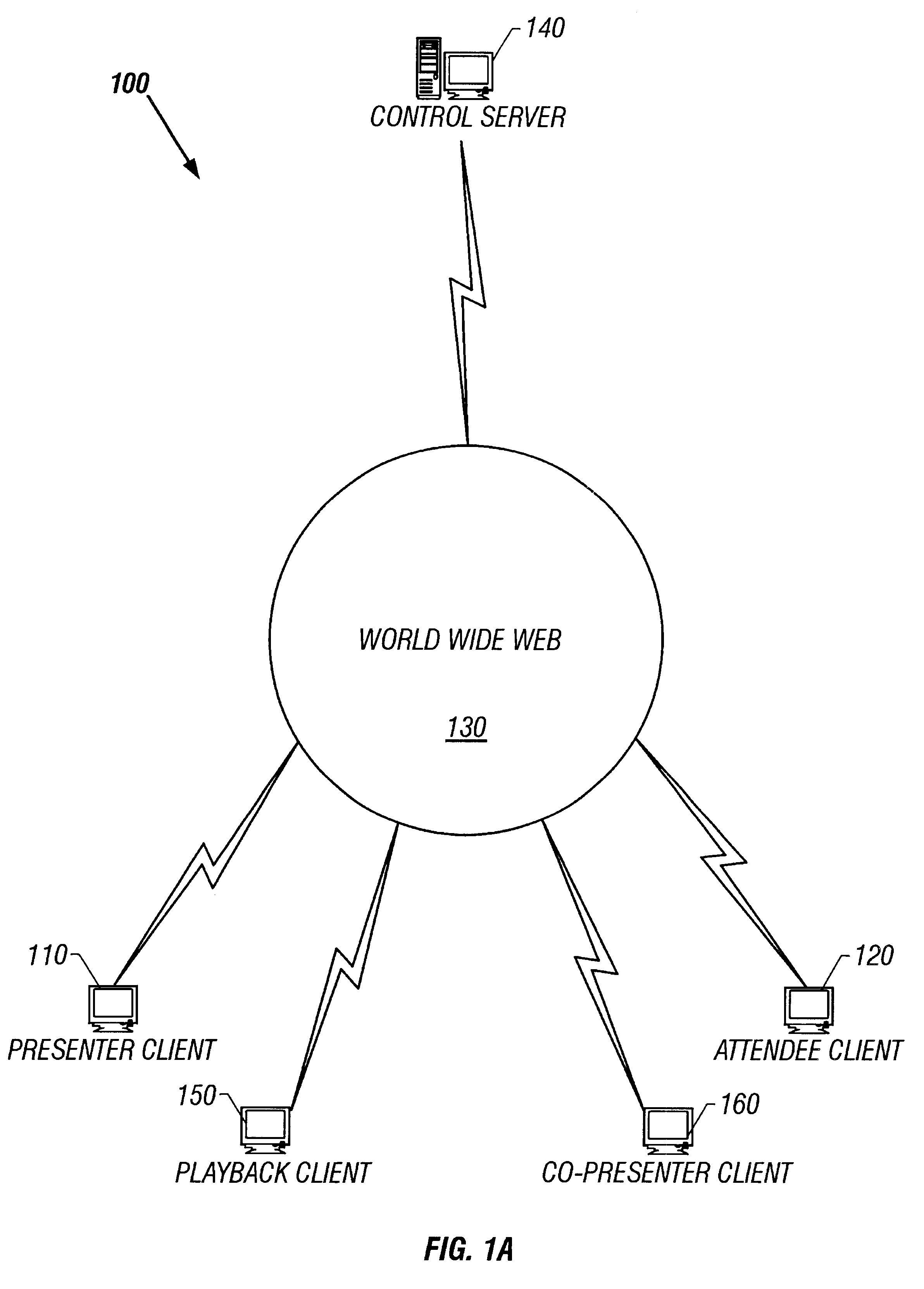
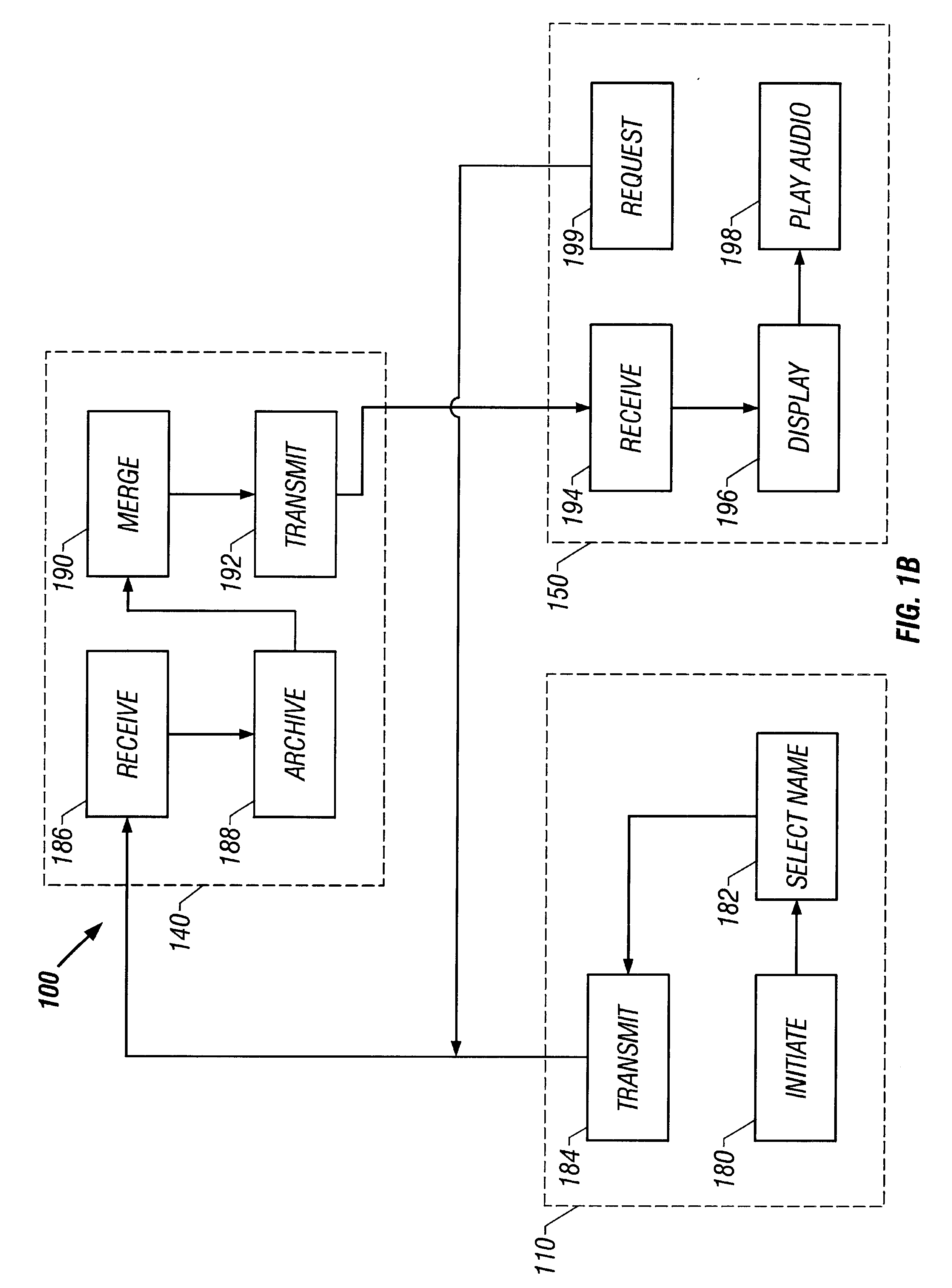
System and method for record and playback of collaborative Web browsing session
InactiveUS6535909B1Cost-effectiveSynchronised browsingWeb data retrievalNetwork connectionWorld Wide Web
A collaborative Web browsing session may take place over a network, allowing the presenter on a first computer to direct the audio and visual components of a browser on one or more second computers. The second computer is instructed to log into a control site that downloads an active control, such as an applet, to the second computer. The present invention allows a collaborative Web browsing session ("session"), as created by the presenter and witnessed by one or more users on second computers, to be recorded and archived by the control site. When a user of a computer is connected to the control site through a communication network such as the World Wide Web, that user may log into the control site and request to view an archived session. The session will then be replayed by the control site on the user's computer, directing the audio and visual components of the browser on the user's computer as if the user was attending the live session. The recorded session replays the events of the live session in real time such that the playback experience contains the same audio and visual events that took place when the session was originally being recorded.
Owner:RED HAT +1
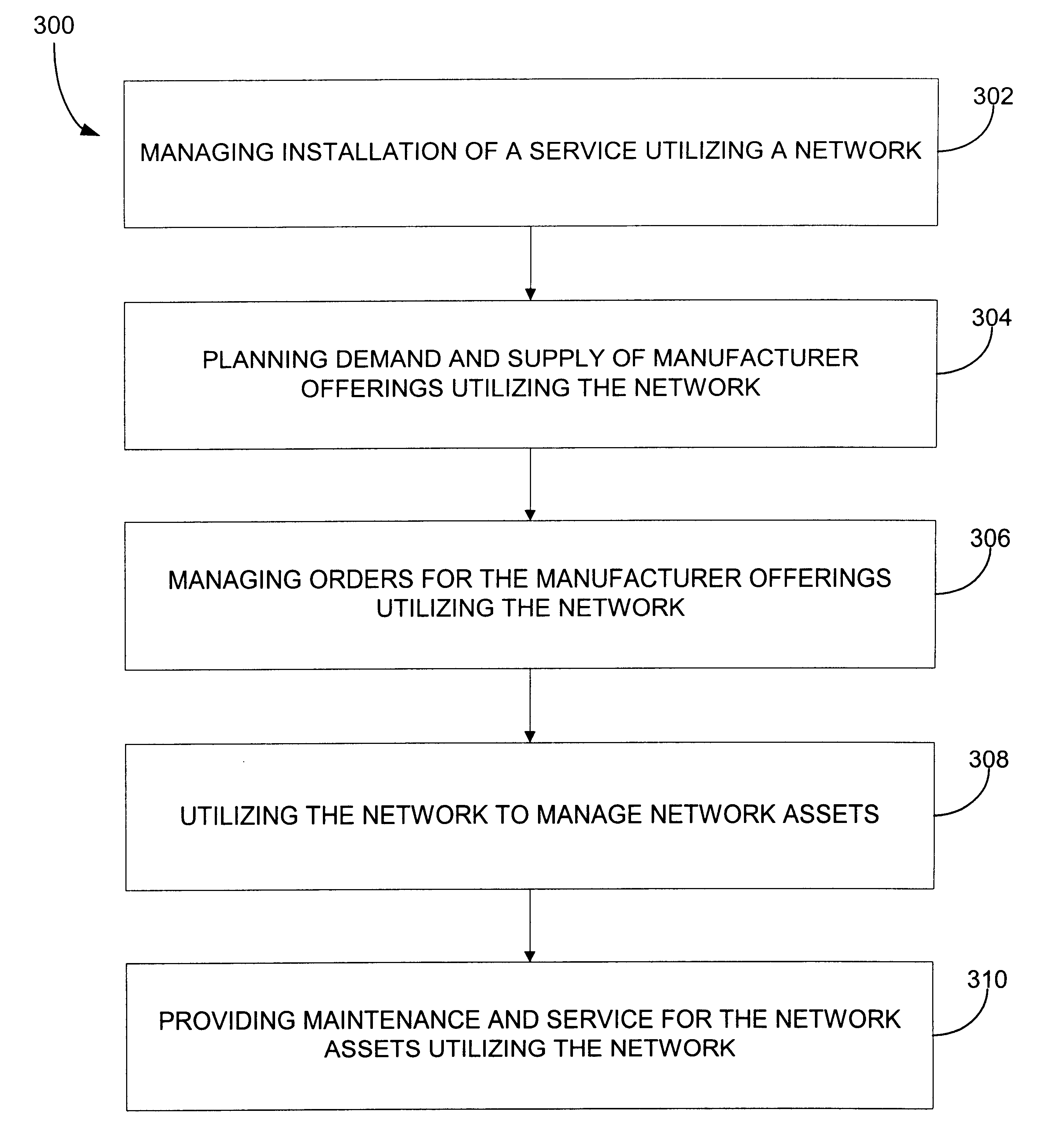
Providing collaborative installation management in a network-based supply chain environment
InactiveUS6606744B1Interconnection arrangementsSpecial service for subscribersWeb applicationService provision
A system, method and article of manufacture are provided for collaborative installation management in a network-based supply chain environment. According to an embodiment of the invention, telephone calls, data and other multimedia information are routed through a network system which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. The system includes integrated Internet Protocol (IP) telephony services allowing a user of a web application to communicate in an audio fashion in-band without having to pick up another telephone. Users can click a button and go to a call center through the network using IP telephony. The system invokes an IP telephony session simultaneously with the data session, and uses an active directory lookup whenever a user uses the system. Users include service providers and manufacturers utilizing the network-based supply chain environment.
Owner:ACCENTURE GLOBAL SERVICES LTD
System for establishing plan to test components of web based framework by displaying pictorial representation and conveying indicia coded components of existing network framework
A system, method, and article of manufacture are provided for planning the testing of components of an existing network framework. First, a pictorial representation of an existing network framework is displayed along with a plurality of components of the existing network framework. Thereafter, the components of the existing network framework are indicia coded in order to convey a plan by which the components of the existing network framework are to be tested. The components may be indicia coded in order to convey an order of the testing or which components of the existing network framework are to be tested.
Owner:ACCENTURE GLOBAL SERVICES LTD
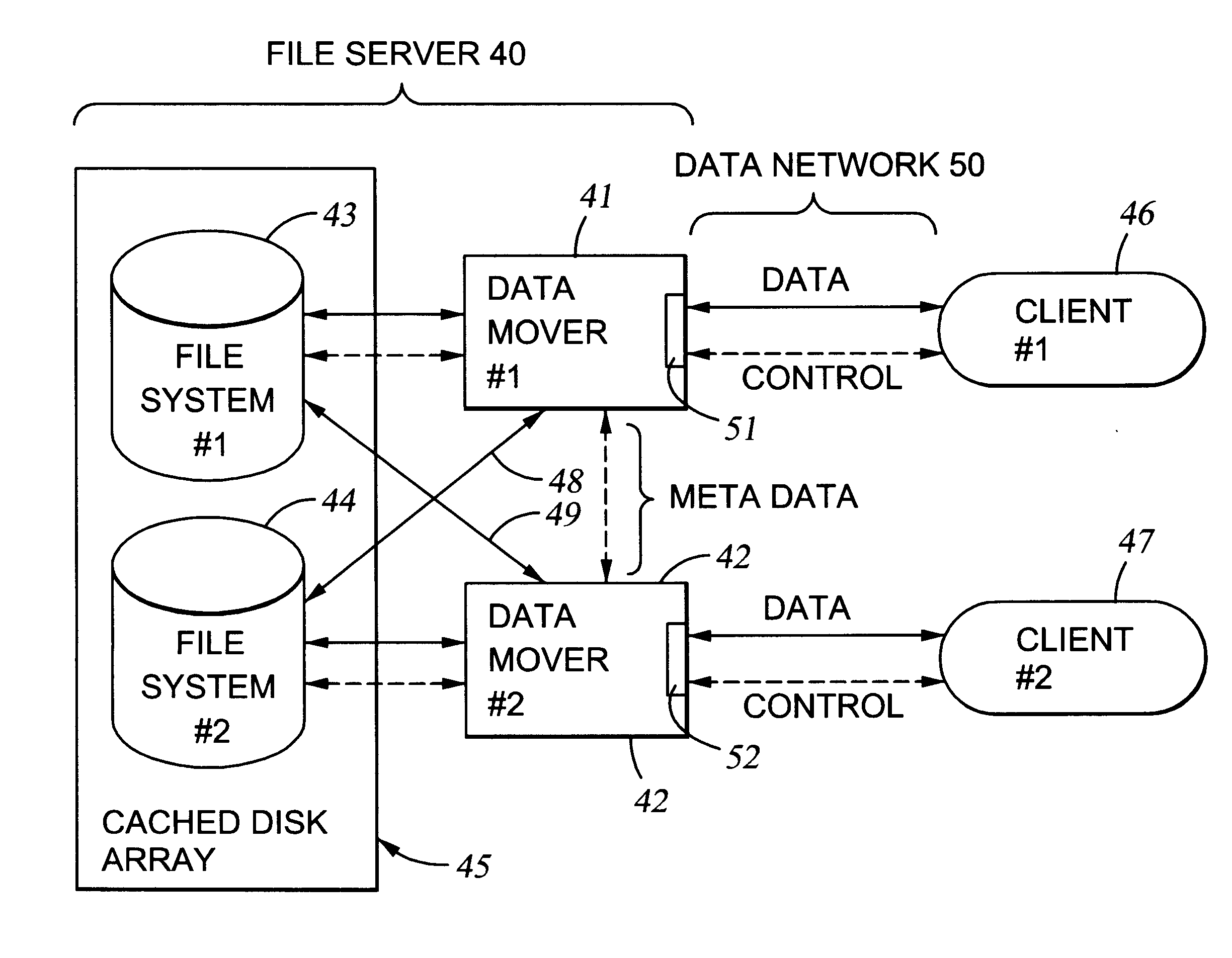
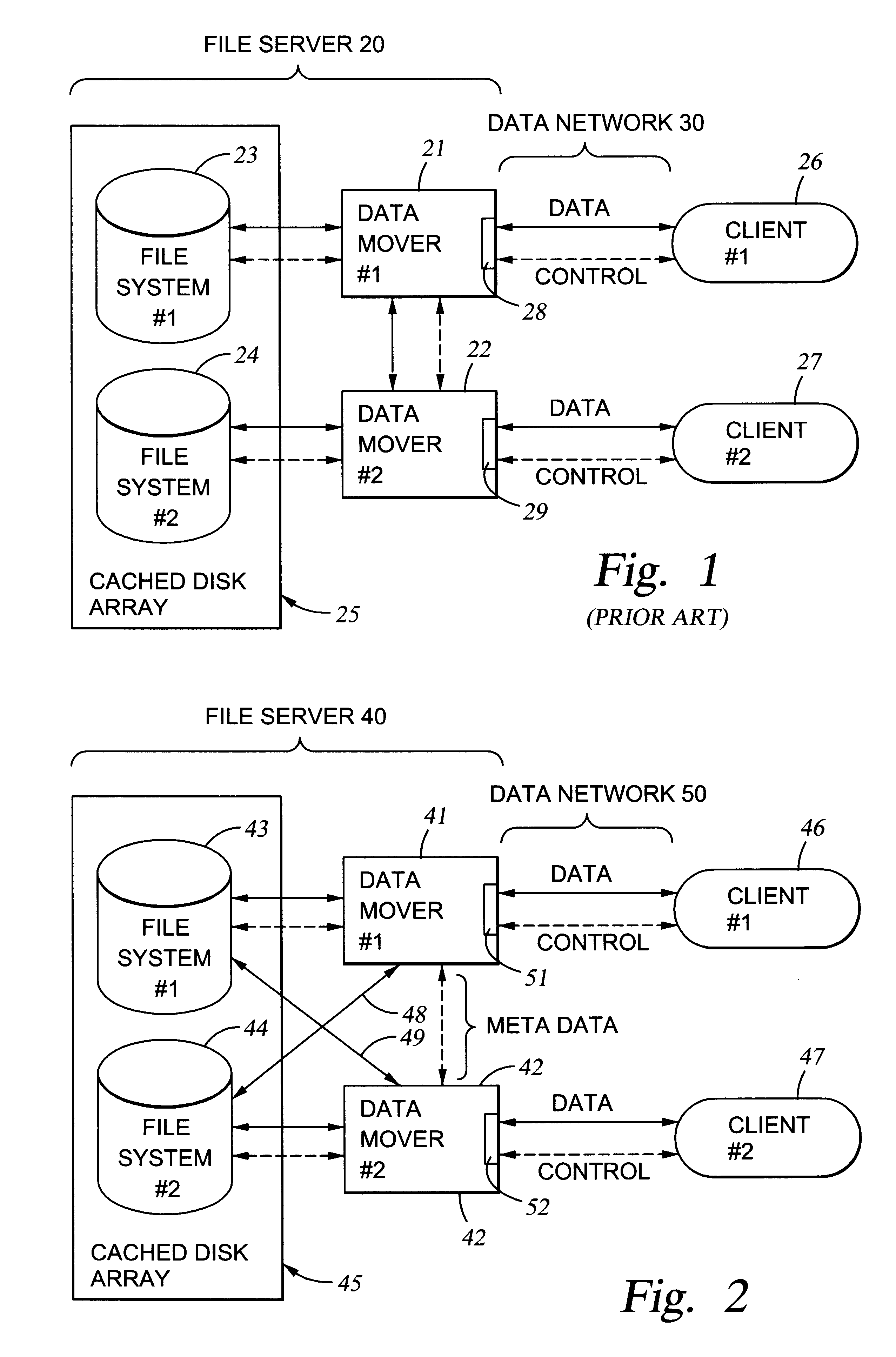
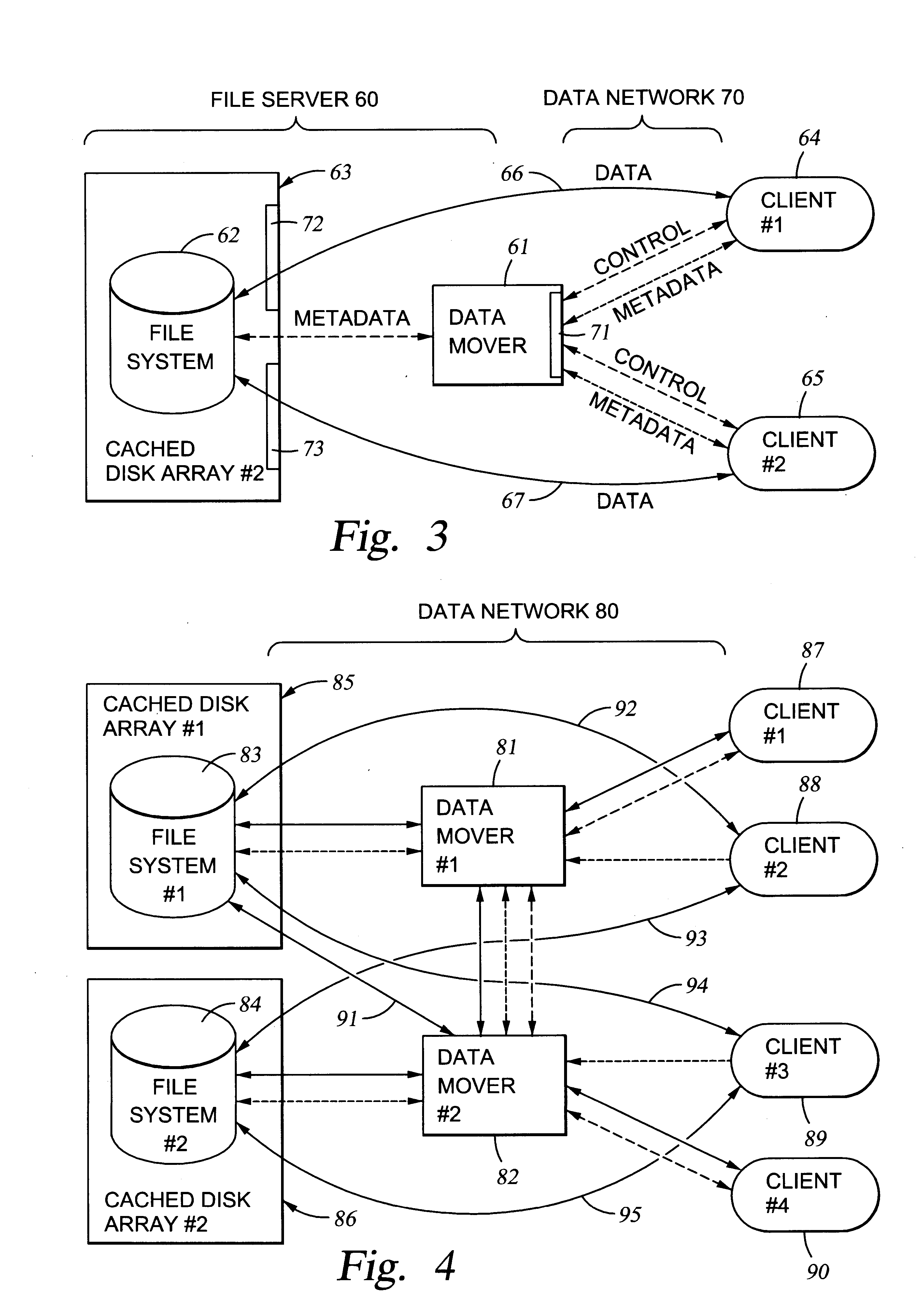
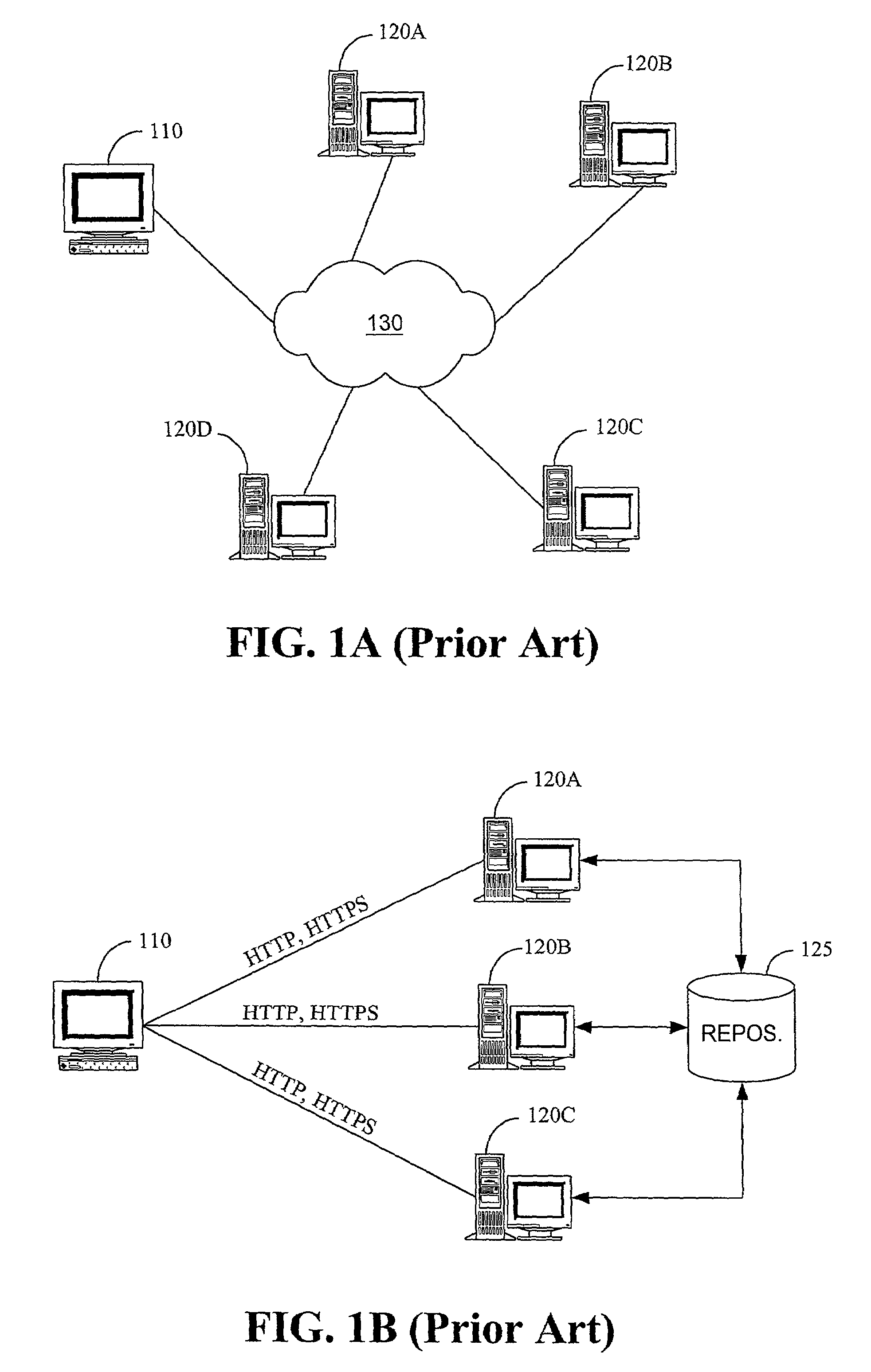
File server system using file system storage, data movers, and an exchange of meta data among data movers for file locking and direct access to shared file systems
InactiveUS6324581B1Digital data information retrievalMultiple digital computer combinationsFile systemData access
A plurality of data mover computers control access to respective file systems in data storage. A network client serviced by any of the data movers can access each of the file systems. If a data mover receives a client request for access to a file in a file system to which access is controlled by another data mover, then the data mover that received the client request sends a metadata request to the data mover that controls access to the file system. The data mover that controls access to the file system responds by placing a lock on the file and returning metadata of the file. The data mover that received the client request uses the metadata to formulate a data access command that is used to access the file data in the file system over a bypass data path that bypasses the data mover computer that controls access to the file system.
Owner:EMC IP HLDG CO LLC
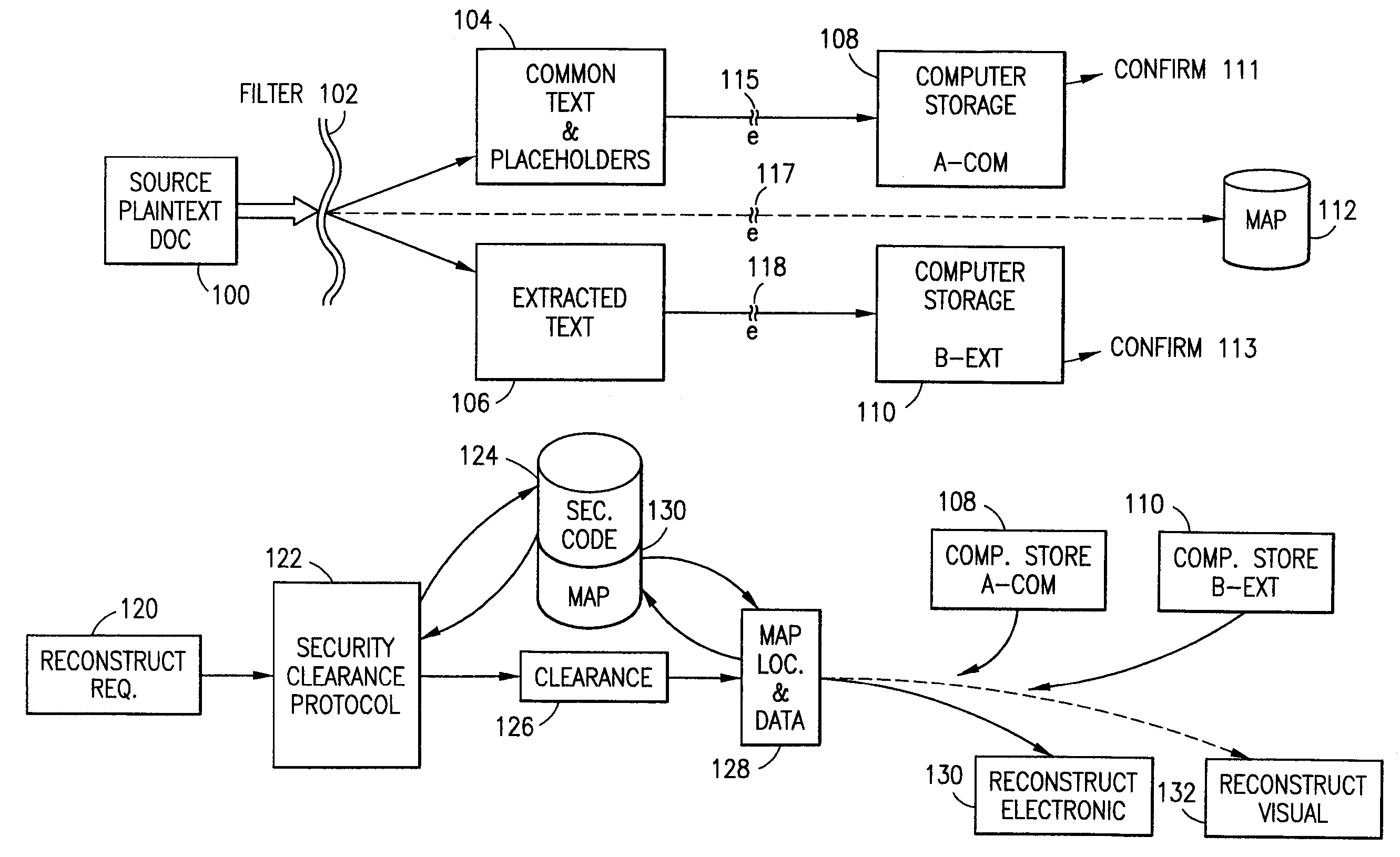
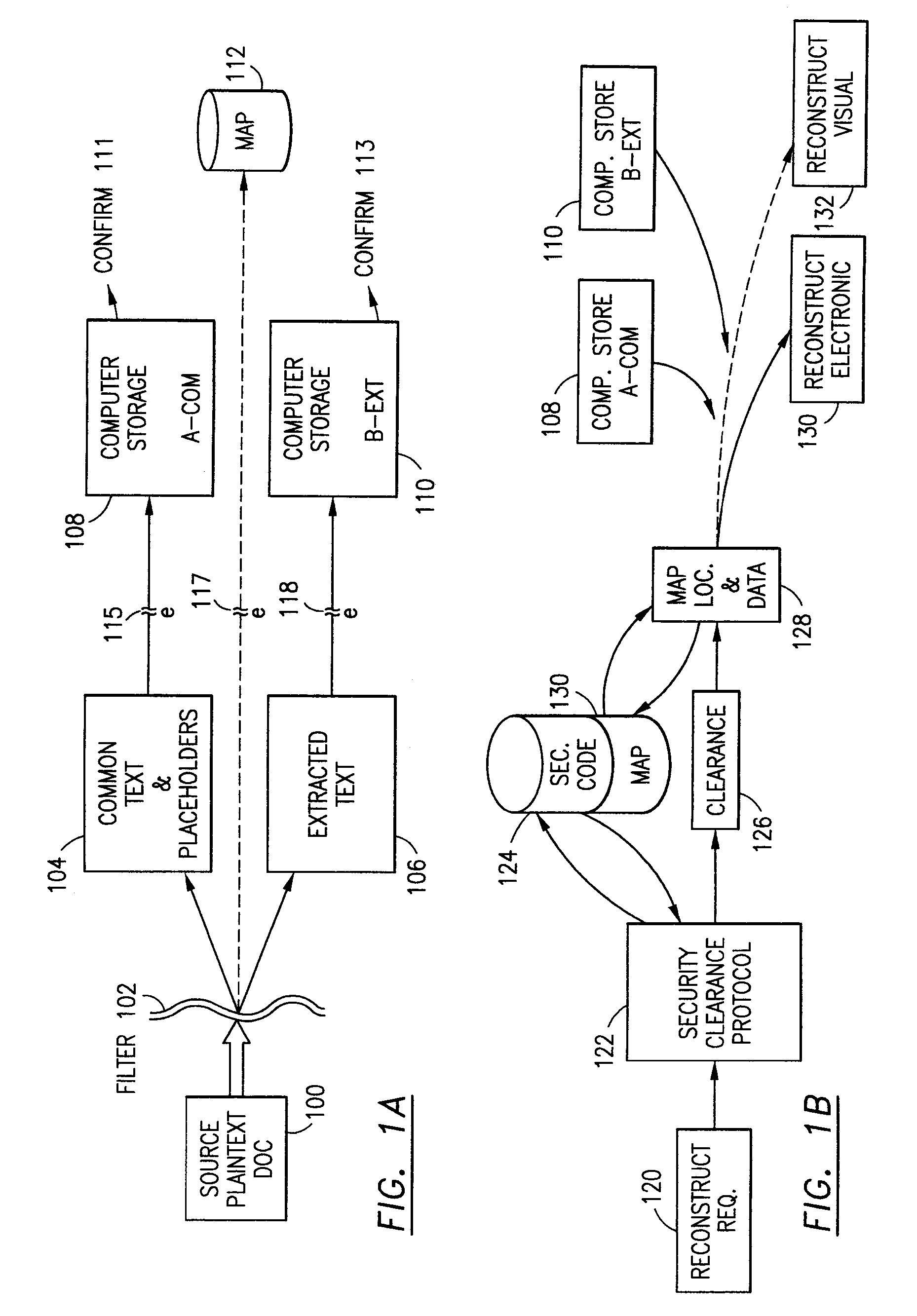
Data security system and method
ActiveUS7103915B2Memory loss protectionDigital data processing detailsPlaintextInformation processing
The method for securing data includes establishing a group of security sensitive items, filtering data and extracting and separating the security items from remainder data. The filtered data are separately stored (locally on a PC or on another computer in a LAN or WAN or on the Internet.) A map may be generated. The filter and / or map may be destroyed or stored. The data input, extracted data and remainder data may be deleted from the originating computer. Encryption may be utilized to enhance security (including transfers of data, filter and map). Reconstruction of the data is permitted only in the presence of a predetermined security clearance. A plurality of security clearances may be used to enable a corresponding plurality of partial, reconstructed views of the plaintext (omitting higher security words). A computer readable medium containing programming instructions and an information processing system is encompassed.
Owner:DIGITAL DOORS
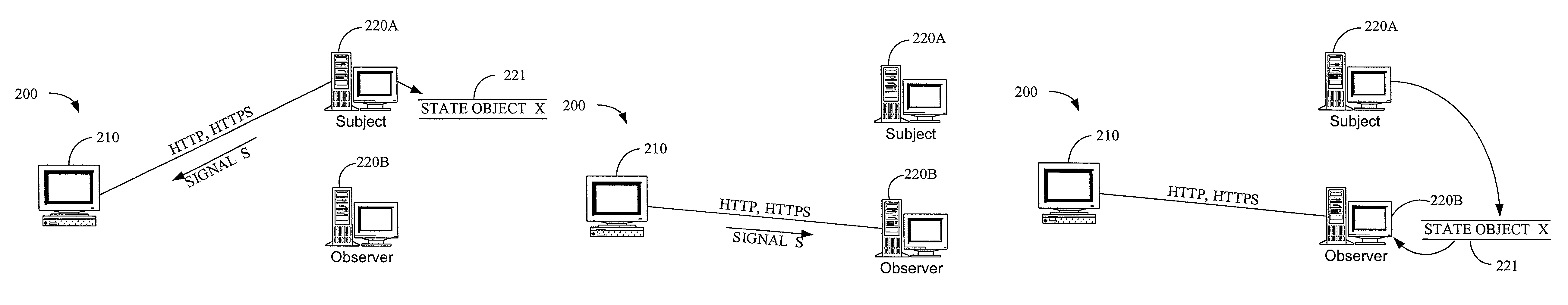
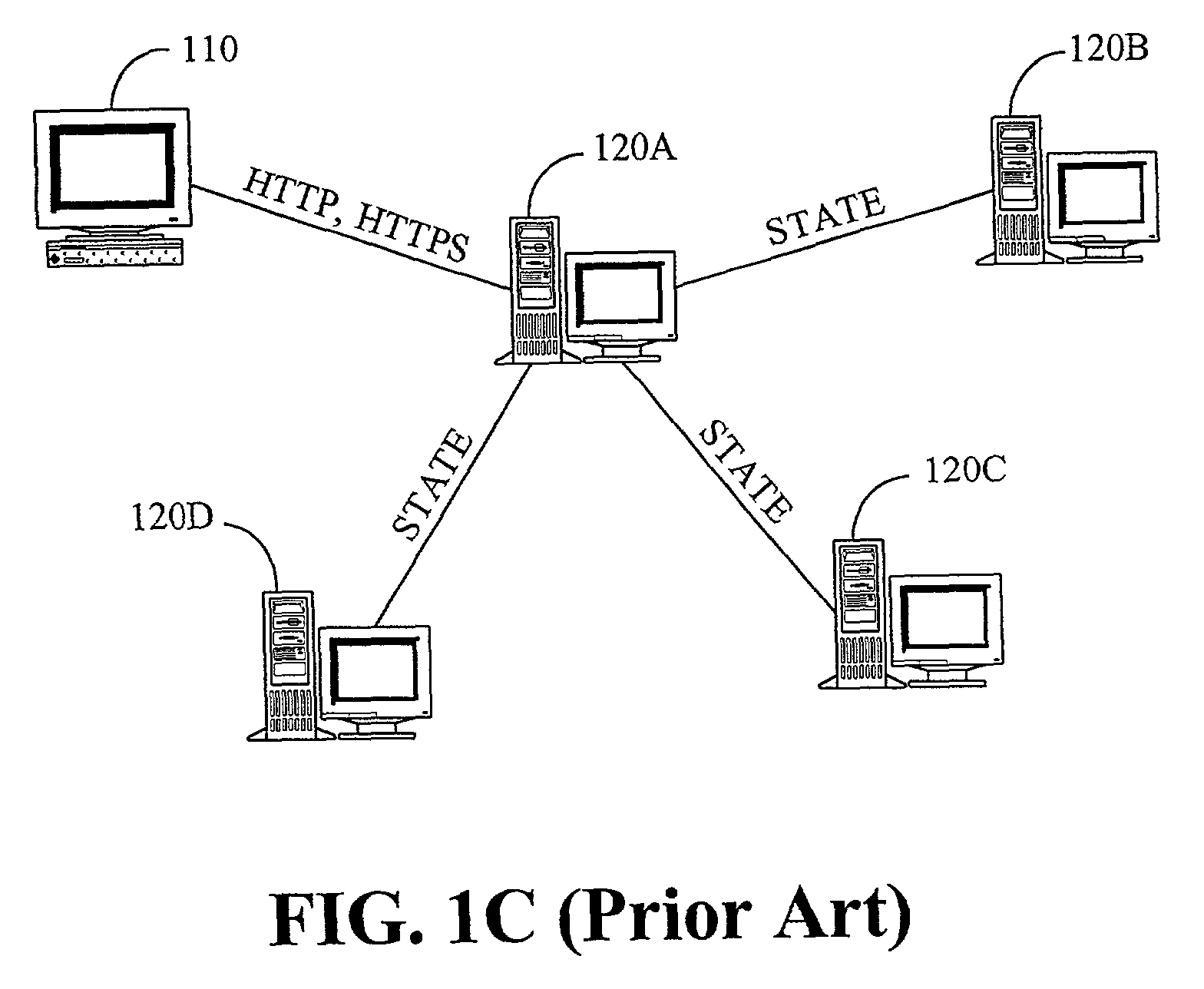
System and method for maintaining consistent independent server-side state among collaborating servers
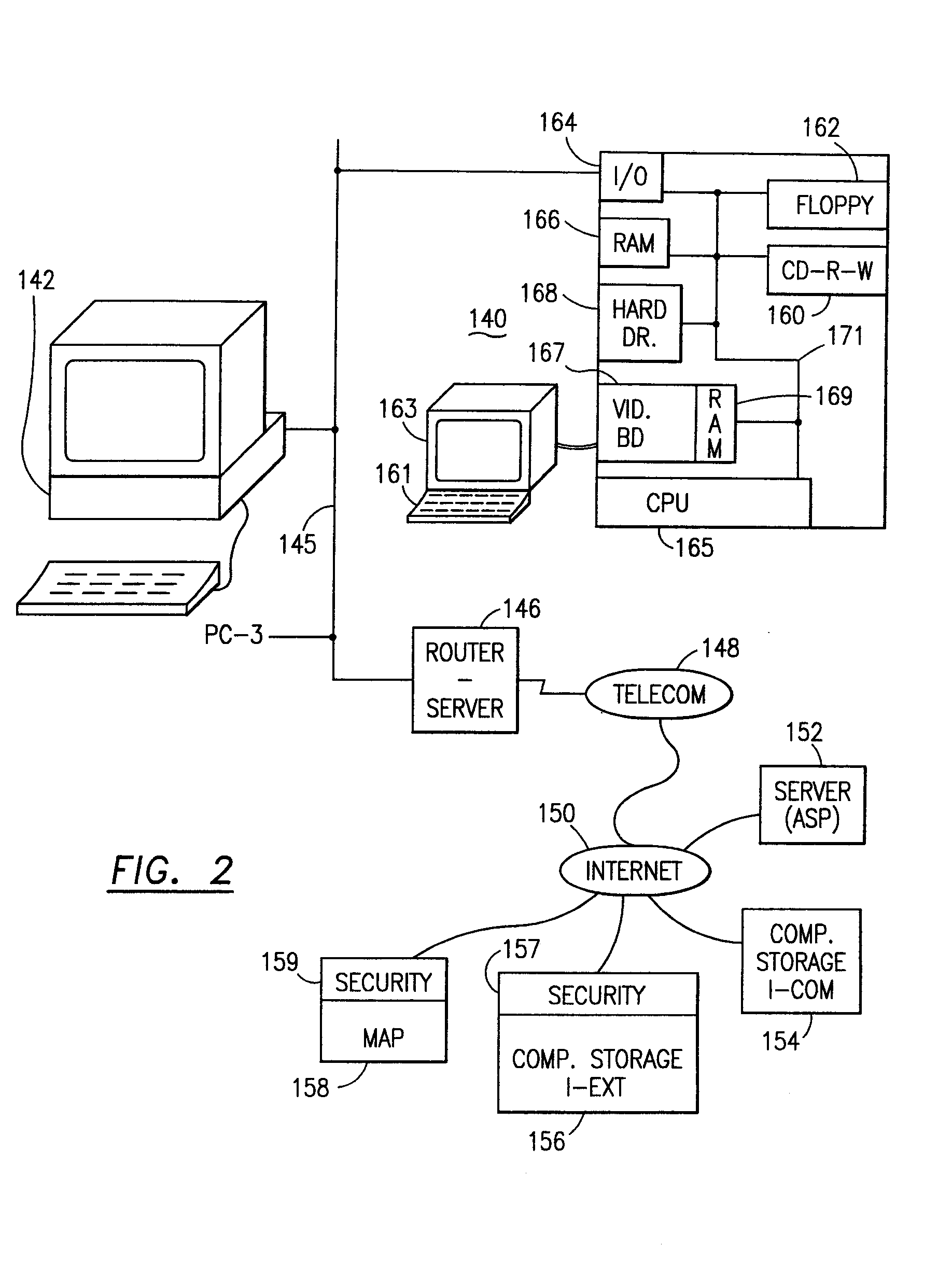
ActiveUS7024451B2Less couplingWork lessMultiple digital computer combinationsSecuring communicationClient-sideServer-side
A system and method are provided for maintaining consistent server-side state across a pool of collaborating servers with independent state repositories. When a client performs an event on a collaborating server which affects such state on the server, it publishes notification of the event into a queue maintained in client-side state which is shared by all of the collaborating servers in the pool. As the client makes requests to servers within the pool, the queue is thus included in each request. When a collaborating server needs to access its server-side state in question, it first discerns events new to it from the queue and replicates their effects into such server-side state. As a result, the effects of events upon server-side state are replicated asynchronously across the servers in the pool, as the client navigates among them.
Owner:META PLATFORMS INC
System and method for scheduling broadcast of and access to video programs and other data using customer profiles
InactiveUS6088722AMinimize memory requirementFacilitate text retrievalTelevision system detailsAnalogue secracy/subscription systemsTelevision systemData source
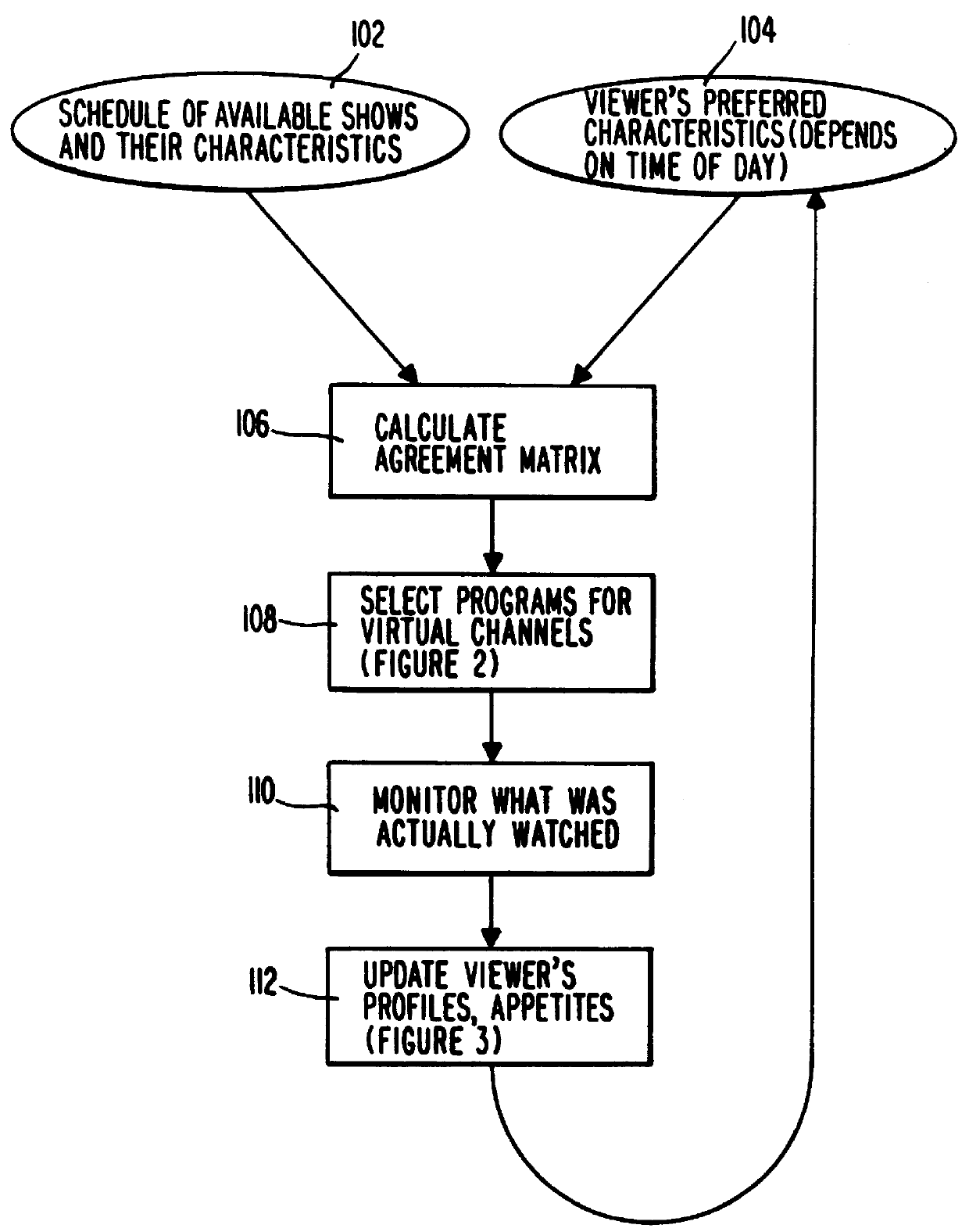
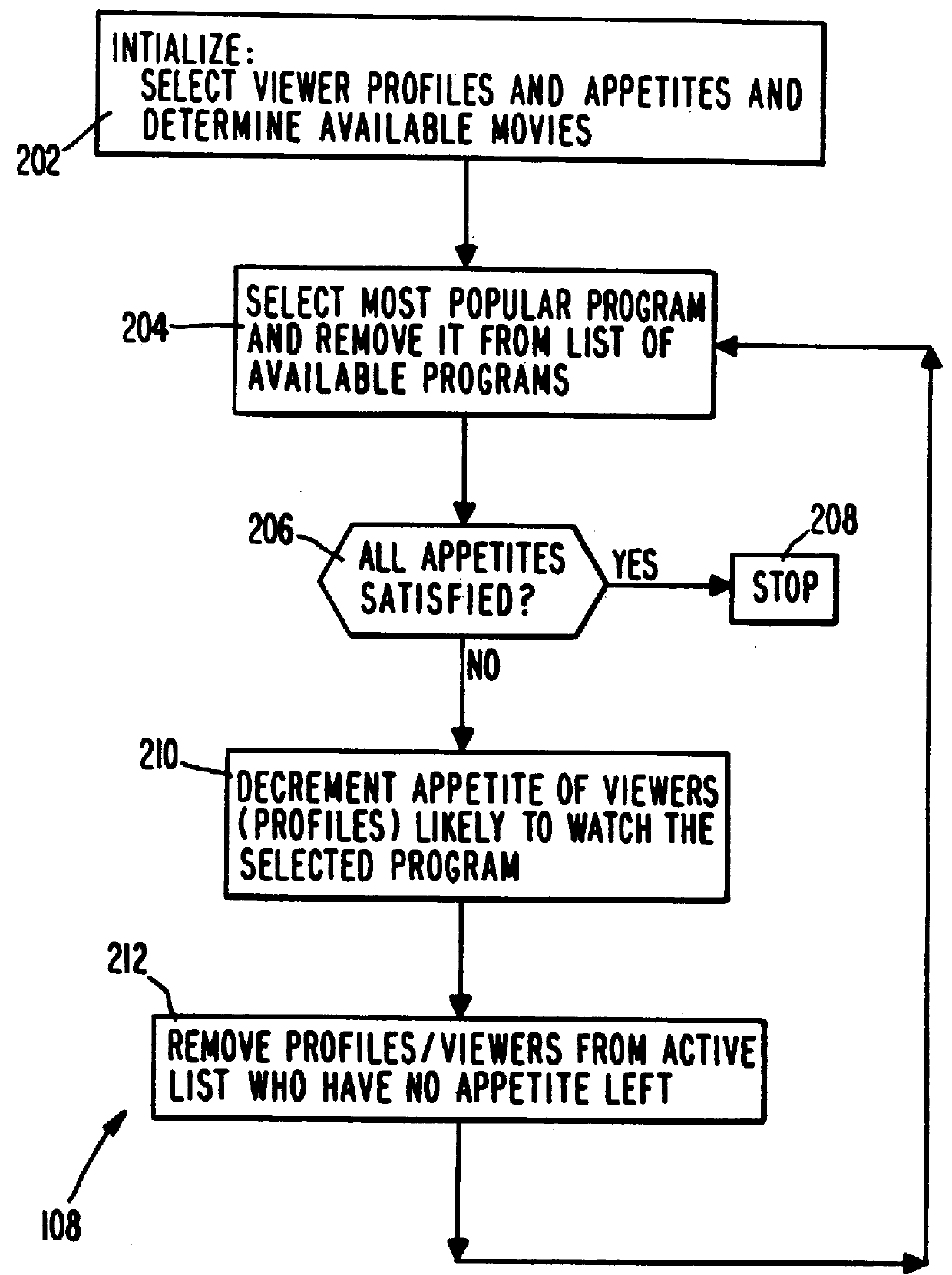
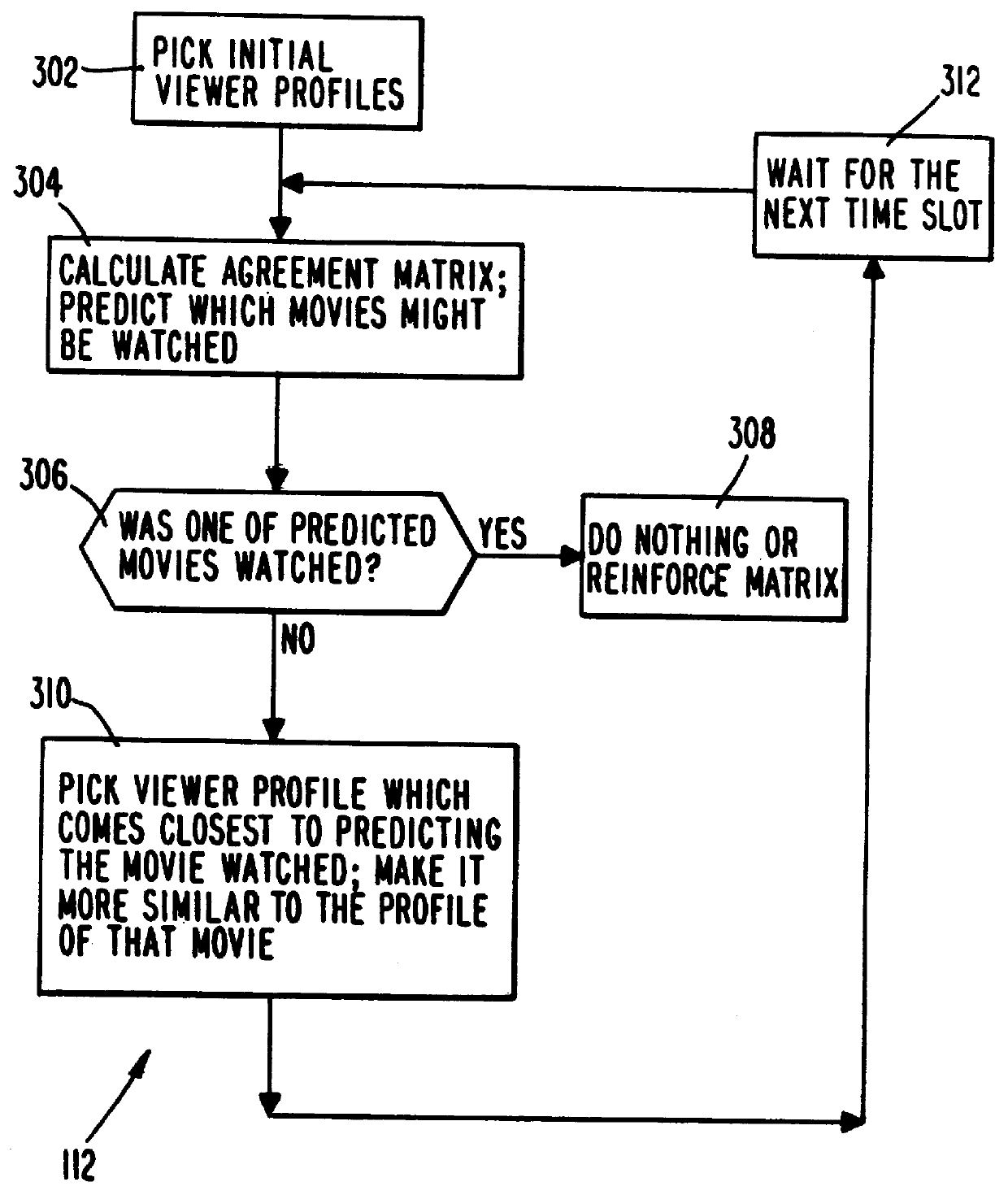
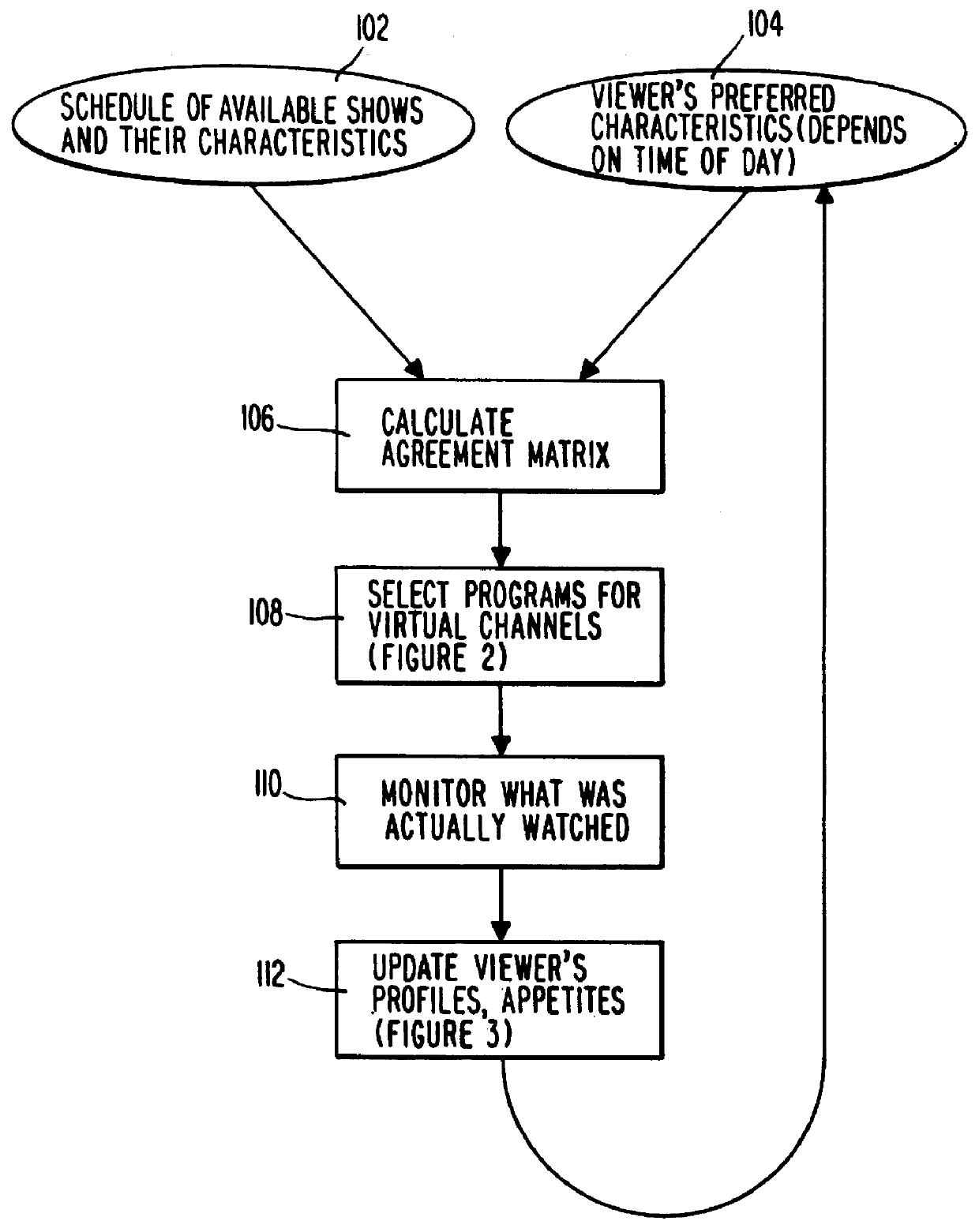
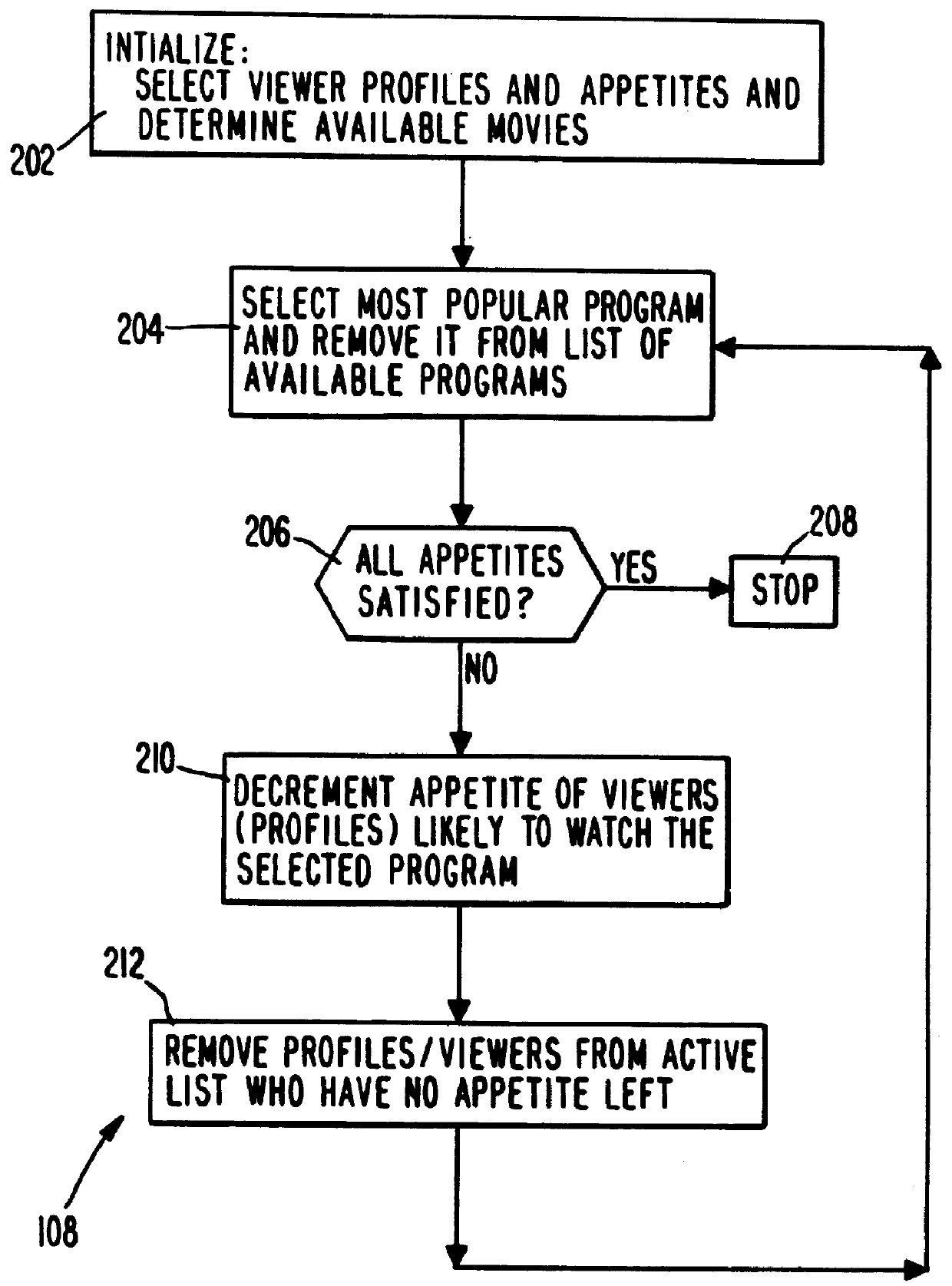
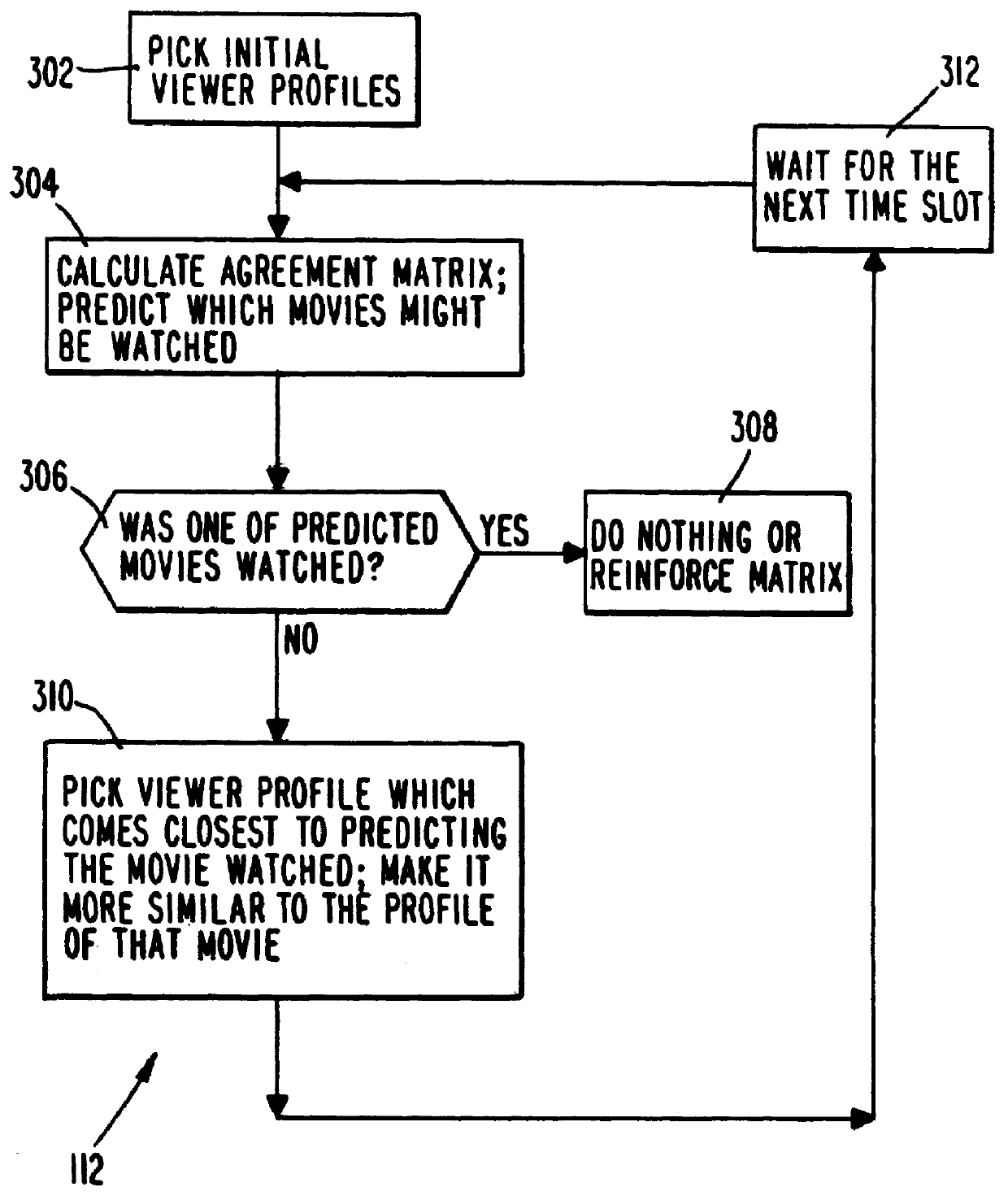
PCT No. PCT / US95 / 15429 Sec. 371 Date Dec. 24, 1997 Sec. 102(e) Date Dec. 24, 1997 PCT Filed Nov. 29, 1995 PCT Pub. No. WO96 / 17467 PCT Pub. Date Jun. 6, 1996A system and method for scheduling the receipt of desired movies and other forms of data from a network, which simultaneously distributes many sources of such data to many customers, as in a cable television system. Customer profiles are developed for the recipient describing how important certain characteristics of the broadcast video program, movie, or other data are to each customer. From these profiles, an "agreement matrix" is calculated by comparing the recipient's profiles to the actual profiles of the characteristics of the available video programs, movies, or other data. The agreement matrix thus characterizes the attractiveness of each video program, movie, or other data to each prospective customer. "Virtual" channels are generated from the agreement matrix to produce a series of video or data programming which will provide the greatest satisfaction to each customer. Feedback paths are also provided so that the customer's profiles and / or the profiles of the video programs or other data may be modified to reflect actual usage, and so that the data downloaded to the customer's set top terminal may be minimized. Kiosks are also developed which assist customers in the selection of videos, music, books, and the like in accordance with the customer's objective profiles.
Owner:FRED HERZ PATENTS
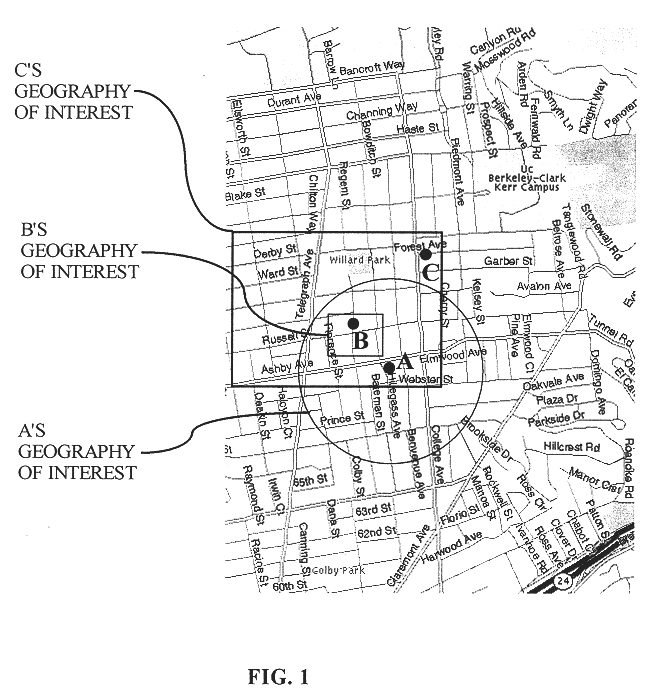
Dynamically matching users for group communications based on a threshold degree of matching of sender and recipient predetermined acceptance criteria
InactiveUS6480885B1Quality of communicationReduce in quantitySpecial service provision for substationMultiprogramming arrangementsPersonalizationWeb service
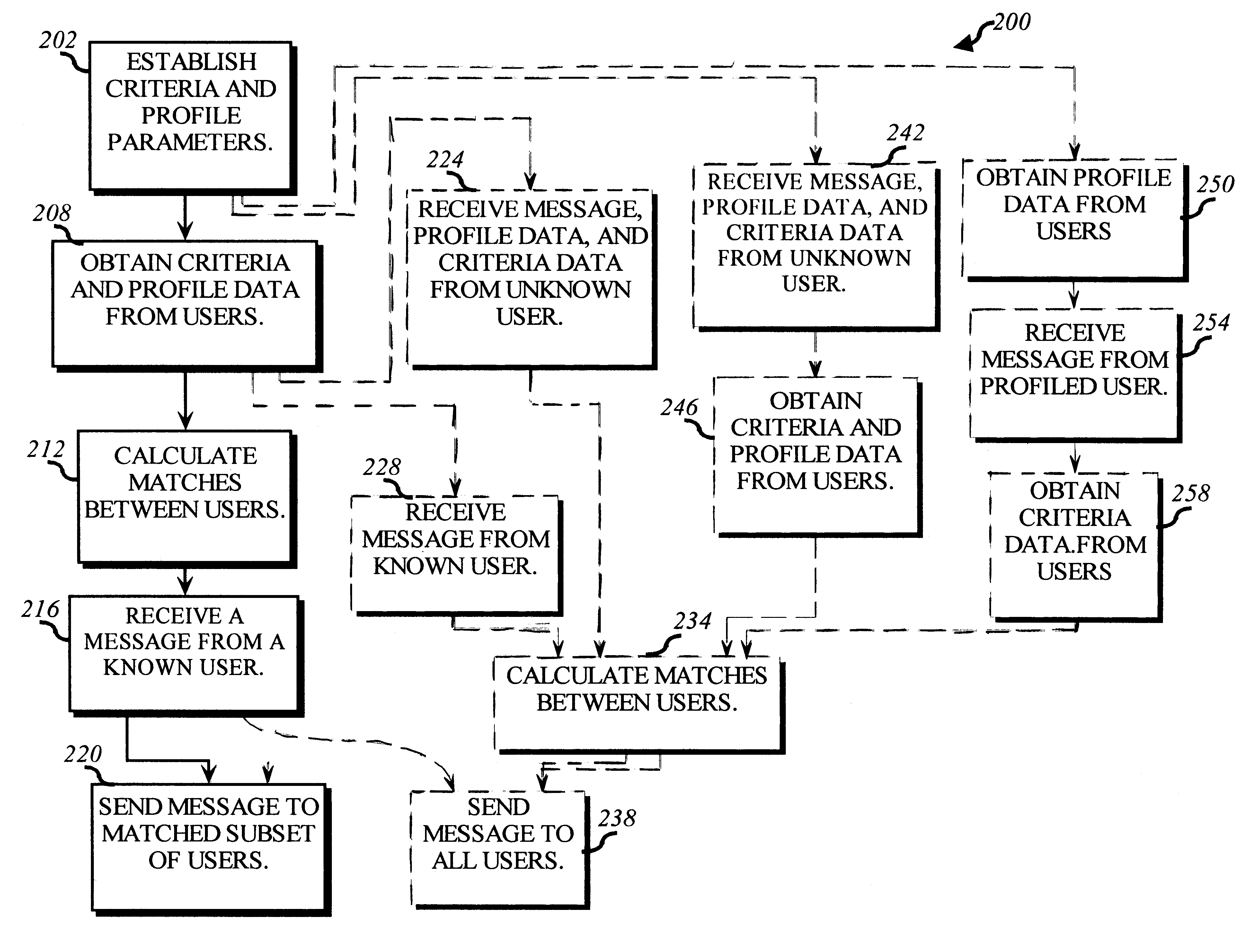
A method for enabling users to exchange group electronic mail by establishing individual profiles and criteria, for determining personalized subsets within a group. Users establish subscriptions to an electronic mailing list by specifying user profile data and acceptance criteria data to screen other users. When a user subscribes, a web server establishes and stores an individualized recipient list including each matching subscriber and their degree of one-way or mutual match with the user. When the user then sends a message to the mailing list, an email server retrieves 100% her matches and then optionally filters her recipient list down to a message distribution list using each recipient's message criteria. The message is then distributed to matching users. Additionally, email archives and information contributions from users are stored in a database. A web server creates an individualized set of web pages for a user from the database, containing contributions only from users in his recipient list. In other embodiments, users apply one-way or mutual criteria matching and message profile criteria to other group forums, such as web-based discussion boards, chat, online clubs, USENET newsgroups, voicemail, instant messaging, web browsing side channel communities, and online gaming rendezvous.
Owner:TUMBLEWEED HLDG LLC
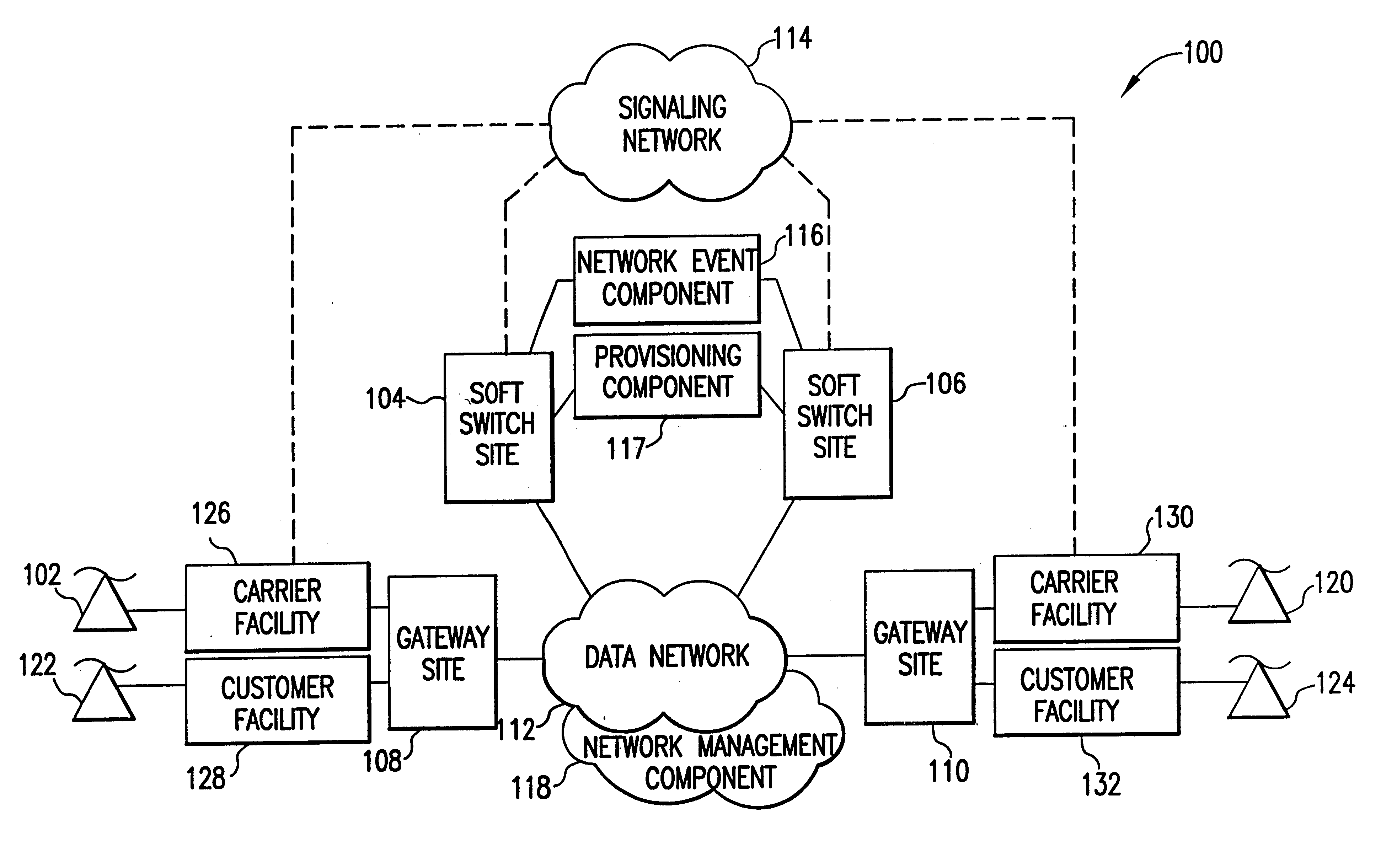
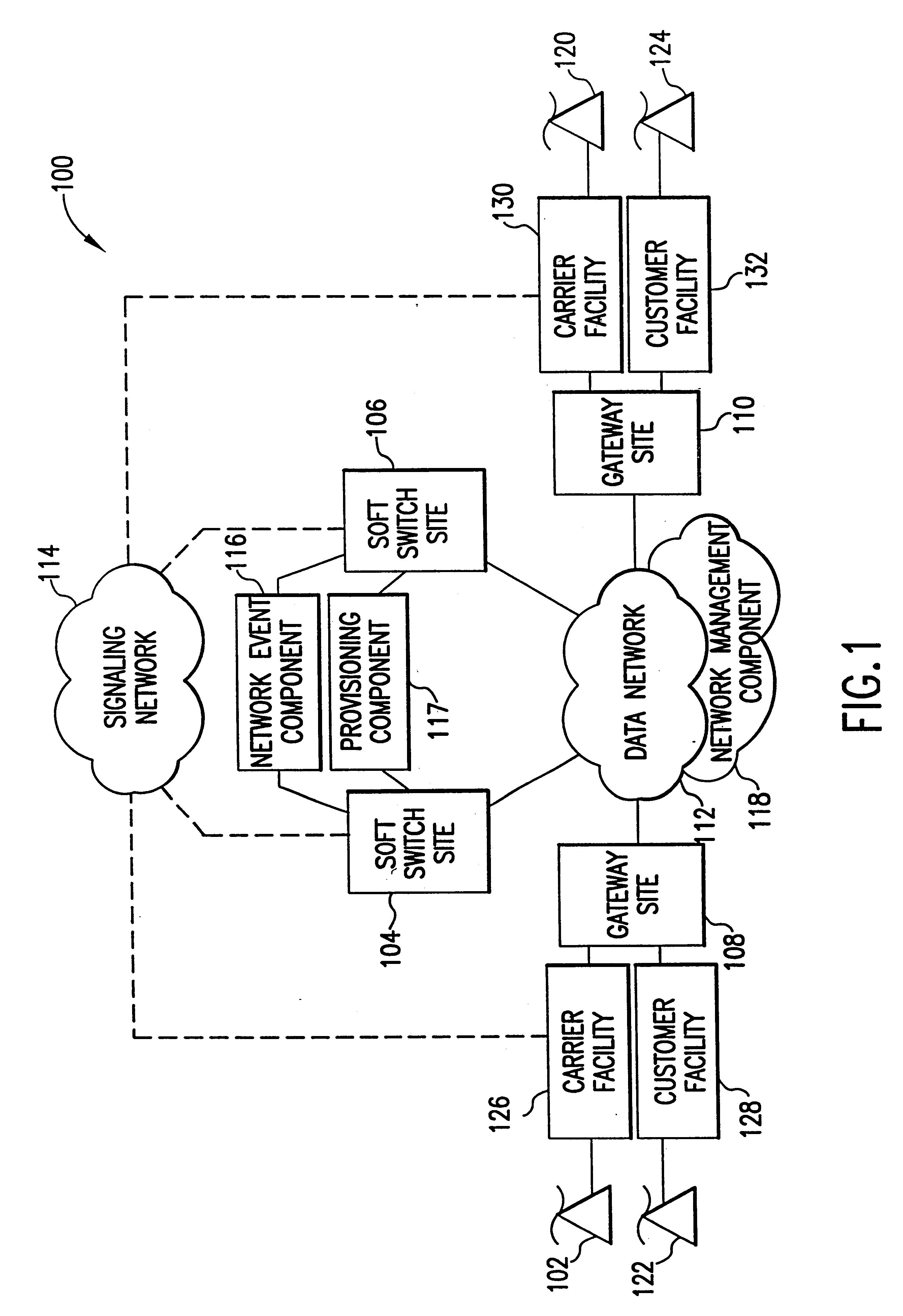
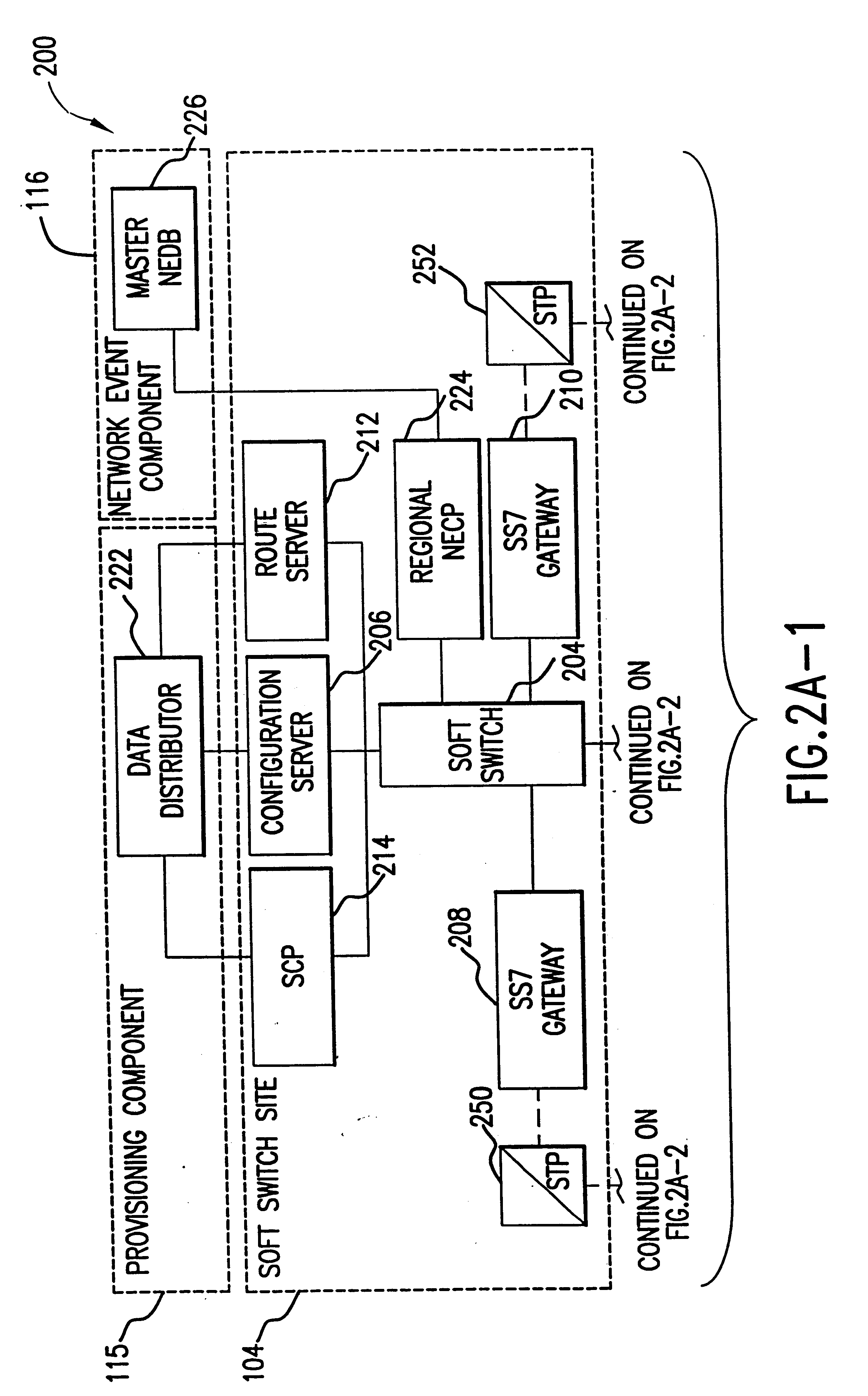
Voice over data telecommunications network architecture
InactiveUS6614781B1Interconnection arrangementsDc level restoring means or bias distort correctionNetwork operations centerNetwork architecture
The present invention describes a system and method for communicating voice and data over a packet-switched network that is adapted to coexist and communicate with a legacy PSTN. The system permits packet switching of voice calls and data calls through a data network from and to any of a LEC, a customer facility or a direct IP connection on the data network. The system includes soft switch sites, gateway sites, a data network, a provisioning component, a network event component and a network management component. The system interfaces with customer facilities (e.g., a PBX), carrier facilities (e.g., a LEC) and legacy signaling networks (e.g., SS7) to handle calls between any combination of on-network and off-network callers.The soft switch sites provide the core call processing for the voice network architecture. The soft switch sites manage the gateway sites in a preferred embodiment, using a protocol such as the Internet Protocol Device Control (IPDC) protocol to request the set-up and tear-down of calls. The gateway sites originate and terminate calls between calling parties and called parties through the data network. The gateway sites include network access devices to provide access to network resources. The data network connects one or more of the soft switch sites to one or more of the gateway sites. The provisioning and network event component collects call events recorded at the soft switch sites. The network management component includes a network operations center (NOC) for centralized network management.
Owner:LEVEL 3 COMM LLC
Information distribution and processing system
InactiveUS7508789B2Reduce loadSufficient amountTelevision system detailsTimetable based automatic information retrievalDigital dataHandling system
An information distribution and processing system contains a remote site, a sender and a receiving apparatus. The remote site contains a first set of digital data. The sender delivers a second set of digital data to the receiving device. In one embodiment of the present invention, the receiving device contain a timing device for automatically receiving the second set of digital data at predetermined times. The second set of digital data contains a first set of displayable data, a second set of displayable data, at least one non-displayable symbol, and at least one linking reference associated with the second set of displayable data. If desired, a user can select the second set of displayable data. The associated linking reference is sent to the remote site. The associated linking reference is used by the remote site to search for the additional information, and returns the requested information to the user.
Owner:ONLINE NEWS LINK
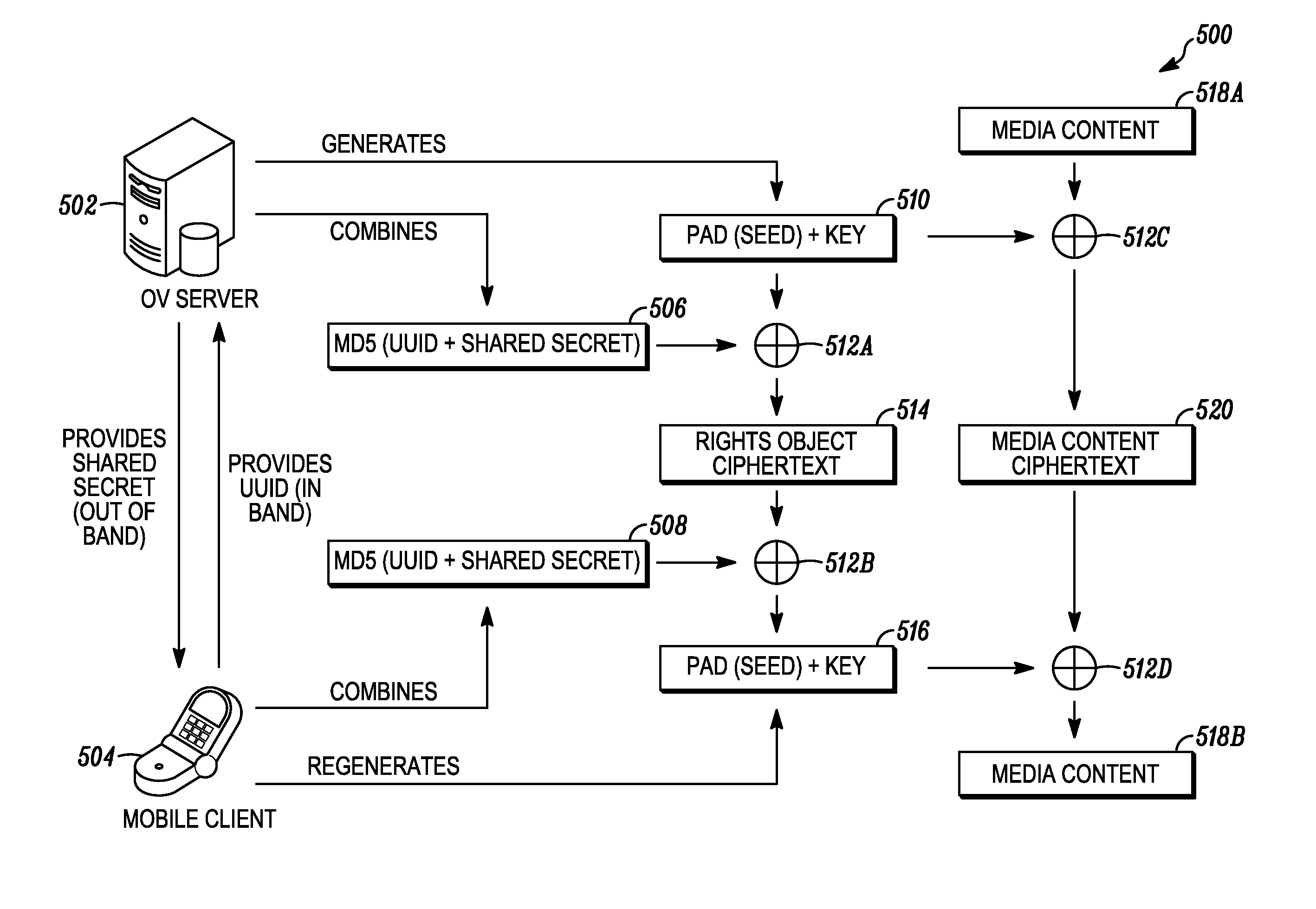
Digital rights management in a mobile environment
ActiveUS20110225417A1Facilitating access to contentOptimization of content deliveryOffice automationResourcesComputer hardwareDigital rights management
Embodiments provide a method that causes a plurality of virtual machine instructions to be interpreted for indications of a mobile device's hardware identification information, thus forming a plurality of hardware instruction interpretations. The embodiment also combines each of the plurality of hardware instruction interpretations and hashes the combination to form a quasi-hardware device identifier. An encryption process is based on the quasi-hardware encryption device identifier and the media is then encrypted using the encryption process. The encrypted media is transferred to the mobile device wherein the mobile device decrypts the media based at least in part on the mobile device's internal knowledge of the quasi-hardware device identification.
Owner:DIRECTV LLC
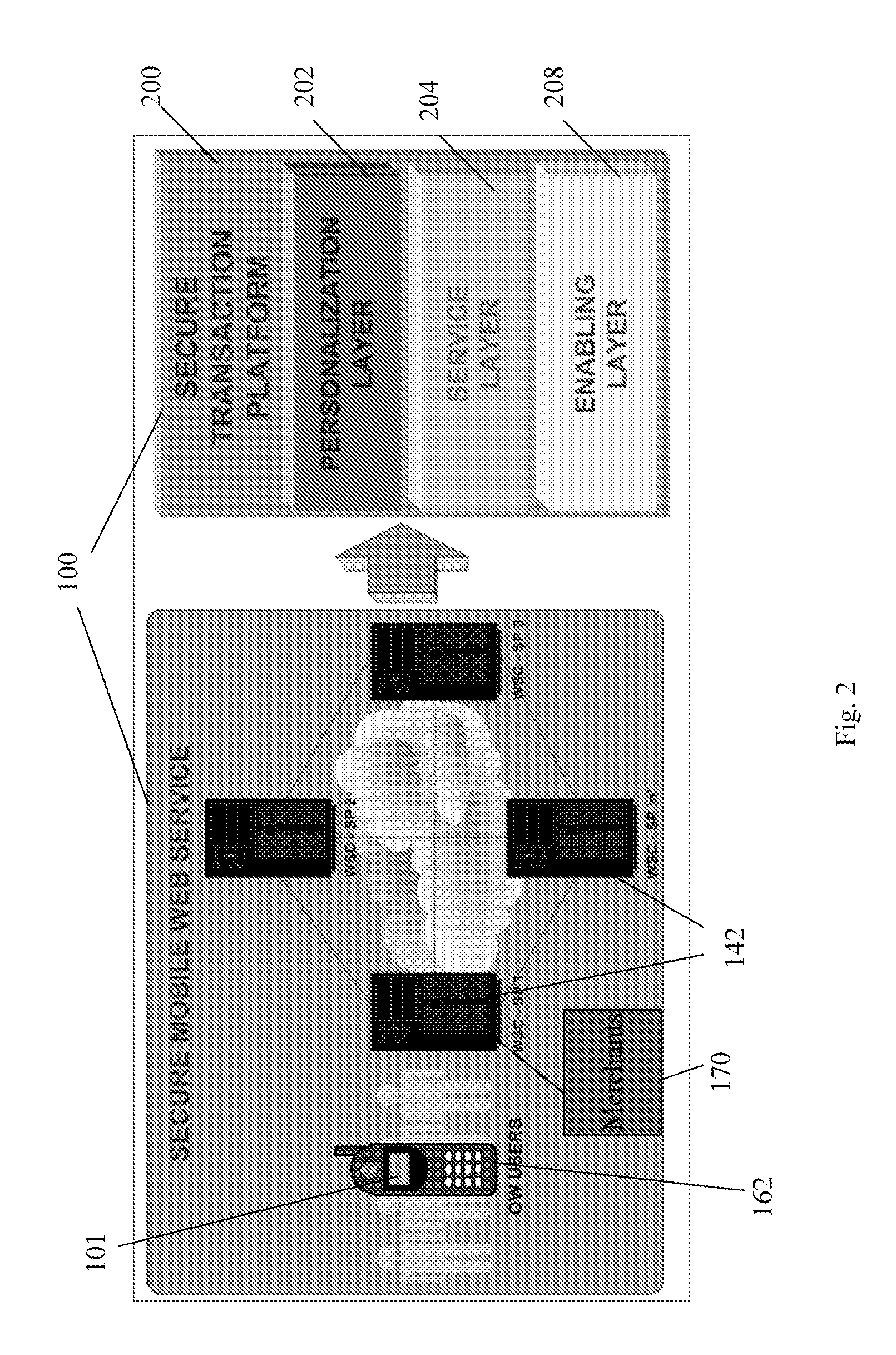
Transactional services
InactiveUS20070198432A1High level of throughputHigh level of efficiencyCryptography processingComputer security arrangementsTransaction serviceDatabase
Owner:MASTERCARD MOBILE TRANSACTIONS SOLUTIONS
System and method for scheduling broadcast of and access to video programs and other data using customer profiles
InactiveUS6020883ATelevision system detailsAnalogue secracy/subscription systemsTelevision systemData source
A system and method for scheduling the receipt of desired movies and other forms of data from a network which simultaneously distributes many sources of such data to many customers, as in a cable television system. Customer profiles are developed for the recipient describing how important certain characteristics of the broadcast video program, movie or other data are to each customer. From these profiles, an "agreement matrix" is calculated by comparing the recipient's profiles to the actual profiles of the characteristics of the available video programs, movies, or other data. The agreement matrix thus characterizes the attractiveness of each video program, movie, or other data to each prospective customer. "Virtual" channels are generated from the agreement matrix to produce a series of video or data programming which will provide the greatest satisfaction to each customer. Feedback paths are also provided so that the customer's profiles and / or the profiles of the video programs or other data may be modified to reflect actual usage. Kiosks are also developed which assist customers in the selection of videos, music, books, and the like in accordance with the customer's objective profiles.
Owner:PINPOINT
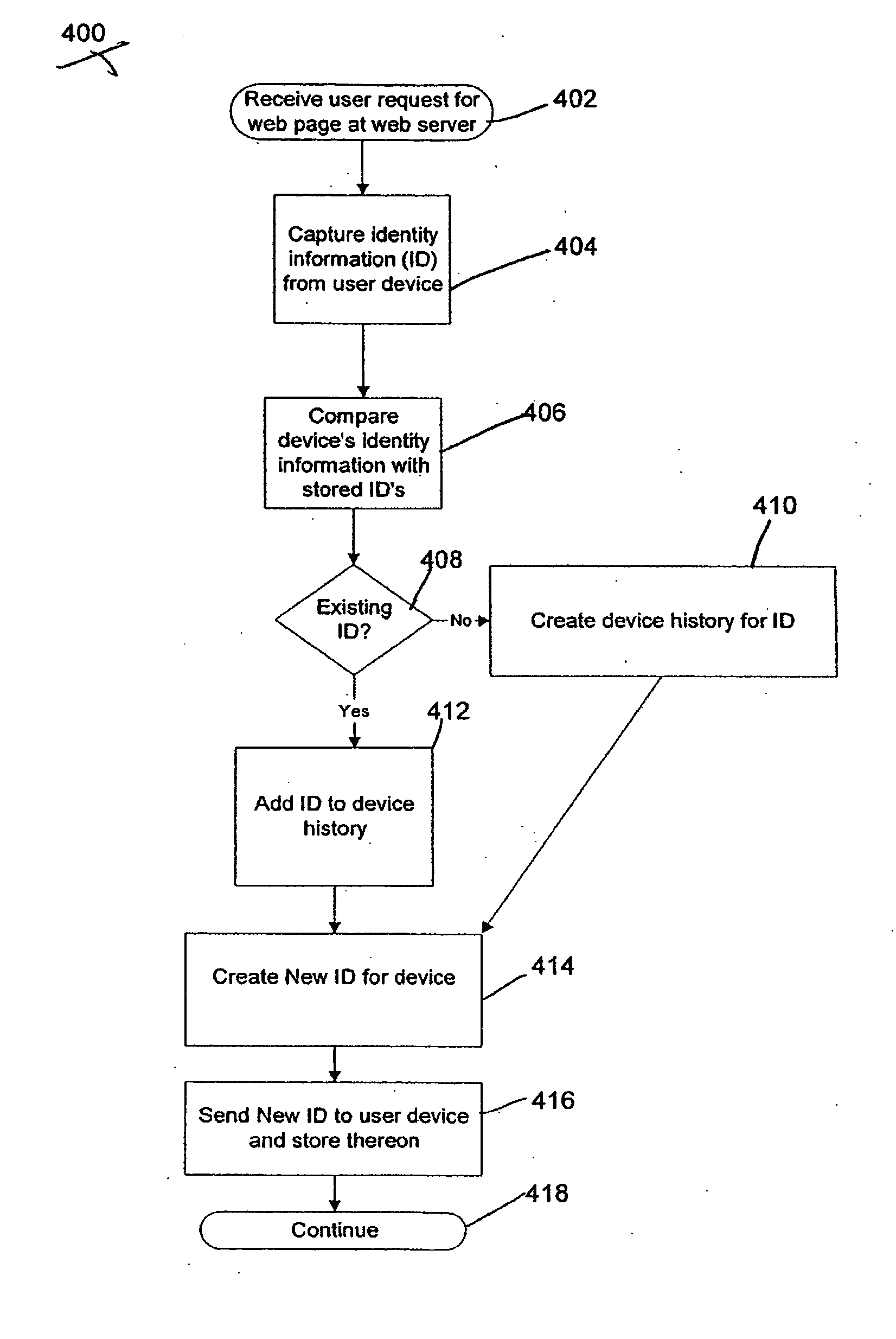
System and method for fraud monitoring, detection, and tiered user authentication
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
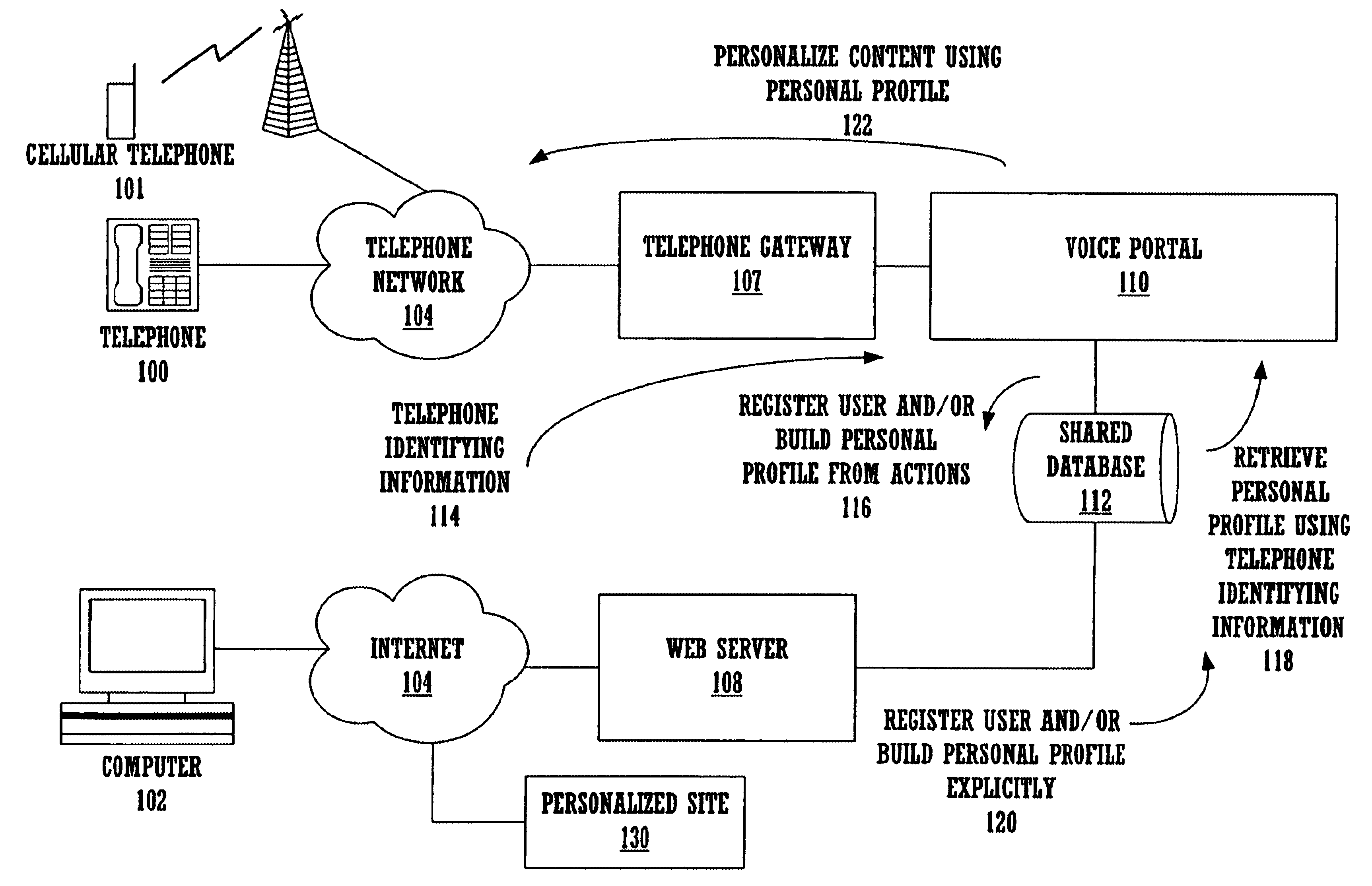
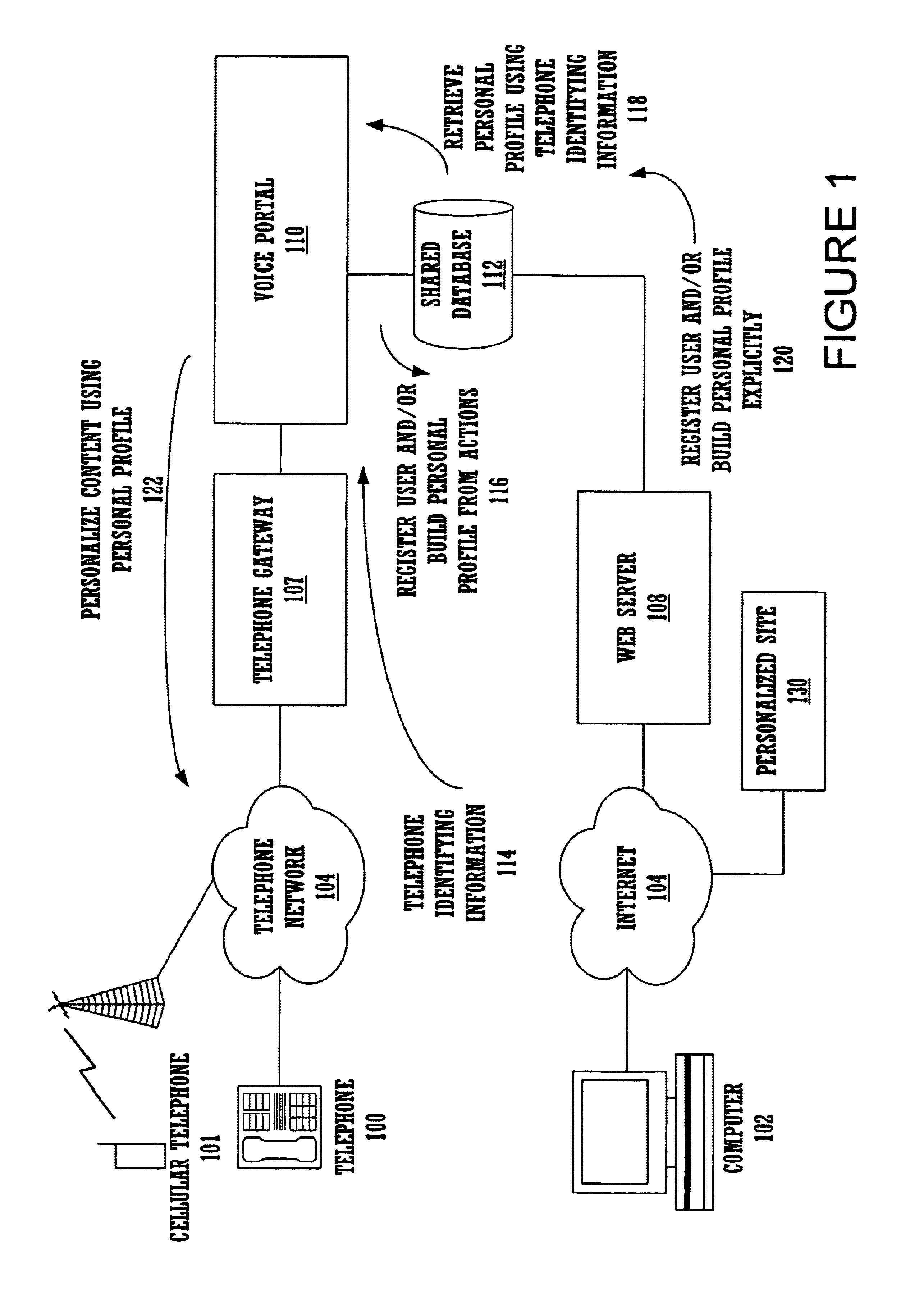
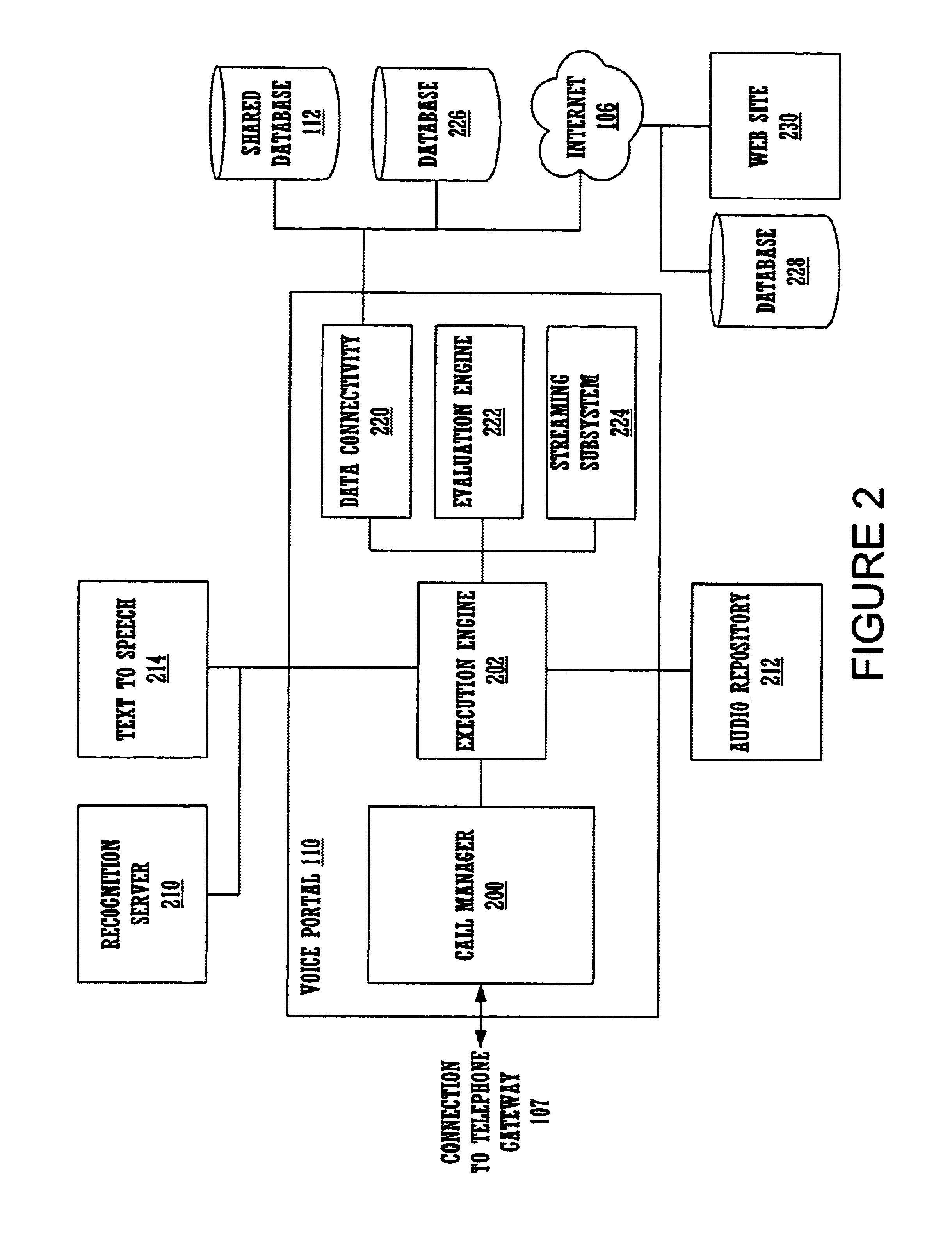
Method and apparatus for content personalization over a telephone interface with adaptive personalization
InactiveUS6842767B1Shorten speedIncrease volumeMultiple digital computer combinationsAutomatic exchangesPersonalizationHuman language
A method and apparatus for providing personalized information content over telephones is described. The creation of a voice portal is supported by the invention. Embodiments of the invention use telephone identifying information such as the calling party's number to identify, or create, user profiles for customization. The personalized content is specific to that user based on her / his telephone identifying information and may be further customized based on the current time, current date, the calling party's locales, and / or the calling party's dialect and speech patterns. Also, the telephone identifying information may support targeted advertising, content, and purchasing recommendations specific to that user. The system may use a voice password and / or touch-tone login system when appropriate to distinguish the caller or verify the caller's identity for specific activities. Typically, embodiments of the invention will immediately present a caller personalized content based on her / his profile using the appropriate dialect as well as the caller's preferred content. Profiles can be constructed as the caller uses embodiments of the invention as well as through explicit designation of preferences. For example, as the user selects topics, as well as particular content, a record of actions can be maintained. This record of actions can be used to provide suggestions and direct the personalization of the system for the user.
Owner:MICROSOFT TECH LICENSING LLC
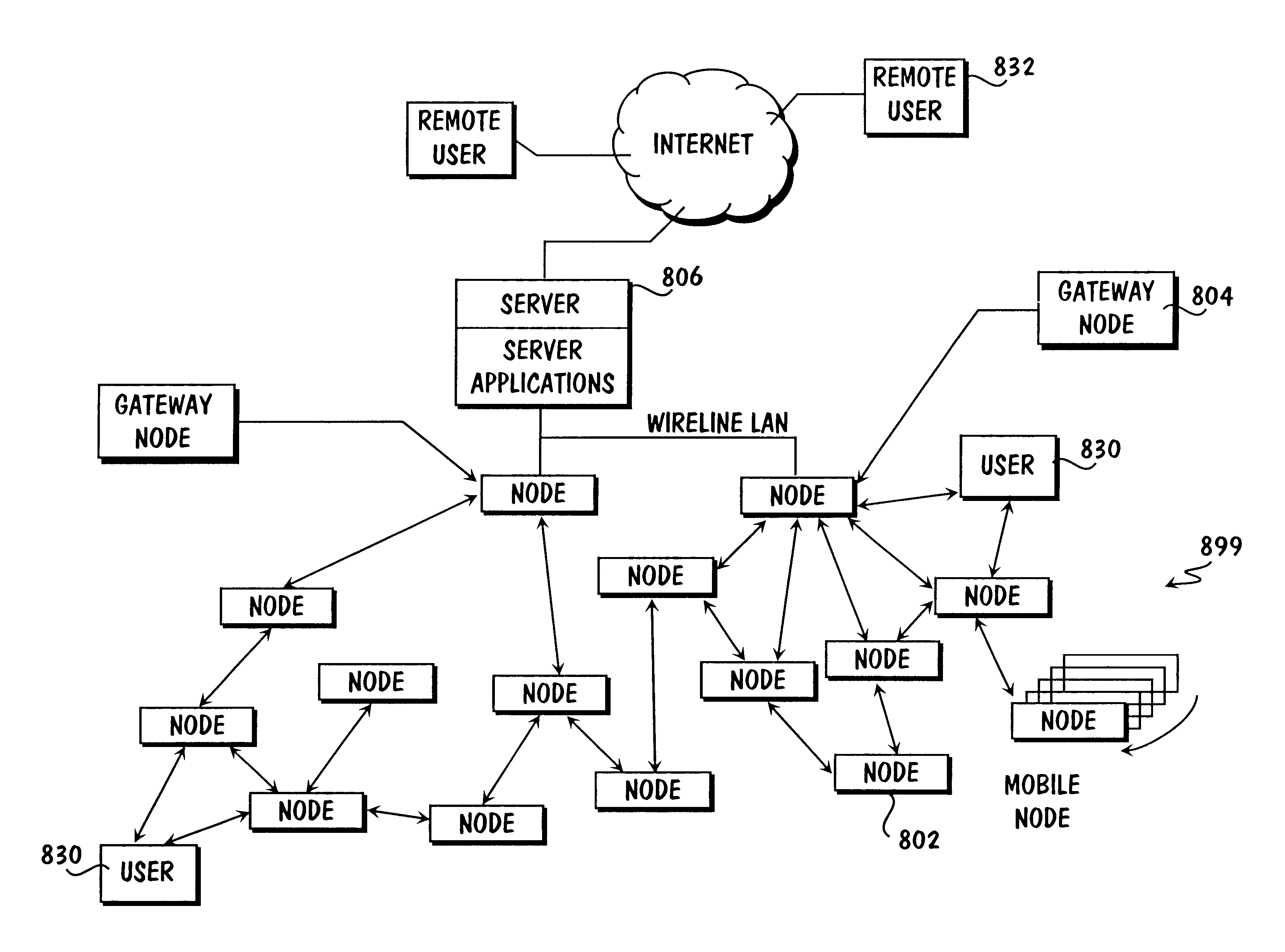
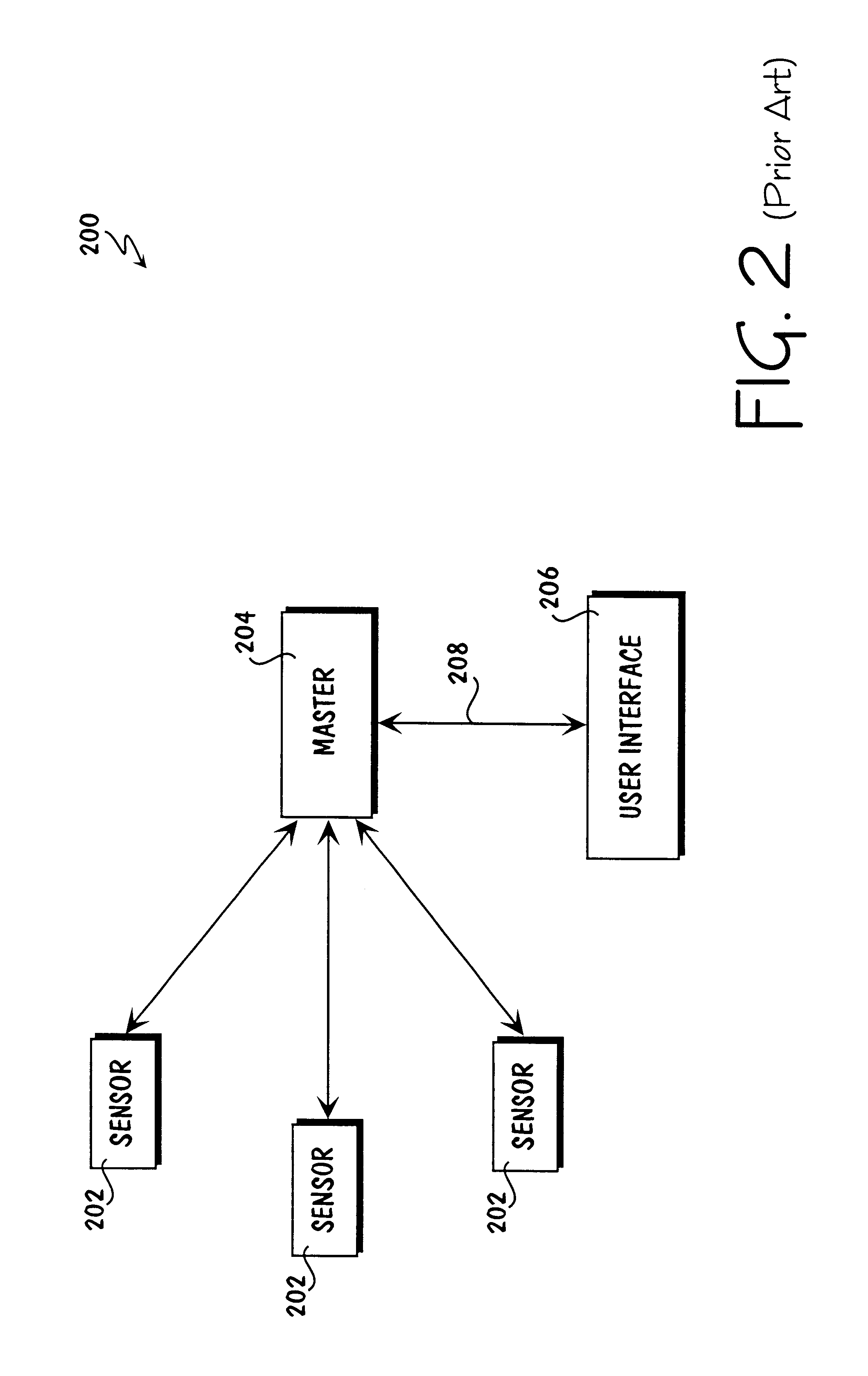
Method and apparatus for internetworked wireless integrated network sensor (WINS) nodes
InactiveUS6859831B1Ease real-time operating system issueImprove adaptabilitySpecific access rightsAnti-theft devicesReconfigurabilityMonitoring and control
The Wireless Integrated Network Sensor Next Generation (WINS NG) nodes provide distributed network and Internet access to sensors, controls, and processors that are deeply embedded in equipment, facilities, and the environment. The WINS NG network is a new monitoring and control capability for applications in transportation, manufacturing, health care, environmental monitoring, and safety and security. The WINS NG nodes combine microsensor technology, low power distributed signal processing, low power computation, and low power, low cost wireless and / or wired networking capability in a compact system. The WINS NG networks provide sensing, local control, remote reconfigurability, and embedded intelligent systems in structures, materials, and environments.
Owner:INTELLECTUAL VENTURES I LLC
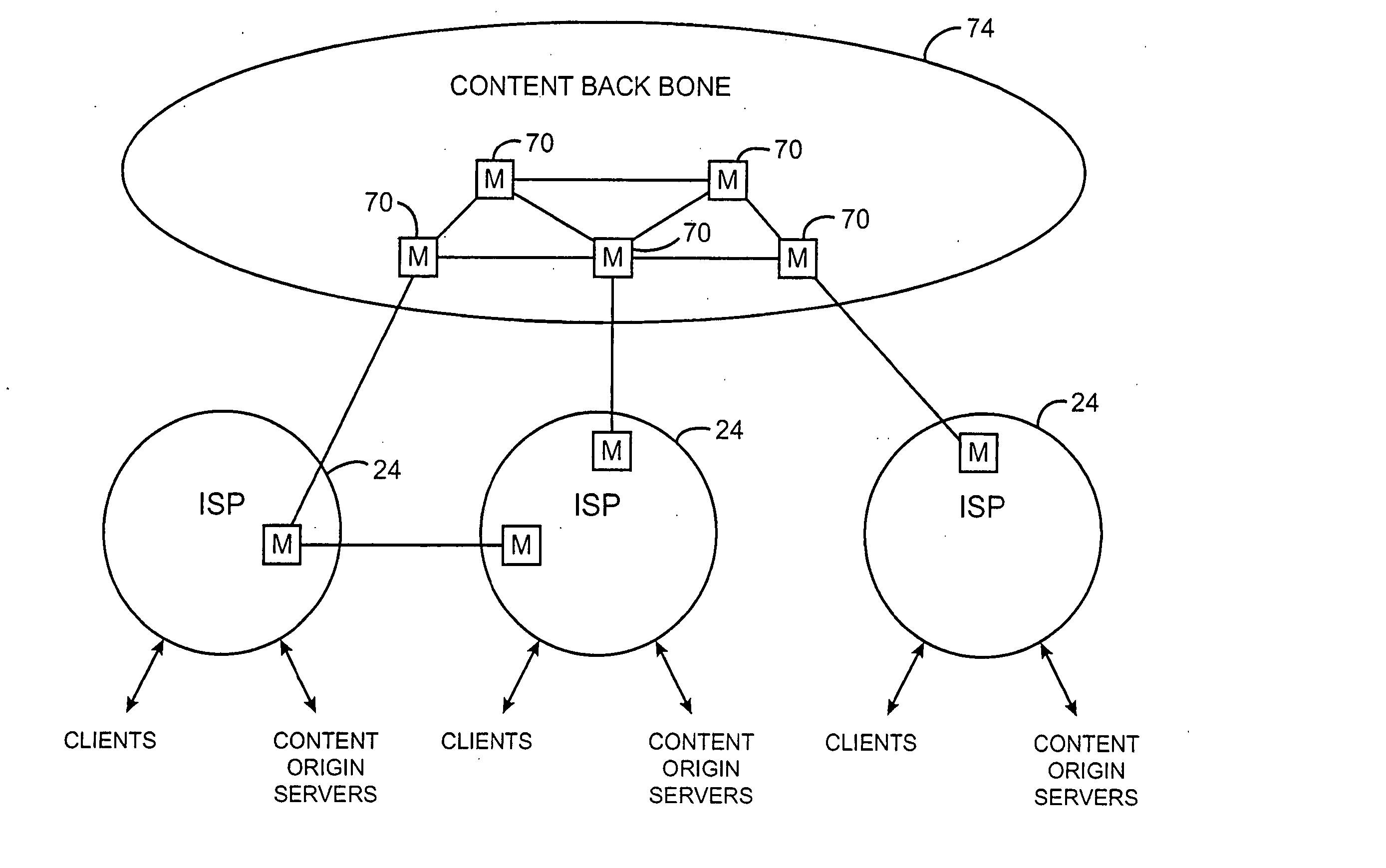
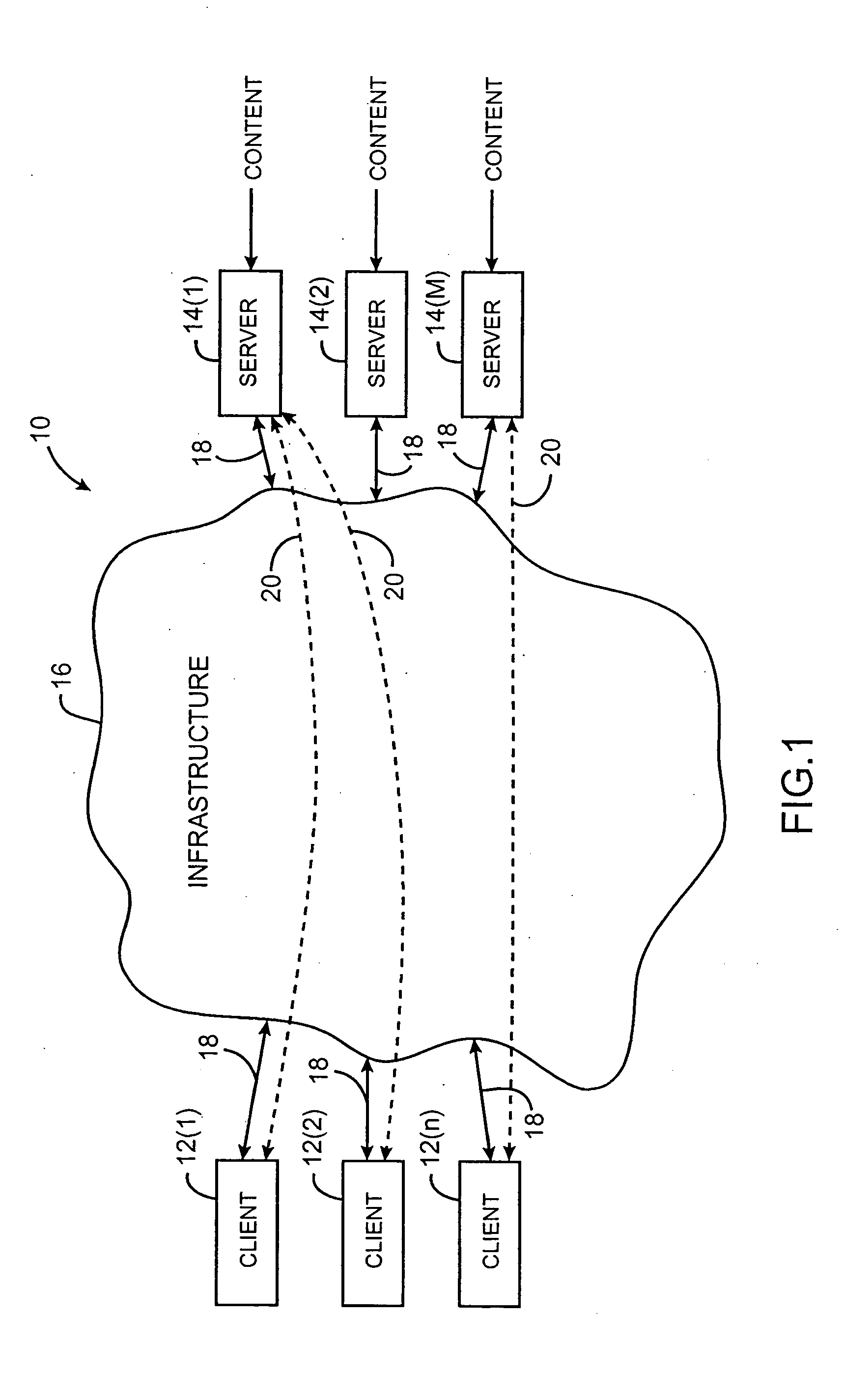
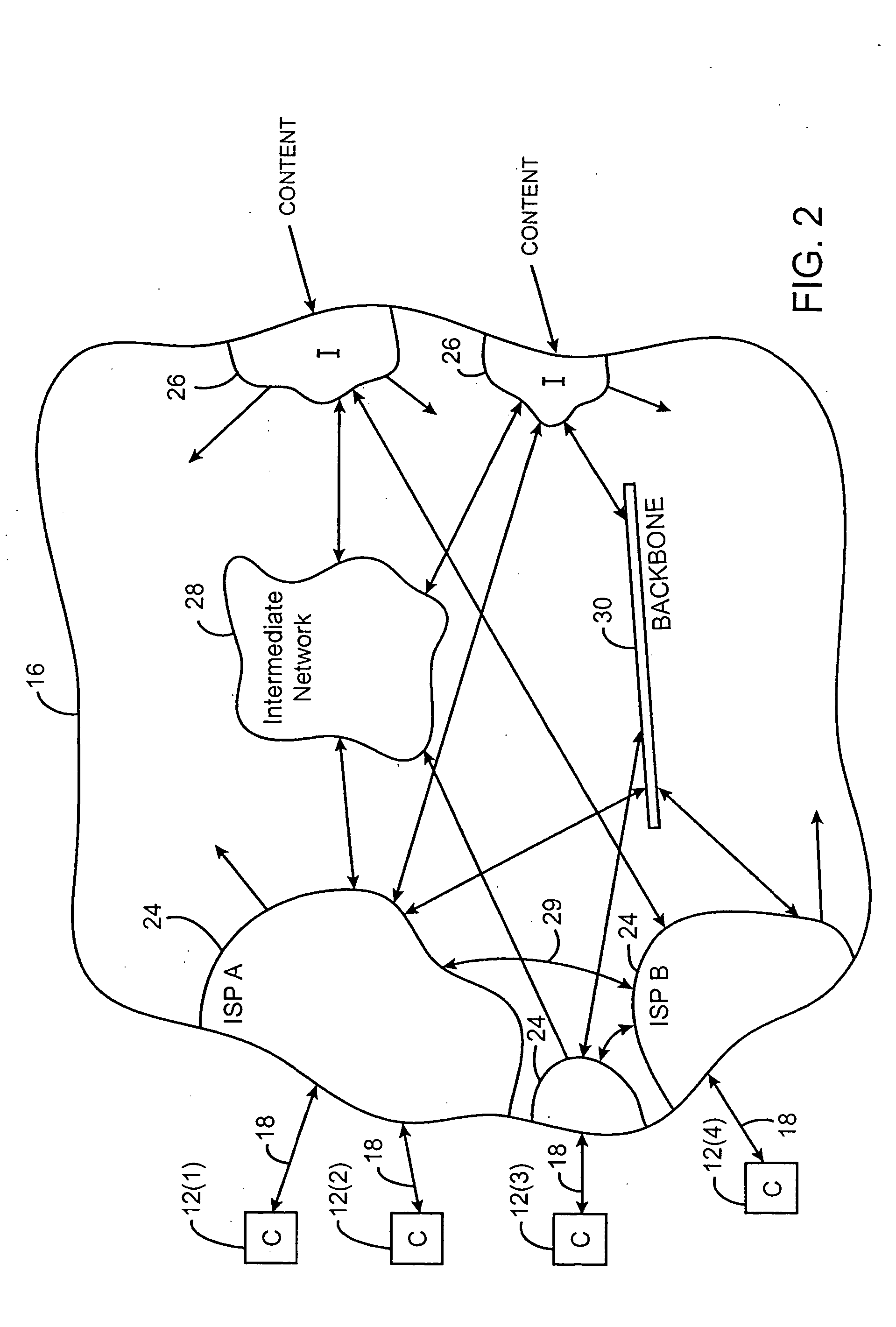
Content distribution system for operation over an internetwork including content peering arrangements
InactiveUS20050010653A1Special service provision for substationMultiple digital computer combinationsContent distributionDomain name
In a network interconnecting a plurality of content providers and a plurality of clients, for providing content to a client, each of the plurality of content providers is coupled to at least one content distribution network of a plurality of content distribution networks, wherein the client is coupled to at least one of the plurality of content distribution networks and a request for the content is sent from the client to a redirector node that receives requests, wherein a redirector at the redirector node provides an address for a server available to serve the requested content. When the client's content distribution network is a primary content distribution network for the content provider providing the requested content, redirecting the client to a server within the client's content distribution network. When the client's content distribution network is not a primary content distribution network for the content provider but the client's content distribution network has a content peering relationship with a primary content distribution network for the content provider, redirecting the client to a server within the client's content distribution network. When the client's content distribution network is not a primary content distribution network for the content provider and the client's content distribution network does not have a content peering relationship with a primary content distribution network for the content provider, redirecting the client to a server outside the client's content distribution network. The redirecting can be done using a domain name service (DNS) server that responds to requests for domain name resolution that include metadata encoding for the content being requested and / or attributes of the resolution request other than a domain name or explicit client / redirector communication to perform the redirection.
Owner:GOOGLE LLC
Authentication services using mobile device
InactiveUS20060206709A1Payment architectureATM softwaresInternet Authentication ServiceMobile device
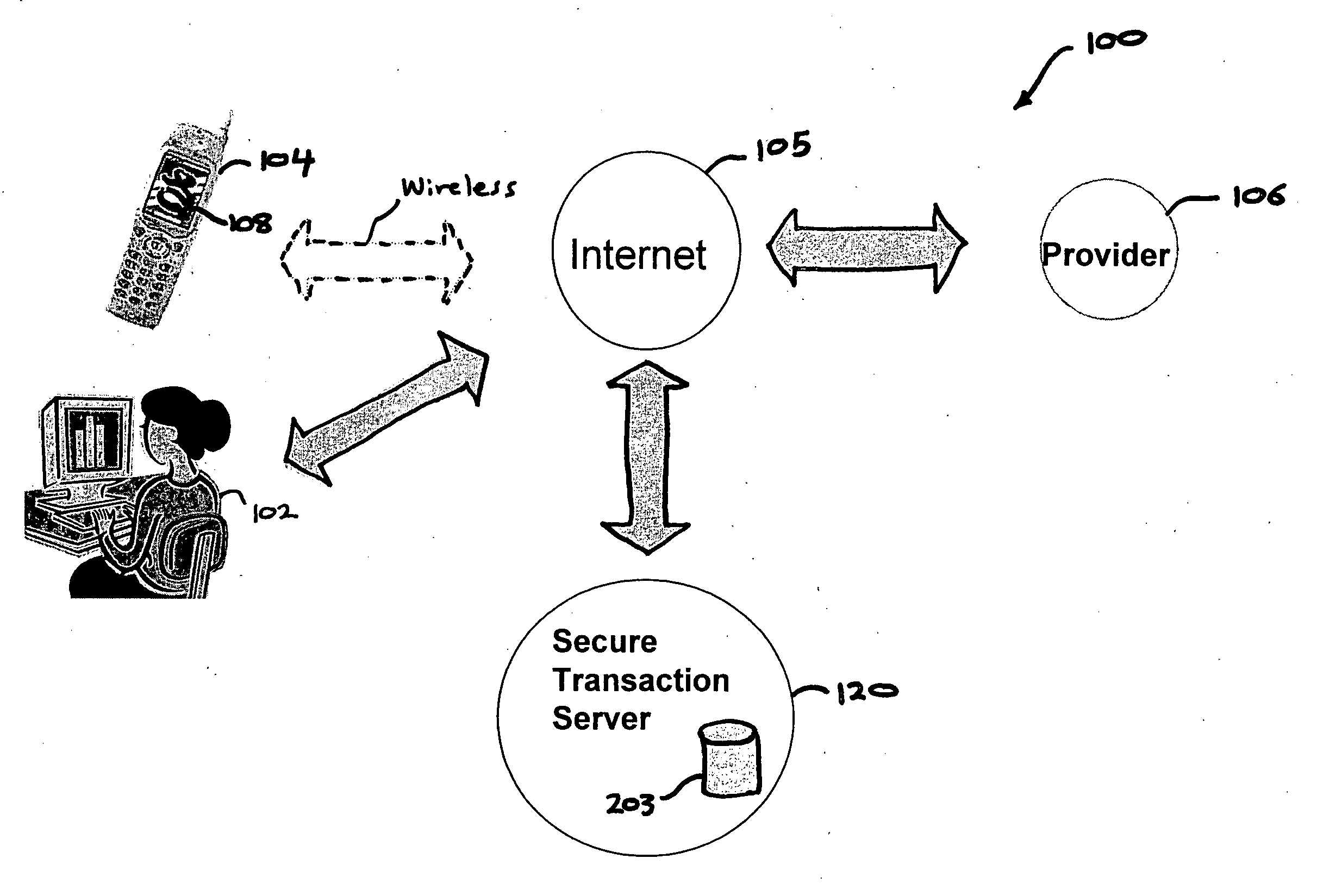
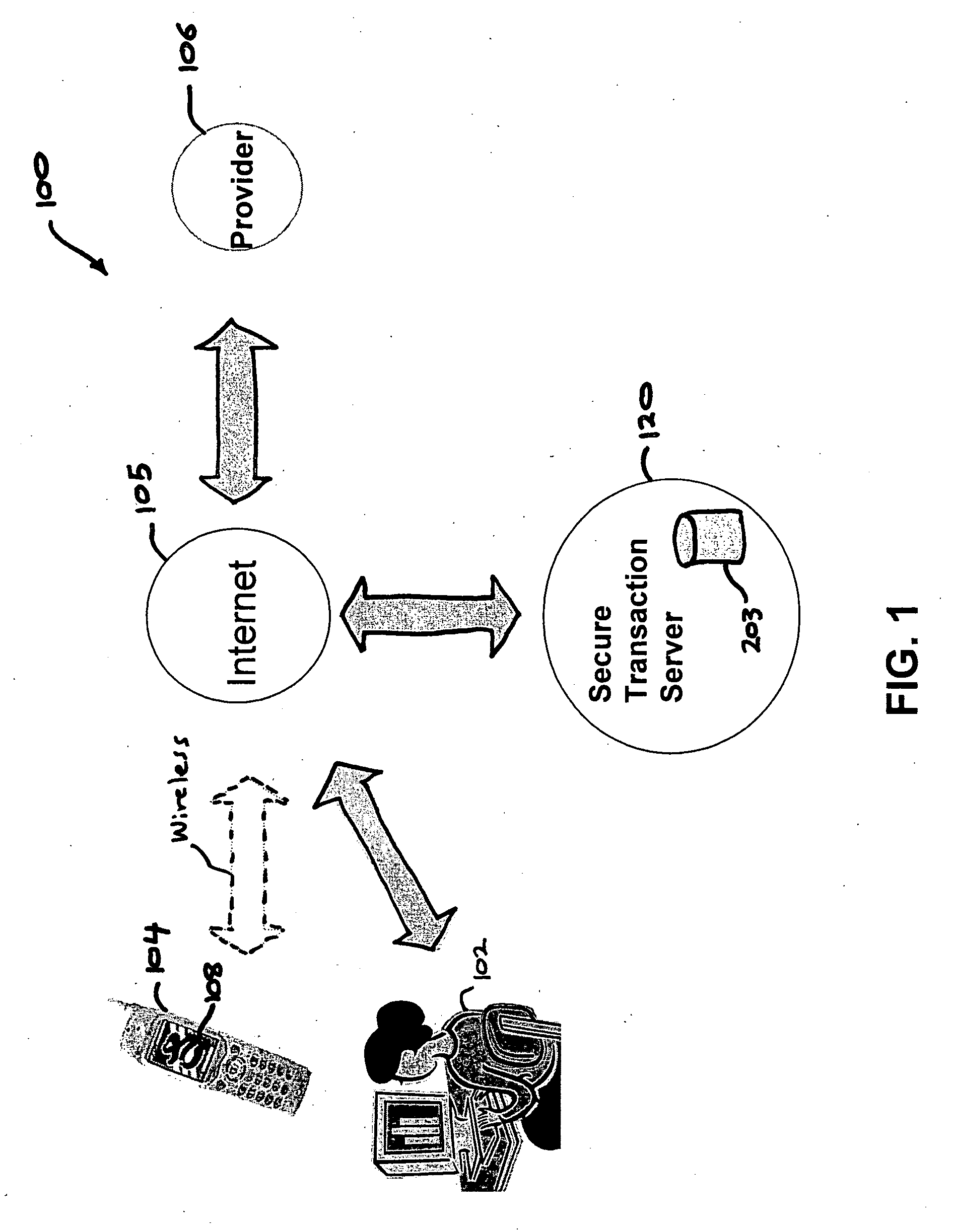
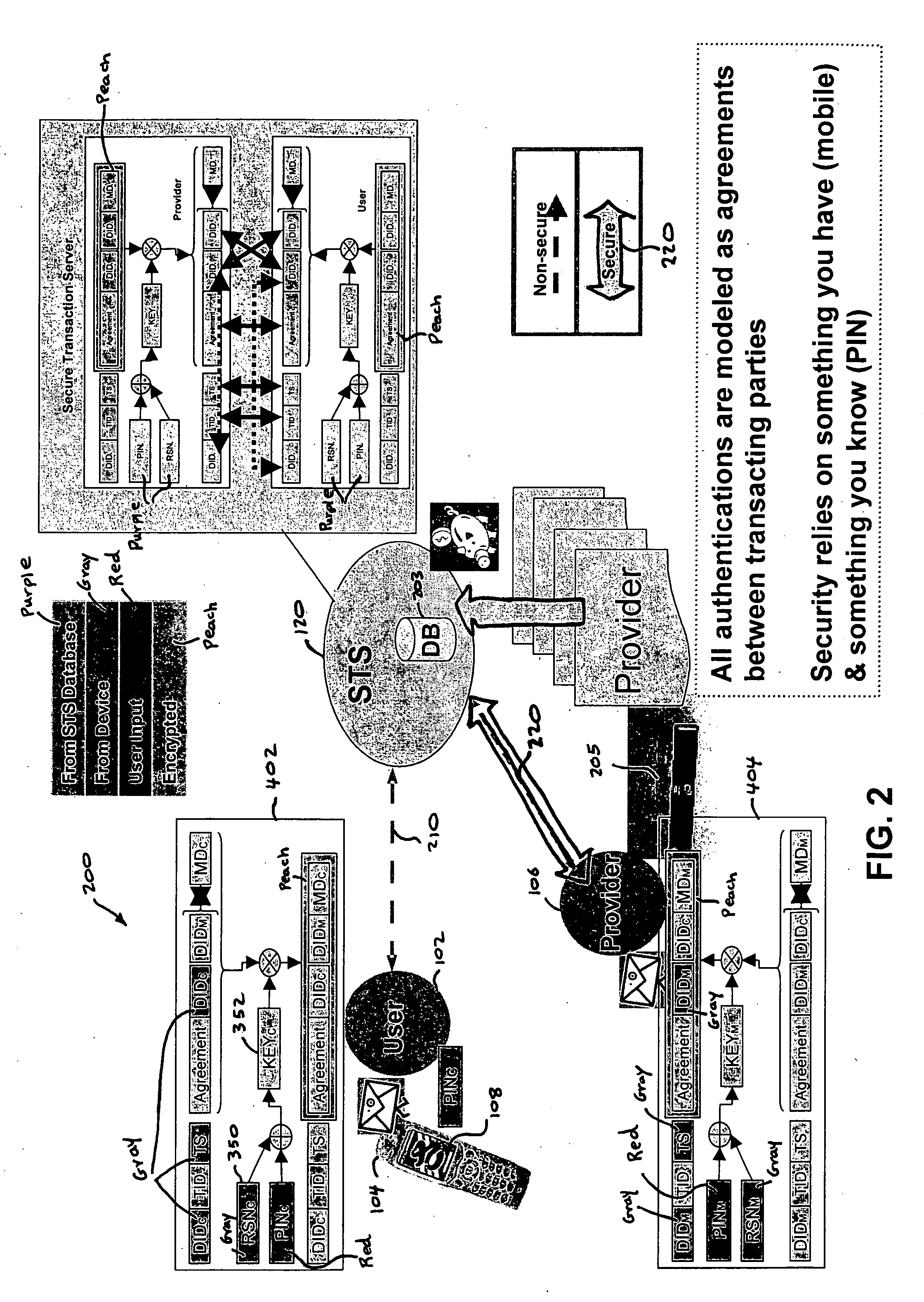
A method, and an apparatus performing the method, is provided by authenticating a mobile device communicably connectable to a wireless network by an authentication parameter from a secure transaction server (STS), as a mobile device authenticator; providing an STS correlation between a personal identification entry (PIE) and the mobile device authenticator; and inputting, by a user, the PIE and a provider action, to the mobile device authenticator to transmit a transformed secure user authenticable authorization request to the STS over the wireless network to authorize an action with a provider.
Owner:PCMS HOLDINGS INC
Place specific buddy list services
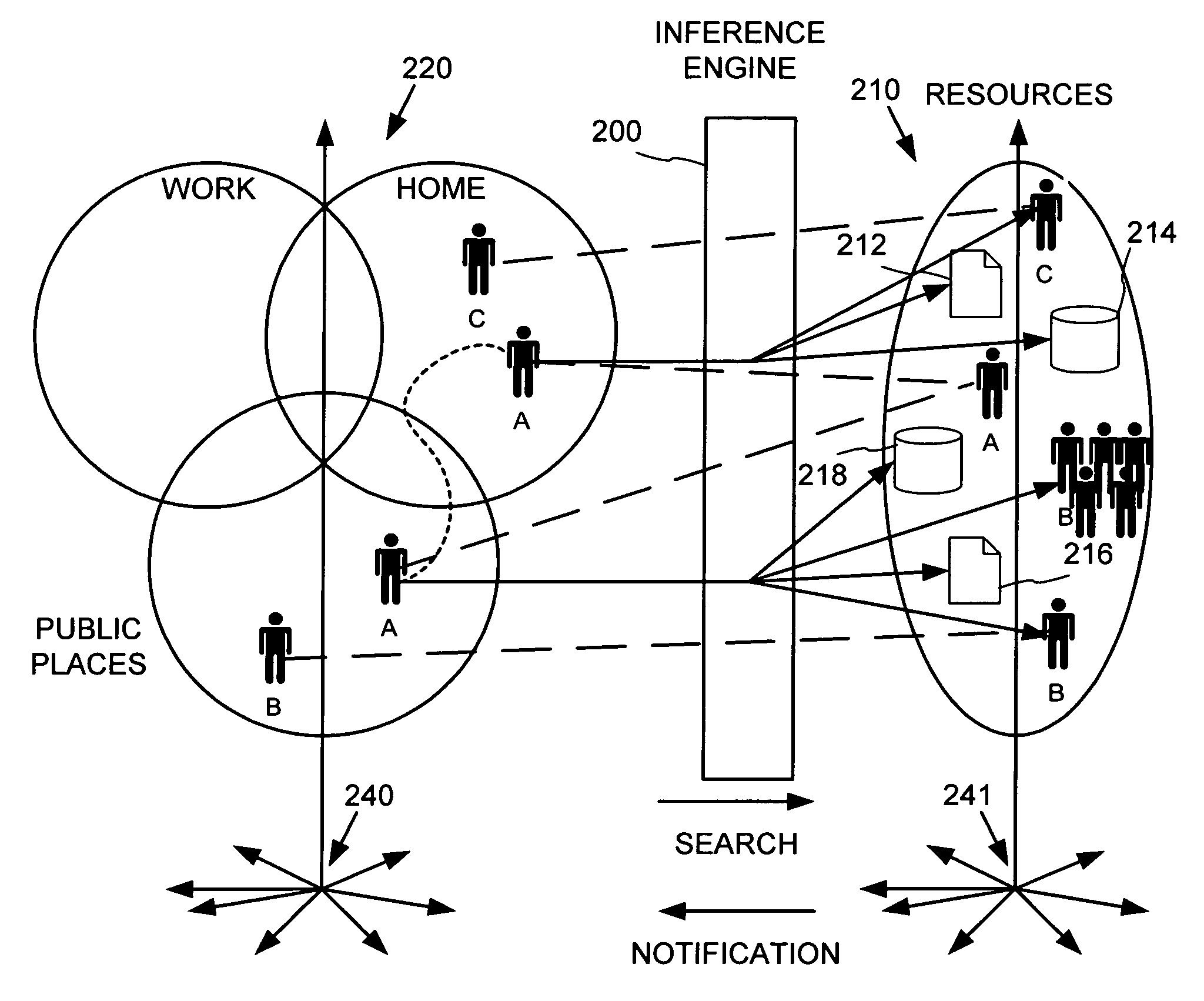
InactiveUS6968179B1Information formatSpecial service for subscribersWorld Wide WebPositioning equipment
An information service provides search and notifications to inform when certain people (e.g., friends, family, business contacts, etc.) are nearby so as to facilitate communications with those people. Users may define lists of people whose locations may be tracked by positioning equipment based on personal communications / computing devices carried by the people. The information service processes this people and place data to identify those of the listed people that are in the user's vicinity, and provide notifications and user-initiated search results informing the user such as via the user's personal communications / computing device.
Owner:MICROSOFT TECH LICENSING LLC
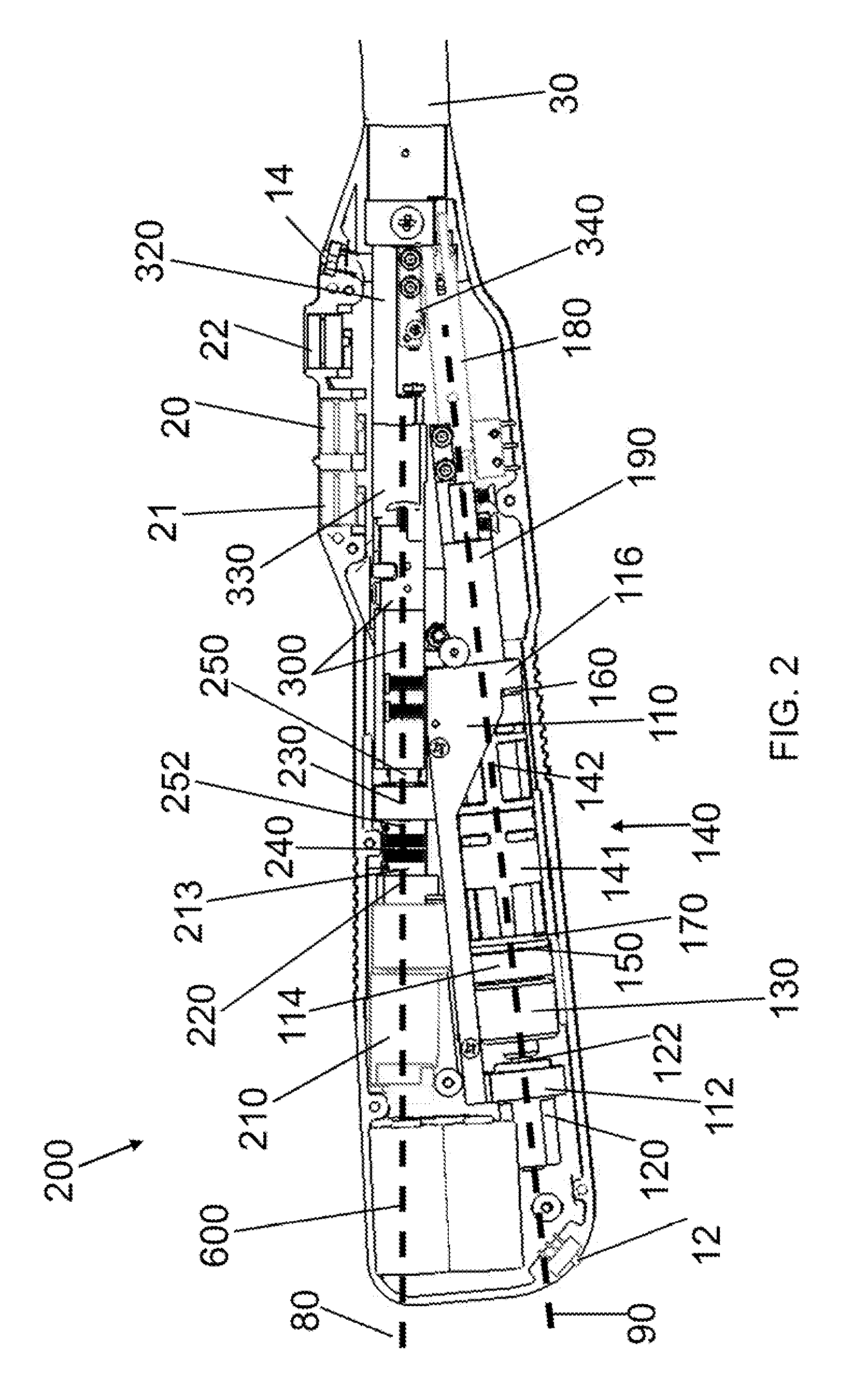
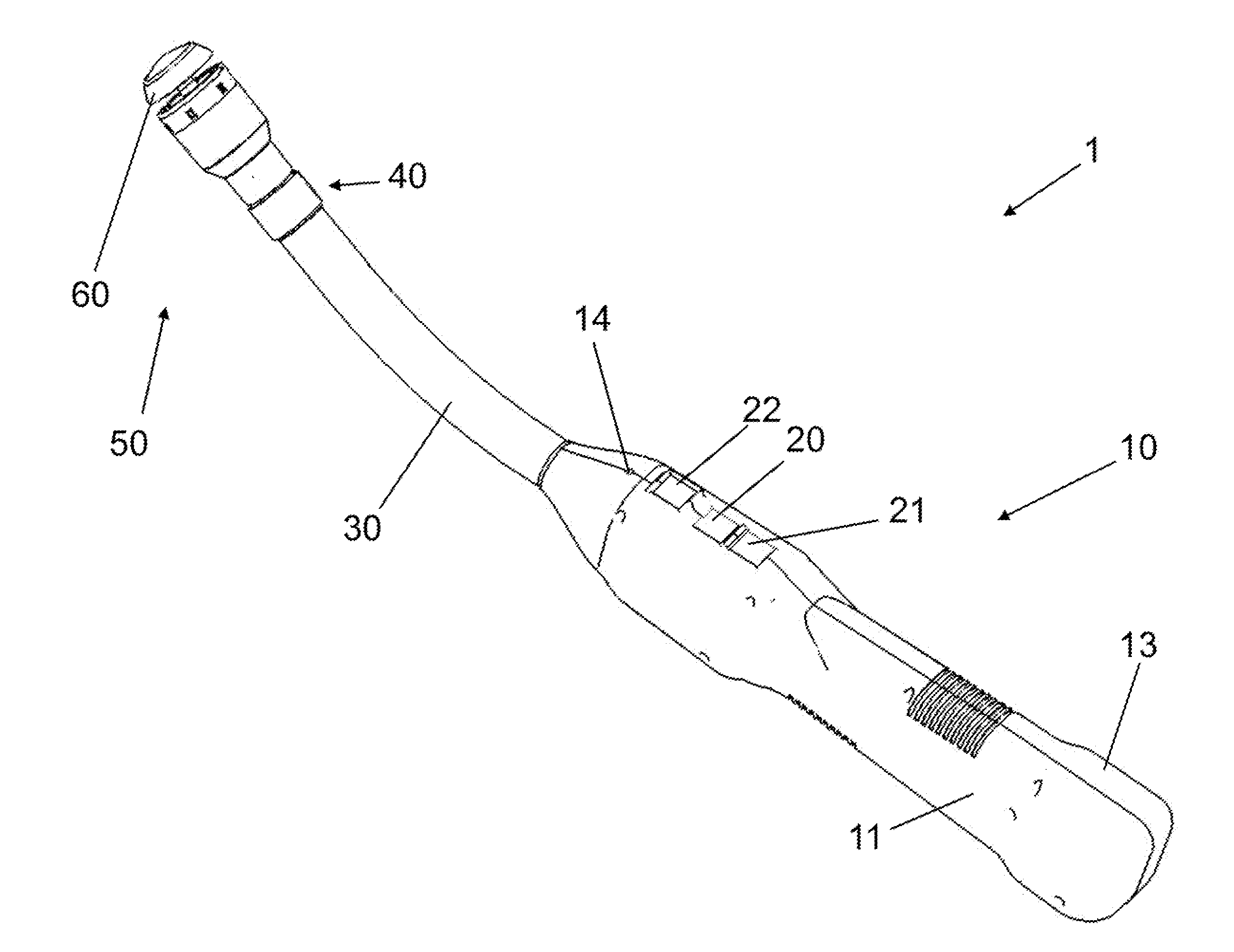
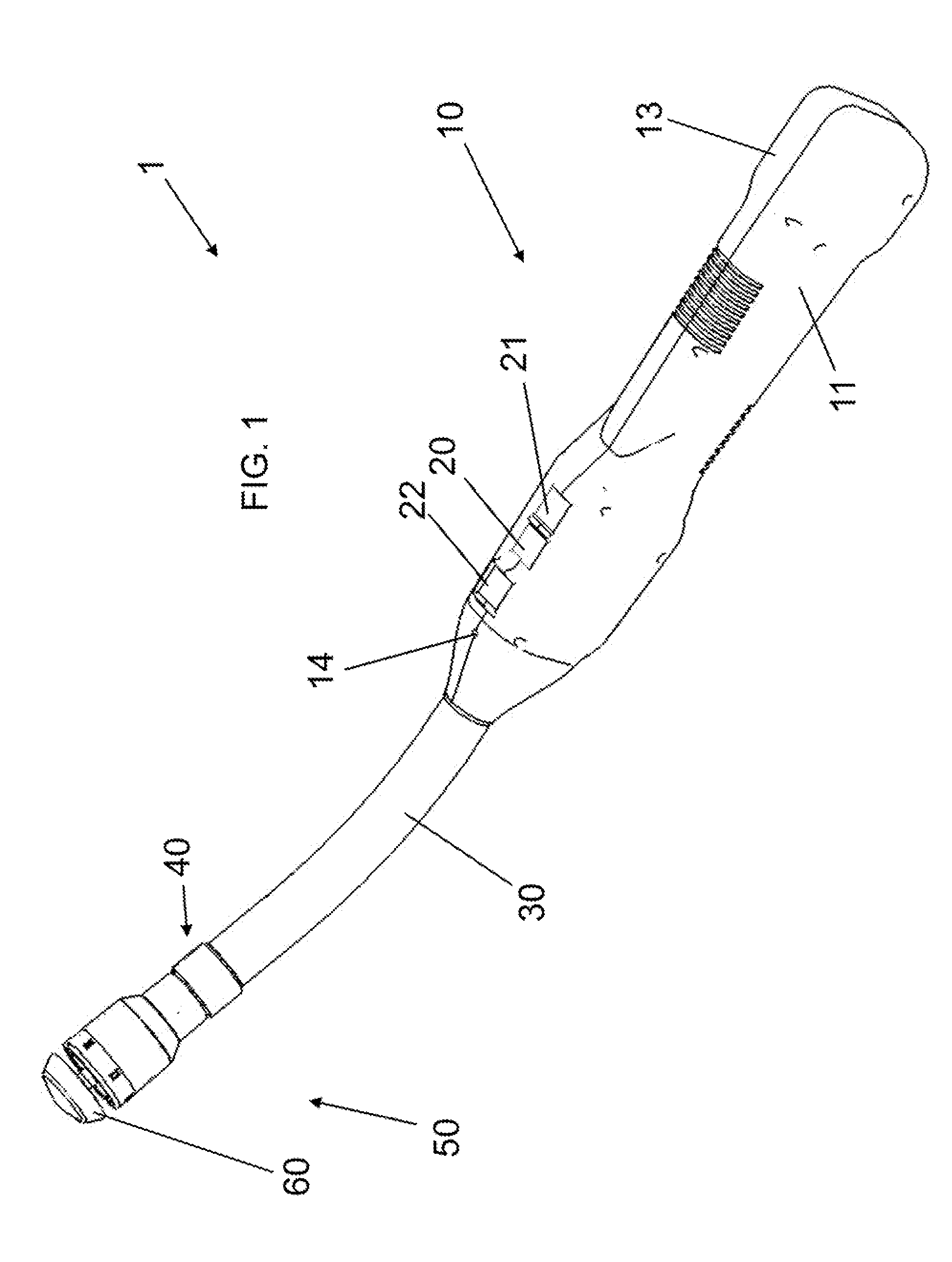
Electrically Self-Powered Surgical Instrument With Cryptographic Identification of Interchangeable Part
ActiveUS20080185419A1Reduce manufacturing difficultyReduce manufacturing costSuture equipmentsStapling toolsElectricityEngineering
A surgical instrument, includes a surgical end effector having a receiving portion for removably receiving therein an interchangeable part. The receiving portion has a communication connection. A handle connected to the end effector actuates the end effector. The handle has a controller electrically connected to the communication connection for authenticating the interchangeable part when placed at the end effector. An interchangeable part is removably connected to the receiving portion and has an encryption device electrically removably connected to the communication connection when placed at the receiving portion. The encryption device authenticates the interchangeable part when queried by the electric controller.
Owner:CILAG GMBH INT
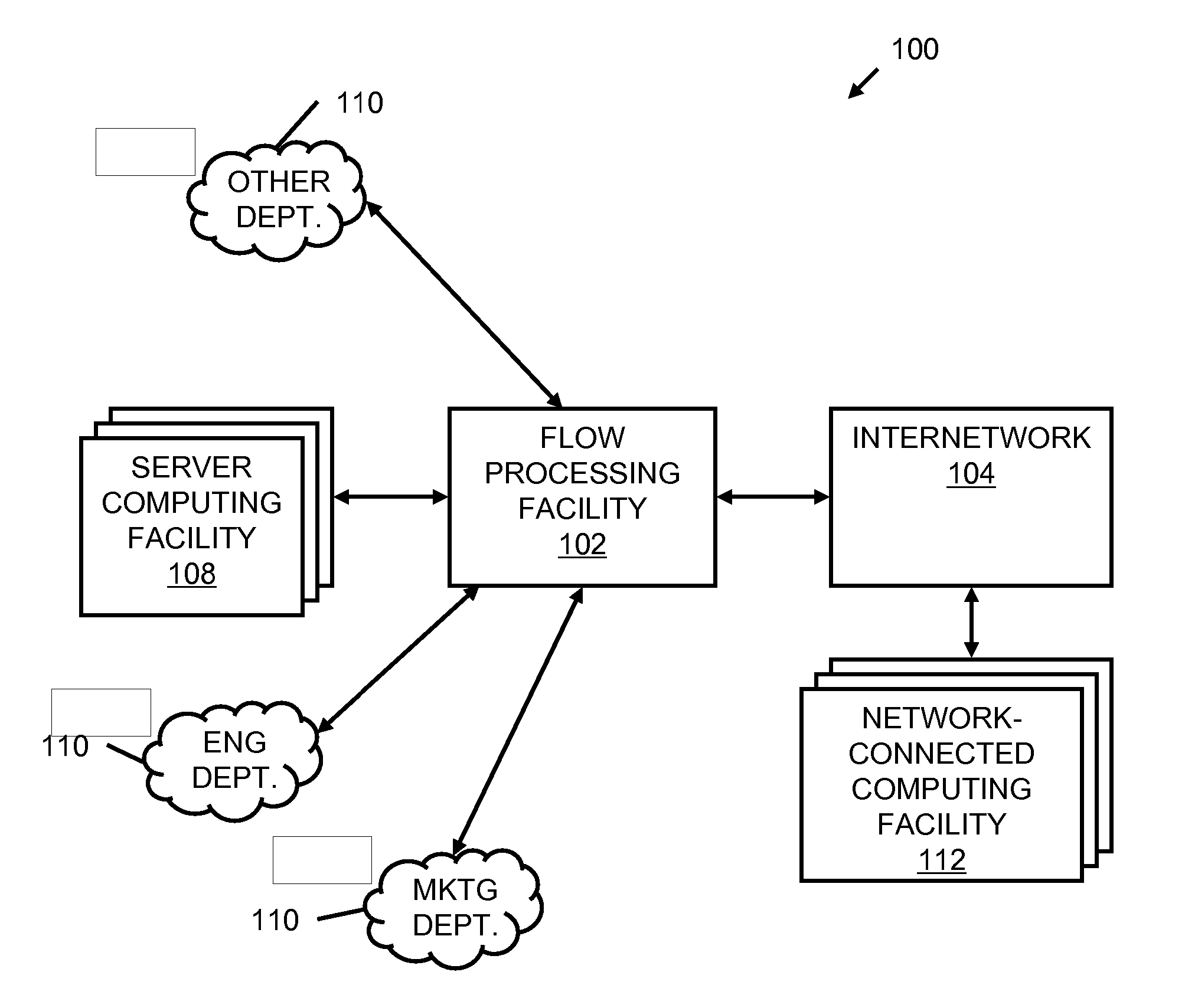
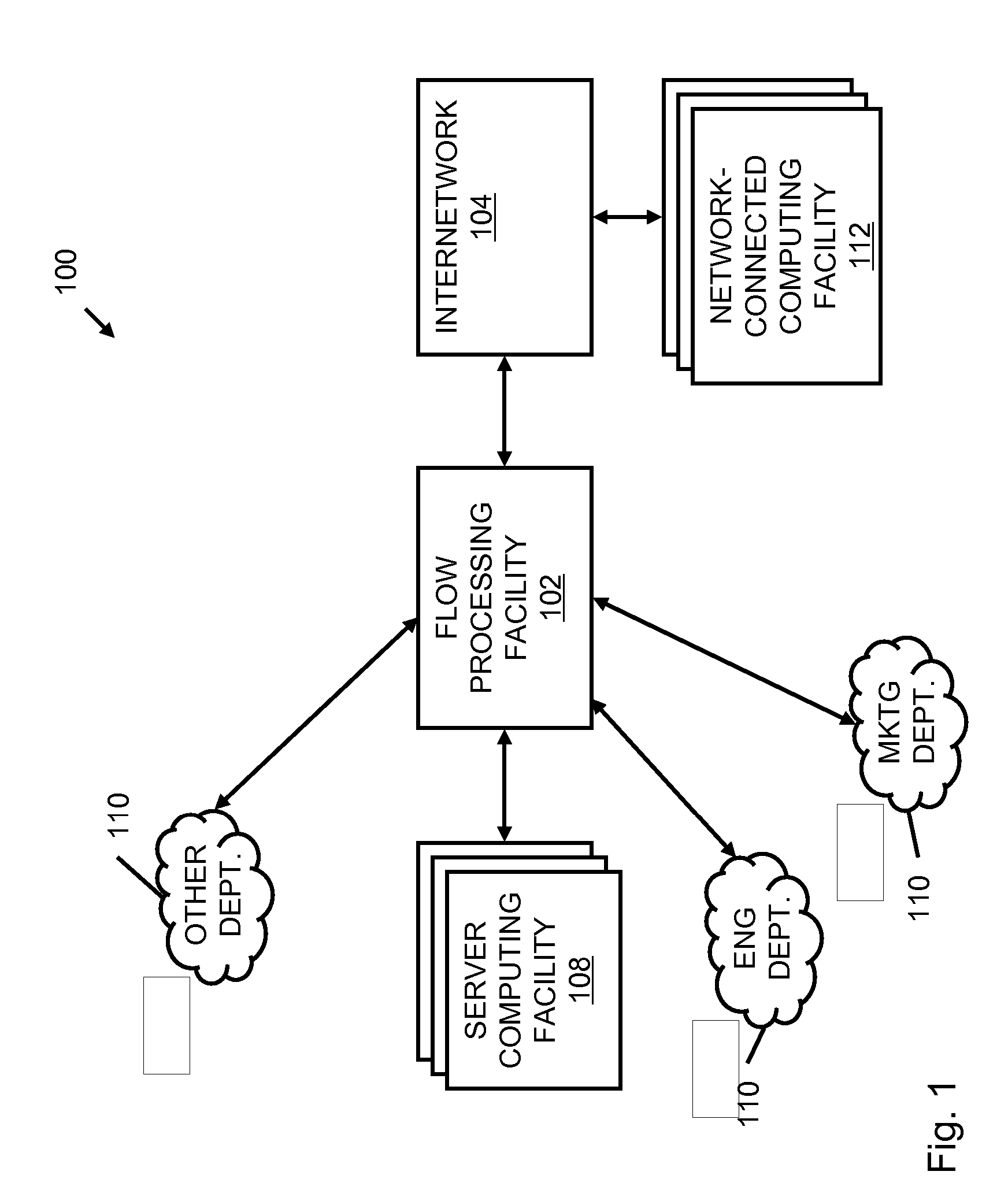
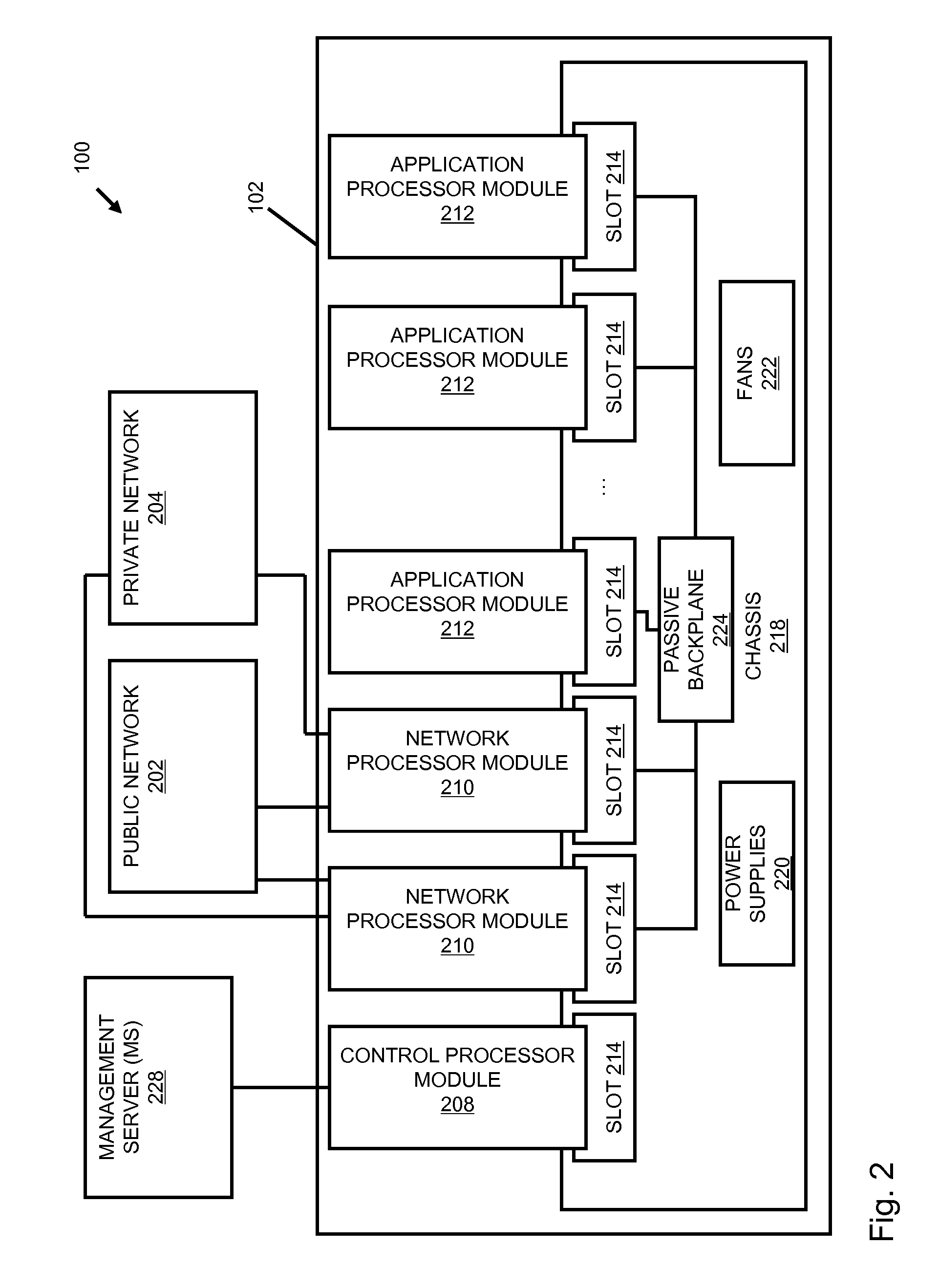
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
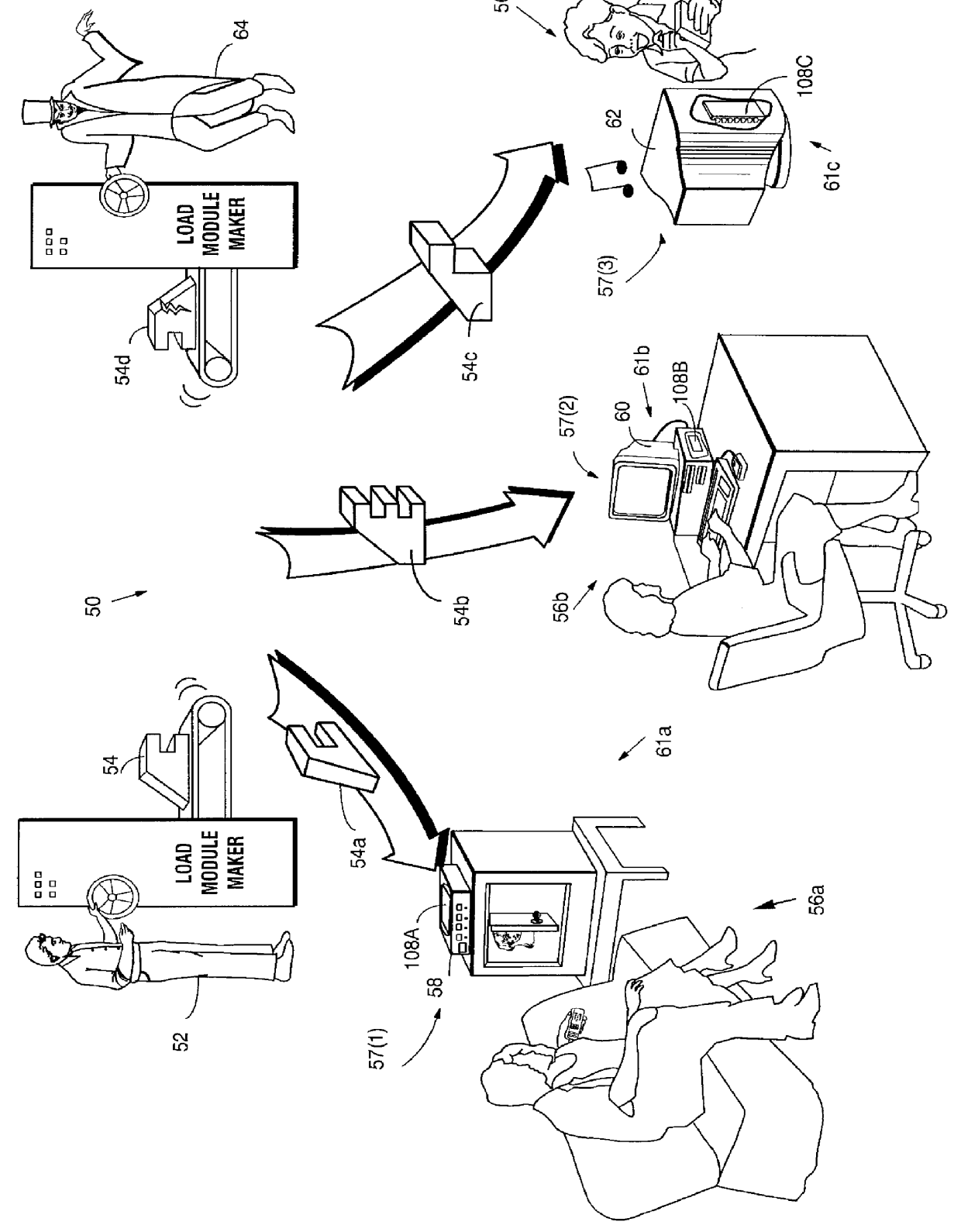
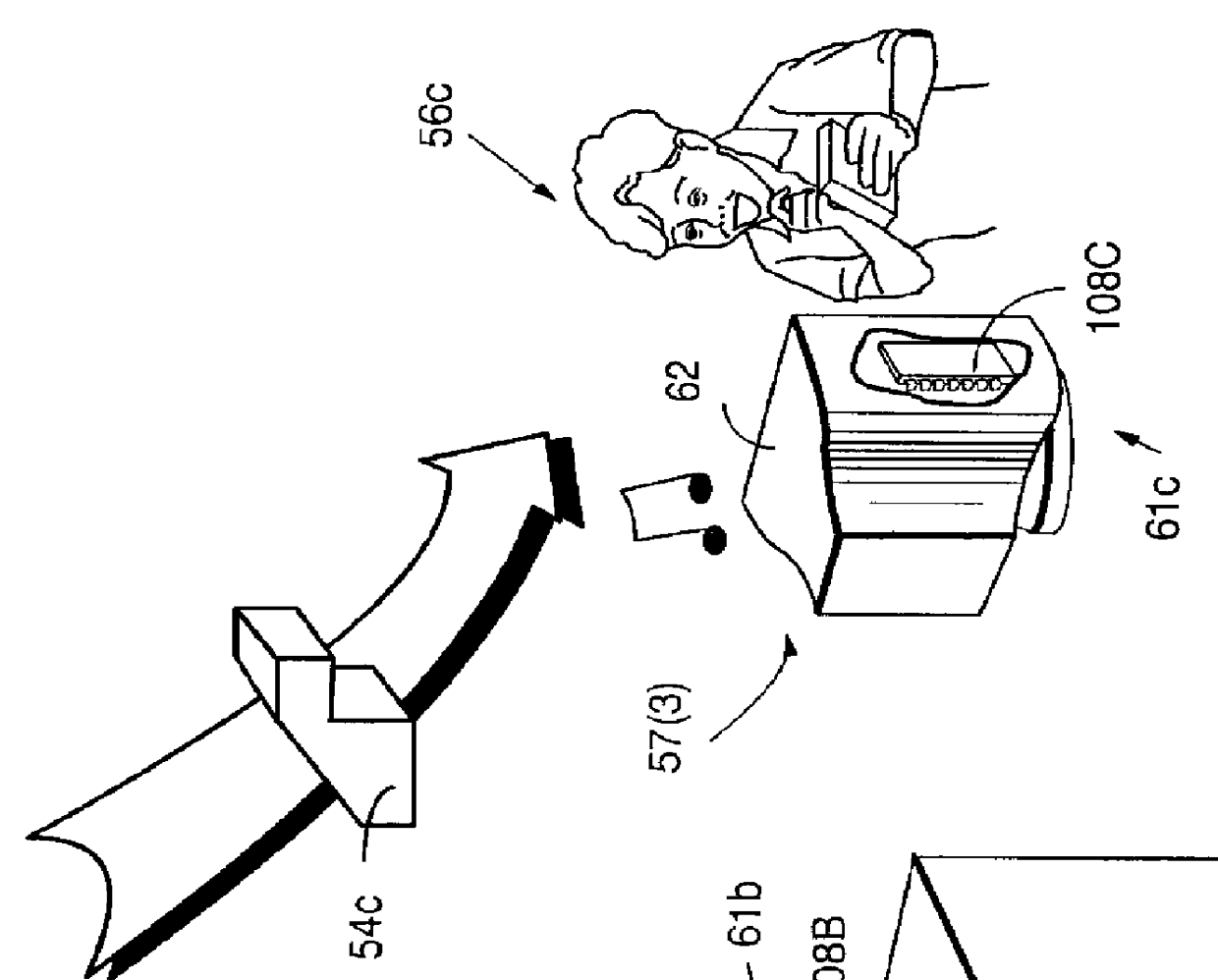
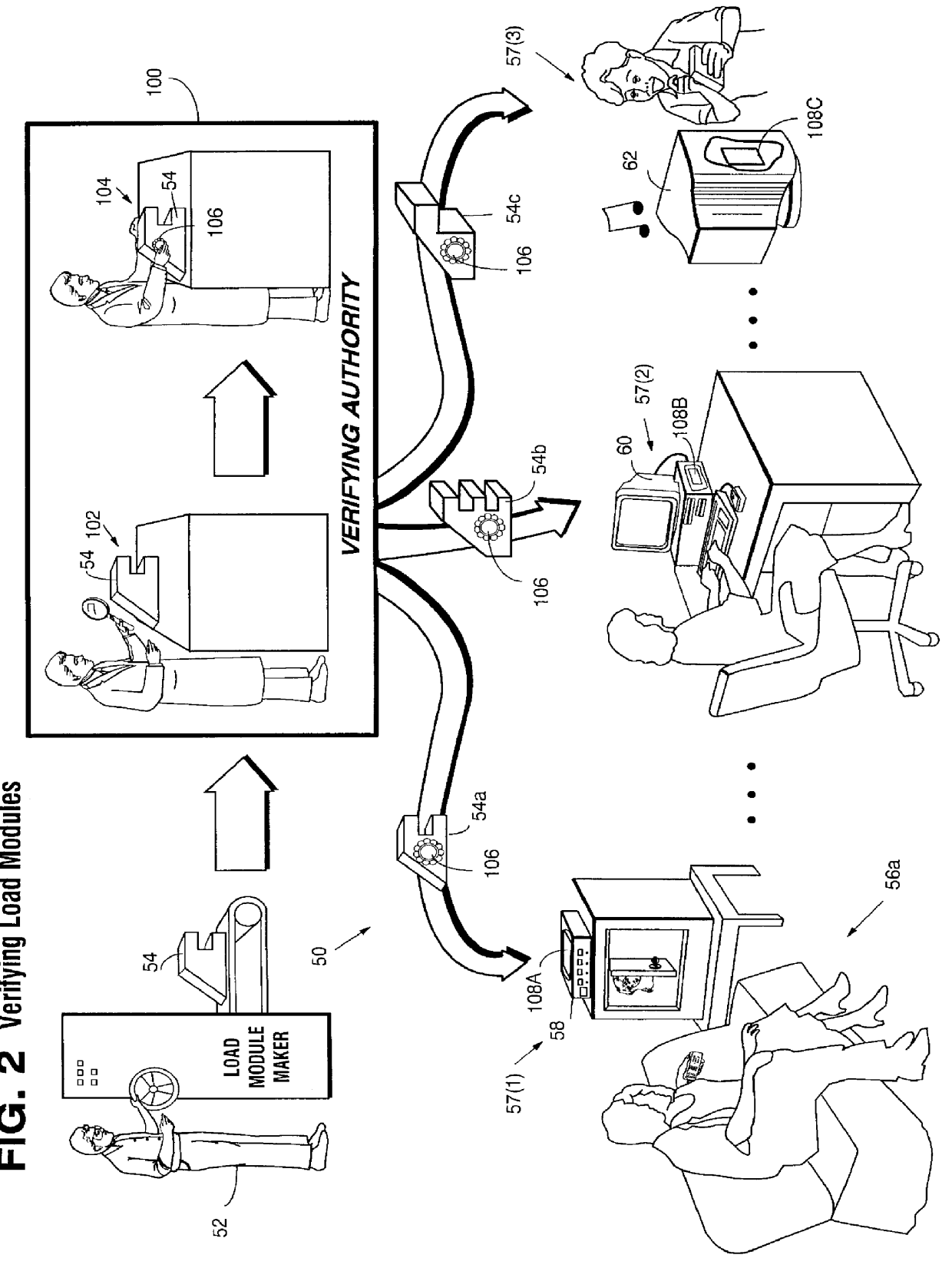
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
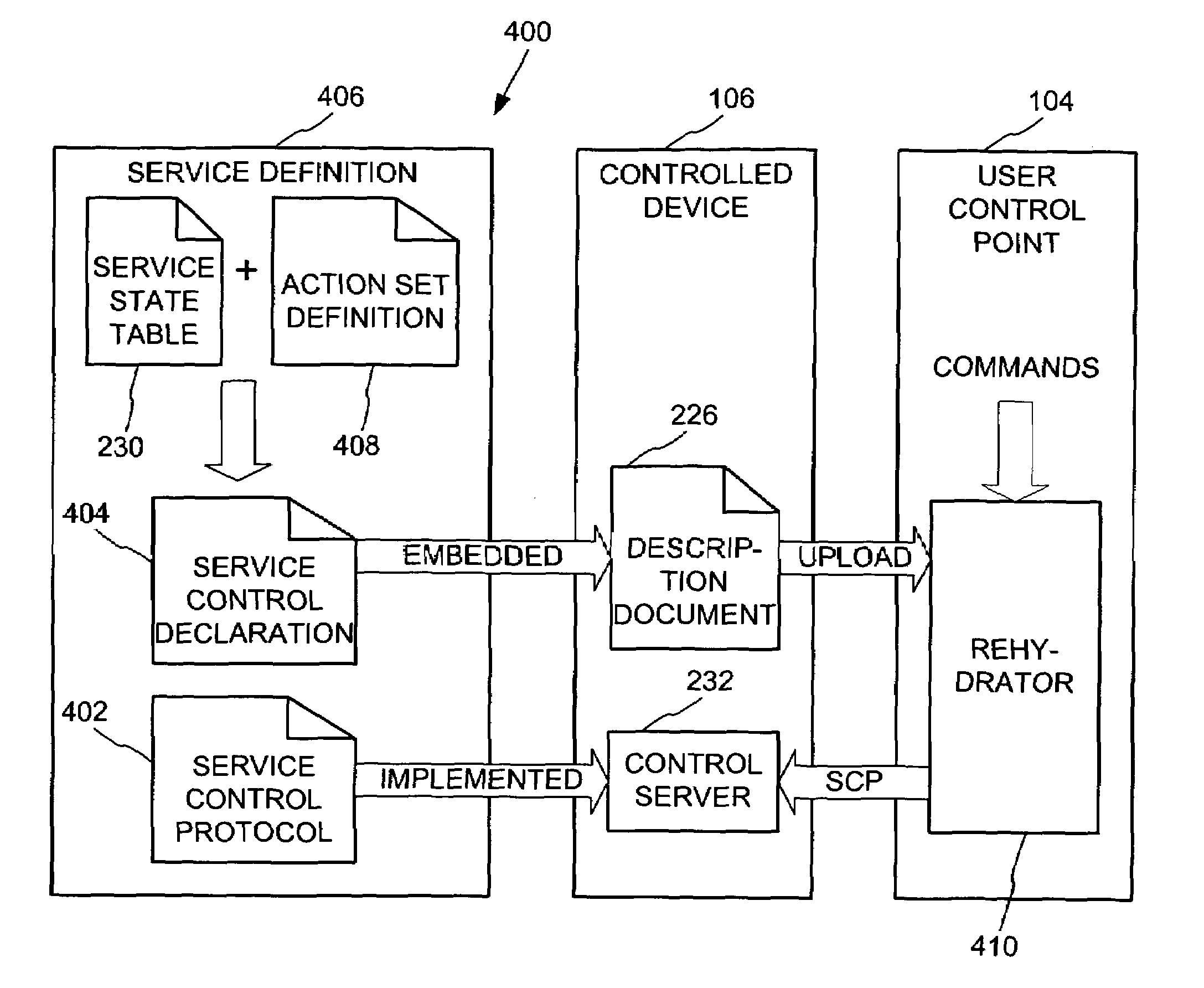
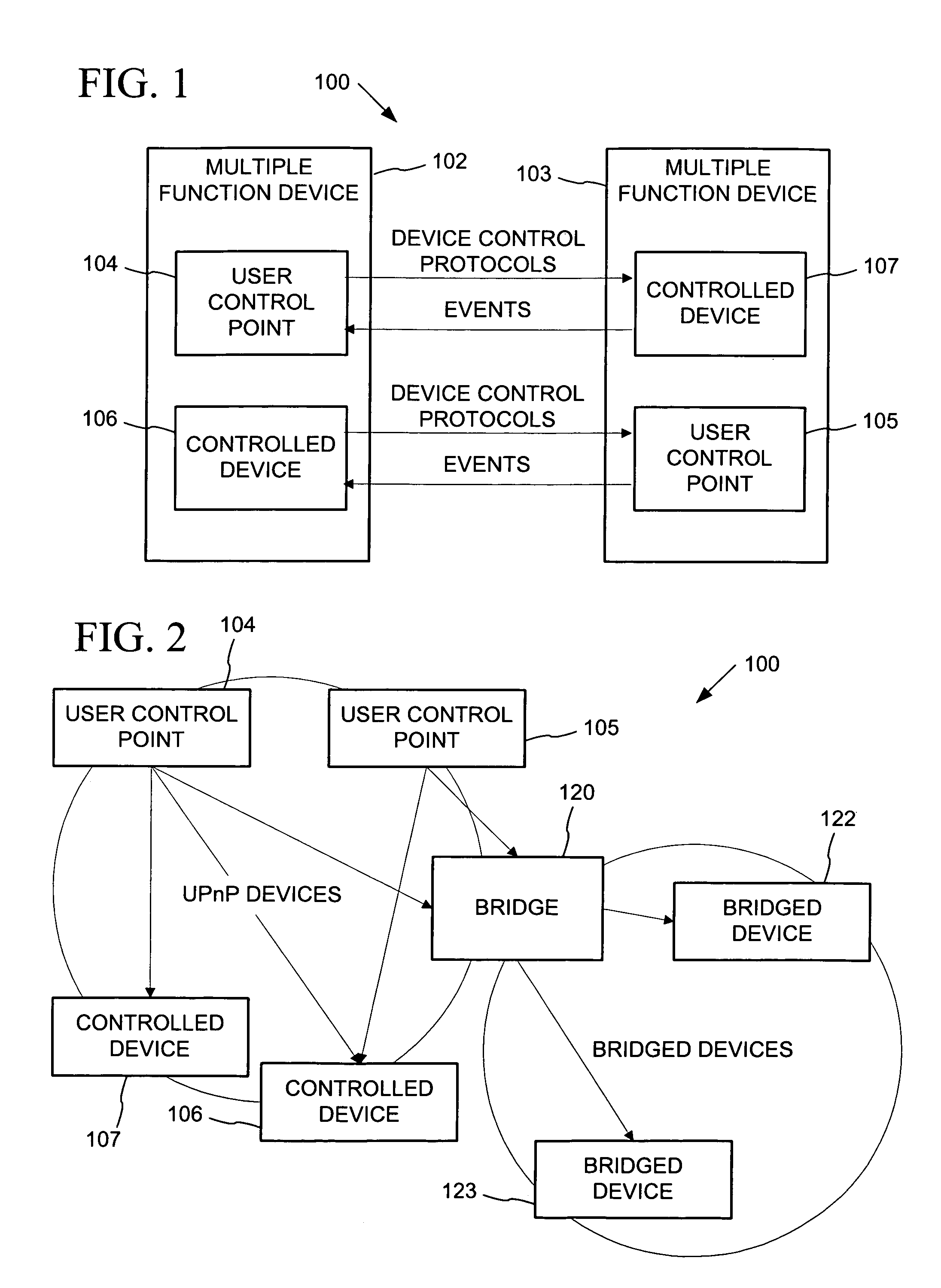
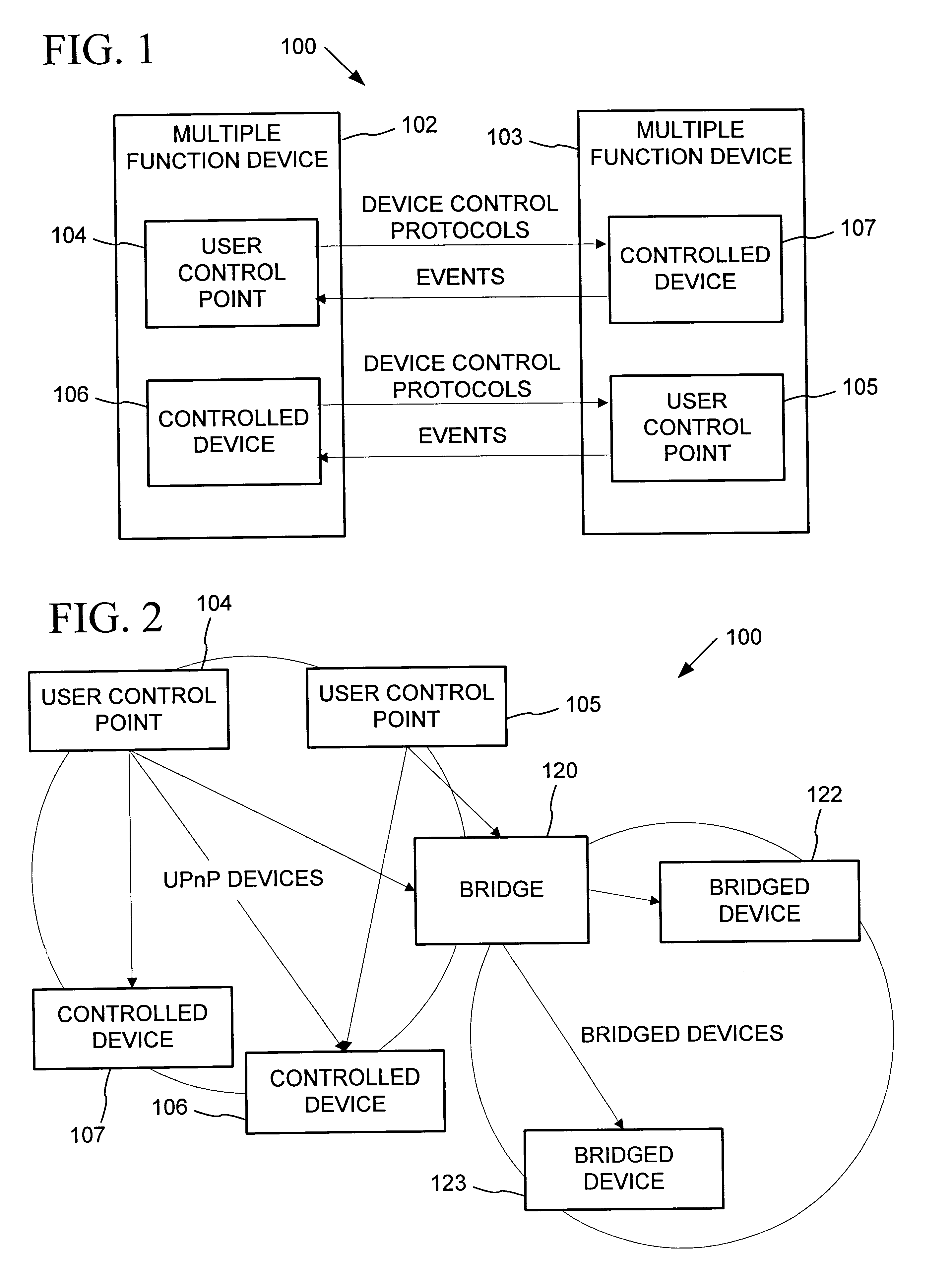
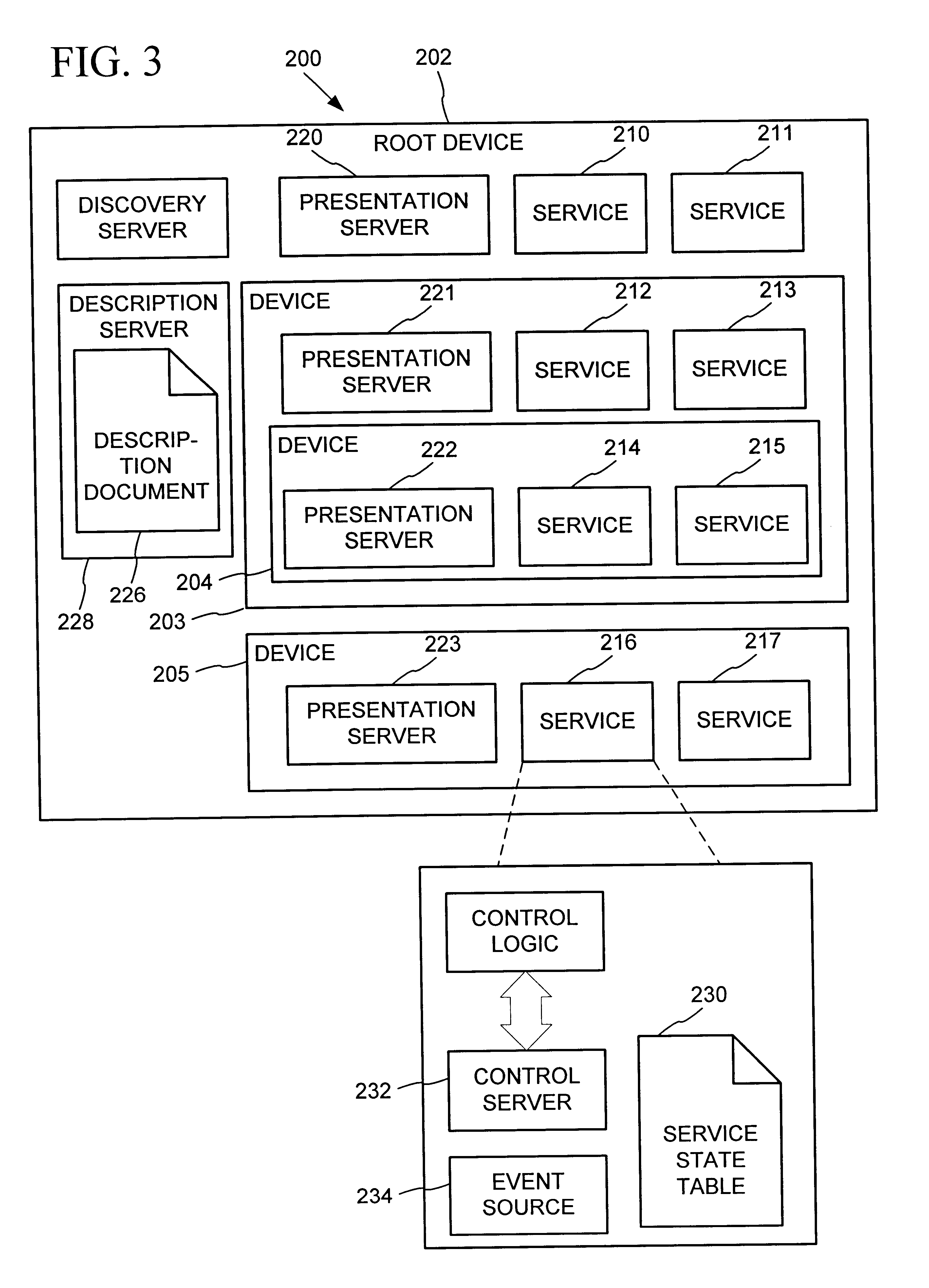
Data driven remote device control model with general programming interface-to-network messaging adapter
InactiveUS7085814B1CostConnectivity solutionMultiple digital computer combinationsNetworks interconnectionService protocolData description
A general programmatic interface-to-network messaging adapter exposes a suitable object integration interface or application programming interface to applications on a controller device and sends network data messages to invoke services or query status of a controlled device. The adapter maps application calls to the interface into network data messages according to service protocols of the controlled device. The general adapter provides the interface suitable to any specific service of a controlled device based on a data description of the interface, and converts the application calls to network data messages based on a data description of a protocol and format for network data messages to interact with the specific service. Once the interface / messaging description is obtained, applications on the controller device can programmatically interact with the adapter, and the adapter then handles appropriate message exchanges with the service of the controlled device. The general adapter allows controller device applications to be written using object-oriented programming, while avoiding code download.
Owner:ROVI TECH CORP
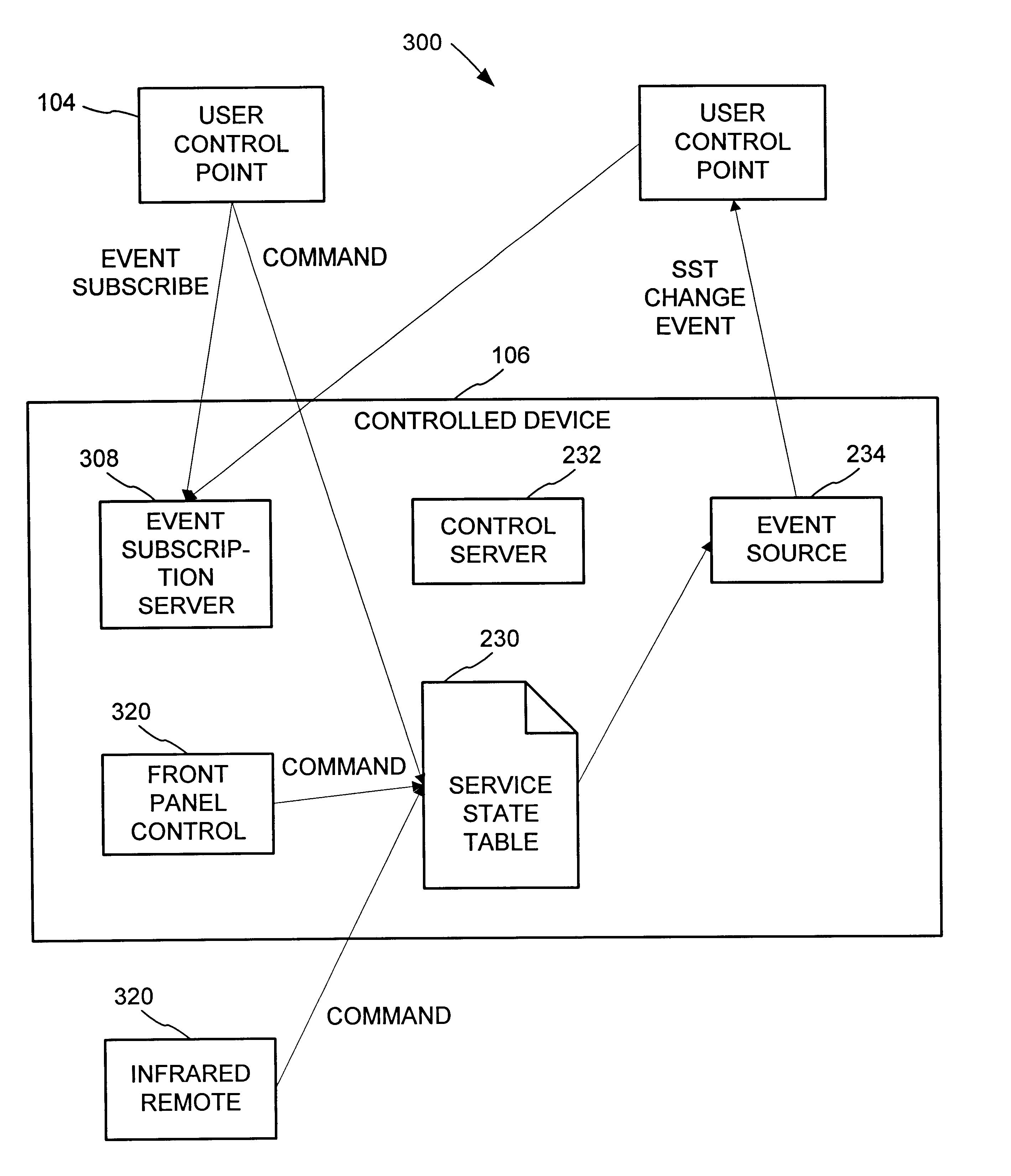
Synchronization of controlled device state using state table and eventing in data-driven remote device control model
InactiveUS6725281B1Falling in priceIncrease speedMultiple digital computer combinationsSecuring communicationEvent synchronizationEvent model
Controlled devices according to a device control model maintain a state table representative of their operational state. Devices providing a user control point interface for the controlled device obtain the state table of the controlled device, and may also obtain presentation data defining a remoted user interface of the controlled device and device control protocol data defining commands and data messaging protocol to effect control of the controlled device. These user control devices also subscribe to notifications of state table changes, which are distributed from the controlled device according to an eventing model. Accordingly, upon any change to the controlled device's operational state, the eventing model synchronizes the device's state as represented in the state table across all user control devices.
Owner:ROVI TECH CORP
Authenticating Wireless Person-to-Person Money Transfers
InactiveUS20070255662A1Facilitates manualFacilitates automated load functionalityDebit schemesLock-out/secrecy provisionWireless transmissionComputer science
A technique is used to ensure the authenticity of a wireless transmission source which is requesting a transaction to be performed by a system. The transaction may be a person-to-person money transfer or other value exchange transaction. The wireless transmission source may be a mobile phone or other similar device. The wireless transmission source transmits a key with the transaction request. The system will determine the authenticity of the transmission based on the transmitted key. If the transmission is determined to be authentic, the transaction will be acted upon. Various approaches for determining authenticity are discussed. The technique may also be used to prevent acting upon duplicate transmissions.
Owner:OBOPAY MOBILE TECH INDIA PTE LTD
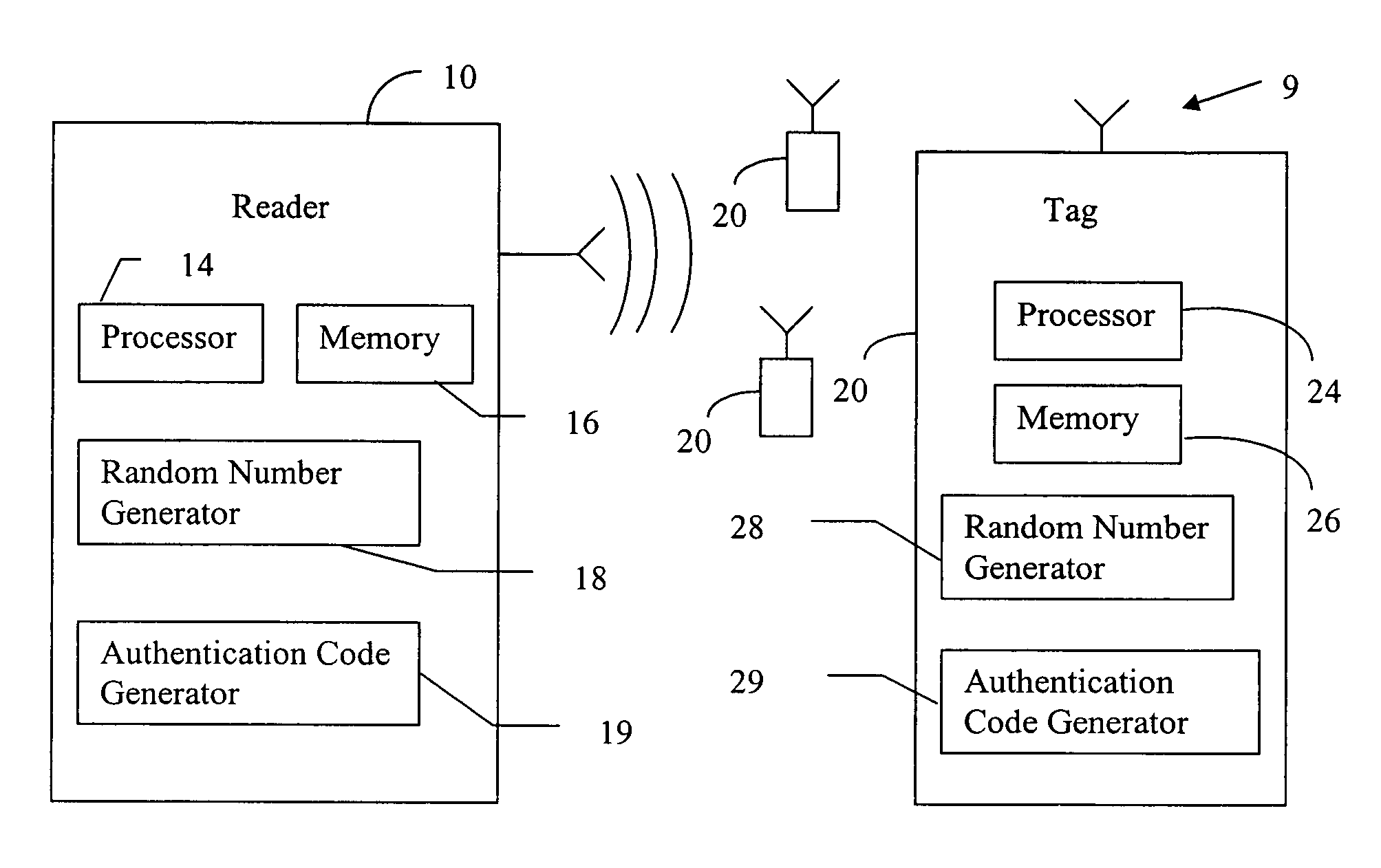
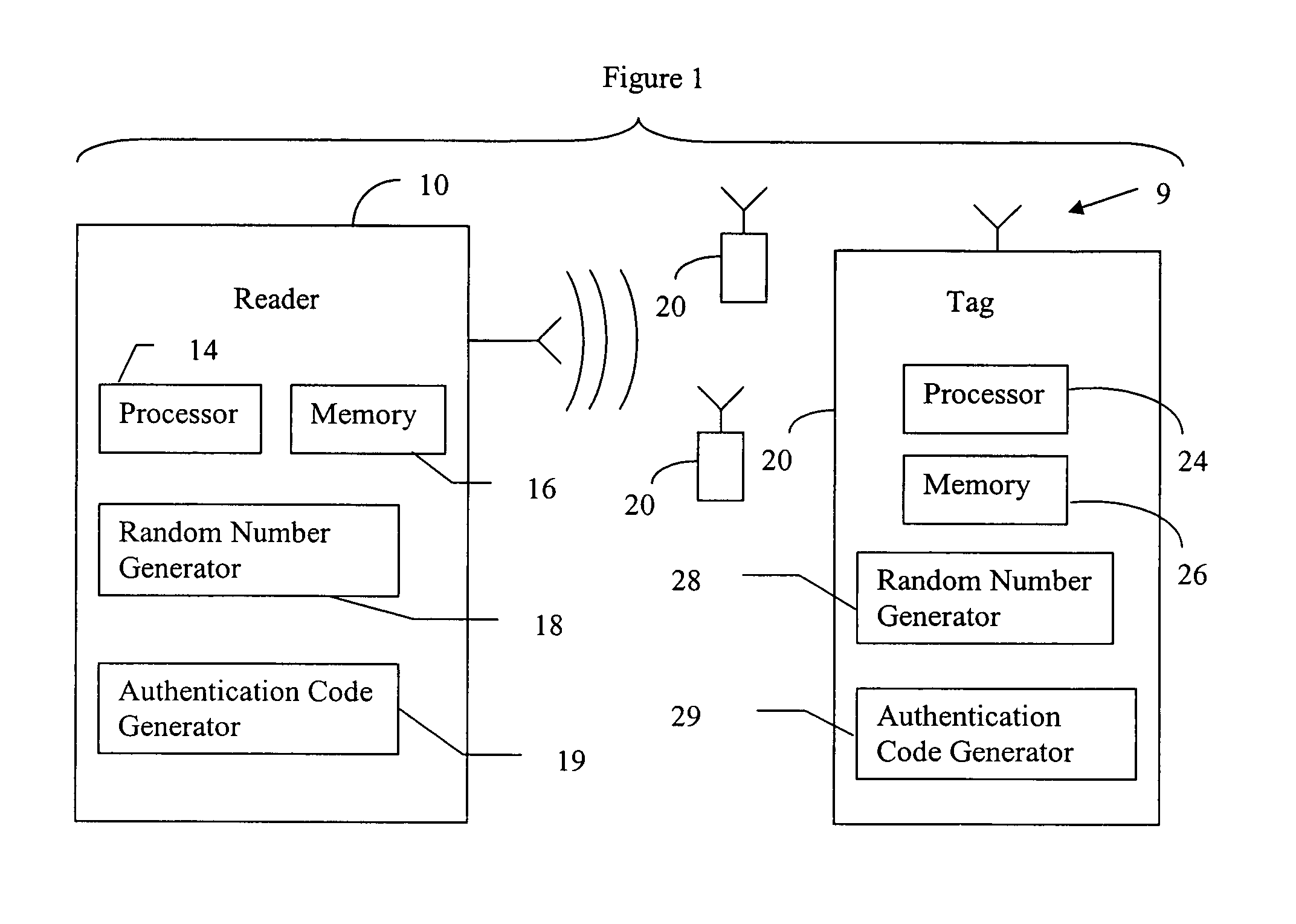
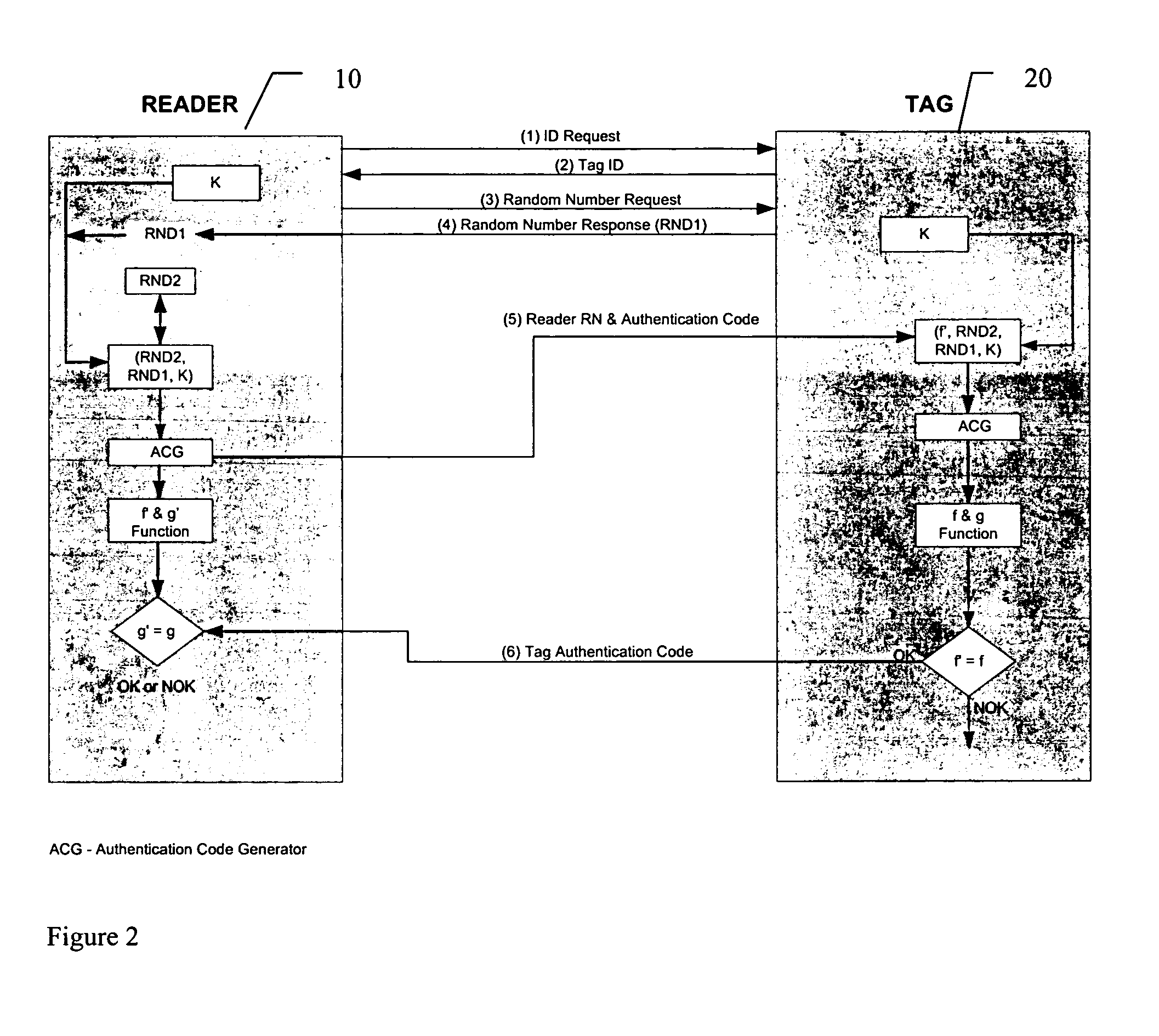
RFID mutual authentication verification session
ActiveUS7450010B1Privacy can be assuredElectric signal transmission systemsDigital data processing detailsMutual authenticationComputer security
Owner:AMTECH SYST
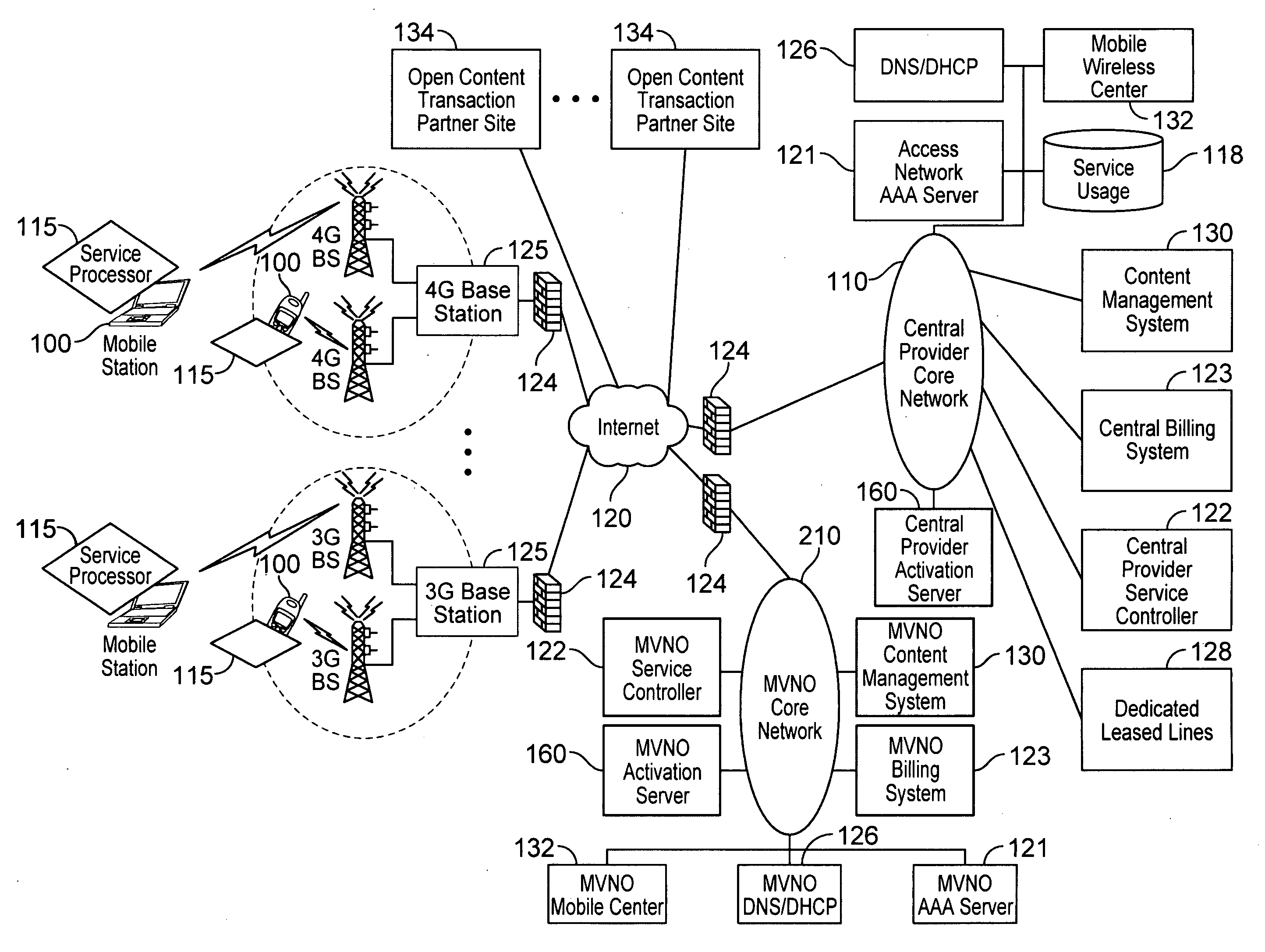
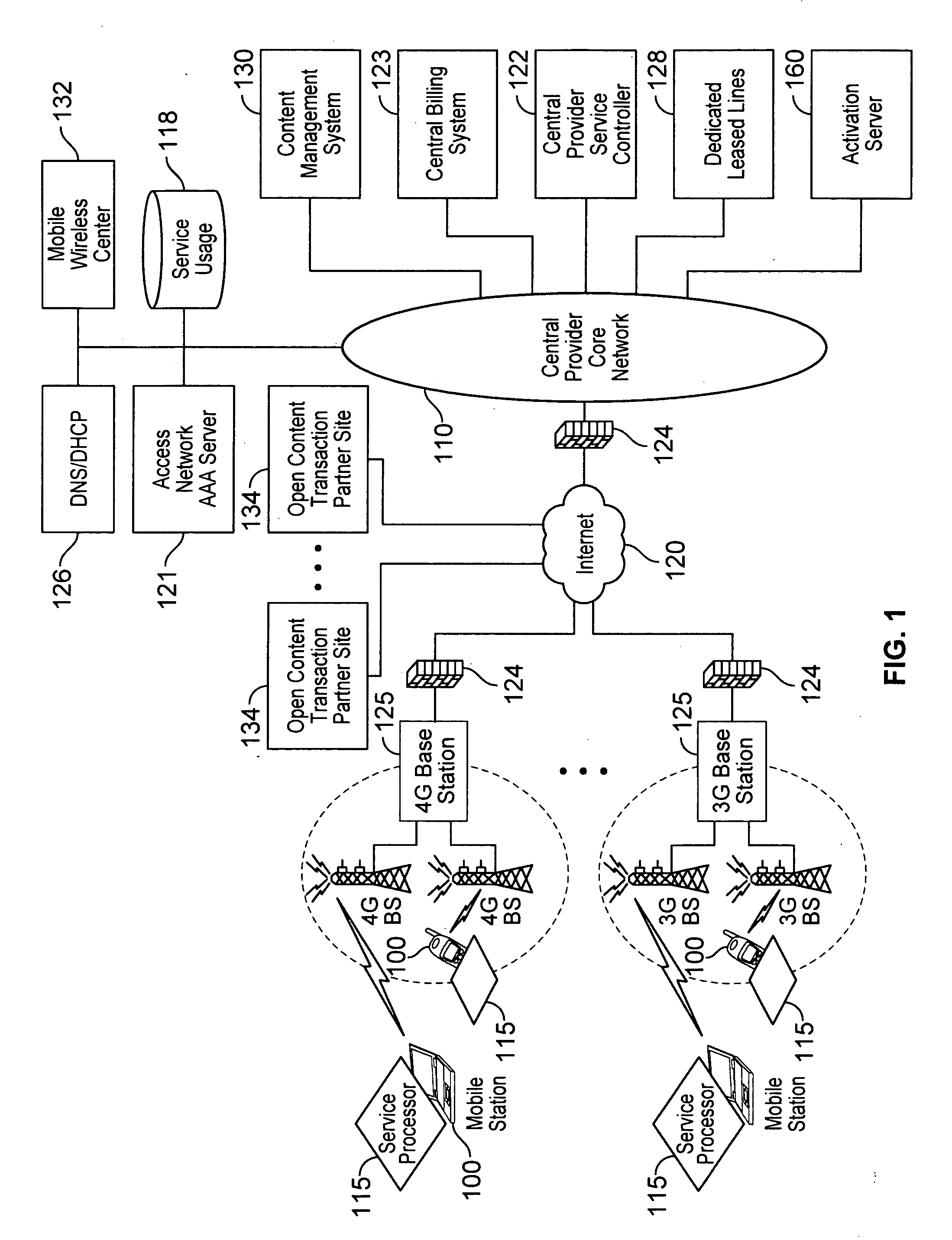
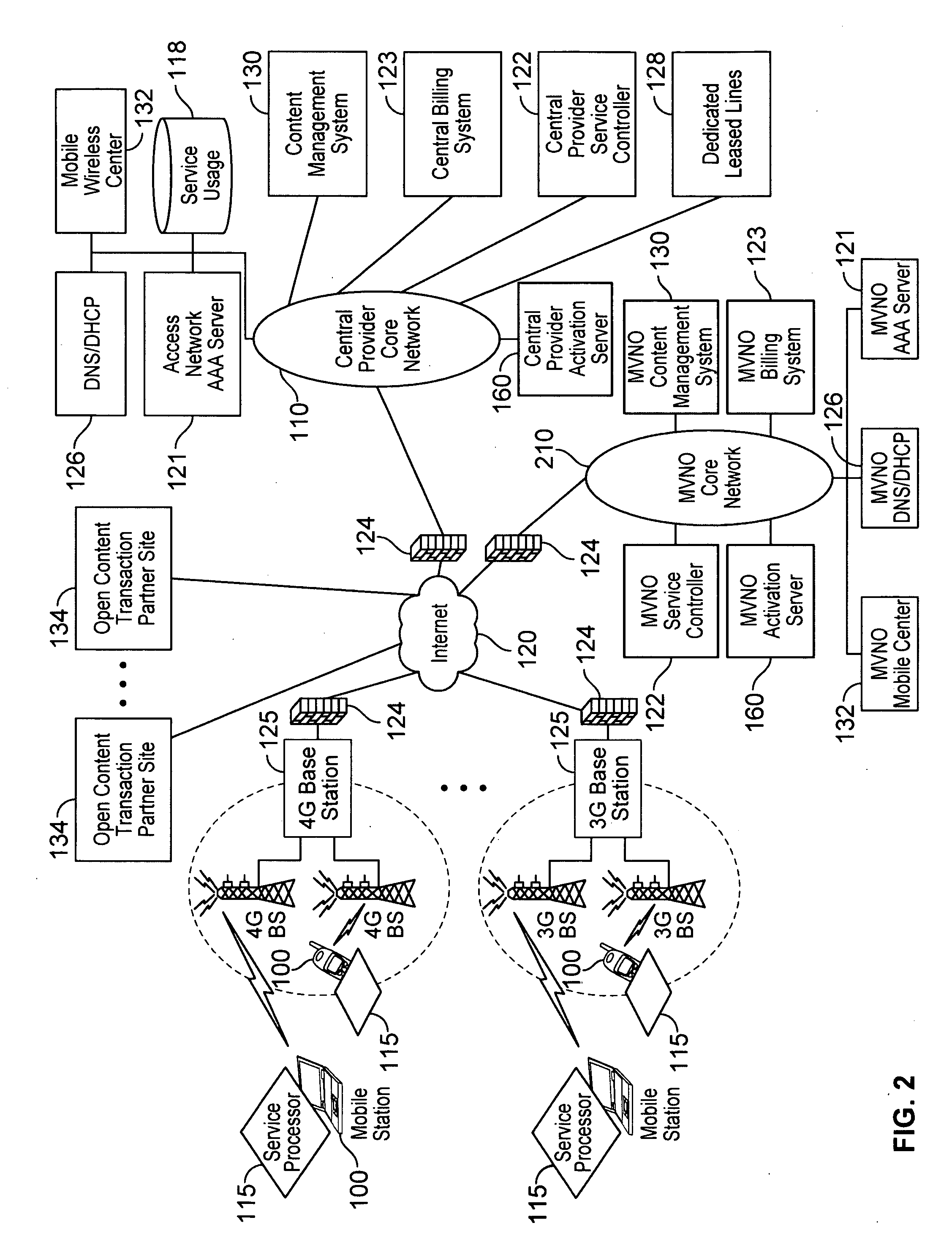
Automated device provisioning and activation
ActiveUS20100192212A1Digital data processing detailsTechnology managementCommunications systemBiological activation
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device stores a set of device credentials for activating the communications device for a service on a network; and sends an access request to the network, the access request including the set of device credentials.
Owner:HEADWATER RES LLC
Methods for Cryptographic Identification of Interchangeable Parts for Surgical Instruments
ActiveUS20100230465A1Comfortably fit into a user's handReduce manufacturing difficultySuture equipmentsStapling toolsEngineeringActuator
A method for encrypted authentication of interchangeable parts of a surgical instrument includes providing a surgical end effector at a distal end of a handle of the surgical instrument and electrically connecting an authentication controller within the handle to a receiving portion of the end effector. An interchangeable part is removably placed at the receiving portion. The interchangeable part is authenticated with the authentication controller when the interchangeable part is seated in the end effector.
Owner:CILAG GMBH INT
Verifiable device assisted service policy implementation
ActiveUS20100188975A1Error preventionFrequency-division multiplex detailsCommunications systemCommunication device
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service policy for assisting control of the communications device use of a service on a network; and monitors use of the service based on the service policy, in which the implementation of the service policy is verified.
Owner:HEADWATER RES LLC
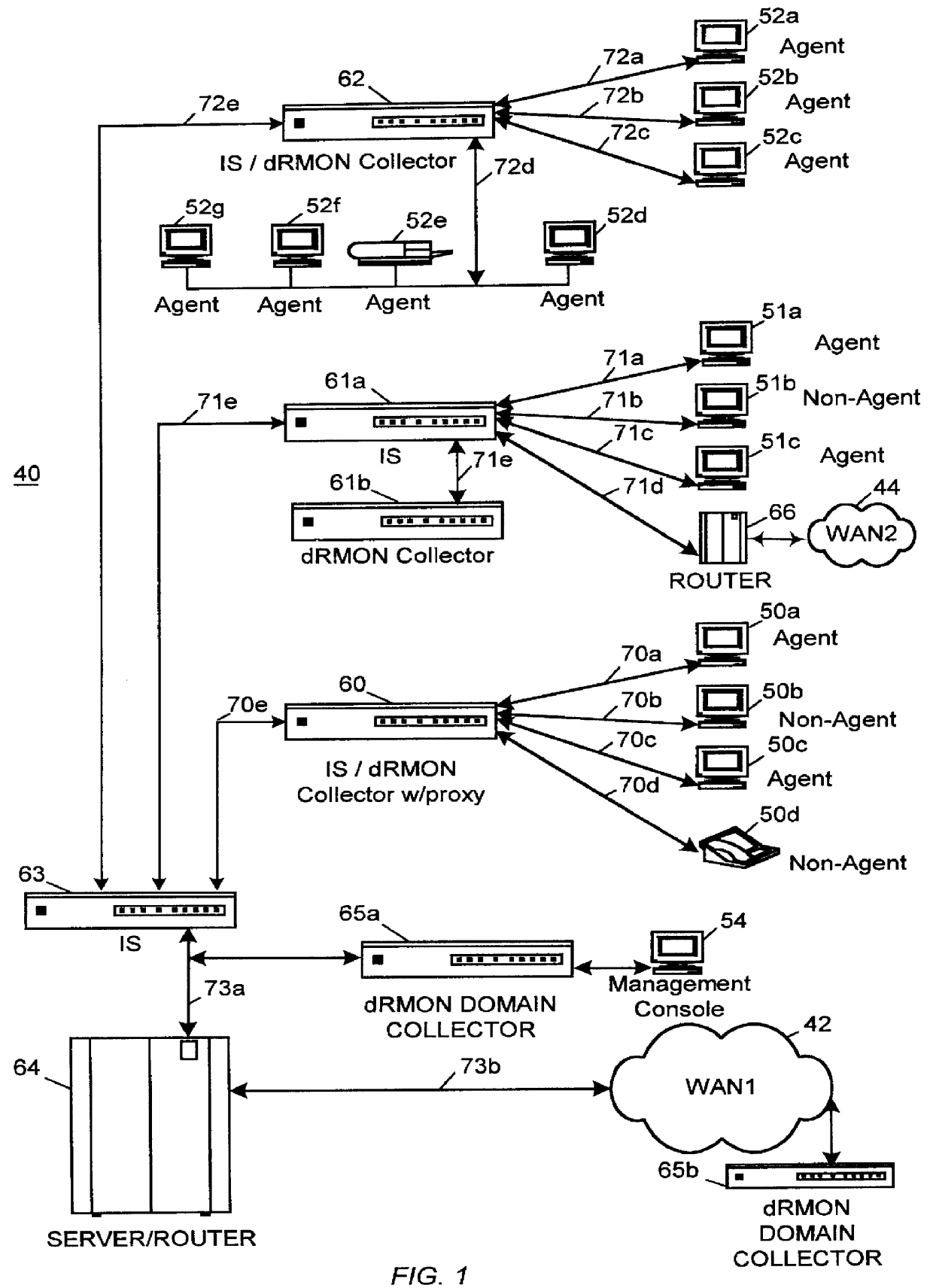
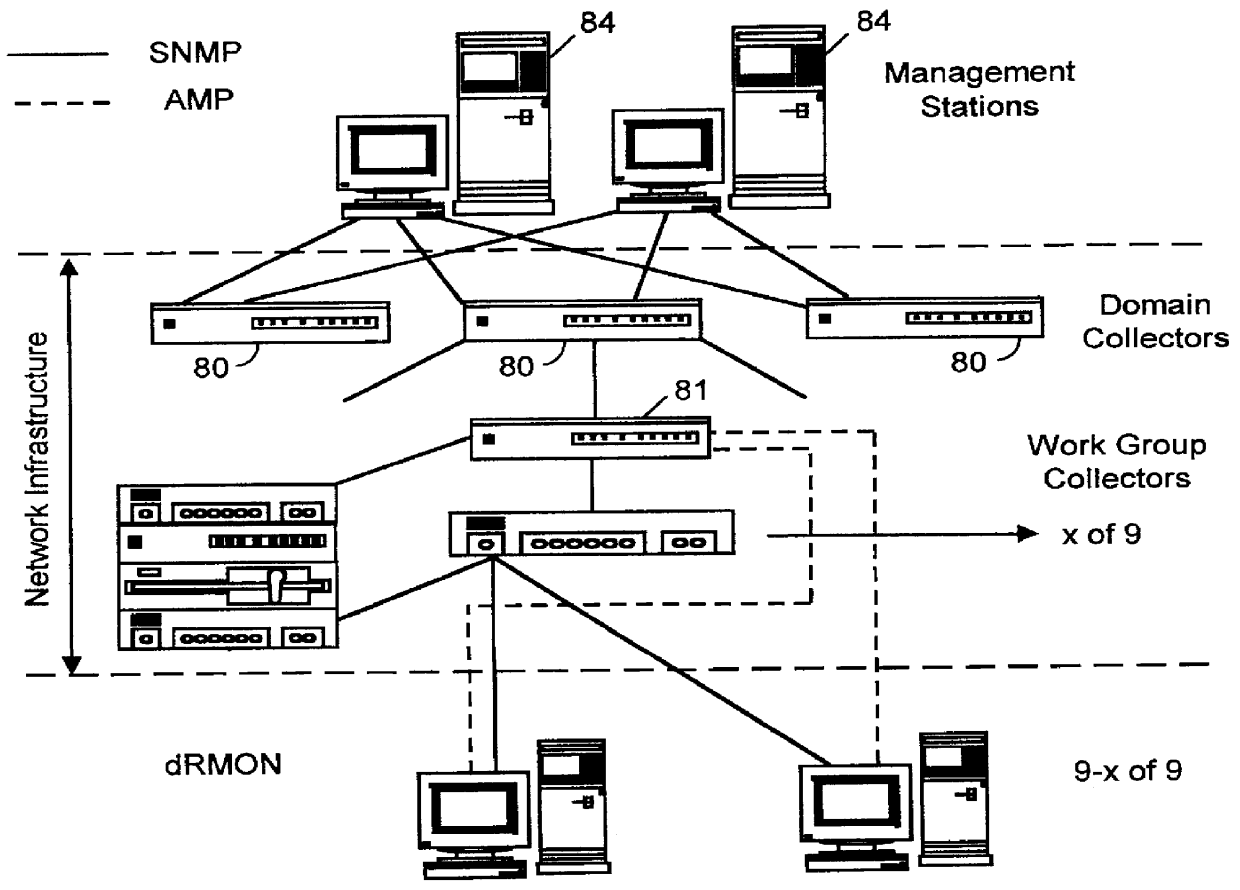
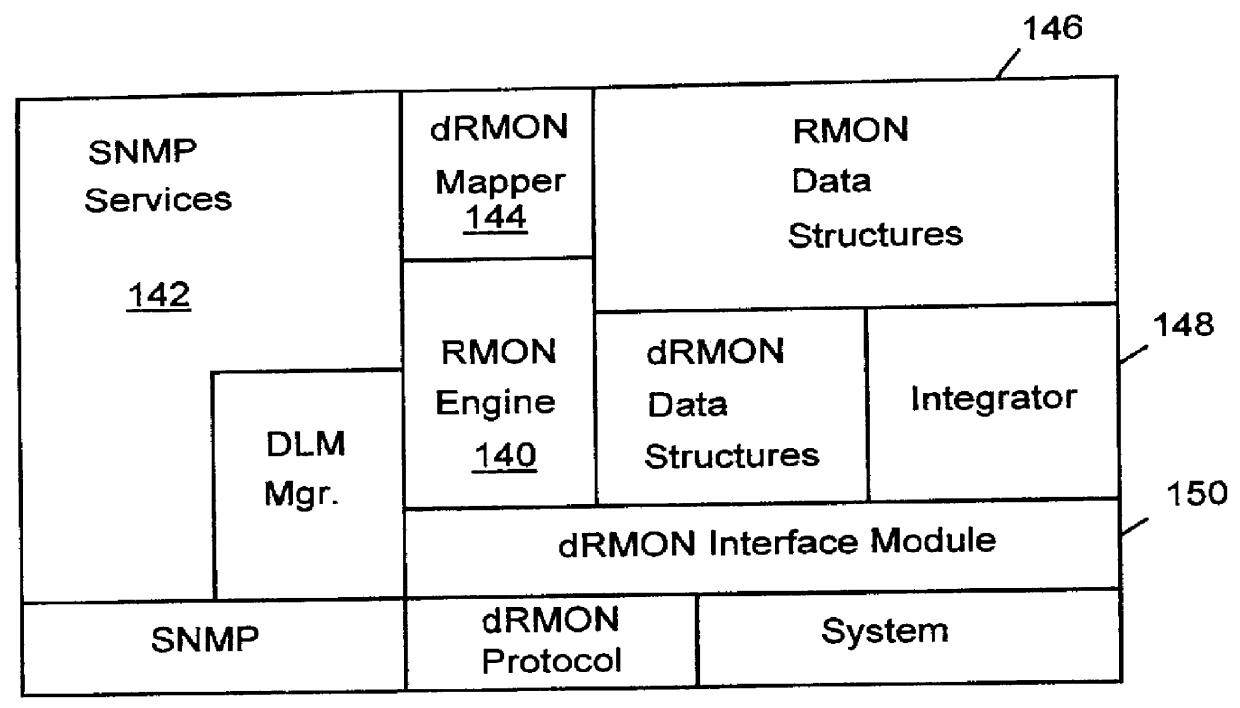
Distributed remote monitoring (dRMON) for networks
InactiveUS6108782AError preventionFrequency-division multiplex detailsNetwork operating systemOperational system
Distributed remote monitoring (dRMON) of network traffic and performance uses distributed nodes to collect traffic statistics at distributed points in the network. These statistics are forwarded to collectors which compile the statistics to create combined views of network performance. A collector may mimic a prior art, non-distributed, network probe and may interact with network management software as though it were a stand alone network probe thereby simplifying a user's interaction with the distributed system. The invention is designed to work in accordance with a variety of standard network management protocols including SNMP, RMON, and RMON2 but is not limited to those environments. The invention has applications in a variety of communication system environments including local area networks, cable television distribution systems, ATM systems, and advanced telephony systems. A specific embodiment of the invention solves is particularly optimized to work in LAN environments with end systems running under Windows-compatible network operating systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com