Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
132 results about "Active directory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Active Directory Federation Services (AD FS) is a single sign-on service. With an AD FS infrastructure in place, users may use several web-based services (e.g. internet forum, blog, online shopping, webmail) or network resources using only one set of credentials stored at a central location, as opposed to having to be granted a dedicated set of credentials for each service.
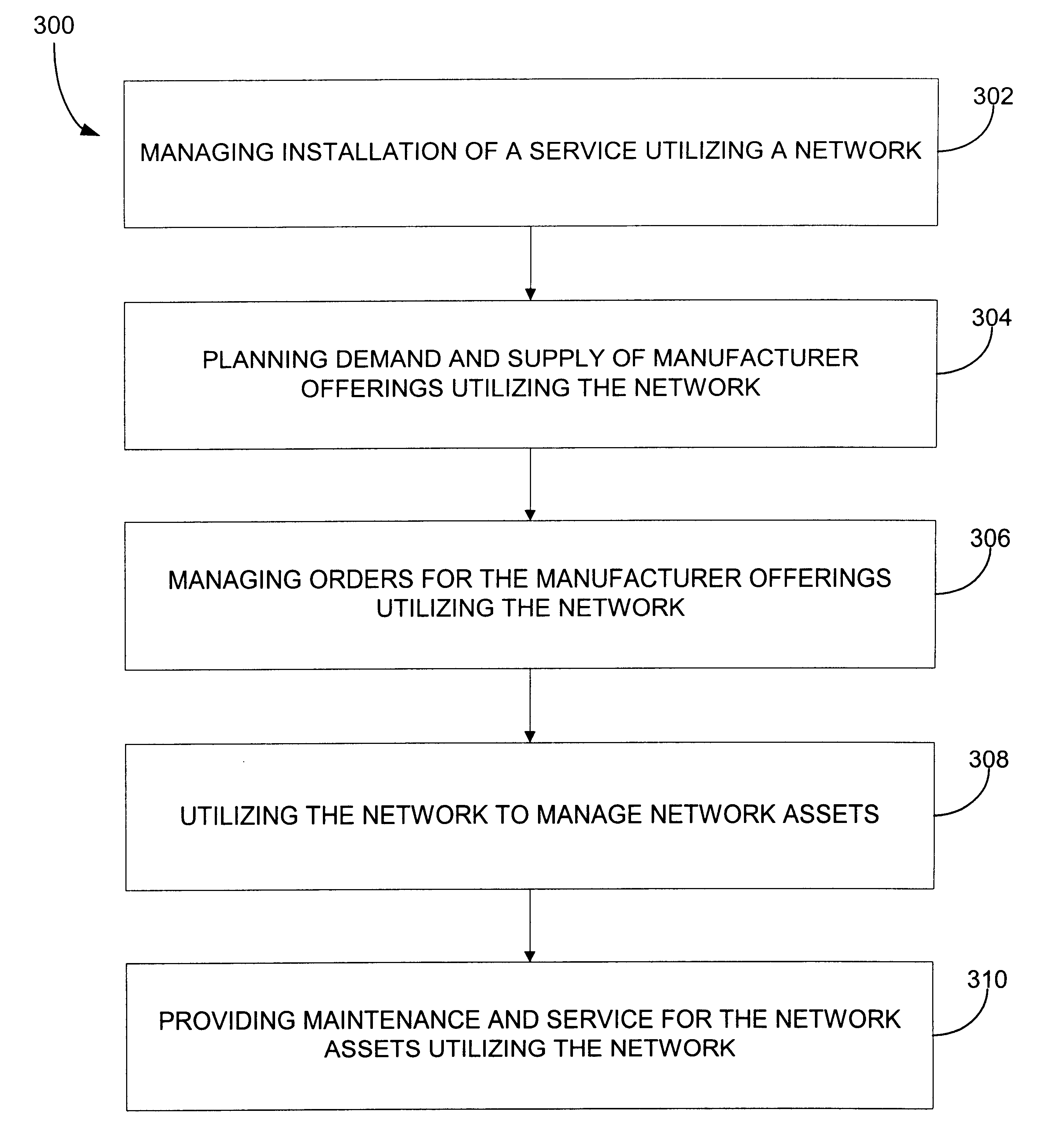
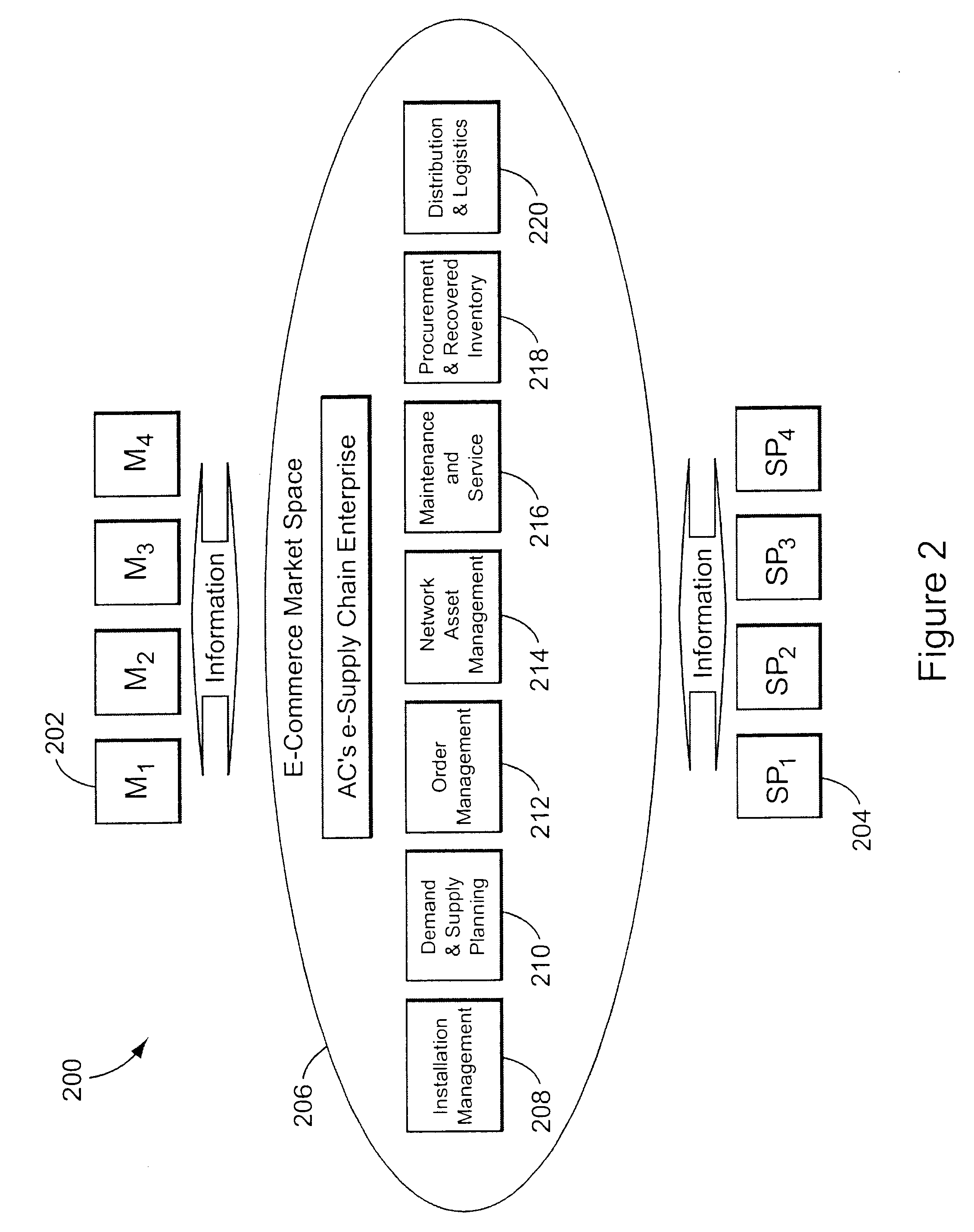
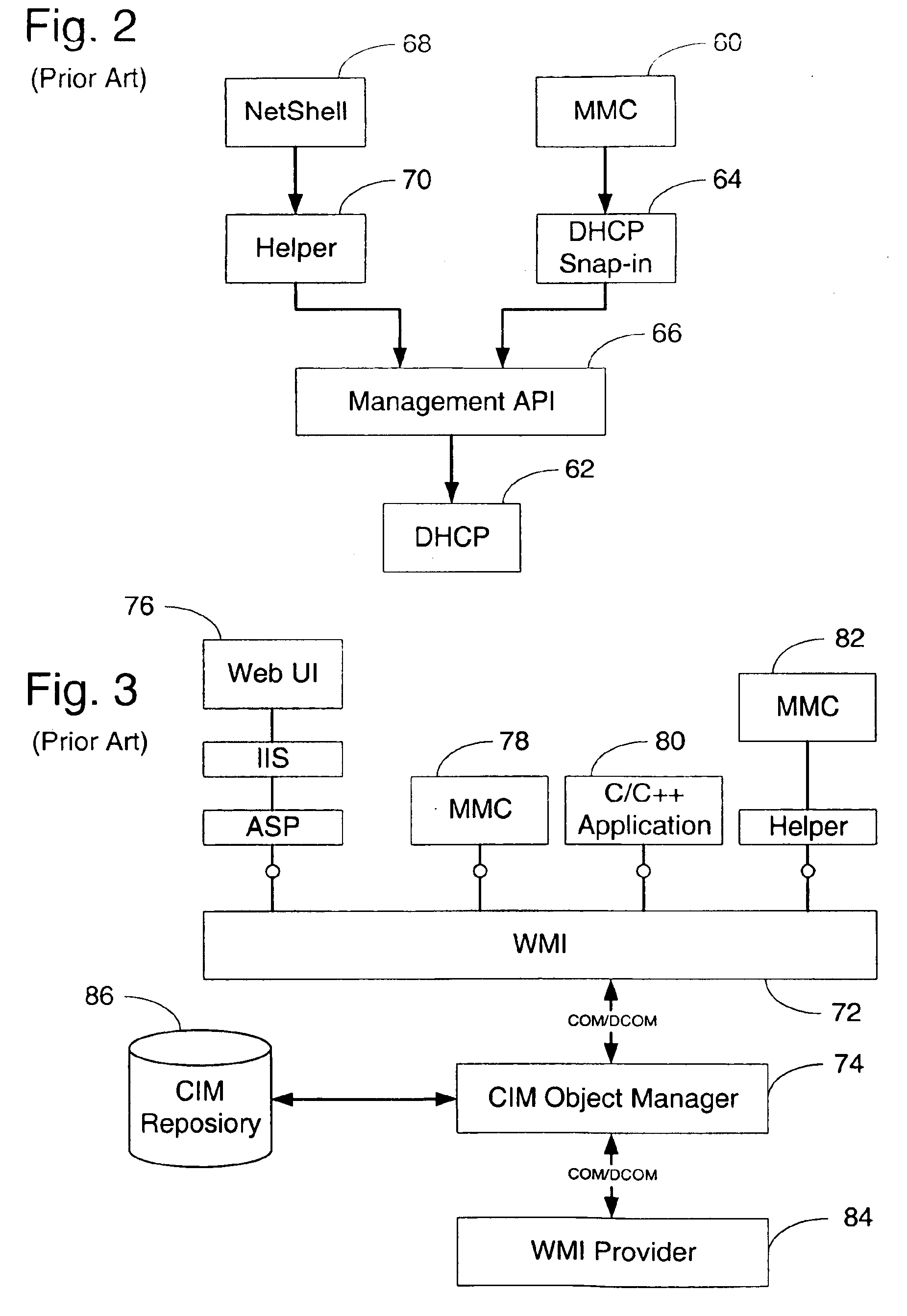
Providing collaborative installation management in a network-based supply chain environment
InactiveUS6606744B1Interconnection arrangementsSpecial service for subscribersWeb applicationService provision
A system, method and article of manufacture are provided for collaborative installation management in a network-based supply chain environment. According to an embodiment of the invention, telephone calls, data and other multimedia information are routed through a network system which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. The system includes integrated Internet Protocol (IP) telephony services allowing a user of a web application to communicate in an audio fashion in-band without having to pick up another telephone. Users can click a button and go to a call center through the network using IP telephony. The system invokes an IP telephony session simultaneously with the data session, and uses an active directory lookup whenever a user uses the system. Users include service providers and manufacturers utilizing the network-based supply chain environment.
Owner:ACCENTURE GLOBAL SERVICES LTD
System and method for launching a resource in a network
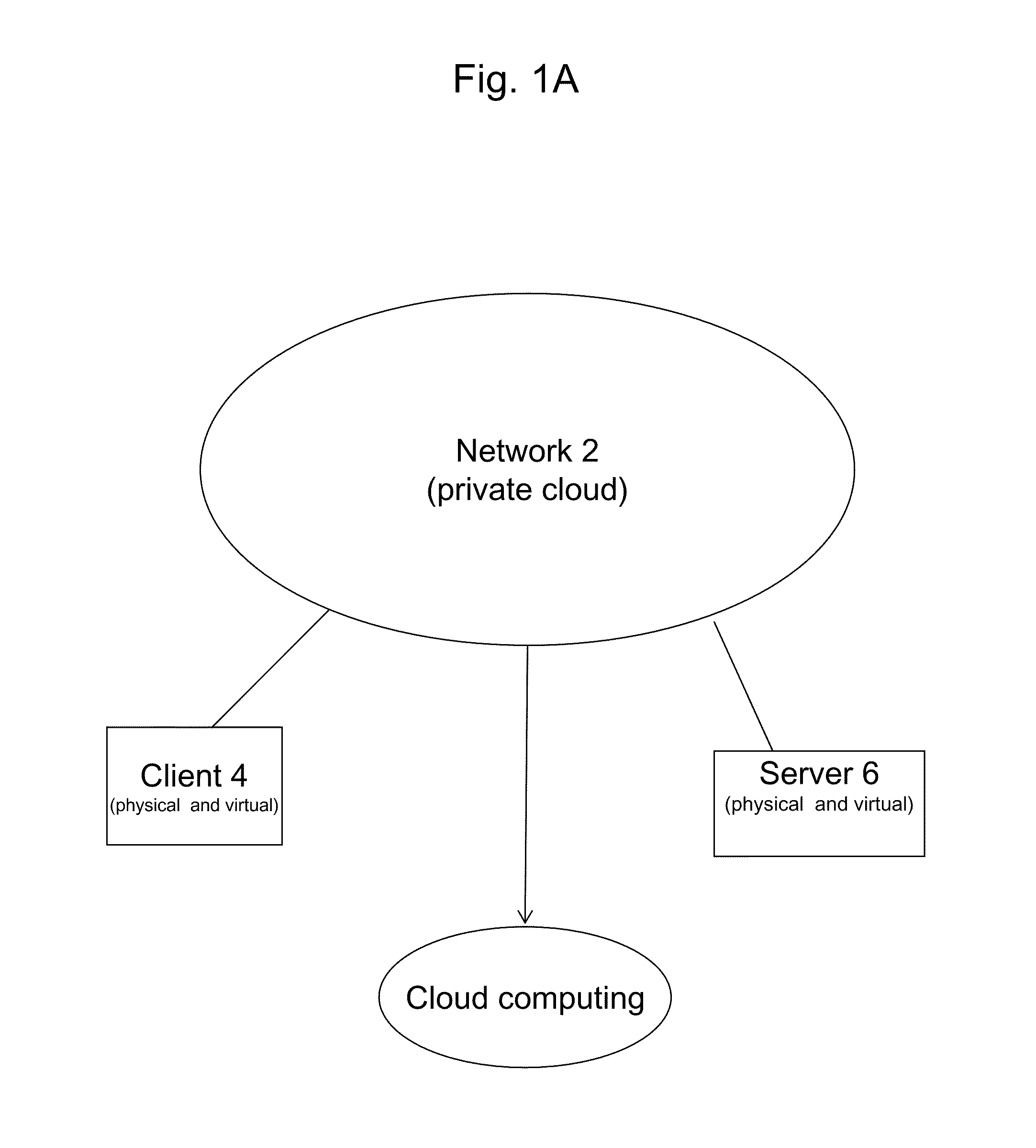
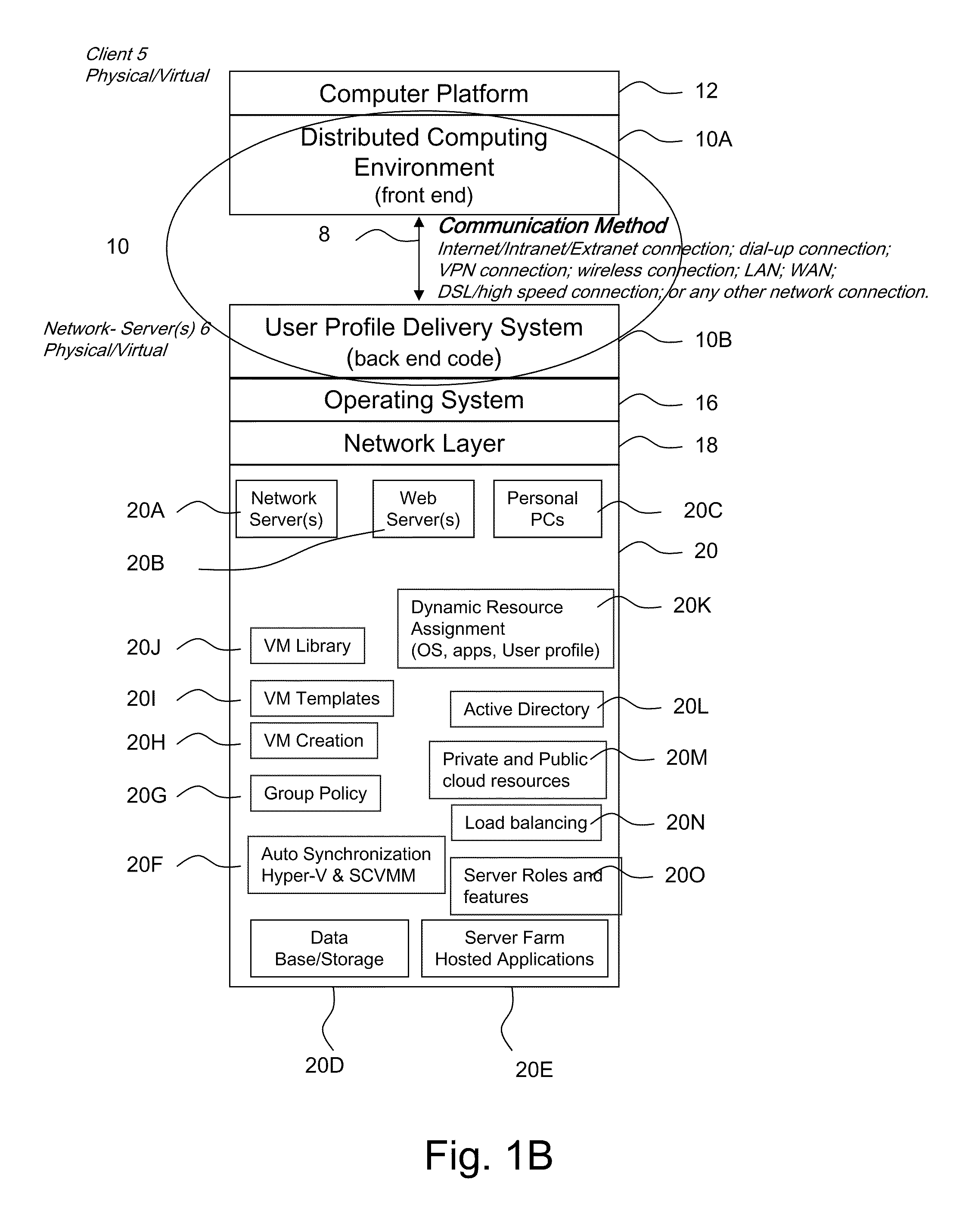
ActiveUS20110251992A1Provide controlDigital data processing detailsWireless commuication servicesOperational systemDirectory structure
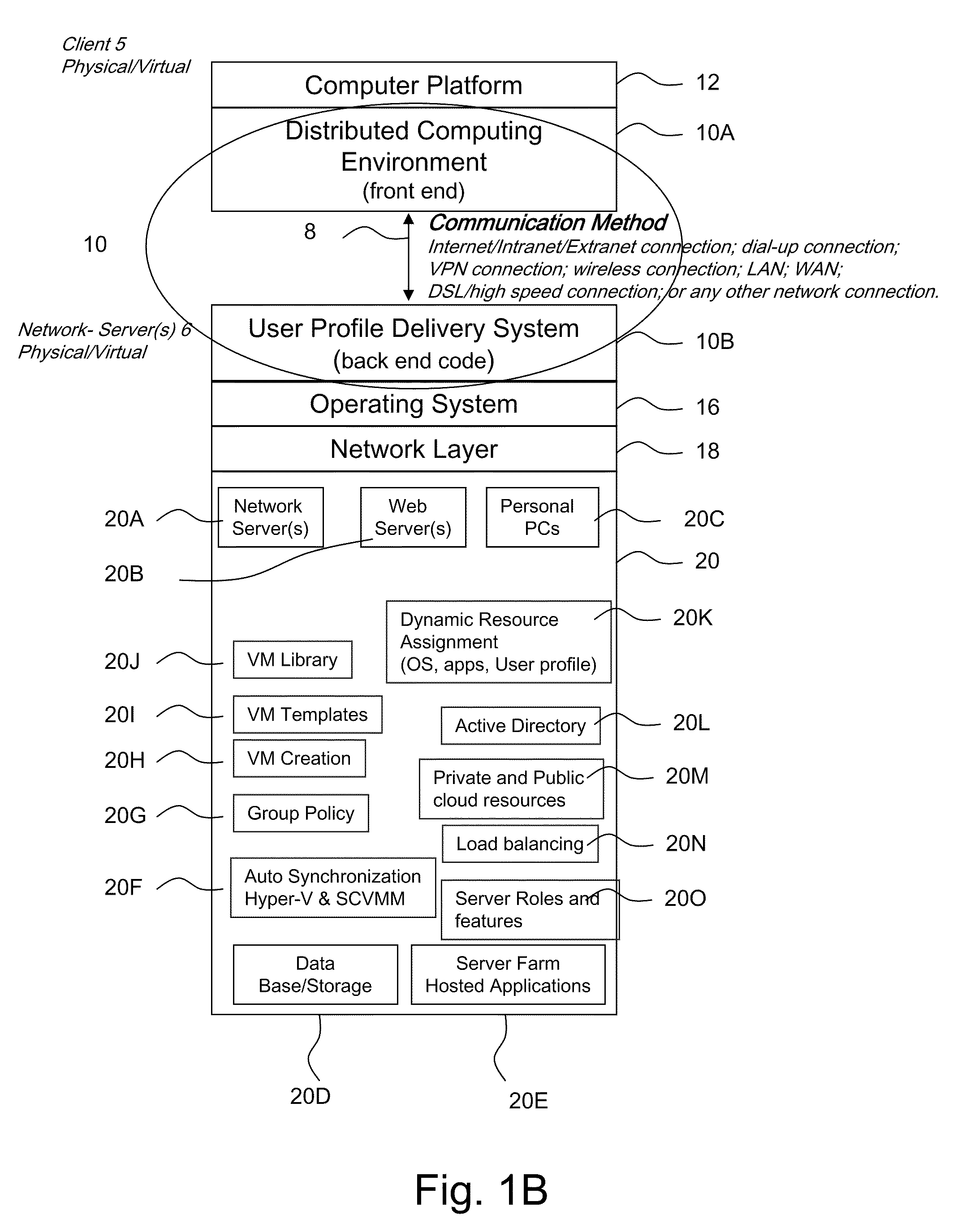
The disclosure provides a system and method for a client connected to a server to a resource in a network. For the system a virtual machine module is provided to access a library and to create virtual machine templates and to create virtual machines from the virtual machine templates. The virtual machine module provides to a host machine in the network access to machines, user profile settings and instances of an application in the network and to multiple operating systems. The client has: access to an instance of the resource; an access module to provide the client with communication to access to the server using load balancing algorithms to access the file using Remote Desktop Protocol (RDP) commands; and an authentication module providing access to a directory structure accessed by the server using Microsoft Group Policy Objects (GPOs) and Active Directory (AD) services to authenticate the client with the server.
Owner:DESKTOPSITES
Back-end decoupled management model and management system utilizing same
InactiveUS6871346B1Easy to manageDigital data processing detailsMultiprogramming arrangementsWeb-Based Enterprise ManagementWindows management instrumentation
Presented is a web-based enterprise management compliant management framework whose back end components are decoupled from the various user interfaces available for accessing the management system. In the Windows environment, the management system of the instant invention is also compliant with the Windows management instrumentation (WMI) requirements. This management system includes WMI providers which implement standard interfaces which decouple all semantic and syntactic checks from the user interface and which provide common error strings, help, etc. to a user regardless of the user interface being used. The providers of the management system of the instant invention store and access data in the active directory. As such, these providers present a customizable user interface which may be based on a user's expertise level and which may be dynamically localized to the user's preferred language. Transaction support is also provided which prevents multiple users from changing the same attributes at the same time through different user interfaces.
Owner:MICROSOFT TECH LICENSING LLC
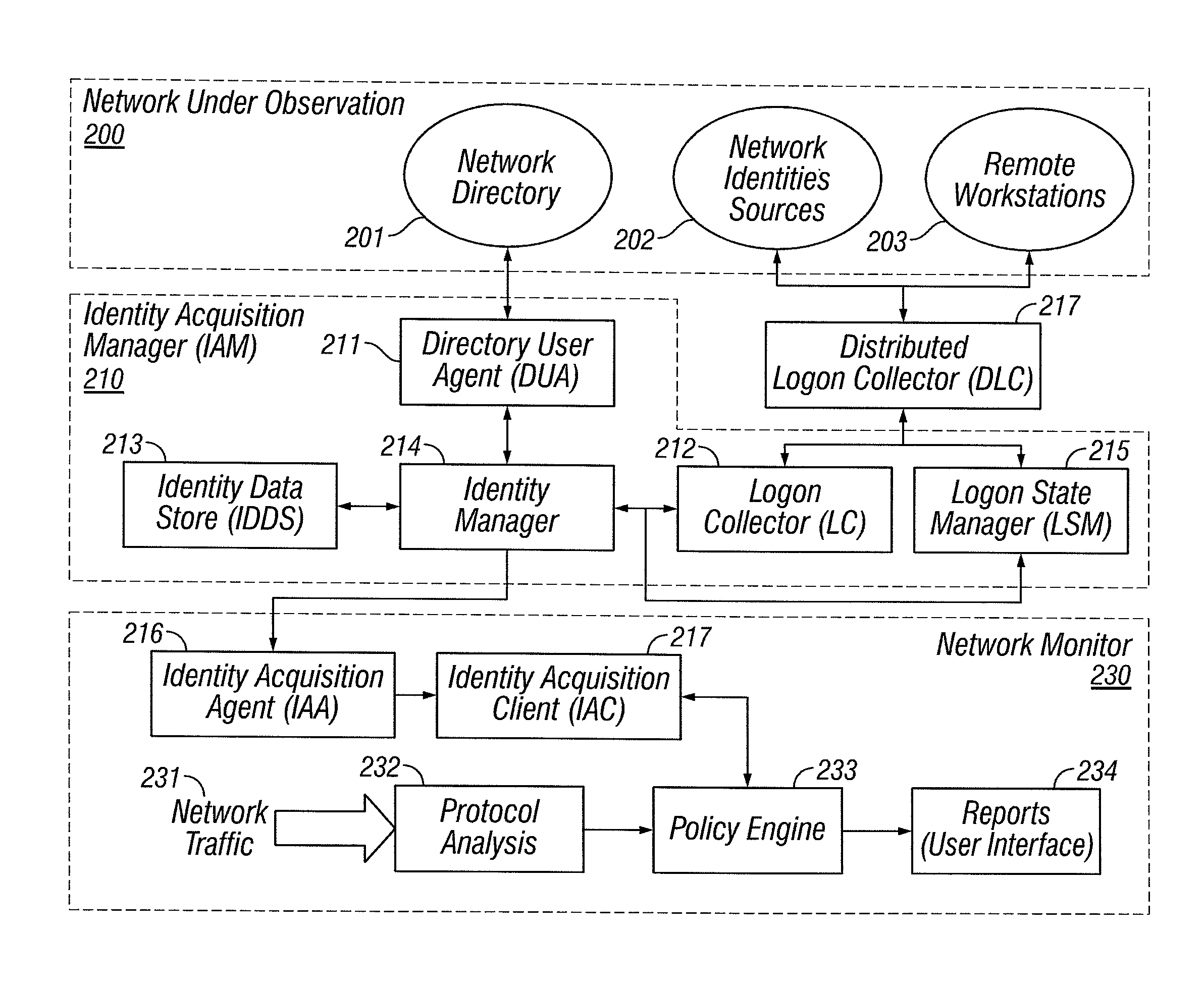
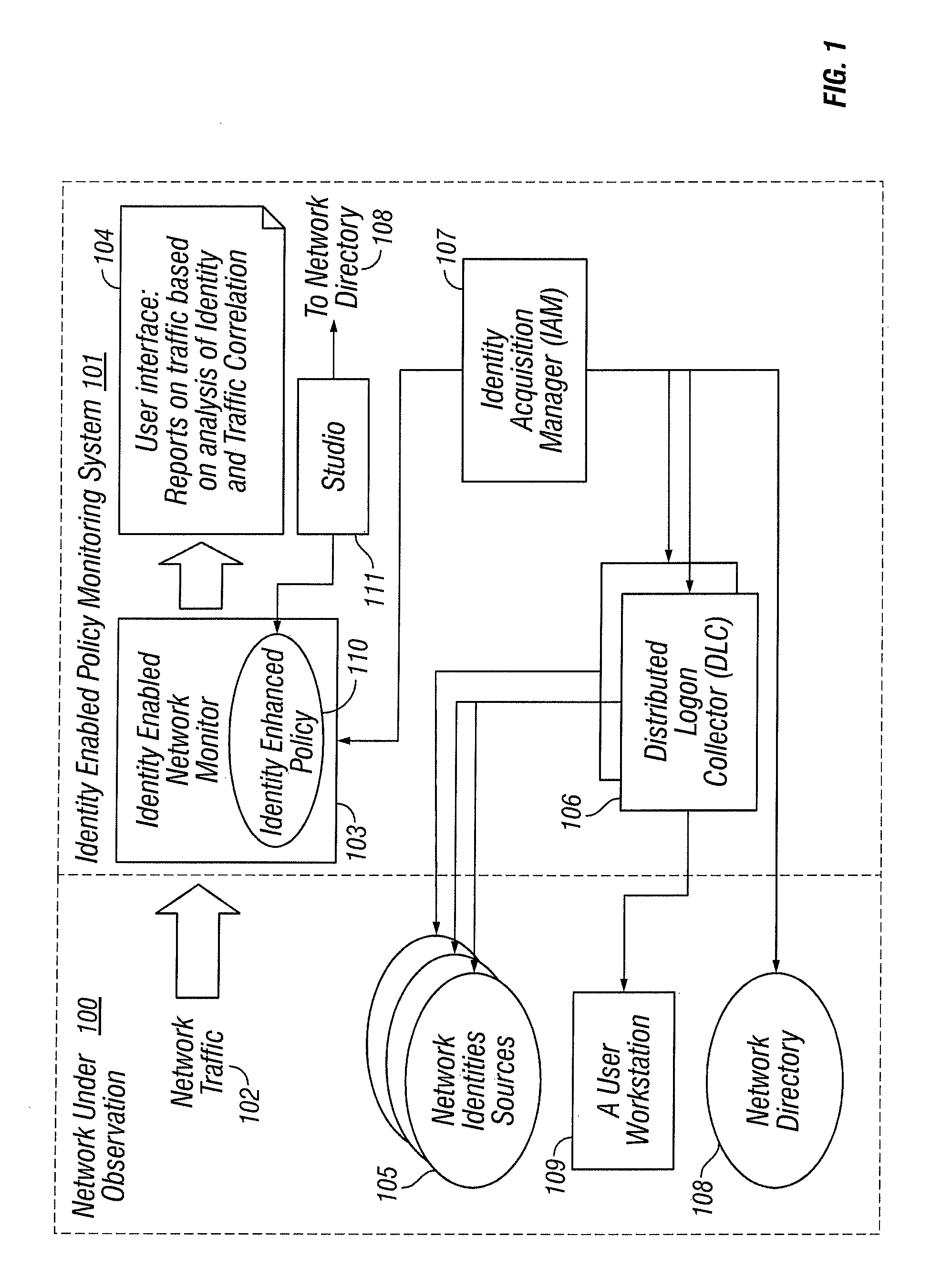
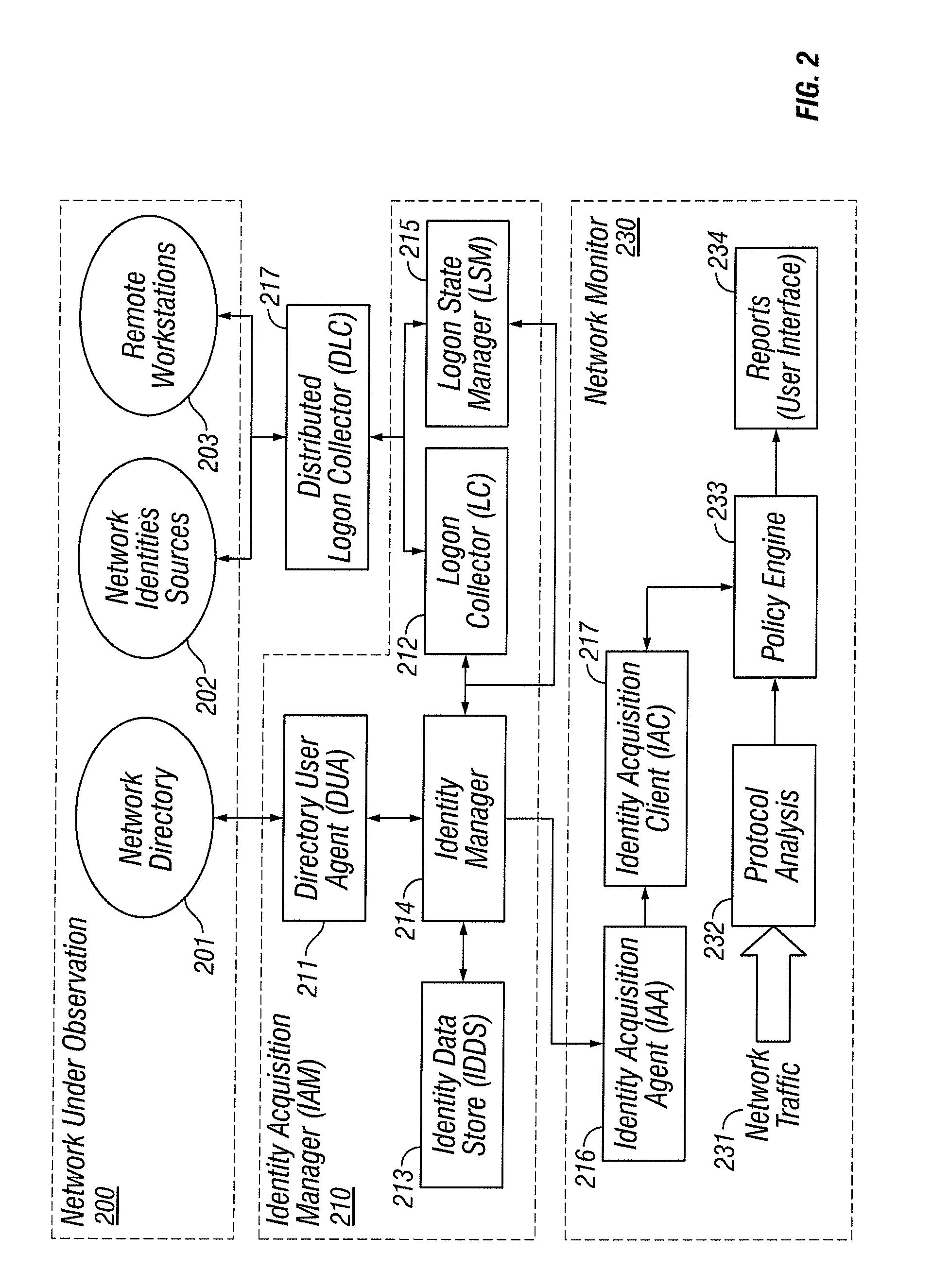
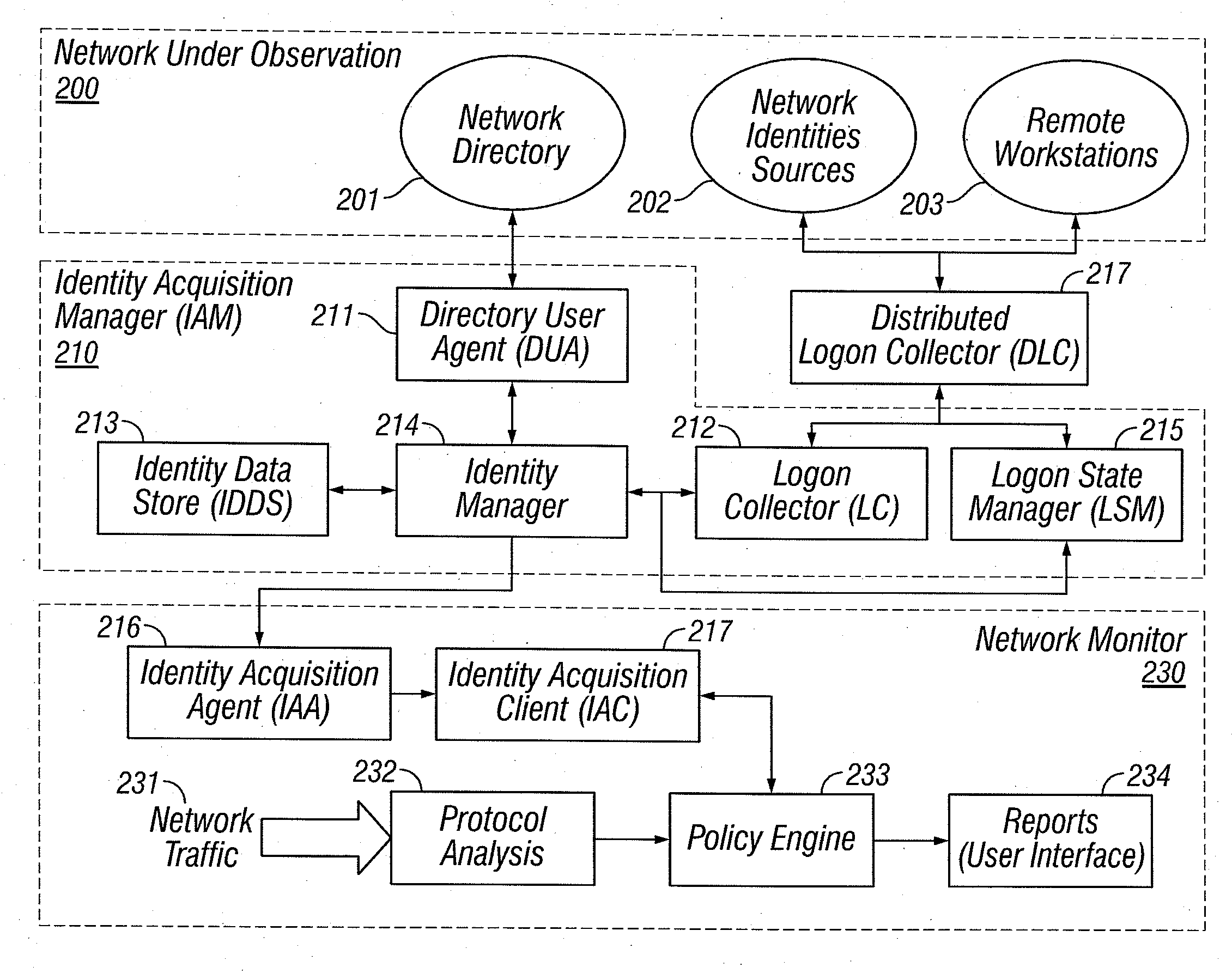
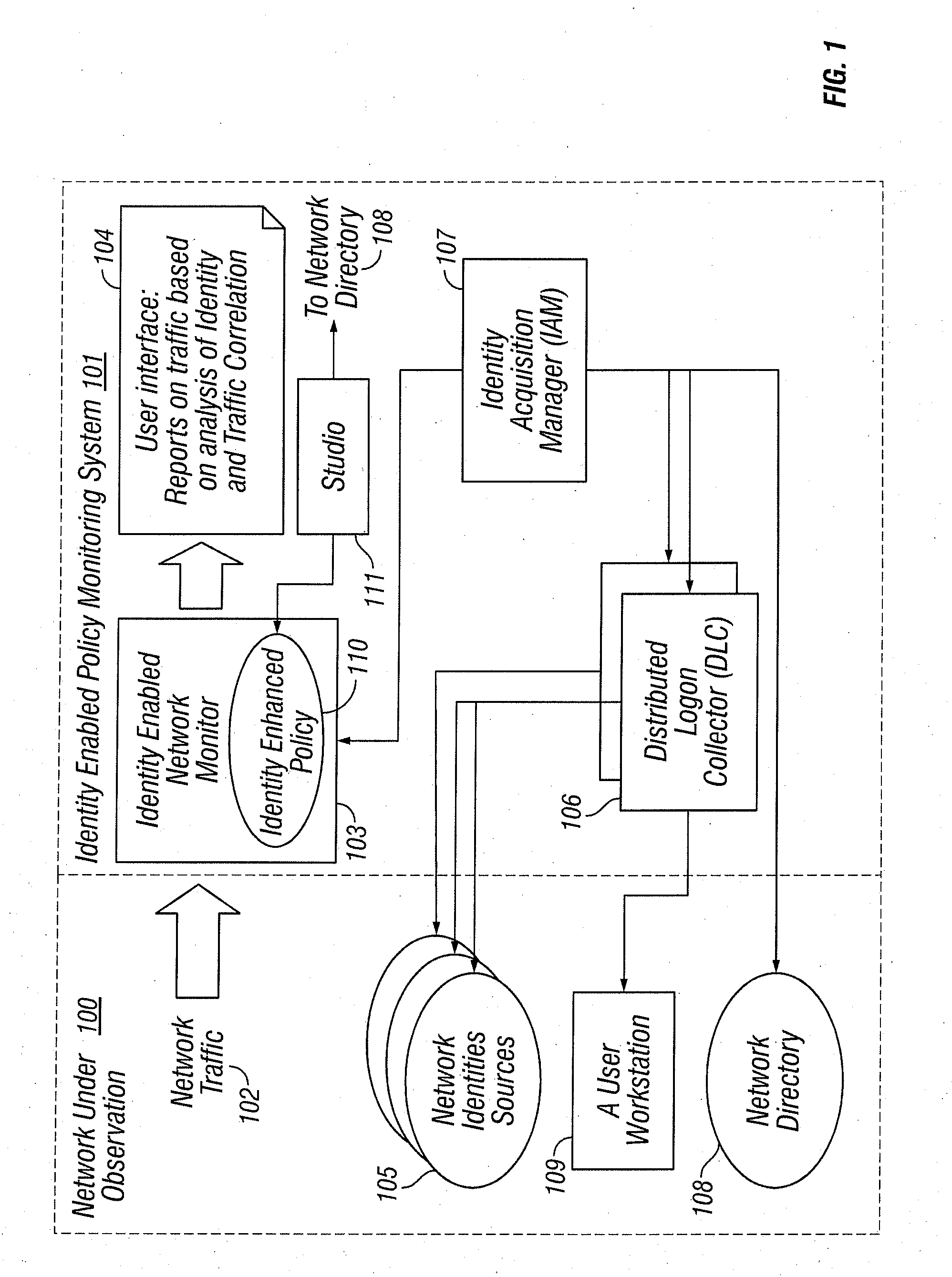
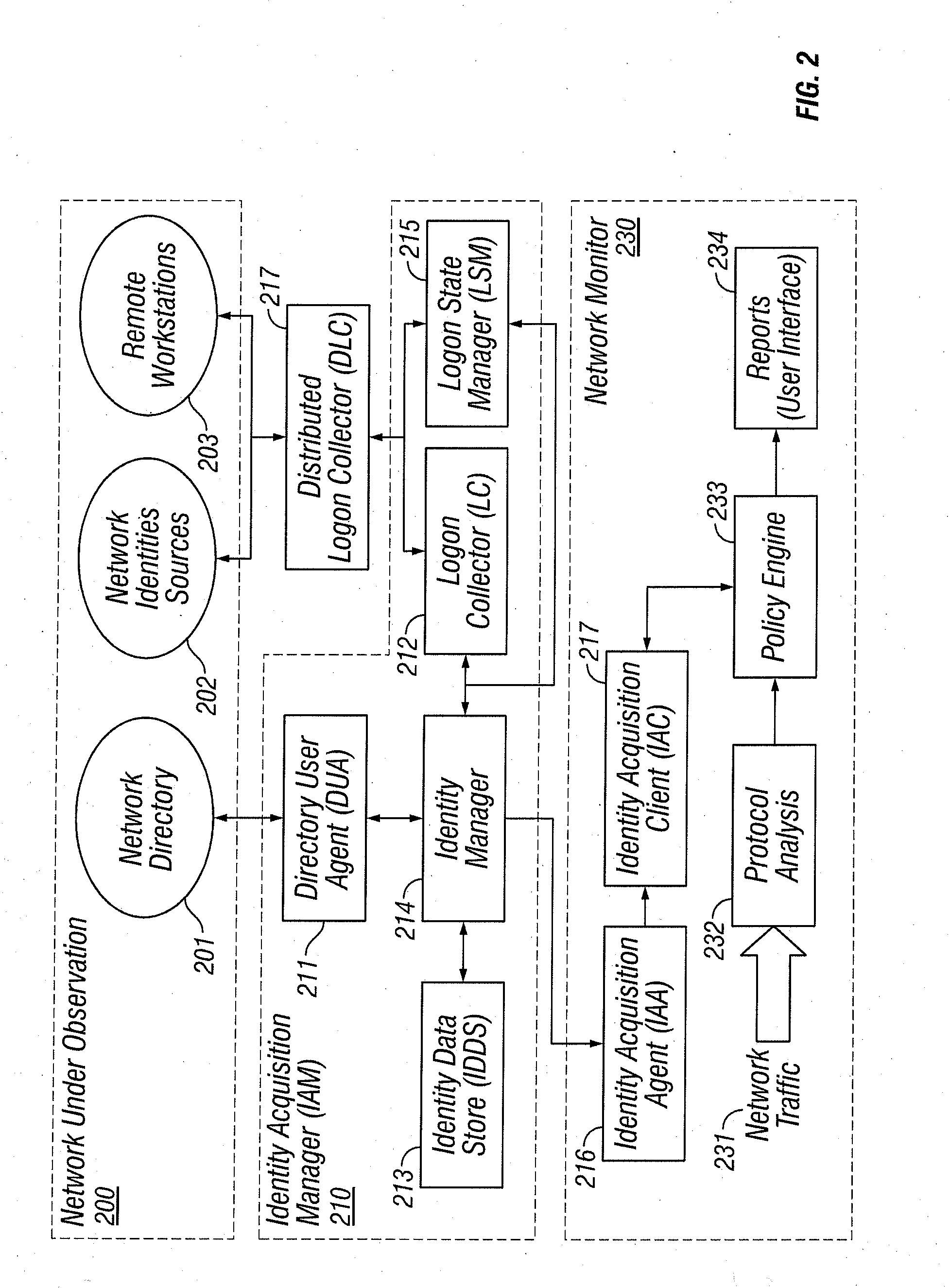
Identities correlation infrastructure for passive network monitoring
ActiveUS8584195B2Policy language is enhancedDigital data processing detailsComputer security arrangementsWorkstationPassive network monitoring
User names and user groups serve as the basis of a formal policy in a network. A passive monitor examines network traffic in near real time and indicates: which network traffic is flowing on the network as before; which users or user groups were logged into workstations initiating this network traffic; and which of this traffic conforms to the formal policy definition. In one embodiment of the invention, users and user groups are determined by querying Microsoft® Active Directory and Microsoft® Windows servers, to determine who is logged onto the Microsoft® network. Other sources of identity information are also possible. The identity information is then correlated with the network traffic, so that even traffic that does not bear on the Microsoft® networking scheme is still tagged with identity
Owner:MUSARUBRA US LLC
Identities Correlation Infrastructure for Passive Network Monitoring
ActiveUS20080109870A1Policy language is enhancedDigital data processing detailsComputer security arrangementsTraffic capacityPassive network monitoring
User names and user groups serve as the basis of a formal policy in a network. A passive monitor examines network traffic in near real time and indicates: which network traffic is flowing on the network as before; which users or user groups were logged into workstations initiating this network traffic; and which of this traffic conforms to the formal policy definition. In one embodiment of the invention, users and user groups are determined by querying Microsoft® Active Directory and Microsoft® Windows servers, to determine who is logged onto the Microsoft® network. Other sources of identity information are also possible. The identity information is then correlated with the network traffic, so that even traffic that does not bear on the Microsoft® networking scheme is still tagged with identity
Owner:MUSARUBRA US LLC
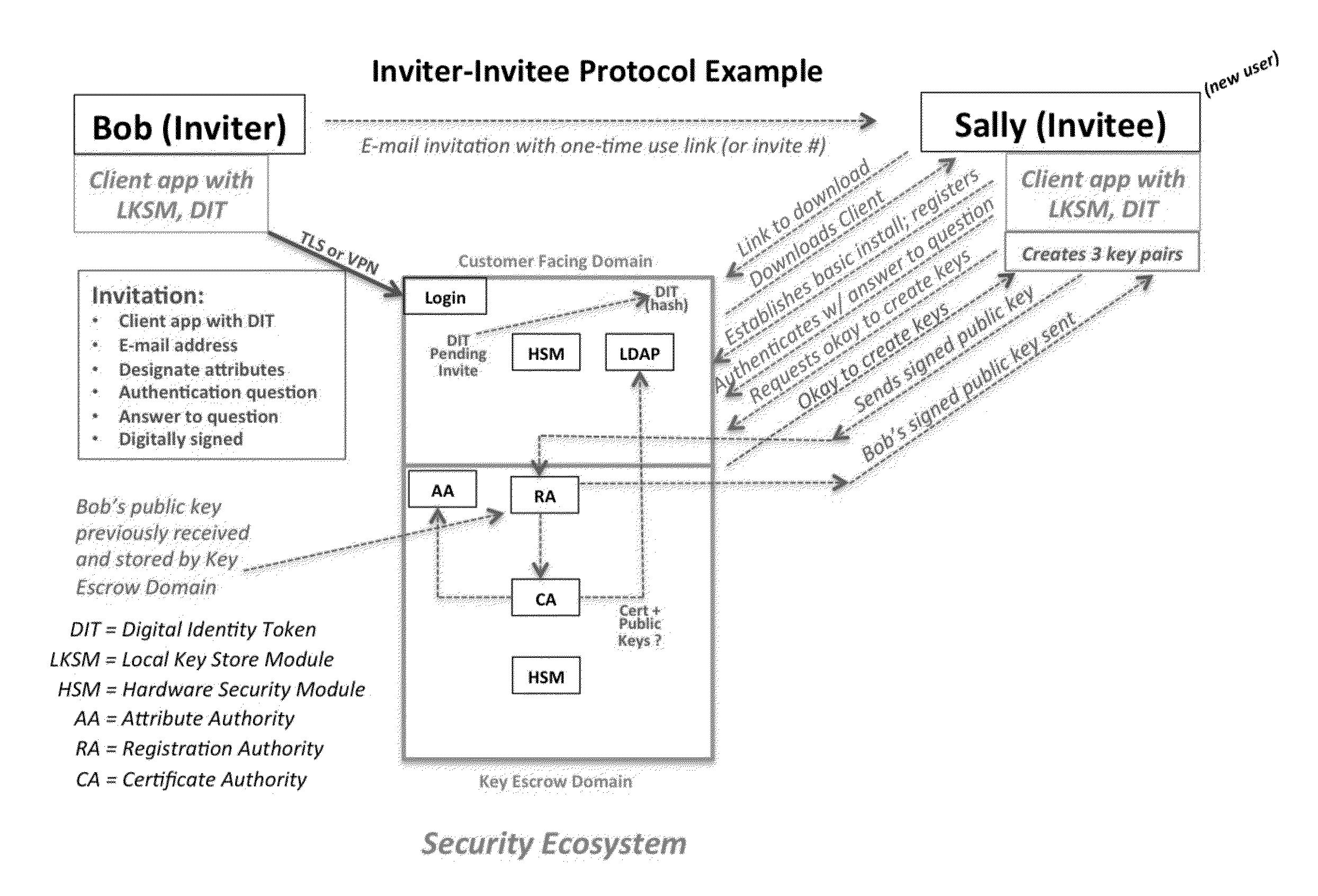
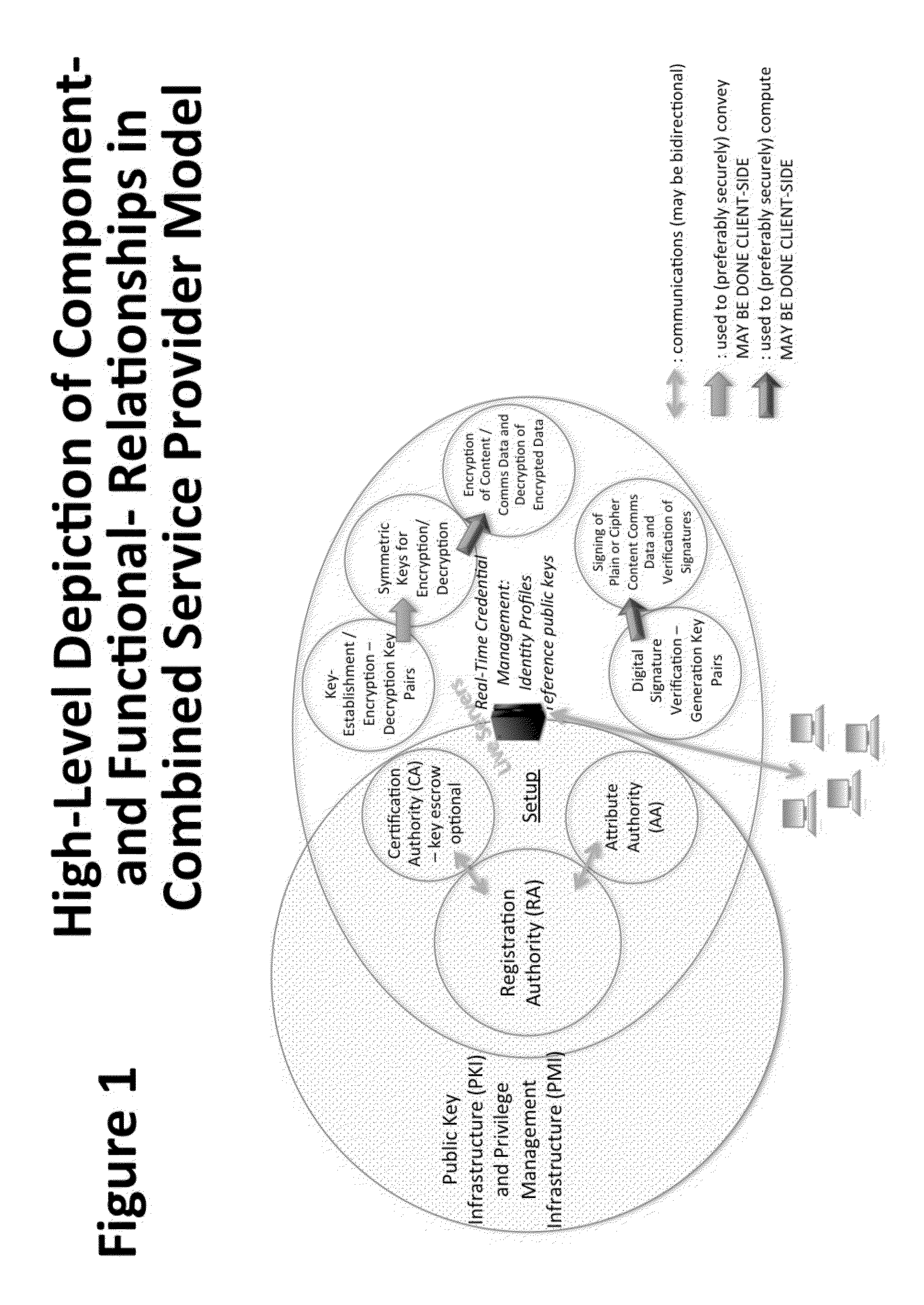
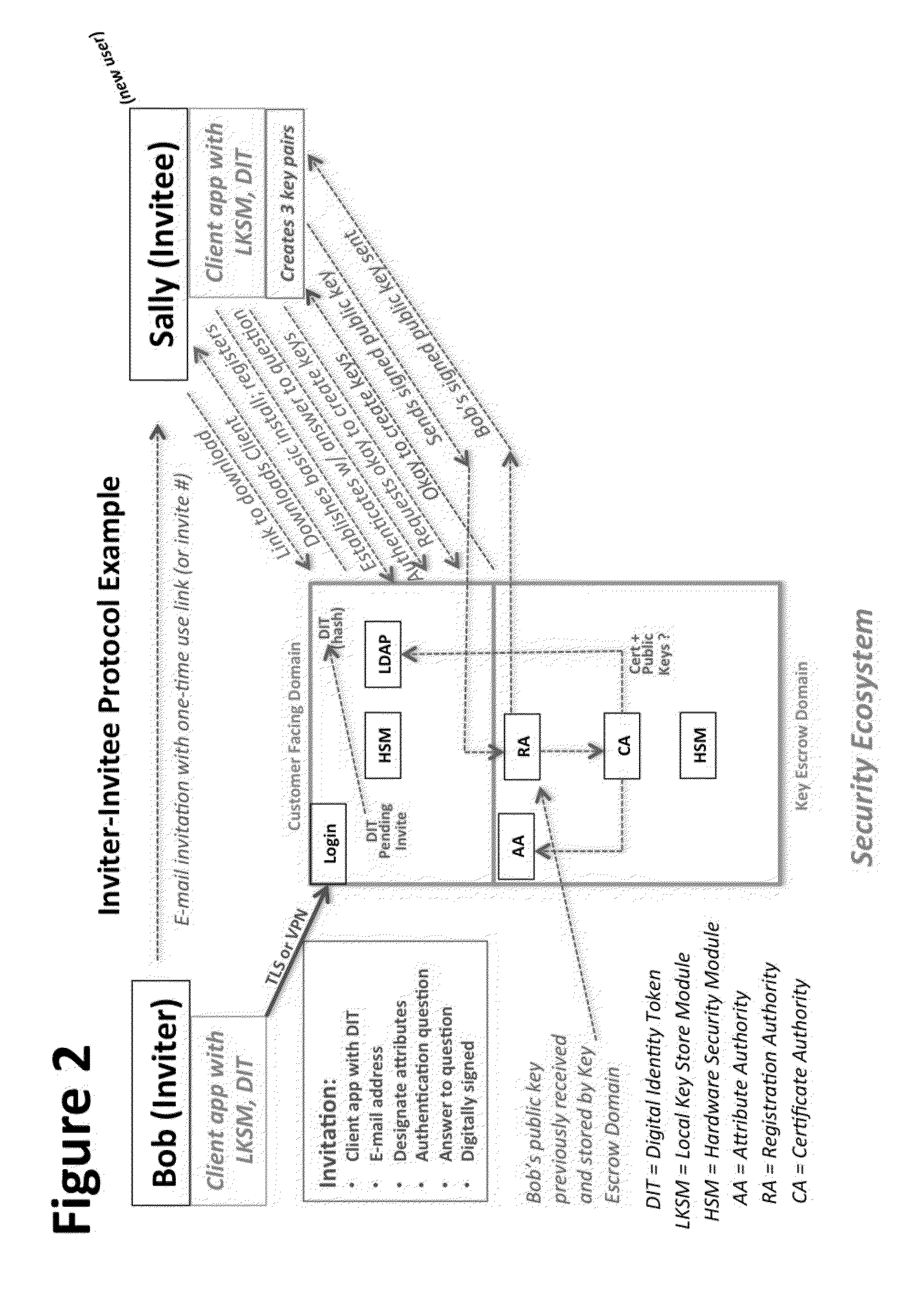
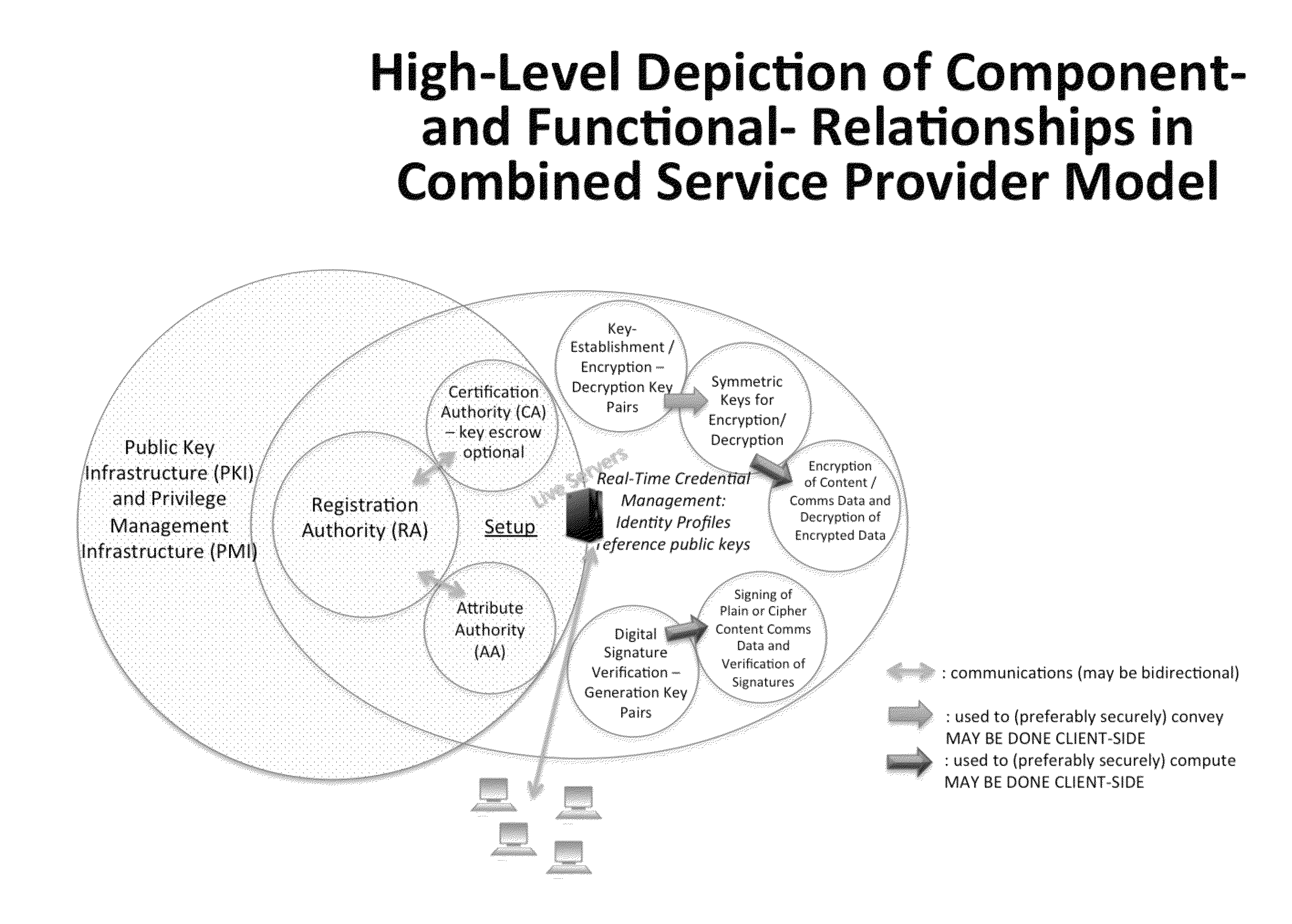
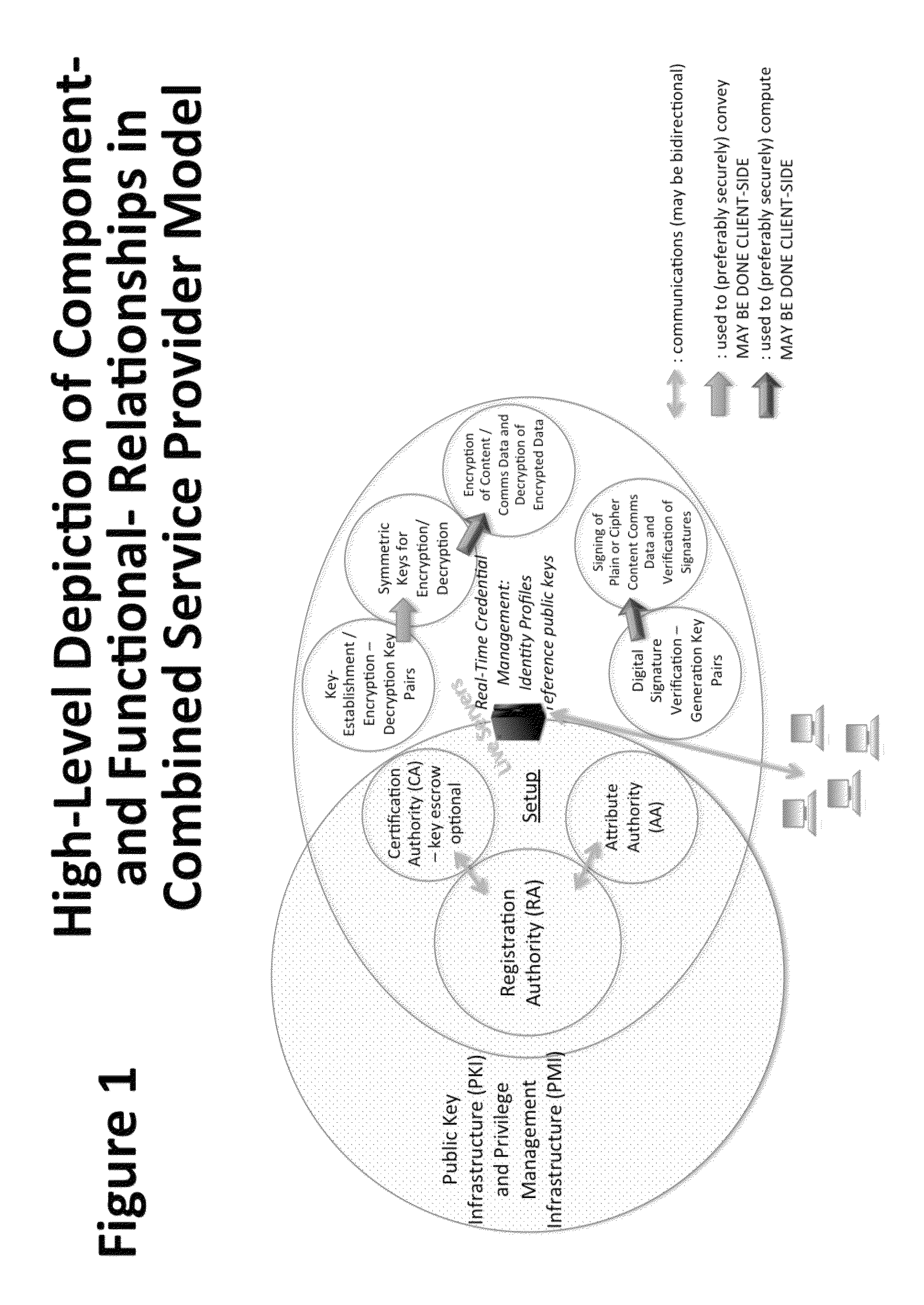
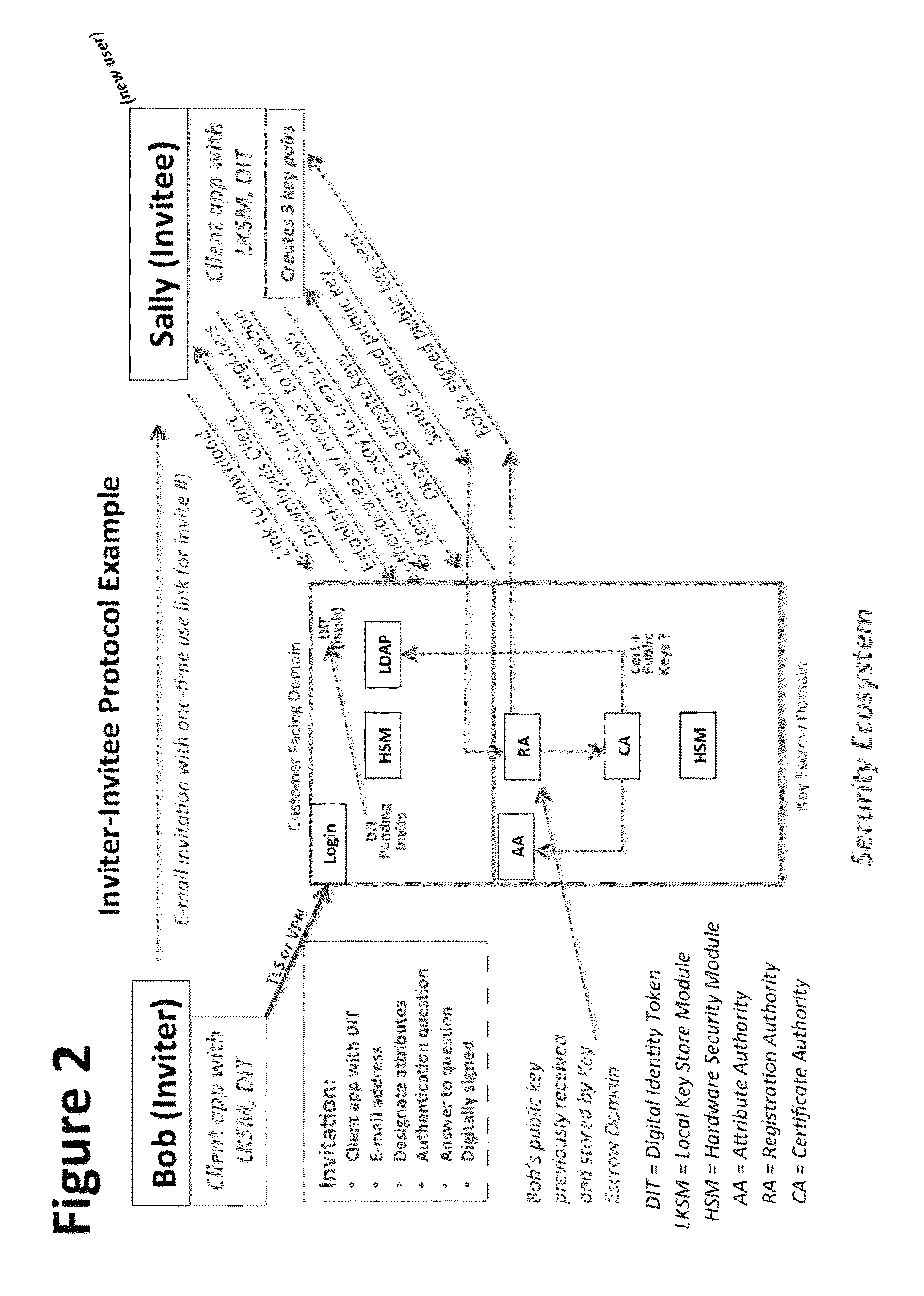
System and Method to Enable PKI- and PMI- Based Distributed Locking of Content and Distributed Unlocking of Protected Content and/or Scoring of Users and/or Scoring of End-Entity Access Means - Added
ActiveUS20150312233A1Key distribution for secure communicationUser identity/authority verificationTrust relationshipThin client
A central server configured with an Attribute Authority (“AA”) acting as a Trusted Third Party mediating service provider and using X.509-compatible PKI and PMI, VPN technology, device-side thin client applications, security hardware (HSM, Network), cloud hosting, authentication, Active Directory and other solutions. This ecosystem results in real time management of credentials, identity profiles, communication lines, and keys. It is not centrally managed, rather distributes rights to users. Using its Inviter-Invitee protocol suite, Inviters vouch for the identity of Invitees who successfully complete the protocol establishing communication lines. Users establish and respond to authorization requests and other real-time verifications pertaining to accessing each communication line (not end point) and sharing encrypted digital files. These are auditable, brokered, trusted-relationships where such relationships / digital agreements can each stand-alone (for privacy) or can leverage build-up of identity confidence levels across relationships. The service is agnostic to how encrypted user content is transported or stored.
Owner:T CENT
System and method for launching a resource in a network
ActiveUS8732182B2Digital data processing detailsWireless commuication servicesOperational systemDirectory structure
Owner:DESKTOPSITES
iSCSI boot drive system and method for a scalable internet engine
InactiveUS20050138346A1Digital computer detailsProgram loading/initiatingOperational systemThe Internet
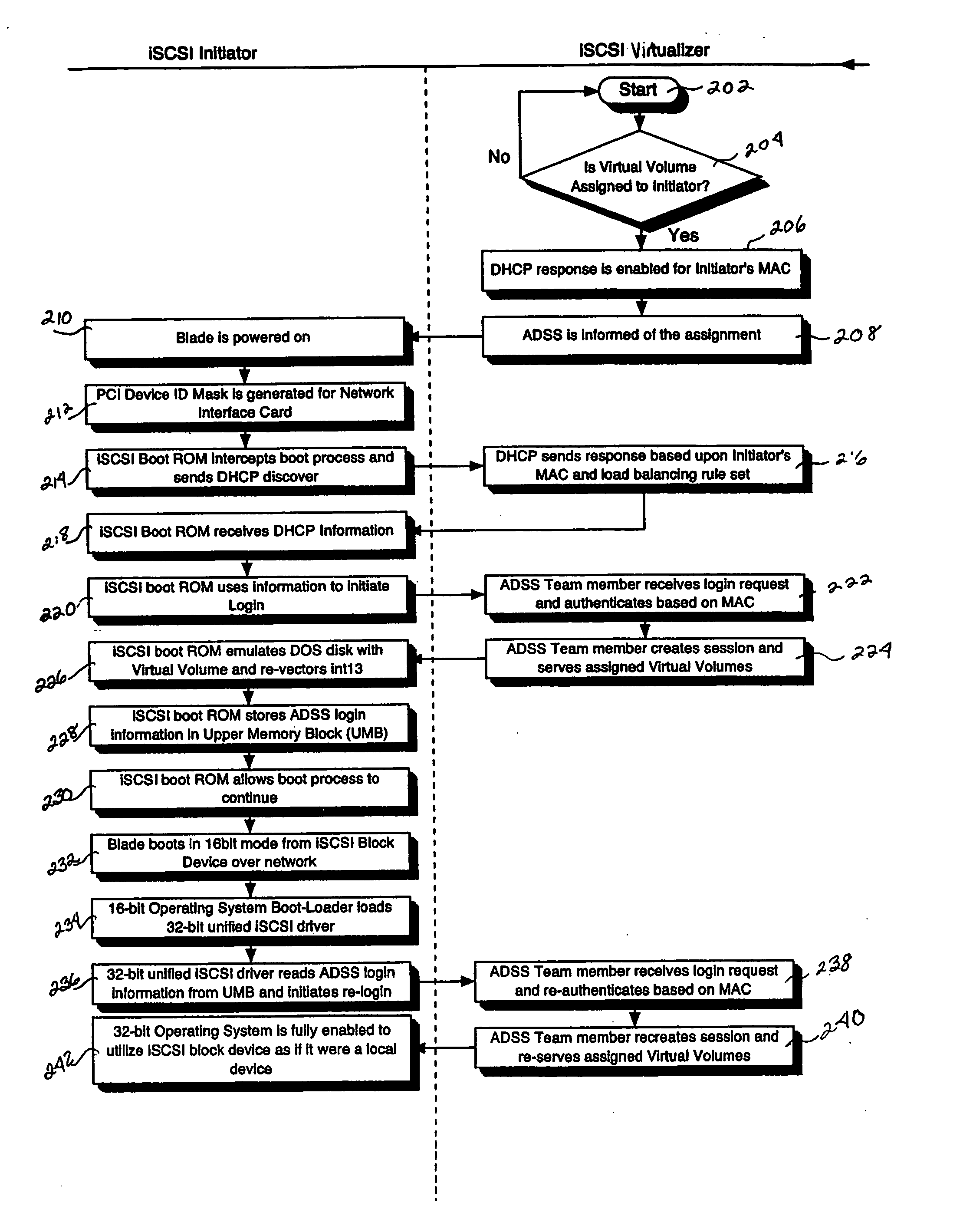
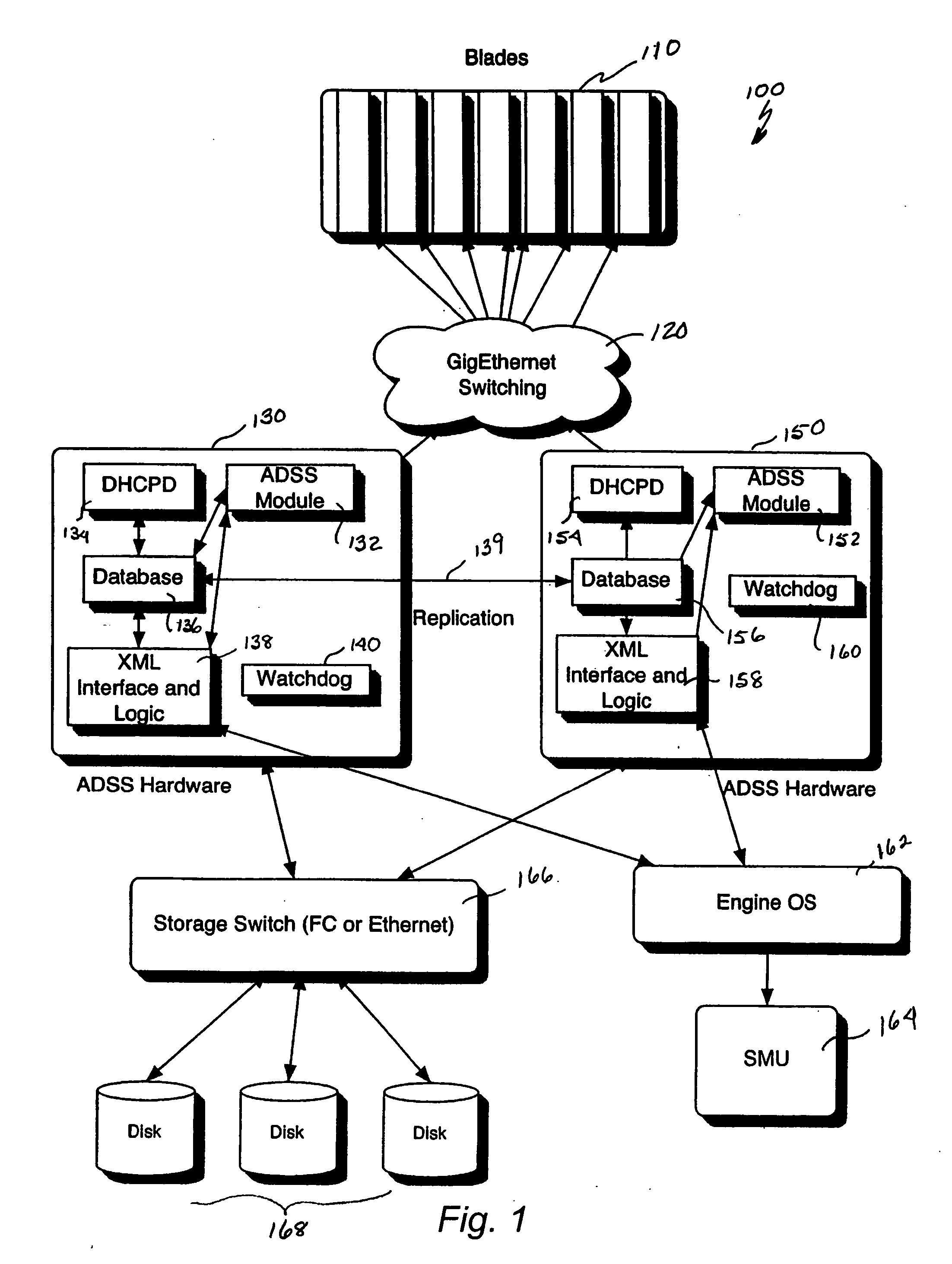
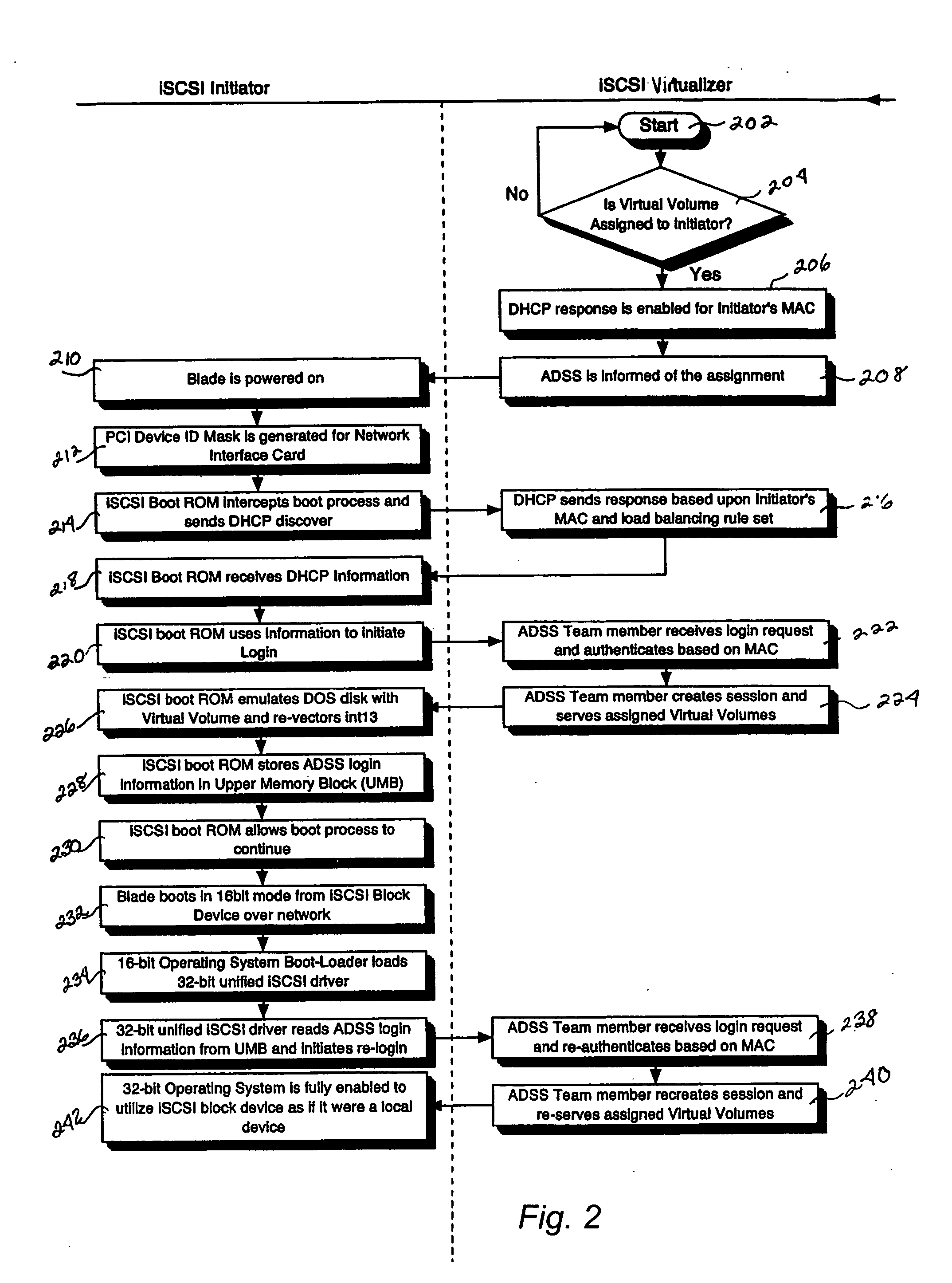
A system for remote booting of a server generally includes a client initiator, an iSCSI virtualizer, and an iSCSI initiator. The client initiator requests access to the server and the iSCSI virtualizer receives the access request. Then, the iSCSI initiator acts upon the request received by the iSCSI virtualizer to initiate login to the server through use of an iSCSI Boot ROM on the server and to emulate a disk operating system through use of the iSCSI Boot ROM, which enables the server to boot. The server boots in both an 8-bit and a subsequent 32-bit mode. The iSCSI Boot ROM appears as a local device upon the completion of the server boot. The iSCSI virtualizer authenticates the login at least twice. The iSCSI virtualizer includes a pair of replicated active directory service servers (ADSS).
Owner:RPX CORP
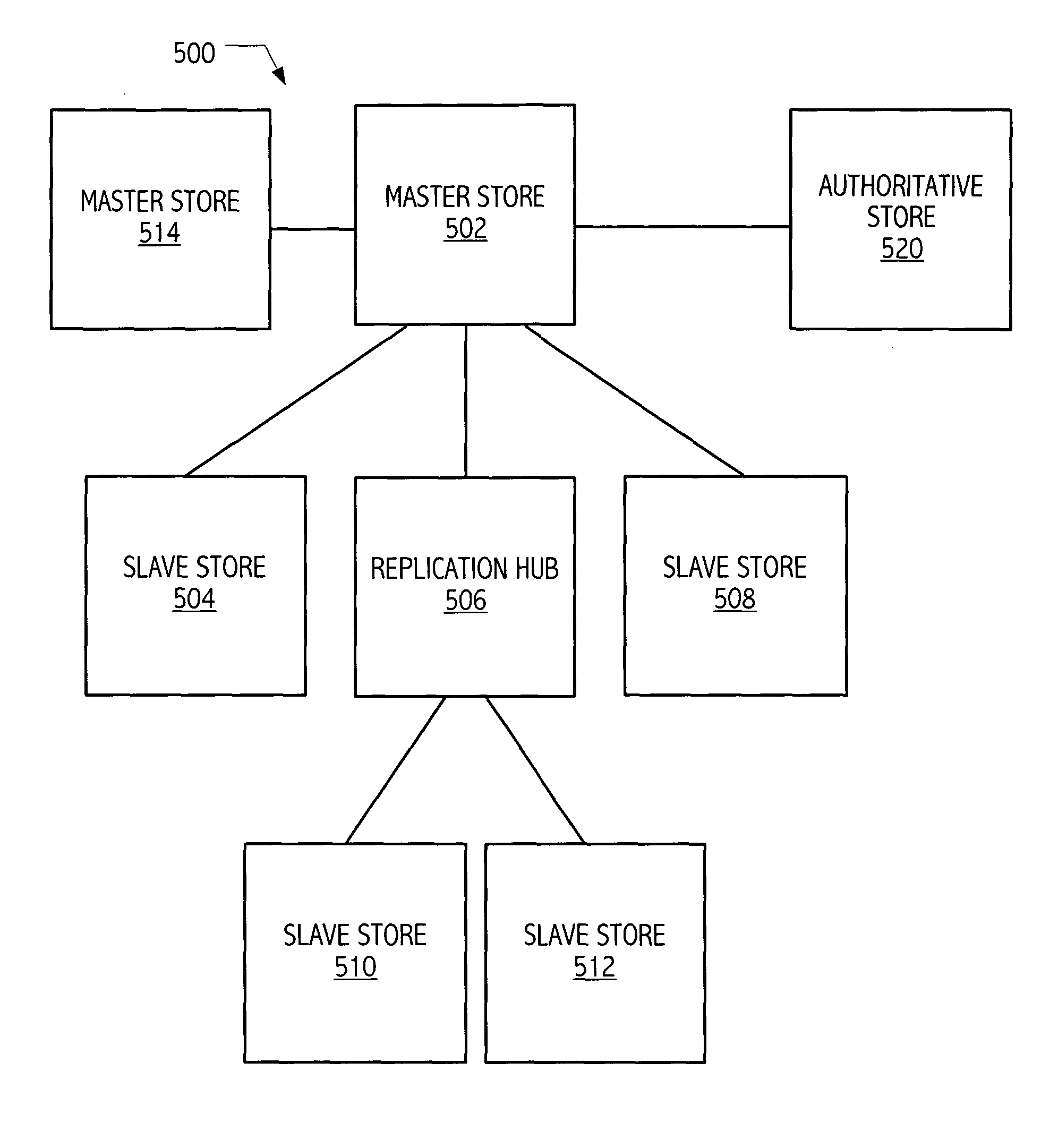
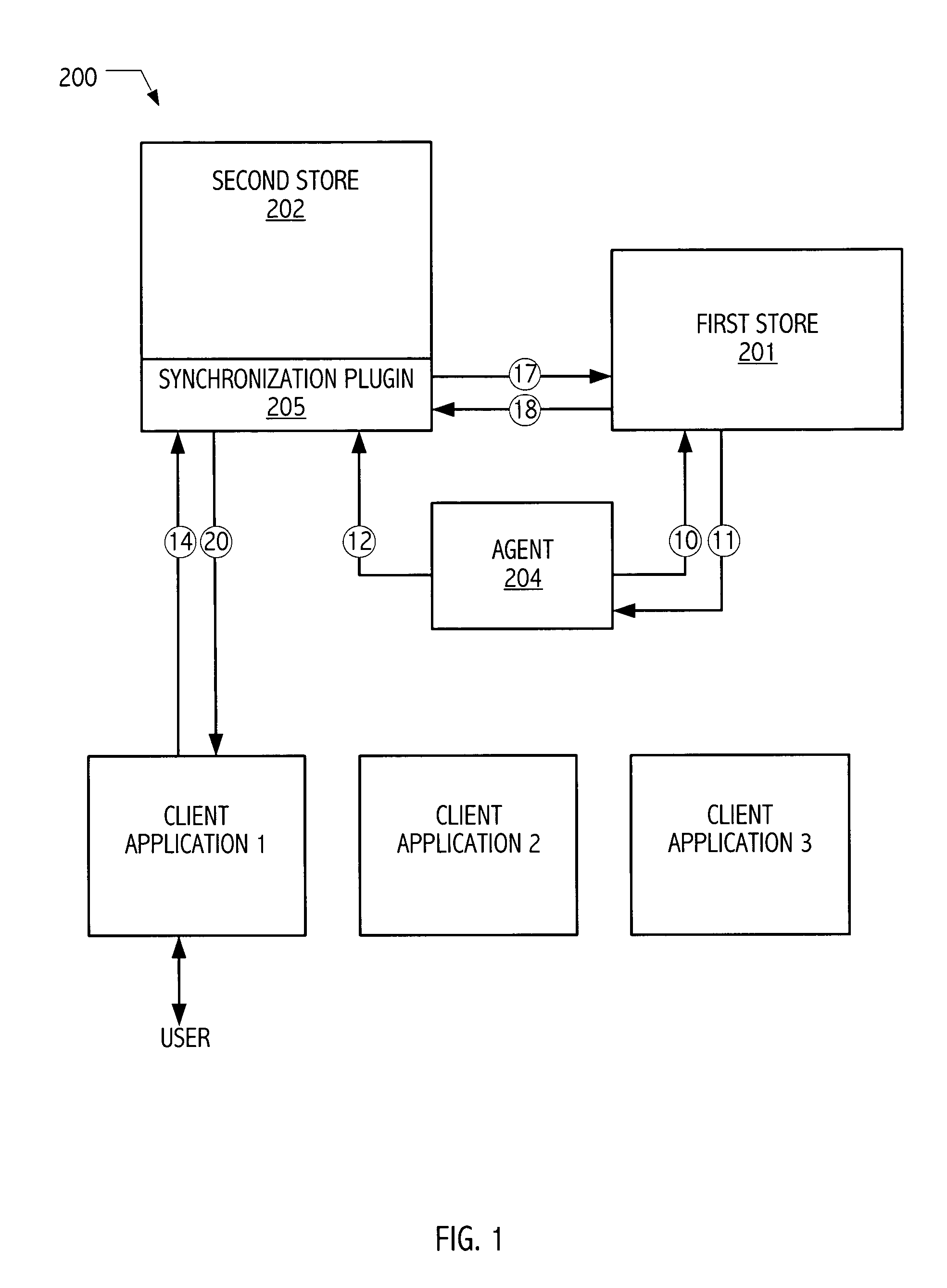
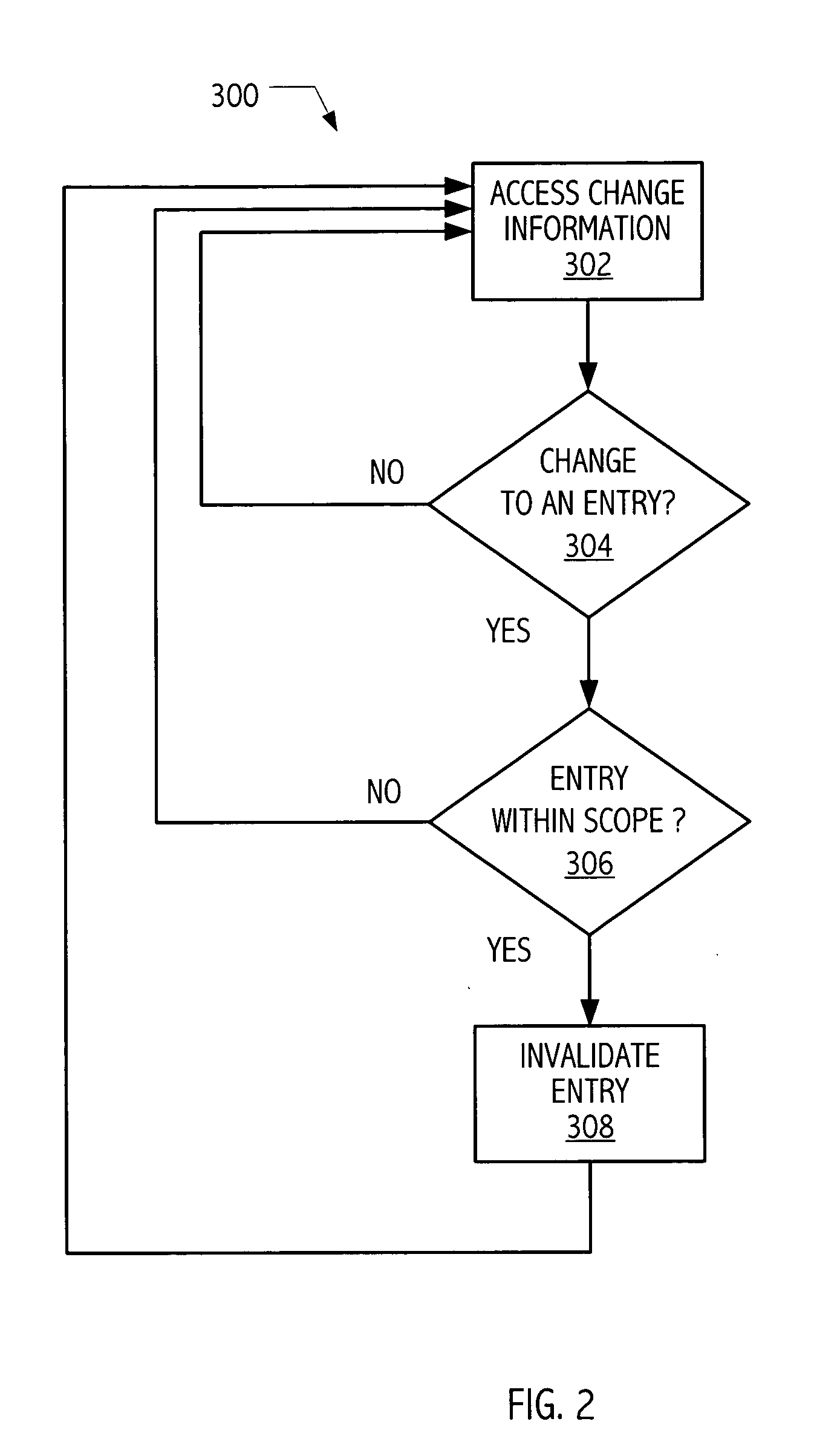
Synchronization facility for information domains employing replicas
InactiveUS20040117667A1Digital data processing detailsMultiple digital computer combinationsOperational systemInformation propagation
Mechanisms have been developed for synchronizing information, e.g., password or other access credential information, amongst replicated directory spaces or repositories. In some exemplary realizations, directory spaces are embodied as directory servers, services or similar components of computer operating systems, including LDAP, UDDI, Active Directory or other standardized or proprietary directory environments. In one embodiment in accordance with the present invention, a method includes invalidating an entry of at least one replica store. The invalidation of the entry of the replica store triggers information synchronization of a corresponding invalidated entry of a master store to a corresponding entry of an authoritative store on a next attempt to authenticate against the invalidated entry of the replica store. The method may include propagating information of the synchronized master store entry to at least one other replica store.
Owner:SUN MICROSYSTEMS INC
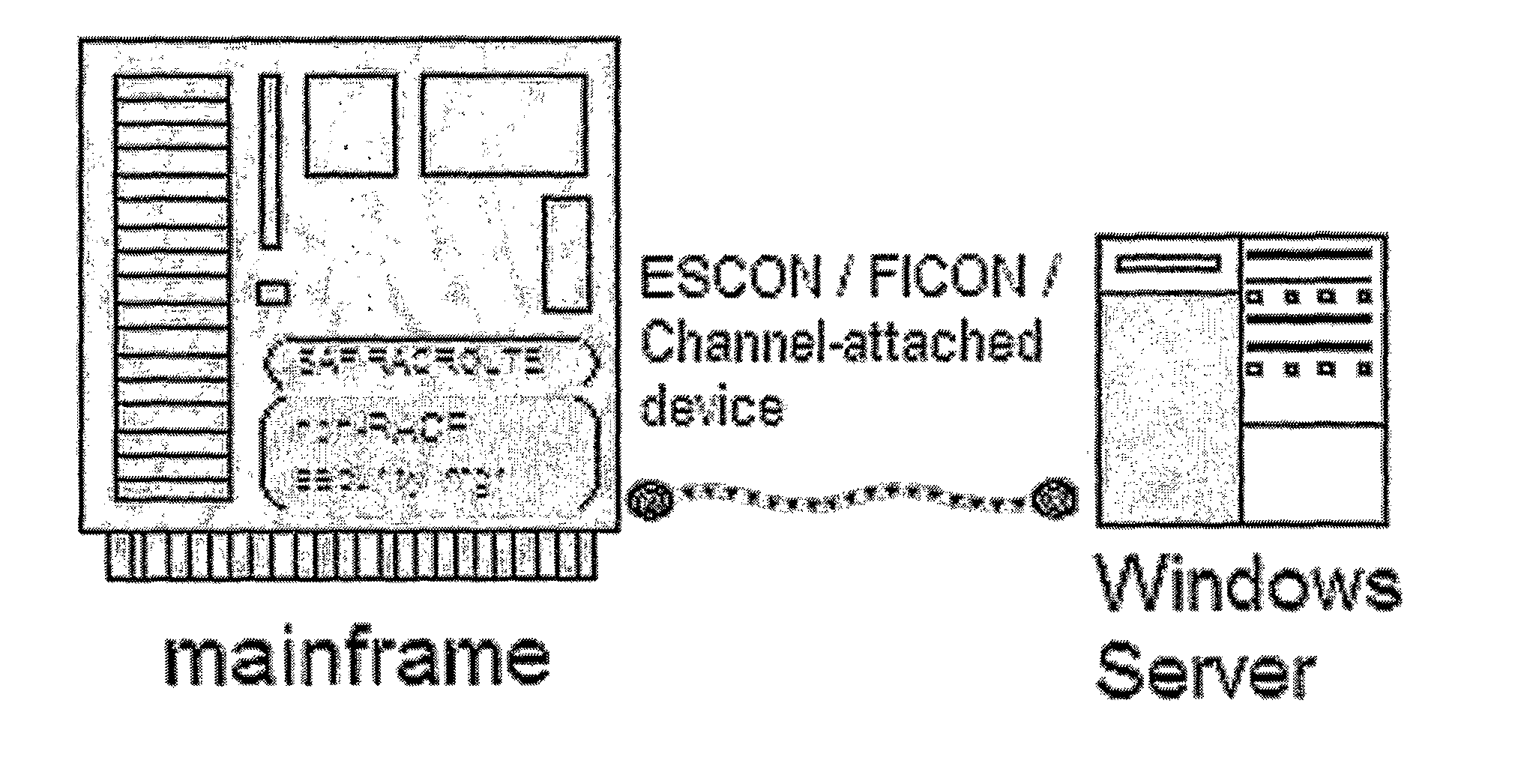
Translation Engine for Computer Authorizations Between Active Directory and Mainframe System
InactiveUS20080263640A1Extended processing timeImproved security flexibilityDigital data processing detailsComputer security arrangementsComputer accessMainframe computer
The invention provides a method and system of implementing a high performance “non-RACF external security-manager product,” which maintains and translates a merged single source of authorizations to both mainframe and Microsoft Windows Active Directory (AD) systems. In one embodiment, a method comprises generating at a server computer access information for a mainframe computer indicative of mainframe authorization for a set of users, receiving from the mainframe computer information indicative of an authorization request, the information indicative of the authorization request identifying a user trying to access the mainframe computer, and sending at least a portion of the access information from the server computer to the mainframe computer, the portion of the access information including mainframe access information for the user.
Owner:REDPHONE SECURITY INC
Active Directory-based uniform authentication realizing method applied to TV station
InactiveCN101605030ARealize the function of cross-domain single sign-onUser identity/authority verificationSoftware engineeringTelevision station
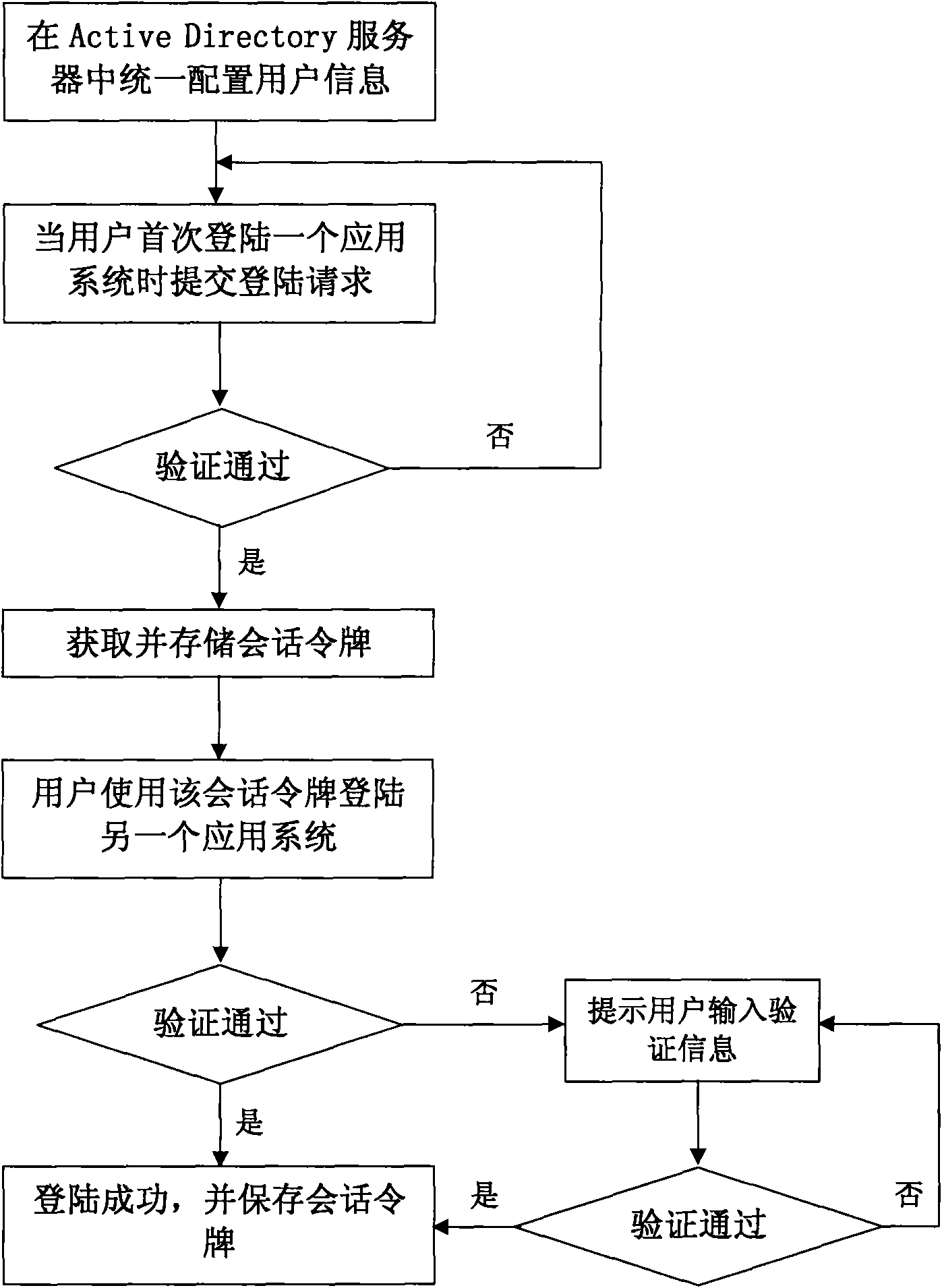
The invention discloses a uniform authentication realizing method, in particular to an Active Directory-based uniform authentication realizing method applied to a backbone network of a TV station. The prior uniform authentication method can not cross a domain and uniformly authenticates among a plurality of browsers simultaneously. The method comprises the following steps: firstly, user information is uniformly configured in an Active Directory server; when a user successfully logs in one application system for the first time, a conversation token is obtained and stored; when the user logs in the other application system by the conversation token, the application system authenticates the legality of the conversation token by the Active Directory server; and if the conversation token is qualified, login is successful. The system can realize the single login of all application systems in different domains in the TV station, and the application systems can be of a B / S or C / S structure.
Owner:CHINA DIGITAL VIDEO BEIJING
Event-Based User State Synchronization in a Cloud Storage System
InactiveUS20170177613A1Overcome problemsEasy maintenanceDatabase distribution/replicationDigital data authenticationFile systemCloud storage system
Cloud storage systems and methods are described for providing event-based user state synchronization among the various cloud elements. A global user directory is maintained on a remote cloud storage system. The global user directory includes a plurality of global user definitions associated with a plurality of user accounts, where each of the user accounts has access to at least one of a remote file system (RFS) hosted by the remote cloud storage system and a local file system (LFS) hosted by a local cloud storage system. As global user definition are altered on the remote cloud storage system, user events are generated and communicated to the local cloud storage system, where they are applied to synchronize the local user definitions with the global user definitions. The invention facilitates centralized control of user definitions, near real-time event delivery to local cloud storage systems, and separation of authentication processes from customers' active directory services.
Owner:EGNYTE
Systems and methods for multi-factor authentication
ActiveUS9118656B2User identity/authority verificationElectric digital data processingControl systemPrivate network
Requests to gain access to secure resources are adjudicated according to authentication policies that include rules based on user-states derived from multiple heterogeneous access-control systems. Comprehensive user authentication and access control based on rules and policies that encompass a user's status in multiple access-control systems, including both logical access (e.g., Active Directory, RADIUS, Virtual Private Network, etc.) as well as physical access (e.g., card-based) control systems, may be realized.
Owner:IMPRIVATA
On-chip network system supporting cache coherence and data request method
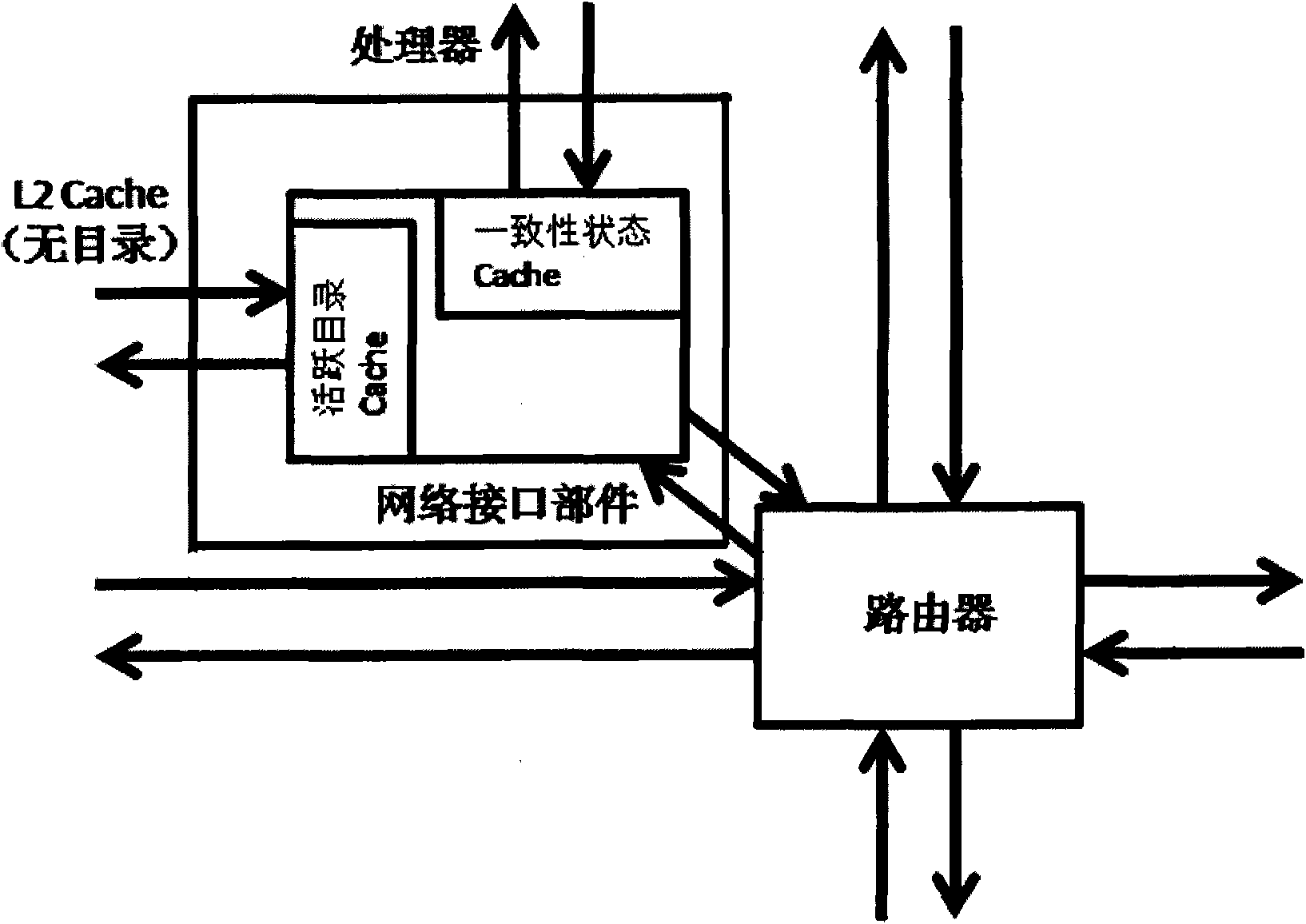
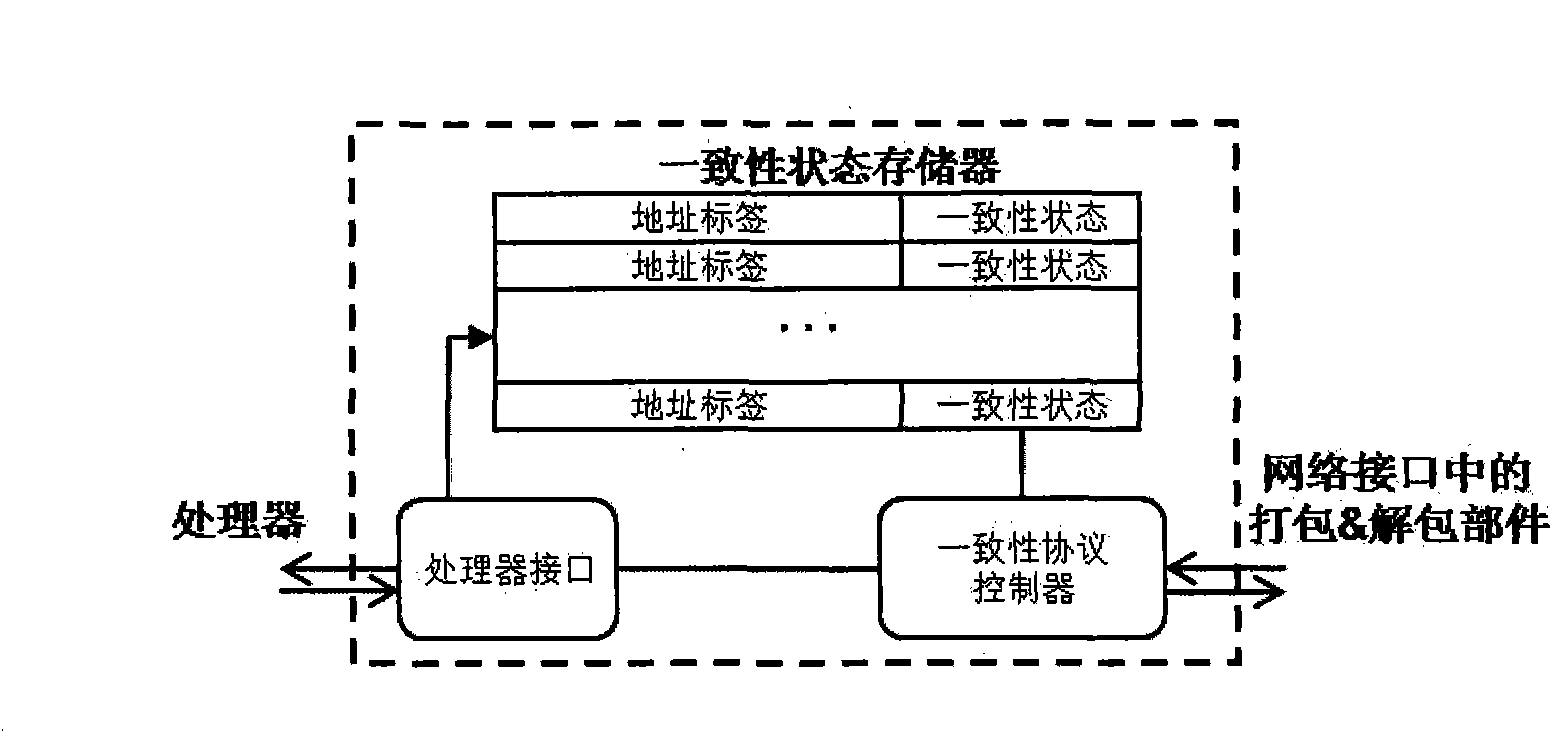
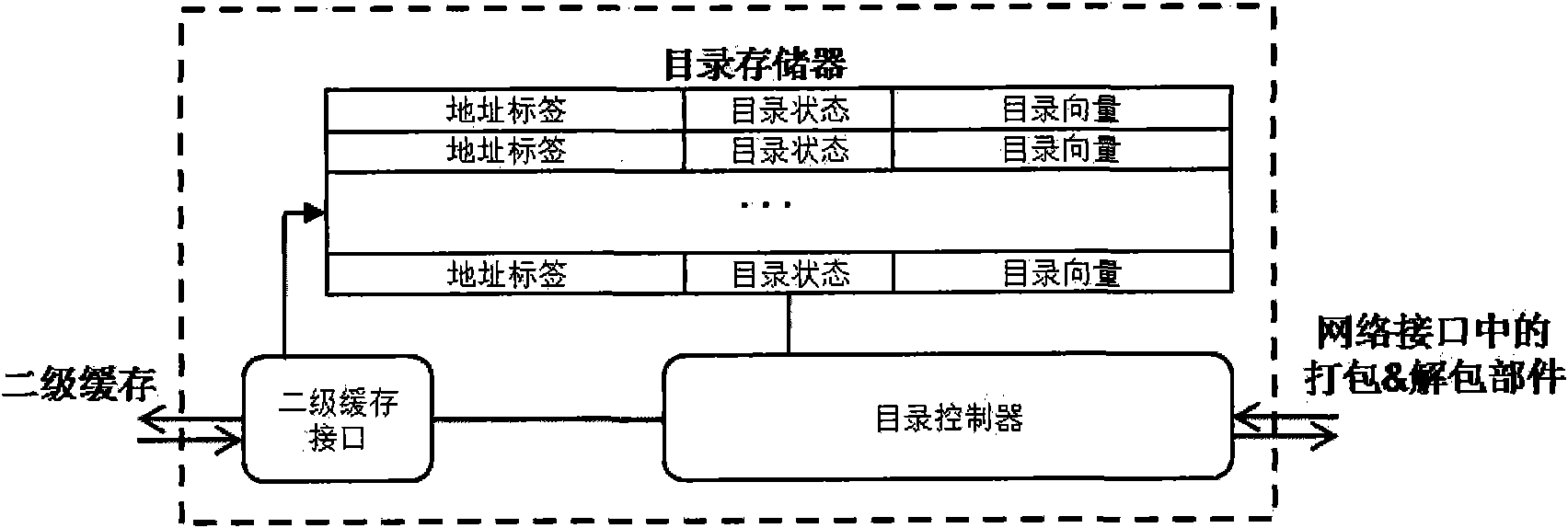
InactiveCN101958834ASimplify the design processSimplify the verification processDigital computer detailsData switching networksCache accessStructure of Management Information
The invention discloses an on-chip network system supporting cache coherence. The network system comprises a network interface part and a router, wherein the network interface part is connected with the router, a multi-core processor and a second level cache; a consistent state cache connected with the multi-core processor is additionally arranged in the network interface part and is used for storing and maintaining the consistent state of a data block in a first level cache of the multi-core processor; and an active directory cache connected with the second level cache is also additionally arranged in the network interface part and is used for caching and maintaining the directory information of the data block usually accessed by the first level cache. Coherence maintenance work is separated from the work of a processor, directory maintenance work is separated from the work of the second level cache, and the directory structure in the second level cache is eliminated, so that the design and the verification process of the multi-core processor are simplified, the storage cost of a chip is reduced, and the performance of the multi-core processor is improved. The invention also discloses a data request method of the system.
Owner:TSINGHUA UNIV
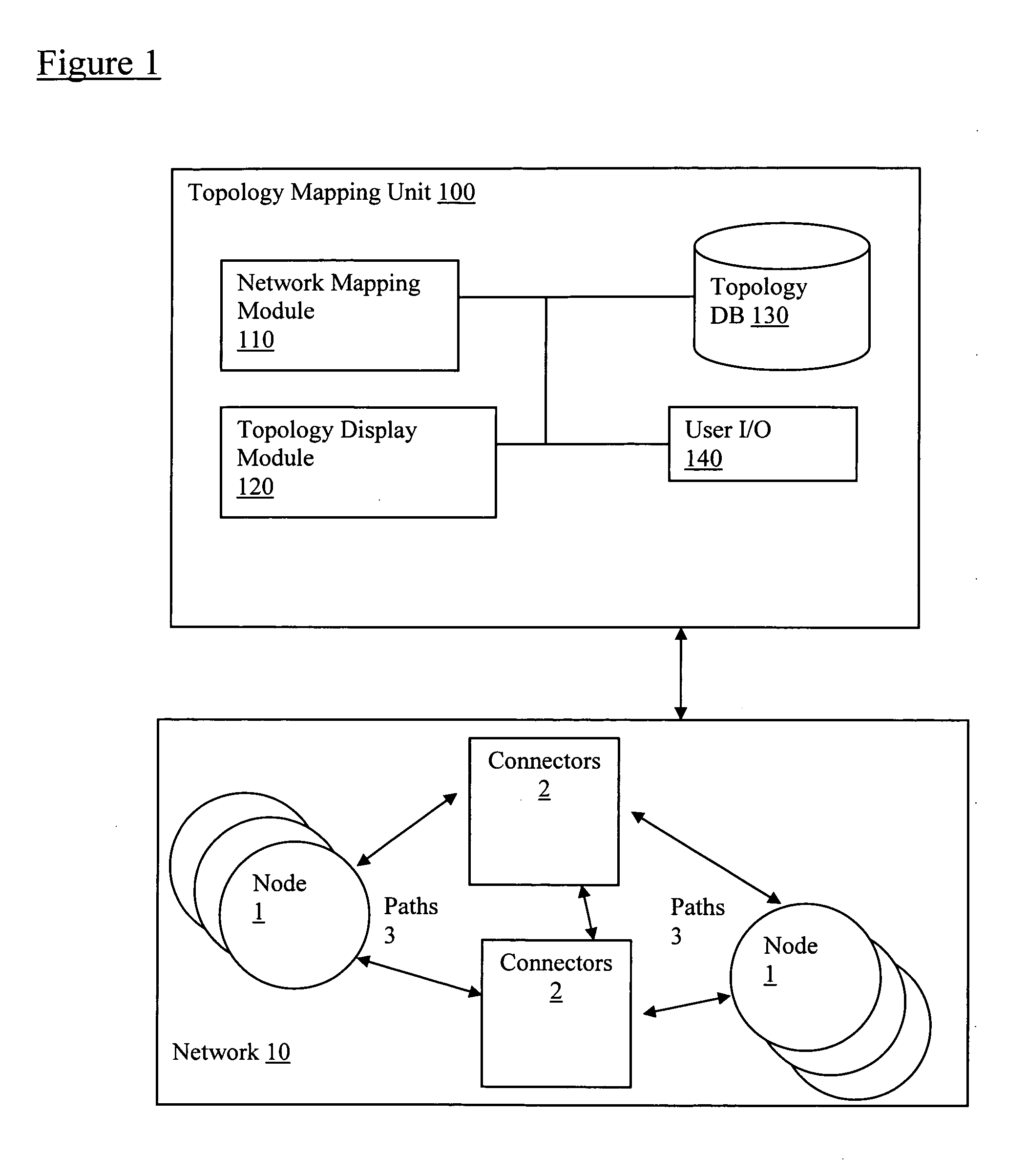
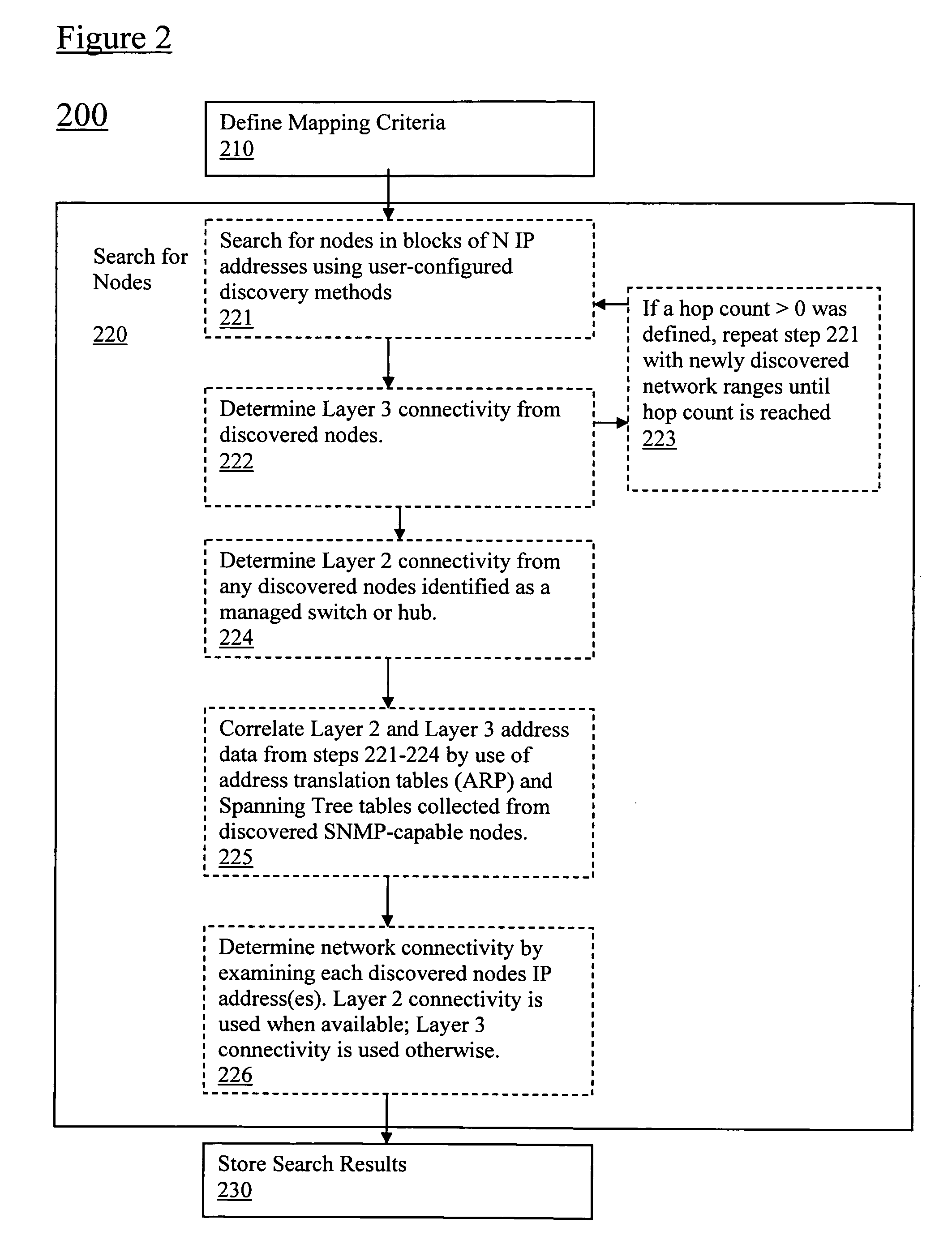
Filtering of map topology based on network discovery characteristics
Embodiments of the present application enable a user to map a network topology and to then dynamically filter the map display by hiding or showing nodes based on discovery characteristics, such as Simple Network Management Protocol (SNMP) status, Active Directory (AD) Domain Controllers (DC) status, group membership status, etc. to allow customization of maps views. In particular, a topology mapping is formed by collecting topology data of a network and storing this topology data. Filtering criteria are received from a user, and the stored topology data is filtered using this received filtering criteria. The filtered topology data is then displayed to the user.
Owner:SOLARWINDS WORLDWIDE
Distributed High Availability Agent Architecture
ActiveUS20180083977A1Database distribution/replicationDigital data protectionAgent architectureCloud base
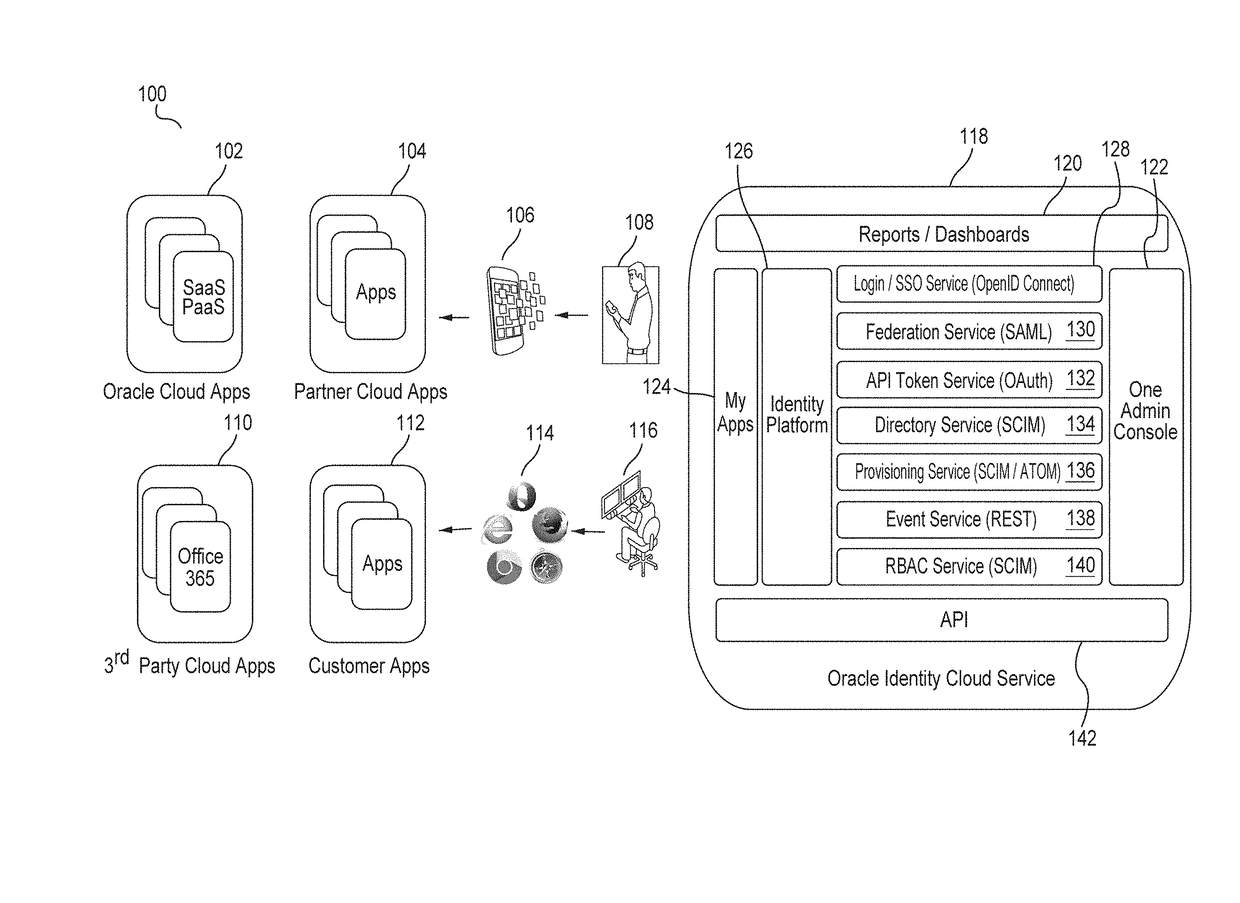
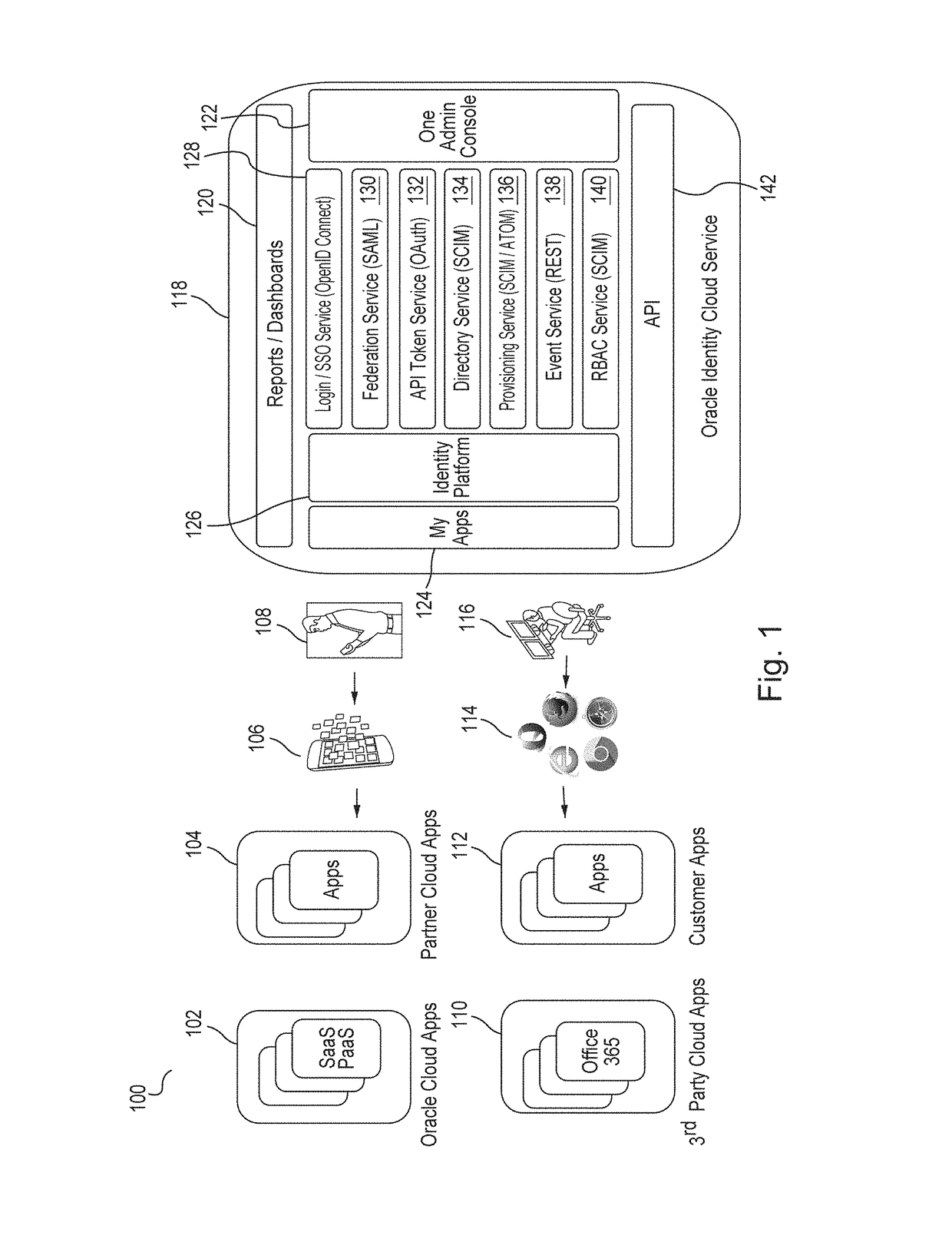
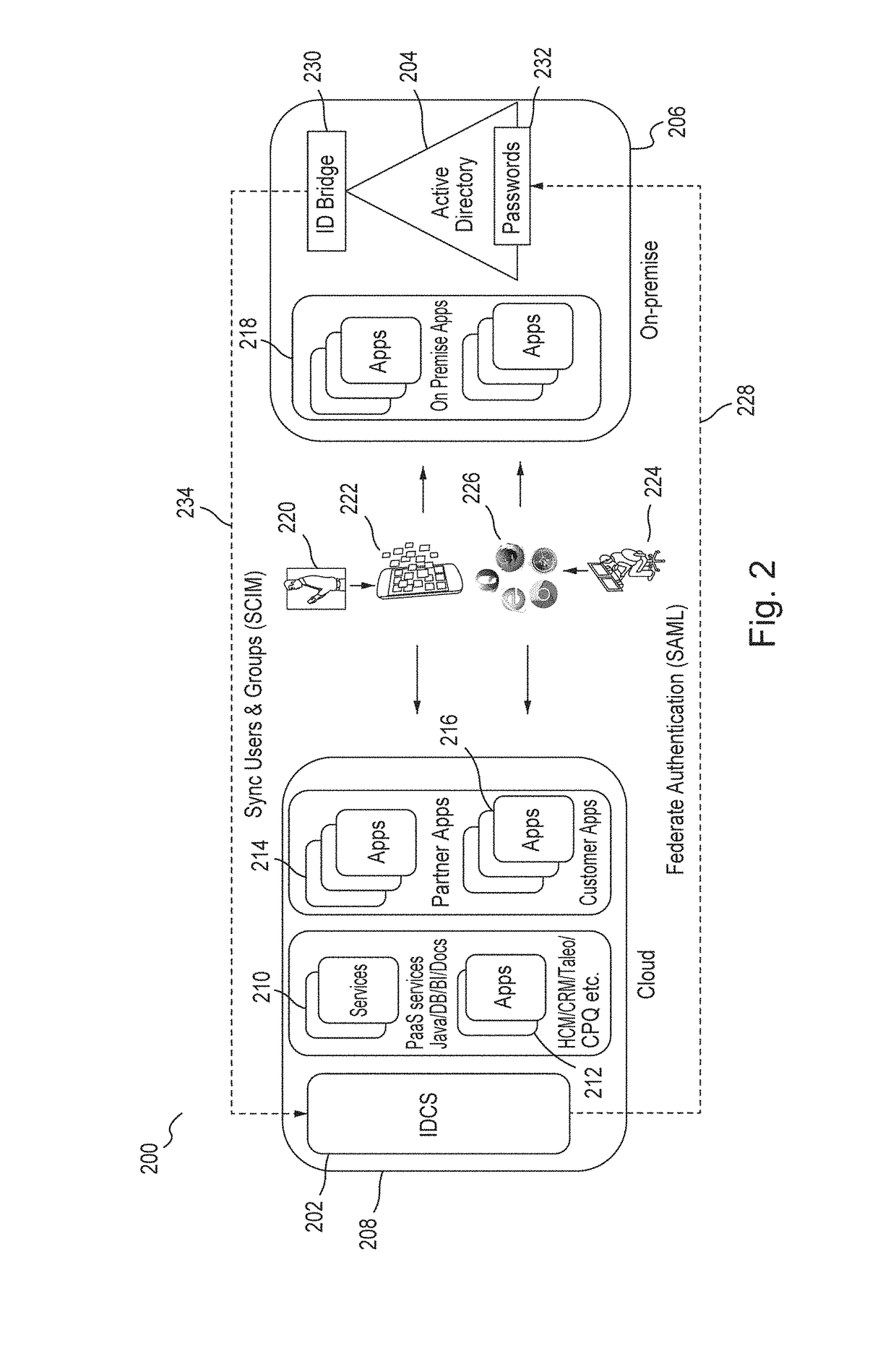
A high availability (HA) Identity Bridge (IDBridge) between an on-premises Active Directory (AD) and a cloud-based Identity Cloud Service (IDCS) is provided. A connection to an AD, coupled to a first network, is established. A connection to an IDCS, coupled to a second network, is established, the IDCS including a System for Cross-domain Identity Management (SCIM) directory. A plurality of selectable AD OUs are displayed in a GUI, and a selection of one or more OUs is then received. Each member group of the selected OUs is displayed in the GUI, and a selection of one or more member groups of the selected OUs is then received. The users of the selected OUs and the selected member groups of the selected OUs are monitored to identify users and groups that have been added, modified or deleted. The identified users and groups are then synchronized to the SCIM directory.
Owner:ORACLE INT CORP
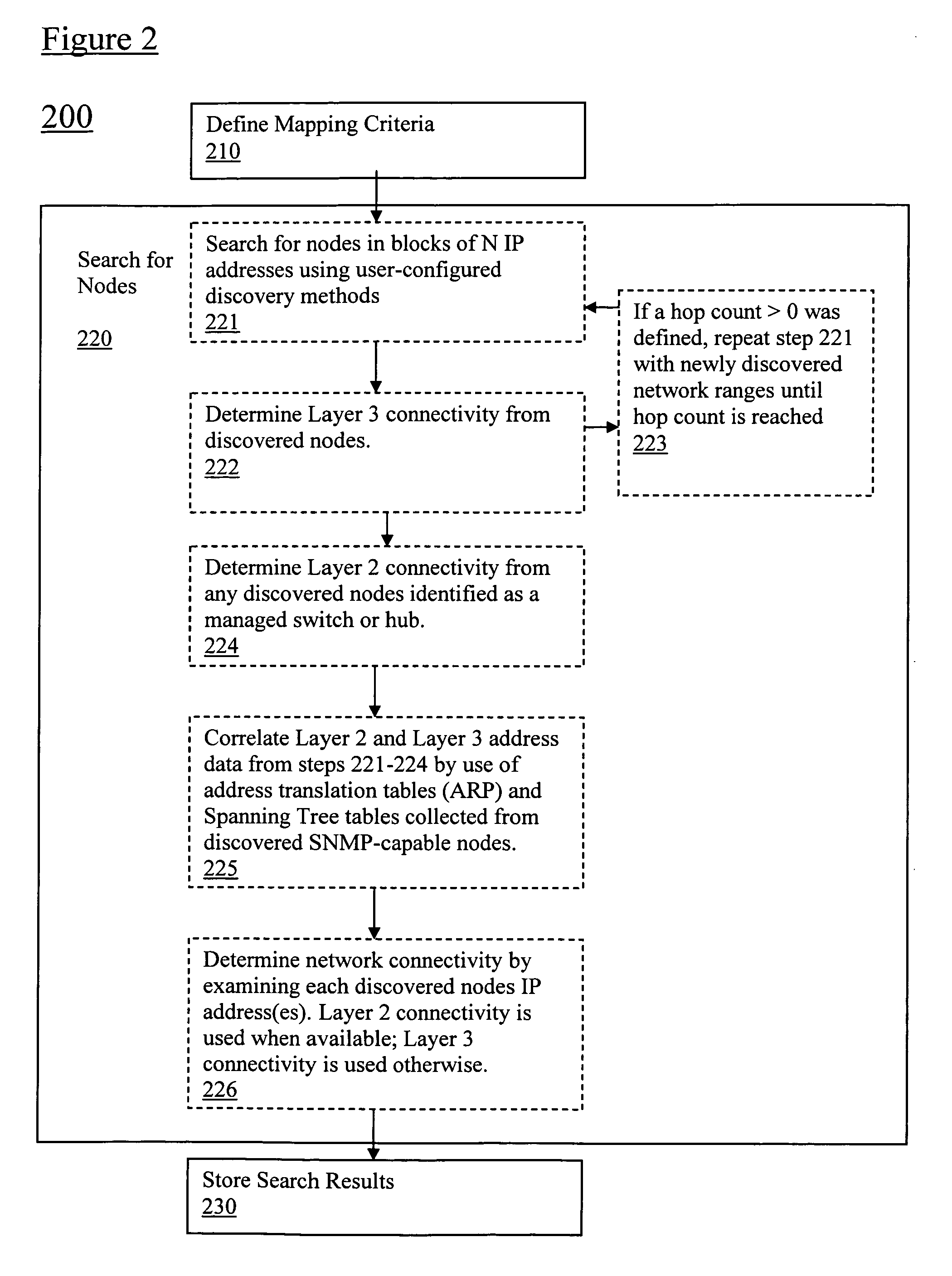
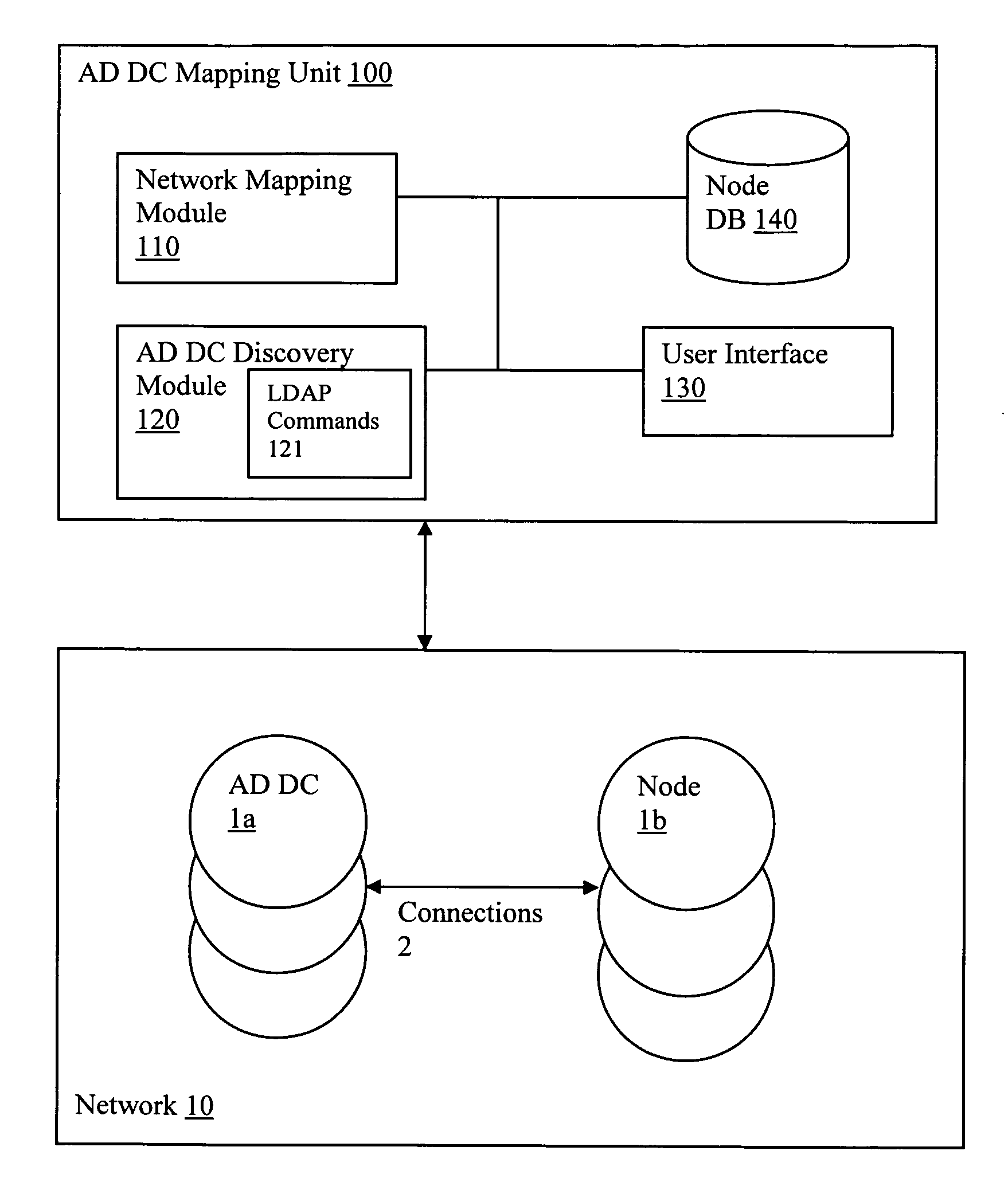
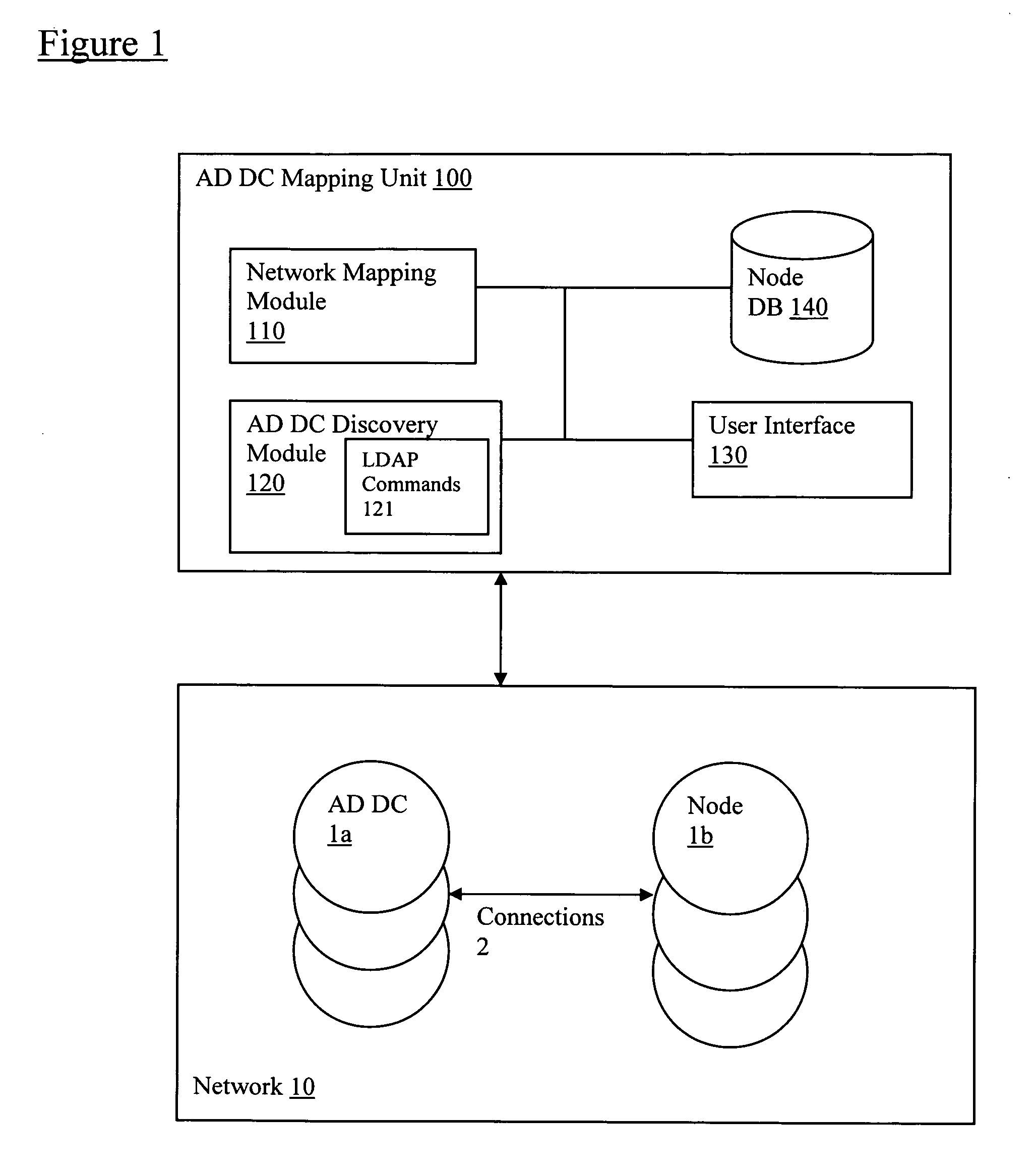
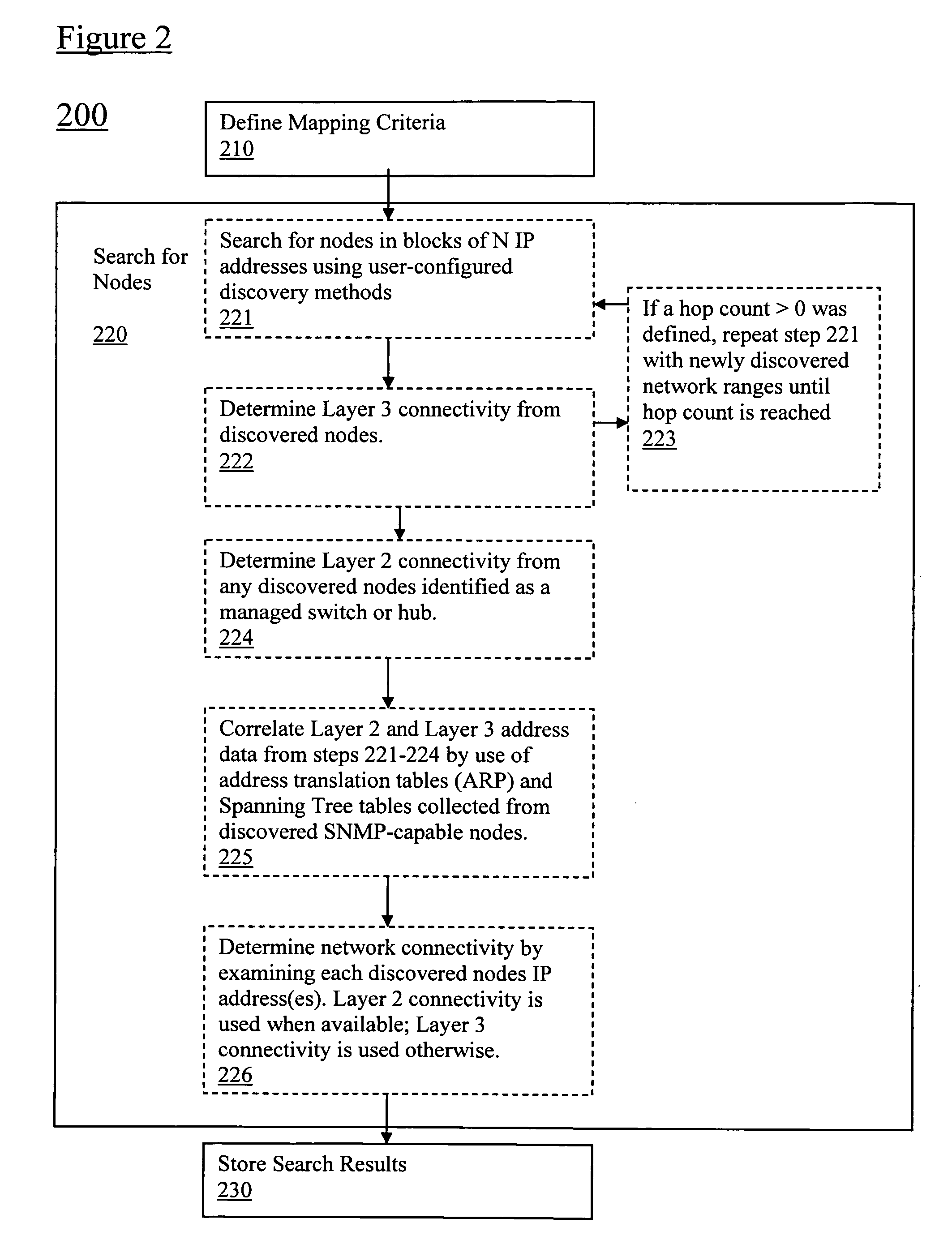
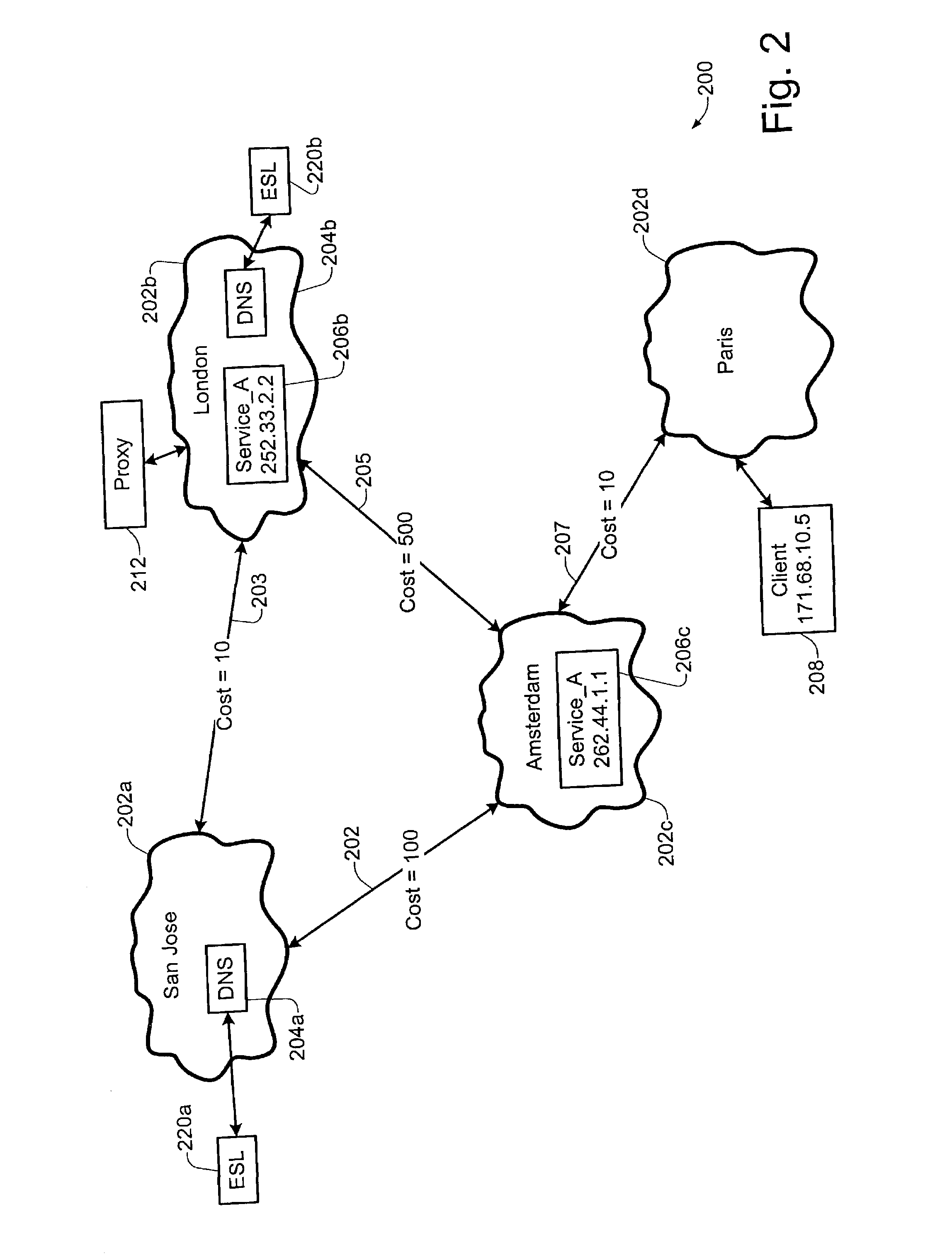
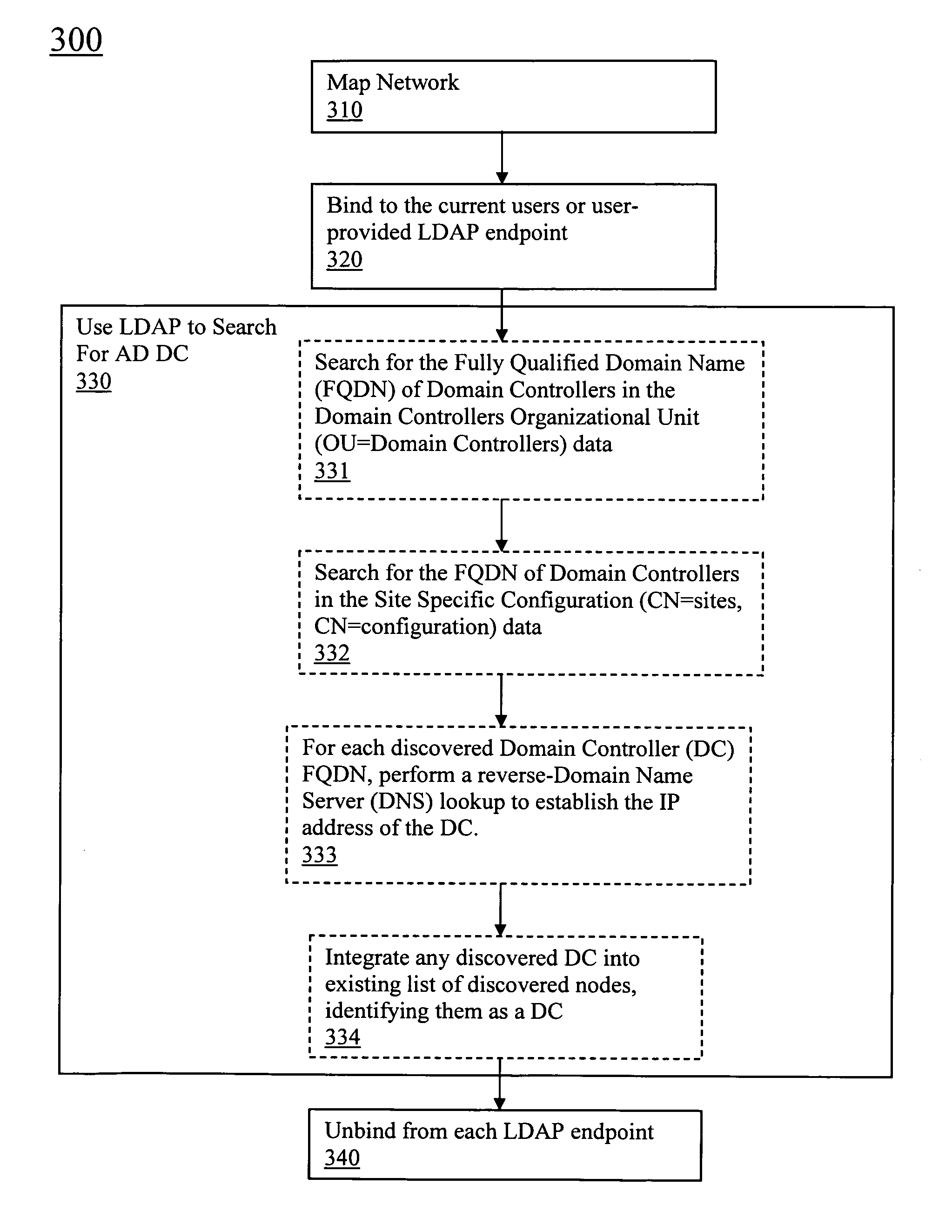
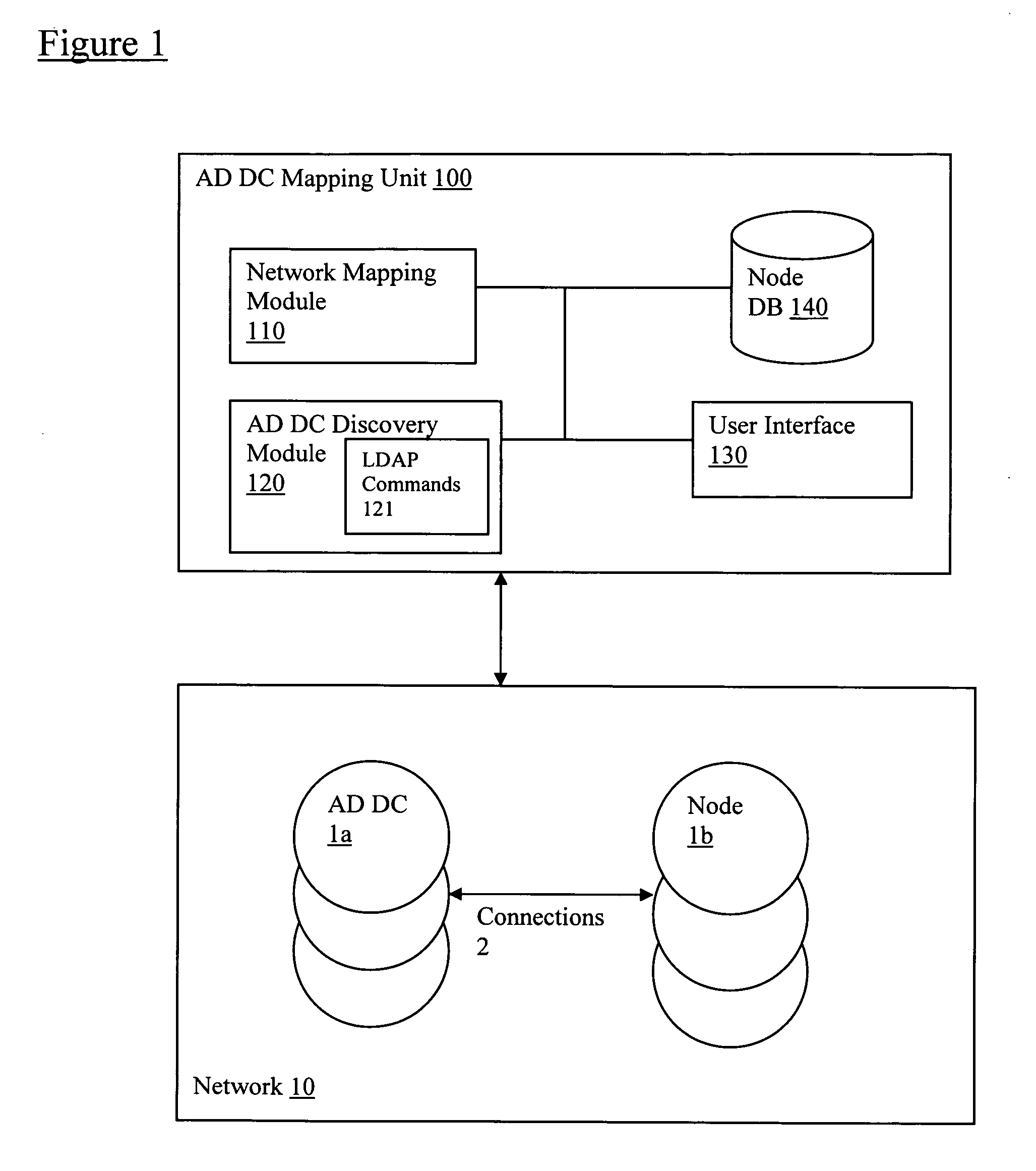
Discovery and visualization of active directory domain controllers in topological network maps
ActiveUS20090285120A1Digital computer detailsData switching by path configurationIp addressSynthetic data
Active directory (AD) Domain Controllers (DC) discovery includes determining the topology of the network, such as the nodes and connections in the network. For example, synthetic data may be transferred within the network and traced to determine the presence and relationships of the various network components. Alternatively, other mapping techniques are based upon mapping a known set of nodes to determine the relationship of the nodes. Next, Lightweight Directory Access Protocol (LDAP) commands are forwarded to the various nodes to identify the AD DC within a range of IP addresses discovered during the mapping of to the topology of the network.
Owner:SOLARWINDS WORLDWIDE
System and method to enable PKI- and PMI-based distributed locking of content and distributed unlocking of protected content and/or scoring of users and/or scoring of end-entity access means—added
ActiveUS9270663B2Key distribution for secure communicationUser identity/authority verificationTrust relationshipApplication software
A central server configured with an Attribute Authority (“AA”) acting as a Trusted Third Party mediating service provider and using X.509-compatible PKI and PMI, VPN technology, device-side thin client applications, security hardware (HSM, Network), cloud hosting, authentication, Active Directory and other solutions. This ecosystem results in real time management of credentials, identity profiles, communication lines, and keys. It is not centrally managed, rather distributes rights to users. Using its Inviter-Invitee protocol suite, Inviters vouch for the identity of Invitees who successfully complete the protocol establishing communication lines. Users establish and respond to authorization requests and other real-time verifications pertaining to accessing each communication line (not end point) and sharing encrypted digital files. These are auditable, brokered, trusted-relationships where such relationships / digital agreements can each stand-alone (for privacy) or can leverage build-up of identity confidence levels across relationships. The service is agnostic to how encrypted user content is transported or stored.
Owner:T CENT
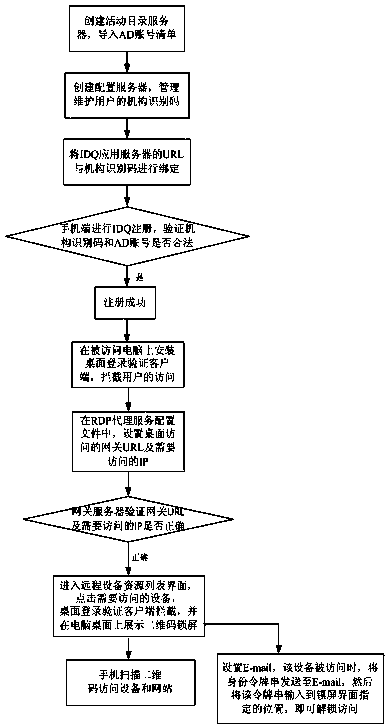
Double-factor identity verification method based on intelligent equipment
InactiveCN103986584AEnsure safetyImprove securityUser identity/authority verificationApplication serverValidation methods
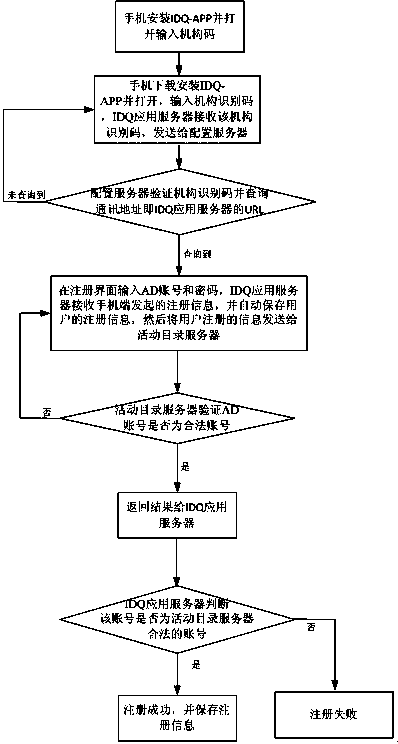
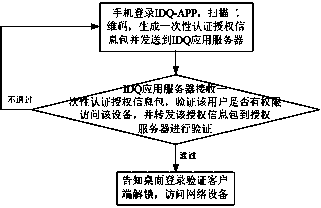
The invention discloses a double-factor identity verification method based on intelligent equipment, which is used for solving the problems of inconvenient operation and low safety of user account numbers and network equipment caused by inputting account numbers and passwords during logging in a long-distance website in the prior art. The double-factor identity verification method based on the intelligent equipment comprises the following steps: establishing an active directory server, and guiding an AD (Active directory) account number list into the active directory server; establishing a configuration server, and managing and maintaining an organization identifying code of a user; binding a URL (Uniform Resource Locator) of an IDQ (internet data query) application server and the organization identifying code; and carrying out IDQ registration at a mobile phone terminal, verifying whether the organization identifying code and the AD account number are legal, if the organization identifying code and the AD account number are legal, registering successfully, otherwise, registering unsuccessfully; and visiting the equipment and a website by using a mobile phone. The double-factor identity verification method has the advantages that the mobile phone is used for scanning real-time alteration two-dimension codes generated by using a verification server so as to carry out login access of network resources, a conventional login manner of inputting the account numbers and the passwords by using a conventional keyboard is replaced, and the safety of the user account numbers and network equipment is greatly guaranteed.
Owner:上海金融云服务集团安全技术有限公司
Service locator technique implemented in a data network
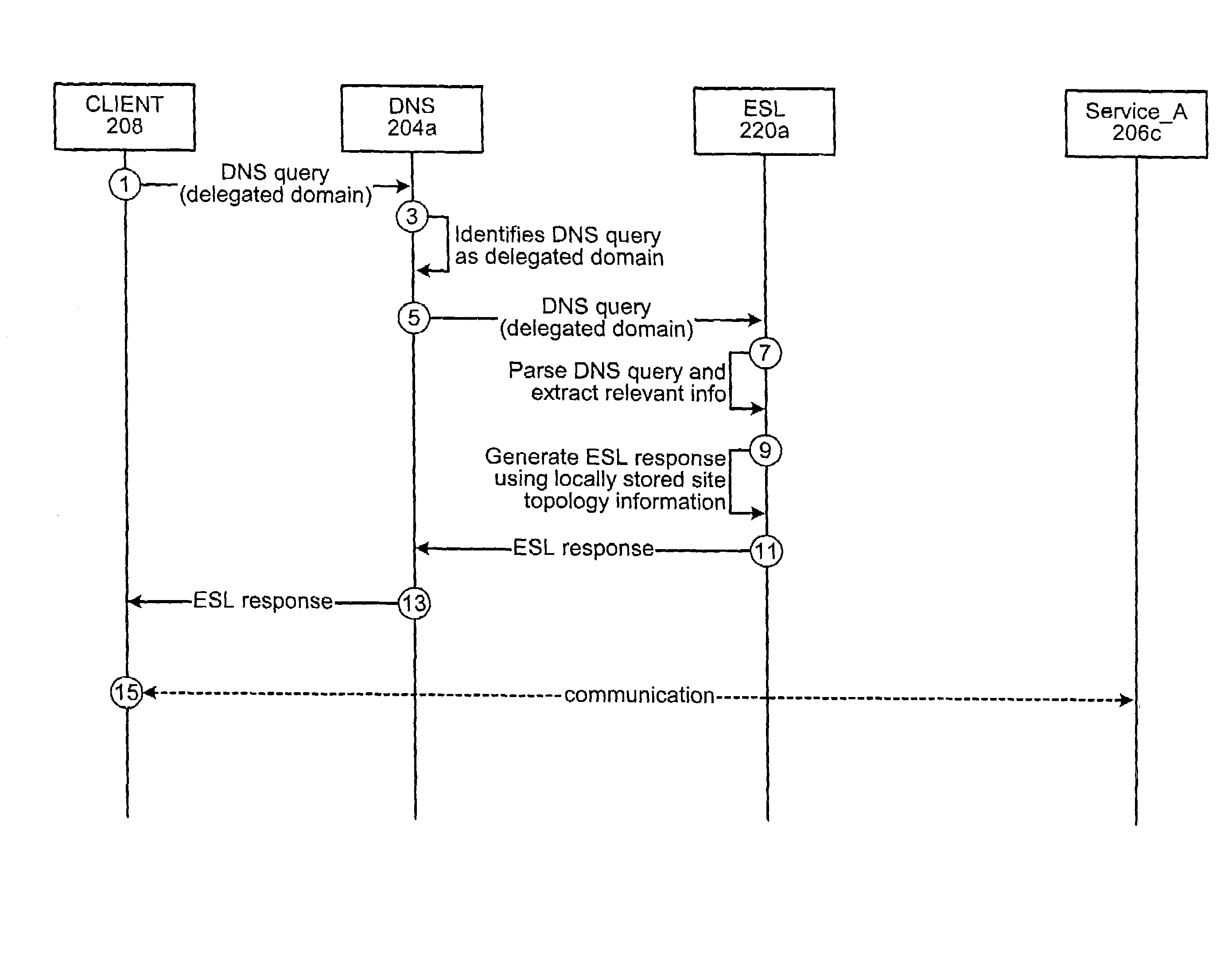
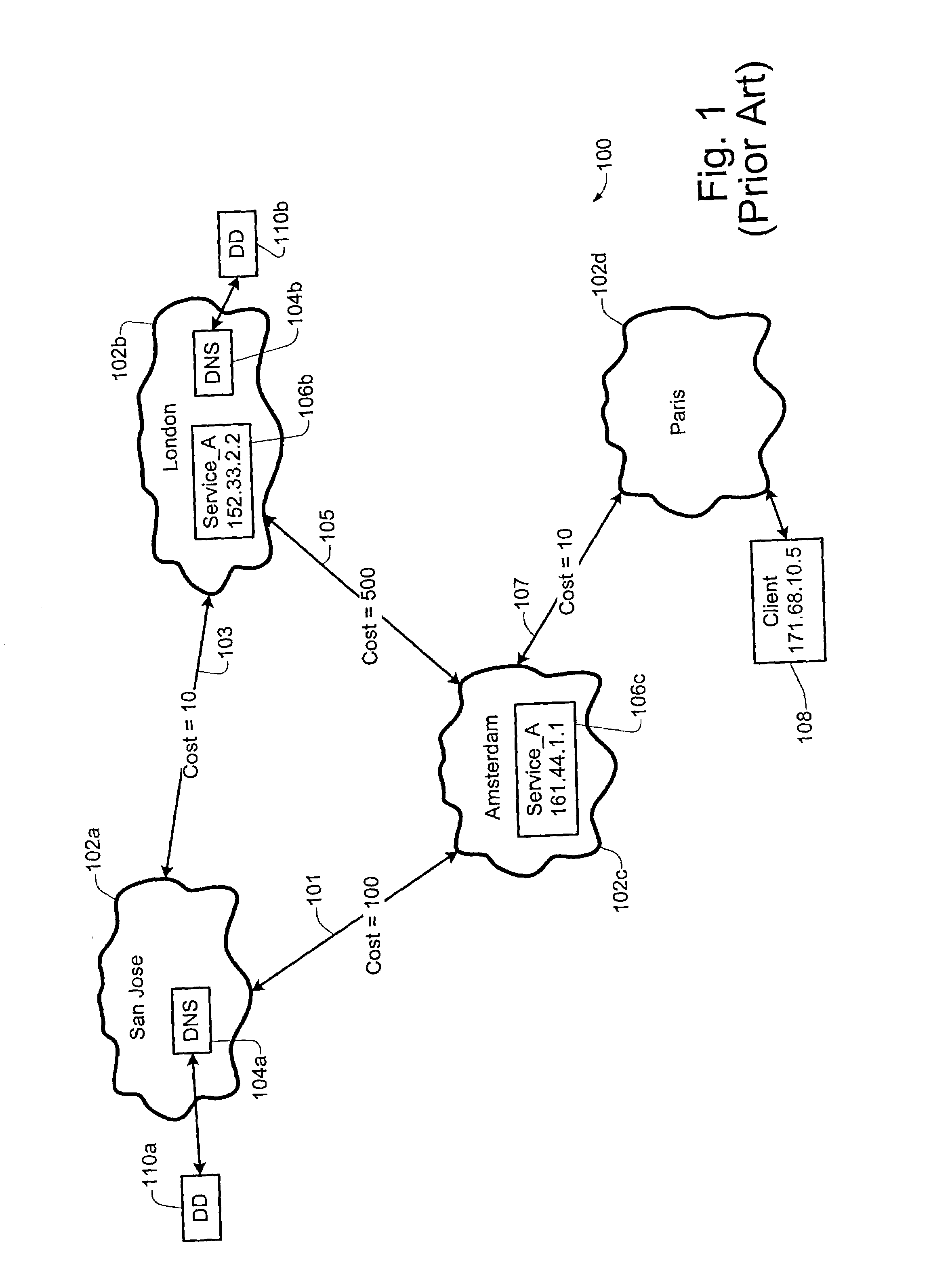
ActiveUS7523170B1Function increaseMultiple digital computer combinationsElectric digital data processingNetwork addressingNetwork address
A service locator technique is described. According to a specific embodiment, the service locator technique may be configured to provide a distributed DNS-based service which may be used for locating services in a given enterprise, network and / or sub-network. According to one implementation, an ESL device of the present invention may be configured to use Microsoft Active Directory replication topology to determine, for example, the locality of the requester, and / or to determine a network address of the closest or most optimal service provider for that requester. Moreover, according to specific embodiments of the present invention, the service locator technique of the present invention may provide a proxy management mechanism in order to allow various network devices (e.g. DNS servers, etc.) to query selected ESL servers for desired information on behalf of any number of clients and / or proxies.
Owner:CISCO TECH INC
Discovery and visualization of active directory domain controllers in topological network maps
ActiveUS8045486B2Digital computer detailsData switching by path configurationIp addressSynthetic data
Active directory (AD) Domain Controllers (DC) discovery includes determining the topology of the network, such as the nodes and connections in the network. For example, synthetic data may be transferred within the network and traced to determine the presence and relationships of the various network components. Alternatively, other mapping techniques are based upon mapping a known set of nodes to determine the relationship of the nodes. Next, Lightweight Directory Access Protocol (LDAP) commands are forwarded to the various nodes to identify the AD DC within a range of IP addresses discovered during the mapping of to the topology of the network.
Owner:SOLARWINDS WORLDWIDE
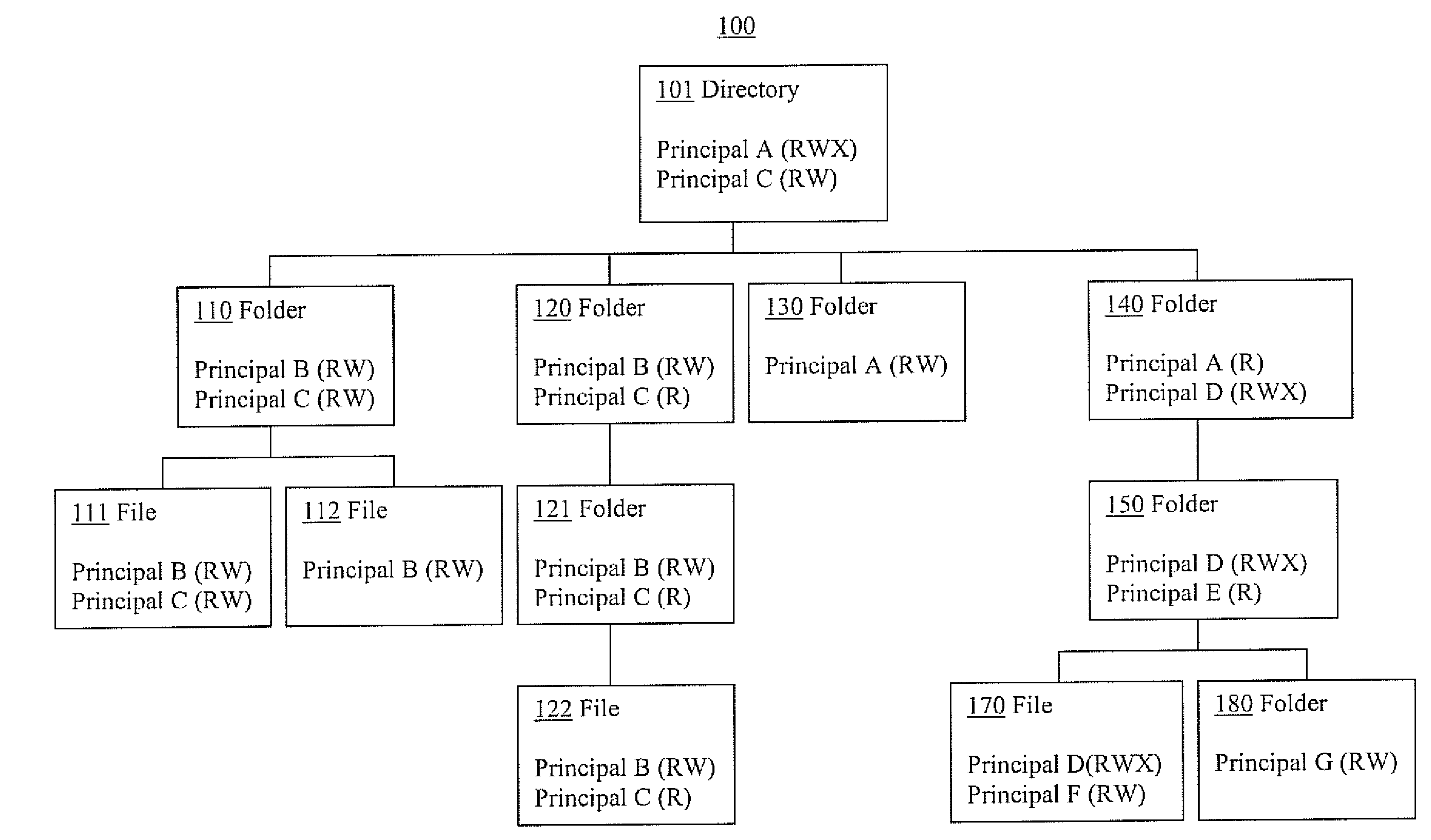
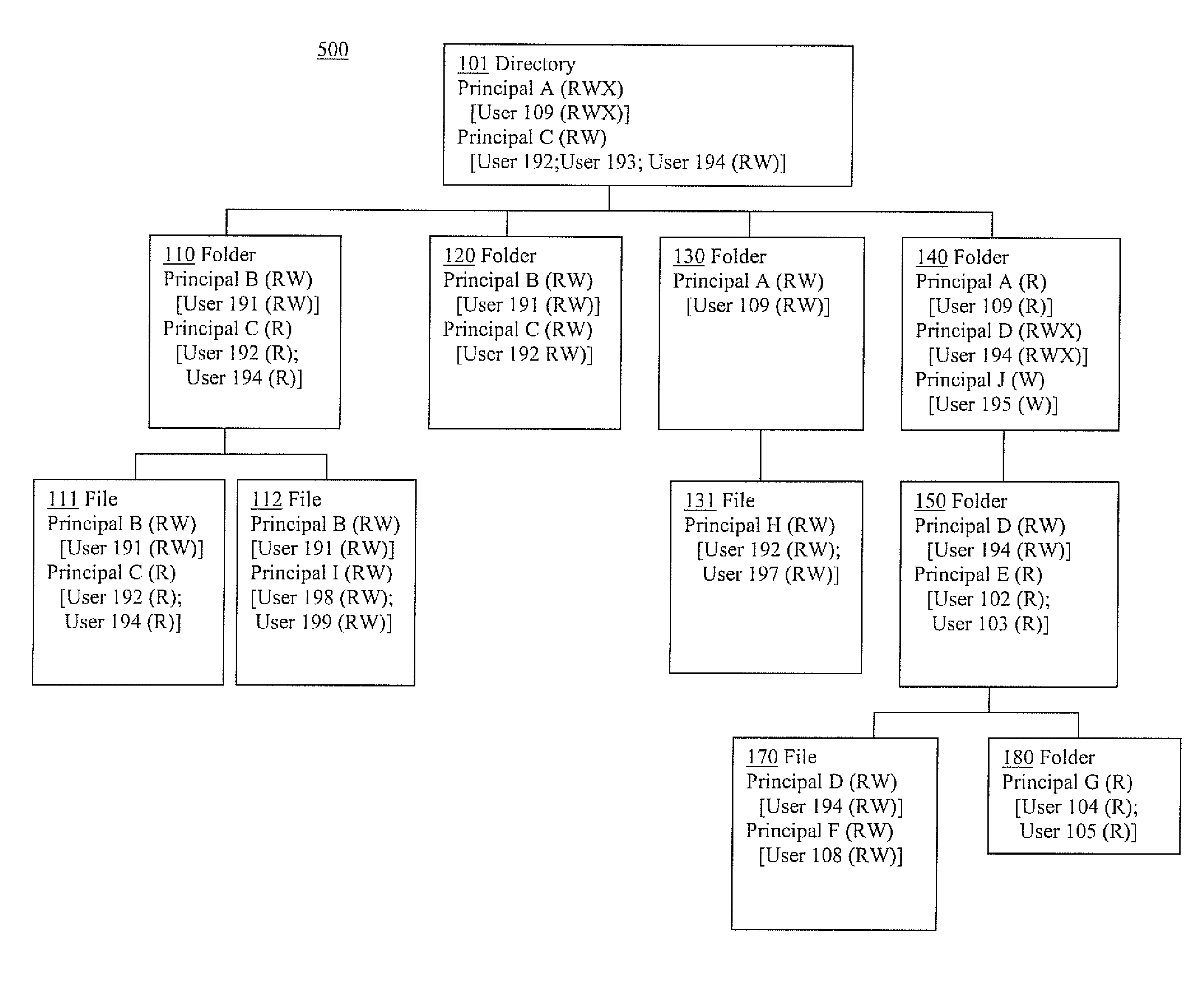
Permission tracking systems and methods
InactiveUS20120011161A1Digital data processing detailsComputer security arrangementsGraphicsGraphical user interface
Systems and methods for permission maintenance are presented. In one embodiment, a permission maintenance method includes: gathering permission indication information including permission indications associated with various stored information; analyzing the permission indication information including analyzing potential permission indication origination; and creating interface presentation information based upon results of the analyzing the permission indications, wherein the interface presentation information includes information related to potential origination of a permission indication. The gathering can include scanning a file system and collecting active directory information. The analyzing can include determining the type of access a principal is given to a file. The analyzing can also include determining if a principal is associated with a group and the type of permissions given to the group. In one exemplary implementation, the permission indication information is organized in accordance with potential permission indication origination. In one embodiment, the interface presentation information is presented in a Graphical User Interface, including a permission indicator and the information related to potential origination of the permission indicator.
Owner:VERITAS TECH
Permission tracking systems and methods
InactiveUS8959115B2Digital data processing detailsDigital data protectionGraphicsGraphical user interface
Systems and methods for permission maintenance are presented. In one embodiment, a permission maintenance method includes: gathering permission indication information including permission indications associated with various stored information; analyzing the permission indication information including analyzing potential permission indication origination; and creating interface presentation information based upon results of the analyzing the permission indications, wherein the interface presentation information includes information related to potential origination of a permission indication. The gathering can include scanning a file system and collecting active directory information. The analyzing can include determining the type of access a principal is given to a file. The analyzing can also include determining if a principal is associated with a group and the type of permissions given to the group. In one exemplary implementation, the permission indication information is organized in accordance with potential permission indication origination. In one embodiment, the interface presentation information is presented in a Graphical User Interface, including a permission indicator and the information related to potential origination of the permission indicator.
Owner:VERITAS TECH
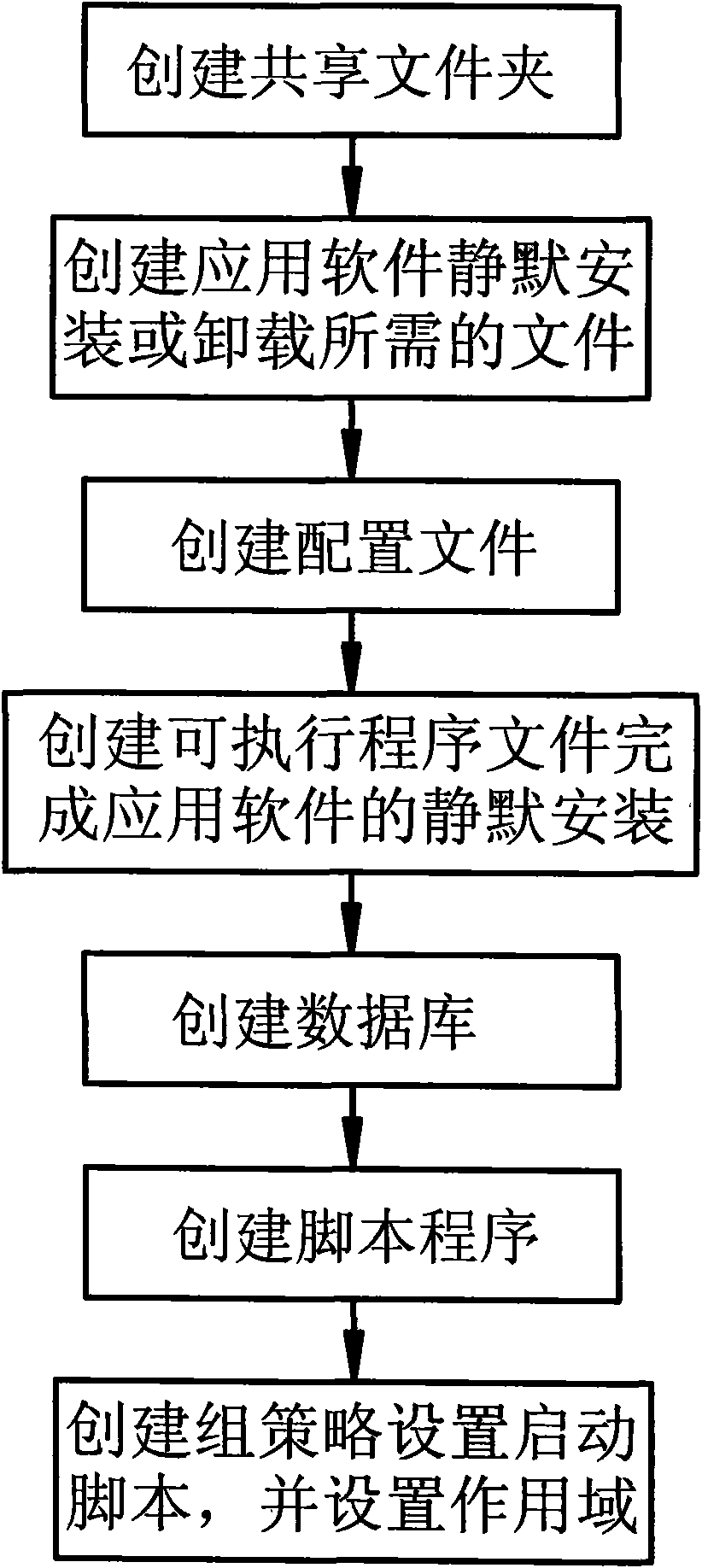
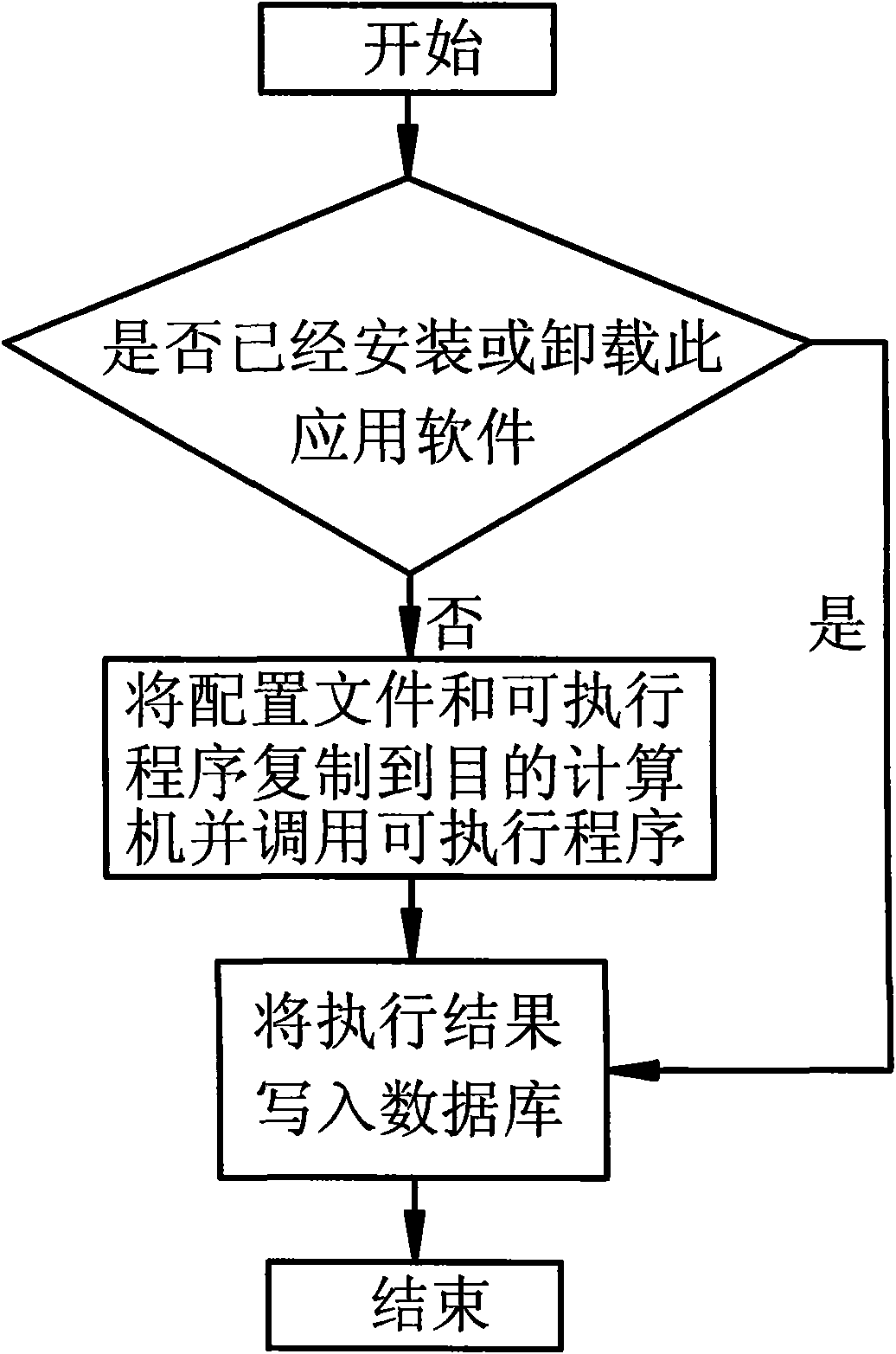
Method for automatically installing or uninstalling application software of computers and a device thereof
InactiveCN101515238AFlexible and automatic installationFlexible offloadingProgram loading/initiatingSupport groupApplication software
The invention discloses a method for automatically installing or uninstalling application software of computers and a device thereof; the device comprises a booting script supporting group policy based on Windows Server 2003 active directory; the method comprises the followings steps: executing appointed script programs through the group policy during booting of the computer, creating a shared folder on a server; creating program files required by silent installation or uninstallation and storing the program files in the shared folder, creating a configuration file for storing the shared path of the files obtained in the previous step, creating the path stored according to the configuration file, creating a database for storing the results of installing or uninstalling application software of the target computer, creating booting script programs, and creating new group policy to set the scripts as booting scripts and establish link between the booting scripts and an organization unit. The invention has the positive effects of achieving the flexible automatic installation or uninstallation of application software, facilitating use, simplifying the operations, returning the installation results and reducing the human intervention.
Owner:LUXI CHEM GRP
System and method for authenticating remote users
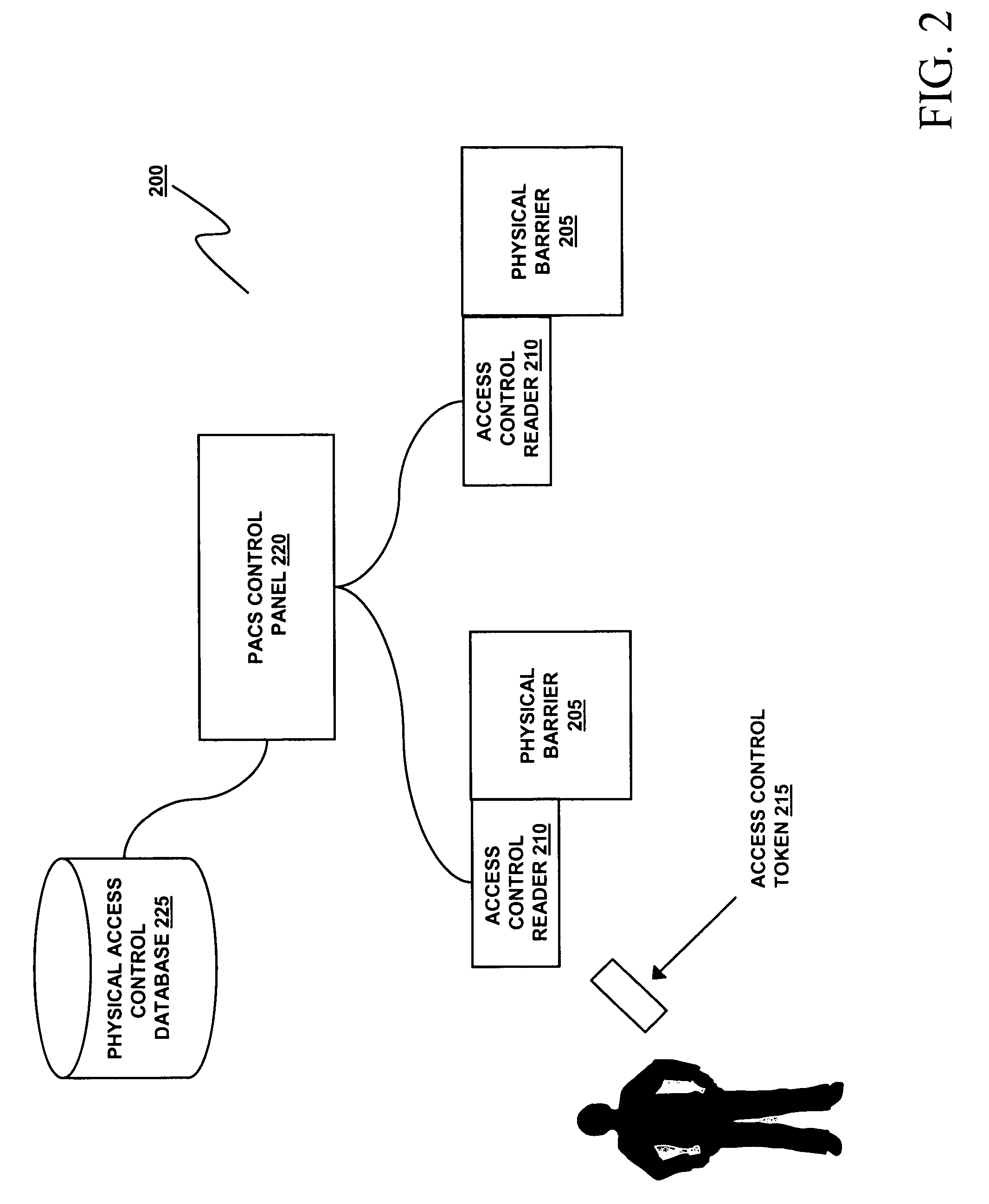
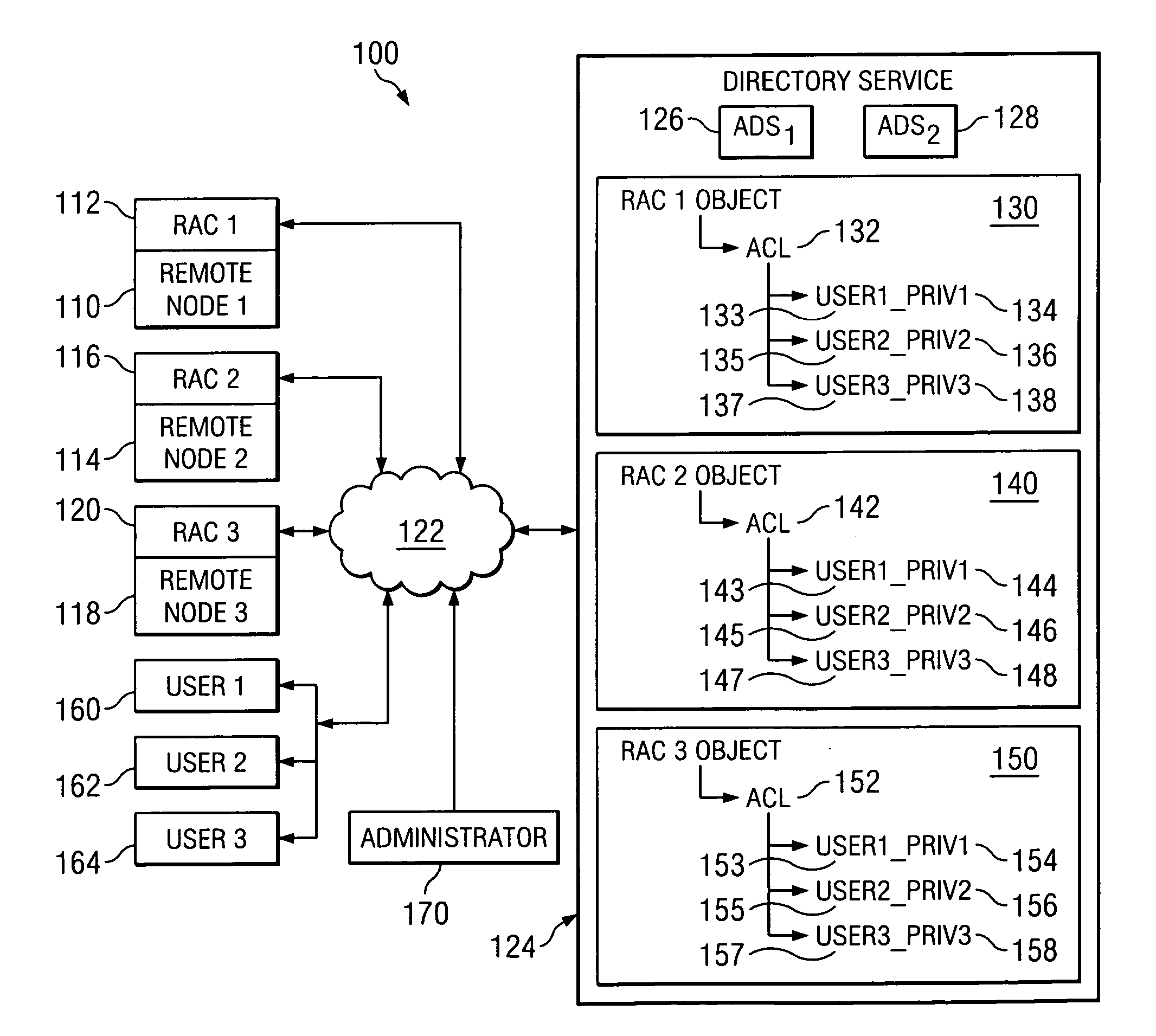
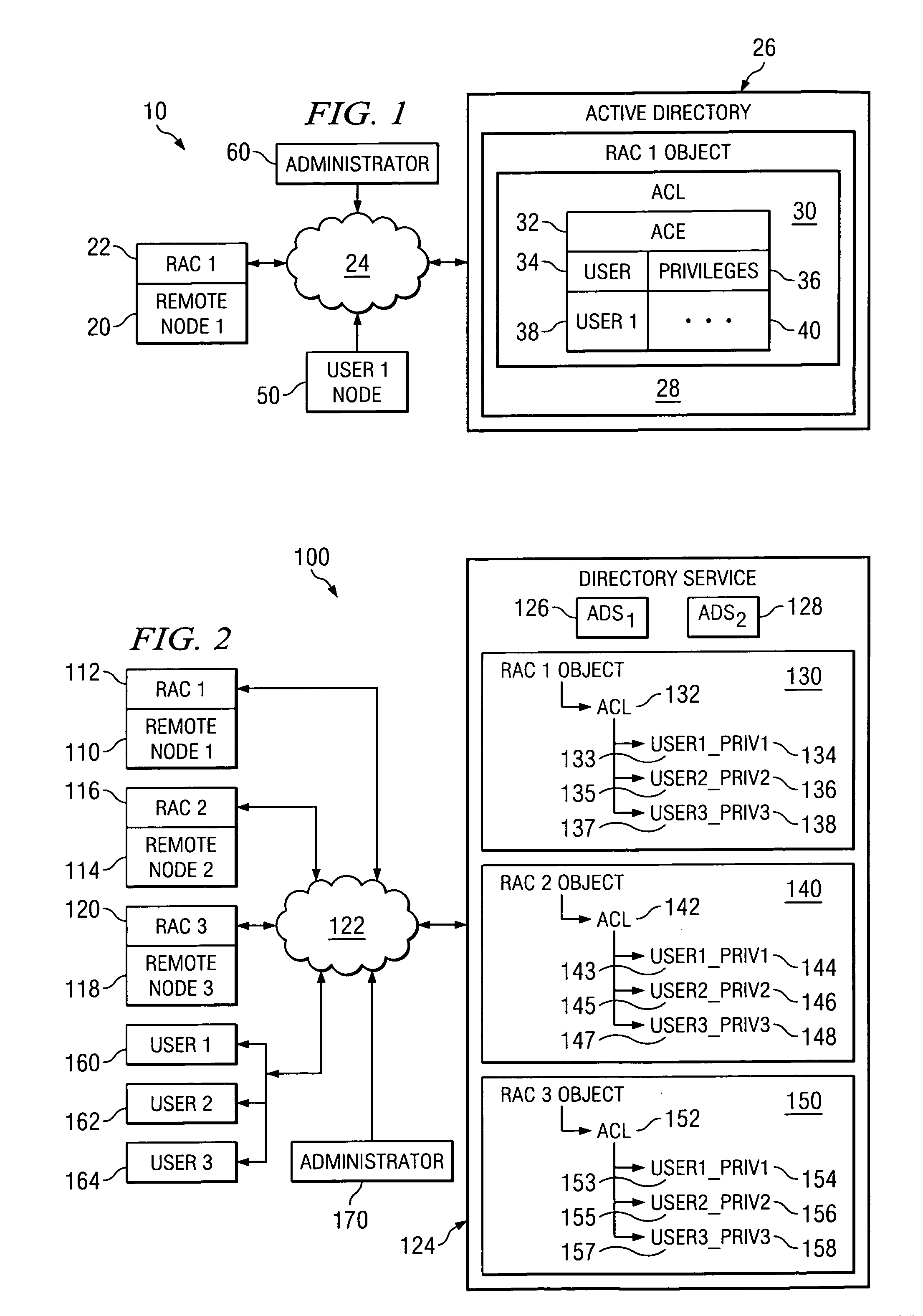
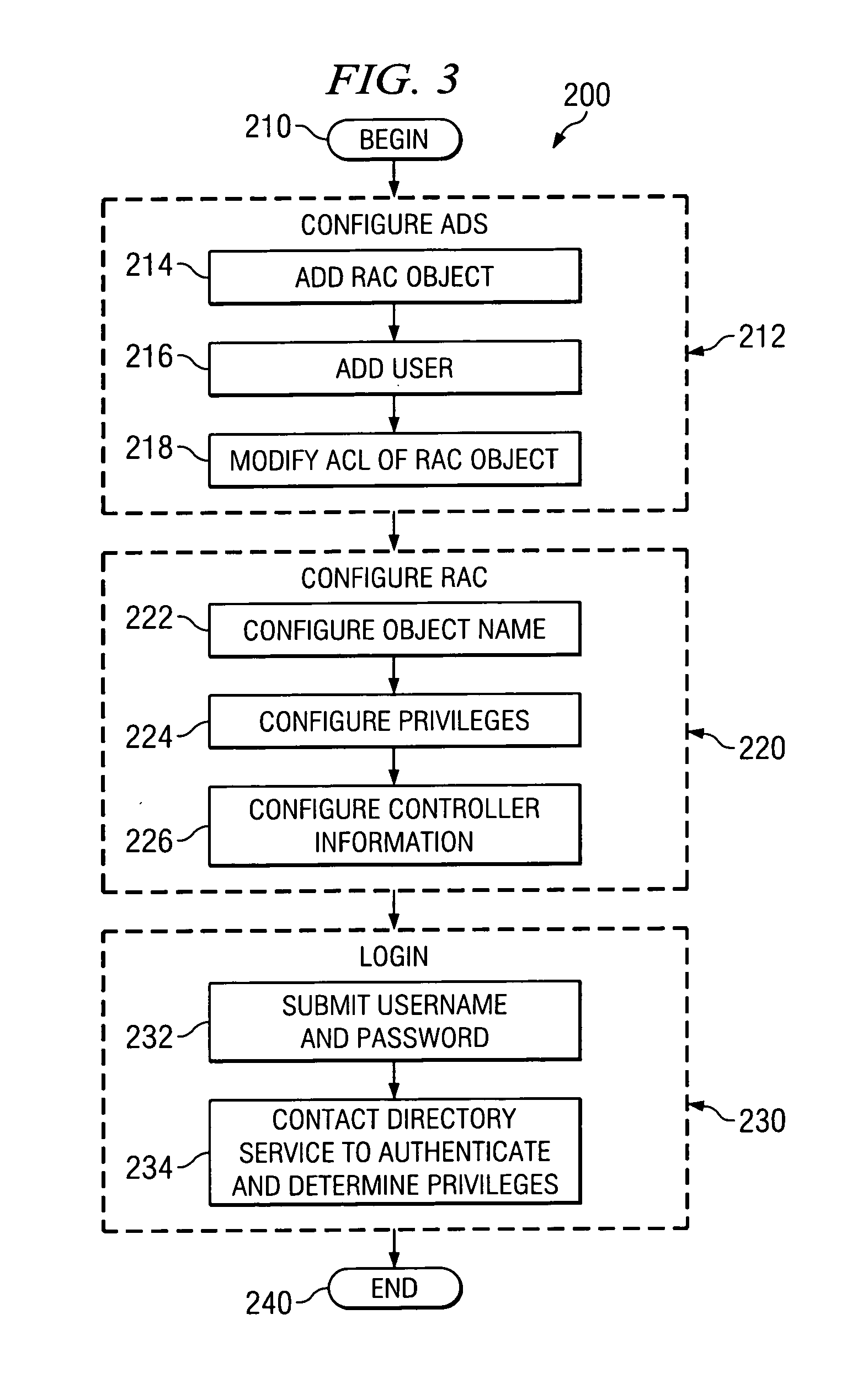
An Active Directory (AD) is utilized to authenticate a remote user to a server or node by providing an object corresponding to the node. The object include an Access Control Entry (ACE) that is listed within an Access Control List (ACL). The ACE also lists privileges that are designated for each specified user. The AD is then queried by the Remote Access Card of a node to authenticate the username and password of a remote user and to determine the privileges granted to such user.
Owner:DELL PROD LP
Unified identity authentication system based on cloud platform
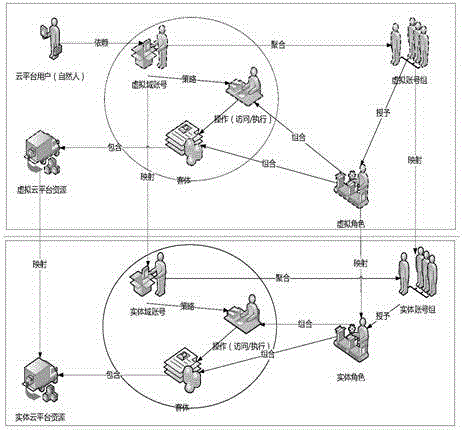
ActiveCN105429999ASolve management problemsSolve control problemsTransmissionCentralized managementVirtual computing
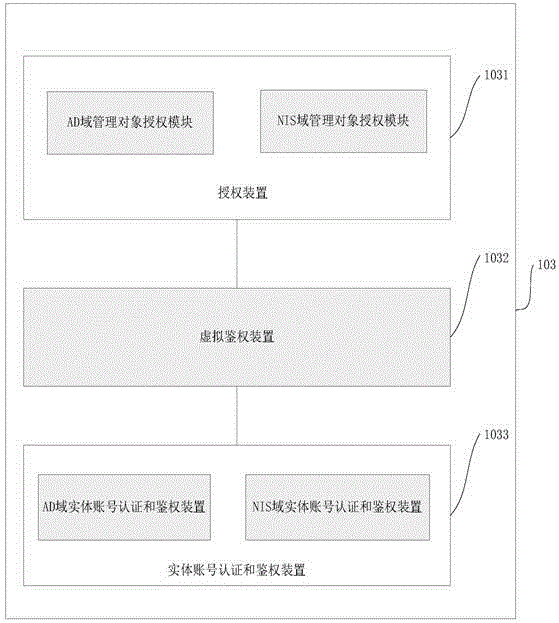
The invention discloses a unified identity authentication system based on a cloud platform, comprising a management subsystem (101) which carries out centralized management to a user, a virtual computing resource, a virtual software resource and a virtual identity object and is responsible for correlation relationship management of the user and the virtual object; a mapping subsystem (102) which maps the virtual object and an entity object managed by the management subsystem (101); an access control subsystem (103) which defines the authority of the mapped entity object; a data storage subsystem (104) which stores the data, the entity AD (active directory) domain data and the entity NIS (network information service) domain data used by the management subsystem (101), wherein the user has an AD domain account and an NIS domain account, the entity object comprises an entity AD group and an entity NIS group, the AD is an active directory, NIS is network information service. Management and control problems of resource access authority after unified authentication are effectively solved by using the unified identity authentication system.
Owner:UNITED ELECTRONICS
Method and system for implementing dynamic catalog based on regulation
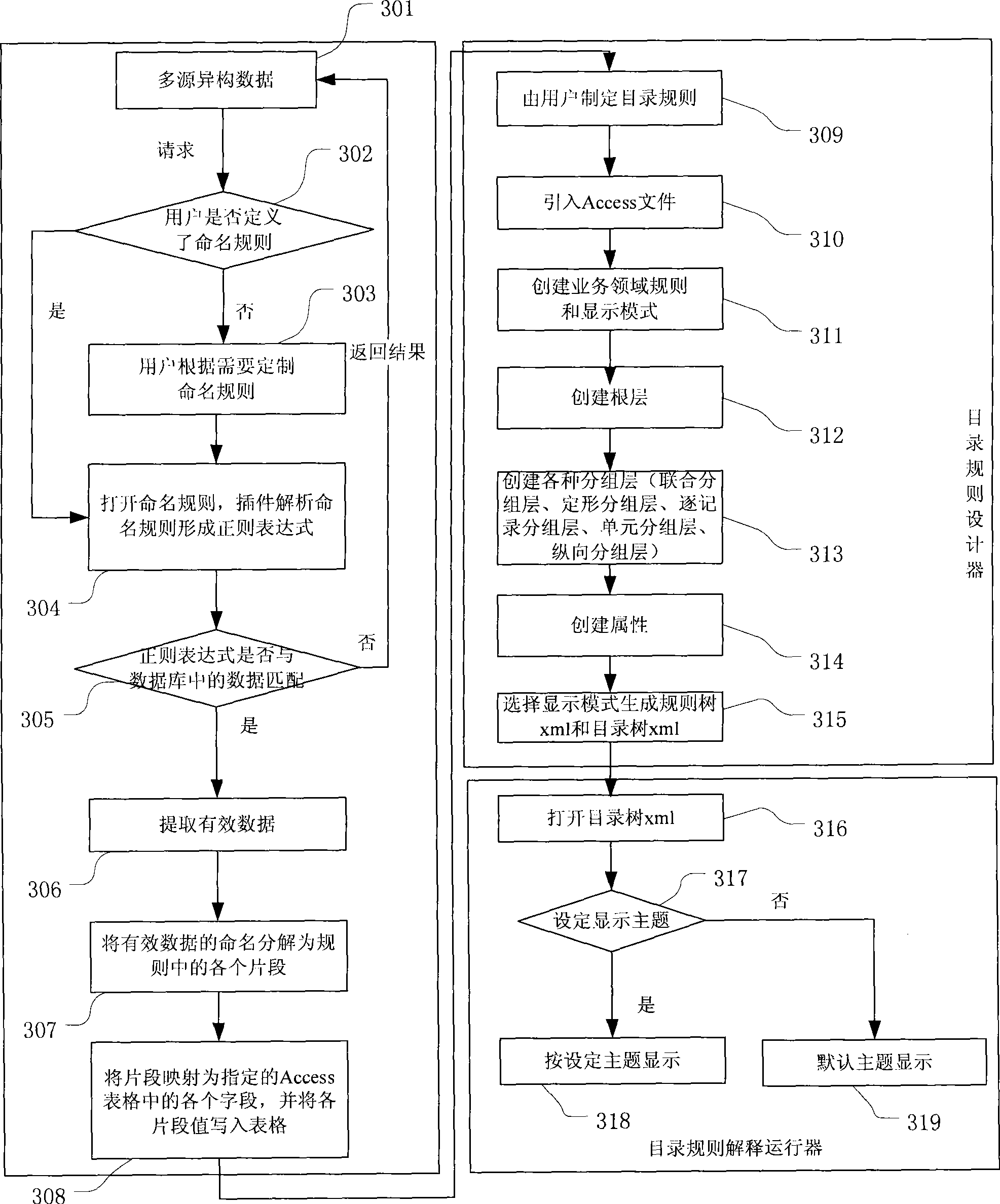
ActiveCN101464879AReal-timeHave needsSpecial data processing applicationsExtensible markupDynamic data
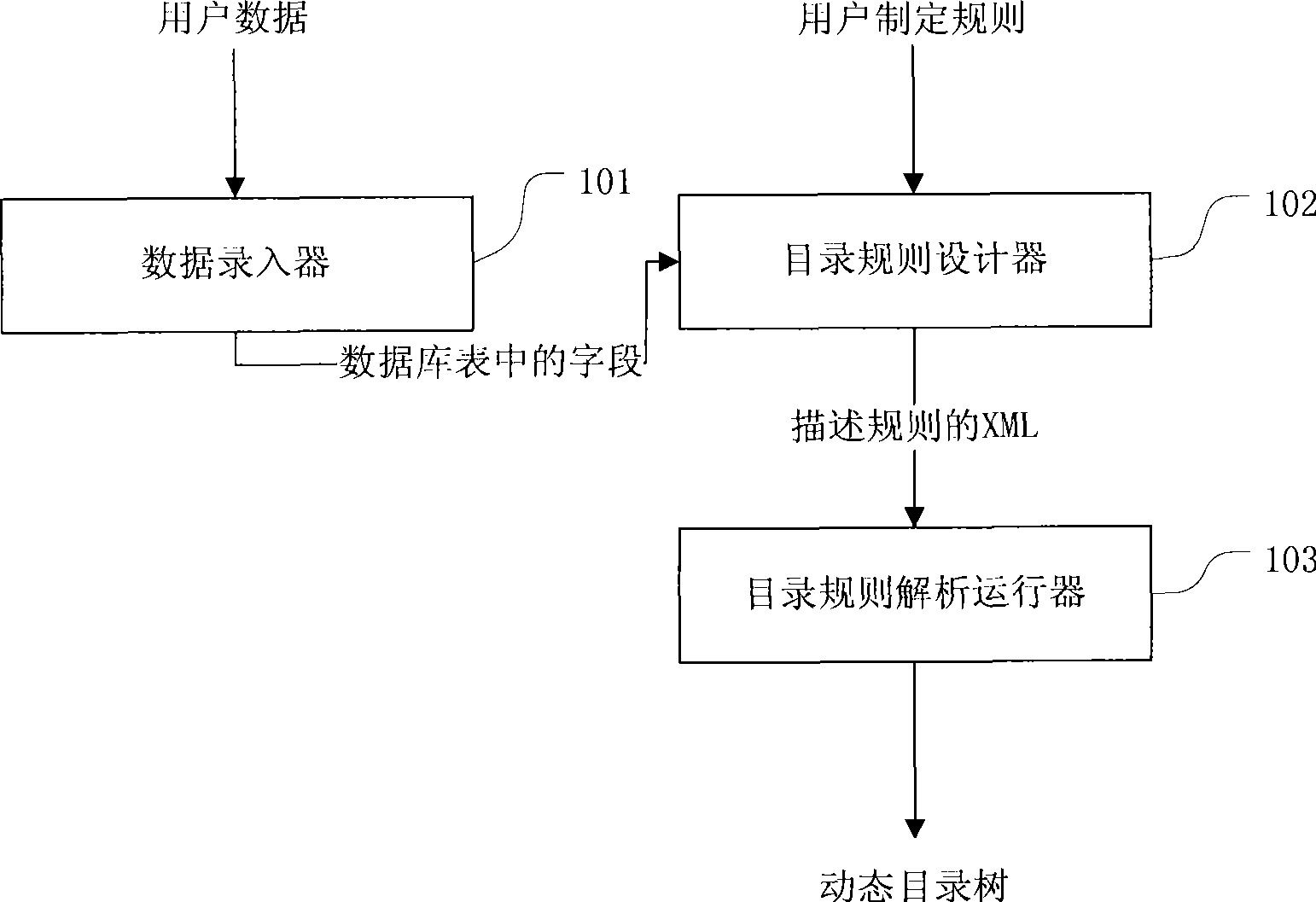
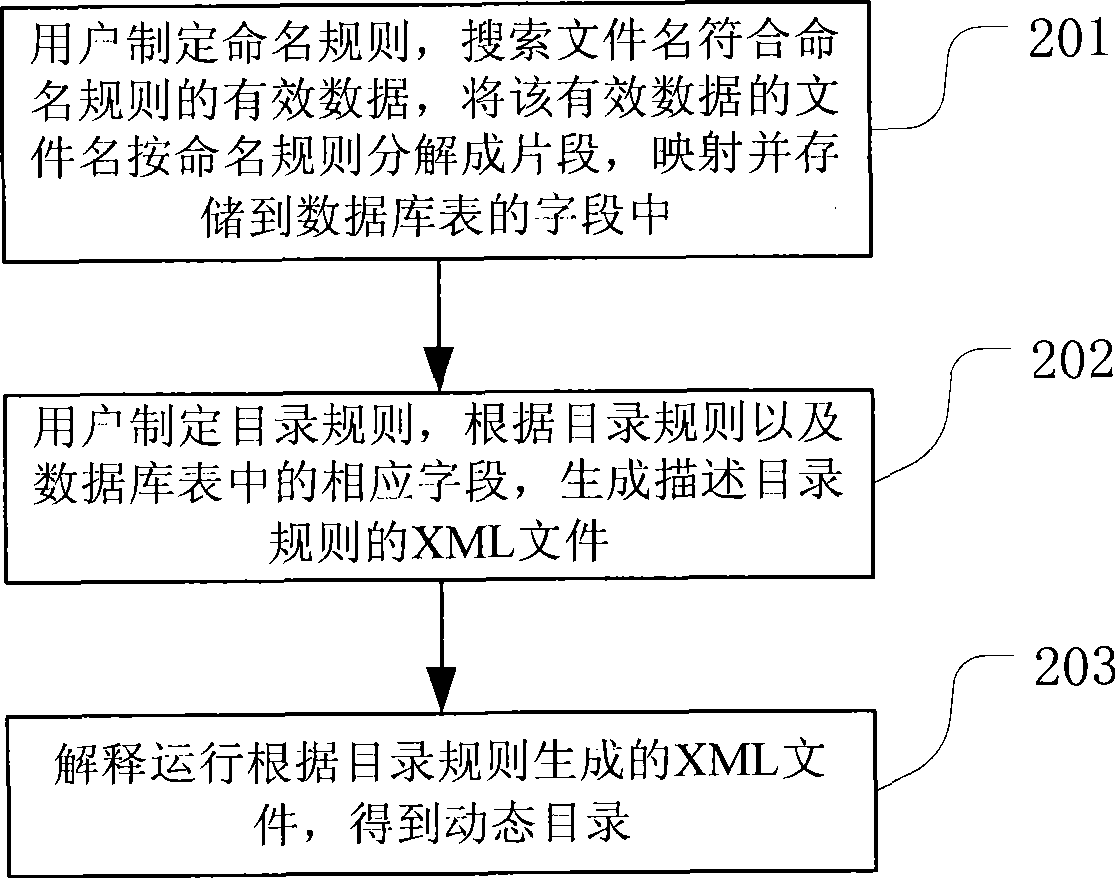
The invention discloses a method and a system for realizing active directory based on rules. Directory rules are set by a user; extend markup language (XML) files used for describing directory rules are generated by a directory rule designer according to the directory rules set by the user and corresponding fields in a database table; and the XML file is interpreted and run by a directory rule running interpreter, so as to obtain a dynamic directory tree. A dynamic data directory provided by the invention provides the user with the method for effectively managing multi-source heterogeneous data, particularly managing spatial data; and the invention has the advantages of dynamics, real time for users and randomness of application demand.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN) +1
Redundancy device for aircraft electric brake pressure sensor and method for controlling redundancy device
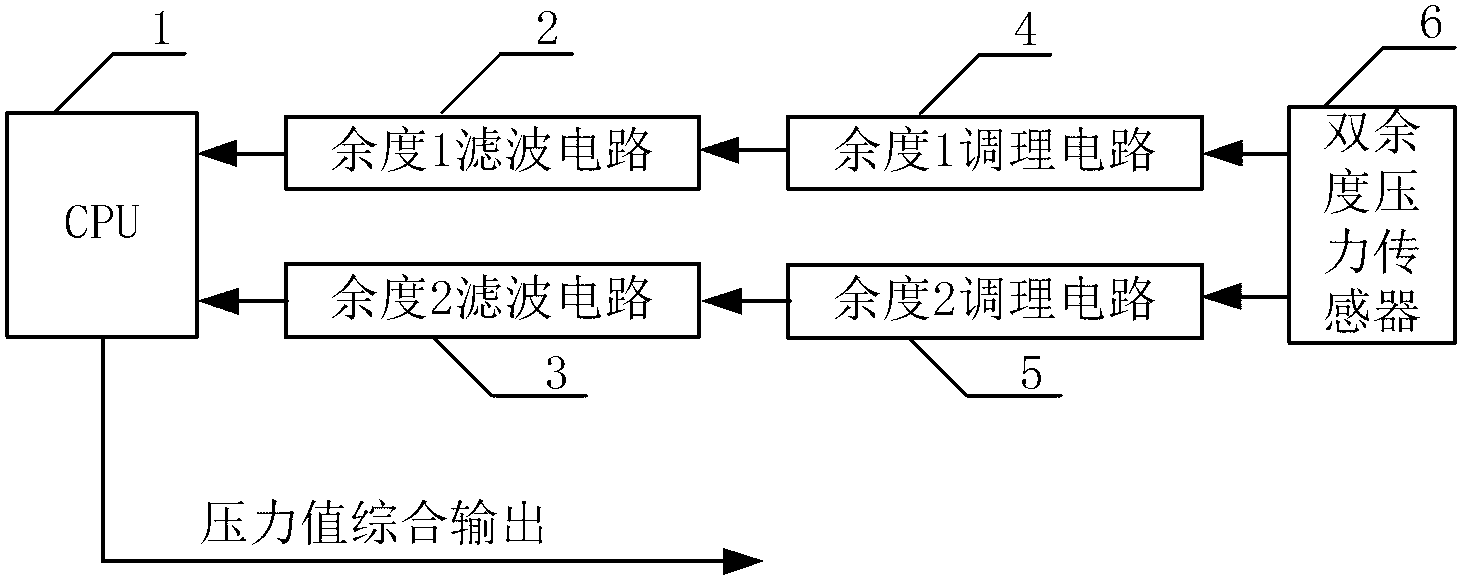
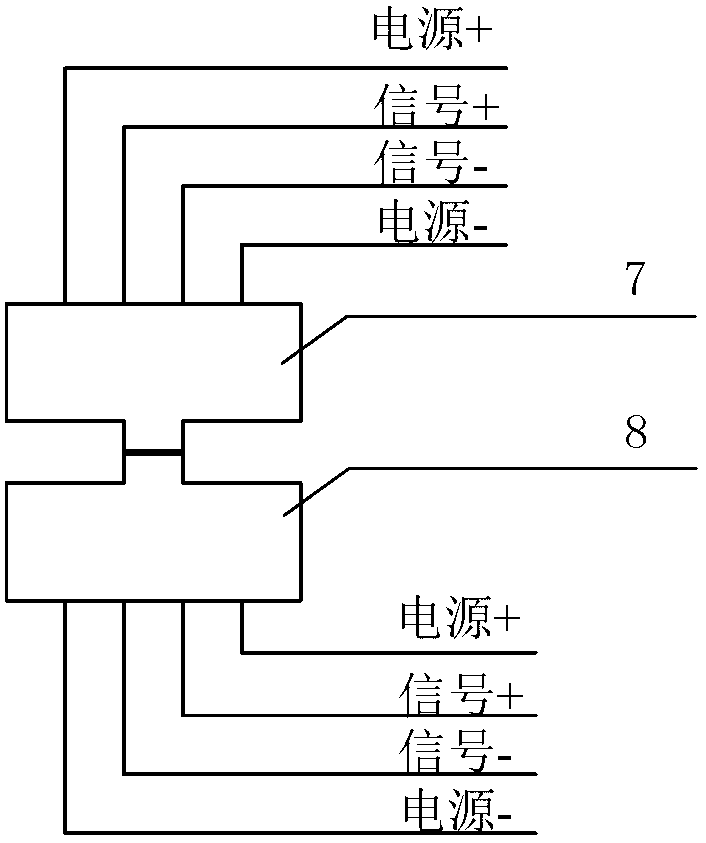
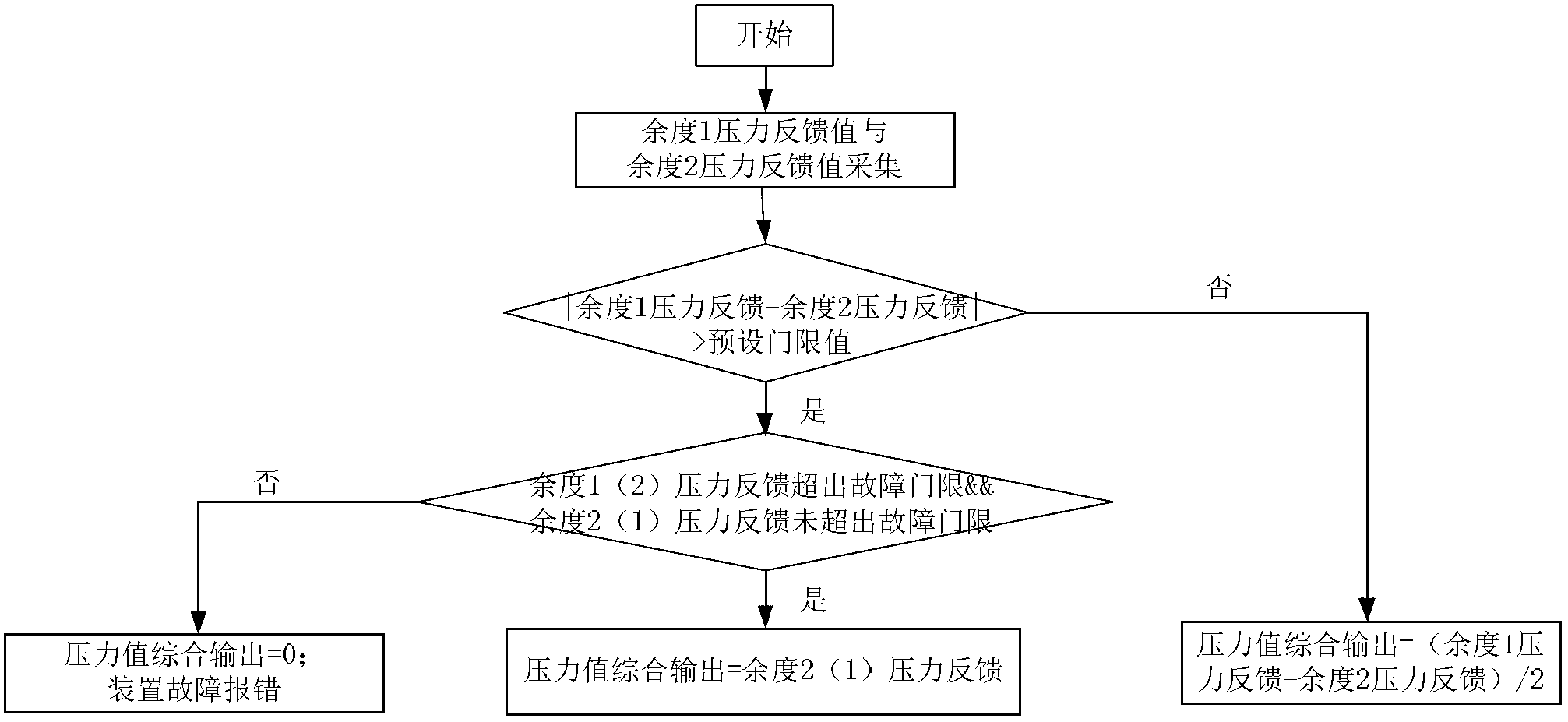
InactiveCN102706505AReduce mistakesHigh precisionApparatus for force/torque/work measurementElectricityPressure sensor
The invention discloses a redundancy device for an aircraft electric brake pressure sensor and a method for controlling the redundancy device. Double redundancy pressure sensors acquire the brake pressure of the same points on an aircraft braked wheel and output two channels of brake pressure values; an adjustment circuit respectively adjusts the brake pressure values as voltage values which can be identified by an active directory (AD) port of a central processing unit (CPU); and the voltage values are respectively filtered by a filter circuit and input to the CPU. The invention has the advantages that when the redundancy pressure sensors normally operate, the accuracy of the pressure sensors can be improved; and when a certain redundancy pressure sensor fails, failure points are automatically detected, the redundancy pressure sensor which fails is isolated, aircraft brake pressure is continuously monitored by using the normal pressure sensor, and the reliability of the aircraft electric brake pressure sensor is effectively improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
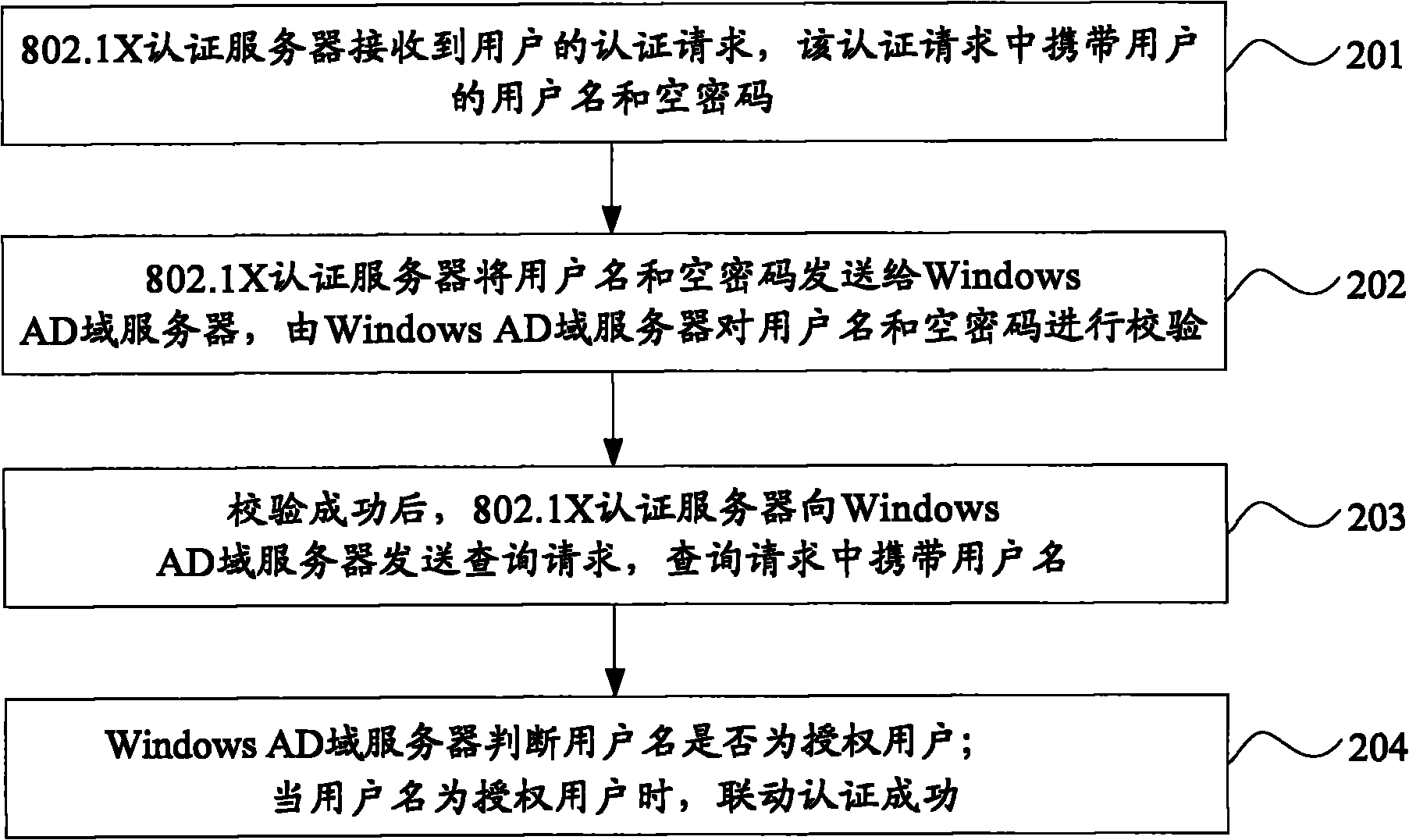
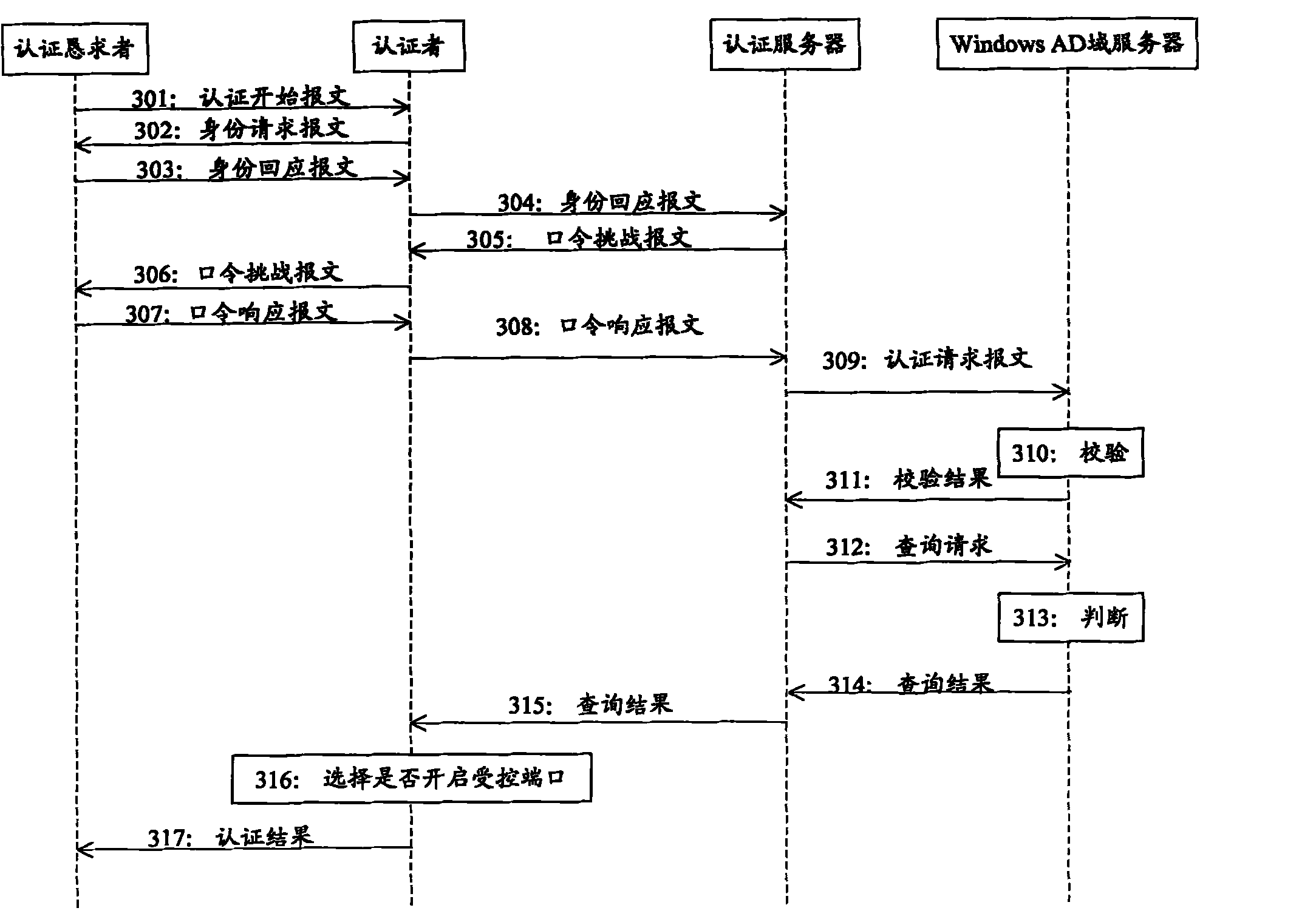
Authentication method, server and system
ActiveCN101986598AThe Drawbacks of Controlling Unrestricted Access to the NetworkLow costUser identity/authority verificationPasswordAuthentication server
The invention provides an authentication method, an authentication server and an authentication system. The authentication method is used for realizing the linkage authentication of 802.1X and a Windows active directory (AD) domain, and comprises that: an 802.1X authentication server receives an authentication request carrying a username and a blank password of a user from the user; the 802.1X authentication server transmits the username and the blank password to a Windows AD domain server which verifies the username and the blank password; after the username and the blank password pass the verification, the 802.1X authentication server transmits a query request carrying the username to the Windows AD domain server; the Windows AD domain server judges whether the username belongs to an authorized user or not; and if the username belongs to the authorized user, the linkage authentication is successfully finished.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
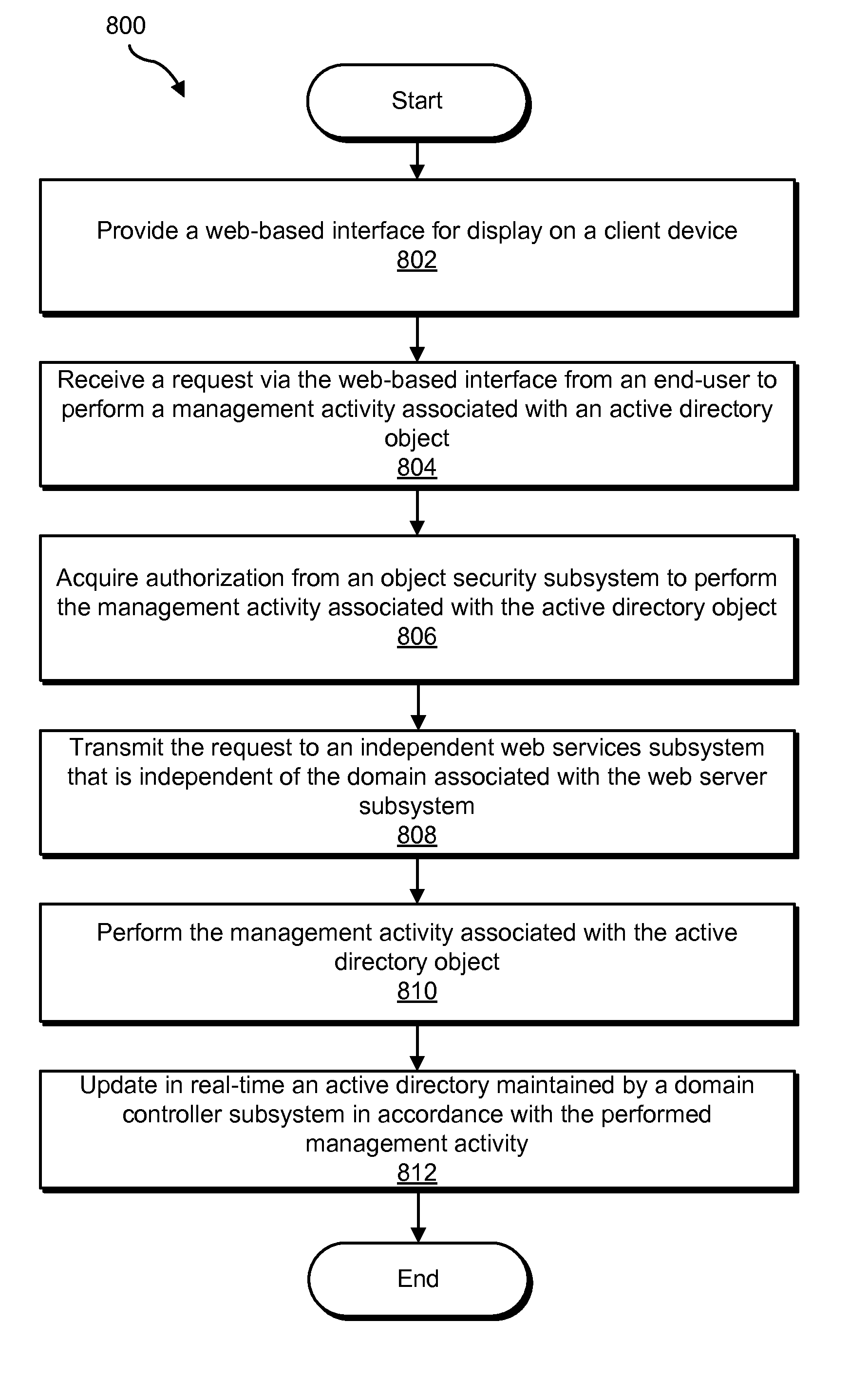
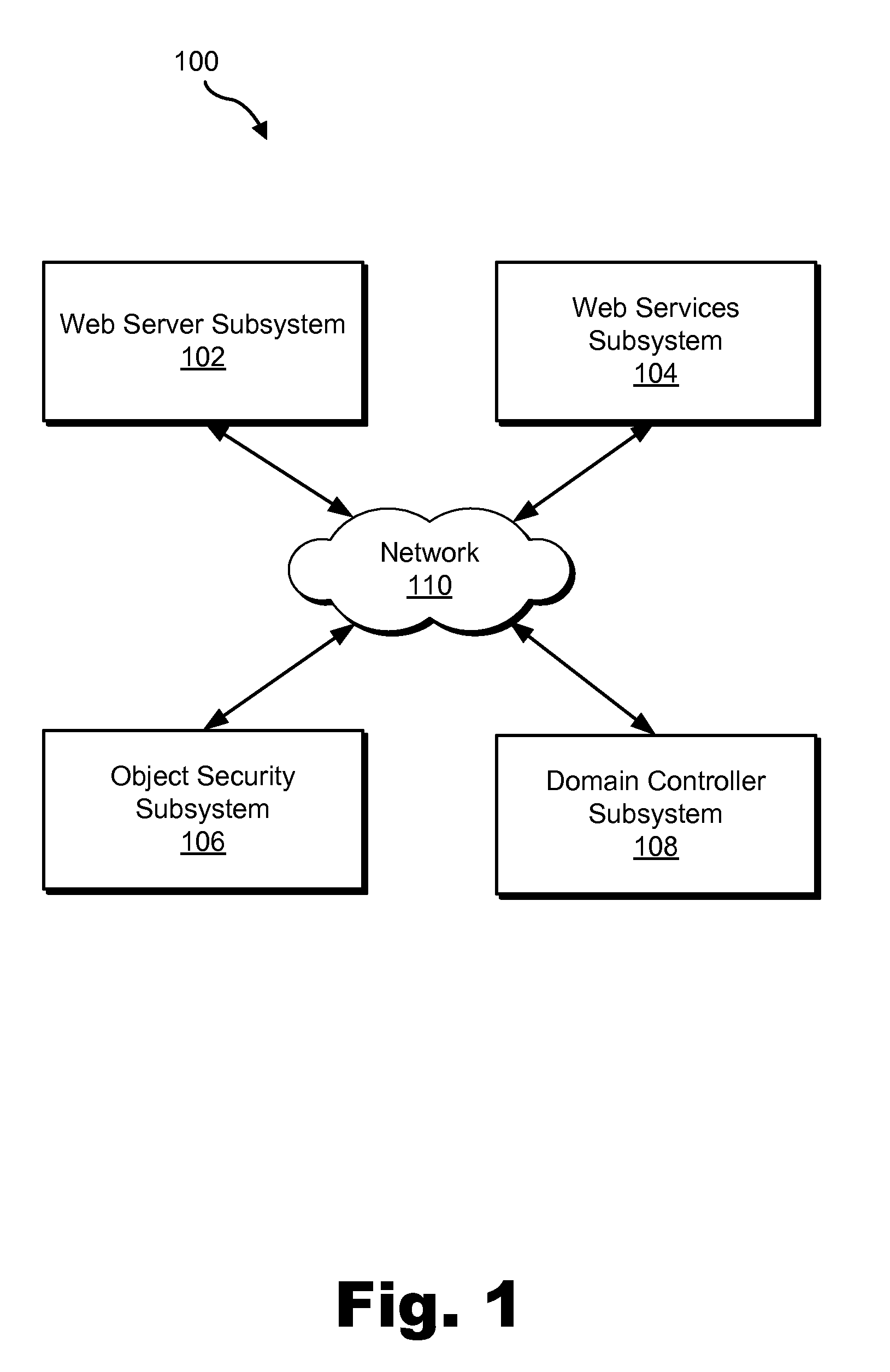
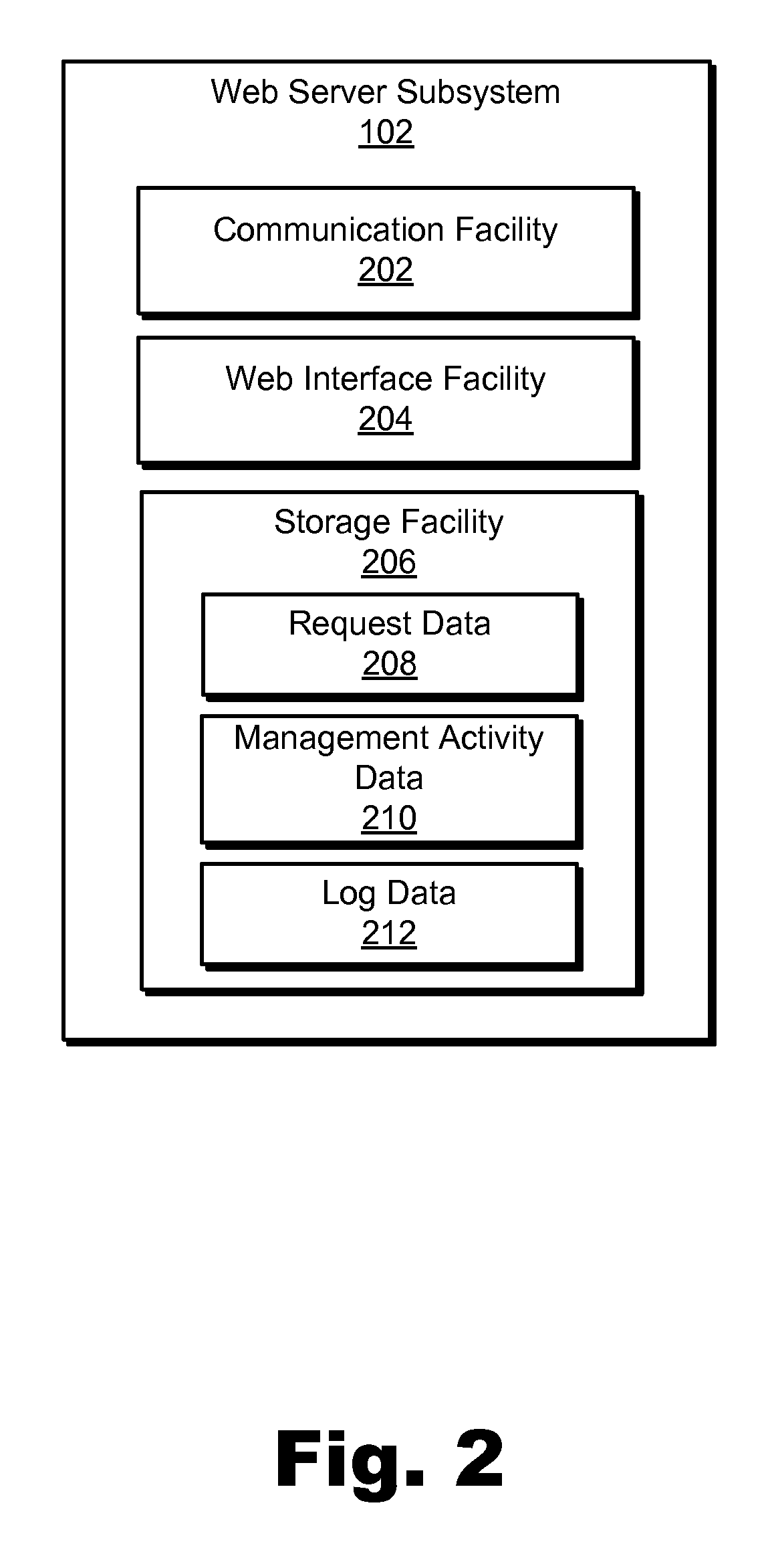
Active Directory Object Management Methods and Systems
ActiveUS20110047206A1Digital data processing detailsDigital data protectionWeb serviceNetwork service
An exemplary method includes providing, by a web server subsystem, a web-based interface for display on a client device within a domain associated with the web server subsystem, receiving, by the web server subsystem, a request via the web-based interface from an end-user to perform a management activity associated with an active directory object, acquiring, by the web server subsystem, authorization from an object security subsystem to perform the management activity associated with the active directory object, transmitting, by the web server subsystem, the request to a web services subsystem that is independent of the domain associated with the web server subsystem, performing, by the web services subsystem, the management activity associated with the active directory object, and updating in real-time, by the web services subsystem, an active directory maintained by a domain controller subsystem in accordance with the performed management activity. Corresponding methods and systems are also disclosed.
Owner:VERIZON PATENT & LICENSING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com