Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
188 results about "Virtual identity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Virtual identity. Related Terms. In online virtual communities, such as online chat rooms or in online games, a virtual identity is one created by the human user that acts as an interface between the physical person and virtual person other users see on their computer screen. See also avatar.
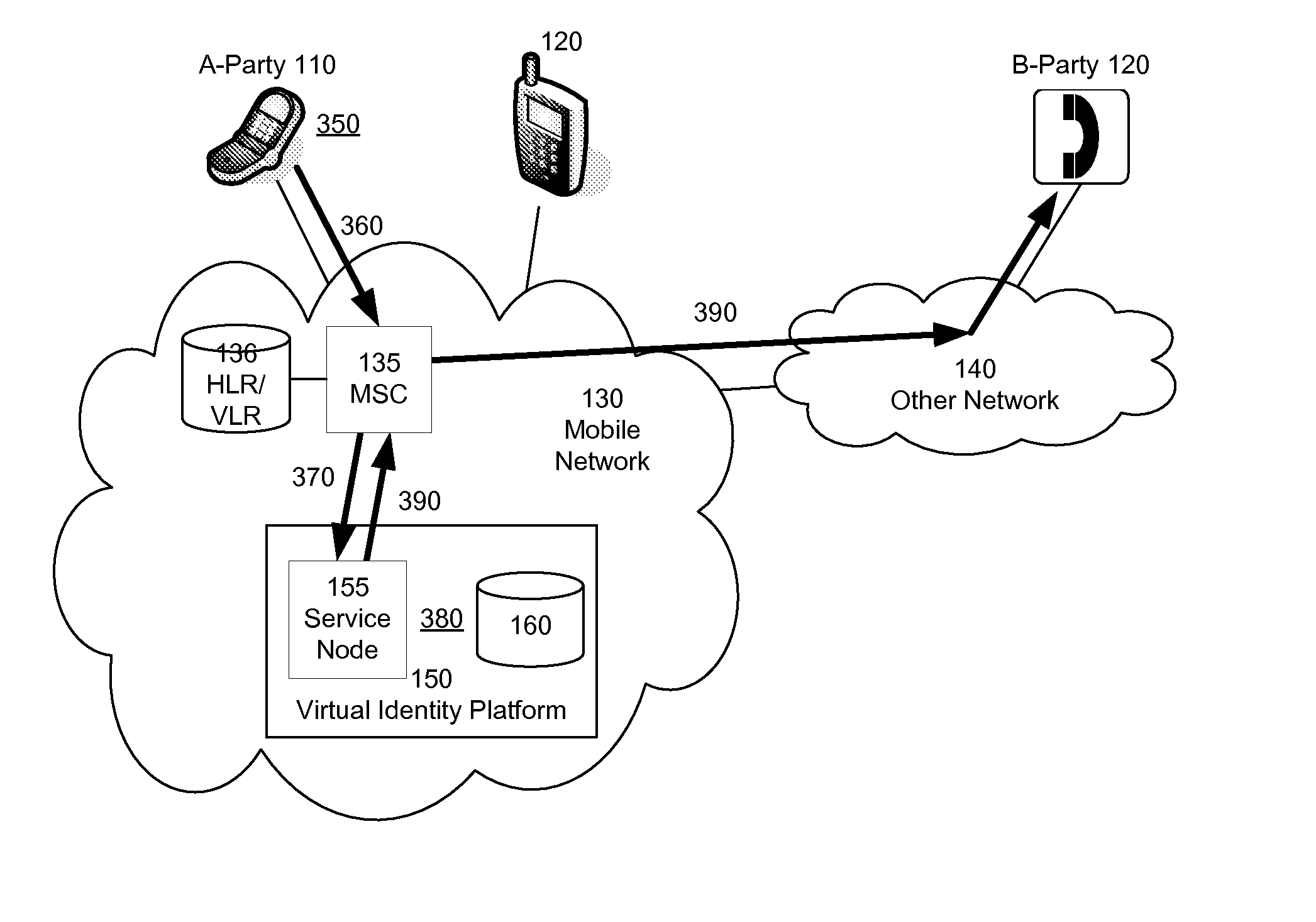
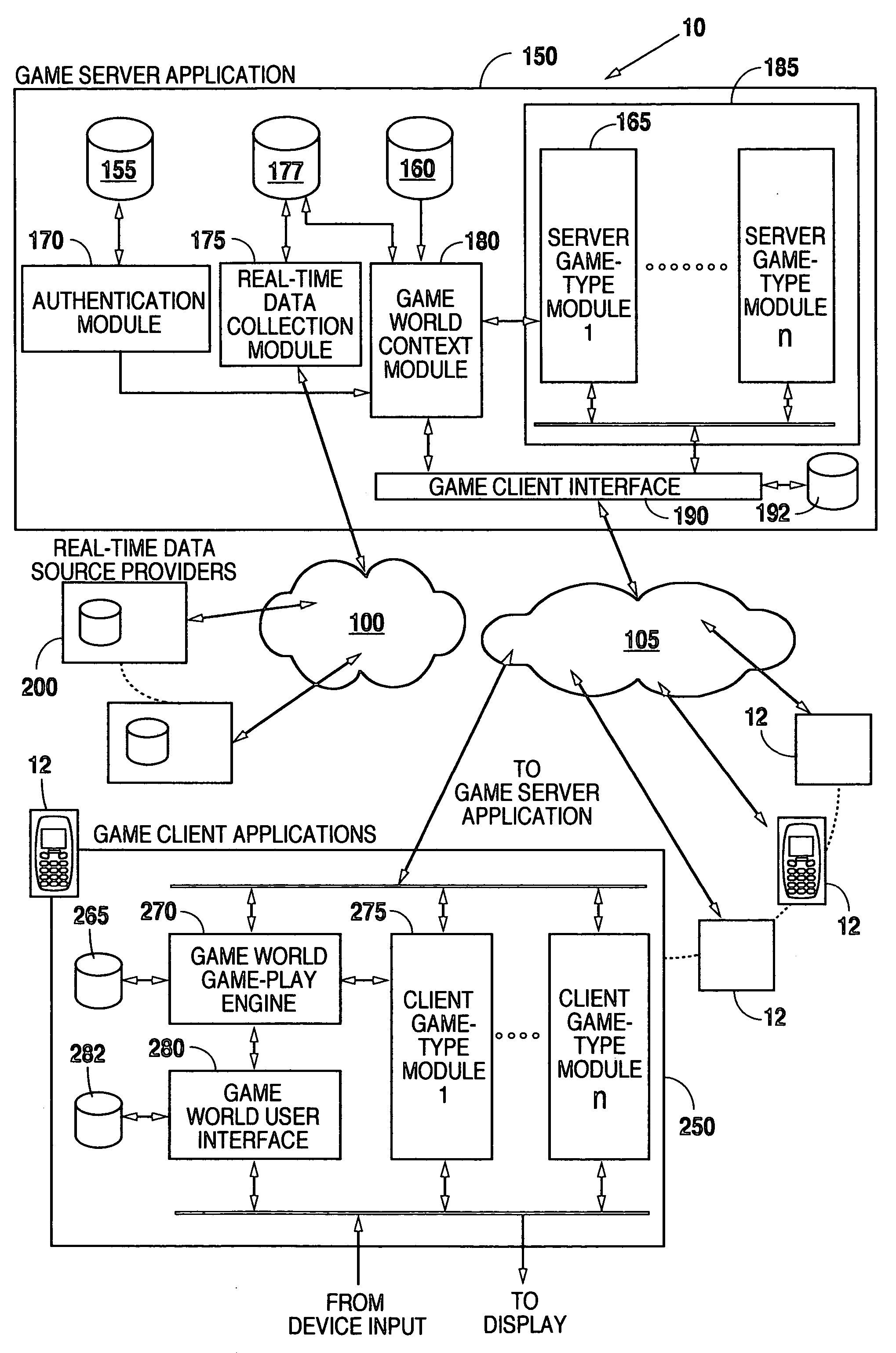
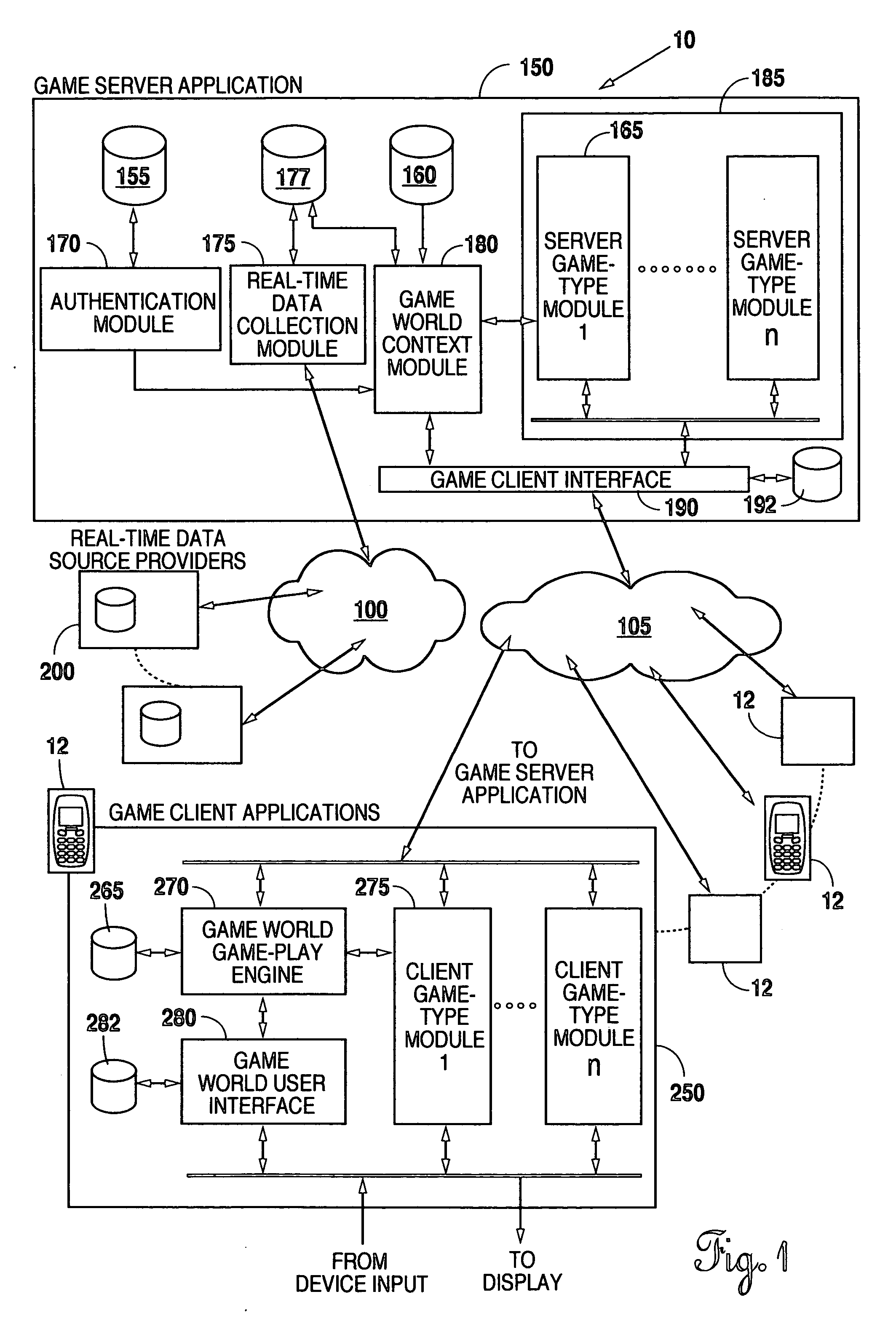
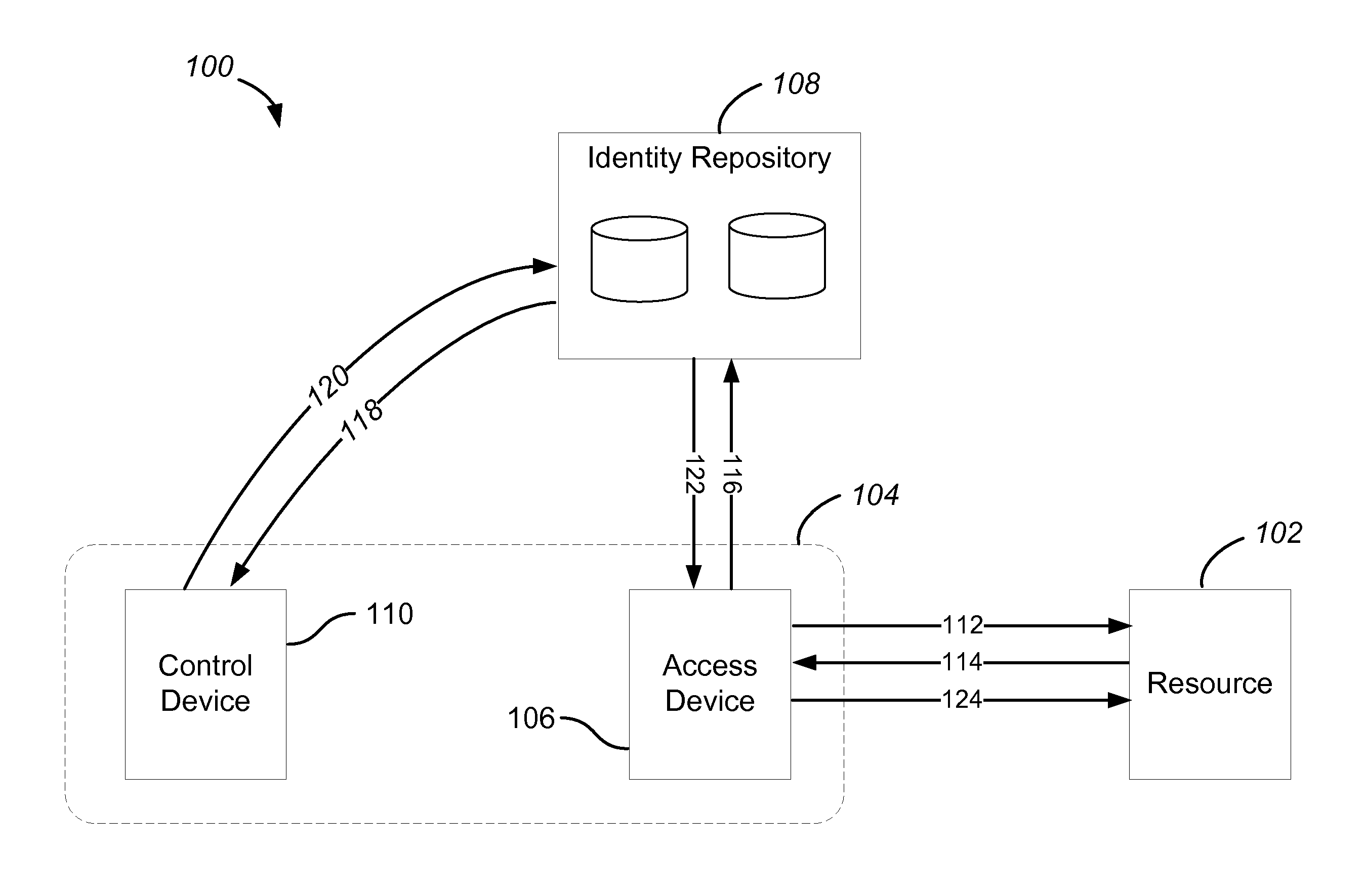
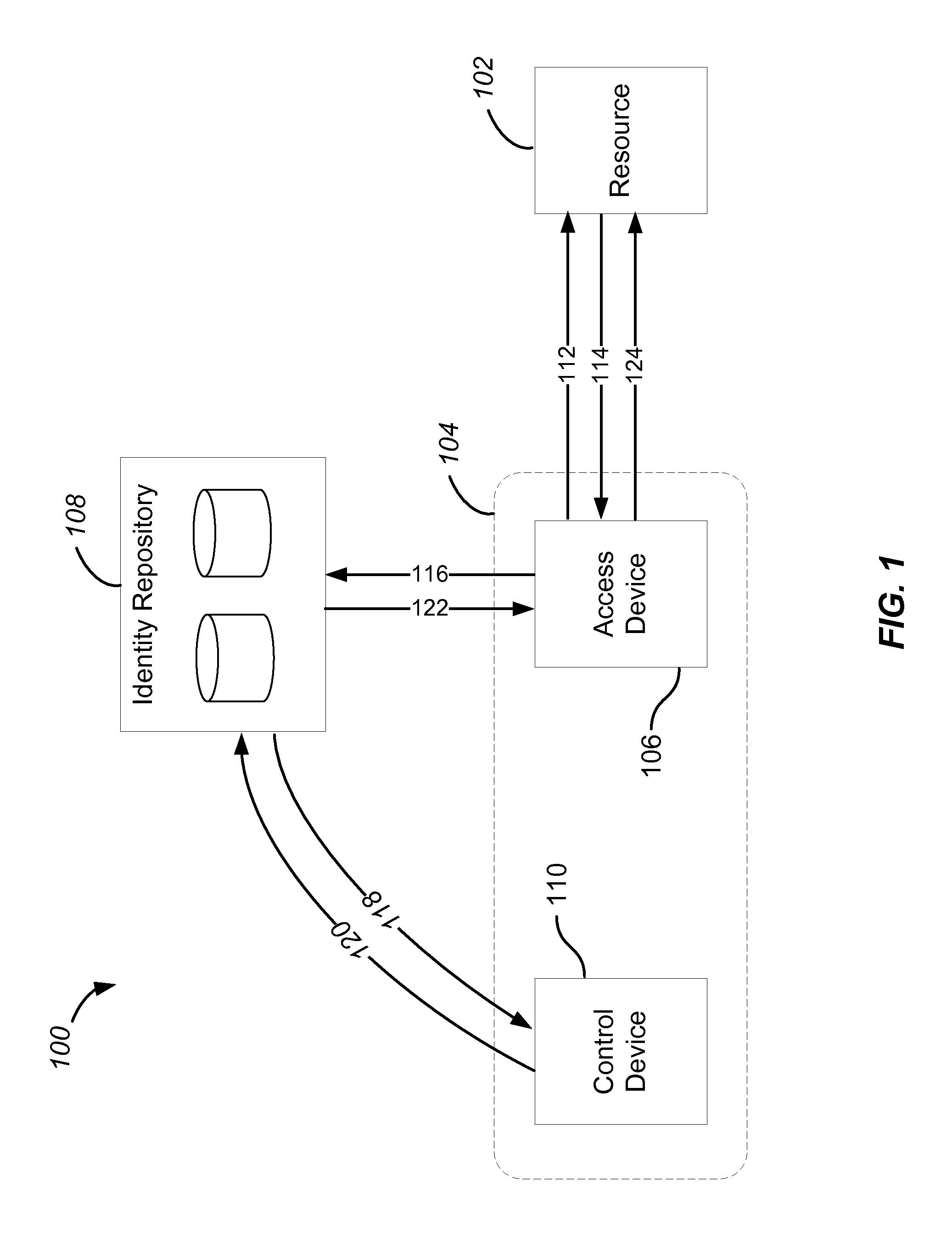
Dynamic Processing of Virtual Identities for Mobile Communications Devices
InactiveUS20070105531A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareMobile device
Virtual identities are created, where the virtual identities correspond to the primary identity of a mobile communications device or are based on the authentication of a mobile communications device. In this way, the same mobile device can send communications from different identities (e.g., different phone numbers) and / or receive communications at different identities. In one implementation, a virtual identity platform includes an identity database that makes associations between virtual identities and primary identities.
Owner:JIBE MOBILE
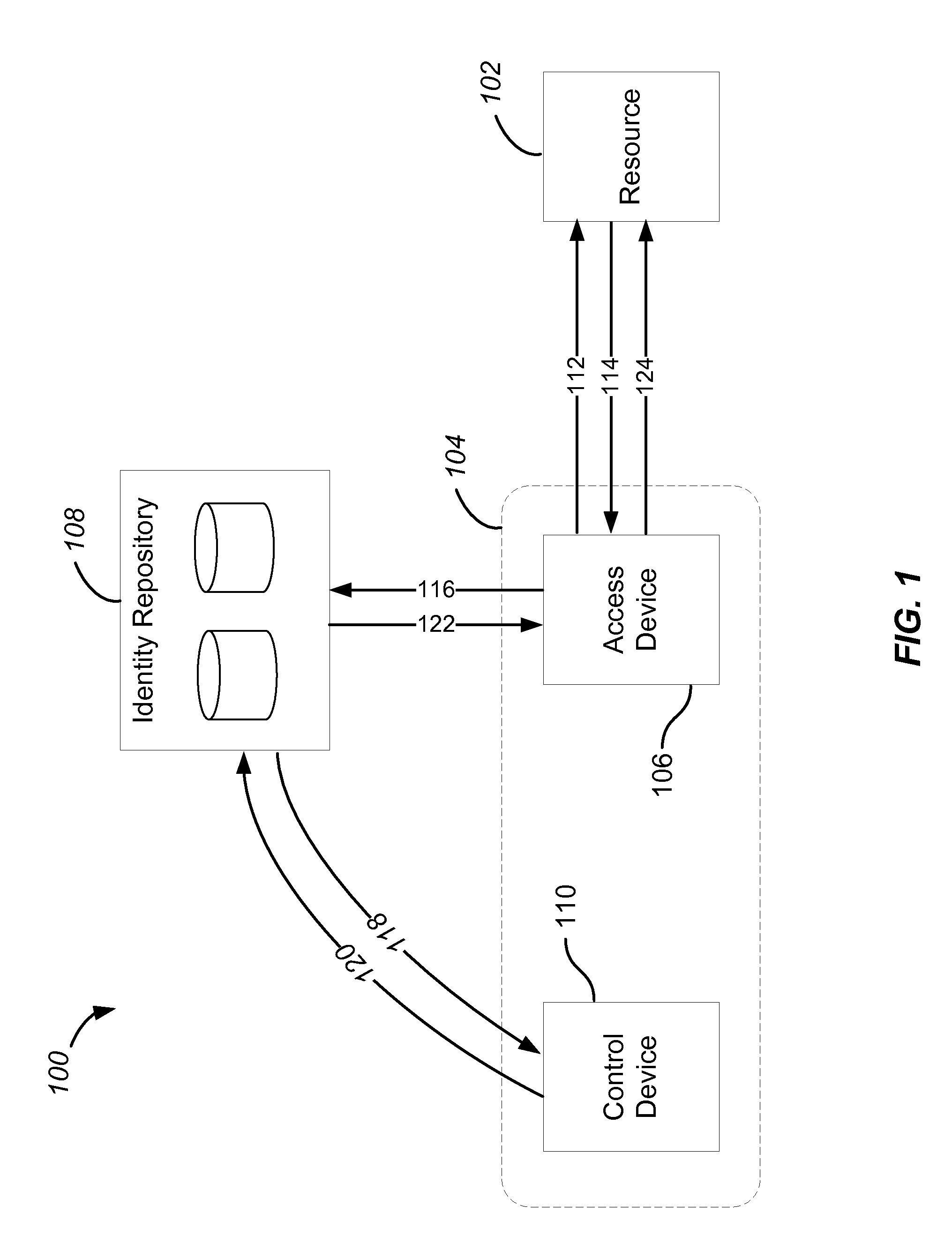
Virtual Identity Credential Issuance and Verification Using Physical and Virtual Means
InactiveUS20180254909A1Promote disseminationUser identity/authority verificationPublic key infrastructure trust modelsMachine-readable mediumElectronic equipment
Systems, methods, and non-transitory machine readable medium for authenticating an identity of a user and facilitating a transaction between the user and a relying party include establishing a communication path with a first electronic device of the user, receiving, an identity credential data points of the user from an identity credential issuer, receiving an identity credential issued by the identity credential issuer from the user, authenticating the identity credential received from the user with the identity credential data points of the user from the identity credential issuer, storing the authenticated identity credential of the user as a virtual identity credential in the memory, establishing a communication path with a second electronic device of the relying party, and facilitating transmission of identity credential information or identity credential verification commands between the user and the relying party.
Owner:LAMARK SOLUTIONS INC
Interrelated game and information portals provided within the context of an encompassing virtual world
InactiveUS20050043097A1Reduce inconvenienceFunction increaseVideo gamesSpecial data processing applicationsVirtual worldVirtual game
A method and system is provided for a virtual game world in which multiple players may play a plurality of games. Each player has a persistent and dynamic virtual identity that is relevant to and affected by the player's activity in each of the games. The games provide the opportunity for the various players to interact with each other, regardless of the actual physical location of the respective players. Preferably, the games provide the opportunity for players to cheat, including conspiring to cheat among multiple players, and accuse other players of cheating. Cheating and accusation of cheating may have positive or negative consequences to the respective players. The games, which are located at specific locations in the virtual world, are preferably provided with location-specific information from corresponding locations in the real world.
Owner:SPIDERMONK ENTERTAINMENT
System and method for interactively collaborating within a secure online social networking community
InactiveUS20100241611A1Eliminate needMove quicklyDigital data processing detailsMultiple digital computer combinationsApplication softwareDocumentation
Interactive collaboration within a secure, server-based social networking community integrated with a secured document management system includes at least one of a plurality of professional functionalities and a plurality of integrative functionalities to members having a member virtual identity within the community. Members may assemble into a network of members that excludes at least one member of the community. Integrative functionalities include allowing networks of members to share documents in a remote secured environment and exclude access to documents from those not belonging to a particular network. Members may also access software applications to remotely create, delete, edit and manage documents and view information about documents in a plurality of customizable and selectable viewing options.
Owner:ZUBER THOMAS
System and method for interactively collaborating within a secure online social networking community
InactiveUS20100241971A1Multiple digital computer combinationsOffice automationApplication softwareDocumentation
Interactive collaboration within a secure, server-based social networking community integrated with a secured document management system includes at least one of a plurality of professional functionalities and a plurality of integrative functionalities to members having a member virtual identity within the community. Members may assemble into a network of members that excludes at least one member of the community. Integrative functionalities include allowing networks of members to share documents in a remote secured environment and exclude access to documents from those not belonging to a particular network. Members may also access software applications to remotely create, delete, edit and manage documents and view information about documents in a plurality of customizable and selectable viewing options.
Owner:ZUBER THOMAS
Methods and systems for pairing devices
ActiveUS20130198516A1Eliminate needMultiple keys/algorithms usagePublic key for secure communicationComputer hardwareVirtual identity
A method of pairing an unregistered device with a virtual identity may include, at a first repository: receiving a request from the unregistered device, sending a pairing code and an identifier to the unregistered device, receiving the pairing code from a registered device, and sending the identifier to the registered device. The method may also include, at a second repository, receiving the pairing code and secret information from the registered device, receiving the pairing code in a transmission associated with the unregistered device, associating the unregistered device with the virtual identity using the pairing code, and sending the secret information to the unregistered device.
Owner:NEUSTAR
Virtual Identity System and Method for Web Services
InactiveUS20100049790A1Improve experienceAdvertisementsNatural language data processingThird partyWeb application
A comprehensive identity management system for users of multiple Web applications. The system supports multiple standards spanning both inbound and outbound single sign-on and integration with an application directory for coupling discovery of third-party applications with single sign-on.
Owner:INFINITY IP BANK INT SUZHOU COMPANY
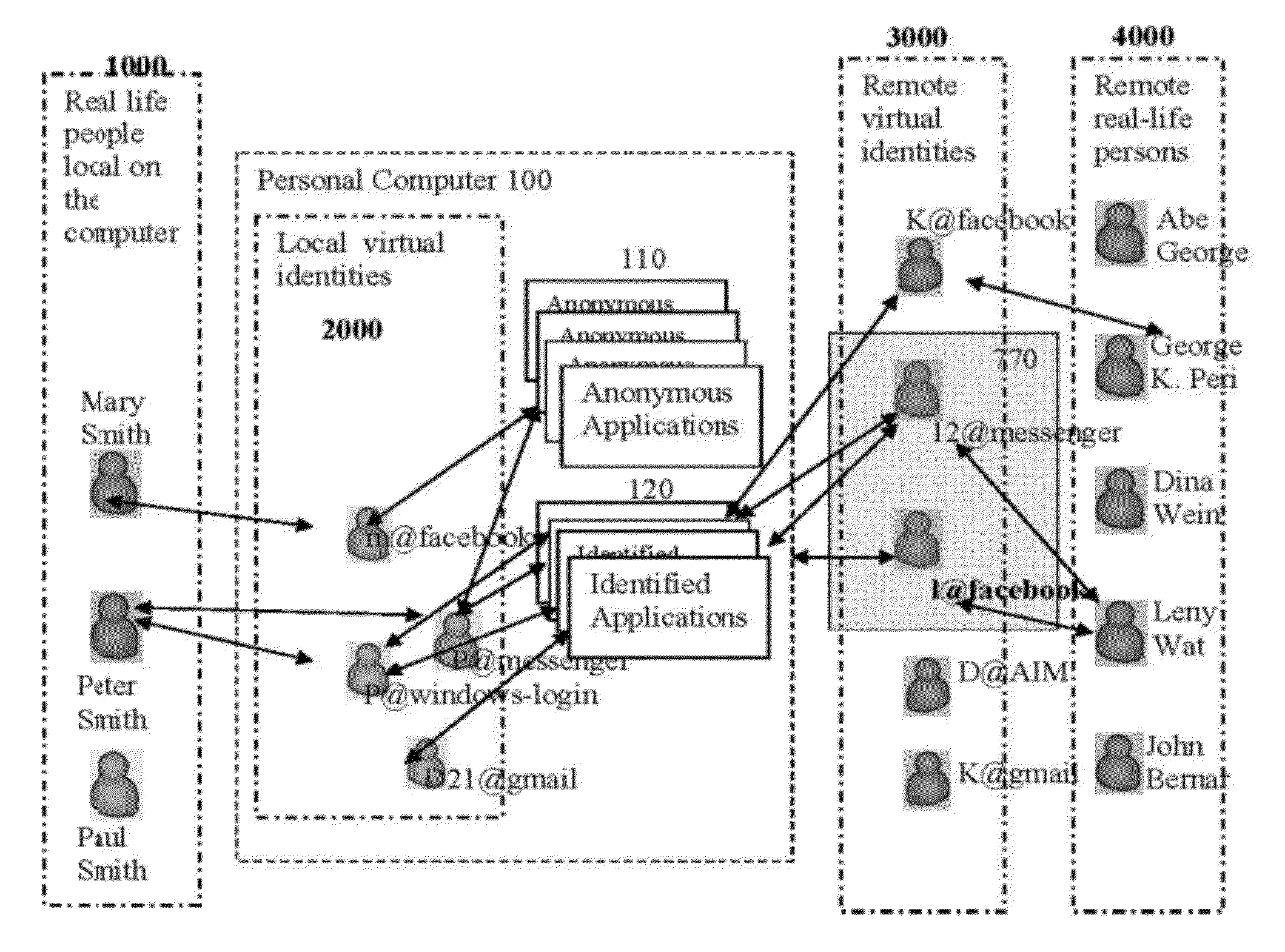
Multi-identity network social intercourse system and implementation method
InactiveCN101599993APrivacy protectionGive full play to personal imaginationData switching networksEngineeringSystem structure
The invention discloses a multi-identity network social intercourse system and an implementation method. The steps thereof are as follows: A: registering to be a member; B: logging on by using a registered user name obtained in the step A, and filling in the personnel information and a head portrait of real identity; C: a user chooses whether activating the virtual identity or not; D: activating the virtual identity, and filling out the information of the virtual identity; E: according to the requirement of the member, choosing the switching of the identities, and switching into the state with two identities; F: according to the identity switching of the step E, the switched state is the state of real identity; and G: according to the identity switching of the step E, the switched state is the state of virtual identity. The identities are respectively connected with the personnel information, the relationship, the resources and the application and operation of the system. The invention favorably protects the privacy of the user, and favorably combines real-name registration with the anonymous registration, thereby providing a flexible and intimate platform for the user. The user can establish a stable network of social relationship, gain real friendship, etc. The system has the advantages of simple structure and easy operation.
Owner:WUHAN ZHONG PIN TECH
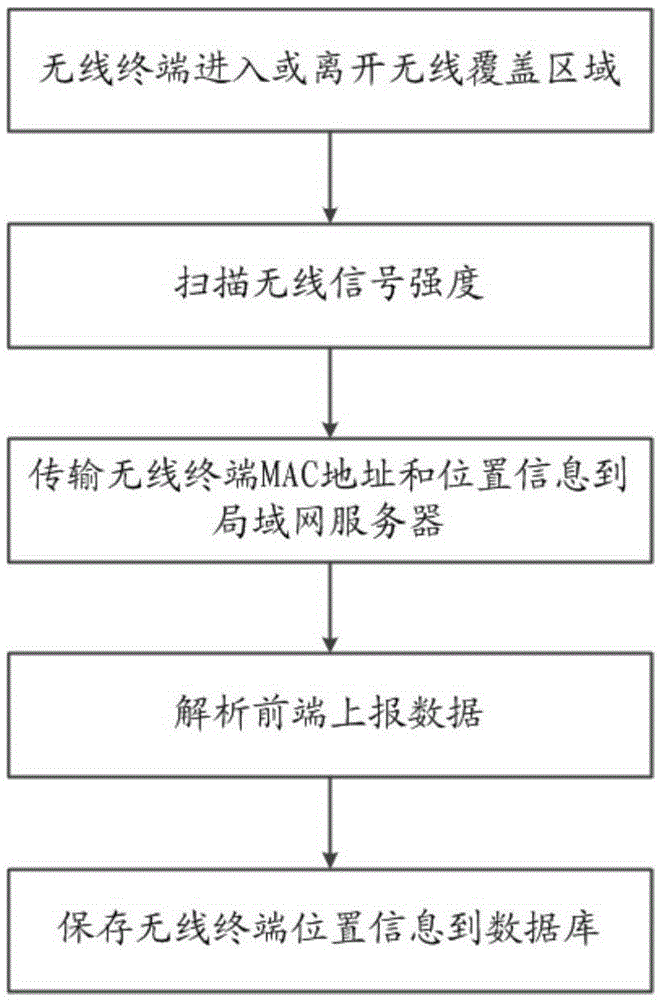
Public place wireless internet access security management system and operation method thereof
InactiveCN105357480ALock accuratelyClosed circuit television systemsLocation information based serviceVideo monitoringWireless internet access
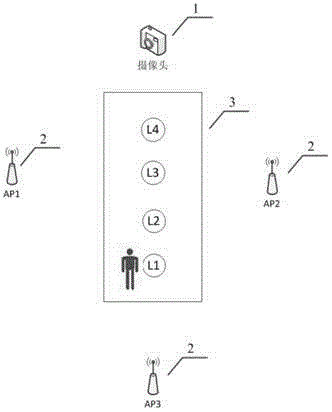
The invention discloses a public place wireless internet access security management system and an operation method thereof. The system comprises a video monitoring unit, a wireless scanning unit and a terminal motion track sketching unit; a video monitor carries out face identification, triggers a joint tracking action; an associated AP positions a wireless terminal according to location information of a person, and builds an association between a terminal MAC address and the identity of the person; MAC of the tracked person is issued to an intersection monitor AP; and warning is carried out on an entrance event and a disappearing event of the MAC, so as to sketch the motion track of the person. On the basis that a public security system naturally has mass data of human face data, the video monitor is combined with an AP scanning technology; depth recognition and virtual identity query of a wireless message are not needed; through linkage with a security system, accurate identification and tracking of the identity of the person can be achieved; and the public place wireless internet access security management system has the advantage that front-end equipment is low in cost..
Owner:HANGZHOU DUNCHONG SCI & TECH
Methods and systems for secure identity management
ActiveUS20130205136A1Eliminate needMultiple keys/algorithms usagePublic key for secure communicationInternet privacyIdentity management
Owner:NEUSTAR
Methods and systems for managing virtual identities
InactiveUS20120317217A1Accurate identityMultiple digital computer combinationsDigital data authenticationHuman–computer interactionCurrent user
A method of monitoring a plurality of user generated interaction sessions. The method comprises providing a list of a plurality of defined users, where each defined user is associated with at least one response to a user-application interaction of a respective defined user with one of a plurality of defined applications accessible via a client terminal, identifying a current user of the client terminal from the plurality of defined users and at least one current interacted application from the plurality of defined applications, selecting a at least one respective response according to the at least one current interacted application and the current user, and triggering the at least one respective response.
Owner:UNITED PARENTS ONLINE
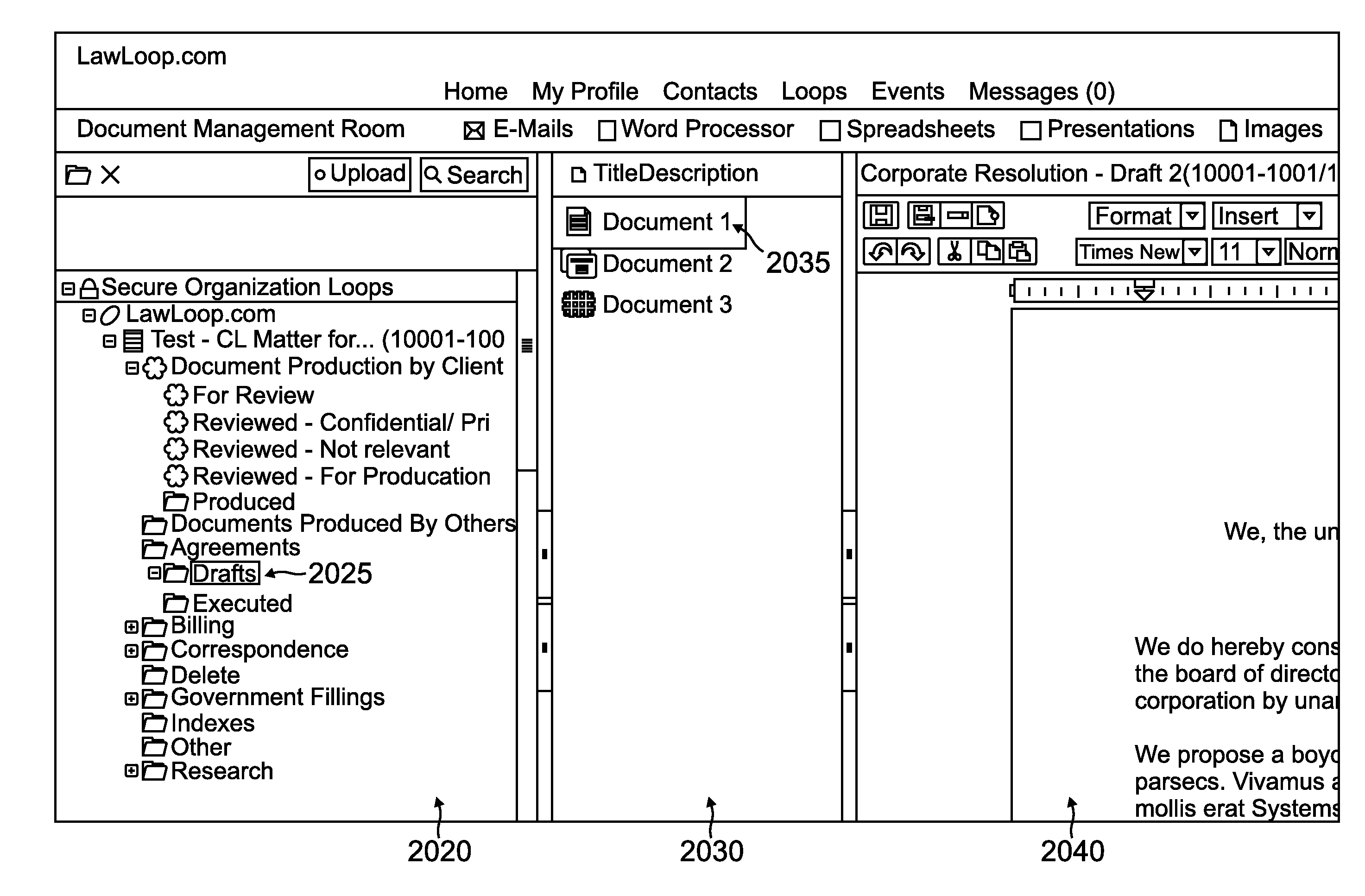
Method for providing alias folders in a document management system
ActiveUS20110213806A1Interference be notEliminate needDigital data processing detailsOffice automationPersonalizationDocument preparation
Interactive collaboration within a secure, server-based social community integrated with a secured document management system that includes at least one of a plurality of professional functionalities and a plurality of integrative functionalities to members having a member virtual identity within the community. Members of the community may create a personalized custom set of folders within the document management system, which customized arrangement allows the members to view documents, files, and folders as they desire. By creating these personalized custom “alias” folders, the members rearrange folders to be more accessible to themselves, while leaving the actual files and folders unchanged as viewed by every other member of the community. Members or a network administrator may also grant permission to other members of the network to access alias folders of each other member.
Owner:ONELOOP
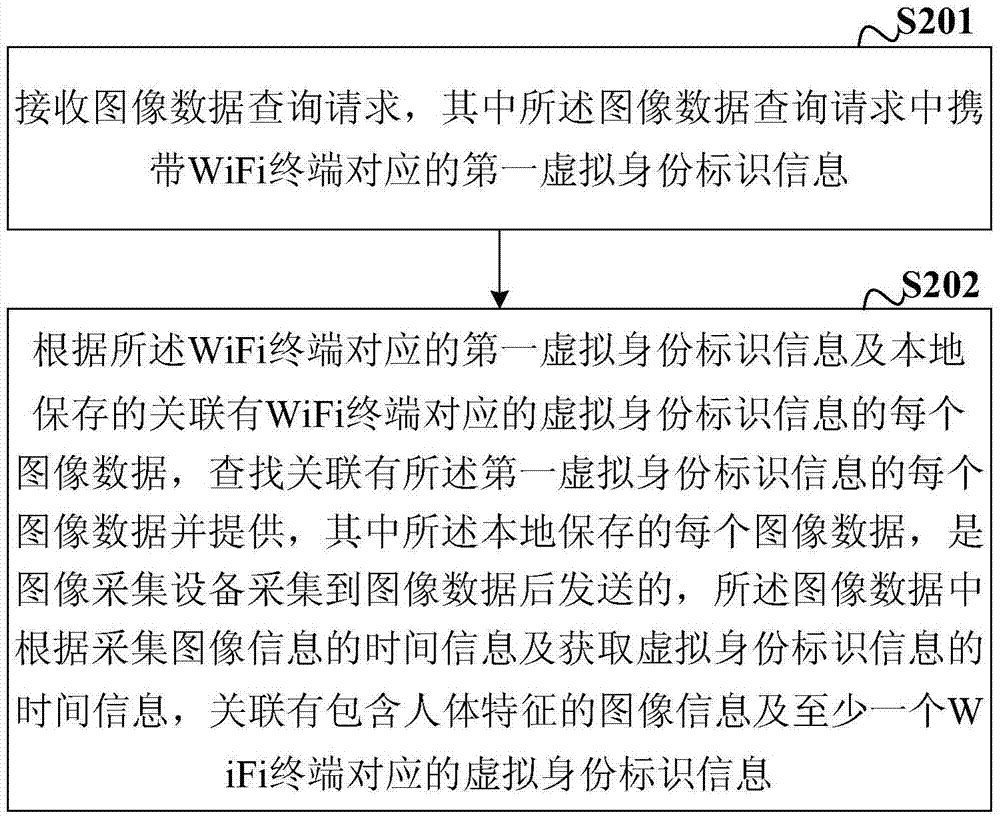
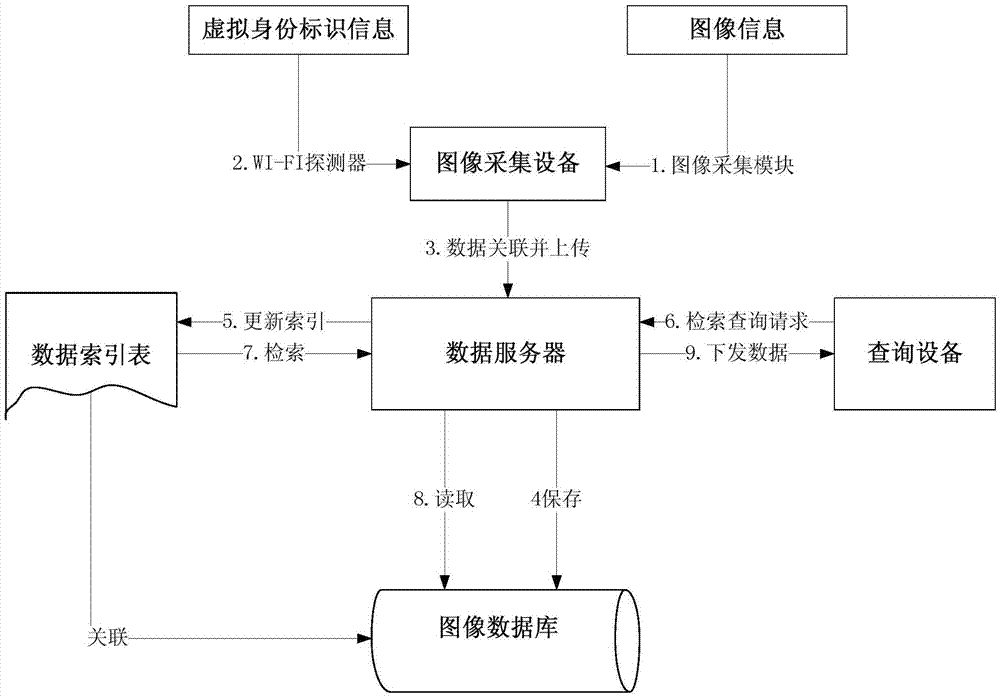
Image data collection, querying and video monitoring method, device and system
InactiveCN106899827AImprove accuracyClosed circuit television systemsTime informationVideo monitoring
The embodiment of the invention discloses an image data collection, querying and video monitoring method, device and system. The method comprises the steps: enabling a data server to receive a querying request with the first virtual identity information corresponding to a WiFi terminal, and then searching and providing each piece of image data related with the first virtual identity information according to the first virtual identity information corresponding to the WiFi terminal and locally stored image data correlated with the virtual identity information corresponding to the WiFi terminal, wherein the locally stored image data is transmitted after the image collection device collects the image data, and the image data is related with the image information comprising human body features and the virtual identity information corresponding to at least one WiFi terminal according to the time information of the image information collection and the information of time in obtaining the virtual identity information.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Methods and systems for device disablement
ActiveUS20130198834A1Eliminate riskMultiple keys/algorithms usagePublic key for secure communicationComputer hardwareDevice Identifiers
A method for disabling a device associated with a virtual identity may include receiving, from the device, a request to use the virtual identity, where the request that may include a passcode guess and a device identifier. The method may also include determining that the passcode guess does not authorize use of the virtual identity and incrementing a number of incorrect passcode guesses received within a time interval. The method may additionally include determining that the number of incorrect passcode guesses received within the time interval is greater than or equal to a threshold. The method may further include storing an indication that subsequent requests associated with the device identifier should not authorize use of the virtual identity.
Owner:NEUSTAR
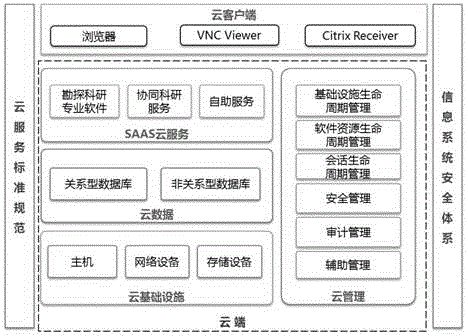
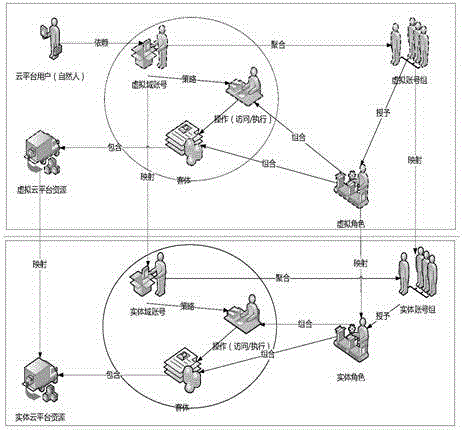
Unified identity authentication system based on cloud platform
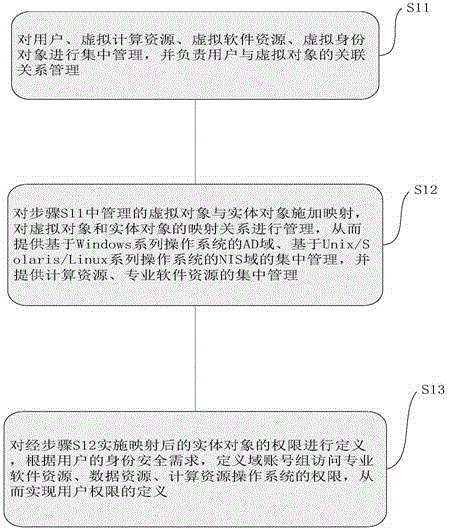
ActiveCN105429999ASolve management problemsSolve control problemsTransmissionCentralized managementVirtual computing
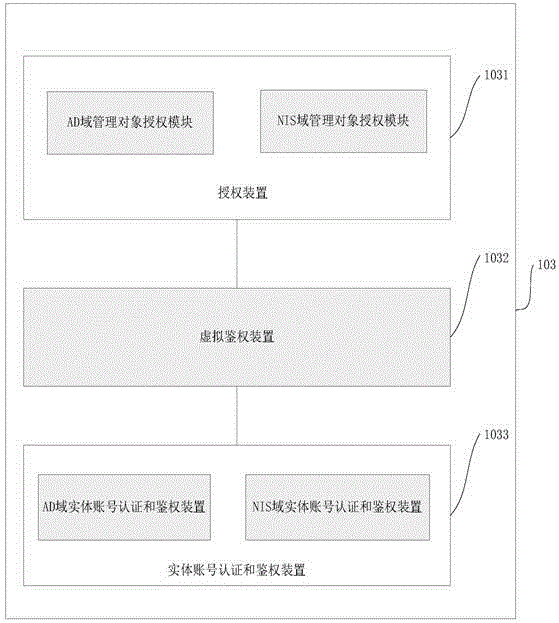
The invention discloses a unified identity authentication system based on a cloud platform, comprising a management subsystem (101) which carries out centralized management to a user, a virtual computing resource, a virtual software resource and a virtual identity object and is responsible for correlation relationship management of the user and the virtual object; a mapping subsystem (102) which maps the virtual object and an entity object managed by the management subsystem (101); an access control subsystem (103) which defines the authority of the mapped entity object; a data storage subsystem (104) which stores the data, the entity AD (active directory) domain data and the entity NIS (network information service) domain data used by the management subsystem (101), wherein the user has an AD domain account and an NIS domain account, the entity object comprises an entity AD group and an entity NIS group, the AD is an active directory, NIS is network information service. Management and control problems of resource access authority after unified authentication are effectively solved by using the unified identity authentication system.
Owner:UNITED ELECTRONICS
Method for implementing multi-virtual identify of one mobile phone number in mobile immediate communication
InactiveCN101090548AImprove experienceWide range of contactsSpecial service for subscribersRadio/inductive link selection arrangementsClient-sideComputer science
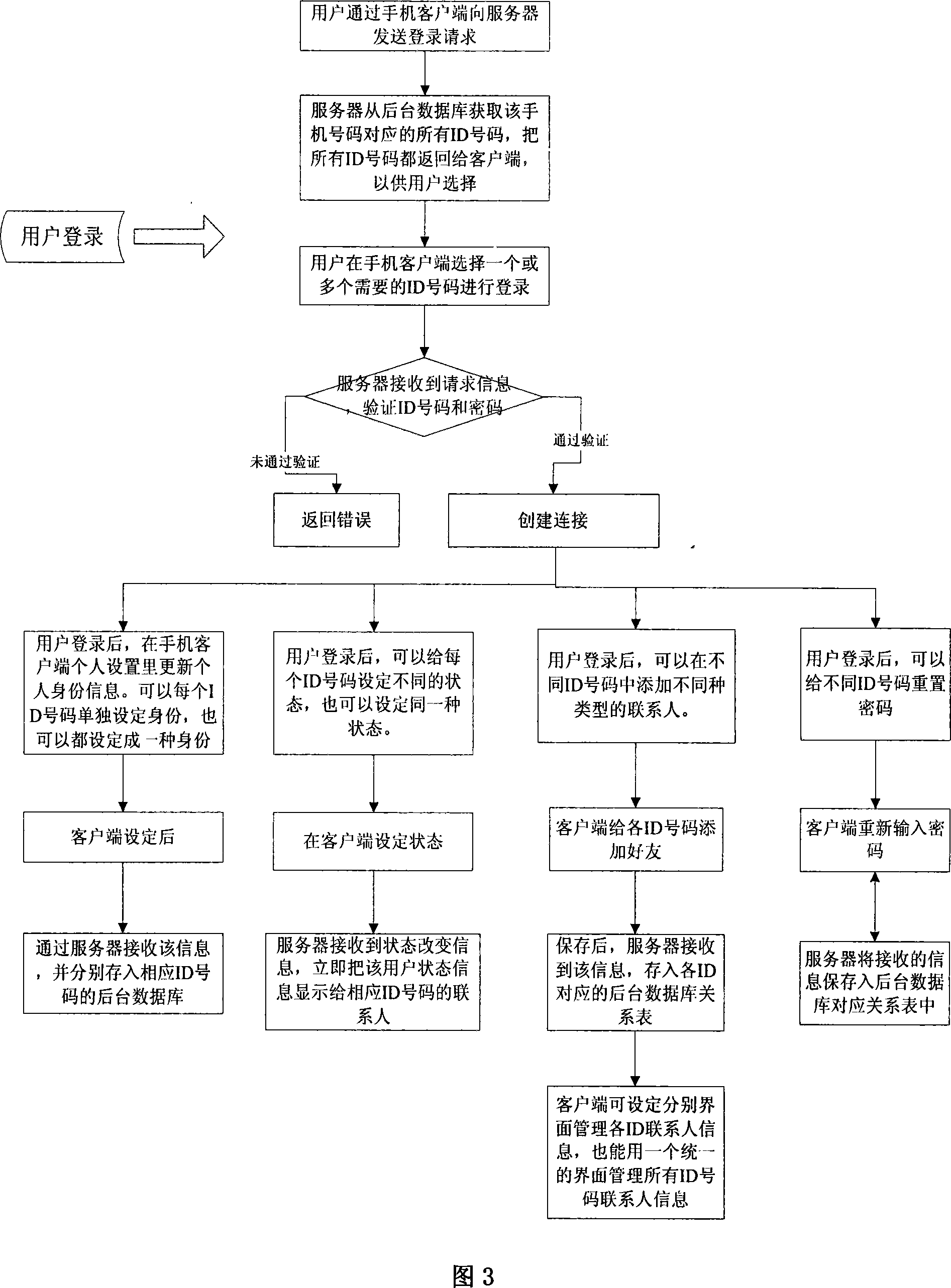
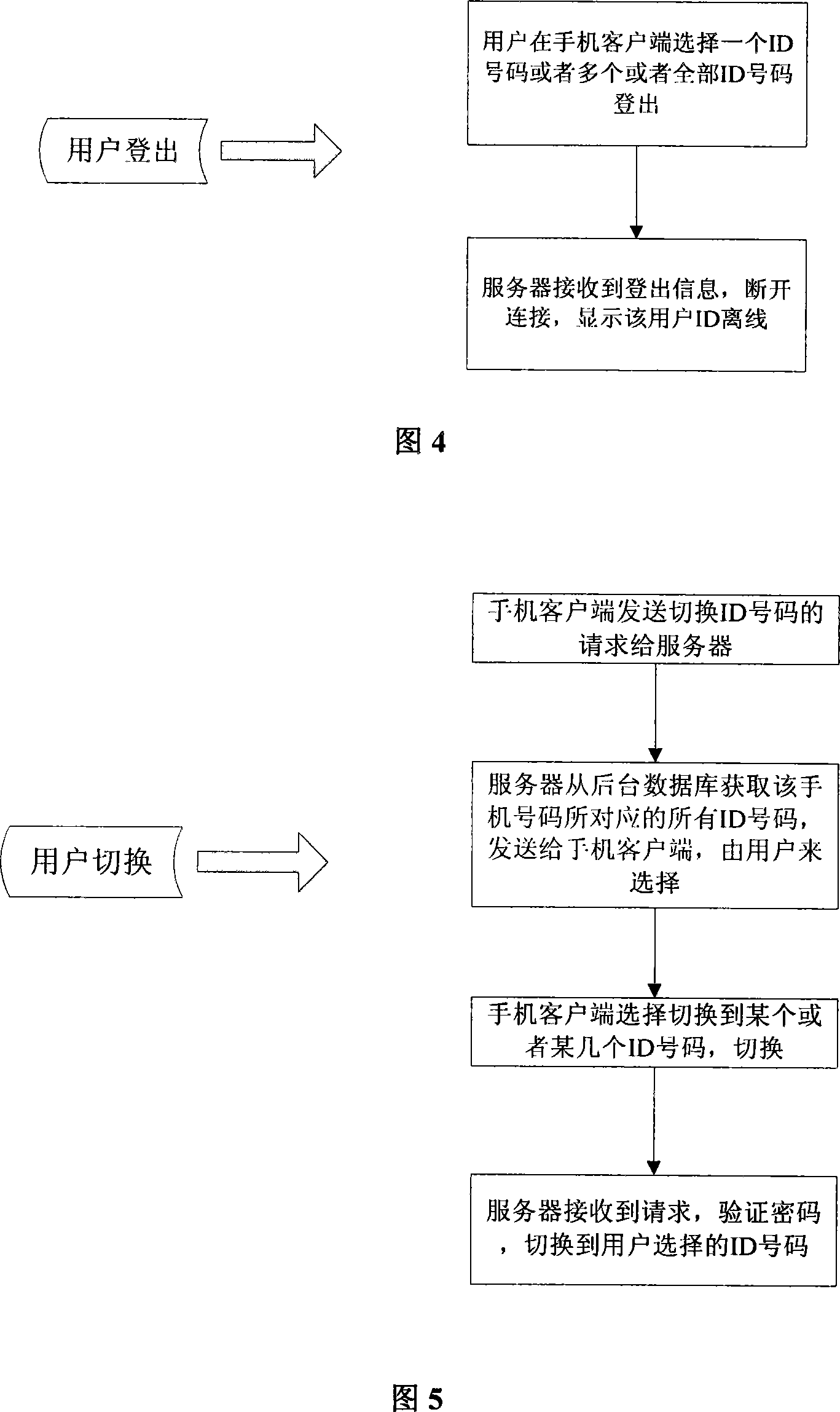
This invention relates to a method for realizing multiple virtual identities by a cell phone number in mobile prompt communication characterizing that said server includes a corresponding relationship list that one number corresponding to multiple prompt communicated ID numbers, namely, one number includes multiple virtual prompt communicated identities. The method includes a registration flow, a cancel flow, a log-on flow, a log-out flow, a switch flow, a cipher-getting back flow and a background statistic flow.
Owner:蒋晓海
Virtual identity association recognition method and device
ActiveCN107404408AEasy and Accurate AcquisitionData switching networksGeographic siteTheoretical computer science
The embodiments of the present invention provide a virtual identity association recognition method and device. The method includes the following steps that: pre-stored access information corresponding to accounts and the account types of the accounts are obtained, wherein the access information of the accounts comprises one kind of information selected from the geographical locations of terminals that log in the accounts and time periods when the terminals are located in the geographical locations when the accounts are in login states; the parameter values of association parameters between the accounts are calculated according to the access information corresponding to the accounts and a pre-constructed calculation model of the association parameters; and association relationships between the accounts are determined according to the calculated parameter values of the association parameters, the account types and a preset association relationship recognition algorithm. When being applied to virtual identity association recognition, the virtual identity association recognition method and device of the invention can identify association relationships between the accounts of different types of service platforms.
Owner:BEIJING UNIV OF POSTS & TELECOMM
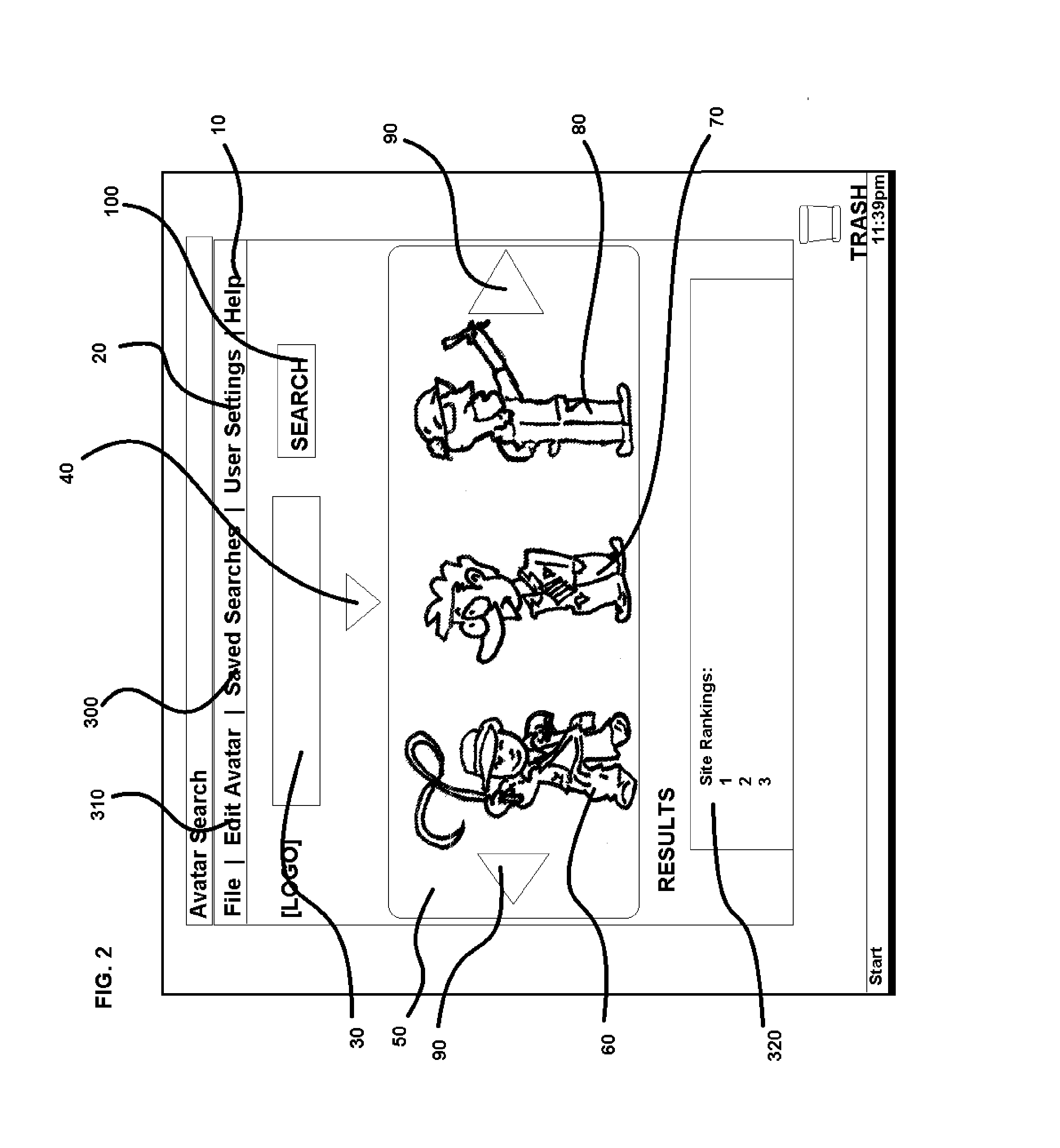
Avatar-based Search Tool
ActiveUS20140214785A1Rapidly and easily selectDigital data information retrievalDigital data processing detailsAnimationA* search algorithm
A method of performing a digital search, wherein the result set returned is additionally narrowed via a virtual personality, represented by an animated avatar selected by the user prior to enacting the search. The avatar consists of a virtual identity, which, when reduced to keyword characteristics and then applied to a search algorithm, enables the filtering of result sets according to the inferred desires of the hypothetical individual instantiated by the virtual identity itself, expressed as an avatar.
Owner:EDBERG MARK C
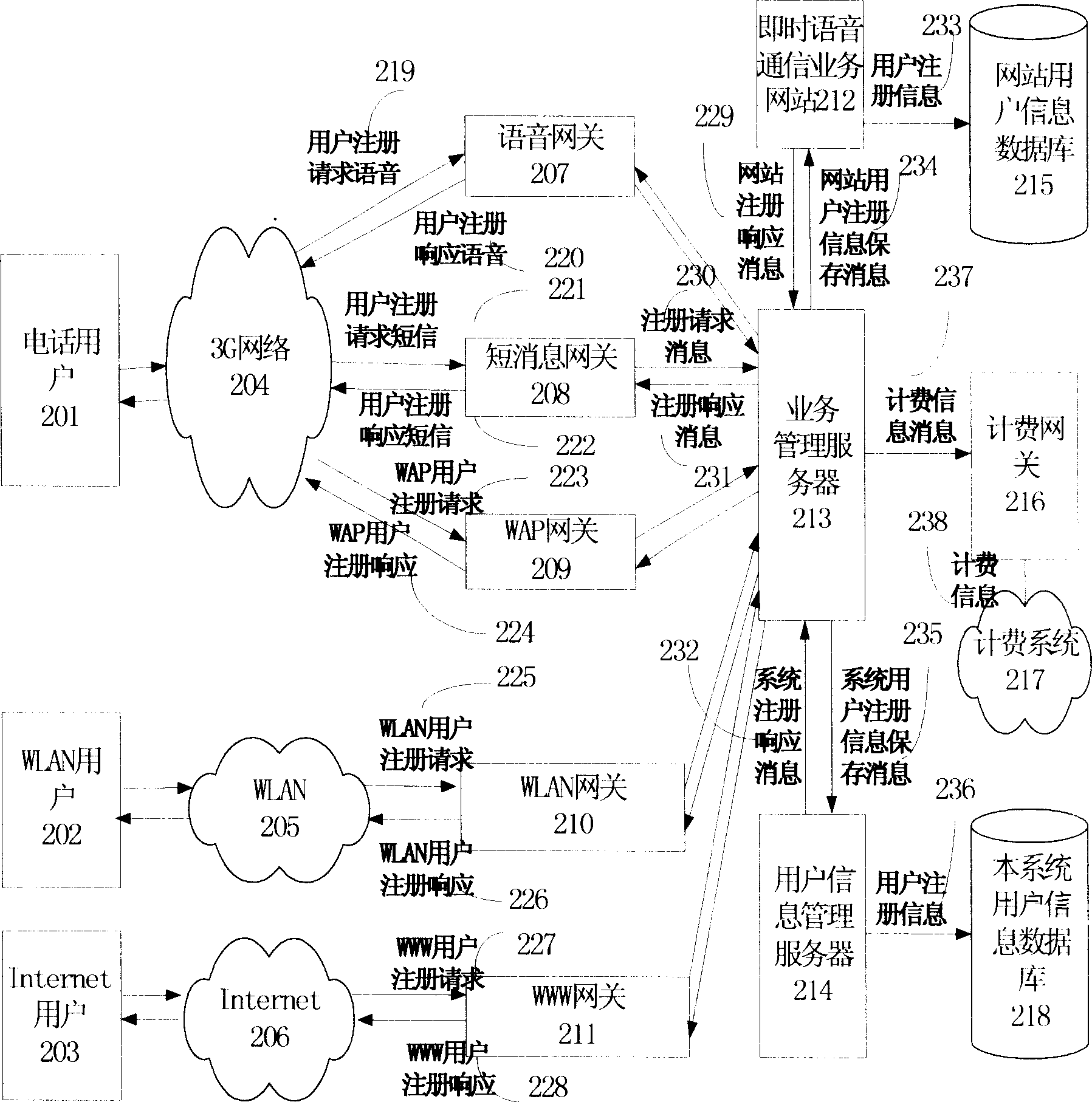
Immediate voice communication method for implementing interactive of 3G network and internet
This invention is related to the method of realizing the instant phonetic communication that the 3G network and the Internet are alternant, using the instant phonetic communication service system on the internet. The system includes the following device: the phonetic gateway, the short message gateway, the WAP gateway, the WLAN gateway, the WWW gateway, the instant phonetic communication service net station, the service managing server and the fare account gateway. The 3G network telephone number of the user is corresponding to the virtual identity number in the Internet instant phonetic communication service net station in this system, to realize the instant phonetic communication service among the 3G telephone users, and between the 3G telephone users and the Internet users. This method brings a new service alternating way into the 3G network, breaks out the limit between the 3G network and the Internet network, and realizes the service amalgamation of the 3G network and the Internet network.
Owner:BEIJING NORTHEN FIBERHOME TECH CO LTD
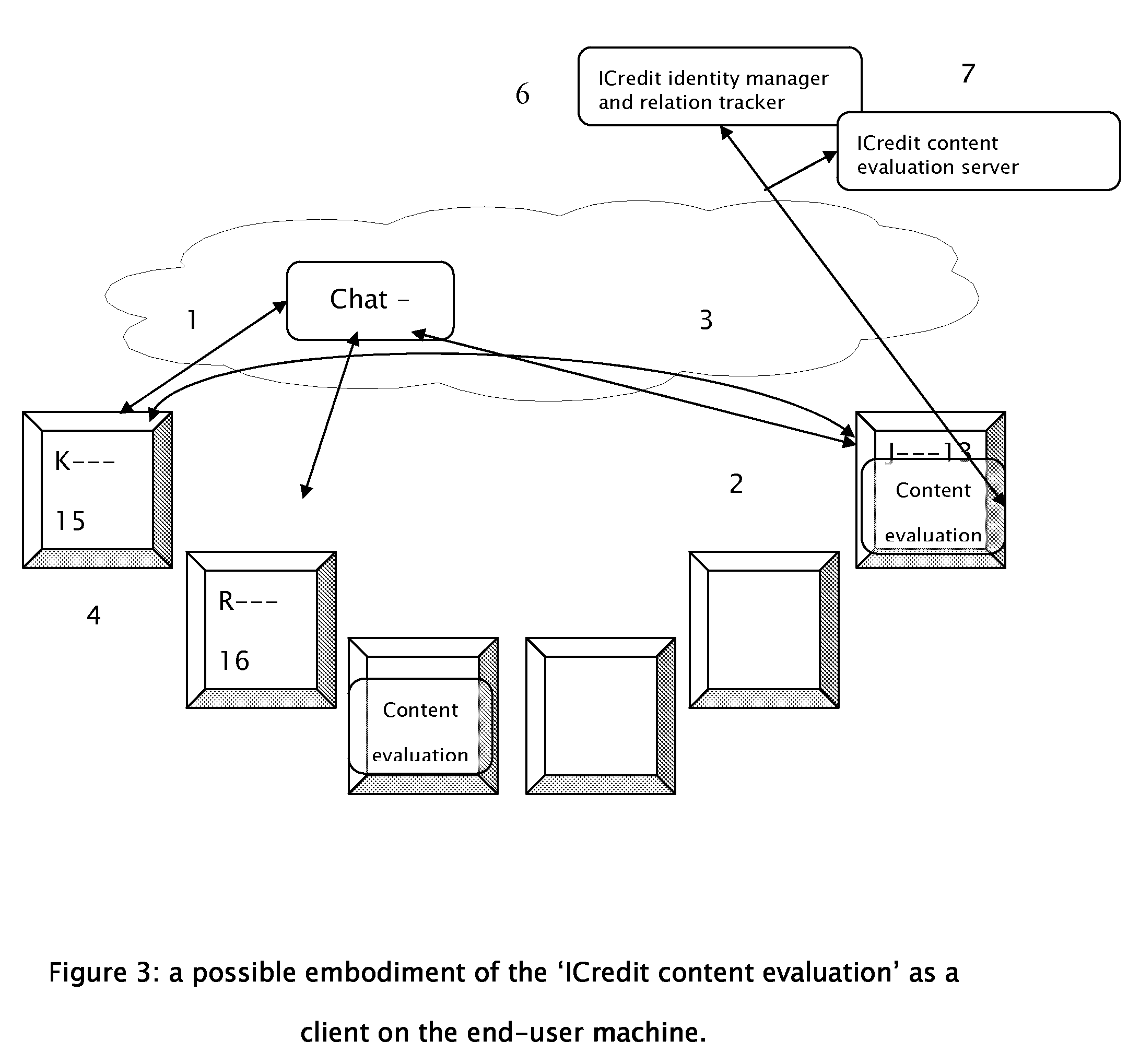
Methods and systems for managing virtual identities in the internet
InactiveUS20110029618A1Negative ICreditMultiple digital computer combinationsOffice automationTime managementComputer science
The present invention discloses methods and systems for managing and maintaining identities over time within the practically anonymous Internet environment. Said system and methods provide protection by tracking identities of partners over time, within multiple relations and over-riding common practices for identity switching.
Owner:UNITED PARENTS ONLINE
System for securing inbound and outbound data packet flow in a computer network
InactiveUS7373655B1Simplify the authorization processDigital data processing detailsMultiple digital computer combinationsNetwork packetEnd user
A method provides for control of access to network resources. A virtual identity machine resides in the network and is pre-authorized to access certain network resources. End users desiring access to those network resources attempt to logically connect to the virtual identity machines. If the logical connection attempt is successful, then the end user assumes the virtual identity of the virtual identity machine and has access to all of the same information that was available to the virtual identity machine.
Owner:AMERICAN PATENTS LLC
Unified identity authentication method based on cloud platform
ActiveCN105577656ASolve resource problemsSolve control problemsDigital data authenticationTransmissionCentralized managementVirtual computing
The invention relates to a unified identity authentication method based on a cloud platform. The method comprises the steps of: managing information, wherein users, virtual calculation resources, virtual software resources and virtual identity objects are integrally managed, and associated relations between the users and the virtual objects are managed; mapping the objects, wherein the managed virtual objects in the information managing step are mapped to entity objects, and mapping relations between the virtual objects and the entity objects are managed; and controlling access, wherein authority of the entity objects after the object mapping step is defined, and data, entity AD domain data, entity NIS domain data used in the information managing step are stored in a preset database of the cloud platform. The unified identity authentication method effectively solves the problems of resource access authority management and control of different coordination after the unified authentication.
Owner:UNITED ELECTRONICS
System and method for managing information objects
ActiveUS7941785B2Reduce and eliminate disadvantageReduce and eliminate and problemDigital data processing detailsUnauthorized memory use protectionInformation objectDatabase
A system and method for managing information on a network using an identity index may include a software program stored on a computer-readable medium which is operable to associate one or more users with the information objects that define the user. The software program can maintain a “virtual identity” for each user, the virtual identity comprising a list of information objects (e.g., accounts) associated with the user and the identities of resources at which the information objects can be found. The list of information objects may include an information object identifier for each information object. The software program may maintain a resource definition for each identified resource. The resource definition may include a set of connection parameters that can be used by the software program to connect to the corresponding resource.
Owner:SUN MICROSYSTEMS INC
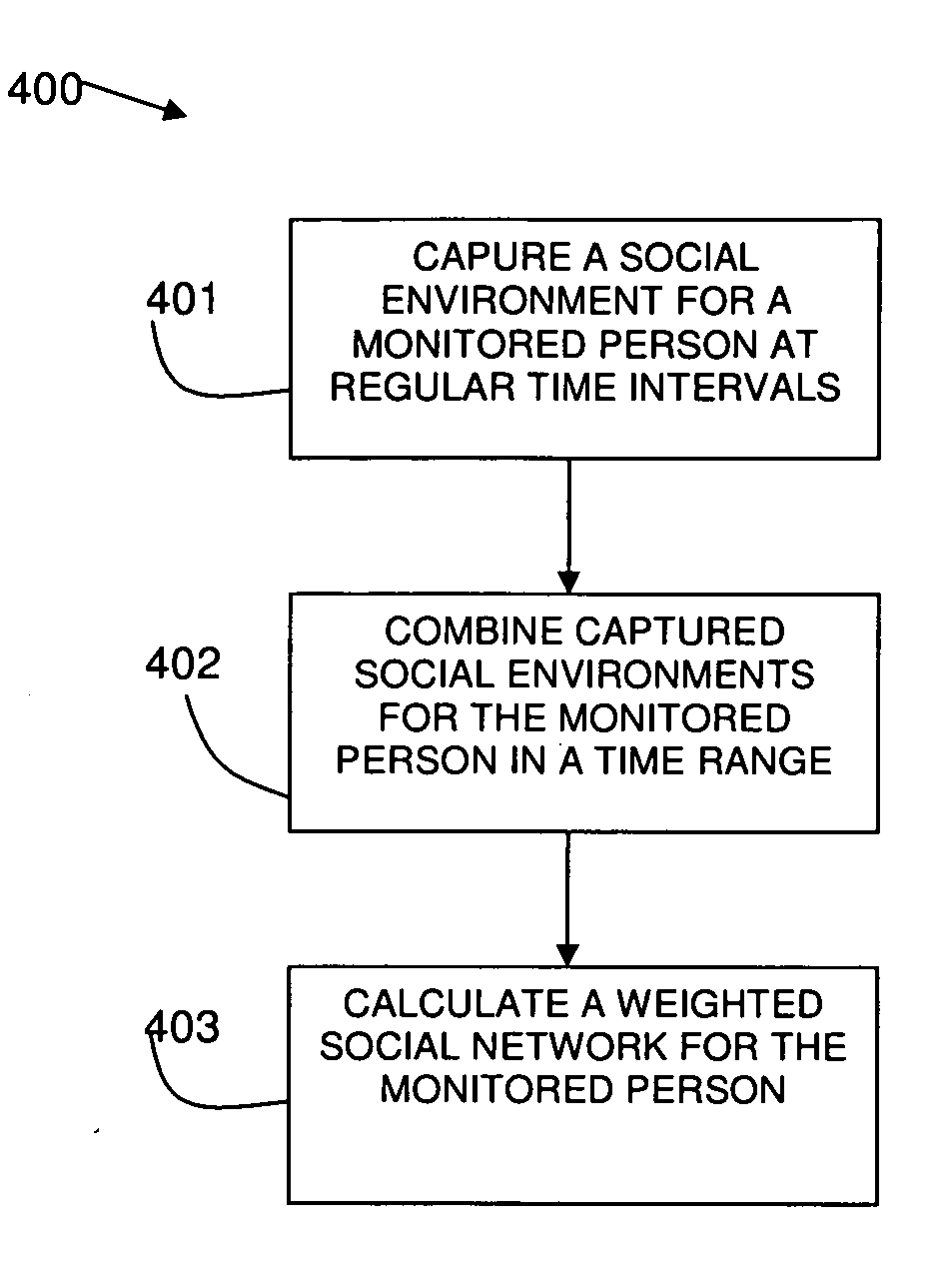
Method and System for Obtaining Social Network Information
A method and system for obtaining social network information are provided. The method includes capturing a social environment at a given time including capturing a set of identities in a predefined proximity to a monitored identity at the given time, wherein an identity is an identity of a real person or a virtual identity, and recording parameters of the social environment. The method then combines the captured social environments in a time range for a monitored identity and analyses the combined captured social environments in the time range to provide a social network for the monitored identity including weightings of the relationships between the monitored identity and the captured identities. The monitored identity and the captured identities may be avatars and the predefined proximity may be a proximity to a virtual location. Alternatively or additionally, the monitored identity and the captured identities may be identities of real people or groups of people, and the predefined proximity may be a proximity to a real location.
Owner:IBM CORP
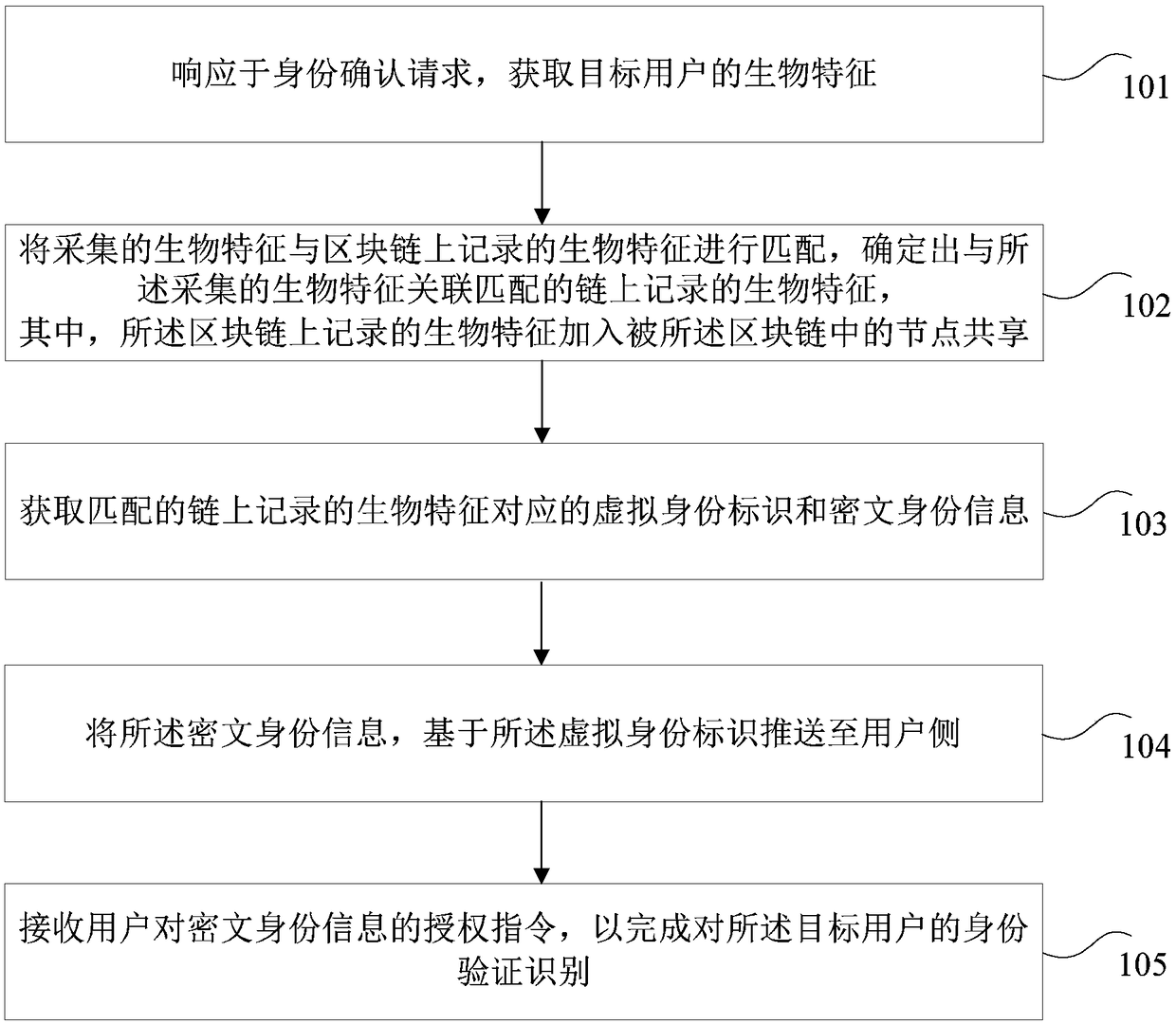
Authentication identification method, electronic device, and computer-readable storage medium
PendingCN109359601AInhibit entryStrong process controllabilityBiometric pattern recognitionMatching and classificationCiphertextAuthorization
The invention discloses an authentication identification method, an electronic device, and a computer-readable storage medium.. The method comprises the following steps of: matching the collected biometrics with the biometrics recorded on the block chain to determine the biometrics recorded on the chain that is associated with the collected biometrics, wherein, the biometrics recorded on the blockchain are added to the nodes shared by the block chain; acquiring virtual identity and ciphertext identity information corresponding to the biometric features recorded on the matching chain; pushingthe ciphertext identity information to a user side based on the virtual identity; receiving an authorization instruction of the user to the ciphertext identity information to complete the authentication identification of the target user. The scheme solves the technical problems that the user's biometric information is not controllable and universal in the existing identification and authenticationprocess, and achieves the technical effect of effectively improving the universality, security and reliability of the biometric information.
Owner:PING AN TECH (SHENZHEN) CO LTD
Method for providing alias folders in a document management system
ActiveUS8112713B2Eliminate needDigital data processing detailsOffice automationPersonalizationDocumentation procedure
Interactive collaboration within a secure, server-based social community integrated with a secured document management system that includes at least one of a plurality of professional functionalities and a plurality of integrative functionalities to members having a member virtual identity within the community. Members of the community may create a personalized custom set of folders within the document management system, which customized arrangement allows the members to view documents, files, and folders as they desire. By creating these personalized custom “alias” folders, the members rearrange folders to be more accessible to themselves, while leaving the actual files and folders unchanged as viewed by every other member of the community. Members or a network administrator may also grant permission to other members of the network to access alias folders of each other member.
Owner:ONELOOP
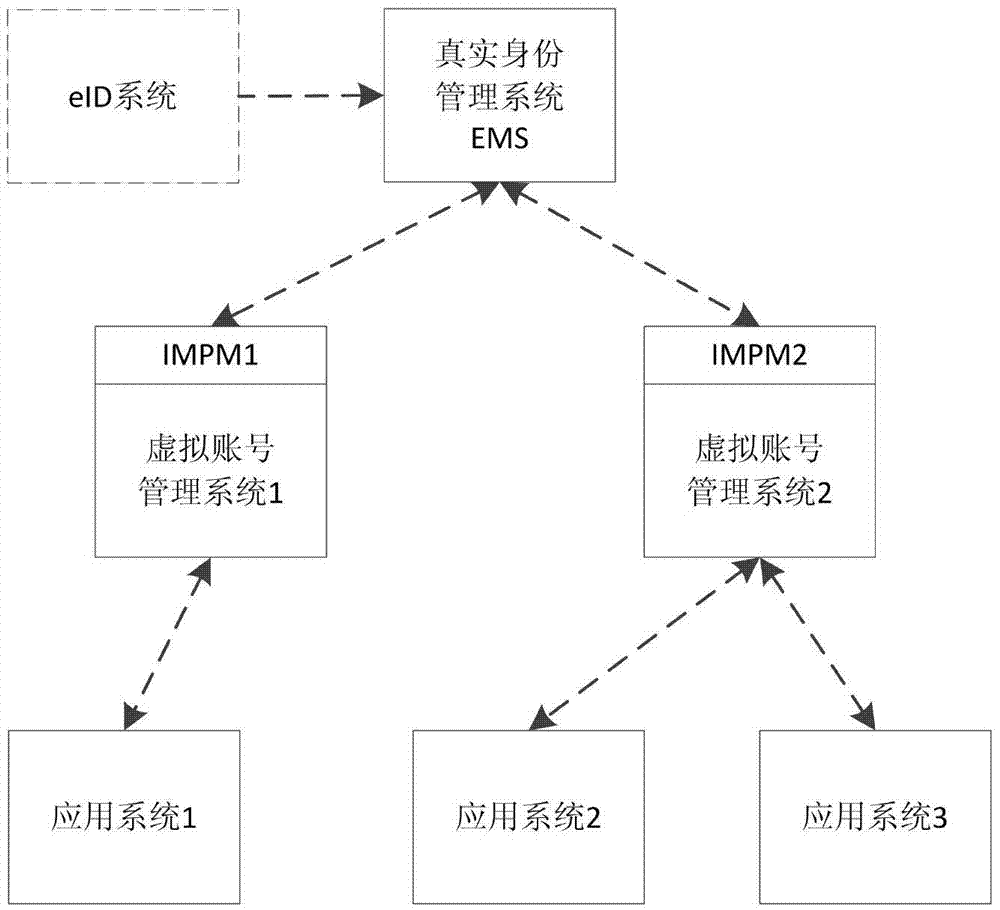
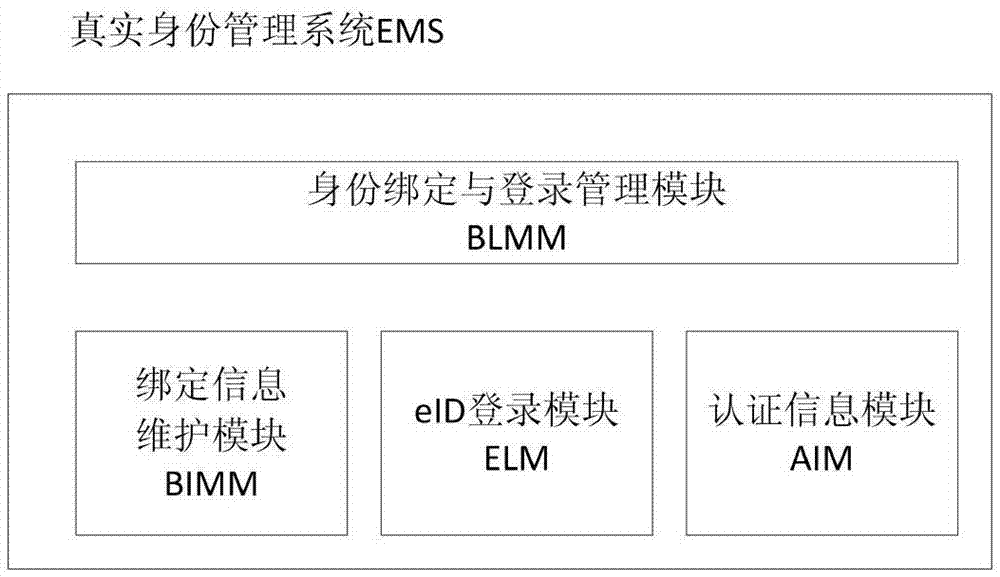
EID security control method and system based on eID
The invention discloses an EID security control method and system based on eID. The system comprises a virtual identity management system VIMS and an EID management system EMS of a target application system AS, wherein the VIMS is used for authenticating a user; if authentication is passed, a binding request is generated, and sent to the EMS; when the user accesses the AS, a login request is generated, and sent to the EMS; the EMS is used for authenticating the user according to the binding request; if authentication is passed, the Ie of the eID identity of the user is returned; then, the Ie is bound with account numbers Iv and V included in the binding request; then, a binding result is sent to the VIMS; the user is authenticated according to the login request; if authentication is passed, authentication result information is generated according to a returned virtual account number set {I} and the identifier E of the EMS, and returned to the VIMS; and the VIMS obtains the virtual account number Iv included therein, and processes access of the user.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Network user identity recognition method
ActiveCN109978016AHigh precisionEffective association identificationCharacter and pattern recognitionIdentity recognitionSimilarity analysis
The invention requests to protect an identity recognition method between a network identity and a real identity, comprising the following steps of: firstly, collecting real identity data of a specificobject in reality and specified network user data; then, formatting processing is performed on the acquired user identity data, and required information in the user identity data is extracted; Then,the relevance between the virtual identity and the real identity is mined and analyzed, and similarity analysis of basic identity information is carried out; then, virtual identity description information of the user is mined and analyzed through content information published on the network by the user, an association relationship between the virtual identity description information and the real identity description information is established in combination with a knowledge base, and correlation analysis of the identity description information is carried out; and finally, fusing the calculation results of the similarity of the basic identity information and the correlation of the identity description information, and inferring the relationship between the specified virtual identity and thereal identity. The public opinion supervision method is helpful for forensics investigation of specific user identities in cases, and public opinion supervision efficiency is improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Data sharing method and system, electronic equipment and storage medium
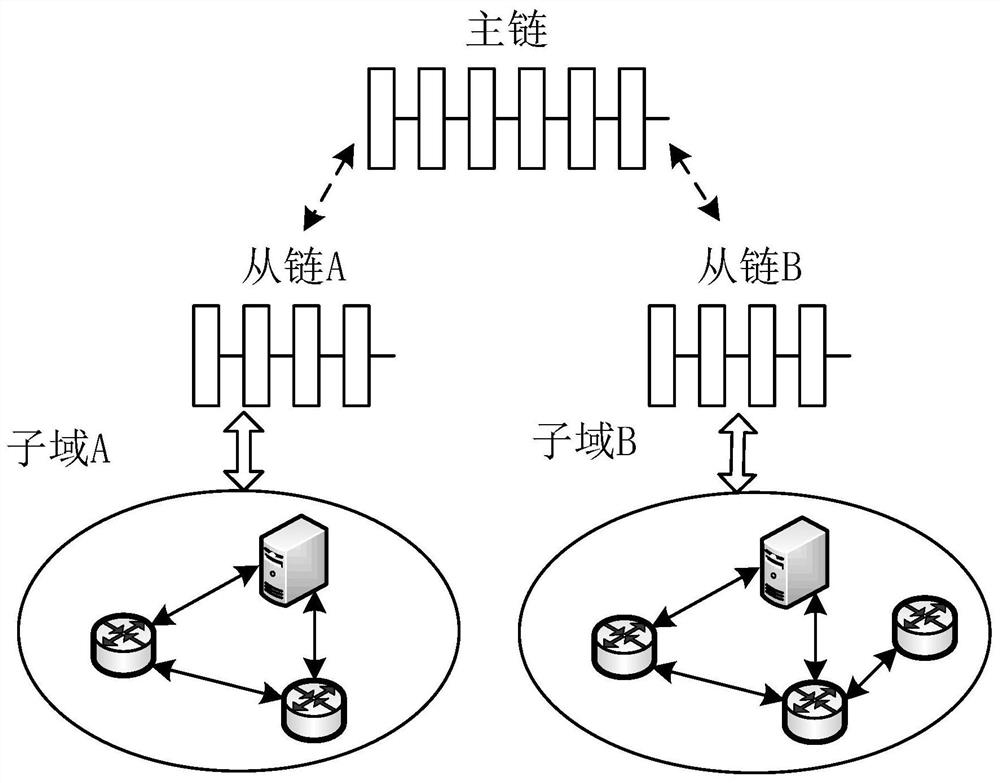
PendingCN112434313AAchieve the effect of sharingAvoid exposureDatabase distribution/replicationDigital data protectionComputer networkEngineering
The invention provides a data sharing method. The data sharing method comprises the steps of building a trust alliance block chain according to an Internet of Things application scene and an equipmentgeographic position, wherein the trust alliance block chain comprises a main chain and at least one slave chain, each slave chain corresponds to a sub-domain, and each sub-domain comprises a leader node; establishing a virtual slave chain on the trust alliance block chain; enabling a leader node in each sub-domain of the trust alliance block chain to designate a node in the sub-domain of the leader node as a federated learning node of the sub-domain, allocate a virtual identity to the federated learning node of the sub-domain, and join the virtual slave chain; and enabling each federated learning node to perform joint training of a neural network model by using the data generated in the sub-domain of the federated learning node, establishing the same federated learning model, and completing data sharing among the sub-domains. The invention further provides a data sharing system, electronic equipment and a storage medium.
Owner:BEIJING UNIV OF POSTS & TELECOMM
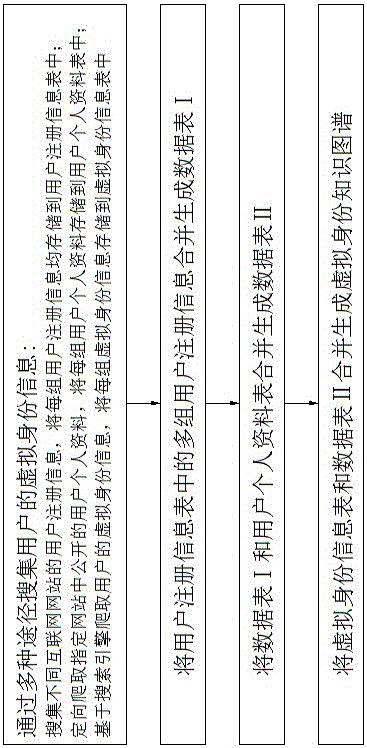
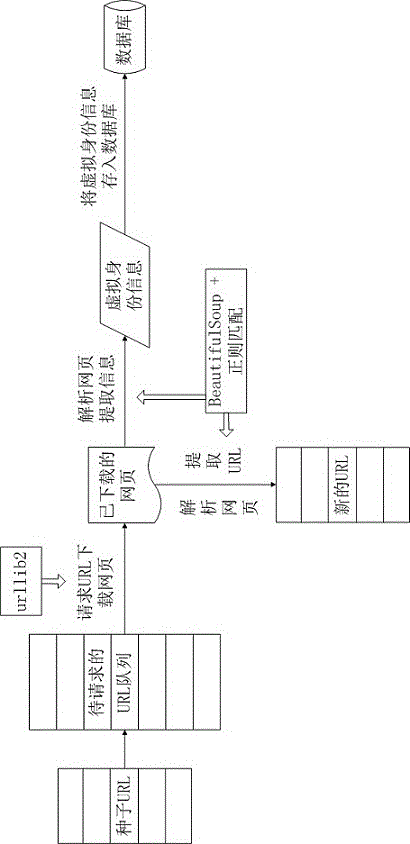
Virtual identity knowledge graph establishing method for aiming at network threat discovery
ActiveCN106230829AIncrease breadthImprove the efficiency of traceabilityTransmissionUser - individualKnowledge graph
The invention discloses a virtual identity knowledge graph establishing method for aiming at network thread discovery, wherein the method belongs to the field of network virtual identity tracking. The method aims to settle a technical problem of reducing time in searching virtual identity information for improving network tracking and tracing efficiency. The method comprises the steps of (1), searching the virtual identity information of a user through a plurality of ways which comprise searching user registration information of different Internet websites, directionally crawling user individual information which is disclosed in a preset website, and crawling the virtual identity information of the user based on a searching engine; (2), combining a plurality of sets of user registration information in a user registration information table for generating a data sheet I, (3), combining the data sheet I with a user individual information sheet for generating a data sheet II; and (4), combining a virtual identity information sheet with the data sheet II for generating the virtual identity knowledge graph. The identity information is searched through the virtual identity knowledge graph, thereby reducing time in searching the virtual identity information and improving efficiency in network tracking and tracing.
Owner:INSPUR COMMON SOFTWARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com