Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2809 results about "Public security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
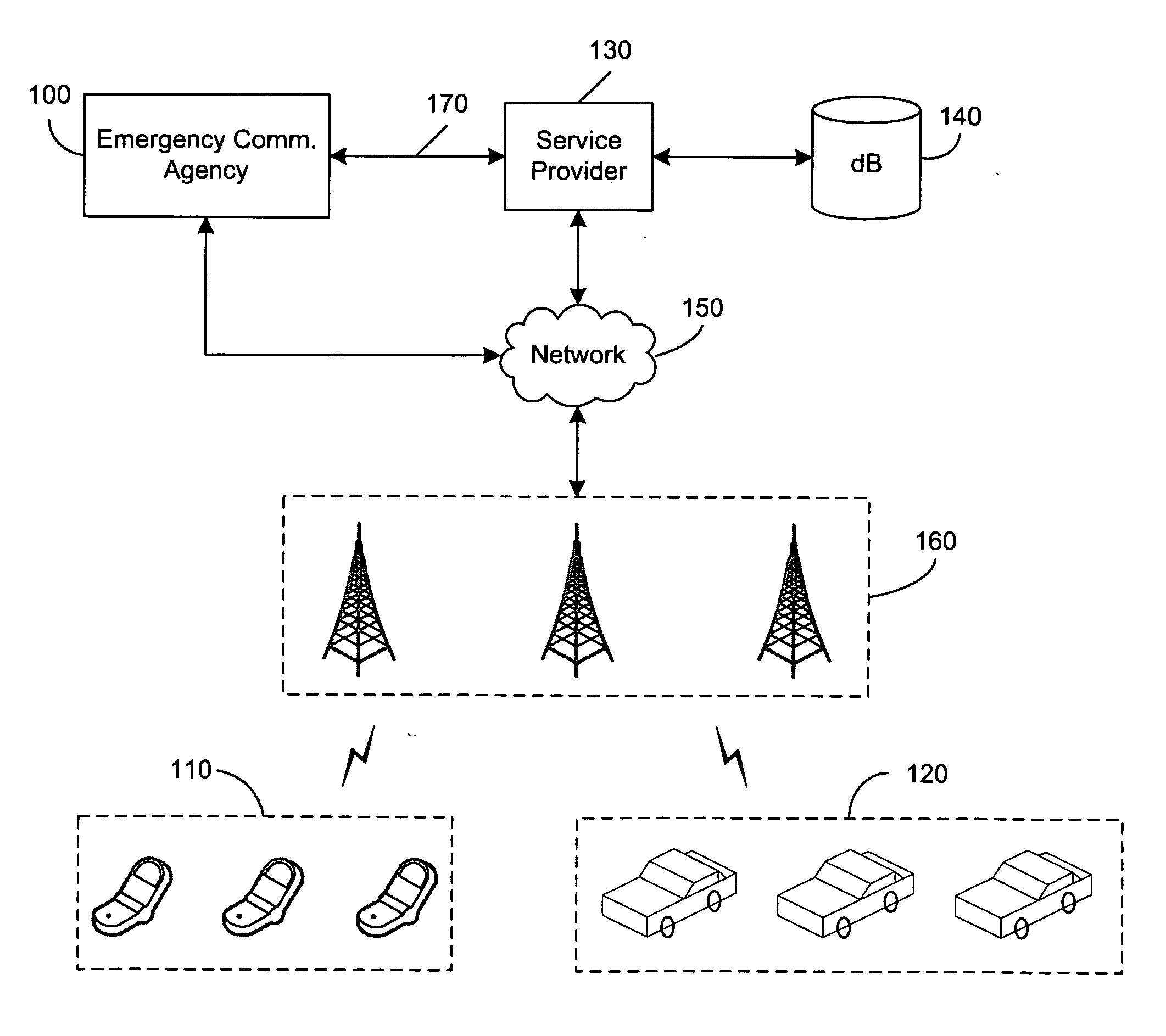
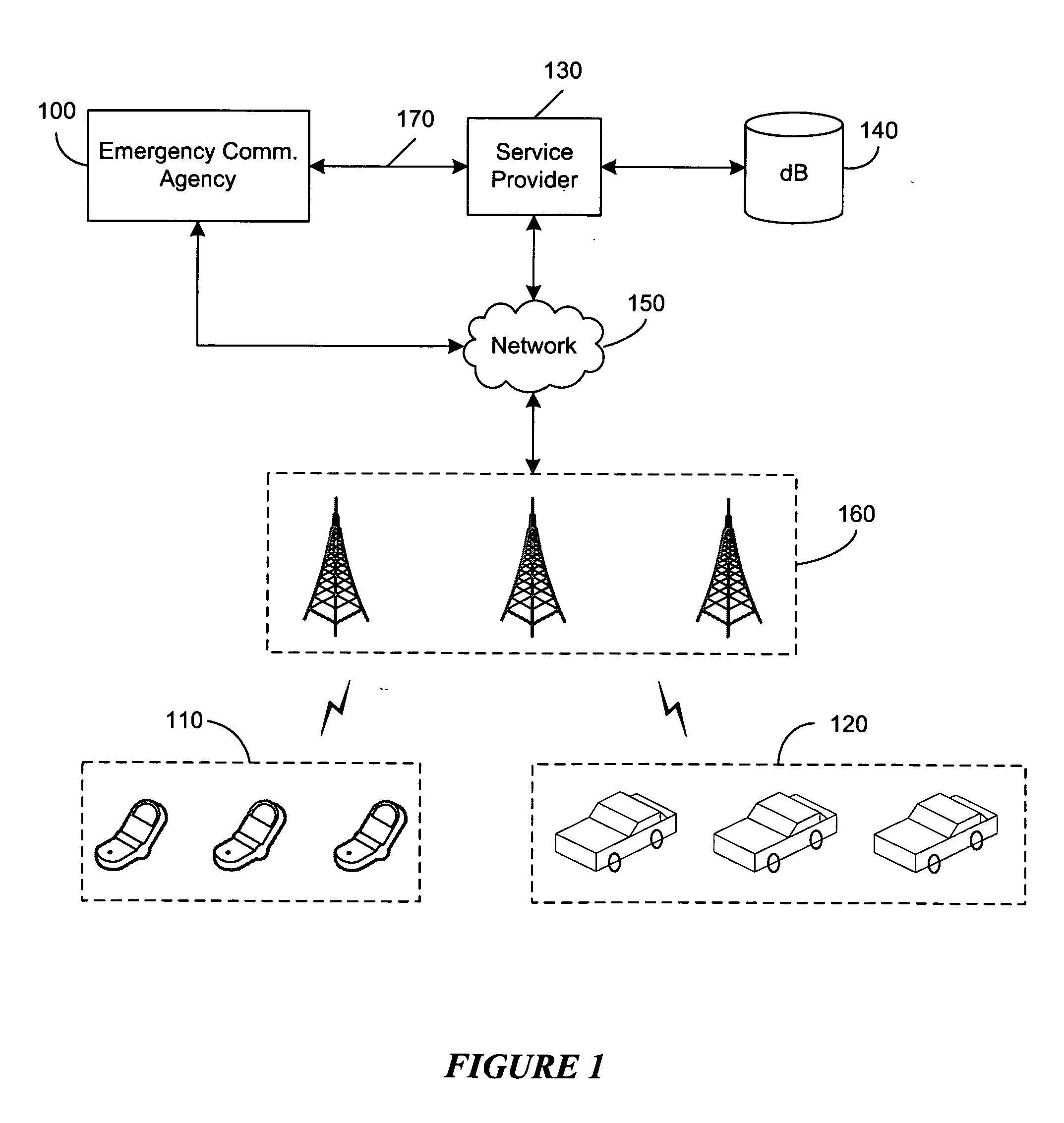
Public security is the function of governments which ensures the protection of citizens, persons in their territory, organizations, and institutions against threats to their well-being – and to the prosperity of their communities.
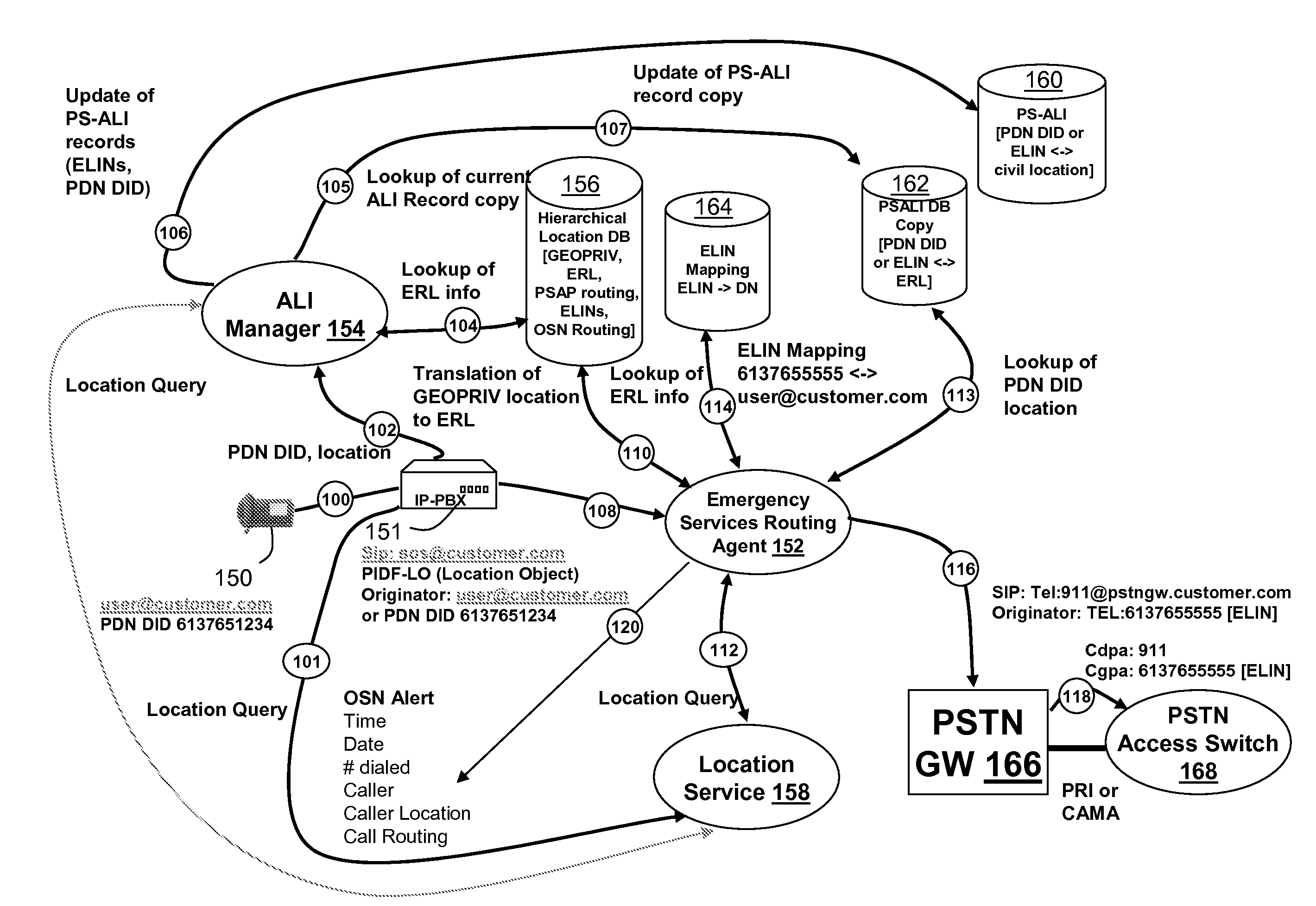
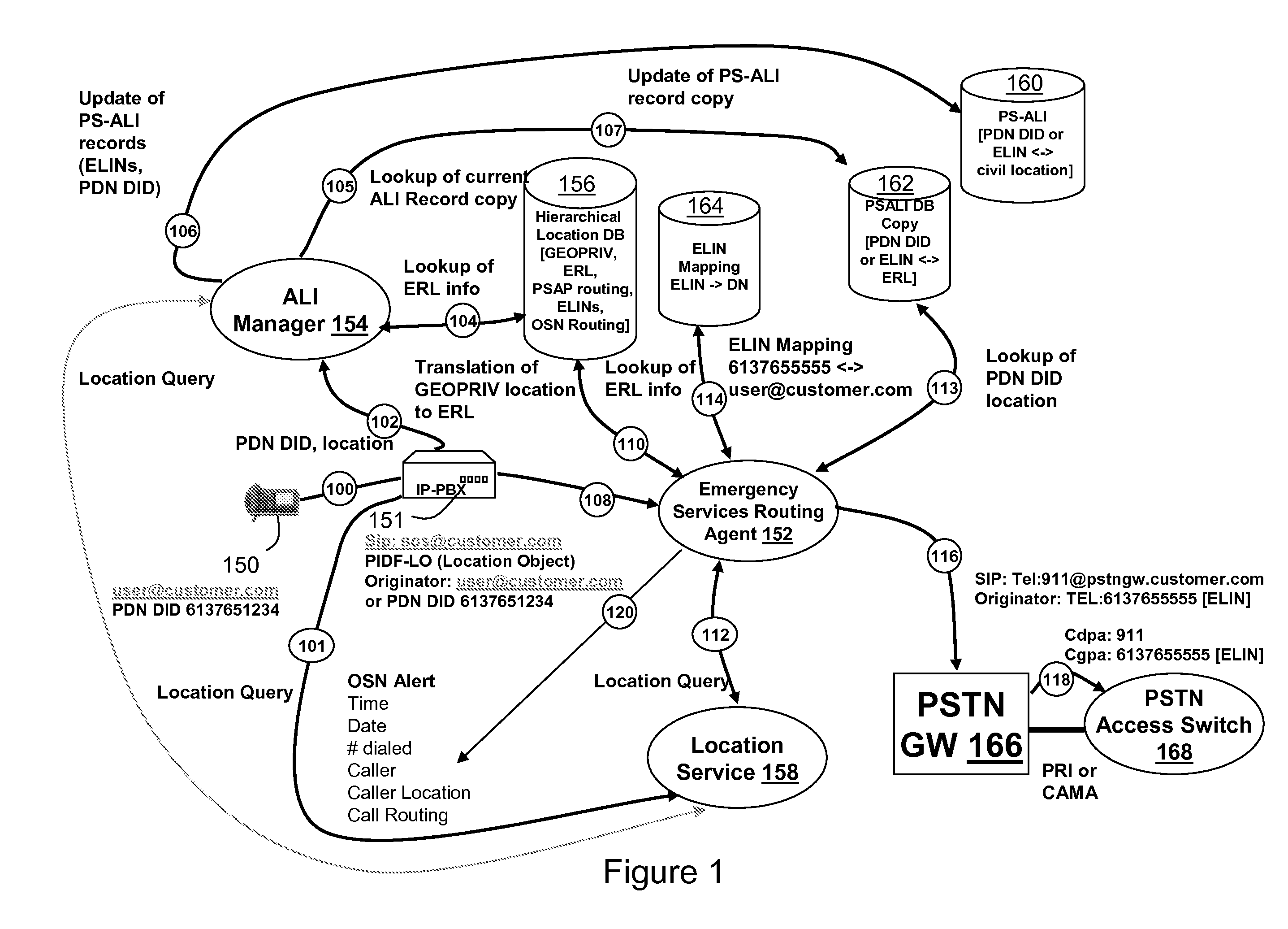
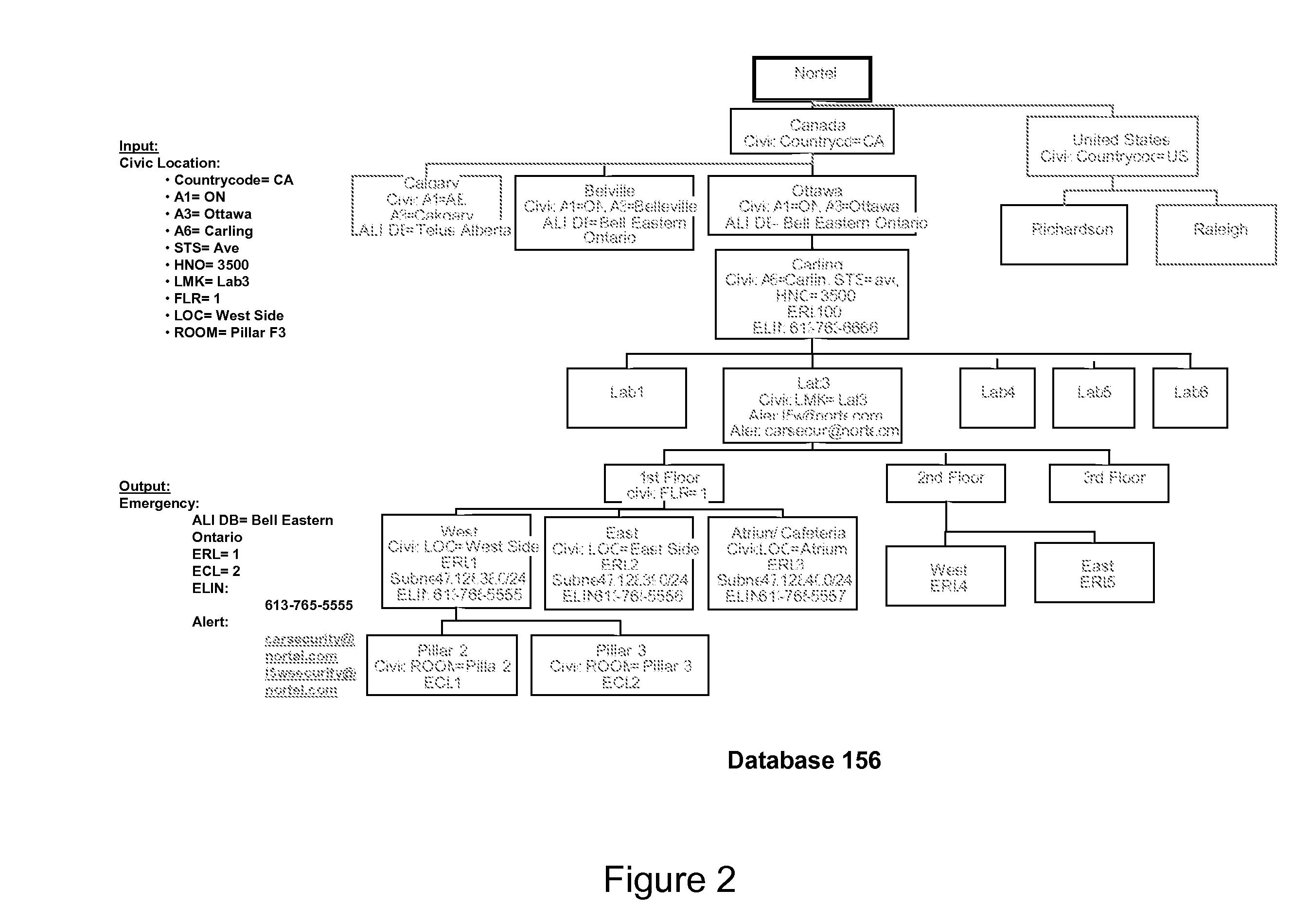
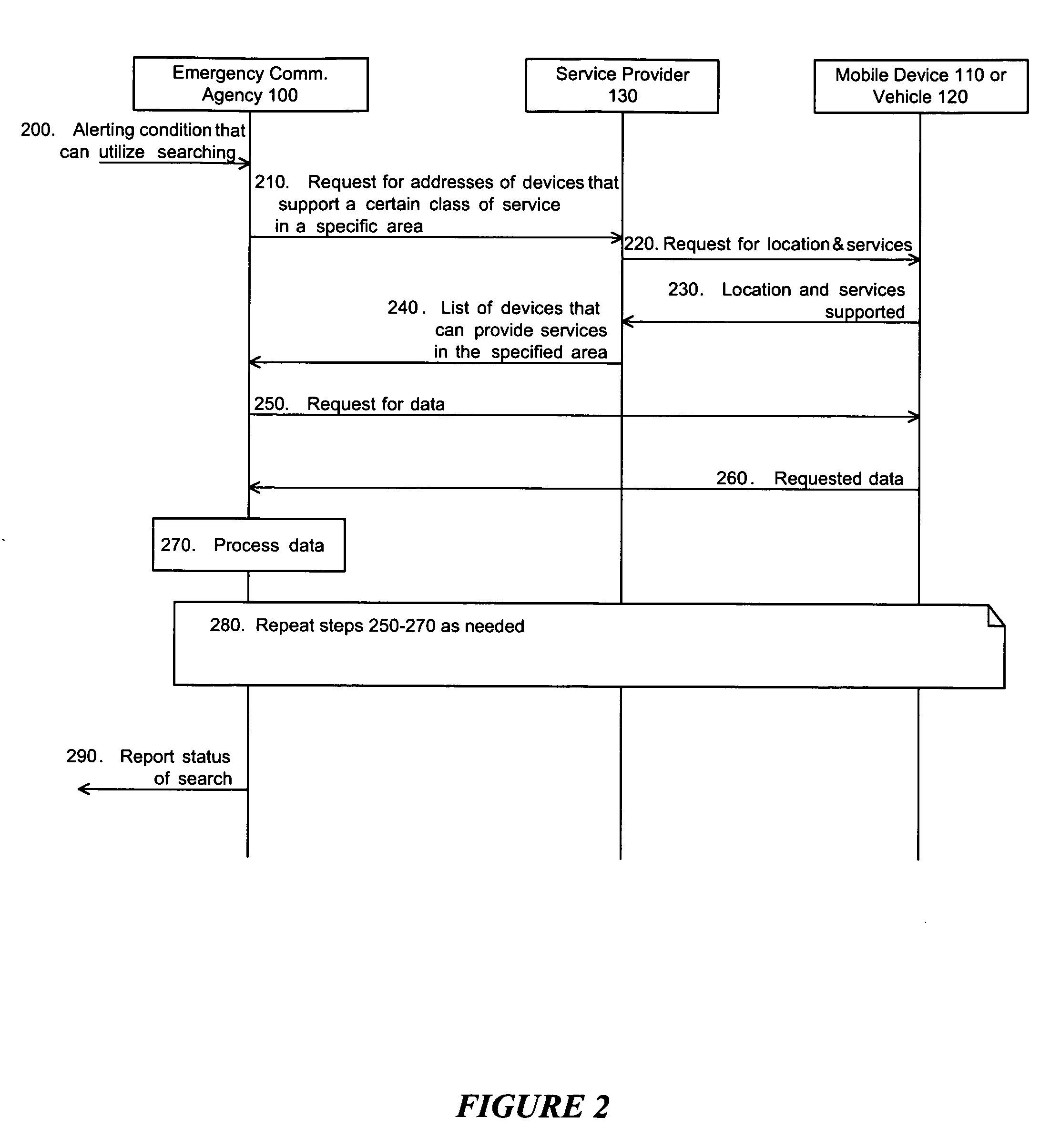
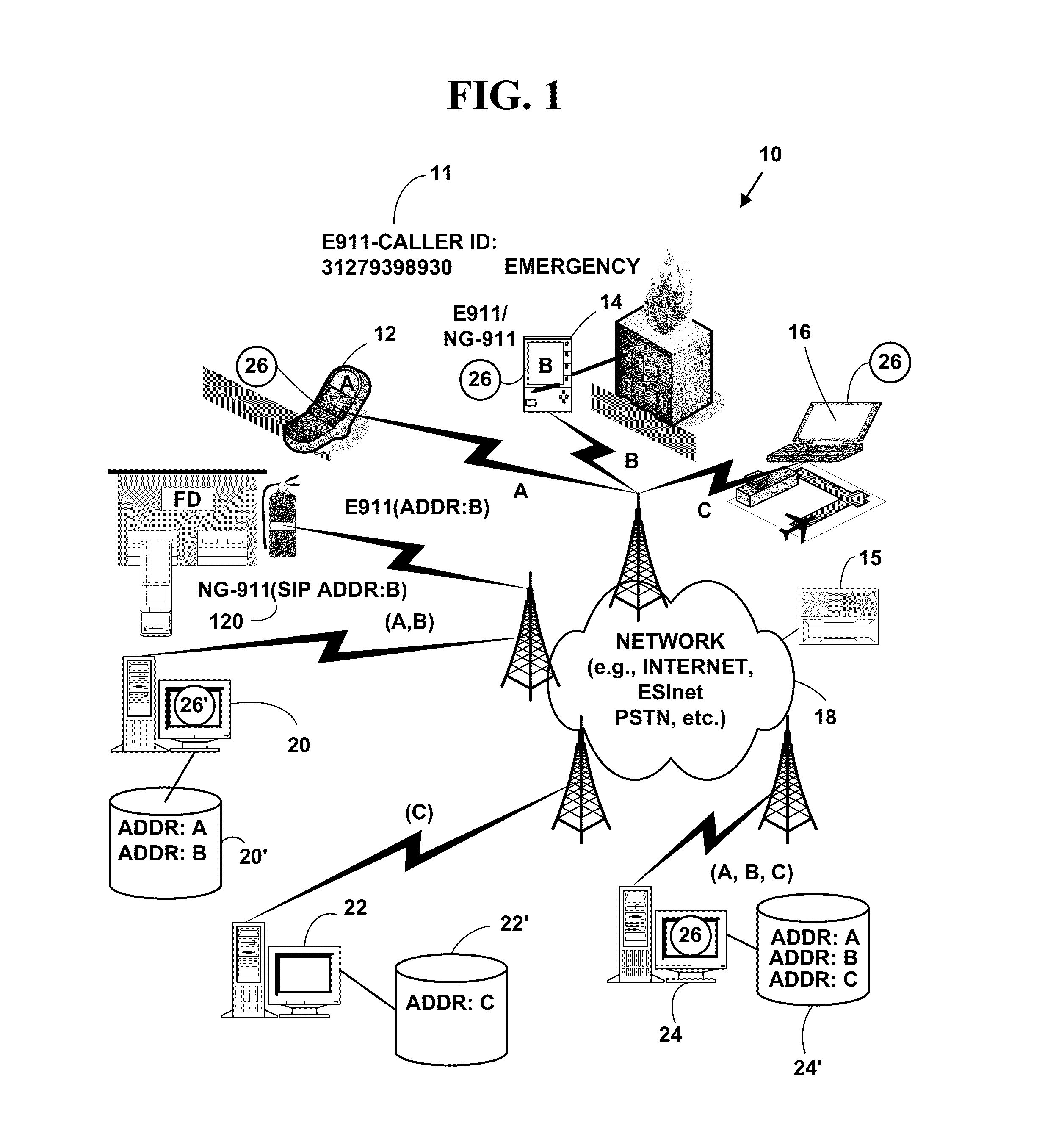
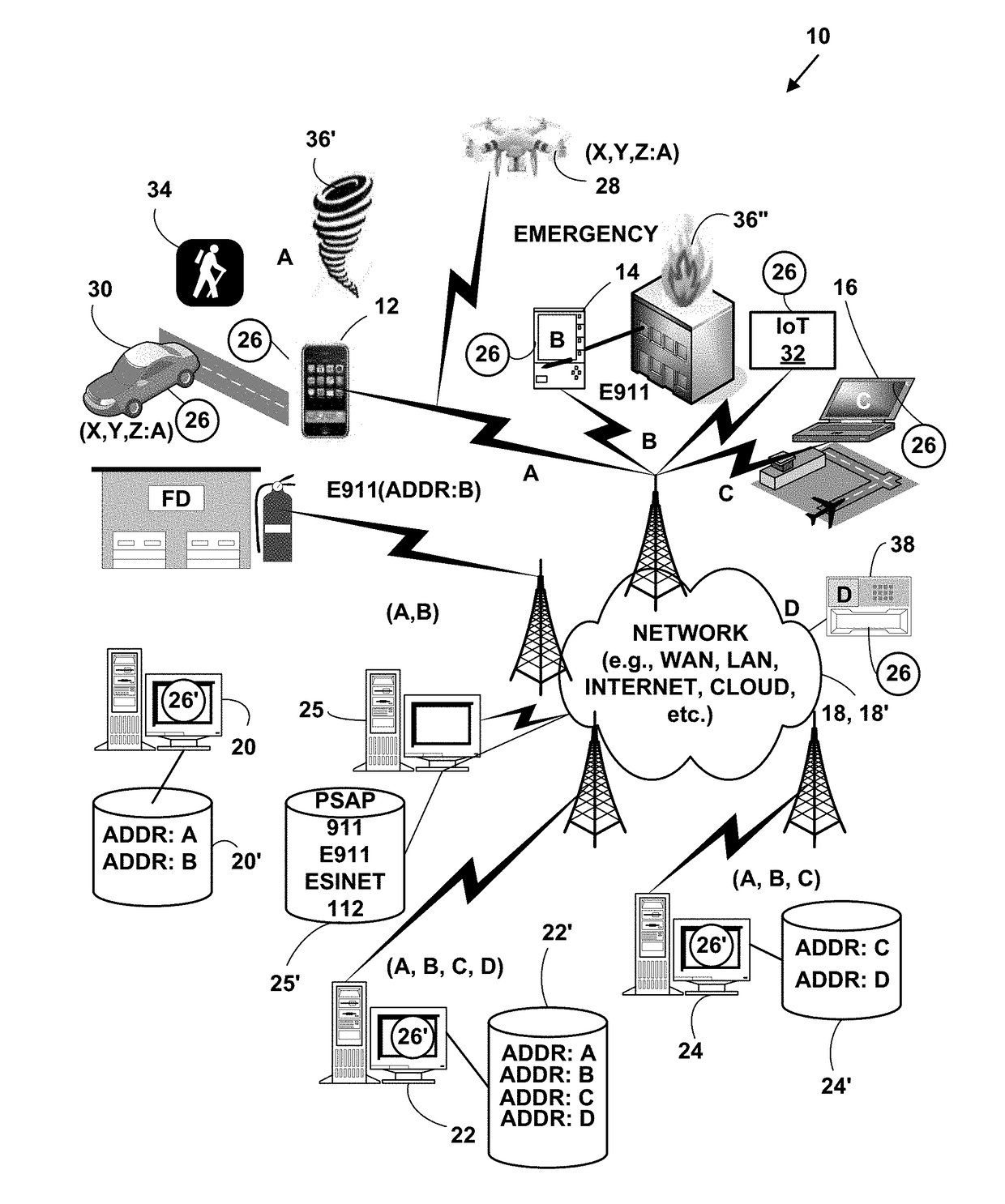
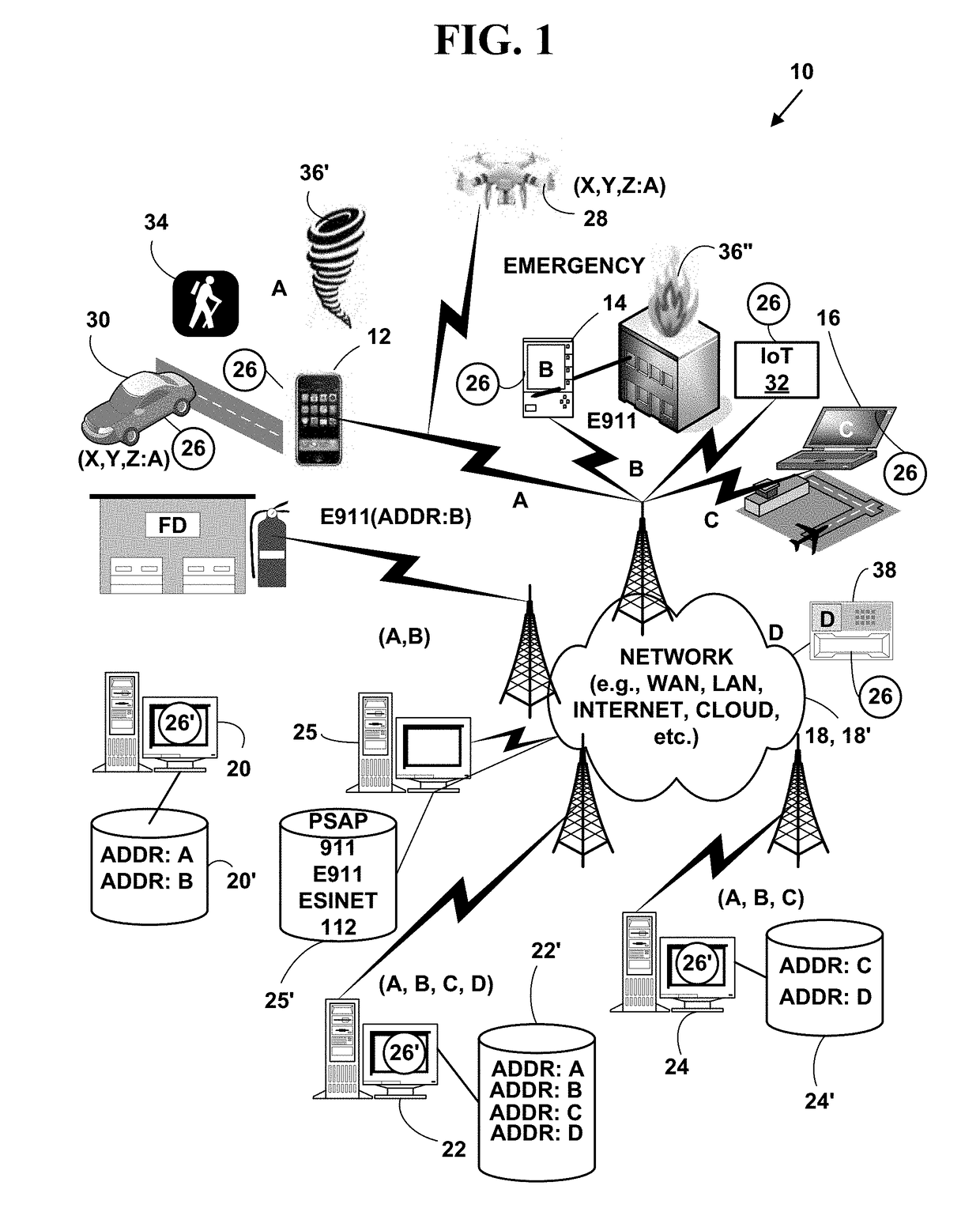
Adaption of emergency calls to the emergency services network based on caller location
ActiveUS20080037715A1Highly integratedEasy to carryTelephonic communicationComputer scienceEmergency situations
The invention includes a technique for integrating emergency calling for VoIP users with legacy emergency services to facilitate adapting to the evolving emergency services network and the services that are available in a given location. Generic location information provided by (or determined for) VoIP emergency callers, typically in civic or geodetic formats, is translated into Emergency Response Locations (ERLs) defining an area, such as an area within an enterprise premises, in which the caller is located. The translated location information is conveyed to the Public Safety Answering Point (PSAP) with the emergency call in for form of the ANI (Automatic Number Identification) or calling line identification number. An appropriate route / gateway is then selected to be used to reach the PSAP appropriate for the caller's location, and an emergency call notification to the appropriate local emergency response personnel is generated within the enterprise based on the caller's location.
Owner:AVAYA INC
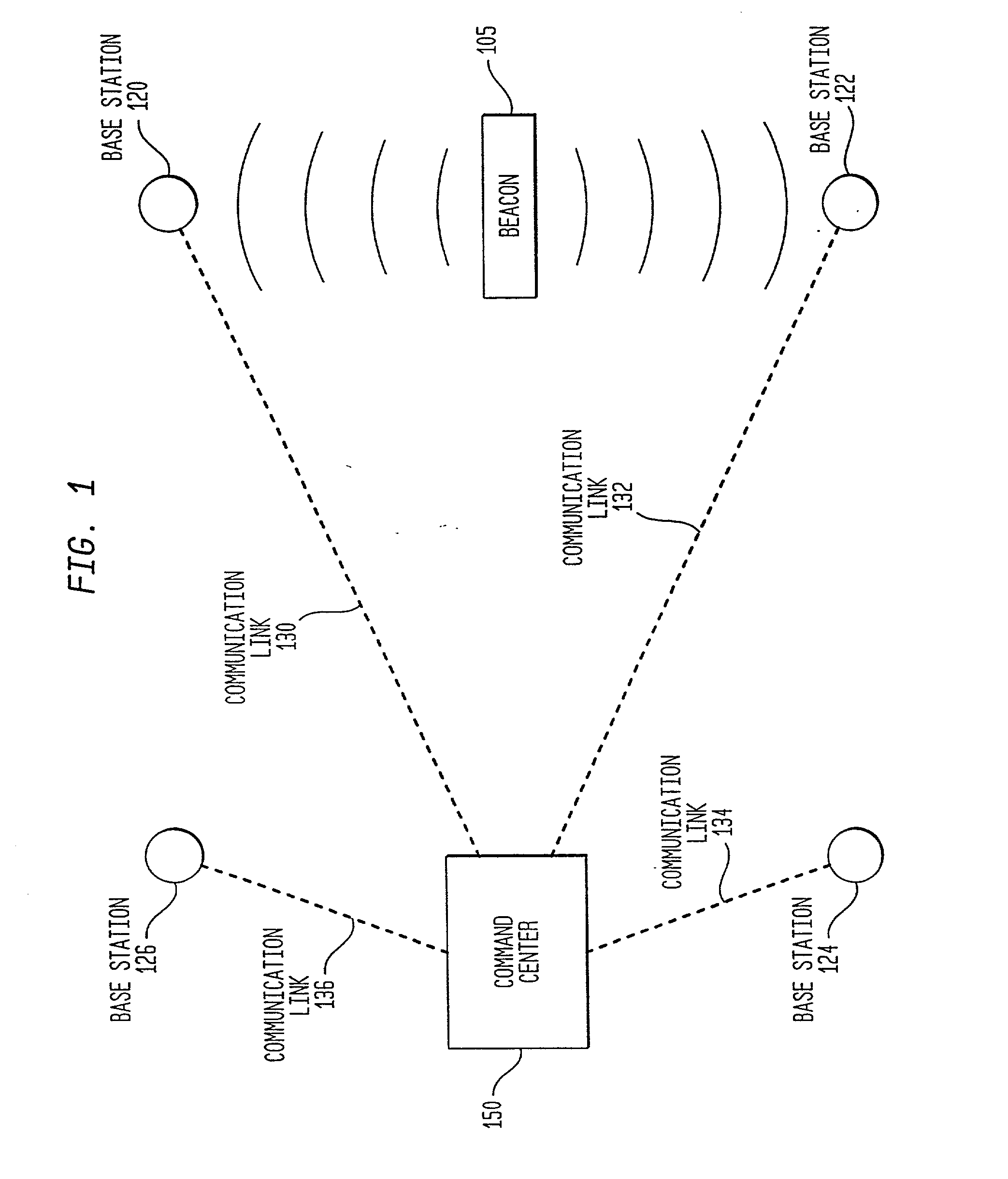
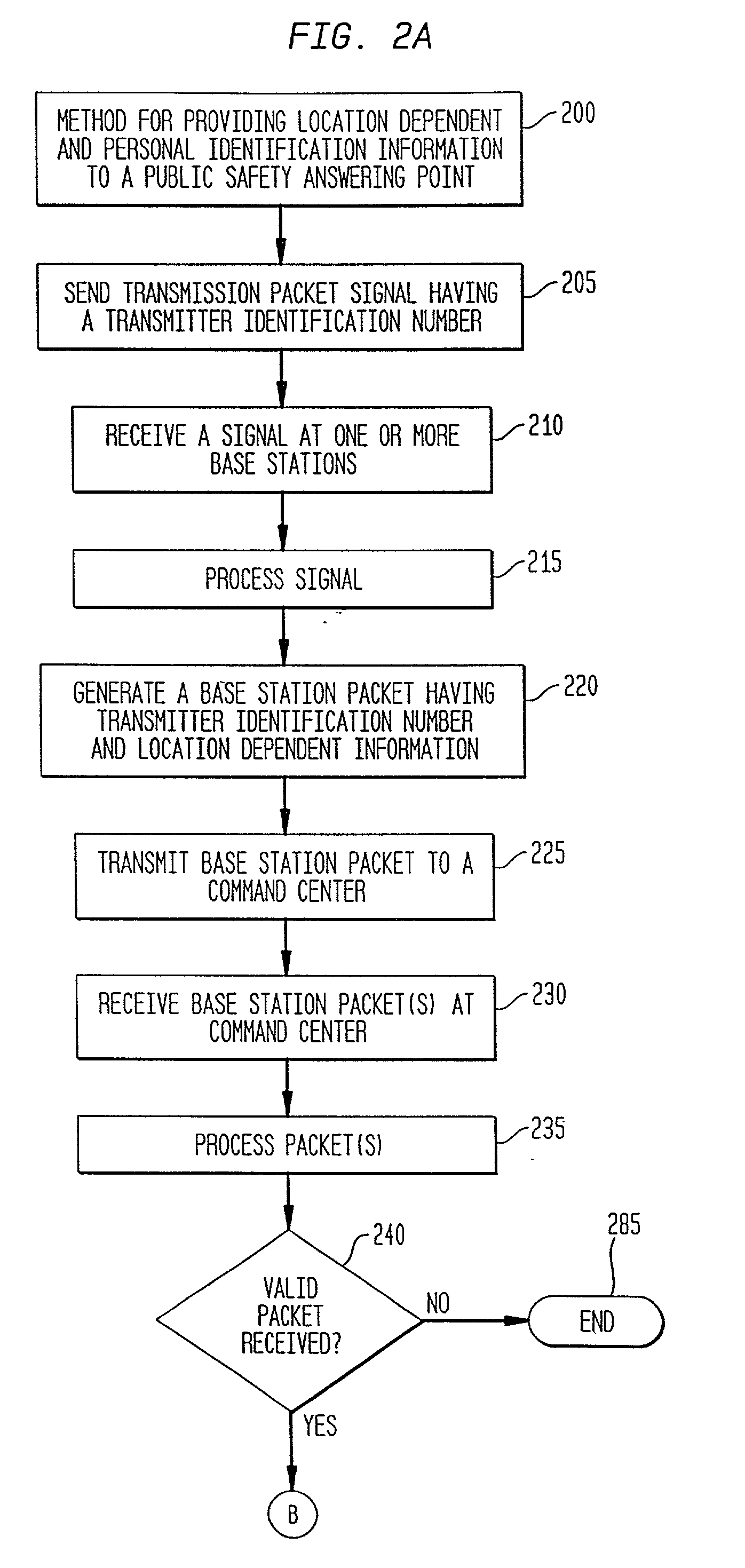
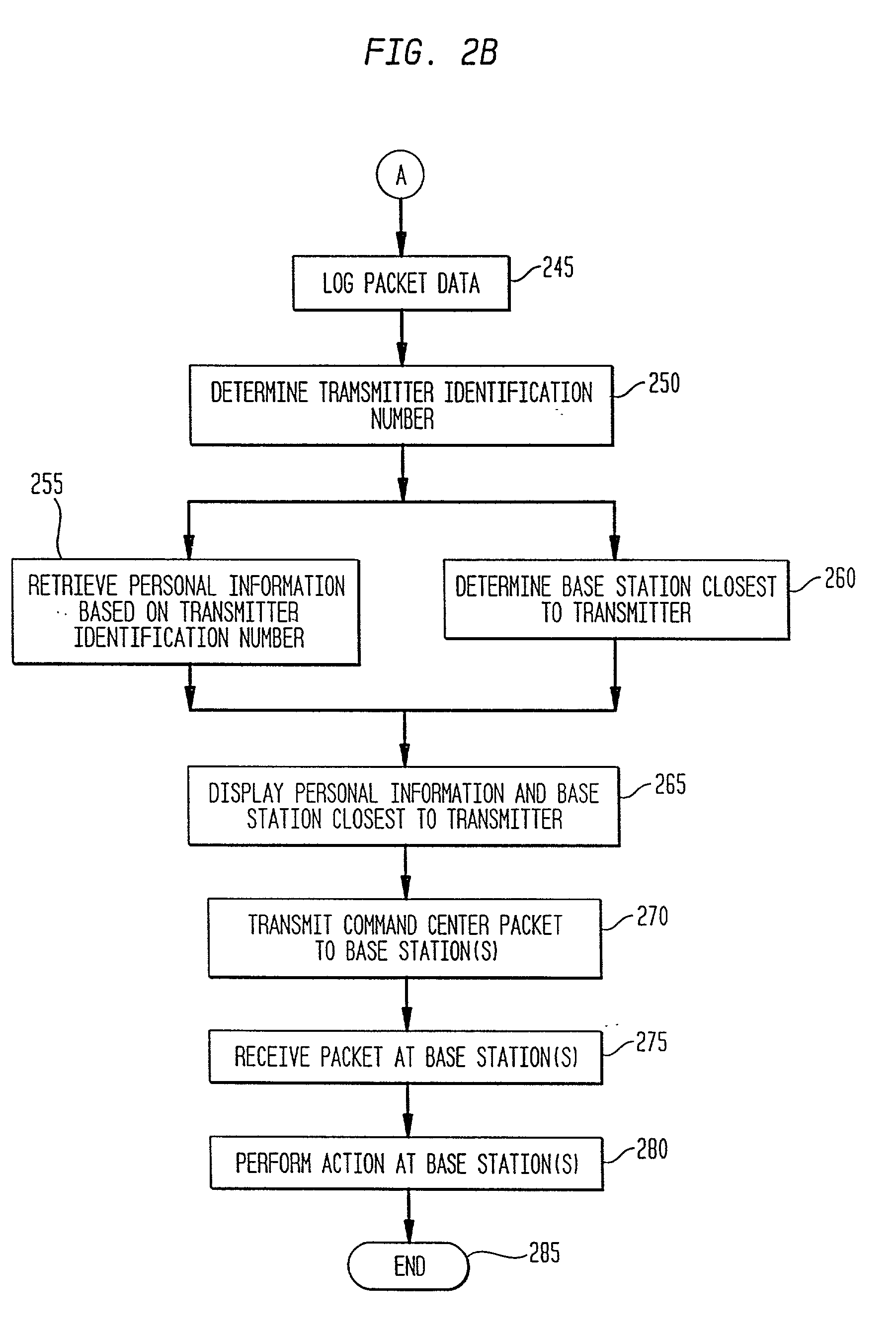
Method and system for providing location dependent and personal identification information to a public safety answering point
InactiveUS20010034223A1Emergency connection handlingTelephonic communicationNetwork packetSignal processing
A method and system are provided for sending location dependent and personal identification information to a public safety answering point. Base stations for receiving a transmission packet signal having a transmitter identification number are located throughout an area where personal security coverage is desired. Whenever a personal security transmitter is activated, it is received by one or more base stations. Each base station has a signal receiving unit for receiving a transmission packet signal and a signal processing unit for processing a transmission packet signal and generating a base station packet. Base station packets contain both a transmitter identification number and location information about the activated transmitter. After a base station packet is generated, it is sent to a command center for processing. If a valid base station packet is received at a command center, information contained in the base station packet is used to determine the closest base station to the activated transmitter and to retrieve personal identification information about the person to whom the transmitter was issued. This location and personal identification information is then displayed at the command center or public safety answering point.
Owner:MARYLAND UNIV OF COLLEGE PARK
Emergency communications for the mobile environment
InactiveUS20070139182A1Beneficial and mannerEmergency connection handlingConnection managementInformation processingTelematics
Systems and methods for two-way, interactive communication regarding emergency notifications and responses for mobile environments are disclosed. In accordance with one embodiment of the present invention, a specific geographic area is designated for selective emergency communications. The emergency communications may comprise text, audio, video, and other types of data. The emergency notification is sent to users' mobile communications devices such as in-vehicle telematics units, cellular phones, personal digital assistants (PDAs), laptops, etc. that are currently located in the designated area. The sender of the emergency message or the users' service provider(s) may remotely control cameras and microphones associated with the users' mobile communications devices. For example, a rear camera ordinarily used when driving in reverse may be used to capture images and video that may assist authorities in searching for a suspect. The users' vehicles may send photographs or video streams of nearby individuals, cars and license plates, along with real-time location information, in response to the emergency notification. Image recognition algorithms may be used to analyze license plates, vehicles, and faces captured by the users' cameras and determine whether they match a suspect's description. Advantageously, the present invention utilizes dormant resources in a highly beneficial and time-saving manner that increases public safety and national security.
Owner:MOTOROLA INC
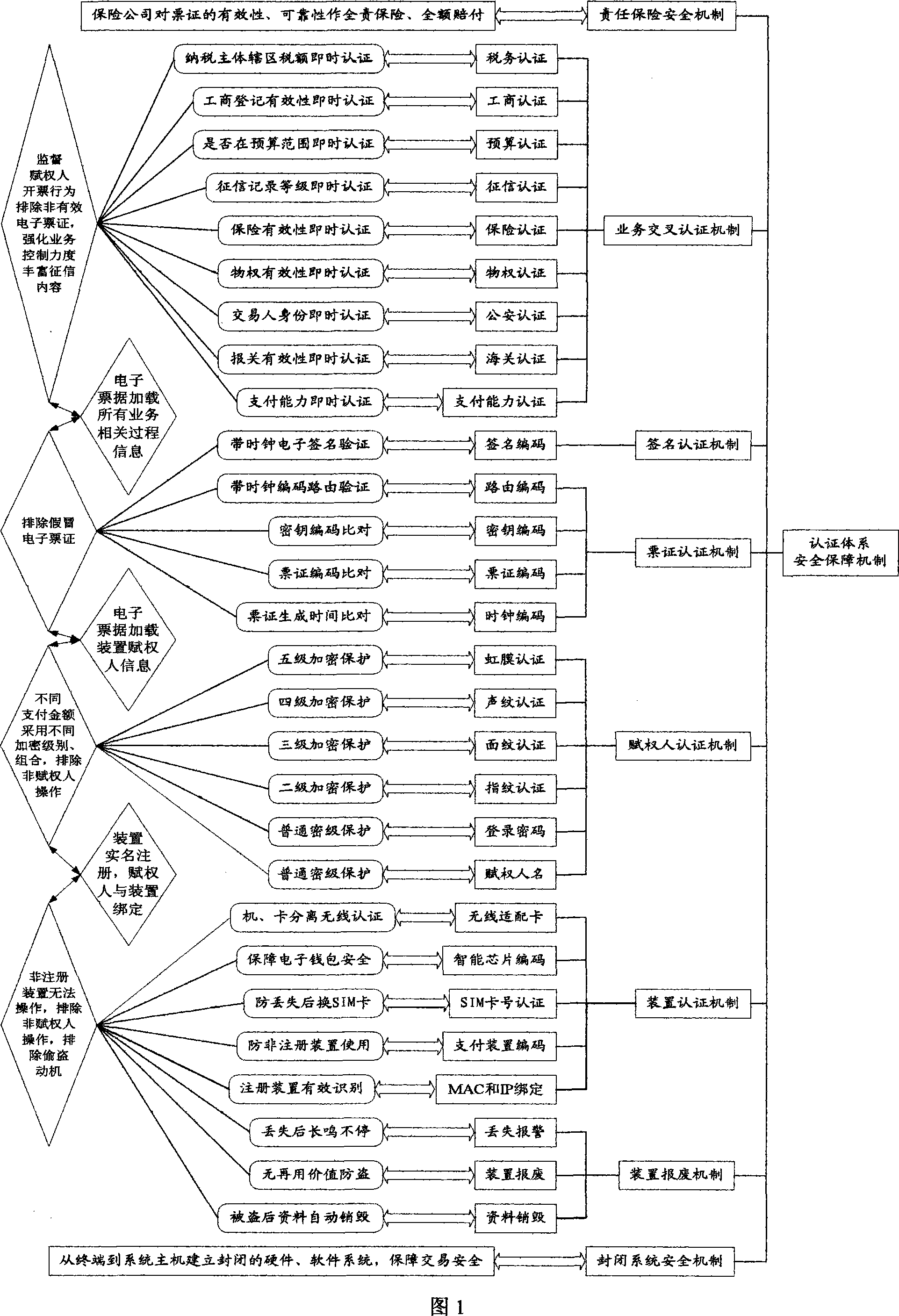
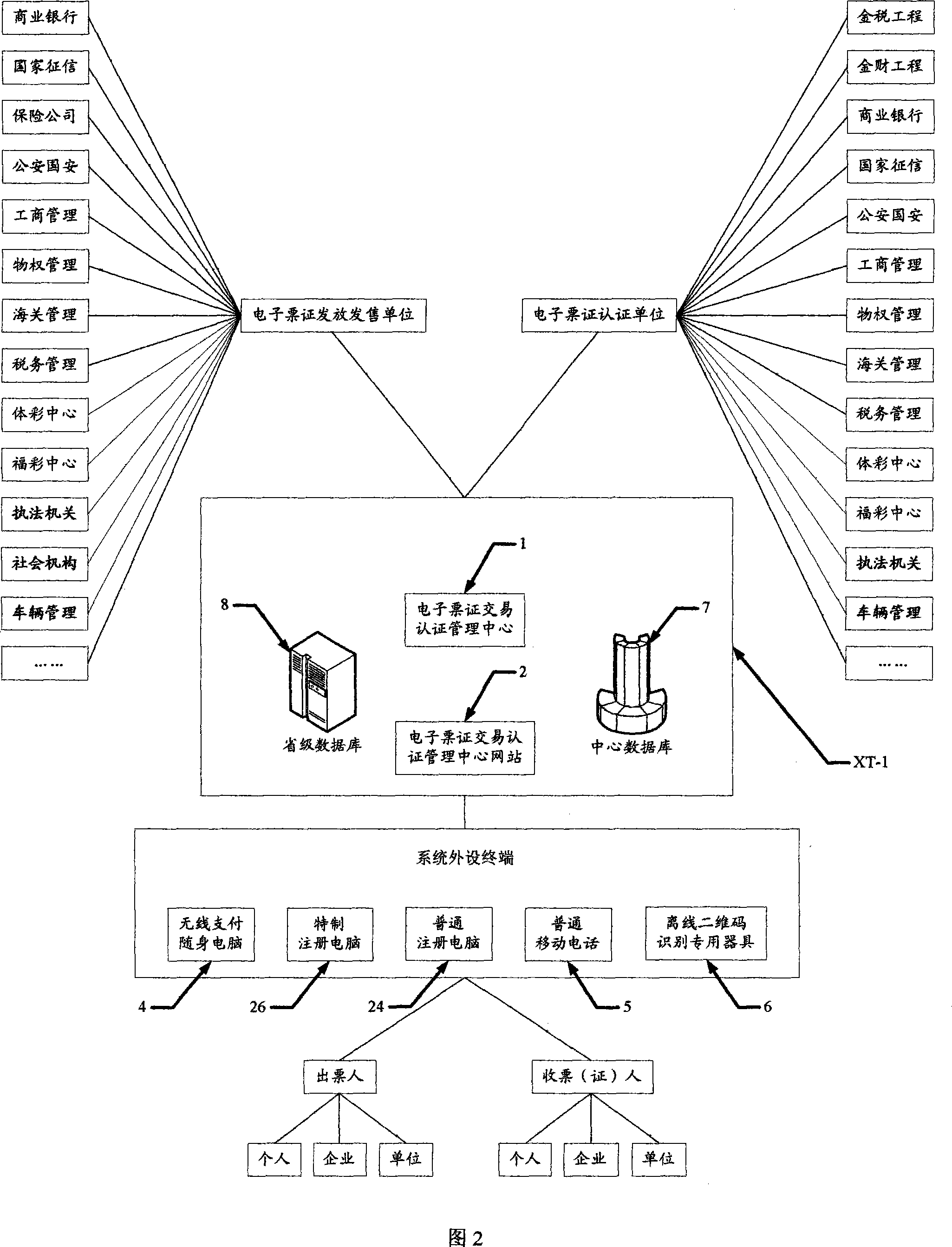
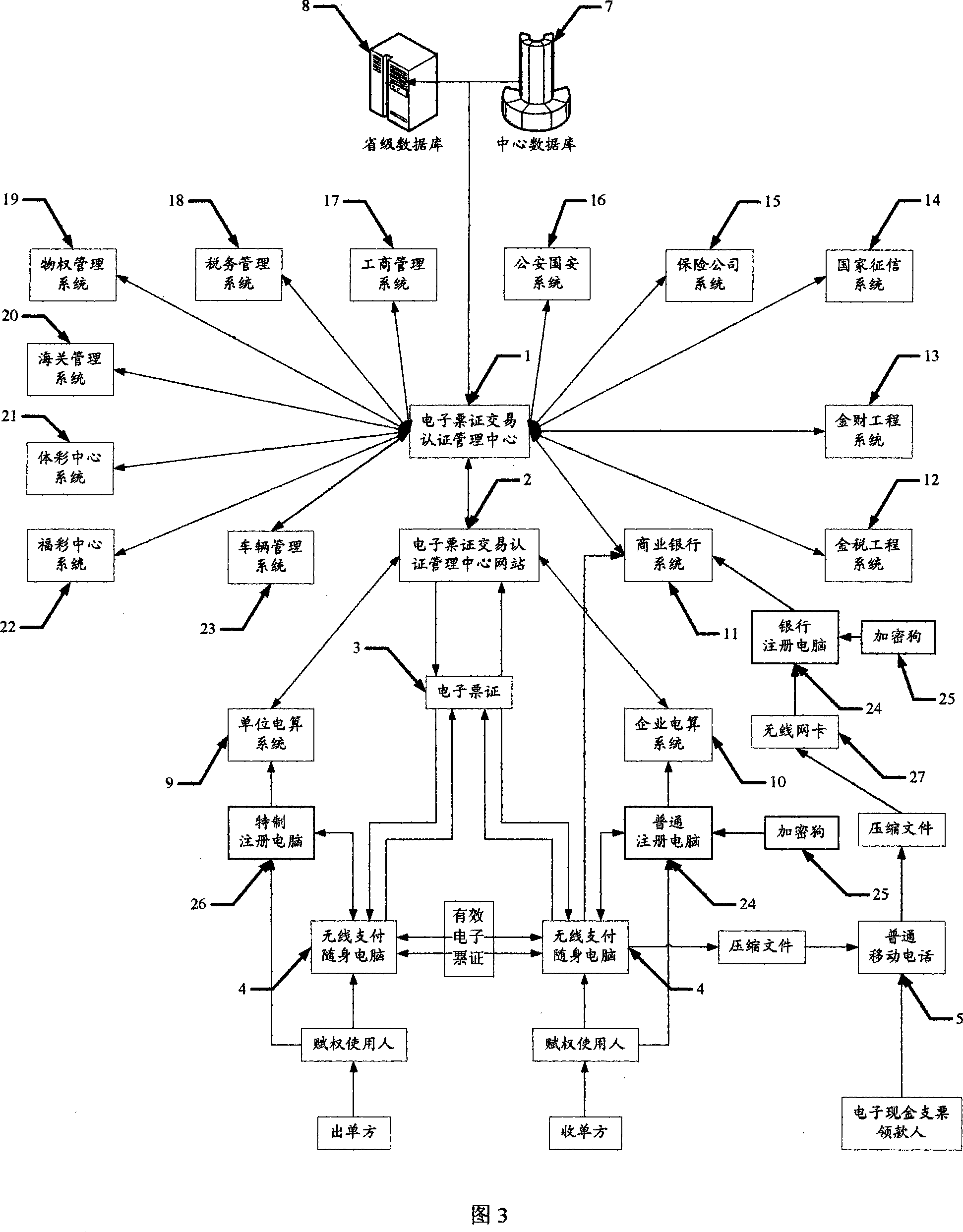
Method for managing electronic ticket trade certification its carrier structure, system and terminal
InactiveCN101075316APrevent forgeryPrevent tamperingAcutation objectsFinanceComputer scienceManagement system
A certification-managing method of electronic ticket transaction includes setting up certification-management center of electronic ticket transaction; connecting said center to fax office, financial office, commercial bank, public security, etc; registering user with real name on terminal; purchasing and downloading electronic ticket; finalizing ticket filling, certifying, electronic signing and locking; exchanging ticket through transaction-certification network station of ticket for realizing integrated certification in order to ensure truth of ticket.
Owner:SICHUAN ZHENGDAOTIANHE INFORMATION TECH
Monitoring and security system and method
InactiveUS20060125620A1Enhancing customer loyaltyFrequency-division multiplex detailsRegistering/indicating working of vehiclesHand heldEngineering
A system and method simplifying, combining and improving vehicle and personal diagnostic monitoring and reporting, automatic vehicle emergency event notification, personal emergency distress notification, vehicle and personal location notification, vehicle and personal threat notification and remote vehicle operation (door locks, lights, horn and other systems). System and method include a device within the vehicle, or carried by an individual, and having a wireless communication capability, providing two way communication of data via a hand-held device or key fob, and a remote call center capable of storing, analyzing and assessing services required and communicating back the results of that assessment. Services would include roadside mechanic assistance, towing, informed Public Safety Answering Point (PSAP) notification (including assessment of severity of emergency) and threat notification.
Owner:SMITH TIMOTHY D +1
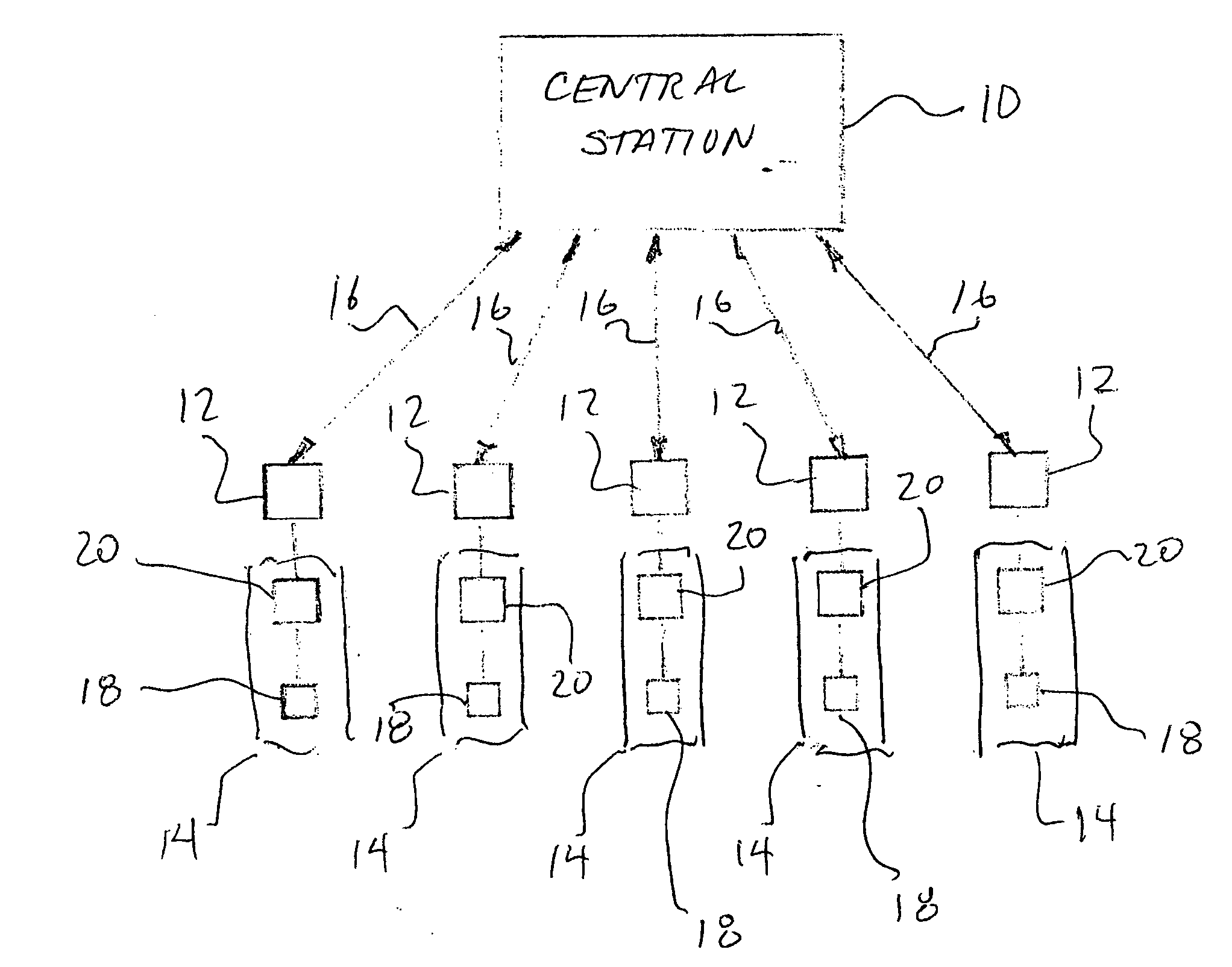
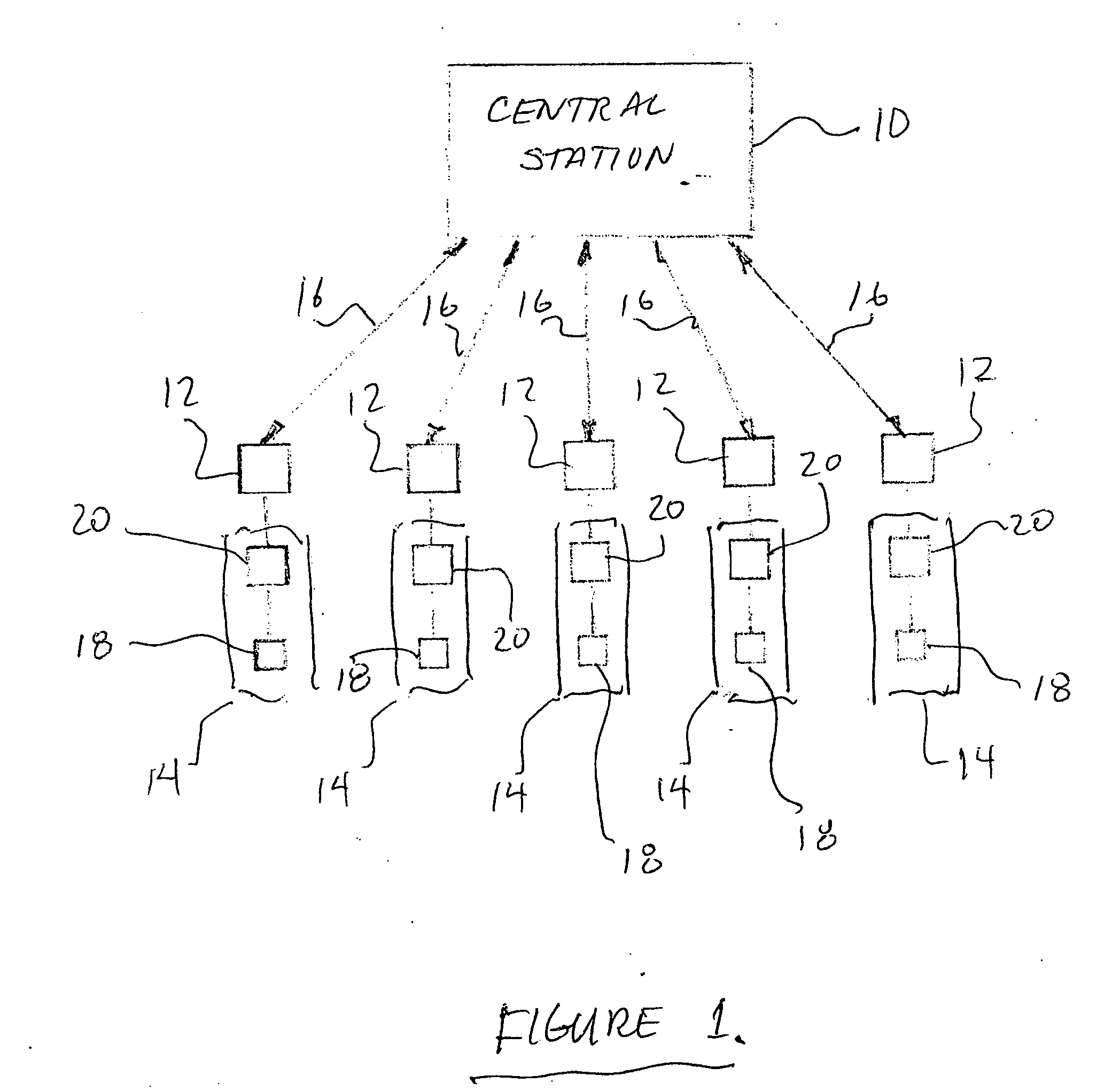
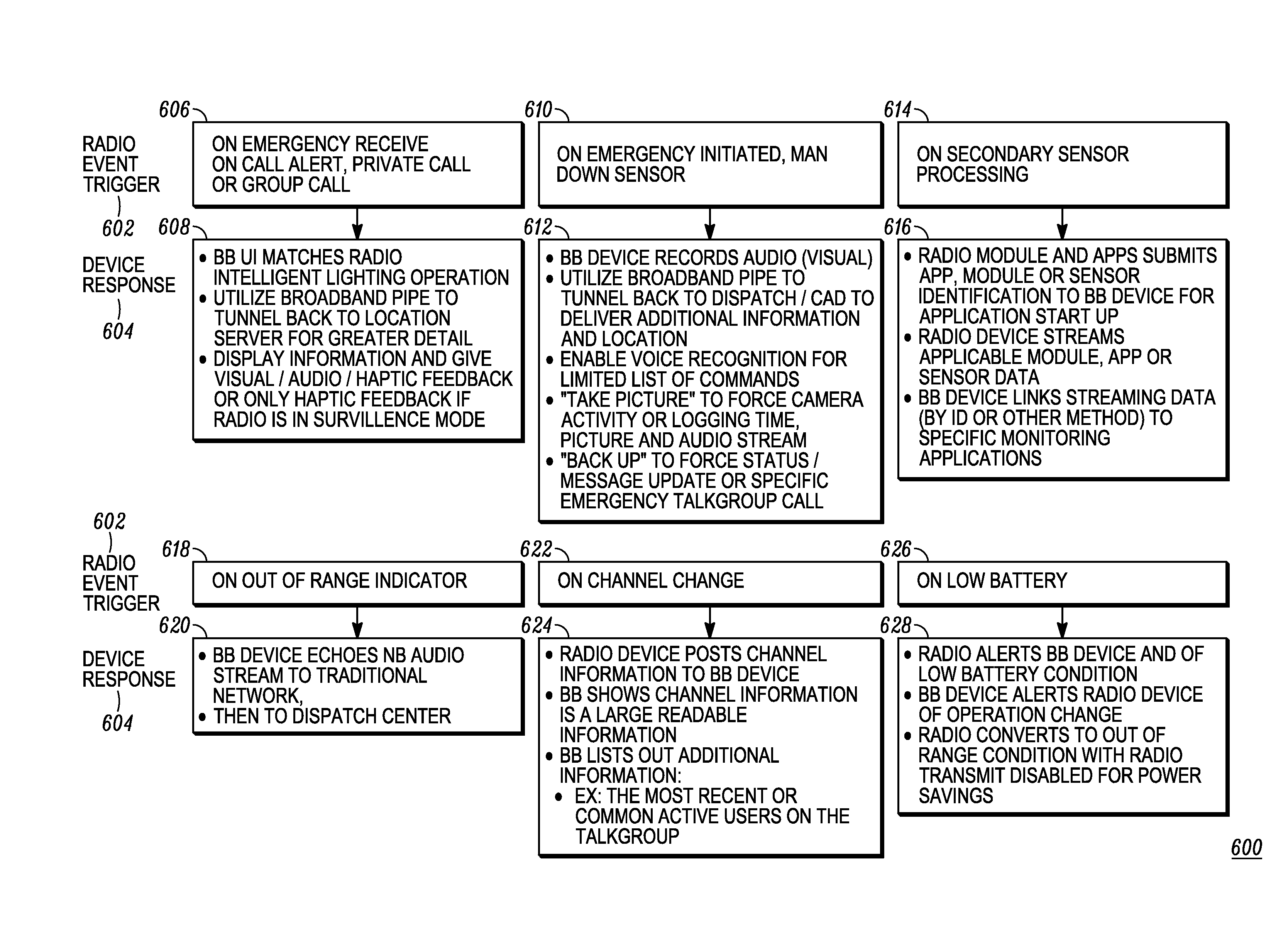
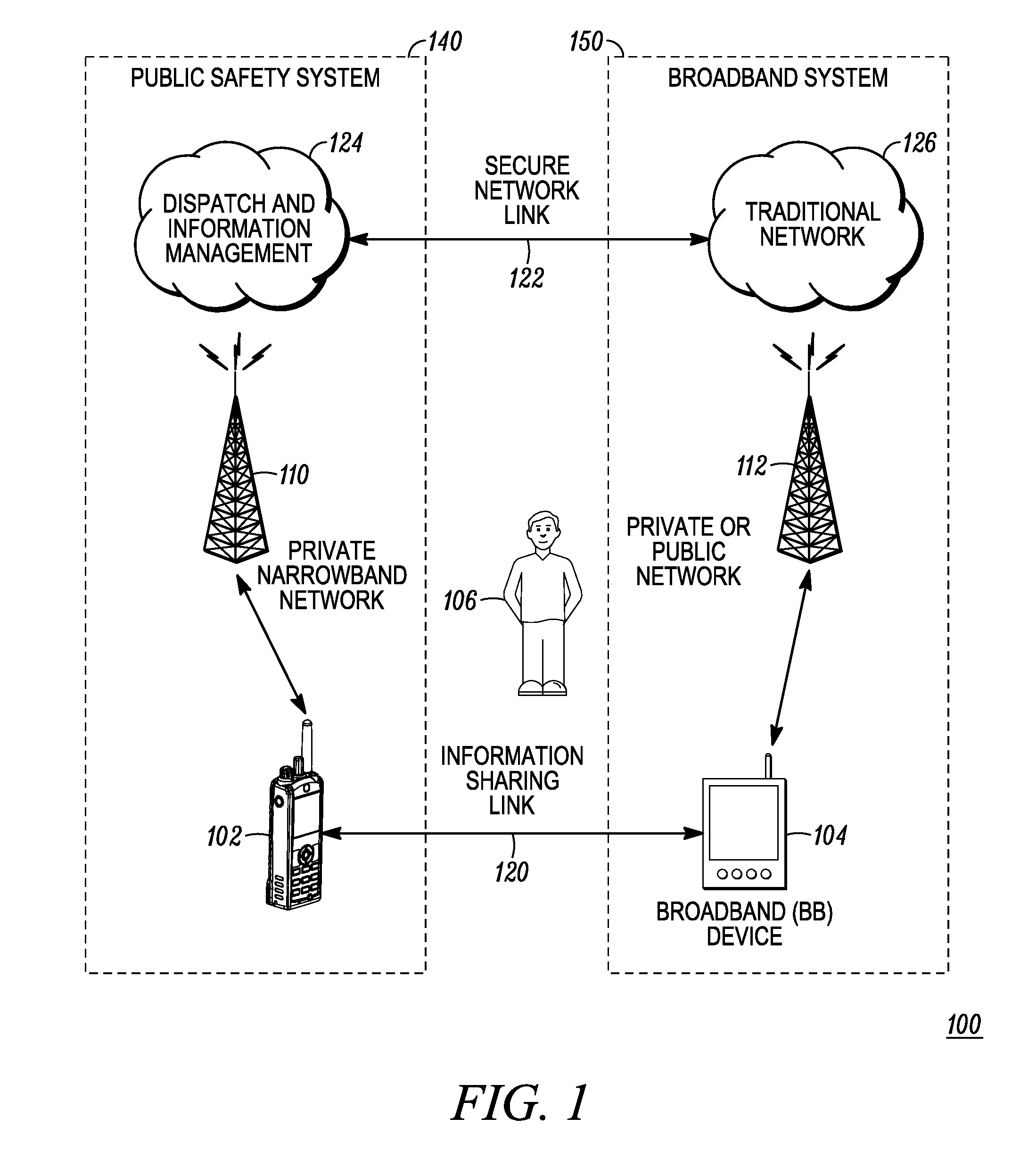
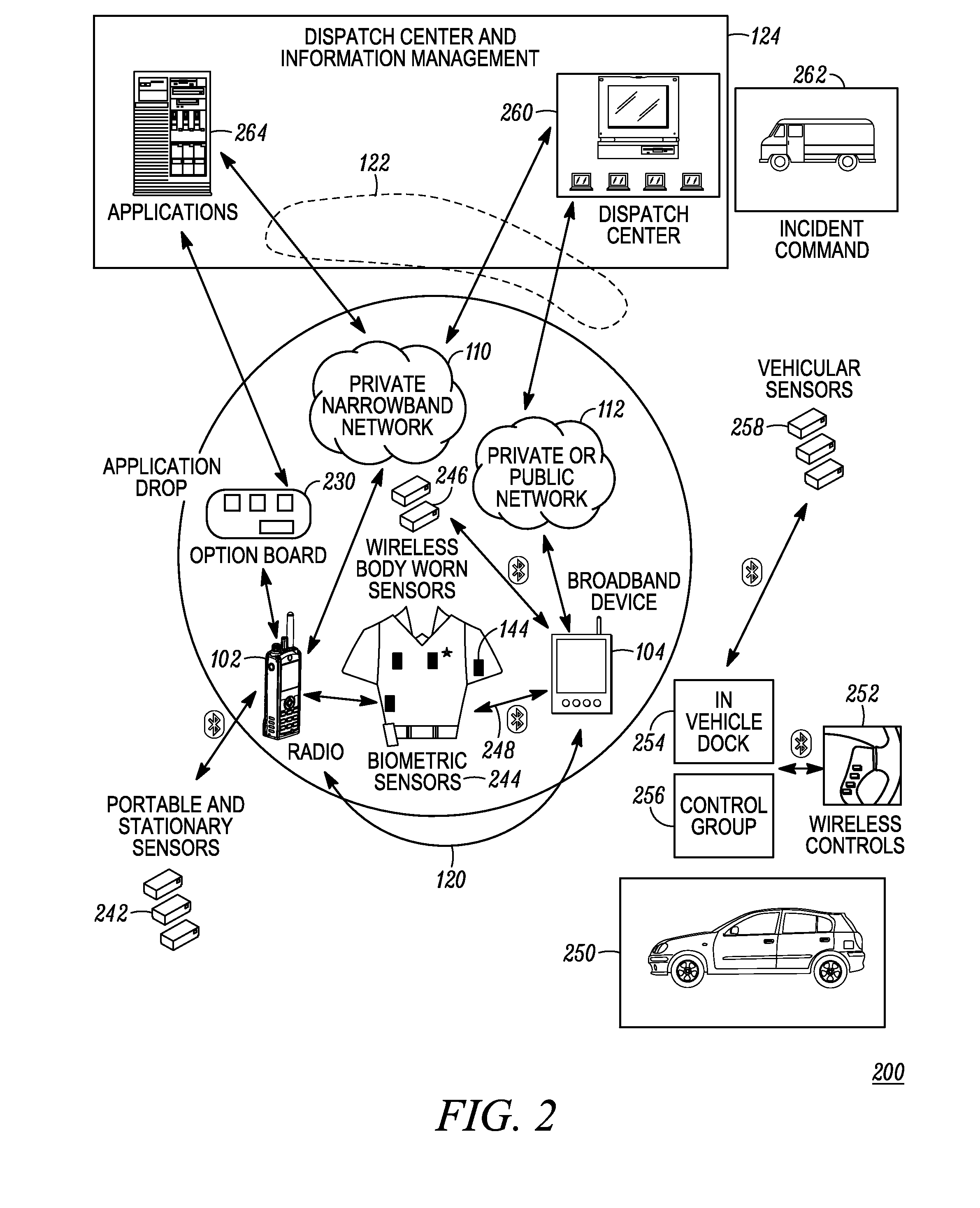
Enhanced public safety communication system
ActiveUS20110237287A1Emergency connection handlingNetwork topologiesCommunication deviceBroadband communication
A communication system (100) provides collaboration between narrowband communication devices (102) and broadband communication devices (104) operating over different networks. The communication devices (102, 104) are linked to provide peer-to-peer communication that supports the dissemination of public safety information to a public safety personnel user utilizing the devices. Applications within the devices (102, 104) automatically control features amongst the plurality of devices for redundancy of critical information, removal of non-critical information and power management. Context information can also be examined and shared between amongst the devices.
Owner:MOTOROLA SOLUTIONS INC
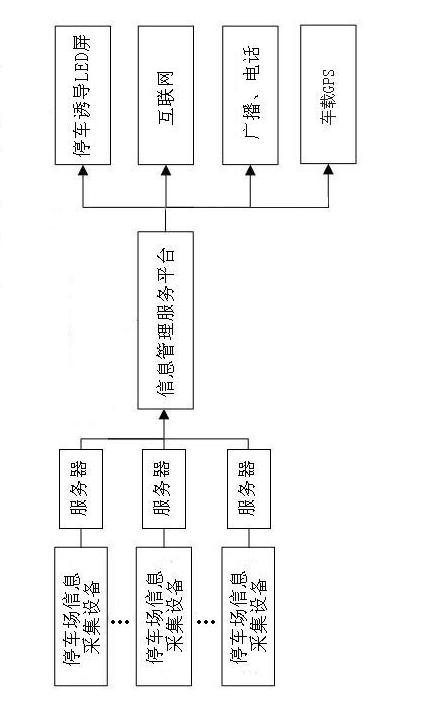
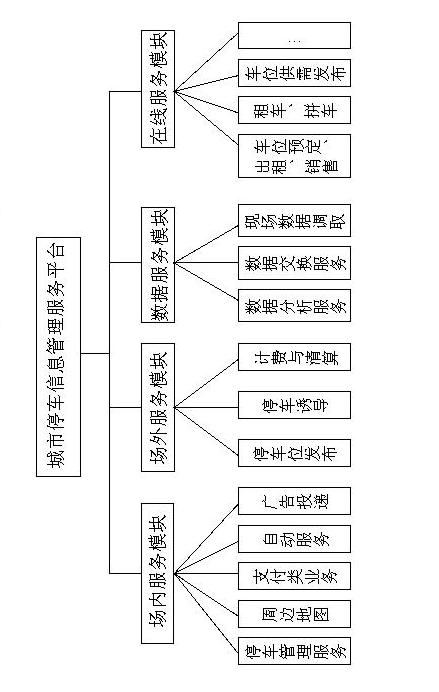
Intelligent parking-place public service system
ActiveCN102622871ATo achieve transparent useEasy to operateData processing applicationsIndication of parksing free spacesInformatizationParking space
The invention relates to the field of application systems orienting to industry and enterprise informatization in electronic information and provides an intelligent parking-place public service system. The intelligent parking-place public service system comprises parking-place information acquisition equipment, a parking-place internal parking data server, an information management service platform and an information issuing terminal. The intelligent parking-place public service system provided by the invention has the advantages that the intelligent parking-place public service system orienting to cities is reformed into a component of a smart city, so that shortage resources of parking spots can be fully shared, the decision-making basis is provided for the urban parking planning of a government, guidance is provided for trip parking of a vehicle owner, further the traffic can be eased, data support is provided for public safety management, and simultaneously the parking place that the vehicle owner often comes in and goes out is reformed into a service channel, so that the vehicle owner can enjoy the service nearby.
Owner:WUHAN ID TECH CO LTD
System and method for creating, storing, and updating local dynamic MAP database with safety attribute
ActiveUS20140358414A1Analogue computers for vehiclesInstruments for road network navigationVolumetric Mass DensityData mining
DSRC (Dedicated short range communication) is expected to play a significant role in Transportation applications for Public Safety and Traffic Management. Some of the key applications especially safety and mobility application requires an accurate representation of the road segments. Accordingly, here, in one example, we describe a method and infrastructure for DSRC V2X (vehicle to infrastructure plus vehicle) system. This presentation, e.g., adds the following improvements on the existing technologies, as some of the examples: (a) Using Speed-Profiles for identifying Intersections / mandatory-stops / Speed-limits, etc. Also, the extension of the map coverage using speed profile data. (b) Vehicular density identification for determining confidence of generated MAP. (c) Mechanisms for identifying Lane Attributes, like Lane-Width, Lane-Connections, Possible Movement states, average travel-time on the lane, etc. In this presentation, we provide various methods and systems to manage and update such maps and its corresponding information, plus many variations on those.
Owner:HARMAN INT IND INC
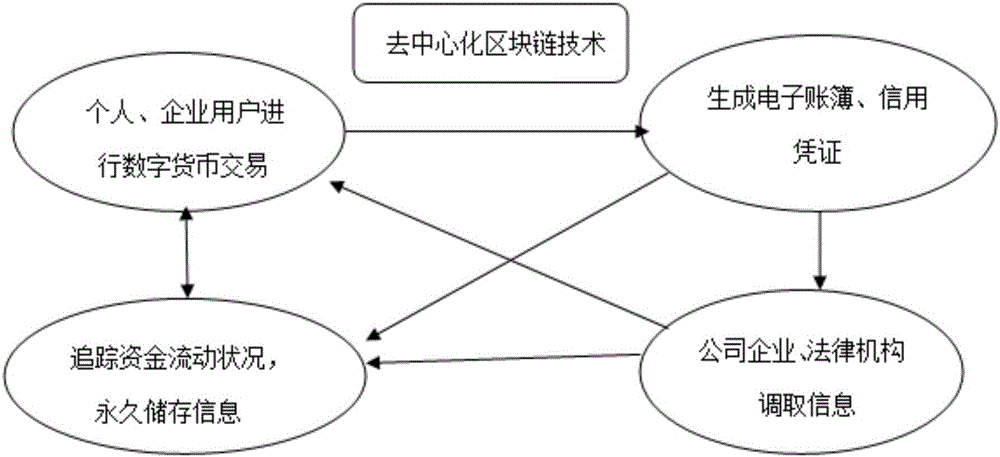
Method of carrying out digital currency trading through block chain technology
InactiveCN105844505AWith decentralized storageNo hidden costsBuying/selling/leasing transactionsDigital currencyData records
The invention discloses a method for conducting digital currency transactions through block chain technology. The method is as follows: individual and enterprise users conduct digital currency transactions through decentralized block chain technology, and generate electronic account book information and various transaction vouchers after the transaction , all data records are stored on the nodes of the blockchain, and companies, legal agencies or public security organs retrieve information from any node to track and investigate the flow of funds, and store the information permanently.
Owner:深圳市新世纪启航科技开发有限公司
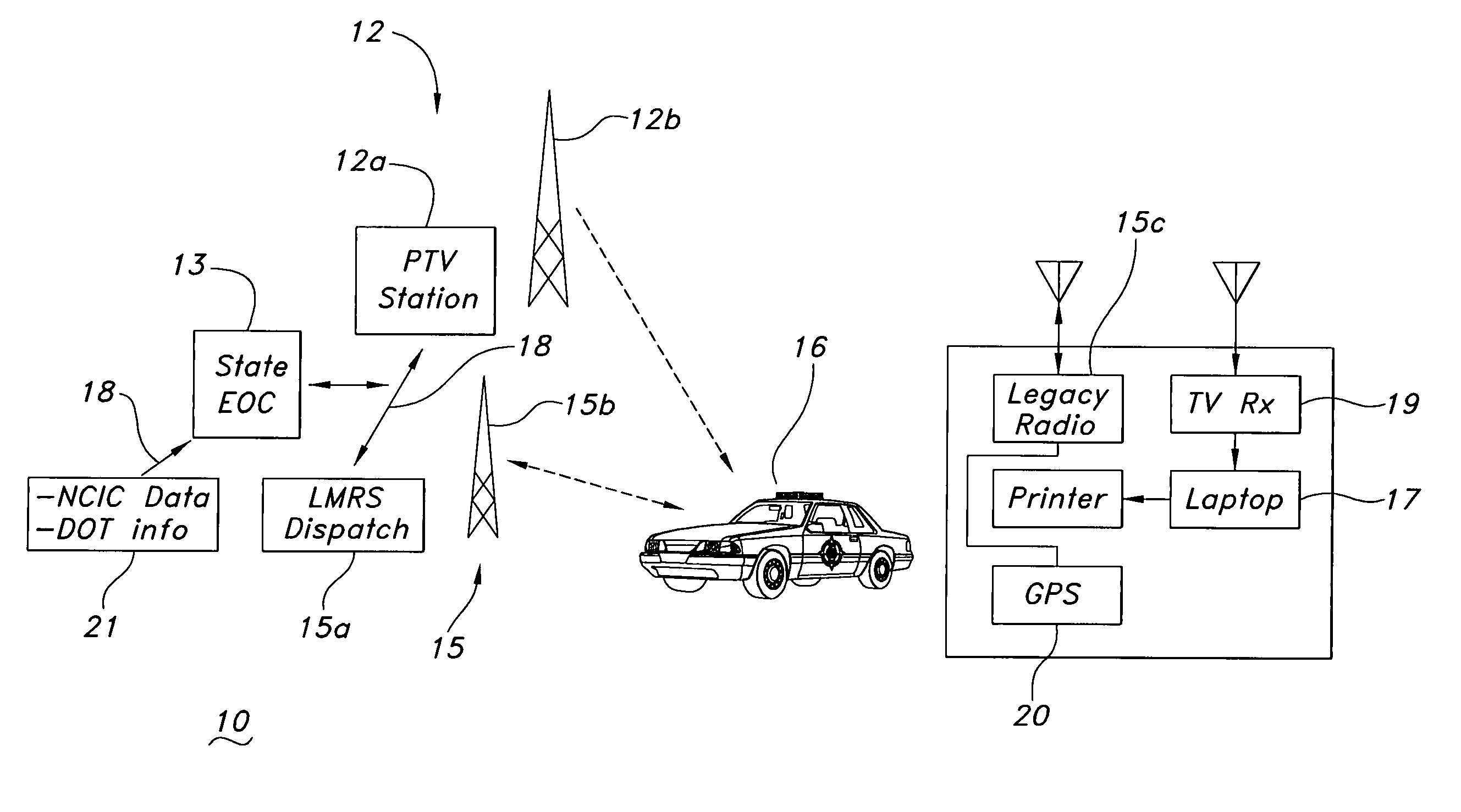
Public safety communications network using asymmetric receive/transmit channels
ActiveUS7783316B1Increase data rateQuality improvementTelevision system detailsError preventionGeolocationLand mobile radio system
A public safety communications network uses asymmetric channels for receiving requests for data from a mobile client over a narrowband land mobile radio system (LMRS) channel and delivering wideband data over a digital television (DTV) network channel to a DTV datacast receiver with the mobile client. An emergency operations center connected to the LMRS receives and processes the data requests and forwards the requested data. DTV network stations have a data multiplex insertion system for inserting the requested data into a DTV signal. The DTV network may be a public television network. An addressing system identifies unique mobile client addresses and unique mobile client group addresses and selects a DTV transmitter for delivering response messages in accordance with the addresses. A forward error correction (FEC) regulation system is used in transmitting requested data with FEC strength regulated as a function of historical bit-error-rate or receive power for a geographical location.
Owner:ROCKWELL COLLINS INC
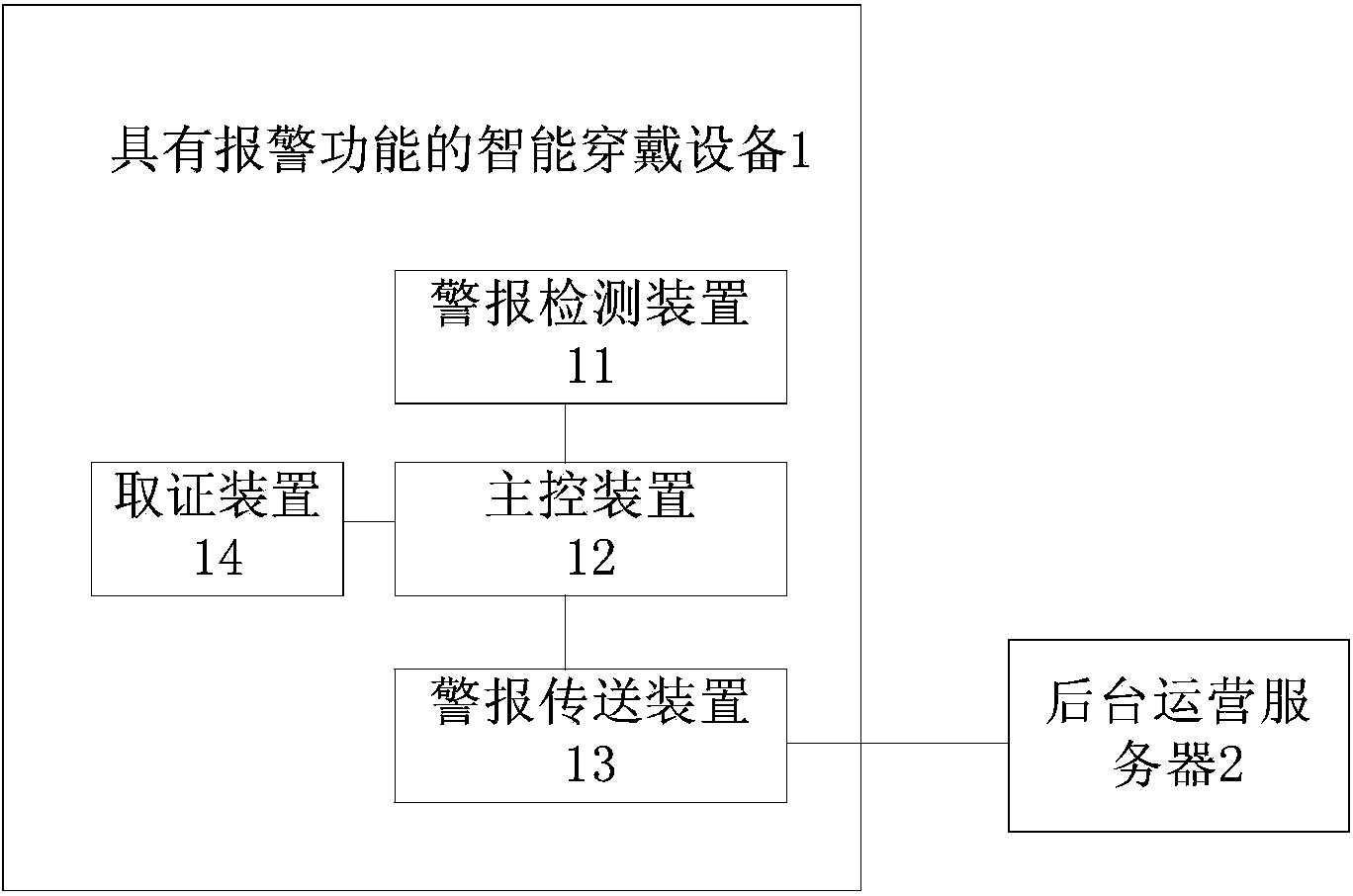
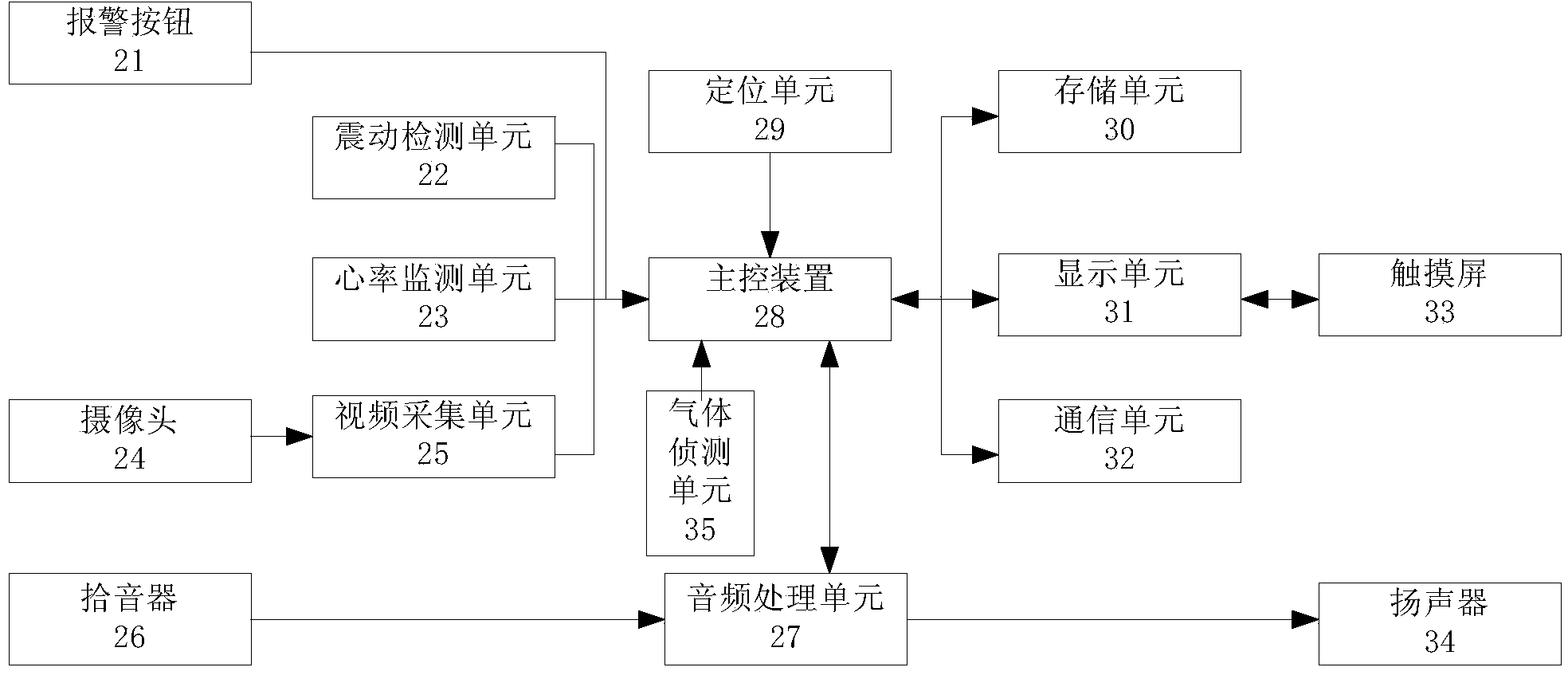
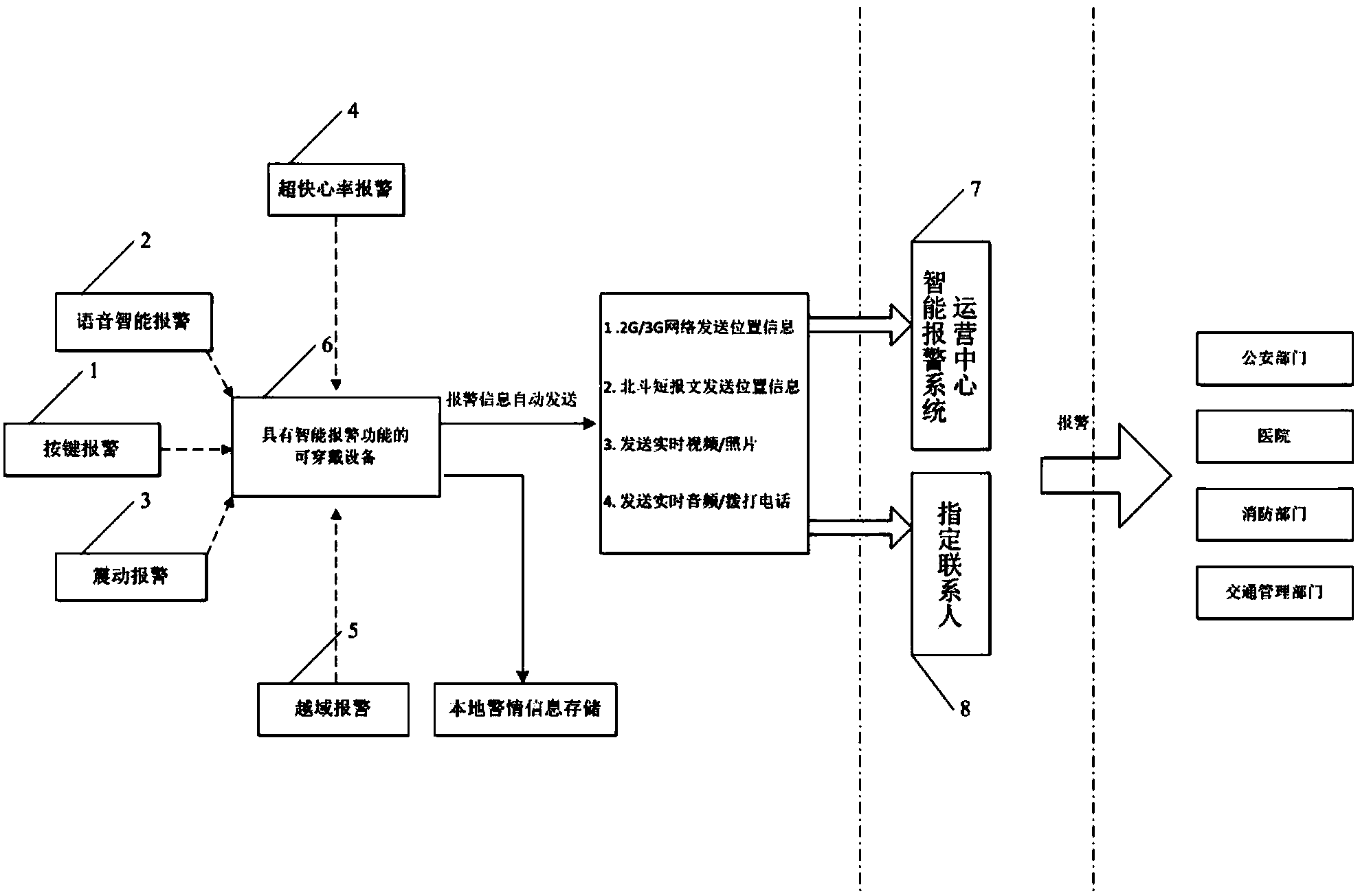
Intelligent wearing equipment with warning function and system
InactiveCN104346902AWith alarm functionFunctionalDiagnostic recording/measuringSensorsManufacturing intelligenceFood safety
The invention discloses intelligent wearing equipment with a warning function and an intelligent wearing system. The intelligent wearing equipment comprises a warning detecting device, a main control device, an evidence obtaining device and a warming transmitting device. The warning detecting device is used for sending a warning signal to the main control device when an abnormal situation is judged to occur; the main control device is used for carrying out warning processing according to the warning signal; the evidence obtaining device is used for obtaining evidence obtaining information, and the warming transmitting device is used for sending the warning information and the evidence obtaining information to a background operating server. According to the intelligent wearing equipment and the intelligent wearing system disclosed by the invention, many kinds of warning modes are supported, the warning information is automatically sent to the background server and can be simultaneously sent to a designated contact person, and the warning information is sent to a public security department, a medical department, a fire department, a traffic management department for police situation processing by the background server, so that the intelligent wearing equipment and the intelligent wearing system have the functions of environmental safety monitoring and food safety monitoring, the situation that nobody accepts warning can be avoided, and the intelligent wearing equipment and the intelligent wearing system have the characteristics of more comprehensive and effective warning function, wider triggering mode, warning-mode concealing property and product intellectualization.
Owner:瞿洪桂
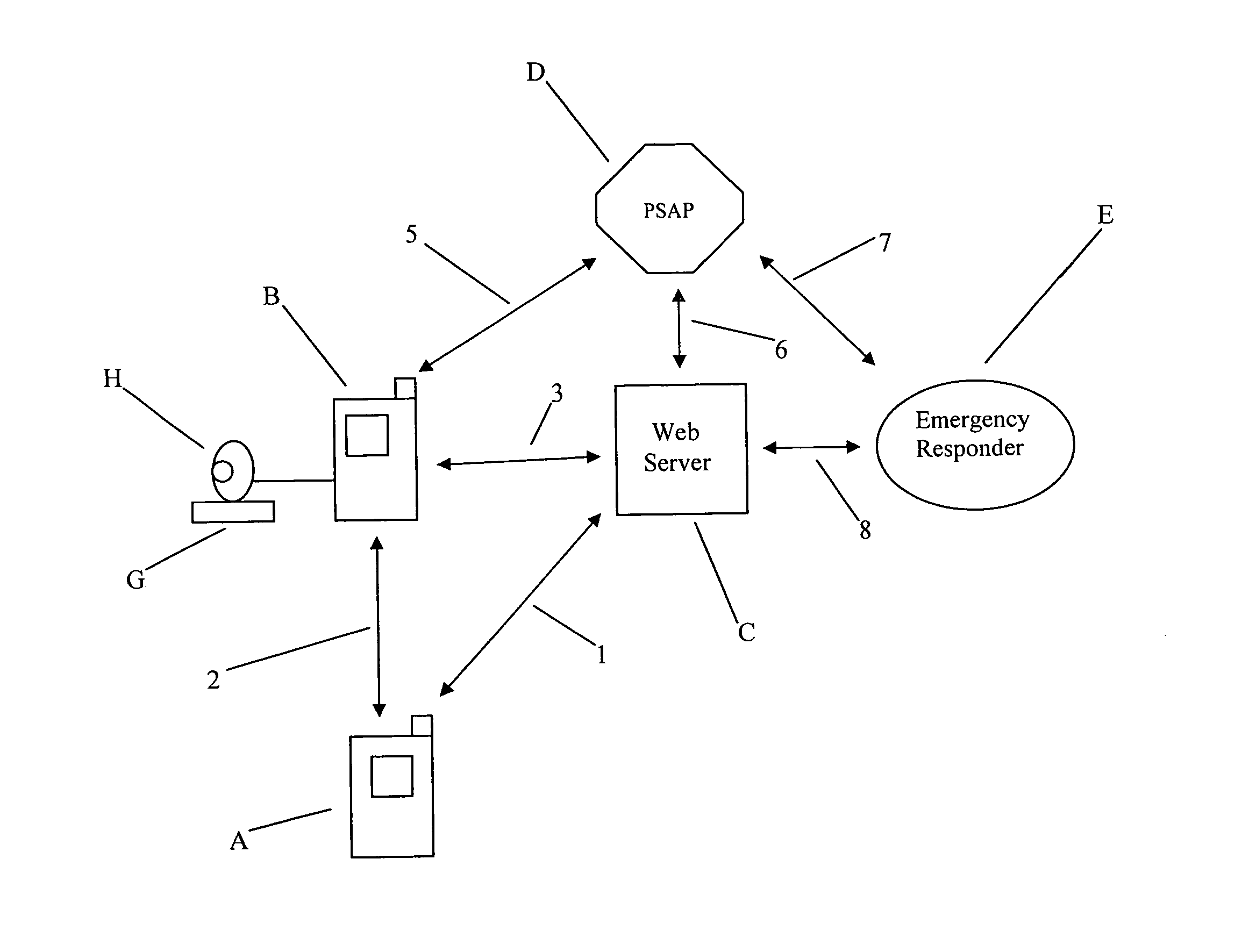
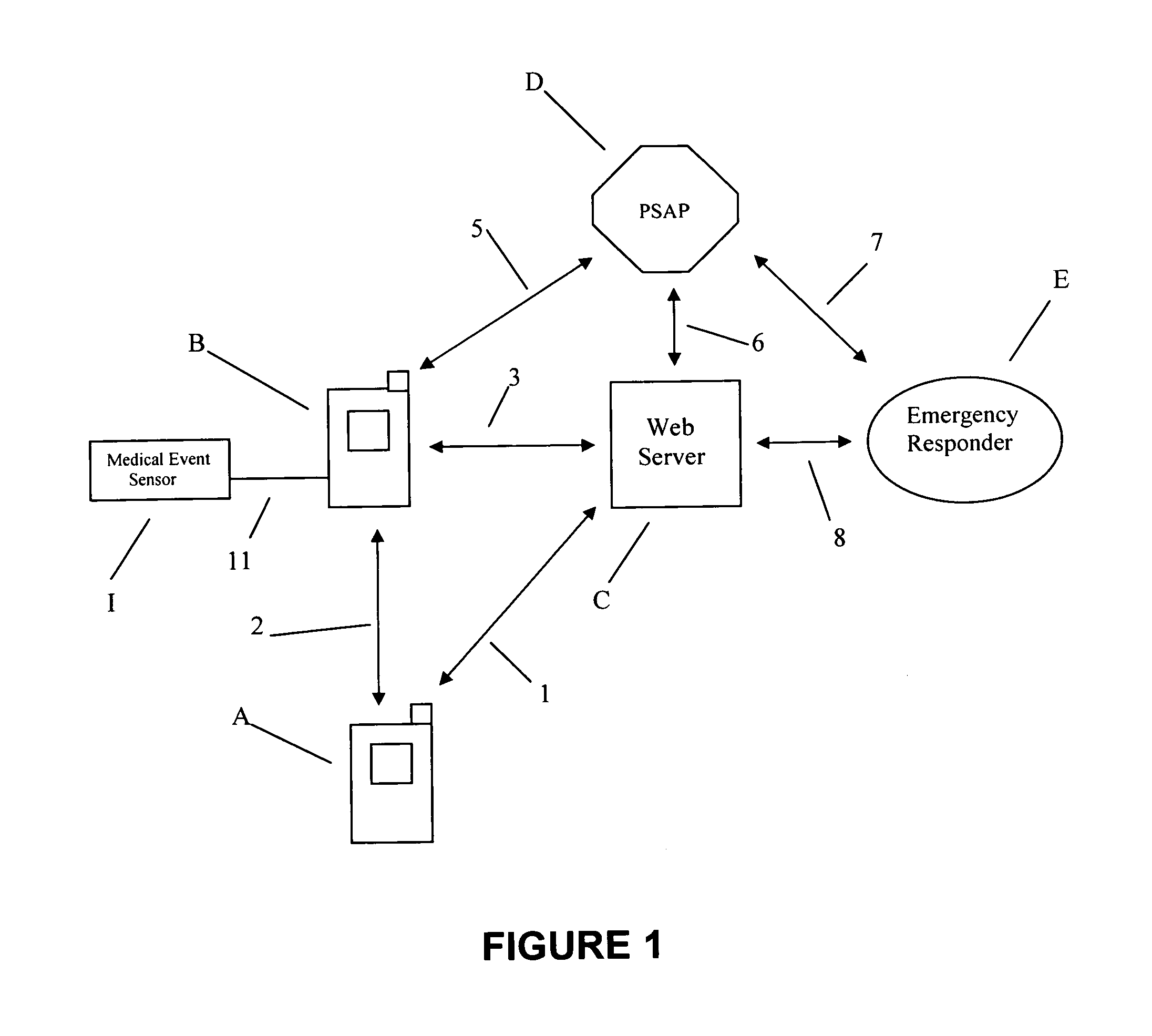
Network server emergency information accessing method
InactiveUS8868028B1Emergency connection handlingDevices with sensorSatellite trackingCall forwarding
Methods are disclosed for using an Internet server with access to a data base of PSAP (Public Safety Answering Point) jurisdiction boundaries and telephone numbers to track the location of a wireless communication device and to determine a PSAP telephone number to call to request emergency services at the location of said wireless communication device using telephone company provided location information. Methods are disclosed for establishing conference call connections between a person, a PSAP and a remote wireless communication device. Also disclosed are methods for establishing an Explicit Call Transfer call connection that redirects a call from a person to a wireless communication device to the telephone of a PSAP having jurisdiction over the location of said remote wireless communication device. Alzheimer tracking devices, offender monitoring devices, medical alert notification devices, satellite tracking devices and child safety telephone embodiments of the current invention are also disclosed.
Owner:KALTSUKIS CALVIN L
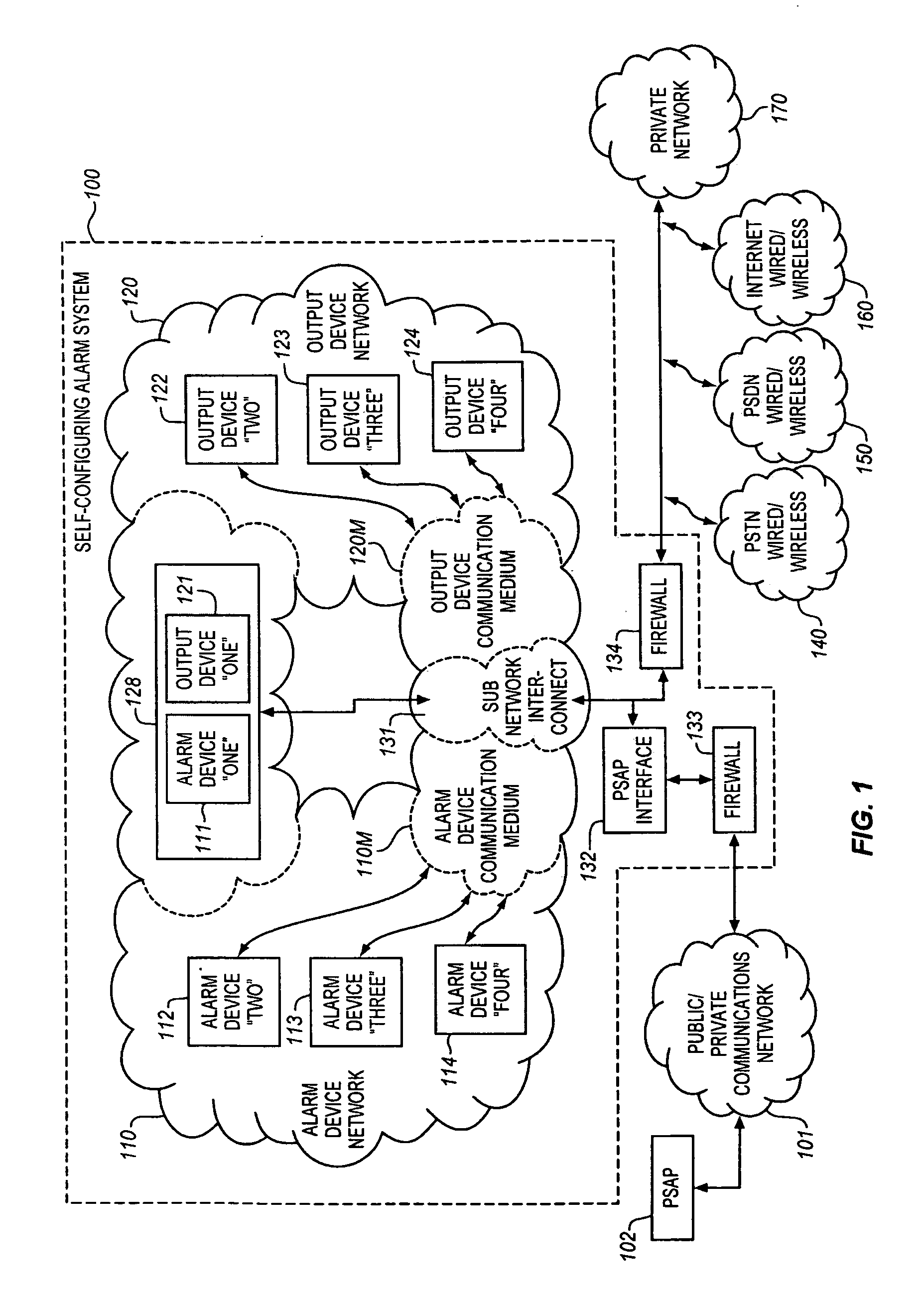
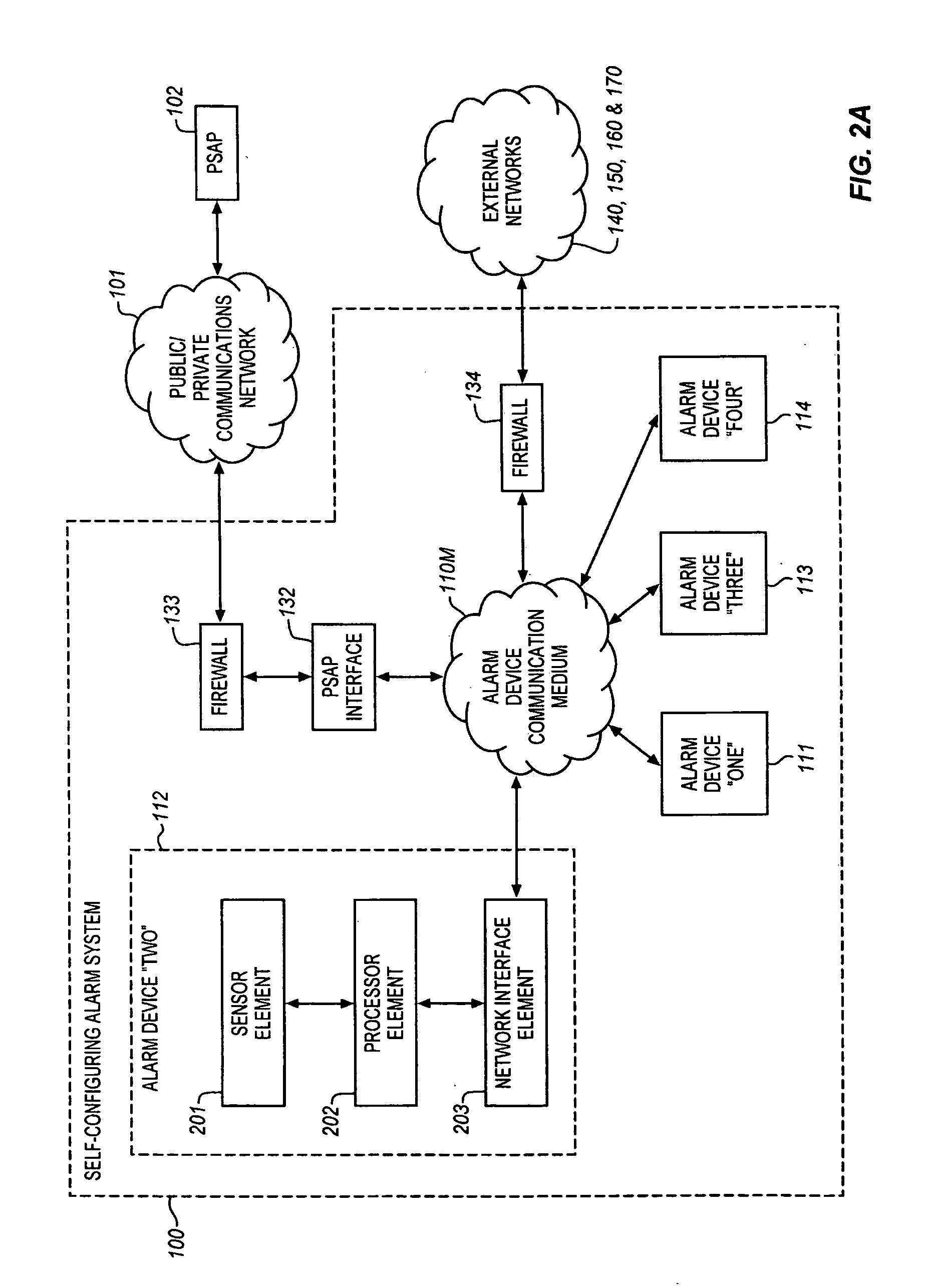
Self-configuring emergency event alarm system having connection to a public safety answering point
ActiveUS20080309486A1Easy to installSimple and safe operationEmergency connection handlingNetwork topologiesEngineeringOutput device
The present Self-Configuring Alarm System uses a decentralized (ad hoc or mesh) architecture where any node is capable of autonomously reporting the alarm event directly to all other nodes in the ad hoc network independent of where the alarm event occurred. In addition, the Self-Configuring Alarm System includes a plurality of autonomous output devices which function to provide an audible alarm that directs the occupants to the location of the hazard and / or provides an indication of the nature of the detected hazard or whether an indication of the hazard has been received at a Public Safety Answering Point (PSAP) that serves the dwelling or locale. The alarm networks and output networks may not be coextensive in their coverage areas.
Owner:KNAPP INVESTMENT
Face recognition method based on Gabor wavelet transform and local binary pattern (LBP) optimization
InactiveCN102024141AReduce distractionsShort storage timeCharacter and pattern recognitionGabor wavelet transformHigh dimensional
The invention relates to a face recognition method based on Gabor wavelet transform and local binary pattern (LBP) optimization. Two-dimensional Gabor wavelet transform can associate pixels of adjacent areas so as to reflect the change conditions of image pixel gray values in a local range from different frequency scales and directions. The feature extraction and the classification recognition are carried out on the basis of a face image two-dimensional Gabor wavelet transform coefficient. For a high-dimensional Gabor wavelet transform coefficient, overall histogram features are extracted by adopting the LBP, and then the image is blocked by utilizing priori knowledge to extract the features of each piece of LBP local histogram. The method has better recognition rate, better robustness to illumination and wide using prospect in the fields of biometric recognition and public security monitoring.
Owner:SHANGHAI UNIV
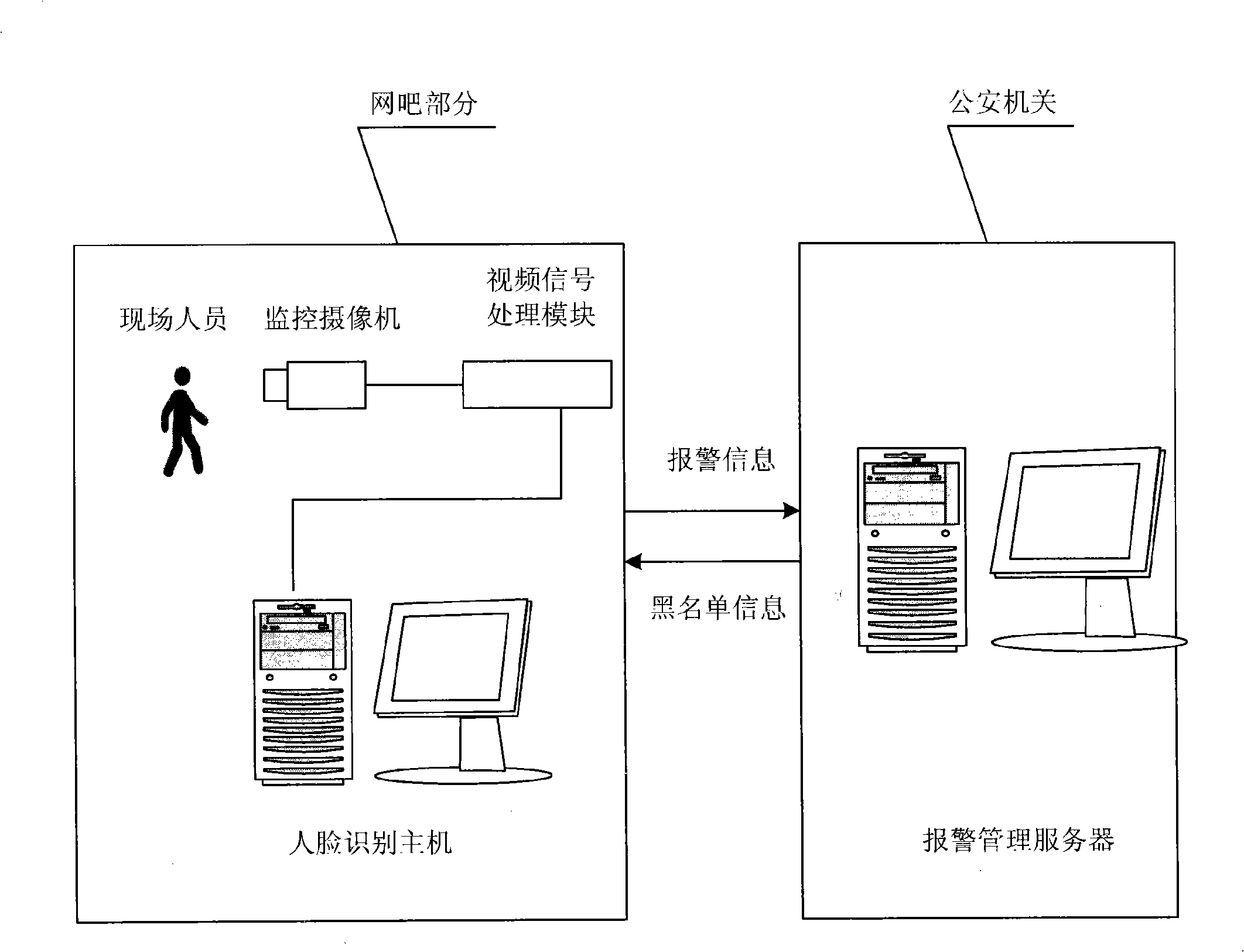
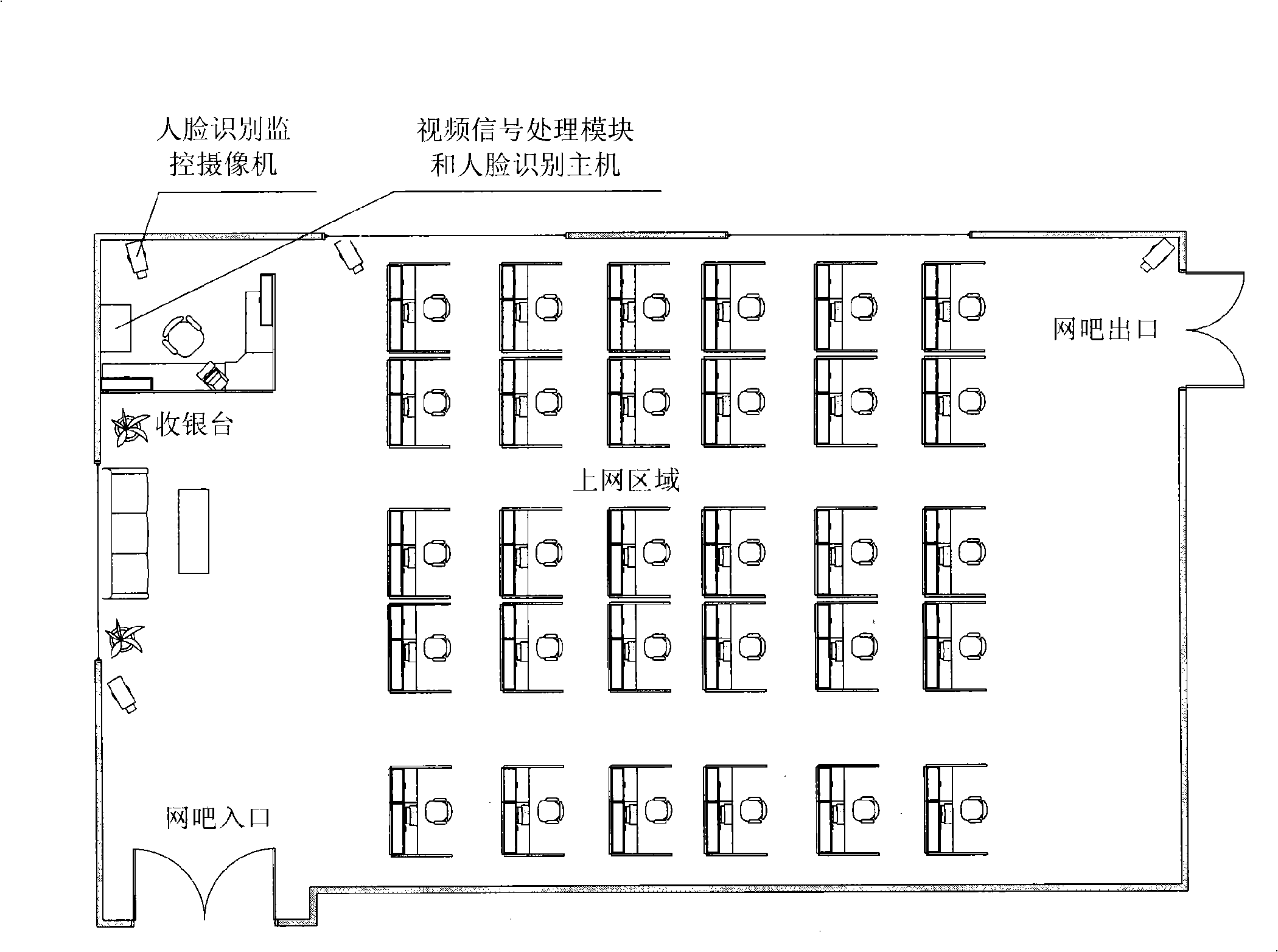
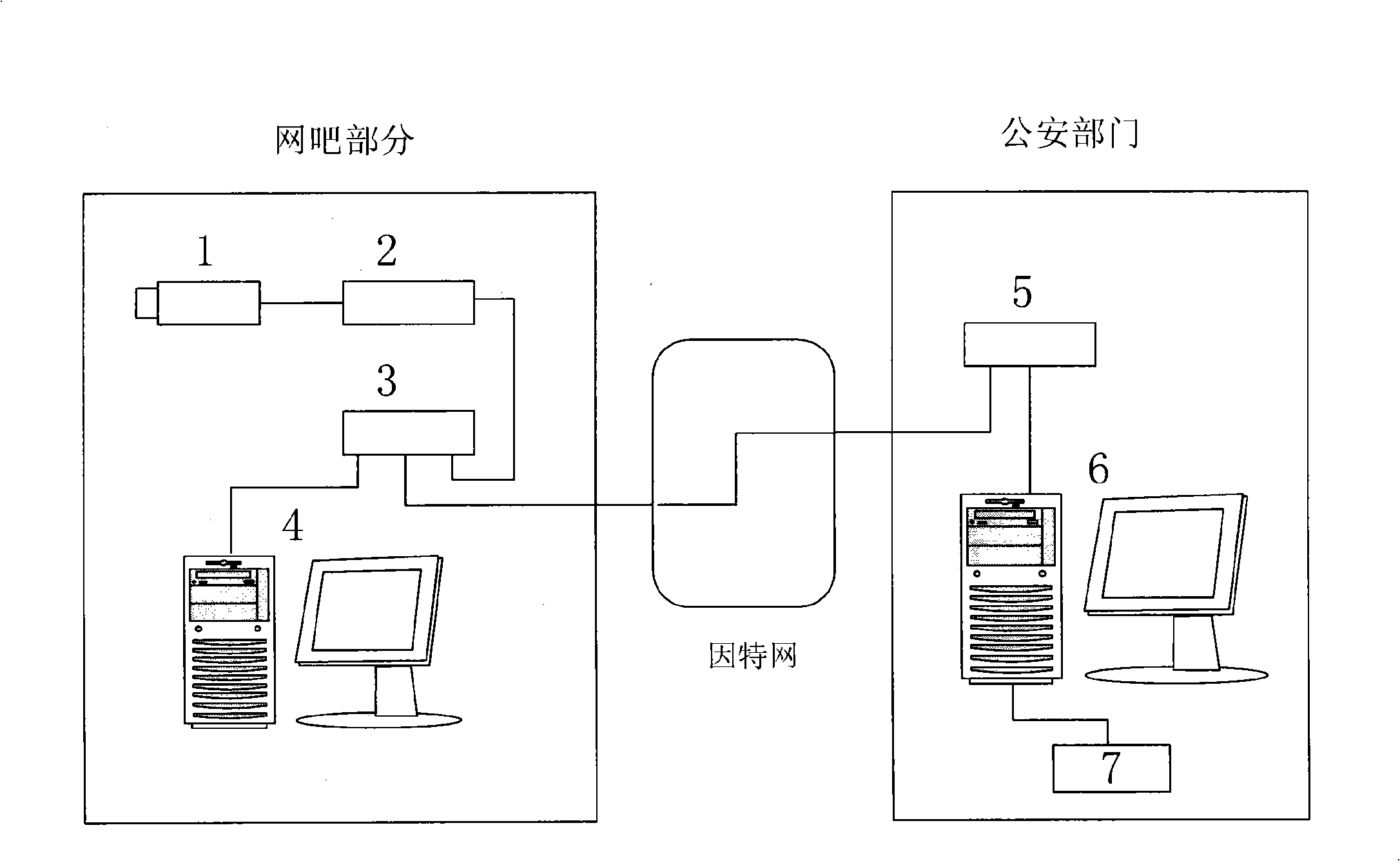
Internet bar monitoring and warning system based on human face recognition technology
InactiveCN101404107AHigh degree of intelligenceSafe and fast to useCharacter and pattern recognitionClosed circuit television systemsPattern recognitionAlarm message
The invention relates to a monitoring alarm system of an internet bar based on the face recognition technology, which comprises a monitoring camera, a video signal processing module, a face recognition host and an alarm management server. The monitoring camera carries out face video image acquisition and transmits the acquired face video images to the video signal processing module for video image processing; the video signal processing module transmits the processed video signals and the face images to the face recognition host; the face recognition host carries out comparative recognition processing on the face images according to face database of a blacklist; and if the matching is successful, alarm messages are transmitted to the alarm management server for alarming by a computer network. By adopting the monitoring alarm system of the internet bar based on the face recognition technology, whether the persons to be found appear can be automatically judged and automatic alarming is carried out, therefore, the system is safe and fast, has stable and reliable working performance and wide application range, greatly improves the degree of monitoring intellectualization of the internet bar and can provide clues for the police to solve cases, thereby being beneficial to improving the efficiency of ministry of public security for solving cases.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
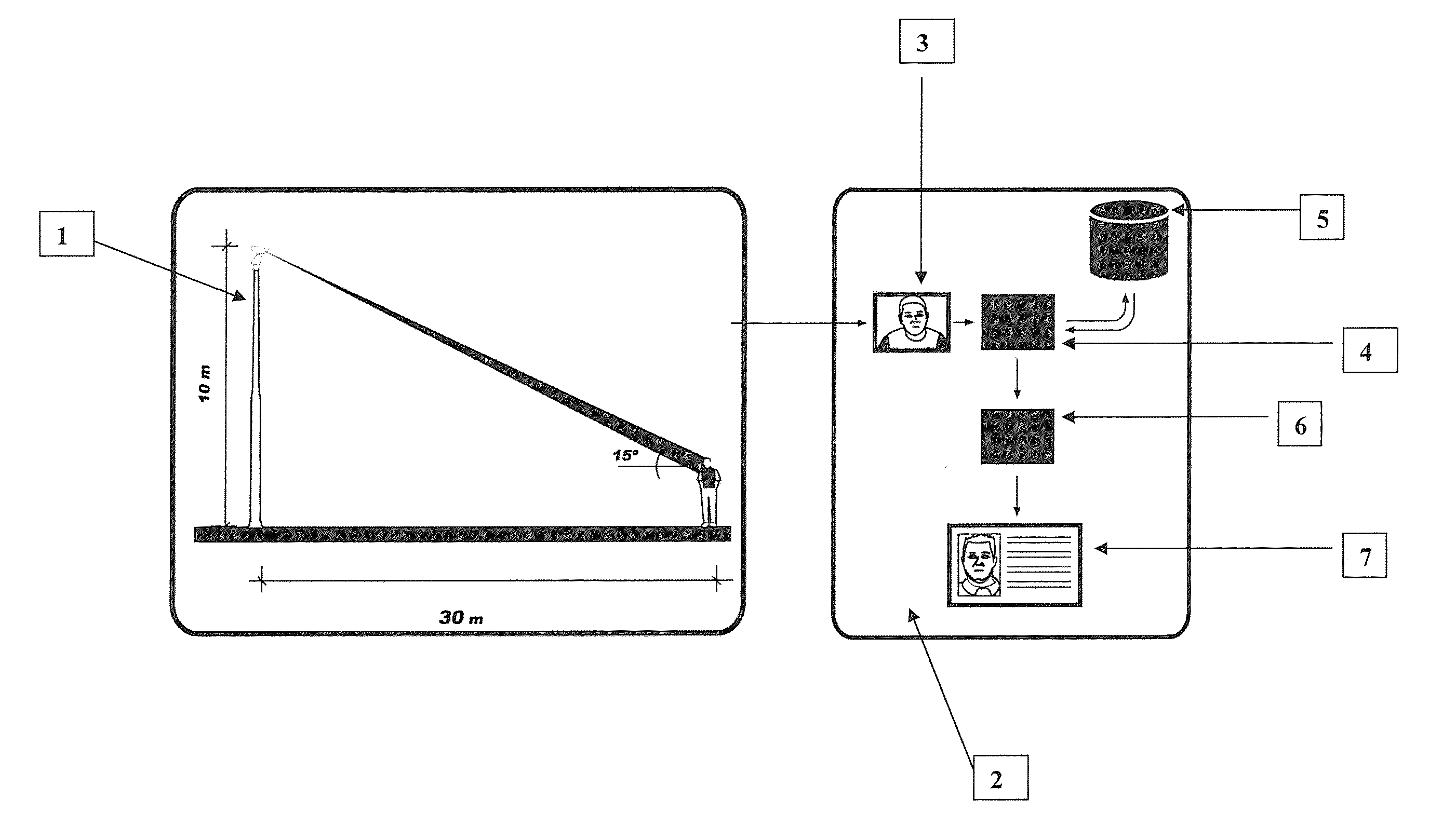
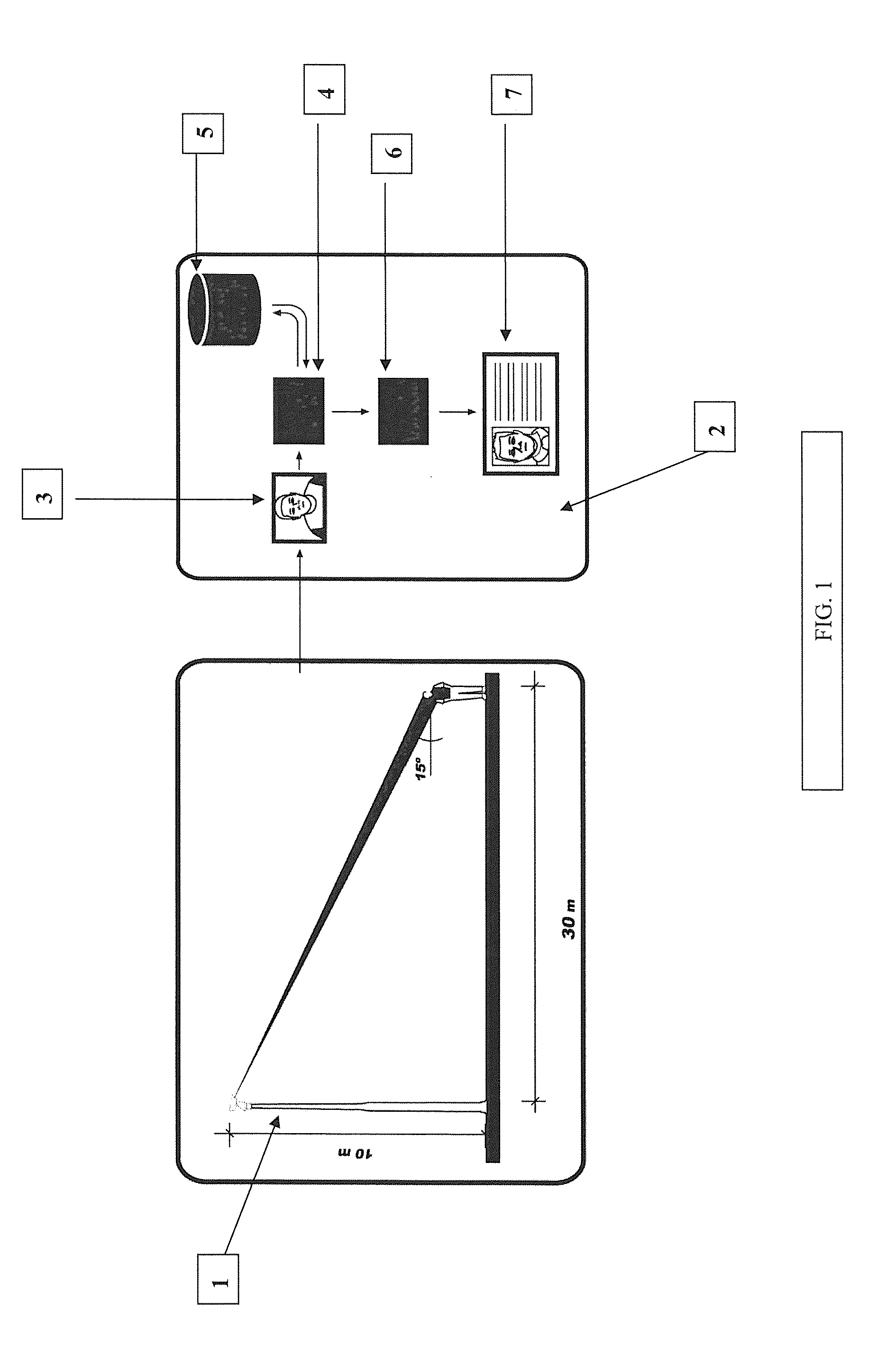
Remote and digital data transmission systems and satellite location from mobile or fixed terminals with urban surveillance cameras for facial recognition, data collection of public security personnel and missing or kidnapped individuals and city alarms, stolen vehicles, application of electronic fines and collection thereof through a personal id system by means of a multifunctional card and collection of services which all of the elements are communicated to a command center
InactiveUS20100177193A1Character and pattern recognitionColor television detailsDigital dataSurveillance camera
This invention is related to a remote and digital data transmission system and satellite location from mobile or fixed terminals with urban surveillance cameras for facial recognition, detector of gunshots, data collection of public security personnel and missing or kidnapped individuals, city alarms and vehicles control collecting traffic violations and detection of stolen vehicles, all modules communicated to a command center comprising the combination of a close-up camera placed on a post or structure, camera by means of which a photograph is taken, said photograph is sent to the command center (2) by means of a data link providing the photograph (3), in real time, said photograph is sent to a global module (4) which transmits it to a security filter (5) for its analysis and once the information is confirmed it sends it back to the module (4), and from here it is sent to the individuals identification module (6), and it edits the photograph or card with all data (7) with an arrangement of a series of microphones (8) coupled to a structure and an electronic switchboard (9), said arrangements enable the recognition of sound signatures such as gunshots in different noise intensities, and said command center acts as an information CPU to register the payment of fines by means of automatic traffic violations and different public services addressed to the corresponding individuals by means of a control system of sole identity with capacity in addition for application of payments.
Owner:GLOBAL SIGHT S A DE
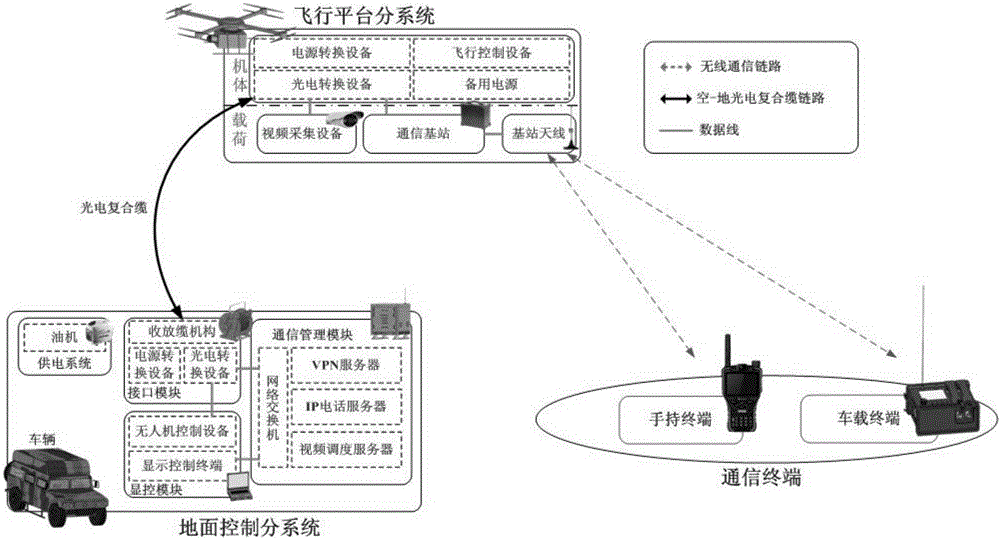
Emergency communication and support system based on tethered unmanned aerial vehicle and method
ActiveCN105223958AQuick set upRealize real-time two-way transmissionTelevision conference systemsClosed circuit television systemsSupporting systemFire protection
The invention relates to an emergency communication and support system based on a tethered unmanned aerial vehicle and a method. The system comprises a flying platform subsystem, a ground control subsystem, a photoelectricity composite cable and a communication terminal. The flying platform subsystem comprises the unmanned aerial vehicle. A communications base station, a base station antenna and a video capturing device are arranged on the unmanned aerial vehicle. The ground control subsystem is connected with the flying platform subsystem through the photoelectricity composite cable, and controls and communicates with the flying platform subsystem through the photoelectricity composite cable. The photoelectricity composite cable transmits ground power to the flying platform subsystem, and realizes space data two-way optical fiber transmission. The communication terminal establishes communication connection with the ground control subsystem and the flying platform subsystem. The system and the method, which are provided by the invention, have the technical advantages of long air time, signal blind spot prevention and real-time air video capturing, and can be used for low-cost cluster communication and video support system solutions in the fields of public security, terrorism countering, high-rise building fire protection and the like.
Owner:CHINA NAT ELECTRONICS IMP & EXP CORP
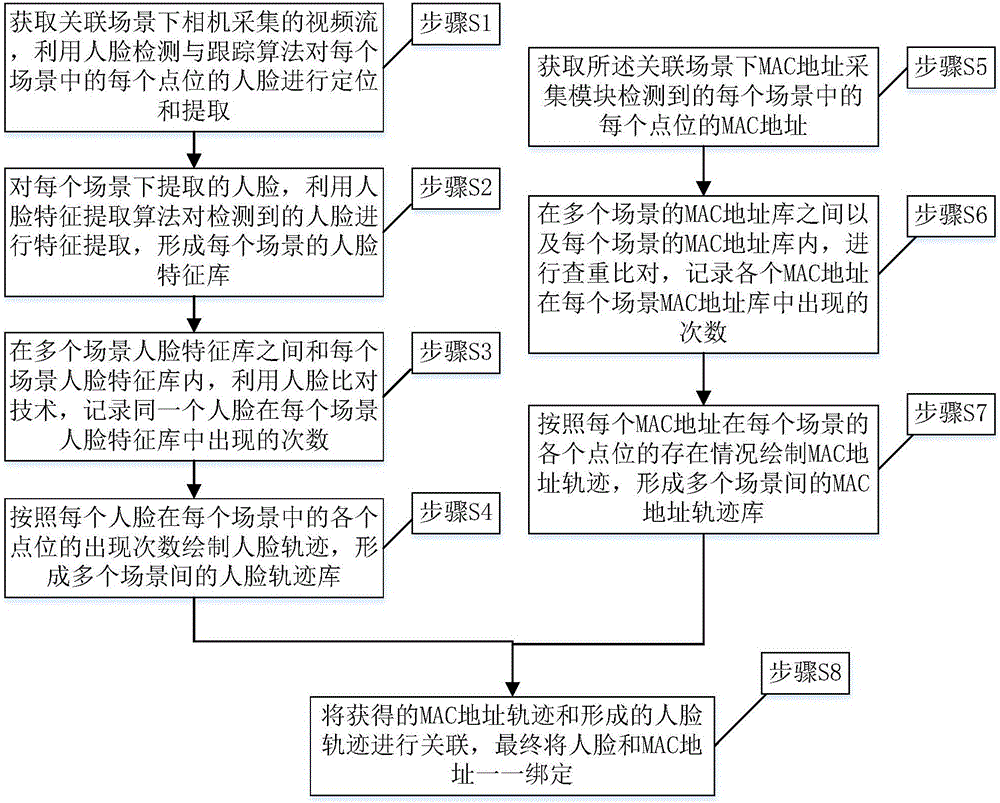
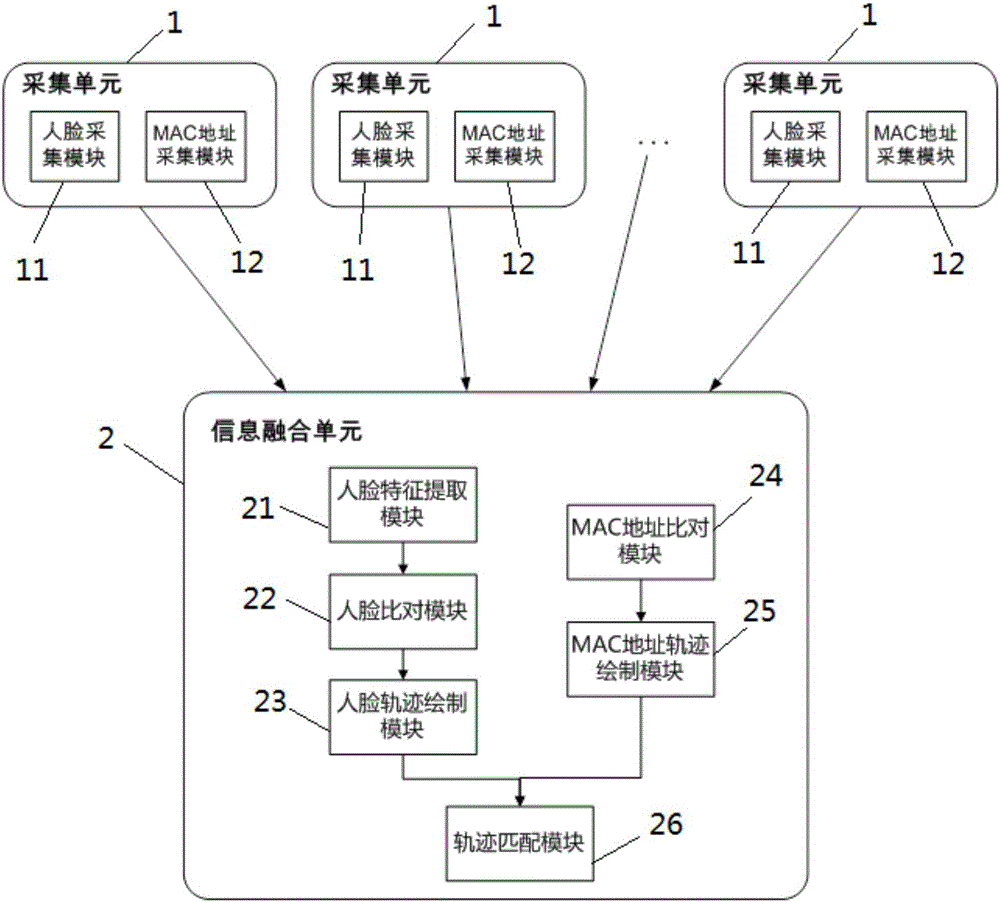
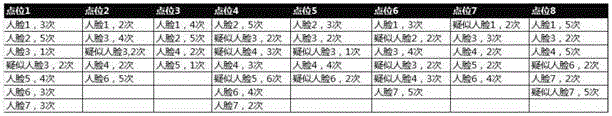
Method and system for associating MAC addresses with face information
ActiveCN105790955ASolve the problem of inaccurate identity verificationTelevision system detailsUser identity/authority verificationHigh probabilityMobile device
The invention provides a method and a system for associating MAC addresses with face information. The method comprises a step of acquiring a face track in multiple scenes, a step of acquiring an MAC address track in multiple scenes, and a step of matching the face track with the MAC address track. One MAC address track is selected from an MAC address track library, a face sequence of the highest probability is looked for in all face tracks through track matching, and a group of association data of 'MAC address + matching faces' is obtained. Track matching is repeated to get a plurality of groups of association data of 'MAC address + matching faces'. By matching MAC addresses with faces based on the uniqueness of the MAC addresses of mobile equipment carried by pedestrians, the problem that identity confirmation based on the face recognition technology only is inaccurate is solved, and a strong support is provided for the public security and criminal investigators to look for suspects quickly.
Owner:深圳市博康智能信息技术有限公司
Systems and methods related to continuous performance improvement
InactiveUS20080059292A1Improvement of professional performanceImprove performanceResourcesData acquisition and loggingState LicensureContinual improvement process
Systems and methods for the continuous improvement of performance. The present systems and methods provide the art with a mechanism for the continuous assessment of the performance of users. By measuring professional performance against benchmarks, standards, and goals, the present invention allows the art to assess continuously and in real time any gaps or deficiencies in performance of the user. The present invention also preferably provides users with performance improvement pathways that are targeted to address the deficiencies and shortcomings of each individual user. The present invention further provides a mechanism by which users may routinely evaluate their own performance and compare it against industry standards and peer groups. Through the present invention, users may also track activities related to their certification, licensure, or credentials and tie those to particular performance improvement pathways. The present invention is particularly useful within medical, legal, engineering, law enforcement, and public safety sectors.
Owner:PREMIER HEALTHCARE SOLUTIONS
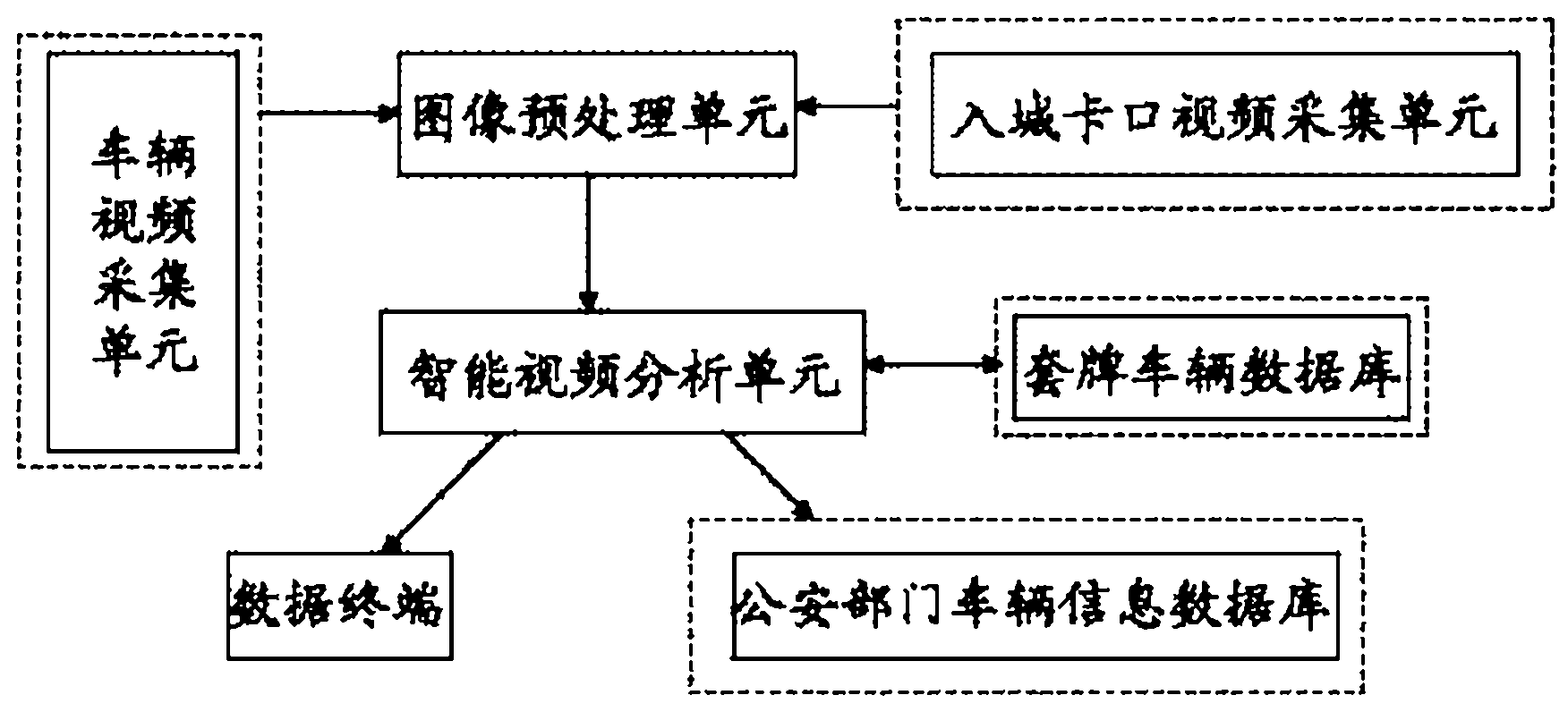
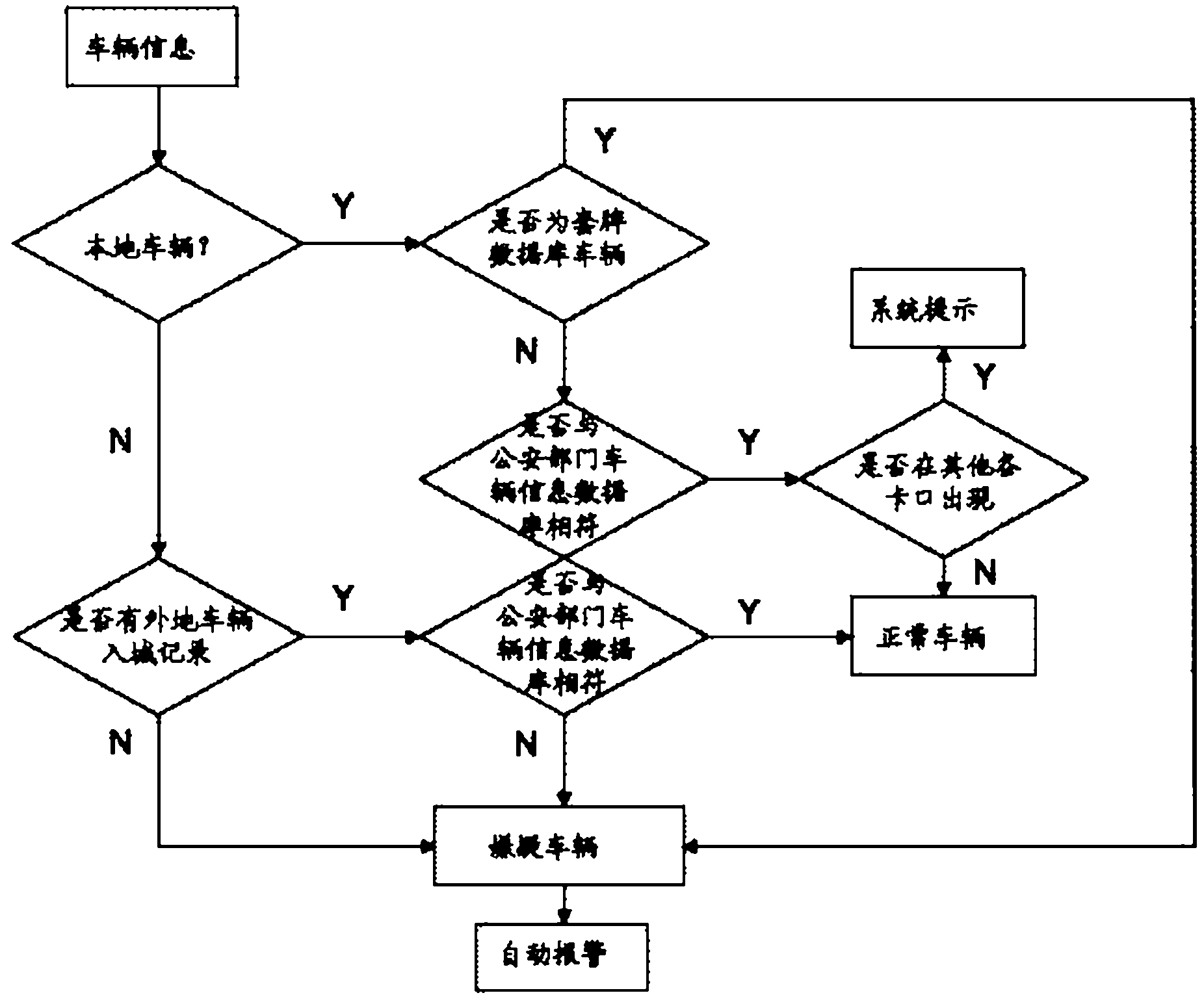
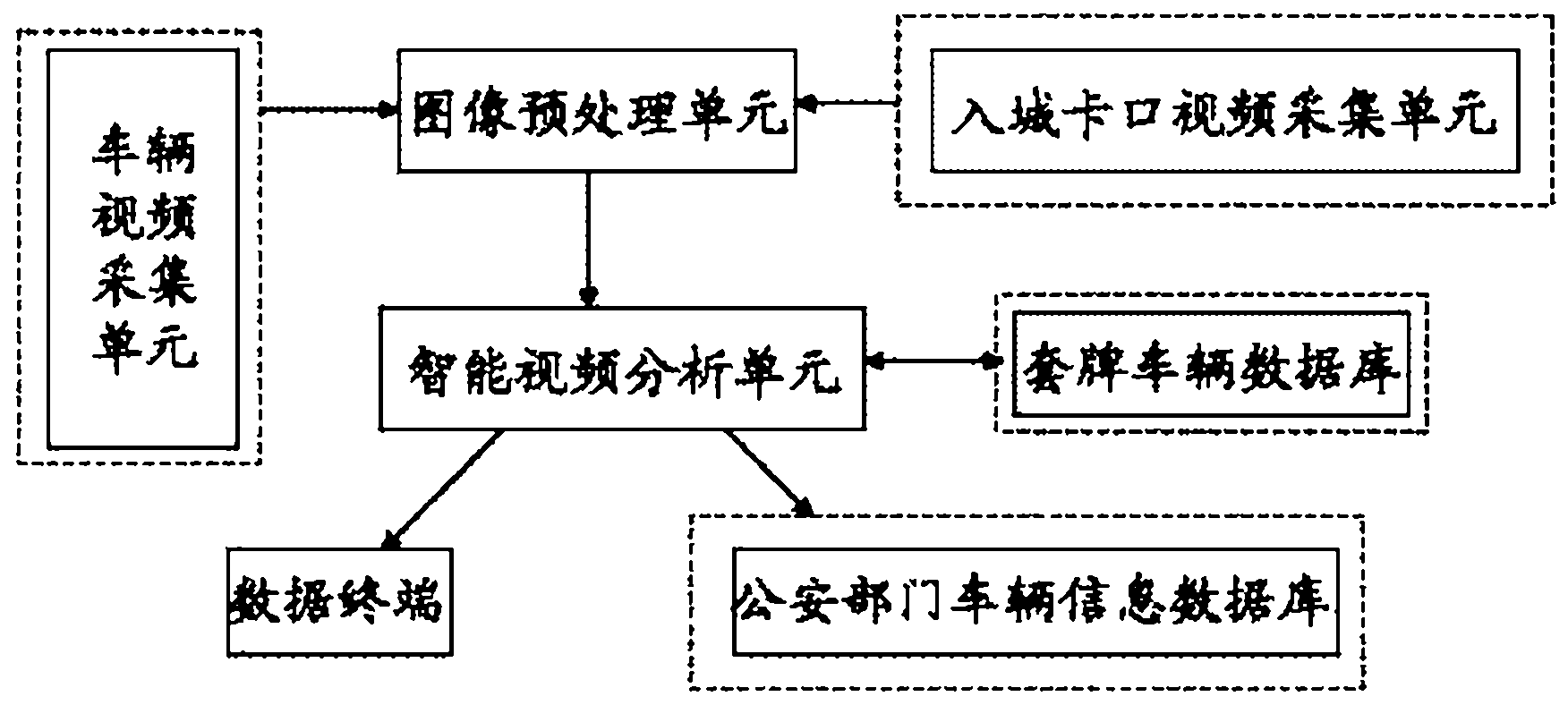
Intelligent video analyzing system and method for automatically identifying fake plate vehicle
InactiveCN102426786AReduce participationImprove accuracyRoad vehicles traffic controlCharacter and pattern recognitionComputer visionImage pre processing
The invention discloses an intelligent video analyzing system and method for automatically identifying a fake plate vehicle. The system comprises a video collecting unit, an image preprocessing unit, an intelligent video analyzing unit and a database, wherein after vehicle video information collected by the video collecting unit is processed by the image preprocessing unit, and is then transmitted to the intelligent video analyzing unit, the vehicle information and the database information are compared by the intelligent video analyzing unit, and the vehicle information is analyzed, matched and judged by software so as to automatically identify a suspected vehicle and carry out system prompt or alarm. By adopting the technical scheme disclosed by the invention, the participation of personnel is greatly reduced, the identification accuracy and efficiency are increased, and the intelligent video analyzing system and method disclosed by the invention can be used for assisting the public security bureau and the criminal investigation department to carry out real-time monitoring on the fake plate, false plate and counterfeit plate vehicles in the illegal criminal cases.
Owner:NANJING GANGWAN INFORMATION TECH CO LTD
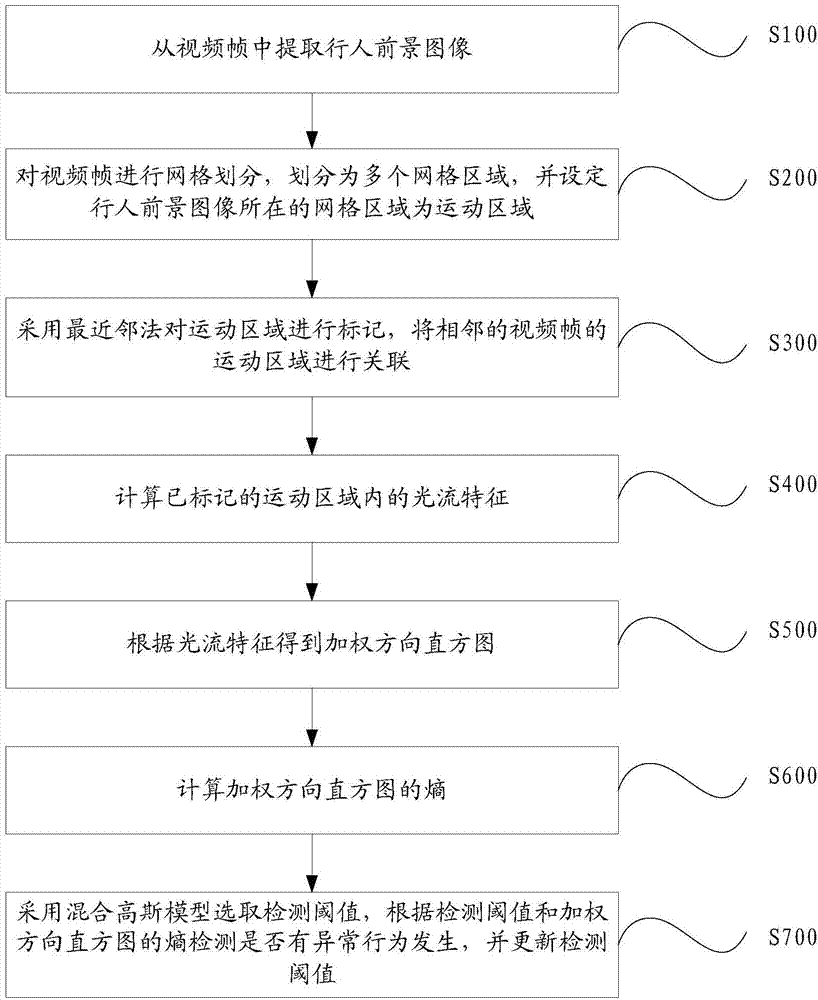
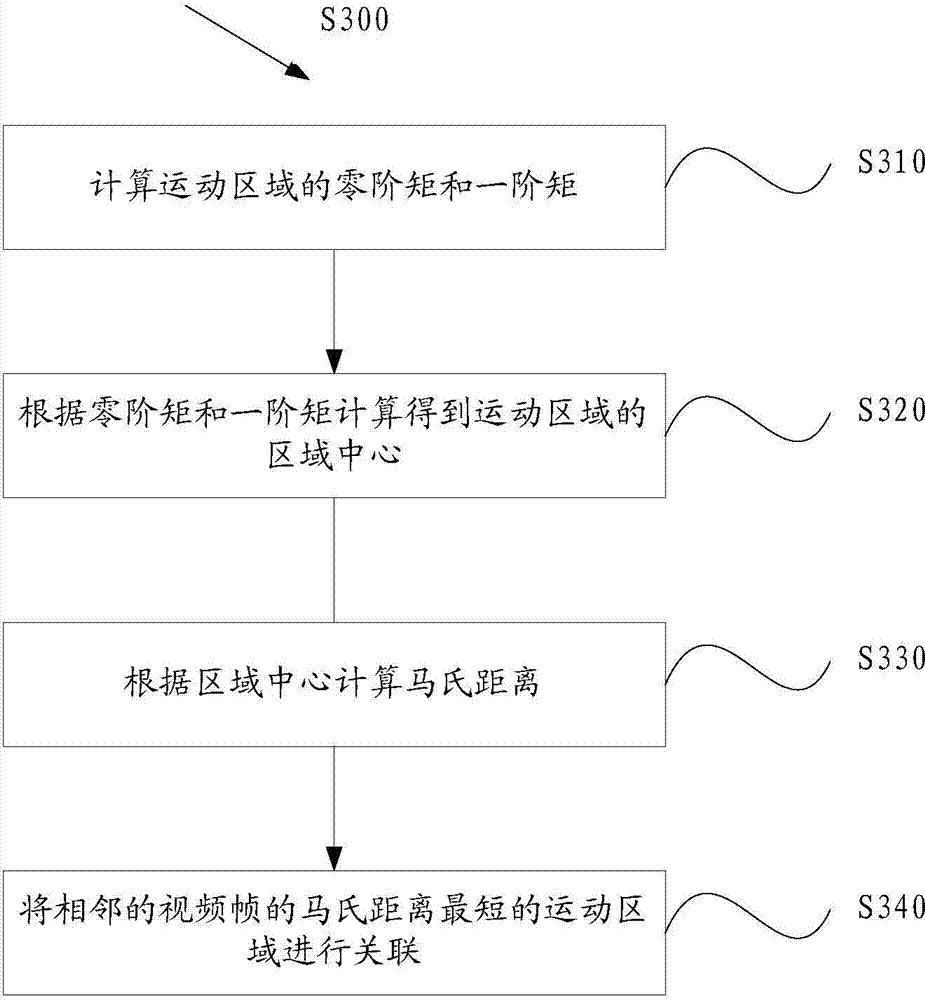
Video analysis based abnormal behavior detection method and system
ActiveCN104123544AReduce workloadEndanger public safetyCharacter and pattern recognitionAnomalous behaviorNear neighbor
The invention provides a video analysis based abnormal behavior detection method and system. The video analysis based abnormal behavior detection method comprises the following steps of extracting pedestrian foreground images from video frames; performing mesh generation on the video frames to divide the video frames into a plurality of mesh areas and setting the mesh areas in which the pedestrian foreground images are arranged to be movement areas; marking the movement areas through a nearest neighbor method and correlating the movement areas of the adjacent video frames; calculating light stream characteristics of the marked movement areas; obtaining a weighting direction histogram according to the light stream characteristics; calculating entropy of the weighting direction histogram; selecting a detection threshold value through a Gaussian mixture model, detecting whether an abnormal behavior is generated or not according to the detection threshold value and the entropy of the weighting direction histogram and updating the detection threshold value. The nested state machine based deduction process control method can automatically detect the abnormal behavior in a video scene, avoid the abnormal behavior disturbing the public plate order and endangering the public security and personal safety, reduce personnel workload and avoid potential risks caused by leak detection and error detection.
Owner:CRSC COMM & INFORMATION GRP CO LTD
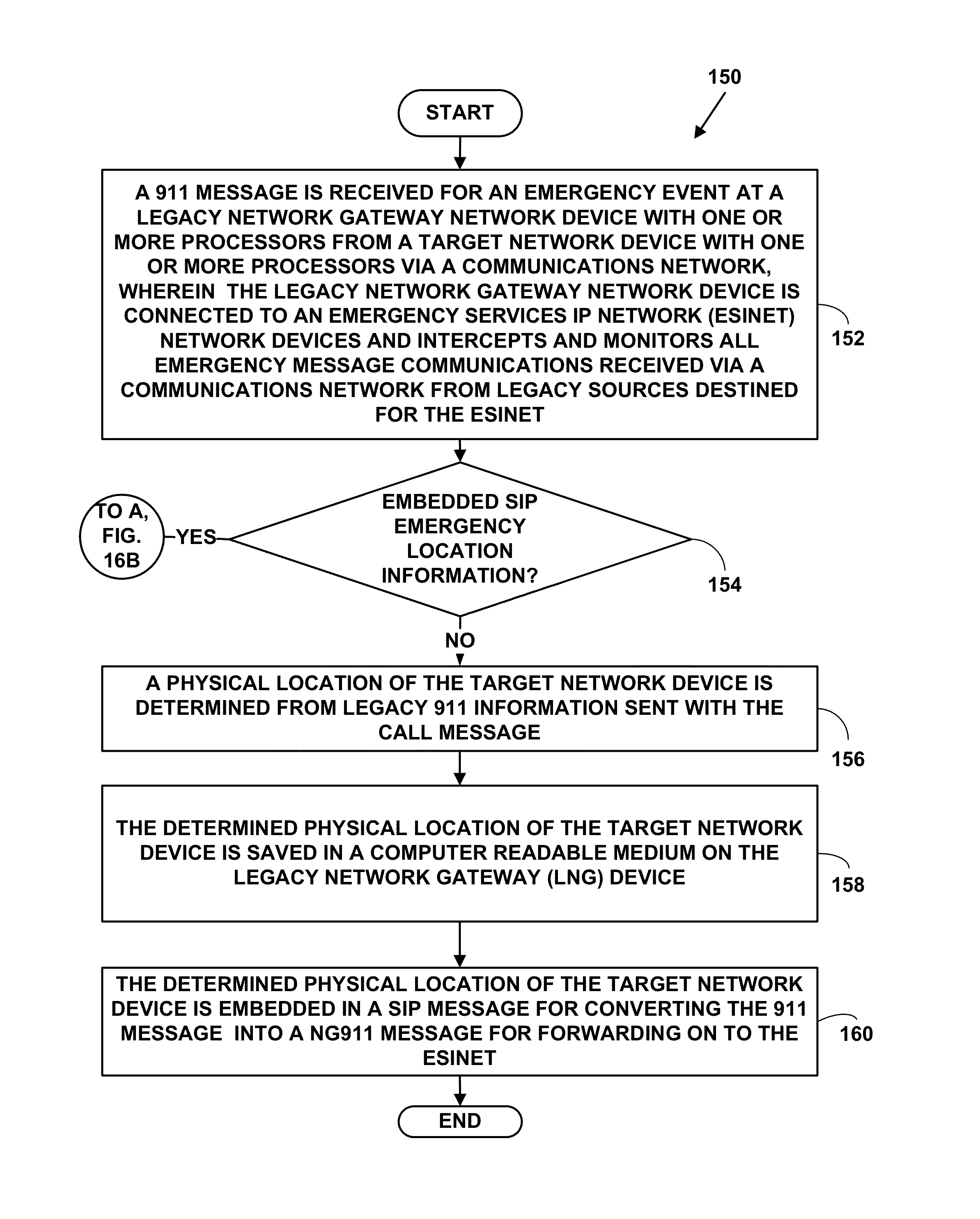
Emergency location information gateway for public safety answering points (PSAPs) and method of use
ActiveUS8442481B2Emergency connection handlingTelephonic communicationSession Initiation ProtocolProtocol for Carrying Authentication for Network Access
The emergency location information gateway provides Public Safety Answering Points (PSAPs) with the capability to receive NG911-compliant (i.e., Session Initiation Protocol (SIP-based) and / or SIP-Voice over Internet Protocol (VoIP)) and other types emergency calls including embedded emergency location information and determine a physical location of a mobile or non-mobile target network device based on the embedded emergency location information. Conversely, a legacy network gateway (LGN) enables the conversion of traditional 911, and E911 calls into NG911 calls for transport and dissemination by so-called Emergency Services IP networks, or ESInets.
Owner:EVERBRIDGE
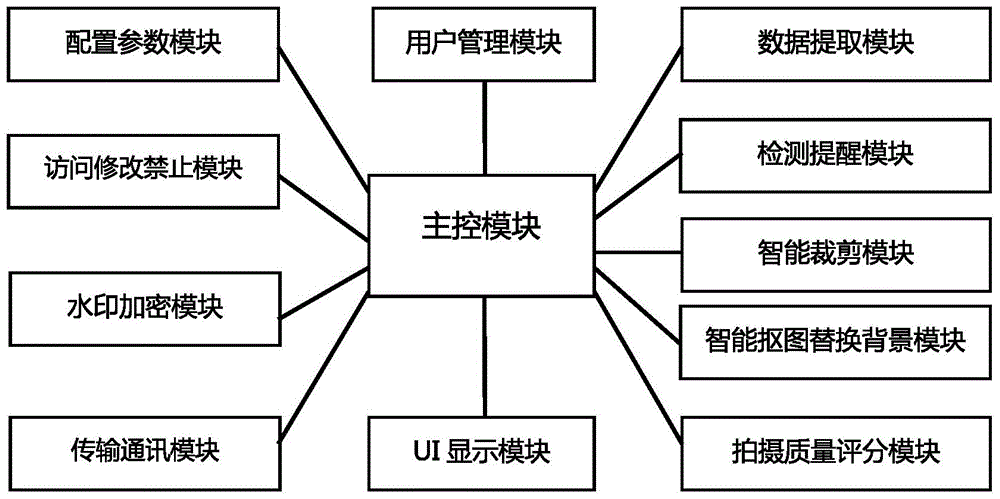
Certificate picture camera and certificate picture photographing method
ActiveCN105120167AMeet the requirements of public security industry standardsPrevent tamperingTelevision system detailsImage analysisComputer graphics (images)Quality assessment
The invention discloses a certificate picture camera and a certificate picture photographing method. The certificate picture camera comprises a parameter configuration module, a data obtaining module, a detection reminding module, an intelligent cutting module and a photographing quality grading module. The certificate picture photographing method comprises the following steps: detecting whether photographing parameters of an intelligent terminal camera satisfy certificate picture photographing requirements or not, and if not, configuring the photographing parameters; obtaining sensor data of an intelligent terminal, portrait characteristic data, luminance data, definition data and chromaticity distortion data of a preview frame image, judging whether relevant standard requirements of a legal certificate picture are satisfied or not, and if so, obtaining original image data after pressing a photographing button; cutting the original image data so as to obtain a standard-sized original picture of the certificate picture; grading the shooting quality of the original picture of the certificate picture, and giving a suggestion according to a comprehensive grading result. According to the invention, users can photograph the certificate picture satisfying government and public security industrial standard requirements in a self-service manner.
Owner:GUANGZHOU XINGFU NETWORK TECH
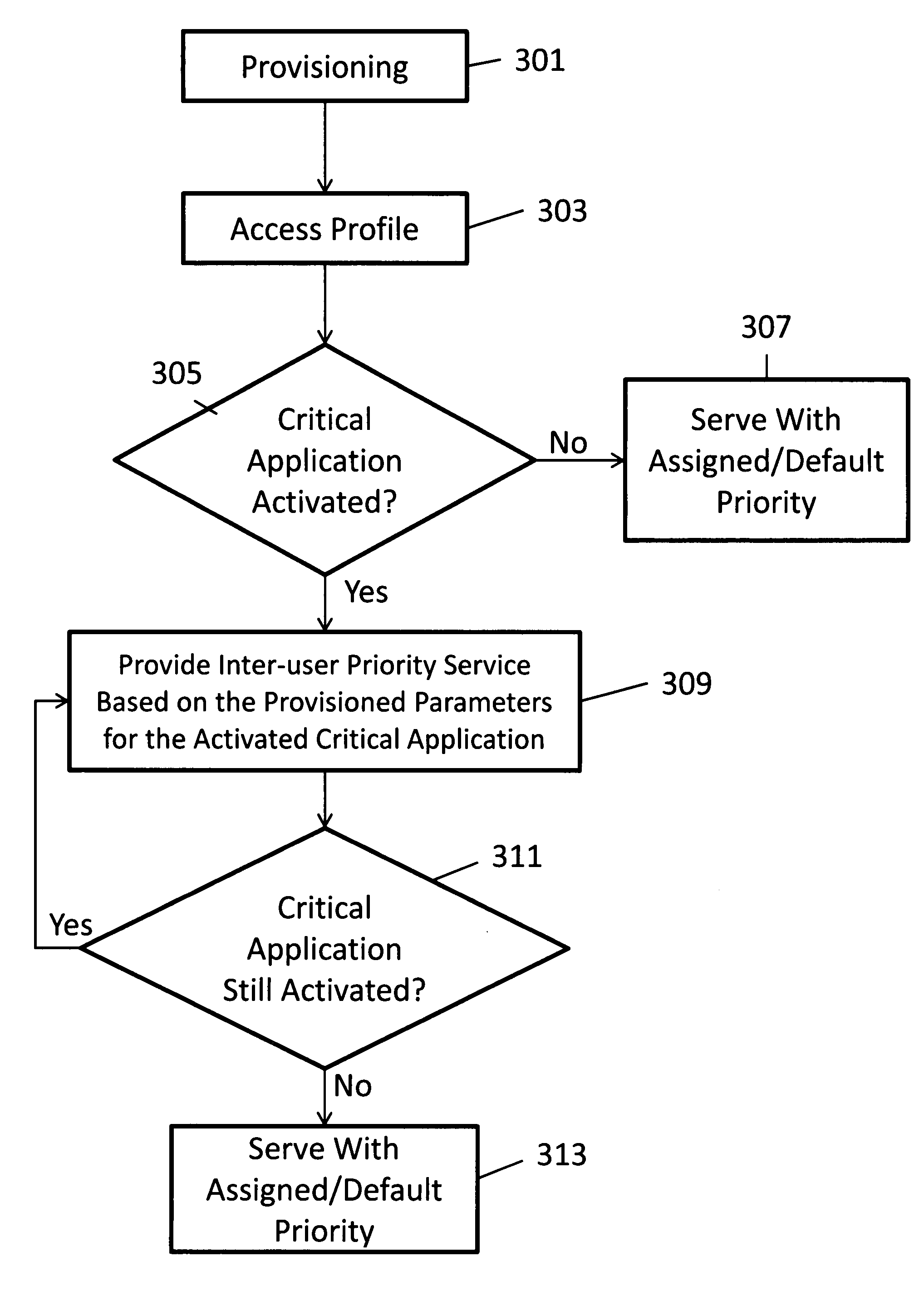
Application-based enhancement to inter-user priority services for public safety market
InactiveUS20090144740A1Maximum capacity/effectivenessGood serviceEmergency connection handlingNetwork traffic/resource managementAccess networkApplication software
A system and method for application based enhancement to the traditional per-user based inter-user priority services is provided. This method includes provisioning a user's profile, not only with an assigned inter-user priority, but also with zero, one or more specified and provisioned applications that are considered as critical applications which require special preferential treatment by the access network. The method continues with accessing the inter-user priority profile associated for sessions established for the user. The system then recognizes that a session may have been assigned to at least one provisioned critical application. The system may then provide inter-user priority services operative to provide the specified preferential treatment for at least the critical applications associated with the session when the critical application(s) are activated. In this form, the critical applications are better served including protection again congestion and availability of resources whenever they are needed. This system may grant preferential treatment on a session and / or application basis so that there will be no impact on other general applications when no critical applications are activated. This is especially useful for public safety implementation where protecting the mission-critical communication is a fundamental requirement.
Owner:LUCENT TECH INC
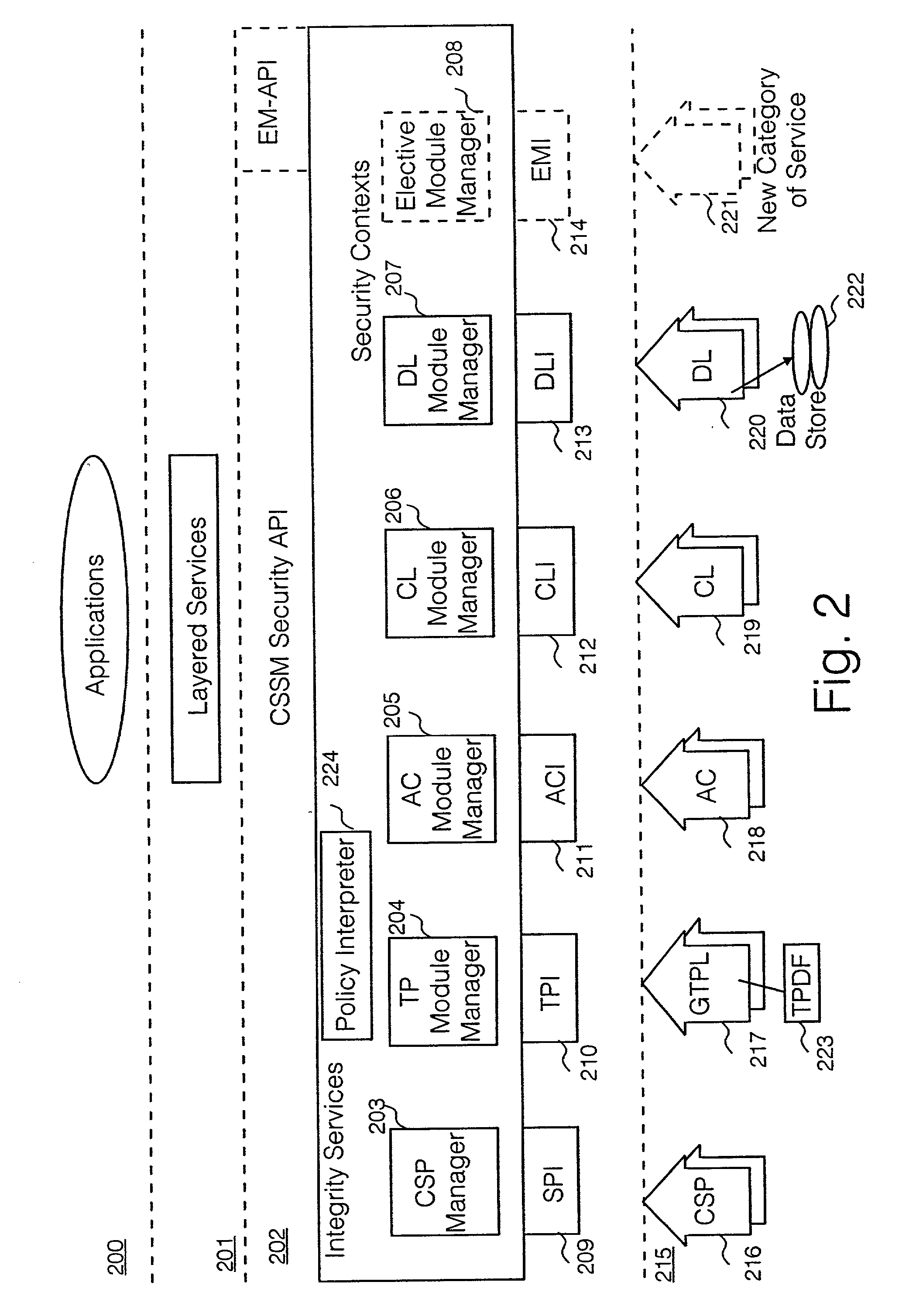
Security policy applied to common data security architecture
InactiveUS20010018746A1Digital data processing detailsUser identity/authority verificationHard codingSemantics
An improved architecture is provided, based upon the prior art common data security architecture, with the modification of adding in a generic trust policy library (217) at an add-in security modules layer (215) and a policy interpreter (224) at a common security services manager layer (202), so that individual users may provide sets of trust policies in the form of a trust policy description file (223), which uses a generic policy description language provided by the architecture. The architecture provides a generic method of incorporating trust policies into a computing platform in a manner which avoids a prior art problem of the semantics of trust policies which are hard-coded in prior art trust policy modules (117). The architecture also improves management flexibility. In the present disclosure, a generic policy description language is provided, which enables different users to define the semantics of a plurality of trust policies.
Owner:HEWLETT PACKARD DEV CO LP
Method and system for managing public safety in at least one of unknown, unexpected, unwanted and untimely situations via offering indemnity in conjunction with wearable computing and communications devices
InactiveUS20160330601A1Facilitate public safetyEnhanced qualitative and quantitativeData processing applicationsEmergency connection handlingEngineeringWearable computer
Embodiments of the present invention disclose design, deployment and implementation of systems capable of facilitating managing public safety (or security) in one or more situations, and methods thereof, in accordance with the principles of the present invention. Specifically, the systems may facilitate managing public safety (or security) in one or more situations of at least one of danger, untoward incident, accident, emergency, loss and death with one or more enhanced qualitative and quantitative features, such as minimal vulnerability, real-time notification ability and automatic evidence manageability, thereby facilitating timely prevention, Quick Response (QR) or (Just-In-Time or JIT) response, speedy trial, effective prosecution, easy enforceability and policing, and methods thereof in accordance with the principles of the present invention.
Owner:SRIVASTAVA VIKAS
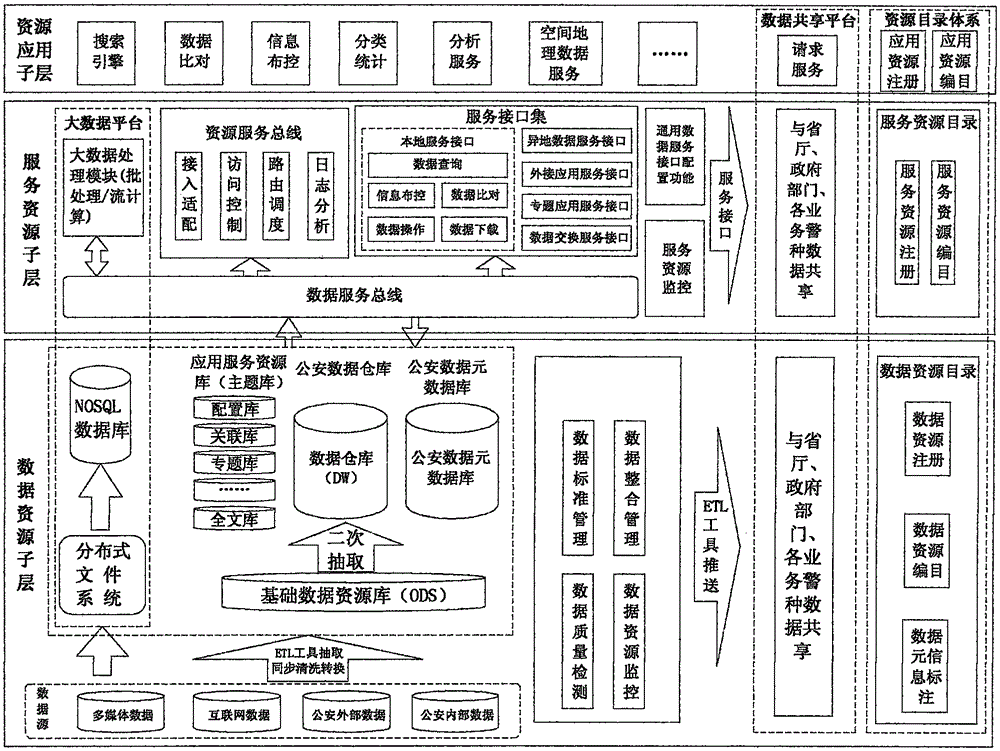
Method based on police affair big data center service construction
ActiveCN105554070AImprove and improve handlingImprove and enhance the technical service guarantee capability of data sharingRelational databasesTransmissionData platformData treatment
The invention discloses a method based on police affair big data center service construction. Through building of a police affair cloud data service layer, functions of data collection, data arrangement, data sharing and data analysis are realized, and the police affair cloud data service layer includes a data recourse sublayer, a service resource sublayer, a resource application sublayer, a data sharing platform and a big data platform. According to the method provided by the invention, through building of the police affair cloud data service layer, the functions of all police data collection, data arrangement, data sharing and data analysis are realized, the capability and level of technical service assurance of data processing and data sharing of a public security organization are comprehensively improved, a data mining and analysis capability is perfected and improved, and open and efficient data sharing application and data analysis and mining services are provided for all the police.
Owner:北京中科云集科技有限公司
Combination carbon monoxide and wireless E-911 location alarm
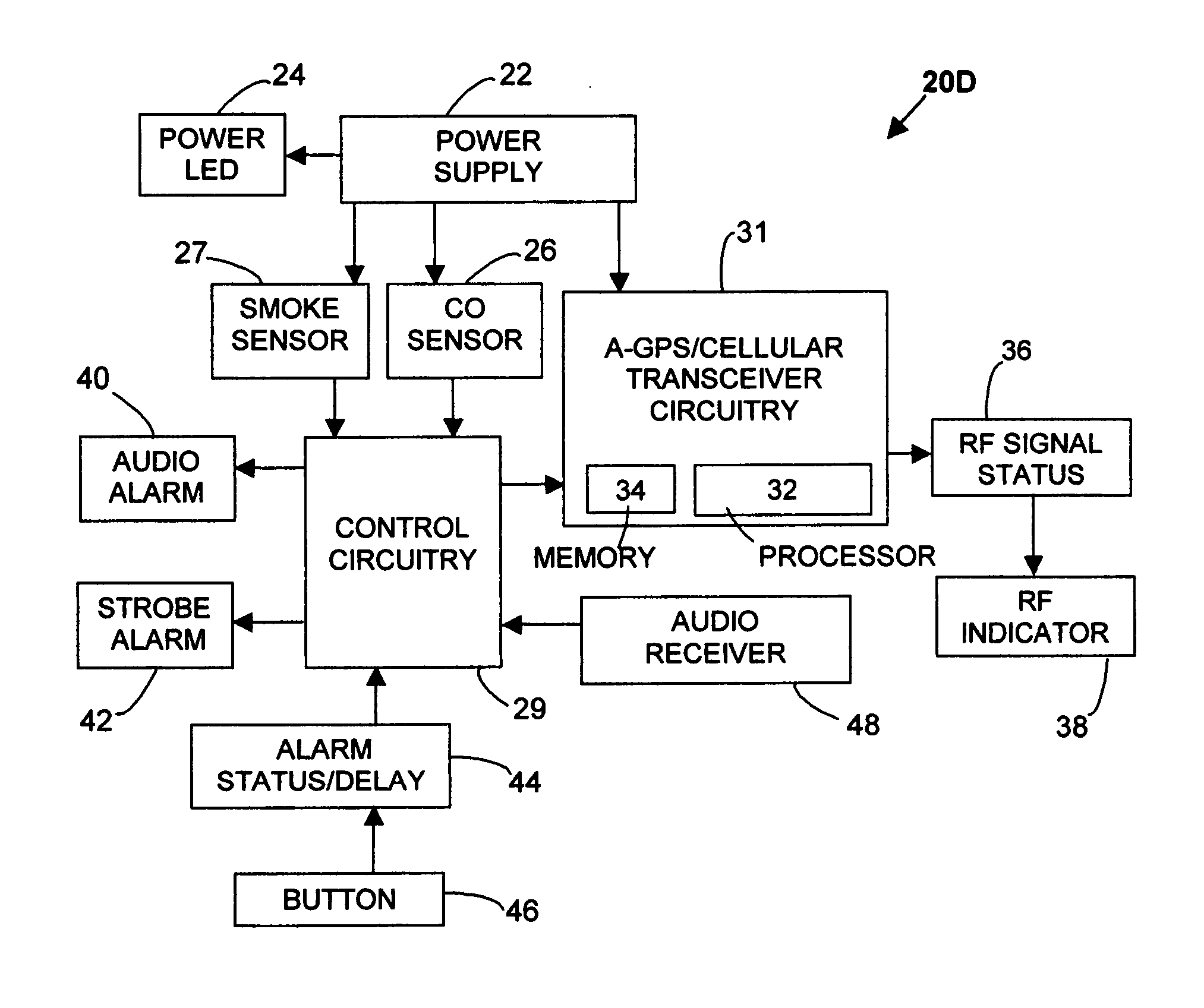
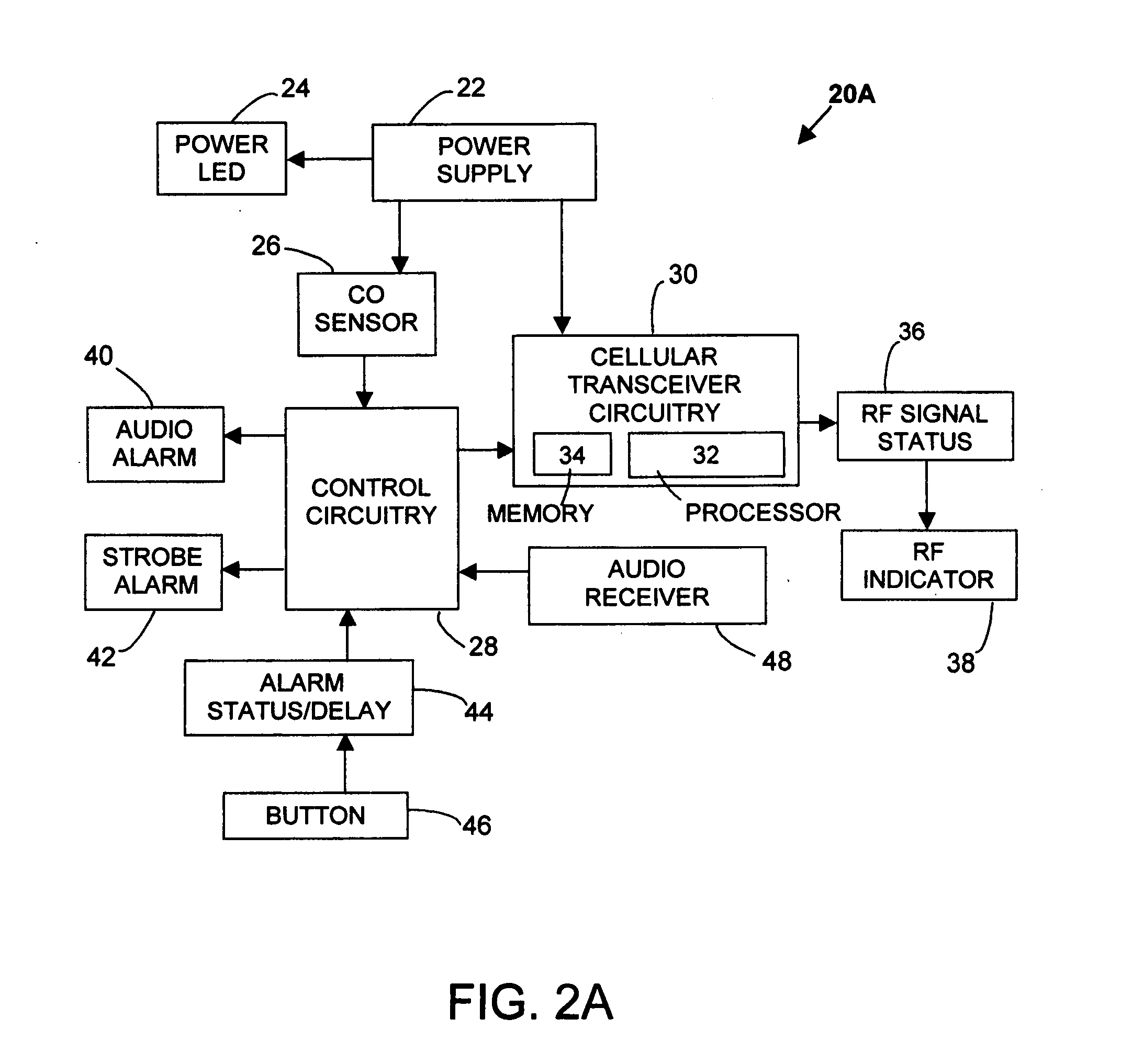
ActiveUS20050200492A1Increase carbon monoxide safetyProvide capabilityElectric signalling detailsFire alarm smoke/gas actuationTransceiverIncident report
The present invention provides a device and method for automatically reporting and determining the geographic location of potential carbon monoxide emergencies utilizing wireless E-911 location systems. The combination carbon monoxide and wireless E-911 location alarm in its main device embodiment comprises a self-contained carbon monoxide alarm interfaced with a cellular transceiver, which operates in existing wireless E-911 location systems. The cellular transceiver is a cellular processor with integrated memory for storing emergency identification data for automated carbon monoxide emergency incident reporting to 911 public safety answering point operators. In one mode of operation, upon sensing the presence of carbon monoxide, the cellular transceiver automatically initiates a 911 emergency call, transmitting emergency identification information over a wireless E-911 location system to a 911 public safety answering point operator, who dispatches public safety personnel to the location of the emergency carbon monoxide incident.
Owner:WOODARD NOEL +1
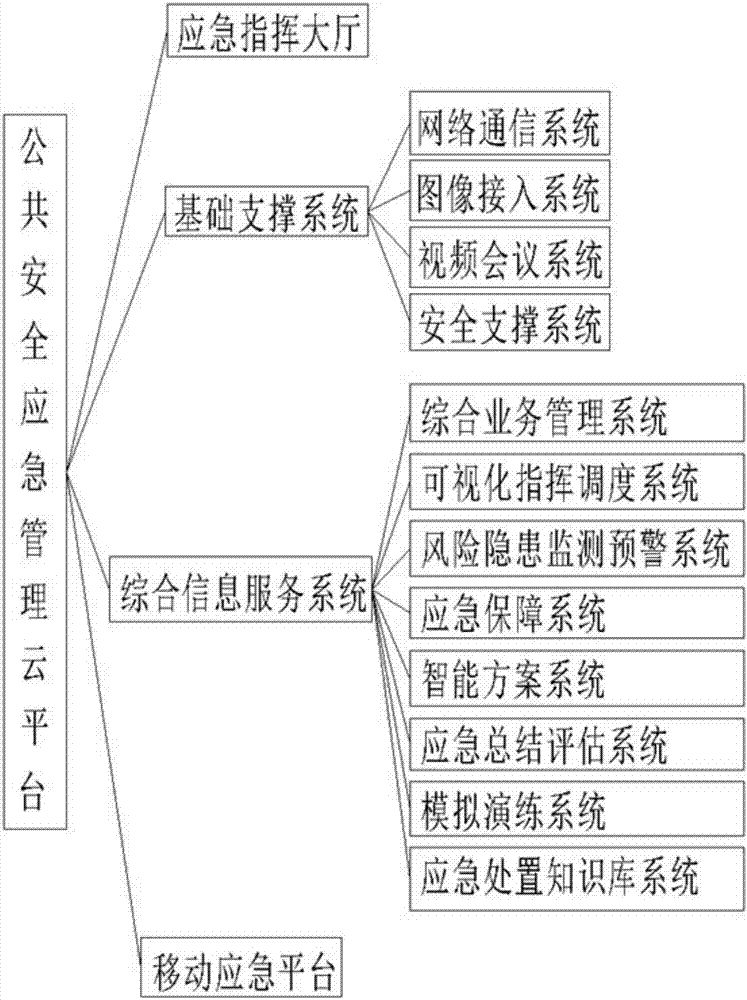
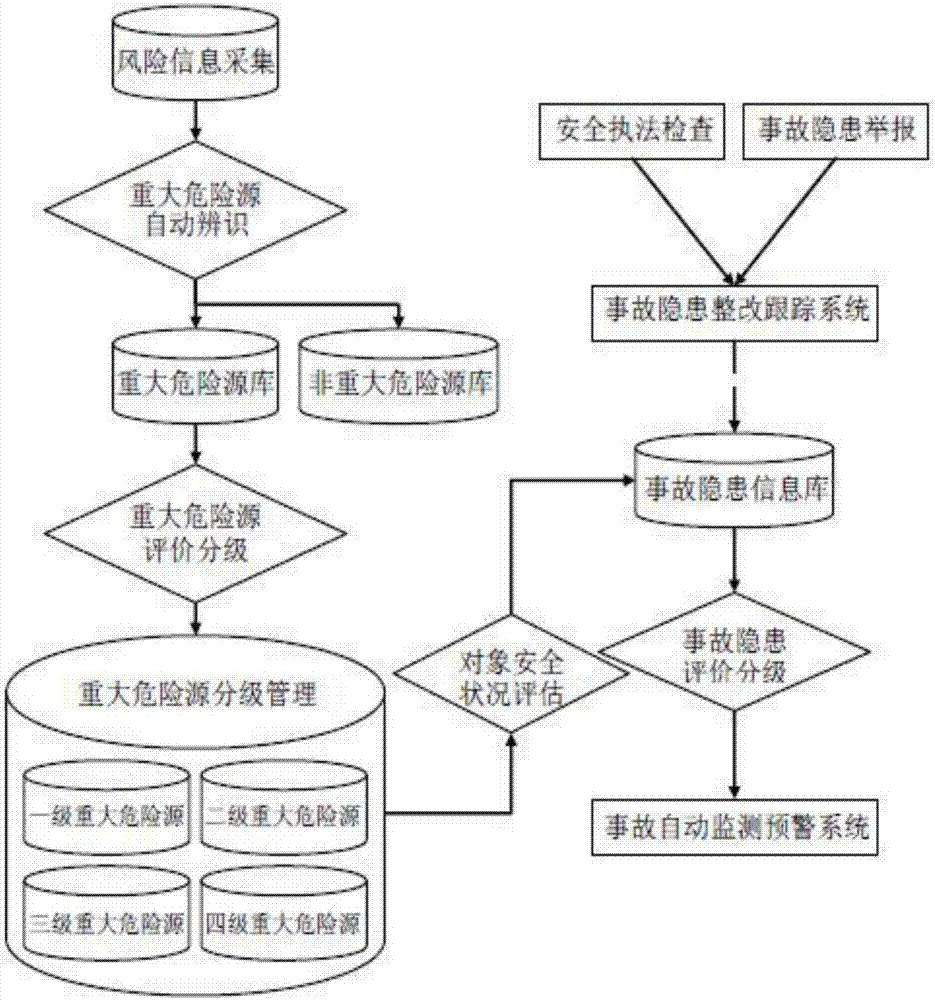
Computer simulation system of public security emergency management and simulation method
InactiveCN106991633AModerate disposal fastFast rebuildData processing applicationsDesign optimisation/simulationEmergency rescueCommand system
The present invention relates to a computer simulation system of public security emergency management and a simulation method. A public security emergency management cloud platform is upwards connected with an emergency command platform, is downwards connected with the town and street emergency command systems, is transversely connected with the municipal special emergency command platforms on the basis of integrating the data resources and the communication network resources of the conventional various systems, thereby realizing the monitoring, the prediction, the early warning, the auxiliary decision-making and the command and dispatch, and providing the comprehensive information services for the emergency rescue and command, the accident deduction, the emergency disposal training and the emergency hedge skill training. The public security emergency management cloud platform comprises an emergency command hall, a basic supporting system, a comprehensive information service system and a mobile emergency platform, enables the generation of the security incidents, the natural disasters and the man-made disasters and the loss brought by the security accidents to be reduced, protects the economy, and maintains the sustained steady and coordinated development of the society. By establishing the security risk evaluation and early warning, the simulation system and the simulation method have the very important significance for improving the social public security emergency rescue of our country, the risk evaluation and the comprehensive management.
Owner:JIANGSU YUANWANG SHENZHOU SOFTWARE CO LTD
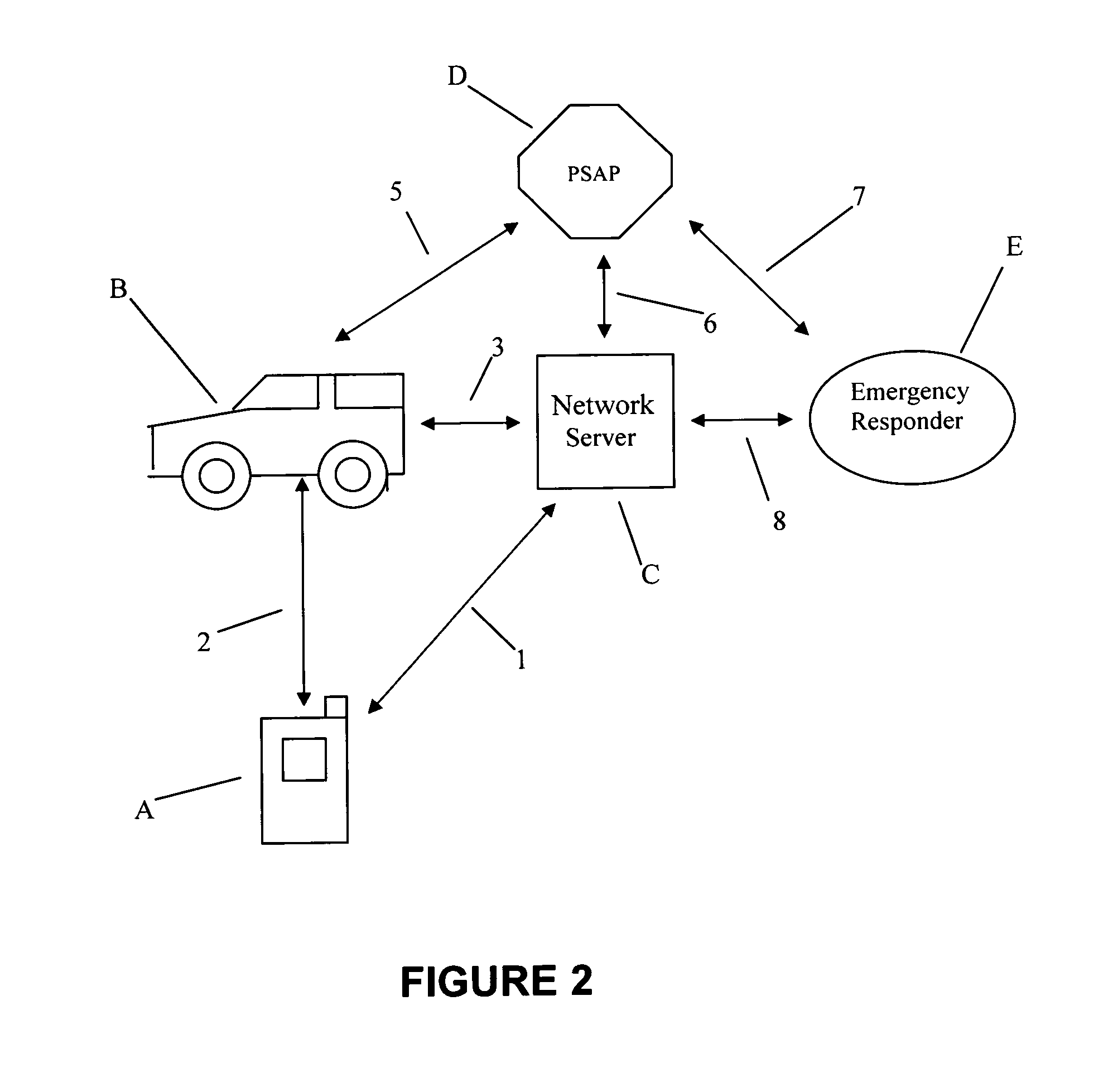
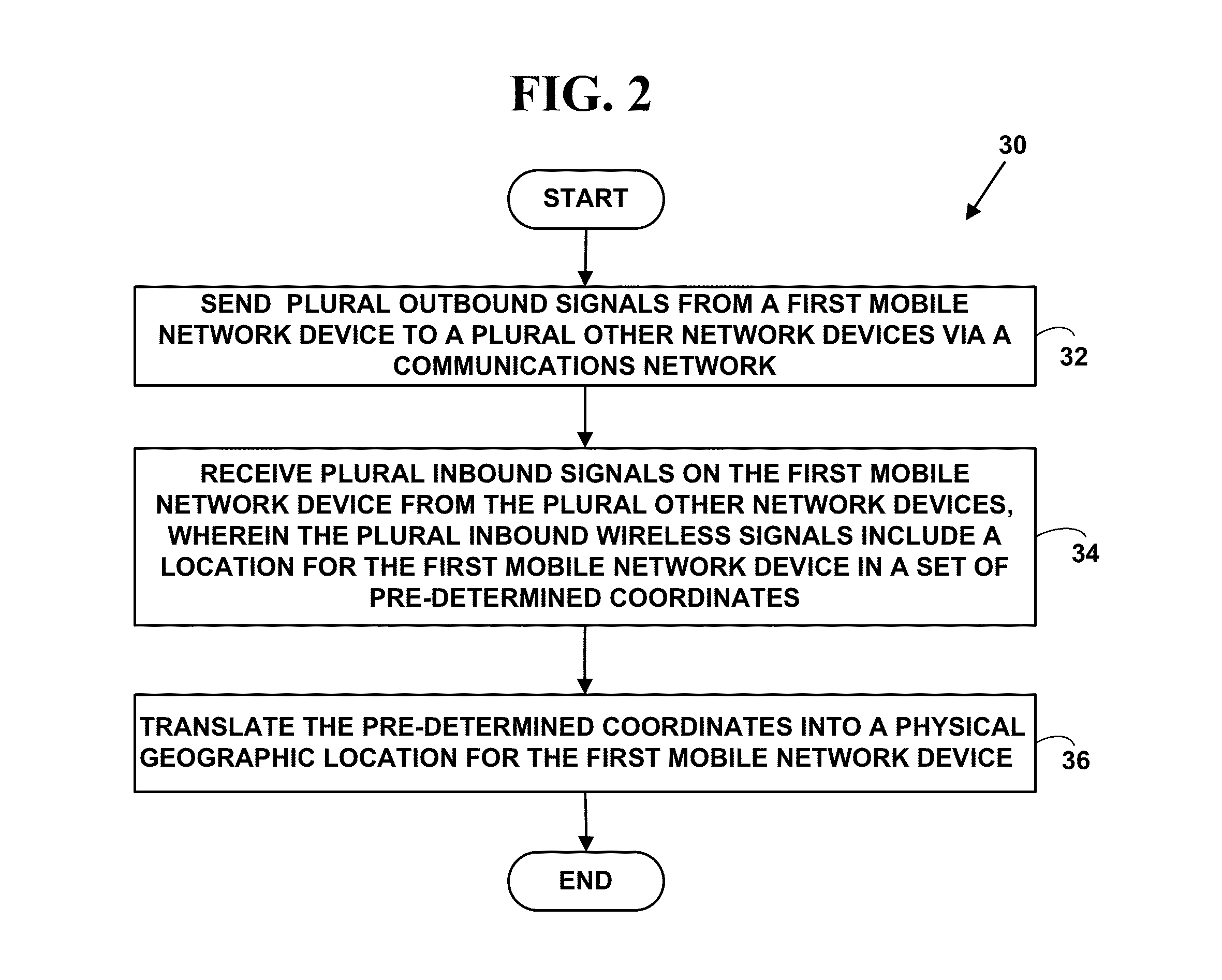
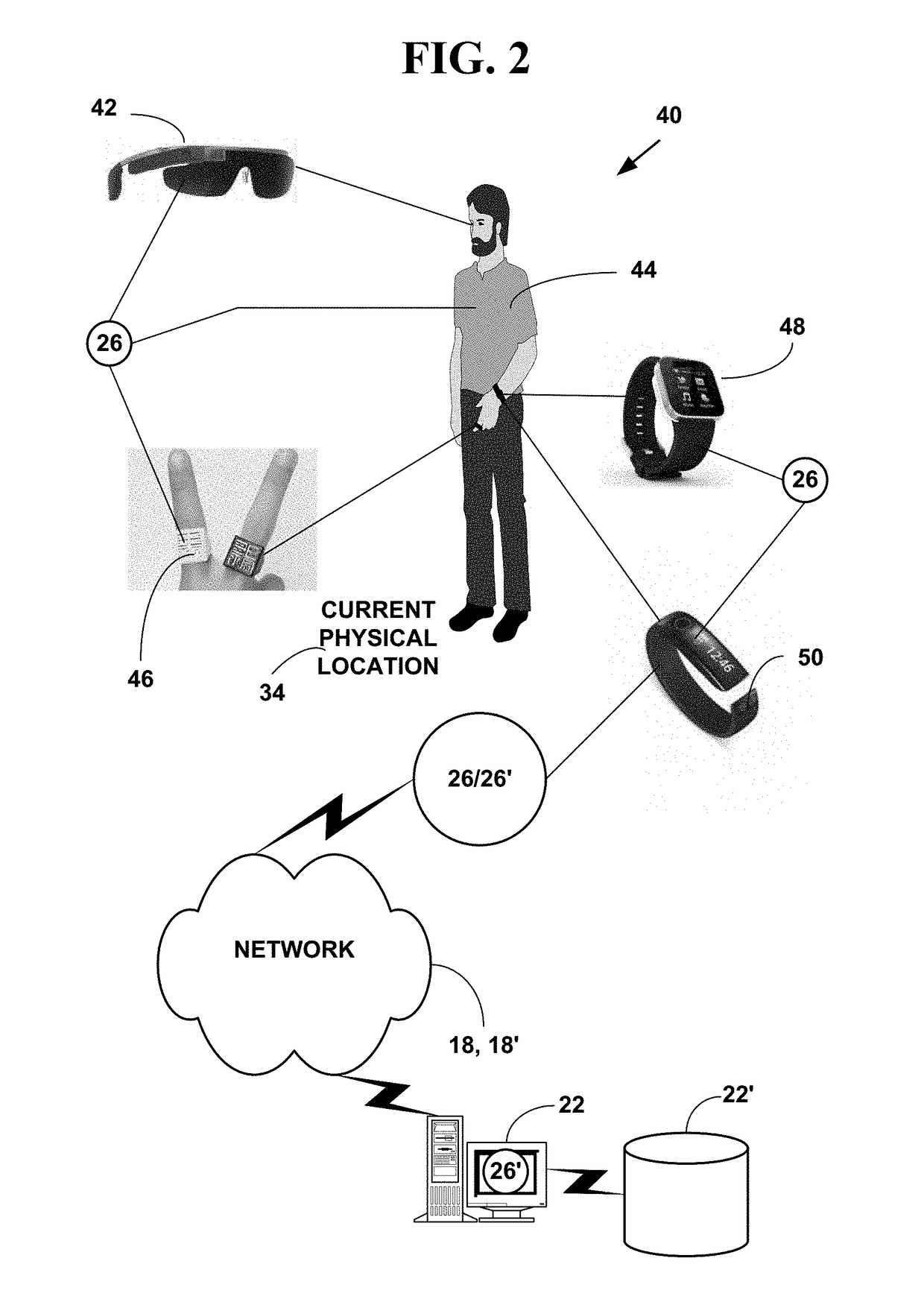
Method and system for locating a network device in an emergency situation
A method and system for locating a network device in an emergency situation. Current physical location information is obtained for a network device every time it registers on a network or moves to a new physical location. The current physical location is sent and received in an encrypted format to and from the network device. When the network device initiates an emergency message (e.g. 911, E911, NG911, text-to-911, 112, etc.) based on an emergency event (e.g., weather, crime, fire, natural disaster, medical, terrorist, military, etc.), the emergency message includes the encrypted current physical location information for the network device. The current physical location information is decrypted and the emergency message is immediately routed in real-time to an appropriate Public Safety Answering Point (PSAP). The appropriate PSAP is immediately notified in real-time so emergency responders (e.g., police, fire, medical, etc.) can be dispatched to the current physical location of the network device.
Owner:EVERBRIDGE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com