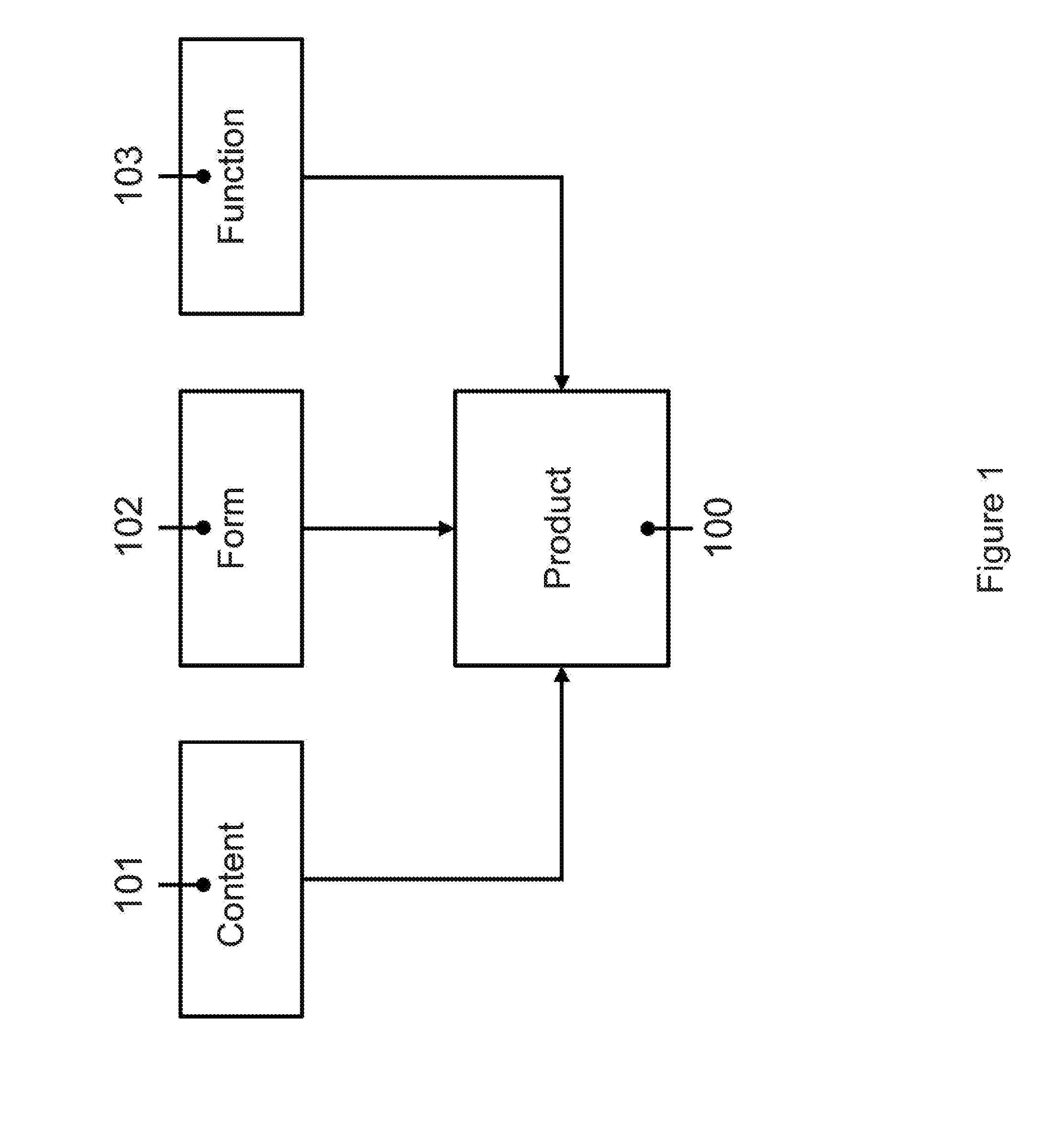
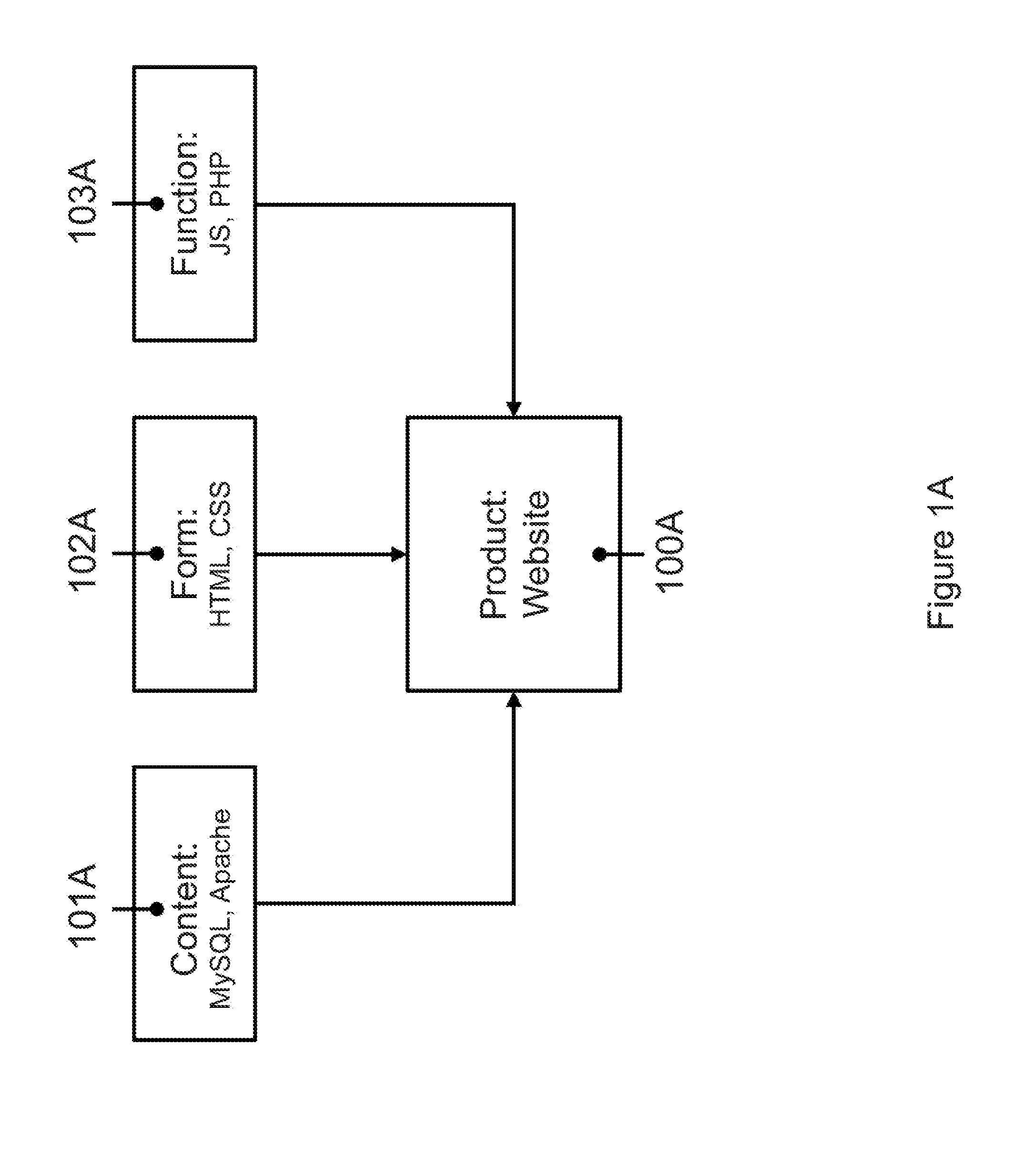
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2184 results about "Data resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
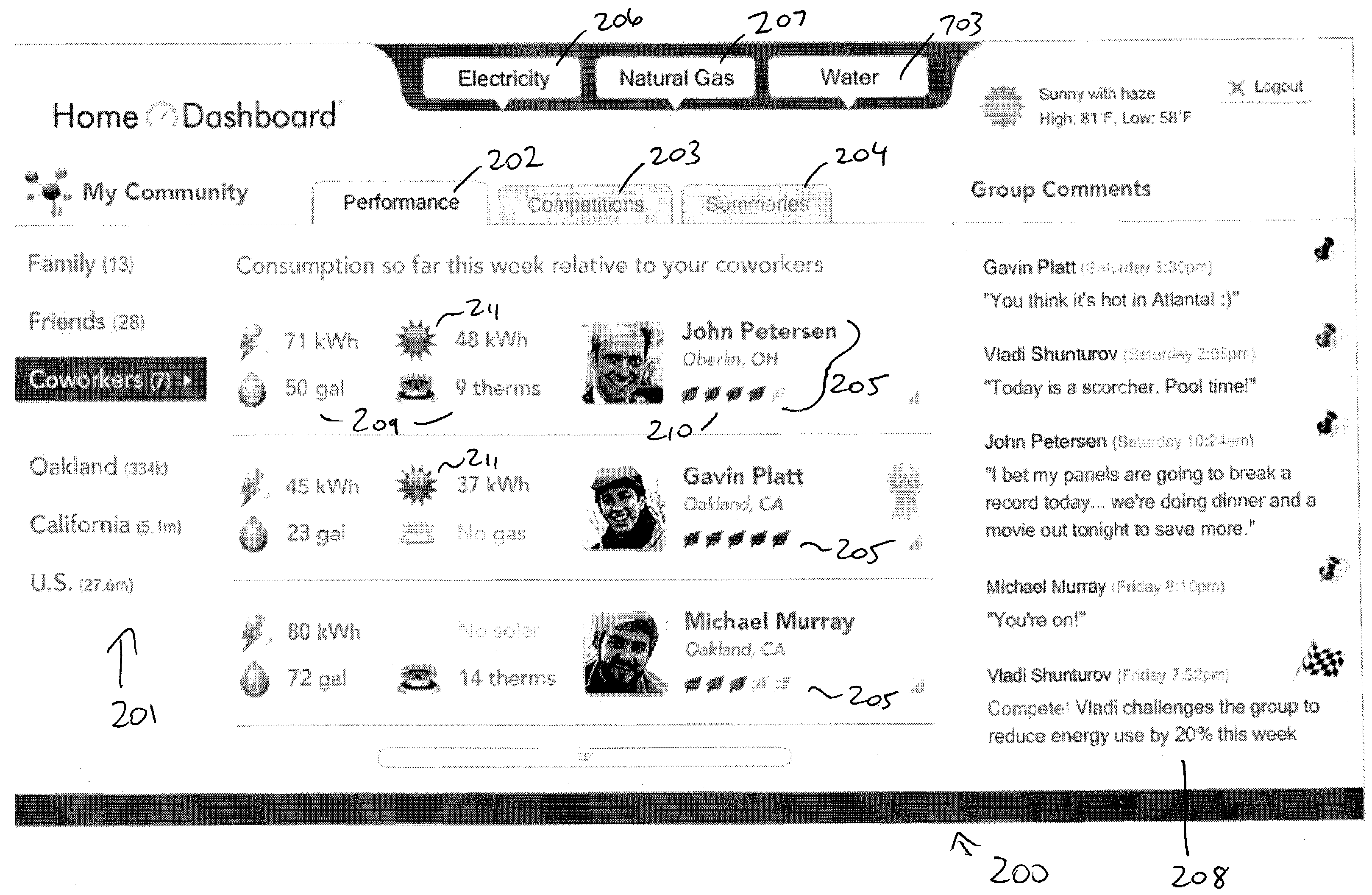
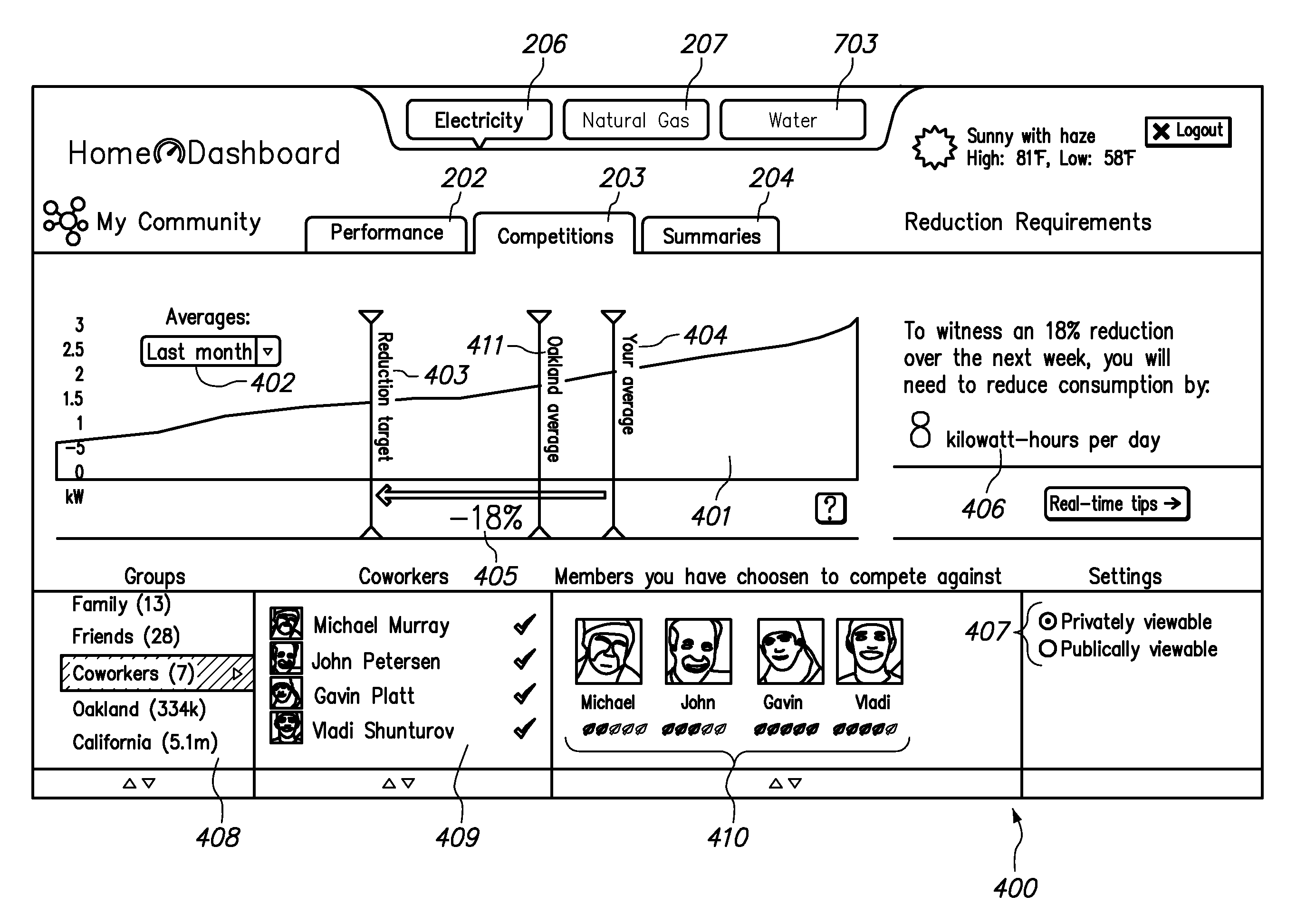
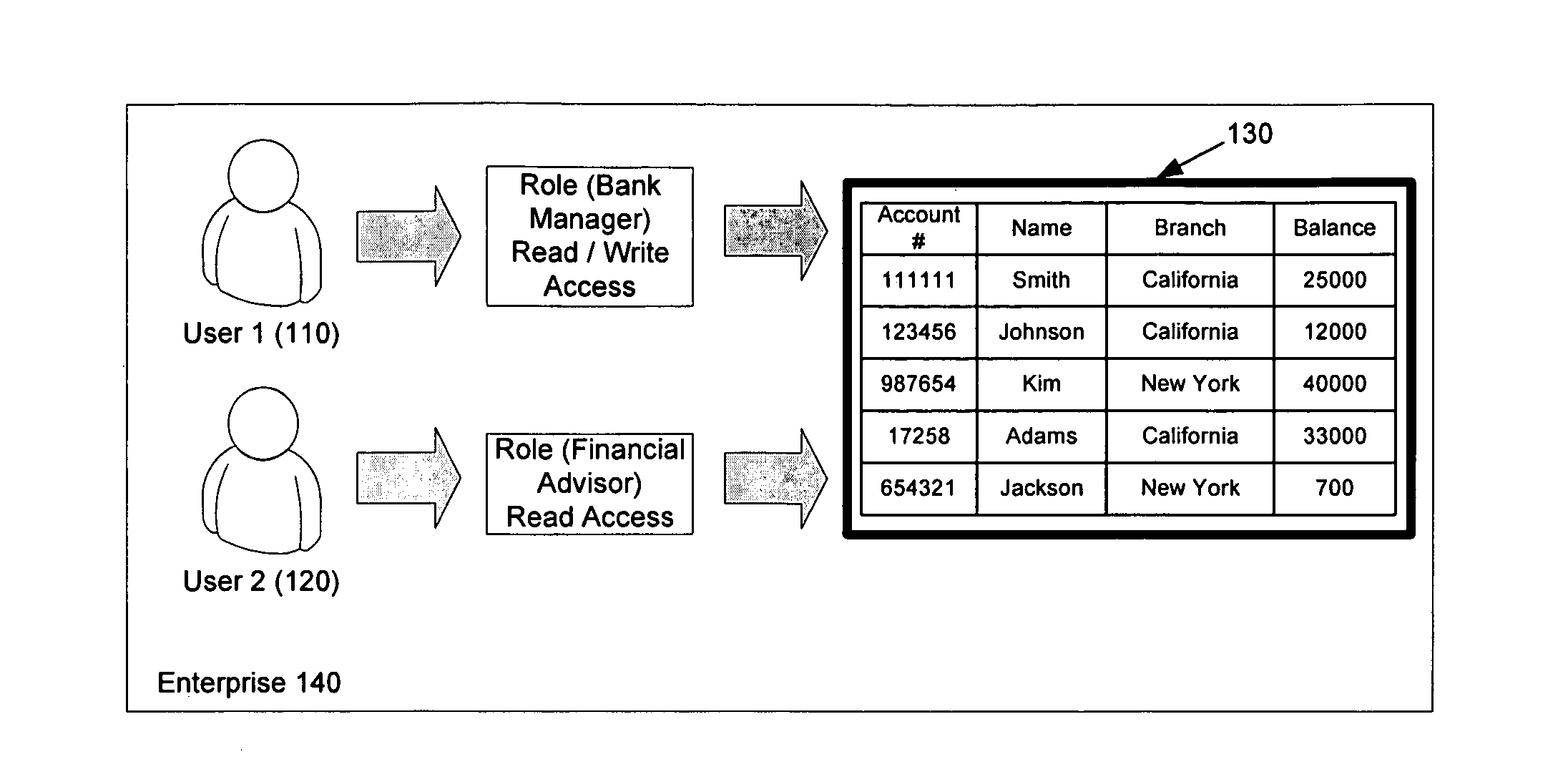
Collecting, sharing, comparing, and displaying resource usage data
ActiveUS20080306985A1Easy to compareThe effect is highlightedOffice automationCommerceGraphicsInteractive displays
Resource usage data is automatically collected for an individual, house-hold, family, organization, or other entity. The collected data is transmitted to a central repository, where it is stored and compared with real-time and / or historical usage data by that same entity and / or with data from other sources. Graphical, interactive displays and reports of resource usage data are then made available. These displays can include comparisons with data representing any or all of community averages, specific entities, historical use, representative similarly-situated entities, and the like. Resource usage data can be made available within a social networking context, published, and / or selectively shared with other entities.
Owner:ABL IP HLDG
Method and system for managing partitioned data resources
InactiveUS6922685B2Easy accessEnhanced interactionFinancePayment protocolsApplication softwareClient-side
Owner:EKMK LLC
Method and system for managing partitioned data resources
InactiveUS20050240621A1Easy accessEnhanced interactionFinancePayment protocolsData storeData resources
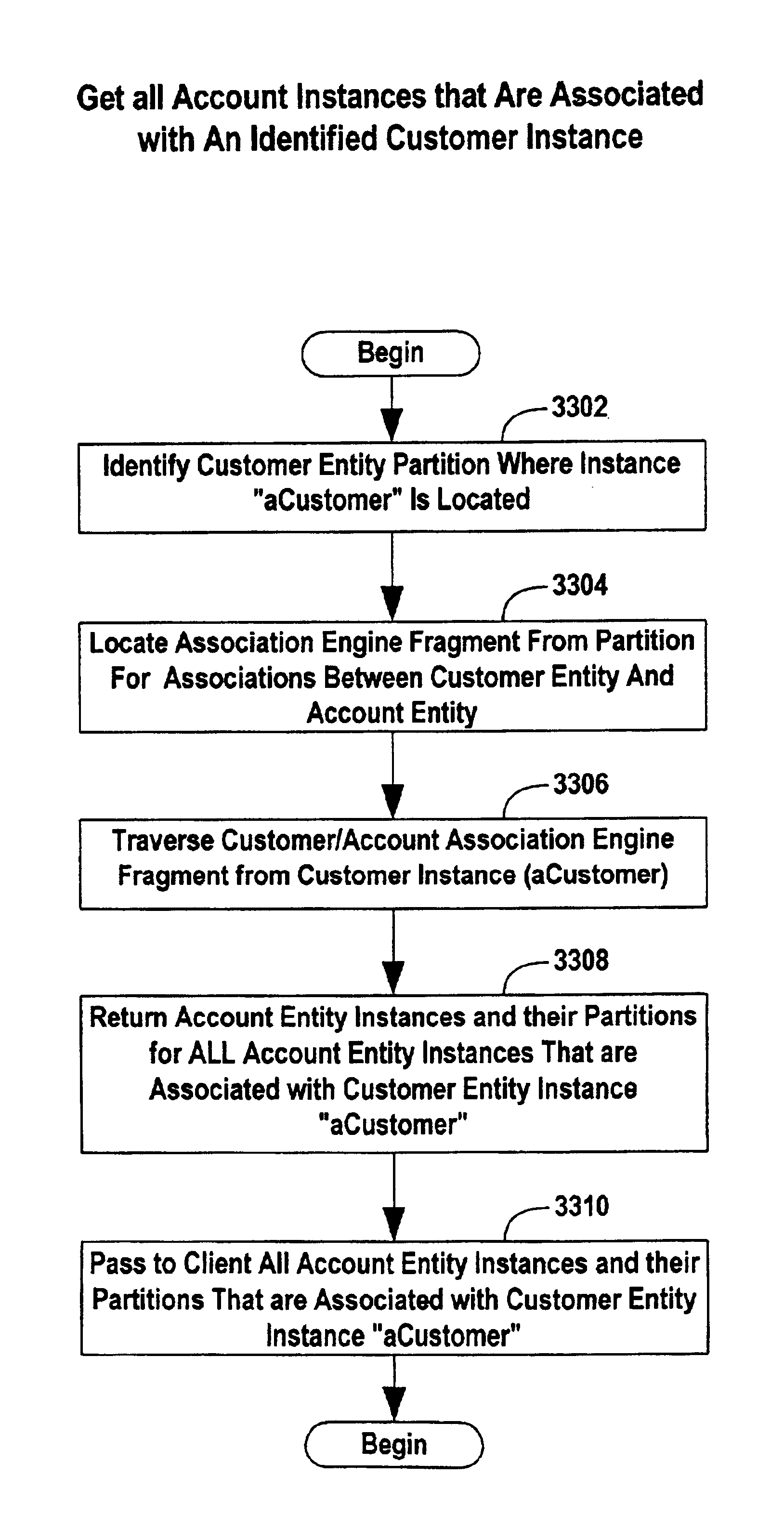
In accordance with an exemplary embodiment of the present invention, association forming entities are: a) maintained as objects in a like manner to the data objects being associated; and 6) are themselves partitioned objects comprising two or more association fragments, each association fragment being mostly concerned with the interfaces to a particular data object participating in the association. In accordance with an exemplary embodiment of the present invention, each association fragment affiliated with a particular data object is stored in a location that enhances the ease of interaction between the association fragment and the data object. For example, where a first data object and second data object are maintained in data stores at some distance from one another, physically or logically, then a first association fragment will be located with or near to the first data object and a second association fragment will be located with or near the second data object, at least within the same partition. This arrangement may be preferable because the volume of interaction between a data object and its respective association fragment may far outweigh the interaction needed between the two association fragments. This arrangement may also be preferable as the volume of interaction between a client application and both the data object and respective association fragment may exceed the interaction needed between the two association fragments. Some interactions will employ only one of the association fragments with the net result being a reduction in communications requirements and an improvement in performance. The present invention further provides for defining logical domains which are arbitrary and entirely orthogonal to partitions.
Owner:EKMK LLC
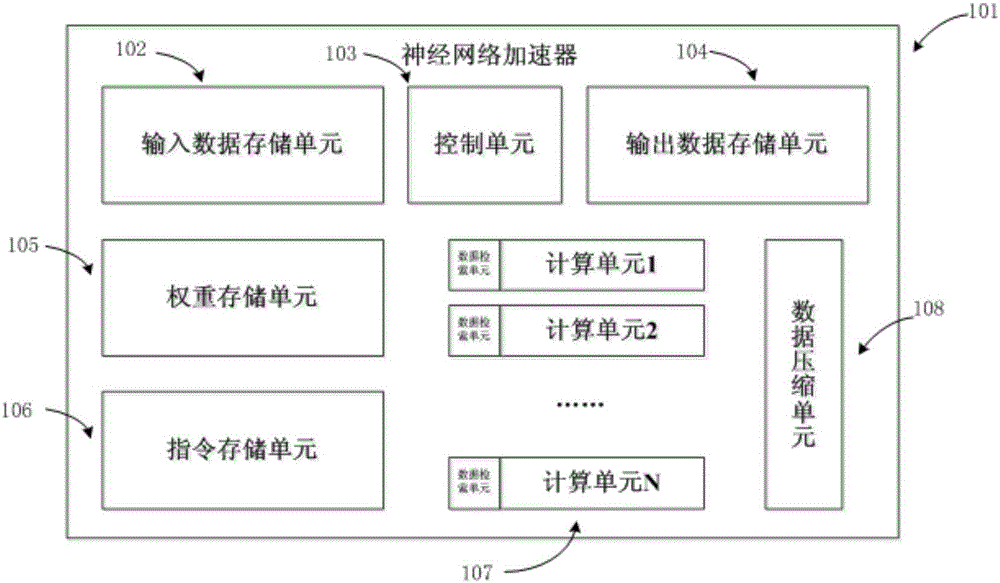
Neutral network processor based on data compression, design method and chip
ActiveCN106447034AIncrease computing speedImprove computing efficiencyPhysical realisationEnergy efficient computingOperating instructionData compression
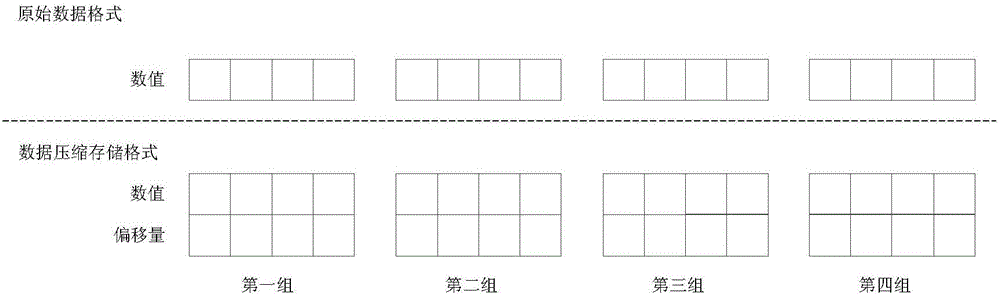
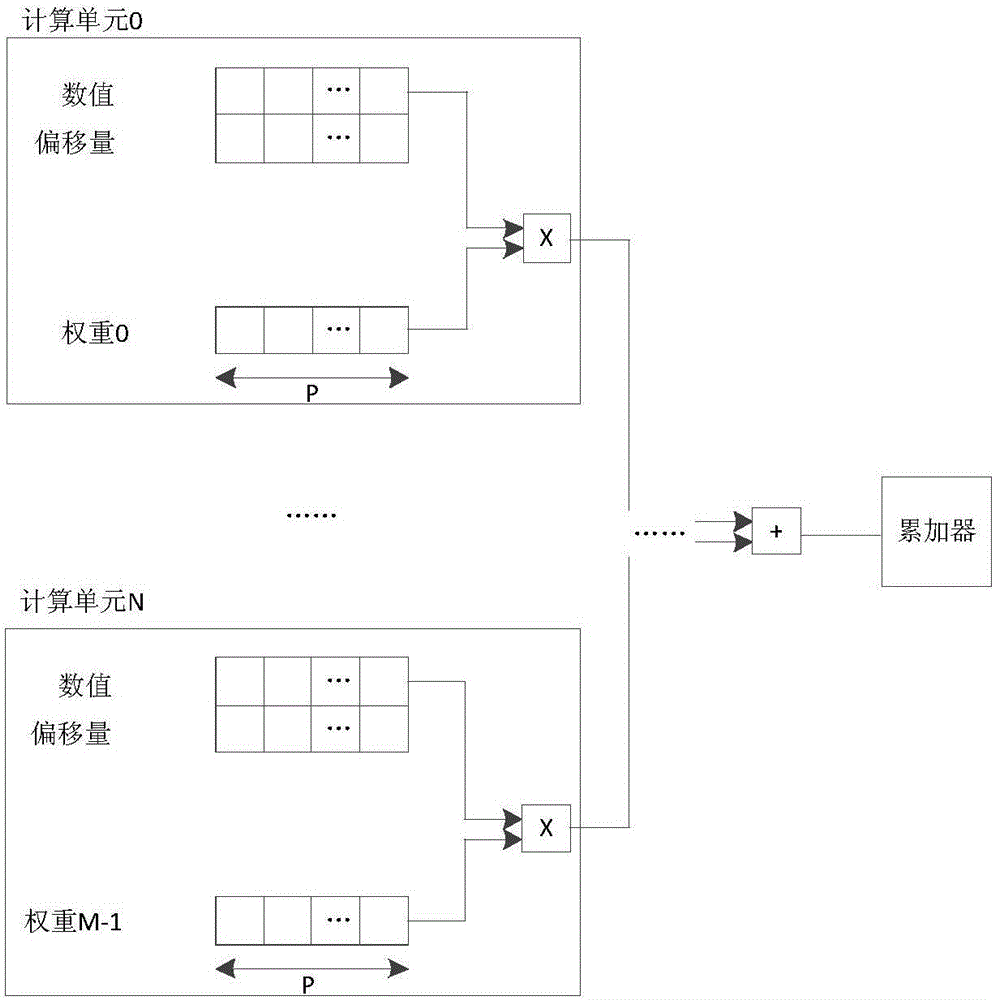
The invention provides a neutral network processor based on data compression, a design method and a chip. The processor comprises at least one storage unit used for storing operating instructions and data participating in calculation, at least one storage unit controller used for controlling the storage unit, at least one calculation unit used for executing calculation of a neutral network, a control unit connected with the storage unit controllers and the calculation units and used for acquiring instructions stored by the storage unit through the storage unit controllers and analyzing the instructions to control the calculation units, and at least one data compression unit used for compressing data participating in calculation according to a data compression storage format. Each data compression unit is connected with the corresponding calculation unit. Occupancy of data resources in the neutral network processor is reduced, the operating rate is increased, and energy efficiency is improved.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
System and method for preventing data corruption in computer system clusters
InactiveUS7631066B1Reduce failover timeImprove the problemError detection/correctionDigital computer detailsCluster systemsComputerized system
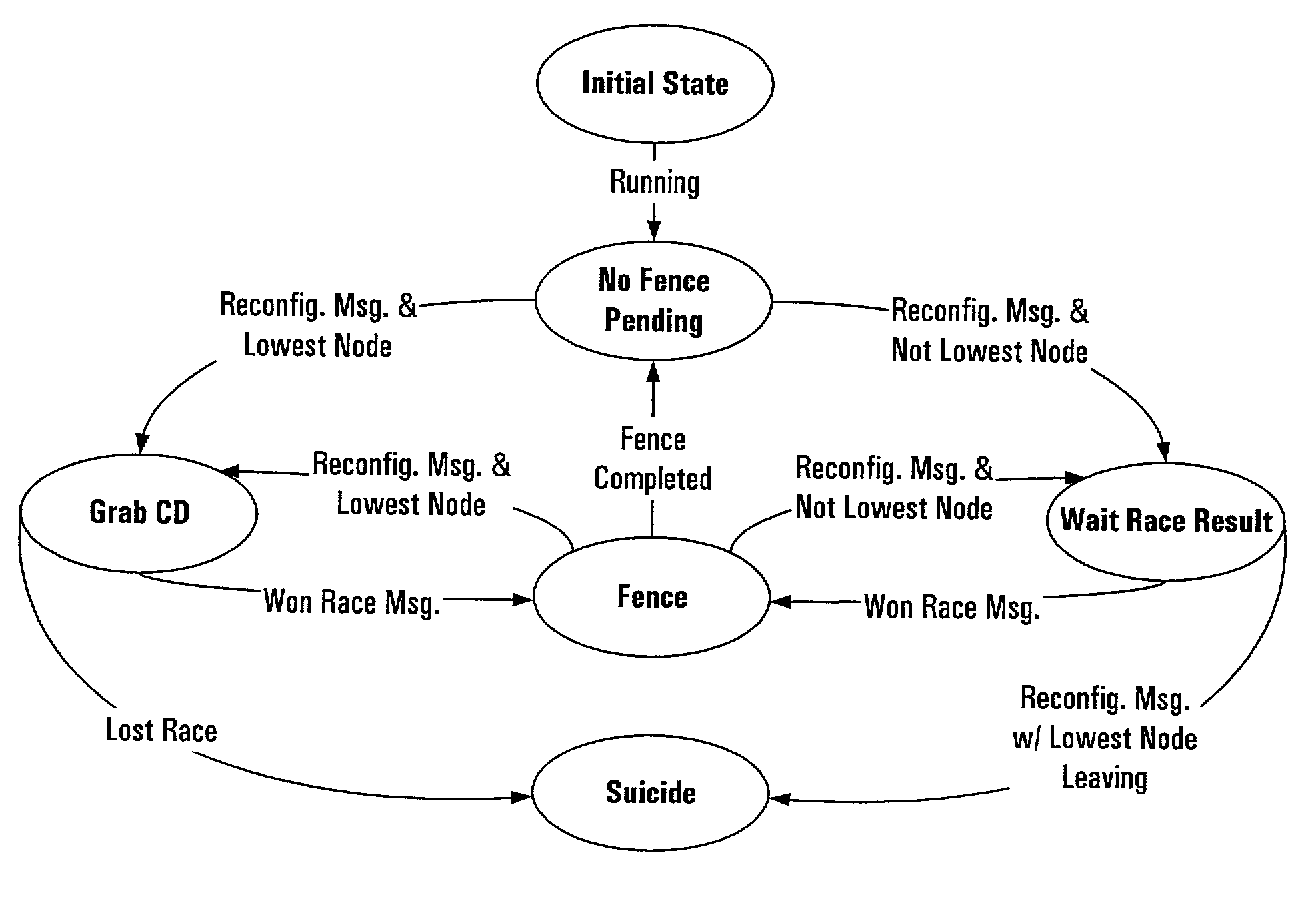
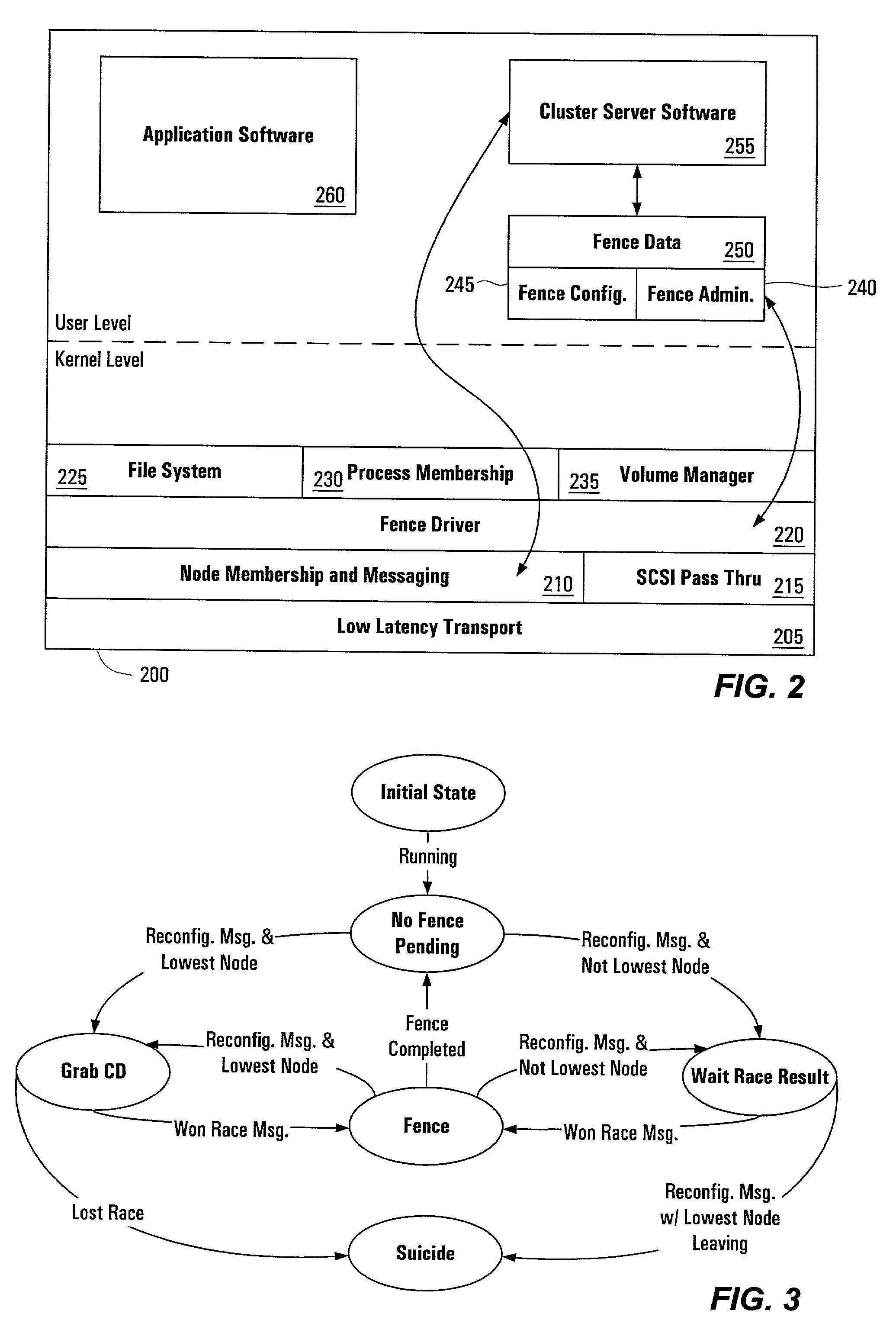
Systems, methods, apparatus and software can make use of coordinator resources and SCSI-3 persistent reservation commands to determine which nodes of a cluster should be ejected from the cluster, thereby preventing them from corrupting data on a shared data resource. Fencing software operating on the cluster nodes monitors the cluster for a cluster partition (split-brain) event. When such an event occurs, software on at least two of the nodes attempts to unregister other nodes from a majority of coordinator resources. The node that succeeds in gaining control of the majority of coordinator resources survives. Nodes failing to gain control of a majority of coordinator resources remove themselves from the cluster. The winning node can also proceed to unregister ejected nodes from shared data resources. These operations can be performed in parallel to decrease failover time. The software can continue to execute on all nodes to prevent additional problems should a node erroneously attempt to reenter the cluster.
Owner:SYMANTEC OPERATING CORP
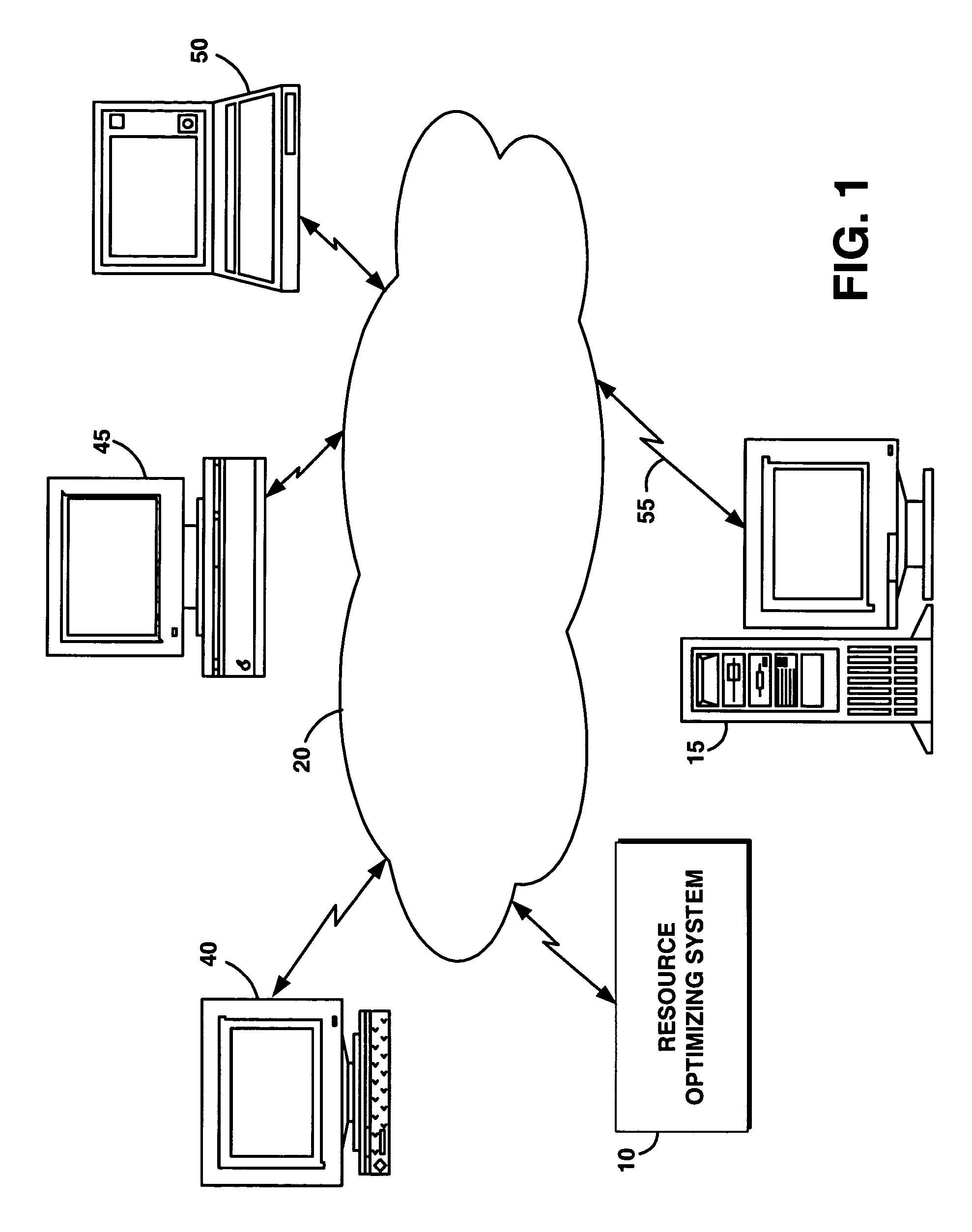
System and method for automatically and dynamically optimizing application data resources to meet business objectives
ActiveUS20050015641A1Provide flexibilityMinimize impactEmergency protective arrangements for automatic disconnectionSpecial data processing applicationsQuality of serviceData availability
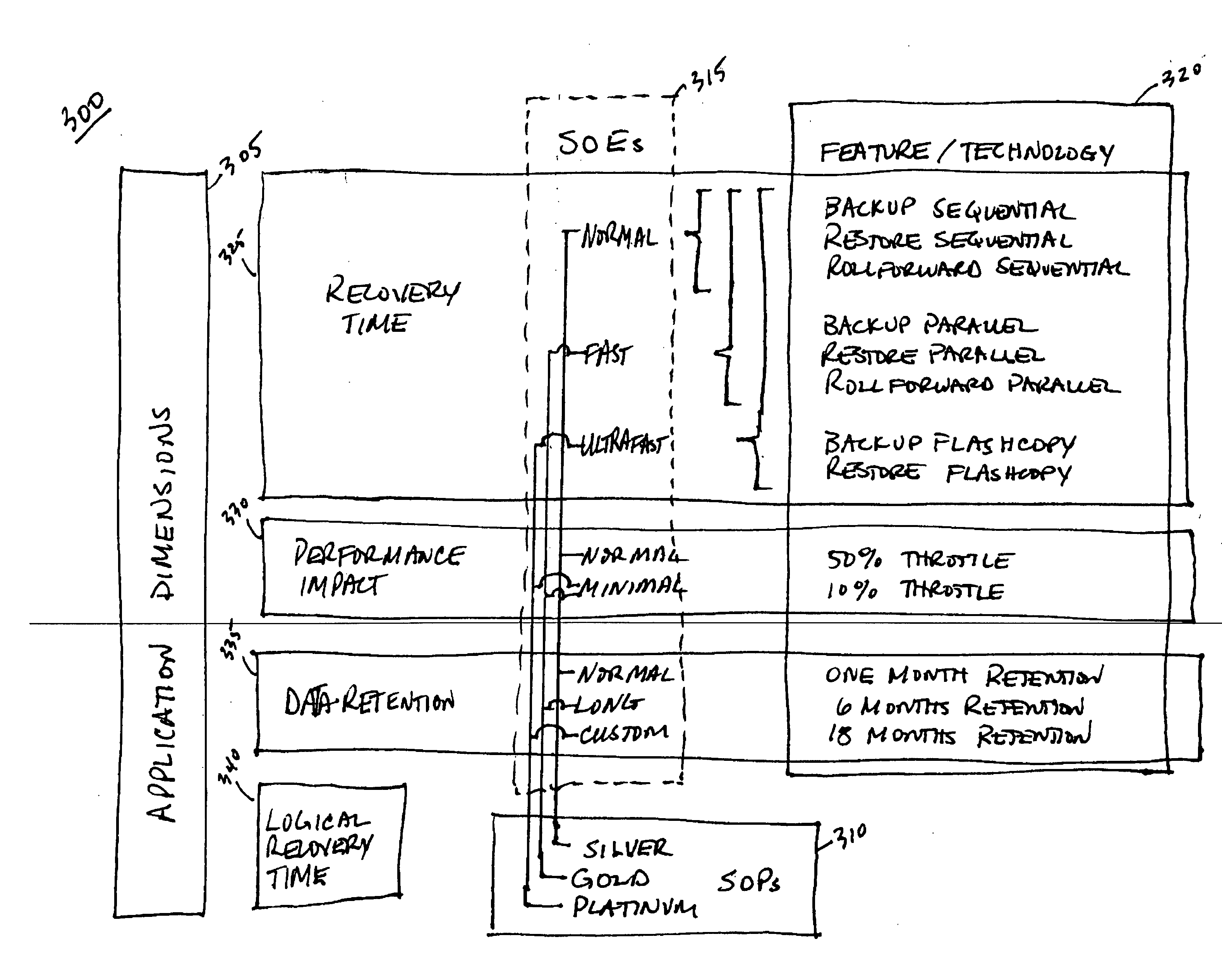
A system and method to automatically and dynamically optimize available resources to meet application data availability and business objectives. In one embodiment, a backup and data recovery system continually and dynamically adjust to the backup and recovery or restore process depending on the customer's environment, workload, and business objectives. Acceptable tolerance of downtime due to recovery and backup impacts the customer's business or system operation. From this high-level business requirement, the present system determines the backup and recovery plan details. The present system accepts application data availability policies based on business objectives, and devises, executes and refines a resource optimal backup and recovery strategy required to deliver the desired quality of service in the environments that have dynamically changing application workloads, business objectives, and hardware / software infrastructure technologies. In addition, the present system performs backups outside blocked windows to minimize the impact on the customer's system.
Owner:TREND MICRO INC
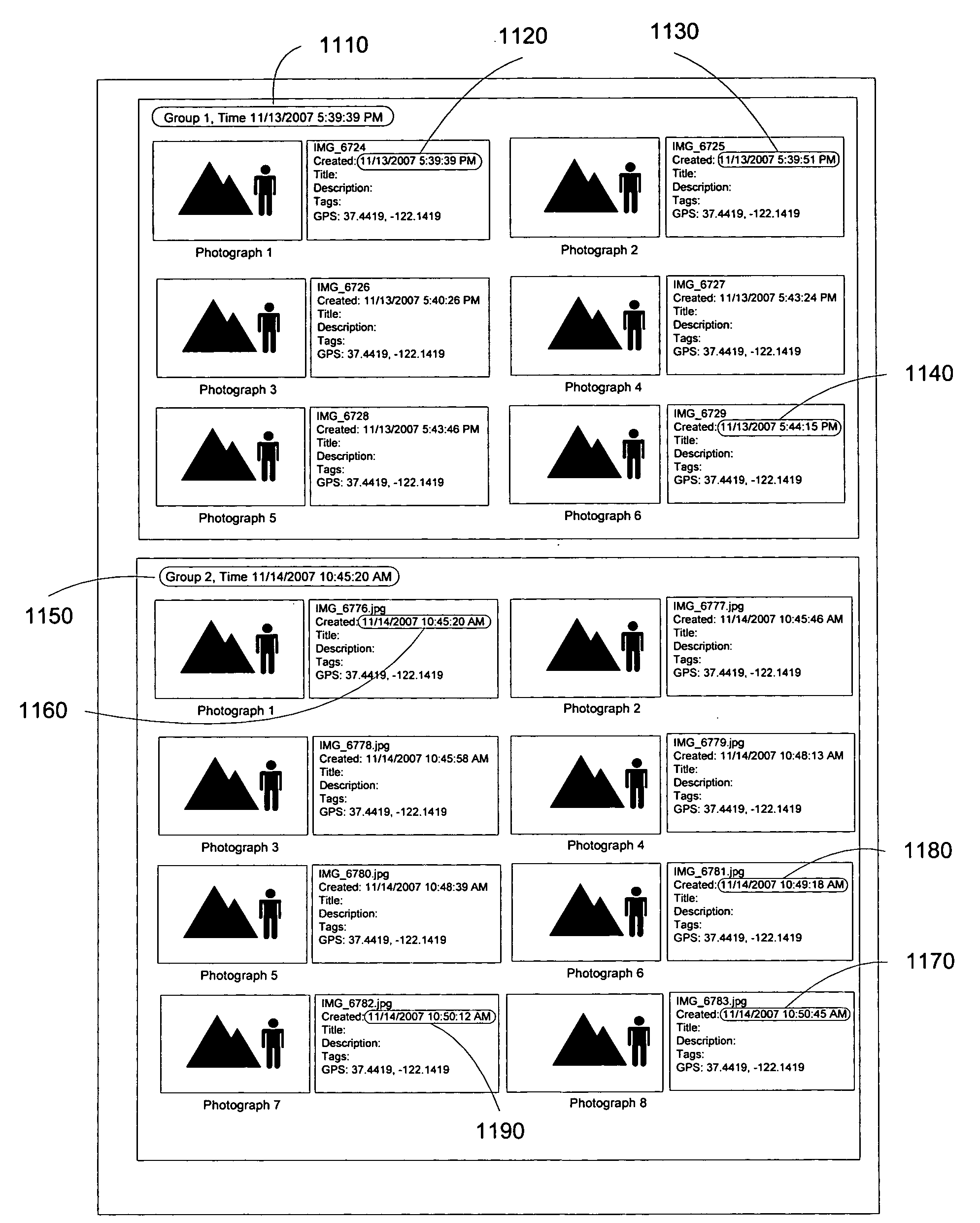
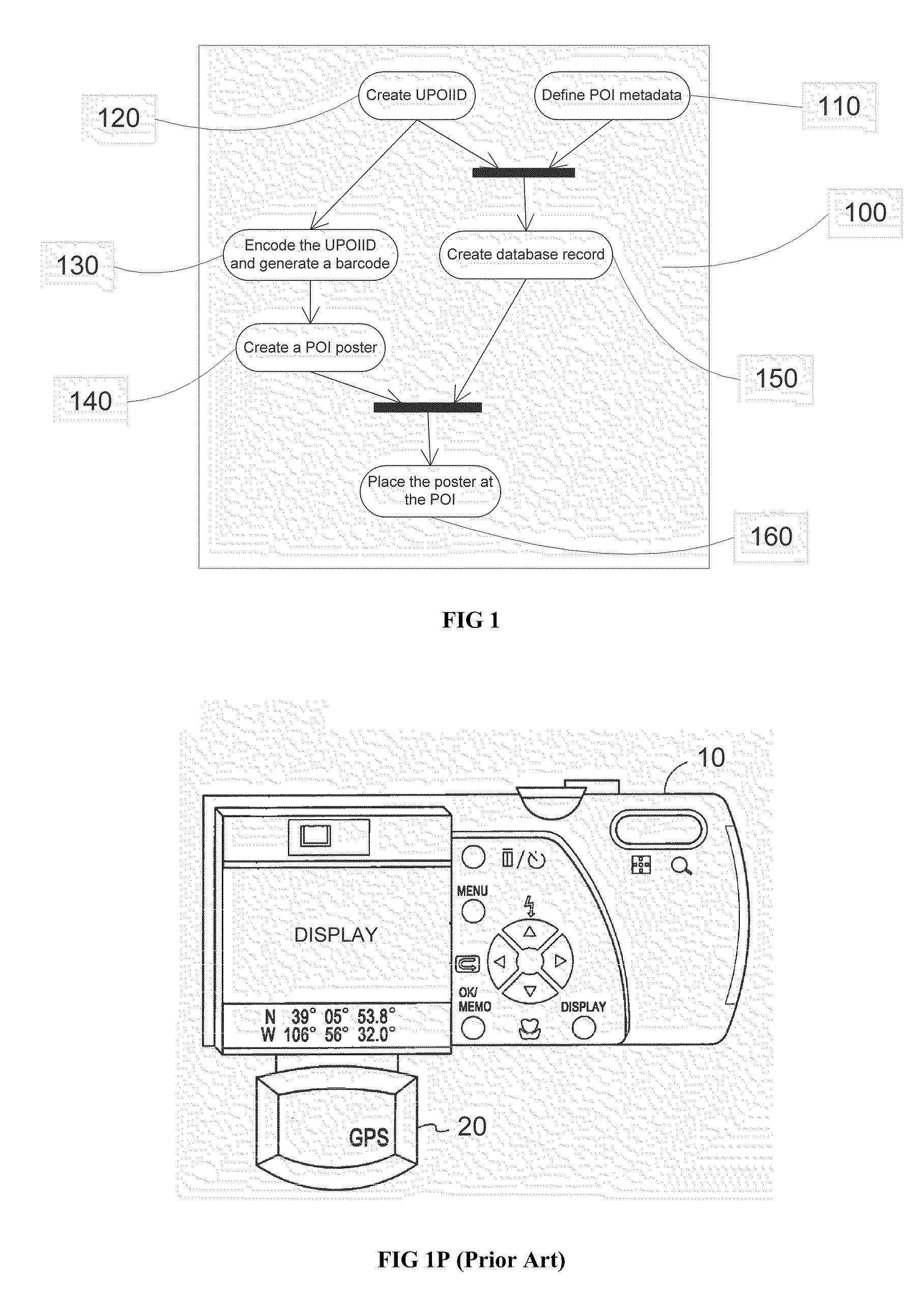
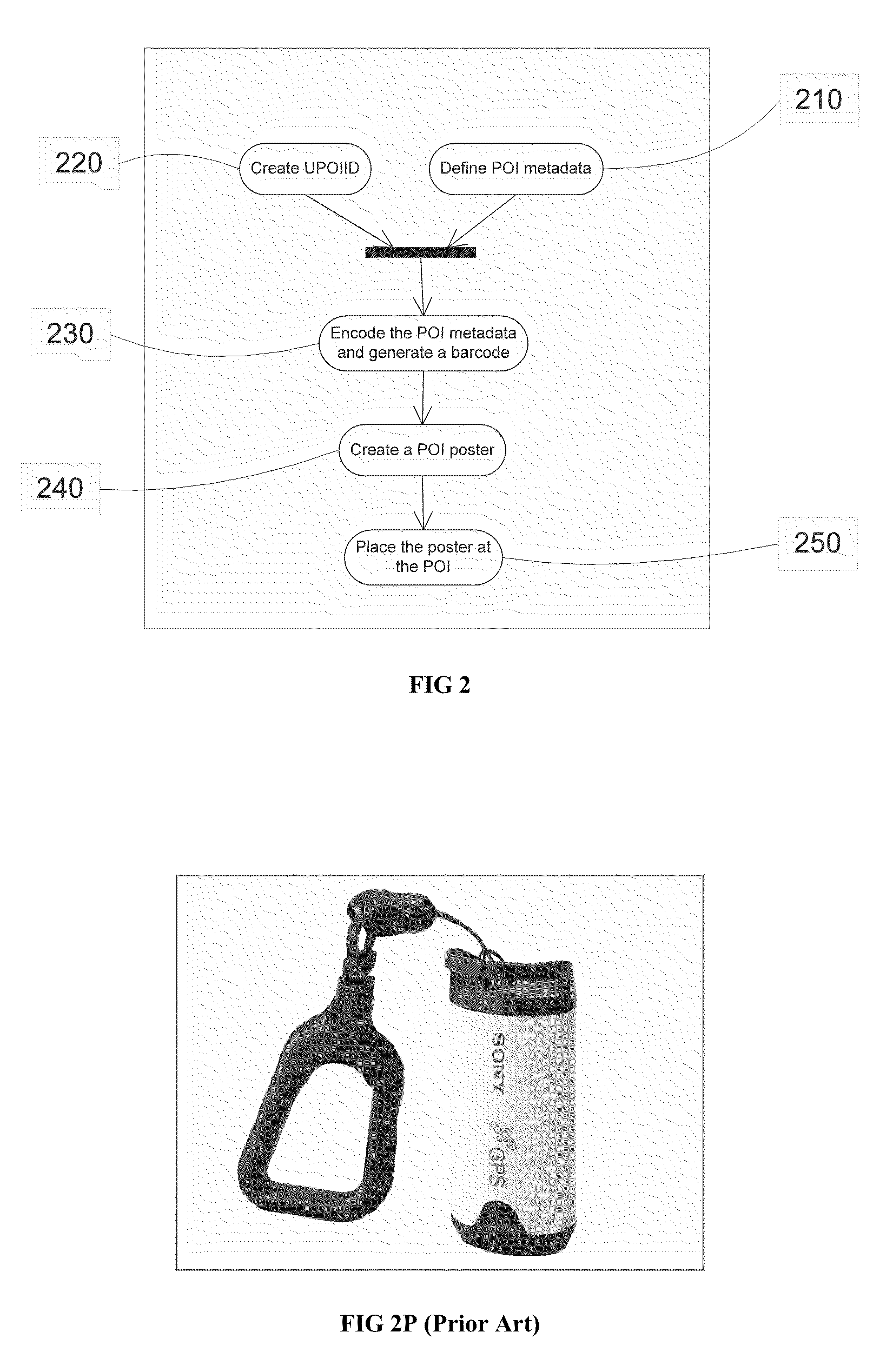
Method of Automatically Tagging Image Data
InactiveUS20100076976A1Eliminate needDigital data processing detailsGeographical information databasesLocation detectionInformation resource
The present invention provides a method of automatic tagging of image data taken at geographical locations, which represent points of interest (POI). In addition to the image data, each image file contains image metadata, which is structured information about the image data resources. The metadata of a POI includes its title, description, associated keywords, geographical identification data, etc., and it describes the POI as a resource of information. Each POI has its unique identifier that connects it to a record in a database, which contains the metadata of a plurality of POIs. The auto-tagging method, subject to the present invention, identifies the POI where image data has been taken. It then retrieves POI metadata from the database or reads it directly from an information tag placed within the POI, and assigns this metadata to all the image files containing image data taken at the POI. In particular, this invention focuses on barcode representation of the unique POI identifier (UPIID) and of its metadata (if the metadata is read directly during the image taking process). The implementation of this method does not require additional devices for location detection (such as GPS), and is applicable to all digital cameras regardless of type and complexity.
Owner:SOTIROV ZLATKO MANOLOV +1
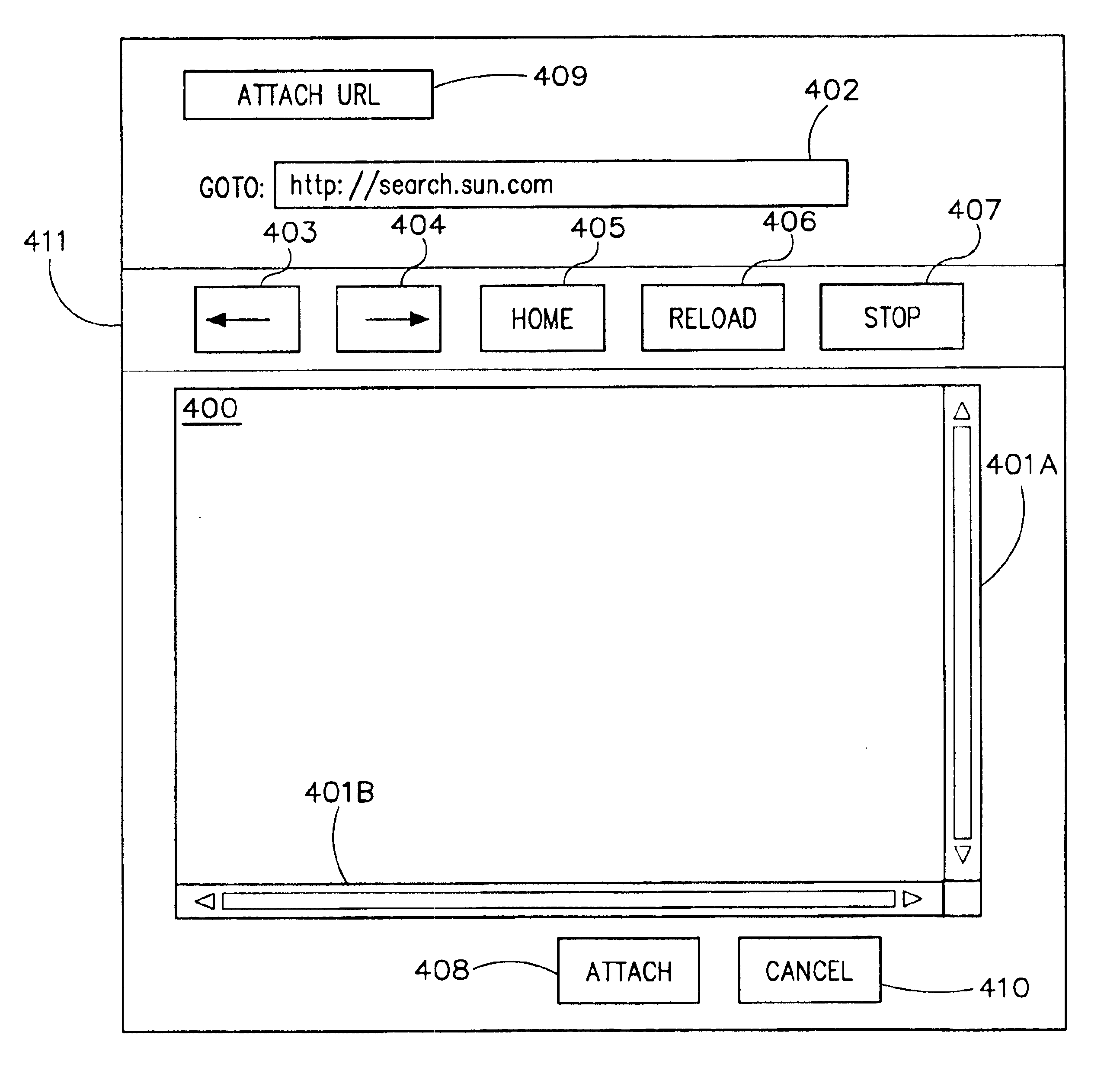
Method and apparatus for selecting attachments
InactiveUS6859213B1Cathode-ray tube indicatorsInput/output processes for data processingGraphicsDocumentation procedure
A method and apparatus for selecting attachments. When a sender indicates in an e-mail application or applet that an attachment is to be associated with an e-mail message, an attachment chooser window is presented. The attachment chooser window provides a browser-based graphical user interface (GUI) which allows a sender to browse data resources, such as HTML documents and associated links. An attachment mechanism is provided by which a sender can choose a currently displayed data resource for attachment in an e-mail message. In one embodiment, the attachment mechanism allows a user to select whether the attachment is retrieved and attached to an e-mail message as a resource locator (such as a URL) of the chosen data resource, or whether source data of the data resource is retrieved and attached to the e-mail message as one or more source files.
Owner:ORACLE INT CORP
Method and system of providing a search tool
InactiveUS20110010367A1High response rateDigital data information retrievalDigital data processing detailsData miningRapid response
A system and method of providing information to improve efficiency of human searchers obtaining information on behalf of users is described. A first responder to a request is provided with specialized tools for responding to a request. An initial evaluation of a query may be used to determine the responder and the type of tools which will be provided initially. A toolset which allows rapid responses based on data resources, common queries, and contextual information of a user, a request, partially matching queries and previous responses to previous queries is used to improve the probability that a first responder may provide a suitable response to a query.
Owner:CHACHA SEARCH
Distributed data storage system and method
InactiveUS20030187853A1Maximum system efficiencyImprove efficiencyOffice automationSpecial data processing applicationsMass storageSoftware distribution
A distributed data storage system and method comprising a highly integrated mass storage controller system permitting distributed management and control of data storage is disclosed. The present invention in some preferred embodiments permits mass storage media to be made available on a network in a fashion to permit global access, while automatically handling many high-level file access and data integrity / security / control functions normally associated with a host operating system. This integration and redistribution of functionality permits spatial diversification of data resources, automatic mirroring of data, fault isolation, data security, and a plethora of other control functions to be integrated into the mass storage device. This integration permits peer-to-peer communication between mass storage devices to both unburden the host data consumers but also isolate the data management functions from the data presentation functions normally associated with host systems. Exemplary embodiments of the present invention as applied to specific preferred system contexts include but are not limited to distributed data storage in a networked environment, brokered data access metering, database access / control, data backup, journaling, checkpointing, and automated software distribution.
Owner:HENSLEY ROY AUSTIN +1
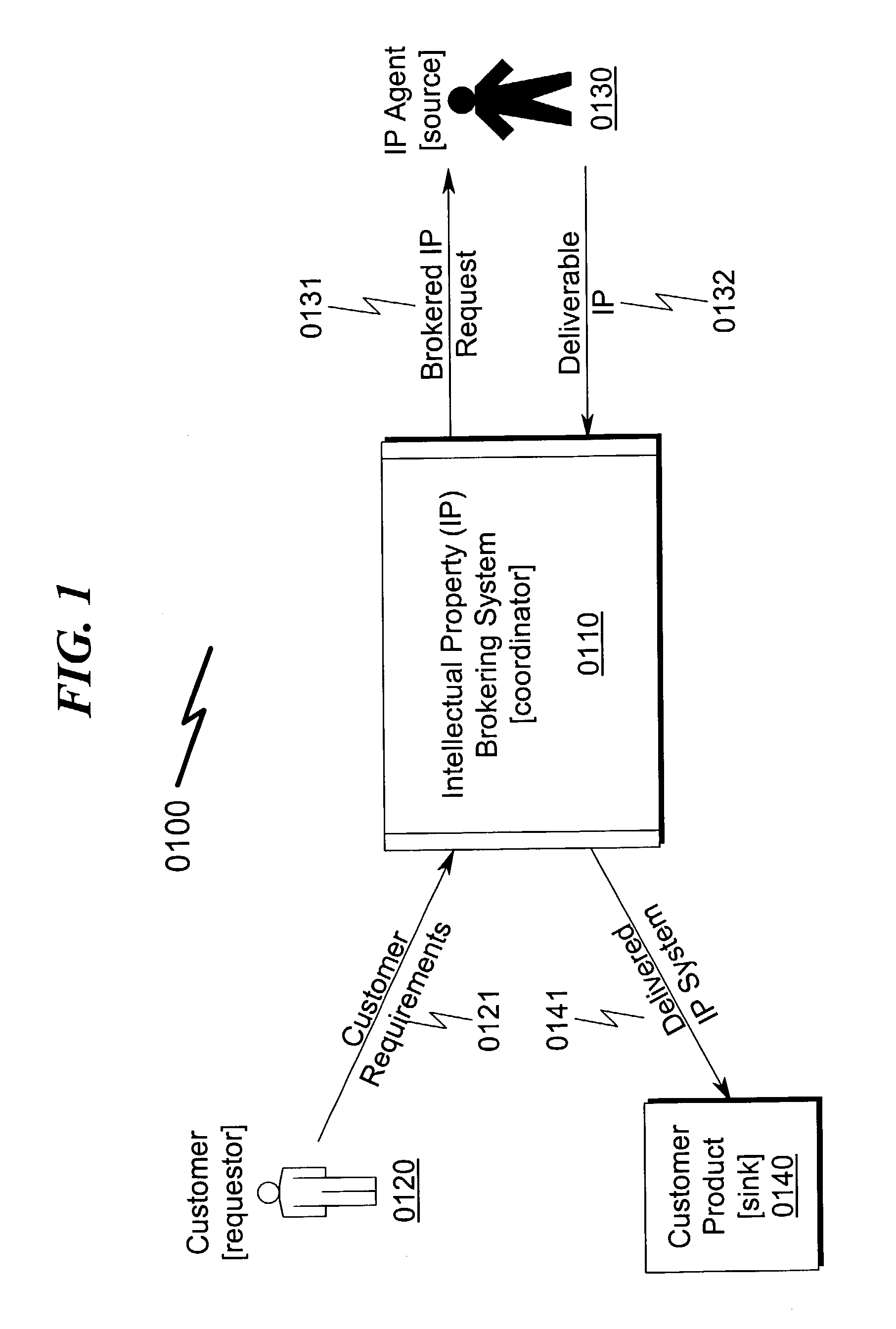
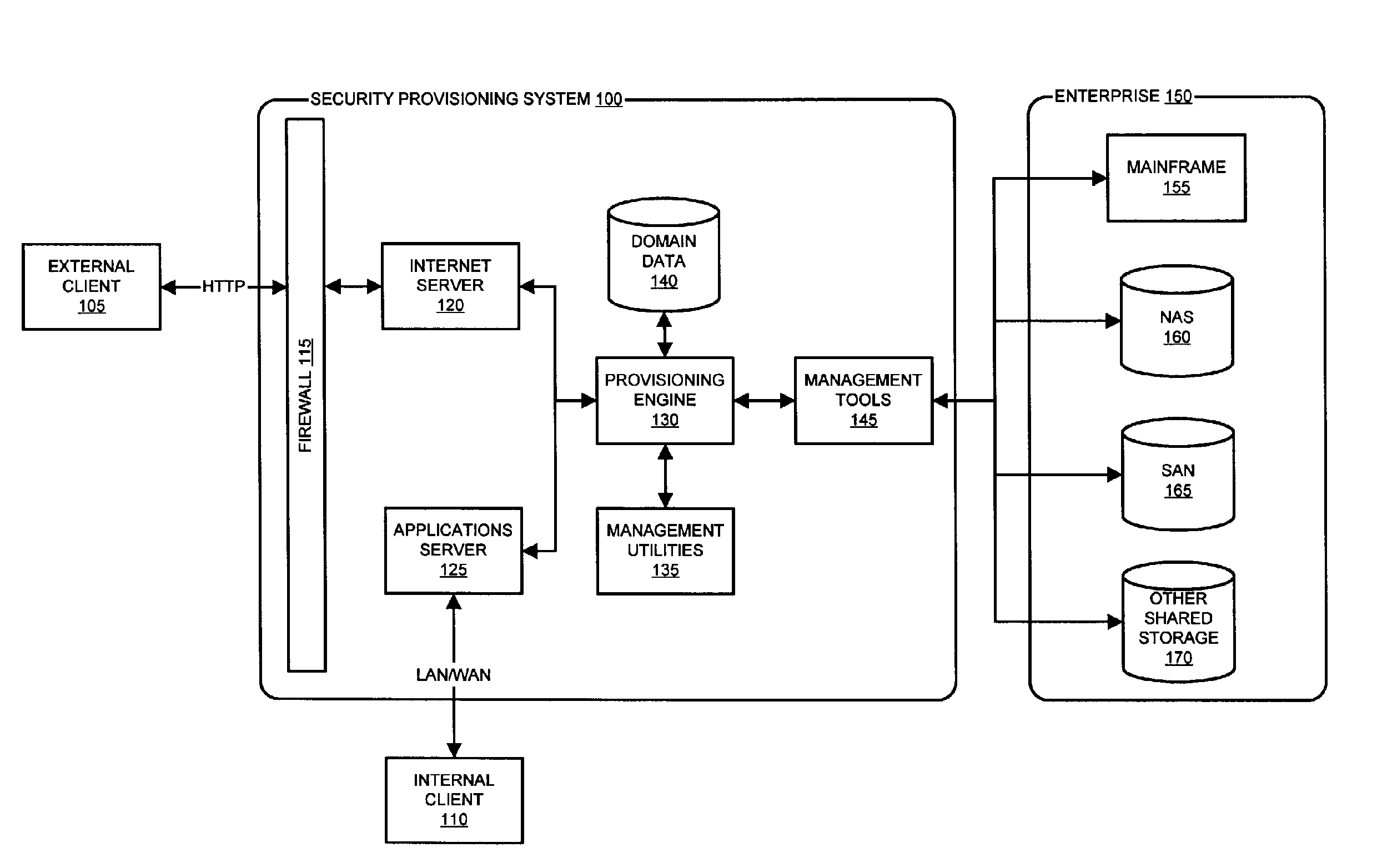
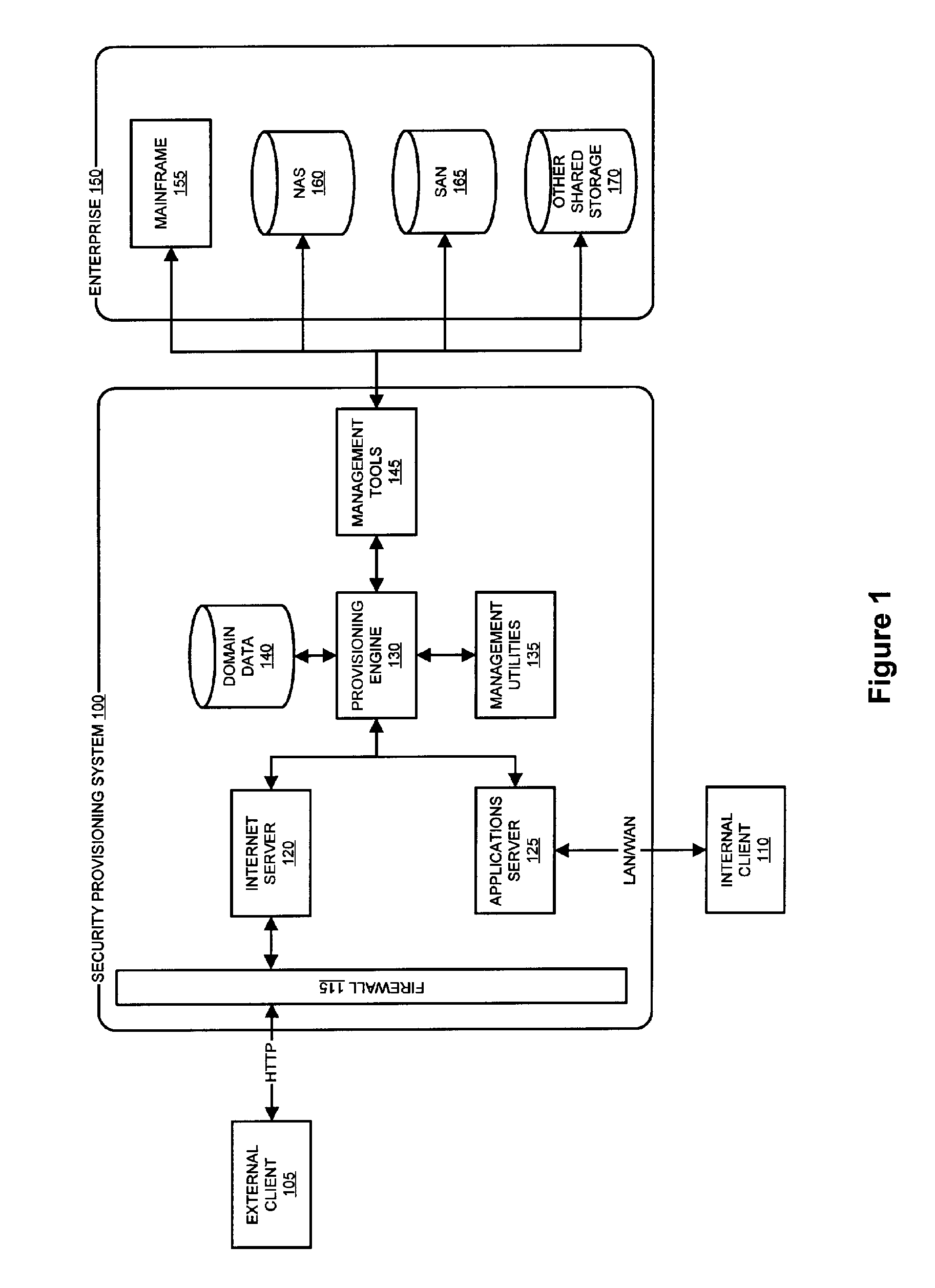
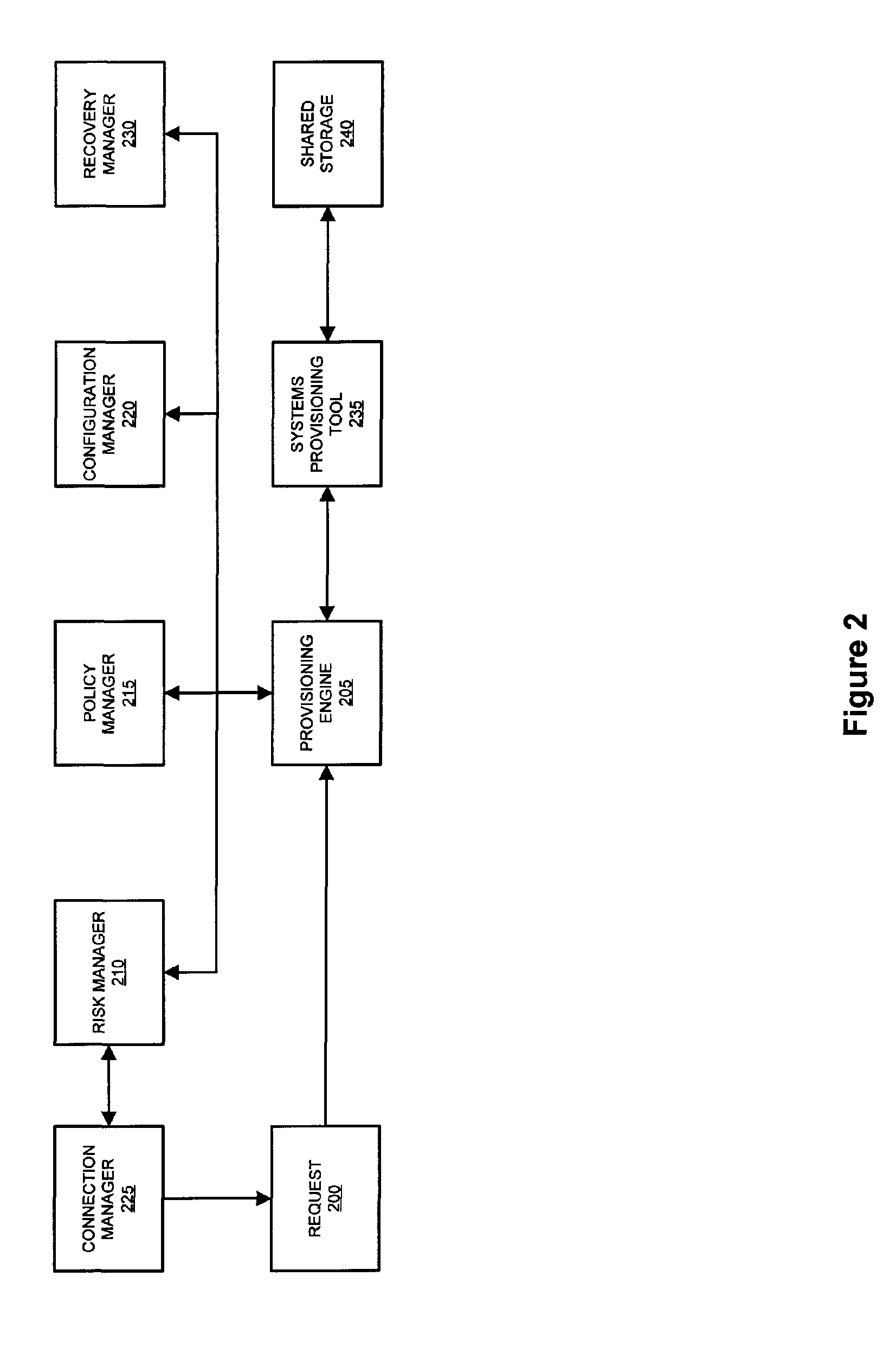
System and method for dynamic security provisioning of data resources
InactiveUS8266670B1Memory loss protectionUnauthorized memory use protectionComputer hardwareSecurity domain
The present invention facilitates the dynamic provisioning of data assets in a shared storage environment. The invention provides a system and method for dynamically provisioning and de-provisioning shared storage resources based on multi-dimensional decision criteria. By employing specialized computing components configured to assess a data asset and requestor of a data asset, a provisioning engine is able to transform the input from the computing components into a specific configuration of shared storage resource provisioning and security controls. According to the rules and policies applying to a security domain, the provisioning engine may dynamically allocate shared storage resources in a manner that is both safe and efficient for the data asset.
Owner:LIBERTY PEAK VENTURES LLC
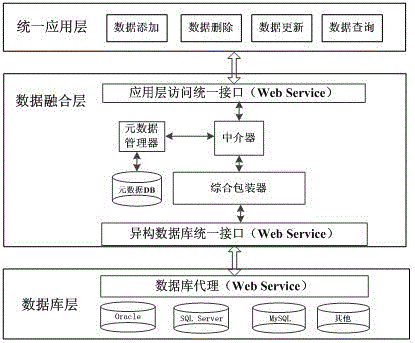
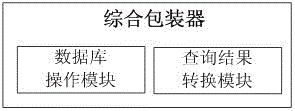
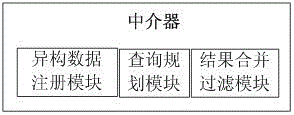
Multi-source heterogeneous database fusion system and data query method thereof
InactiveCN104008135AAchieve integrationEfficient integrationSpecial data processing applicationsMetadata managementSystem maintenance
The invention provides a multi-source heterogeneous database fusion system and a data query method thereof. The system comprises a database layer, a data fusion layer and a uniform application layer. The database layer is composed of heterogeneous databases and agencies of the heterogeneous databases. The data fusion layer is used for fusing information of all heterogeneous data sources, and is responsible for data access of the heterogeneous data sources and coordinating the information of all the data sources, and specifically comprises a metadata data base (DB), a metadata manager, a comprehensive wrapper, a mediator, an application layer access uniform interface and a heterogeneous database uniform interface. The uniform application layer is the user of the heterogeneous database fusion system and can have access to shared data resources of the heterogeneous databases by fusing middle layers. The multi-source heterogeneous database fusion system and the data query method of the multi-source heterogeneous database fusion system solve the problems in heterogeneous database fusion and overcome the defects of an existing database fusion technology. The system can conduct transparent query on all the heterogeneous databases on the condition that local databases are not affected, and the maintenance cost of the system is reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
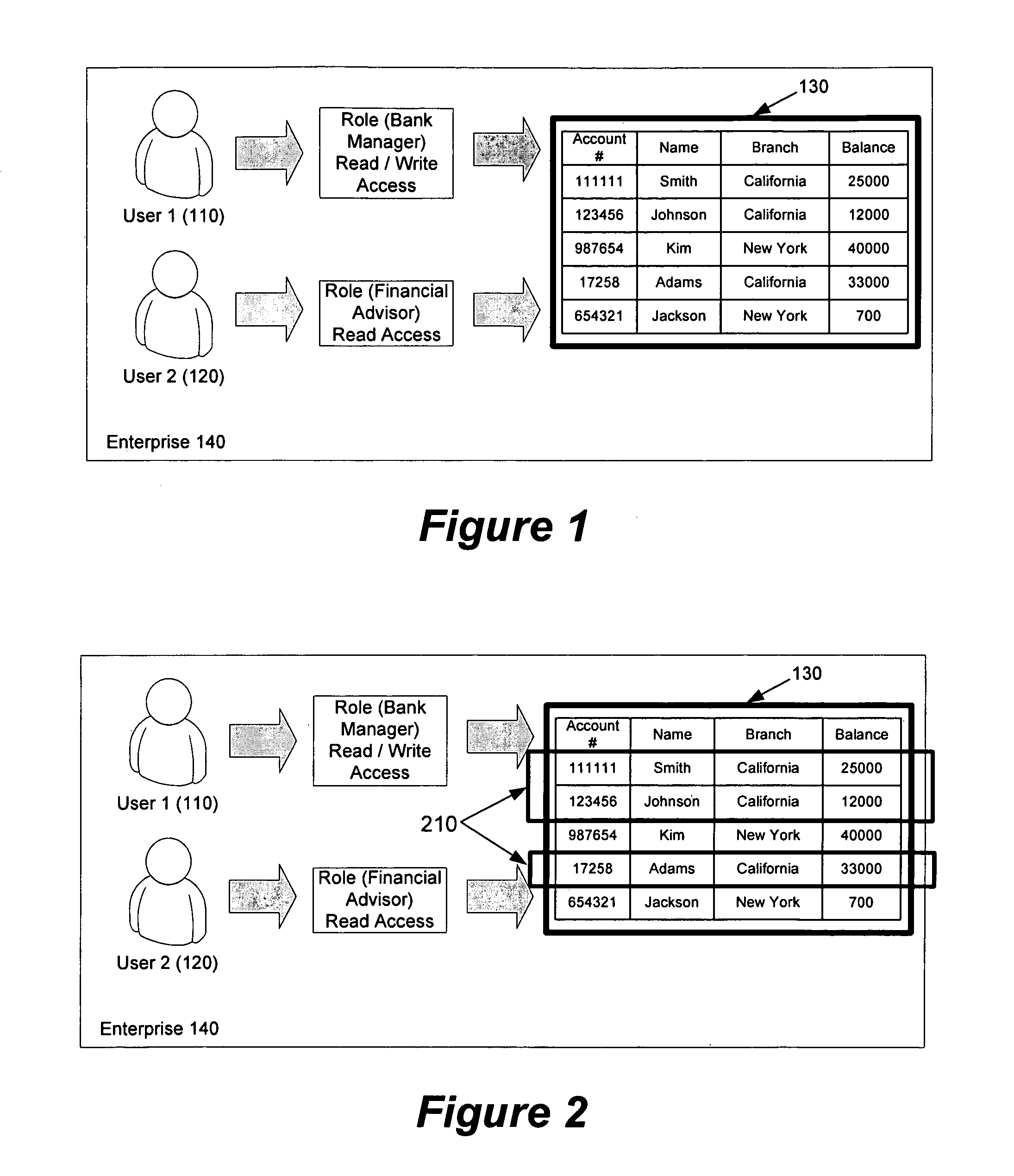
Collecting, sharing, comparing, and displaying resource usage data
ActiveUS8176095B2Save resourcesConservation usageDigital data processing detailsOffice automationGraphicsInteractive displays
Resource usage data is automatically collected for an individual, household, family, organization, or other entity. The collected data is transmitted to a central repository, where it is stored and compared with real-time and / or historical usage data by that same entity and / or with data from other sources. Graphical, interactive displays and reports of resource usage data are then made available. These displays can include comparisons with data representing any or all of community averages, specific entities, historical use, representative similarly-situated entities, and the like. Resource usage data can be made available within a social networking context, published, and / or selectively shared with other entities.
Owner:ABL IP HLDG
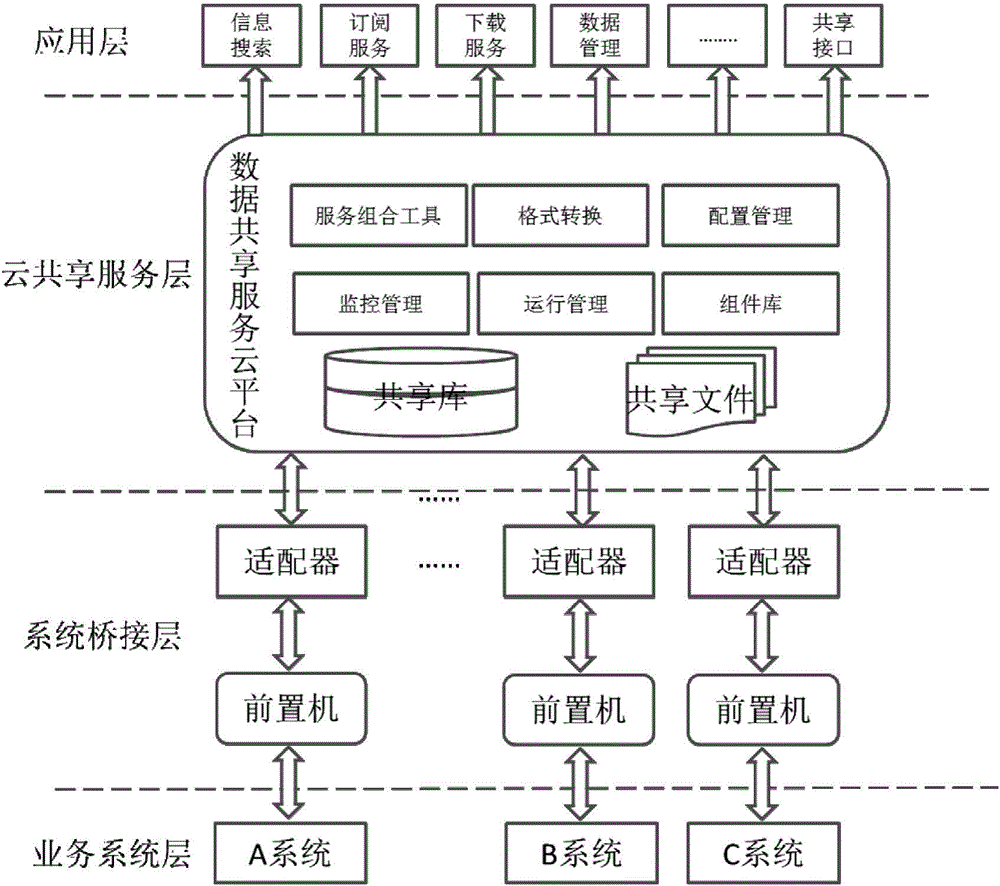
Data sharing exchange model and method based on cloud computation
The invention discloses a data sharing exchange model and a method based on cloud computation. The model comprises a data sharing service module, a data exchange service module, a management service module, an enterprise service bus, a front-end exchange database and a front-end interchanger, wherein the data sharing service module is used for realizing distributed heterogeneous data resource sharing; the data exchange service module is used for realizing a heterogeneous data exchange function; the management service module is used for realizing sharing exchange and system management; the enterprise service bus is used for realizing service registration and management; the front-end exchange database is used for realizing an intermediate storage logic information database which is established for information exchange; and the front-end interchanger is used for realizing the function of unified exchange output and input ports of exchange nodes. The method comprises the steps of constructing a data sharing exchange service system based on SaaS (Software as a Service) to share data which is stored in a business database in a distributed way and providing exchange request submission and approval service; using the enterprise service bus to conduct unified management on service and establishing a model of an exchange service business process by virtue of management service to realize dynamic combination of inter-business service; and using the front-end exchange database to conduct exchange, storage and forwarding, and pushing the data to target nodes through the front-end interchanger.
Owner:HOHAI UNIV
Methods, Systems, Apparatus, Products, Articles and Data Structures for Cross-Platform Digital Content
InactiveUS20160048606A1Effective machine readabilityNatural language data processingWebsite content managementDigital contentData resources
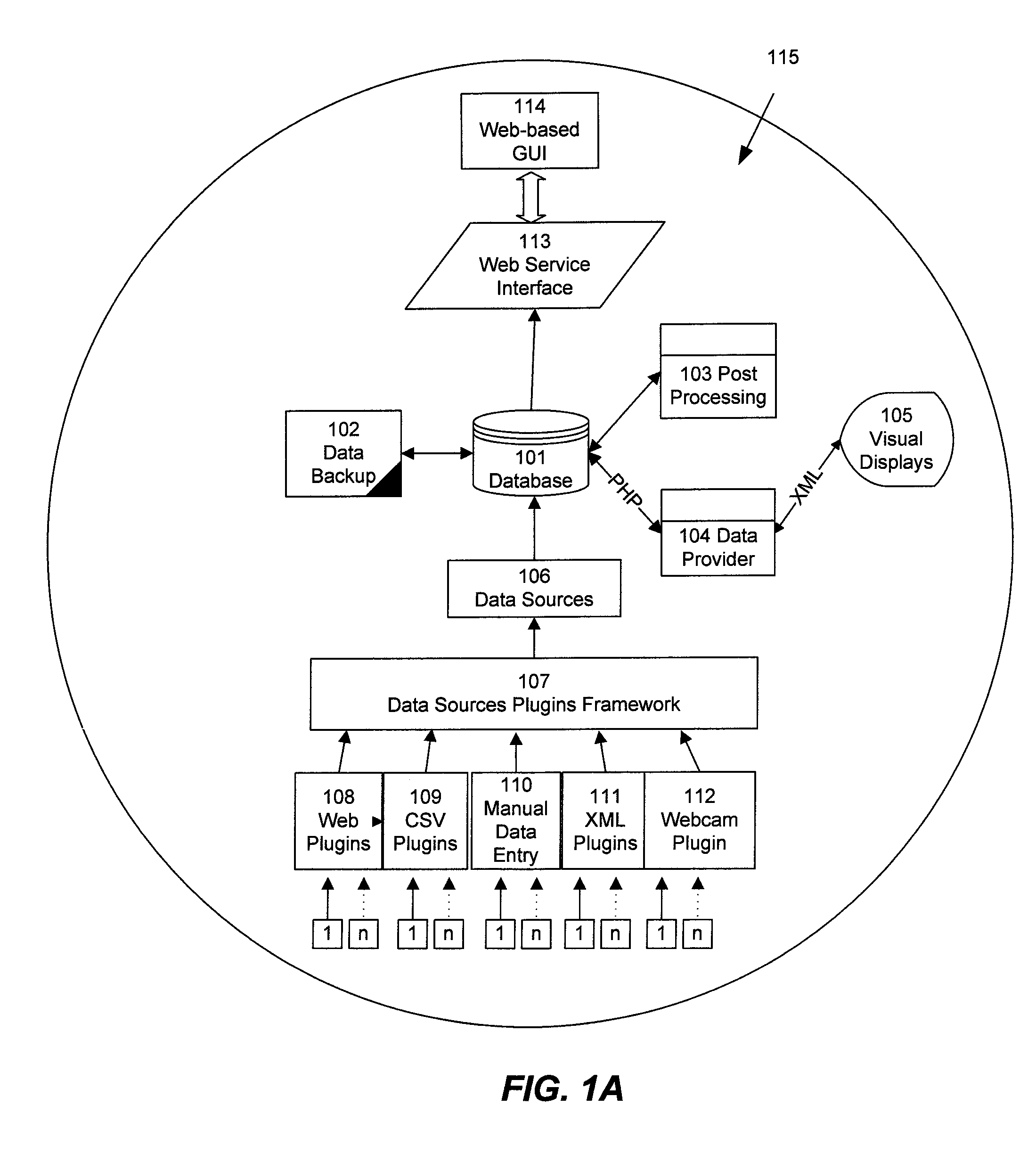
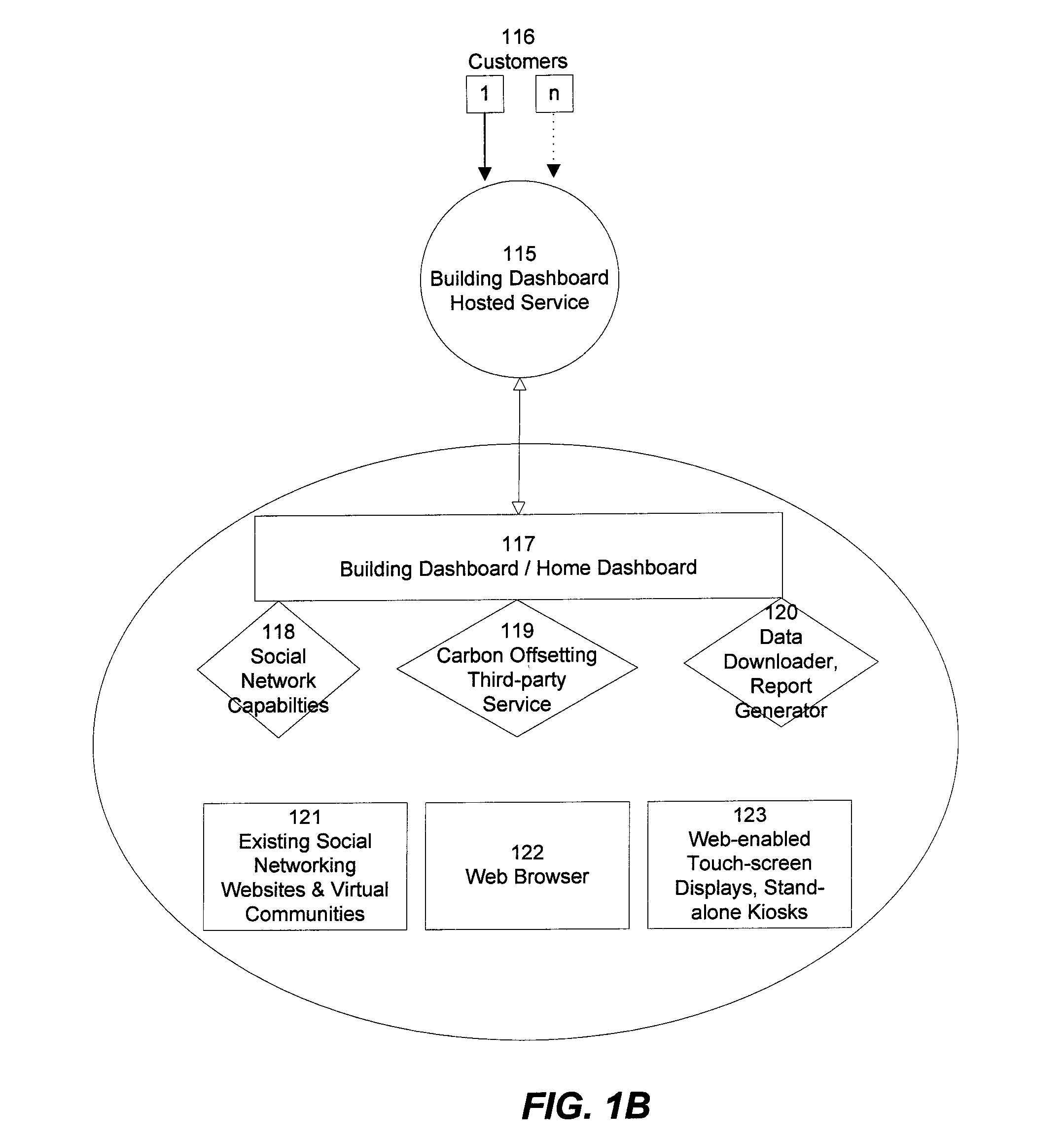
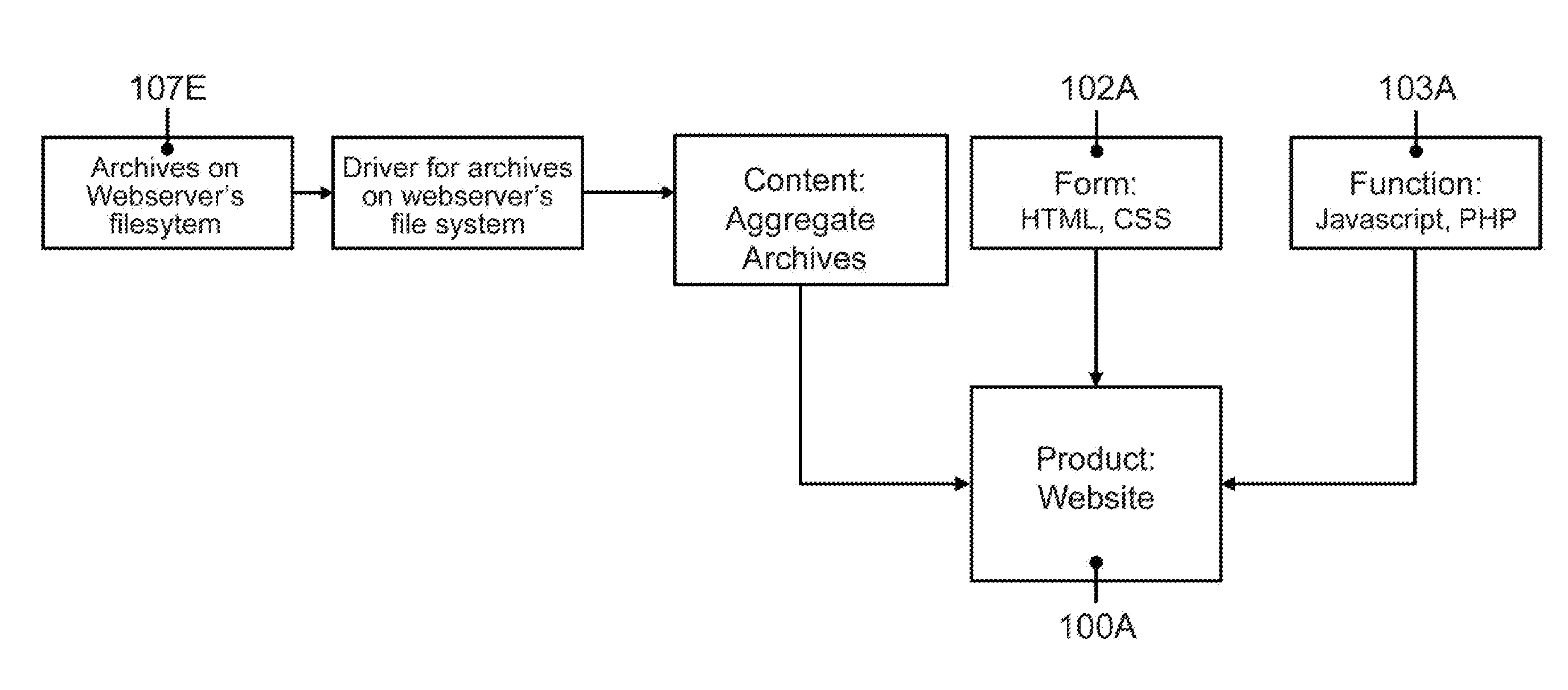
The present invention relates to handling of digital content in cross-platform environments and provides methods, systems, computer readable storage with instructions, and / or products for providing digital content, including the possibility of portions of the content being accessible over a communication network. In one form, the invention provides a functional software product compliant with a predetermined computing platform adapted for cross-platform use that may include: a predetermined form means for presenting content to a user of the product, a predetermined function means for enabling the user of the product to navigate content, and at least one driver means operatively associated with the functional software product for enabling access to content by the predetermined form and function means wherein the driver means is adapted for accessing at least one originating content data resource having a format non-specific to the predetermined computing platform.
Owner:KISS DIGITAL MEDIA
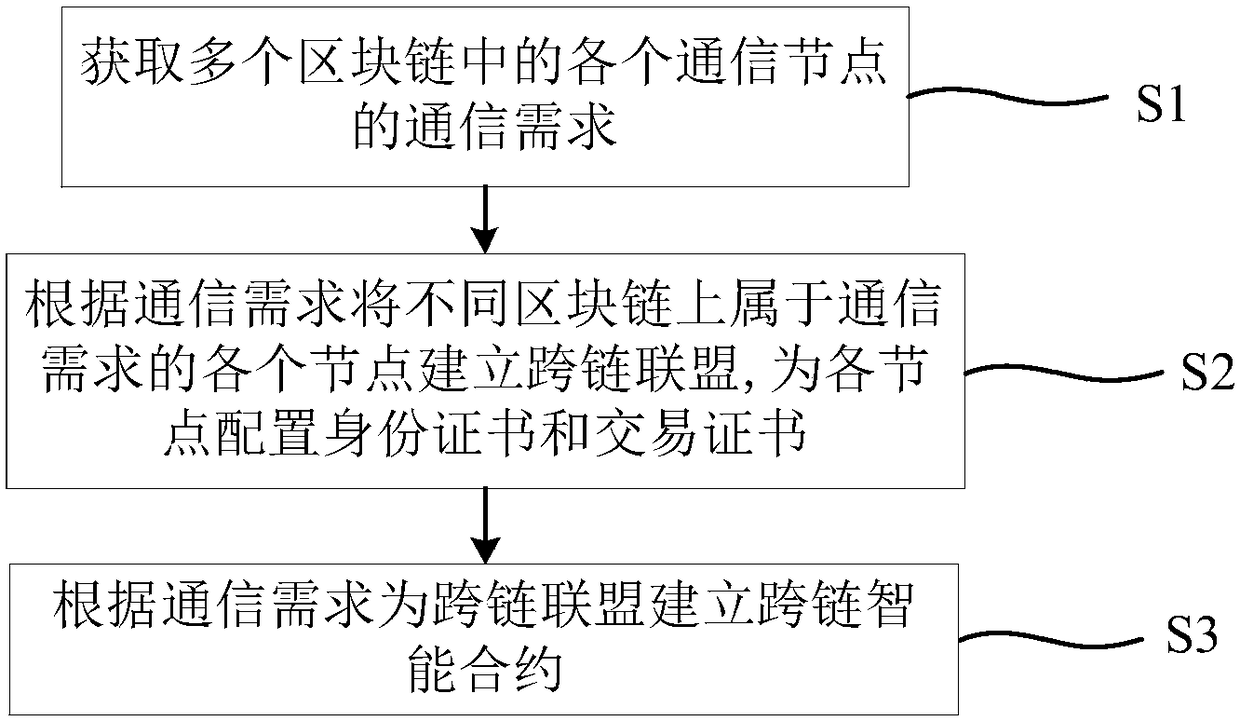
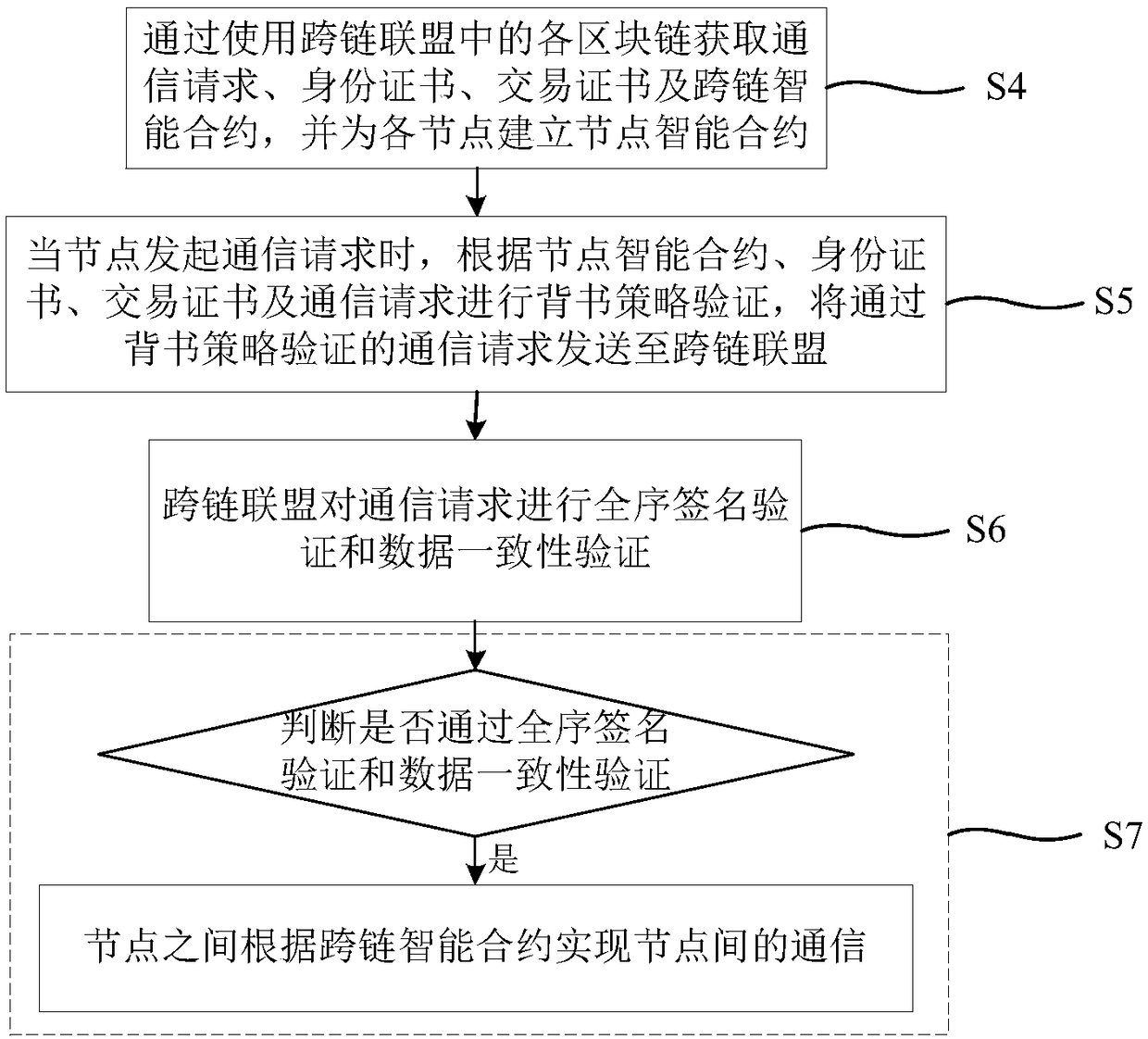
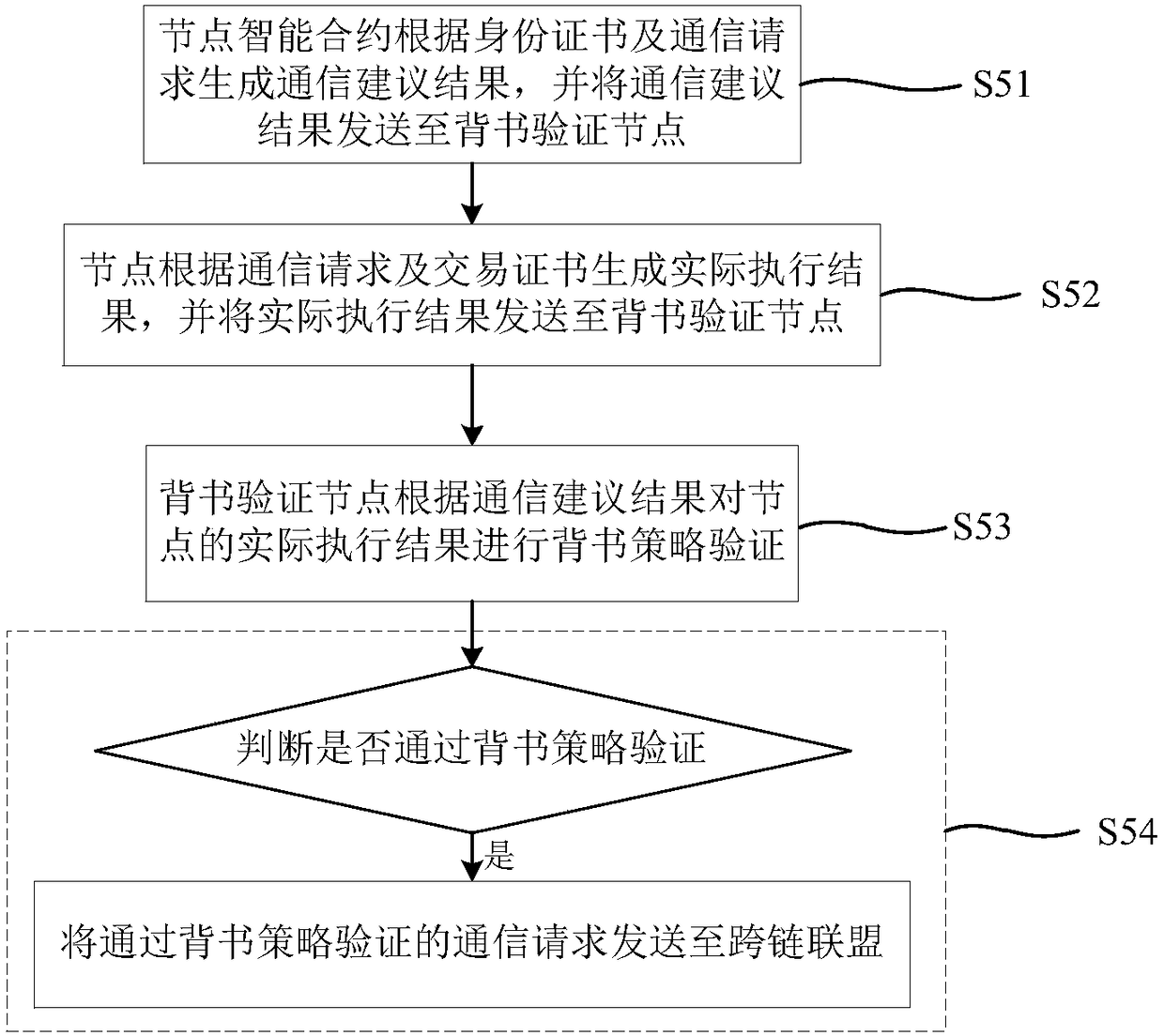
Method for building cross-chain alliance among block chains and block chain cross-chain communication method and system
ActiveCN108256864ARealize the establishmentAchieve sharingTransmissionProtocol authorisationResource utilizationSmart contract
The invention provides a method for building a cross-chain alliance among block chains and a block chain cross-chain communication method and system. The method for building the cross-chain alliance includes: acquiring the communication requirements of various communication nodes in multiple block chains; using the nodes which belong to the communication requirements to build the cross-chain alliance, and configuring identity certificate and transaction certificate; building a cross-chain smart contract. The block chain cross-chain communication method includes: using the various block chainsin the cross-chain alliance to acquire a communication request, and building a node smart contract for each node; if the communication request is initiated, performing endorsement strategy verification on the communication request, performing total order signature verification and data consistency verification, and using the cross-chain smart contract to achieve node communication when the communication request passes the verification. By using the method to build the cross-chain alliance, cross-chain communication among different block chains is achieved, data resources on different block chains can be shared, and resource utilization efficiency is increased.
Owner:无锡三聚阳光知识产权服务有限公司
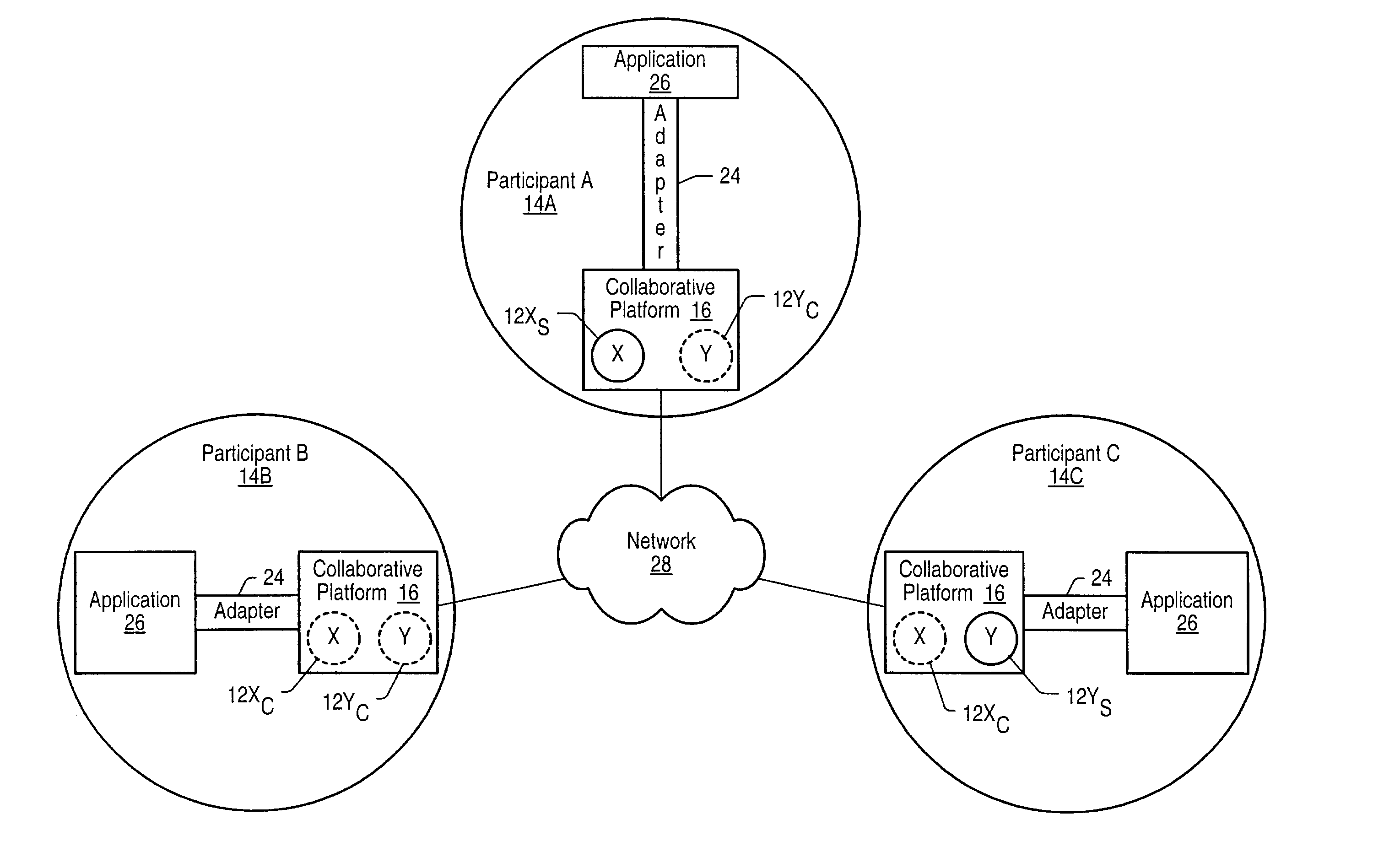
System and method for collaborative data resource representation
InactiveUS20030014513A1Multiple digital computer combinationsDistributed object oriented systemsClient dataClient-side
In a collaborative environment a collaborative platform for each participant may include a collaborative data resource representation for each collaborative data resource used in that collaborative environment. For each collaborative data resource, one of the participants' collaborative platform may be the host or server for that collaborative data resource. The collaborative data resource representation managed by the host collaborative platform is referred to as the server data representation. Every other participants' collaborative platform may manage a client data representation of that collaborative data resource. When an application makes a change to a collaborative data resource, the change is made for the server data representation and then the collaborative platform managing the server data representation sends state information to each client data representation of that collaborative data resource to reflect the change made to the server data representation.
Owner:ADVANCED REALITY
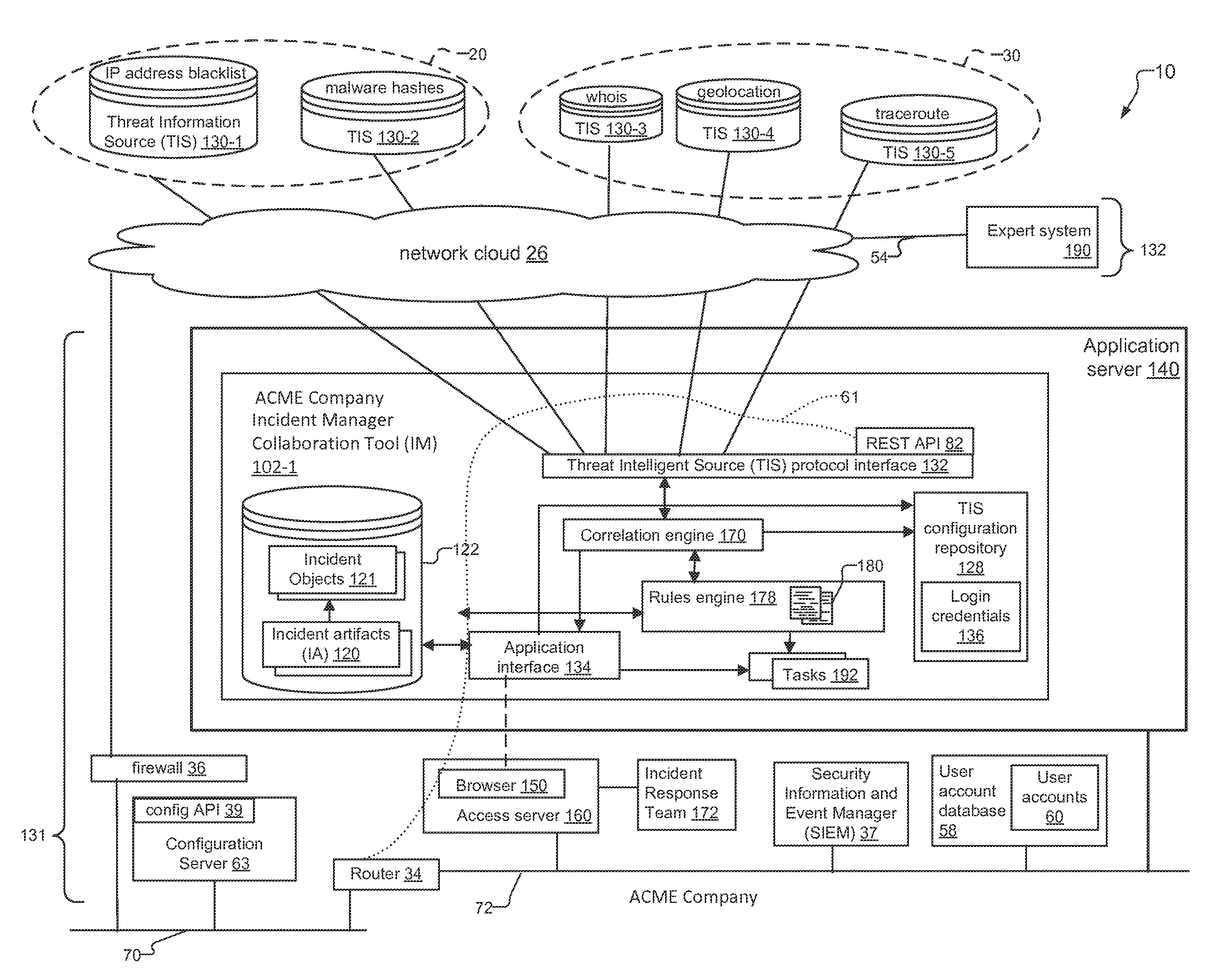
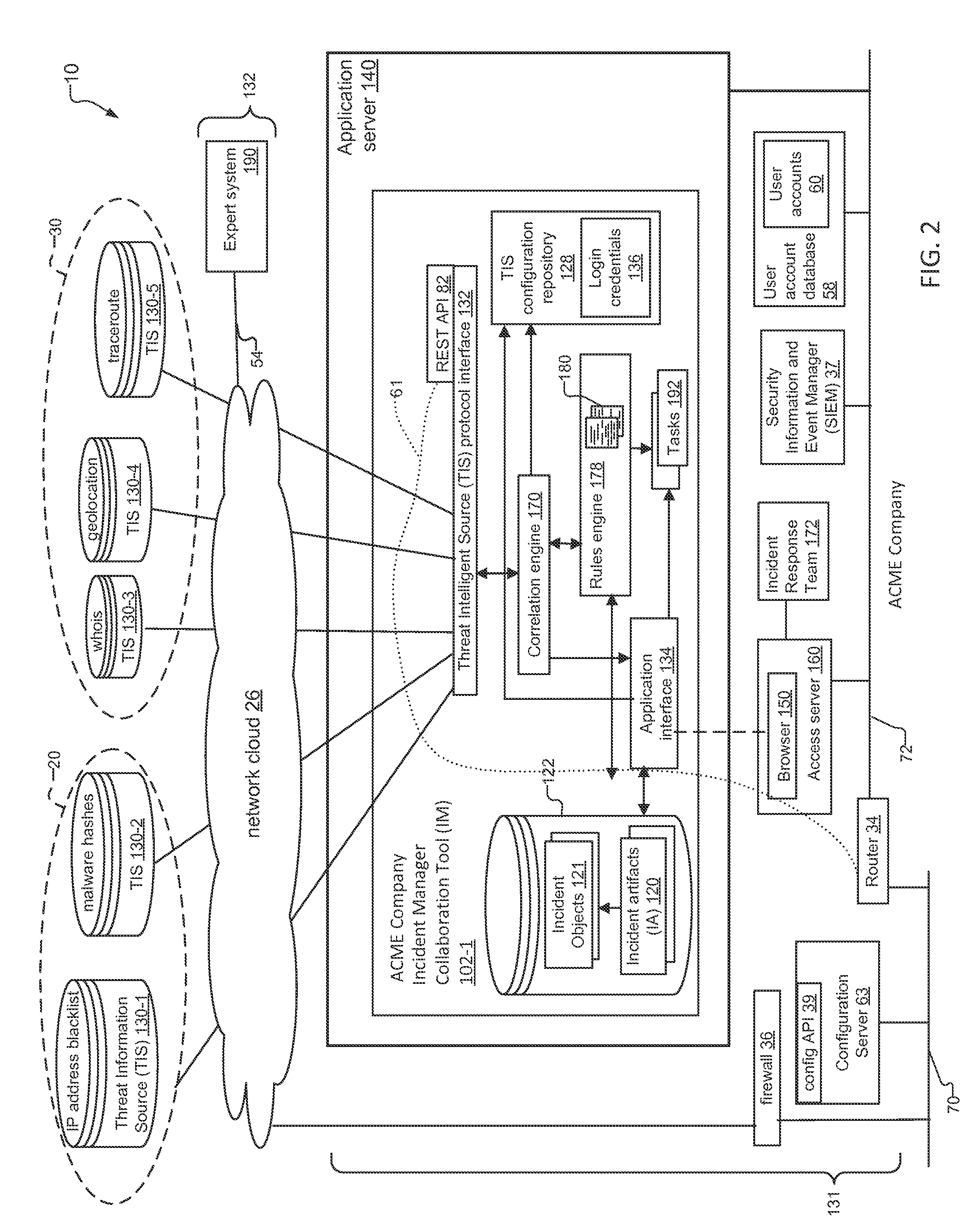
System for Tracking Data Security Threats and Method for Same
ActiveUS20160072836A1Information obtainedMemory loss protectionError detection/correctionIp addressInternet privacy
An incident response system and method for tracking data security incidents in enterprise networks is disclosed. An Incident Manager application (IM) stores incident objects and incident artifacts (IAs) created in response to the incidents, where the incident objects include the information for the incident and the IAs are associated with data resources (e.g. IP addresses and malware hashes) identified within the incident objects. In response to creation of the IAs, the IM issues queries against one or more external threat intelligence sources (TISs) to obtain information associated with the IAs and augments the IAs with the obtained information. In examples, the IM can identify known threats by comparing the contents of IAs against TIS(s) of known threats, and can identify potential trends by correlating the created incident objects and augmented IAs for an incident with incident objects and IAs stored for other incidents.
Owner:GREEN MARKET SQUARE LTD
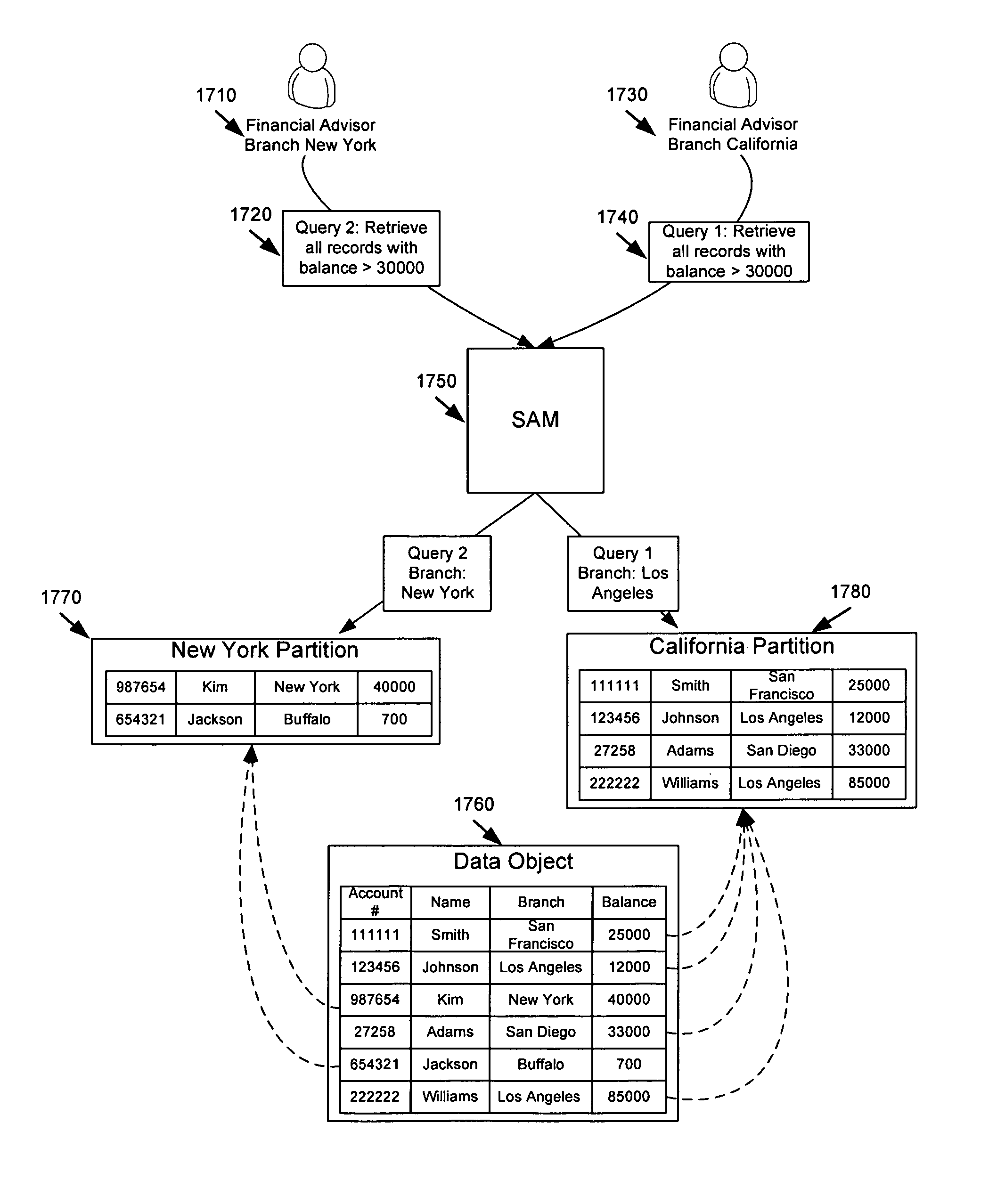
Query server system security and privacy access profiles
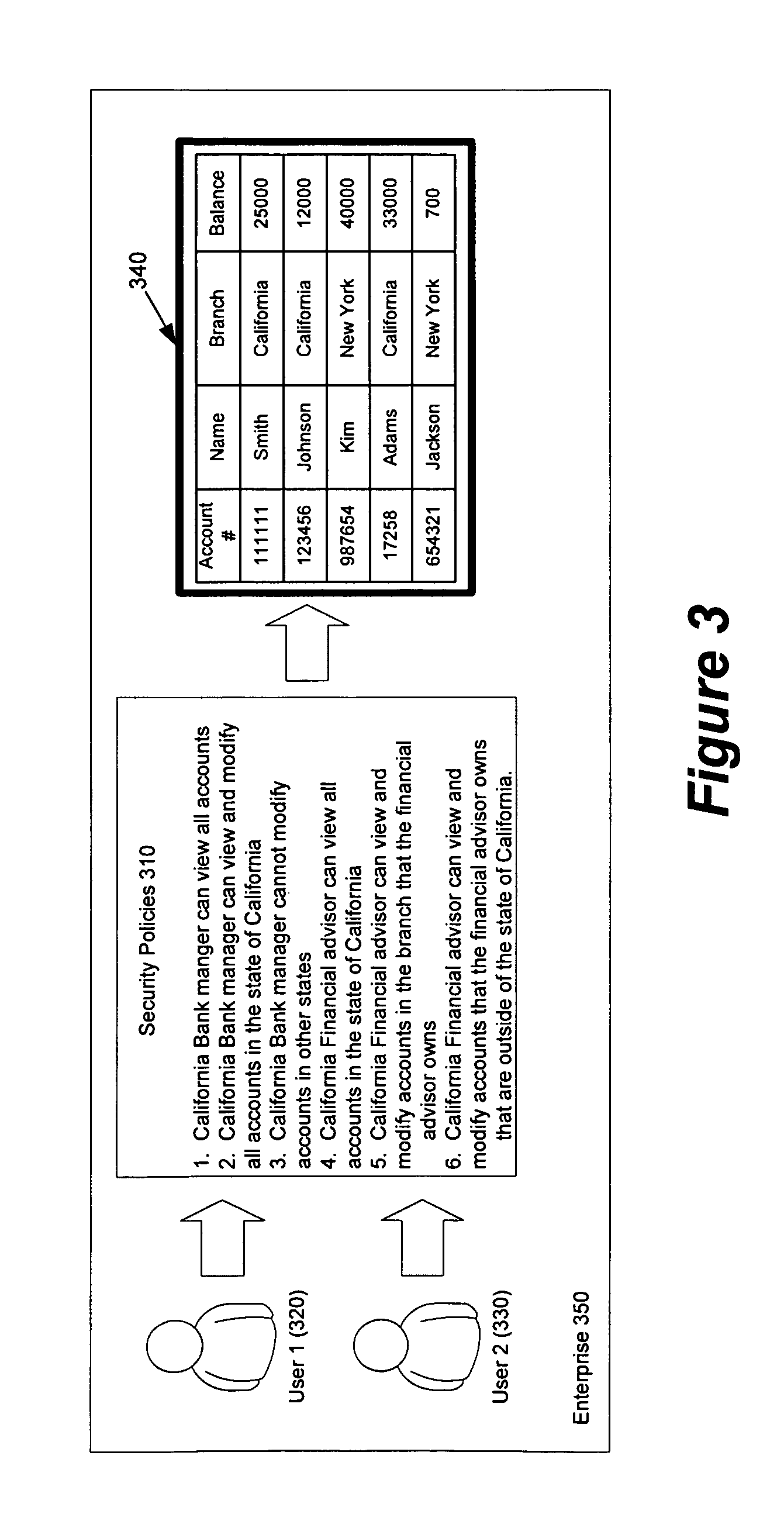
A method of controlling graduated access to data resources within an organization may be performed by assigning security access privileges to organizational roles. When a query is received, the organizational role is associated with the query source. The security access privileges are used to determine the available query data results for the organizational role. Results are provided to the query source based on the security access privileges.
Owner:WHAMTECH
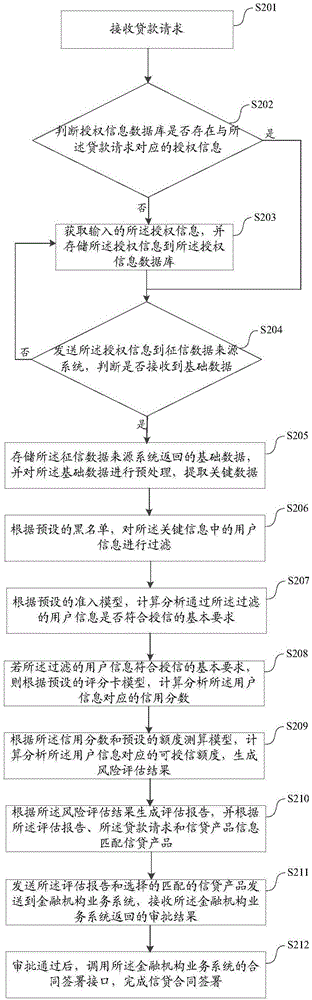
Method and system for internet credit
InactiveCN106780012AQuick buildImprove timelinessFinanceBuying/selling/leasing transactionsManufacturing intelligenceThe Internet
The invention discloses a method and a system for internet credit. The method comprises the following steps of receiving a loan request; obtaining corresponding authorizing information; according to the authorizing information, collecting and storing basic data returned from a credit investigation data resource system, pre-processing the basic data, and extracting key data; calculating and analyzing the key data, and generating risk evaluation results; according to the risk evaluation results, generating an evaluation report, and matching with a credit product. The method has the advantage that according to the pre-stored matched credit product information sent by business systems of multiple financing institutions such as banks, the evaluation report and the user loan request, a suitable credit product is intelligently matched from the integrated multiple credit products and is recommended to the user, so that the problem of single credit product is solved, the intelligent matching of the credit products on Internet on line is realized, the loan requirement of the user is well met, and the user experience is improved.
Owner:深圳微众信用科技股份有限公司
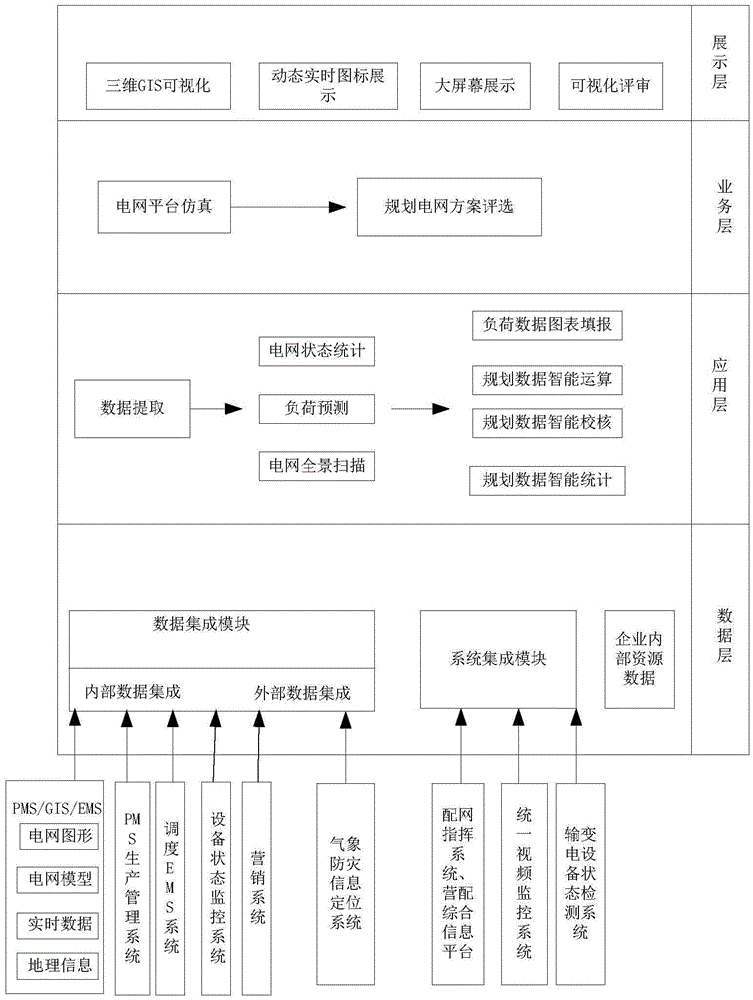
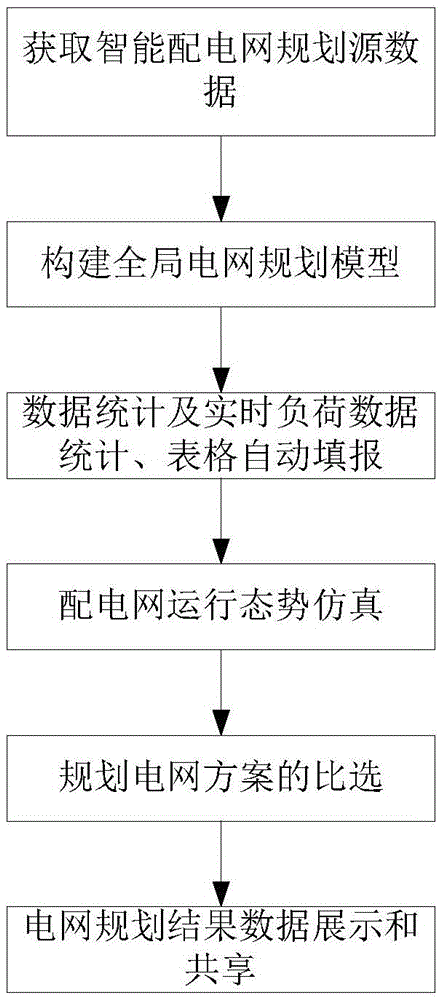
Planning big data management and control system of smart power distribution network and method
ActiveCN105574652ALaying a solid foundation for planning and design informatizationEffectively integrate planning and design data resourcesResourcesInformation technology support systemTime informationStatistical analysis
The invention discloses a planning big data management and control system of a smart power distribution network and a method. The system comprises that a data layer constructs a global power network planning model; a basic data dictionary containing power network devices, graph standards and power network operation information is built; an application layer carries out statistic analysis and real time load actual measurement analysis to the power network devices and power network operation states in a set region; automatic filling of power network load data graphs, intelligent operation of planning data, intelligent verification of the planning data and intelligent statistics and summary of the planning data are realized; a service layer selects planning power network schemes; a display layer carries out centralized display, share and information issue to the planning and design achievement. According to the system and the method of the invention, through taking multi-source massive data such as basic geographic information, power network space and attribute thematic information and power network operation real time information as cores, planning and design data resources in the system are effectively integrated, a power network planning and design integrated information platform is built, and power network planning and design information-based foundation is tamped.
Owner:RES INST OF ECONOMICS & TECH STATE GRID SHANDONG ELECTRIC POWER +1
Method and system for data-structure management
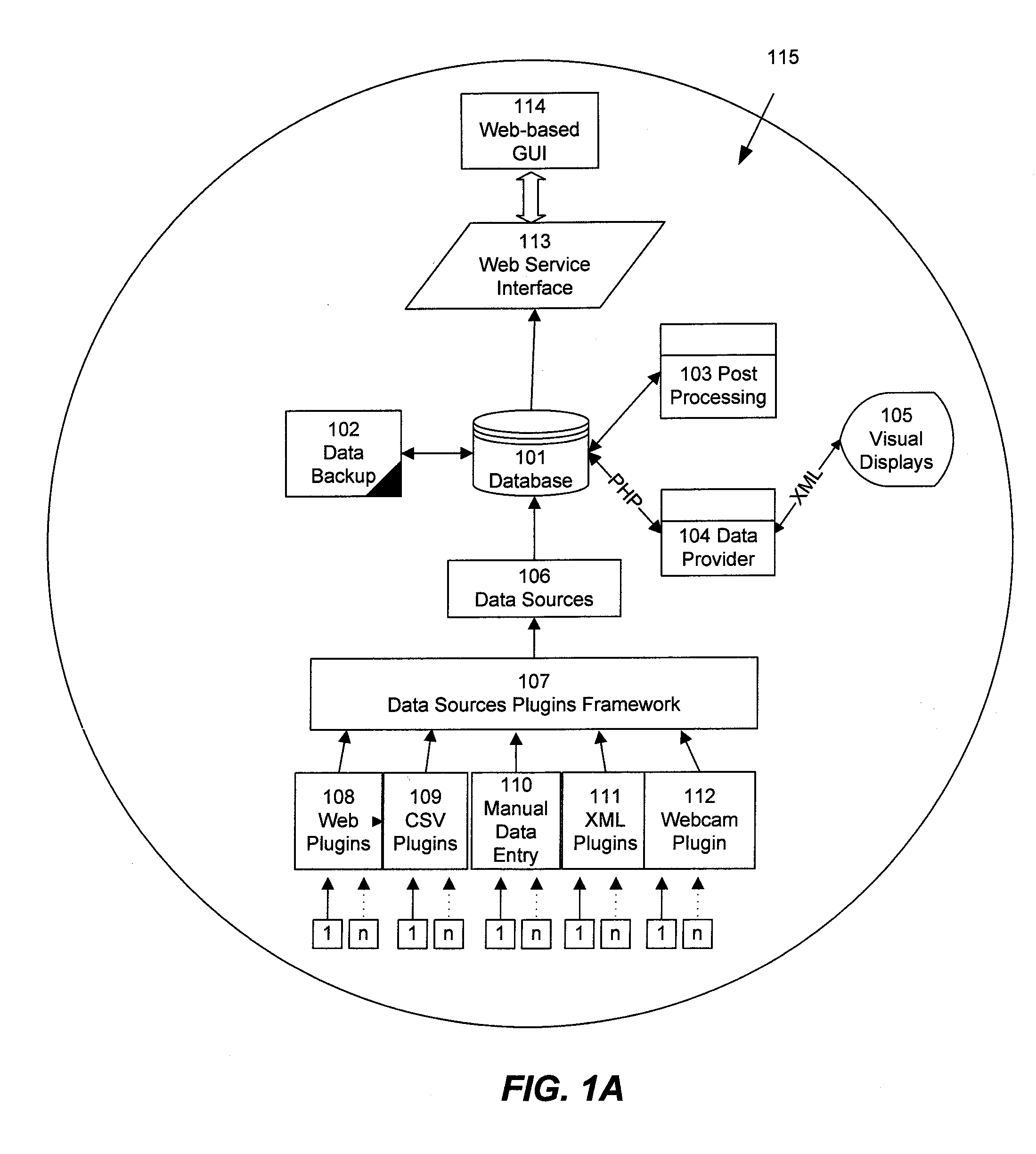
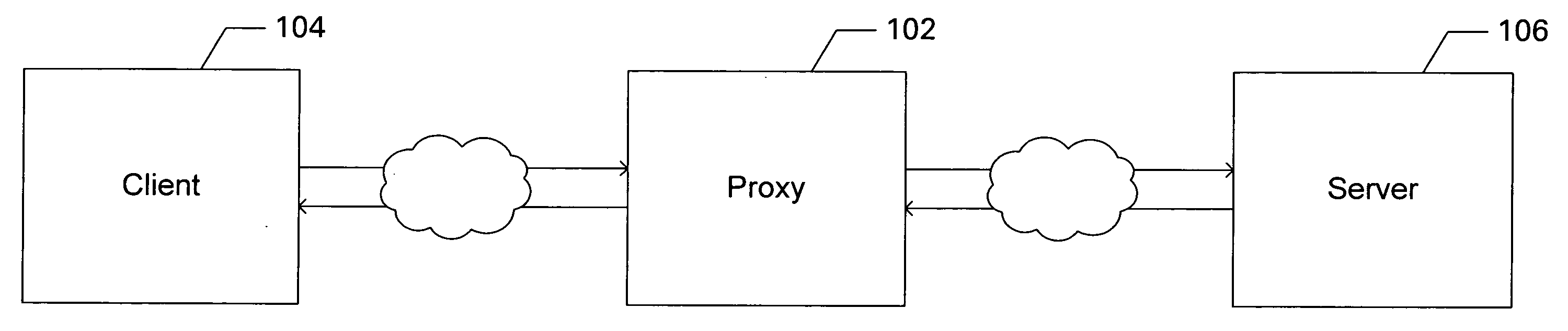
InactiveUS20080016216A1Efficient methodMultiple digital computer combinationsTransmissionTimerDistributed computing
Embodiments of the present invention are directed to computationally efficient methods and systems for managing connection-associated and exchange-associated resources within network proxies. In one embodiment of the present invention, a circular connection-switch queue is employed for allocating, de-allocating, and maintaining connection-based or exchange-based data resources within a proxy. The connection-switch queue includes a free pointer that identifies a next connection-switch queue entry for allocation, and an idle pointer that is incremented continuously or at fixed intervals as timers associated with connection-switch entries expire. In an alternate embodiment, the connection-switch queue includes a free pointer, an idle pointer, and a clear pointer.
Owner:SECURE64 SOFTWARE
Method for achieving automatic synchronization of multi-source heterogeneous data resources
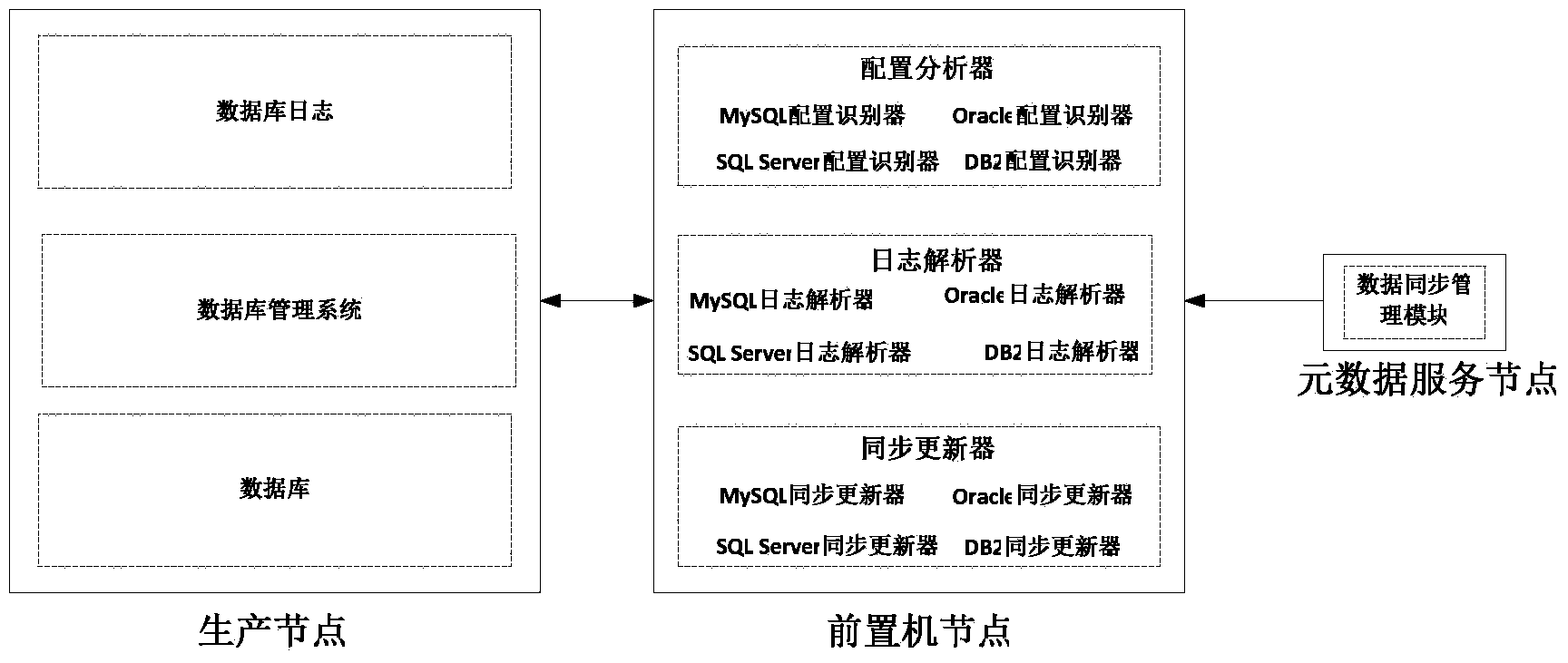
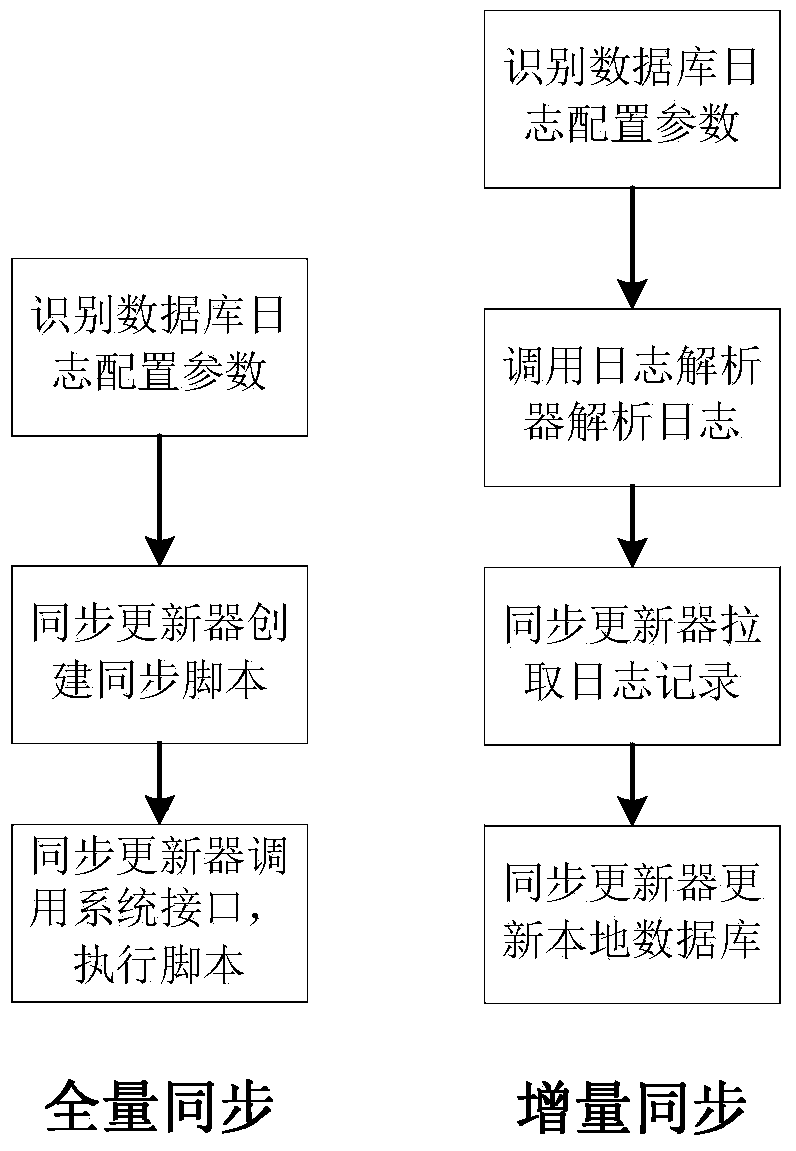
ActiveCN103617176AAchieve synchronizationReduce configuration difficultySpecial data processing applicationsData synchronizationComputer science
The invention relates to a method for achieving automatic synchronization of multi-source heterogeneous data resources. A metadata service node, a service node and a production node are related in the method, the metadata service node is responsible for storing a data dictionary in a distributed heterogeneous database system, the service node is responsible for analyzing user requests in the distributed heterogeneous database system and carrying out synchronization with a database on the production node periodically, and the production node is responsible for requests such as inquiring and updating in a corresponding production application system, wherein the service node is formed by a configuration recognizer, a blog parser and a data synchronizer, the configuration recognizer is used for analyzing the configuration of a source database on the production node and selecting a feasible synchronizing mode, the blog parser is used for analyzing blogs of different dataset systems and is a component for first-phase preparing work of an increment synchronization mode, and the data synchronizer carries out data synchronization according to the synchronizing mode of the configuration recognizer. The method for achieving the automatic synchronization of the multi-source heterogeneous data resources enables the automatic synchronization of the multi-source heterogeneous data resources to be achieved, and can be used in data resource processing.
Owner:GUANGDONG ELECTRONICS IND INST
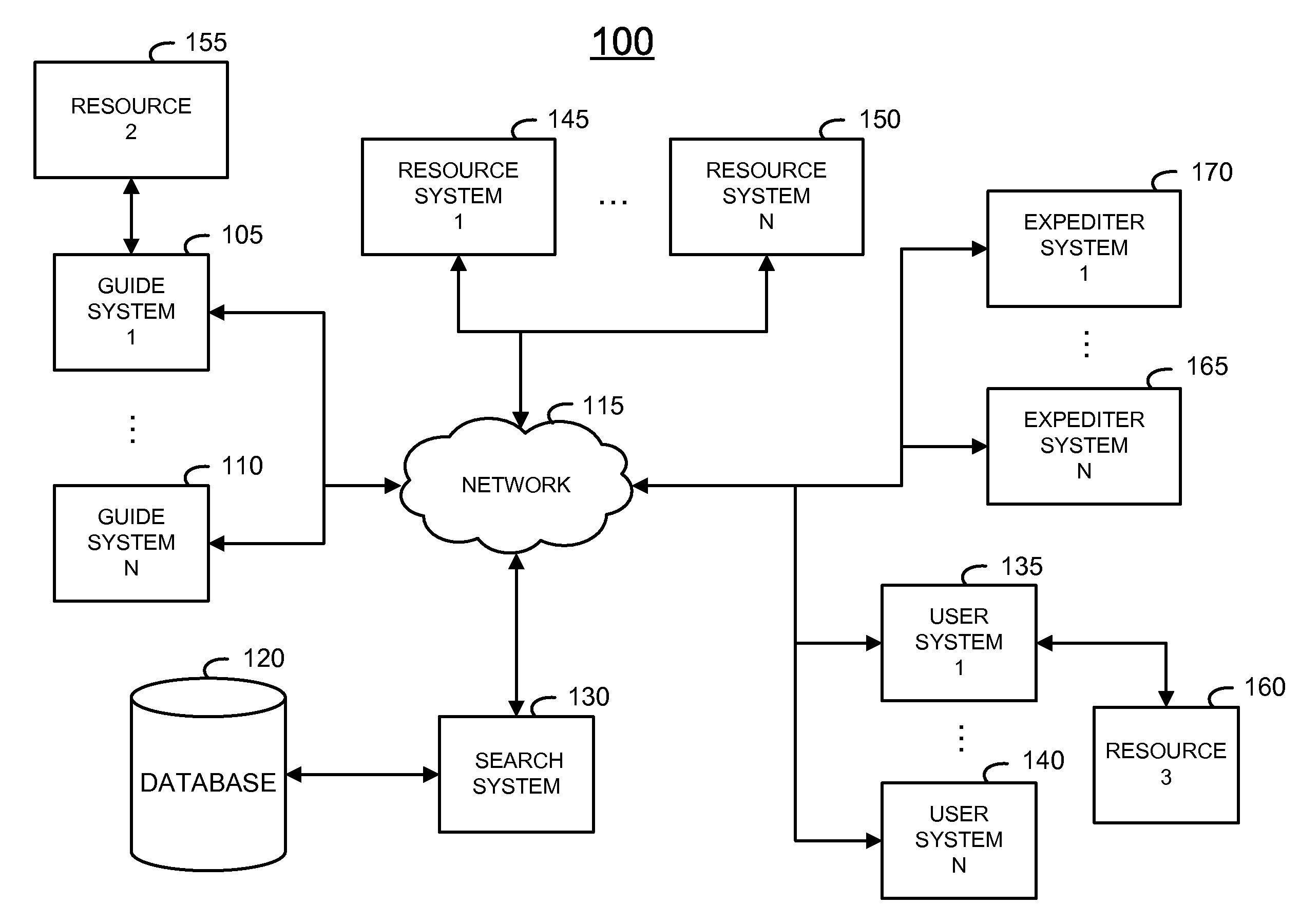
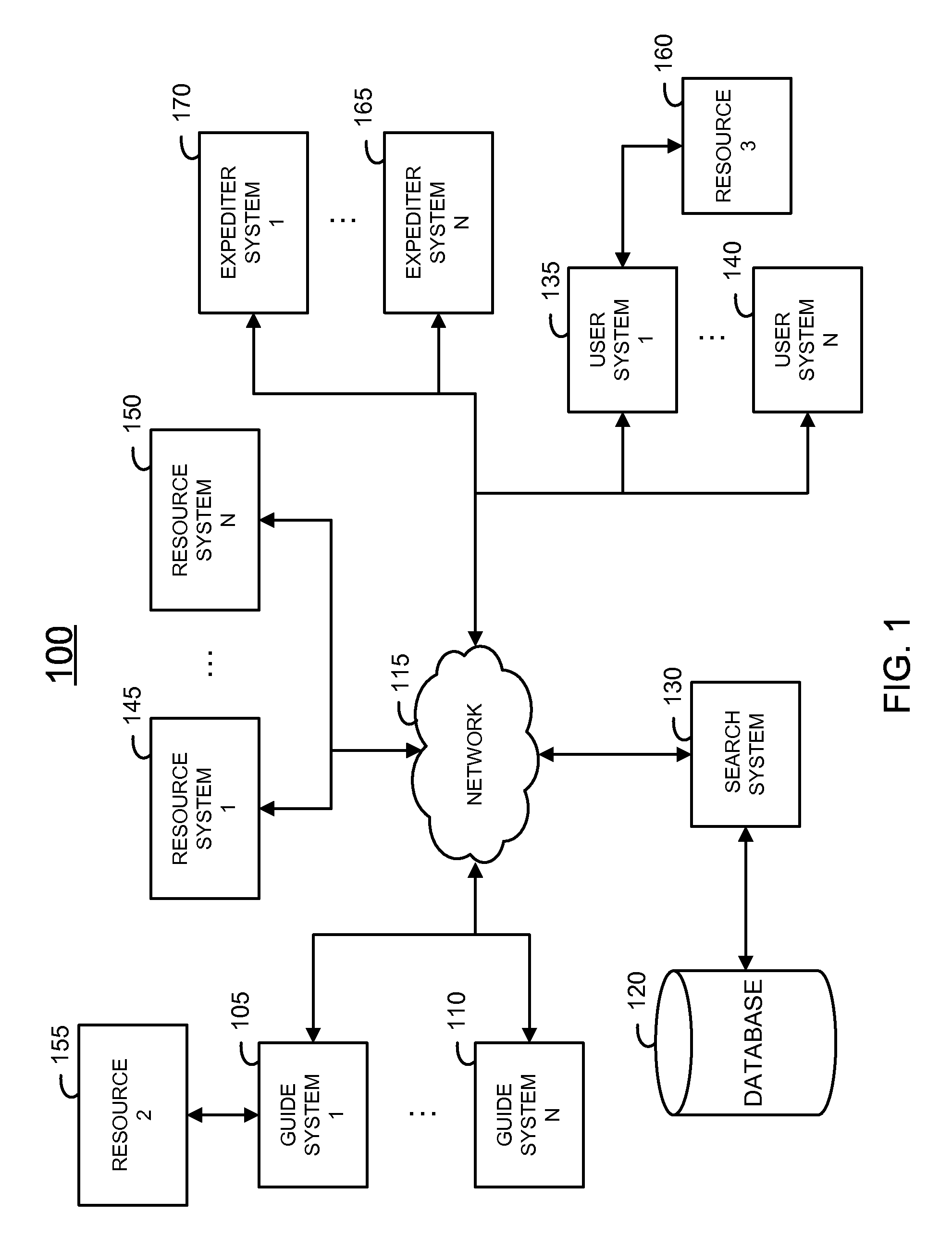
System and method for efficiently securing enterprise data resources
ActiveUS8327419B1Digital data processing detailsUnauthorized memory use protectionBusiness enterpriseData mining
Some embodiments provide a system and method that secures access to data objects of an enterprise that includes multiple data objects and multiple user applications that access data attributes of the data objects. In some embodiments, access is provided by secure resources that (1) filter a set of the data objects using a user attribute to identify a subset of data attributes of the data objects and (2) performing a query by identifying the secure resources accessible by the user based on the particular user attribute and retrieving data attributes from the secure resources according to the query.
Owner:INFORMATICA CORP
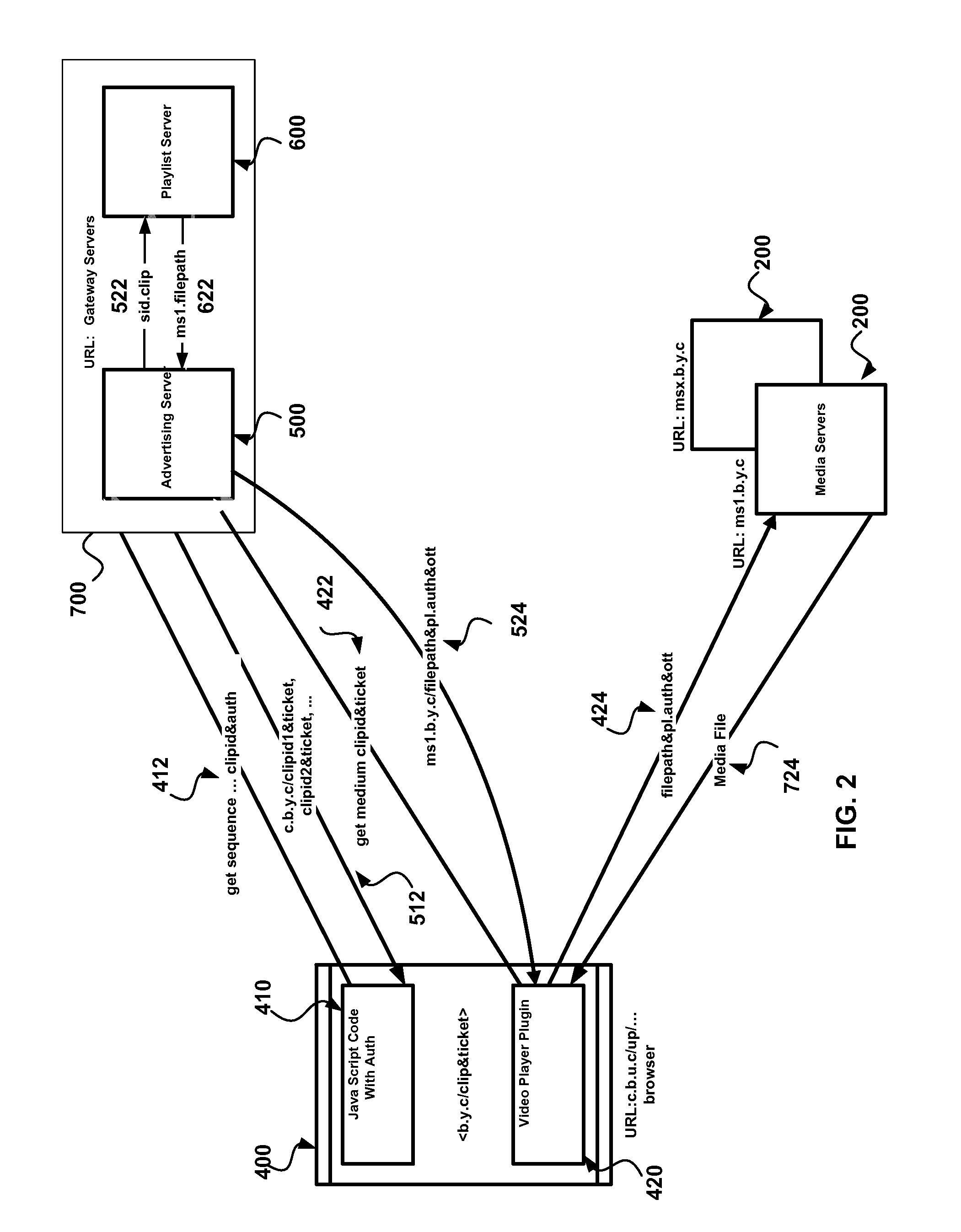
Method and system for securely streaming content
ActiveUS20090235347A1Digital data processing detailsUser identity/authority verificationAuthorization certificateWhitelist
A system and method for securely streaming media. The system includes a gateway server that receives requests for access to a secured data resource from an end users. The request include an authorization ticket and a referring website. The gateway server validates the authorization ticket using a secret key shared with the referring website, and validates the referring website by verifying that referring website is on a white-list for the secured data resource. The gateway server selects a data server to service the request, and formats a data server access request containing the data server location and data server request parameter data and transmits the data server access request to the end users. When end users transmit the data server access requests to a data server, the data server validates the request and transmits it to the end user.
Owner:VERIZON PATENT & LICENSING INC
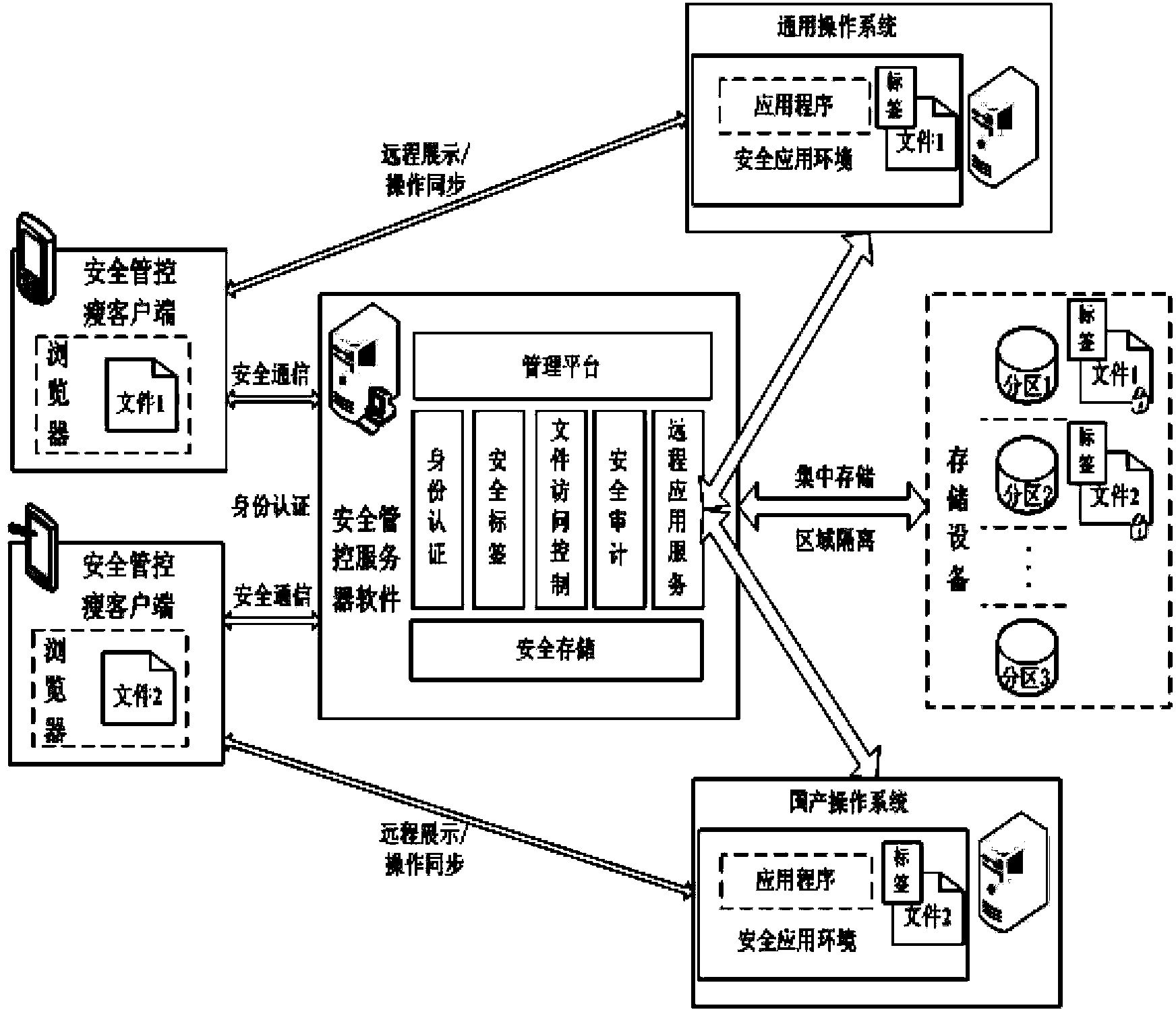
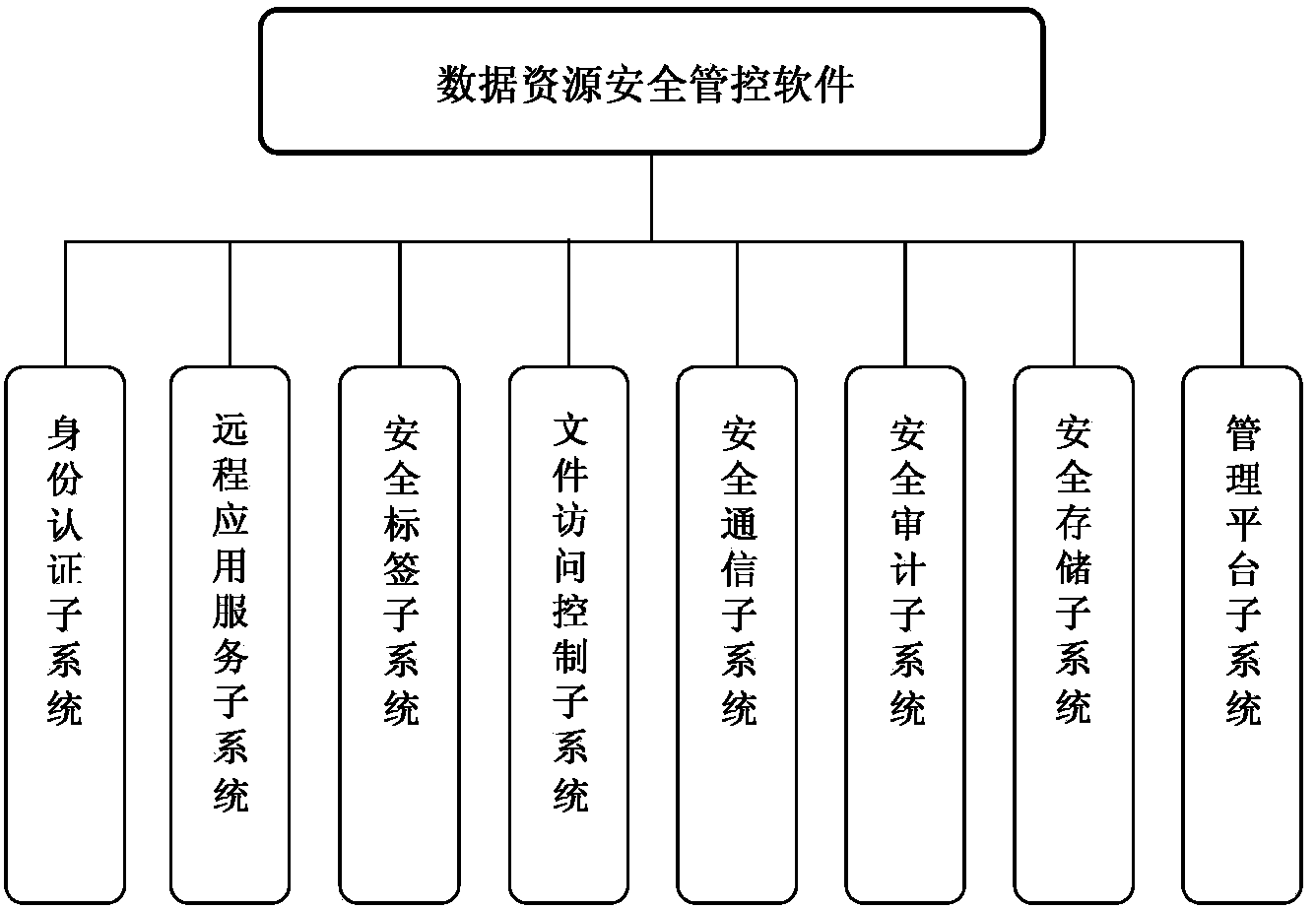
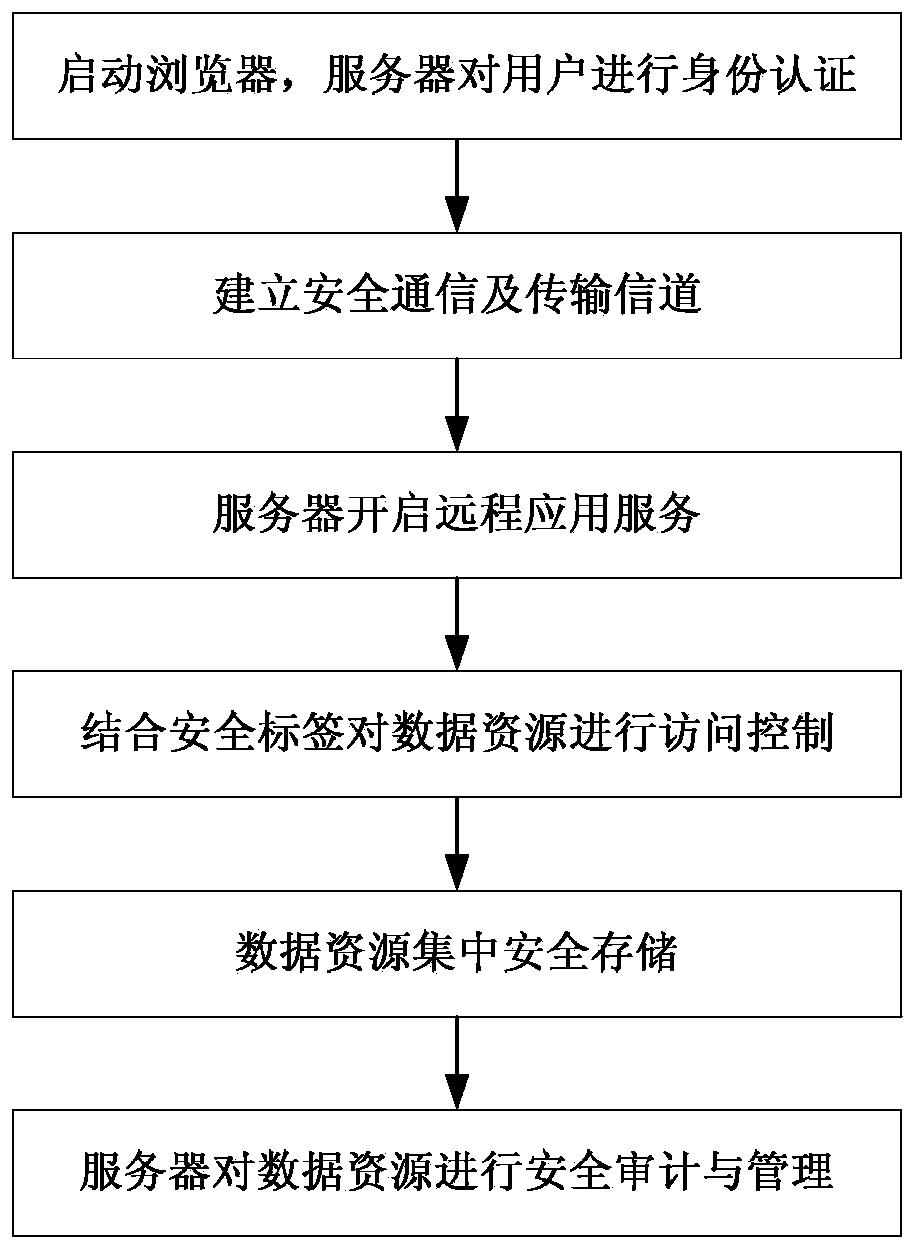
Data resource security control method in thin client mode
ActiveCN103441986AEfficient identificationEnsure authenticityDigital data protectionTransmissionThin clientServer-side
The invention belongs to the field of network security, and particularly relates to a data resource security control method in a thin client mode. The data resource security control method in the thin client mode comprises eight subsystems, namely the identity authentication subsystem, the remote application service subsystem, the security label subsystem, the file access control subsystem, the security communication subsystem, the security audit subsystem, the security storage subsystem and the management platform subsystem. Storage and control of files are mainly performed on a background server, the files are stored in different partitions according to user types or security levels of the files, the files are stored and protected, and a server side can not recognize the content of the files. When a user needs to have access to and process the files, the user logs in on a browser, identity authentication is conducted between the user and a server, and then file access connection is established. The files of a thin client are processed on the server side (provided by a physical application server or a virtual application server), no application or agent needs to be installed on the thin client, and interface interoperability is supported by related services released by remote application services.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
Cloud platform for achieving distributed isomerous data sharing and data sharing method thereof
InactiveCN103607469AReal-time extraction strategyTiming Extraction StrategyTransmissionData cloudSoftware
The invention relates to the technical field of multi-source data processing, in particular to a cloud platform for achieving distributed isomerous data sharing and a data sharing method thereof. A system is composed of a sharing data cloud application layer, a cloud sharing data service layer, a system bridging layer and a service system layer. The three-layer data sharing and accessing control technology is adopted, and a data owner carries out setting on the synchronization mode and the sharing mode of sharing data by using adapter software running in a front-end processor and data resource management software running in a cloud end respectively, and carries out secondary confirmation on switching of the sharing data by setting certain operation procedures. Cloud end backup is carried out on the shared data through format transformation. The cloud platform for achieving the distributed isomerous data sharing and the data sharing method thereof solve the sharing problem of isomerous data, and can be applied to the sharing processing of multi-source isomerous data.
Owner:CLOUD COMPUTING CENT CHINESE ACADEMY OF SCI
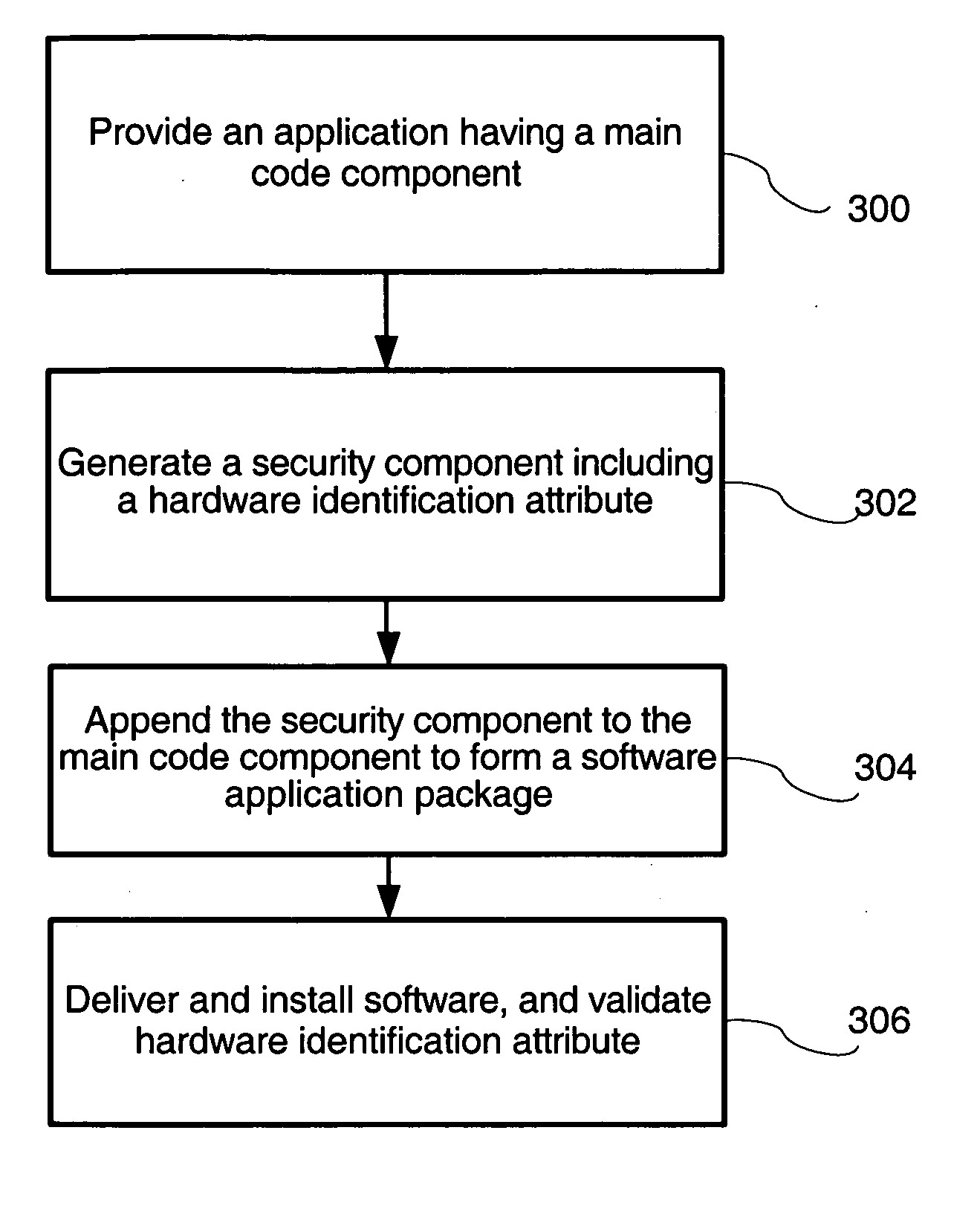
Digital rights management system based on hardware identification
InactiveUS20060064756A1Digital data processing detailsAnalogue secracy/subscription systemsComputer hardwareDigital rights management system
A method for digital rights management is provided. The method is used for managing the right to use a digital software application having a main code component including application code and data resources. The method generates a security component including a hardware identification attribute and appends the security component to the main code component to form a software application package. When the software application package is installed on a hardware device, the security component enables the software application only if the hardware identification attribute is also present in the hardware device.
Owner:INVENTEC APPLIANCES CORP
System and method for efficiently securing enterprise data resources
ActiveUS8166071B1Digital data processing detailsComputer security arrangementsInternet privacyApplication software
Some embodiments provide a system and method that secures access to data objects of an enterprise that includes multiple data objects and multiple user applications that access data attributes of the data objects. In some embodiments, secure access is provided via a secure resource that secures access to data attributes of at least two objects by defining access control permissions for the secure resource and applying the defined access control permissions to the data attributes of the secure resource.
Owner:INFORMATICA CORP
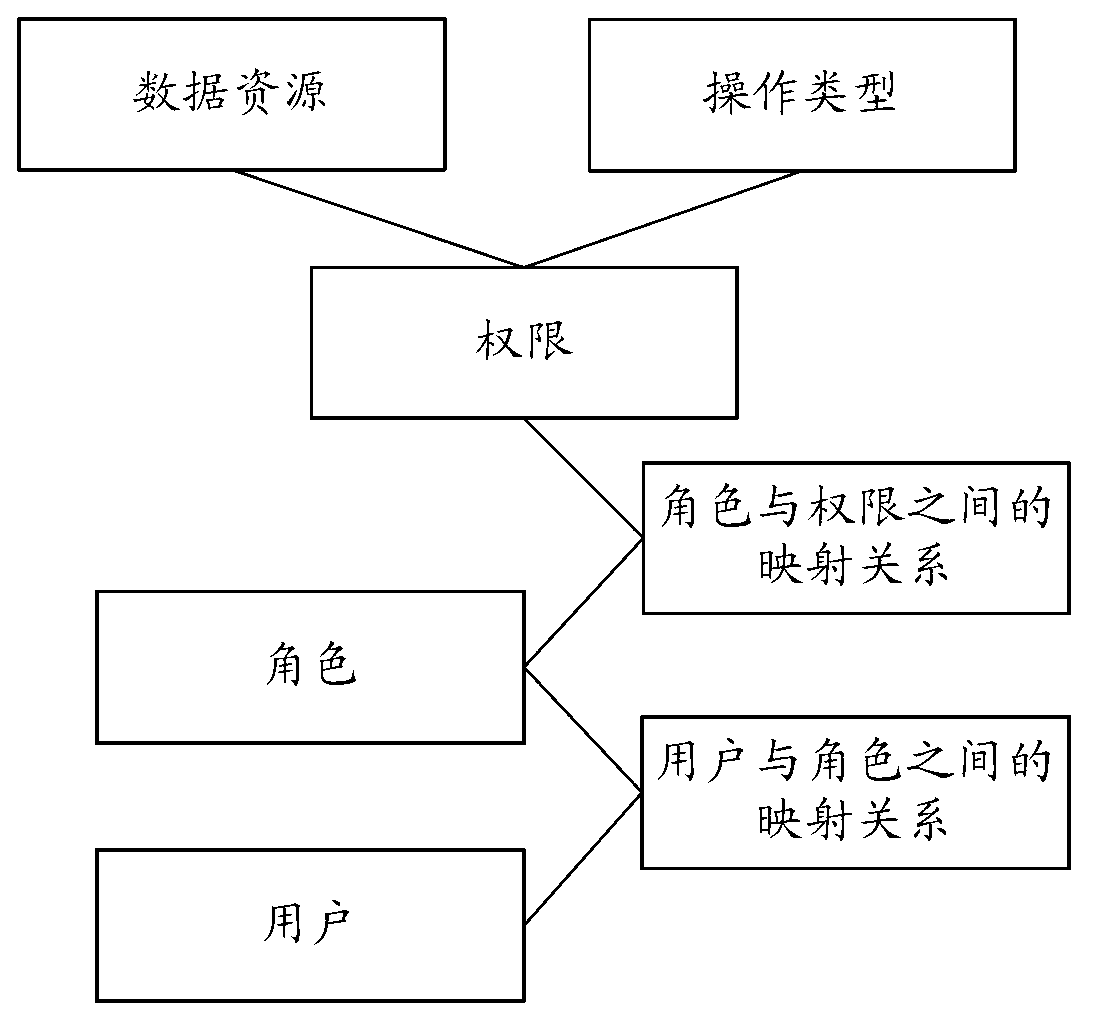
Service system authority management method, equipment and system
ActiveCN103078859AImprove the ability of authority managementDigital data authenticationTransmissionGranularityComputer terminal
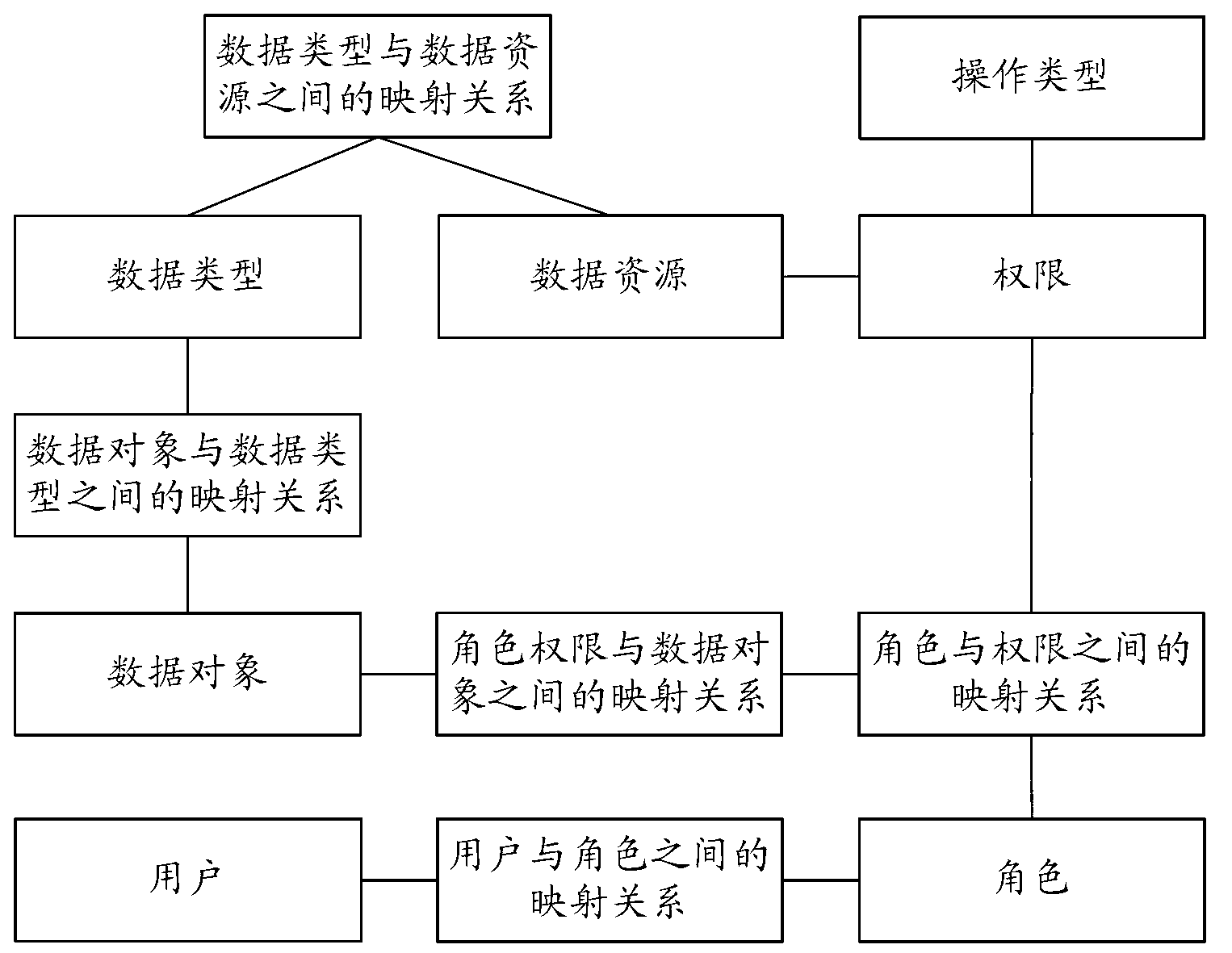
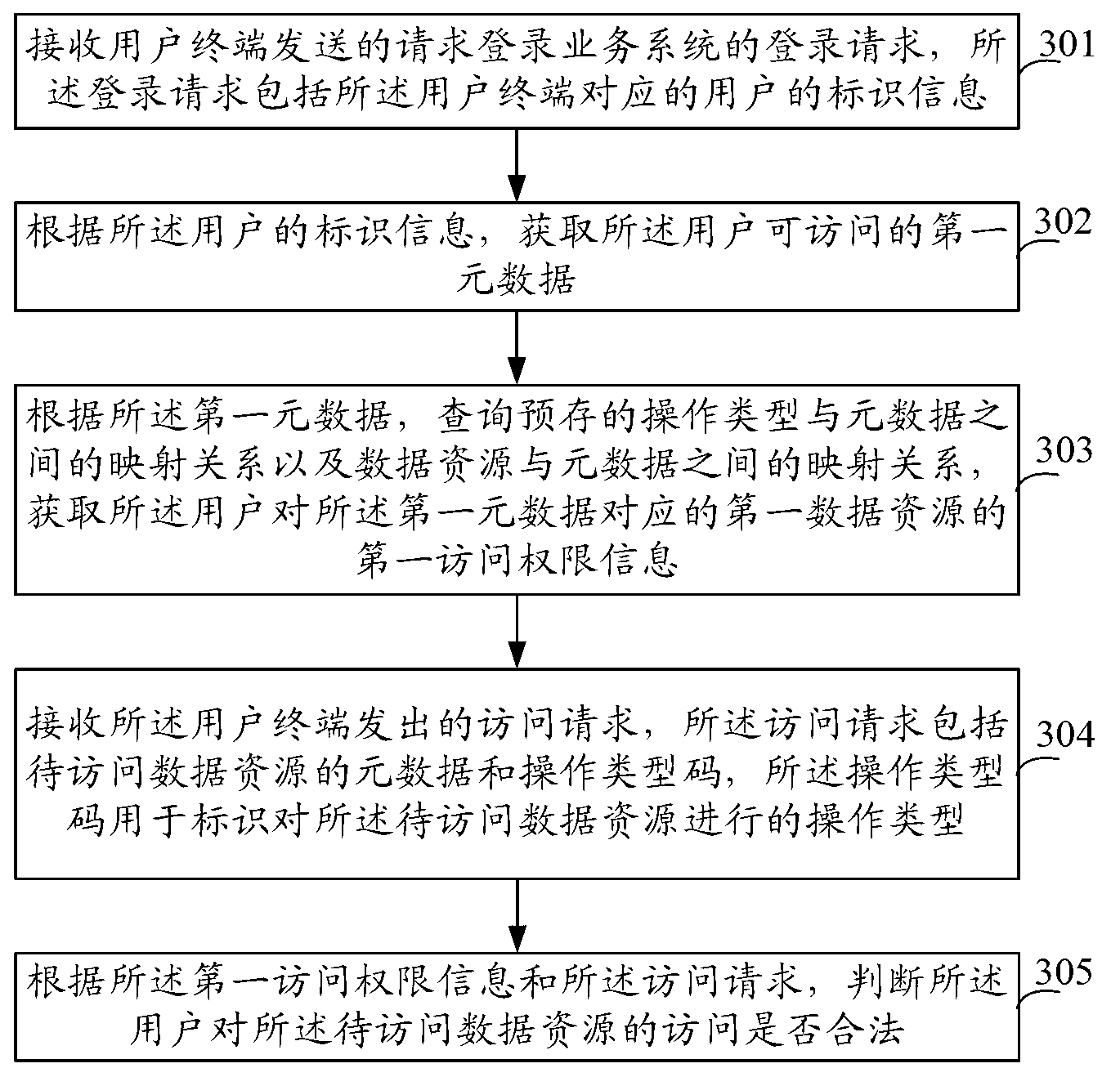
The embodiment of the invention provides a service system authority management method, service system authority management equipment and a service system authority management system. The method comprises the following steps that the login request sent by a user terminal is received, the login request comprises marking information of users, a first metadata capable of being visited by the users is obtained according to the marking information of the users, the mapping relationship between the preset operation type and the metadata and the mapping relationship between the data resource and the metadata are inquired according to the first metadata, the first visit authority information of the users is obtained, the visit request sent by the user terminal is received, the visit request comprises the metadata of data resources to be visited and the operation type codes, and whether the visit to the data resources to be visited by the users is legal or not is judged according to the first visit authority information and the visit request. The mapping relationship is built in advance, the fine granularity grading visit authority control on the data resources of the service system is realized, and the authority management capability on the service system is improved.
Owner:PUTIAN NEW ENERGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com