Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
122 results about "Incident response" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An incident response team or emergency response team (ERT) is a group of people who prepare for and respond to any emergency incident, such as a natural disaster or an interruption of business operations. Incident response teams are common in public service organizations as well as in organizations. This team is generally composed of specific members designated before an incident occurs, although under certain circumstances the team may be an ad hoc group of willing volunteers.
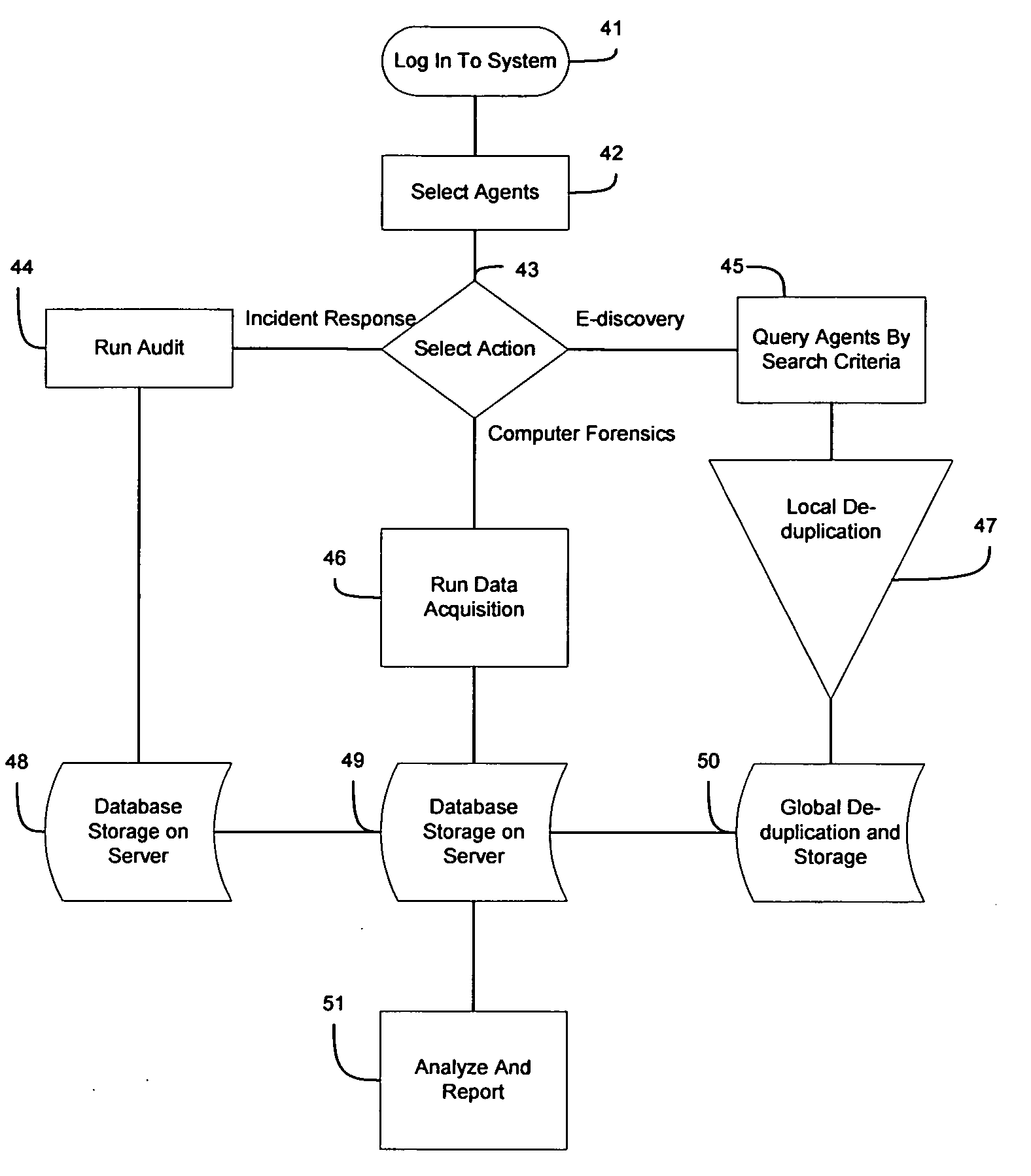
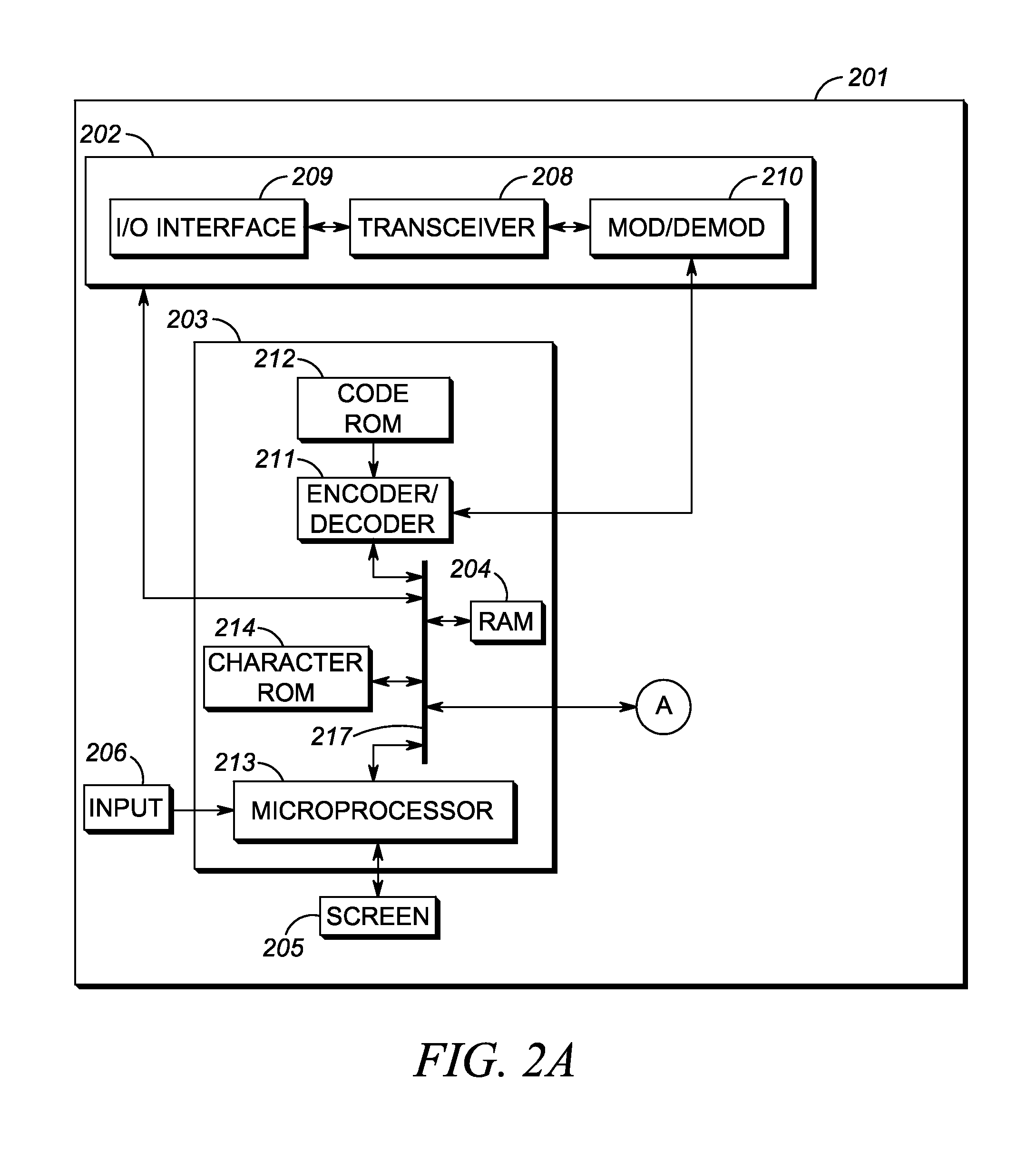
Computer forensics, e-discovery and incident response methods and systems
InactiveUS20090164522A1Secure transmissionCommunication securityMultiple digital computer combinationsTransmissionUser inputElectronic discovery
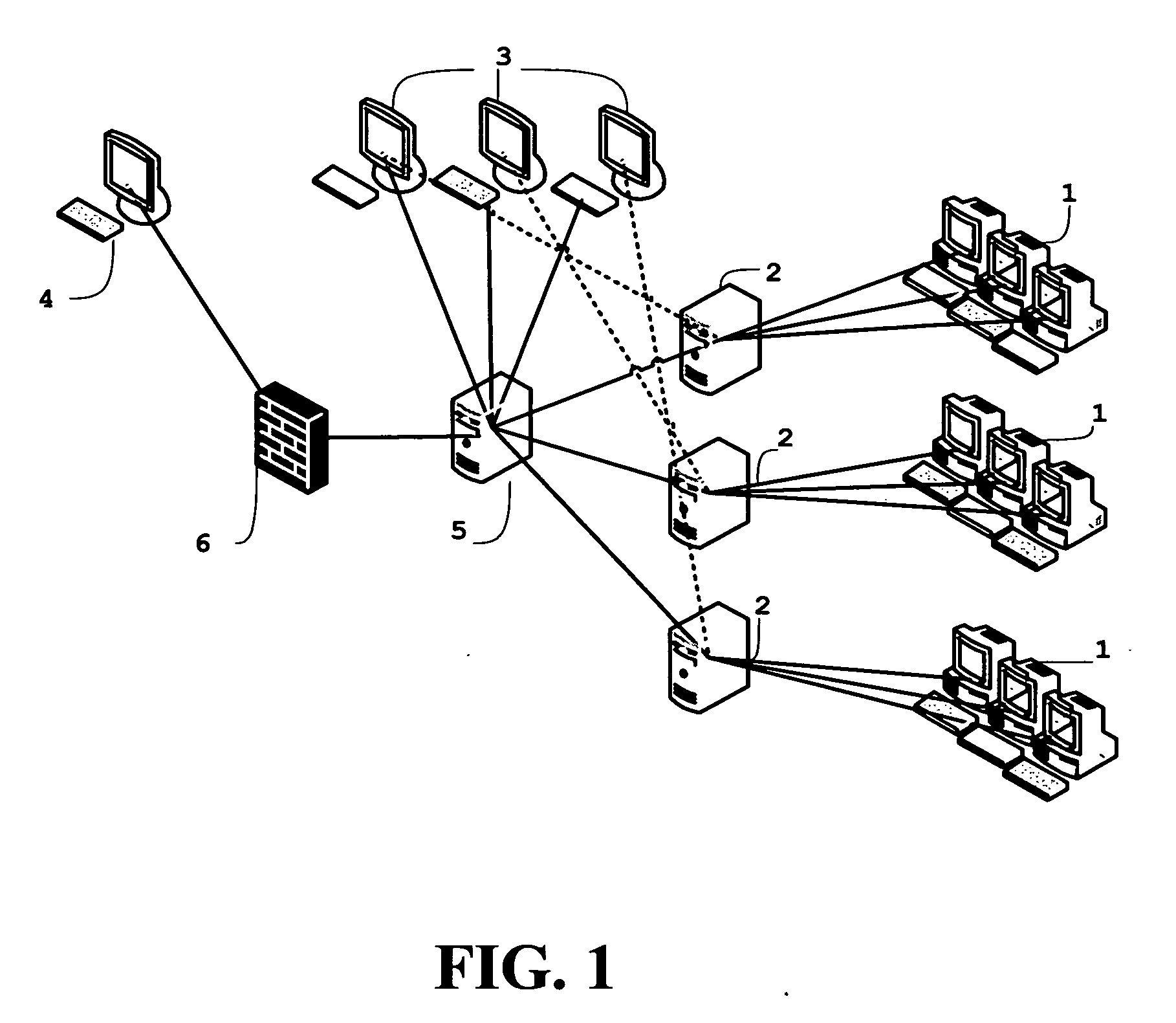
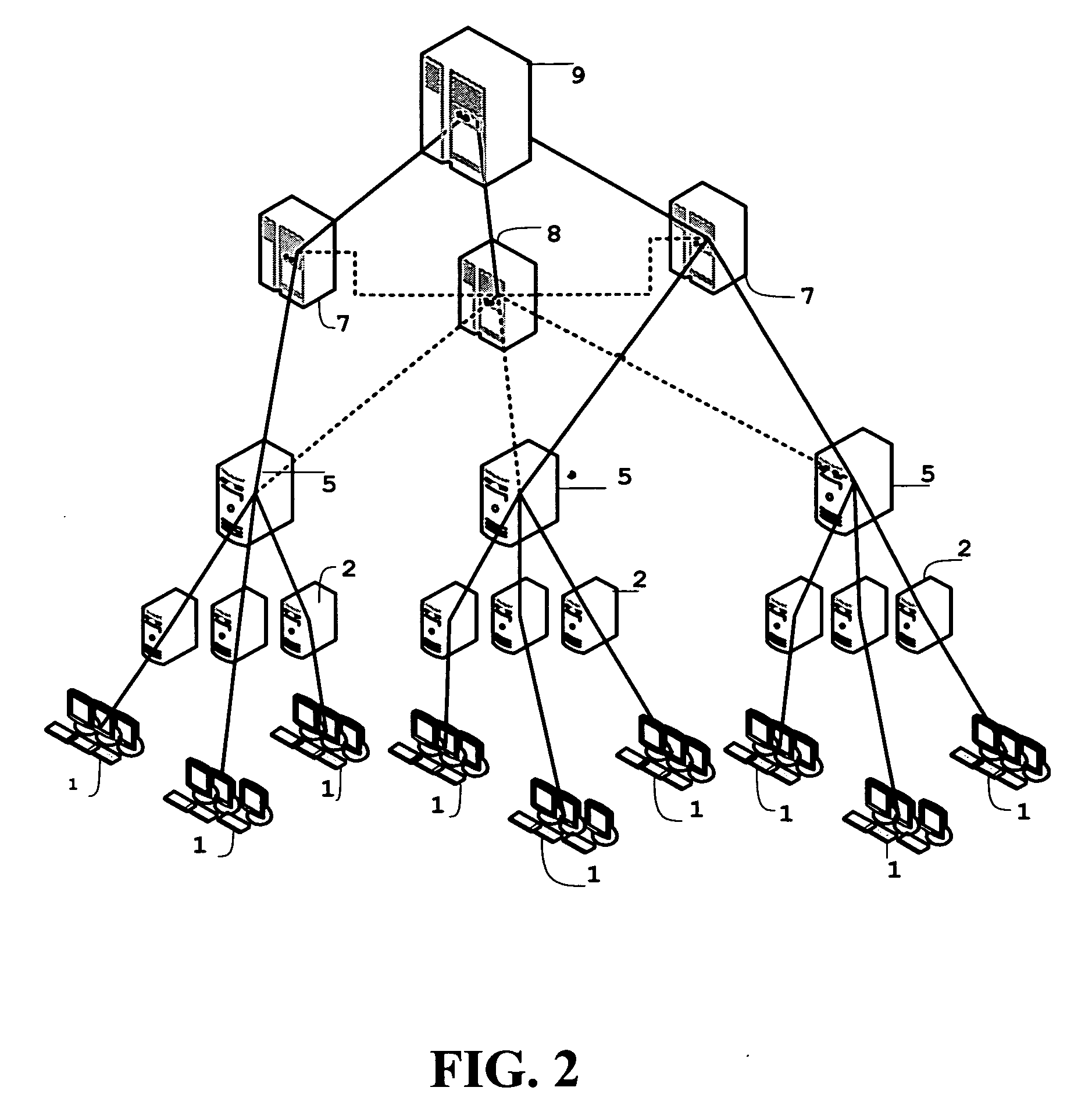
Systems and methods for collection of volatile forensic data from active systems are described. In an embodiment of the methods, a selected set of forensics data items can be selected. Runtime code capable of launching data collection modules from a removable storage device with little or no user input is generated and stored on the device. The collection of forensic data can then be accomplished covertly using the removable storage device by a person with minimal training. In another embodiment, pre-deployed agents in communication with servers and controlled by console software can collect forensic data covertly according to schedule, immediately at the command of an analyst using a remote administrative console, or in response to a triggering event.
Owner:E FENSE
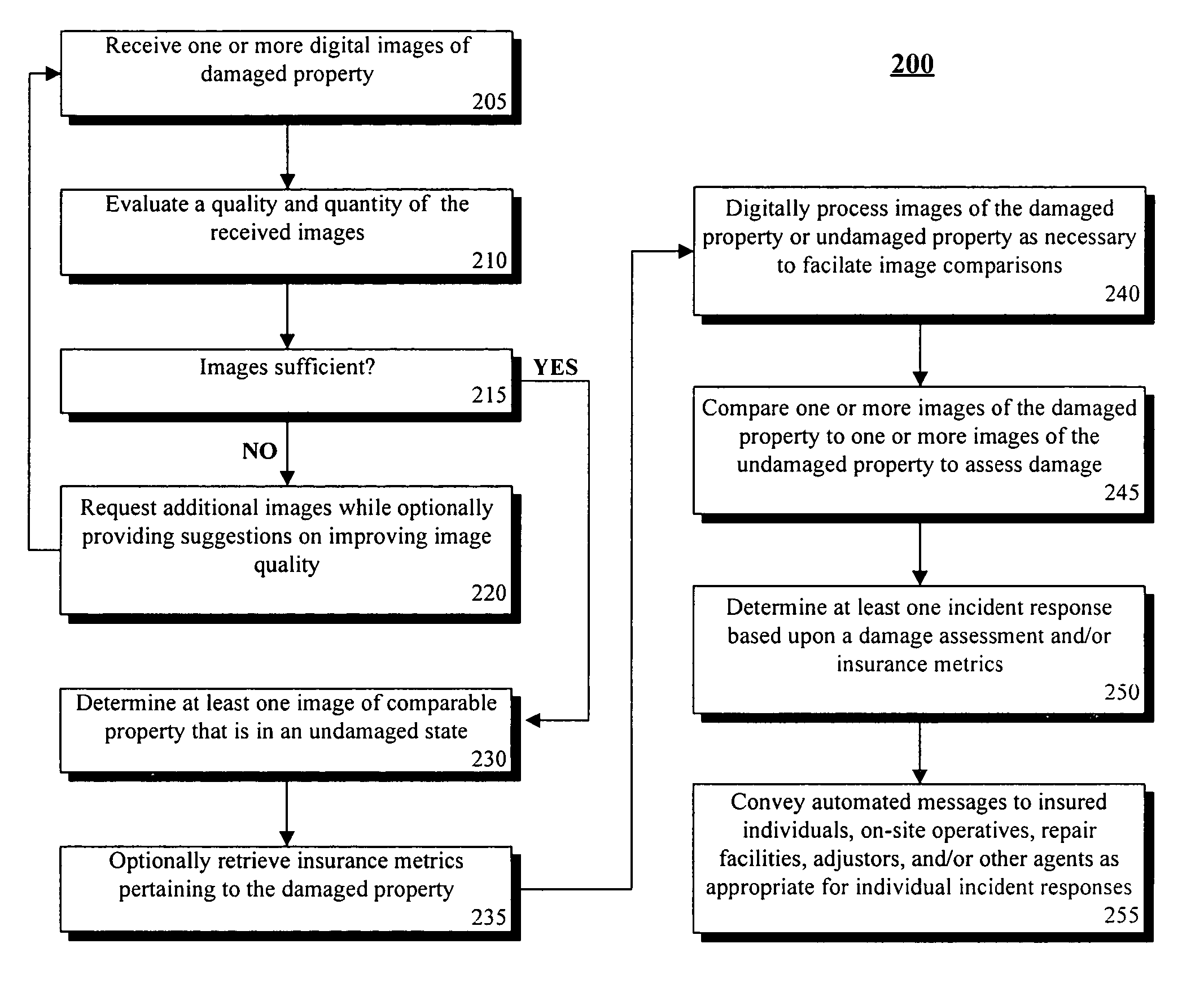
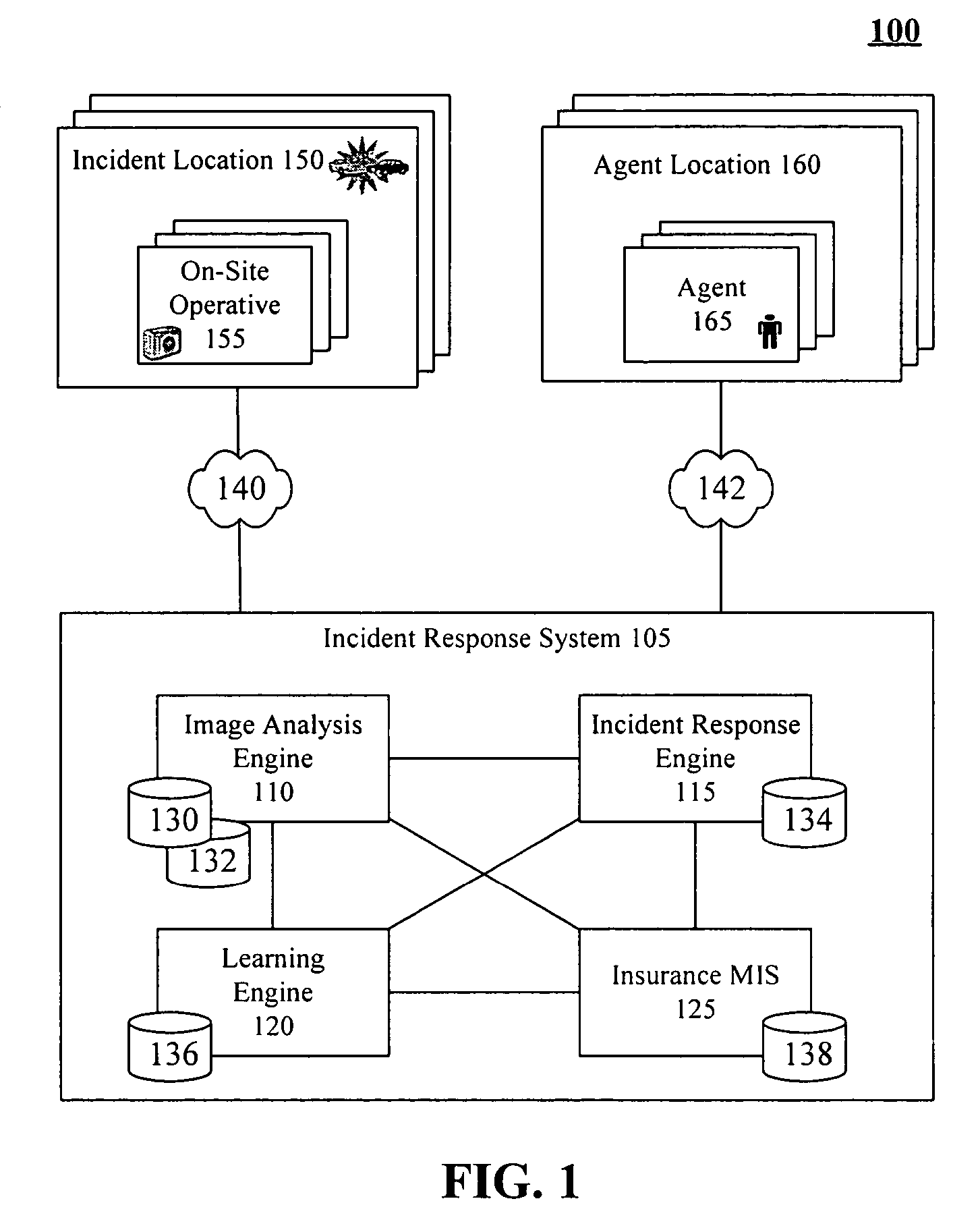
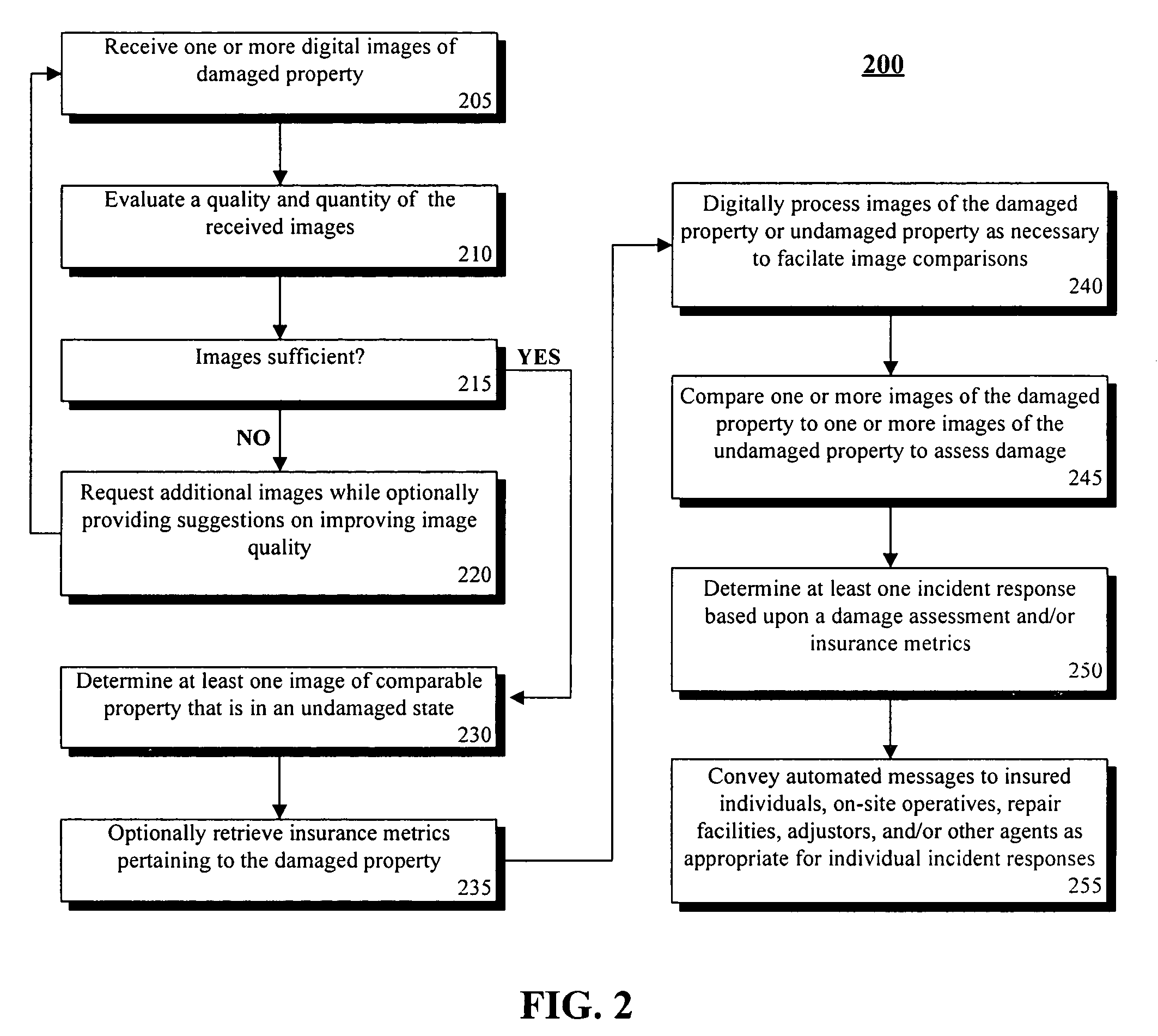
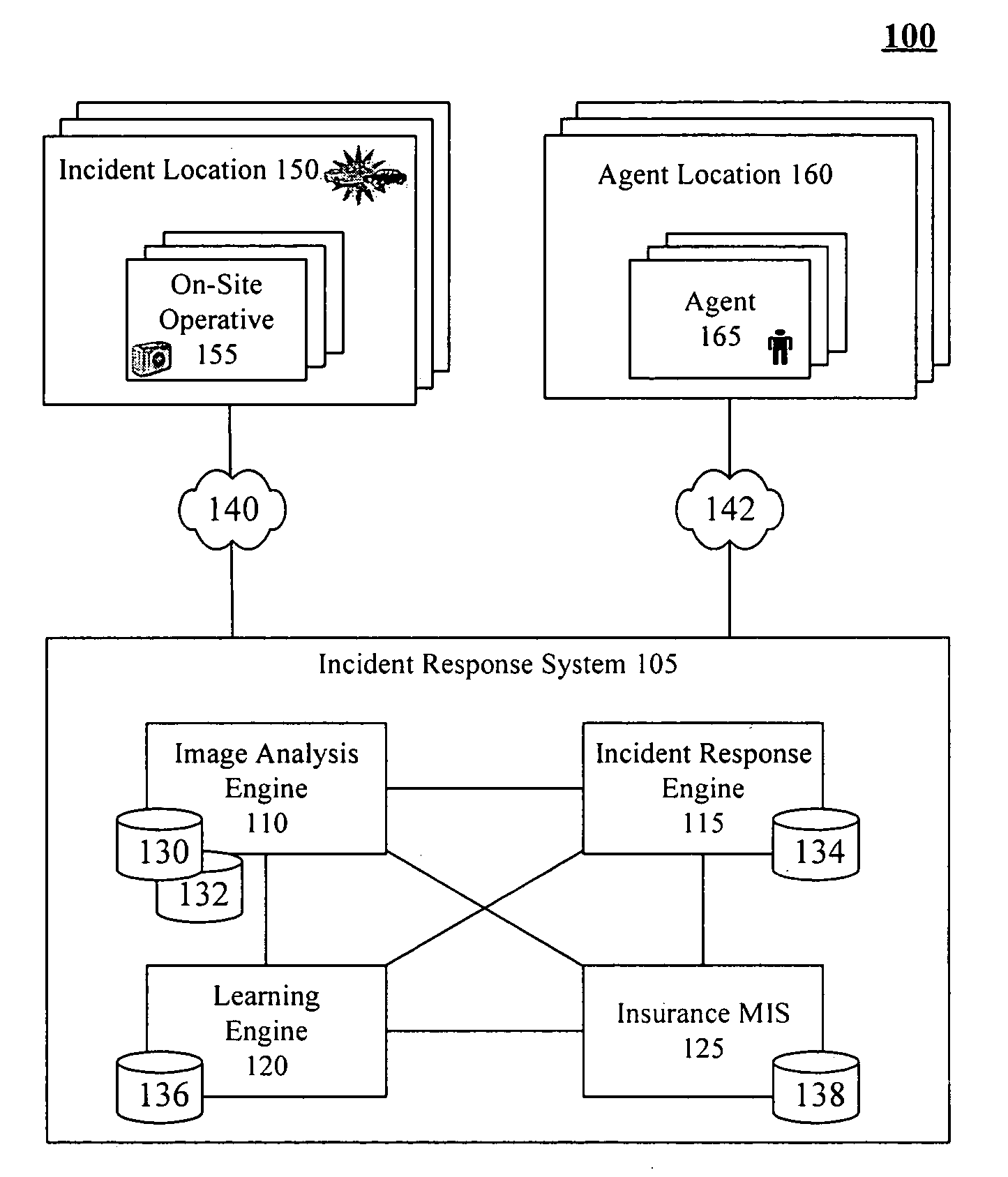
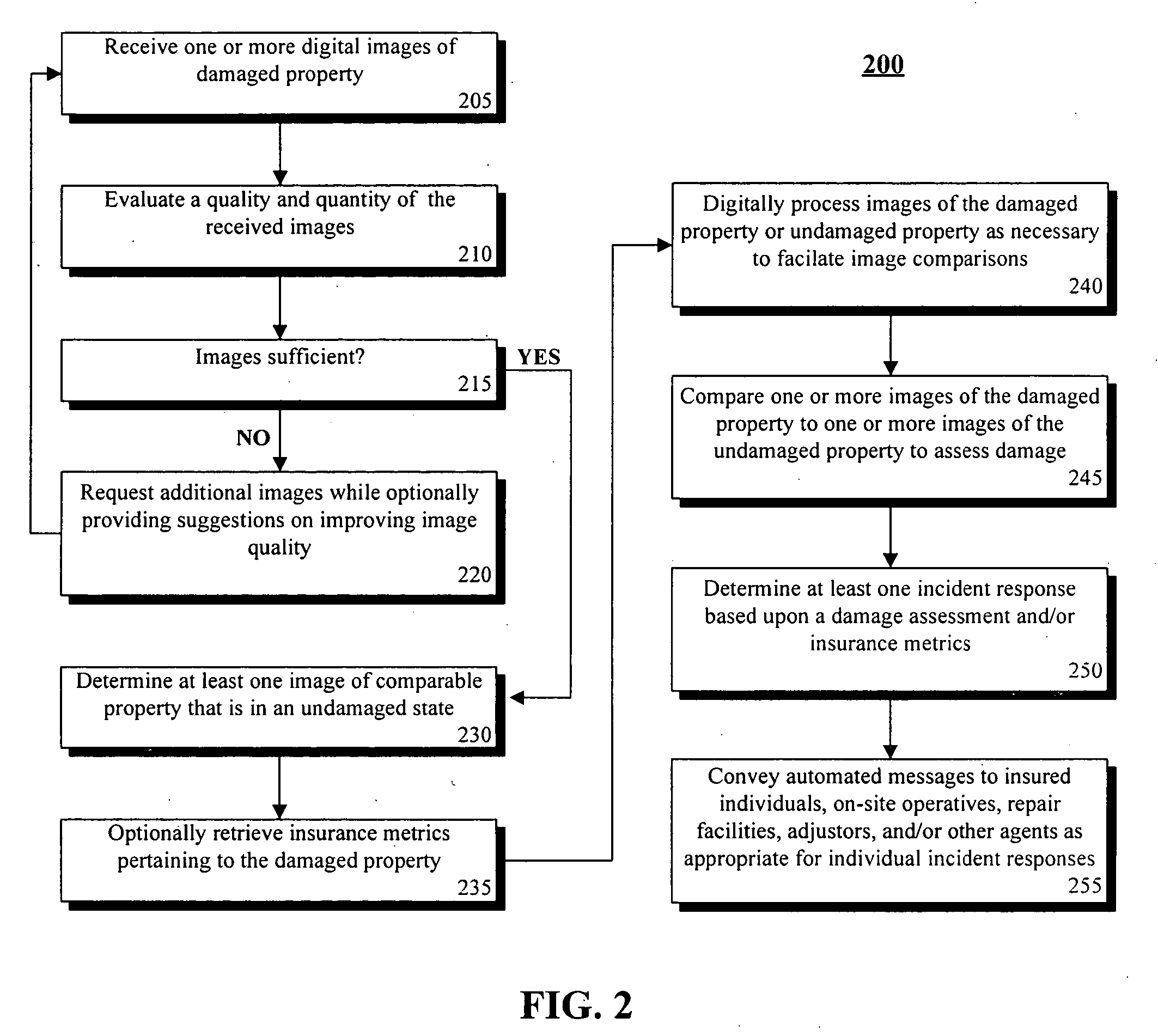
Rapid business support of insured property using image analysis
InactiveUS7809587B2Increase the number ofProcessing speedFinanceOffice automationImaging analysisHuman agent
Owner:LINKEDIN
Rapid business support of insured property using image analysis
InactiveUS20050251427A1Increase the number ofSpeed up claim processFinanceOffice automationImaging analysisHuman agent
A method of providing rapid business support of insured property using image analysis can include the step of receiving at least one digital image of damaged property. Damage can be automatically accessed for insurance purposes based upon the received images. An incident response can be automatically determined based at least in part upon the damage assessment. Incident responses can include, but are not limited to, tendering a claim payoff offer, referring a claim to a human agent, providing repair instructions, and / or arranging for a physical damage assessment of the damaged property.
Owner:LINKEDIN
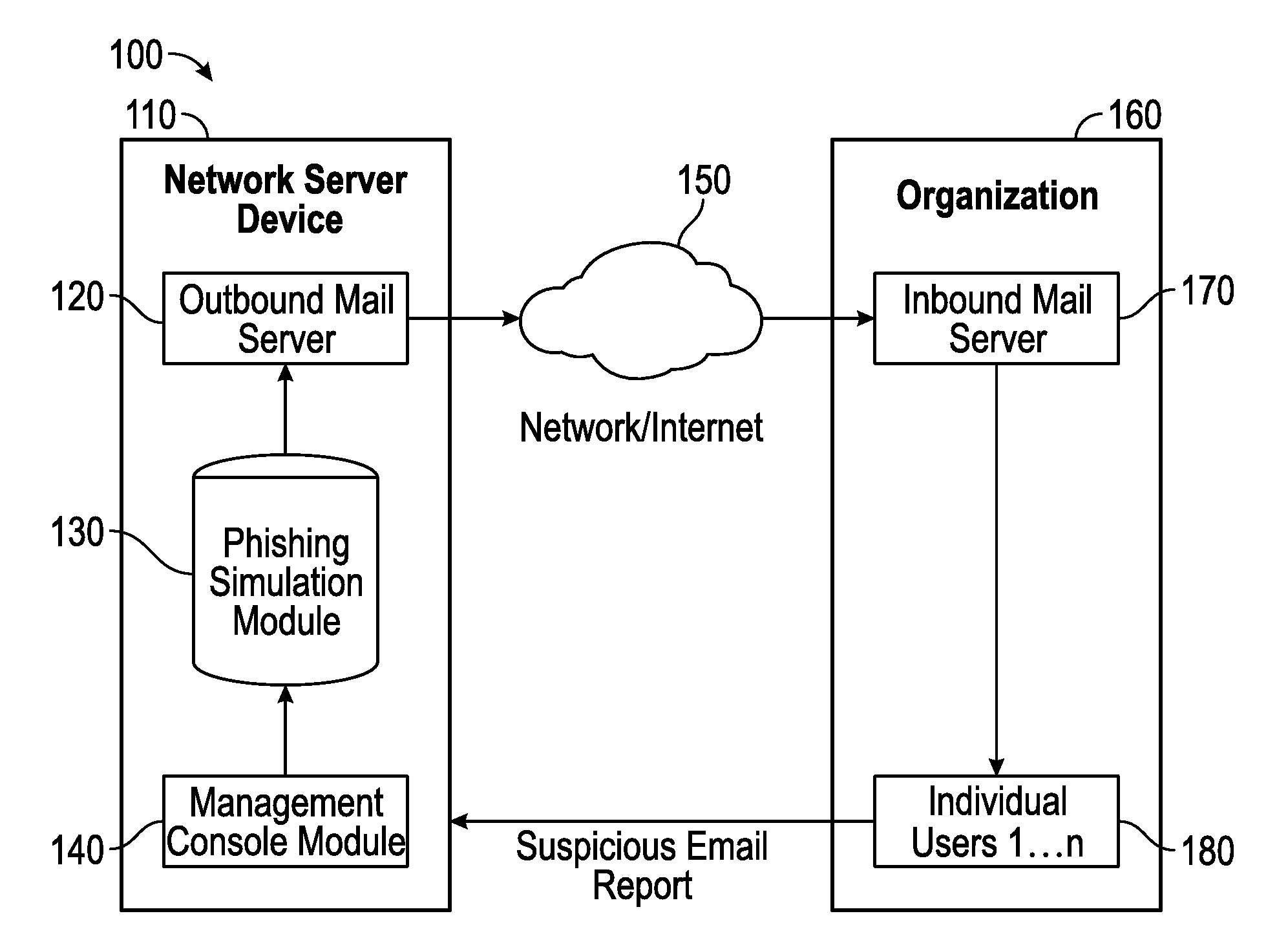
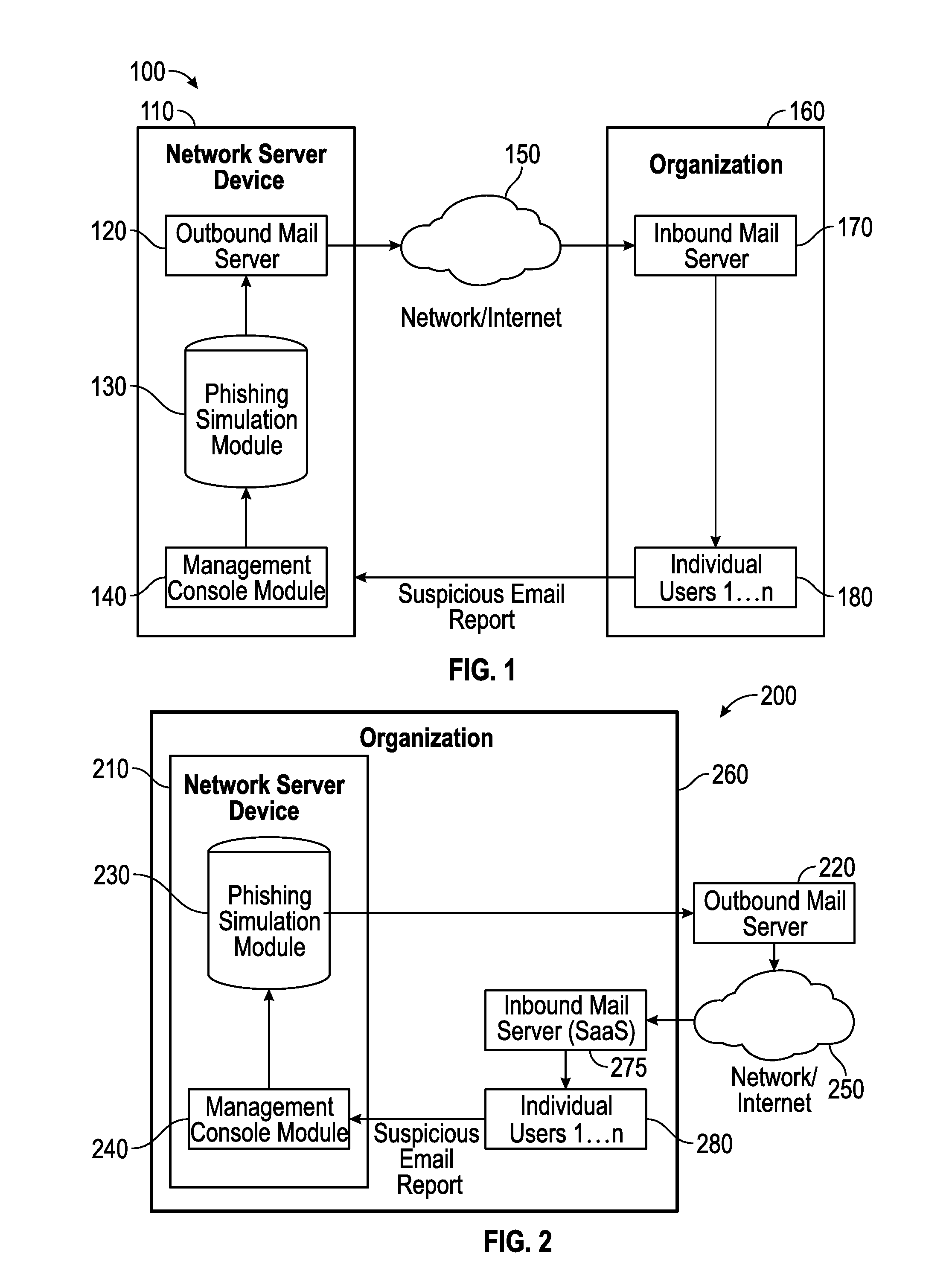
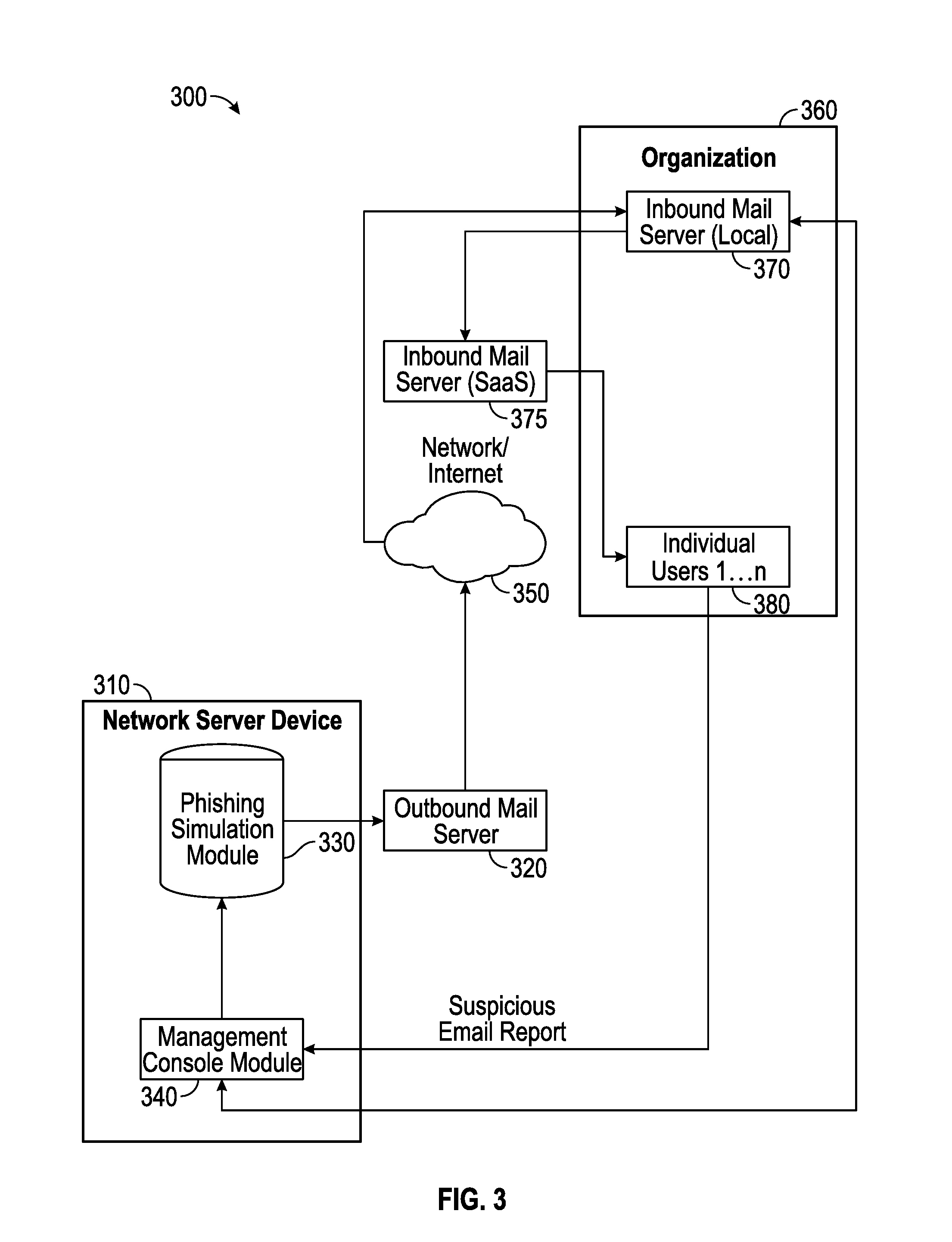
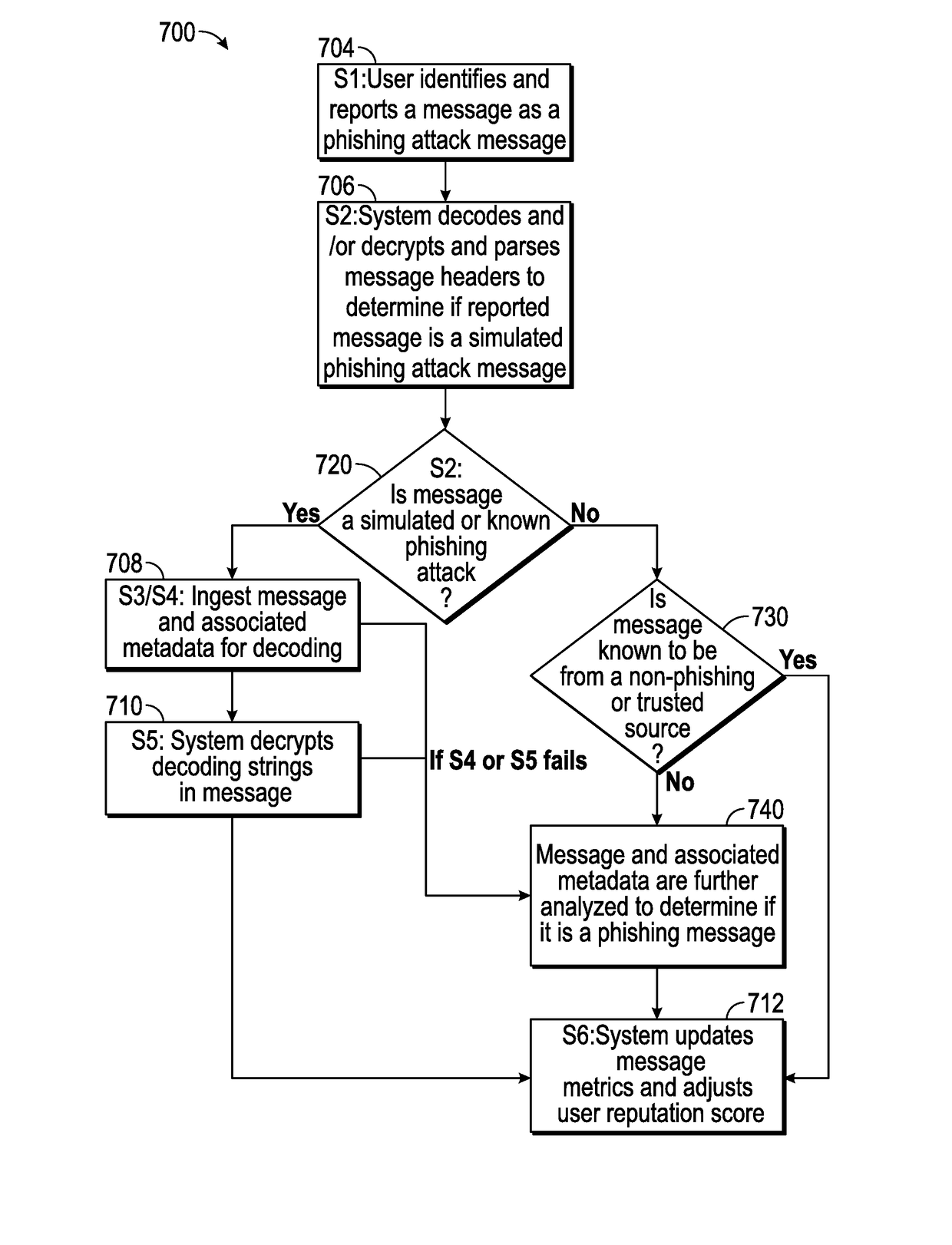
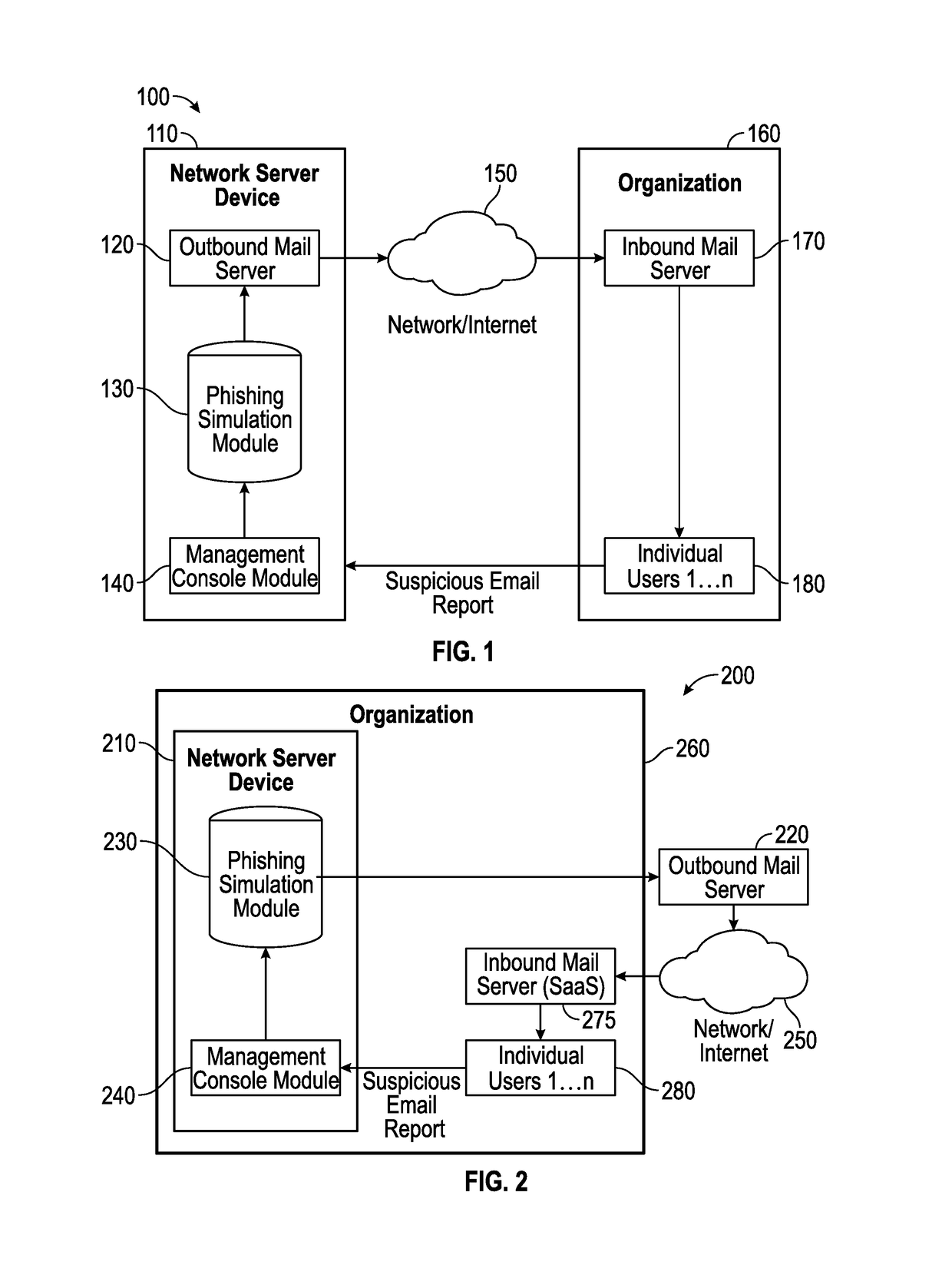
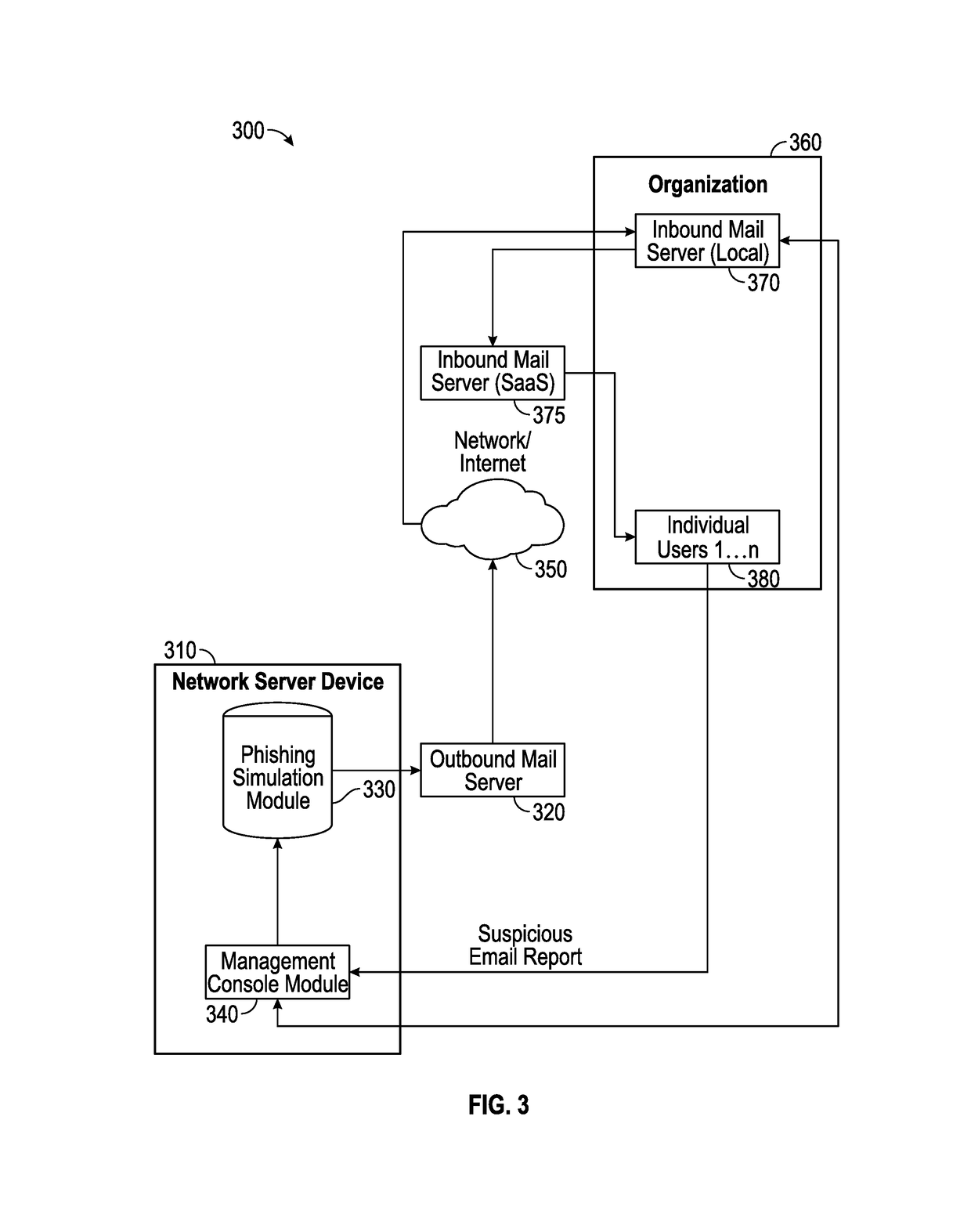
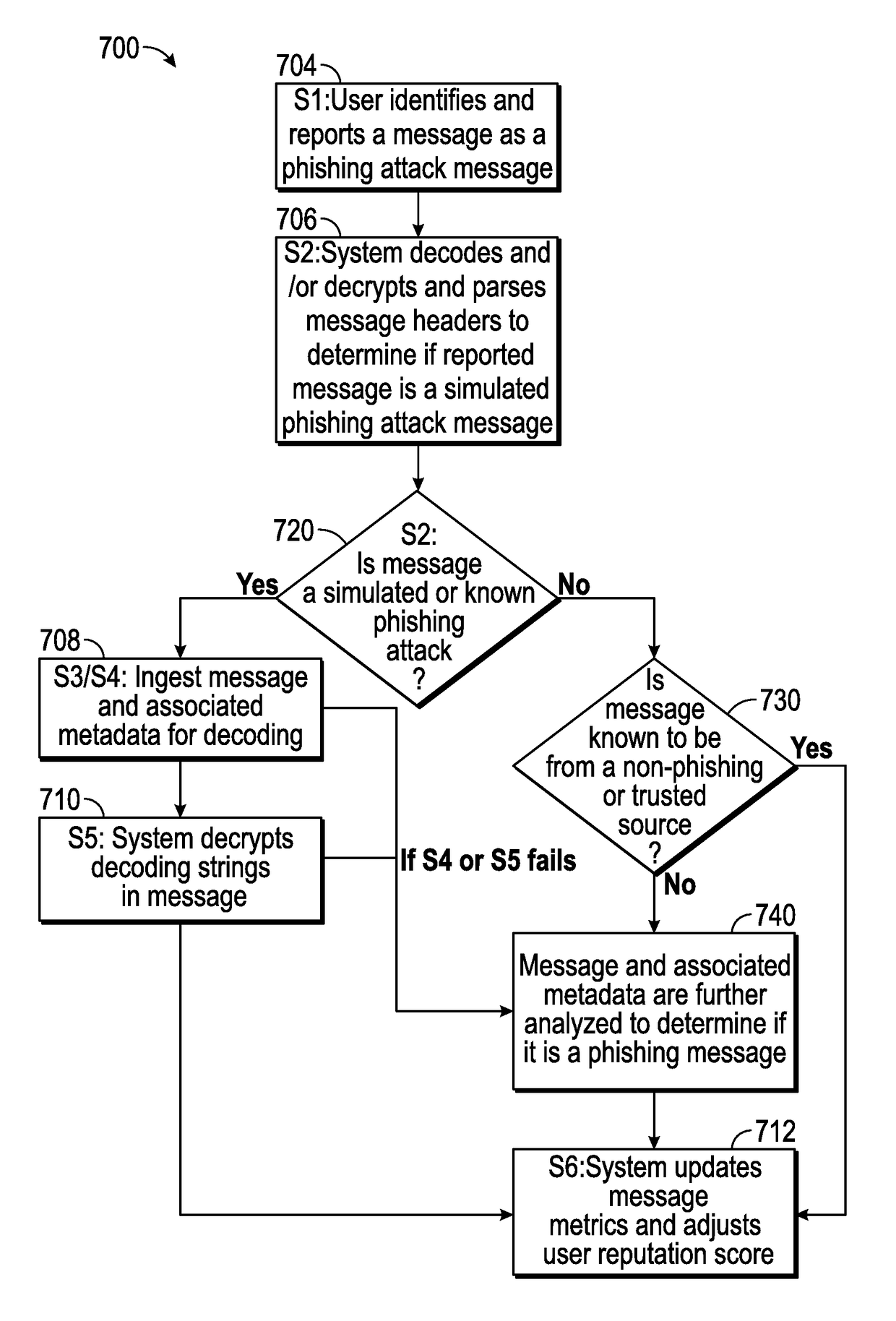
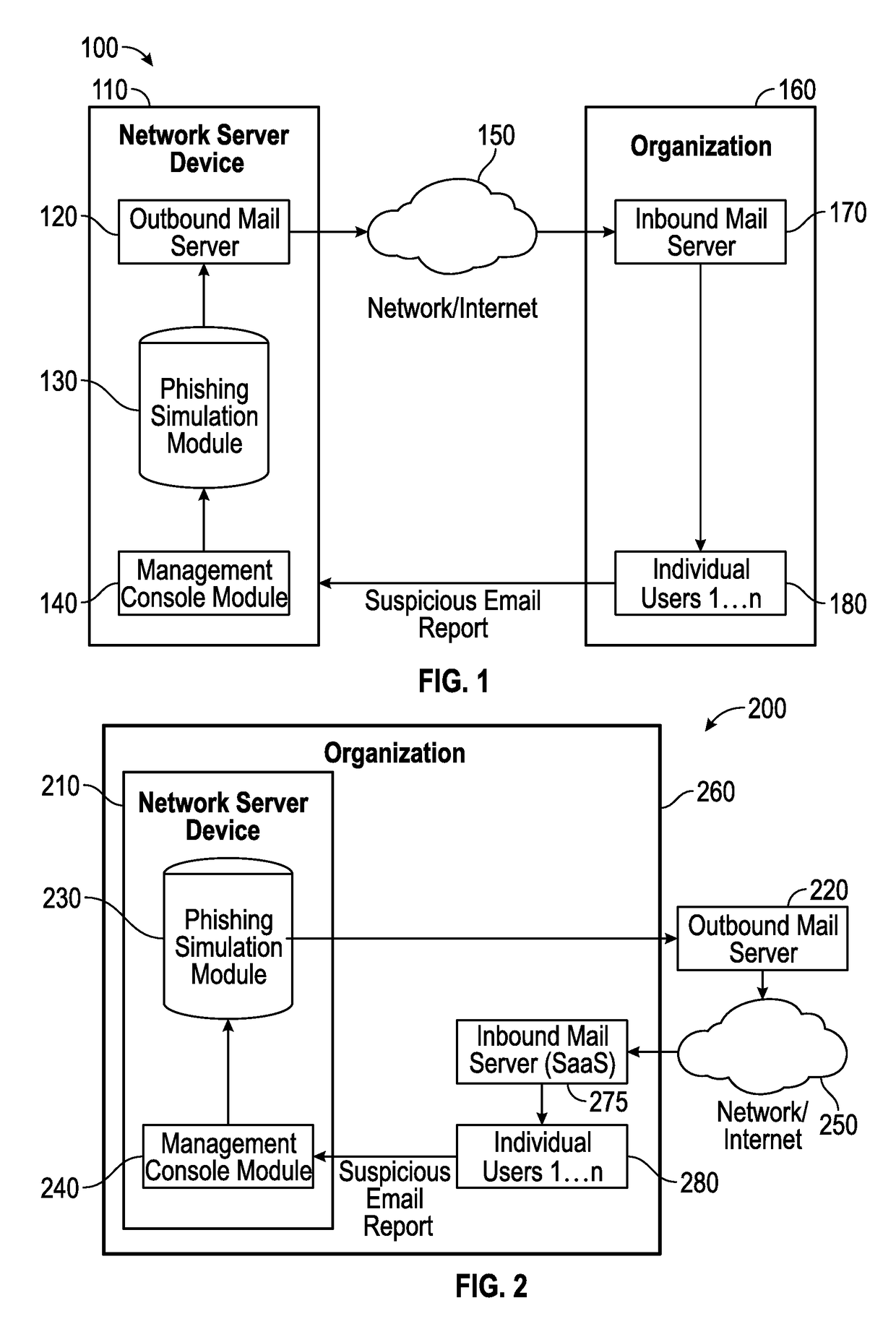
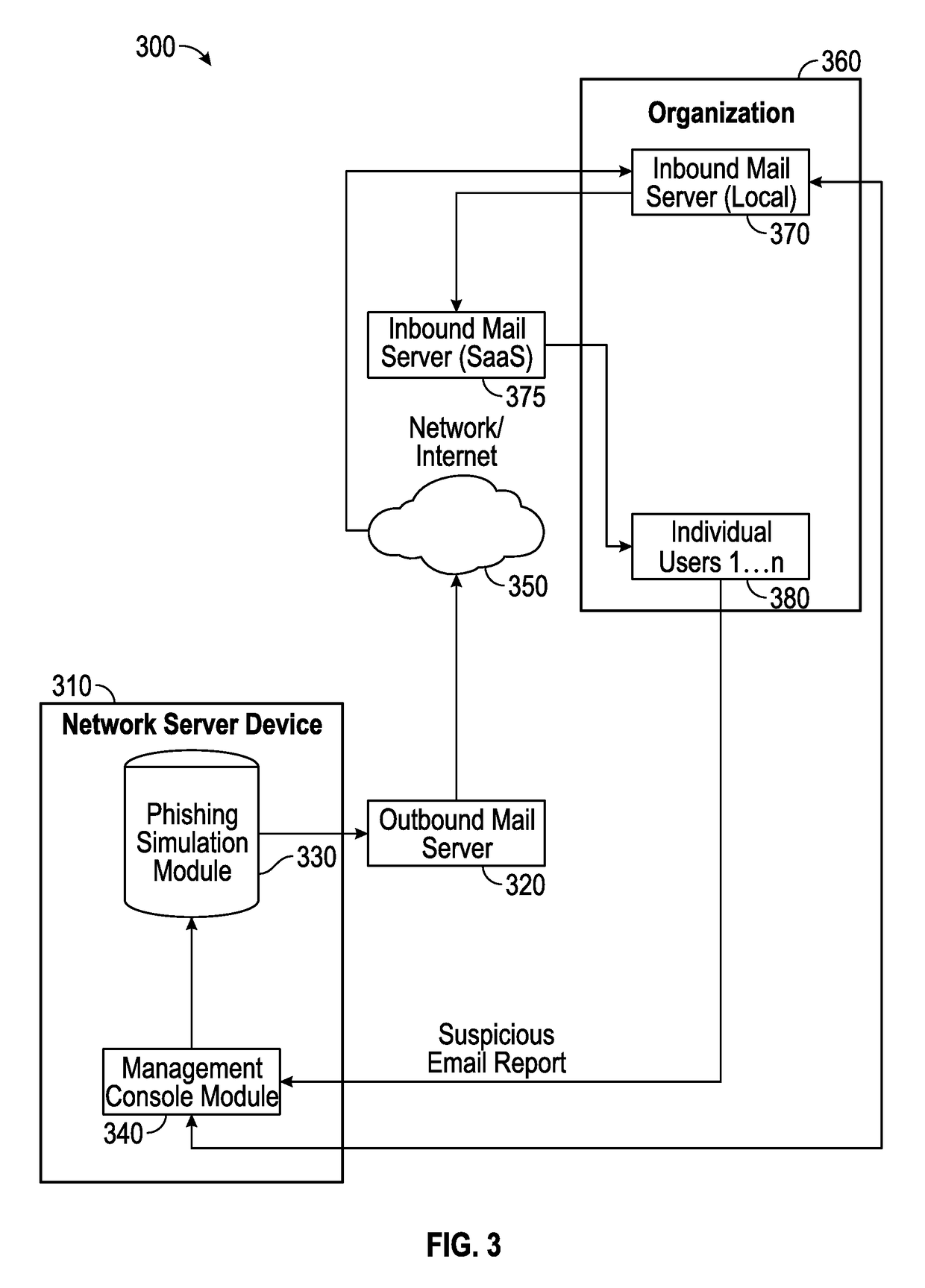
Suspicious message processing and incident response
ActiveUS20160301705A1Improve scoreReduce the overall heightData switching networksSpecial data processing applicationsMessage processingComputer science
The present invention relates to methods, network devices, and machine-readable media for an integrated environment for automated processing of reports of suspicious messages, and furthermore, to a network for distributing information about detected phishing attacks.
Owner:COFENSE INC
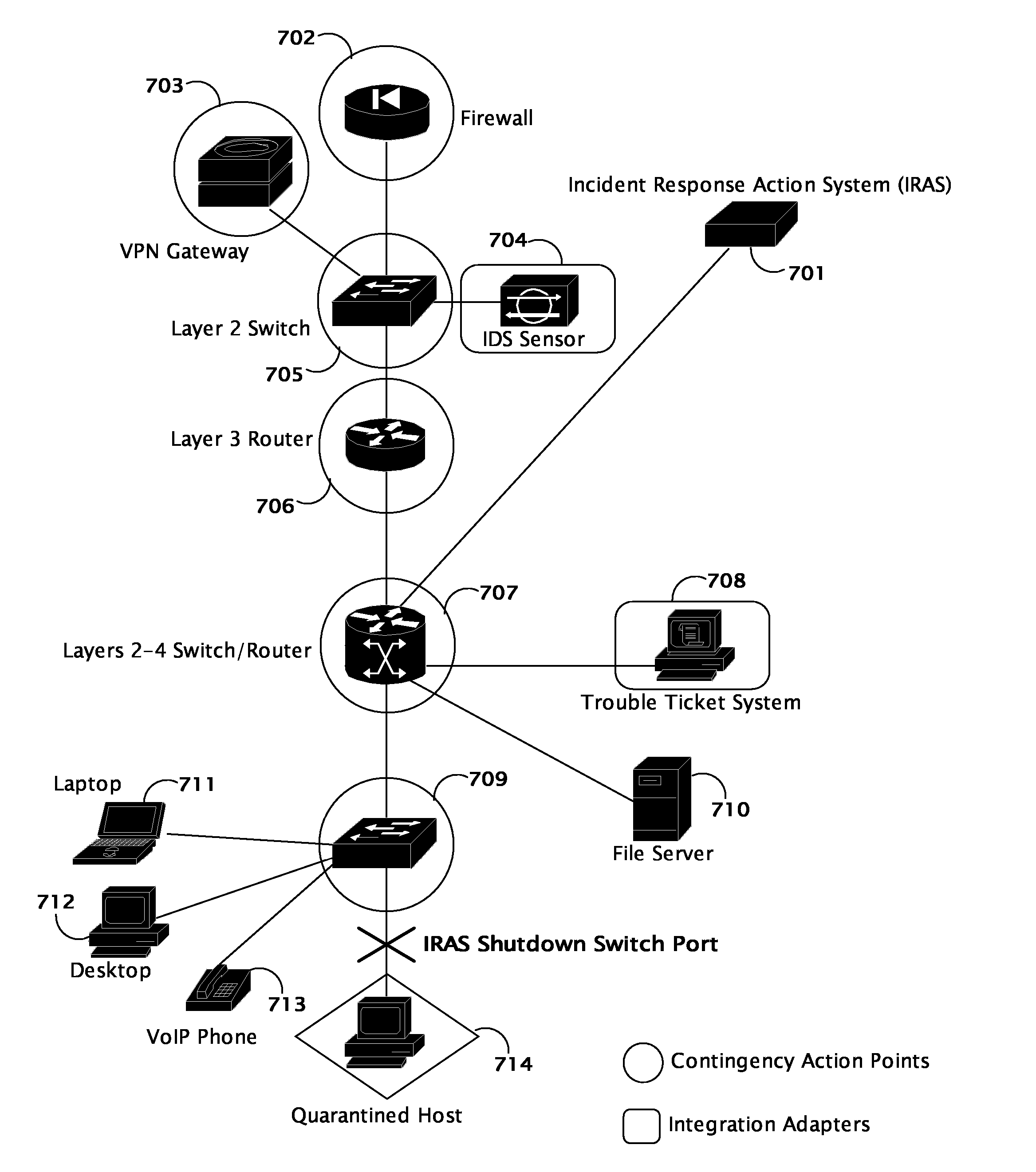
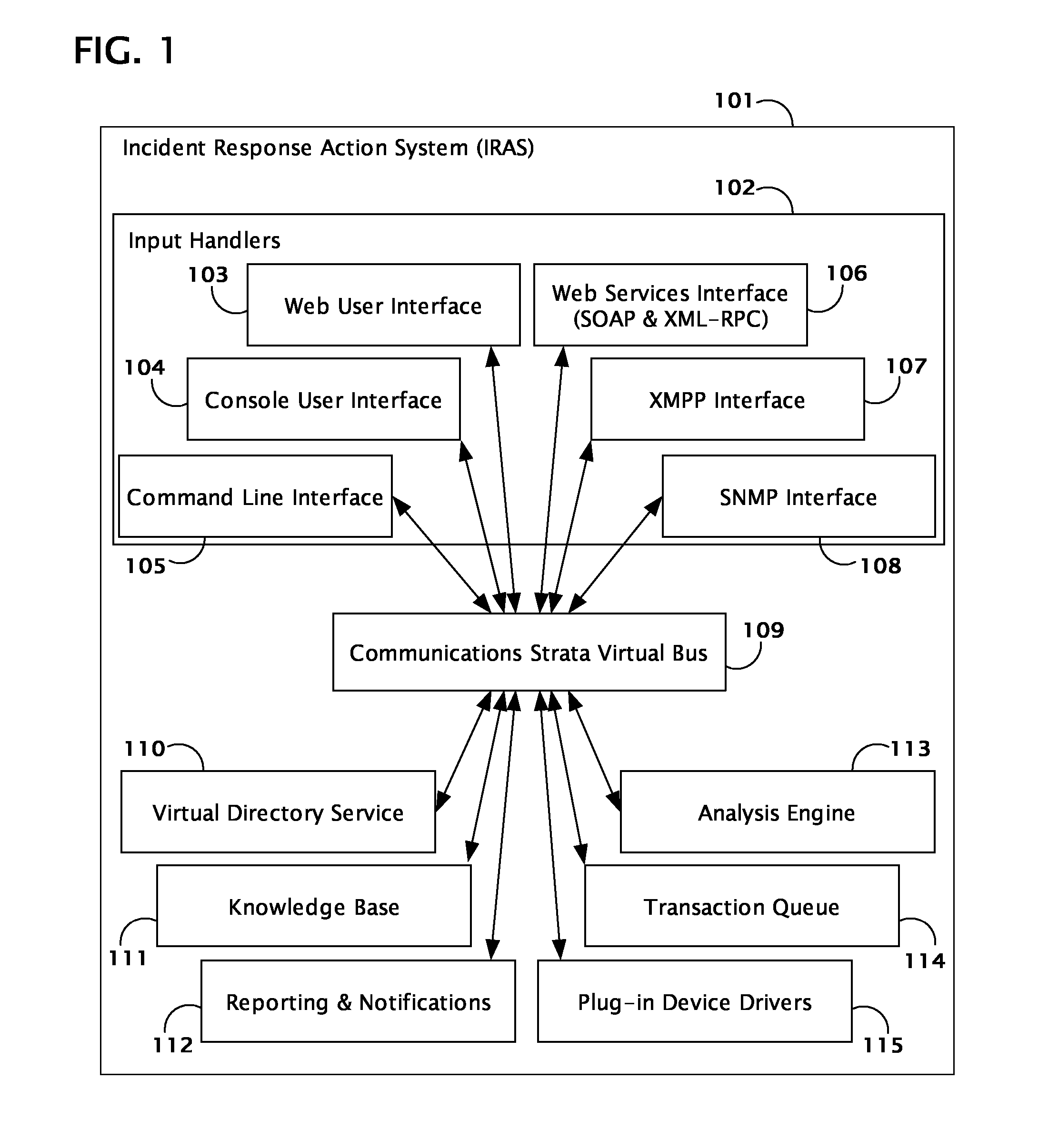
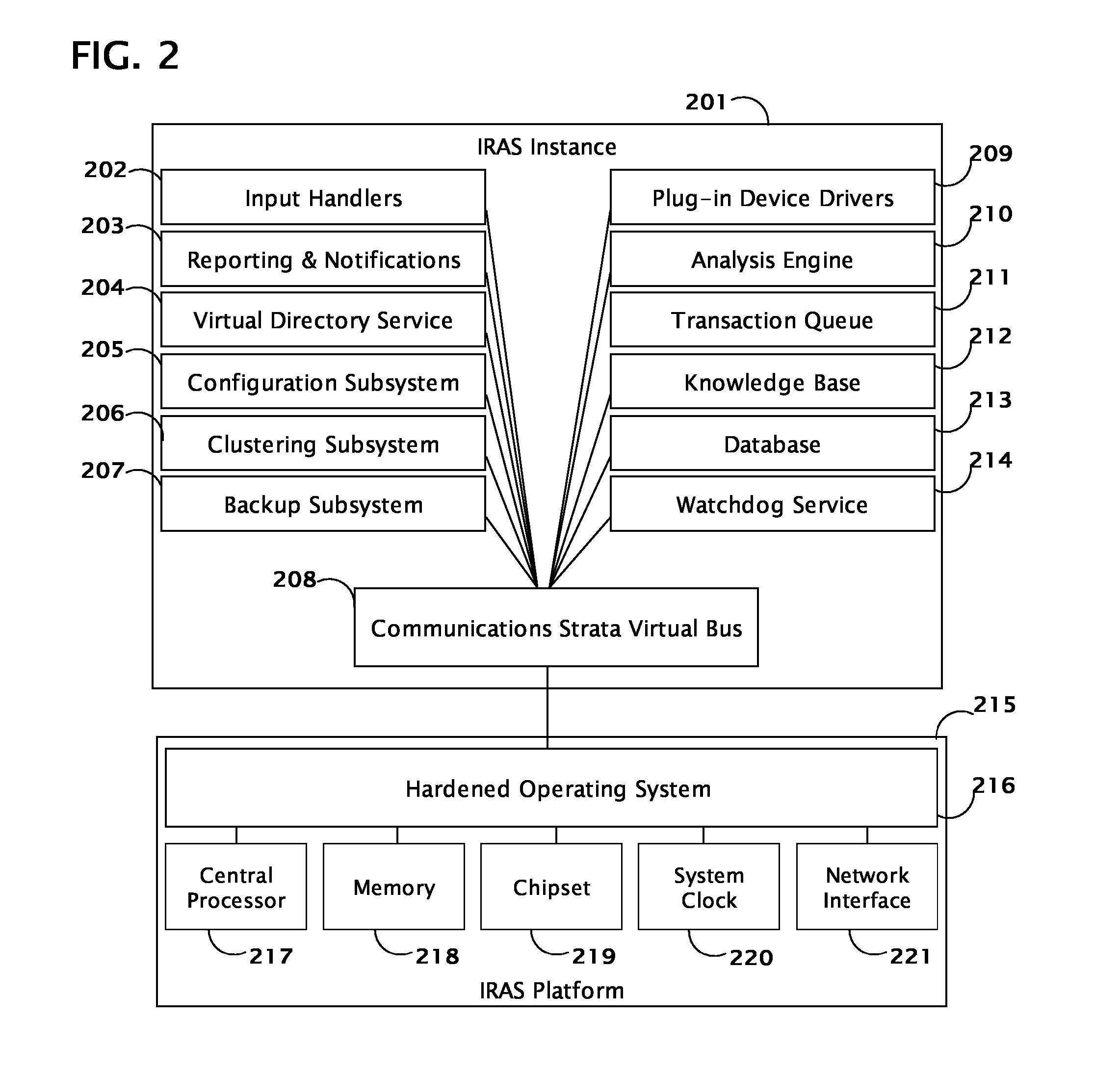
System and method for coordinating network incident response activities
ActiveUS20060212932A1Improve responseReduce decreaseMemory loss protectionError detection/correctionCountermeasureNetwork connection
The present invention provides a system and method to process information regarding a network attack through an automated workflow that actively reconfigures a plurality of heterogeneous network-attached devices and applications to dynamically counter the attack using the network's own self-defense mechanisms. The present invention leverages the security capabilities present within existing and new network-attached devices and applications to affect a distributed defense that immediately quarantines and / or mitigates attacks from hostile sources at multiple points simultaneously throughout the network. In a preferred embodiment, deployed countermeasures are automatically lifted following remediation activities.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Suspicious message processing and incident response
ActiveUS20170237776A1Improve acuityShorten the timeTransmissionSpecial data processing applicationsMessage processingPhishing attack
Owner:COFENSE INC
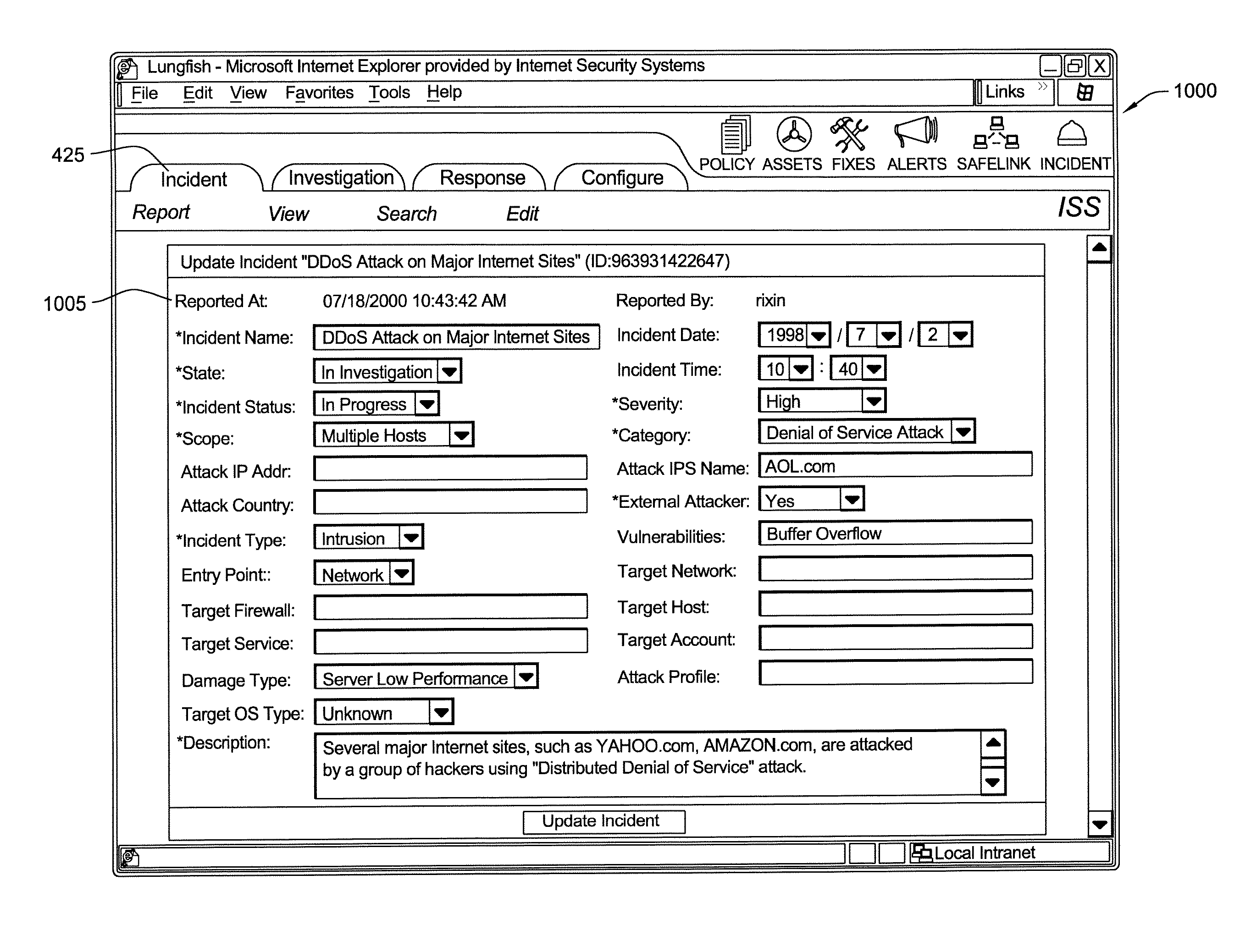
Method and System for Creating a Record for One or More Computer Security Incidents
ActiveUS20080016569A1Avoid unsafe incidentsMemory loss protectionError detection/correctionSafety management systemsDigital Signature Algorithm
A security management system can log, investigate, respond, and track computer security incidents that can occur in a networked computer system. In other words, the security management system can produce a security record of information related to the tracking of suspicious computer activity or actual computer security threats, such as denial of service attacks or other similar compromises to computers or computer networks. The security record can include, but is not limited to, date and times of computer security incidents, a name for a particular security incident, a security management system user, and a potential source of the computer security incident. The security record can be designed as a running log that saves or records all activity of a computer incident source as well as the activity of the security team responding to the computer incident source. To produce the security record, all data that relates to a computer incident and all data that relates to a computer incident response can be sent to a separate protected database, where data is protected by digital signature algorithms (DSAs).
Owner:KYNDRYL INC
Critical incident response management systems and methods
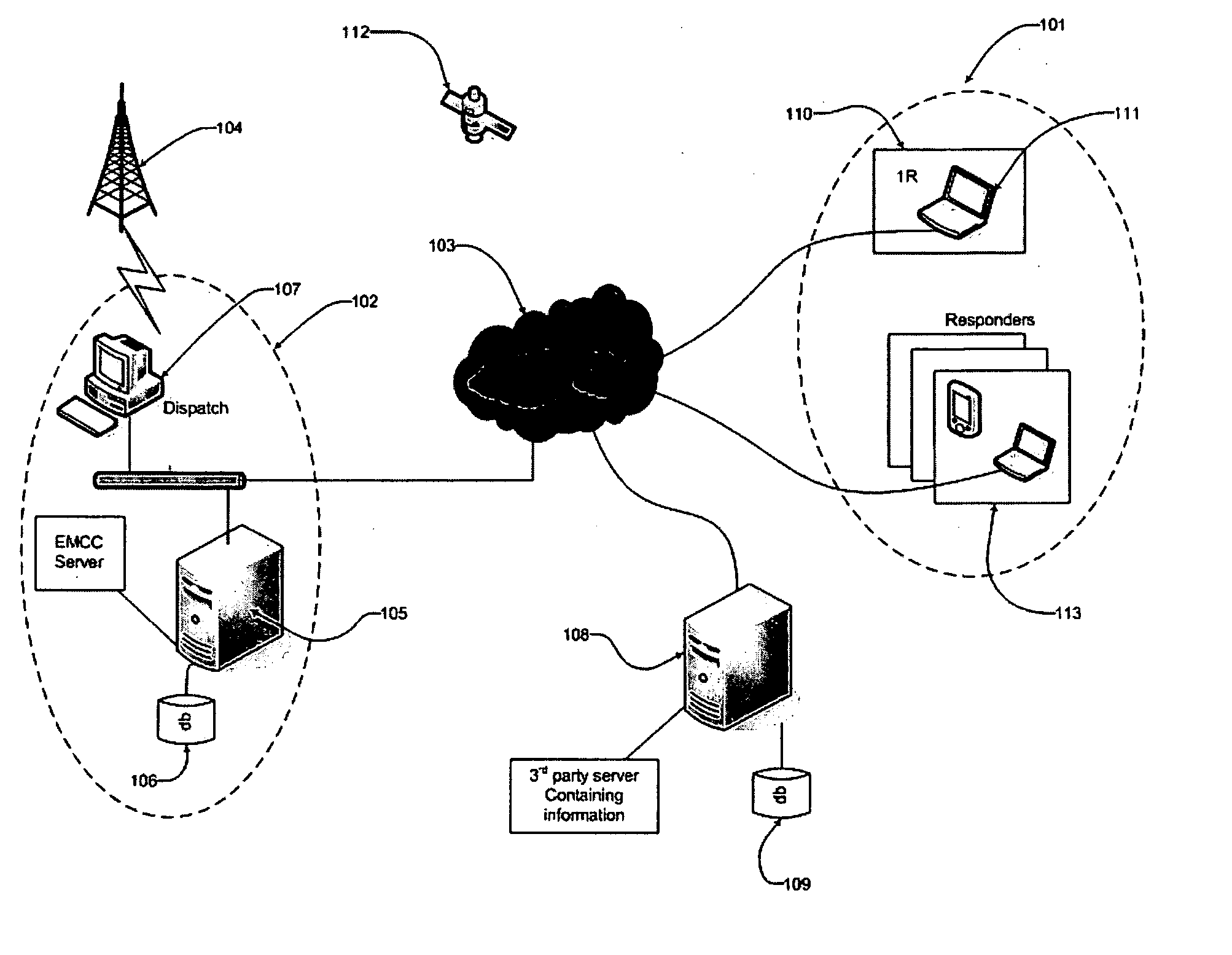
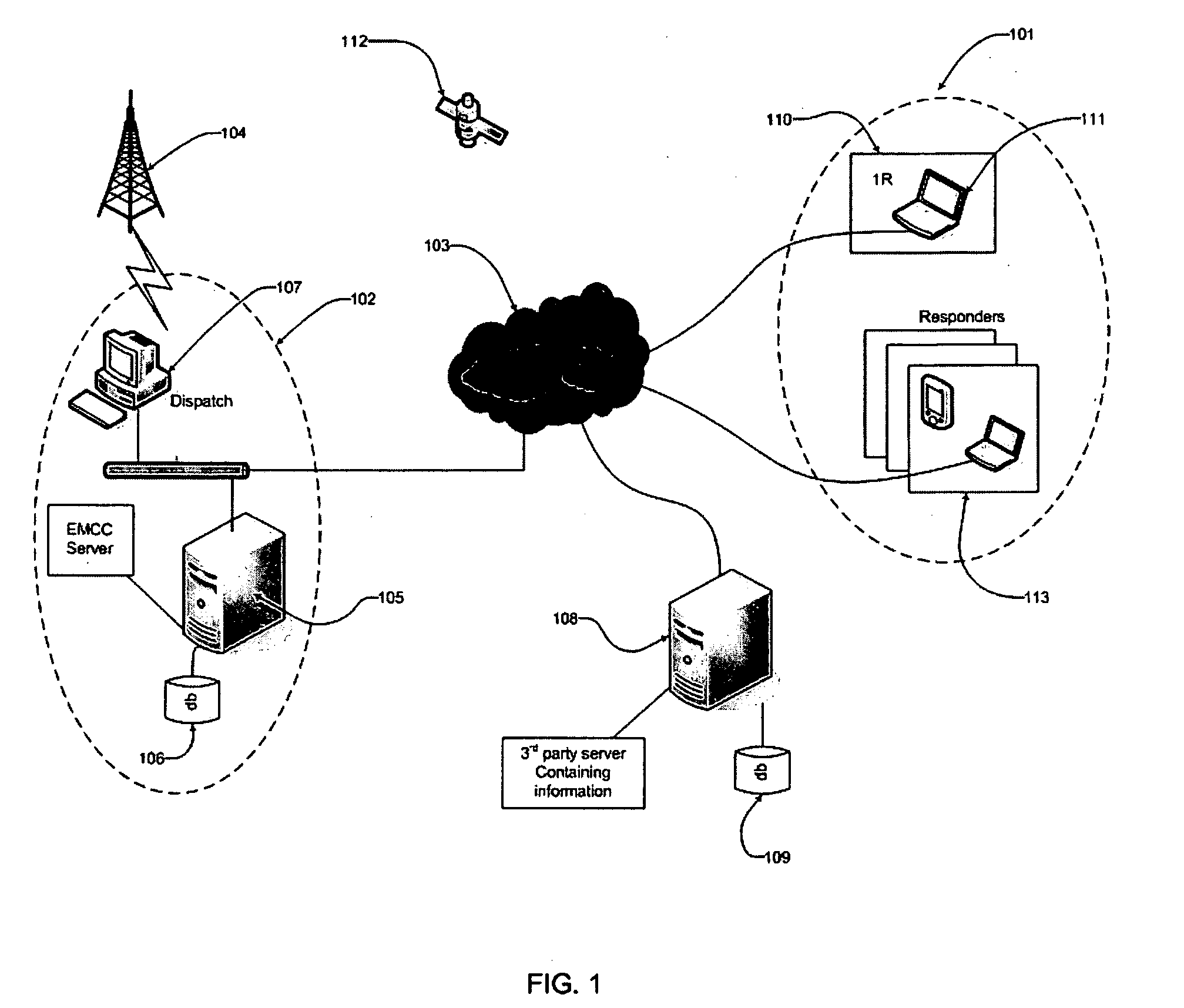
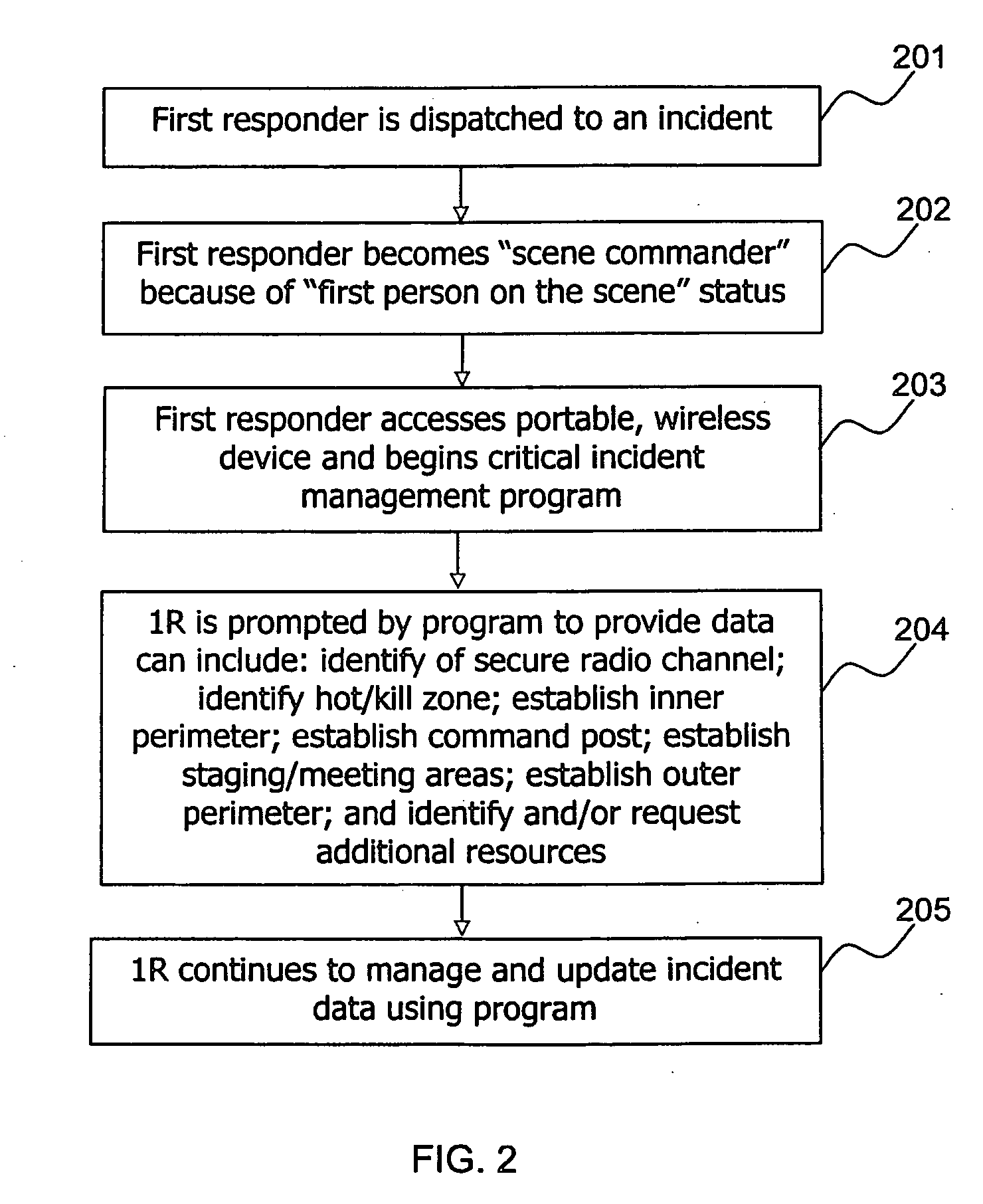
InactiveUS20070103294A1Easy to manageFrequency-division multiplex detailsTime-division multiplexLocation based systemsGeolocation
Systems and methods may enable first incident responder management and support. System and methods enabled by software may utilize communications networks and location based systems such as the Global Positioning System (GPS) to locate the incident and response units, and to relay and share critical incident management information for use by other emergency response operators associated with an emergency scene. Maps and icons may be accessed and utilized over devices in the field. Software modules enable a system operator to use maps and a selection of user interface objects such as custom icons symbolizing a list of responders (police, fire, rescue, military) called forward and may designate specific geographic positions for managing a crisis.
Owner:CODE 9000
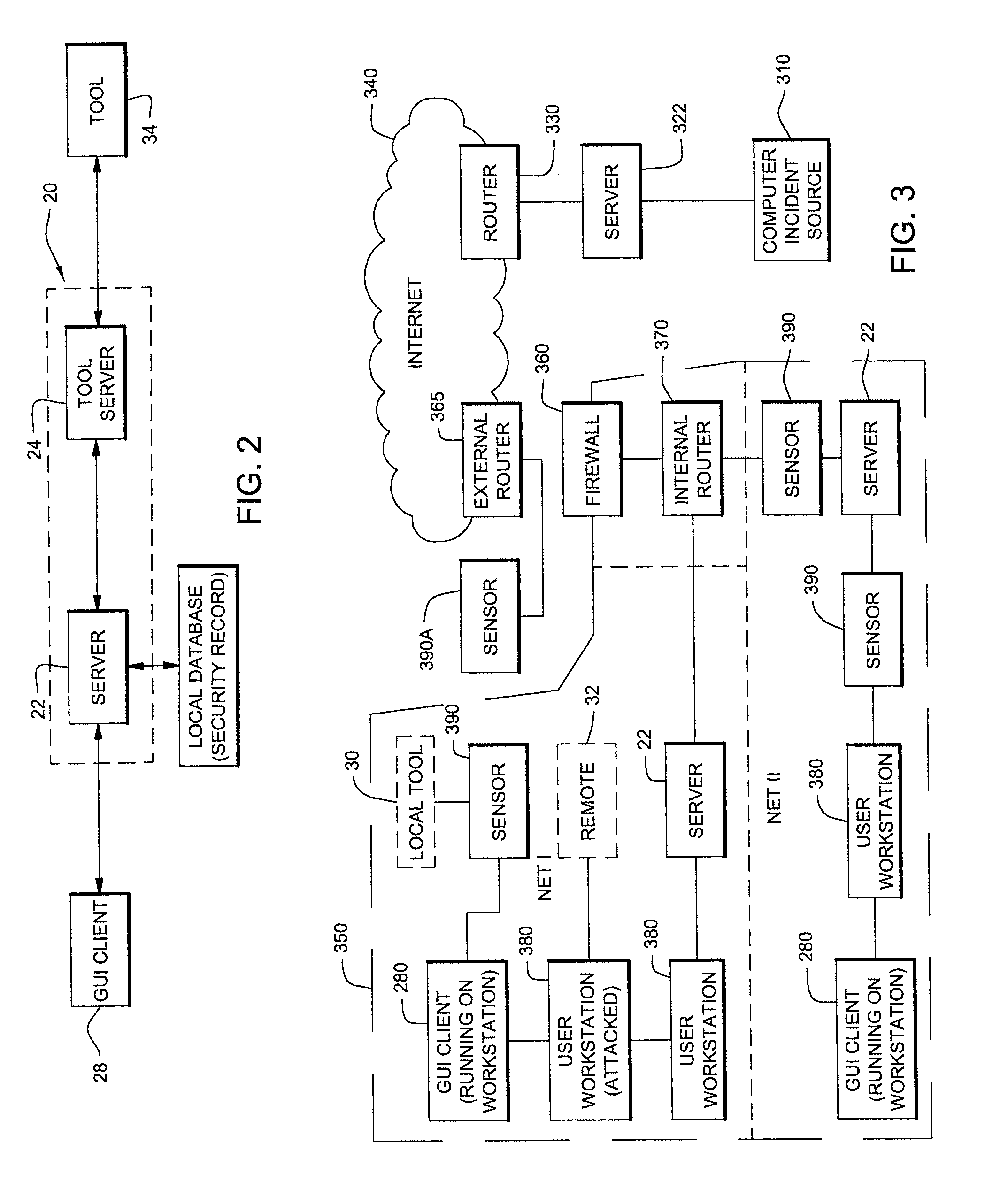
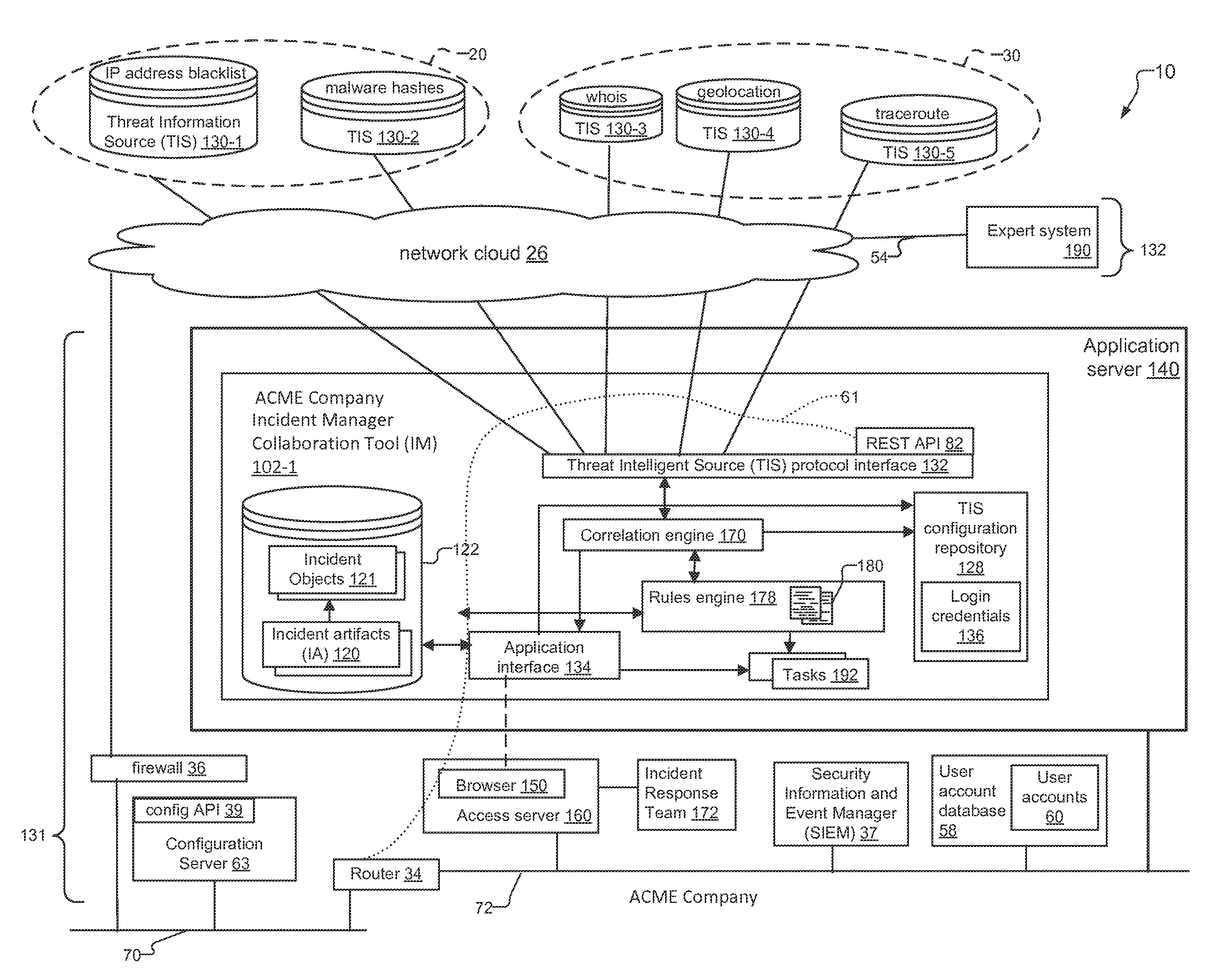
System for Tracking Data Security Threats and Method for Same
ActiveUS20160072836A1Information obtainedMemory loss protectionError detection/correctionIp addressInternet privacy
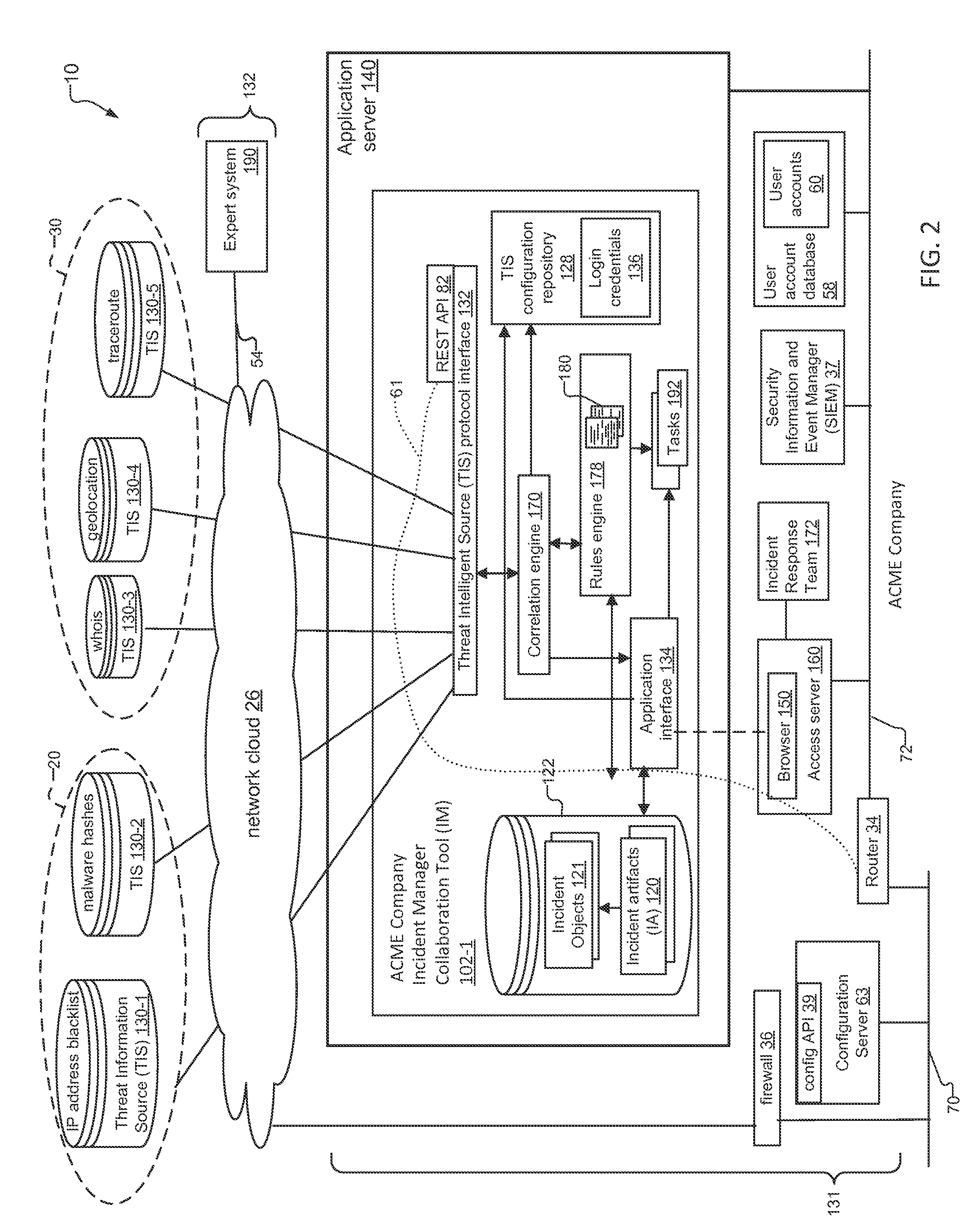
An incident response system and method for tracking data security incidents in enterprise networks is disclosed. An Incident Manager application (IM) stores incident objects and incident artifacts (IAs) created in response to the incidents, where the incident objects include the information for the incident and the IAs are associated with data resources (e.g. IP addresses and malware hashes) identified within the incident objects. In response to creation of the IAs, the IM issues queries against one or more external threat intelligence sources (TISs) to obtain information associated with the IAs and augments the IAs with the obtained information. In examples, the IM can identify known threats by comparing the contents of IAs against TIS(s) of known threats, and can identify potential trends by correlating the created incident objects and augmented IAs for an incident with incident objects and IAs stored for other incidents.
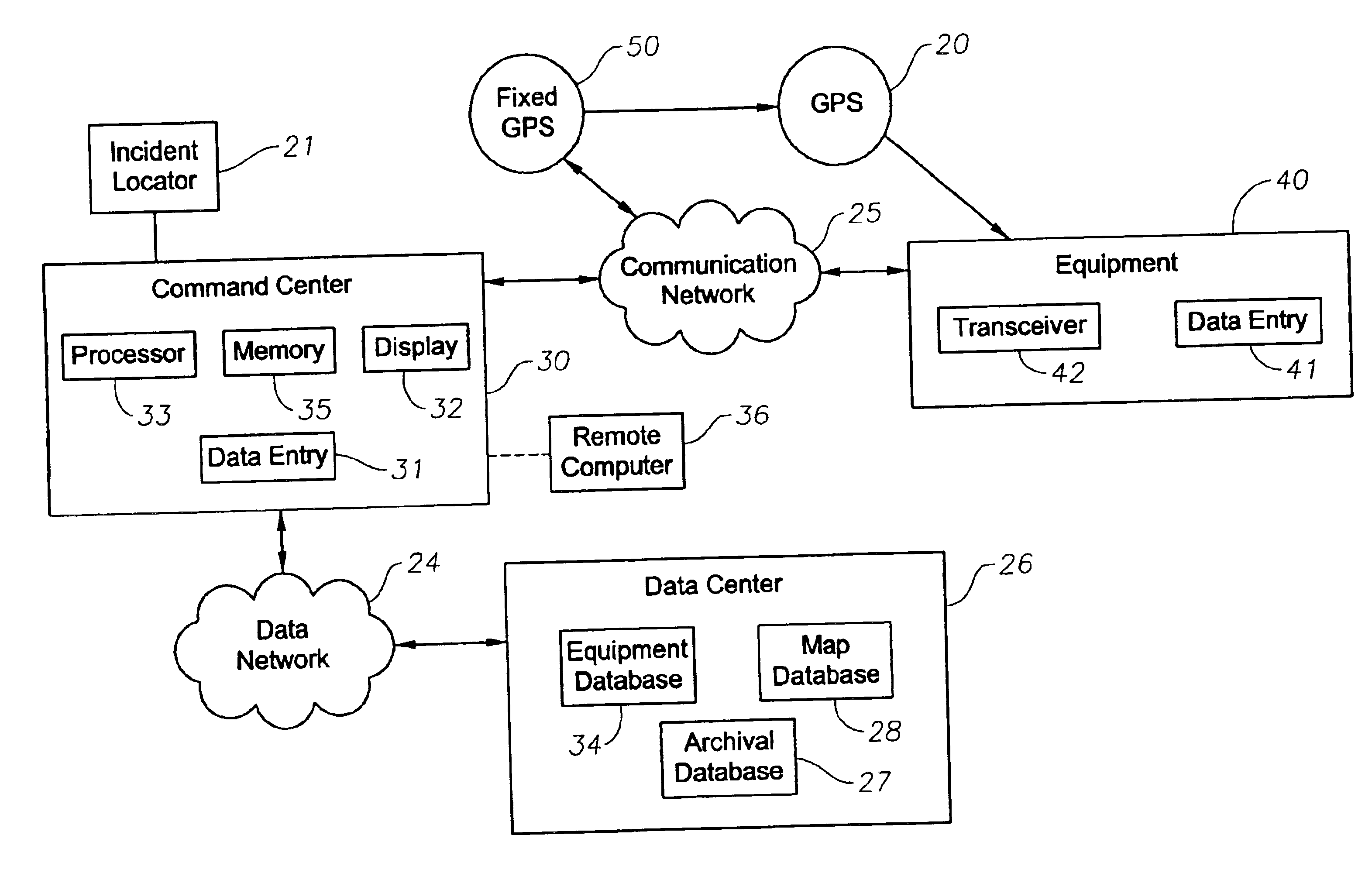
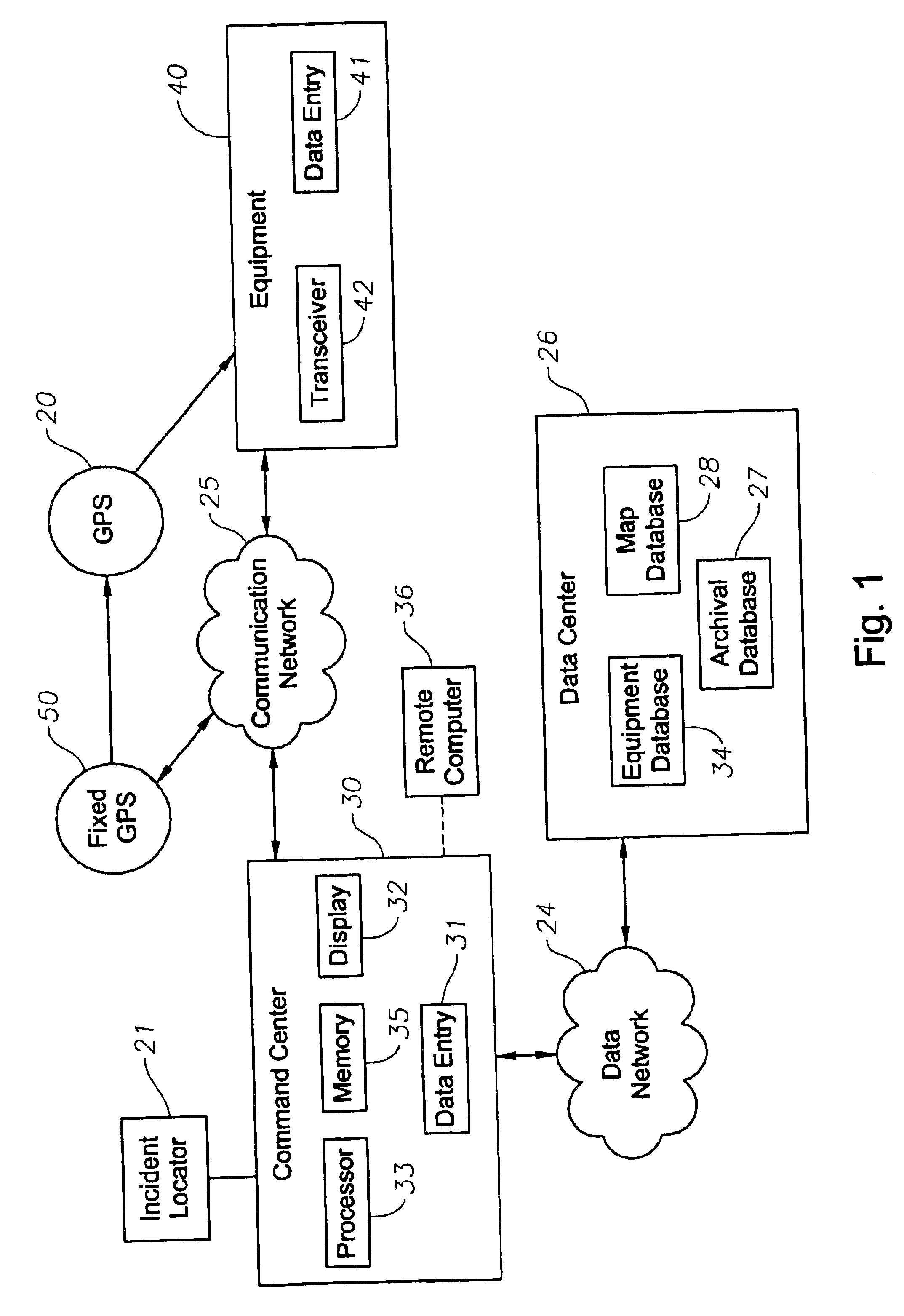
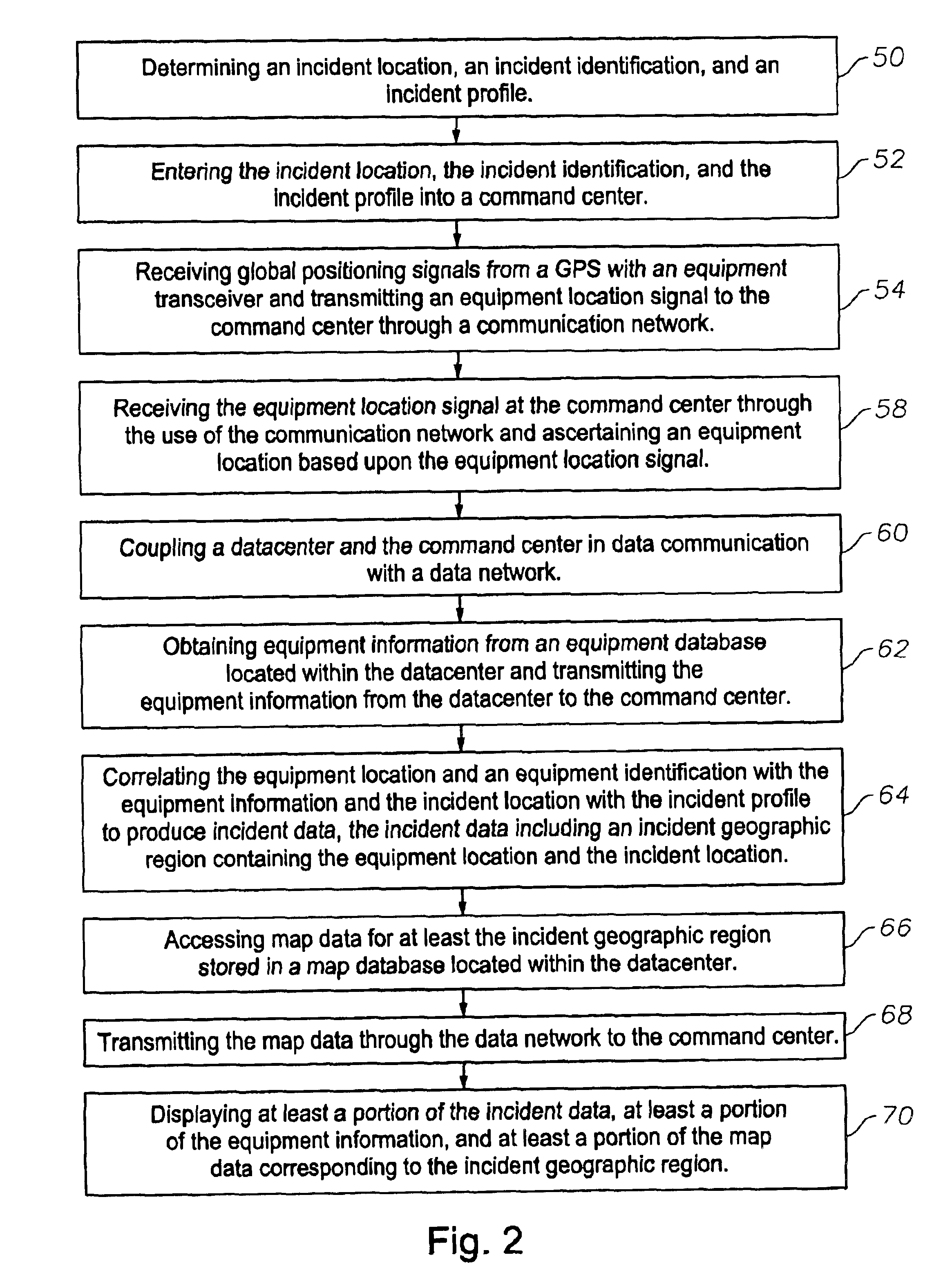
Owner:GREEN MARKET SQUARE LTD
Interactive system for monitoring and inventory of emergency vehicles and equipment and associated methods
A system on interactive tracking and inventorying of incident response equipment and associated methods is provided. The system and methods enable command centers to determine the geographic location of all available emergency response equipment that are capable of responding to an incident. The systems and methods allow the inventory to be updated as equipment and personnel are spent during the course of the incident. The location of the equipment and personnel can be viewed on a topography map, as well as an aerial map, to enable the incident command to determine the atmospheric surroundings of each piece of equipment. The maps can be superimposed so that more than one type of map data can be viewed simultaneously.
Owner:CONCENTRAX
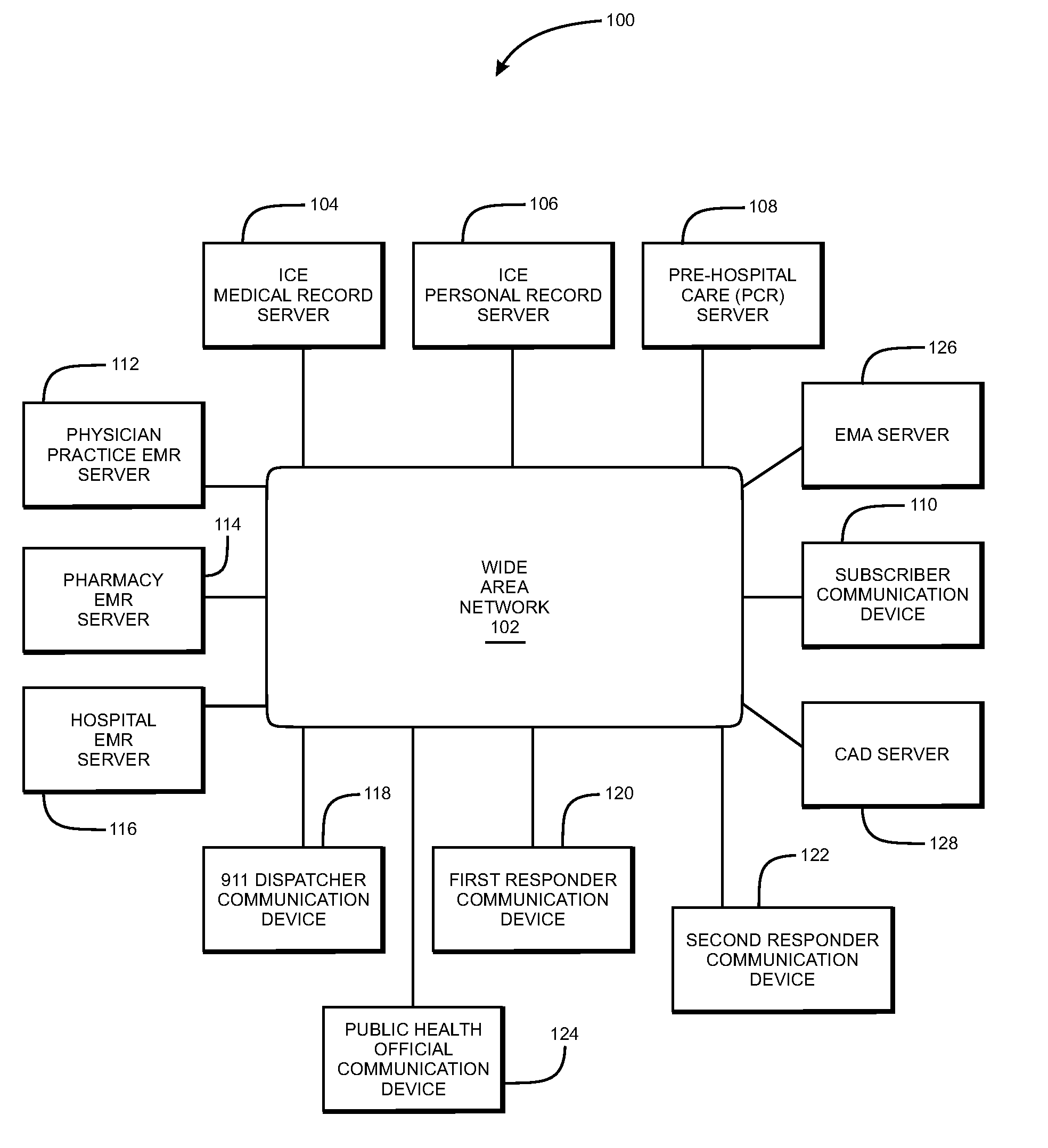
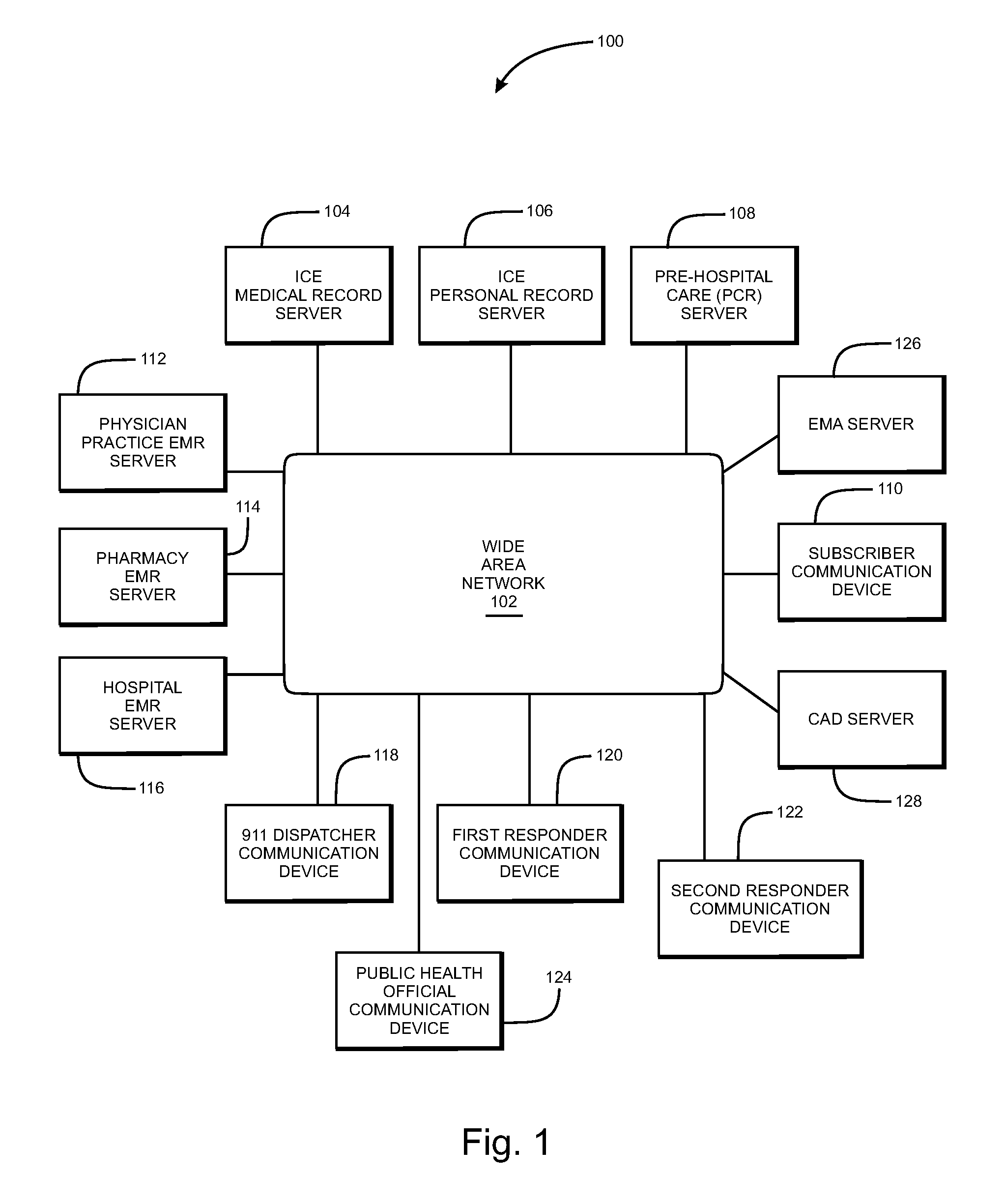
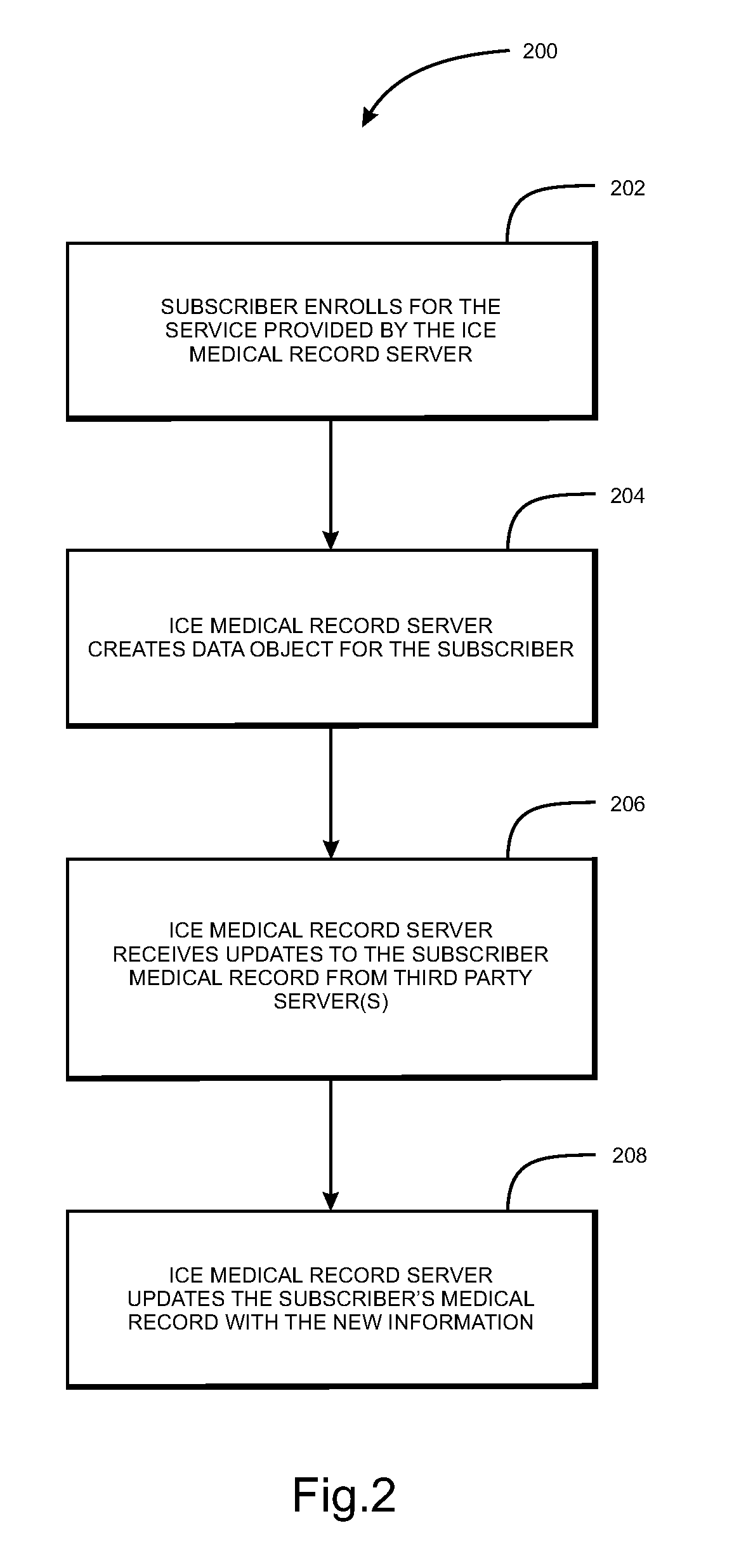
System and method of aggregating and disseminating in-case-of-emergency medical and personal information
InactiveUS20070250348A1Data processing applicationsPatient personal data managementMedical recordCommunication device
A system for aggregating and disseminating in-case-of-emergency (ICE) medical information to medical units. The system includes an ICE medical record server that stores medical records of respective subscribers, and automatically receive updates from health service entities visited by subscribers. When contacted by emergency dispatchers or first responders, the server sends subscribers medical information to first responders, emergency management agencies directly, via a dispatcher, or via a computer aided dispatch (CAD) system. The medical information may be arranged, emphasized, and / or filtered in a manner relevant to the on-going emergency. A communication device may wirelessly receive the medical information and pre-populate a pre-hospital care form with the information, which may be further orally annotated by the first responder. The completed PCR may then be sent to a PCR server for subsequent access by medical units that subsequently treat the subscriber. The medical server may further assist a public health agency to disseminate emergency information to selected subscribers, responders, and public health alerting systems. An ICE personal server for storing important personal documents is also disclosed. A PCR server is also disclosed that can disseminate aggregate PCR information in near real-time to an emergency management agency (EMA) system for developing incident response plans during a wide area emergency.
Owner:VITAL DATA TECH
Suspicious message processing and incident response
ActiveUS9906554B2Improve acuityShorten the timeTransmissionSpecial data processing applicationsMessage processingPhishing attack
The present invention relates to methods, network devices, and machine-readable media for an integrated environment for automated processing of reports of suspicious messages, and furthermore, to a network for distributing information about detected phishing attacks.
Owner:COFENSE INC
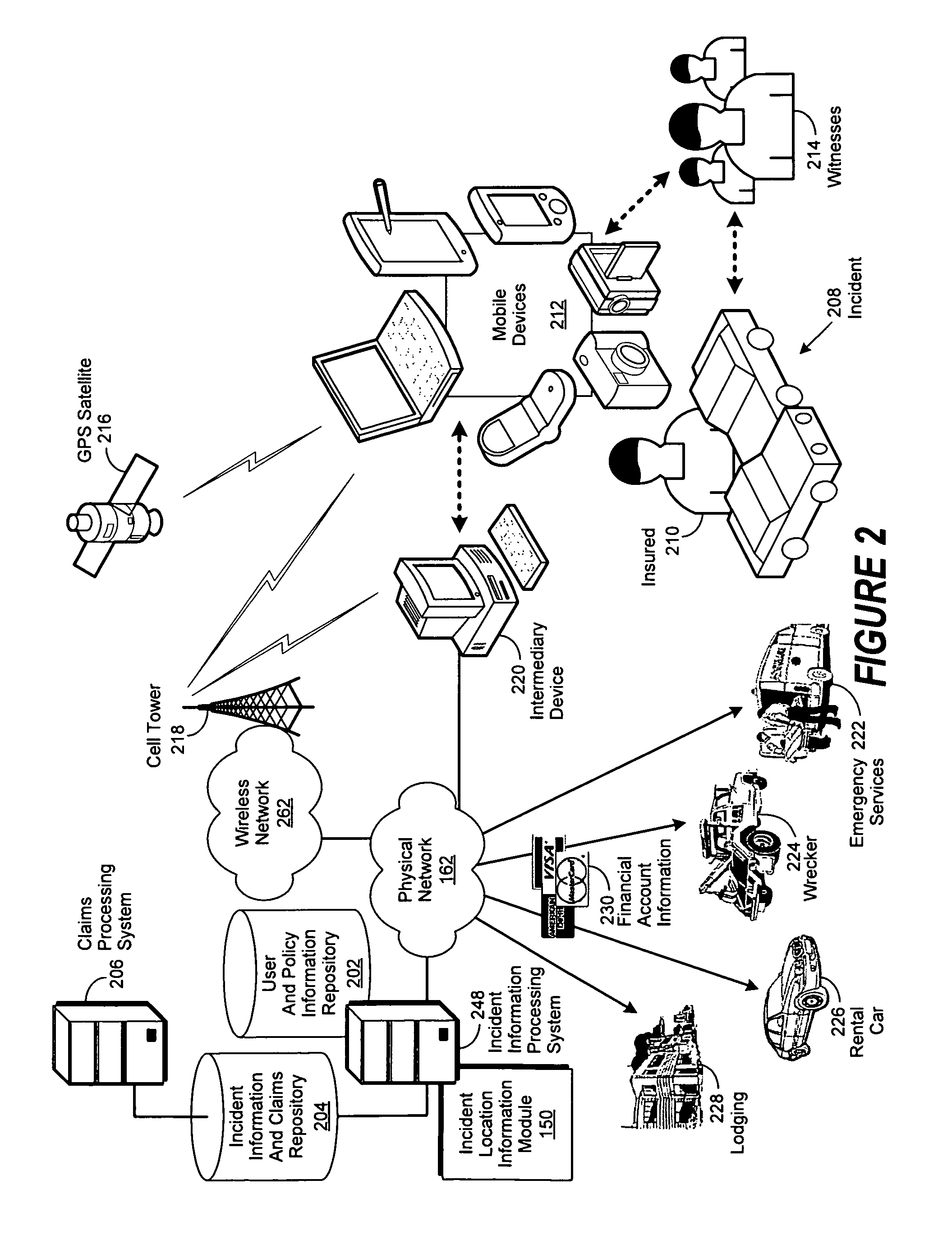
Systems and methods for claims processing via mobile device
A method, system and computer-usable medium are disclosed for the processing of information collected by a mobile device at the site of an incident. An incident information processing system, comprising an incident location information module, receives incident information provided in a communication originated from a mobile device. The received incident information is processed by the incident location information module to provide location information, which is then used to provide incident response services. Image and audio information relating to the incident are likewise provided by the mobile device for processing into incident information. Incident statement questions are generated by the incident information processing system and are then presented via the mobile device for response by various parties associated with the incident. Responses to the questions are collected via the mobile device, processed into incident statements, and stored in the incident information and claims repository.
Owner:USAA
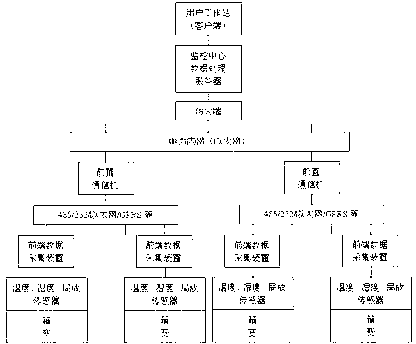
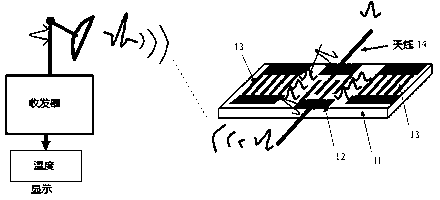
Power distribution net box type transformer environmental parameters on-line monitoring system
ActiveCN103107597AReal-time online security monitoringSolve the problem of power supplyCircuit arrangementsInformation technology support systemTransformerData acquisition
The invention relates to a power distribution net box type transformer environmental parameters on-line monitoring system which includes the steps that aiming at any one of box-type transformer substations, the power distribution net box type transformer environmental parameters on-line monitoring system is provided with a plurality of sensors, wherein at least the temperature of a high pressure charged body in the environmental parameters of the box-type transformer substations, the high frequency partial discharge, the temperature and humidity in the box-type substation are monitored correspondingly by the sensors, and the monitored data of the various sensors are received and sent to a front-end data acquisition unit of a monitoring center based on a wired or wireless communication mode. The data processing server device of the monitoring center carries out the storage and processing analysis for the received data to generate a real-time dynamic monitoring curve and produces an audible and visual alarm when the monitored data exceed a set threshold value, and meanwhile the alarm information can notify attendants in the relevant areas in a text message form, so that the time of incident response is shortened and the economic loss is reduced.
Owner:SHANGHAI OUYI INTELLIGENT NETWORK +3
Real-time Deployment of Incident Response Roadmap
ActiveUS20140278664A1Effectively actEasy to understandTesting/monitoring control systemsSubstation equipmentInformation securityComputer science
In various representative aspects, a method and a system that guide an incident response team to efficiently respond to an information security incident based on a roadmap are disclosed herein. A delegated incident response lead may oversee the whole process, including the creation of the roadmap, the performance of the team members, and the statuses of all tasks. When an incident occurs, incident response team members are notified, and delegated tasks in the roadmap are laid out. With a secure collaboration platform, the incident response team may work together in a secure, uncompromised environment.
Owner:FORTINET
Automatic testing method, device, equipment and system
ActiveCN104699598AGuaranteed performance qualitySolve problems where the performance quality of the application cannot be adequately guaranteedSoftware testing/debuggingComputer terminalTest phase
The invention discloses an automatic testing method, device, equipment and system and belongs to the technical field of computers. The method comprises the following steps: implementing an automated script to test a test case; in the implementing process of the automated script, collecting the performance data of the test case and / or a mobile terminal, and obtaining a performance test report form of the test case according to the performance data. As the method collects the performance data of the test case and / or the mobile terminal and obtains the performance test report form of the test case according to the performance data in the implementing process of the automated script, the method solves the problem that in the prior art, a test of an application program is only a basic incident response test and the performance quality of the application program cannot be fully ensured, and achieves the effects of automatically collecting and analyzing the performance data in the test phase of the application program, reducing the labor cost, and fully ensuring the performance quality of the application program.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
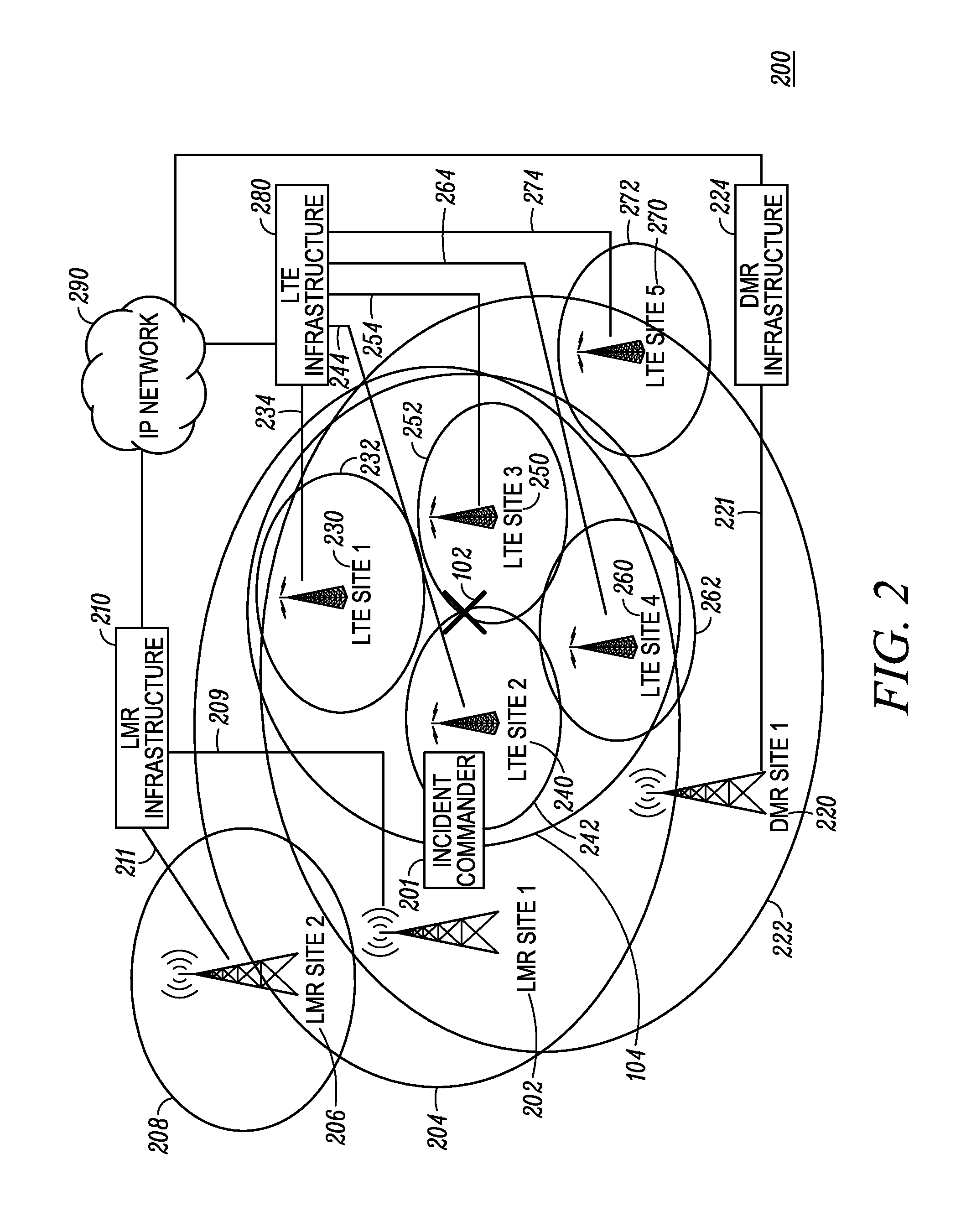
Dynamically re-configured incident scene communication based on incident scene factors
An incident commander computing device dynamically reconfigures subscriber unit usage of radio access networks by first identifying, based at least on a type of incident occurring within a particular geographic area, a first incident response group having a first higher priority for responding to the incident and a second incident response group having a second lower priority for responding to the incident, then identifying a first higher priority radio access network having a sufficient coverage level across the particular geographic area and a second lower priority radio access network having a sufficient coverage level across the particular geographic area, and finally assigning the first incident response group to the first higher priority radio access network and assigning the second incident response group to the second lower priority radio access network.
Owner:MOTOROLA SOLUTIONS INC
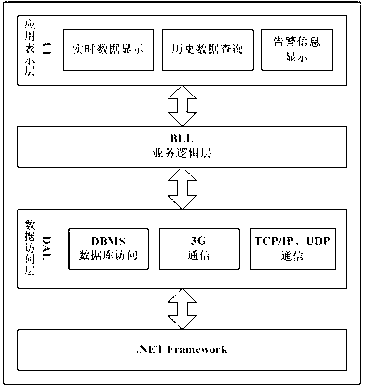
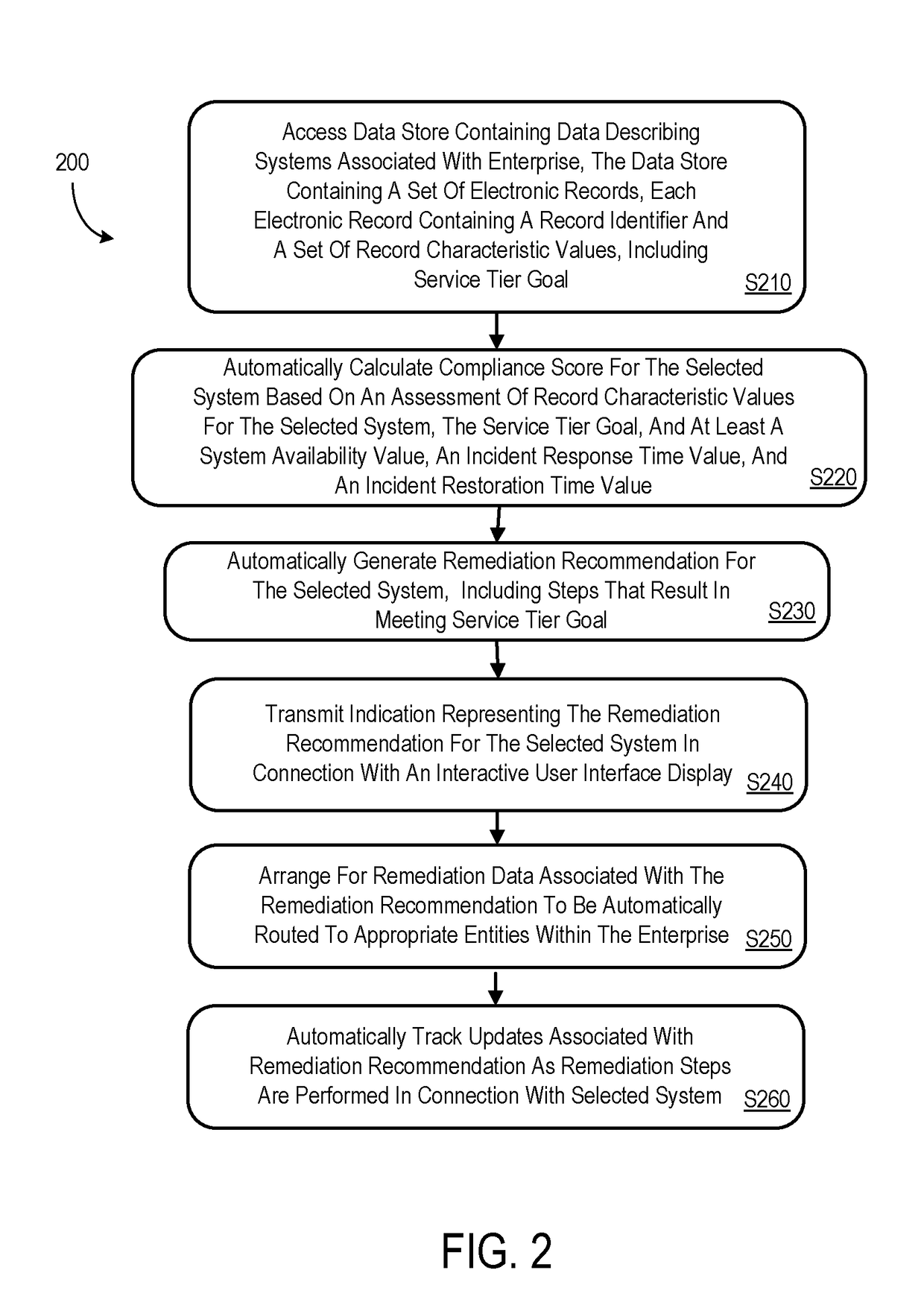
System compliance assessment utilizing service tiers
A data store may contain data describing systems associated with an enterprise. The data store may contain electronic records, each containing a record identifier and a set of record characteristic values, including a service tier goal. A compliance score may be automatically calculated based on an assessment of record characteristic values, the service tier goal, and at least a system availability value, an incident response time value, and an incident restoration time value. A remediation recommendation may be generated, including steps that, when performed, will result in the selected system meeting the service tier goal. An indication representing the remediation recommendation may then be transmitted in connection with an interactive user interface display. According to some embodiments, remediation data is automatically routed to appropriate entities within the enterprise and updates associated with the remediation recommendation are automatically tracked as remediation steps are performed in connection with the selected system.
Owner:HARTFORD FIRE INSURANCE
GPS Pathfinder Cell Phone And Method
ActiveUS20090182587A1Improve effectivenessQuick instructionsFinanceRoad vehicles traffic controlComputer networkNormal cell
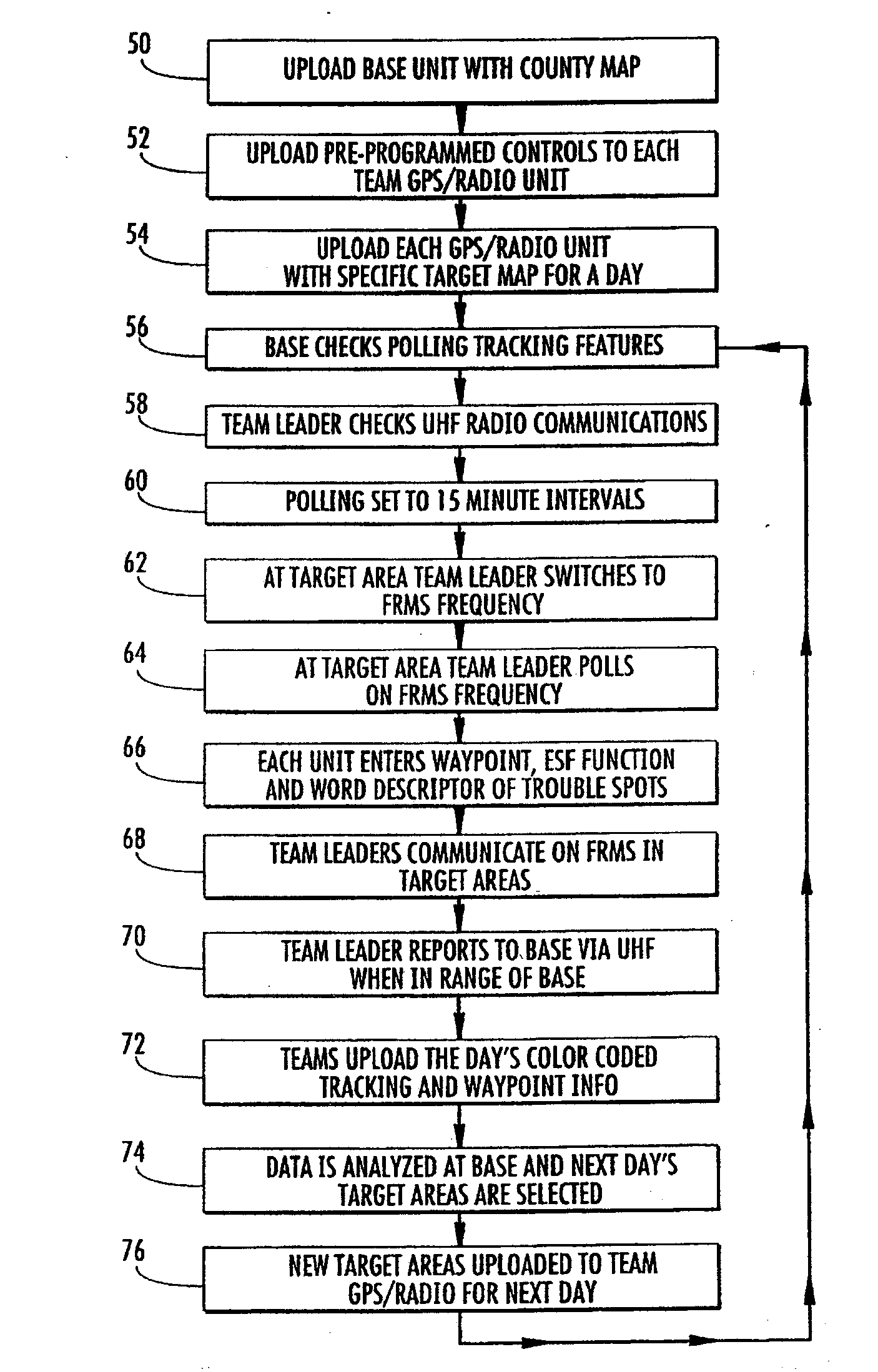
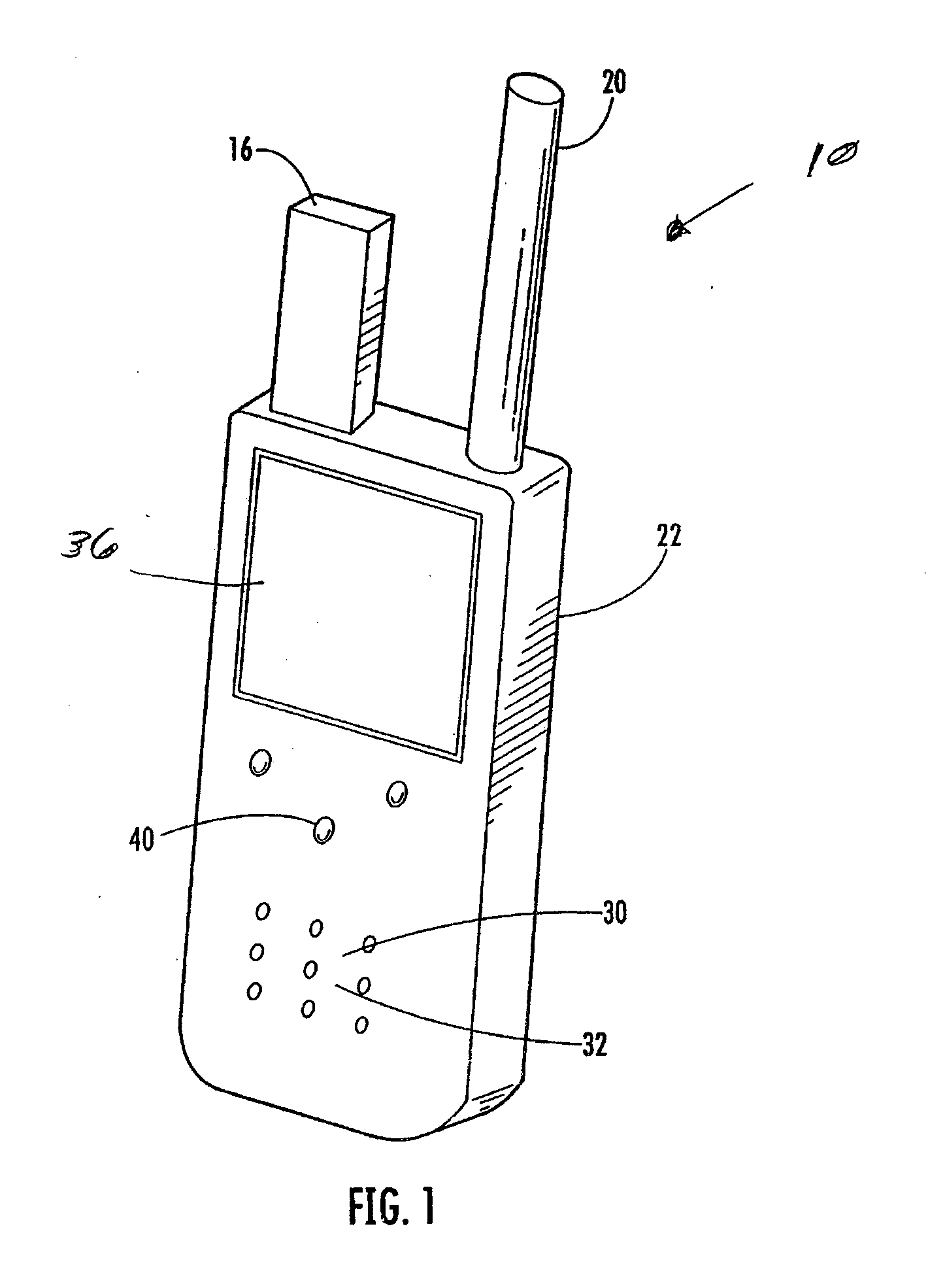
A device and system for use in emergency management operations before and after a disaster. The device incorporates a GPS and a radio with very simplified, pre-programmed instructions which are uploaded automatically in the device's memory via wireless technology prior to the unit's first use at a disaster site. Maps of areas to be searched are uploaded into the device and the areas covered during the search are retained in the devices' memory. A unique feature enables the searcher to quickly indicate a specific need or service at a particular location during the search, which information automatically is geocoded and time / date stamped once the user saves the information inputted. Via wireless technology areas that have been searched during an operational period are downloaded to a base unit and areas to be searched the following operational period are uploaded to the portable units at the beginning of the day. Radios on the units can enable the searchers to audibly communicate with each other without cell towers. The system can be employed by cleanup teams, insurance adjusters, and any number of post incident response teams both focused on short and long term recovery operations. The entire system is designed to be self contained to operate when normal cell and Internet systems are damaged or destroyed. The system can quickly organize, sort, and edit the data collected by field users for daily and future analysis and documentation or any and all disaster operations.
Owner:SPHINX IND INC
System and method for disaster training, simulation, and response
A system for conducting simulations of disaster and hazardous incident responses to assist in the organization, planning, and testing of the response of healthcare and other institutions to such incidents. A series of modules are used to enter personnel resource information into the system, design and create disaster and hazardous incident scenarios, assign personnel to incident command system (ICS) roles, and conduct a simulation with said personnel taking appropriate responsive actions. Personnel may interface with the system through a program creating a dashboard interface. Personnel can access an ICS organization chart, and use it to initiate messages and communications, conduct meetings, take actions, and assign subordinate positions. Personnel can view the status of the response actions in real-time. Standard and custom reports can be created and viewed. The system also can be used to respond to a real incident using the same interface and methods practiced in the simulation.
Owner:DNI HLDG
Incident response management system and method
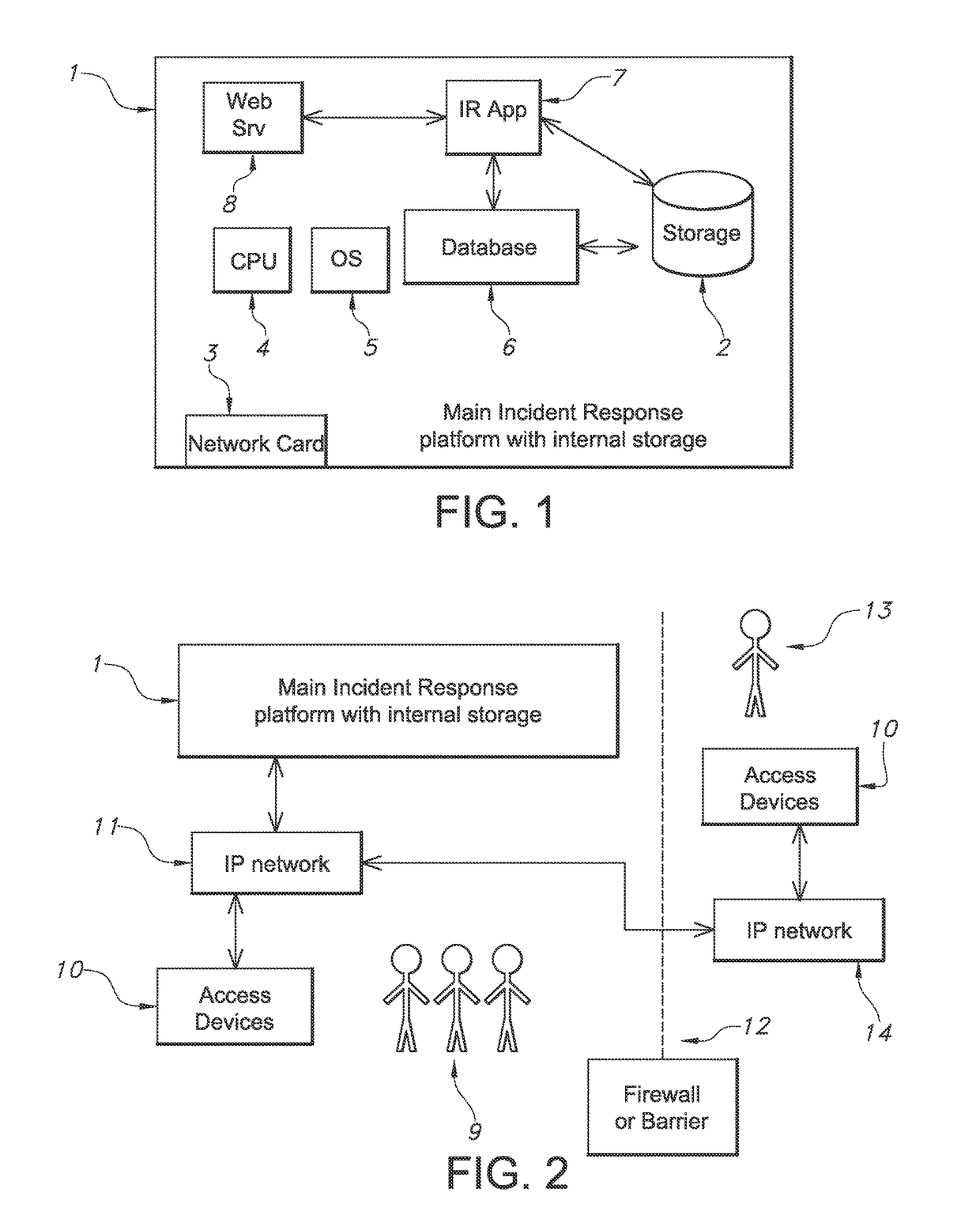
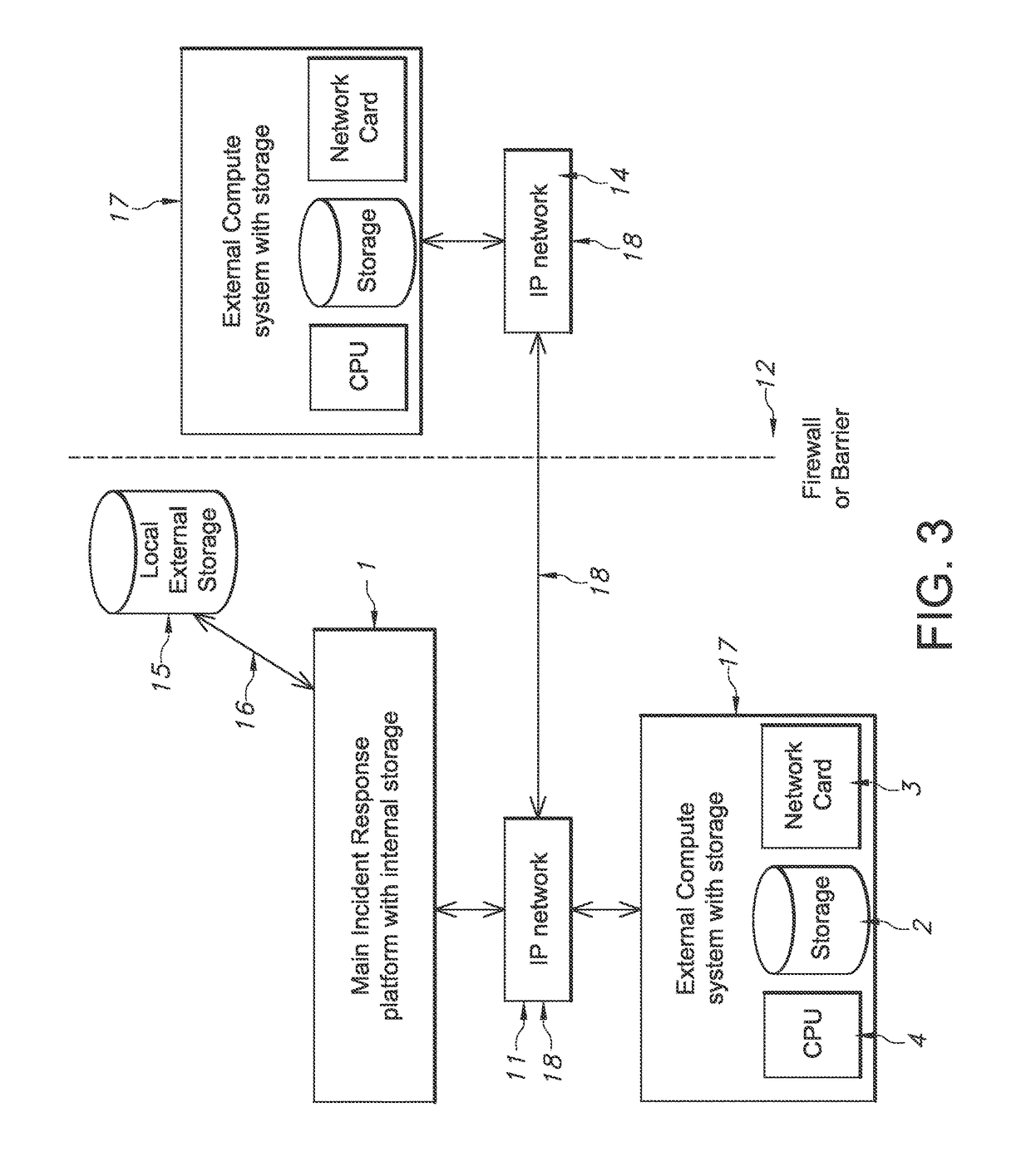
ActiveUS9697352B1Error detection/correctionPlatform integrity maintainanceOperational systemInternet privacy
A computer-implemented incident response management system, and corresponding method in which an incident response application is provided having a user interface; at least one central processing unit; an operating system and a database communicably coupled to said incident response application. The incident response application is configured to: receive, via said user interface, notification of a cyber or information security incident, together with data objects representative of entities related to said incident, files and / or data found during said incident, and / or observed actions and / or outcomes related to said incident; provide, via said user interface, an interactive representation of said incident, including information represented by said data objects, to selected users; receive, in the form of one or more Indicators of Compromise, data related to the detection of system compromise in connection with one or more of said data objects; and store said Indicators of Compromise in connection with a respective incident.
Owner:LOGICALLY SECURE LTD
System for multi-phase management of a natural disaster incident
InactiveUS20120047187A1Digital data processing detailsGeographical information databasesNatural resourceNatural disaster
A computerized system for multi-phase management of a natural disaster incident is disclosed. In one embodiment of the invention, the computerized system incorporates a pre-incident risk reduction management module, a crisis response management module, and a restoration and rehabilitation management module to correspond to these three distinct phases of managing a natural disaster incident. This multi-phase natural disaster management system can be utilized by private entities, community groups, state, national, and / or international agencies to assist prevention or reduction of damage to human and natural resources in a particular disaster incident. Furthermore, the multi-phase natural disaster management system can assist or enable protection of lives, health, and safety of community members and disaster incident response personnel. A prioritization model in the pre-incident risk management module can take an empirical or subjective weighting factor in evaluating a particular geographic section to optimize disaster prevention and management.
Owner:DAUS STEVEN J
GPS pathfinder method and device
InactiveUS20080246652A1Quick instructionsBeacon systems using radio wavesDevices with GPS signal receiverProgram instructionComputer science
A device and system for use in the early stages of search and recovery after a disaster. The device incorporates a GPS and a radio with very simplified, pre-programmed instructions which are uploaded automatically in the device's memory via wireless technology prior to the unit's first use at a disaster site. Maps of areas to be searched are uploaded into the device and the areas covered during the search are retained in the devices' memory. A unique feature enables the searcher to quickly indicate a specific need or service at a particular location during the search. Via wireless technology Areas that have been searched during a day are downloaded to a base unit and areas to be searched the following day are uploaded to the portable units at the beginning of the day. Radios on the units enable the searchers to audibly communicate with each other. The system can be employed by cleanup teams, insurance adjusters also and any number of post incident response teams both focused on short and long term recovery operations.
Owner:DISASTER SOLUTIONS LLC
GPS pathfinder cell phone and method
ActiveUS8154440B2Improve effectivenessQuick instructionsFinanceDevices with GPS signal receiverComputer scienceIncident response
A device and system for use in emergency management operations before and after a disaster. The device incorporates a GPS and a radio with very simplified, pre-programmed instructions which are uploaded automatically in the device's memory via wireless technology prior to the unit's first use at a disaster site. Maps of areas to be searched are uploaded into the device and the areas covered during the search are retained in the devices' memory. A unique feature enables the searcher to quickly indicate a specific need or service at a particular location during the search, which information automatically is geocoded and time / date stamped once the user saves the information inputted. Via wireless technology areas that have been searched during an operational period are downloaded to a base unit and areas to be searched the following operational period are uploaded to the portable units at the beginning of the day. Radios on the units can enable the searchers to audibly communicate with each other without cell towers. The system can be employed by cleanup teams, insurance adjusters, and any number of post incident response teams both focused on short and long term recovery operations. The entire system is designed to be self contained to operate when normal cell and Internet systems are damaged or destroyed. The system can quickly organize, sort, and edit the data collected by field users for daily and future analysis and documentation or any and all disaster operations.
Owner:SPHINX IND INC
Personalized Situation Awareness Using Human Emotions and Incident Properties
ActiveUS20180053503A1Optimal response plan generationNatural language translationEmergency connection handlingPersonalizationComputer science
The disclosure provides systems and methods for generating and delivering situational-dependent incident responses. An incident response is generated based on incident characterizations as well as emotional data pertaining to a reporting person. The generated response may also involve an interactive component in order to obtain further situational details from the reporting person and other sources, thereby further refine the response and recommendations. Persons reporting incidents are aided by appropriate recommendations and assistance from appropriate service providers.
Owner:IBM CORP
Automated incident response method and system
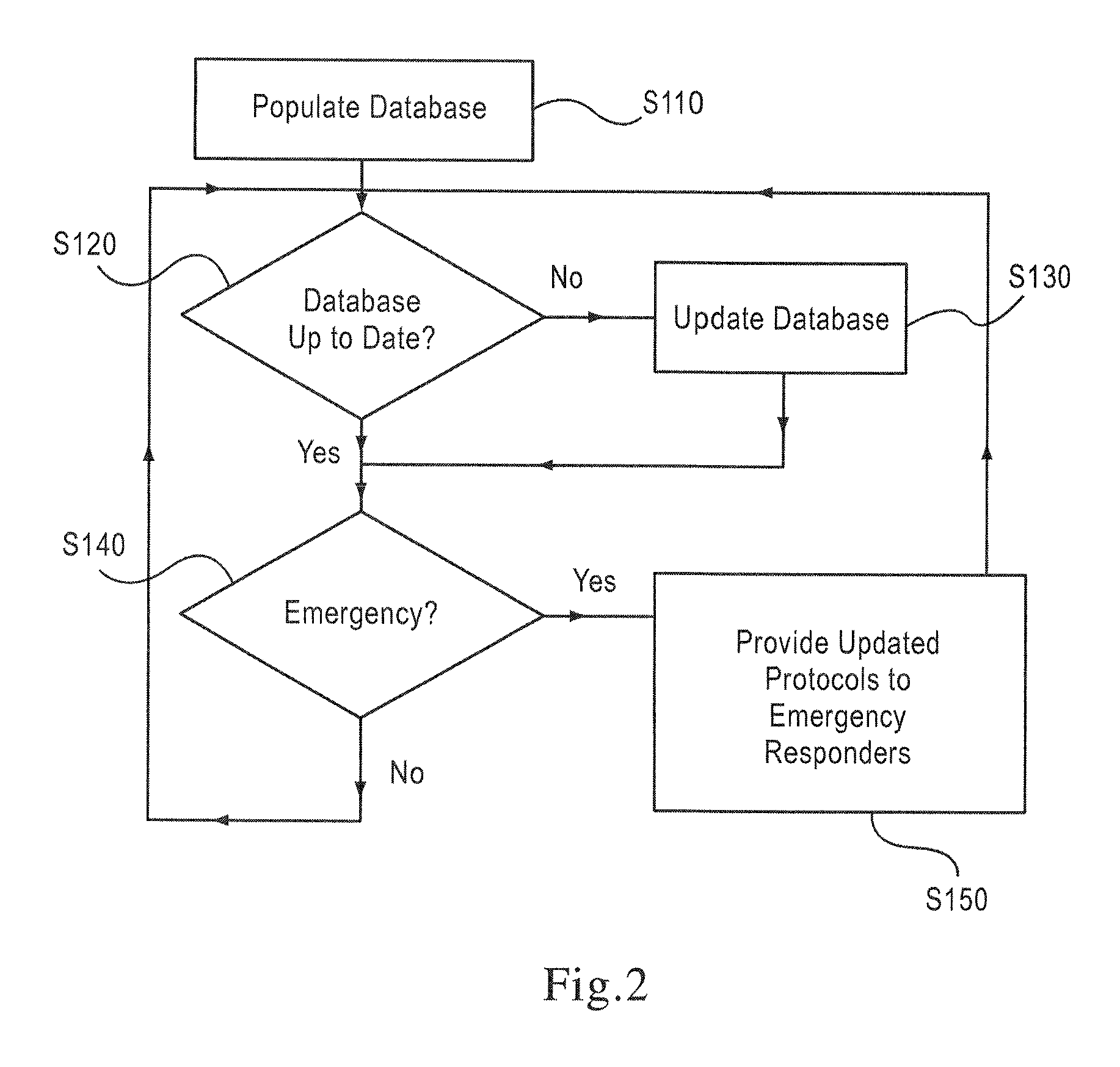
ActiveUS20090276489A1Improve national and international responseImprove efficiencyTelemedicineMultiple digital computer combinationsEmergency medical dispatchComputer science
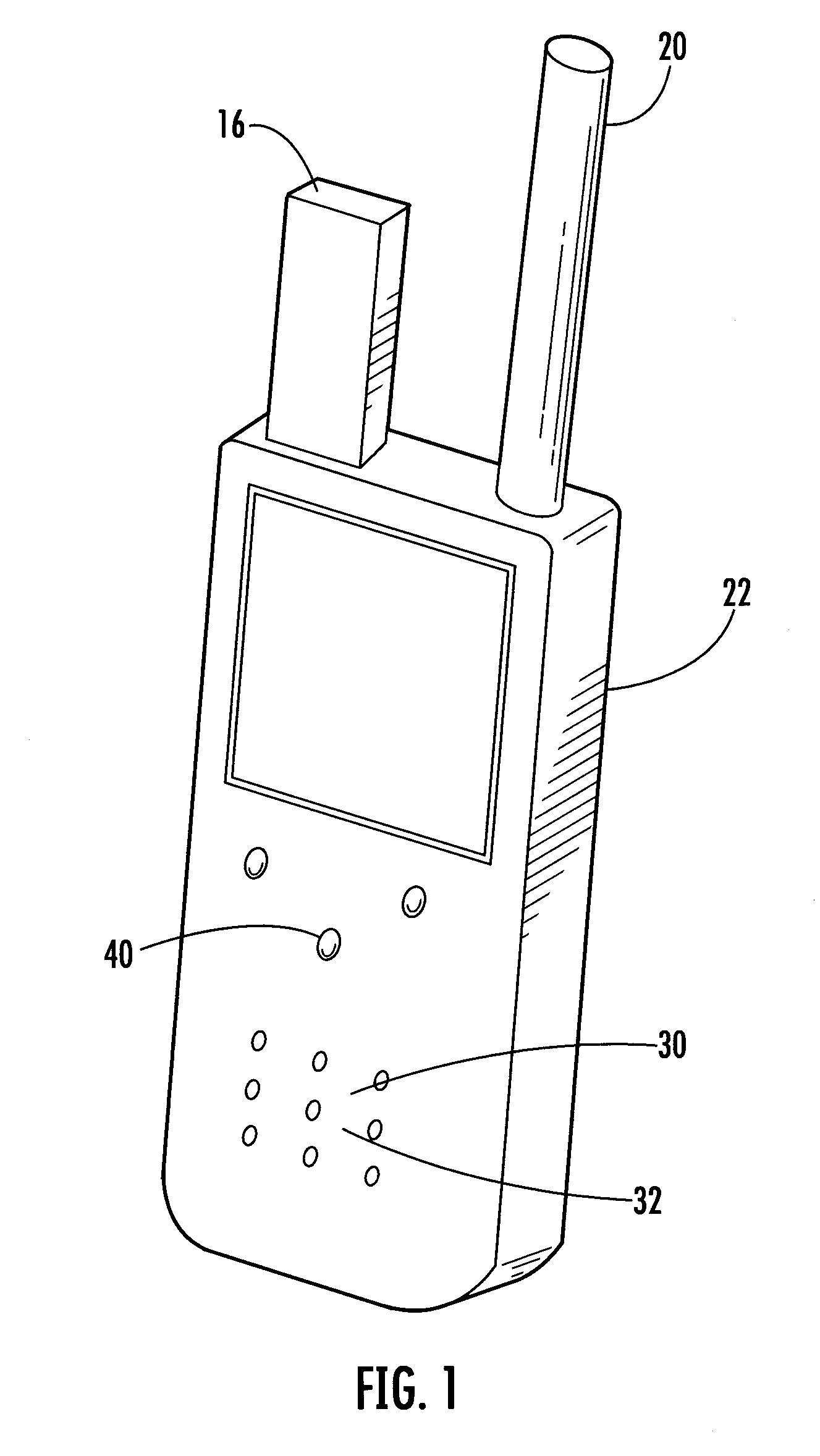
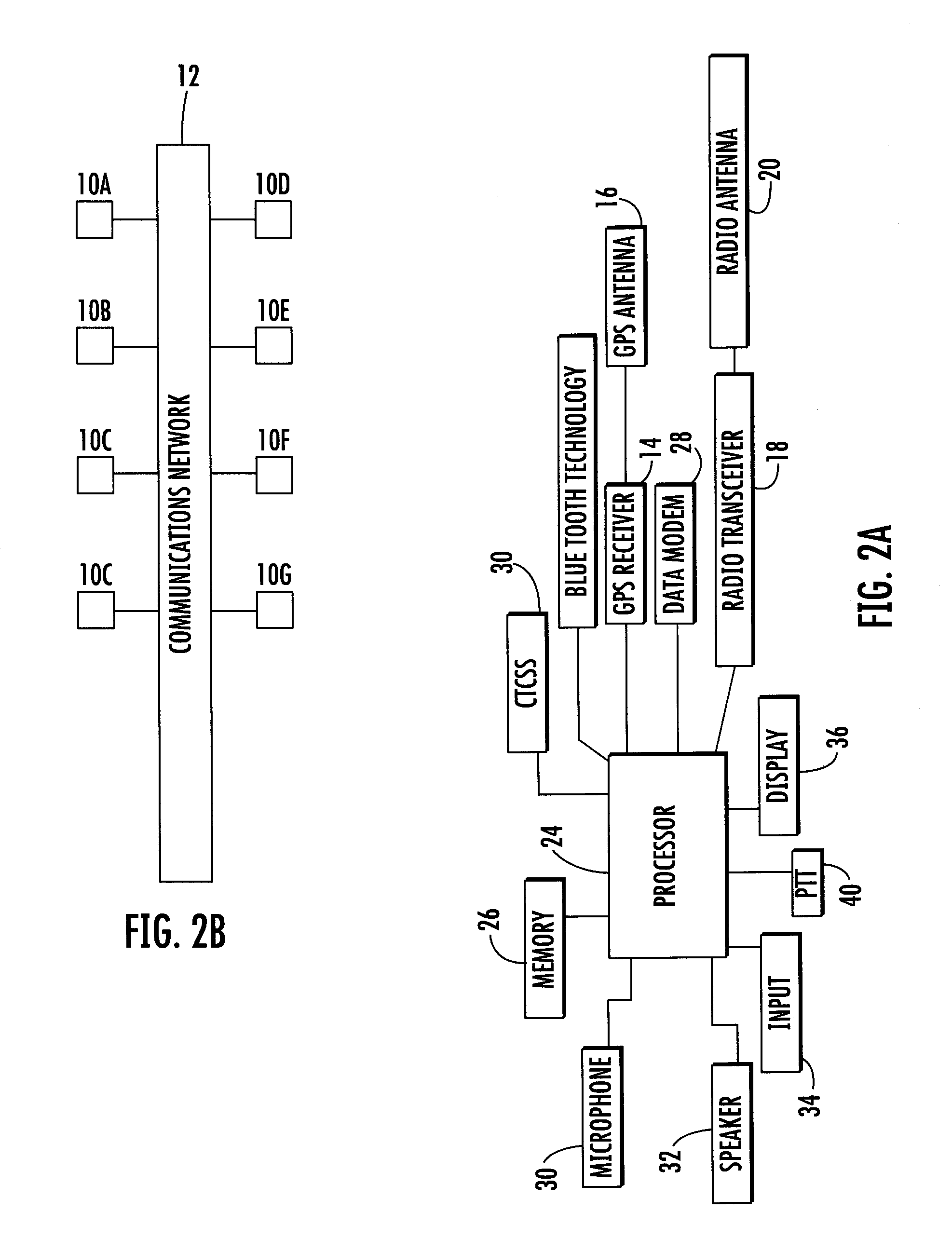
An automated emergency response method and system to remotely and timely update emergency response protocols, such as Emergency Medical Dispatch Protocol Reference Systems (EMDPRS), is provided. A method and system to remotely and timely update the EMDPRS in a controlled, consistent and timely manner is also provided. A method that can provide accurate, up-to-date and consistent EMDPRS provides the advantage of increasing operator readiness and efficiency in responding to an emergency, and increases the chances of success in dealing with the emergency.
Owner:VITALCLICK
Incident aware service operations for wireless infrastructure
ActiveUS20140148115A1Telephonic communicationBroadcast service distributionWireless mesh networkService Request Block
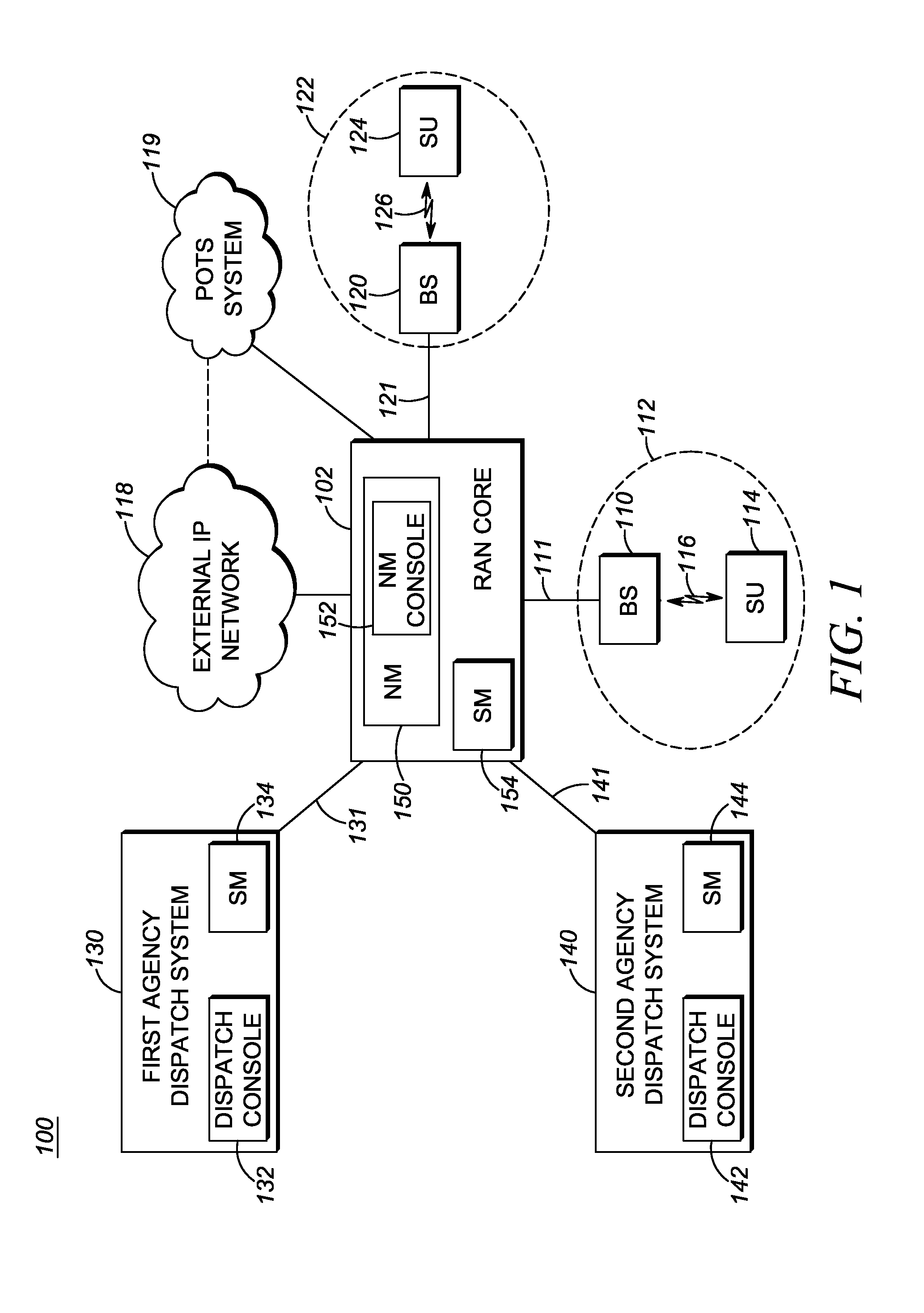
In a two-way radio frequency (RF) communications system having a plurality of subscriber units (SUs) and a supporting infrastructure including a wireless core network, a service request is received indicating one of a device, application, and transport link that will be removed from service. One or more SUs out of the plurality of SUs are identified that will be impacted by the removal from service. A determination is then made of whether any one of the SUs is currently involved in an incident response. For each SU determined to be currently involved in an incident response, it is determined whether the respective incident response is of a non-interruptible incident response type. Responsive to determining that a SU is currently involved in a non-interruptible incident response, a notification is caused to appear at a network management console or a dispatch console, and the service request is at least temporarily suspended.
Owner:MOTOROLA SOLUTIONS INC
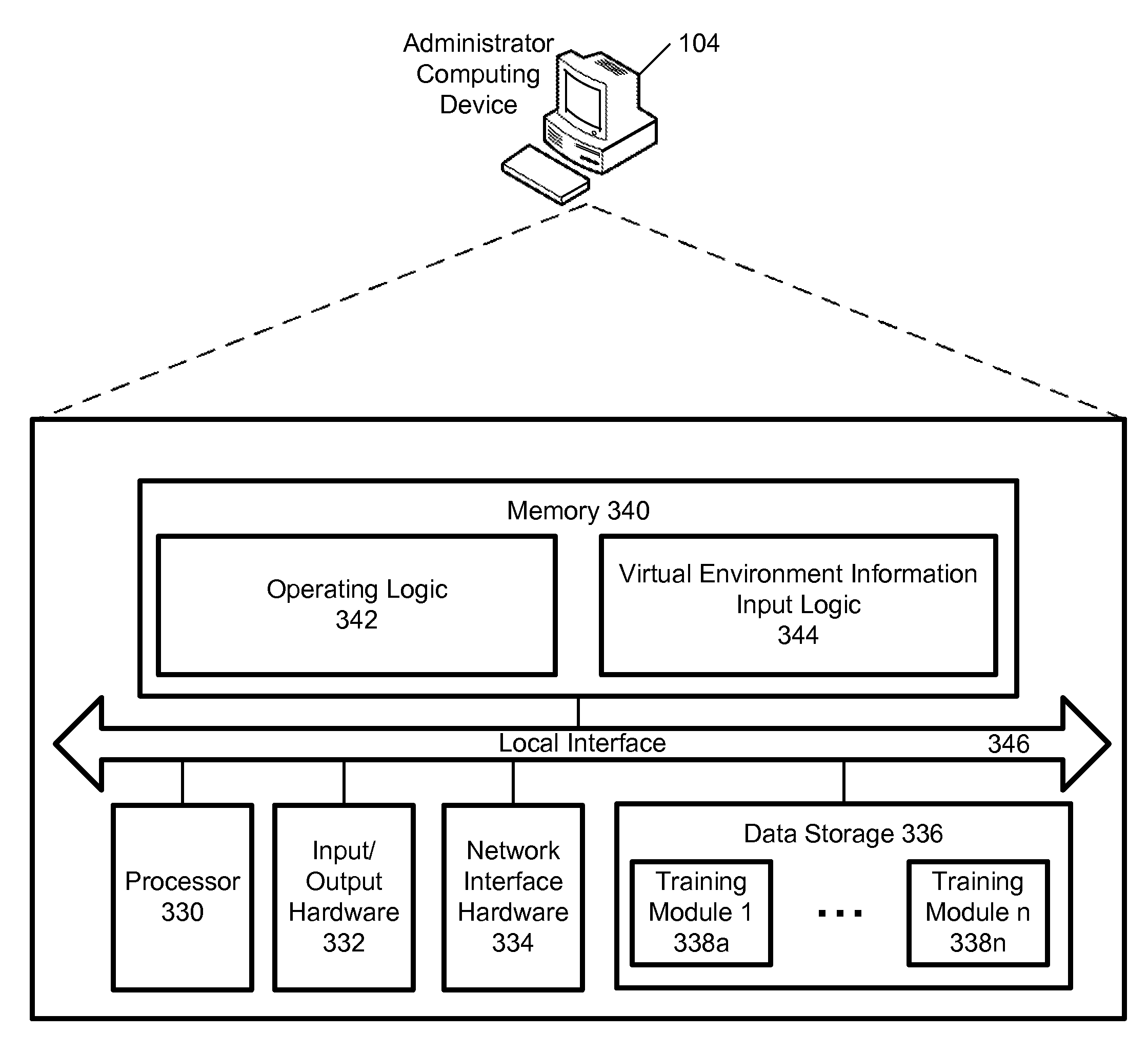
Virtual Environment For Critical Incident Response Training
Methods, systems, and computer-readable media for critical incident response training are disclosed. A method of prompting a user of a computing device to choose how a user avatar should interact with a three-dimensional virtual environment in response to a critical incident includes displaying the three-dimensional virtual environment on a display device. The three-dimensional virtual environment graphically represents a physical environment. The method further includes displaying the user avatar that represents the user on a display device. The user avatar is positioned in the three-dimensional virtual environment. The method further includes simulating the critical incident in the three-dimensional virtual environment, and prompting the user to choose how the user avatar should interact with the three-dimensional virtual environment in response to the simulated critical incident.
Owner:ENVIROQUEST
Role-Based Control of Incident Response in a Secure Collaborative Environment
Various systems and method for incident response may benefit from role-based control. More particularly, role-based control of incident response may be of benefit in a secure collaborative environment. A method can include determining, by a computer for a computer-controlled workflow, whether filtering is activated. The method can also include determining, by the computer when filtering is activated, whether a threshold severity level is met by the workflow or whether a critical data type is implemented in the workflow. The method can further include alerting, by the computer, an attorney about the workflow when the threshold is met or the critical data type is implemented.
Owner:FORTINET
System and method for coordinating network incident response activities
ActiveUS8850565B2Improve responseReduce decreaseMemory loss protectionError detection/correctionCountermeasureNetwork connection
The present invention provides a system and method to process information regarding a network attack through an automated workflow that actively reconfigures a plurality of heterogeneous network-attached devices and applications to dynamically counter the attack using the network's own self-defense mechanisms. The present invention leverages the security capabilities present within existing and new network-attached devices and applications to effect a distributed defense that immediately quarantines and / or mitigates attacks from hostile sources at multiple points simultaneously throughout the network. In a preferred embodiment, deployed countermeasures are automatically lifted following remediation activities.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com