Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
680 results about "Phishing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
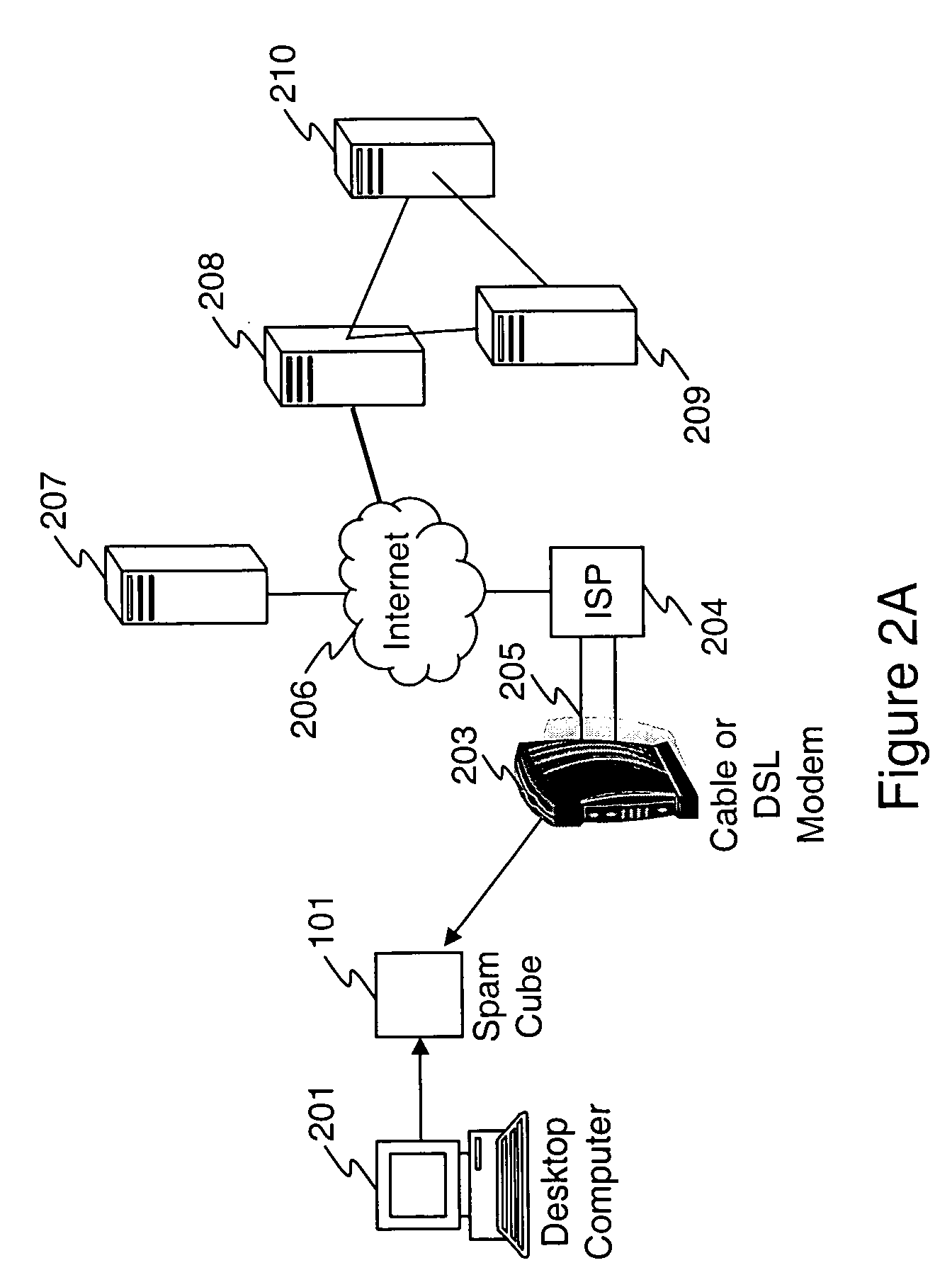
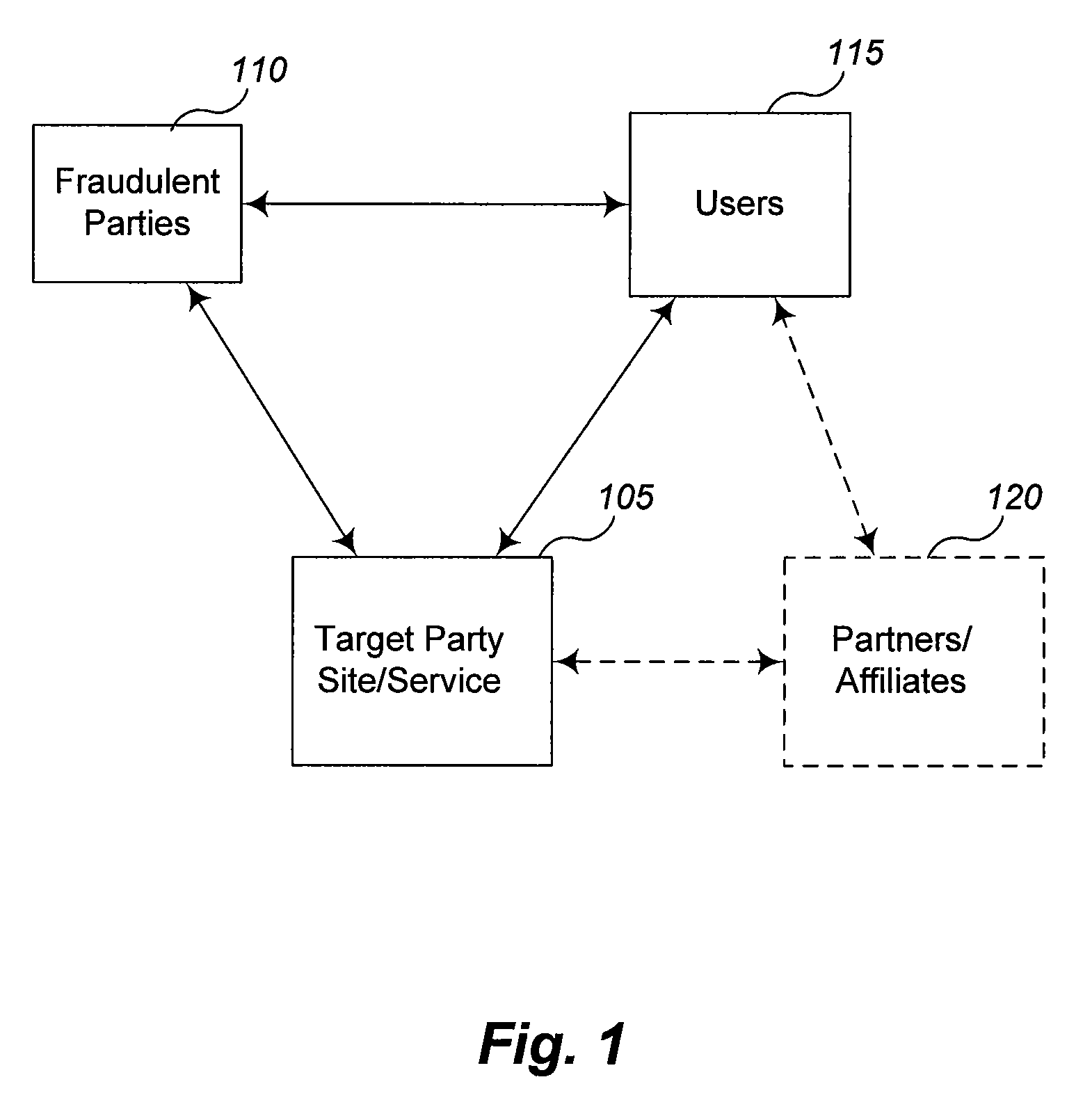
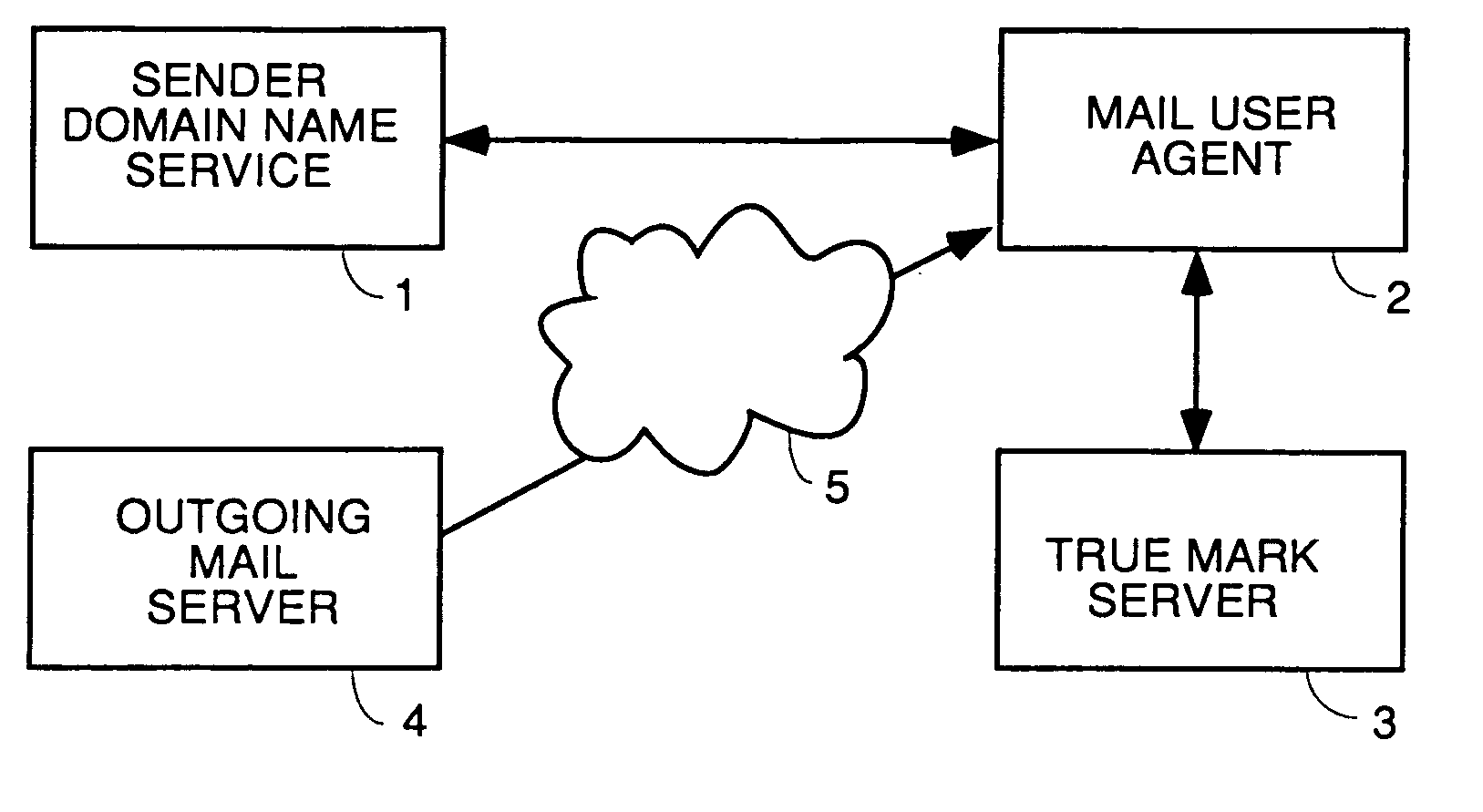
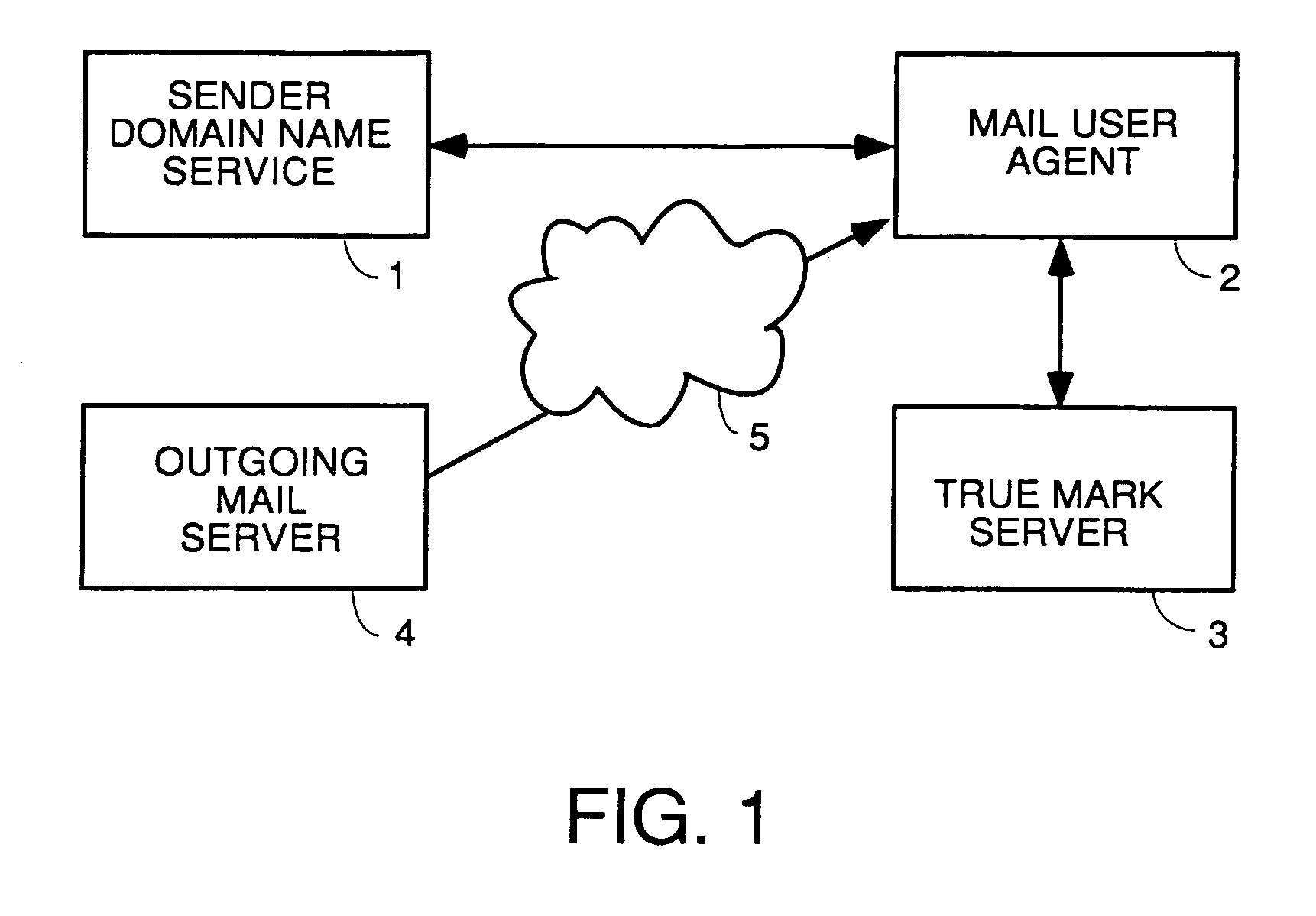
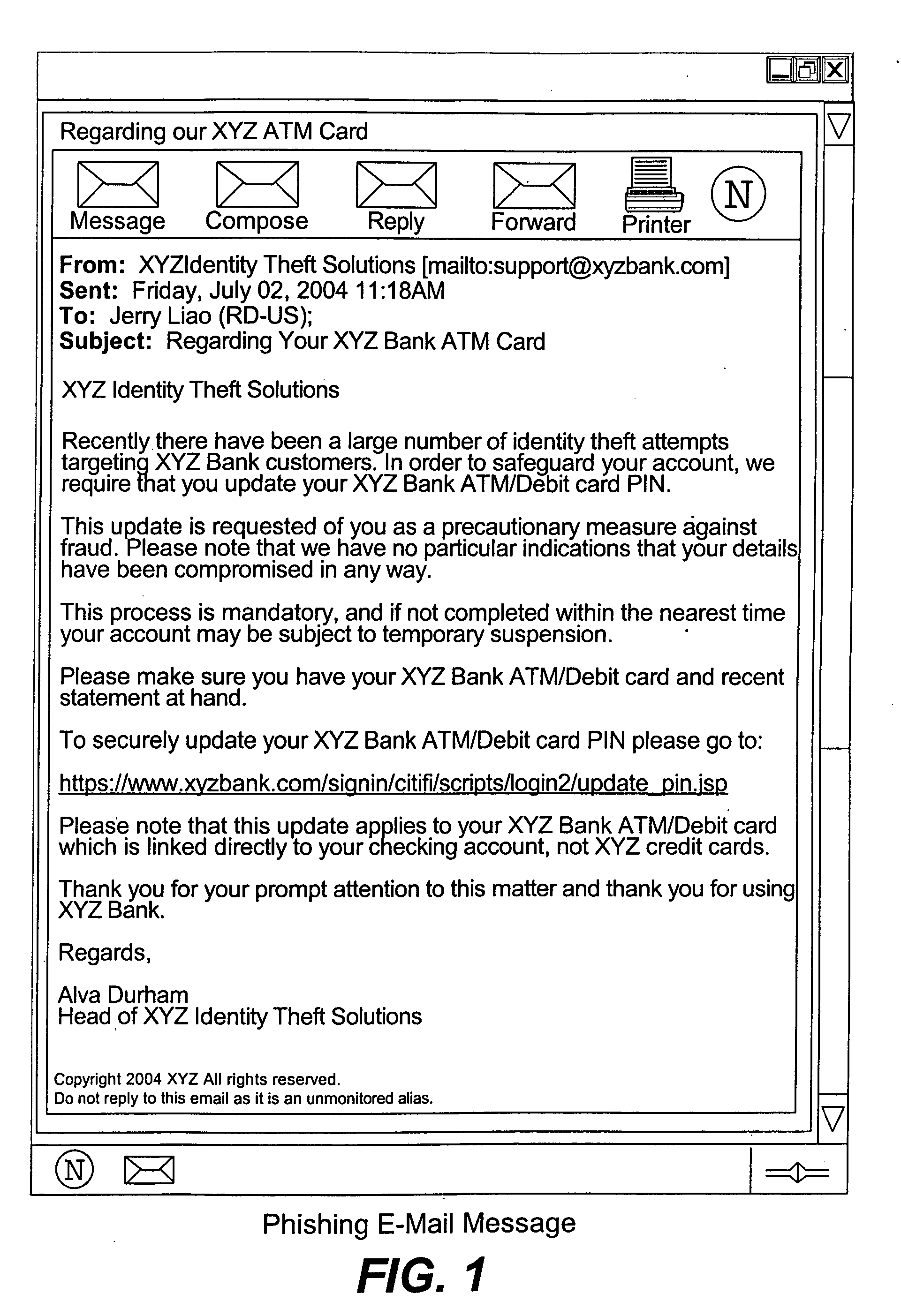
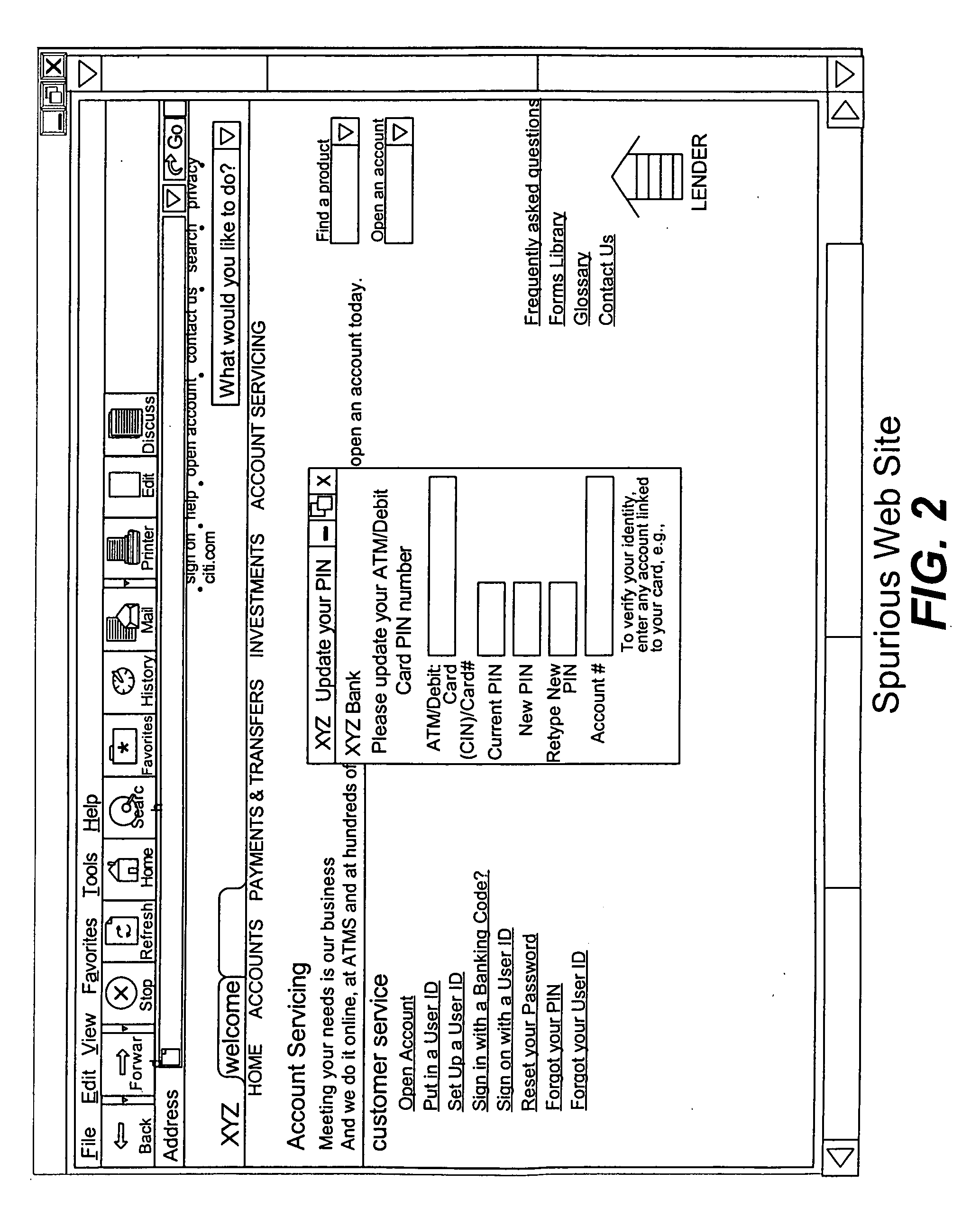
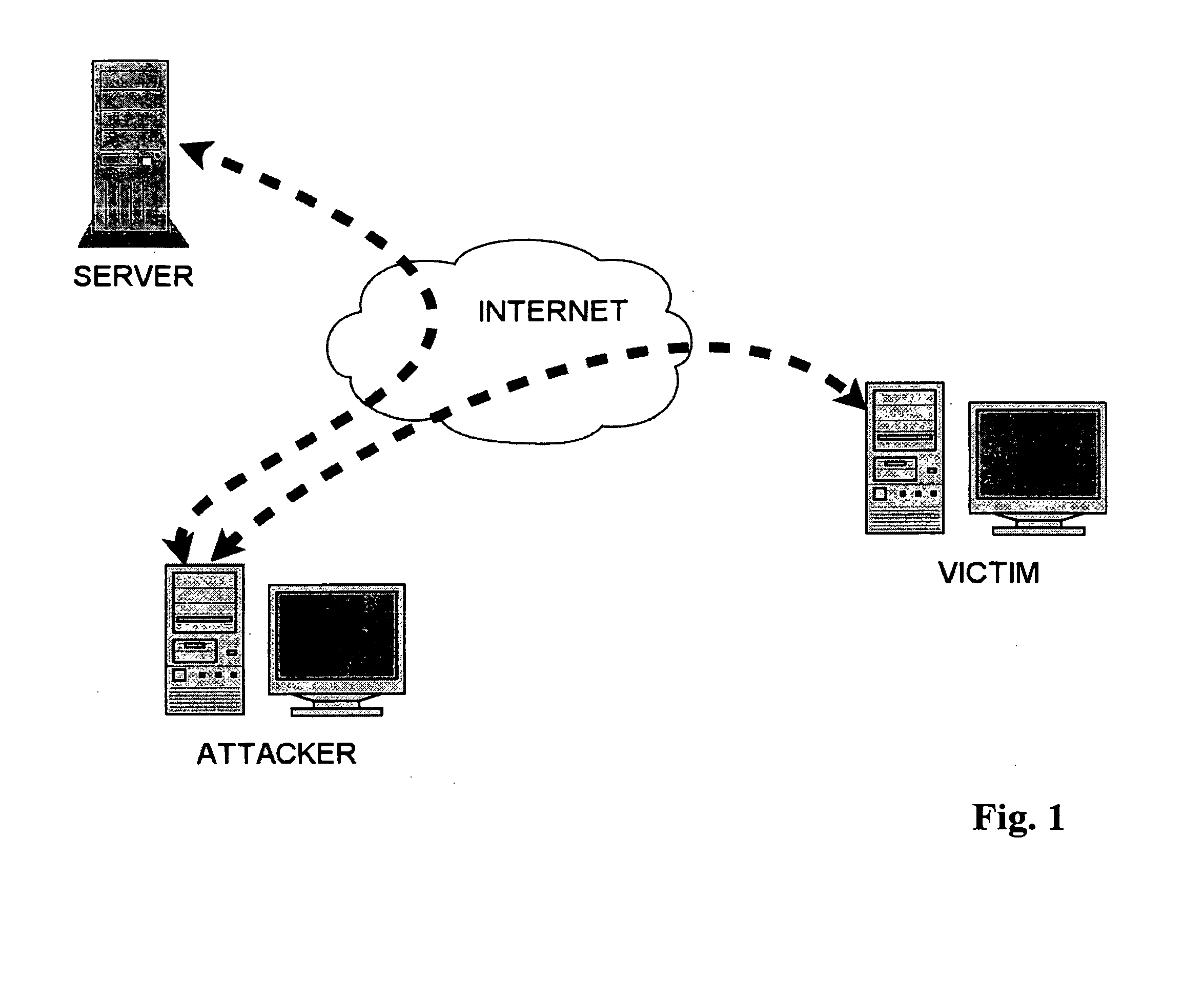
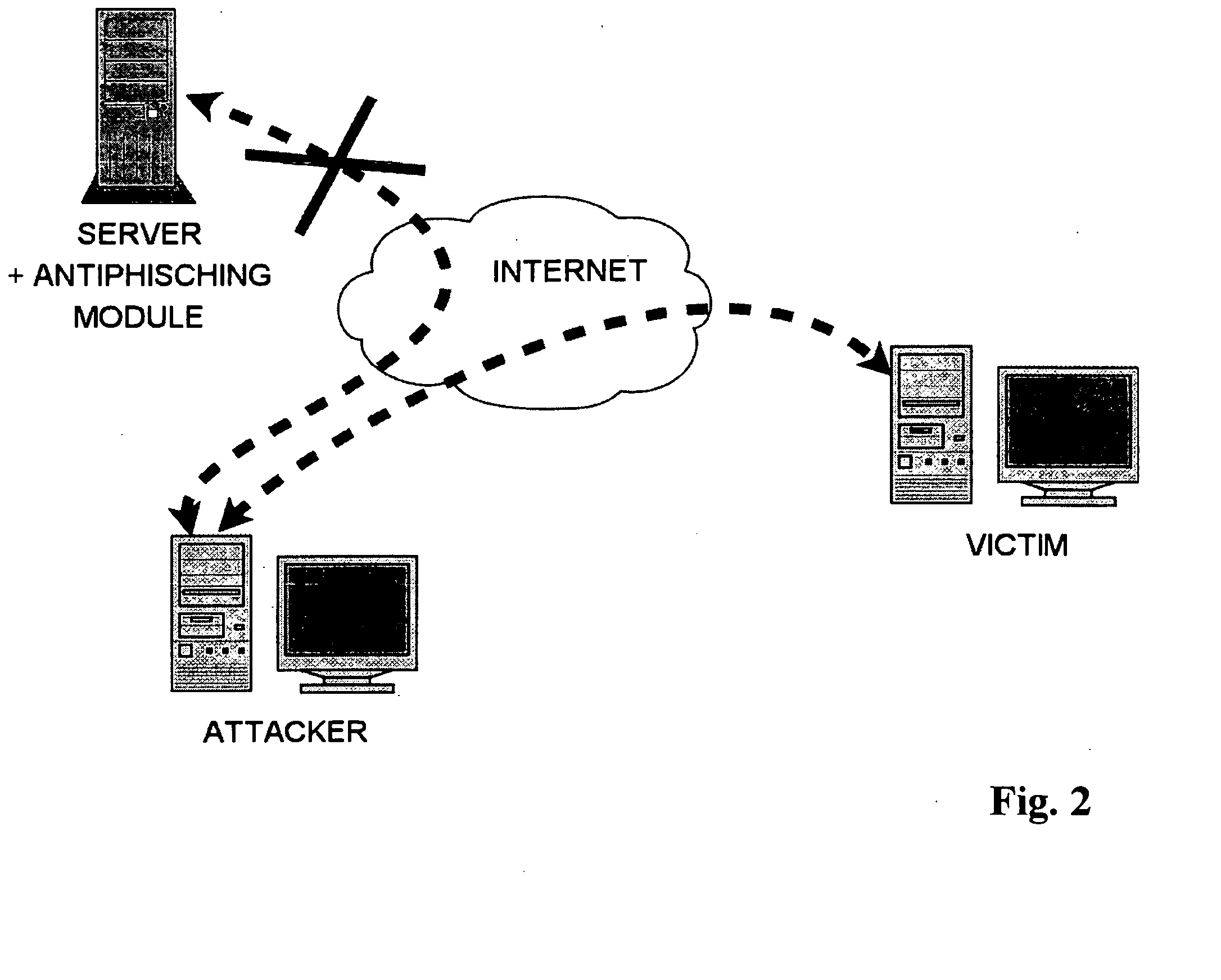
Phishing is the fraudulent attempt to obtain sensitive information such as usernames, passwords and credit card details by disguising oneself as a trustworthy entity in an electronic communication. Typically carried out by email spoofing or instant messaging, it often directs users to enter personal information at a fake website which matches the look and feel of the legitimate site.
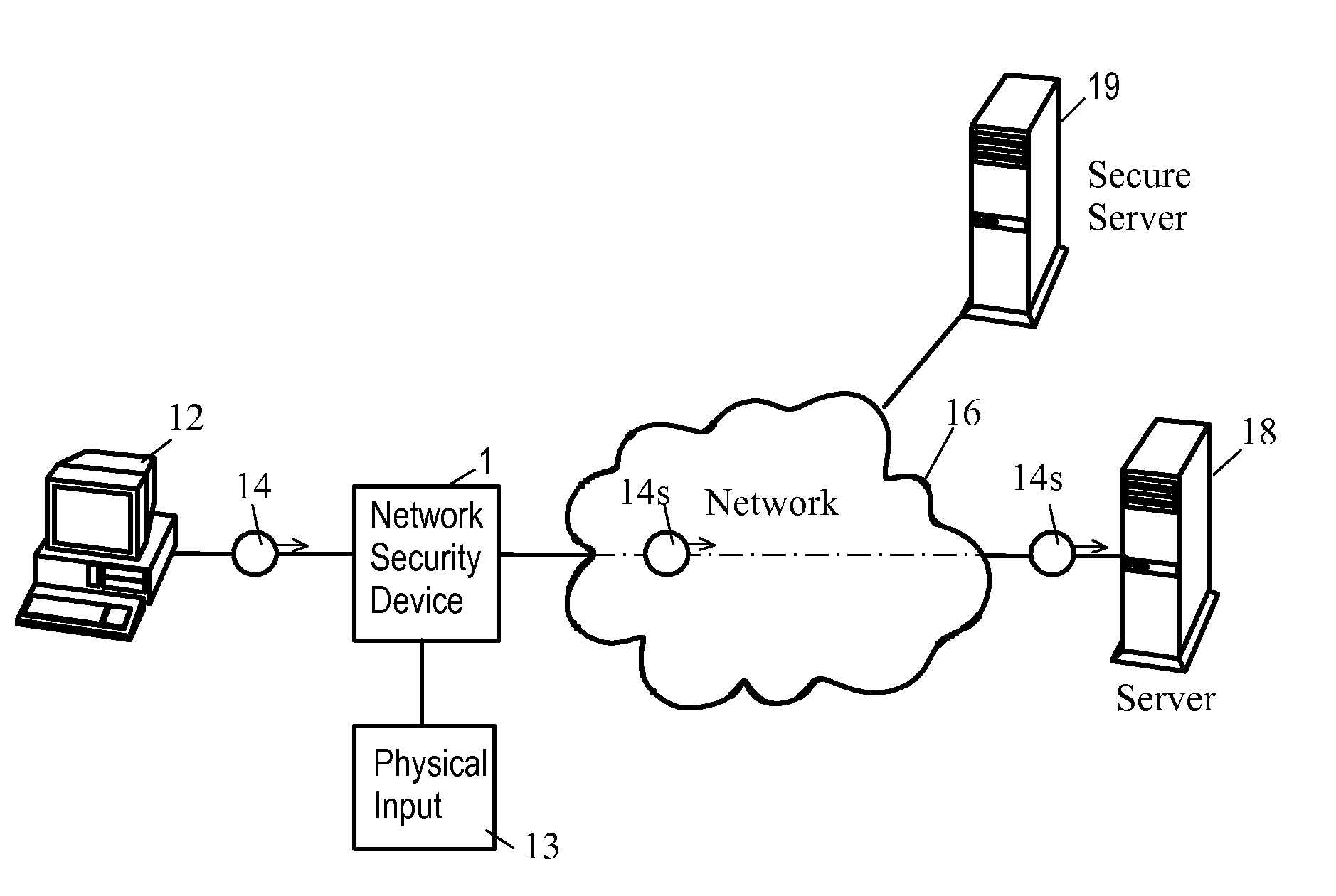
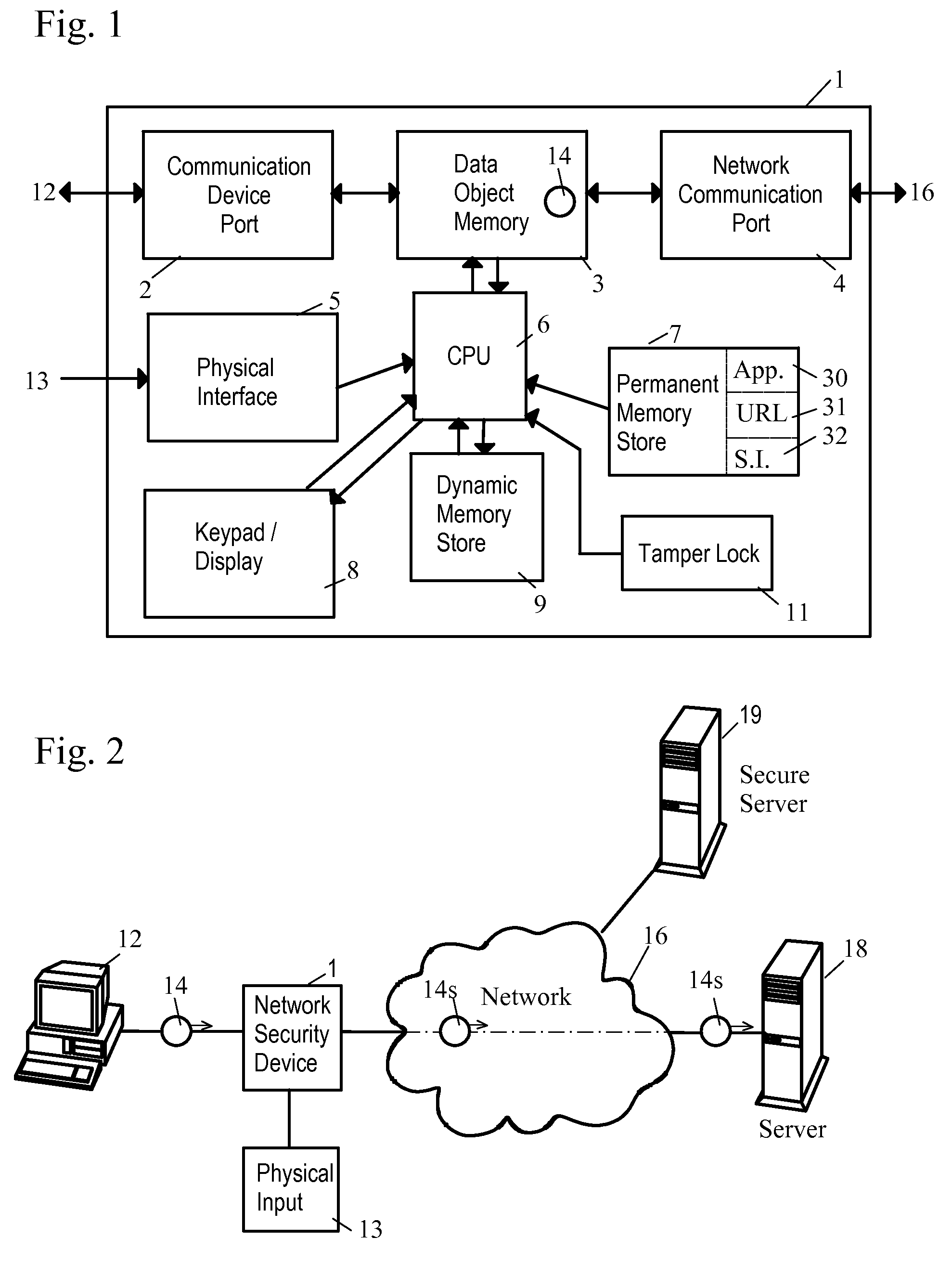
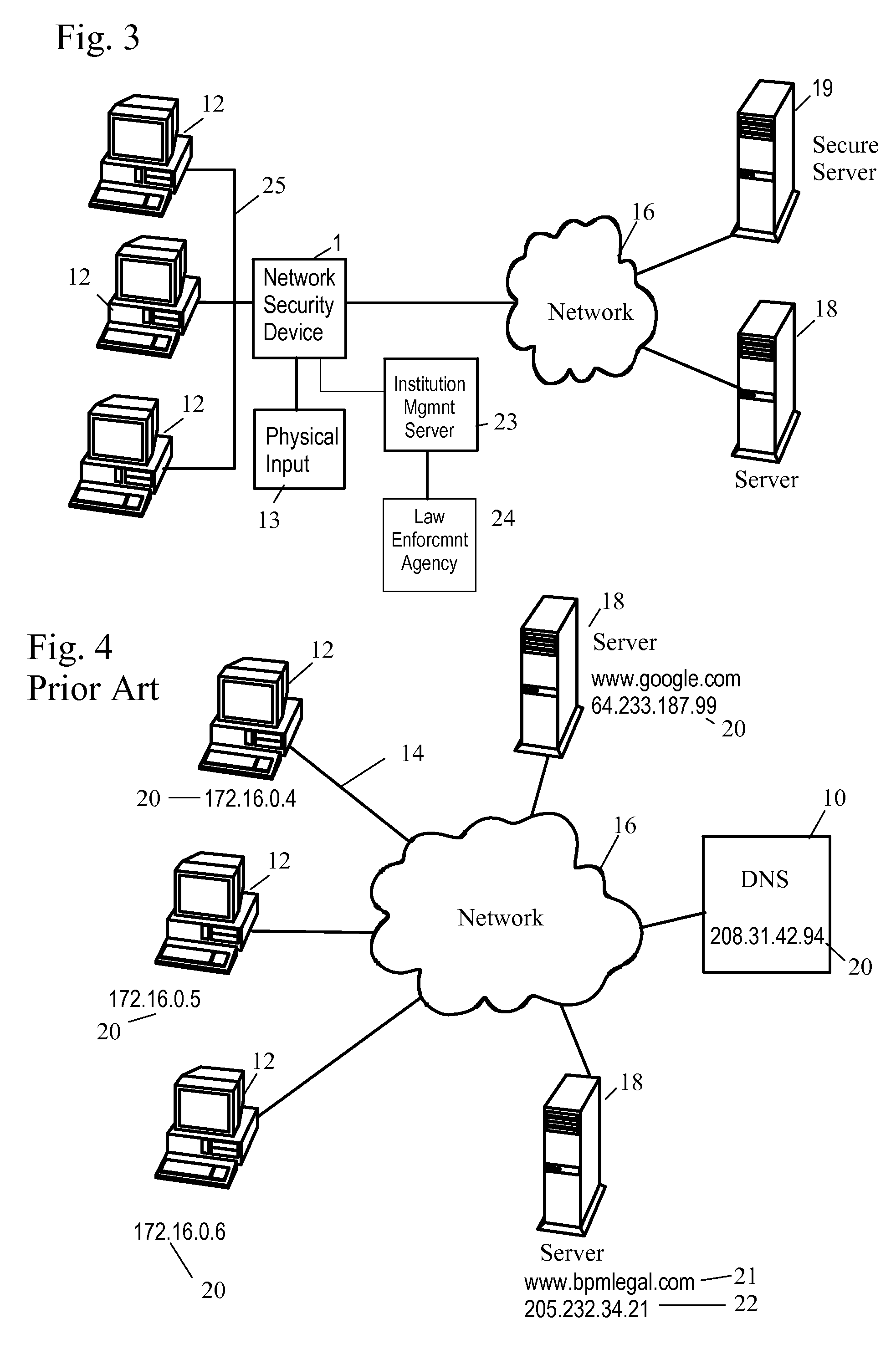
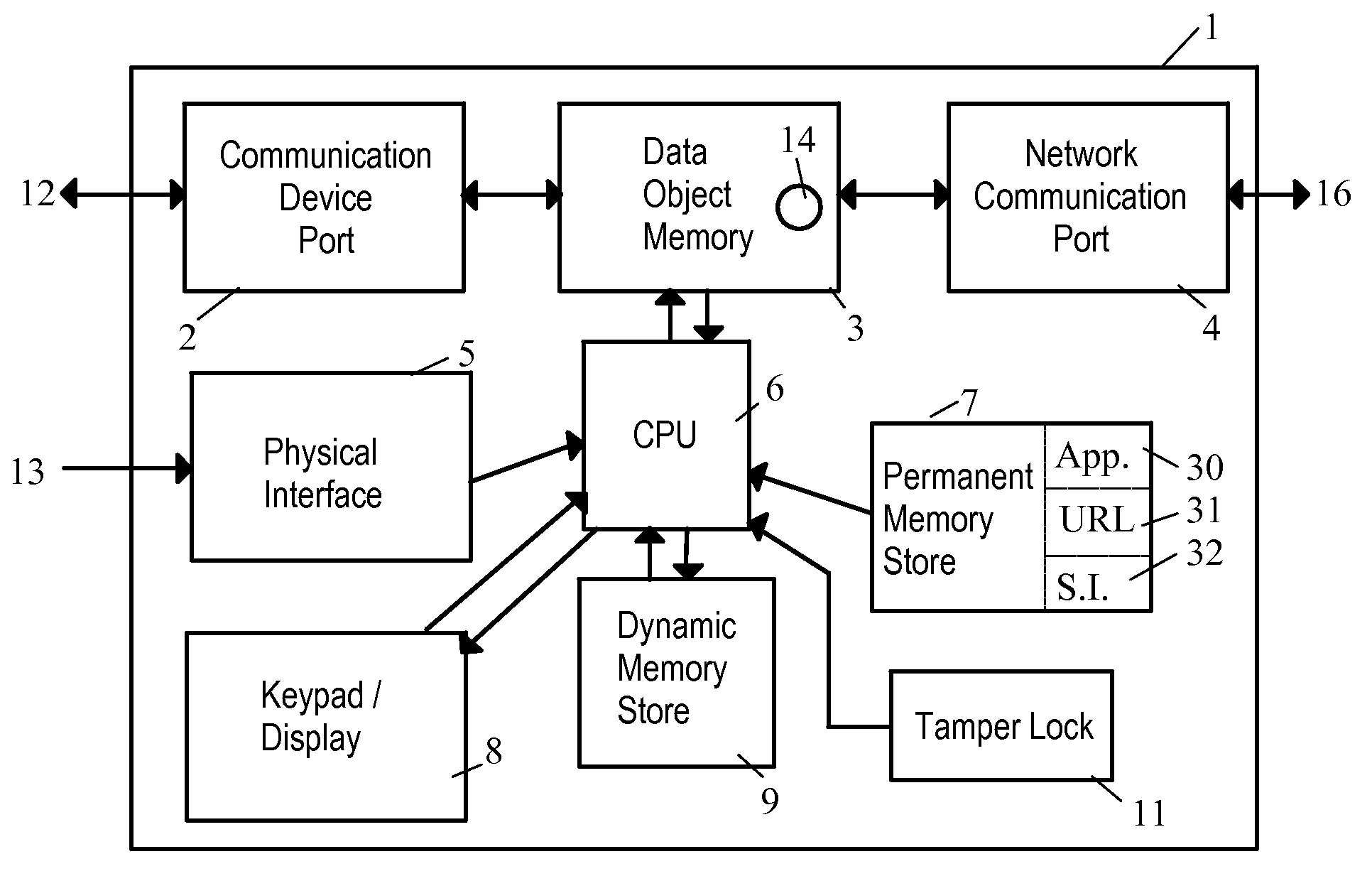
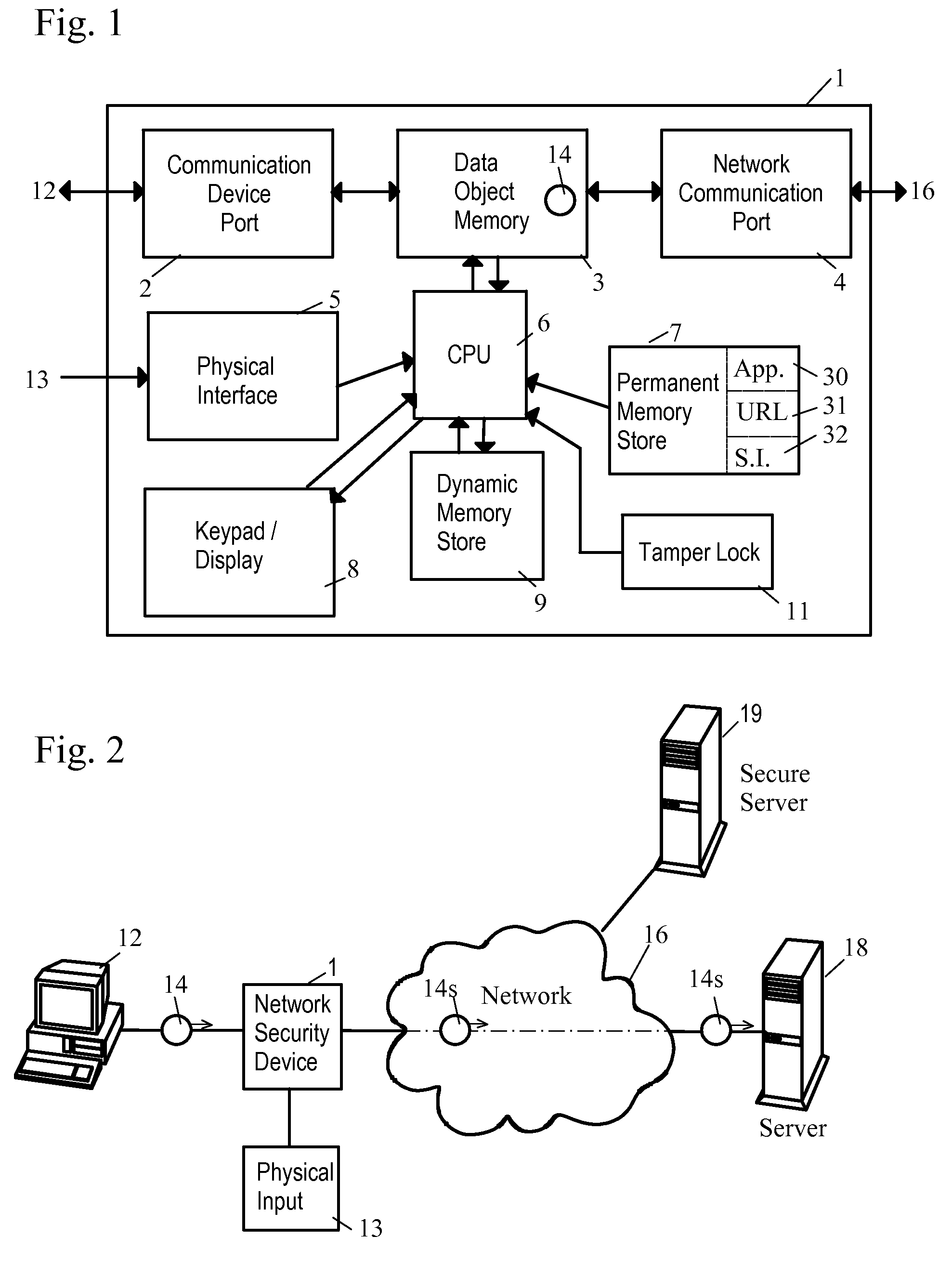
Network Security Device
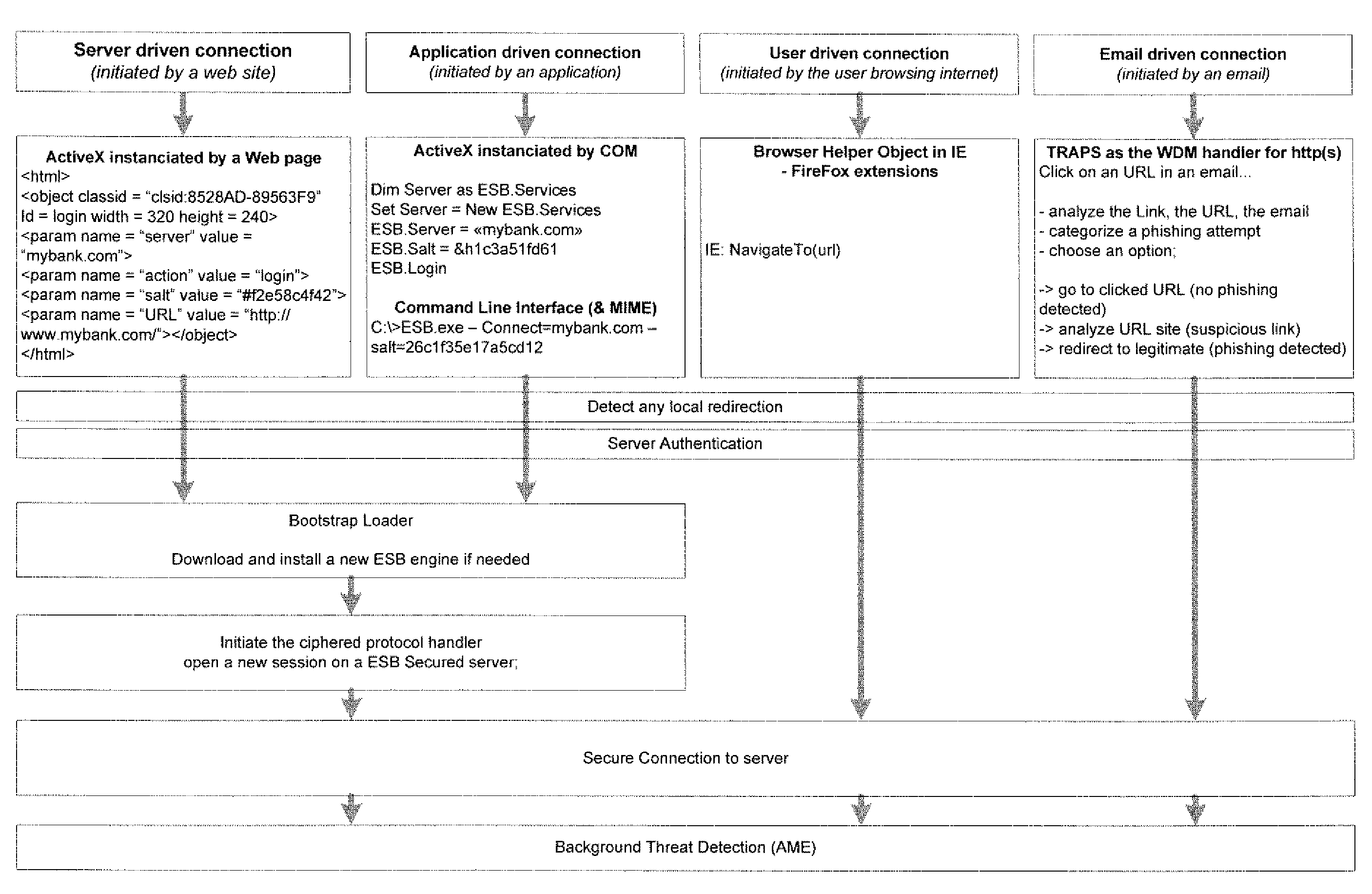
ActiveUS20070261112A1Function providedFacilitate law enforcement effortDigital data processing detailsUser identity/authority verificationNetwork packetDatapath
A network security device which acts as an “airlock” for traffic between a communications device and a network. Data is screened using rules based analysis by the security device to counter various threats, including viruses, phishing, attempts to “hijack” communications, communications with known malicious addresses or unknown addresses, and transmission of sensitive information. Data packets can be reassembled into files for screening, and decoded or expanded as necessary, but is never executed. The data path for the data being screened is kept separate from the operations of the network security device itself, so that the device is incorruptible—its programming cannot be compromised from outside sources. Updates for rules and entry of sensitive data for screening, etc., must be done through a physical interface, not via the normal data communications channel. The device is invisible—it cannot be “seen” by the network, and thus cannot be attacked.
Owner:ELECTRO GUARD CORP
Method and apparatus for regulating data flow between a communications device and a network
ActiveUS7890612B2Digital data processing detailsComputer security arrangementsTraffic capacityData stream
A network security device which acts as an “airlock” for traffic between a communications device and a network. Data is screened using rules based analysis by the security device to counter various threats, including viruses, phishing, attempts to “hijack” communications, communications with known malicious addresses or unknown addresses, and transmission of sensitive information. Data packets can be reassembled into files for screening, and decoded or expanded as necessary, but is never executed. The data path for the data being screened is kept separate from the operations of the network security device itself, so that the device is incorruptible—its programming cannot be compromised from outside sources. Updates for rules and entry of sensitive data for screening, etc., must be done through a physical interface, not via the normal data communications channel. The device is invisible—it cannot be “seen” by the network, and thus cannot be attacked.
Owner:ELECTRO GUARD CORP
Apparatus and method for analyzing and filtering email and for providing web related services
InactiveUS20060184632A1Eliminate the problemSoftware engineeringDigital data processing detailsService provisionSpamming
The inventive methodology provides an integrated plug and play solution designed to protect home networks against spam, phishing emails, viruses, spyware as well as other similar threats. The described content filtering appliance can be used for processing of web and email traffic implemented and can be deployed as a stand-alone appliance. In one implementation, the content processing appliance utilizes backend content filtering provided by a remote scanning service accessed via a network. The system employs network level analysis and translation of content and executes various procedures to handle the network traffic. In an embodiment of the invention, the appliance is provided with an automatic remote updating capability, wherein the software and data used by the appliance can be updated remotely via a network. Finally, the appliance may also implement parental controls.
Owner:MARINO JOSEPH P
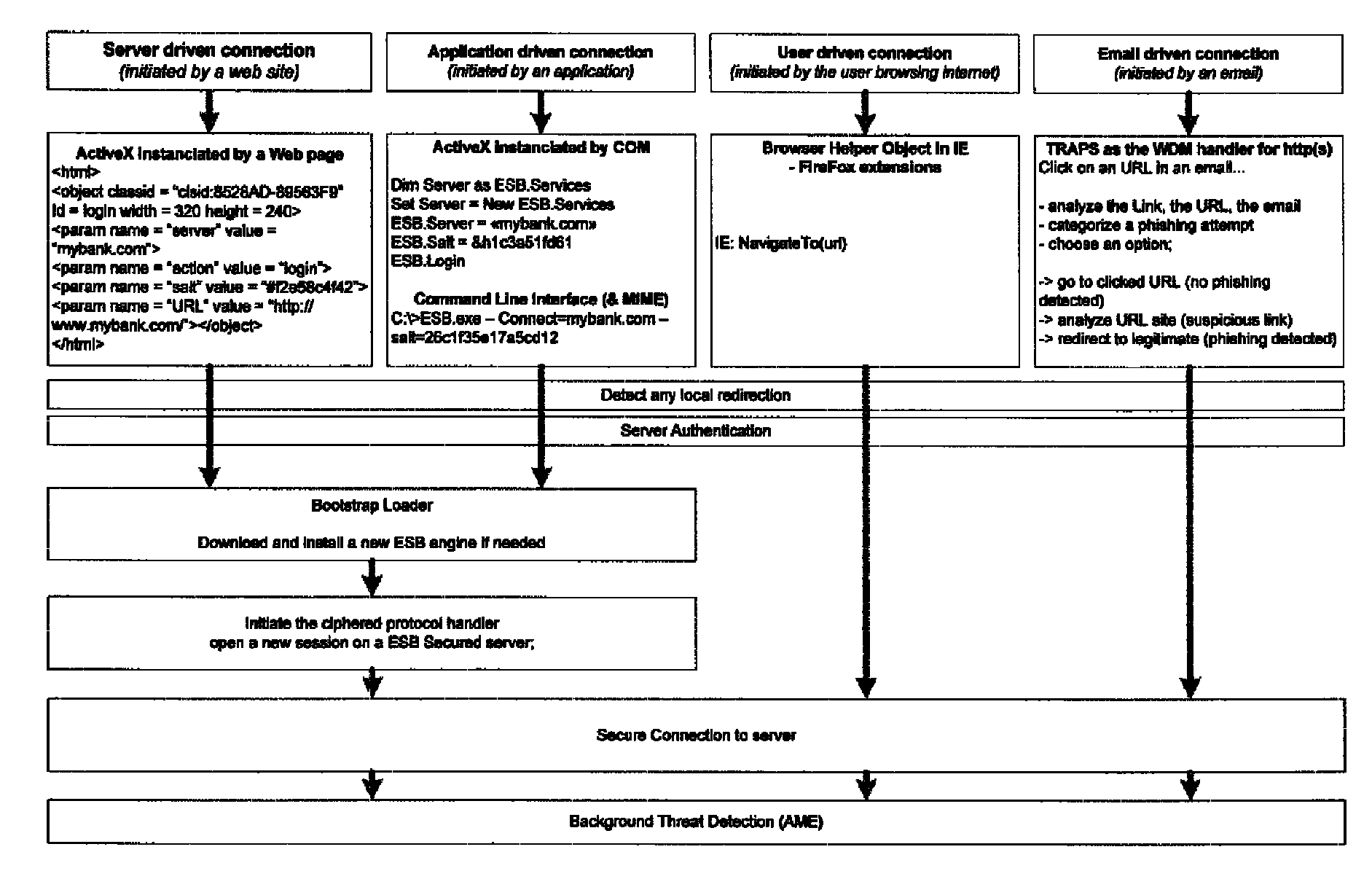
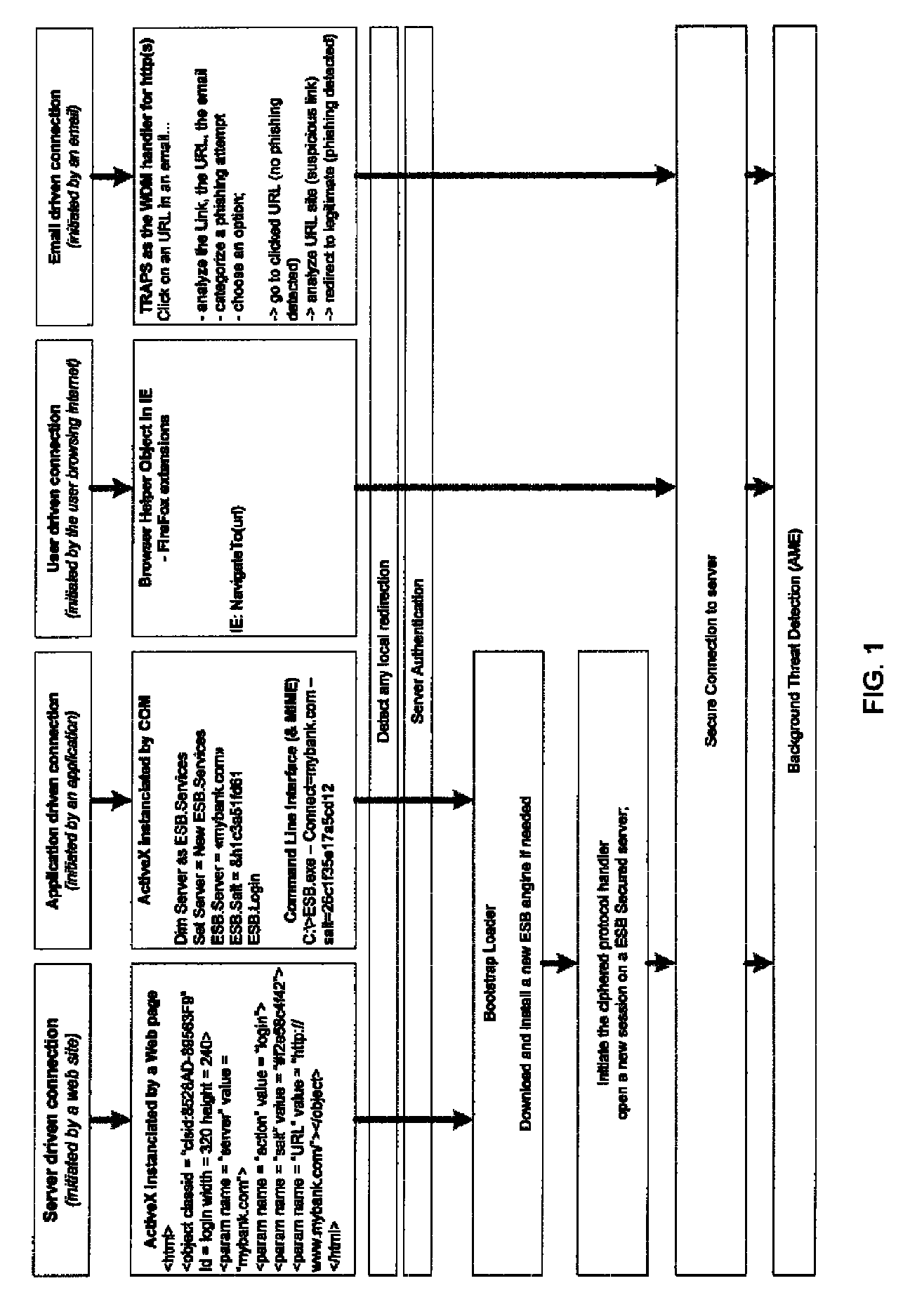
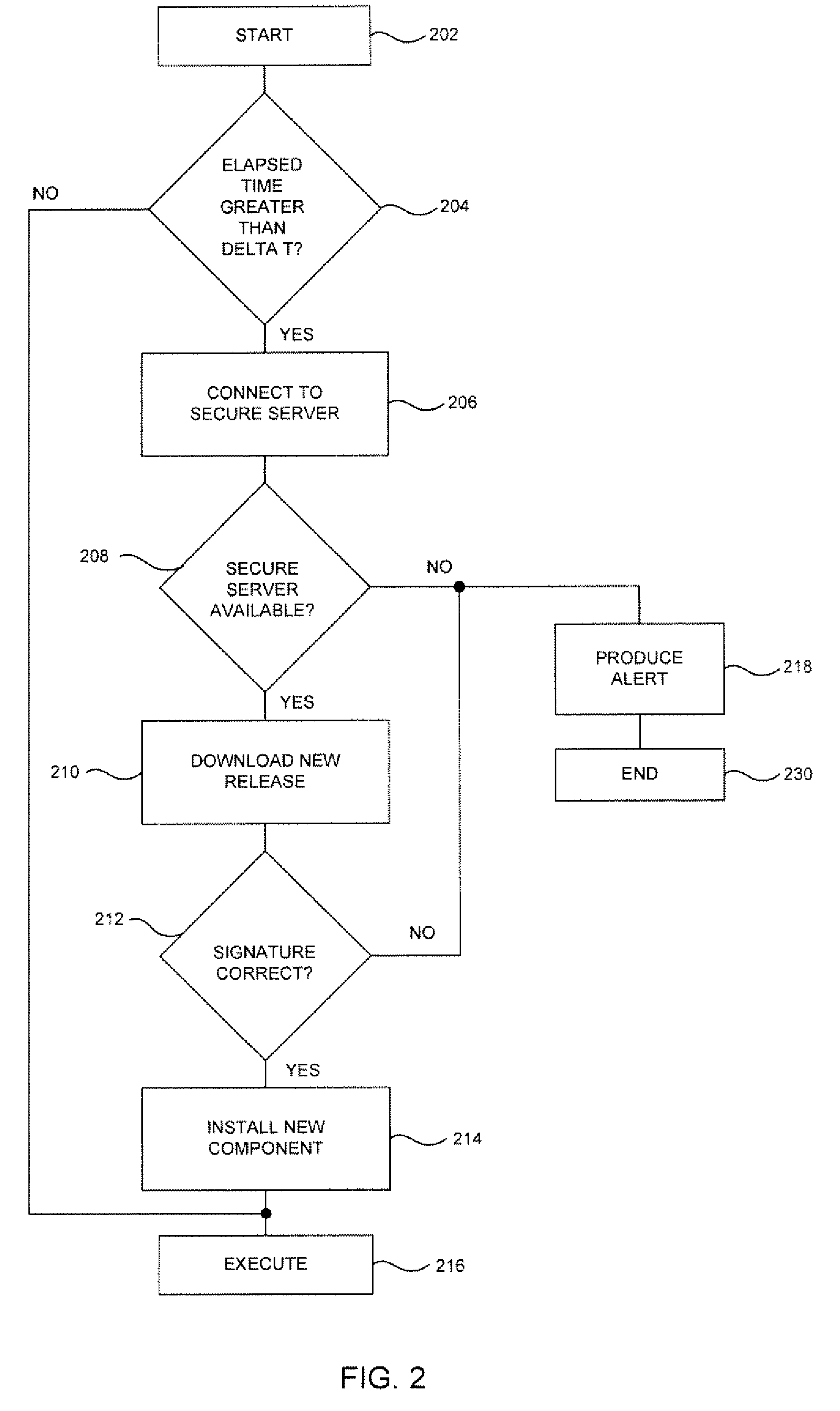
System and method for authentication, data transfer, and protection against phishing
ActiveUS8578166B2Key distribution for secure communicationDigital data processing detailsElectronic communicationStructure of Management Information
Methods and systems for secure electronic data communication over public communication networks. A secure data communication component may be utilized to implement a communication protocol. New versions of the data communication component may be generated, with each version containing a different communication protocol. Source code of the data communication component may be modified using a polymorph engine to create a functionally-equivalent component having a different code structure. An anti-phishing component may intercept a link in an electronic communication activated by a user, analyze the link and the electronic communication, determine a phishing risk to the user posed by the link, and direct the user to a location indicated by the link or redirect the user to a valid location. A server authentication component may detect and prevent DNS attacks, injections, and defacing activities.
Owner:MORGAMON
Mobile web protection
InactiveUS20120324568A1Computer security arrangementsMultiple digital computer combinationsEvaluation resultWeb browser
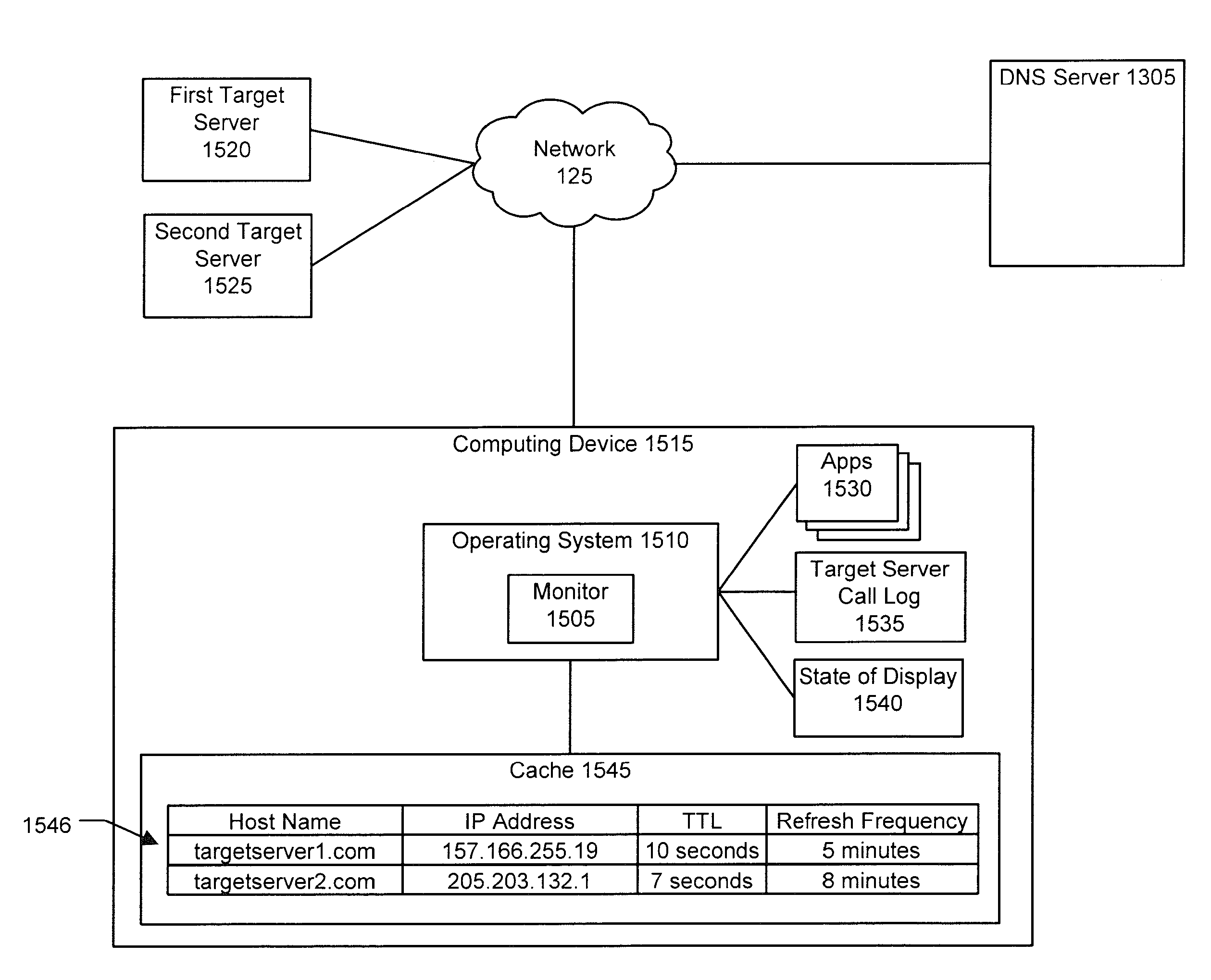
On a mobile communications device, visiting a link from a messaging application or web browser may result in an undesired action, such as visiting a phishing site, downloading malware, causing unwanted charges, using too much battery, or the device being exploited. In an implementation, a mobile application intercepts a request including an identifier associated with an action to be performed by another application on the device and evaluates the identifier to determine when the request should be permitted, blocked, or conditionally permitted. The client may use local data or make a request to a server to evaluate the identifier. In an implementation, server communications are optimized to minimize latency by caching evaluation results on the device, proactively priming the device's DNS cache, optimizing when DNS lookups are performed, and adapting evaluation policy based on factors such as the source of the request, and the currently active network connection.
Owner:LOOKOUT MOBILE SECURITY
Automated identification of phishing, phony and malicious web sites
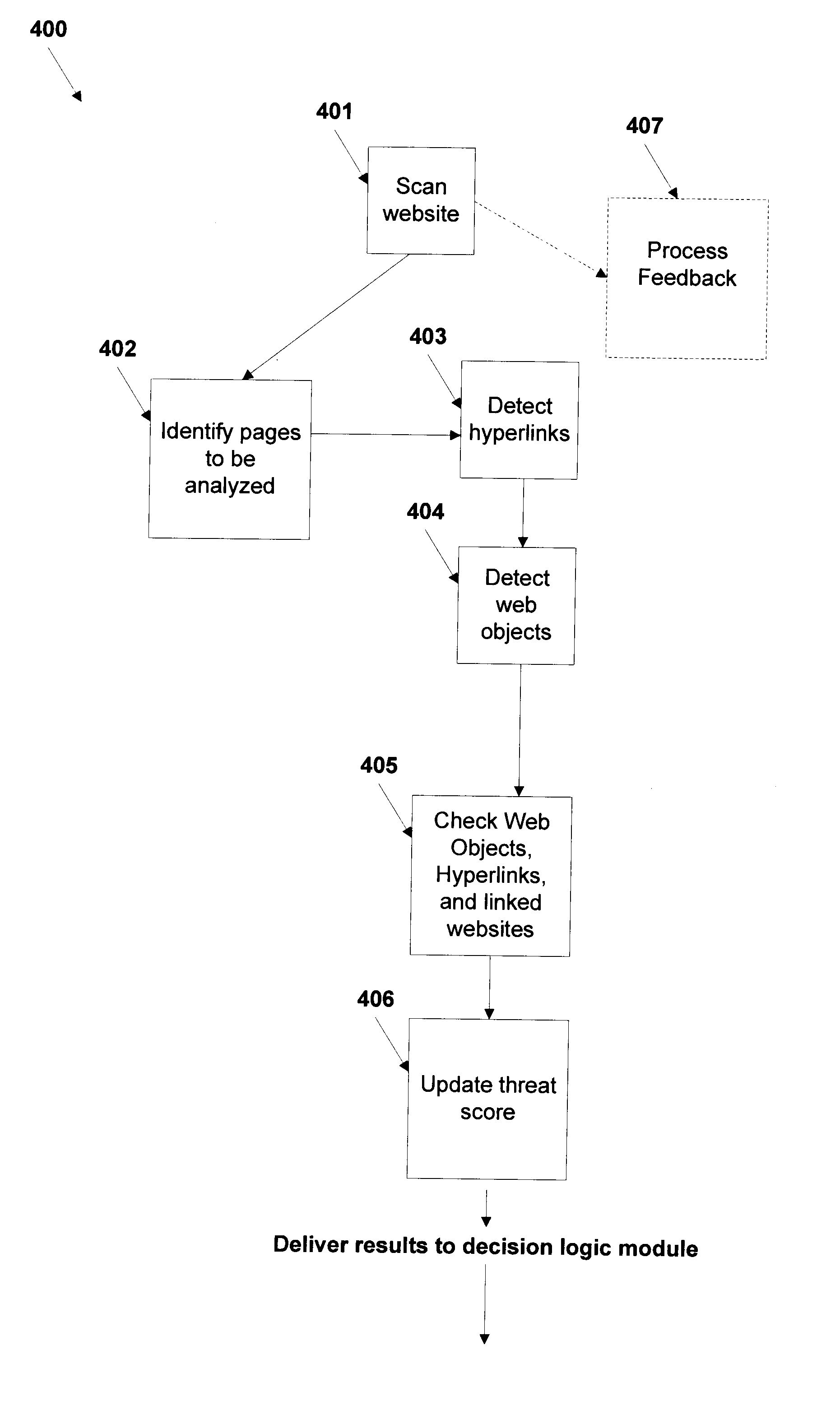
A method and system for automated identification of phishing, phony, and malicious web sites are disclosed. According to one embodiment, a computer implemented method, comprises receiving a first input, the first input including a universal resource locator (URL) for a webpage. A second input is received, the second input including feedback information related to the webpage, the feedback information including an indication designating the webpage as safe or unsafe. A third input is received from a database, the third input including reputation information related to the webpage. Data is extracted from the webpage. A safety status is determined for the webpage, including whether the webpage is hazardous by using a threat score for the webpage and the second input, wherein calculating the threat score includes analyzing the extracted data from the webpage. The safety status for the webpage is reported.
Owner:CLOUDFLARE
Mutual authentication security system with detection and mitigation of active man-in-the-middle browser attacks, phishing, and malware and other security improvements.
ActiveUS20170346851A1Multiple keys/algorithms usagePublic key for secure communicationWeb sitePhishing
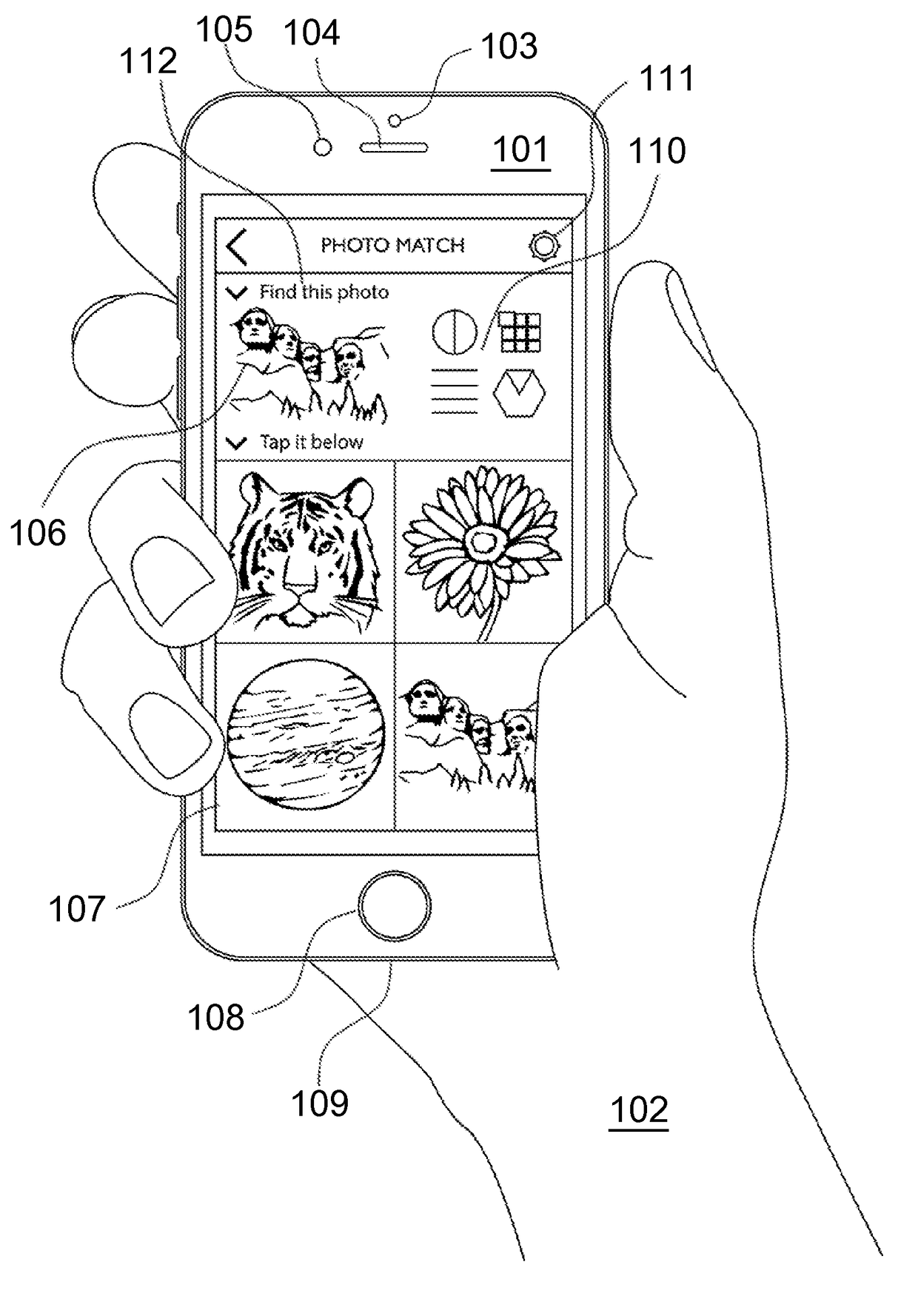
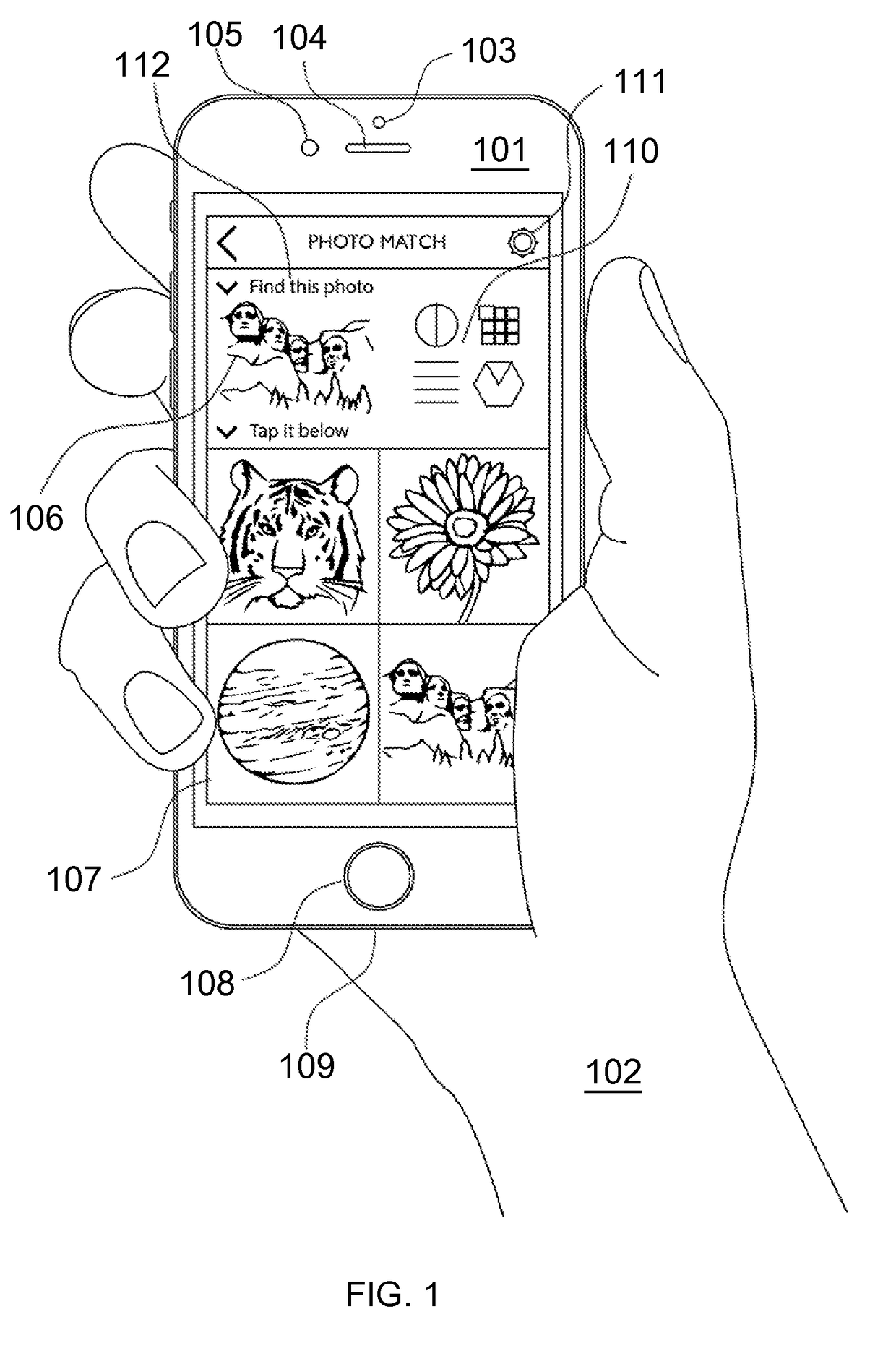
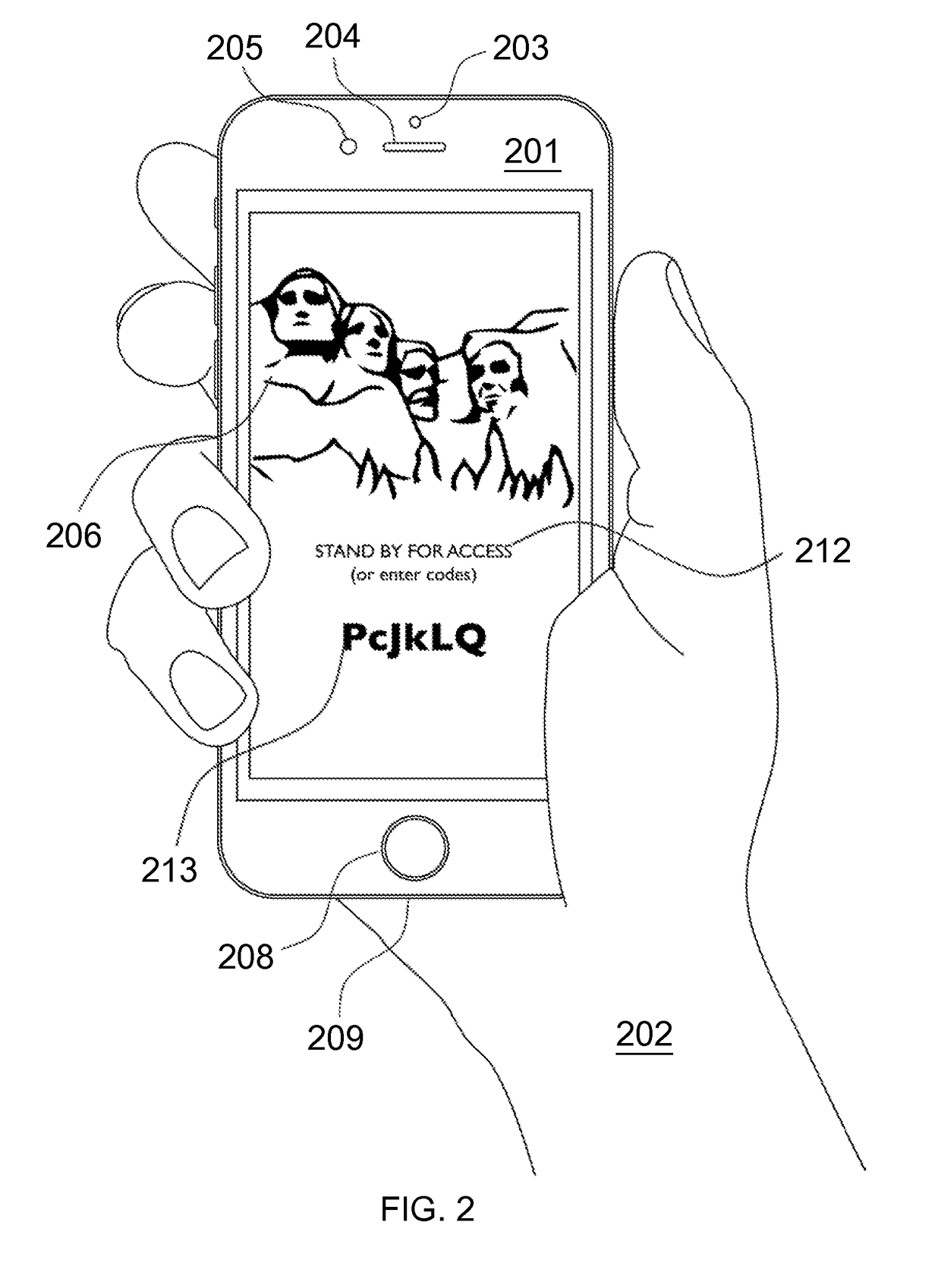
A strong, unified and comprehensive new computer security and authentication solution is disclosed. It is ideal for everyday users, and invents faster and easier enrollments, faster usage, easier usage, numerous aspects of stronger security including token based rapid mutual-authentication with protection against phishing, MitM, malware and user carelessness, secure resilience against token loss or theft, continuing protection in harsh situations, non-repudiation benefits, biometric encryption, code self-defenses, improved deployment, lower costs, new revenue opportunities, and more. One aspect's flow, visually-enforced mutual-authentication is: customer visits protected web site's login page, gets identified via Cookies, site displays one random photograph on said page, triggers customer's smartphone to automatically show a grid of random photos, one of which matches the login page photo, and customer taps it to login. Disclosed techniques teach how to block fraudulent sites and activity by preventing these producing any matching photo the customer can tap.
Owner:DRAKE CHRISTOPHER NATHAN TYRWHITT
System and method for authentication, data transfer, and protection against phishing
ActiveUS20090077383A1Key distribution for secure communicationDigital data processing detailsElectronic communicationPhishing
Methods and systems for secure electronic data communication over public communication networks. A secure data communication component may be utilized to implement a communication protocol. New versions of the data communication component may be generated, with each version containing a different communication protocol. Source code of the data communication component may be modified using a polymorph engine to create a functionally-equivalent component having a different code structure. An anti-phishing component may intercept a link in an electronic communication activated by a user, analyze the link and the electronic communication, determine a phishing risk to the user posed by the link, and direct the user to a location indicated by the link or redirect the user to a valid location. A server authentication component may detect and prevent DNS attacks, injections, and defacing activities.
Owner:MORGAMON
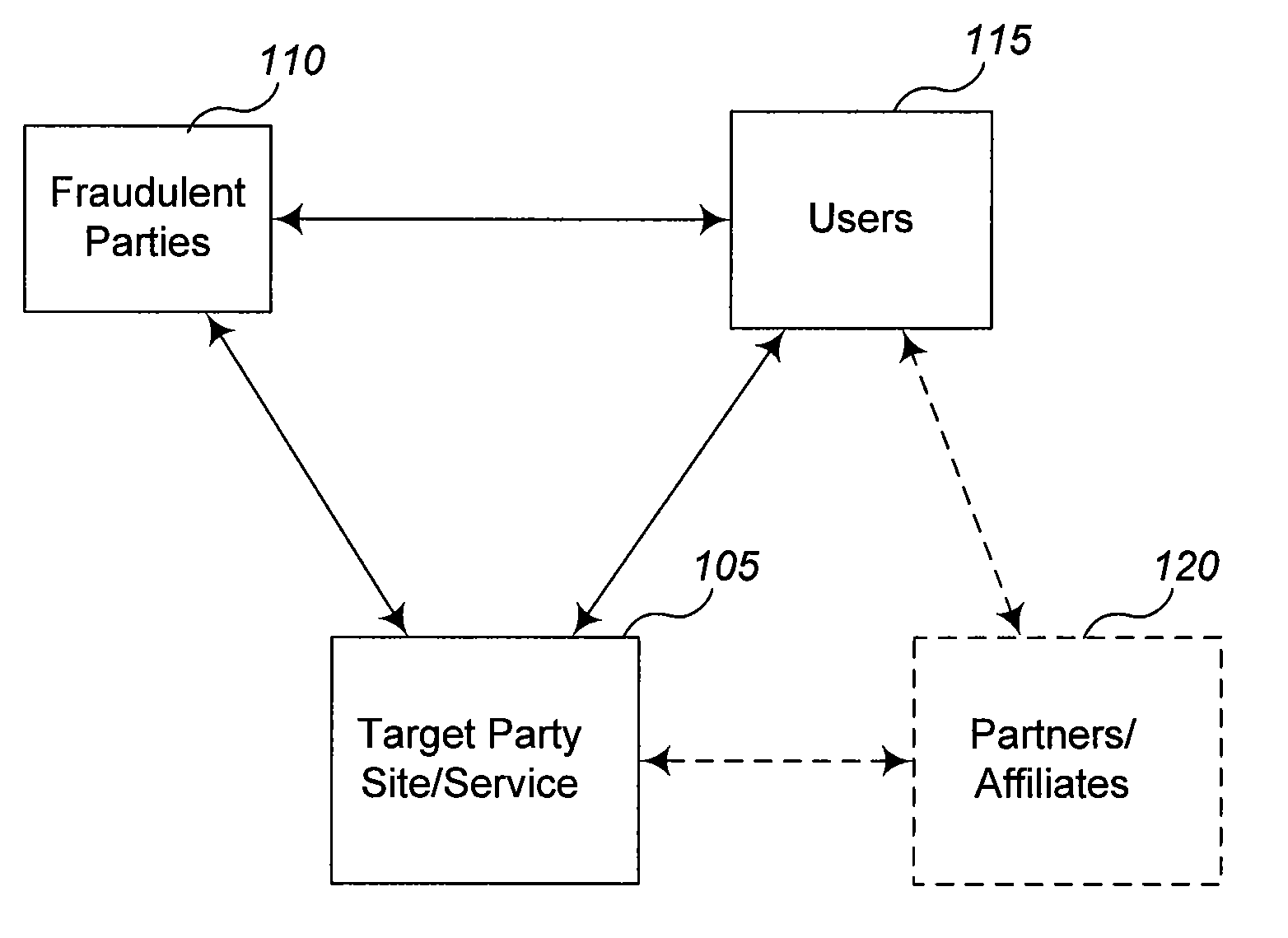
Methods and systems for analyzing data related to possible online fraud
ActiveUS20060069697A1Data processing applicationsDigital data processing detailsWeb siteAnalysis data
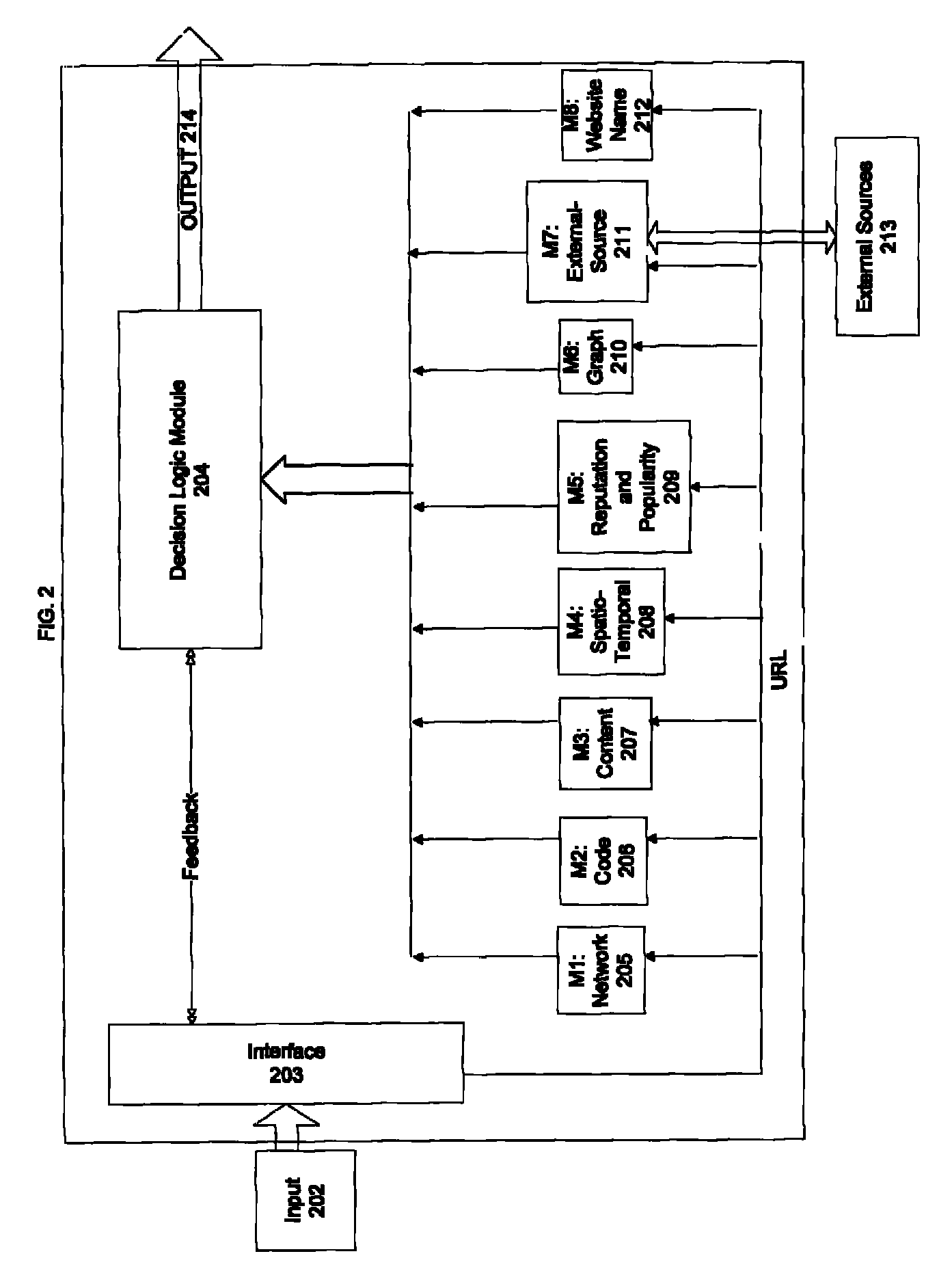
Various embodiments of the invention provide methods, systems and software for analyzing data. In particular embodiments, for example, a set of data about a web site may be analyzed to determine whether the web site is likely to be illegitimate (e.g., to be involved in a fraudulent scheme, such as a phishing scheme, the sale of gray market goods, etc.). In an exemplary embodiment, a set of data may be divided into a plurality of components (each of which, in some cases, may be considered a separate data set). Merely by way of example, a set of data may comprise data gathered from a plurality of data sources, and / or each component may comprise data gathered from one of the plurality of data sources. As another example, a set of data may comprise a document with a plurality of sections, and each component may comprise one of the plurality of sections. Those skilled in the art will appreciate that the analysis of a particular component may comprise certain tests and / or evaluations, and that the analysis of another component may comprise different tests and / or evaluations. In other cases, the analysis of each component may comprise similar tests and / or evaluations. The variety of tests and / or evaluations generally will be implementation specific.
Owner:OPSEC ONLINE LTD
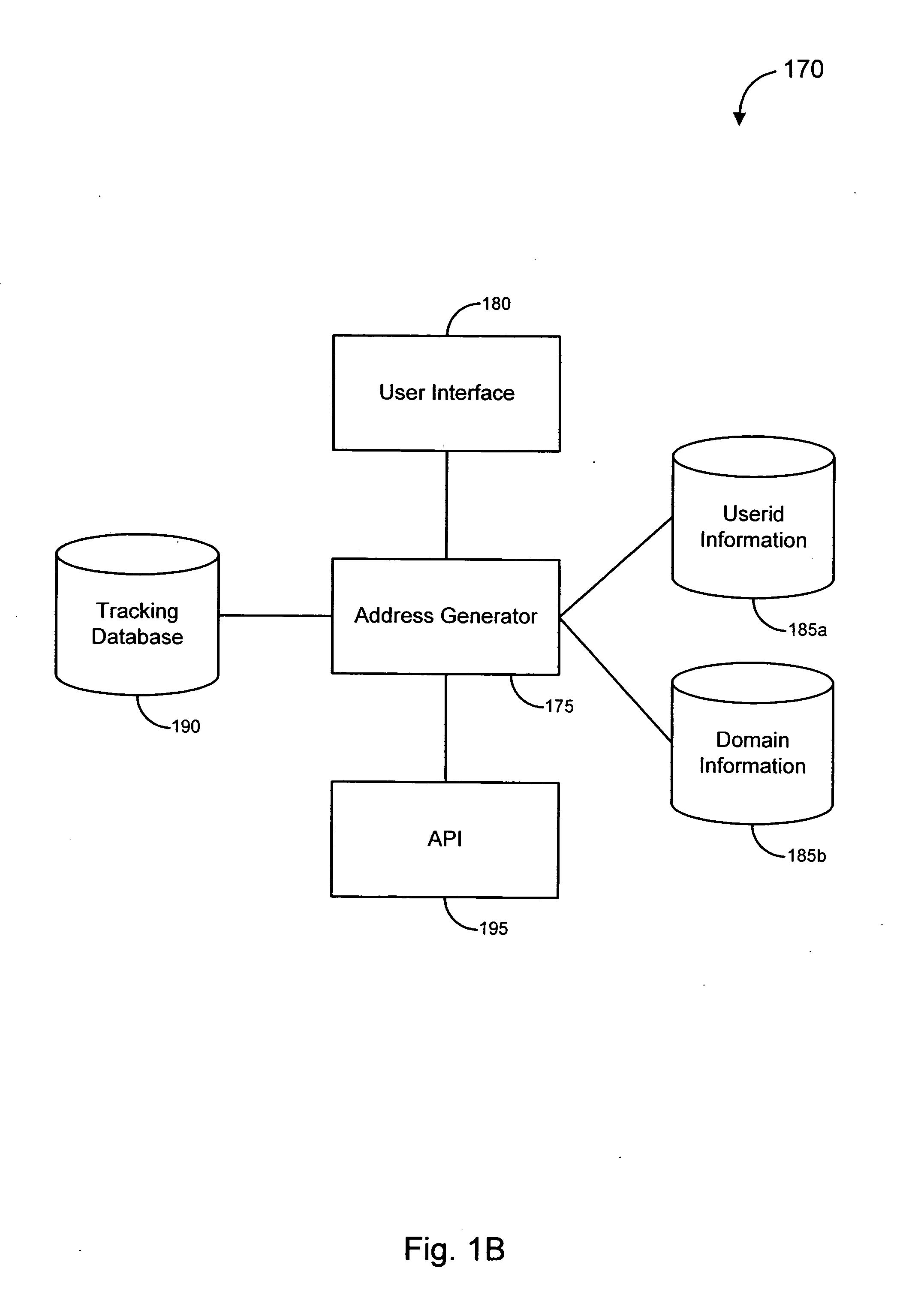
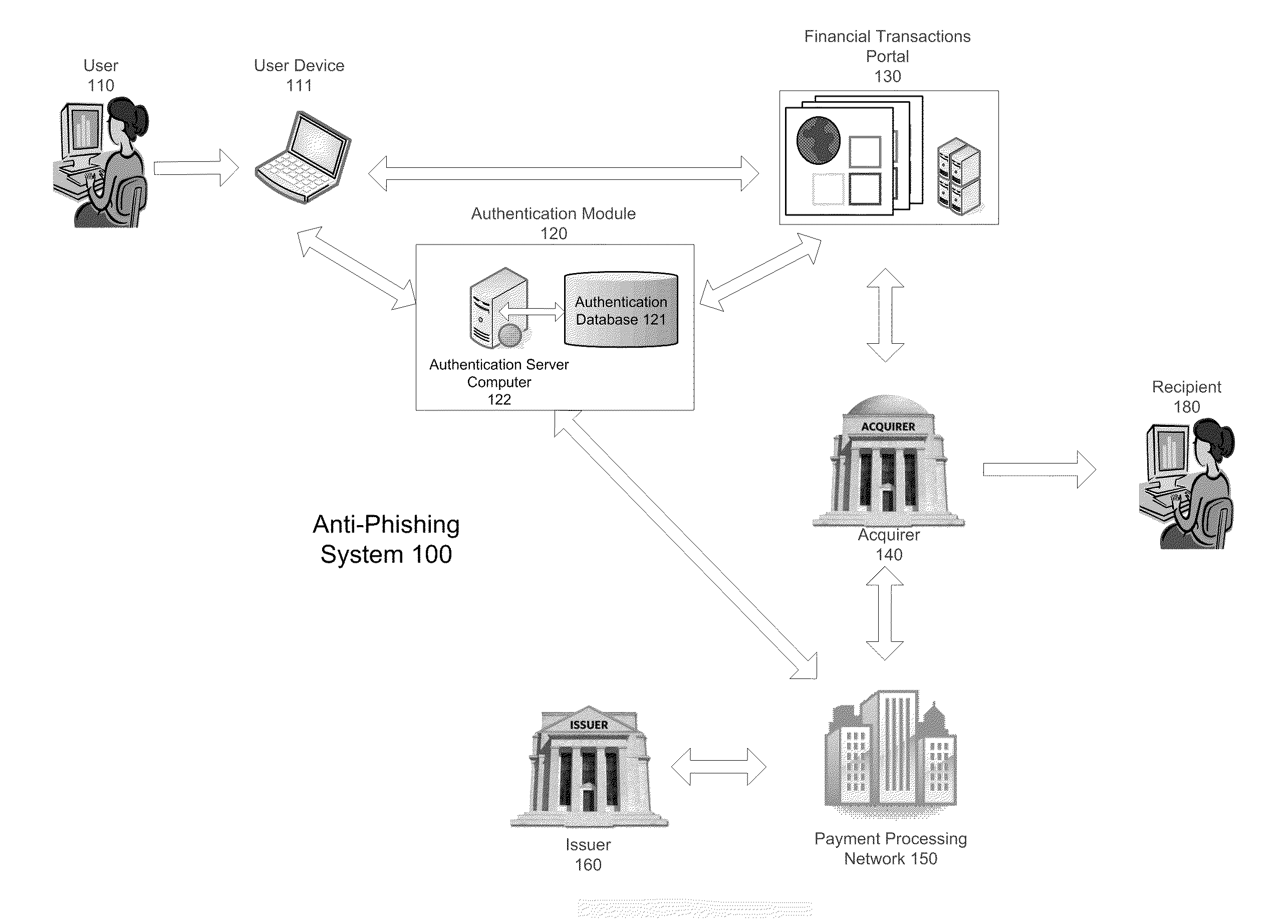
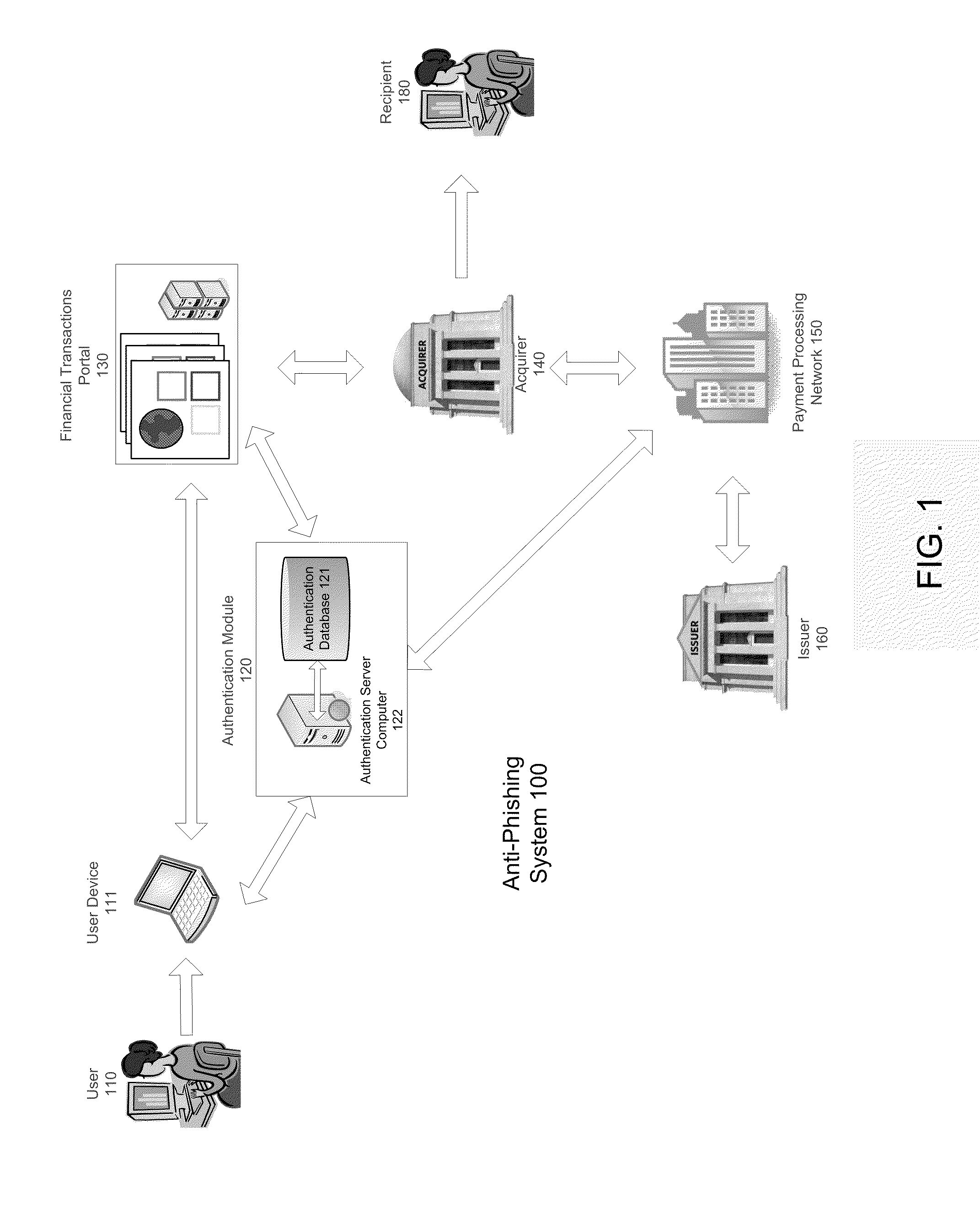
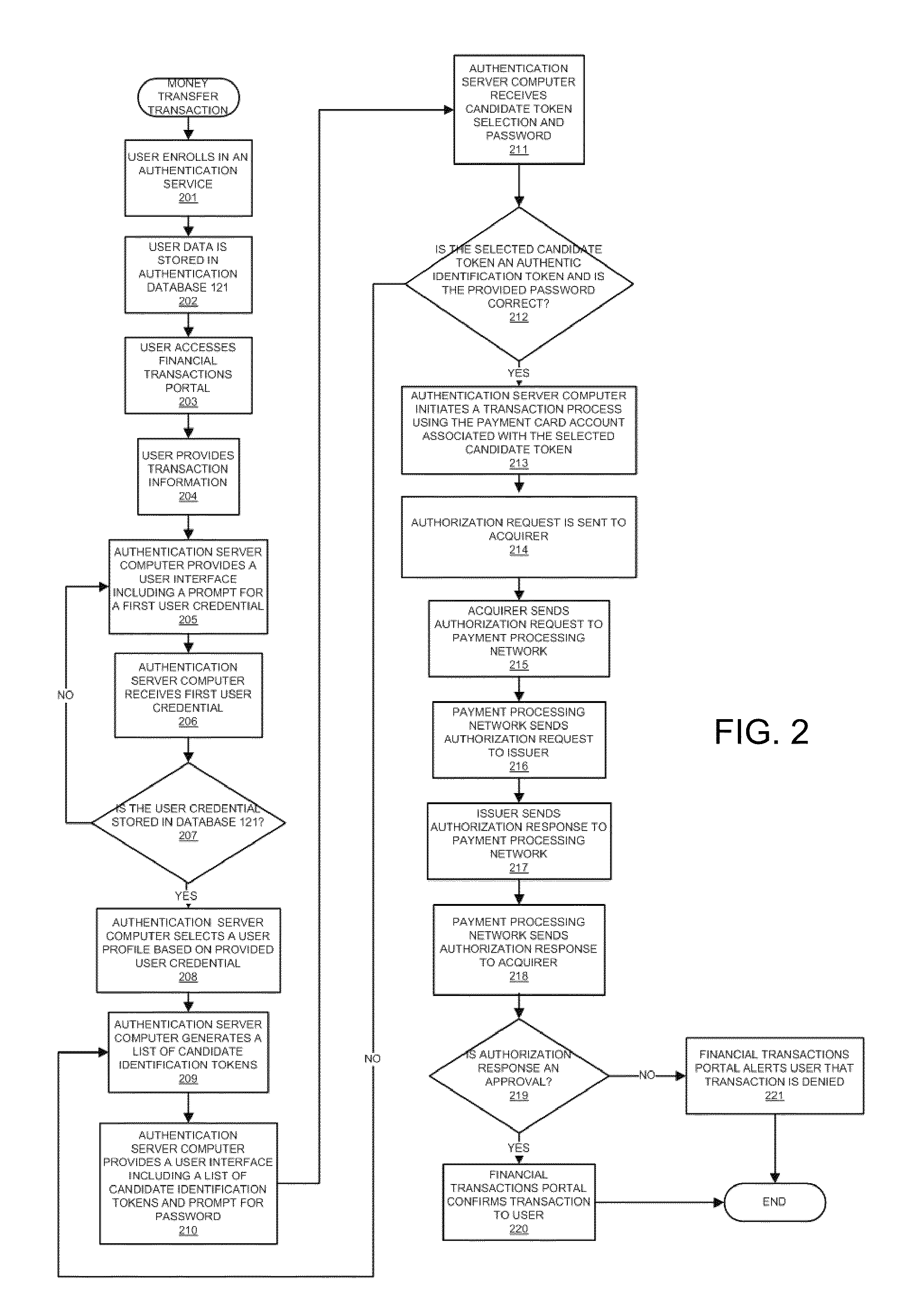
Anti-phishing system and method including list with user data
InactiveUS20110093397A1Improve securityIncrease speedPayment architectureOffice automationPhishingUser interface
A server computer is disclosed. It comprises a processor and a computer readable medium coupled to the processor. The computer readable medium comprises code executable by the processor for implementing a method comprising: (i) receiving a request to conduct a transaction, (ii) providing a user interface to a user in response to the request, wherein the user interface includes a list of candidate identification tokens, wherein the list of candidate identification tokens includes an authentic identification token and one or more non-authentic identification tokens, wherein the authentic identification token is associated with a user account.
Owner:VISA INT SERVICE ASSOC
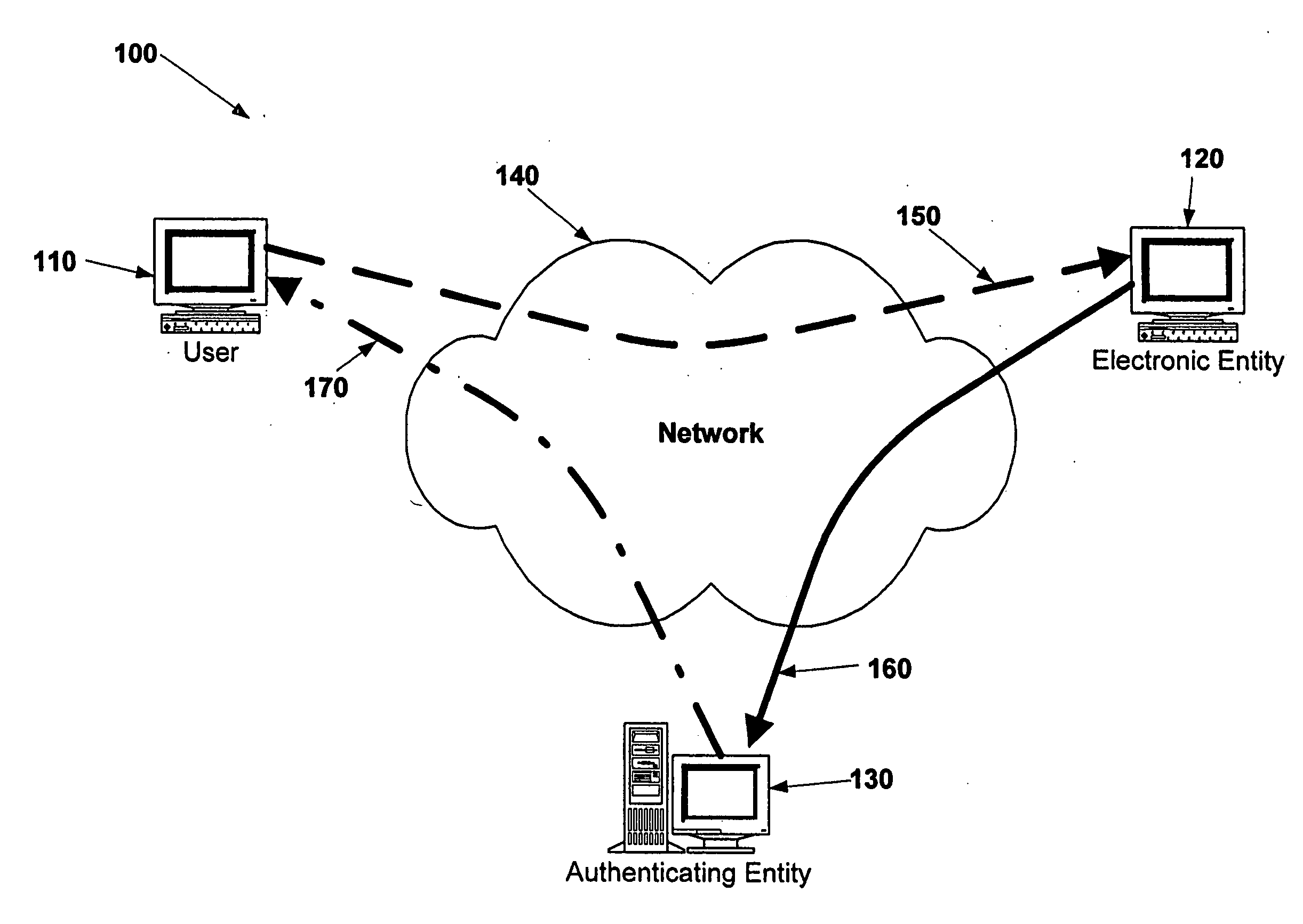
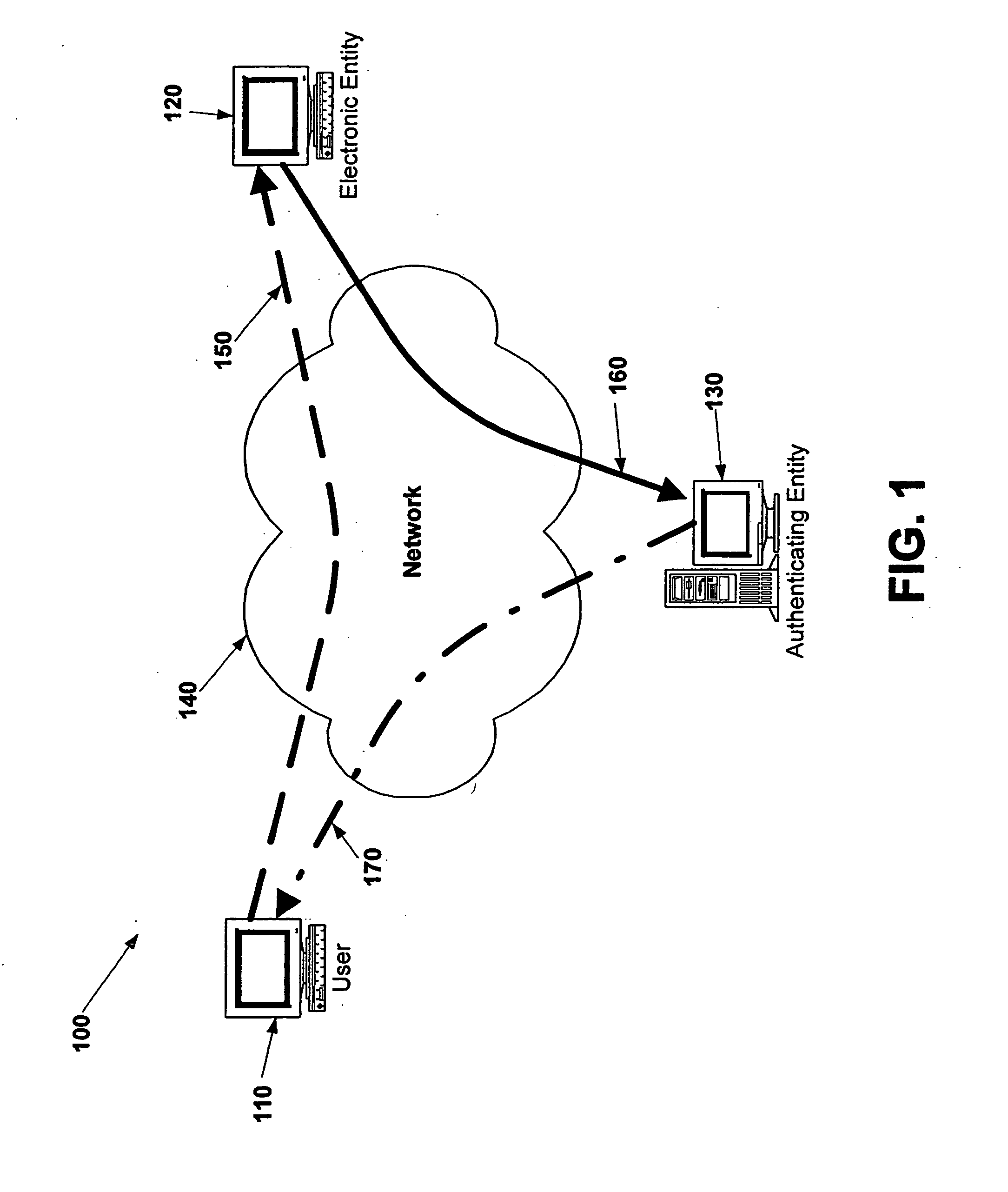
Electronic verification systems
ActiveUS20060200855A1Verify authenticityPrevent account hijacking and frustrate fraudulent electronic transactionsDigital data processing detailsUser identity/authority verificationObject basedThe Internet
A verification system which can be used over electronic networks, such as the Internet, to help prevent phishing, electronic identity theft, and similar illicit activities, by verifying the authenticity of electronic entities (for example, websites). Users and electronic entities register with an authenticating entity. The authenticating entity shares an encryption method with registered electronic entities and establishes a secret code for each registered electronic entity. The secret code is combined with other information and encrypted before being transmitted over the network to ensure that the secret code cannot be compromised. Also disclosed are systems for virtual token devices, which provided object-based authentication without a physical device. Also disclosed are dynamic media credentials, which display nearly-unique behavior, previously specified and known to a user, to assist in verifying the authenticity of the presenter.
Owner:SYCCURE INC
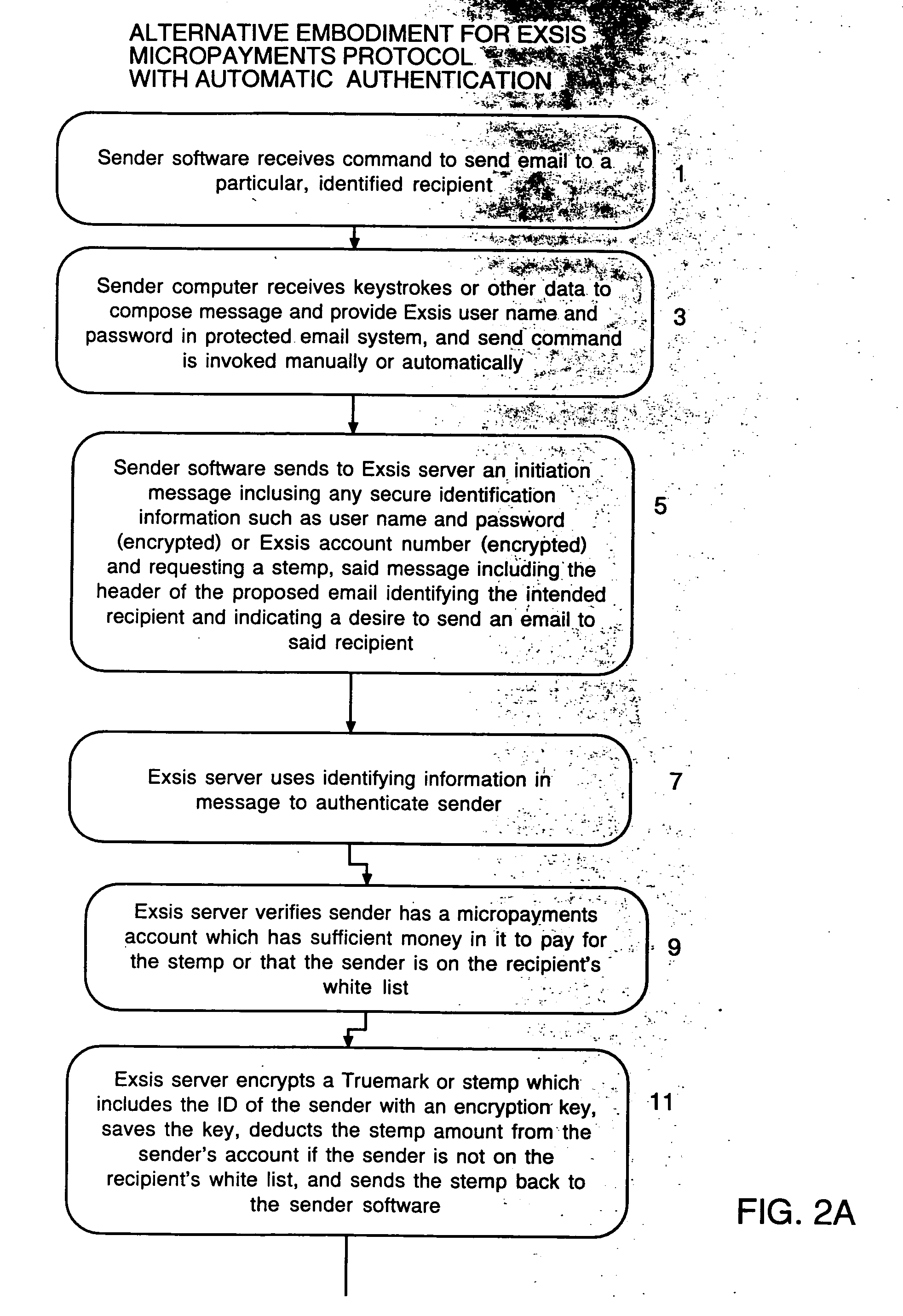
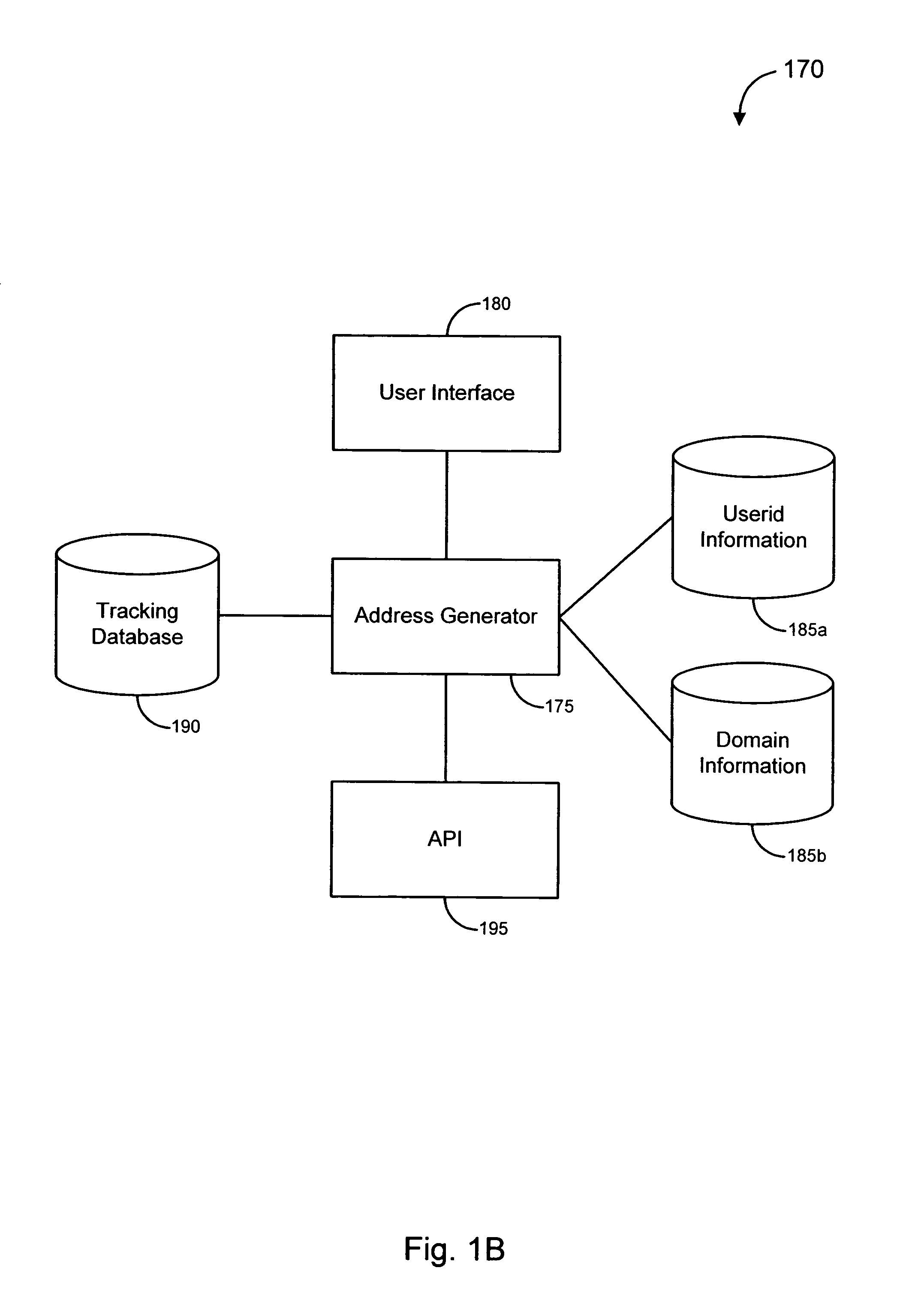
User interface and anti-phishing functions for an anti-spam micropayments system
ActiveUS20060075028A1Control contentEffective controlMultiple digital computer combinationsFlotationTrademarkSpamming
Owner:ICONIX INC
Detecting fraudulent activity by analysis of information requests
Techniques are described for use in inhibiting attempts to fraudulently obtain access to confidential information about users. In some situations, the techniques involve automatically analyzing at least some requests for information that are received by a Web site or other electronic information service, such as to determine whether they likely reflect fraudulent activities by the request senders or other parties that initiate the requests. For example, if a request is being made to a Web site based on a user's interaction with a third-party information source (e.g., another unaffiliated Web site) that is not authorized to initiate the request, the third-party information source may be a fraudulent phishing site or engaging in other types of fraudulent activity. If fraudulent activity is suspected based on analysis of one or more information requests, one or more actions may be taken to inhibit the fraudulent activity.
Owner:AMAZON TECH INC
Advanced responses to online fraud
Various embodiments of the invention provide solutions (including inter alia, systems, methods and software) for dealing with online fraud. In particular, various embodiments of the invention provide advanced responses to an identified instance of online fraud. Such advanced responses can incorporate one or more of a variety of strategies for defeating an attempt by a server to filter and / or otherwise avoid responses to its fraudulent activity. Merely by way of example, in accordance with some embodiments, one or more HTTP responses to a server's request (such as an online form, etc.) may be submitted and / or transmitted for reception by the server. In some cases, each of the submitted responses may appear to comprise valid information responsive to the server's request. In other cases, one or more countermeasures may be implemented to defeat an attempt by a phisher (or any other operator of an illegitimate server) to filter responses.
Owner:OPSEC ONLINE LTD
Methods and systems for analyzing data related to possible online fraud
Various embodiments of the invention provide methods, systems and software for analyzing data. In particular embodiments, for example, a set of data about a web site may be analyzed to determine whether the web site is likely to be illegitimate (e.g., to be involved in a fraudulent scheme, such as a phishing scheme, the sale of gray market goods, etc.). In an exemplary embodiment, a set of data may be divided into a plurality of components (each of which, in some cases, may be considered a separate data set). Merely by way of example, a set of data may comprise data gathered from a plurality of data sources, and / or each component may comprise data gathered from one of the plurality of data sources. As another example, a set of data may comprise a document with a plurality of sections, and each component may comprise one of the plurality of sections. Those skilled in the art will appreciate that the analysis of a particular component may comprise certain tests and / or evaluations, and that the analysis of another component may comprise different tests and / or evaluations. In other cases, the analysis of each component may comprise similar tests and / or evaluations. The variety of tests and / or evaluations generally will be implementation specific.
Owner:OPSEC ONLINE LTD
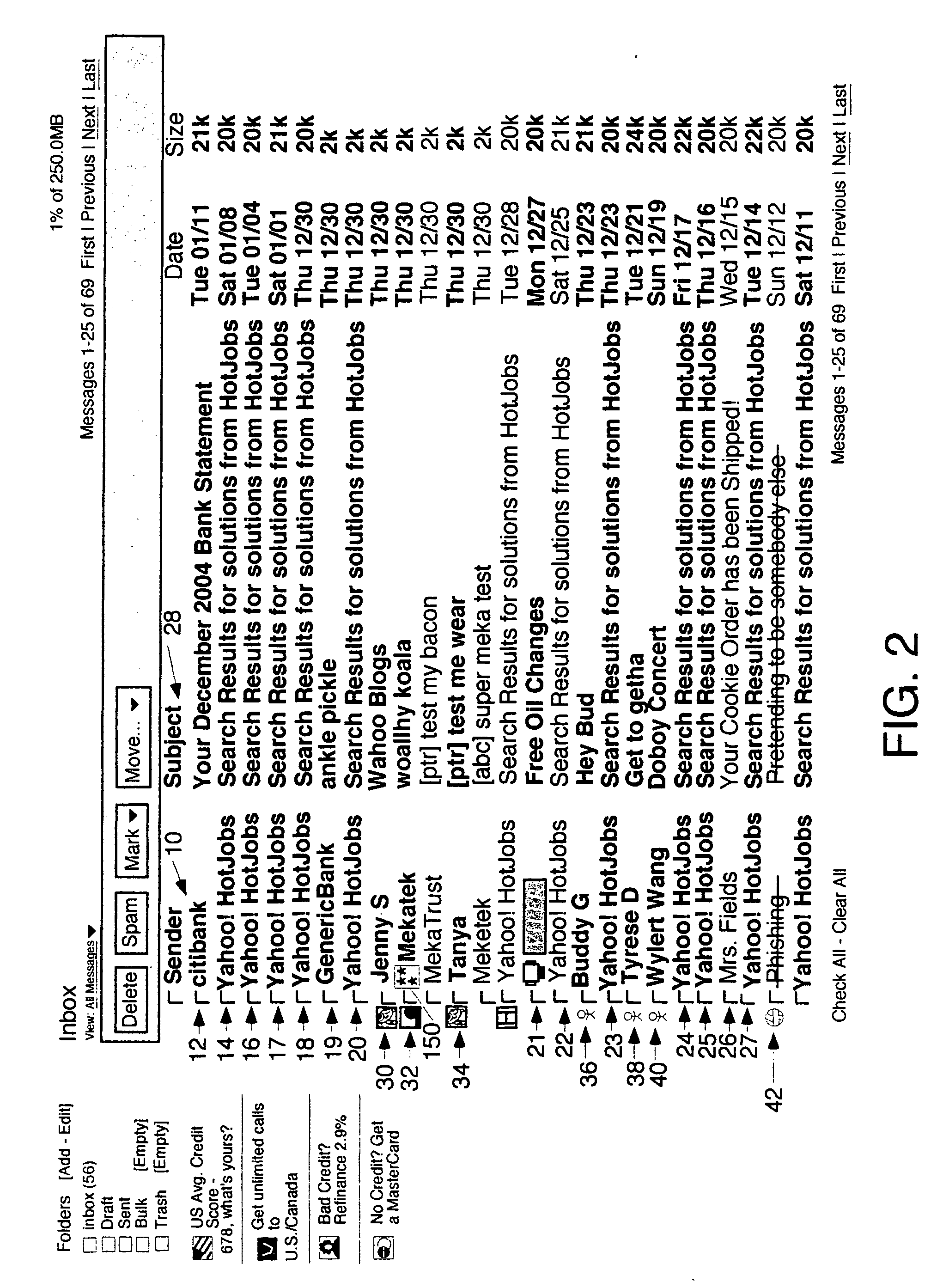
User interface for email inbox to call attention differently to different classes of email
InactiveUS20070005702A1Multiple digital computer combinationsData switching networksGraphicsPhishing
A user interface for email users which calls attention to one or more categories of emails in different ways. In some species, at least three categories are used: branded senders with Trumarks; white list buddies; and fraudulent emails which are either not from the domain they purport to be from or in which the content was tampered. The preferred embodiment authenticates emails from branded senders and displays them with the sender's Truemark. Branded sender emails have their Truemarks displayed in the sender column of a list view in the preferred embodiment. In a preferred embodiment, white list senders have either an icon or other graphic or photo they choose displayed to the left or right of the sender column with their name in the sender column. In a preferred embodiment, fraudulent emails have a fraud icon displayed to the left or right of the sender column with a warning in the sender column. Antiphishing processing is also disclosed.
Owner:ICONIX INC
Controlling hostile electronic mail content
InactiveUS20060101334A1Reduce harmSimple technologyNatural language data processingComputer security arrangementsHyperlinkJScript
Owner:TREND MICRO INC
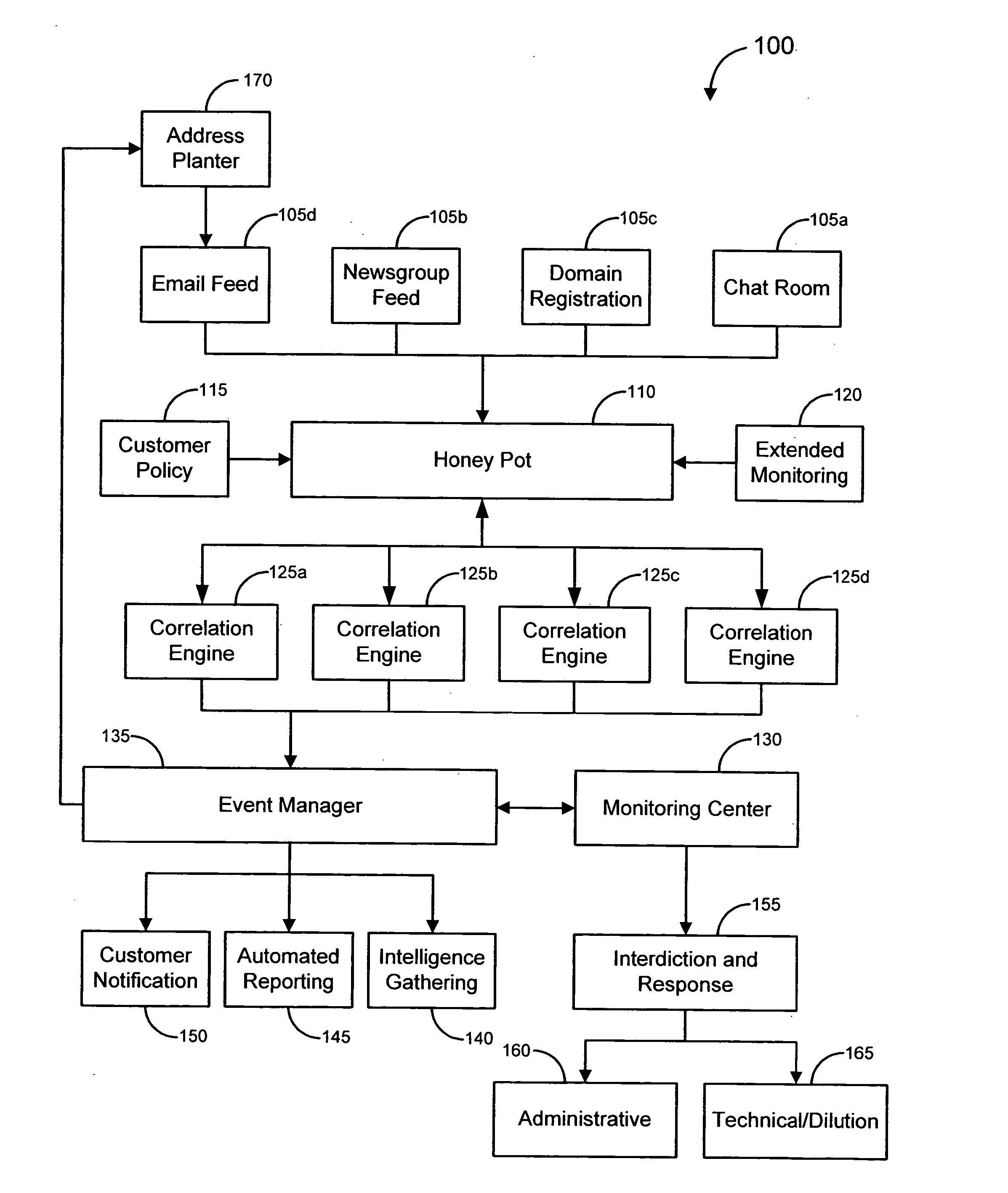
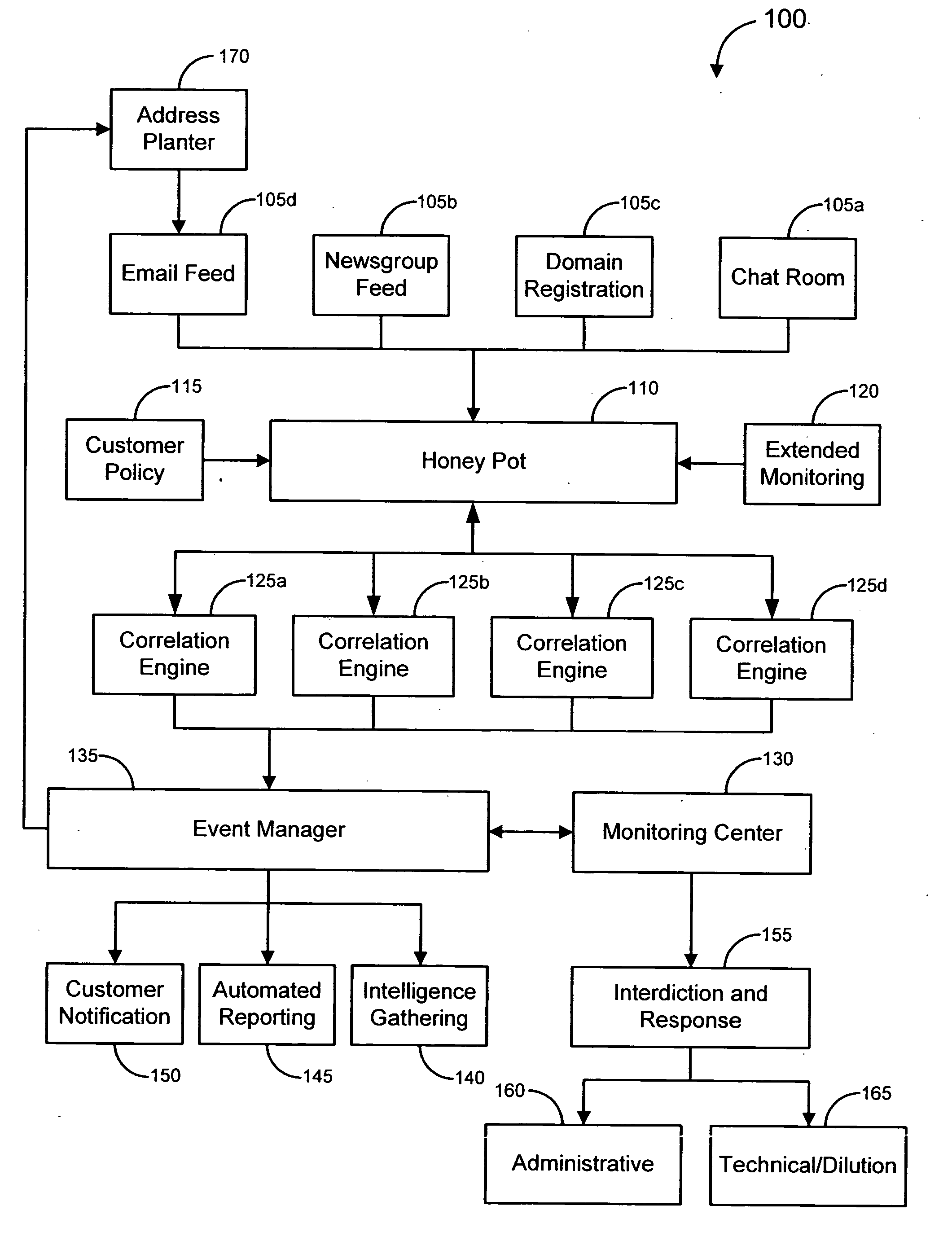
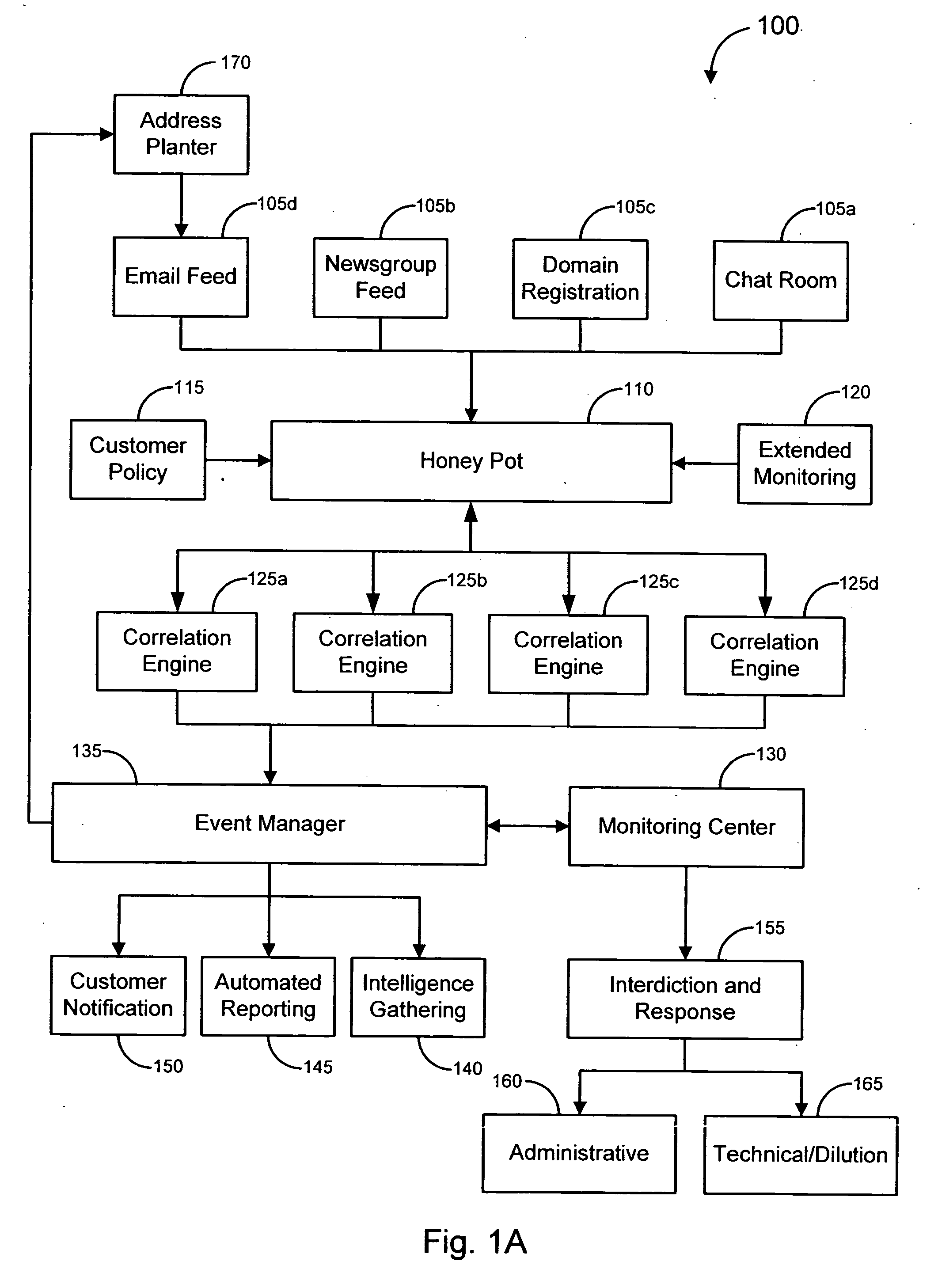
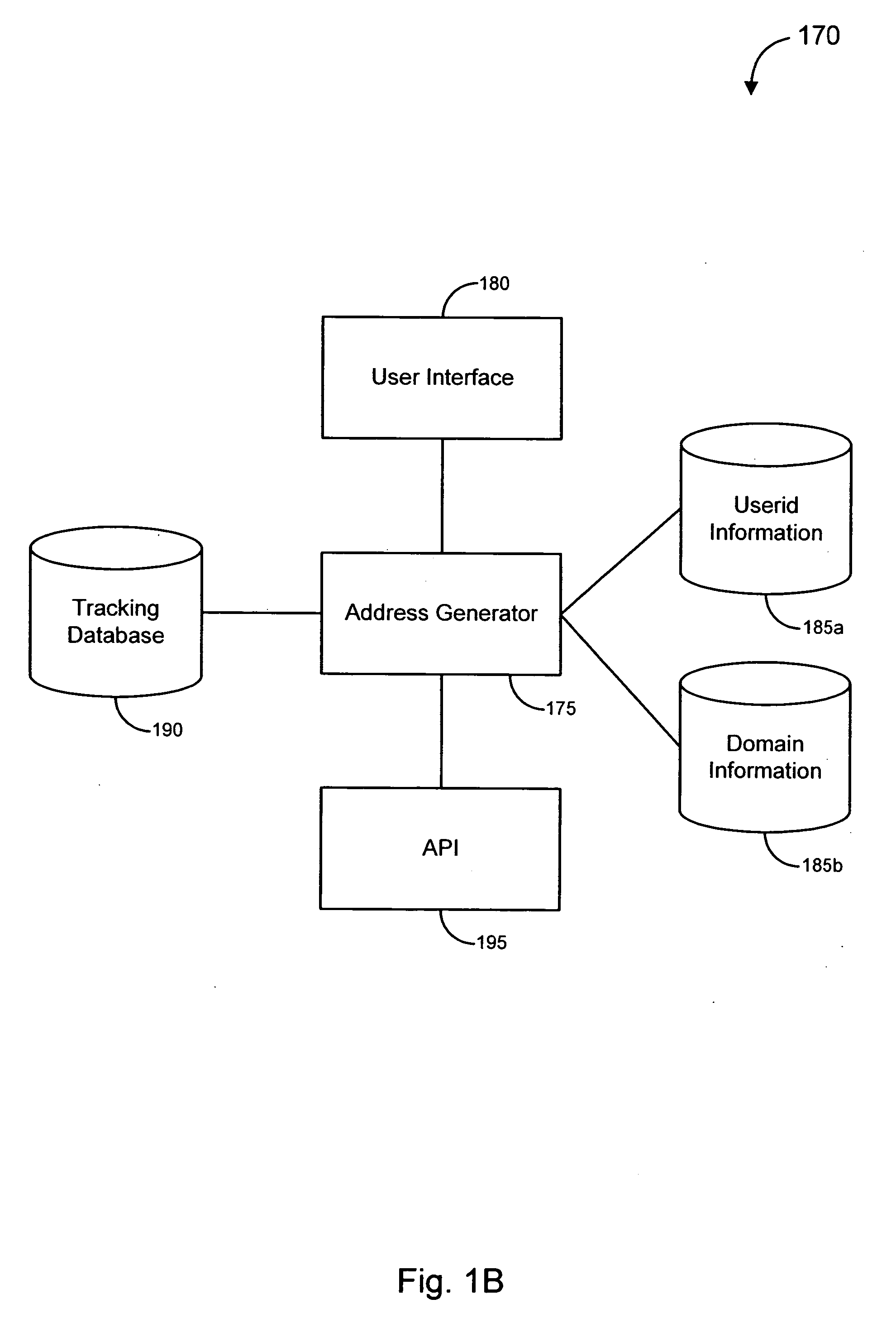
Systems and methods for identifying and mitigating information security risks
ActiveUS20120124671A1High level of realismRaise the possibilityDigital data processing detailsAnalogue secracy/subscription systemsUnique identifierPhishing
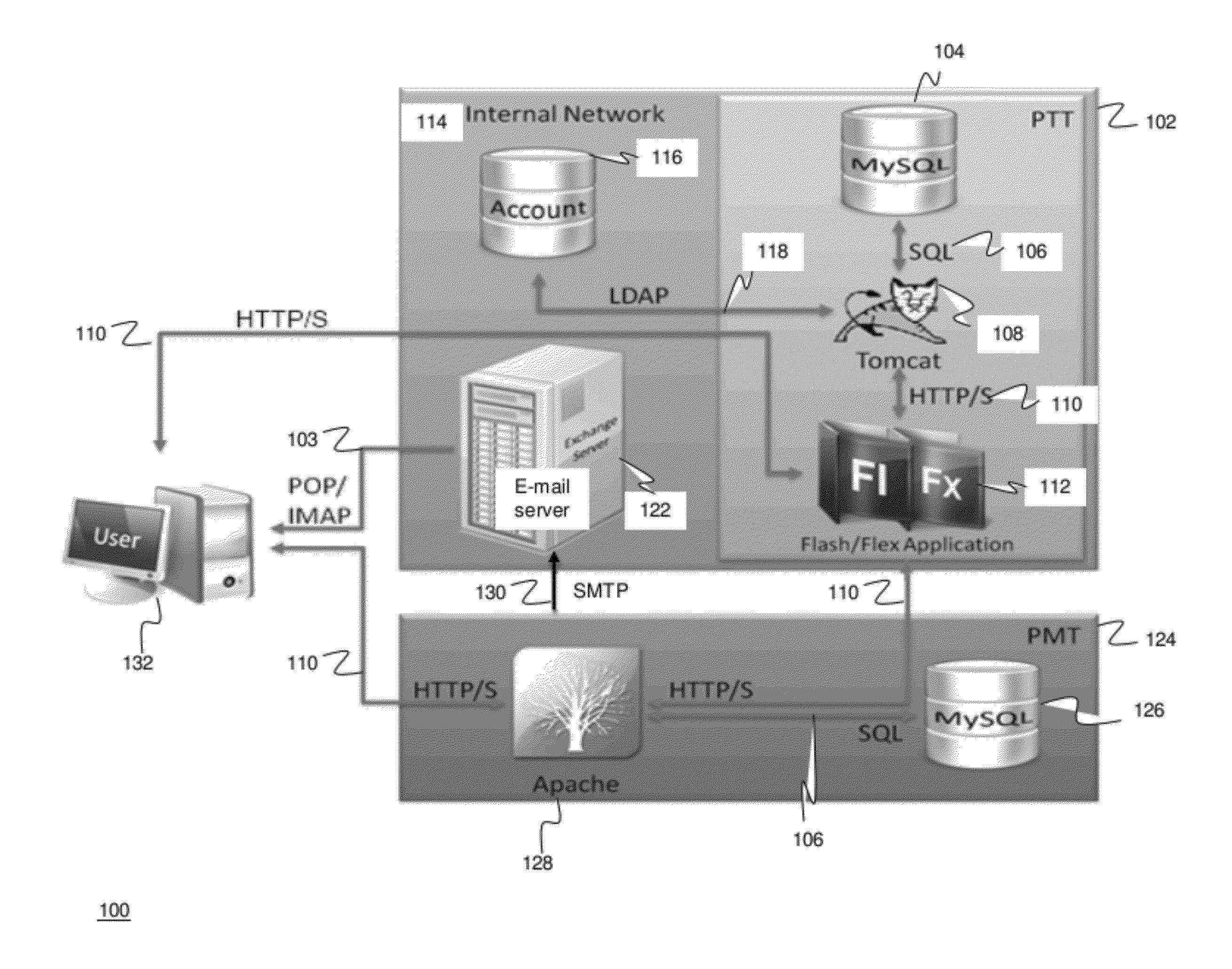
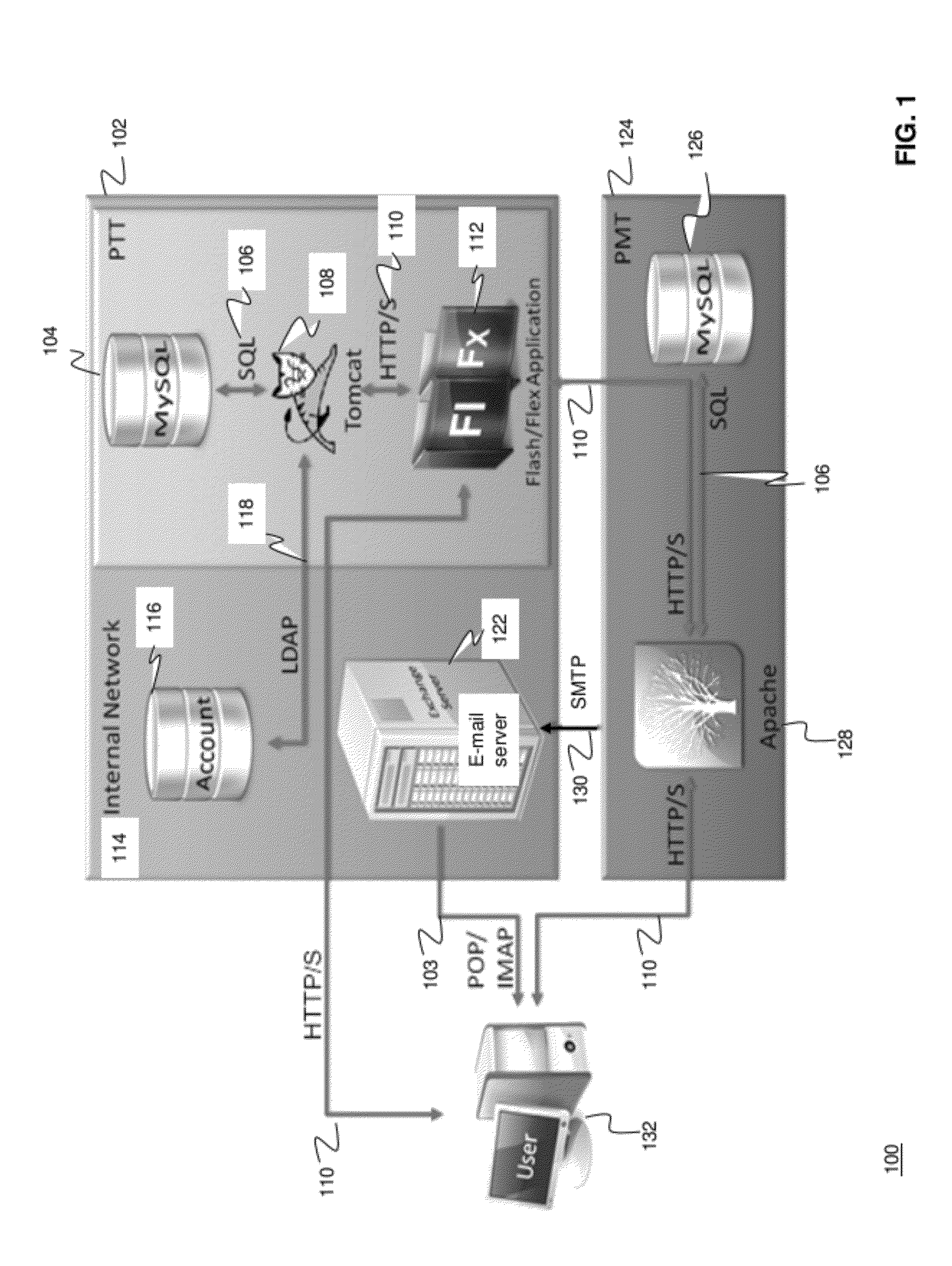
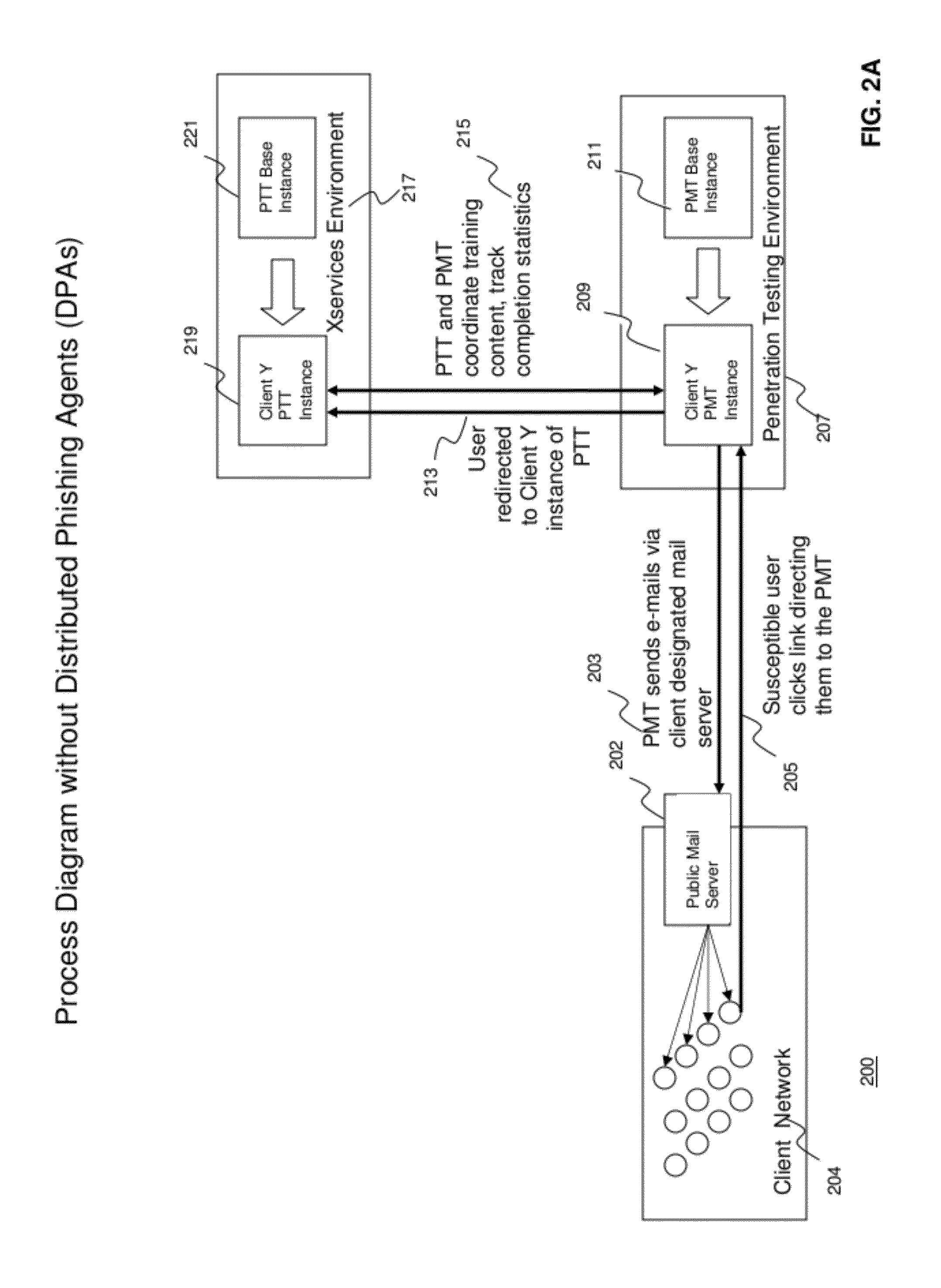
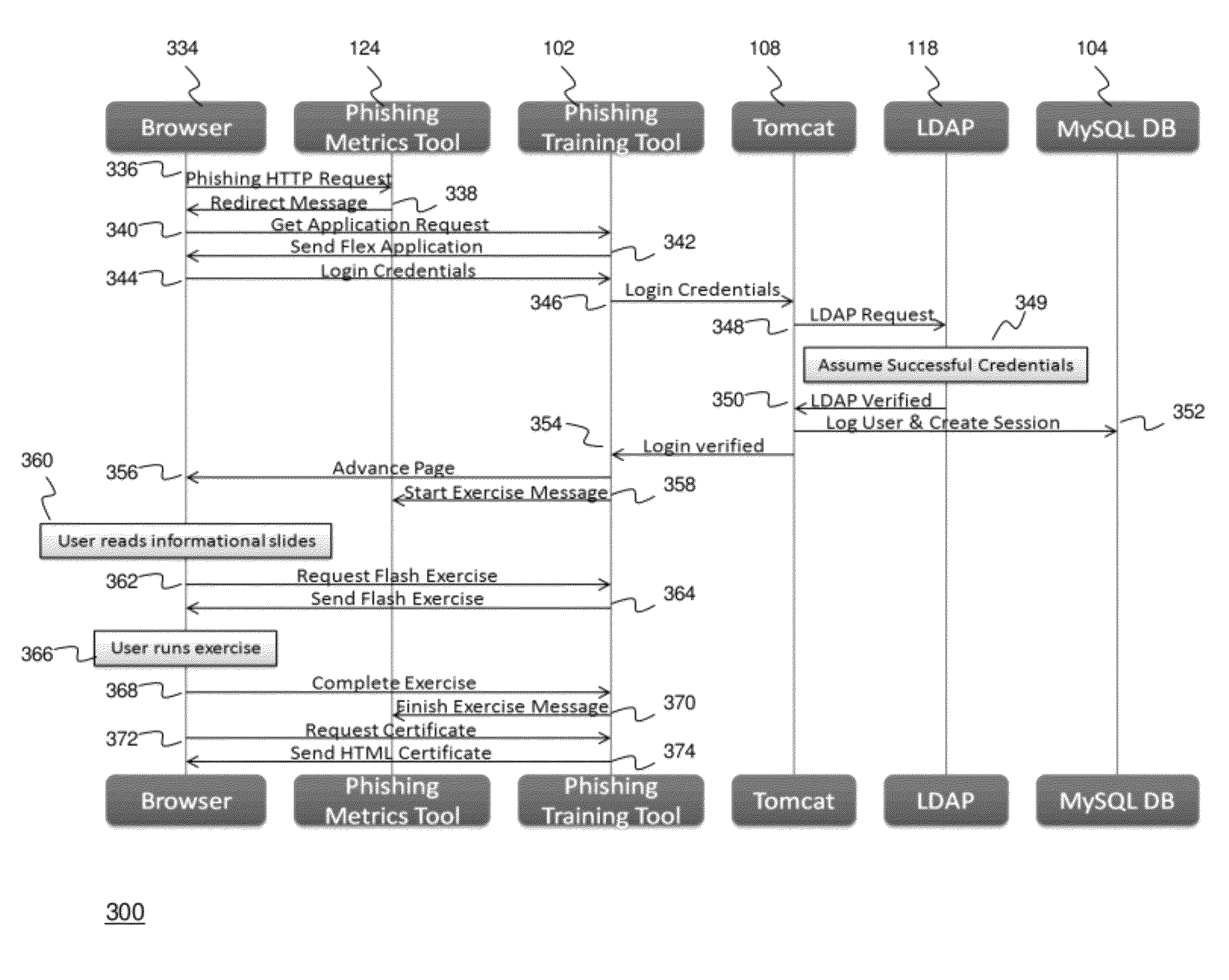
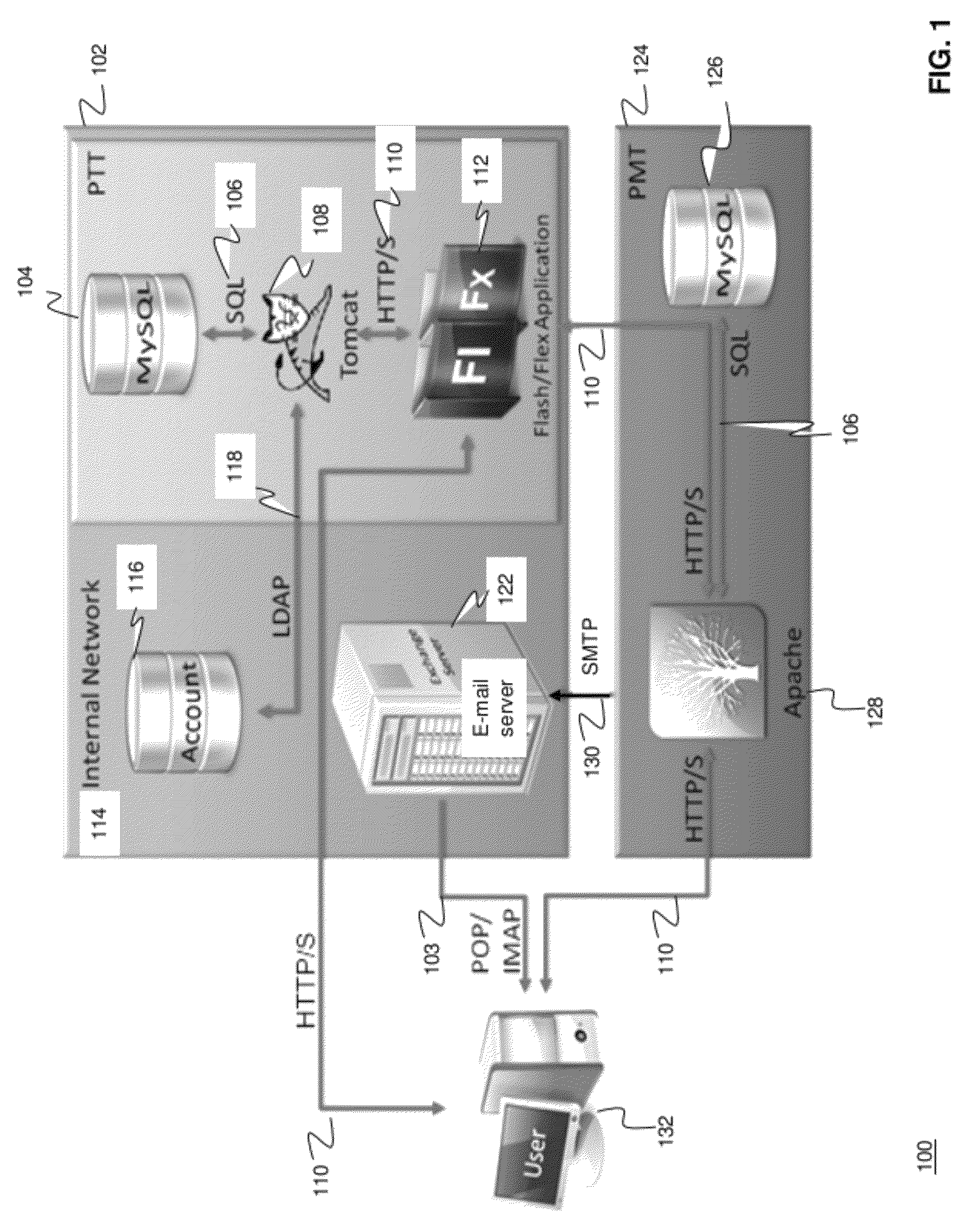
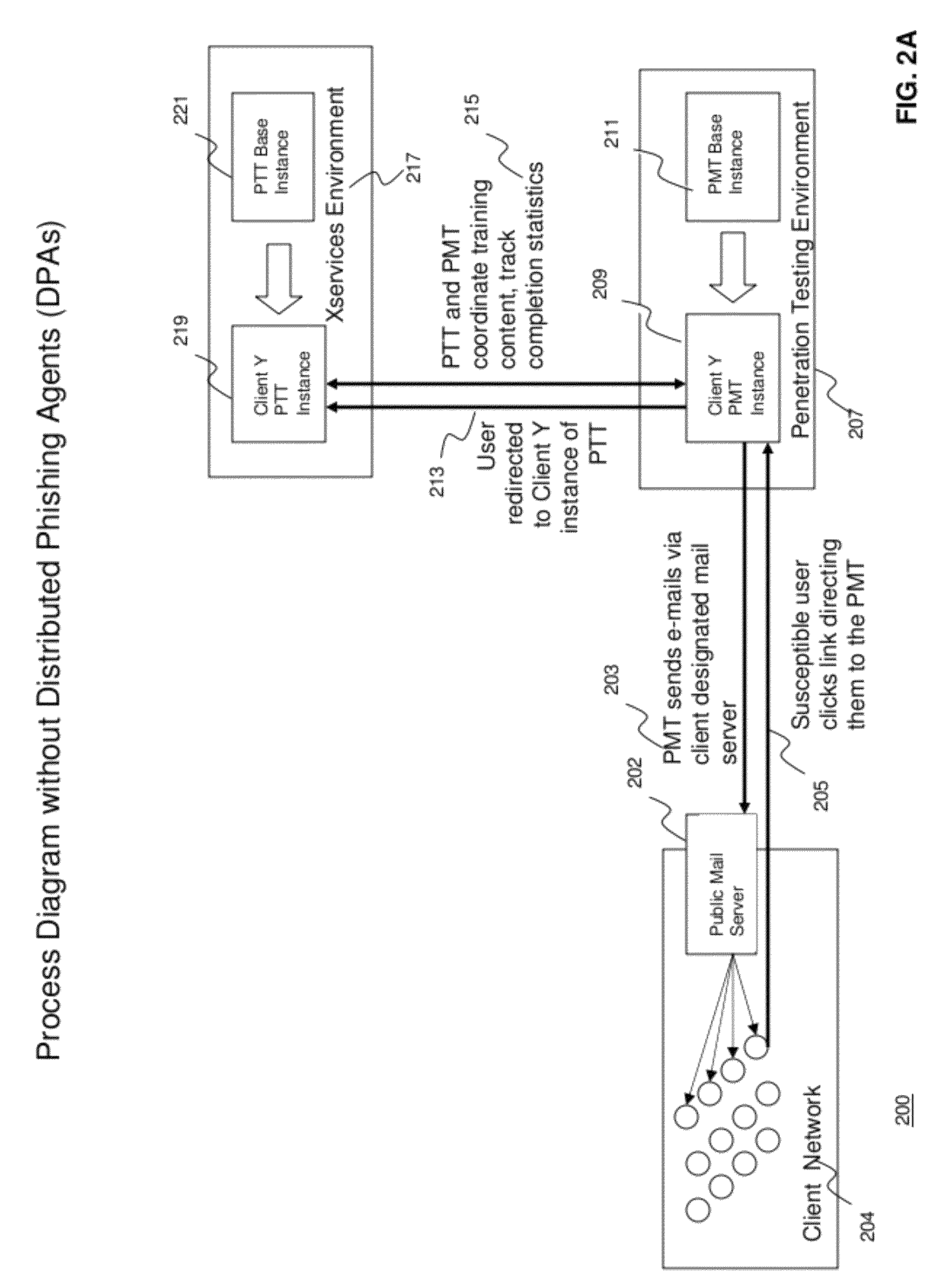
Methods and systems for Sustained Testing and Awareness Refresh against Phishing threats (STAR*Phish™) are disclosed. In an embodiment, a method assigns schemes and unique identifiers to target e-mail addresses associated with a user accounts. The method delivers e-mail messages to the targeted e-mail addresses, the e-mail messages comprising an HTTP request and a unique identifier associated with each of the user accounts. The method then receives, at a Phishing Metric Tool (PMT), a response including the unique identifier. The PMT logs training requirements for the user accounts, tracks response metrics for the training requirements, and redirects the respective HTTP requests to a phishing training tool (PTT). The PTT sends a notification of the user account identities and the unique identifiers to the PMT and returns a status for the training requirements for the user accounts. Upon completion of the training, the PMT sends completion notifications for the user accounts.
Owner:BOOZ ALLEN HAMILTON INC
Email filtering system and method
ActiveUS20060129644A1Effective filteringMultiple digital computer combinationsData switching networksSpammingFilter system
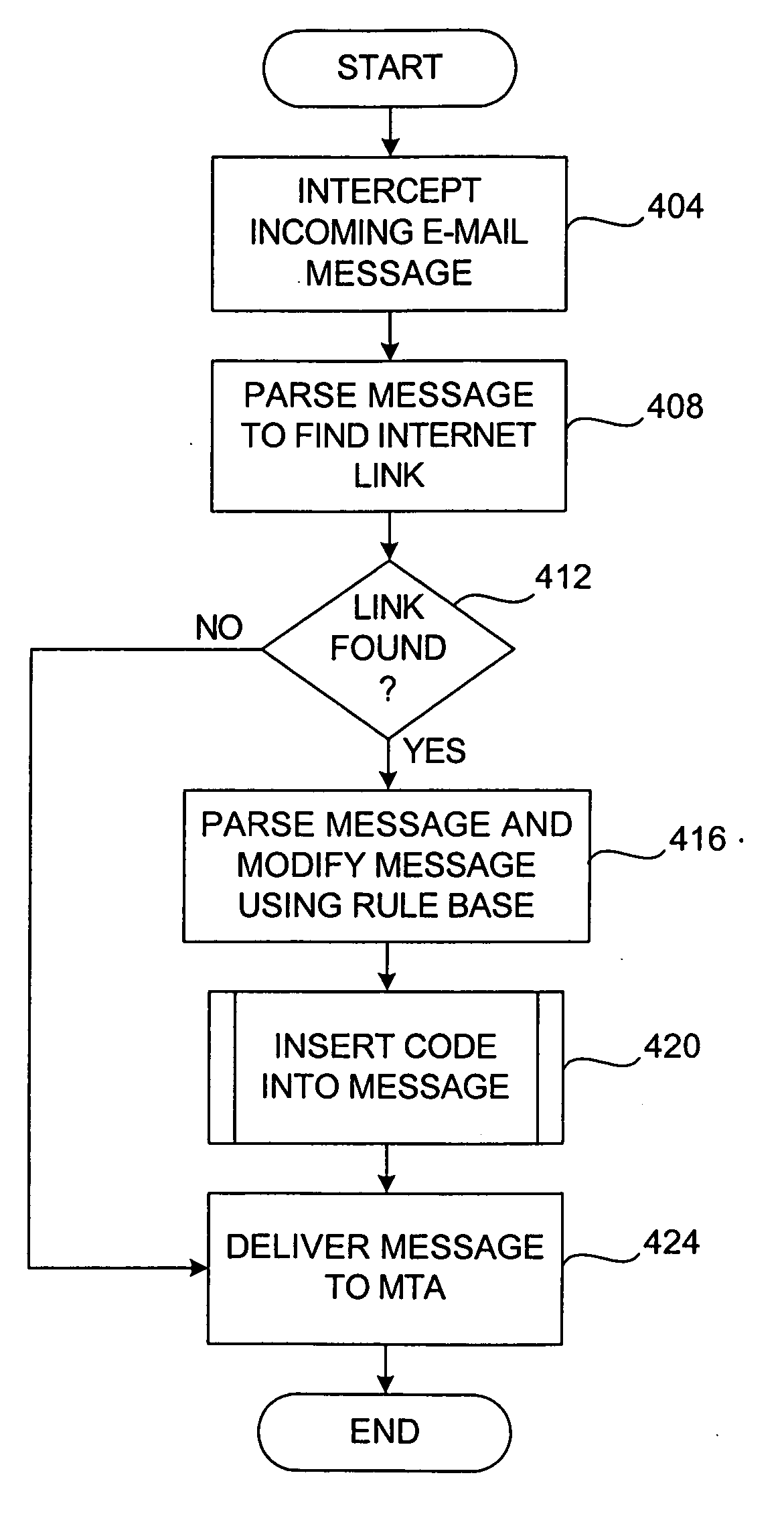
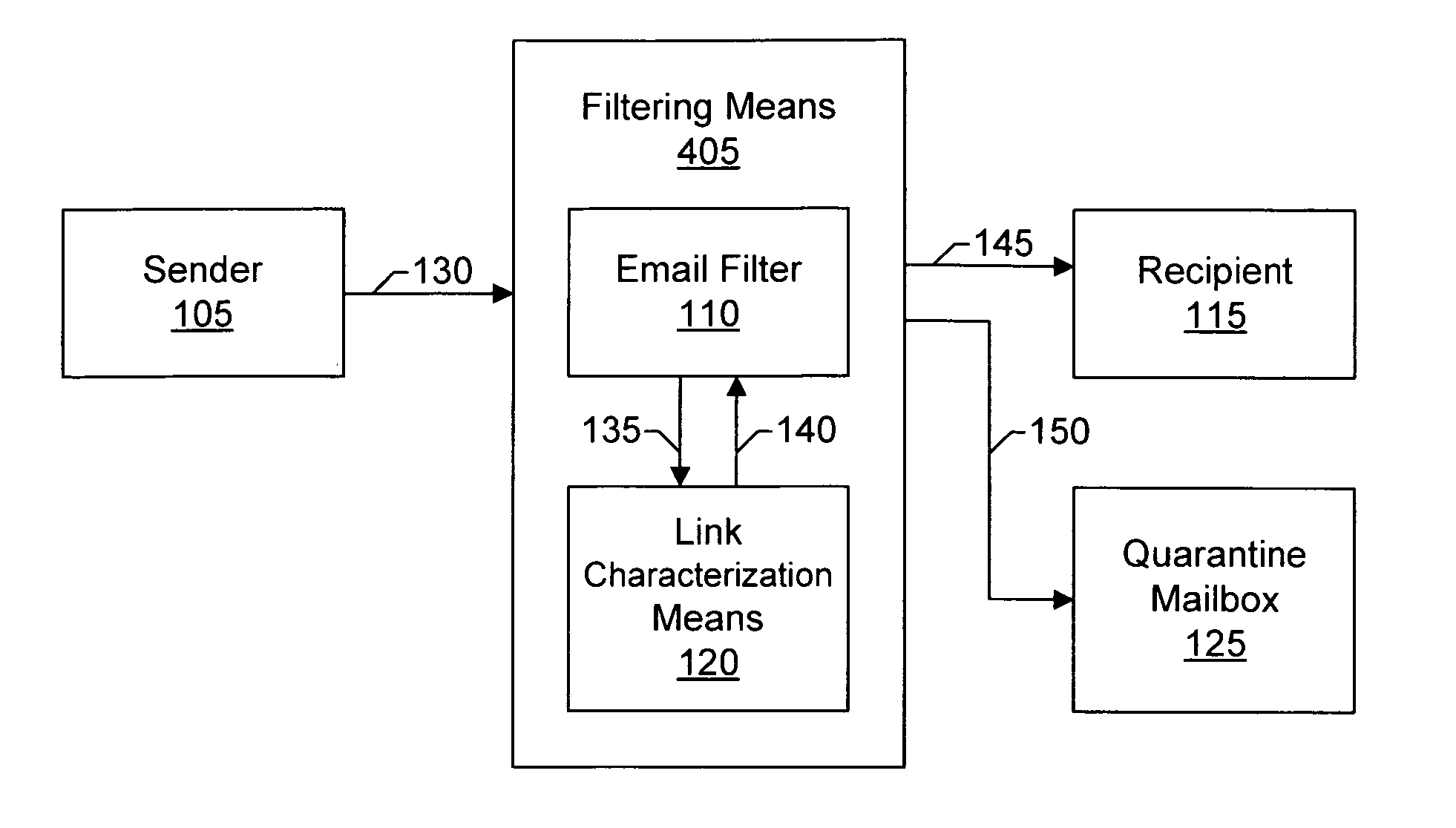
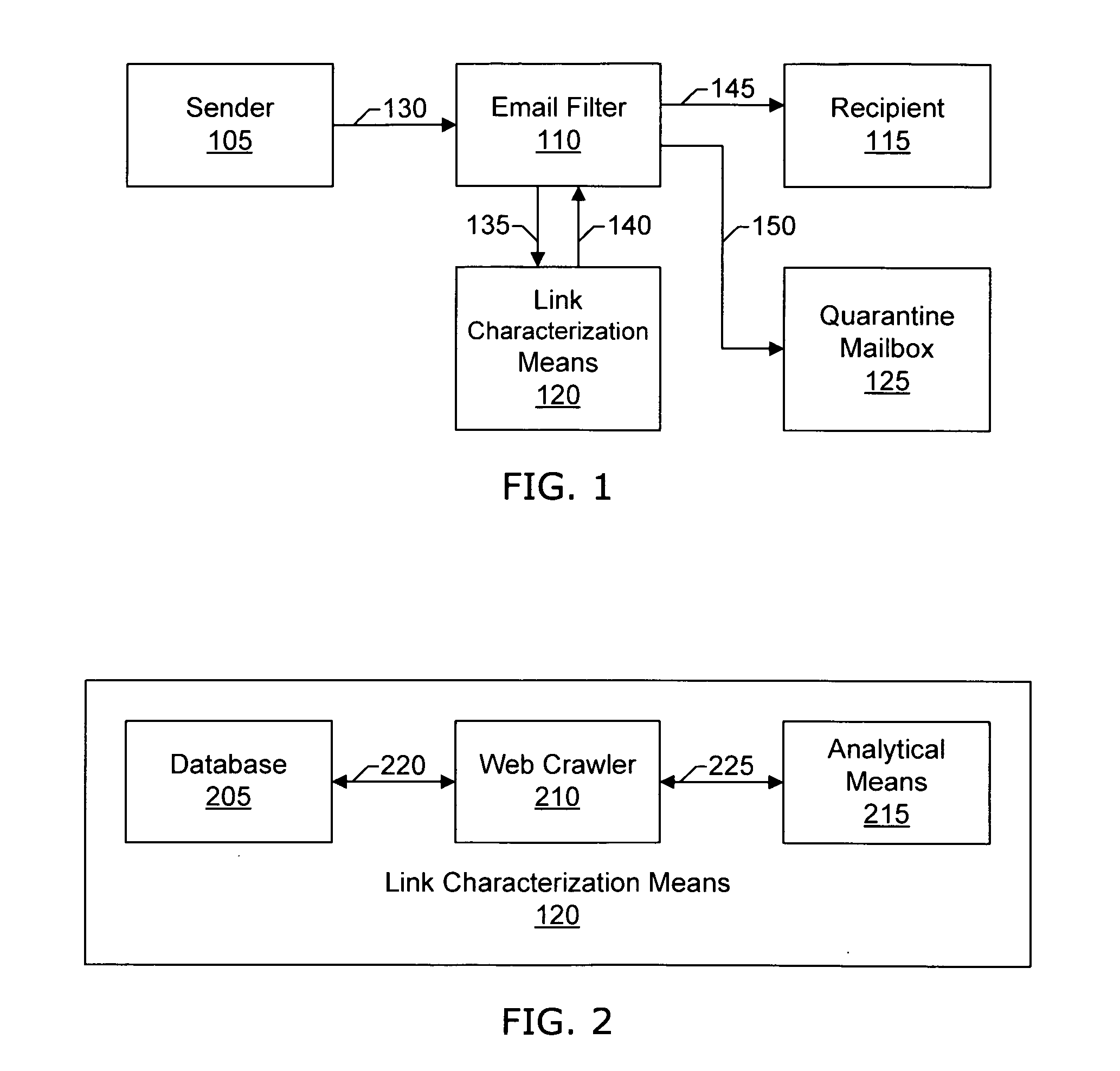
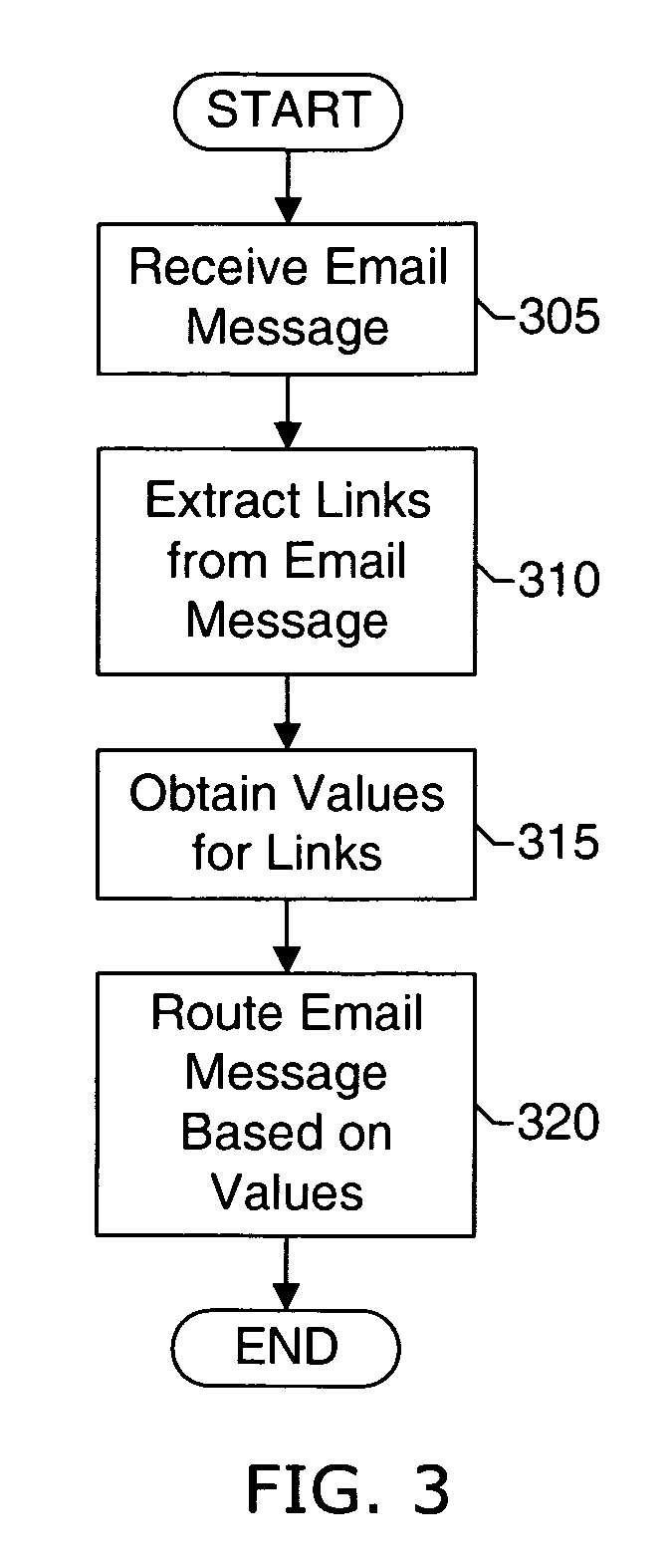
Systems and methods of the present invention allow filtering out spam and phishing email messages based on the links embedded into the email messages. In a preferred embodiment, an Email Filter extracts links from the email message and obtains desirability values for the links. The Email Filter may route the email message based on desirability values. Such routing includes delivering the email message to a Recipient, delivering the message to a Quarantine Mailbox, or deleting the message.
Owner:GO DADDY OPERATING
Anti-phishing system and method
An anti-phishing system and method includes monitoring a user input data stream input to a computing device, identifying, in the user input data stream, one or more characters corresponding to a trigger event related to private information of a user, and taking an action to protect the private information based on identifying the one or more characters corresponding to the trigger event.
Owner:GOOGLE LLC
Email anti-phishing inspector
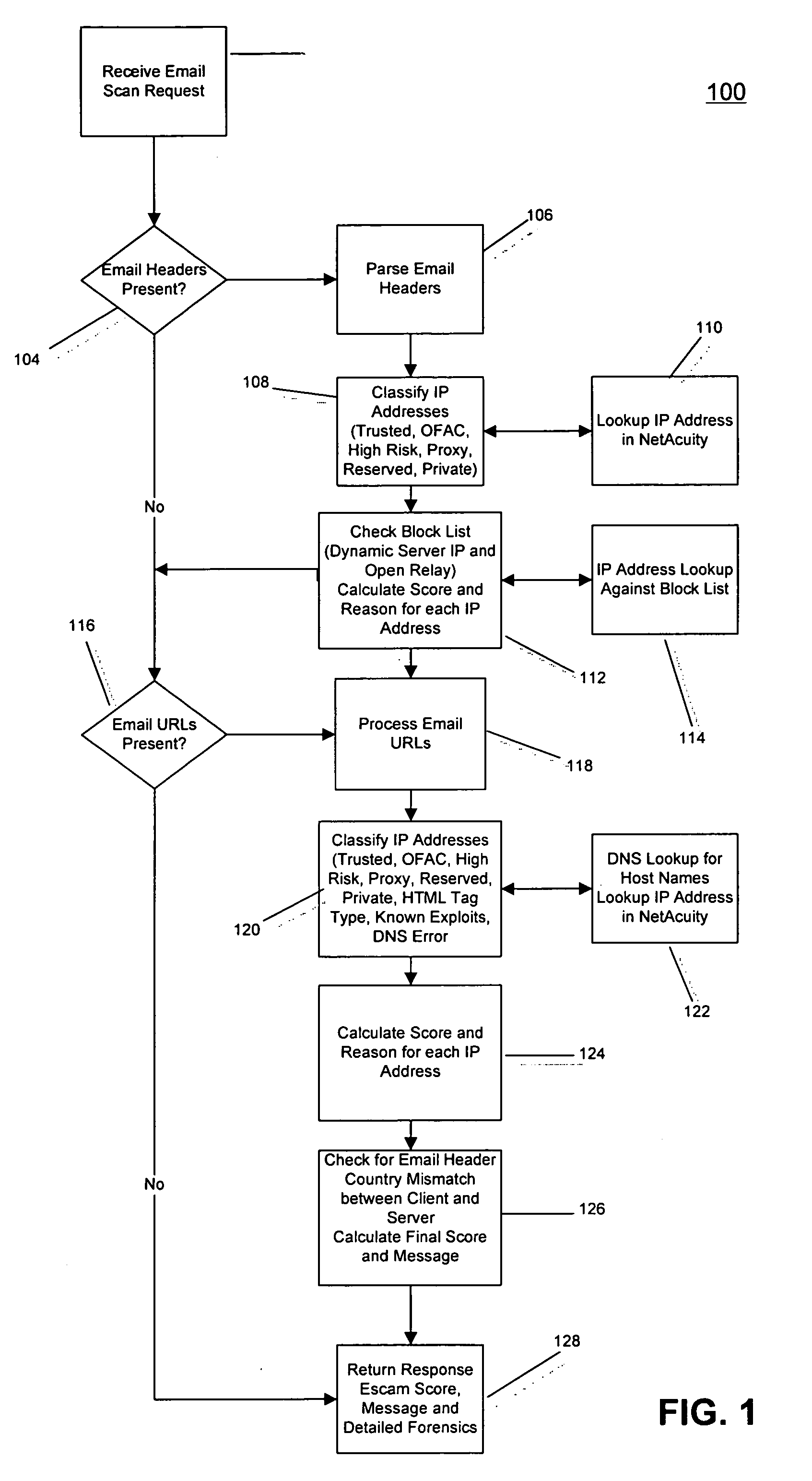
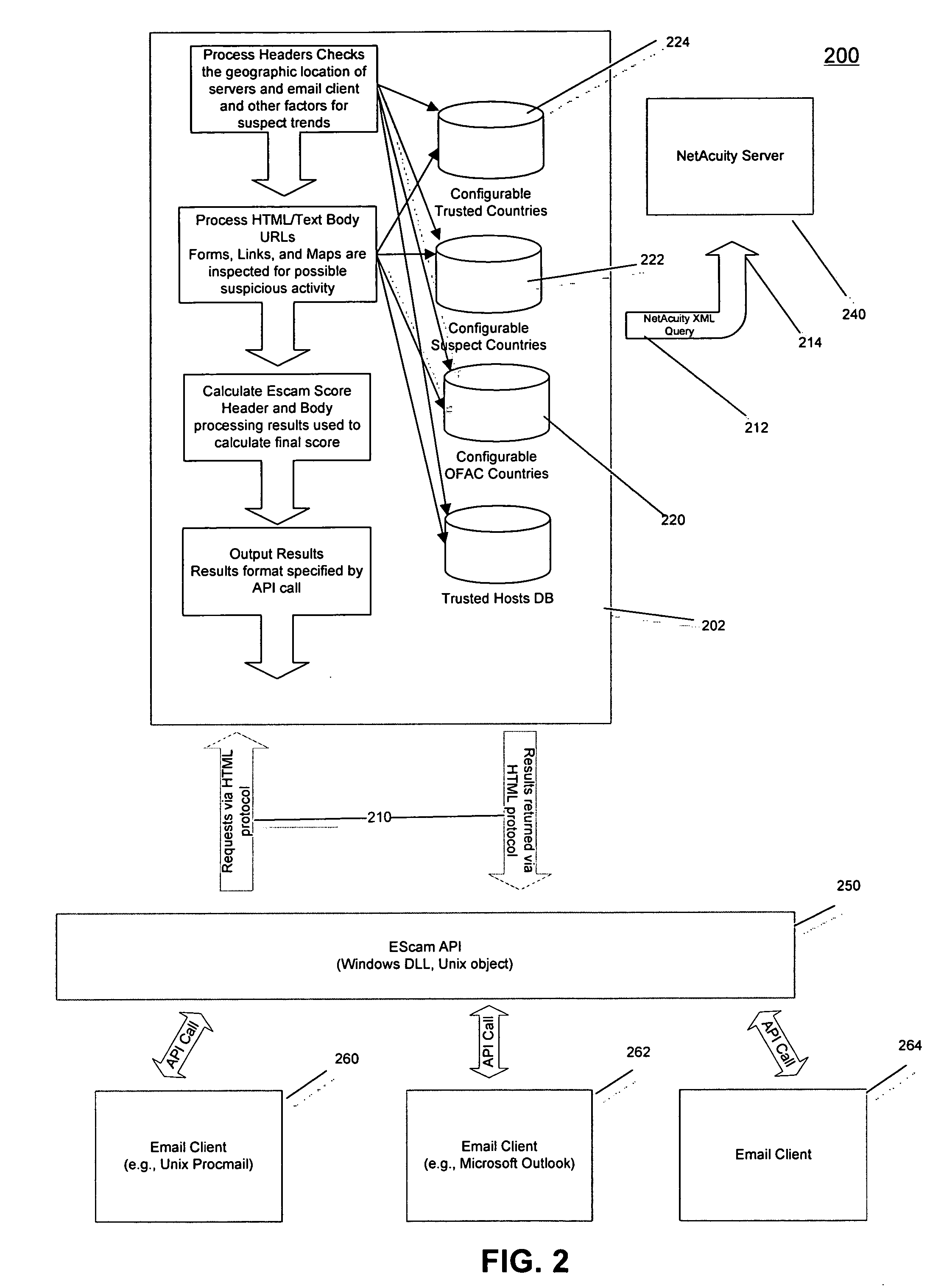
InactiveUS20060168066A1Multiple digital computer combinationsDigital data authenticationUniform resource locatorPhishing
A method, system, and computer program product are provided for implementing embodiments of an EScam Server, which are useful for determining phishing emails. Methods, systems, and program products are also provided to implement embodiments of a Trusted Host Miner, useful for determining servers associated with a Trusted URL, a Trusted Host Browser, useful for communicating to a user when links are Trusted URLs, and a Page Spider, useful for determining on-site links to documents which request a user's confidential information.
Owner:DIGITAL ENVOY
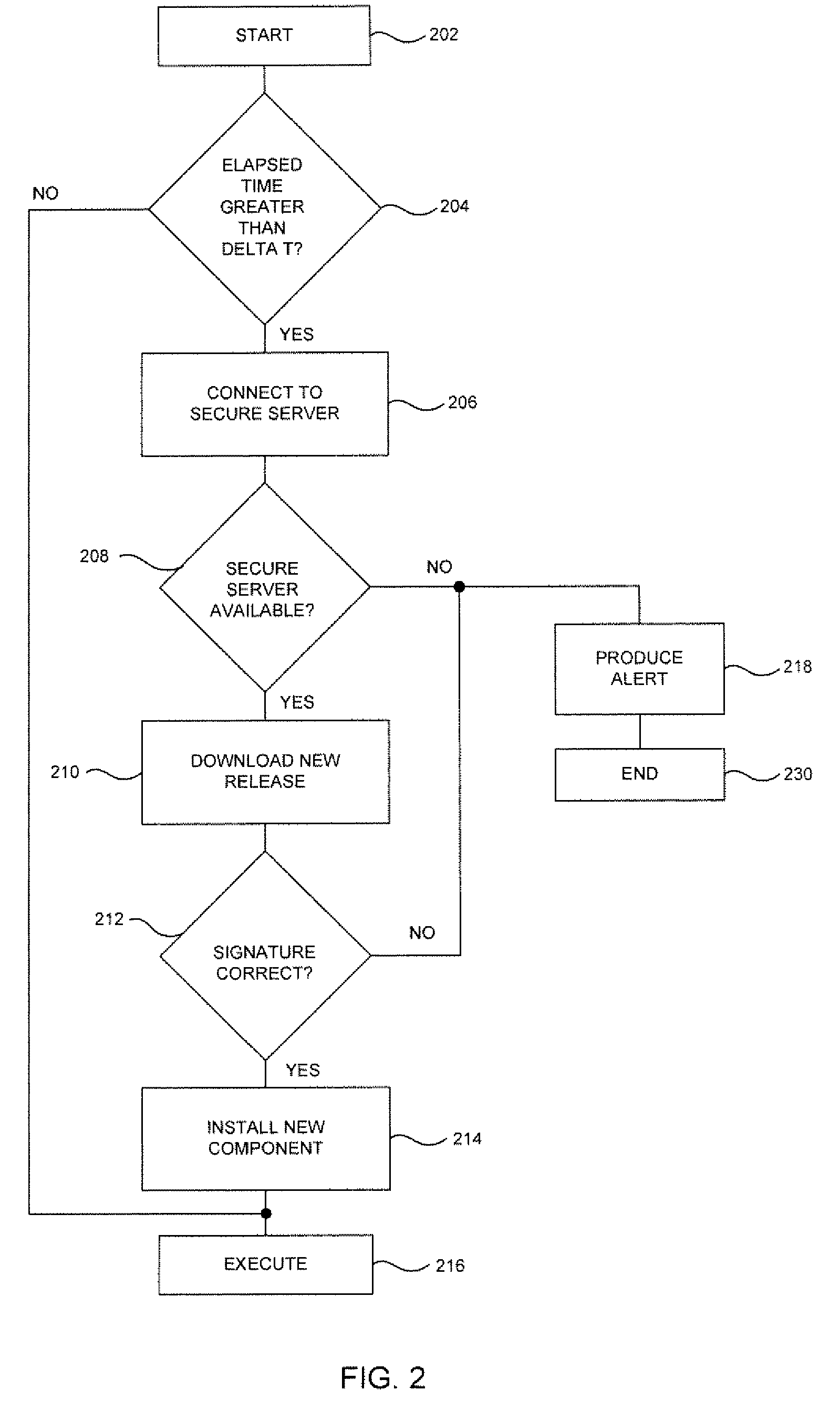
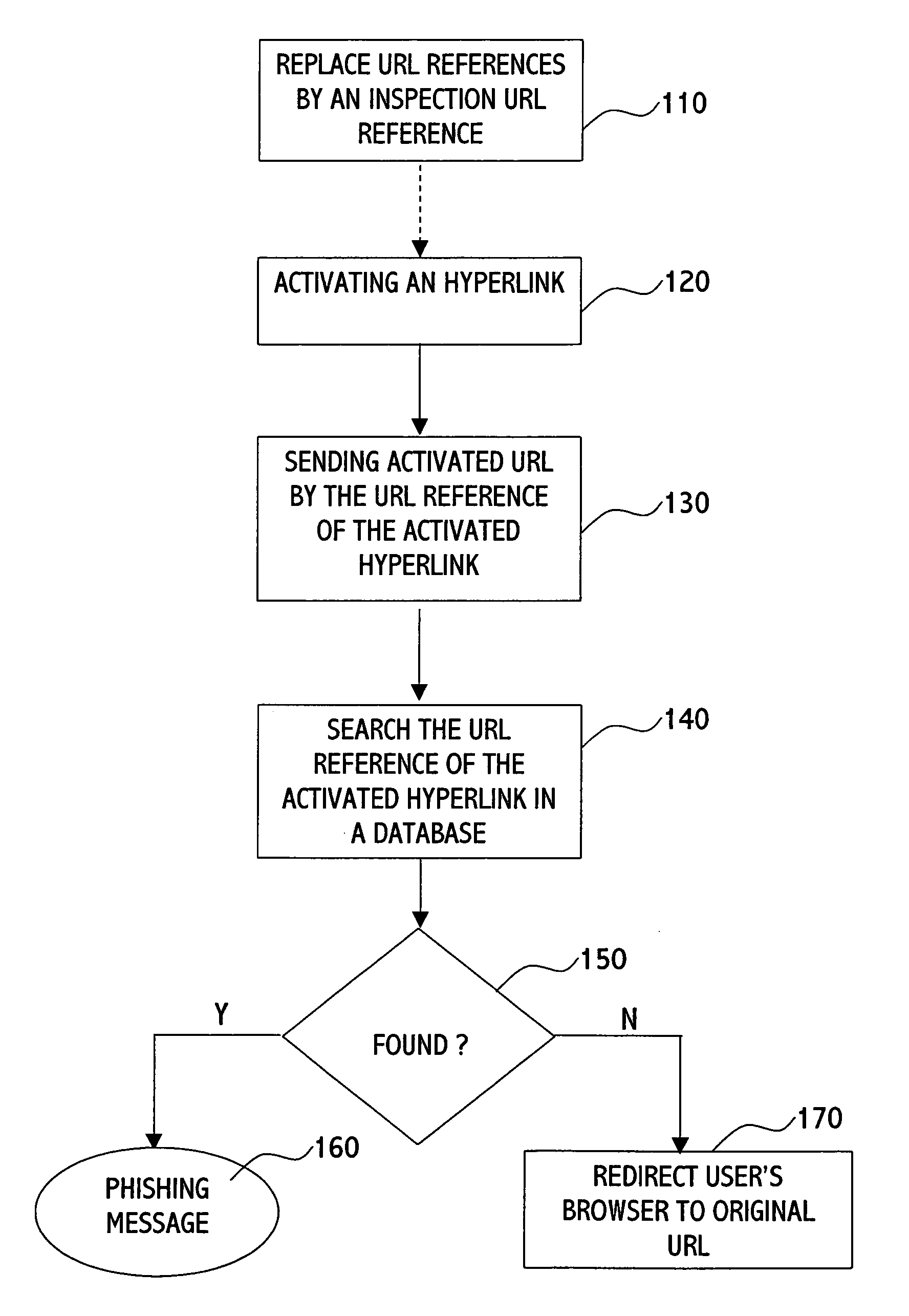
Method and system for blocking phishing scams
The present invention is directed to a method for blocking phishing, the method comprising the steps of: upon activating a hyperlink within an email message by a user's email client: sending the original URL reference of the hyperlink to a phishing inspection utility; testing the original URL reference by the phishing inspection utility for being a phishing URL; if the original URL is not found as phishing URL, directing a browser of the user to the original URL. The method may further comprise the step of: replacing the original URL reference of the hyperlink with a URL reference of the phishing inspection utility; and setting the original URL reference as a parameter to the URL reference of the phishing inspection utility, thereby on activating the hyperlink providing to the inspection utility the URL reference to be tested.
Owner:ALADDIN KNOWLEDGE SYSTEMS
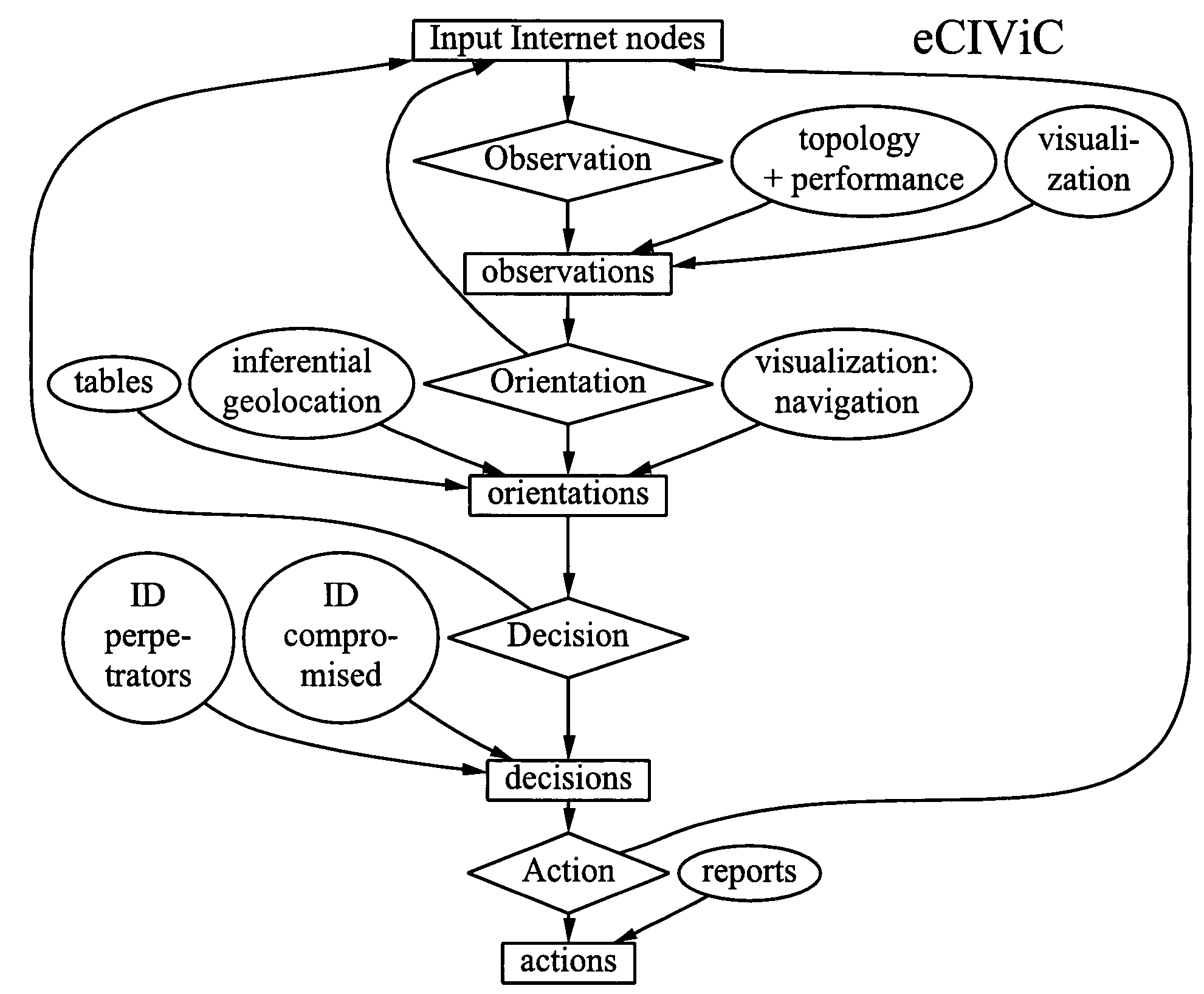
Method and system for detecting distributed internet crime
InactiveUS8560413B1Investigated betterWide viewingFinanceComputer security arrangementsDomain nameGeotargeting
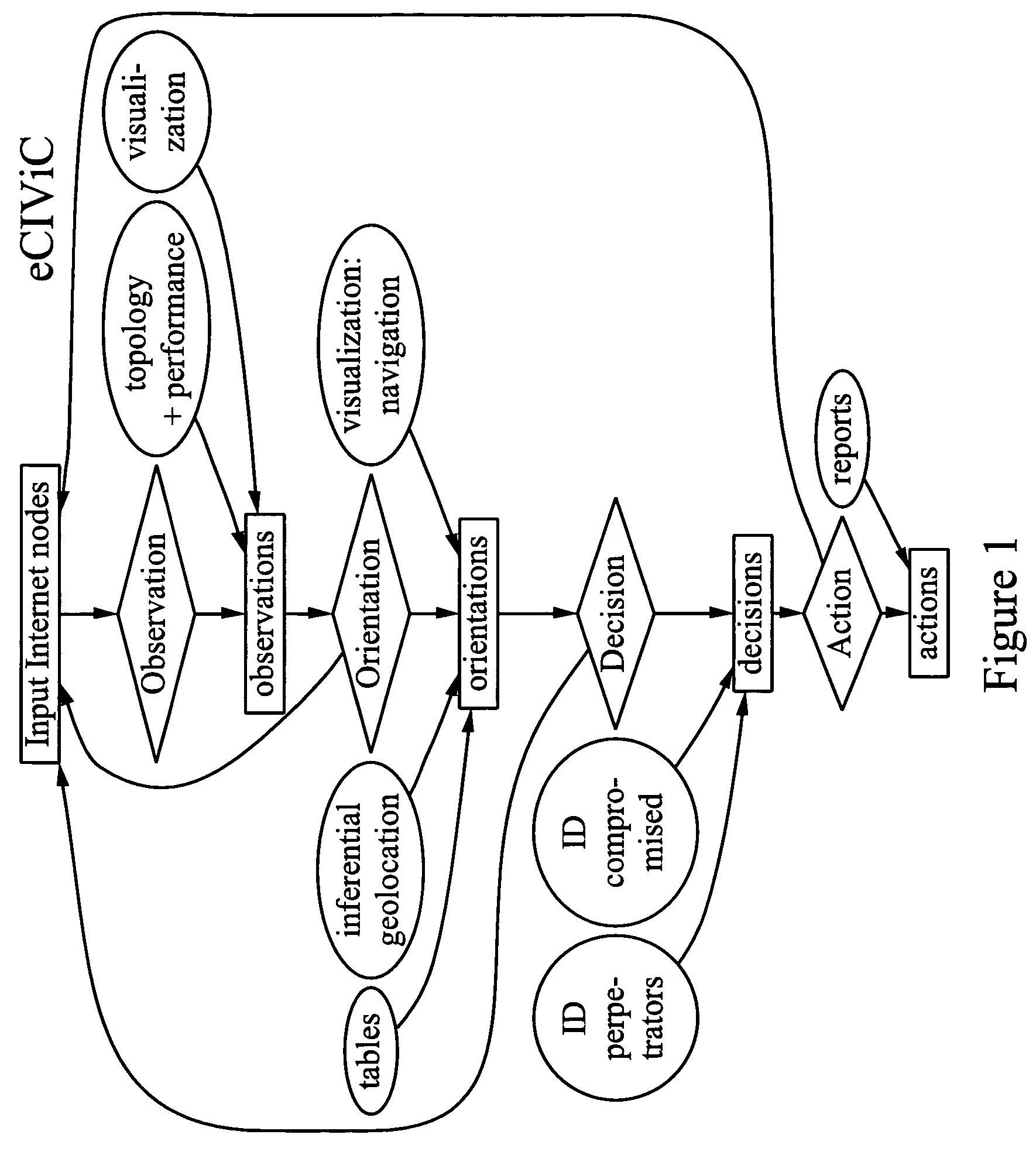
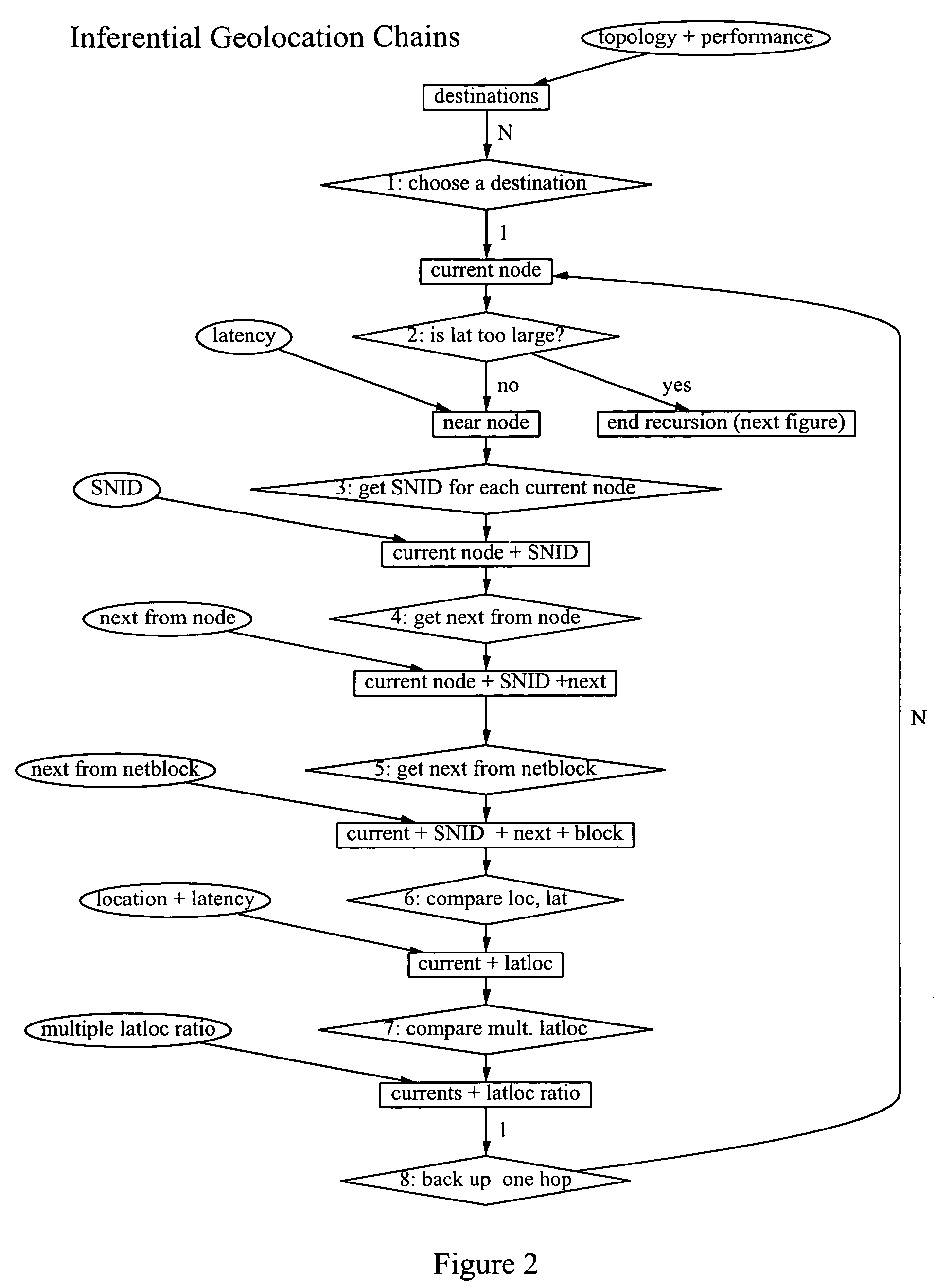
The invention broadly comprises a method and service of visualization of Internet nodes involved in distributed electronic crime in order to see patterns of actionable intelligence, such as multiple phishing nodes hosted at the same hosting center, or domain names registered in one country that are actually in another country or nodes related by one or more aspects, such as specific criminal attack campaign, target or technical weakness exploited to ease commandeering of the node. The invention involves collecting topological and latency data including changes over time and using the data to determine probable topological and geographical locations of single or multiple nodes, as well as inferential geolocation.
Owner:QUARTERMAN JOHN S +2
Method and apparatus for detecting phishing attempts solicited by electronic mail
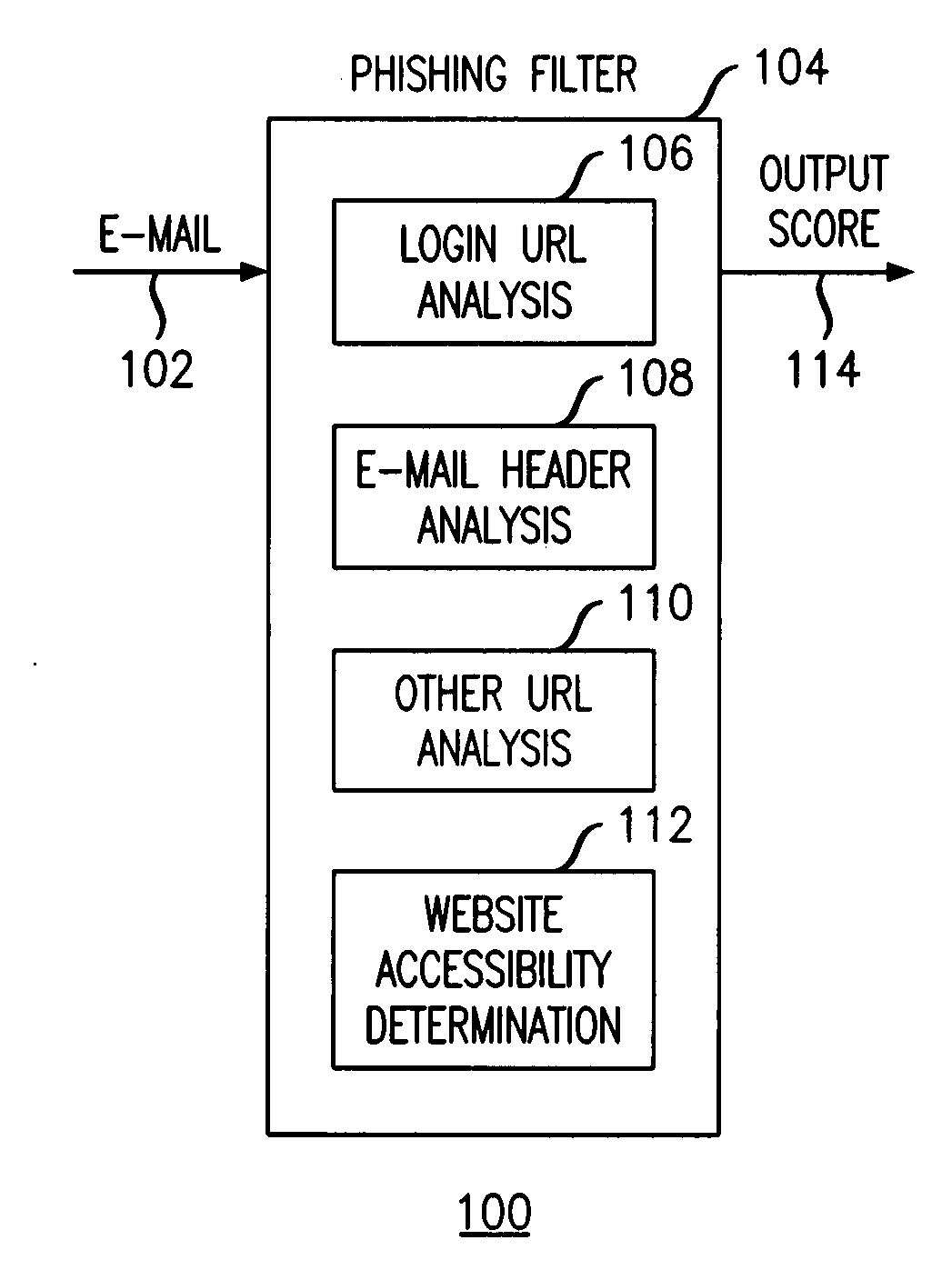
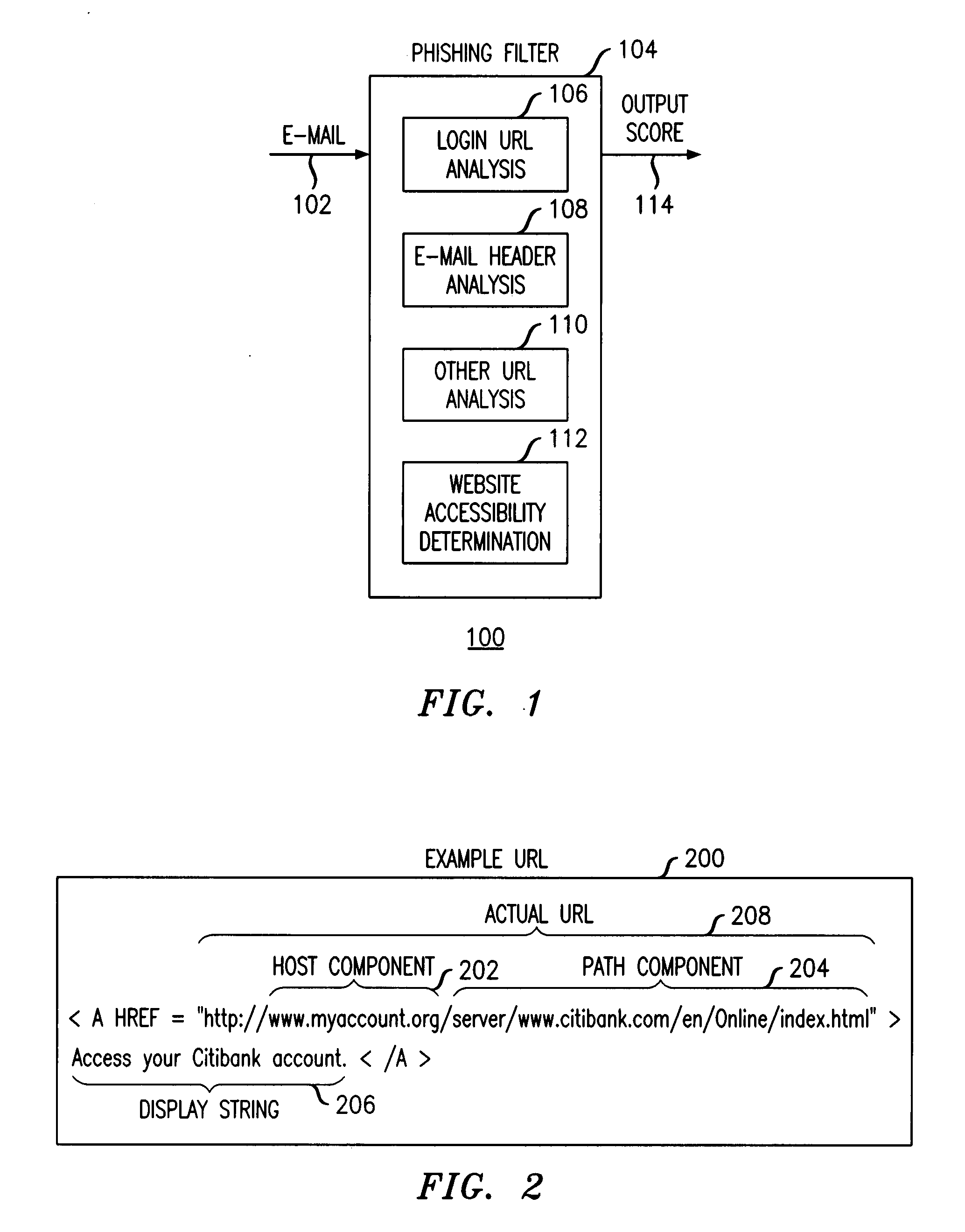
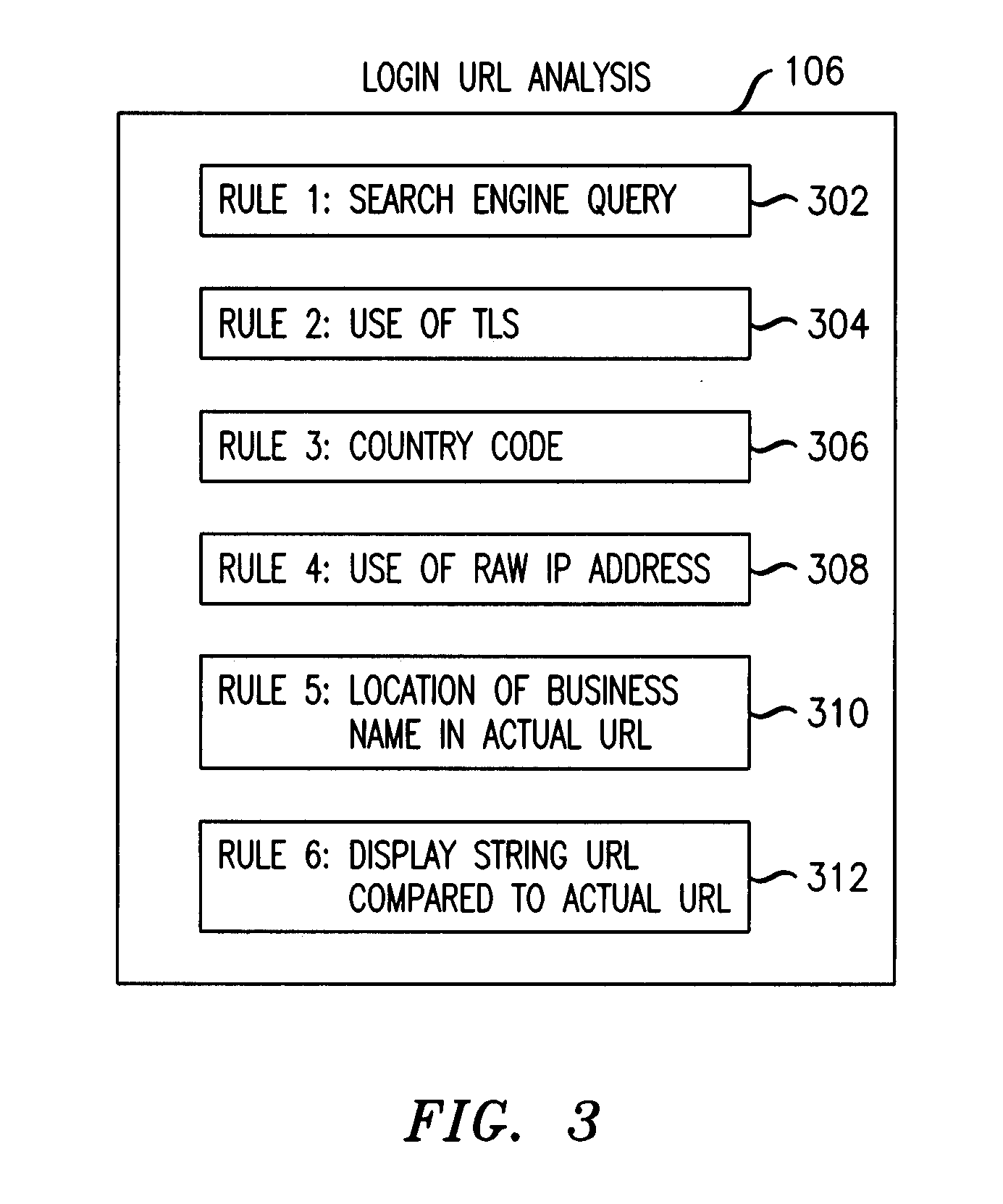
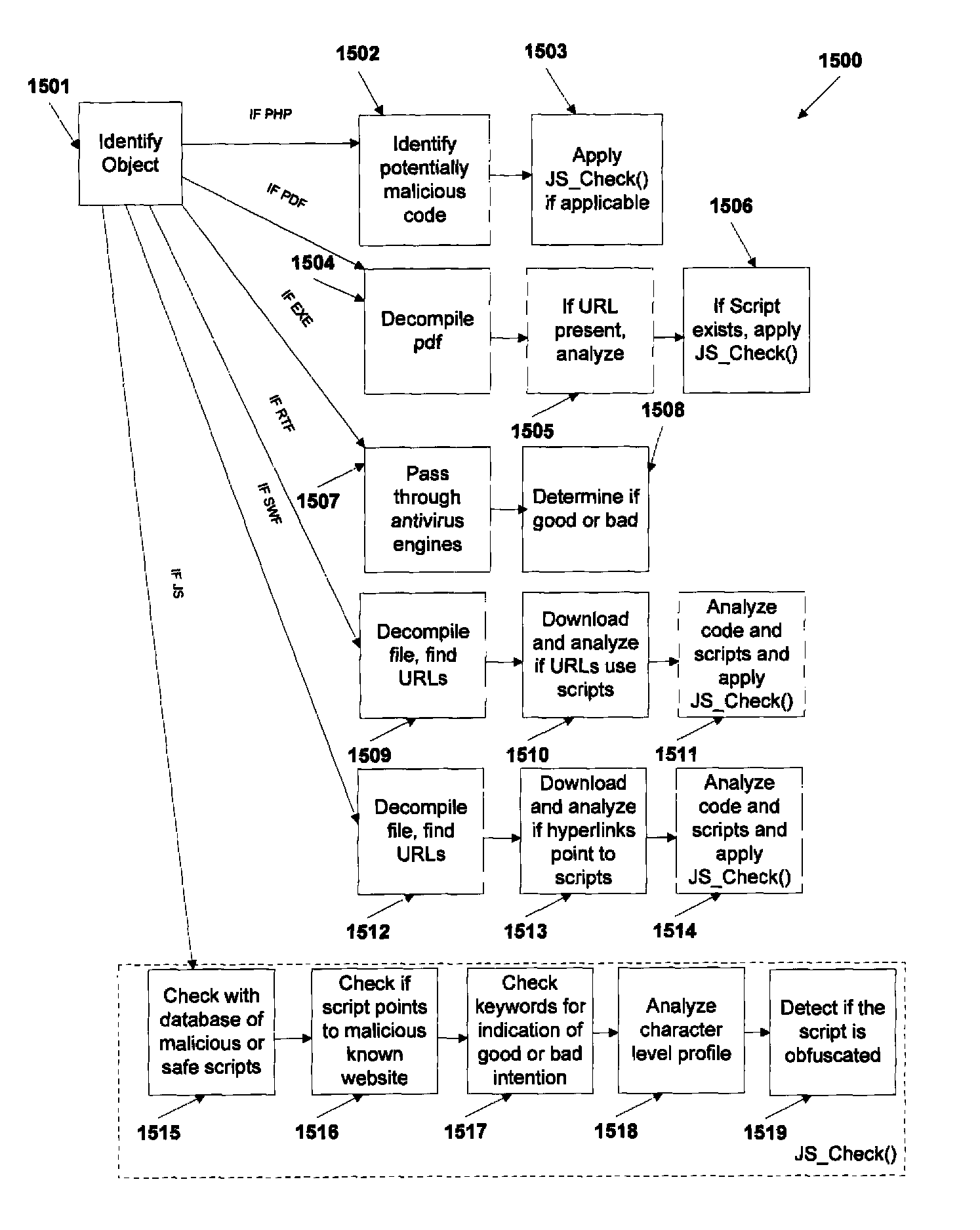
InactiveUS20090089859A1Digital data processing detailsUser identity/authority verificationKeyword analysisHeuristic
A phishing filter employs a plurality of heuristics or rules (in one embodiment, 12 rules) to detect and filter phishing attempts solicited by electronic mail. Generally, the rules fall within the following categories: (1) identification and analysis of the login URL (i.e., the “actual” URL) in the email, (2) analysis of the email headers, (3) analysis across URLs and images in the email other than the login URL, and (4) determining if the URL is accessible. The phishing filter does not need to be trained, does not rely on black or white lists and does not perform keyword analysis. The filter may be implemented as an alternative or supplemental to prior art spam detection filters.
Owner:ALCATEL-LUCENT USA INC
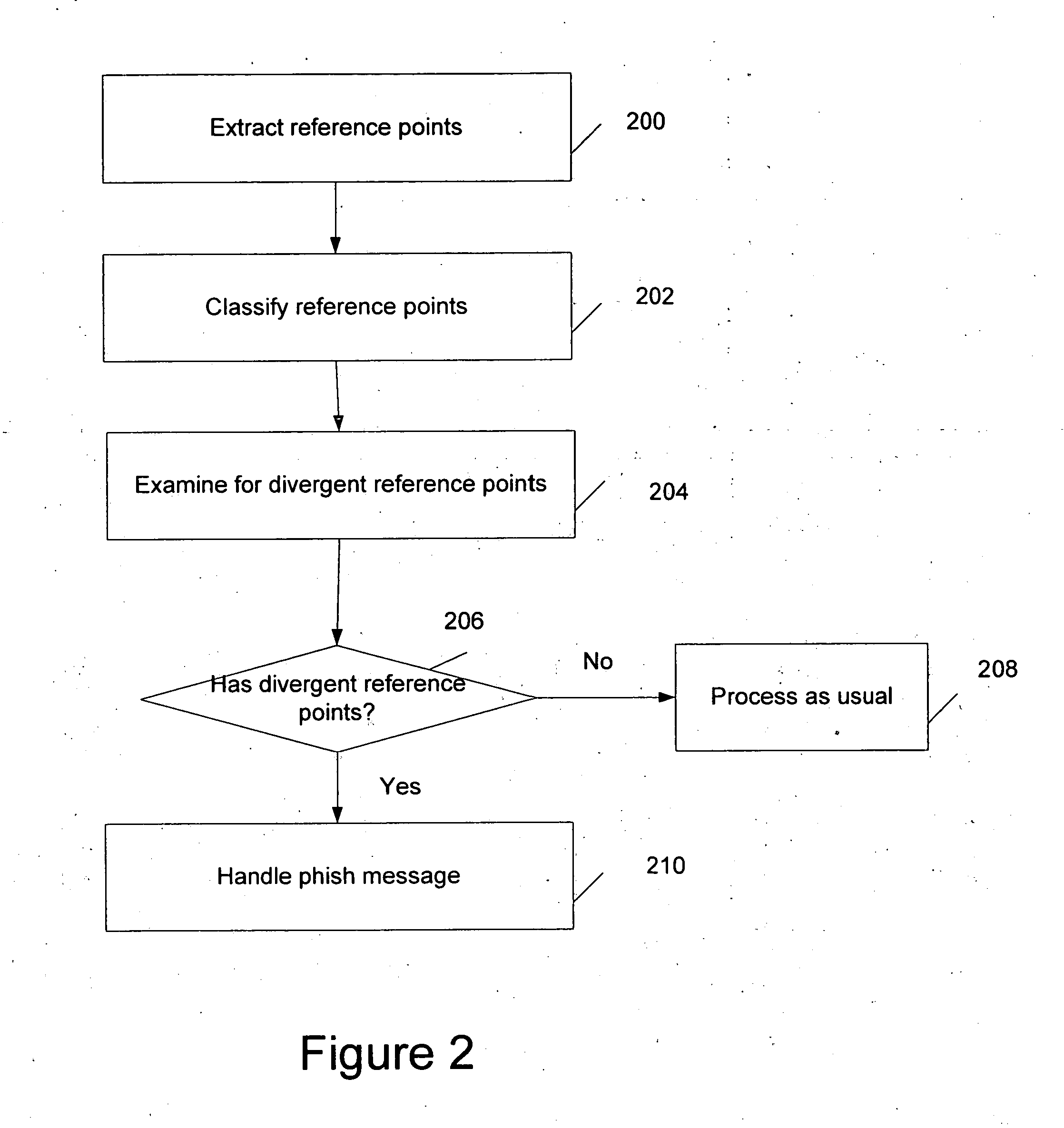
Fraudulent message detection
A technique for classifying a message is disclosed. In some embodiments, the technique comprises extracting a plurality of reference points, classifying the plurality of reference points, and detecting that the message is a phish message based on the classified reference points. In some embodiments, the technique comprises identifying a plurality of fraud indicators in the message, applying a statistical analysis on the plurality of fraud indicators; and determining whether the message is a fraudulent message based on the analysis.
Owner:DELL PROD LP
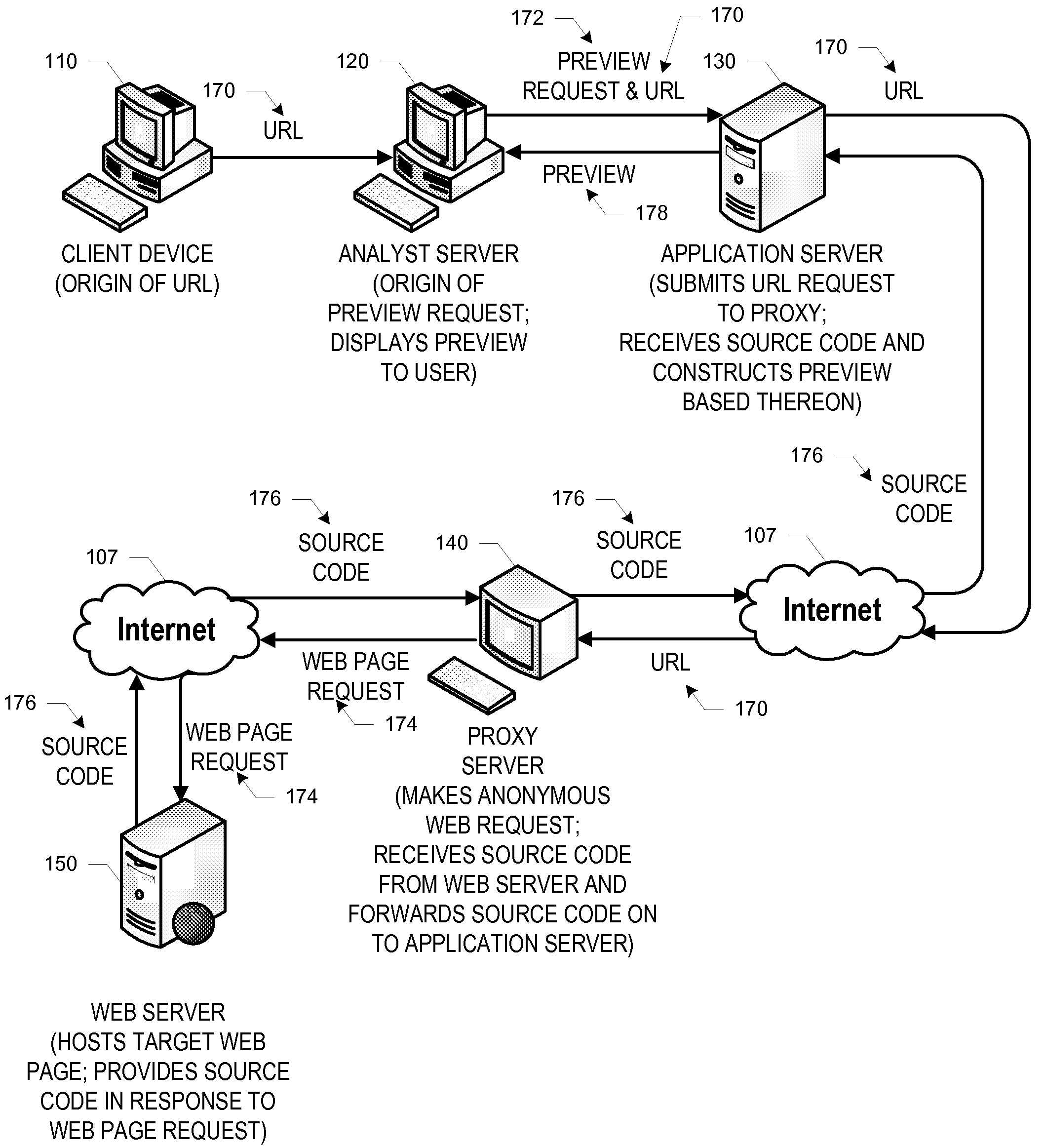
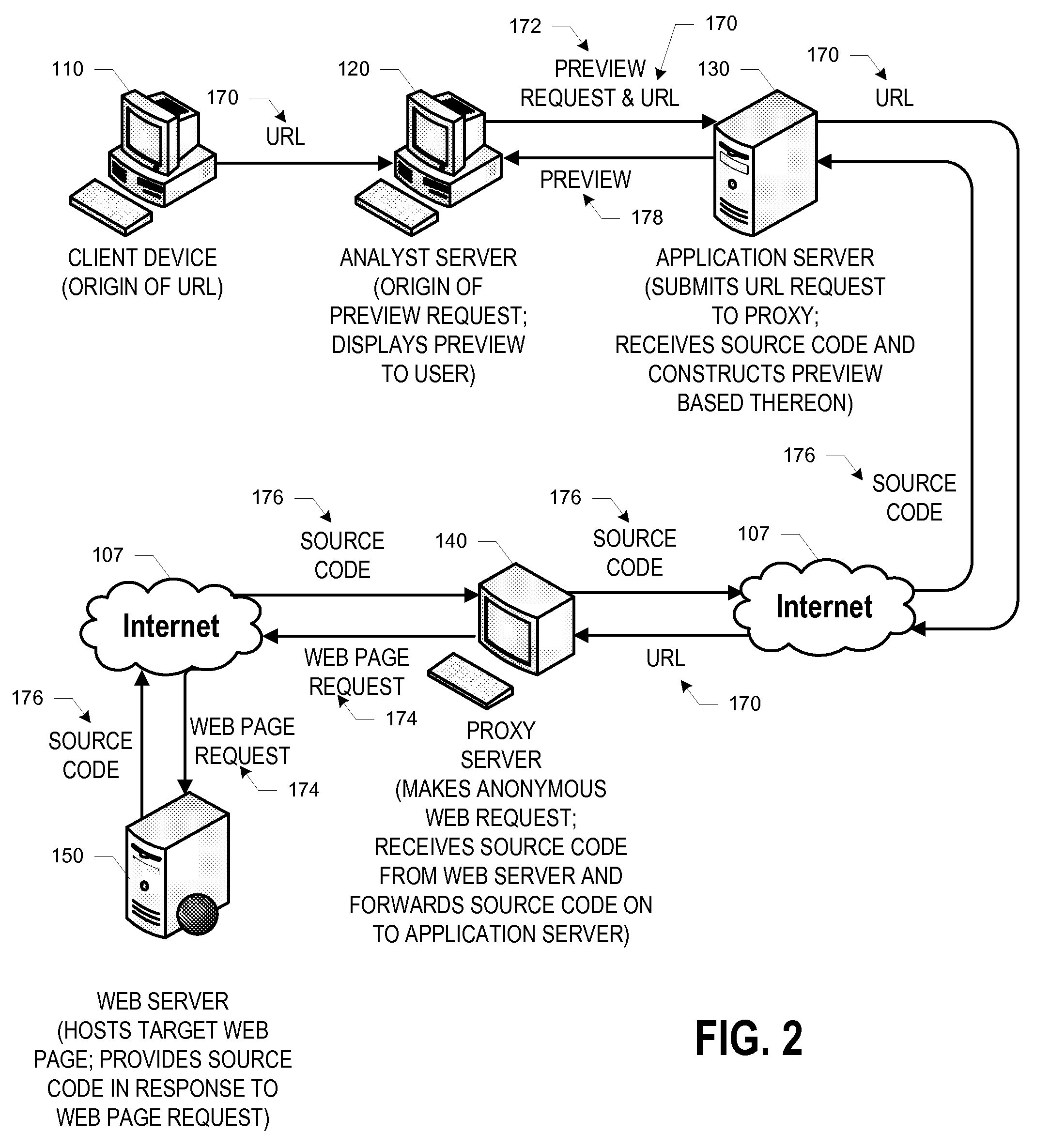
Browser preview
ActiveUS20110022559A1Safely previewingEnvironment safetyInput/output for user-computer interactionDigital data information retrievalMalwarePhishing
In general, embodiments of the invention relate to systems, methods, and computer program products for previewing, in a safe environment, a given web page that is or may be conducting dangerous or fraudulent activity, including malware distribution and phishing activity. More particularly, embodiments of the invention relate to previewing a given web page in a safe environment by obtaining and breaking down the source code behind the given web page and constructing a preview of the web page without any potentially harmful images, scripts, executables, and / or the like.
Owner:BANK OF AMERICA CORP
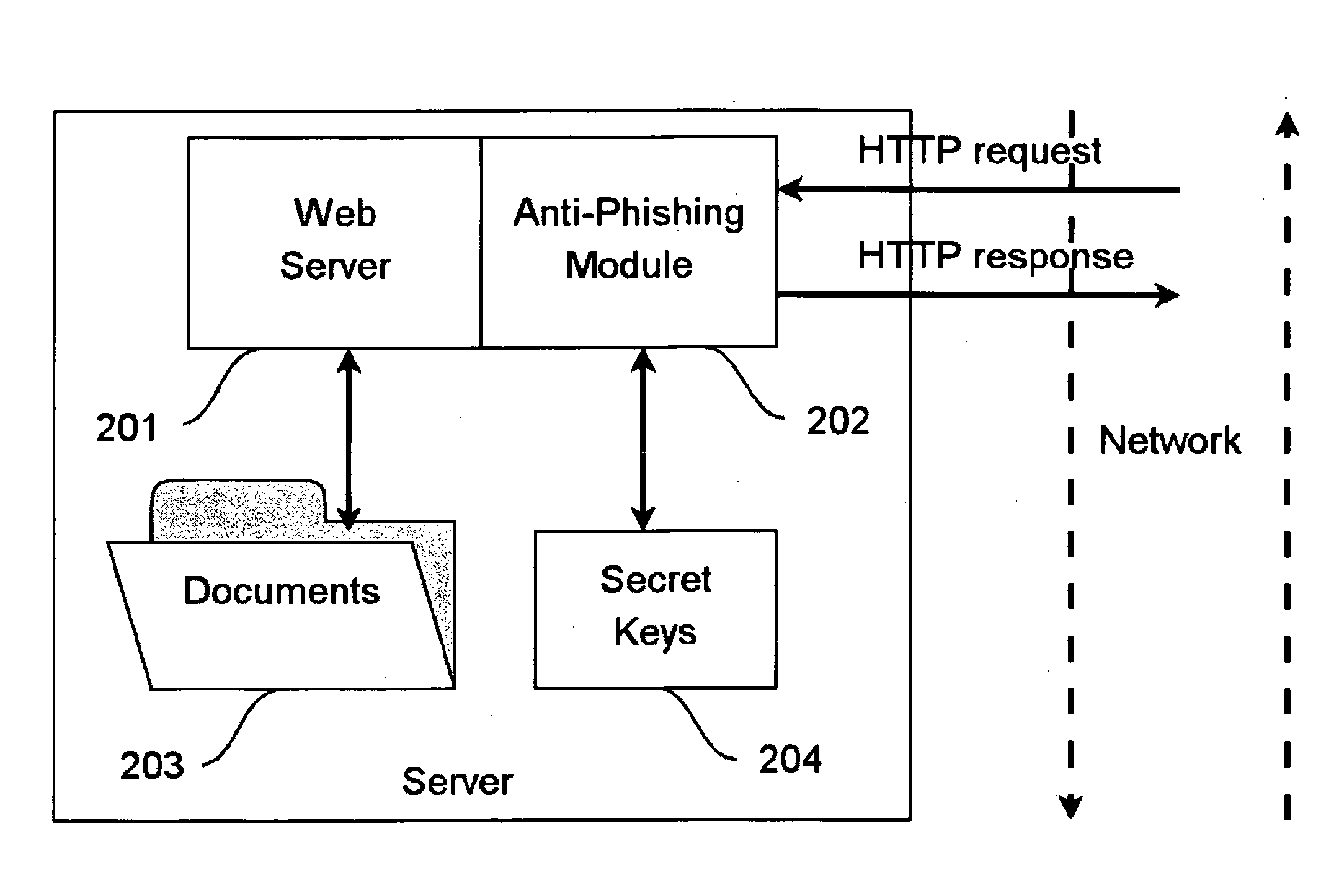
Method for providing web application security
InactiveUS20090292925A1Memory loss protectionError detection/correctionClient-sideApplication software
A method for an HTTP server to decide whether a remote client is victim of a phishing ttack, comprising: —receiving a first HTTP request from the remote client on said HTTP Server; —responding to said first HTTP request, wherein a token is added to the response submitted to said remote client; —receiving a second HTTP request on said HTTP server; —judging whether the second HTTP request includes said token; —judging whether the token originates from said remote client; —processing the HTTP request when said remote client has really issued the second HTTP request.
Owner:ZEUS TECHNOLOGY +1
Automated identification of phishing, phony and malicious web sites
A method and system for automated identification of phishing, phony, and malicious web sites are disclosed. According to one embodiment, a computer implemented method, comprises receiving a first input, the first input including a universal resource locator (URL) for a webpage. A second input is received, the second input including feedback information related to the webpage, the feedback information including an indication designating the webpage as safe or unsafe. A third input is received from a database, the third input including reputation information related to the webpage. Data is extracted from the webpage. A safety status is determined for the webpage, including whether the webpage is hazardous by using a threat score for the webpage and the second input, wherein calculating the threat score includes analyzing the extracted data from the webpage. The safety status for the webpage is reported.
Owner:CLOUDFLARE
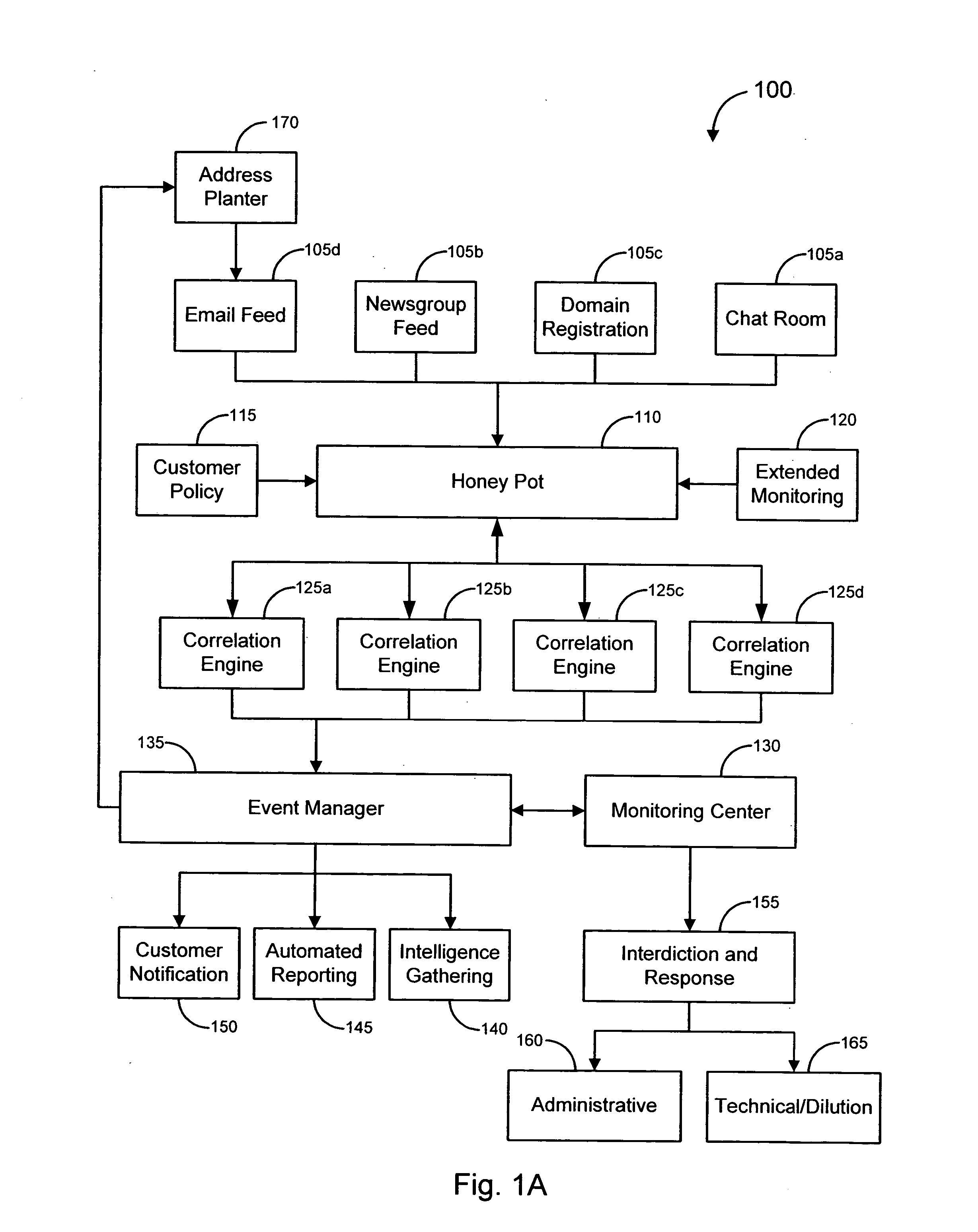
Systems and methods for identifying and mitigating information security risks
ActiveUS8793799B2High level of realismRaise the possibilityMemory loss protectionDigital data processing detailsUnique identifierPhishing
Methods and systems for Sustained Testing and Awareness Refresh against Phishing threats (STAR*Phish™) are disclosed. In an embodiment, a method assigns schemes and unique identifiers to target e-mail addresses associated with a user accounts. The method delivers e-mail messages to the targeted e-mail addresses, the e-mail messages comprising an HTTP request and a unique identifier associated with each of the user accounts. The method then receives, at a Phishing Metric Tool (PMT), a response including the unique identifier. The PMT logs training requirements for the user accounts, tracks response metrics for the training requirements, and redirects the respective HTTP requests to a phishing training tool (PTT). The PTT sends a notification of the user account identities and the unique identifiers to the PMT and returns a status for the training requirements for the user accounts. Upon completion of the training, the PMT sends completion notifications for the user accounts.
Owner:BOOZ ALLEN HAMILTON INC
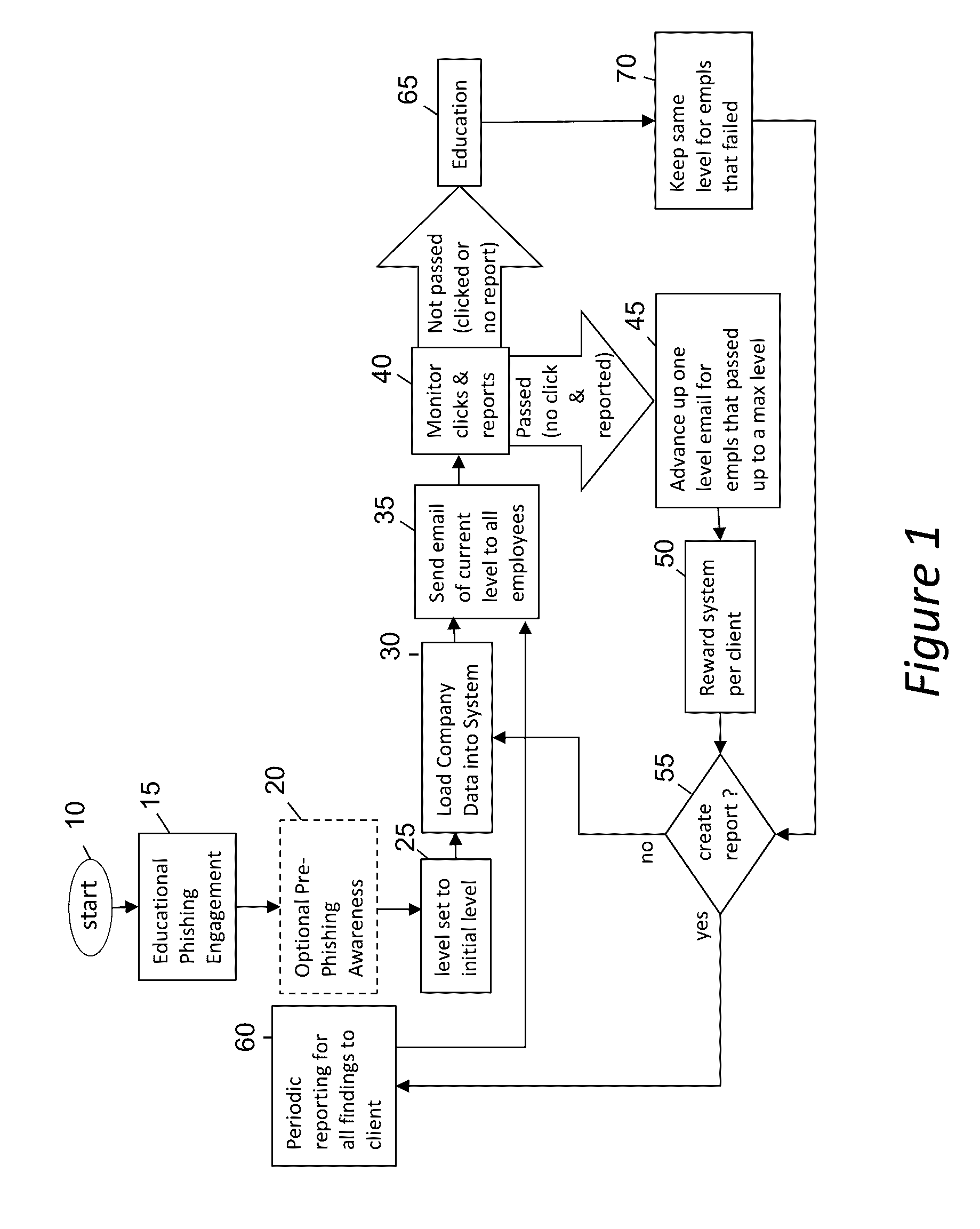
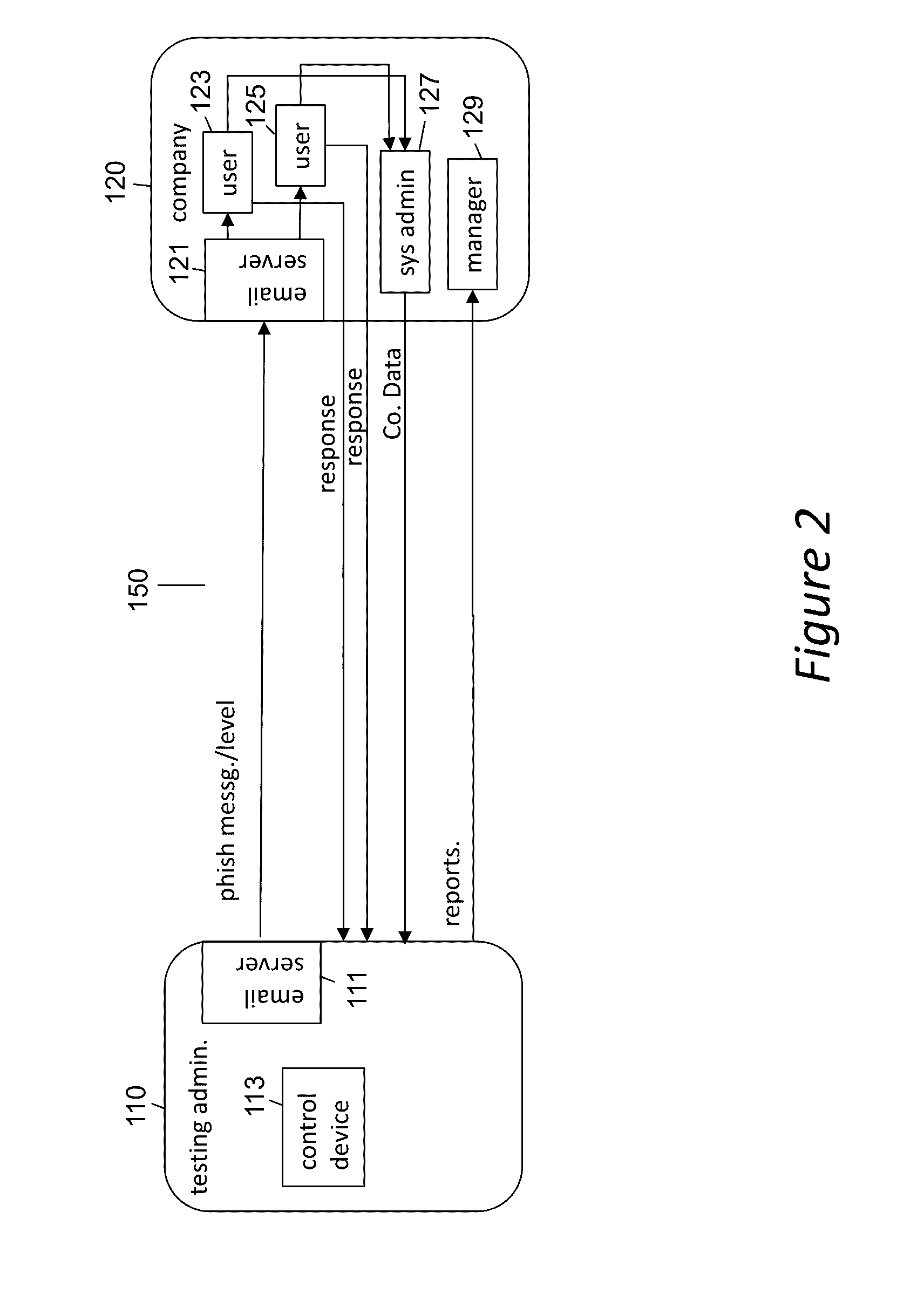
Phishing-as-a-Service (PHaas) Used To Increase Corporate Security Awareness
ActiveUS20160330238A1Increasing corporate information securityImprove the level ofData switching networksMaximum levelThe Internet
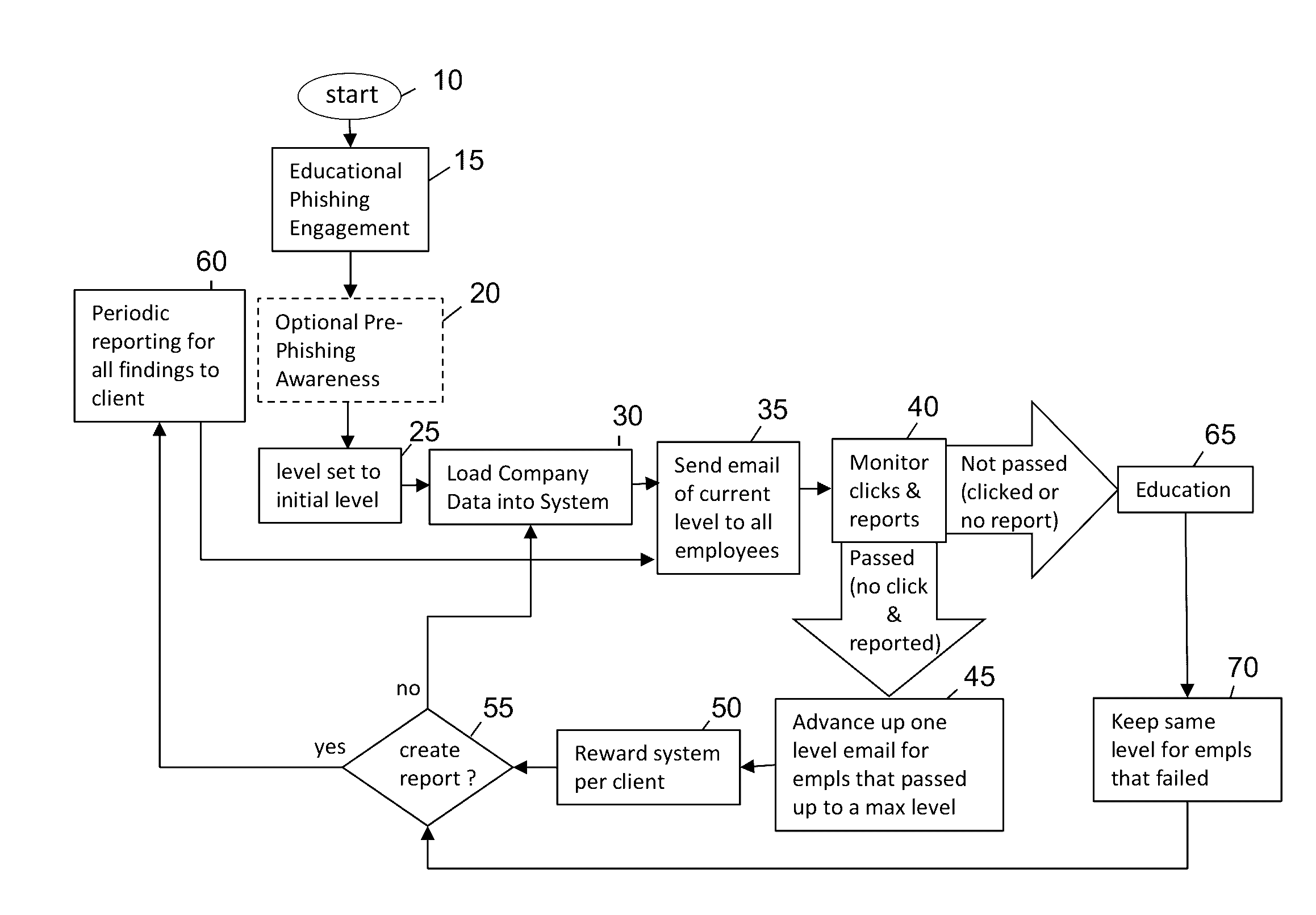
An enhanced system is provided through a network such as the Internet that provides integrated network security (phishing) testing and training. The current system increases corporate security of users that can receive and send electronic messages in an entity, by creating and storing a set of phish messages, each classified by a difficulty level. The electronic addresses of the users are acquired and stored. A current difficulty level is set for all users to an initial level. A phish message of the current difficulty level for a given user is selected and sent to the user. The system monitors if the user clicks on or reports the phish message. If the user does not click on the phish message and reports it, the user's current level is increased up to a maximum level. Those that do not pass the test are provided on-line education. The above steps are repeated for all users until the testing is completed providing targeted phishing education to those which need it most.
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com