Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
391 results about "Spamming" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Spamming is the use of messaging systems to send an unsolicited message (spam), especially advertising, as well as sending messages repeatedly on the same site. While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging spam, Internet forum spam, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam. It is named after Spam, a luncheon meat, by way of a Monty Python sketch about a restaurant that has Spam in every dish and where patrons annoyingly chant "Spam" over and over again.
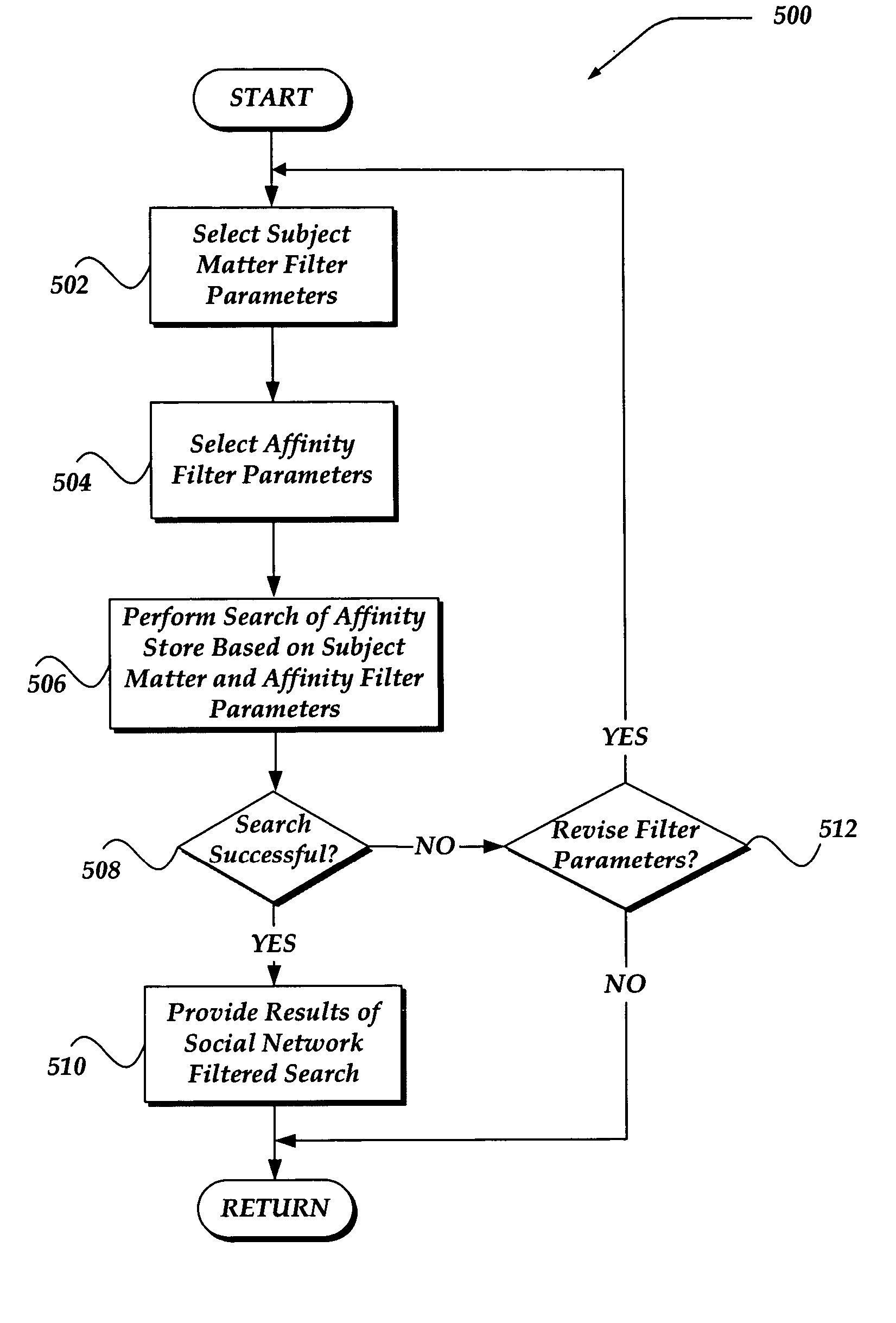
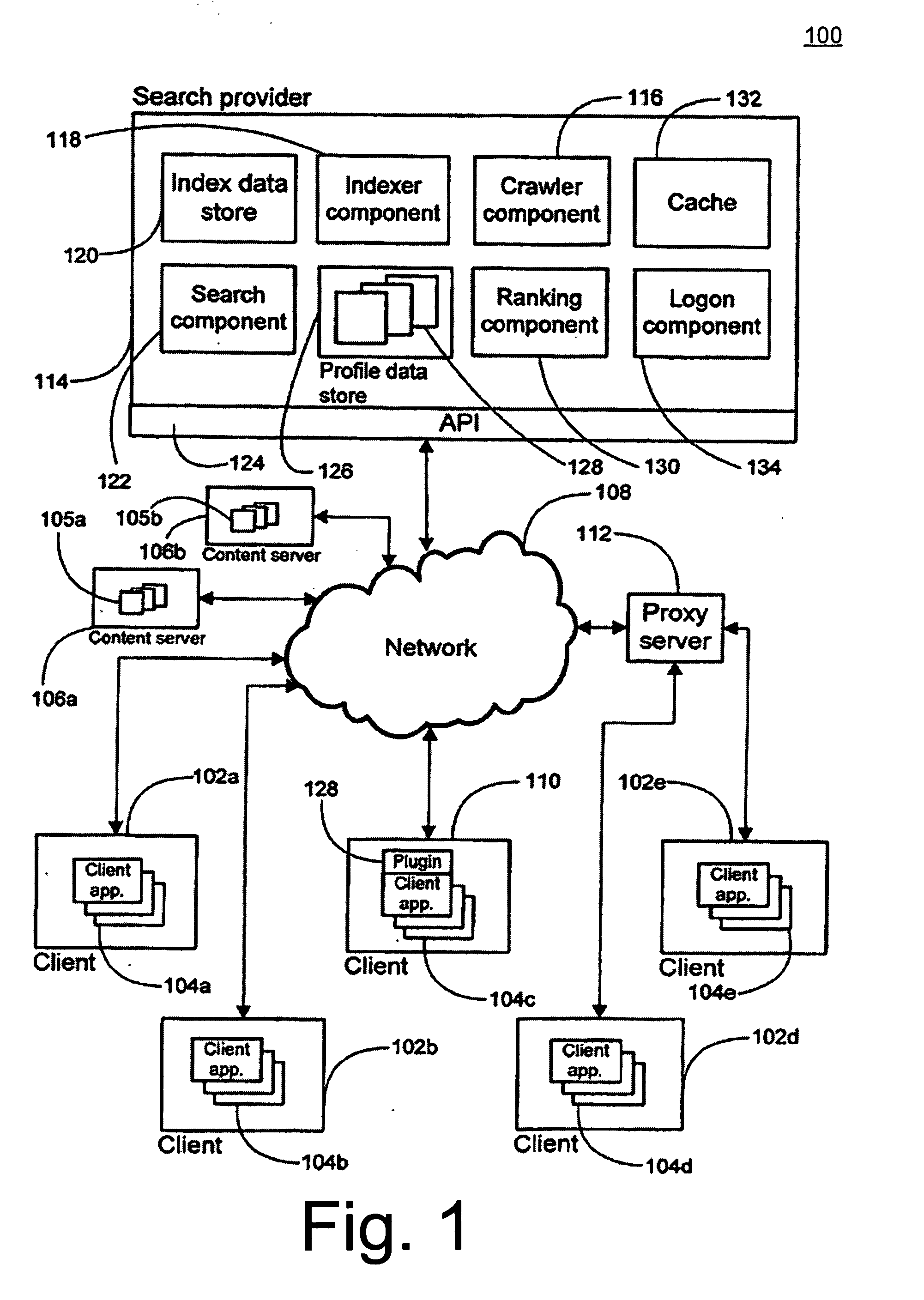
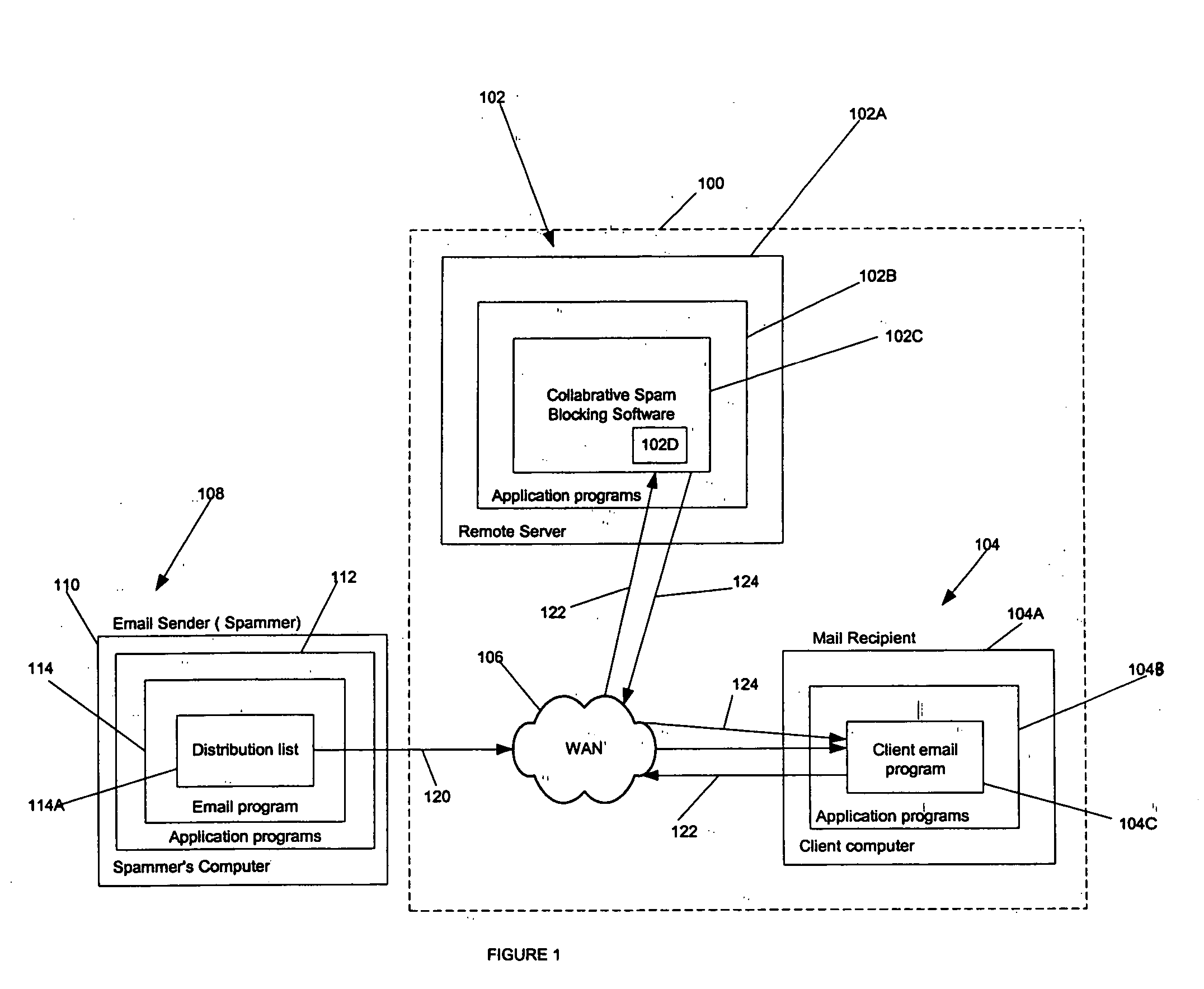
System and method of information filtering using measures of affinity of a relationship
ActiveUS20050171955A1Data processing applicationsData switching networksAffinity measurementSpamming
A system, apparatus, and method are directed towards enabling information filtering using measures of an affinity of a relationship between subscribers of an online portal system. The affinity of a relationship may be determined based, in part, on the tracking of various online behaviors of and between subscribers of the portal system. Any of a variety of behaviors may be tracked, including message communications between subscribers, participation in instant messaging groups, purchases, activities, categories, and so forth. Such behaviors may be employed to determine a level of trust (or affinity) between subscribers of the portal system. This affinity measurement may be used to filter various information, including, but not limited to, product recommendations, ratings, polling queries, advertising, social network communications, personal ads, search results, and the like. Moreover, this affinity measurement may also be employed to perform message spam detection.
Owner:SLACK TECH LLC
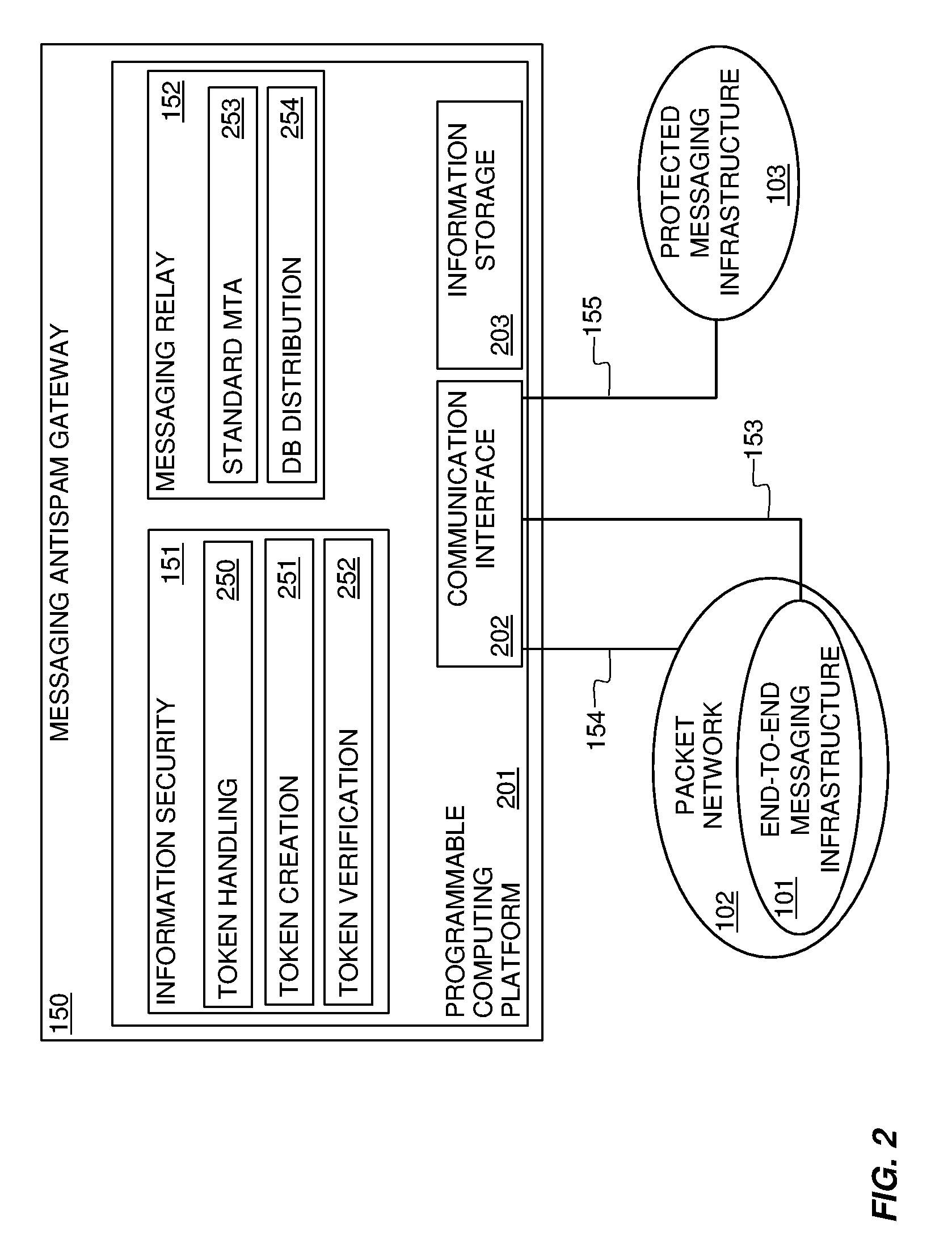
Systems and methods for preventing spam and denial of service attacks in messaging, packet multimedia, and other networks
InactiveUS20050132060A1Low costRaise priorityMultiple digital computer combinationsData switching networksData packSpamming
A system, various methods, and various apparatuses are provided for the purpose of supplying and including in an electronic message or multimedia session signalling unit a valid cryptographic authentication token, verifying said token's validity upon arrival of said message or signalling unit, and thereby providing message recipients or session parties with the assurance that said message or signalling unit is from a valid sender. A system, apparatus, and various methods are further provided for the purpose of protecting legitimate application traffic and the network elements exchanging it from intrusion by wild packets attempting to consume application resources and thereby deny service to legitimate users or network elements. A system, various methods, and various apparatuses are further provided for the purpose of enabling legitimate advertising via electronic messages, relying upon message and sender authentication to assure both advertisers and viewers of advertising messages that all participants are valid, legitimate, and accountable for any abuse that may occur.
Owner:AUTOUPTODATE LLC
Apparatus and method for analyzing and filtering email and for providing web related services
InactiveUS20060184632A1Eliminate the problemSoftware engineeringDigital data processing detailsService provisionSpamming
The inventive methodology provides an integrated plug and play solution designed to protect home networks against spam, phishing emails, viruses, spyware as well as other similar threats. The described content filtering appliance can be used for processing of web and email traffic implemented and can be deployed as a stand-alone appliance. In one implementation, the content processing appliance utilizes backend content filtering provided by a remote scanning service accessed via a network. The system employs network level analysis and translation of content and executes various procedures to handle the network traffic. In an embodiment of the invention, the appliance is provided with an automatic remote updating capability, wherein the software and data used by the appliance can be updated remotely via a network. Finally, the appliance may also implement parental controls.
Owner:MARINO JOSEPH P
Spam filtering system and method
InactiveUS9177293B1Multiple digital computer combinationsOffice automationEmail addressFilter system
A spam filter system and method, for maintaining at least one database of permitted email addresses; automatically communicating with an email server, and selectively downloading and storing email not corresponding to entries in the database; automatically sending a challenge message in response to messages from non-permitted email addresses; if an appropriate response is received to the challenge message, adding the non-permitted email address to the database of permitted email addresses; and automatically restoring downloaded email messages from email addresses which become permitted.
Owner:COUSINS INTPROP
Dynamic message filtering
ActiveUS20050076084A1Reduce in quantityMake fastError detection/correctionGenetic modelsSpammingWhitelist
Dynamically filtering and classifying messages, as good messages, bulk periodicals, or spam. A regular expression recognizer, and pre-trained neural networks. The neural networks distinguish “likely good” from “likely spam,” and also operate at a more discriminating level to distinguish among the three categories above. A dynamic whitelist and blacklist; sending addresses are collected when the number of their messages indicates the sender is good or a spammer. A dynamically selected set of regular expressions input to the neural networks.
Owner:MAILGATE LLC
Method and system for categorizing and processing e-mails based upon information in the message header and SMTP session
InactiveUS20050198159A1Multiple digital computer combinationsData switching networksWeb siteSpamming
Owner:ABACA TECH CORP
System and method for the classification of electronic communication
InactiveUS20060168006A1Multiple digital computer combinationsData switching networksElectronic communicationSpamming
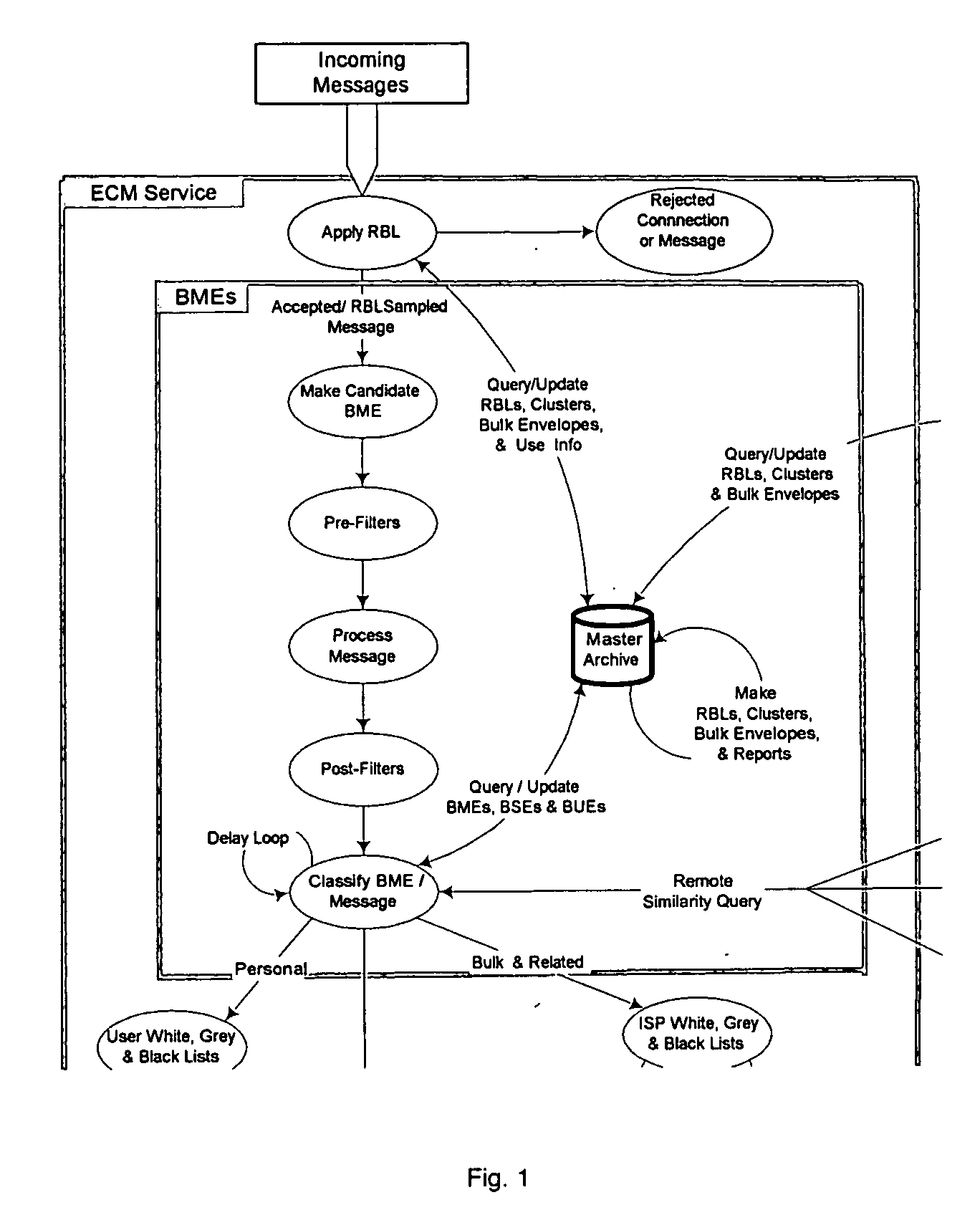
From an electronic message, we extract any destinations in selectable links, and we reduce the message to a “canonical” (standard) form that we define. It minimizes the possible variability that a spammer can introduce, to produce unique copies of a message. We then make multiple hashes. These can be compared with those from messages received by different users to objectively find bulk messages. From these, we build hash tables of bulk messages and make a list of destinations from the most frequent messages. The destinations can be used in a Real time Blacklist (RBL) against links in bodies of messages. Similarly, the hash tables can be used to identify other messages as bulk or spam. Our method can be used by a message provider or group of users (where the group can do so in a p2p fashion) independently of whether any other provider or group does so. Each user can maintain a “gray list” of bulk mail senders that she subscribes to, to distinguish between wanted bulk mail and unwanted bulk mail (spam). The gray list can be used instead of a whitelist, and is far easier for the user to maintain.
Owner:METASWARM INC
Spam filtering with probabilistic secure hashes
ActiveUS20060036693A1Multiple digital computer combinationsData switching networksSpammingComputer science
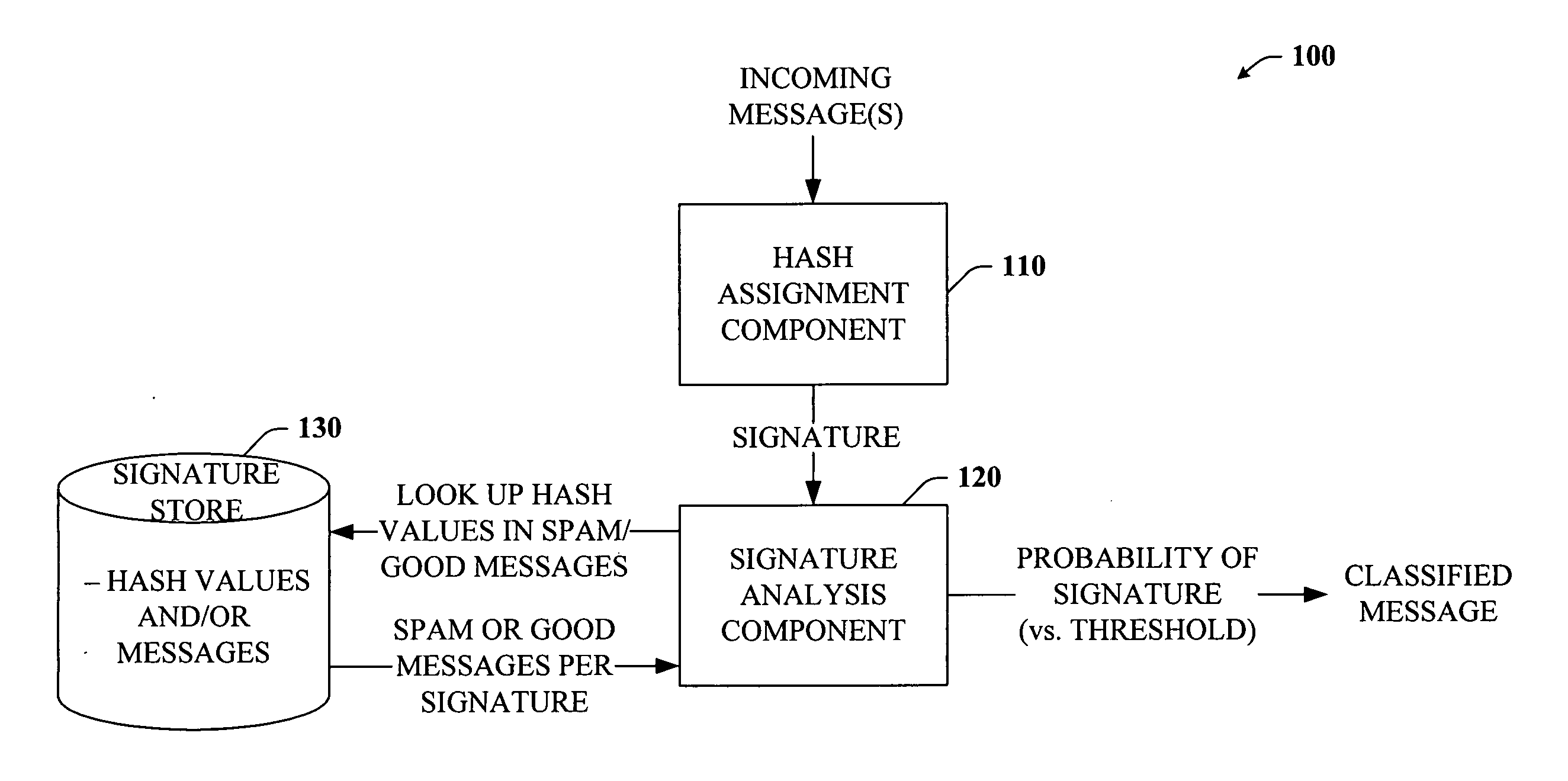
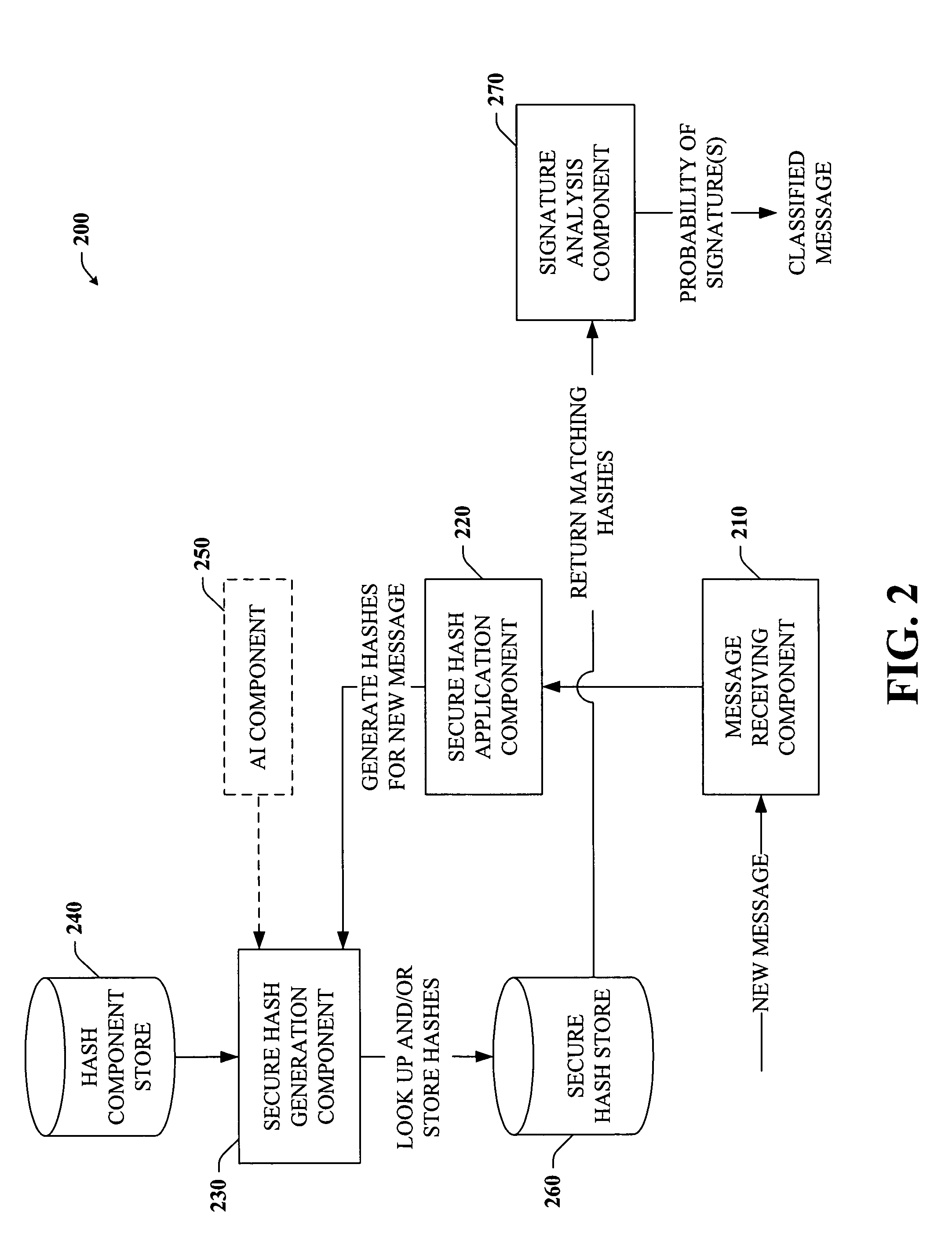
Disclosed are signature-based systems and methods that facilitate spam detection and prevention at least in part by calculating hash values for an incoming message and then determining a probability that the hash values indicate spam. In particular, the signatures generated for each incoming message can be compared to a database of both spam and good signatures. A count of the number of matches can be divided by a denominator value. The denominator value can be an overall volume of messages sent to the system per signature for example. The denominator value can be discounted to account for different treatments and timing of incoming messages. Furthermore, secure hashes can be generated by combining portions of multiple hashing components. A secure hash can be made from a combination of multiple hashing components or multiple combinations thereof. The signature based system can also be integrated with machine learning systems to optimize spam prevention.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for collaborative tag suggestions
InactiveUS20070174247A1Increase coverageLeast effortMetadata text retrievalDigital data processing detailsSpammingCommon Criteria
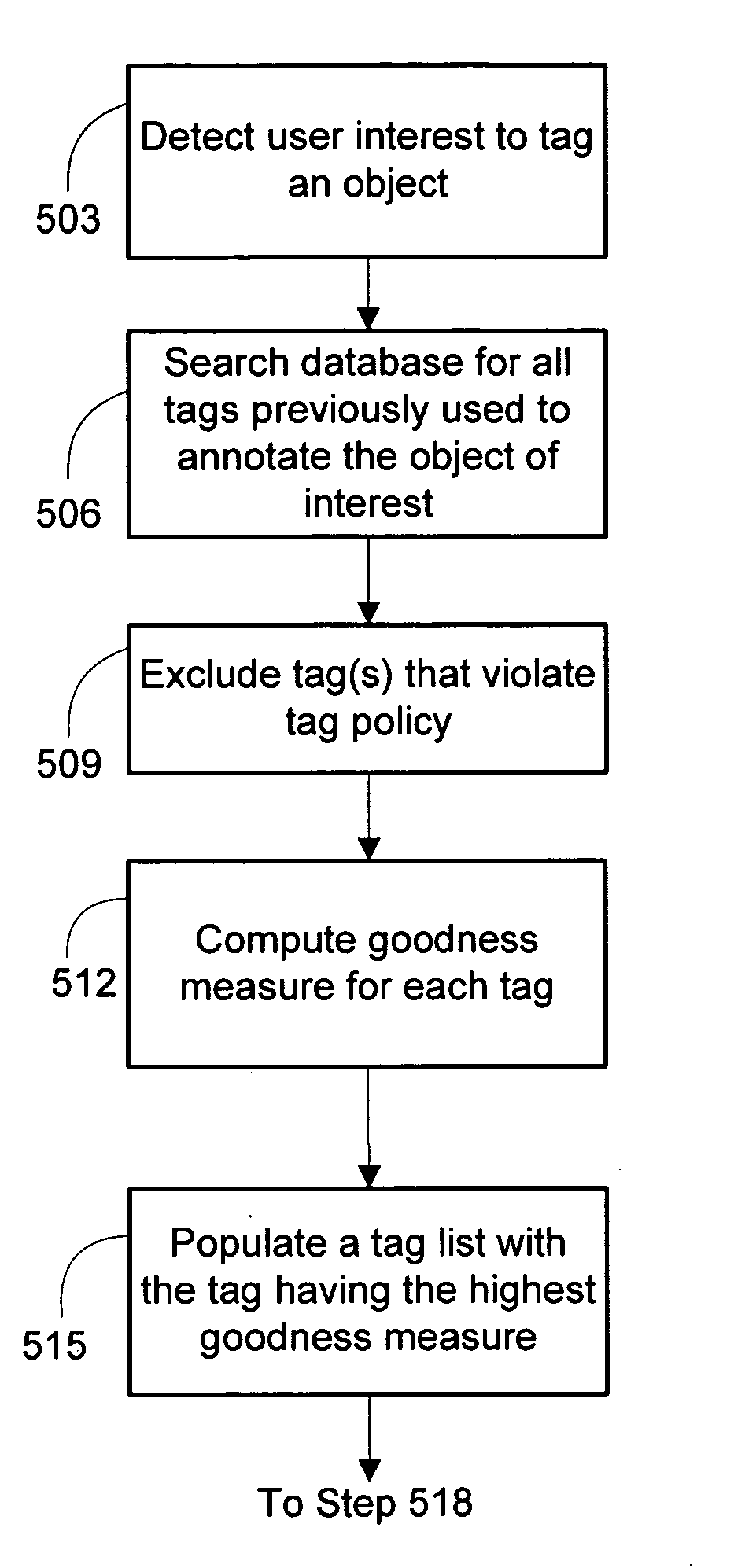
A set of general criteria have been defined to improve the efficacy of a tagging system, and have been applied to present collaborative tag suggestions to a user. The collaborative tag suggestions are based on a goodness measure for tags derived from collective user authorities to combat spam. The goodness measure is iteratively adjusted by a reward-penalty algorithm during tag selection. The collaborative tag suggestions can also incorporate other sources of tags, e.g., content-based auto-generated tags.
Owner:R2 SOLUTIONS
Selective electronic messaging within an online social network for SPAM detection
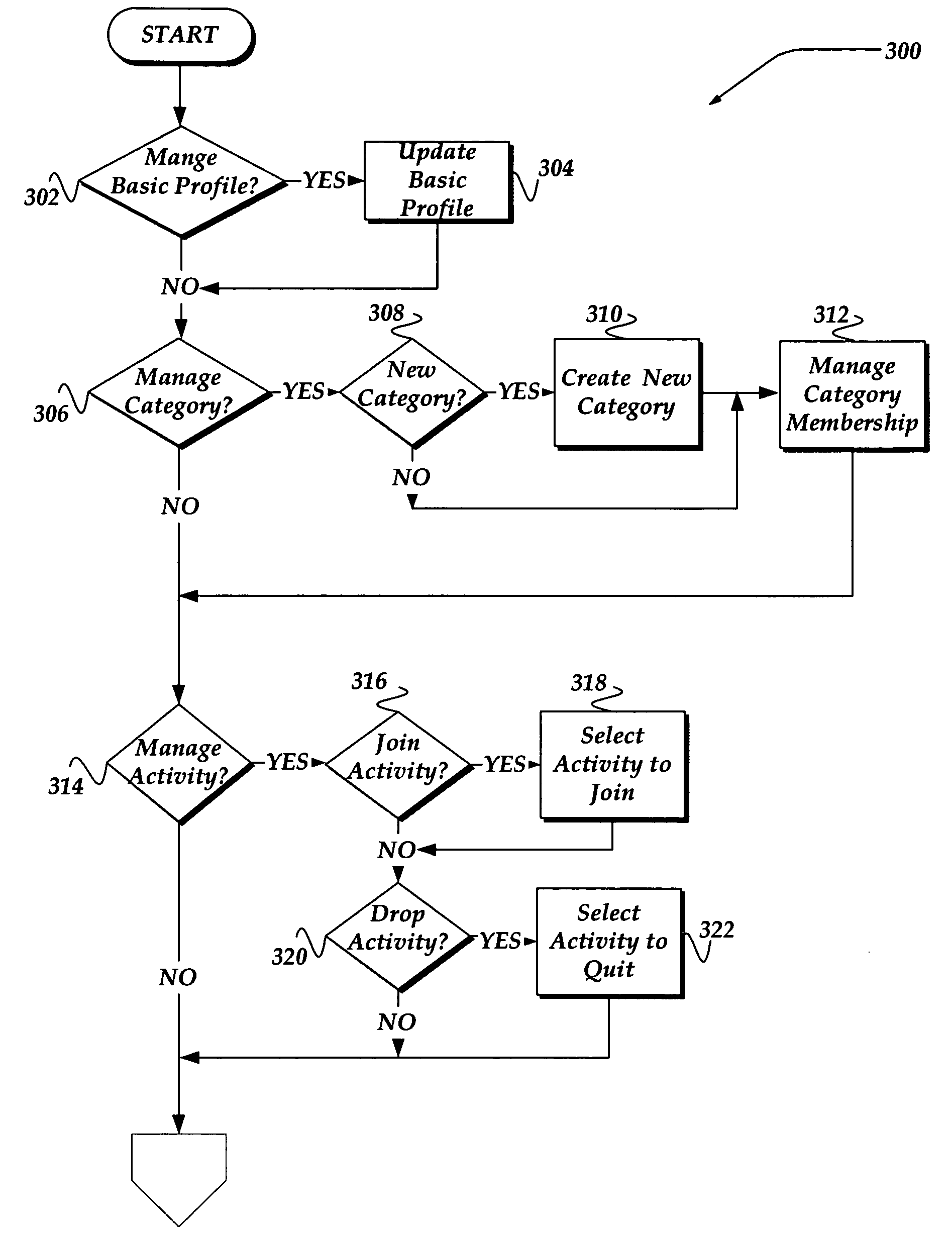
A method, apparatus, and system are directed towards communicating a message within a social network based, in part, on user-defined criteria. The user-defined criteria may be applied towards filtering outgoing and / or incoming messages. The user-defined criteria may include degrees of separation between members of the social network, a relationship to the prospective recipient, as well as criteria based, in part, on activities, such as dating, employment, hobbies, and the like. The user-defined criteria may also be based on a group membership, a strength of a relationship, and the like. Such user-defined relationship criteria may then be employed to determine to whom a message may be sent, as well from whom a message may be received.
Owner:OATH INC
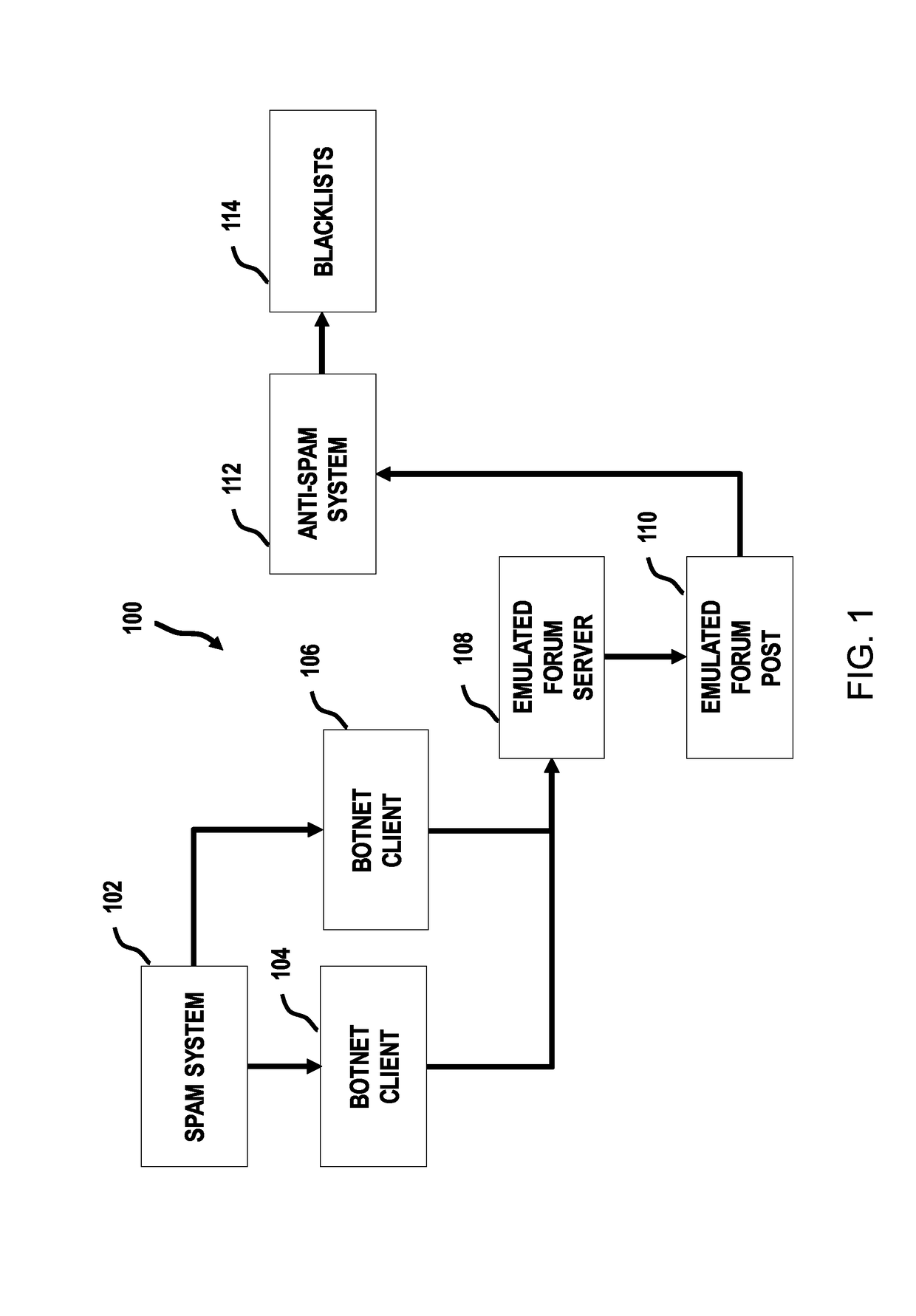
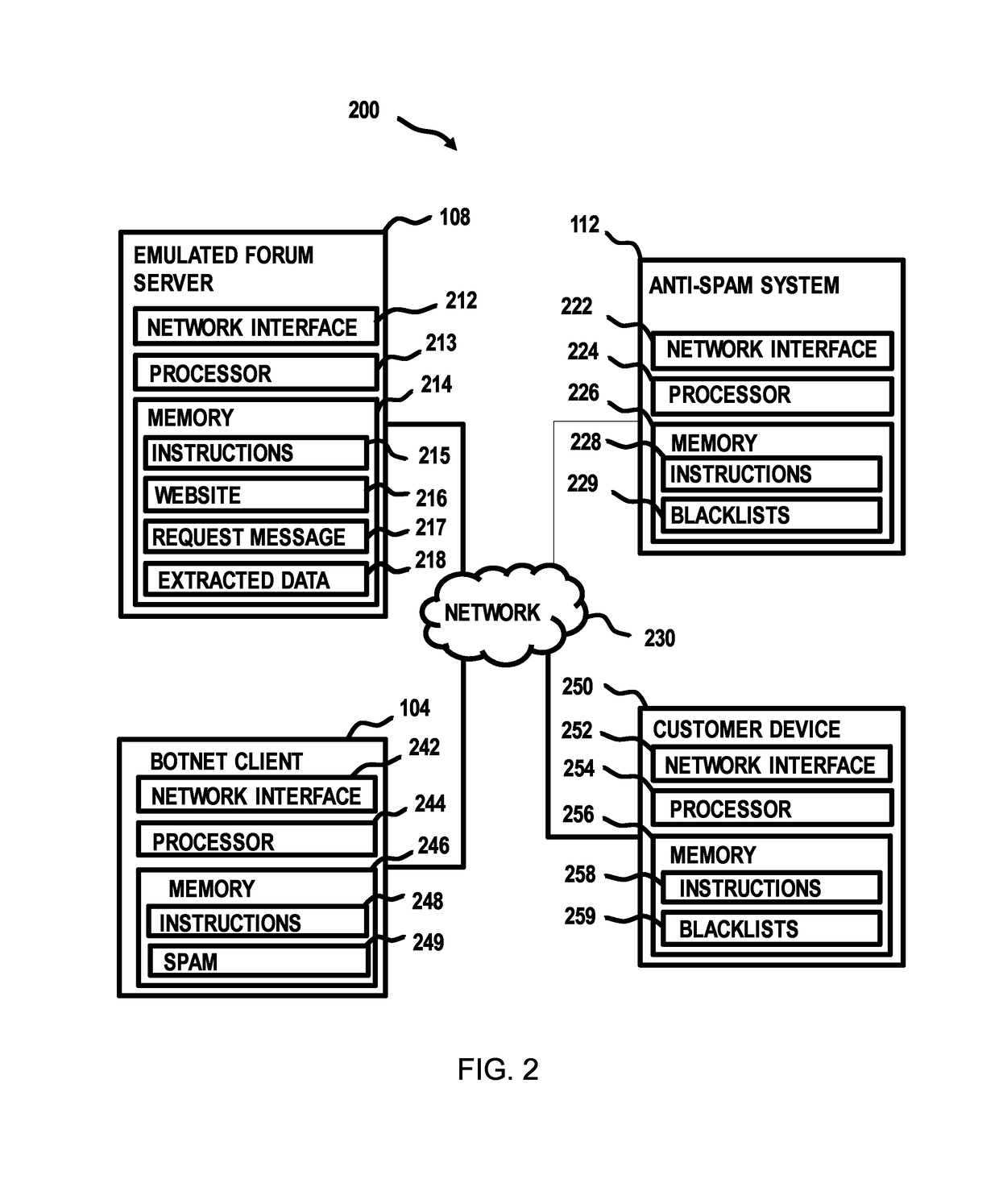
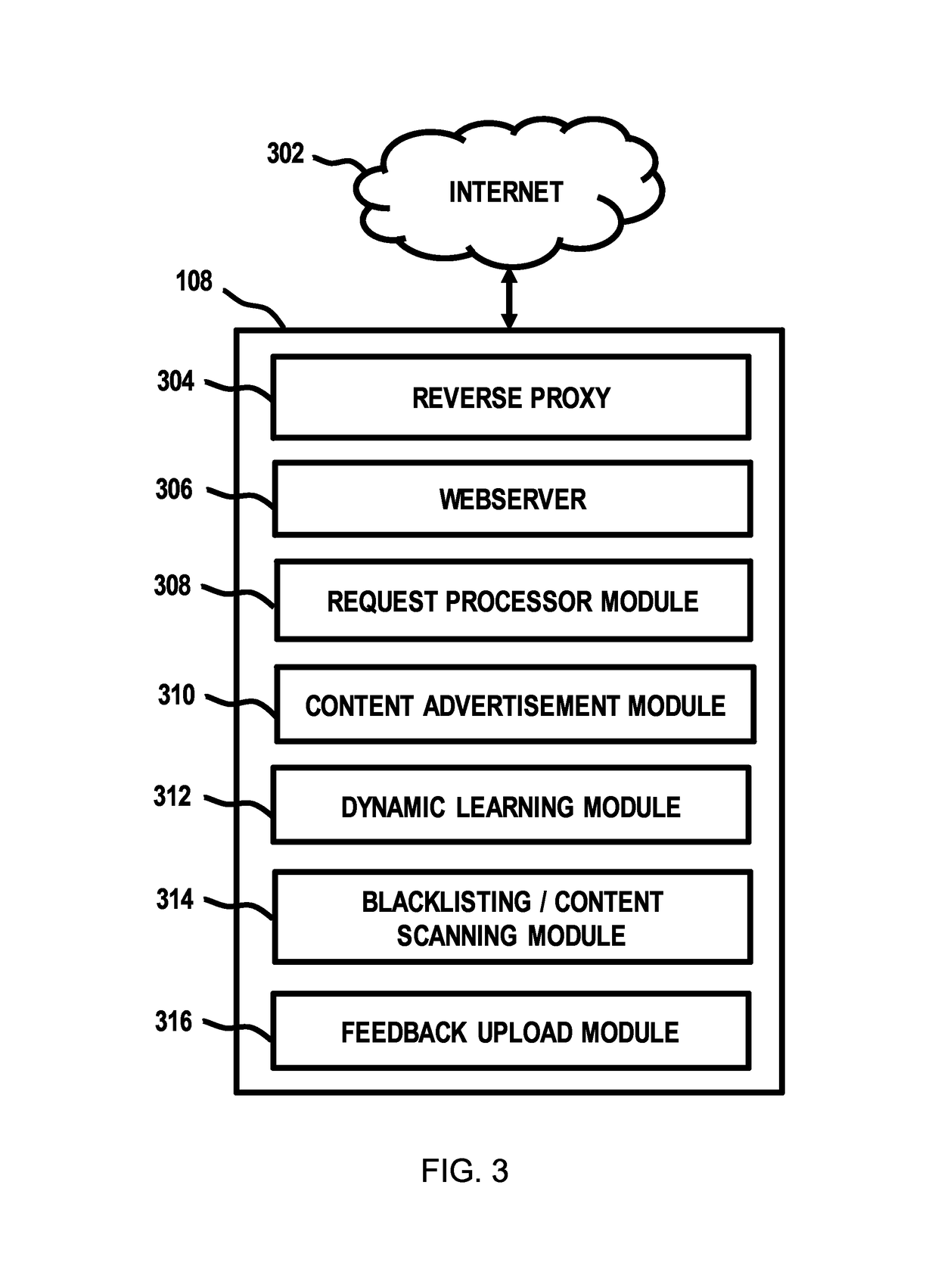
Attracting and analyzing spam postings
One or more processors generate a website mimicking a virtual message board. One or more processors receive a request message directed to the website. One or more processors analyze the request message for evidence that the request message originates from a source of spam. In response to a determination that the request message likely does originate from a spam source, one or more processors provide data about the spam source to an anti-spam system.
Owner:INT BUSINESS MASCH CORP
User interface and anti-phishing functions for an anti-spam micropayments system
ActiveUS20060075028A1Control contentEffective controlMultiple digital computer combinationsFlotationTrademarkSpamming
Owner:ICONIX INC
Prevention of outgoing spam
InactiveUS20050021649A1Facilitates mitigating spammer manipulationFacilitates detecting and preventingData processing applicationsComputer security arrangementsSpammingSubject matter
The subject invention provides for a system and method that facilitates detecting and preventing spam in a variety of networked communication environments. In particular, the invention provides several techniques for monitoring outgoing communications to identify potential spammers. Identification of potential spammers can be accomplished at least in part by a detection component that monitors per sender at least one of volume of outgoing messages, volume of recipients, and / or rate of outgoing messages. In addition, outgoing messages can be scored based at least in part on their content. The scores can be added per message per sender and if the total scores) per message or per sender exceeds some threshold, then further action can be taken to verify whether the potential spammer is a spammer. Such actions include human-inspecting a sample of the messages, sending challenges to the account, sending a legal notice to warn potential spammers and / or shutting down the account.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for categorizing and processing e-mails
InactiveUS20050091320A1Good reputationMultiple digital computer combinationsData switching networksData packSpamming
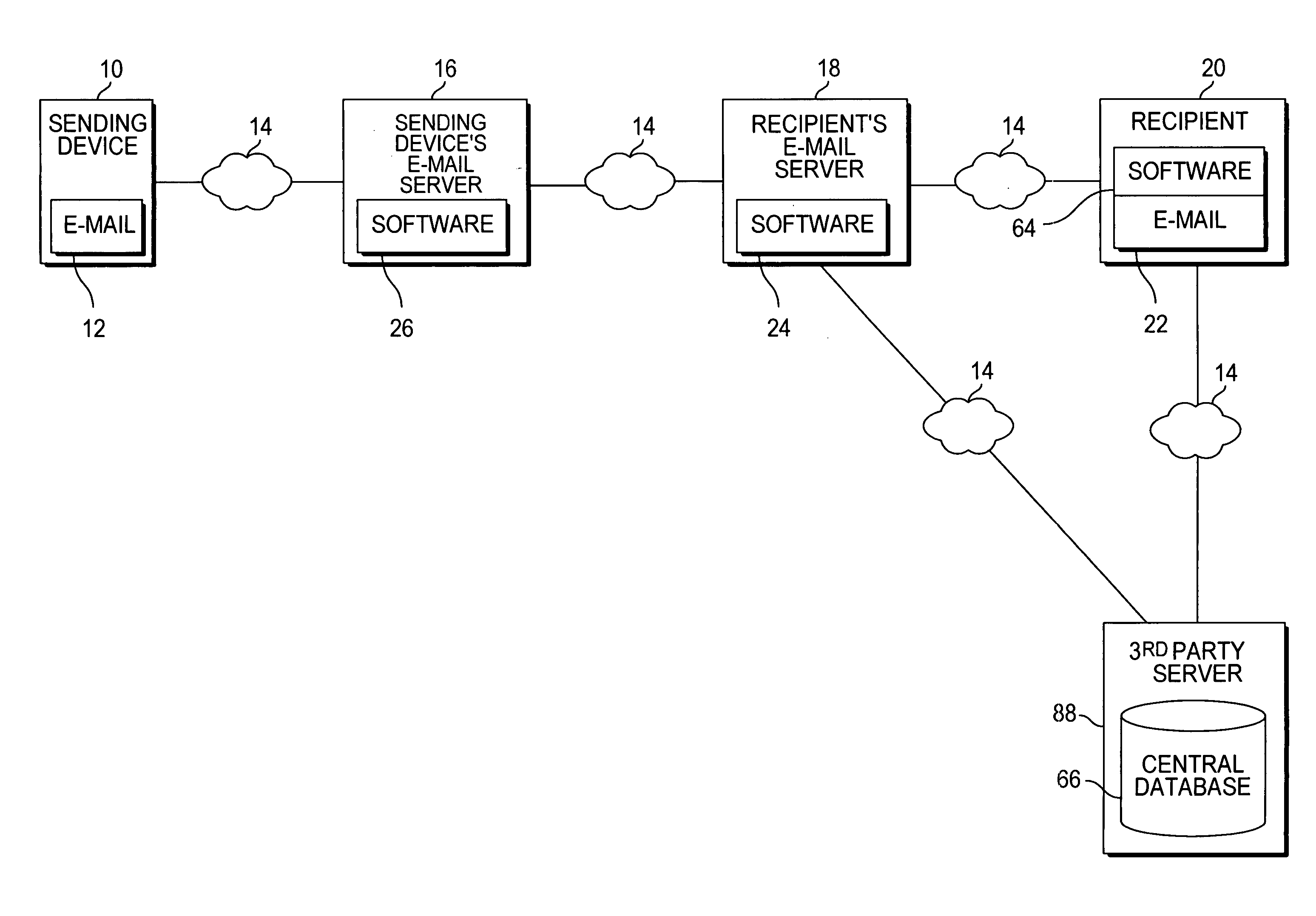
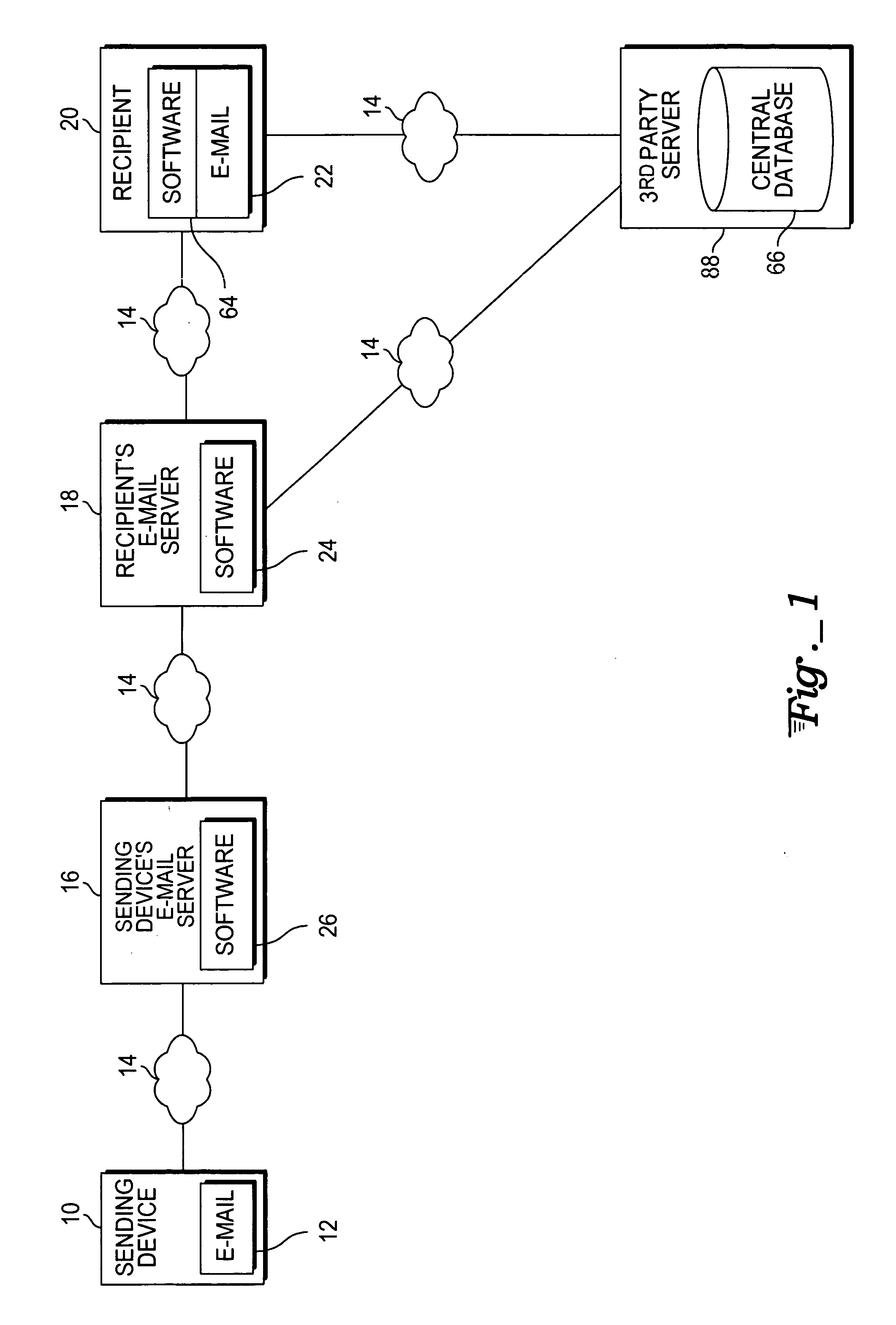
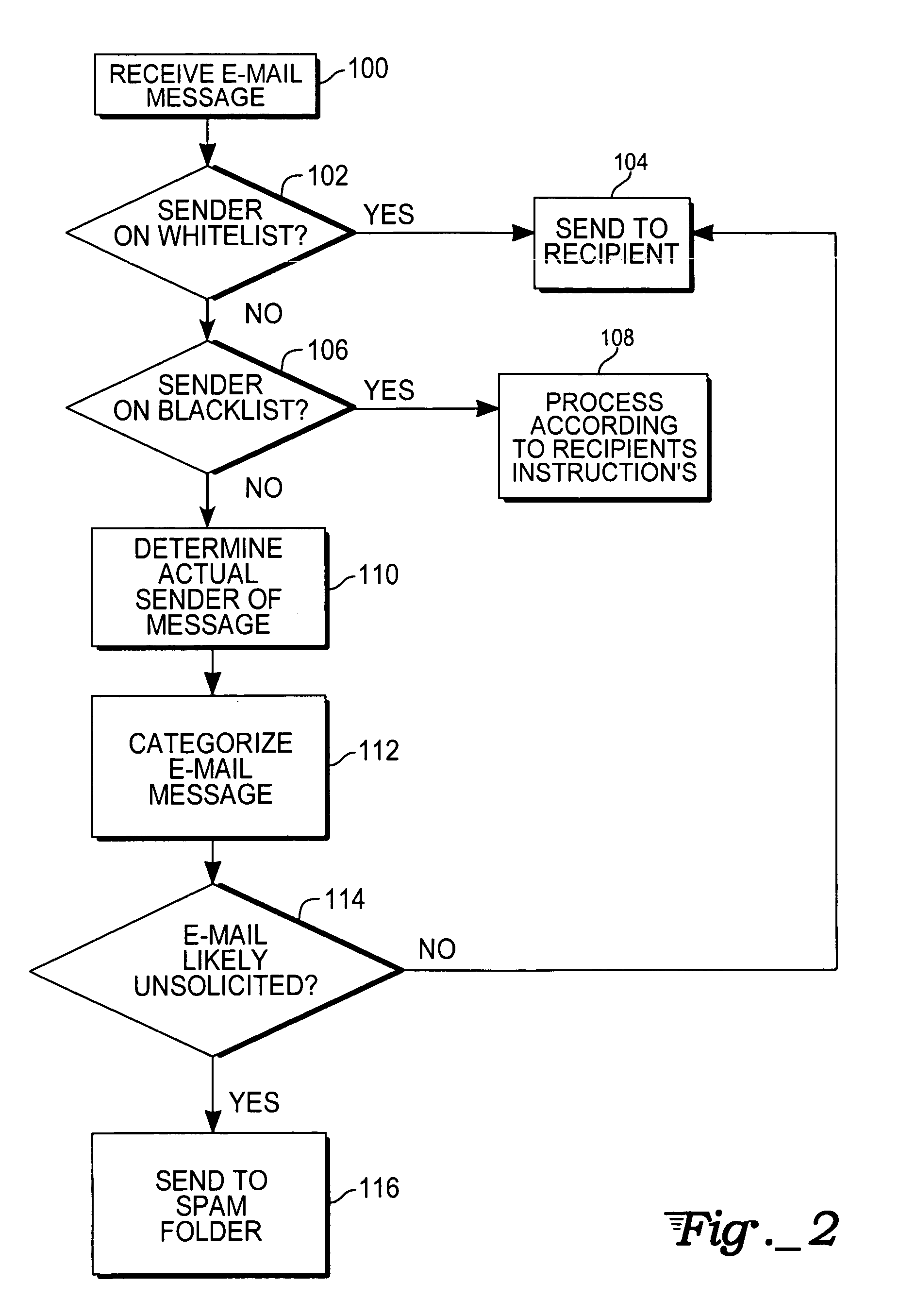
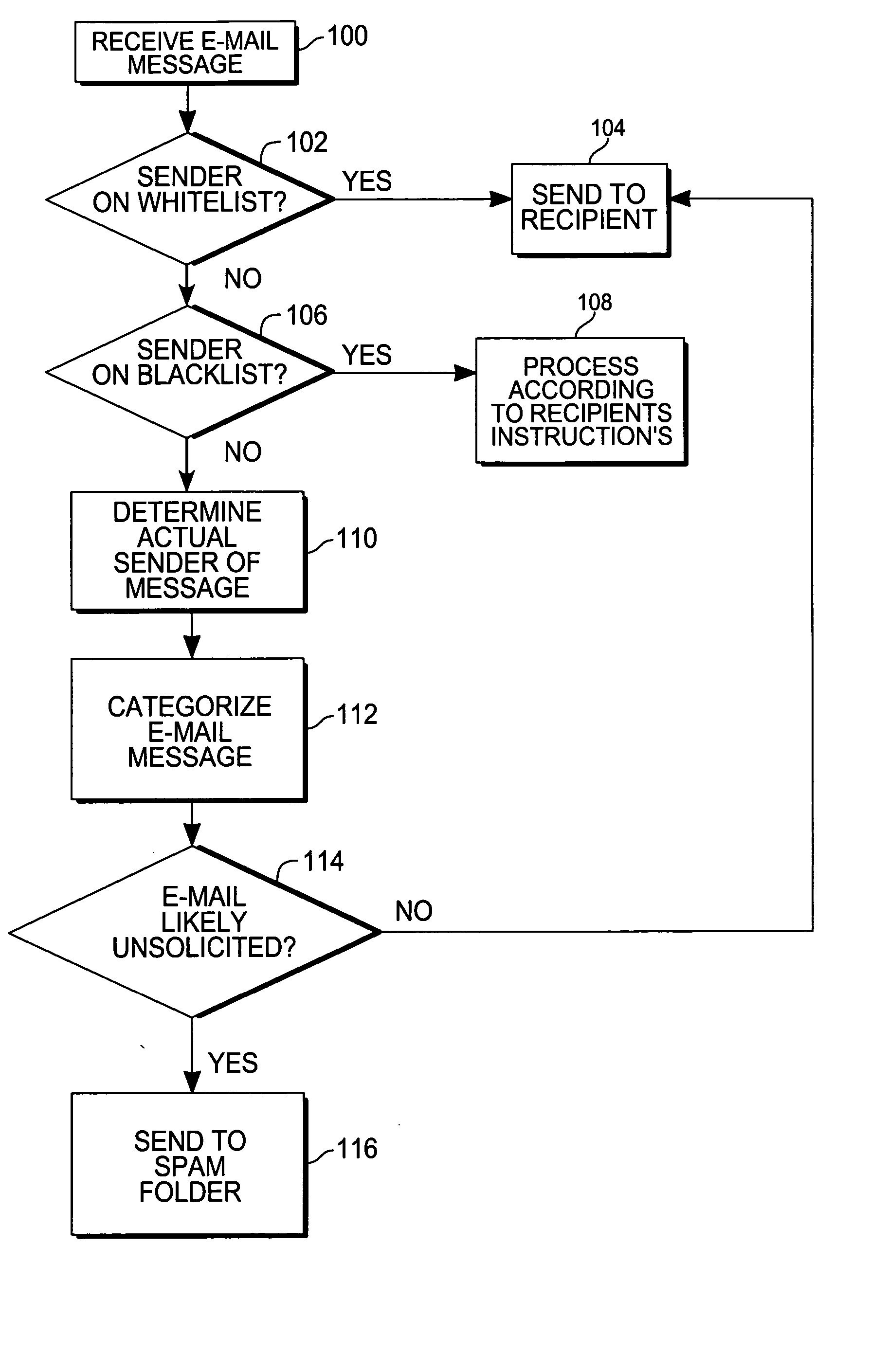
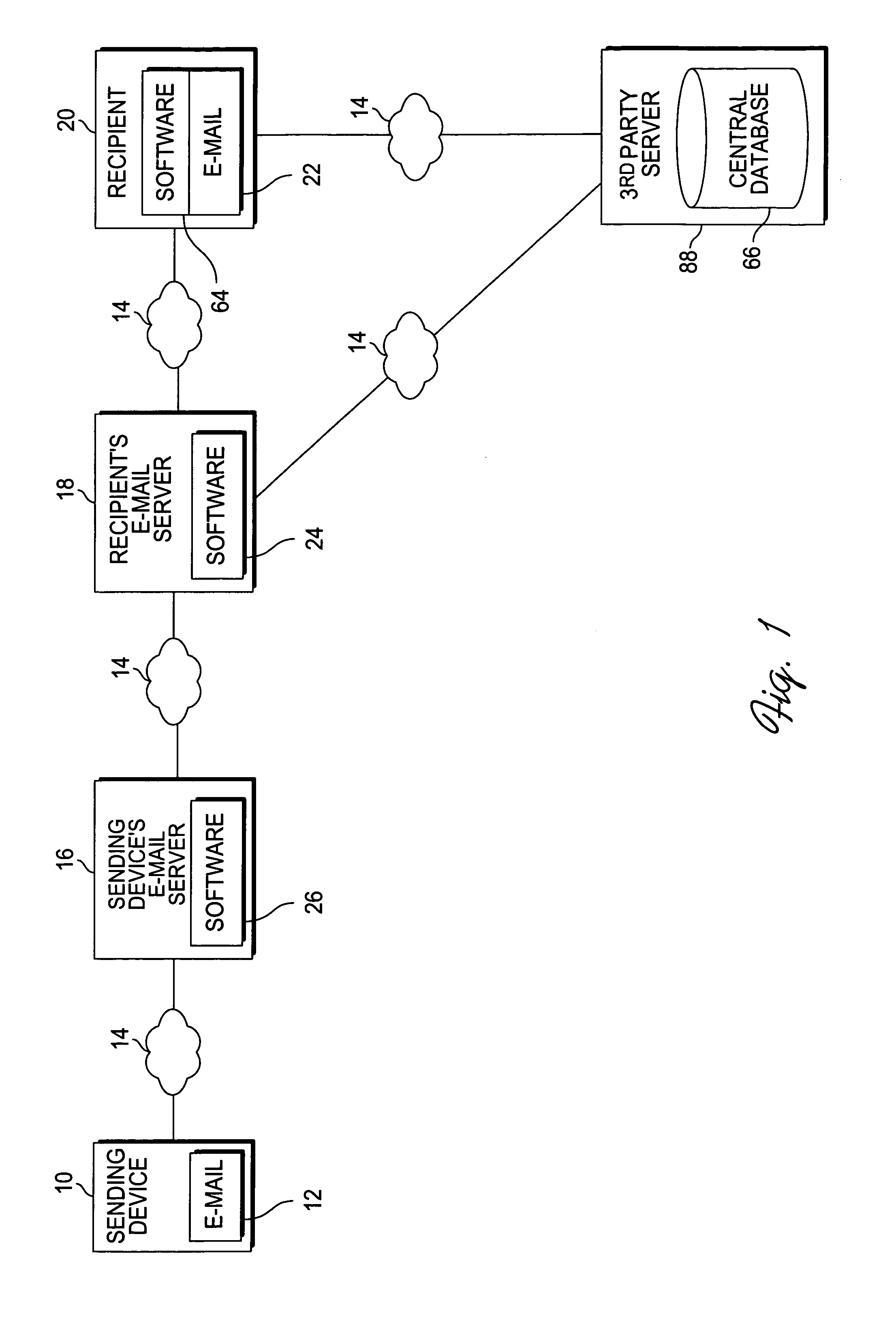
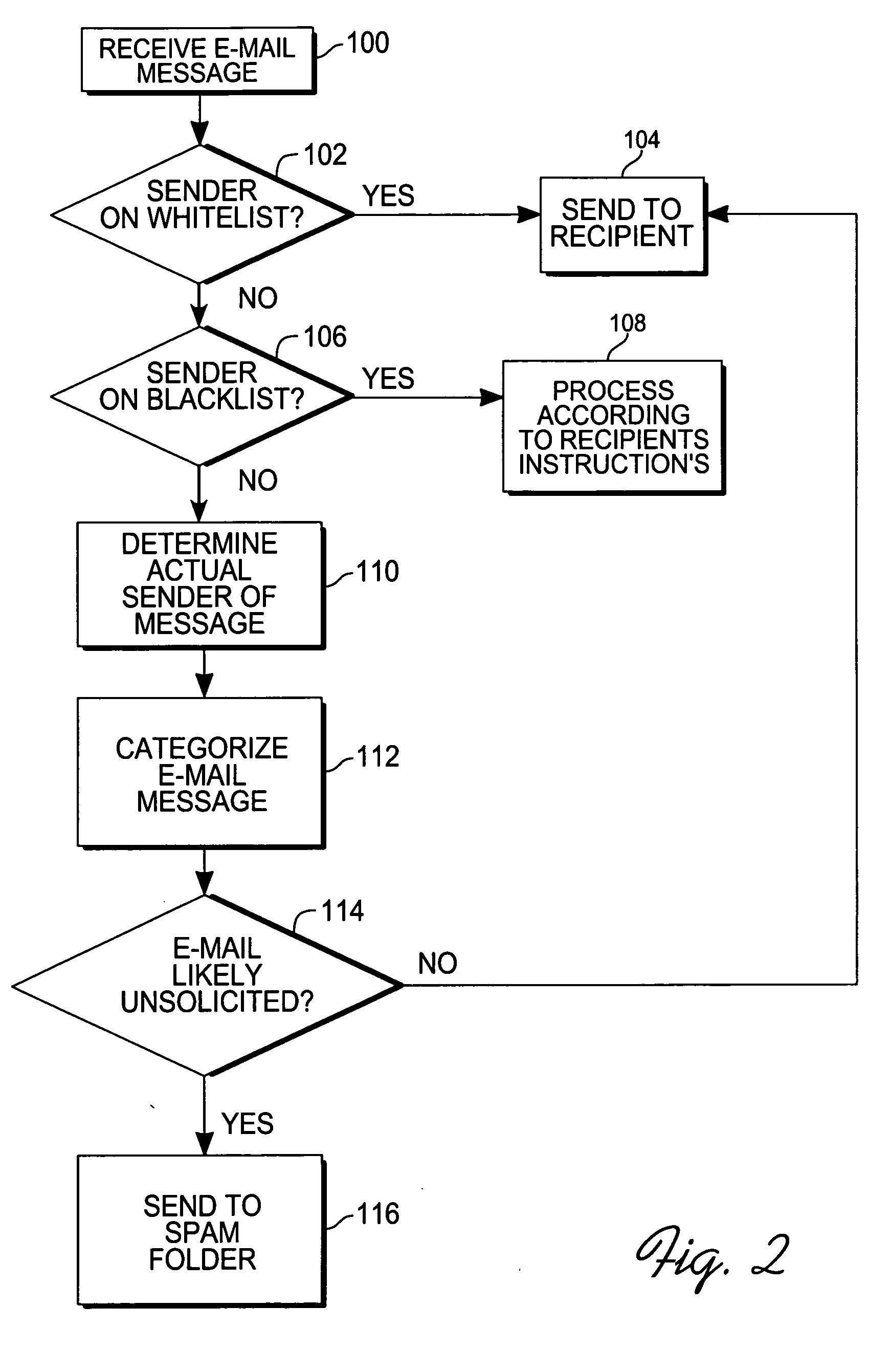
An e-mail filtering method and system that categorize received e-mail messages based on information about the sender. Data about the sender is contained in the message and is used to identify the actual sender of the message using a signature combining pieces of information from the message header or derived from information in the message header. This and other information about the message is then sent by each member of an e-mail network to one or more central databases (in one embodiment, the information will also be stored at a database associated with the recipient's e-mail program and filtering software) which stores the information and compiles statistics about e-mails sent by the sender to indicate the likelihood that the e-mail is unsolicited and determine the reputation of the sender (a good reputation indicates the sender does not send unwanted messages while a bad reputation indicates the sender sends unsolicited e-mail messages). Information from the central database is then sent to recipients in order to determine the likelihood that a received e-mail message is spam (information may also be obtained from the local database associated with the recipient's e-mail program and filtering software).
Owner:ABACA TECH CORP
Spam prevention
InactiveUS20050097179A1Cheap and simpleEasily recreatedDigital data processing detailsUser identity/authority verificationInternet privacySpamming
Owner:ORME GREGORY MICHAEL
Adaptive spam message detector
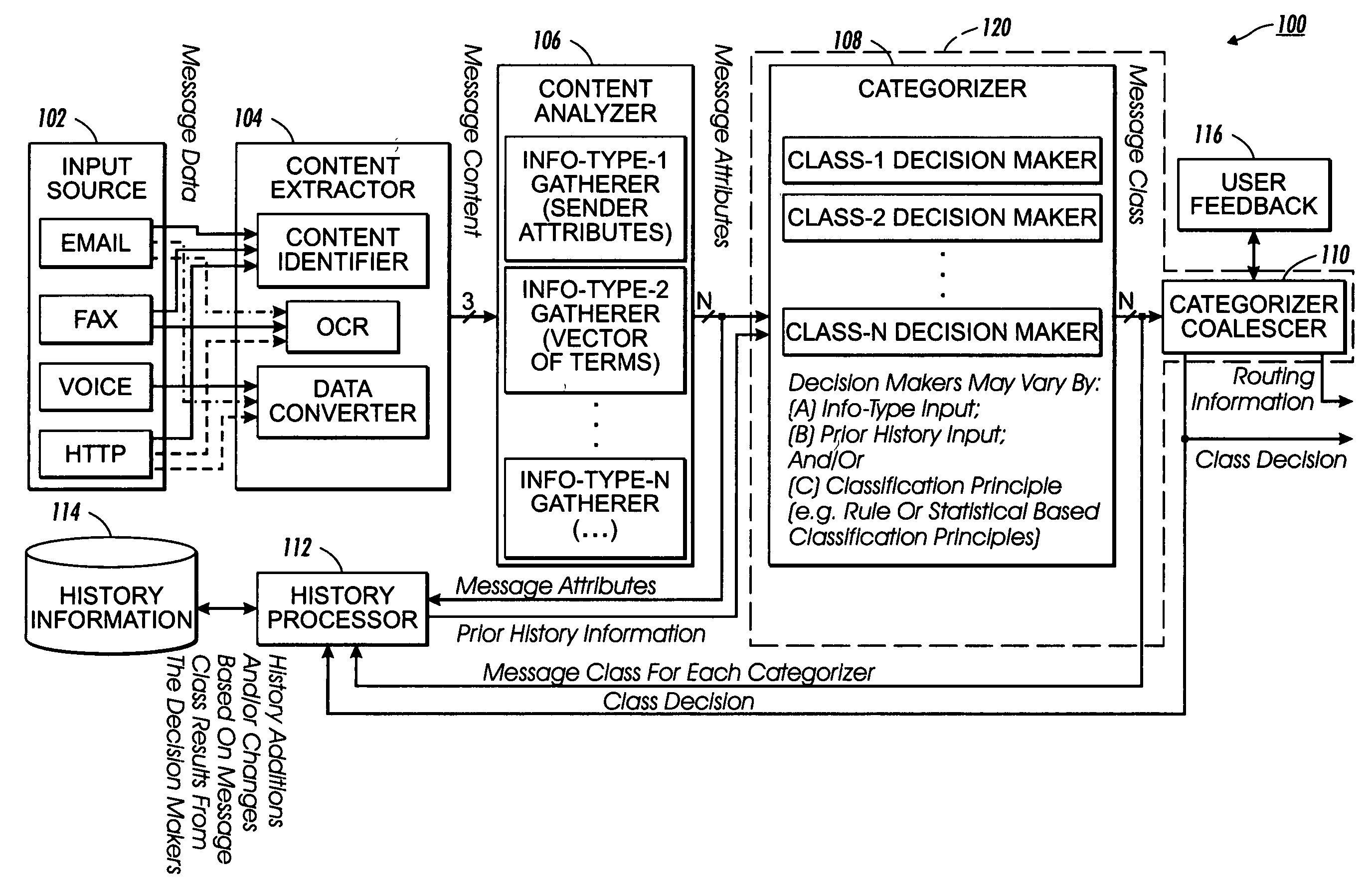
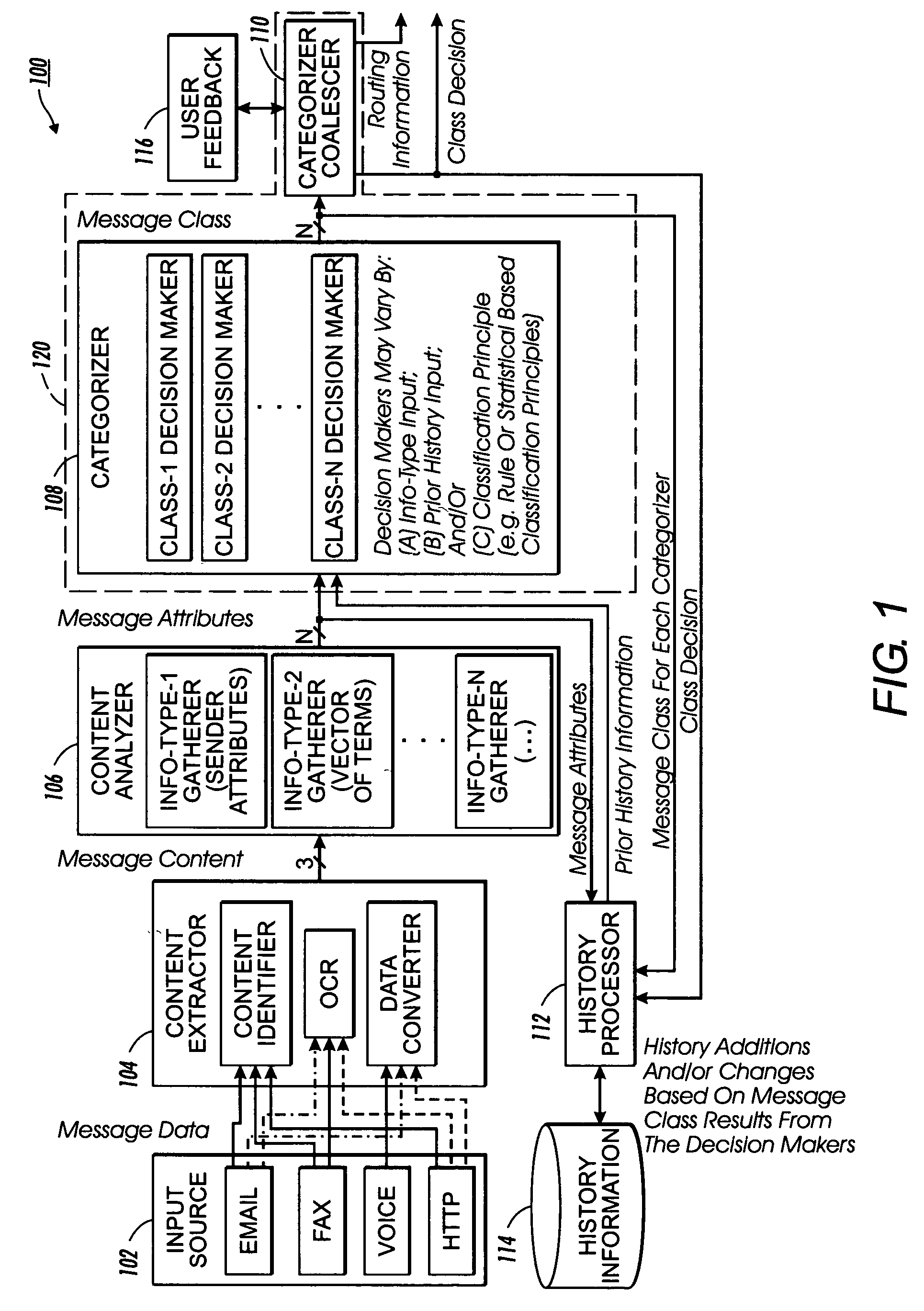
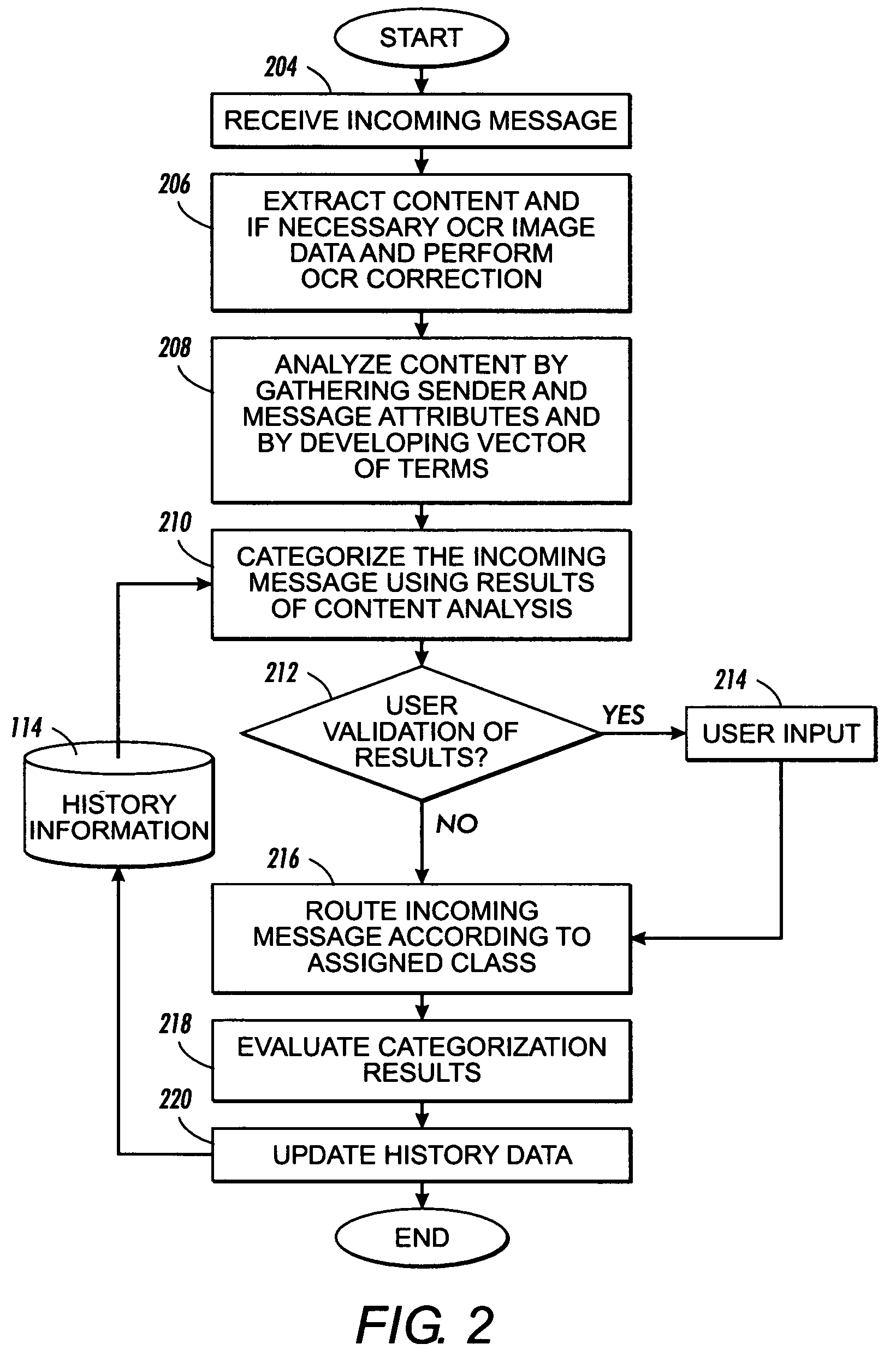
InactiveUS20060123083A1Loss of productivityWasted attentionMultiple digital computer combinationsData switching networksInformation typeDecision maker
Electronic content is filtered to identify spam using image and linguistic processing. A plurality of information type gatherers assimilate and output different message attributes relating to message content associated with an information type. A categorizer may have a plurality of decision makers for providing as output a message class for classifying the message data. A history processor records the message attributes and the class decision as part of the prior history information and / or modifies the prior history information to reflect changes to fixed data and / or probability data. A categorizer coalescer assesses the message class output by the set of decision makers together with optional user input for producing a class decision identifying whether the message data is spam.
Owner:XEROX CORP
Public relations communication methods and systems
InactiveUS20060059129A1Easily search for informationEasy to getWeb data indexingData switching networksEmail addressSpamming
An arrangement for distributing information from Information Providers (IP) to Information Recipients (IR) that utilizes the email system and the Internet to communicate with popular hardware devices—computers, PDAs, cellular phones, etc. IRs receive information anonymously and only the information desired. IPs do not need to “spam” the world in the hope of getting their information into the right hands because it is organized in a manner that allows IRs to receive exactly what they are looking for. Information is provided by an IP to an IR in response to a request from an IR. A PR server organizes and stores information uploaded by IPs, retrieves information requested by an IR and sends an automated response to the IR. A web domain is associated with the PR server provides a common email addressing scheme for communicating between the PR server and the IRs.
Owner:AZUMA HIDEYUKI
Method and system for categorizing and processing e-mails
ActiveUS20050080856A1Good reputationMultiple digital computer combinationsData switching networksSpammingScreening method
An e-mail filtering method and system that categorize received e-mail messages based on information about the sender. Data about the sender is contained in the message and is used to identify the actual sender of the message using a signature combining pieces of information from the message header or derived from information in the message header. This and other information about the message is then sent by each member of an e-mail network to one or more central databases (in one embodiment, the information will also be stored at a database associated with the recipient's e-mail program and filtering software) which stores the information and compiles statistics about e-mails sent by the sender to indicate the likelihood that the e-mail is unsolicited and determine the reputation of the sender (a good reputation indicates the sender does not send unwanted messages while a bad reputation indicates the sender sends unsolicited e-mail messages). Information from the central database is then sent to recipients in order to determine the likelihood that a received e-mail message is spam (information may also be obtained from the local database associated with the recipient's e-mail program and filtering software).
Owner:PROOFPOINT INC
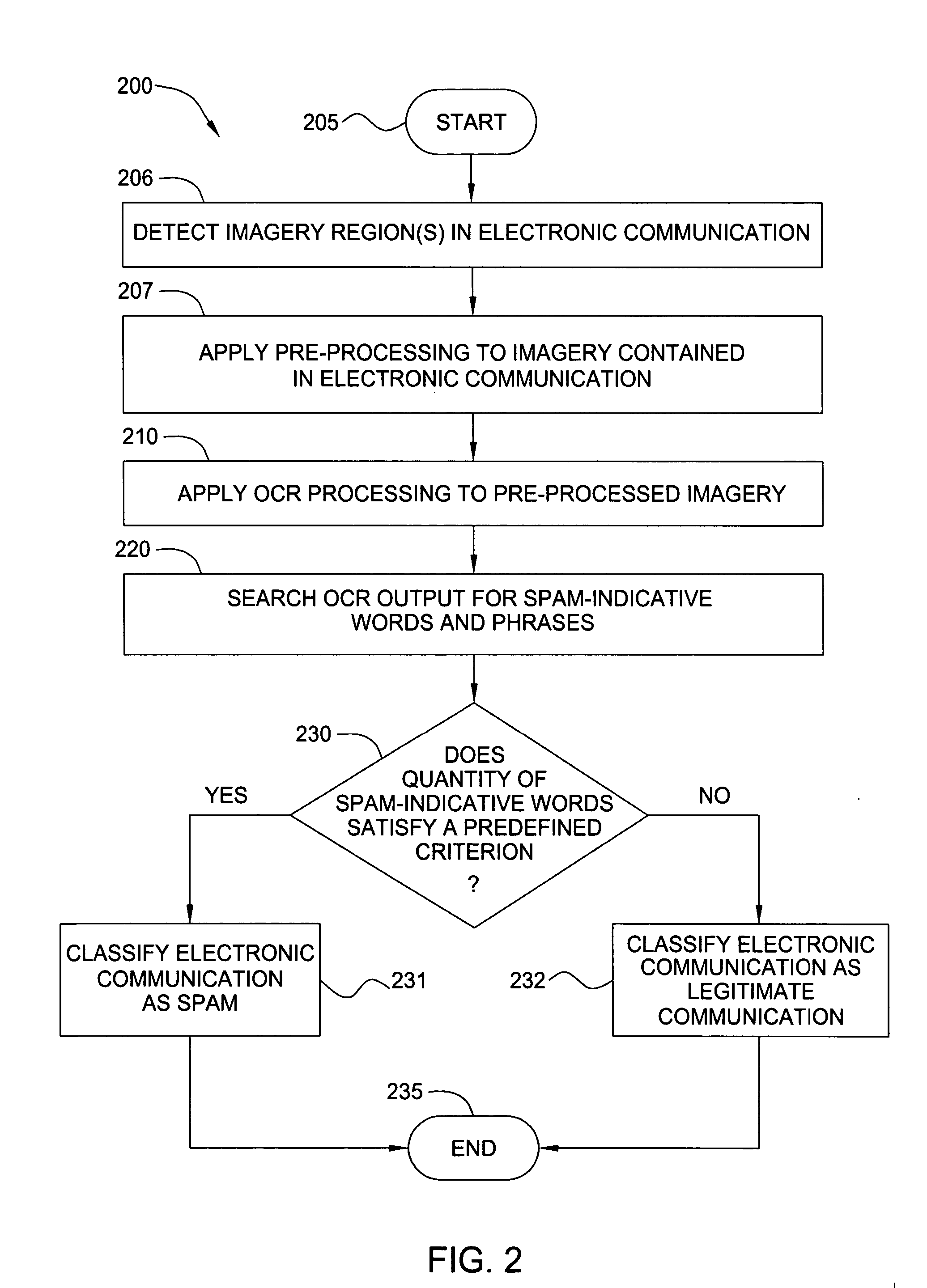
Method and apparatus for analysis of electronic communications containing imagery
InactiveUS20050216564A1Multiple digital computer combinationsData switching networksElectronic communicationSpamming
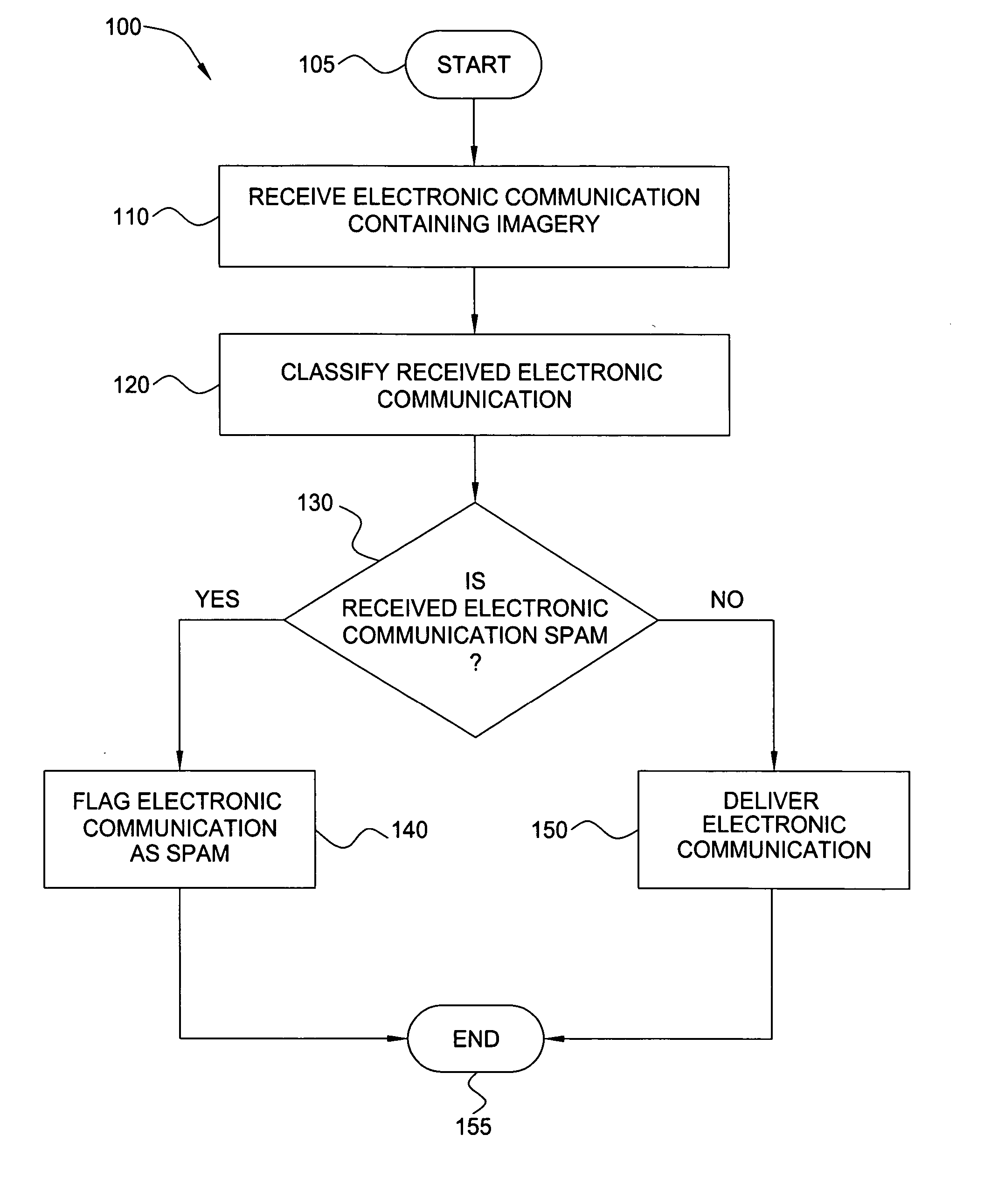
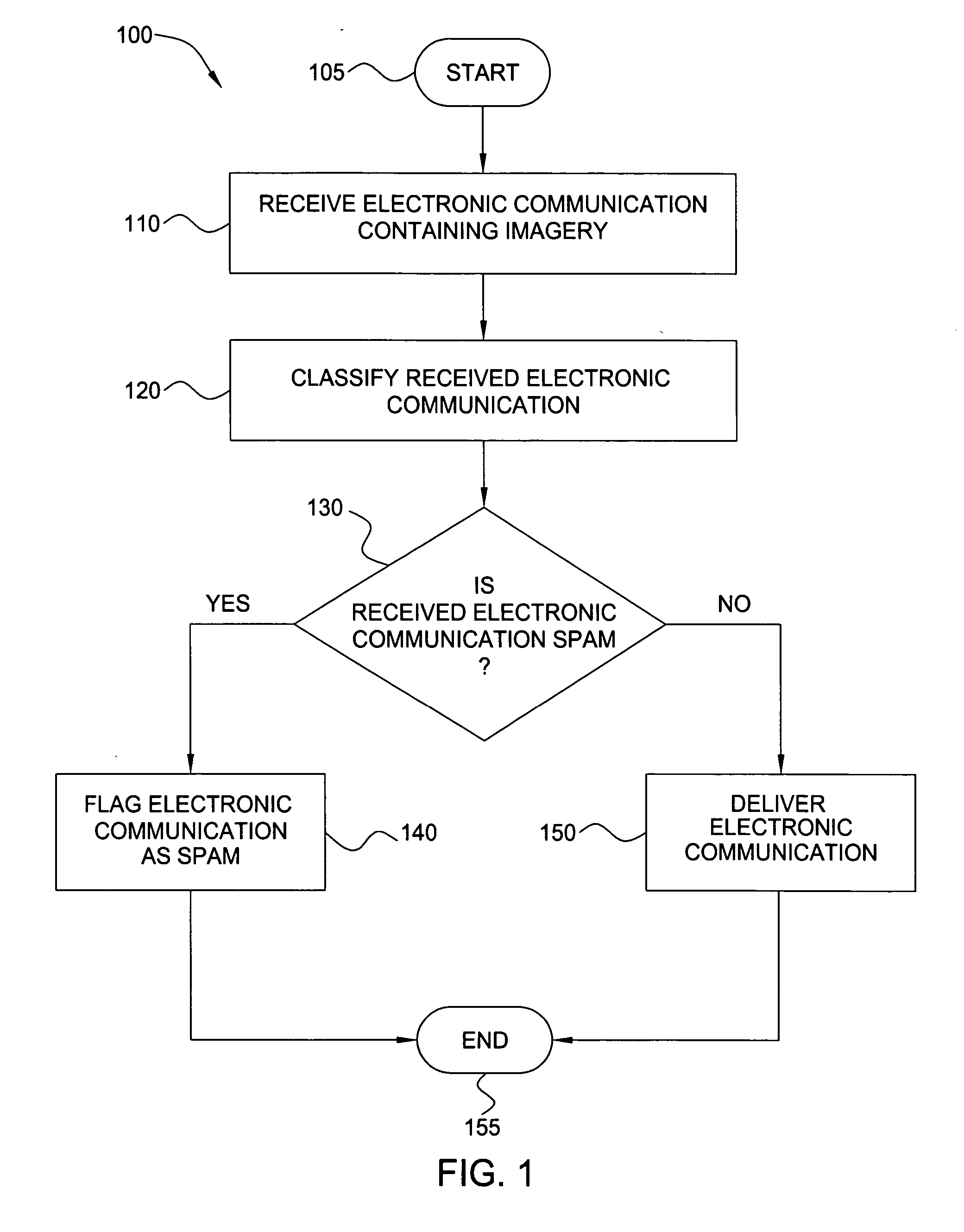
A method and apparatus are provided for analyzing an electronic communication containing imagery, e.g., to determine whether or not the electronic communication is a spam communication. In one embodiment, an inventive method includes detecting one or more regions of imagery in a received electronic communication and applying pre-processing techniques to locate regions (e.g., blocks or lines) of text in the imagery that may be distorted. The method then analyzes the regions of text to determine whether the content of the text indicates that the electronic communication is spam. In one embodiment, specialized extraction and rectification of embedded text followed by optical character recognition processing is applied to the regions of text to extract their content therefrom. In another embodiment, keyword recognition or shape-matching processing is applied to detect the presence or absence of spam-indicative words from the regions of text. In another embodiment, other attributes of extracted text regions, such as size, location, color and complexity are used to build evidence for or against the presence of spam.
Owner:SRI INTERNATIONAL
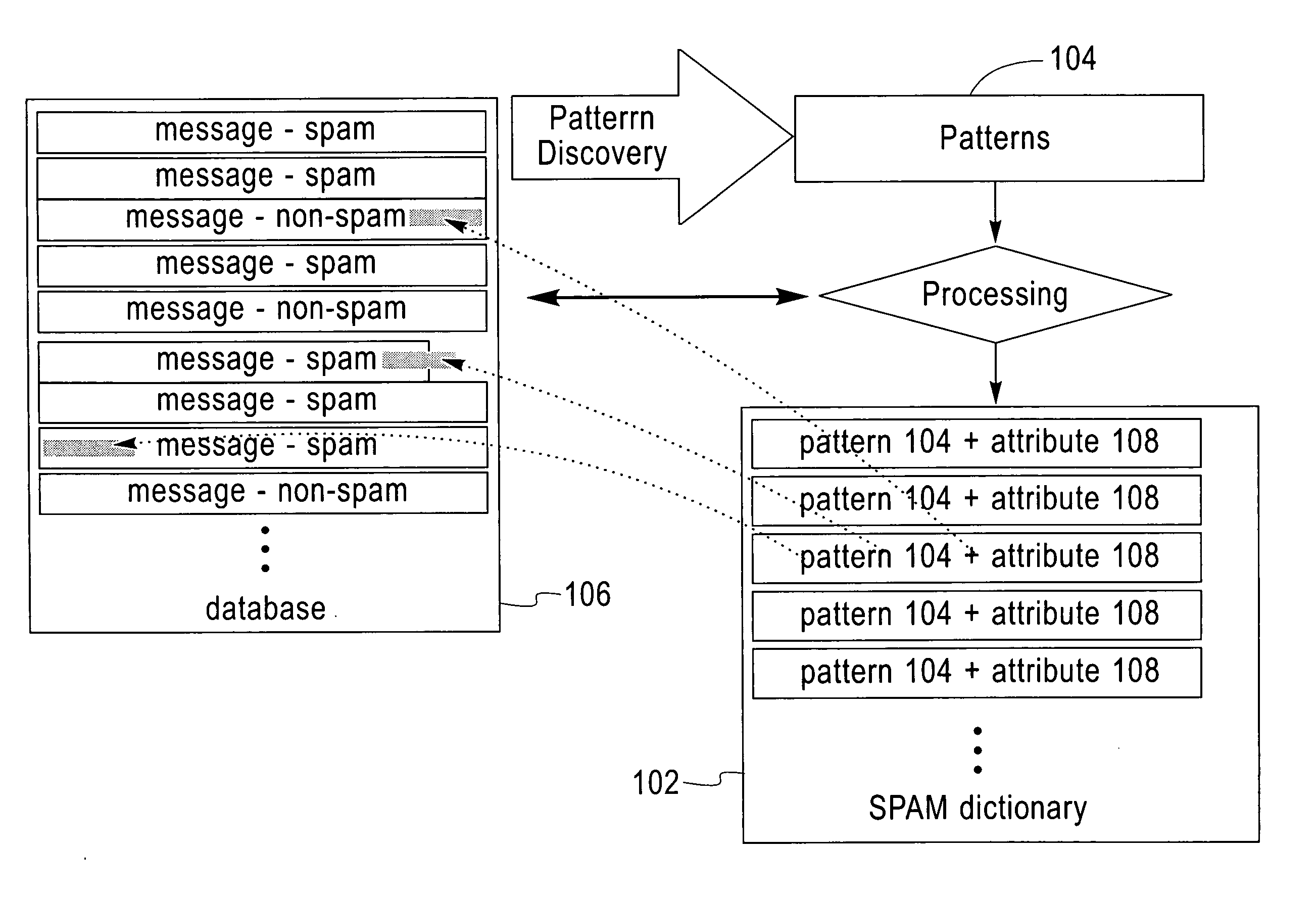
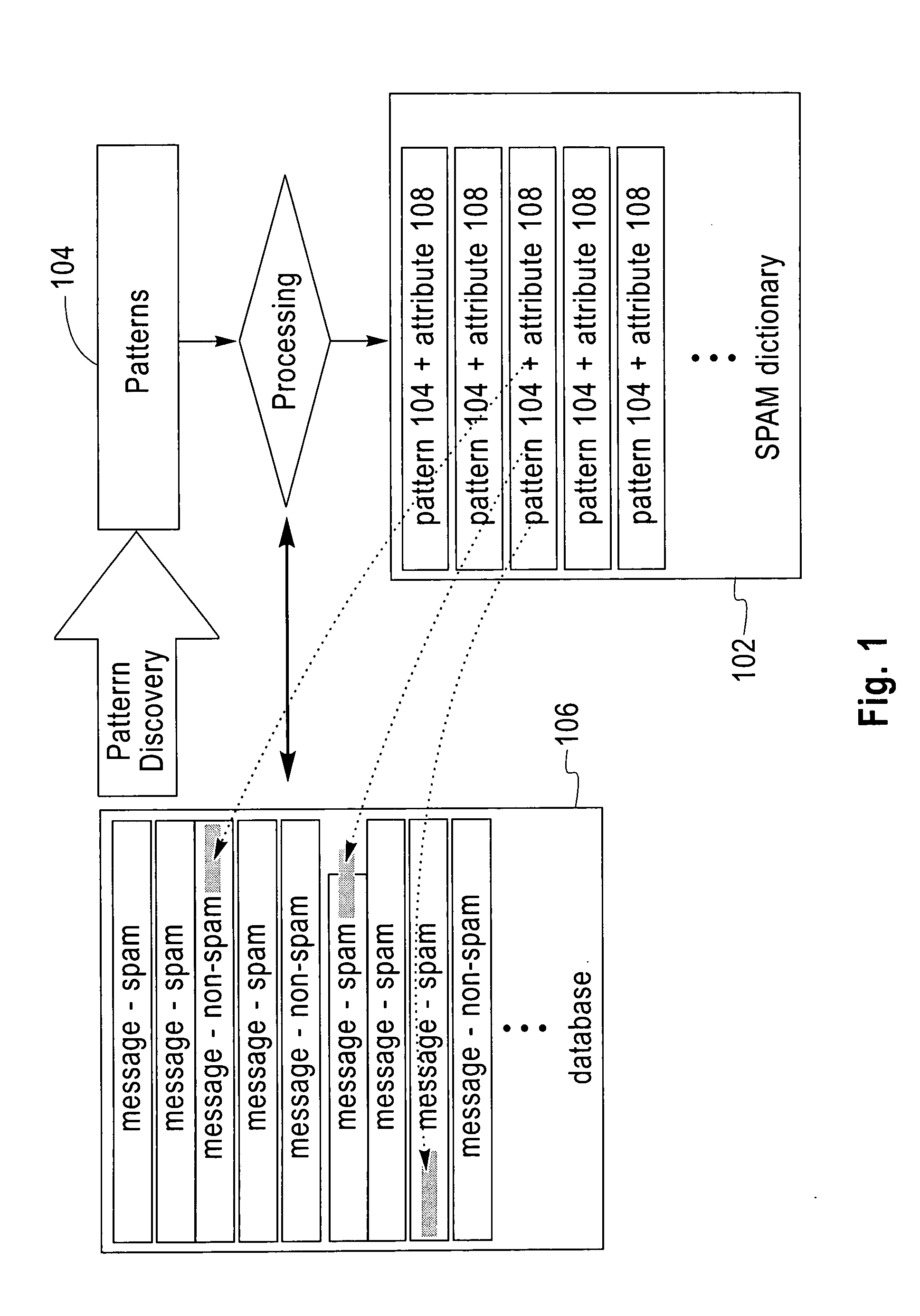
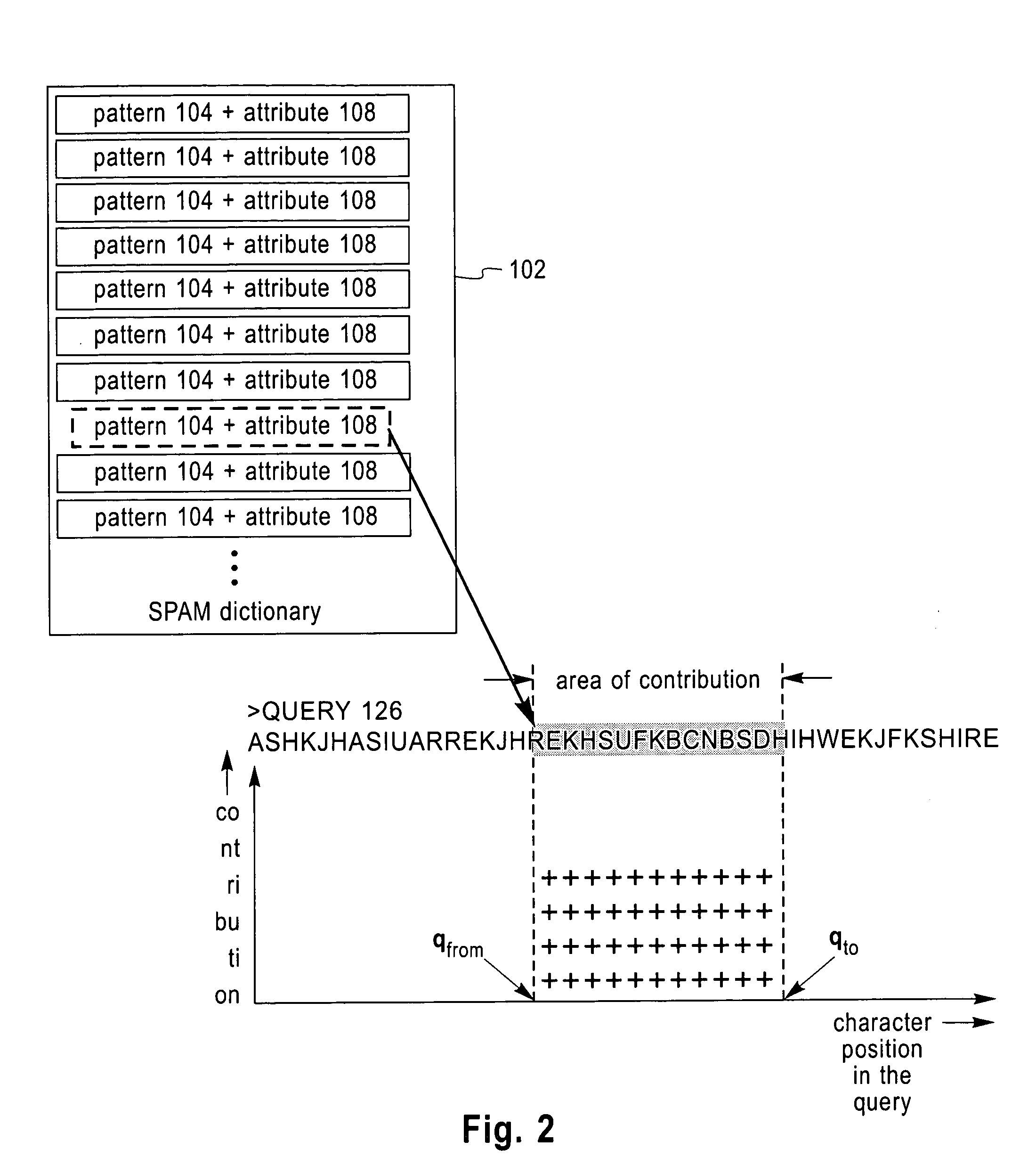
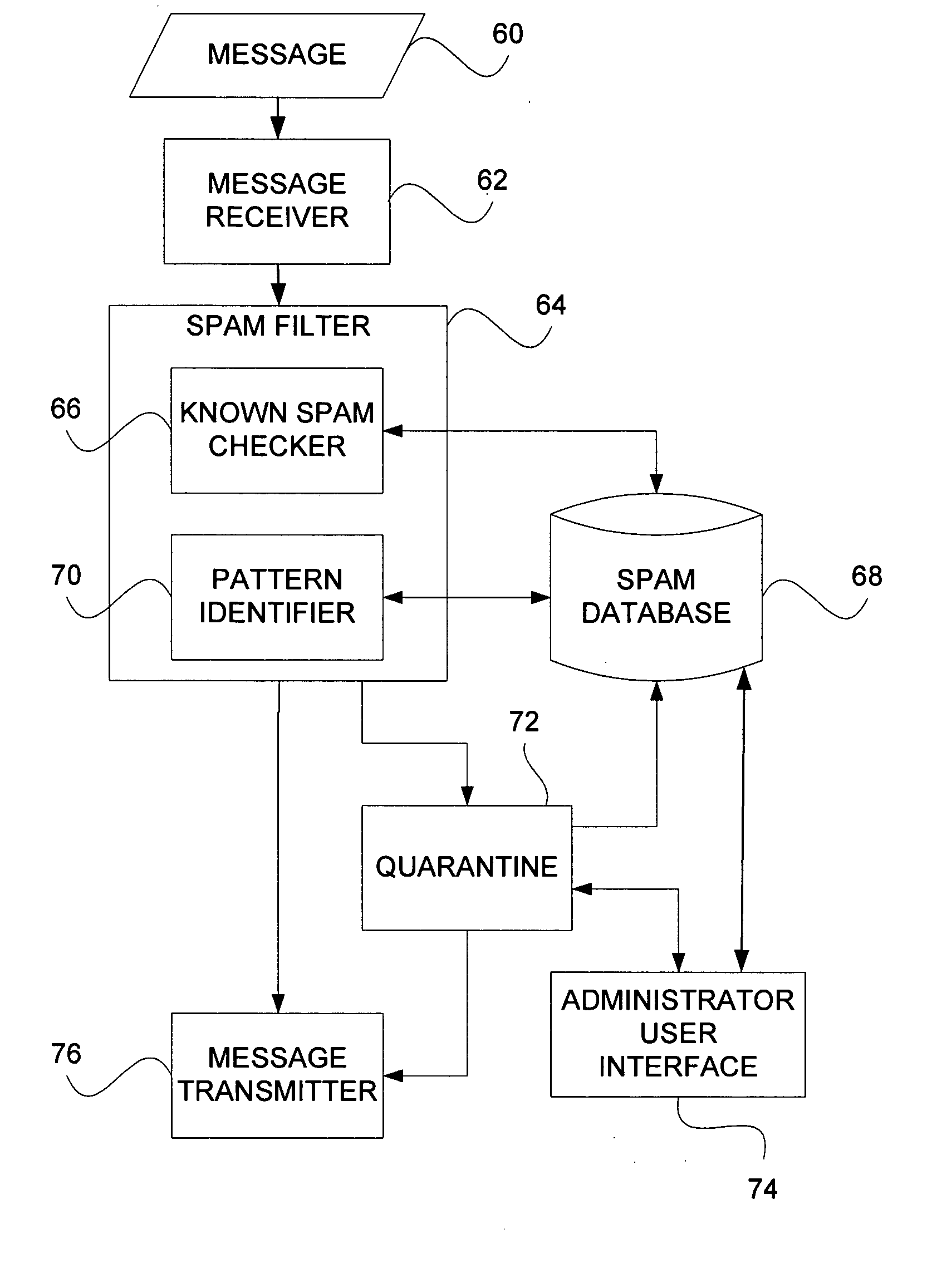
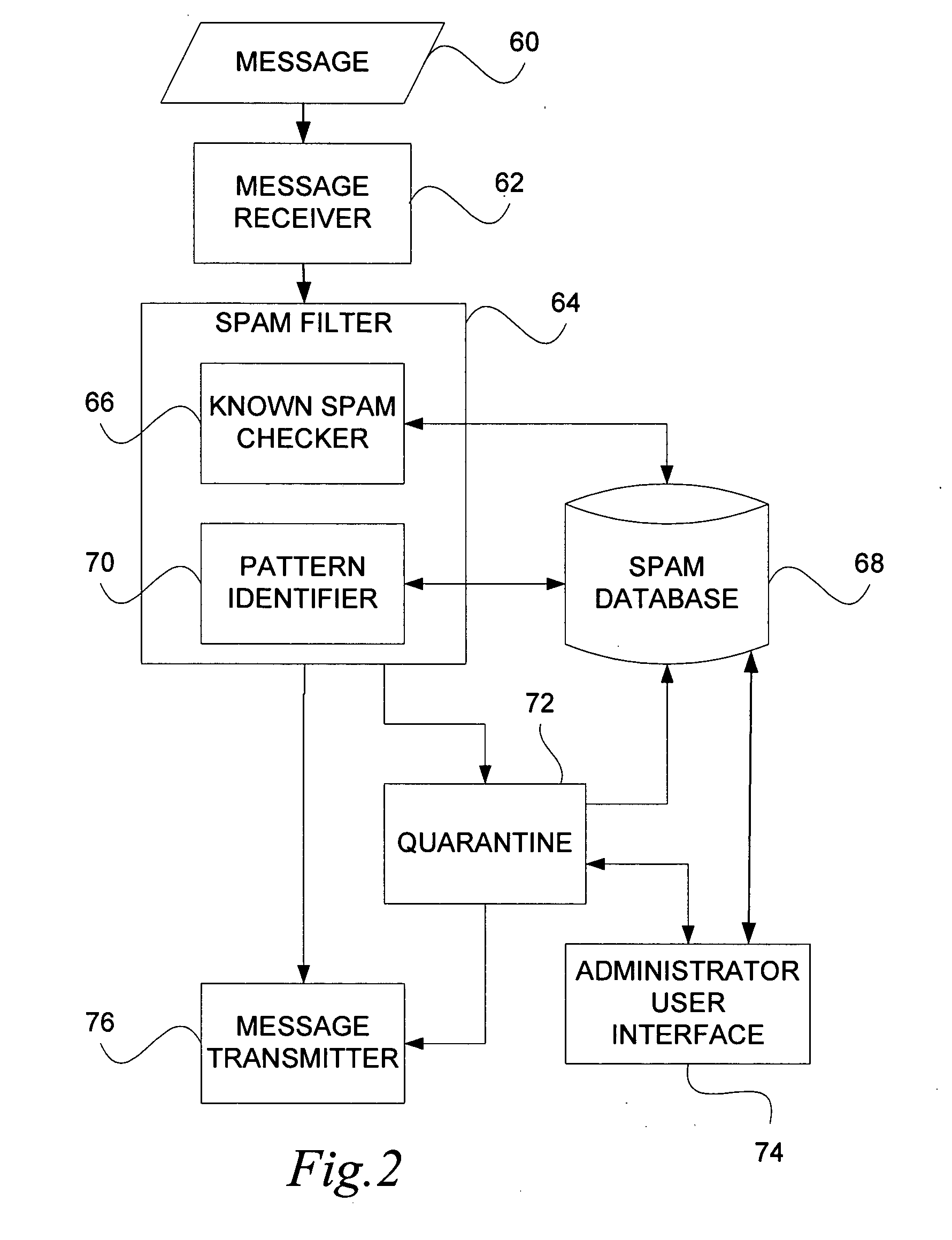
Method and apparatus for the automatic identification of unsolicited e-mail messages (SPAM)
Techniques for annotating email messages. In one aspect of the invention, a method is provided for annotating a query email message. According to the method, patterns associated with a database, comprising annotated email messages, which may typically be known unwelcome email messages (“SPAM), are accessed, as by use of a pattern discovery algorithm (e.g. the Teiresias pattern algorithm). Attributes are assigned to the patterns based on the annotated SPAM email messages. The patterns with assigned attributes are used to analyze the query email message.
Owner:IBM CORP
Origination/destination features and lists for spam prevention
ActiveUS20050022008A1Easy to buildFacilitate improvingDigital data processing detailsMultiple digital computer combinationsEmail addressIp address
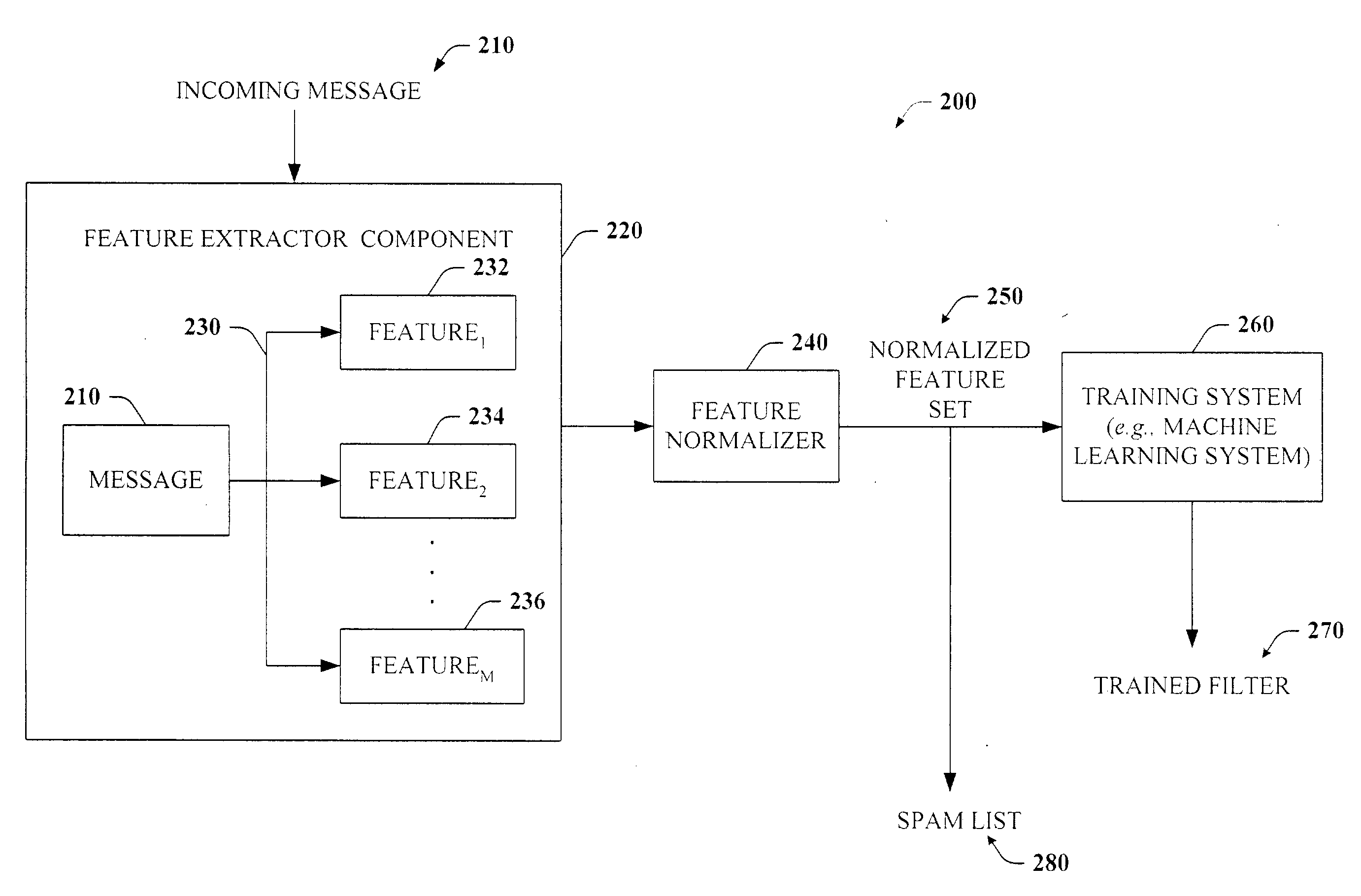
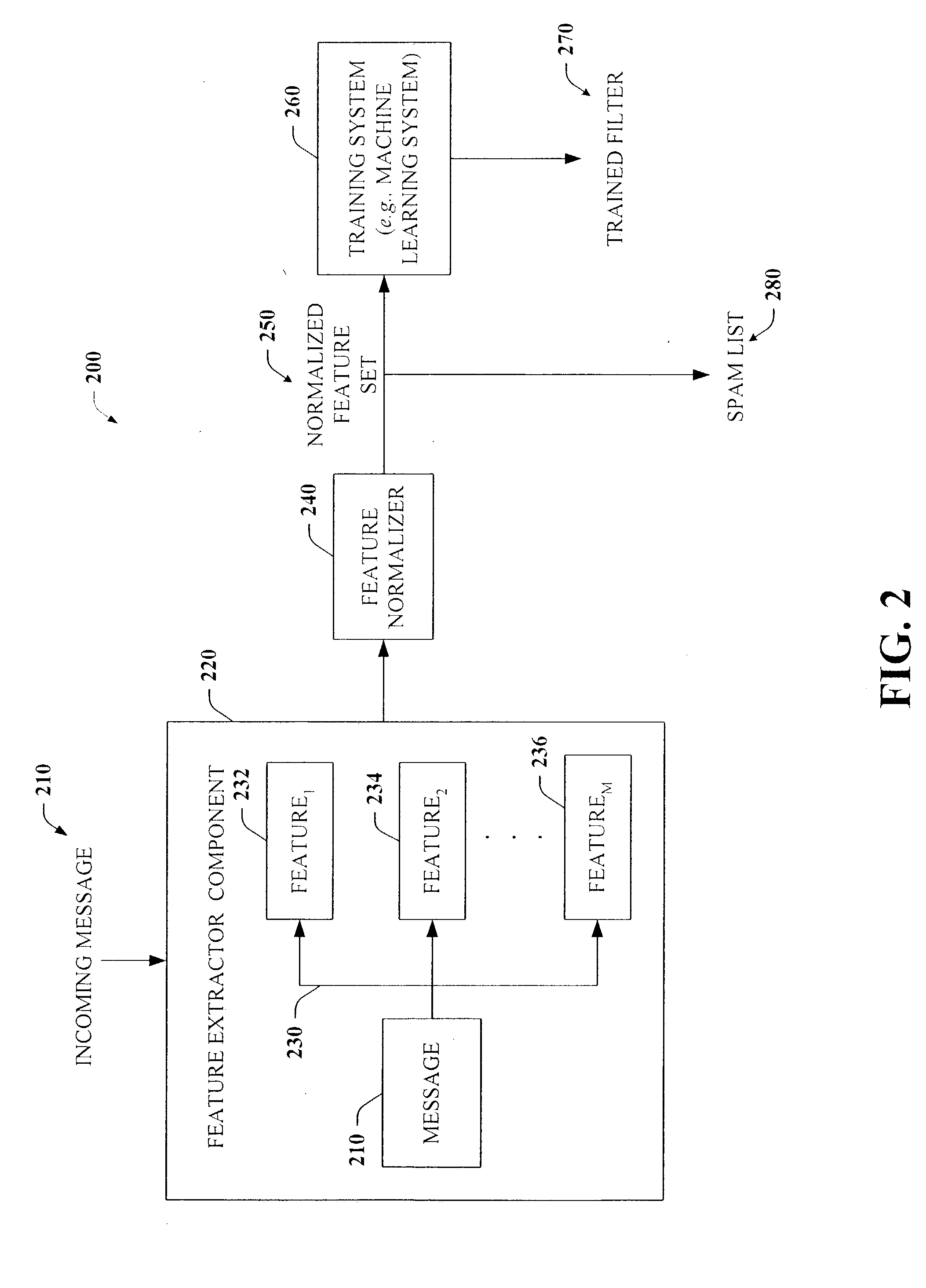
The present invention involves a system and method that facilitate extracting data from messages for spam filtering. The extracted data can be in the form of features, which can be employed in connection with machine learning systems to build improved filters. Data associated with origination information as well as other information embedded in the body of the message that allows a recipient of the message to contact and / or respond to the sender of the message call be extracted as features. The features, or a subset thereof, can be normalized and / or deobfuscated prior to being employed as features of the machine learning systems. The (deobfuscated) features can be employed to populate a plurality of feature lists that facilitate spam detection and prevention. Exemplary features include an email address, an IP address, a URL, an embedded image pointing to a URL, and / or portions thereof.
Owner:MICROSOFT TECH LICENSING LLC
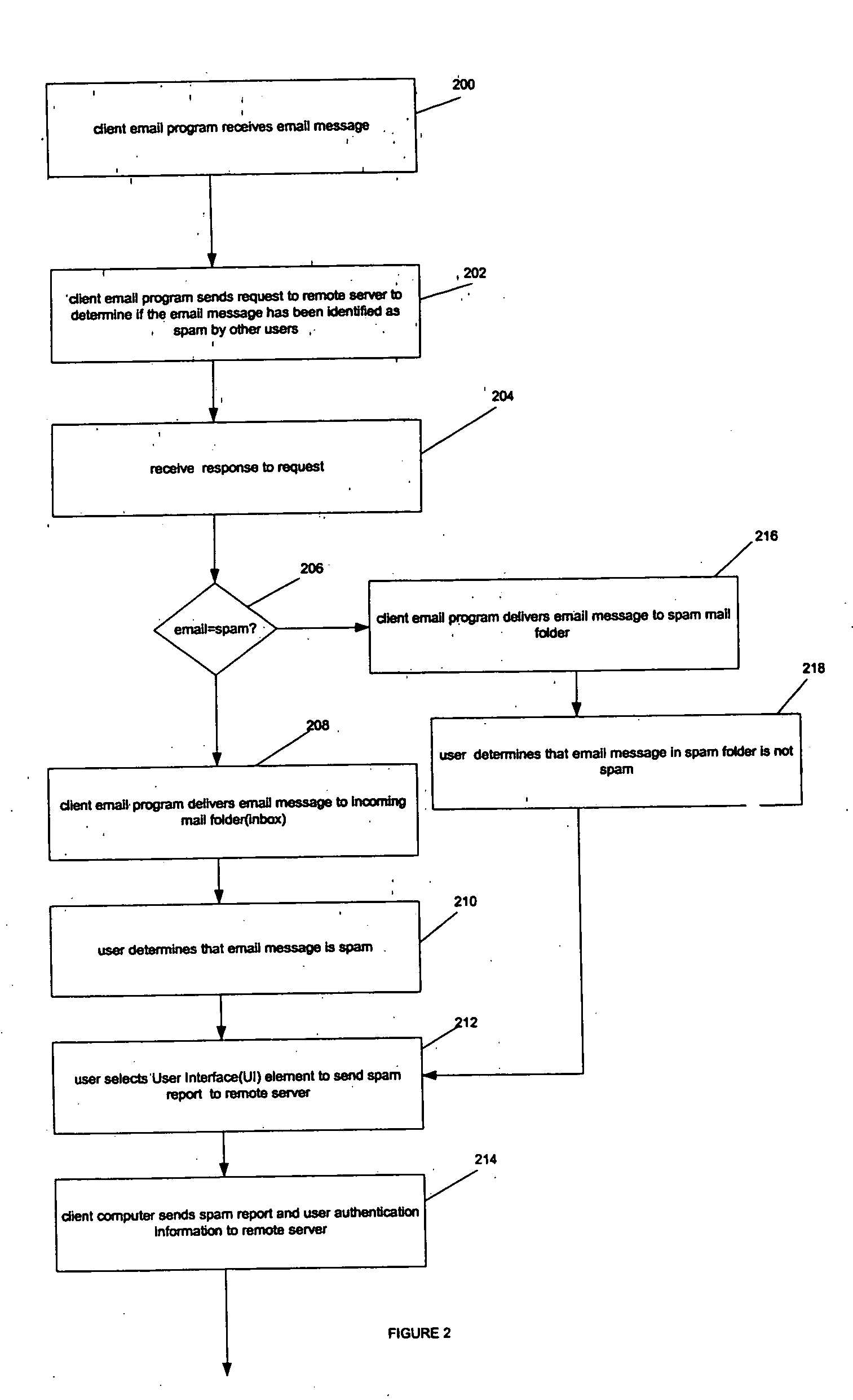
Method and apparatus to block spam based on spam reports from a community of users
ActiveUS20050114452A1Digital data processing detailsUser identity/authority verificationInternet privacyTrust factor
In one embodiment, a method for operating a server is provided. The method comprises receiving a plurality of reports from a community of users, each report identifying an email message as spam or not spam; and determining if the email message is spam based on a number of the reports received from the community of users, and a trust factor associated with each user.
Owner:PROOFPOINT INC
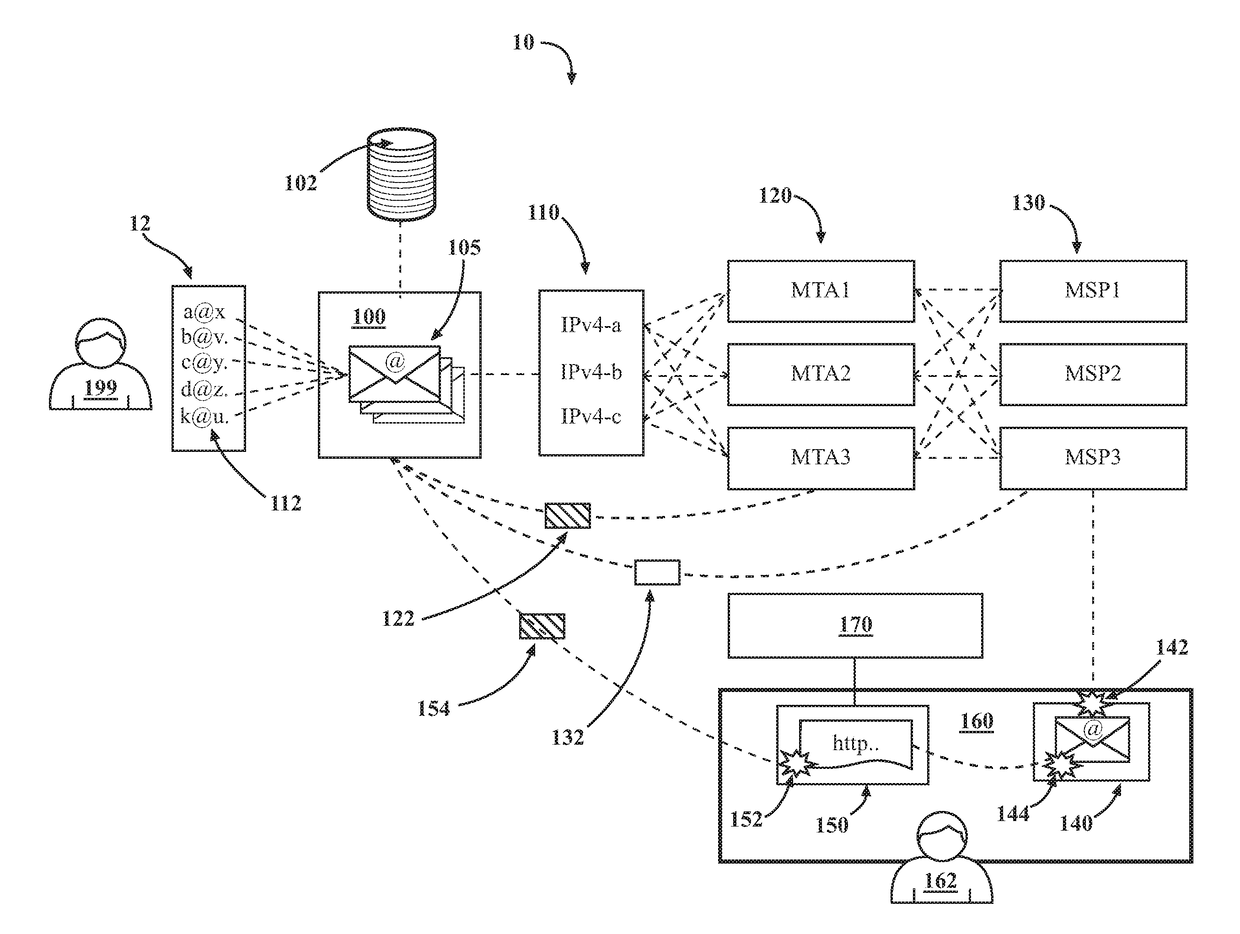
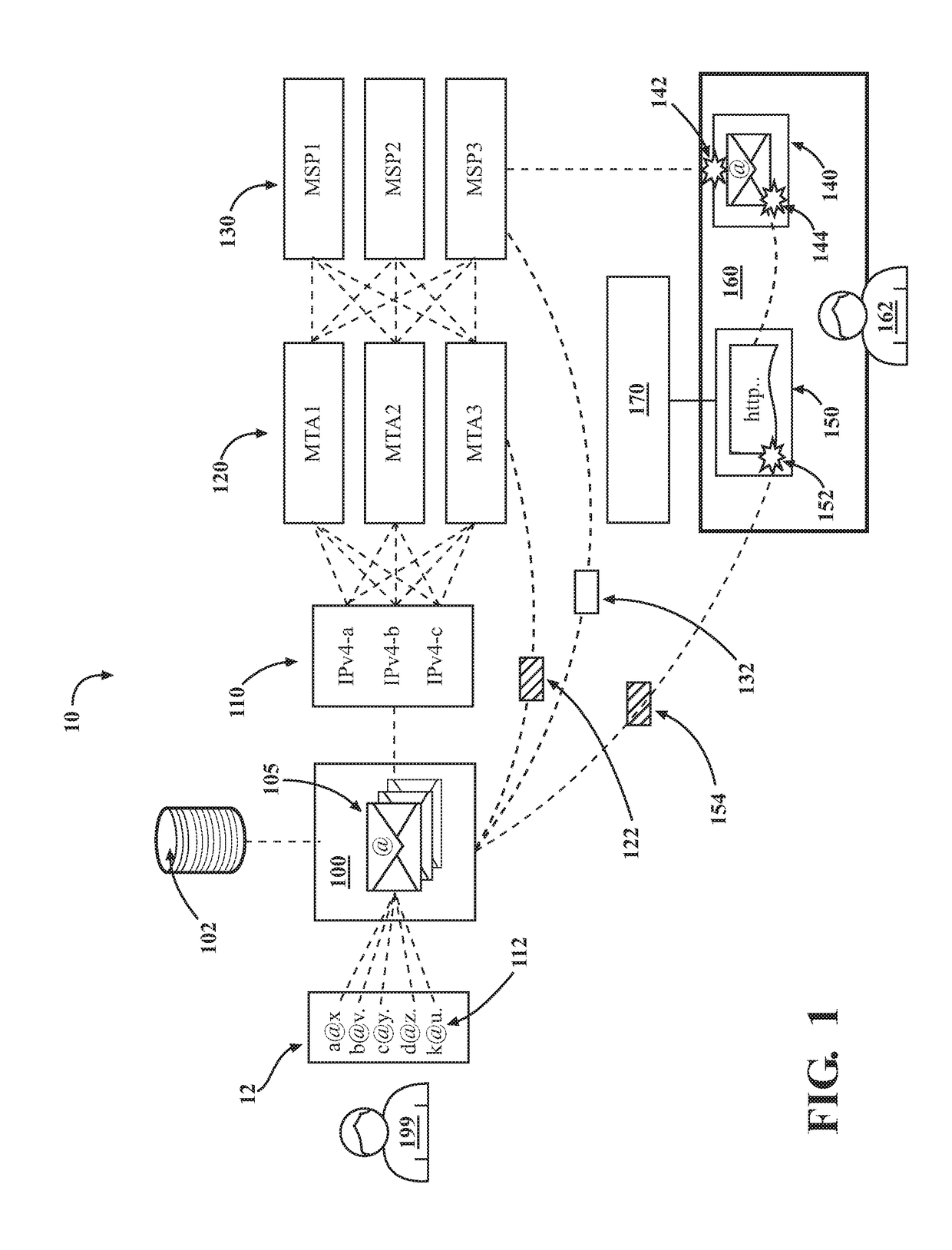
Introducing a new message source into an electronic message delivery environment
ActiveUS20180219830A1Reduce riskMaximizing numberMathematical modelsAdvertisementsMessage deliveryBlack list
Owner:HUBSPOT
Messaging spam detection
InactiveUS20060026242A1Multiple digital computer combinationsData switching networksEmail addressTelecommunications
Detecting unsolicited messages (spam) by aggregating information across multiple recipients and / or across the same or differing messaging protocols. Multiple messages are analyzed to detect a call to action pattern that specifies a target communication address with which the recipients are requested to communicate, such as an email address, an Internet address, a telephone number, and the like. Once a frequency threshold of messages containing the call to action pattern is reached, subsequent messages are temporarily quarantined for evaluation by a human operator. If the human determines that the messages are not spam, the human can release the quarantined messages, and indicate that future messages with the call to action pattern are not to be delayed. Conversely, if the human determines that the messages are spam, the human can delete the messages in quarantine, and indicate that all future messages with that call to action pattern are to be deleted automatically.
Owner:WIRELESS SERVICES CORP
Email filtering system and method
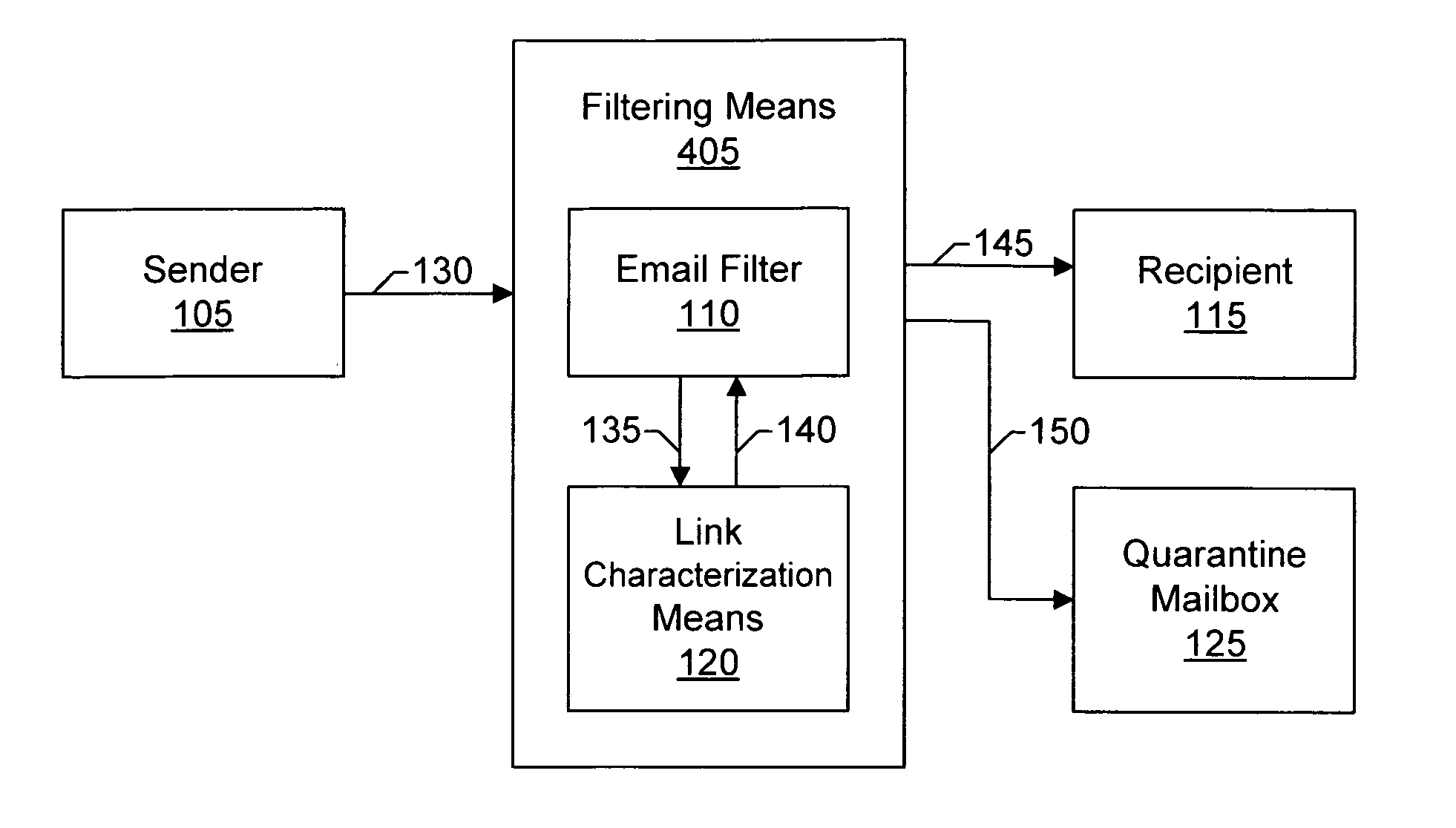
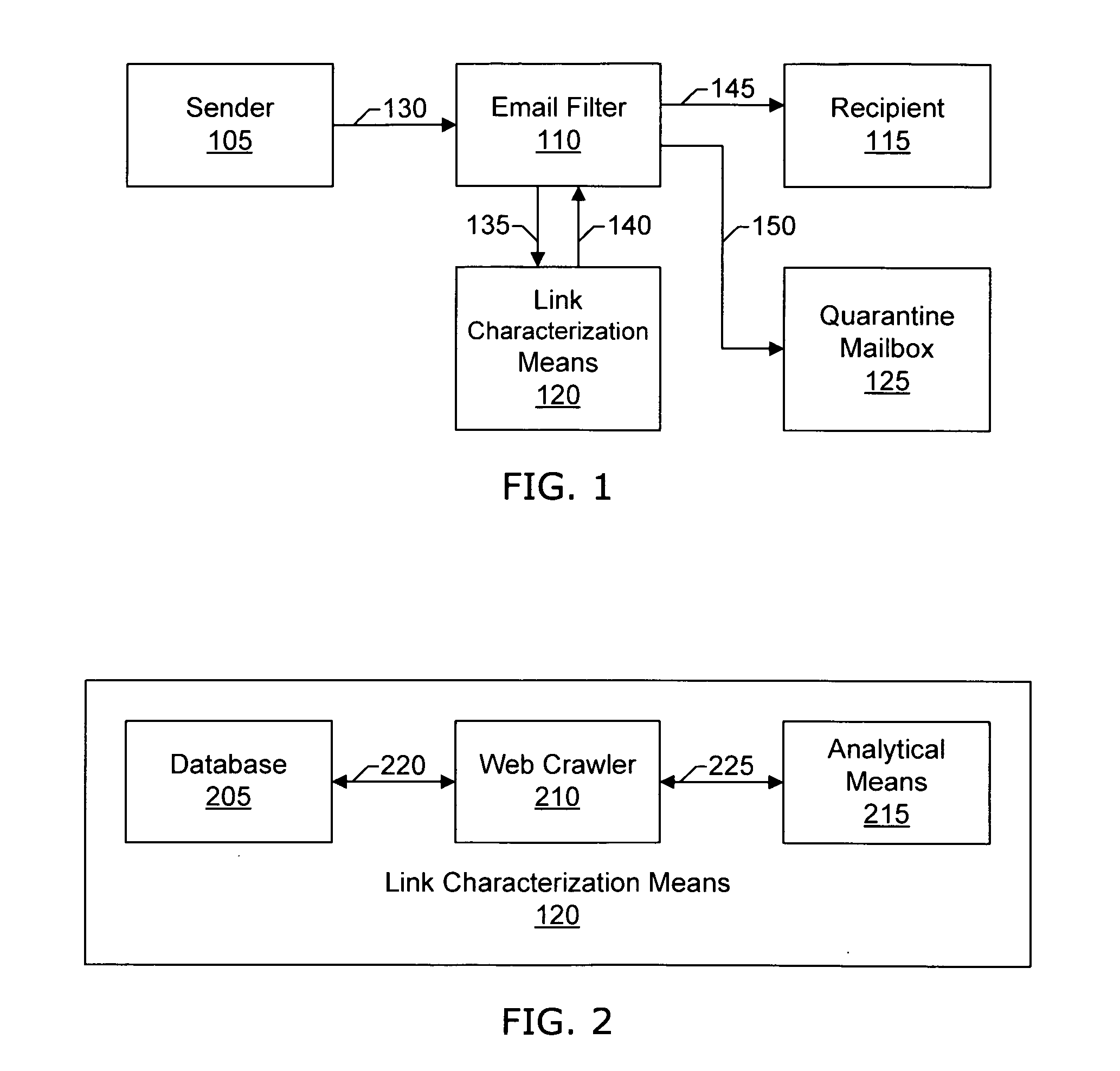
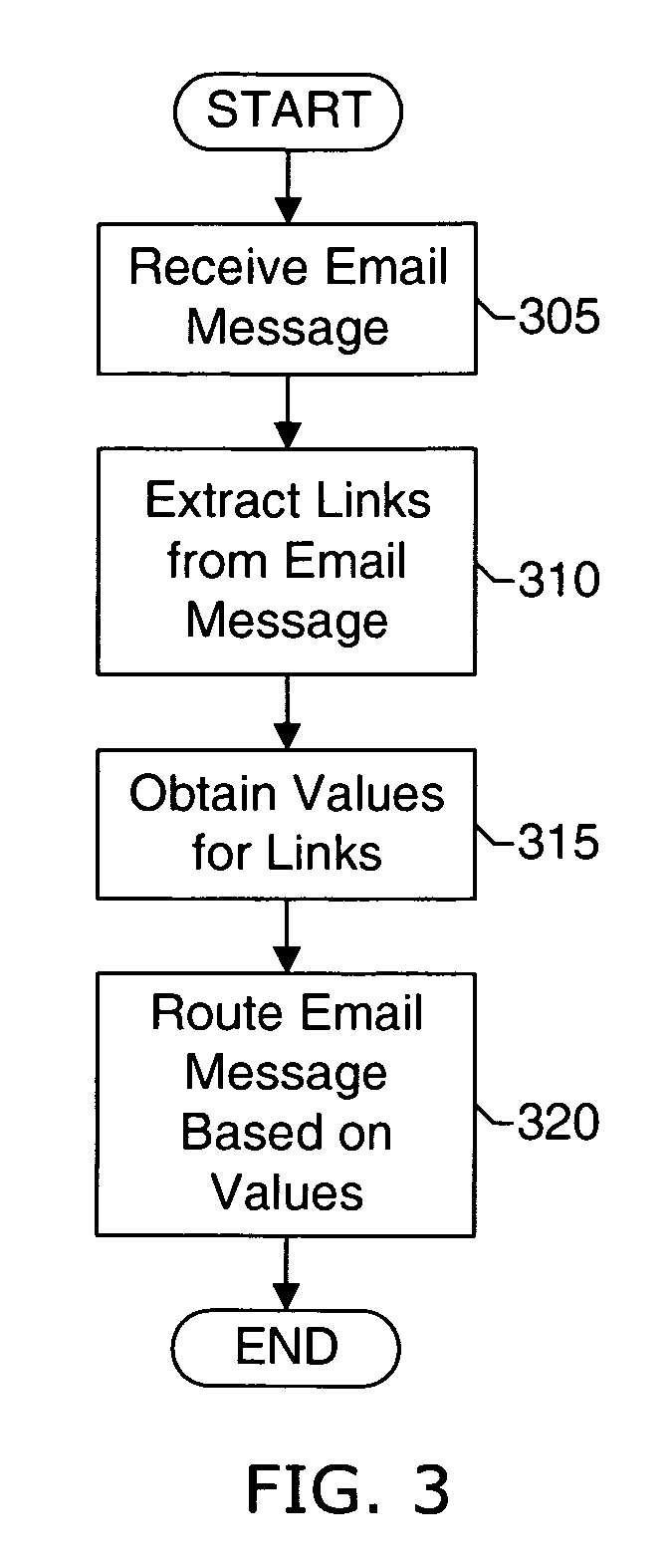
ActiveUS20060129644A1Effective filteringMultiple digital computer combinationsData switching networksSpammingFilter system
Systems and methods of the present invention allow filtering out spam and phishing email messages based on the links embedded into the email messages. In a preferred embodiment, an Email Filter extracts links from the email message and obtains desirability values for the links. The Email Filter may route the email message based on desirability values. Such routing includes delivering the email message to a Recipient, delivering the message to a Quarantine Mailbox, or deleting the message.
Owner:GO DADDY OPERATING
System and method for compounded marketing
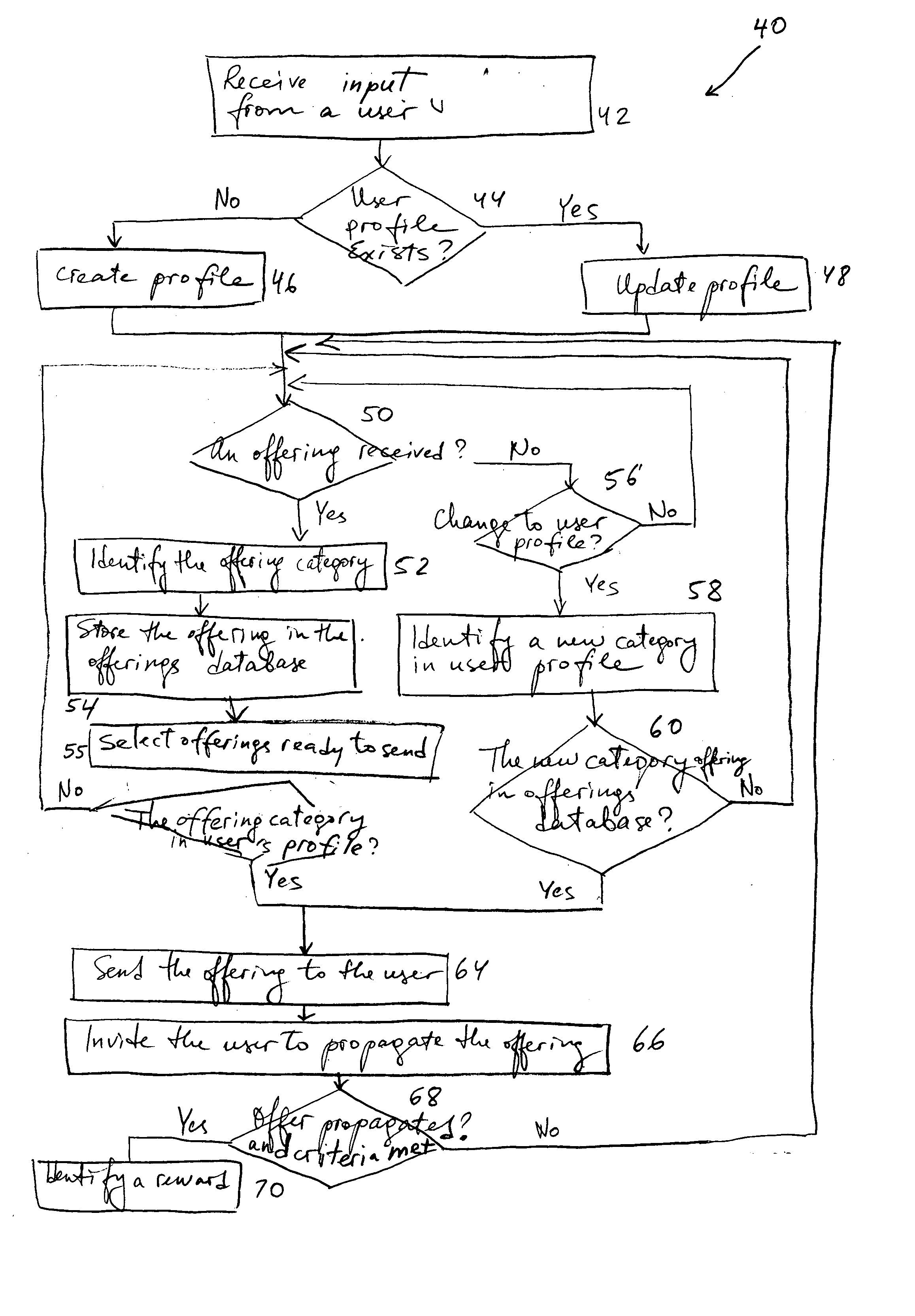
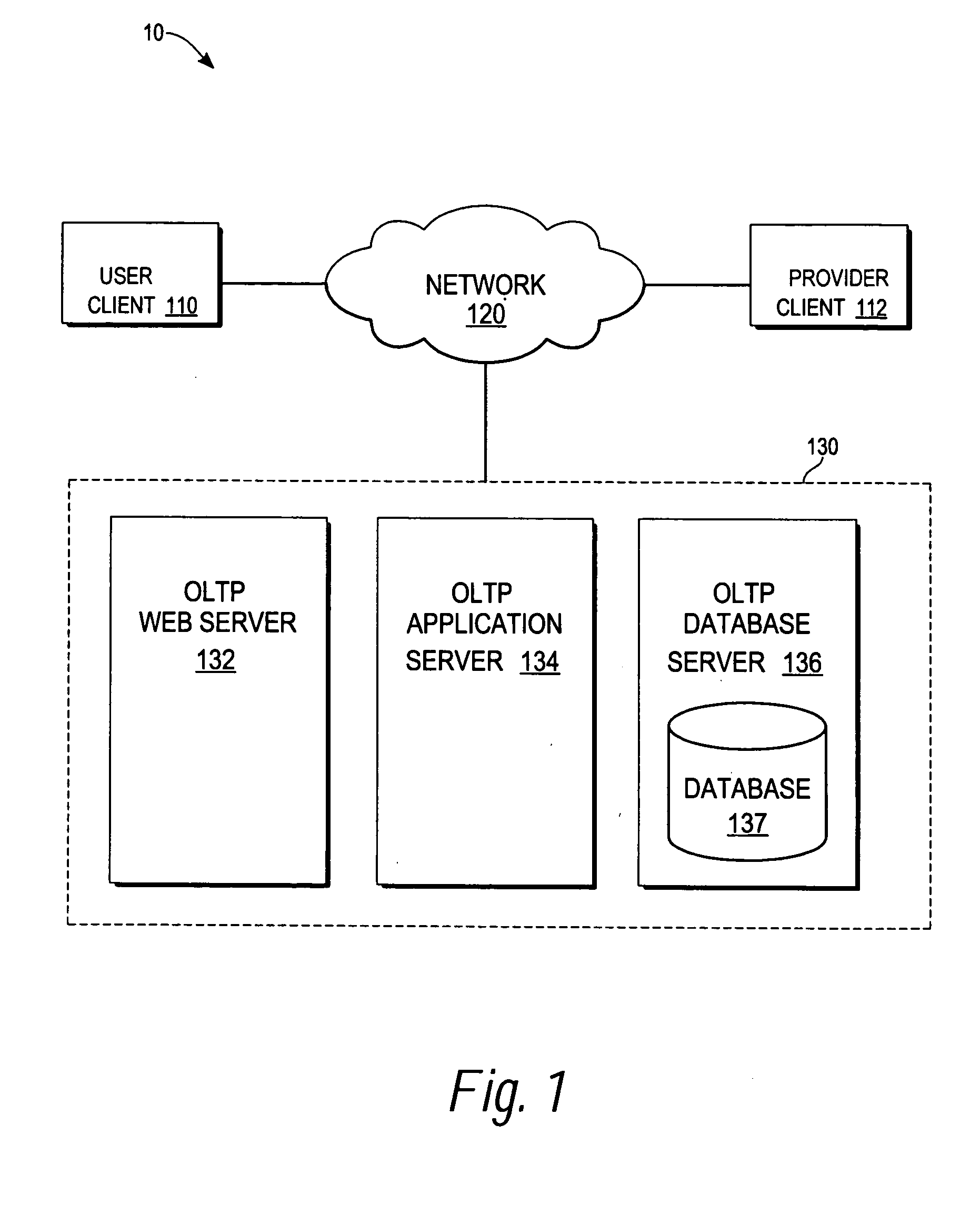
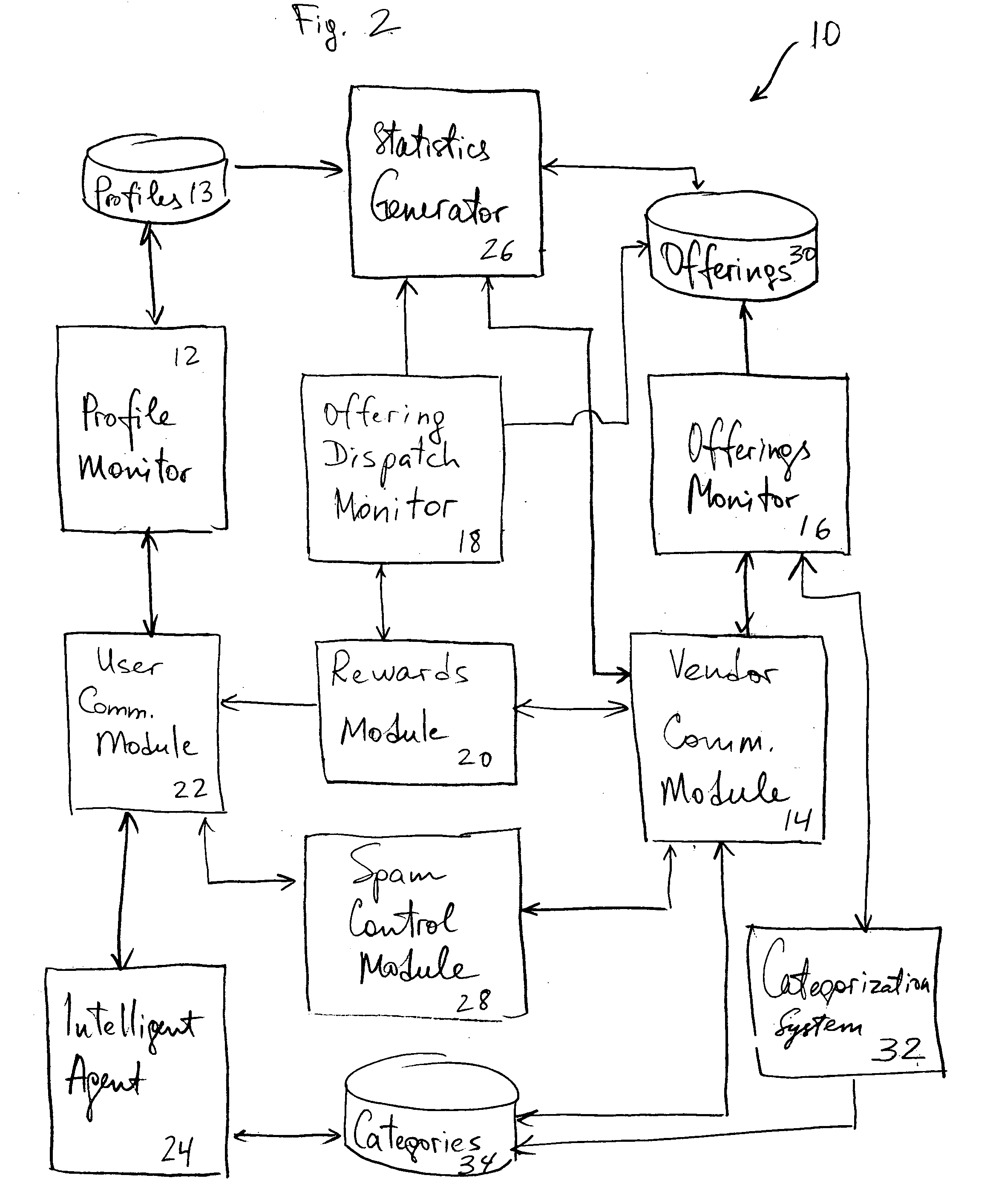
InactiveUS20050004837A1Facilitate communicationSpecial data processing applicationsMarketingThird partyUser profile
A system and method to facilitate computer-based commerce is presented. The system may including a module to facilitate communicating a vendor offering to a user if the offering is within a category designated by the user as being acceptable for receipt of such offering. The acceptable categories may be stored in user profiles, a user profile being updated when the user chooses to add or remove an interest category. When a vendor offering is received, the offering is categorized and stored in an offerings database. The vendor offering is then matched with a category in the user profile When the vendor offering is communicated to the user, the user's address or the user's identity is not revealed to the vendor. If a user chooses to propagate a vendor offering to another user, the user may be entitled to a reward. The reward may be designated to the user or to a third party. A spam control module may also be provided to identify spam complaints and to take actions in response to the spam complaints.
Owner:SHARENET
Email filtering methods and systems
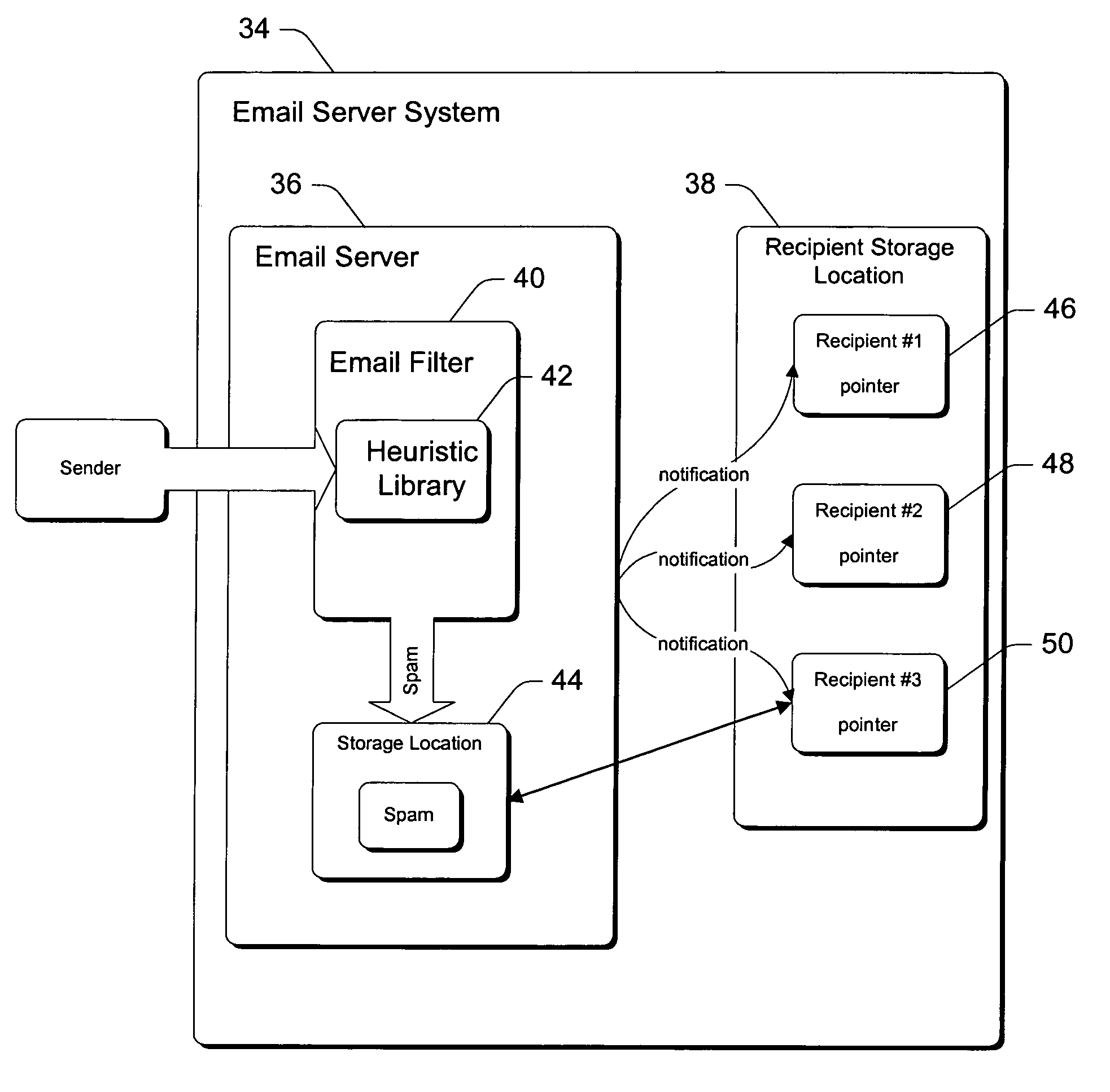
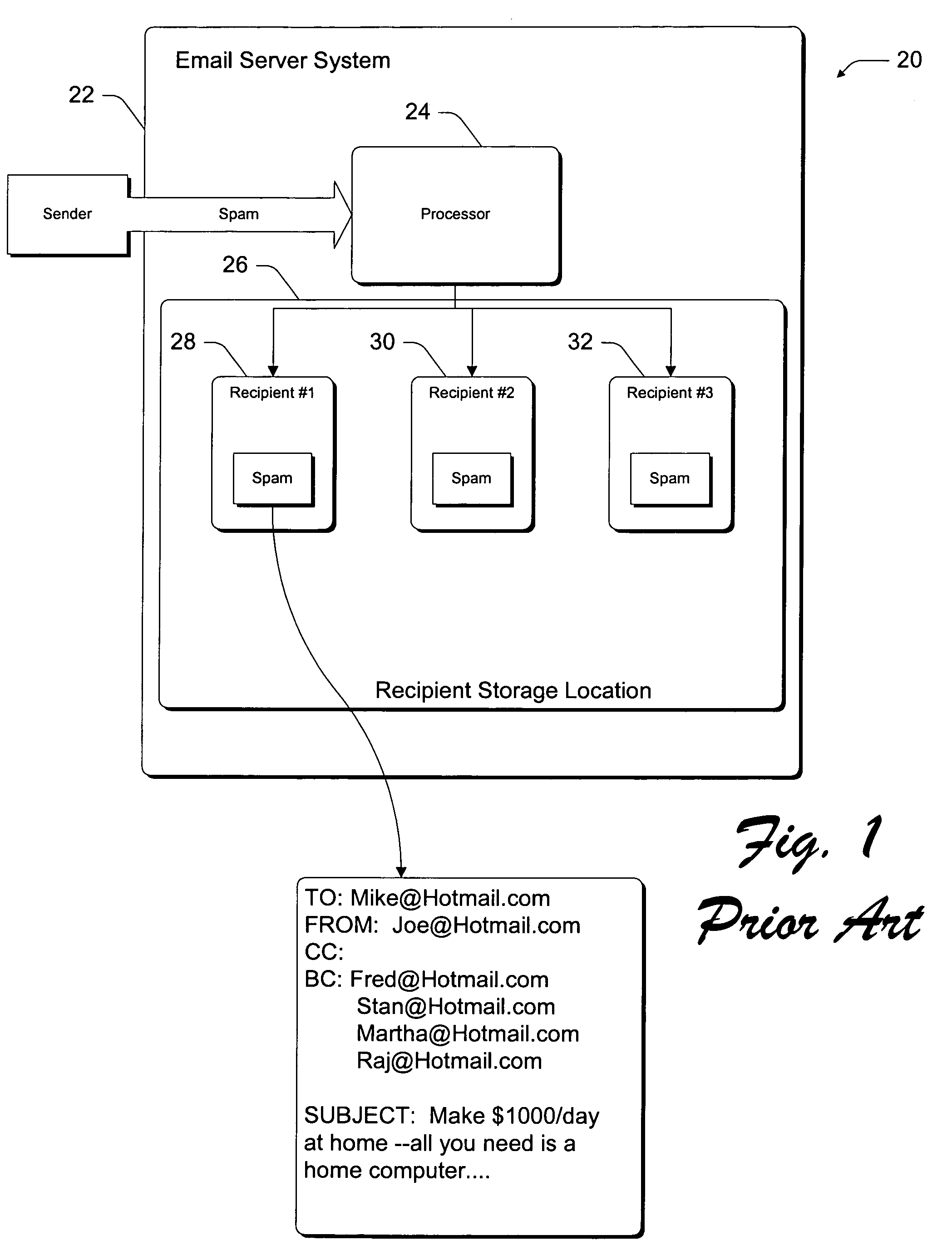
InactiveUS7072942B1Improve the level ofReduce the impactMultiple digital computer combinationsTransmissionService provisionSystem impact
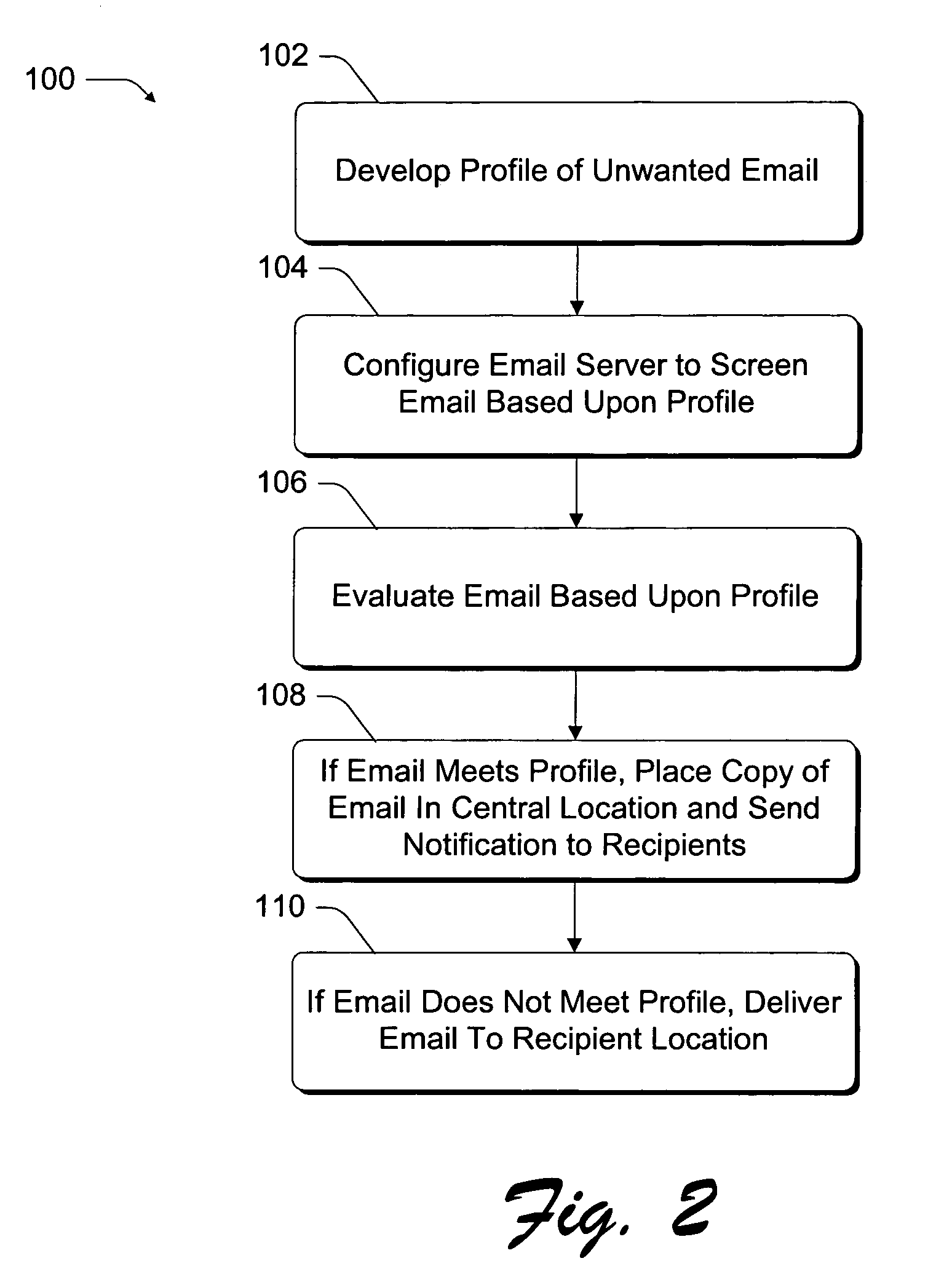
Various embodiments of the invention address two critical problems that current email service providers face. First, there is the problem of maintaining high levels of customer service when email server systems are inundated with spam. Second, there is the problem of reducing the system-wide impact that spam has on the email delivery system. Current embodiments are directed to determining whether an email message is an unwanted bulk email message without necessarily considering the message that is conveyed by any portion of the email message. Through analyses of patterns of delivery of these email messages, profiles are built that allow an email server to ascertain whether there is a likelihood that any one particular email message constitutes an unwanted email message. If an email message is determined to likely constitute an unwanted email message, then memory-saving measures are implemented. In preferred embodiments, one copy of the email message is saved at a central, shared location that can be accessed by each of the intended recipients. This avoids having to replicate the email message across the system for each of the recipients.
Owner:MICROSOFT TECH LICENSING LLC
Domain name system security network
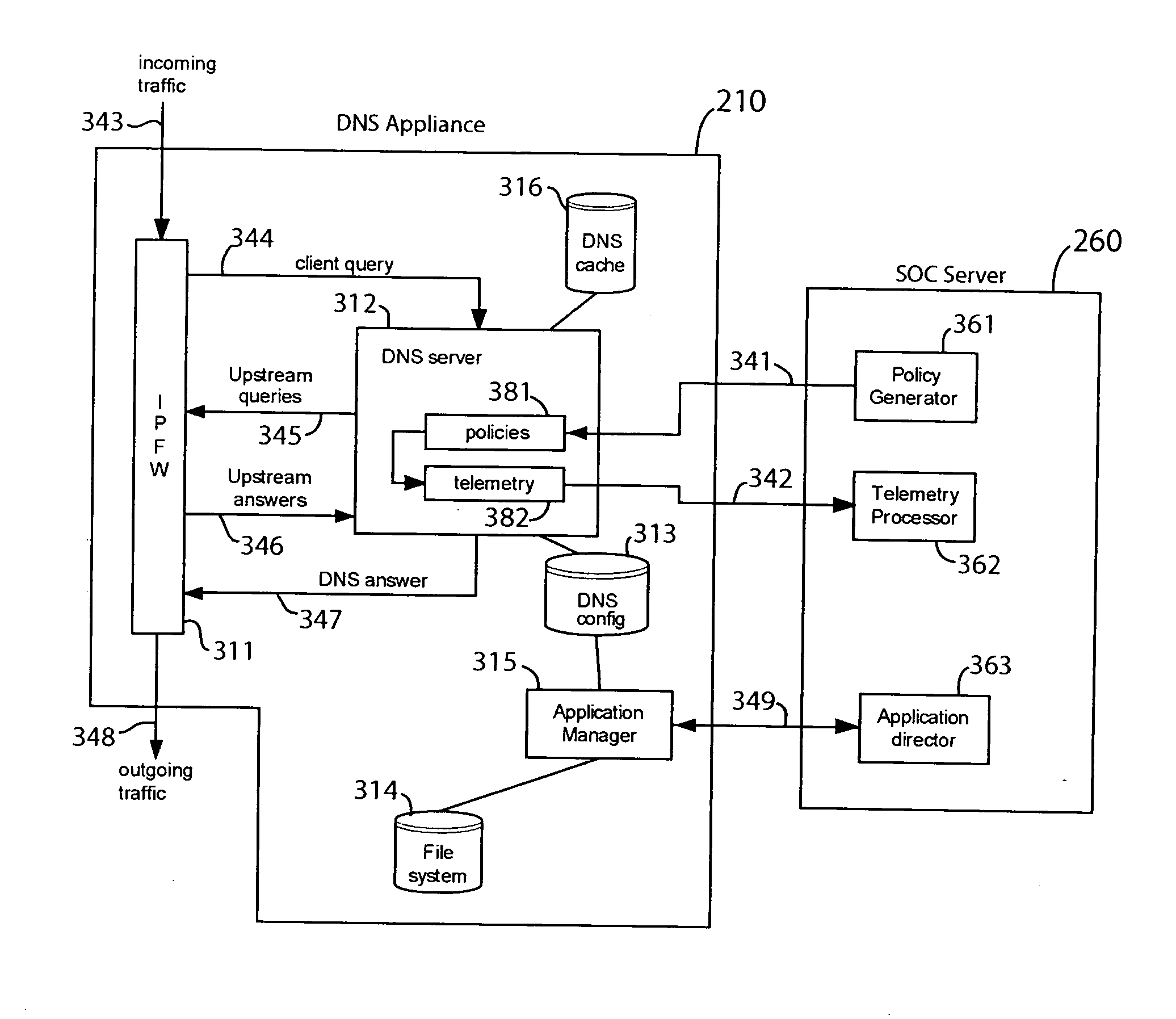
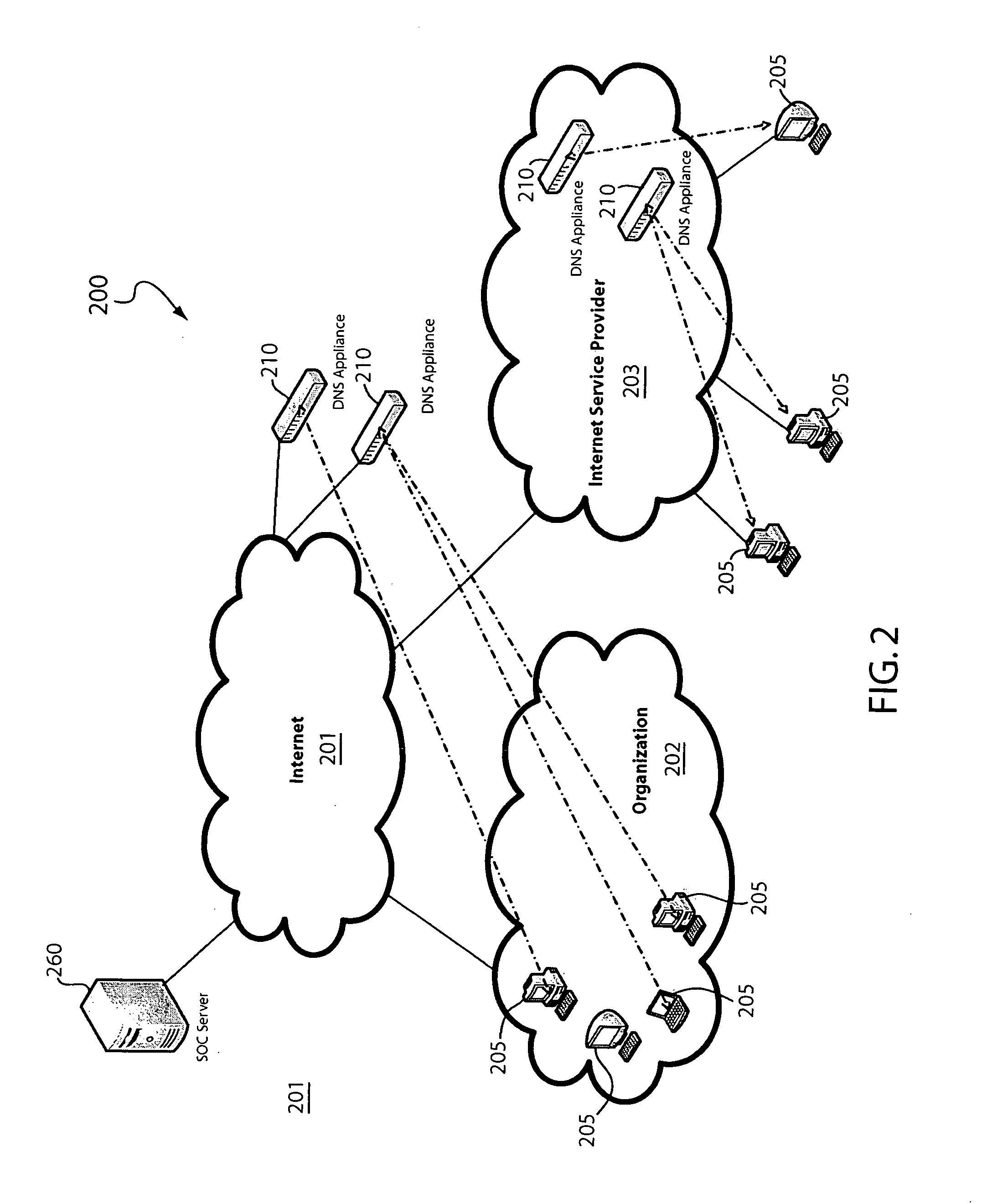
In one embodiment, a DNS security network includes several DNS appliances and a security operations center (SOC) server computer. The SOC server computer may receive telemetry data from the DNS appliances, the telemetry data comprising information about DNS client queries received in the respective DNS appliances. From the telemetry data, the SOC server computer may generate security policies for distribution to the DNS appliances. The security policies may be used by the DNS appliances to determine whether a DNS client query is originated by a client computer performing a prohibited activity (e.g., sending spam, communicating with a zombie control computer, navigating to a prohibited website, etc.). An answer to a client query may be replaced or discarded altogether in cases where the originator is performing a prohibited activity.
Owner:TREND MICRO INC
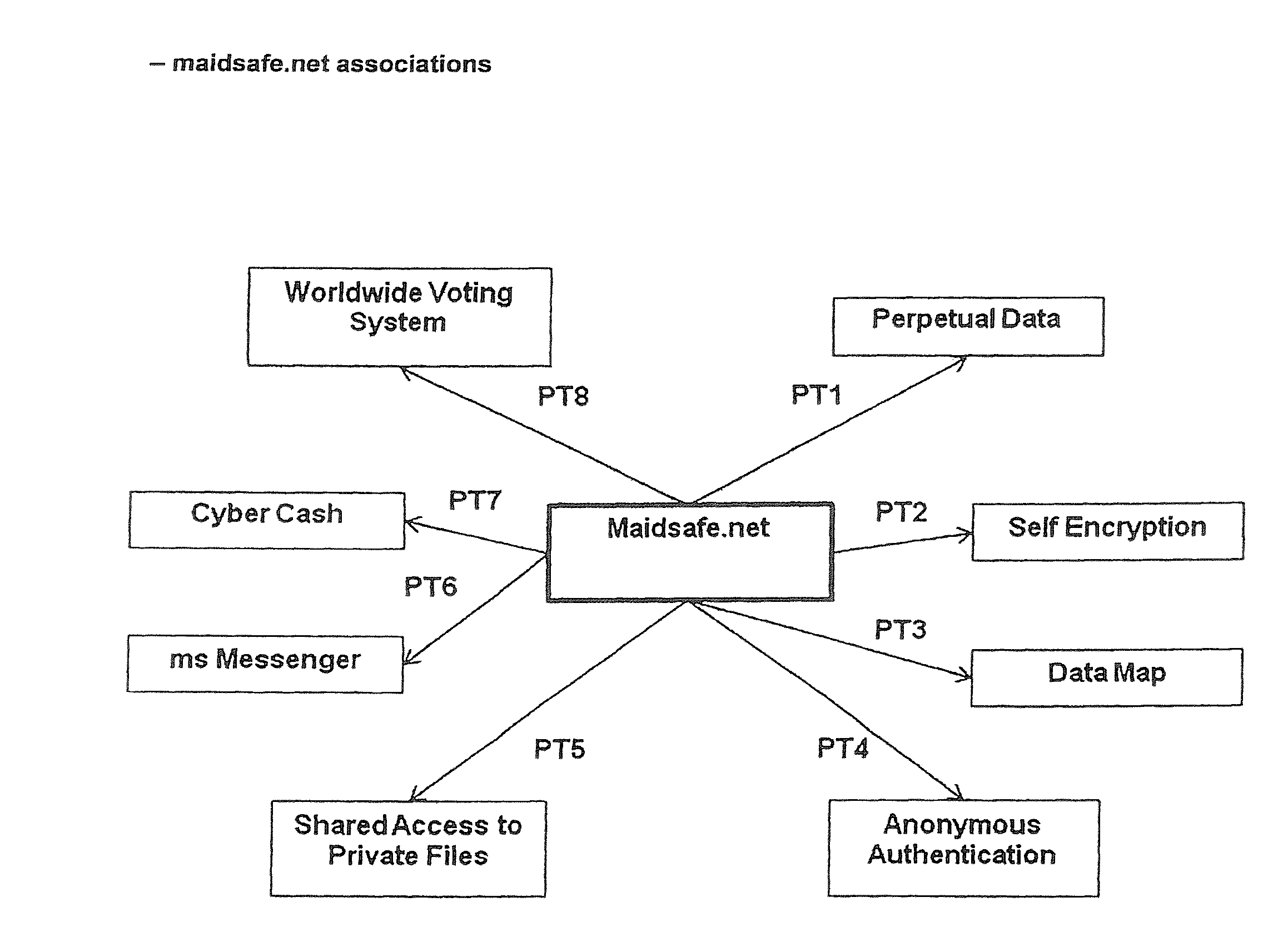
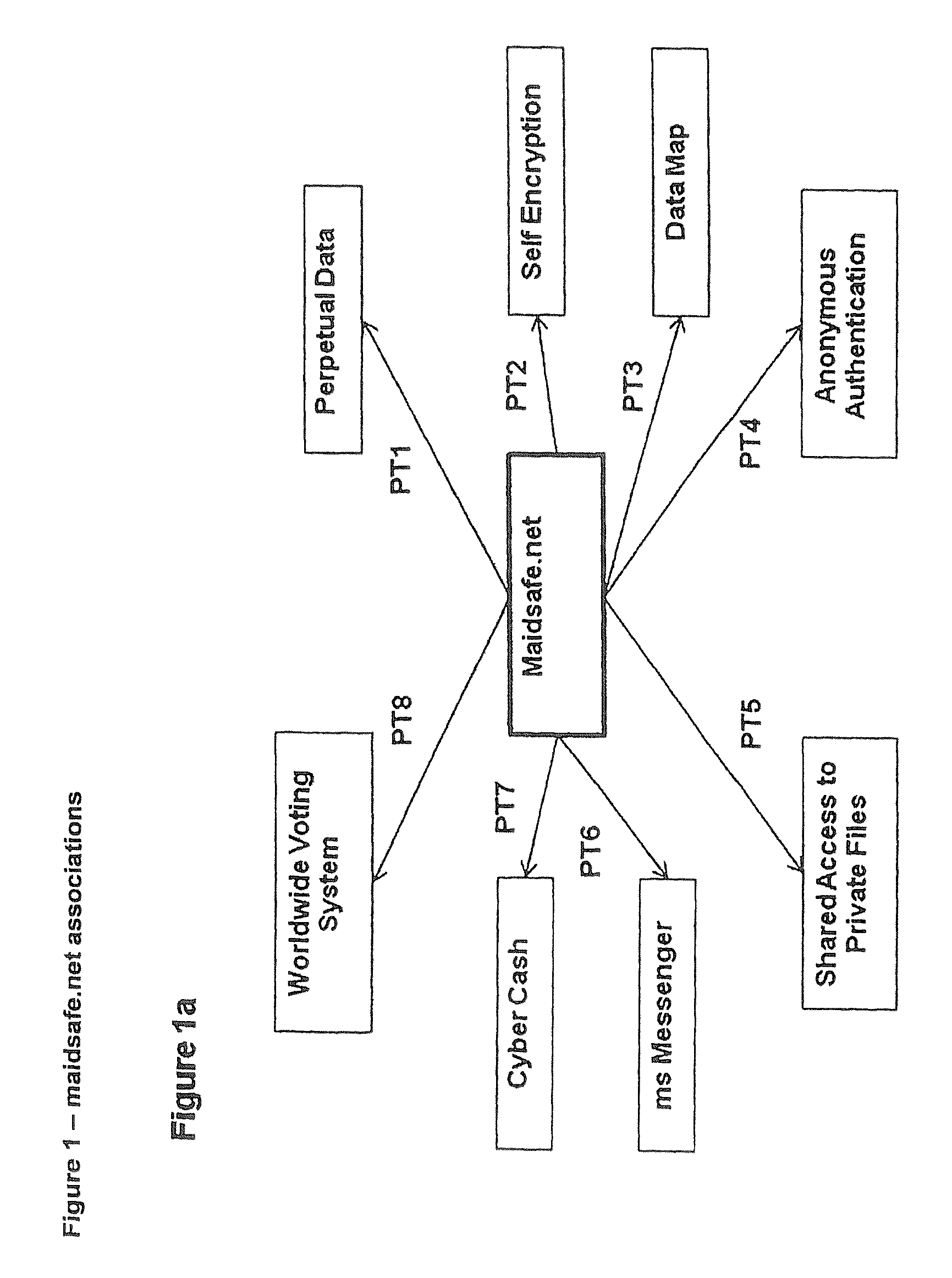
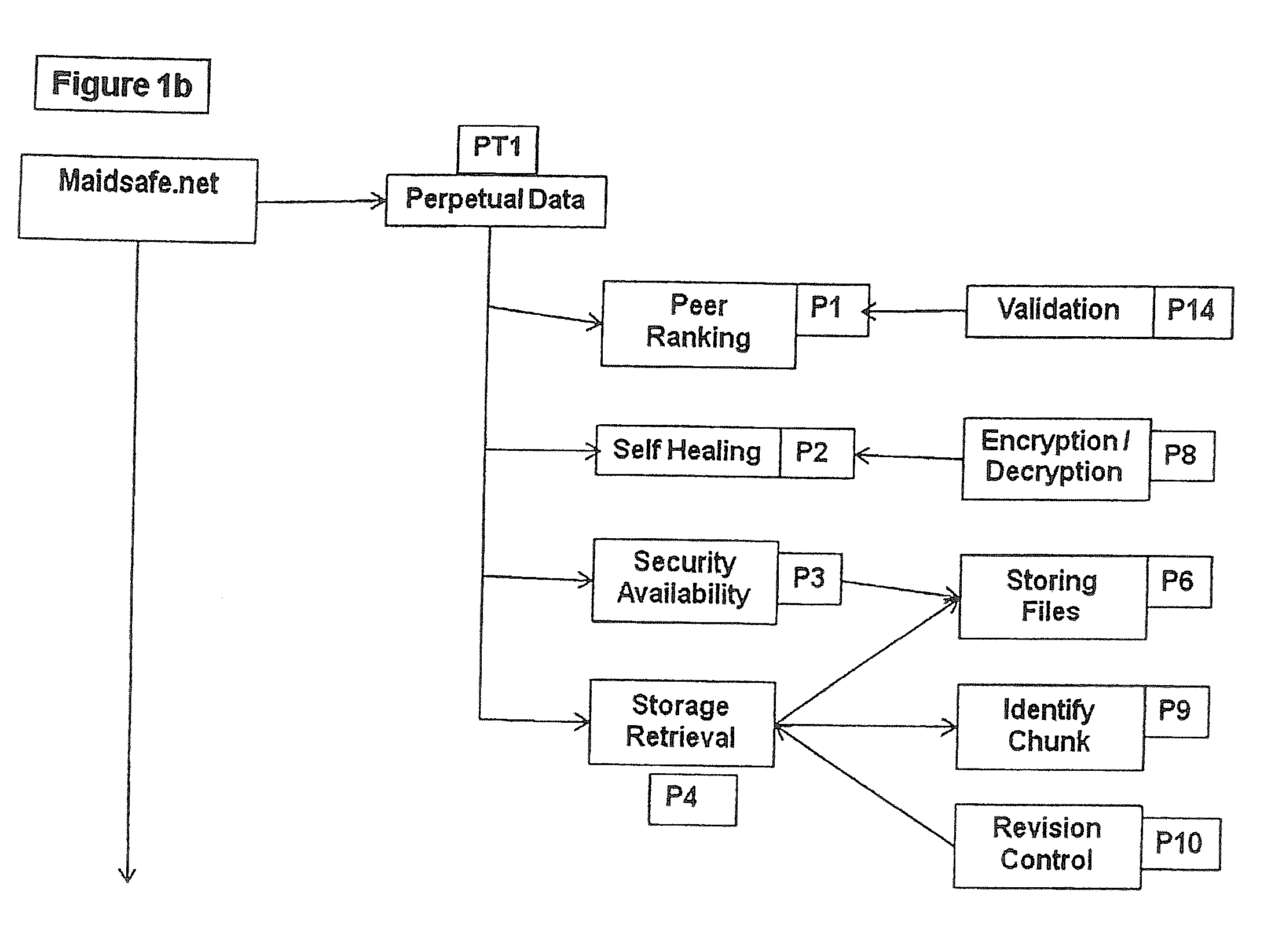
Maidsafe.net
InactiveUS20100064354A1Maintain validityEasy to set upDigital data processing detailsAnalogue secracy/subscription systemsSecure communicationVendor lock-in
This invention is a network that is defined by its novel approach to privacy, security and freedom for its users. Privacy by allowing access anonymously, security by encrypting and obfuscating resources and freedom by allowing users to anonymously and irrefutably be seen as genuine individuals on the network and to communicate with other users with total security and to securely access resources that are both their own and those that are shared by others with them. Further, this invention comprises a system of self healing data, secure messaging and a voting system to allow users to dictate the direction of development of the network, whereby adoption or denial of proposed add-ons to the network will be decided. System incompatibilities and security breaches on networks and the Internet are addressed by this invention where disparity and tangents of development have had an undue influence. The functional mechanisms that this invention provides will restore open communications and worry-free access in a manner that is very difficult to infect with viruses or cripple through denial of service attacks and spam messaging, plus, it will provide a foundation where vendor lock-in need not be an issue.
Owner:UNIV OF CALIFORNIA IRVINE
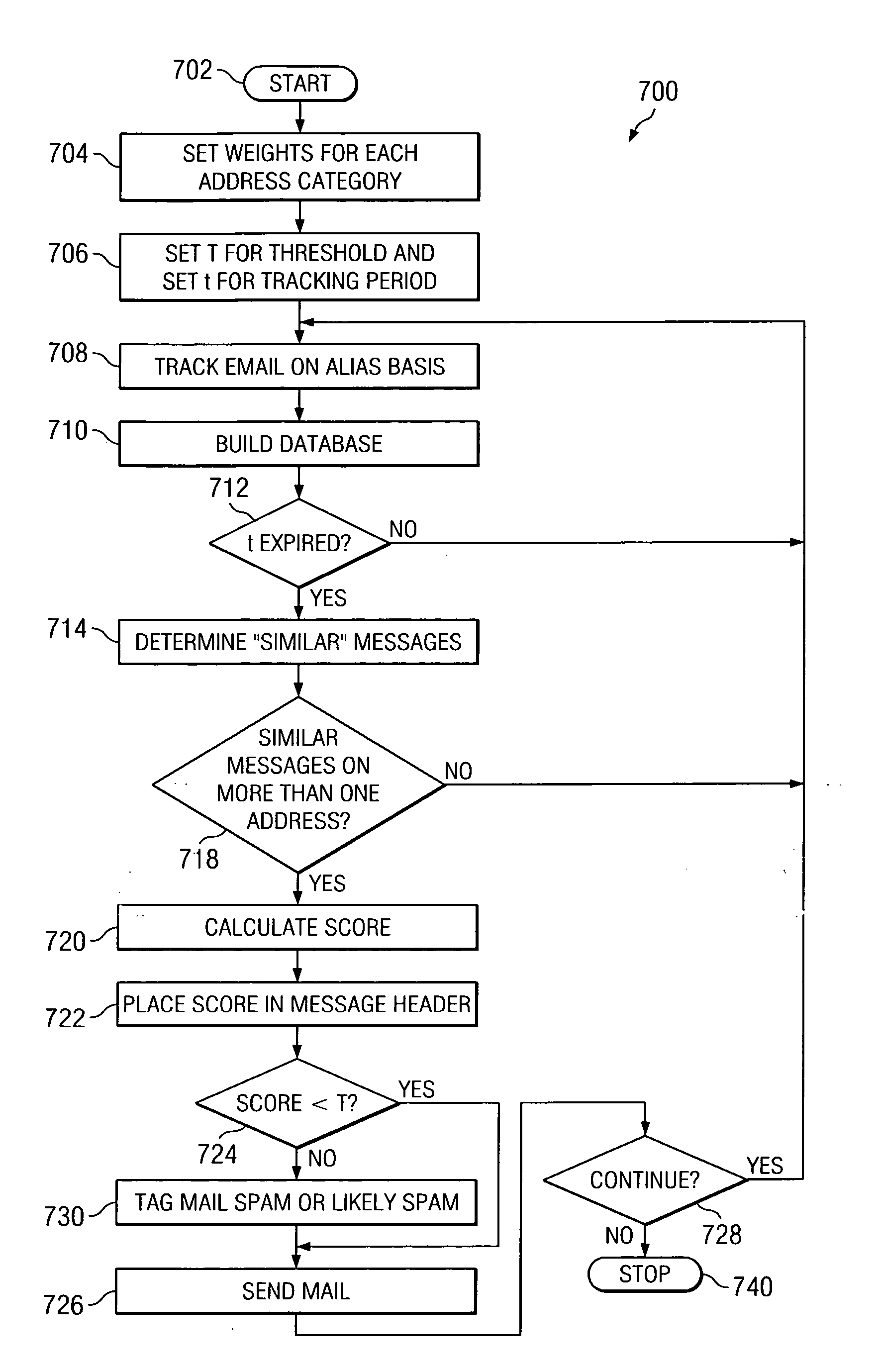
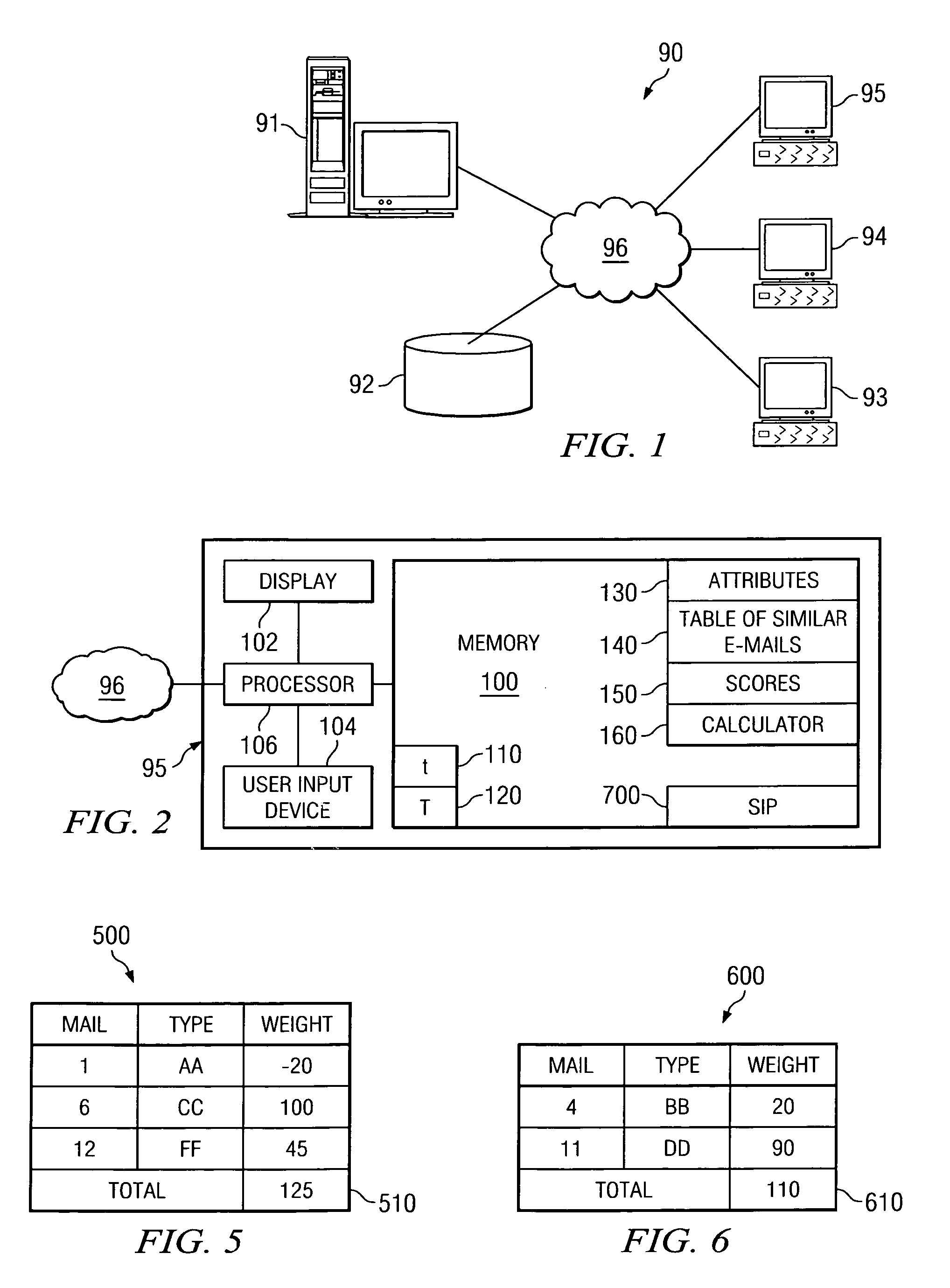
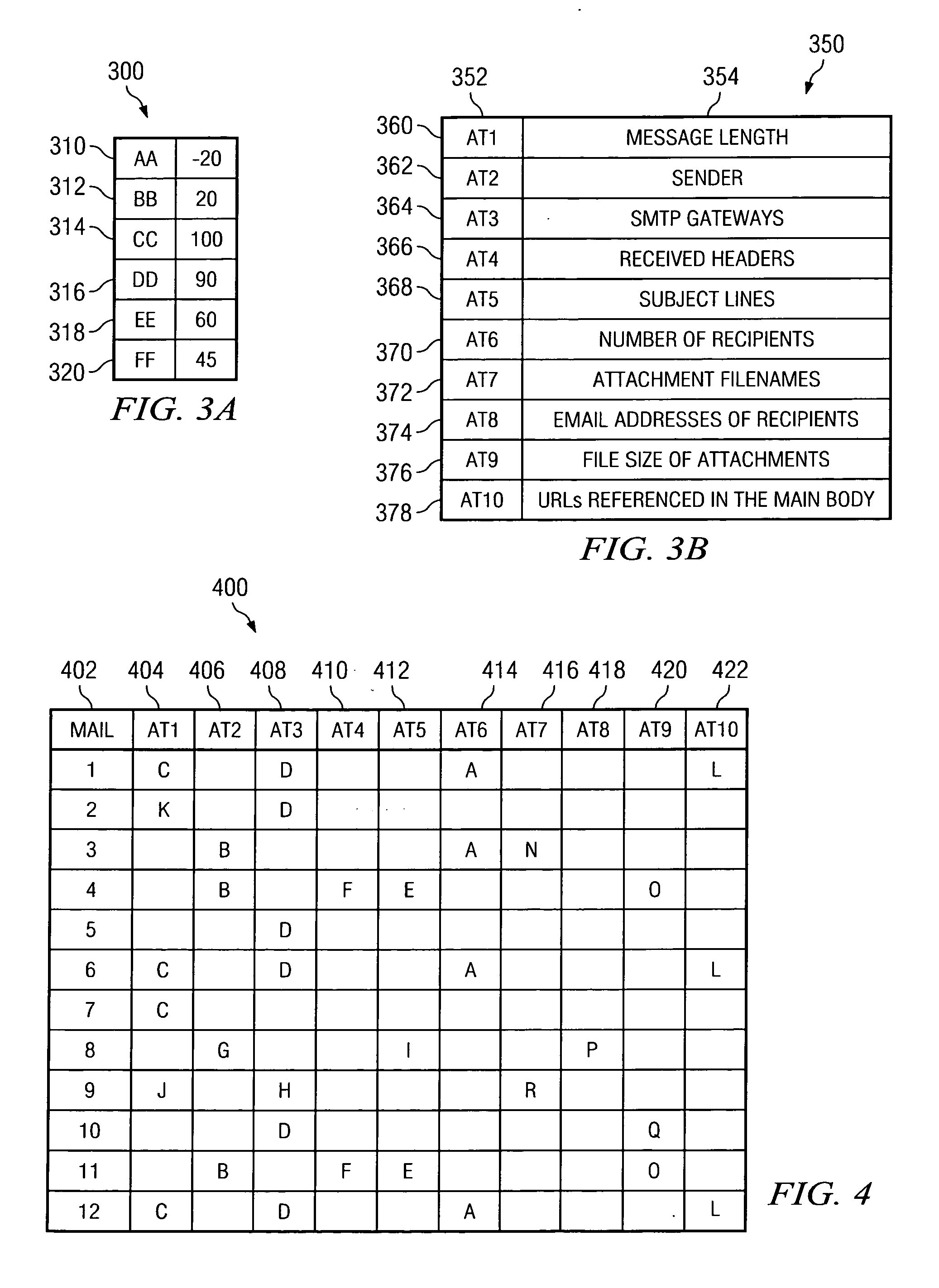
Method and apparatus for scoring unsolicited e-mail
A method for filtering spam is disclosed comprising the steps of: assigning weights to a plurality of recipient e-mail addresses; determining a set of similar e-mails from a plurality of e-mails sent to the recipient addresses; calculating a score based for each set of similar e-mails; placing the score in the header of the e-mail; determining whether the score exceeds a threshold; and responsive to determining that the score exceeds the threshold, tagging and / or filtering the e-mail.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com