Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35 results about "Security operations center" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
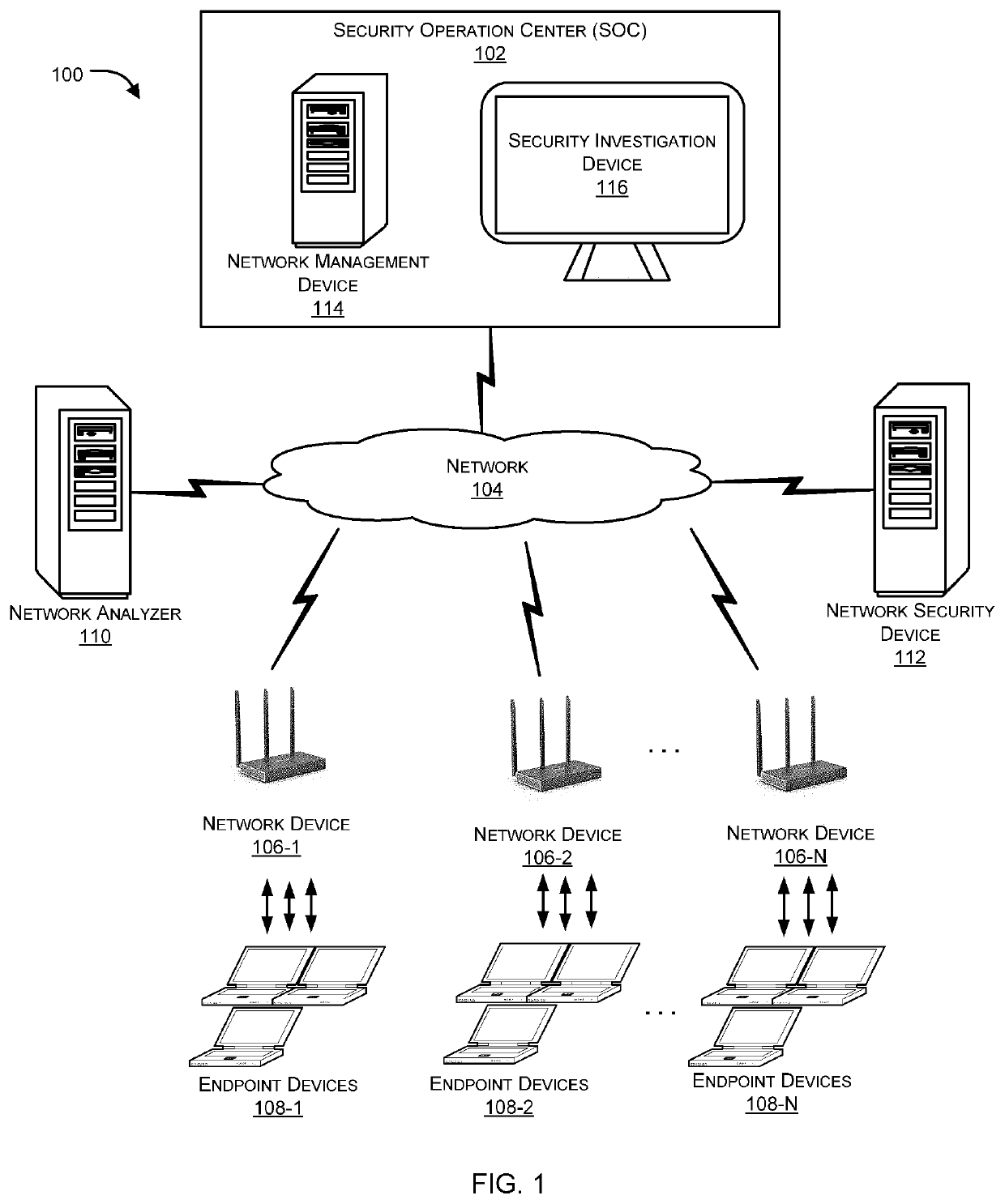
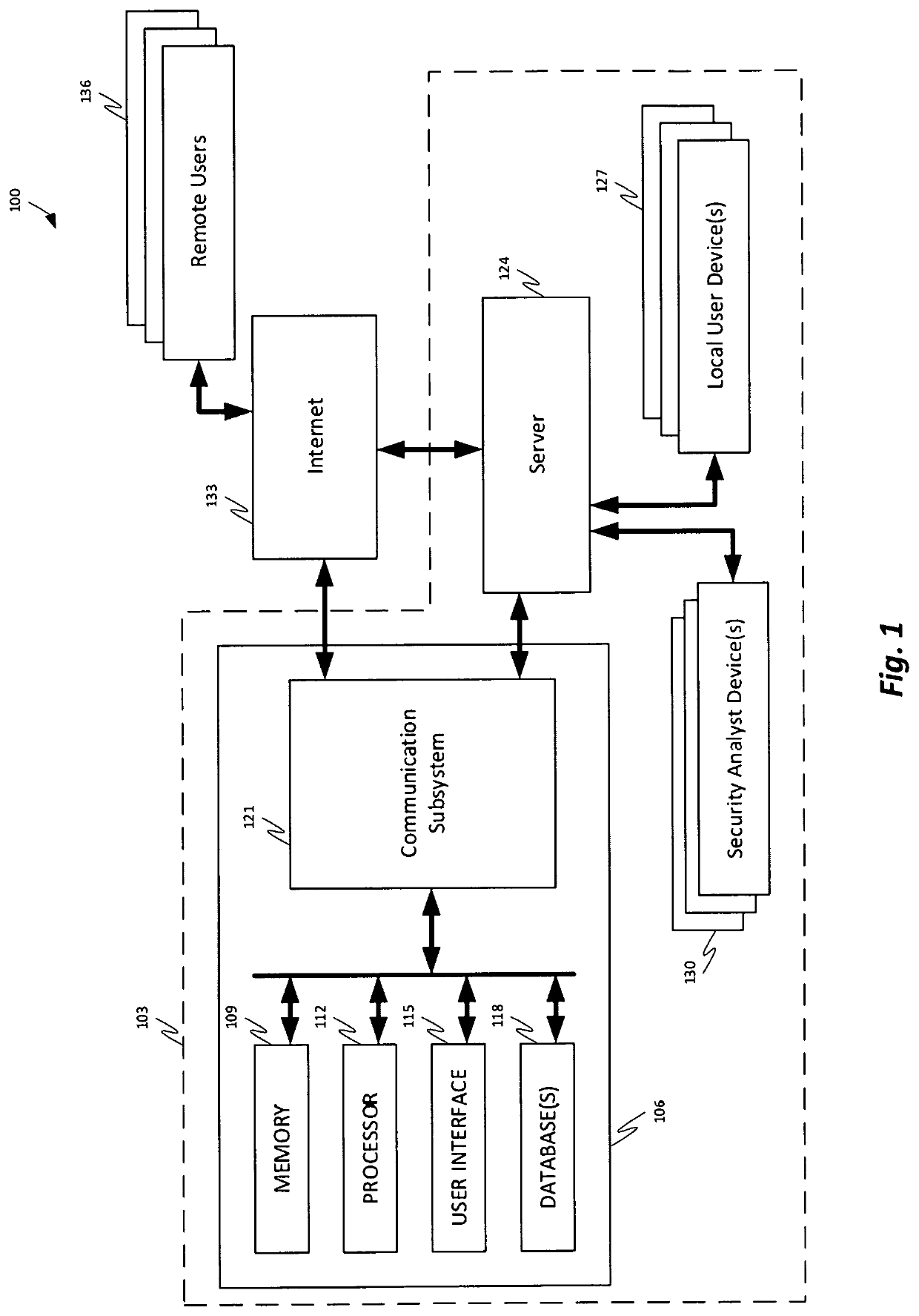
A security operations center (SOC) is a centralized unit that deals with security issues on an organizational and technical level. A SOC within a building or facility is a central location from where staff supervises the site, using data processing technology. Typically, a SOC is equipped for access monitoring, and controlling of lighting, alarms, and vehicle barriers.
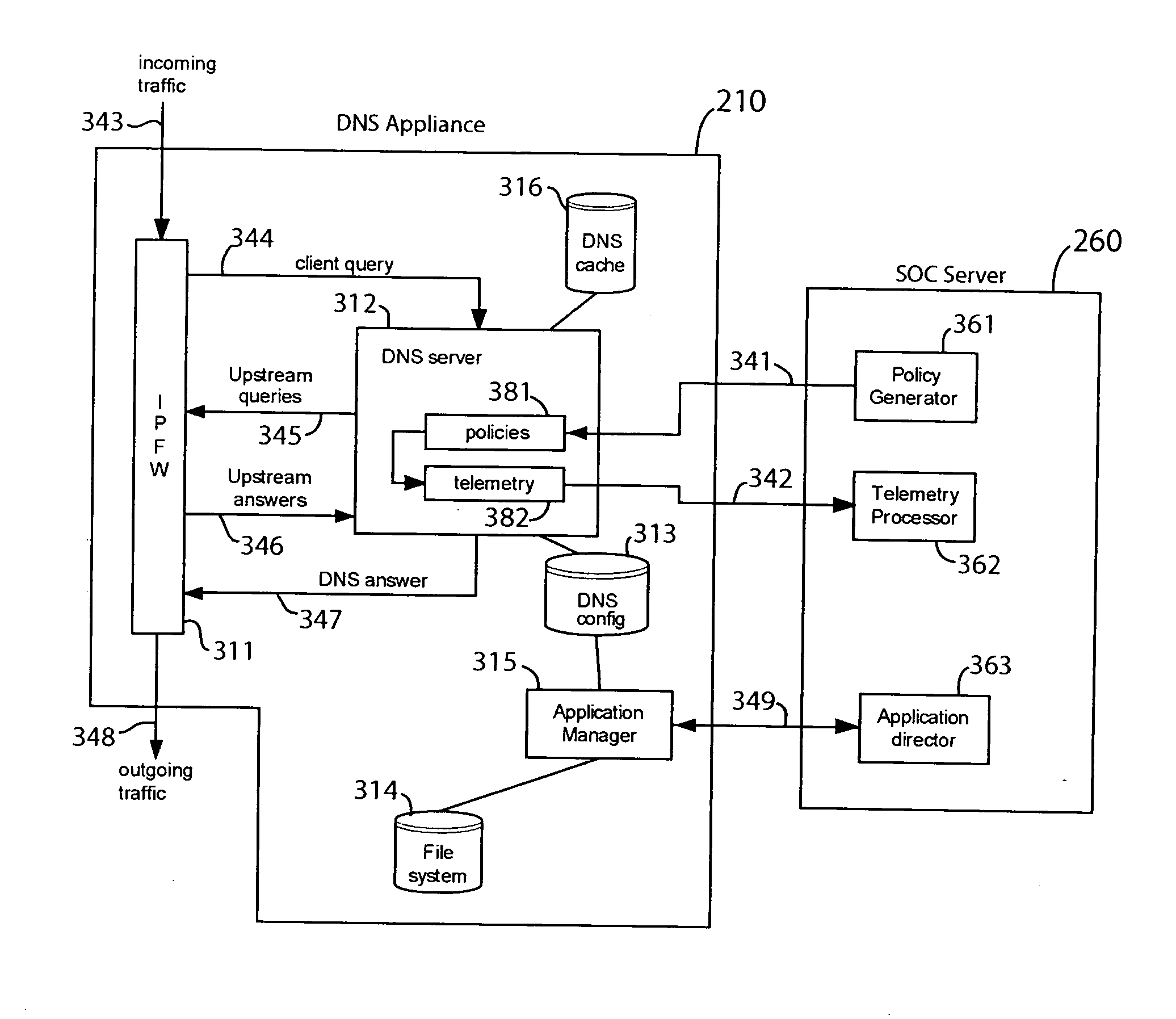
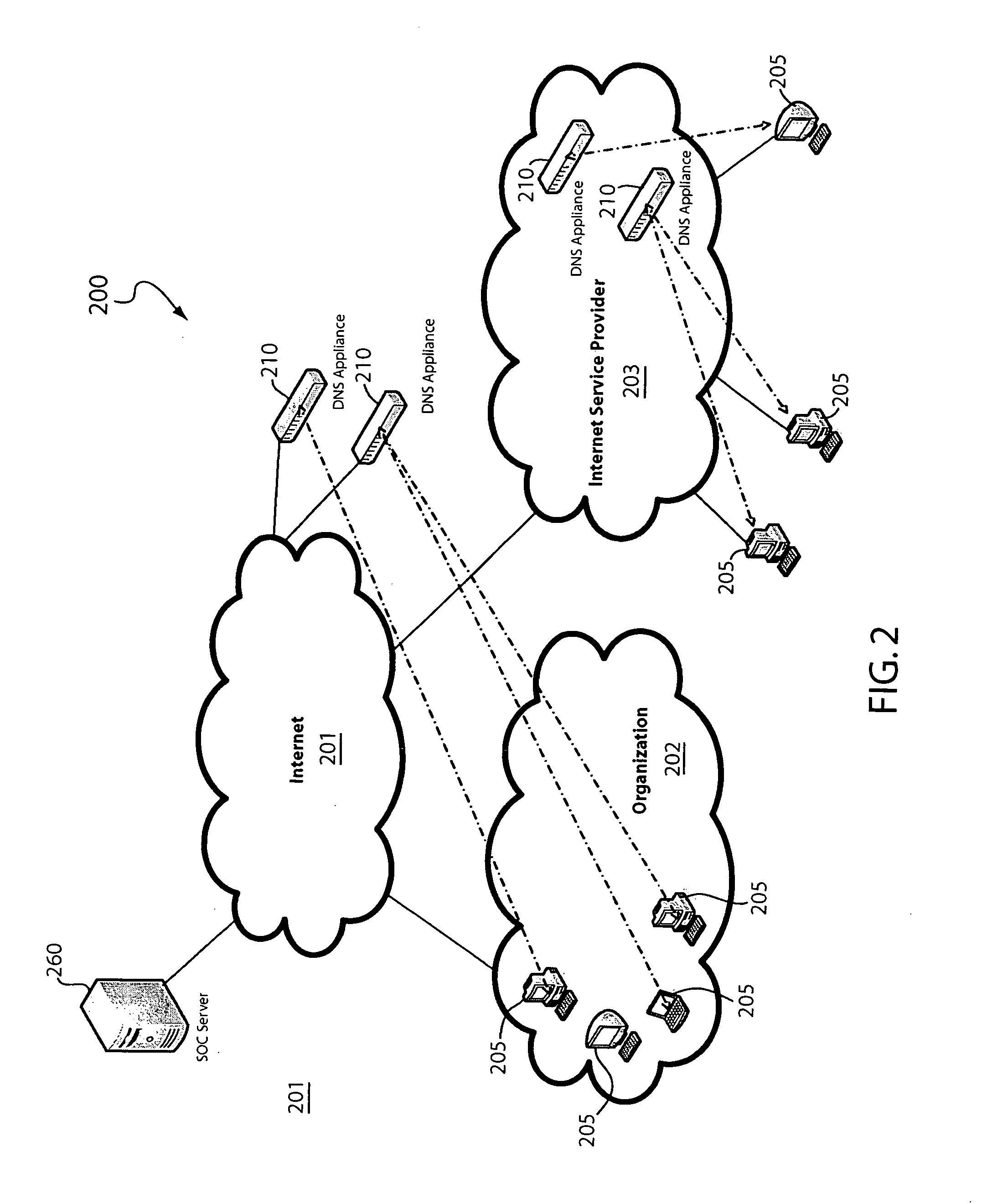
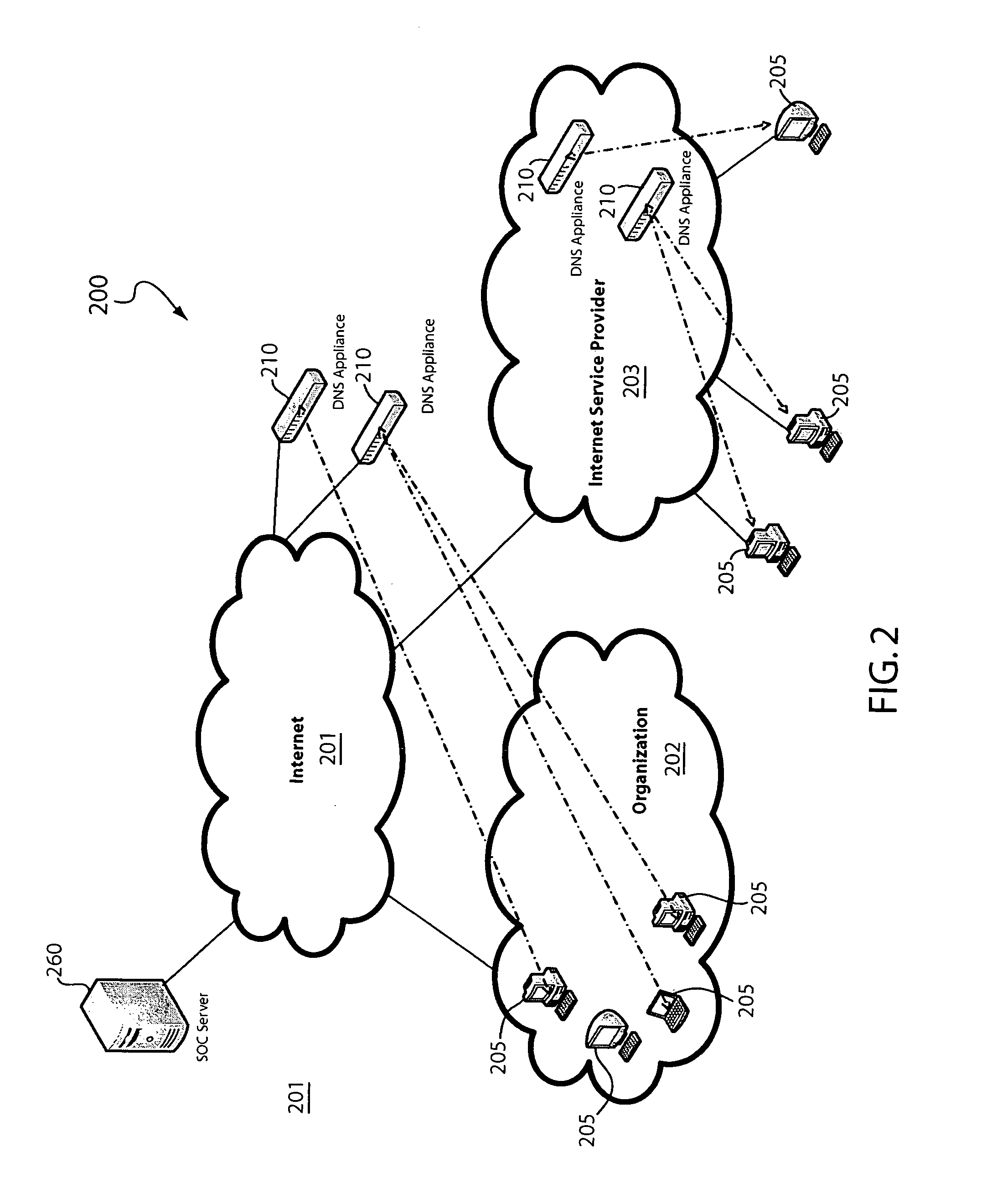
Domain name system security network
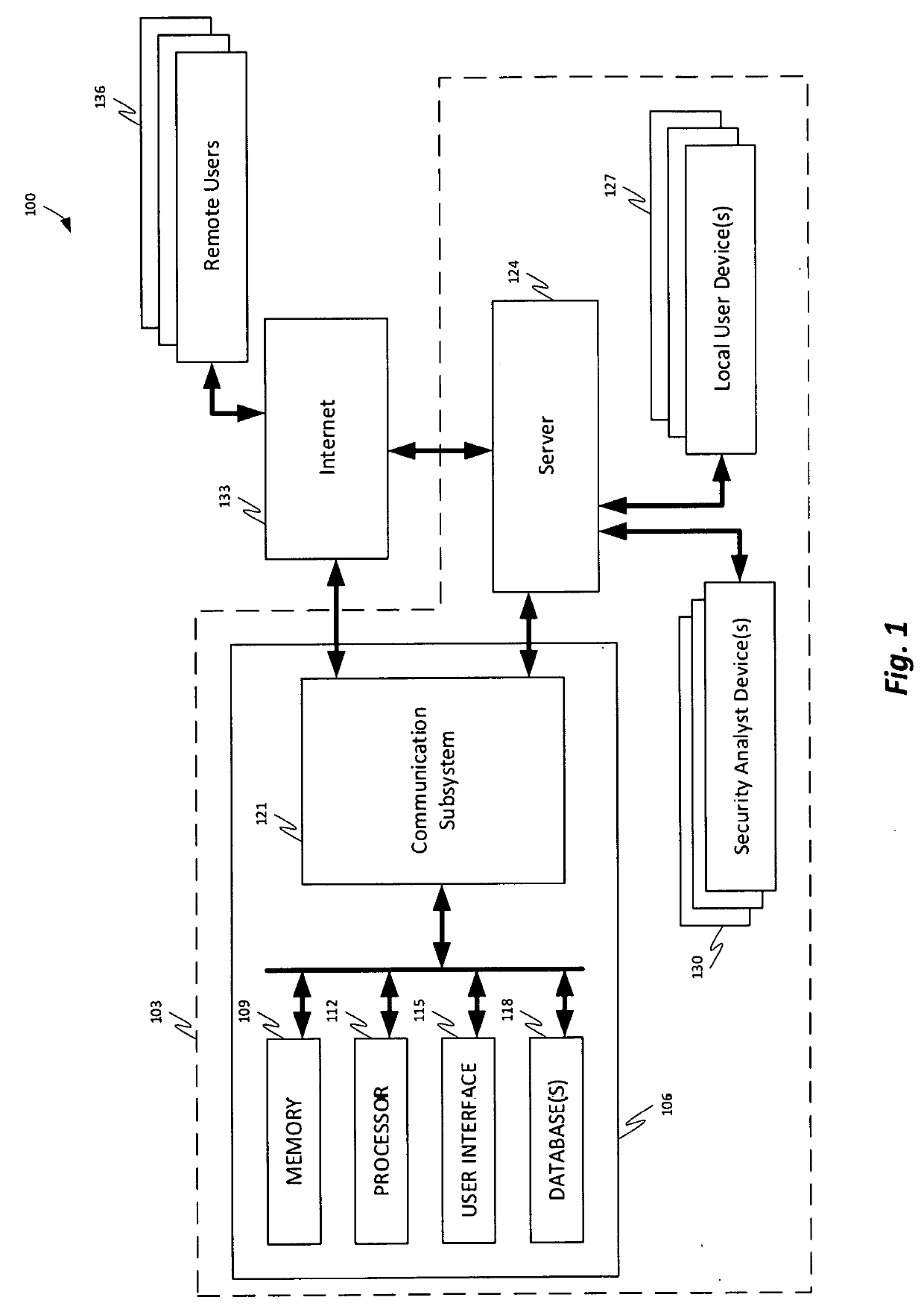
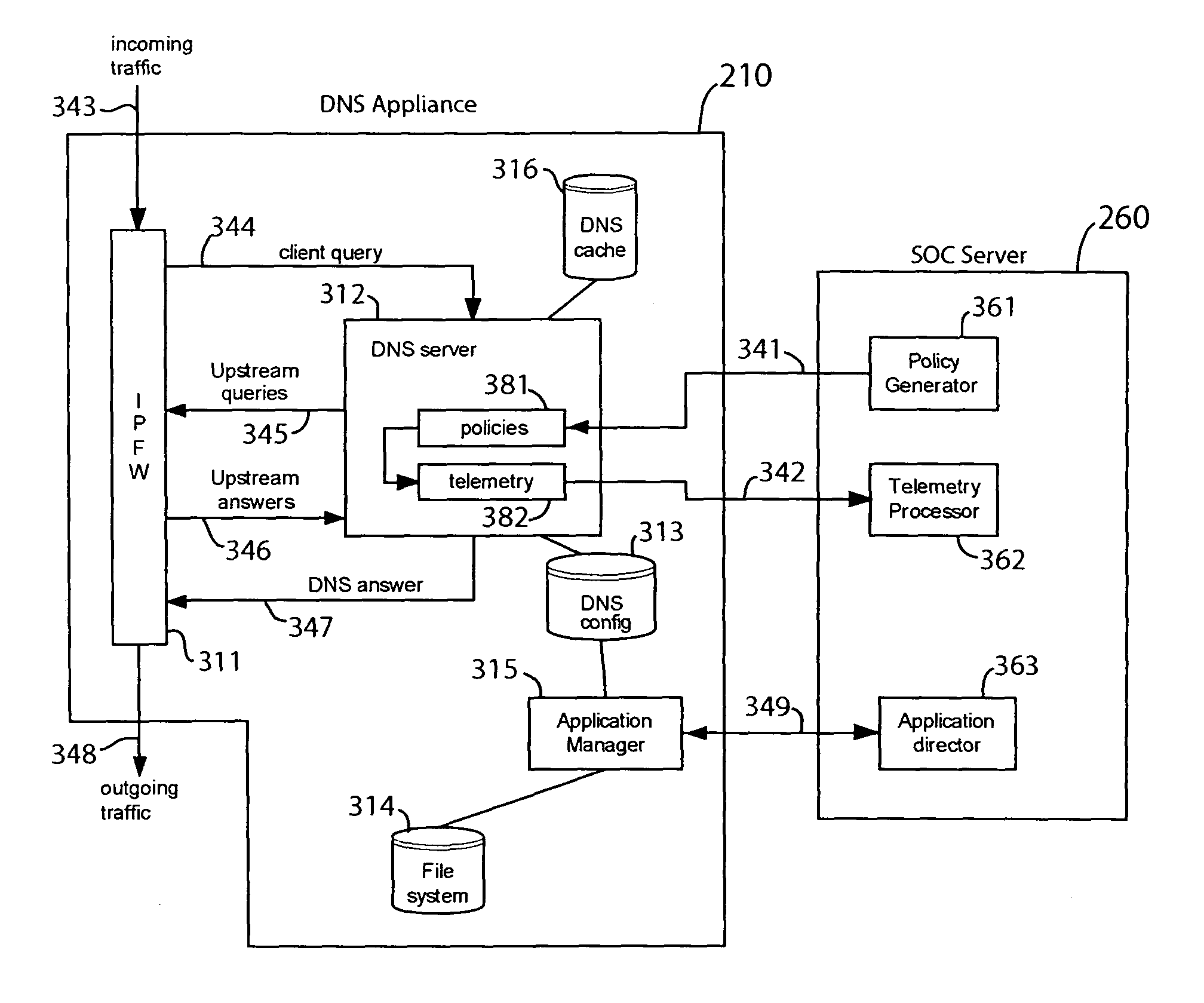
In one embodiment, a DNS security network includes several DNS appliances and a security operations center (SOC) server computer. The SOC server computer may receive telemetry data from the DNS appliances, the telemetry data comprising information about DNS client queries received in the respective DNS appliances. From the telemetry data, the SOC server computer may generate security policies for distribution to the DNS appliances. The security policies may be used by the DNS appliances to determine whether a DNS client query is originated by a client computer performing a prohibited activity (e.g., sending spam, communicating with a zombie control computer, navigating to a prohibited website, etc.). An answer to a client query may be replaced or discarded altogether in cases where the originator is performing a prohibited activity.
Owner:TREND MICRO INC
Computer-implemented method for determining computer system security threats, security operations center system and computer program product
ActiveUS20180167402A1Ensure resource securityReduce processComputer security arrangementsMachine learningRisk levelSecurity operations center
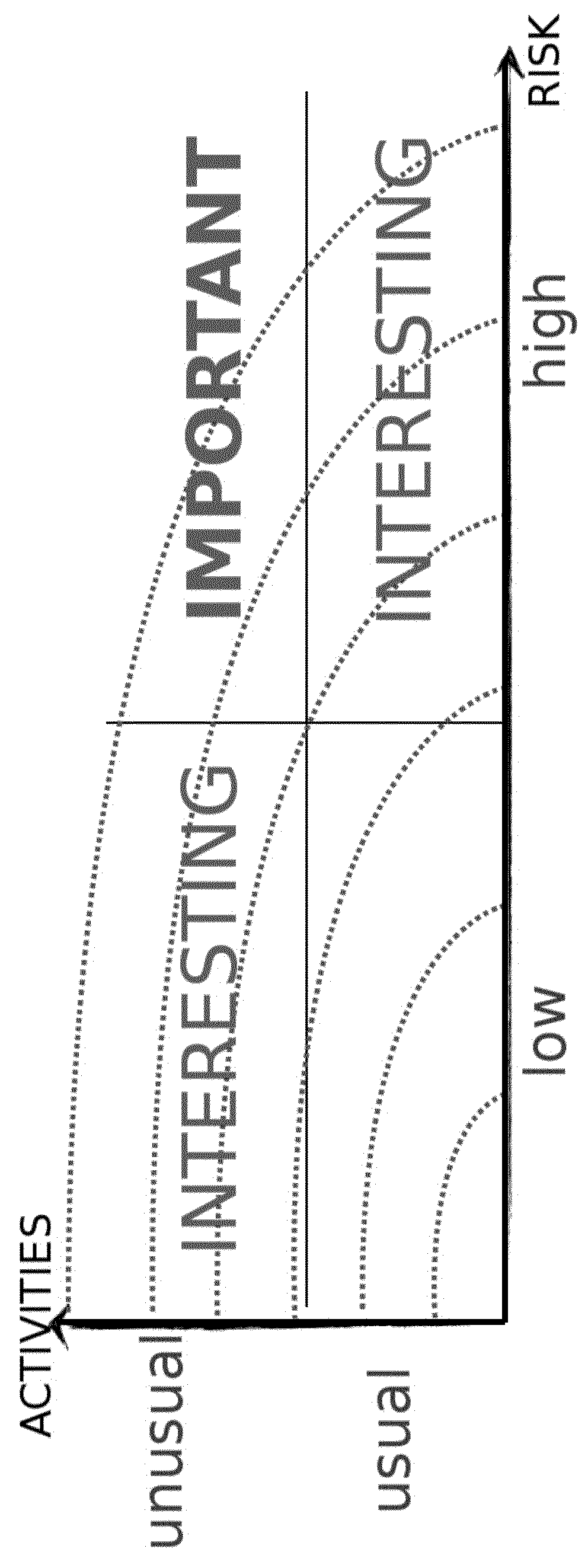
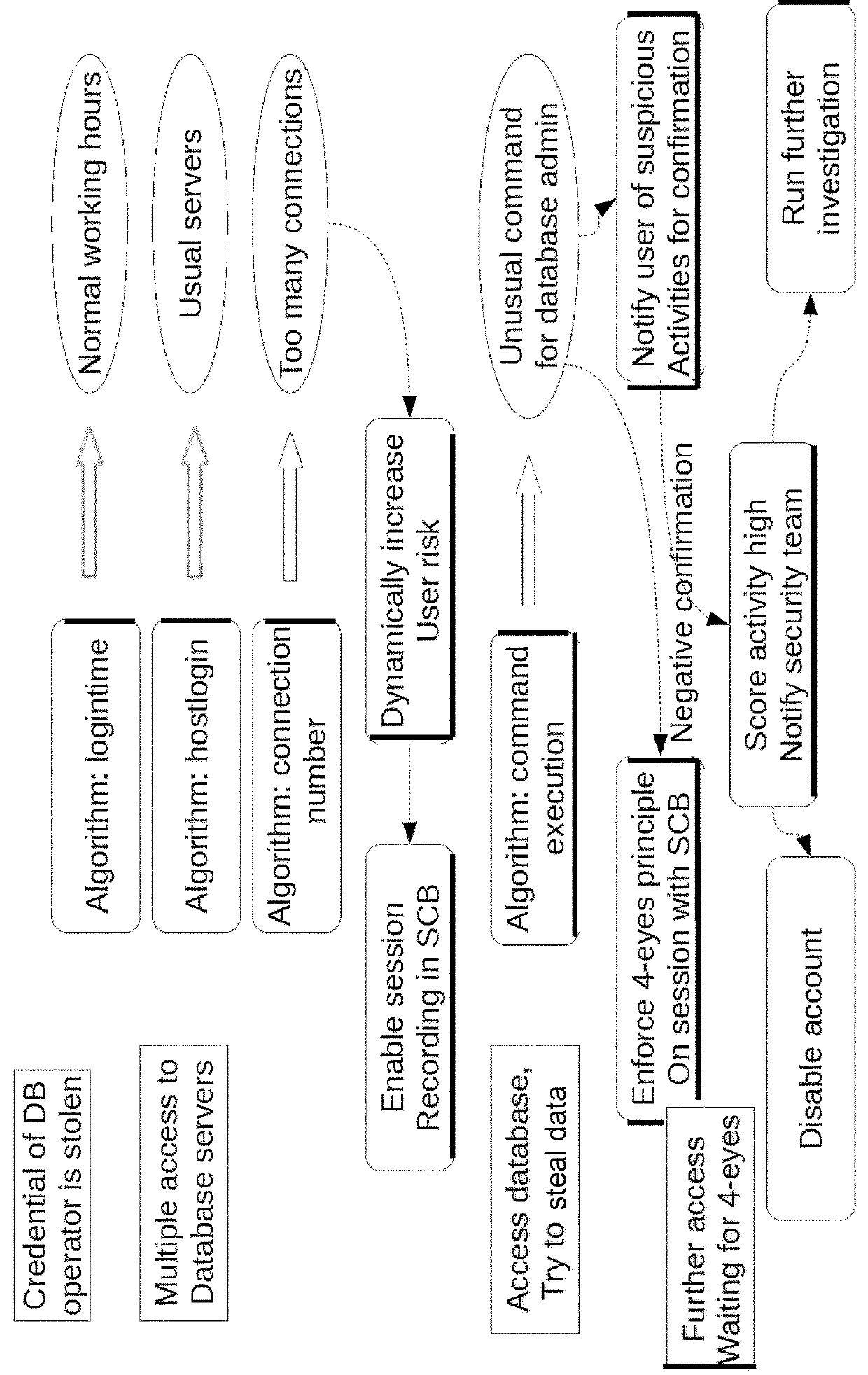
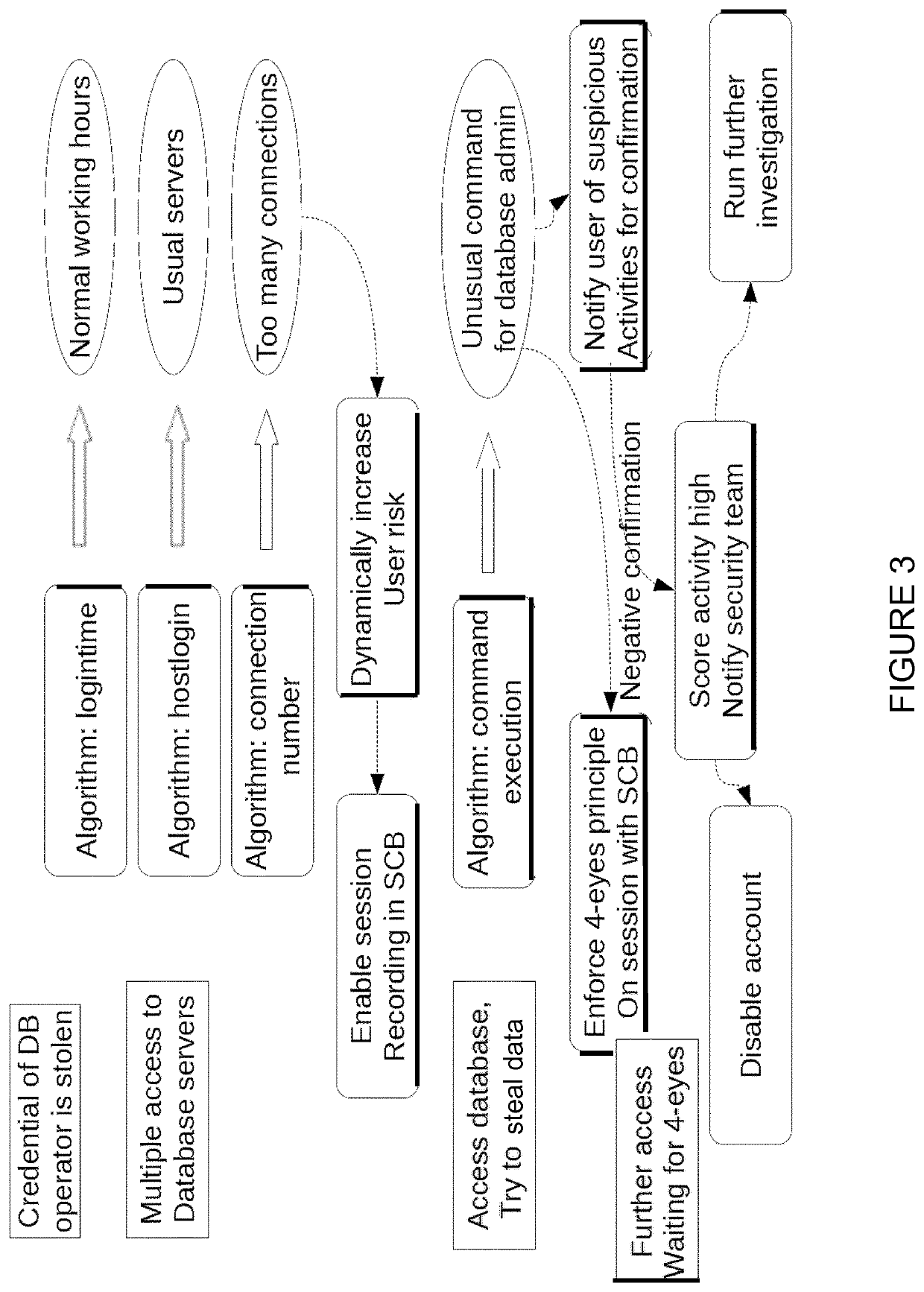
A computer-implemented method for determining computer system security threats, the computer system including user accounts established on the computer system, the method including the steps of: (i) for a plurality of user accounts, assigning a risk level to each account; (ii) in a time interval, for a plurality of events, wherein each event is linked to a respective user account, assigning an event score relating to deviation from normal behavior of each event with respect to the respective user account; (iii) in the time interval, for the plurality of events, calculating an event importance which is a function of the respective event score and the respective user account risk level; (iv) prioritizing the plurality of events by event importance, and (v) providing a record of the plurality of events, prioritized by event importance.
Owner:BALABIT SA
Total Property Intelligence System
ActiveUS20180211115A1Multiple keys/algorithms usagePublic key for secure communicationPhysical securityApplication software
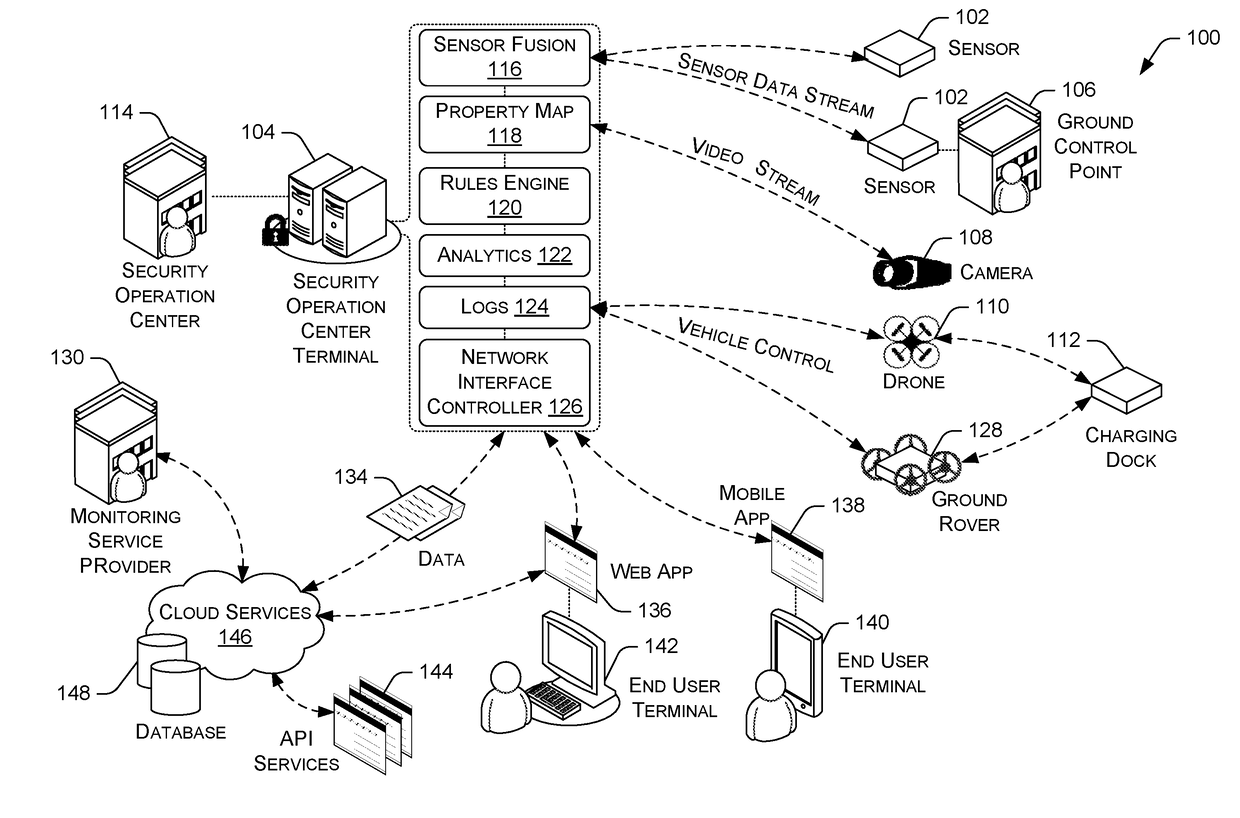
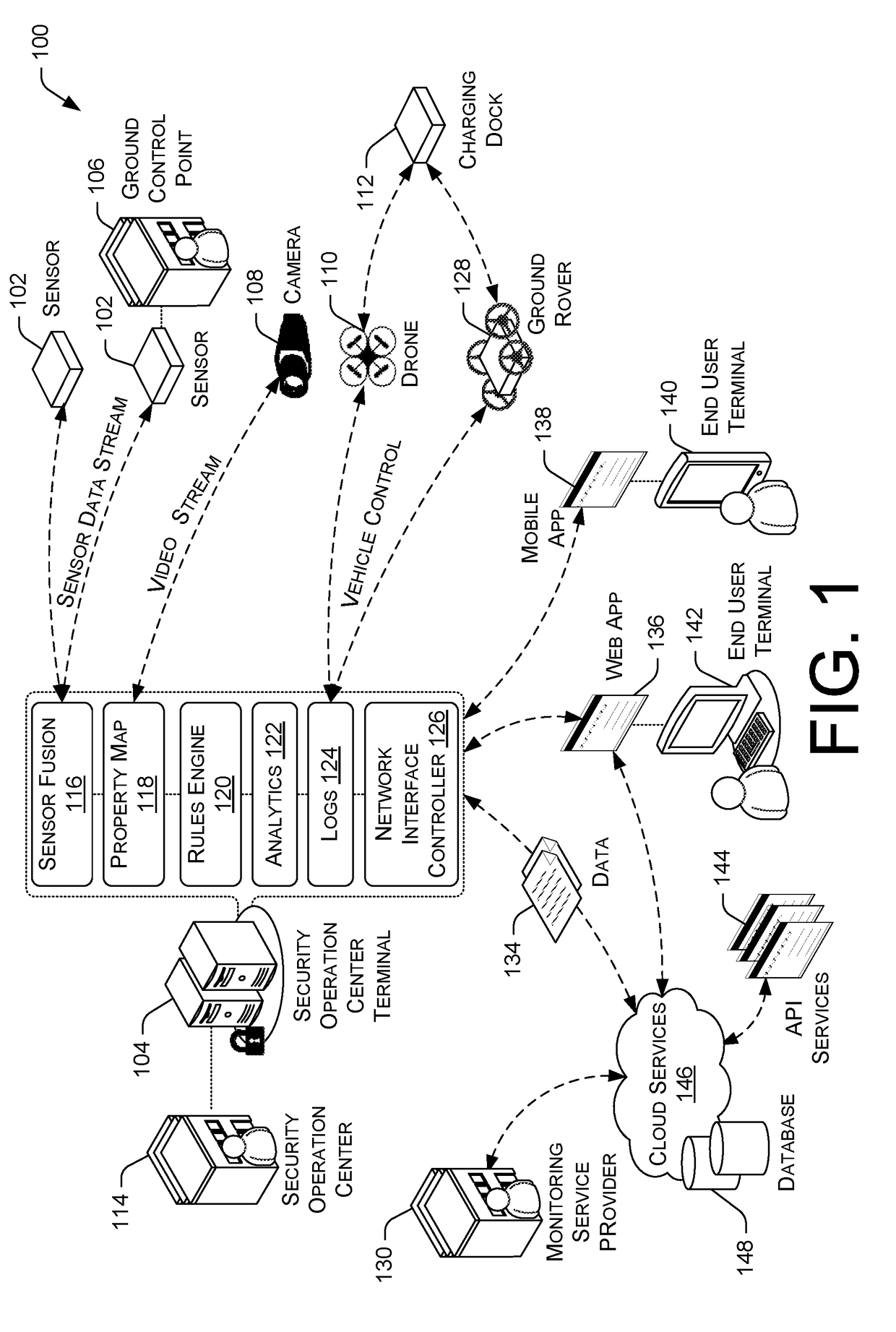
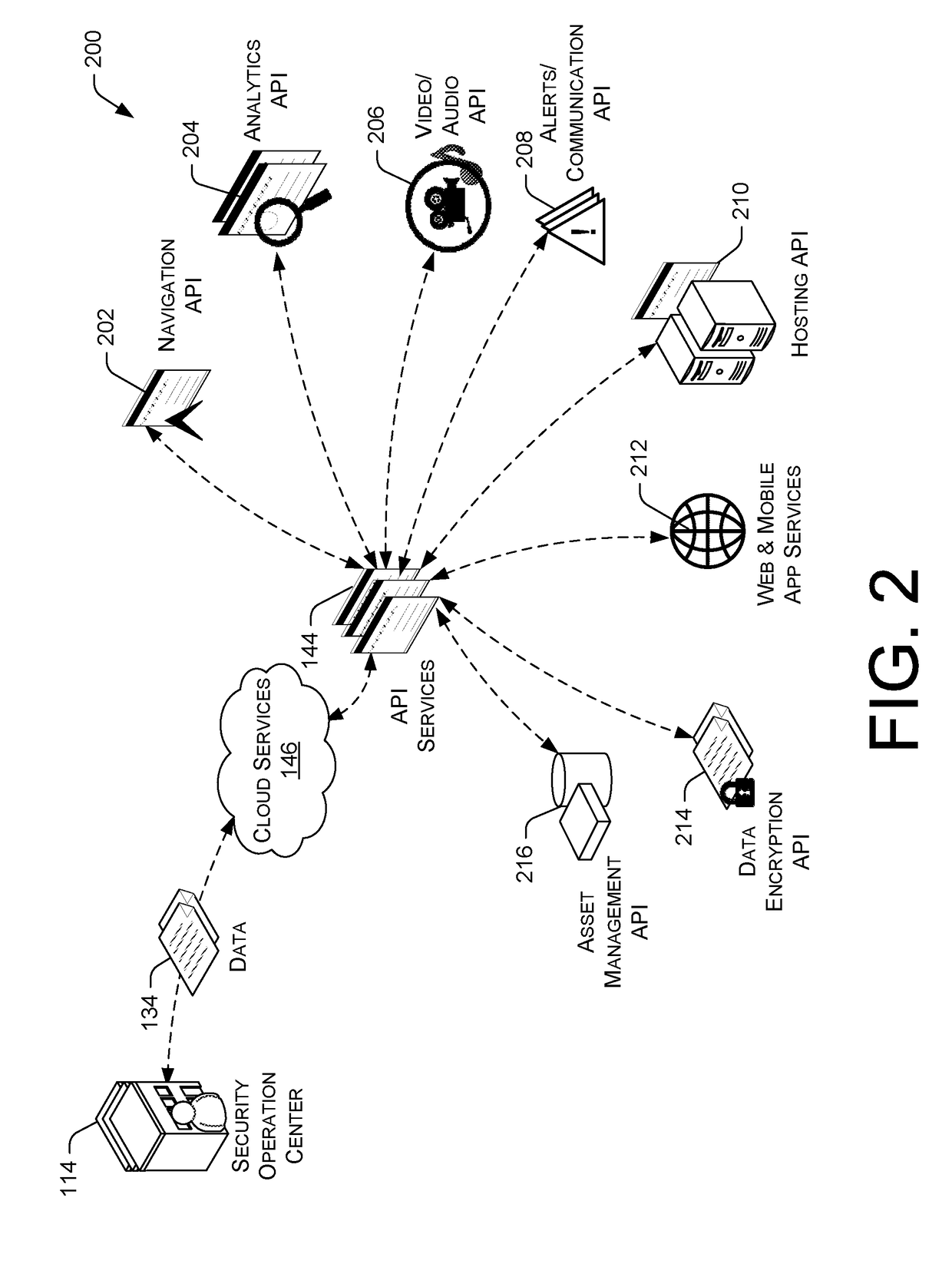
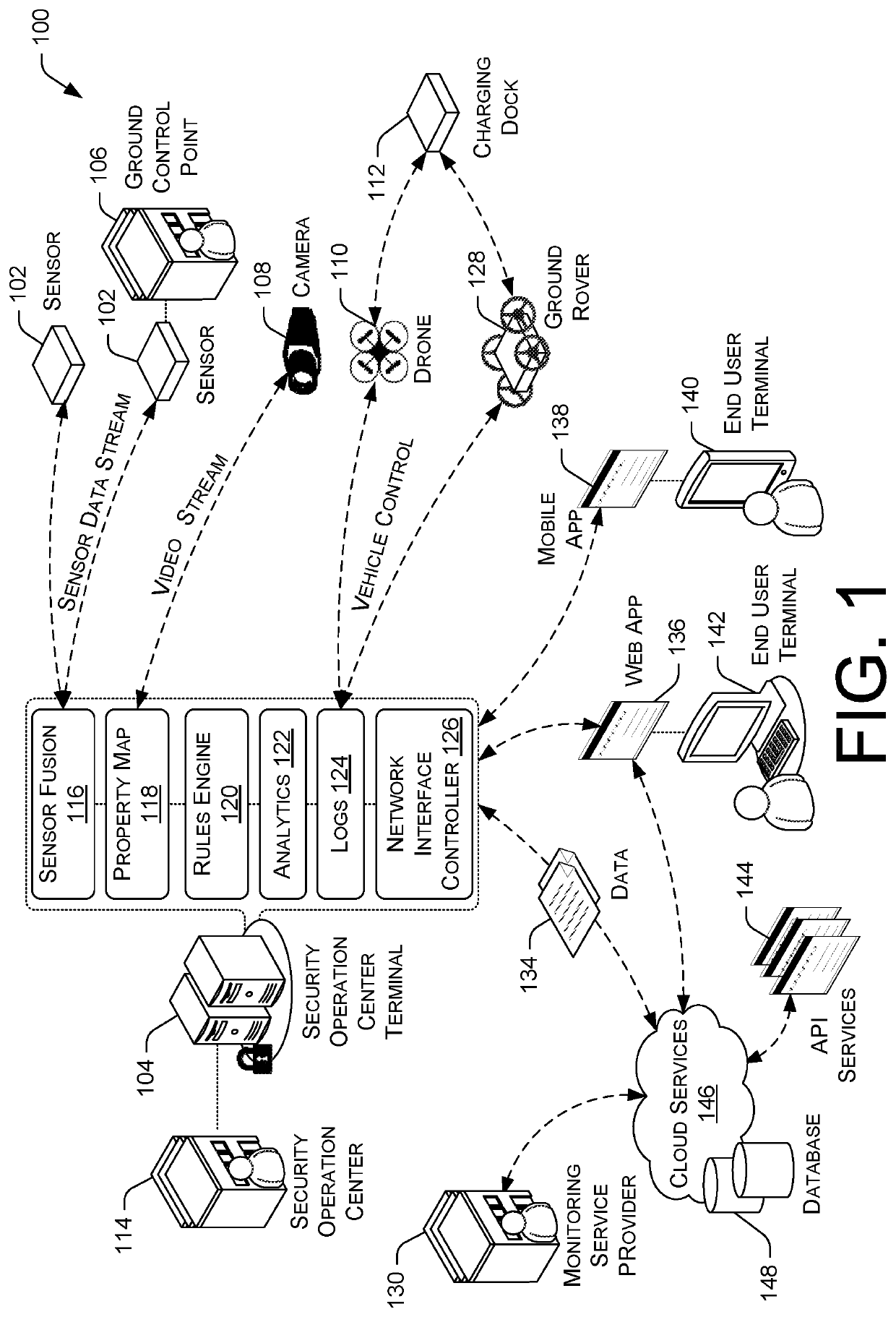
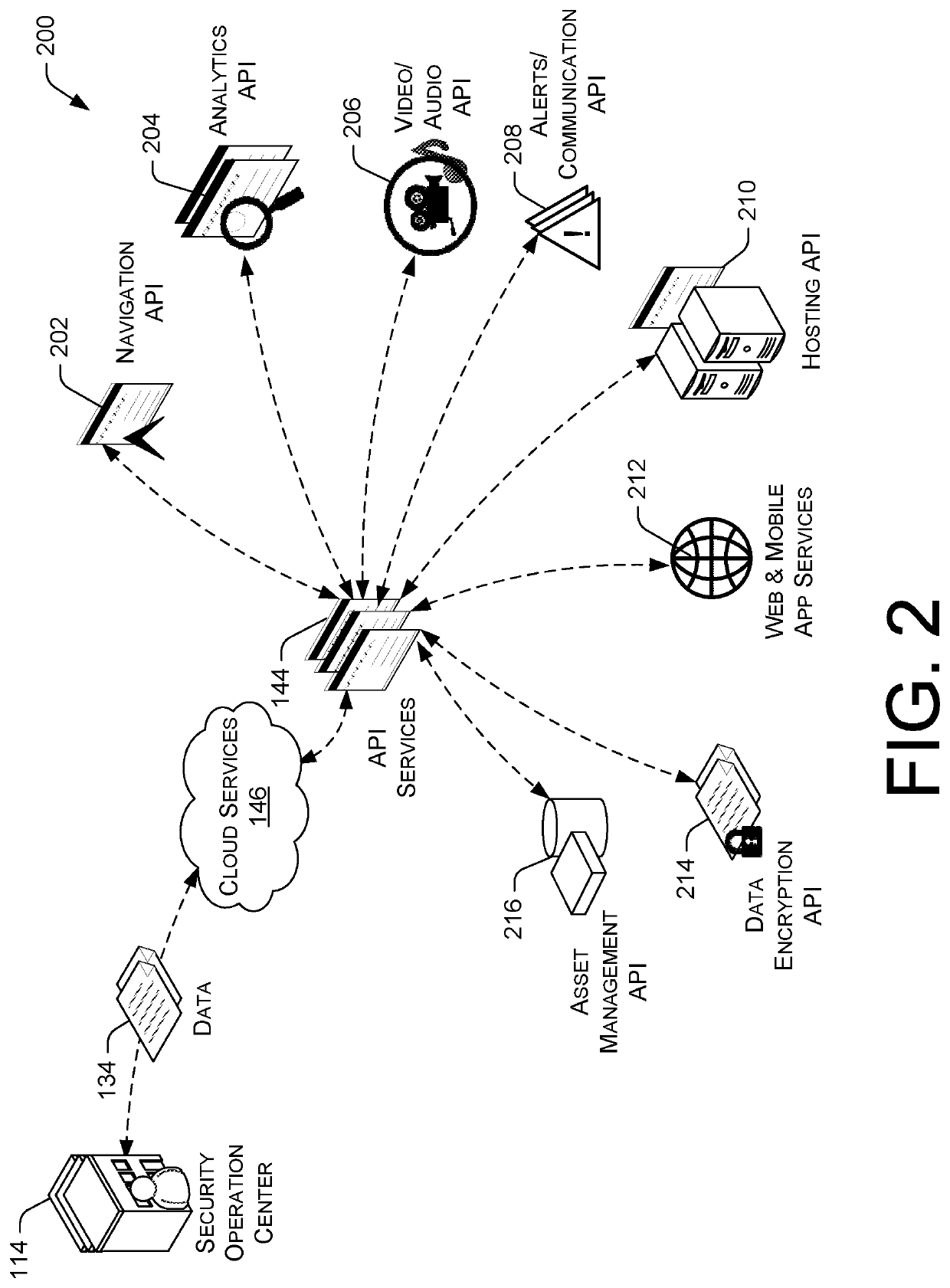
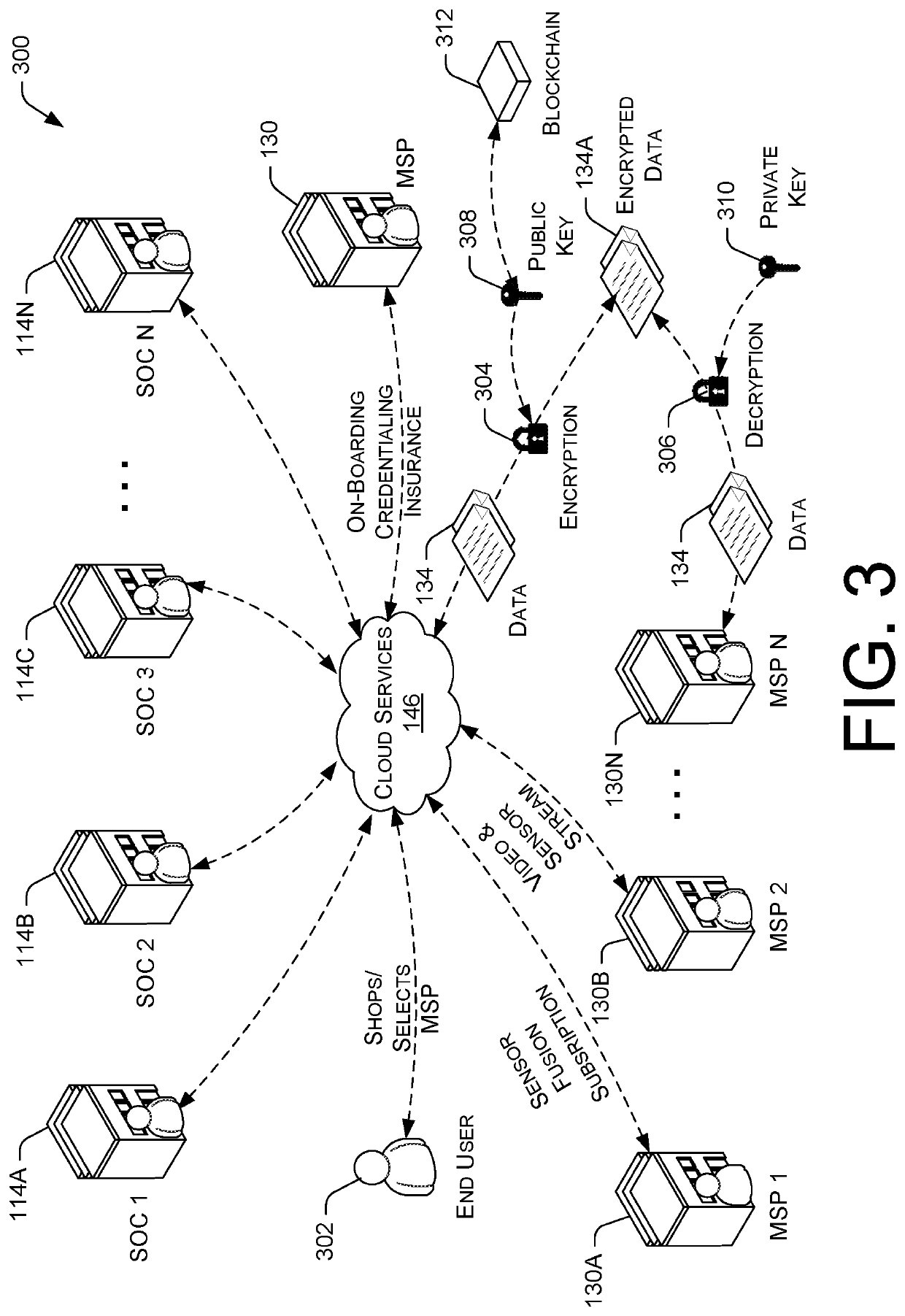
A total property security system may be implemented to conduct security and surveillance operations. The system includes security operations centers that are connected to one or more sensors and vehicles for collecting and transmitting surveillance data to a database hosted on cloud services. The collected surveillance data is analyzed in order to automatically deploy security measures and / or recommend courses of action using a rules engine that can be configured to client-specific or user-specific security needs. The cloud services can provide a set of application program interface services that can act on the surveillance operations center. Sensor fusion data and other surveillance data can be also transmitted to vetted monitoring service providers on a subscription basis to provide physical security services to the area within the property perimeter. During the subscription period, the selected monitoring service providers can obtain time-based encryption token for accessing surveillance data.
Owner:KLEIN MATIAS
Computer-implemented method for determining computer system security threats, security operations center system and computer program product
ActiveUS10681060B2Improve securityQuick and efficientPlatform integrity maintainanceMachine learningRisk levelSecurity operations center
A computer-implemented method for determining computer system security threats, the computer system including user accounts established on the computer system, the method including the steps of: (i) for a plurality of user accounts, assigning a risk level to each account; (ii) in a time interval, for a plurality of events, wherein each event is linked to a respective user account, assigning an event score relating to deviation from normal behavior of each event with respect to the respective user account; (iii) in the time interval, for the plurality of events, calculating an event importance which is a function of the respective event score and the respective user account risk level; (iv) prioritizing the plurality of events by event importance, and (v) providing a record of the plurality of events, prioritized by event importance.
Owner:BALABIT SA
Active machine learning system for hazardous host detection
ActiveCN106790256ARealize detectionRealize the alarmTransmissionSecurity information and event managementDeep belief network
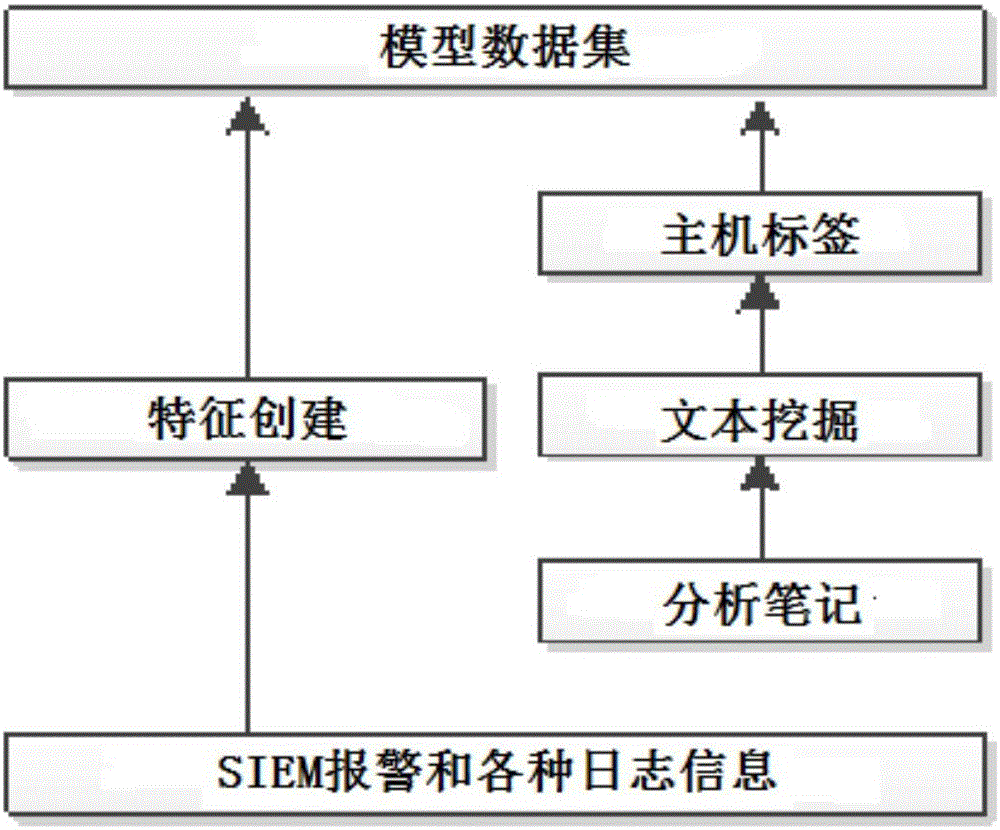
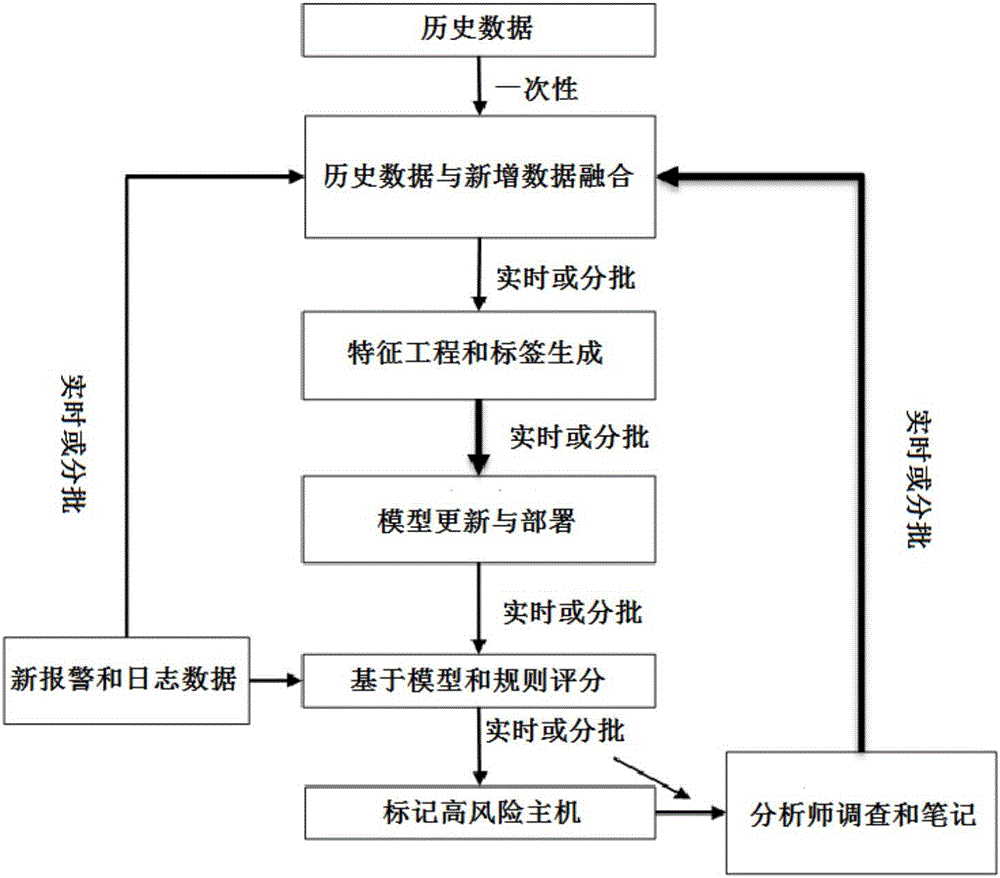
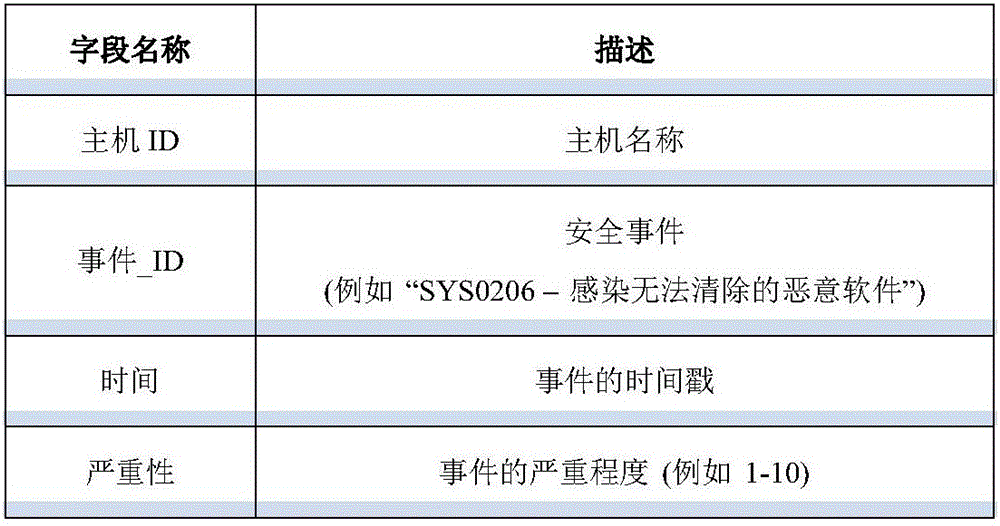
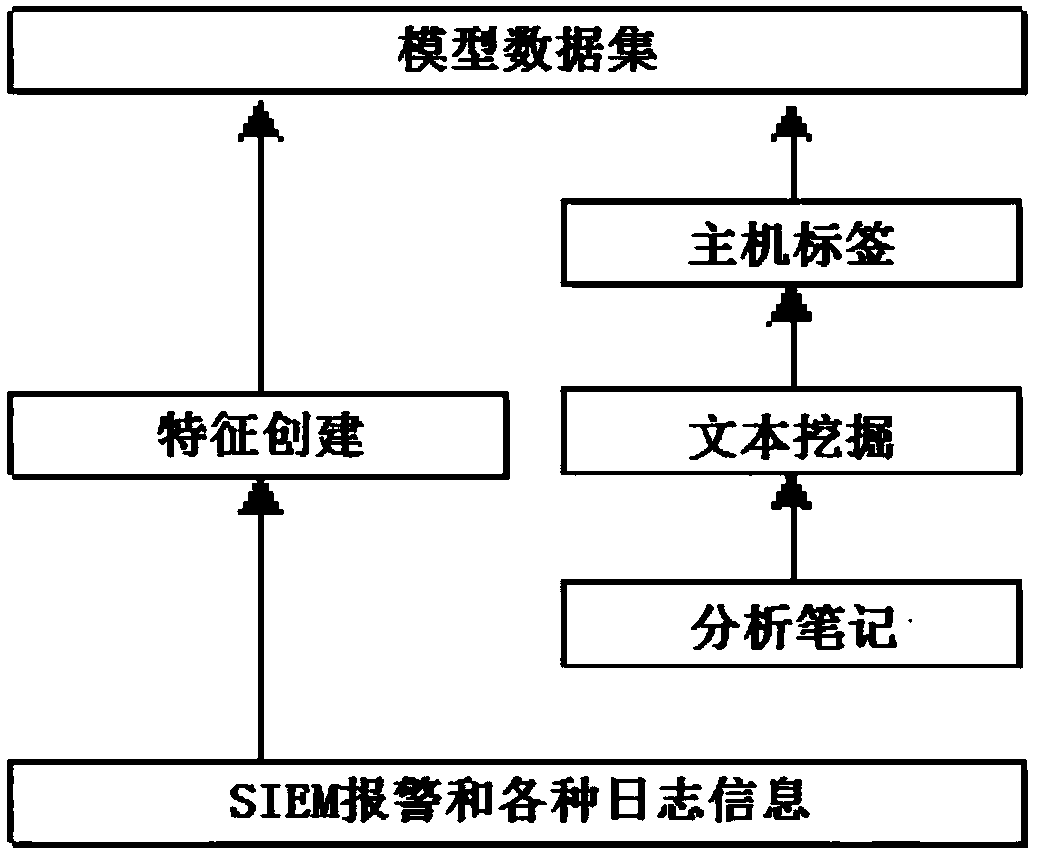
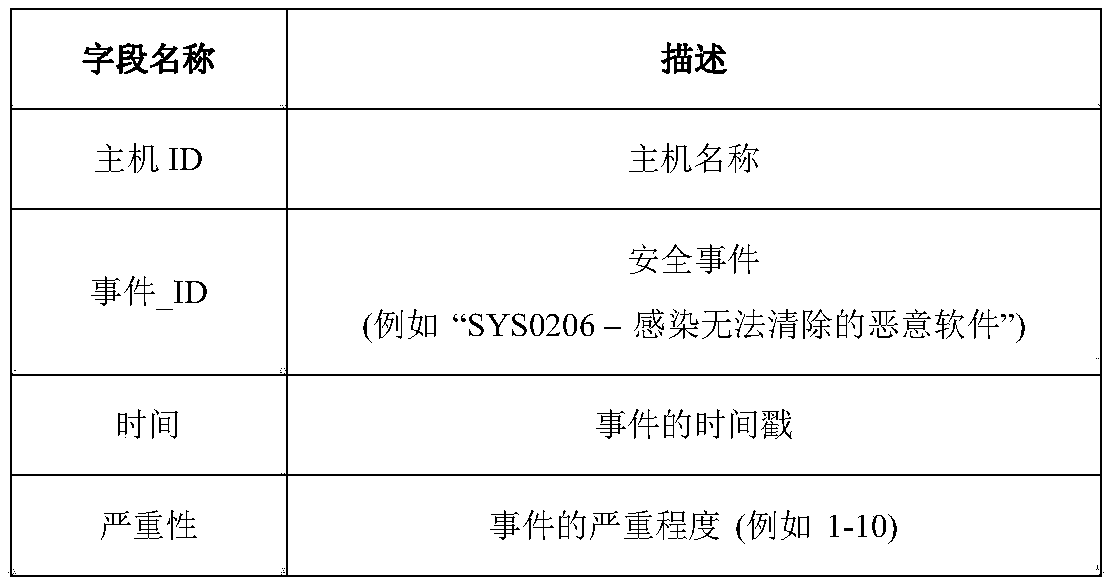
The invention discloses an active machine learning system for hazardous host detection. Hosts high in possibility of being destroyed are marked by the aid of SIEM (security information and event management) warning information, various safety logs and research notes of analysts. The active machine learning system comprises parts including data collection, feature engineering, mark production, machine learning, feedback algorithms of active learning analyst insights, real-time warning and the like; natural language progressing, text mining and graphics-based methods are adopted, targets are generated and characteristics are created for machine learning; a machine learning mechanism of deep belief network, multilayer deep neutral network, random forest, support vector machine, Logistic regression and the like are adopted for machine learning. The hazardous hosts in the network can be accurately detected, false alarm rate is greatly reduced, host security detection requests and SOC (security operation center) actual investigation are considered, important security events can be handled in time, and labor cost is reduced while network security monitoring capability is improved.
Owner:浙江航芯科技有限公司
Implementing method and system for could security service
InactiveCN104601530ARespond quicklyEasy to handleTransmissionSecurity operations centerSecurity as a service
The invention discloses an implementing method and an implementing system for cloud security service. The method includes the steps that: security middleware receives an executing message from a cloud security operating center, wherein the security middleware is preset in a security engine layer, and the cloud security operating center is preset in a managing layer; the security middleware executes corresponding dynamic security operation according to the executing message, and thereby obtaining an execution result; the security middleware dynamically regulate a cloud security strategy according to the execution result. According to the implementing method and system for cloud security service, the efficiency for quickly responding to security threat and dealing with security events in the case of no manual intervention can be improved.
Owner:ZTE CORP
Expressway rescue system with forewarning analysis function for electric vehicles and method of the same
ActiveCN106627421AGuaranteed safe operationSafe and stable jobDetection of traffic movementElectric/fluid circuitSecurity operations centerEmergency rescue
The invention discloses an expressway rescue system with forewarning analysis function for electric vehicles and a method of the same. The expressway rescue system with forewarning analysis function for the electric vehicles and the method of the same comprises operational centers. The operational centers make decisions after analyzing and judging operating data in the running process of vehicles and send decision information to the rescue centers or vehicle-mounted systems installed on the vehicles through network. The operational centers or the vehicle-mounted systems installed on the vehicles dispatch according to the decision information received. The rescue centers or security operation centers generate the final analysis results according to the exception handling model and achieve event storage, early warning analysis and rescue guidance according to the data uploaded by the vehicle mounted system. The expressway rescue system with forewarning analysis function for the electric vehicles and the method of the same have the advantages of being capable of analyzing general failure of the charging facilities for expressway electric vehicles and elements of affecting the expressway electric vehicles charging, formulating an emergency rescue plan of the expressway electric vehicles, better ensuring the safe operation of the electric vehicles on the expressway, and ensuring the safety and stability of the charging facilities.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +2
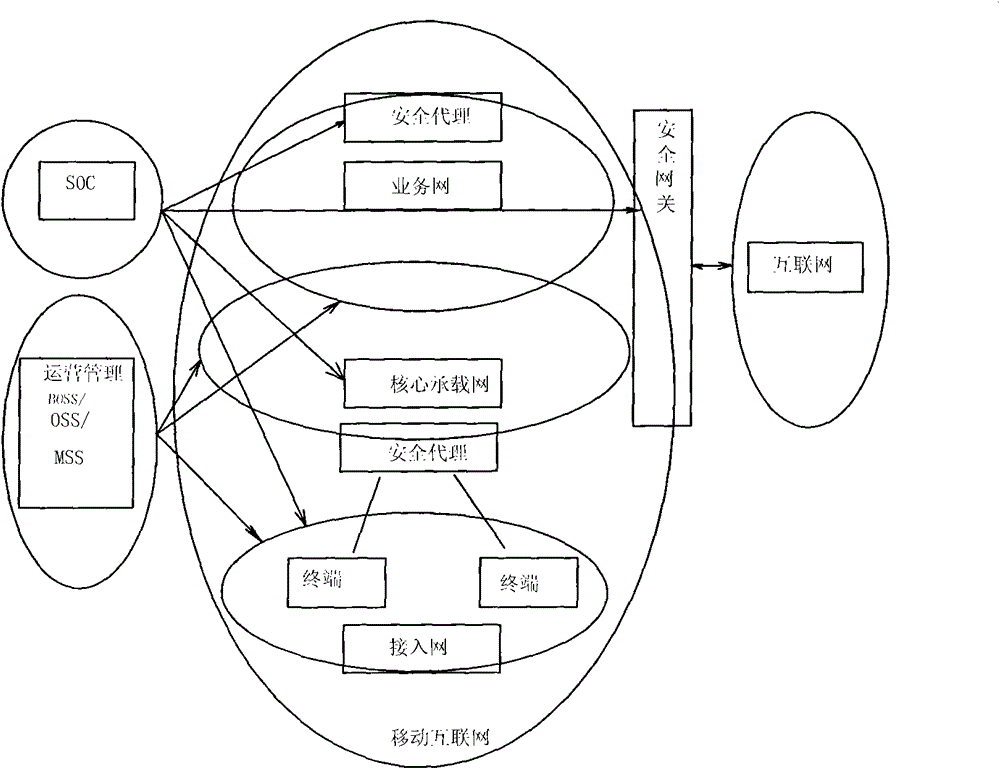
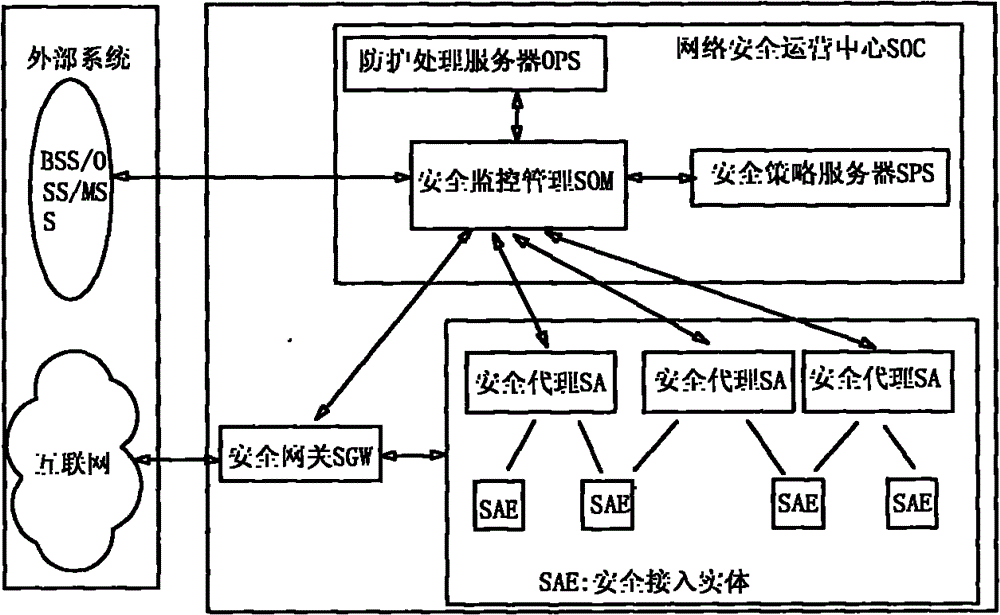
Hierarchical type mobile internet security monitoring and protecting system
ActiveCN101789948AImprove safe operation capabilitiesEnsure safetyData switching networksSecurity arrangementArea networkInteroperability Problem
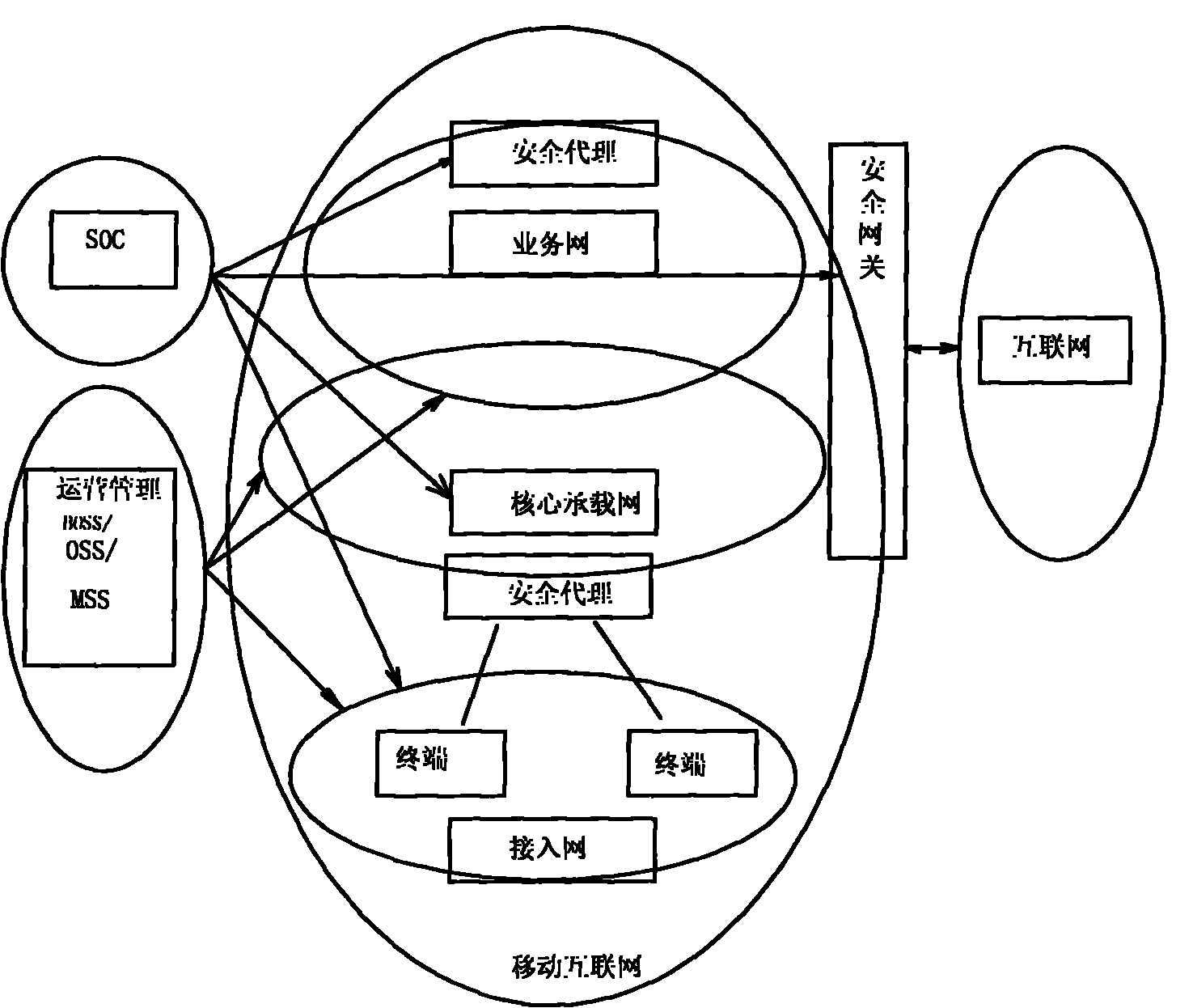
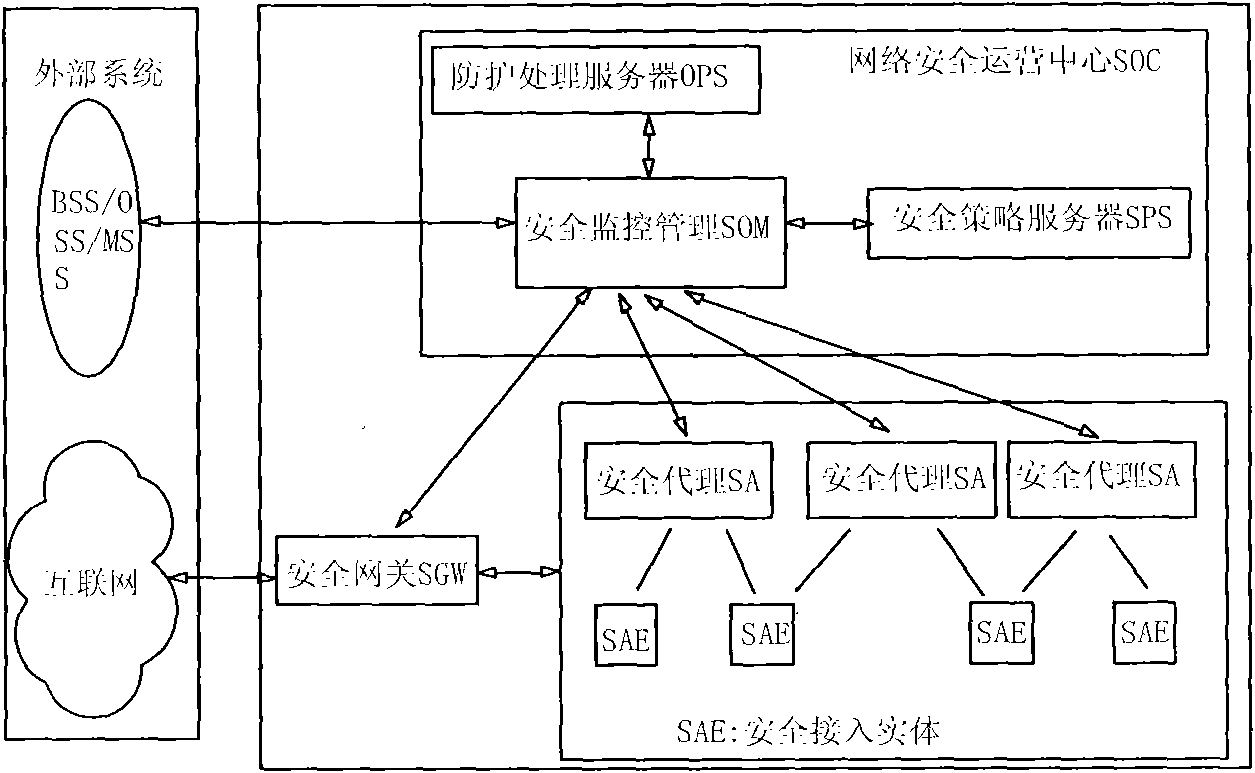
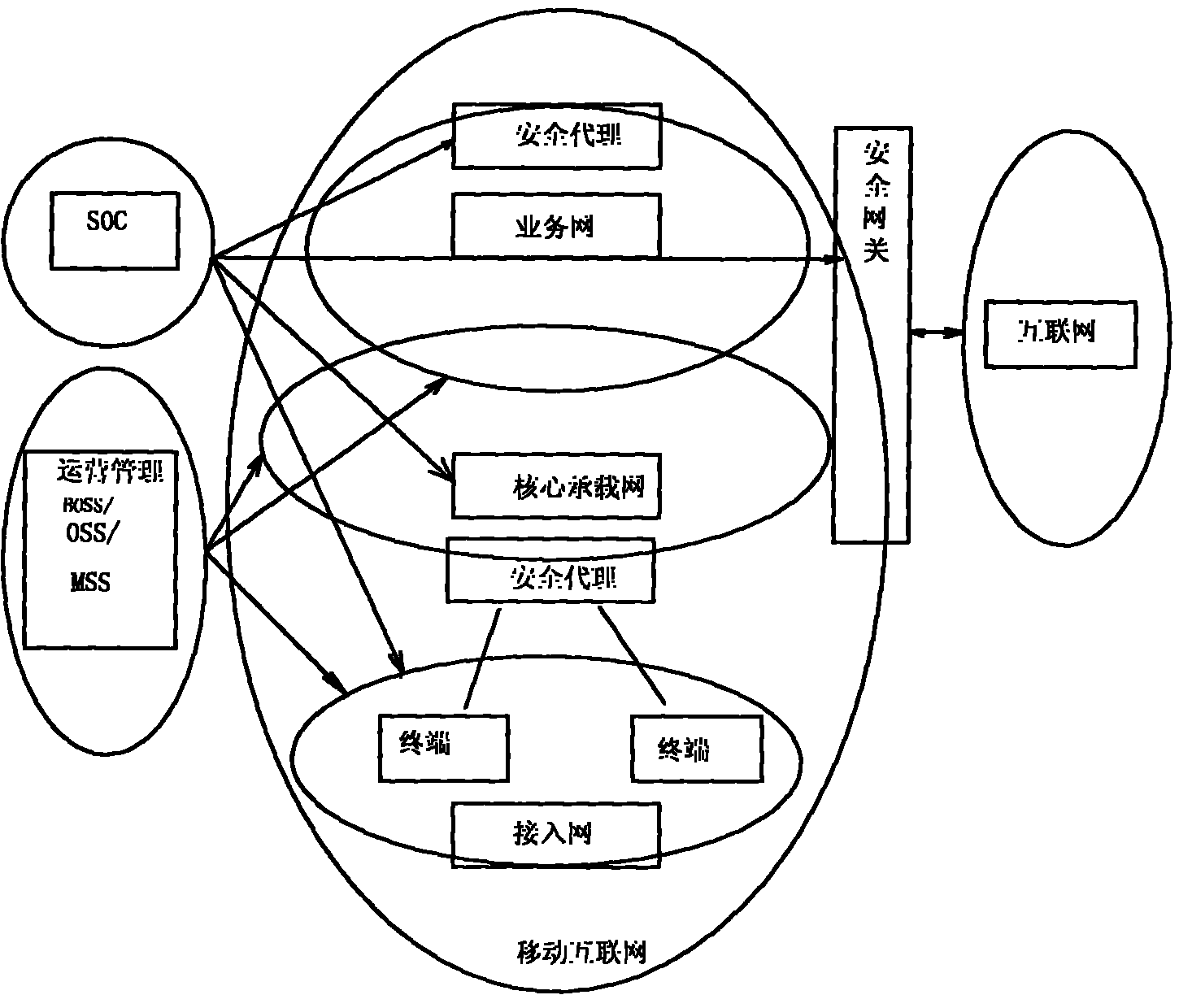
The invention provides a hierarchical type mobile internet security monitoring and protecting system. A set of complete mobile internet security monitoring and protecting system is provided by adopting an active security monitoring and protecting technology, an intelligent detecting and analyzing technology and a customer service-oriented quality assurance policy on the basis of the further research on the characteristics of performability and maintainability of the mobile internet. The system comprises three layers of functional groups including a security operation center (SOC), a security gateway (SGW), a security access entity (SAE), and defines the basic attribute of each functional entity and the interoperability relation among the functional entities. The SOC is in charge of overall security operation monitoring management, the SGW is in charge of the flux security detection from common internet to the mobile internet, a security agent (SA) is in charge of the security monitor of in-out flux of network nodes or domestic area networks, and the SAE is in charge of monitoring the safe access and the safe operation of various types of terminals.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
Threat information integration system and method for industrial environment
InactiveCN109547479AImprove work efficiencyCharacter and pattern recognitionTransmissionSecurity operations centerSafety management systems
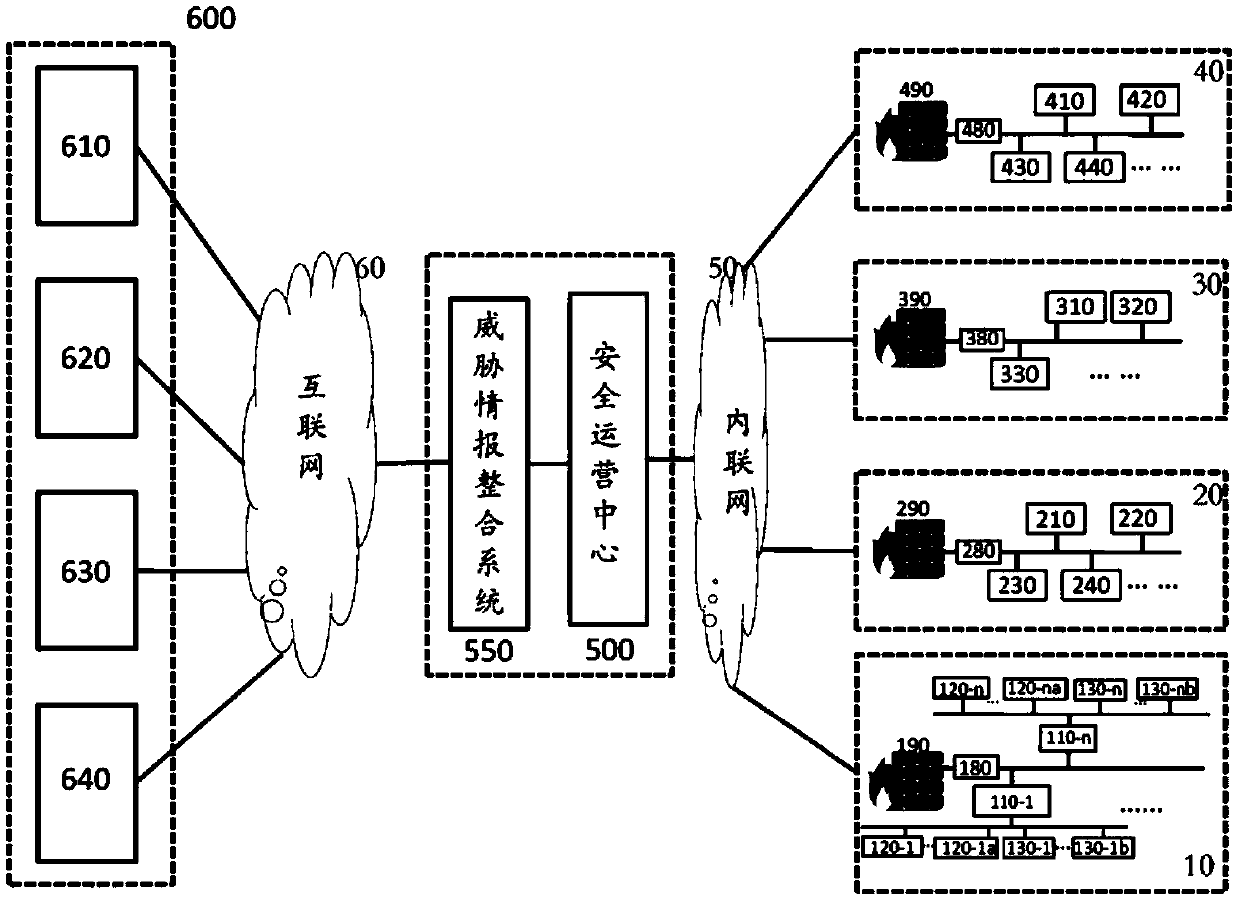
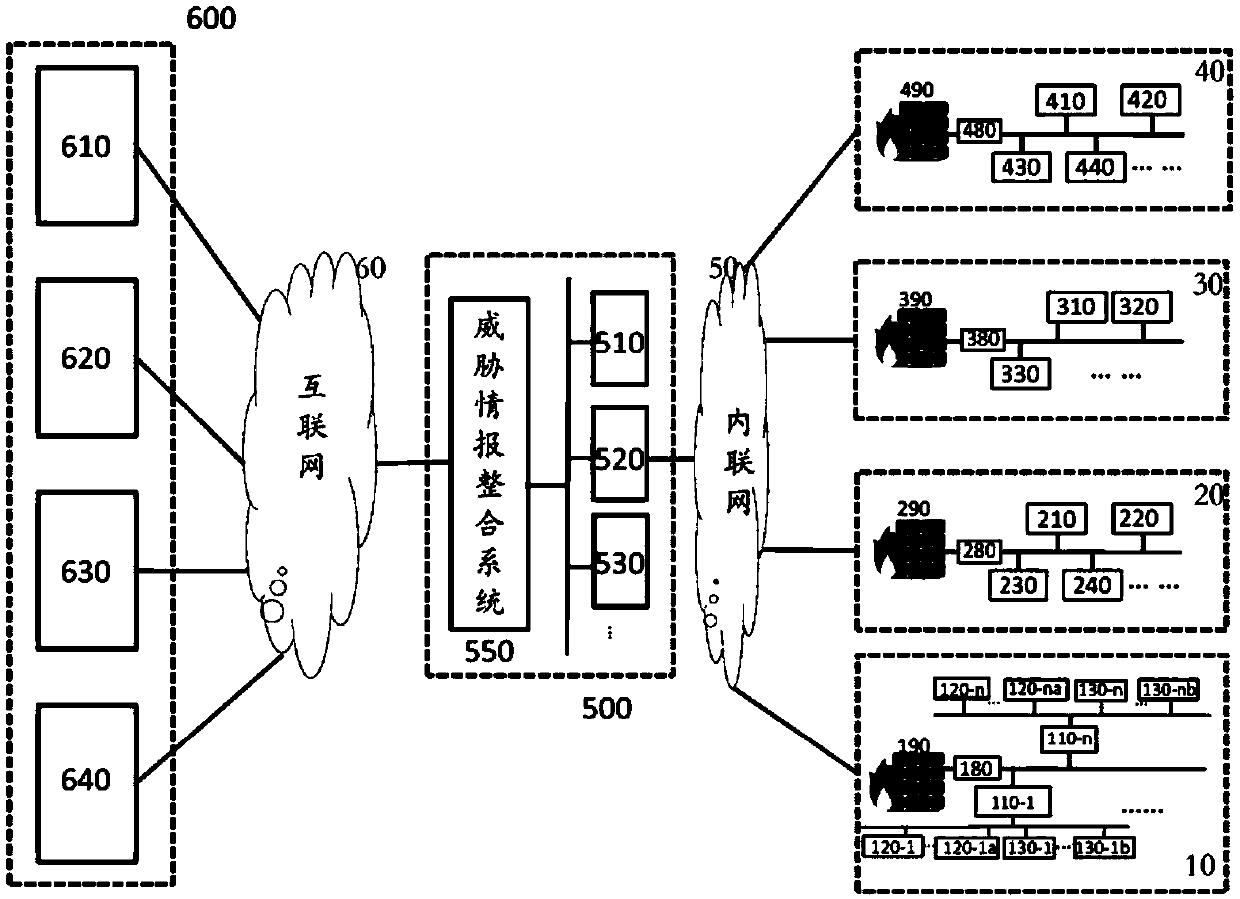
The invention discloses a threat information integration system and method for an industrial environment. The threat information integration system collects original threat information data from at least one external threat information source and converts the original threat information data to be in a standard format, performs clustering analysis on the threat information data in the standard format by utilizing a non-supervised machine learning algorithm, verifies obtained threat information data clusters, classifies the threat information data clusters according to calculation characteristics of target network assets, and converts all the data in the threat information data clusters in a corresponding category of a target network to be in a data format operable for a target network security operation center. A security management system has more pertinence in the aspects of threat detection and event response; only the threat information data conforming to the target network characteristics can be converted to be in the data format operable for the target network security operation center, so that the working efficiency of the security operation center during use of external threat information is greatly improved.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +2
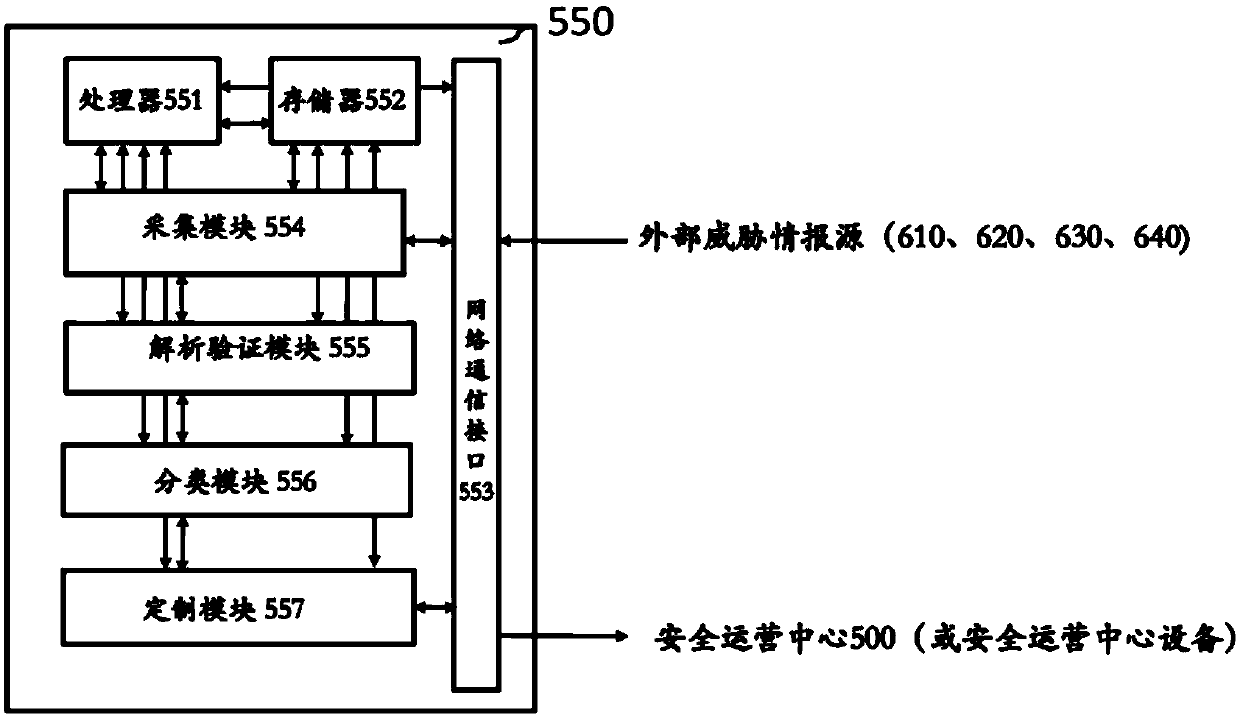
Dynamically modeling workloads, staffing requirements, and resource requirements of a security operations center
A method and associated systems for dynamically modeling workloads, staffing requirements, and resource requirements of a security operations center. A processor receives an average rate at which the center receives threats, an average time needed to handle a threat, a target time within which the center desires to respond to a threat, and a target service level that characterizes a goal of handling a certain portion of a workload within certain constraints. The processor develops a model of the operations center and allows the user to fine-tune the model by proposing what-if scenarios. The processor uses statistical methods that time-distribute characteristics of the workload and uses staff-availability information to translate the model into an interval capacity plan, which the user may further fine-tune by proposing additional scenarios. The processor continues to refine the model by comparing real-world results with the capacity plan's forecasts and by considering further user input.
Owner:IBM CORP
Systems and methods of responding to cyber security threats
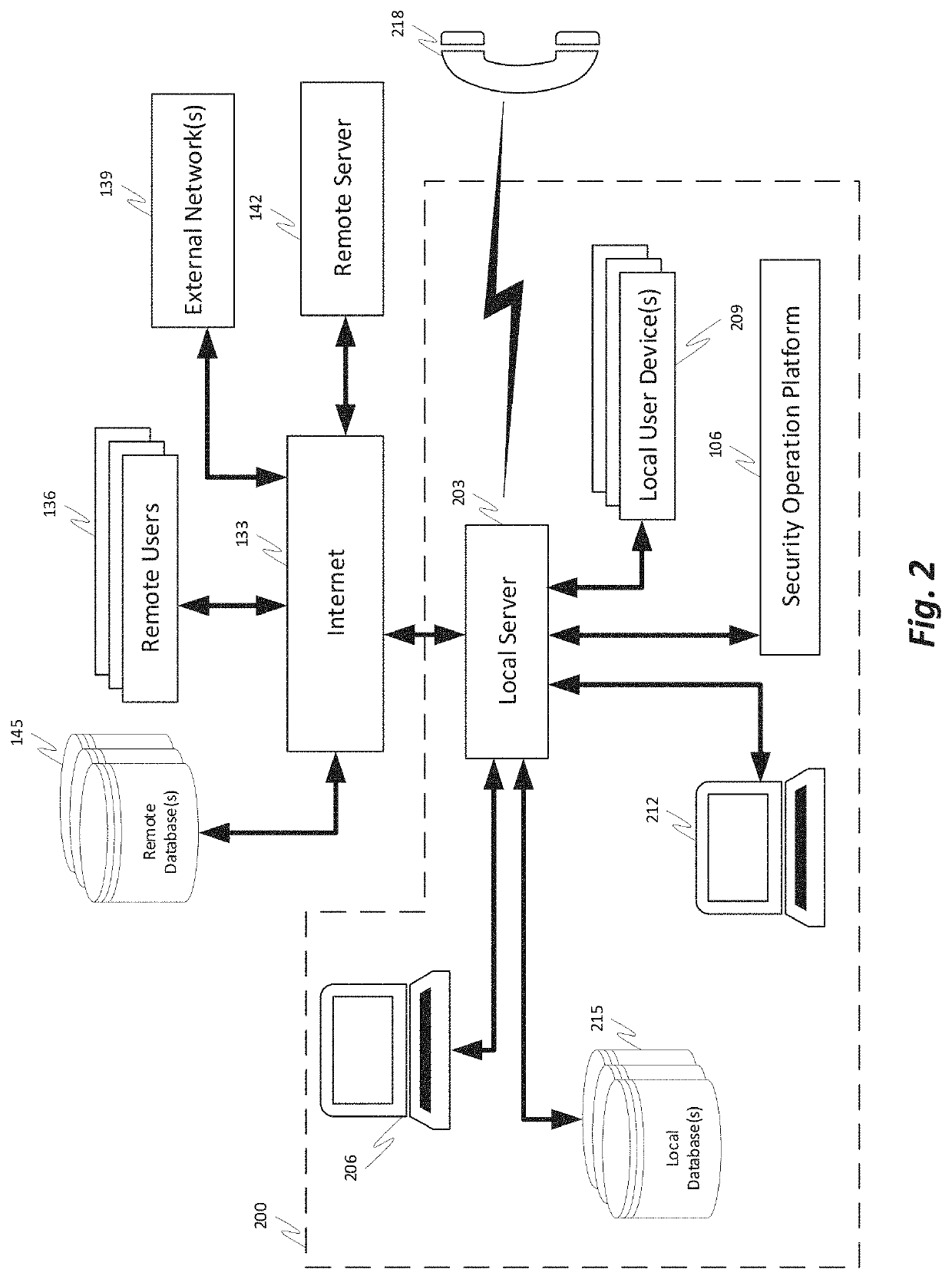
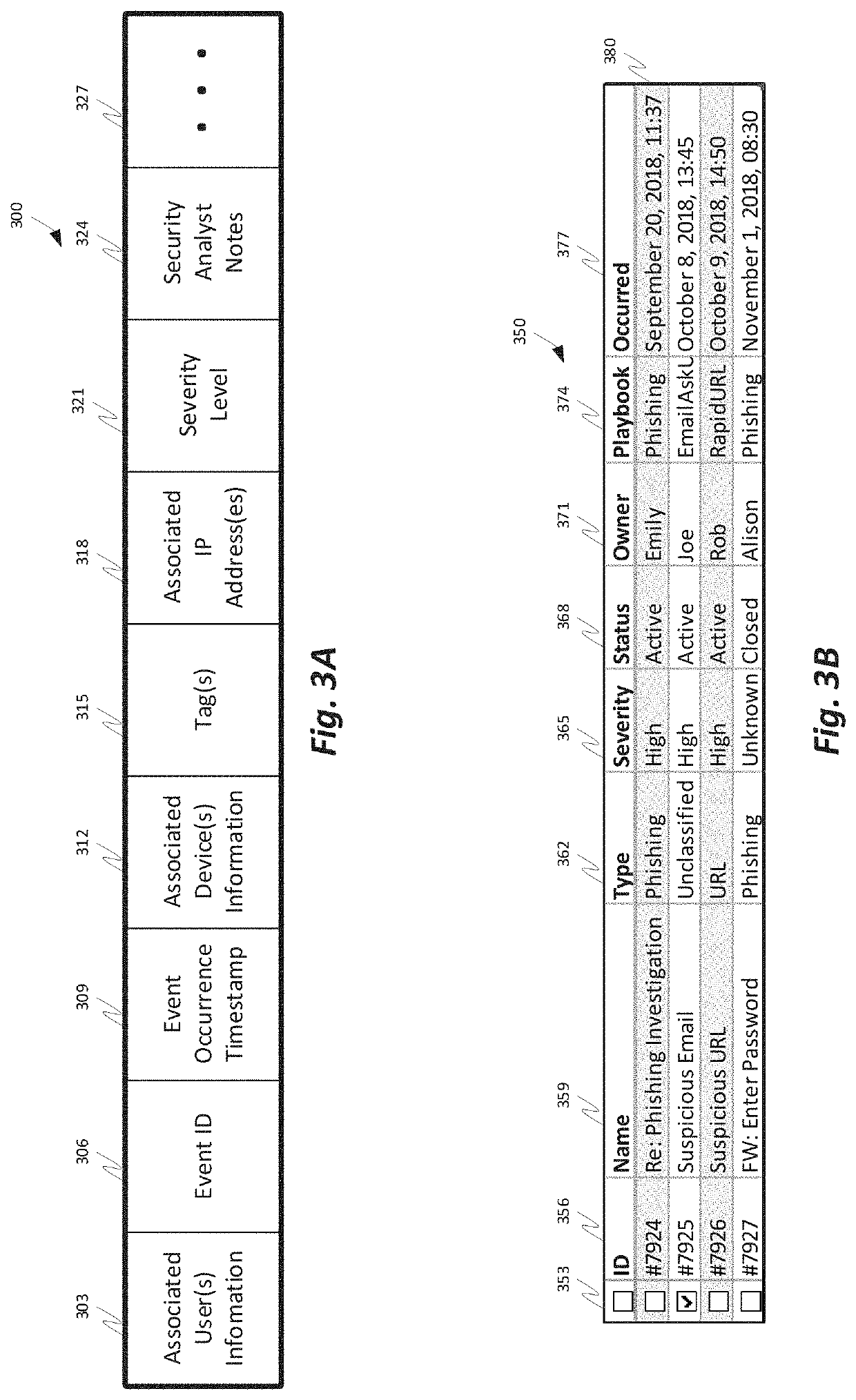
A comprehensive security operation platform with artificial intelligence capabilities which may collaborate and / or automate tasks, including complex and / or redundant security tasks. An automated system may assist security analysts and security operations center managers in discovering security incidents. A comprehensive security operations platform may combine intelligent automation scale and collaborative human social learning, wisdom and experience. An automated system may empower security analysts to resolve incidents faster and reduce redundancy through collaboration with peers in virtual war rooms. An automated system may automate security analyst work by executing tasks from the war room or by following playbooks defined by the security analysts.
Owner:PALO ALTO NETWORKS INC
Domain name system security network
In one embodiment, a DNS security network includes several DNS appliances and a security operations center (SOC) server computer. The SOC server computer may receive telemetry data from the DNS appliances, the telemetry data comprising information about DNS client queries received in the respective DNS appliances. From the telemetry data, the SOC server computer may generate security policies for distribution to the DNS appliances. The security policies may be used by the DNS appliances to determine whether a DNS client query is originated by a client computer performing a prohibited activity (e.g., sending spam, communicating with a zombie control computer, navigating to a prohibited website, etc.). An answer to a client query may be replaced or discarded altogether in cases where the originator is performing a prohibited activity.
Owner:TREND MICRO INC
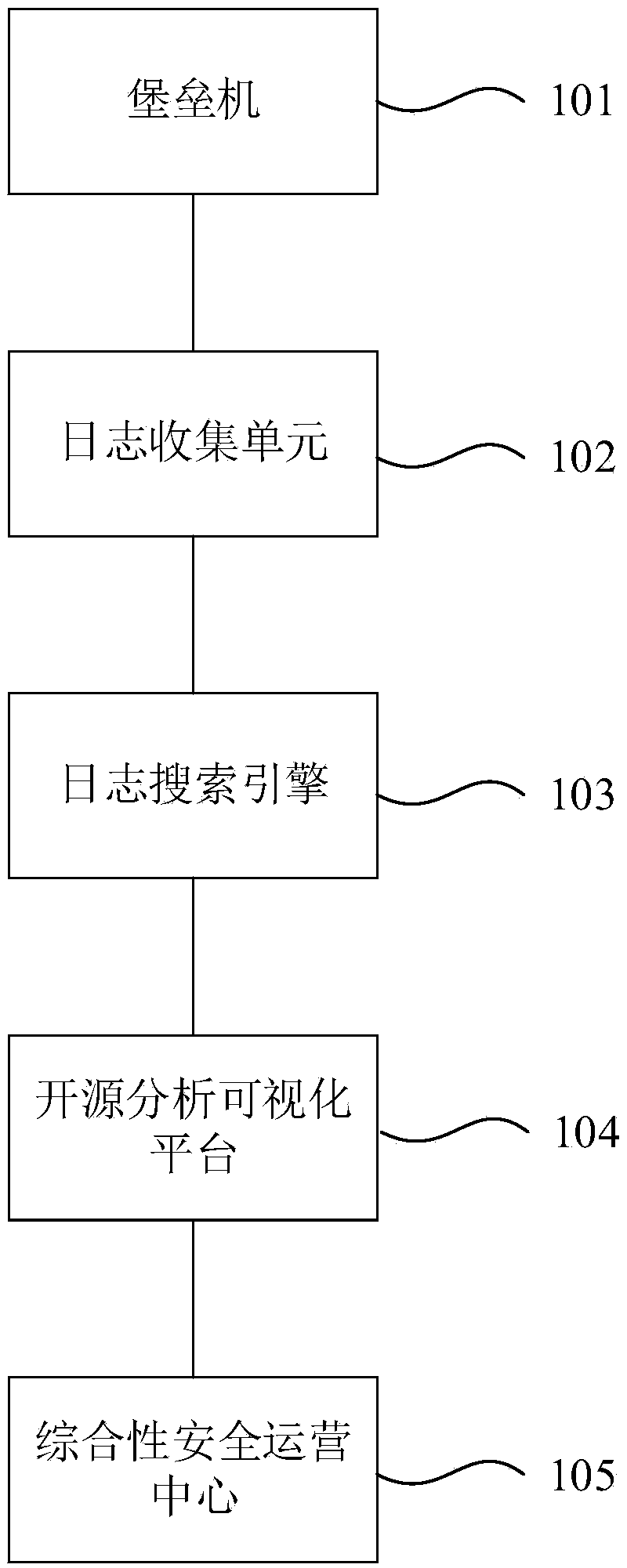
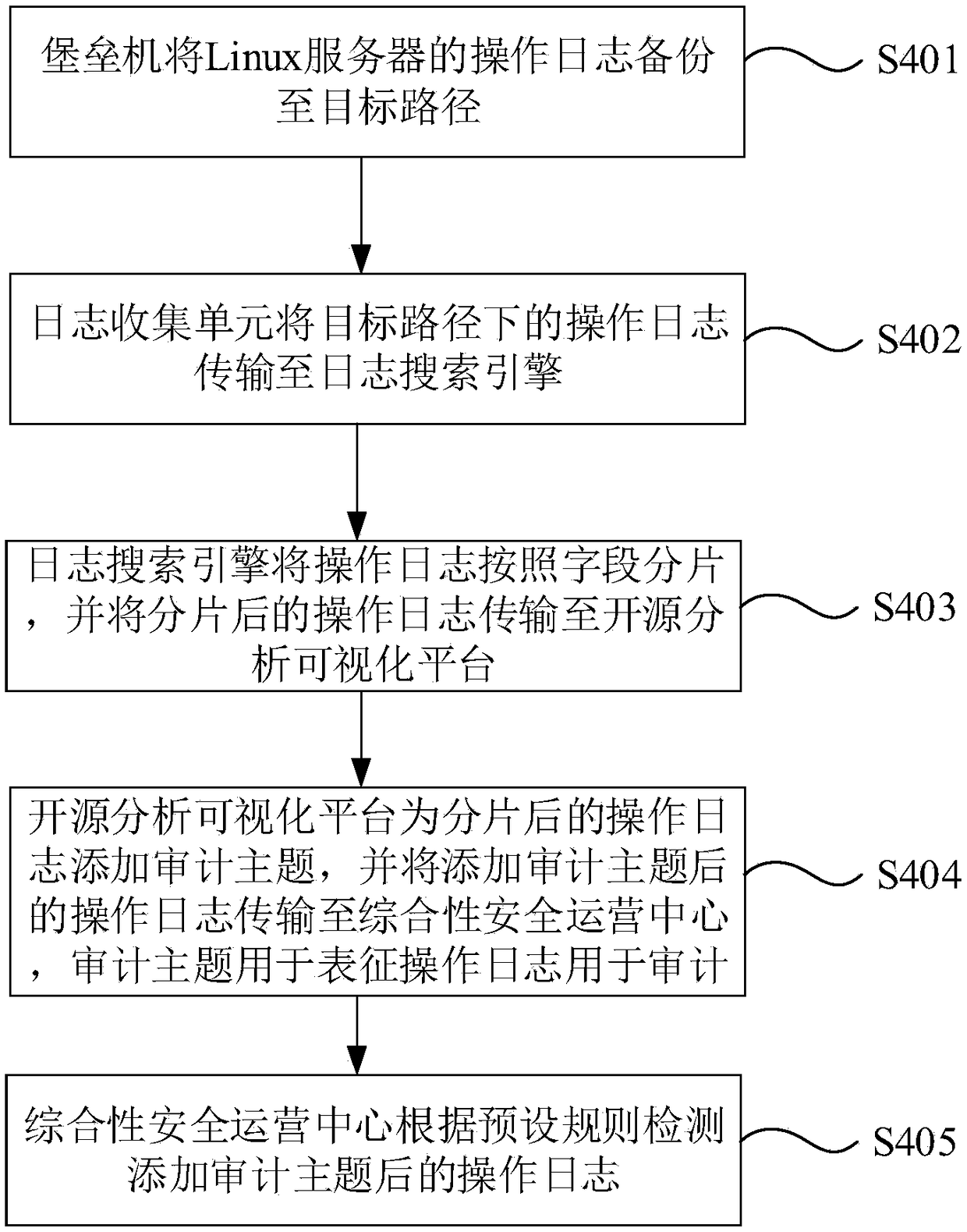
Linux operation log audit system and method
ActiveCN109033813AEnsure safetyAvoid lossHardware monitoringPlatform integrity maintainanceSecurity operations centerGNU/Linux
The invention discloses a Linux operation log audit system and method. The Linux operation log audit system comprises a fortress machine, a log search engine, a log collection unit, an open source analysis visual platform and a comprehensive safety operation center. The fortress machine is used for backing up the operation logs of the Linux server to the target path; the log collection unit is used for transmitting the operation log under the target path to the log search engine. The log search engine is used for slicing the operation log according to the fields and transmitting the sliced operation log to the open source analysis visualization platform. The open source analysis visual platform is used to add audit topics to the fragmented operation logs; the comprehensive safety operationcenter is used to detect the operation logs after adding audit topics according to the preset rules. The invention can audit the Linux operation log in real time, and timely alarms.
Owner:携程旅游信息技术(上海)有限公司
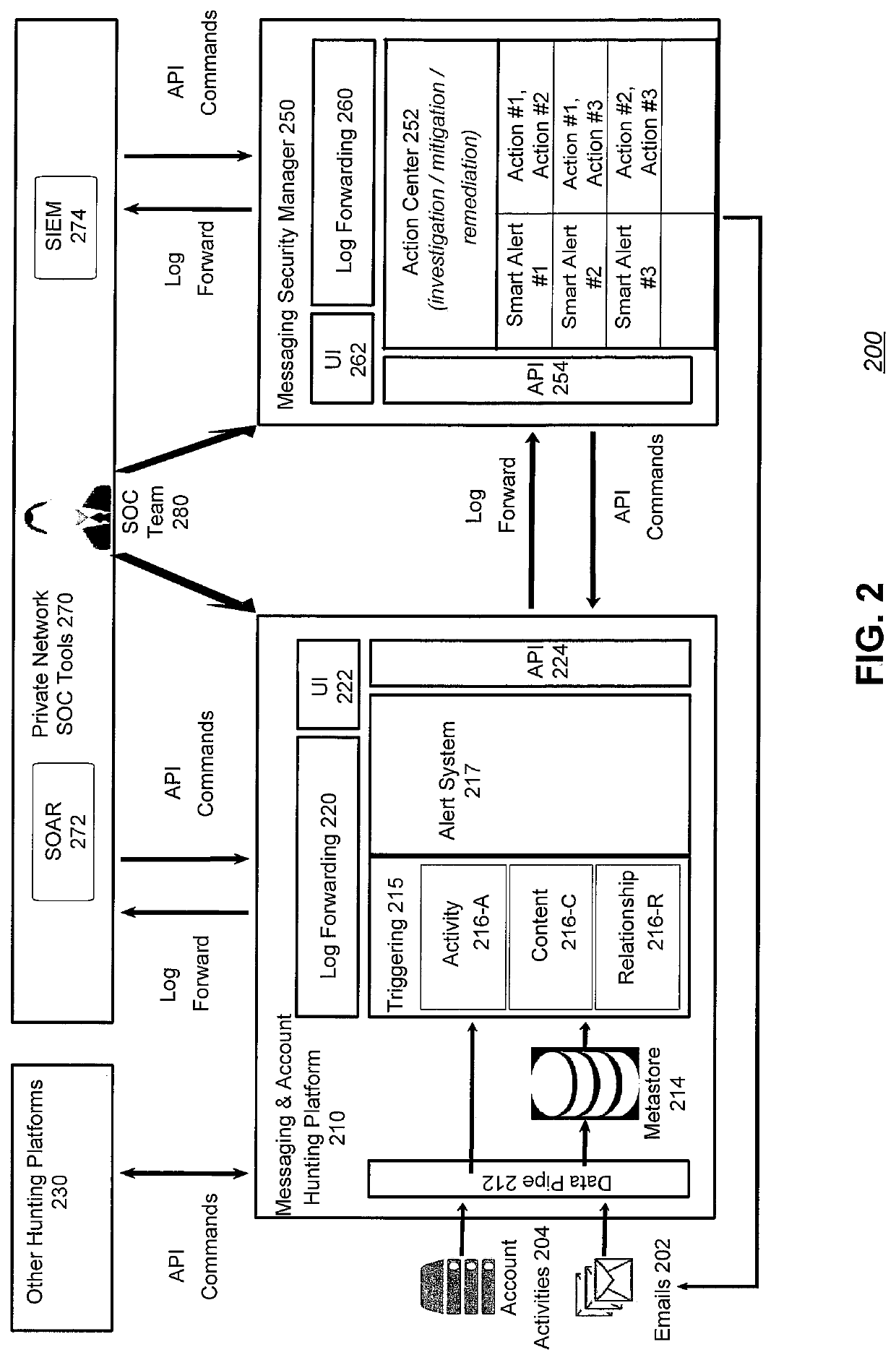
Systems and methods for detecting and responding to anomalous messaging and compromised accounts
ActiveUS11128649B1Metering/charging/biilling arrangementsAccounting/billing servicesSecurity operations centerMessage delivery
One embodiment disclosed relates to a system for detecting anomalous messaging, discovering compromised accounts, and generating responses to threatened attacks. The system utilizes API commands and log forwarding for interaction and communication between a messaging and account hunting platform, other hunting platforms, an action center, and a security operations center. Another embodiment relates to a method of, and system for, performing a complete root cause analysis. Another embodiment relates to a method of, and system for, anomaly discovery which may advantageously utilize reference data to correlate different anomalies for reporting as a single incident.
Owner:TREND MICRO INC
Collaborative analysis method of information security operation centers
ActiveCN104378364AComprehensive judgmentImprove accuracyTransmissionSecurity operations centerCorrelation analysis
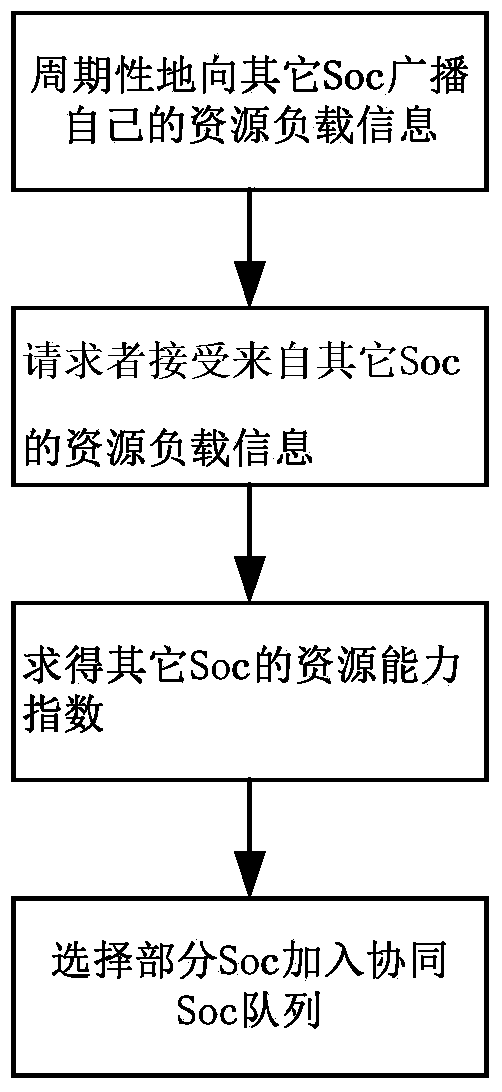
The invention relates to the technical field of information safety, in particular to a collaborative analysis method of information security operation centers. An internetwork collaborative module of one of the security operation centers sends suspected threat information, then a safety event management module analyzes the suspected threat information, and it is determined that a threat is found if the threat meets the standard of a certain attack event; a receiver finding the threat informs a sender of the suspected threat and other security operation centers of confirmation information through the internetwork collaborative module; a requester takes corresponding measures through a safety strategy library; if the sender does not find the threat by himself, correlation analysis of the second stage is carried out by communication between the sender and other receivers; all the security operation centers take corresponding measures for response after receiving the information. The collaborative analysis method of the information security operation centers achieves the collaborative analysis of the information security operation centers and can be used for the security operation centers for information security operation.
Owner:GUANGDONG ELECTRONICS IND INST
Enterprise security operation center (SOC) Bot
InactiveCN106850293AAccurate identificationImprove detection efficiencyData switching networksSecurity operations centerEnterprise networking
The invention discloses a security operation center (SOC) Bot for assisting an SOC analyst in detecting, surveying and recovering various events in enterprise network security. The SOC Bot comprises the parts of data collection, data identification, data processing, data integration, machine learning, marking and alarming, command execution and the like, and the parts cooperate to finish the functions of enterprise security clue collection, security event monitoring and marking, security threat alarming, and security protection and recovery, provide analysis clues for the SOC security analyst, and execute tasks issued by the security analyst. Through the Bot, the labor intensity of the analyst can be relieved greatly, and the efficiency and automation and intelligence levels of enterprise security detection and maintenance work are increased and raised greatly.
Owner:浙江航芯智控科技有限公司
Systems and methods of network-based intelligent cyber-security
A comprehensive security operation platform with artificial intelligence capabilities which may collaborate and / or automate tasks, including complex and / or redundant security tasks. An automated system may assist security analysts and security operations center managers in discovering security incidents. A comprehensive security operations platform may combine intelligent automation scale and collaborative human social learning, wisdom and experience. An automated system may empower security analysts to resolve incidents faster and reduce redundancy through collaboration with peers in virtual war rooms. An automated system may automate security analyst work by executing tasks from the war room or by following playbooks defined by the security analysts.
Owner:PALO ALTO NETWORKS INC
Intelligent security management system
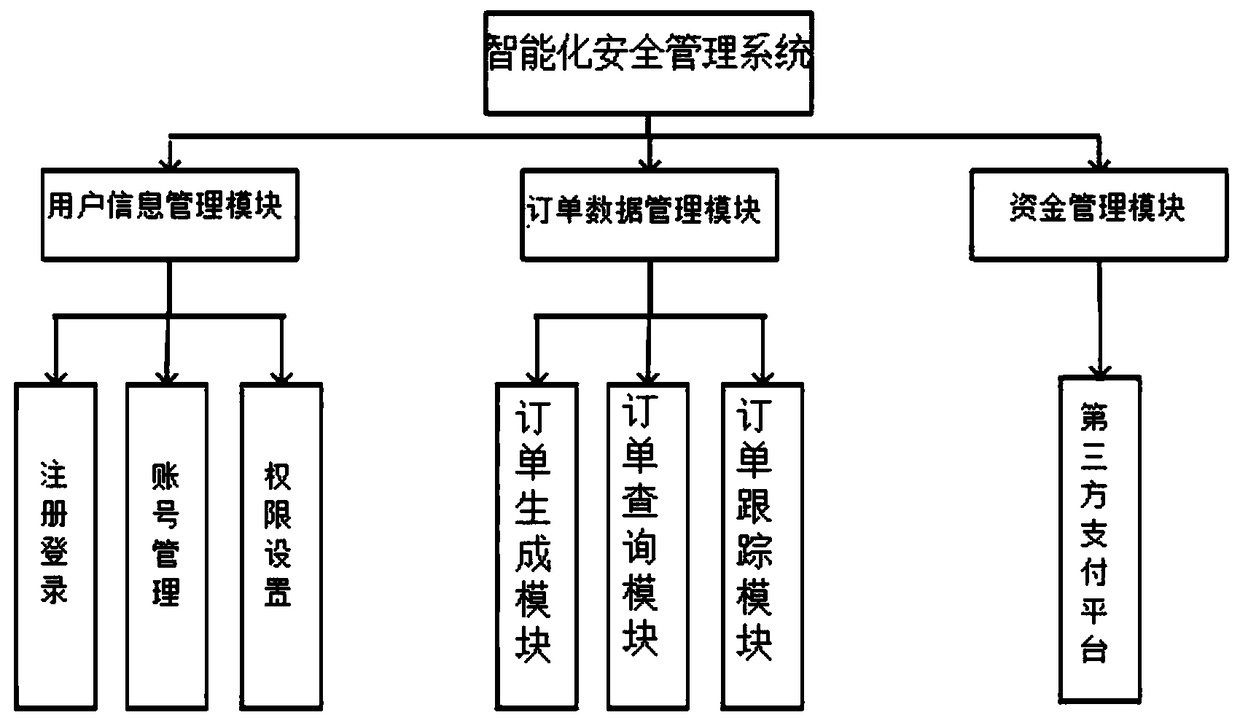
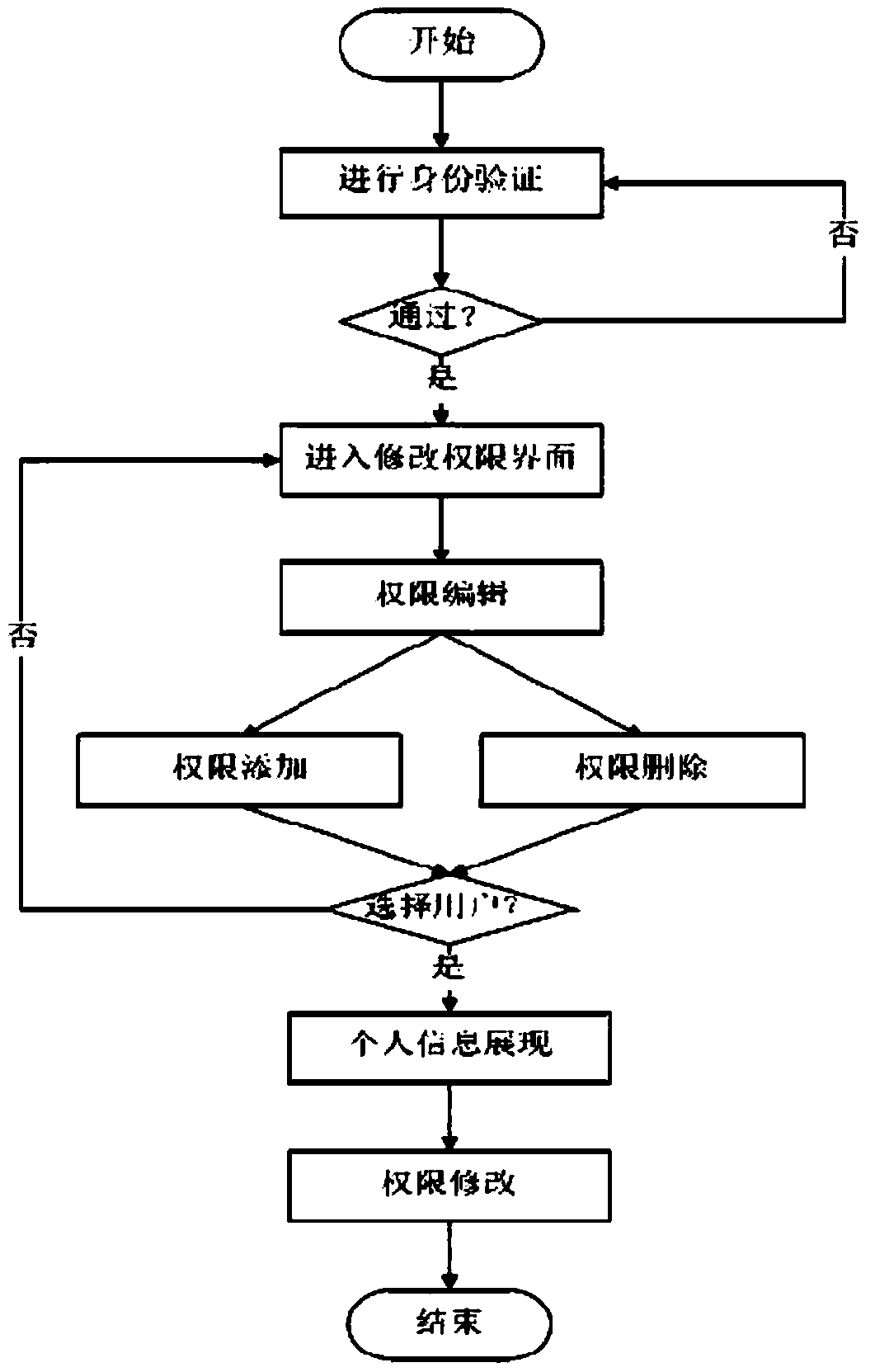
The invention provides an intelligent security management system, and relates to the field of internet application technology. The system includes a user information management module, a fund management module and an order data management module. The user information management module is used for registration and login, member auditing, account number management, permission setting and role assignment. The order data management module includes an order generation module, an order query module and an order tracking module. The fund management module is connected with a third-party payment platform in a butt-joint manner through an API interface, and is used to enable each user to carry out recharging, payment and cash withdrawal operations on an account thereof, audit funds, and monitor andmanage fund flow directions in real time. The system covers security monitoring and management of platform information, data and funds, provides a security-centric intelligent processing and monitoring system for enterprise users, helps an enterprise in realizing counting, which provides a basis of multiple sub-security-operation-centers and supports data, funds and information of ultra-large scales, on the basis of a centralized security running center when a Chuangshijie live-streaming system is used, and can realize real-time monitoring and layer-by-layer management.
Owner:闫俊杰
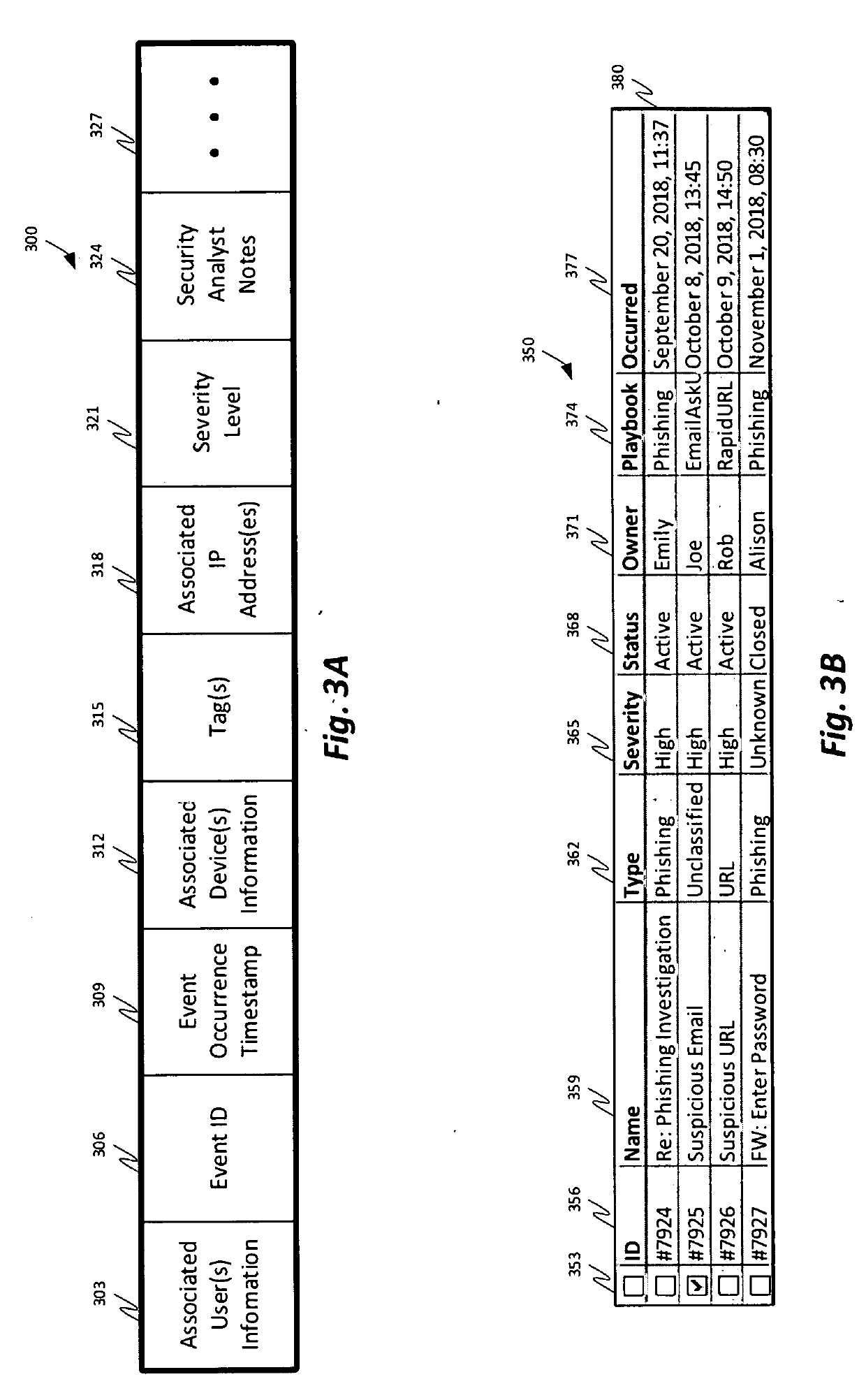
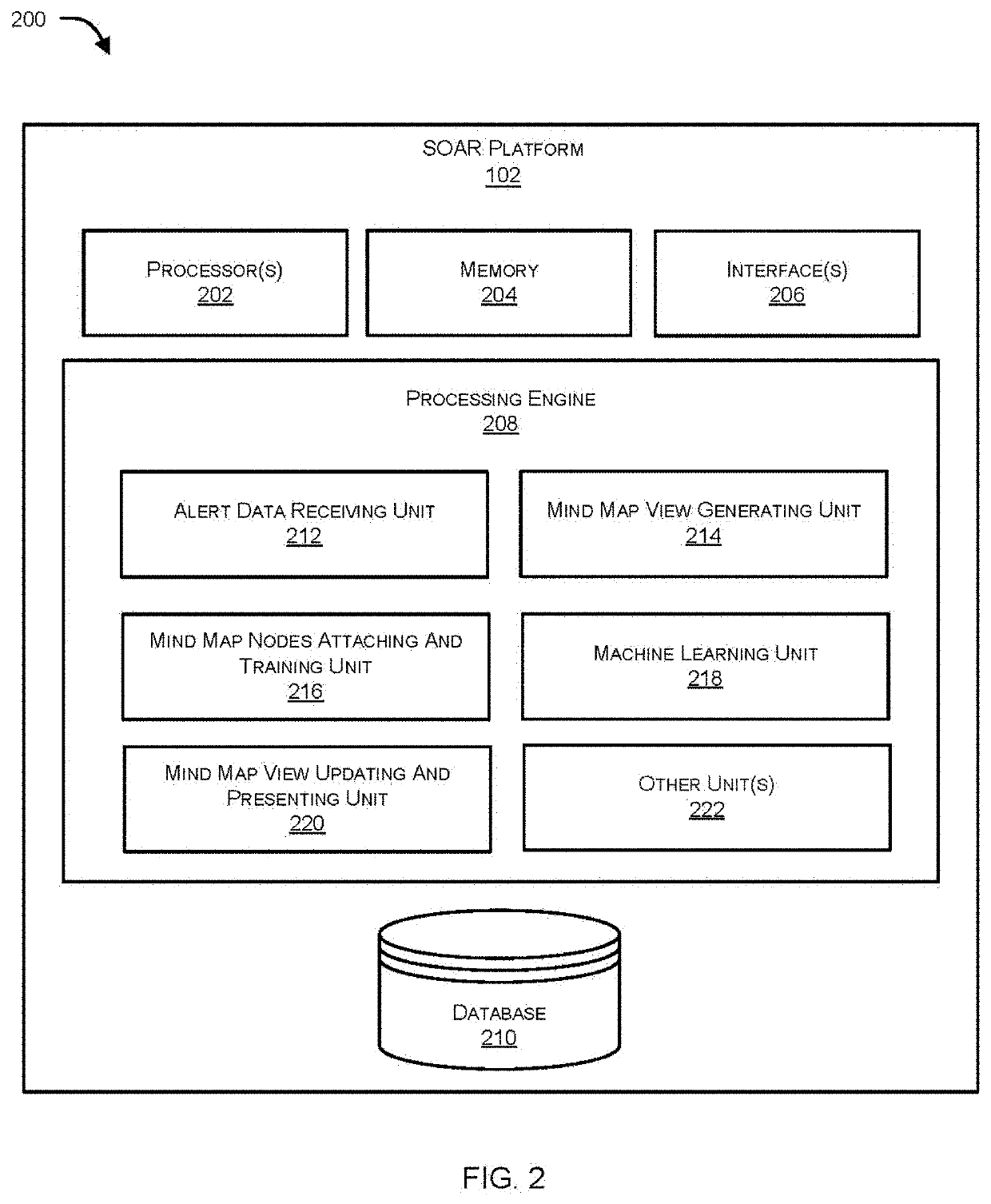
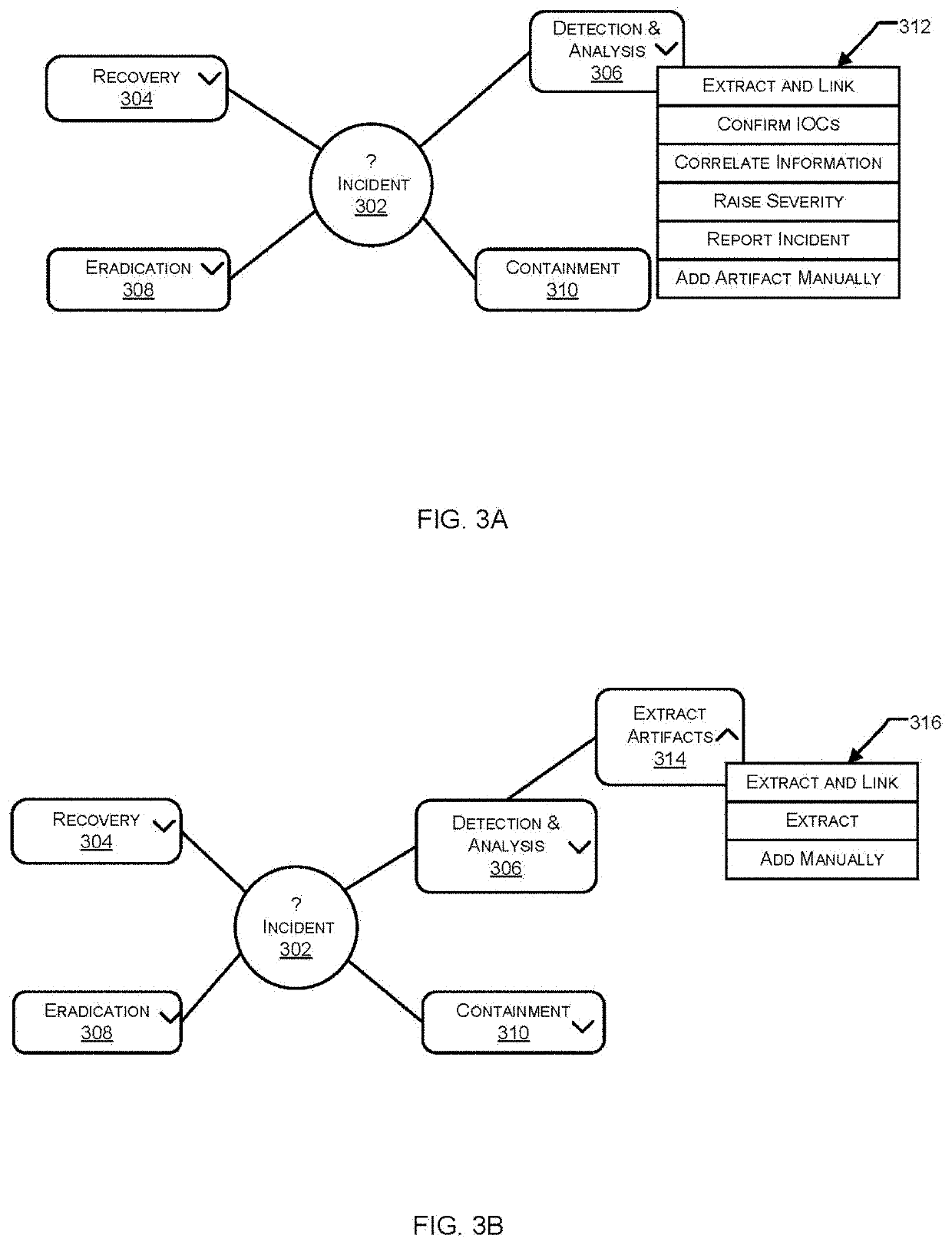
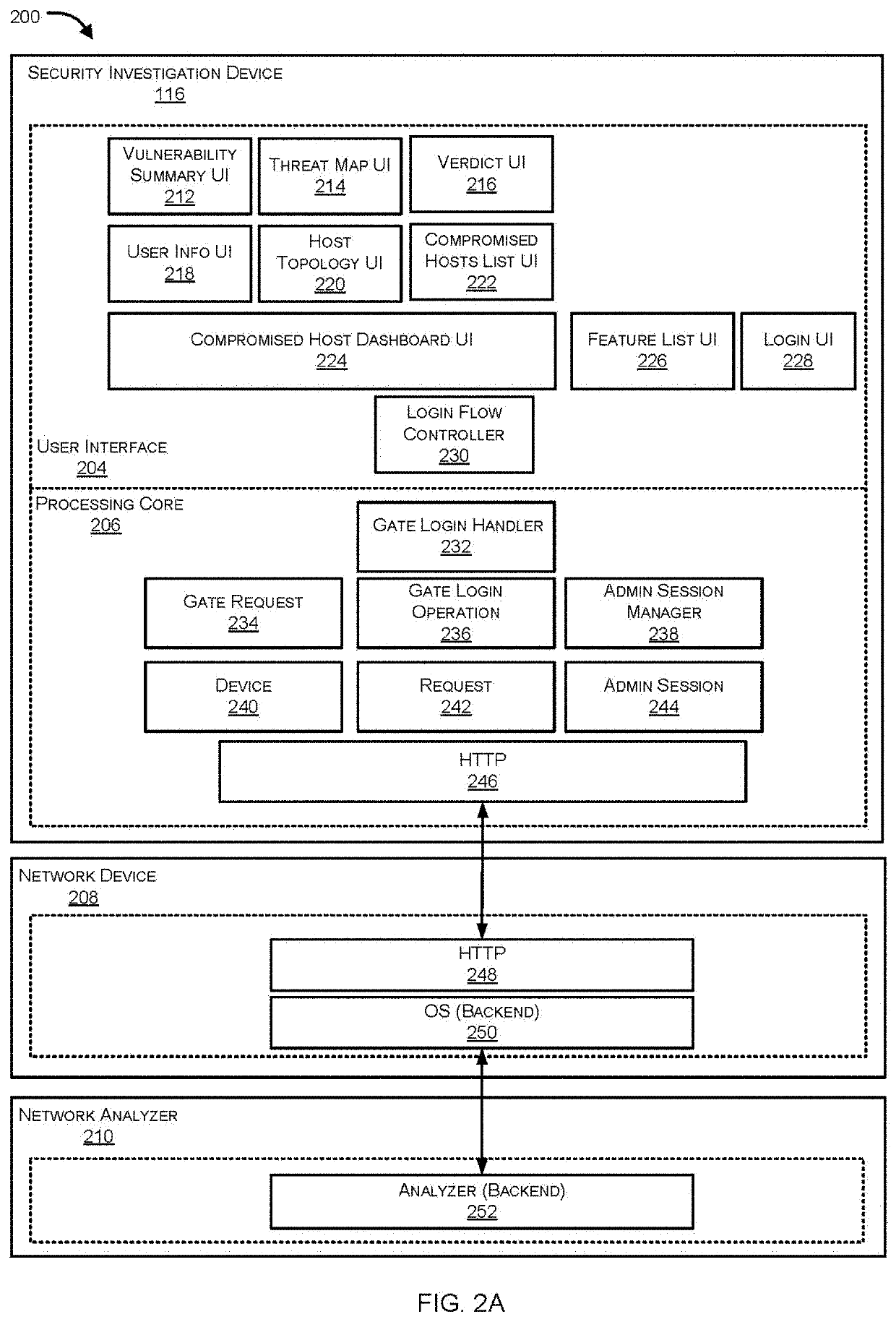
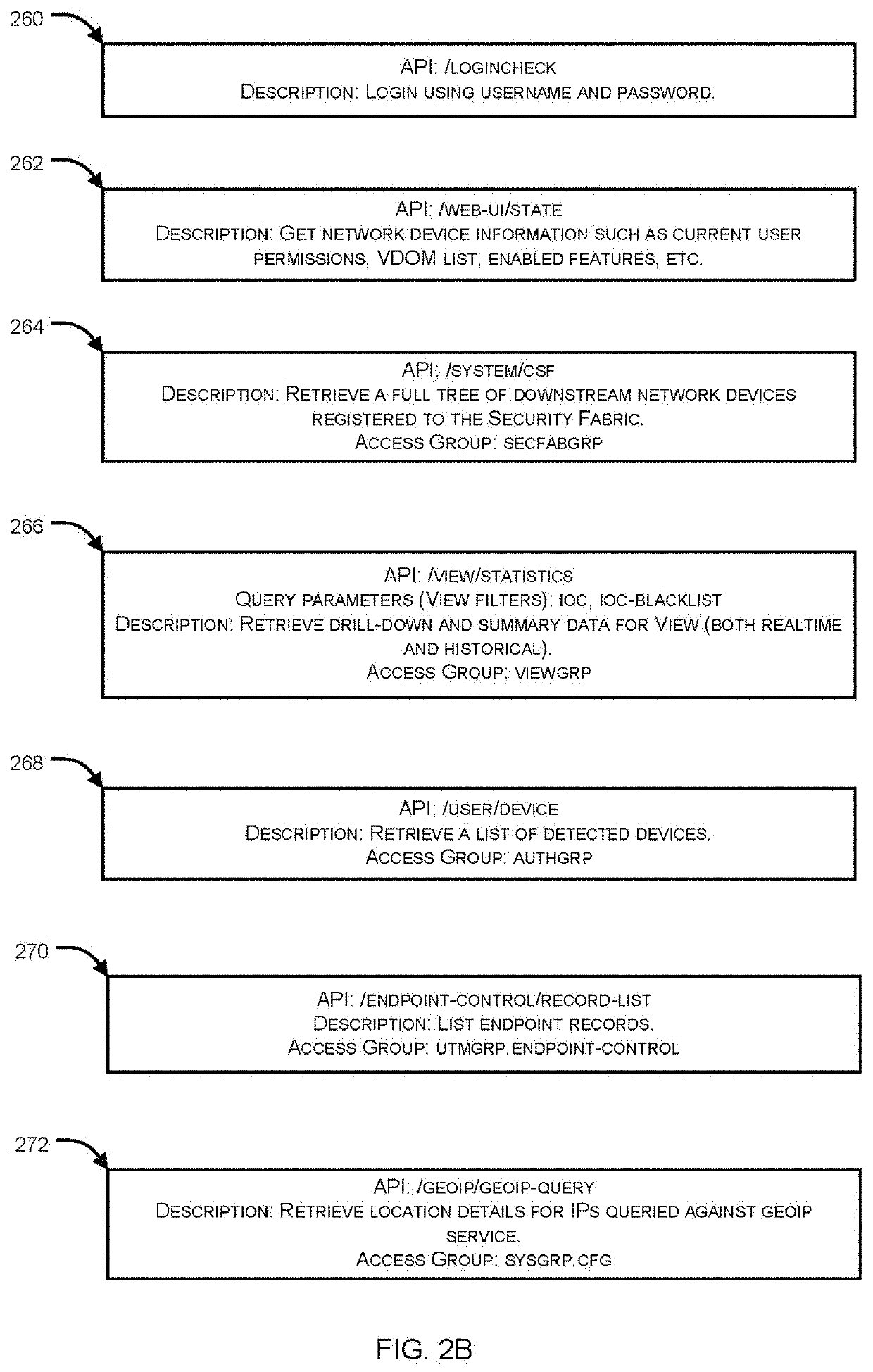
Facilitating security orchestration, automation and response (SOAR) threat investigation using a machine-learning driven mind map approach
InactiveUS20210297427A1Machine learningTransmissionGraphical user interfaceSecurity operations center
Systems and methods for facilitating a mind map approach to a SOAR threat investigation are provided. A SOAR platform operatively coupled with a Security Operation Center (SOC) of a monitored network receives alert data pertaining to an incident. A mind map view is generated within a graphical user interface. The mind map view includes a primary node corresponding to the incident, one or more field nodes associated with the primary node, one or more action nodes based at least on one of the one or more field nodes. Each of the action nodes is associated with one or more dynamic actions selectable by an analyst. Responsive to selection of a dynamic action, at least one field node or a suggested actions associated with a corresponding action node is suggested by a machine-learning engine based on the selection. The mind map view is updated in real time to include the suggestion.
Owner:FORTINET
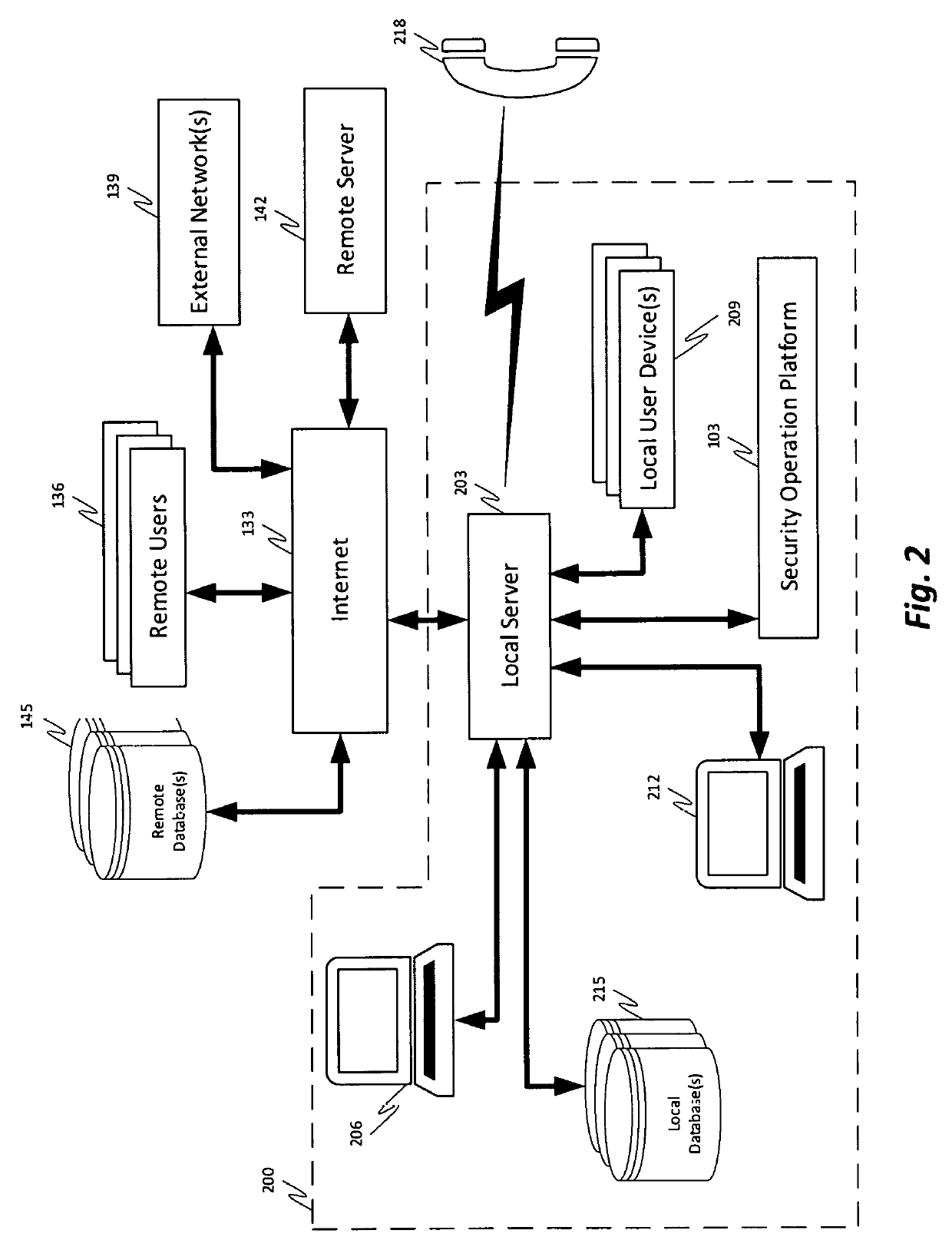
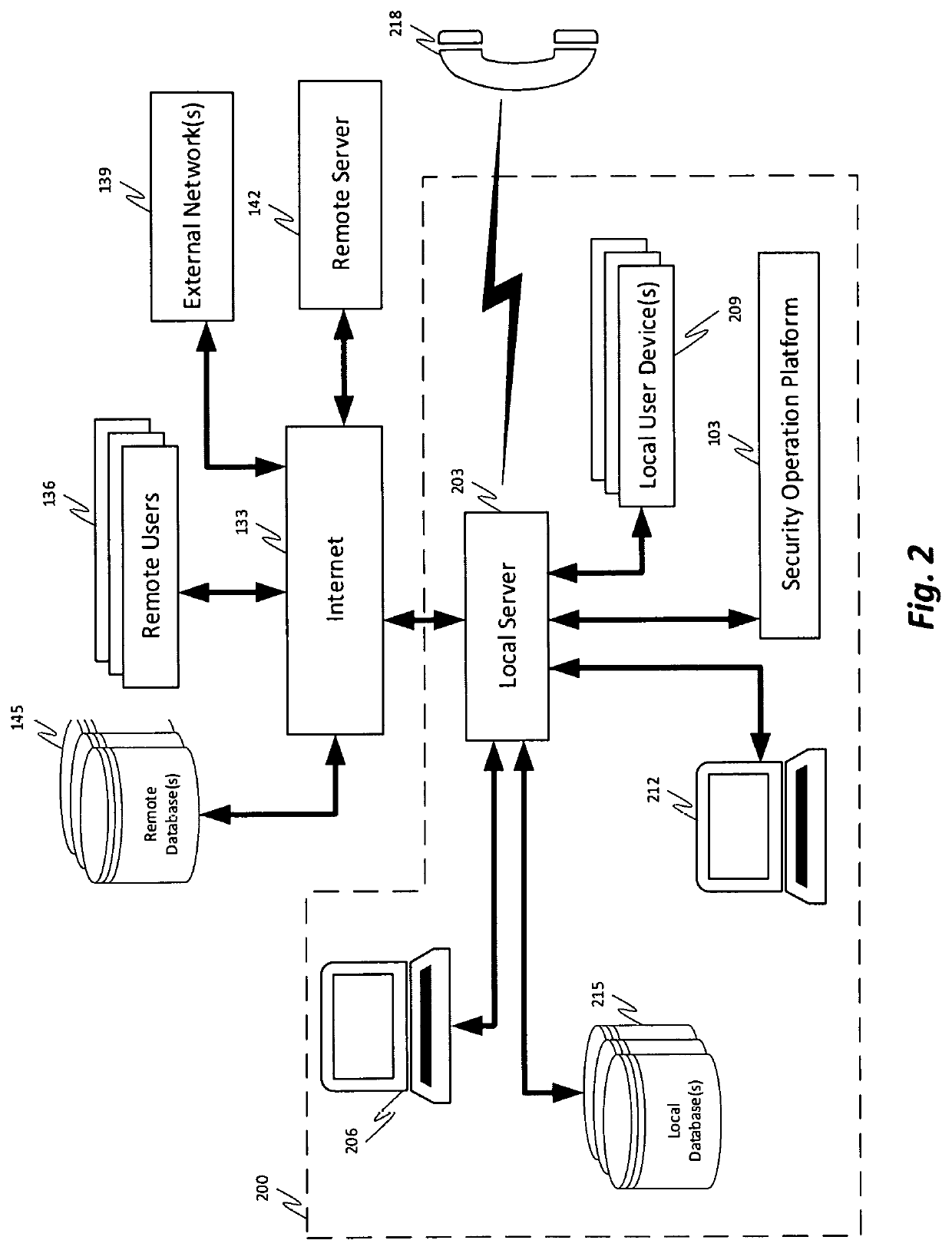
Remote monitoring of a security operations center (SOC)
Systems and methods for remote monitoring of a Security Operations Center (SOC) via a mobile application are provided. According to one embodiment, a management service retrieves information regarding multiple network elements that are associated with an enterprise network and extracts parameters of the monitored network elements from the retrieved information. The management service prioritizes the monitored network elements by determining a severity level associated with security-related issues of the network elements and generates various monitoring views that summarize in real time various categories of potential security-related issues detected by the SOC. Further, the management service assigns a priority to each monitoring view and displays a video on the display device that cycles through monitoring views in accordance with their respective assigned priorities.
Owner:FORTINET
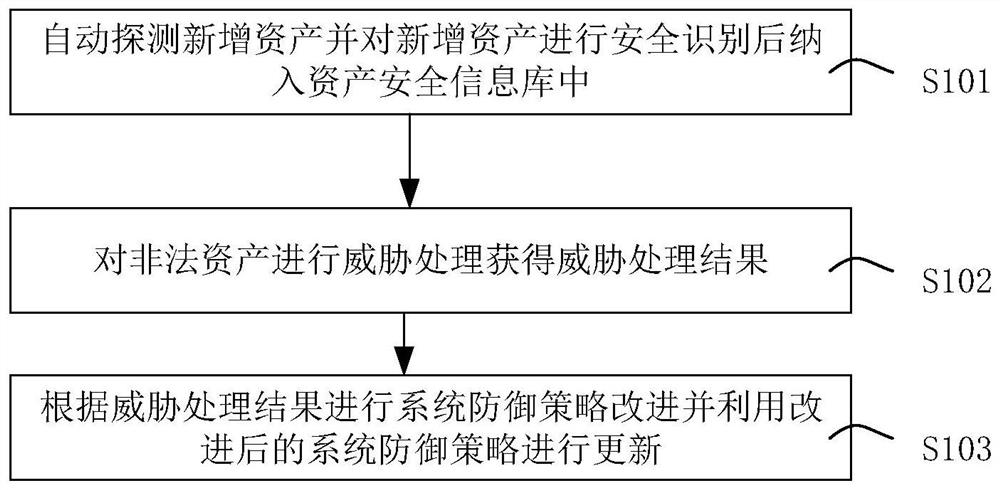
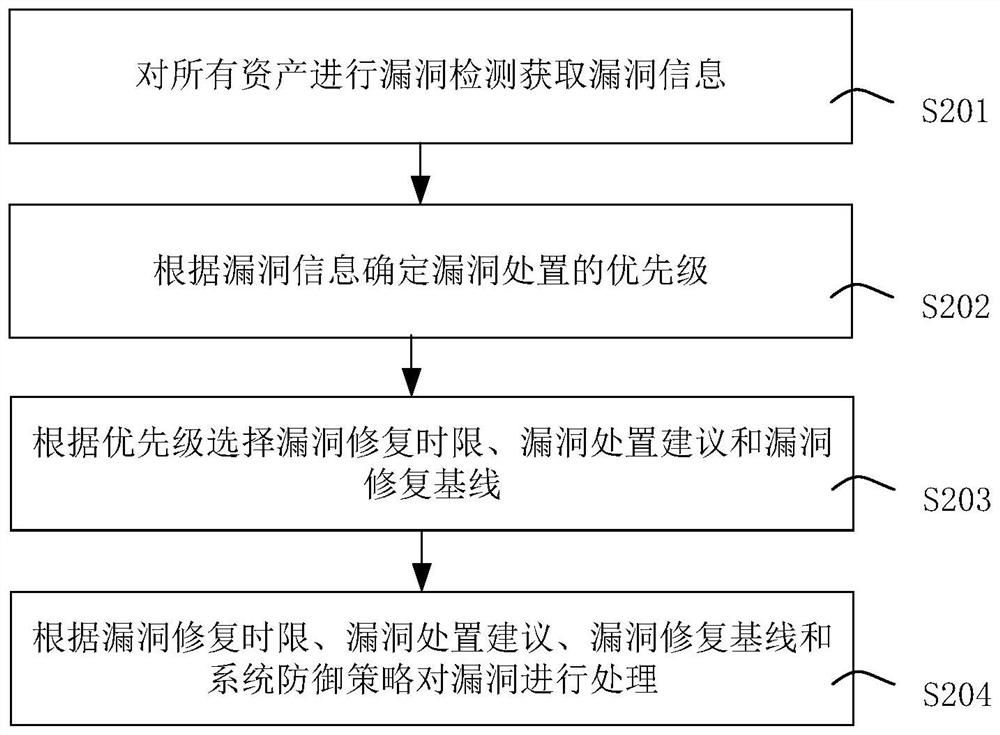
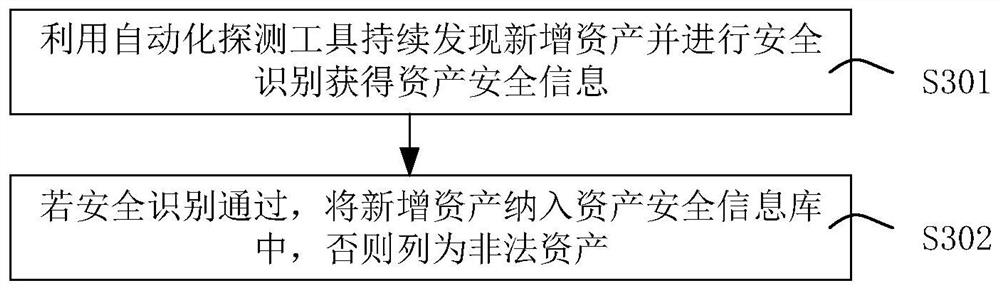
Data center operation and maintenance security management and control method and device
PendingCN114329498AImprove securitySolve management problemsPlatform integrity maintainanceData centerIT service management
The invention provides a data center operation and maintenance safety management and control method and device, and belongs to the technical field of finance, and the method comprises the steps: automatically detecting newly-added assets, and carrying out the safety recognition of the newly-added assets; performing threat processing on the illegal assets to obtain a threat processing result; and improving a system defense strategy according to a threat processing result, and updating by using the improved system defense strategy. According to the invention, by constructing the operation and maintenance security management and control platform of the data center, the problems that a security operation center and situation awareness cannot communicate with an asset management platform, an IT service management platform, a big data analysis platform and a data bus, and the source of security information is relatively single are solved; the problem of security asset isolation is also solved, and the management problem of security assets and threat intelligence is solved by using the CMDB.
Owner:工银科技有限公司 +1
Total property intelligence system
ActiveUS11010614B2Multiple keys/algorithms usagePublic key for secure communicationPhysical securityEngineering
A total property security system may be implemented to conduct security and surveillance operations. The system includes security operations centers that are connected to one or more sensors and vehicles for collecting and transmitting surveillance data to a database hosted on cloud services. The collected surveillance data is analyzed in order to automatically deploy security measures and / or recommend courses of action using a rules engine that can be configured to client-specific or user-specific security needs. The cloud services can provide a set of application program interface services that can act on the surveillance operations center. Sensor fusion data and other surveillance data can be also transmitted to vetted monitoring service providers on a subscription basis to provide physical security services to the area within the property perimeter. During the subscription period, the selected monitoring service providers can obtain time-based encryption token for accessing surveillance data.
Owner:KLEIN MATIAS
Active Machine Learning System for Dangerous Host Monitoring
ActiveCN106790256BRealize detectionRealize the alarmTransmissionSecurity information and event managementDeep belief network
The invention discloses an active machine learning system for hazardous host detection. Hosts high in possibility of being destroyed are marked by the aid of SIEM (security information and event management) warning information, various safety logs and research notes of analysts. The active machine learning system comprises parts including data collection, feature engineering, mark production, machine learning, feedback algorithms of active learning analyst insights, real-time warning and the like; natural language progressing, text mining and graphics-based methods are adopted, targets are generated and characteristics are created for machine learning; a machine learning mechanism of deep belief network, multilayer deep neutral network, random forest, support vector machine, Logistic regression and the like are adopted for machine learning. The hazardous hosts in the network can be accurately detected, false alarm rate is greatly reduced, host security detection requests and SOC (security operation center) actual investigation are considered, important security events can be handled in time, and labor cost is reduced while network security monitoring capability is improved.
Owner:浙江航芯科技有限公司
Playbook based data collection to identify cyber security threats
A comprehensive security operation platform with artificial intelligence capabilities which may collaborate and / or automate tasks, including complex and / or redundant security tasks. An automated system may assist security analysts and security operations center managers in discovering security incidents. A comprehensive security operations platform may combine intelligent automation scale and collaborative human social learning, wisdom and experience. An automated system may empower security analysts to resolve incidents faster and reduce redundancy through collaboration with peers in virtual war rooms. An automated system may automate security analyst work by executing tasks from the war room or by following playbooks defined by the security analysts.
Owner:PALO ALTO NETWORKS INC
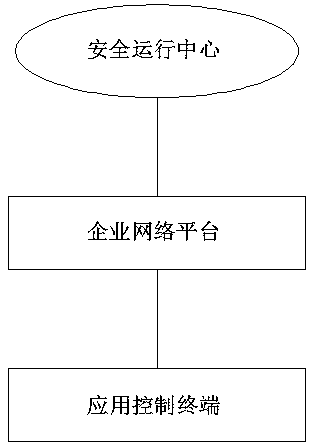
Special network security supervision system for enterprises
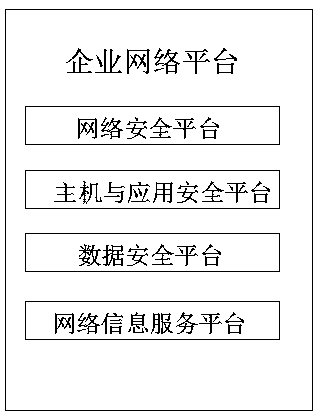
InactiveCN110708340AImprove securityComprehensive strategyData switching networksPrivate networkInformation resource
The invention discloses a special network security supervision system for enterprises, which is characterized by comprising a security operation center, an enterprise network platform and an application control terminal, the safety operation center can formulate comprehensive safety configuration and strategies for enterprises, reasonably plan and use information resources and monitor an enterprise network in real time, and the enterprise network platform can monitor all operation data information in the enterprise private network in real time. In the present invention, the enterprise special-purpose network safety supervision system adopts a structure system of one center, four platforms and five control terminals. The supervision effect of step-by-step permeation of the enterprise private network is realized; relatively unified network supervision of the enterprise private network is also realized, abnormal transmission and exchange of data in the network and in the network can be prevented through real-time monitoring of various network access devices and control terminals in the enterprise private network, and data loss or leakage caused by loopholes of the enterprise private network is prevented.
Owner:深圳市高德信通信股份有限公司
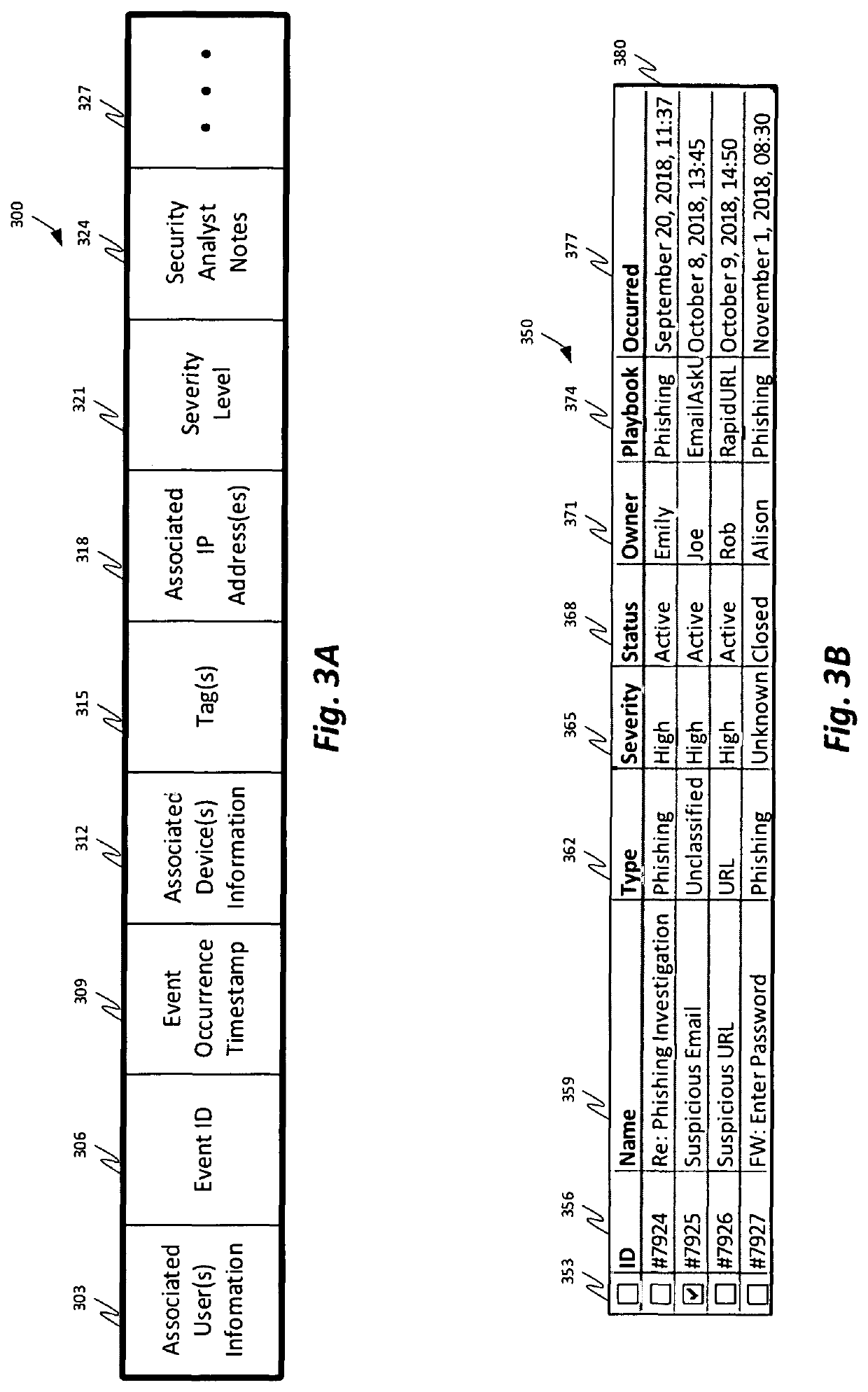
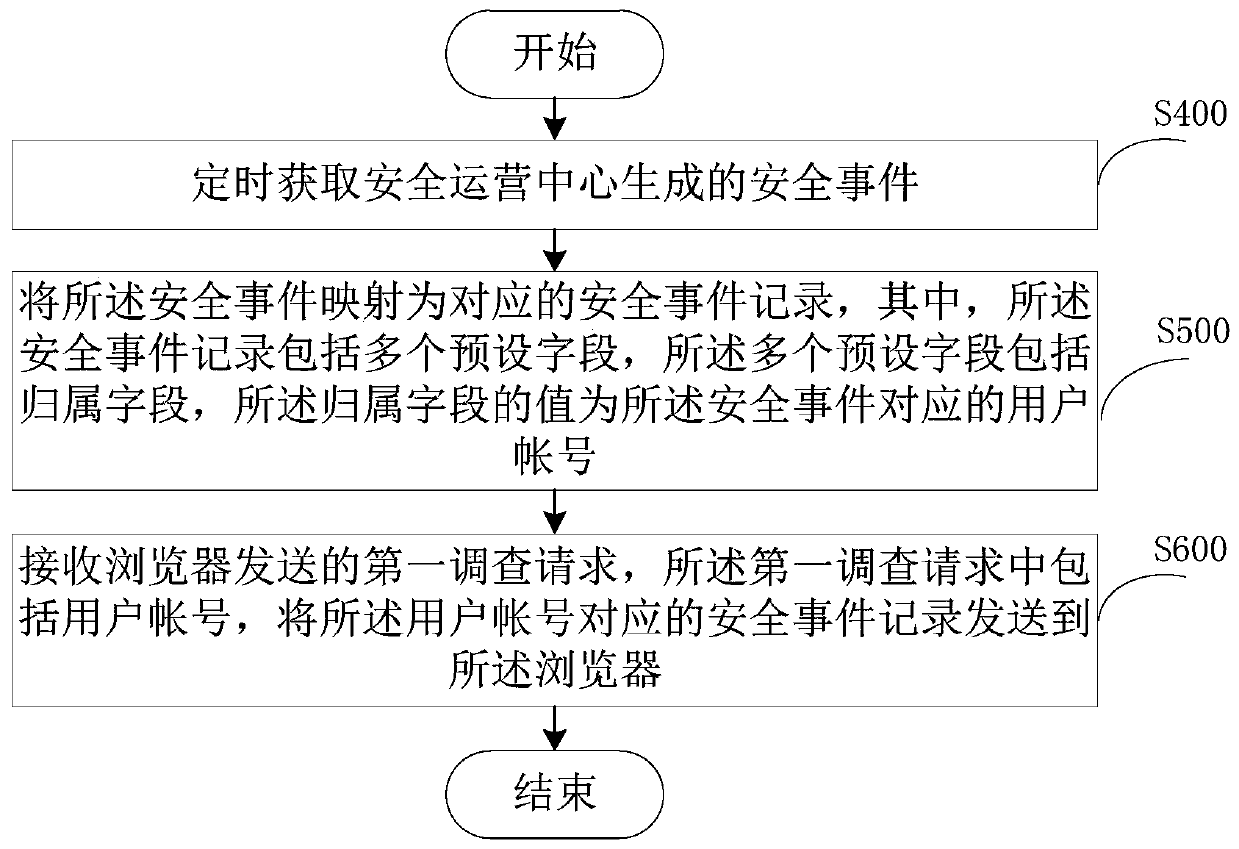
Security Incident Handling Method
ActiveCN106330909BSimple and fast searchReduce resource requirementsData switching networksSecurity operations centerComputer terminal
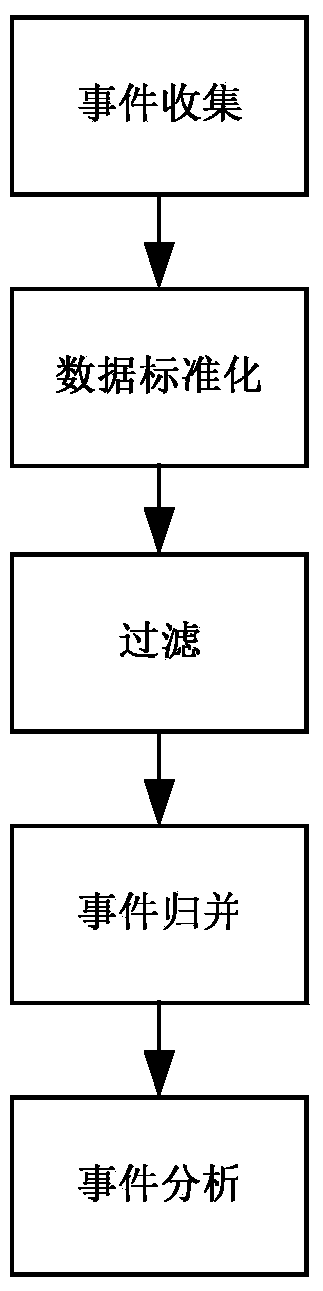
The embodiment of the invention provides a security event handling method, comprising the following steps: regularly acquiring security events generated in a security operation center; mapping the security events to corresponding security event records; receiving a first investigation request sent by a browser, wherein the first investigation request includes user accounts; and sending the security event records corresponding to the user accounts to the browser. According to the method provided by the invention, a user terminal can directly access the security events of a server side through the browser without installing a client, and because the client does not need to be connected with the server side to implement multi-channel event monitoring, the memory resource occupancy and performance influences of the server side can be greatly reduced, and the problem that events cannot be followed up and traced back due to mixed storage of original logs and the events on an SOC platform can be solved.
Owner:华青融天(北京)软件股份有限公司
Hierarchical type mobile internet security monitoring and protecting system
ActiveCN101789948BImprove safe operation capabilitiesEnsure safetyData switching networksSecurity arrangementArea networkSecurity operations center
The invention provides a hierarchical type mobile internet security monitoring and protecting system. A set of complete mobile internet security monitoring and protecting system is provided by adopting an active security monitoring and protecting technology, an intelligent detecting and analyzing technology and a customer service-oriented quality assurance policy on the basis of the further research on the characteristics of performability and maintainability of the mobile internet. The system comprises three layers of functional groups including a security operation center (SOC), a security gateway (SGW), a security access entity (SAE), and defines the basic attribute of each functional entity and the interoperability relation among the functional entities. The SOC is in charge of overall security operation monitoring management, the SGW is in charge of the flux security detection from common internet to the mobile internet, a security agent (SA) is in charge of the security monitor of in-out flux of network nodes or domestic area networks, and the SAE is in charge of monitoring the safe access and the safe operation of various types of terminals.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
A Collaborative Analysis Method for Information Security Management Center
ActiveCN104378364BComprehensive judgmentImprove accuracyTransmissionInformation security risk managementSecurity operations center
The invention relates to the technical field of information safety, in particular to a collaborative analysis method of information security operation centers. An internetwork collaborative module of one of the security operation centers sends suspected threat information, then a safety event management module analyzes the suspected threat information, and it is determined that a threat is found if the threat meets the standard of a certain attack event; a receiver finding the threat informs a sender of the suspected threat and other security operation centers of confirmation information through the internetwork collaborative module; a requester takes corresponding measures through a safety strategy library; if the sender does not find the threat by himself, correlation analysis of the second stage is carried out by communication between the sender and other receivers; all the security operation centers take corresponding measures for response after receiving the information. The collaborative analysis method of the information security operation centers achieves the collaborative analysis of the information security operation centers and can be used for the security operation centers for information security operation.
Owner:GUANGDONG ELECTRONICS IND INST
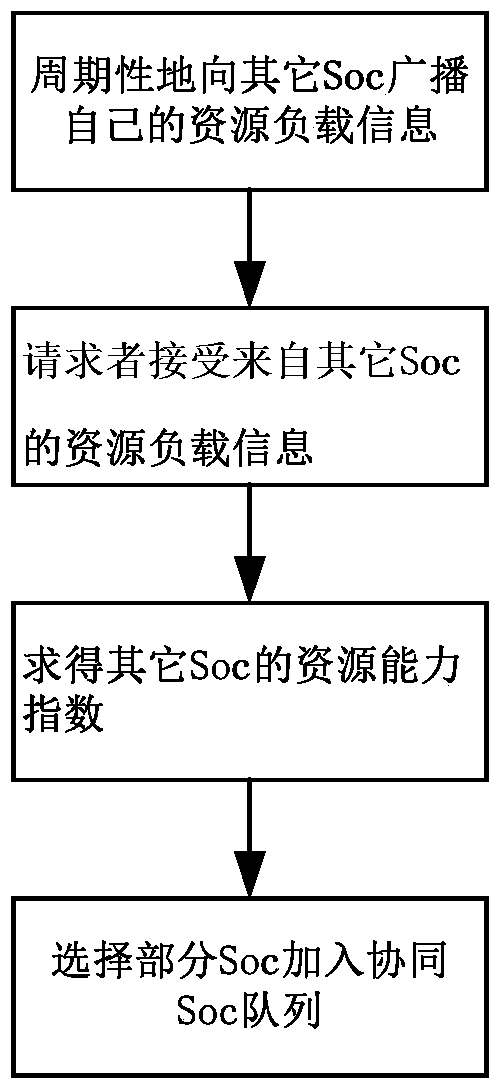
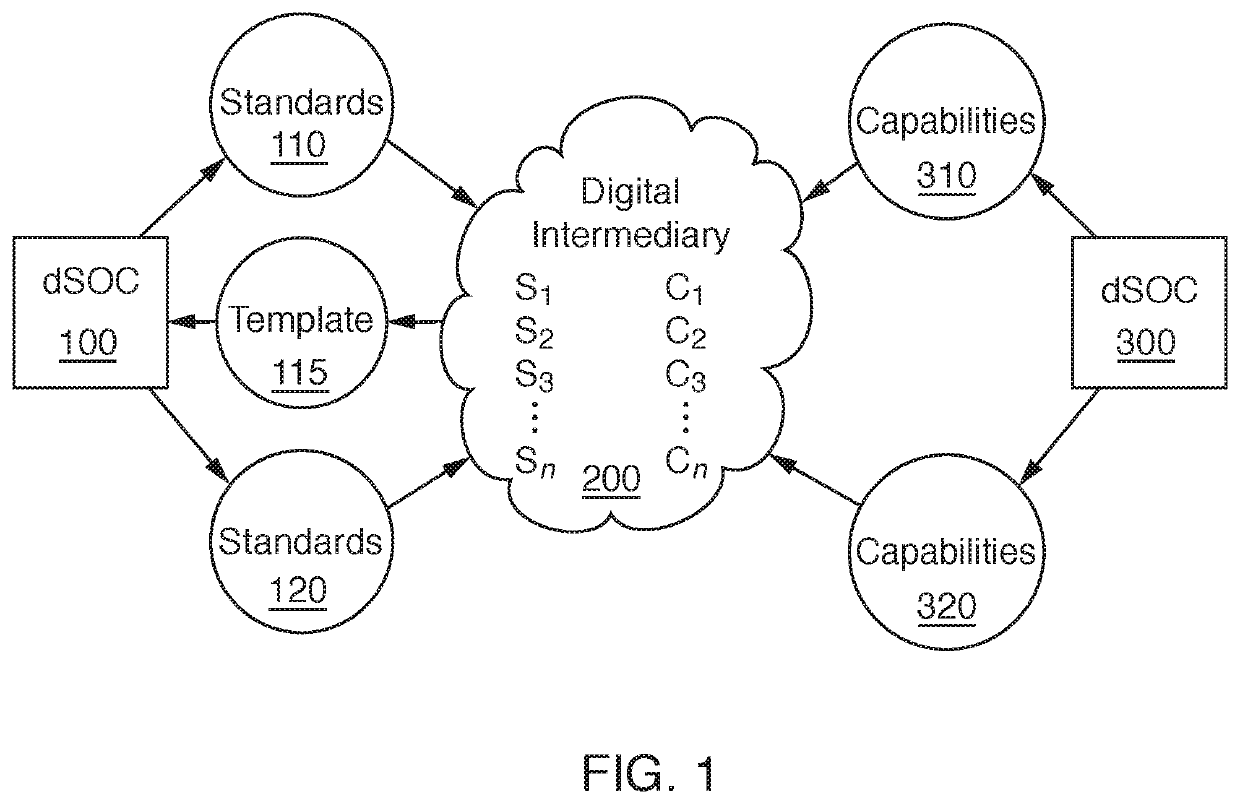
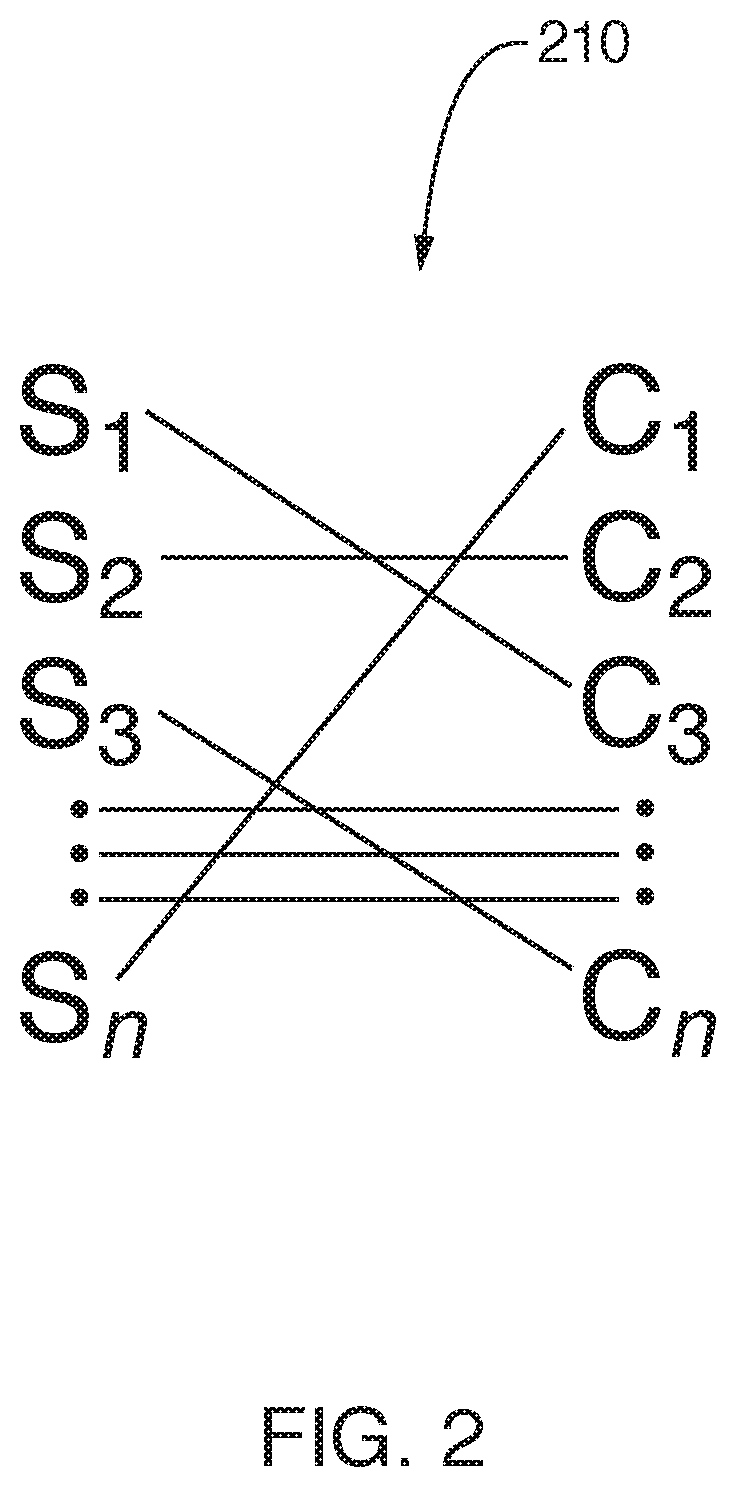
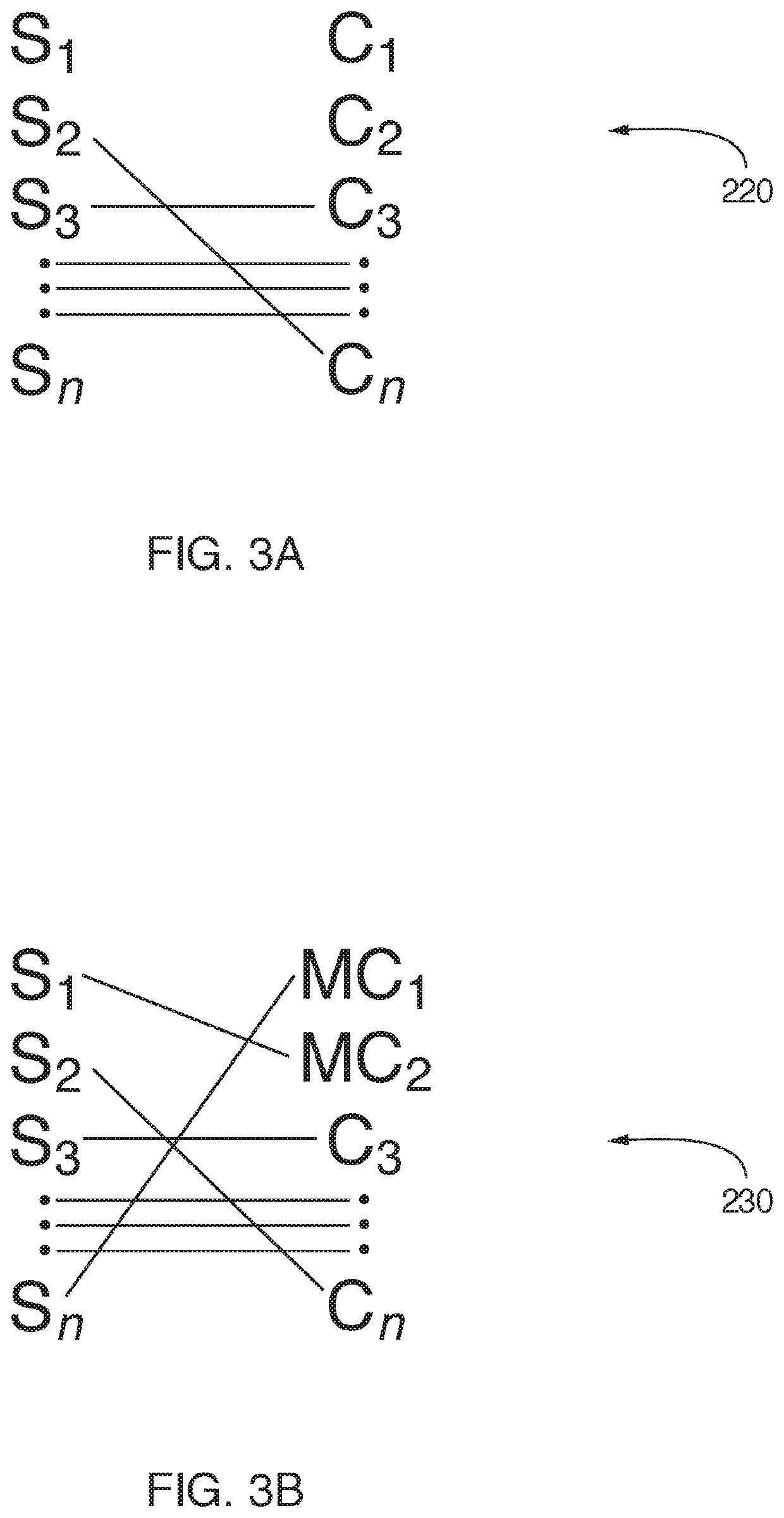
Methods, apparatuses and systems for negotiating digital standards and compliance
InactiveUS20220038507A1Shorten the timeFacilitate complianceDigital data authenticationPlatform integrity maintainanceElectronic accessThird party
Apparatuses, methods and systems for negotiating digital security standards and compliance between associated computing devices of a distributive security operation center (dSOC) and a personal security operation center (pSOC). Commonly, an enterprise / dSOC has the need of the services of a third-party / employee / pSOC to meet the business needs of the enterprise. The business needs of the enterprise often require electronic access by the third-party / employee / pSOC to confidential, private or sensitive information or data possessed by the enterprise. Onloading the third-party / employee / pSOC to the enterprise's electronic business operations required ensuring that the devices used by the third-party / employee / pSOC digital security capabilities which comply with the enterprise's digital security standards. The present invention provided apparatuses, methods and systems to ensure that the digital security capabilities of the third-party / employee / pSOC meet the technical functionality of the digital security standards of the enterprise. dSOC.
Owner:GUARD DOG SOLUTIONS INC
Security alarm operation data display system
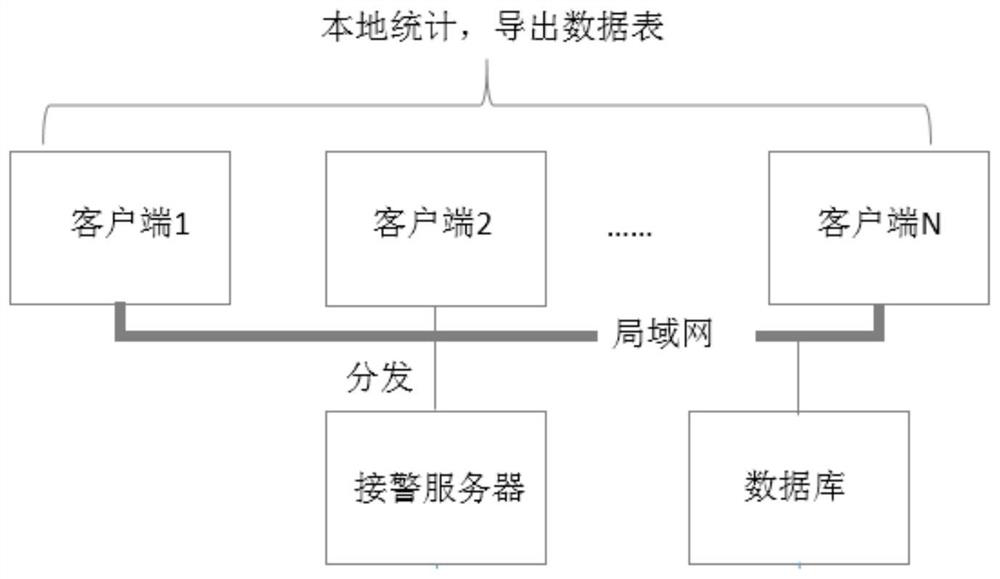
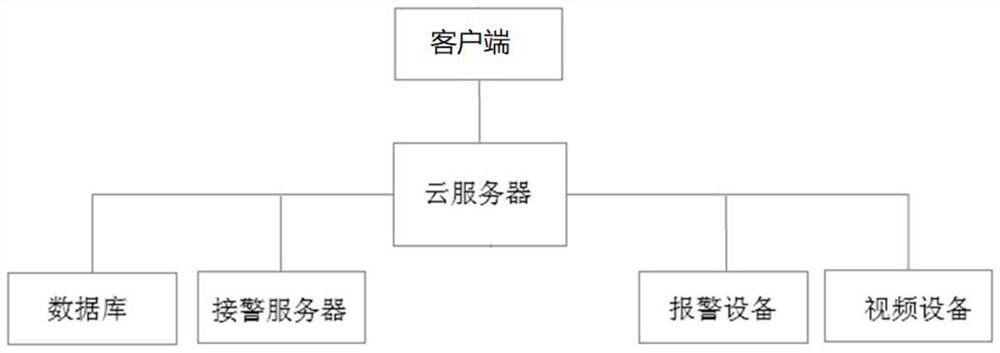
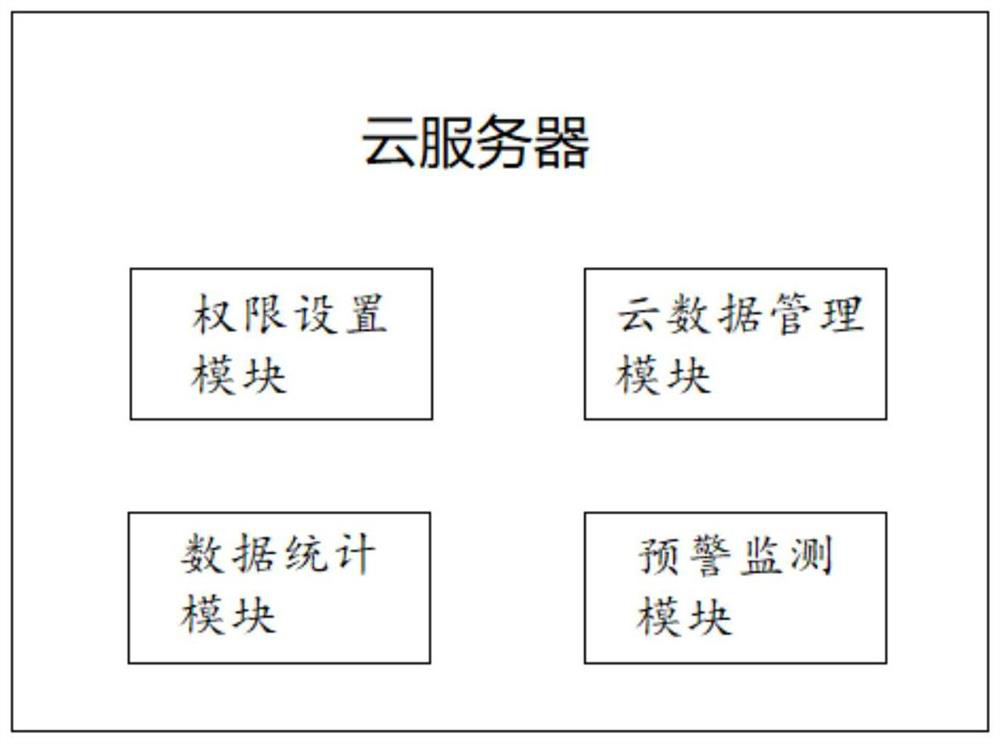
PendingCN112270464AImprove quality serviceRealize integrated managementAlarmsResourcesData displaySecurity operations center
A security alarm operation data display system provided by the present invention comprises a cloud server which is connected with an alarm receiving server of each security operation center and is used for acquiring the security alarm operation data of each security operation center and performing data statistical analysis; and a client which is connected with the cloud server and is used for acquiring the security alarm operation data and the data statistical analysis result from the cloud server according to the authority of a user and displaying the data according to the presentation form set by the user. By adopting the technical scheme of the invention, various requirements of different industries and different customers can be met, and the integrated management of big data by a security operation service center is realized.
Owner:CONGWEN SOFTWARE TECHNOLOGICAL SHENZHEN CITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com