Collaborative analysis method of information security operation centers
A security management and information security technology, applied in the field of collaborative analysis of the information security management center, can solve the problems of insufficient information security threat detection and prevention capabilities, and achieve the effect of improving the accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] To facilitate the understanding of the present invention, the present invention will be described in detail below with reference to specific embodiments.
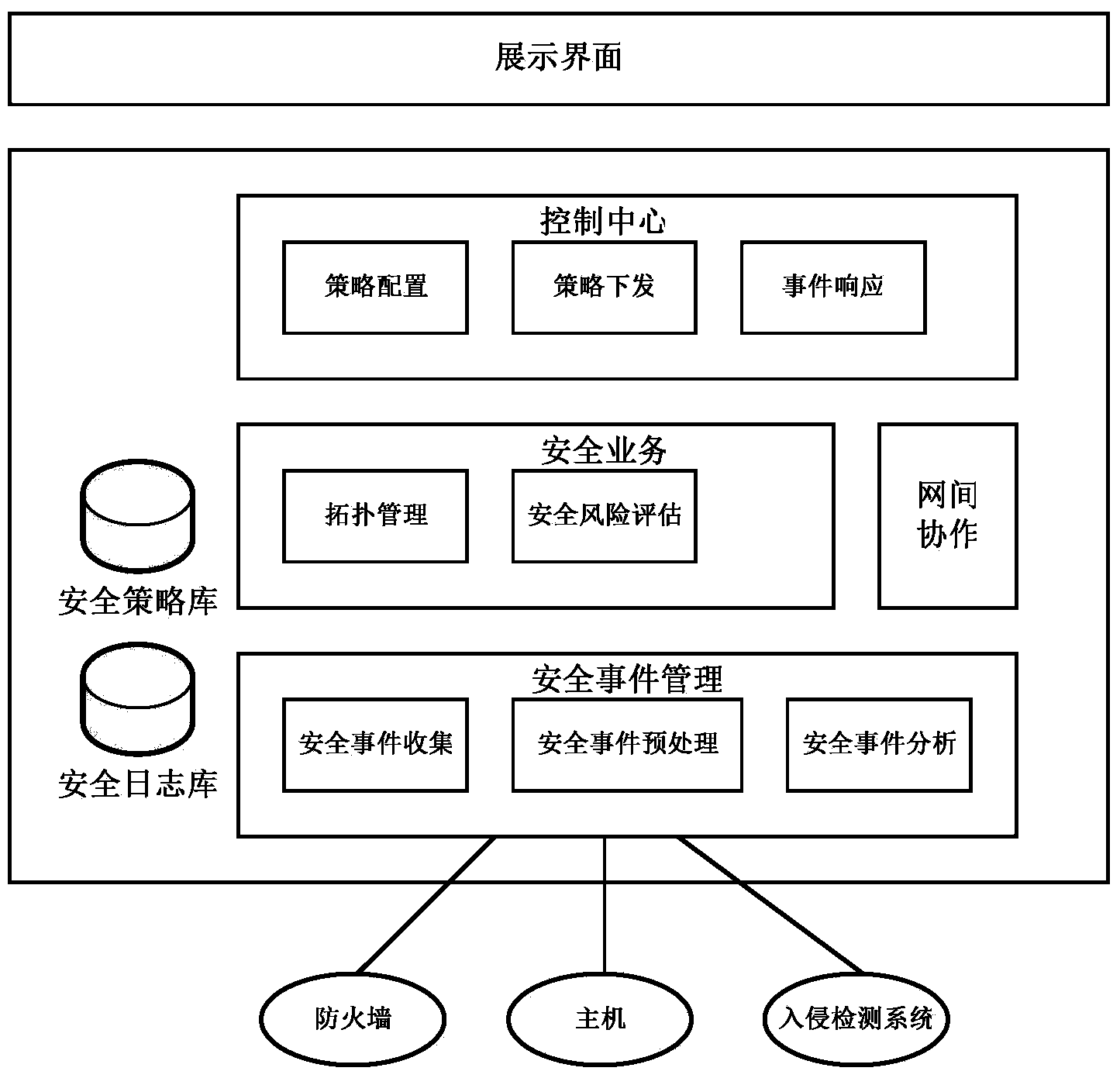
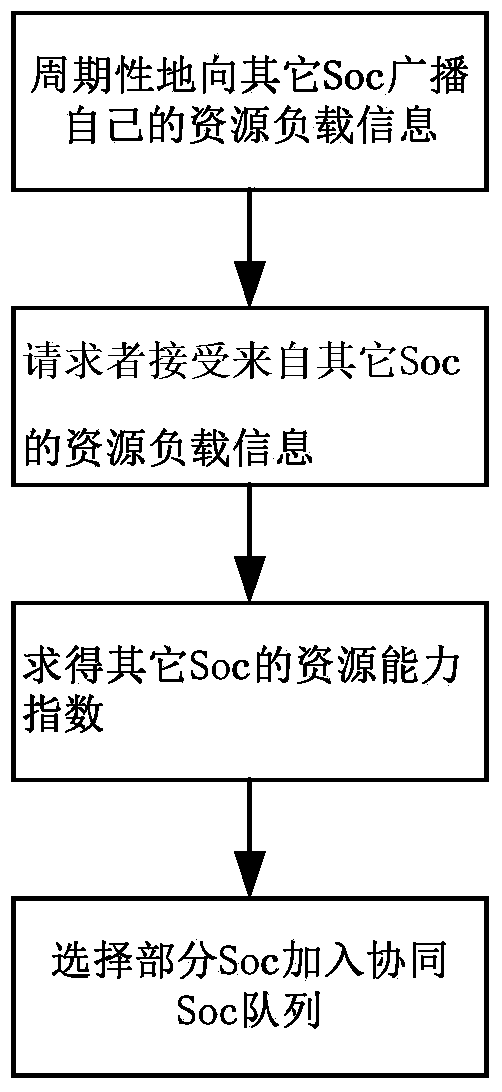
[0041] The system structure of the collaborative safety management center involved in the present invention is as follows figure 1 Shown. The system includes: security event management module, security business module, control center, security policy database, log database, and network collaboration module.
[0042] Security Event Management Module
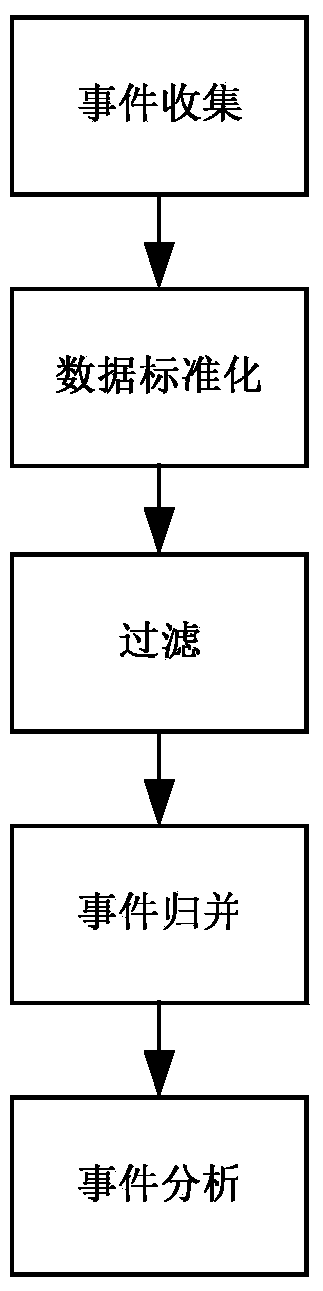
[0043] This module includes: security event collection submodule, security event preprocessing submodule and security event analysis submodule.
[0044] Security event collection submodule
[0045] The security event information sent by various information security devices can be collected in a variety of ways. The collection methods include the following: (1) Collect events based on SNMP Trap and Syslog. (2) Obtain the security related information of the device in various datab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com