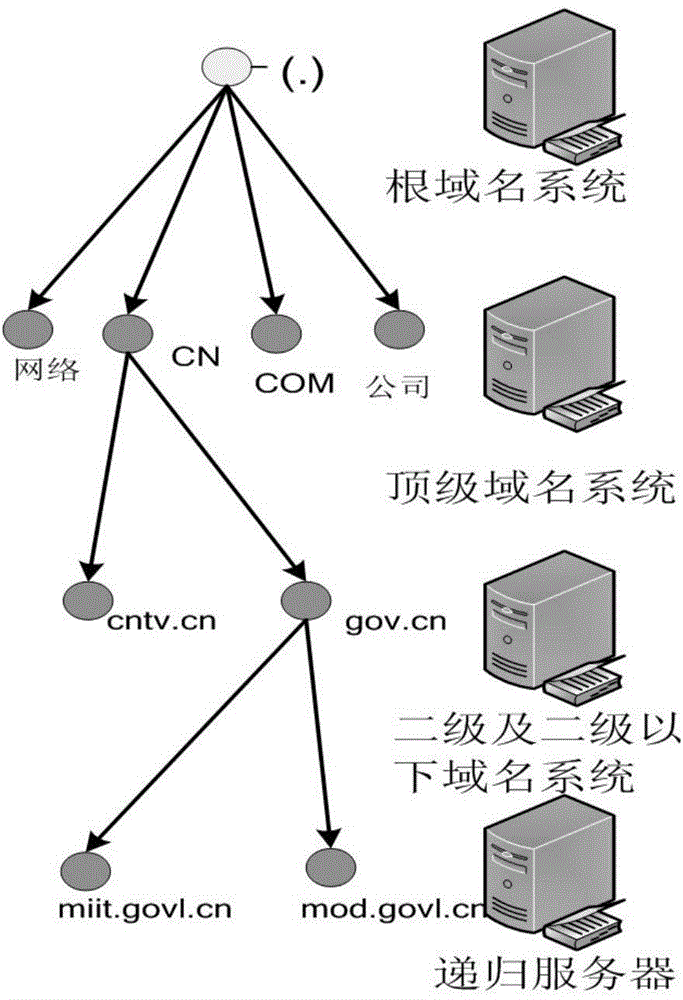
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
39 results about "Dns security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
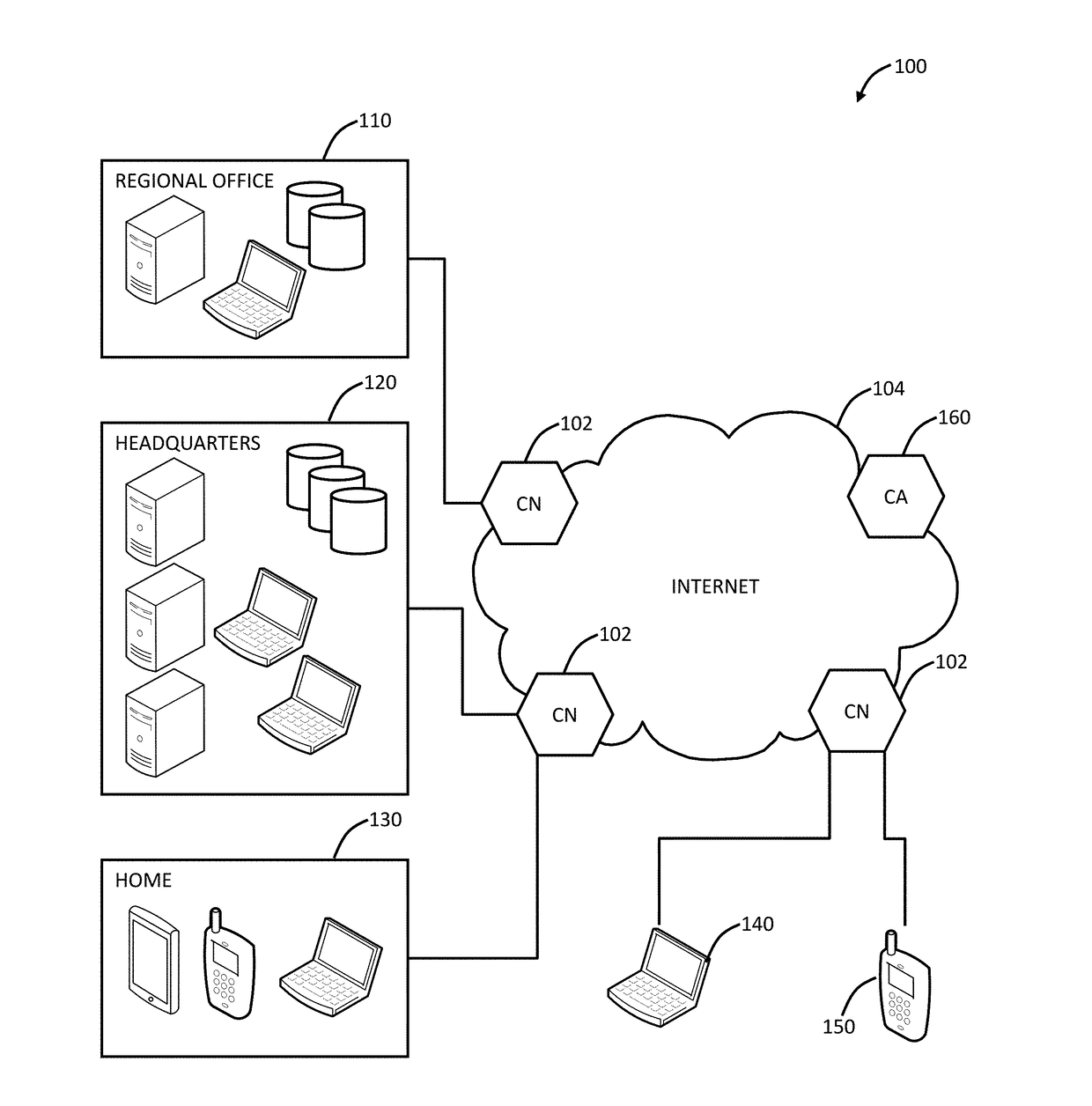
Systems and methods for managing domain name system security (dnssec)
ActiveUS20120117621A1Digital data processing detailsComputer security arrangementsDomain nameComputer network
The present invention is directed towards systems and methods for providing multiple modes of a zone for DNSSEC by an intermediary device. The method includes providing, by a device intermediary to a plurality of clients and a plurality of servers, a plurality of modes of a zone for Domain Name Service. The device receives a selection of a first mode of the zone of the plurality of modes of the zone. The device receives information identifying to enable DNS Security for the selected first mode. The device establishes the zone for DNS in accordance with the selected first mode and with DNS Security enabled.
Owner:CITRIX SYST INC
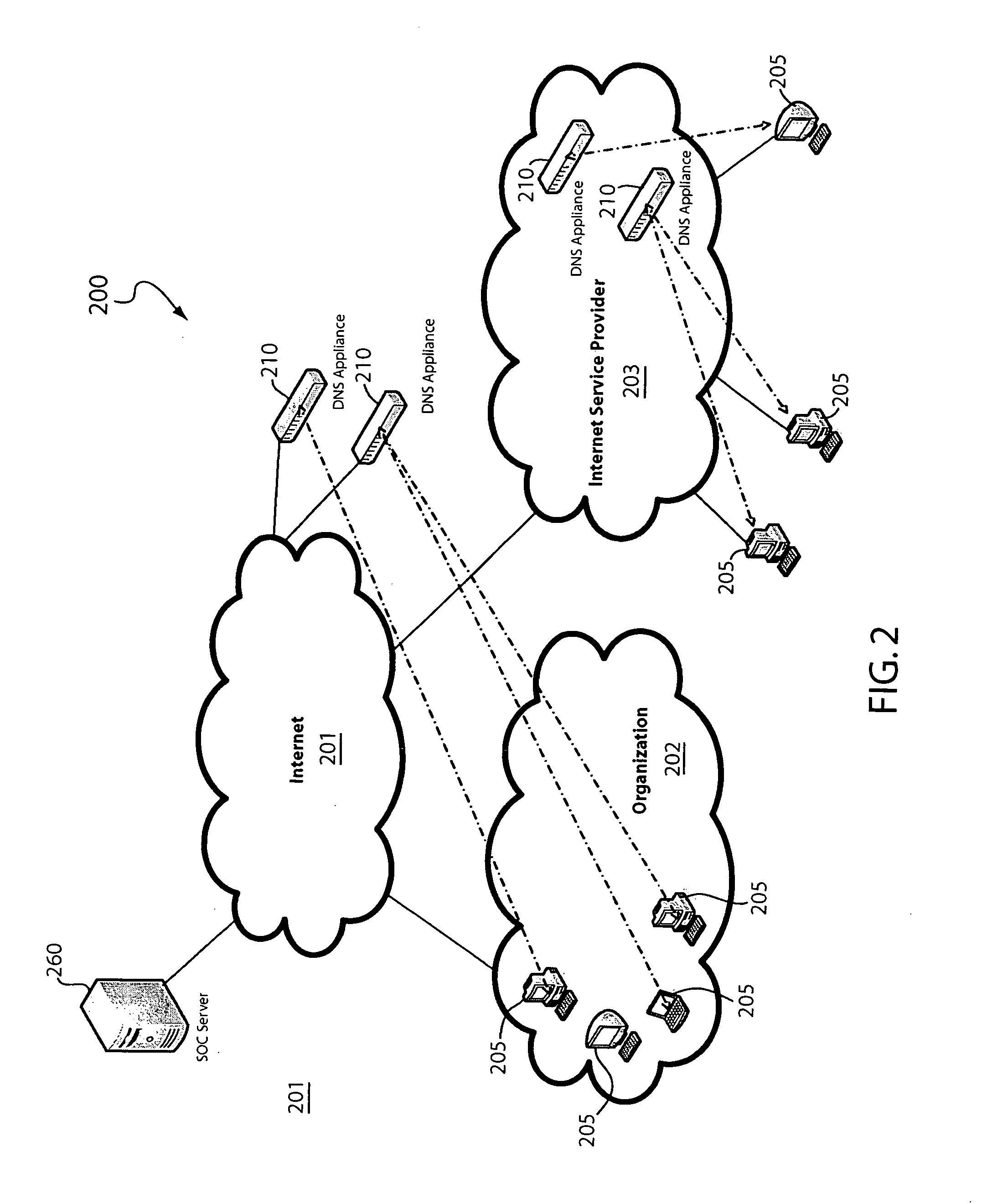
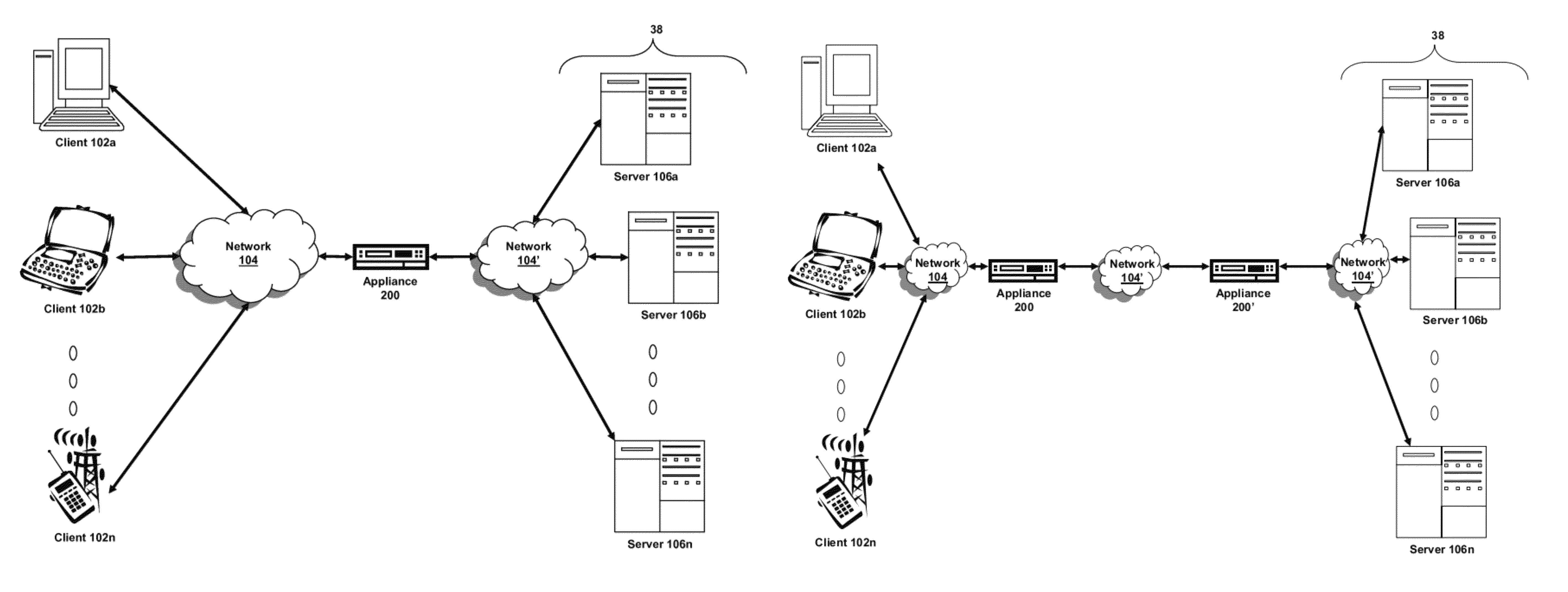
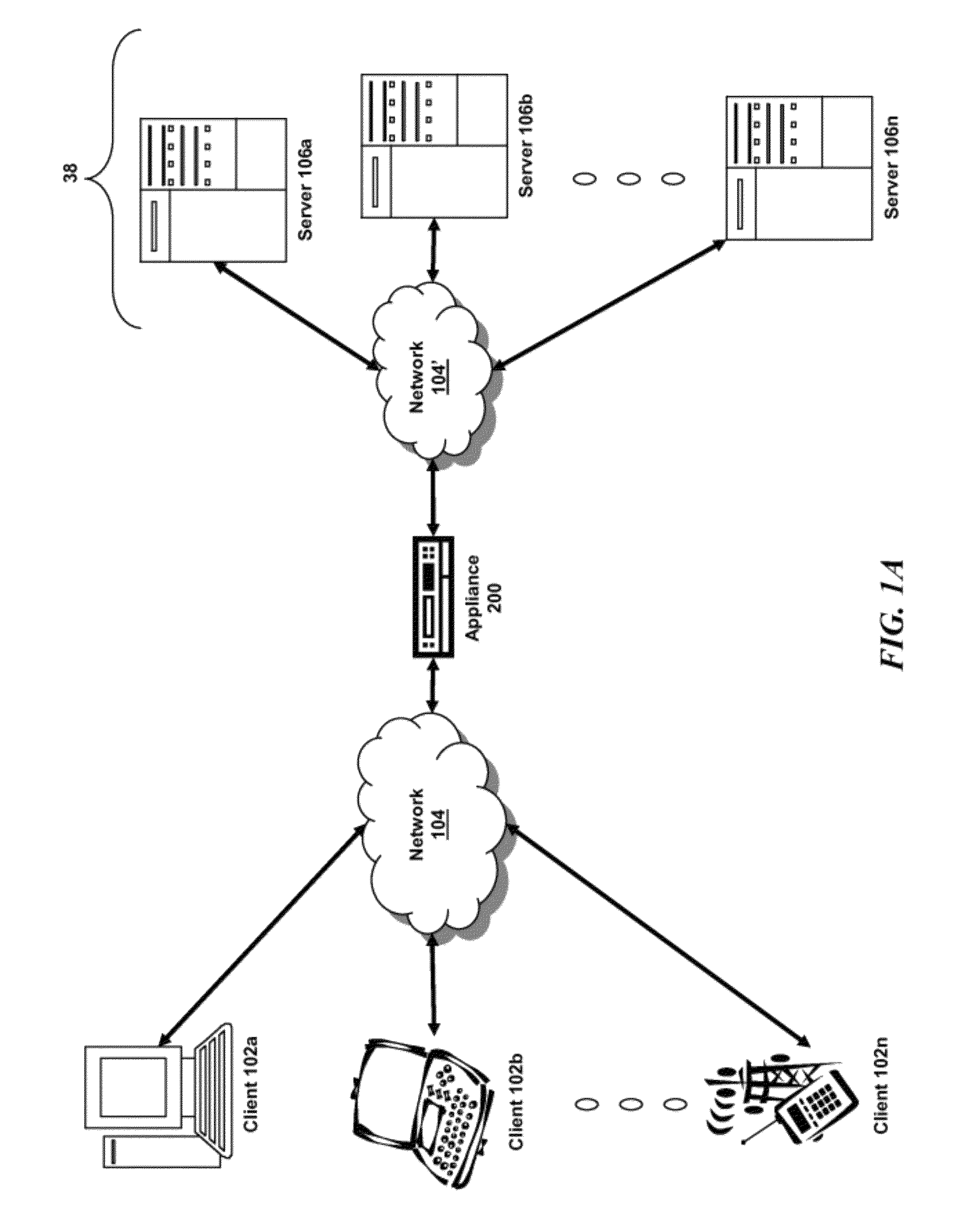
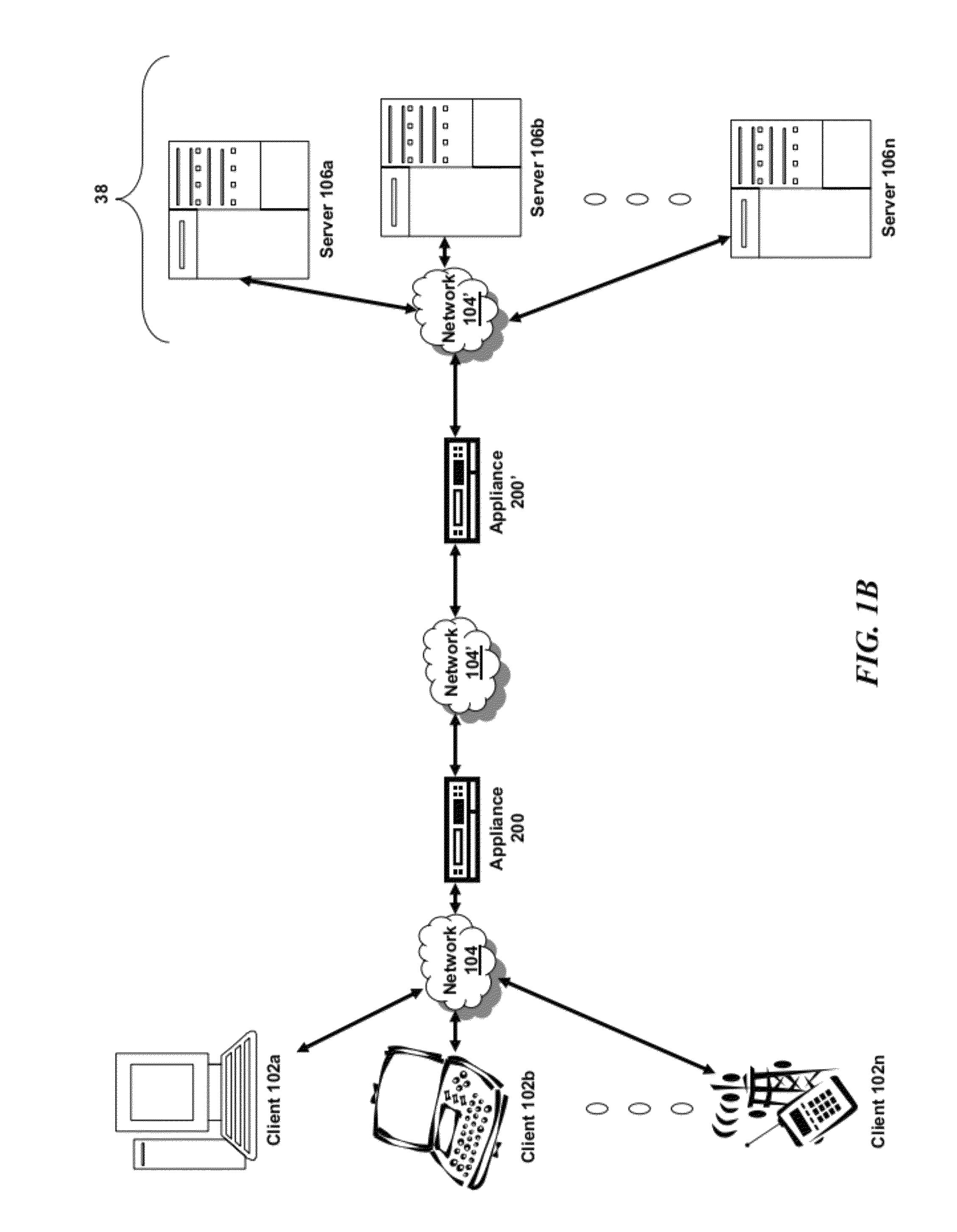
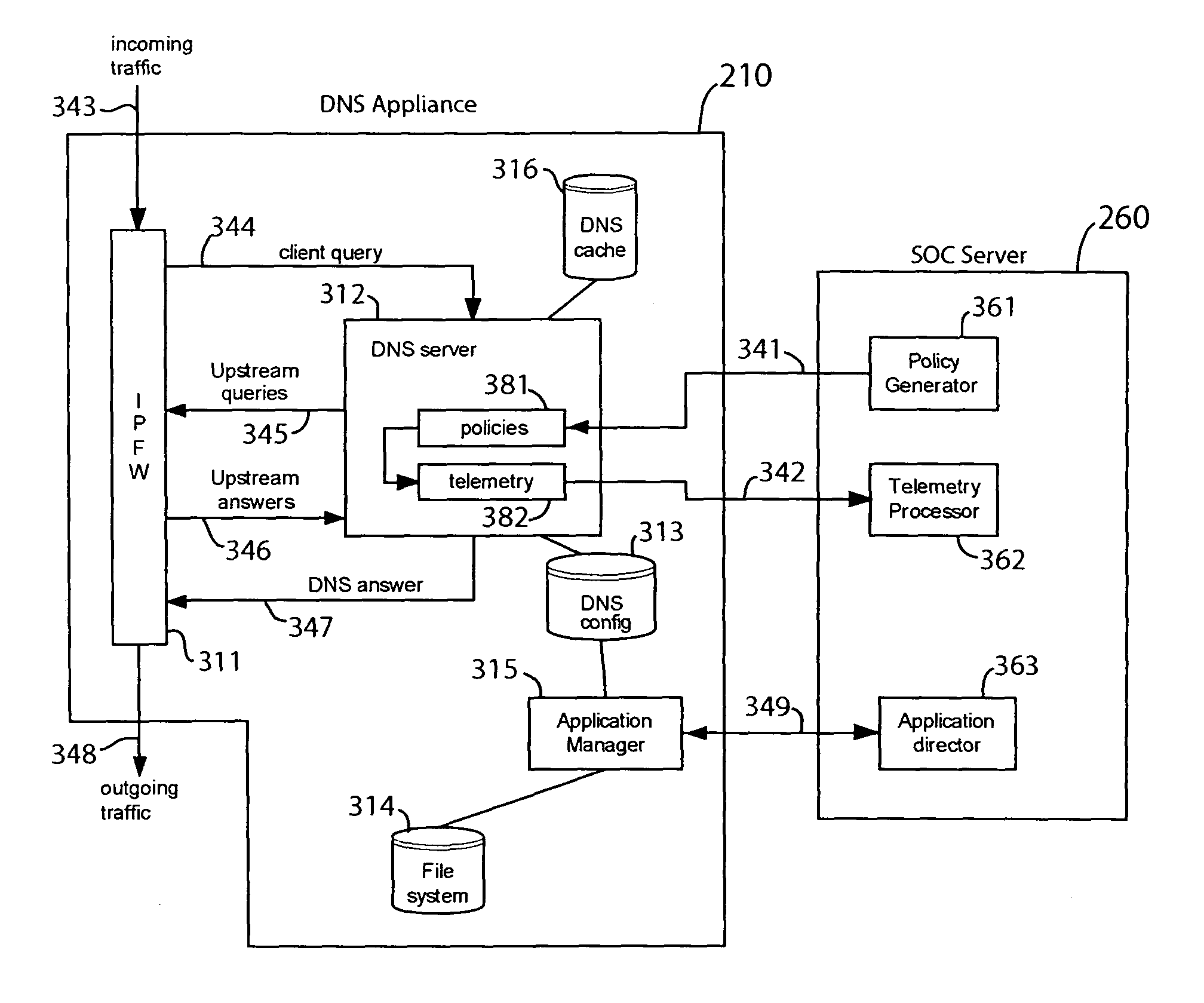
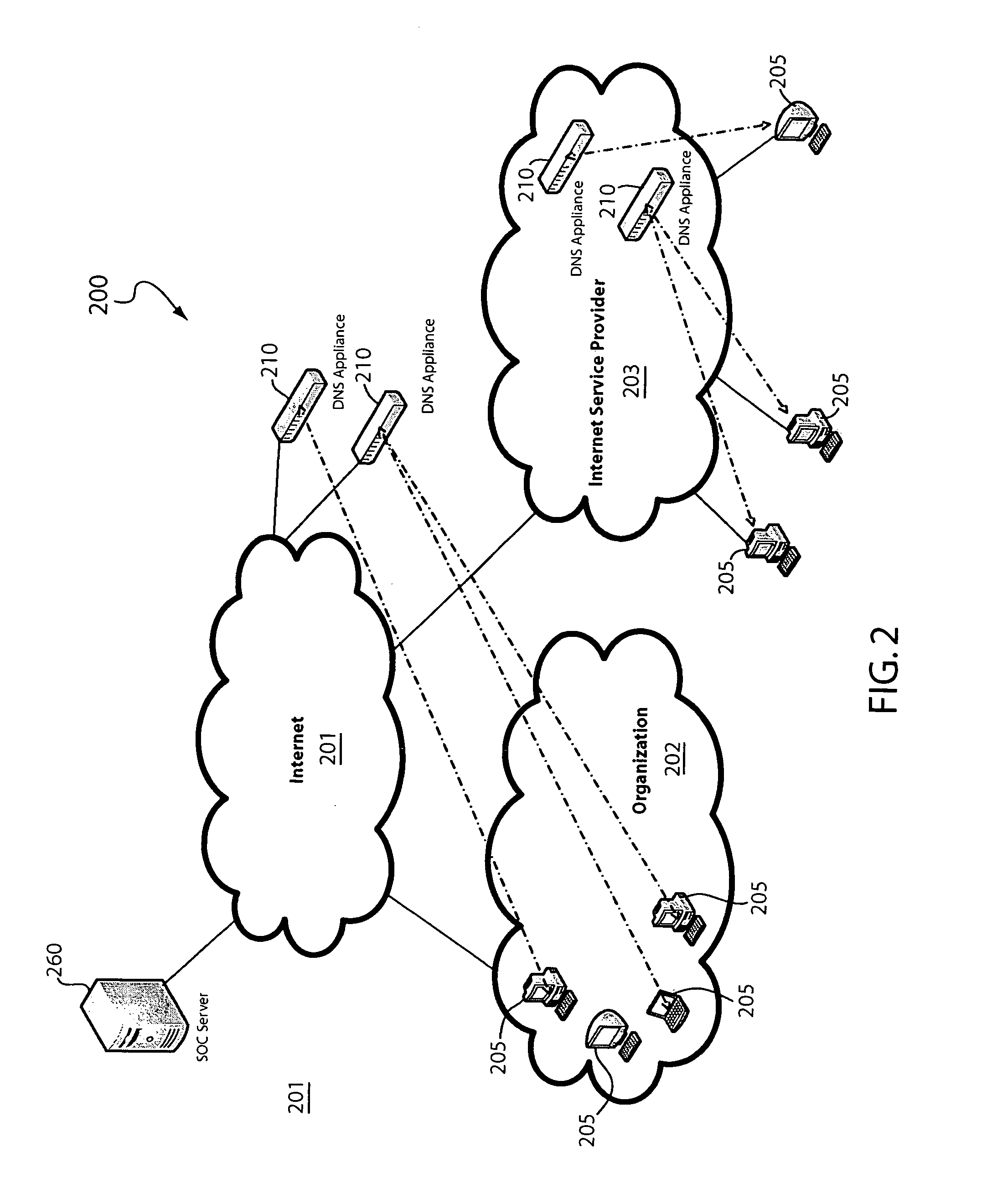
Domain name system security network
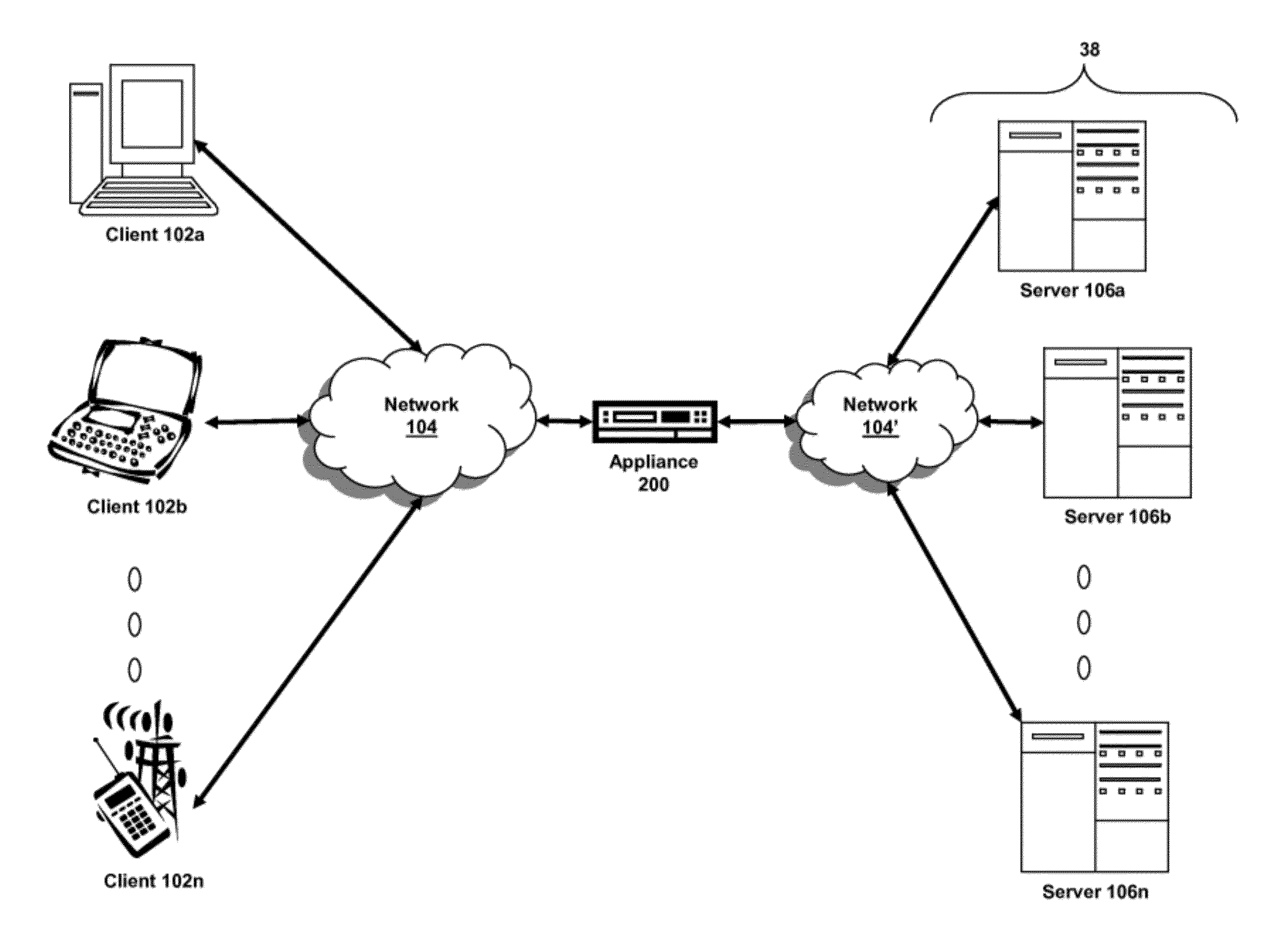
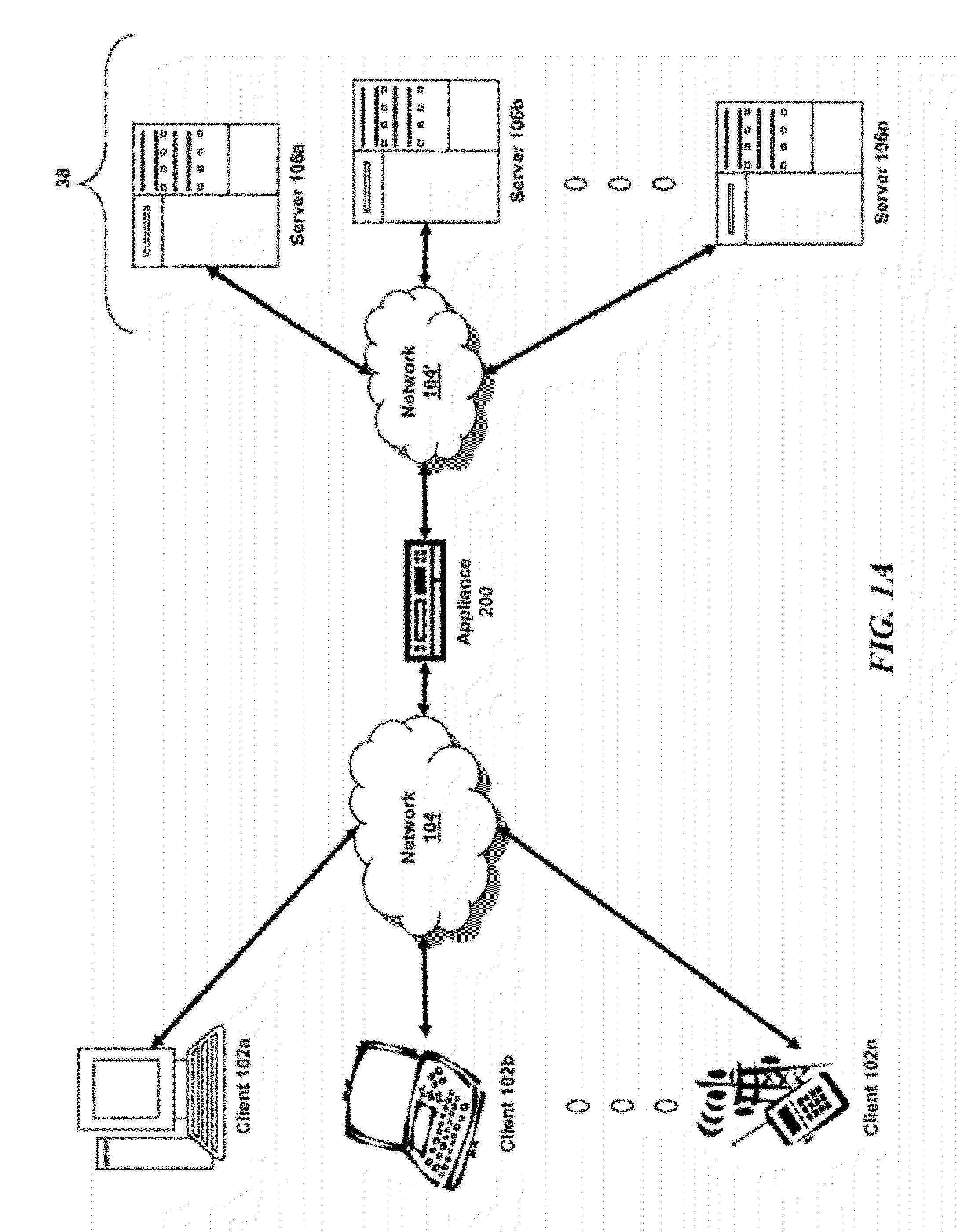
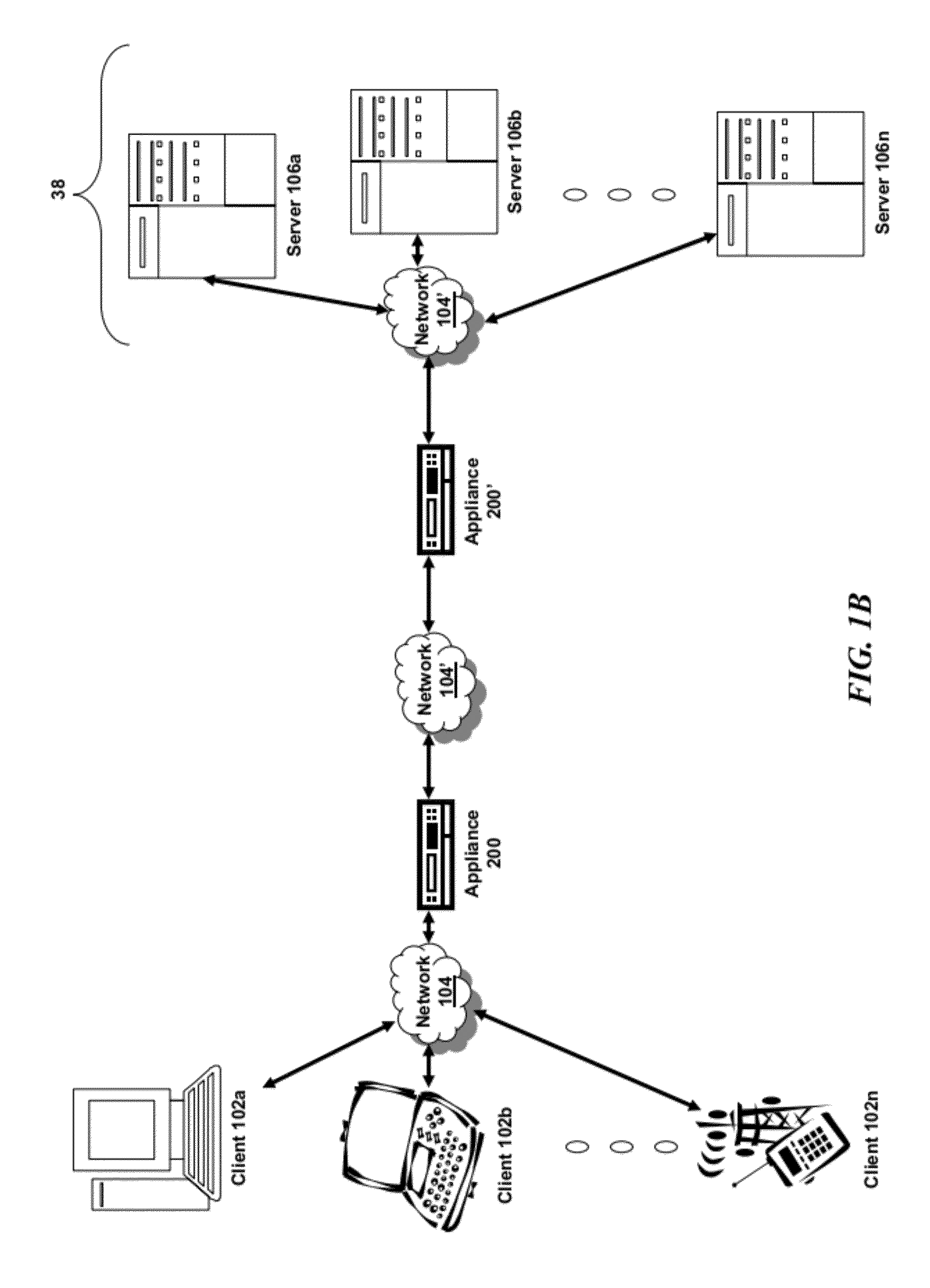
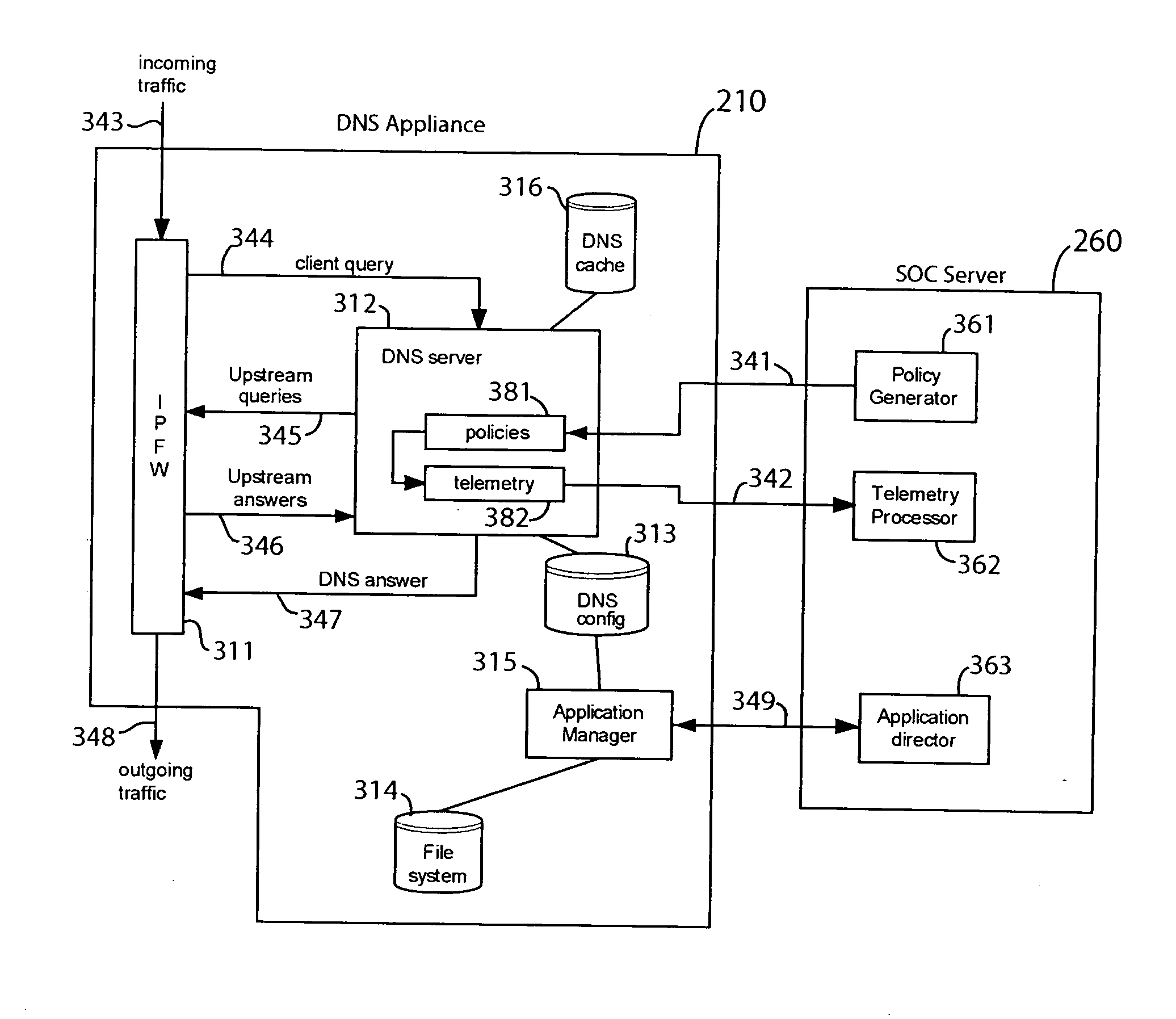
In one embodiment, a DNS security network includes several DNS appliances and a security operations center (SOC) server computer. The SOC server computer may receive telemetry data from the DNS appliances, the telemetry data comprising information about DNS client queries received in the respective DNS appliances. From the telemetry data, the SOC server computer may generate security policies for distribution to the DNS appliances. The security policies may be used by the DNS appliances to determine whether a DNS client query is originated by a client computer performing a prohibited activity (e.g., sending spam, communicating with a zombie control computer, navigating to a prohibited website, etc.). An answer to a client query may be replaced or discarded altogether in cases where the originator is performing a prohibited activity.
Owner:TREND MICRO INC
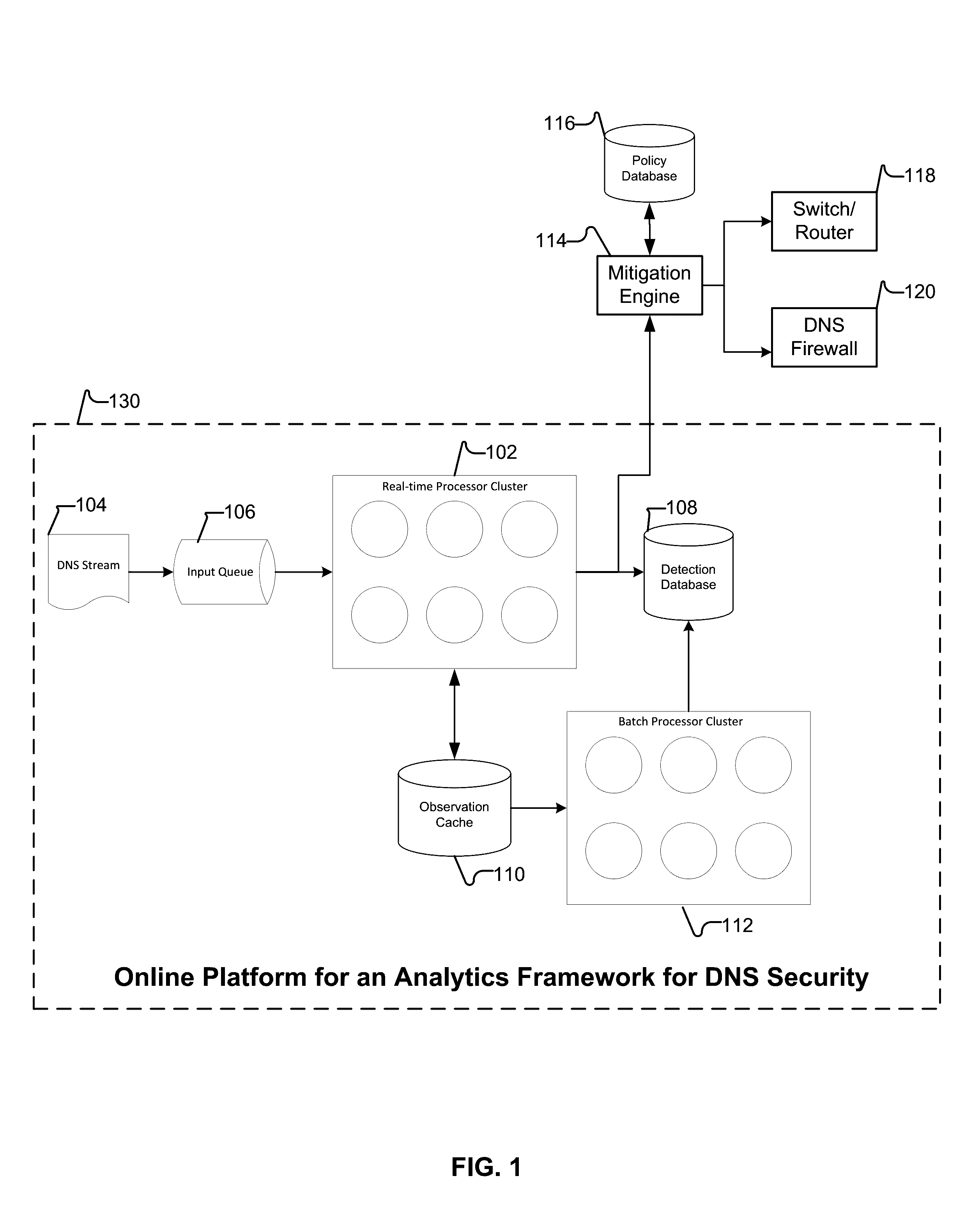
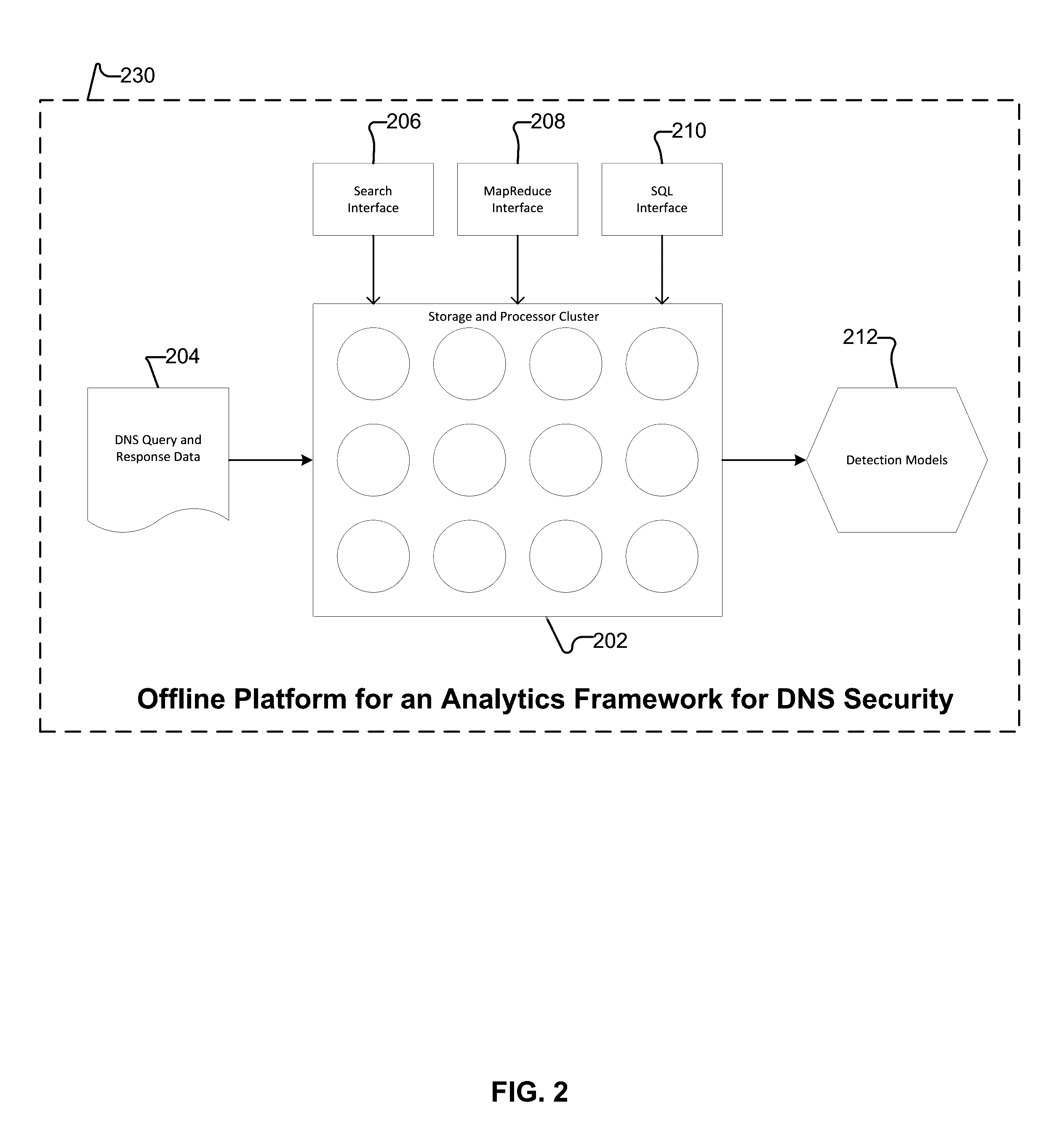
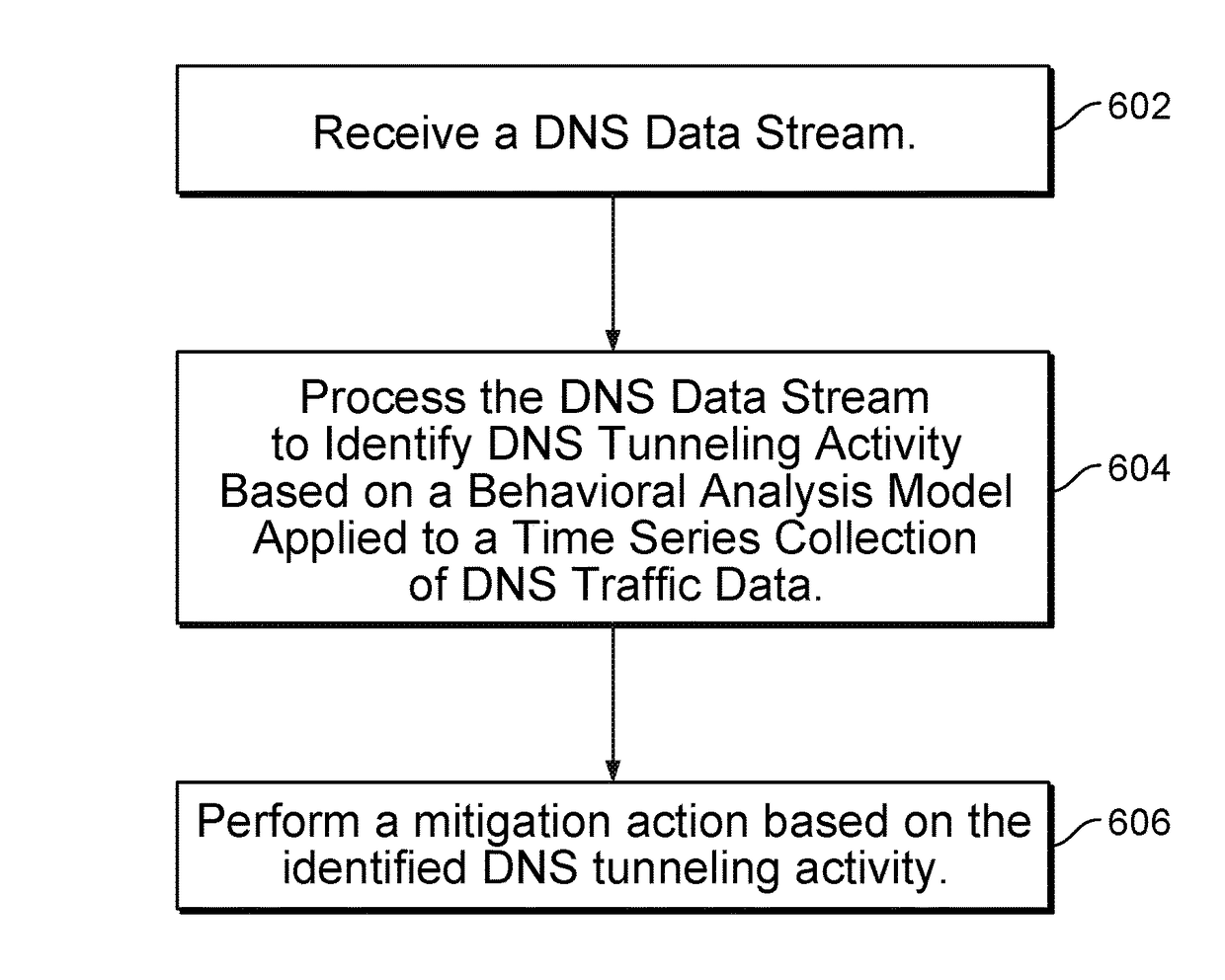
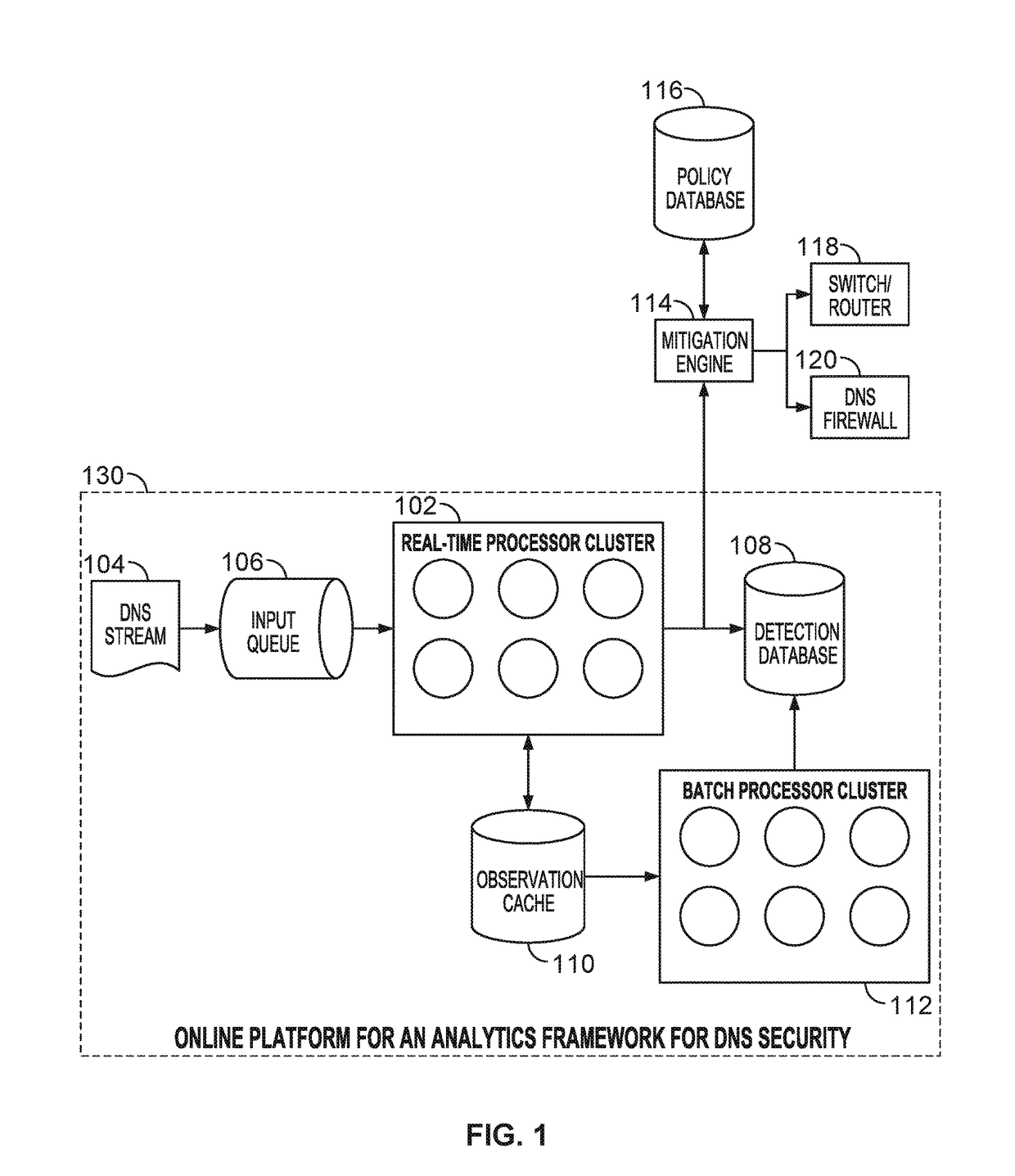
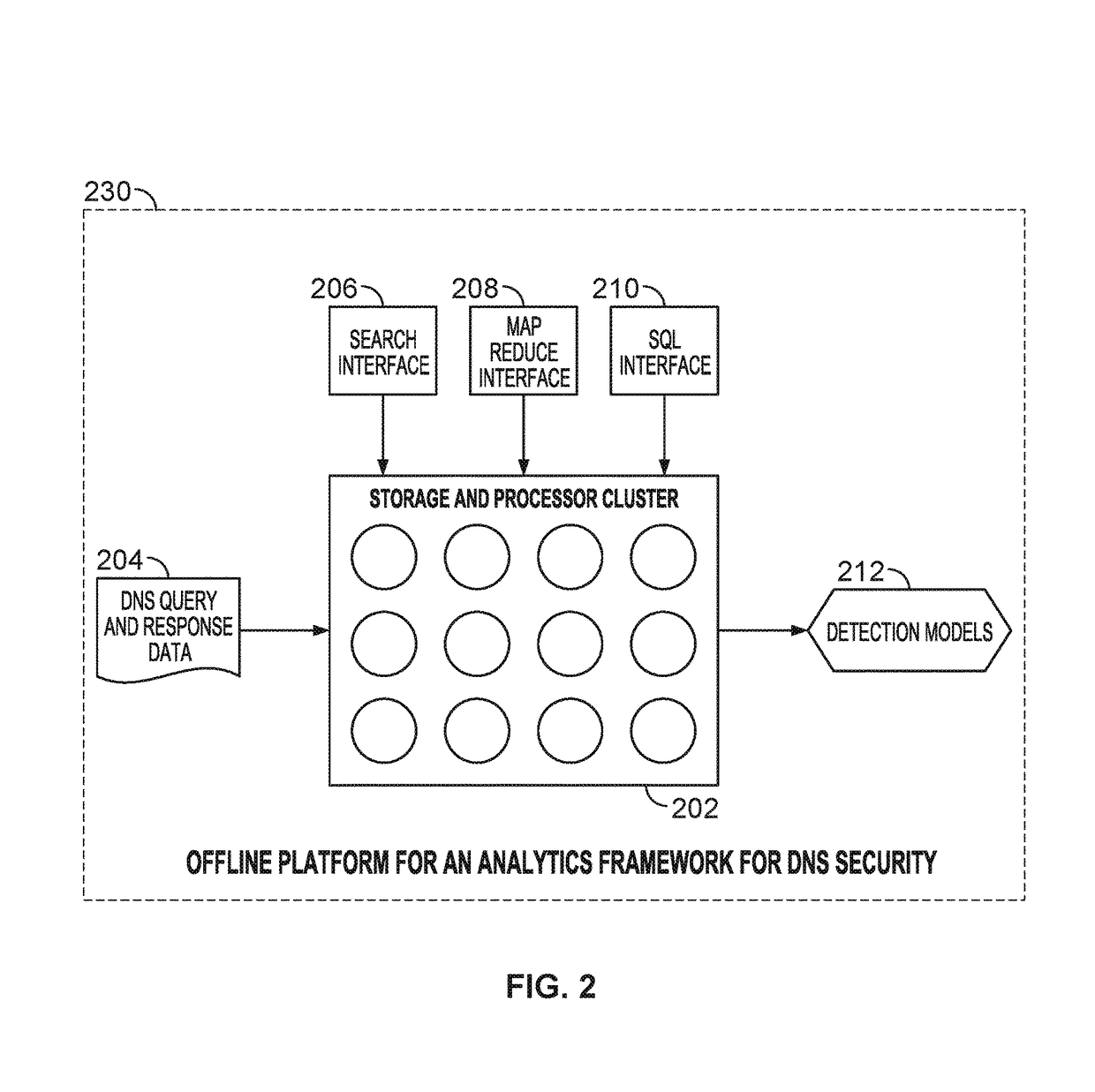
Behavior analysis based DNS tunneling detection and classification framework for network security
New and improved techniques for a behavior analysis based DNS tunneling detection and classification framework for network security are disclosed. In some embodiments, a platform implementing an analytics framework for DNS security is provided for facilitating DNS tunneling detection. For example, an online platform can implement an analytics framework for DNS security based on passive DNS traffic analysis.
Owner:INFOBLOX
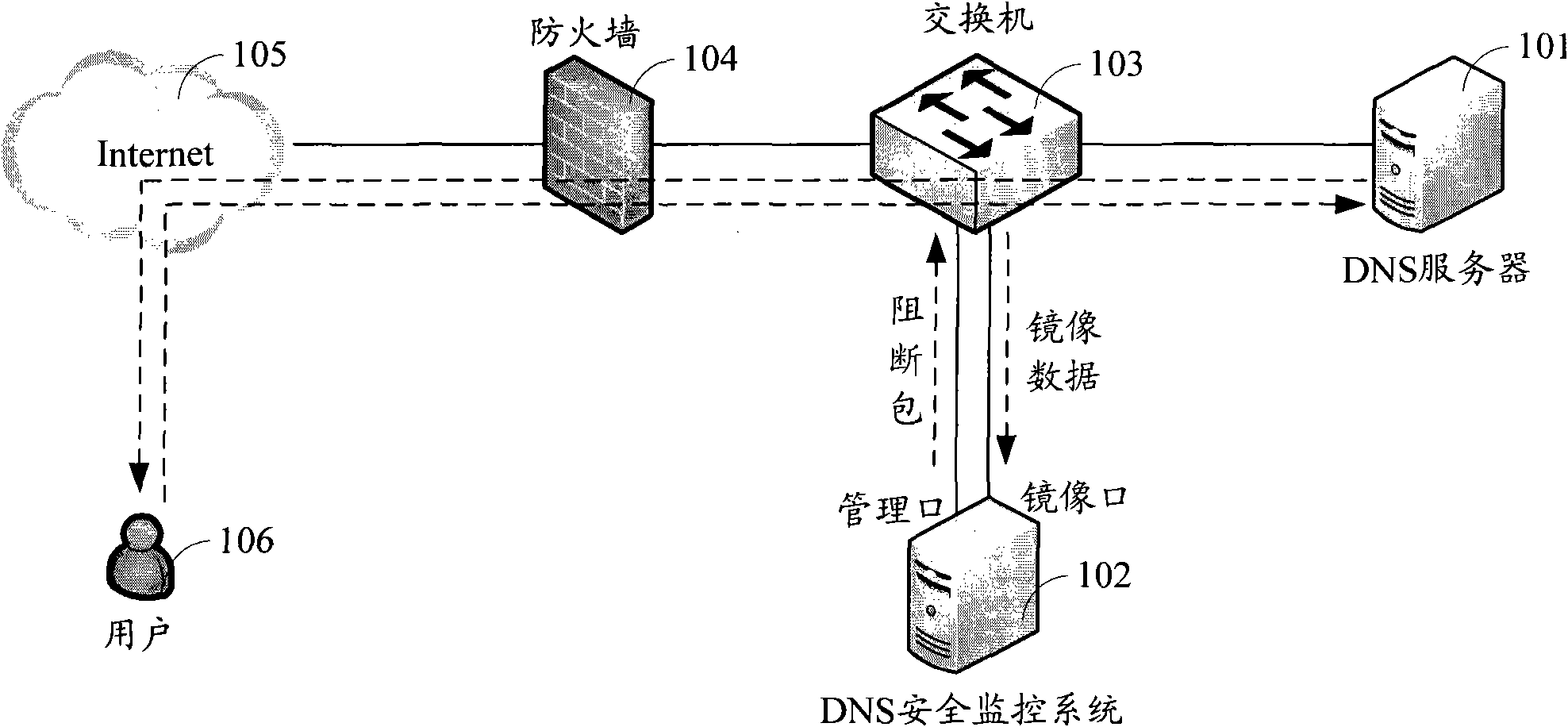
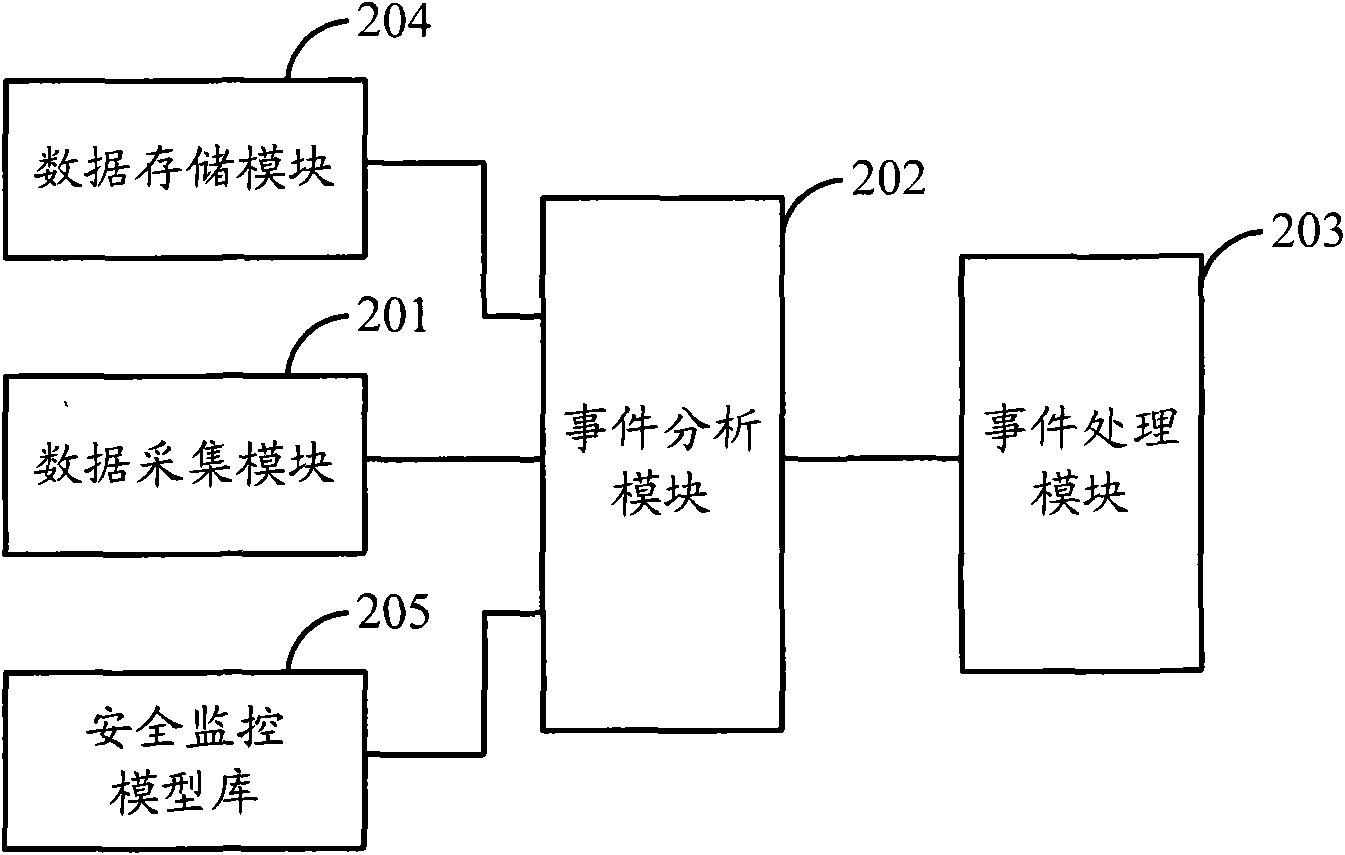
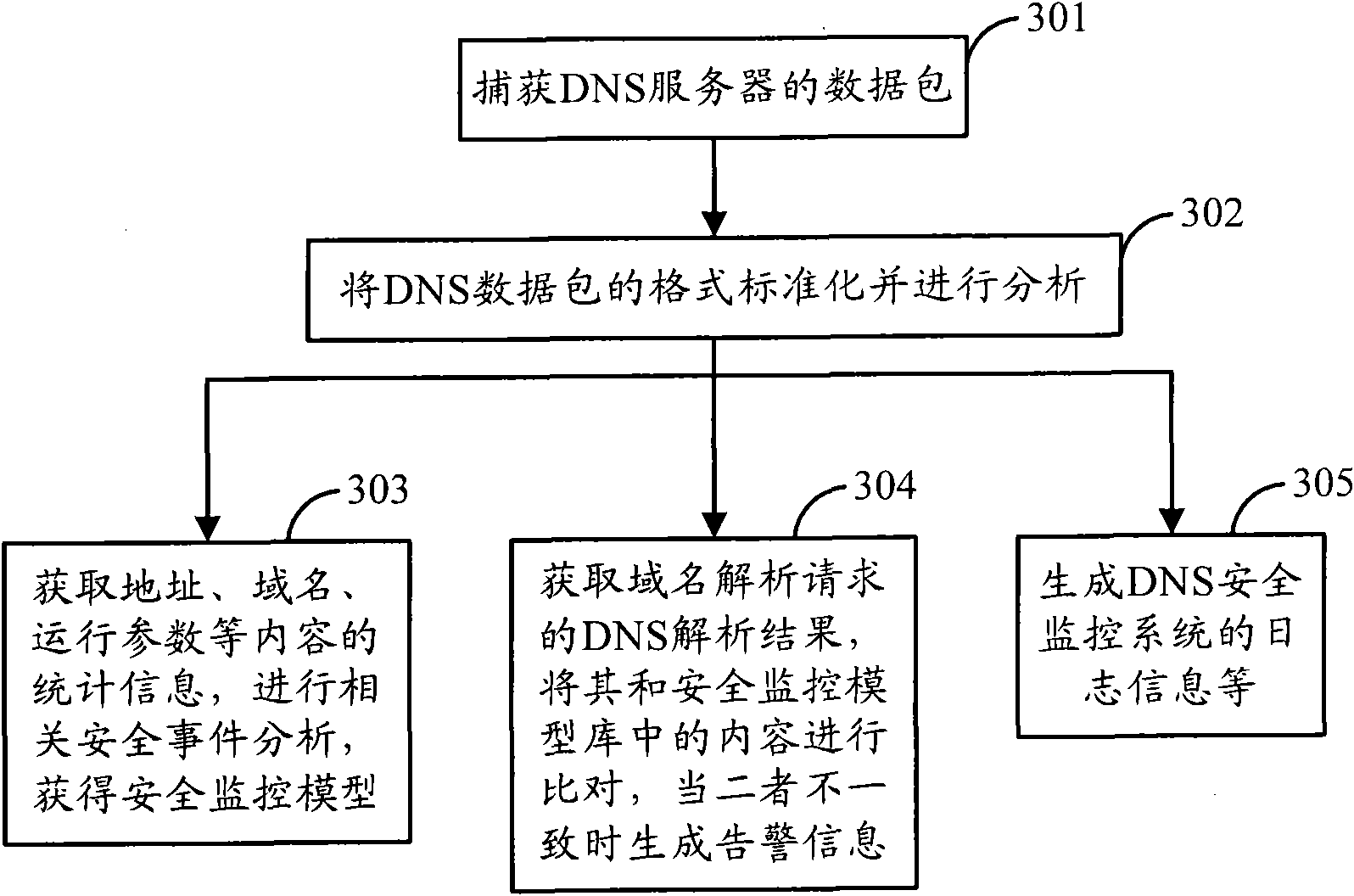
DNS (Domain Name Server) safety monitoring system and method
ActiveCN102082836ARunning does not affectImprove stabilityData switching networksDomain nameData acquisition
The invention discloses a DNS (Domain Name Server) safety monitoring system and method of a domain name resolution system. The DNS safety monitoring system comprises a data acquisition module and an event analysis module, wherein the data acquisition module is used for acquiring the network data of a DNS and providing the network data to the event analysis module; and the event analysis module isused for analyzing the network data and generating a monitoring result. The system and the method can be used for preventing network attacks such as domain name hijacks, site phishing, zombie attacks, and the like and improving the running stability and reliability of the DNS.
Owner:CHINA MOBILE GROUP SICHUAN
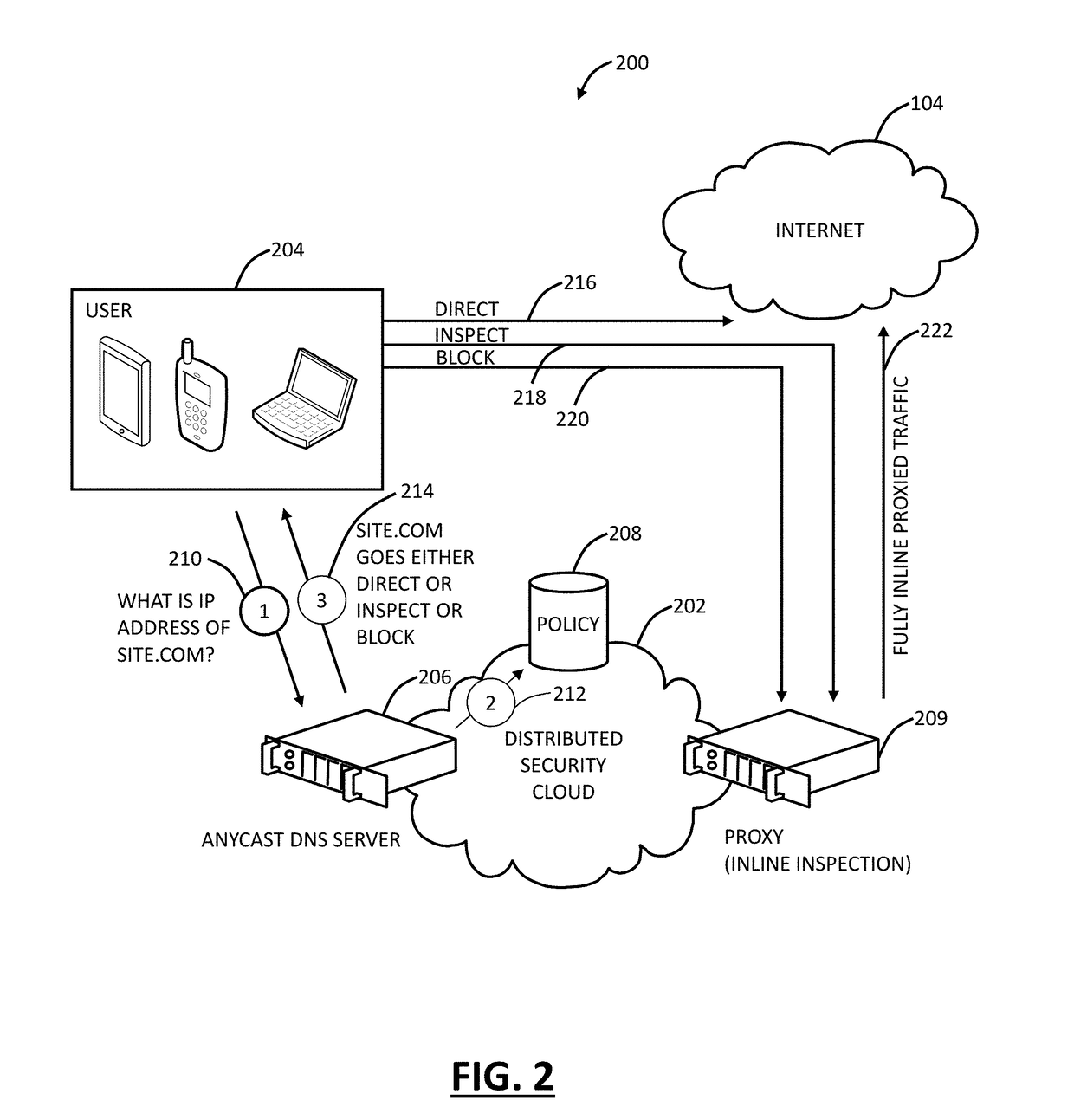
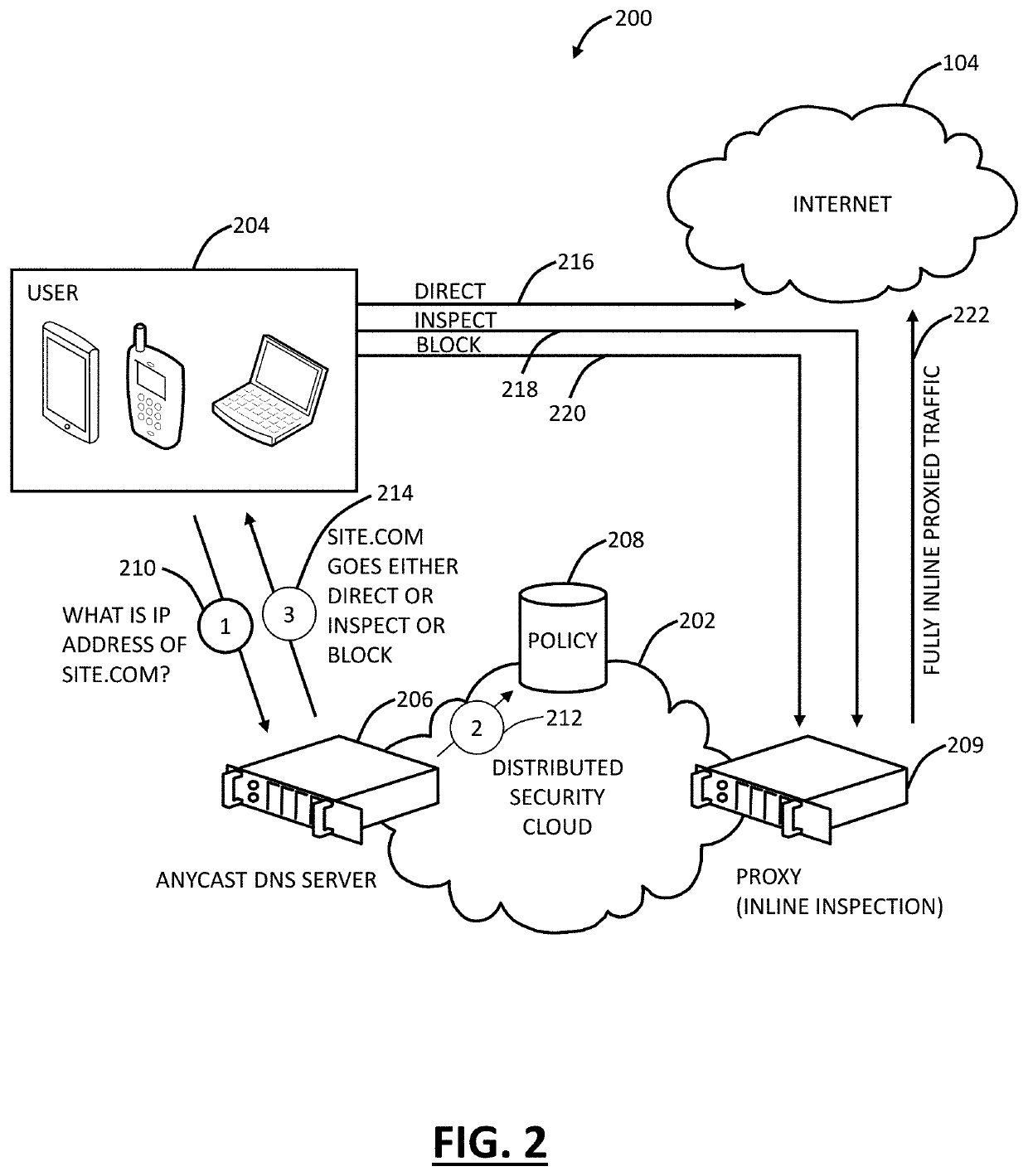
Cloud based security using DNS
A cloud-based security method using Domain Name System (DNS) includes receiving a request from a user device at a DNS server; performing a security check on the request based on a policy look up associated with the user device; responsive to the policy look up, performing a DNS security check on the request; and responsive to the DNS security check, performing one of allowing the request to the Internet; blocking the request based on the policy; and providing the request to inline inspection based on the policy, wherein the request is one of allowed to the Internet or blocked based on the inline inspection.
Owner:ZSCALER INC
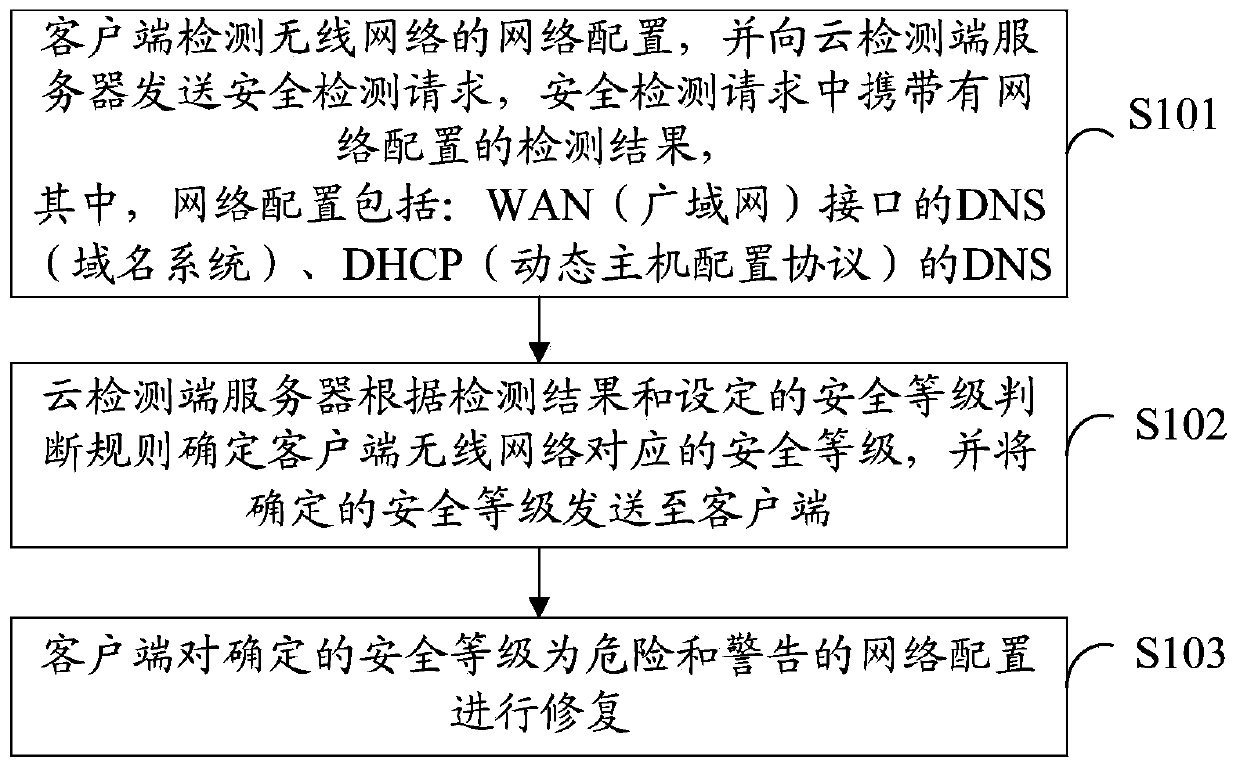
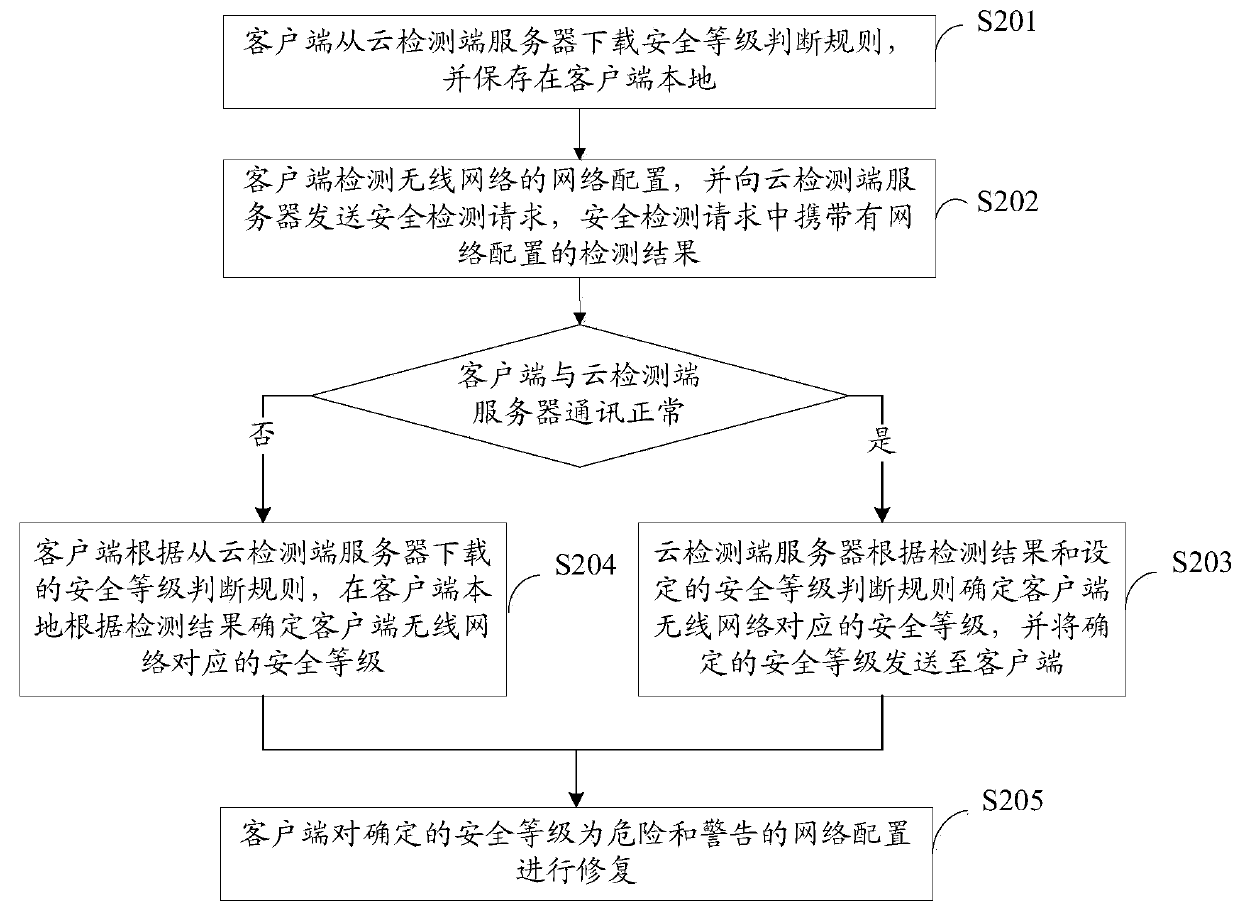
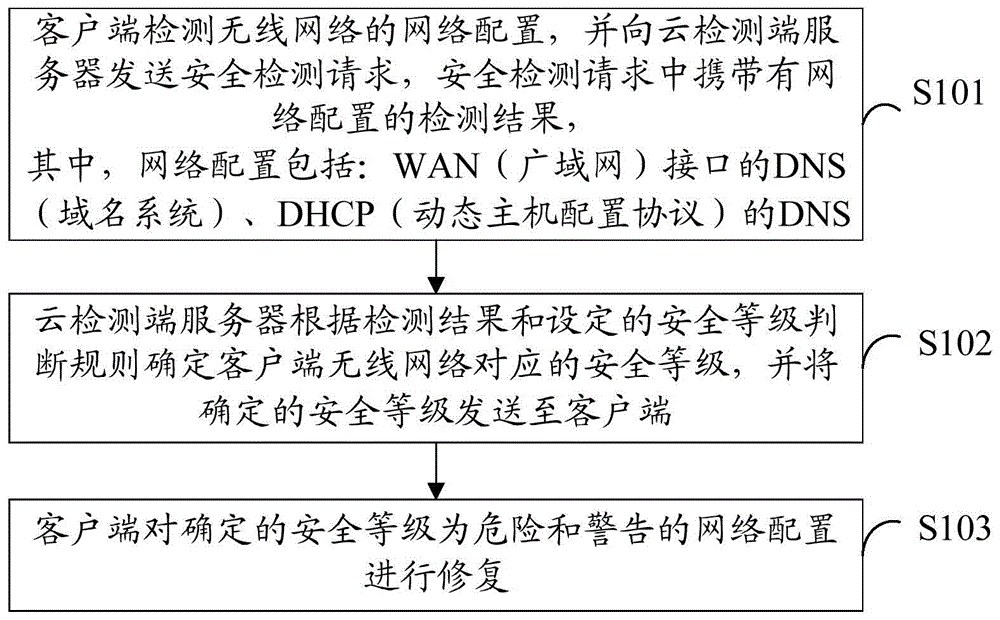
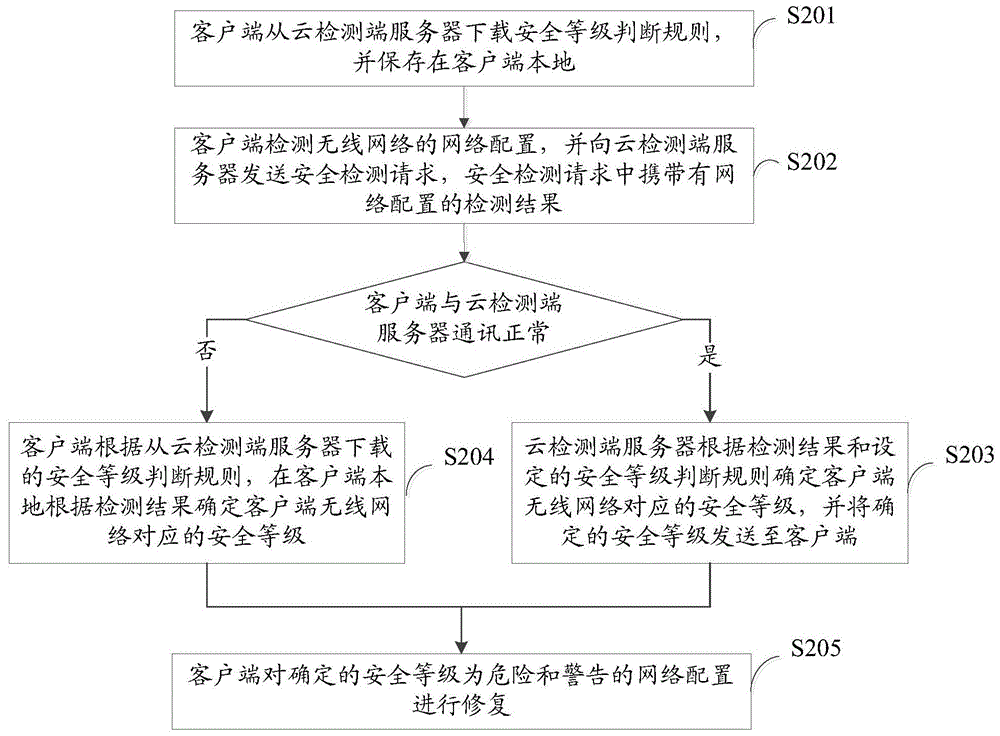
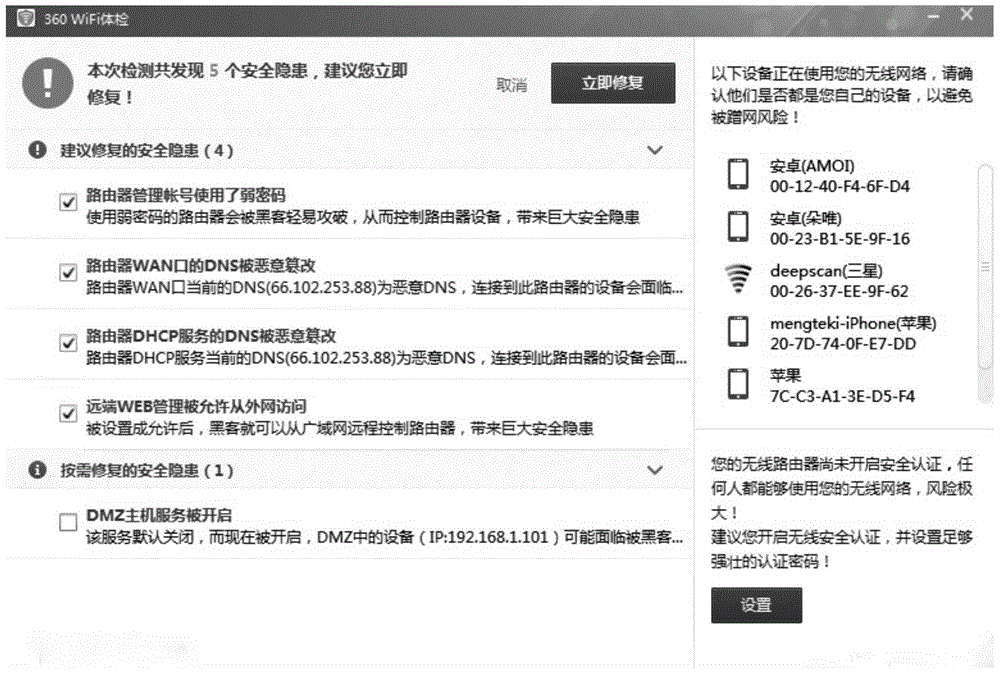
Method and system for security detection and repair of wireless network
The invention provides a method and a system for the security detection and repair of a wireless network. The method for the security detection and repair of the wireless network comprises the following steps: detecting the network configuration of the wireless network and sending a security detection request to a cloud detection side server by a client-side, wherein the detection result of the network configuration is carried in the security detection request; determining the security grade corresponding to the wireless network of the client-side according to the detection result and set security grade judgment rules and sending the determined security grade to the client-side by the cloud detection side server, wherein the security grade judgment rules comprise: if a DNS (Domain Name Server) conforms with a first DNS security rule, the security grade of the DNS is dangerous; if the DNS conforms with a second DNS security rule, the security grade of the DNS is secure; if the DNS conforms with a third DNS security rule, the security grade of the DNS is warning; repairing the network configuration of which the determined security grade is dangerous or warning by the client-side. Through the method and the system, the security risk of the DNS is inhibited and changed.
Owner:三六零数字安全科技集团有限公司
Method and device for prevention of DNS (Domain Name Server) cathe attack
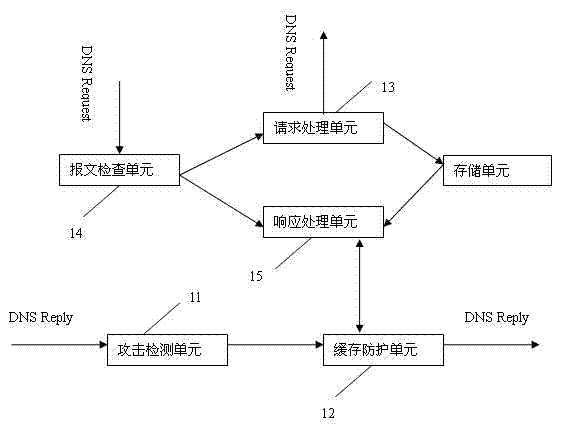
ActiveCN102404318AShorten the effective timeDNS Cache Attack DefenseTransmissionDomain nameComputer network
The invention provides a method and a device for prevention of DNS cathe attack. The device comprises an attack detection unit used for detecting whether a behavior about giving an attack according to the DNS server cathe exists, and adding the attacked domain into a protected list if the behavior exists; a cathe protection unit used for checking whether the domain in a DNS response message is in the protected list when the attack behavior happens, changing the survival time corresponding to the domain into a shorter survival time and sending out the changed response message if the domain is in the protected list. The method and the device for prevention of DNS cathe attack have a very remarkable effect of preventing the attack given to DNS cathe in an exhaustion manner.
Owner:杭州迪普信息技术有限公司
Systems and methods for managing domain name system security (DNSSEC)
ActiveUS8910245B2Digital data processing detailsMultiple digital computer combinationsDomain nameMultiple modes
The present invention is directed towards systems and methods for providing multiple modes of a zone for DNSSEC by an intermediary device. The method includes providing, by a device intermediary to a plurality of clients and a plurality of servers, a plurality of modes of a zone for Domain Name Service. The device receives a selection of a first mode of the zone of the plurality of modes of the zone. The device receives information identifying to enable DNS Security for the selected first mode. The device establishes the zone for DNS in accordance with the selected first mode and with DNS Security enabled.
Owner:CITRIX SYST INC
Domain name system security network
In one embodiment, a DNS security network includes several DNS appliances and a security operations center (SOC) server computer. The SOC server computer may receive telemetry data from the DNS appliances, the telemetry data comprising information about DNS client queries received in the respective DNS appliances. From the telemetry data, the SOC server computer may generate security policies for distribution to the DNS appliances. The security policies may be used by the DNS appliances to determine whether a DNS client query is originated by a client computer performing a prohibited activity (e.g., sending spam, communicating with a zombie control computer, navigating to a prohibited website, etc.). An answer to a client query may be replaced or discarded altogether in cases where the originator is performing a prohibited activity.
Owner:TREND MICRO INC
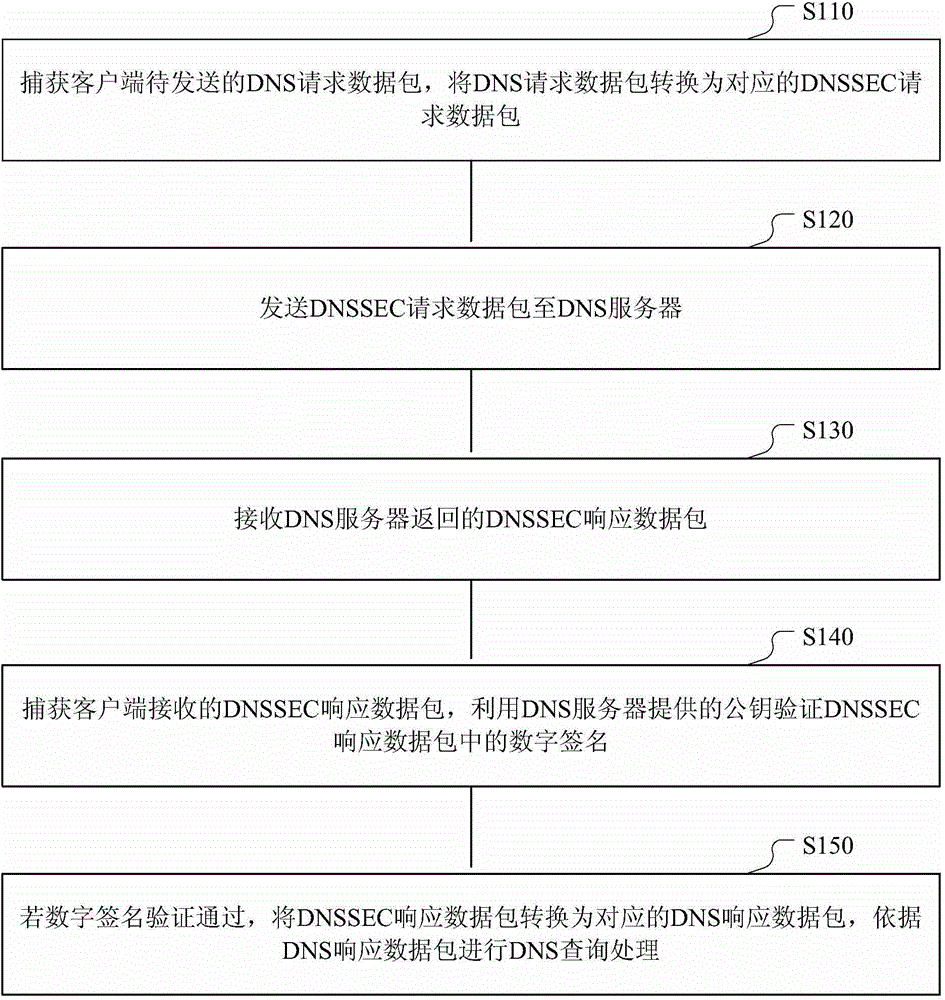
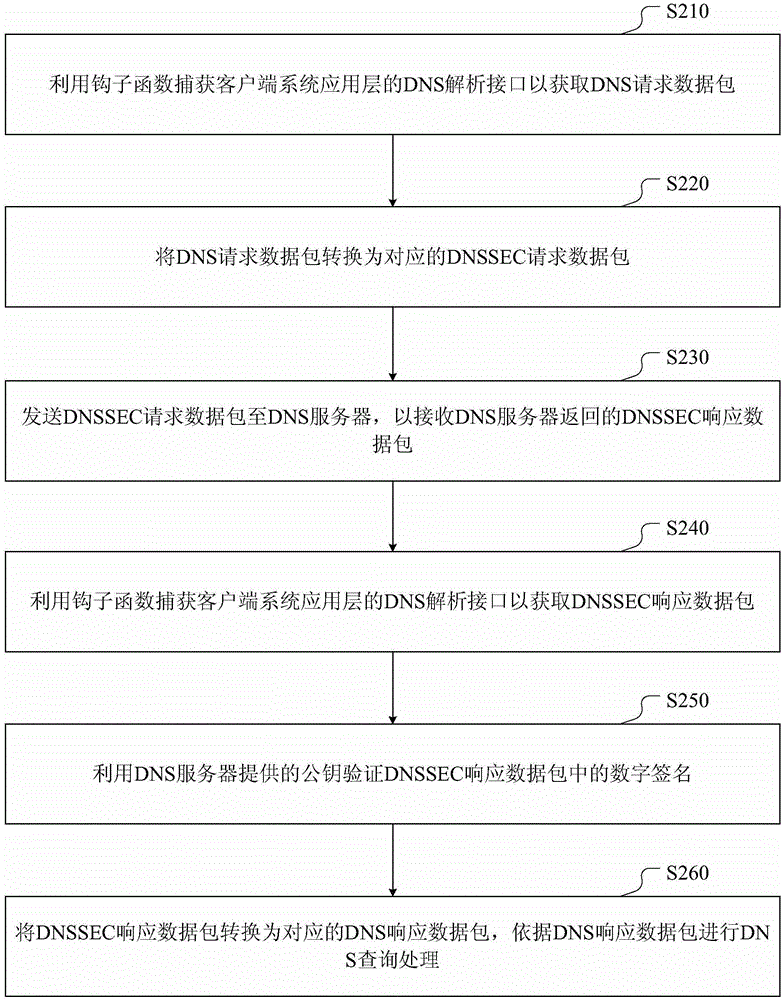
DNS (Domain Name Server) safety querying method and device
The invention discloses a DNS (Domain Name Server) safety querying method and device. The method comprises the steps of capturing a DNS request data packet to be sent by a client; converting the DNS request data packet into a corresponding DNSSEC (Domain Name System Security Extensions) request data packet; sending the DNSSEC request data to a DNS server to receive a DNSSEC response data packet returned by the DNS server; capturing the DNSSEC response data packet received by the client; verifying to a digital signature in the DNSSEC response data packet through a public key provided by the DNS server; if passing the digital signature passes the verification, converting the DNSSEC response data packet into the corresponding DNS response data packet; performing DNS querying processing according to the DNS response data packet. According to the scheme, the method has the advantages that the DNSSEC verification process is applied to the client, and a trust relationship between the client and the closest DNS server is configured, so as to form a complete trust chain with the DNS servers at each level; the truth and integrity of the data can be verified through the client, and thus the problems of DNS hijacking and cheating can be further avoided.
Owner:三六零数字安全科技集团有限公司
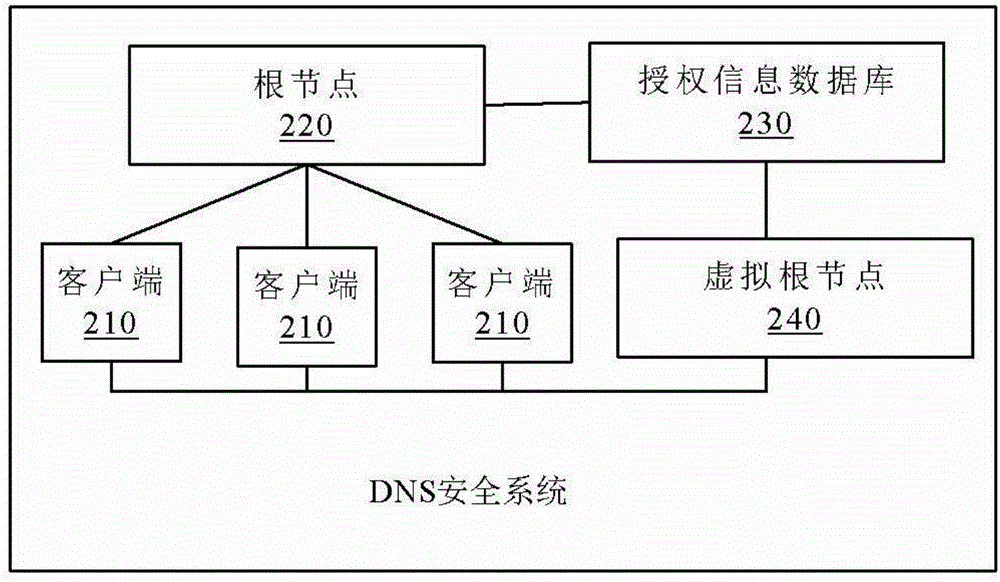
DNS safety system and fault processing method thereof
ActiveCN103957286AReduce single point of failureImprove defense against attacksTransmissionClient-sideFault handling
The invention provides a DNS safety system and a fault processing method thereof. The DNS safety system comprises at least one client end, a root node, an authorization information database and a virtual root node. The at least one client end is configured to initiate a DNS request. The root node is configured to provide authorization information for the DNS request. The authorization information database is configured to store all DNS requests and the corresponding authorization information in a specific area. The virtual root node is configured to call the corresponding authorization information from the authorization information database to provide analysis services for the corresponding client end when DNS analysis breakdown happens to the root node. The DNS safety system and the fault processing method thereof can improve the safety and the stability of DNS analysis.
Owner:BEIJING QIHOO TECH CO LTD +2
DNS health degree assessment method based on fuzzy comprehensive evaluation model
ActiveCN106911536AEfficient detectionFast analysisData switching networksStatistical analysisSecure state
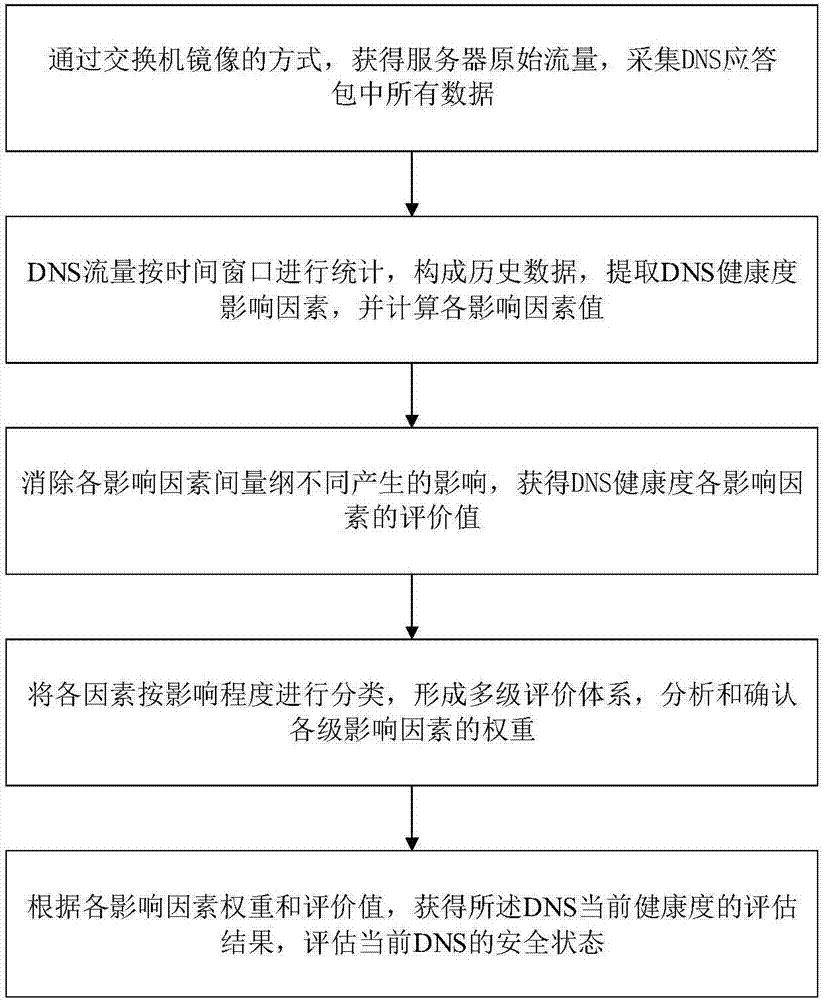
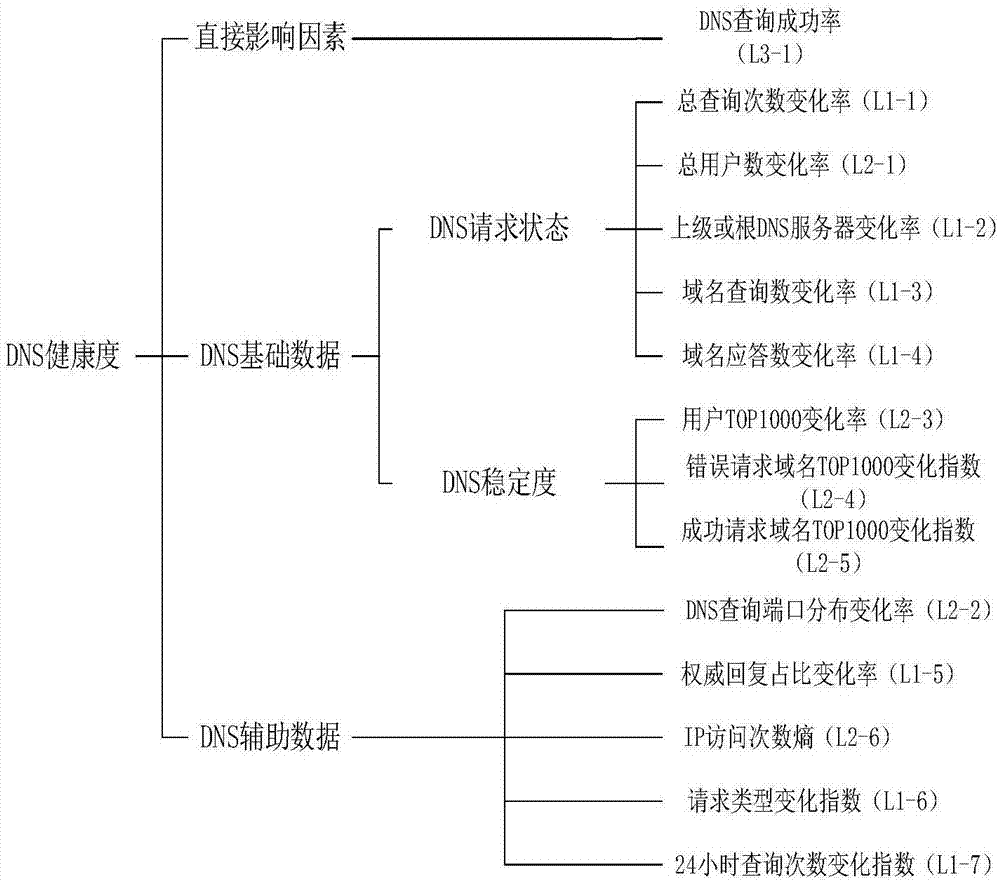
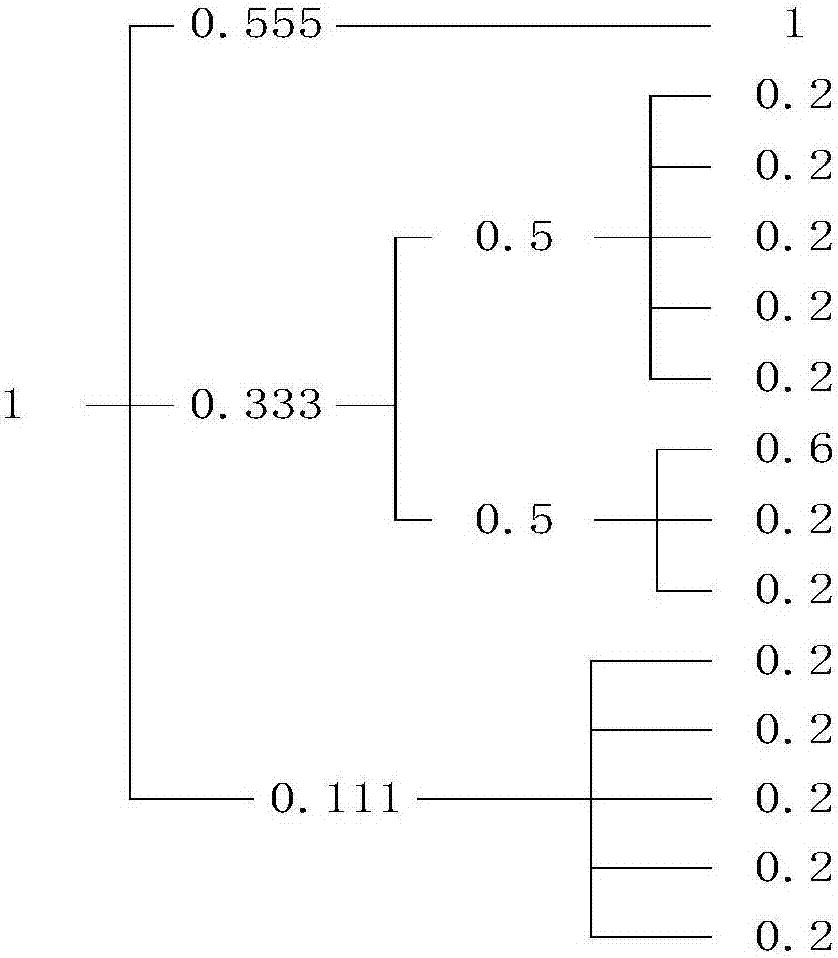
The invention discloses a DNS health degree assessment method based on a fuzzy comprehensive evaluation model. The DNS health degree assessment method comprises the following steps that step 1: server original traffic is acquired through the mode of switch mirroring, and all the data in a DNS response package are acquired; step 2: statistical analysis is performed through the DNS traffic according to a time window so as to form historical data, DNS health degree influence factors are extracted and the value of each influence factor is calculated; step 3: the influence generated by dimension difference between all the influence factors is eliminated so that the evaluation value of each DNS health degree influence factor is acquired; step 4: all the factors are classified according to the degree of influence so as to form a multilevel evaluation system, and the weight of each level of influence factor is analyzed and determined; and step 5: the current DNS security state is assessed according to the weight and the evaluation value of each influence factor so as to acquire the evaluation result of the current health state of the DNS. The characteristics of the current DNS traffic are fully considered so that multiple abnormal conditions of the DNS can be effectively detected.
Owner:SICHUAN UNIV
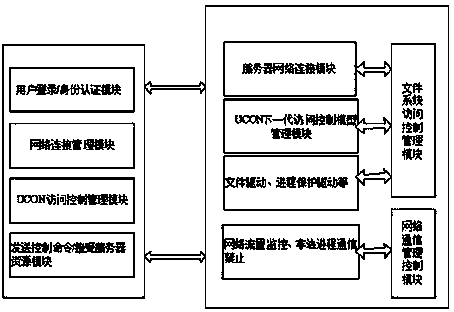
Cloud computing network server inner core safe access method
InactiveCN103457958AEnsure safetyEnsure communication securityTransmissionCommunications securityVirtualization
The invention relates to the technical field of cloud computing network server inner core safe access, in particular to a cloud computing network server inner core safe access method. According to the cloud computing network server inner core safe access method, actual requirements of cloud computing safety are combined, and a next-generation network access control model (UCON) is utilized. The UCON not only has the capacity of a traditional access control model, but also integrates the ability of credible management and digital right management. The UCON access control model is used to control system resources in the storage and document layer. The access control model capable of being tailored in a custom-made mode is adopted on a server virtualization platform to protect the safety of cloud computing virtualization. In a network layer, and DDOS is attacked against, DNS safety communication monitoring is conducted. Illegal access is discovered and forbidden in time so as to ensure server communication safety.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Behavior analysis based DNS tunneling detection and classification framework for network security
New and improved techniques for a behavior analysis based DNS tunneling detection and classification framework for network security are disclosed. In some embodiments, a platform implementing an analytics framework for DNS security is provided for facilitating DNS tunneling detection. For example, an online platform can implement an analytics framework for DNS security based on passive DNS traffic analysis.
Owner:INFOBLOX
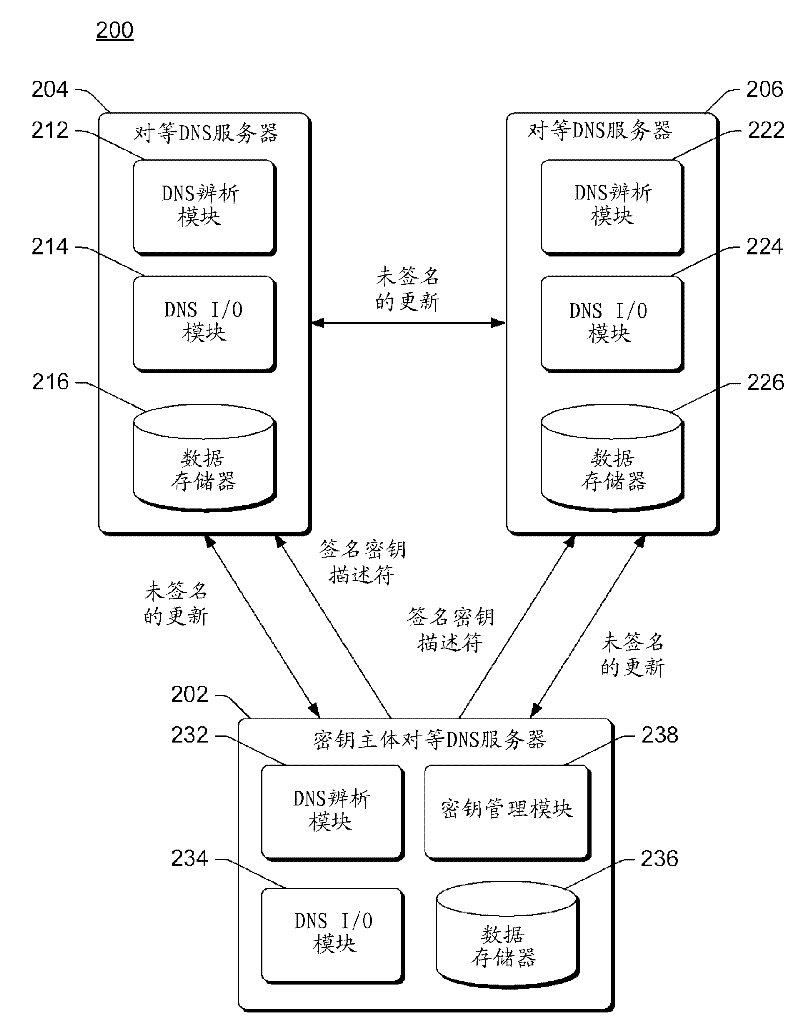
Supporting DNS security in a multi-master environment
ActiveCN102546176AKey distribution for secure communicationUser identity/authority verificationComputer networkDomain Name System
Multiple peer domain name system (DNS) servers are included in a multi-master DNS environment. One of the multiple peer DNS servers is a key master peer DNS server that generates one or more keys for a DNS zone serviced by the multiple peer DNS servers. The key master peer DNS server can also generate a signing key descriptor that identifies the set of one or more keys for the DNS zone, and communicate the signing key descriptor to the other ones of the multiple peer DNS servers.
Owner:MICROSOFT TECH LICENSING LLC
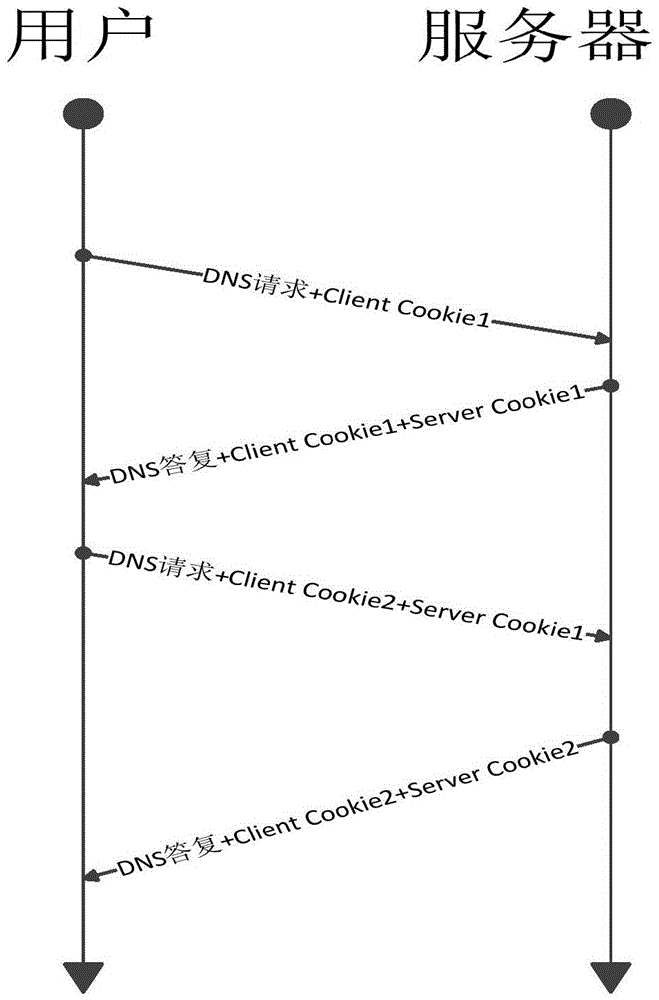
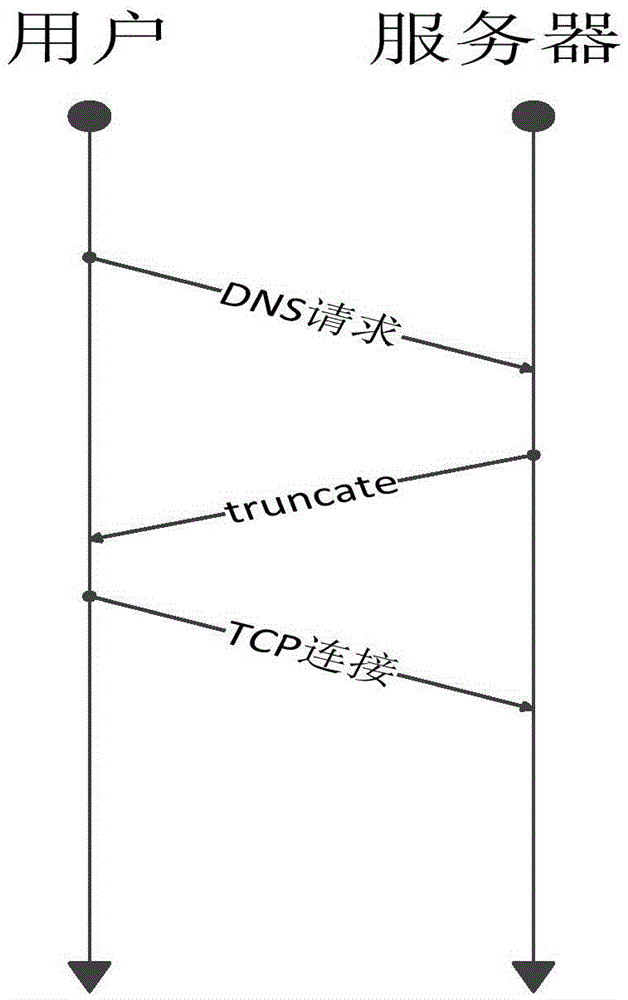
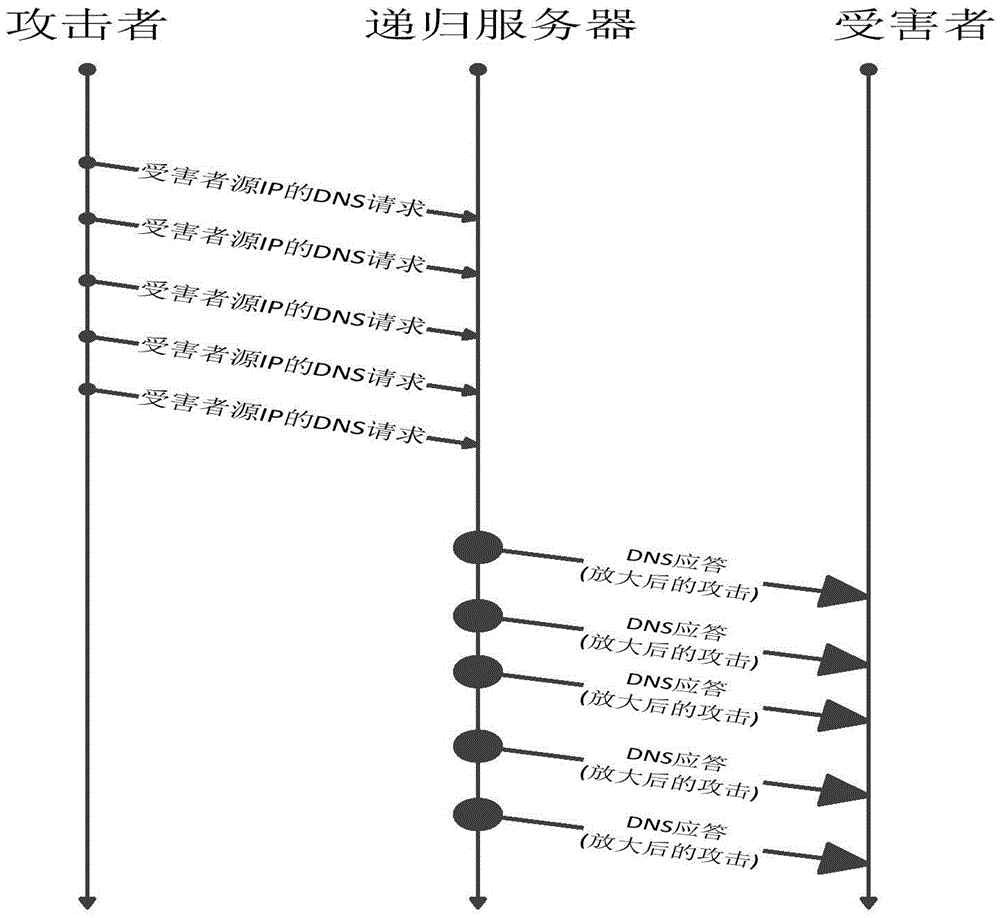
Solution for coping with reflection amplification attacks of domain name system (DNS) server
The invention belongs to the technical field of domain name system (DNS) security protection, and particularly relates to a solution for coping with reflection amplification attacks of a DNS server. The solution comprises the following steps that: a field of cookie is added into a pseudo resource record of EDNS0; a user generates random cookie while sending a request, and a recursive server checks whether the cookie exists or not after reception of the request, and returns truncate to require the user to perform retransmission by using a transmission control protocol (TCP) if the cookie does not exist; if the cookie exists, the recursive server checks whether the request carries Server Cookie or not, returns the Server Cookie together with Client Cookie if the request does not carry the Server Cookie, checks whether Server Cookie of the user is consistent with the Server Cookie generated by the recursive server if the request carries the Server Cookie, returns the Server Cookie and the Client Cookie to the user if the Server Cookie of the user is consistent with the Server Cookie, and returns the truncate to require the user to perform retransmission by using the TCP if the Server Cookie of the user is not consistent with the Server Cookie; and the user checks whether the Client Cookie is the same as the random cookie or not, receives the data if the Client Cookie is the same as the random cookie, and discards the data if the Client Cookie is not the same as the random cookie.
Owner:BEIJING INTERNET INST +1
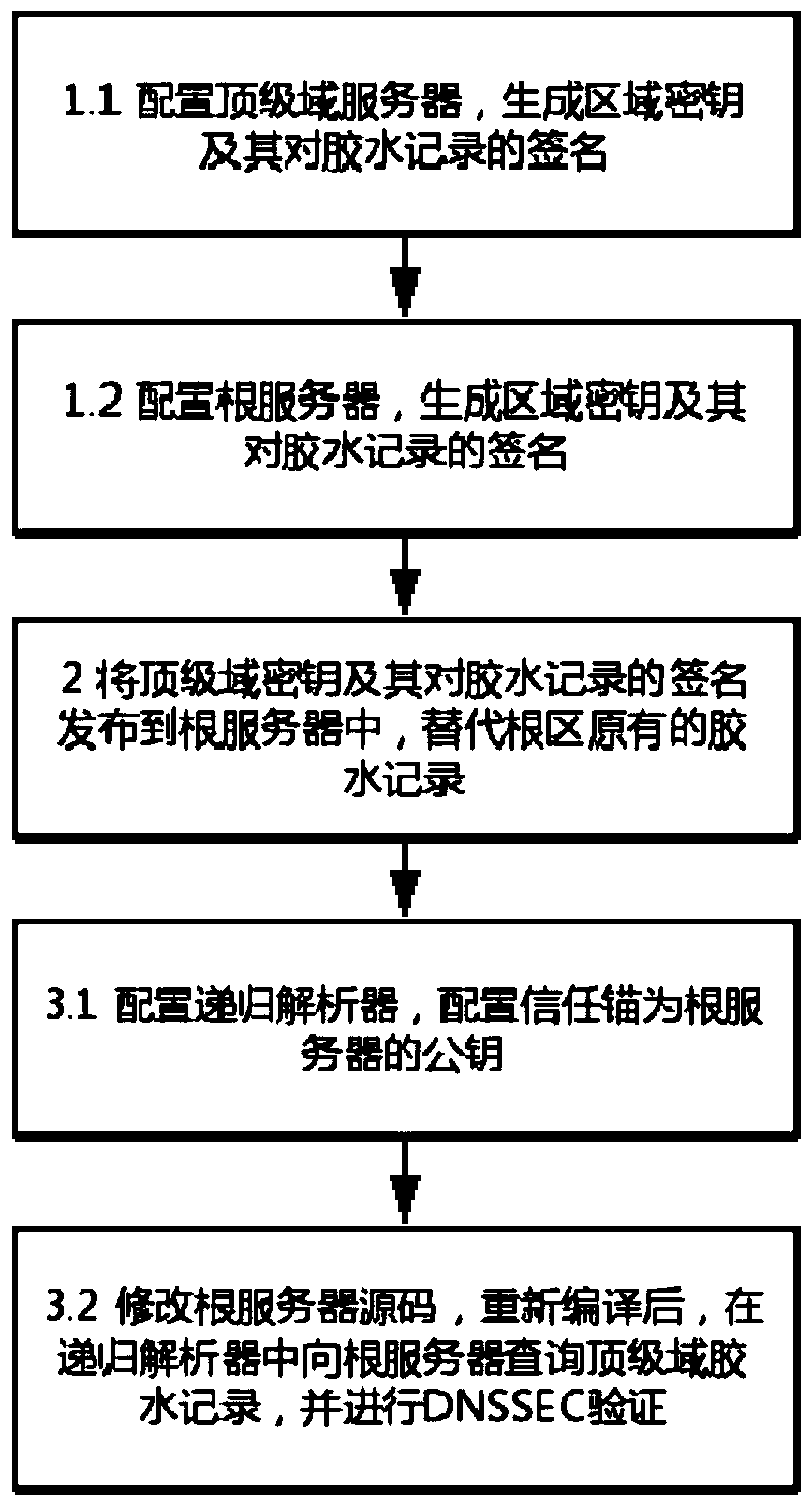
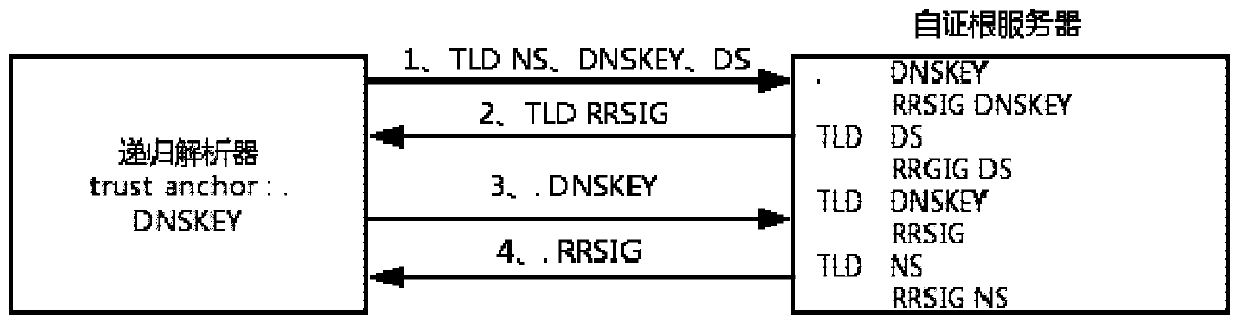
Self-certified root implementation method based on open source DNS software
ActiveCN110071810AImprove securitySelf-Certifying Root ImplementationKey distribution for secure communicationUser identity/authority verificationSelf certifiedOpen source
The invention discloses a self-certified root implementation method based on open source DNS software, and relates to the technical field of DNS security improvement. The invention aims to solve the problem that the root area glue record is tampered due to the fact that a signature mechanism for the root area glue record is not provided in an existing DNSSEC scheme. The method comprises the following steps: generating a regional key and a signature of the regional key to a glue record in a root server and a top-level domain server; and releasing the top-level domain key and the glue record signature thereof to a root server to replace the original glue record of the root region, and querying the top-level domain glue record from the root server on a recursive analyzer and carrying out DNSSEC verification. According to the self-certified root scheme, potential safety hazards that glue records in a DNSSEC scheme may be tampered are improved, and the safety of the glue records in the rootregion is improved by adding signatures of the glue records in the root region. By modifying the source code of the open source DNS software, a trust chain of glue recording from the root domain to the top domain is established in the root region, and self-certification of the root is achieved.
Owner:HARBIN INST OF TECH
DNS end-to-end analysis method capable of ensuring safety and privacy
InactiveCN105357212AFix security issuesSolve protection problemsTransmissionClient-sideAnalysis method
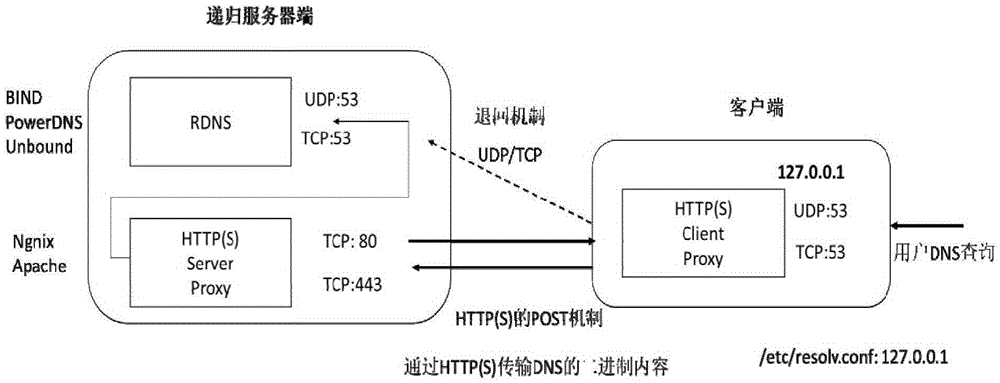
The invention belongs to the technical field of DNS security protection and especially relates to a DNS end-to-end analysis method capable of ensuring safety and privacy. The method comprises the following steps: a configuration file of a client operating system is configured with an address of a recursive server; a client sends a DNS query message to a local 127.X.X.X address, and a client proxy process receives the query message and establishes HTTP or HTTPS connection with a proxy of the recursive server; the client adopts a POST interaction mode to sent data to the recursive server, and the DNS message is sent to the proxy of the recursive server through the HTTP or HTTPS in the form of binary content; when a DNS response message IS received from the recursive server, the DNS response message is sent to the client by adopting the process opposite to the DNS query message; and when the cache of the recursive server does not have the DNS query message, the recursive server sends a DNS request to an authoritative server through DNSSEC.
Owner:BEIJING INTERNET INST +1
Cloud based security using DNS
A cloud-based security method using Domain Name System (DNS) includes receiving a request from a user device at a DNS server; performing a security check on the request based on a policy look up associated with the user device; responsive to the policy look up, performing a DNS security check on the request; and responsive to the DNS security check, performing one of allowing the request to the Internet; blocking the request based on the policy; and providing the request to inline inspection based on the policy, wherein the request is one of allowed to the Internet or blocked based on the inline inspection.
Owner:ZSCALER INC
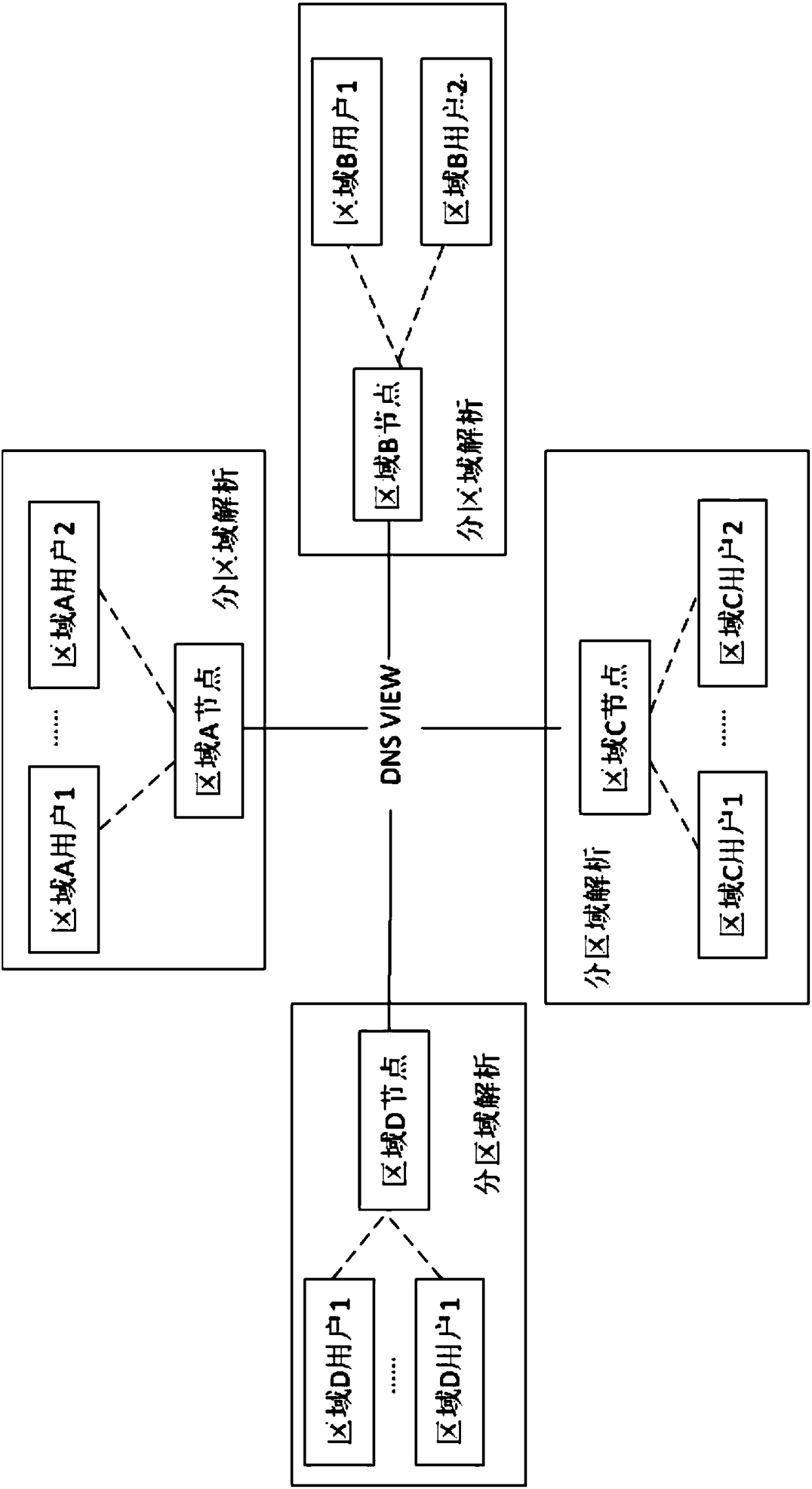
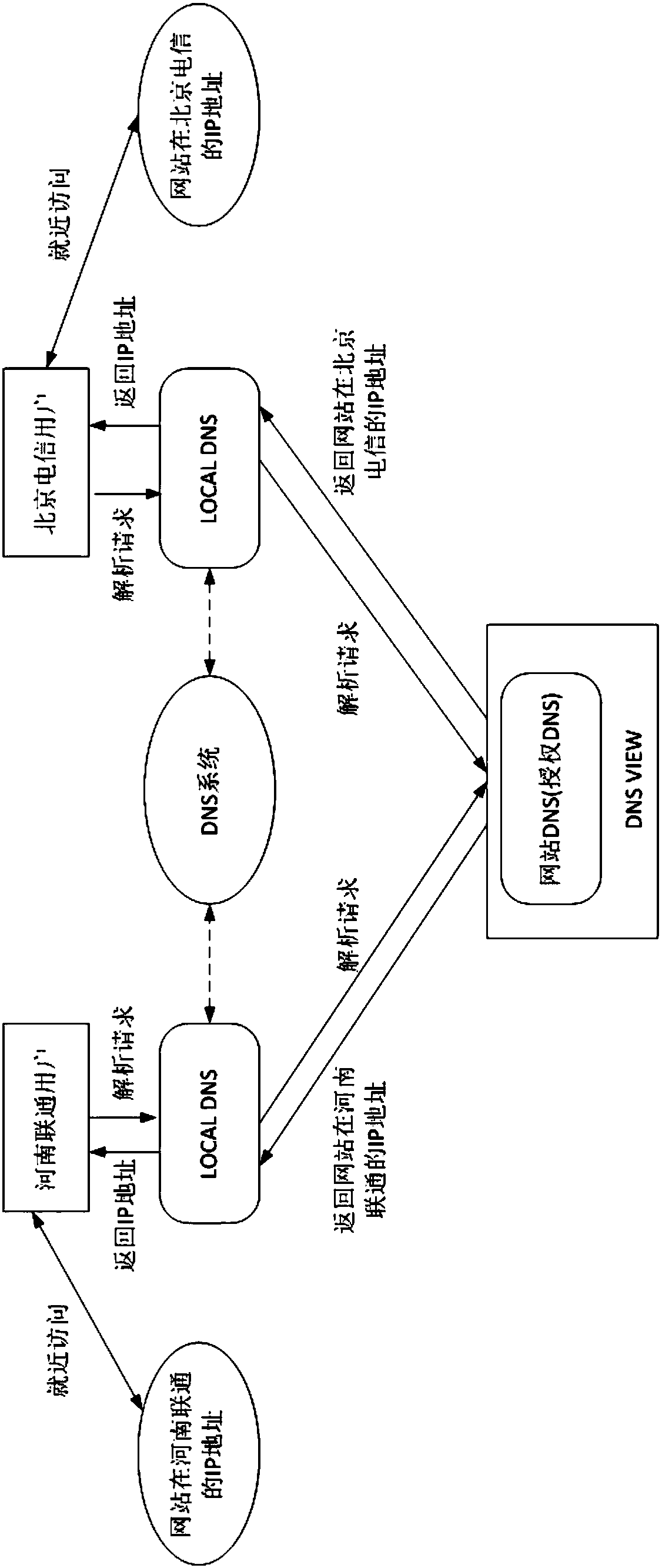
A method for improving DNS safety and performance
The invention discloses a method for improving DNS safety and performance. Through a DNS VIEW function, domain name resolutions can be carried out by different DNS authorized servers according to different areas, corresponding IP addresses can be returned, proximity resolutions and load balancing can be achieved, and the situation that resolutions are carried out by concentrating on one or severalauthorized DNS servers can be avoided. Compared with the prior art, the method can increase the coverage area of authoritative servers and improve service performance, and the nodes of the authoritative servers can be resolved proximally for different regions of the country. The prevention areas of DNS authoritative servers can be effectively extended because of the dispersion of DNS authority, and therefore, DNS attacks can be effectively defended, and the safety of the DNS authority can be increased.
Owner:北京云端智度科技有限公司
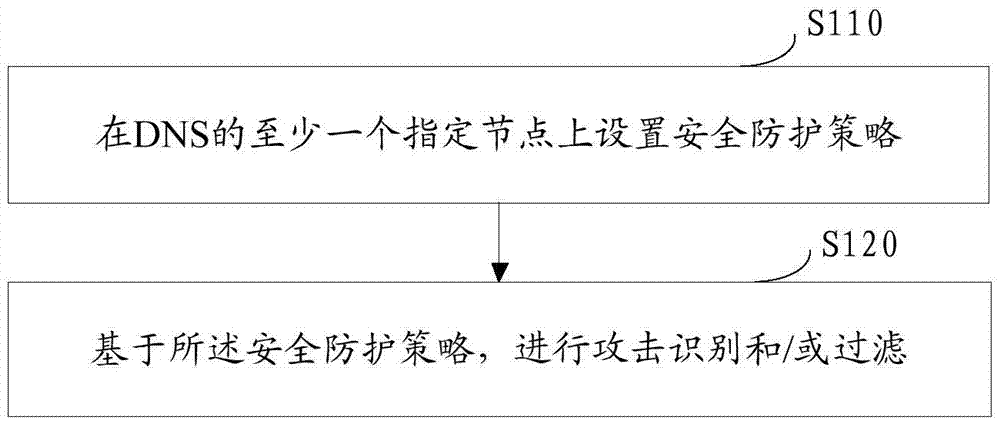
Security protection method and device for domain name system (DNS) and DNS
ActiveCN106953830AImprove response rateImprove response efficiencyTransmissionDomain nameDomain Name System
The embodiment of the invention discloses a security protection method and device for a domain name system (DNS) and the DNS. The security protection method for the DNS comprises the following steps: setting a security protection strategy on at least one specified node of the DNS; and performing attack identification and / or filtering based on the security protection strategy.
Owner:CHINA MOBILE GRP FUJIAN CO LTD
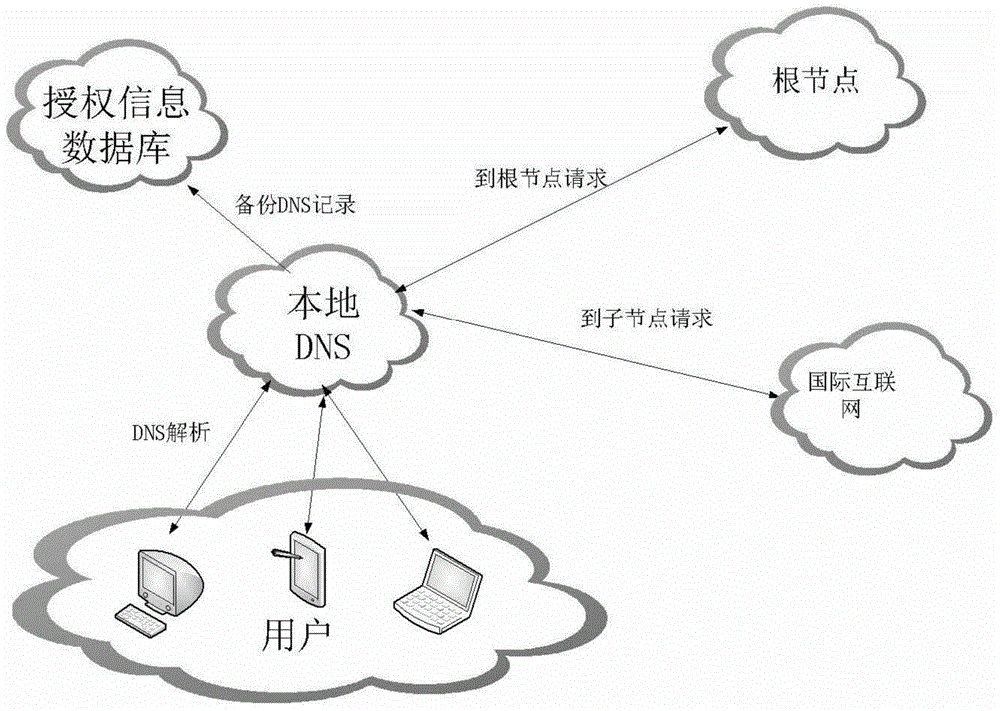
Safe DNS system based on local analysis and DNS security analysis method
ActiveCN104539603AImprove parsing speedAvoid the possibility of hijackingTransmissionSecurity questionCryptography protocols
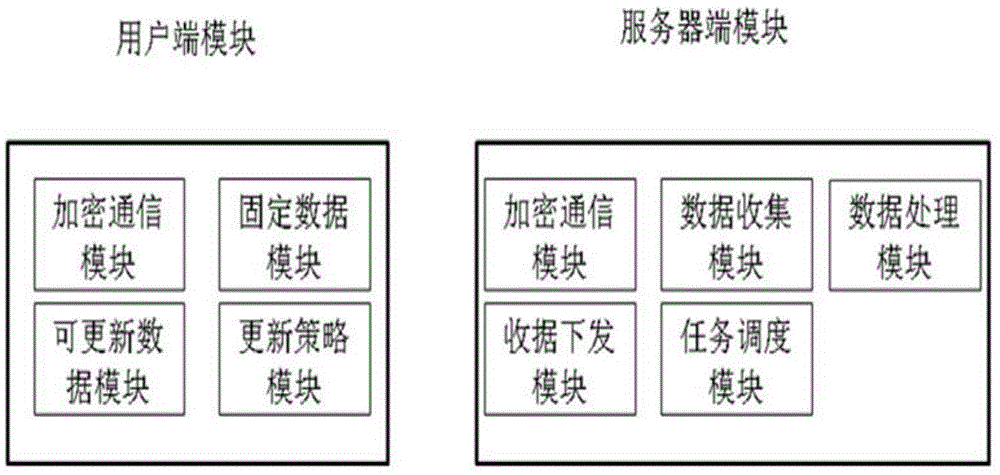
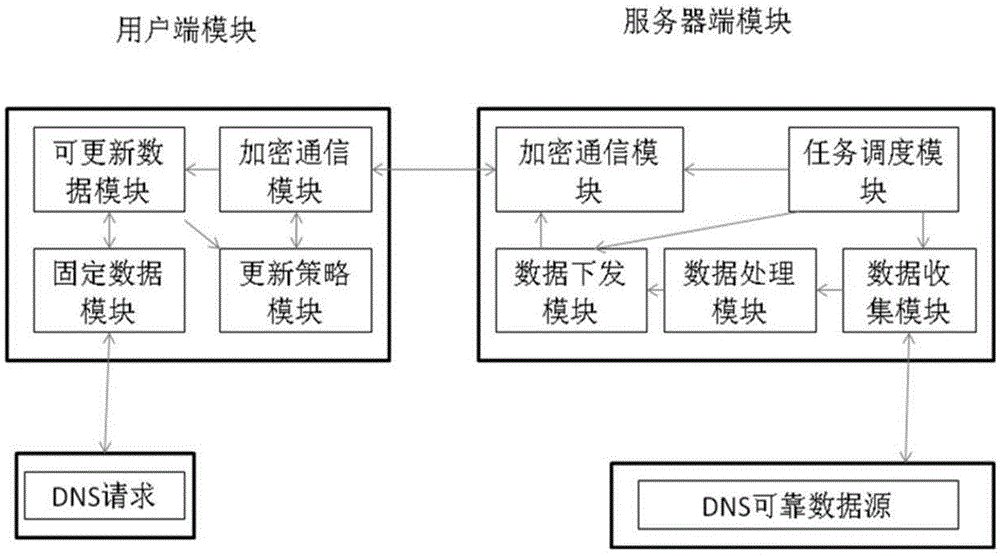
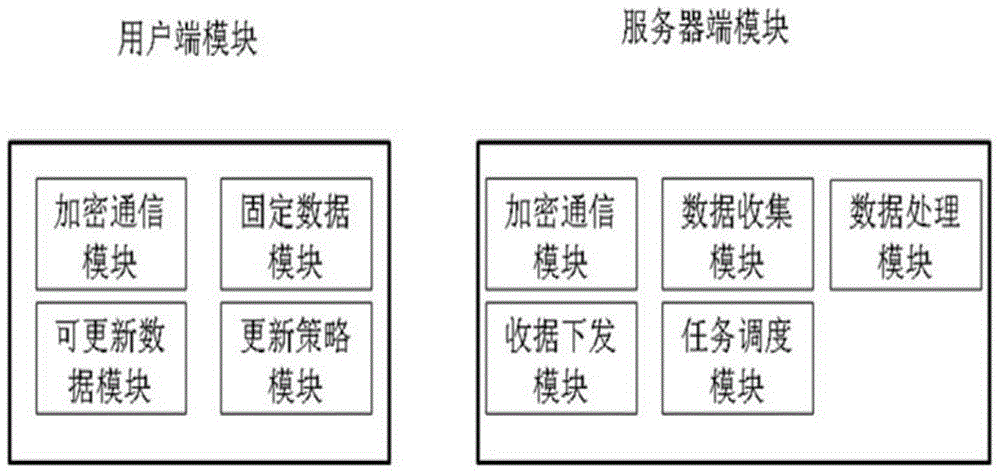
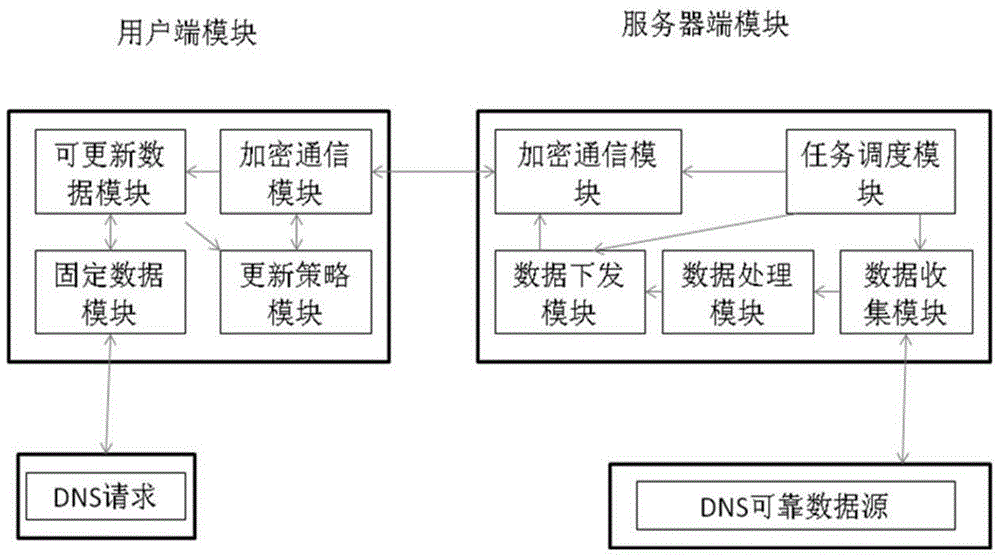
The invention relates to a safe DNS system based on local analysis and a DNS security analysis method. The system comprises a user side module and a server side module, the user side module is deployed in a host of a user, and the server side module is deployed in a provider of a solution; the user side module is in communication with the server side module through a private encryption protocol. The user side module includes an encryption communication module, a fixed data module, an updatable data module and a strategy updating module. The server side module includes an encryption communication module, a data collection module, a data processing module, a data issuing module and a task scheduling module. The DNS security analysis solution which can be achieved rapidly by the common user is provided, the user can promote the security level through independent deployment without waiting the network provider to deploy safety equipment on a large scale, and therefore safety problems are controlled by the user.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Network-based DNS security updating method in MIPv6
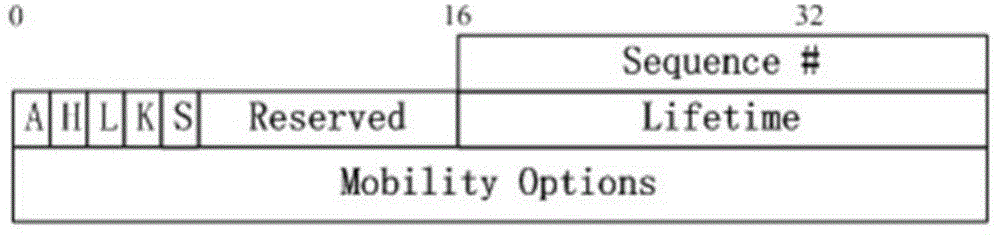
ActiveCN104410728AEnsure safetyImprove the efficiency of update operationsTransmissionDns securityComputer security
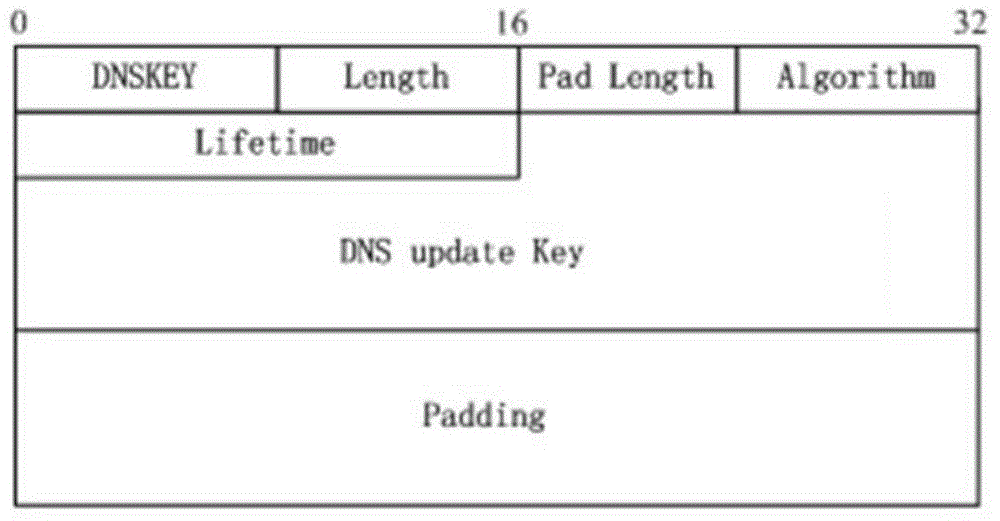
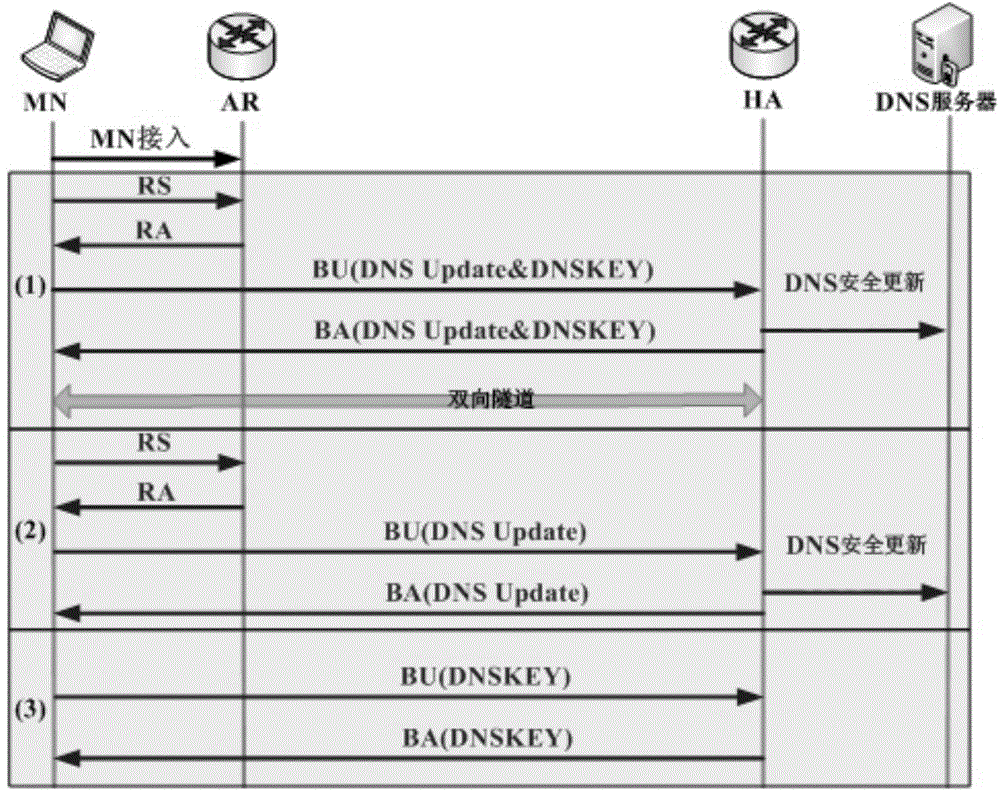
The invention discloses a network-based DNS security updating method in MIPv6. The method comprises the following steps: adding new items with key information for AAAA record updating into Binding Update (BU) of MIPv6, and providing service regulations of the items; transmitting the AAAA updating key of MN to HA through MIPv6 signalling, thereby ensuring the security of the AAAA record and the PTR record updating. By adopting the method, HA takes the duty of DNS updating operation of MN, so that the efficiency of updating operation is improved, dynamic DNS updating of large-scale nodes is supported, and in addition, the operation process of the method is compatible with updating operation defined in later RFC5026.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Using aggregated DNS information originating from multiple sources to detect anomalous DNS name resolutions
A DNS security system collects and uses aggregated DNS information originating from a plurality of client computers to detect anomalous DNS name resolutions. A server DNS security component receives multiple transmissions of DNS information from a plurality of client computers, each transmission of DNS information concerning a specific instance of a resolution of a specific DNS name. The server component aggregates the DNS information from the multiple client computers. The server component compares DNS information received from a specific client computer concerning a specific DNS name to aggregated DNS information received from multiple client computers concerning the same DNS name to identify anomalous DNS name resolutions. Where an anomaly concerning received DNS information is identified, a warning can be transmitted to the specific client computer from which the anomalous DNS information was received.
Owner:CA TECH INC
DHT expanded DNS mapping system and method for realizing DNS security
InactiveCN102045413BImprove compatibilitySolve the hierarchical authorization problemKey distribution for secure communicationComputer networkSchema for Object-Oriented XML
The invention discloses a distributed hash table (DHT) expanded domain name system (DNS) mapping system and a method for realizing DNS security. The mapping system comprises a host with a DNS resolver, a local and authorized DNS server and a DHT server in a DHT ring, wherein the DNS server and the DHT server serving as mapping servers manage mapping information from identity to position together and query mapping information for the host. The system synthesizes the advantages of the DNS and the DHT, absorbs a DNS tree structure, supports hierarchical query of the mapping information, is provided with reasonable commercial and trust models, and succeeds the advantages of DHT redundancy backup, strong robustness and the like; and the system can be realized on the basis of the conventional DNS mapping system so as to reduce a large amount of financial resource and manpower of network construction. A complete trust chain is established between the DHT ring and the upper DNS server, a transaction signature (TSIG) key is automatically distributed by using an ID management server positioned in an identity and position separation architecture, and the original DNS signature (DNSSEC) and TSIG security mechanisms of the DNS are ensured to be completely realized in the DHT expanded DNS mapping system.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method and system for wireless network security detection and repair
The present invention provides a method and system for security detection and repair of a wireless network, wherein the method for security detection and repair of a wireless network includes: a client detects a network configuration of a wireless network, sends a security detection request to a cloud detection terminal server, The security detection request carries the detection result of the network configuration; the cloud detection server determines the security level corresponding to the wireless network of the client according to the detection result and the set security level judgment rules, and sends the determined security level to the client. Judgment rules include: if the DNS conforms to the first DNS security rule, then the DNS security level is dangerous; if the DNS conforms to the second DNS security rule, then the DNS security level is safe; if the DNS conforms to the third DNS security rule, then the DNS security level is Warning; the client makes repairs to network configurations identified as dangerous and warning. Through the present invention, the security risk of DNS tampering is curbed.
Owner:三六零数字安全科技集团有限公司
A method and device for preventing dns cache attack
ActiveCN102404318BShorten the effective timeDNS Cache Attack DefenseTransmissionDomain nameComputer network
The invention provides a method and a device for prevention of DNS cathe attack. The device comprises an attack detection unit used for detecting whether a behavior about giving an attack according to the DNS server cathe exists, and adding the attacked domain into a protected list if the behavior exists; a cathe protection unit used for checking whether the domain in a DNS response message is in the protected list when the attack behavior happens, changing the survival time corresponding to the domain into a shorter survival time and sending out the changed response message if the domain is in the protected list. The method and the device for prevention of DNS cathe attack have a very remarkable effect of preventing the attack given to DNS cathe in an exhaustion manner.
Owner:杭州迪普信息技术有限公司
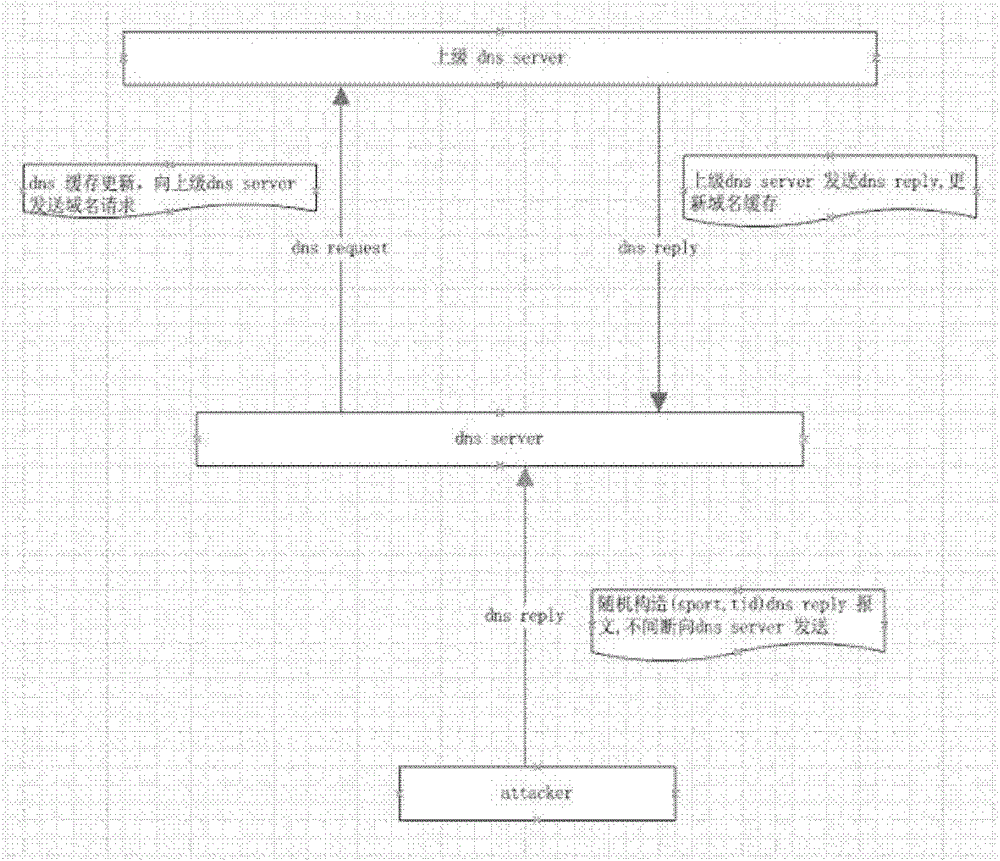
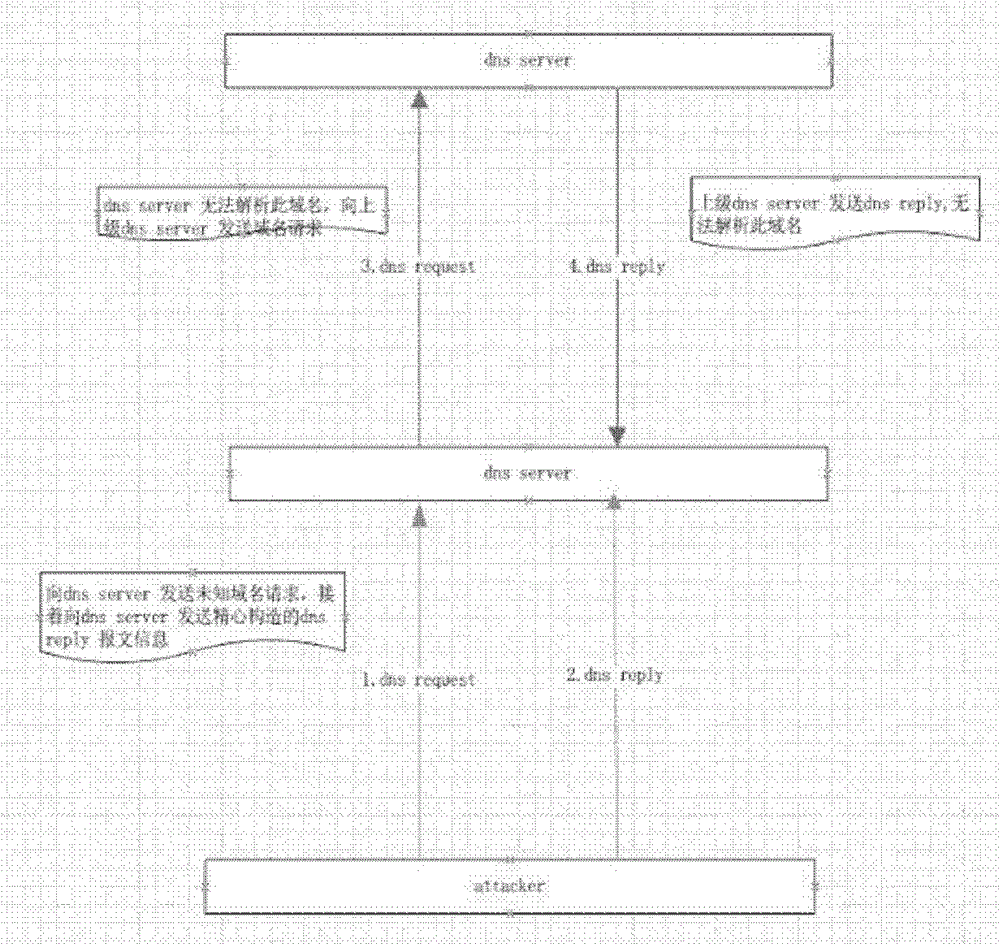
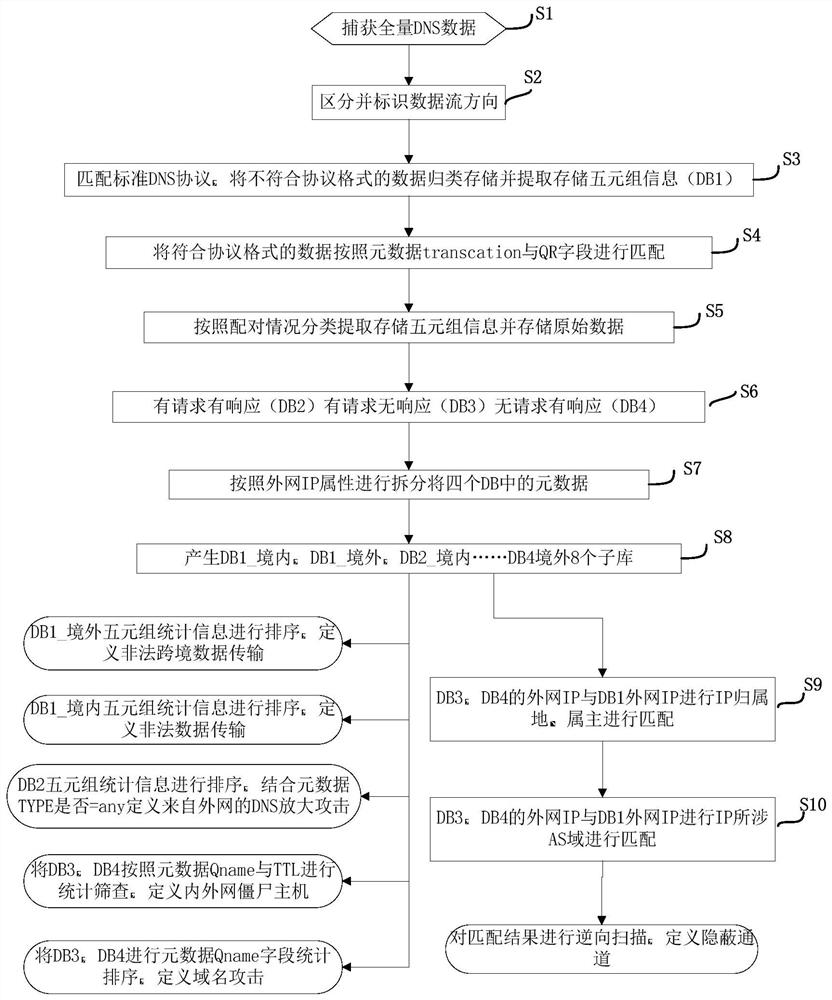
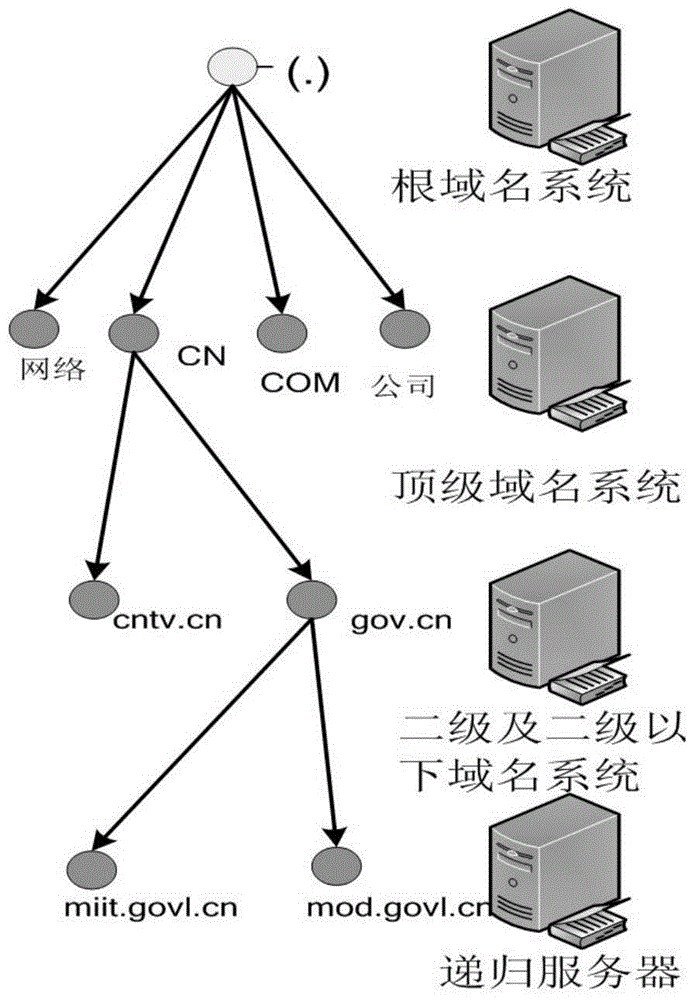
A method for dns protection and data leakage prevention based on metadata analysis
The invention relates to a method for DNS protection and data leakage prevention based on metadata analysis. The method first extracts the original data and metadata of the full amount of DNS data and stores them in scientific classification; The extended metadata knowledge base (IP, AS domain owner, etc.) that comes with the system can easily and quickly locate and find various DNS security events; at the same time, through cross-validation between sub-datasets, seemingly unrelated DNS data behavior is accurately and quickly defined as malicious data behavior, such as covert covert data transmission or remote control behavior. Through the invention, the DNS behavior in the deployed network environment can be scientifically and reasonably supervised and visualized. Provide highly accurate technical support for security management and policy implementation.
Owner:北京大天信息技术有限公司
Safe dns system and dns safe parsing method based on local parsing
ActiveCN104539603BImprove parsing speedAvoid the possibility of hijackingTransmissionSecurity questionSecurity level
The invention relates to a local resolution-based secure DNS system and a DNS security resolution method. The system includes a client module and a server module. The client module is deployed on the user's own host, and the server module is deployed by the solution provider. The client module and the server module communicate through a private encryption protocol. The client module includes: an encrypted communication module, a fixed data module, an updateable data module, and an update policy module; the server-side module includes: an encrypted communication module, a data collection module, a data processing module, a data delivery module, and task scheduling module. The present invention provides a DNS security analysis solution that can be quickly implemented by ordinary users. Users can complete the improvement of security levels through autonomous deployment without waiting for network providers to deploy security devices on a large scale, thereby controlling security issues in the hands of users themselves.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
A centralized DNS security monitoring method applied to routers
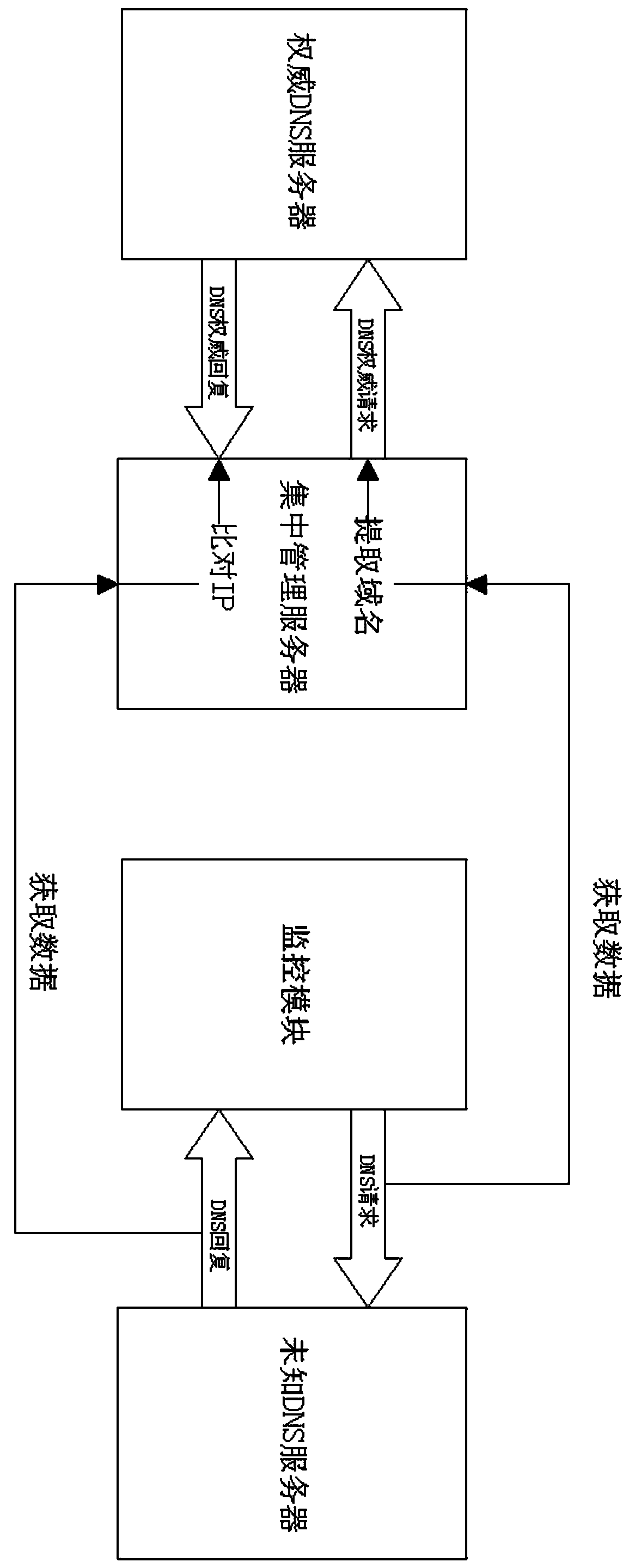
The invention discloses a centralized DNS security monitoring method applied to a router. A monitoring module is deployed on the router, and each time the router initiates a DNS resolution request to the DNS server, the detailed data of the request is recorded and transmitted to the centralized management server; centralized management The server extracts the domain name field in the detailed data of the request, uses this domain name field as the domain name to initiate a DNS resolution authoritative request to the authoritative DNS server, and records the reply data after receiving the authoritative request. The monitoring module records the reply data of the request and passes it to the centralized Manage the server; compare with the reply data of the authoritative request; monitor the existing DNS resolution process to obtain the DNS resolution request and reply data, submit them to the centralized management server, and use the request data of the resolution process to request the authoritative DNS domain name again The server compares the acquired safety reply data with the reply data to determine whether the DNS resolution process is safe.
Owner:CHENGDU QIANNIU INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com