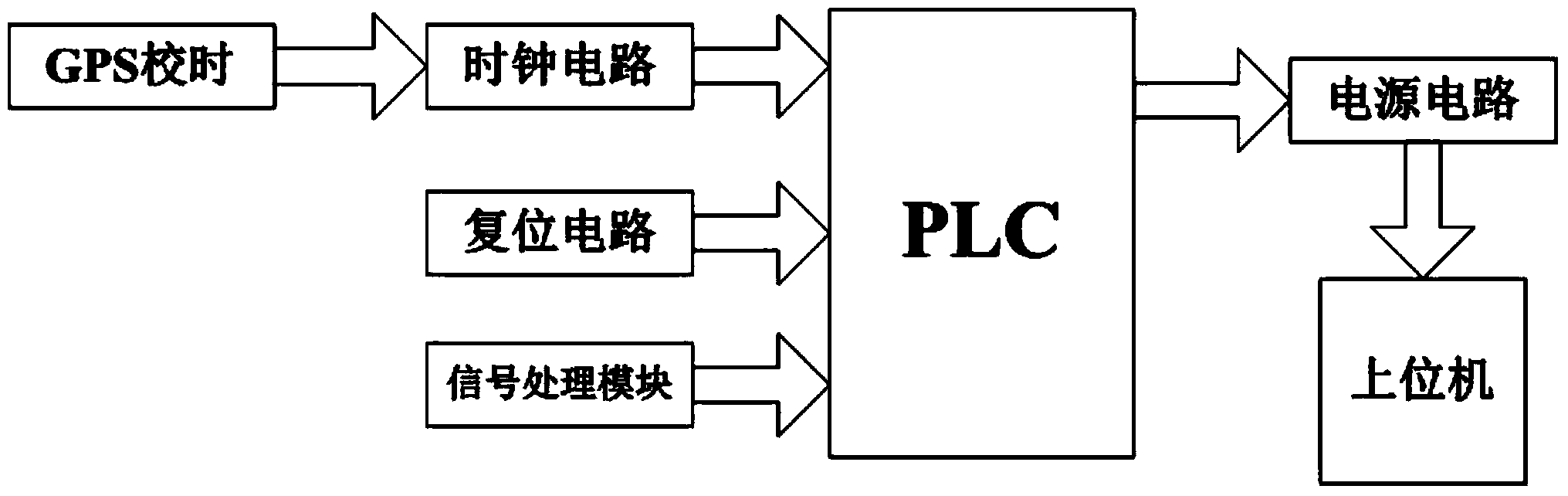
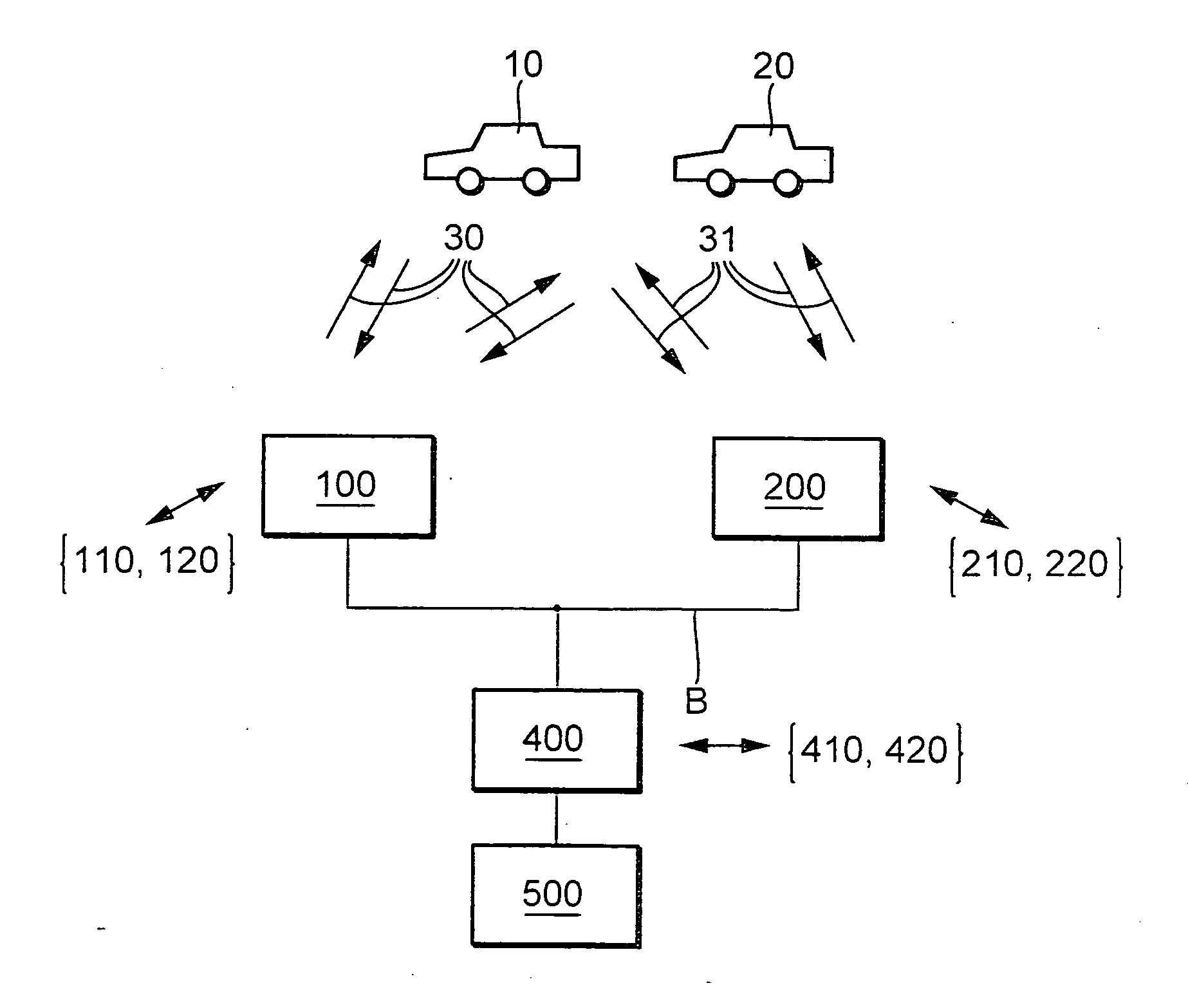
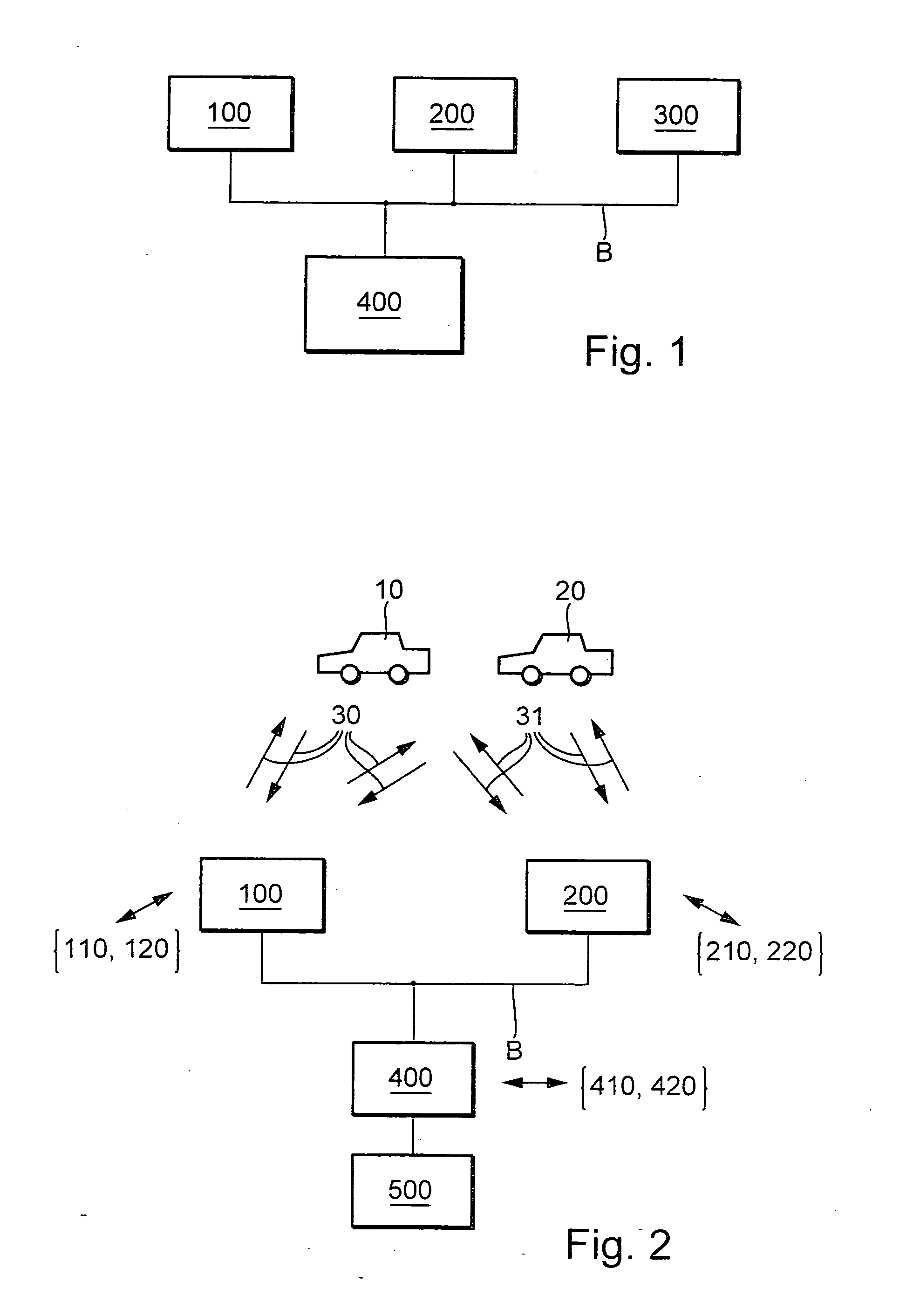
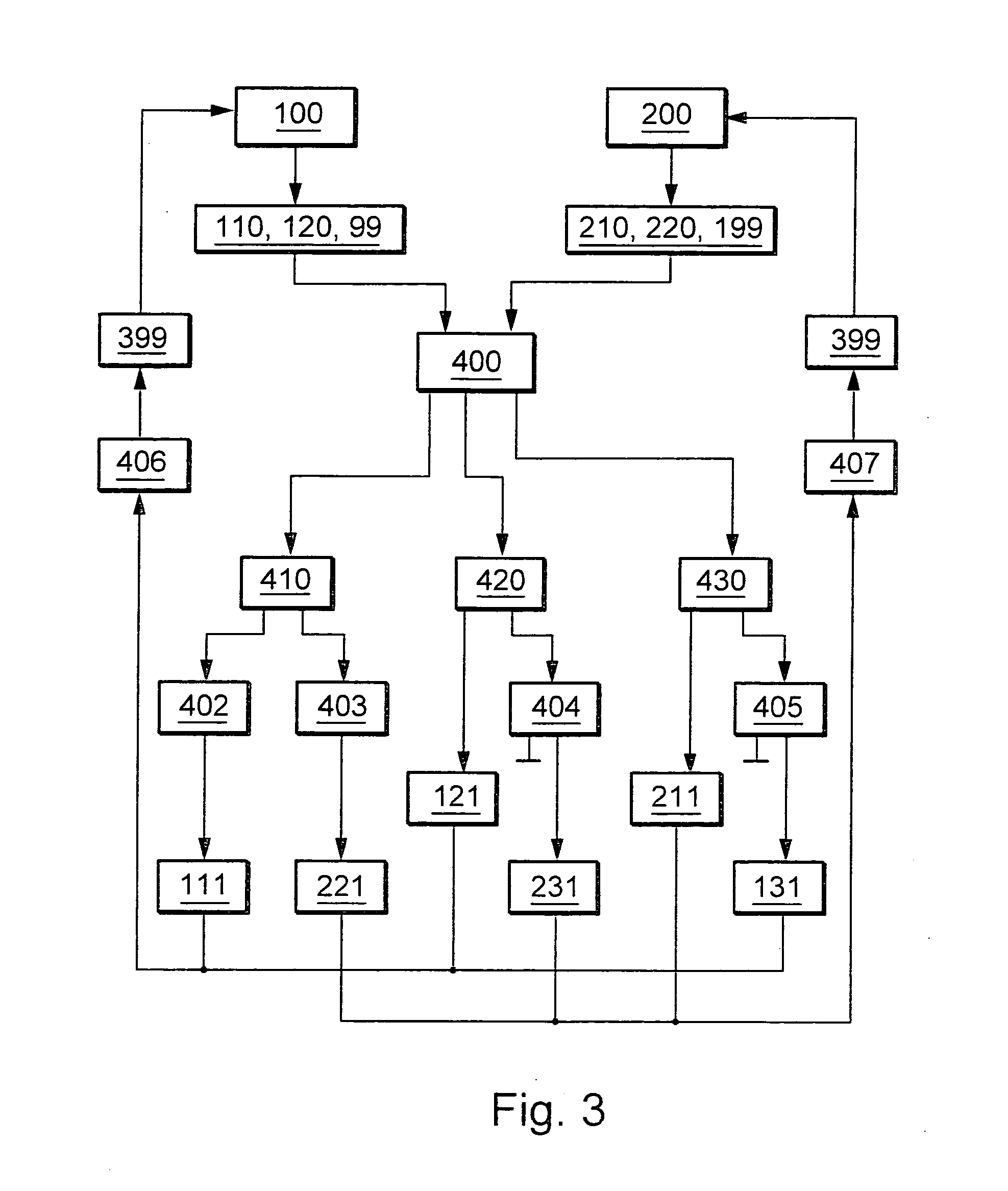
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4771results about How to "Reduce false alarm rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
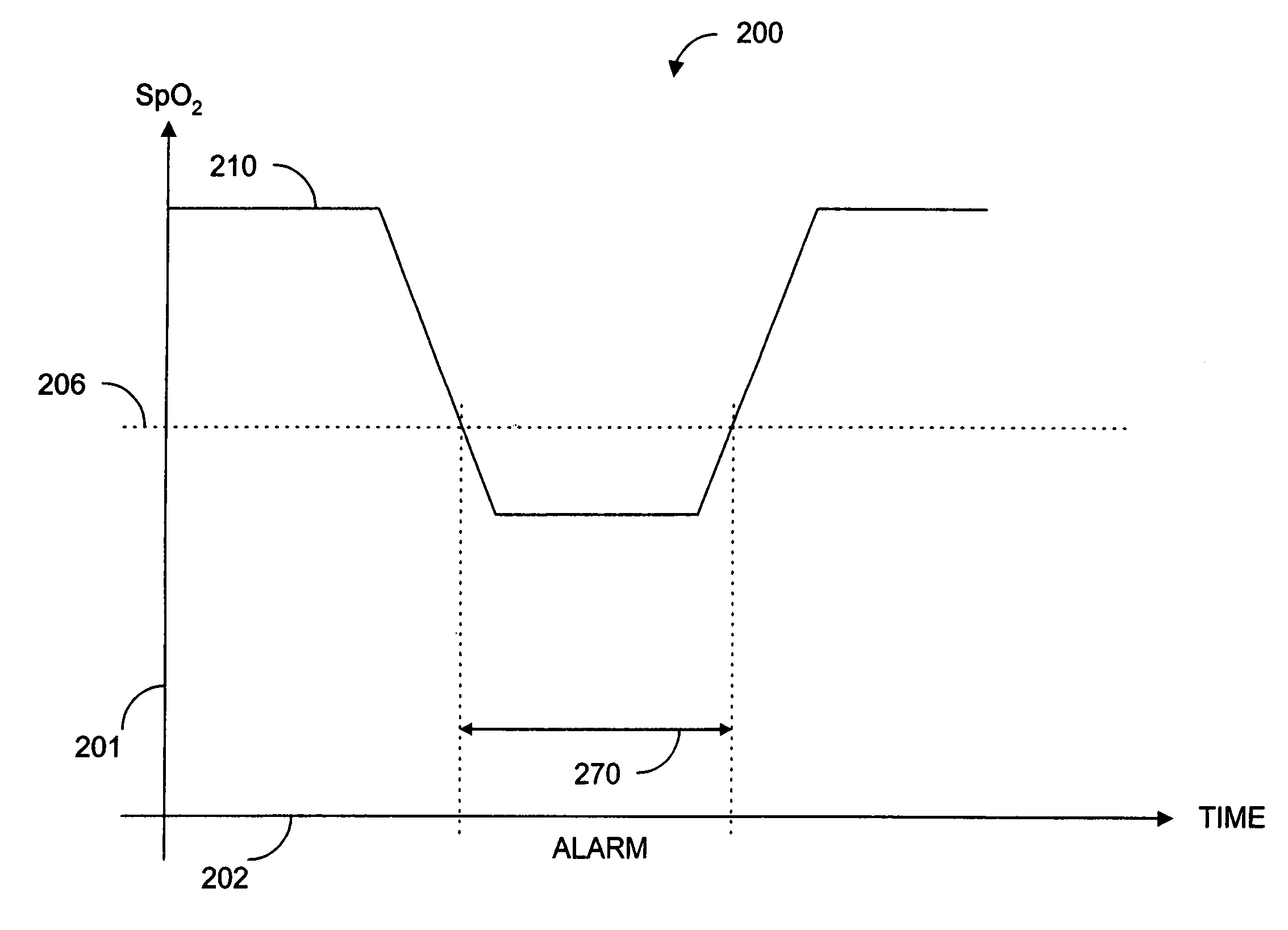
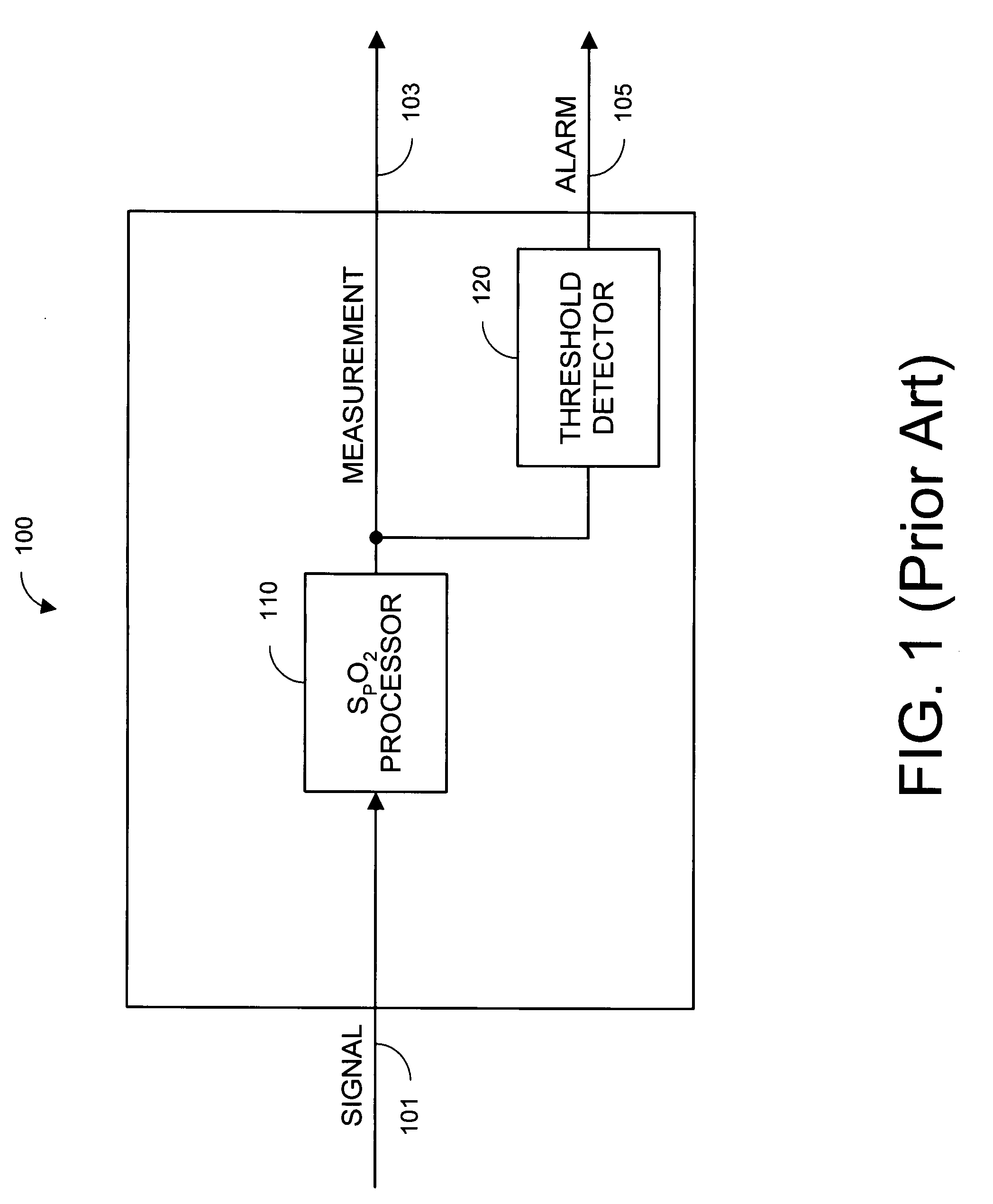
Parallel measurement alarm processor
InactiveUS7030749B2Waste caregiver resourcesReduce false alarm rateComputer controlResistance/reactance/impedenceNormal rangeComputer science
An alarm processor suppresses alarms when a physiological parameter is below a predetermined value but recovering toward a normal range.
Owner:JPMORGAN CHASE BANK NA
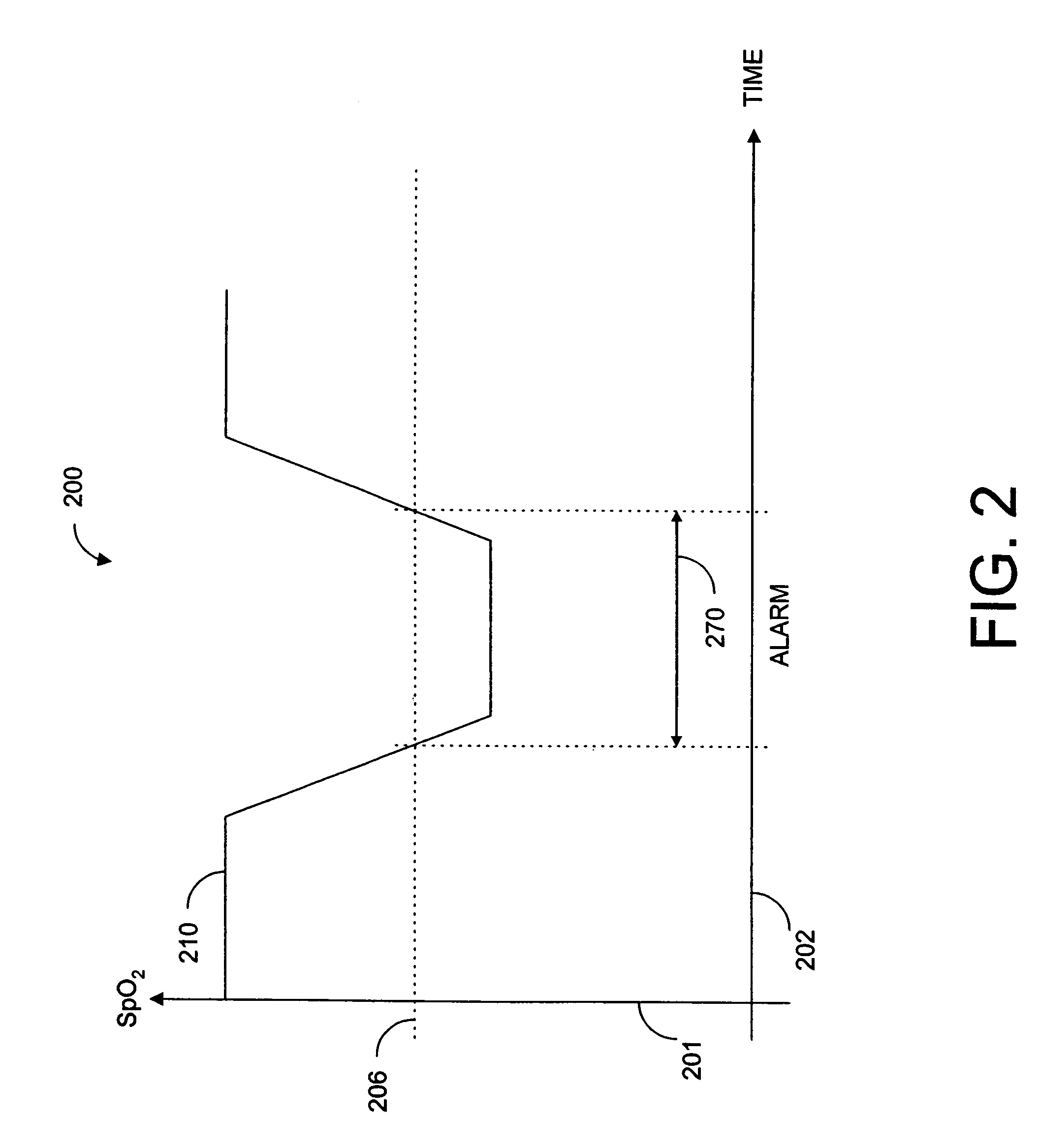
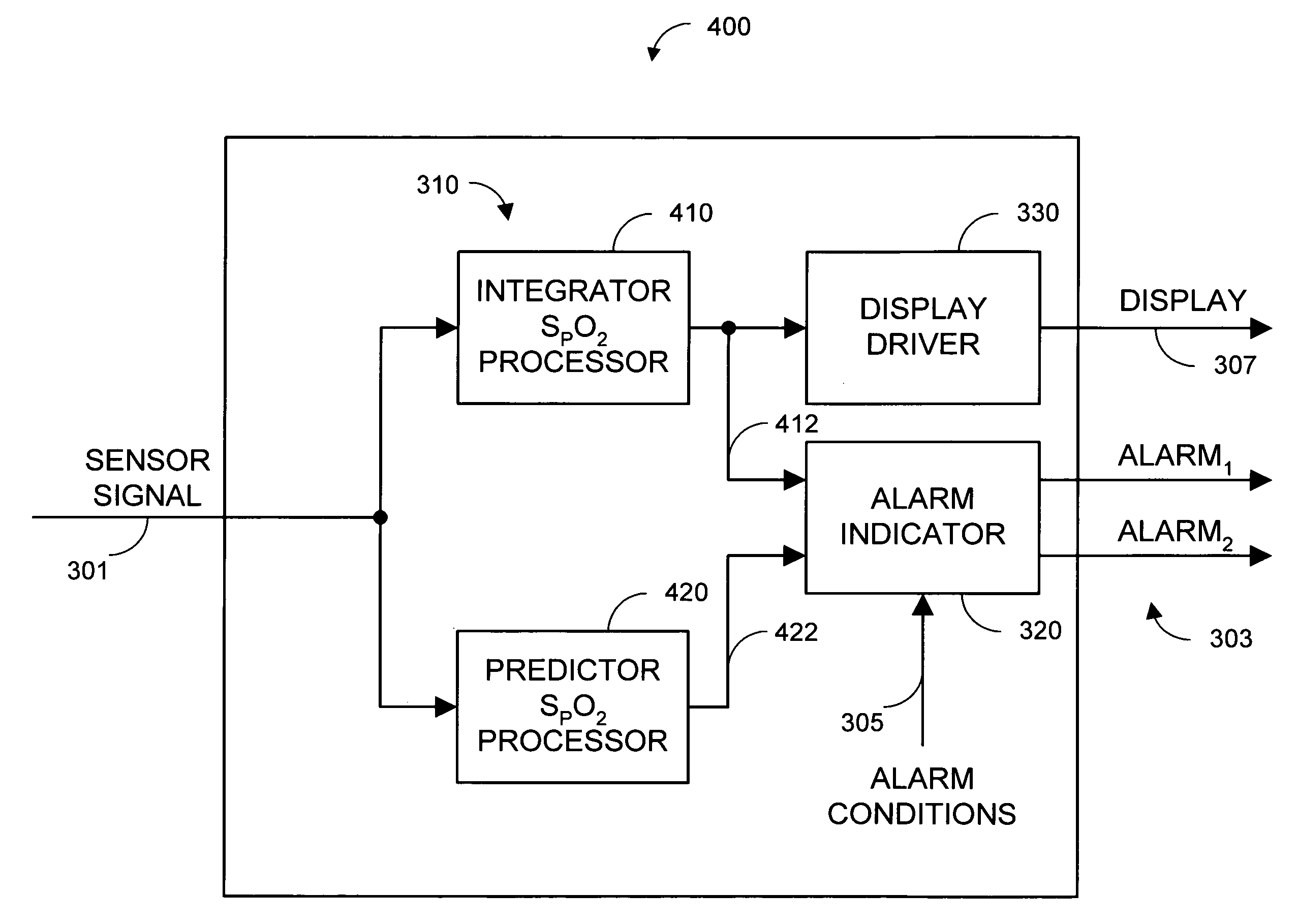
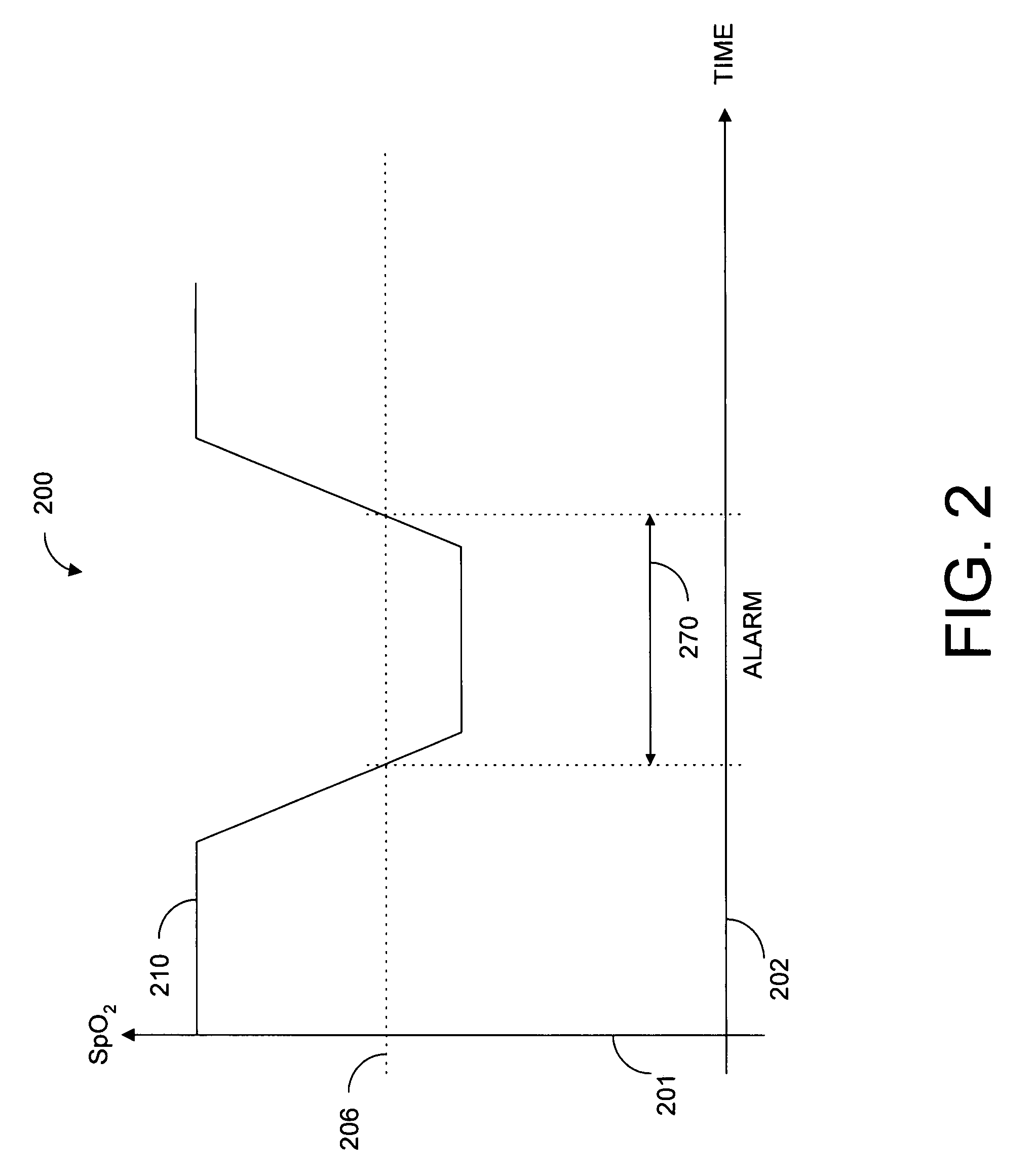
Parallel alarm processor
InactiveUS7355512B1Waste caregiver resourcesReduce false alarm rateEvaluation of blood vesselsSensorsLower limitOxygen Saturation Measurement
A parallel alarm processor has a threshold detector, a pattern extractor, a predetermined reference pattern, a first alarm and a second alarm. The threshold detector has a first output responsive to relatively long duration oxygen desaturations. The pattern extractor has a second output responsive to relatively short duration oxygen desaturations. The predetermined reference pattern is indicative of a series of intermittent oxygen desaturations. A first alarm is triggered when the first output crosses a lower limit threshold. A second alarm is triggered when the second output matches the predetermined reference pattern. In an embodiment, an integrator inputs smoothed oxygen saturation measurements to the threshold detector, and a predictor inputs predictive oxygen saturation measurements to the pattern extractor.
Owner:JPMORGAN CHASE BANK NA
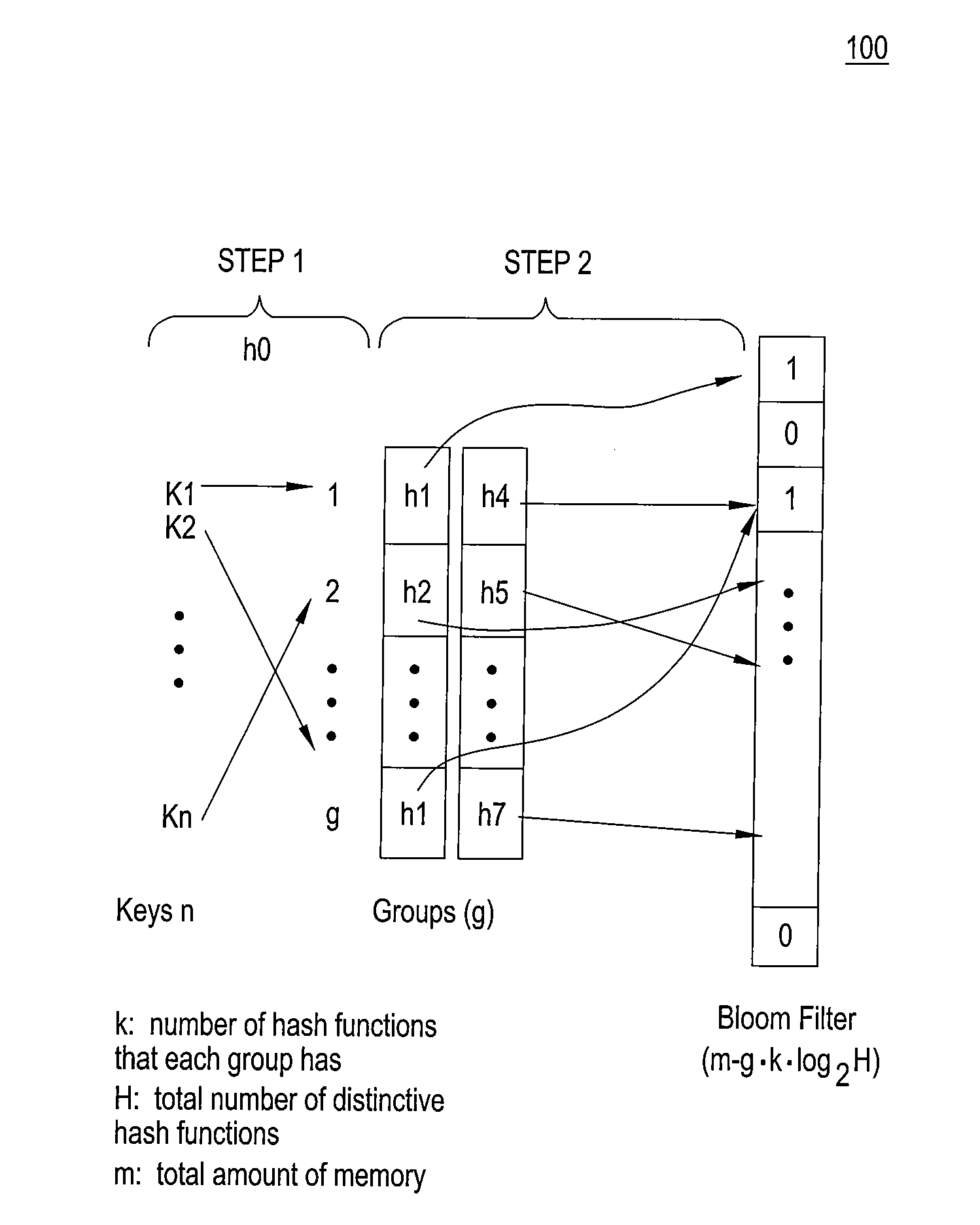
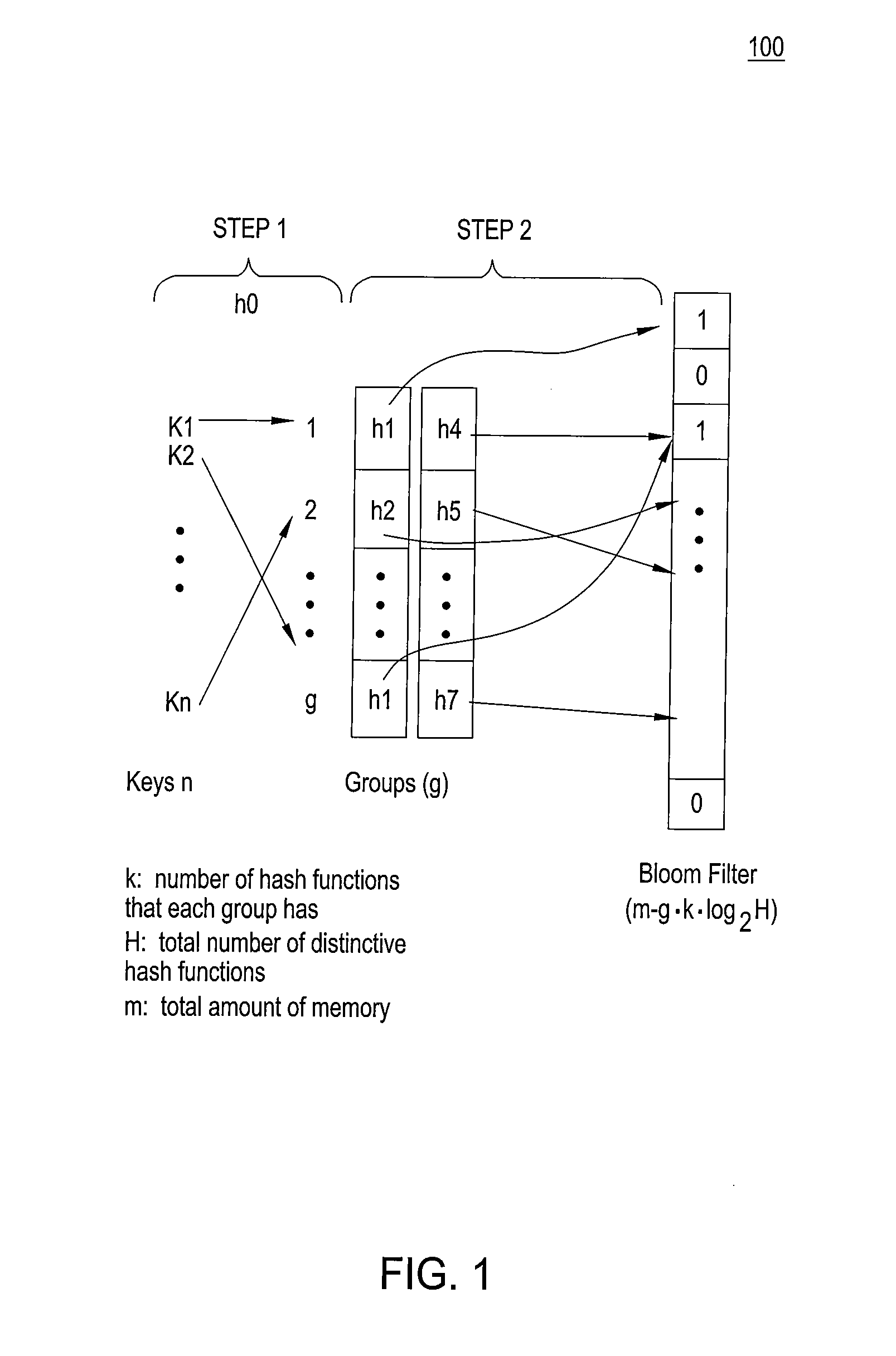
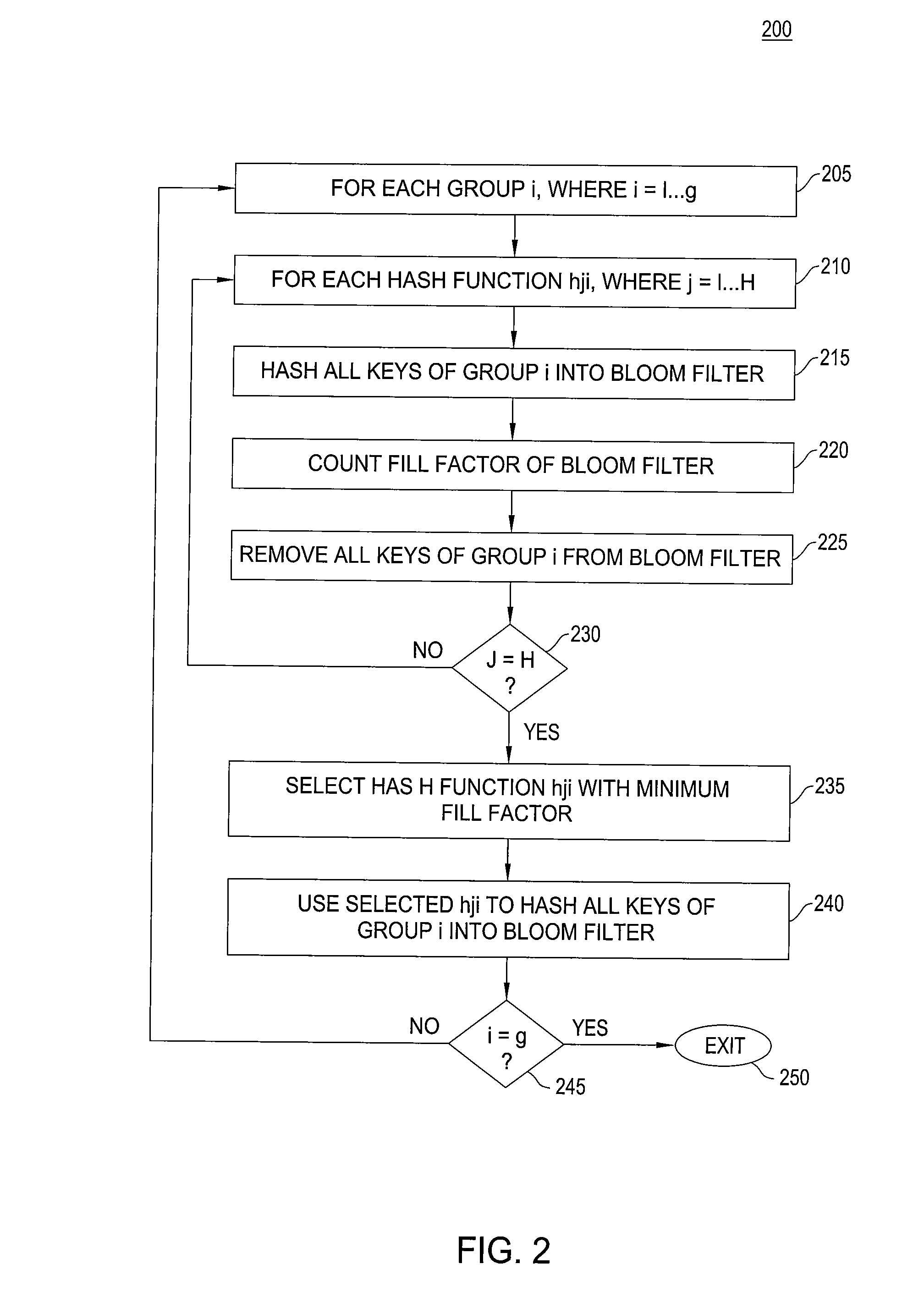
High accuracy bloom filter using partitioned hashing
ActiveUS20080313132A1Reduce false alarm rateReduce the probability of false positivesTransmissionSpecial data processing applicationsHash functionTheoretical computer science
A method and system for generating a bloom filter by mapping into respective groups each of a plurality of initial keys according to a first hash function and mapping each group hashed key into a bloom filter using k respective hash functions.
Owner:ALCATEL-LUCENT USA INC
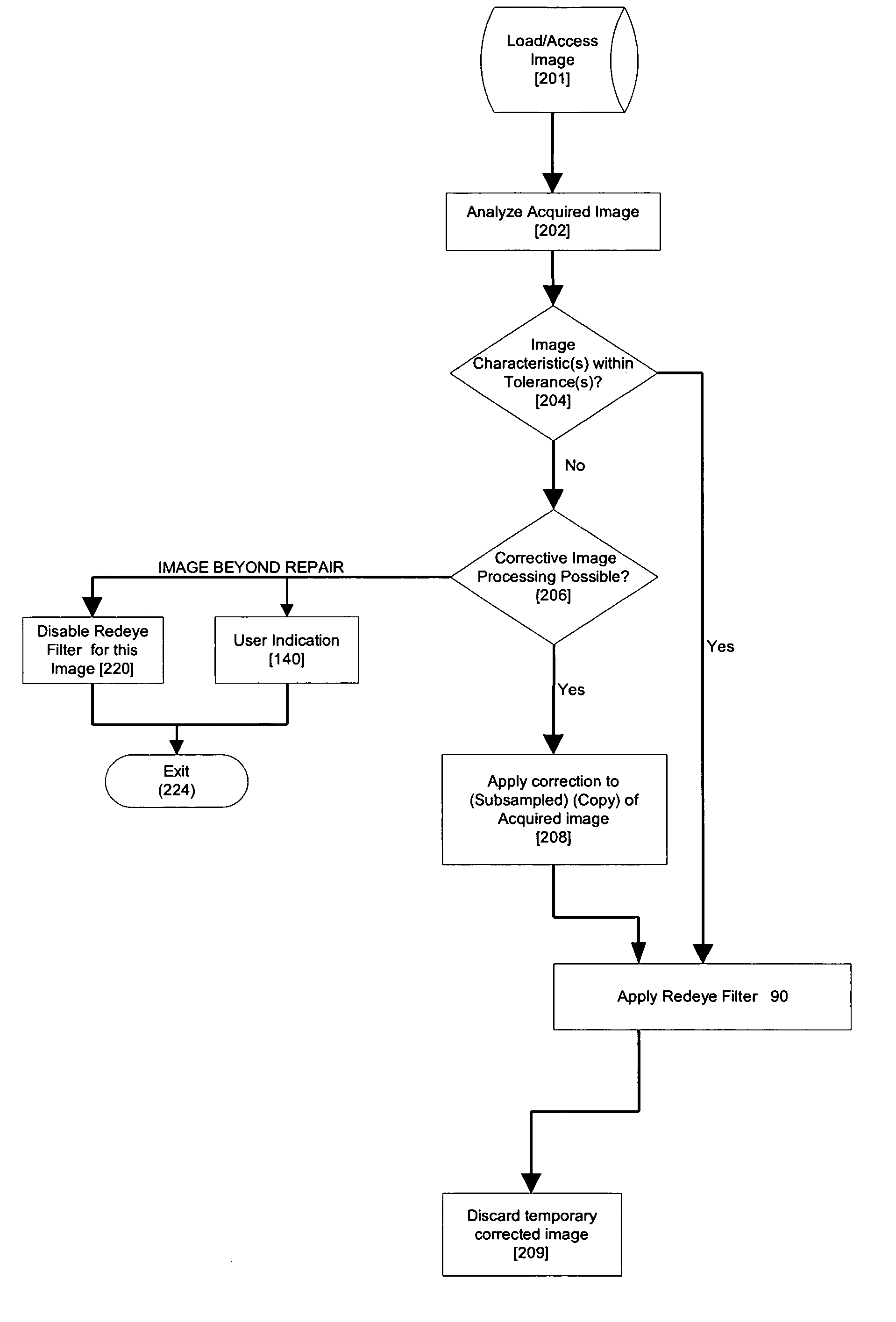
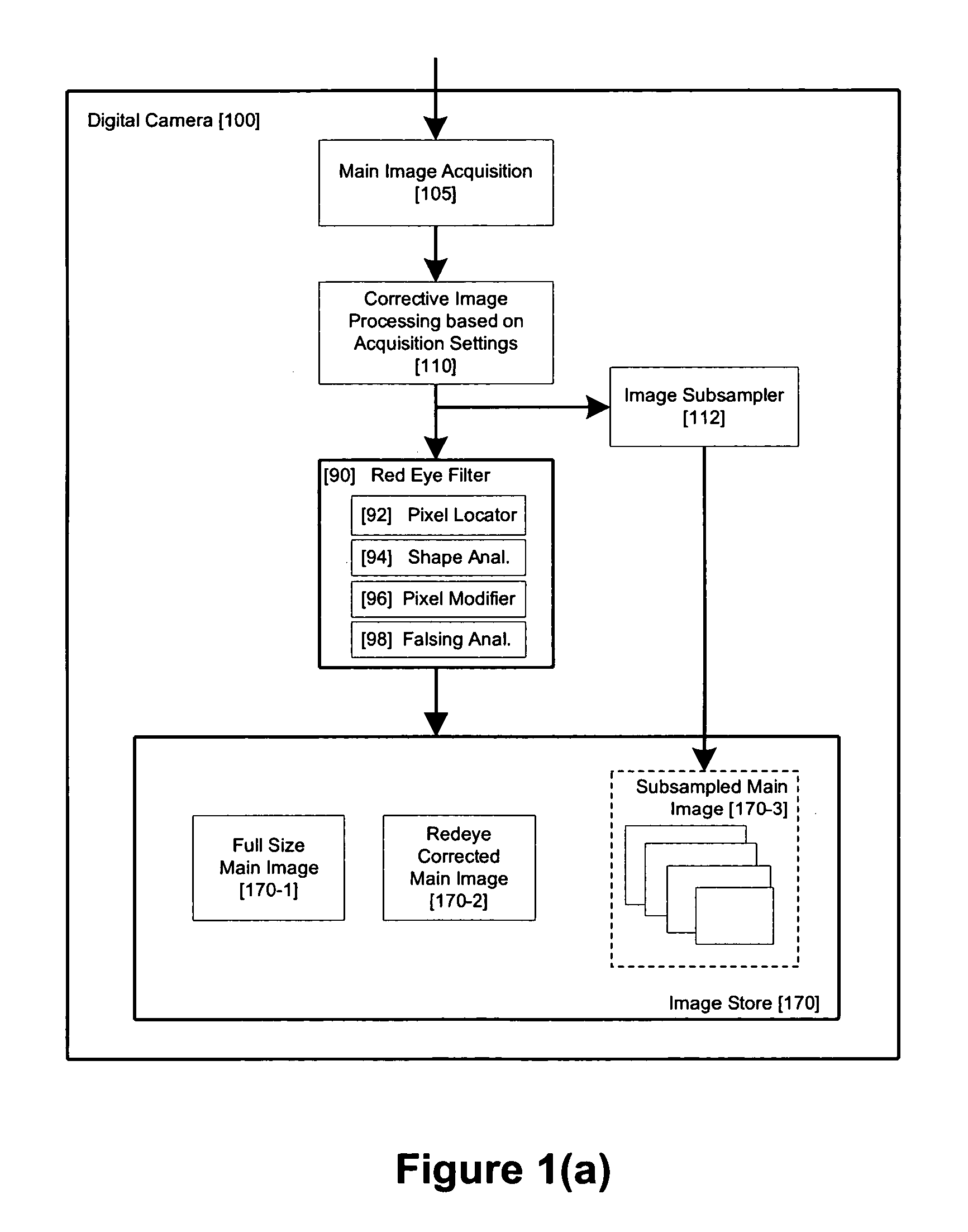
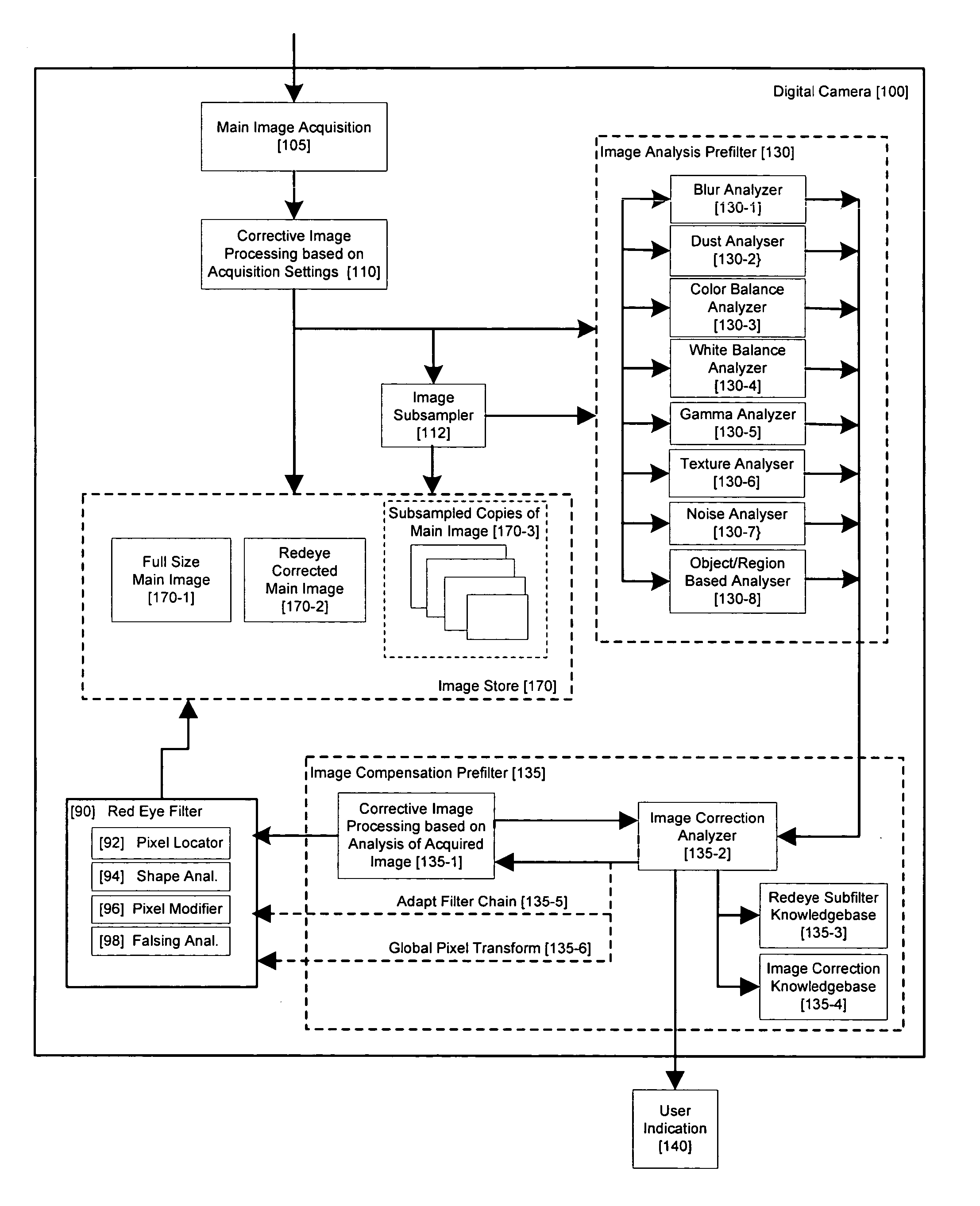
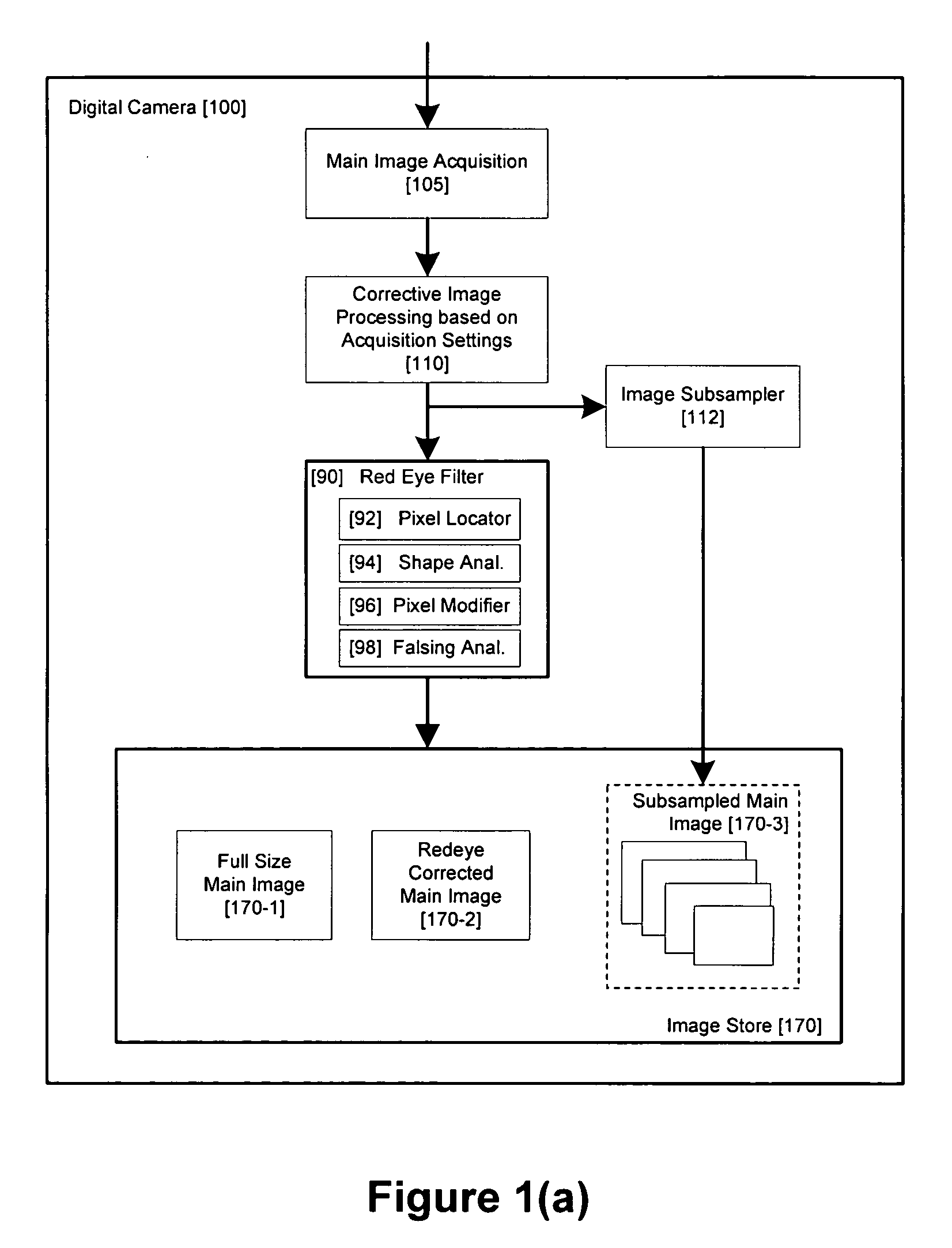
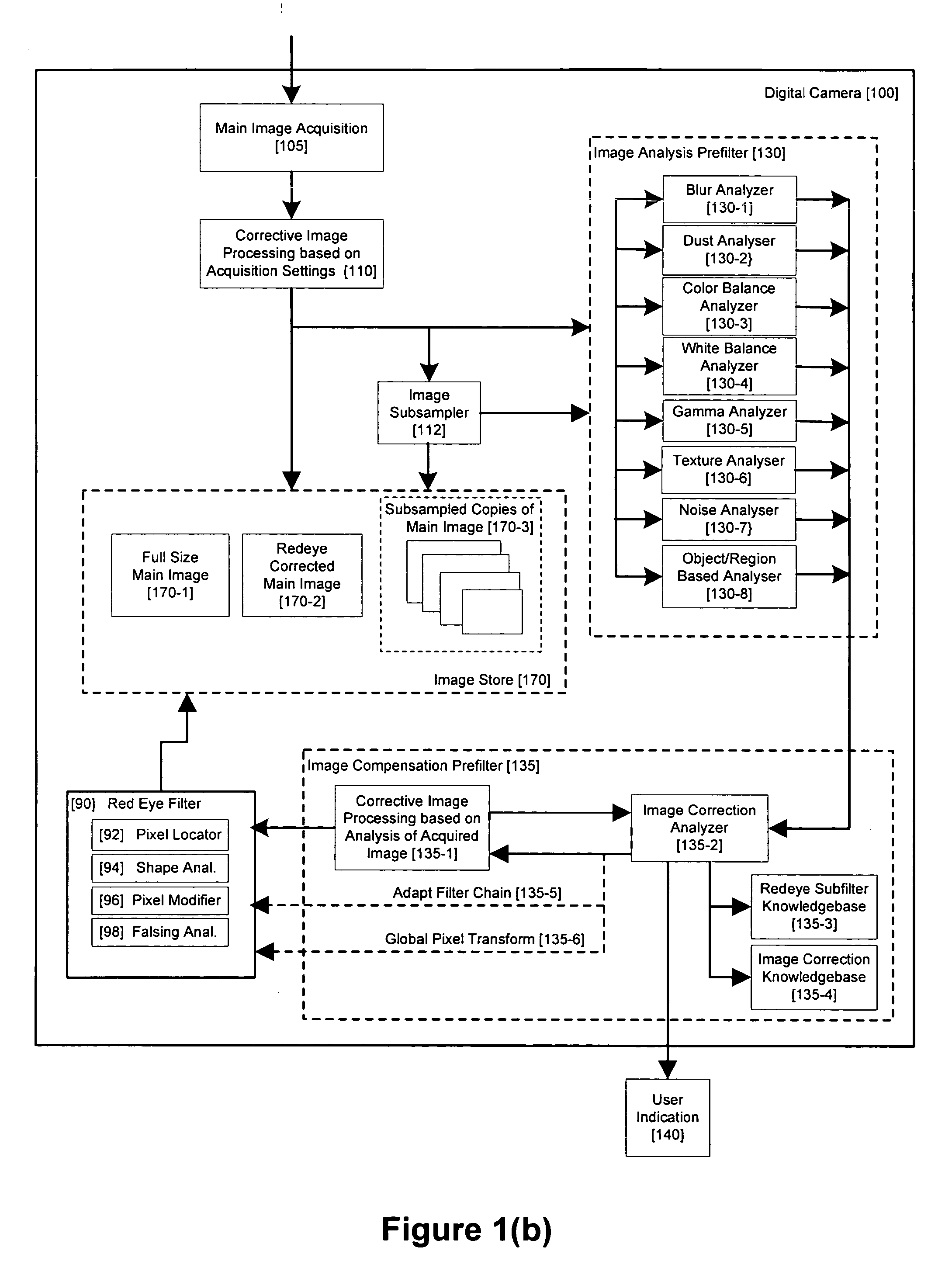
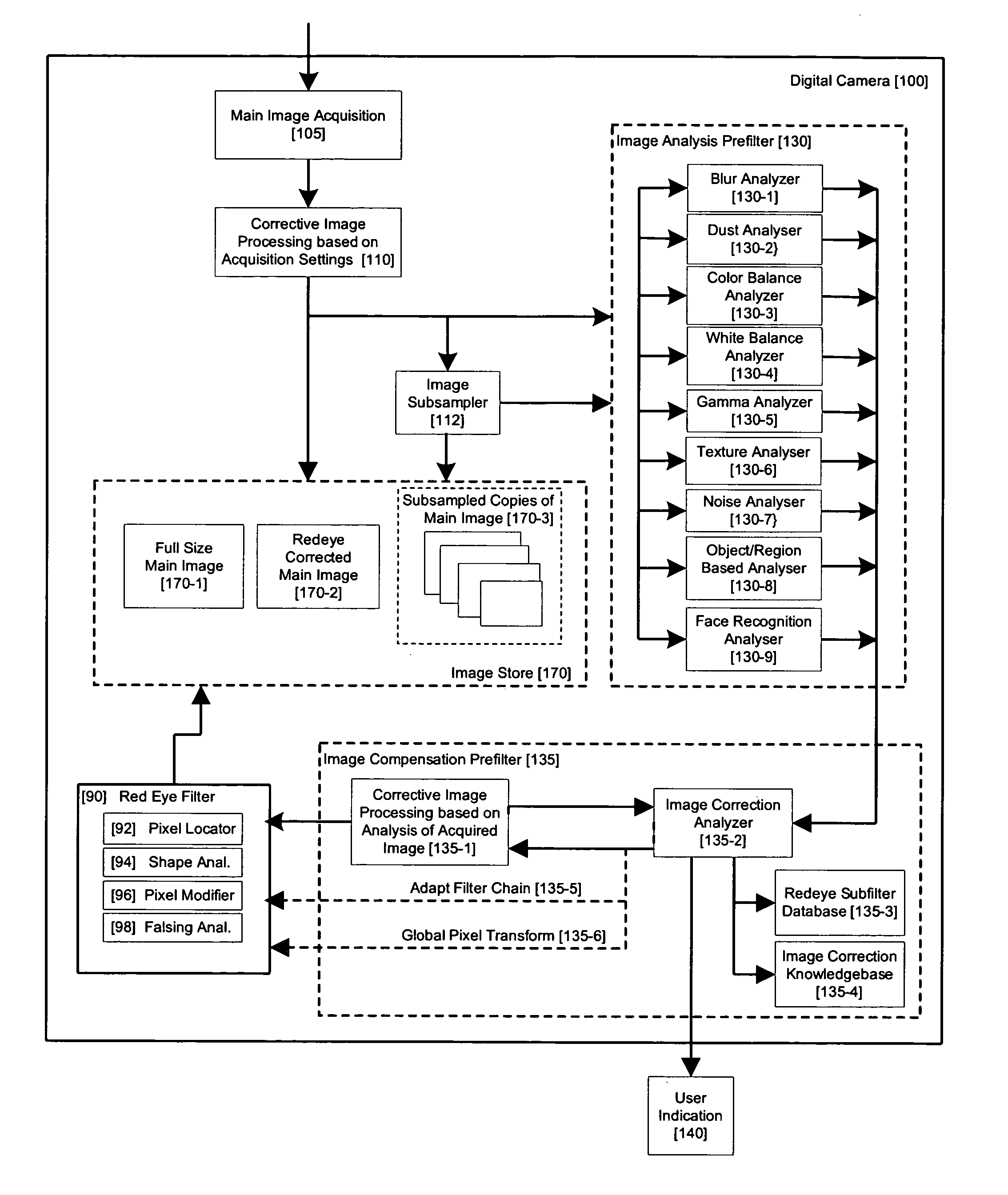
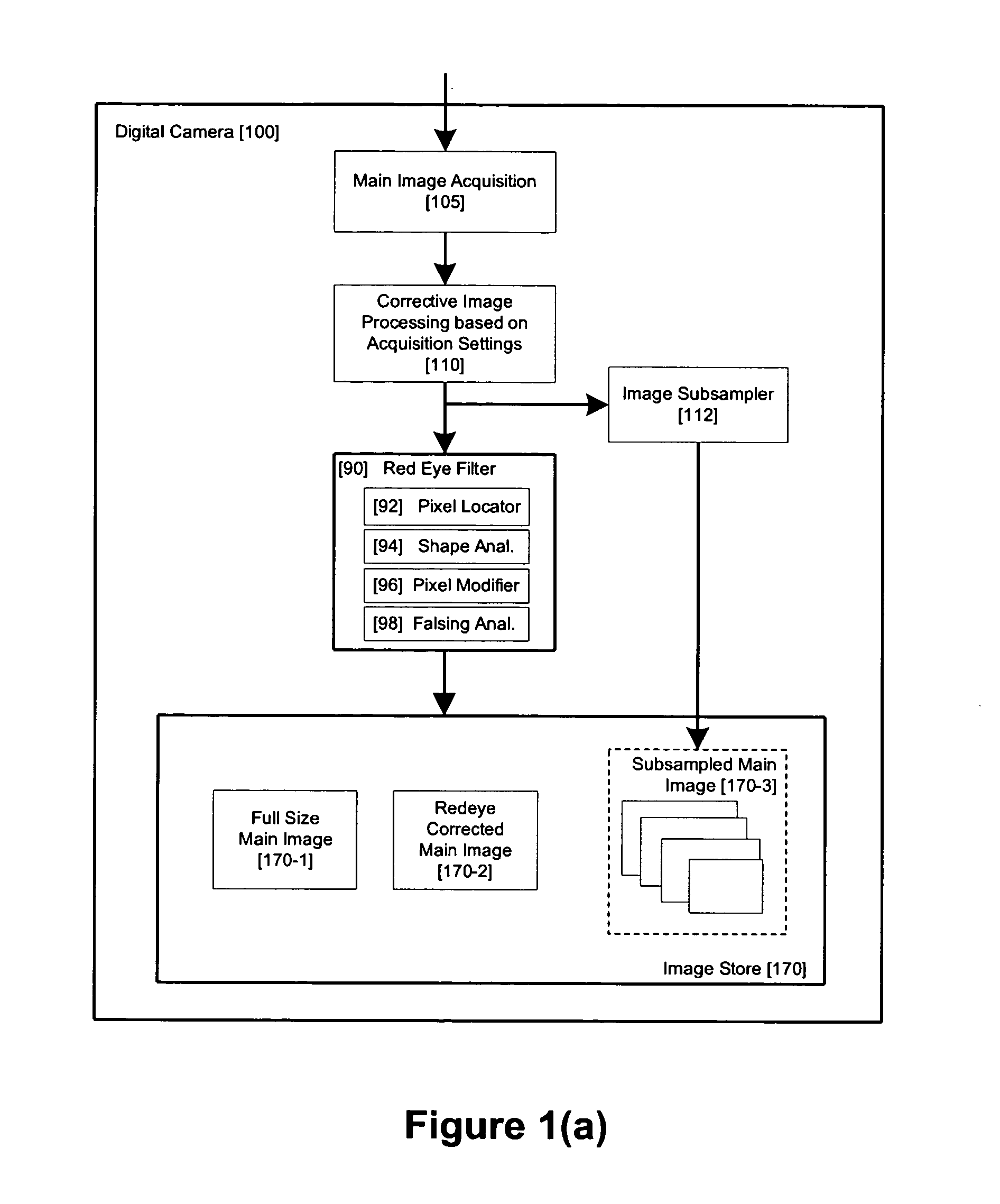
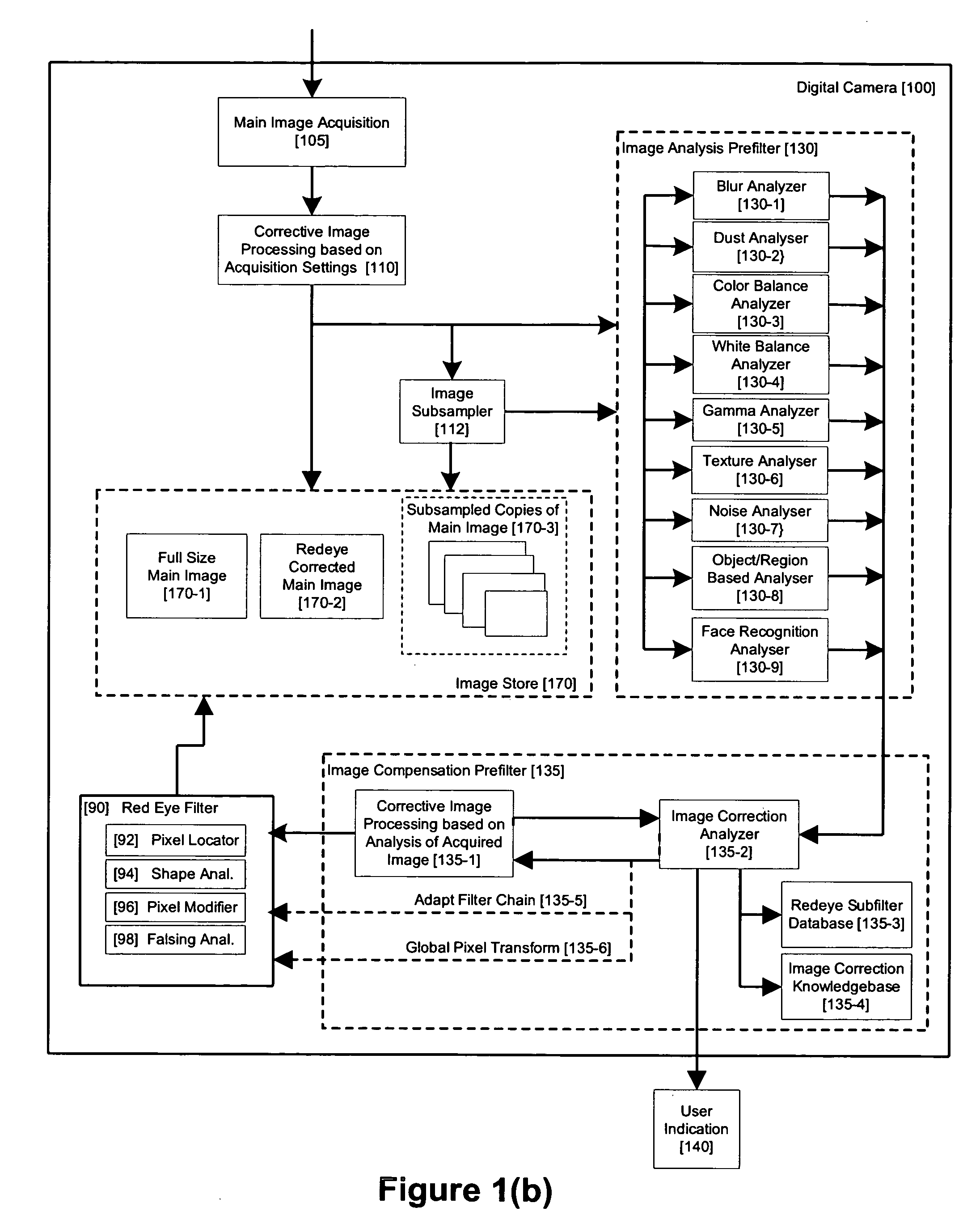
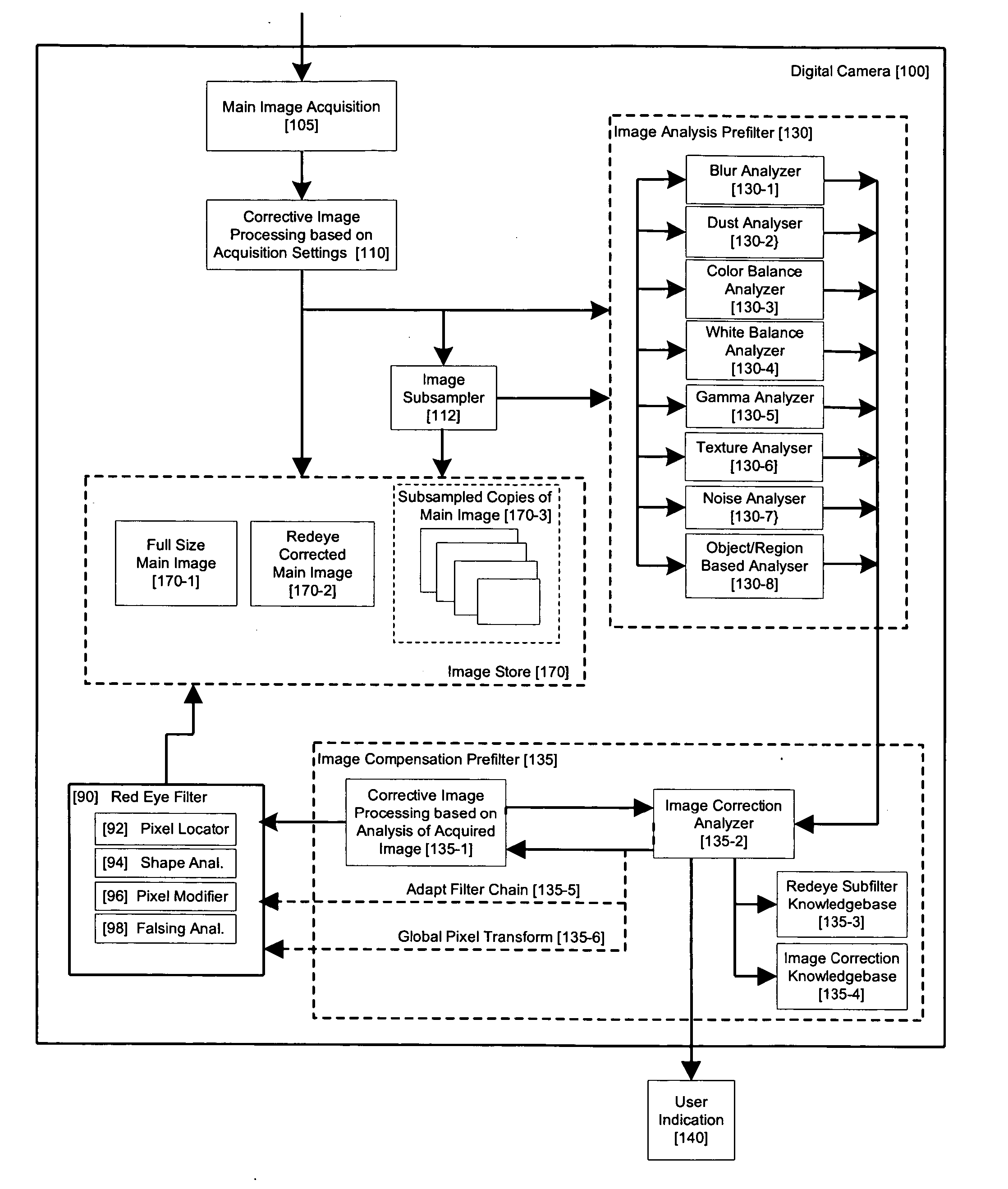
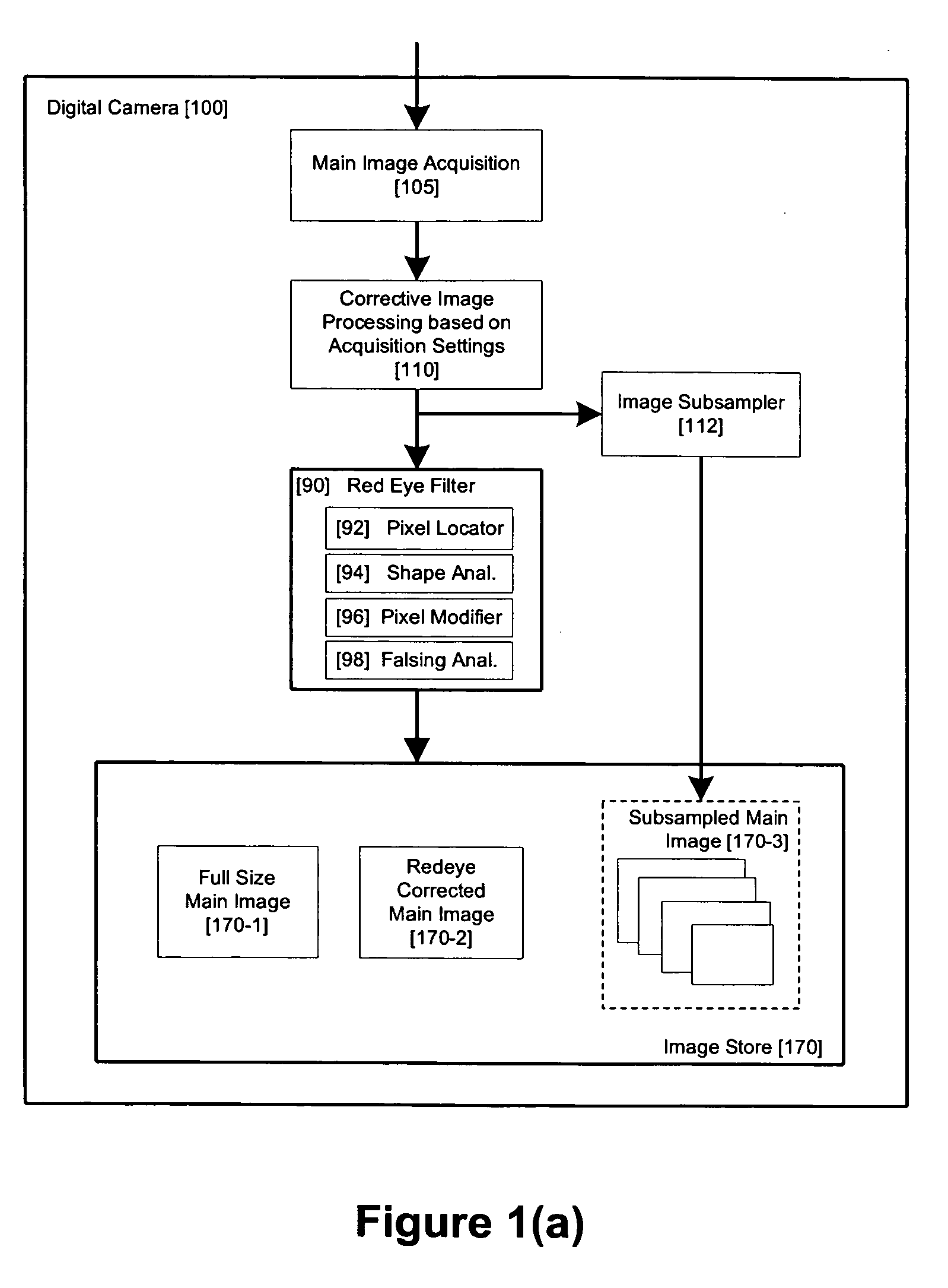
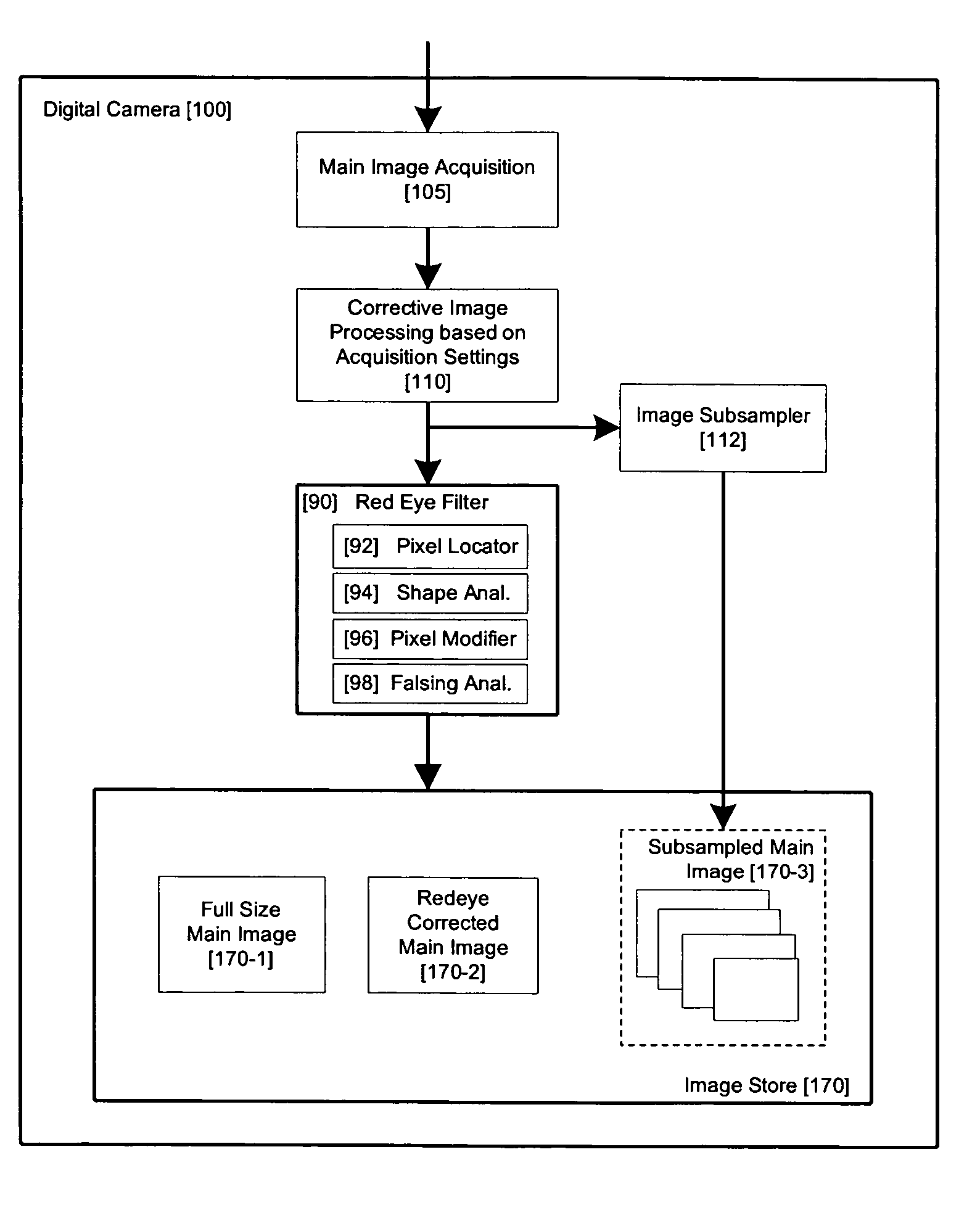
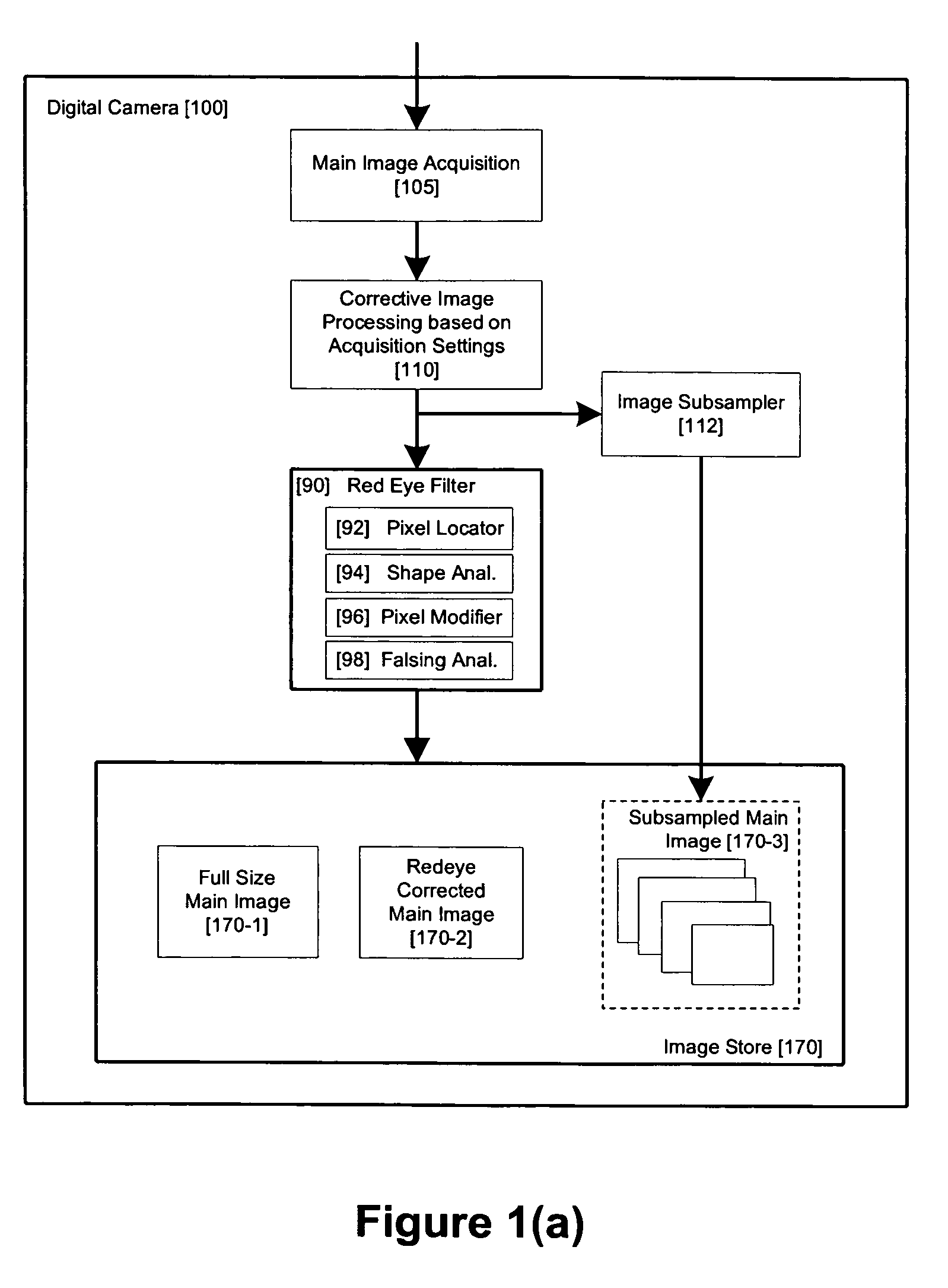
Method and apparatus for red-eye detection in an acquired digital image
ActiveUS20060120599A1Reduce false alarm rateIncrease success rateImage enhancementImage analysisImaging qualityDigital image
A method for red-eye detection in an acquired digital image comprises acquiring a first image and analyzing the first acquired image to provide a plurality of characteristics indicative of image quality. The process then determines if one or more corrective processes can be beneficially applied to the first acquired image according to the characteristics. Any such corrective processes are then applied to the first acquired image. Red-eye defects are then detected in a second acquired image using the corrected first acquired image. Defect detection can comprise applying a chain of one or more red-eye filters to the first acquired image. In this case, prior to the detecting step, it is determined if the red-eye filter chain can be adapted in accordance with the plurality of characteristics; and the red-eye filter is adapted accordingly.
Owner:FOTONATION LTD
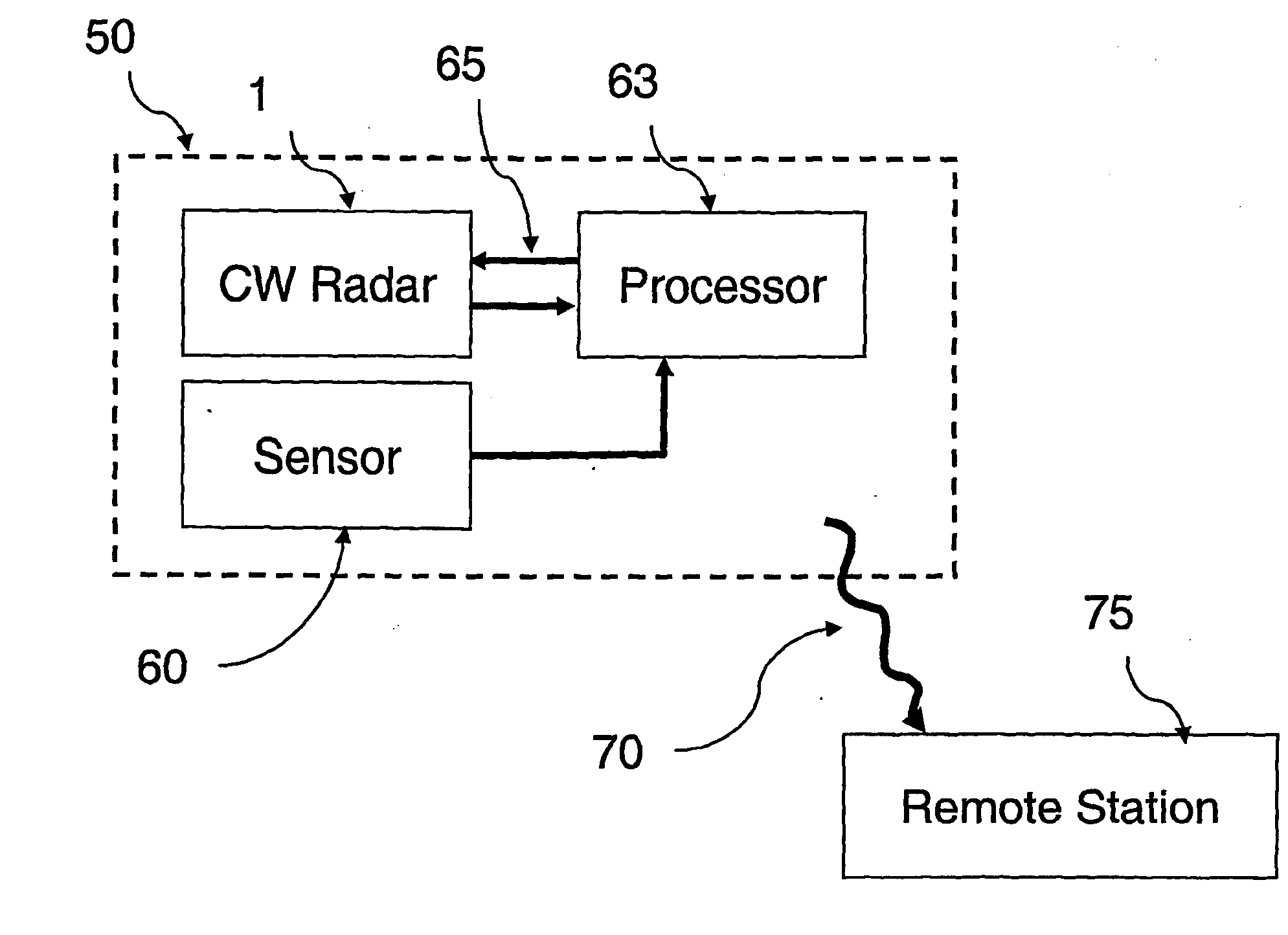
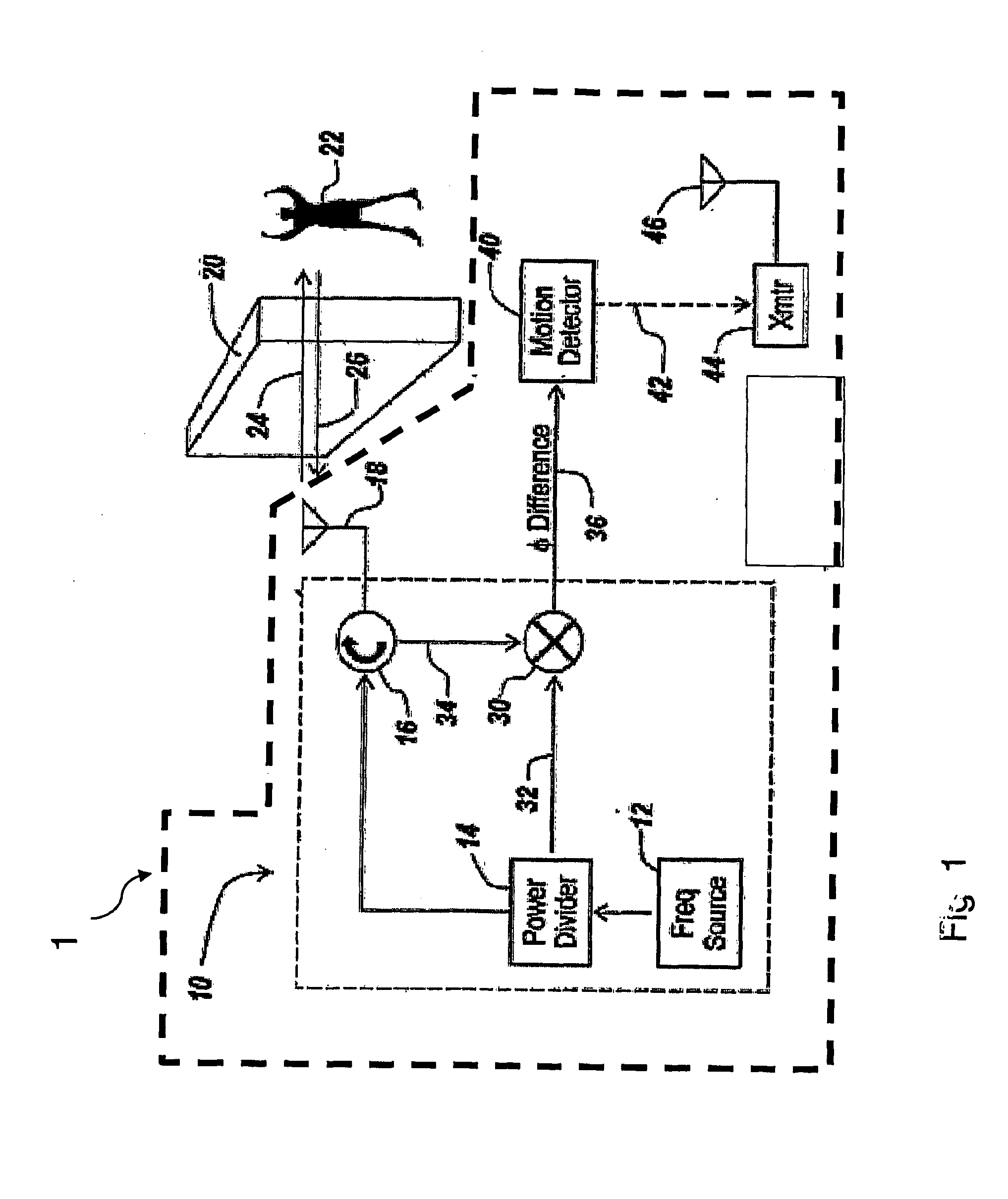
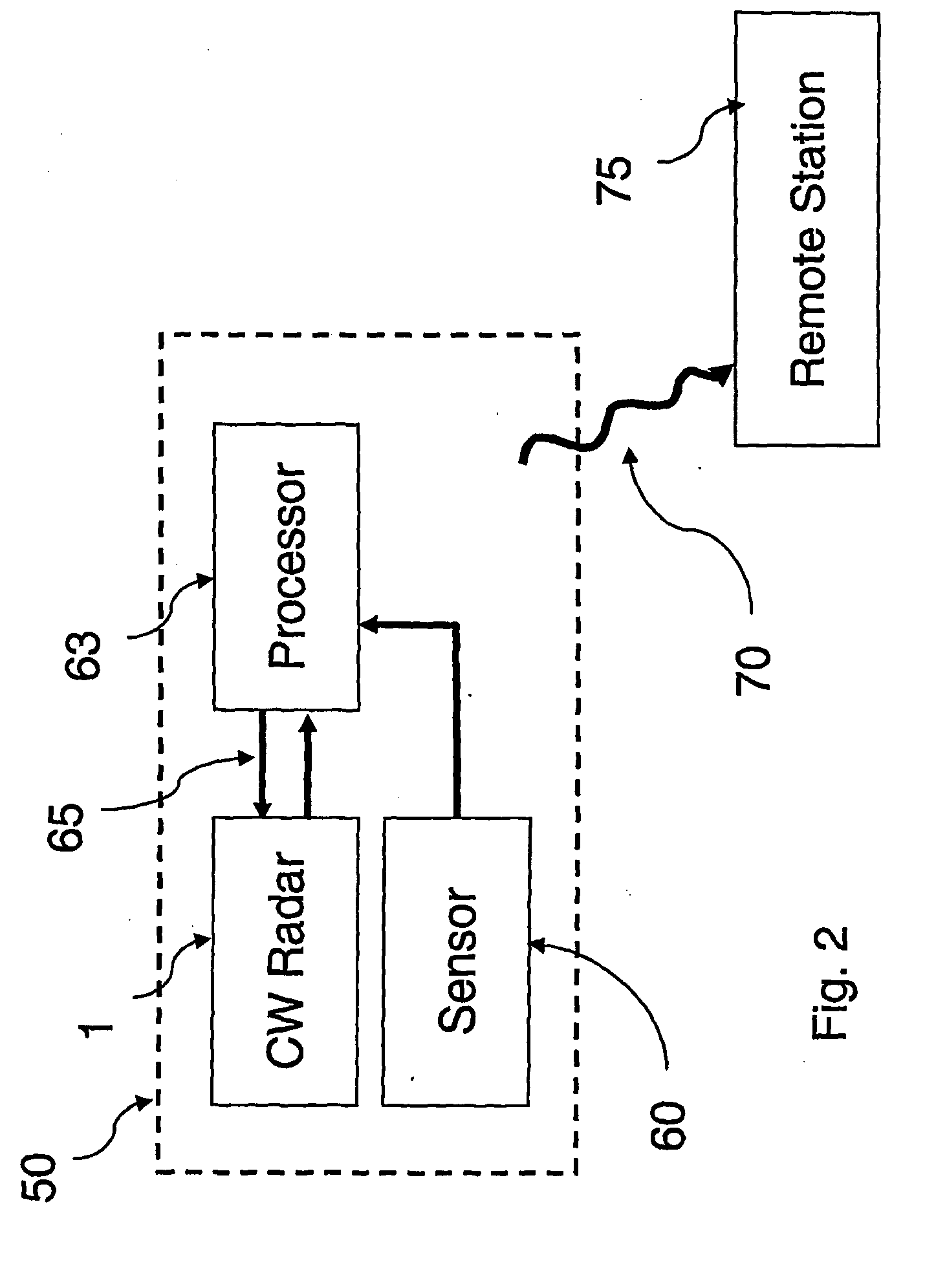
Motion Detection Systems Using CW Radar in Combination With Additional Sensors
ActiveUS20090303100A1Reduce power consumptionImprove discriminationRadio wave reradiation/reflectionRadarFalse alarm
Whether or not the CW radar is utilized for through-the-wall detection, additional one or more sensors are used with the CW radar to confirm the motion detection result or to in fact turn on the CW radar once motion or the physical presence of an individual has been sensed, thereby to provide confirmation of a less-reliable sensor with the use of the more reliable CW radar. Thus, the addition of other sensors provides lower power consumption, lower false alarm rates and better discrimination and classification of moving objects.
Owner:III HLDG 1
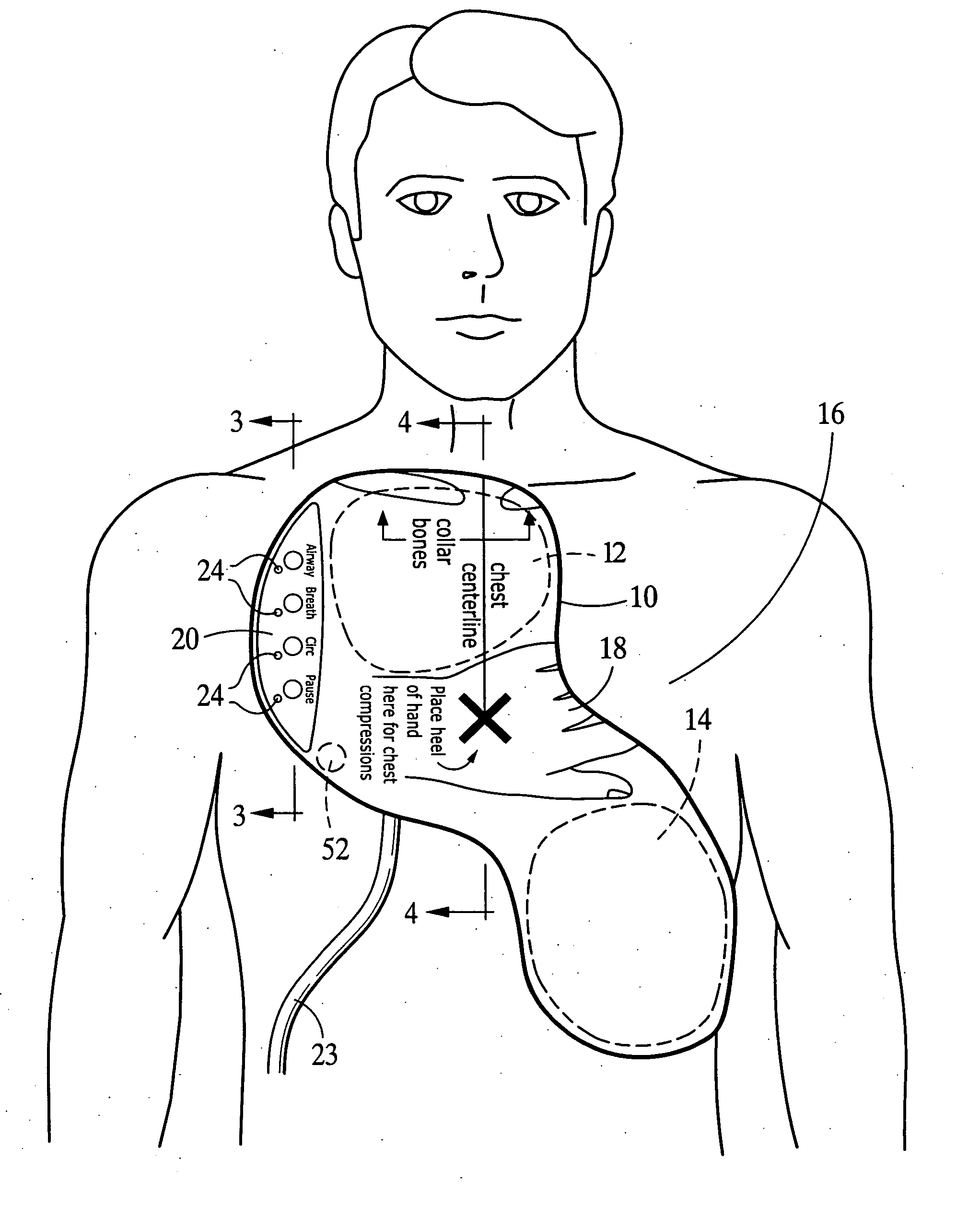
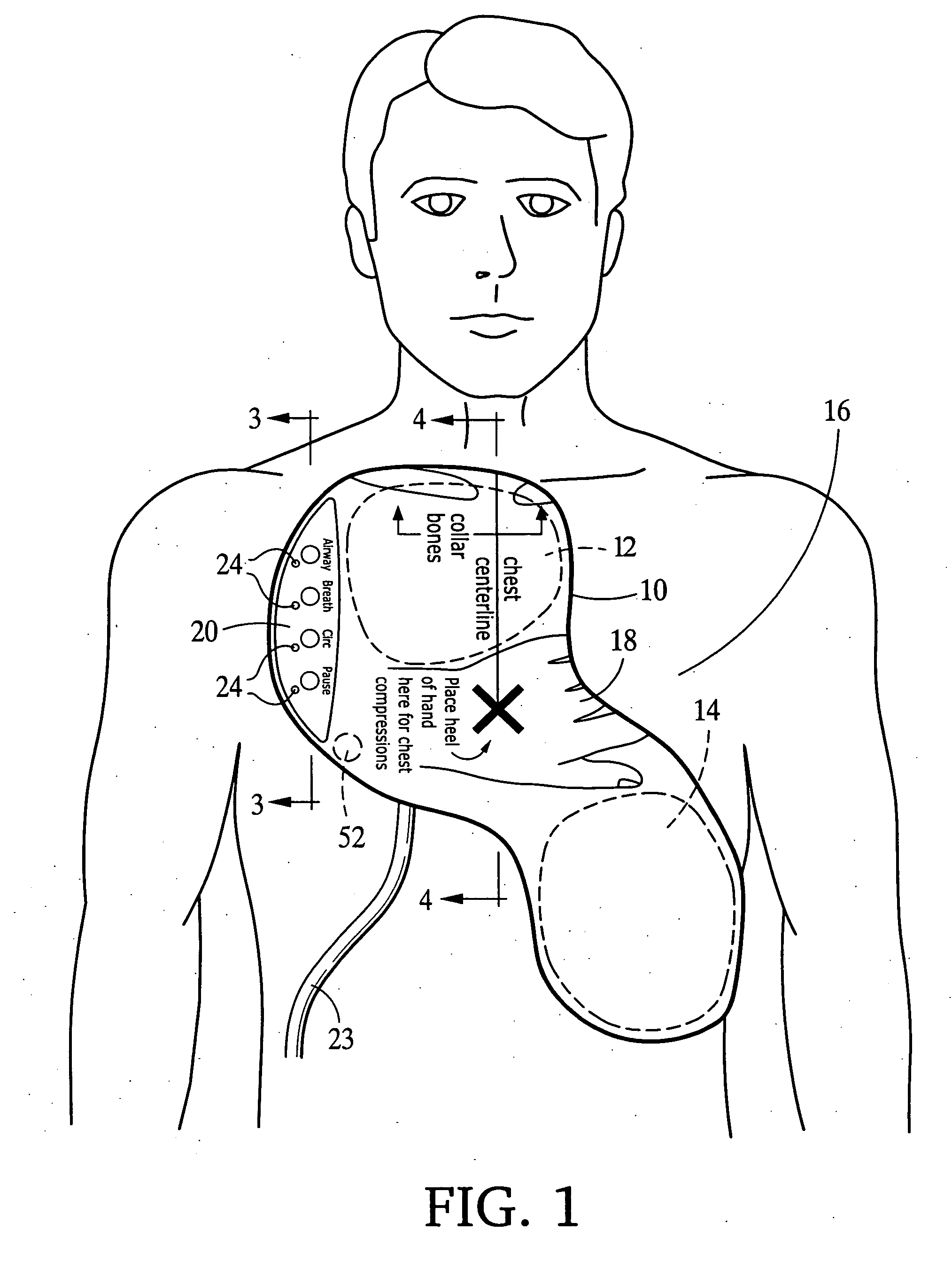
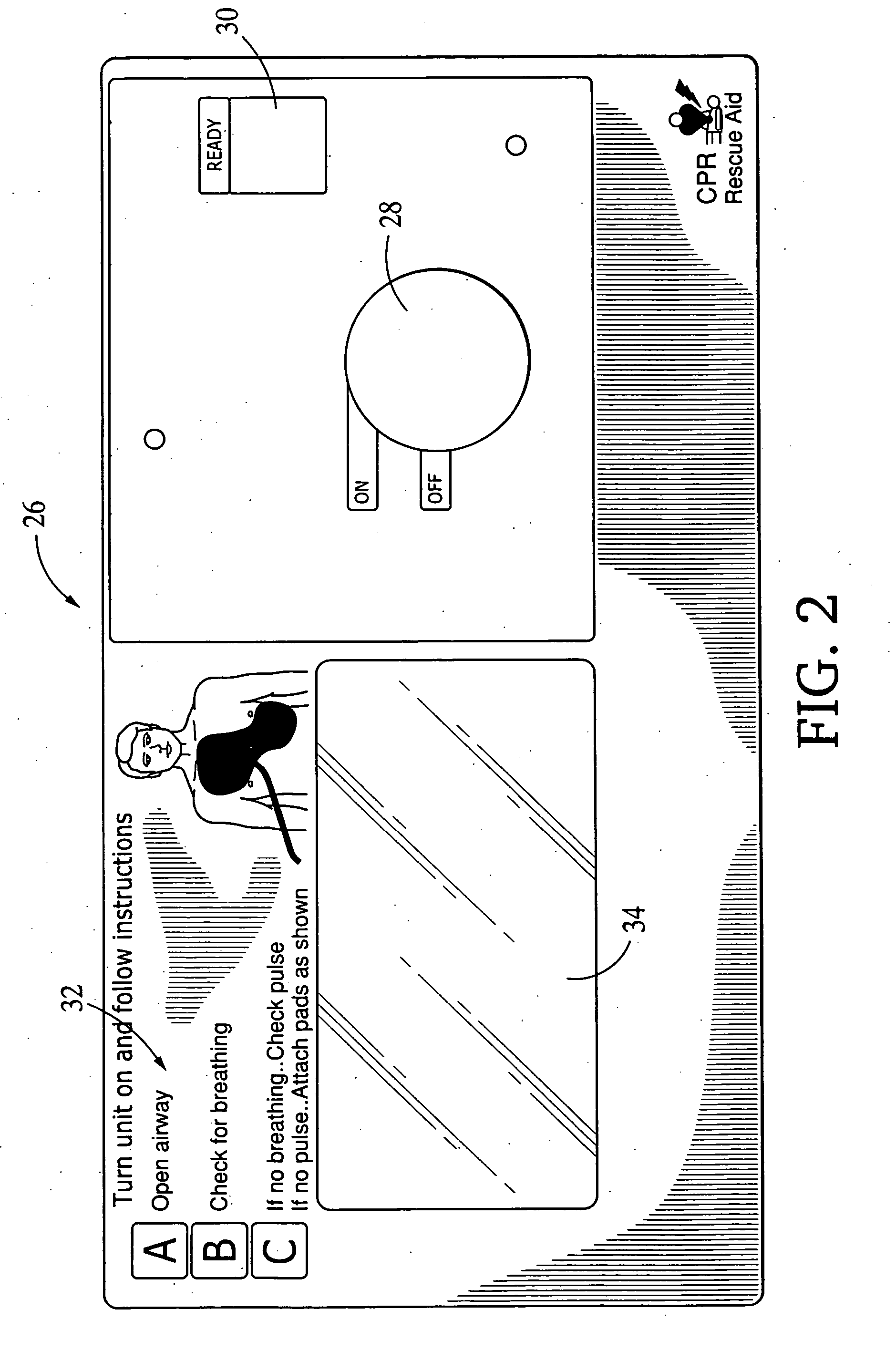
Integrated resuscitation
InactiveUS20050131465A1Widely distributedLow costHeart defibrillatorsStethoscopeElectricityElectrical connection
A resuscitation system for use by a rescuer for resuscitating a patient, comprising at least two high-voltage defibrillation electrodes, a first electrical unit comprising circuitry for providing resuscitation prompts to the rescuer, a second electrical unit separate from the first unit and comprising circuitry for providing defibrillation pulses to the electrodes, and circuitry for providing at least one electrical connection between the first and second units. In another aspect, at least two electrical therapy electrodes adapted to be worn by the patient for extended periods of time, circuitry for monitoring the ECG of the patient, an activity sensor adapted to be worn by the patient and capable of providing an output from which the patient's current activity can be estimated, and at least one processor configured for estimating the patient's current activity by analyzing the output of the activity sensor, analyzing the ECG of the patient, and determining whether electrical therapy should be delivered to the electrodes.
Owner:ZOLL MEDICAL CORPORATION
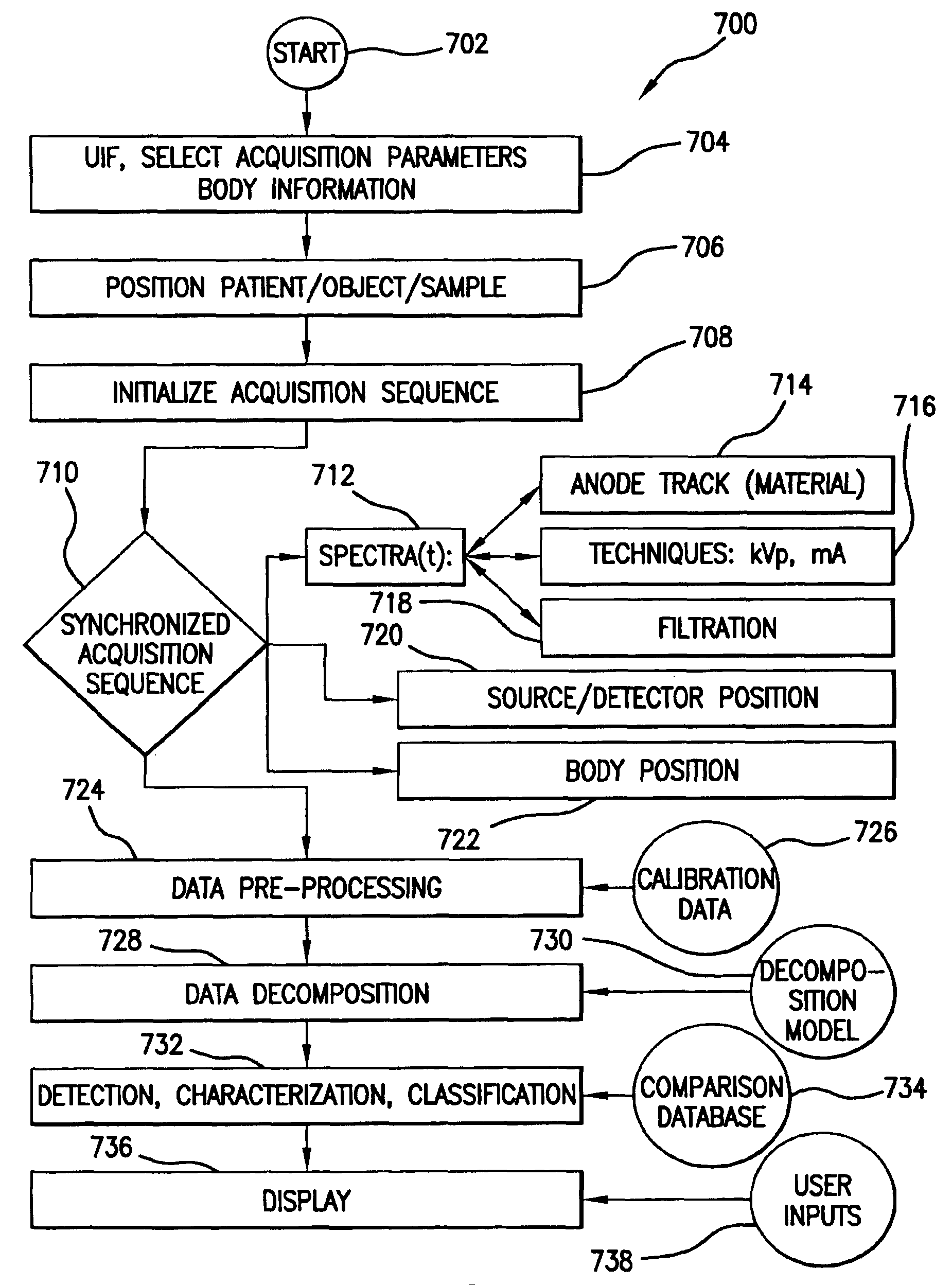
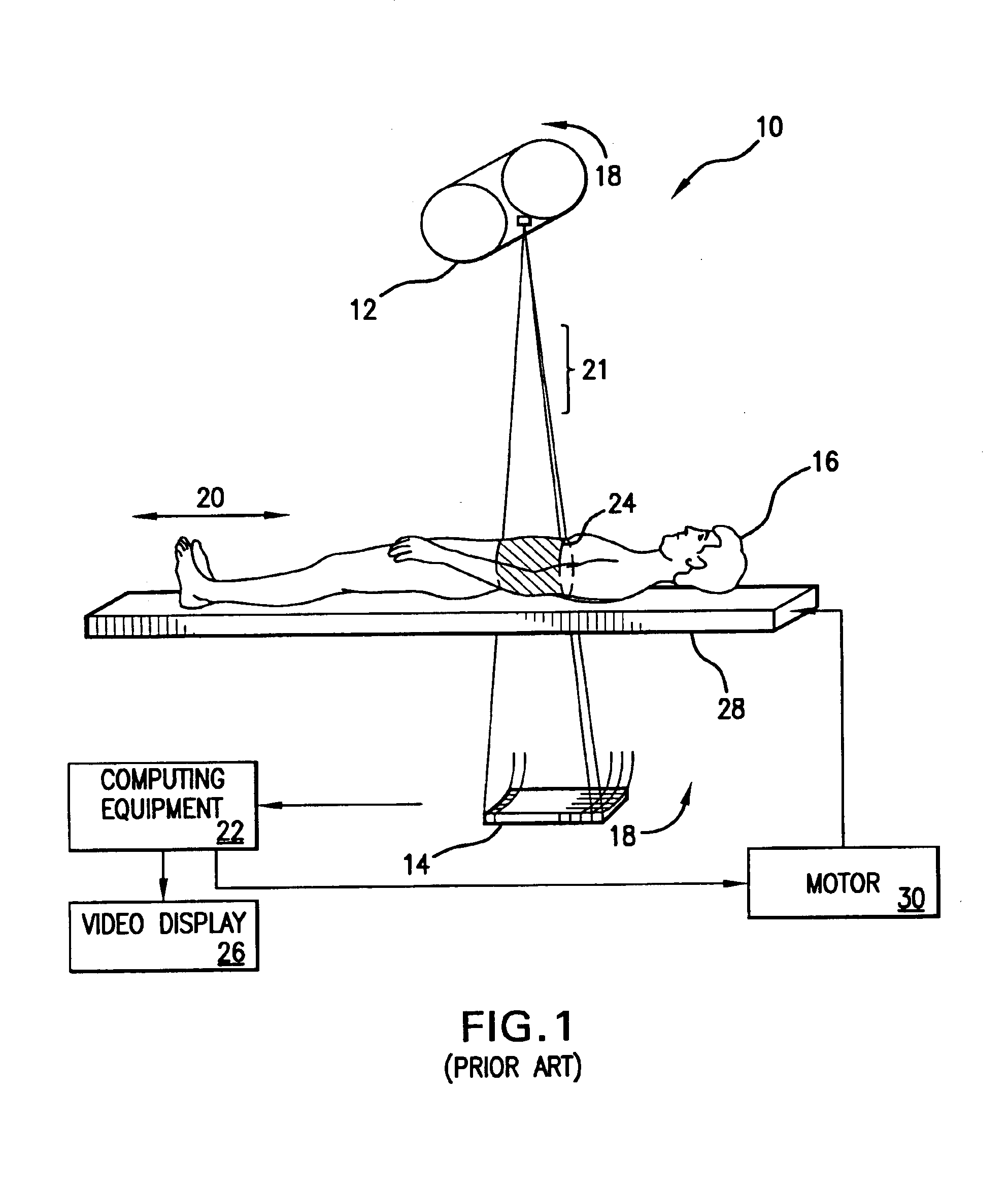
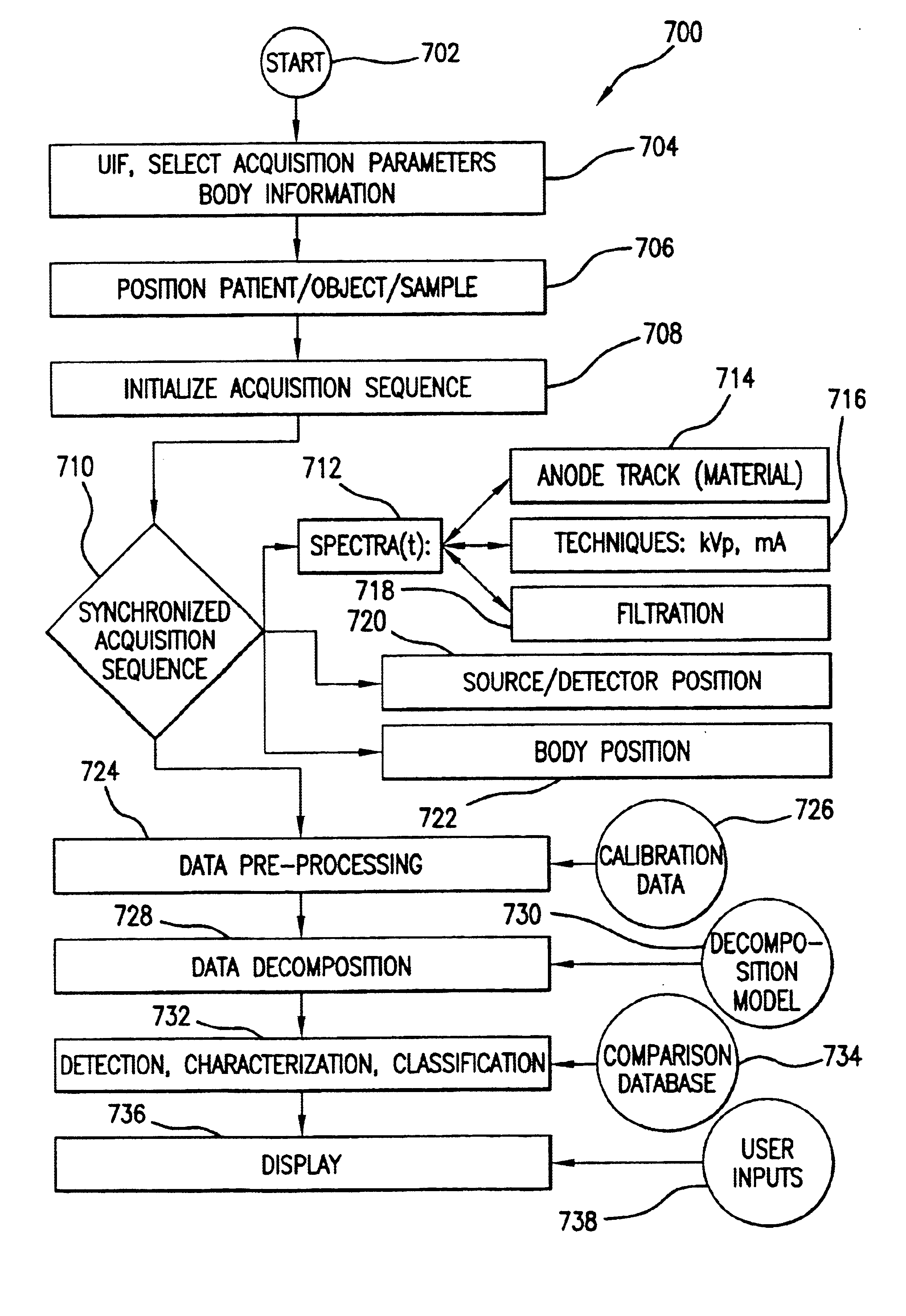
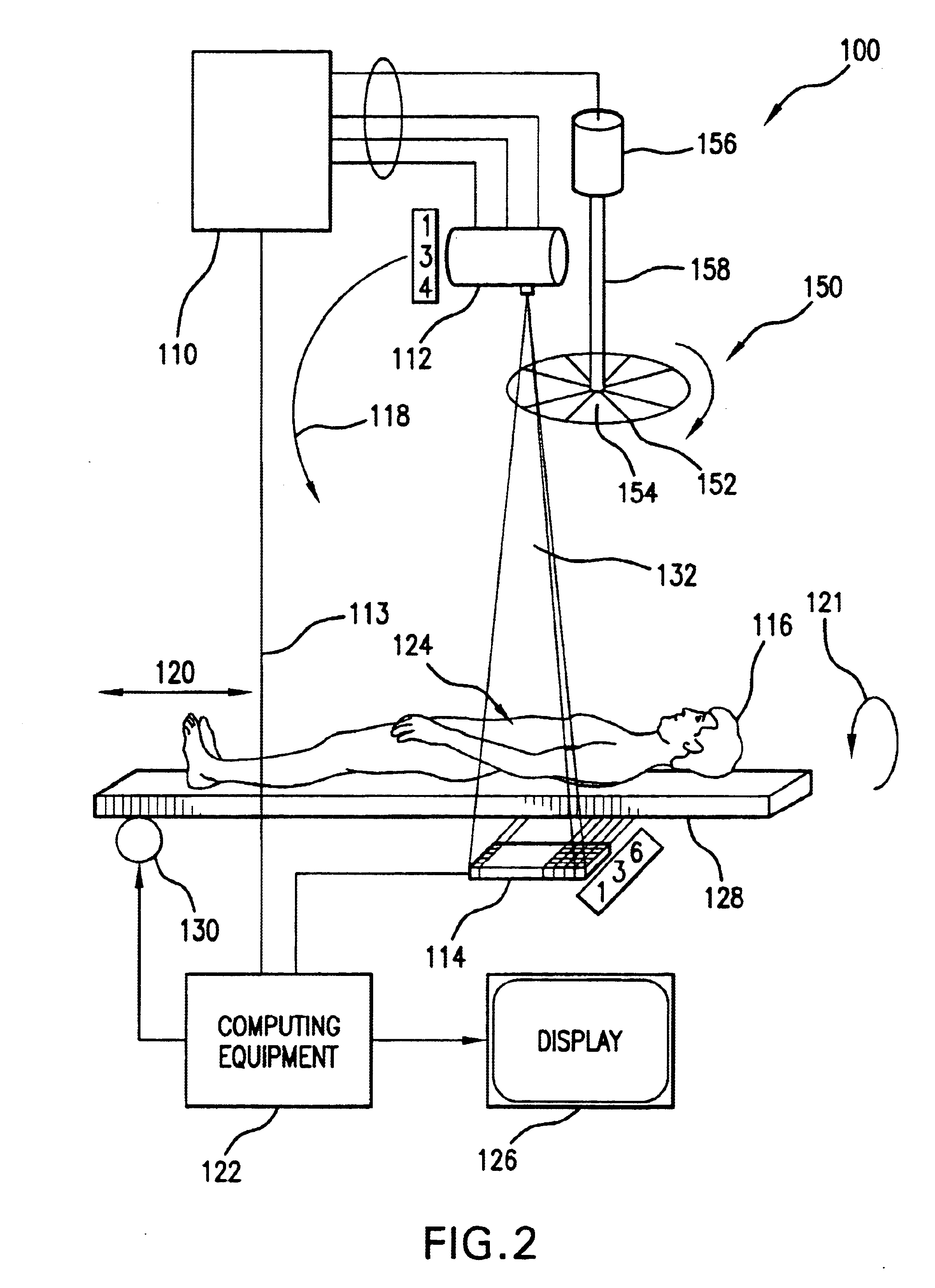
Dynamic multi-spectral X-ray projection imaging
InactiveUS6950492B2Good curative effectPromote resultsMaterial analysis using wave/particle radiationRadiation/particle handlingFiltrationX-ray
A multispectral X-ray imaging system uses a wideband source and filtration assembly to select for M sets of spectral data. Spectral characteristics may be dynamically adjusted in synchrony with scan excursions where an X-ray source, detector array, or body may be moved relative to one another in acquiring T sets of measurement data. The system may be used in projection imaging and / or CT imaging. Processed image data, such as a CT reconstructed image, may be decomposed onto basis functions for analytical processing of multispectral image data to facilitate computer assisted diagnostics. The system may perform this diagnostic function in medical applications and / or security applications.
Owner:FOREVISION IMAGING TECH LLC
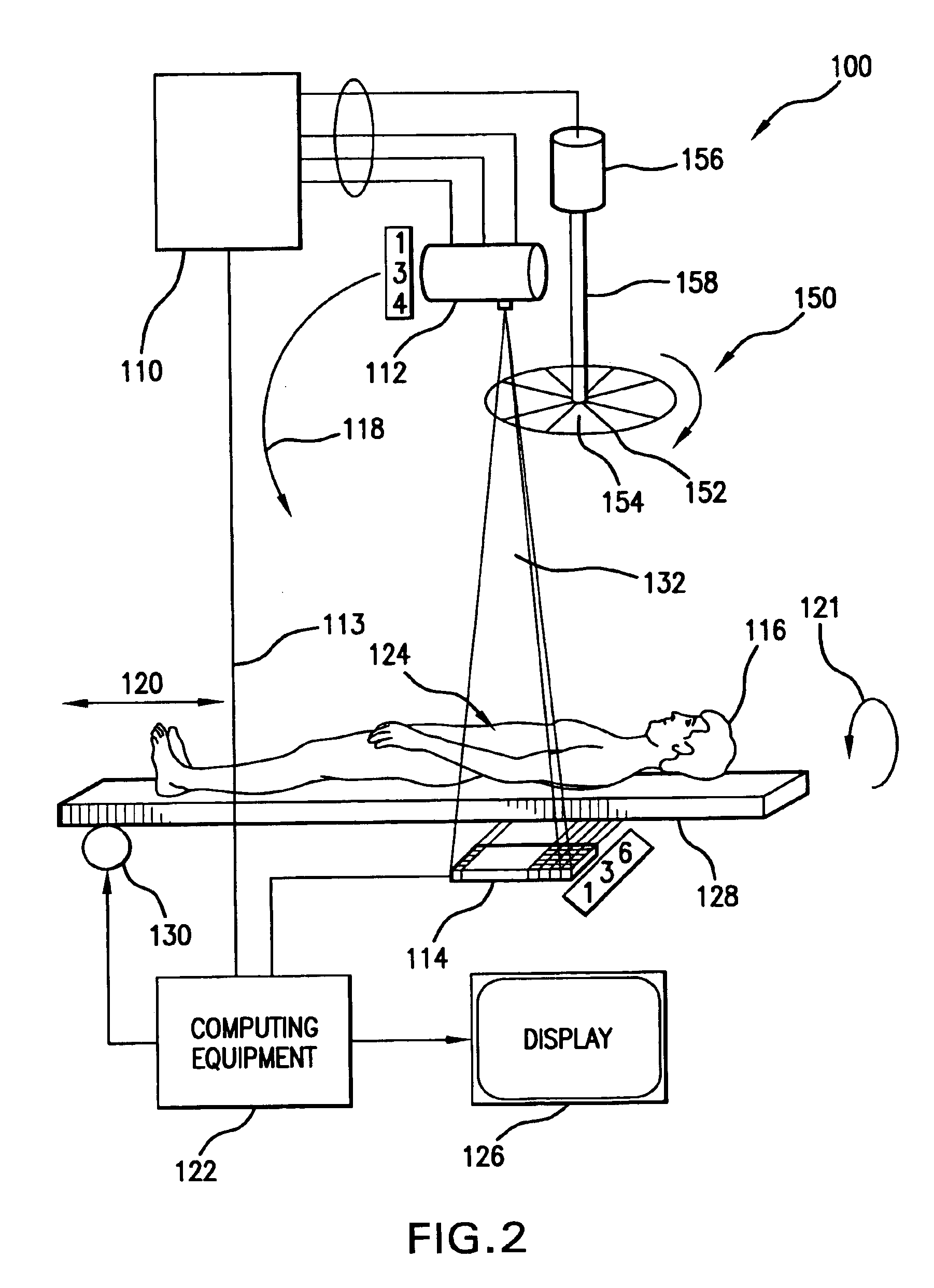
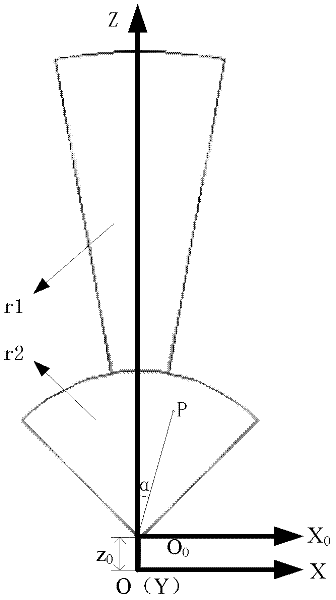
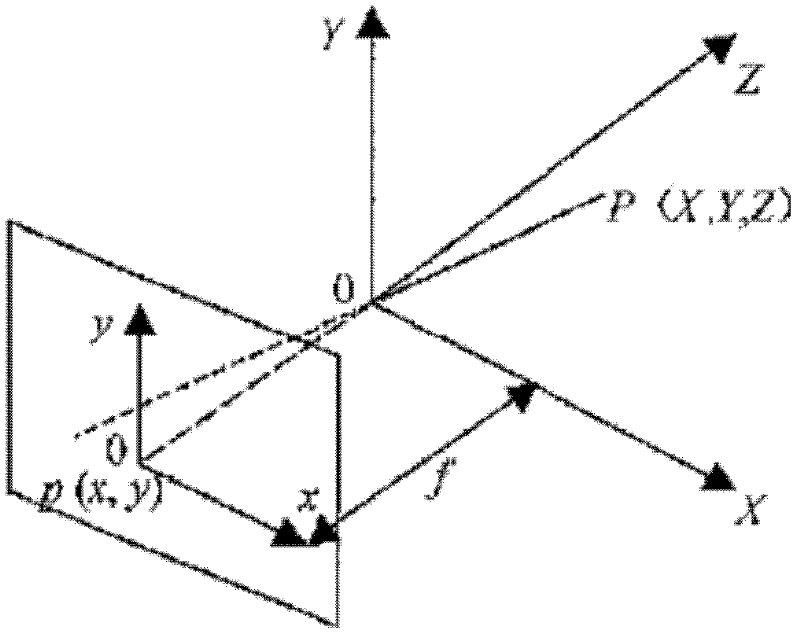
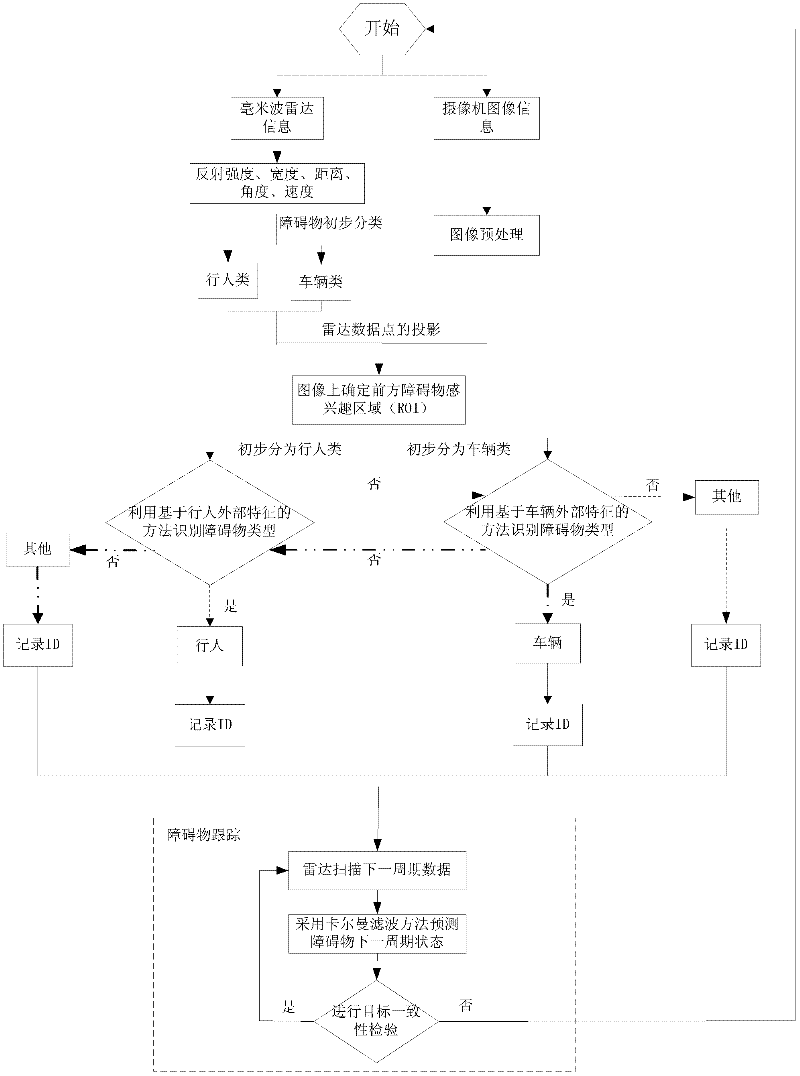
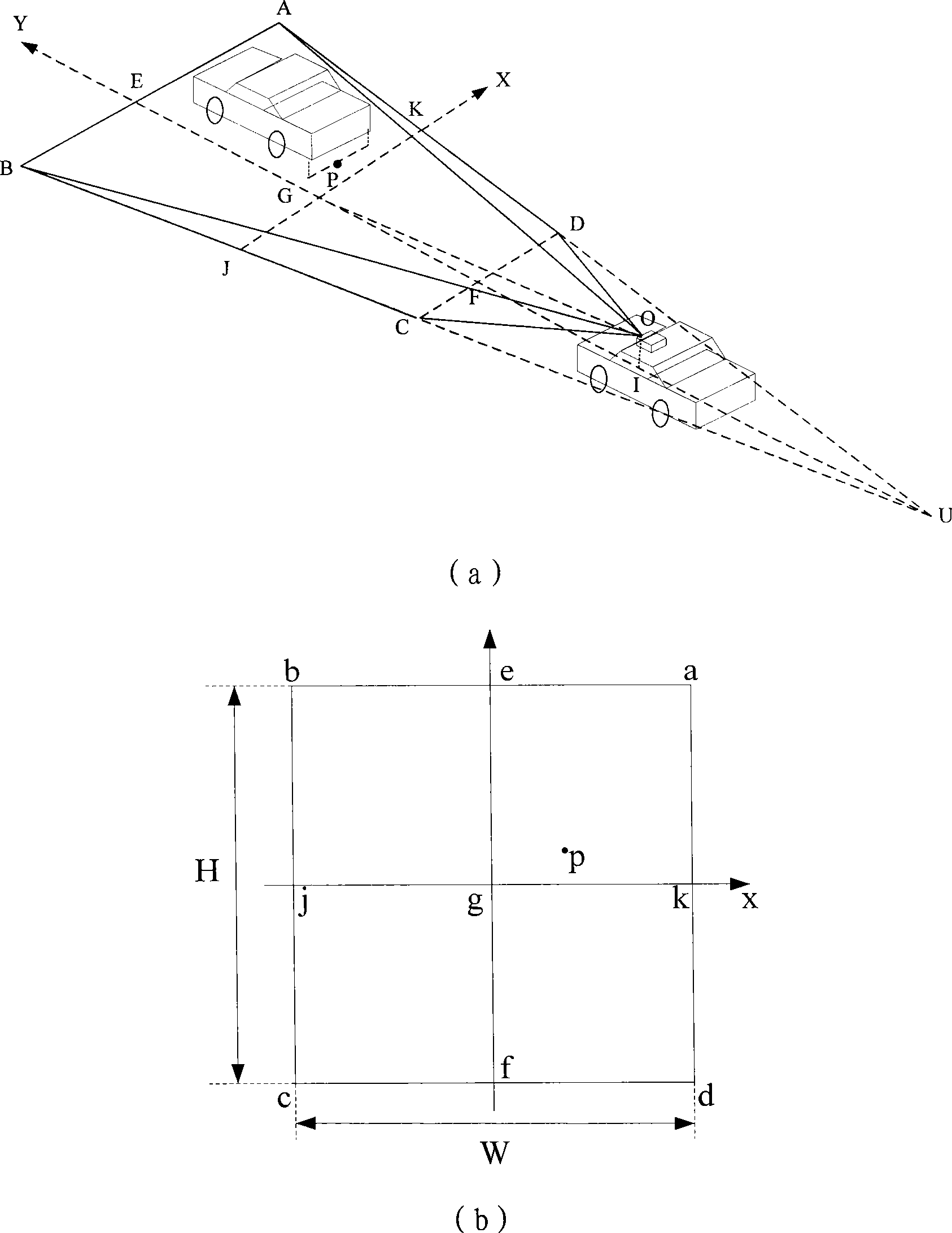
Method for detecting and tracking obstacles in front of vehicle
InactiveCN102508246ASolve problems that are difficult to classify and identify at the same timeSolve elusive problemsPhotogrammetry/videogrammetryCharacter and pattern recognitionCamera imageImaging processing
The invention discloses a method for detecting and tracking obstacles in front of a vehicle, aiming to overcome the defect and shortage in detection and tracking of obstacles in front of the vehicle by using a single-type sensor. The method comprises the following steps of: 1. establishing a relation for realizing data conversion between a millimeter wave radar coordinate system and a camera coordinate system; 2. receiving, resolving and processing the millimeter wave radar data, and carrying out preliminary classification on the obstacles; 3. synchronously collecting a camera image and receiving millimeter wave radar data; 4. classifying the obstacles in front of the vehicle: 1) projecting scanning points of the millimeter wave radar data on a camera coordinate system by combining the methods of millimeter wave radar and monocular vision, and establishing a region of interest (ROI) of the obstacles on the image; 2) carrying out preliminary classification on different obstacles in theROI established on the image, and confirming the types of the obstacles by using different image processing algorithms; and 5. tracking the obstacles in front of the vehicle.
Owner:JILIN UNIV
Method and apparatus for red-eye detection in an acquired digital image
ActiveUS20060093212A1Reduction of false positiveLower requirementImage enhancementTelevision system detailsImaging qualityDigital image
A method for red-eye detection in an acquired digital image comprises acquiring a first image and analyzing the first acquired image to provide characteristics indicative of image quality. The process then determines if one or more corrective processes can be beneficially applied to the first acquired image according to the characteristics. Any such corrective processes are then applied to the first acquired image. Red-eye defects are then detected in a second acquired image using the corrected first acquired image. Defect detection can comprise applying one or more, or a chain of two or more, red-eye filters to the first acquired image. In this case, prior to the detecting step, it is determined if the red-eye filter or red eye filter chain can be adapted in accordance with the characteristics. The red-eye filter may be adapted accordingly.
Owner:FOTONATION LTD
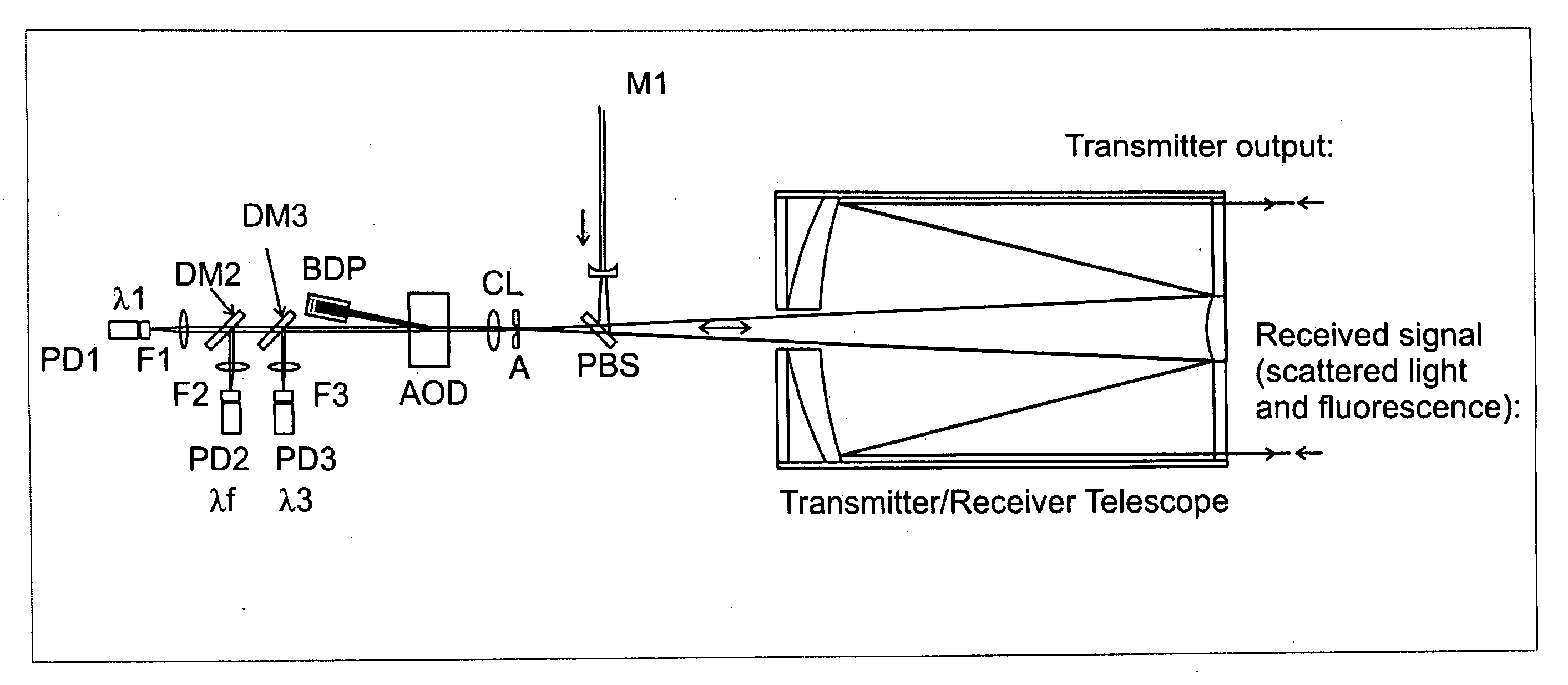
Enhanced portable digital lidar system
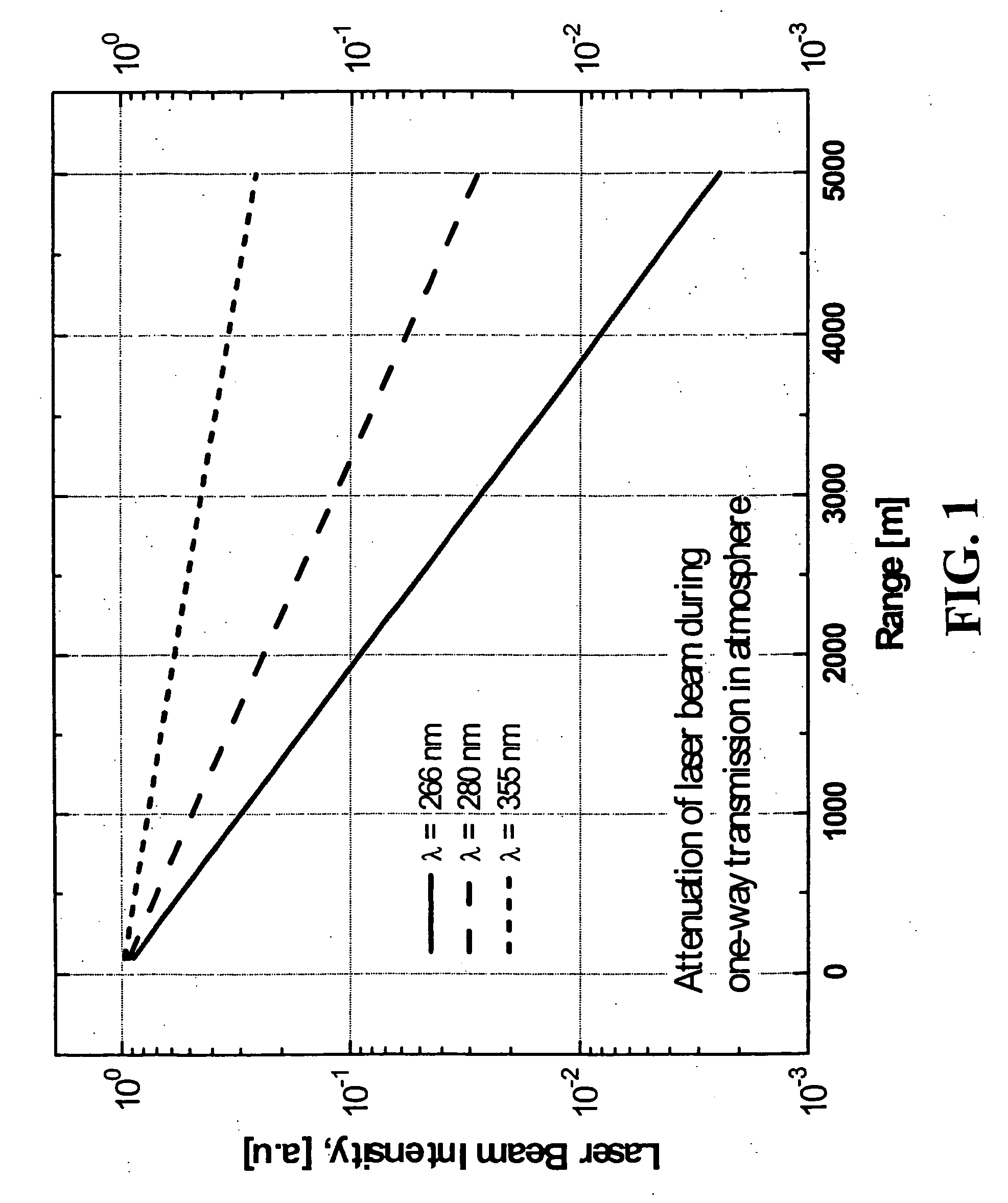
InactiveUS20060231771A1Easy to set upEasy maintenancePhotometryMaterial analysis by optical meansSpectral bandsFluorescence
A system for detecting airborne agents. The system can include a laser source that provides laser pulses of at least two wavelengths, a transmitter that transmits the laser pulses, and a coupling mechanism configured to remotely couple the laser pulses between the laser source and the transmitter. The system can include a receiver receives both elastically backscattered signals from airborne agents and fluorescence signals from the airborne agents. The system can include a telescope both transmits a collimated laser beam of the laser pulse from the transmitter to a far field and receives the elastically backscattered signals and the fluorescence signals from the far field. The system can include a detection system having at least one of a backscatter optical detector that detects the elastically backscattered signals and one or more fluorescence optical detectors that detect the fluorescence signals in selected spectral band(s) from the airborne agents.
Owner:SCI & ENG SERVICES
Method and apparatus for red-eye detection in an acquired digital image using face recognition
InactiveUS20060093238A1Reduction of false positiveLower requirementImage enhancementImage analysisImaging qualityDigital image
A method for red-eye detection in an acquired digital image comprises acquiring a first image and analysing the first acquired image to provide a plurality of characteristics indicative of image quality. The analysing step may also include recognizing one or more faces or types of face in the first acquired image, and performing the correction accordingly. The process then determines if one or more corrective processes can be beneficially applied to the first acquired image according to the characteristics. Any such corrective processes are then applied to the first acquired image. Red-eye defects are then detected in a second acquired image using the corrected first acquired image. Defect detection can comprise applying a chain of one or more red-eye filters to the first acquired image. In this case, prior to the detecting step, it is determined if the red-eye filter chain can be adapted in accordance with the plurality of characteristics: and the red-eye filter is adapted accordingly.
Owner:STEINBERG ERAN +3
Dynamic multi-spectral CT imaging
InactiveUS6950493B2Good curative effectPromote resultsMaterial analysis using wave/particle radiationRadiation/particle handlingX-rayDetector array
A multispectral X-ray imaging system uses a wideband source and filtration assembly to select for M sets of spectral data. Spectral characteristics may be dynamically adjusted in synchrony with scan excursions where an X-ray source, detector array, or body may be moved relative to one another in acquiring T sets of measurement data. The system may be used in projection imaging and / or CT imaging. Processed image data, such as a CT reconstructed image, may be decomposed onto basis functions for analytical processing of multispectral image data to facilitate computer assisted diagnostics. The system may perform this diagnostic function in medical applications and / or security applications.
Owner:FOREVISION IMAGING TECH LLC
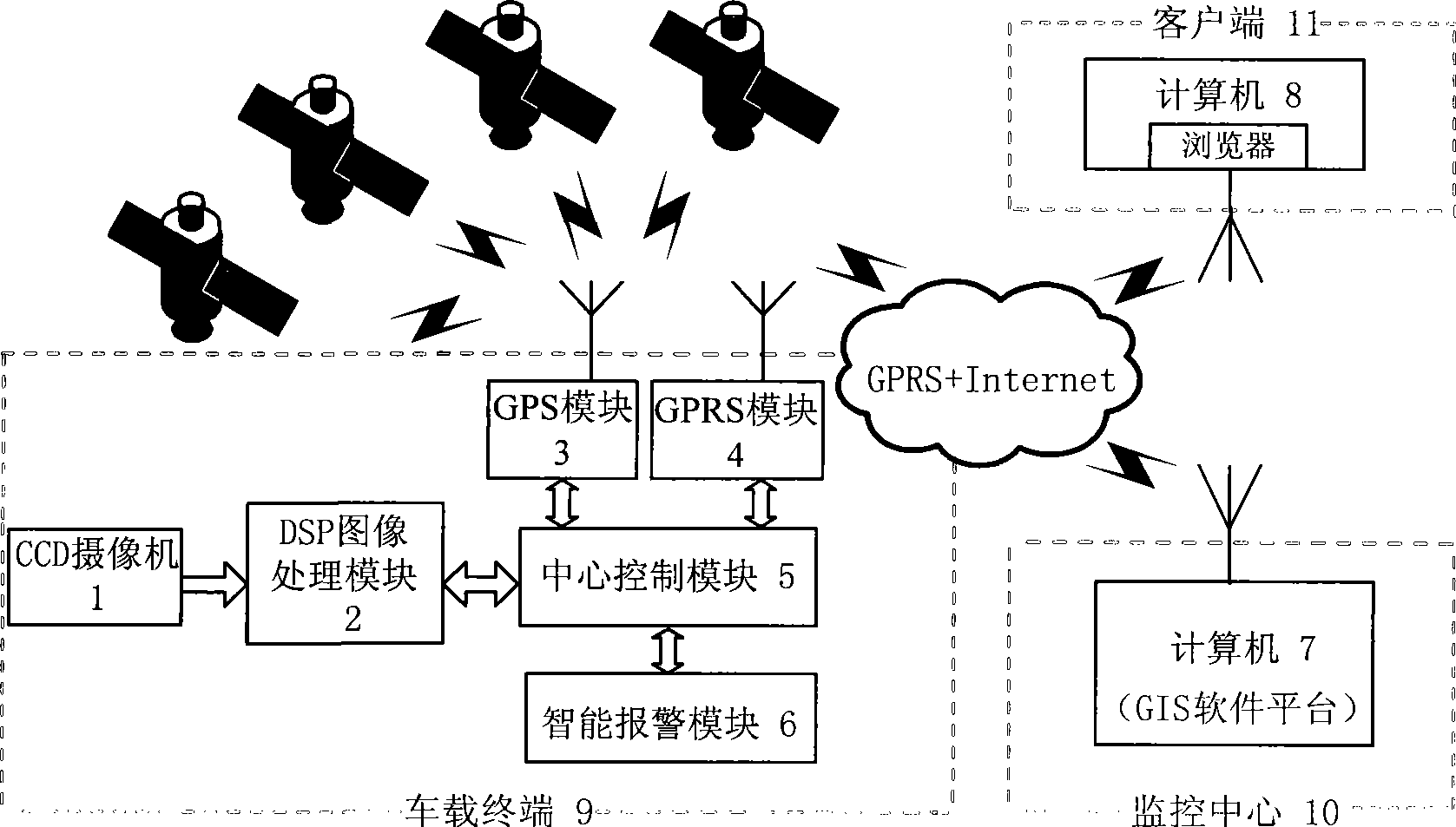
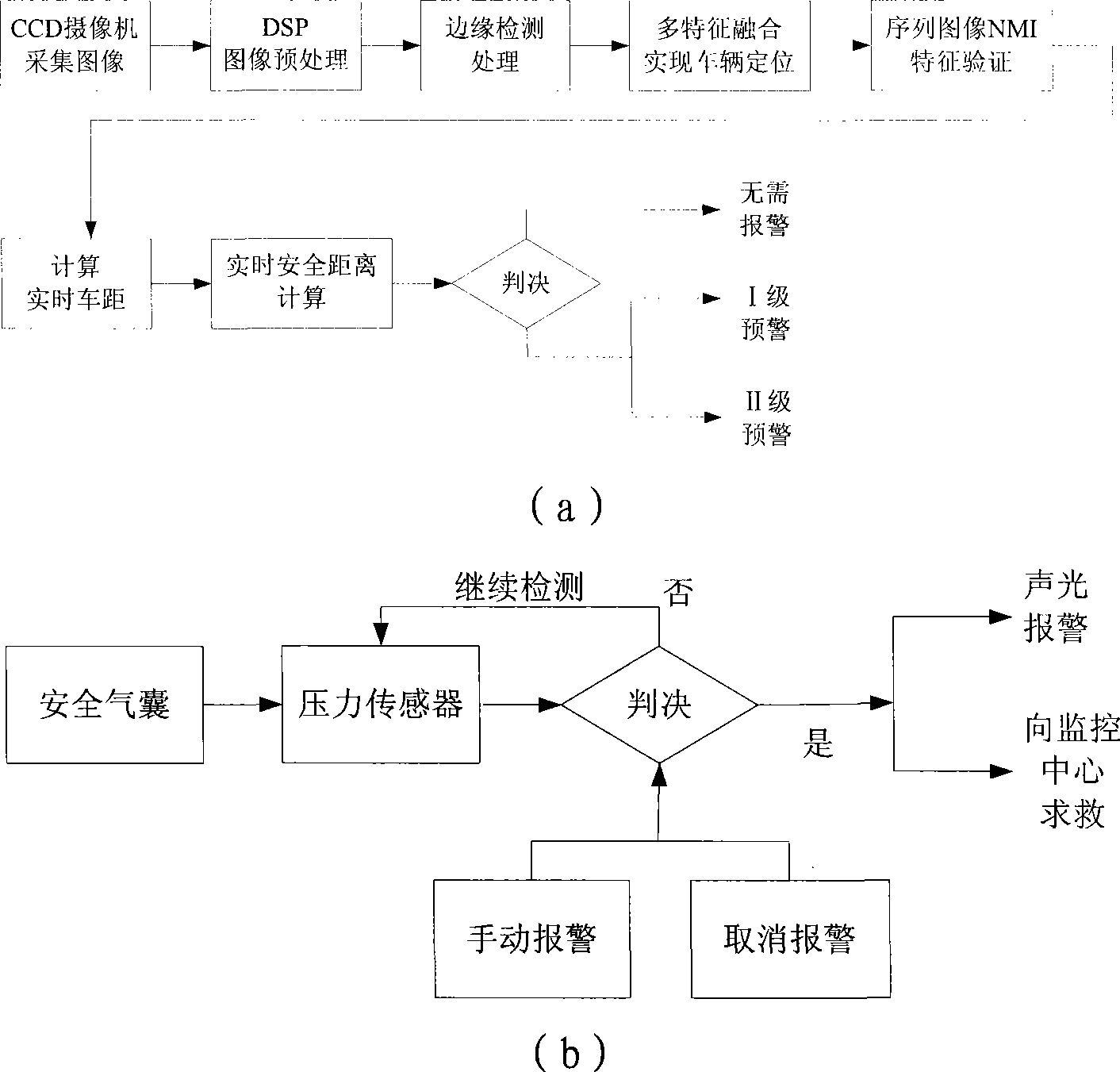
Vehicle intelligent alarming method and device
InactiveCN101391589AImprove securityEfficient detectionPedestrian/occupant safety arrangementSignalling/lighting devicesMobile vehicleMachine vision
The invention relates to an on-board intelligent alarming method and a device, wherein, the method combines a longitudinal anti-collision pre-warning method based on the single-eye vision and an accident automatic help-calling method, realizes preventing the rear-end accidents, strives for helping time, reduces injuries and deaths, effectively prevents the collision accidents and personnel deaths caused by the collision, and improves the running safety of the automobile; the device mainly comprises three parts: an on-board terminal, a monitoring center and a user end; the method and the device use the machine vision technique to differentiate the moving vehicles in the front, have high precision and wide visible range, can effectively probe the obstacles, reduce the error reporting possibility and prevent the collision accidents. The method and the device can improve the safety of the vehicle, thus having extremely large application value and prospect.
Owner:SHANGHAI UNIV
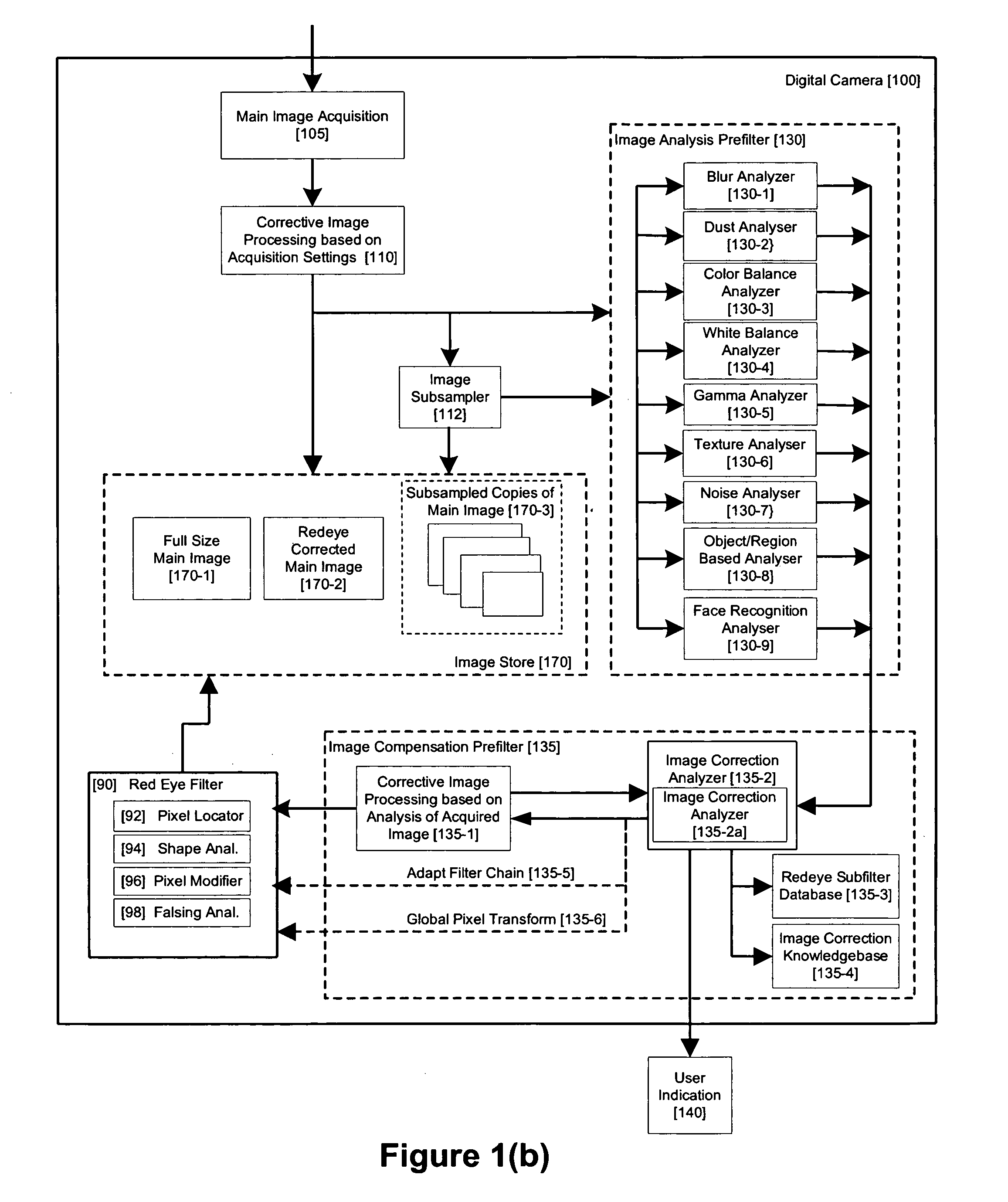
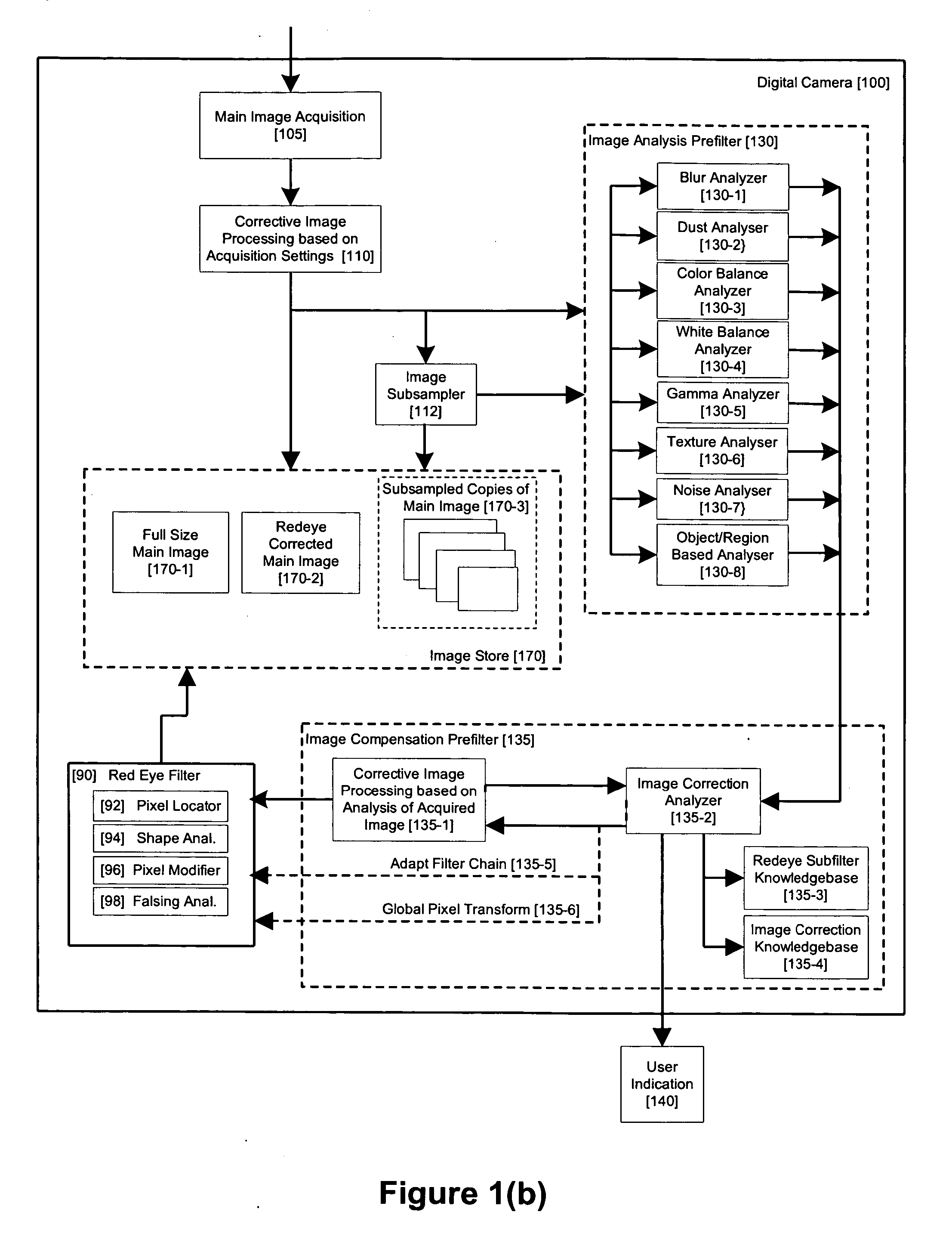
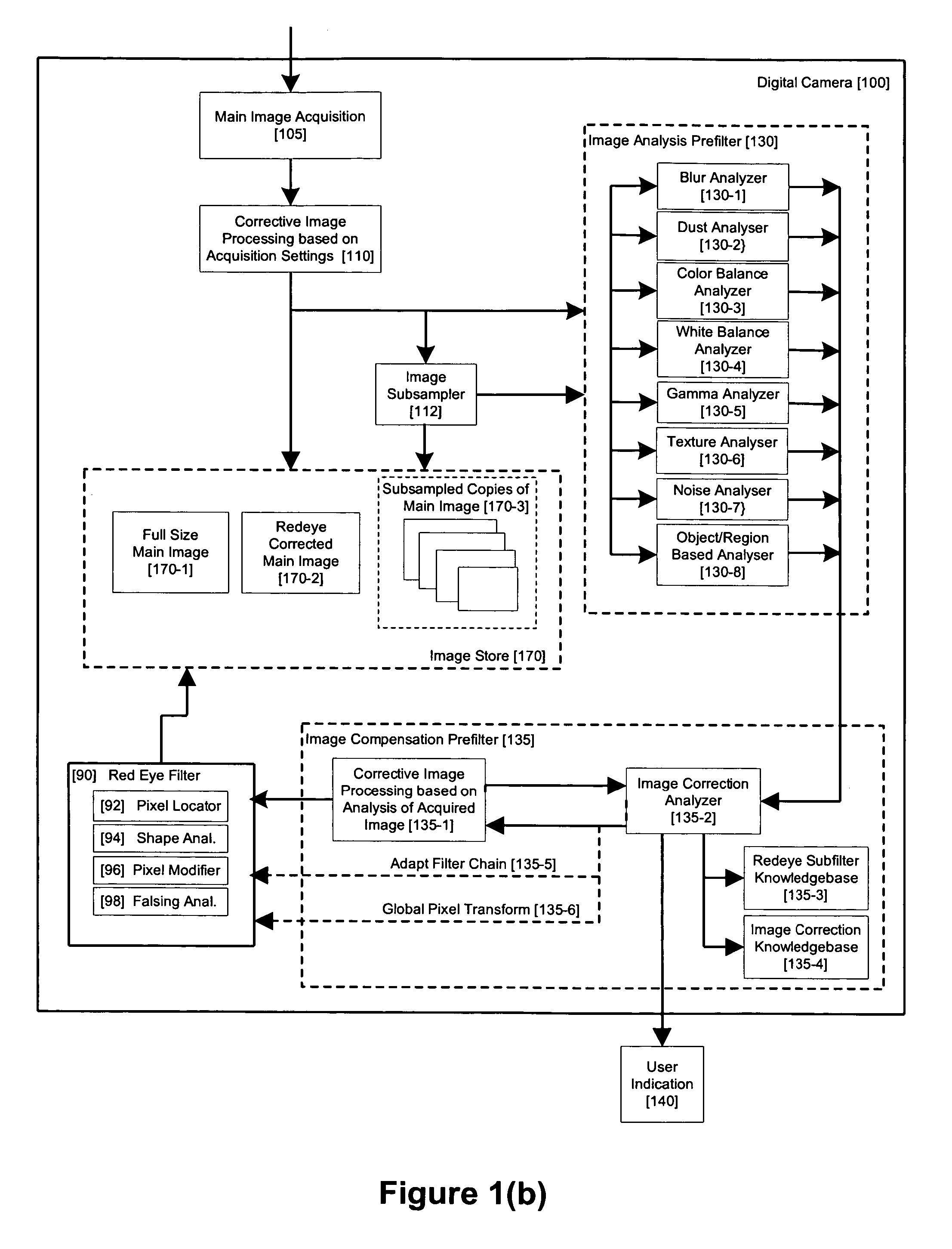
Method and apparatus for red-eye detection in an acquired digital image based on image quality pre and post filtering
ActiveUS20060093213A1Reduce false alarm rateIncrease success rateImage enhancementImage analysisImaging qualityImage correction
A method for red-eye detection in an acquired digital image comprises acquiring a first image and analyzing the first acquired image to provide characteristics indicative of image quality. The process then determines if one or more corrective processes can be beneficially applied to the first acquired image according to the characteristics. Any such corrective processes are applied and red-eye defects are detected in an established order established according to determination and analysis of characteristics of the corrective process and / or resulting image qualities. Defect correction can comprise applying one or more image correction operations, or a chain of two or more red-eye filters to the first acquired image. In this case, prior to the detecting step, it is determined if the red-eye filter or red eye filter chain should be applied before or after image corrective processes and whether the red eye filter can be adapted in accordance with the characteristics. The red-eye filter and the order in which it is executed in relation to the various image corrective operations may be adapted accordingly.
Owner:FOTONATION LTD
Short-range frequency-modulation continuous wave FMCW radar anti-interference method
ActiveCN101089653AWork reliablyEasy to implementRadio wave reradiation/reflectionContinuous waveFrequency modulation
An anti-interfering method of short-range FMCW radar includes designing a set of pseudo-random code according to occasion of radar, distributing different pseudo-random code to different radar operated at different area, applying different pseudo-random code to modulate frequency start-point of FM emission signal for the same radar on each cycle, making frequency-mixture on received echo signal by utilizing emission signal, using filter to filter off interference signal and applying FM signal processing means to treat reserved usable signal for obtaining object distance and speed information in high resolution.
Owner:南京精益安防系统科技有限公司
Mobile phone telephone and message anti-disturbance and private communication method and system
InactiveCN101184264AImprove filtering effectOptimize the effect of anti-harassmentRadio/inductive link selection arrangementsSubstation equipmentPrivate communicationSocial statistics
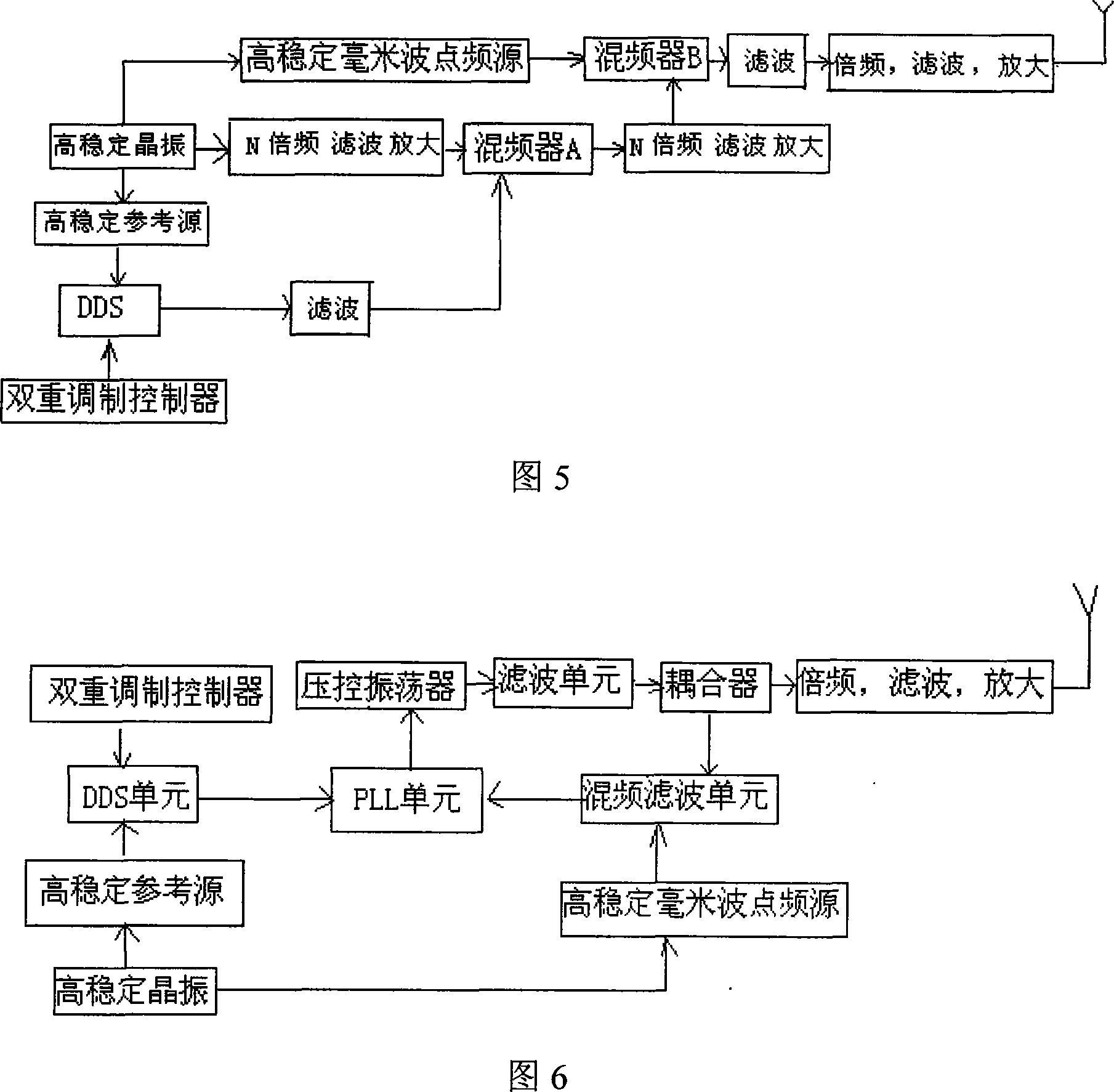
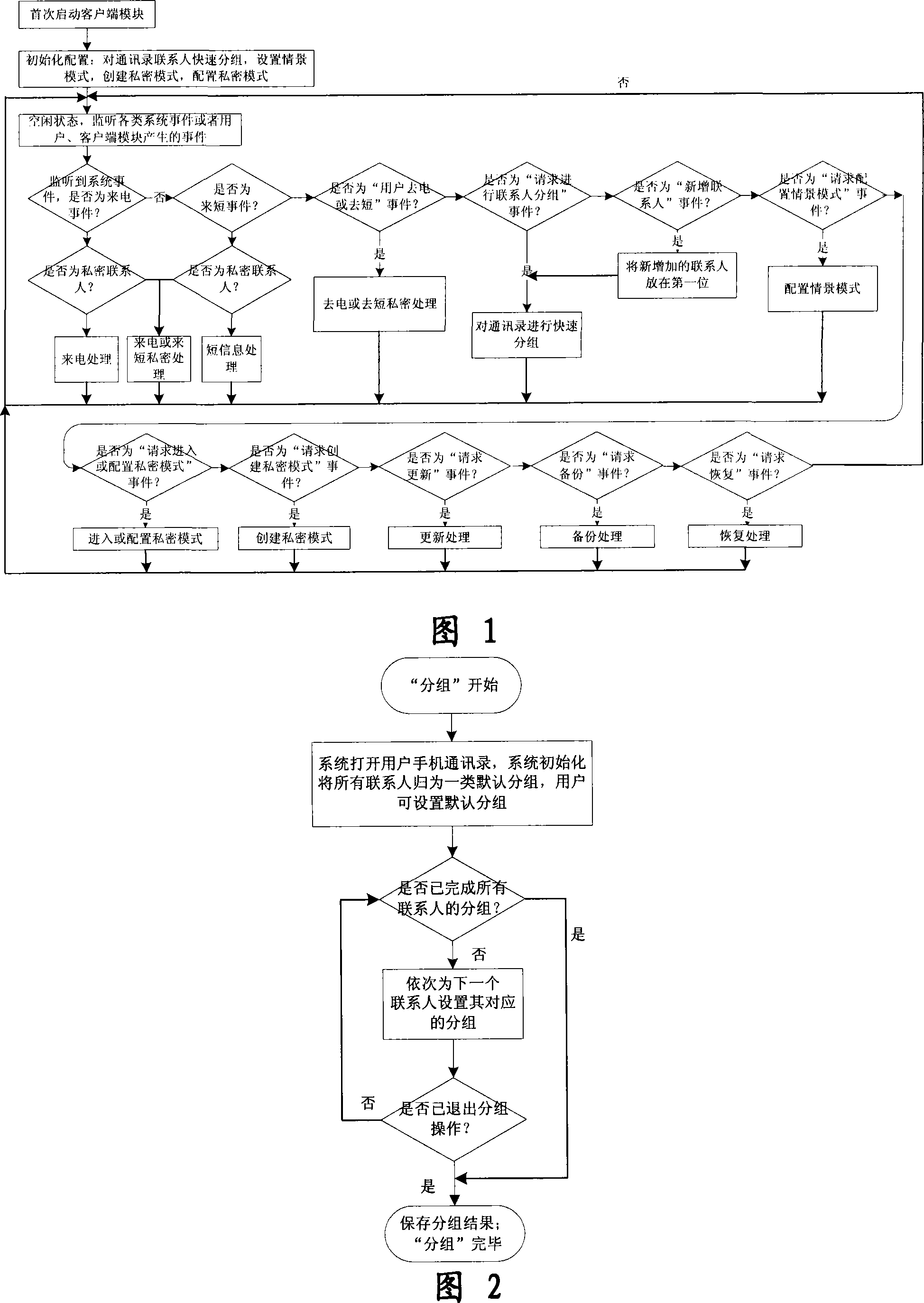
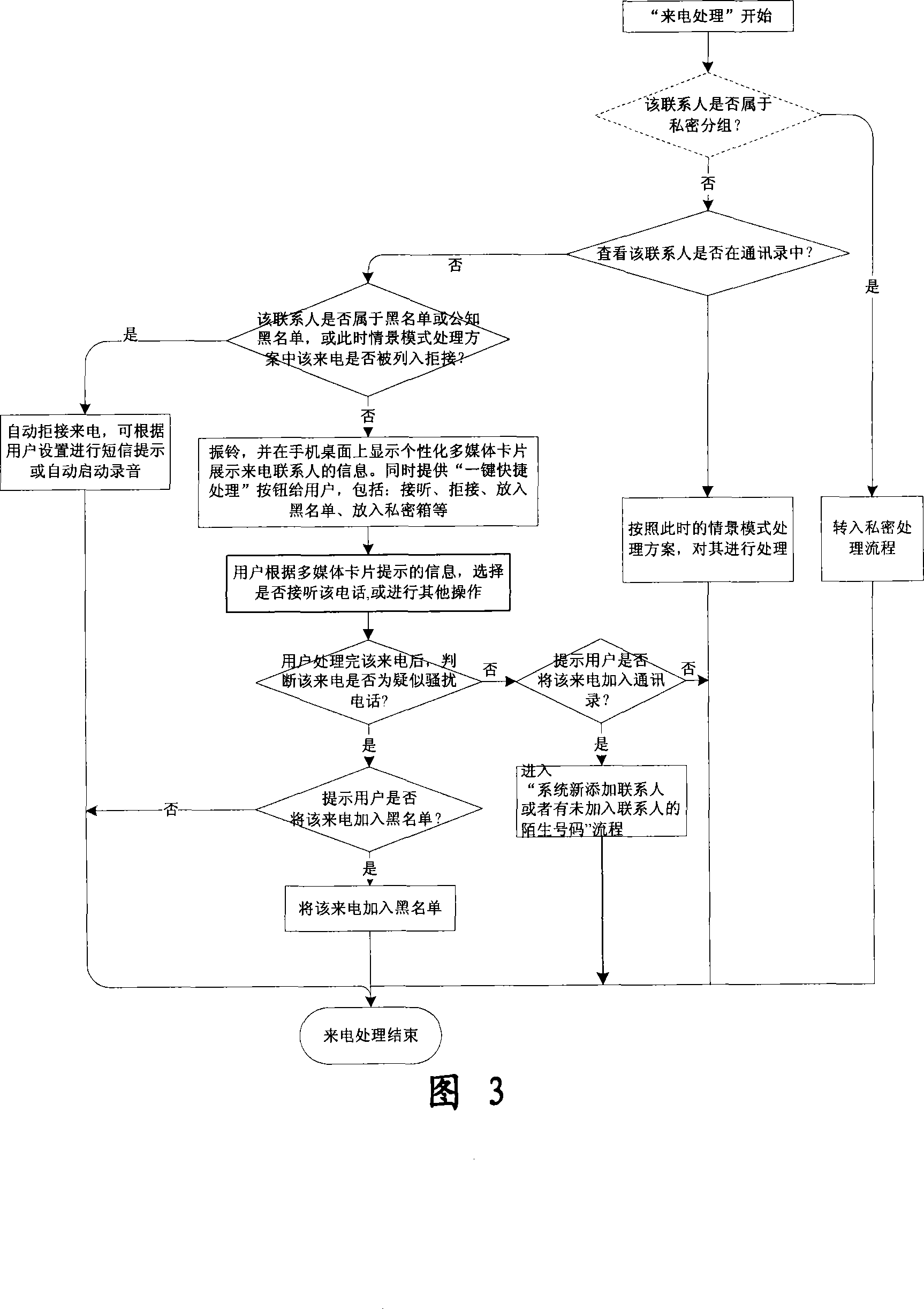
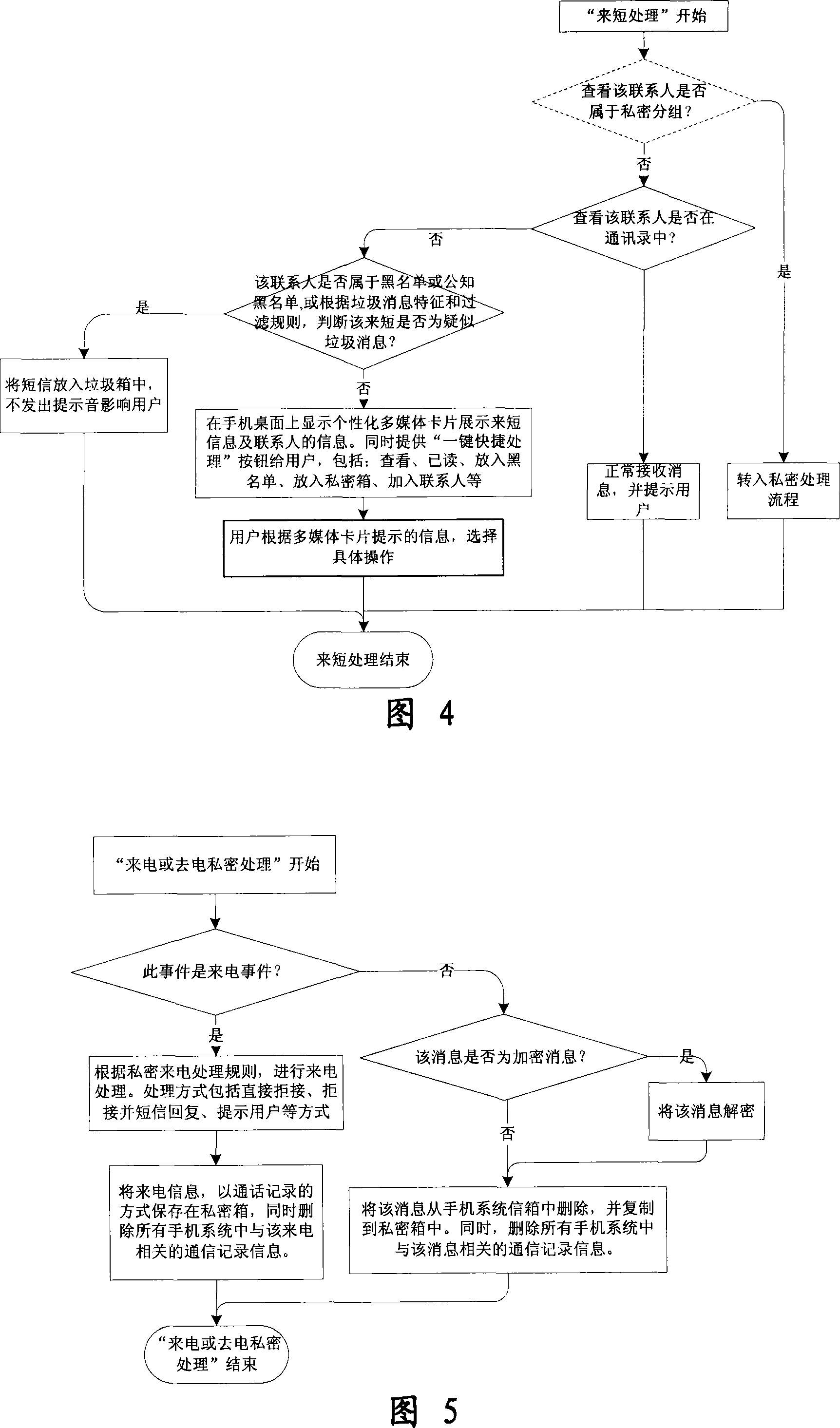
The invention relates to a processing method and the system of anti-harassment of mobile phone calls and messages and private communication, which is as follow: when grouping the contacts in the mobile phone address list according to different classes, a private group of private communicating contacts is added, and different scene modes of the user are set; when receiving a mobile phone call or a message (text message, multimedia message), depending on the grouping sort of the contact of the incoming call or the message or the multimedia message, and the current scene of the user, together with the behavior characteristics of the harassing call and the spam message with the database information of the public harassing message issued by the authoritative institution or obtained from social statistics, the corresponding process to the call, the message and the multimedia message of the mobile phone is executed to reduce harassment; meanwhile the communication records of incoming, dialed calls and message, multimedia message with the contacts in the private grouping are encrypted and preserved to protect the personal privacy of the user. The invention has the advantages of adopting the operating steps of uniform process, and resolving synthetically the harassment of calls, messages and multimedia messages for the mobile phone and the private protection.
Owner:BEIJING NETQIN TECH
Multiple-sensor and multiple-object information fusing method
InactiveCN1389710AExpand coverageImprove the detection rateBeacon systems using radio wavesAiming meansFeature extractionAlgorithm
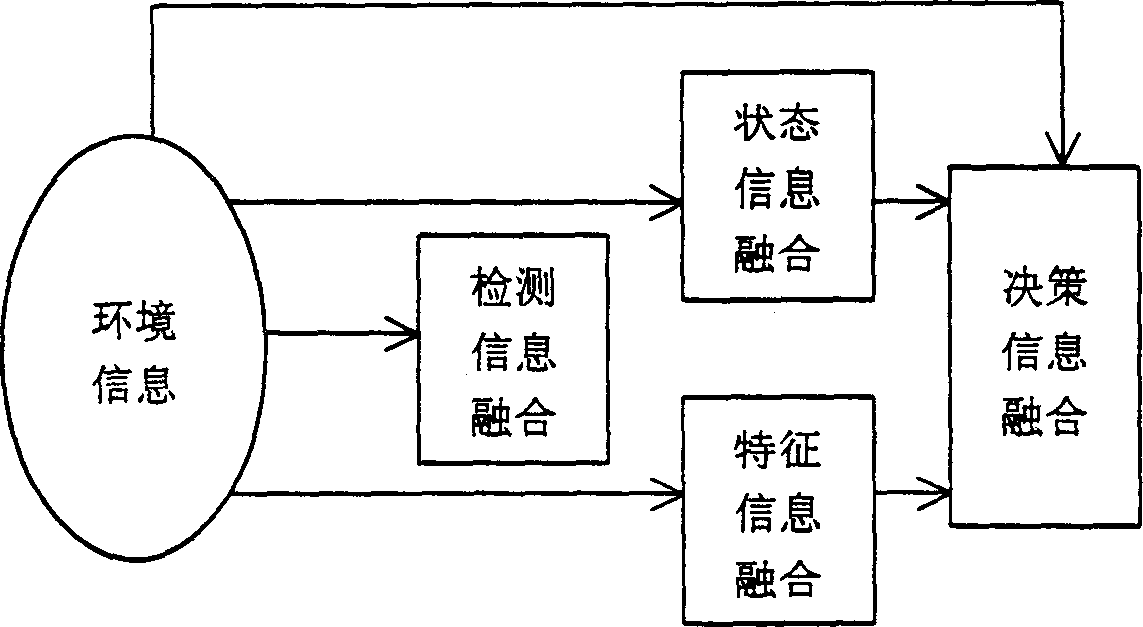
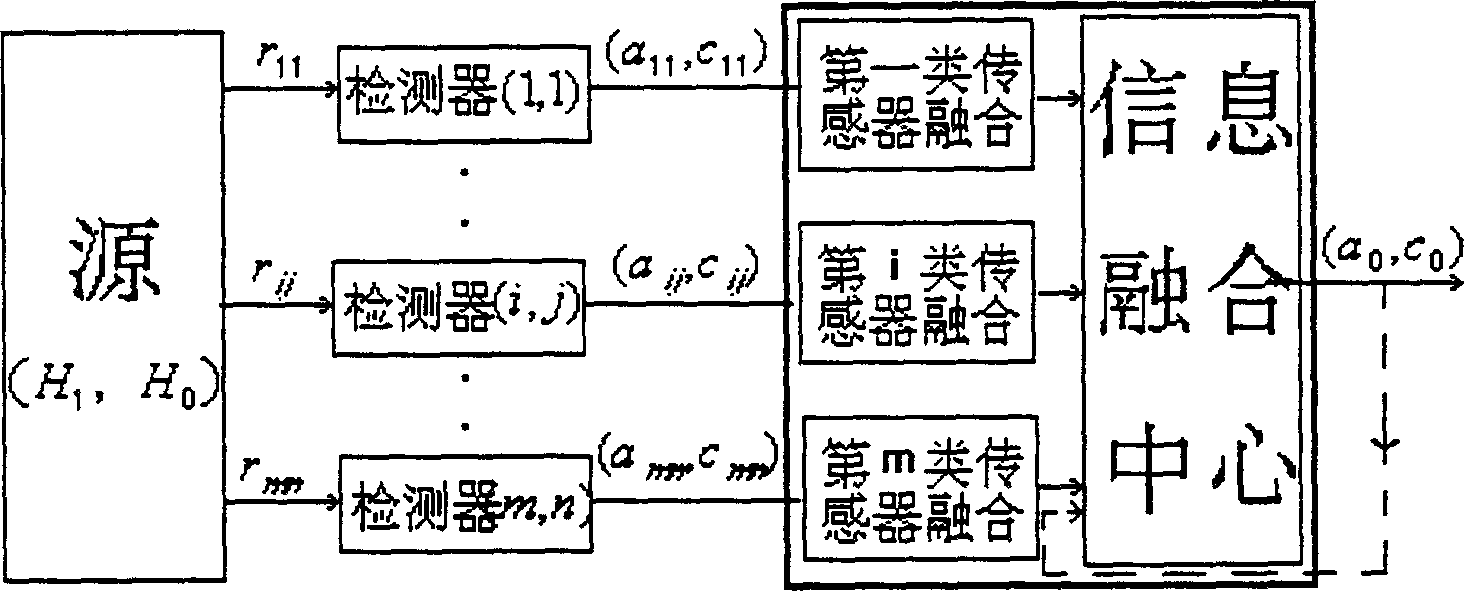
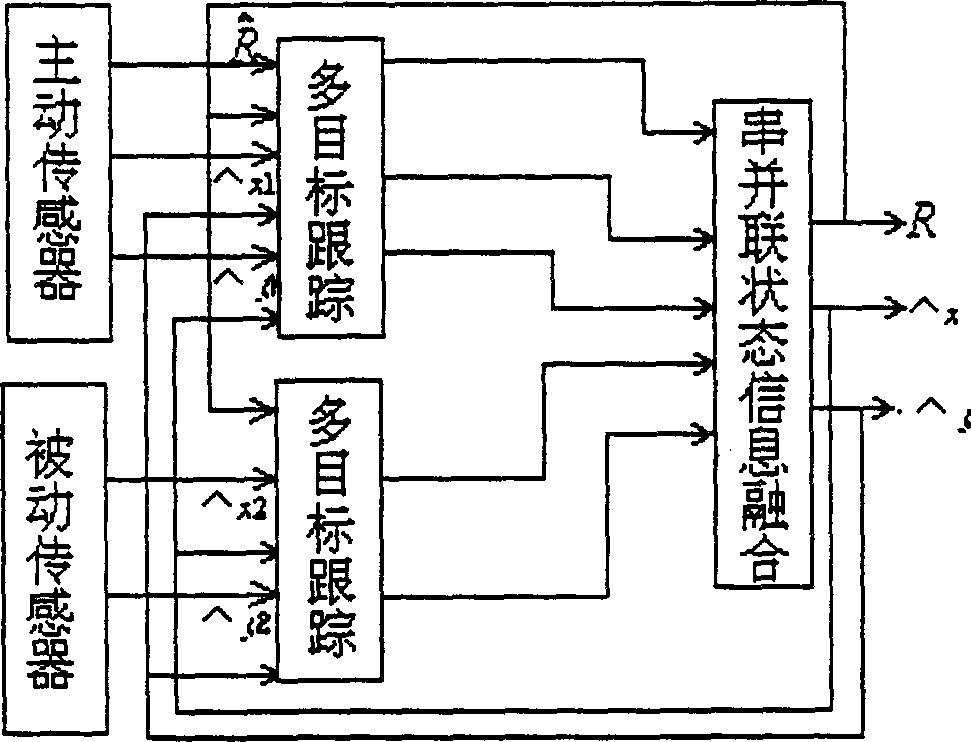
Transducers of different distributions detect the existence of targets of environment first and a test information composition system mixes the results detected by transducers to follow up the state and pick-up the character of the target. The state information composition system and the character dinformation composition system composite the traced states and identification results of character vector separately by each transducer to get relative accurate state parameter and identified results and information composition makes the entire systematic composition to provide favorable decision for next step, to increase systematic detecting probability, estimated accuracy and identified probability and more resonable algorithm.
Owner:SHANGHAI JIAO TONG UNIV
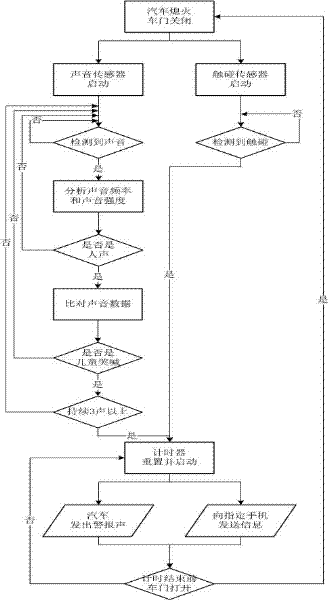
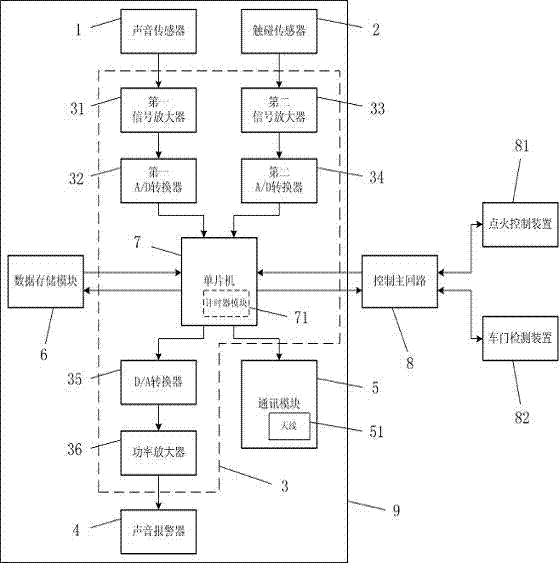
Vehicle-mounted child omission reminder device and detection method thereof
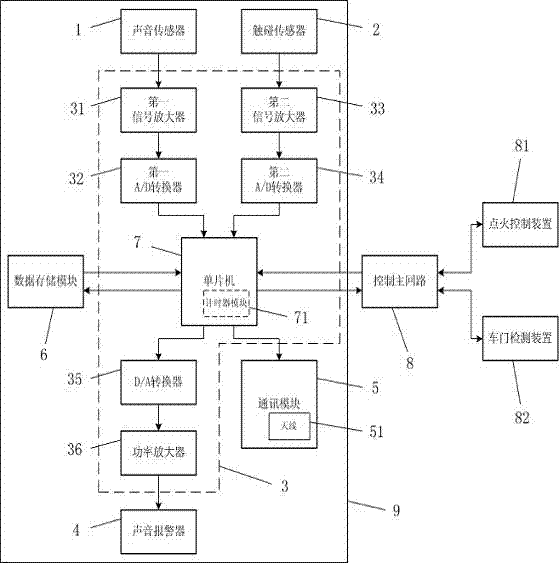
ActiveCN102259629AEffective reminderImprove reliabilityPedestrian/occupant safety arrangementAlarmsComputer moduleComputer science
The invention discloses a vehicle-mounted child leaving reminding device and a vehicle-mounted child leaving detection method. The device comprises a voice sensor, a touch sensor, a main control module, a voice alarm, a communication module and a data storage module, wherein the voice sensor and the touch sensor are connected with the signal input end of the main control module; the voice alarm and the communication module are connected with the signal output end of the main control module; the data storage module is connected with the main control module; after an automobile is power off andan automobile door is closed through detection, the voice sensor and the touch sensor are started and respectively perform detection in voice and touch modes; when at least one detection result indicates that a child is left in the automobile, the automobile sends alarm voice and sends information to a specified mobile phone; and an initial state is returned when the automobile door is opened through detection. By the vehicle-mounted child leaving reminding device and the vehicle-mounted child leaving detection method, people around the automobile and specific related personnel can be effectively reminded when the child is left in the automobile.
Owner:ZHEJIANG GEELY AUTOMOBILE RES INST CO LTD +1
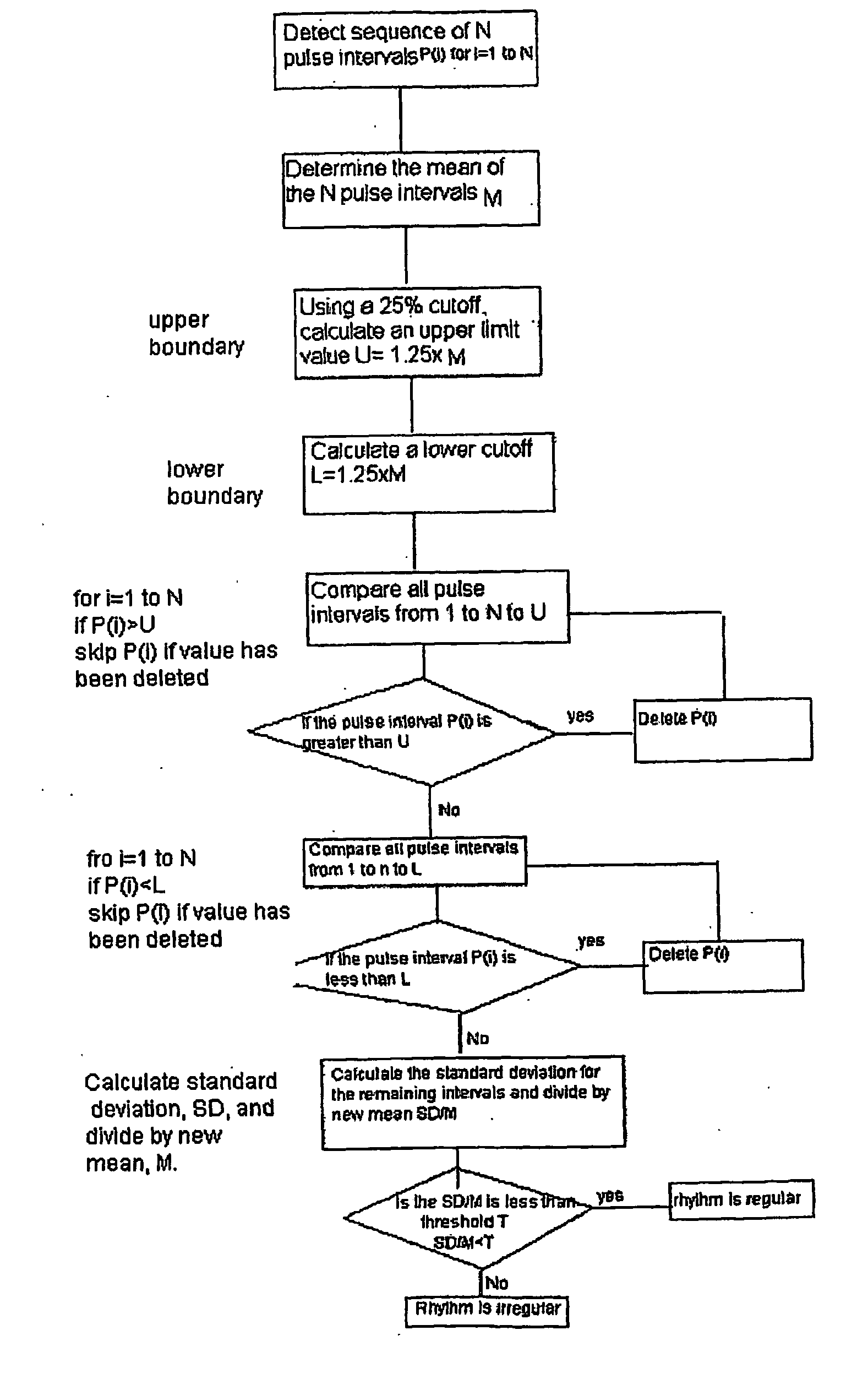
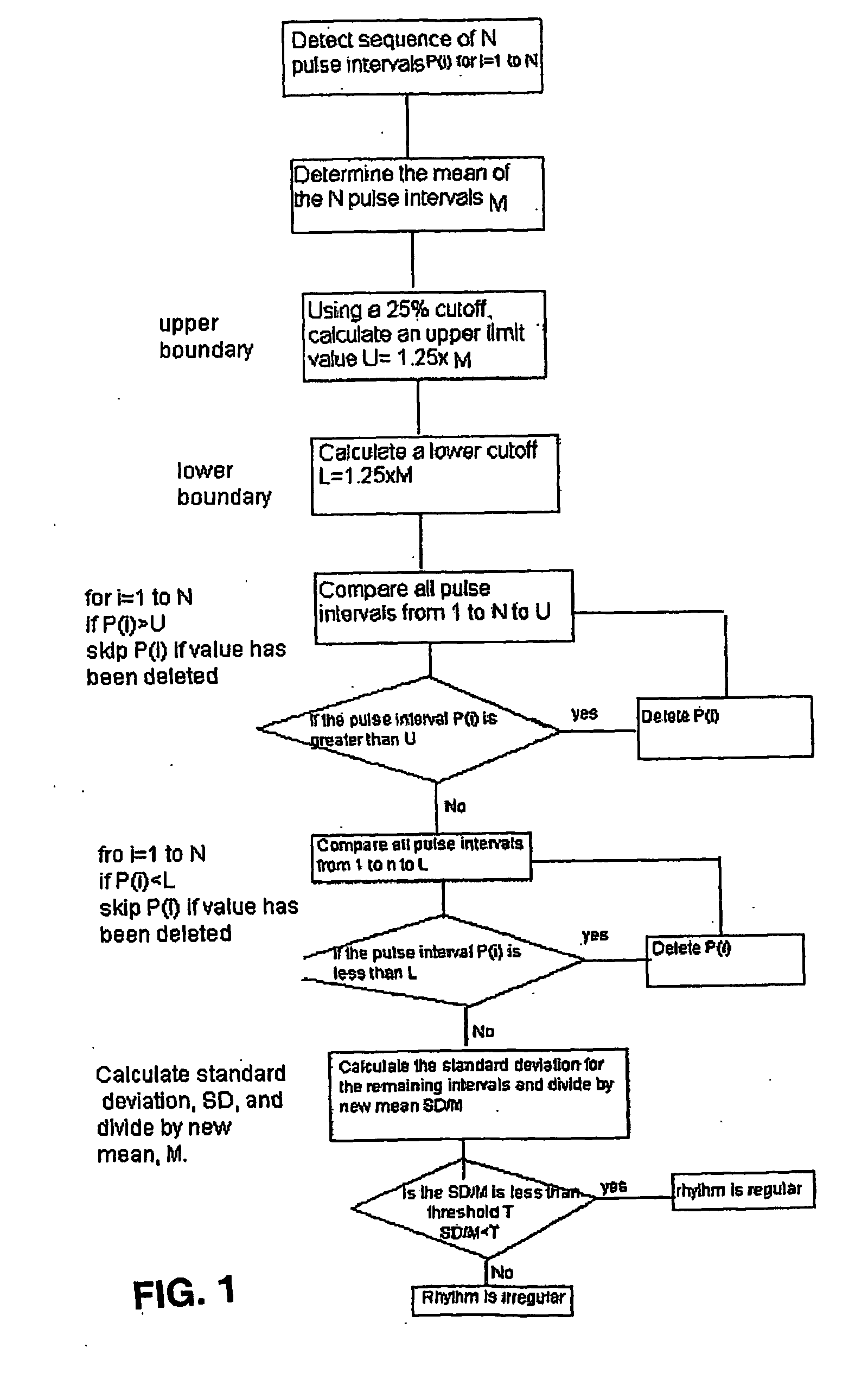
Detecting Atrial Fibrillation, Method of and Apparatus for
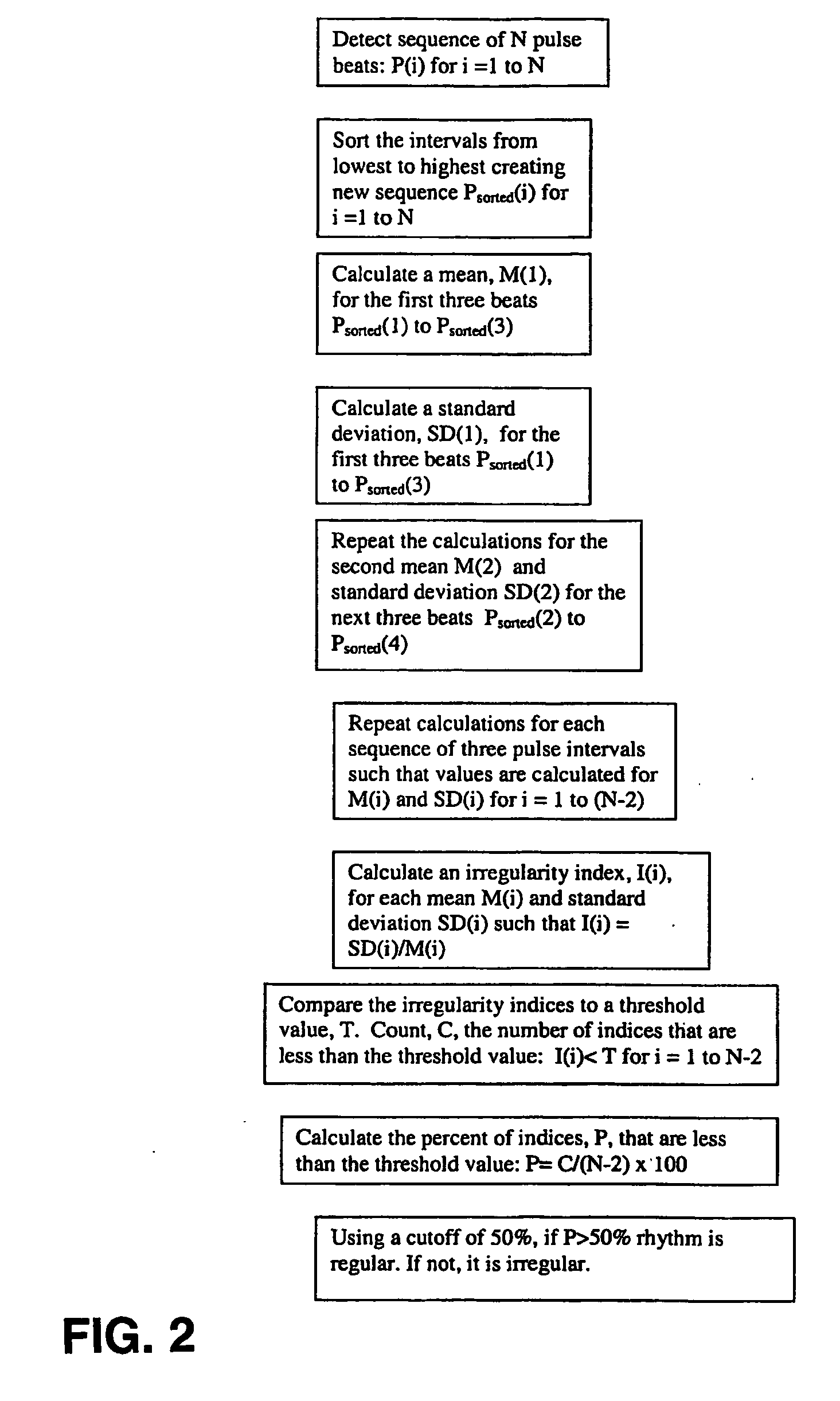
ActiveUS20090012412A1Avoid detectionReduce false alarm rateElectrotherapyElectrocardiographyAtrial fibrillationPulse rhythm
A method and apparatus to determine possible atrial fibrillation or absence of atrial fibrillation that includes detecting pulse rhythms from a succession of time intervals each corresponding to a respective interval of time between successive pulse beats; analyzing the detected pulse rhythms to make a determination of possible atrial fibrillation; indicating the possible atrial fibrillation from the determination; or making a determination of the absence of atrial fibrillation.
Owner:WIESEL JOSEPH
Contactless respiration monitoring of a patient
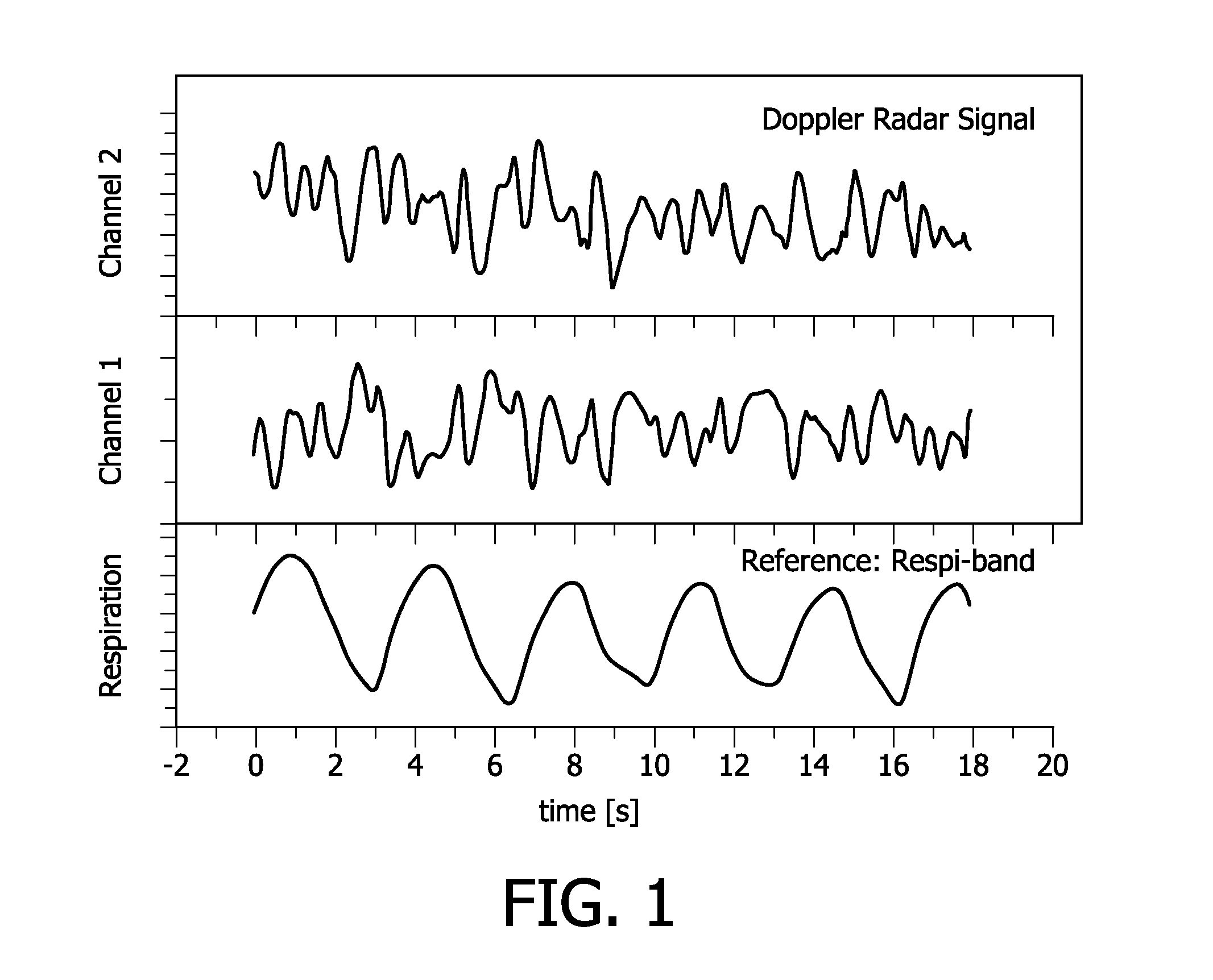
ActiveUS20110112425A1Easy to handleReliable of direction changeRespiratory organ evaluationSensorsPhase shiftedRadar
The invention relates to a method for detection of respiration of a patient comprising the following steps: emitting an electromagnetic signal towards the patient; receiving a reflected electromagnetic signal reflected from the patient; converting the reflected electromagnetic signal, yielding a first signal; phase-shifting the reflected electromagnetic signal and converting the phase-shifted reflected electromagnetic signal, yielding a second signal; determining a first vector being defined by the time derivatives of the first signal and the second signal, for a common first point in time; determining a second and vector being defined by the time derivatives of the first signal and the second signal, for a common second point in time; and calculating the scalar product of the normalized first vector and the normalized second vector as an indicator value for a change from expiration to inspiration of the patient or vice versa. A change from expiration to inspiration of the patient or vice versa is preferably indicated if the indicator value is below a threshold value, preferably below a value of 0. In this way, a possibility for contactless remote respiration monitoring of a patient based on the Doppler radar principle is provided which is reliable and easy to handle.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Log based computer system fault diagnosis method and device
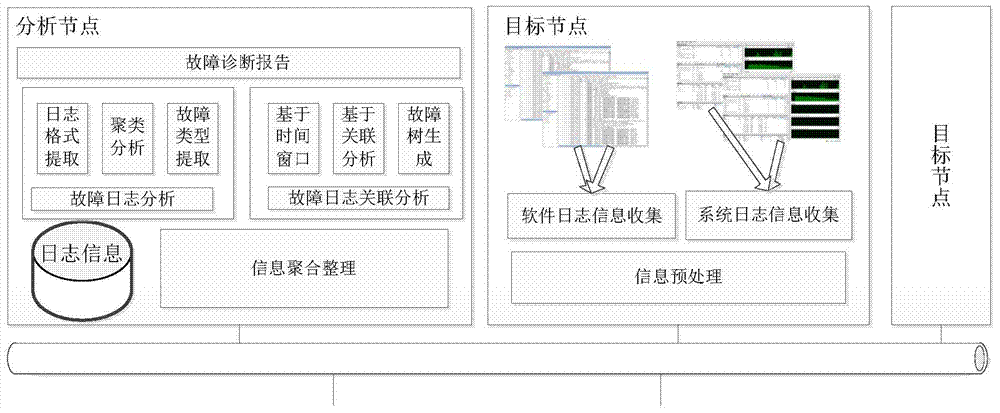
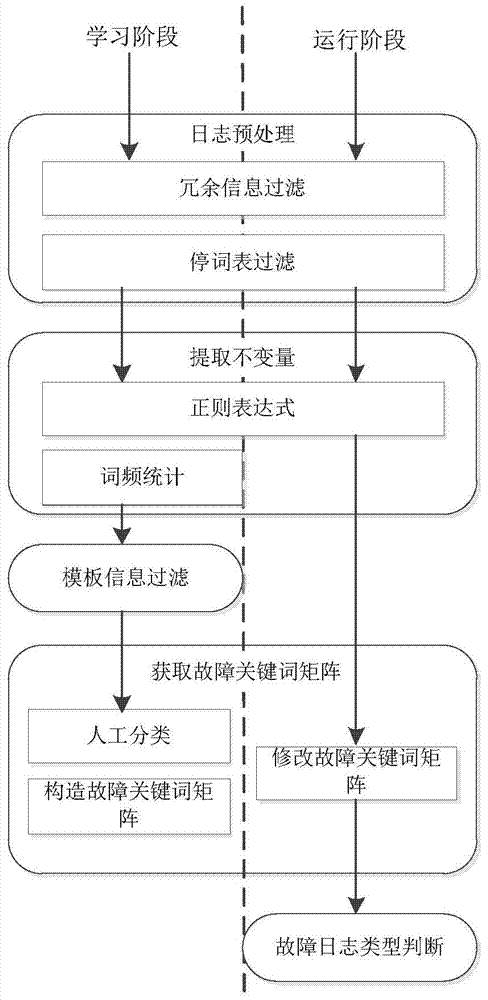
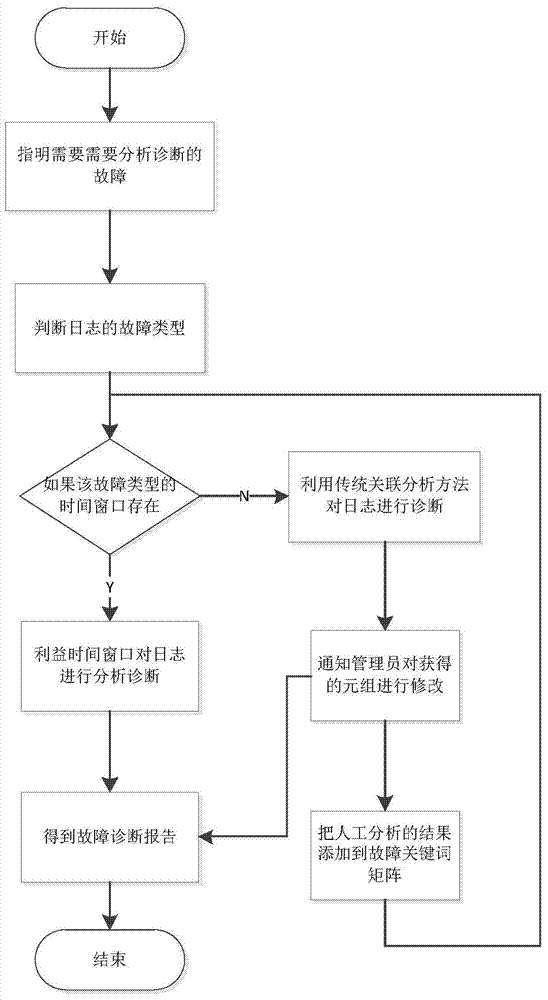
InactiveCN103761173AConvenient and rapid fault classificationProcessing speedDetecting faulty computer hardwareHardware monitoringProcess systemsLog management
The invention discloses a log management and fault diagnosis method and device under multiple hosts. The method comprises fault log collection, fault log analysis and fault log correlation analysis. Fault log collection comprises collecting fault logs of all hardware and software in the cluster and storing the logs in a log server uniformly. Fault log analysis comprises filtering the fault logs, extracting log template information and classifying the logs according to log types. Fault log correlation analysis comprises performing fault reason analysis by using log analysis results and combining time windows, clustering the related faults caused by the same fault into a category and trying to find the root of the type of the faults. The method and the device are capable of analyzing the system operation condition effectively, assisting administrators to process system faults and improving the fault type determination accuracy.
Owner:HUAZHONG UNIV OF SCI & TECH
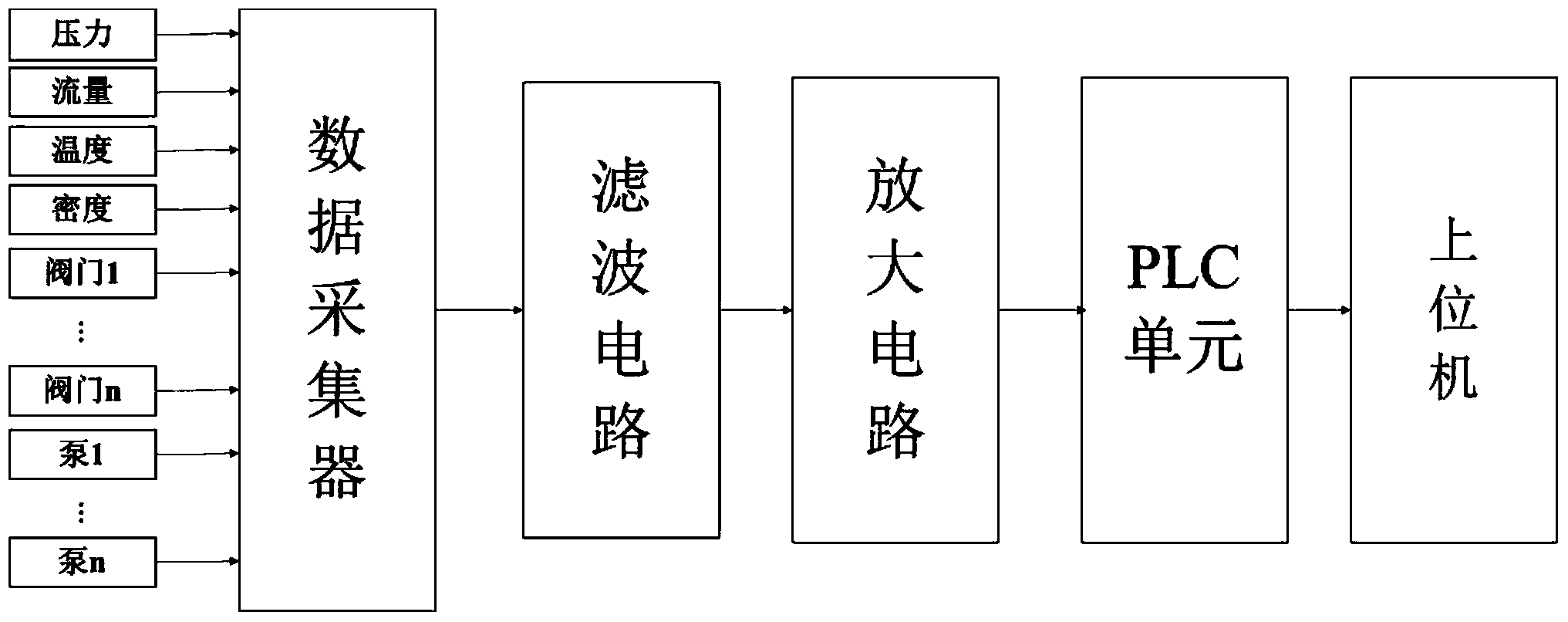
Oil pipeline network leakage intelligent self-adaptation monitoring system and method based on big data
InactiveCN103939749ASimple methodHigh sensitivityFluid-tightness measurementPipeline systemsTraffic capacityMonitoring system
The invention provides an oil pipeline network leakage intelligent self-adaptation monitoring system and method based on big data, and belongs to the technical field of pipeline network internal detection methods. By means of the system and method, a large number of data collected on site can be effectively analyzed in reasonable time, the state of a pipeline network can be obtained by means of an intelligent self-adaptation method, and accordingly a topological structure of the pipeline network is obtained. By means of a flow balance method and with the combination of an information consistency theory, whether the pipeline network leaks is analyzed, and the method is visual, simple, high in sensitivity and low in false alarm rate. Besides, precise warning is well carried out on detection of small leakage amount and slow leakage. By means of a generalized regression neural network, leakage positioning of the pipeline network is carried out, and accuracy of a result is improved. Accordingly, leakage detection and positioning problems of the pipeline network are solved by means of strategies based on the big data and the intelligent self-adaptation method, and meanwhile the aims of high precision and high accuracy can be achieved.
Owner:NORTHEASTERN UNIV LIAONING
Method and device for data exchange and processing
InactiveUS20050021201A1Improve efficiencyDelayed decisionVehicle testingAmplifier modifications to reduce noise influenceProcessing elementData exchange
A method and a device are proposed for the exchange and the processing in common of object data between sensors and a processing unit, position data and / or speed data and / or additional object attributes (size, identification, markings) of sensor objects and fusion objects being transmitted and processed.
Owner:ROBERT BOSCH GMBH
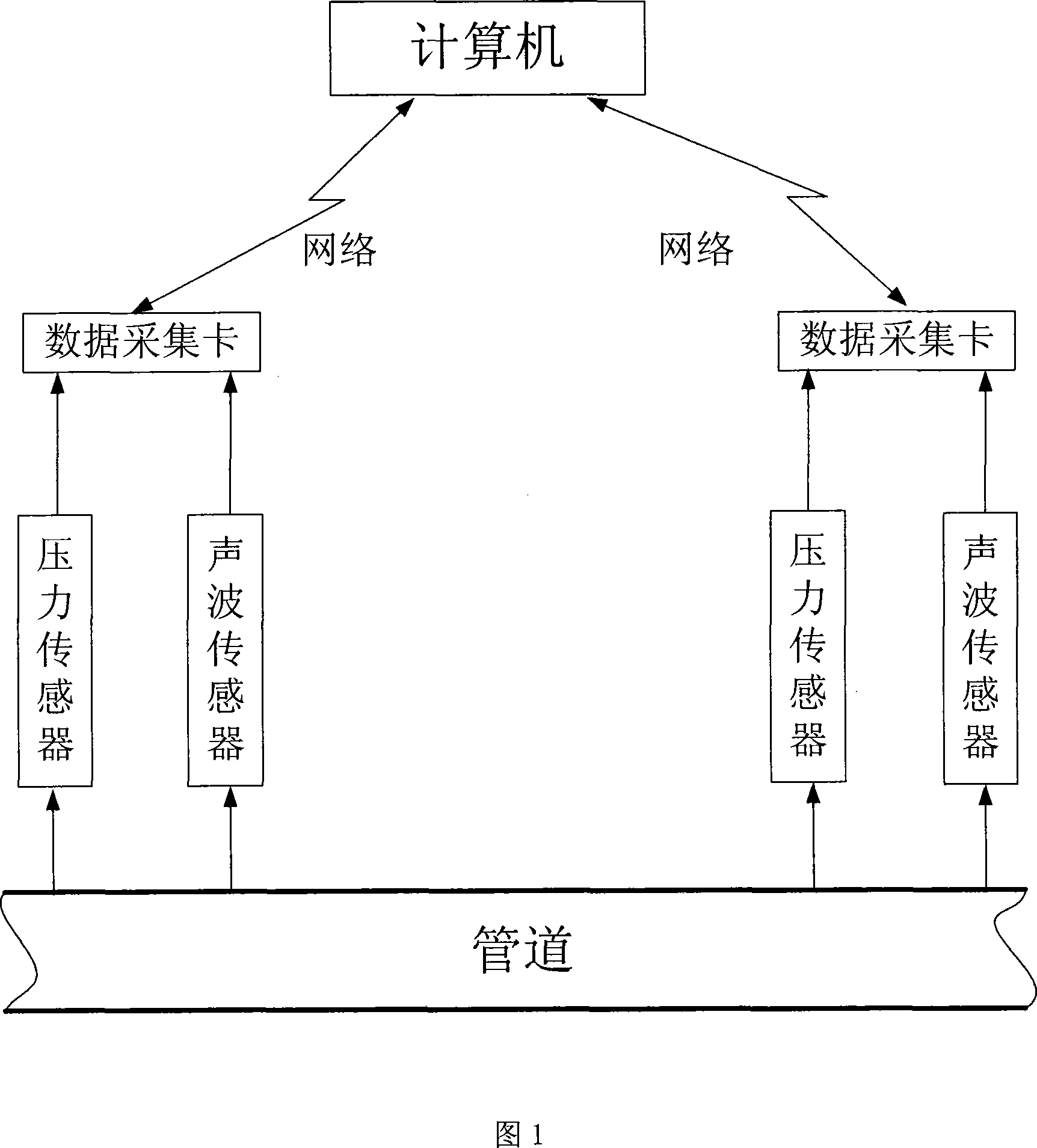
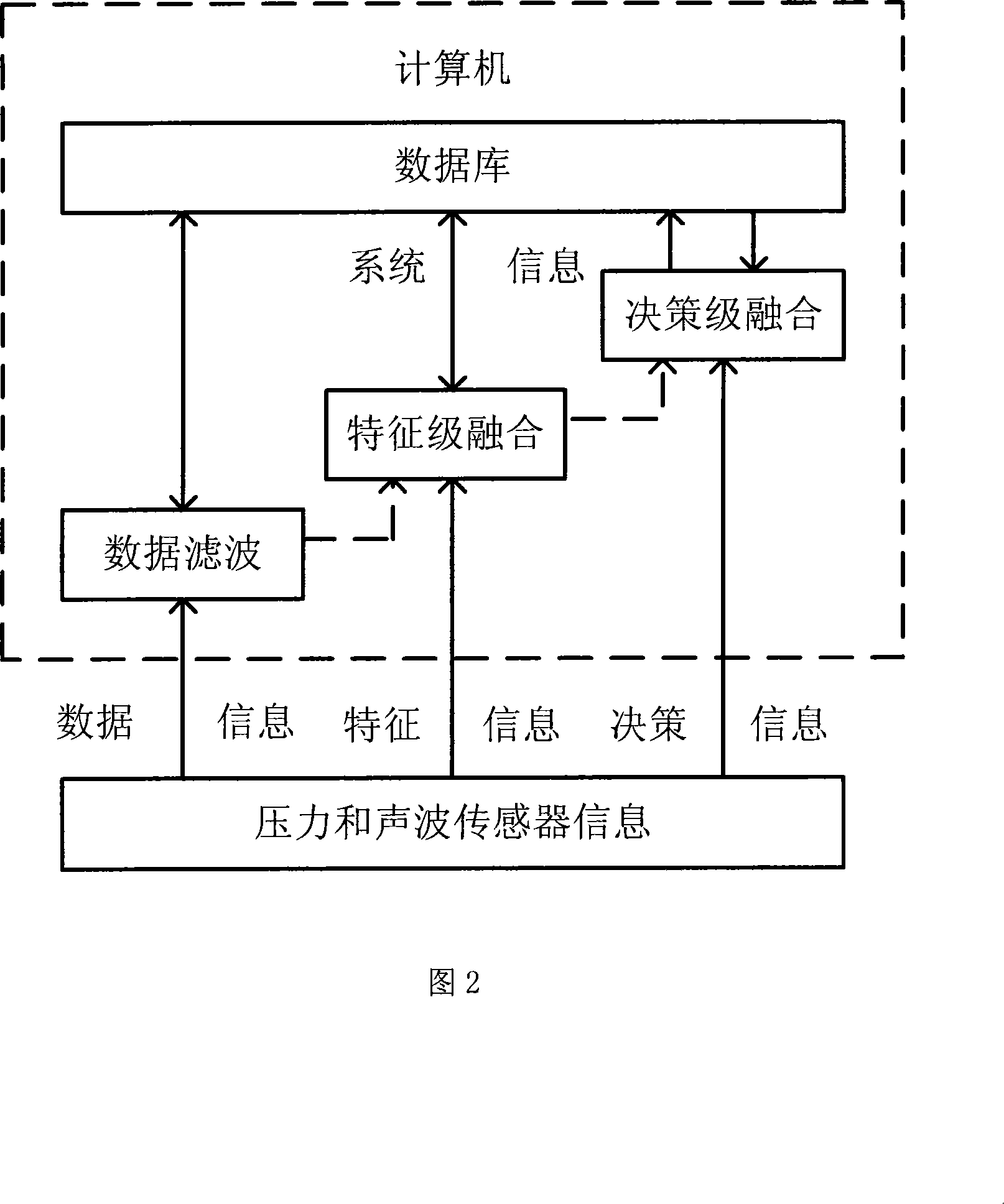
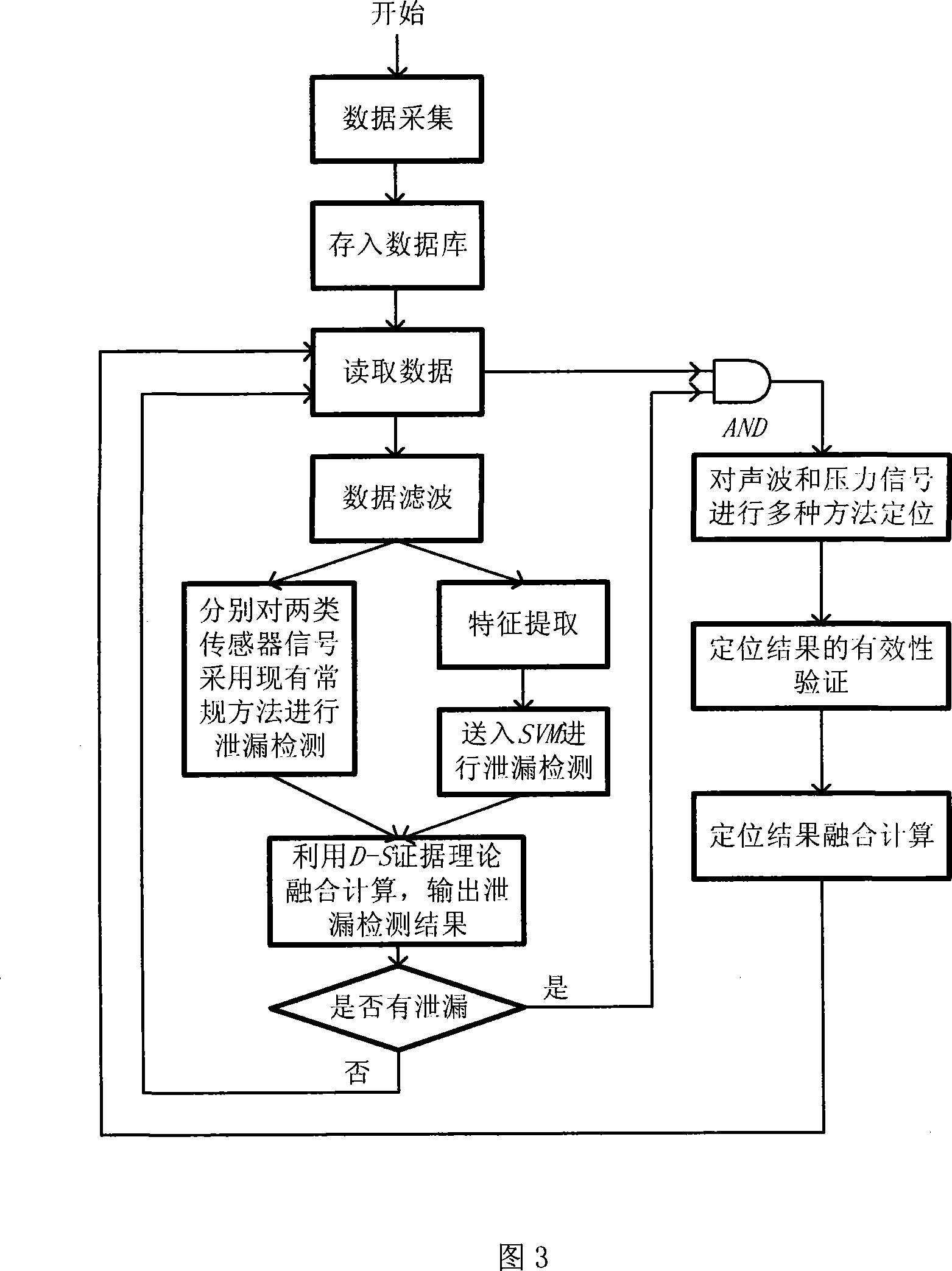
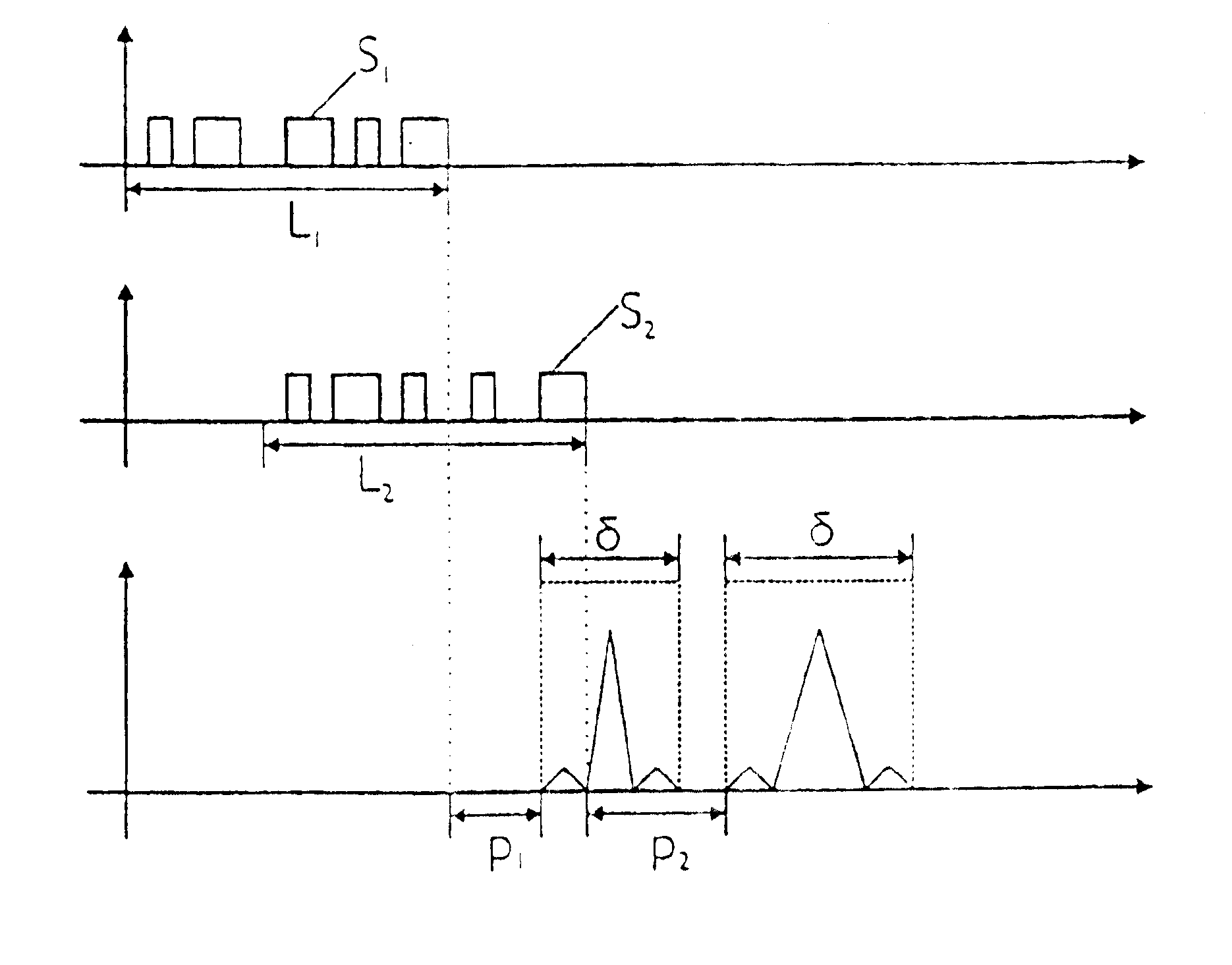
Leakage detecting and locating method based on pressure and sound wave information amalgamation
ActiveCN101196872AHigh precisionReduce false alarm ratePipeline systemsSpecial data processing applicationsThree levelAcoustic wave
A leakage detection location method based on pressure and sound information integration is provided, which belongs to the technology field of an oil (gas) pipeline fault diagnosis, and is characterized by leakage detection and leakage location based on information integration. The former comprises: separately acquiring the measurement data of the pressure on the upperstream end and downstream end of the pipeline and a sound wave sensor, sending the data to a computer and gaining final detection results through three levels processing including data filtering, characteristic level integration and decision level integration. If the detection result shows leakage, starting leakage location process based on information integration. The process first carries out leakage location by separately adopting the signals of two kinds of sensors and a plurality of different leakage location algorithms and finally gains the location results via integration of the location results based on the same sensor and different location methods and two levels processing based on the integration of the location results of two kinds of different sensors. The method can effectively reduce the false positive rate and false negative rate and improve the location precision.
Owner:TSINGHUA UNIV
Wirless network
InactiveUS6901104B1Reduces pulse amplitudeReliably recognizePower managementAmplitude-modulated carrier systemsStart timeWireless network
A wireless network is disclosed including at least one base station and a plurality of assigned terminals for exchanging user data and control data. The base station is arranged for transmitting the start time of at least one signaling sequence of at least terminal. For evaluating the signaling sequences transmitted by the terminals, the base station includes a device for correlating a received signaling sequence and for detecting the pulse evolving from a received and correlated signaling sequence. A terminal generates a signaling sequence by folding two code sequences.
Owner:KONINKLJIJKE PHILIPS NV +1
Integrated biological and chemical sensors
InactiveUS6955787B1The process is fast and accurateOptical signal enhancementVibration measurement in solidsWave amplification devicesDual modeSurface acoustic wave
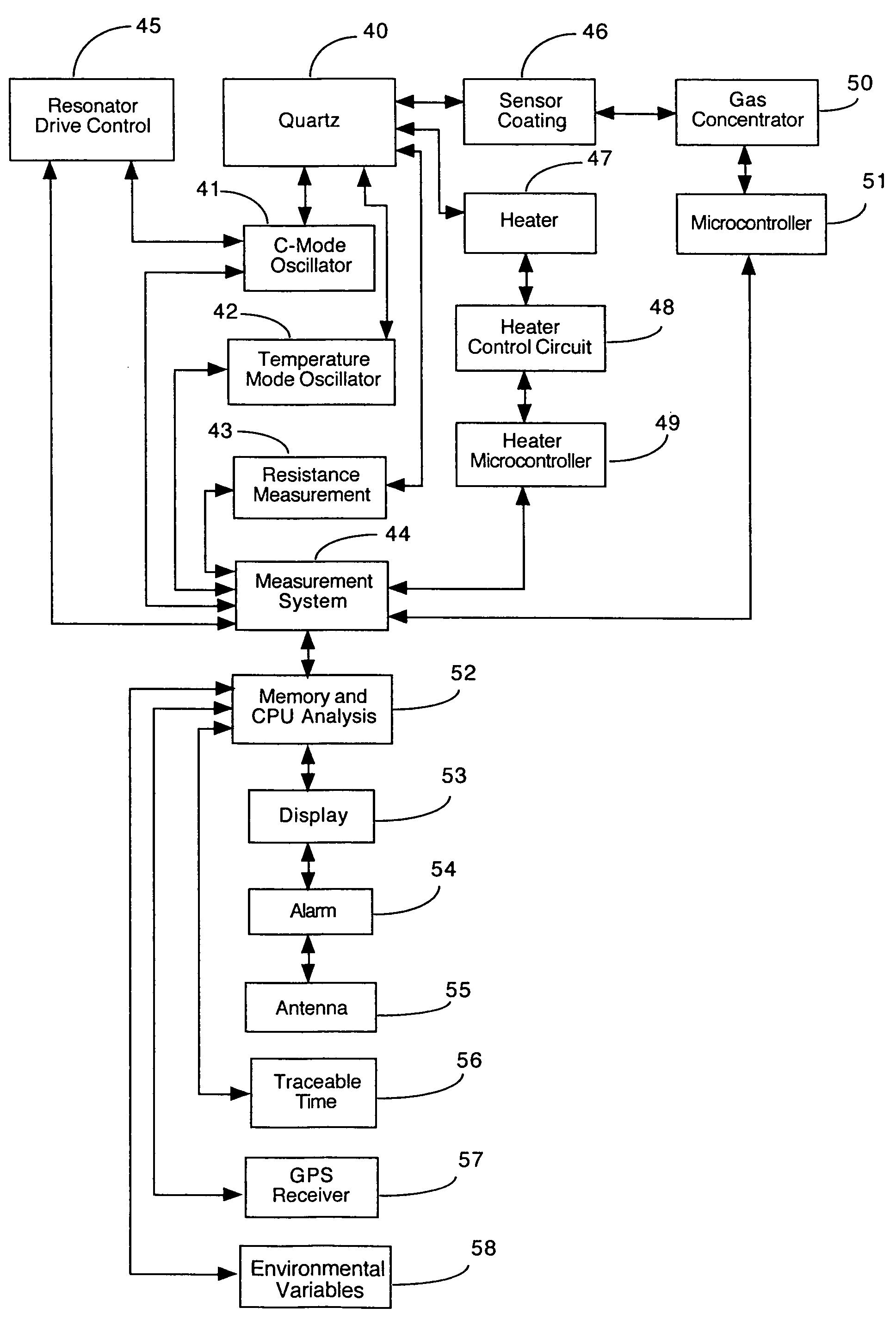
An array of piezoelectric resonators used in a sensor device in order to identify chemical and biological agents. The resonators can operate as bulk acoustic wave (BAW), surface acoustic wave (SAW), or Love mode devices. The sensor device integrates gravimetric, calorimetric, thermal gravimetric, voltage gravimetric and optical detection methods into one sensor system, improving the accuracy of identifying hazardous agents. For gravimetric detection, dual-mode resonators provide simultaneous calorimetric and gravimetric data, one type from each mode. Resonators with heaters on the surfaces will provide thermal gravimetric data. An optical detector can be used to analyze the optical signal from the surface of a coated resonator. Additionally, voltage gravimetric measurements can be made with an electric field set up between the resonator and an external electrode. Thermal voltage gravimetric measurements can be made by adding an integrated heater on the resonator with an external electrode. An alarm can be activated upon the identification of a hazardous agent. The sensor device can utilize other valuable information, including traceable time, GPS location, and variables related to temperature, humidity, air speed, and air direction.
Owner:HANSON WILLIAM PAYNTER
Detecting Outliers in Network Traffic Time Series
ActiveUS20100030544A1Reduce false alarm rateComputationally efficientAnalogue computers for electric apparatusTransmissionTraffic capacityOutlier
According to an aspect of the invention, a system and method is configured to detect time series outliers in network traffic.
Owner:RIVERBED TECH LLC
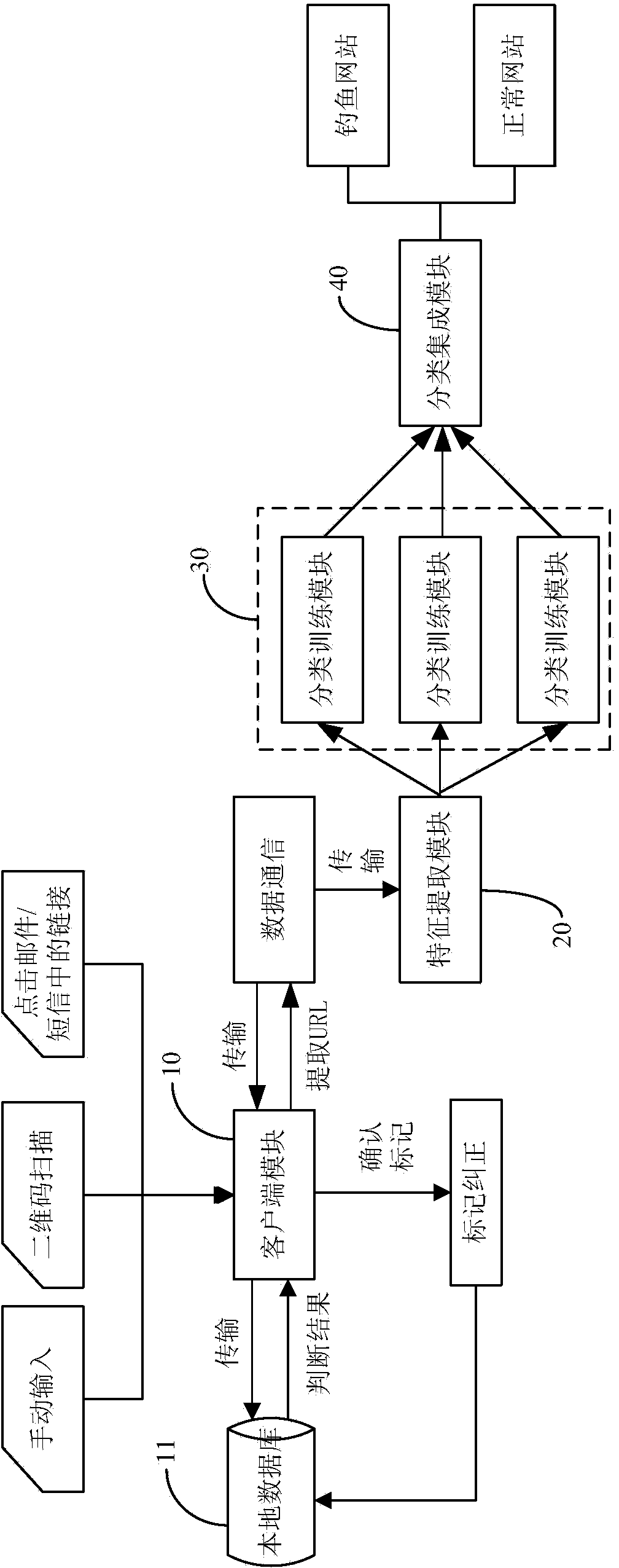
Method and system for detecting Chinese phishing website
ActiveCN104217160AImprove classification efficiencyReduce false alarm ratePlatform integrity maintainanceSpecial data processing applicationsFeature vectorWeb site
The invention discloses a method and a system for detecting a Chinese phishing website. The method comprises the following steps: S1, acquiring a URL (Uniform Resource Locator) by a client; S2, extracting URL features and website page content features as feature vectors respectively; S3, performing classification trainings on the feature vectors through an SVM (Support Vector Machine), an extended website page content feature NBC (Naive Bayes Classifier), a decision tree algorithm and a link and form processing method; S4, performing classification integration on classification training results, and judging whether a website with the URL is a phishing website. According to the method and the system, the URL features and the website page content features are extracted as the feature vectors, the corresponding classification trainings are performed through the SVM, the NBC, the decision tree algorithm and the corresponding processing of links and forms, prediction results are integrated by virtue of classification integration to obtain a final result, and therefore the classification accuracy is greatly improved.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
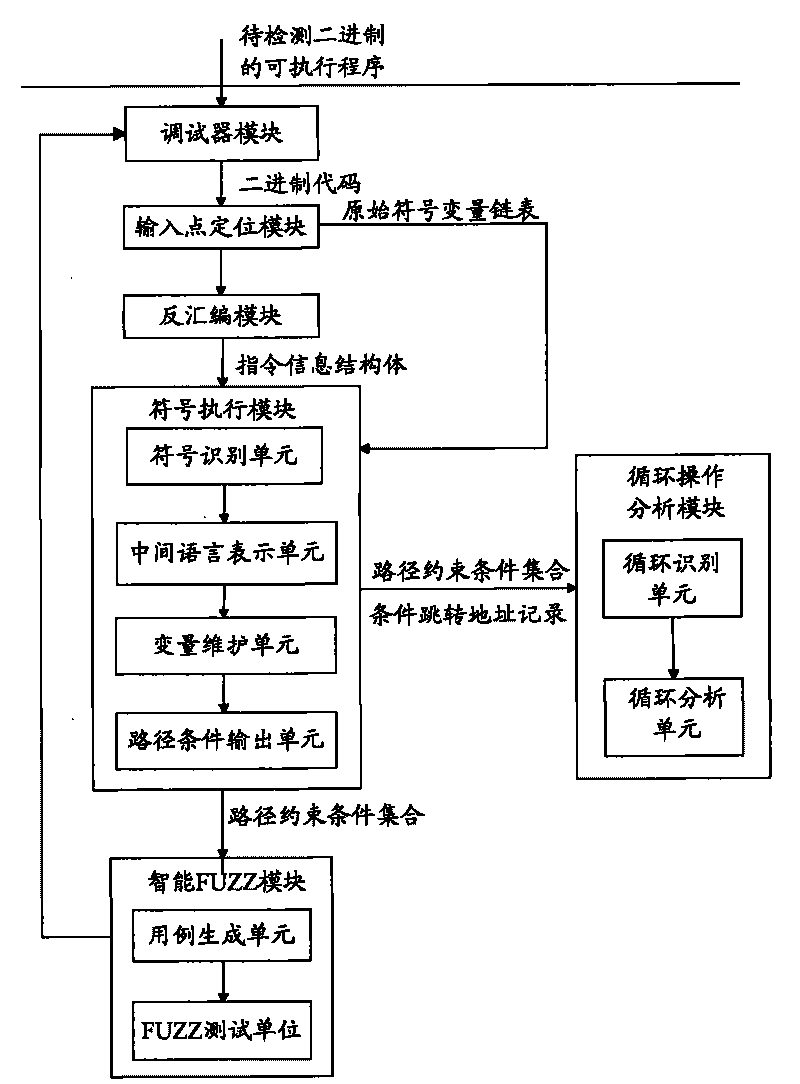
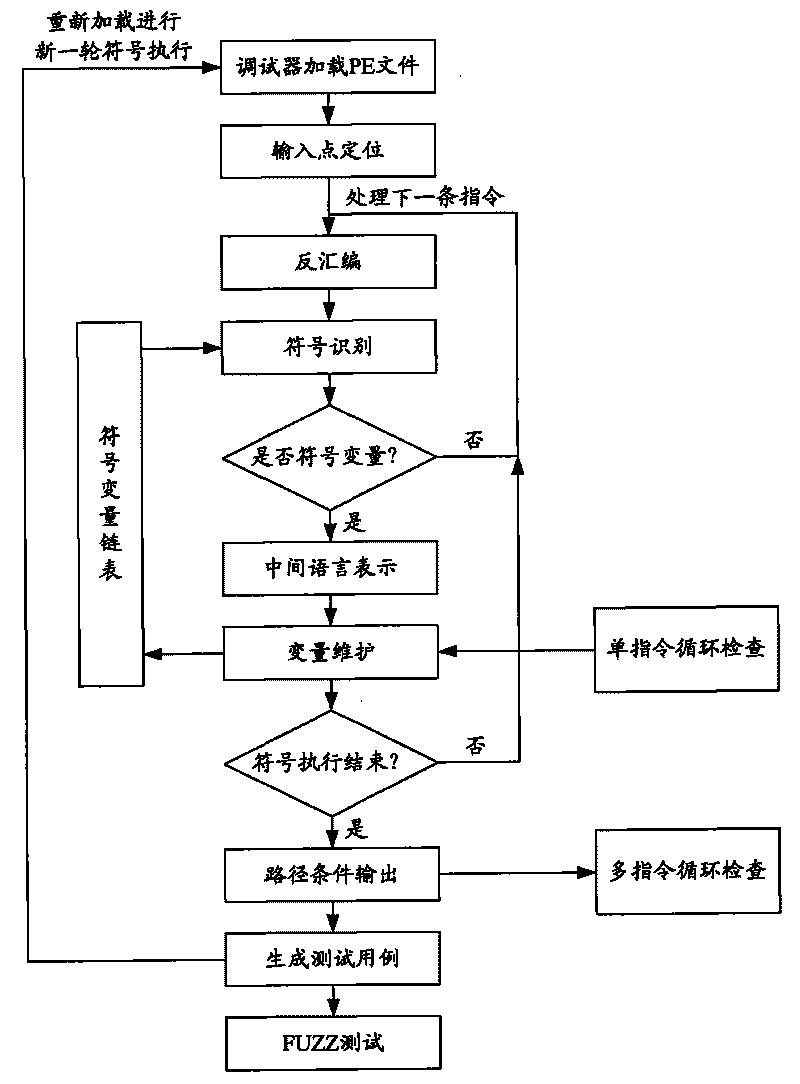
Detector for binary-code buffer-zone overflow bugs, and detection method thereof
InactiveCN101714118AGuaranteed feasibilityGuaranteed accuracyMultiprogramming arrangementsSoftware testing/debuggingBuffer overflowSource code
The invention provides a detector for binary-code buffer-zone overflow bugs, and a detection method thereof. The detector comprises six functional modules, namely a debugger module, an input point positioning module, a disassembling module, a symbolic execution module, a loop operation analysis module and an intelligent FUZZ test module. Differing from static symbolic execution, the detection method dynamically loads programs through the self-developed debugger module to synchronously performing symbolic execution and single-step practical execution, and then applies a model to solve each difficulty in binary code analysis so as to test path coverage and detect overflow bugs in accordance with all executable programs of PE format under a Windows platform. The detection can also provide propagation paths of input data and other important information related to bug formation cause while positioning the bugs, only analyzes the selves of the executable programs, needs no source codes, is unrelated to the species of source codes and development tools, and is extensive in applicable occasions, so the detection method has good prospects for popularization and application.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method and apparatus for red-eye detection in an acquired digital image based on image quality pre and post filtering
ActiveUS7436998B2Reduce false alarm rateIncrease success rateImage enhancementImage analysisImaging qualityImage correction
A method for red-eye detection in an acquired digital image comprises acquiring a first image and analyzing the first acquired image to provide characteristics indicative of image quality. The process then determines if one or more corrective processes can be beneficially applied to the first acquired image according to the characteristics. Any such corrective processes are applied and red-eye defects are detected in an established order established according to determination and analysis of characteristics of the corrective process and / or resulting image qualities. Defect correction can comprise applying one or more image correction operations, or a chain of two or more red-eye filters to the first acquired image. In this case, prior to the detecting step, it is determined if the red-eye filter or red eye filter chain should be applied before or after image corrective processes and whether the red eye filter can be adapted in accordance with the characteristics. The red-eye filter and the order in which it is executed in relation to the various image corrective operations may be adapted accordingly.
Owner:FOTONATION LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com