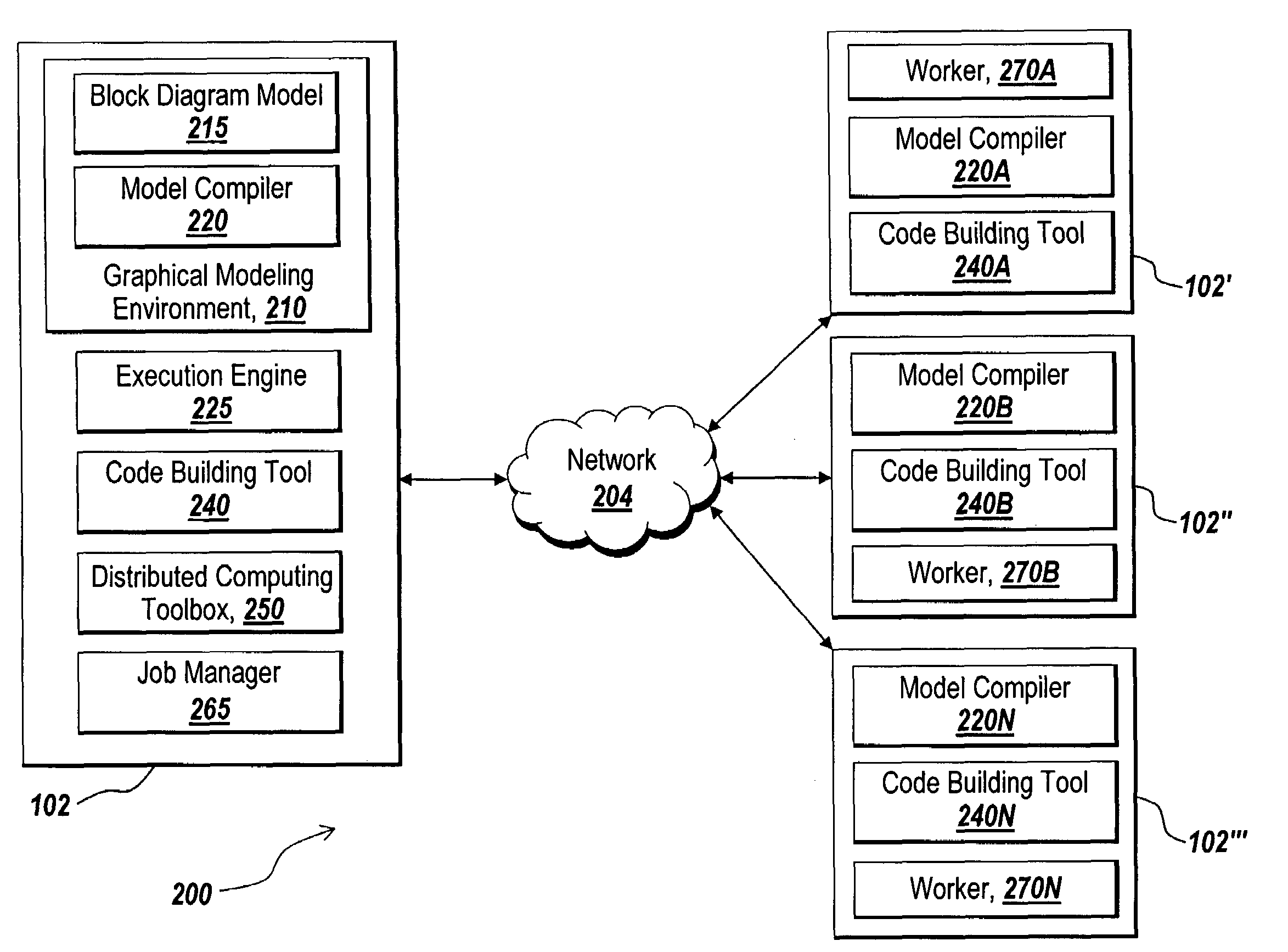
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2417results about "Analogue computers for electric apparatus" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
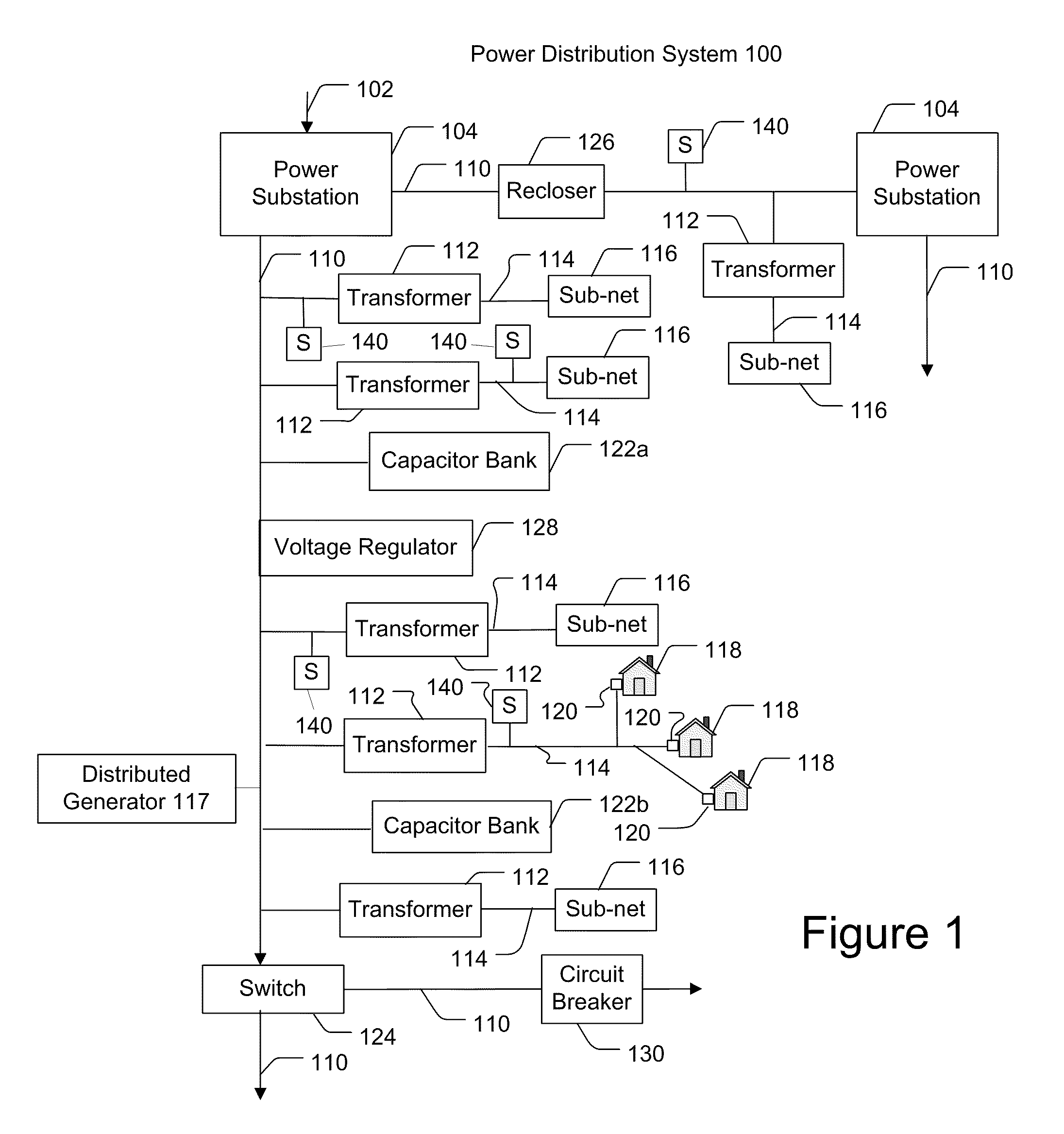
Optimization of microgrid energy use and distribution
ActiveUS20100179704A1Optimize energy distributionOptimize energy useBatteries circuit arrangementsLevel controlPersonalizationMicrogrid
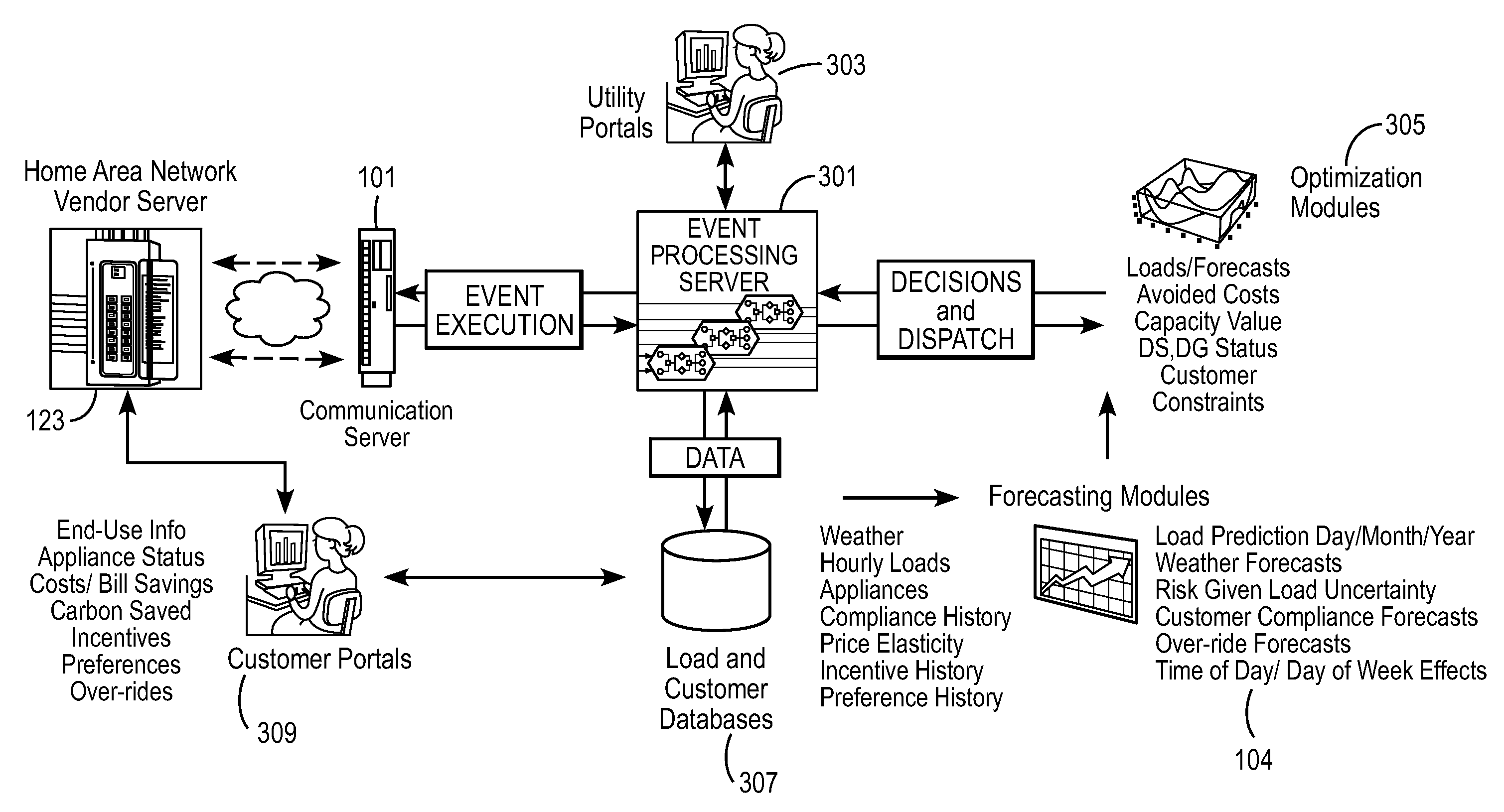
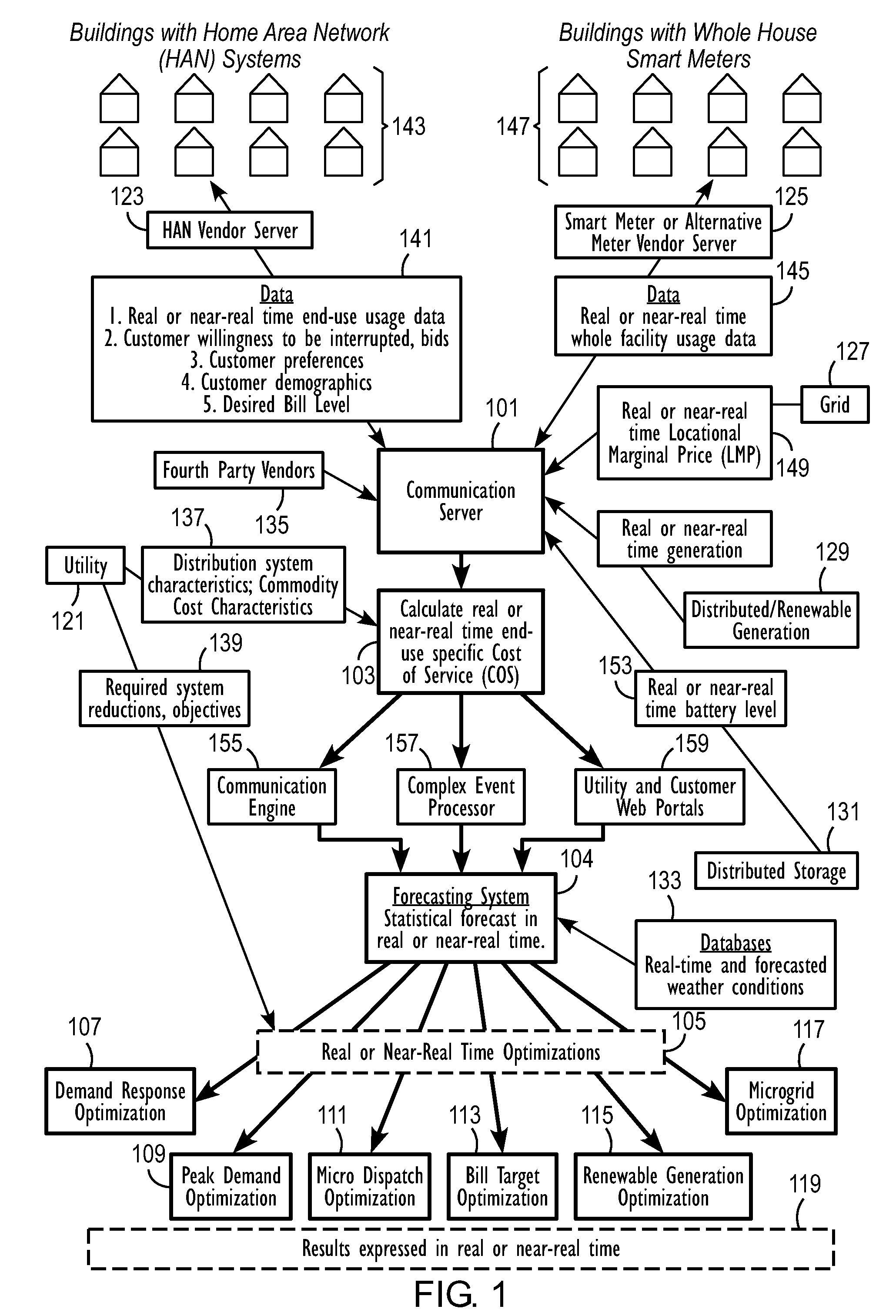
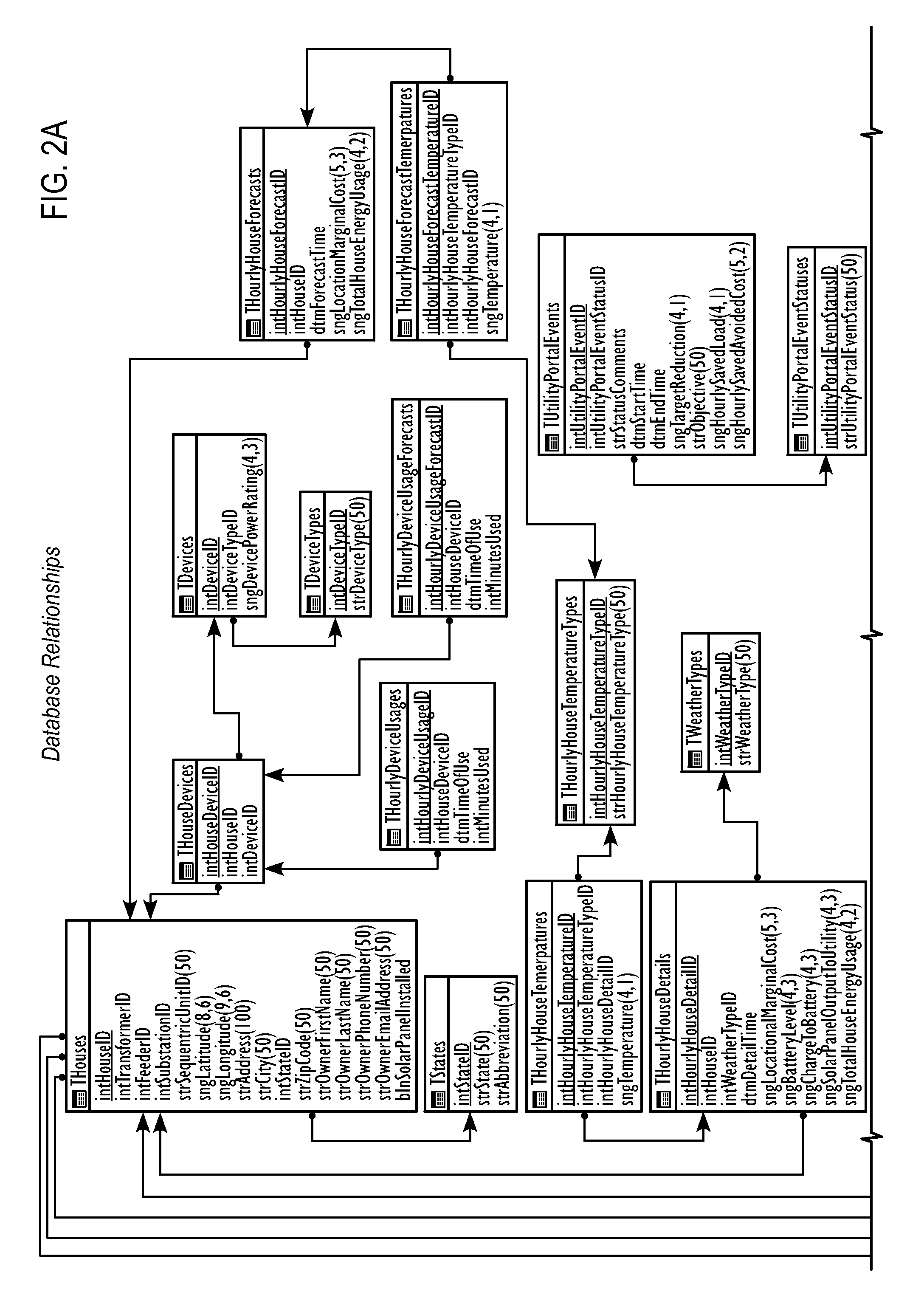
An energy distribution may include a server and one or more databases. The system may communicate with an energy provider to receive energy provider data, at least one information collector to receive information collector data such as individualized energy usage data, customer preferences, and customer or location characteristics, and the one or more databases for receiving data for optimization. The system may calculate a cost of service or avoided cost using at least one of the individualized energy usage data and a system generation cost at a nearest bus. The system may also forecast individualized demand by end-use, individualized demand by location, energy prices, or energy costs. The system may optimize energy distribution, energy use, cost of service, or avoided cost using the forecasted individualized demand by end-use, the forecasted individualized demand by location, the forecasted energy prices, and the forecasted energy costs.
Owner:INTEGRAL ANALYTICS
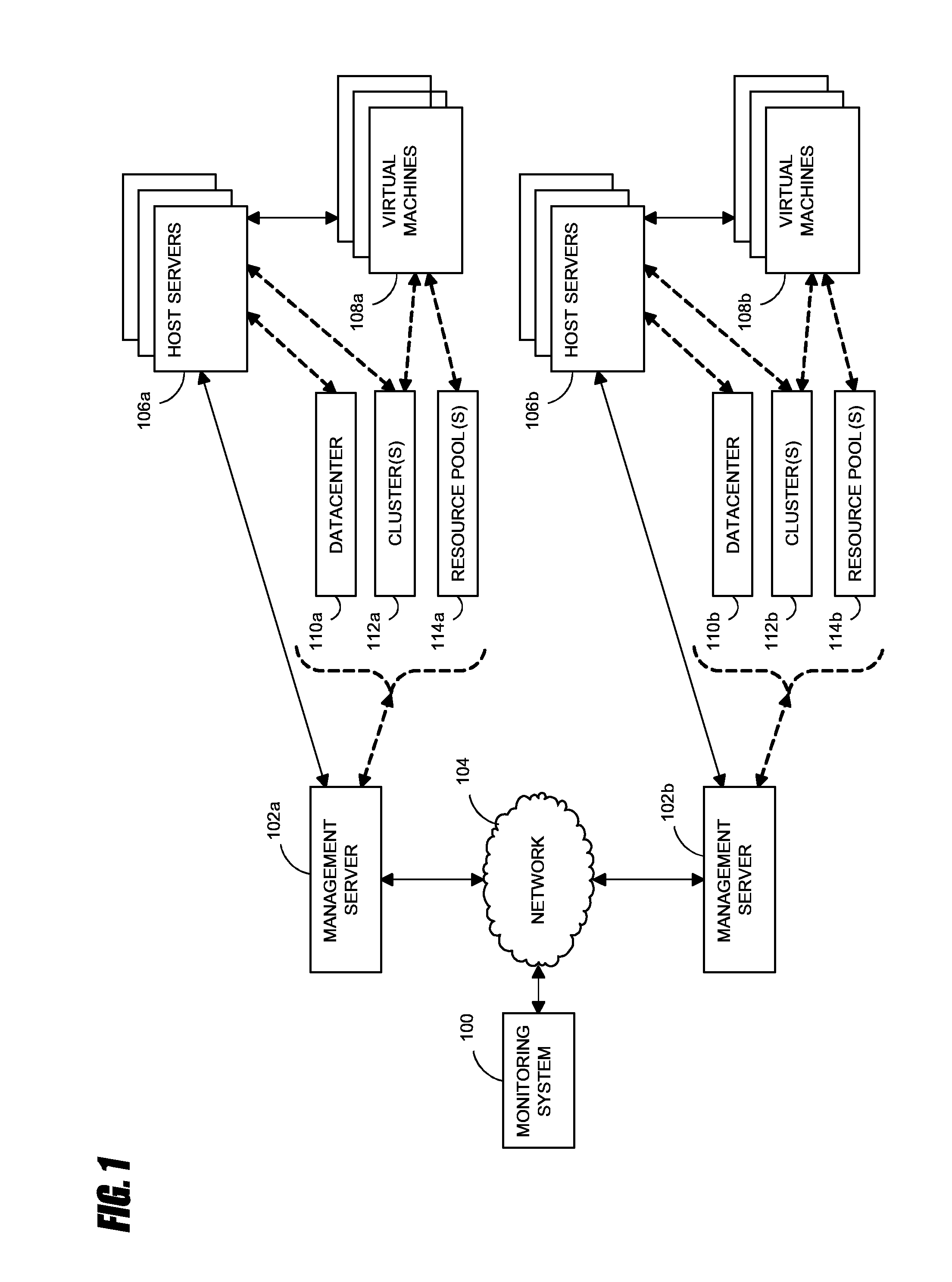
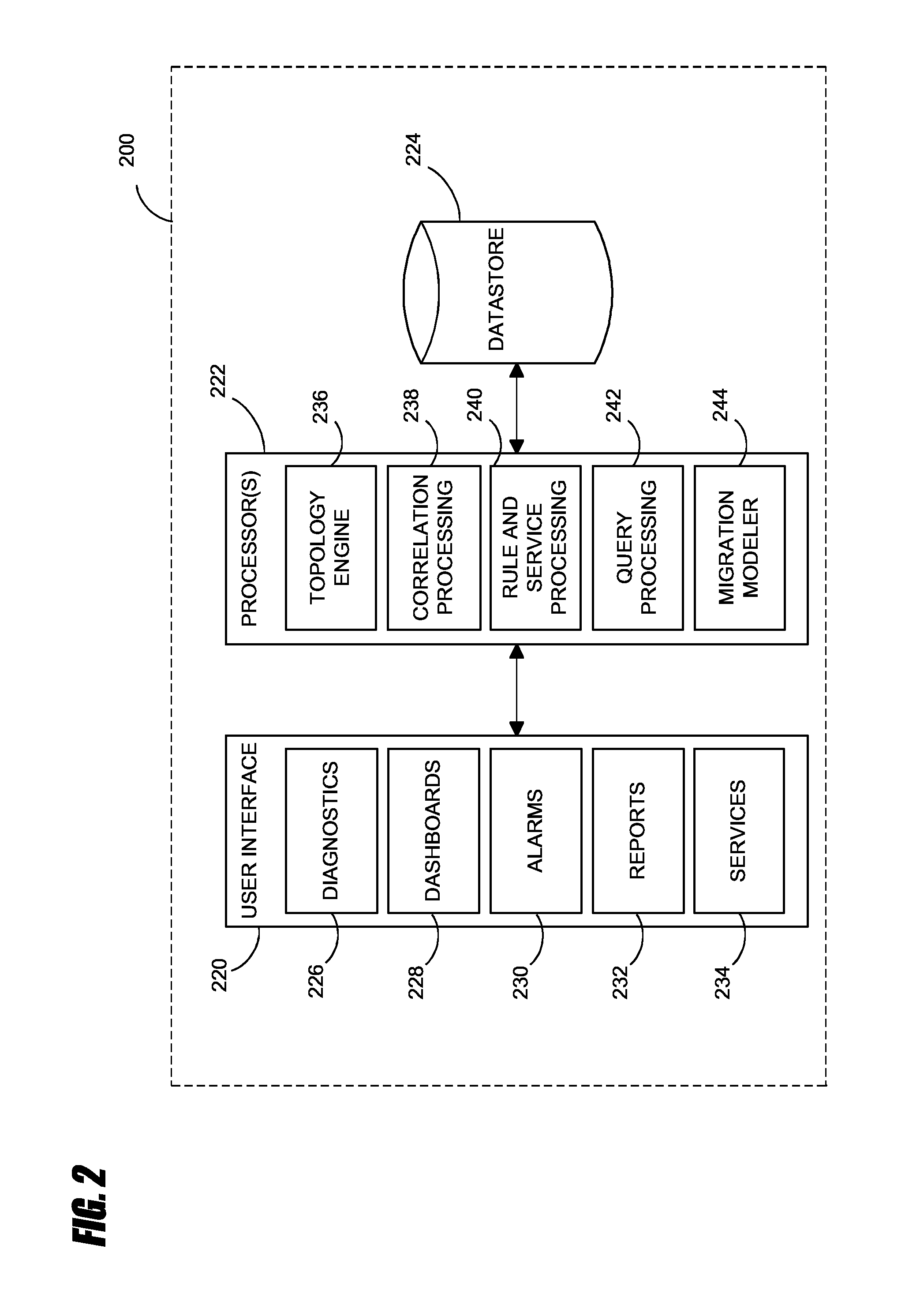
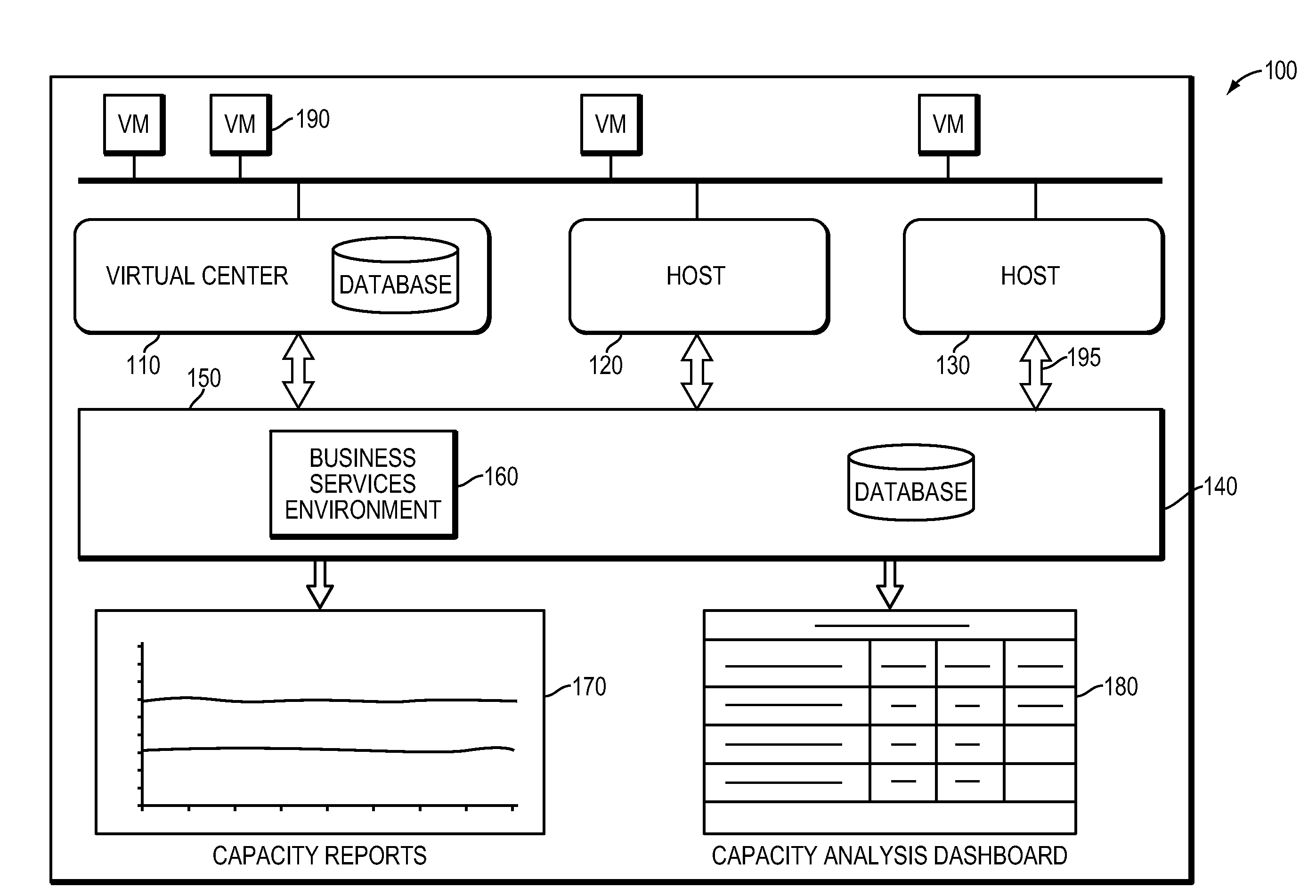
Systems and methods for analyzing performance of virtual environments
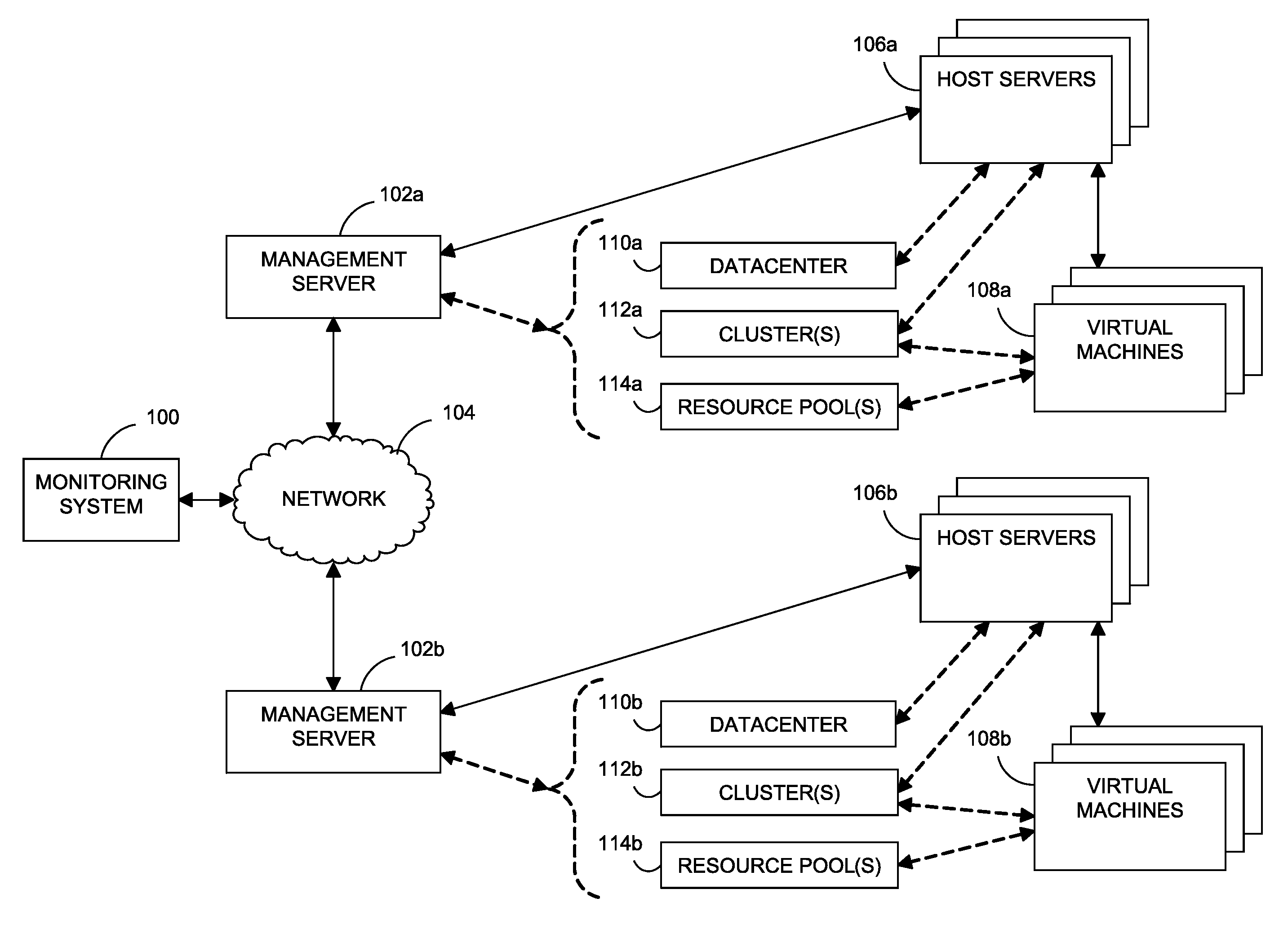
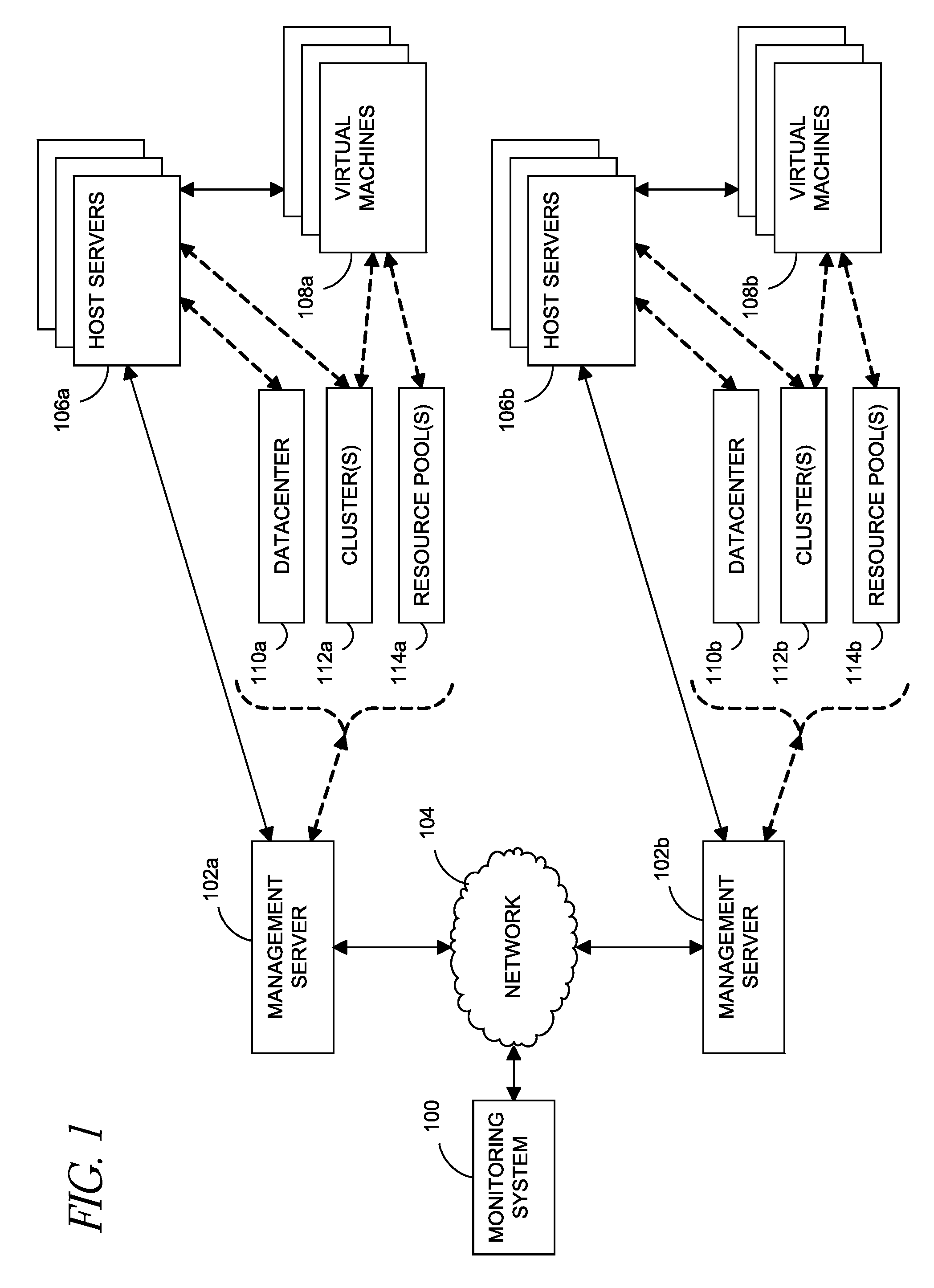
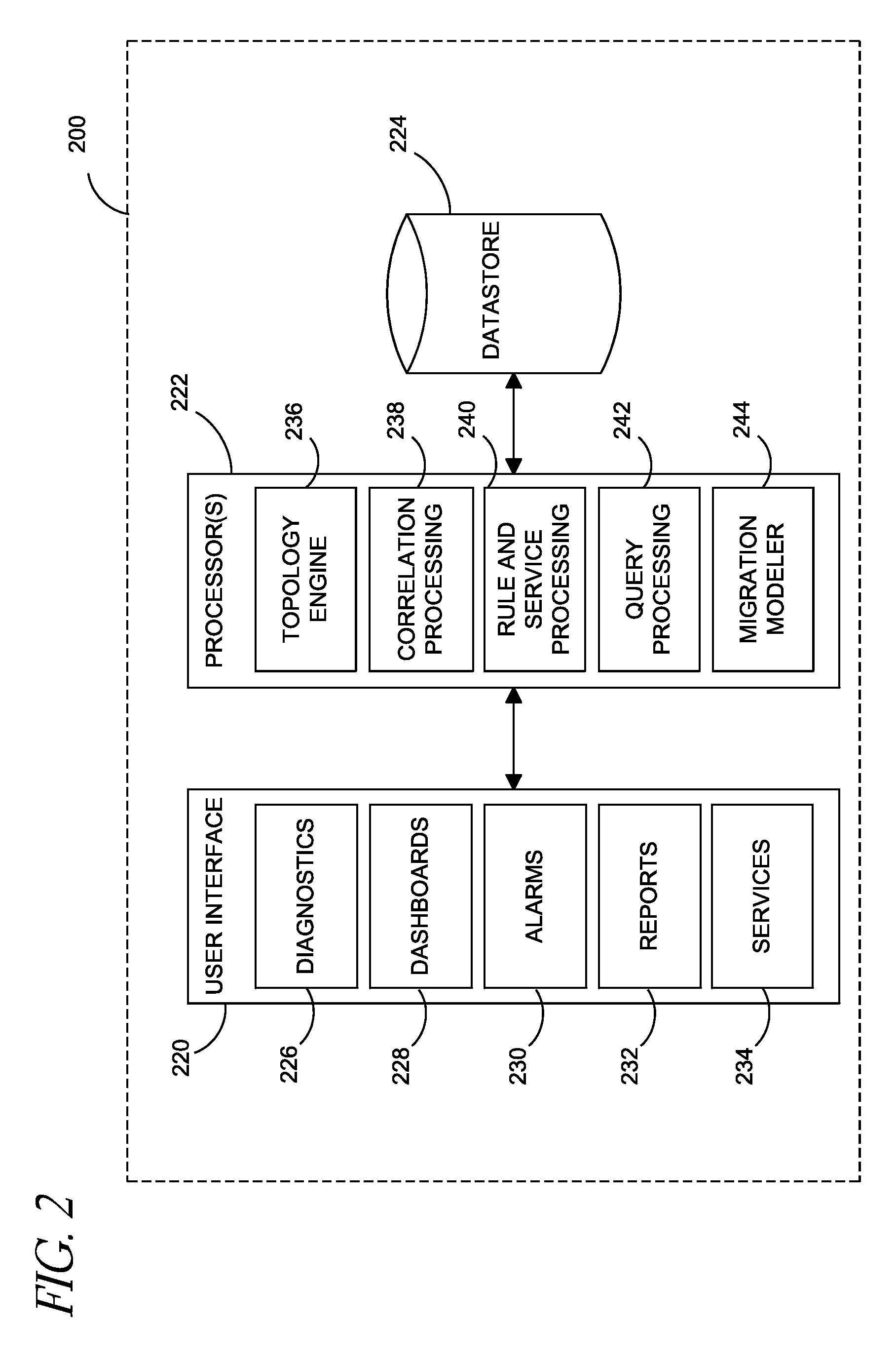
InactiveUS8175863B1Effective and efficient diagnosisResource allocationError detection/correctionMonitoring systemSmart surveillance
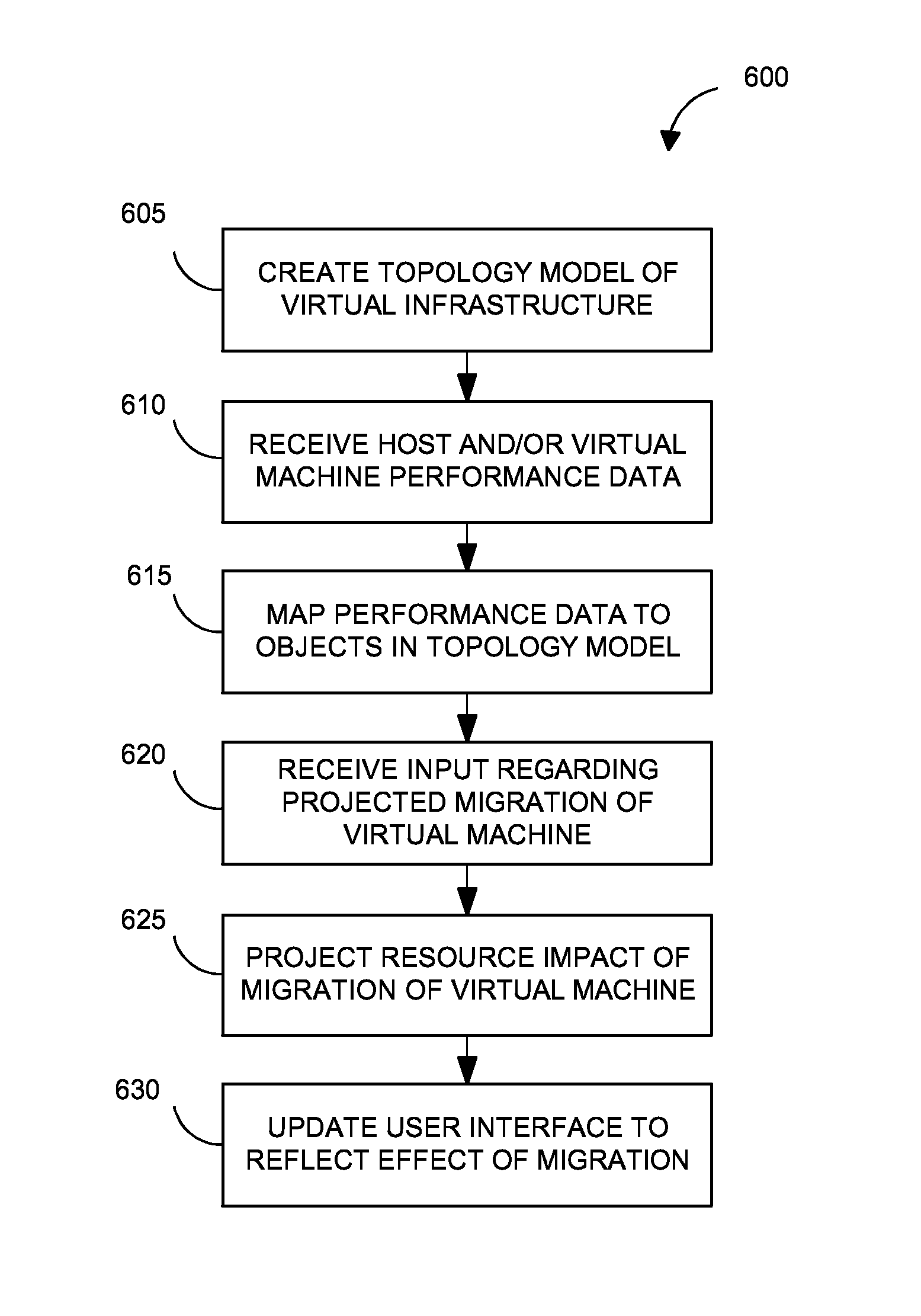
Intelligent monitoring systems and methods for virtual environments are disclosed that understand various components of a virtual infrastructure and how the components interact to provide improved performance analysis to users. In certain examples, a monitoring system assesses the performance of virtual machine(s) in the context of the overall performance of the physical server(s) and the environment in which the virtual machine(s) are running. For instance, the monitoring system can track performance metrics over a determined period of time to view changes to the allocation of resources to virtual machines and their location(s) on physical platforms. Moreover, monitoring systems can utilize past performance information from separate virtual environments to project a performance impact resulting from the migration of a virtual machine from one physical platform to another.
Owner:QUEST SOFTWARE INC
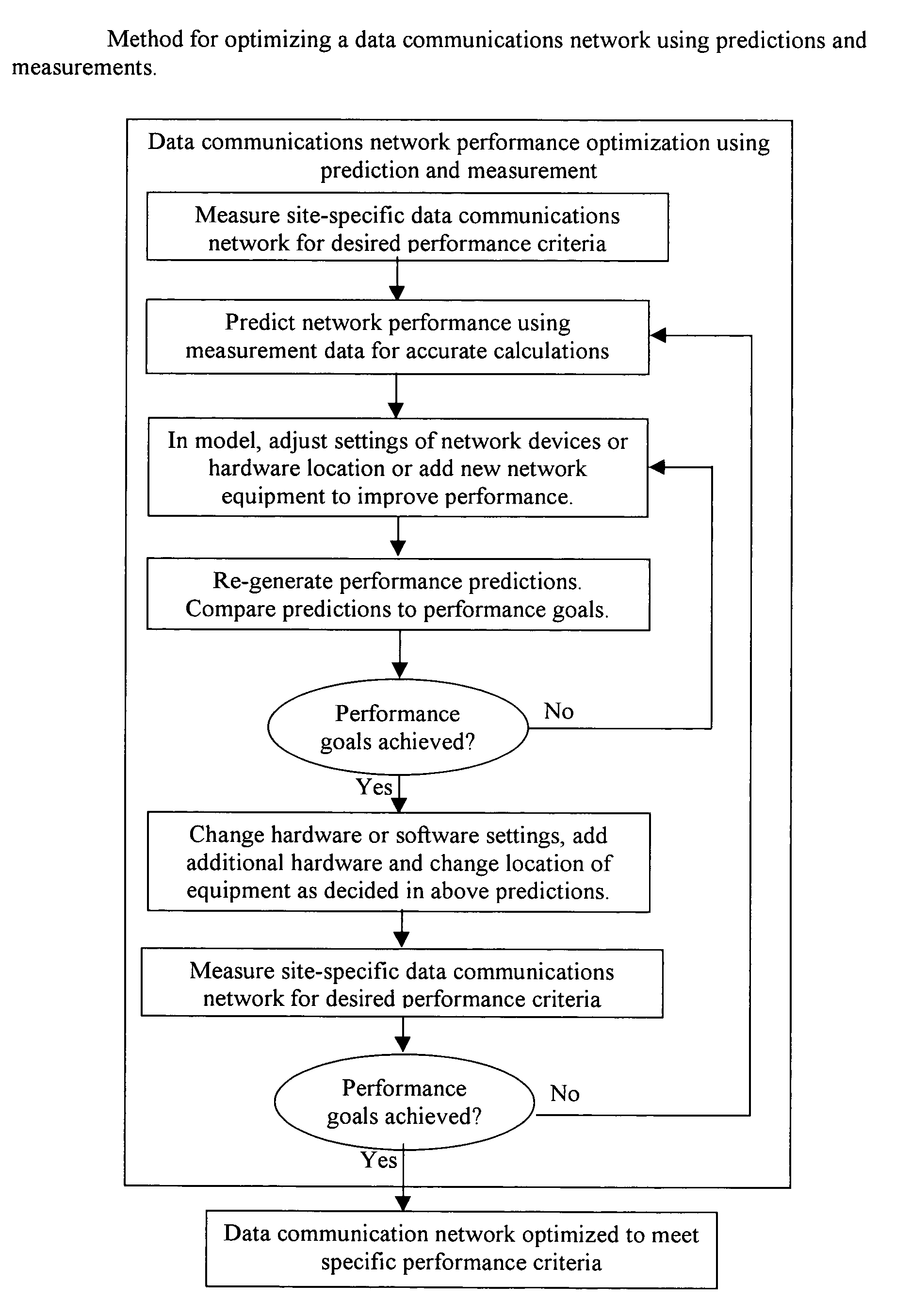
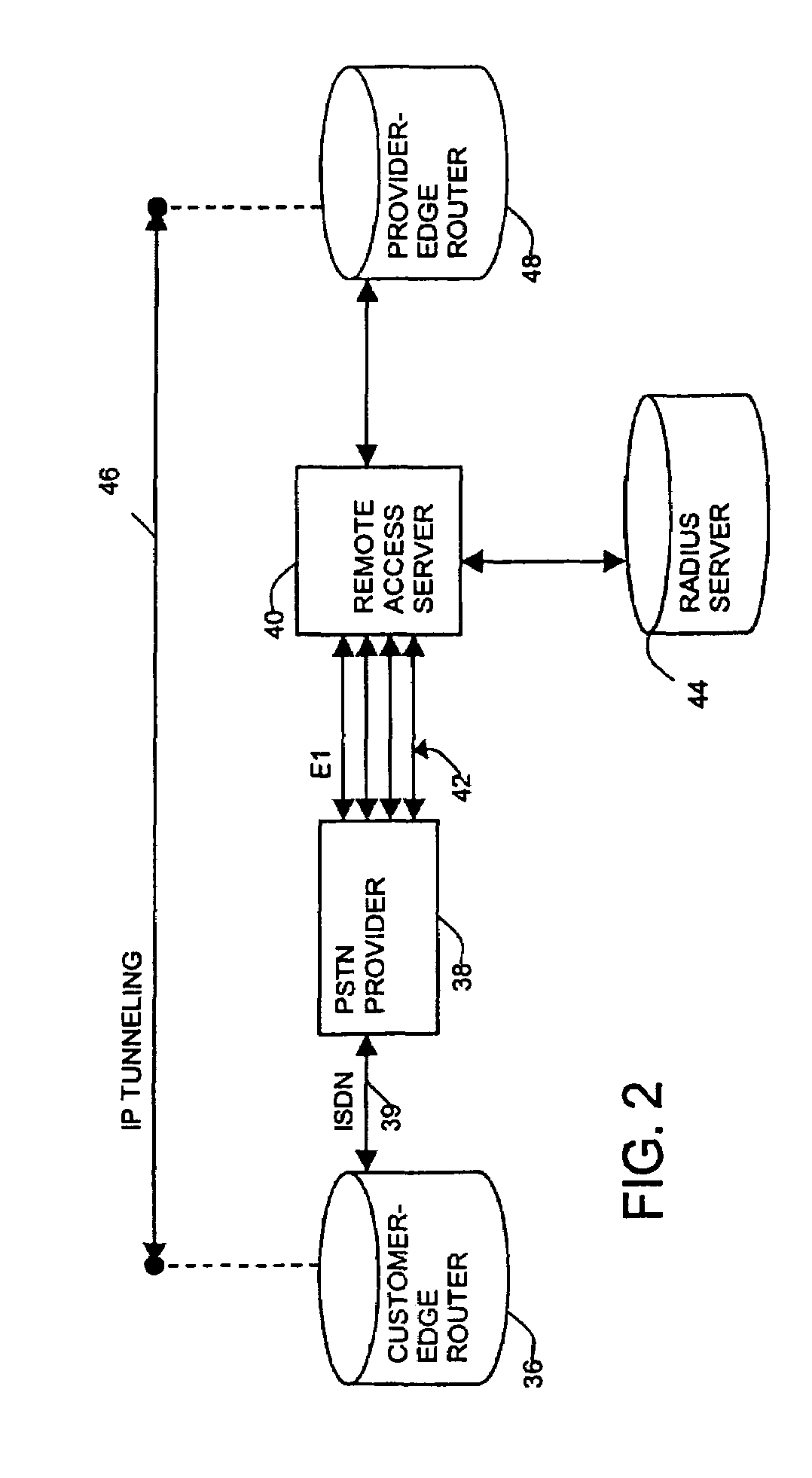
System and method for design, tracking, measurement, prediction and optimization of data communication networks
InactiveUS6973622B1MeasuringImprove performanceAnalogue computers for electric apparatusData switching by path configurationRadio propagationSpecific model
Owner:EXTREME NETWORKS INC
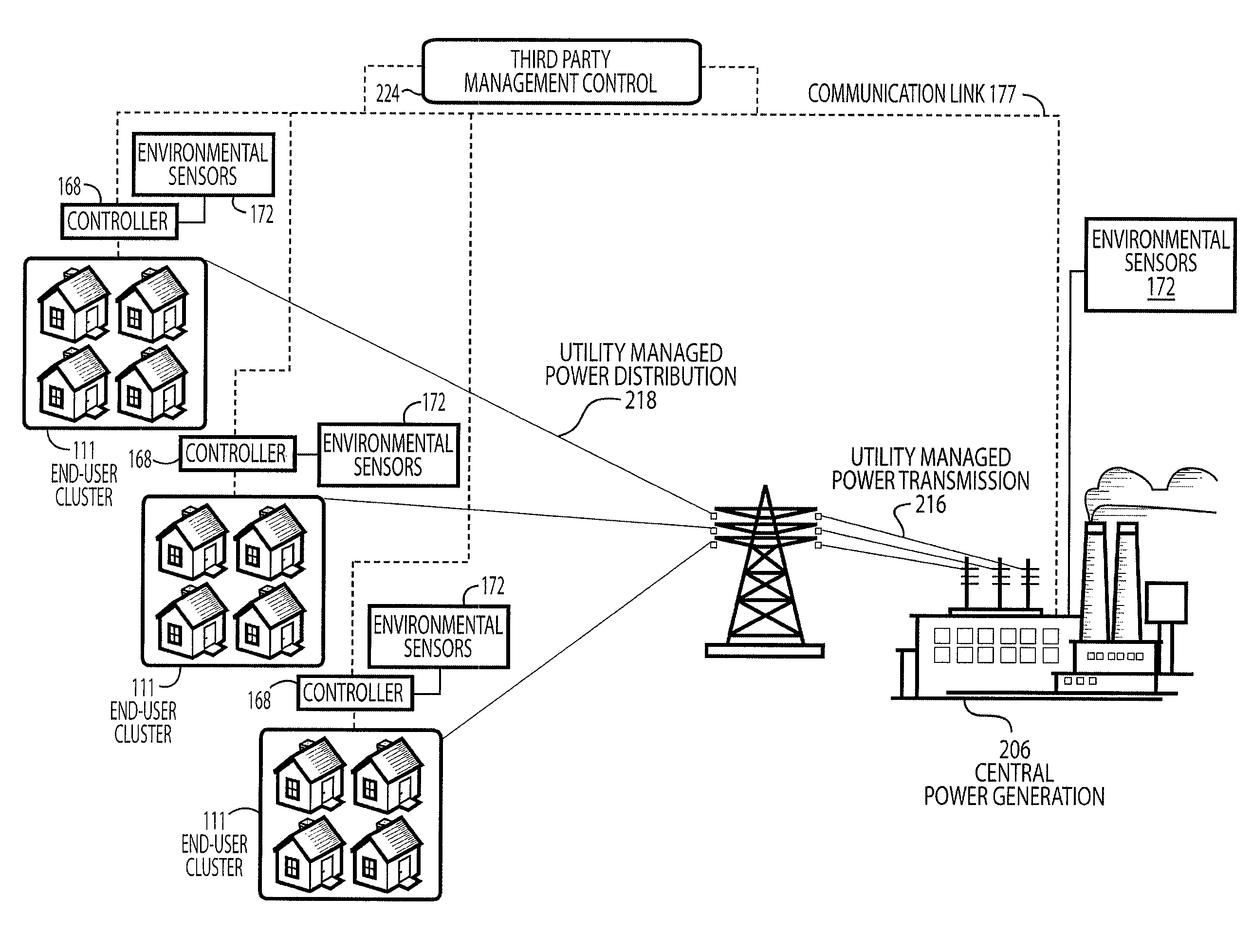
Utility managed virtual power plant utilizing aggregated thermal energy storage
Disclosed is a system and method for providing power generation and distribution with on-site energy storage and power input controlled by a utility or a third party manager. The system allows a utility manager to decide and direct how energy is delivered to a customer on both sides of the power meter, while the customer directs and controls when and how much energy is needed. In the disclosed embodiments, the utility controls the supply (either transmitted or stored) and makes power decisions on a system that acts as a virtual power plant, while the end-user retains control of the on-site aggregated power consumption assets. The disclosed systems act to broker the needs of the utility and end-user by creating, managing and controlling the interface between these two entities.
Owner:BLUE FRONTIER LLC
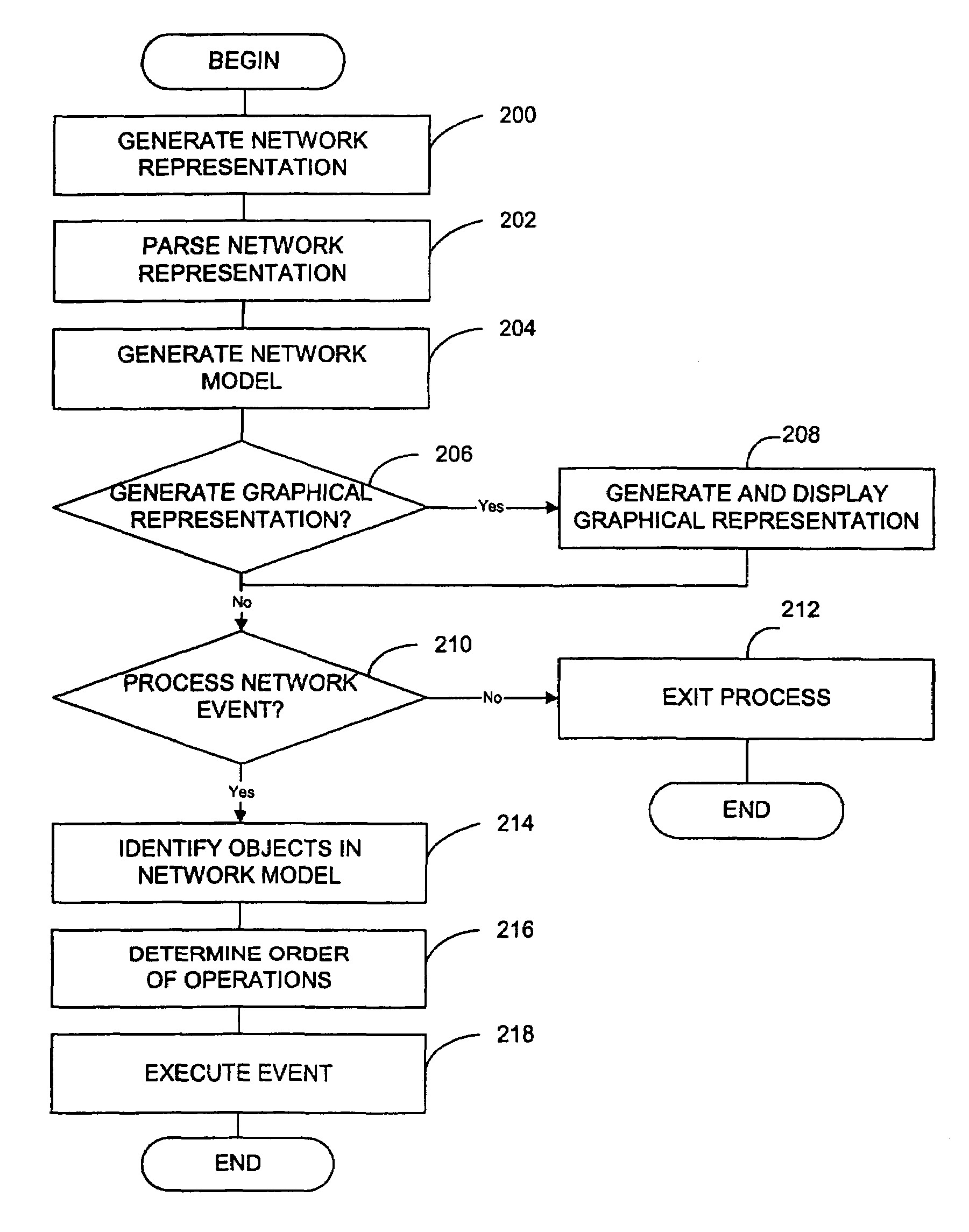
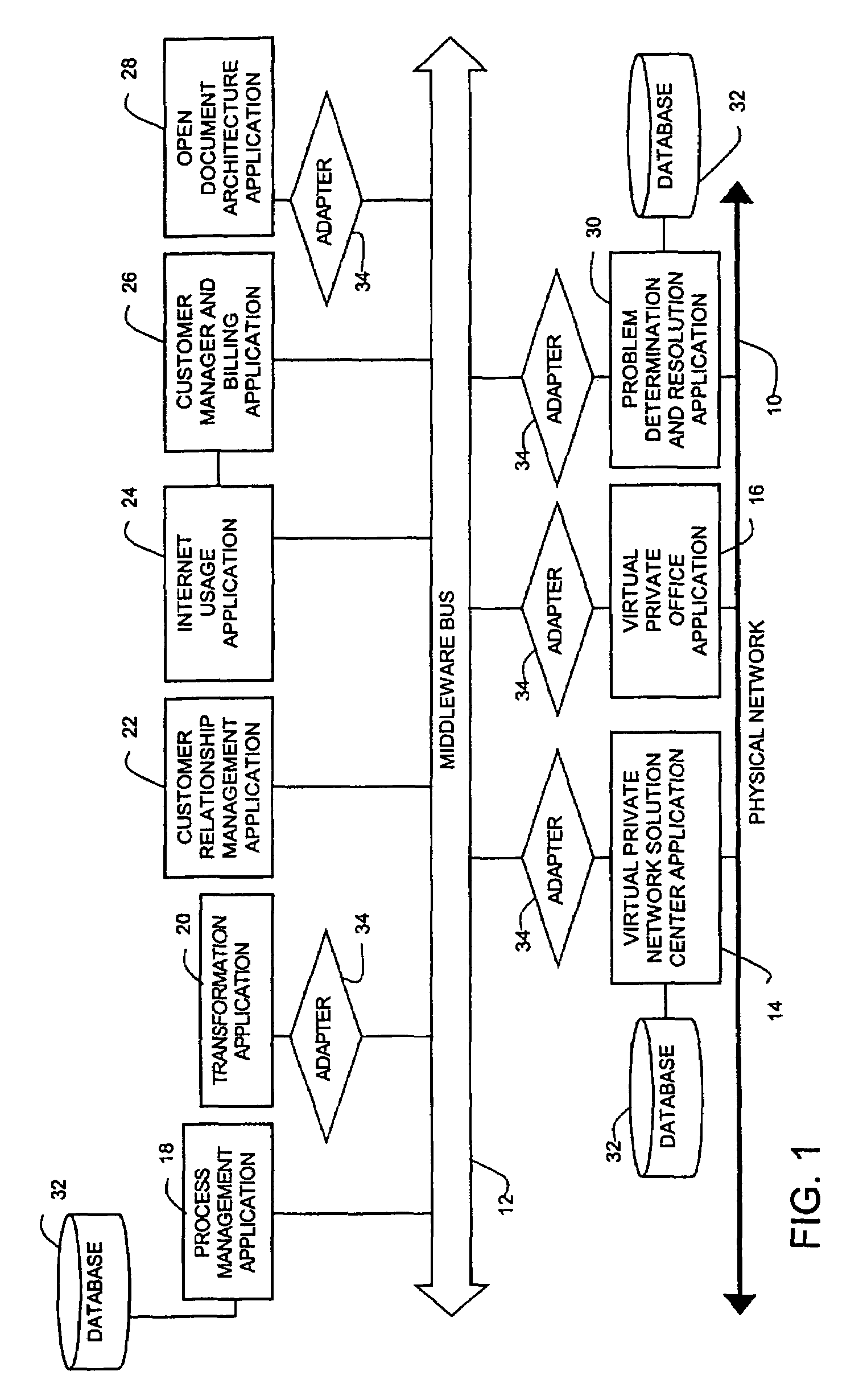
Method and system for modelling a communications network
ActiveUS7392300B2Analogue computers for electric apparatusDigital computer detailsOrder of operationsNetwork model
A system and method of modelling a communications network using a computer system is disclosed, the method including generating a network representation using computer-readable code that represents structured information; parsing the network representation; generating a network model using the parsed network representation, the network model including a plurality of network objects and relationships between the plurality of network objects; and storing the network model in memory. Any type of network may be modeled. The computer-readable code may be any suitable language or instructions for representing structured information such as, for example, extensible mark-up language (XML). A network inventory adapter receives the network representation from the network. The network inventory adapter is a software component that may be used to connect applications to the network. The network inventory adapter receives the network representation from the network and reads and parses the network representation to determine which network objects are to be operated on and the order of operation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
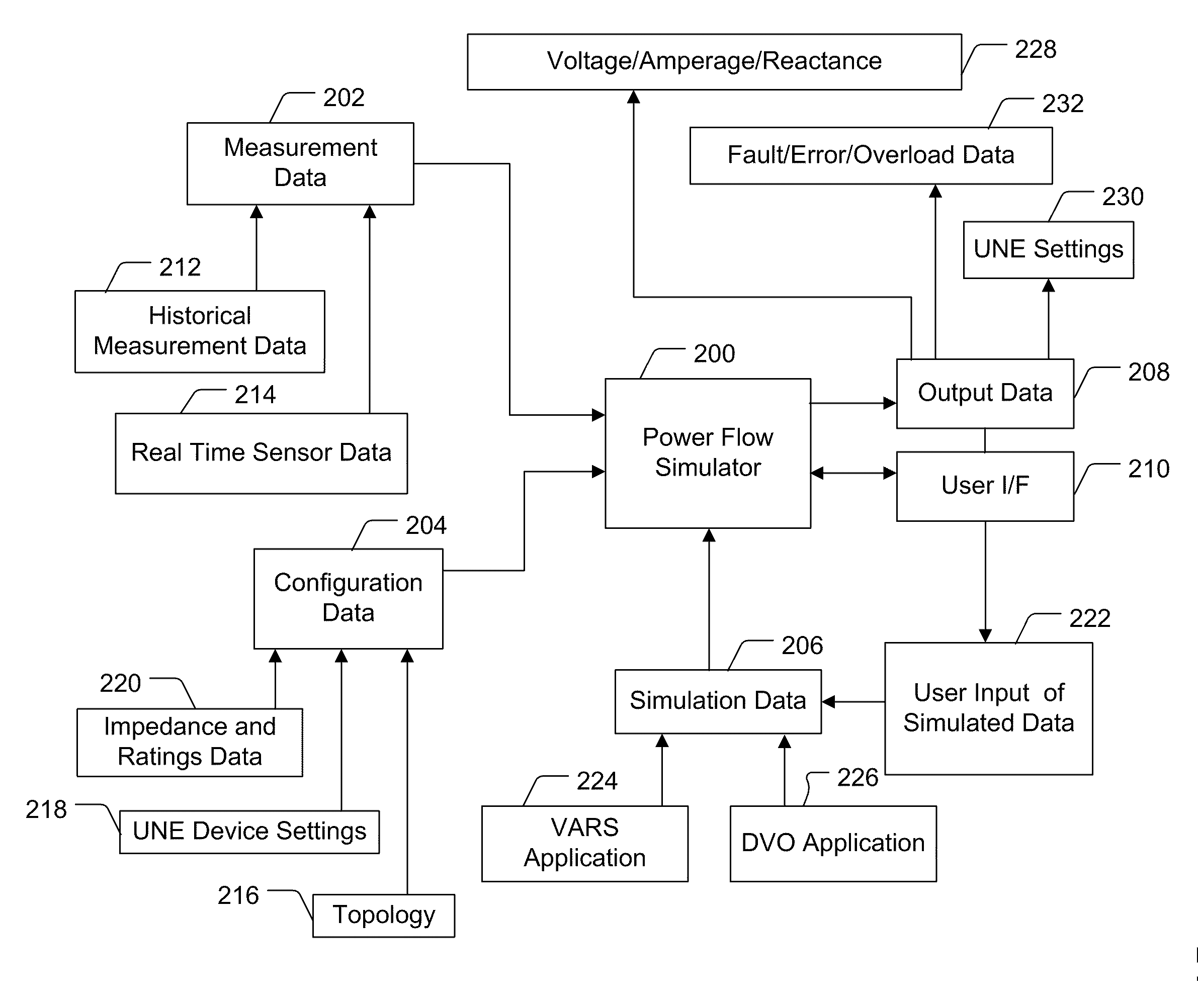
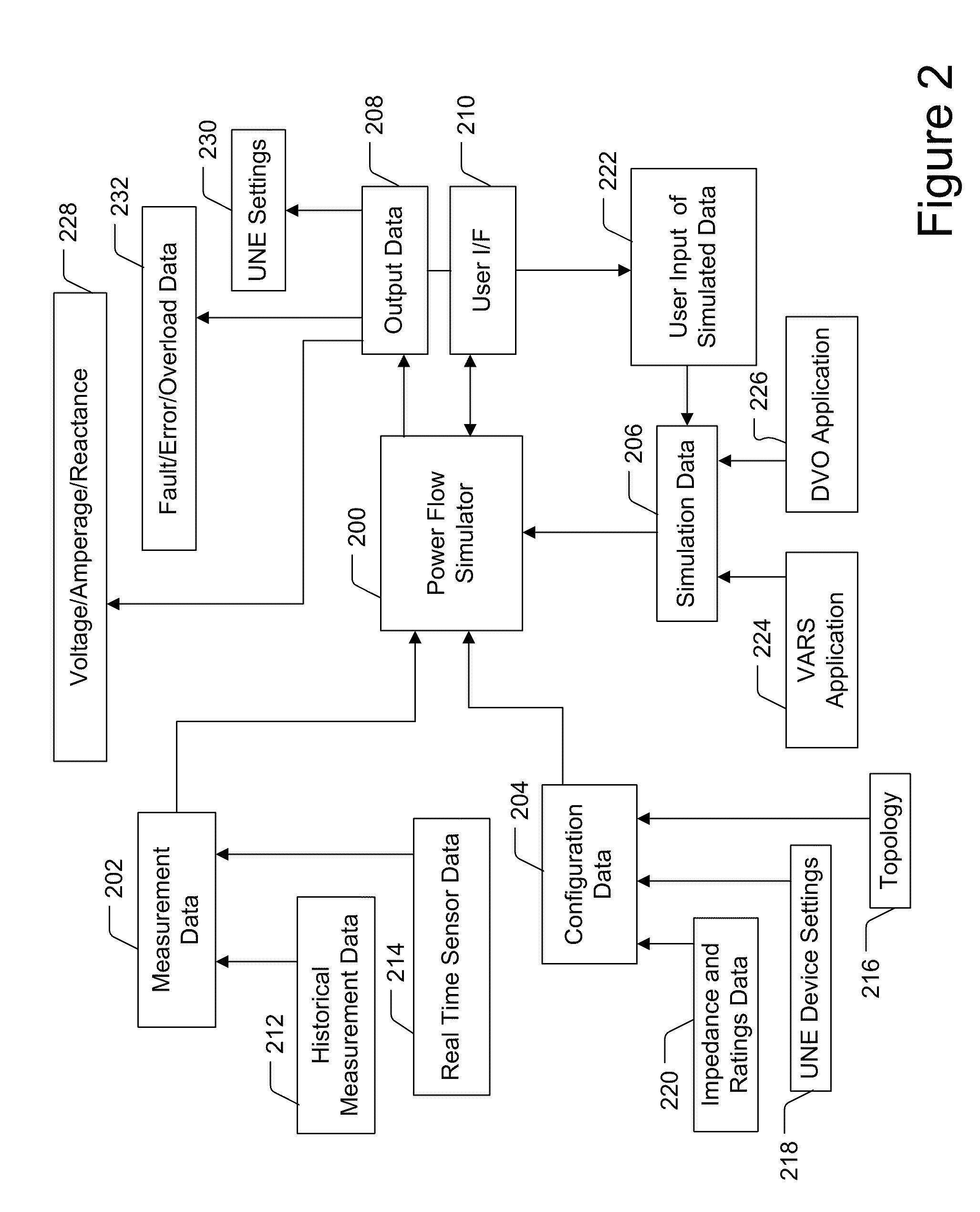
Power Flow Simulation System, Method and Device
InactiveUS20120022713A1Mechanical power/torque controlLevel controlDistribution systemElectric power
Embodiments of the present invention provide power flow analysis and may process electrical power distribution system data in real time to calculate load, current, voltage, losses, fault current and other data. The power flow analysis system may include a detailed data model of the electrical power distribution system, and may accept a variety of real time measurement inputs to support its modeling calculations. The power flow analysis system may calculate data of each of the three distribution system power phases independently and include a distribution state estimation module which allows it to incorporate a variety of real time measurements with varying degrees of accuracy, reliability and latency.
Owner:S&C ELECTRIC
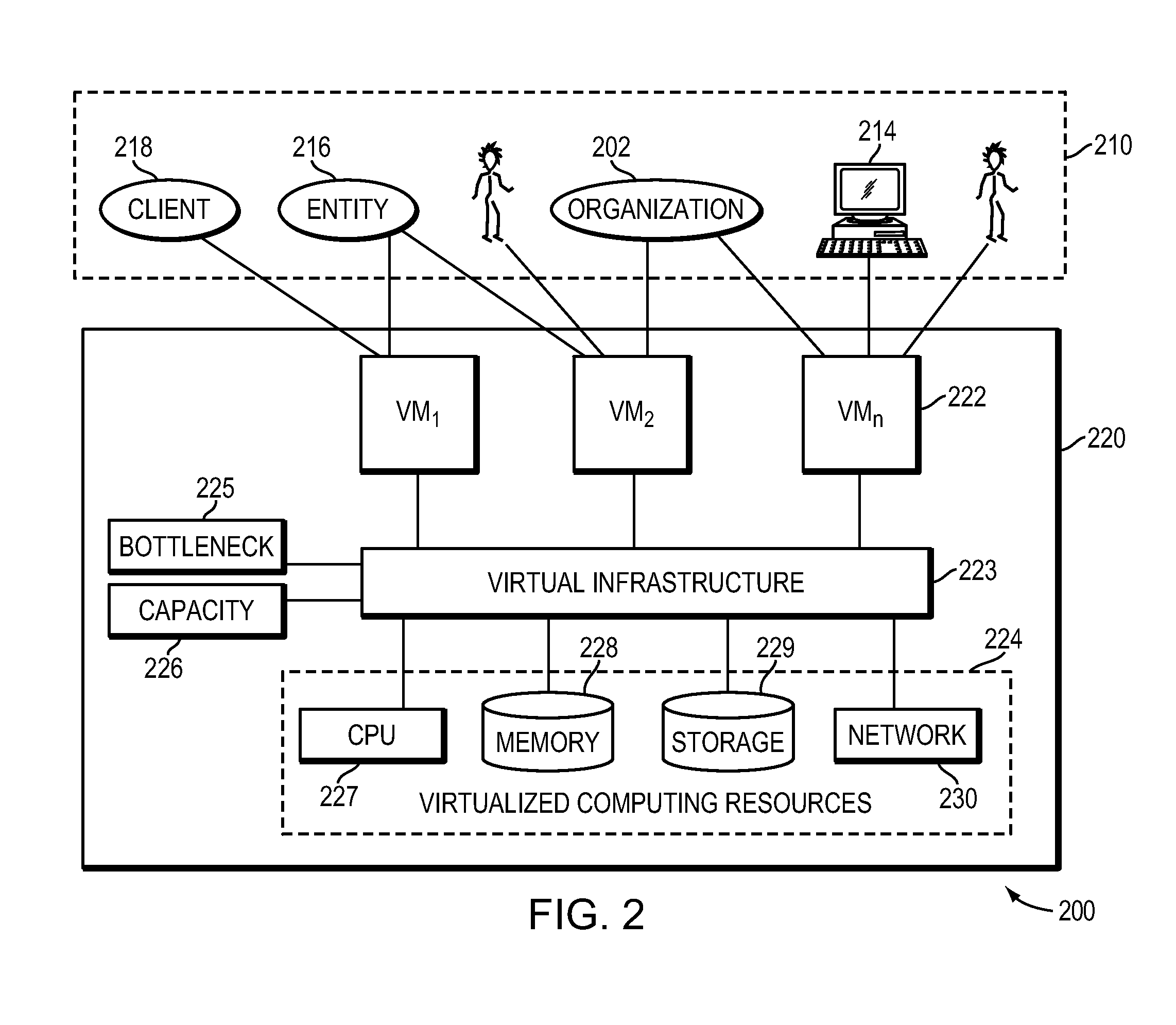
Method, System and Apparatus for Managing, Modeling, Predicting, Allocating and Utilizing Resources and Bottlenecks in a Computer Network
ActiveUS20090300173A1Shorten the timeLow costAnalogue computers for electric apparatusDigital computer detailsVirtualizationResource allocation
A method and apparatus for managing, modeling, predicting, allocating and utilizing resources and bottlenecks in a computer network managing, predicting and displaying of capacity, allocating and utilizing of resources, as well as actual and potential performance-degrading resource shortages in a computer network, is provided. Specifically, exemplary implementations of the present invention provide a method, system and apparatus for calculating, detecting, predicting, and presenting resource allocation, utilization, capacity bottlenecks and availability information, in a computer network, particularly in a virtualized computer environment.
Owner:QUEST SOFTWARE INC
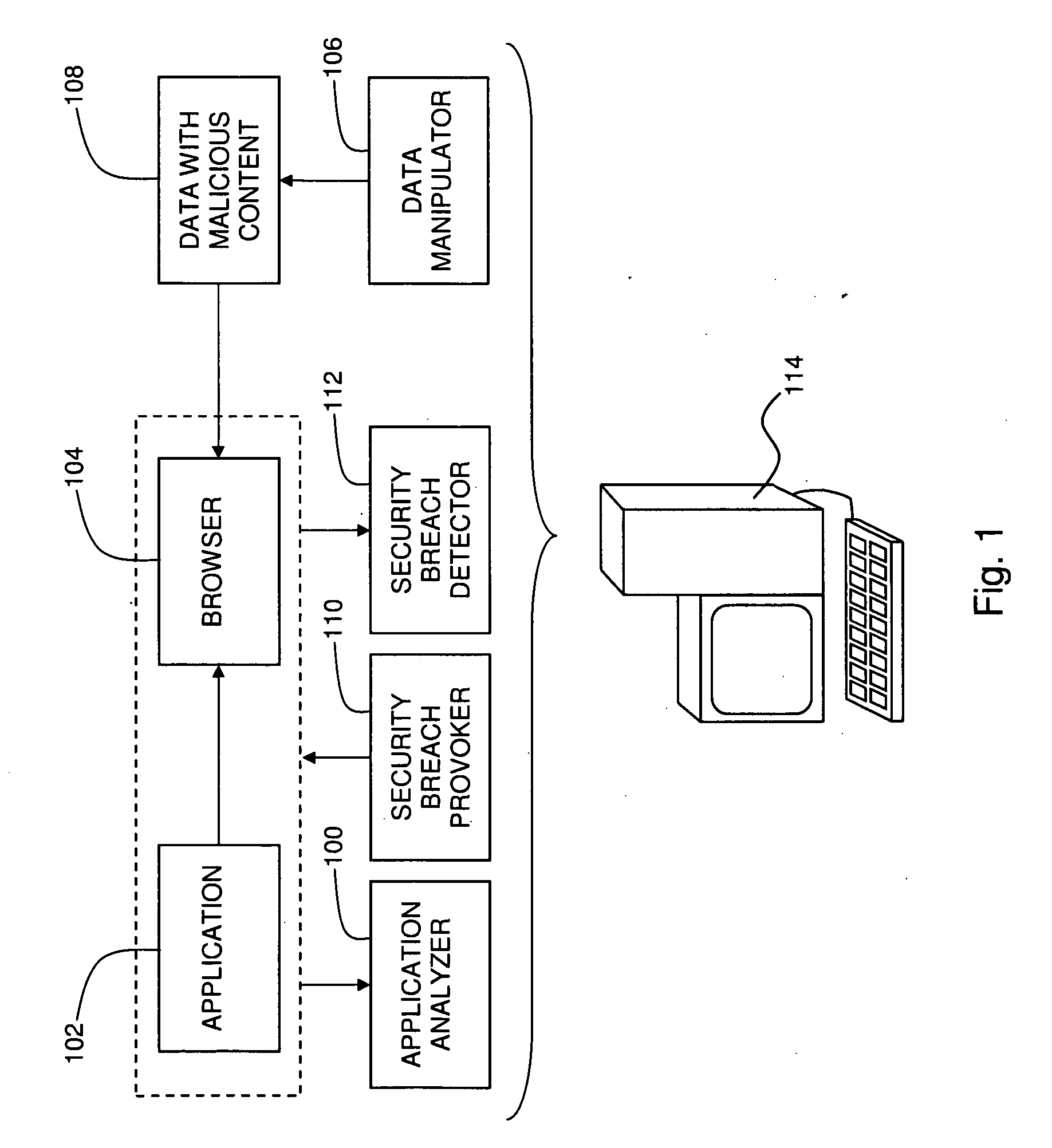
Identifying Security Breaches Caused by Web-Enabled Software Applications
Identifying a security breach caused when a computer-based software application uses a computer-based web browser application, including identifying at least one function within a computer-based software application that causes a computer-based web browser application to access data from a source that is external to the software application, at least partially replacing the data with malicious content that is configured to cause a predefined action to occur when the malicious content is accessed by the web browser application, where the predefined action is associated with a known security breach when the predefined action occurs subsequent to the malicious content being accessed by the web browser application, causing the software application to perform the function, and determining whether the predefined action is performed.
Owner:IBM CORP
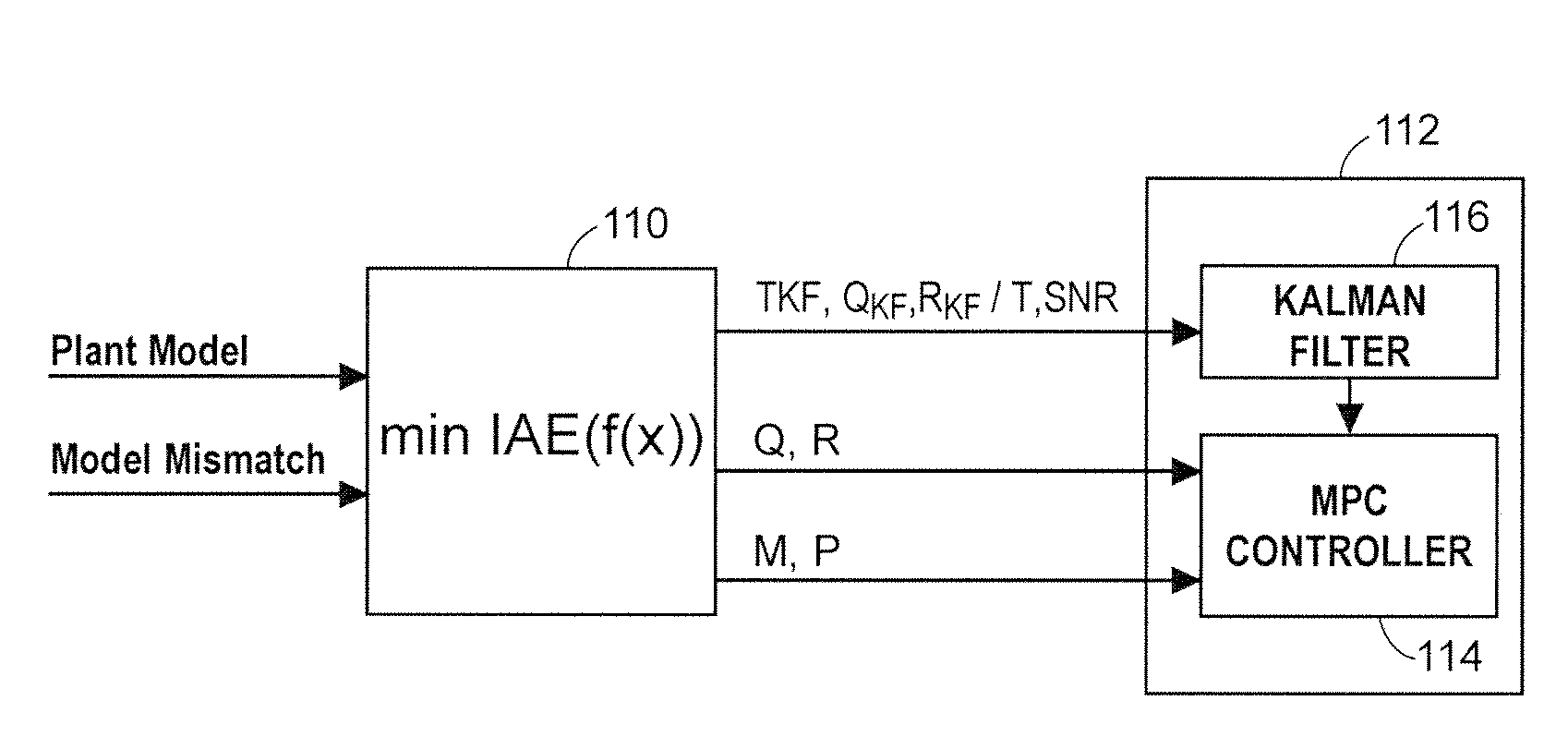
Robust adaptive model predictive controller with tuning to compensate for model mismatch
ActiveUS20090198350A1Improve immunityImprove performanceComputer controlSimulator controlClosed loopPredictive controller
An MPC adaptation and tuning technique integrates feedback control performance better than methods commonly used today in MPC type controllers, resulting in an MPC adaptation / tuning technique that performs better than traditional MPC techniques in the presence of process model mismatch. The MPC controller performance is enhanced by adding a controller adaptation / tuning unit to an MPC controller, which adaptation / tuning unit implements an optimization routine to determine the best or most optimal set of controller design and / or tuning parameters to use within the MPC controller during on-line process control in the presence of a specific amount of model mismatch or a range of model mismatch. The adaptation / tuning unit determines one or more MPC controller tuning and design parameters, including for example, an MPC form, penalty factors for either or both of an MPC controller and an observer and a controller model for use in the MPC controller, based on a previously determined process model and either a known or an expected process model mismatch or process model mismatch range. A closed loop adaptation cycle may be implemented by performing an autocorrelation analysis on the prediction error or the control error to determine when significant process model mismatch exists or to determine an increase or a decrease in process model mismatch over time.
Owner:FISHER-ROSEMOUNT SYST INC
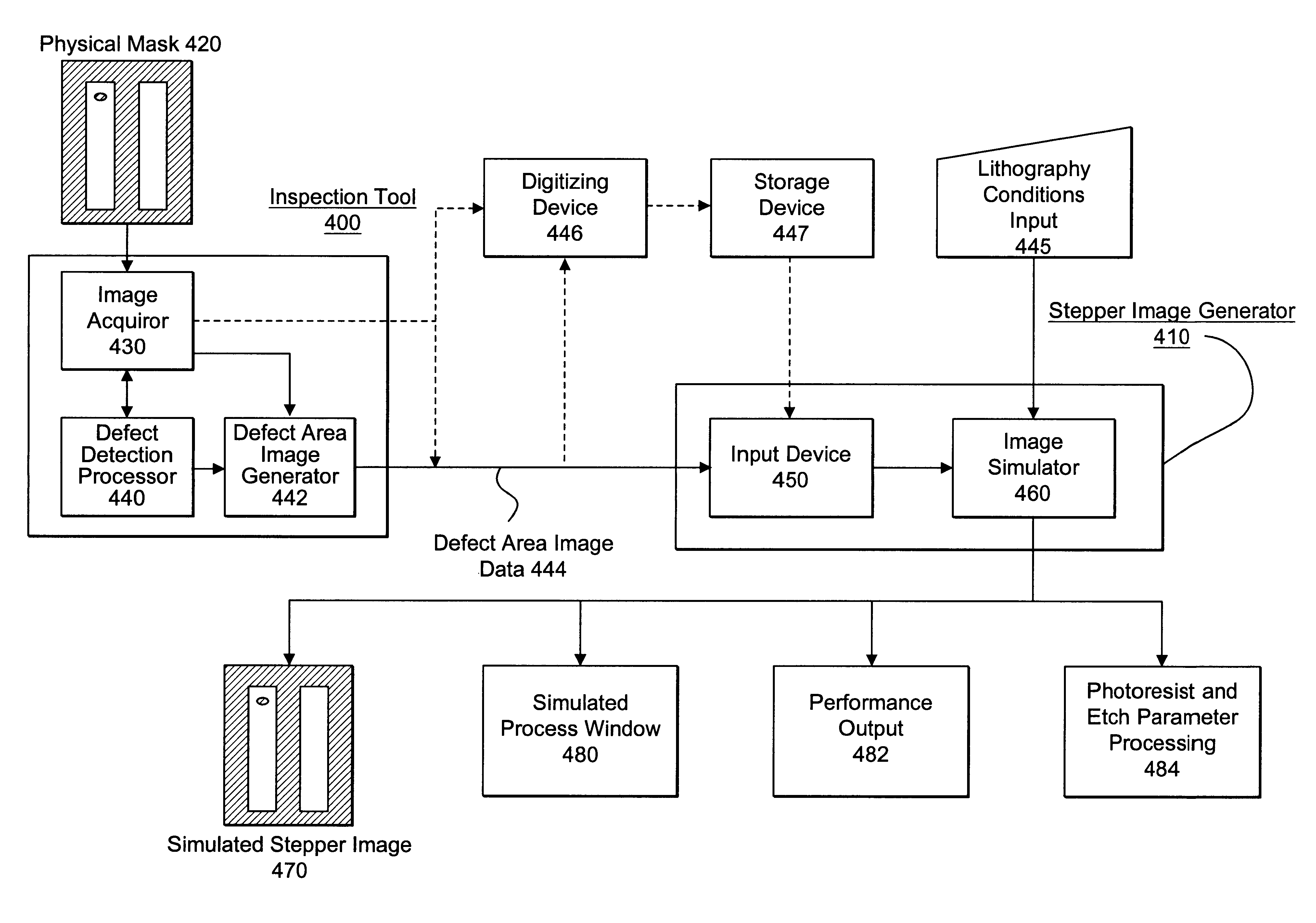
Visual inspection and verification system
A method and apparatus for inspecting a photolithography mask for defects is provided. The inspection method comprises providing a defect area image to an image simulator wherein the defect area image is an image of a portion of a photolithography mask, and providing a set of lithography parameters as a second input to the image simulator. The defect area image may be provided by an inspection tool which scans the photolithography mask for defects using a high resolution microscope and captures images of areas of the mask around identified potential defects. The image simulator generates a first simulated image in response to the defect area image and the set of lithography parameters. The first simulated image is a simulation of an image which would be printed on a wafer if the wafer were to be exposed to an illumination source directed through the portion of the mask. The method may also include providing a second simulated image which is a simulation of the wafer print of the portion of the design mask which corresponds to the portion represented by the defect area image. The method also provides for the comparison of the first and second simulated images in order to determine the printability of any identified potential defects on the photolithography mask. A method of determining the process window effect of any identified potential defects is also provided for.
Owner:SYNOPSYS INC
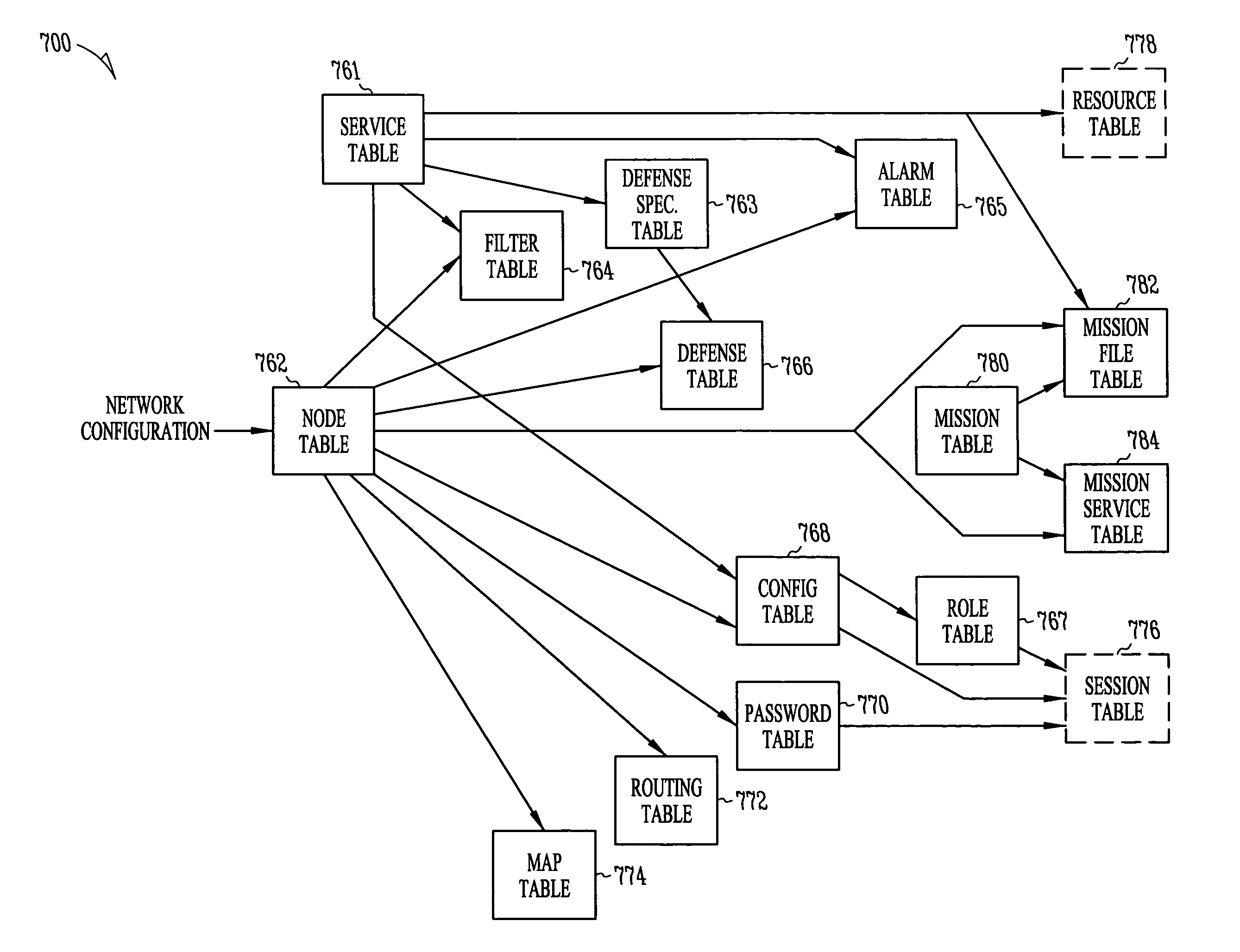
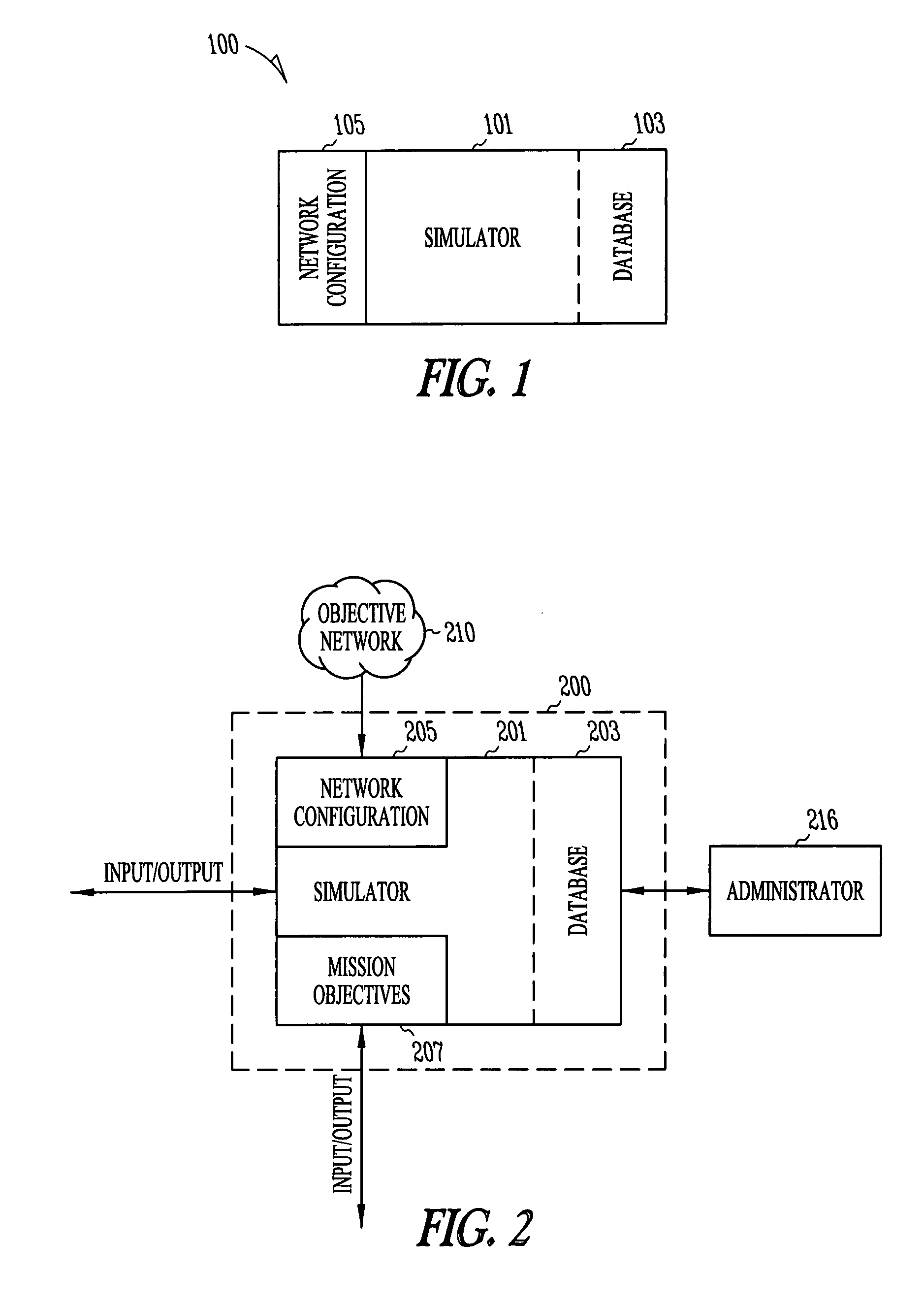
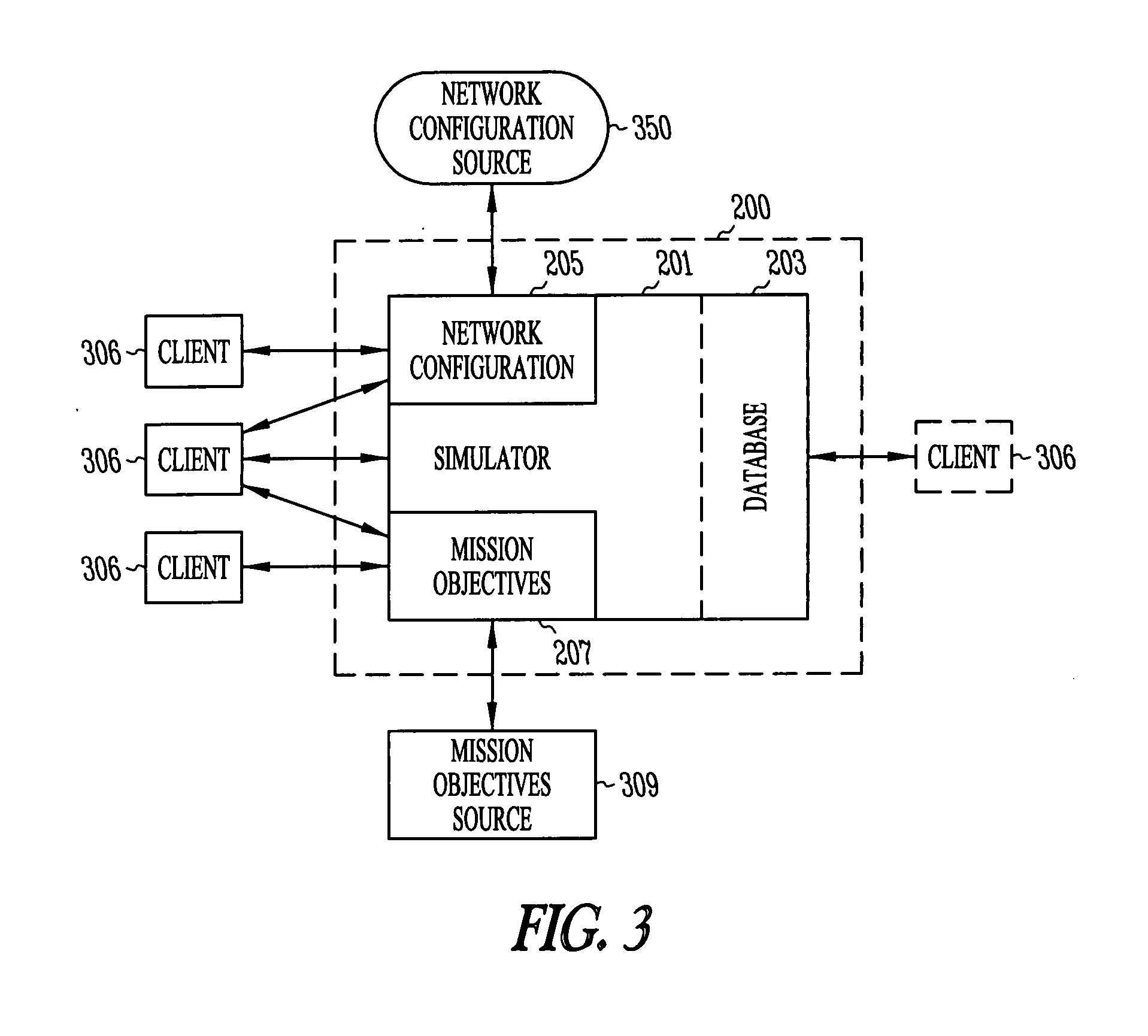
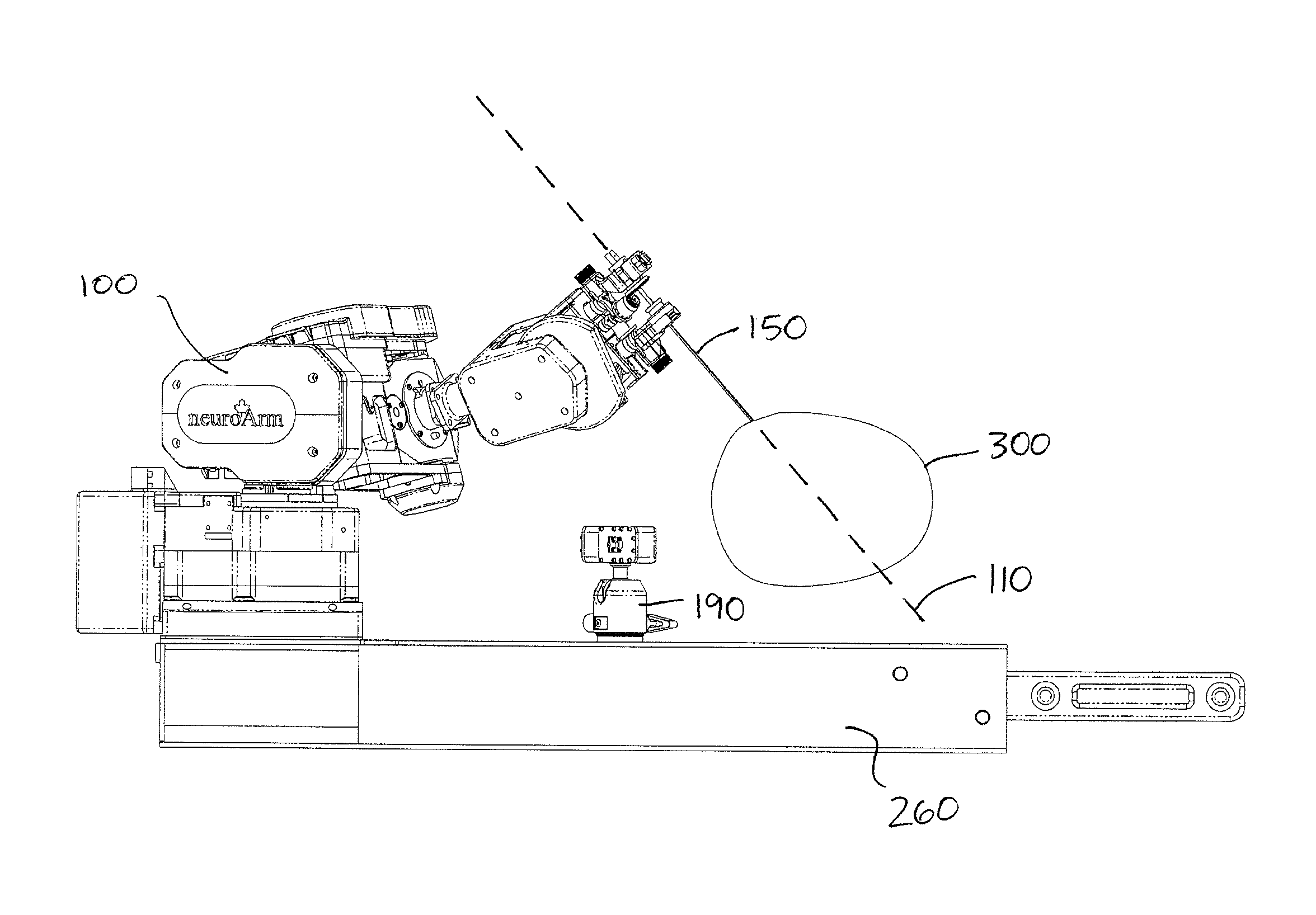
Network security modeling system and method
InactiveUS7315801B1Analogue computers for electric apparatusDigital computer detailsNetwork security policyVulnerability
A network security modeling system which simulates a network and analyzes security vulnerabilities of the network. The system includes a simulator which includes a network vulnerabilities database and a network configuration module having network configuration data. The simulator determines vulnerabilities of the simulated network based on the network configuration data and the vulnerabilities database.
Owner:MCAFEE LLC
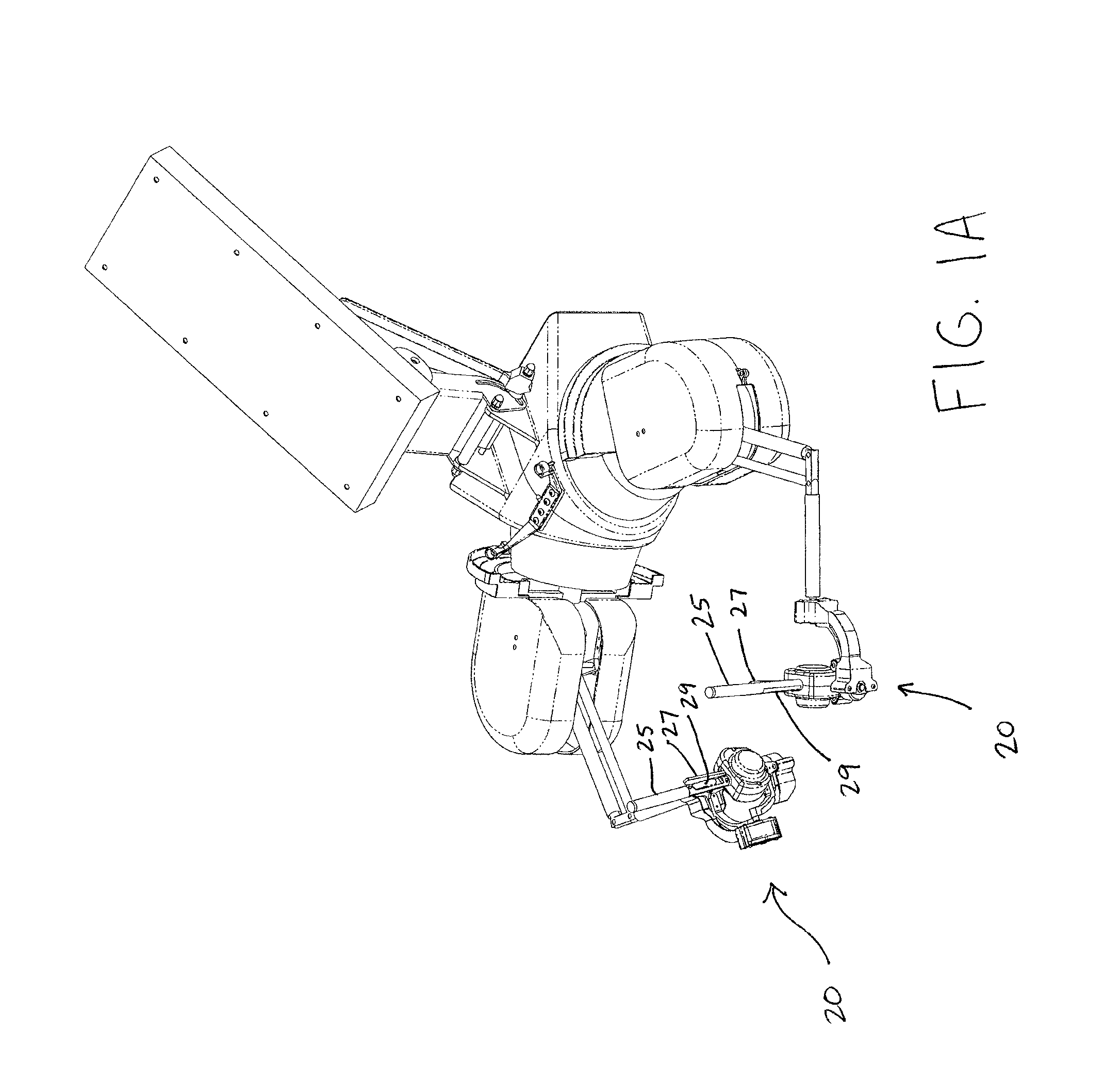
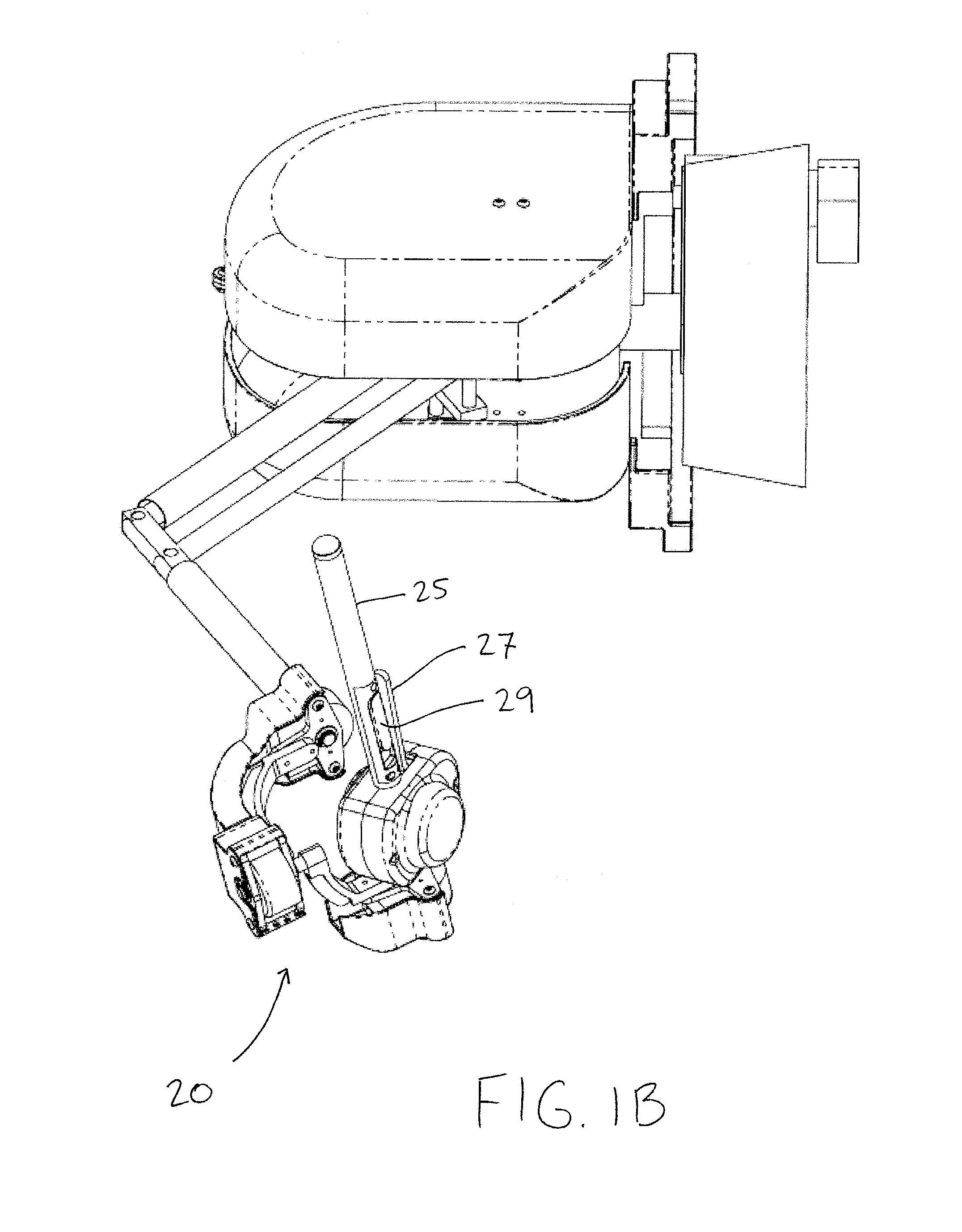
Methods, devices, and systems for non-mechanically restricting and/or programming movement of a tool of a manipulator along a single axis
ActiveUS8560118B2Programme-controlled manipulatorMechanical/radiation/invasive therapiesMedical robotEngineering
Owner:DEERFIELD IMAGING INC
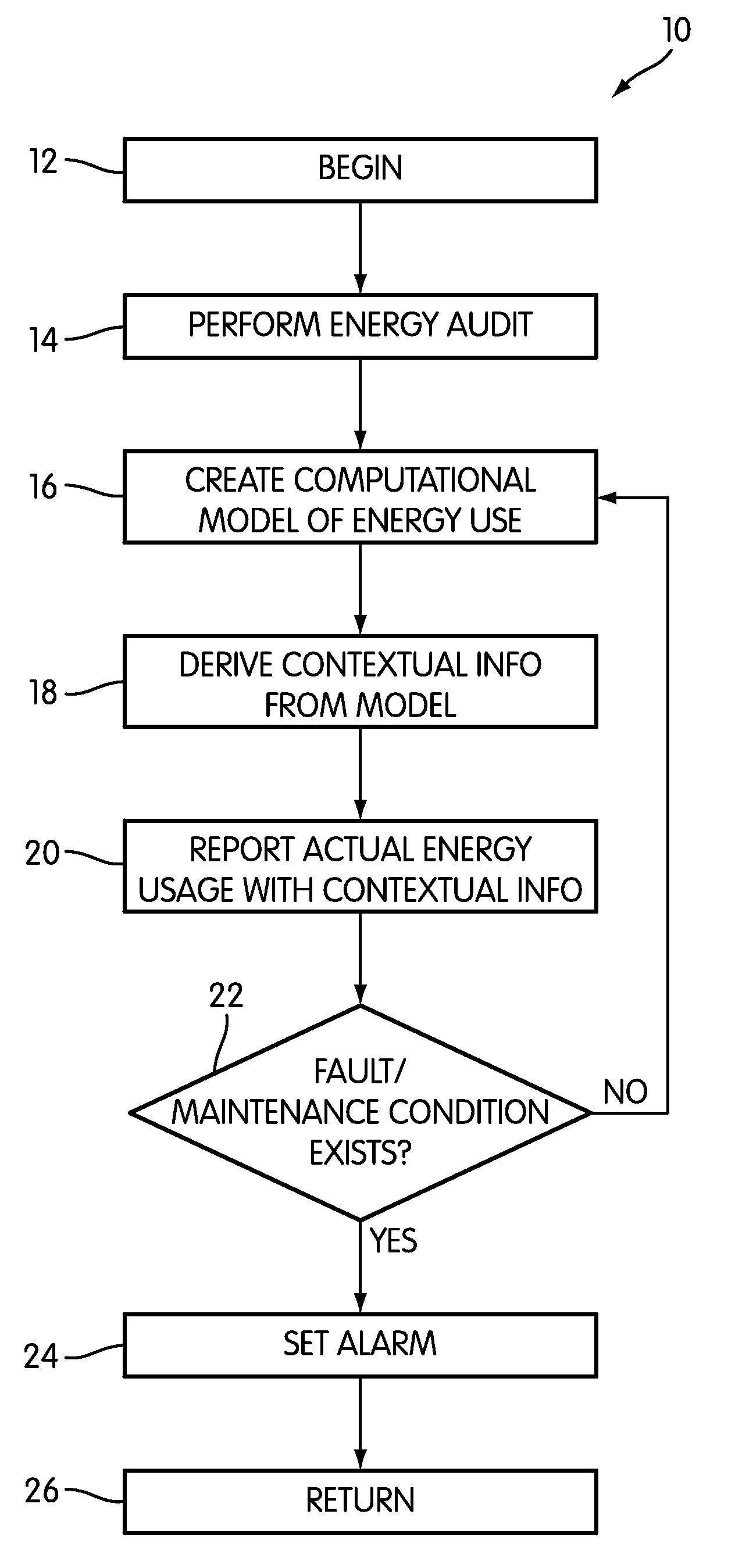
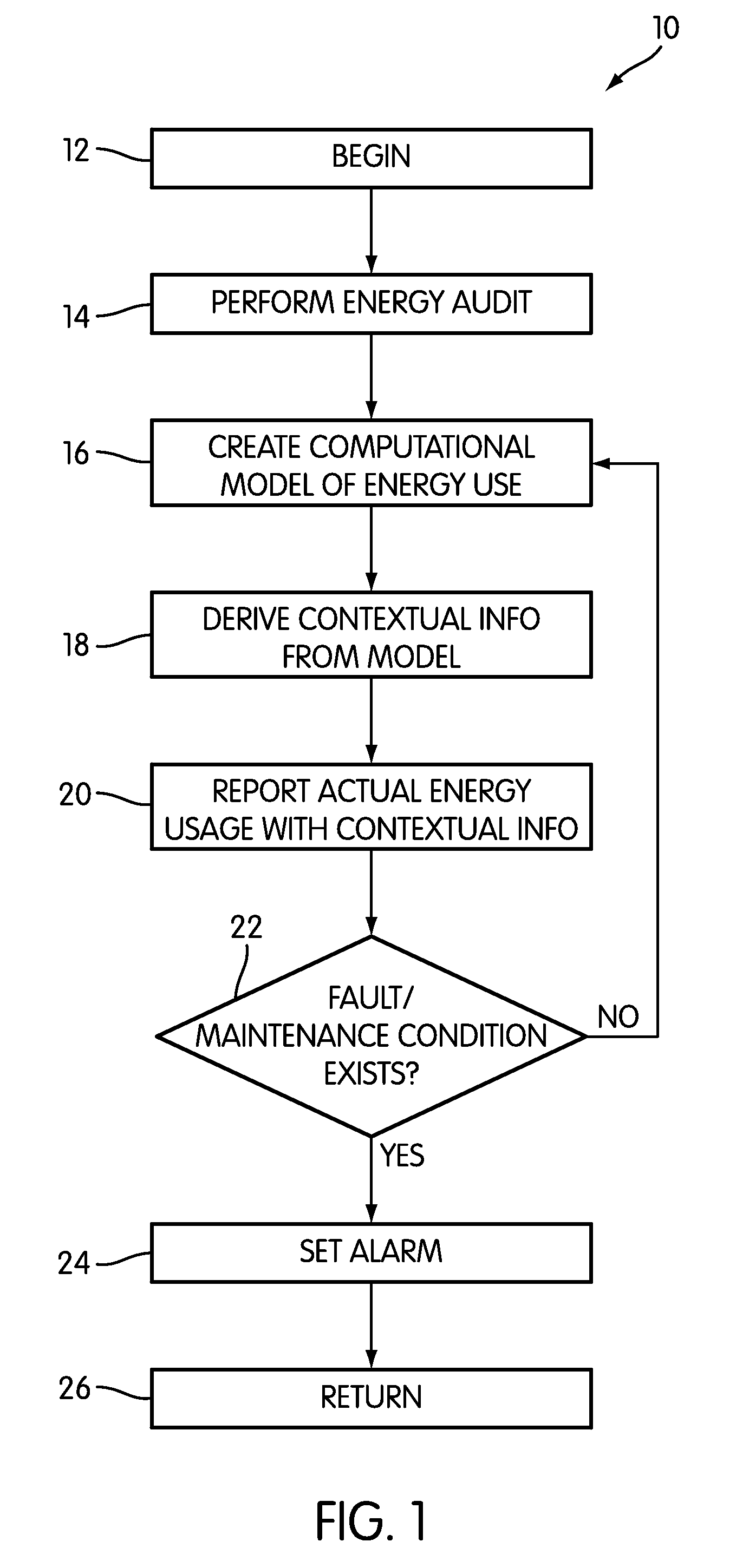
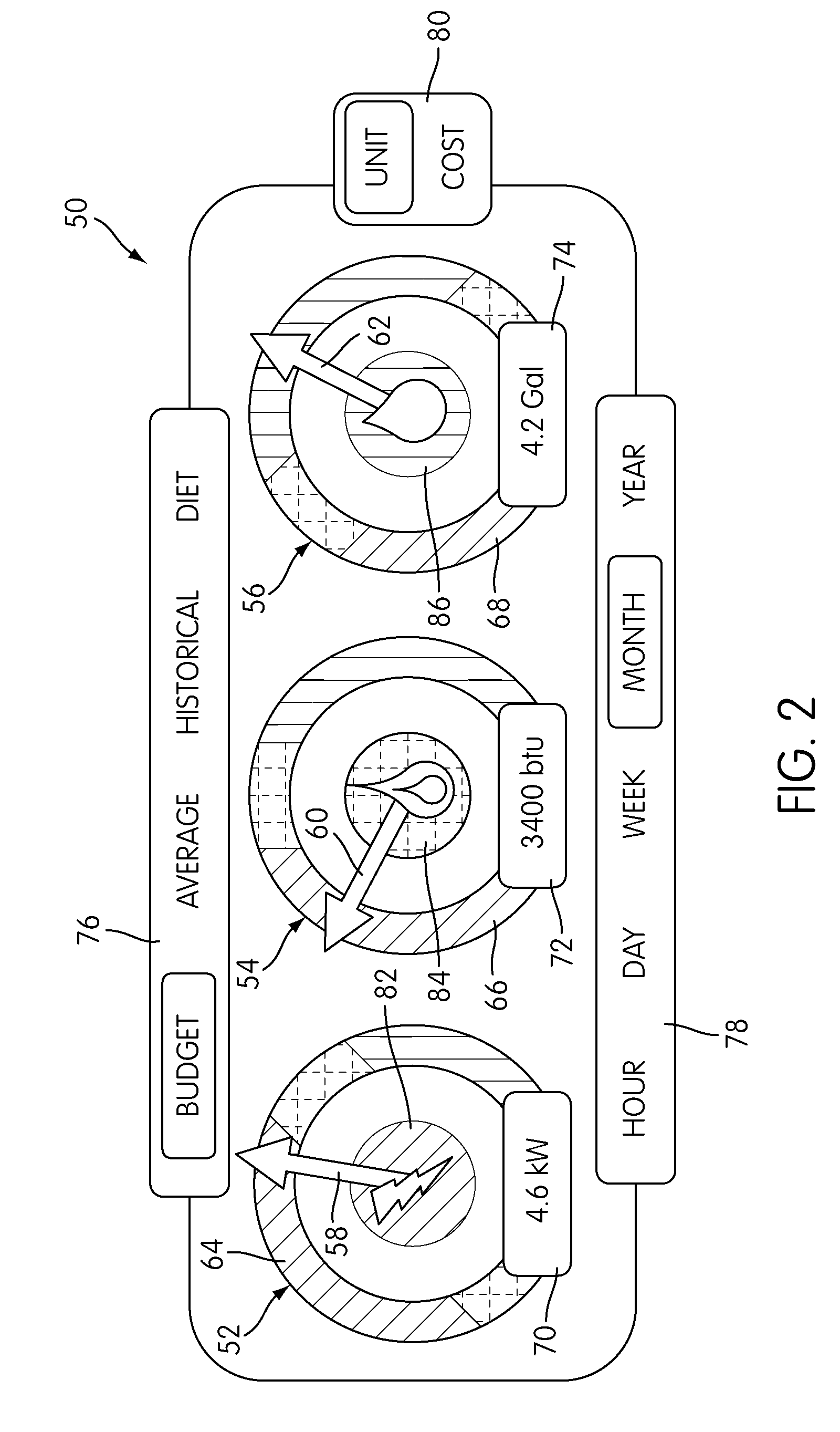
Building Energy Usage Auditing, Reporting, and Visualization
Systems and methods for energy monitoring and for providing the user with contextual information on the energy usage of a building area are disclosed. The methods may comprise performing an energy audit of a building and using the audit data and a building physics simulator to construct a computational model of the building's energy usage. An energy budget may be derived based on the computational model. The building's actual energy usage is reported with contextual information on energy usage from the computational model, the energy budget, historical data on energy usage, and other sources. The systems generally include energy monitoring hardware, a building physics simulator engine, and an interface. The interface may be implemented in hardware or software. The components of the system may be located in one building, or a central monitoring station with a building physics simulator engine may communicate with energy monitoring hardware in several buildings.
Owner:RECURVE
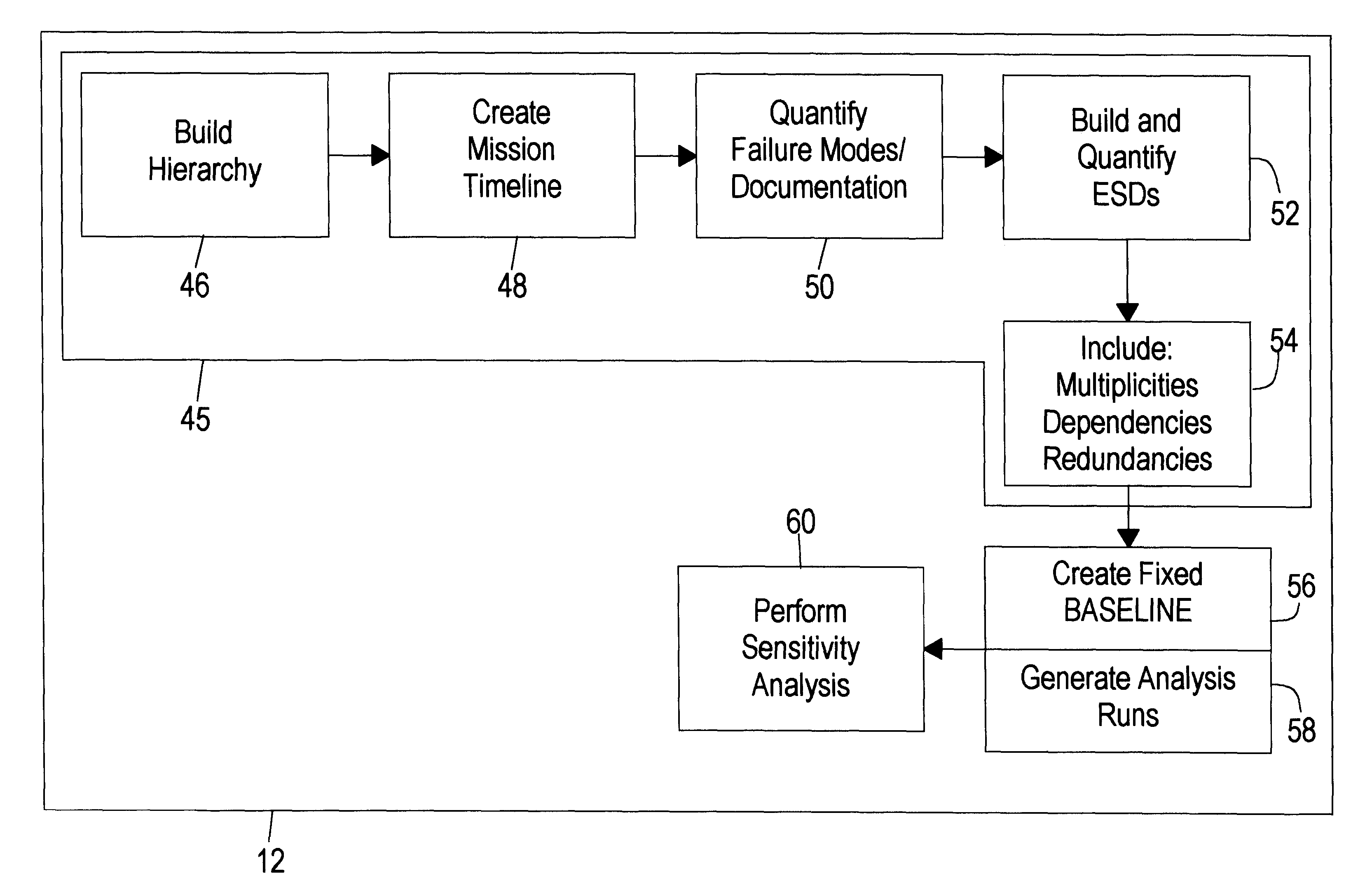
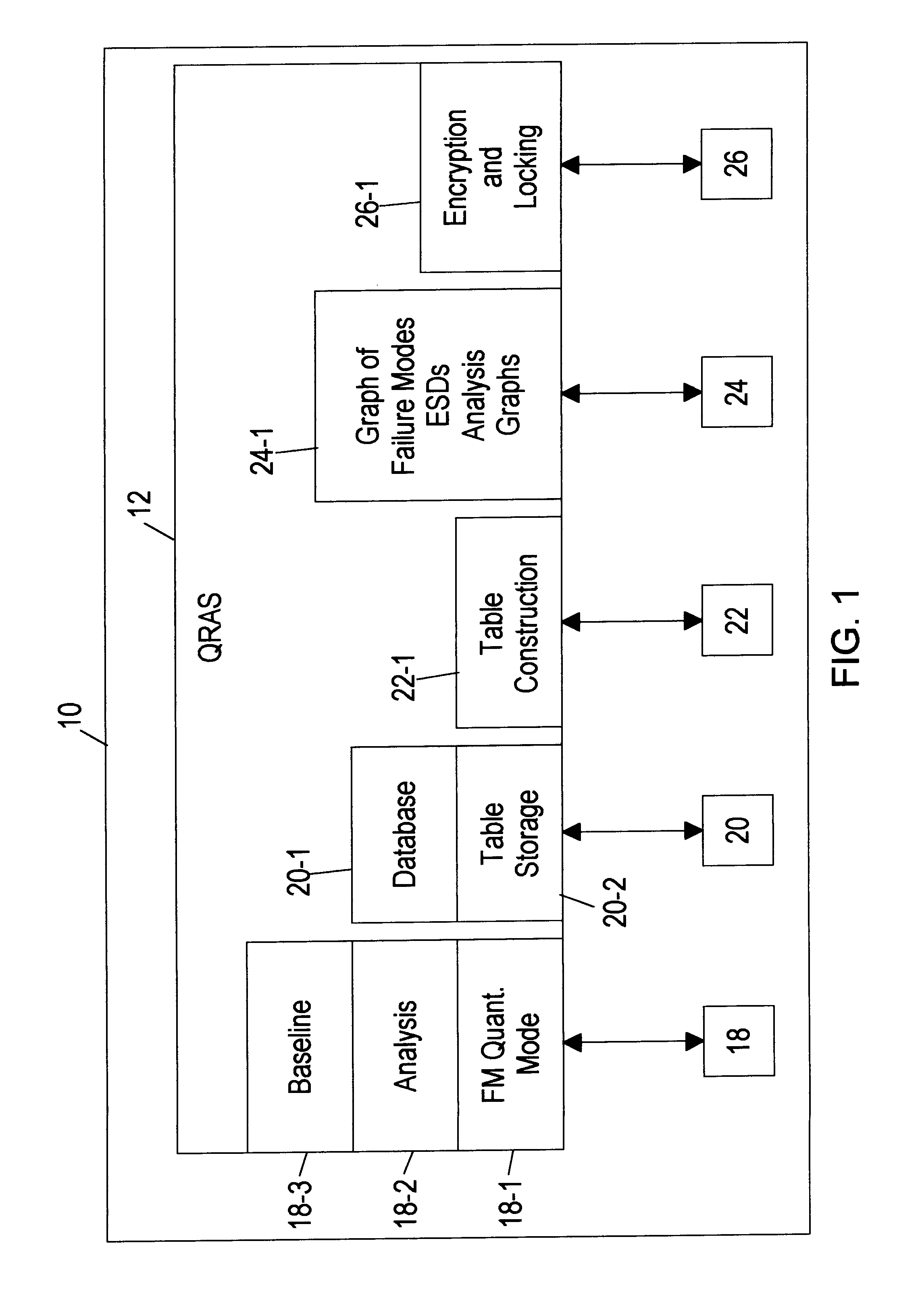
Quantitative risk assessment system (QRAS)
A quantitative risk assessment system (QRAS) builds a risk model of a system for which risk of failure is being assessed, then analyzes the risk of the system corresponding to the risk model. The QRAS performs sensitivity analysis of the risk model by altering fundamental components and quantifications built into the risk model, then re-analyzes the risk of the system using the modifications. More particularly, the risk model is built by building a hierarchy, creating a mission timeline, quantifying failure modes, and building / editing event sequence diagrams. Multiplicities, dependencies, and redundancies of the system are included in the risk model. For analysis runs, a fixed baseline is first constructed and stored. This baseline contains the lowest level scenarios, preserved in event tree structure. The analysis runs, at any level of the hierarchy and below, access this baseline for risk quantitative computation as well as ranking of particular risks. A standalone Tool Box capability exists, allowing the user to store application programs within QRAS.
Owner:NAT AERONAUTICS & SPACE ADMINISTATION U S GOVERNMENT AS REPRESENTED BY THE ADMINISTATOR +1
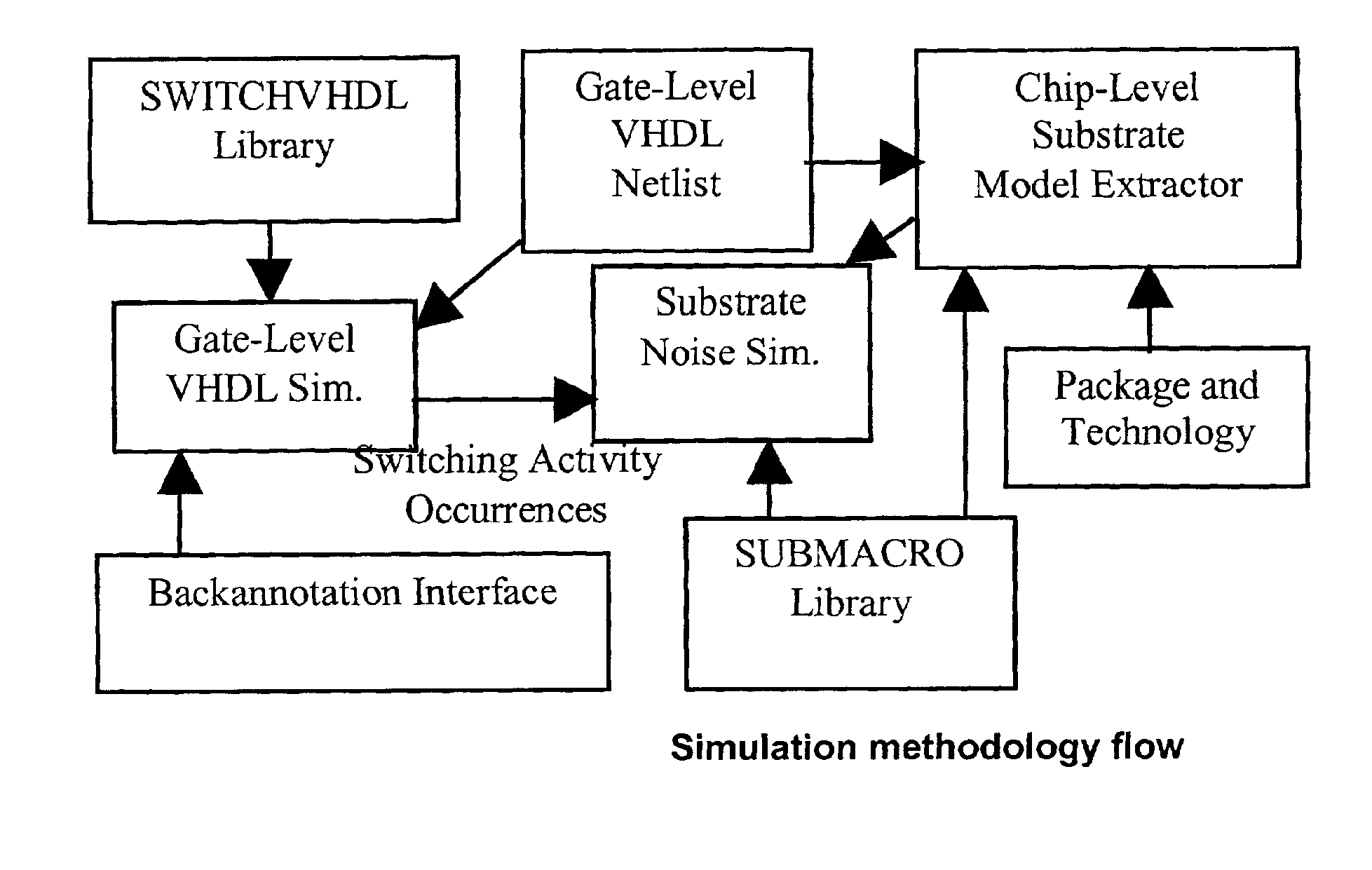
Method, apparatus and computer program product for determination of noise in mixed signal systems
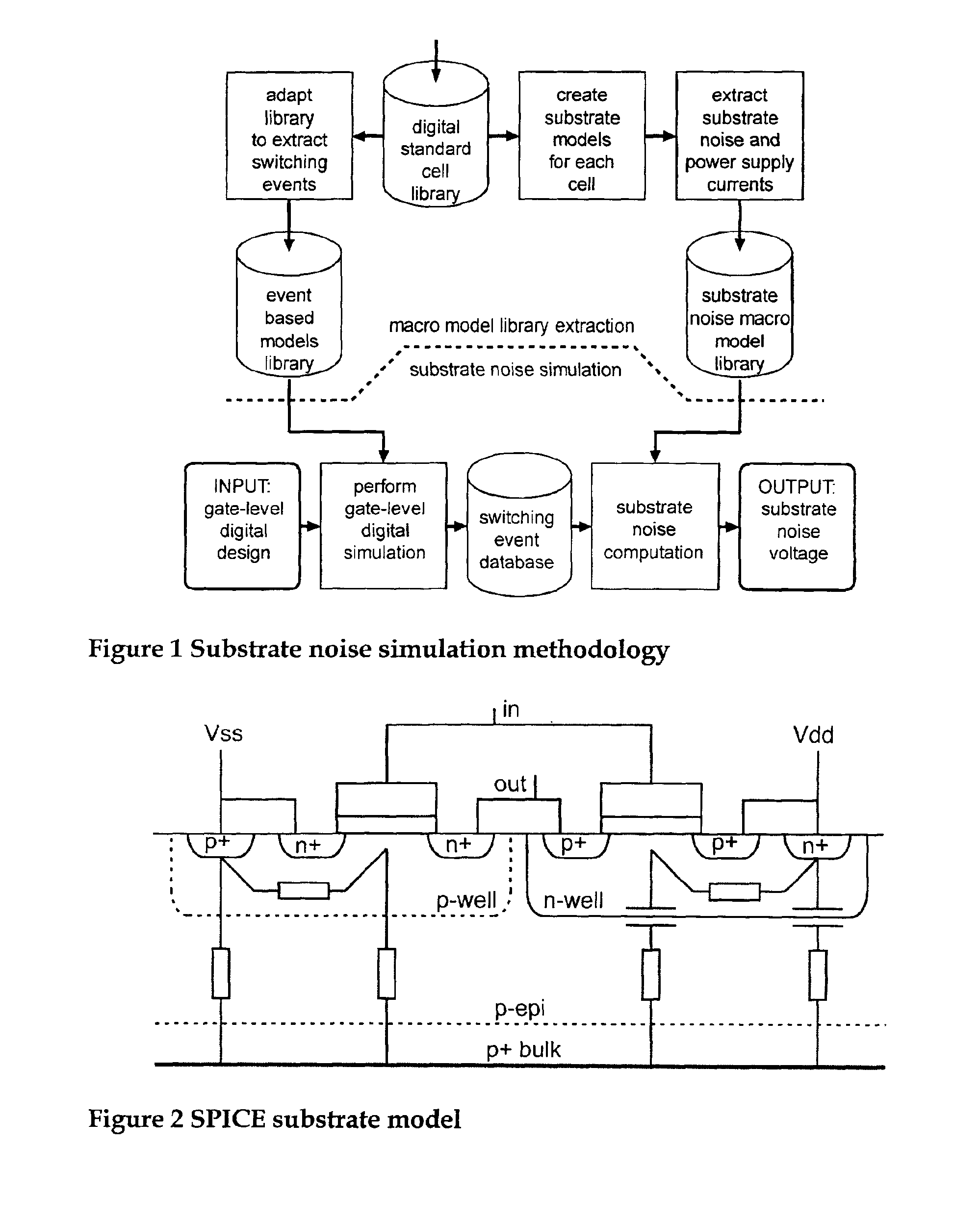
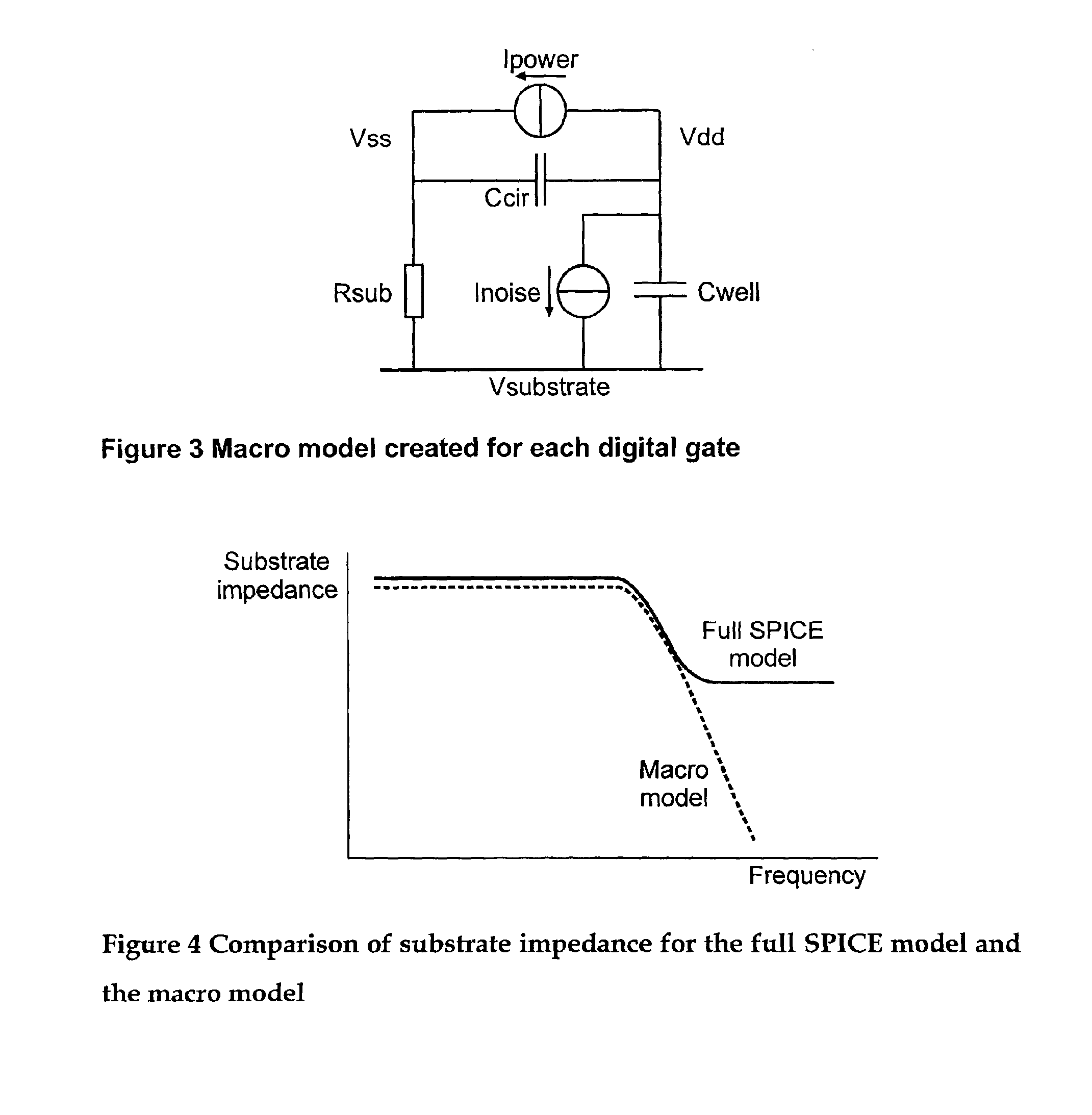
InactiveUS6941258B2Fast and accurate determinationAnalogue computers for electric apparatusDetecting faulty computer hardwareEngineeringSignaling system
A simulation system is described for computing the overall signal generated in a substrate by a digital system comprising a plurality of gates associated with the substrate, wherein each gate is configured to perform a switching event. Output of a transistor-level model is compared with output of a lumped circuit model for each gate and the substrate, and signal contributions from each gate and switching event are determined based on the comparison. The system determines switching event signals for each of the plurality of gates. The signal contributions and the switching event signals are combined, and a combined lumped circuit model is derived based on a combination of lumped circuit models of the plurality of gates. The overall signal is computed based on the combined gate signal contributions and switching event signals, which are configured as an input to the combined lumped circuit model.
Owner:INTERUNIVERSITAIR MICRO ELECTRONICS CENT (IMEC VZW)
Method for categorizing, describing and modeling types of system users
InactiveUS6853966B2Good suitImprove performanceSoftware engineeringAnalogue computers for electric apparatusSimulationBehavior type
Owner:SBC TECH RESOURCES
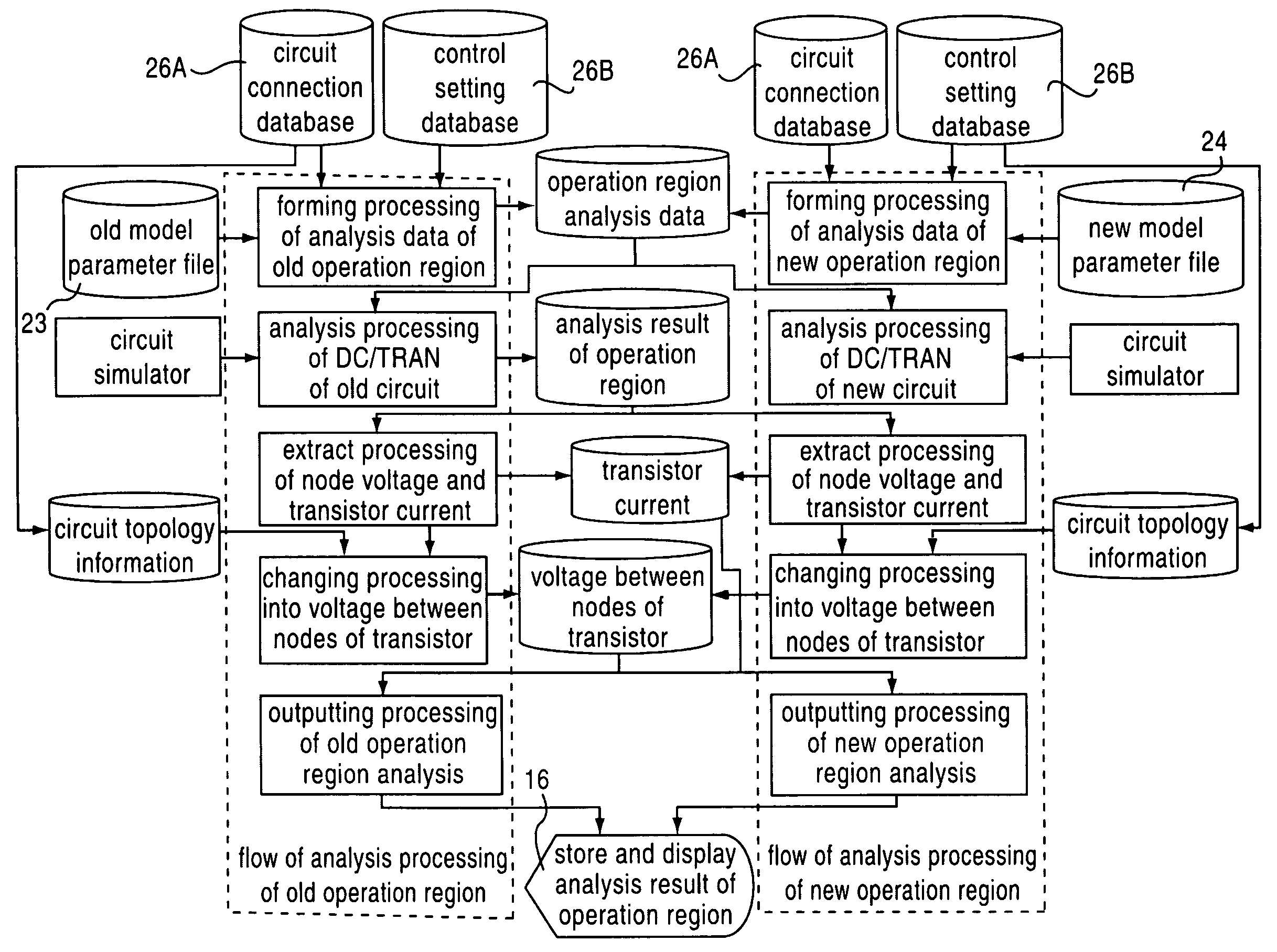
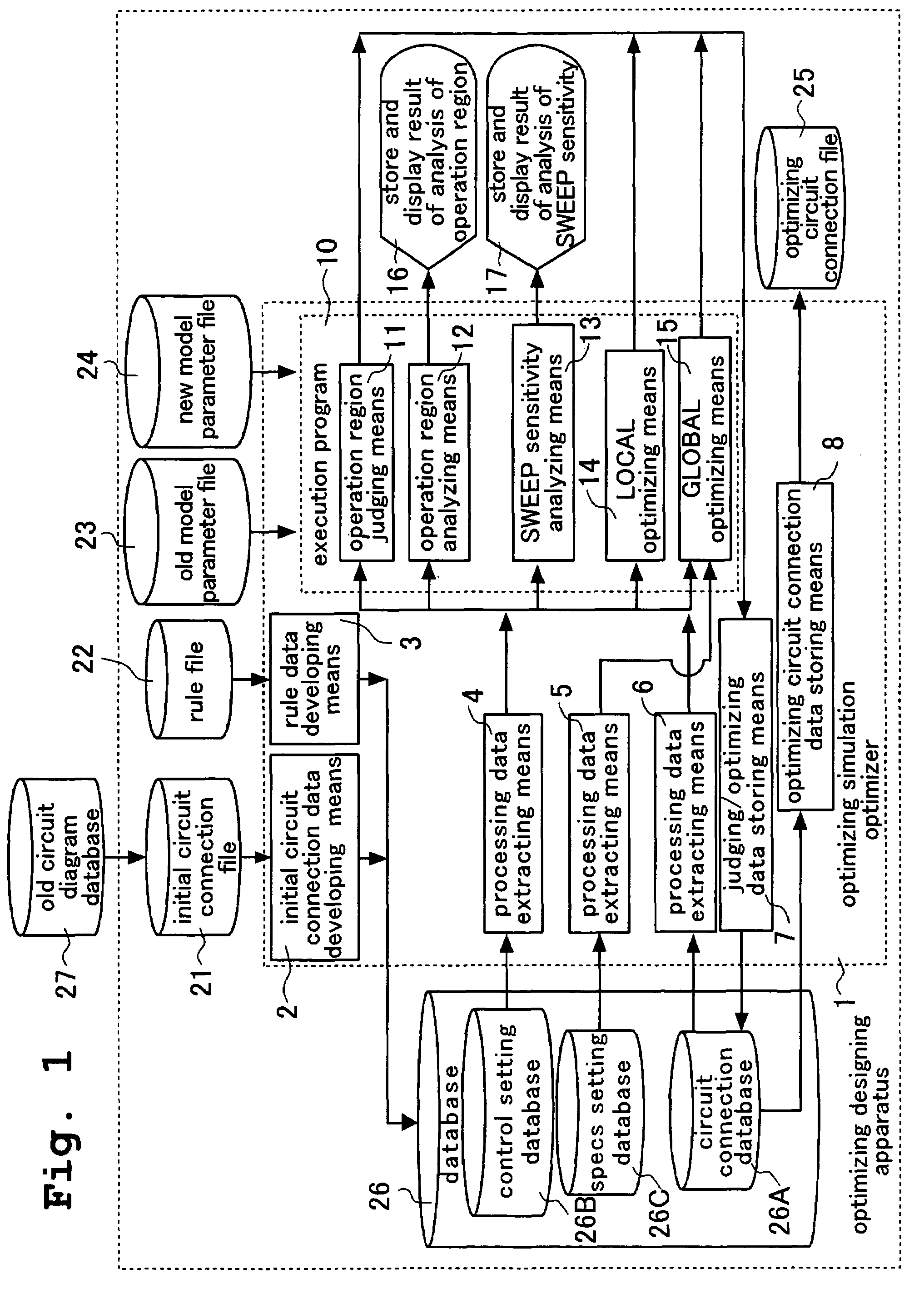
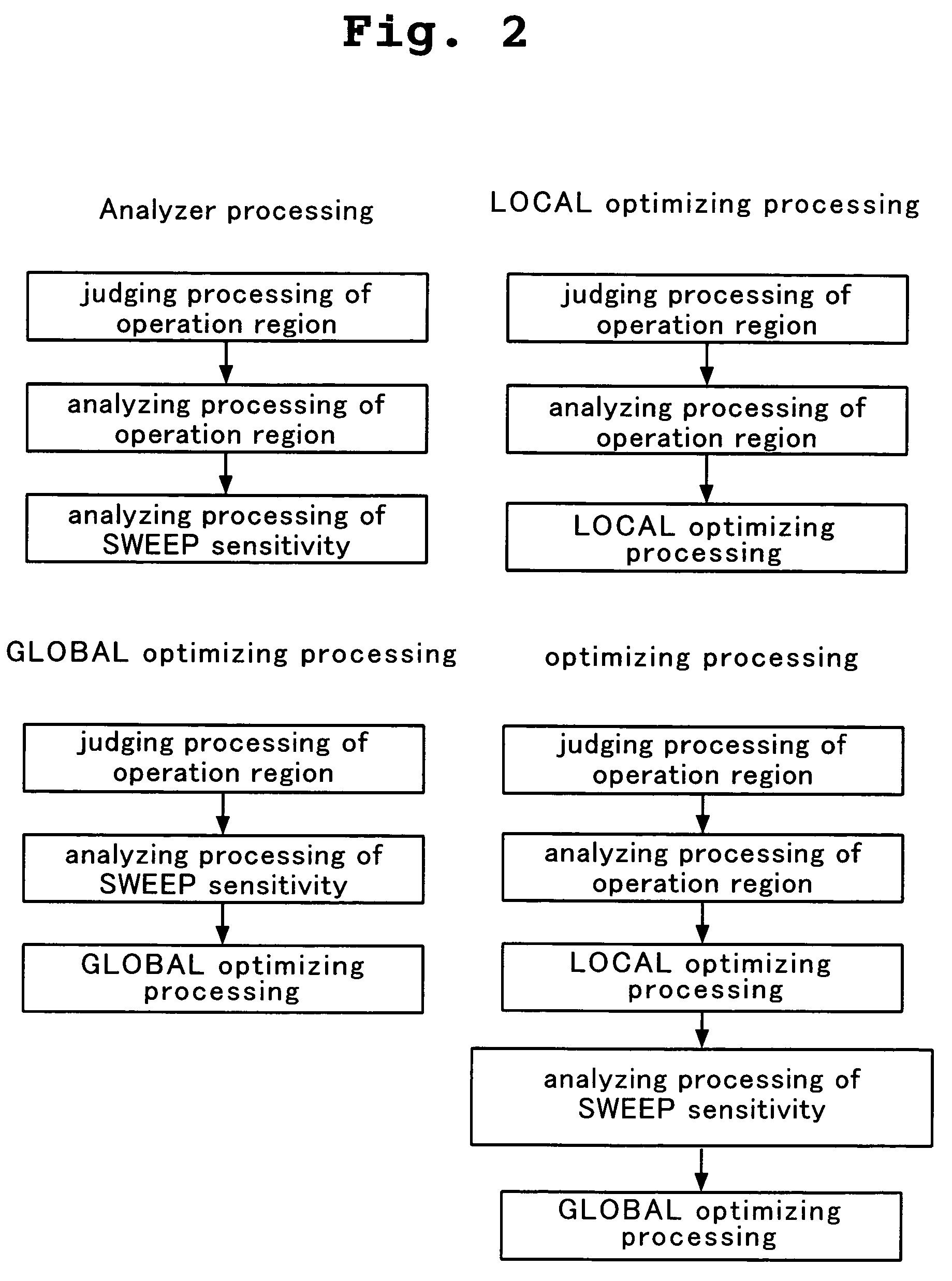
Optimizing designing apparatus of integrated circuit, optimizing designing method of integrated circuit, and storing medium in which program for carrying out optimizing designing method of integrated circuit is stored
ActiveUS7155685B2Easy to carryAnalogue computers for electric apparatusSemiconductor/solid-state device manufacturingLinear regionRegion analysis
It is an object of the present invention to provide a method, an apparatus and a program having high optimization precision and capable of obtaining an answer required by a designer in a short time by combining optimization between individual transistors and optimization as the entire circuit, or by appropriately combining judgment of an operation region, an analysis of the operation region and a SWEEP sensitivity analysis when the optimization is carried out. An optimizing designing apparatus of an integrated circuit for designing a circuit, comprises operation region judging means for adjusting an operation region (linear region, saturation region) of the circuit, operation region analysis means for displaying liner characteristics (Ids-Vgs characteristics) of the circuit and saturation characteristics (Ids-Vds characteristics) of the circuit, and SWEEP sensitivity analysis means for displaying variation in output characteristics of the circuit.
Owner:ABLIC INC
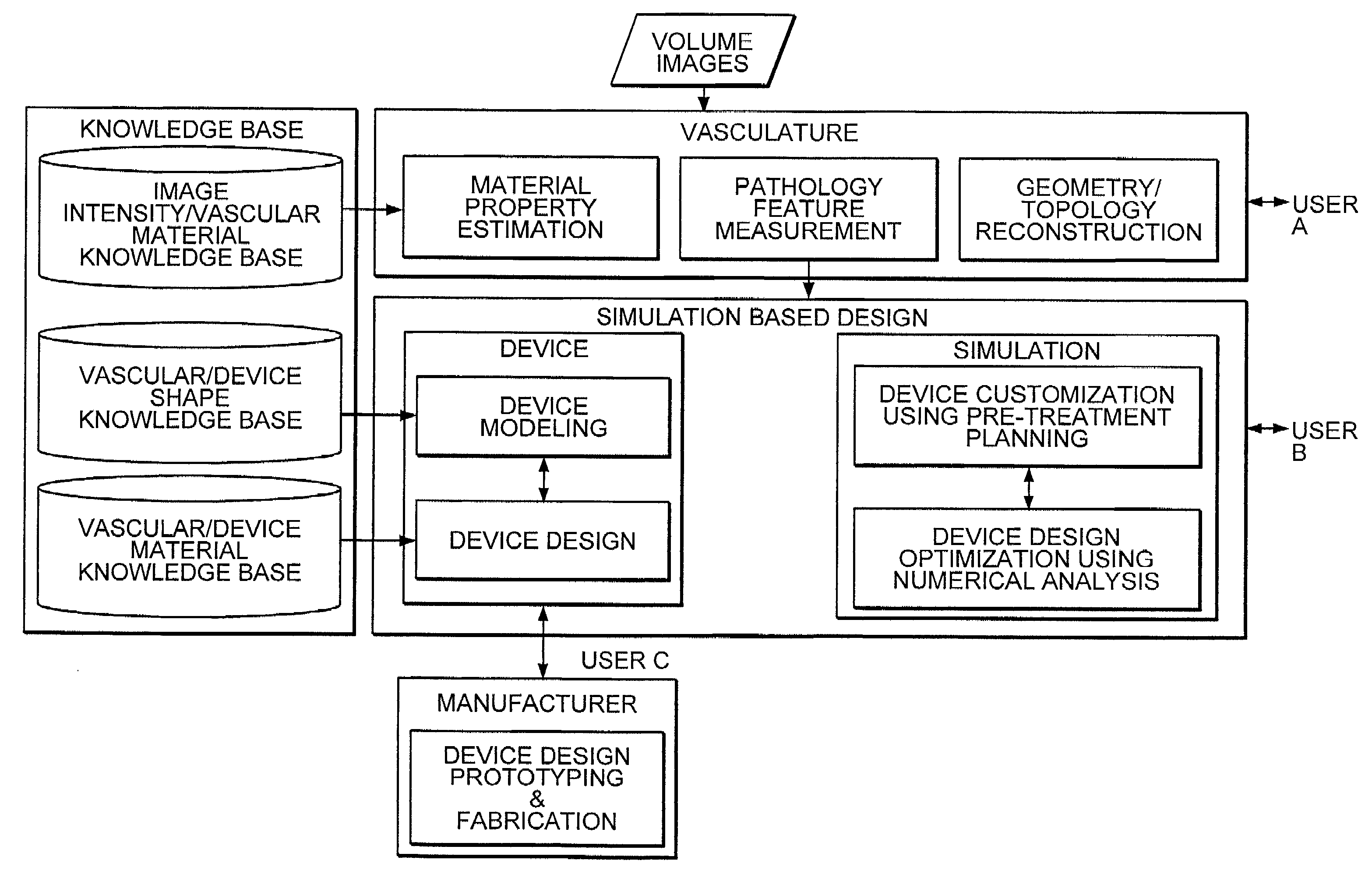
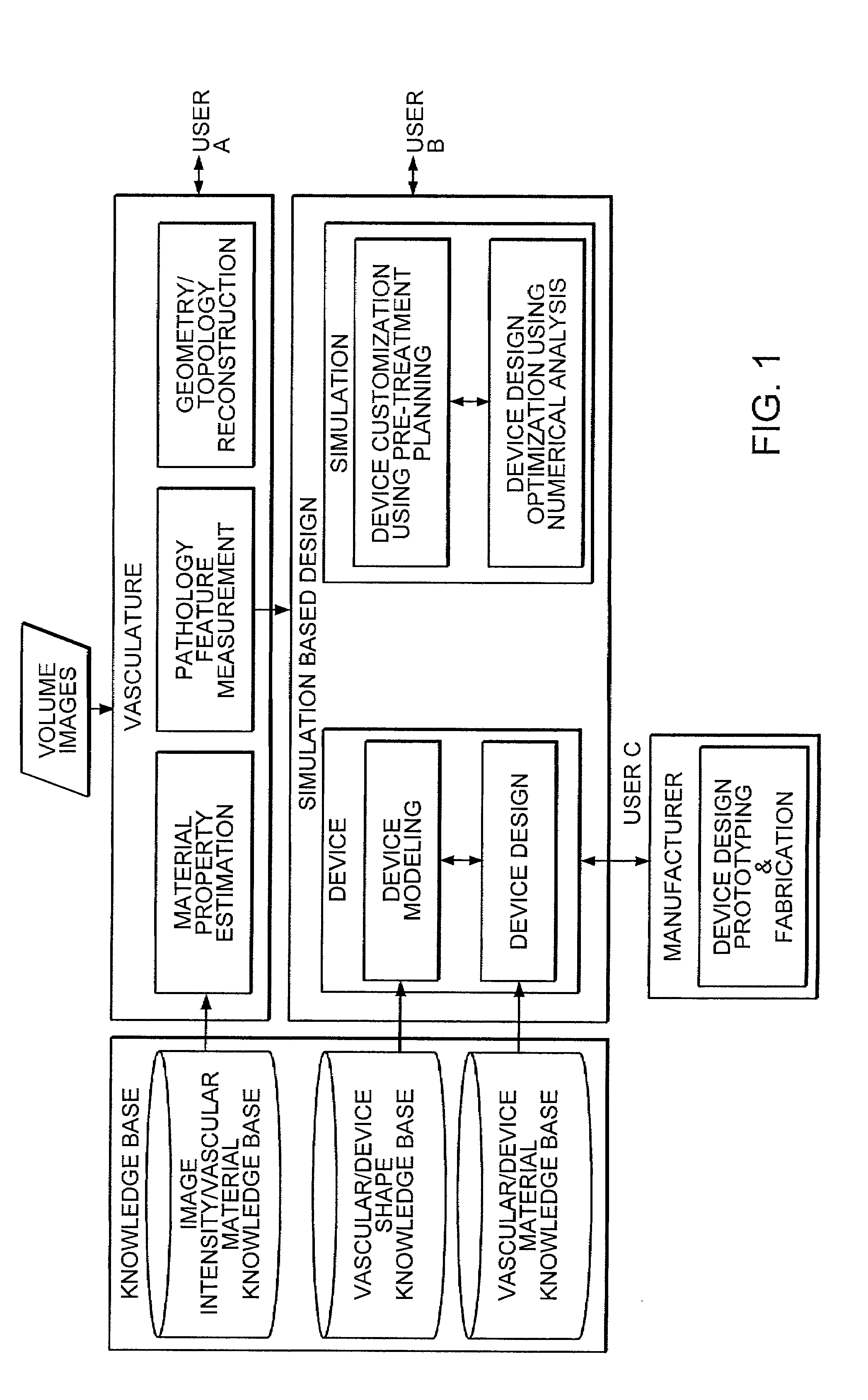
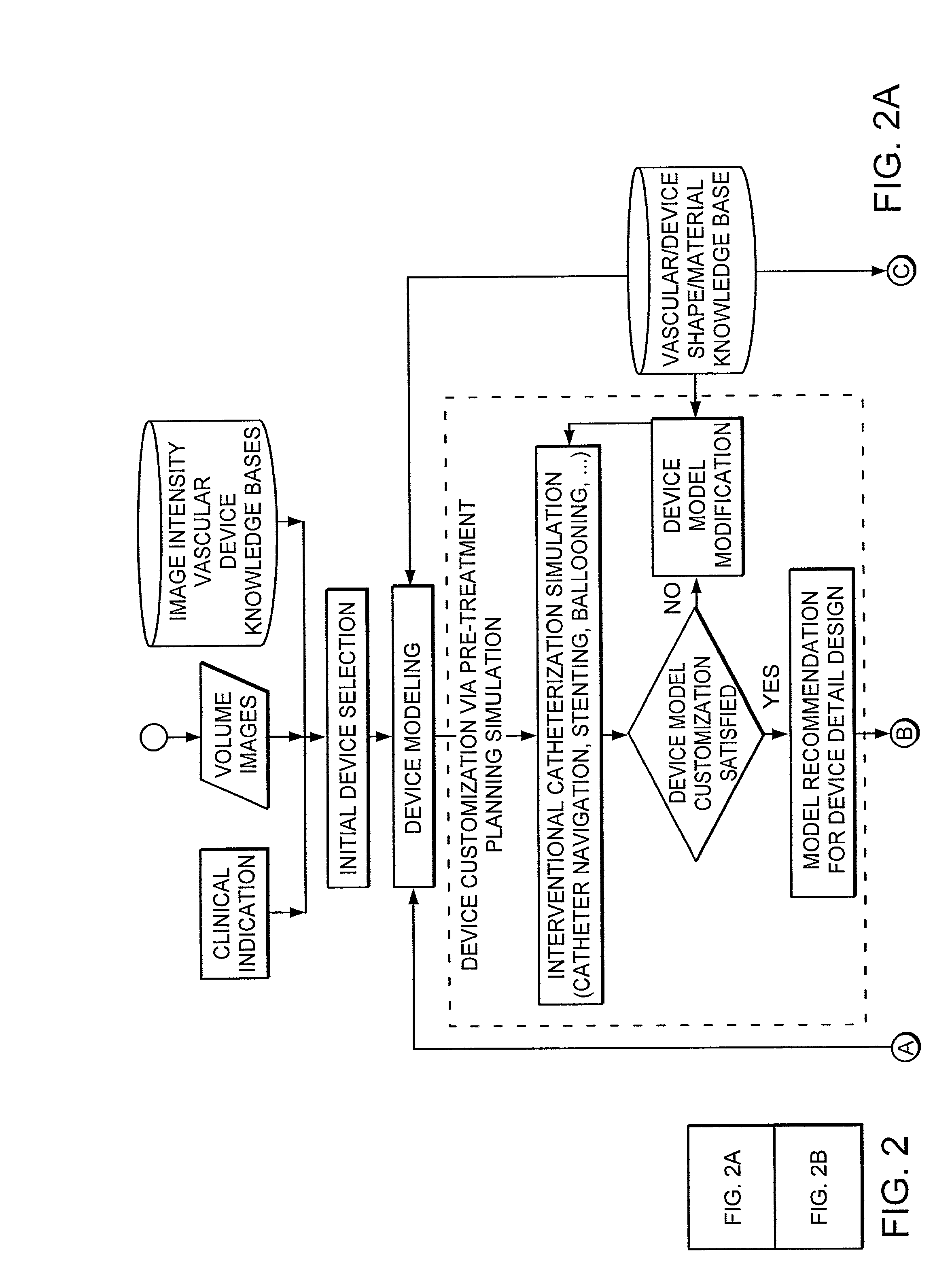
Simulation method for designing customized medical devices
The invention provides a system for virtually designing a medical device conformed for use with a specific patient. Using the system, a three-dimensional geometric model of a patient-specific body cavity or lumen is reconstructed from scanned volume images such as obtained x-rays, magnetic resonance imaging (MRI), computer tomography (CT), ultrasound (US), angiography or other imaging modalities. Knowledge of the physical properties of the cavity / lumen is obtained by determining the relationship between image density and the stiffness or elasticity of tissues in the body cavity or lumen and is used to model interactions between a simulated device and a simulated body cavity or lumen.
Owner:AGENCY FOR SCI TECH & RES +1
Radiation treatment plan making system and method
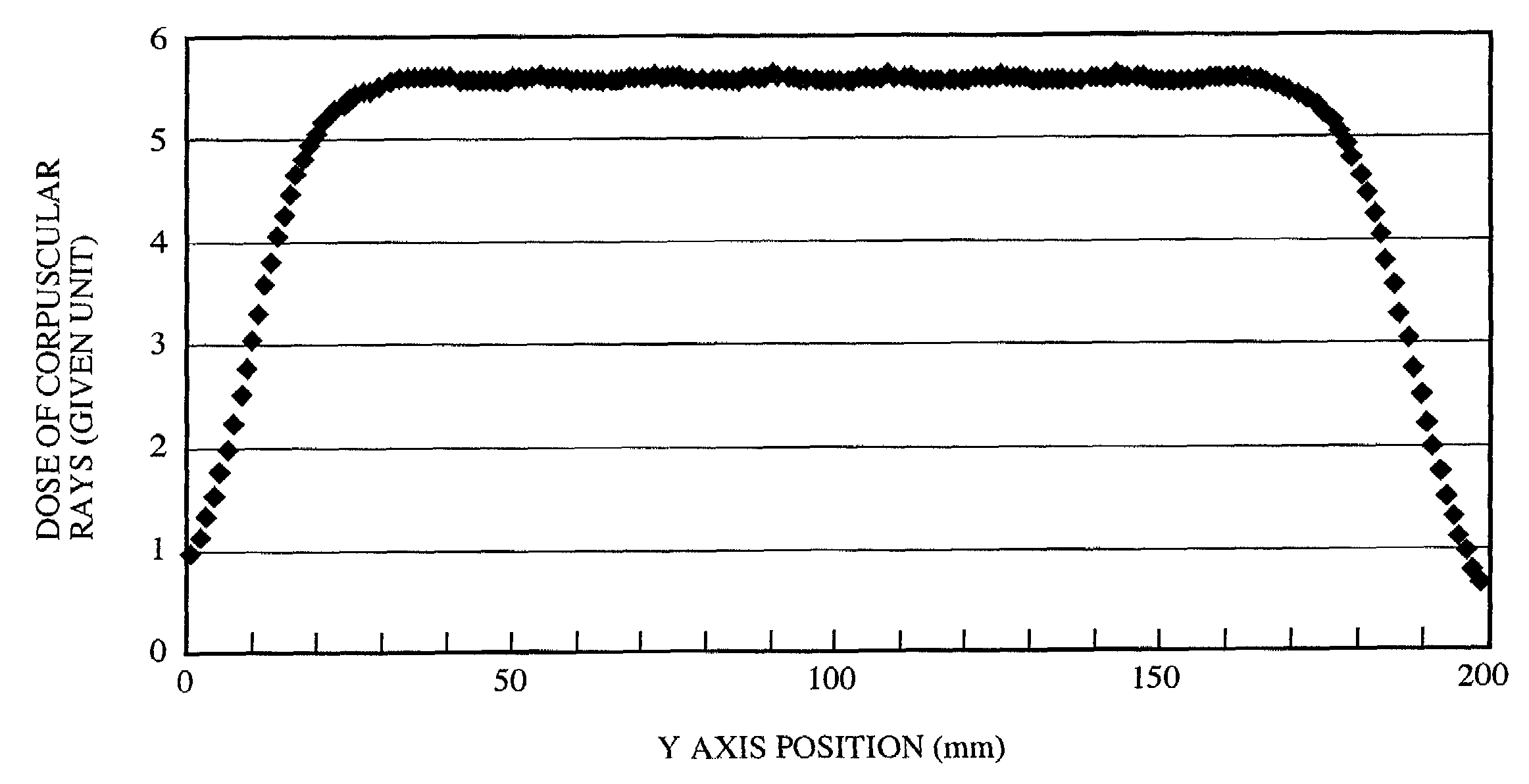
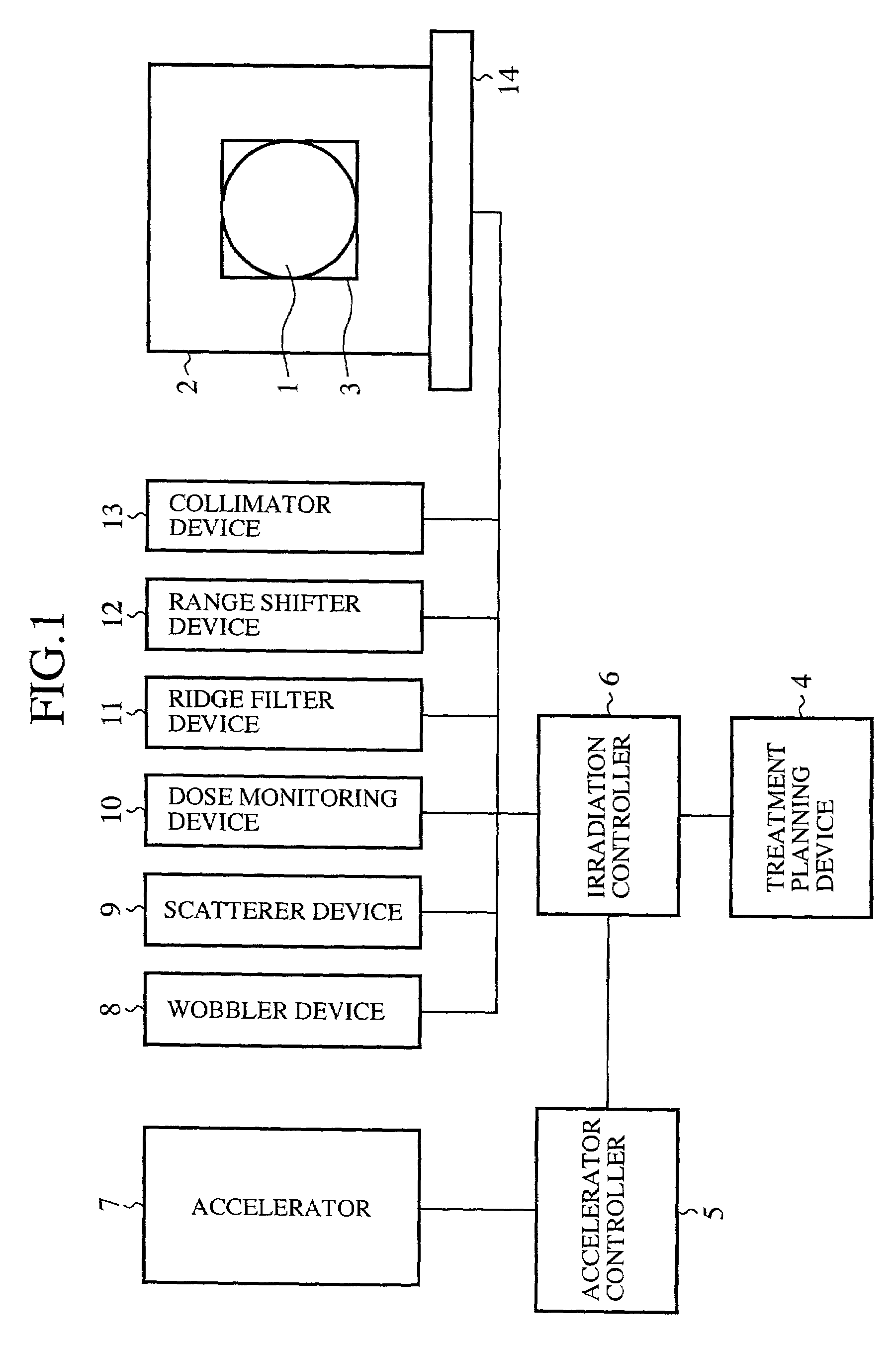
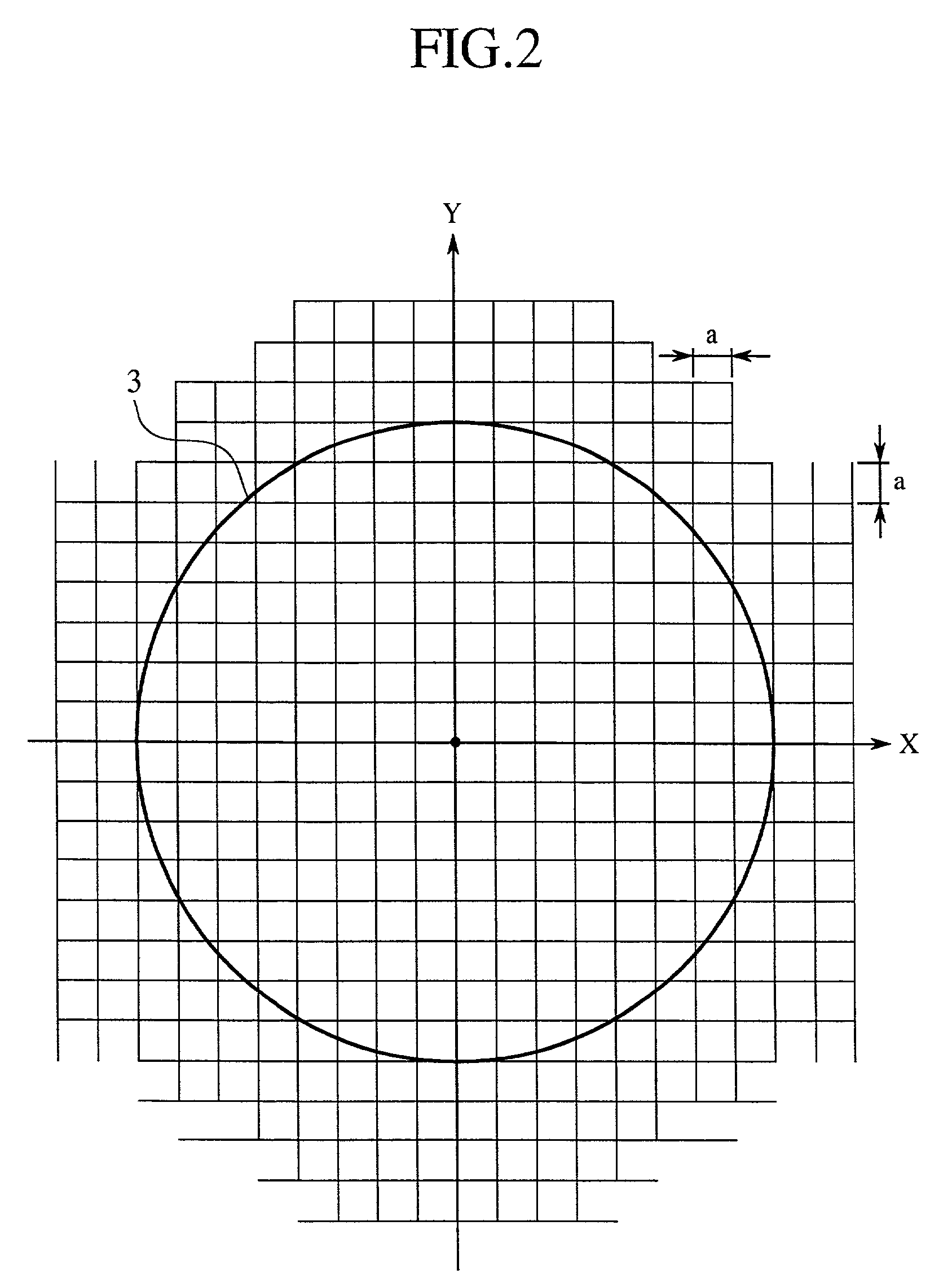
InactiveUS7054801B2Improve efficiencyImprove flatnessAnalogue computers for electric apparatusAnalogue computers for chemical processesParticle beamRadiation exposure
A radiation exposure region to be irradiated with particle beams and a peripheral region thereof are respectively divided into pluralities of exposure regions, radiation treatment simulation for applying particle beams according to the shape of each divided exposure region is performed, and a radiation treatment condition is obtained for causing the flatness of the radiation exposure region to be in a desired range, and a dose of particle beams applied to the unit exposure region of the peripheral region to be minimum. Thus, the problem of low efficiency of radiation is solved.
Owner:MITSUBISHI ELECTRIC CORP
Integrated circuit devices and methods and apparatuses for designing integrated circuit devices
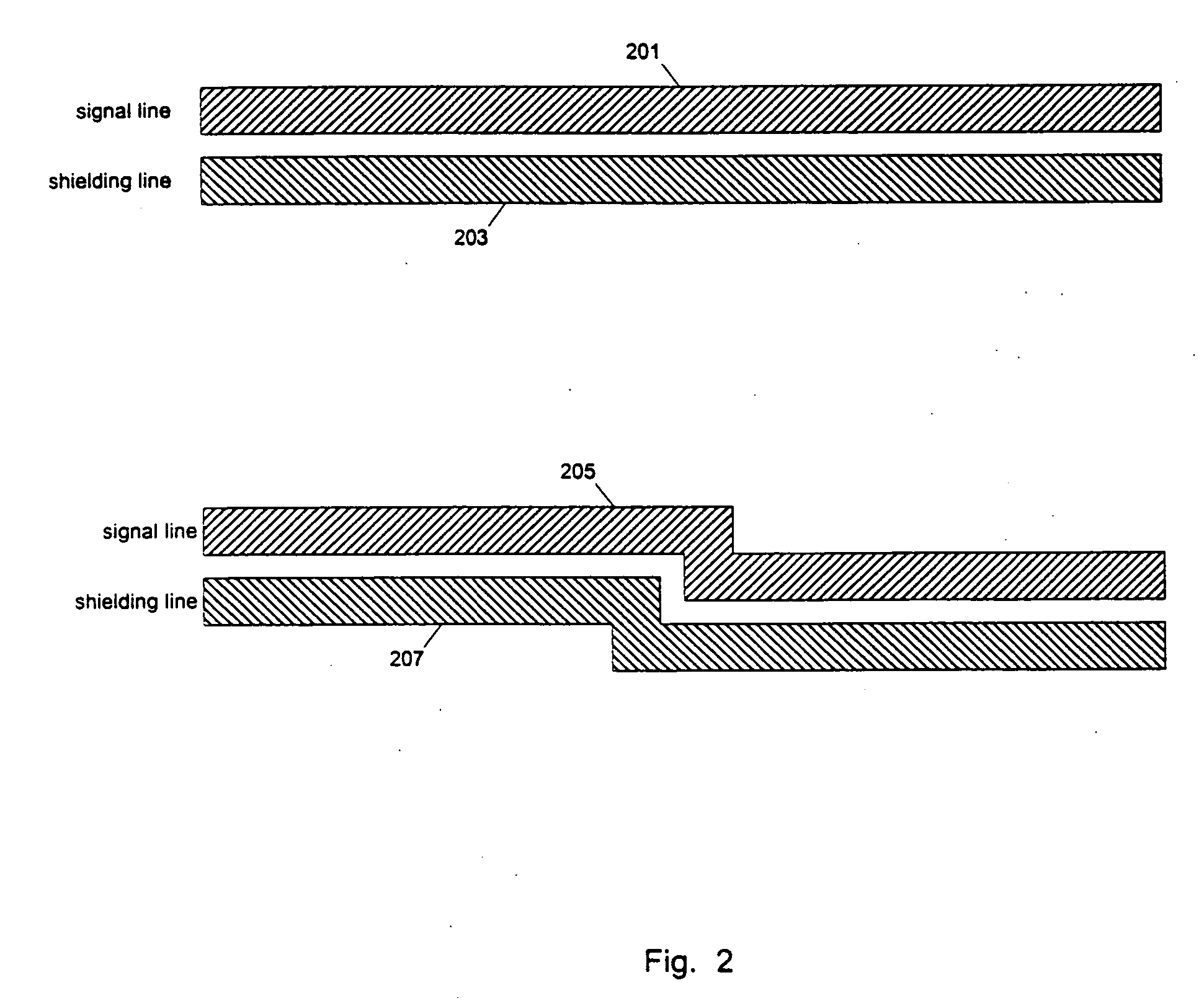
ActiveUS20060095872A1Reduce temperature changesSemiconductor/solid-state device detailsAnalogue computers for electric apparatusCapacitanceCapacitive coupling
Methods and apparatuses to design an Integrated Circuit (IC) with a shielding of wires. In at least one embodiment, a shielding mesh of at least two reference voltages (e.g., power and ground) is used to reduce both the capacitive coupling and the inductive coupling in routed signal wires in IC chips. In some embodiments, a type of shielding mesh (e.g., a shielding mesh with a window surrounded by a power ring, or a window with a parser set of shielding wires) is selected to make more routing area available in locally congested areas. In other embodiments, the shielding mesh is used to create or add bypass capacitance. Other embodiments are also disclosed.
Owner:SYNOPSYS INC
Common shared memory in a verification system
InactiveUS20110307233A1LessSimilar performance levelAnalogue computers for electric apparatusCAD circuit designCoded elementWorkstation
The debug system described in this patent specification provides a system that generates hardware elements from normally non-synthesizable code elements for placement on an FPGA device. This particular FPGA device is called a Behavior Processor. This Behavior Processor executes in hardware those code constructs that were previously executed in software. When some condition is satisfied (e.g., If . . . then . . . else loop) which requires some intervention by the workstation or the software model, the Behavior Processor works with an Xtrigger device to send a callback signal to the workstation for immediate response.
Owner:CADENCE DESIGN SYST INC
Optimum buffer placement for noise avoidance
InactiveUS6117182AEasy to insertAnalogue computers for electric apparatusCAD circuit designIntegrated circuitElectrical conductor
A method for optimal insertion of buffers into an integrated circuit design. A model representative of a plurality of circuits is created where each circuit has a receiving node coupled to a conductor and a source. A receiving node is selected from the modeled plurality of circuits and circuit noise is calculated for the selected receiving node utilizing the circuit model. If the calculated circuit noise exceeds an acceptable value an optimum distance is computed from the receiving node on the conductor for buffer insertion. In a multi-sink circuit merging of the noise calculation for the two receiving circuits must be accomplished. If an intersection of conductors exists between the receiving node and the optimum distance a set of candidate buffer locations is generated. The method then prunes inferior solutions to provide an optimal insertion of buffers.
Owner:GLOBALFOUNDRIES INC
Distributed model compilation
ActiveUS7509244B1Shorten the timePromote generationAnalogue computers for electric apparatusComputation using non-denominational number representationGraphicsParallel computing
Methods and systems are provided for partitioning and distributing the model processing of a graphical model to provide an executable form of the graphical model. The methods and systems determine tasks of the model processing that can be processed separately and concurrently from other tasks. A distribution scheme for distributing the model processing tasks is determined that considers the characteristics of the model processing tasks in view of the characteristics of available computing resources. Variations of partitioning and distributing the model processing tasks can be determined to provide for distributed processing in an optimized or desired manner. The results of the distributed processing of the model processing tasks are obtained and combined to provide an executable form for the graphical model.
Owner:THE MATHWORKS INC
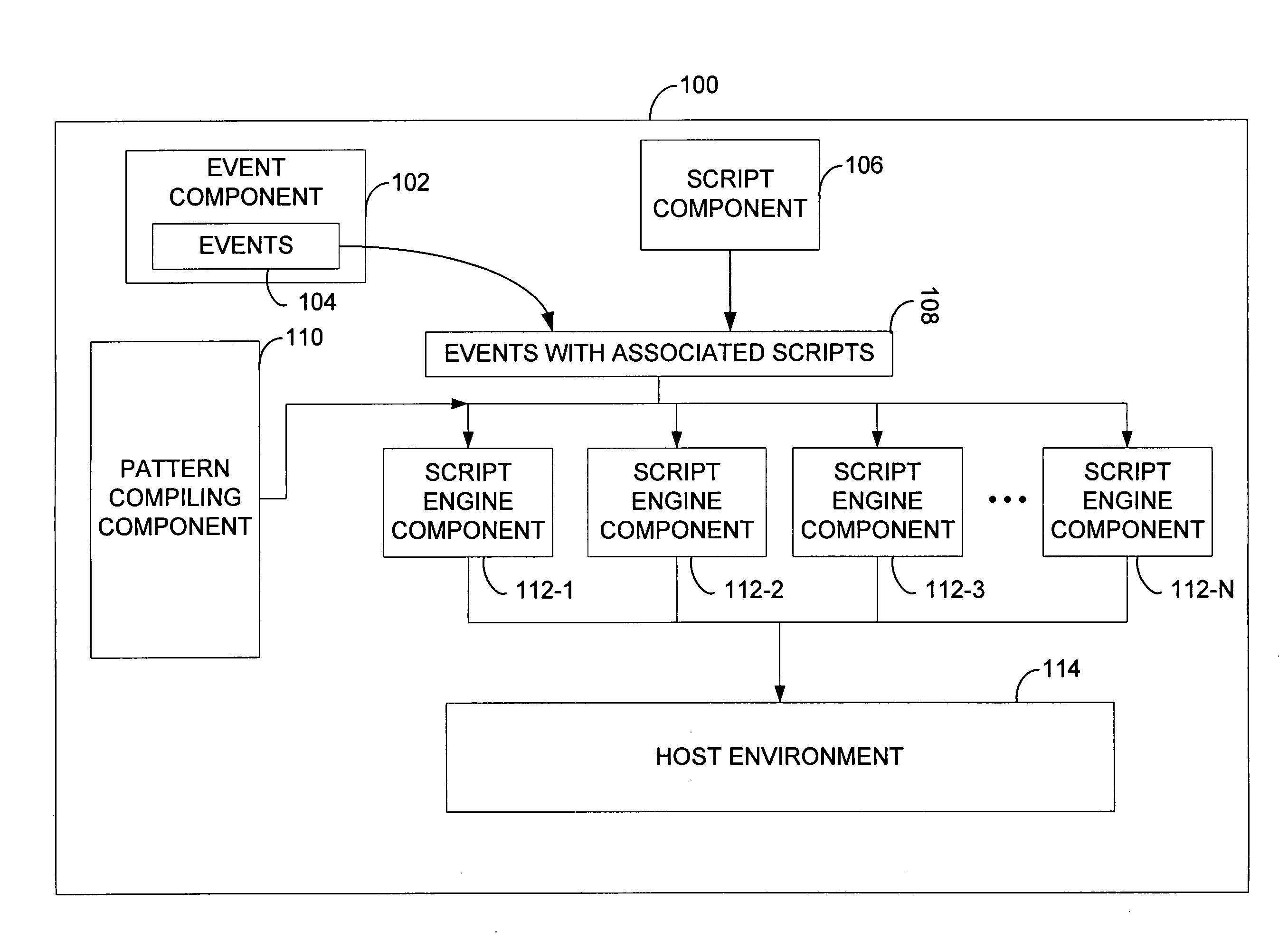
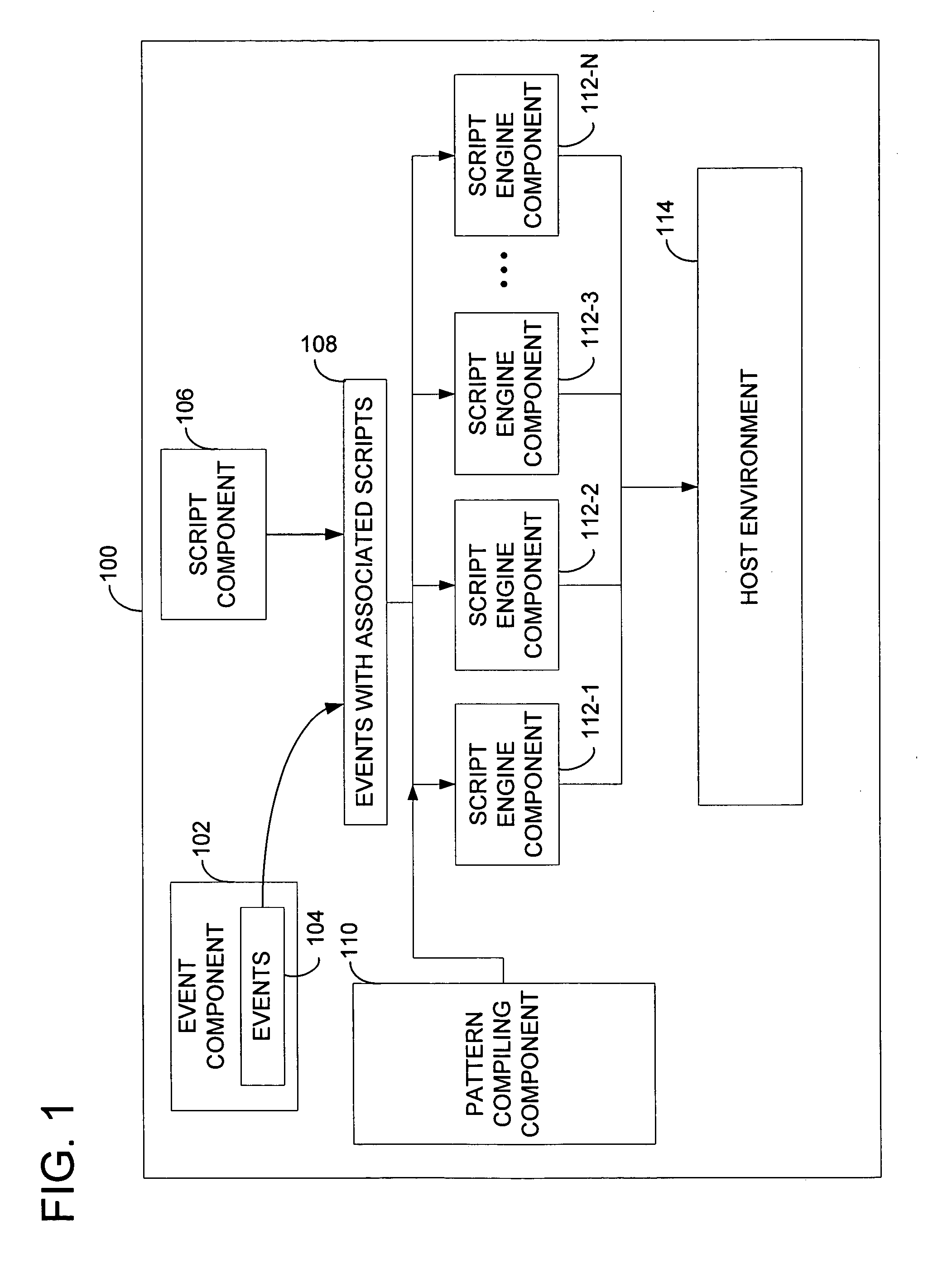
Recognizing event patterns from event streams
System and method for identifying a pattern. A method of the invention compiles a pattern description where the pattern description defines a series of a first event and a second event relating to the first event. The first event is received and includes a type parameter data, a time parameter data, and a substance parameter data. A system of the invention includes a script component for associating or attaching a first script to the first event. The first script defines the type, time, and substance parameters of the second event as a function of the parameters of the first event according to the pattern description. A pattern recognition engine executes the attached first script and the executed script identifies the second event and thereby identifies the pattern.
Owner:MICROSOFT TECH LICENSING LLC
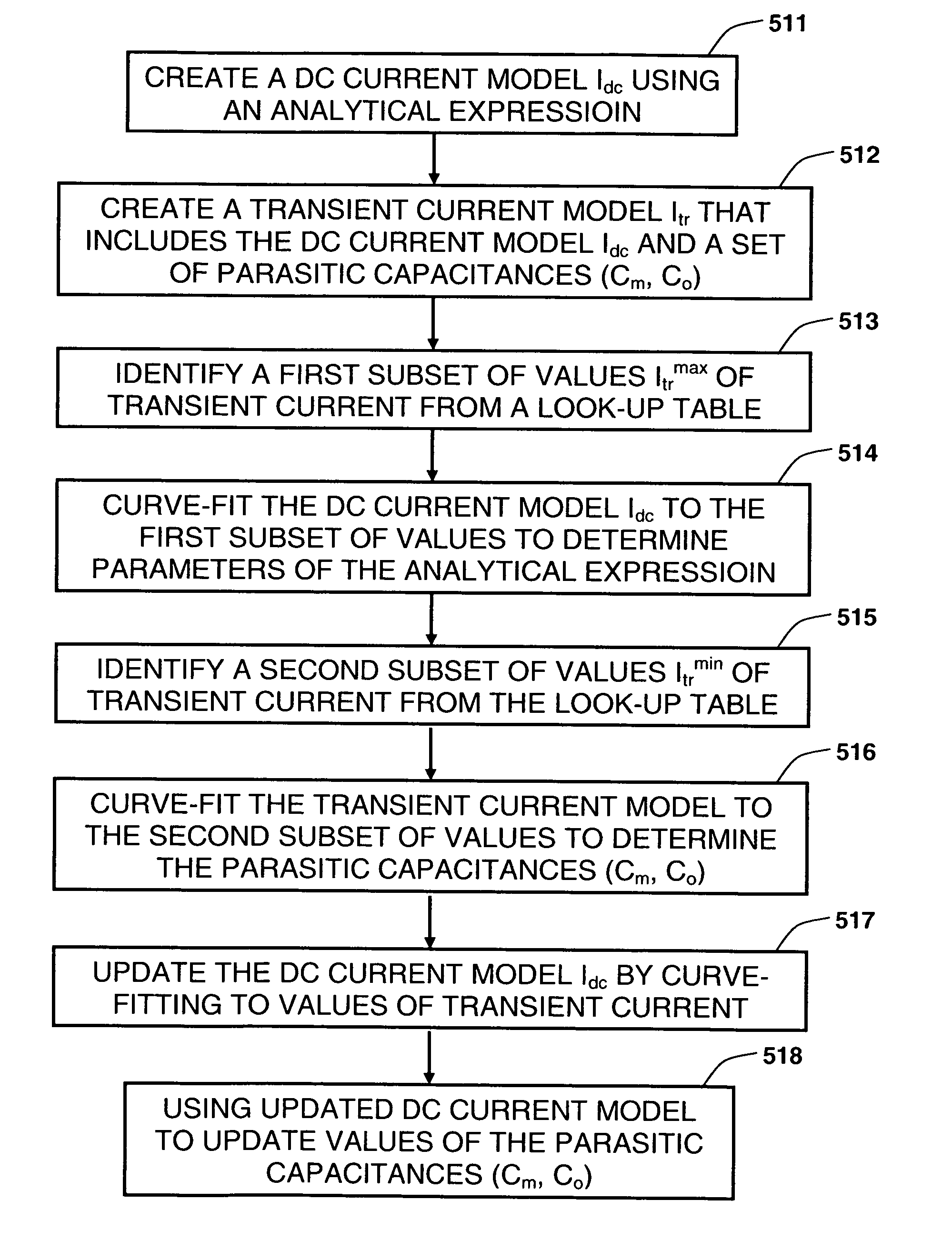
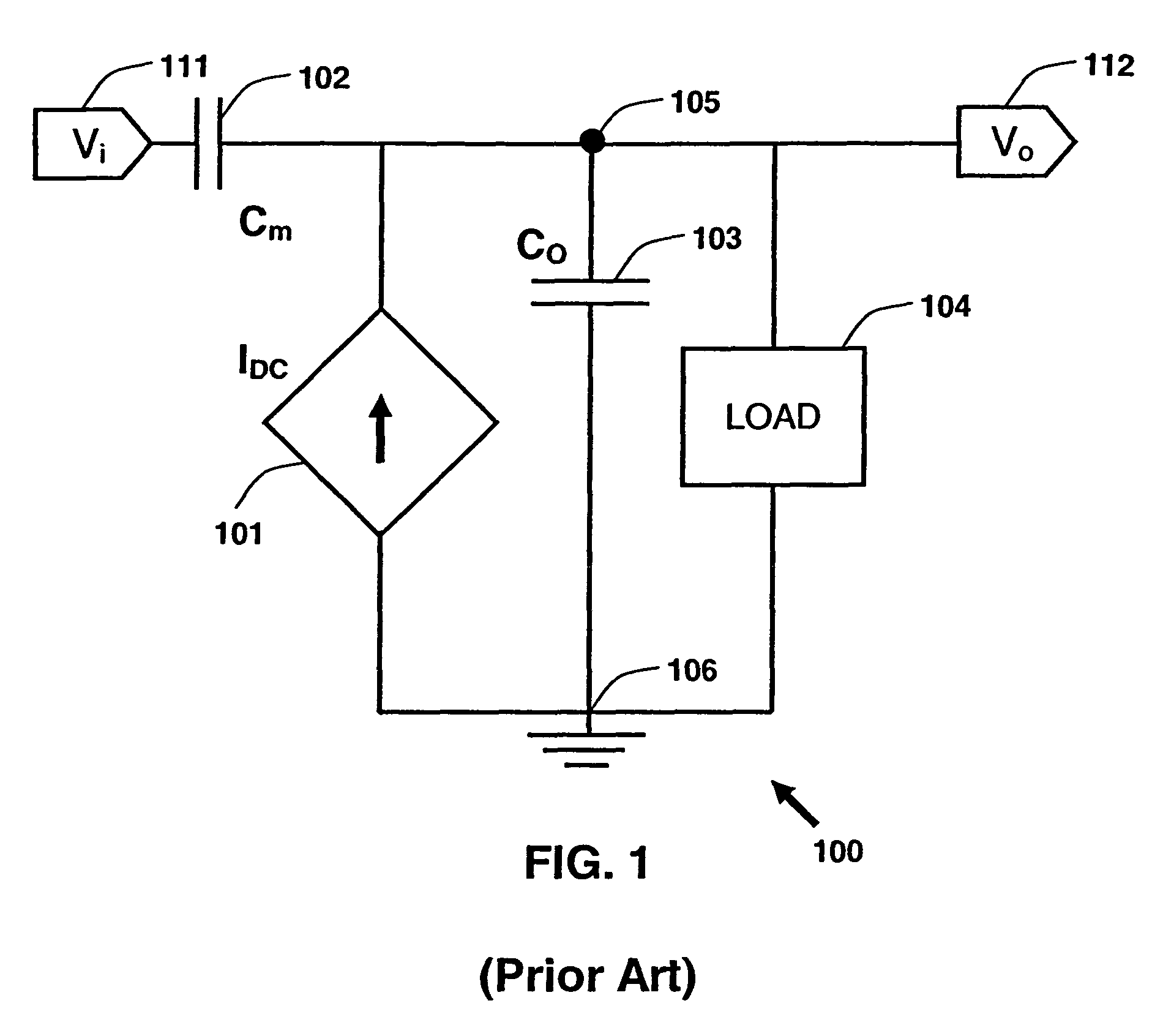
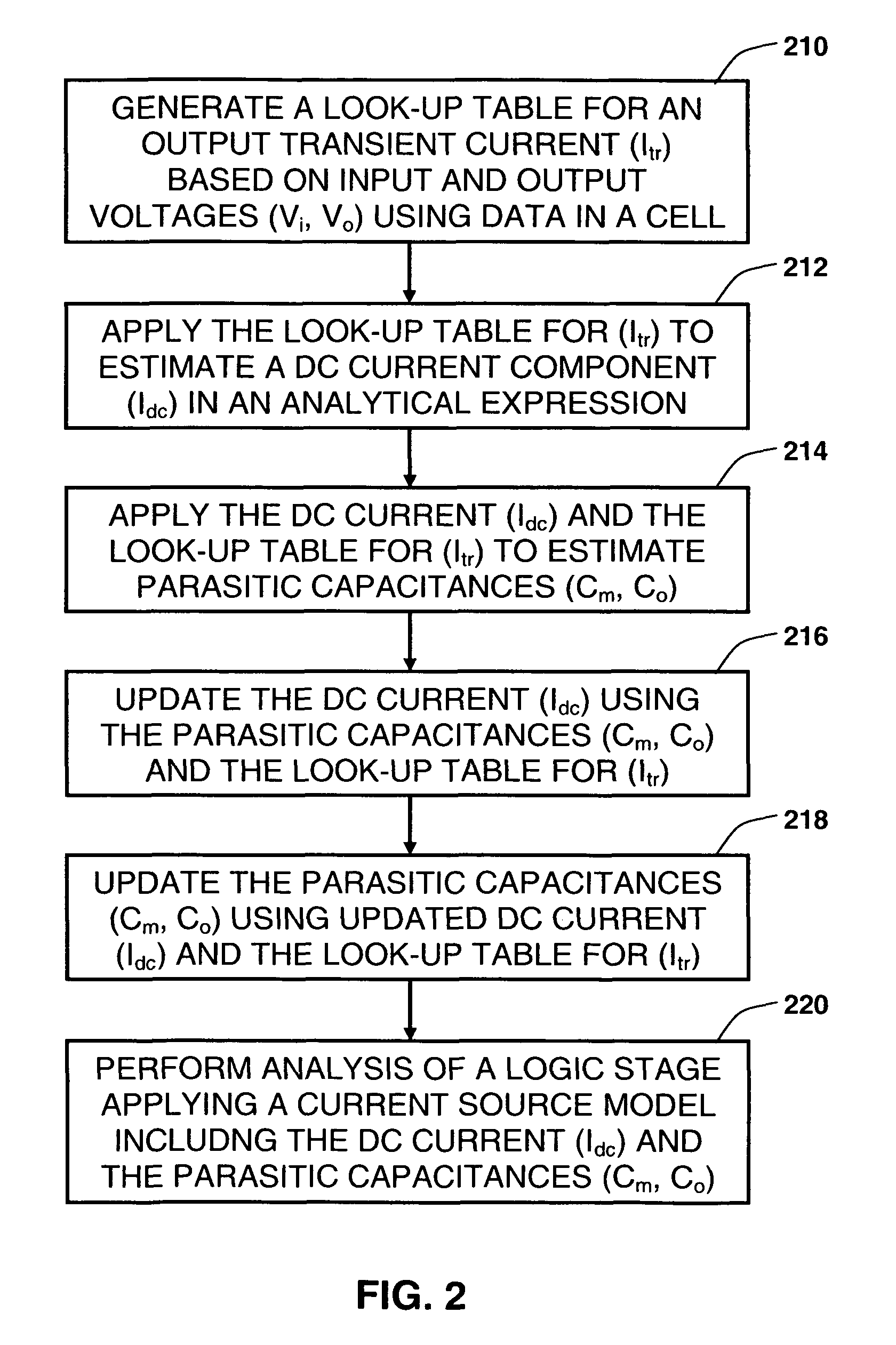
Synthesizing current source driver model for analysis of cell characteristics
InactiveUS7761275B2Analogue computers for electric apparatusCAD circuit designParasitic capacitanceEngineering
A method for performing an analysis of at least one logic stage in a netlist, which include one or more drivers, is provided. The method includes operations of generating at least one look-up table for an output transient current to be based on values of input and output voltages using data available from a cell library; synthesizing analytically at least one current source model, which includes a DC component and a plurality of parasitic capacitances, using the look-up table; simulating the logic stage using the current source model to model the drivers; and obtaining characteristics of the simulated logic stage. A system and a machine-readable medium for performing the method are also provided.
Owner:INT BUSINESS MASCH CORP
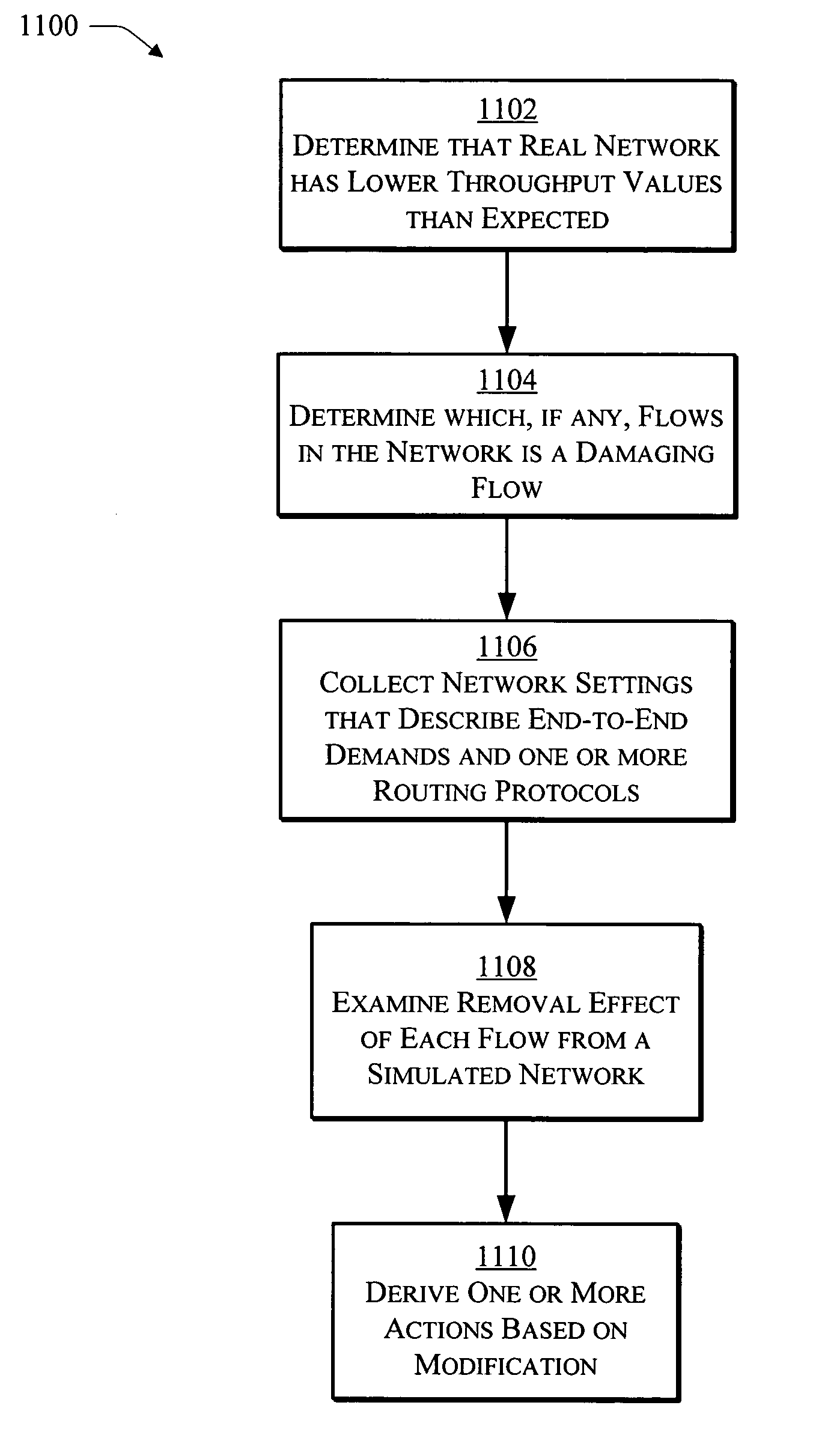
What-if analysis for network diagnostics
InactiveUS20050169186A1Improve network performanceProvide feedbackError preventionFrequency-division multiplex detailsNetwork simulationNetwork performance
A network troubleshooting framework is described. In an implementation, a method includes generating a first estimation of network performance by a simulator based on network settings obtained from a network, estimating the new performance under an alternative setting by providing the alternative setting to the network simulation and observing the simulation output, repeating the procedure for other alternative settings, and suggesting the alternative setting that improves network performance.
Owner:MICROSOFT TECH LICENSING LLC
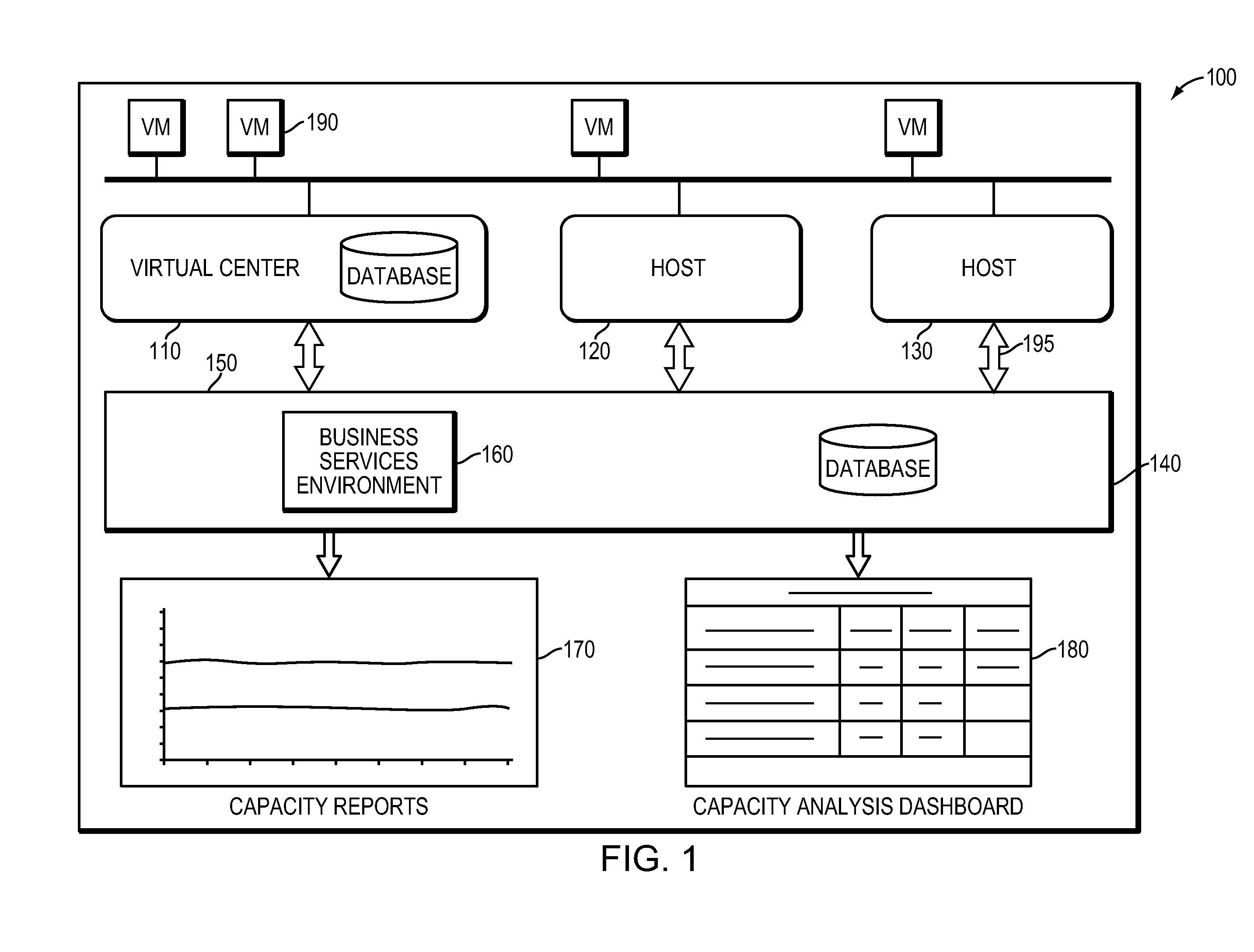
Systems and methods for analyzing performance of virtual environments
ActiveUS20120284713A1Effective and efficient diagnosisDigital data processing detailsError detection/correctionMonitoring systemSimulation
Intelligent monitoring systems and methods for virtual environments are disclosed that understand various components of a virtual infrastructure and how the components interact to provide improved performance analysis to users. In certain examples, a monitoring system assesses the performance of virtual machine(s) in the context of the overall performance of the physical server(s) and the environment in which the virtual machine(s) are running. For instance, the monitoring system can track performance metrics over a determined period of time to view changes to the allocation of resources to virtual machines and their location(s) on physical platforms. Moreover, monitoring systems can utilize past performance information from separate virtual environments to project a performance impact resulting from the migration of a virtual machine from one physical platform to another.
Owner:QUEST SOFTWARE INC
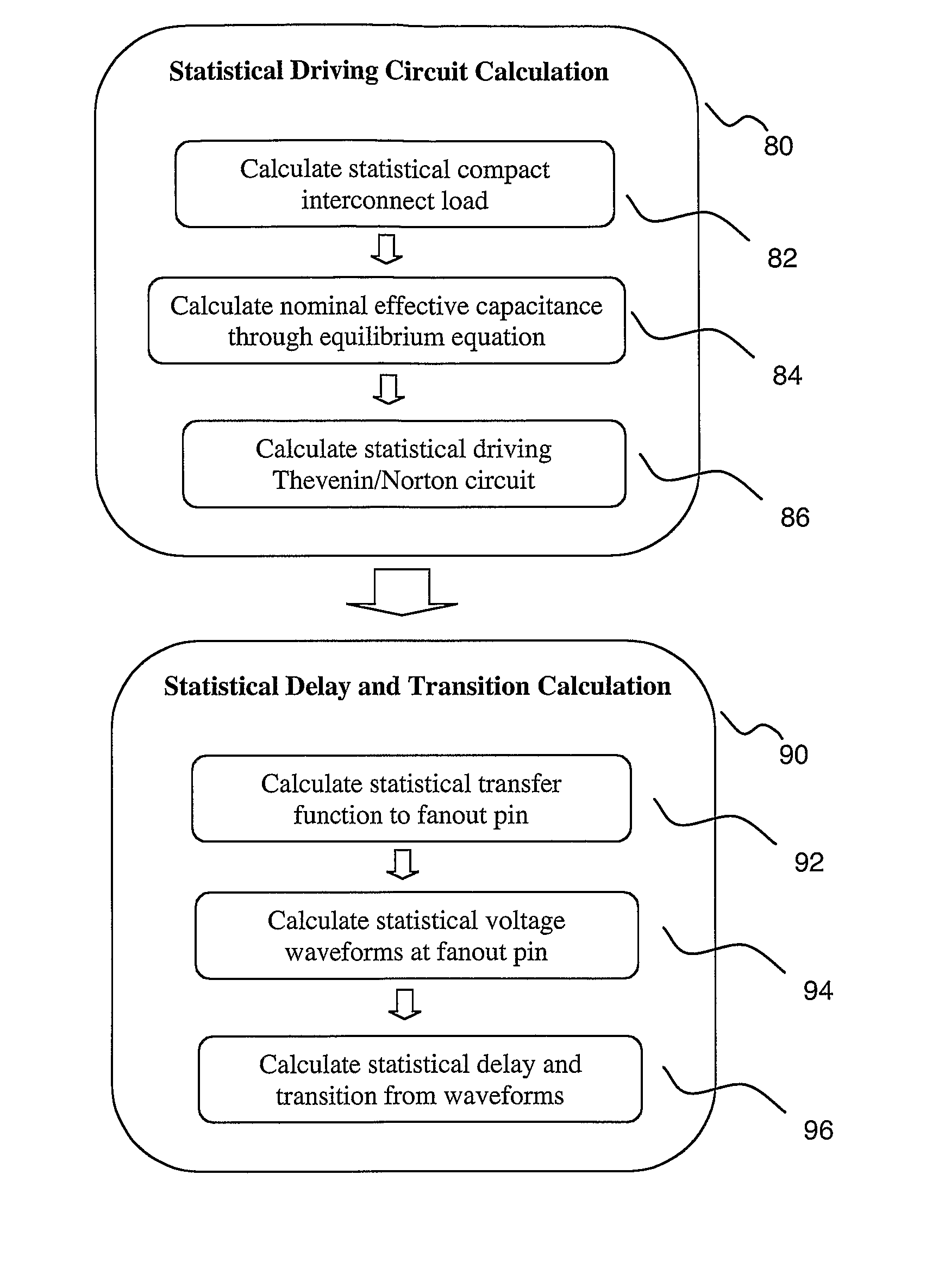
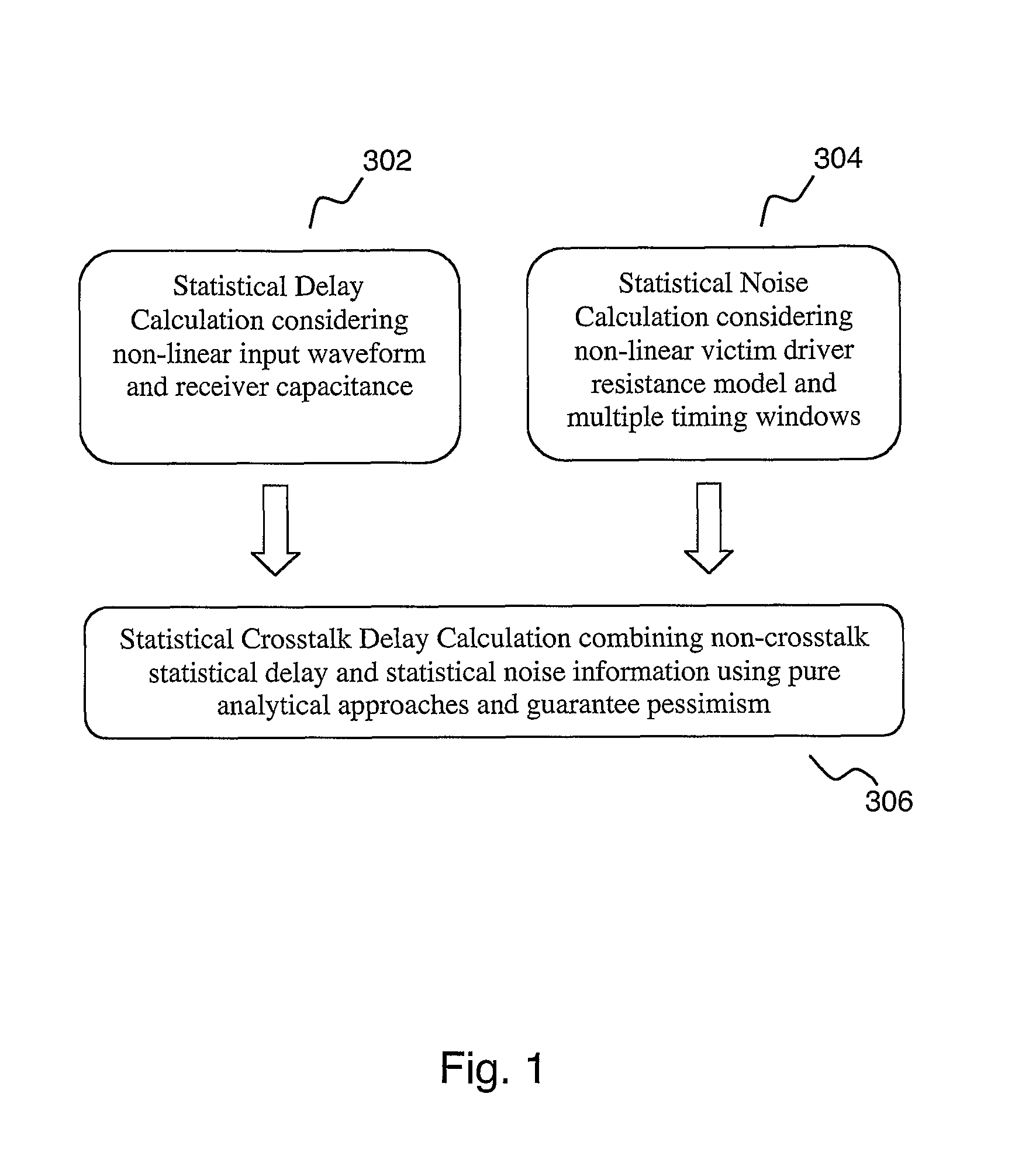
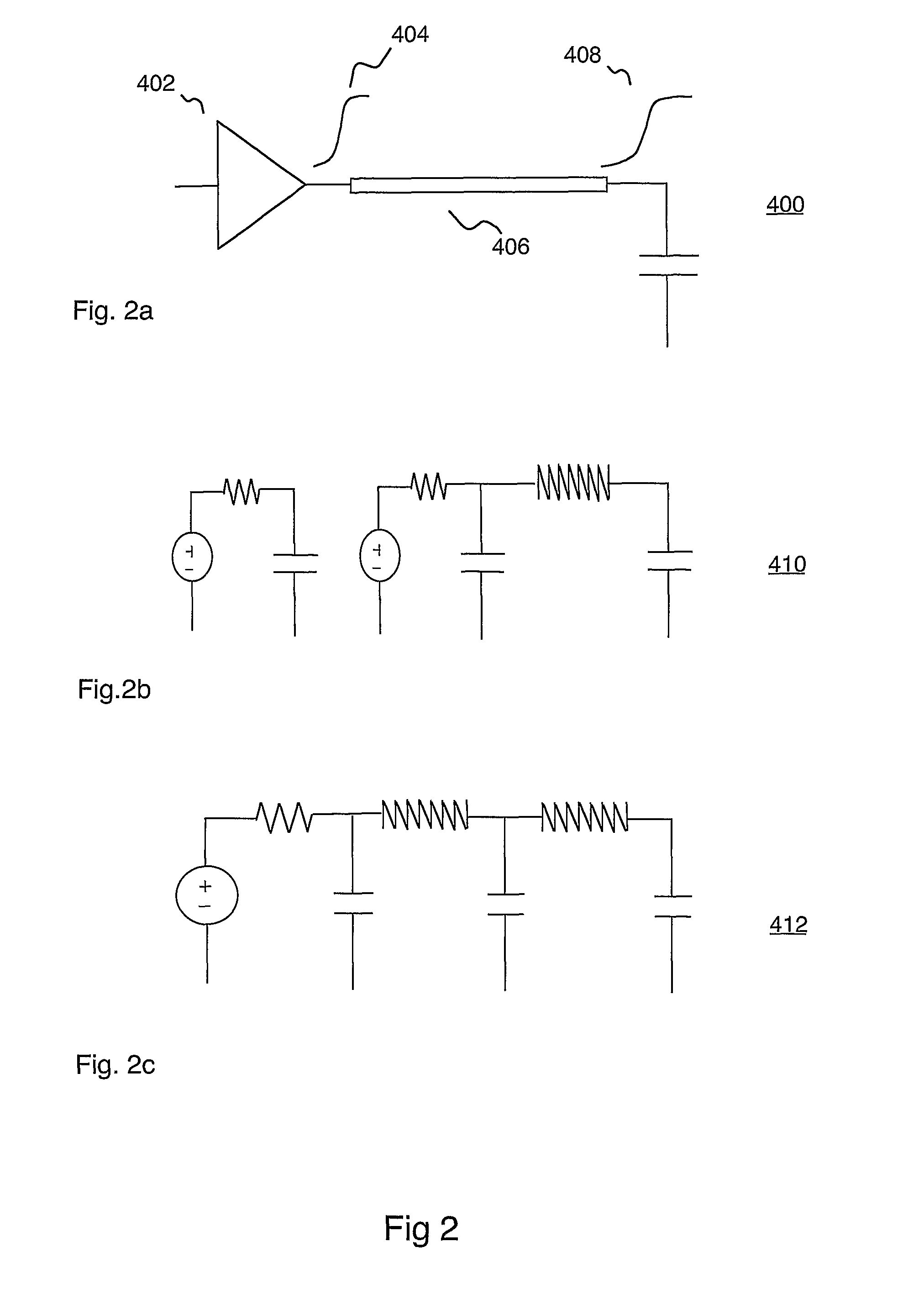
Statistical delay and noise calculation considering cell and interconnect variations
ActiveUS7890915B2Efficiently delayEfficiently sensitivityAnalogue computers for electric apparatusComputation using non-denominational number representationNumerical stabilityComputer science
The electrical circuit timing method provides accurate nominal delay together with the delay sensitivities with respect to different circuit elements {e.g., cells, interconnects, etc.) and variational parameters (e.g., process variations; environmental variations). All the sensitivity computations are based on closed-form formulas; as a consequence, the method provides rapidly and at low cost high accuracy and high numerical stability.
Owner:SYNOPSYS INC
Method and apparatus for generating an application for an automation control system
InactiveUS6643555B1Analogue computers for electric apparatusMultiprogramming arrangementsControl systemPhysical model
An apparatus and method of generating an application for a control system. A control process is defined by a physical model and a topological model. An application generator utilizes the physical and topological models to generate an application for the control system.
Owner:SCHNEIDER AUTOMATION INC
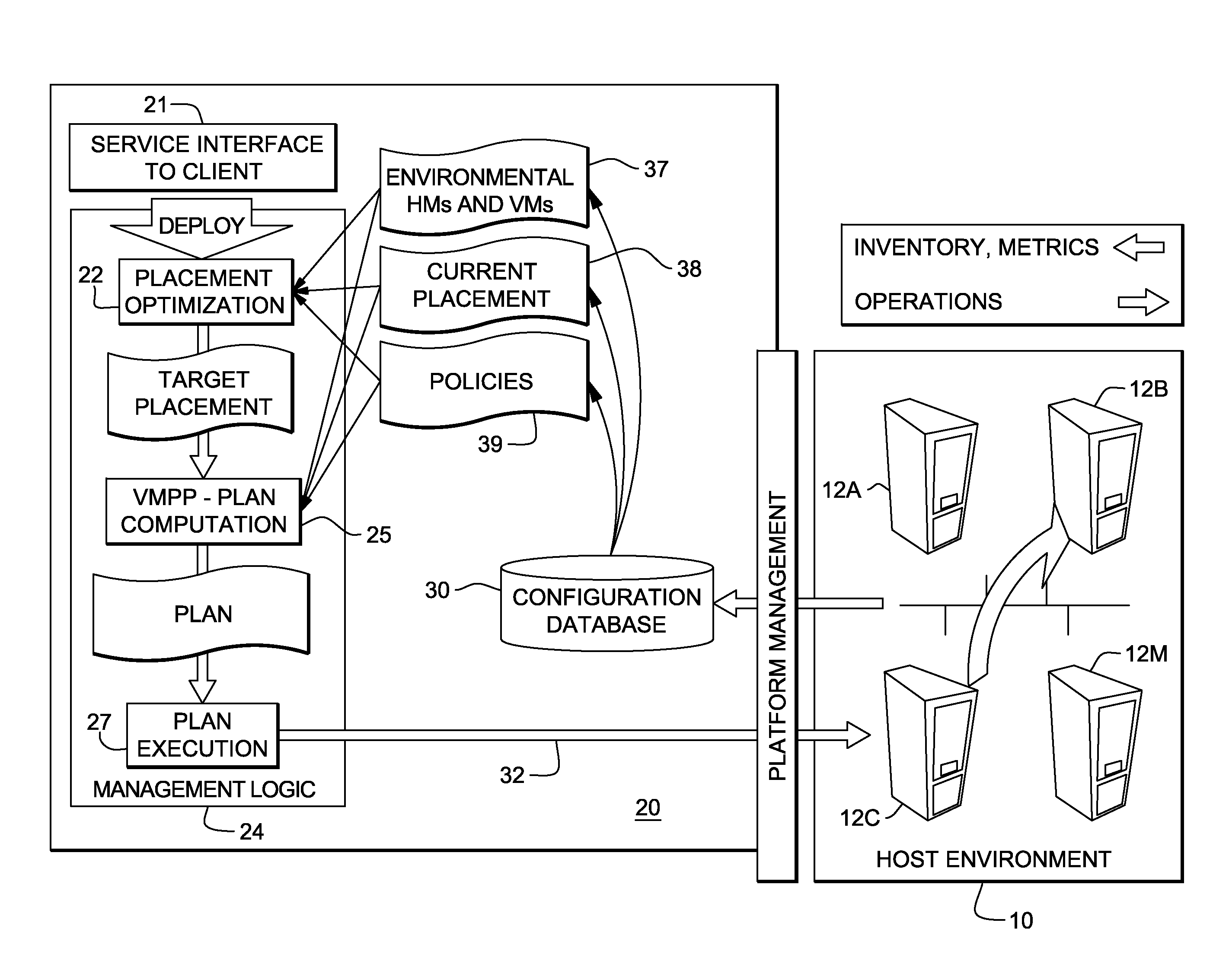
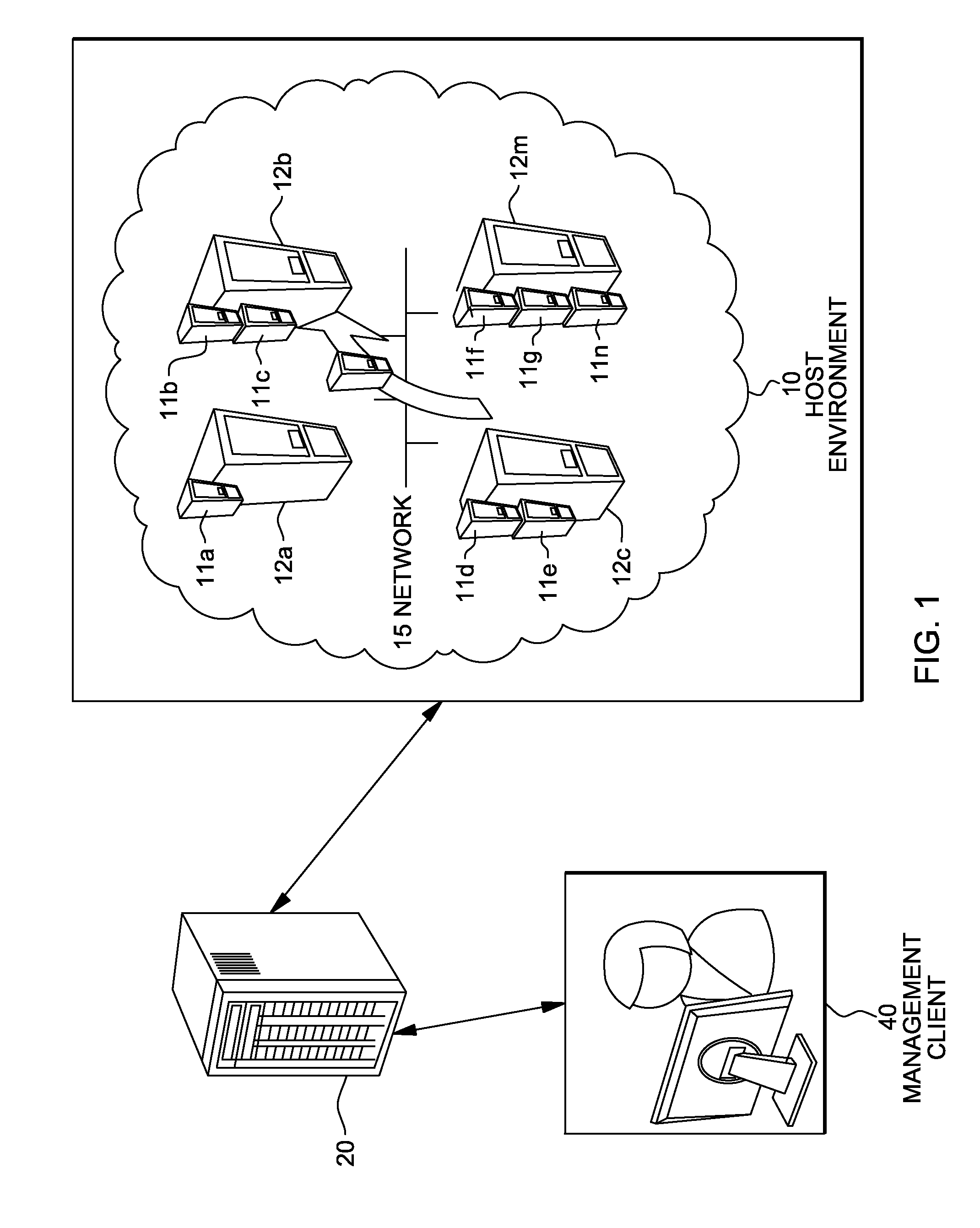
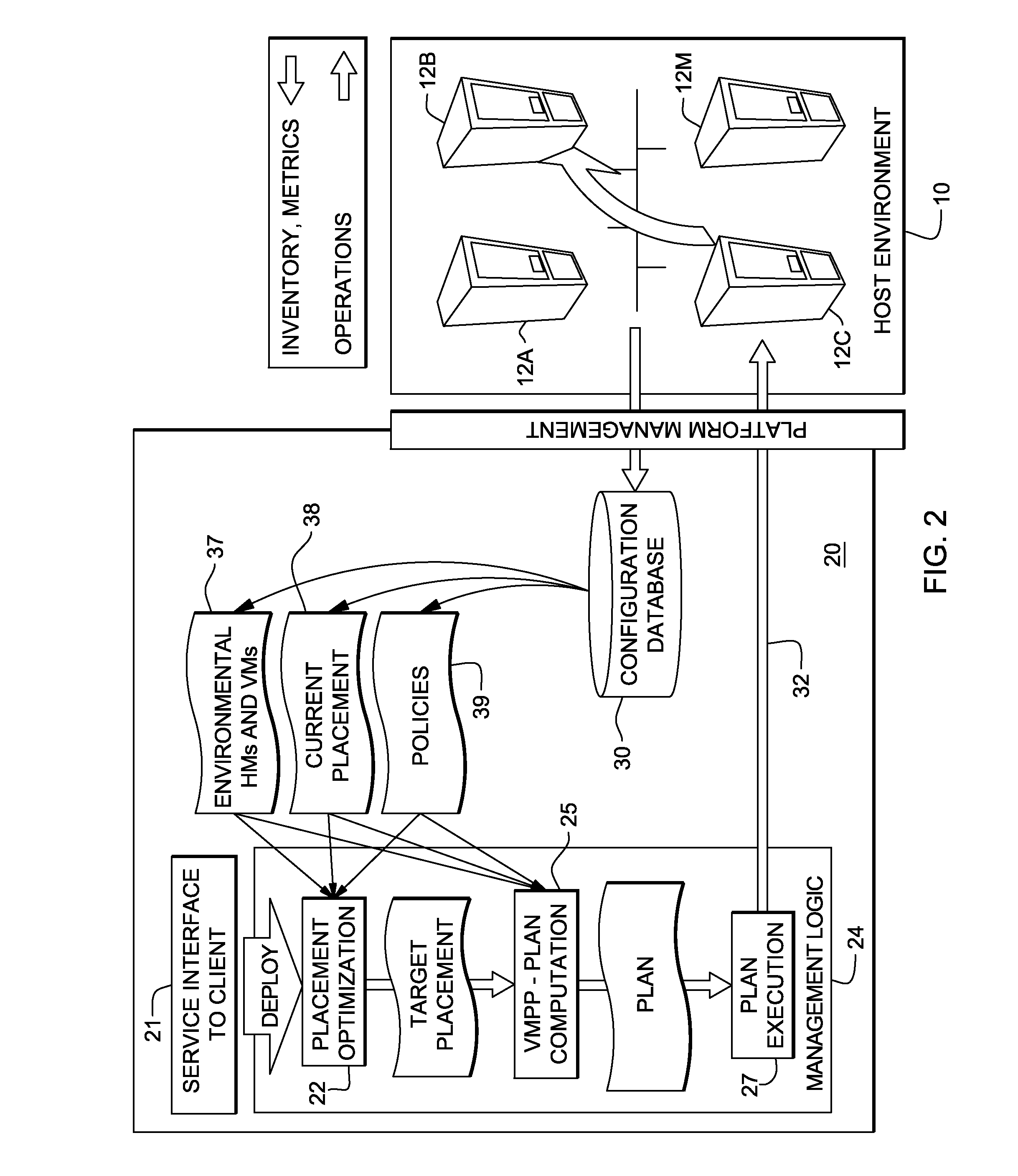
System and method for deploying virtual machines in a computing environment
InactiveUS20100250744A1Cycle brokenEffect is temporaryDigital data processing detailsAnalogue computers for electric apparatusGraphicsDirected graph
A system and method for planning placement of virtual machines VMs in a computing environment comprising a set of hosting machines HM. The method includes constructing a bipartite directed graph-based model that represents both a current and a target placement states, both including virtual machine nodes v in VM and nodes h in HM. Using a technique of graph pruning, the method iteratively generates a plan for achieving a desired target placement starting from the current placement without temporarily violating any policy or resource constraint. The application of the pruning algorithm to VM deployment automation necessarily defines a new model. The methodology employed safely manages concurrent changes in a datacenter, so that the environment can adjust faster to changing constraints. Furthermore, the present invention allows detection of migration cycles, caused by deadlocked combinations of capacity and policy constraints, and resolving them.
Owner:IBM CORP
Popular searches
Load forecast in ac network Analogue computers for control systems Buying/selling/leasing transactions Material dimension control Complex mathematical operations Power network operation systems integration Energy storage Power supply for data processing Ac network load balancing Control using feedback
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com