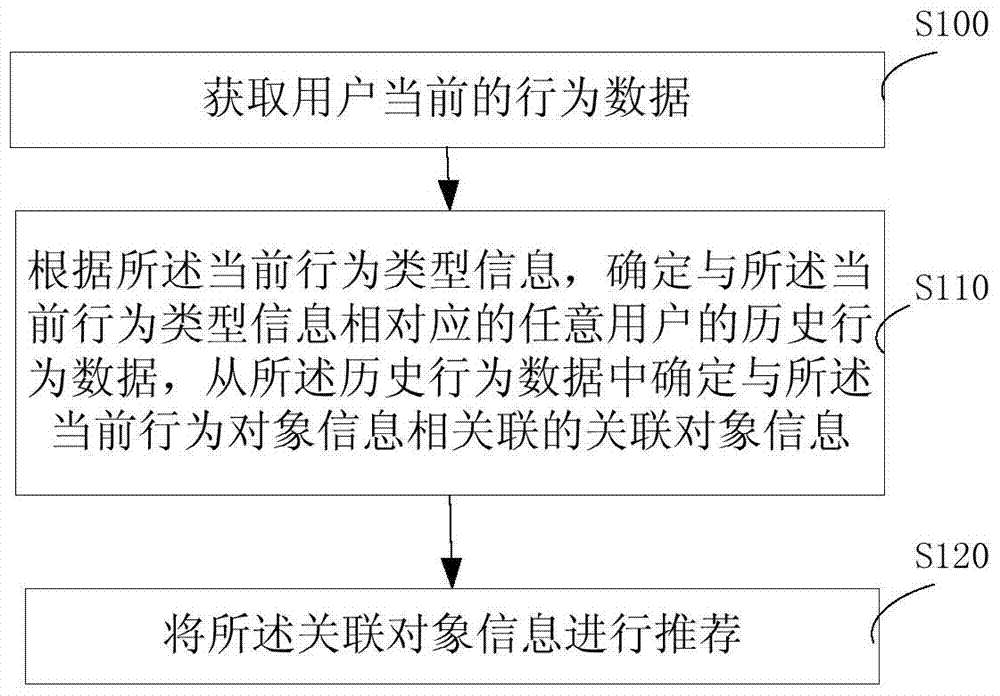
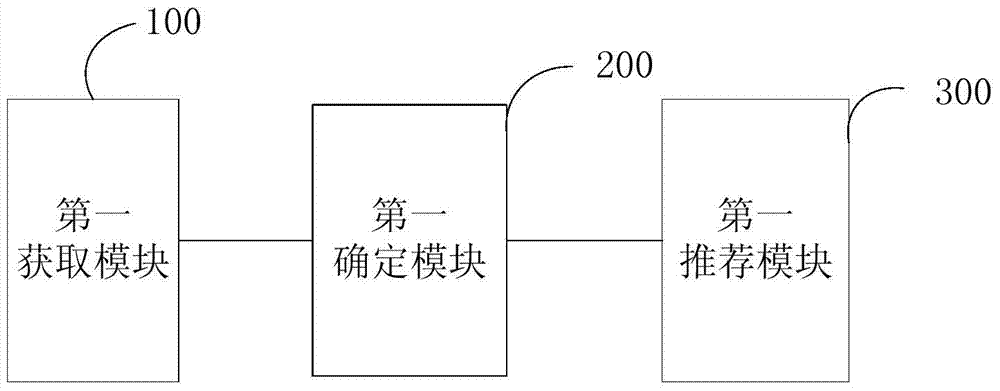
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
212 results about "Behavior type" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Two Basic Kinds of Behavior. There are only two kinds of behavior in humans and other animals. One kind of behavior is called Operant Behavior because it “operates”, or acts, upon the environment. Most important, operant behavior is controlled by its consequences.
Visual programming method and its system
InactiveUS6366300B1Improve efficiencyReduce developmentProgramme controlData processing applicationsProgramming languageGraphics
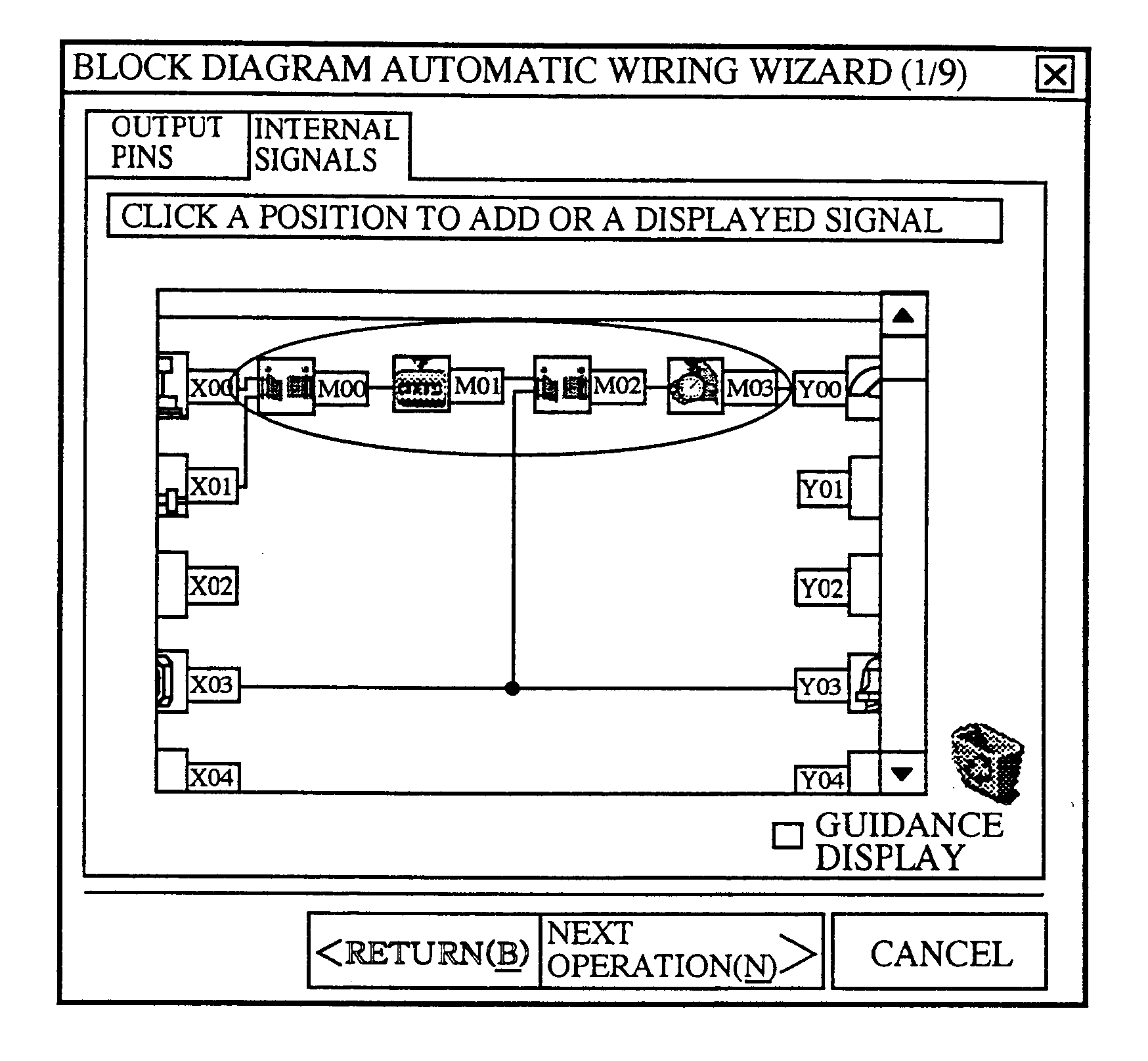
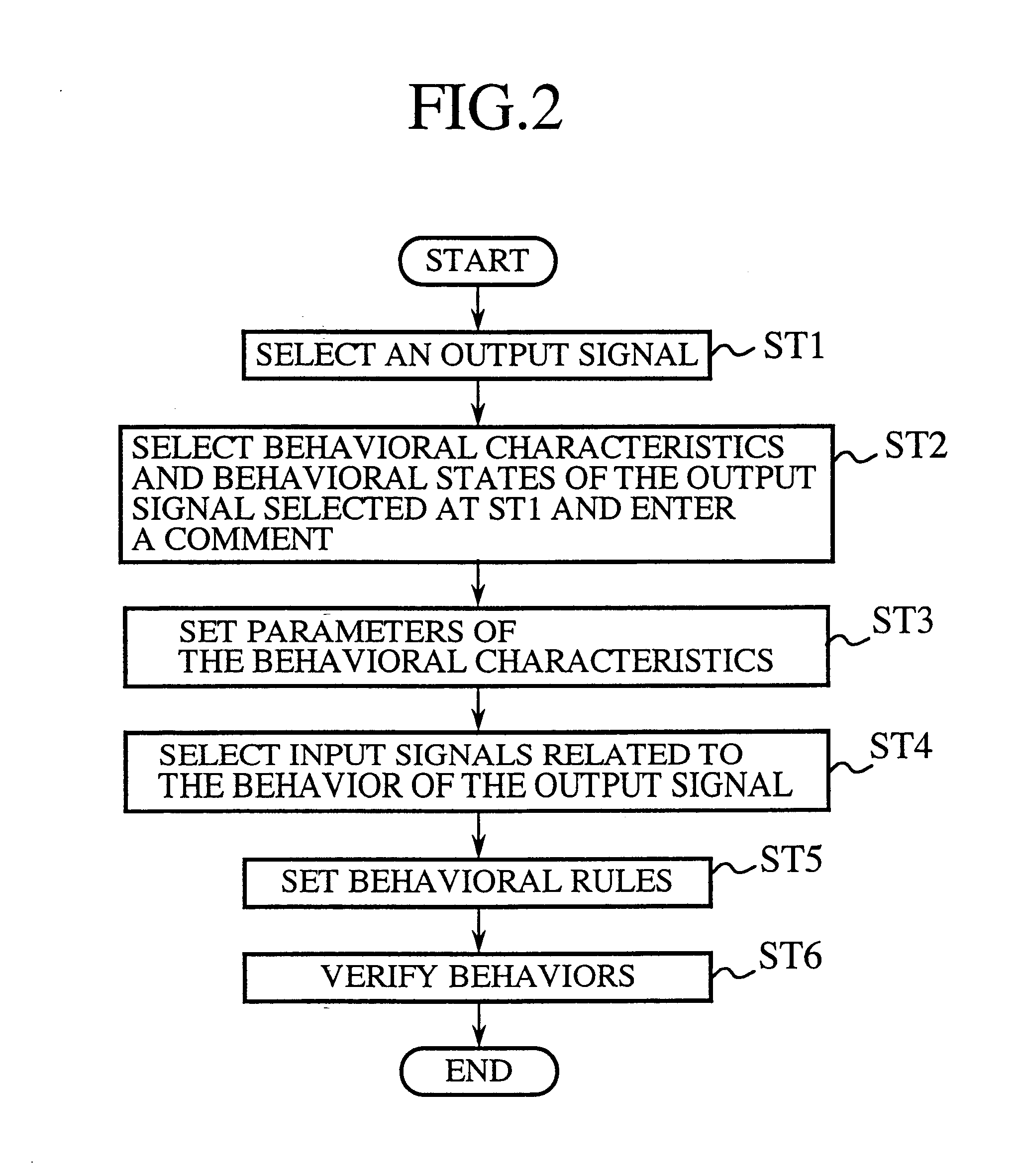
The user is allowed to automatically generate a program by using a visual programming method and a system adopting the method for automatically generating a program wherein an object selection means 8 is used for selecting a behavioral graphical object defining the behavior of a load connected thereto, a behavior selection means 9 is used for selecting the type of the behavior of the behavioral graphical object, a relevant object selection means 10 is used for selecting relevant graphical objects related to the behavior of the behavioral graphical object and a behavioral rule setting means 11 is used for setting behavioral rules of the behavioral graphical object whereas a behavioral characteristic selection unit 3509 is used for selecting a behavior of a behavioral graphical object selected by using a behavioral object selection unit 3508, behavioral condition setting unit 3510 is used for setting conditions for the behavior of the behavioral graphical object and a relevant object selection unit 3511 is used for defining a relation.
Owner:MITSUBISHI ELECTRIC CORP
Method for categorizing, describing and modeling types of system users
InactiveUS6853966B2Good suitImprove performanceSoftware engineeringAnalogue computers for electric apparatusSimulationBehavior type
Owner:SBC TECH RESOURCES
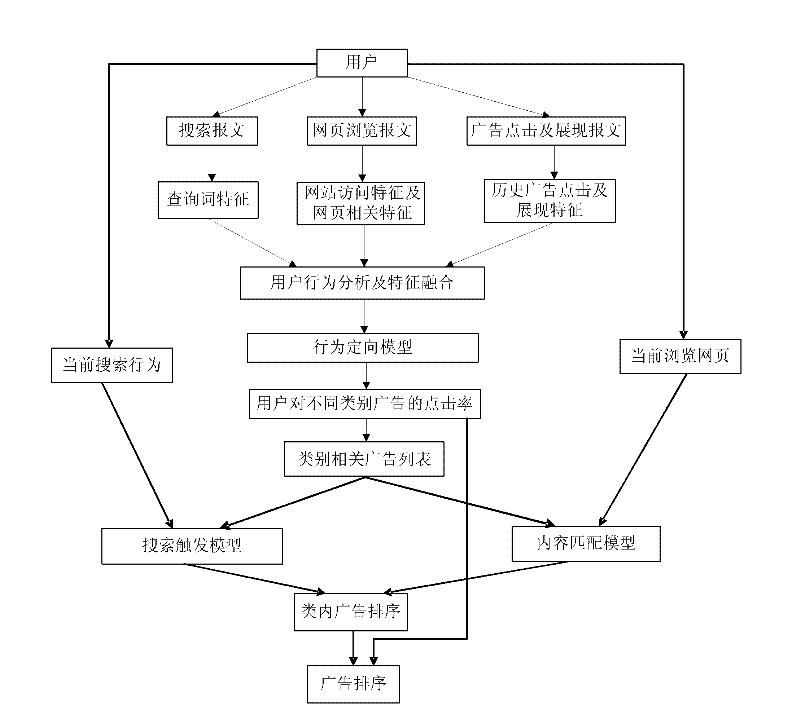
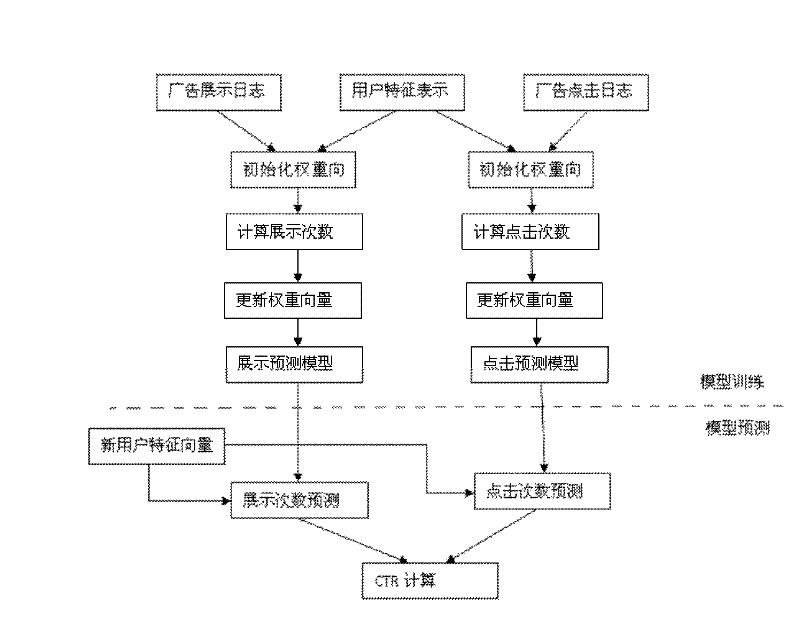
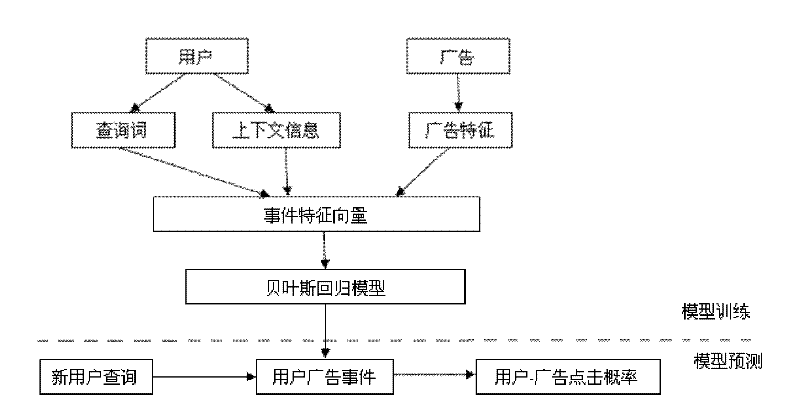
Method and device for predicting advertisement click rate based on user behaviors
InactiveCN102346899AAccurate sortingCommerceSpecial data processing applicationsData miningClick-through rate
The invention discloses a method and device for predicting advertisement click rate based on user behaviors. The method comprises the following steps of: behavior directional prediction: training a behavior directional model by analyzing the user behaviors, and predicting the click rates of the user on different types of advertisements to obtain a predicted value of the click rate; in-type sorting: sorting the advertisements of each type according to the current behavior type of the user to obtain an in-type advertisement sorting list; and comprehensive sorting: sorting the click rates of all advertisements according to the predicted value of click rate and the in-type advertisement sorting list to obtain a comprehensive sorting list. Through the method disclosed by the invention, a prediction model can be established for each type of advertisements so as to sort the advertisements more accurately according to the type characteristics of the advertisements.
Owner:亿赞普(北京)科技有限公司
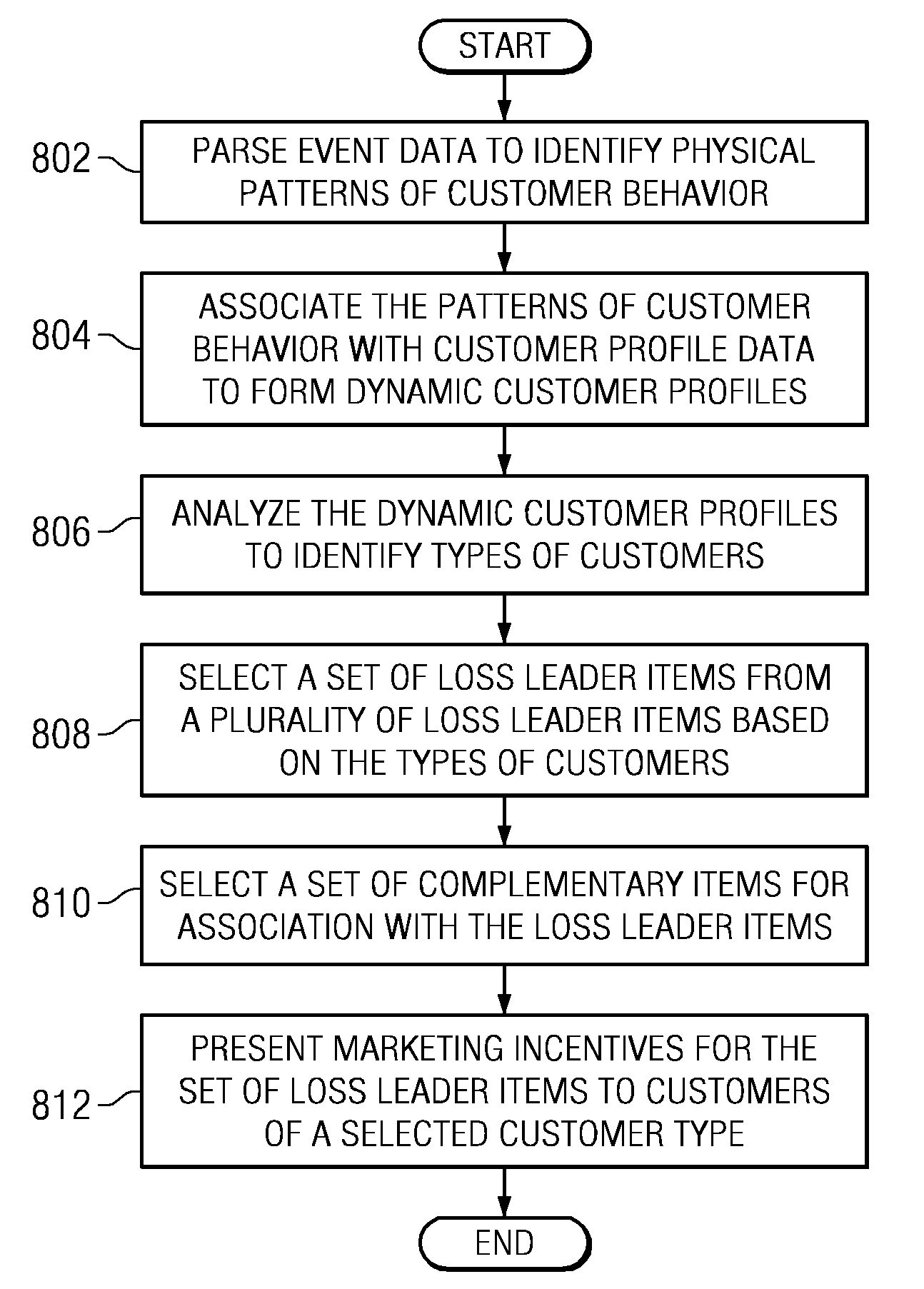
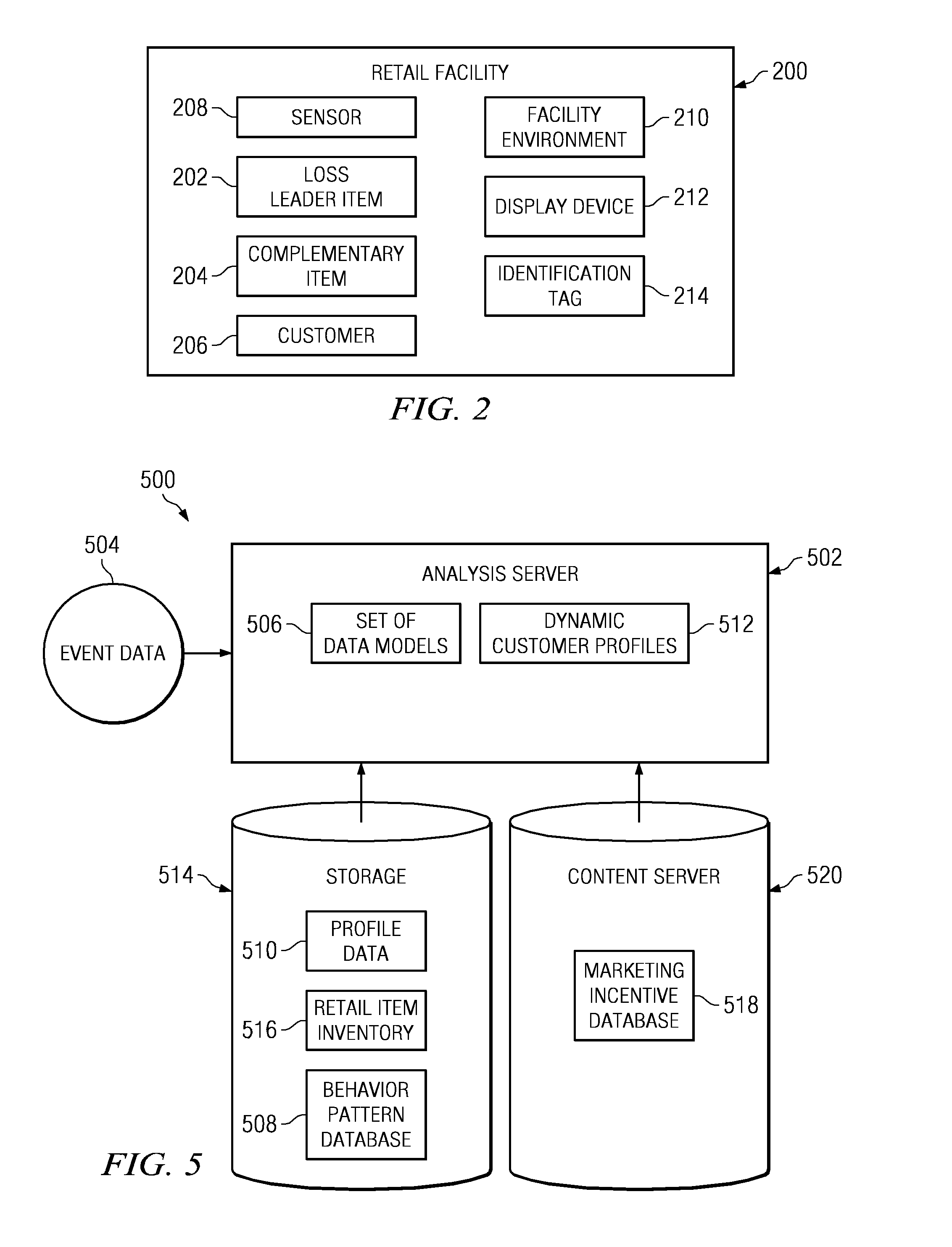
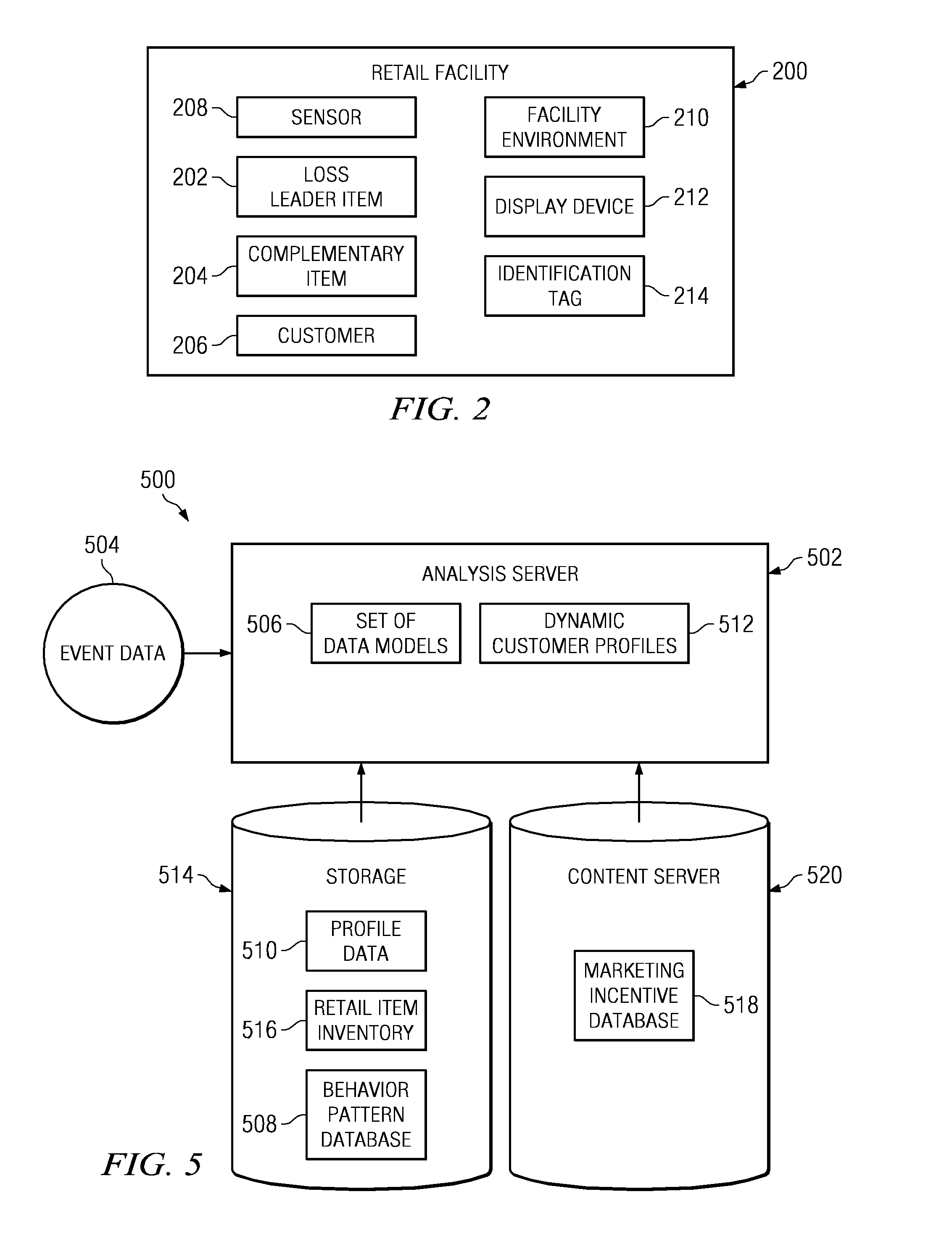
Method and apparatus for identifying customer behavioral types from a continuous video stream for use in optimizing loss leader merchandizing
A computer implemented method, apparatus, and computer usable program product for optimizing loss leader merchandizing. The process parses event data to identify physical patterns of customer behavior, wherein the event data is derived from a continuous video stream captured at a retail facility, and associates the physical patterns of customer behavior with customer profile data to form dynamic customer profiles. The process then analyzes the dynamic customer profiles to identify types of customers and presents marketing incentives for a set of loss leader items to customers of a selected customer type, wherein the set of loss leader items are selected based on the dynamic profiles.
Owner:IBM CORP
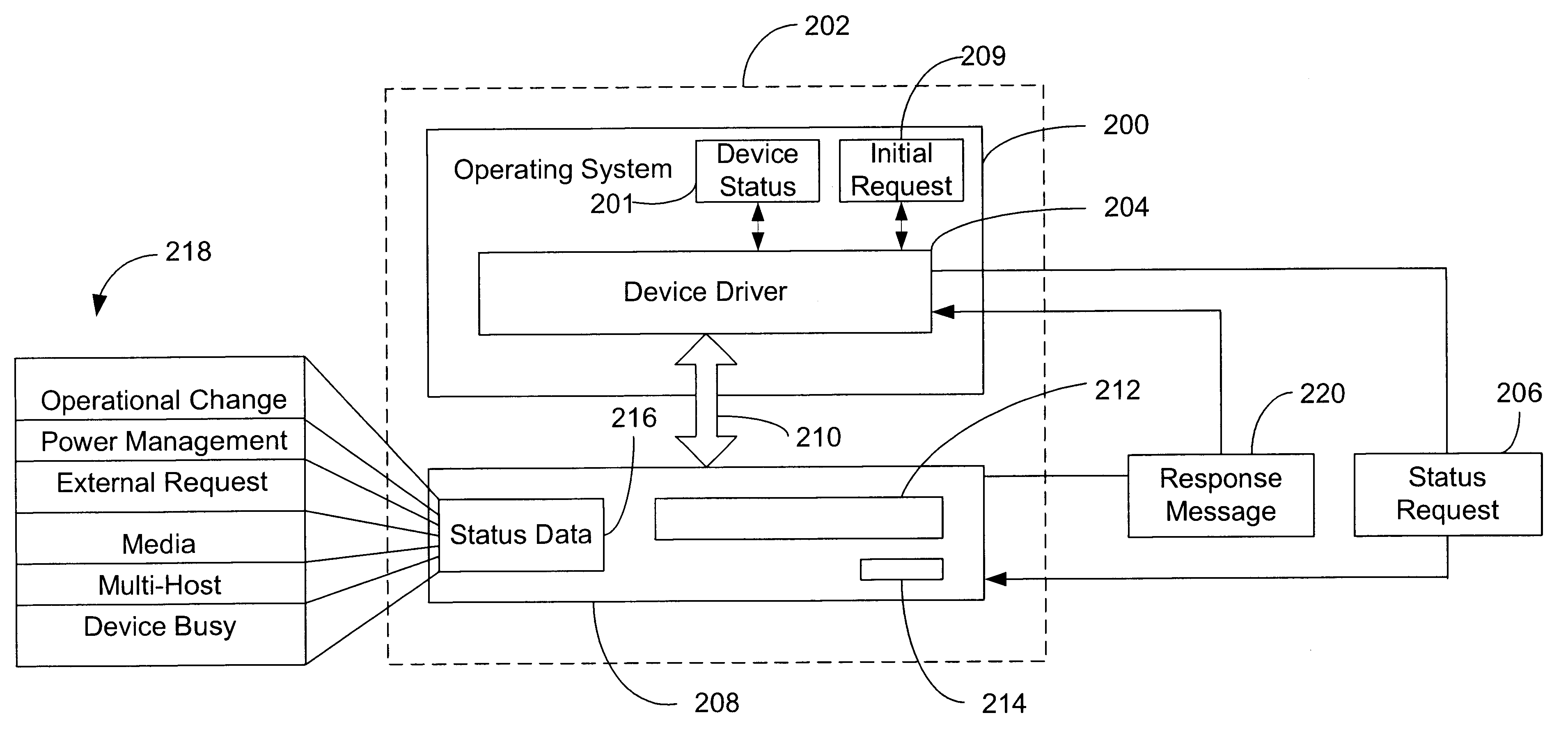
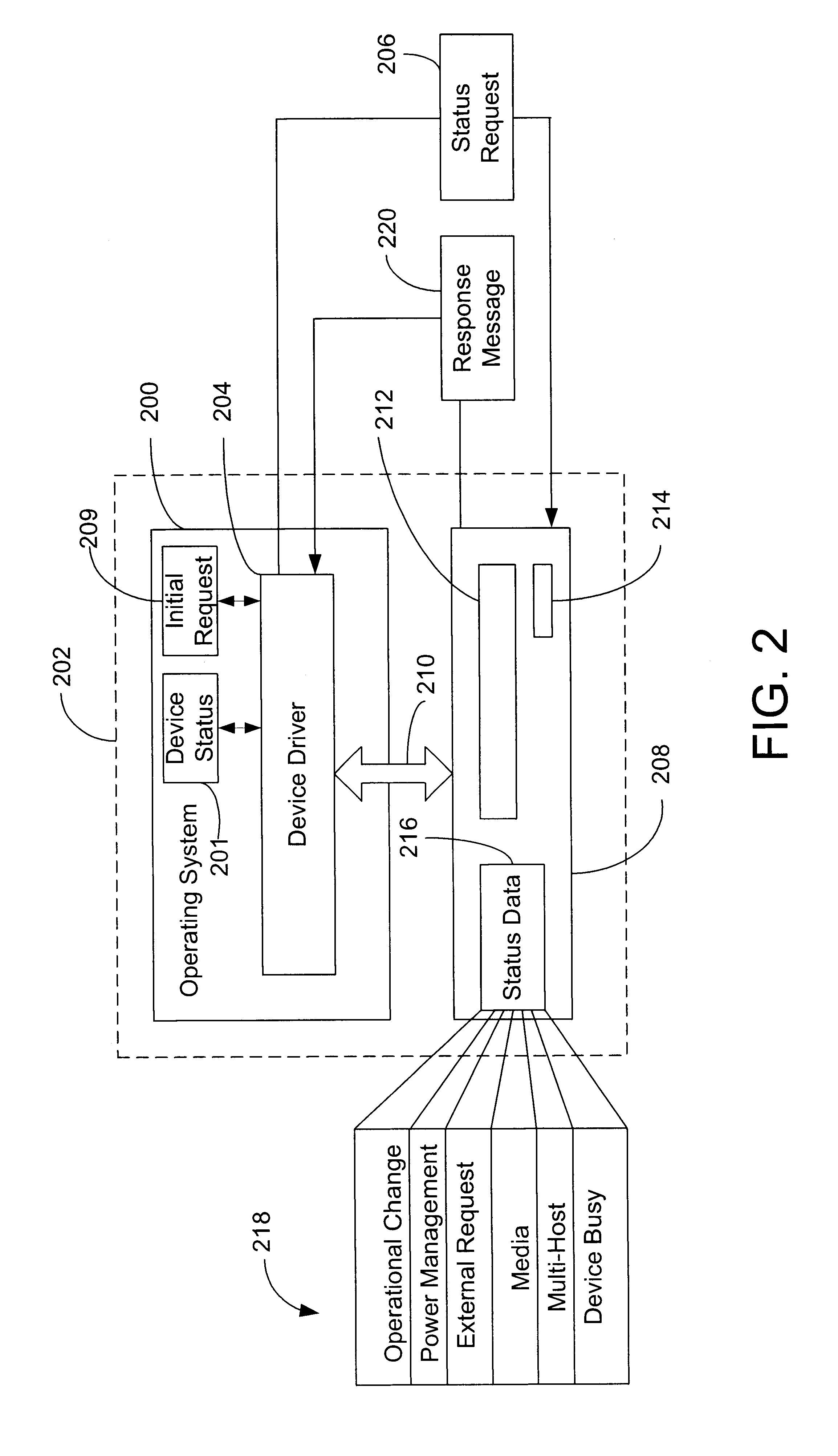
Method for determining status of a computer device and detecting device behavior in response to a status request
A method and system allows a device driver to obtain the status of a device that may exhibit one of two distinct behaviors in responding to status requests that designate a plurality of event types associated with a device. Devices exhibiting the first behavior respond to the status requests by providing the status for the highest priority event type designated in the status request. Device exhibiting the second behavior respond to the status requests by providing the status for the highest priority event type that has undergone a status change. In one implementation, the device driver transmits a series of distinct status requests such that the status of all event types can be determined. In a related aspect of the invention, the device driver also analyzes the response message to determine if the device exhibits the second behavior type. When the second behavior type is detected, only a single type of status request is sent to obtain the status of all event types.
Owner:MICROSOFT TECH LICENSING LLC
Method for identifying abnormal motion in video and system thereof
InactiveCN106571014AEliminate the effects ofImprove accuracyCharacter and pattern recognitionAlarmsPattern recognitionVideo sequence
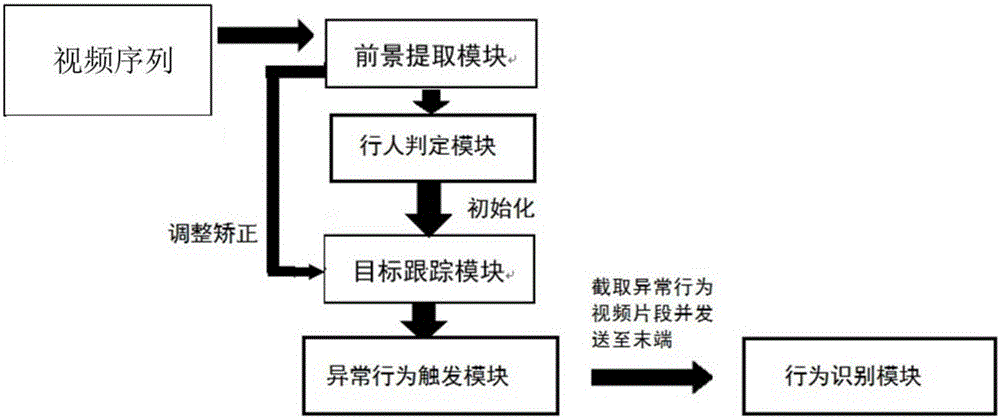
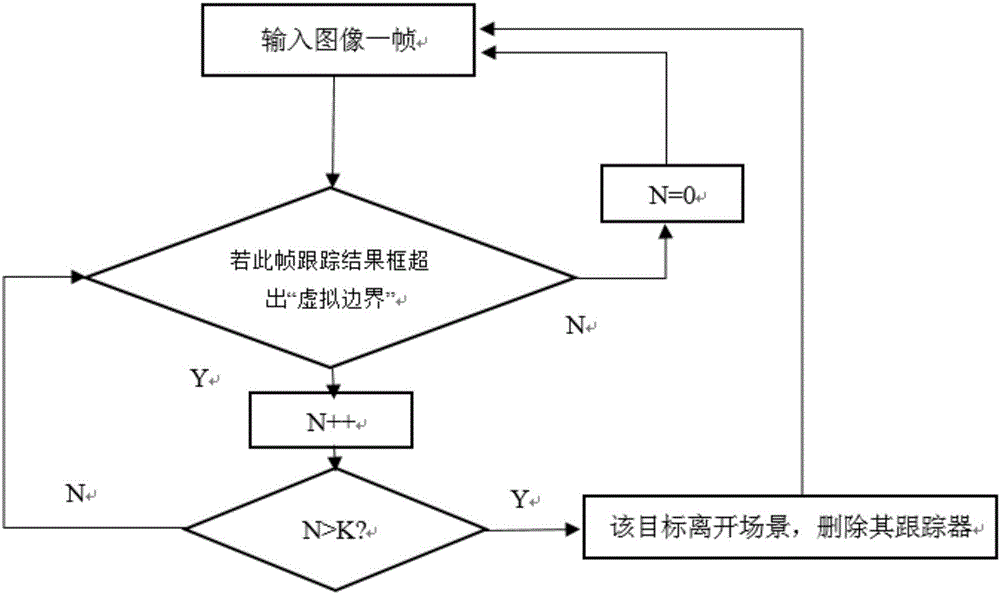
The invention discloses a method for identifying abnormal motion in a video. The method comprises the steps that an area of which the pixels have certain change is extracted from a video sequence through a foreground extraction module; a movement target detected by the foreground extraction module is judged through a pedestrian judgment module, and a rectangular box judged to be a pedestrian is kept and transmitted to a target tracking module; each identified target in the scene is continuously tracked in a multi-target way through the target tracking module; the posture of each target tracked by the target tracking module within each frame of time is judged through an abnormal behavior trigger module and behavior analysis is performed on the abnormal behavior; and the abnormal behavior is processed and computed into a video segment through a behavior identification module, and the abnormal behavior is alarmed and the behavior type of the abnormal behavior is identified. The invention also discloses a system for identifying the abnormal motion in the video. The problem that abnormal behavior (falling down) detection of massive video data cannot be performed in real time can be solved and the detection accuracy can be greatly enhanced.
Owner:SHANGHAI VSI INTELLIGENT TECH
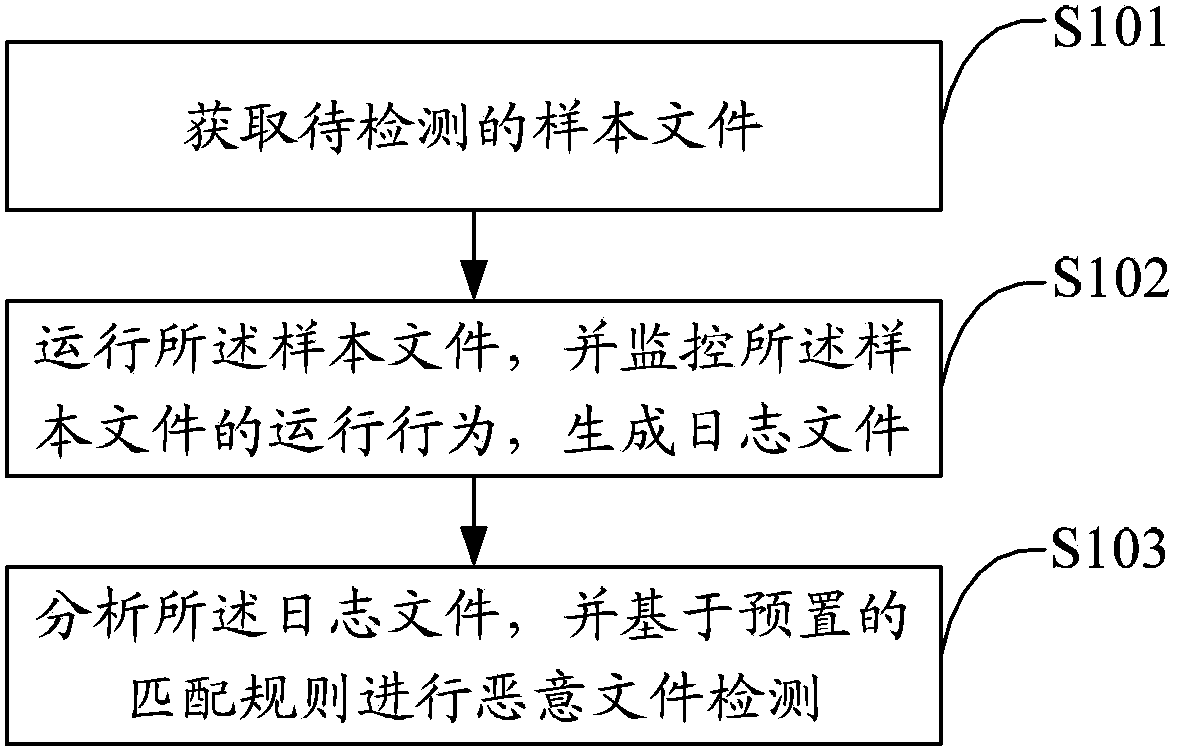
Malicious file detection method and device
ActiveCN103839003AImprove analysis efficiencyImprove detection accuracyPlatform integrity maintainanceAnti virusSoftware
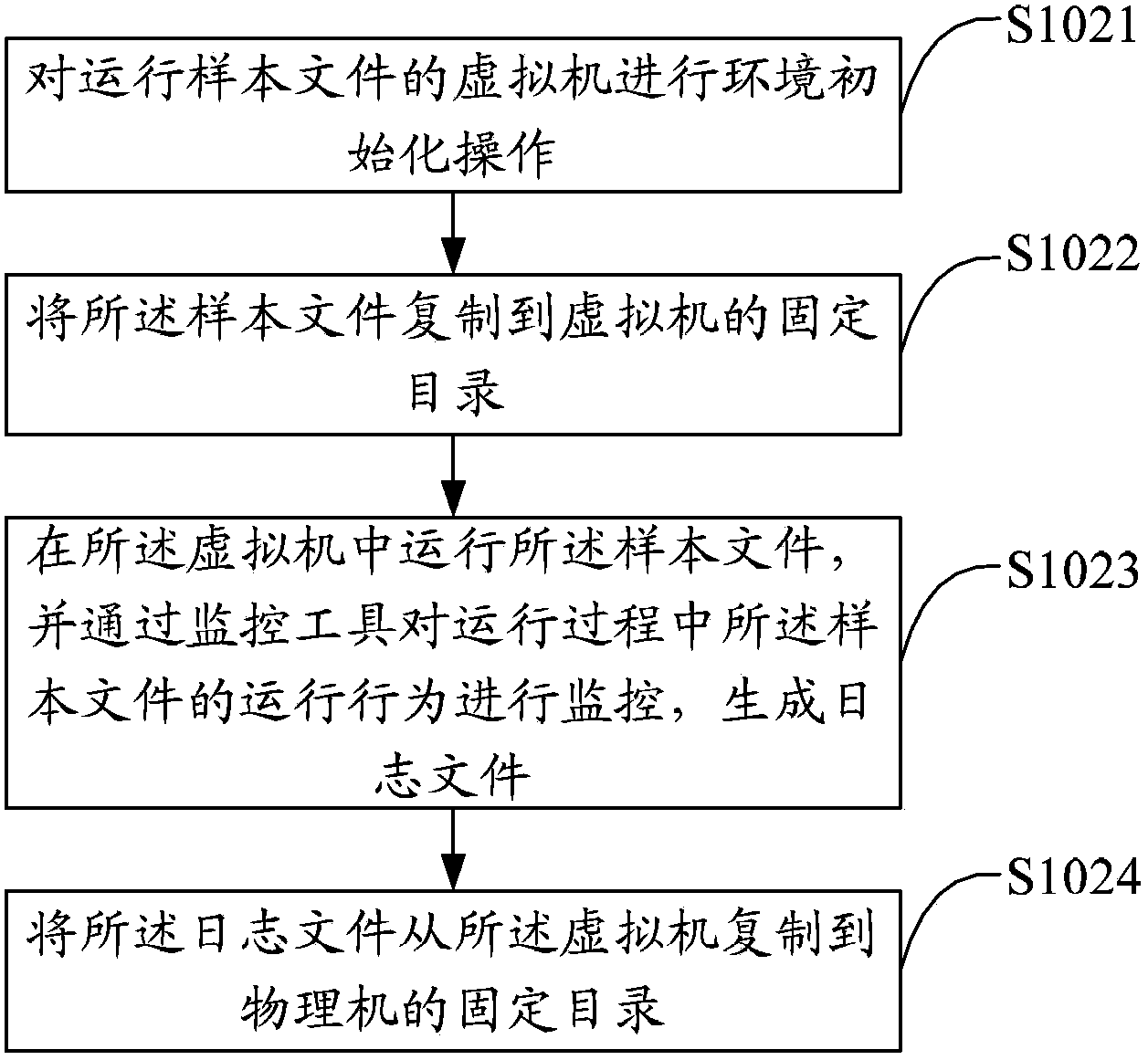
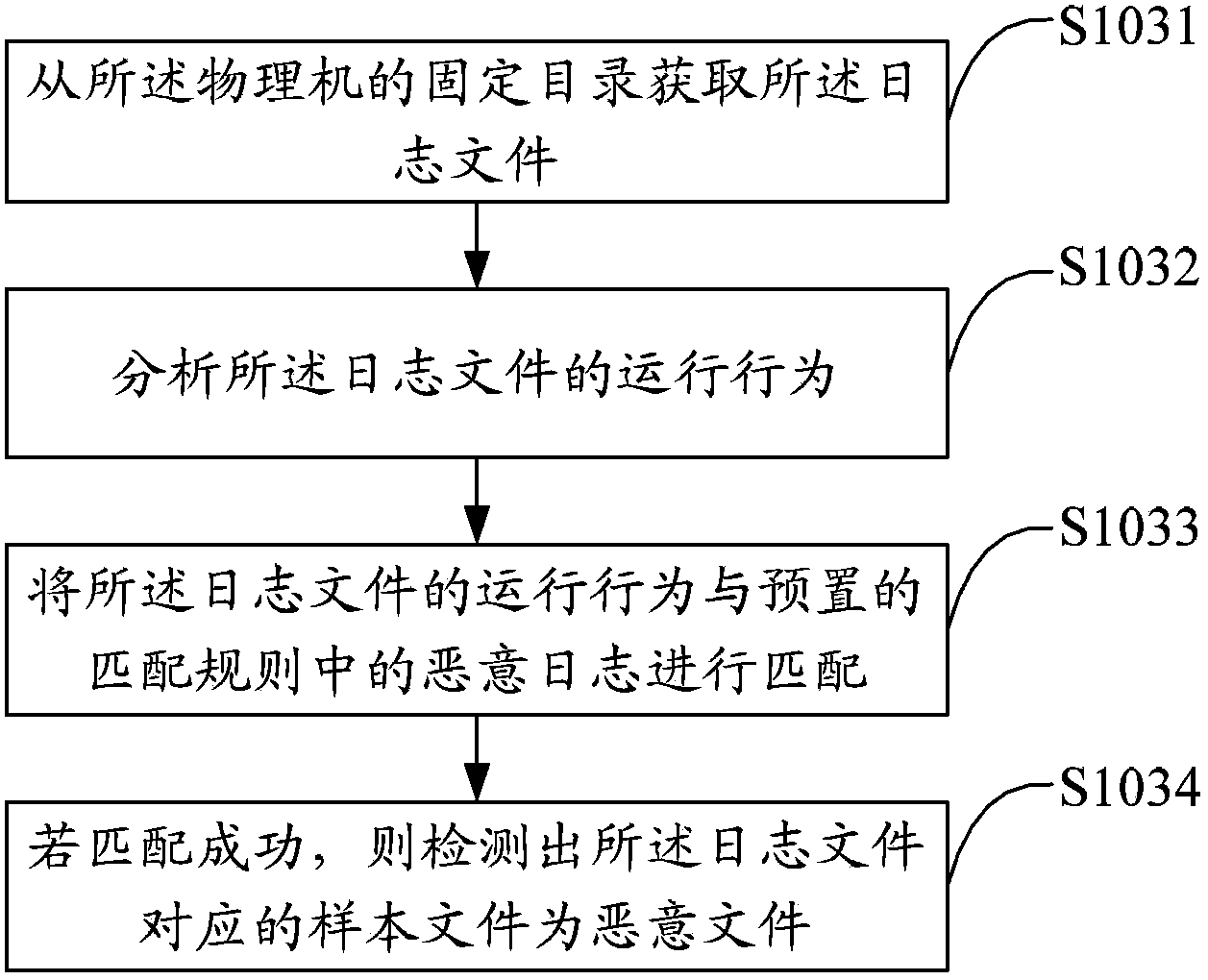
The invention discloses a malicious file detection method and device. The method includes the steps of obtaining a sample file to be detected; operating the sample file, monitoring operation behaviors of the sample file and generating a log file; analyzing the log file, and carrying out malicious file detection based on a preset matching rule. The sample file is operated in a virtual machine, a monitoring program is operated in the virtual machine, the operation behaviors of the sample file are recorded to generate the log file, then the log file is matched according to an extracted feature rule, and finally malicious file detection of the sample file is achieved. By means of the method, virus analysis efficiency can be greatly improved, new samples which can not be detected by anti-virus programs in the prior art or a certain type of samples of a specific behavior type can be found timely, and accordingly detection accuracy of virus samples is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
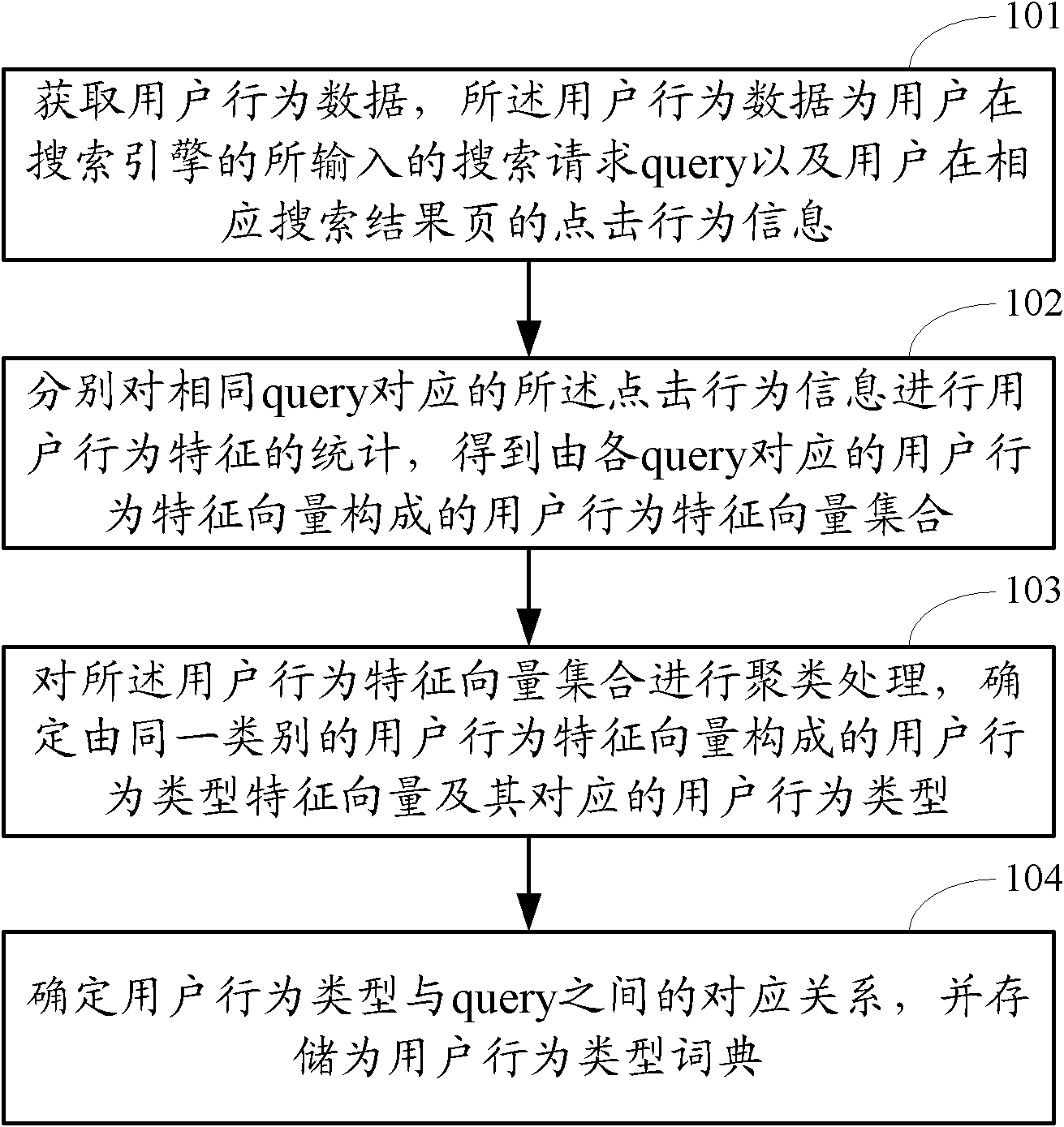
Classification method and device for user network behaviors and search method and device for user network behaviors
ActiveCN102760138AImprove accuracySpecial data processing applicationsFeature vectorNetwork behavior
The invention discloses classification method and device for users' network behaviors and search method and device for users' network behaviors. The classification method includes: data of user behaviors is acquired, the data of the user behaviors include queries input in an search engine by users and information of clicks performed on corresponding search engine results pages by the users; information of the clicks corresponding to the same query are counted in terms of user behavior features, and a user behavior feature vector set consisting of user behavior feature vectors corresponding to the queries is obtained; the user behavior feature vector set is clustered to determine a user behavior pattern feature vector consisting of same patterns of the user behavior feature vectors and a user behavior pattern corresponding to the user behavior pattern feature vector; correspondence between the user behavior patterns and the queries is determined and is stored as a user behavior pattern dictionary. Post-search clicks performed by the users are classified, and accordingly accuracy in services or applications based on user behavior data is improved effectively.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Method of managing slowly changing dimensions
InactiveUS6847973B2Data processing applicationsMulti-dimensional databasesSlowly changing dimensionData mart
A method of managing slowly changing dimensions in a dimensional database, such as a dimensional data mart, is disclosed. The method consists of providing a dimension template for each dimension undergoing slow changes, which template assigns a behavior to each column of the dimension table. When a row of dimensional data is to be delivered to the dimension table, the table is searched for a record having the key value of the row of data to be delivered. If such a record exists and if any attributes of the row to be delivered have their values changed compared with the existing record, the table is updated according to the behavior type assigned to these attributes in the dimension template, either by overwriting the existing record with the record to be delivered or by creating a new record or records.
Owner:IBM CORP
Abnormal behavior detection method and system
ActiveCN110135319AImprove versatilityEnhance expressive abilityCharacter and pattern recognitionNeural architecturesVideo monitoringPattern recognition
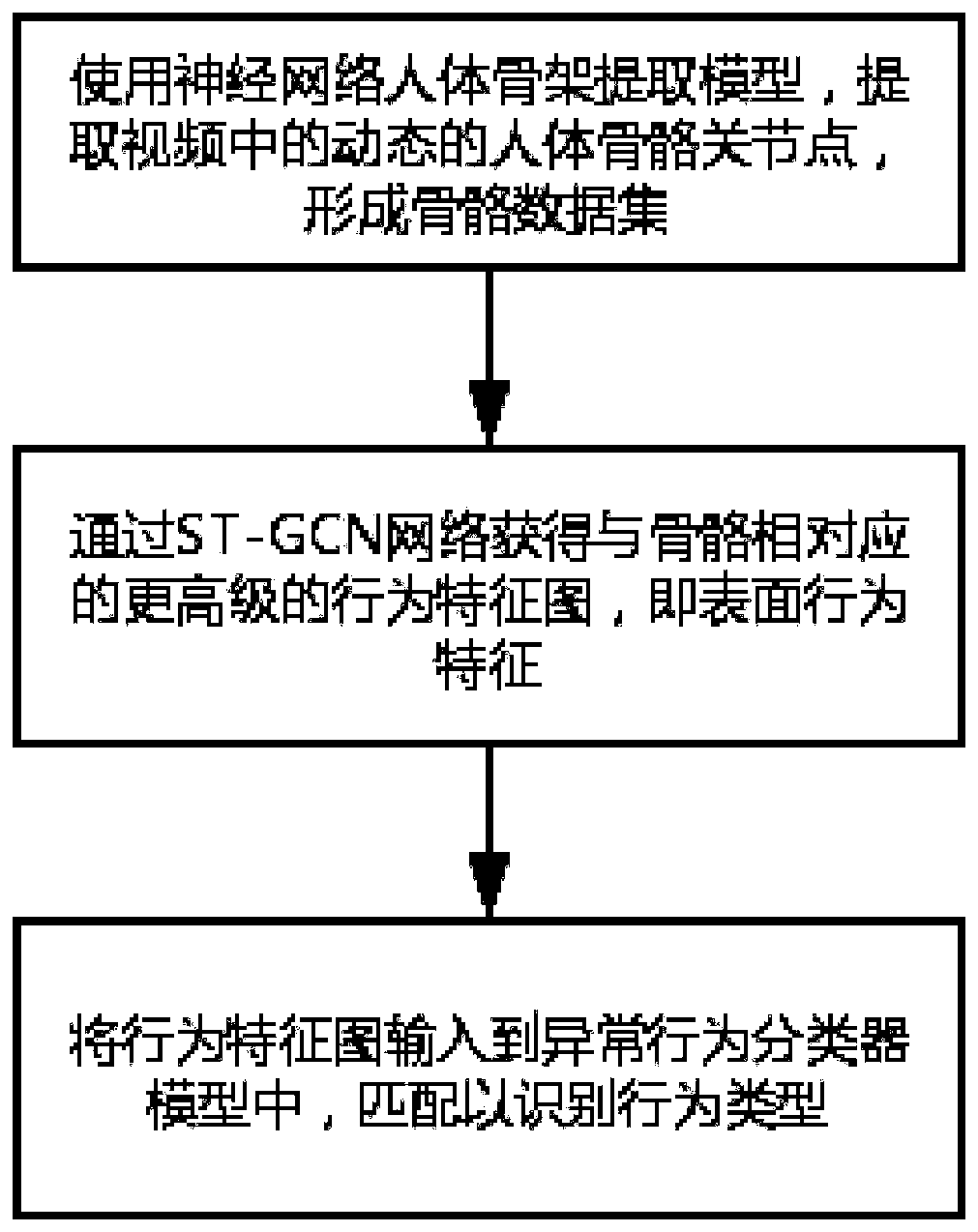
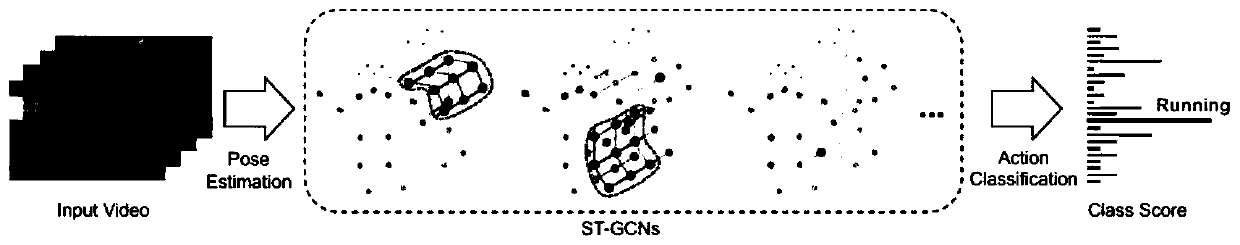
The invention discloses an abnormal behavior detection method, which comprises the following steps of: extracting dynamic human skeleton joints in a video by using a neural network human skeleton extraction model to form a skeleton data set; obtaining a higher-level behavior feature map corresponding to the bone, namely surface behavior features, by an ST-GCN network; and inputting the behavior feature map into the abnormal behavior classifier model, and performing matching to identify the behavior type. The invention also discloses an abnormal behavior detection system which comprises a videomonitoring module and a network model integration module. According to the method, various human body behaviors and a large amount of human body skeleton data can be accurately and efficiently processed, and abnormal behaviors appearing in video monitoring can be automatically identified.
Owner:GUANGZHOU UNIVERSITY
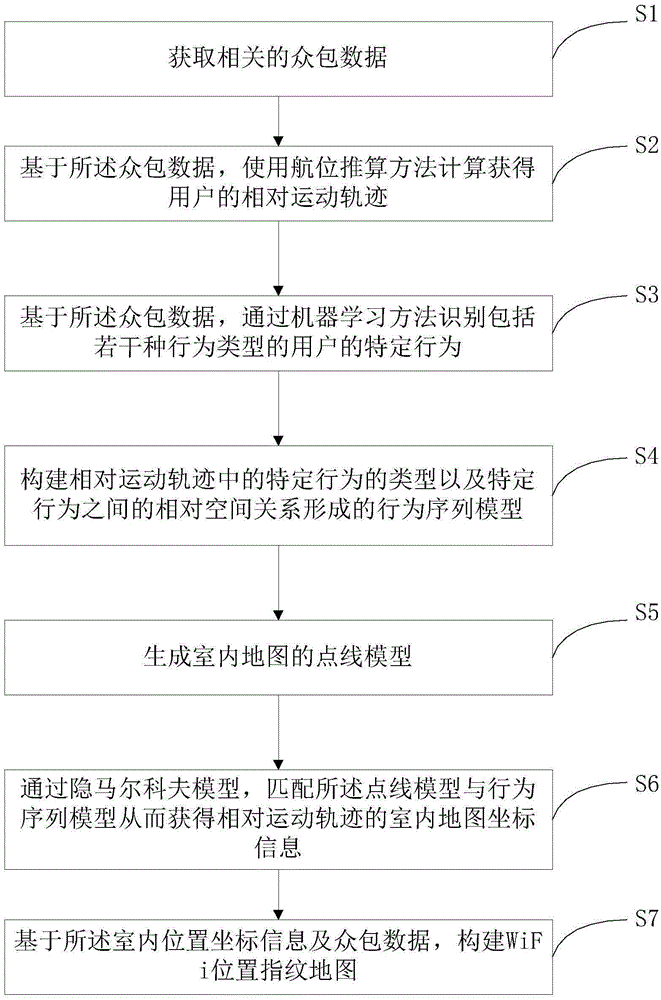
Wi-Fi location fingerprint map building method and system based on crowd-sourcing
ActiveCN105263113ASolve the problem of time-consuming and labor-intensive constructionImprove timelinessLocation information based serviceSequence modelRelative motion
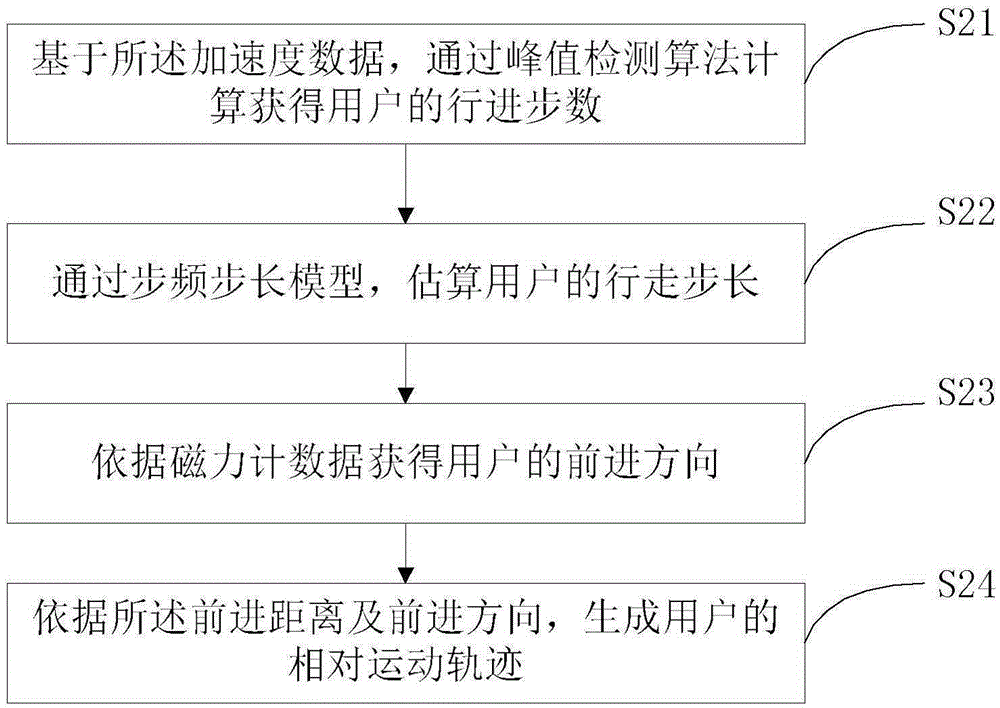
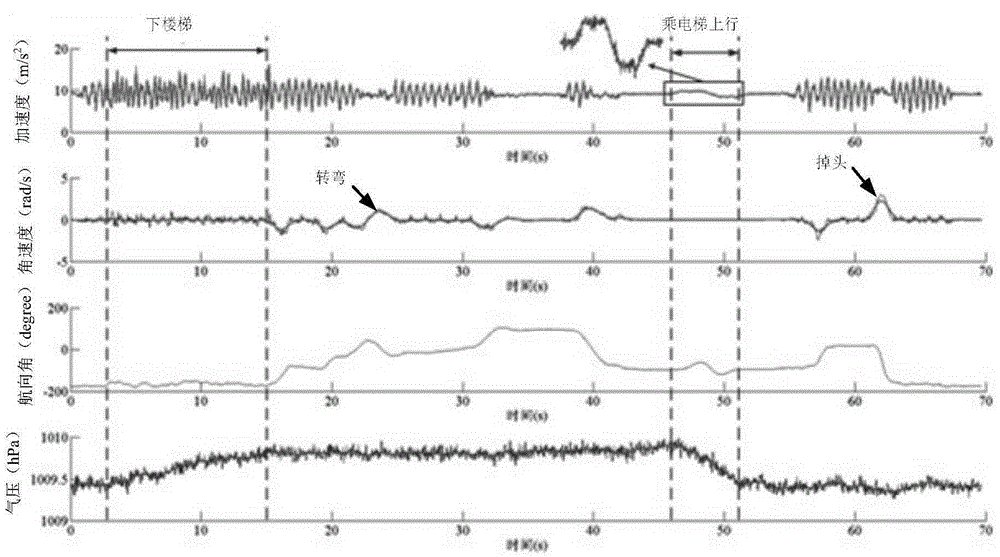
The invention provides a Wi-Fi location fingerprint map building method and a system based on crowd-sourcing. The method comprises the steps as follows: acquiring relevant crowd-sourcing data; using a dead reckoning approach to calculate the relative motion trajectory of a user based on the crowd-sourcing data; identifying specific behaviors of the user including a plurality of behavior types through machine learning; building a behavior sequence model formed by the types of the specific behaviors in the relative motion trajectory and the relative spatial relationship between the specific behaviors; generating a point-line model of an indoor map, and matching the point-line model with the behavior sequence model through a hidden Markov model to obtain the indoor map coordinate information of the relative motion trajectory; and finally, building a Wi-Fi location fingerprint map based on the indoor location coordinate information and the crowd-sourcing data. The Wi-Fi location fingerprint map is built and updated automatically based on the crowd-sourcing data.
Owner:SHENZHEN UNIV
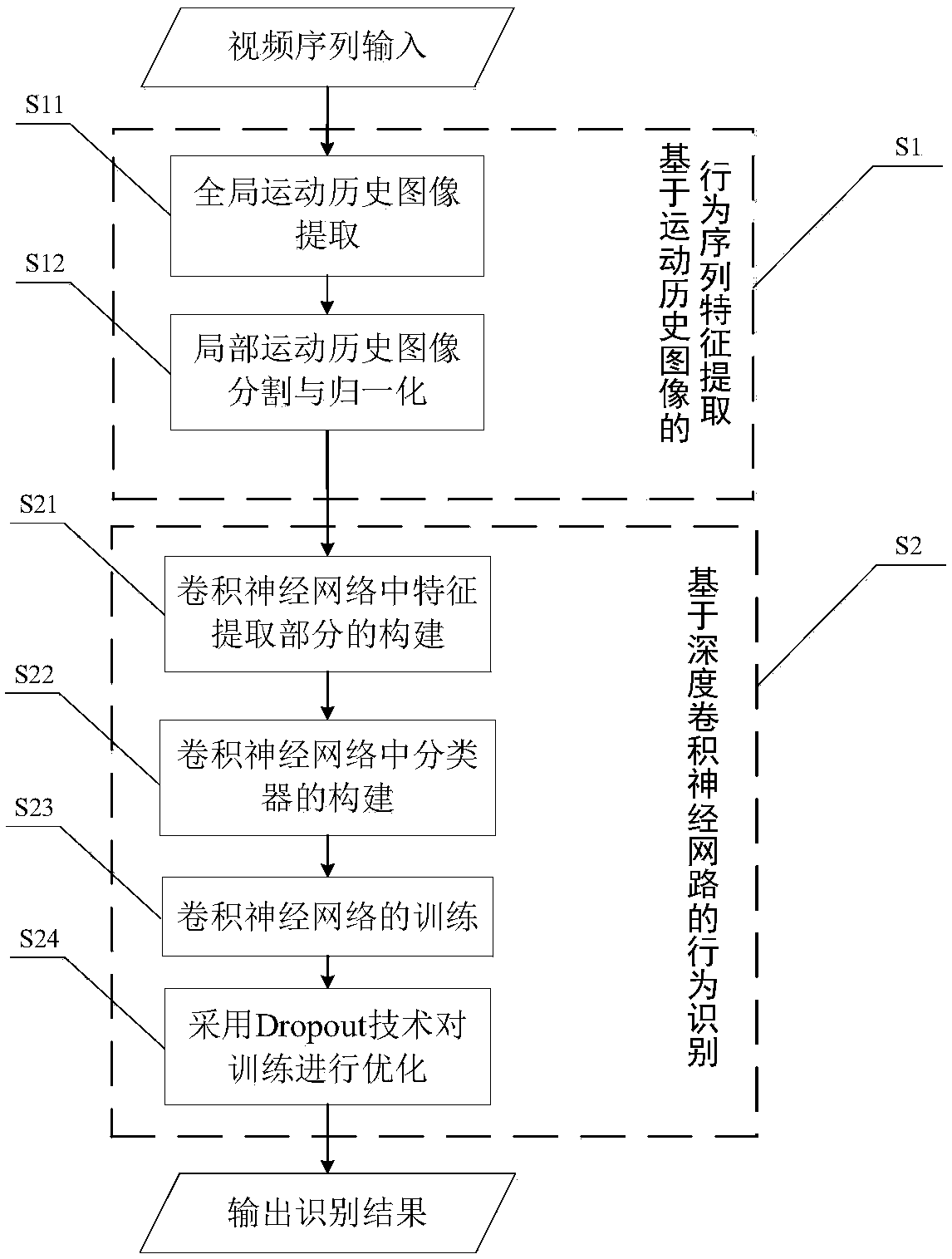
Motion history image and convolutional neural network-based behavior identification method
ActiveCN108133188ASuppress overfittingReduce complexityImage enhancementImage analysisStochastic gradient descentVideo sequence
The invention discloses a motion history image and convolutional neural network-based behavior identification method. The method comprises the following steps of S1, obtaining an input original videoimage, and processing the input original video image through a motion history image-based behavior sequence feature extraction method; and S2, performing behavior identification on a local motion history image by adopting a deep convolutional neural network-based method to obtain a behavior type classifier, and finally outputting a behavior identification result through the behavior type classifier. The motion history image is calculated in an original video sequence, so that the to-be-processed information amount is reduced and key time-space information in behavior identification is extracted; and by taking the motion history image as an input, a deep convolutional neural network is established, then the network is trained by utilizing a stochastic gradient descent method and a Dropout policy, and finally behavior type identification is realized. The method can be effectively applied to online real-time behavior identification.
Owner:WUHAN UNIV OF TECH
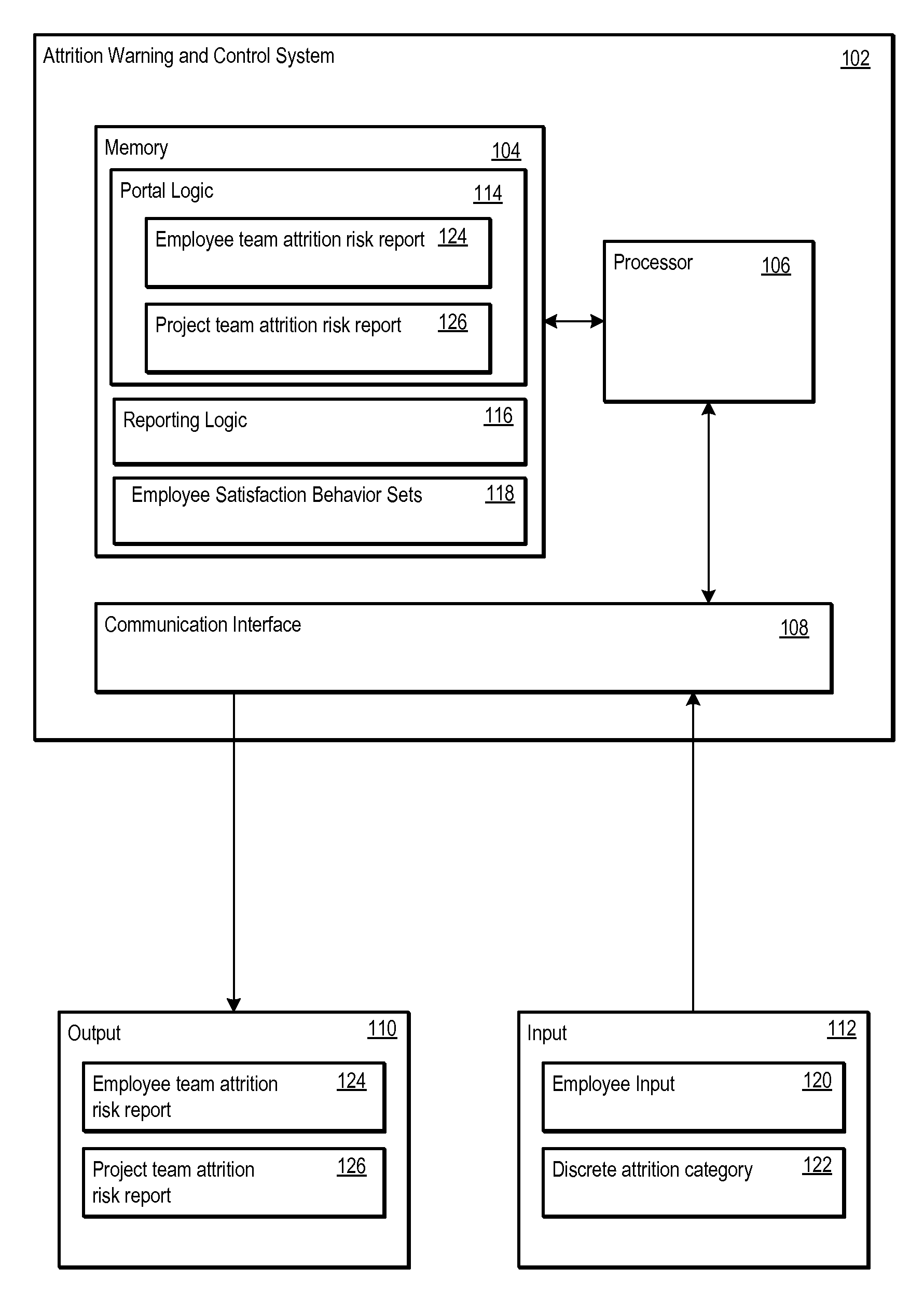
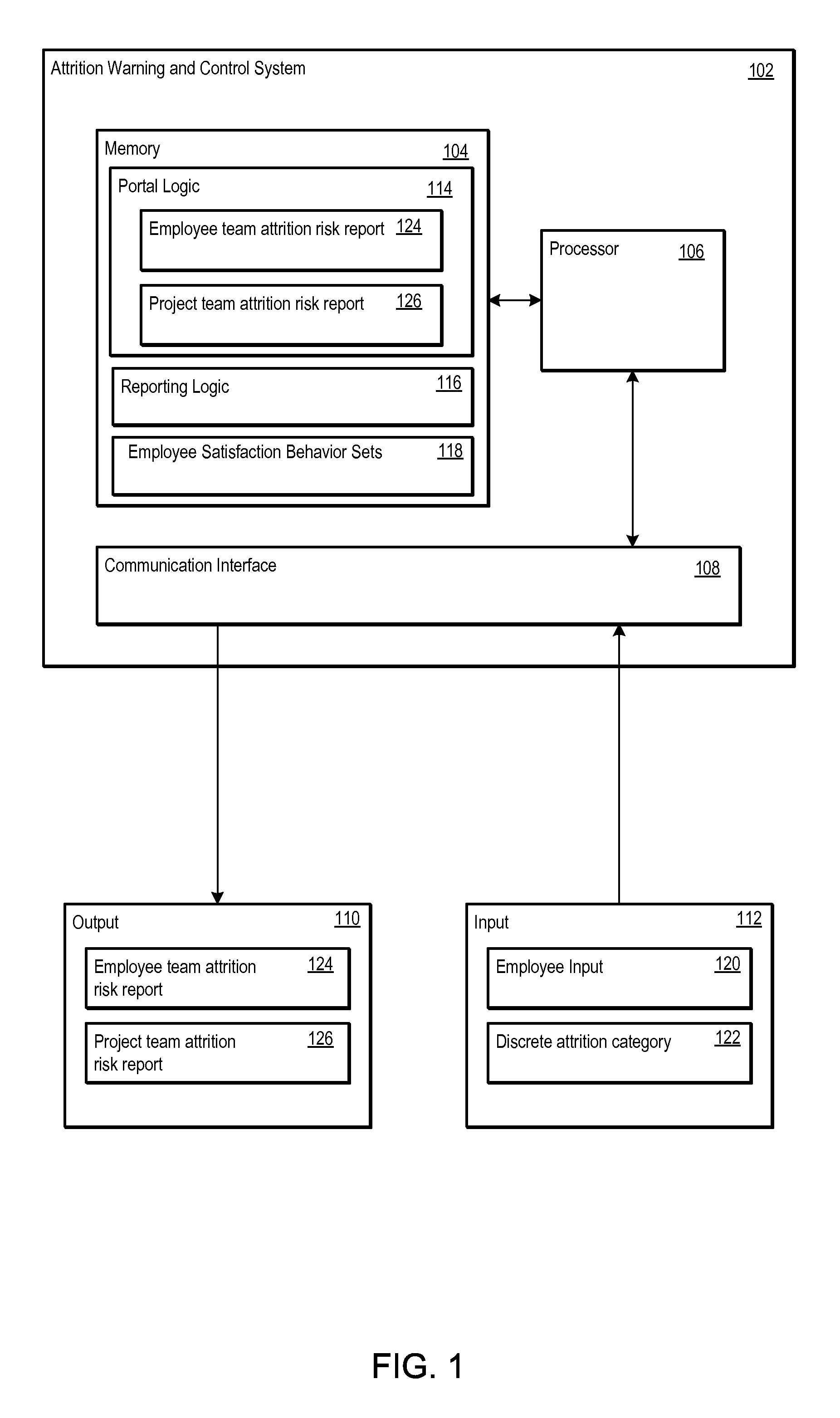
Attrition Warning and Control System
An attrition warning and control system informs an employer as to the risk of attrition for an employee. The employee is assigned a discrete attrition category. The discrete attrition category is determined from an employee satisfaction behavior. The employee satisfaction behavior may be categorized according to its behavior type. Portal logic executed by the attrition warning and control system generates employee team attrition risk reports for employee teams. The portal logic also builds project team attrition risk reports from the employee team attrition risk reports. Reporting logic executed by the attrition warning and control system delivers the discrete attrition category, employee satisfaction behavior, the employee team attrition risk reports, and the project team attrition risk reports through an authorized connection via a communication interface.
Owner:ACCENTURE GLOBAL SERVICES LTD
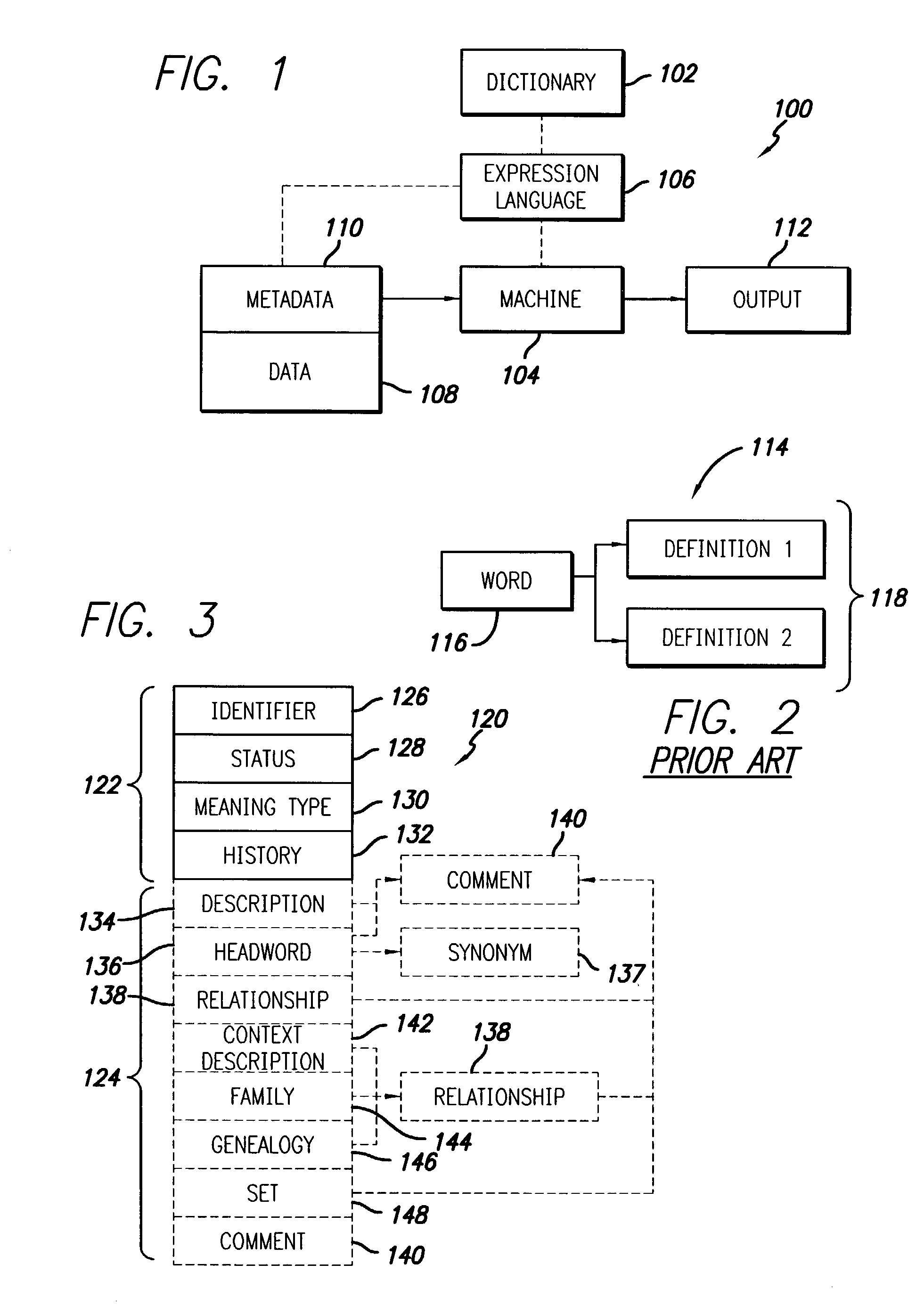
Data dictionary method
InactiveUS20030221171A1Complete understandingText processingDigital computer detailsTheoretical computer scienceRights management
A method for creating a rights data dictionary for definition of terms of a rights expression language is disclosed. The data dictionary may be used in computer operations on rights expression metadata, such as for digital rights management applications. The data dictionary may also be used for translating between expressions in different rights expression languages, thereby enabling interoperability of rights expressions. The rights data dictionary is organized according to a hierarchical schema. Terms are added to the data dictionary according to specified rules that relate to a basic term set, and in particular, are begotten from act type terms. The schema includes a "context" term of the basic term set that is assigned a meaning signifying a circumstance in which at least the basic action occurs. Other terms may be developed from the context term and defined by their relationship to it.
Owner:CONTECS DD LLC (US)
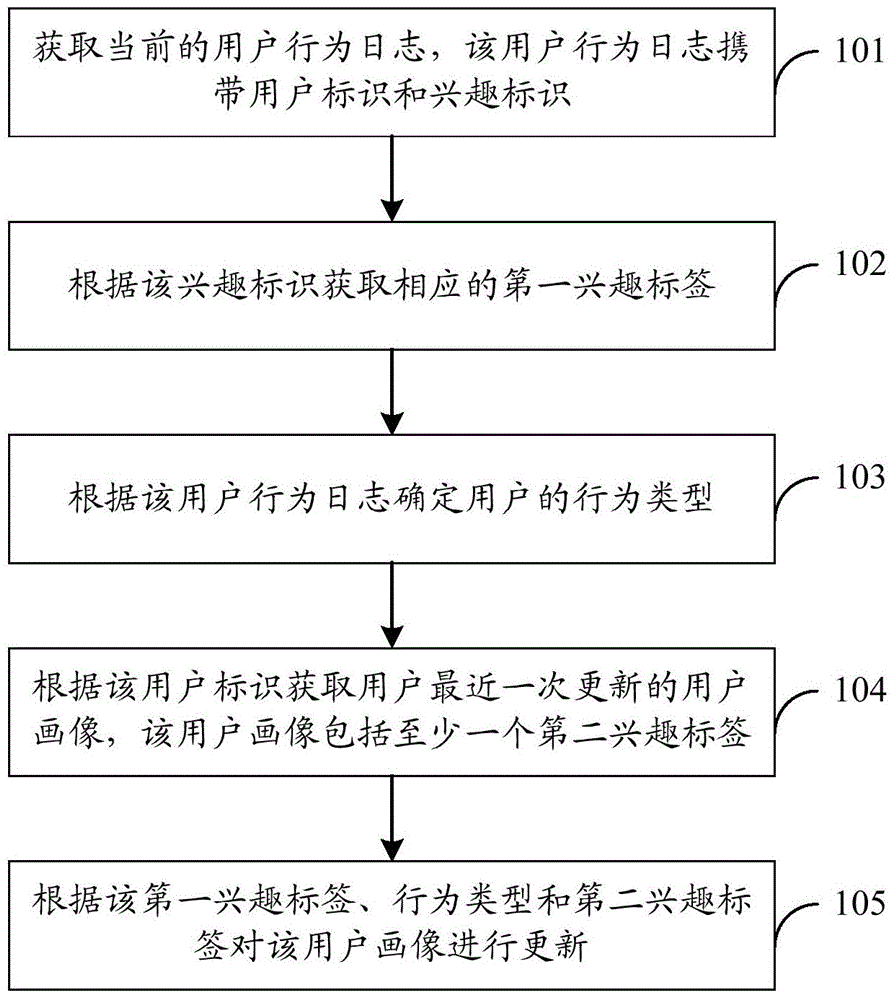
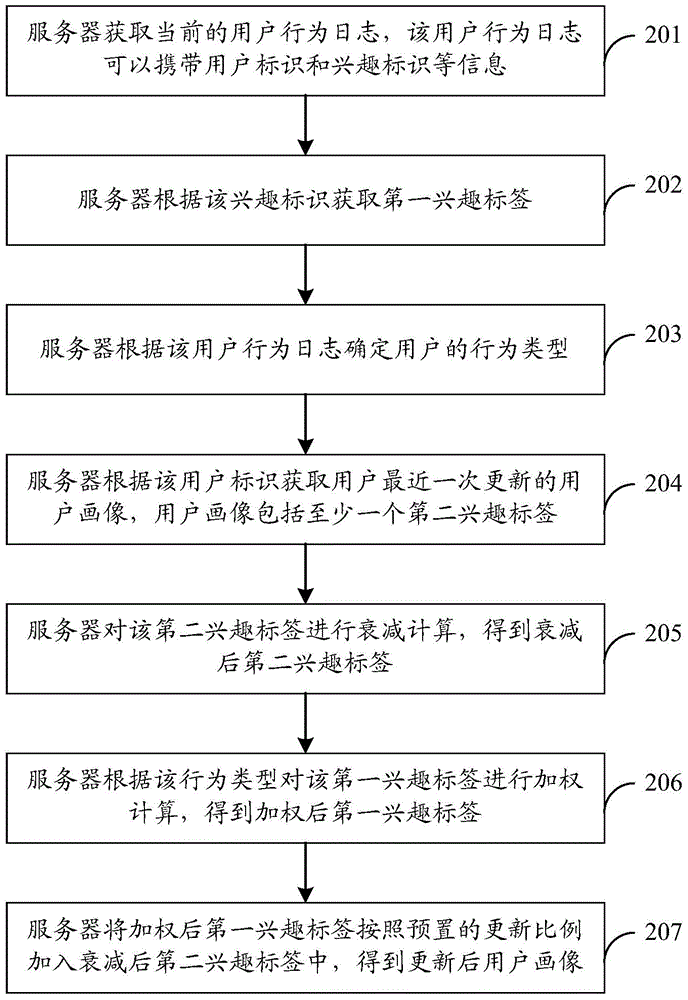
User portrait updating method, apparatus and system
InactiveCN105005587AAvoid untimely updatesImprove update effectSpecial data processing applicationsData miningCurrent user
An embodiment of the invention discloses a user portrait updating method, apparatus and system. According to the embodiment of the invention, the method comprises the steps of: obtaining a current user behavior log; obtaining a corresponding first interest label according to interest identifiers carried in the user behavior log; determining the user behavior type according to the user behavior log; obtaining a user portrait updated most recently according to the interest identifiers in the user behavior log; and updating the user portrait according to the first interest label, the behavior type and a second interest label carried in the user portrait. According to the technical scheme, the user portrait can be updated in real time, the consumption of stored resources can be reduced, the calculated amount is reduced, and the processing efficiency is improved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Recommendation method, recommendation device and server
ActiveCN104731830AImprove experienceReduce invalid browsingSpecial data processing applicationsMarketingData miningWeb page
Owner:TENCENT TECH (SHENZHEN) CO LTD
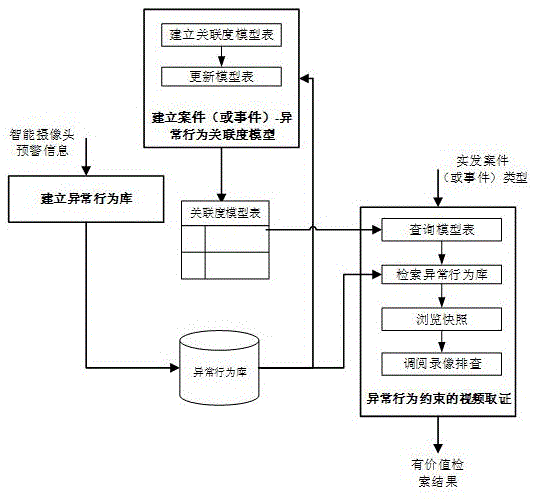
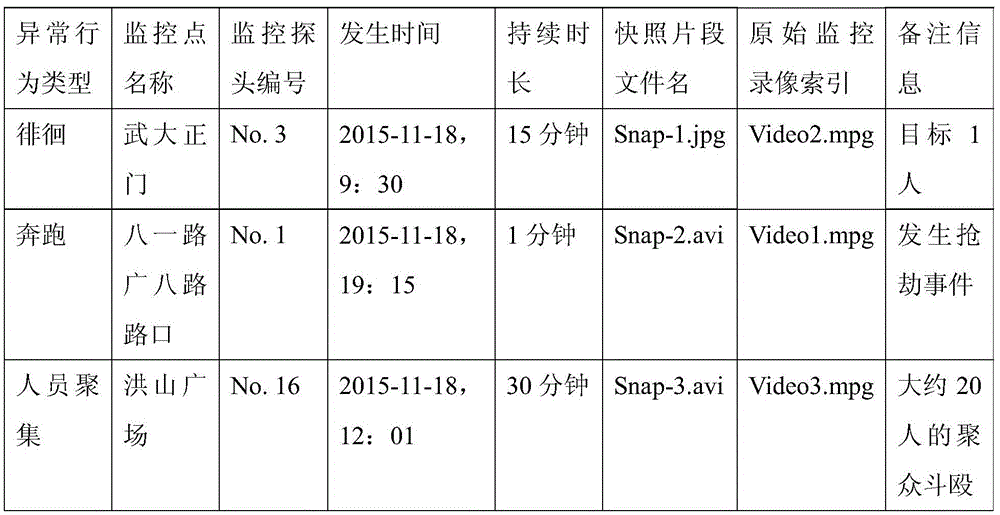
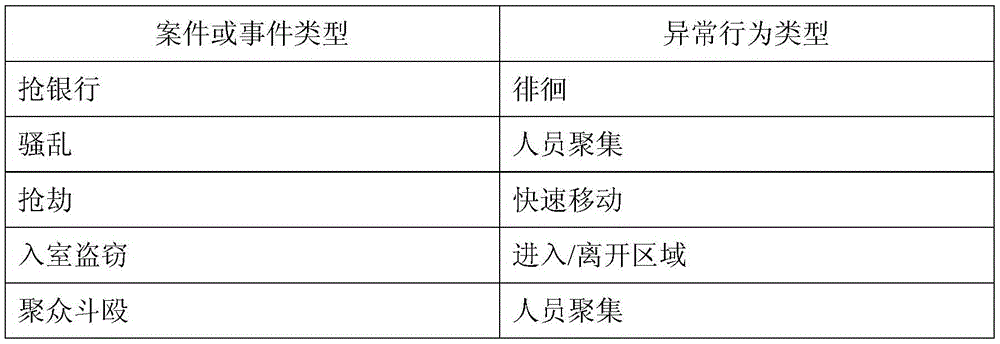
Video big data rapid searching method and system constrained by abnormal behavior early-warning information
ActiveCN105653690AImprove discovery efficiencyReduce the size of monitoring pointsSpecial data processing applicationsVideo retrievalVideo monitoring
The present invention discloses a video big data rapid searching method and system constrained by abnormal behavior early-warning information, wherein a massive video monitoring data clue investigation range is constrained by using abnormal behavior early-warning information sent out by an intelligent monitoring camera. The method comprises: receiving abnormal behavior early-warning information of a front-end intelligent camera, and establishing an abnormal behavior library; establishing a correlation model table, wherein the correlation model table stores a correlation between a case or event type and an abnormal behavior type; and according to the correlation model table, searching the abnormal behavior library, and positioning a corresponding valuable clue of monitoring point The method and system disclosed by the technical scheme of the present invention significantly reduce the size of recording data called in the video searching process and greatly improve valuable clue discovery efficiency.
Owner:WUHAN UNIV
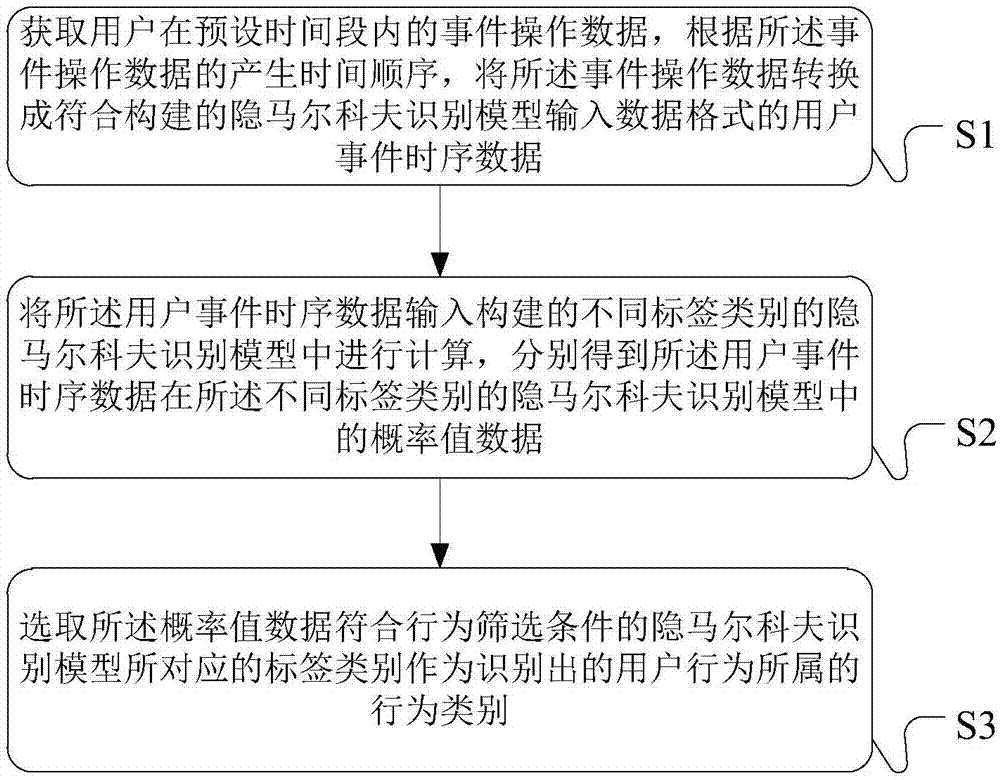
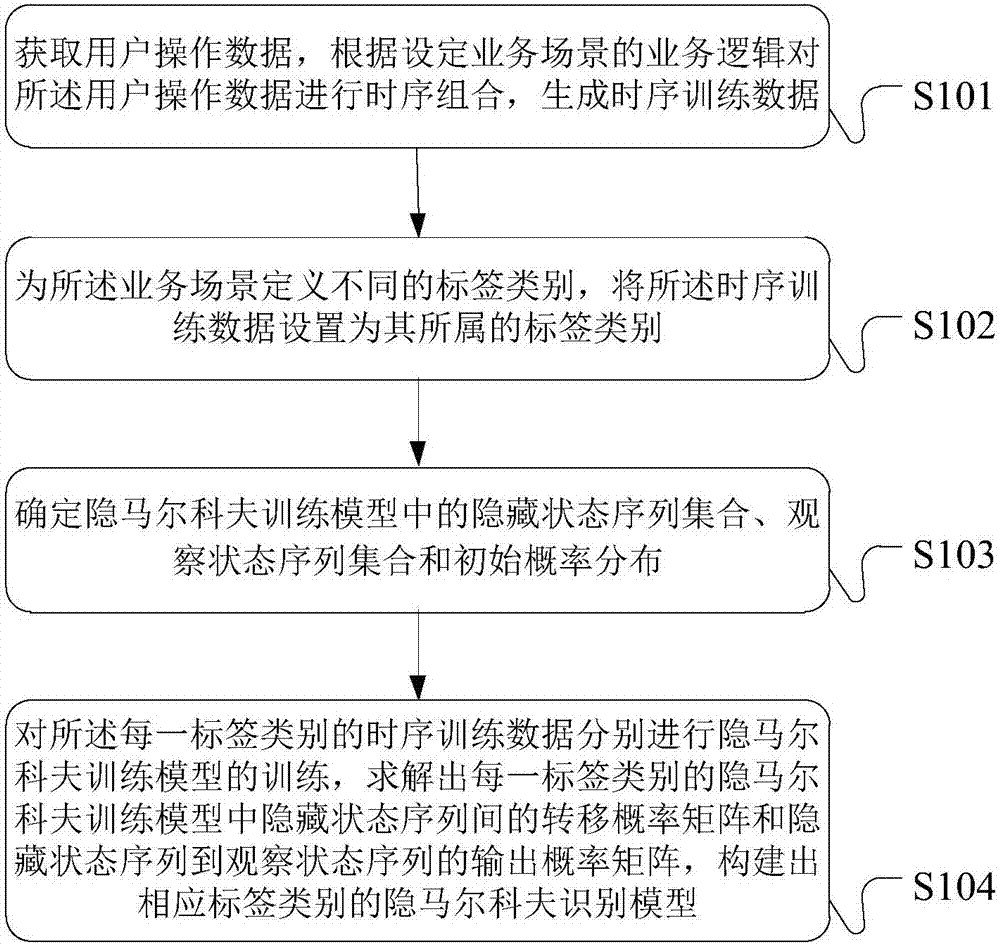
Event time sequence data processing method, device and system for recognizing user behaviors
ActiveCN107402921AAccurate identificationImprove reliabilityFinanceResourcesOperational behaviorDependability
The invention provides an event time sequence data processing method, device and system for recognizing user behaviors. The method comprises the steps of obtaining event operation data of a user within a preset period of time, and converting the event operation data into user event time sequence data conforming to constructed hidden Markov recognition model input data formats; inputting user event time sequence data into the constructed hidden Markov recognition models of different label types for calculating to obtain probability value data of the user event time sequence data in the hidden Markov recognition models of different label types; selecting label types corresponding to the hidden Markov recognition models with the probability value data conforming to the screening condition as the behavior type to which the recognized user s behavior belongs. By means of the event time sequence data processing method, on the basis of time sequence user s behavior data, recognized user s behaviors of the user are judged, the user operation behavior recognition result accuracy and reliability are improved, and the user s risk operation behavior recognition and control prevention effects are improved.
Owner:ADVANCED NEW TECH CO LTD
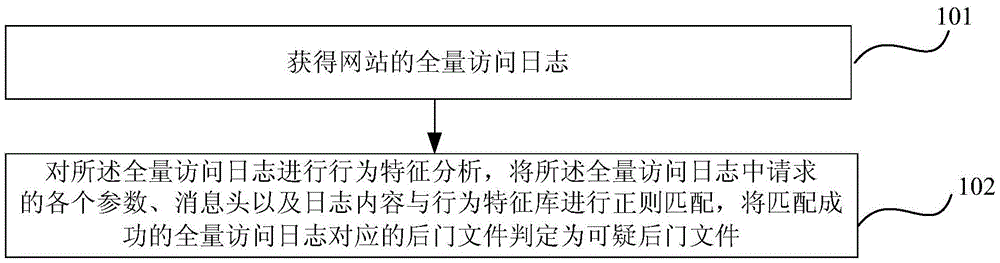
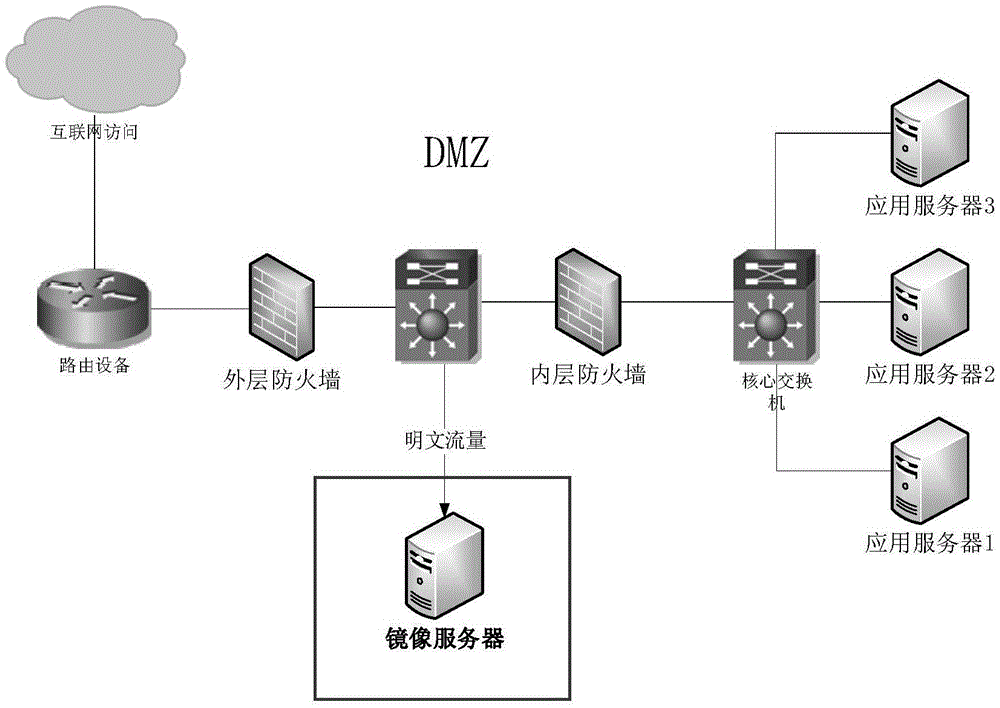
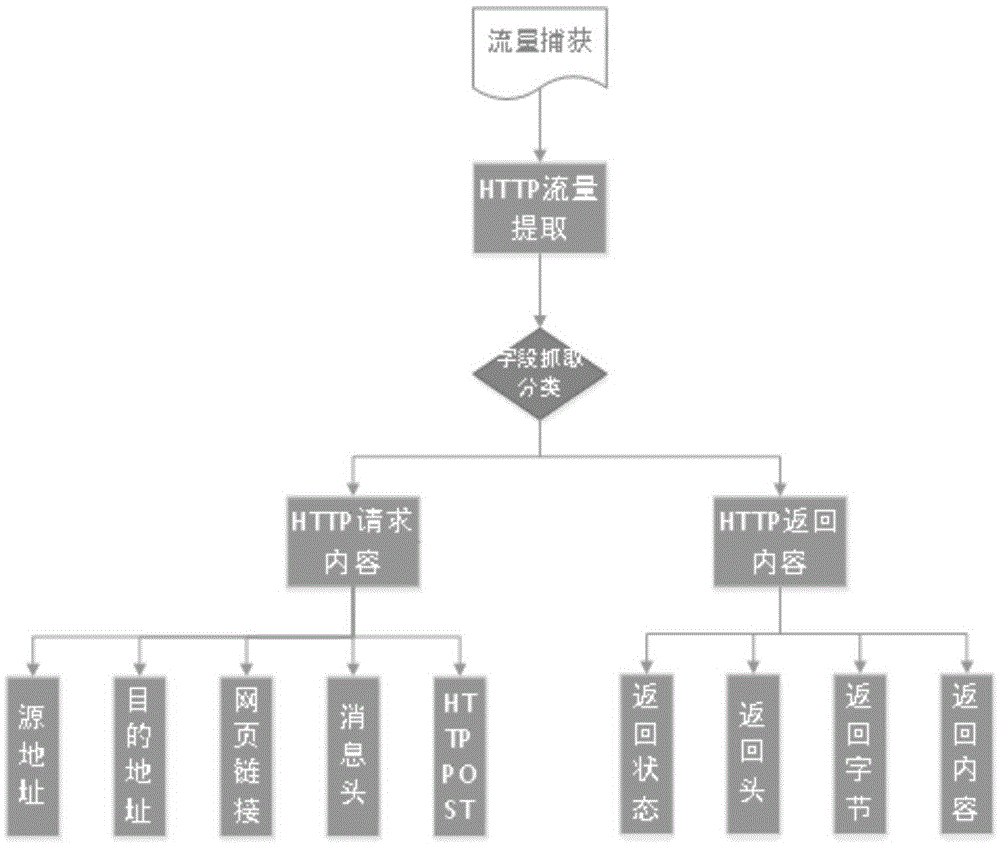
Webshell detection method and apparatus based on total access log analysis
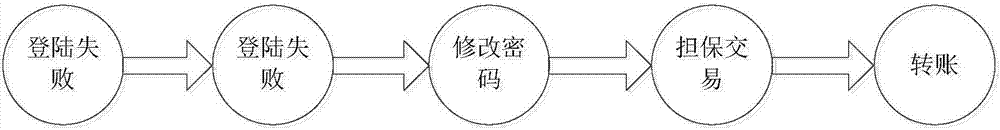
The invention relates to a webshell detection method and apparatus based on total access log analysis. The method includes that the total access log of a website are obtained; the total access log is subjected to characteristic analysis, the request parameters, message headers, and returned data content in the total access log are subjected to regular matching with the behavior characteristic database of the webshell, and the matched corresponding webshell files in the total access log are determined as suspected back-door files. The webshell behavior types, names, and the corresponding total access log of the suspected webshell files are sent to a log server and are alarmed. The method is suitable for detecting the scenes that hackers control the directly uploaded webshell deformed files and encrypted files, and embed the webshell files to normal files to carry out attacks, and makes up the defects of file hash comparison, common function comparison or other webshell detection methods.
Owner:CHINA UNIONPAY
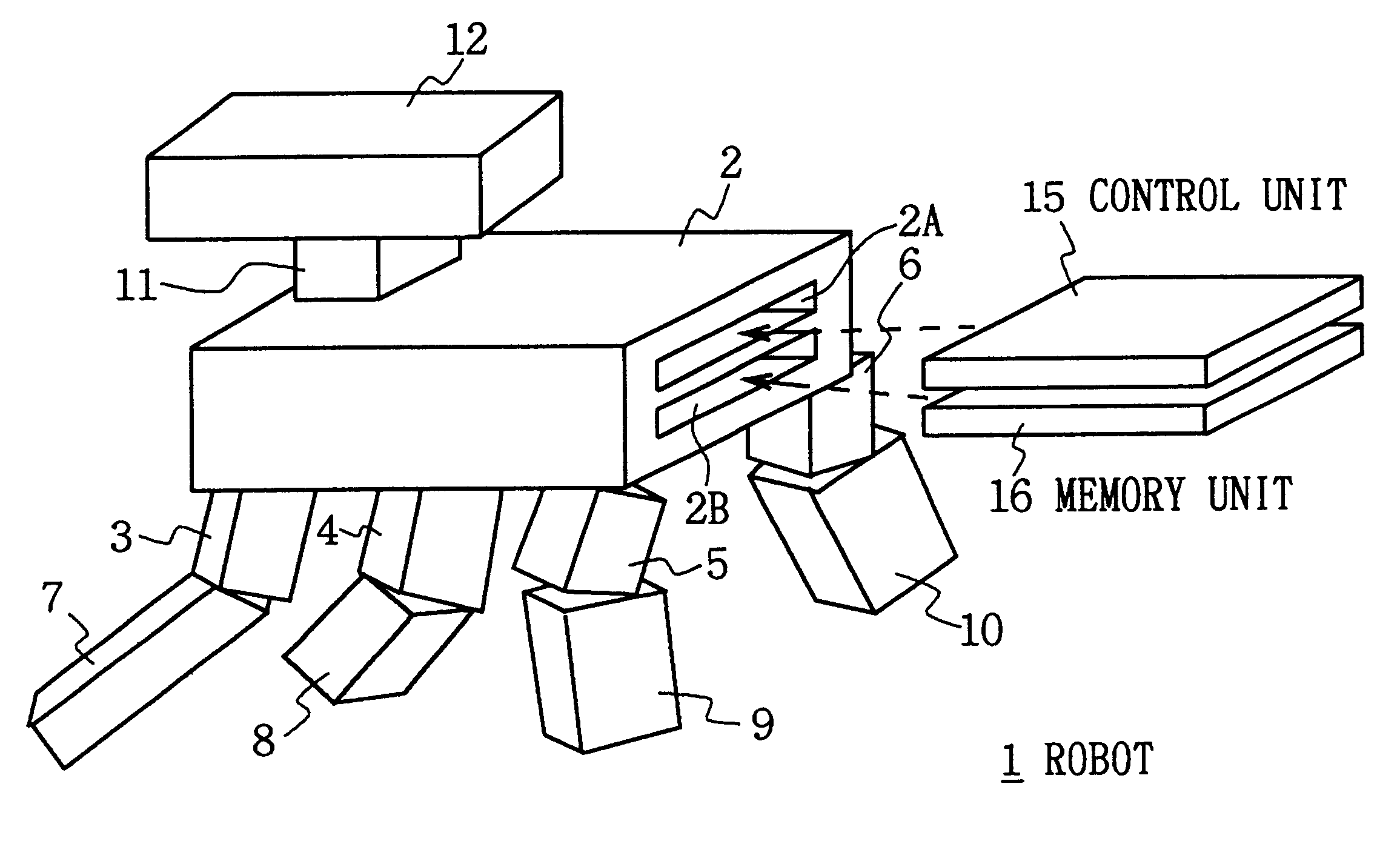
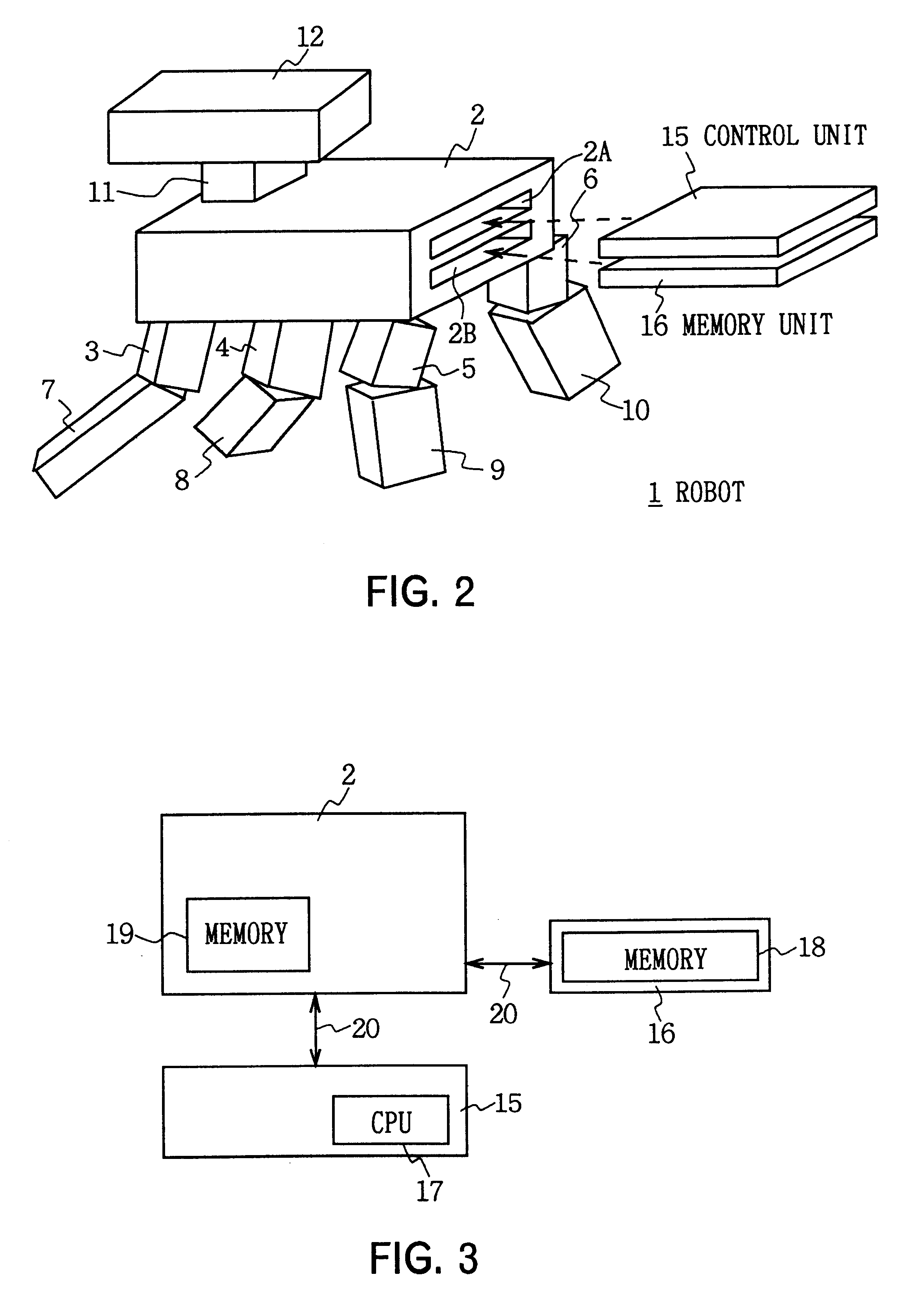
Robot device
InactiveUS6321140B1Promote exchangeSlow changeProgramme-controlled manipulatorComputer controlEmbedded systemBehavior type
A robot device having a plurality of component units connected together and controller detachably mounted on one of the component units for driving and controlling each the component units in a prescribed state. The control device is easily exchangeable for another control device. The robot device may further include a storing device detachably mounted on the respective component unit for storing desired behavior type information. The storing device is readily exchangeable for another storing device having stored therein different behavior type information.
Owner:SONY CORP
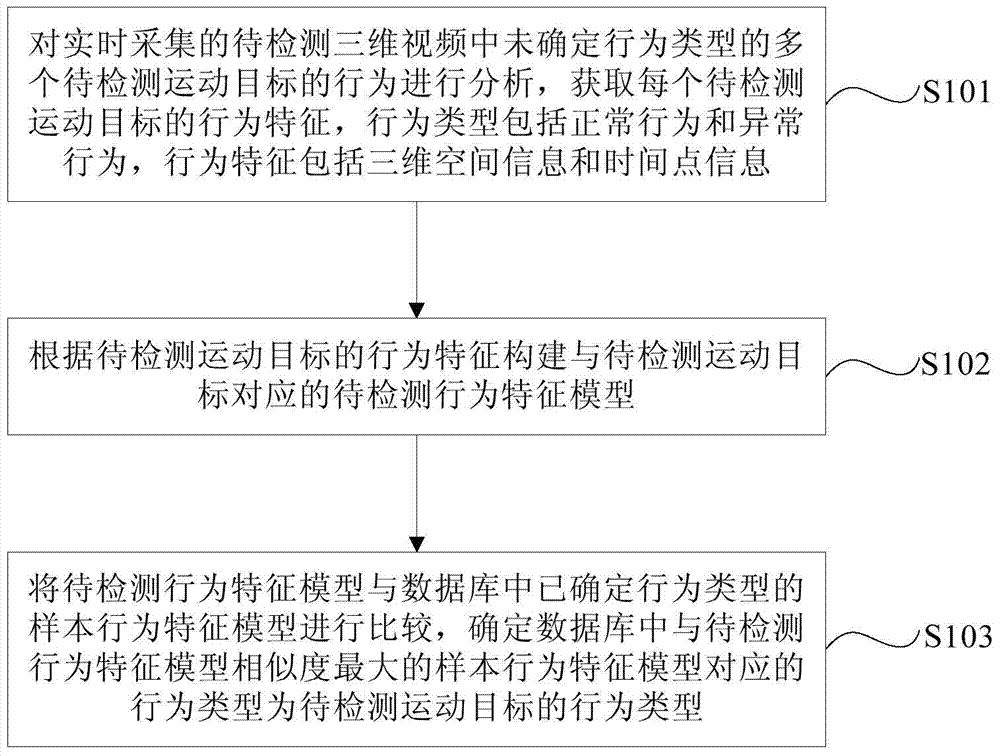
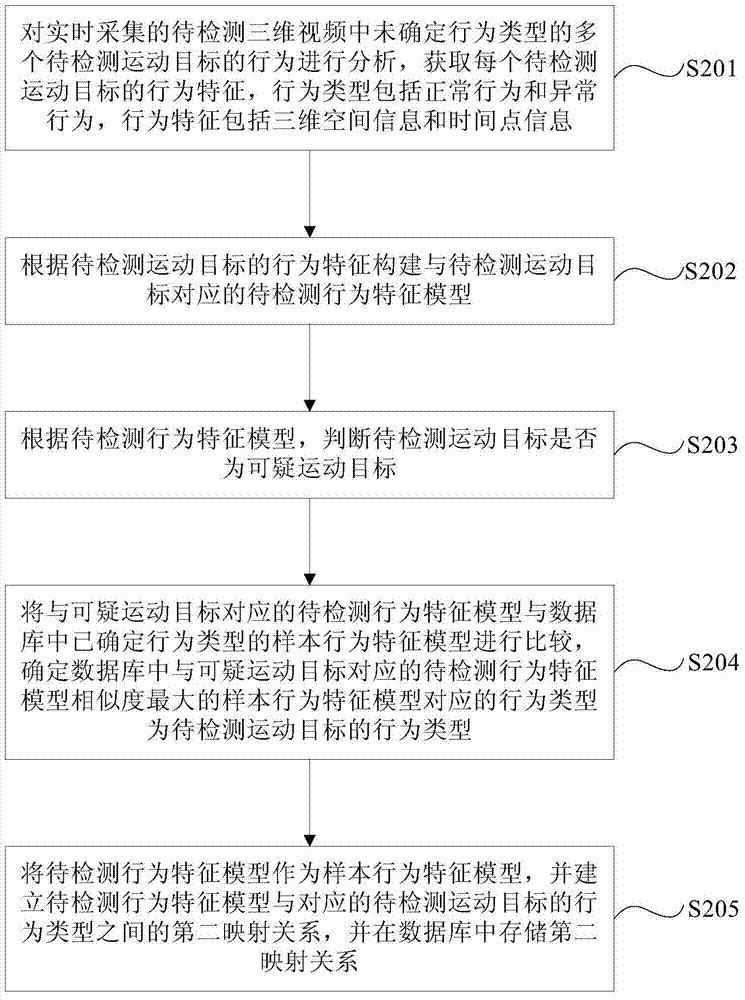
Method and device for detecting abnormal behaviors
The invention provides a method and device for detecting abnormal behaviors. The method comprises the steps that behaviors of a plurality of moving objects, to be detected, with undetermined behavior types are analyzed, the moving objects to be detected are collected in a three-dimensional video in real time, the behavior feature of each moving object to be detected is obtained, the behavior types comprise normal behaviors and the abnormal behaviors, and the behavior features comprise three-dimensional space information and point-in-time information; corresponding behavior feature models to be detected are constructed according to the behavior features of the moving objects to be detected; the behavior feature models to be detected are compared with sample behavior feature models with determined behavior types in a database, and behavior types corresponding to the sample behavior feature models most similar to the behavior feature models to be detected in the database are determined to be the behavior types of the moving objects to be detected. According to the method and device for detecting the abnormal behaviors, the problems that due to the fact that pedestrians are blocked seriously, analysis errors of the behavior features of the moving objects are large, and the accuracy of a detection result is low are solved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
An abnormal behavior detection method based on a linear dynamic system and a deep network
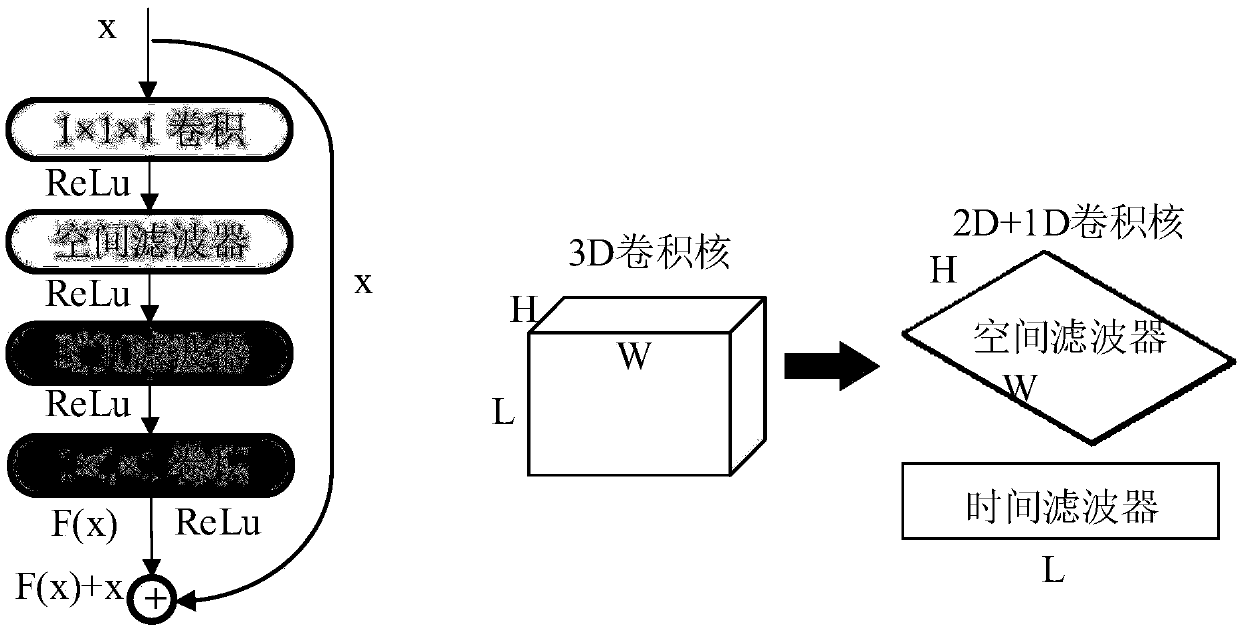
ActiveCN109670446AImprove feature extractionIncrease the number of layersCharacter and pattern recognitionNeural architecturesSupport vector machineFeature extraction
The invention provides an abnormal behavior detection method based on a linear dynamic system and a deep network. An LDS dynamic system model and a TSN deep learning network are combined, the space-time feature information of actions is extracted through the TSN, then action features are connected in series through an LDS to form complete behavior features, and finally the behavior type is judgedthrough a support vector machine (SVM). According to the method, the 3D convolutional network is established on the basis of the residual network, and the 3D convolutional kernel is established in a 2D+1D form, so that the network parameter quantity is reduced, and the problem that the original 3D network cannot preload the weight is solved. A residual 3D network is introduced into the TSN structure, so that the feature extraction capability of the network is improved. The number of network layers is increased, and the fitting capability of the network is improved. According to the invention,the high-precision identification of long-sequence abnormal actions can be realized, and finally the accurate monitoring of abnormal behaviors is realized.
Owner:QUANZHOU INST OF EQUIP MFG
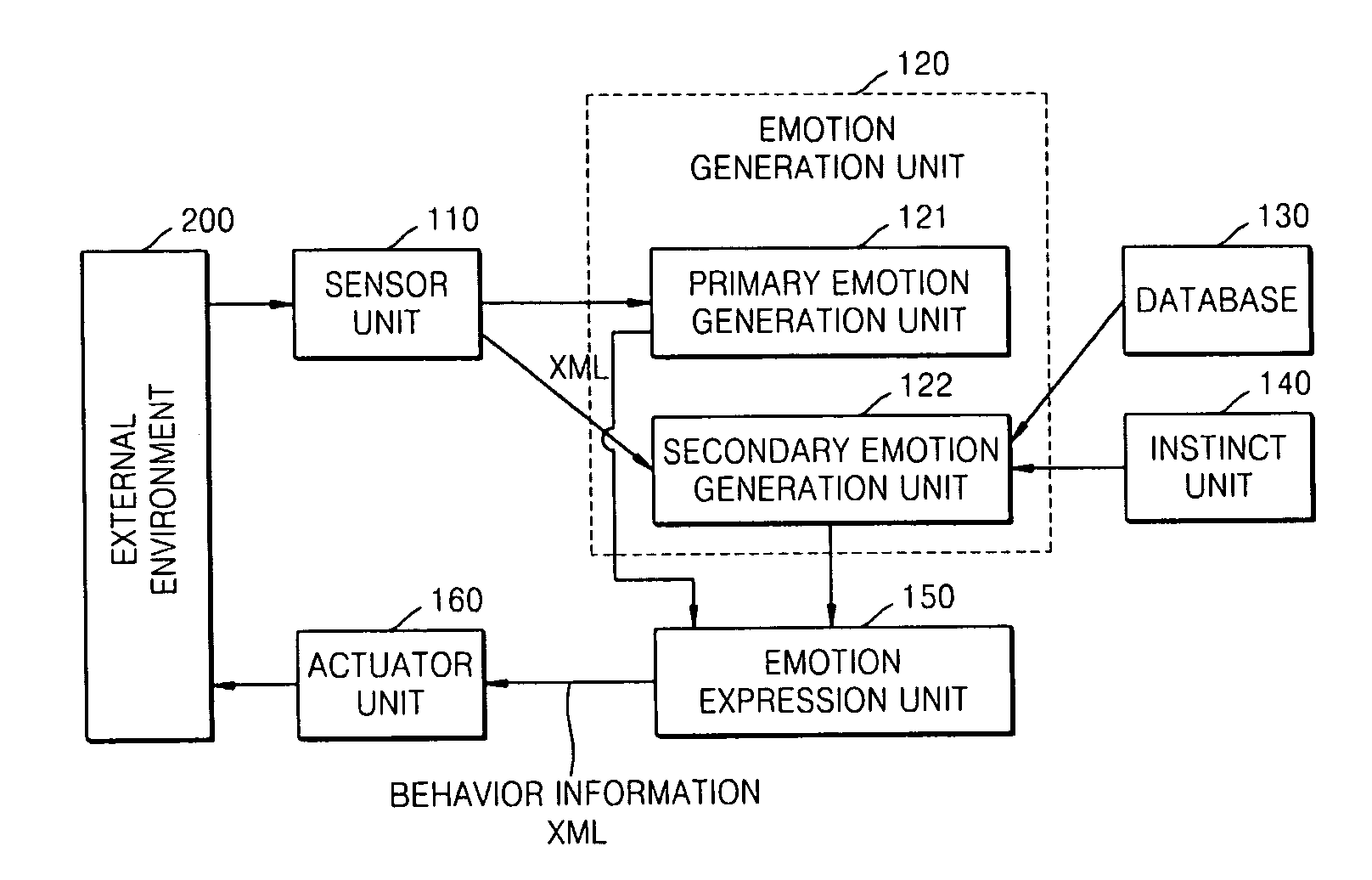
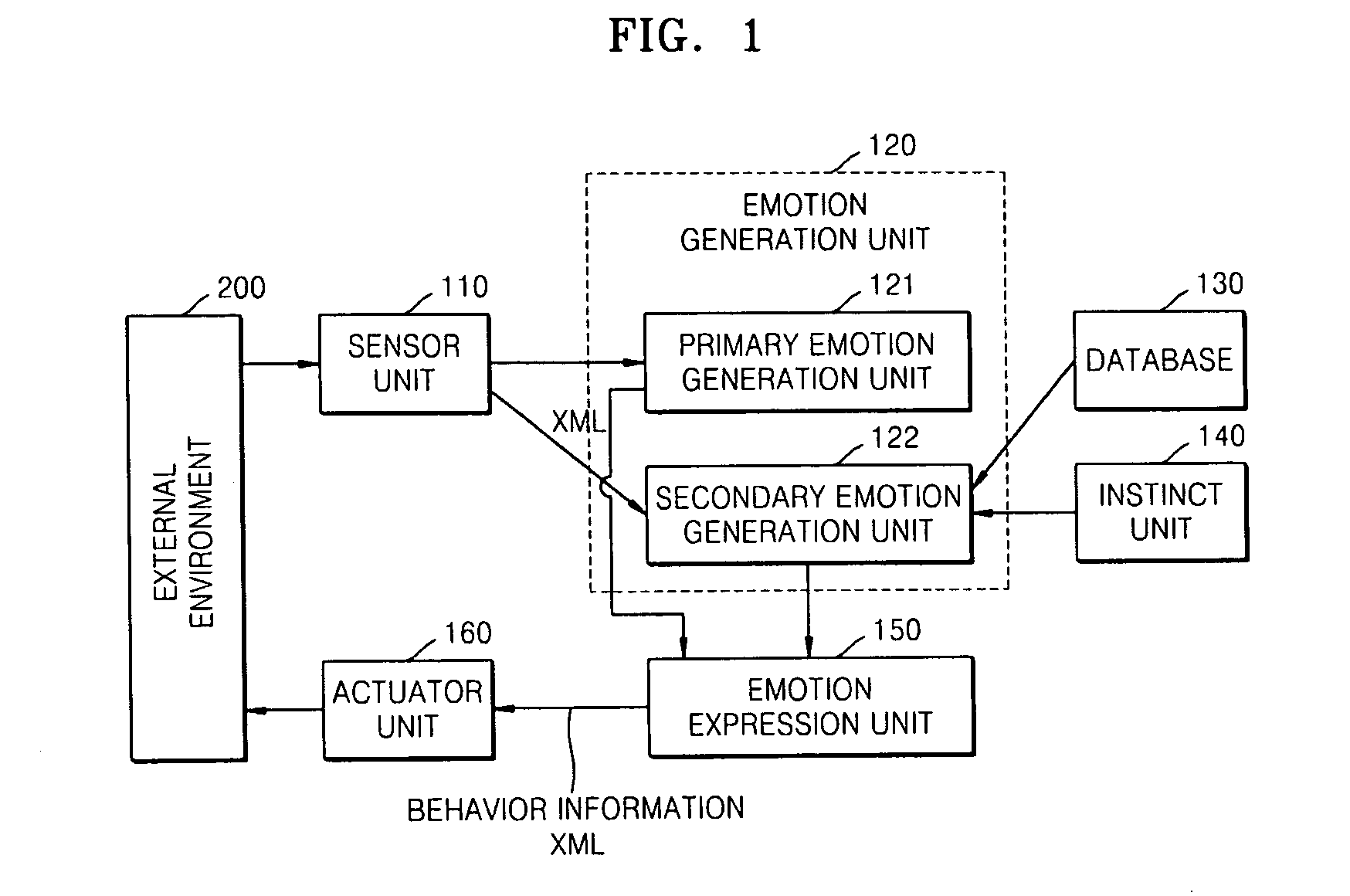
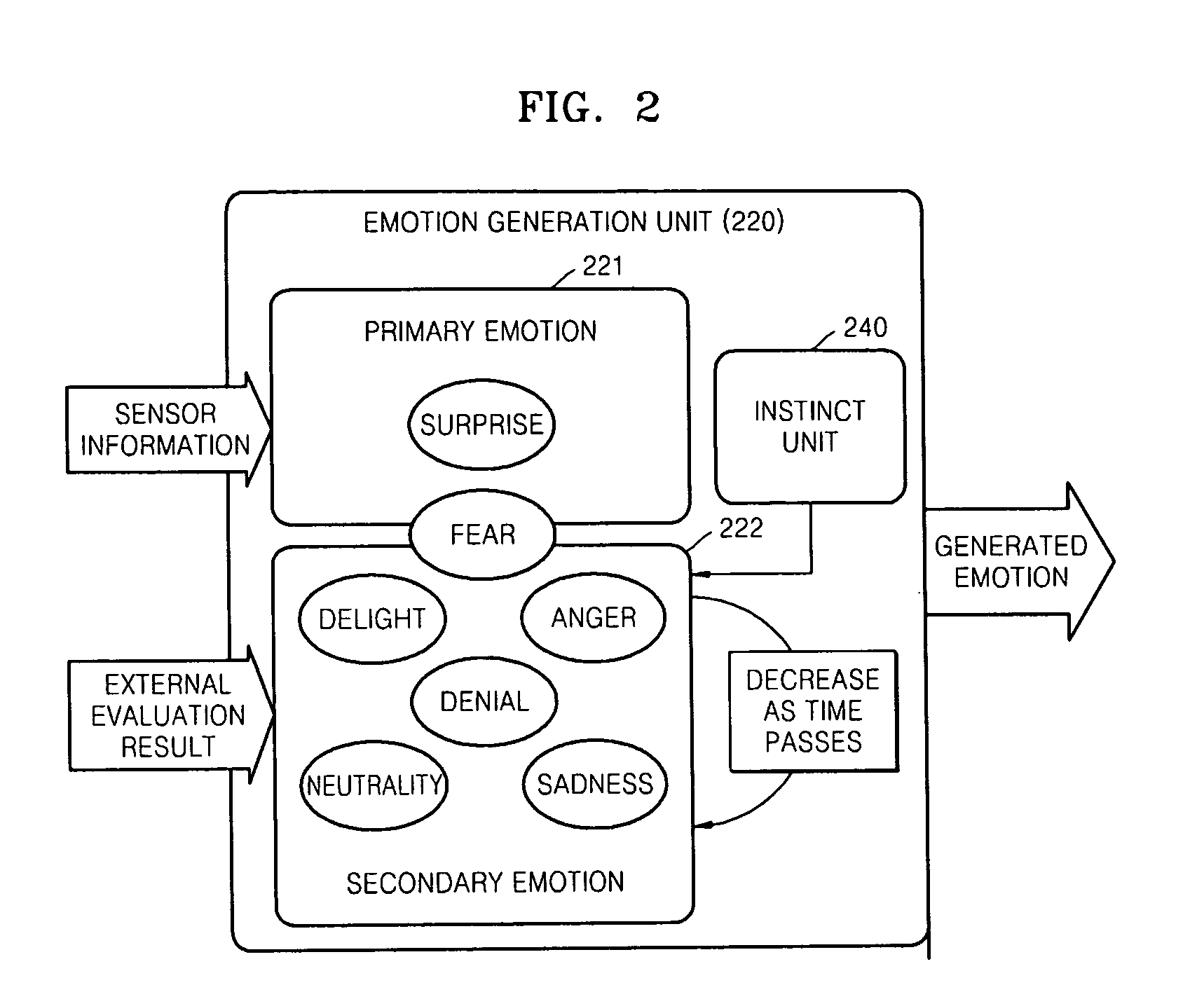
Robot for generating multiple emotions and method of generating multiple emotions in robot
A robot for generating multiple emotions is provided. The robot includes a sensor unit sensing external environment information, a database unit storing a predetermined list including information on types of behavior the robot is allowed, a user's reaction corresponding to each behavior of the robot, and favorite objects of the robot, a primary emotion generation unit generating an emotion corresponding to characteristics of the sensed information when the sensed information exceeds a predetermined threshold value, and a secondary emotion generation unit generating an emotion corresponding to characteristics of the sensed information based on the information sensed by the sensor unit, the list stored in the database unit, the amount of internal power of the robot, internal information on the robot indicating the existence of an operational error and an elapse of time.
Owner:ELECTRONICS & TELECOMM RES INST
Apparatus, method and article for providing vehicle event data
ActiveUS20150134142A1Registering/indicating working of vehiclesDigital data processing detailsDashboardAccelerometer
Detected events such as impacts, accidents, breakdowns, and types of driving behaviors based on feedback from tilt, gravity, accelerometers and / or shock sensors within a portable electrical power storage device such as a battery and / or within a vehicle (e.g., an electric scooter) are communicated to the user's mobile device, dashboard display and / or backend systems over wired and / or wireless communication channels. The communication of the events and types of events are logged and automatically aggregated from multiple vehicles for further analysis to determine various potential system-wide safety issues and to track event history on an individual per-user or individual per-scooter basis or individual per-battery basis. Such event data may also be transferred accordingly via the battery exchange process at the online exchange machine through a memory device attached to the battery that stores the event data.
Owner:GOGORO
Game user behavior analysis method and computer readable storage medium
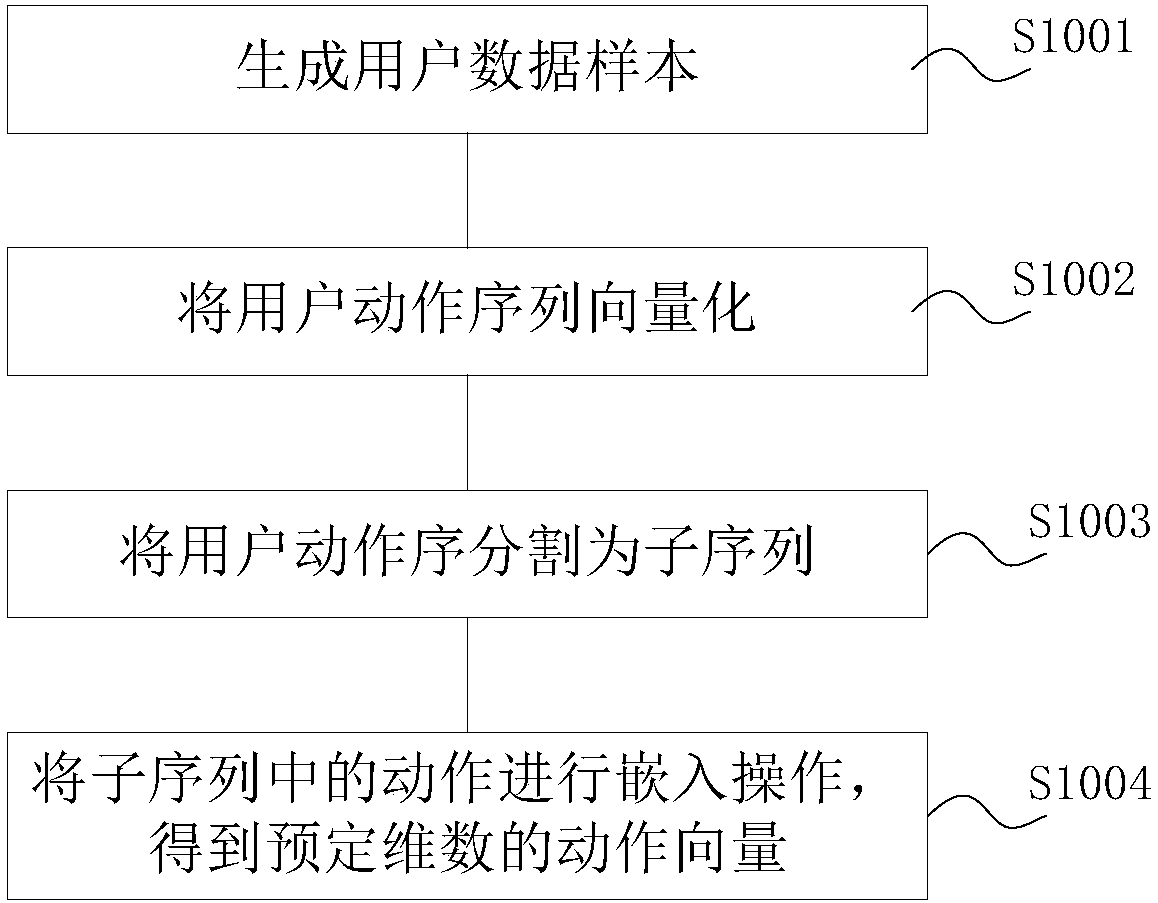
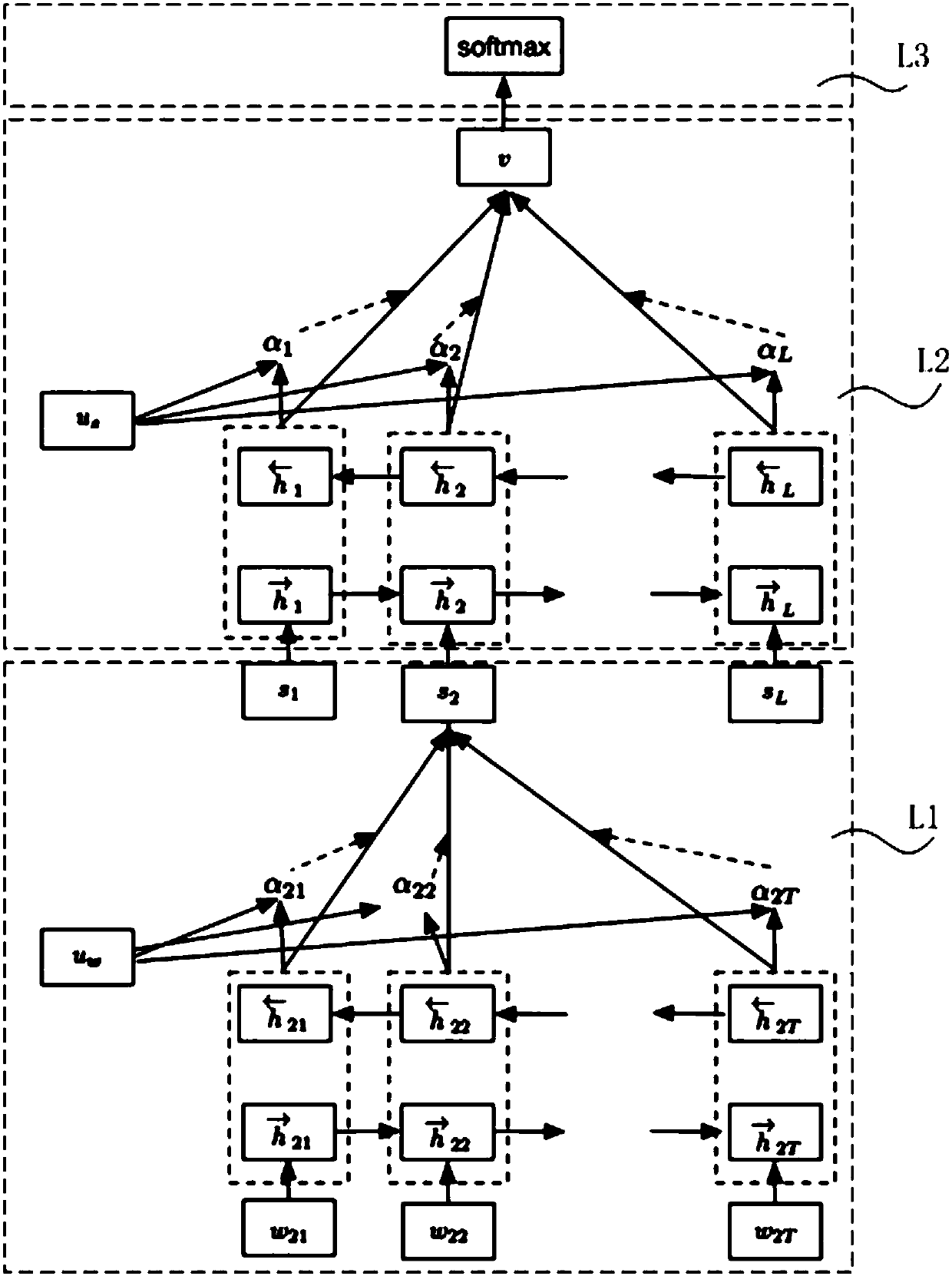
ActiveCN107944915AReduce churnImprove game contentBiological neural network modelsMarket data gatheringPaymentAttention model
The invention provides a user behavior analysis method and a computer readable storage medium. The method comprises the following steps that a neural network model including a cyclic neural network model and an attention model is trained by using user behavior data samples so as to acquire the corresponding weight value of each motor of different behavior types of users, wherein the user behaviordata samples include the motion sequences of different behavior types of users. The objective reasons of loss of the user or the behavior of no paying and other behaviors caused by the game can be analyzed in a short period of time by acquiring the weight relation between the motion sequences of the user in the game and the loss of the user and user payment, and the game content can be improved ina targeted way through the result obtained by analysis so that loss of the user can be reduced and even the user can be attracted back to the game.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
A pedestrian abnormal behavior identification method based on 3D convolution
PendingCN109635790AStay recognizableReduce computing costCharacter and pattern recognitionNeural architecturesNerve networkData set
The invention discloses a pedestrian abnormal behavior identification method based on 3D convolution. The pedestrian abnormal behavior identification method comprises the steps of S1, creating a dataset containing abnormal behaviors such as fighting, dog walking and falling; S2, in combination with the latest video behavior identification scheme, constructing a 3D convolutional neural network considering both precision and speed; S3, preprocessing the images in the data set, and sending the preprocessed images into a 3D convolutional neural network to obtain a video abnormal behavior recognition model; And S4, inputting a tested pedestrian monitoring video, and outputting an abnormal behavior type. According to the identification method provided by the invention, the lightweight 2D convolutional network MobileNet idea is migrated to the 3D network, so that the calculation cost can be reduced on the basis of maintaining the identification performance; Meanwhile, a self-adaptive poolinglayer and a sparse time sampling strategy are adopted, so that a large amount of redundant information and fuzzy noise contained in continuous frames can be reduced.
Owner:HANGZHOU DIANZI UNIV
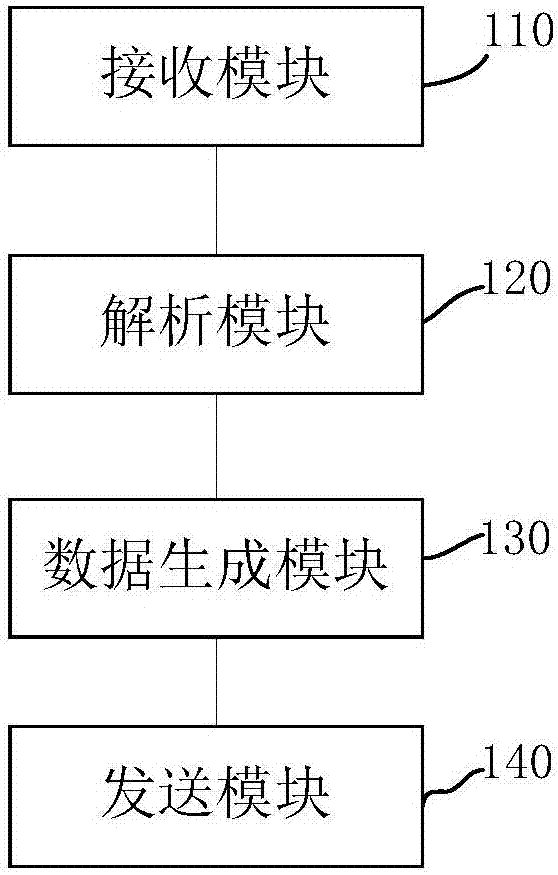
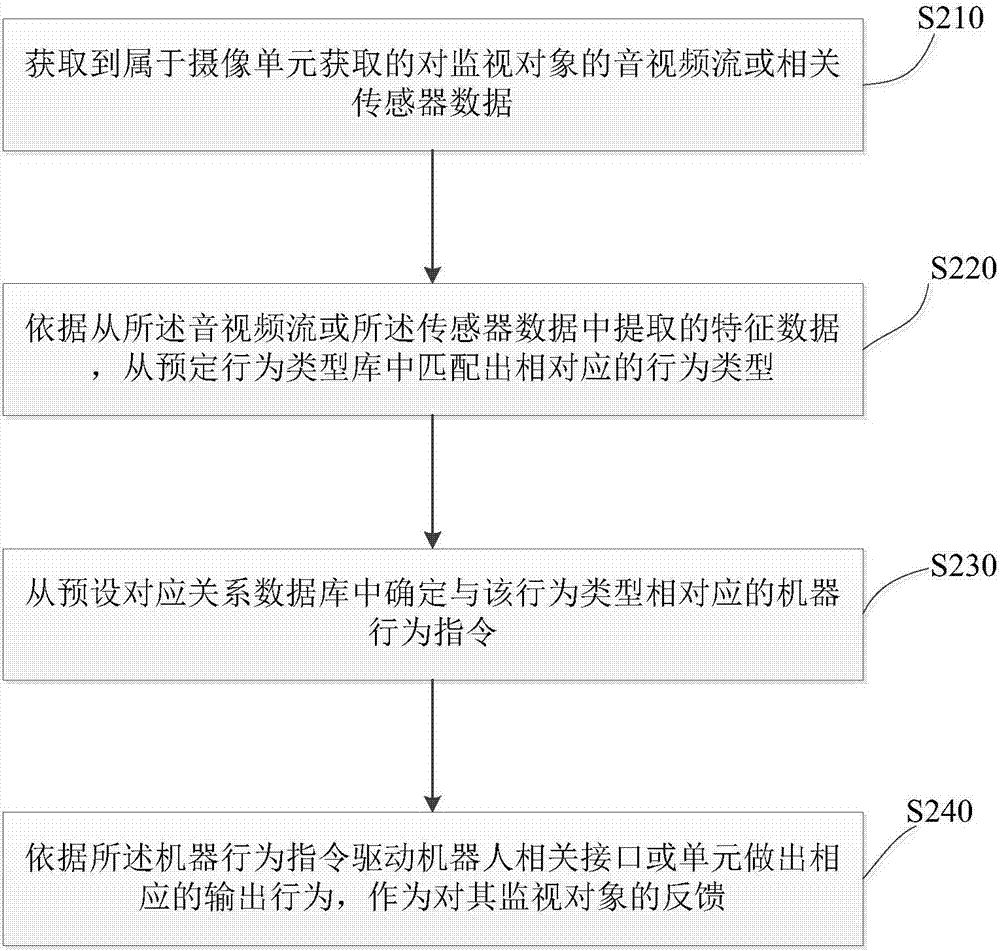
Robot interaction control method, server and robot
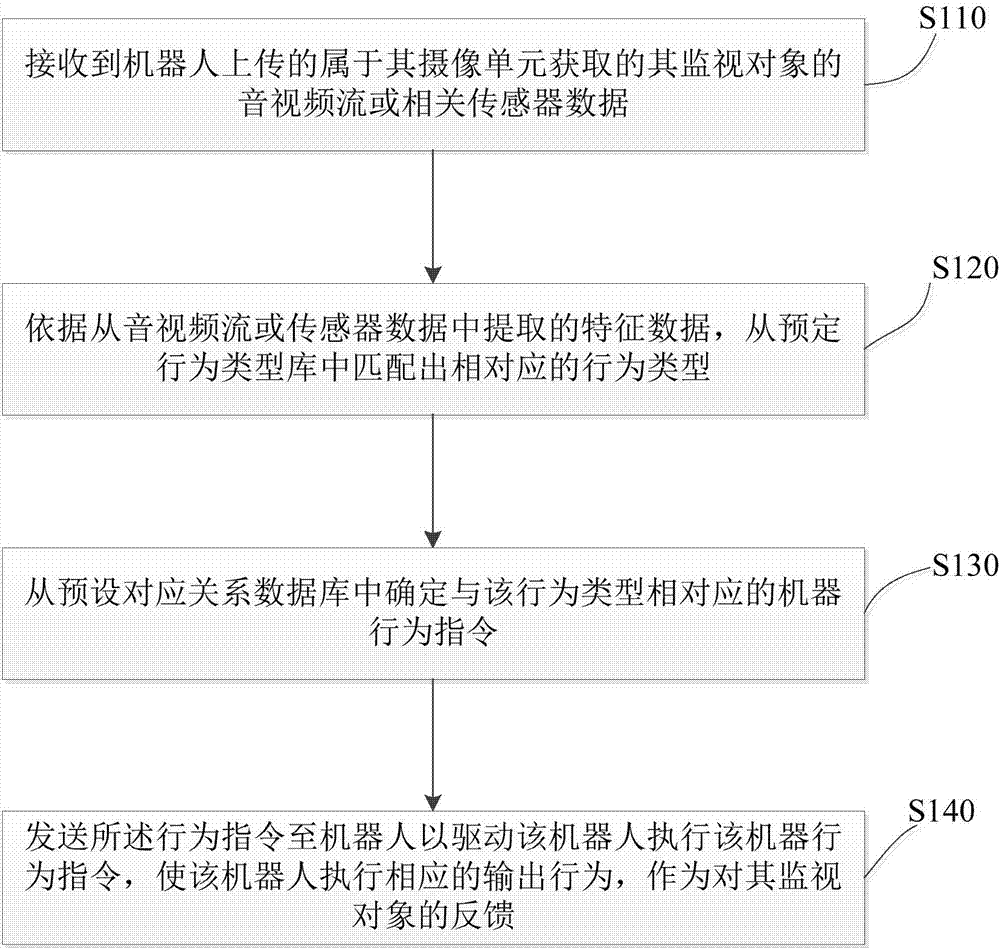
ActiveCN106873773AImprove intelligenceEnhanced interactionInput/output for user-computer interactionGraph readingInteraction controlRelational database
The invention provides a robot interaction control method, a server and a robot. The method comprises the following steps: receiving audio and video streams of a monitored object, which is obtained by a photographing unit and is uploaded by the robot, or related sensor data; matching a corresponding behavior type from a pre-set behavior type library according to the audio and video streams or characteristic data extracted from the sensor data; determining a machine behavior instruction corresponding to the behavior type from a pre-set corresponding relation database; and sending the machine behavior instruction to the robot to drive the robot to execute the machine behavior instruction, so as to enable the robot to execute corresponding output behaviors to be taken as feedback of the monitored object. According to the method and equipment, provided by the invention, the intelligence level of the robot is greatly improved, the interaction between the robot and people is more convenient and forms are more abundant.
Owner:BEIJING QIHOO TECH CO LTD
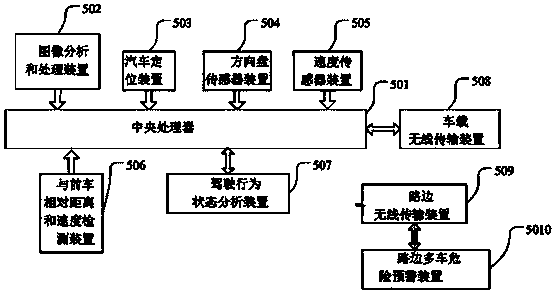
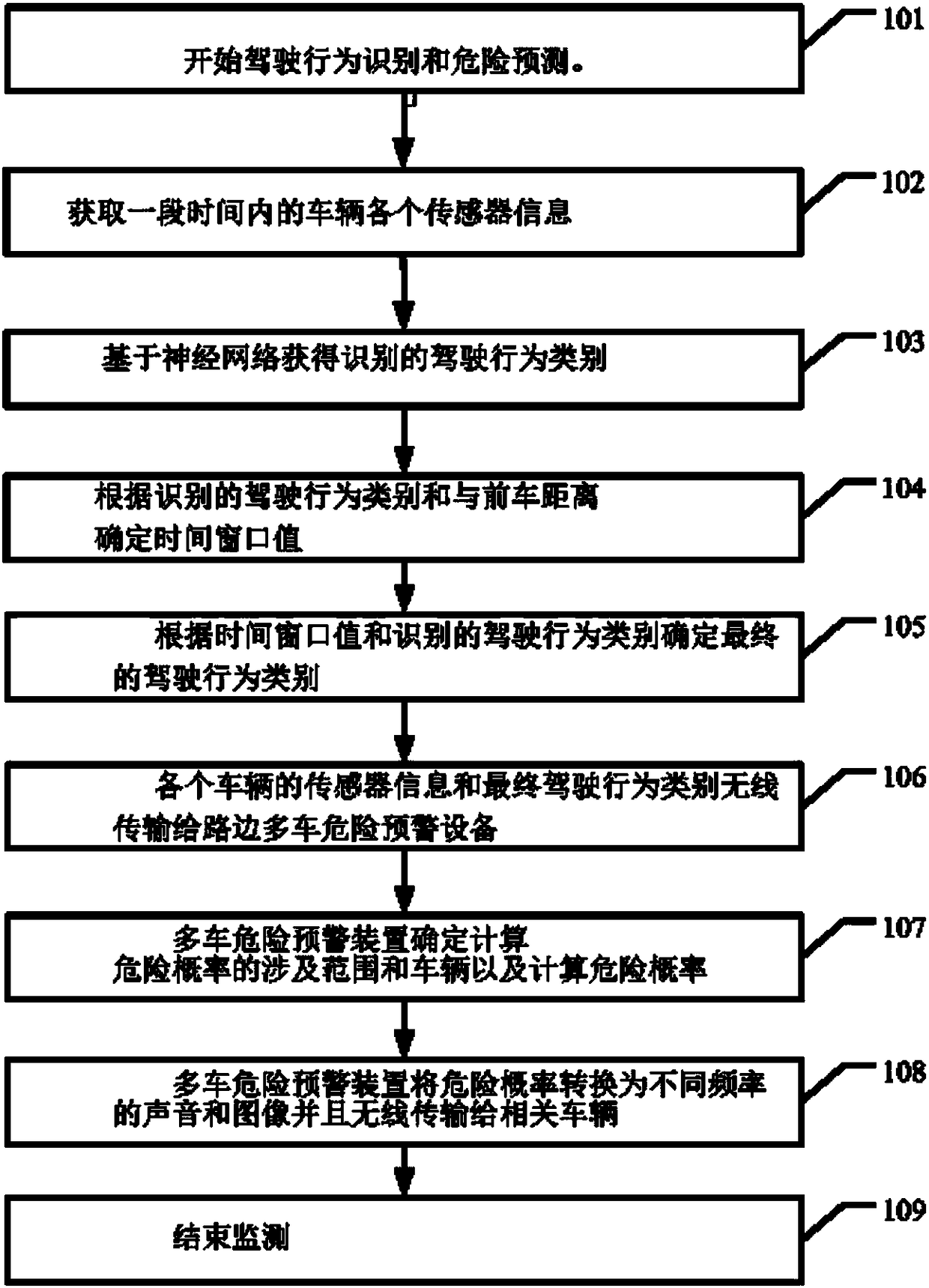
Multi-vehicle driving behavior analysis and danger early warning method and system
PendingCN108428343AEffectively monitor driving conditionsReduce wasteDetection of traffic movementAnti-collision systemsWireless transmissionDriver/operator
The invention discloses a multi-vehicle driving behavior analysis and danger early warning method and system. The method includes the steps that firstly, a driving behavior state analysis device in avehicle obtains driver control and vehicle state feature information in a period of time through vehicle-mounted and in-vehicle sensor systems, inputs the feature information into a trained neural-network-based driving behavior model and determines the corresponding driving behavior class; a vehicle-mounted wireless transmission device transmits related vehicle information and driving behavior type information to a roadside multi-vehicle danger prediction device to calculate the danger probability, converts the danger probability into image and sound danger prompt information and sends the image and sound danger prompt information to related vehicles. By means of the multi-vehicle driving behavior analysis and danger prediction method and system, the driving conditions of multiple vehicleswhich may cause danger can be effectively monitored and mastered, the waste of resources is reduced, and the driving safety and danger prediction efficiency are improved.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
Identifying customer behavioral types from a continuous video stream for use in optimizing loss leader merchandizing
A computer implemented method, apparatus, and computer usable program product for optimizing loss leader merchandizing. The process parses event data to identify physical patterns of customer behavior, wherein the event data is derived from a continuous video stream captured at a retail facility, and associates the physical patterns of customer behavior with customer profile data to form dynamic customer profiles. The process then analyzes the dynamic customer profiles to identify types of customers and presents marketing incentives for a set of loss leader items to customers of a selected customer type, wherein the set of loss leader items are selected based on the dynamic profiles.
Owner:INT BUSINESS MASCH CORP
Multimedia data recommendation method and device, server and storage medium
PendingCN110442790AImprove effectivenessImprove reliabilityDigital data information retrievalSpecial data processing applicationsThe InternetComputer terminal
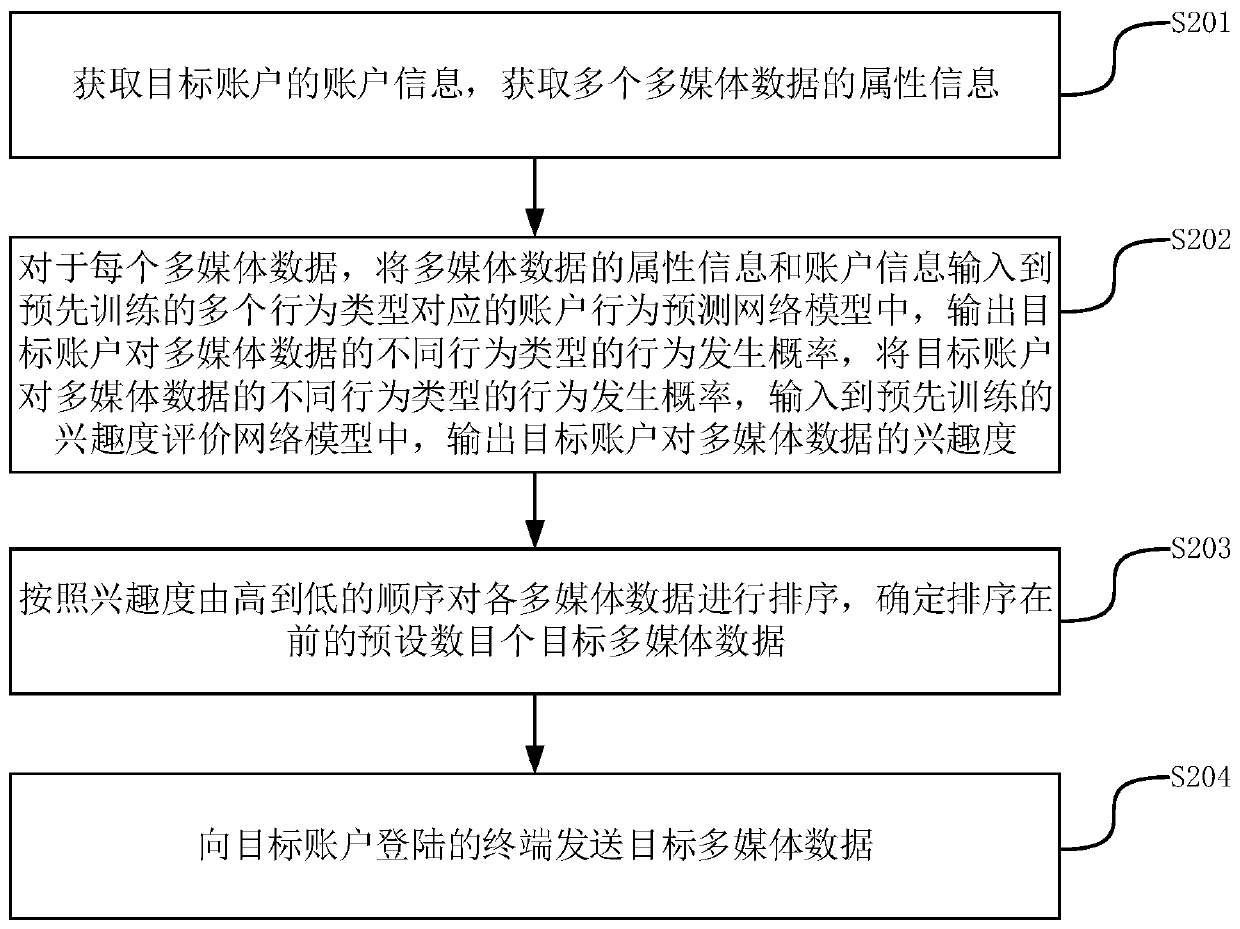
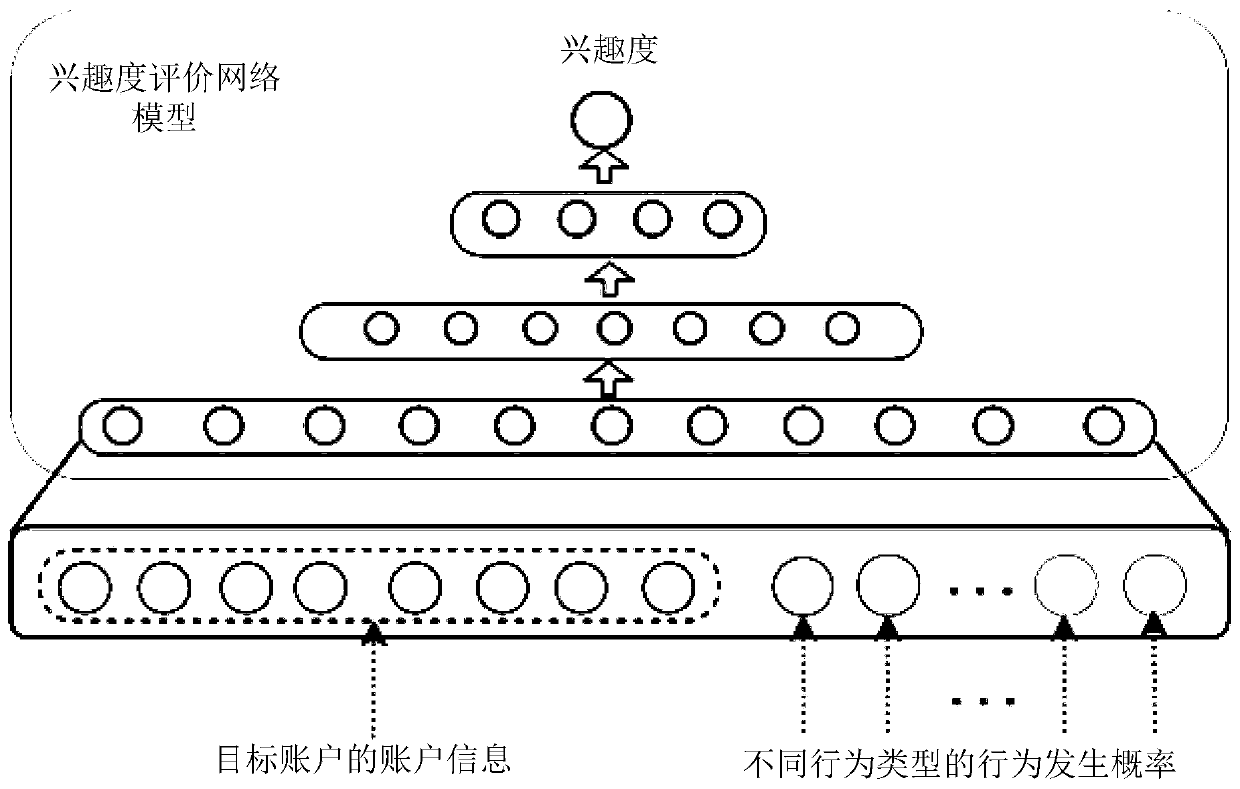
The invention relates to a multimedia data recommendation method and device, a server and a storage medium, and belongs to the technical field of the Internet. The method comprises the following steps: acquiring account information of a target account, and acquiring attribute information of a plurality of multimedia data; for each multimedia data, inputting the attribute information and the account information of the multimedia data into a pre-trained account behavior prediction network model corresponding to a plurality of behavior types, outputting the behavior occurrence probability of thetarget account for different behavior types of the multimedia data, inputting the behavior occurrence probability of the target account for different behavior types of the multimedia data into a pre-trained interestingness evaluation network model, and outputting the interestingness of the target account for the multimedia data; sorting the multimedia data according to the sequence of the interestingness from high to low, and determining a preset number of target multimedia data sorted in the front; and sending the target multimedia data to a terminal logged in by the target account. By adopting the method, the recommendation effectiveness can be improved.
Owner:深圳市雅阅科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com