Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1455 results about "Monitoring program" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
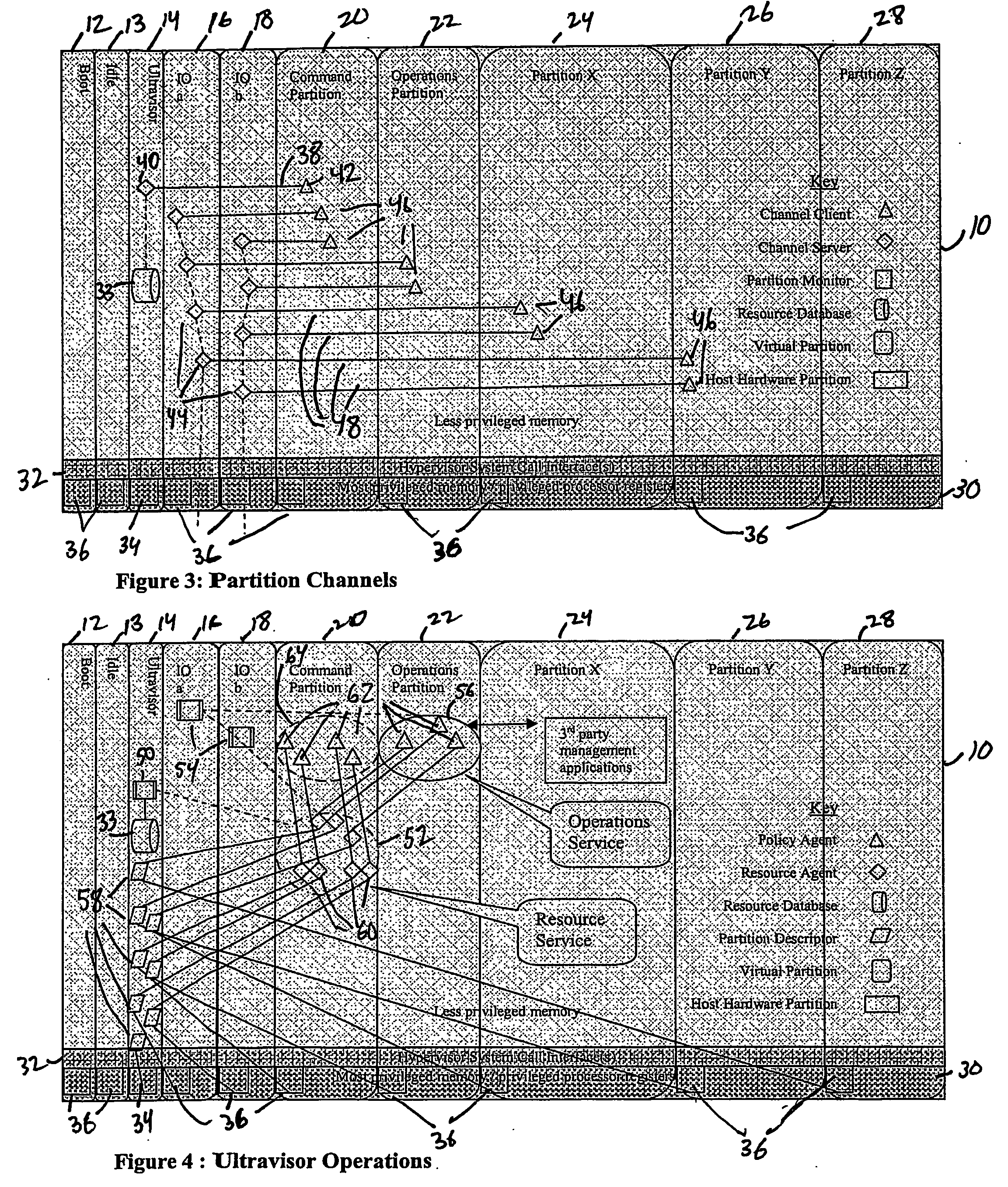
Virtual data center that allocates and manages system resources across multiple nodes
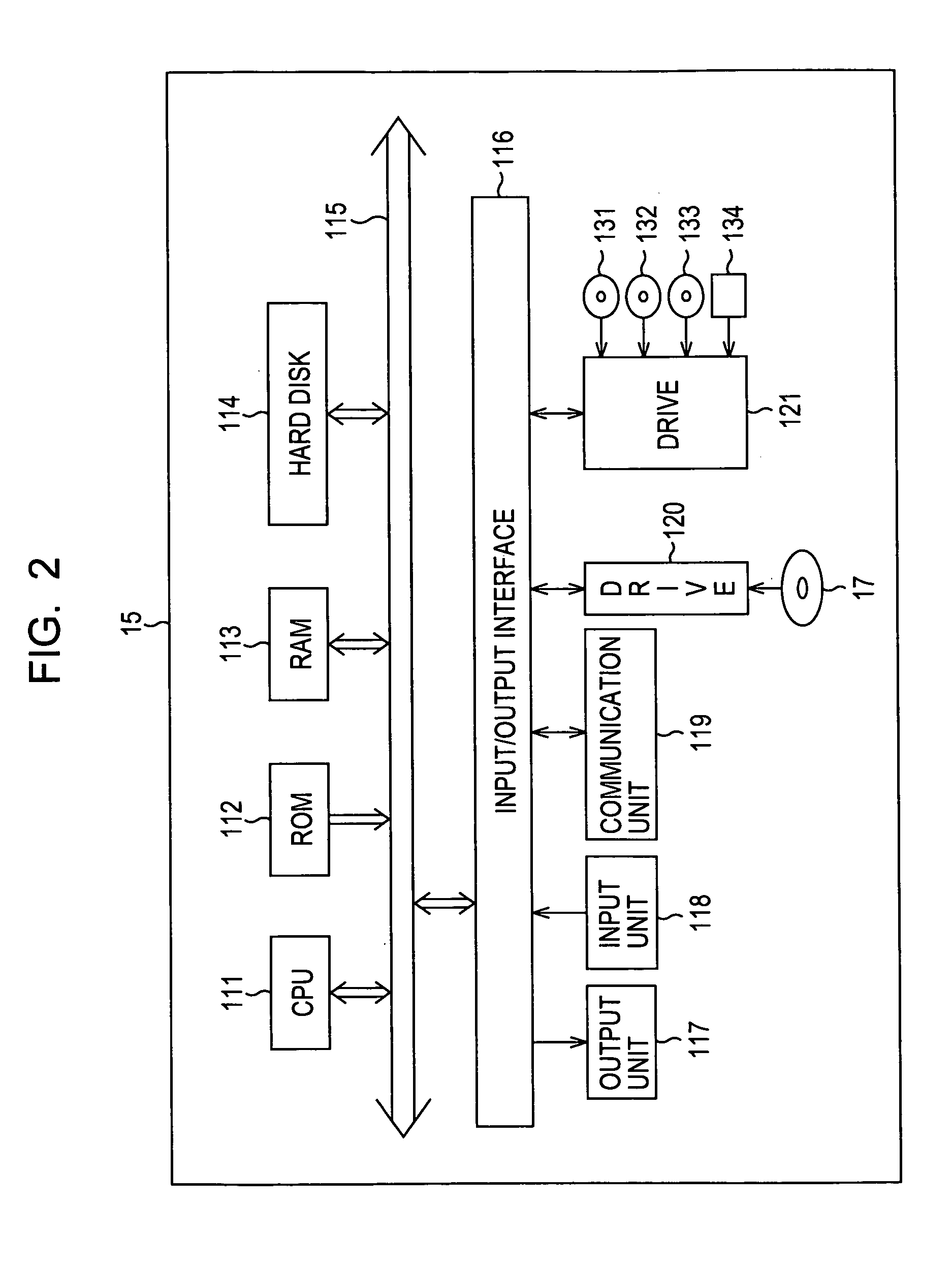
ActiveUS20070067435A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemData center
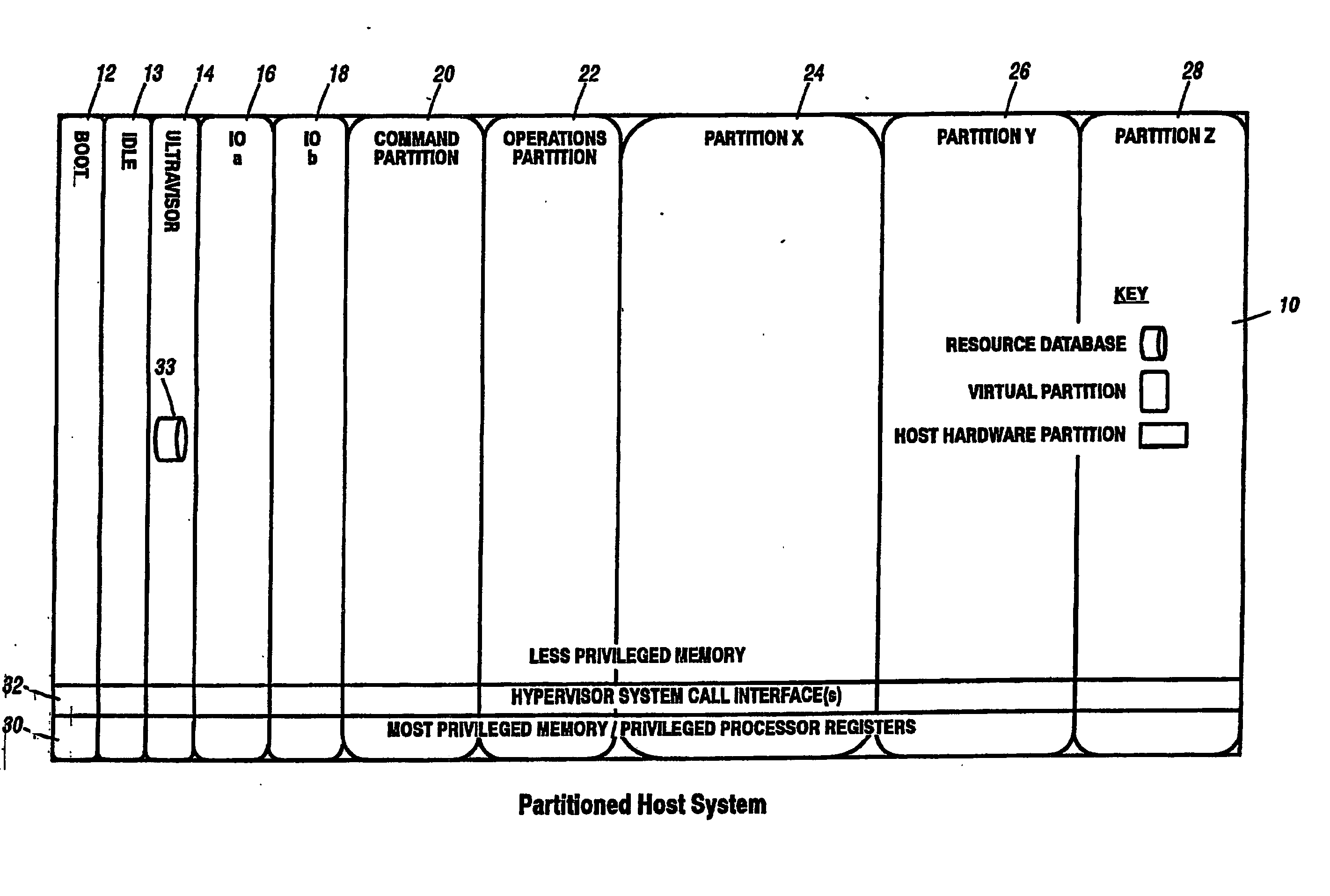
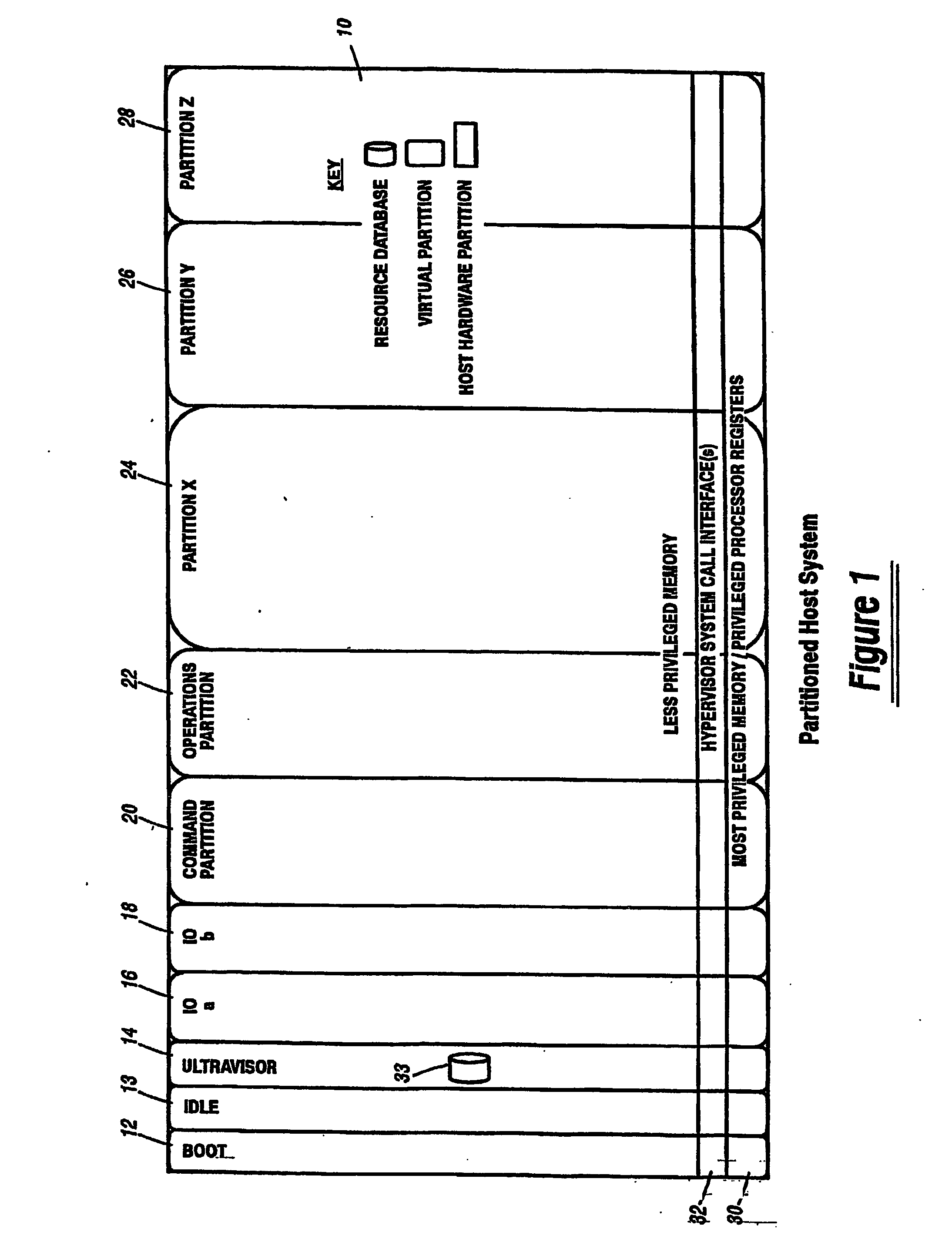
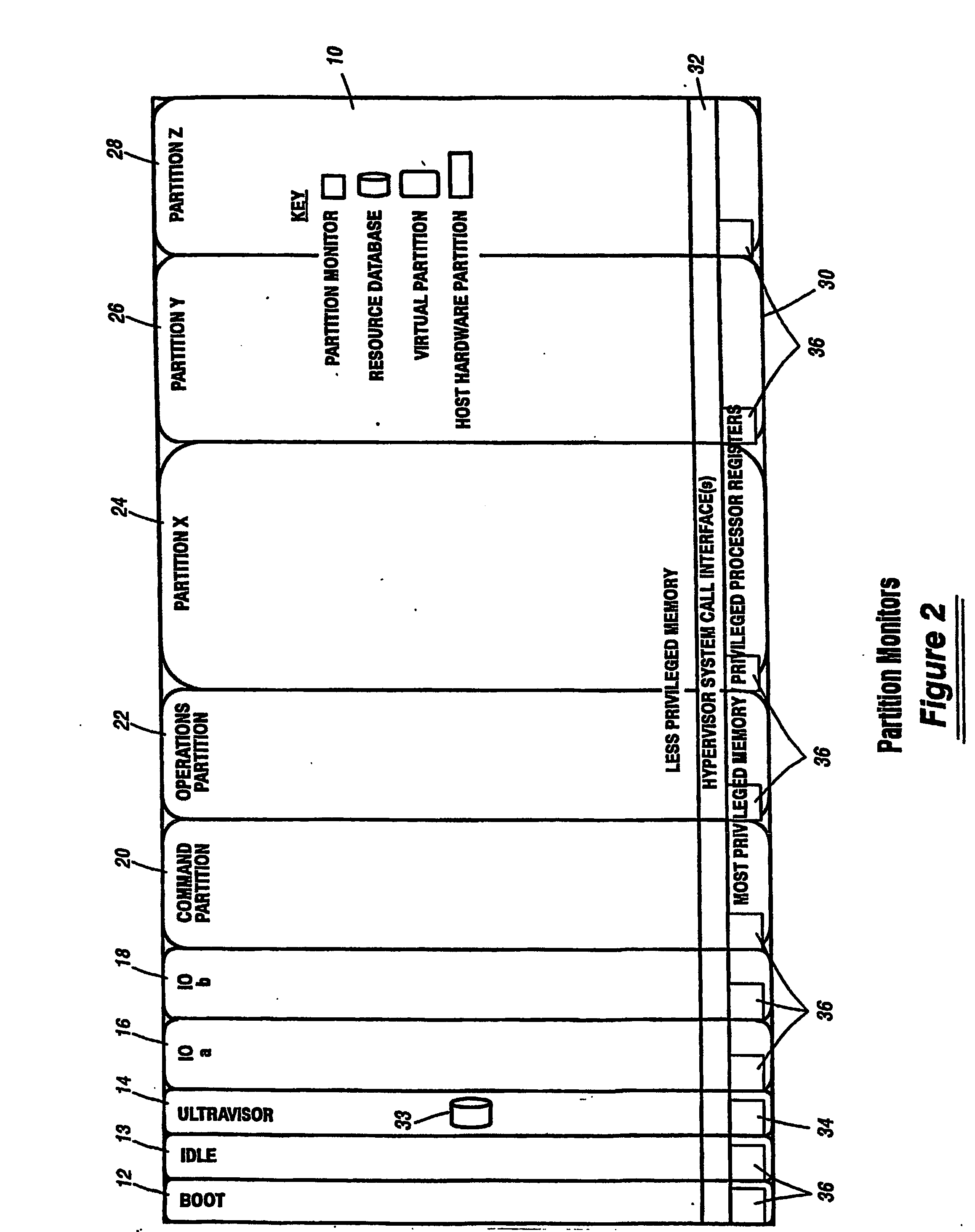
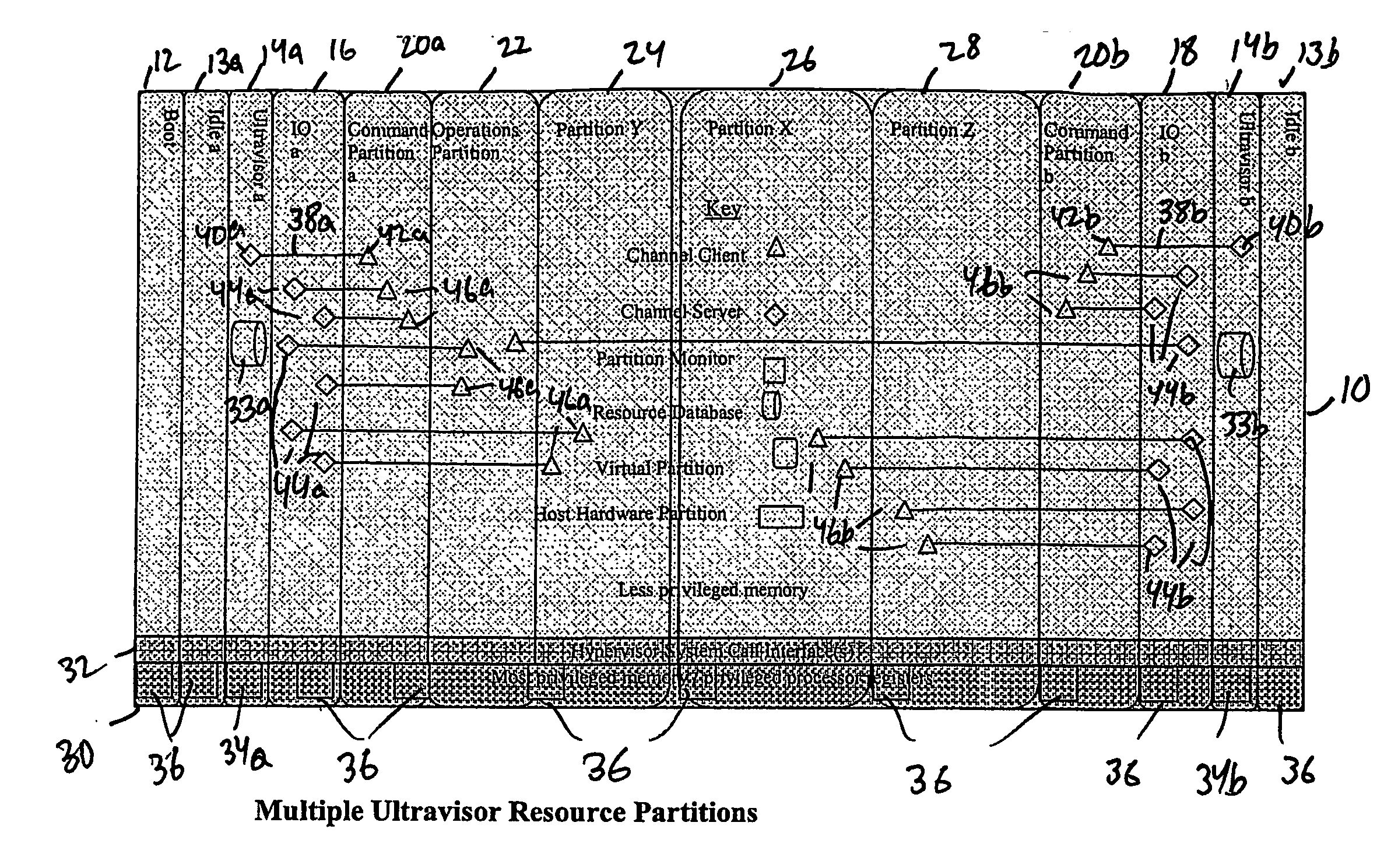
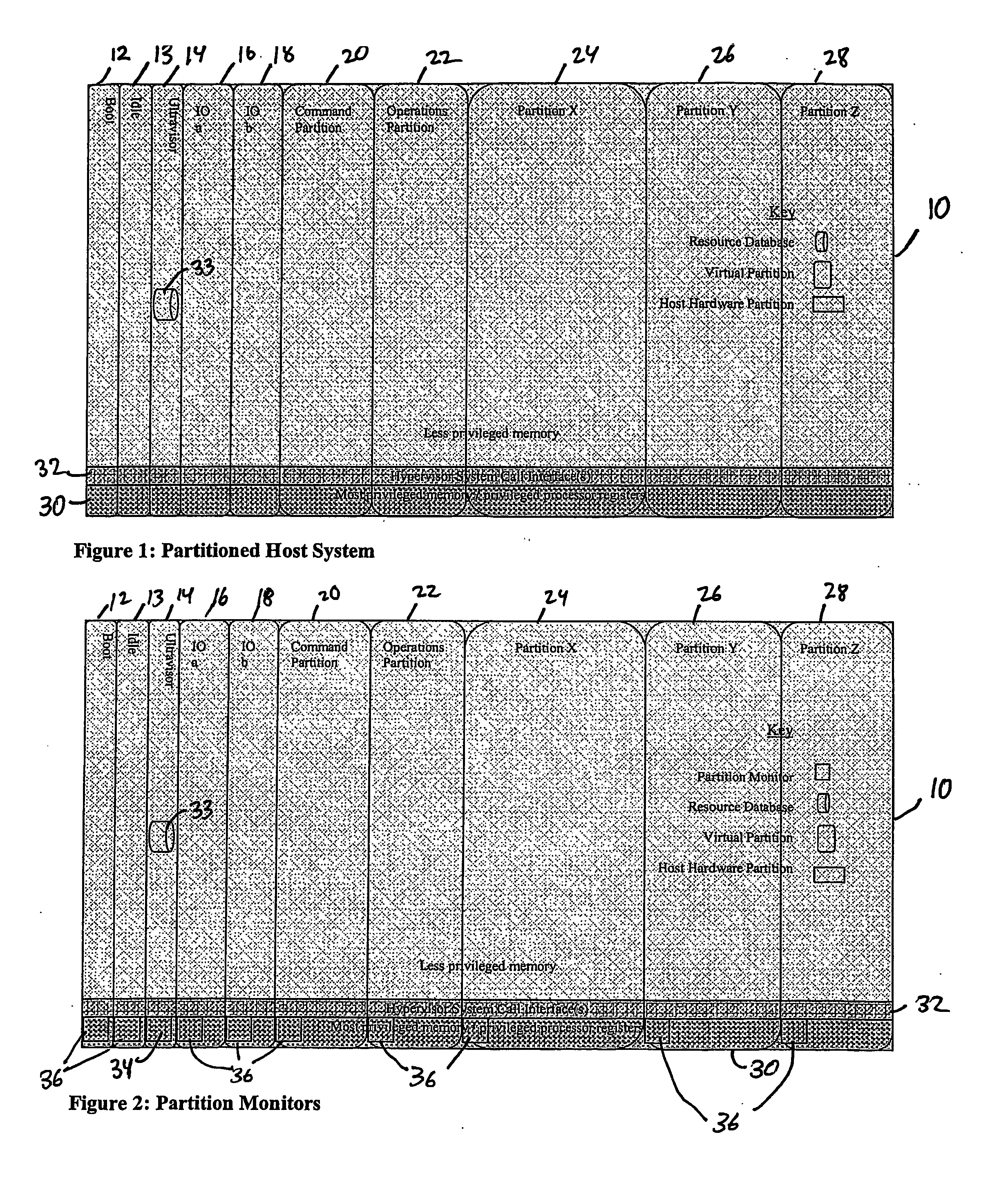
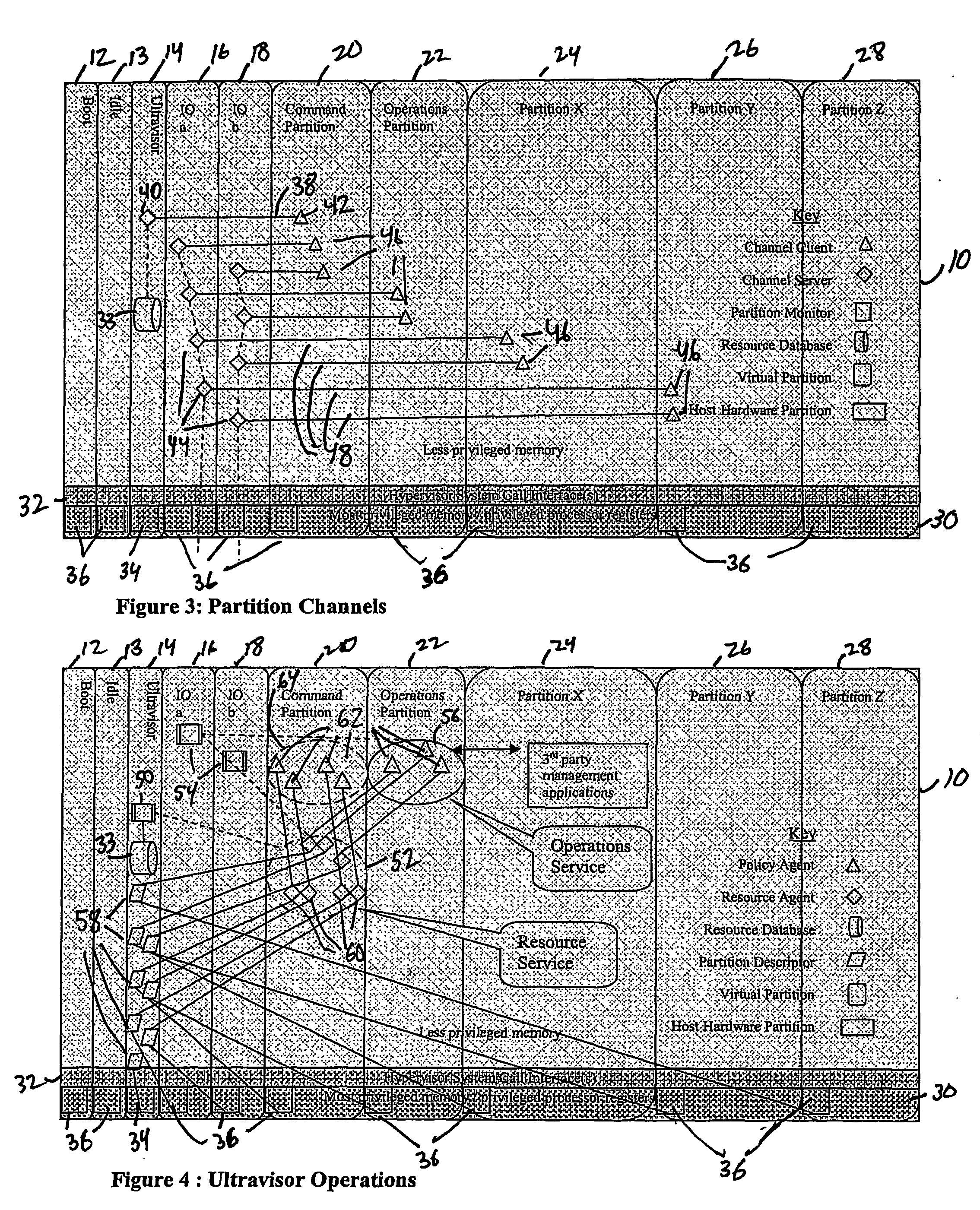
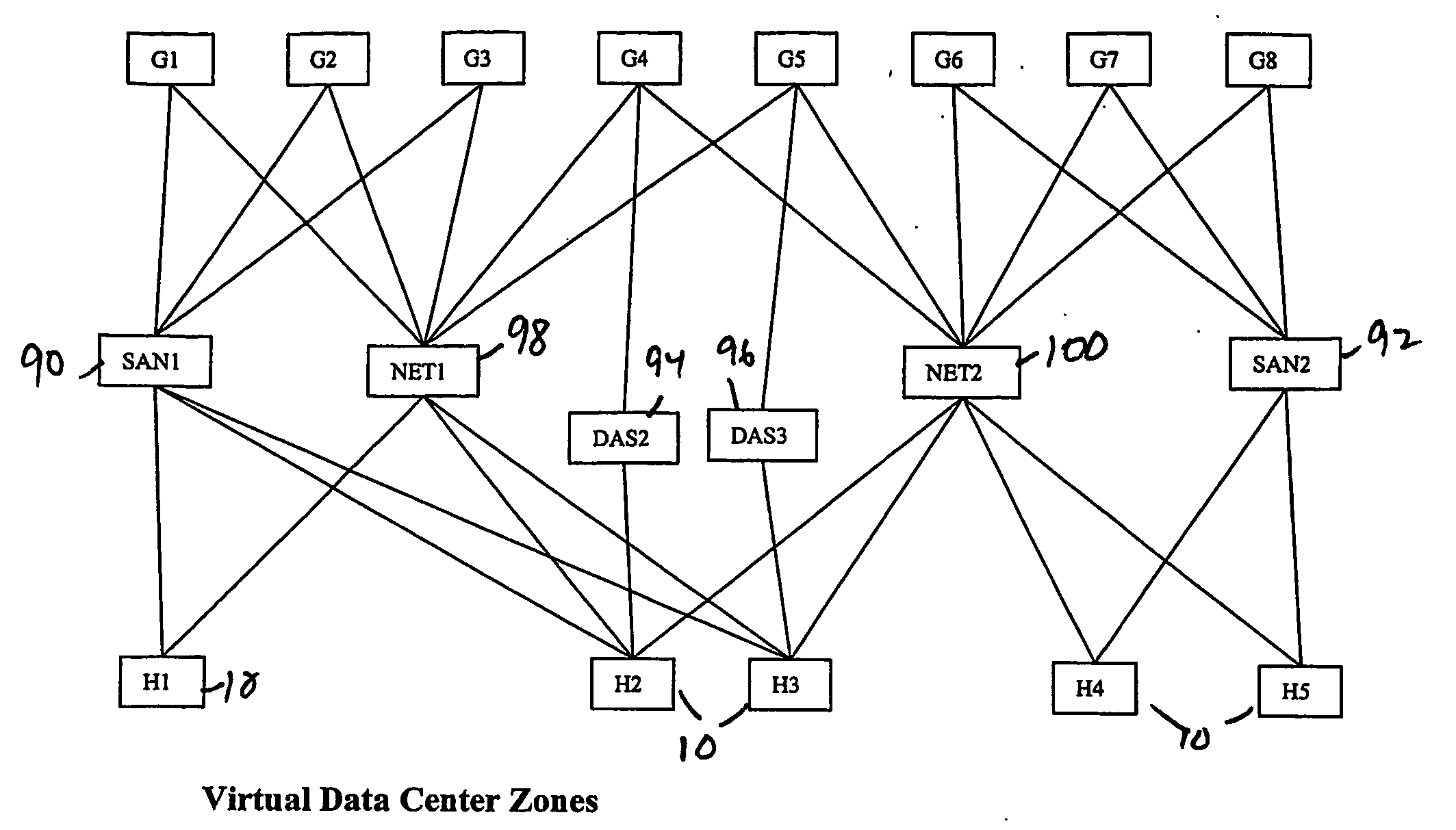
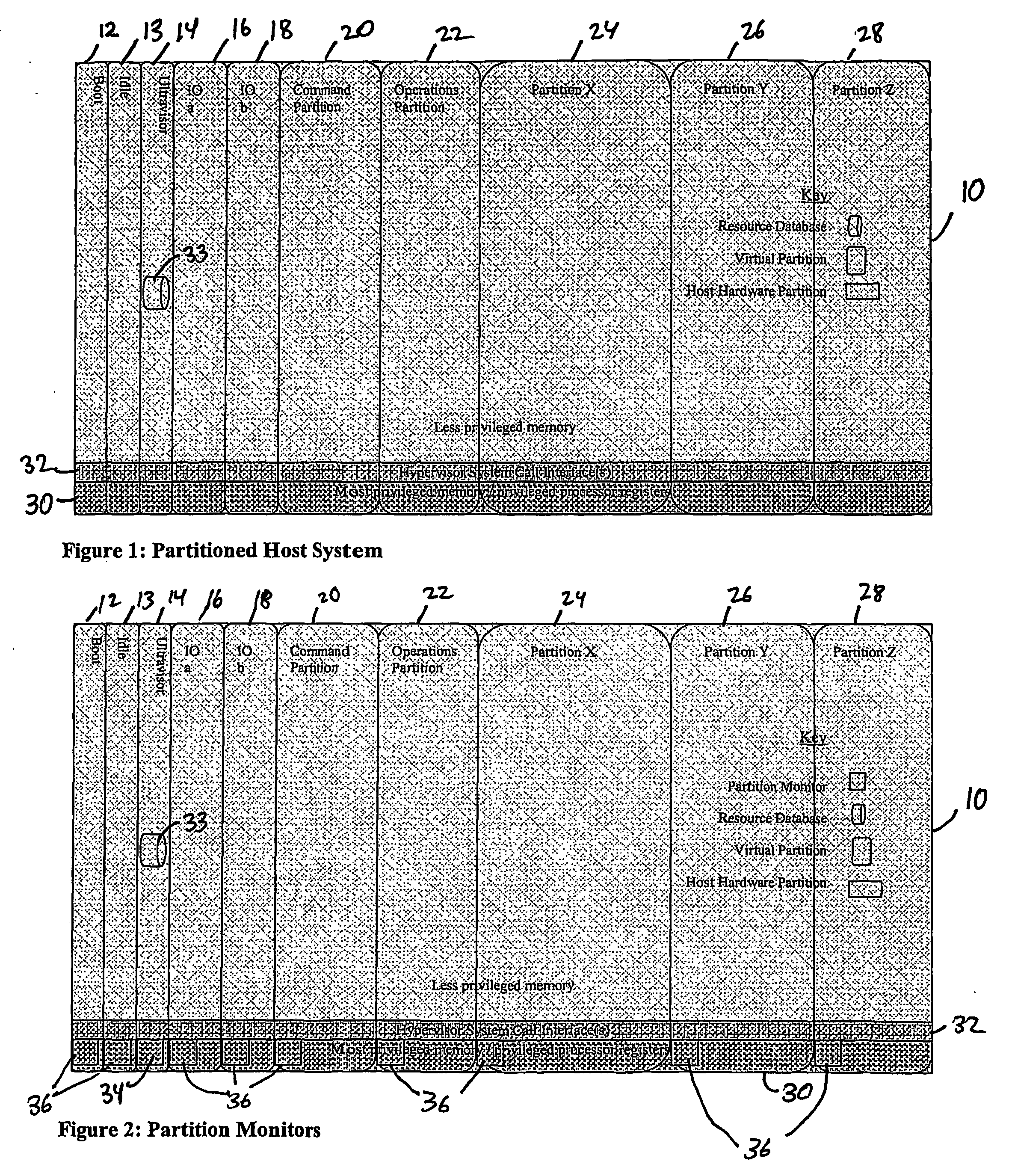
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps. System resources are separated into zones that are managed by a separate partition containing resource management policies that may be implemented across nodes to implement a virtual data center.
Owner:UNISYS CORP
Computer system para-virtualization using a hypervisor that is implemented in a partition of the host system
ActiveUS20070028244A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemSystem call
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps.
Owner:UNISYS CORP
Para-virtualized computer system with I/0 server partitions that map physical host hardware for access by guest partitions
InactiveUS20070061441A1Improve efficiencyImprove securityError detection/correctionDigital computer detailsOperational systemSystem call
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps.
Owner:UNISYS CORP
Location-Aware Fitness Monitoring Methods, Systems, and Program Products, and Applications Thereof
Owner:ADIDAS
Electronic smoking device and data exchange applications
An electronic smoking system includes an electronic smoking device; a pack communicatively linked to the device, the pack configured to hold the device; and a computer communicatively linked to the pack and to at least one communication channel; wherein the communication channel is configured to share data with at least one of a social network, a vendor, a clinical monitoring program, or a data collection program.
Owner:FONTEM HLDG 1
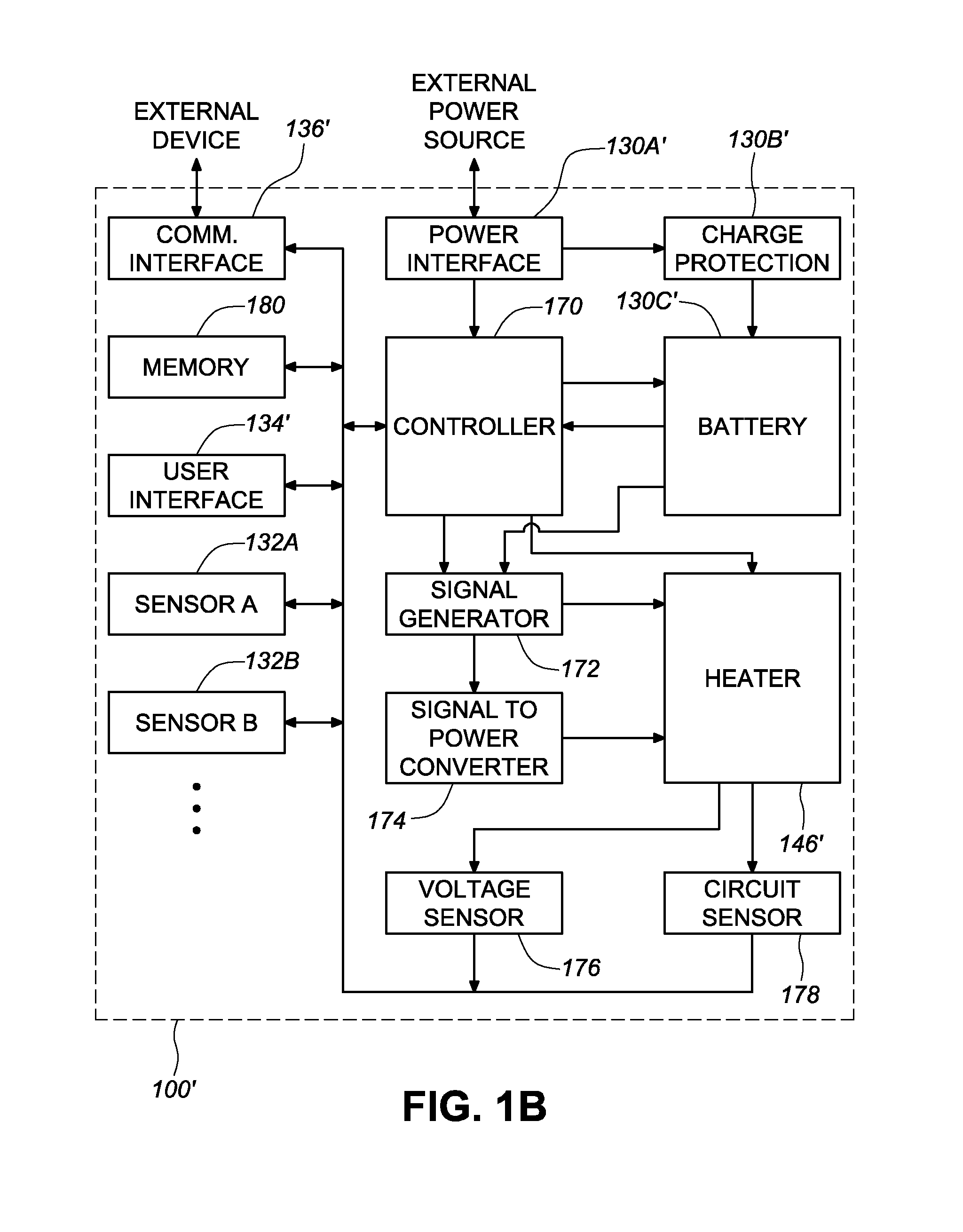
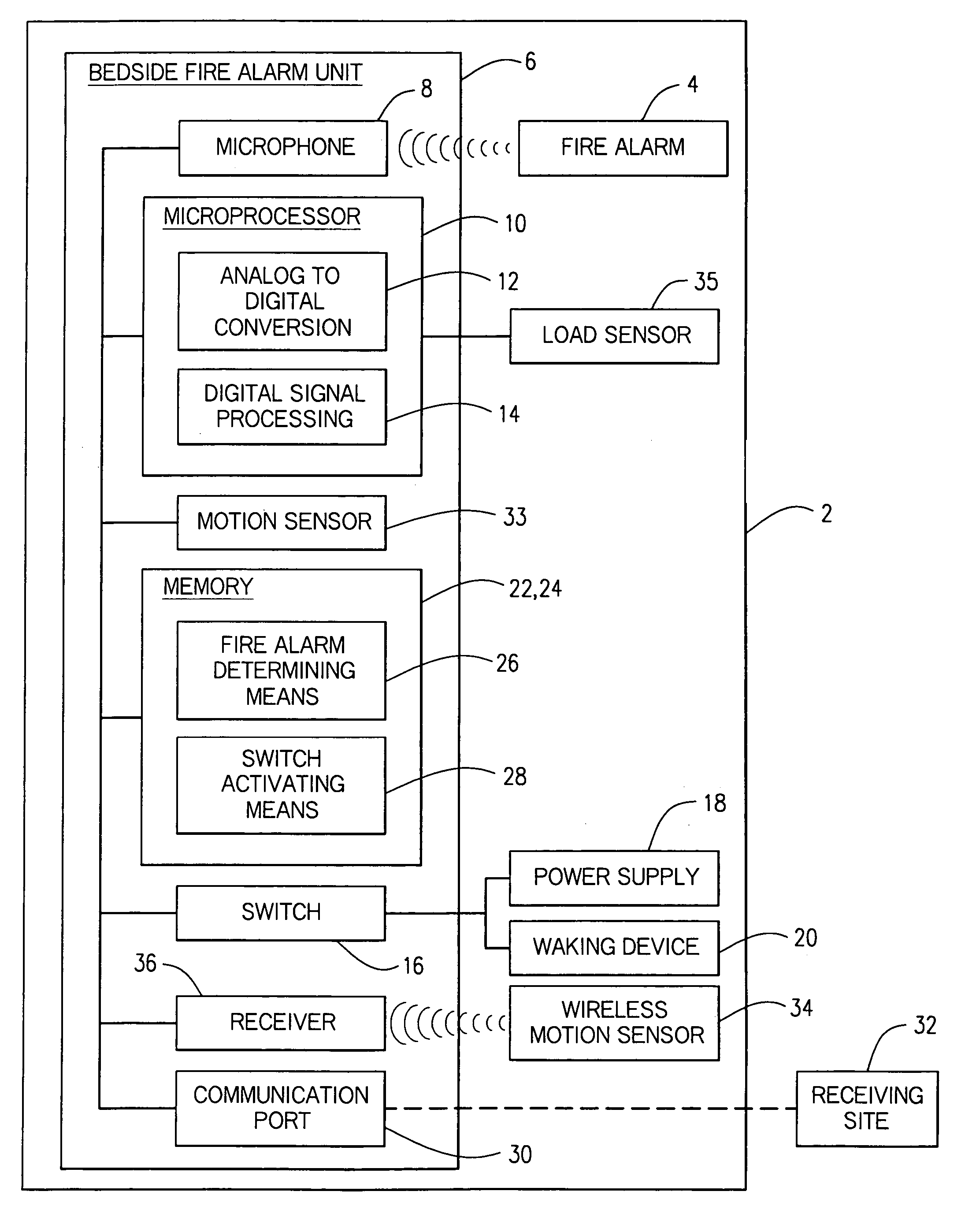
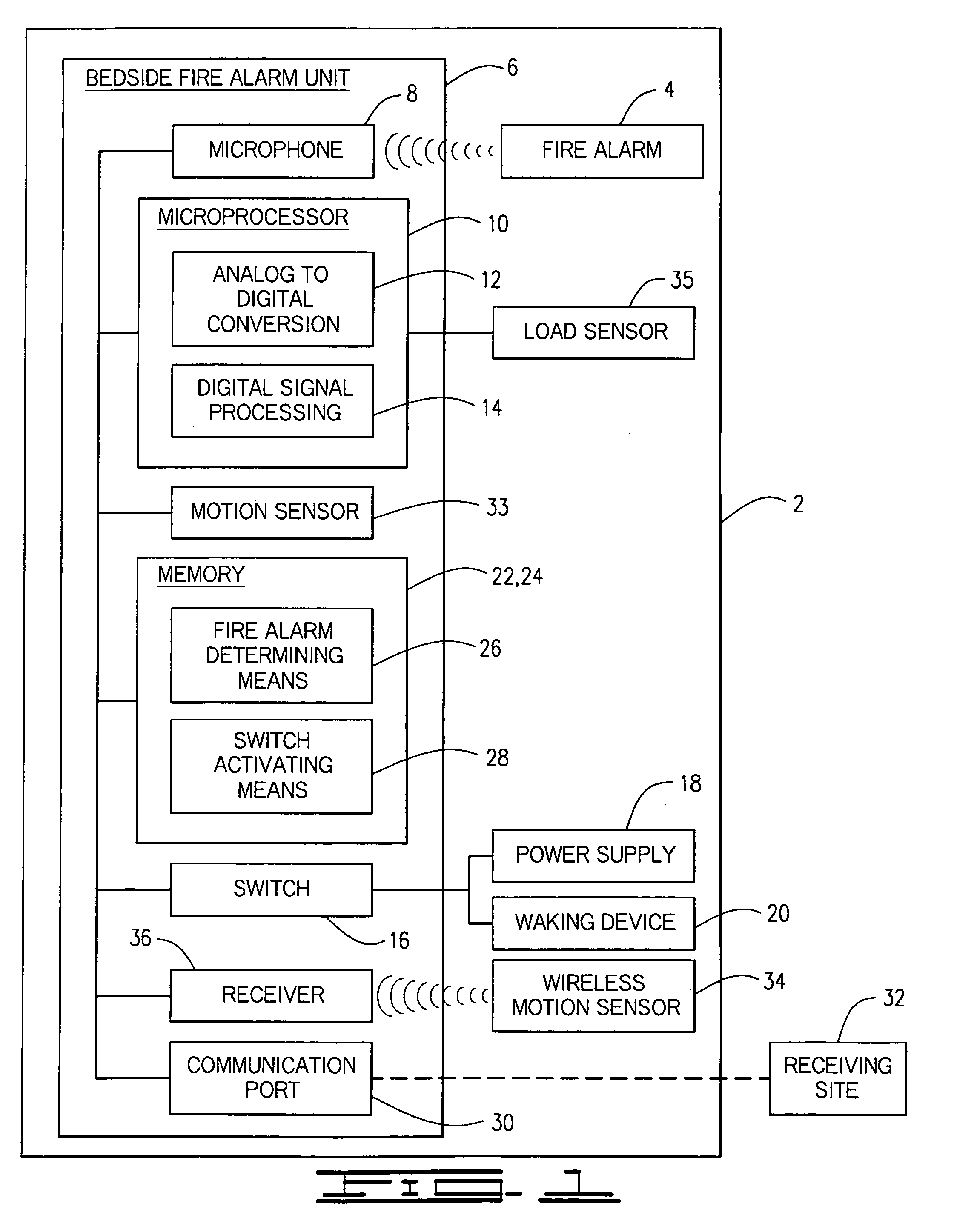
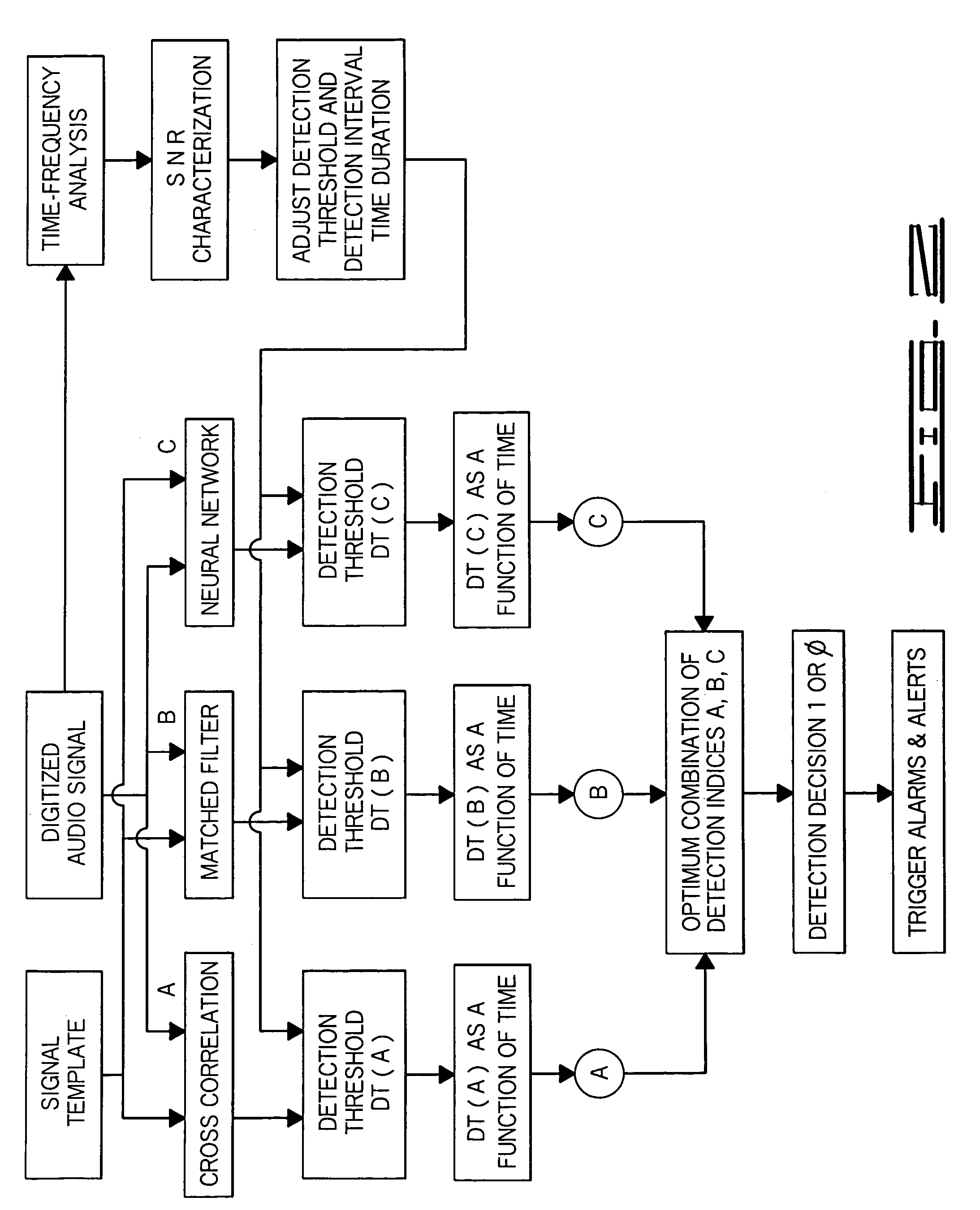
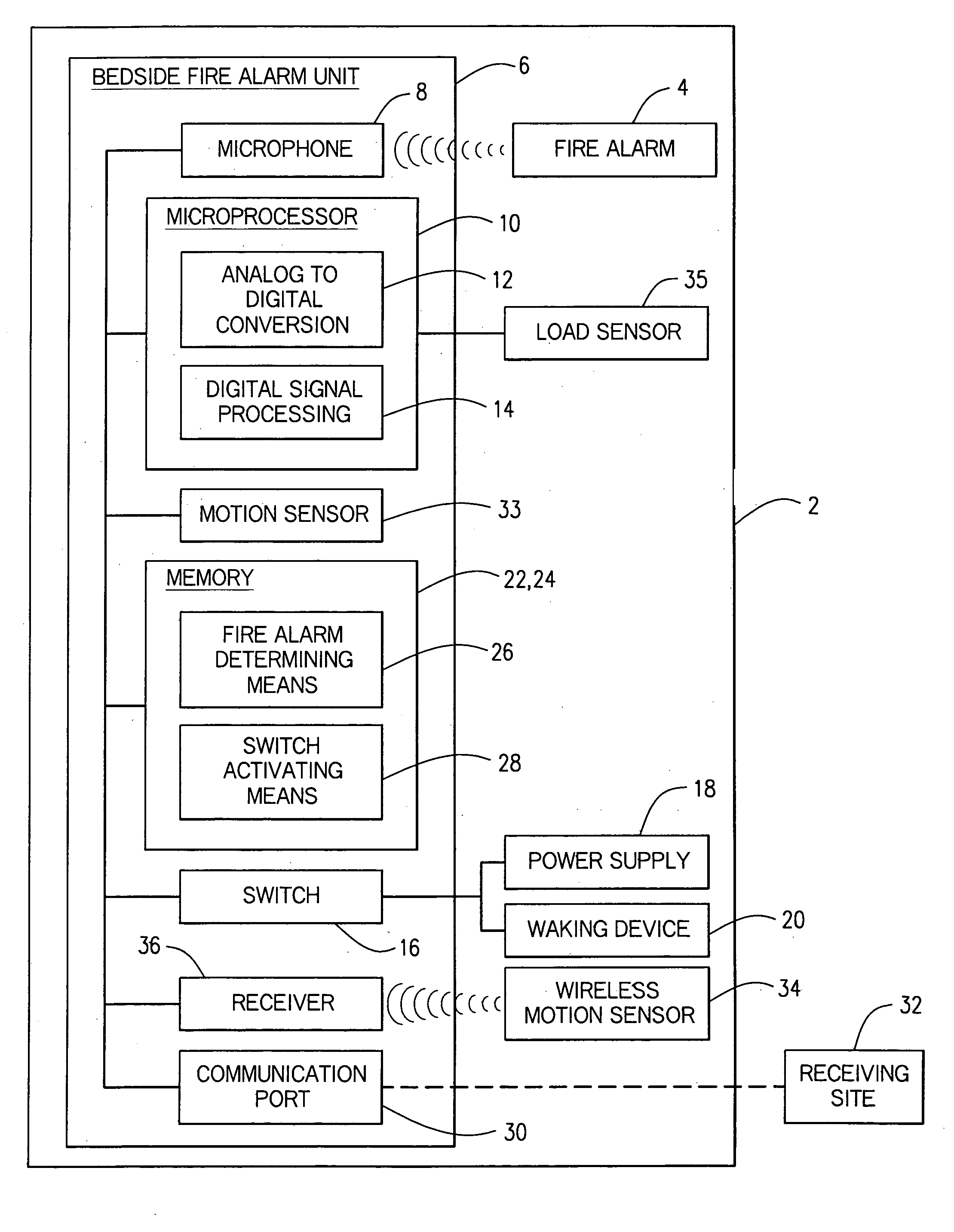
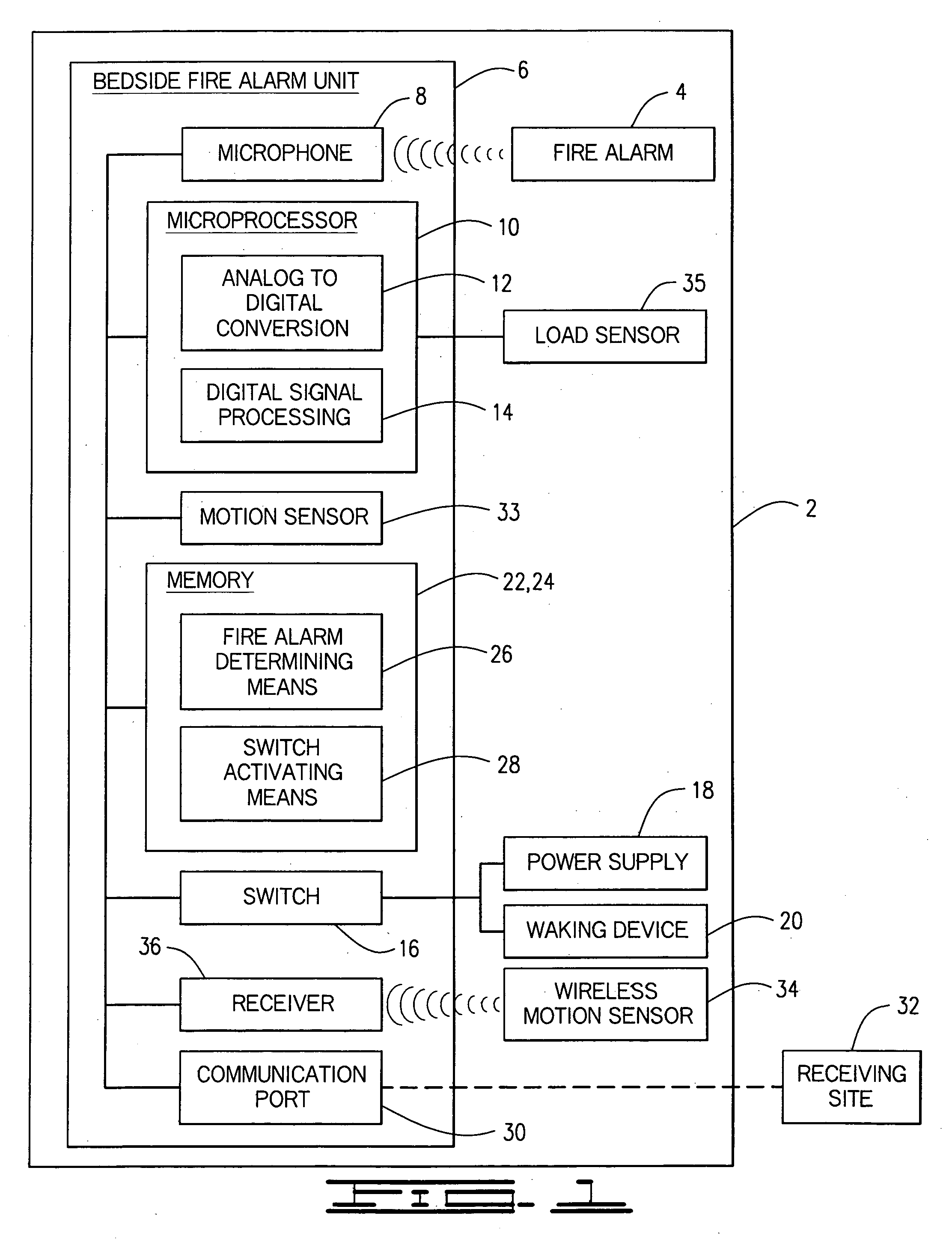
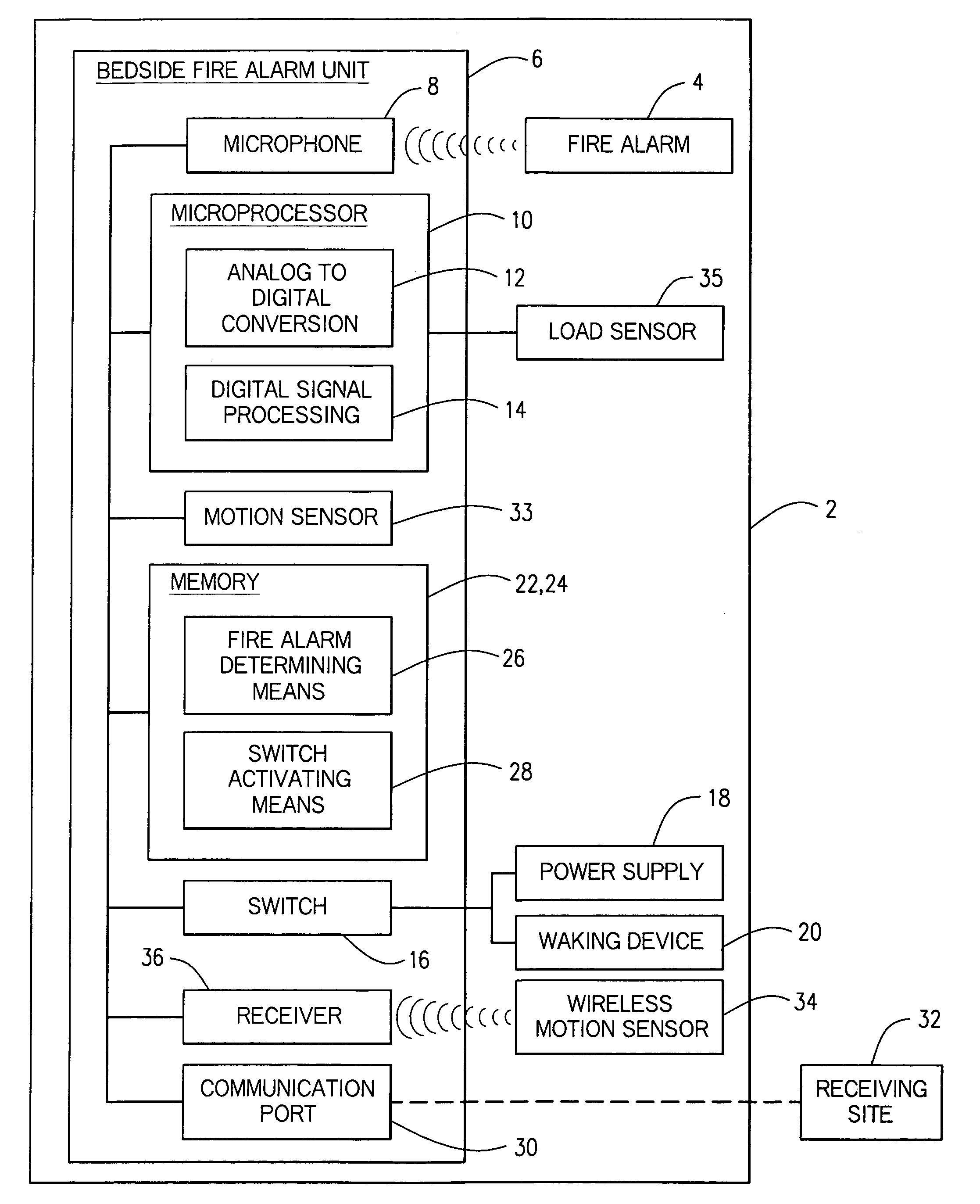
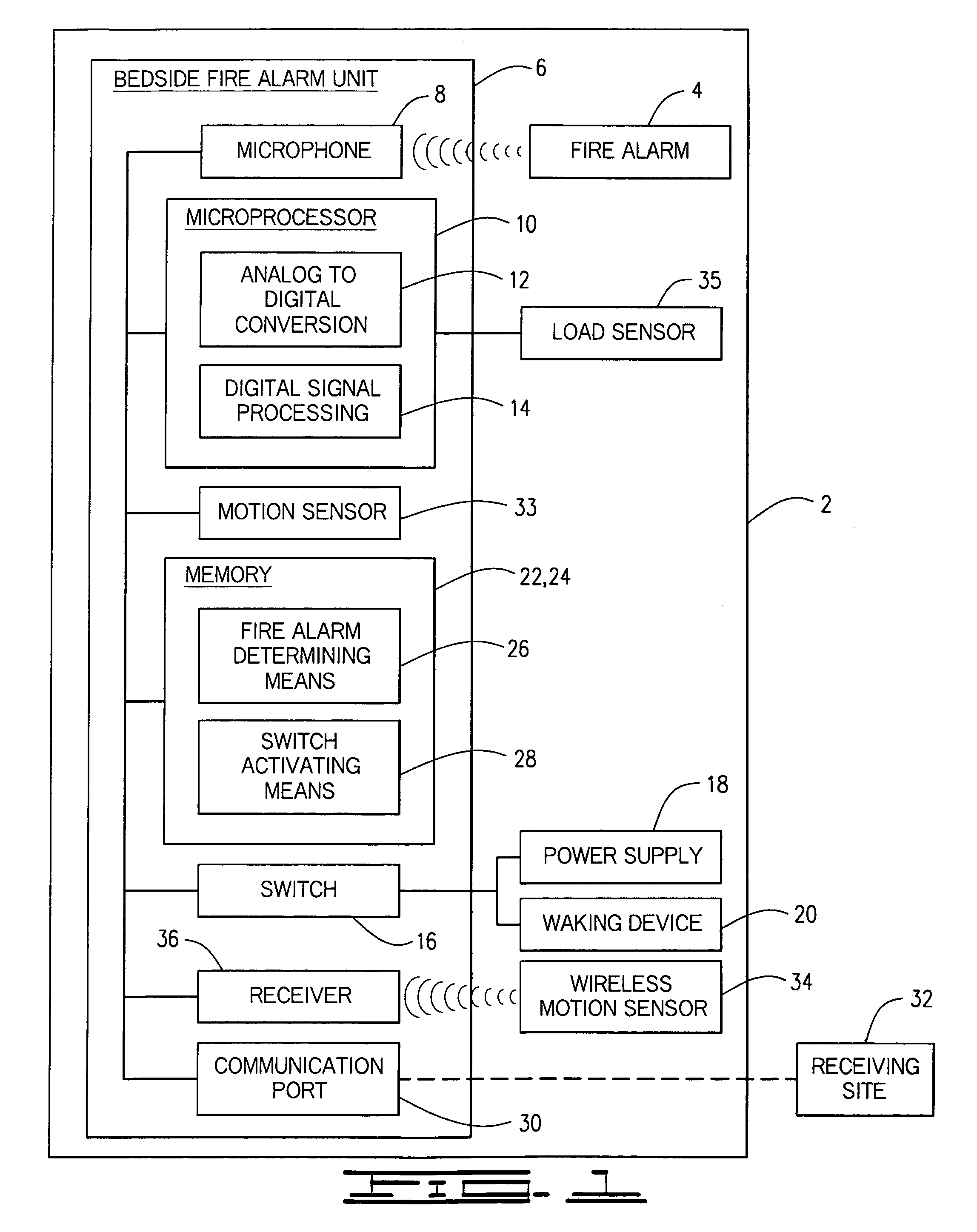
Enhanced fire, safety, security and health monitoring and alarm response method, system and device
Method, system and device useful with conventional personal computers respond automatically to an identified alarm sound by sending a notification signal via the Internet only when a special sound monitoring program is active. Additionally, bedside detection of acoustic alarms is combined with enhanced waking devices to insure the waking of a child or hearing impaired person in response to an emergency. Home safety and security are provided using a bedside unit to monitor audible safety and security alarms and send notification signals to the appropriate communication site. A health monitoring method and system utilizes the bedside device to monitor breathing patterns and other health measuring signals and communicate these patterns and signals to a medical monitoring station.
Owner:INNOVALARM
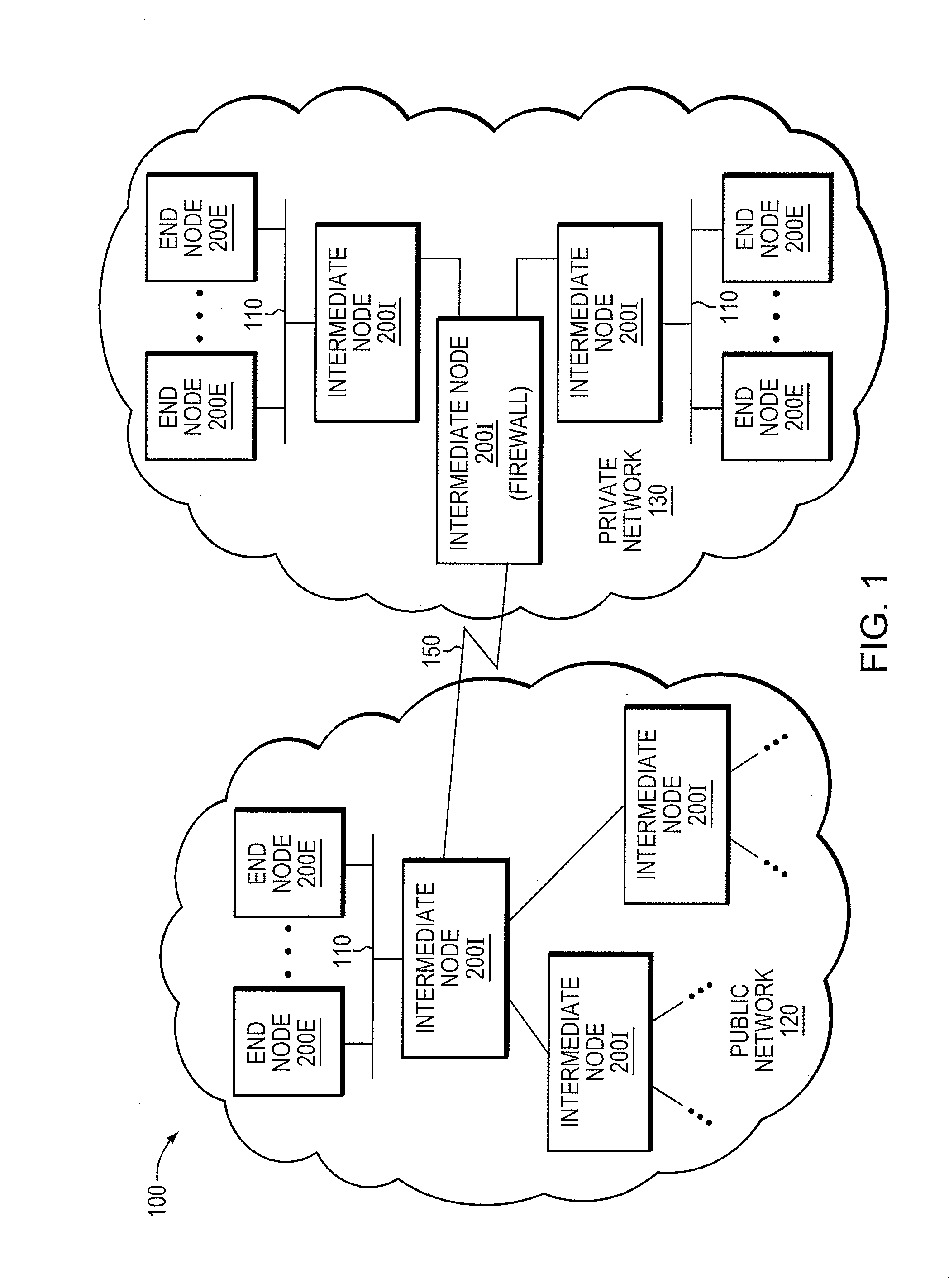
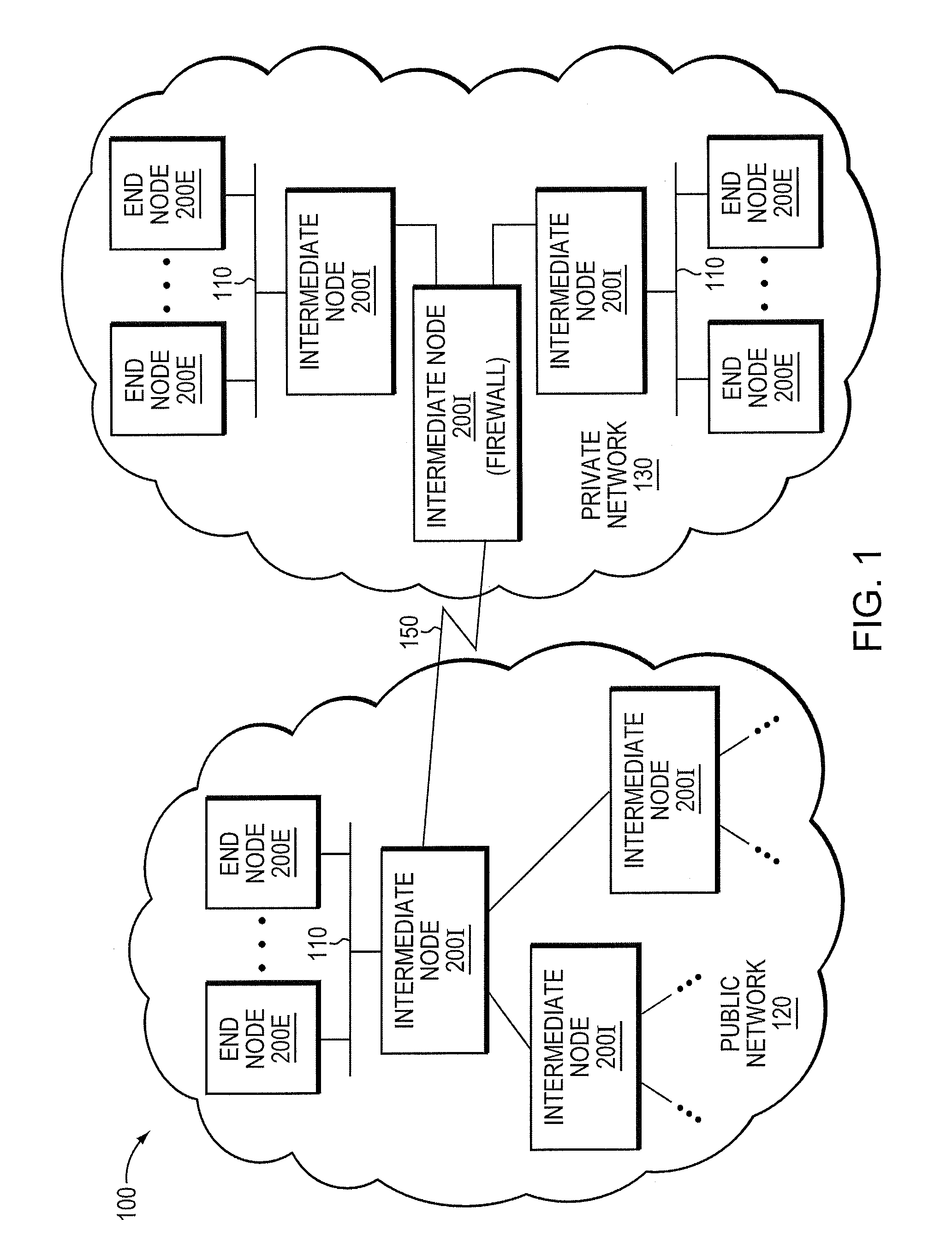
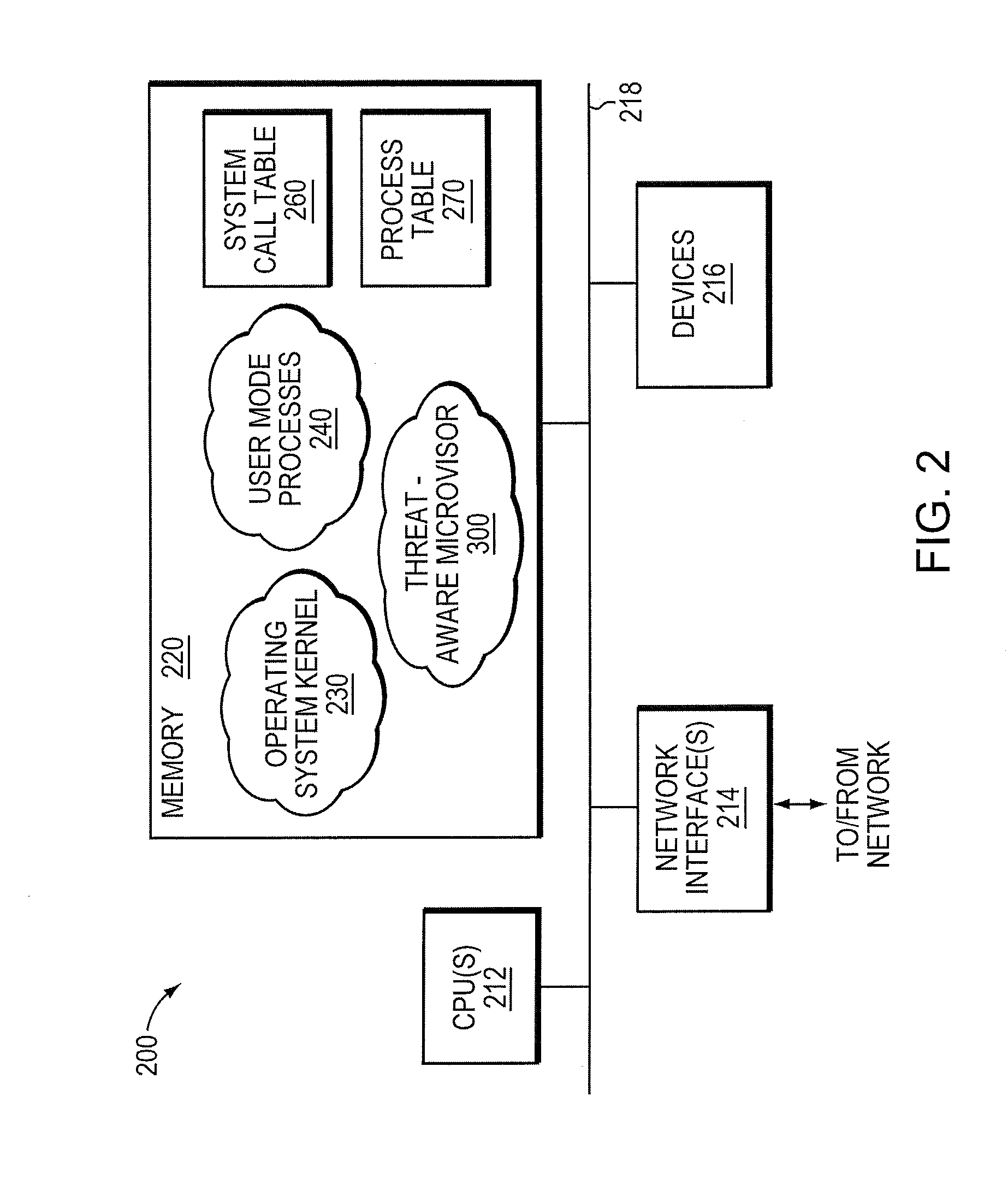
Exploit detection system with threat-aware microvisor
ActiveUS20150199531A1Digital data processing detailsAnalogue secracy/subscription systemsVulnerability detectionThreat intelligence
An exploit detection system deploys a threat-aware microvisor to facilitate real-time security analysis, including exploit detection and threat intelligence, of an operating system process executing on a node of a network environment. The microvisor may be organized as a main protection domain representative of the operating system process. In response to the process attempting to access a kernel resource for which it does not have permission, a capability violation may be generated at the main protection domain of the microvisor and a micro-virtual machine (VM) may be spawned as a container configured to encapsulate the process. The main protection domain may then be cloned to create a cloned protection domain that is representative of the process and that is bound to the spawned micro-VM. Capabilities of the cloned protection domain may be configured to be more restricted than the capabilities of the main protection domain with respect to access to the kernel resource. The restricted capabilities may be configured to generate more capability violations than those generated by the capabilities of the main protection domain and, in turn, enable further monitoring of the process as it attempts to access the kernel resource.
Owner:FIREEYE SECURITY HLDG US LLC
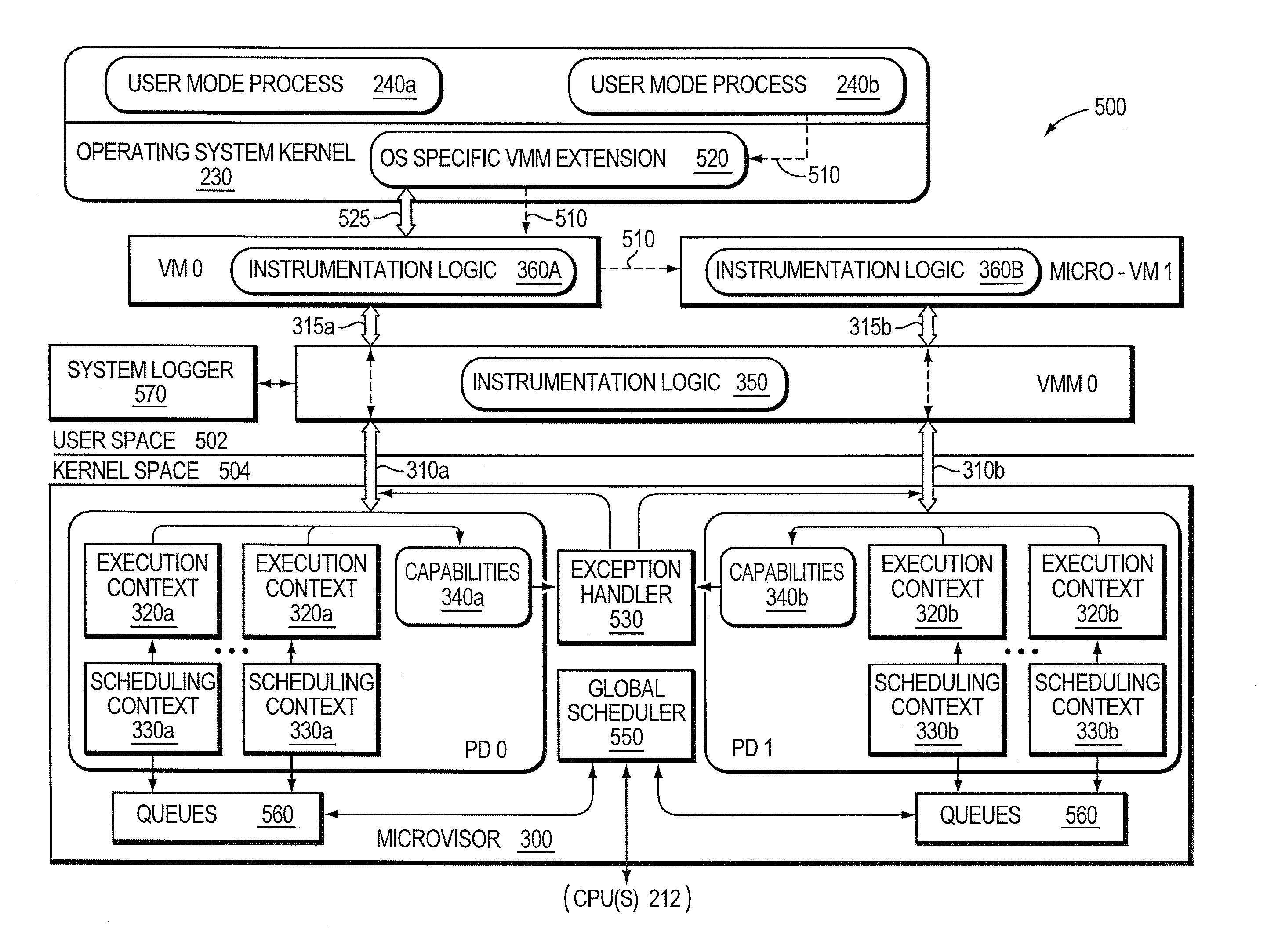
Micro-virtualization architecture for threat-aware microvisor deployment in a node of a network environment
ActiveUS9292686B2Digital data protectionPlatform integrity maintainanceVirtualizationOperational system
A micro-virtualization architecture deploys a threat-aware microvisor as a module of a virtualization system configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing in a memory of a node in a network environment. The micro-virtualization architecture organizes the memory as a user space and kernel space, wherein the microvisor executes in the kernel space of the architecture, while the operating system processes, an operating system kernel, a virtual machine monitor (VMM) and its spawned virtual machines (VMs) execute in the user space. Notably, the microvisor executes at the highest privilege level of a central processing unit of the node to virtualize access to kernel resources. The operating system kernel executes under control of the microvisor at a privilege level lower than a highest privilege level of the microvisor. The VMM and its spawned VMs execute at the highest privilege level of the microvisor.
Owner:MANDIANT +1
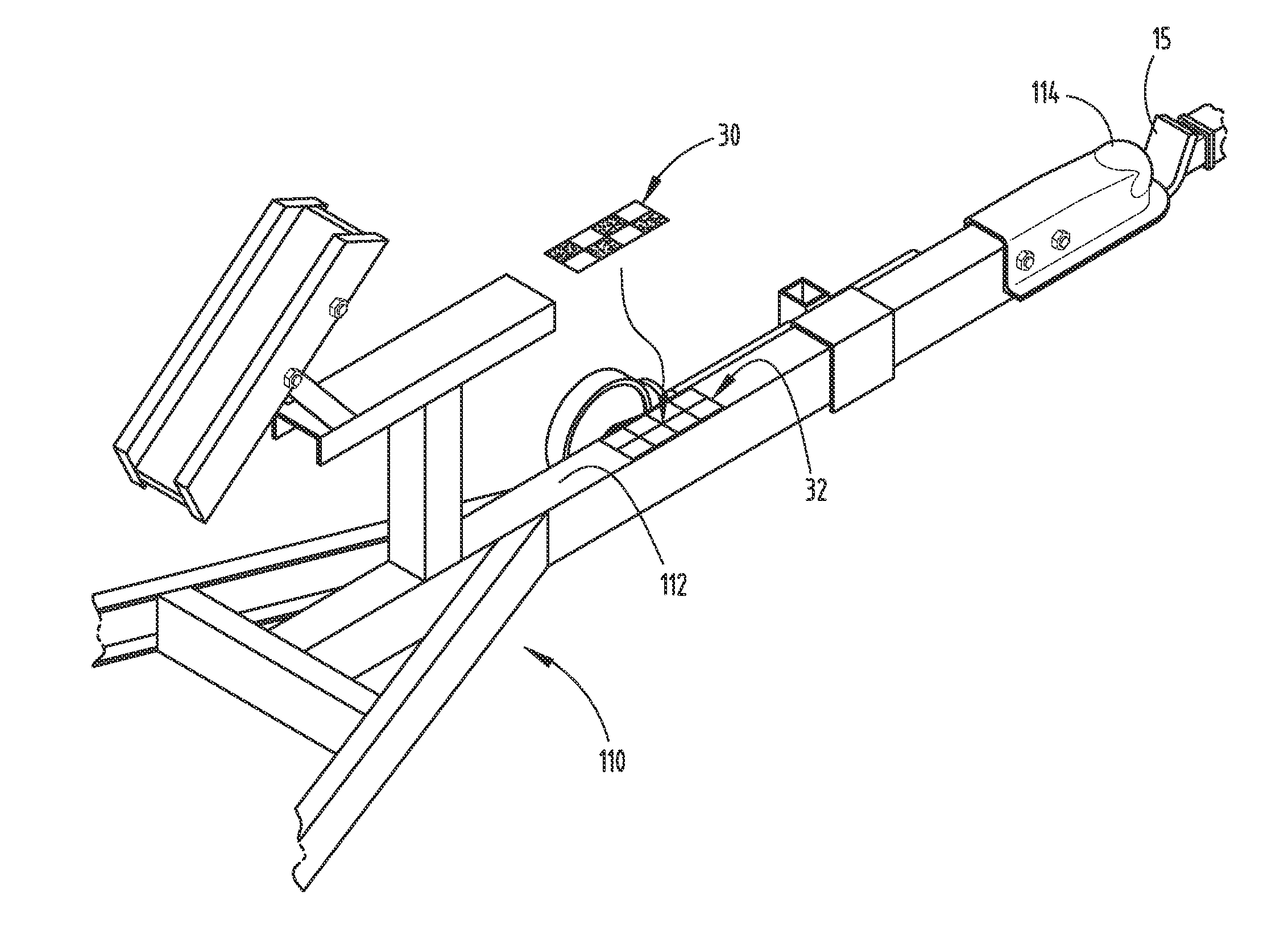
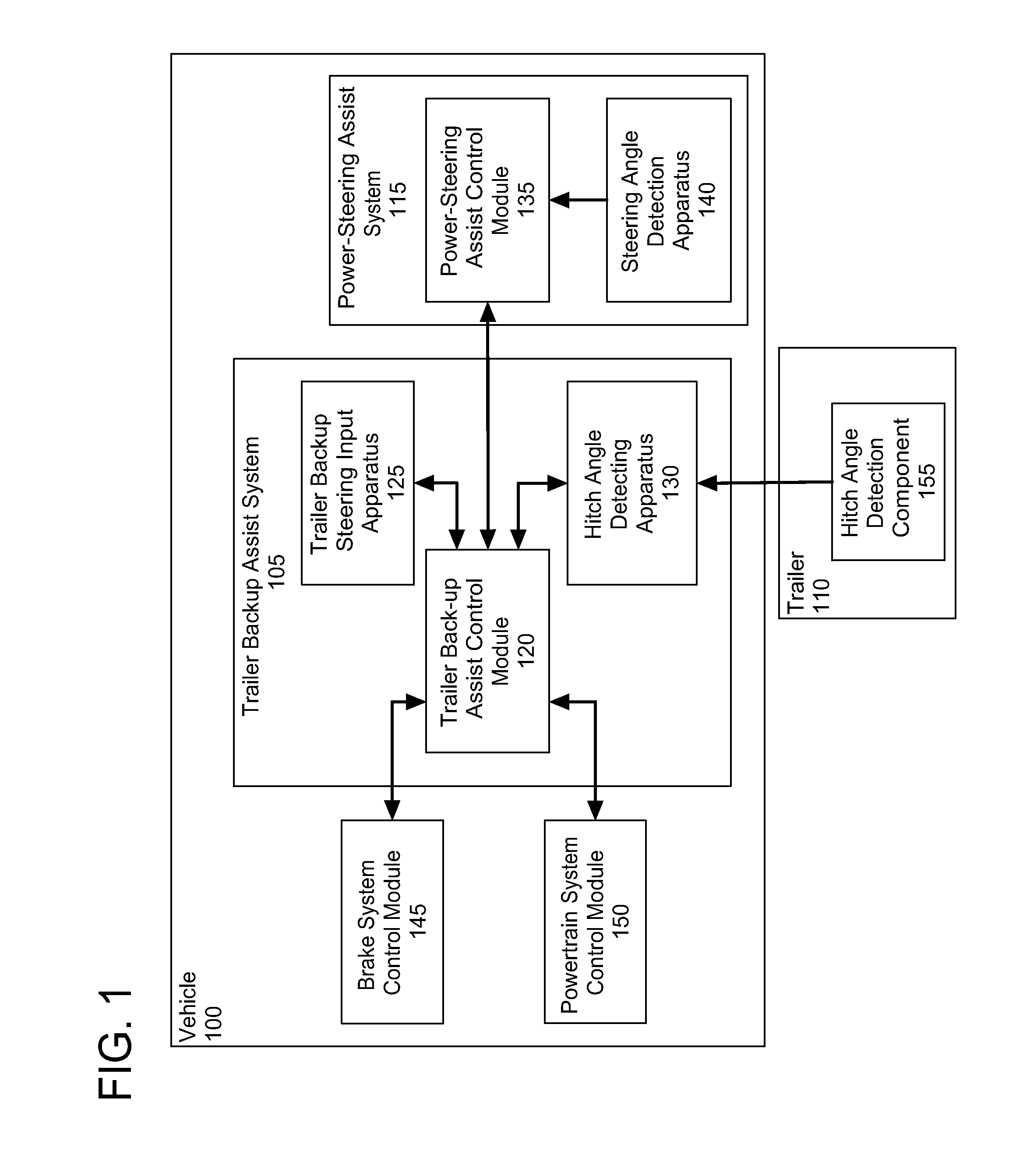
Trailer target placement assist system and method
A vehicle trailer backup assist system and method includes a hitch angle detection apparatus and a target monitor controller. The target monitor controller processes images acquired of the trailer towed by a towing vehicle to assist with placement of a target on the trailer. The target monitor controller also monitors the target and provides feedback to the user as to proper positioning of the target on the trailer. A target move detection routine detects movement of a target by processing the pixels of the image to determine if a new trailer has been connected. Further, a trailer connection monitoring routine monitors for a changed trailer based on loss of the hitch angle or target for a predetermined time period.
Owner:FORD GLOBAL TECH LLC
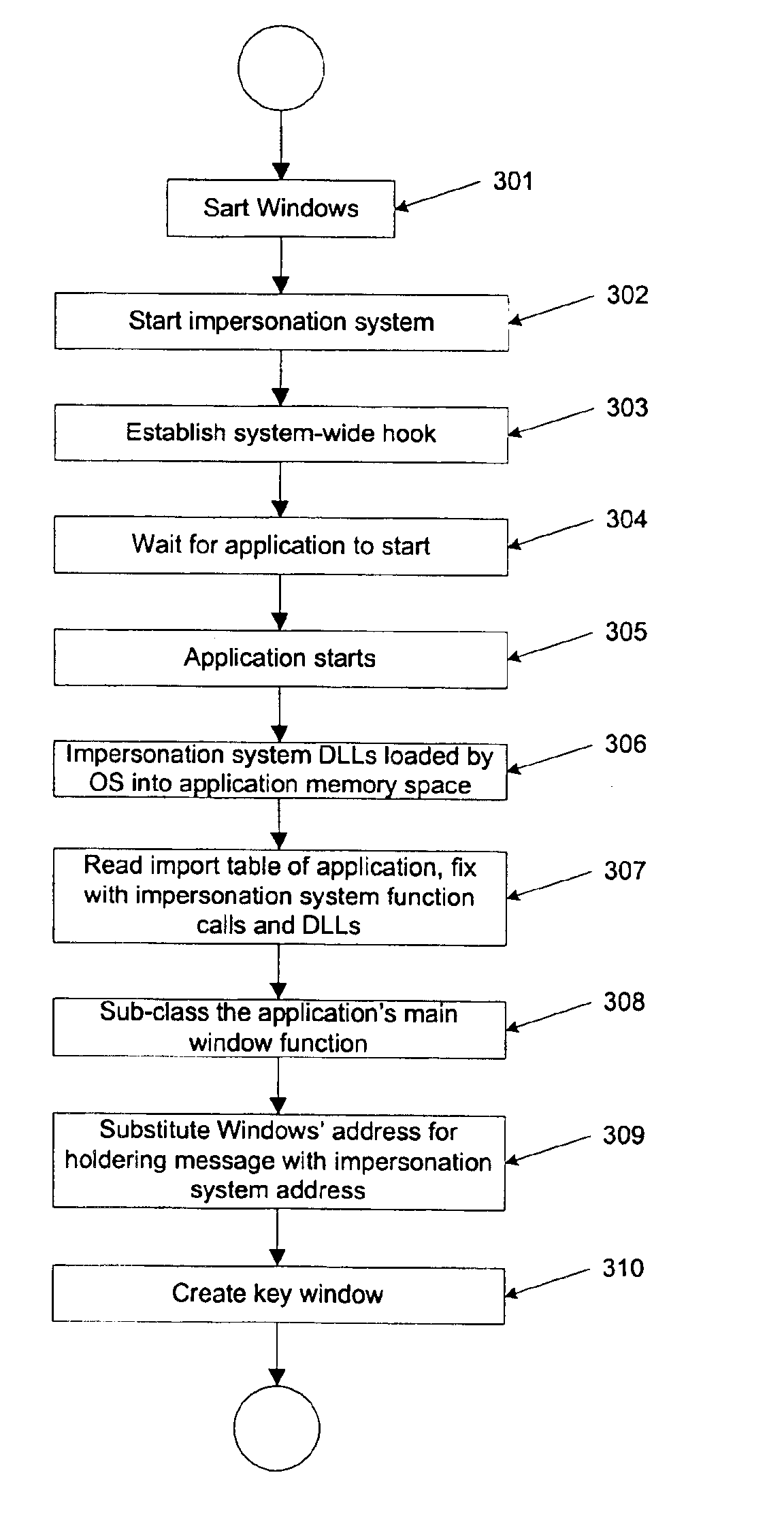
Method and system for seamless integration of preprocessing and postprocessing functions with an existing application program
InactiveUS6874139B2Function increaseWithout compromising file securityHardware monitoringPlatform integrity maintainanceGraphicsOperational system
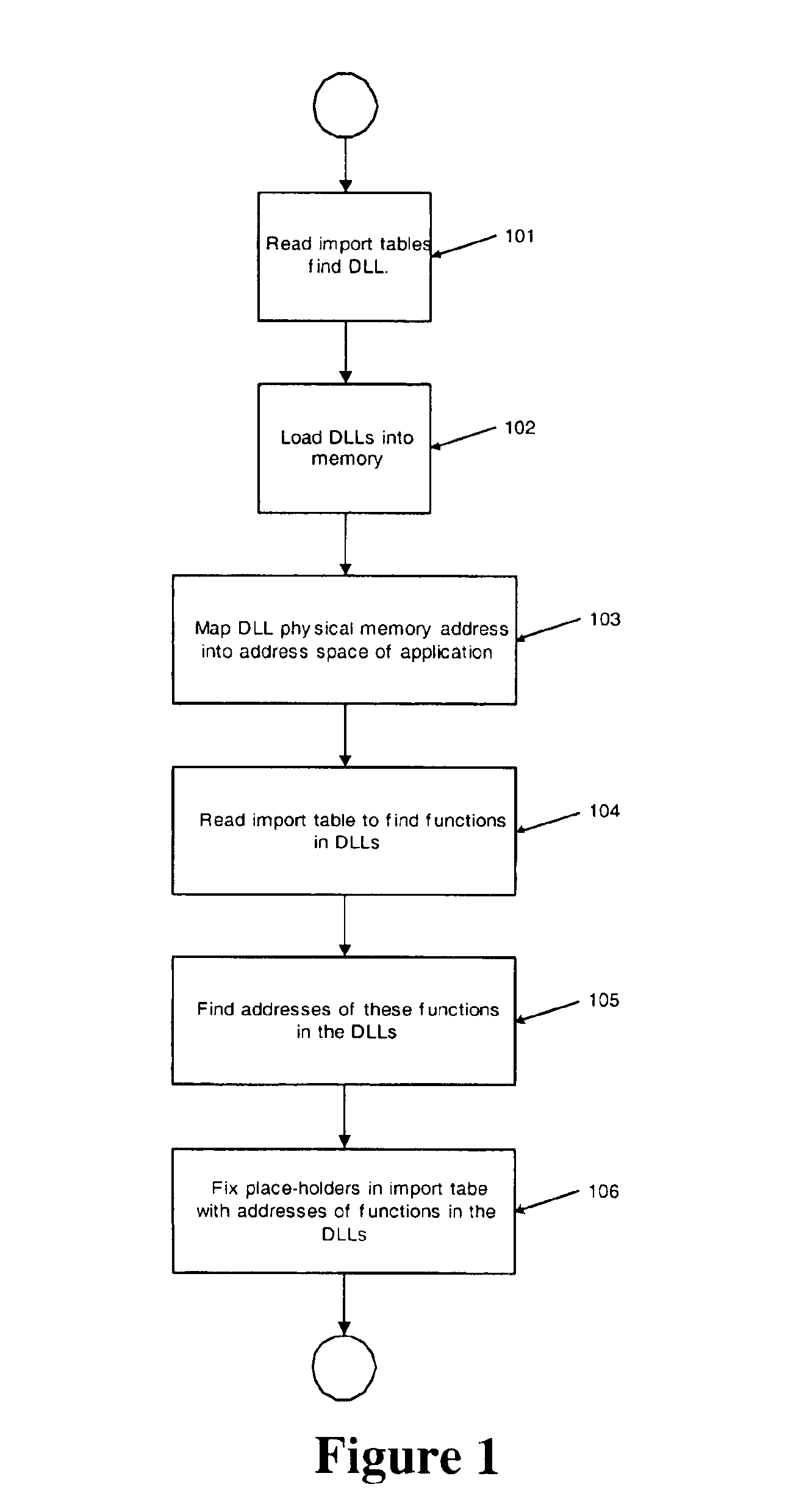
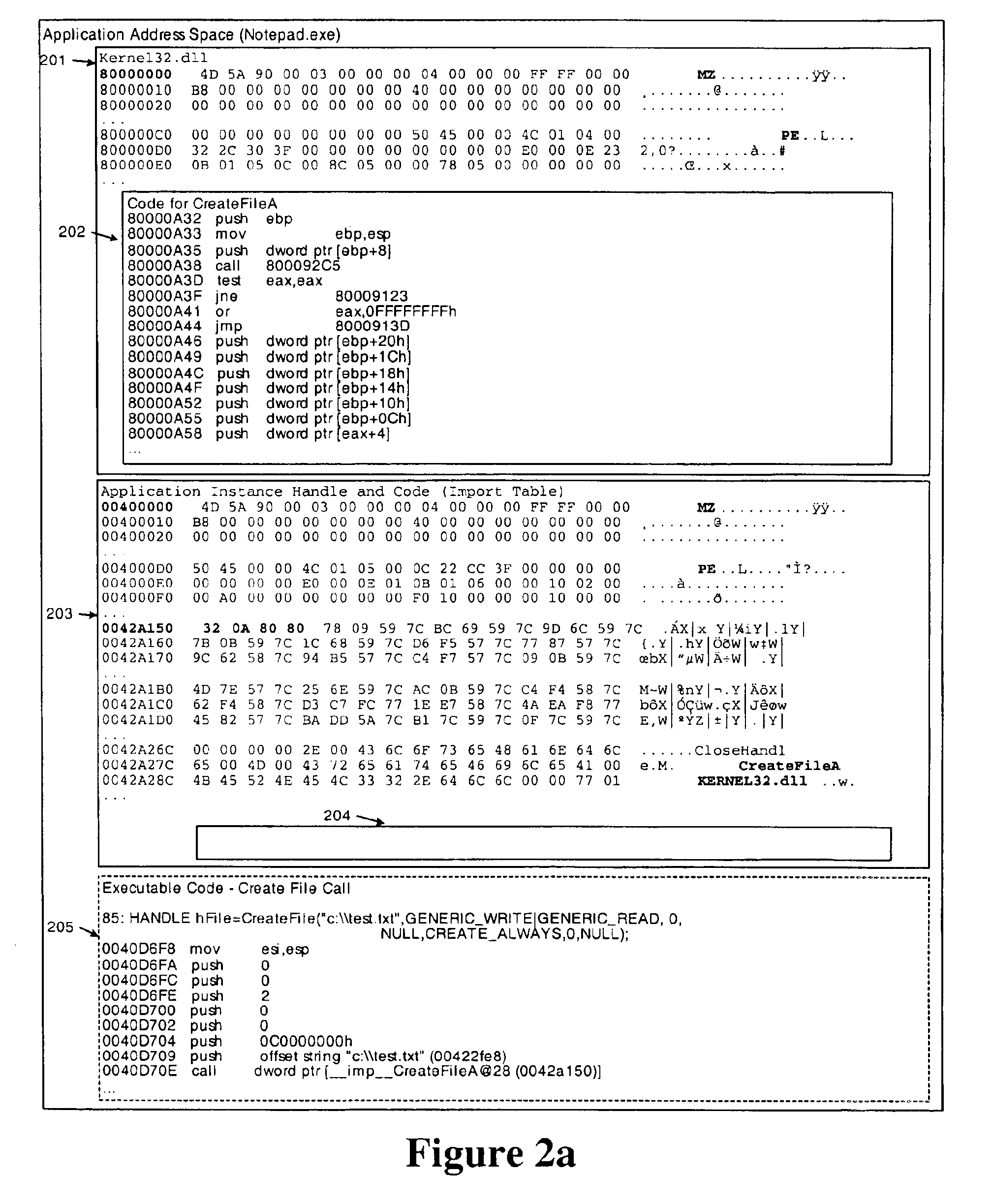
A method for associating file activity of an application with the graphical display of the file on a screen comprises loading by an operating system an executable code of a message monitoring program adapted to monitoring a message sent by an operating system to a document display window. The message monitoring program establishes a system-wide window hook using available operating system API functions associated with one or more functions in a library of the message monitoring program. The message monitoring program library is loaded into the memory space of a newly started application program, the import table of the application is fixed with addresses of functions from the message monitoring program library, and the application's main window function is substituted with a message monitoring program window function.
Owner:CONTROLGUARD SOFTWARE TECH +1
Monitoring system and monitoring method
ActiveUS6977585B2Increase flexibilityFrequency-division multiplex detailsTelephonic communicationMonitoring systemEmbedded system
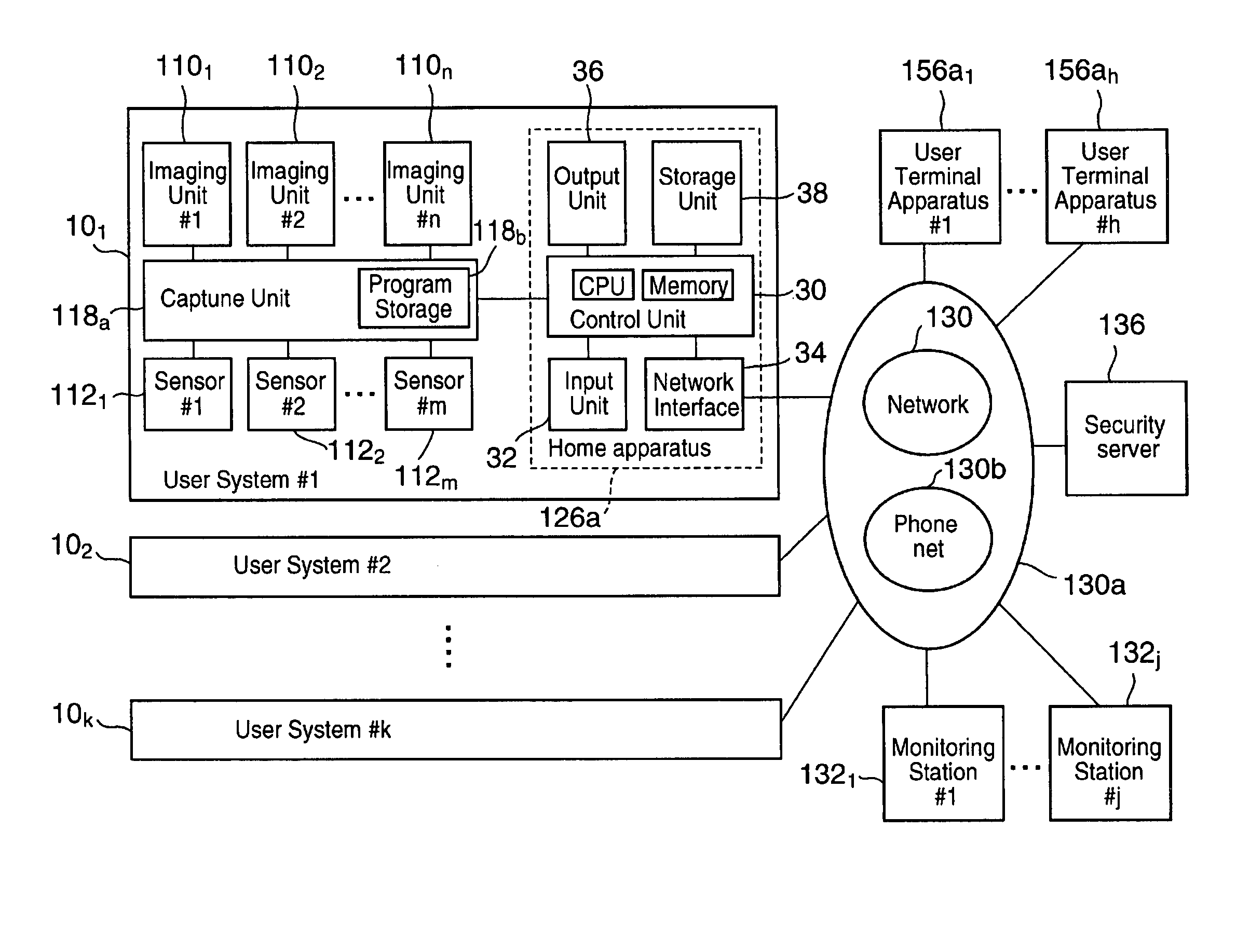
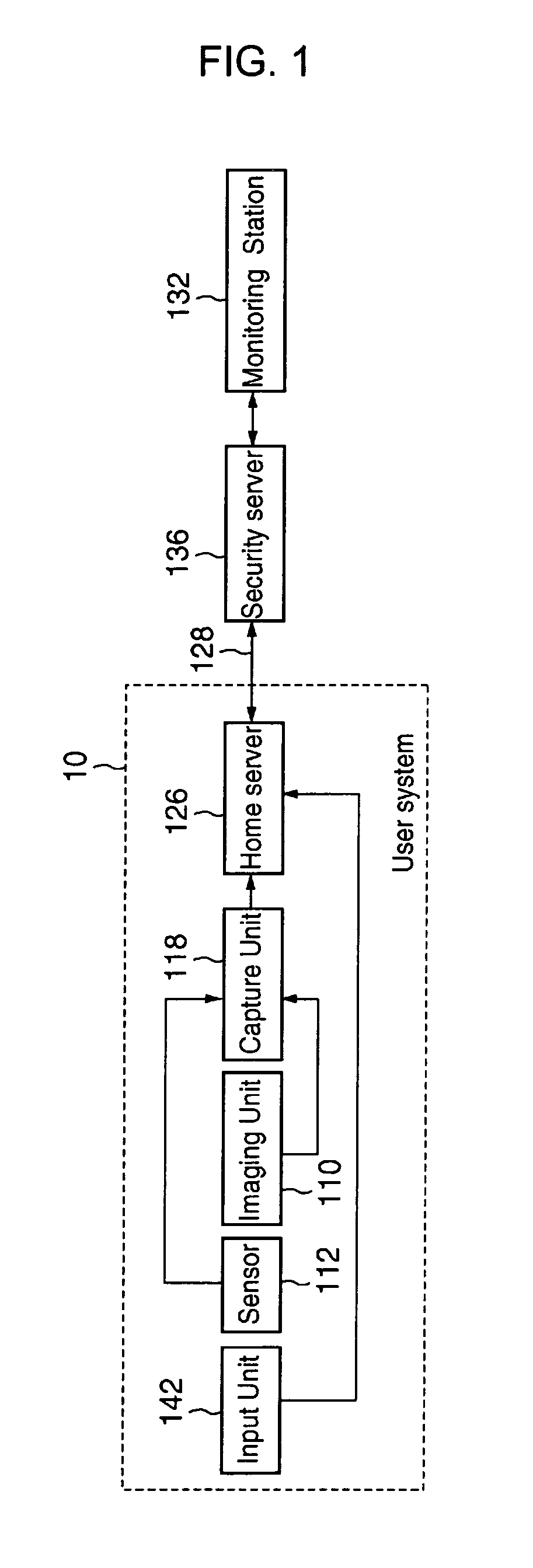
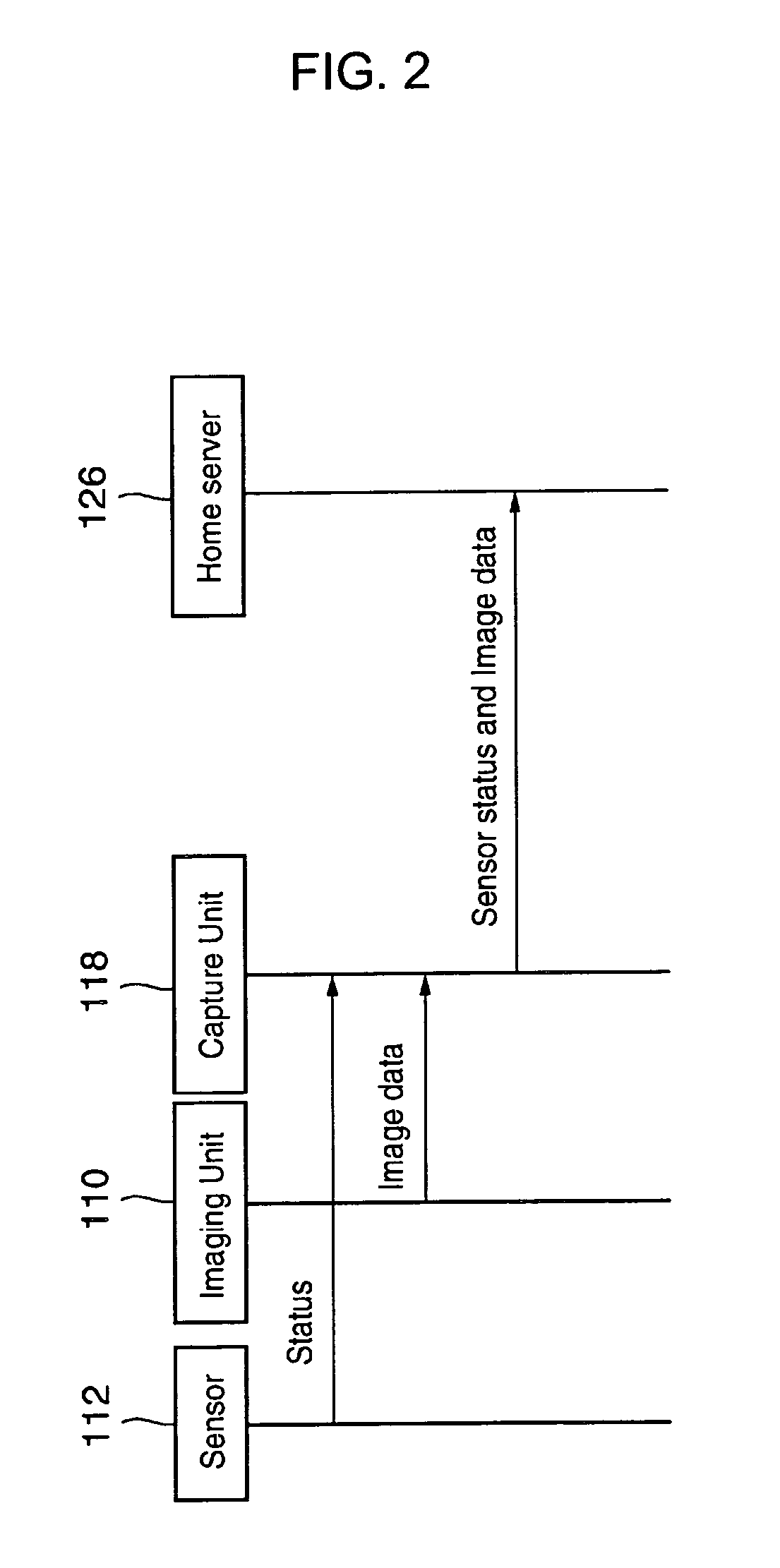
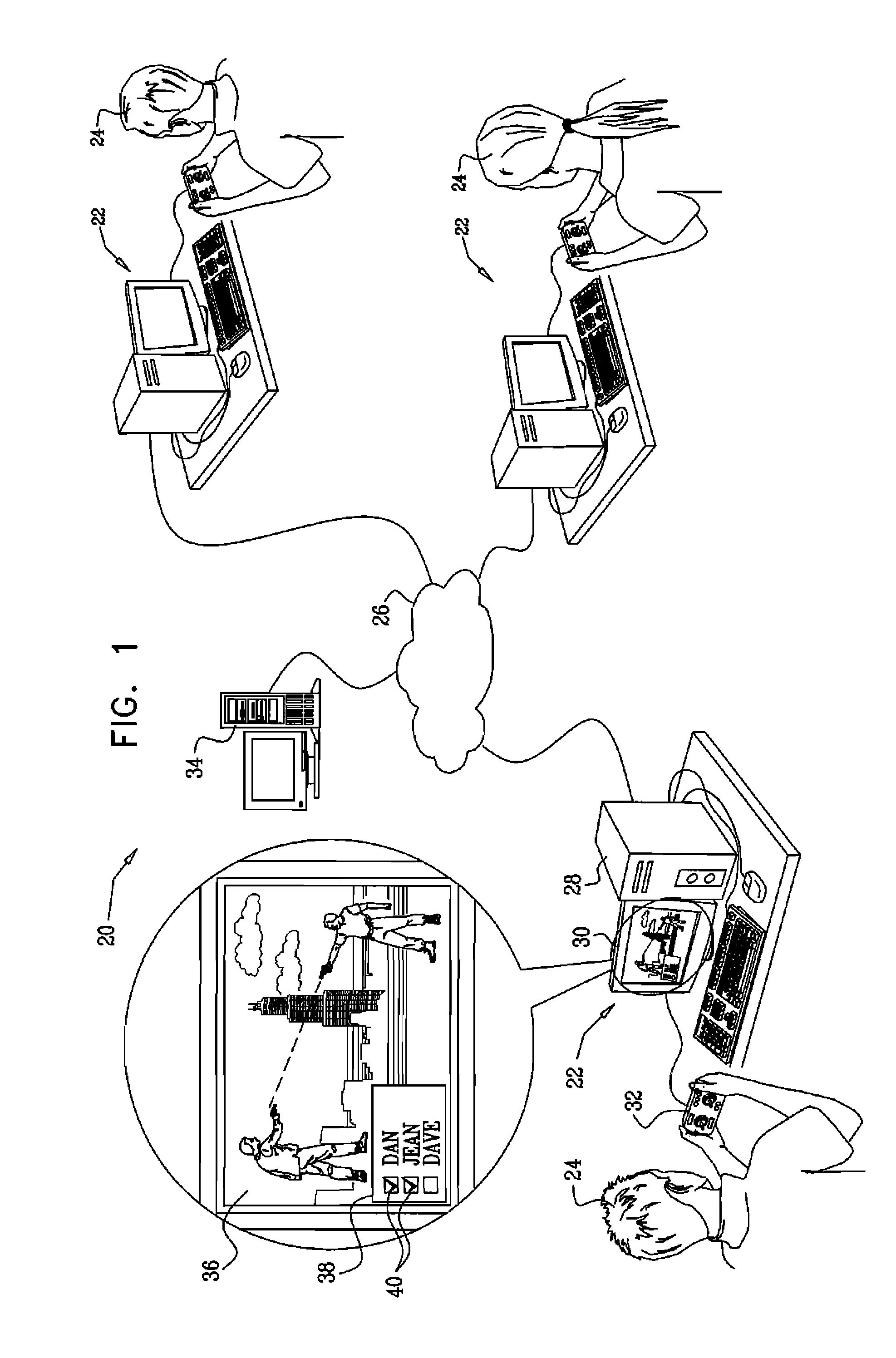
To provide a monitoring system and method that allows customization of a monitoring system and method according to a user's instruction, thereby achieving a higher flexibility in configuring the monitoring scheme. The monitoring system comprises a user system and a security server. The user system includes a capture unit, an input unit, a sensor, an imaging unit and a home server. The home server accepts the user's instructions and configure monitoring program realized by the home server. The user may specify logical connections between imaging unit and sensor, notification rule when the alarm is occurred.
Owner:SONY CORP
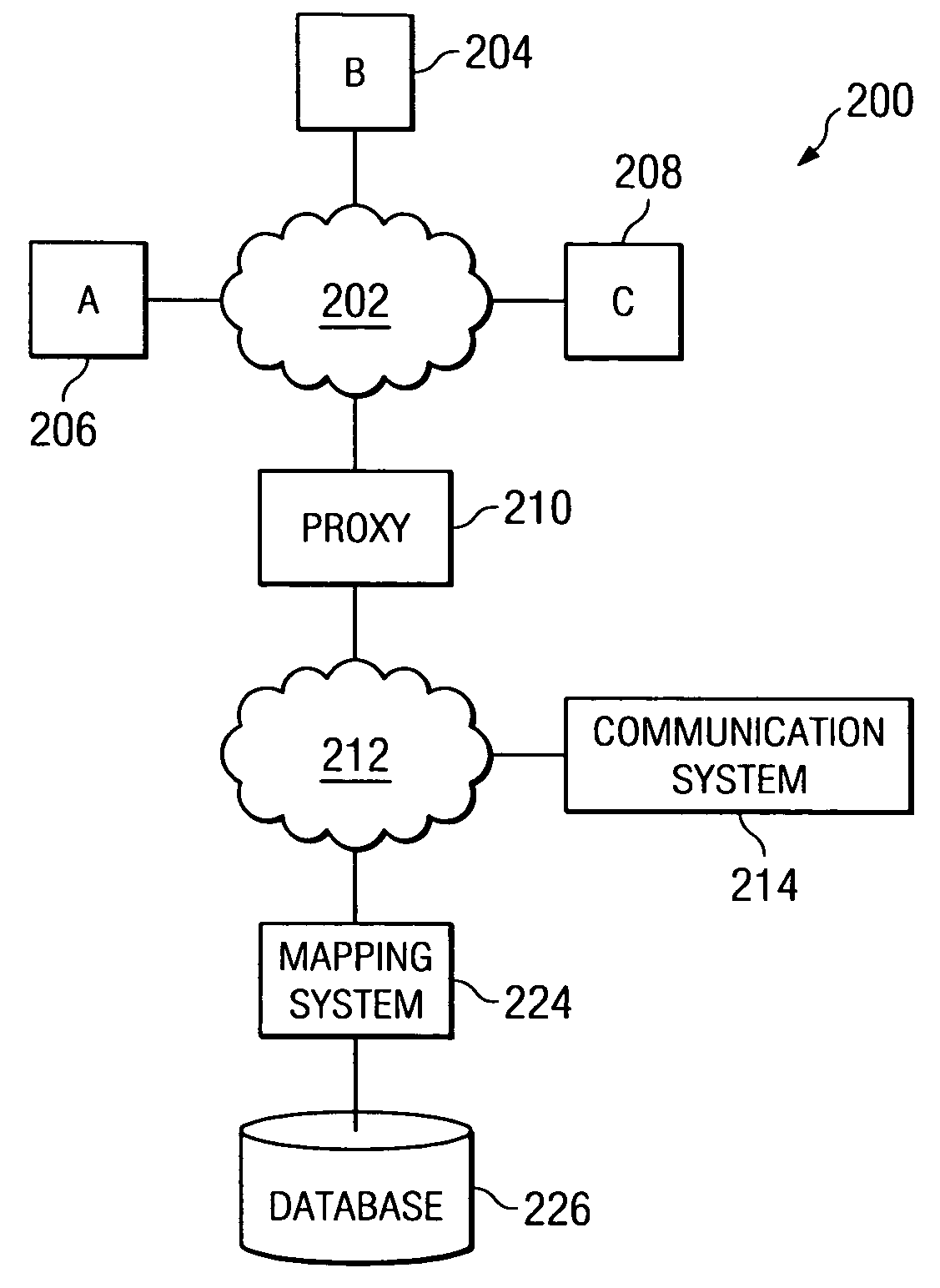
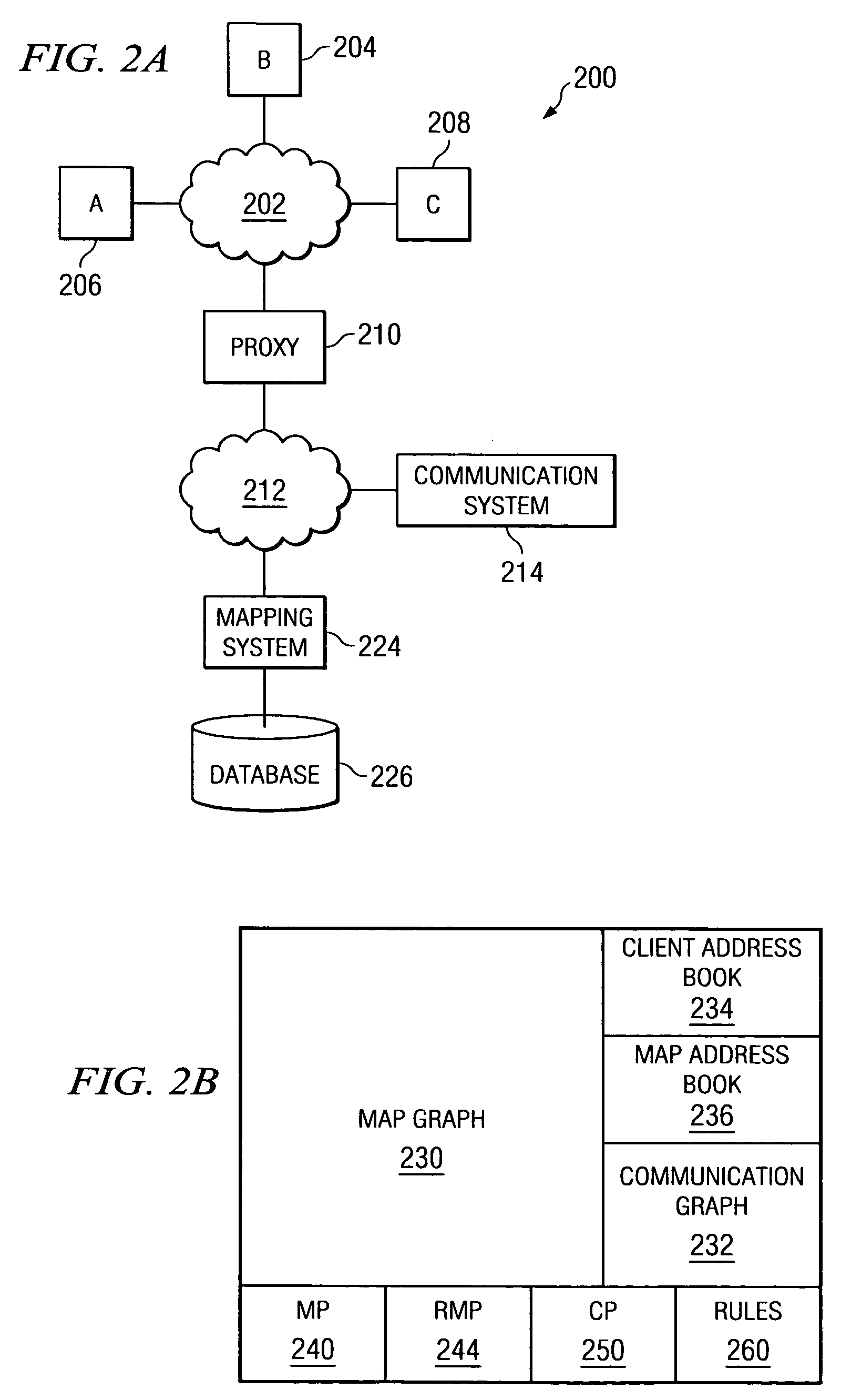
Method for distributing and geographically load balancing location aware communication device client-proxy applications
InactiveUS7428588B2Resource allocationMultiple digital computer combinationsThe InternetApplication software
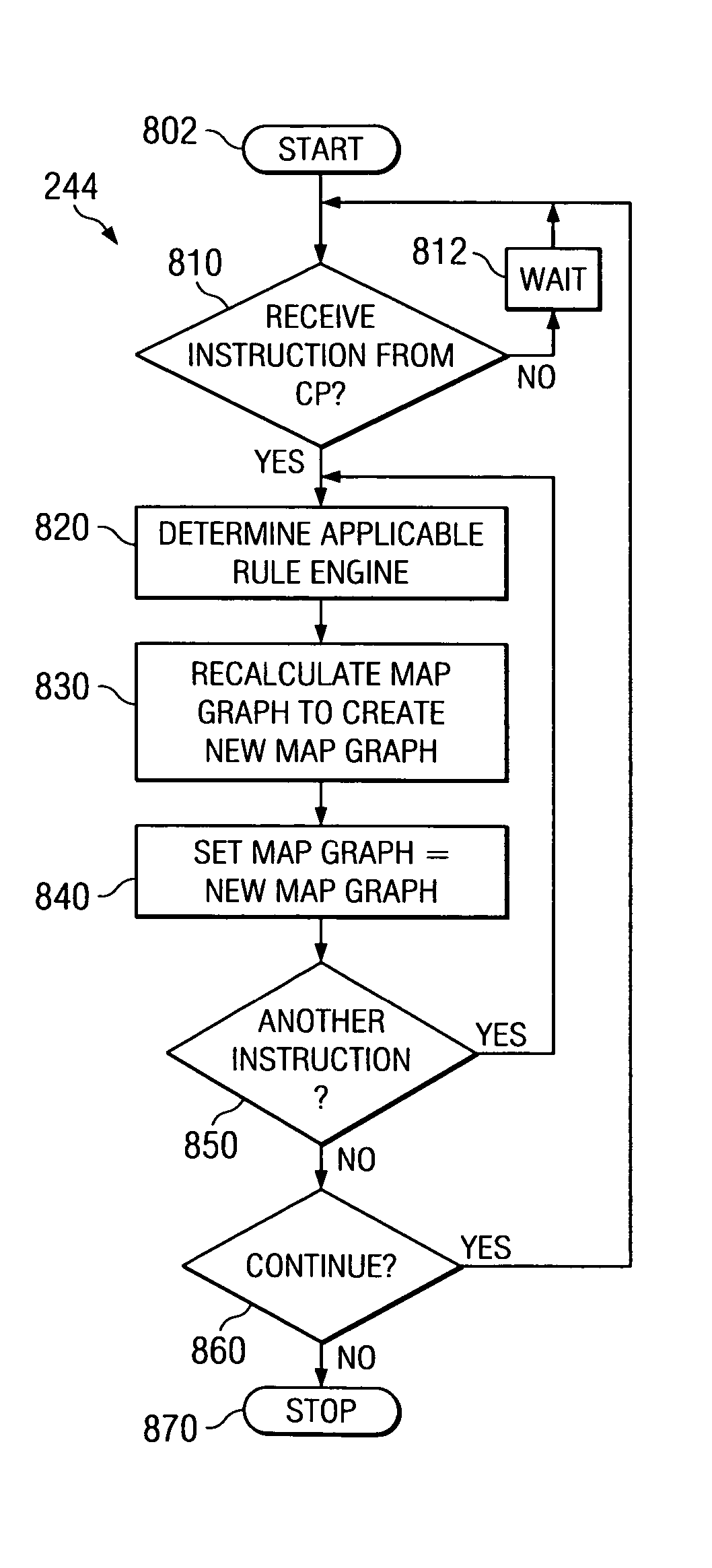
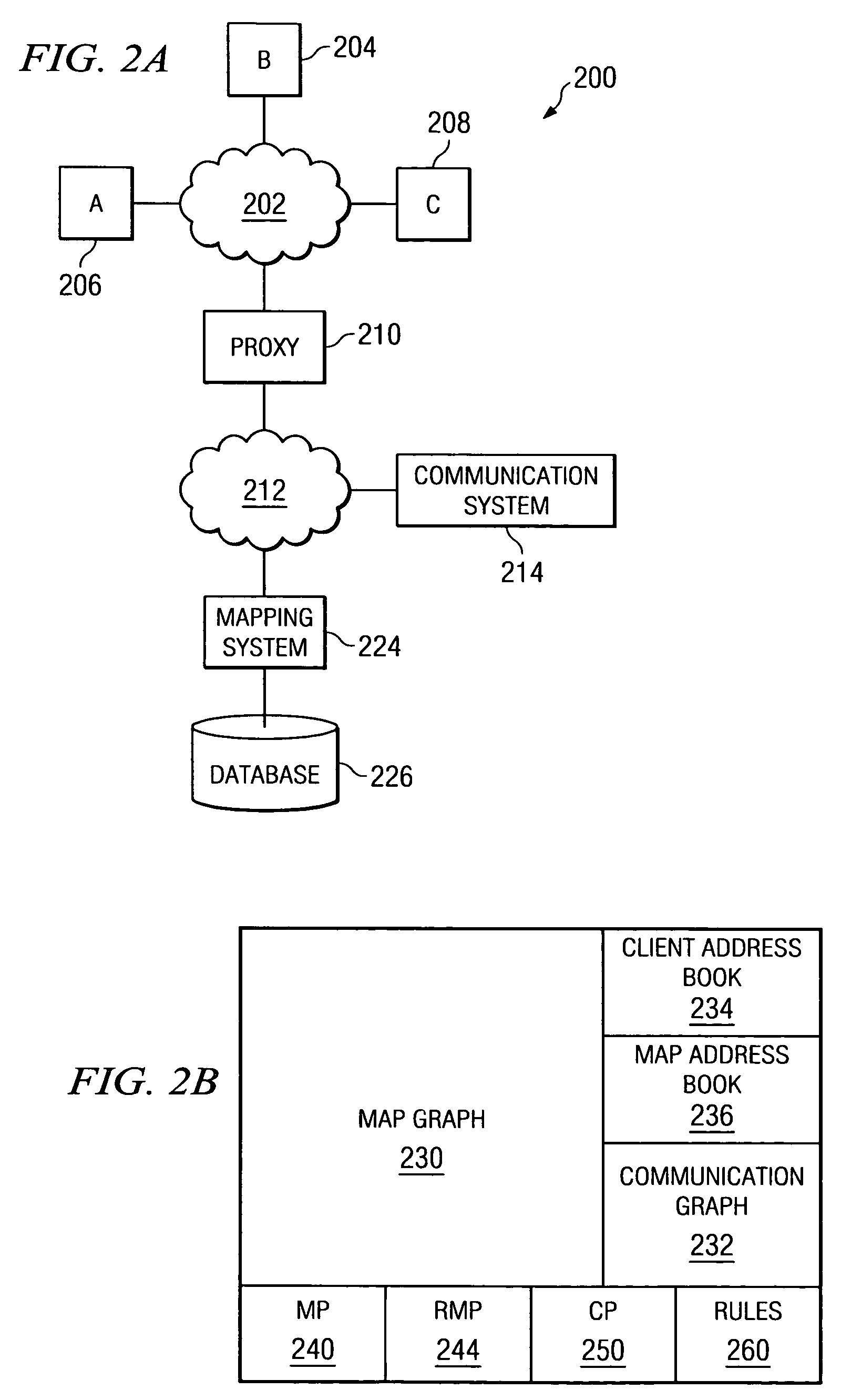
A method and system for balancing server work load for cellular phone client-proxy applications in an environment where the clients change position within a given geographic area is disclosed. The method comprises the steps of mapping, monitoring, automatically re-mapping the system when required, updating a map address book, and updating a client address book. The system has a mapping system and a communication system connected to a plurality of servers, proxy servers and applications by an internal network. The proxy servers are connected to a plurality of clients by the Internet. If a threshold is exceeded, the monitoring program sends a message to a mapping program. Upon receipt of the message, the mapping program uses a rules engine to calculate a new map graph to remove load from an overloaded server (or servers) and to adjust communication requirements for data by reconfiguring partitions.
Owner:ACTIVISION PUBLISHING
Video editor and editing method, recording medium, and program
InactiveUS20060098941A1Television system detailsElectronic editing digitised analogue information signalsTerminal equipmentVideo image
An object of the present invention is to perform speedy editing to produce images including desired features. A disc video monitor program 161 sets an essence mark, which is digital mark data indicating a feature of an image, in metadata related to video content data for displaying images. A video display program 172 controls the display of images based on the video content data. An essence-mark display program 171 controls the display of the temporal position of the image having the feature indicated by the digital mark data based on the metadata in which the essence mark, which is digital mark data, is set. The video-image editing apparatus of the present invention is applicable to a filming terminal device.
Owner:SONY CORP
Method for distributing and geographically load balancing location aware communication device client-proxy applications
InactiveUS20050246711A1Resource allocationMultiple digital computer combinationsClient agentThe Internet
A method and system for balancing server work load for cellular phone client-proxy applications in an environment where the clients change position within a given geographic area is disclosed. The method comprises the steps of mapping, monitoring, automatically re-mapping the system when required, updating a map address book, and updating a client address book. The system has a mapping system and a communication system connected to a plurality of servers, proxy servers and applications by an internal network. The proxy servers are connected to a plurality of clients by the Internet. If a threshold is exceeded, the monitoring program sends a message to a mapping program. Upon receipt of the message, the mapping program uses a rules engine to calculate a new map graph to remove load from an overloaded server (or servers) and to adjust communication requirements for data by reconfiguring partitions.
Owner:ACTIVISION PUBLISHING
Enhanced fire, safety, security, and health monitoring and alarm response method, system and device
ActiveUS20060017558A1Frequency-division multiplex detailsTime-division multiplexResponse methodThe Internet
Method, system and device useful with conventional personal computers respond automatically to an identified alarm sound by sending a notification signal via the Internet only when a special sound monitoring program is active. Additionally, bedside detection of acoustic alarms is combined with enhanced waking devices to insure the waking of a child or hearing impaired person in response to an emergency. Home safety and security are provided using a bedside unit to monitor audible safety and security alarms and send notification signals to the appropriate communication site. A health monitoring method and system utilizes the bedside device to monitor breathing patterns and other health measuring signals and communicate these patterns and signals to a medical monitoring station.
Owner:INNOVALARM
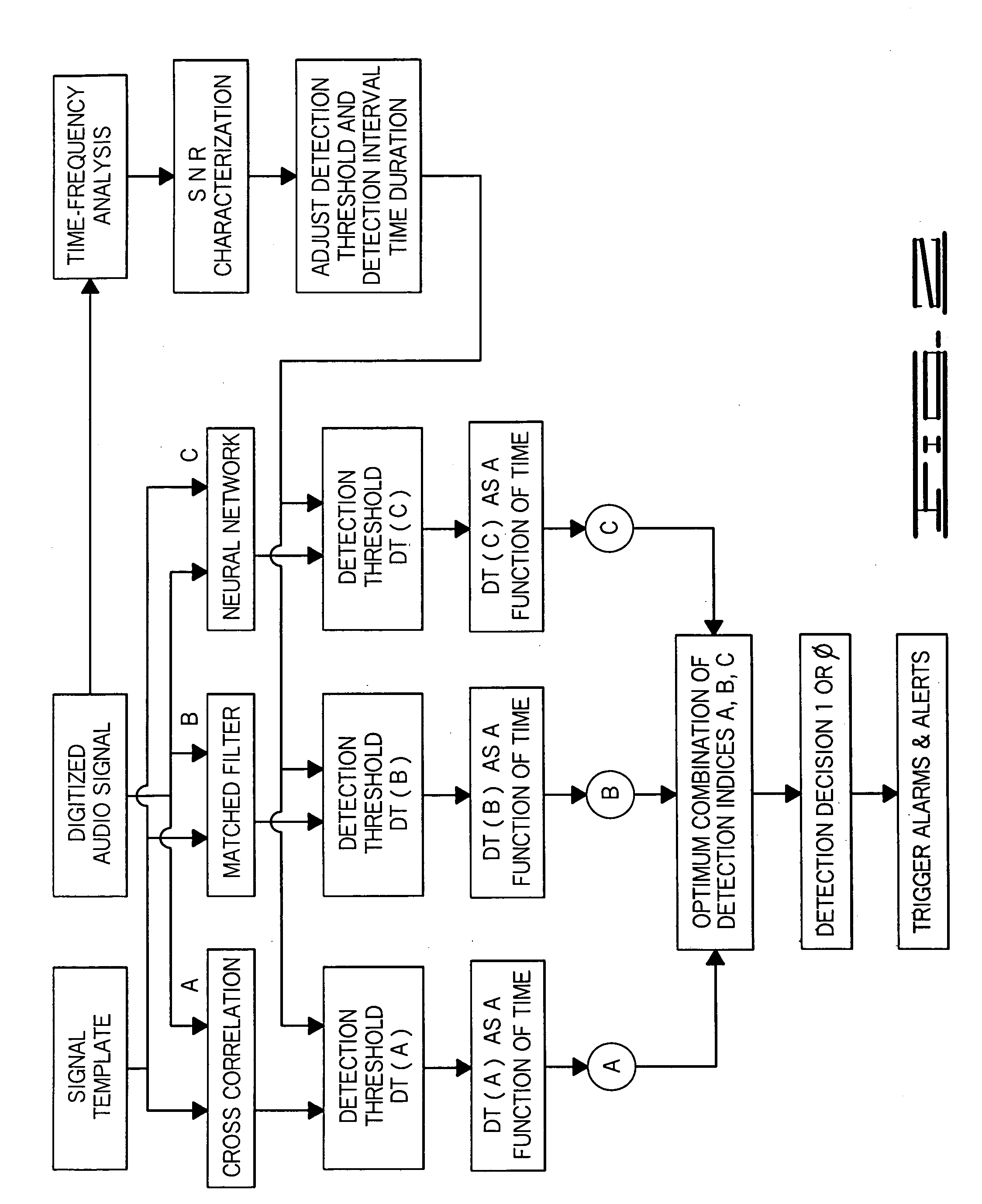
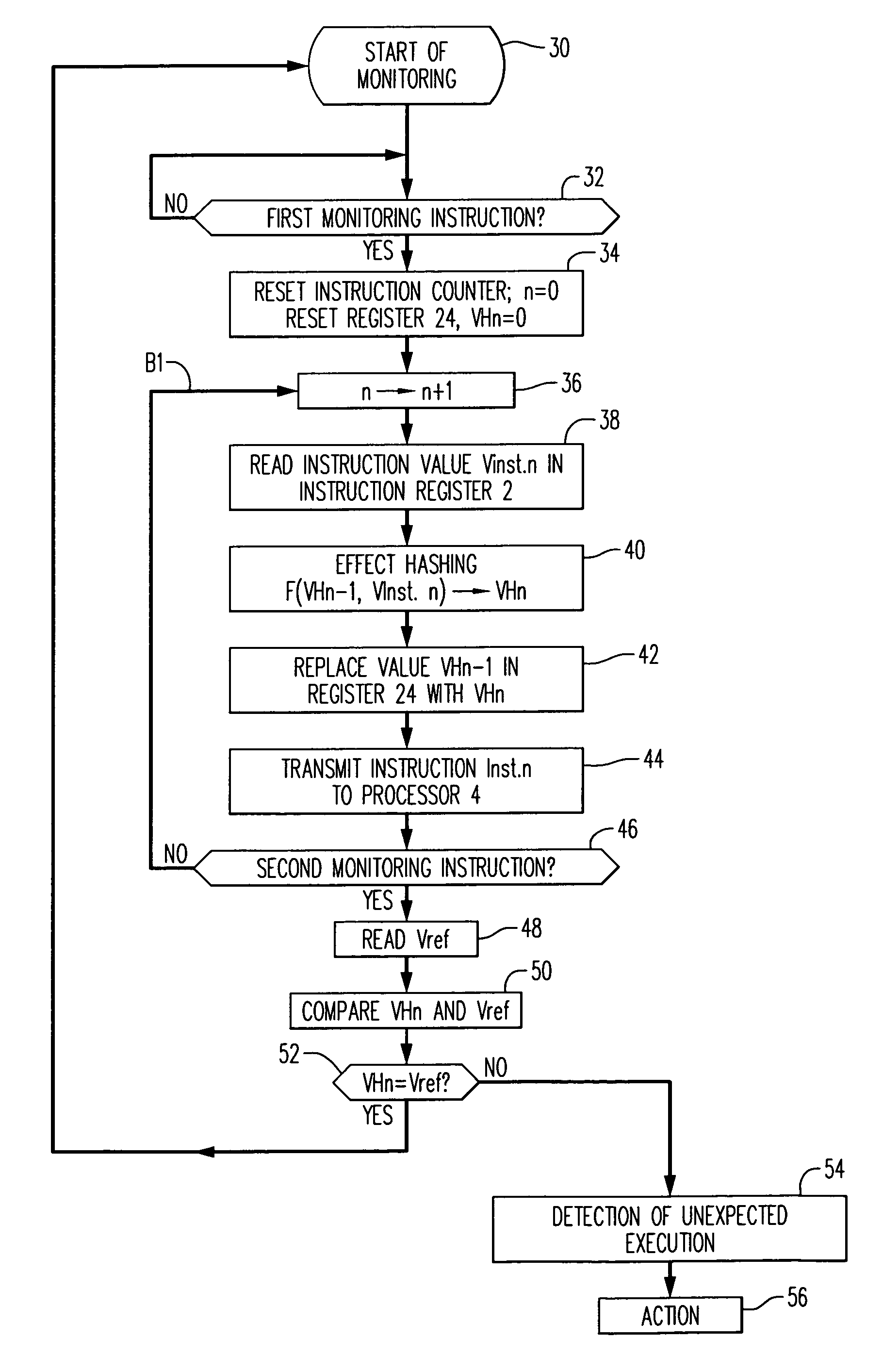
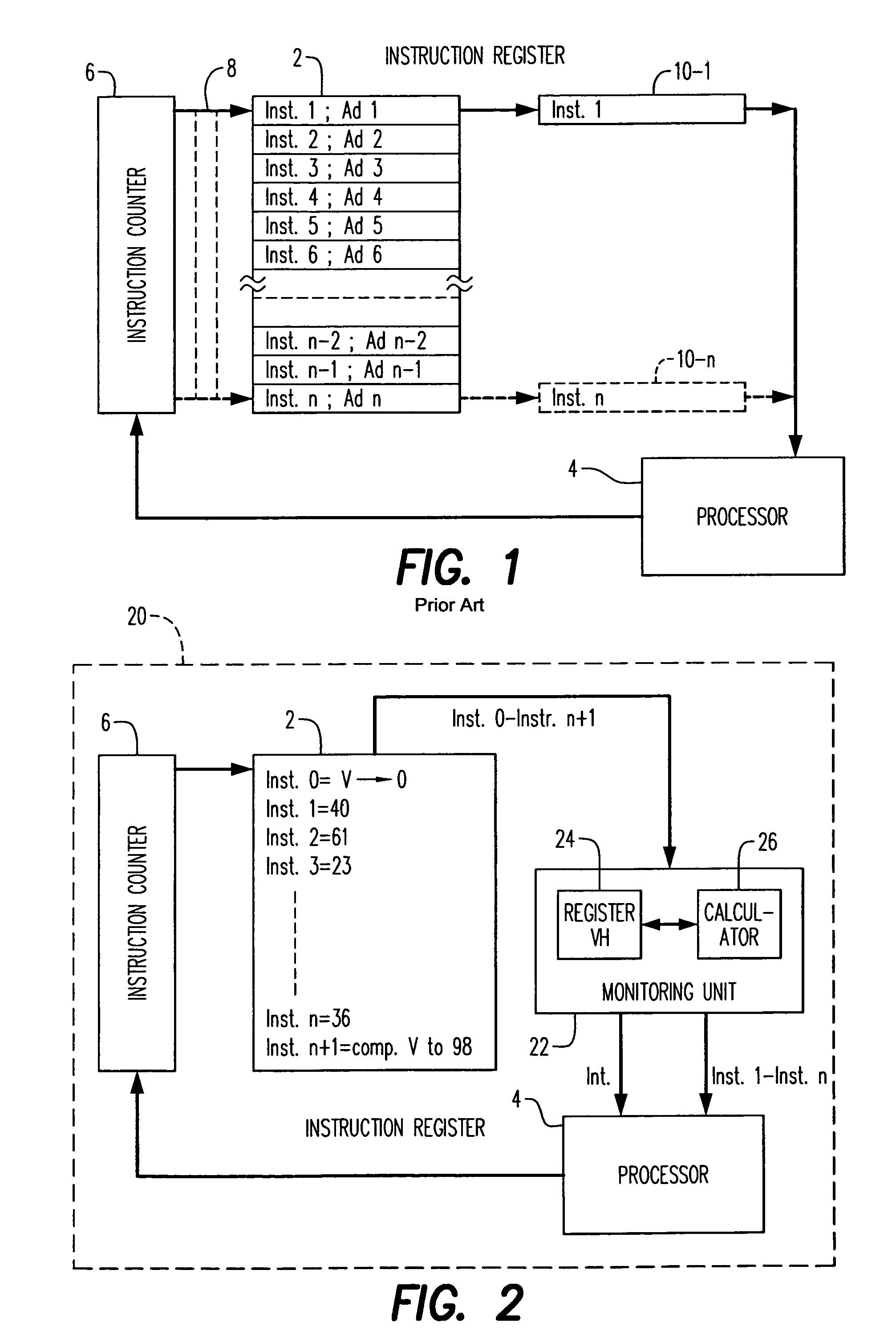
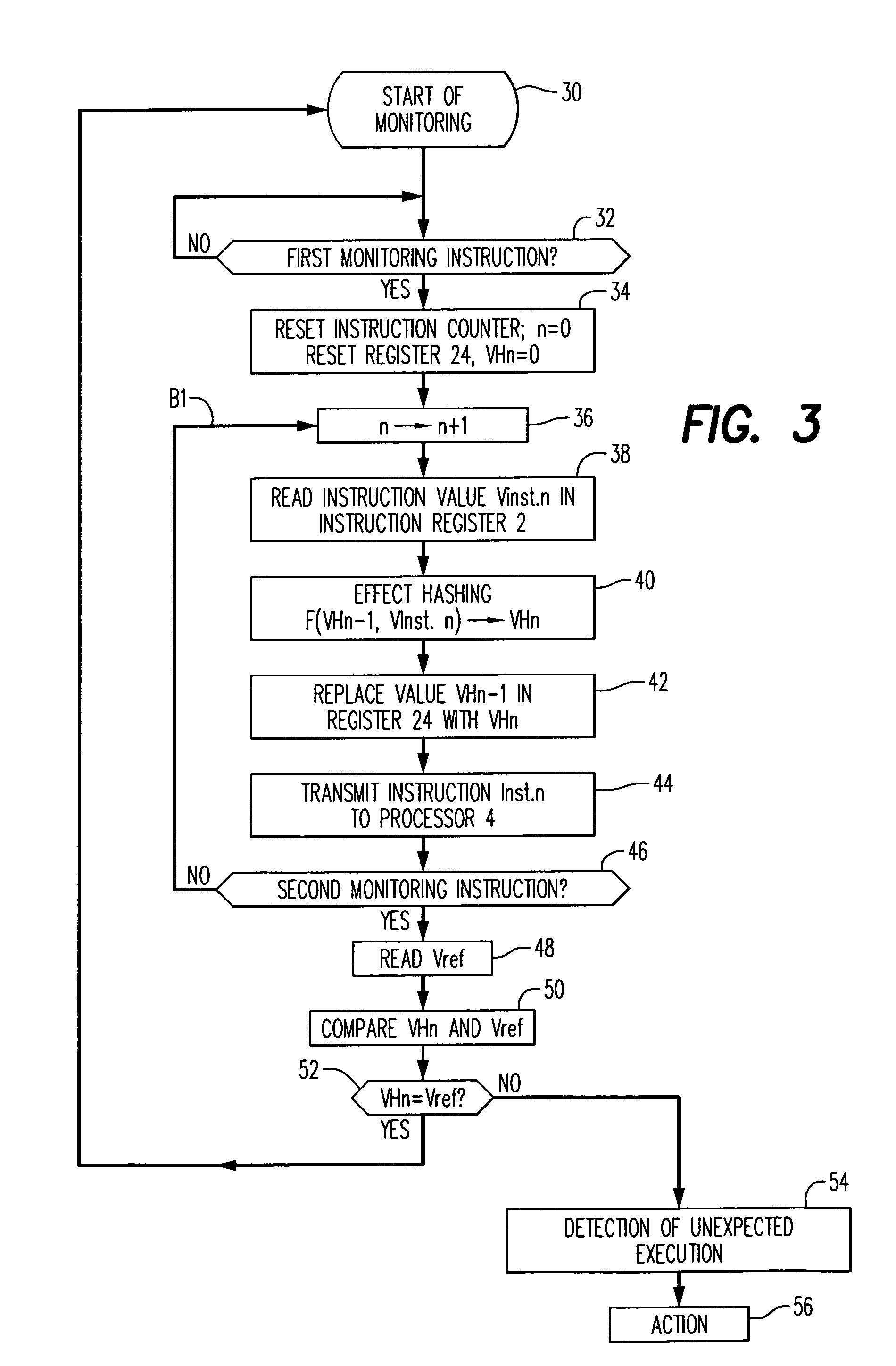
Method for monitoring program flow to verify execution of proper instructions by a processor
InactiveUS7168065B1Save memory spaceEasy to manageDigital computer detailsHardware monitoringComputer scienceProcedure device
In a method for monitoring the flow of execution of a series of instructions of a computer program, a sequence of instructions are transmitted to the processor to execute the monitored program. These instructions are analyzed, and the result of the analysis are verified by referring to reference data recorded with the program. The reference data can include a value predetermined in such a way as to correspond to the result of the analysis produced during the monitoring process only if all the instructions have been actually analyzed during the program flow. The invention also concerns a device for monitoring the program execution, a program device, and a programming device operating according to the monitoring principles.
Owner:GEMPLU
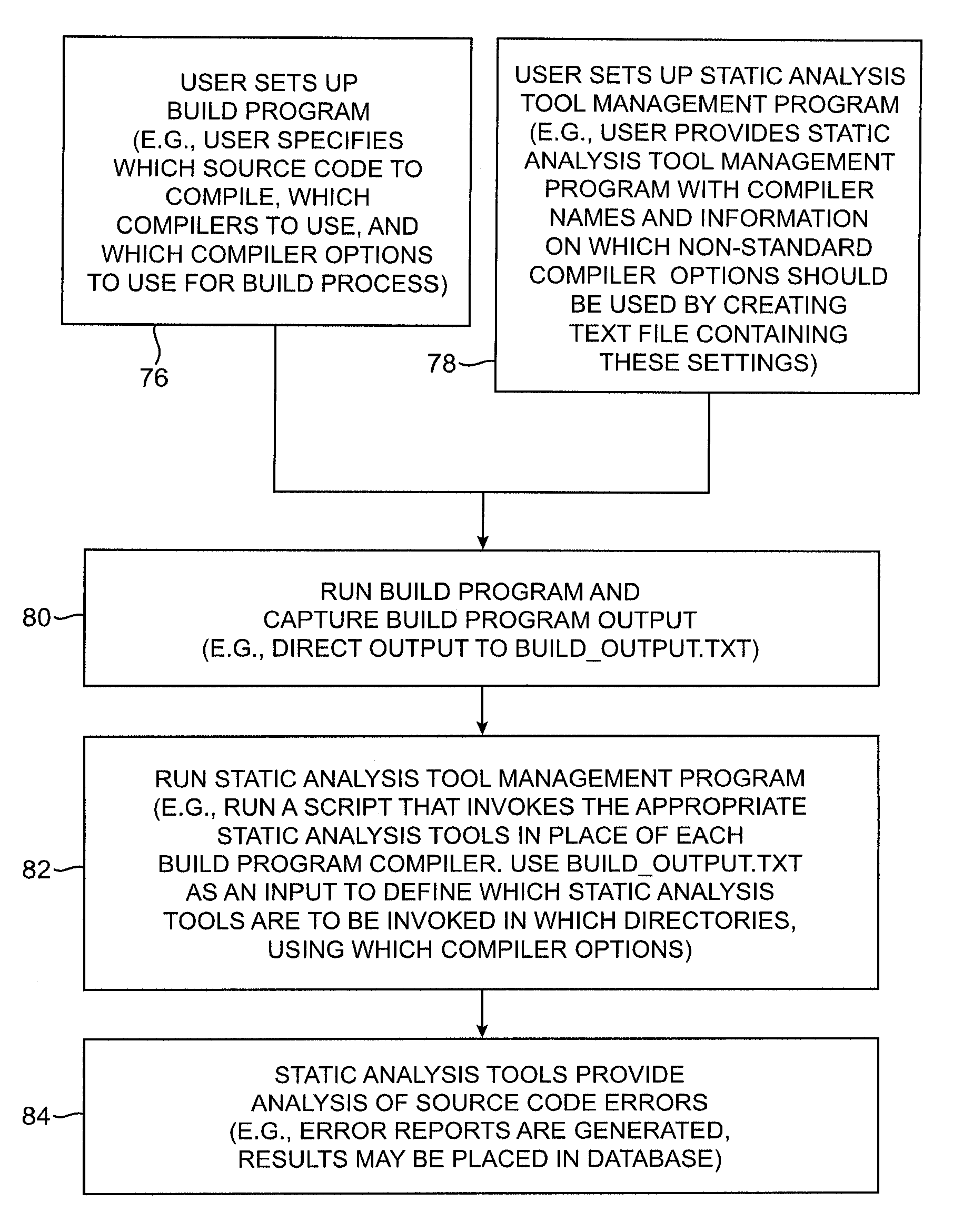
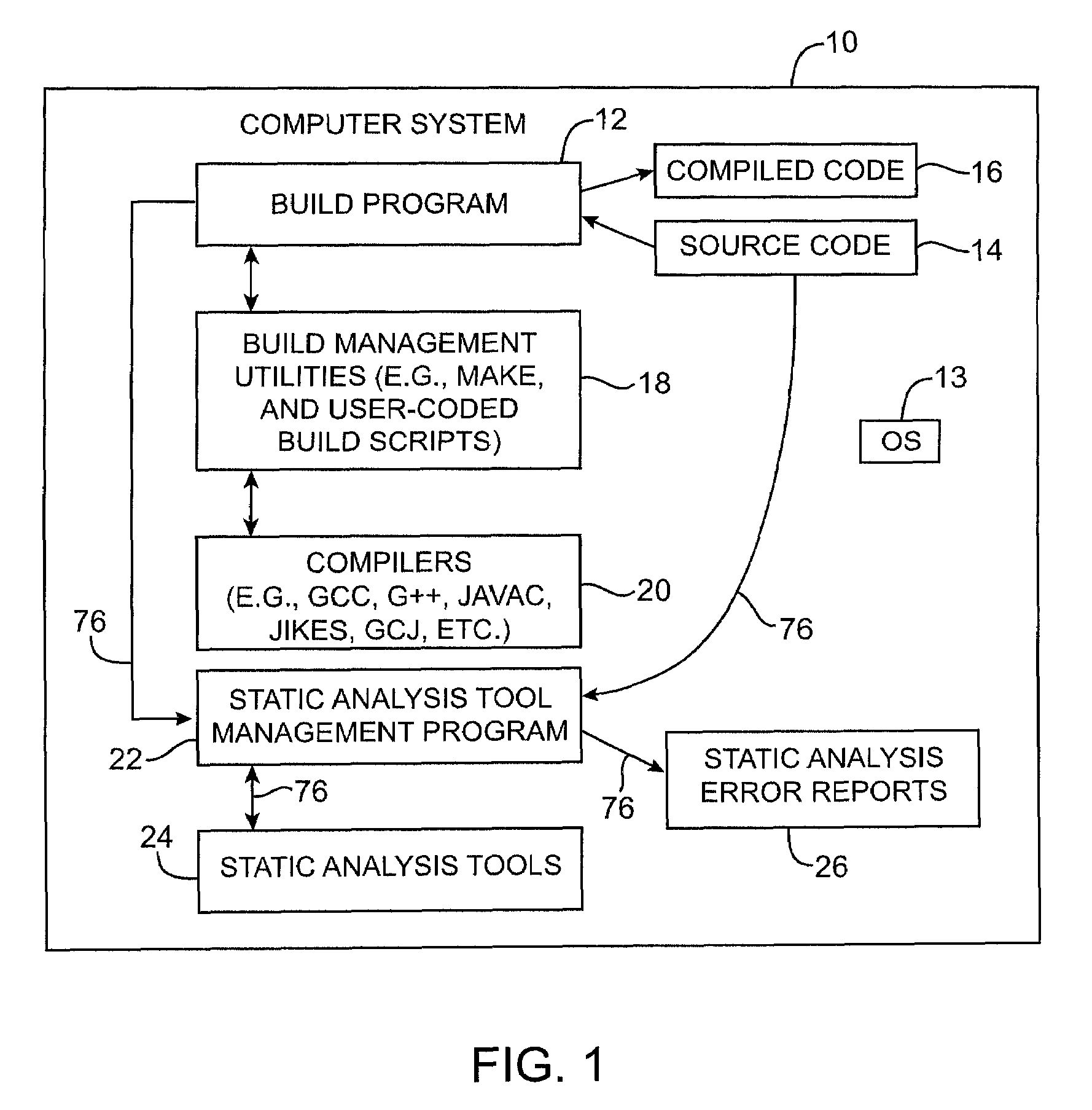
Systems and methods for performing static analysis on source code
Systems and methods are provided for performing static error analysis on source code. A computer system having an operating system may contain a number of source code files. During a normal build process, a build program may be used to set various compilation options and to invoke appropriate compilers that compile the source code files into executable code. Static analysis debugging tools may be used to perform static analysis on the source code files. The appropriate static analysis tools may be invoked using a static analysis tool management program. Directory, path and name modification may be used to invoke the analysis tools. A monitoring program may be used to determine how to invoke the tools. The operating system may be modified so that the static analysis tools are invoked in place of the compilers when the build program is run.
Owner:SYNOPSYS INC
Enhanced fire, safety, security and health monitoring and alarm response method, system and device
ActiveUS7148797B2Frequency-division multiplex detailsTime-division multiplexResponse methodThe Internet
Owner:INNOVALARM
Prevention of cheating in on-line interaction
InactiveUS20080305869A1Prevent cheatingApparatus for meter-controlled dispensingVideo gamesMonitoring programDistributed computing
A method for preventing cheating by users of client computers running a network game program includes installing a monitoring program, independent of the network game program, on a group of the client computers so as to detect, using the monitoring program, an anomalous use of an asset of at least one of the client computers that is indicative of an attempt to cheat in the game program. A message is conveyed over a network to a server from each of at least some of the client computers in the group. The message from each such client computer indicates that the monitoring program has been actuated on the client computer. Responsively to the message, the client computers receive a message from the server at the client computer indicating which ones of the client computers have actuated the monitoring program.
Owner:COGNISAFE
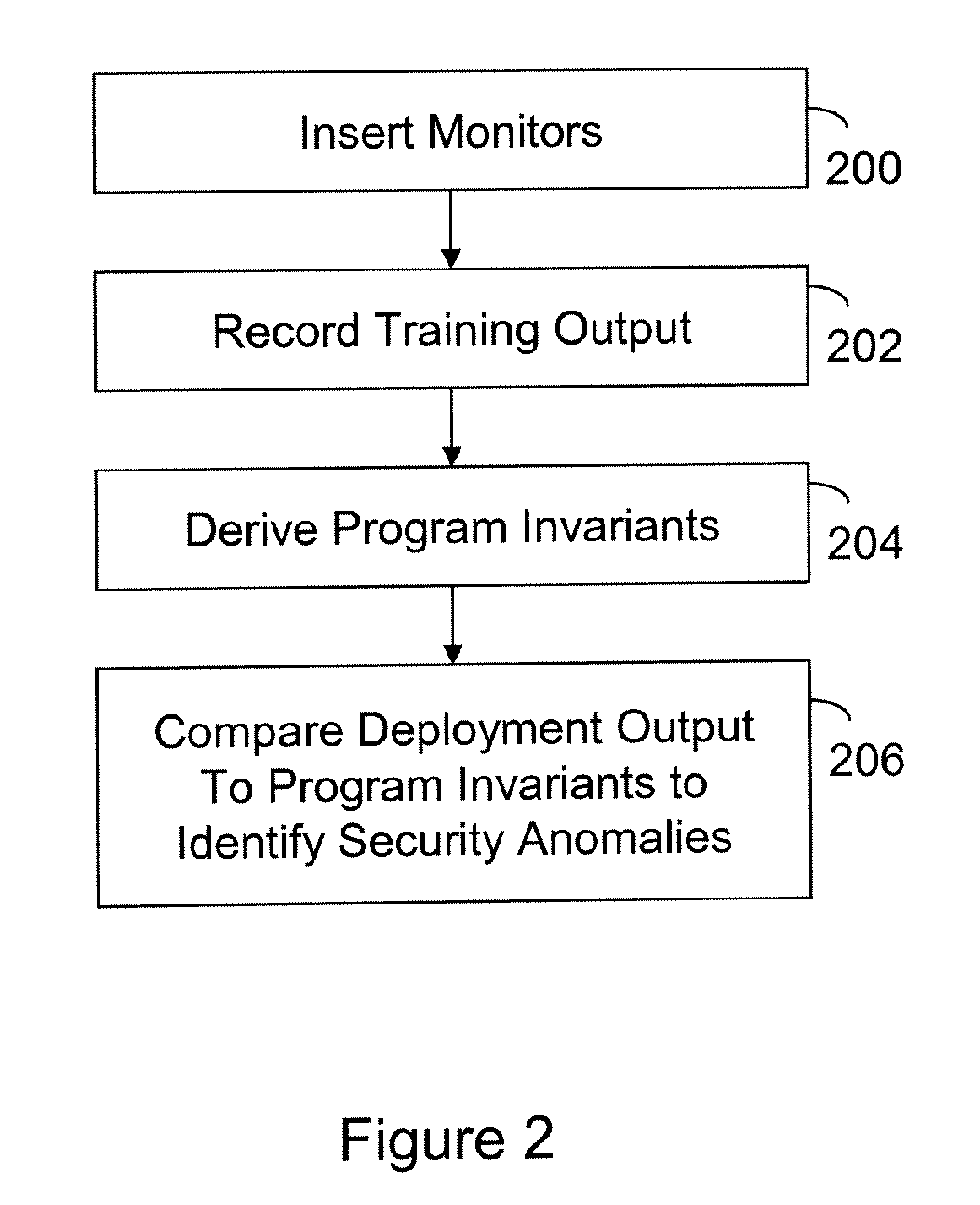
Apparatus and Method for Monitoring Program Invariants to Identify Security Anomalies
InactiveUS20090282480A1Memory loss protectionError detection/correctionTraining phaseComputer engineering
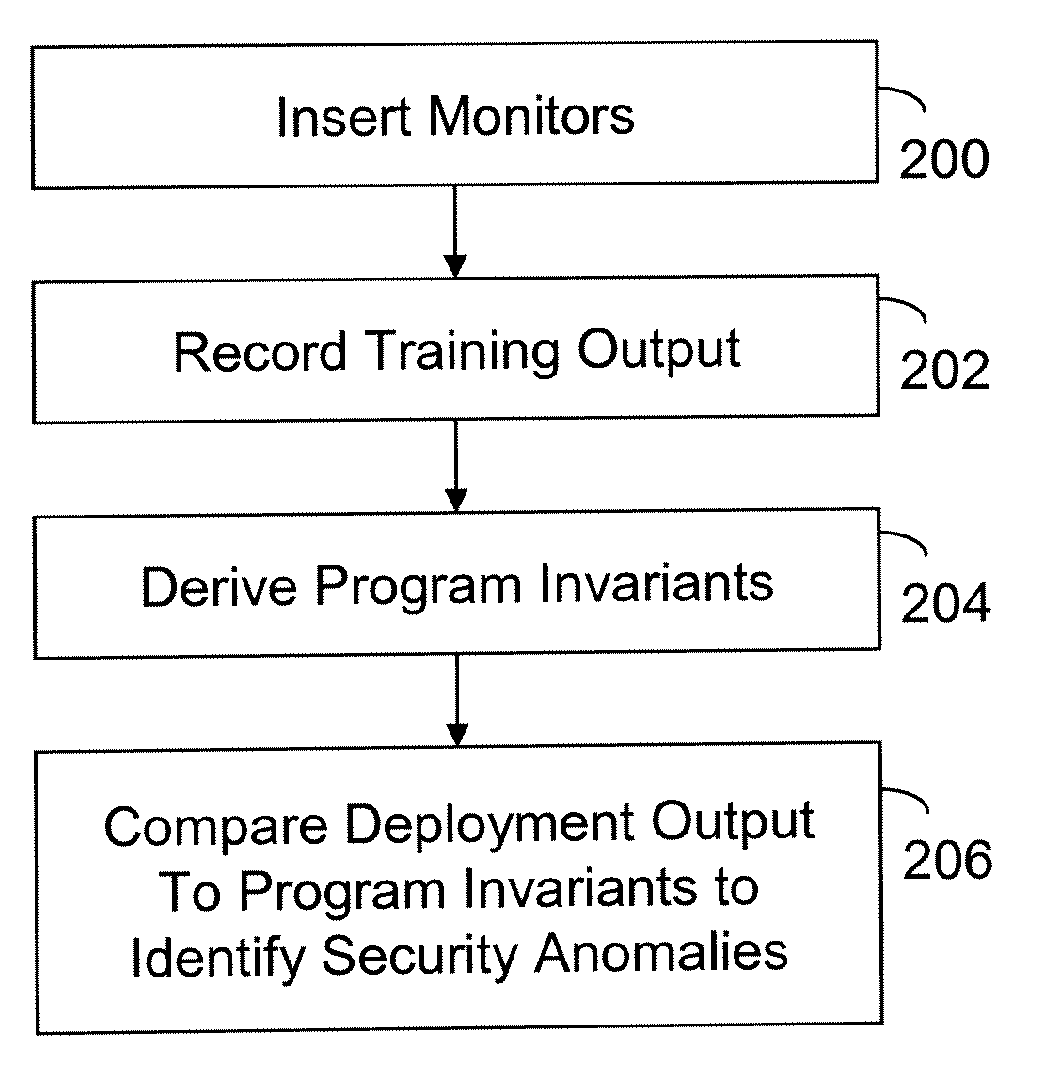
A computer readable storage medium includes executable instructions to insert monitors at selected locations within a computer program. Training output from the monitors is recorded during a training phase of the computer program. Program invariants are derived from the training output. During a deployment phase of the computer program, deployment output from the monitors is compared to the program invariants to identify security anomalies.
Owner:HEWLETT PACKARD DEV CO LP
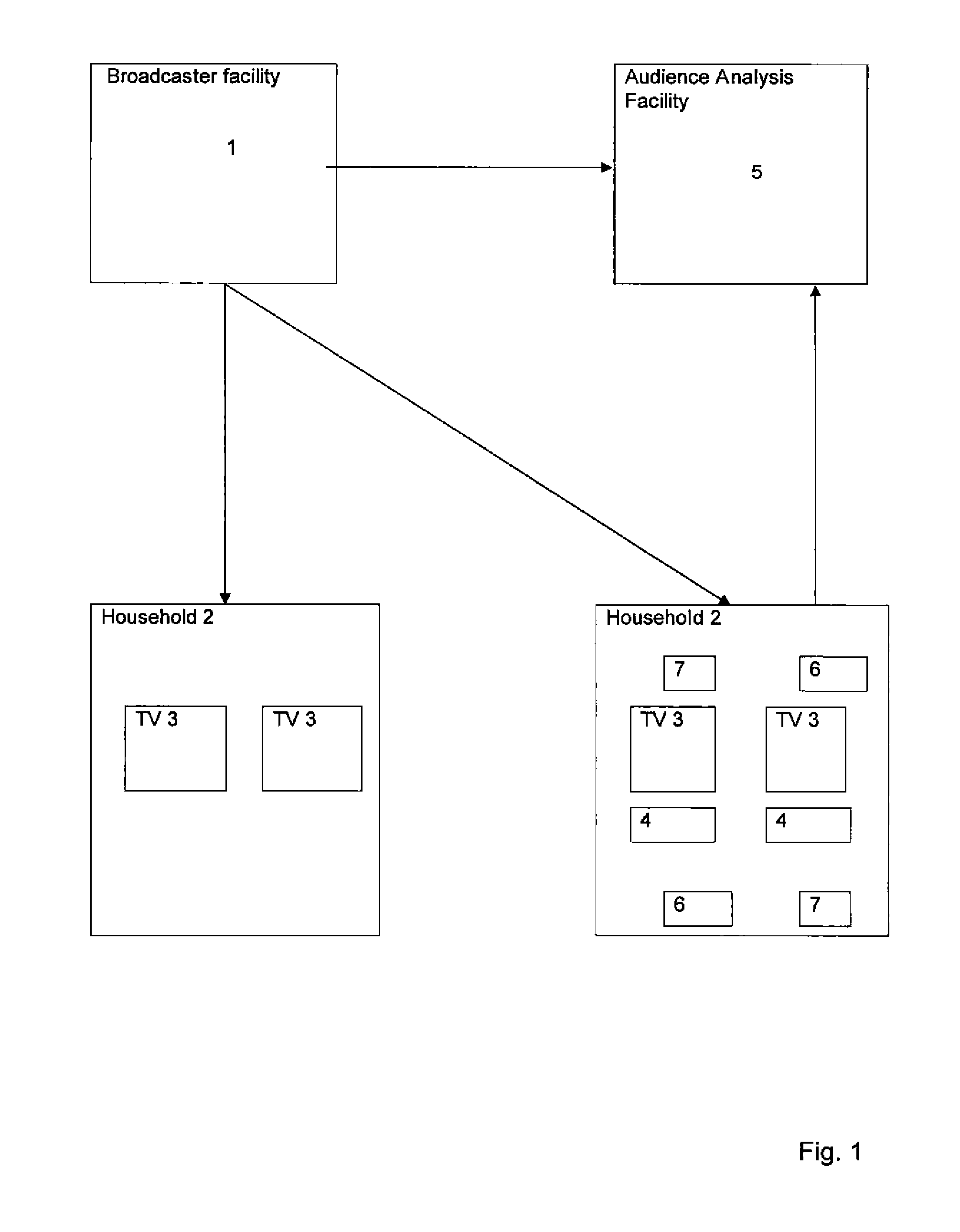
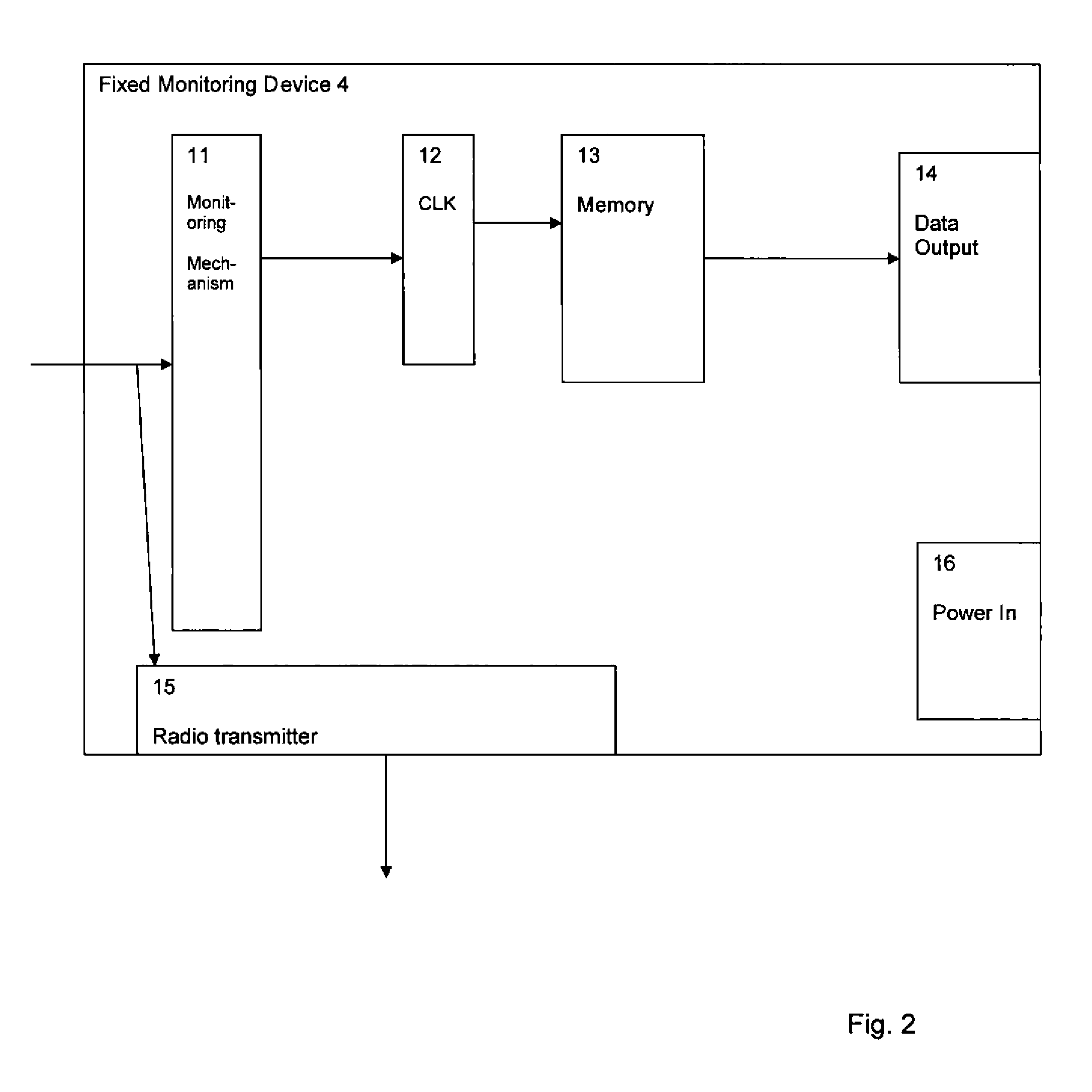
Audience measurement system and monitoring devices
InactiveUS20080148309A1Accurately determineAnalogue secracy/subscription systemsBroadcast information monitoringMonitor equipmentReal-time computing
Audience measurement systems having fixed and portable monitoring devices are provided. Embodiments of the audience measurement system may be suitable for monitoring programs viewed and / or listened to by one or more members of a sample household. The fixed monitoring device may be associated with a particular media device, for example, in the household's home and monitor a received broadcast signal and / or a state of the media device to extract information enabling a received program and / or station to be identified. The portable monitoring device may comprise a receiver for receiving sound of a program emitted by any nearby media device; a data extractor for extracting data from the received sound to enable a program and / or station to be identified. Either a first or a second communicator may be operable to transmit a device present signal in the vicinity of its respective monitoring device, and / or detect the said signal.
Owner:TAYLOR NELSON SOFRES PLC
Apparatus, system, and method for implementing and monitoring breath alcohol testing programs, usually from a fixed point location, such as a home
ActiveUS20110309932A1Avoid the needReduce stepsColor television detailsClosed circuit television systemsThird partyAccelerometer
The invention relates to devices, systems and methods for thwarting attempts to circumvent breath alcohol level testing and monitoring programs. In-home monitoring systems as well as ignition interlock systems are described. Accelerometers and / or compasses are used to detect movement of the device. GPS and image data are collected at the time samples are collected to verify their authenticity. A system is provided for use by a third party service provider to provide reports and notification to monitoring authorities.
Owner:CONSUMER SAFETY TECH
Method and system for monitoring an apparatus for a computer
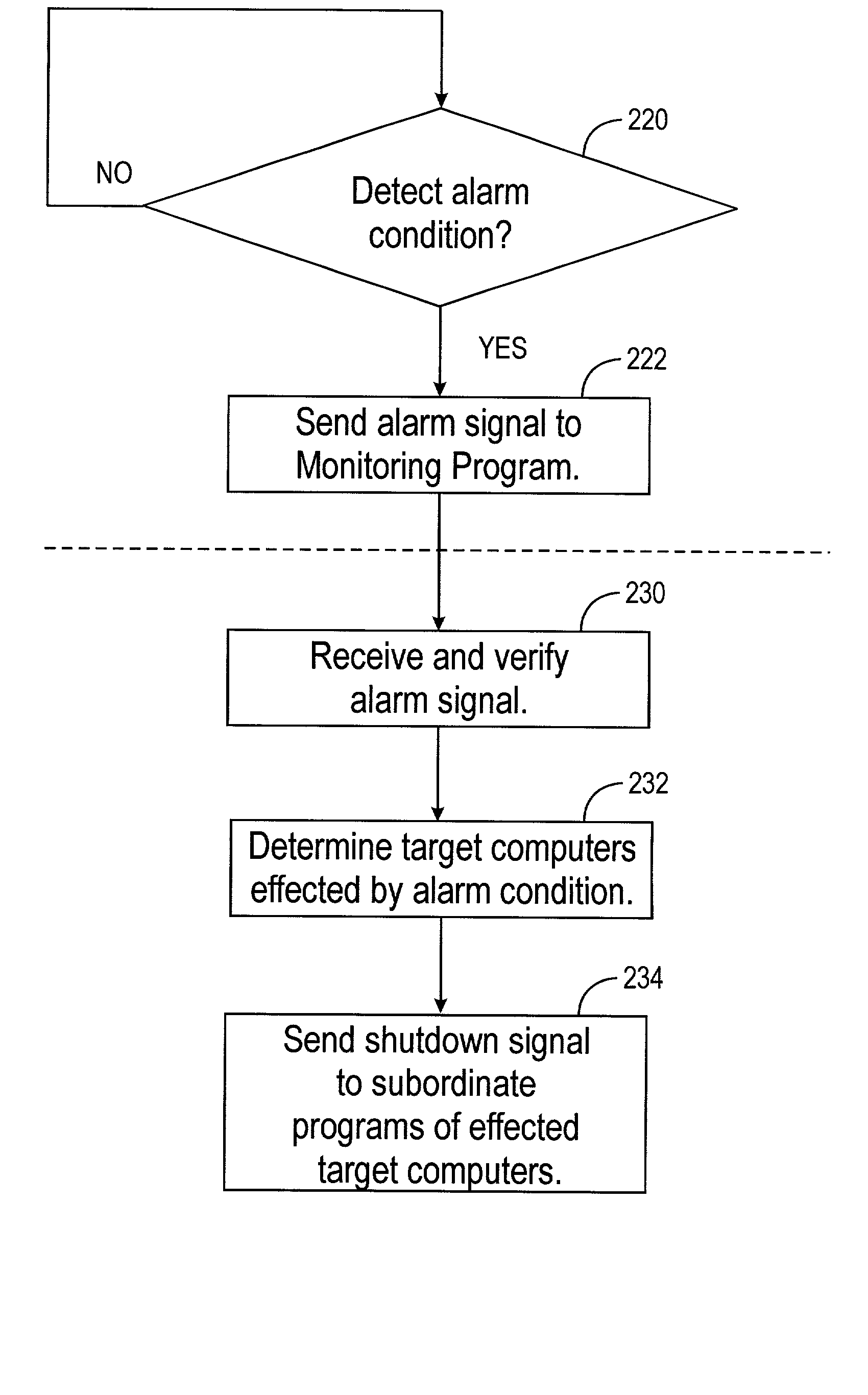
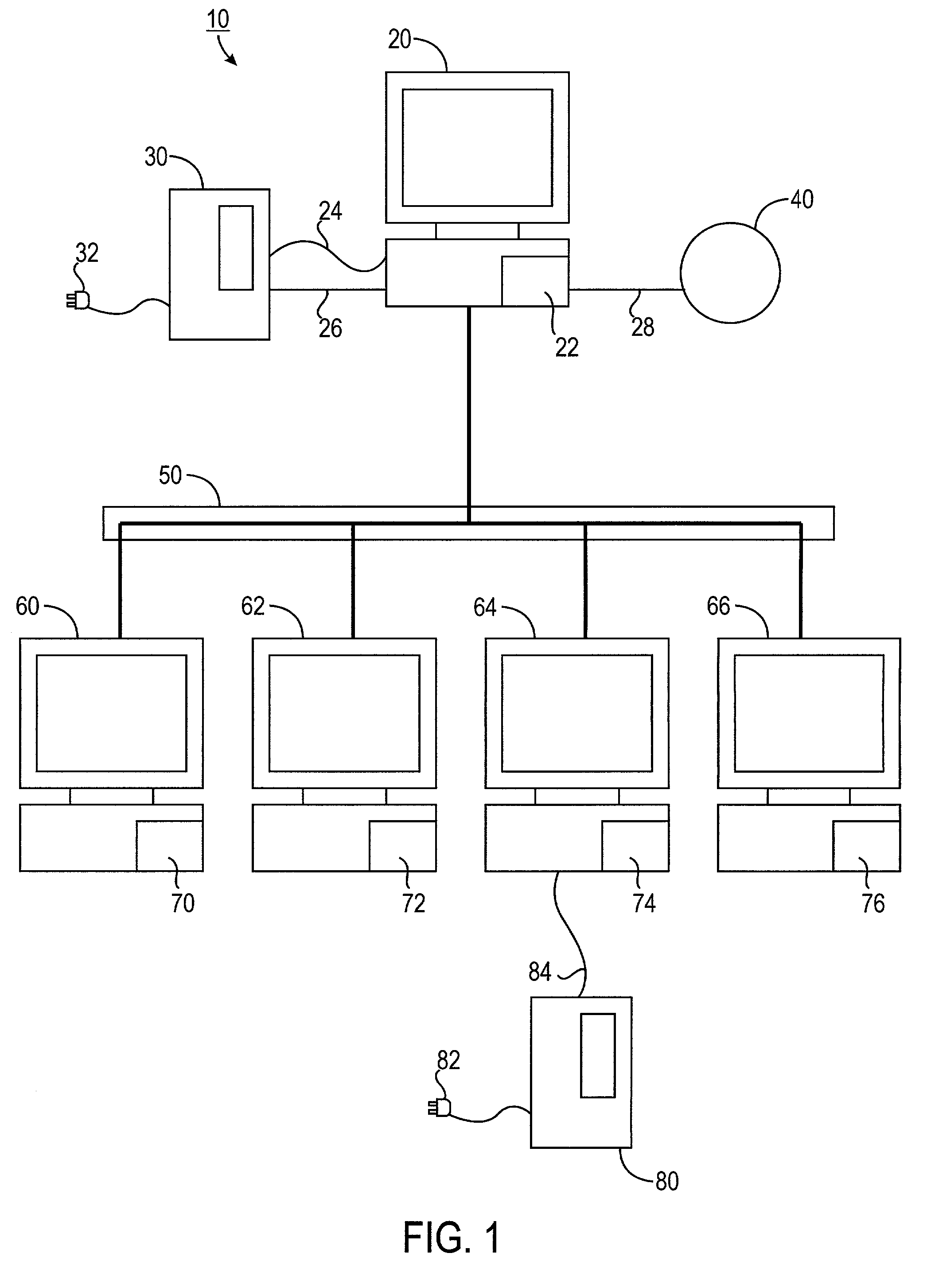
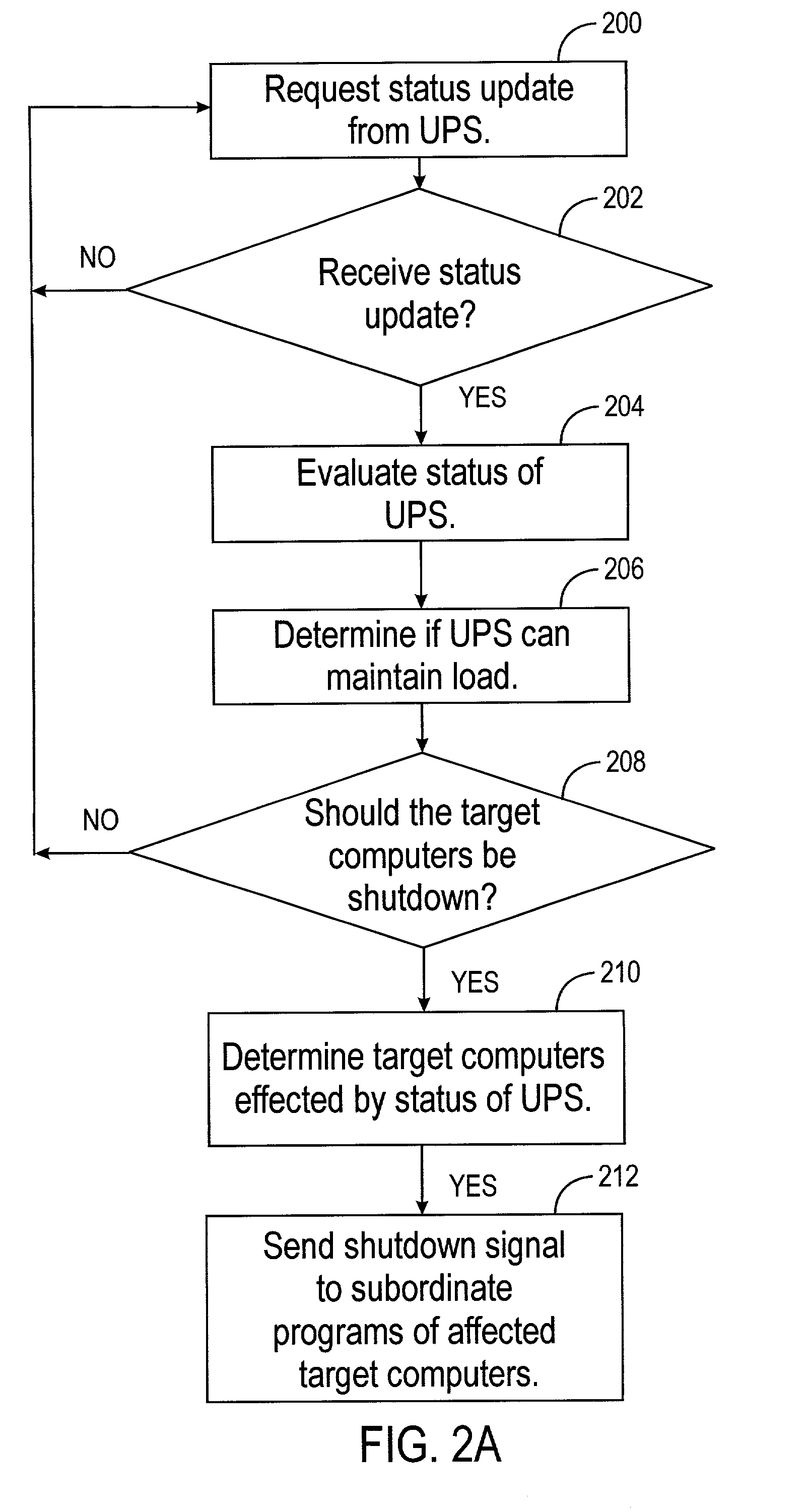
A system for monitoring various support devices of a computer network is disclosed. The network has a monitoring computer with a monitoring program that monitors the devices. The monitoring program is used to configure a subordinate program. Using push technology, the subordinate program is installed on and is run on target computers in the network. The monitoring program monitors operating parameters and alarm signals from the devices. When the monitoring program determines that the devices can no longer support its load, the monitoring computers sends a shut down instruction to the affected target computers. The subordinate program executes a shutdown routine for the target computer based on the shutdown instruction sent from the monitoring program. The subordinate program has minimal or no graphical user interface on the target computer and requires no local configuration by the user of the target computer.
Owner:LIEBERT
Active-mode intelligent safety monitoring instrument for car
InactiveCN101857008ARapid situationQuick alarmAnti-theft devicesAlarmsElectrical batterySolar battery
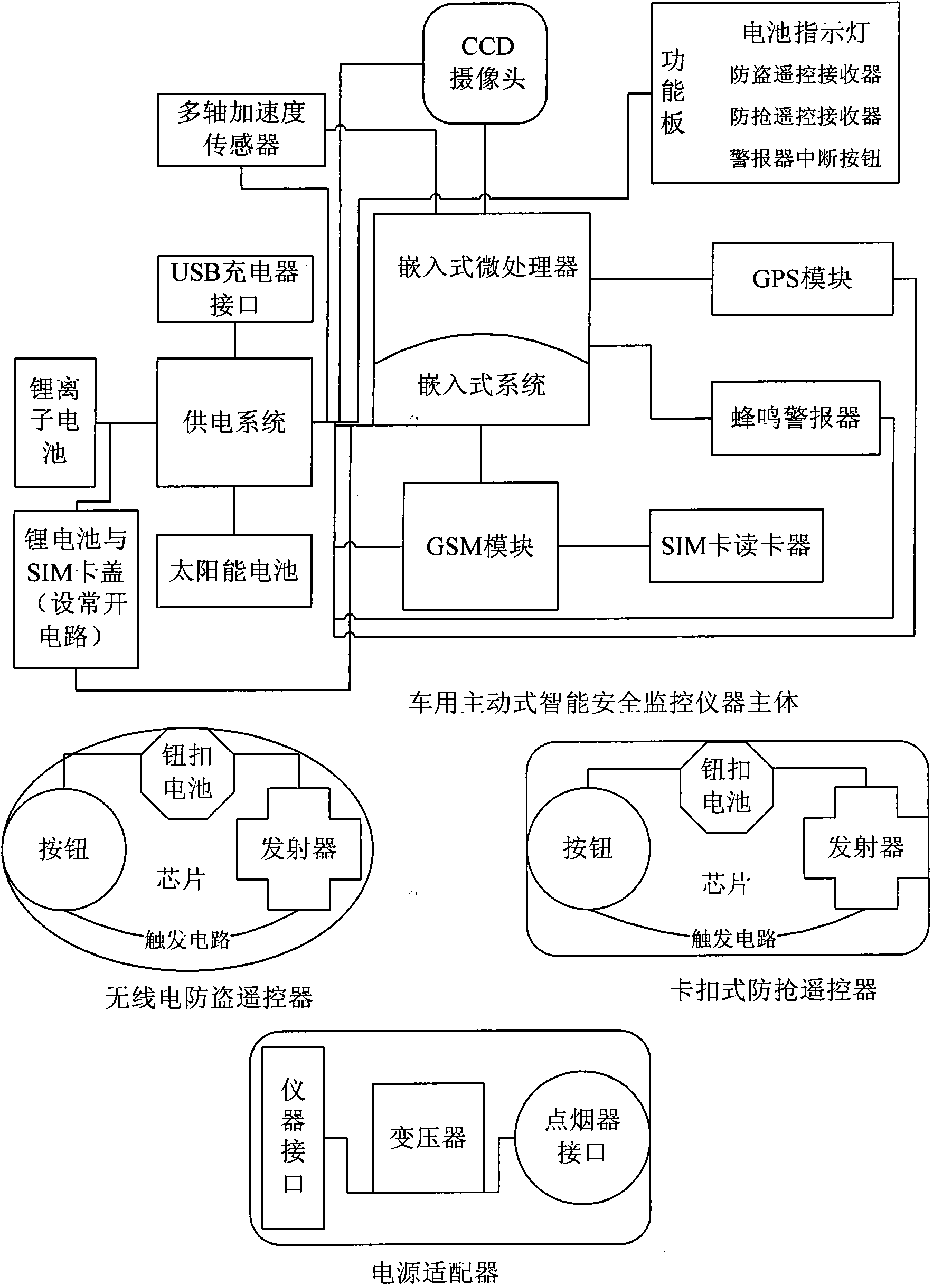
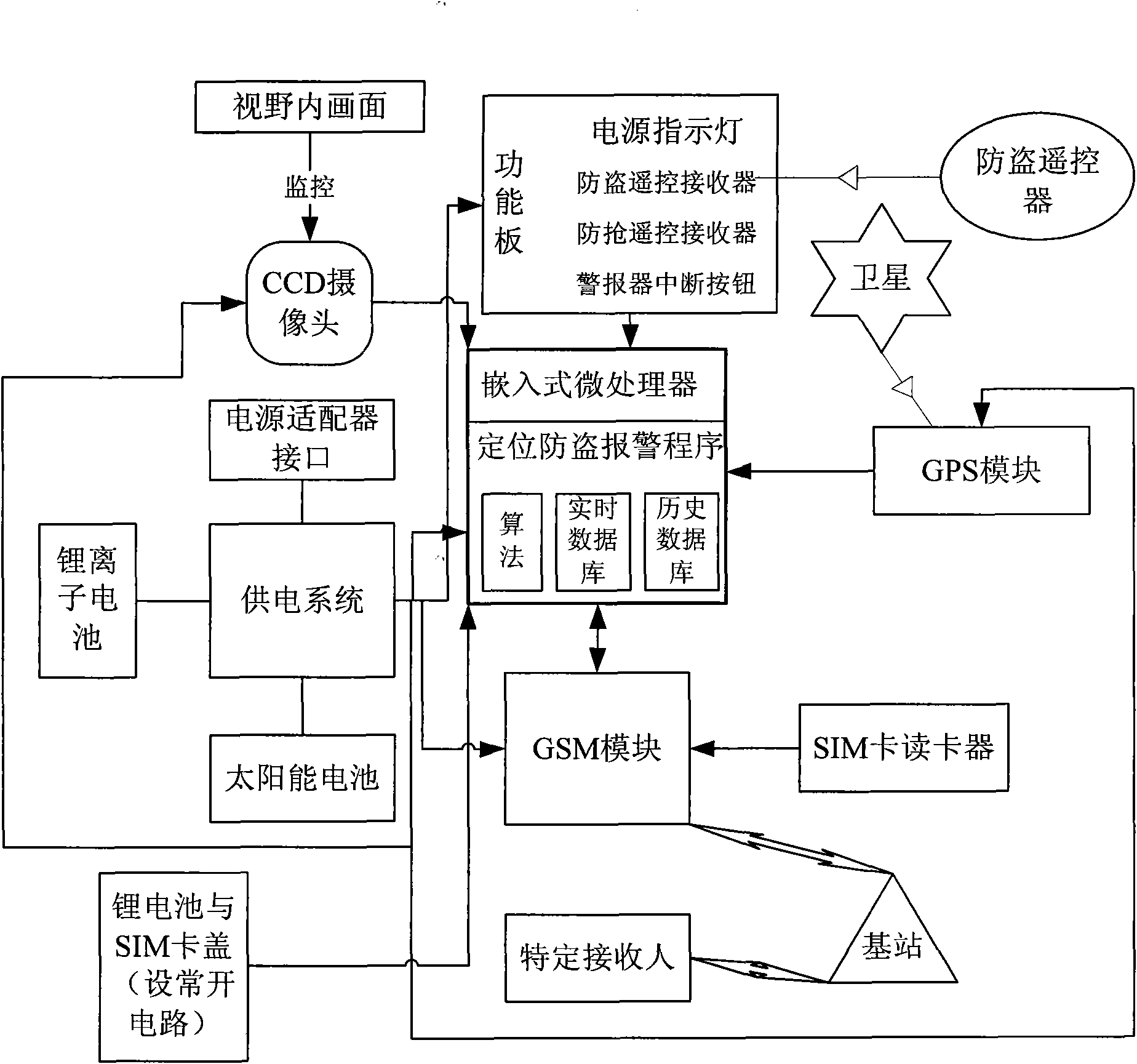
The invention relates to the field of the car electronic and artificial intelligent field, and particularly discloses an active-mode intelligent safety monitoring instrument for a car and a monitoring method thereof. The active-mode intelligent safety monitoring instrument for the car comprises an embedded system (comprising a microprocessor, a monitoring program and relevant algorithm, which are cured inside a chip), a GPS module, a GSM module, an SIM card reader, an alarming device, a CCD camera, a multi-axis acceleration sensor, a power supply system (a lithium battery, a solar battery and a power supply adapter interface), an integrated circuit board, a shell (comprising a functional plate and a battery cover), an antitheft remote controller, a buckling-type rubbery-prevention remote controller and a power supply adapter. The instrument utilizes the GPS to realize the positioning, displacement bulgur prevention, speed measurement and timing, utilizes GSM to realize the auxiliary positioning and the SMS automatic alarming, utilizes the CCD combination mode to identify and monitor the fatigue driving, robbery and accident state and utilizes the acceleration sensor to detect the accident state. The instrument can realize the functions such as mobile positioning, over-speed alarming, positioning antitheft automatic alarming, positioning robbery-prevention alarming, fatigue driving prevention and warning, traffic accident automatic positioning, alarming and help, and the like.
Owner:CHANGSHU ROADVECHILE INTELLIGENT ELECTRONICS
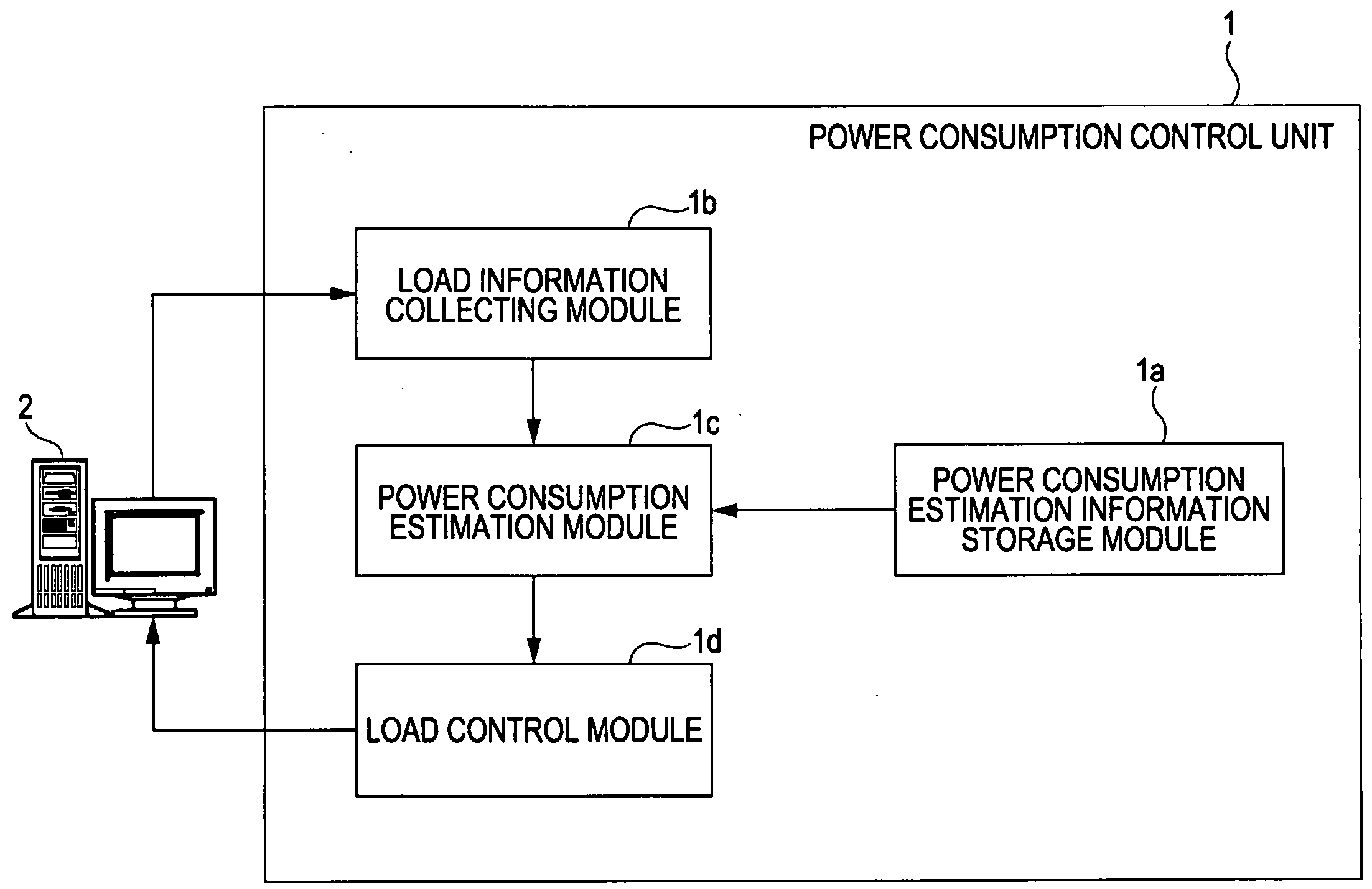
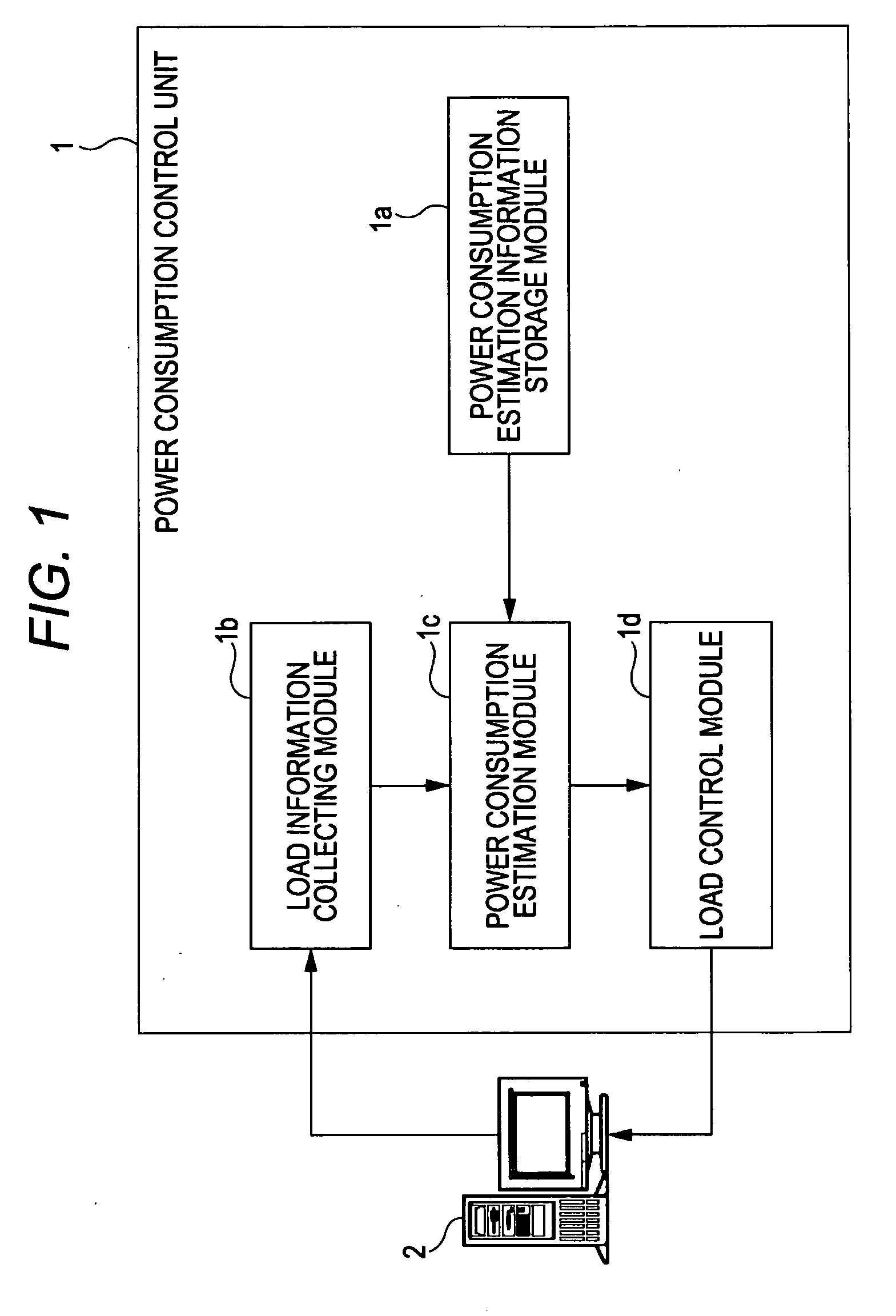
Storage medium for storing power consumption monitor program, power consumption monitor apparatus and power consumption monitor method
A power consumption monitor device monitors power consumption of one or more devices through a network. The monitor device includes a storage unit, a load information collecting unit and a power consumption estimation unit. The storage unit stores power consumption estimation information indicating a relation between power consumption and processing load of the one or more devices. The load information collecting unit collects load information indicating the processing load of the one or more devices through the network to the monitor device. The power consumption estimation unit estimates power consumption of the one or more device based on the collected load information and the power consumption estimation information.
Owner:FUJITSU LTD
Automated turnout inspection
ActiveUS20110064273A1Enhancing turnout inspection approachReduce dependenceCharacter and pattern recognitionRailway signalling and safetyRail profileDerailment
A method of inspecting a turnout of a track includes the steps of: capturing images of the components of the turnout; converting each image into a set of coordinates that traces the transverse cross-section of a rail profile; analyzing the rail profile to determine if the rail profile is a profile of arunning rail portion or a component. Upon determination that the image represents a component, taking measurements of the rail profile and applying virtual gauges to the rail profile to check for potentially dangerous conditions of the component; and generating a summary of each cross-section of the rail profile of the component indicating problem areas. The method is used for identifying certain classes of switch or turnout rail conditions which can lead to derailments, and for enhancing the turnout inspection approach currently used. The use of this method as an integrated part of the rail profile monitoring program will reduce reliance on field measurements and will also allow more frequent, comprehensive, and convenient analysis of turnout condition.
Owner:HARSCO CORP
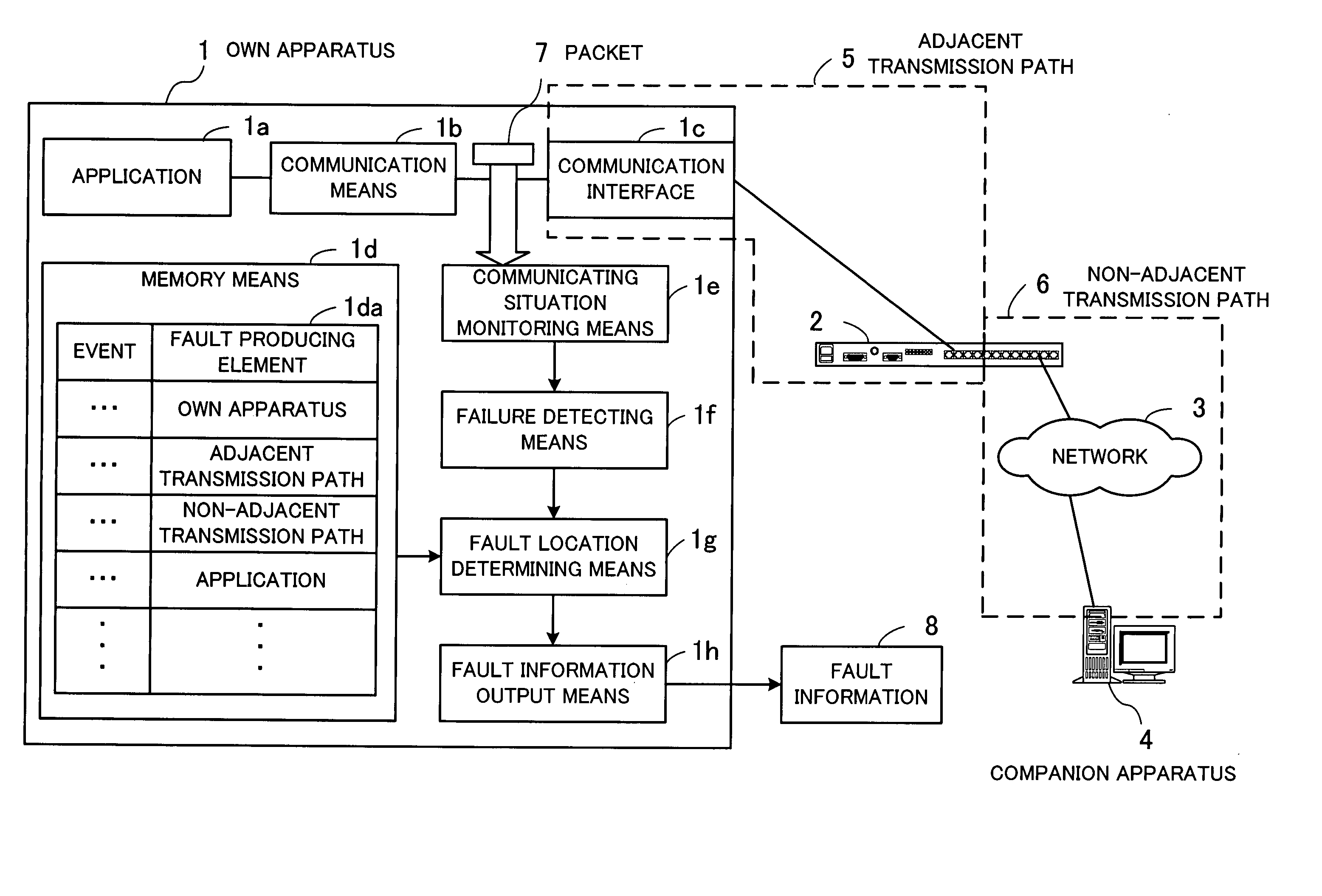
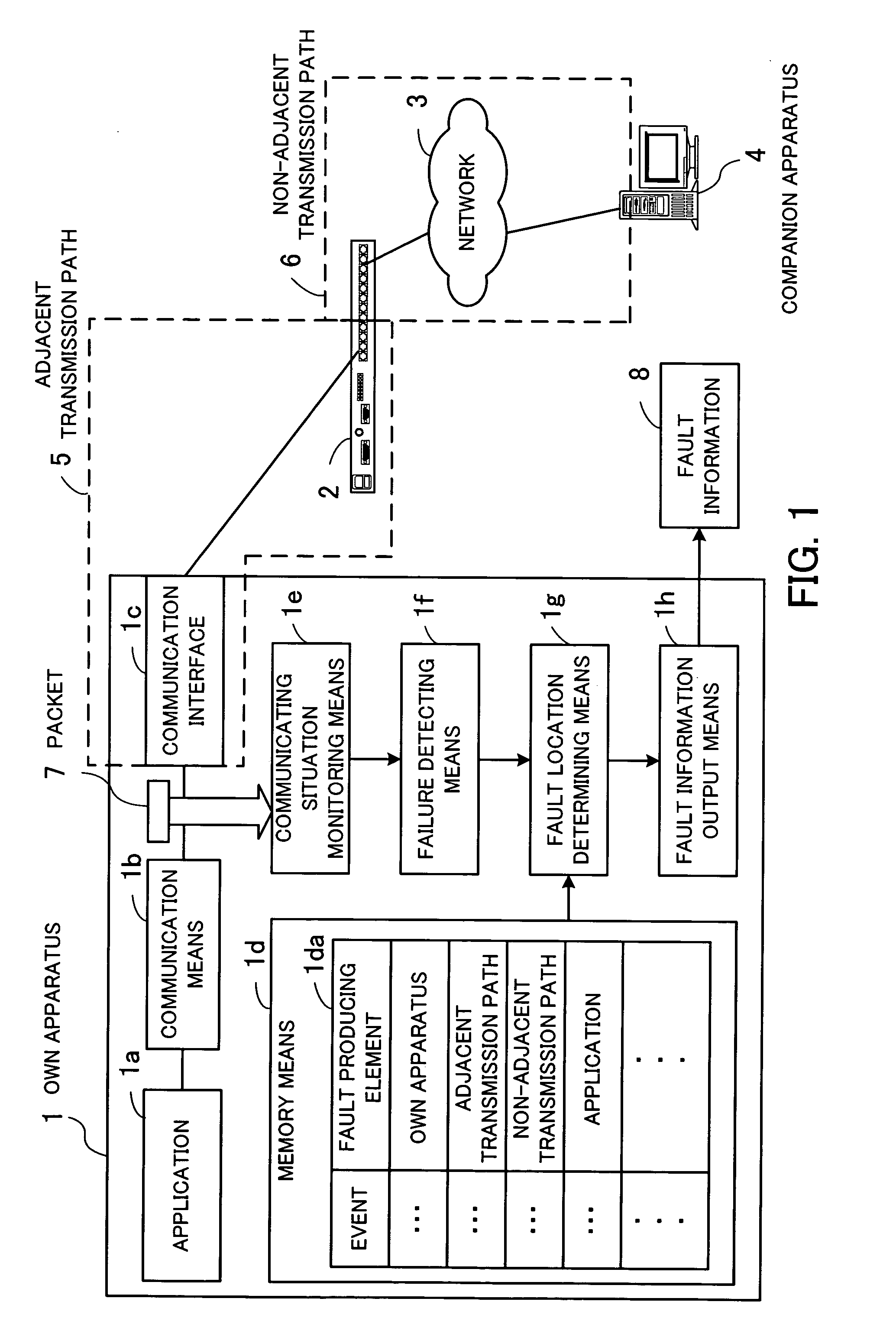
Network monitoring program, network monitoring method, and network monitoring apparatus
InactiveUS20050144505A1Error prevention/detection by using return channelTransmission systemsNetwork monitoringLocation determination
A network monitoring program automatically sorts fault producing locations on a network. A memory unit stores a fault location determining table containing events indicative of failures of communications via the network, the events being associated with classified elements which can be causes of faults on the network. A communication situation monitoring unit monitors communication situations with respect to other apparatus on the network. A failure detecting unit detects an event indicative of a failure from a communication situation detected by the communication situation monitoring unit. A fault location determining unit determines an element which is responsible for the event detected by the failure detecting unit by referring to the fault location determining table. A fault information output unit outputs fault information representative of a determined result from the fault location determining unit.
Owner:FUJITSU LTD
Virtual machine system
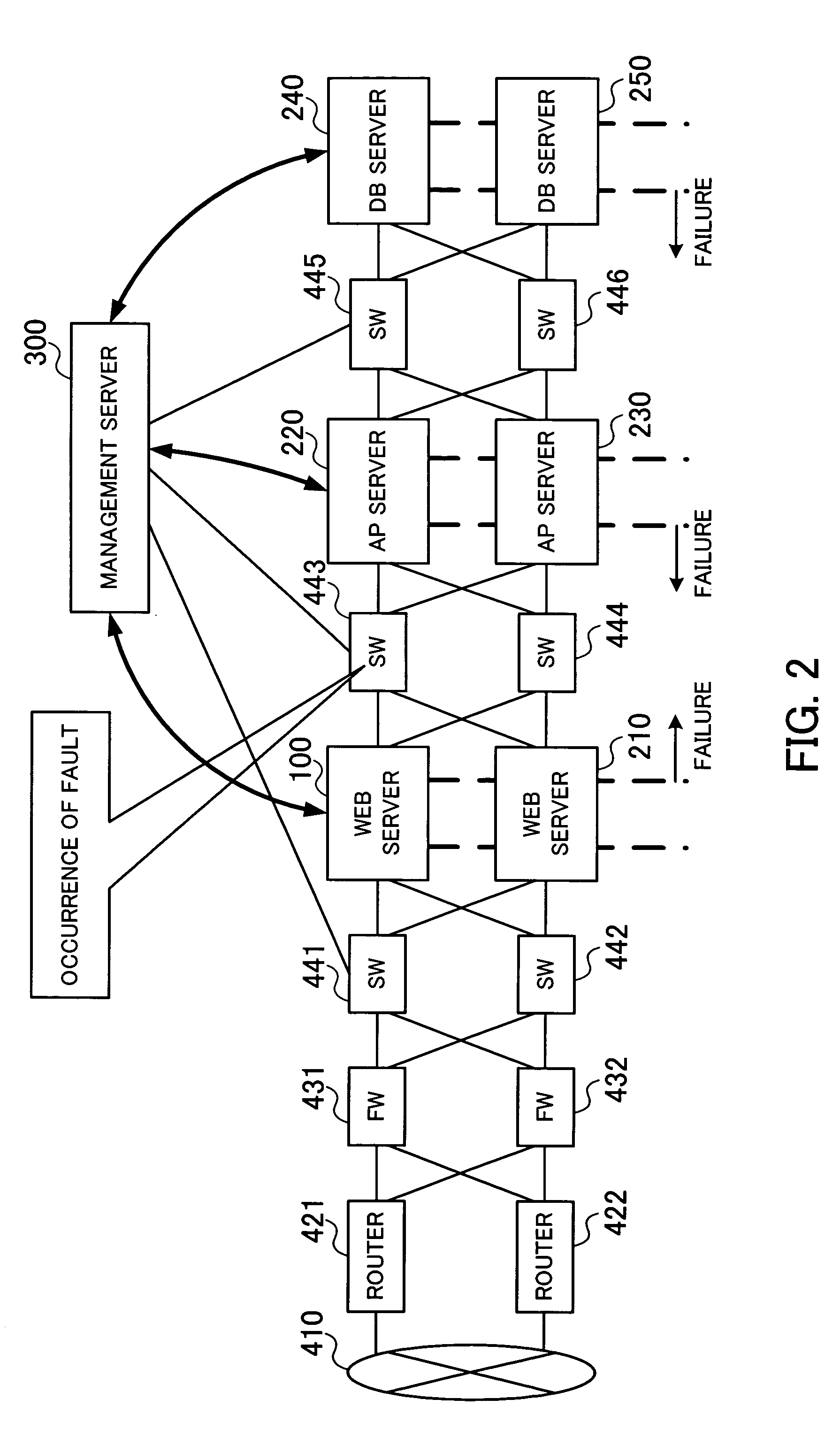
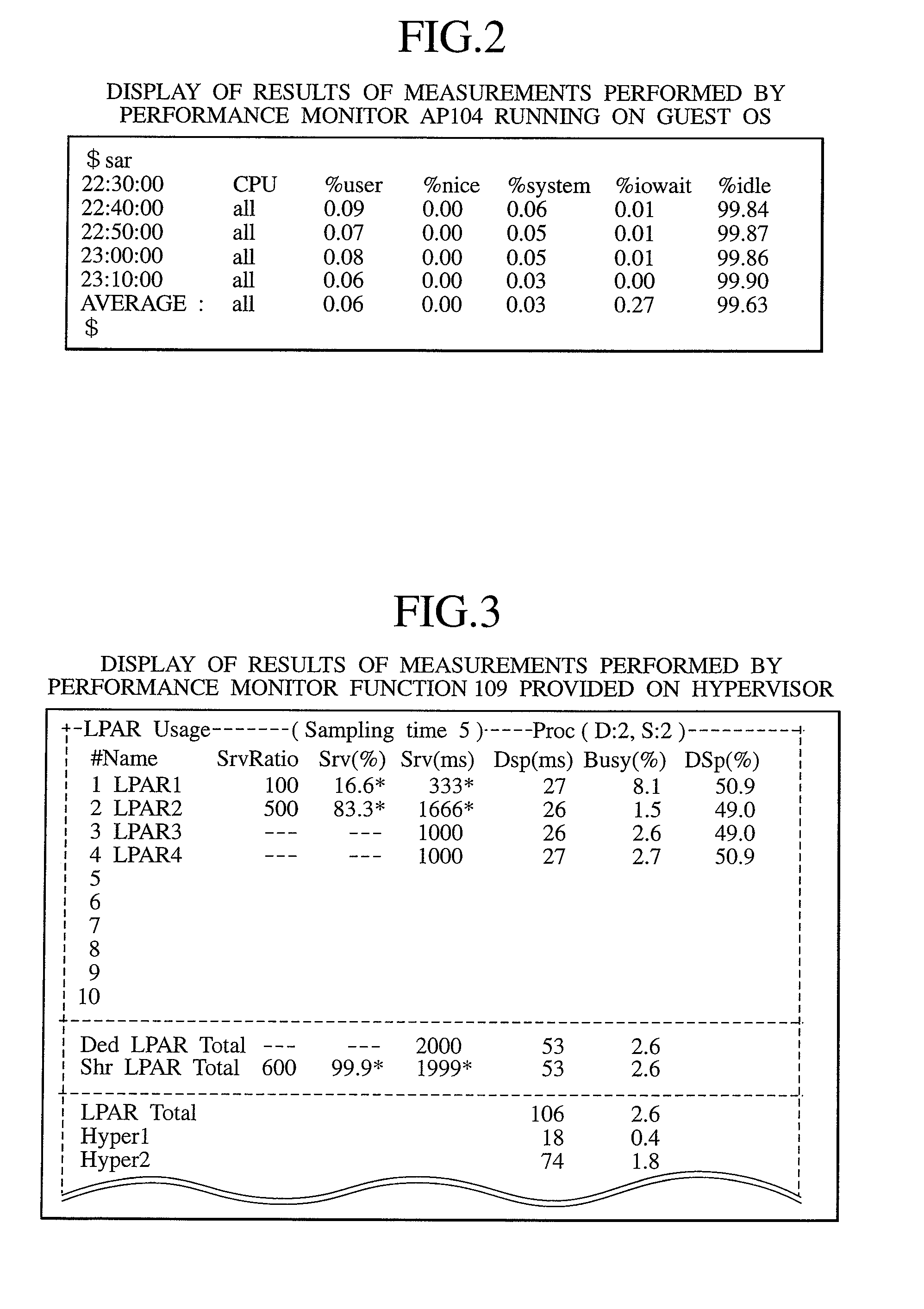
InactiveUS20080222632A1Error detection/correctionMultiprogramming arrangementsVirtual machineHypervisor
A virtual machine system in which a physical CPU busy ratio can be measured in consideration of the status of an assignment of the physical CPU, and the measured CPU busy ratio can be reflected to a CPU busy ratio of each guest OS. An elapsed time counter is provided in a hypervisor, and a hypervisor access interface is provided in each of LPARs and used to read the elapsed time counter from the guest OS. A performance monitor program running on each guest OS calculates, based on a value of the elapsed time counter, the number of sampling timings expected to occur during the time when the physical CPU is not assigned to the LPAR in which the performance monitor program is provided.
Owner:HITACHI LTD
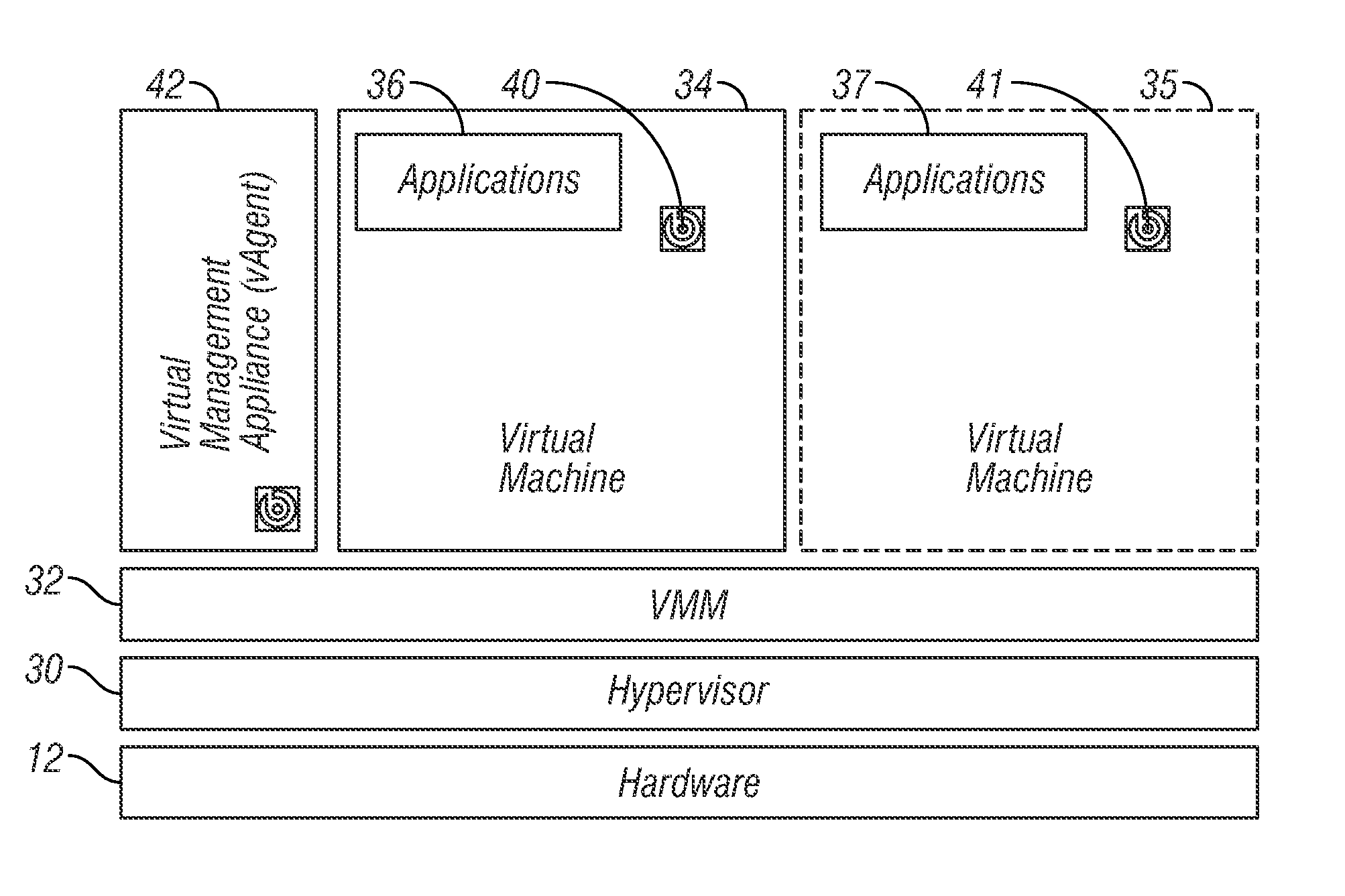
Endpoint-Hosted Hypervisor Management
ActiveUS20110167472A1New of controlNew levelService provisioningDigital data processing detailsOperational systemClient-side
A client hypervisor comprises a virtual agent that runs outside of a system OS and that allows device management independent of the OS and user. The virtual agent is tied to a device and not a specific instance of the OS. Such client hypervisors expose new functionality to ease managing systems. Some of these capabilities come from the persistence and privileges outside the OS. In some embodiments of the invention, this new management functionality is exposed to allow device management via new virtualization concepts, such as multiple VMs per system, VM replacement, snapshot / rollback, etc.
Owner:INT BUSINESS MASCH CORP
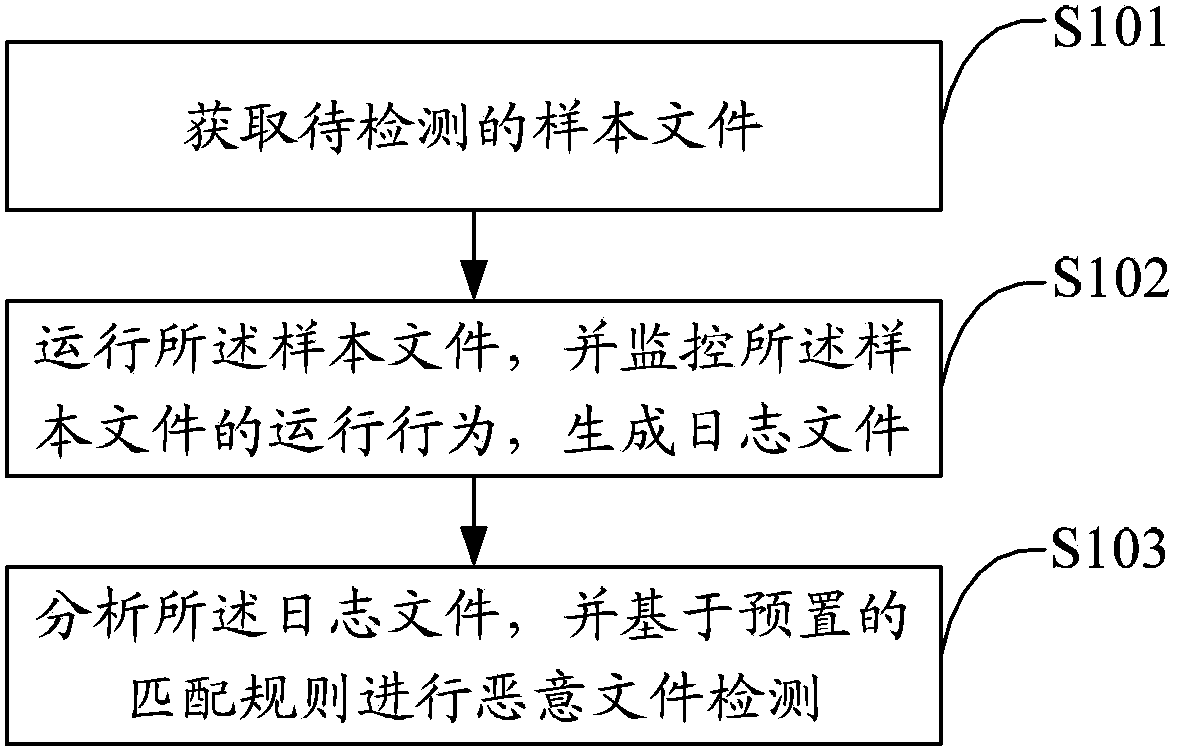
Malicious file detection method and device
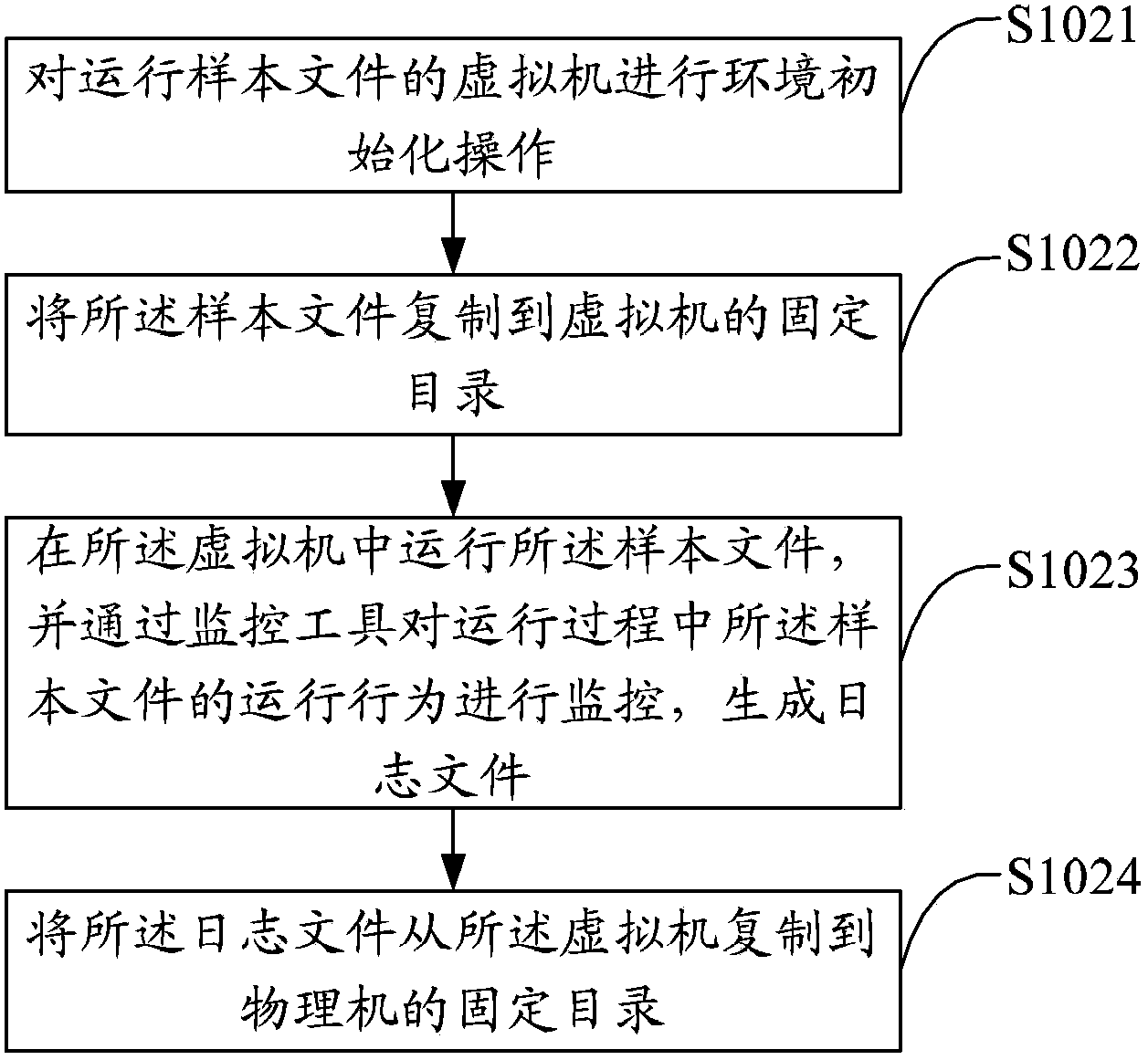
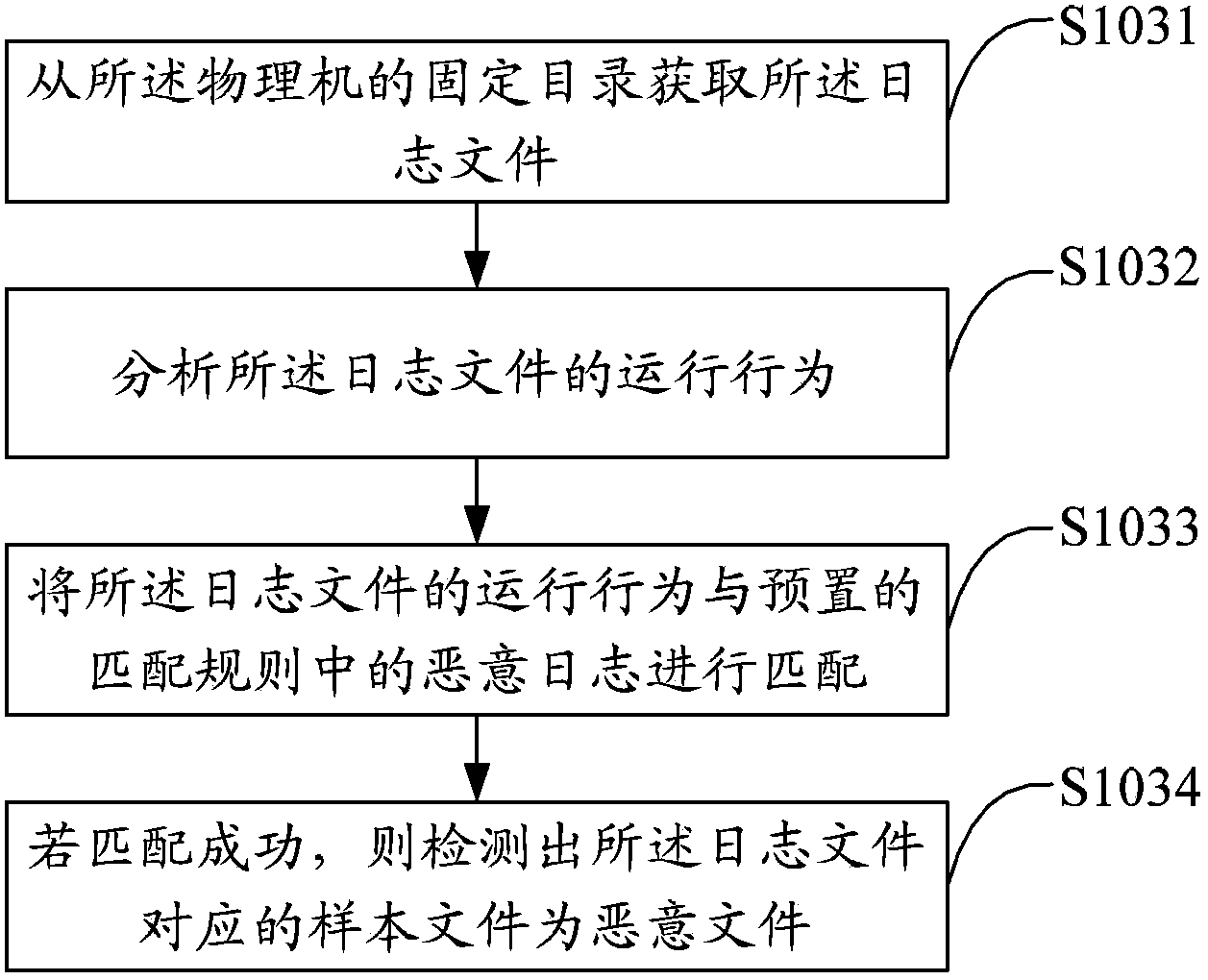
ActiveCN103839003AImprove analysis efficiencyImprove detection accuracyPlatform integrity maintainanceAnti virusSoftware
The invention discloses a malicious file detection method and device. The method includes the steps of obtaining a sample file to be detected; operating the sample file, monitoring operation behaviors of the sample file and generating a log file; analyzing the log file, and carrying out malicious file detection based on a preset matching rule. The sample file is operated in a virtual machine, a monitoring program is operated in the virtual machine, the operation behaviors of the sample file are recorded to generate the log file, then the log file is matched according to an extracted feature rule, and finally malicious file detection of the sample file is achieved. By means of the method, virus analysis efficiency can be greatly improved, new samples which can not be detected by anti-virus programs in the prior art or a certain type of samples of a specific behavior type can be found timely, and accordingly detection accuracy of virus samples is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com