Malicious file detection method and device
A malicious file and detection method technology, applied in computer security devices, instruments, calculations, etc., can solve the problems of low virus analysis efficiency and low detection accuracy, and achieve the effect of improving efficiency and detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
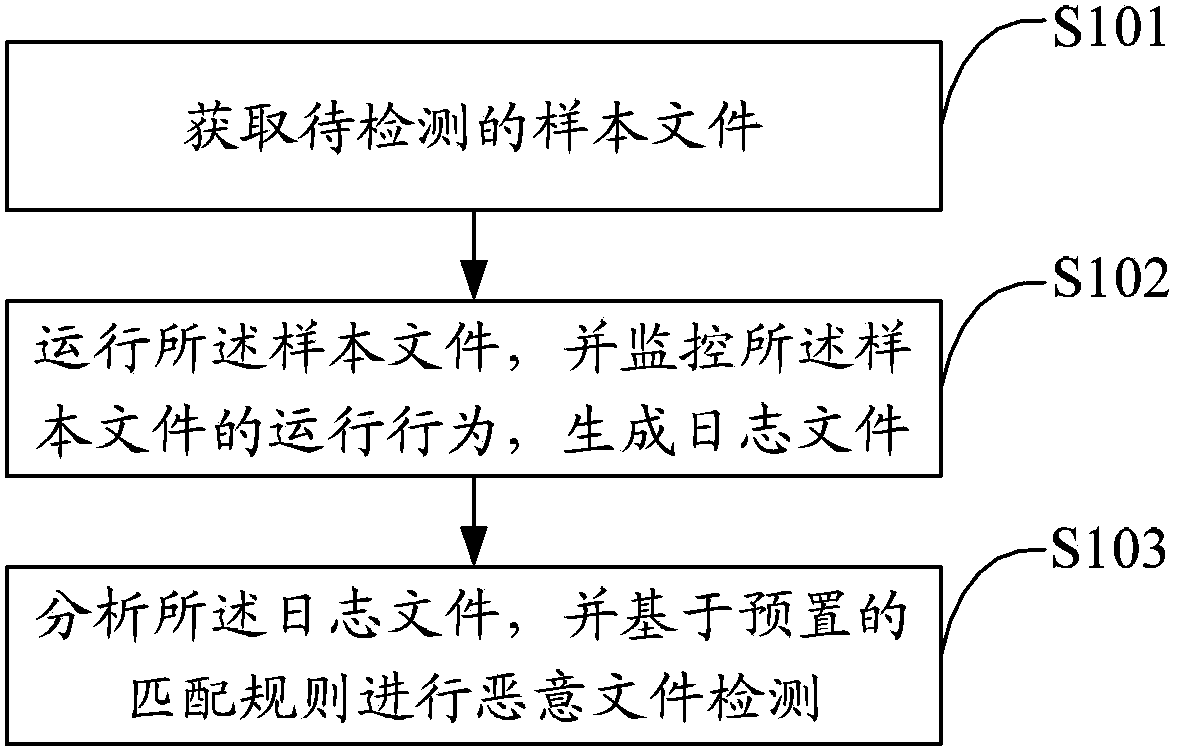
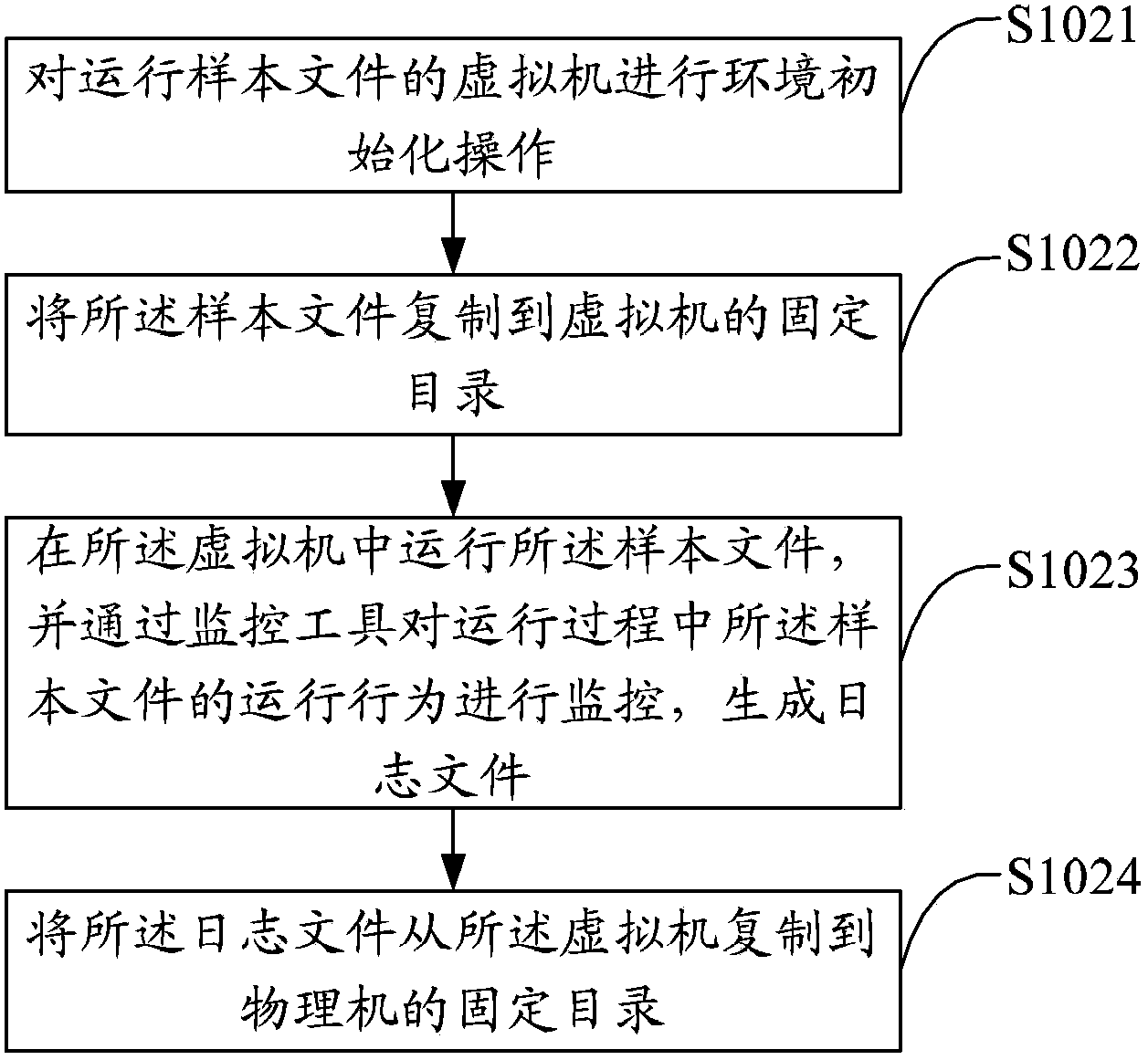
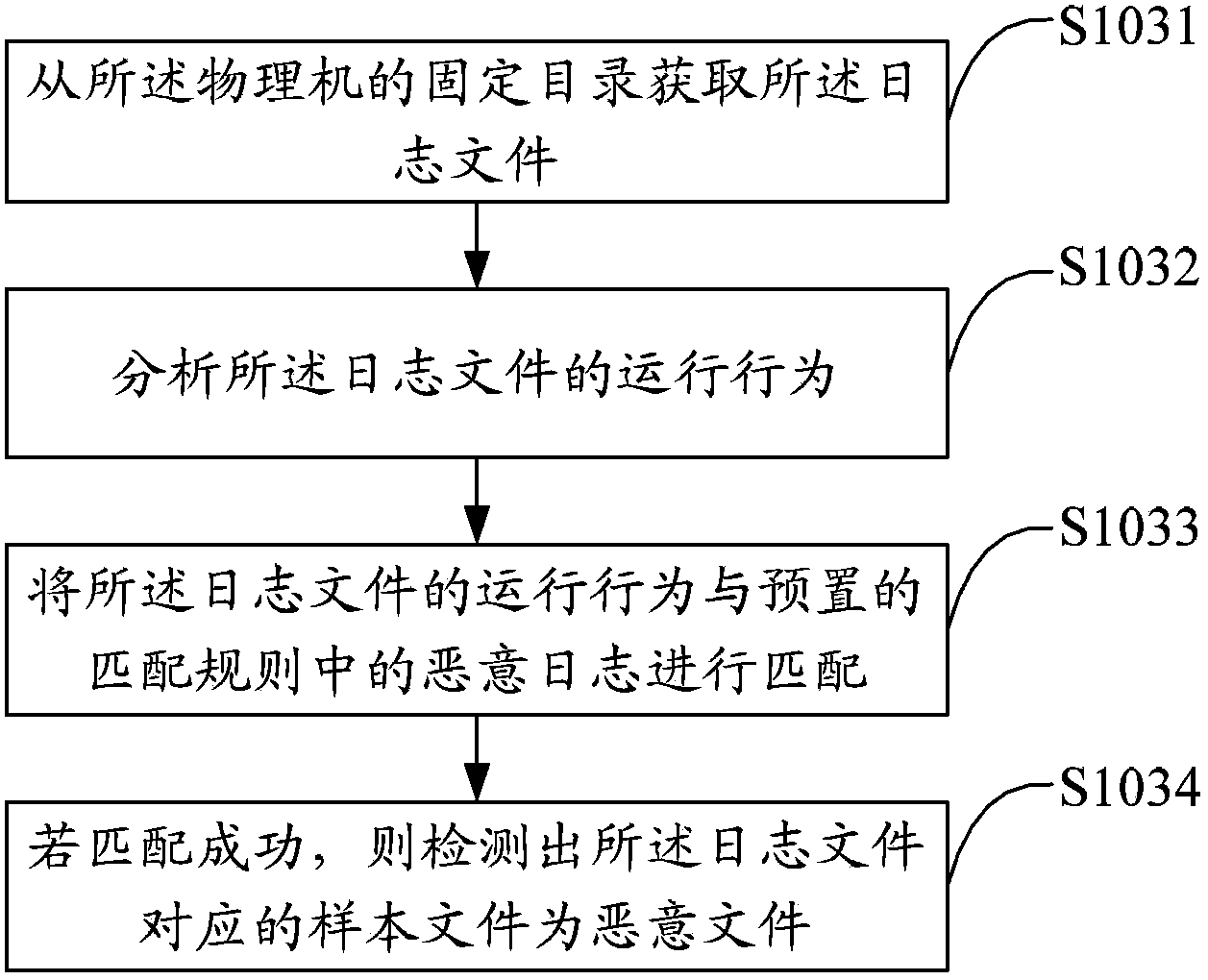
[0027] The solution of the embodiment of the present invention is mainly: by running the sample file in the virtual machine, and then running the monitoring program in the virtual machine, recording the running behavior of the sample file, including reading and writing related to the sample file, registry, network, and process 1. Modify information records to generate log files, and then match these log files through the extracted feature rules. If matched, it indicates that the sample file is a malicious sample, thereby realizing automatic virus behavior analysis.
[0028] Such as figure 1 As shown, a preferred embodiment of the present invention proposes a malicious file detection method, including:
[0029] Step S101, obtaining a sample file to be detected;
[0030] The source of the sample file to be detected may not be limited, for example, it may be downloaded from a specified location.
[0031] The obtained sample files to be tested will be input into the automatic mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com