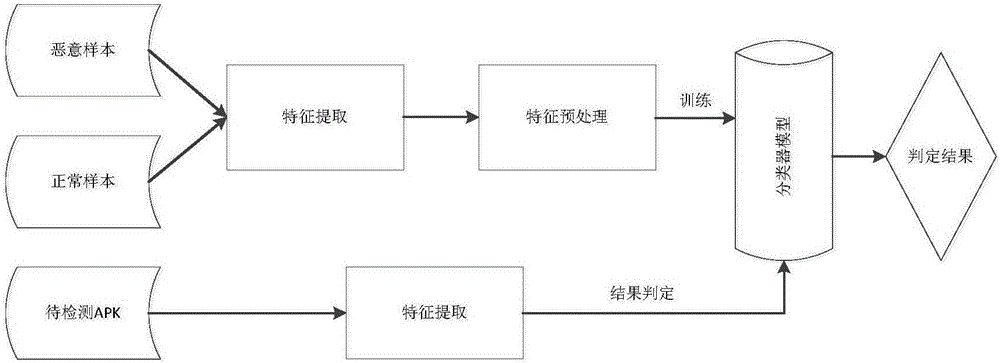
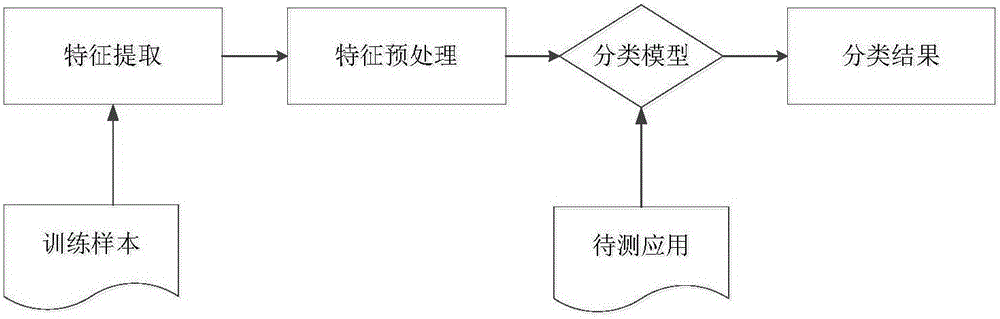
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1397 results about "Virus detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
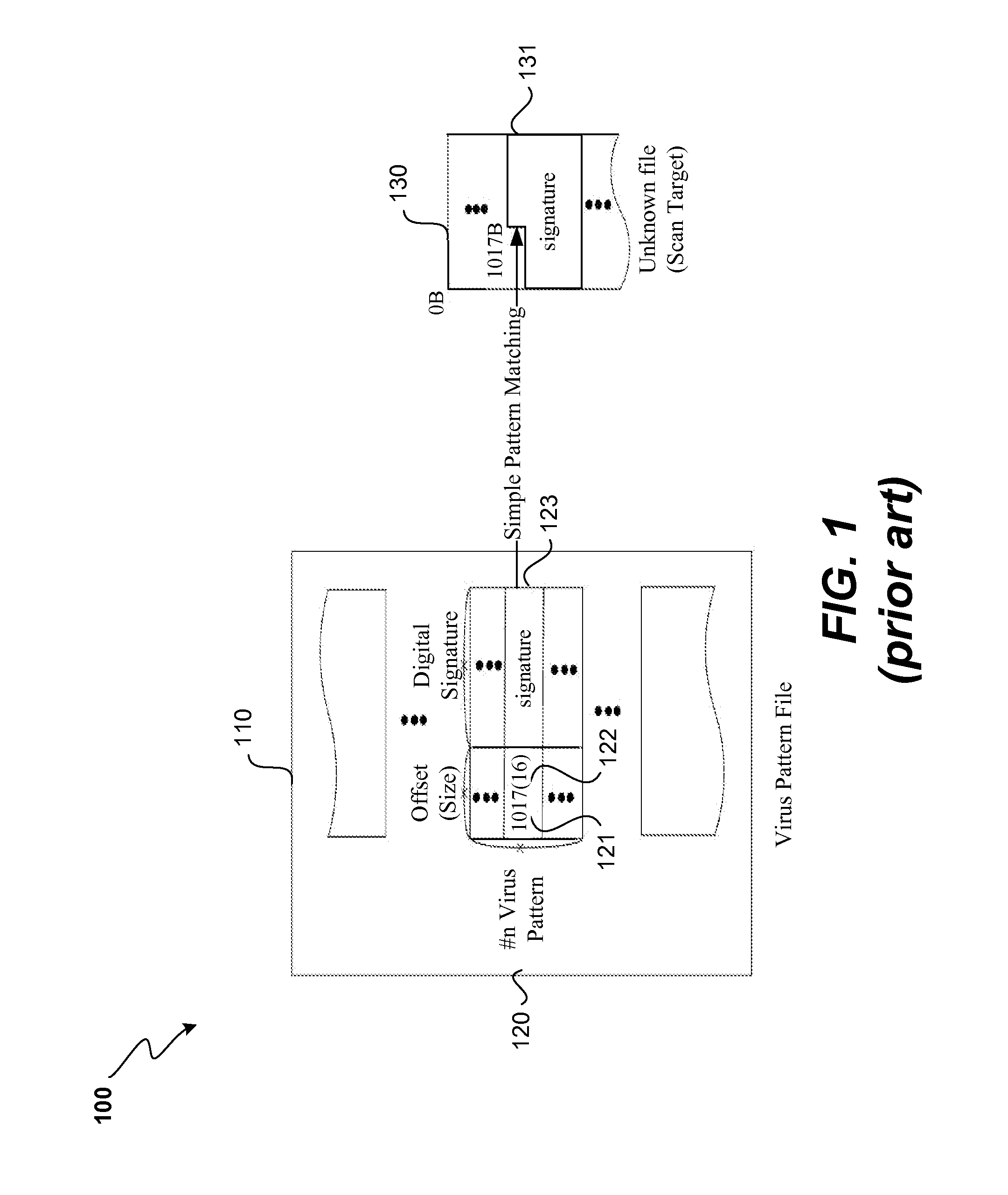
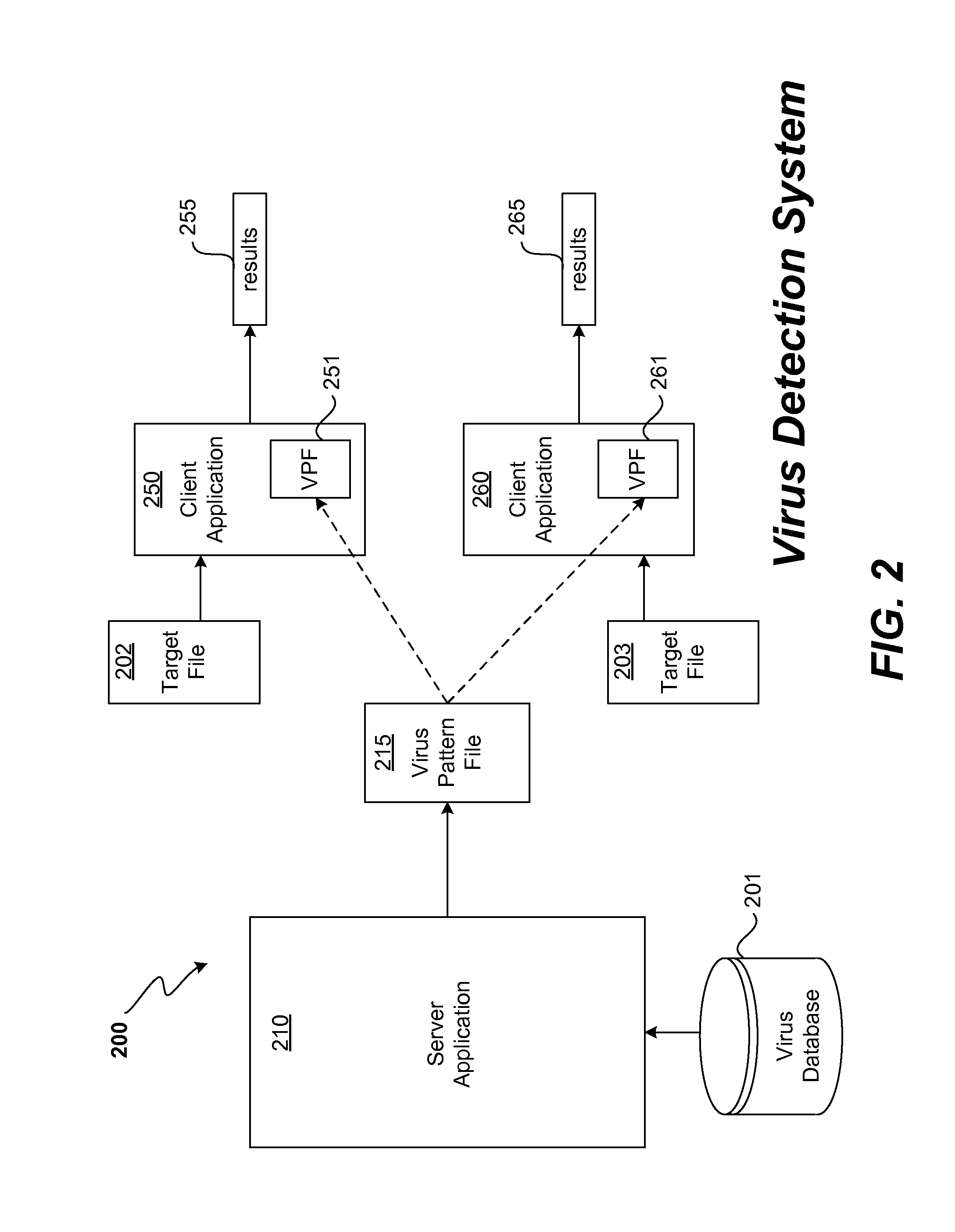
Virus detection techniques can be classified as follows: Signature-based detection uses key aspects of an examined file to create a static fingerprint of known malware. Heuristics-based detection aims at generically detecting new malware by statically examining files for suspicious characteristics without an exact signature match.
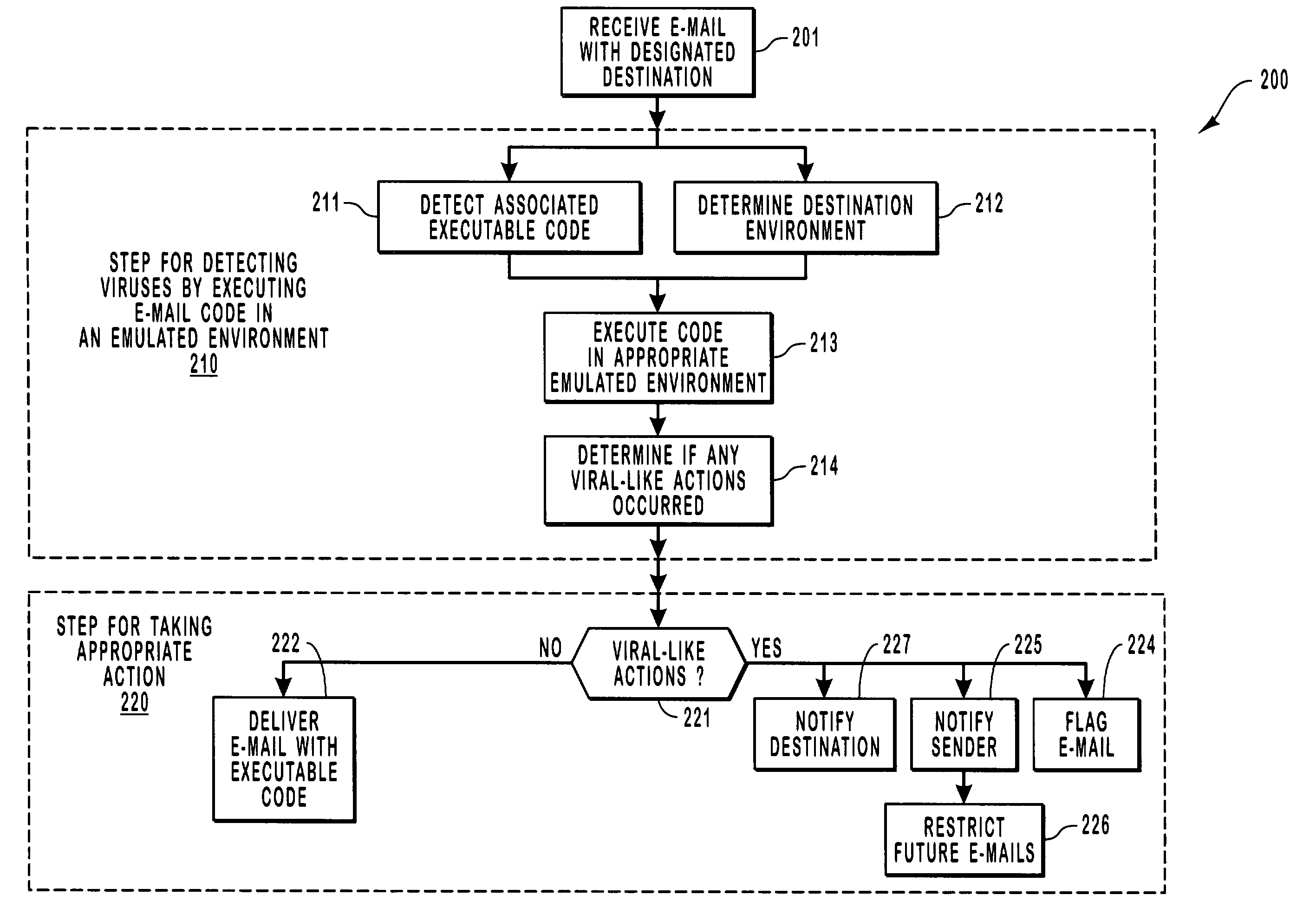
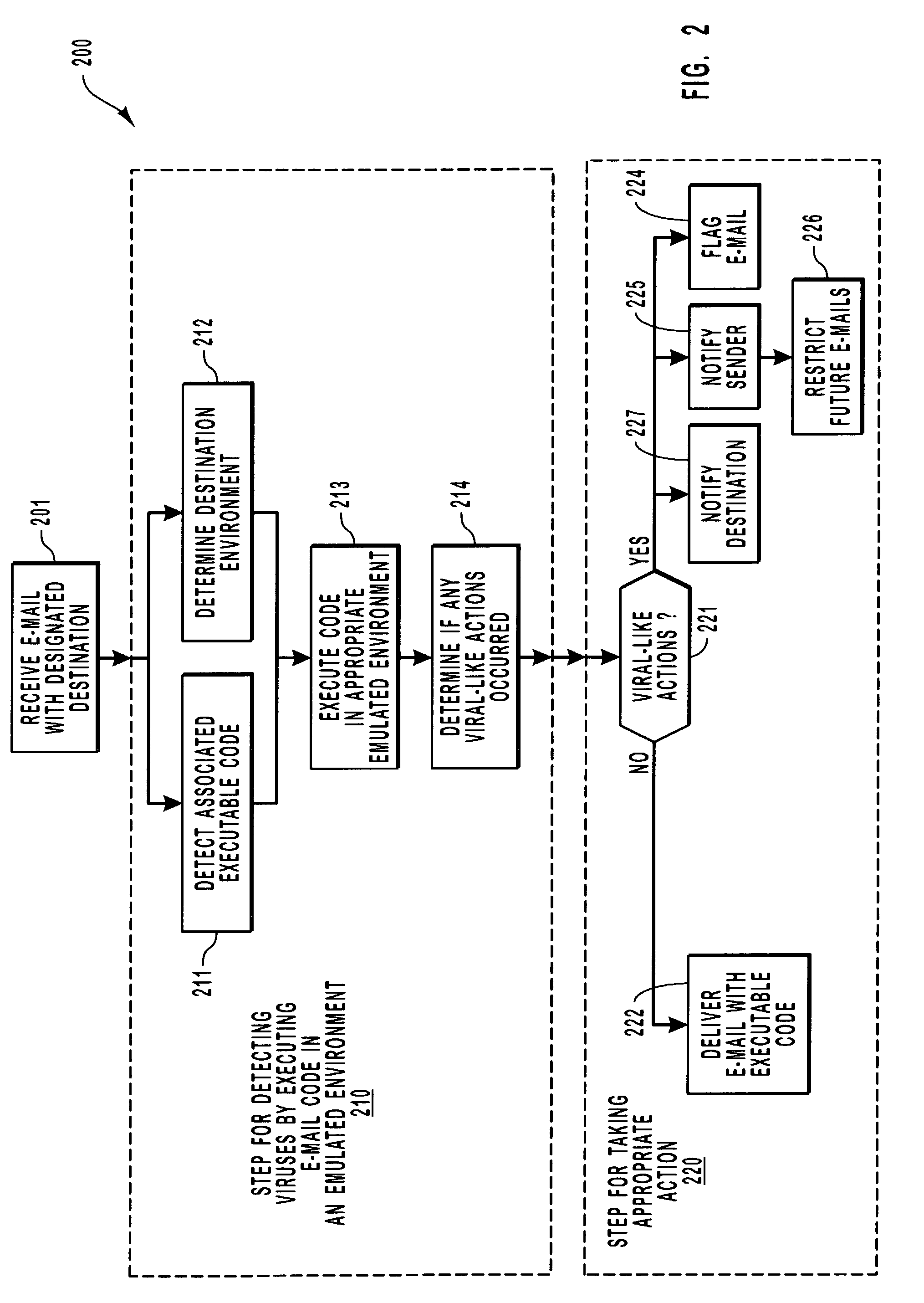
Virus detection by executing e-mail code in a virtual machine
ActiveUS7607171B1Reduce harmAvoid damageMosaic printer telegraph systemMemory loss protectionElectronic mailVirus detection
An intermediary isolation server receives e-mails and isolates any viral behavior from harming its intended destination. After the intermediary receives an e-mail, it determines that the e-mail has associated executable code, and then identifies the environment in which the e-mail code would be executed if delivered. The intermediary then executes the code by emulating how it would be executed in its ultimate environment. If a viral-like behavior is detected, appropriate action is taken to prevent the execution of the code at its intended destination. The attachment is executed in a contained environment that allows for the contained environment to be easily restarted in a clean state.
Owner:AVINTI
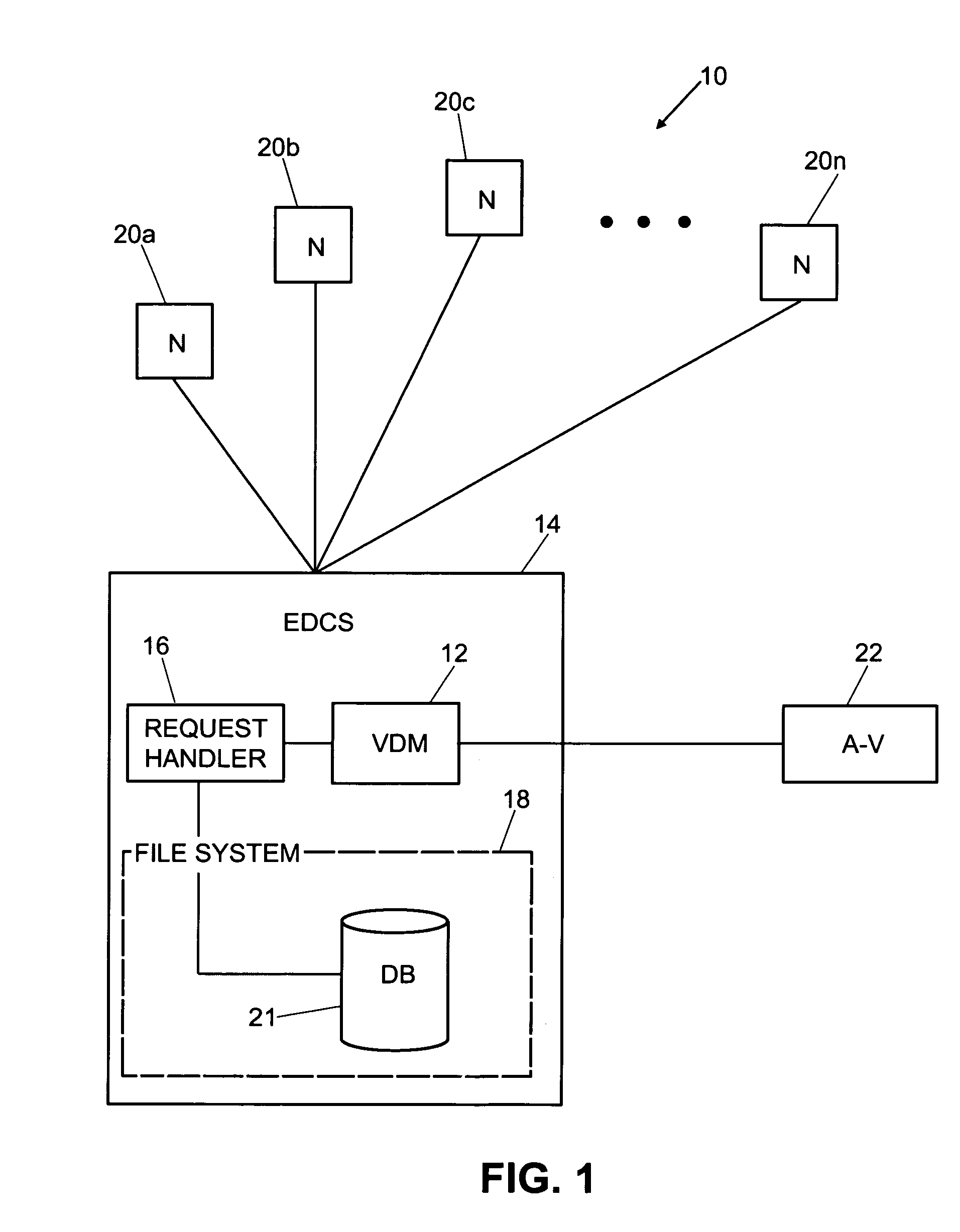
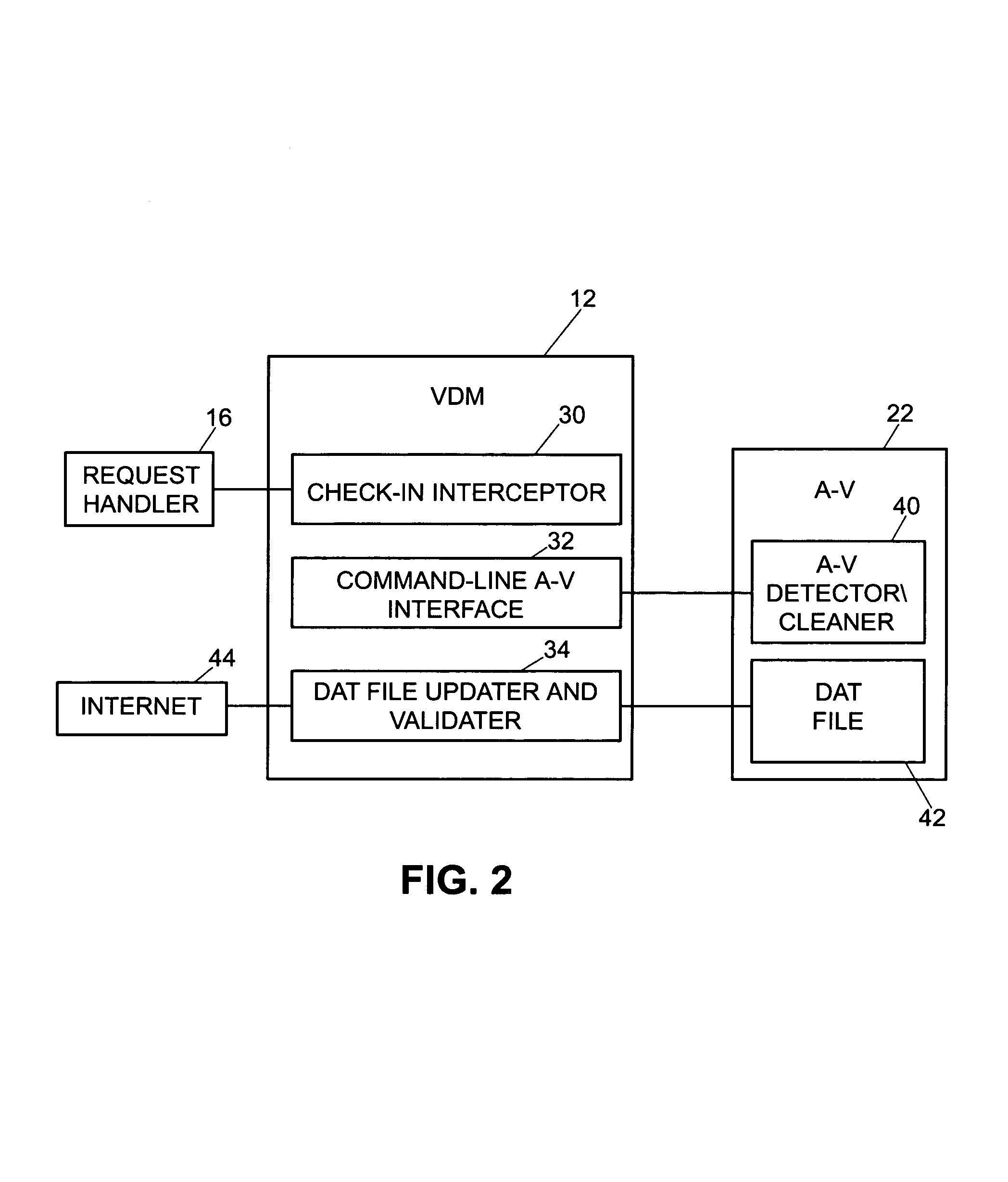
Virus detection and removal system and method for network-based systems
InactiveUS7080407B1Memory loss protectionUnauthorized memory use protectionElectronic documentAnti virus
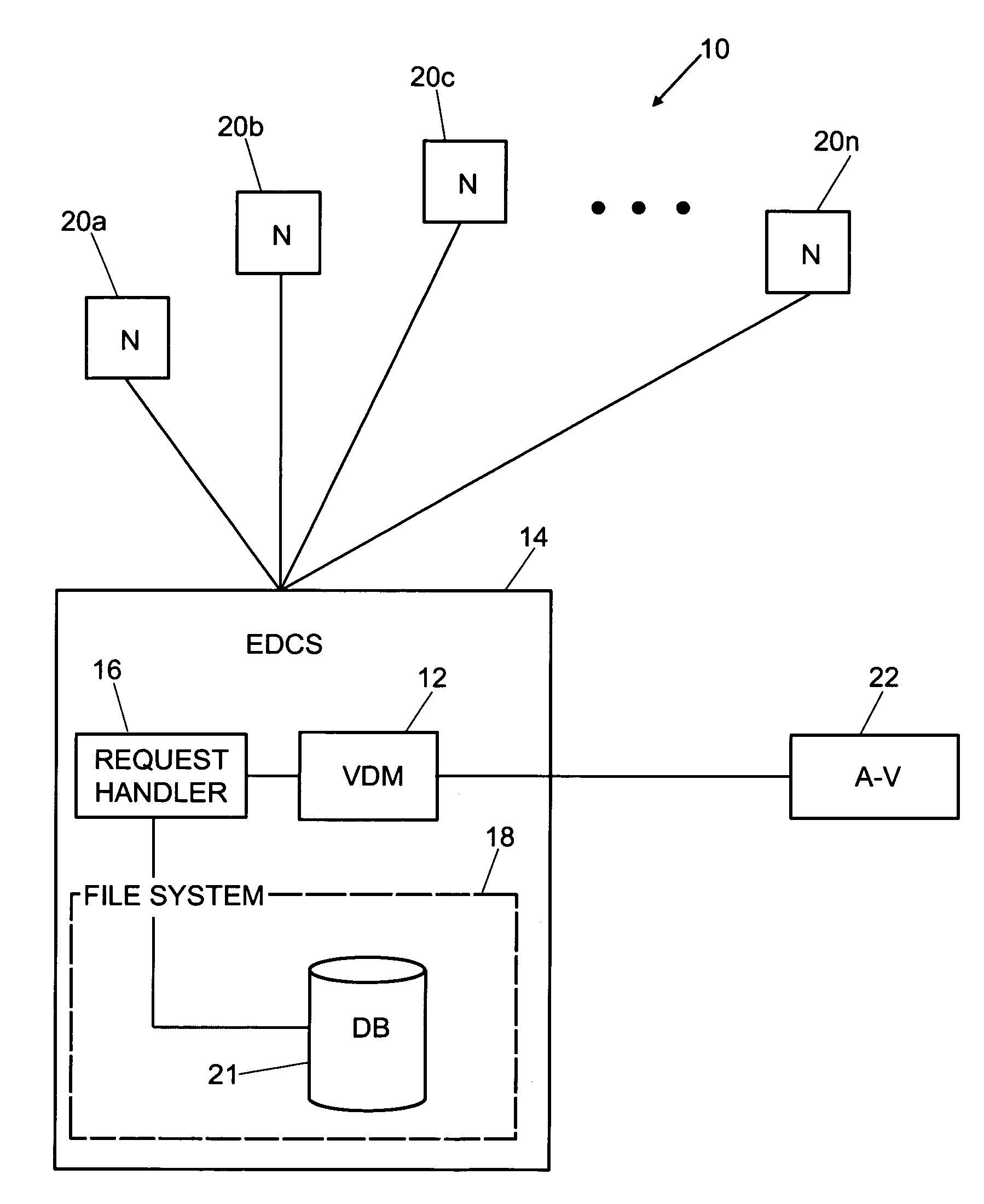
An enhanced virus detection monitoring (VDM) system and method suitable for use with network systems, and in particular electronic document control systems (EDCS) is disclosed. The VDM system intercepts files and documents before they are made available to other users (“check-in”) and inspects the files / documents for virus infection. If a virus infection is found in a file or document, the VDM system invokes anti-virus software to disinfect the file or document. Once the virus has been removed from the file or document, the file (or document) is then made available to other users of the system. If the virus cannot be removed, the file (or document) is not allowed to be checked-in.
Owner:CISCO TECH INC
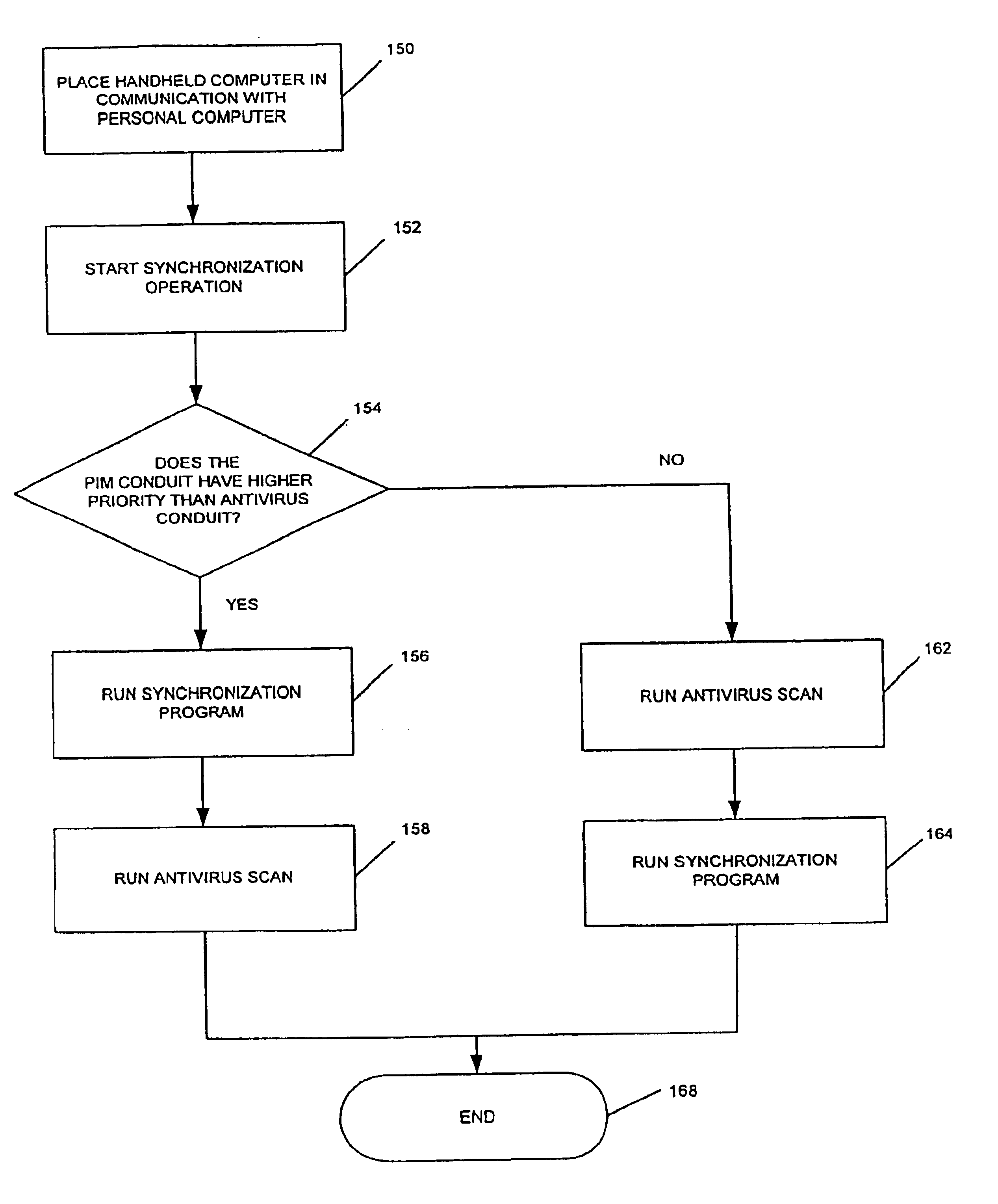
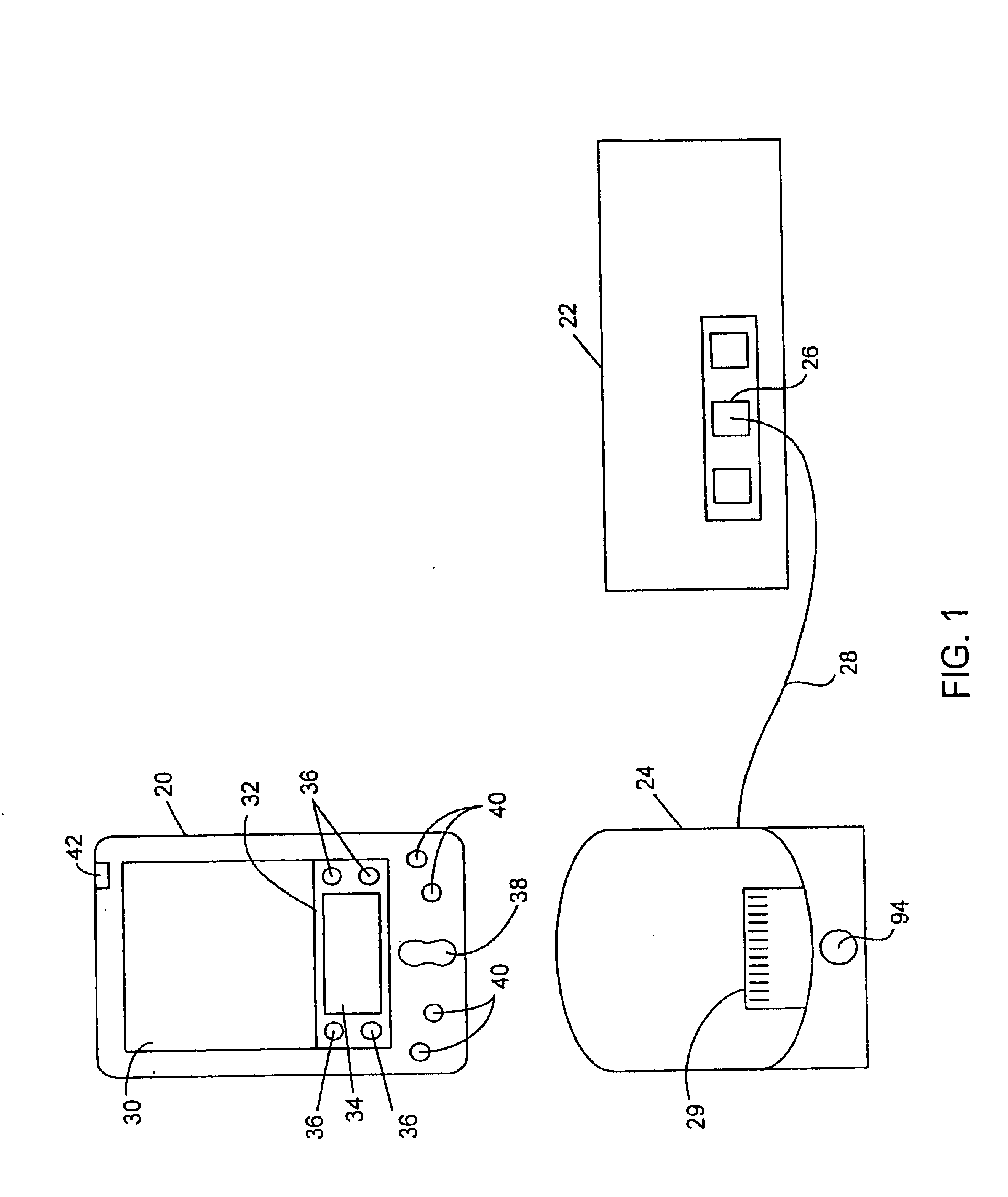
Method and system for detecting viruses on handheld computers
InactiveUS6842861B1Memory loss protectionUnauthorized memory use protectionComputerized systemHand Held Computer
A method and system for detecting viruses on handheld computers. The handheld computer is in communication with a computer system having a virus detection program. The method includes reading data from the handheld computer and writing the data at least temporarily to a database on the computer system. The data is scanned for viruses with the virus detection program. The method further includes updating data on the handheld computer based on results of the scanning.
Owner:MCAFEE INC
Data driven detection of viruses
InactiveUS6851057B1Easy to detectMemory loss protectionUser identity/authority verificationEntry pointData file
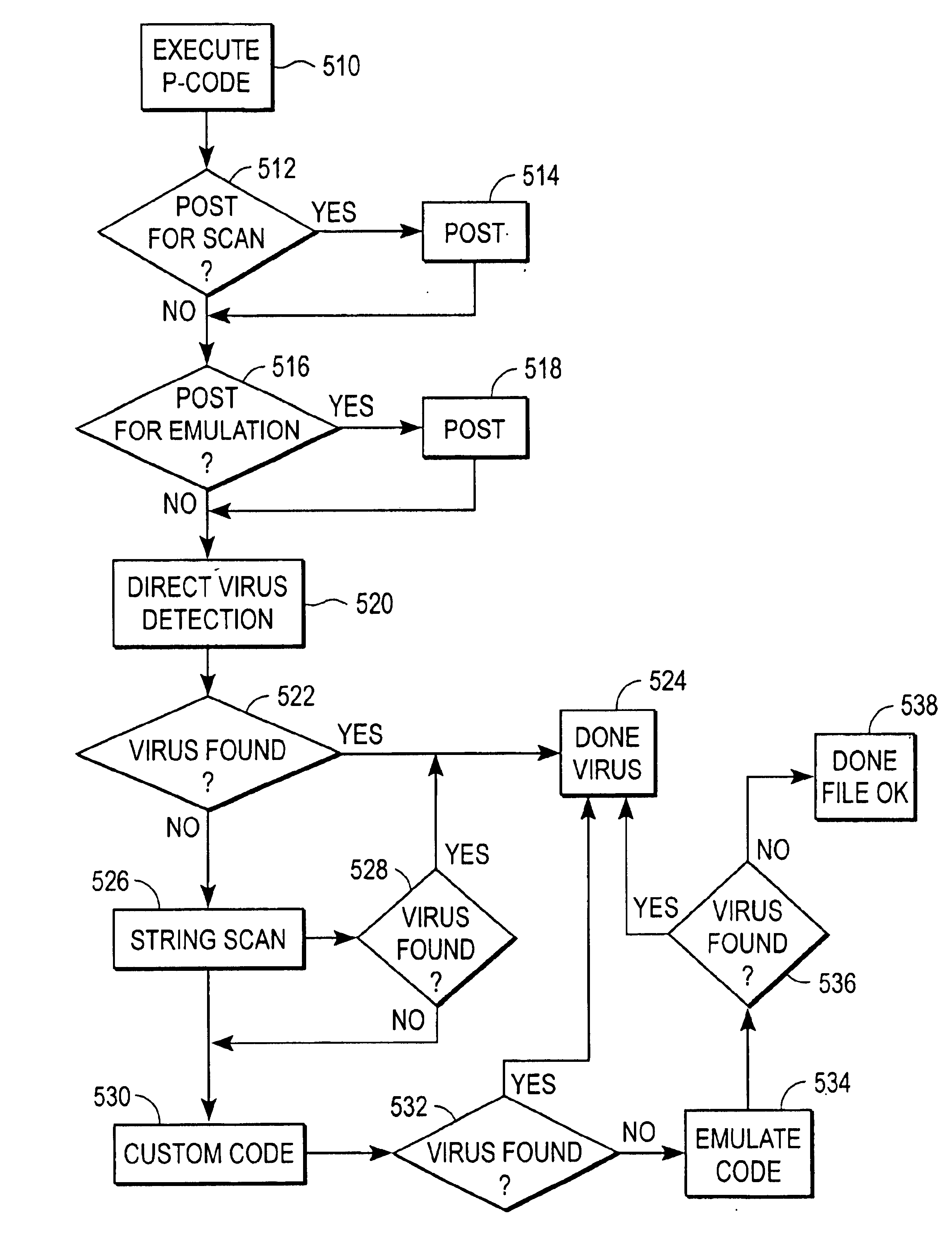
A virus detection system (VDS) (400) operates under the control of P-code to detect the presence of a virus in a file (100) having multiple entry points. P-code is an intermediate instruction format that uses primitives to perform certain functions related to the file (100). The VDS (400) executes the P-code, which provides Turing-equivalent capability to the VDS. The VDS (400) has a P-code data file (410) for holding the P-code, a virus definition file (VDF) (412) for holding signatures of known viruses, and an engine (414) for controlling the VDS. The engine (414) contains a P-code interpreter (418) for interpreting the P-code, a scanning module (424) for scanning regions of the file (100) for the virus signatures in the VDF (412), and an emulating module (426) for emulating entry points of the file. When executed, the P-code examines the file (100), posts (514) regions that may be infected by a virus for scanning, and posts (518) entry points that may be infected by a virus for emulating. The P-code can also detect (520) certain viruses algorithmically. Then, the posted regions and entry points of the file (100) are scanned (526) and emulated (534) to determine if the file is infected with a virus. This technique allows the VDS (400) to perform sophisticated analysis of files having multiple entry points in a relatively brief amount of time. In addition, the functionality of the VDS (400) can be changed by changing the P-code, reducing the need for burdensome engine updates.
Owner:CA TECH INC
Histogram-based virus detection
InactiveUS6971019B1Easy to detectDigital data processing detailsUser identity/authority verificationCode moduleComputer science
A virus detection system (VDS) (400) uses a histogram to detect the presence of a computer virus in a computer file. The VDS (400) has a P-code data (410) for holding P-code, a virus definition file (VDF) (412) for holding signature of known viruses, and an engine (414) for controlling the VDS. The engine (414) contains a P-code interpreter (418) for interpreting the P-code, a scanning module (424) for scanning regions of the file (100) for the virus signatures in the VDF (412), and an emulating module (426) for emulating instructions in the file. The emulating module (426) contains a histogram generation module (HGM) (436) for generating a histogram of characteristics of instructions emulated by the emulating module (426) and a histogram definition module (HDF) (438) for specifying the characteristics to be included in the generated histogram. The emulating module (426) uses the generated histogram (500) to determine how many of the instructions of the computer file (100) to emulate. The emulating module (426) emulates (712) instructions and the HGM (436) generates a histogram of the instructions until active instructions are note detected. When active instructions are not detected (714), a P-code module is executed (722) to analyze the histogram (500) and determine whether a the file (100) contains a virus. The P-code can also decide to extend (728) emulation. The HGM (436) is also used to detect (822) the presence of dummy loops during virus decryption.
Owner:CA TECH INC
Method and system for virus detection using pattern matching techniques
ActiveUS20060161984A1Without precipitous drop in system performanceMemory loss protectionUser identity/authority verificationVirus detectionFilter technique
A method and system for providing virus detection. A virus detection system provides for the use of pattern matching techniques on data at a binary level for virus detection. Whenever an incoming data stream is received, the data stream is segmented into time-based data frames. The time-based data frames are processed to generate associated data frame images utilizing signal processing identification and filter techniques. One or more data frame images are compared to a stored virus image utilizing pattern analysis techniques. A pattern match value associated with each data frame image is generated based on the comparison and a determination is made as to whether or not the pattern match value exceeds a pattern match value threshold. When the pattern match value exceeds the pattern match value threshold, a pattern associated with the virus image is removed from the time-based frames to produce a filtered data stream.
Owner:MICROSOFT TECH LICENSING LLC
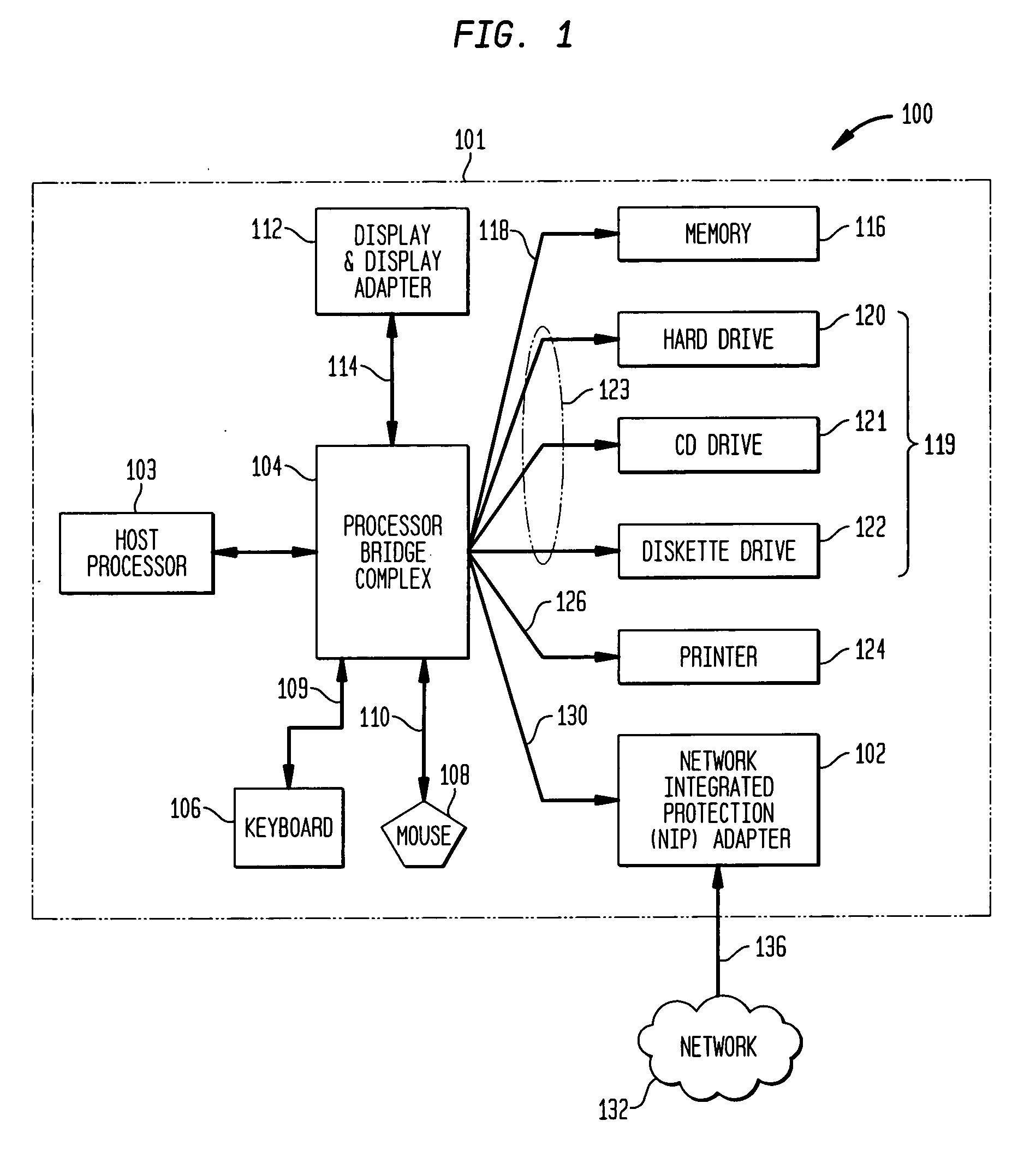
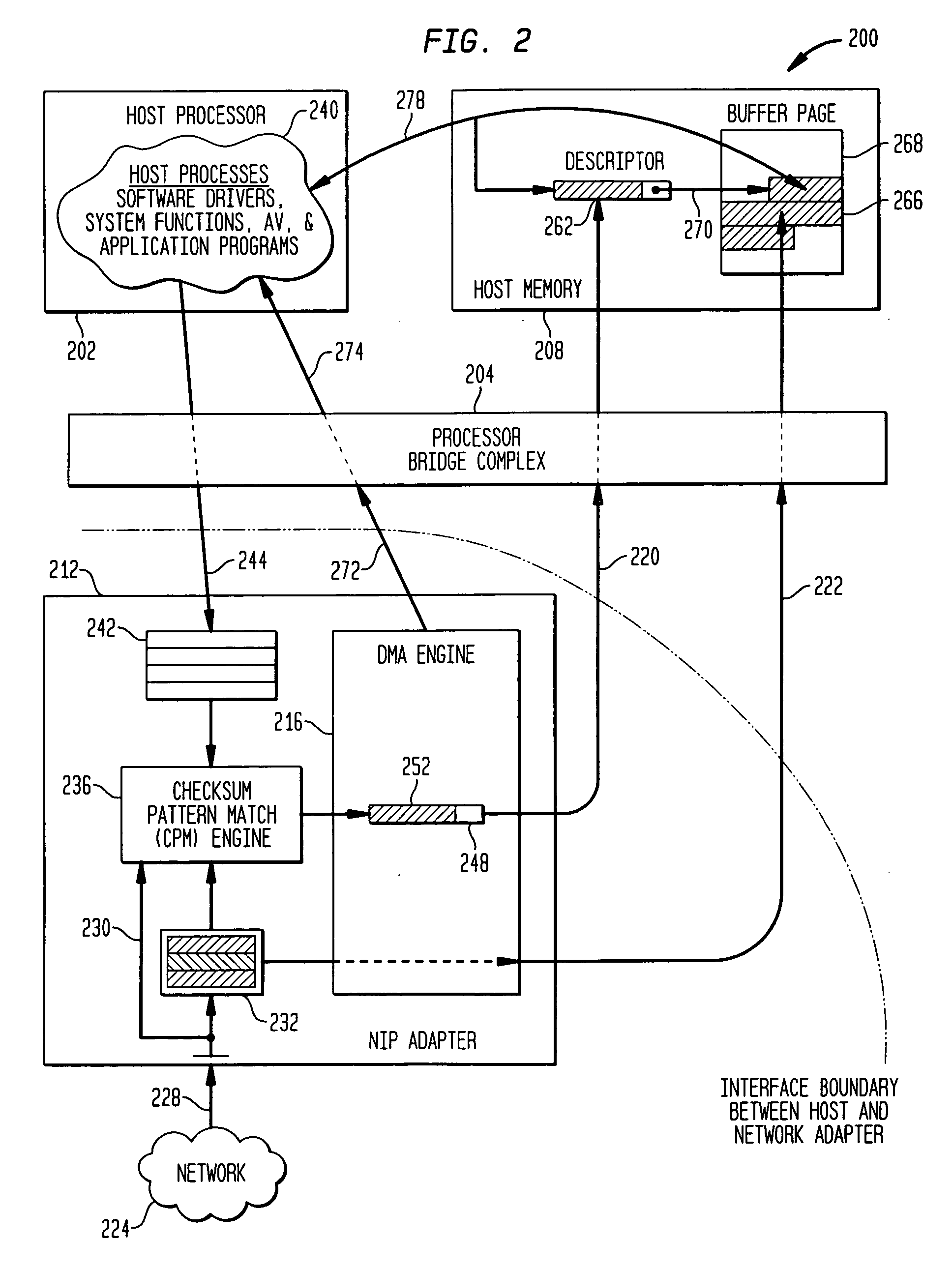
Methods and apparatus for interface adapter integrated virus protection
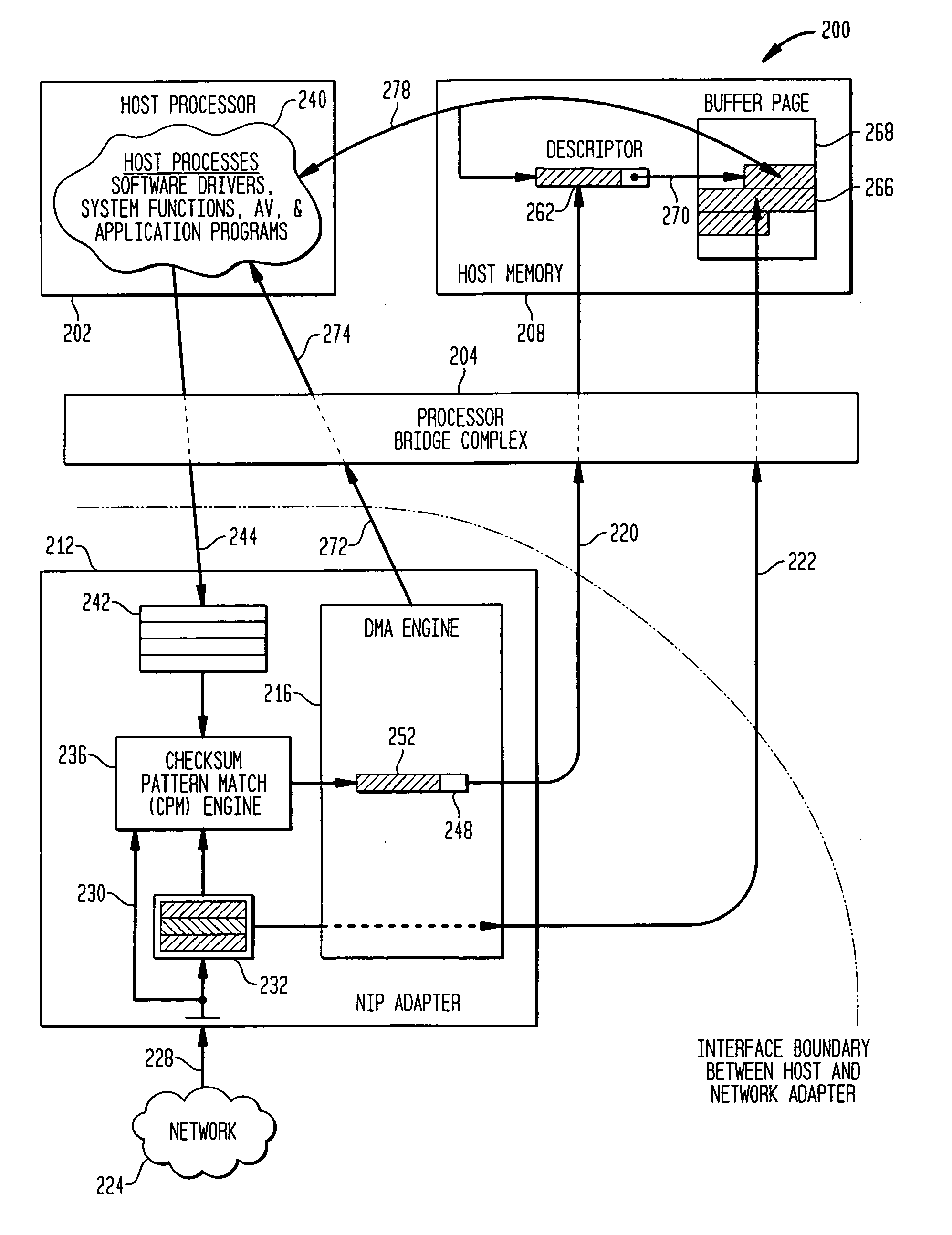
A virus detection mechanism is described in which virus detection is provided by a network integrated protection (NIP) adapter. The NIP adapter checks incoming media data prior to it being activated by a computing device. The NIP adapter operates independently of a host processor to receive information packets from a network. This attribute of independence allows NIP anti-virus (AV) techniques to be “always on” scanning incoming messages and data transfers. By being independent of but closely coupled to the host processor, complex detection techniques, such as using check summing or pattern matching, can be efficiently implemented on the NIP adapter without involving central processor resources and time consuming mass storage accesses. The NIP adapter may be further enhanced with a unique fading memory (FM) facility to allow for a flexible and economical implementation of polymorphic virus detection.
Owner:AVAGO TECH INT SALES PTE LTD
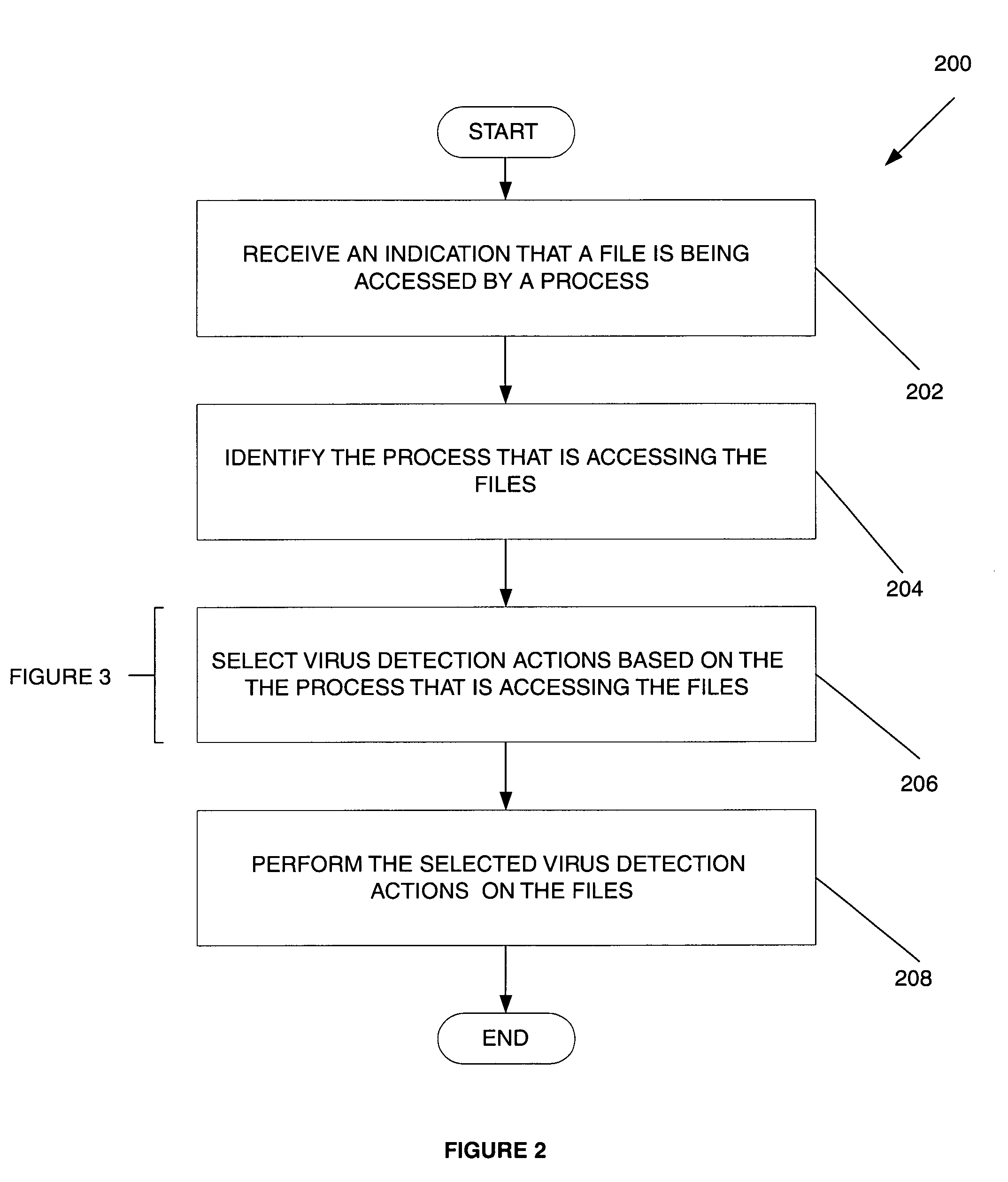
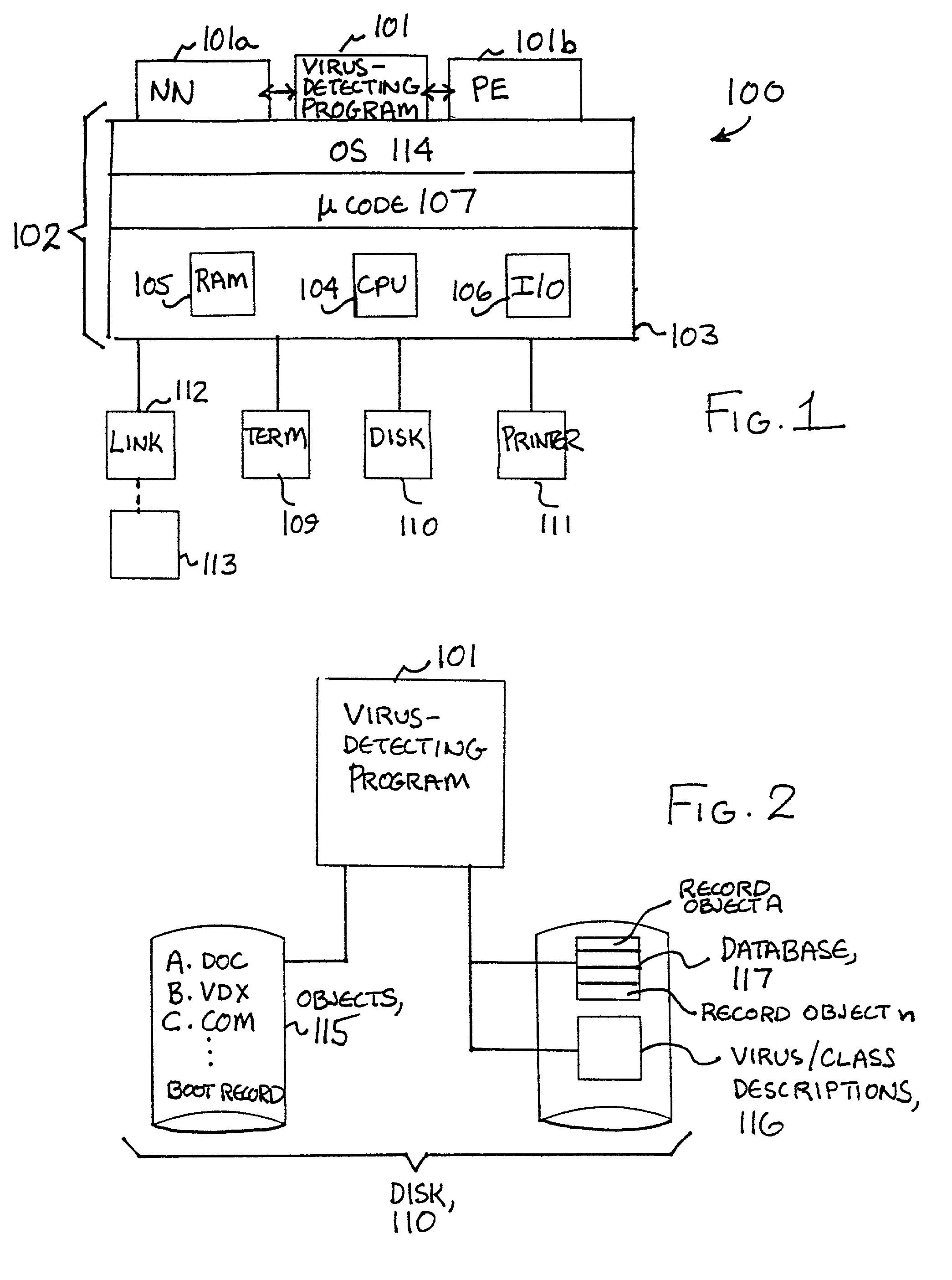
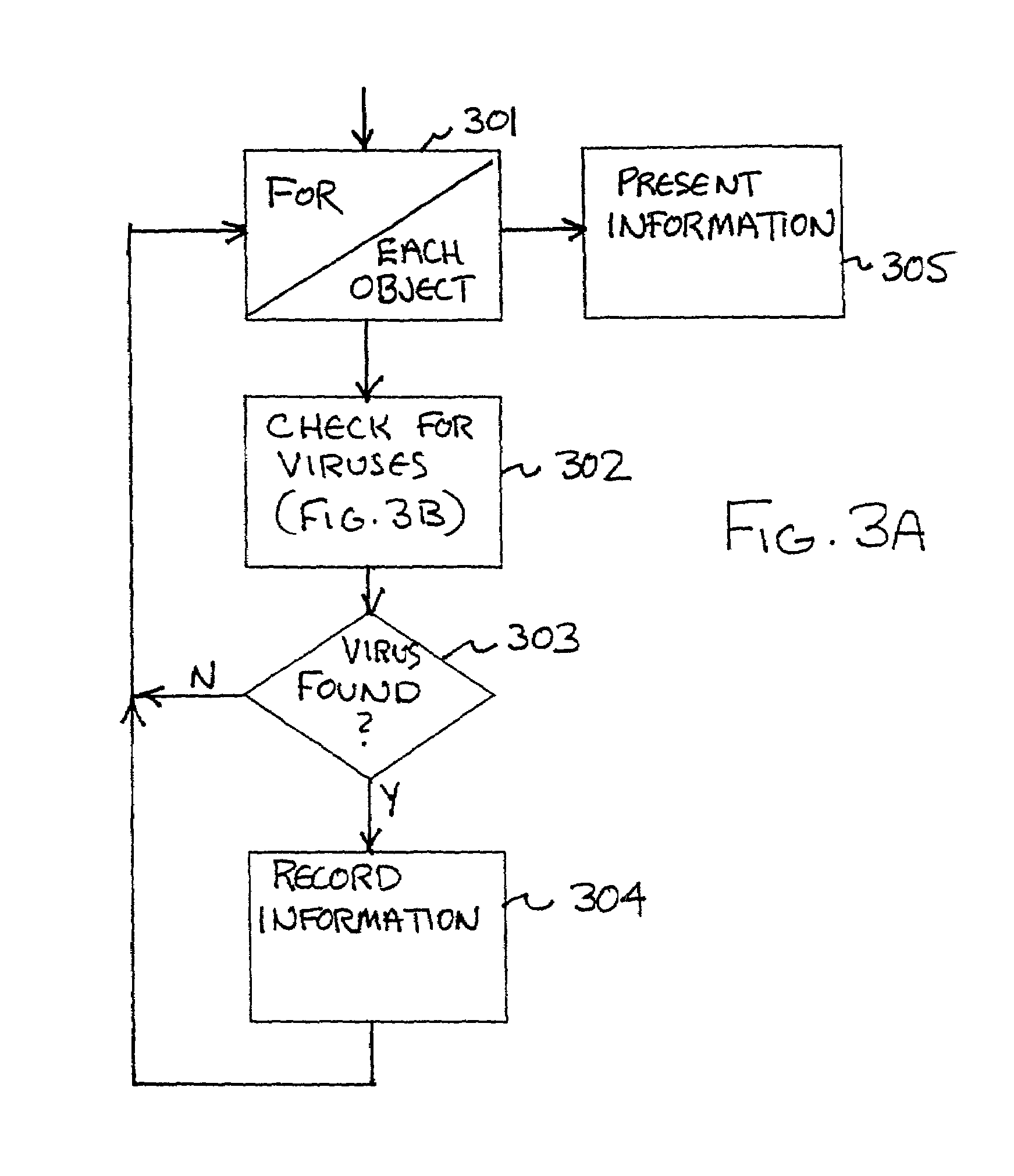
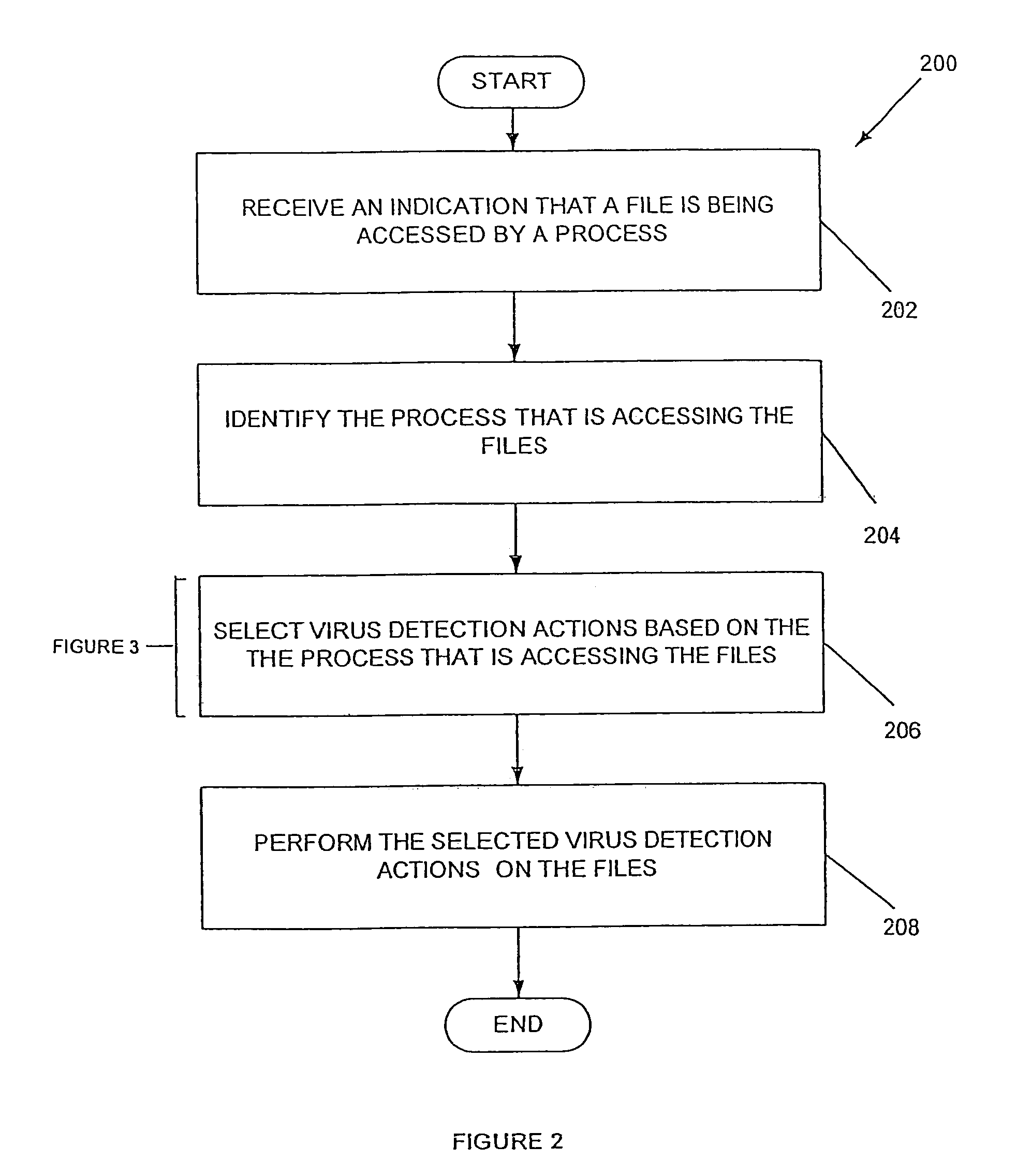
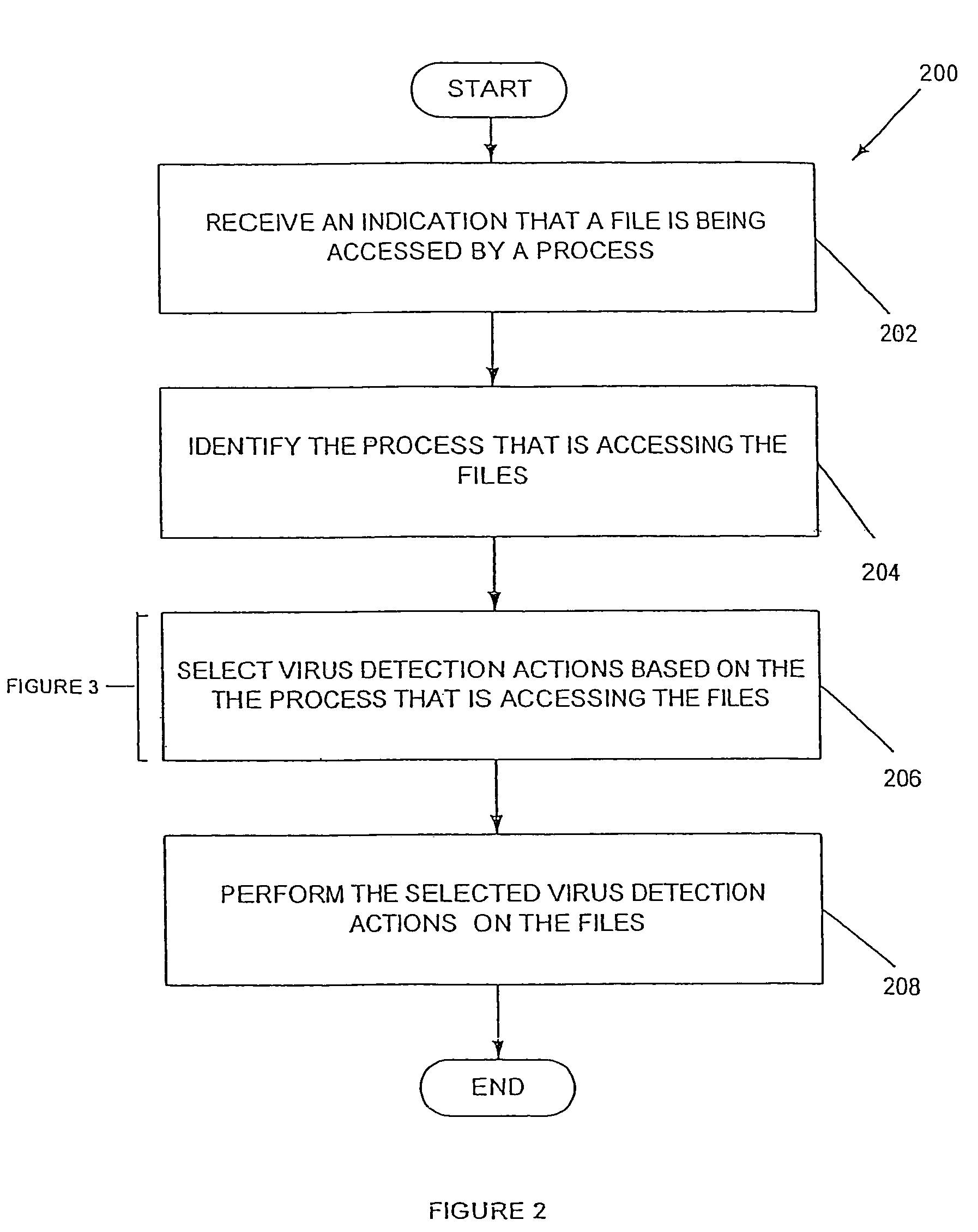
System, method and computer program product for process-based selection of virus detection actions
InactiveUS6973578B1Easy to useMemory loss protectionUnauthorized memory use protectionVirus detectionDatabase
A system, method and computer program product are provided for efficient on-access computer virus scanning of files. Initially, a process for accessing files is identified. Thereafter, virus detection actions are selected based at least in part on the process. The virus detection actions are then performed on the files.
Owner:MCAFEE LLC
Cognizant engines: systems and methods for enabling program observability and controlability at instruction level granularity
ActiveUS20100107252A1Improve performanceEfficient powerMemory loss protectionError detection/correctionGranularityControllability
The present invention is directed to system for and methods of real time observing, monitoring, and detecting anomalies in programs' behavior at instruction level. The hardware assist design in this invention provides fine grained observability, and controllability. Fine grained observability provides unprecedented opportunity for detecting anomaly. Controllability provides a powerful tool for stopping anomaly, repairing the kernel and restoring the state of processing. The performance improvement over pure software approach is estimated to be many orders of magnitudes. This invention is also effective and efficient in detecting mutating computer viruses, where normal, signature based, virus detection is under performing.
Owner:MERTOGUNO SUKAMO
Method and apparatus for increasing virus detection speed using a database
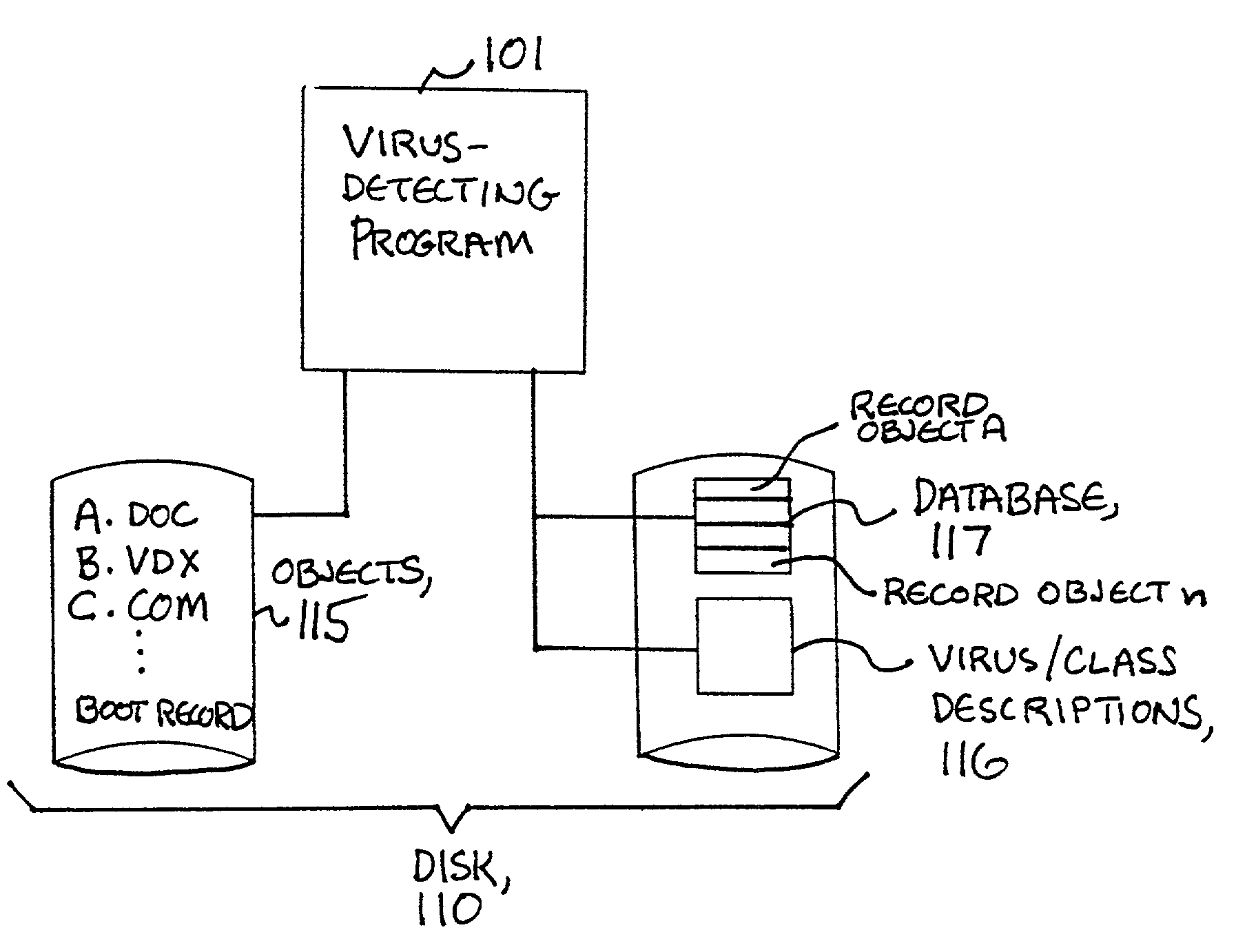
InactiveUS6952776B1Simple technologyLess timeData processing applicationsUnauthorized memory use protectionVirus detectionComputer virus
A virus detection method for use in a computer system that contains at least one object that may potentially become infected with a computer virus. The method has steps of providing a database for storing information that is descriptive of a state of the object as it existed at a point in the past. For an object that is indicated as having a current state that is described by the stored information, another step programmatically examines the object for a presence of a computer virus while assuming that the current state of the object is the same as the state of the object as it existed at the point in the past. The the database stores additional information, beyond what is necessary to determine simply whether or not a particular object, such as a file, has changed. The additional information is employed to achieve a more rapid virus scan, even when the list of viruses being scanned for has changed since a previous scan.
Owner:TREND MICRO INC
System, method and computer program product for selecting virus detection actions based on a process by which files are being accessed
InactiveUS6931540B1Efficient mannerMemory loss protectionUnauthorized memory use protectionComputer scienceDatabase
A system, method and computer program product are provided for on-access computer virus scanning of files in an efficient manner. If no identifier is assigned to a process for accessing files, virus detection actions are selected based at least in part on the identification of the process. Further, an identifier is assigned to the process. Thereafter, virus detection actions may be selected based at least in part on the identifier for accelerating the selection process. In operation, the selected virus detection actions are performed on the files.
Owner:MCAFEE LLC +1
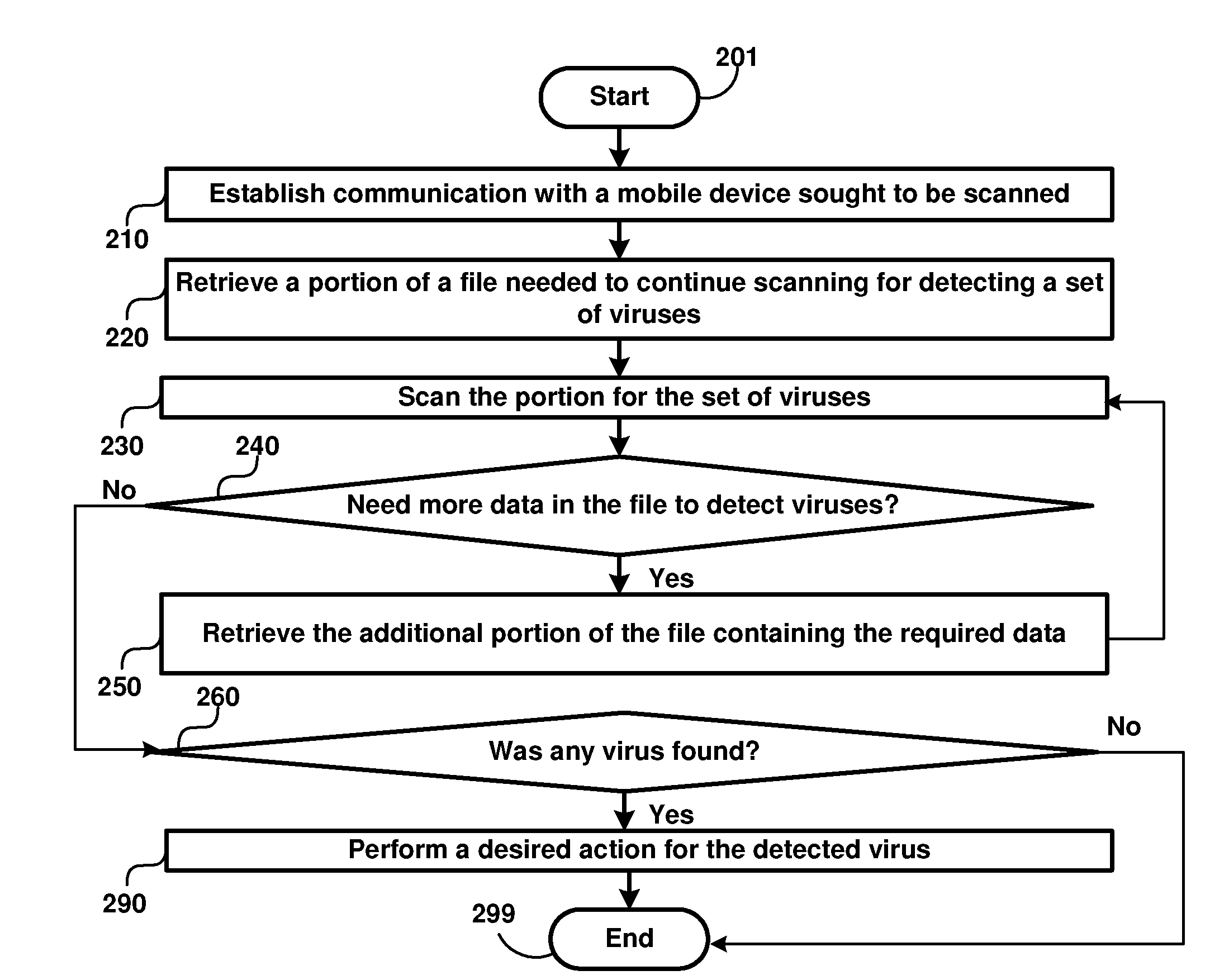
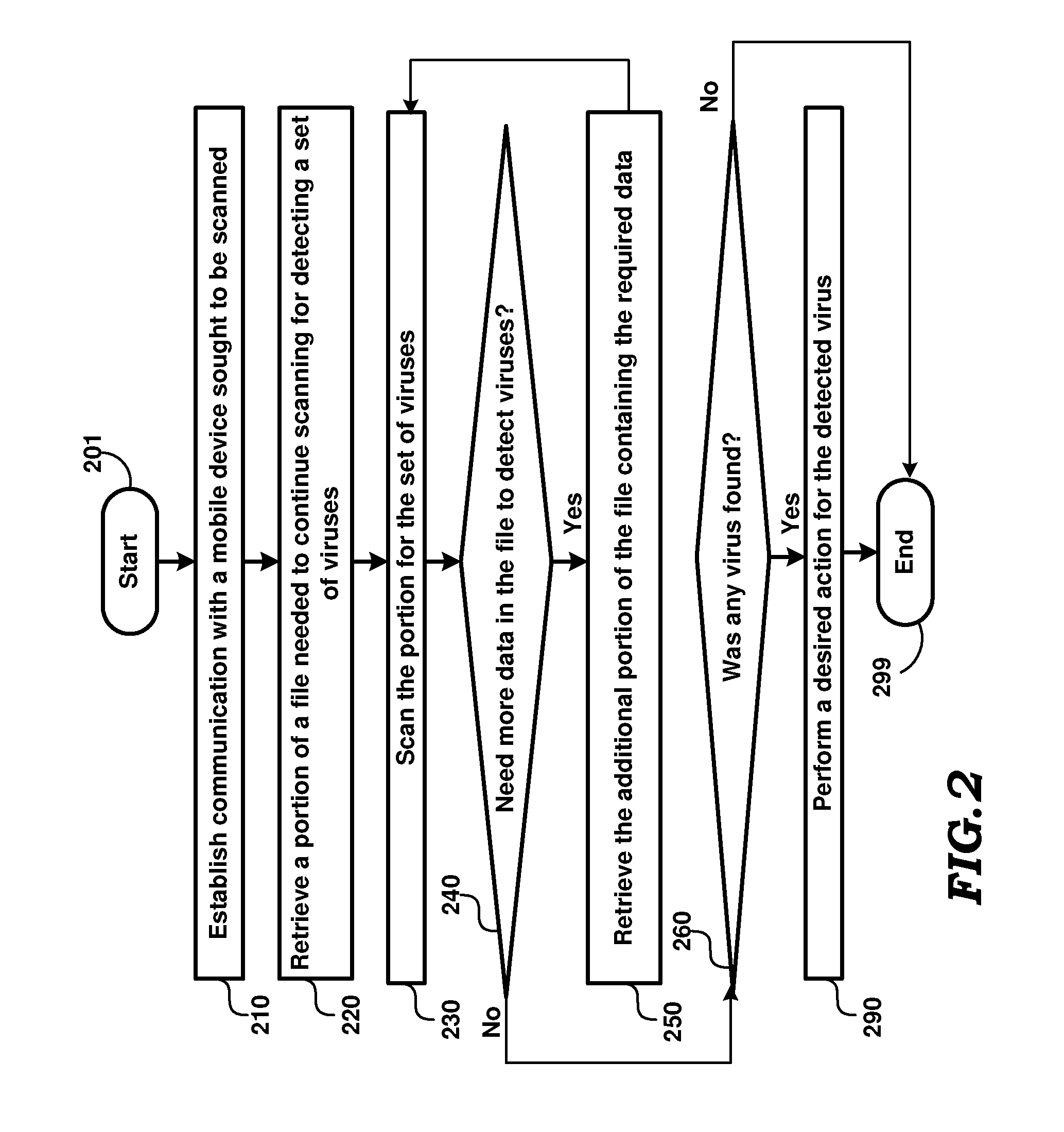
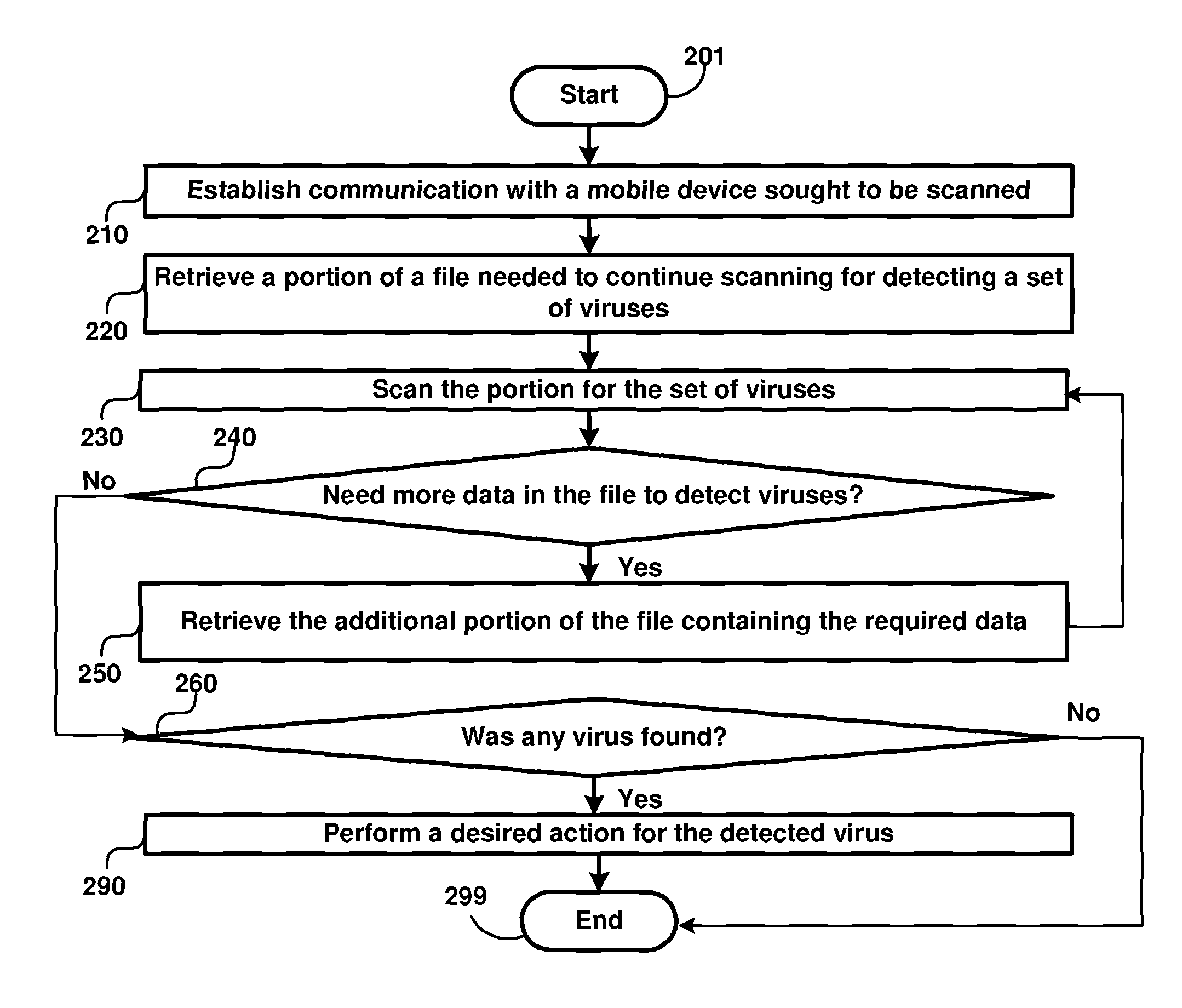
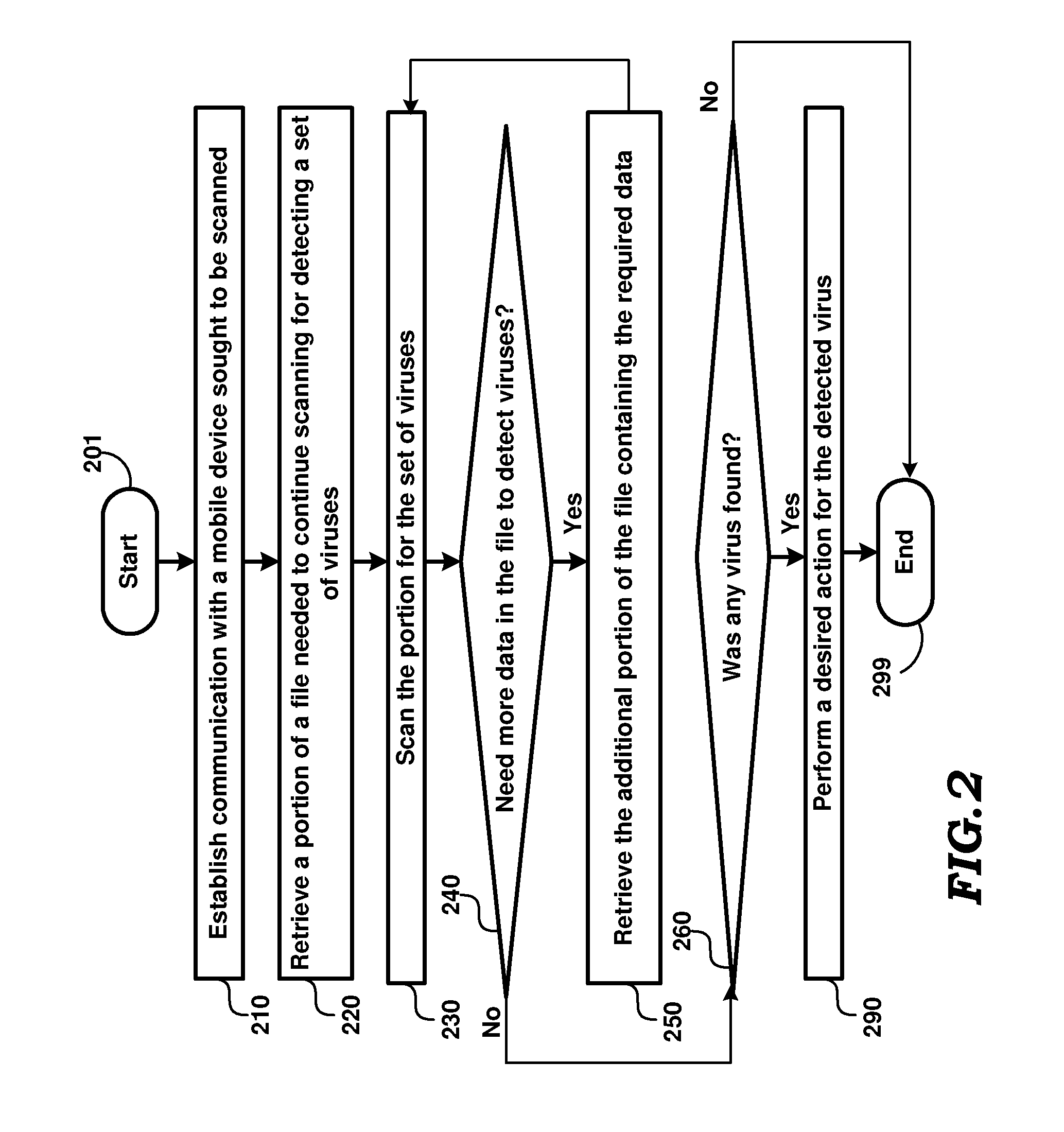
Virus Detection in Mobile Devices Having Insufficient Resources to Execute Virus Detection Software
InactiveUS20080148407A1Memory loss protectionUnauthorized memory use protectionApplication programming interfaceApplication software
A virus scanning system which scans a mobile device / mobile device for files containing viruses even if the files are not executable on the mobile device. Corrective actions such as removing the files can be performed once the viruses are detected. As a result, viruses which are not executable (as being designed for other mobile device types) can also be detected and removed from mobile devices. According to another aspect, a common interface is provided when a virus scanning program requests data from mobile devices, and the computer is provided with different remote application programming interfaces suited to retrieve the specified data from the corresponding mobile devices. As a result, the computer can be extended to integrate scanning of new device types easily. According to one more aspect, a scanning program retrieves only data portions required for continuing the scan operation. According to yet another aspect, the program modules and virus definitions for scanning are received from a server on a network.
Owner:CAT COMP SERVICES PVT
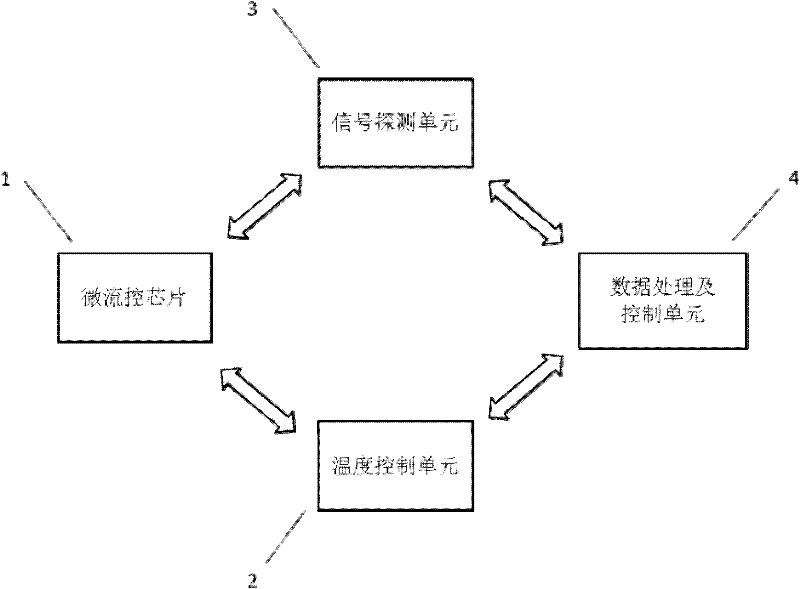
A microfluidic chip for pcr and a real-time pcr virus rapid detection device
InactiveCN102286358AReduce dosageShort injection timeBioreactor/fermenter combinationsBiological substance pretreatmentsTemperature controlFluorescent pcr
The invention relates to a microfluidic control chip which is formed by bonding and sealing PDMS (Polydimethylsiloxane) material integrated with a micro valve, and comprises an upper layer of air control passage, a middle layer of PDMS membrane and a lower layer of microfluidic passage. A real-time PCR virus quick detection device comprises the microfluidic control chip, a temperature control unit, a signal detection unit and a data processing and control unit. The invention designs the microfluidic control chip which is integrated with the micro valve, is in a three-layer PDMS structure, andis used for virus detection and the real-time fluorescent PCR detection device. Compared with the traditional method, the invention has the advantages of short time, less sample usage, quick detection speed, simpleness and convenience in operation, integration and the like.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
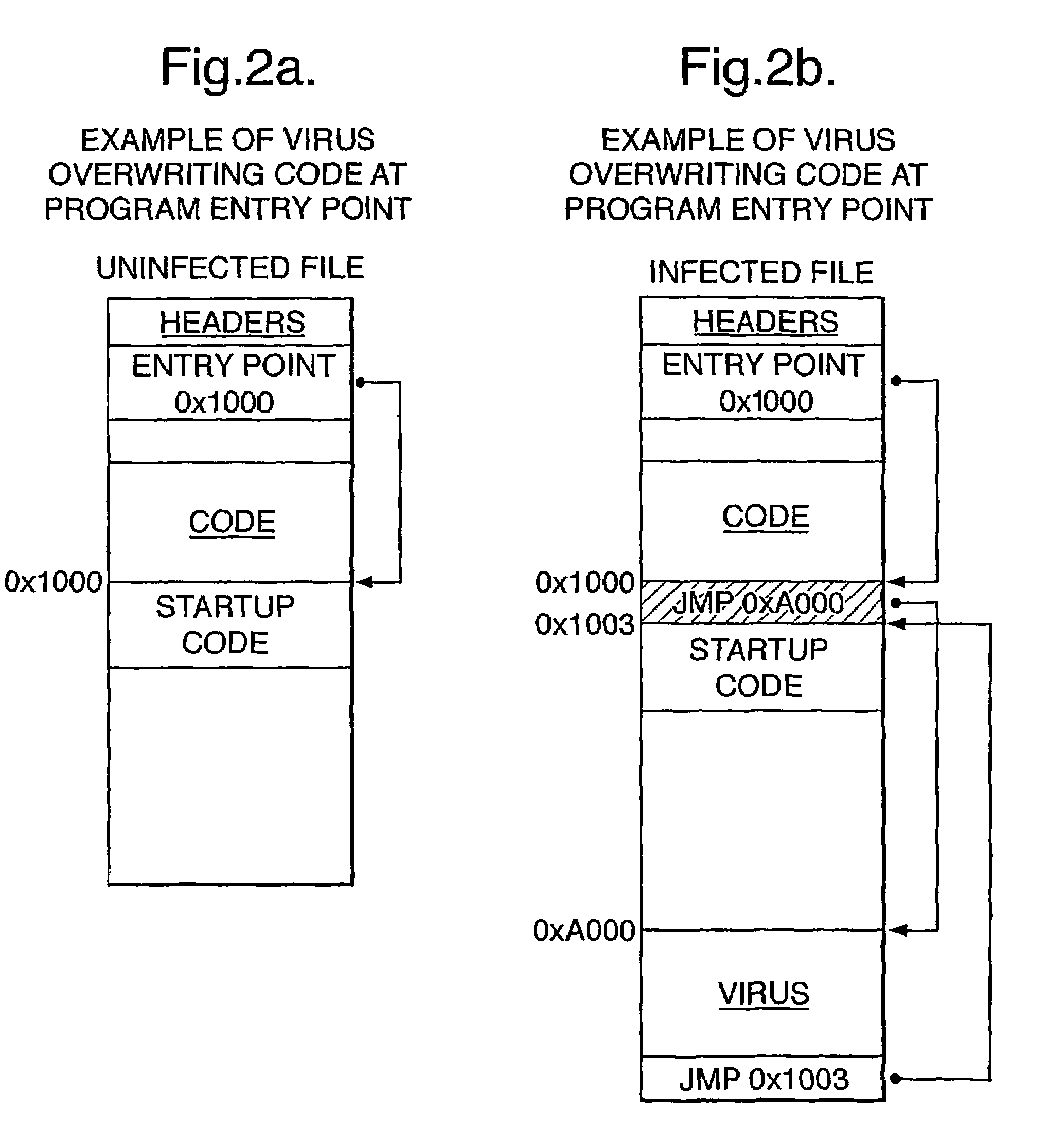
Method of, and system for, heuristically detecting viruses in executable code
ActiveUS7496963B2Significant timeMemory loss protectionDigital data processing detailsHeuristicVirus detection
A method of, and system for, virus detection has a database of known patterns of start-up code for executable images created using a collection of known compilers and uses examination of the start-up code of the image by reference to this database to determine whether or not the executable image is likely to have been subject to infection by viral code. In particular, the system seeks to determine whether the expected flow and execution of the image during start up has had viral code interjected into it. Various heuristics to assist in assessing the likely presence of viral code are disclosed.
Owner:CA TECH INC
Software virus detection methods and apparatus
InactiveUS7093135B1Memory loss protectionUser identity/authority verificationVirus detectionAuthentication
The present invention is a system and method for identifying and securing code, as well as providing virus detection and code authentication. This detection and authentication occurs through modules or components which utilize certification identifiers to authenticate and validate code. Preferred embodiments include macro detection.
Owner:CYBERSOFT
System and method for managing security of general network
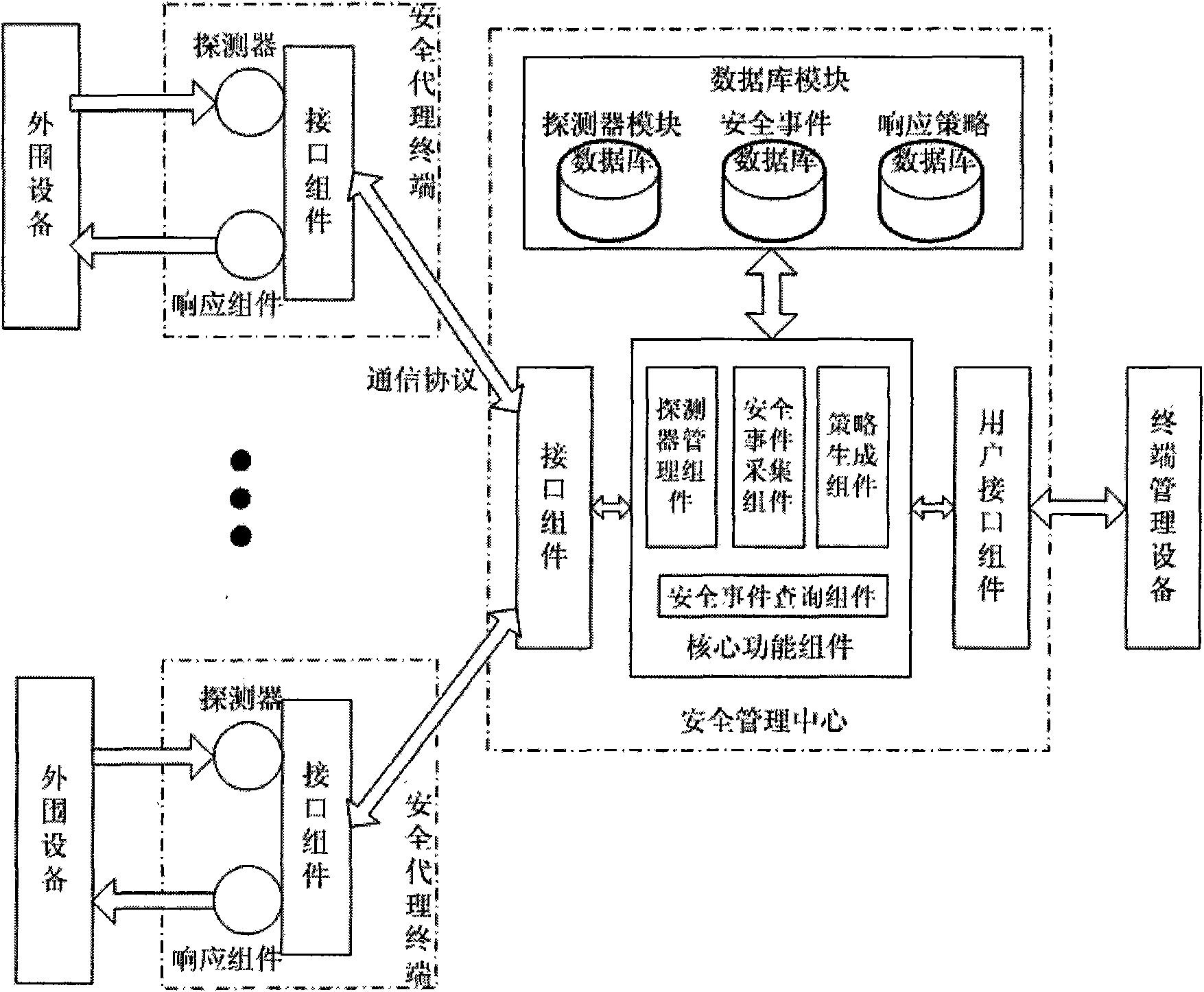
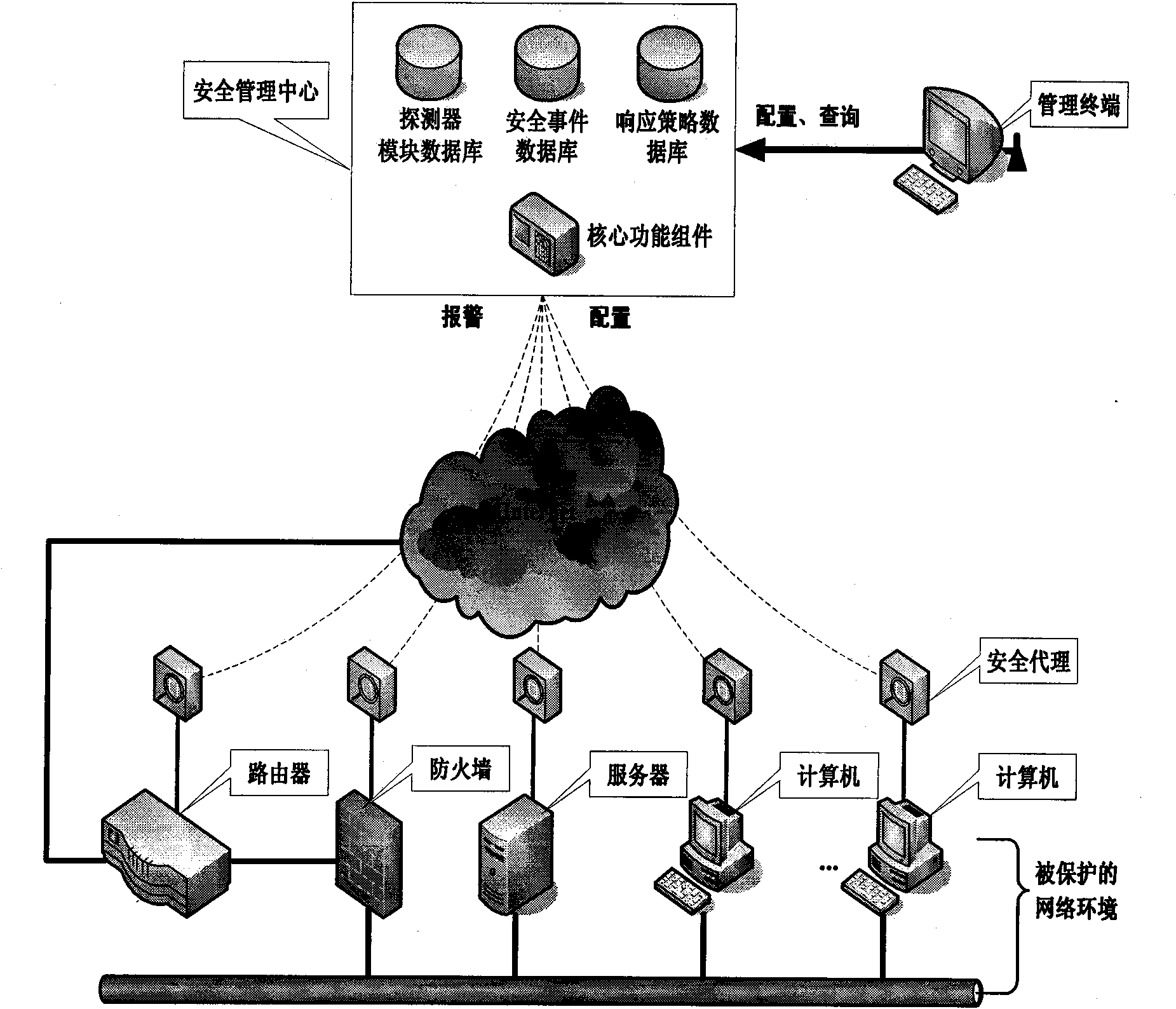
InactiveCN101582883AImprove general performanceIncrease opennessData switching networksDistributed securityProtection system
The invention discloses a system and a method for managing security of a general network, and mainly overcomes the defects of poor openness and expansibility and weak functional completeness existing in the prior network security management system. The system mainly comprises peripheral equipment, a security agent terminal, a security management center and terminal management equipment, wherein the security management center applies security technology of network access control, intrusion detection, virus detection and vulnerability management to the security agent terminal through an interface component, a data base module and a user interface component; and under the unified management and control, all security technology is mutually complemented and matched to detect and control network behaviors, so that a distributed security protection system structure in which security strategies are under central management and the security detection is separately distributed is formed. The system and the method have the advantages of flexible configuration, easy expansion, good openness, support of the different level management, and suitability for the security management and protection of the computer network in governments, colleges and universities, and large- and medium-sized enterprises.
Owner:XIDIAN UNIV
Policy-based data protection
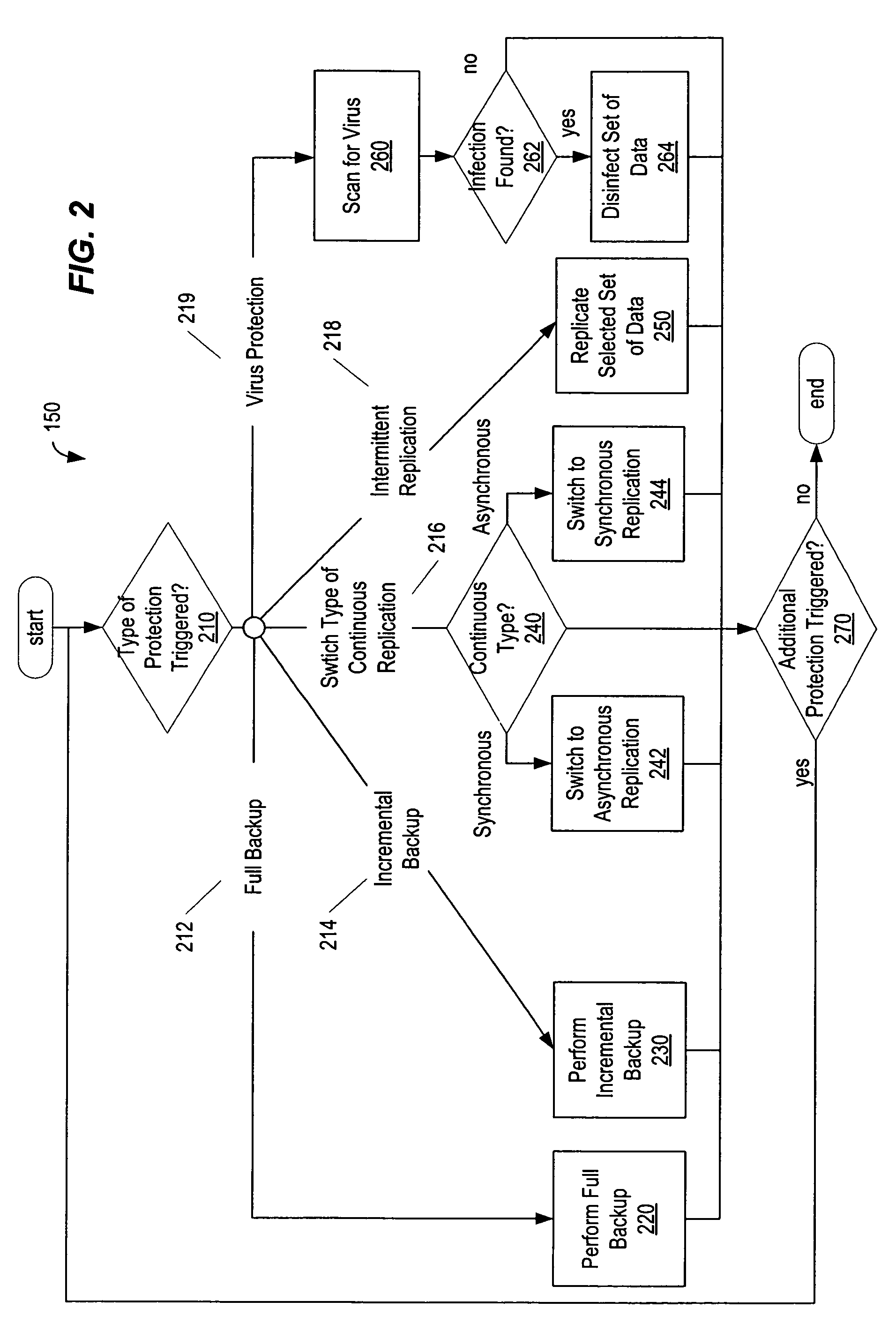
ActiveUS7509468B1Error detection/correctionUnauthorized memory use protectionData setComputerized system
A method, system, computer system, and computer-readable medium to trigger protection of a set of data based upon the type or class of the data in the set and / or an amount of data that has changed since some prior point in time. Types of protection that can be triggered include full backup, incremental backup, switching to a different type of continuous replication, intermittent replication, and virus detection. Using the type of the data as a basis for triggering protection enables the operational significance of different sets of data to be taken into account when allocating protection resources. Data sets may be pre-classified, or an automated determination of the type of a data set may be determined by variables measured at run-time. The amount of the changed data in a set that triggers protection may vary in accordance with the type of the set of data.
Owner:SYMANTEC OPERATING CORP
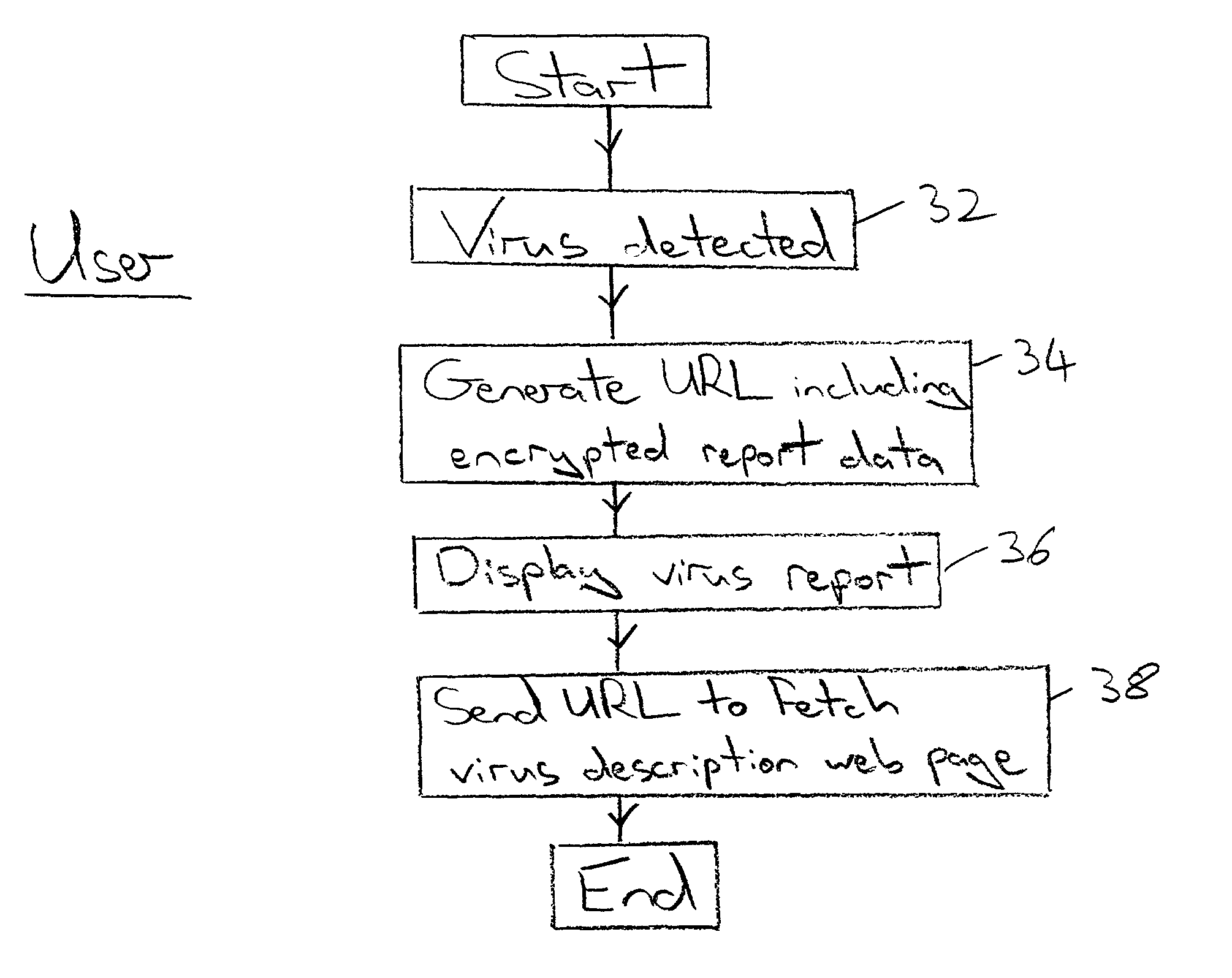
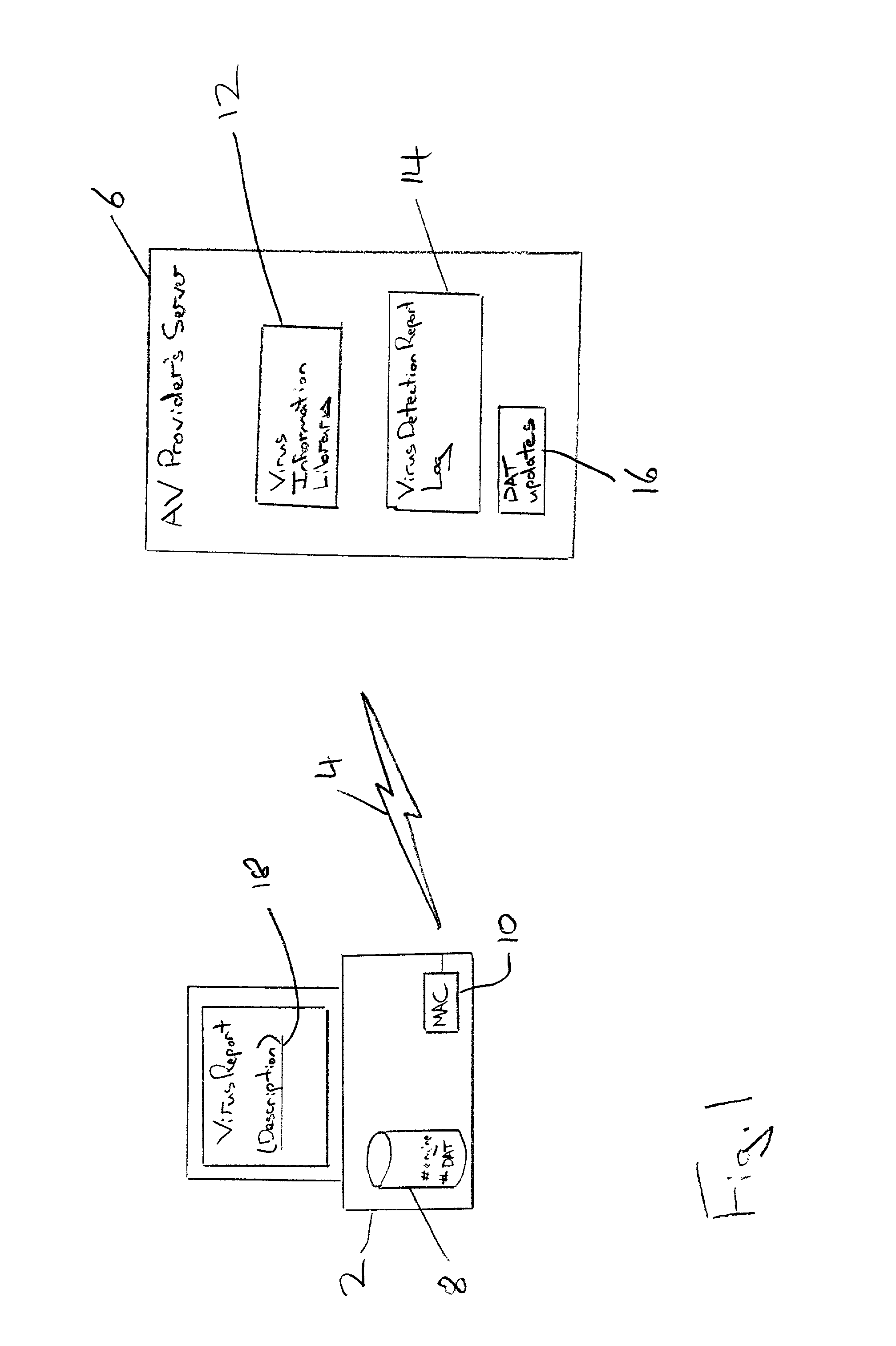
Event reporting between a reporting computer and a receiving computer
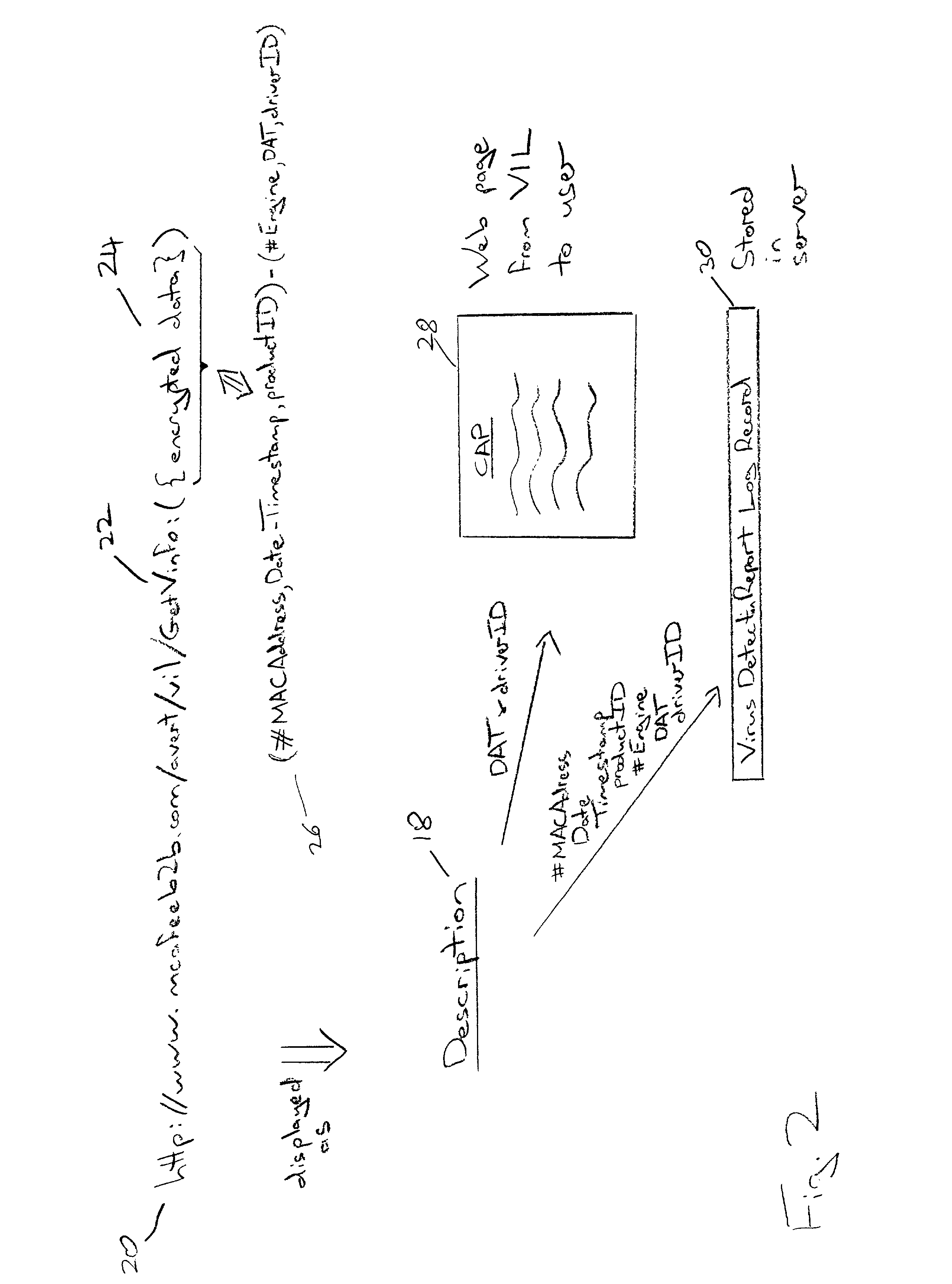
An event report, such as a virus detection event, is sent from a reporting computer 2 to a receiving computer 6 via an internet link 4. The report data may take the form of a URL requesting a web page 28 to be provided by the receiving computer 6, the URL bearing an encrypted form 24 of the report data that is used to identify the requested web page as well as pass further information to the receiving computer 6. Alternatively, the report data may be collated in the reporting computer 2 and passed to the receiving computer 6 when a computer virus definition data update is requested. The report data seeks to uniquely identify the event by incorporating the MAC address of the reporting computer 2, the date, time, computer product identifier, version identifier, update identifier and driver triggered. Additionally, a checksum derived from the infected file together with an indication of the corrective action, if any, taken by the reporting computer 2 may be included. The report data sent to the receiving computer 6 may be used to obtain real life information concerning the prevalence of particular viruses together with information characterising the anti-virus programs and their update status being employed by the user community.
Owner:MCAFEE LLC
Two stage virus detection
ActiveUS8935788B1Improve efficiencyLess iterationMemory loss protectionUnauthorized memory use protectionPattern matchingPhases of clinical research
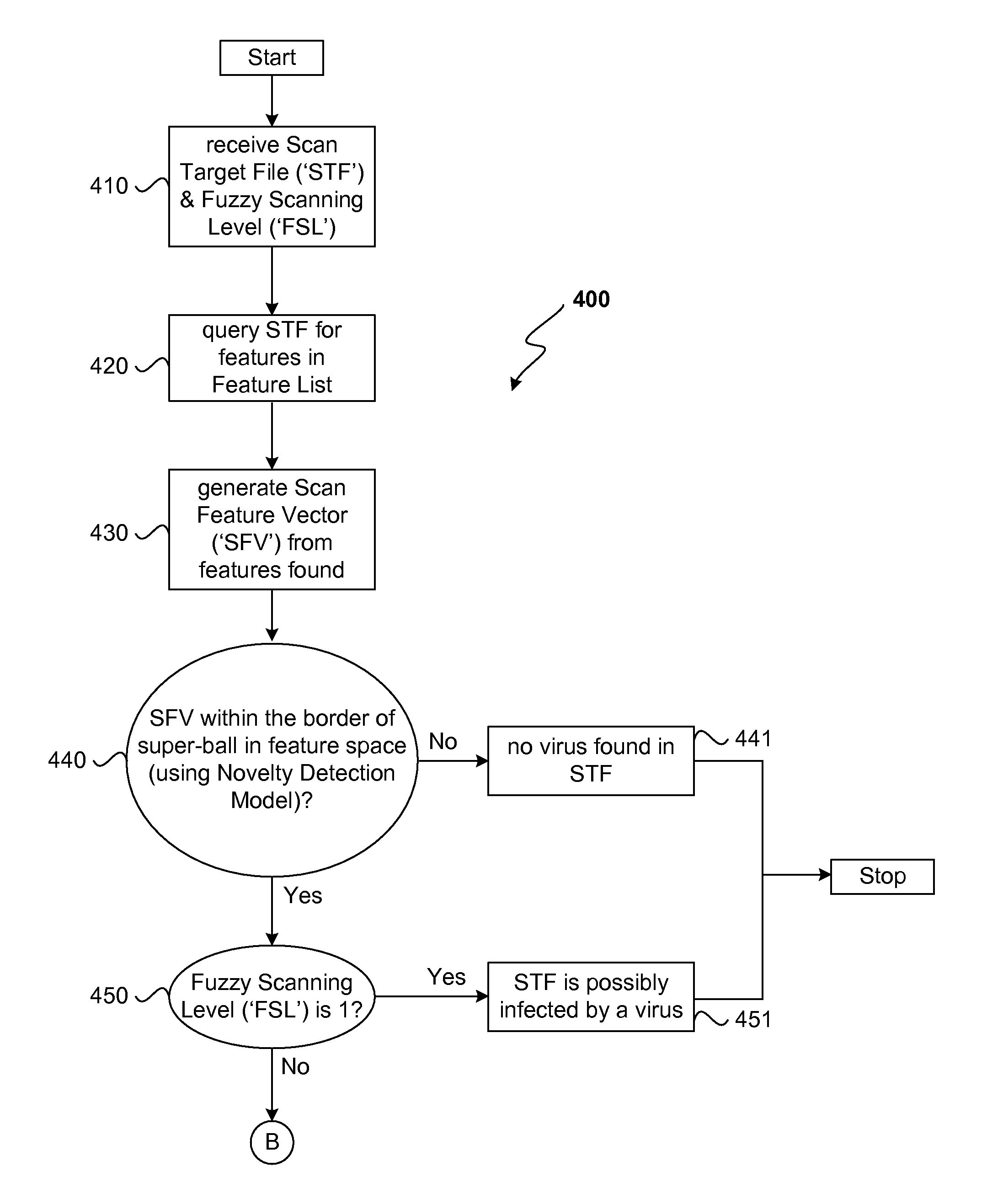
A two stage virus detection system detects viruses in target files. In the first stage, a training application receives a master virus pattern file recording all known virus patterns and generates a features list containing fundamental virus signatures from the virus patterns, a novelty detection model, a classification model, and a set of segmented virus pattern files. In the second stage, a detection application scans a target file for viruses using the generated outputs from the first stage rather than using the master virus pattern file directly to do traditional pattern matching. The results of the scan can vary in detail depending on a fuzzy scan level. For fuzzy scan level “1,” the existence of a virus is returned. For fuzzy scan level “2,” the grant virus type found is returned. For fuzzy scan level “3,” the exact virus name is returned. This invention provides a solution for the problems caused by traditional virus detection solution: slow scanning speed, big pattern file, big burden on computation resource (CPU, RAM etc.), as well as heavy pattern updating traffic via networks.
Owner:TREND MICRO INC
Process-based selection of virus detection actions system, method and computer program product
InactiveUS7251830B1Easy to useMemory loss protectionUser identity/authority verificationSelection systemComputer science
A system, method and computer program product are provided for efficient on-access computer virus scanning of files. Initially, a process for accessing files is identified. Thereafter, virus detection actions are selected based at least in part on the process. The virus detection actions are then performed on the files.
Owner:MCAFEE LLC
Virus detection in mobile devices having insufficient resources to execute virus detection software
InactiveUS7945955B2Memory loss protectionUnauthorized memory use protectionDevice typePublic interface
A virus scanning system which scans a mobile device / mobile device for files containing viruses even if the files are not executable on the mobile device. Corrective actions such as removing the files can be performed once the viruses are detected. As a result, viruses which are not executable (as being designed for other mobile device types) can also be detected and removed from mobile devices. According to another aspect, a common interface is provided when a virus scanning program requests data from mobile devices, and the computer is provided with different remote application programming interfaces suited to retrieve the specified data from the corresponding mobile devices. As a result, the computer can be extended to integrate scanning of new device types easily. According to one more aspect, a scanning program retrieves only data portions required for continuing the scan operation. According to yet another aspect, the program modules and virus definitions for scanning are received from a server on a network.
Owner:CAT COMP SERVICES PVT
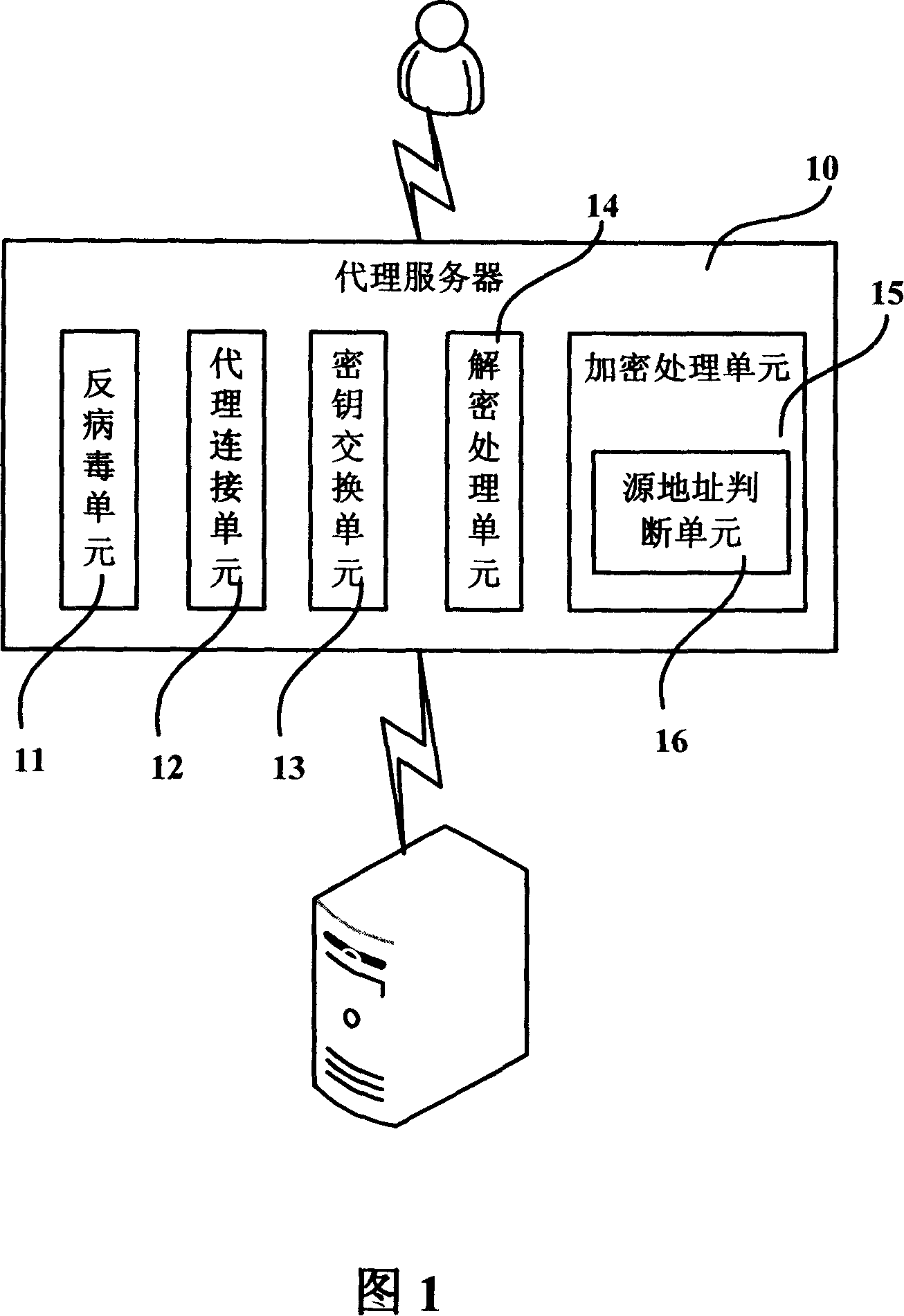
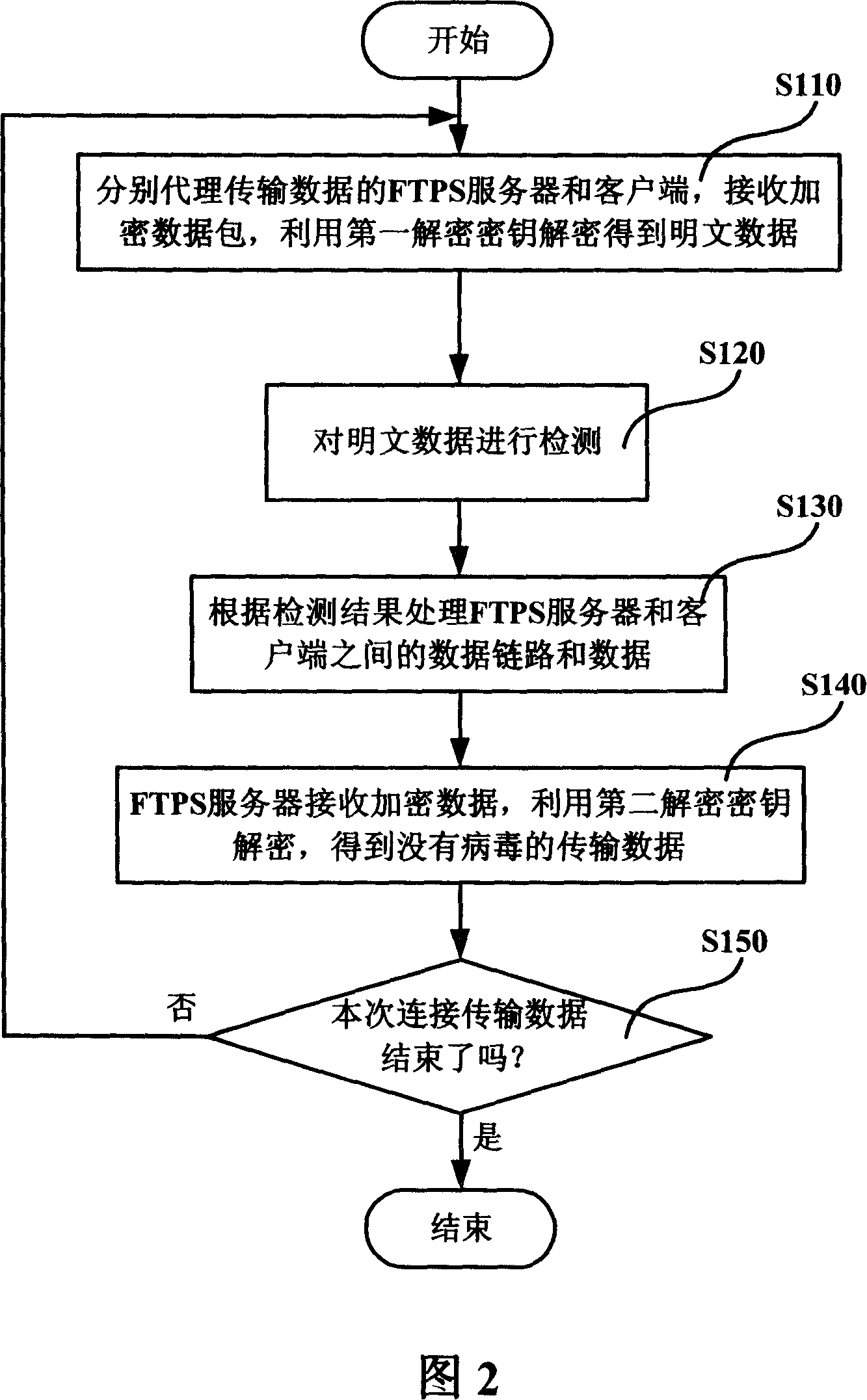
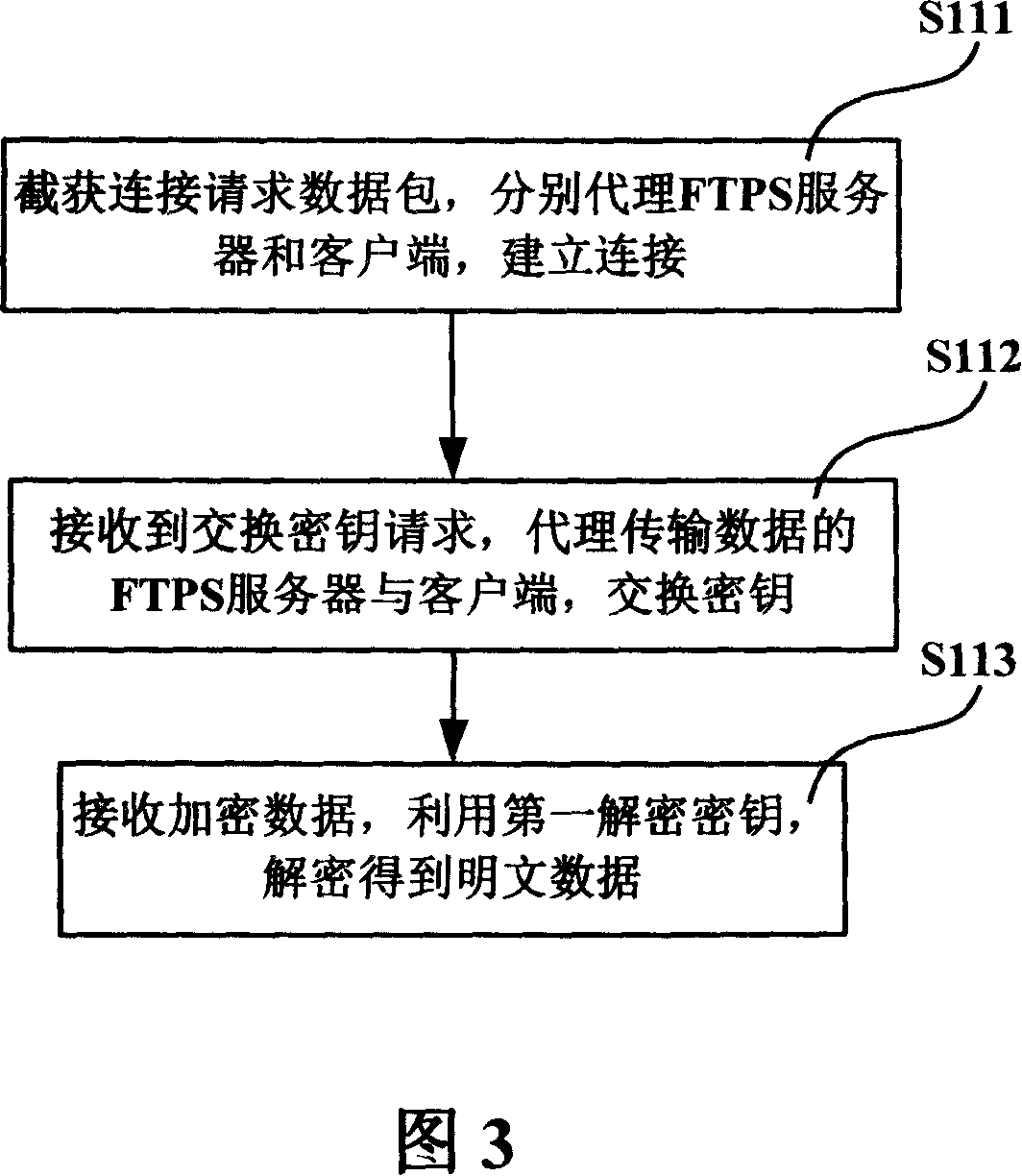
Network enciphered data virus detection and elimination system and proxy server and method
ActiveCN101141244AEliminate transmissionEliminate the risk of leaksSecuring communicationAnti virusPlaintext
The utility model discloses a virus-detection and removing system, proxy server and method used for network encryption data. The system comprises a client, a server, a proxy server and a anti-virus unit, among which when the proxy server encrypts the data communication between the client and the server, the proxy client and the server will receive the transmitted data pack which is decrypted to the plaintext data and then sent to the anti-virus unit for virus examination and removing, so that the safety plaintext data are re-encrypted and then sent to the server. The anti-virus unit can detect and remove the virus from the plaintext data and inform the examining and removing results to the proxy sever, so as to reduce or even remove the network viral transmission via SSL / TLS cryptographic protocol.
Owner:FORTINET
Metamorphic computer virus detection
The executions of computer viruses are analyzed to develop register signatures for the viruses. The register signatures specify the sets of outputs the viruses produce when executed with a given set of inputs. A virus detection system (VDS) (400) holds a database (430) of the register signatures. The VDS (400) selects (710) a file that might contain a computer virus and identifies potential entry points in the file. The VDS (400) uses a virtual machine (422) having an initial state to emulate (714) a relatively small number of instructions at each entry point. While emulating each potential entry point, the VDS builds (716) a register table that tracks the state of a subset of the virtual registers (428). Once the VDS (400) reaches an emulation breakpoint, it analyzes the register table in view of the register signatures to determine whether the file contains a virus.
Owner:CA TECH INC
Static analysis method and static analysis device for Android application program
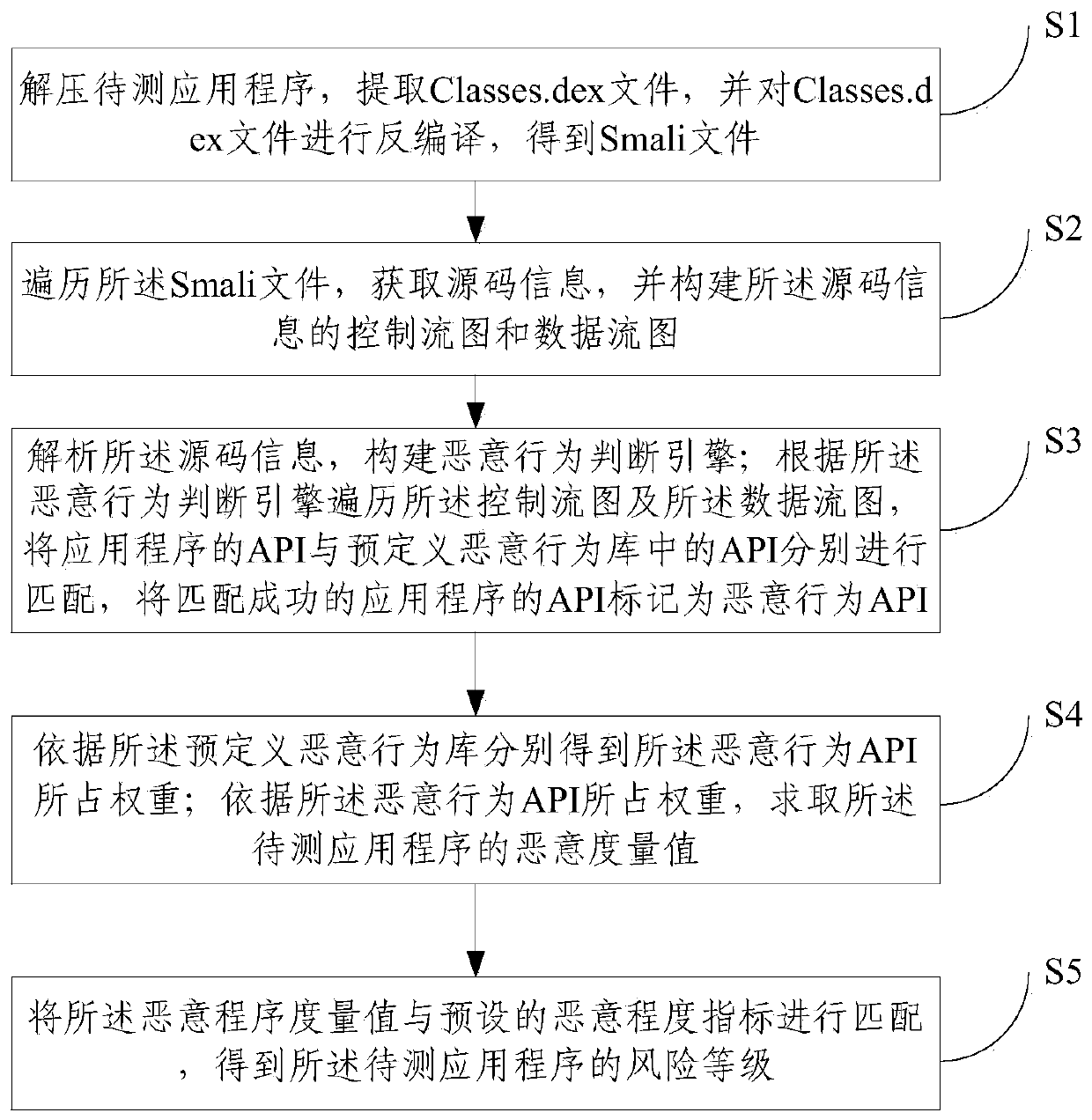
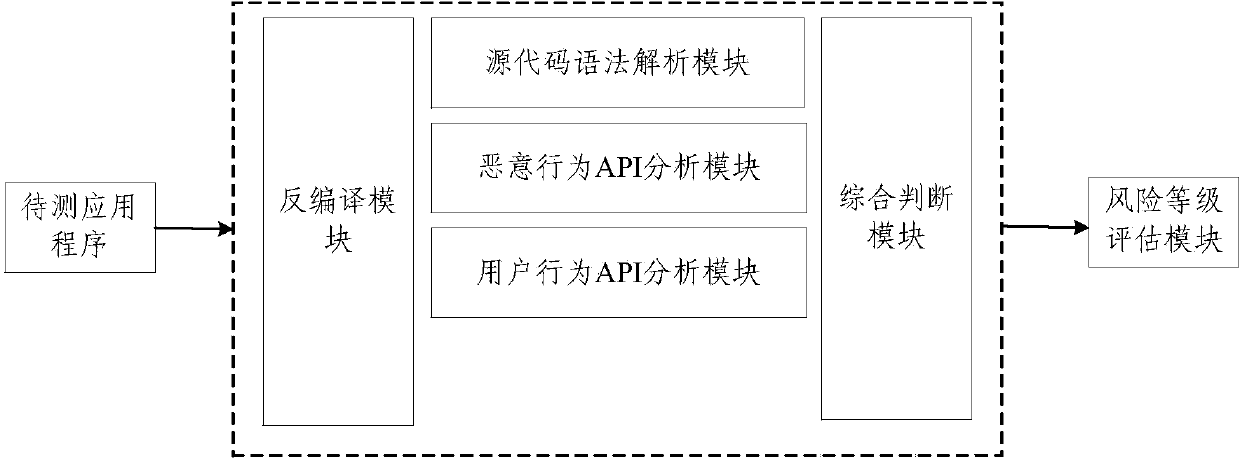
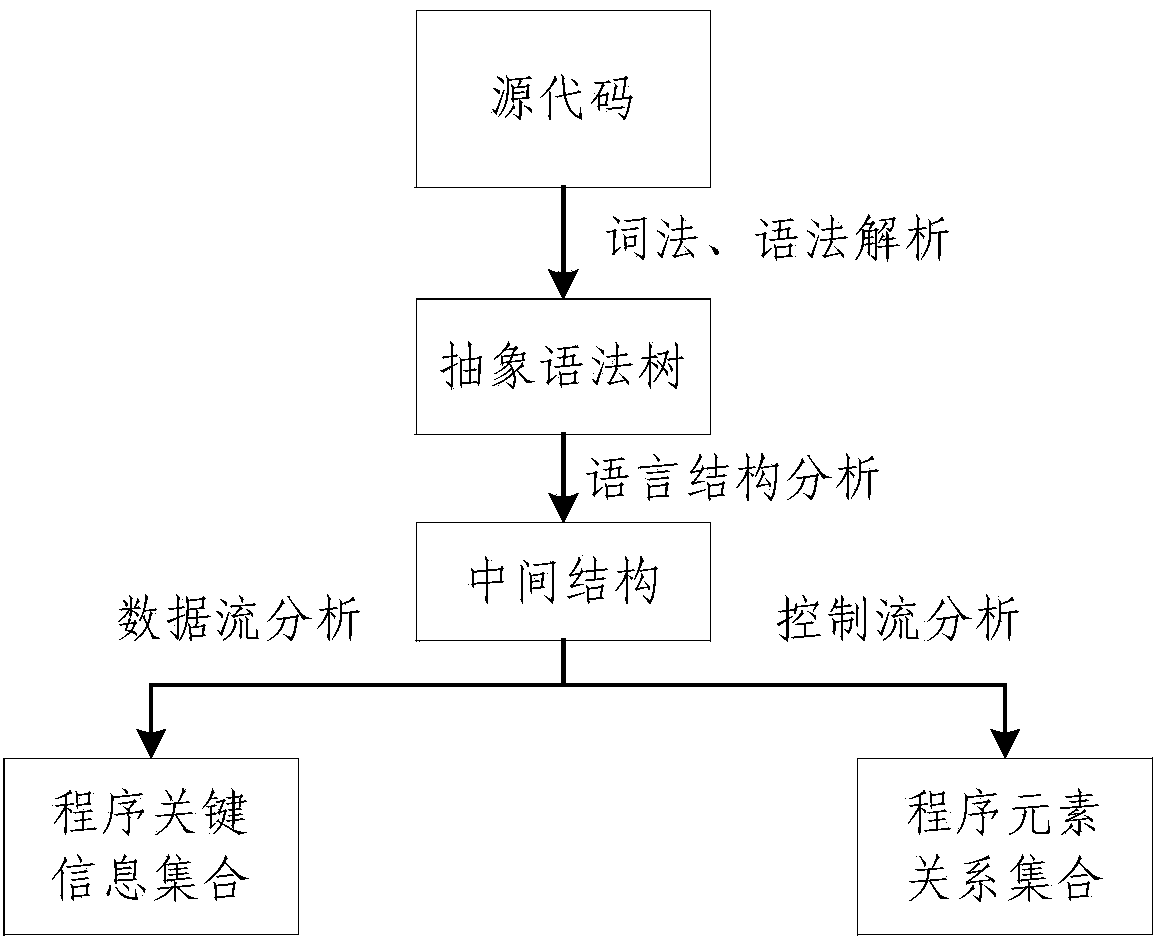
InactiveCN103793650AReduce the risk of miscalculationReduce misjudgmentPlatform integrity maintainanceRisk levelData stream
The invention provides a static analysis method and a static analysis device for an Android application program and relates to the technical field of security detection. The static analysis method includes: S1, unzipping an application program to be detected to obtain a Smali file; S2, traversing the Smali file to acquire a source code information and structuring a control flow diagram and a data flow diagram of the source code information; S3, traversing the control flow diagram and the data flow diagram according to a malicious behavior judging engine to respectively match an API (application program interface) of the application program with another API in a predefined malicious behavior library and marking the successfully matched API of the application program as the malicious behavior API; S4, calculating the malicious measuring value of the application program to be detected; S5, matching the malicious measuring value with a predefined malicious degree index to acquire risk level of the application program to be detected. Through behavior analysis and comprehensive judgment of combined rules, misjudgment rate of virus detection upon the Android application program can be reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Network security detection method and system
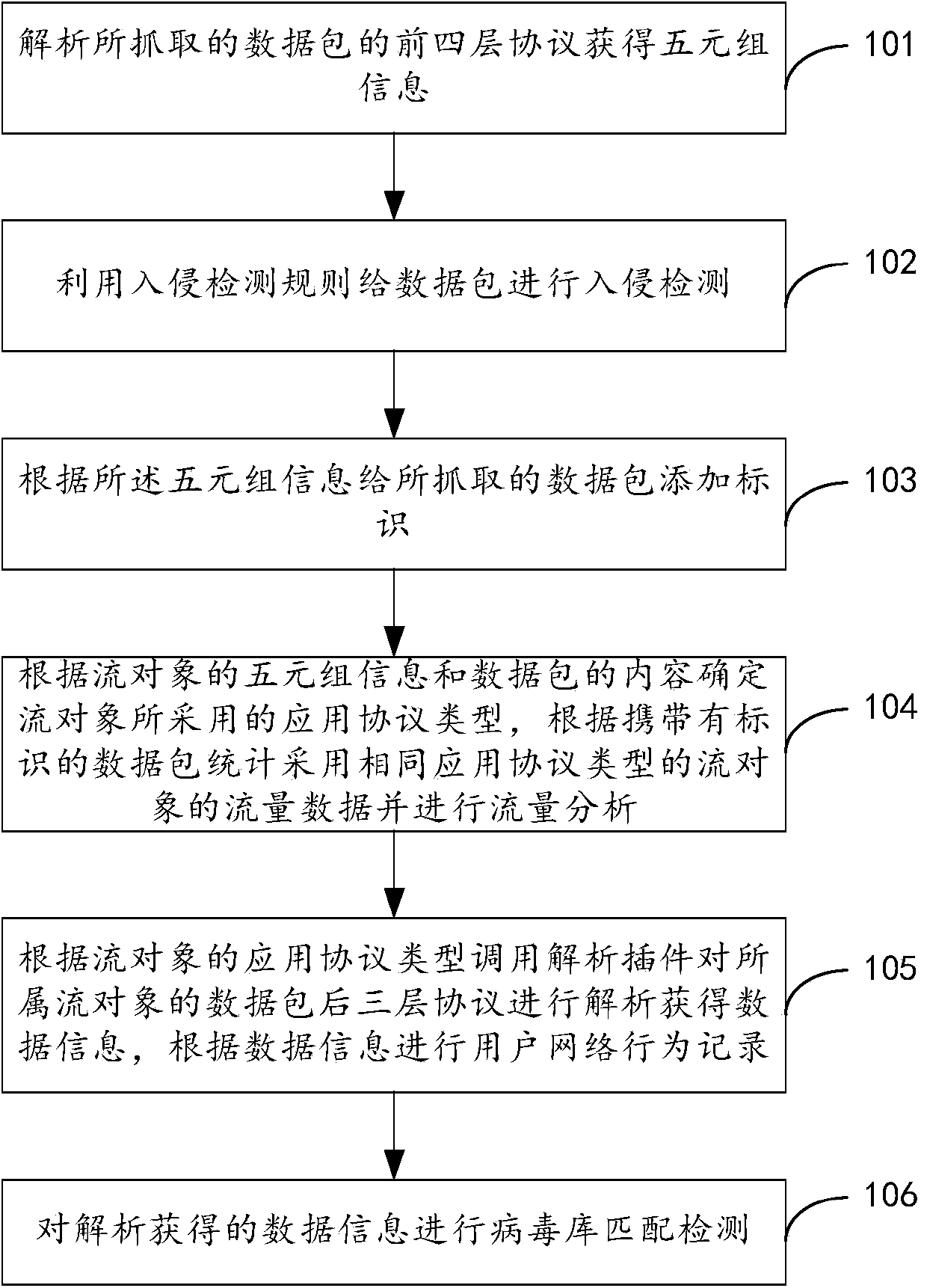
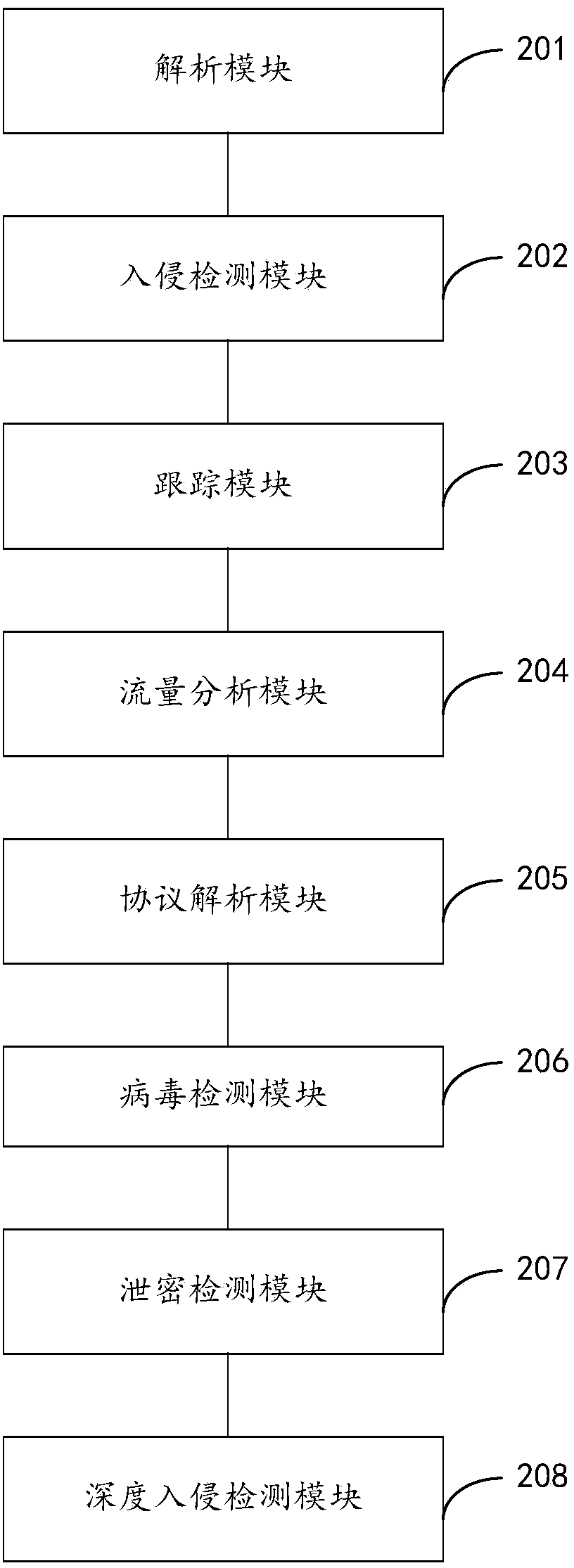
The invention provides a network security detection method and system. First four layers of a protocol of a capture data packet are analyzed to obtain quintuple information; an intrusion detection rule is used to carry out intrusion detection to the data packet; the quintuple information is used to add an identifier to the captured data packet; according to quintuple information of a stream object and a content of the data package, an application protocol type applied in the stream object is determined; according to the data packet with the identifier, flow data of the stream object using the same application protocol type is calculated and undergoes flow analysis; according to the application protocol type of the stream object, an analysis plug-in is used to analyze a data packet application layer protocol of the corresponding stream object so as to obtain data information; according to the data information, a user network behavior record is carried out; and the obtained data information obtained by analyzing is detected by matching a virus database. The intrusion detection, the network behavior detection, the abnormal flow analysis and the virus detection are integrated in one system, and only one interface is needed to realize multiple detection methods of the network access.
Owner:BEIJING TOPSEC SOFTWARE +3
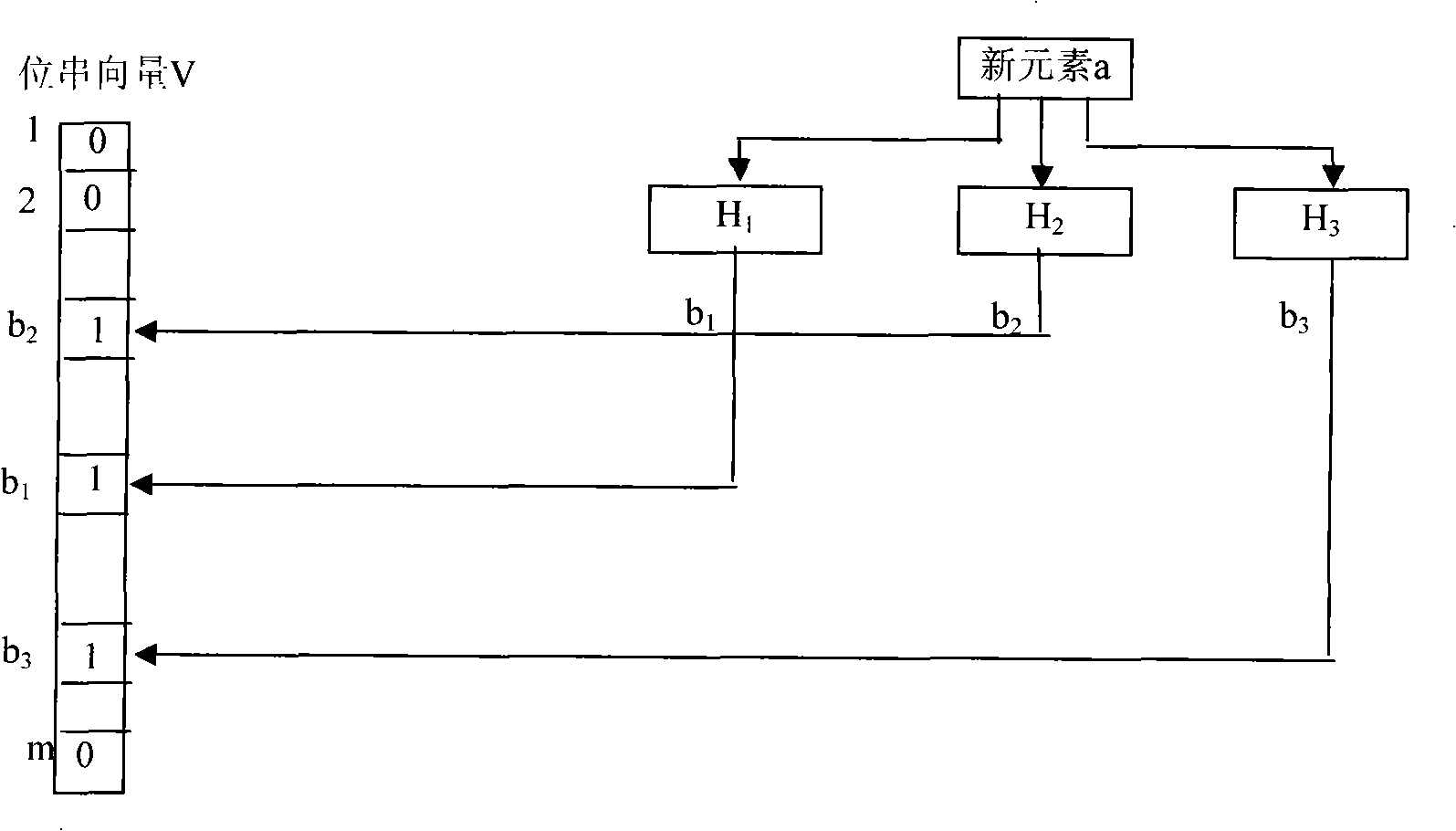
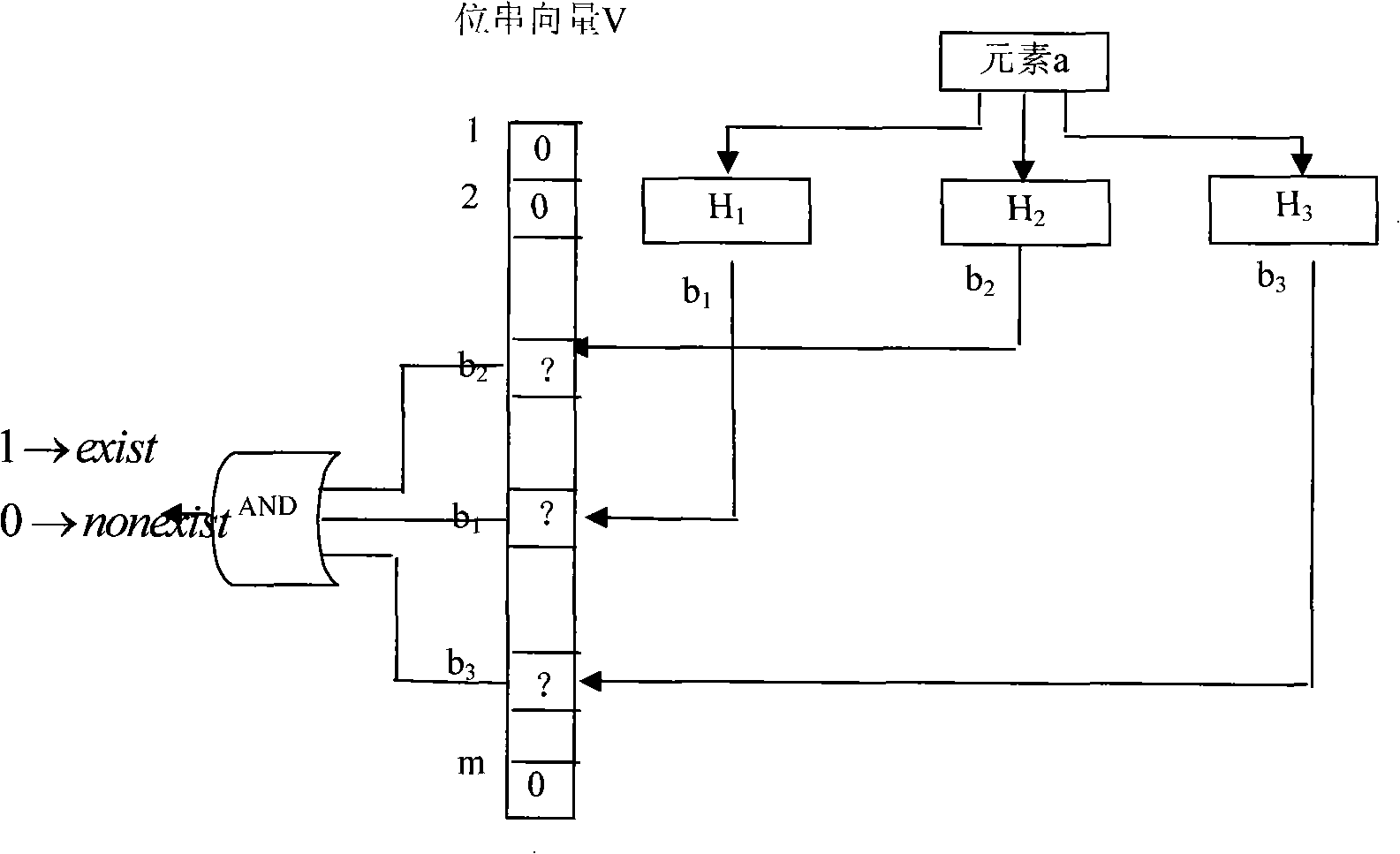
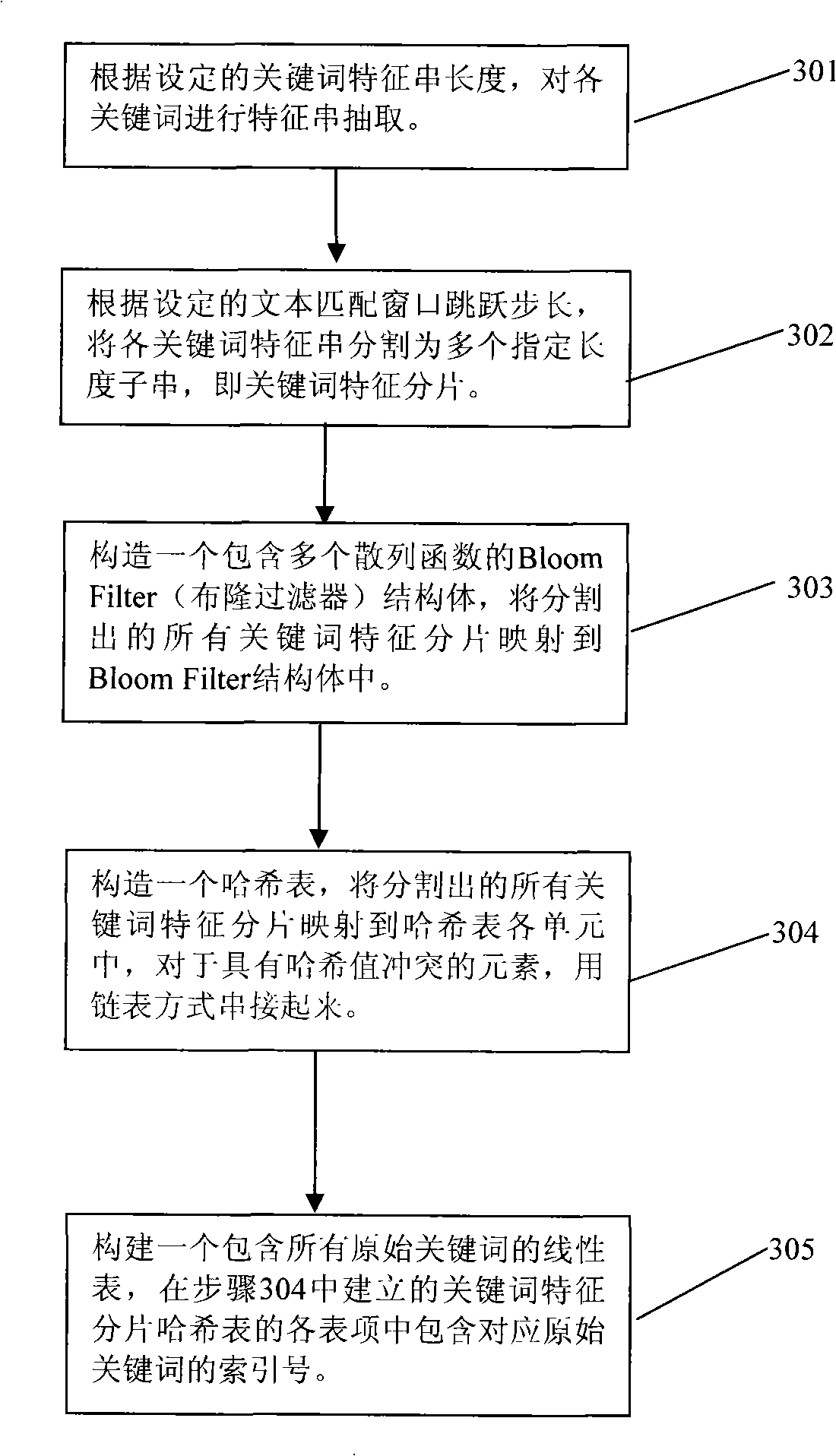
Multi-key-word matching method for rapidly analyzing content
The invention discloses a quick content analysis multi-keyword matching method which includes the preprocessing stage and the pattern matching stage; wherein, the preprocessing stage includes the keyword characteristic string clipping, the establishment of the keyword character segmentation set, the Bloom Filter (bloom filter) construction based on the keyword character segmentation set and the original keyword set linear table construction; the pattern matching stage includes the quick judgment that the text string in the current window is not matched with any keyword characteristic segmentation is realized according to the Bloom Filter; the accurate matching of the text string and the candidate keyword is realized through the character string comparison only under the situation that the quick judgment is failed; the text matching window skips in high speed with continuous multibytes. The quick content analysis multi-keyword matching method utilizes the very low success matching rate of the text for being matched and the keyword to realize the high-speed matching under the large quantity of keywords scene so that the multi-keyword matching method is very applicable to the online virus scanning application such as the virus detection.
Owner:BEIJING VENUS INFORMATION TECH
Android malicious act detection method based on Bayesian network
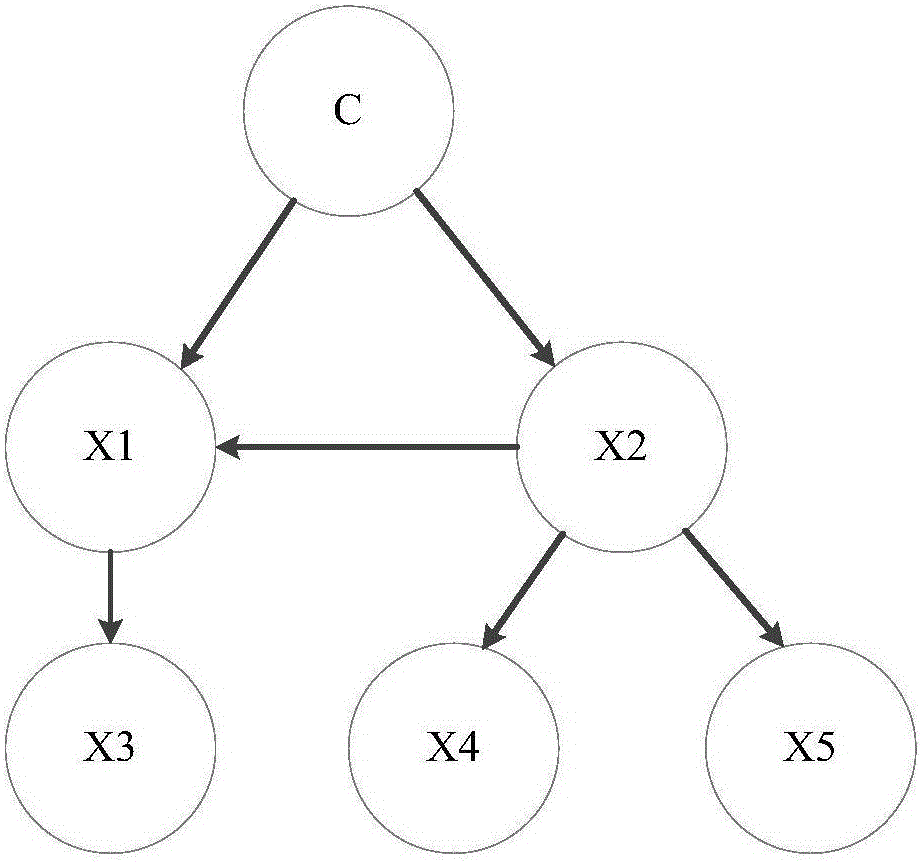
ActiveCN105740712APredicting the Impact of ClassificationEasy to usePlatform integrity maintainanceFeature extractionProbit
The invention discloses an Android malicious act detection method based on the Bayesian network.The method specifically comprises the steps of 1, conducting static feature extraction on an Android application training sample; 2, conducting feature processing, and calculating the correlation degree between feature and category with the chi-squared statistic feature selection approach; 3, establishing an Android software malicious act detection model based on the Bayesian network classification algorithm; 4, inputting an APK extraction feature to be detected into a well trained Bayesian network virus detection model, and calculating the posterior probability of the category of the feature; 5, comparing the two data obtained from the step 4 representing the posterior probability that the APK extraction feature to be detected belongs to the virus category and representing the posterior probability that the APK extraction feature to be detected belongs to the normal category respectively, and taking the category with larger posterior probability as the classification result of the application.The method can effectively detect Android malice applications and reduce the learning time of the Bayesian network to a certain degree.
Owner:HARBIN ENG UNIV
Virus detection system, method and computer program product for handheld computers
InactiveUS20080060075A1Memory loss protectionUnauthorized memory use protectionHand Held ComputerClient-side
A method and system are provided for updating software on a handheld computer in communication with a client computer system operable to connect to a network. Software installed on the handheld computer is identified with the client computer. Moreover, information on the identified software is transmitted from the client computer to a server connected to the network. Further, updated versions of the software installed on the handheld computer are transferred from the server to the client computer based on the identified software that is installed on the handheld computer. Still yet, the software installed on the handheld computer is updated with the updated versions transferred to the client computer.
Owner:MCAFEE LLC
Efficient breeding method of sugarcane health seedling
InactiveCN101361458AEasy to induceImprove survival rateMicrobiological testing/measurementPlant tissue cultureDiseaseShoot apex
The invention relates to a high-efficiency breeding method of healthy seedlings of cane, the method is proposed aiming at the problems that seed performance degenerates, yield is greatly reduced and the quality is reduced, which are caused by that the cane is taken as asexually propagated crop, propagation coefficient is low, the amount of seeds used for cane implantation is large, and after the implantation of a plurality of years, the cane is easy to be infected with a disease; improved type healthy seedlings of the cane can be cultured by nine steps of seedling mild water detoxication processing, seedling sprouting, in vitro peeling inoculation, induction culture, virus check, propagation culture, rootage culture, domesticated seedling-refining and outdoor temporary planting; the method adopts the combination of mild water detoxication and stem tip detoxication with thorough detoxication and good effect; the direct peeling inoculation of the explant does not need to be treated with disinfection processing, has low pollution rate and light browning, and is easy to generate clustering buds by induction; the propagation coefficient is high, the speed is high, the period is short; the seed performance is table, the seedling is strong; the virus detection is precise and accurate; the survival rate of the outdoor temporary planting is high and is up to more than 90 percent; the production cost is low, the efficiency is high, and the method is suitable for industrialized production.
Owner:SUGARCANE RES INST OF YUNNAN ACADEMY OF AGRI SCI
System and method for identifying message propagation
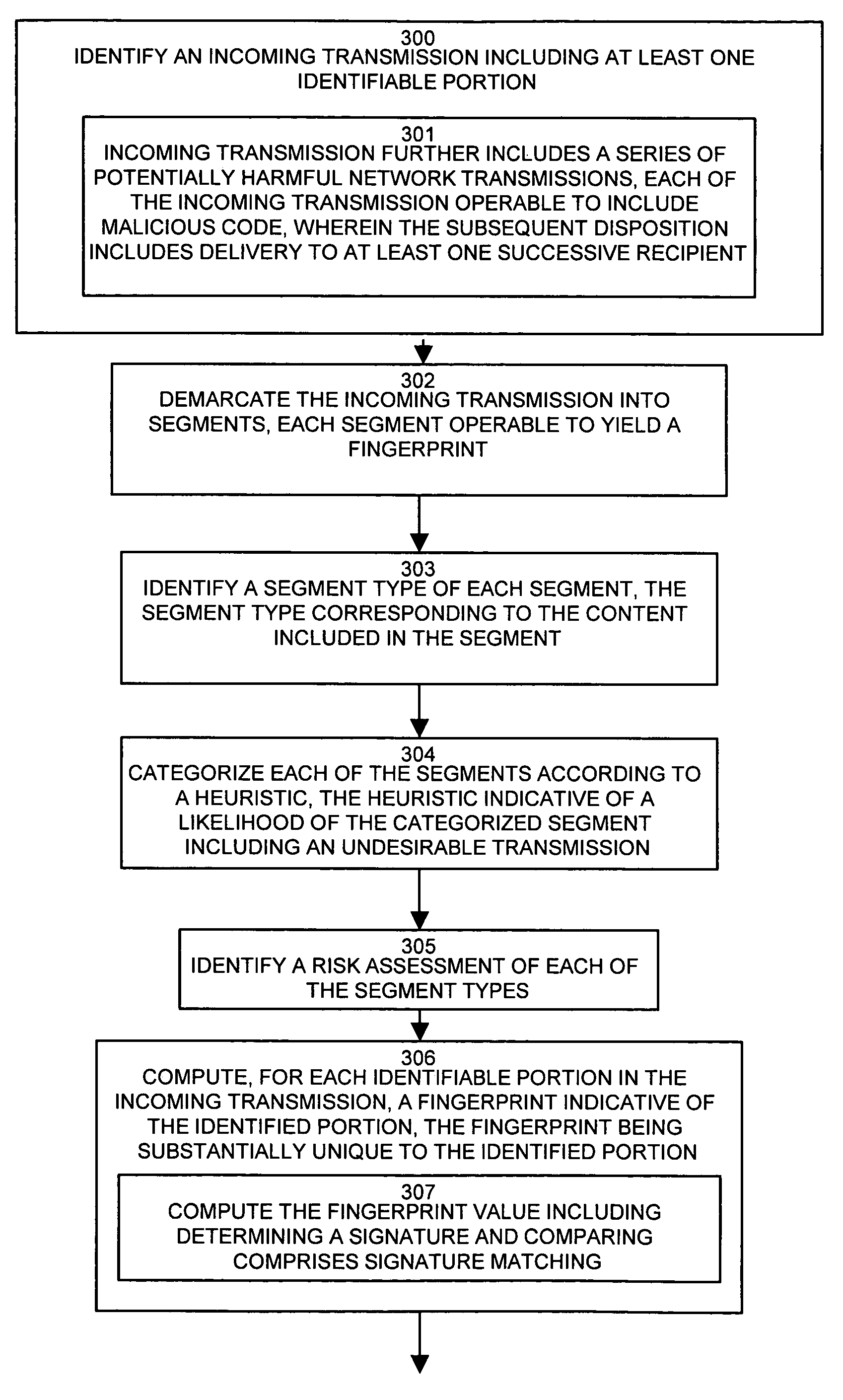
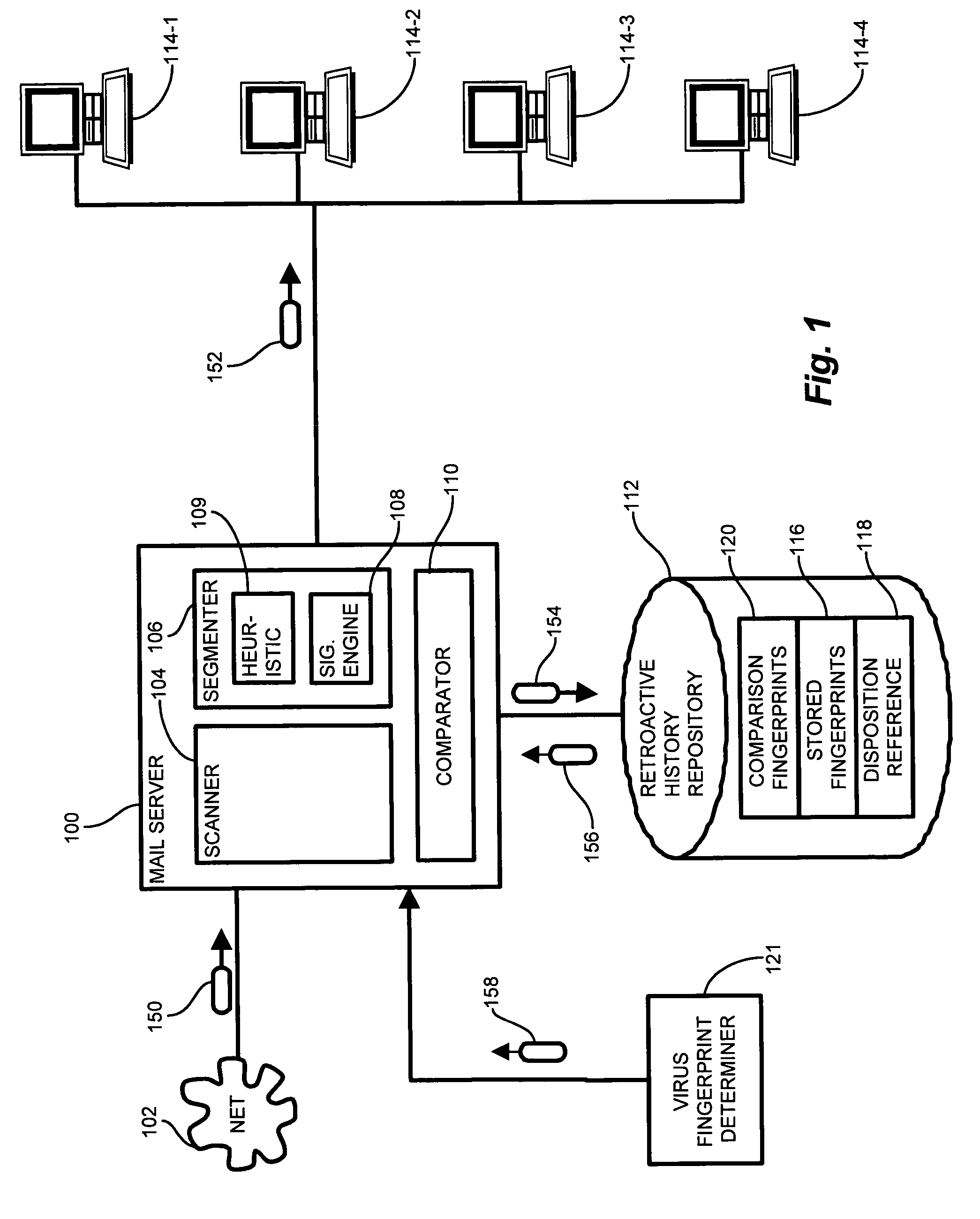
ActiveUS7539871B1Overcomes shortcomingShorten the overall cycleUser identity/authority verificationComputer security arrangementsRemedial actionComputer science
Conventional virus detection software monitors incoming arrivals of network traffic. Retroactive analysis and / or monitoring of previously accepted traffic is not included in the scope of protection. A retroactive virus detection and propagation history tracking mechanism provides identification of successive recipients of a newly discovered virus which may have eluded detection during the lag time prior to effecting the detection of a new virus. A propagation history maintains a set of recipients receiving a potentially harmful transmission. Upon detection of a particular transmission or portion thereof as being a virus, the propagation history contains a set of infected recipients, which the tracking mechanism notifies so as to perform remedial action and contain the virus to the known set of infected recipients. In this manner, configurations of the invention maintain a set of successive recipients of a virus, and retroactively track and contain the newly propagated virus once detected.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com