Network enciphered data virus detection and elimination system and proxy server and method
A proxy server and virus detection technology, applied in the field of network security, can solve the problems that data cannot be checked and attacked, and achieve the effect of reducing the spread of viruses and eliminating the risk of leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
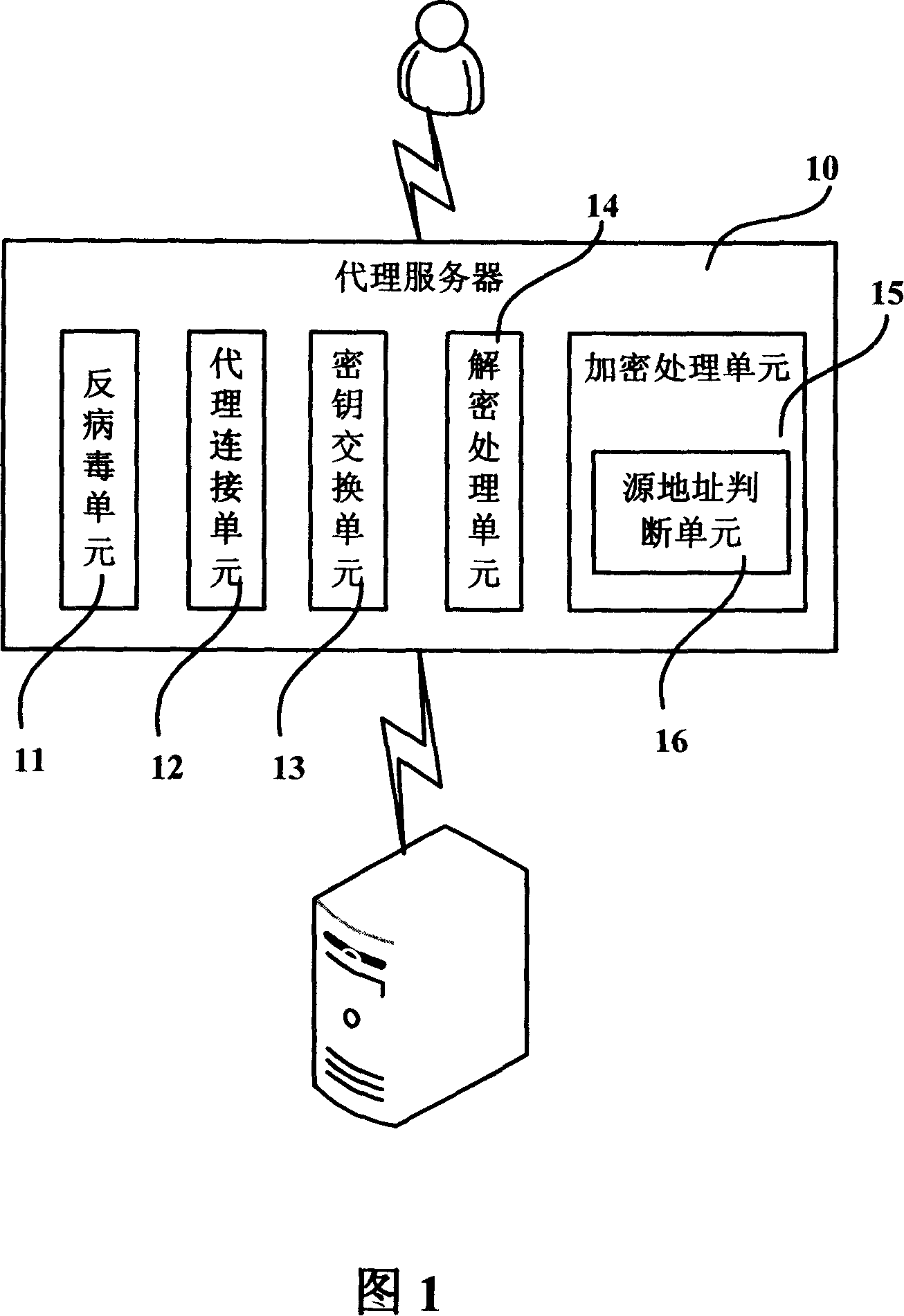
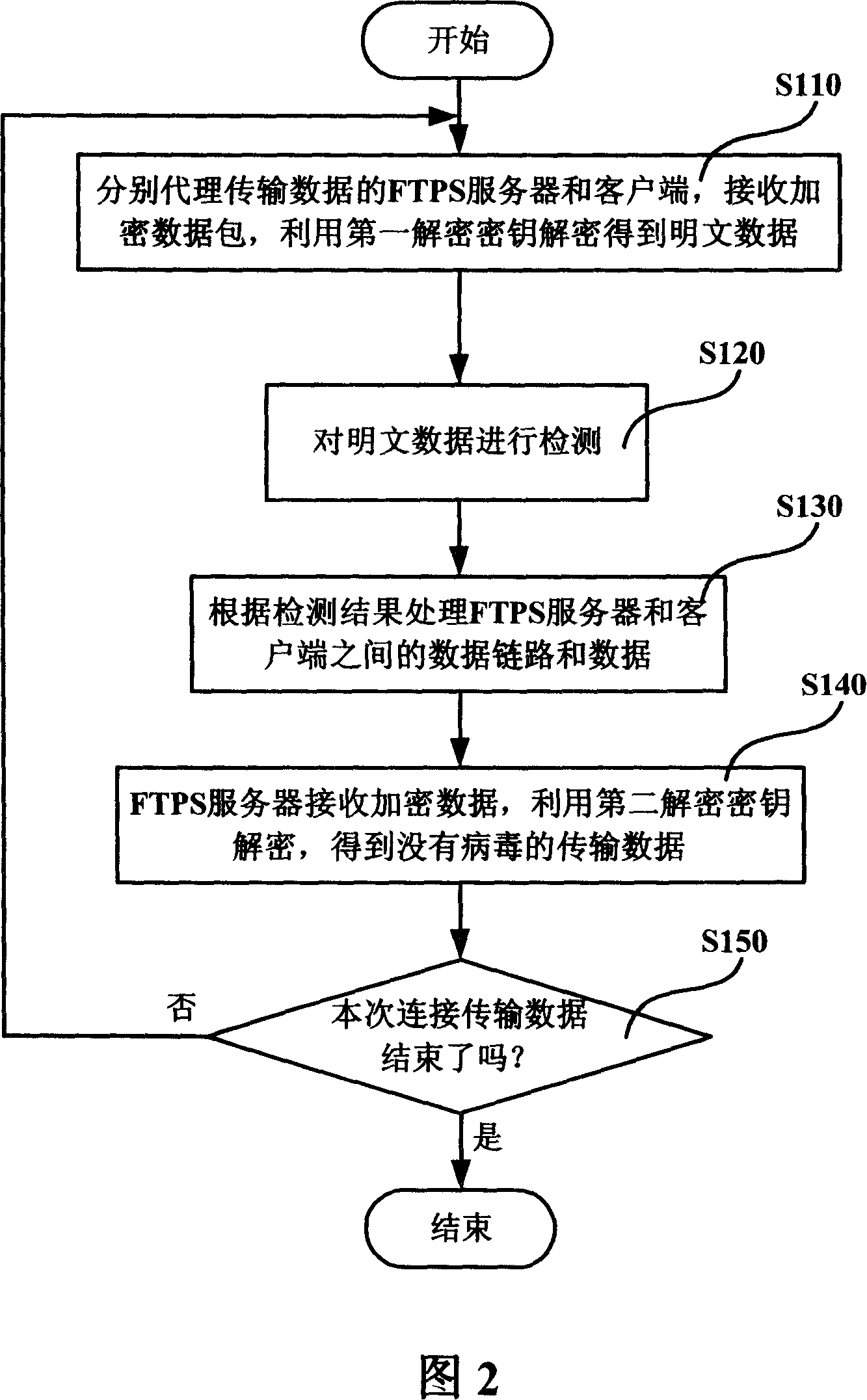
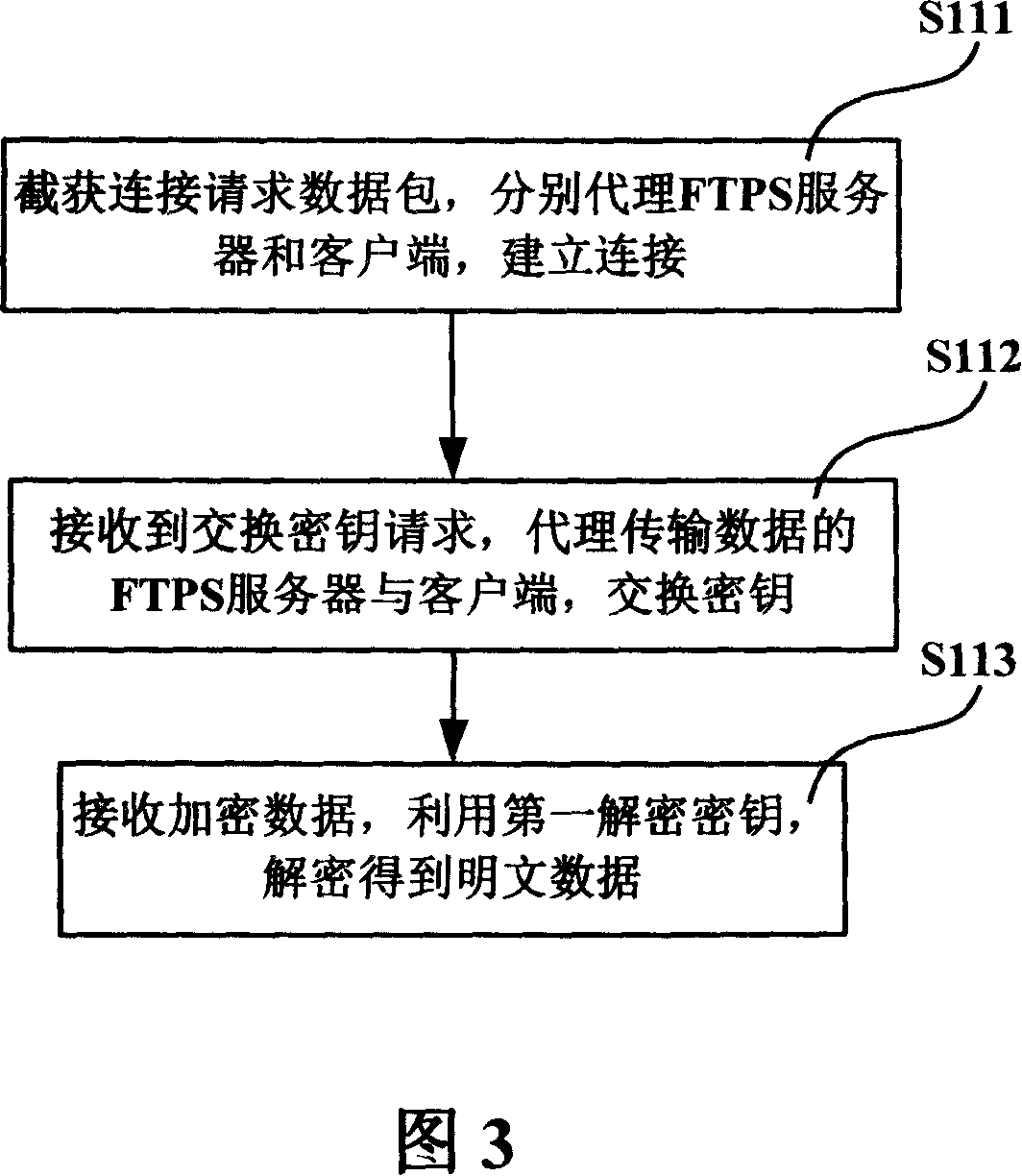
[0086] In the method for network encrypted data virus detection and elimination in Embodiment 1 of the present invention, when the encrypted FTPS protocol data passes through the FTPS proxy server 10, the FTPS proxy server 10 decrypts it into plaintext data, and performs virus detection on the plaintext data According to the detection result, the connection communication link between the FTPS server and the client is processed; for the plaintext data without virus, the FTPS proxy server 10 encrypts the plaintext data again and transmits it to the FTPS server.
[0087] FTPS is an enhanced TFP protocol that uses the standard FTP protocol and instructions in the secure socket layer, adding SSL security functions to the FTP protocol and data channels. FTPS is also known as "FTP-SSL" and "FTP-over-SSL".
[0088] FTP refers to the file transfer protocol, namely File Transfer Protocol, referred to as FTP, is a protocol used to transfer files from one host to another host. The FTP pr...
Embodiment 2
[0123] The method for network encrypted data virus detection and elimination in the embodiment of the present invention two, when encrypted SMTPS protocol data passes through SMTPS proxy server 10, SMTPS proxy server 10 decrypts it into plaintext data; SMTPS proxy server 10 to described plaintext data Carry out virus detection and removal, and process the connection communication link between the SMTPS server and the client according to the detection and elimination results; For the plaintext data that has no virus or virus elimination, the SMTPS proxy server 10 encrypts the plaintext data again and transmits it to SMTPS server.
[0124] SMTPS (SMTP protocol over TLS / SSL), is a simple mail transfer protocol (SMTP, Simple Mail Transfer Protocol) through the secure socket layer, and is an enhanced SMTP protocol that uses standard SMTP protocols and instructions at the secure socket layer , adding SSL security features to the SMTP protocol and data channels. SMTP provides a reli...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com