Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2507 results about "Security check" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
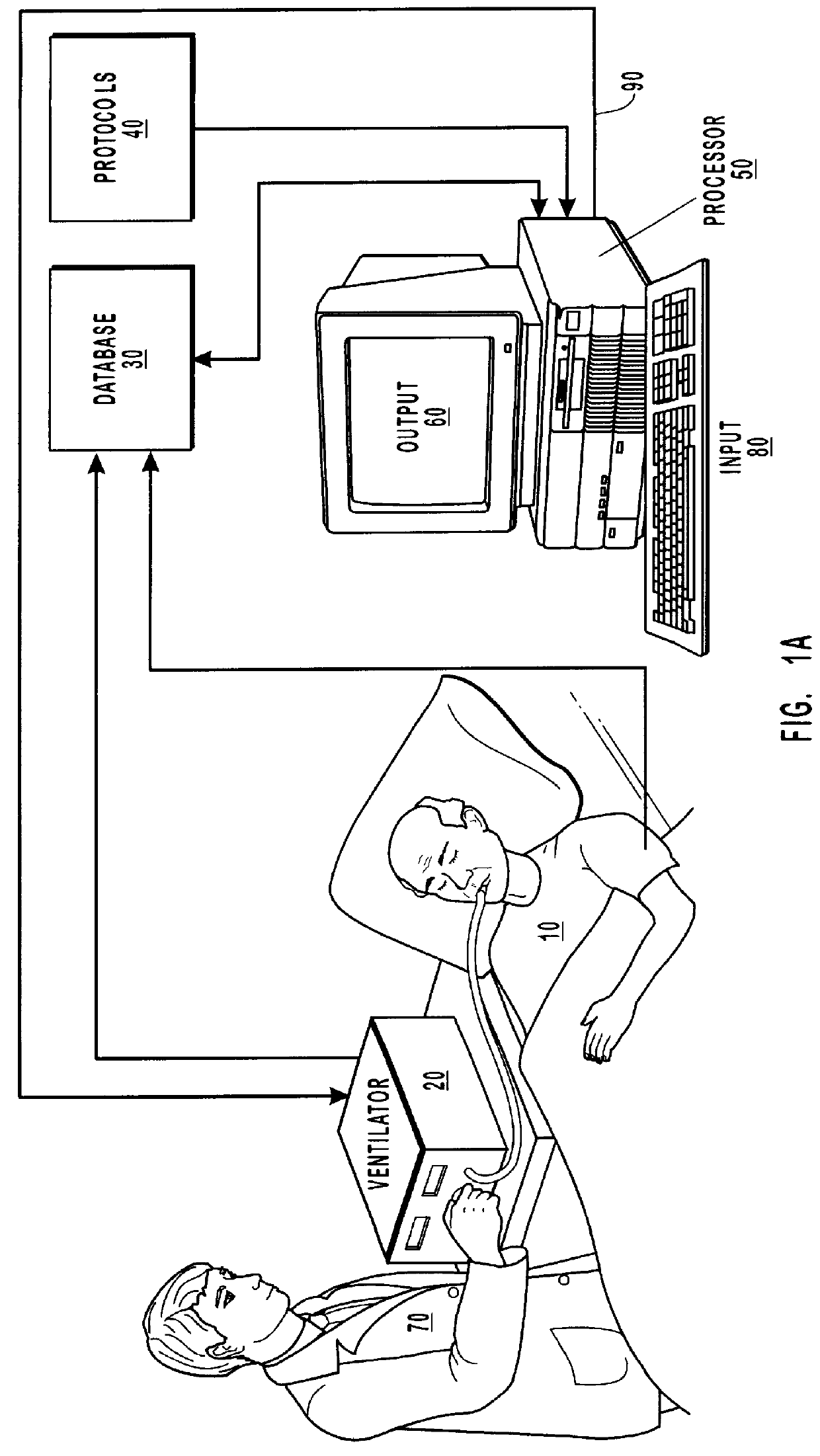
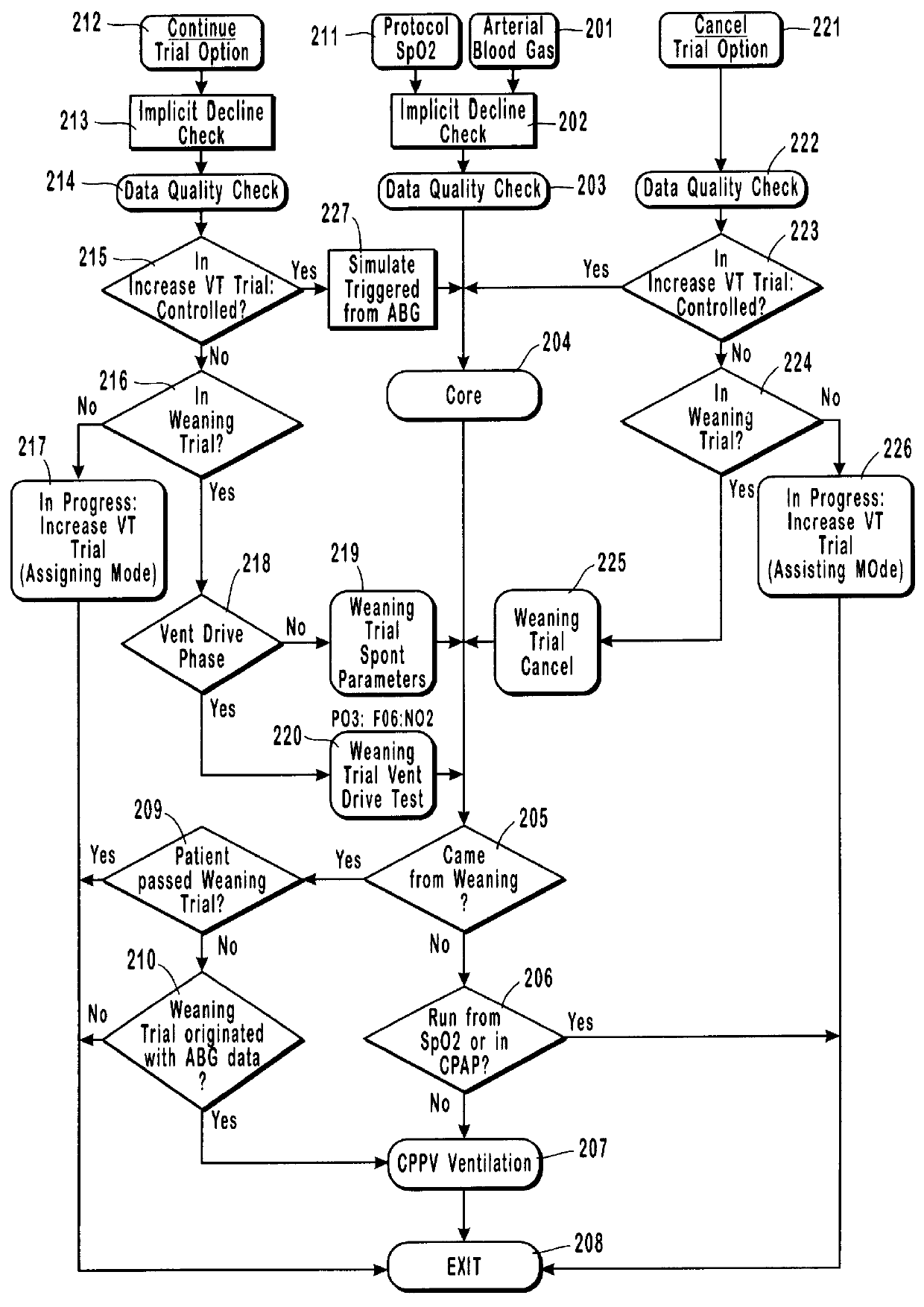
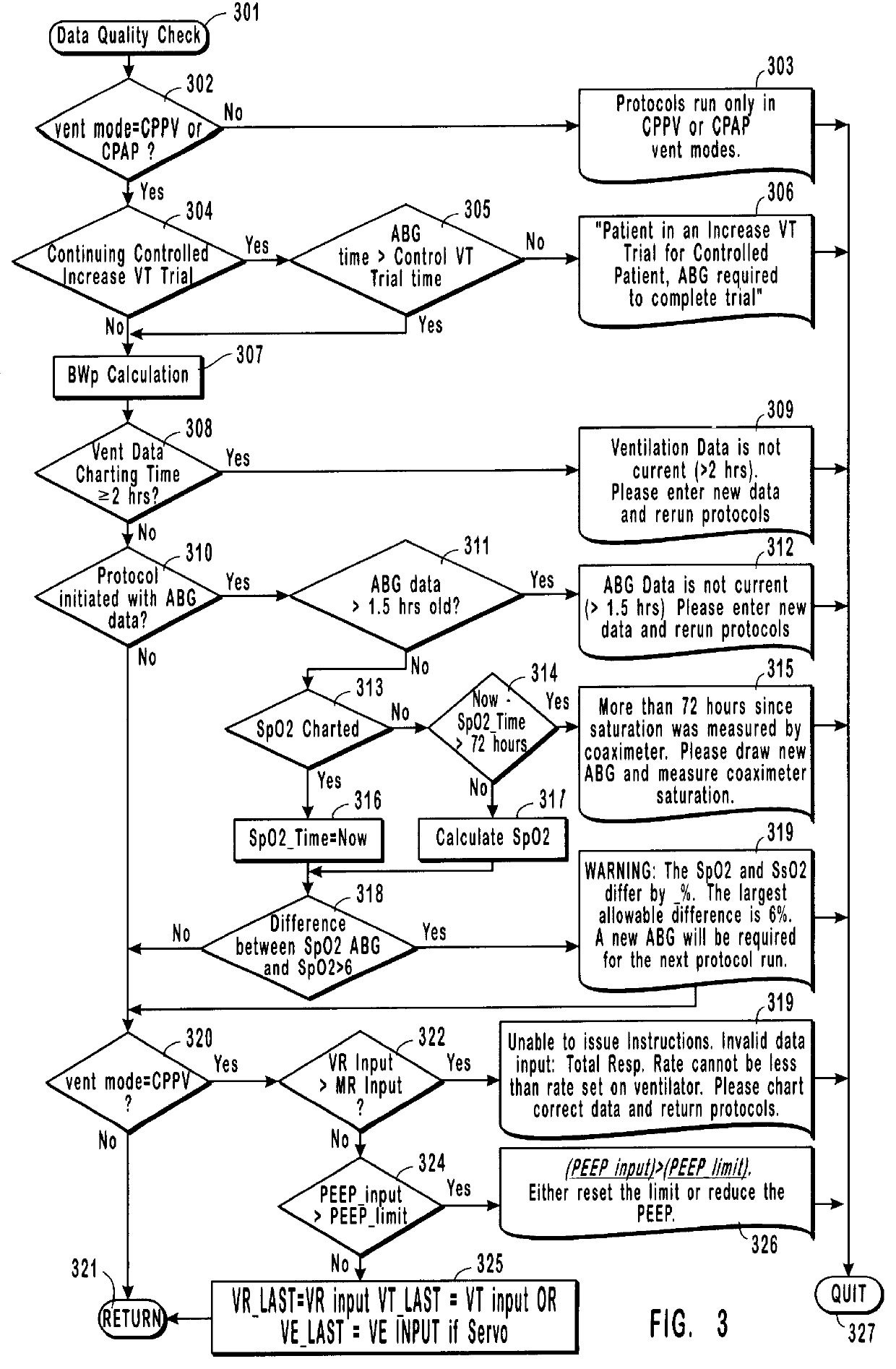
Method and system for patient monitoring and respiratory assistance control through mechanical ventilation by the use of deterministic protocols
InactiveUS6148814AReducing ventilator rateRelieve pressureRespiratorsBreathing masksDiseaseClinical staff
A method and system for managing mechanical ventilation of patients with respiratory disorders is described. The main objective of the system is to generate executable instructions for patient care which take into account a large number of parameters of patient condition and ventilation. Data regarding the state of the patient are stored in a database. Patient data are processed according to a set of protocols which contain rules for patient care decisions arranged in a logical sequence to generate detailed, executable instructions for patient care. Instructions are updated when new data are entered into the database. The data can be acquired in an automated fashion, or the clinician can be instructed to collect and enter new data into the clinical database. Likewise, patient care instructions can be carried out automatically or manually, but it is preferred that instructions are carried out manually as a safety check. The preferred embodiment of the invention includes a computer system, software for processing patient data, and a display device for presenting patient care instructions to the clinician. The system maintains a record of patient data, patient care instructions, whether instructions were followed by the clinical staff, and if not, a reason why.
Owner:INTERMOUNTAIN INTELLECTUAL ASSET MANAGEMENT LLC
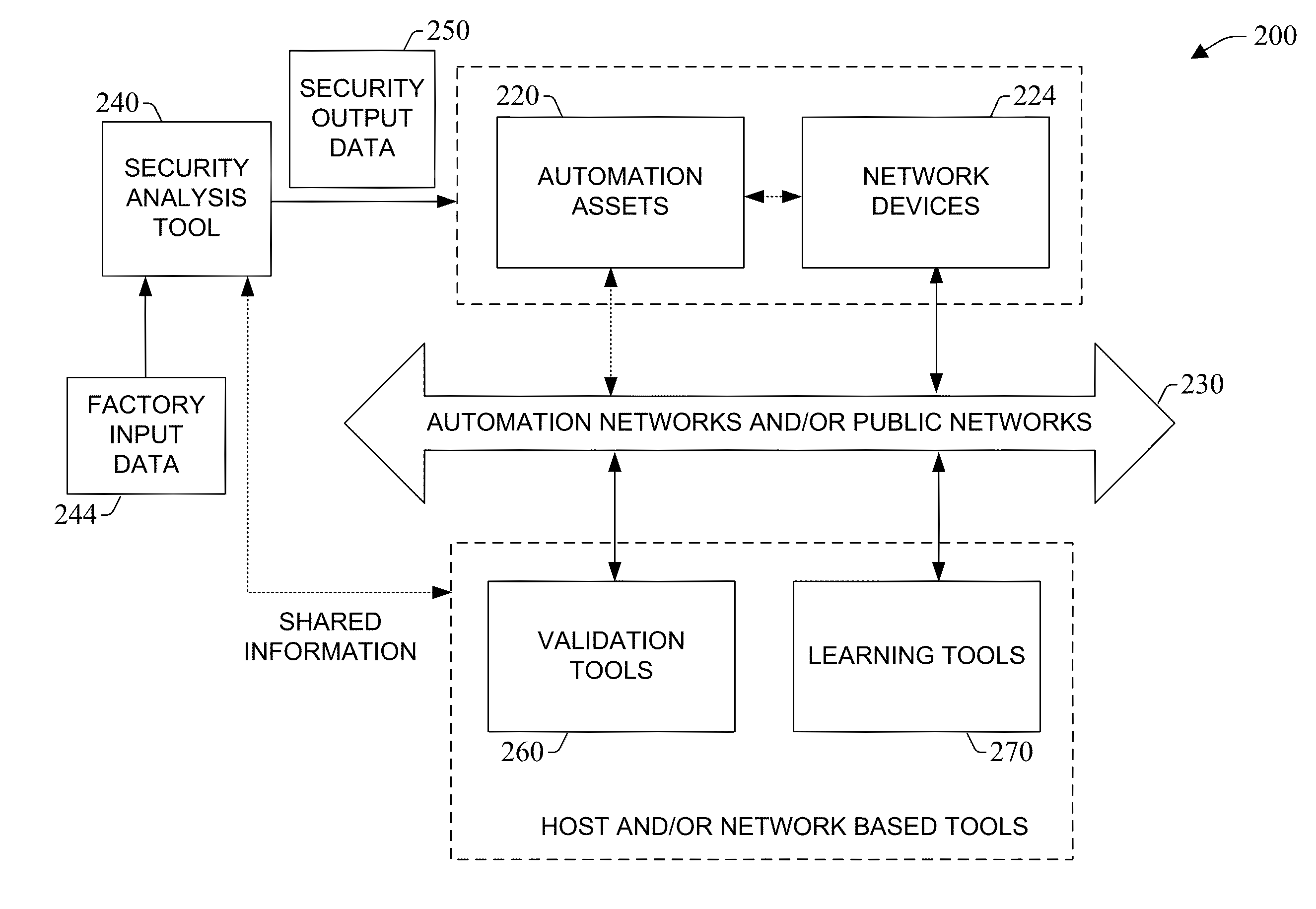
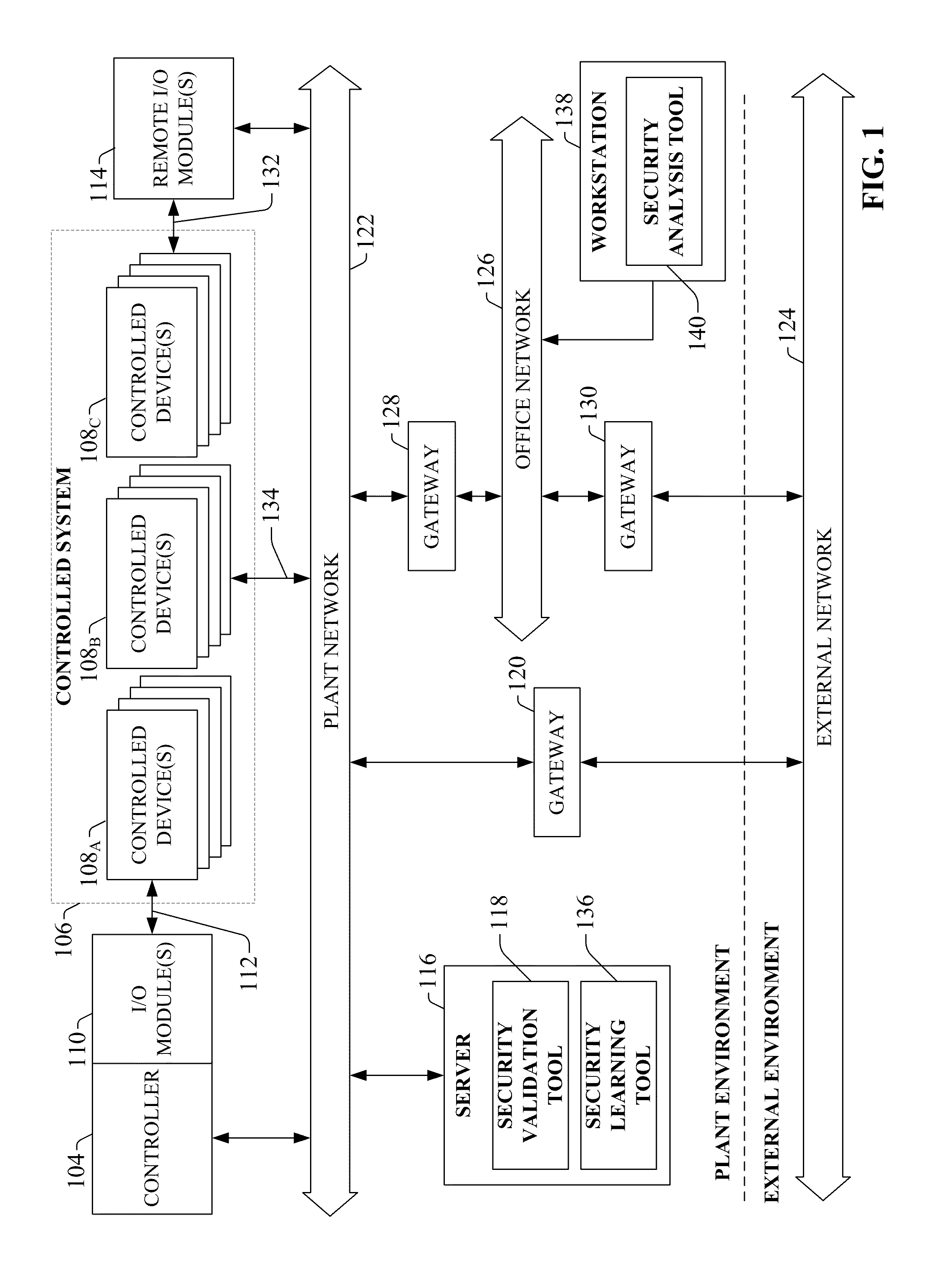
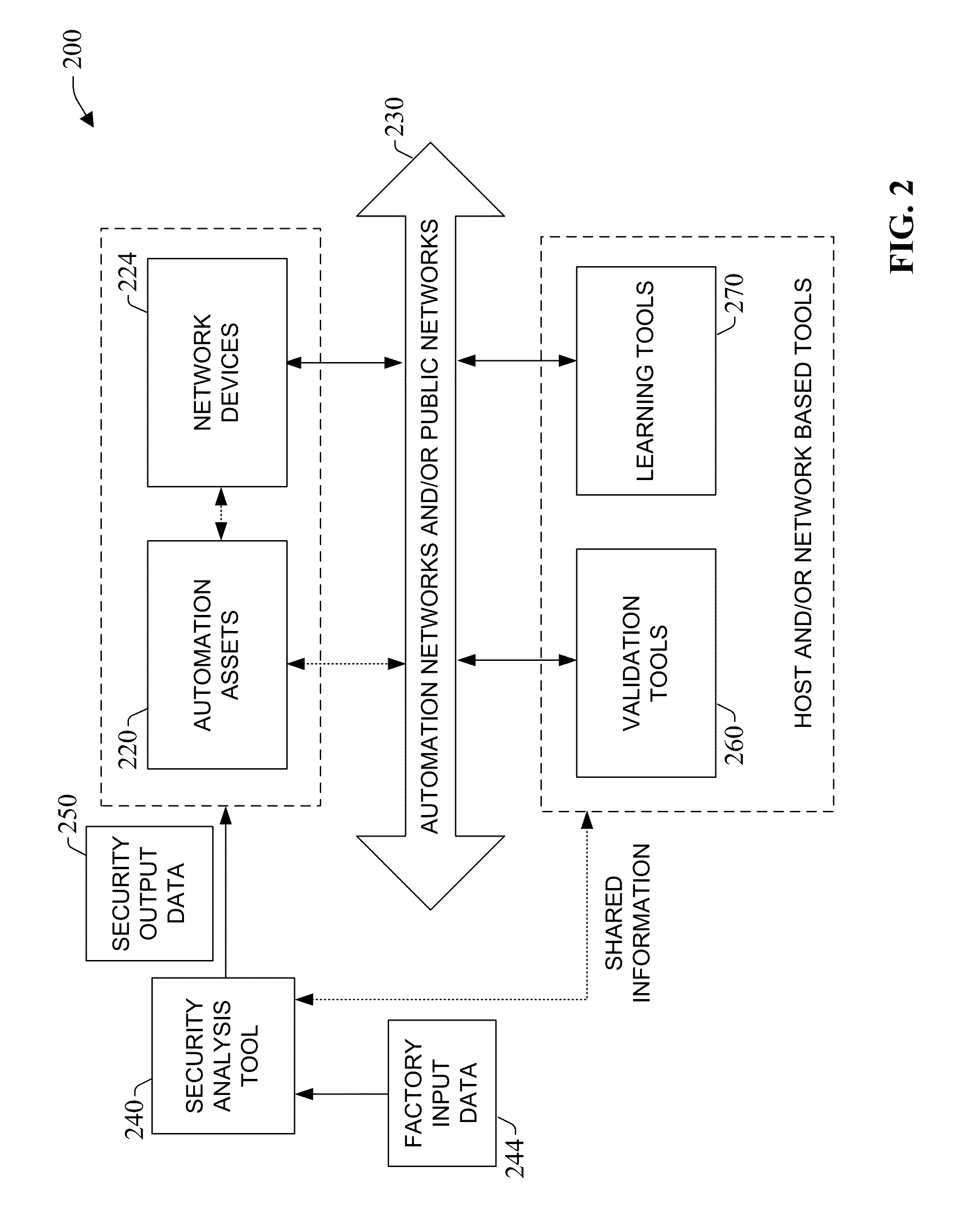
System and methodology providing automation security analysis and network intrusion protection in an industrial environment
ActiveUS20130031037A1Improve integrityFacilitate privacyProgramme controlComputer controlGuidelineEngineering
The present invention relates to a system and methodology facilitating automation security in a networked-based industrial controller environment. Various components, systems and methodologies are provided to facilitate varying levels of automation security in accordance with security analysis tools, security validation tools and / or security learning systems. The security analysis tool receives abstract factory models or descriptions for input and generates an output that can include security guidelines, components, topologies, procedures, rules, policies, and the like for deployment in an automation security network. The validation tools are operative in the automation security network, wherein the tools perform security checking and / or auditing functions, for example, to determine if security components are in place and / or in suitable working order. The security learning system monitors / learns network traffic patterns during a learning phase, fires alarms or events based upon detected deviations from the learned patterns, and / or causes other automated actions to occur.
Owner:ROCKWELL AUTOMATION TECH
Systems and methods for providing access to wireless gaming devices
ActiveUS7644861B2Digital data authenticationApparatus for meter-controlled dispensingComputer networkSecurity check
Systems and methods for controlling access to wireless gaming devices and networks are provided. For example, access is controlled through one or more levels of security check, such as a hard security check instead of or in addition to a soft security check. In a hard security check, the user employs an apparatus such as a card or other physical token that can be used to access the wireless gaming device. Such an apparatus may communicate information that identifies the user to the device or may simply be used to produce a signal without which the device is locked to users.
Owner:CFPH LLC
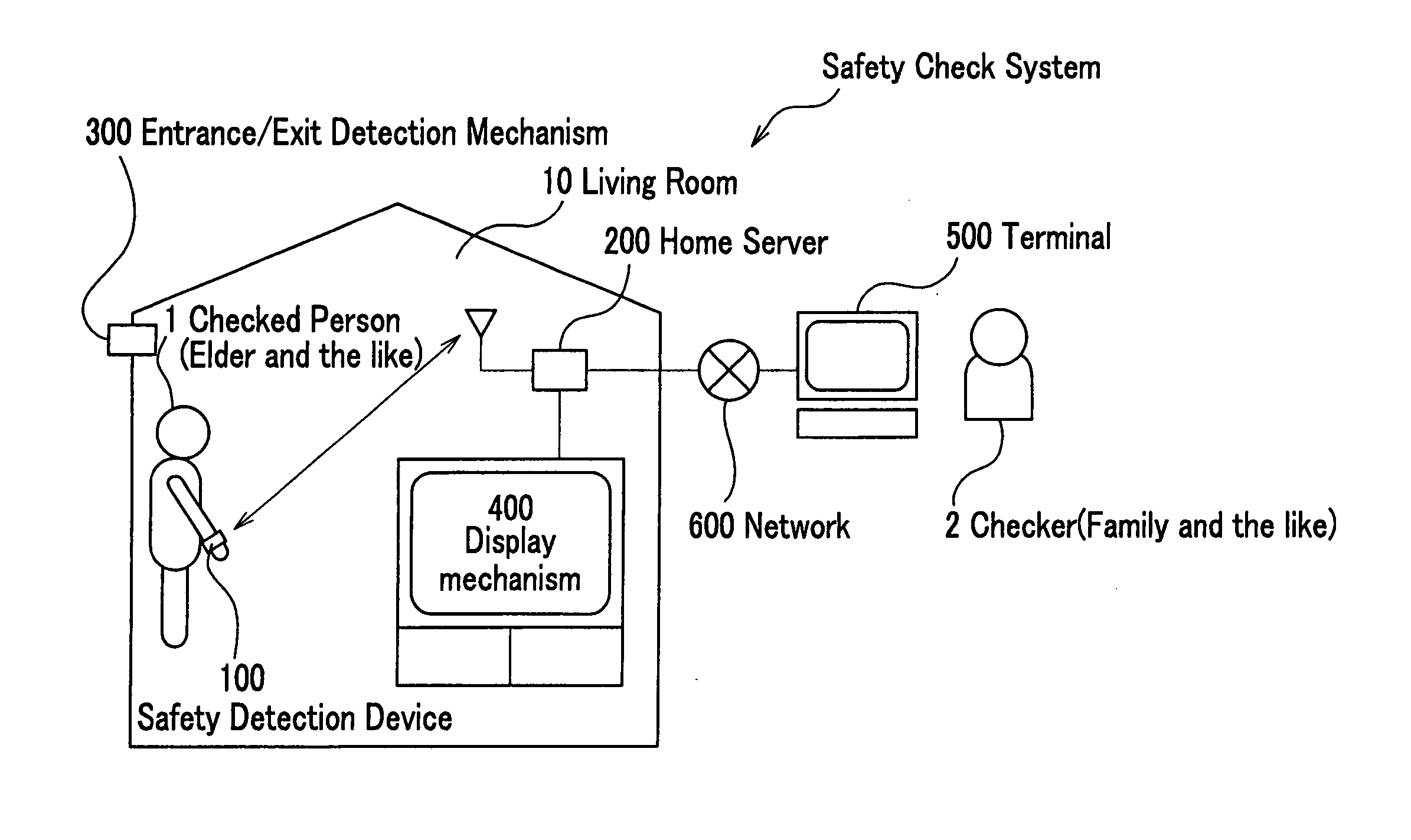
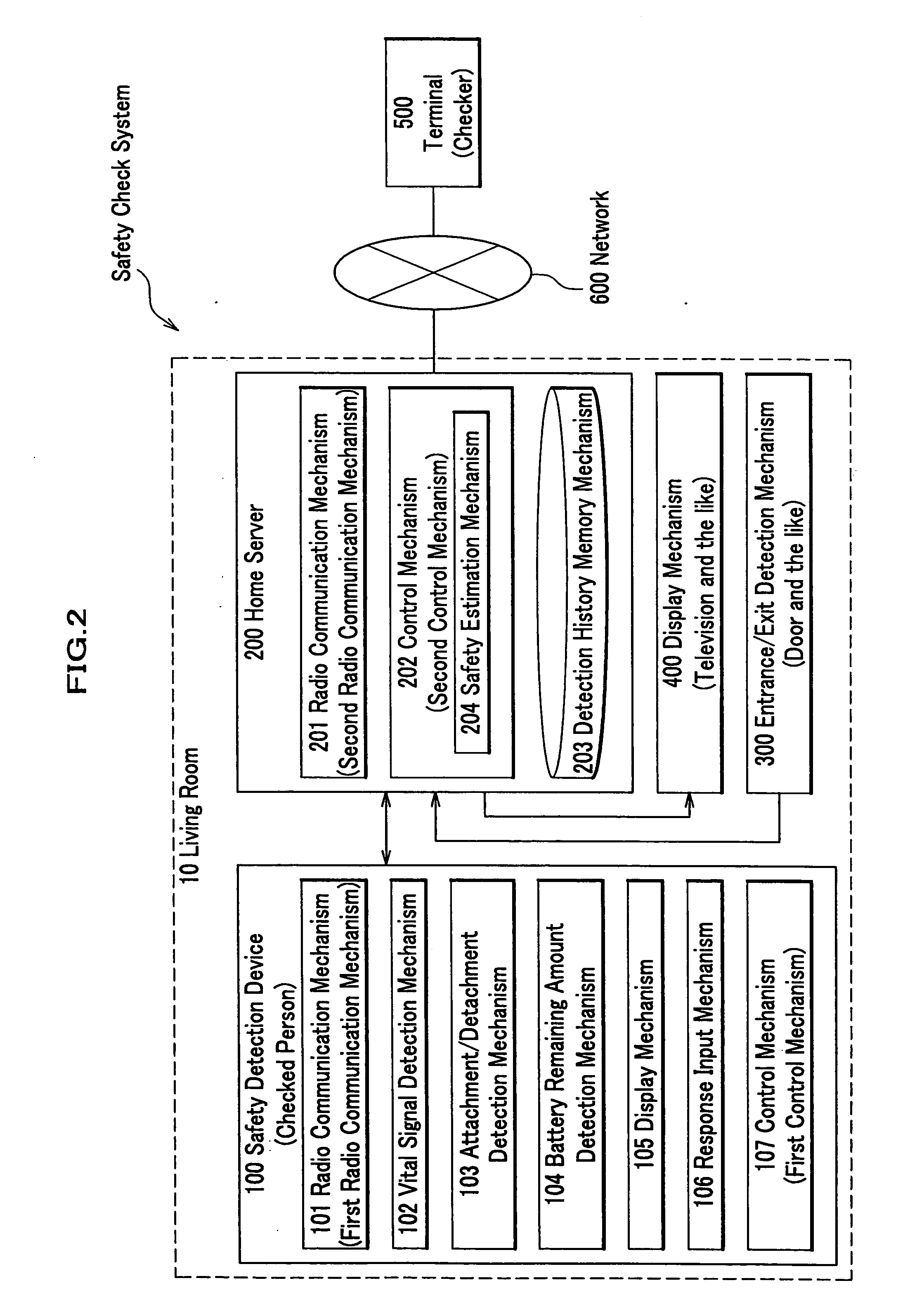
Safety check system, method, and program, and memory medium for memorizing program therefor
A safety check system of the invention is equipped with a safety detection device attached to a body of a checked person, a server for accumulating various pieces of information, and a terminal of a checker for executing a safety check of the checked person, wherein the detection device is equipped with a first radio communication mechanism for making a radio communication with the server, a vital signal detection mechanism for detecting a vital signal of the checked person, and a first control mechanism for creating safety information of the checked person; and the server is equipped with a second radio communication mechanism for making a radio communication with the detection device, a detection history memory mechanism for memorizing a detection history of the checked person, and a second control mechanism for sending the detection history of the checked person in the detection history memory mechanism to the terminal.
Owner:HITACHI LTD
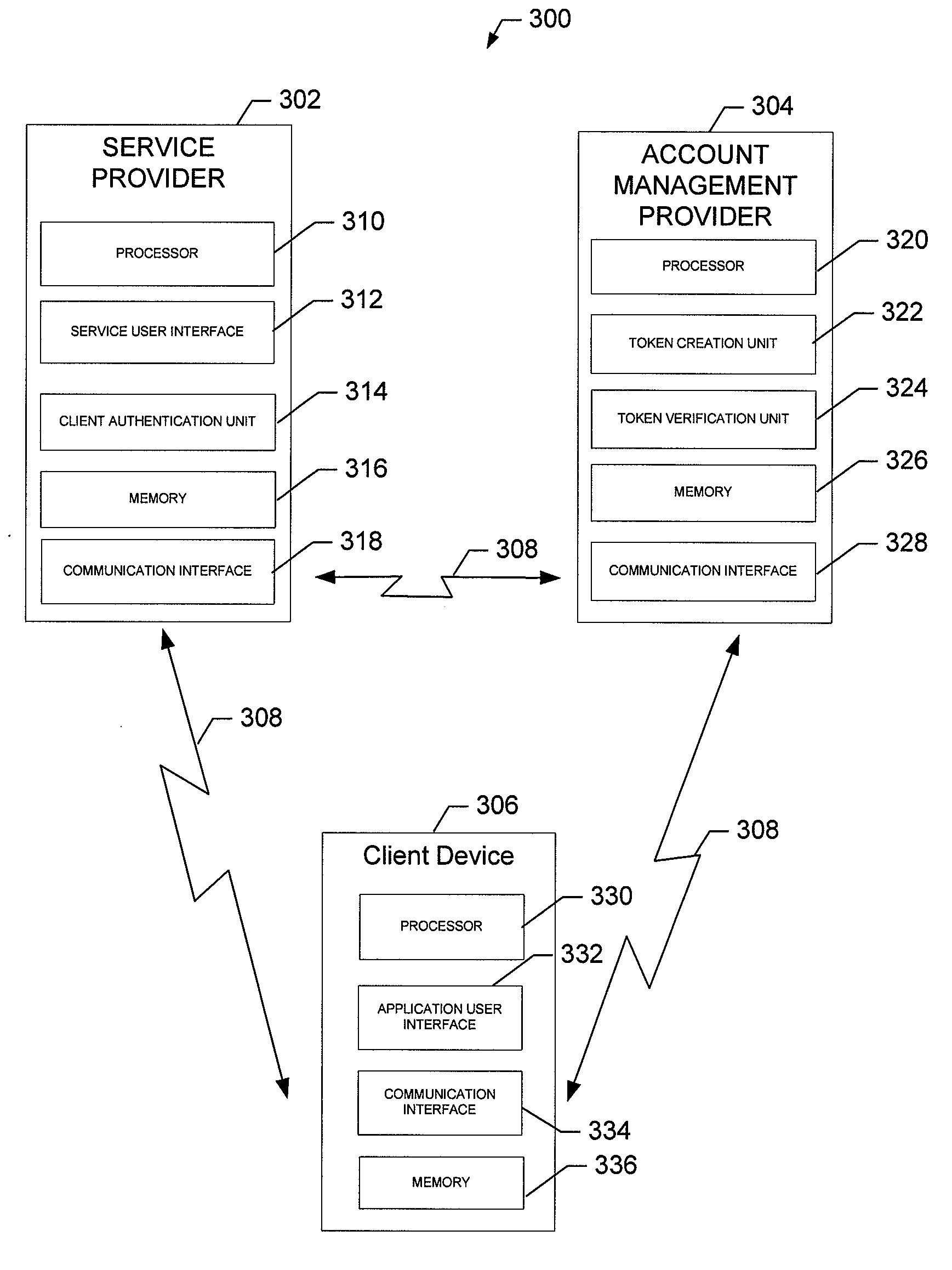
Methods, Apparatuses, and Computer Program Products for Providing a Single Service Sign-On
InactiveUS20090271847A1Enhanced interactionImprove securityDigital data processing detailsUser identity/authority verificationPasswordSecret code
An apparatus may include a processor configured to receive a request for an access token from a remote entity, wherein the request includes an indication of a requested service. The processor may be further configured to determine a request type, wherein the request type may be a user identification and password combination, a request token exchange, or an access token exchange. The processor may be additionally configured to extract one or more parameters included in the request based upon the determined request type and to perform one or more security checks based at least in part upon the one or more extracted parameters. The processor may be further configured to create an access token based at least in part upon the results of the one or more security checks and to provide the access token to the remote entity.
Owner:NOKIA TECHNOLOGLES OY
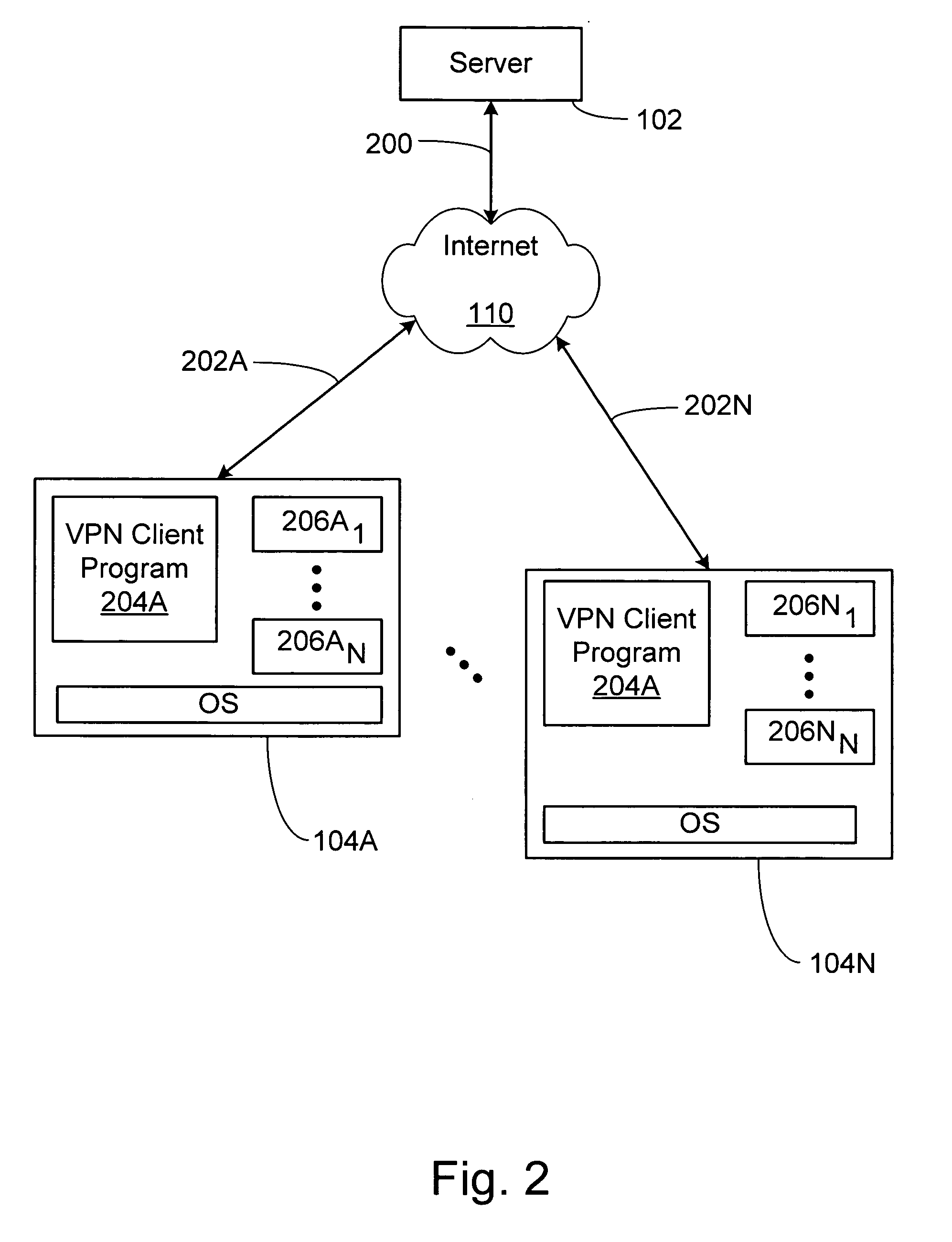
System and method for secure network connectivity
InactiveUS20070101405A1Accurate protectionConnection securityRandom number generatorsMemory loss protectionSecurity checkRemote computer
A system and method to ensure that a remote computer making a VPN connection complies with network security policies. Server-driven security checks may be configured to verify compliance with each access level before access is granted at that level. The security checks may be selected based at least according to the information received from the remote computer. After the server determines that the remote computer complies with the security policy for the requested access level, the server may pass a token to the remote computer, or may grant VPN access to the remote computer. If the remote computer does not comply with the security policy associated with the requested access level but is in compliance with a security policy corresponding to a lower access level, the server may grant the remote computer access to the lower access level.
Owner:BARCLAYS CAPITAL INC
Systems and methods for providing access to wireless gaming devices
ActiveUS20070241187A1Digital data authenticationApparatus for meter-controlled dispensingComputer hardwareSecurity check
Systems and methods for controlling access to wireless gaming devices and networks are provided. For example, access is controlled through one or more levels of security check, such as a hard security check instead of or in addition to a soft security check. In a hard security check, the user employs an apparatus such as a card or other physical token that can be used to access the wireless gaming device. Such an apparatus may communicate information that identifies the user to the device or may simply be used to produce a signal without which the device is locked to users.
Owner:CFPH LLC
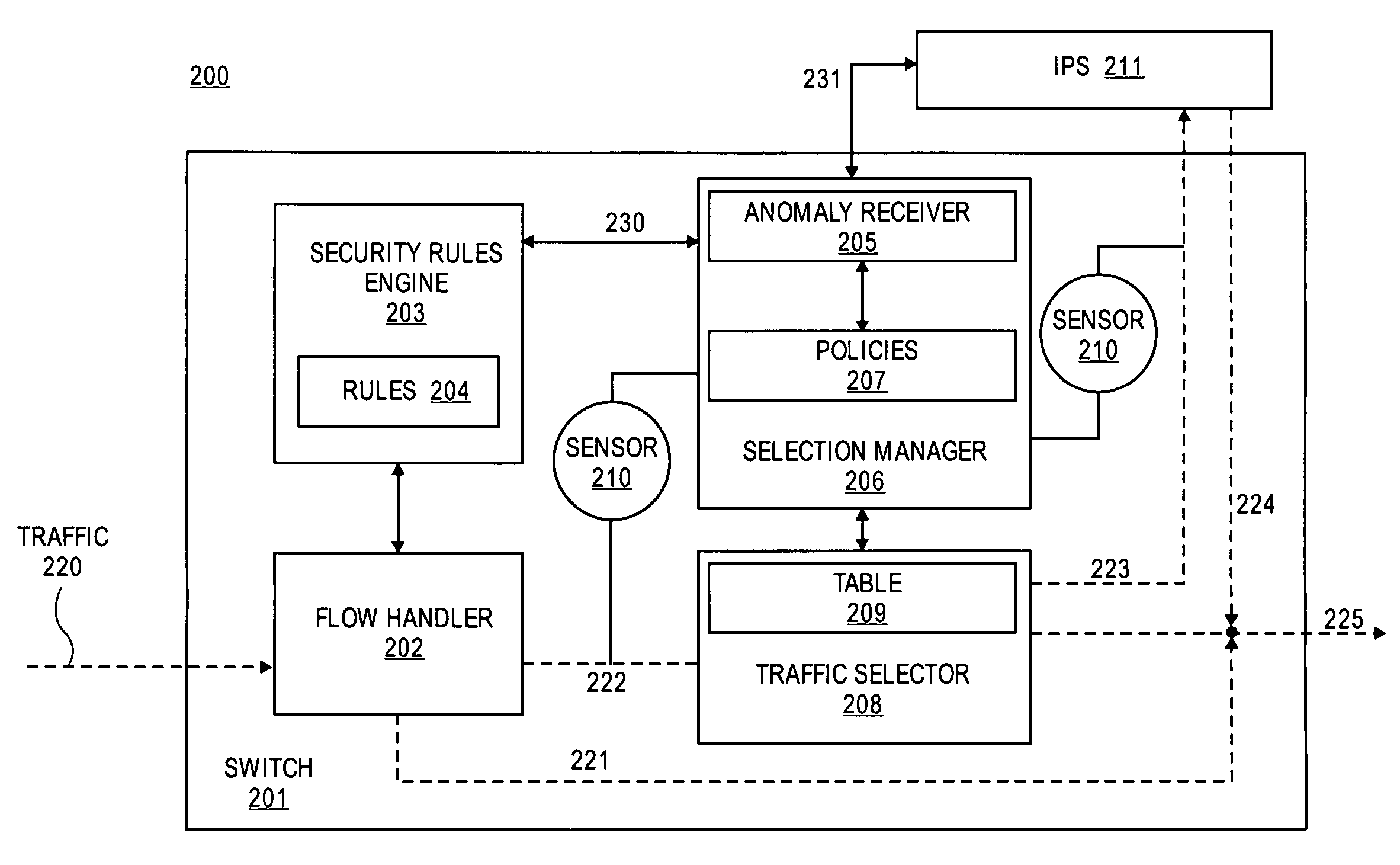
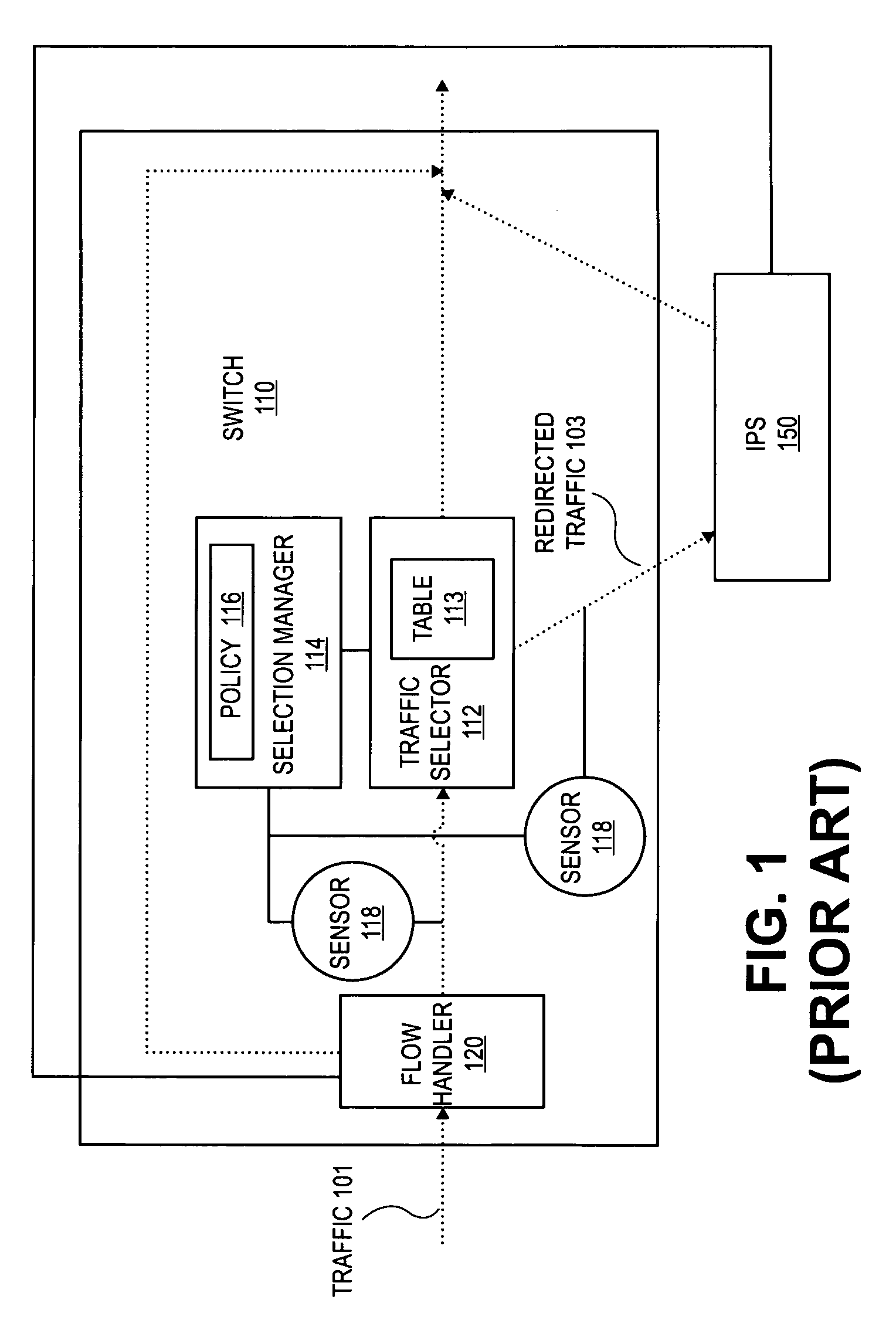
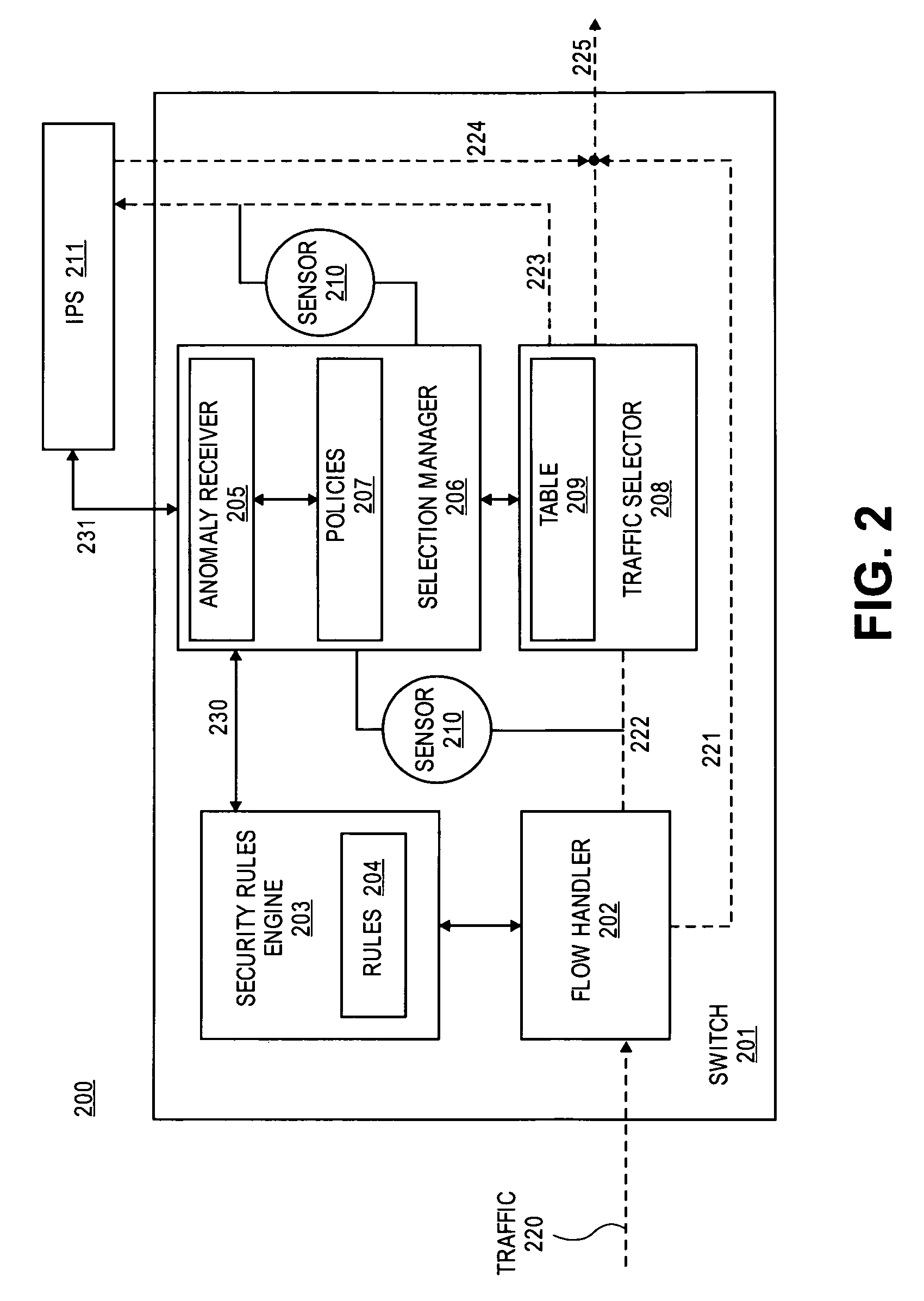
Method and apparatus for dynamic anomaly-based updates to traffic selection policies in a switch
ActiveUS20080163333A1Multiplex system selection arrangementsMemory loss protectionTraffic capacityComputer network
Techniques and architectures to dynamically modify policies used to determine how data in switched network traffic is selected for security inspection. One embodiment of the invention modifies policies used to determine how data in network traffic is redirected from a switch to an intrusion prevention system, without the policy modifications interrupting the handling of network traffic by the switch.
Owner:EXTREME NETWORKS INC
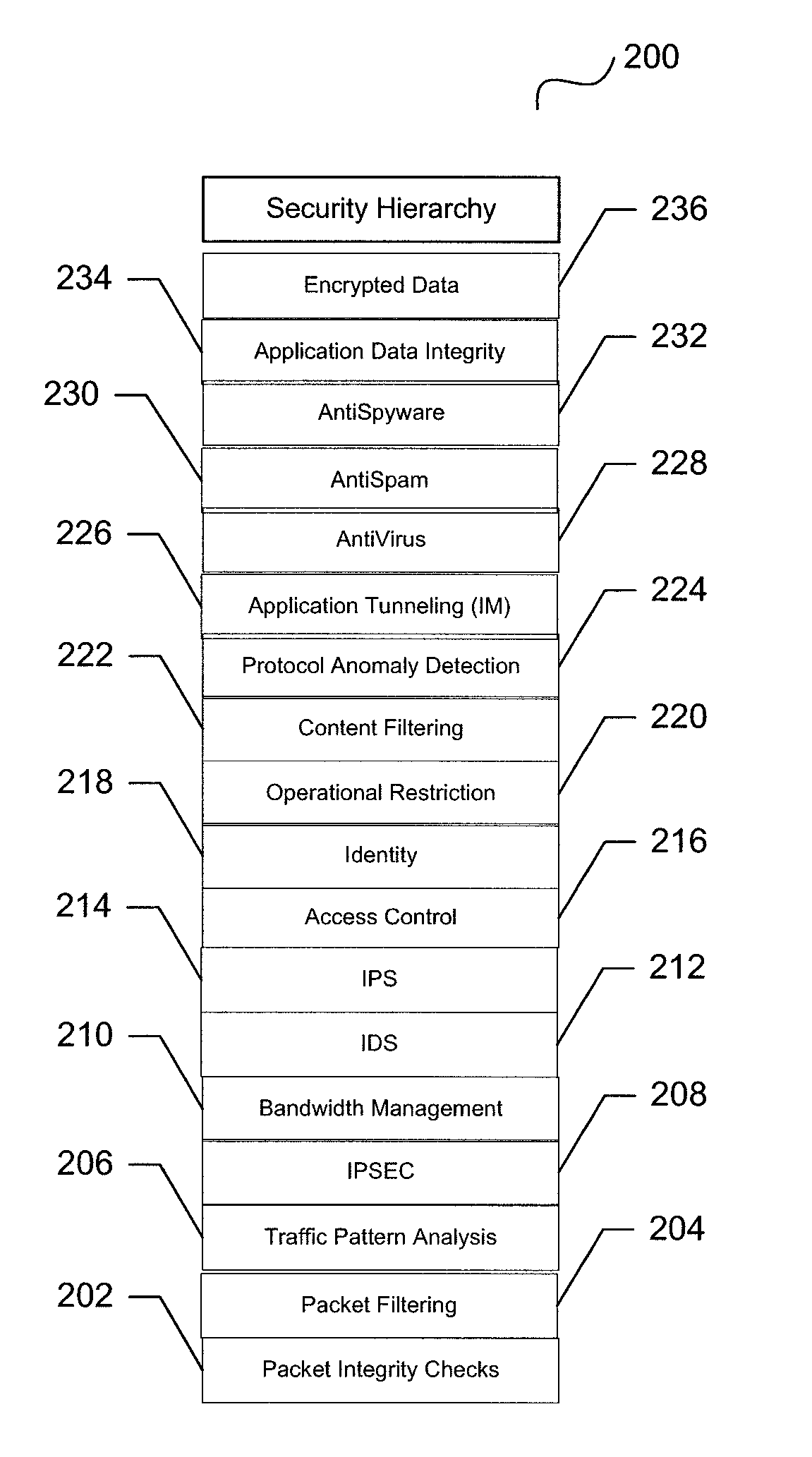
System and method for unified threat management with a relational rules methodology
ActiveUS7735116B1Improve performanceImprove securityDigital data processing detailsUser identity/authority verificationSecurity measurementSecurity Measure
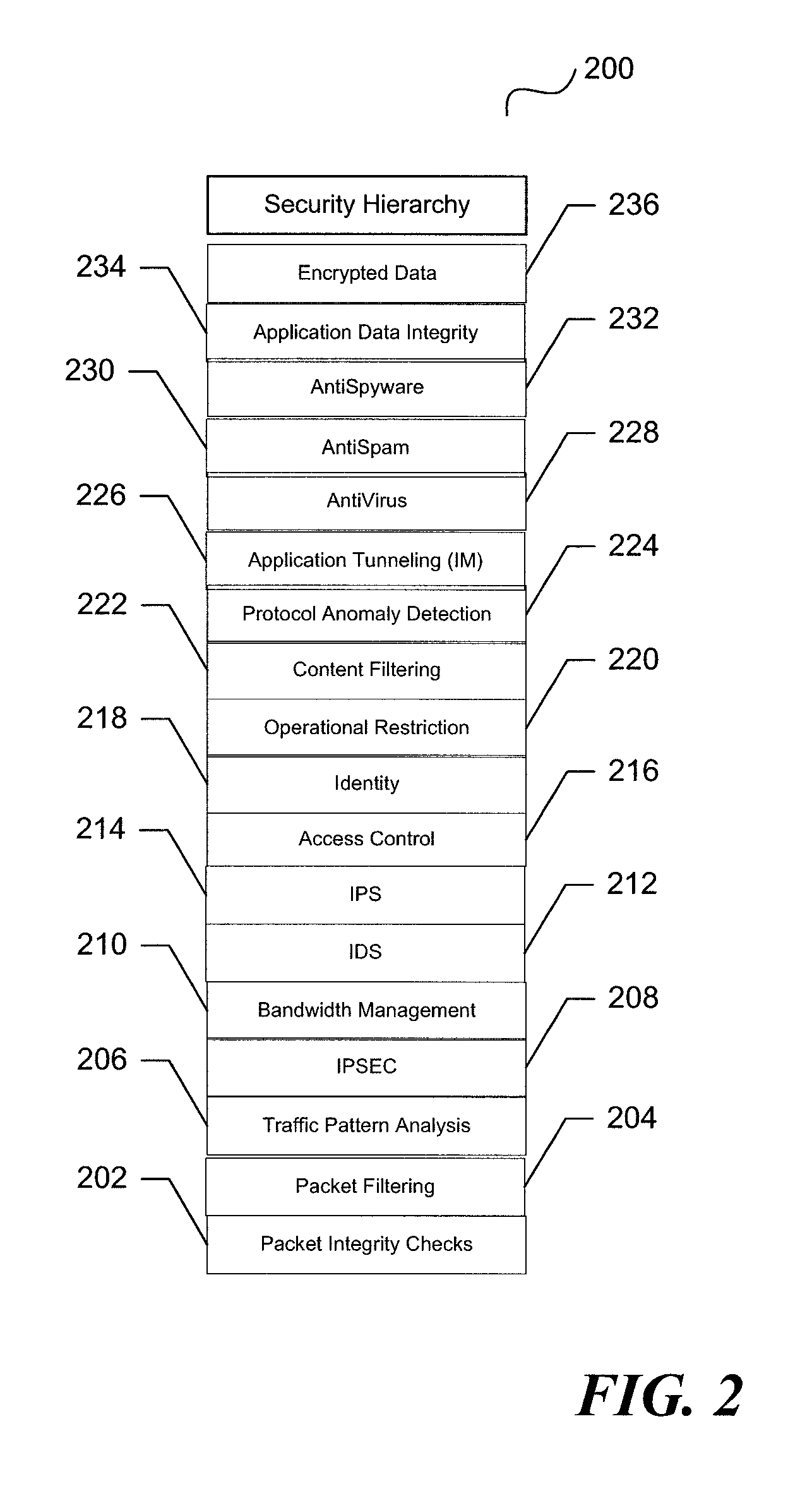
A unified threat management system is provided with a uniform relational rules model. The unified relational rules model provides for the sub-setting of rules and the ability to derive a result based partially from previous security measurements. The sharing of a security check from one security implementation to another using an object-oriented methodology is facilitated. Security policy is divided into specific security features that result in a security hierarchy. The security features may be considered to be listed sequentially, from bottom to top, and form a relationship with one another. These relationships are used to build a current security measure upon a previous security measure and may be used as a pre-cursor when marshalling data content to be validated.
Owner:CA TECH INC
Methods and Systems for Achieving High Assurance Computing using Low Assurance Operating Systems and Processes
ActiveUS20080016313A1Improve protectionImprove securityDigital data processing detailsUnauthorized memory use protectionOperational systemTerm memory
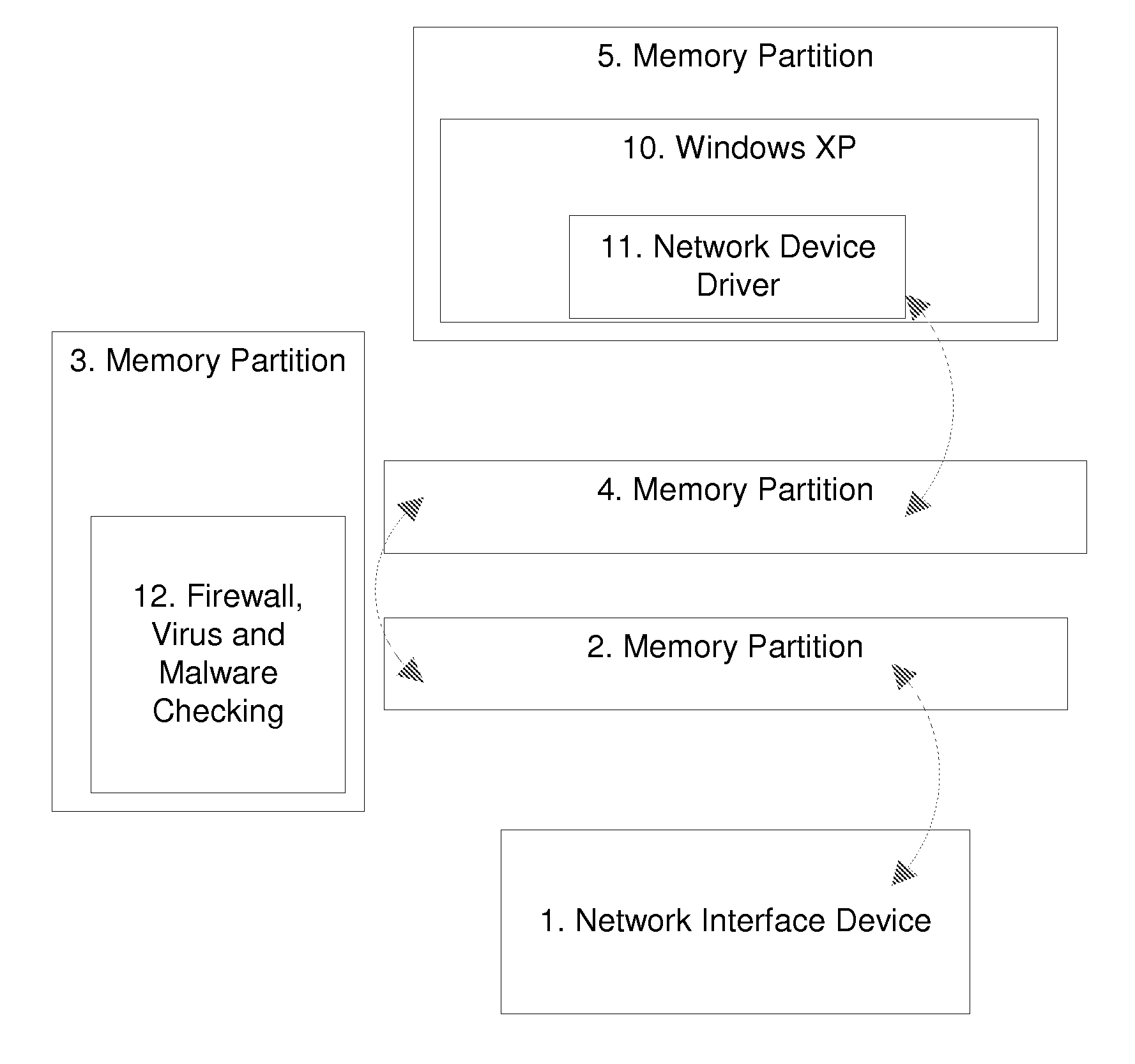
A computing system contains and uses a partitioning microkernel (PMK) or equivalent means for imposing memory partitioning and isolation prior to exposing data to a target operating system or process, and conducts continuing memory management whereby data is validated by security checks before or between sequential processing steps. The PMK may be used in conjunction with an Object Request Broker.
Owner:TECNICA
Memory management system and method providing increased memory access security
Owner:GLOBALFOUNDRIES INC
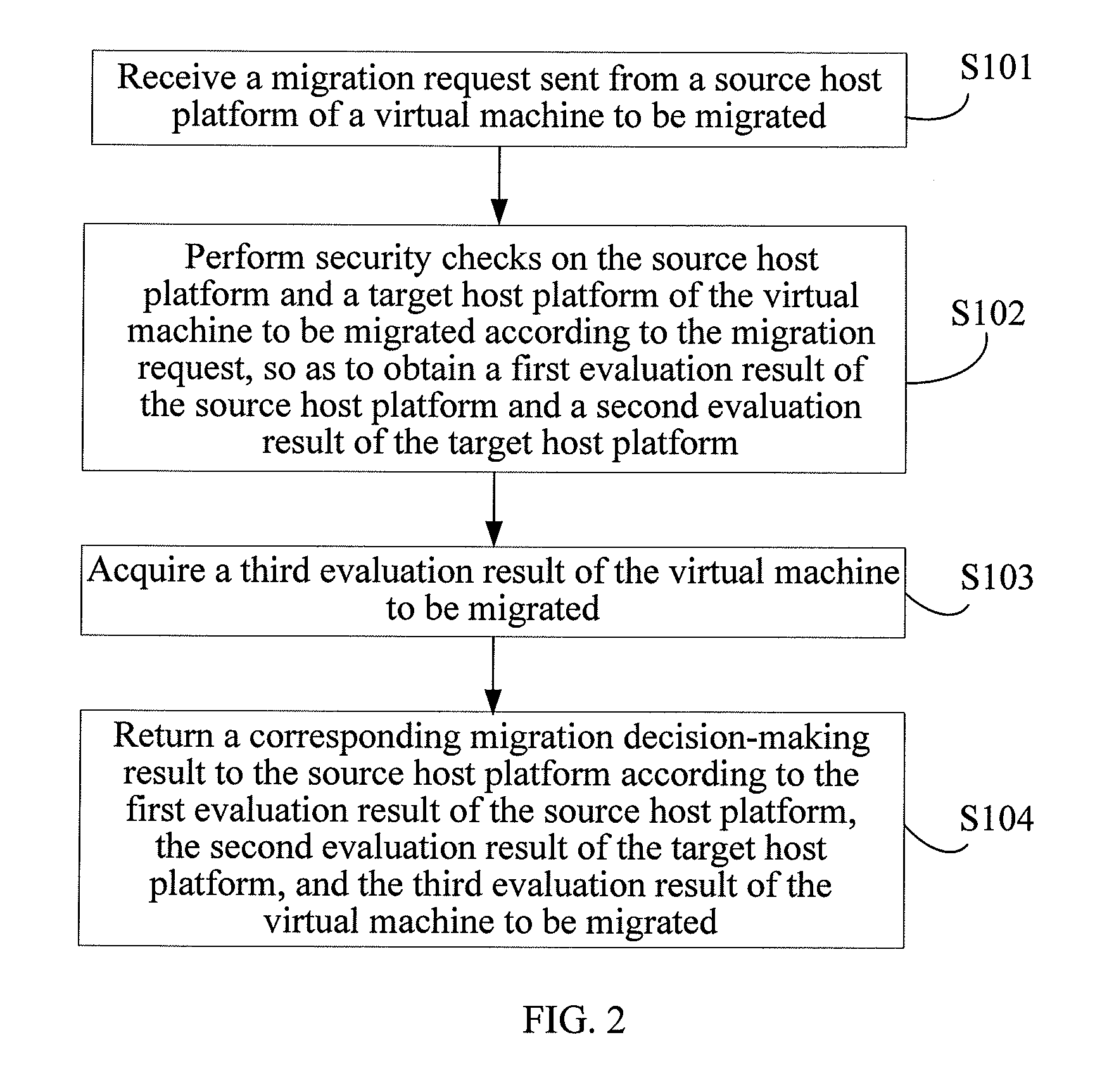
Method, apparatus and system for making a decision about virtual machine migration
ActiveUS20110099548A1Minimize impactImprove accuracyDigital data processing detailsMultiprogramming arrangementsSecurity checkVirtual machine
A method, an apparatus, and a system for making a decision about virtual machine migration includes a source host platform, configured to send a migration request to a Migration Authority (MA), and to migrate the virtual machine to a target host platform according to a received migration decision-making result. The MA is configured to perform security checks on the source host platform and the target host platform, to obtain a first evaluation result of the source host platform and a second evaluation result of the target host platform, acquire a third evaluation result of the virtual machine, and return a corresponding migration decision-making result to the source host platform. The corresponding migration decision-making result indicates whether the virtual machine is permitted to be migrated; and the target host platform of the virtual machine to be migrated, is configured to accept the virtual machine to be migrated.
Owner:HUAWEI TECH CO LTD
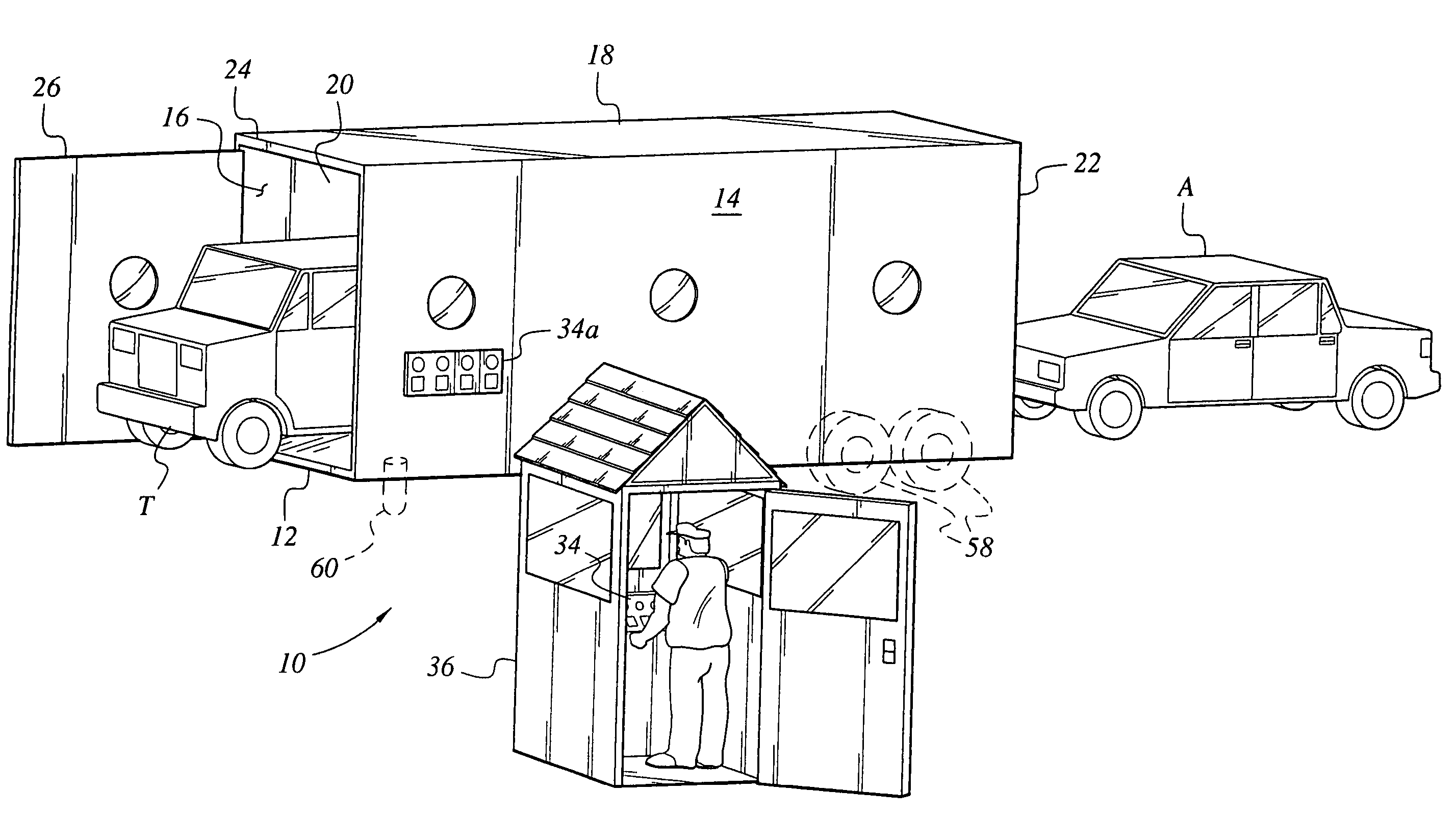
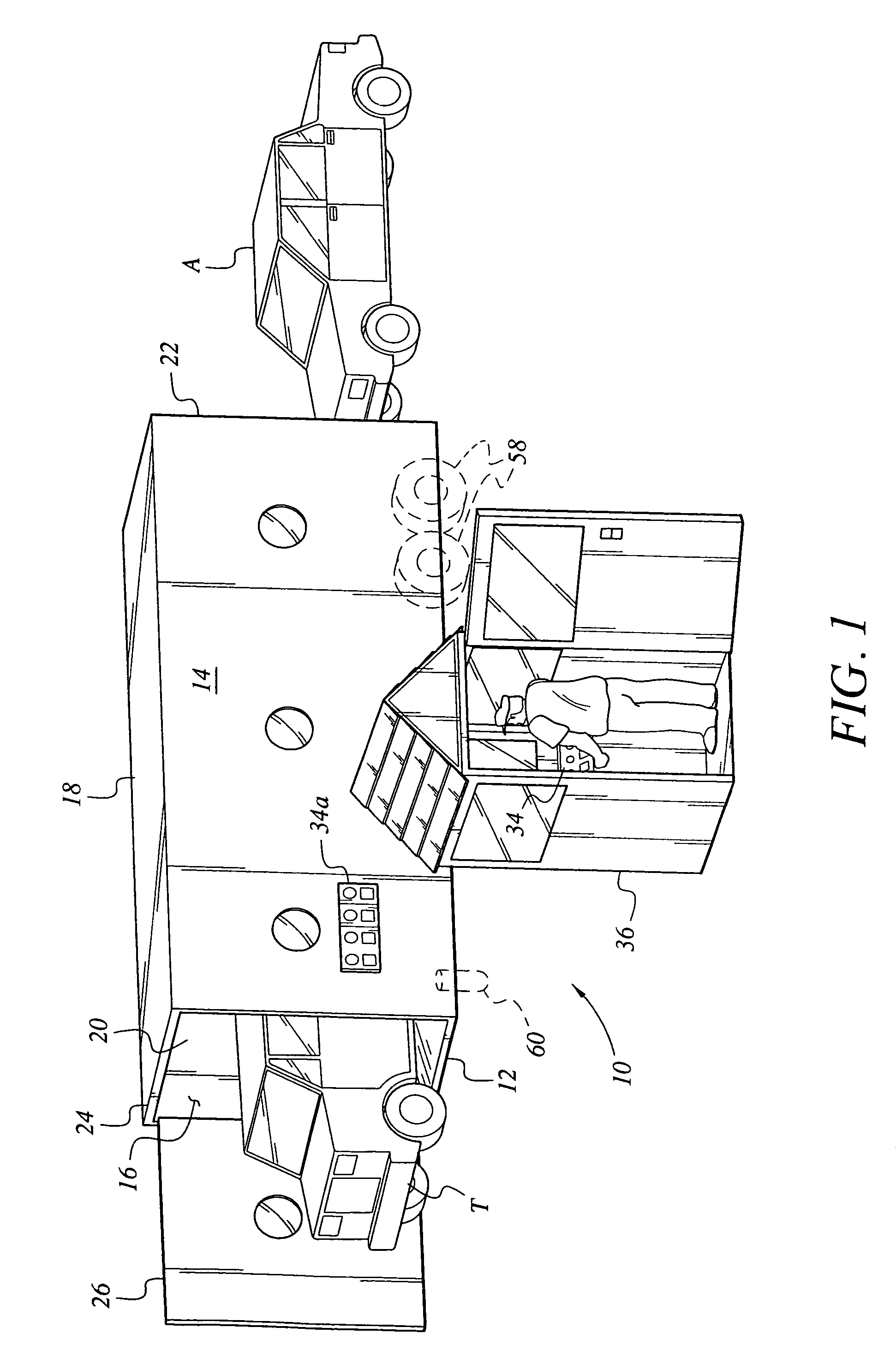
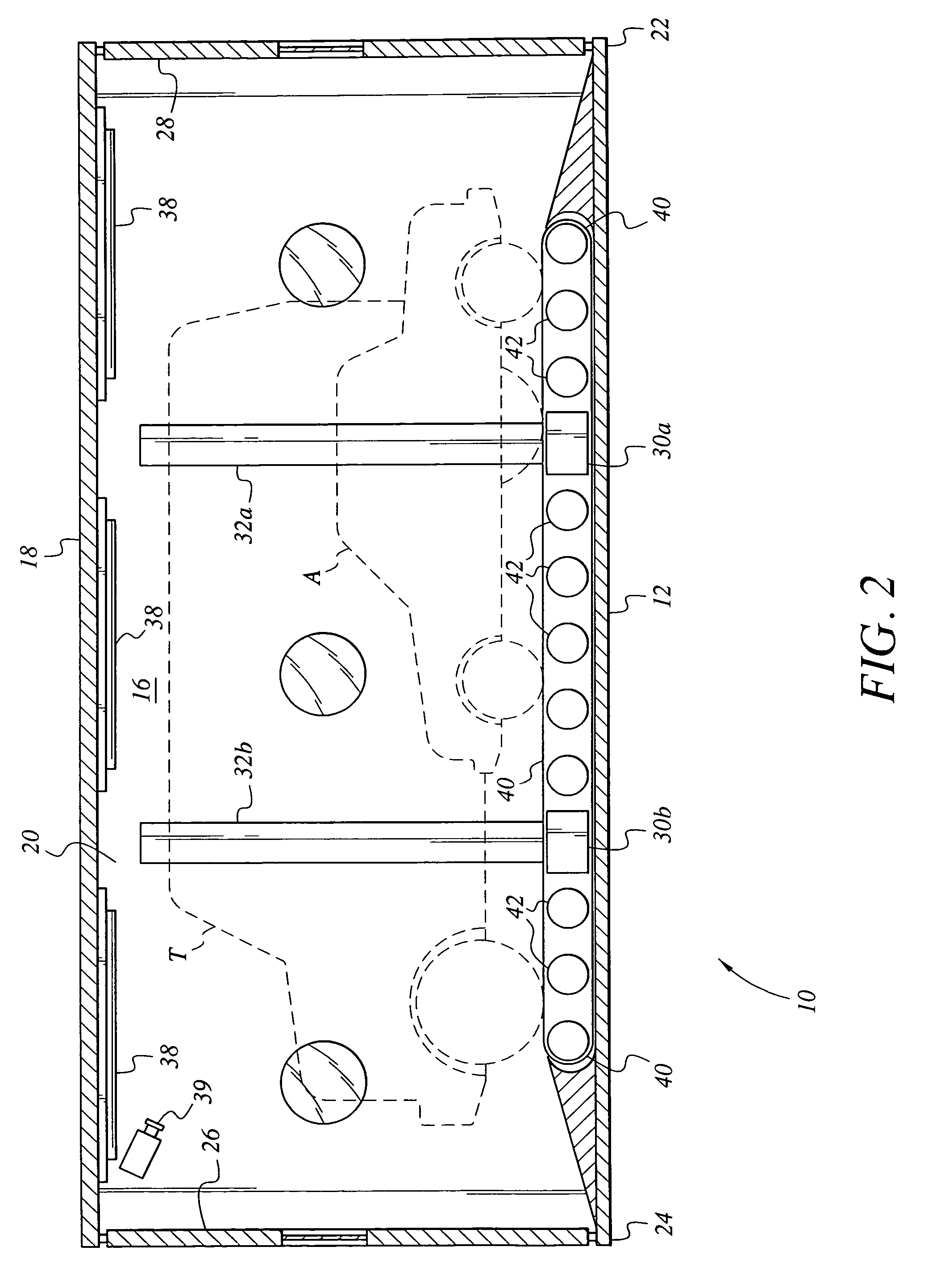
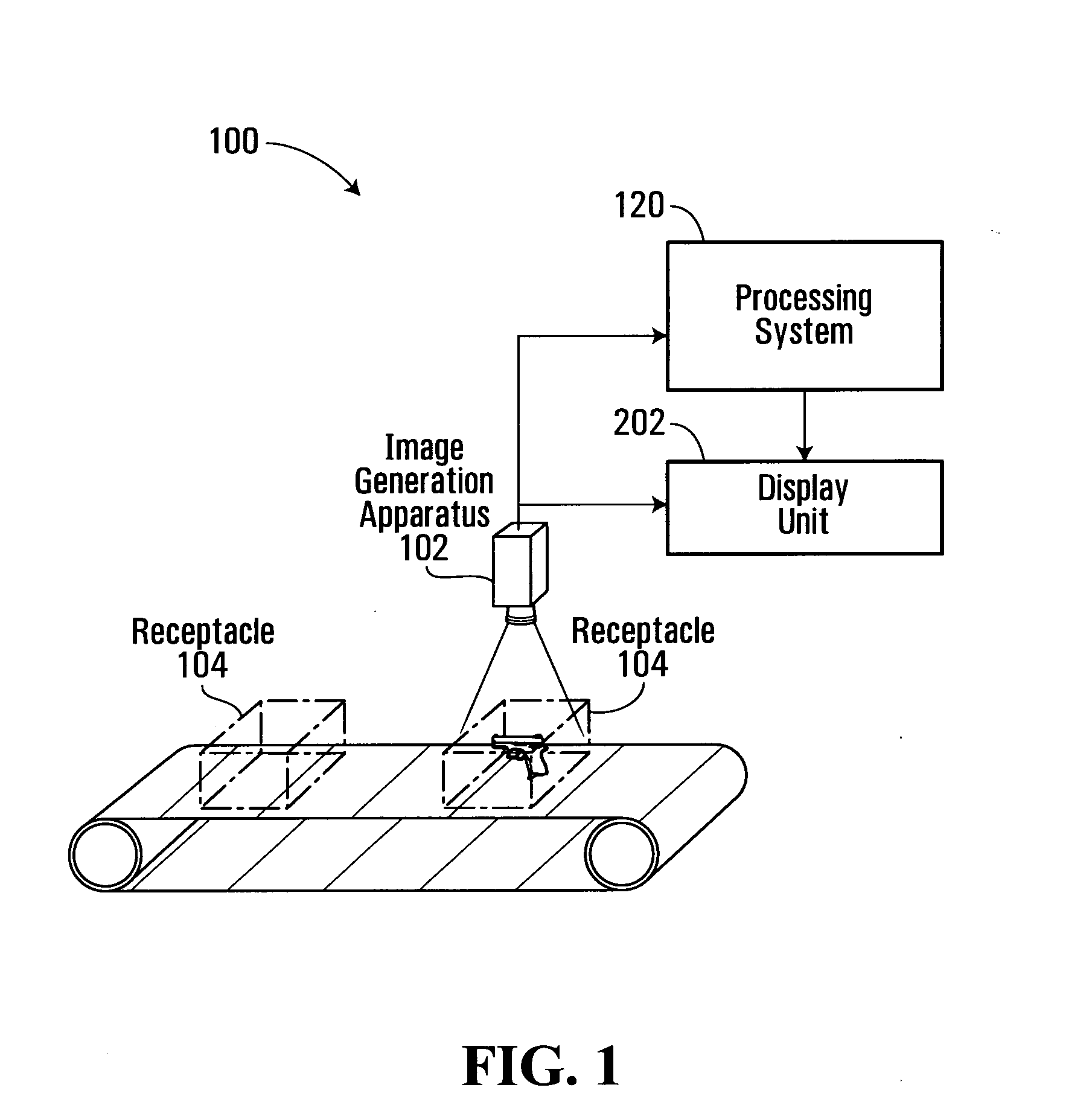
Vehicle security inspection system
ActiveUS6972693B2For quick inspectionRoad vehicles traffic controlError detection/correctionMobile vehicleSurveillance camera
The vehicle security inspection system may include multiple automated detection devices for detecting explosives, weapons, contraband, etc. which may be contained on or within a motor vehicle. The system includes a tunnel or enclosure with a moving conveyor therein. A motor vehicle is driven into the entrance to the enclosure, and conveyed past the series of sensors by the conveyor belt. One or more surveillance cameras may be installed in the enclosure, as well. The various sensors incorporated therein check the vehicle for illegal articles, and the vehicle is released from the enclosure. A control gate may be provided as a door at the exit of the enclosure, and / or as a gate guiding vehicles along their intended route or to a detention area, as appropriate. The system may be provided either as a portable device or as a permanent installation, and / or may be configured as a multiple lane inspection system.
Owner:BROWN BETTY J +1
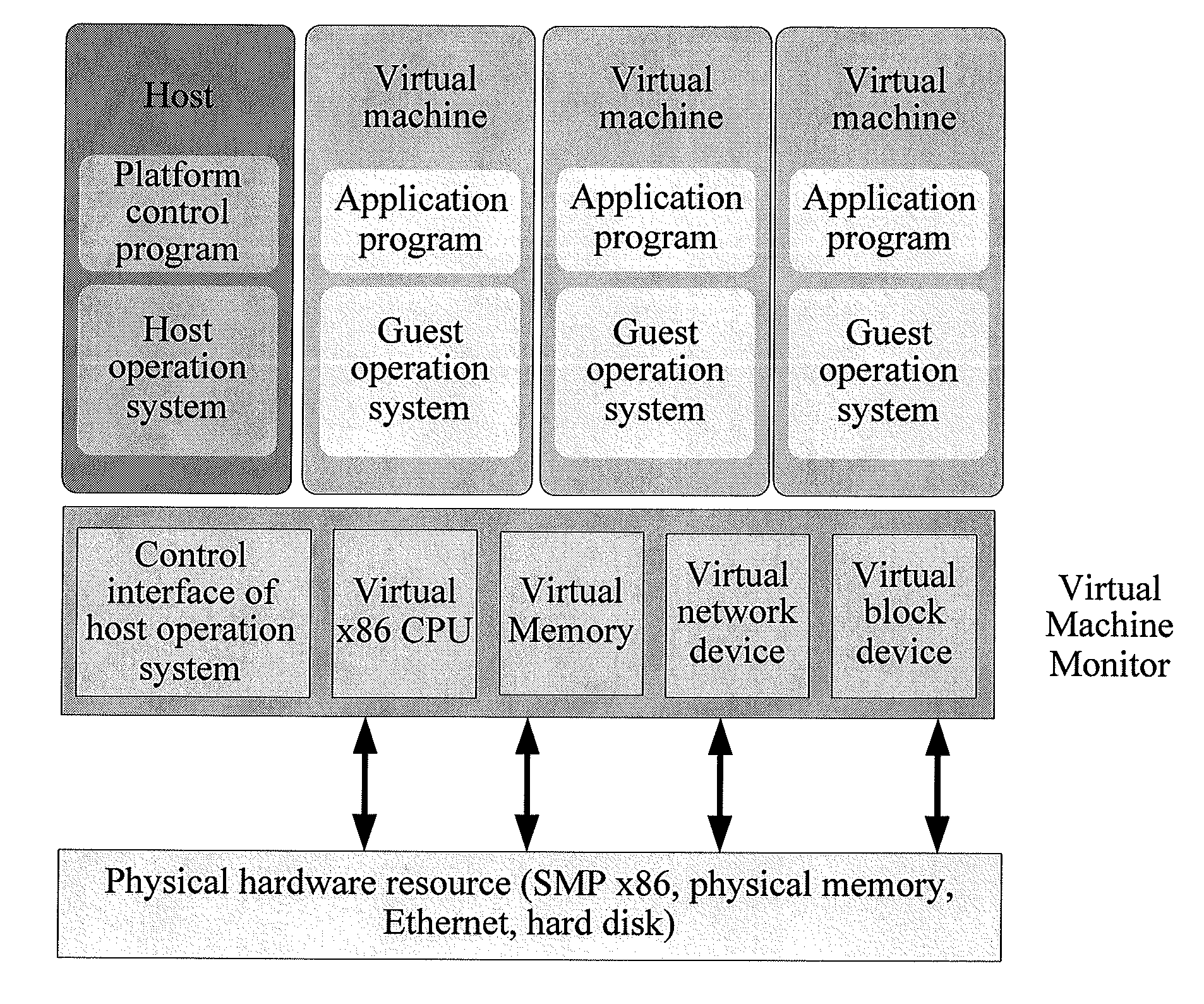
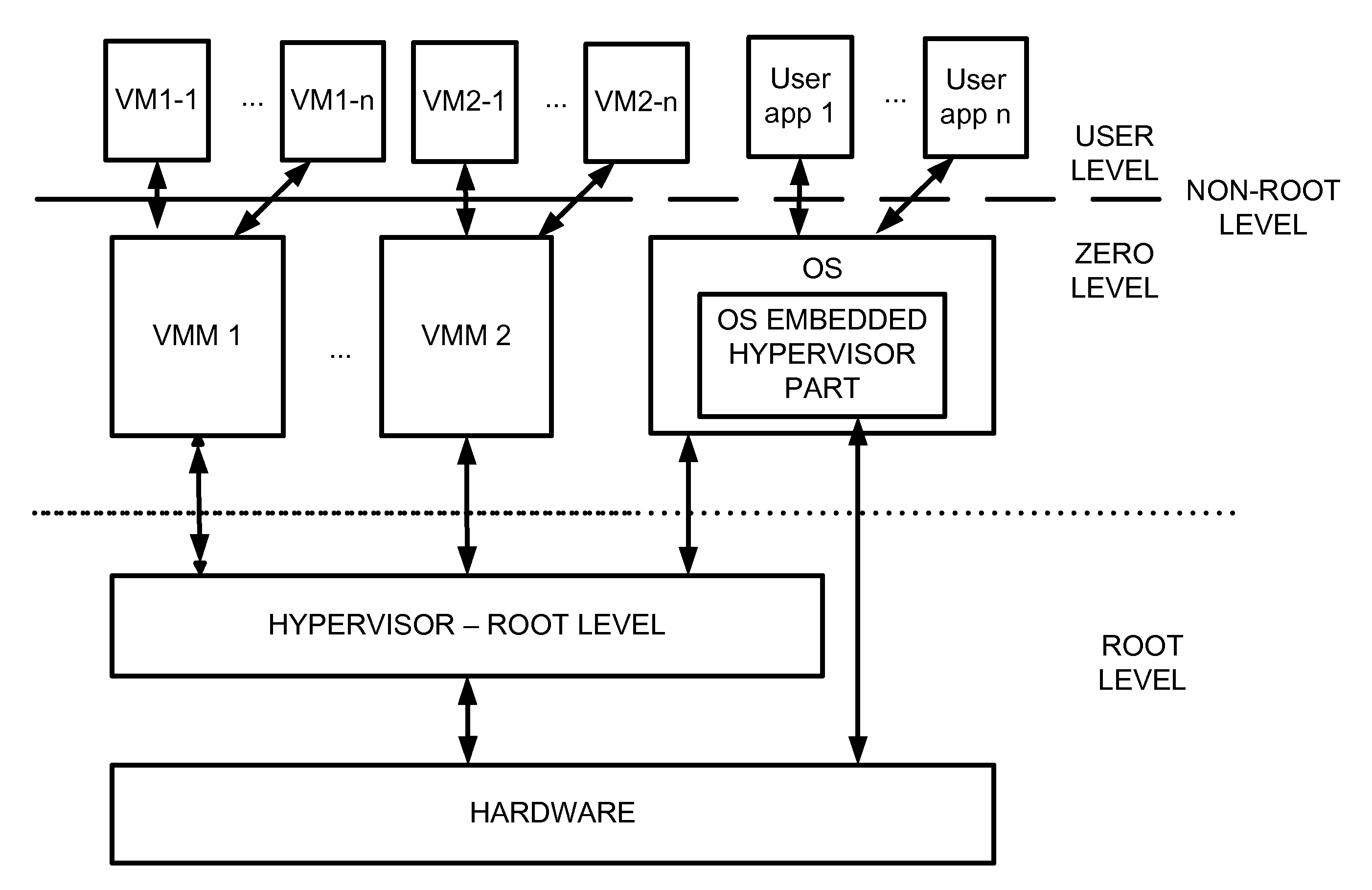
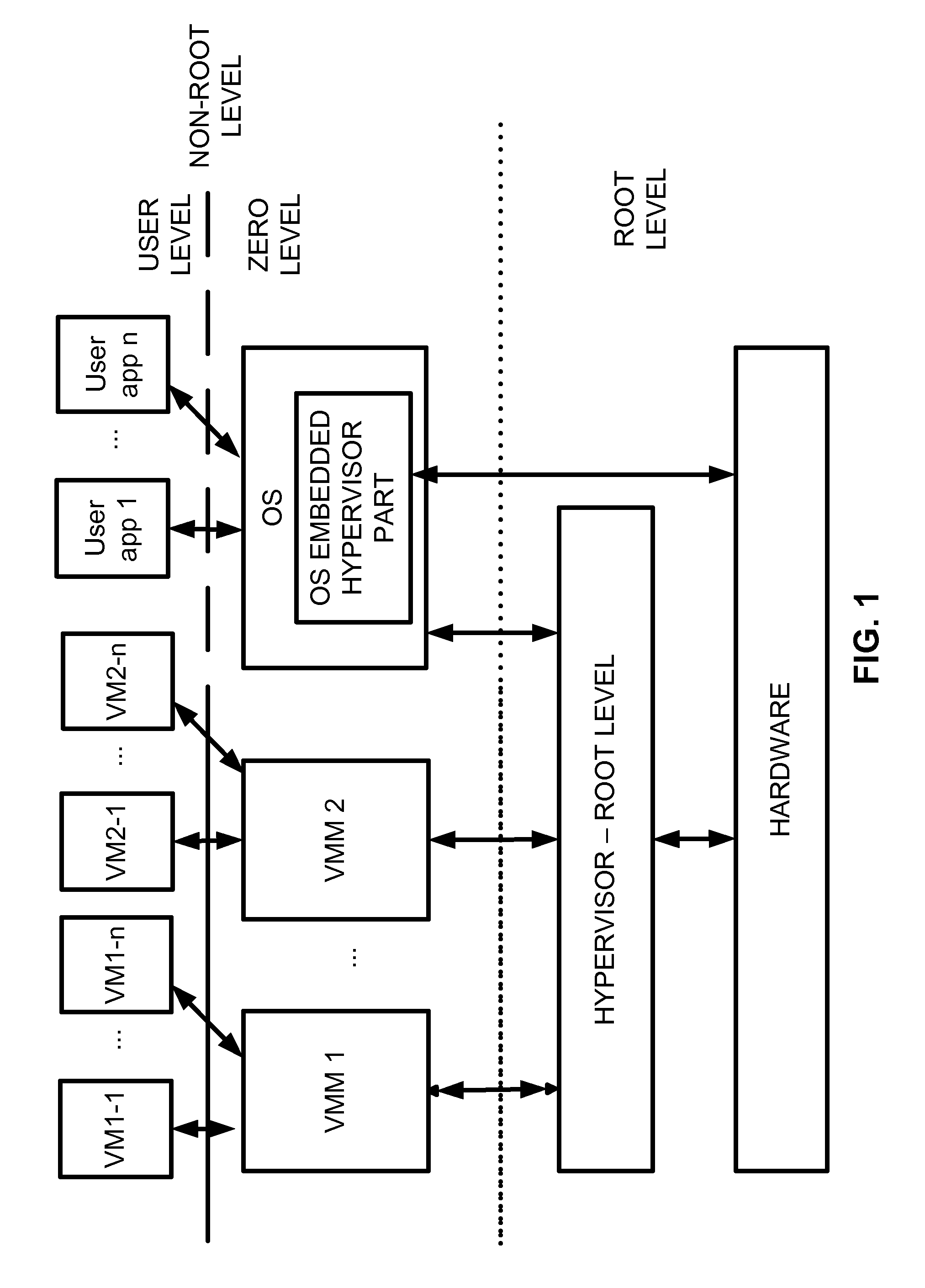
Virtualization system with hypervisor embedded in bios or using extensible firmware interface
A computer system includes a first portion of a Hypervisor is loaded into the memory as a part of an Extensible Firmware Interface upon start up and prior to loading of an operating system. The first portion is responsible for context switching, at least some interrupt handling, and memory protection fault handling. The first portion runs on a root level. An operating system is loaded into a highest privilege level. A second portion of the Hypervisor is loaded into operating system space together with the operating system, and runs on the highest privilege level, and is responsible for (a) servicing the VMM, (b) servicing the VMs, (c) enabling communication between code launched on non-root level with the second portion of the Hypervisor to perform security checks of trusted code portions and to enable root mode for the code portions if allowable. The VMM runs on the highest privilege level. A Virtual Machine is running under control of the VMM. Trusted code runs on non-root level. The first portion of the Hypervisor verifies trusted code portions during their loading or launch time, and the trusted code is executed on root level.
Owner:PARALLELS INT GMBH
Centrally enhanced peer-to-peer resource sharing method and apparatus
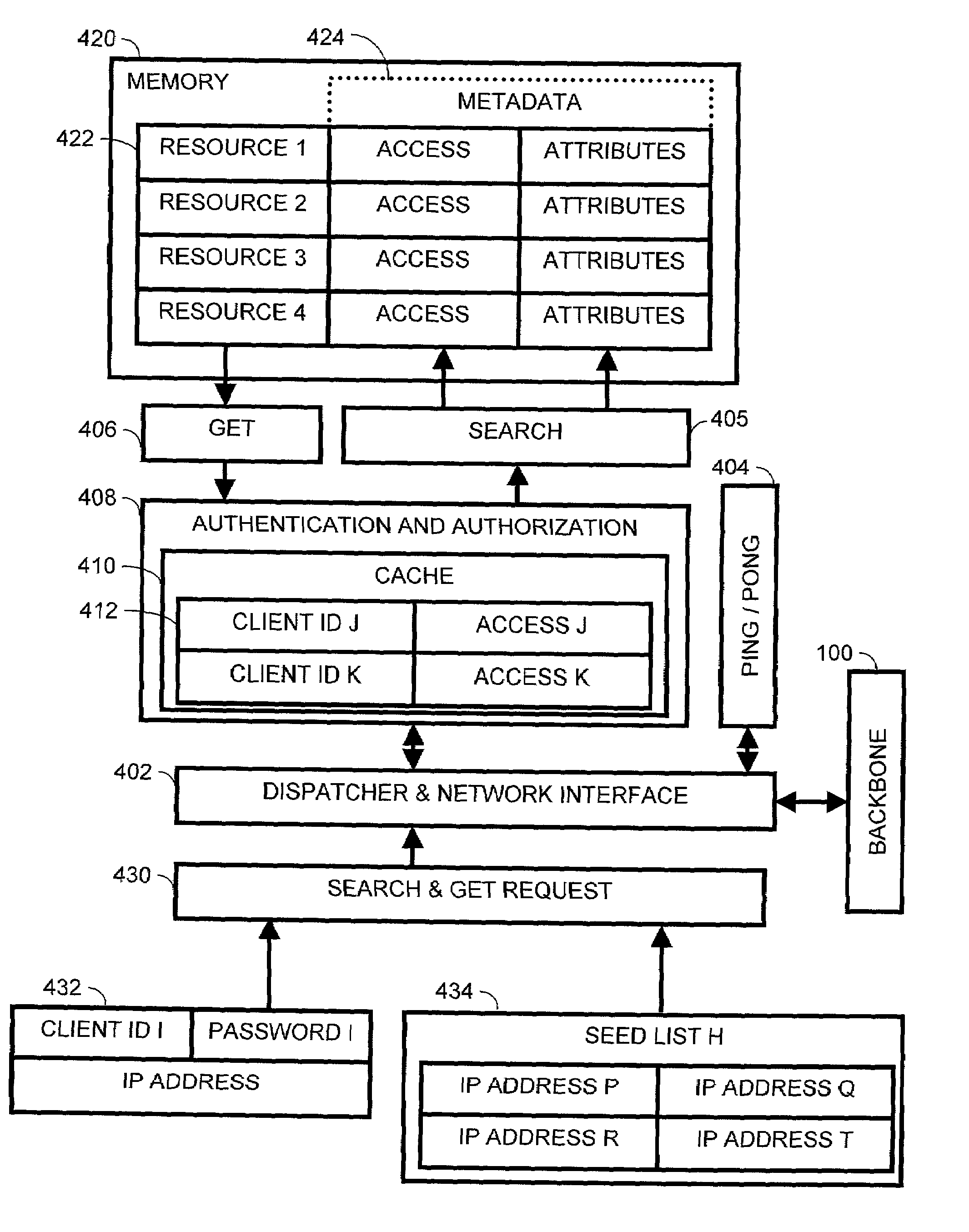
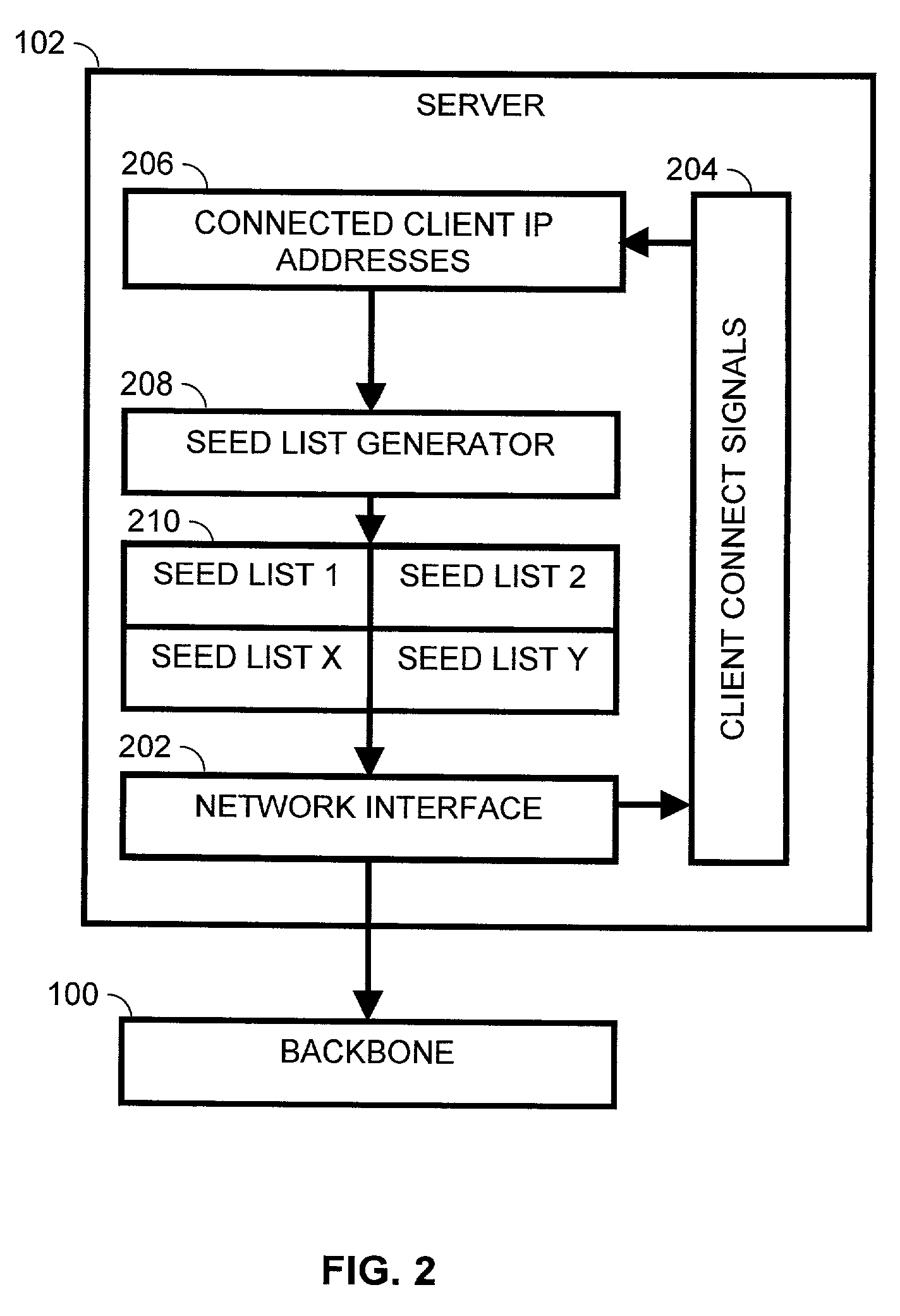
InactiveUS7130921B2Digital data processing detailsMultiple digital computer combinationsSecurity checkClient-side
A peer-to-peer network has a server that maintains a list of addresses of clients connected to the peer-to-peer network. The server generates seed lists for each of the clients connected to the network from the server maintained list. The clients conduct peer-to-peer searches using the seed list provided by the server. The seed lists may be either randomly generated or generated to facilitate network objectives. The clients may periodically request seed list refreshing. The peer-to-peer network may further include authentication and authorization search security checks.
Owner:IBM CORP
Security management device and method
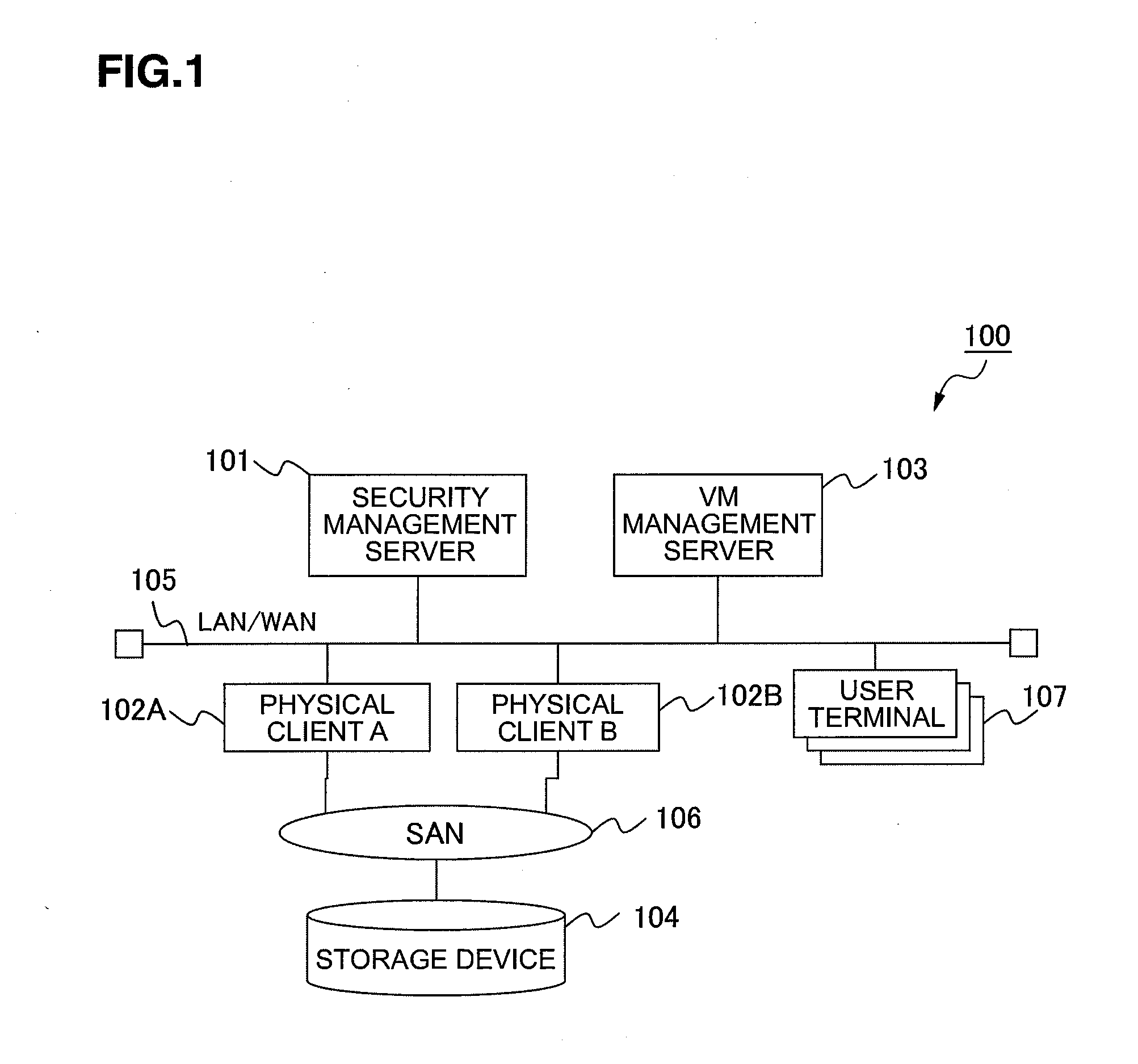
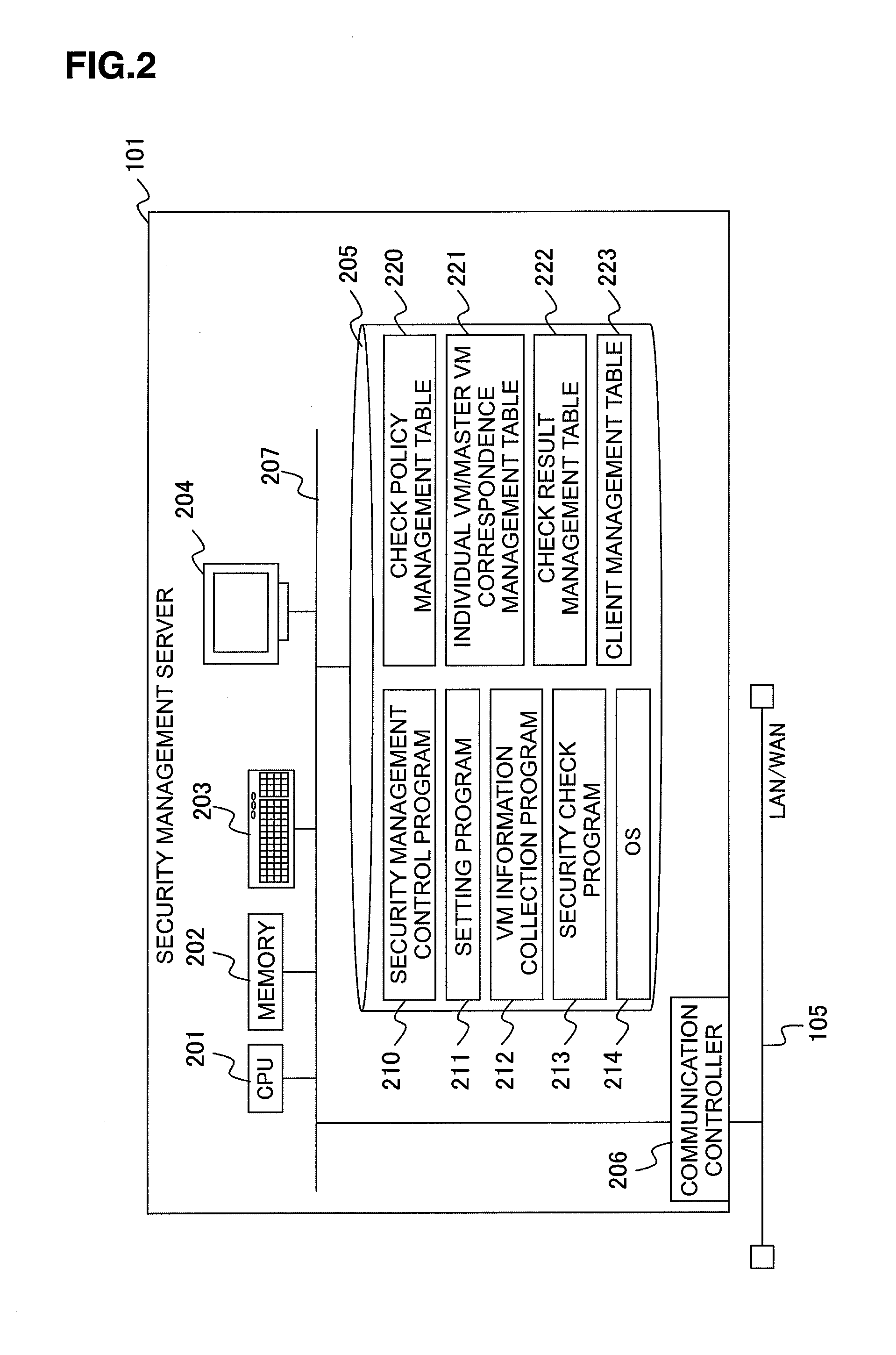
InactiveUS20110047541A1Security check faster and more efficientlySecurity check to be carried out faster and more efficientlyDigital data protectionPlatform integrity maintainanceSecurity checkClient-side
In a case where a master virtual machine, which is constructed on the basis of master information for configuring either part or all of a virtual machine, and an individual virtual machine, which is constructed on the basis of individual information that is configured partially or entirely in accordance with the master information, exist as the types of virtual machines that a physical client provides to a user terminal, a security check of a plurality of virtual machines is selectively executed, with respect to each check item, for a virtual machine of the type corresponding to the contents of the check item.
Owner:HITACHI LTD
Systems and methods for proxying encrypted traffic to protect origin servers from internet threats
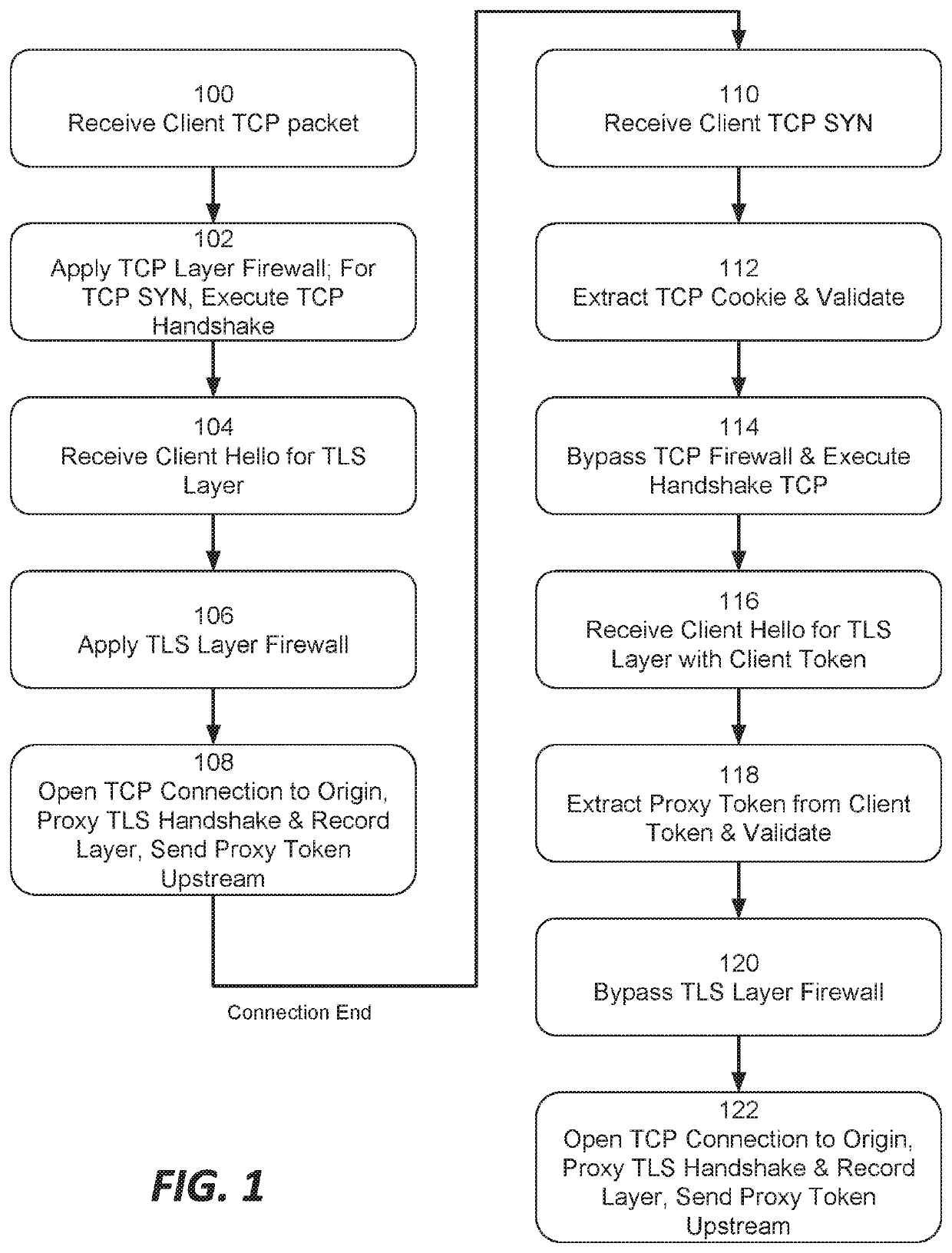
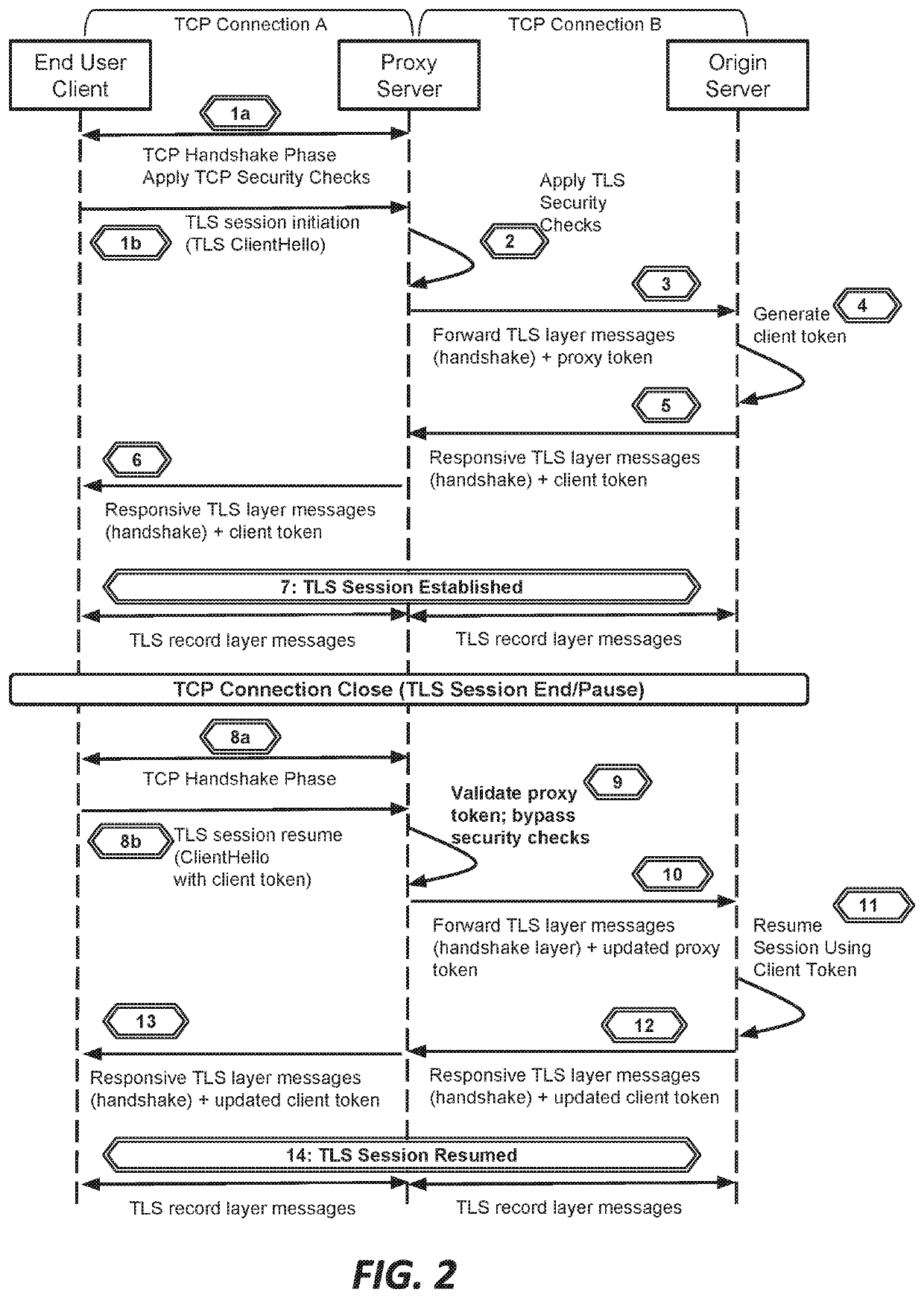
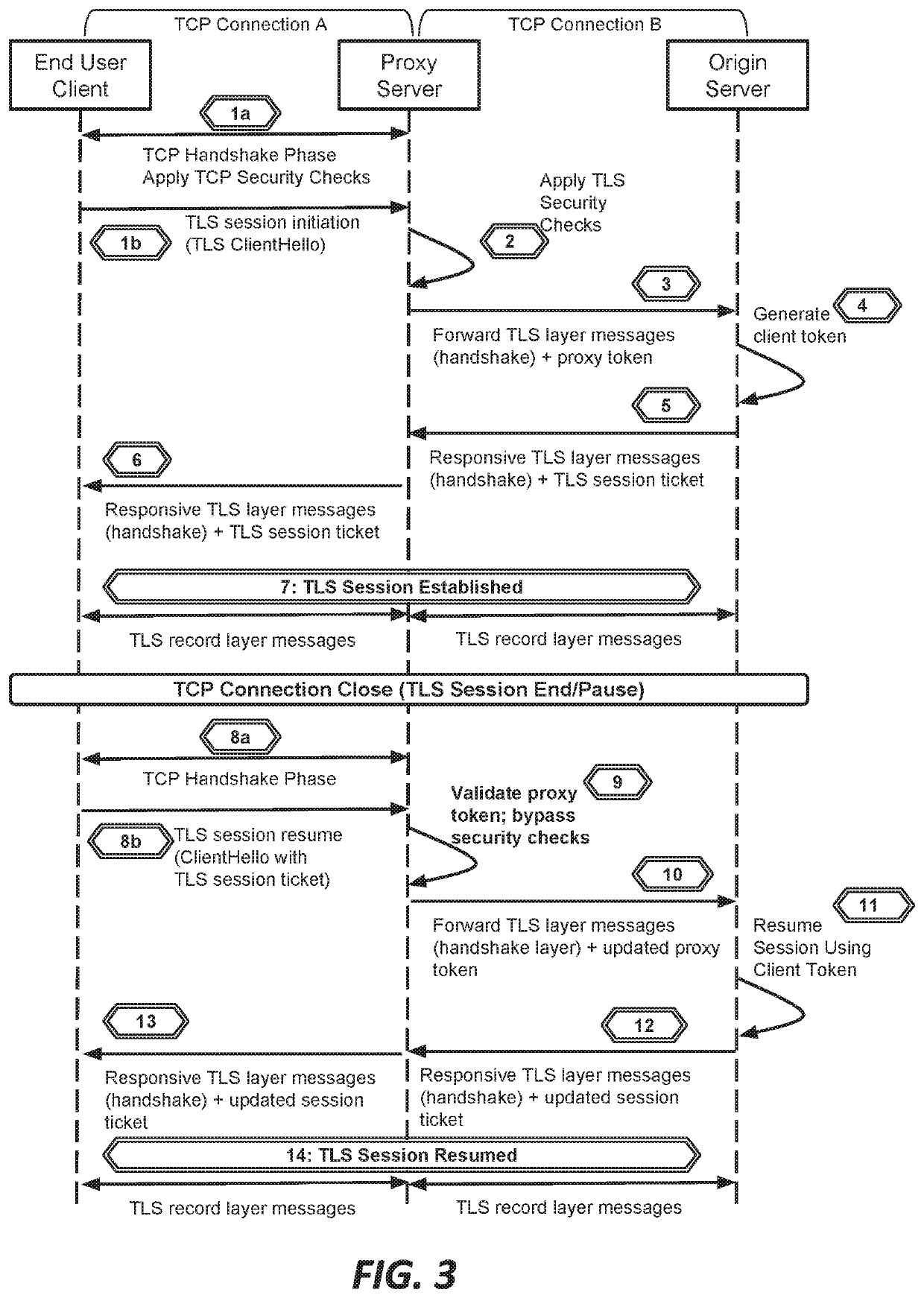
This document describes, among other things, systems and methods for more efficiently resuming a client-to-origin TLS session through a proxy layer that fronts the origin in order to provide network security services. At the time of an initial TLS handshake with an unknown client, for example, the proxy can perform a set of security checks. If the client passes the checks, the proxy can transmit a ‘proxy token’ upstream to the origin. The origin can incorporate this token into session state data which is passed back to and stored on the client, e.g., using a TLS session ticket extension field, pre-shared key extension field, or other field. On TLS session resumption, when the client sends the session state data, the proxy can recover its proxy token from the session state data, and upon successful validation, bypass security checks that it would otherwise perform against the client, thereby more efficiently handling known clients.
Owner:AKAMAI TECH INC
Memory management system and method for providing physical address based memory access security
InactiveUS6823433B1Memory adressing/allocation/relocationUnauthorized memory use protectionManagement unitComputerized system
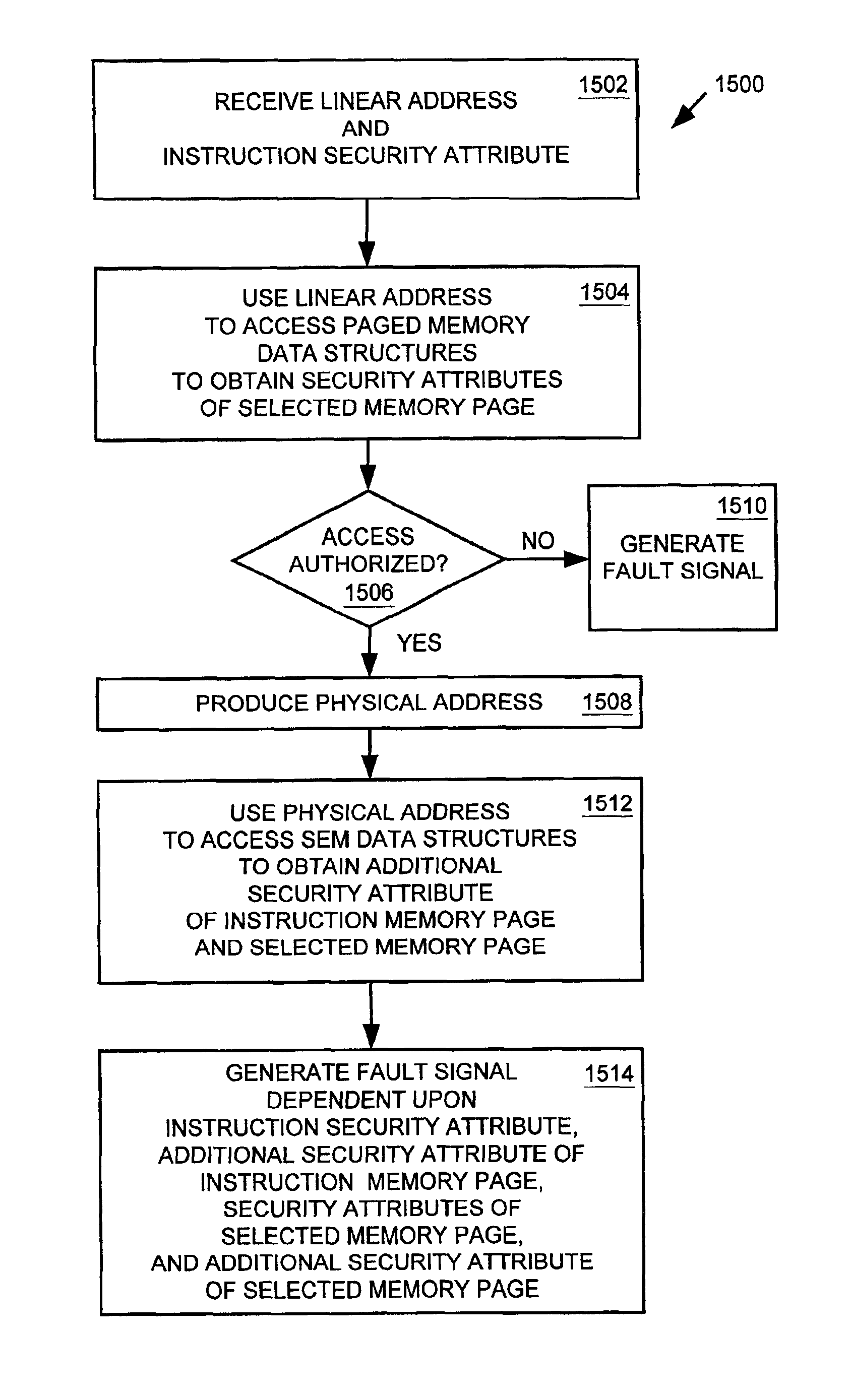
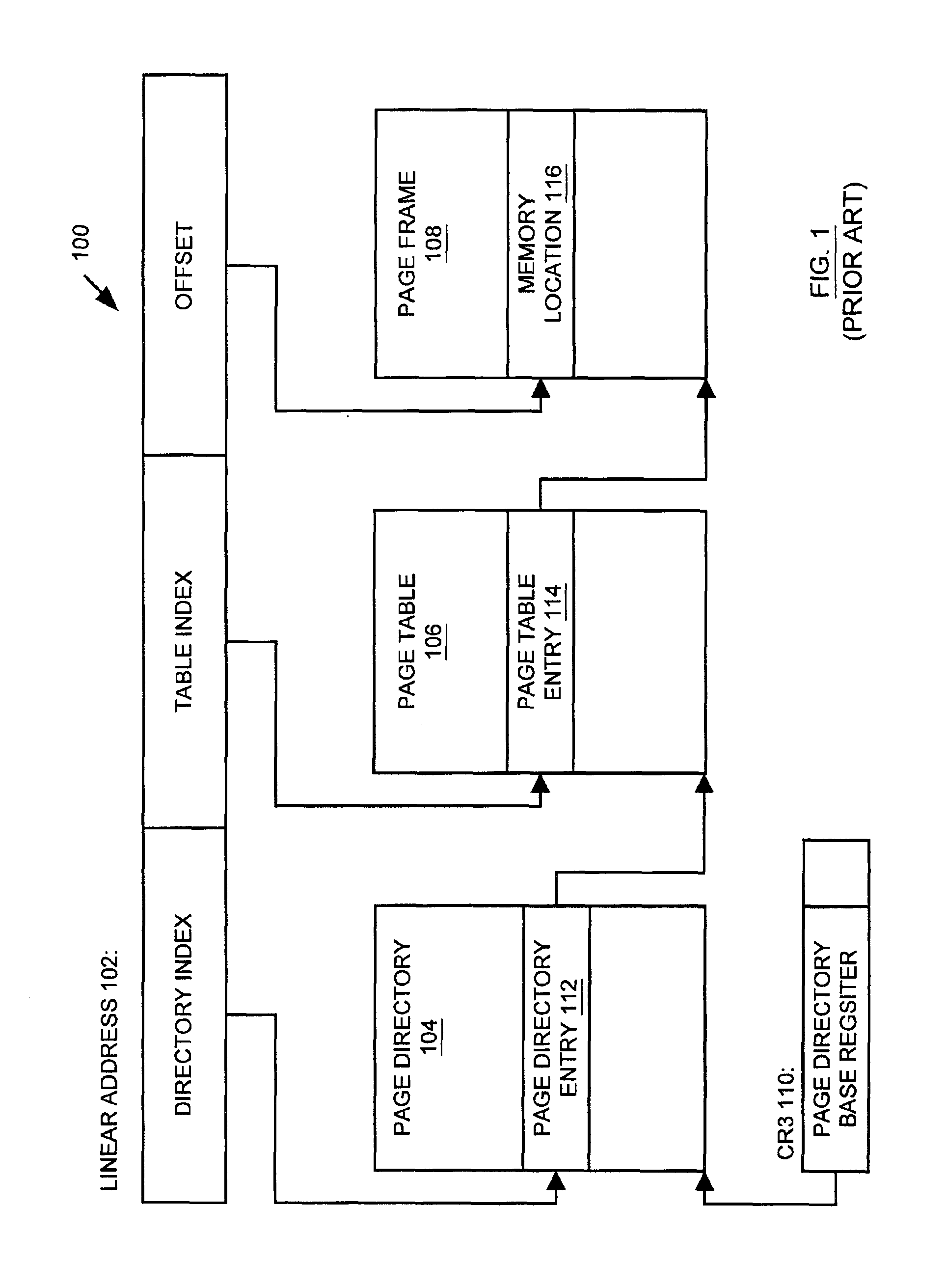
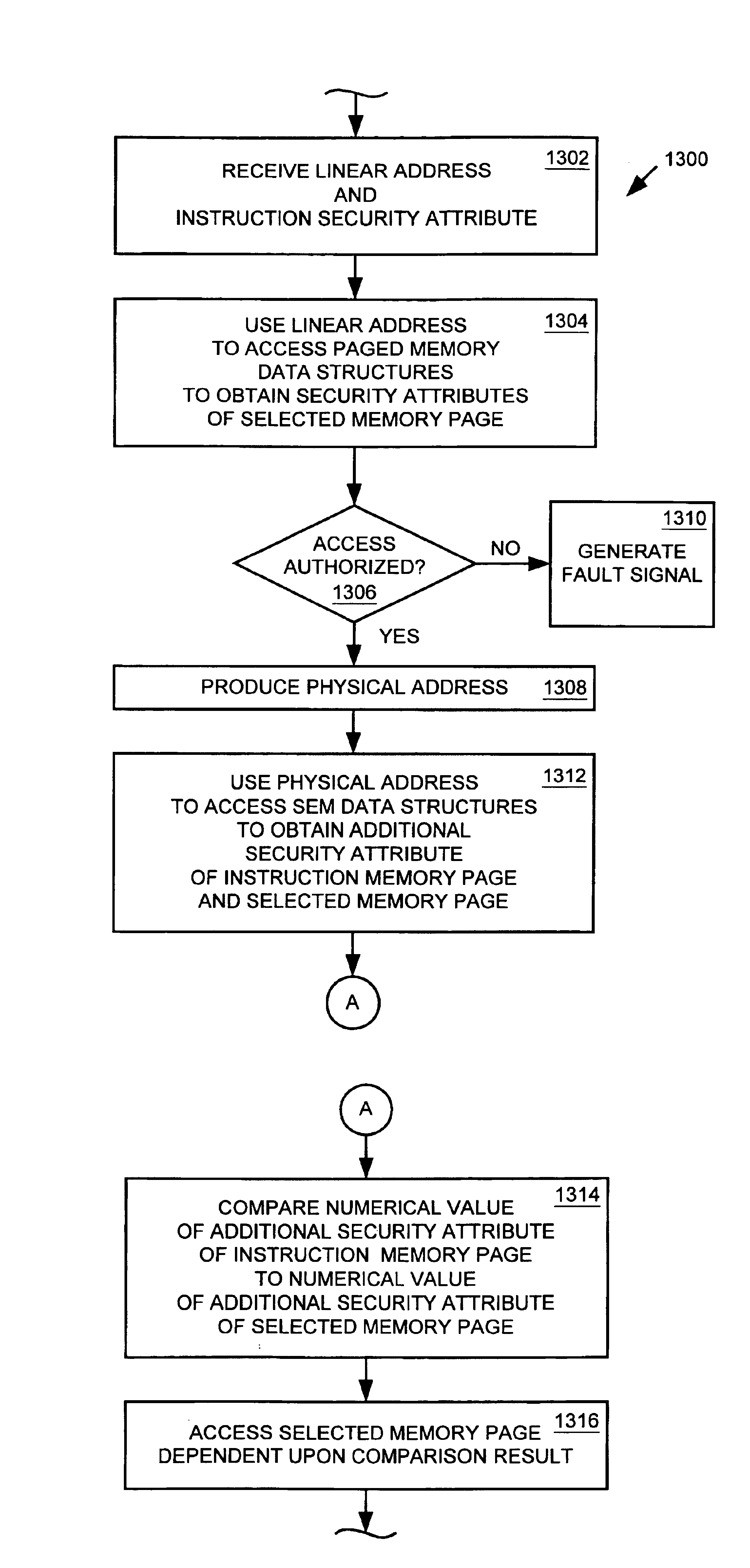
A memory management unit (MMU) is disclosed for managing a memory storing data arranged within a plurality of memory pages. The MMU includes a security check unit (SCU) receiving a physical address generated during execution of a current instruction. The physical address resides within a selected memory page. The SCU uses the physical address to access one or more security attribute data structures located in the memory to obtain a security attribute of the selected memory page, compares a numerical value conveyed by a security attribute of the current instruction to a numerical value conveyed by the security attribute of the selected memory page, and produces an output signal dependent upon a result of the comparison. The MMU accesses the selected memory page dependent upon the output signal. The security attribute of the selected memory page may include a security context identification (SCID) value indicating a security context level of the selected memory page. The security attribute of the current instruction may include an SCID value indicating a security context level of a memory page containing the current instruction. A central processing unit (CPU) is described including an execution unit and the MMU. A computer system is described including the memory, the CPU, and the MMU. A method is described for providing access security for a memory used to store data arranged within a plurality of memory pages. The method may be embodied within the MMU.
Owner:GLOBALFOUNDRIES US INC +1
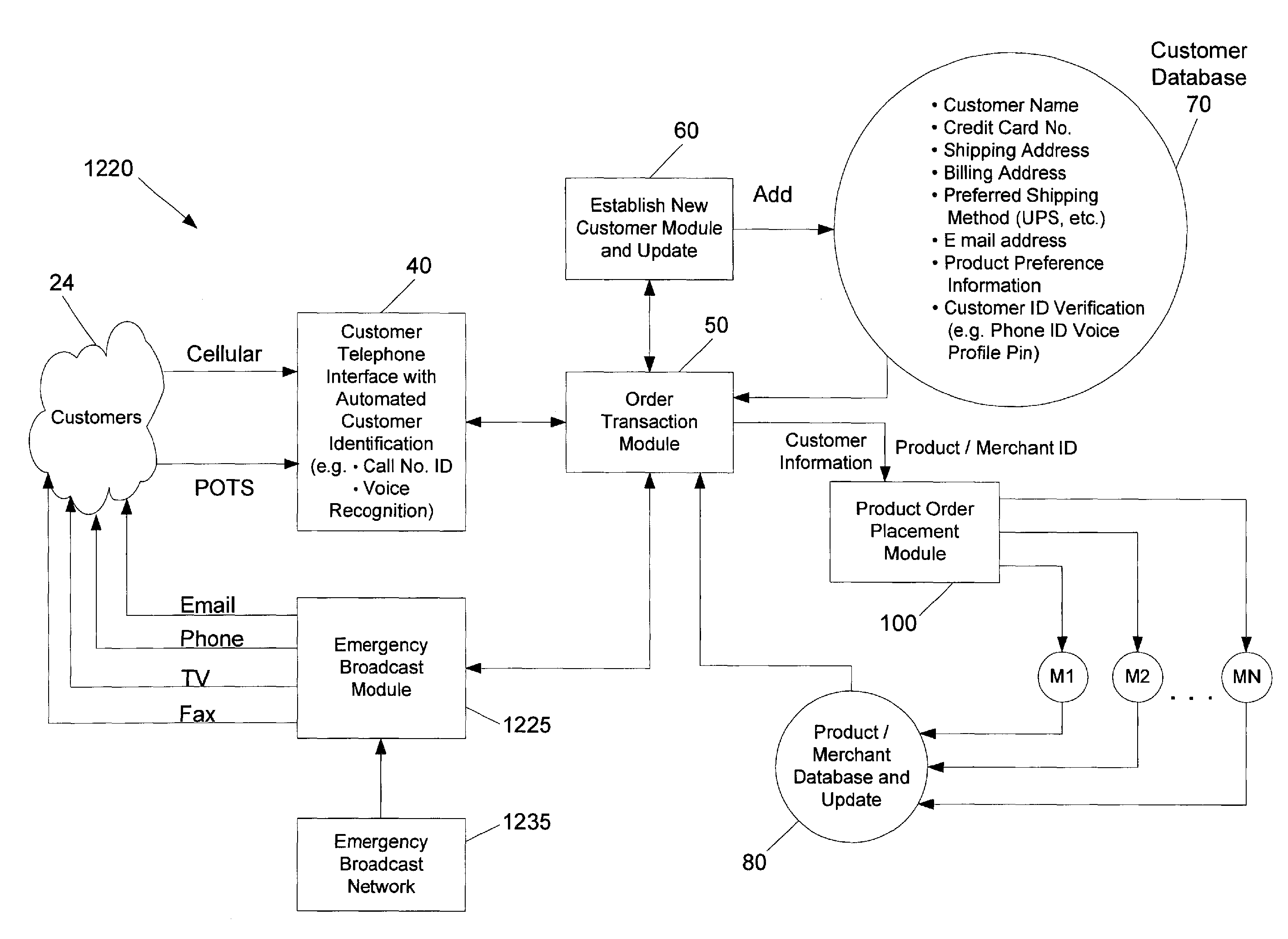
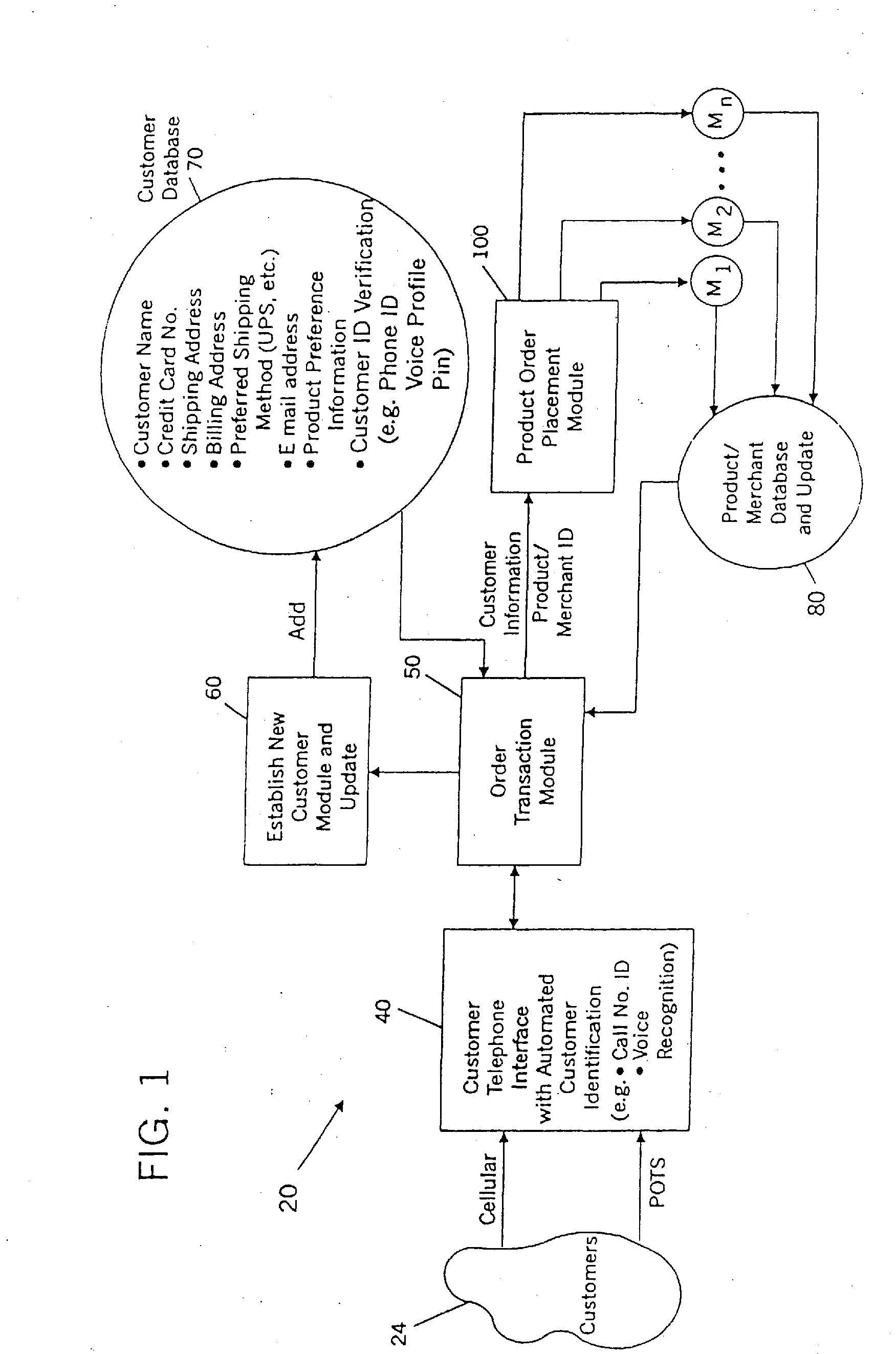
System and Method Permitting Customers to Order Selected Products from a Vast Array of Products Offered By Multiple Participating Merchants and Related Security Publications
InactiveUS20060293971A1Improve securityImprove reliabilityCredit schemesTwo-way working systemsCredit cardProduct order
A universal automated order processing system represents multiple (e.g., hundreds or thousands) participating merchants who offer their products through the system. Customers become qualified for using the system by supplying a set of information (e.g., name, credit card number, shipping address) that is stored in a customer database. When a customer wishes to order a product, the customer calls the system, customer identity is automatically confirmed, the customer enters a product order number and the complete order is routed to the appropriate merchant with the information necessary for the merchant to fulfill the order. Available credit verification and other aspects of credit card transactions may be handled by either the system operator or the merchant. The system operator may offer revolving credit. The system may also be used to provide potential customers of the merchants with free product information. In certain embodiments, the processing system may be used to verify customer identity at security check-in at public transportation sites (e.g., airports) or other public venues (e.g., concerts, sporting events).
Owner:HANGER SOLUTIONS LLC +1
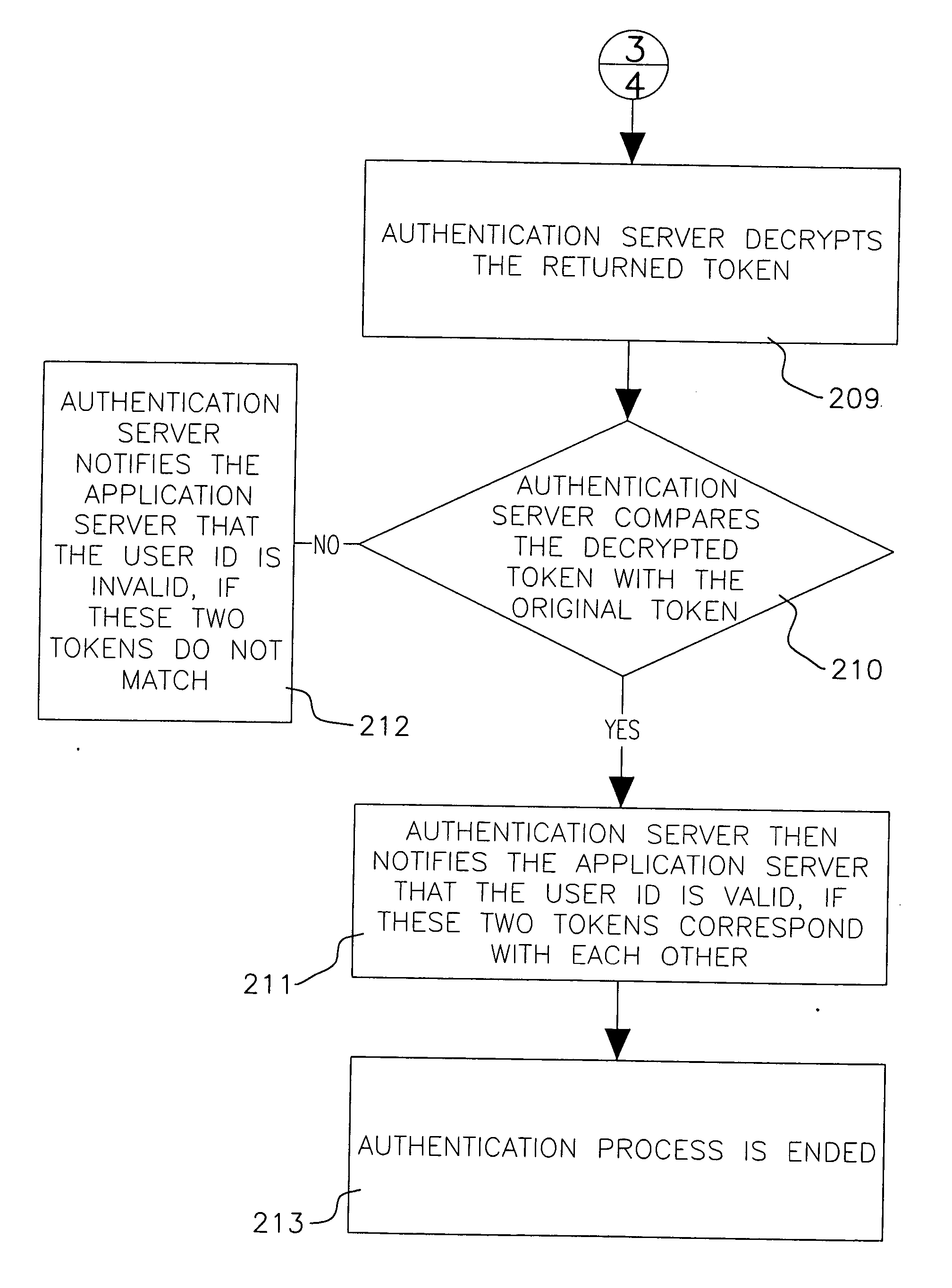
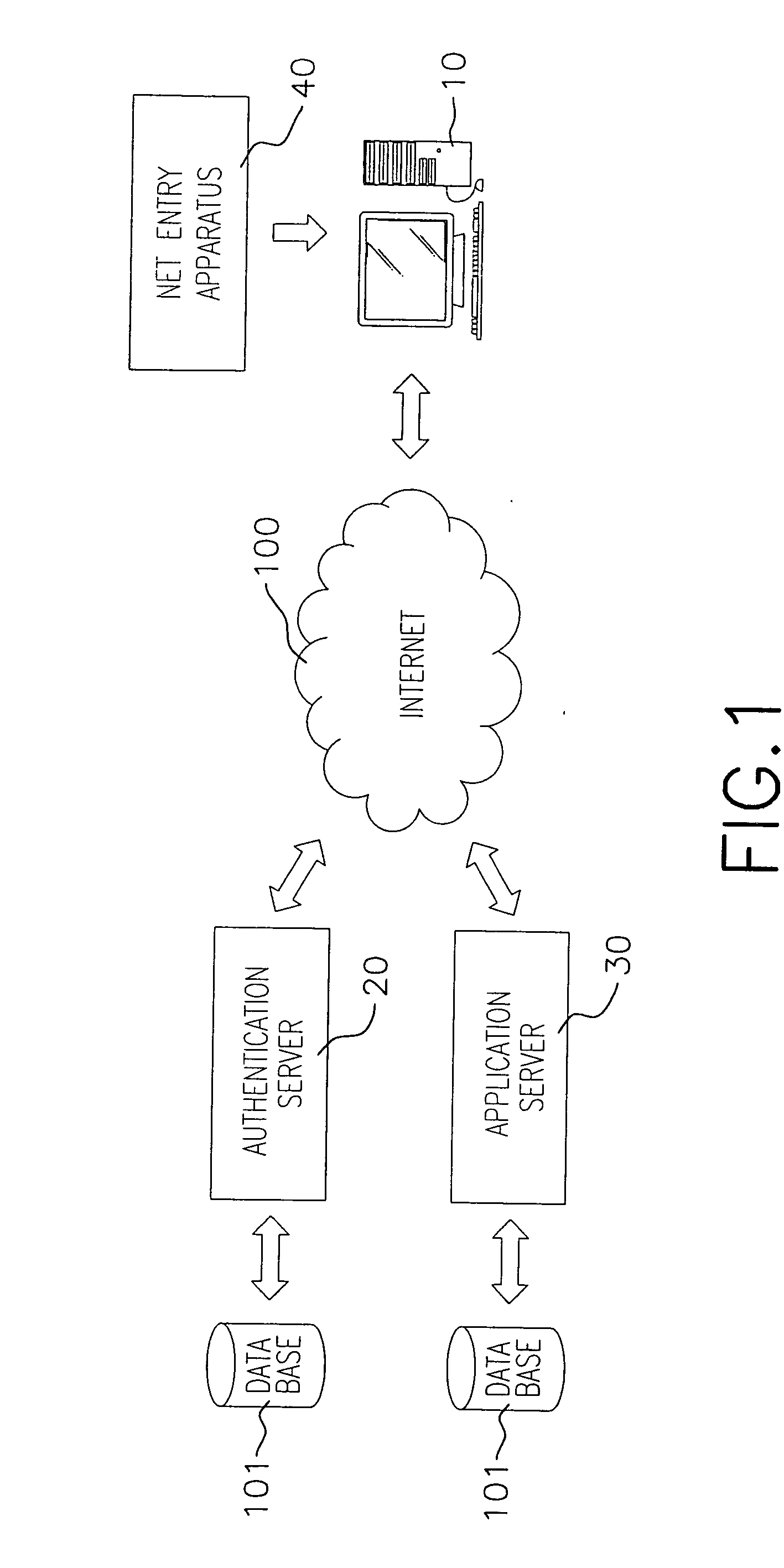
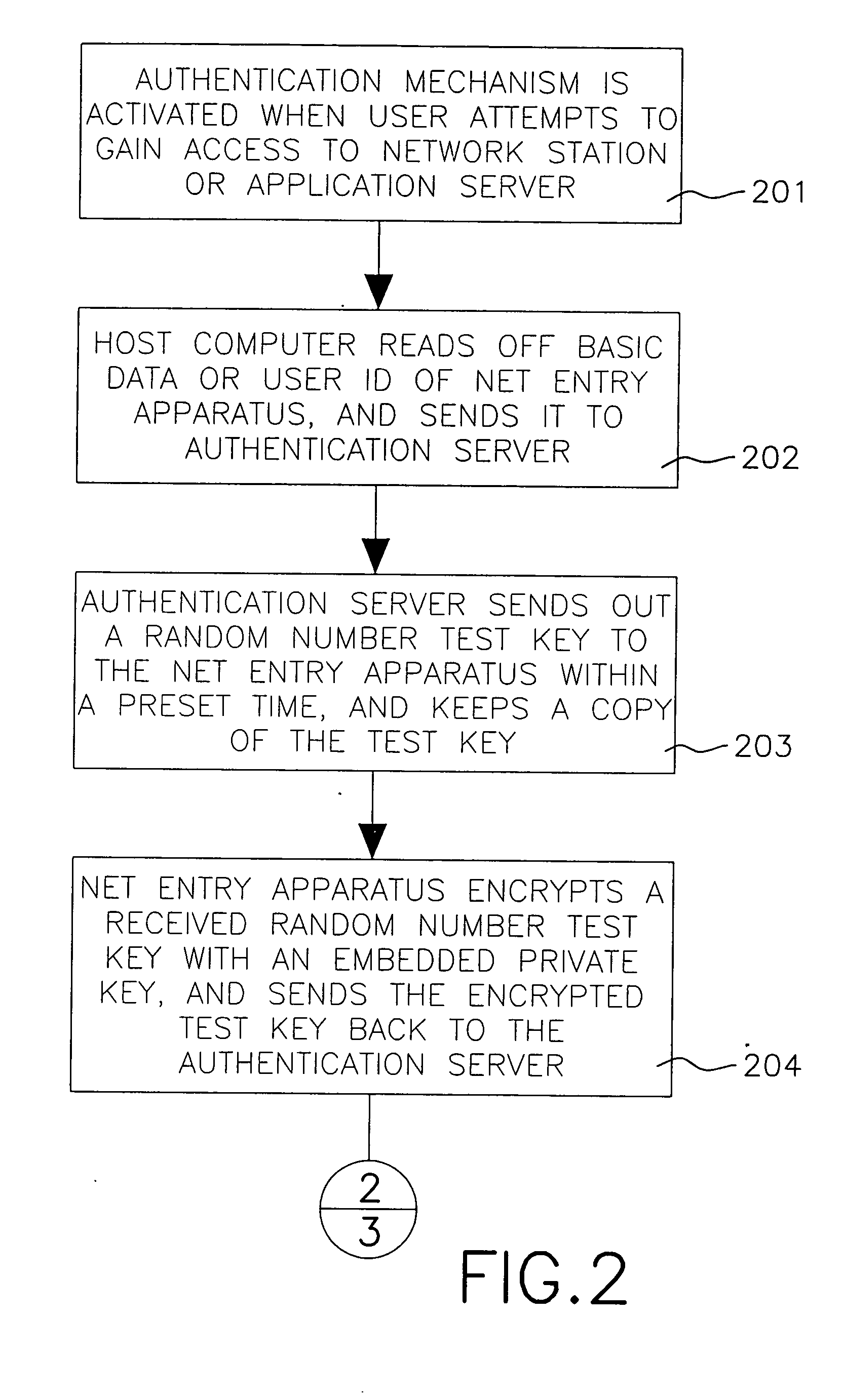
Method of authenticating user access to network stations
InactiveUS20050044377A1Ensure safetyKey distribution for secure communicationUser identity/authority verificationApplication serverPassword
A method of authenticating a user access to network stations is disclosed. Users of the new authentication system do not need to input passwords to gain access to the network stations for on-line transactions, as the authentication job is handled by the authentication server and the net entry apparatus through a host computer. A token is generated dynamically and sent to the application server to which the user intends to gain access, and the verification process is then activated between the authentication server and the application server, which then retrieves a symmetrical copy of the token to compare with the token passed from the application server. If both tokens match up, the user ID has passed the security check. Users are freed from having to memorize different user IDs and passwords to operate many network accounts, with no risk of losing network account numbers and passwords.
Owner:CHOU CHIN INDAL
Apparatus and method for location specific authentication using powerline networking
ActiveUS20050005150A1Stop theftTransmission/receiving by modifying power source waveMemory loss protectionData packEngineering
A mechanism for ensuring the physical location of data processing devices as a security check is provided. With this mechanism, security data is transmitted to data processing devices via an electrical network and is used to perform a security check to determine if the data processing device may operate. The data processing devices may be limited such that they may only power-up, boot-up, or remain operational when they are coupled to the electrical network. Thus, they must be physically located such that they may gain access to the electrical network. In addition, a security check may be used to control which data processing devices may communicate data packets with one another over the data network. When a data packet is received by a data processing device, security data in the data packet is compared against a local history of security data received by the recipient of the data packet via the electrical network. If matching security data is found in the history for the same time represented by an associated timestamp, then the sending data processing device and the receiving data processing device are determined to be present on the same electrical network and may communicate with one another.
Owner:GOOGLE LLC
Check writing point of sale system
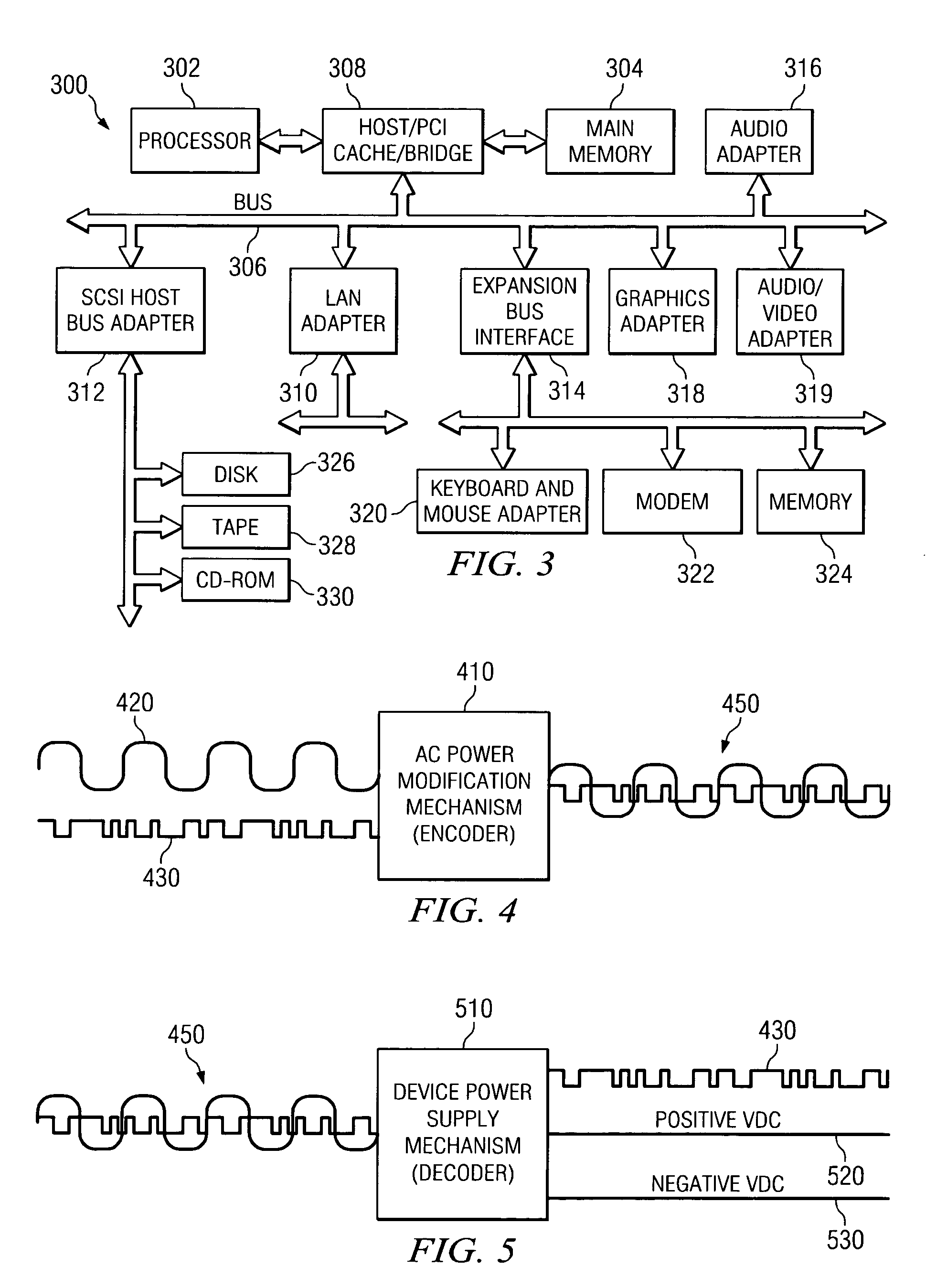
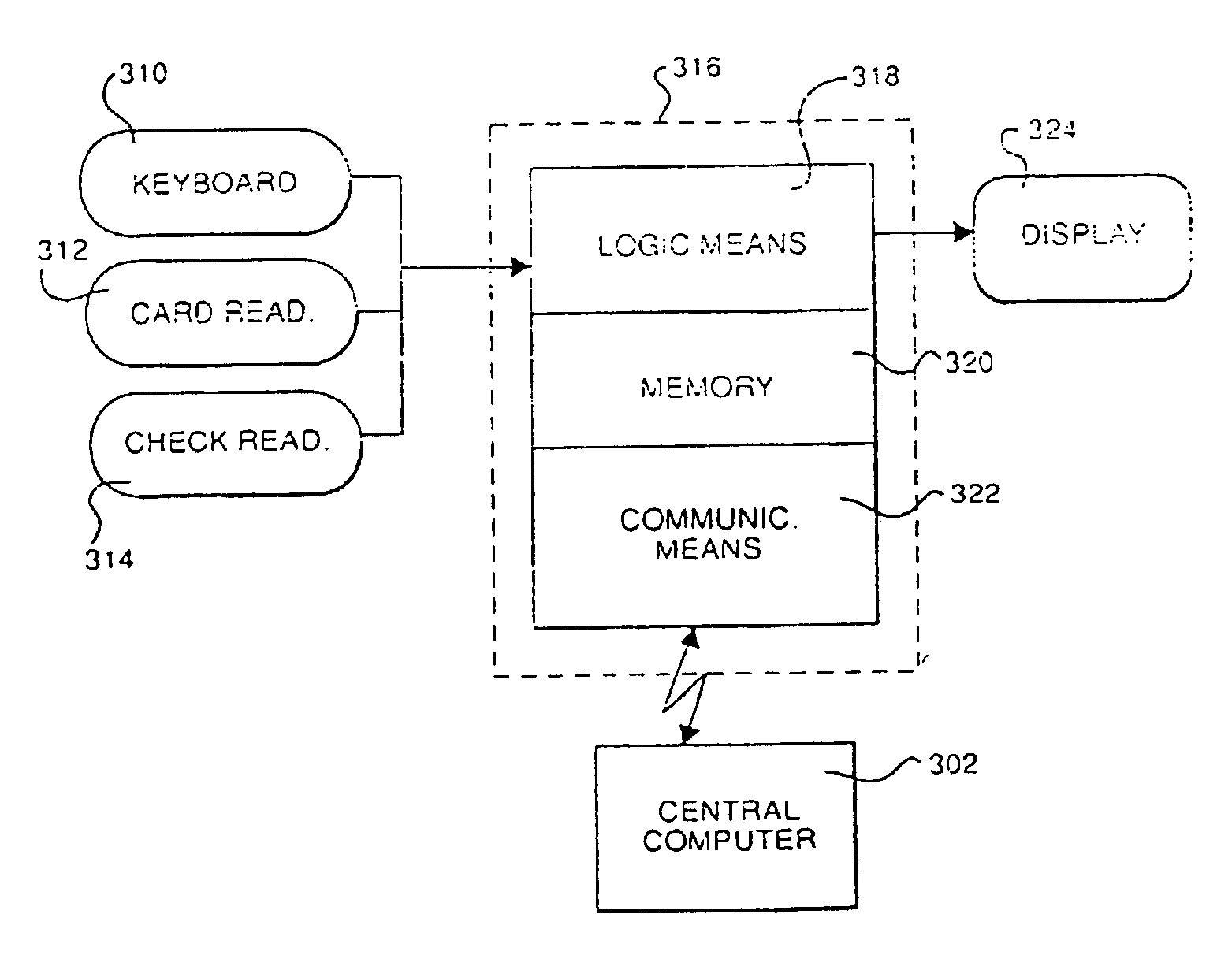
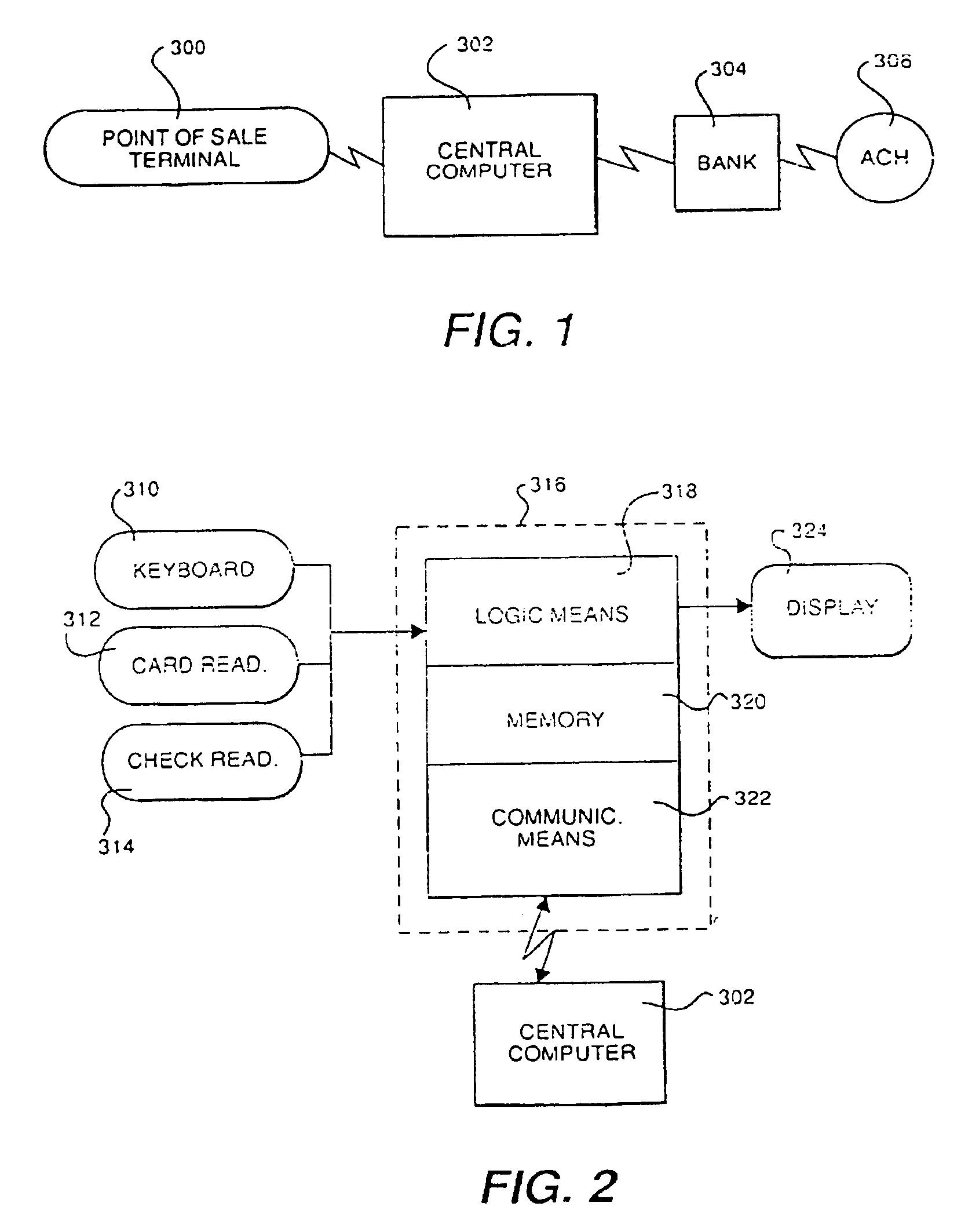
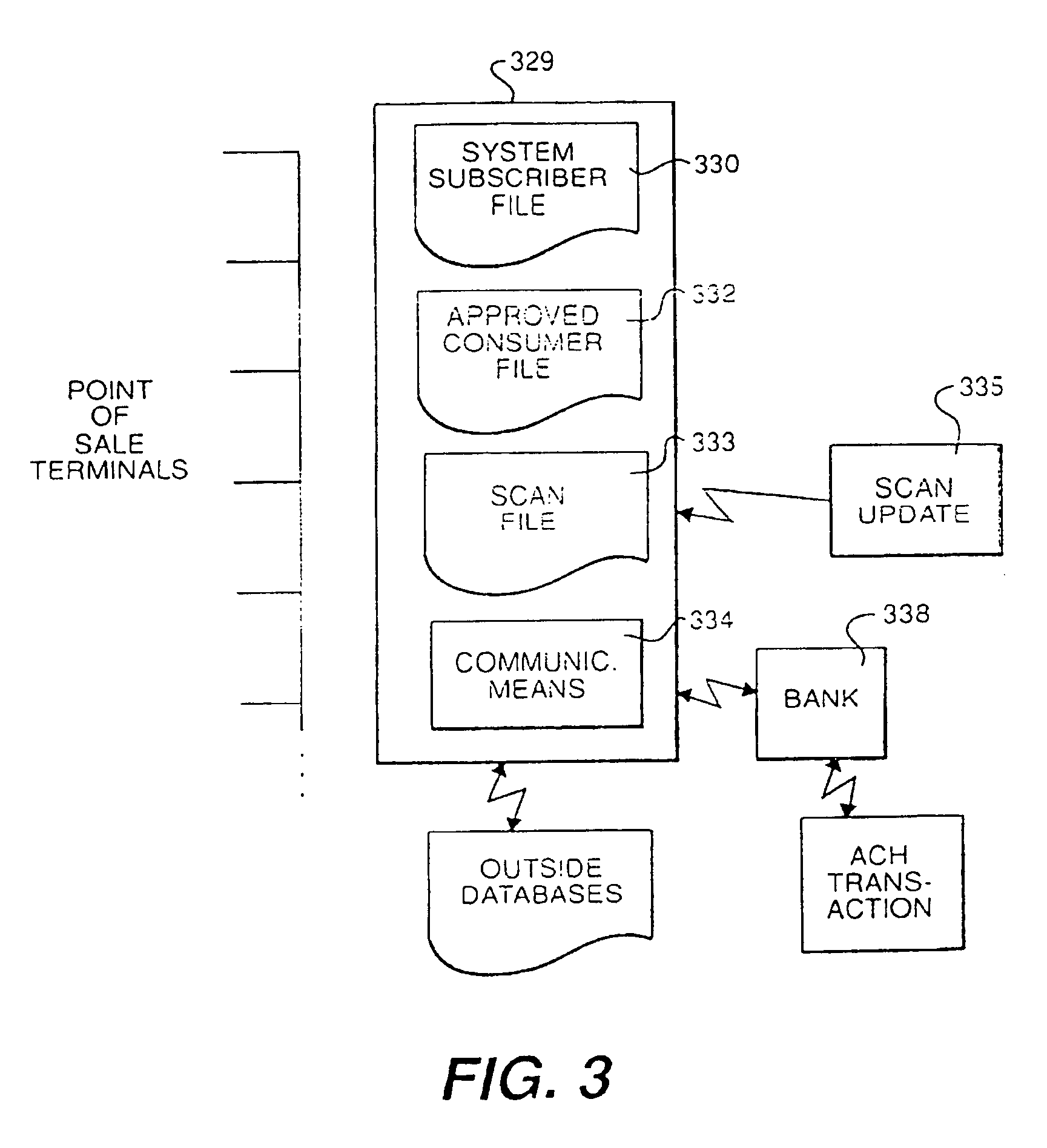
InactiveUSRE40220E1Easy accessEfficient use ofComplete banking machinesFinanceCredit cardSystems design
A point of sale system designed to read information from a consumer's check, credit card, or manual input with a subsequent debiting of a consumer's account and crediting merchant's account for the goods or services provided. Point of sale terminals are designed to accept a form of credit card with a consumer's bank account information encoded thereon or in the alternative to read the MICR number from a consumer's check in order to verify that a consumer has an appropriate balance to conduct the transaction with a given merchant. Thereafter the transaction of that information is transmitted to a central computer system which verifies the consumer's credit worthiness and stores the transaction event information for subsequent bank reconciliation via the ACH or other competing network. The invention eliminates the need for paper checks with all bank reconciliation being accomplished electronically. The present invention also includes fraud protection provisions such as velocity controls, social security checks, and scans. The present invention has the further flexibility to differentiate between “first time” consumer usage and those limits otherwise assigned to “known” consumer accounts. Additionally, there is not need for the present system to retain the consumer's check after verification.
Owner:LML PATENT CORP
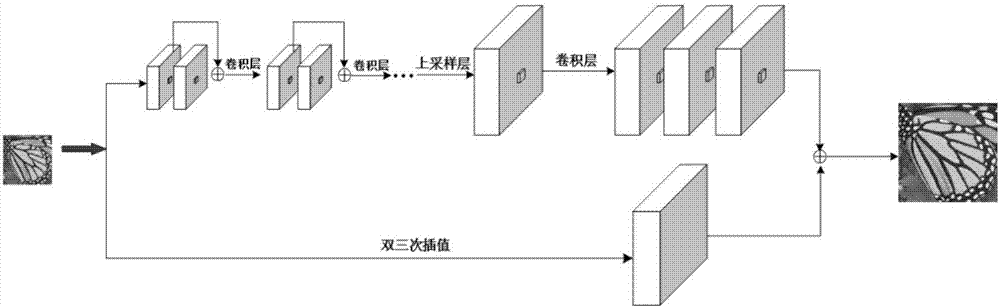
Single-image super-resolution reconstruction method based on deep residual network
InactiveCN107358575AImprove rebuild speedAchieving continuous scalingGeometric image transformationReconstruction methodImage compression
The invention discloses a single-image super-resolution reconstruction method based on a deep residual network. The method of the invention mainly comprises a first step of performing block extraction and pixel averaging processing on an image in a sample image database to obtain a corresponding high resolution and low resolution training image sets; a second step of constructing a deep convolutional neutral network with a residual structure for iterative training, and then inputting the training set obtained in the first step to the neural network constructed in the second step for iterative training; and a third step of according to a data model obtained by training, realizing the continuous up-scaling of the input low resolution image through the combination of iterative operation and an interpolation algorithm. By introducing a deep residual network and introducing an upsampling layer at the end of the network, the method of the invention accelerates the processing speed of the image up-scaling, enhances the display effect of the image details, obtains a better image super-resolution reconstruction effect, and has a wide range of applications in the image high definition display, image compression, security checks and other fields.
Owner:TSINGHUA UNIV
Metering device and process to record engine hour data
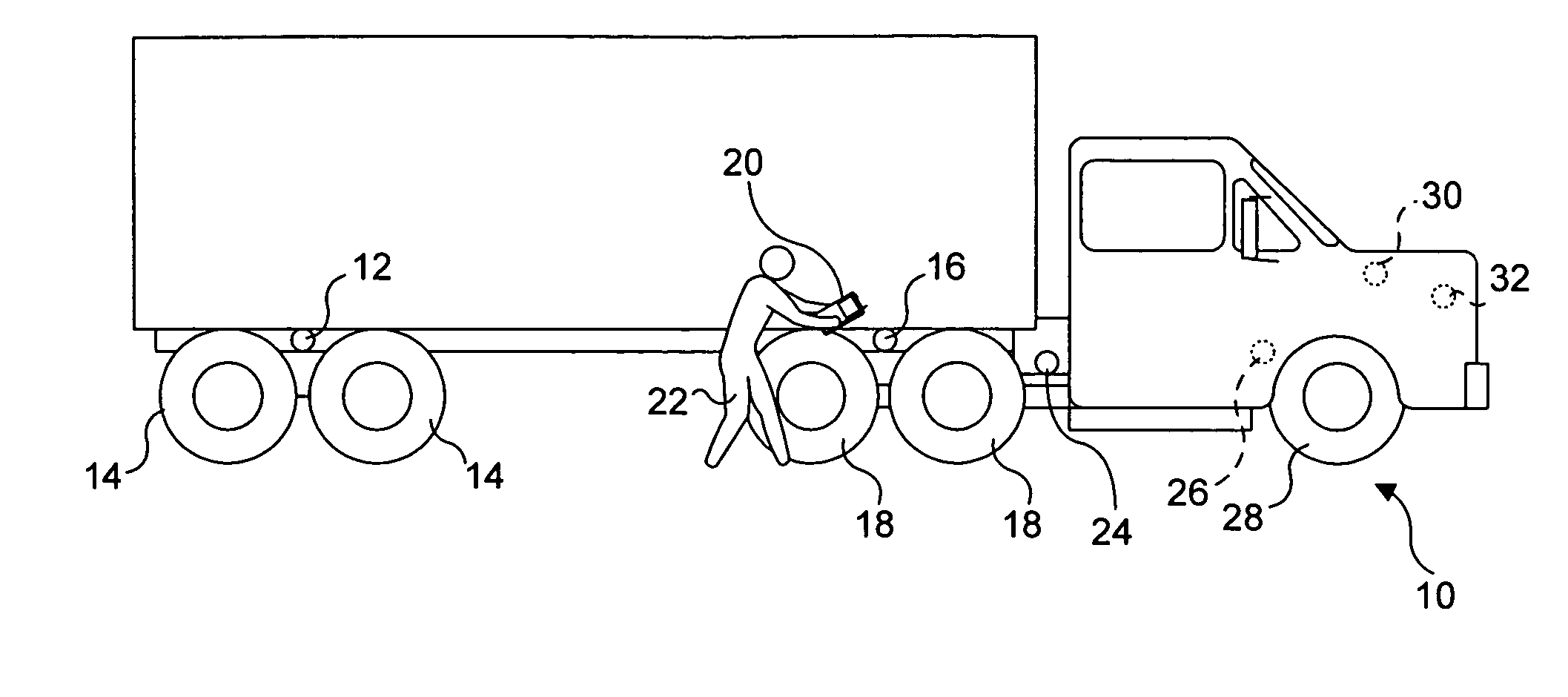
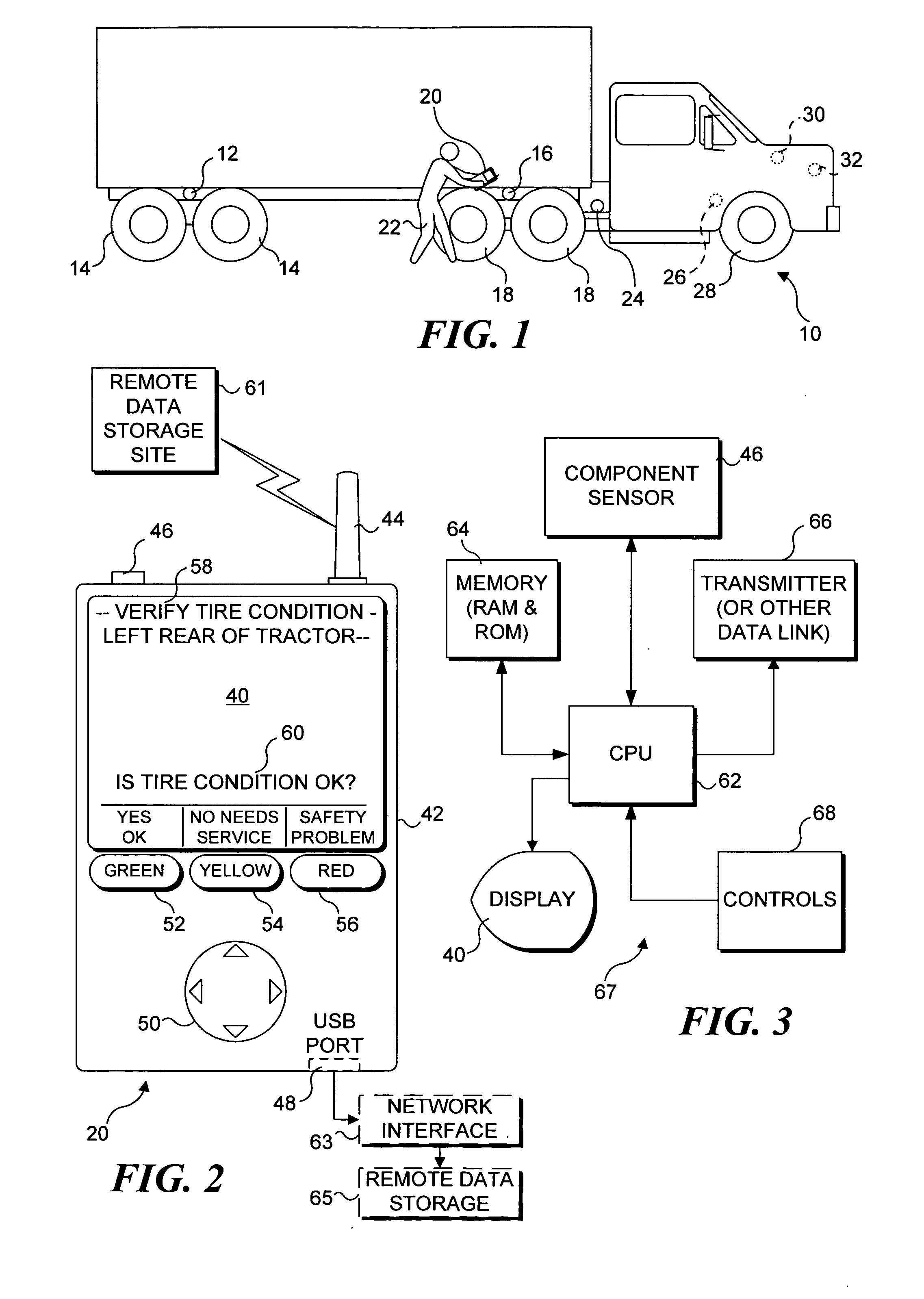
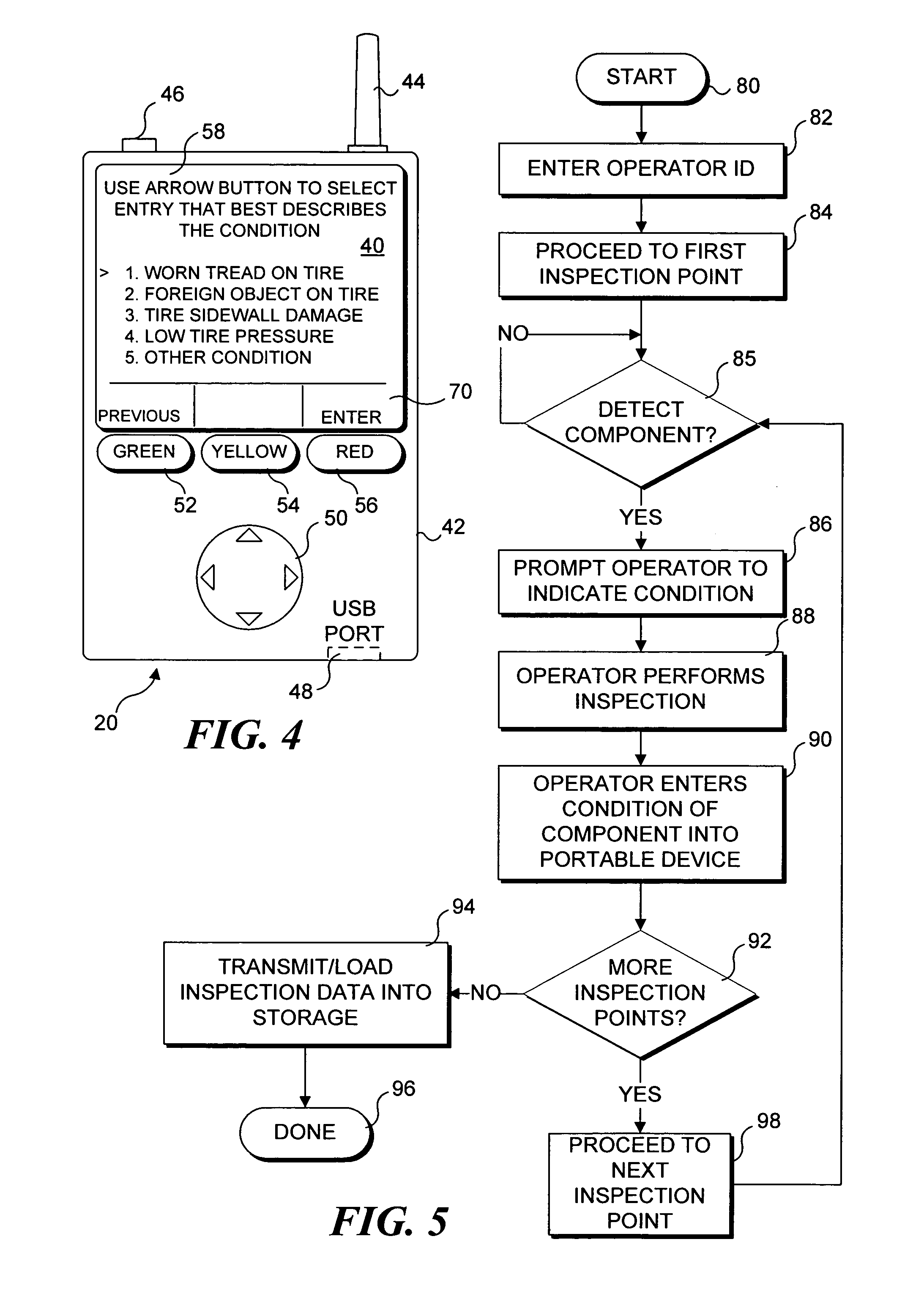
InactiveUS20050256681A1Registering/indicating working of vehiclesRoad vehicles traffic controlHand heldReliability engineering
A handheld, portable device (20, 140 , or 140′ ) is used to store data that indicate an operator was sufficiently close to each of a plurality of components during a safety inspection to actually inspect the components. The portable device includes a sensor (46) that detects tokens (12, 16, 24), such as radio frequency identification tags, which are affixed adjacent to the components. Messages (58) appearing on a display (40, 152) of the portable device prompt the operator to proceed to each checkpoint, determine a state of the component disposed there, and if the component is not operating properly, indicate a plurality of predefined conditions from which the operator can choose to identify the observed condition of the component. The state and condition of each component entered during the safety inspection are stored as data that are subsequently transferred to a remote data storage site over a wire or wireless link.
Owner:ZONAR SYST
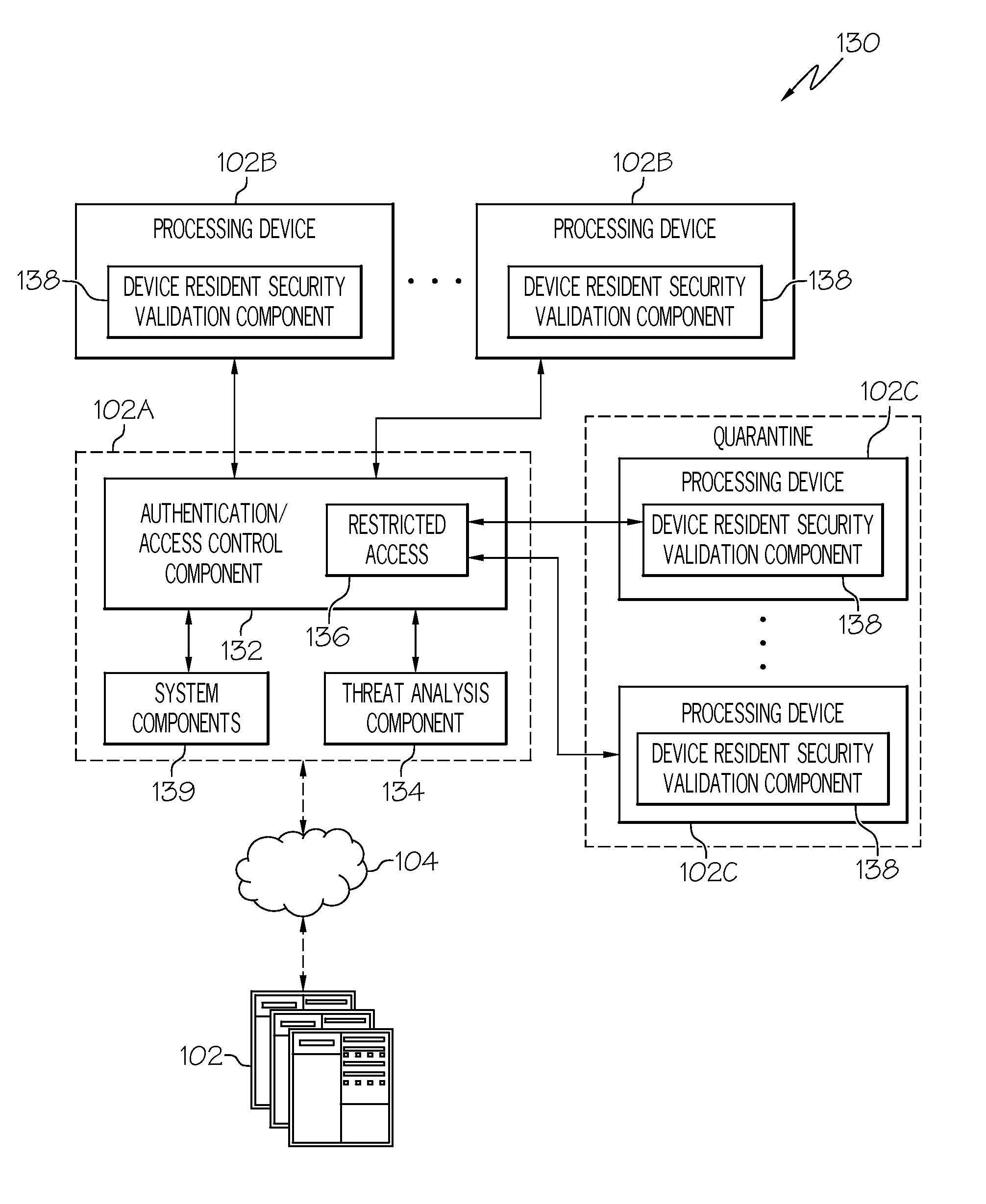
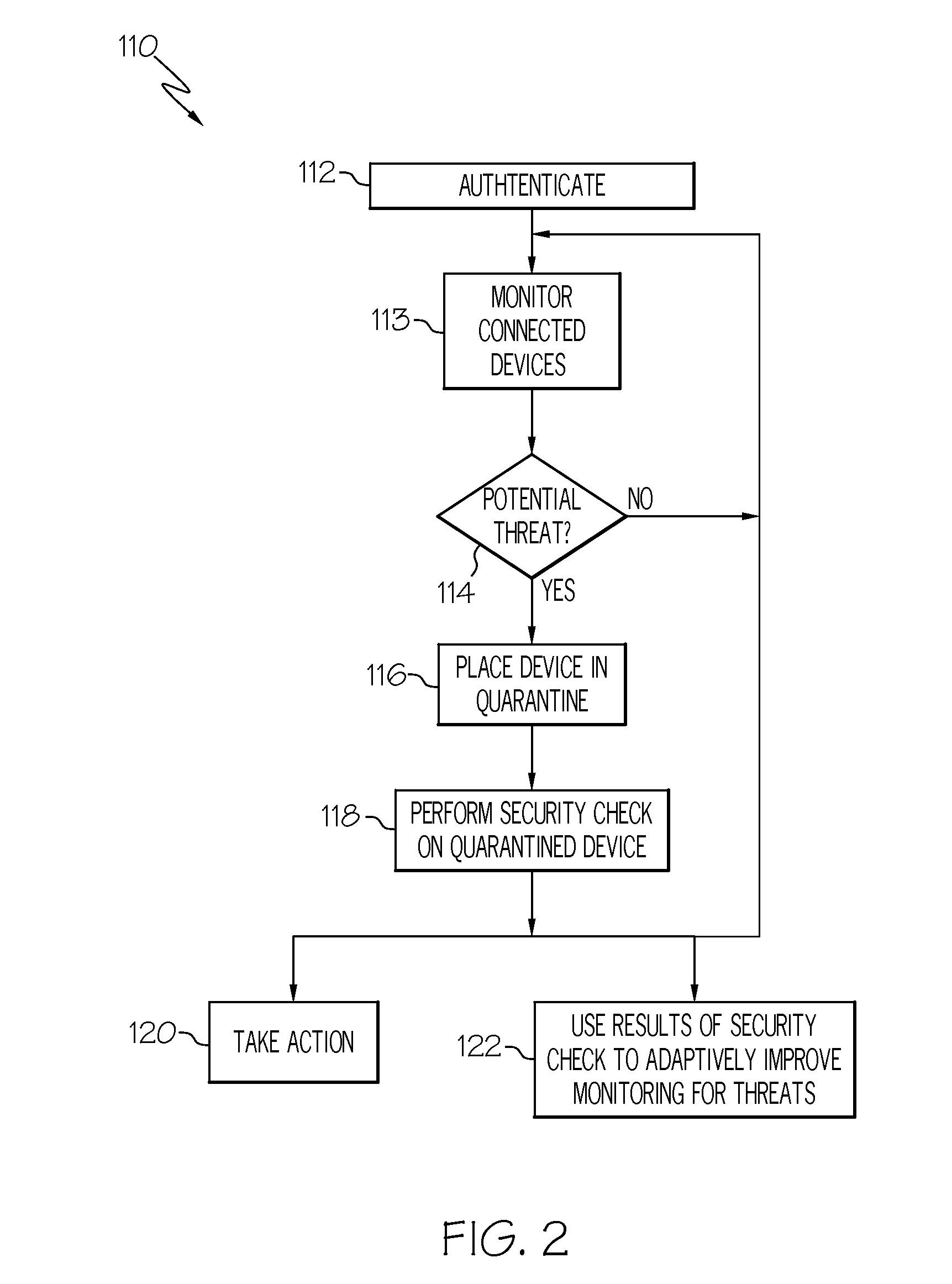
Adaptive Autonomic Threat Detection and Quarantine
InactiveUS20090064334A1Memory loss protectionUnauthorized memory use protectionTraffic capacityQuarantine
Autonomic threat detection is performed by collecting traffic samples of traffic patterns associated with a networked device having a device resident validation module. A threat analysis system is used to recognize a pattern of traffic indicative of a compromised device based at least in part upon the traffic samples. If the samples indicate a compromised device, the device is quarantined and a security check is performed on the device. The security check may include requesting data from the corresponding device resident validation module to determine if the device is compromised, analyzing data from the device resident validation module of the quarantined device and taking an action based upon analysis of the data. At least one of the data from the device resident validation module of the quarantined device or the traffic samples is utilized to autonomically train the threat analysis system to identify compromised devices.
Owner:IBM CORP
Methods and systems for use in security screening, with parallel processing capability
InactiveUS20090175411A1Increase probabilityCharacter and pattern recognitionMaterial analysis by transmitting radiationReference databaseEngineering
A security screening system to determine if an item of luggage carries an object posing a security threat. The security screening system may comprise an input for receiving image data derived from an apparatus that subjects the item of luggage to penetrating radiation, the image data conveying an image of the item of luggage. The security screening system may also comprise a processing module for processing the image data to identify in the image a plurality of regions of interest, the regions of interest manifesting a higher probability of depicting an object posing a security threat than portions of the image outside the regions of interest. The processing module may comprise: a first processing entity for processing a first one of the regions of interest to ascertain if the first region of interest depicts an object posing a security threat; and a second processing entity for processing a second one of the regions of interest to ascertain if the second region of interest depicts an object posing a security threat. The processing of the first and second regions of interest by the first and second processing entity occurs in parallel. Different processing entities may also be used to process in parallel different sets of entries a reference database to determine if an item of luggage carries an object posing a security threat.
Owner:OPTOSECURITY
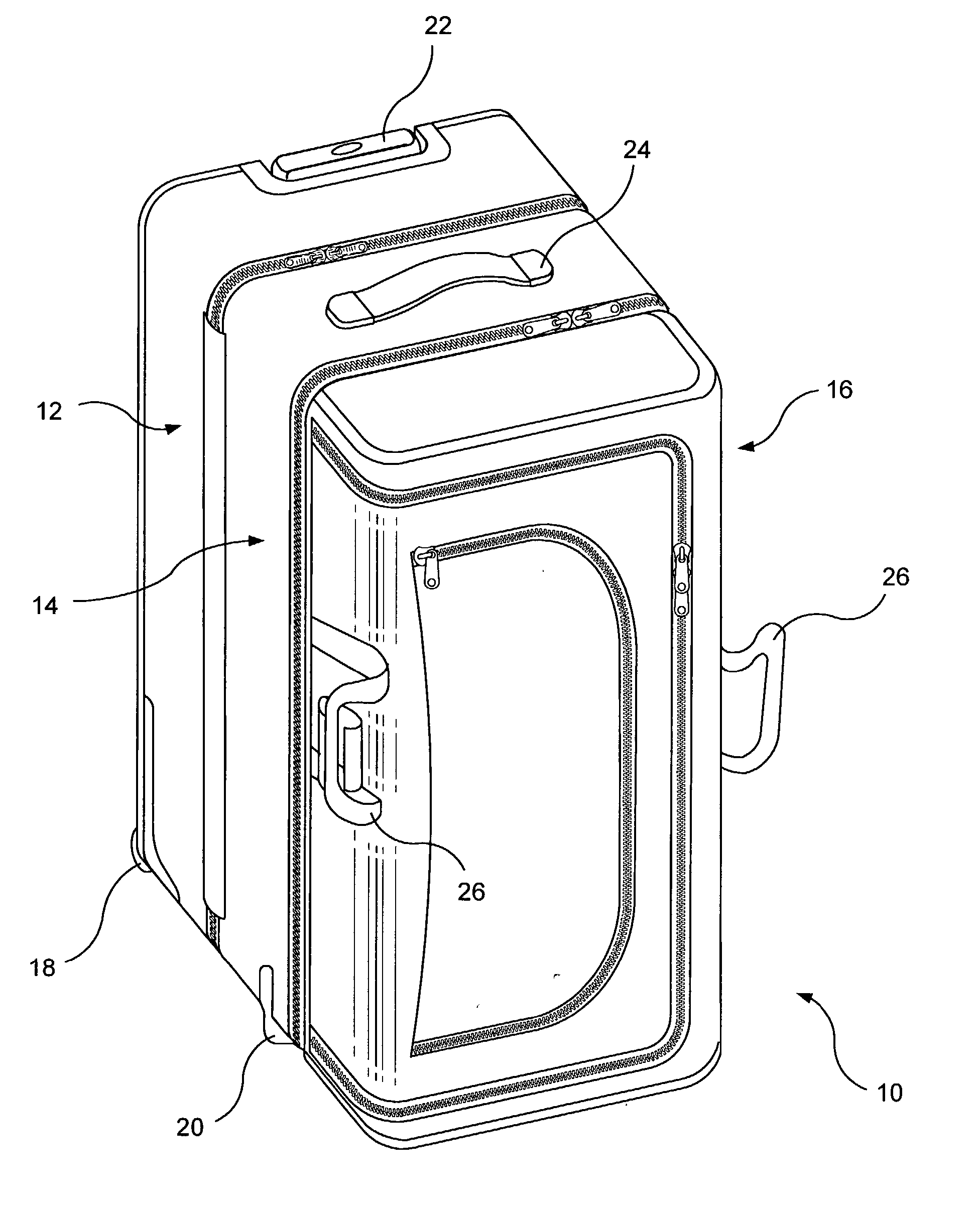
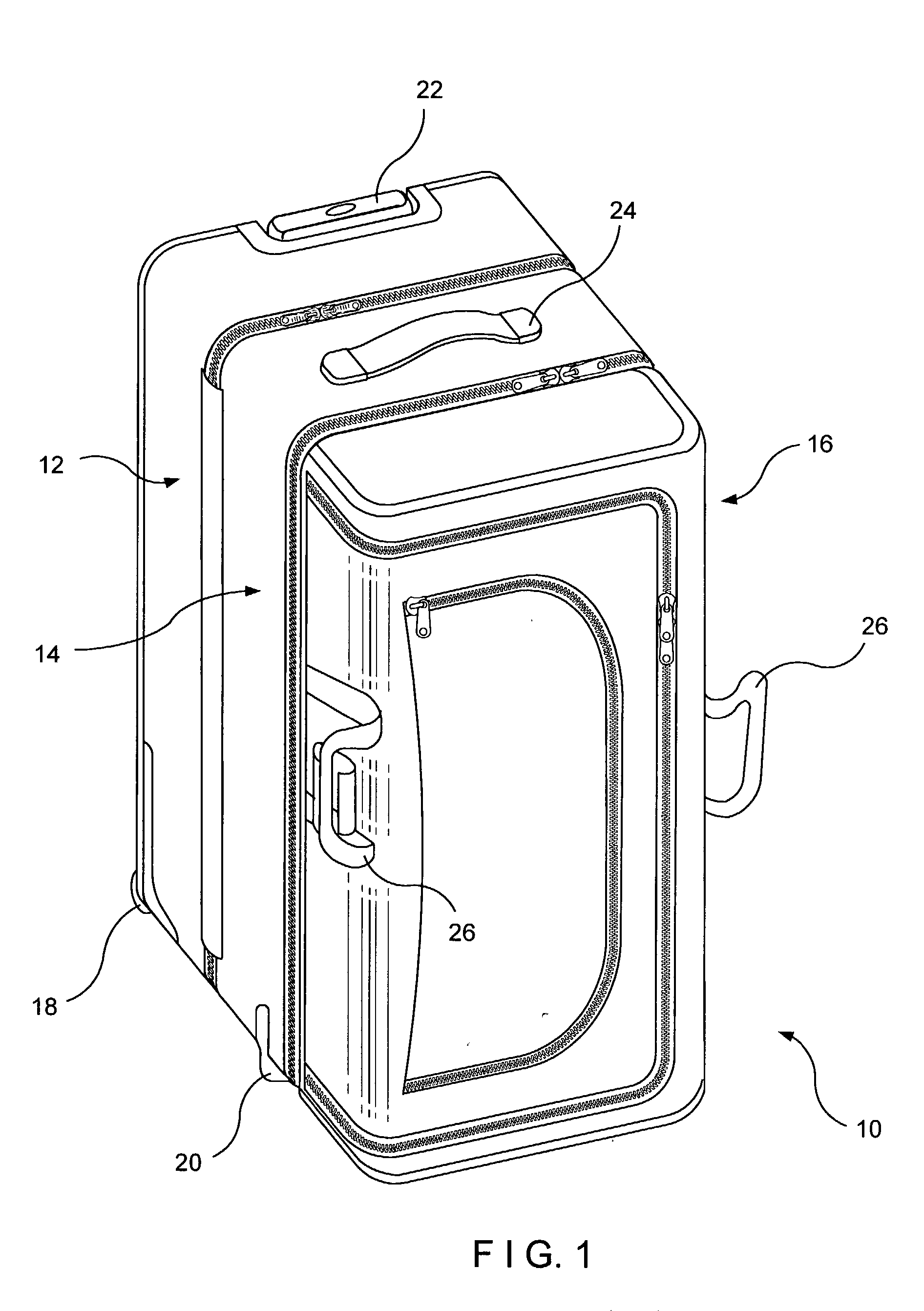
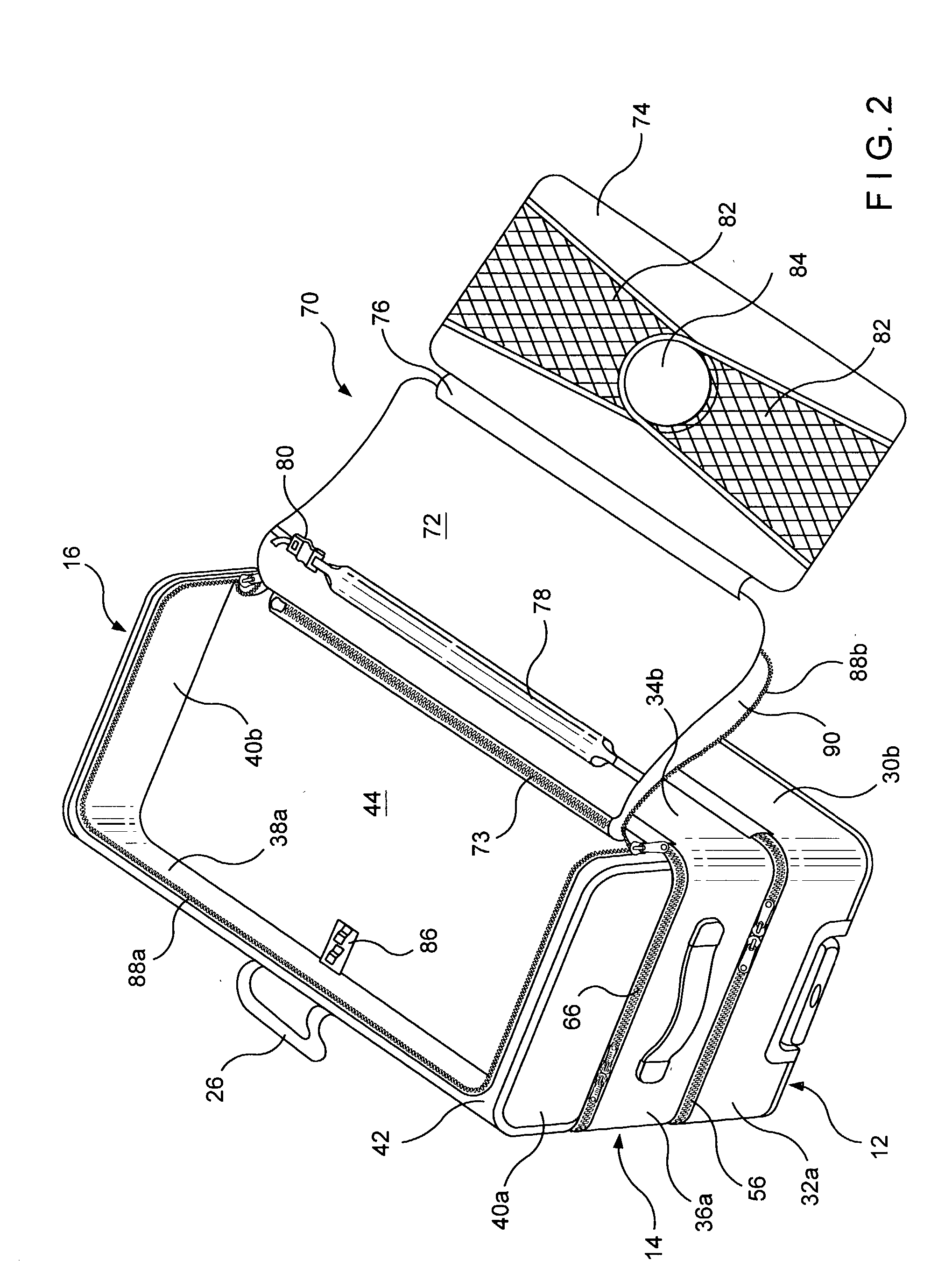
Easy-access bag
An easy-access bag includes three compartments that are hinged together so as to be foldable between a closed position, in which all three compartments form a compact, integral bag for carrying or towing, and an open position, in which all three compartments lie in side-by-side relation to each other and are all simultaneously accessible for packing or unpacking or for security inspections.
Owner:TUMI INC
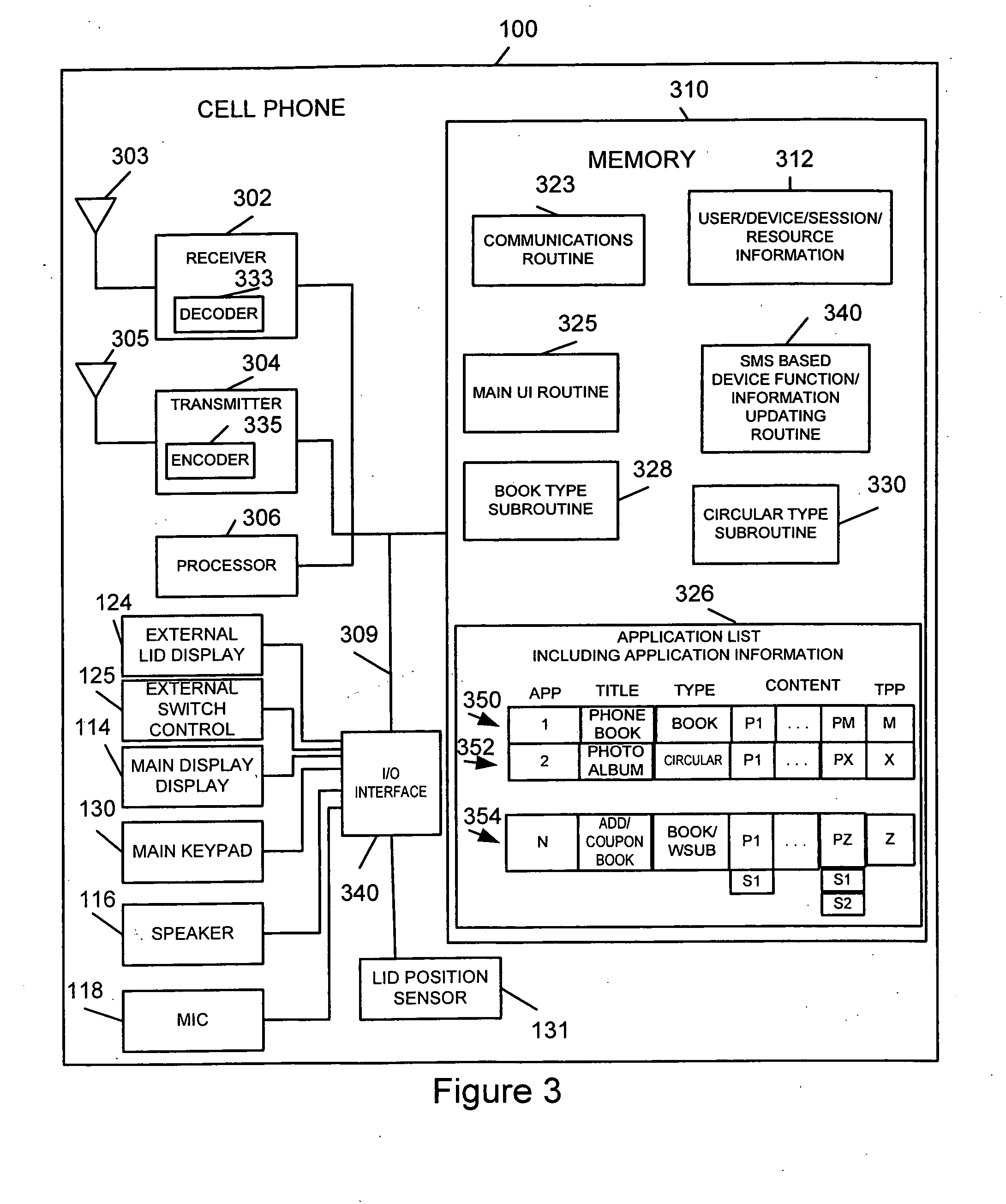
Methods and apparatus for updating a communications device using SMS messages
InactiveUS20070087765A1Substation equipmentRadio/inductive link selection arrangementsComputer hardwareSecurity check
Method and apparatus for using text messages, e.g., SMS messages, to trigger a device update and / or to update a communications device, e.g., cell phone, are described. The cell phone can be updated / programmed from a remote device. The updating can use SMS messages to accomplish the update. An SMS message may include a command and, optionally, other update information in the message body. Received SMS messages are checked to determine if they include an update command. If an update command is present the command is performed after a security check is satisfied. In some but not necessarily all embodiments, a simplified user interface is supported in addition to SMS update features.
Owner:DYNA
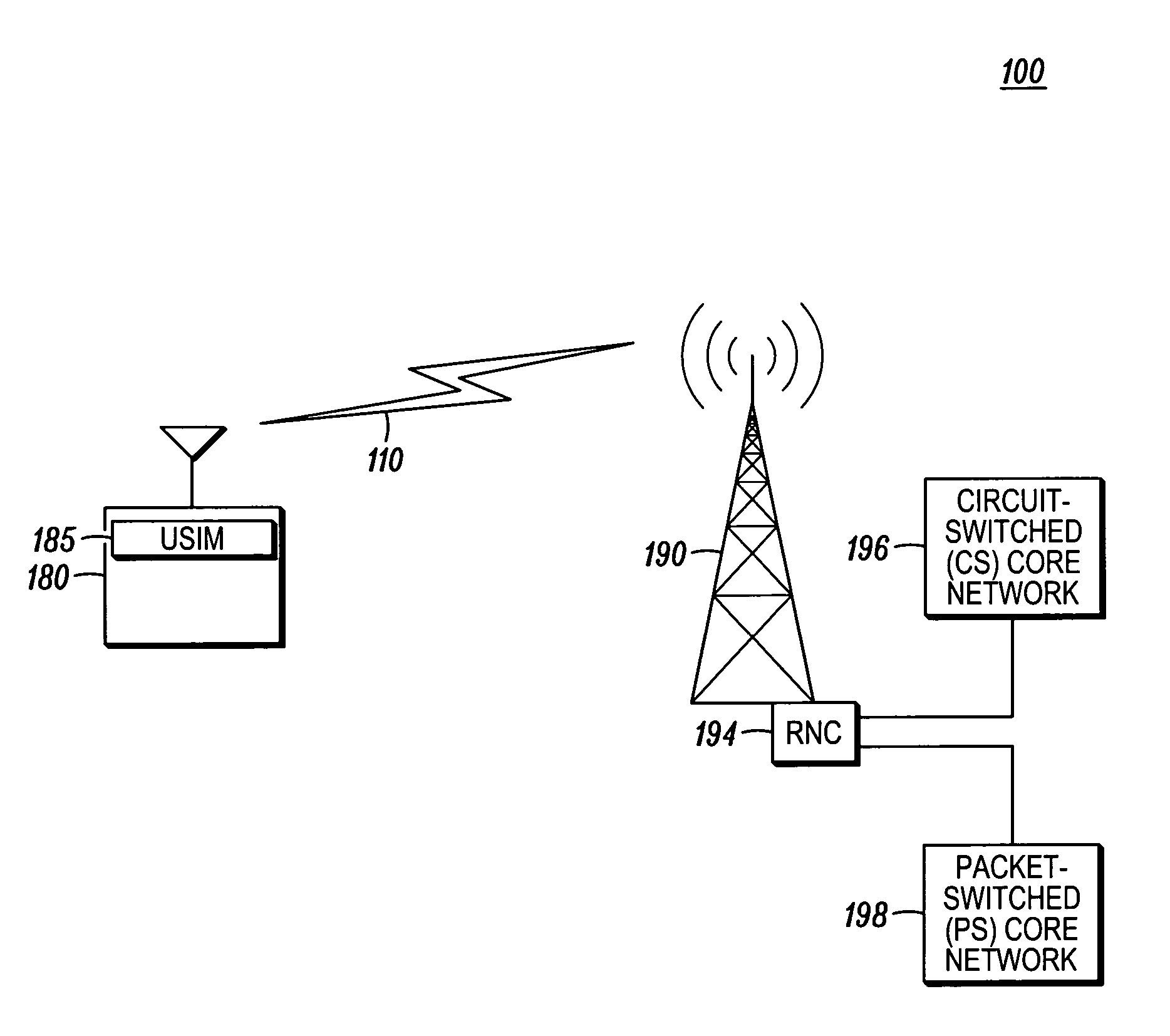
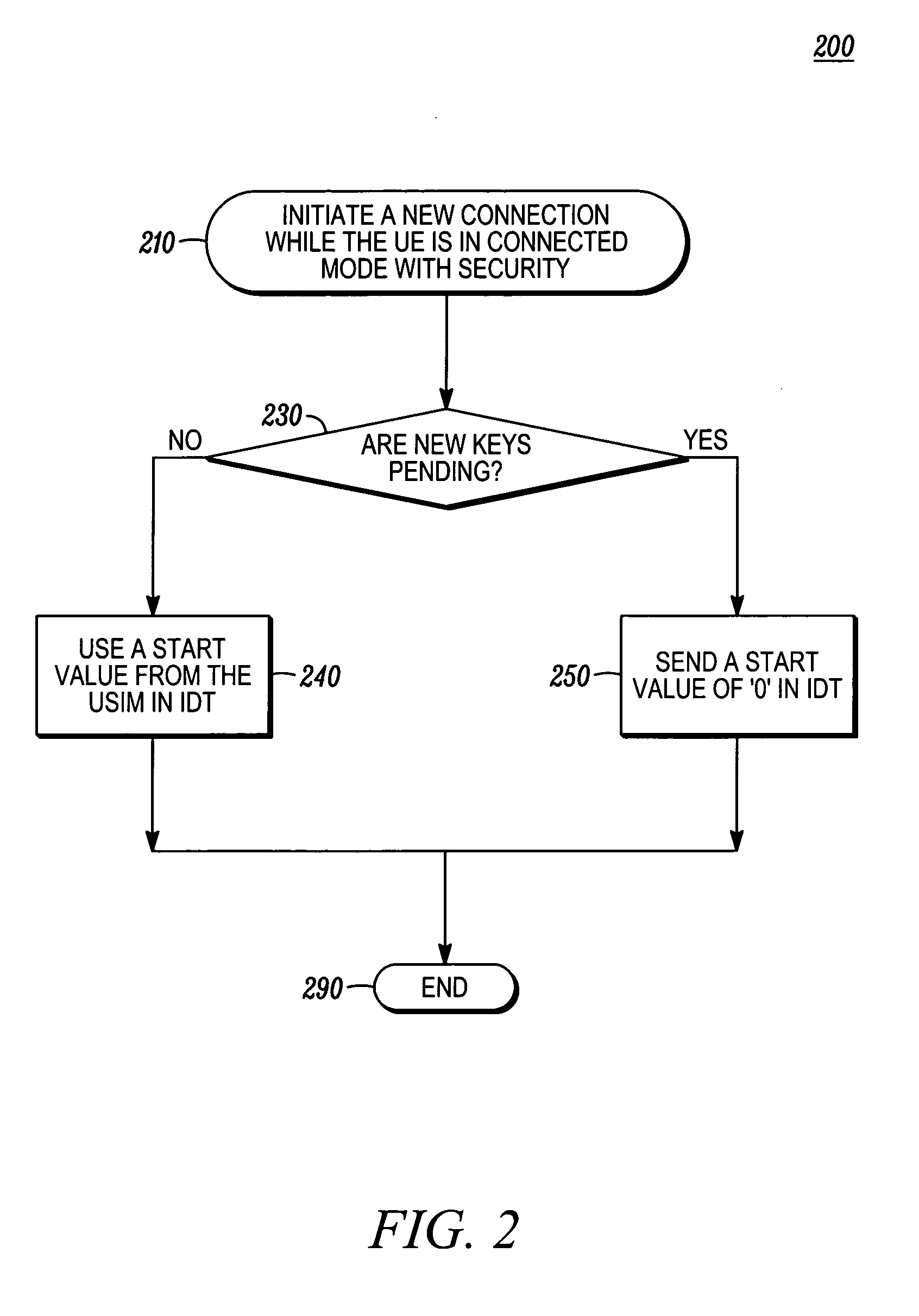
Integrity protection count synchronization method
ActiveUS20070072635A1Synchronisation arrangementUnauthorised/fraudulent call preventionComputer hardwareSecurity check
An integrity protection count synchronization method (200) initiates (210) a new connection when a user equipment (UE) is already in connected mode with a network. If new security keys are pending, the UE sends (250) a START value of zero in an initial direct transfer message. If no new security keys are pending, the UE sends (240) a non-zero START value based on a Universal Subscriber Interface Module (USIM). Sending a START value of zero when new security keys are pending at the UE forces the network's COUNT-I integrity count value to match the zero COUNT-I value at the UE, which prevents call set-up failure due to inability to pass an integrity protection security check.
Owner:GOOGLE TECH HLDG LLC
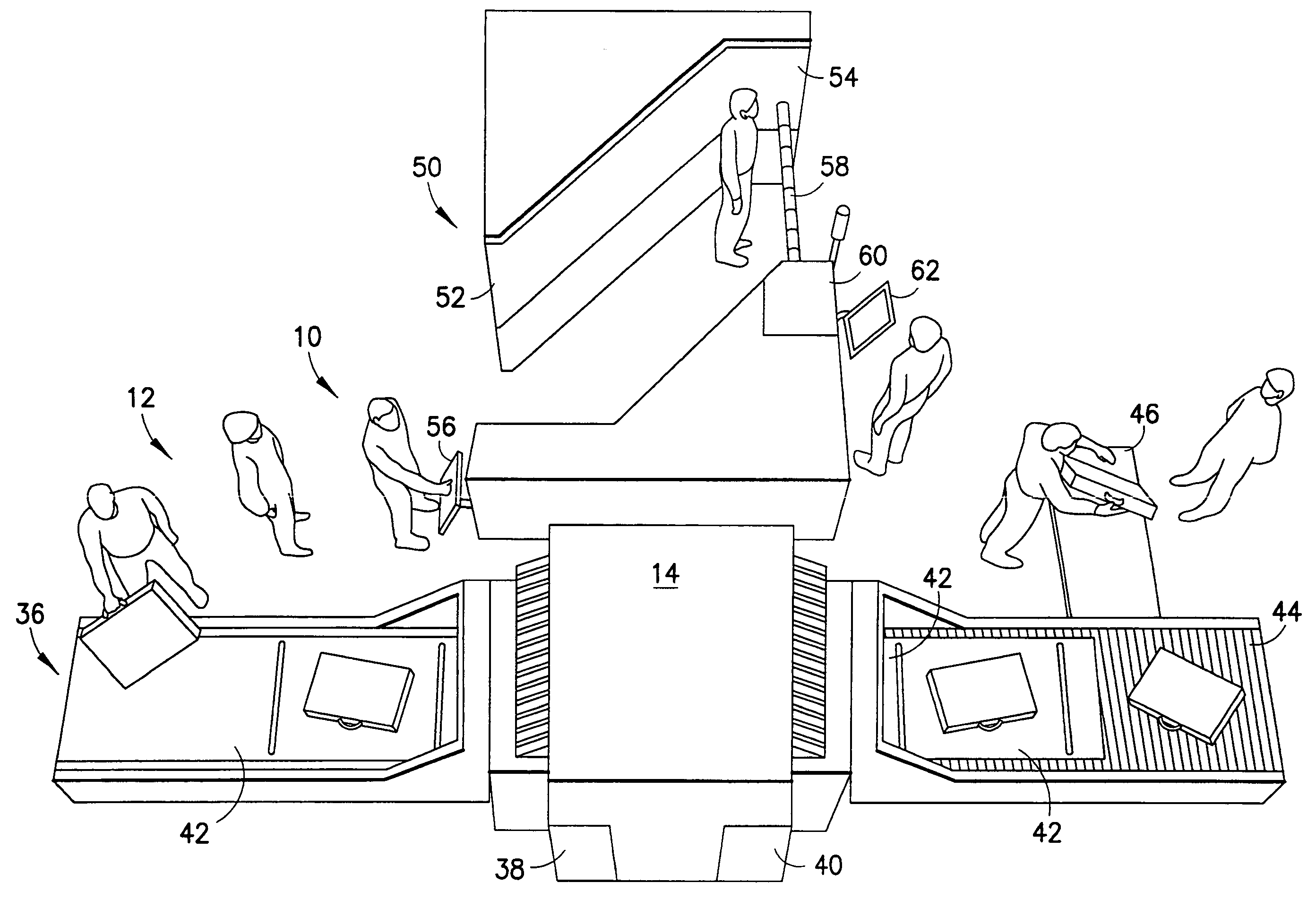
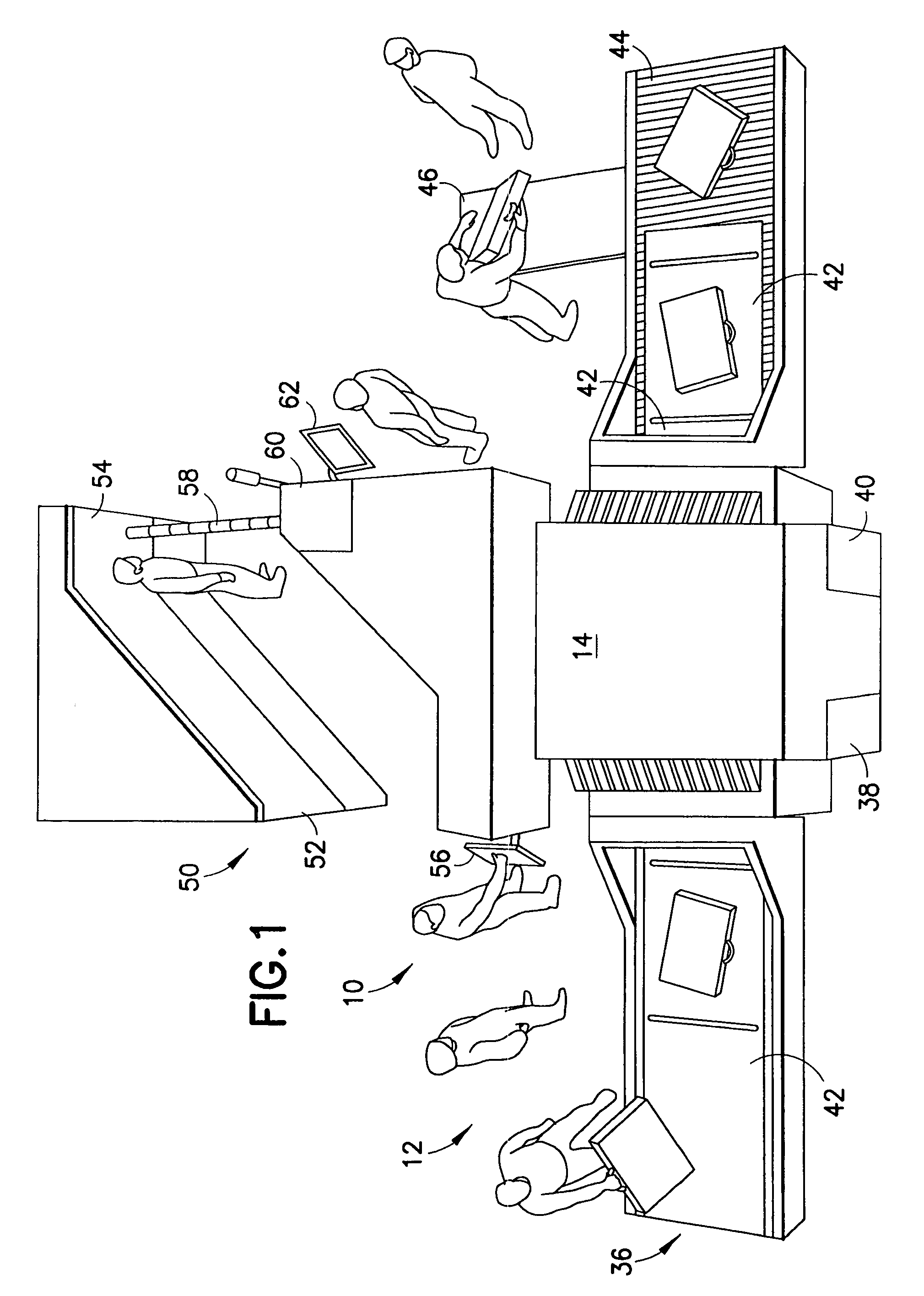
Security checkpoint
ActiveUS7253727B2Individual entry/exit registersGeological measurementsSecurity checkComputer science
A security checkpoint includes a personal scanning portal, a parcel scanning portal and a controller for ensuring substantially simultaneous scanning of a person and the parcel associated with the person. The controller also adjusts the level of scrutiny at each portal based on scanned data received at the other portal and based on information in a database relating to the specific person at the security checkpoint.
Owner:RAPISCAN SYST INC (US)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com