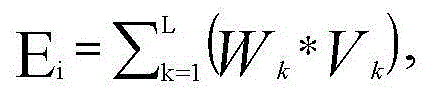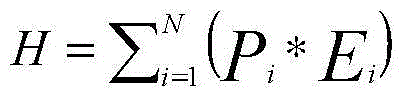Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
71 results about "Security measurement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security measures. n measures taken as a precaution against theft or espionage or sabotage etc. Synonyms: security.
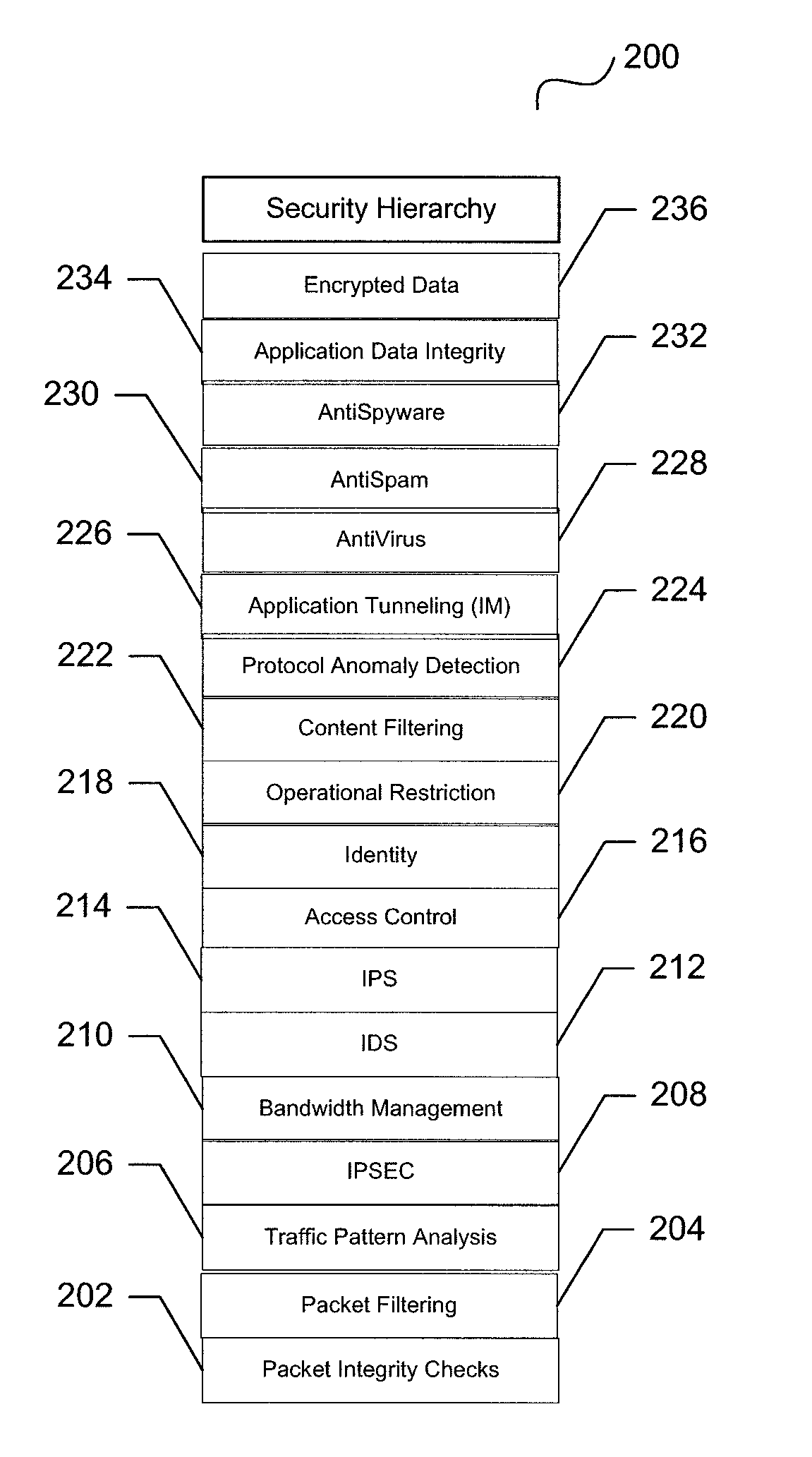
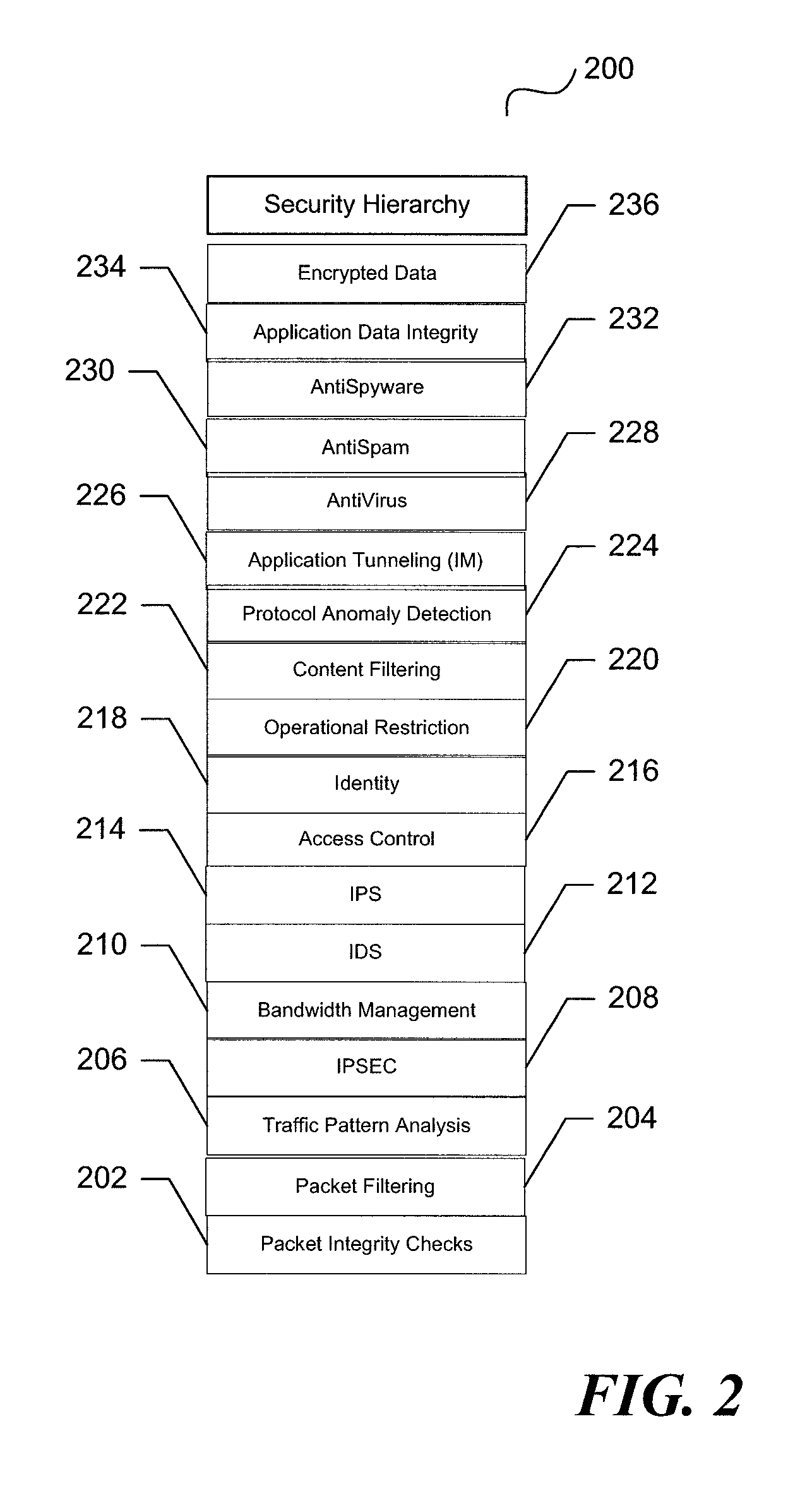
System and method for unified threat management with a relational rules methodology
ActiveUS7735116B1Improve performanceImprove securityDigital data processing detailsUser identity/authority verificationSecurity measurementSecurity Measure
A unified threat management system is provided with a uniform relational rules model. The unified relational rules model provides for the sub-setting of rules and the ability to derive a result based partially from previous security measurements. The sharing of a security check from one security implementation to another using an object-oriented methodology is facilitated. Security policy is divided into specific security features that result in a security hierarchy. The security features may be considered to be listed sequentially, from bottom to top, and form a relationship with one another. These relationships are used to build a current security measure upon a previous security measure and may be used as a pre-cursor when marshalling data content to be validated.
Owner:CA TECH INC
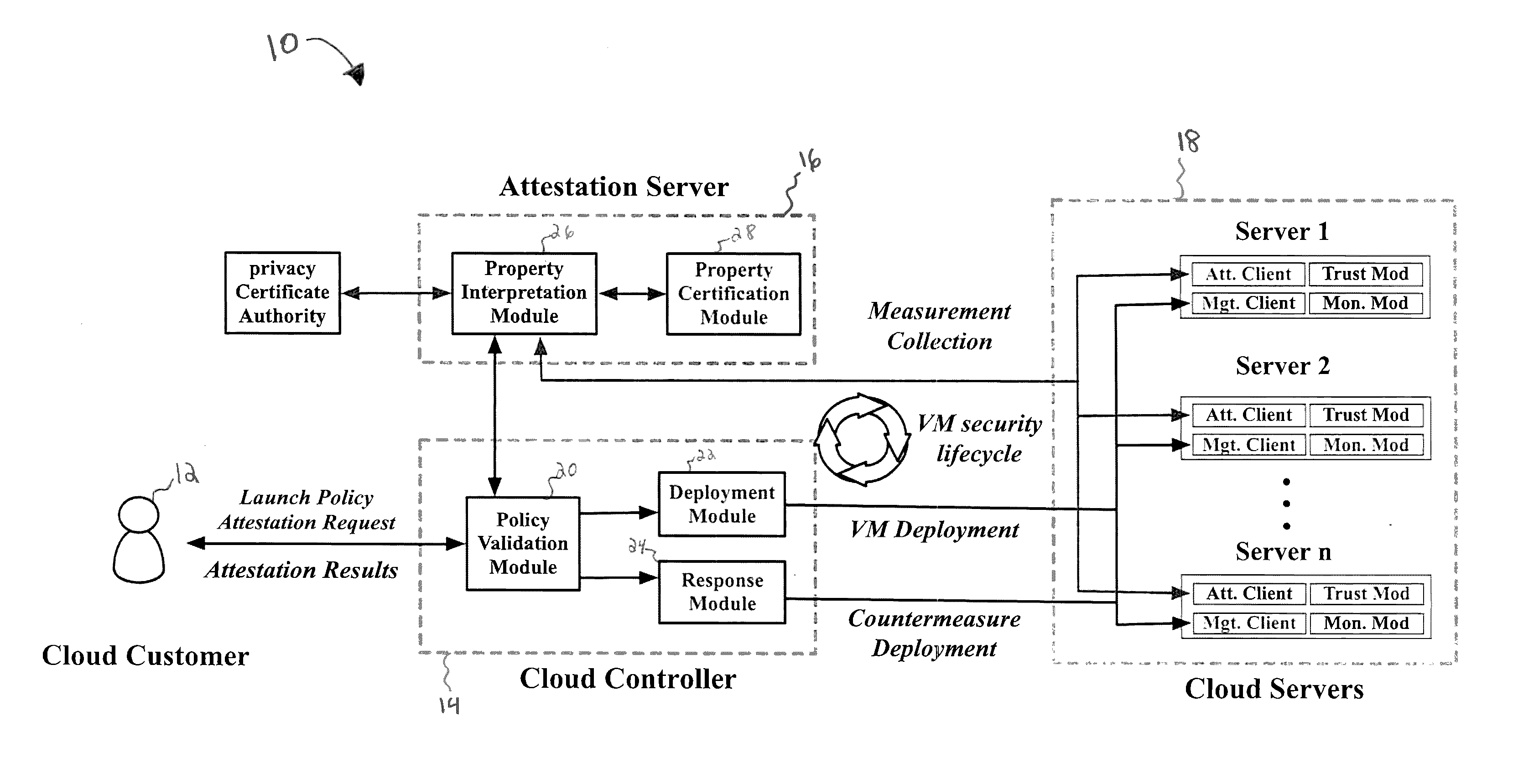
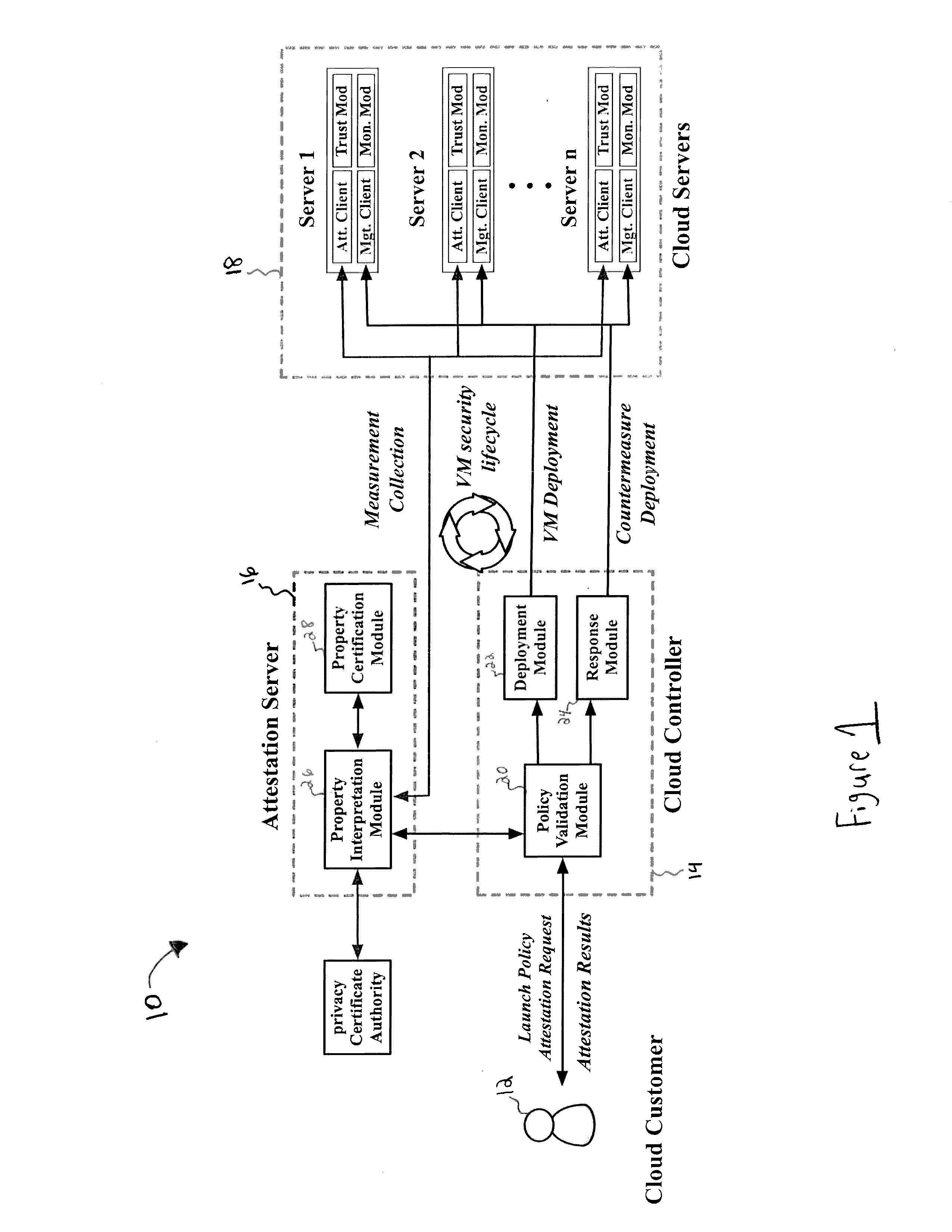
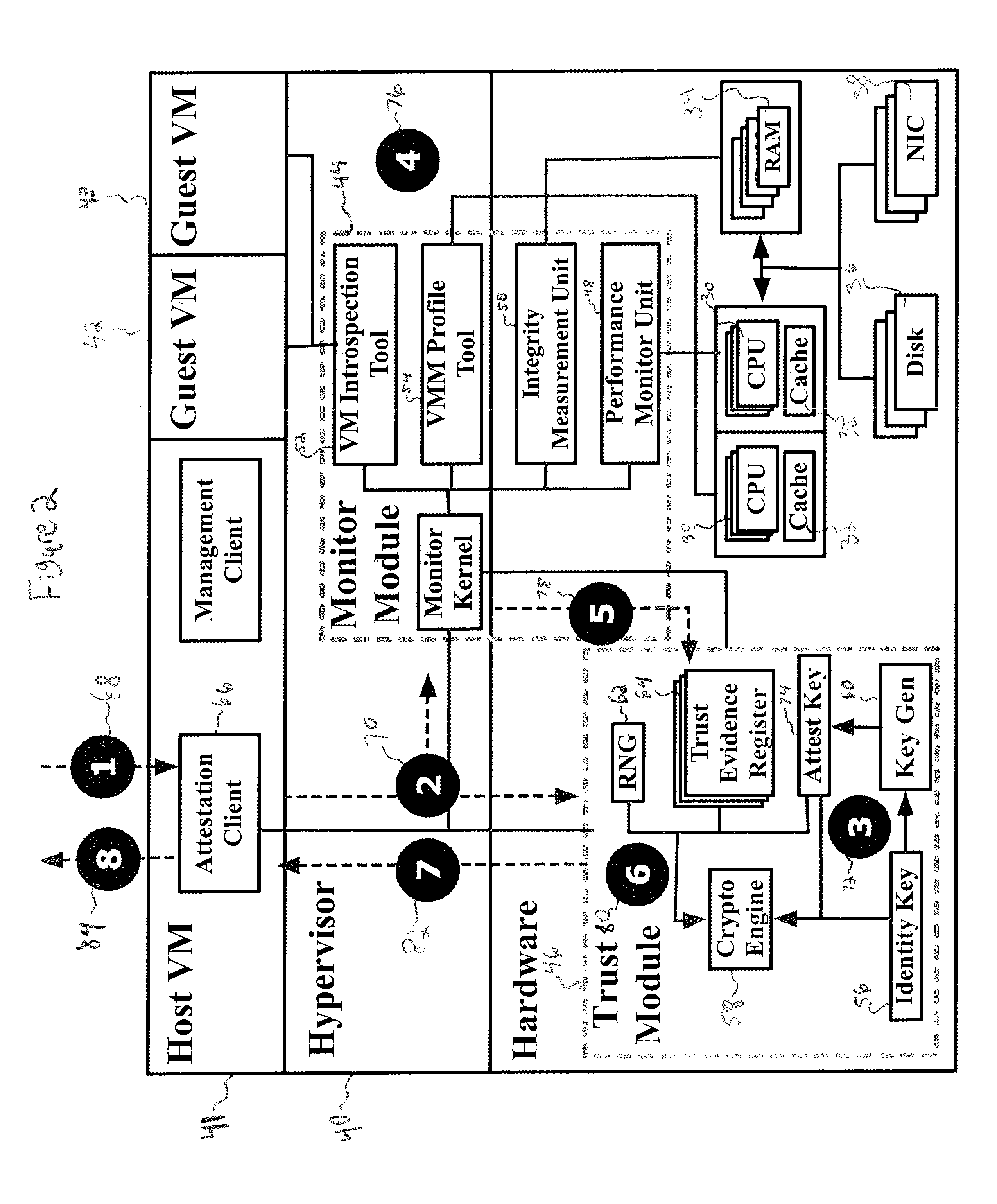
System and Method for Security Health Monitoring And Attestation Of Virtual Machines In Cloud Computing Systems
ActiveUS20160366185A1User identity/authority verificationSoftware simulation/interpretation/emulationSecurity measurementComputer science
A system for security health monitoring and attestation of virtual machines in cloud computing systems is provided. The system includes a cloud server having a virtual machine and a hypervisor. The cloud server collects security measurement information and signs and hashes the security measurement information using a cryptography engine. The system also includes an attestation server for receiving the hashed security measurement information from the cloud server. The attestation server also verifies the signature and hash values, and interprets the security measurement information. The attestation server generates an attestation report based on the verification and interpretation of the security measurement information.
Owner:CORESECURE TECH LLC
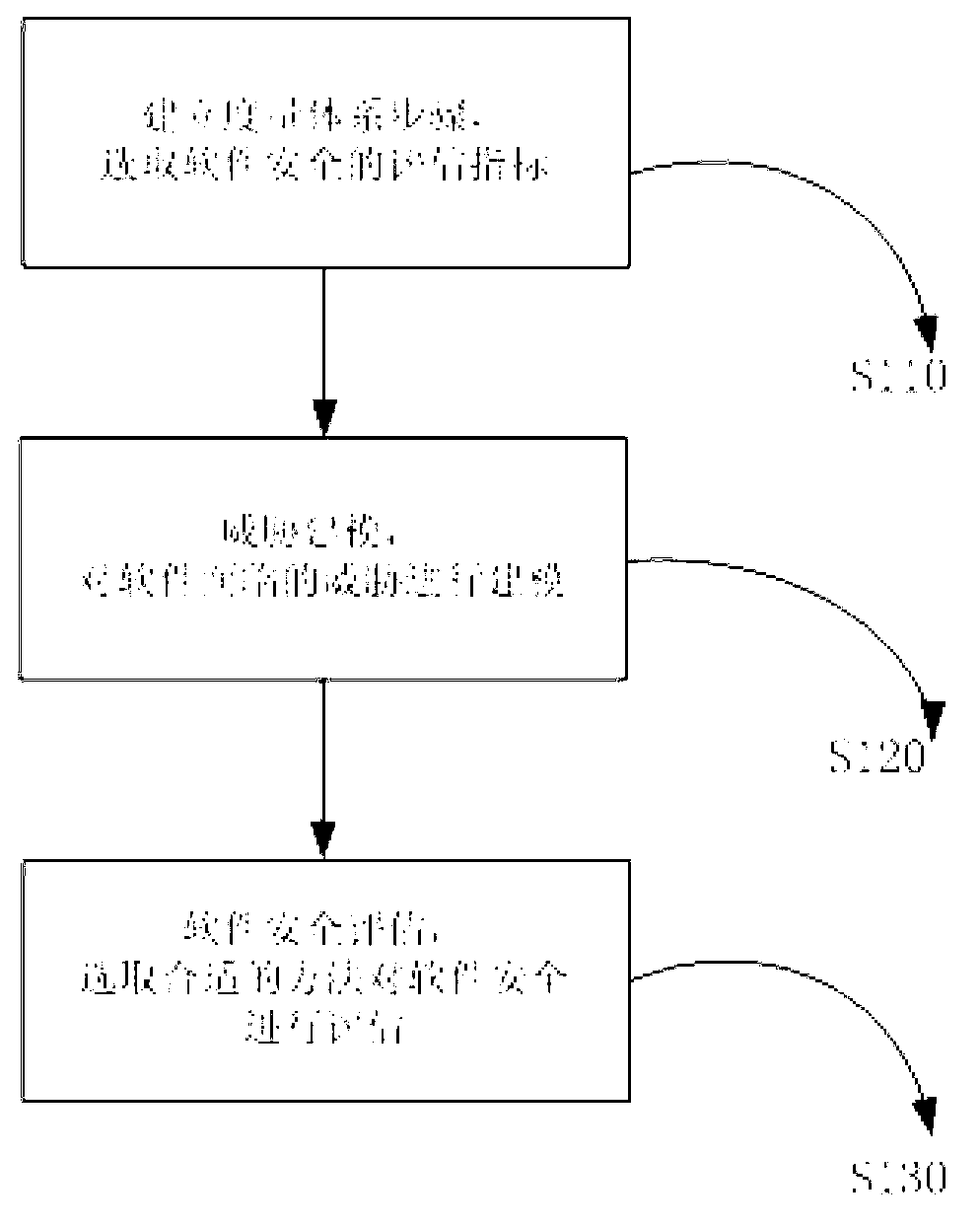
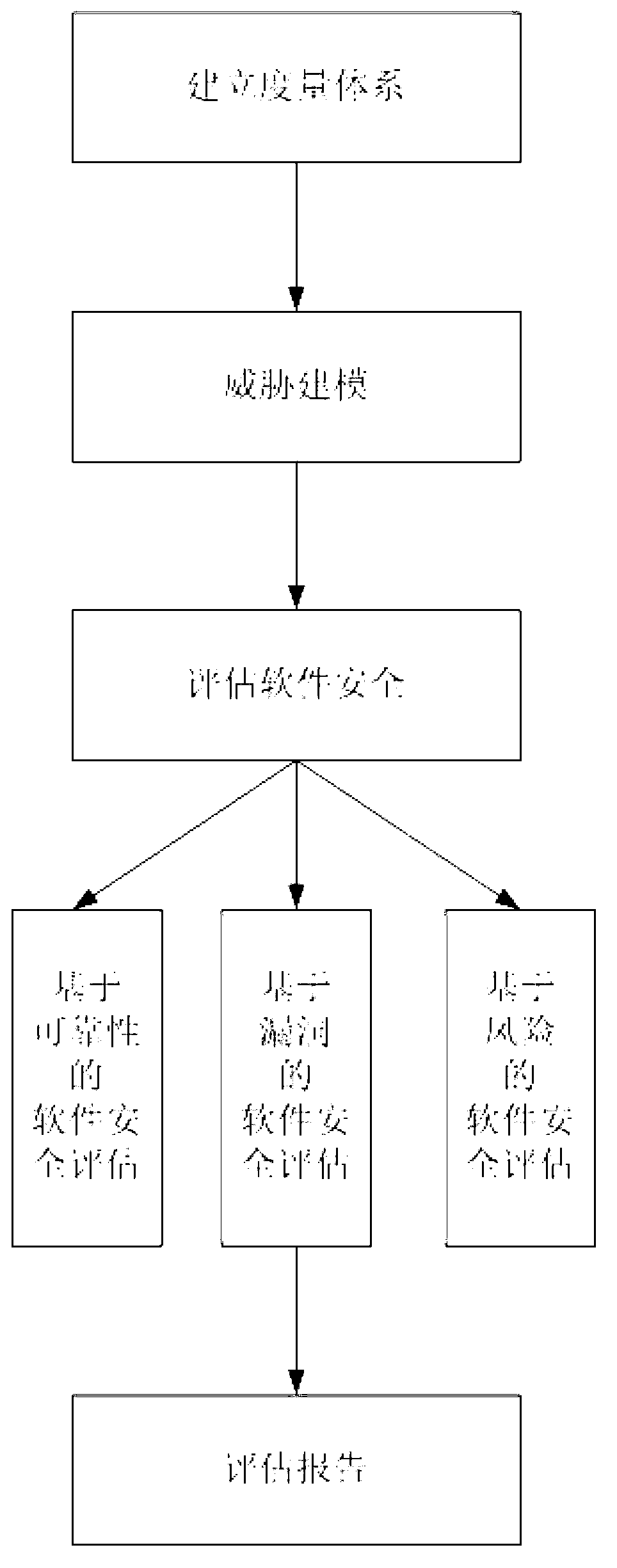
Software running security measurement and estimation method based on network environment
ActiveCN102799822AObjective selectionFull selectionComputer security arrangementsConfidentialityInformation security
The invention discloses a software running security measurement and estimation method based on a network environment, and belongs to a network information security analysis and estimation technology. The method comprises the following steps of: constructing a measurement system, namely selecting a software security estimation index; performing threat modeling, namely modeling a threat of software under the network environment; and estimating the security of the software, namely performing security estimation on the software facing the threat under the network environment according to the estimation index through a software security estimation method based on reliability, a software security estimation method based on bug and a software security estimation method based on risk. The step of constructing the measurement system also comprises a substep of selecting the completeness, the non-repudiation, the confidentiality, the authorization, the availability and the identity checkability as the software security estimation indexes. By the method, the security bug and the risk of the software can be estimated in advance, so that a function and security module of the software can be immediately adjusted, and dangerous events can be effectively controlled and prevented.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT
Enterprise information security management software for prediction modeling with interactive graphs
InactiveUS8516594B2Analysis can be performedLoses credibilityDrawing from basic elementsMemory loss protectionGraphicsSecurity measurement
Various baseline security measurements of assets are collected and calculated by the system. A user creates a what-if scenario by changing one or more baseline security measurements. The system generates interactive, animated graphs that compare the baseline security measurements against the what-if scenario.
Owner:ALLGRESS
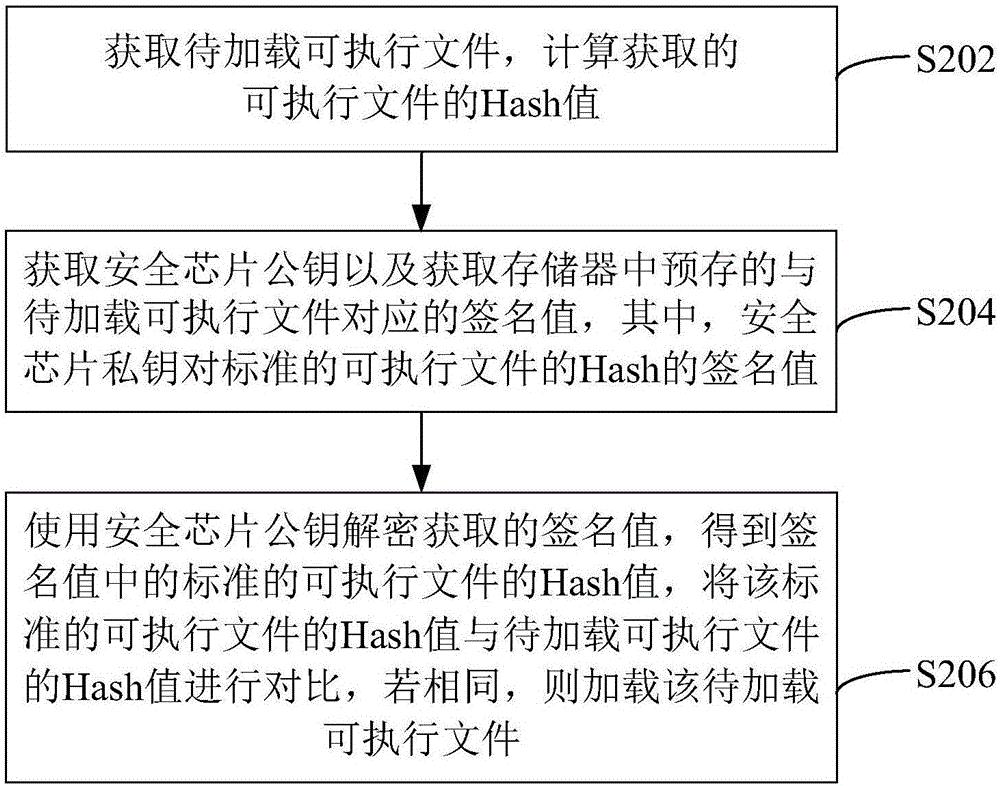
Terminal starting method and device
InactiveCN106156635AGuaranteed reliabilityPlatform integrity maintainanceSecurity measurementOperational system
The present invention relates to a terminal startup method and device. When a terminal startup instruction is detected, the method starts a read-only memory and a security chip of the terminal; verifies whether the key information between the security chips of the read-only memory matches; if so, performs an operation System startup process; calculate the Hash value of the file to be loaded in the operating system; send the Hash value of the file to be loaded into the security chip, and when the matching result is that the Hash value of the file to be loaded matches the security measurement value in the security chip, load the file to be loaded Loading files, due to the read-only characteristics of the read-only memory, can verify whether the security chip is an authorized chip by matching the key information of the read-only memory and the security chip, and load and operate other hardware on the basis of the reliability of the security chip The system's loading authentication realizes the upper-level measurement authentication from the hardware to the operating system and the lower-level startup mode, and the terminal startup security certification is stronger.
Owner:SHENZHEN SINOSUN TECH
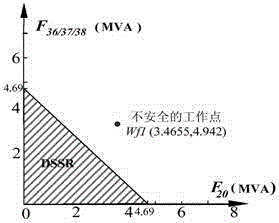
Network N-1 security-region-boundary calculation and security evaluation method
The invention discloses a network N-1 security-region-boundary calculation and security evaluation method and relates to the field of analysis of network security. The method includes: defining network operation work points, network N-1 security and network security regions. The method is a security evaluation method based on the security regions. The security evaluation method based on the security regions is capable of judging the security of a system rapidly without simulating N-1 events one by one and giving measurement of the security. The network N-1 security-region-boundary calculation and security evaluation method is widely applicable to undirected authorized networks such as power grids and communication networks and the like. The general security-region method which is applicable to general networks provides a basis for adjustment of work points and planning of topology and capacity when the general networks are subjected to random attacks. It is found that in the security-region method, a security-distance calculation result is highly identical with an anti-destroying-ability calculation result so that correctness of the security-domain method in security measurement is proved.
Owner:TIANJIN UNIV
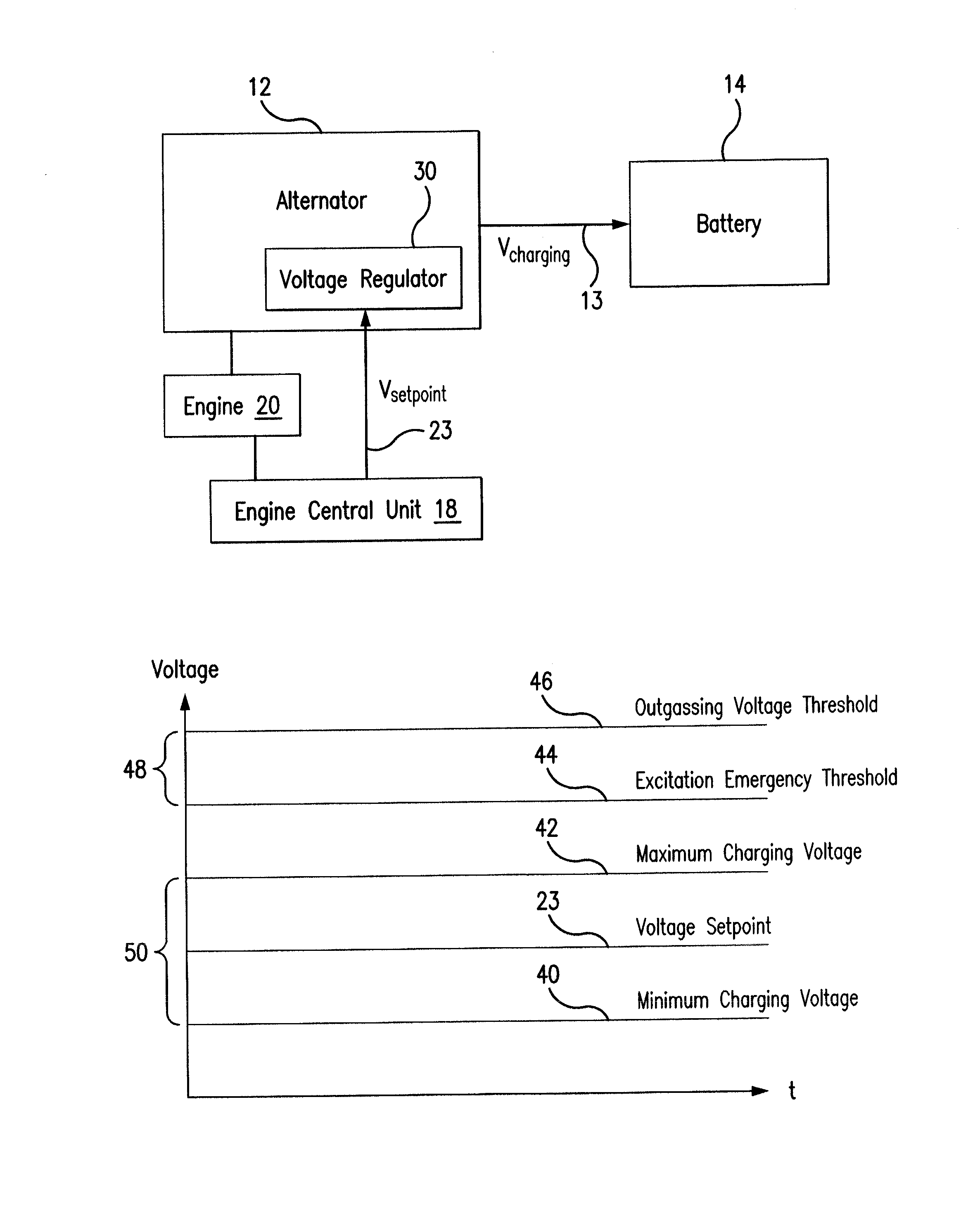
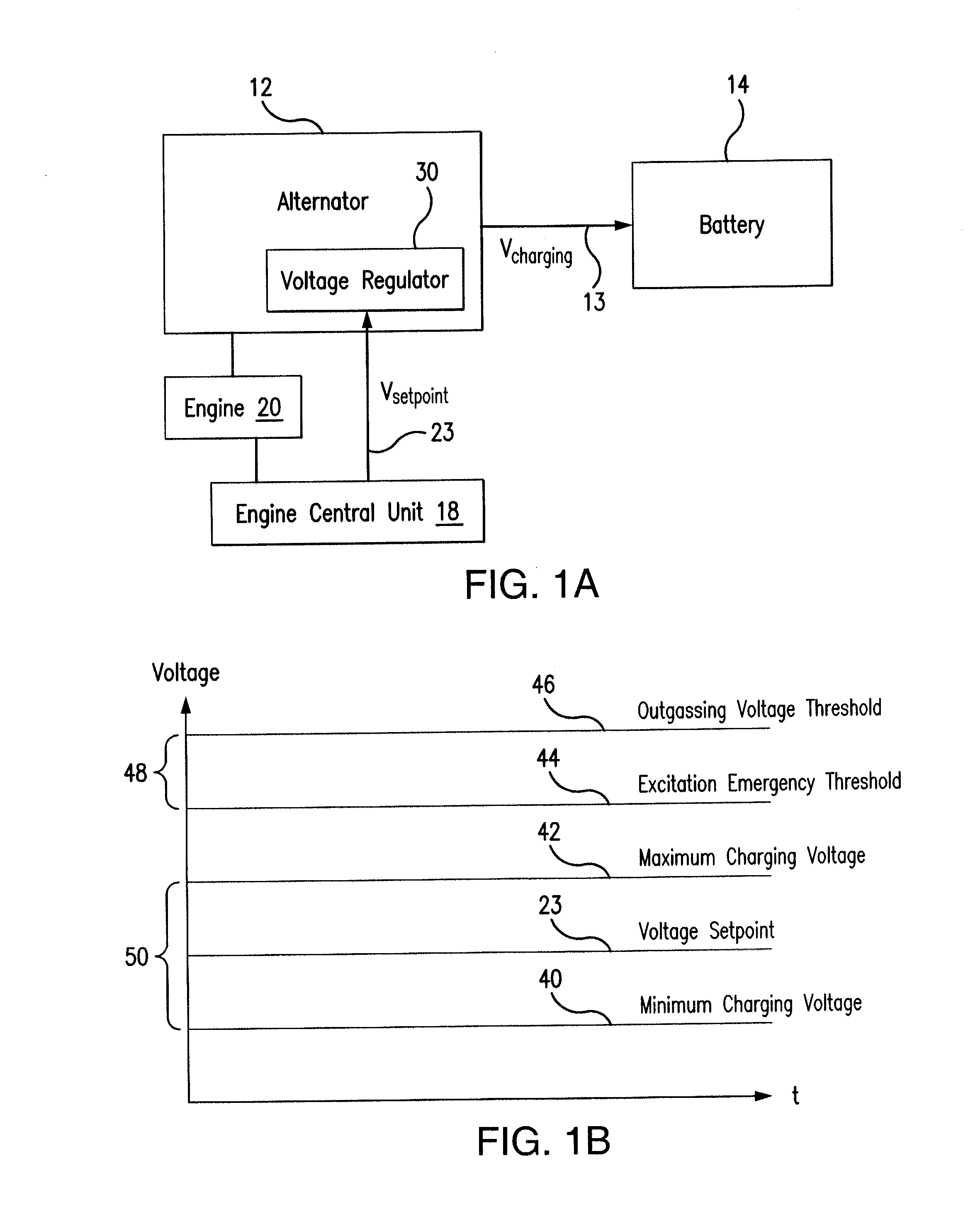
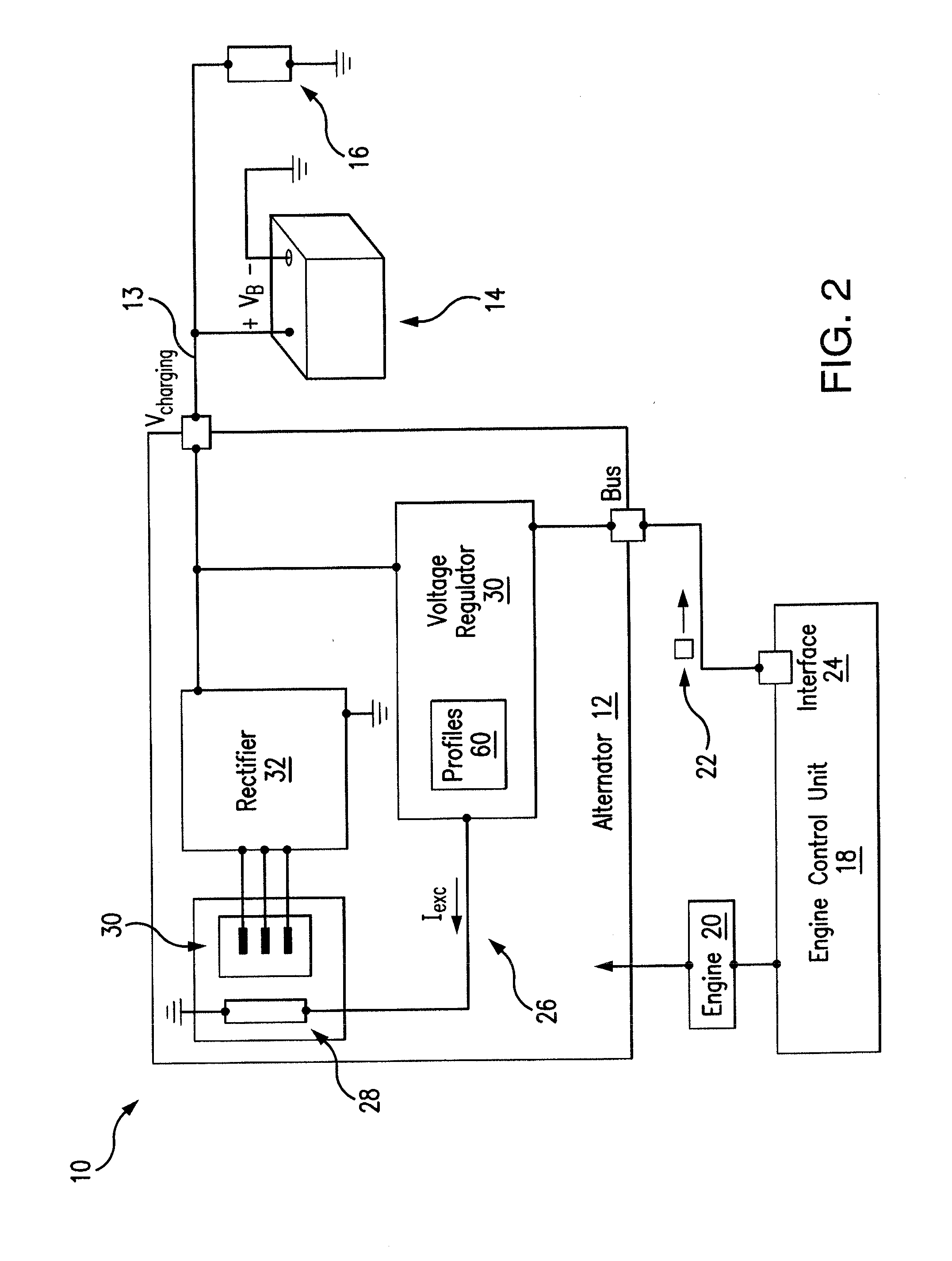
Alternator Control with Temperature-Dependent Safety Feature
ActiveUS20160380567A1Provide securityReduce and eliminate riskGeneration protection through controlEmergency protective circuit arrangementsAlternatorSecurity measurement
A method for controlling an alternator includes determining a temperature-dependent value associated with a battery coupled to an alternator and determining an excitation emergency threshold for the alternator based on the determined temperature-dependent value associated with the battery. The method further includes initiating, by a controller of an alternator, at least one safety measure upon a determination that a voltage associated with the battery exceeds the determined excitation emergency threshold.
Owner:INFINEON TECH AG
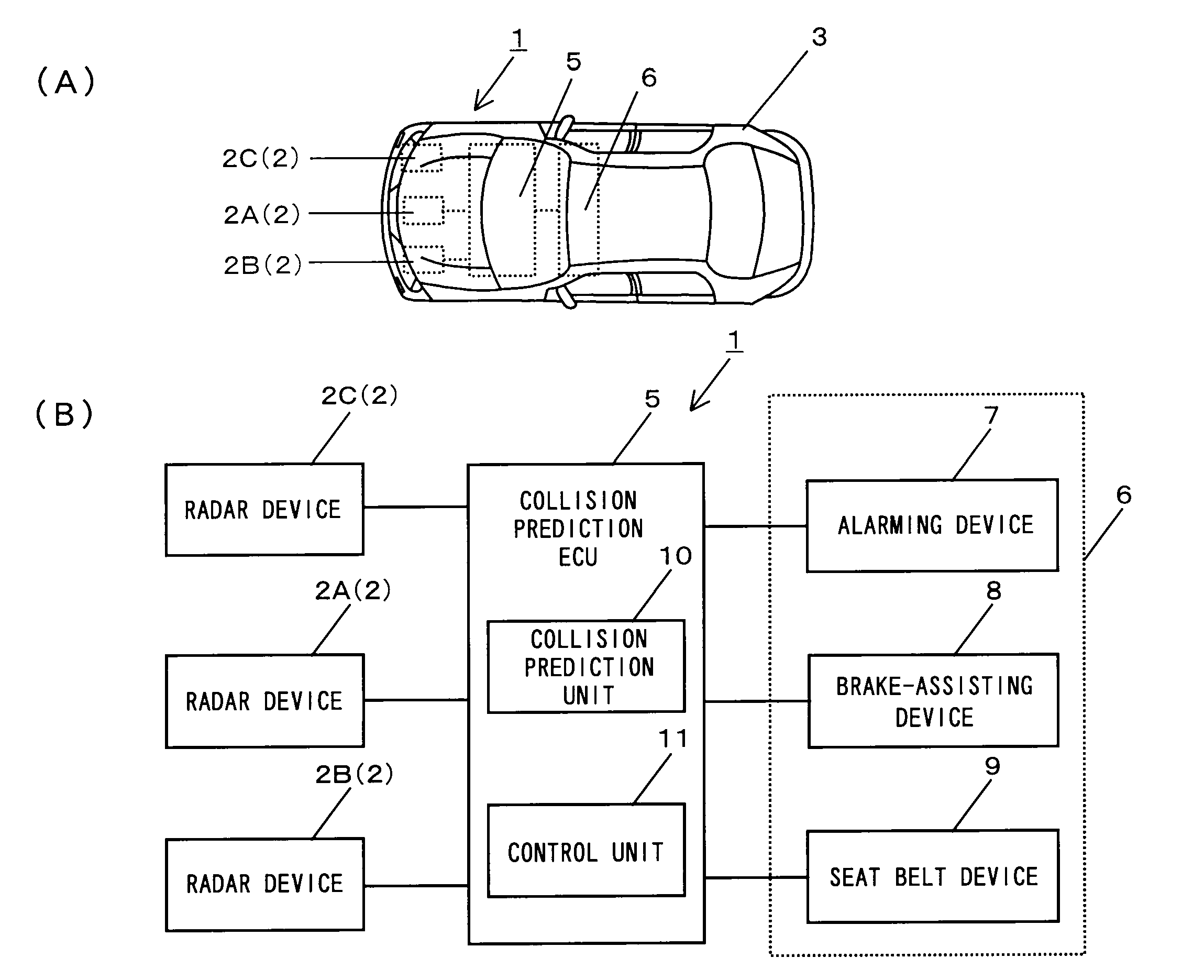
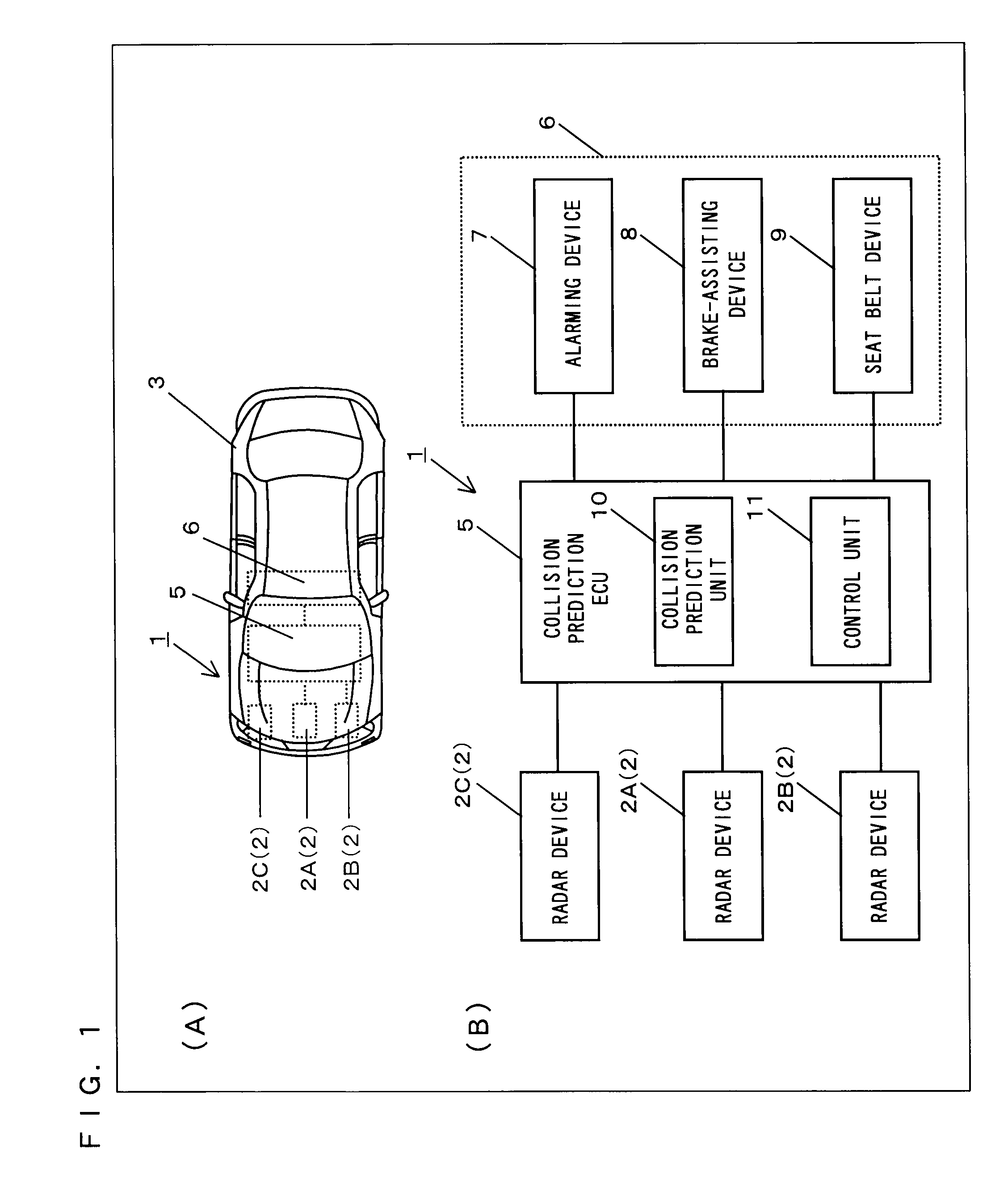
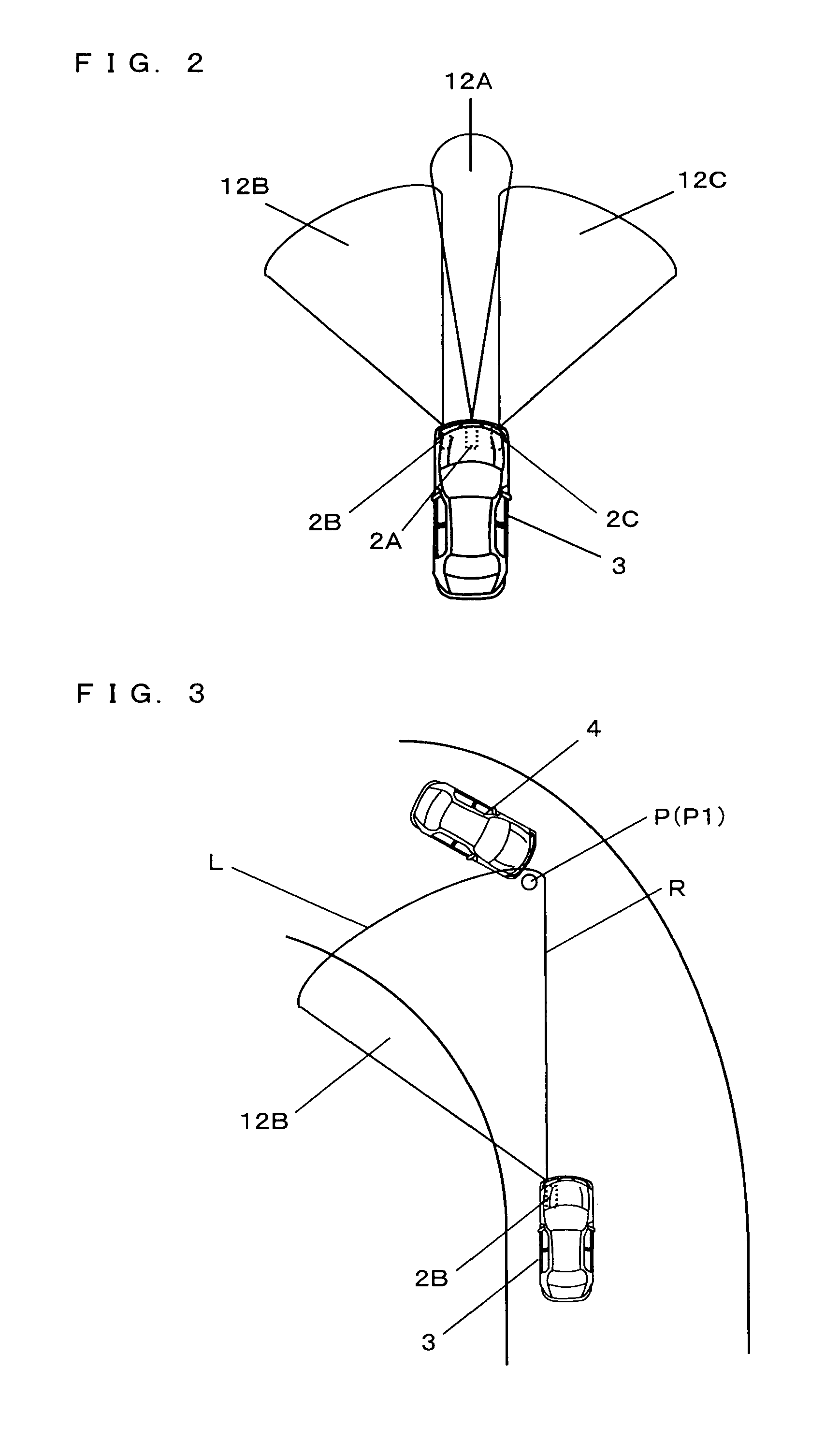
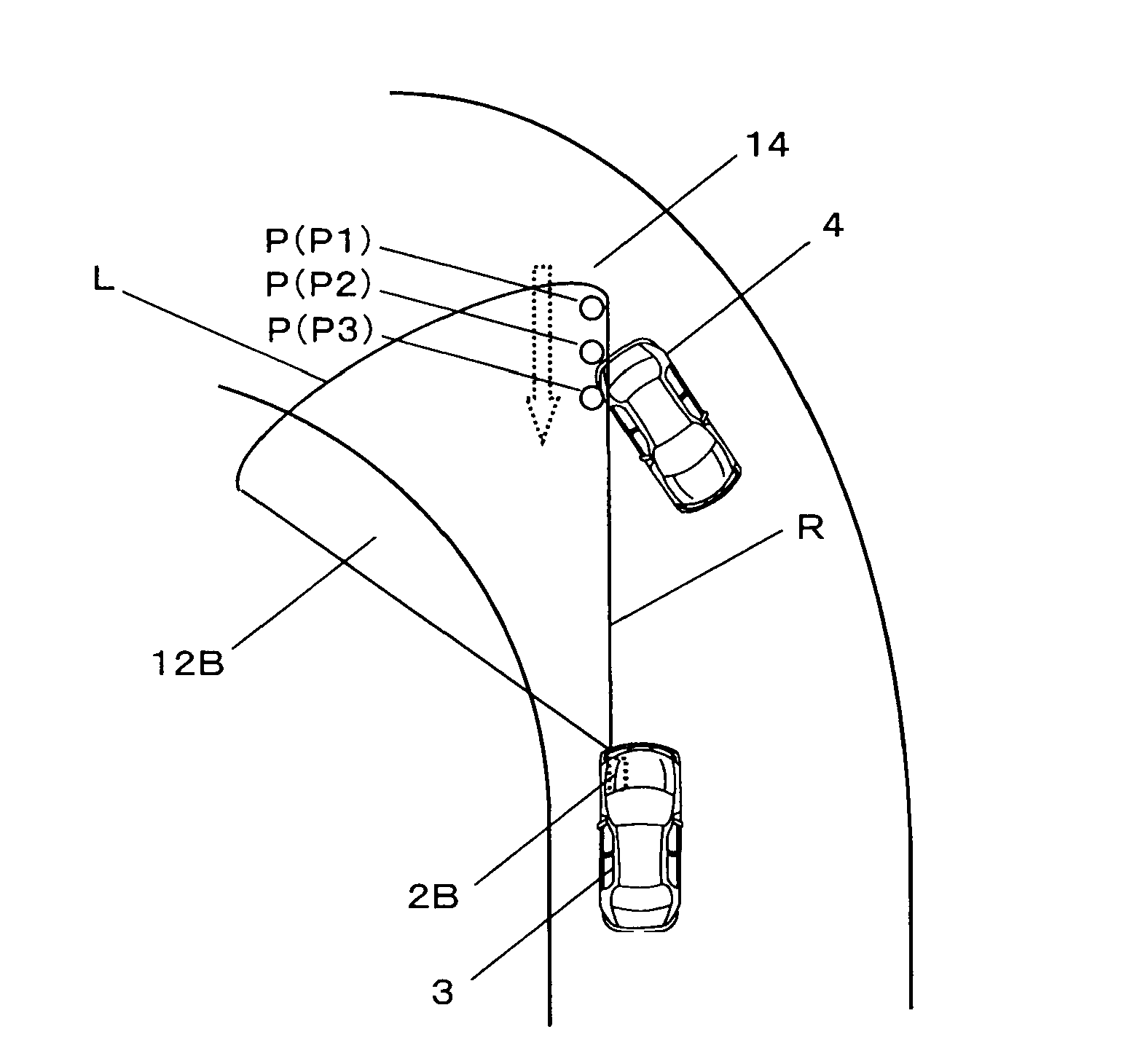
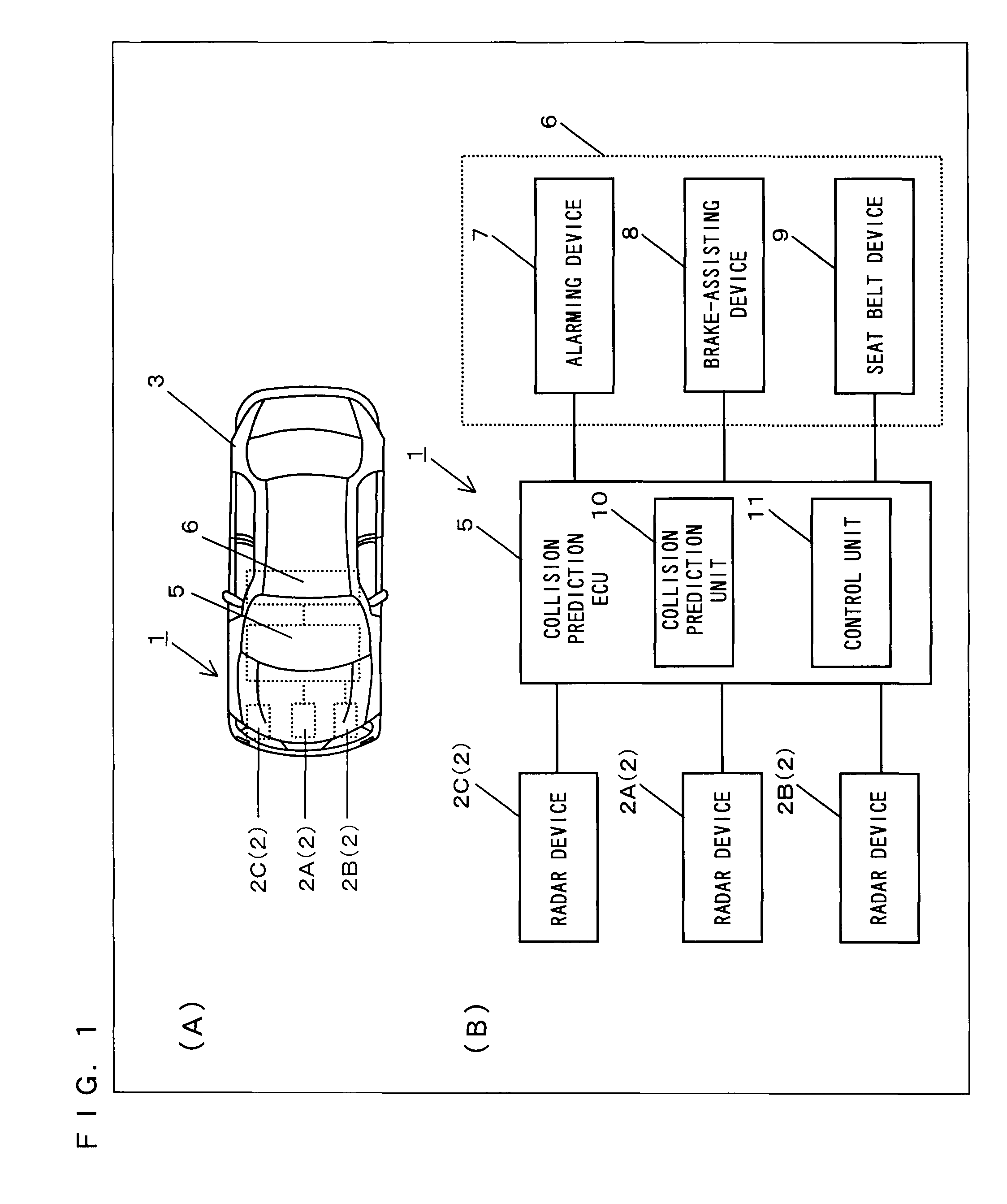
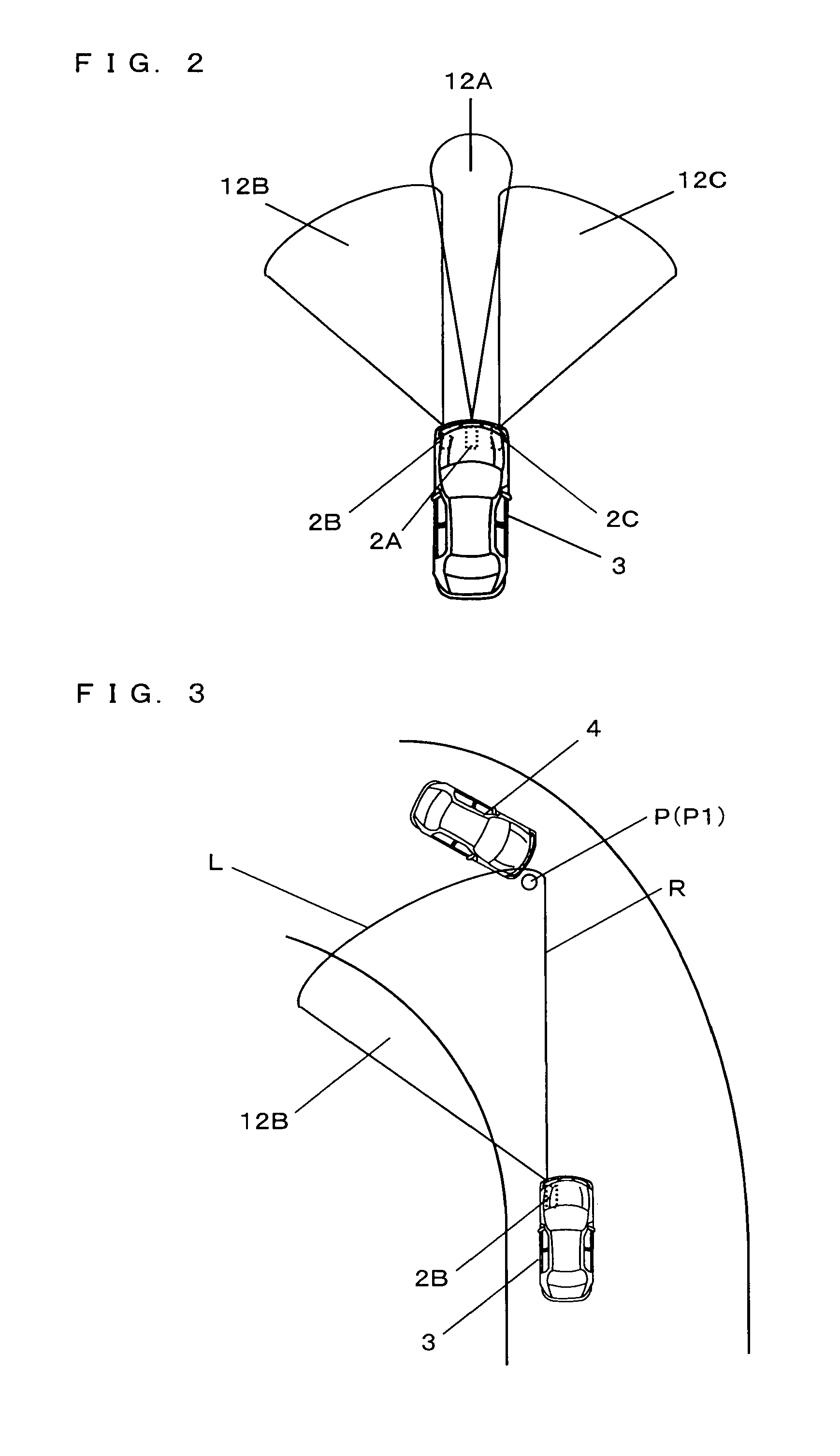
Pre-crash safety system
InactiveUS20100271256A1Pedestrian/occupant safety arrangementAnti-collision systemsSecurity measurementRadar
Provided is a pre-crash safety system in which, even when, due to a movement of a reflection point of a radar wave on a surface of another vehicle, a radar device falsely recognizes that the other vehicle is approaching toward an own-vehicle, such a false recognition does not influence a safety measure operation that is based on a prediction of a collision. The pre-crash safety system causing, when a possibility of a collision between the own-vehicle equipped with a radar device and the other vehicle that approaches the own-vehicle exists after a prediction of a collision therebetween is made, the own-vehicle to conduct a safety measure operation, the pre-crash safety system includes: a collision prediction unit that makes the prediction of a collision between the own-vehicle and the other vehicle that has entered a monitoring area of the radar device; a control unit that causes the own-vehicle to conduct the safety measure operation based on a result of the prediction of a collision by the collision prediction unit, while the control unit does not cause the own-vehicle to conduct the safety measure operation if, after the other vehicle has entered the monitoring area, a reflection point coordinate which represents a reflection point of a radar wave on the other vehicle is positioned within a predefined direction range when viewed from the own-vehicle.
Owner:TOYOTA JIDOSHA KK
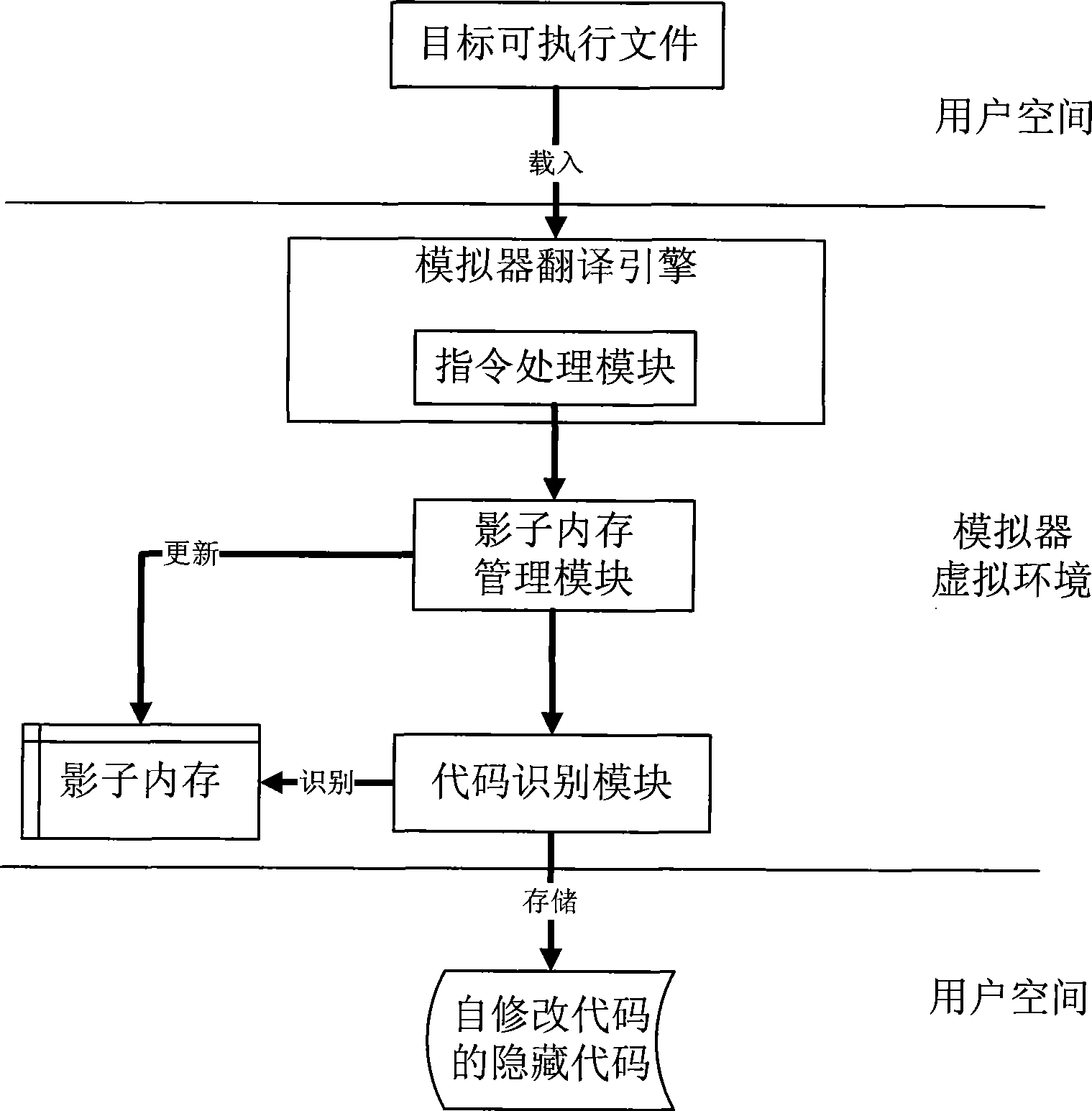
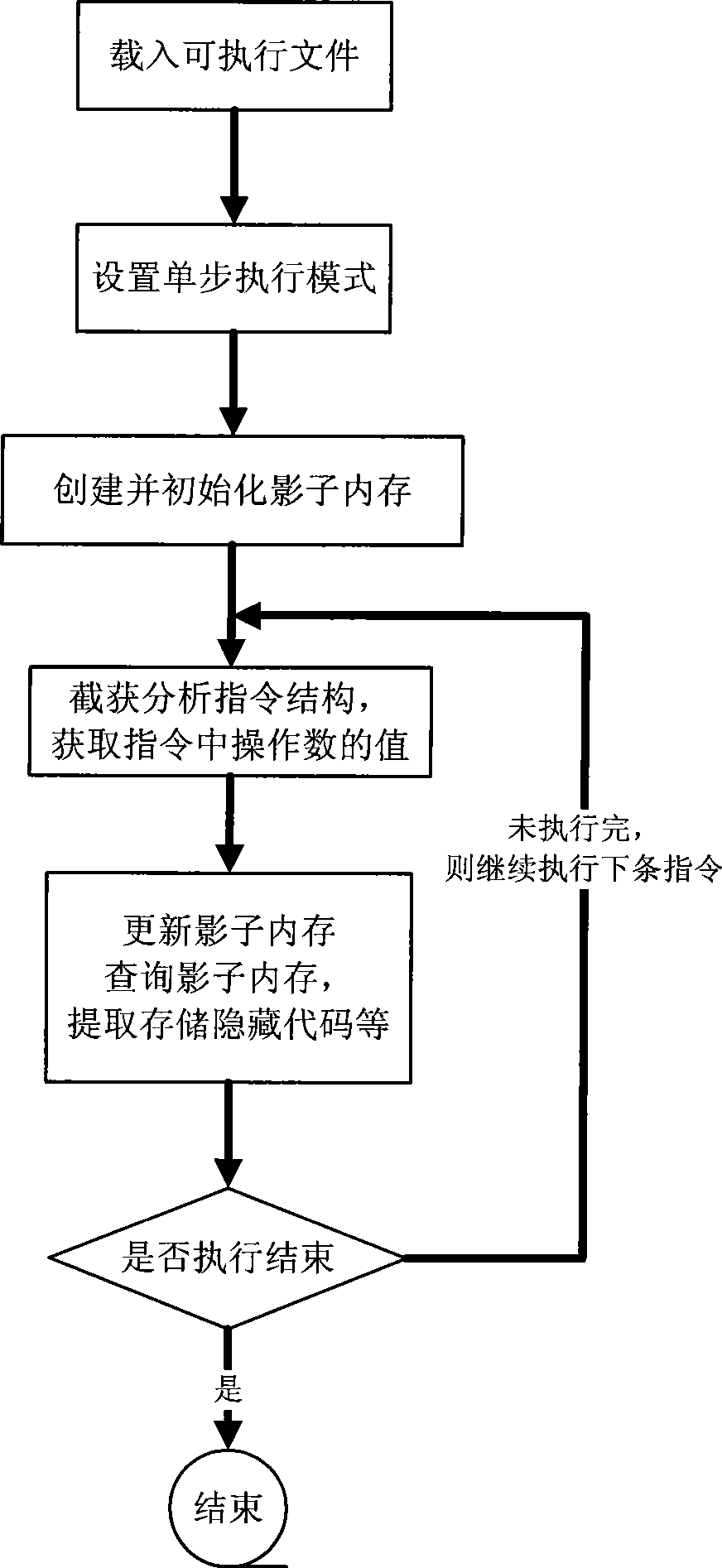
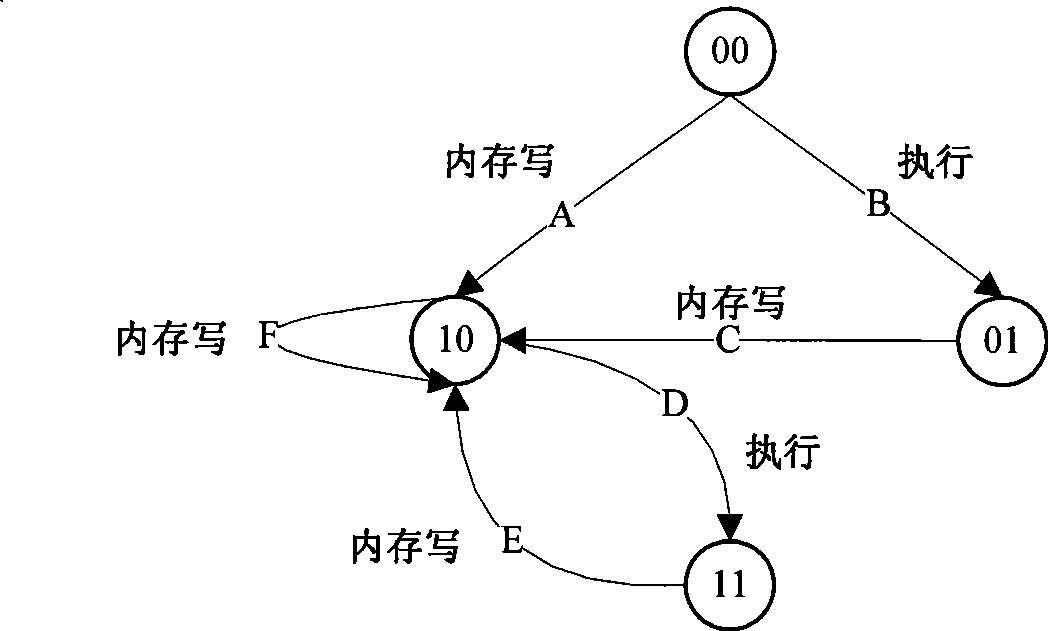
Self-modifying code identification method based on hardware emulator
ActiveCN101458630AImprove analysis efficiencyHigh transparencyProgram controlProgram/content distribution protectionSelf-modifying codeSecurity measurement
The invention belongs to the technical field of software security measurement and evaluation, especially relates to a self-modifying code recognition method based on a hardware simulator. The invention is provided with a marker in the hardware simulator in order to only execute a target executable file by one step and capture a virtual system execute instruction, the information in the process can be executed by using a shadow memory monitoring program, the code which is dynamically released into the memory and is executed can be recognized and executed in the course of program execution, so that data information of the analysis target can be acquired. The data acquisition of the invention is implemented by the simulation hardware, is not executed by placing the malevolence code on a true CPU, so the actual system can not be affected. The invention adopts the hardware simulator as a dynamic analysis platform, which can improve the transparency between the analysis platform and the code and can effectively defend against the detection of the code.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
System and method for processing gas-holder location data
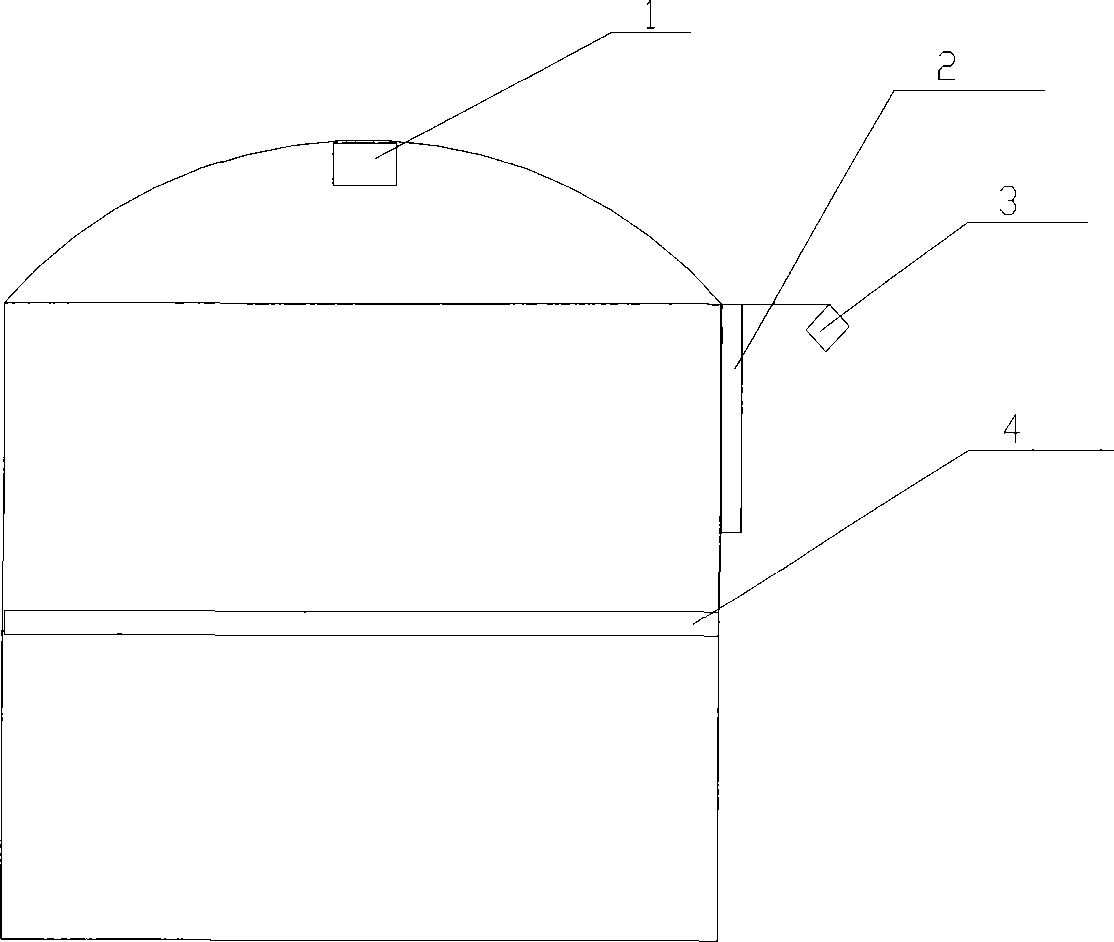
InactiveCN101251402ARealize non-contact measurementRealize no electrical safety measurementMachines/enginesLevel indicatorsEngineeringContact line
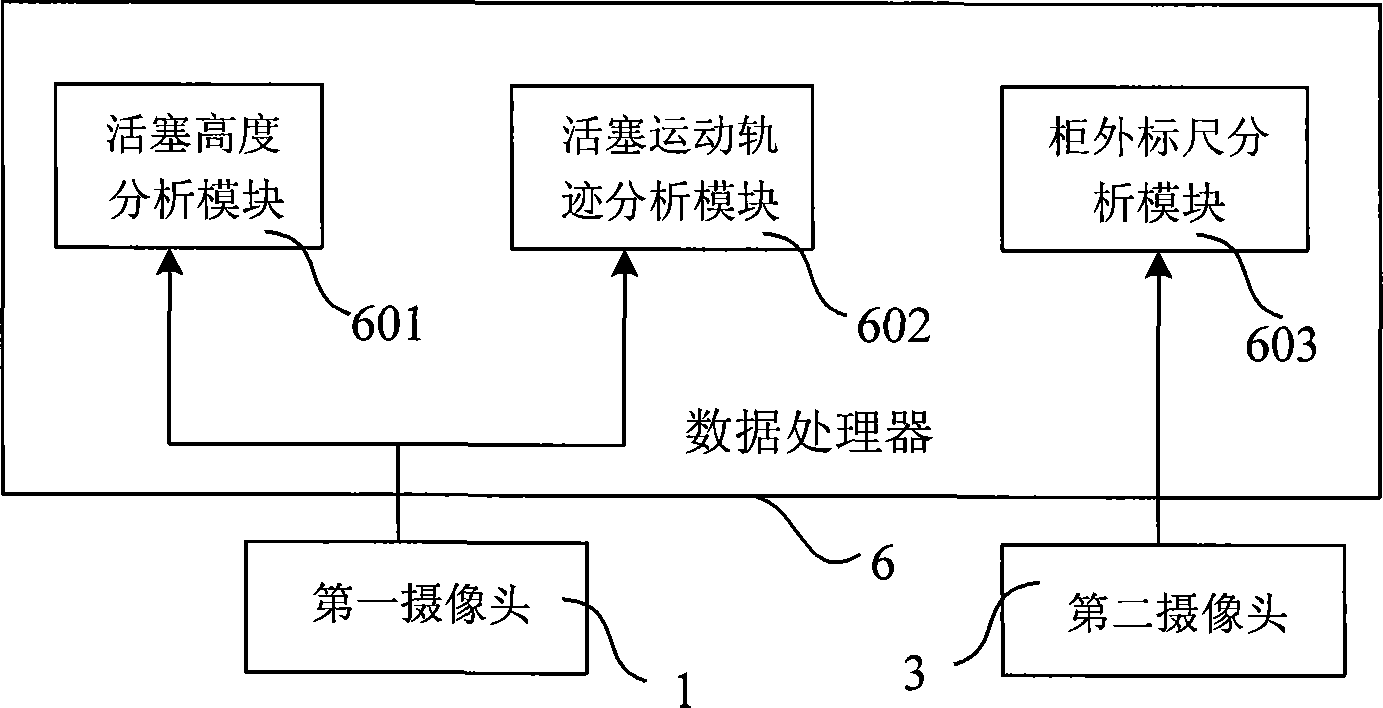
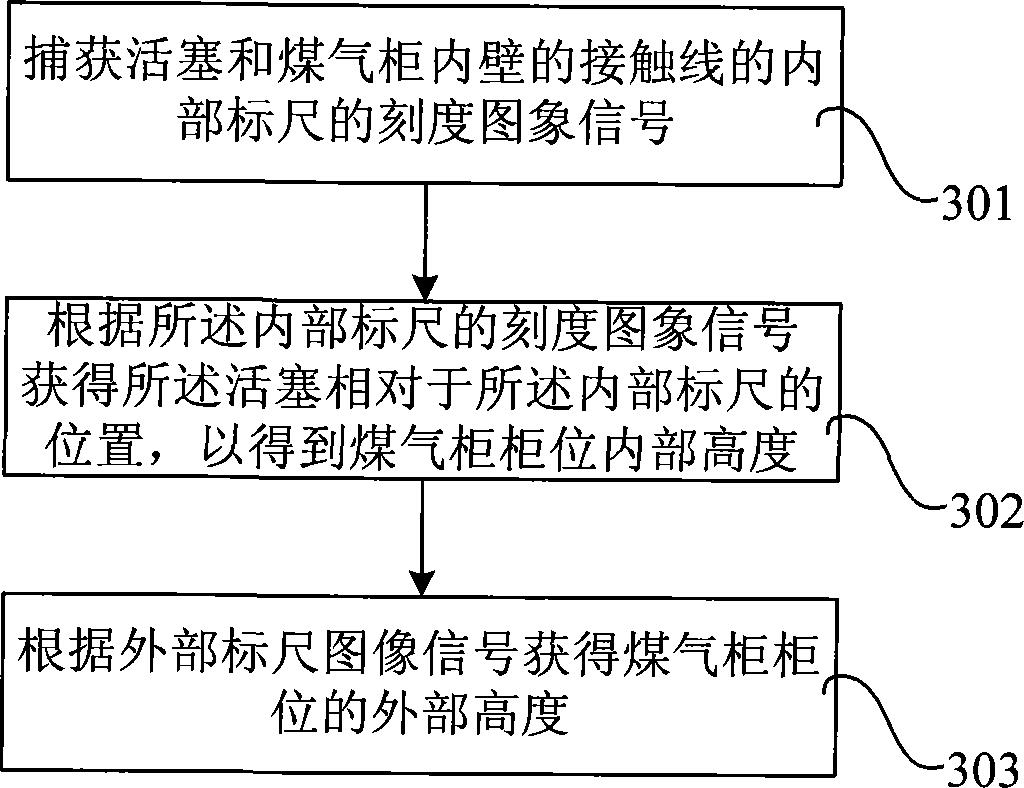
The invention relates to a gas cabinet position data processing system. The gas cabinet position data processing system comprises: an internal scale which captures the calibration image signal of the internal scale of a contact line between a piston and the inner wall of the gas cabinet and sends the captured first image signal; a second camera which is arranged outside the gas cabinet and is used to capture the calibration image signal of an external scale for indicating the height of the gas cabinet; and a data processor which is communicated with a first camera and the second camera through optical fiber communication and is used for obtaining the position of the piston relative to the internal scale according to the calibration image signal of the internal scale to obtain the internal height of the gas cabinet position and simultaneously obtaining the external height of the gas cabinet position according to the calibration image signal of the external scale. The invention also discloses a gas cabinet position data processing method. Thus, the measuring method and the device provided by the invention can not only realize electricity-free safe measurement, but also judge the general operational status of the gas cabinet according to the motion track of the piston of the gas cabinet and guarantee the safe operation of the gas cabinet.
Owner:MCC CAPITAL ENGINEERING & RESEARCH
Security measurement method of industrial control system based on attack graph
ActiveCN112114579AShorten the analysis cycleImprove measurement efficiencyElectric testing/monitoringTotal factory controlAttackRelational table
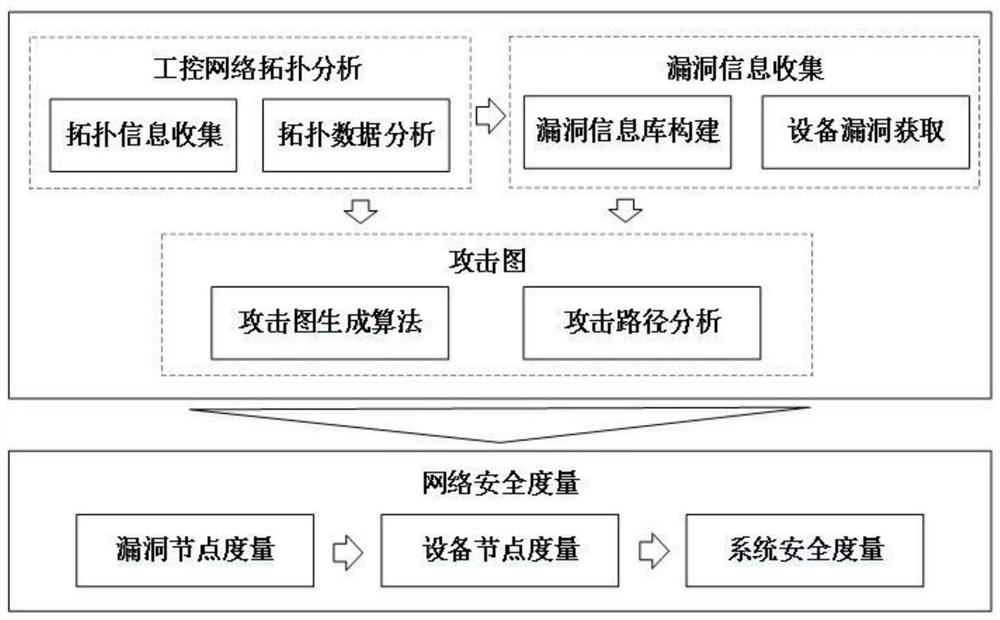
The invention relates to a security measurement method of an industrial control system based on an attack graph. The method comprises the following steps: acquiring the topological structure information of an industrial control network, carrying out detection on equipment of a specific industrial control system, mastering the equipment information in the industrial control network, and carrying out the analysis of the equipment correlation condition; aiming at the detection result of the equipment in the industrial control network, collecting equipment vulnerability information; according to the topological structure and the equipment vulnerability information, storing a format in a graphical format based on a graph database-based method, and adopting nodes and a relationship represent graph structure to generate a system attack graph; and according to the generated system attack graph, performing network security measurement on the specific industrial control system according to threelevels of vulnerability node measurement, equipment node measurement and system security measurement, and analyzing an attack path. According to the method, potential threats are discovered to the greatest extent, the analysis period of the safety measurement of the industrial control system is greatly shortened, the measurement efficiency is improved, and a foundation is laid for the protectionwork of the industrial control system.
Owner:HARBIN INST OF TECH AT WEIHAI
Method and device for confirming safety level of biology identification systemic
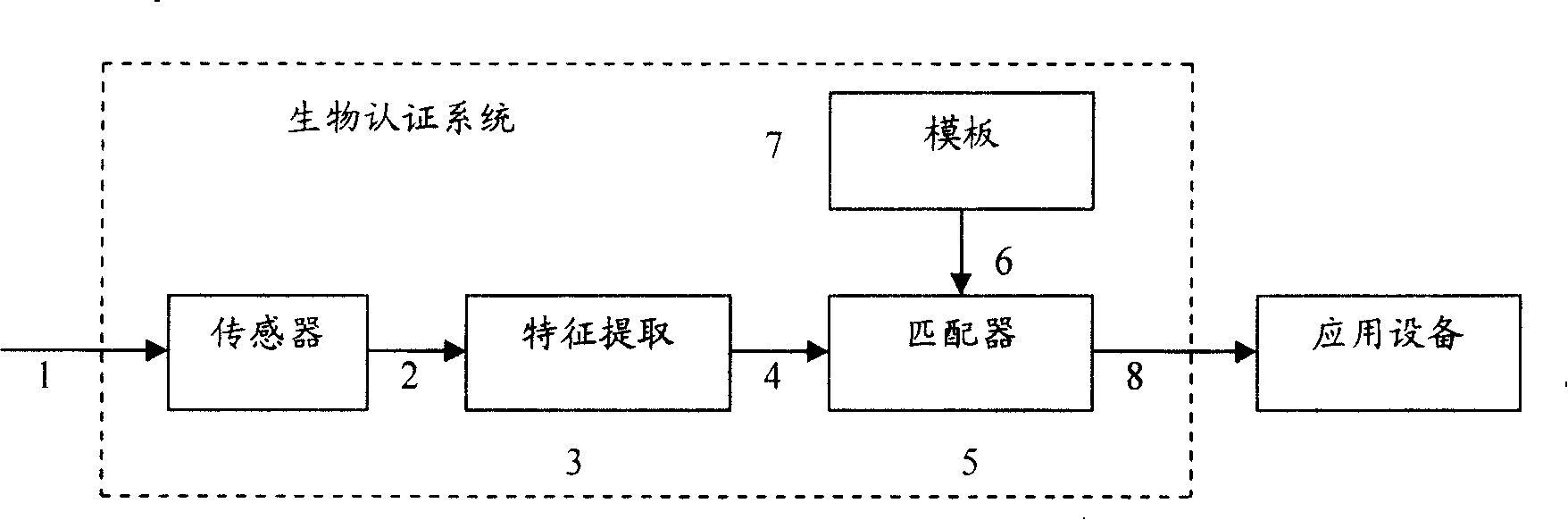
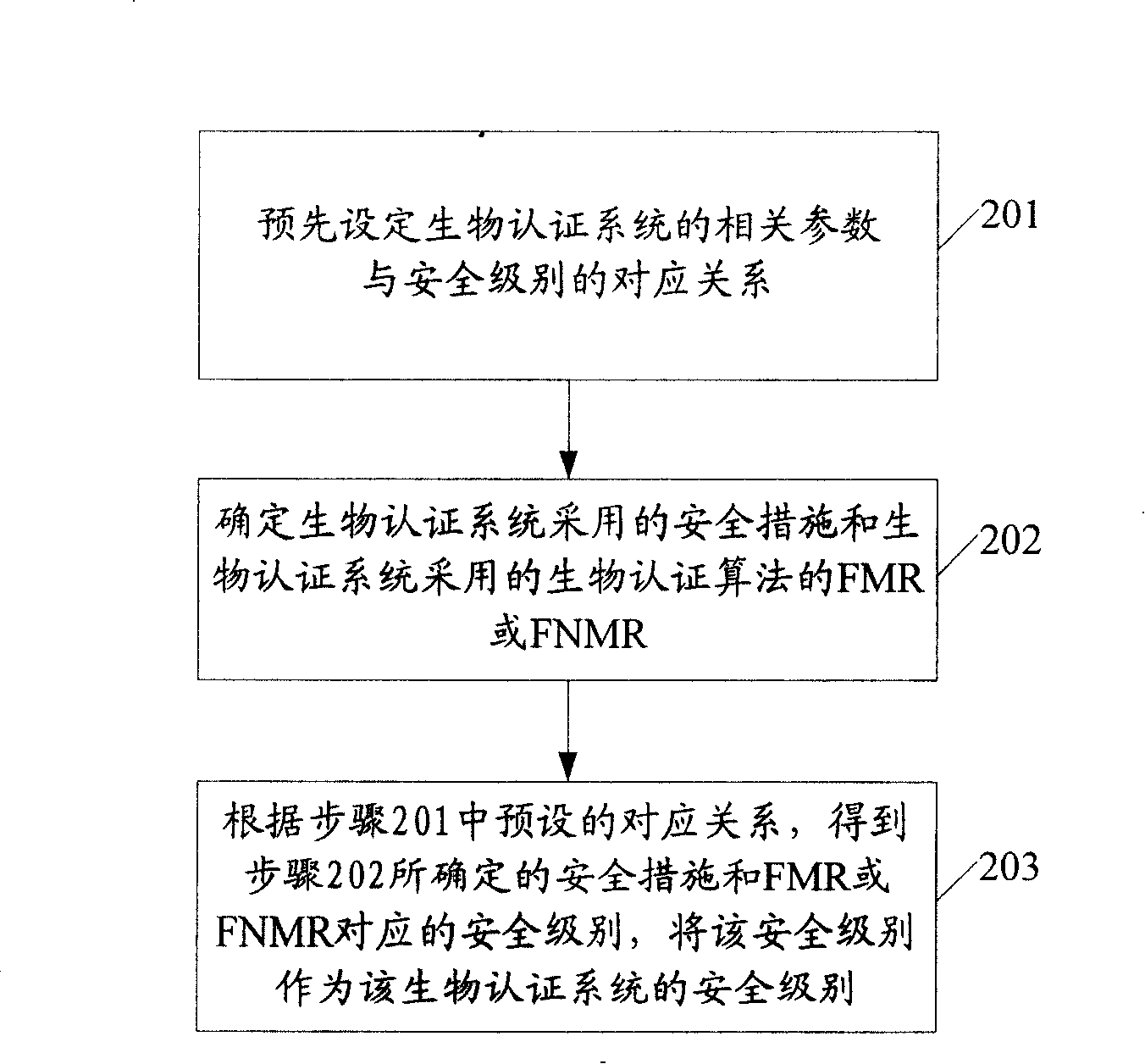
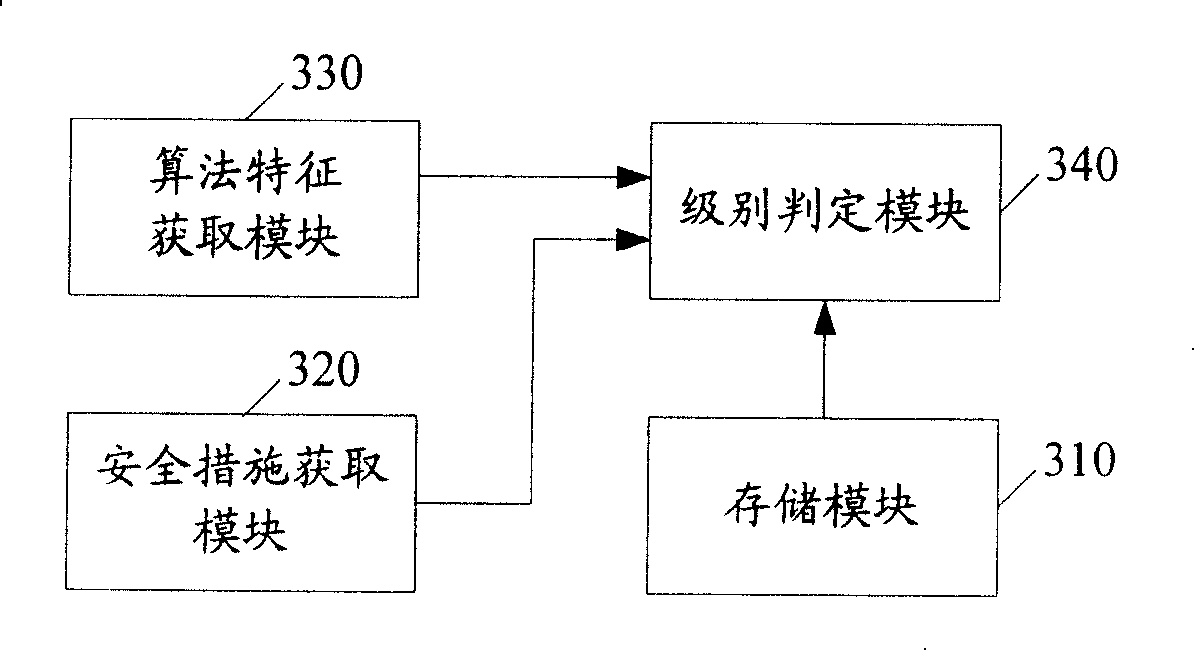
ActiveCN101178755AMeet the needs of different levelsDigital data authenticationSecurity measurementSecurity Measure
The invention embodiment discloses a method for identifying the security grade of a biometric security certificate system, including the procedures as follows: a. setting the corresponding relationship between related parameters and the security grade of the biometric security certificate system in advance, the related parameters comprise the security measurement adopted by the biometric security certificate system and the FMR or the FNMR of biometric certificate calculation adopted by the biometric security certificate system; b. identifying the security measurement adopted by the biometric security certificate system and the FMR or the FNMR of biometric certificate calculation adopted by the biometric security certificate system; c. according to the corresponding relationship preset in procedure a, gaining the corresponding security grades of the security measurement and the FMR or FNMR identified in procedure b, the security grade is regarded as the security grade of the biometric certificate system. The invention embodiment can calibrate the security grade of the biometric certificate system. The invention embodiment also discloses a device for identifying the security grade of the biometric certificate system.
Owner:江苏京生管业有限公司
Systems and methods for using eye signals with secure mobile communications
InactiveCN106462743ATelevision system detailsAcquiring/recognising eyesSecurity measurementSoftware architecture
Apparatus, systems, and methods are provided for secure mobile communications (SMC) by an individual using biometric signals and identification in real time. The apparatus includes a wearable computing device where identification of the user is based on iris recognition, and / or other physiological and anatomical measures. Biometric identity measures can be combined with other security-based information such as passwords, date / time stamps, and device identification. Identity verification can be embedded within information that is transmitted from the device and / or to determine appropriate security measures. SMC addresses security issues associated with the transmission of eye-signal control and biometric identification data using secure interfaces with network devices within a system of systems (SoS) software architecture.
Owner:GOOGLE LLC
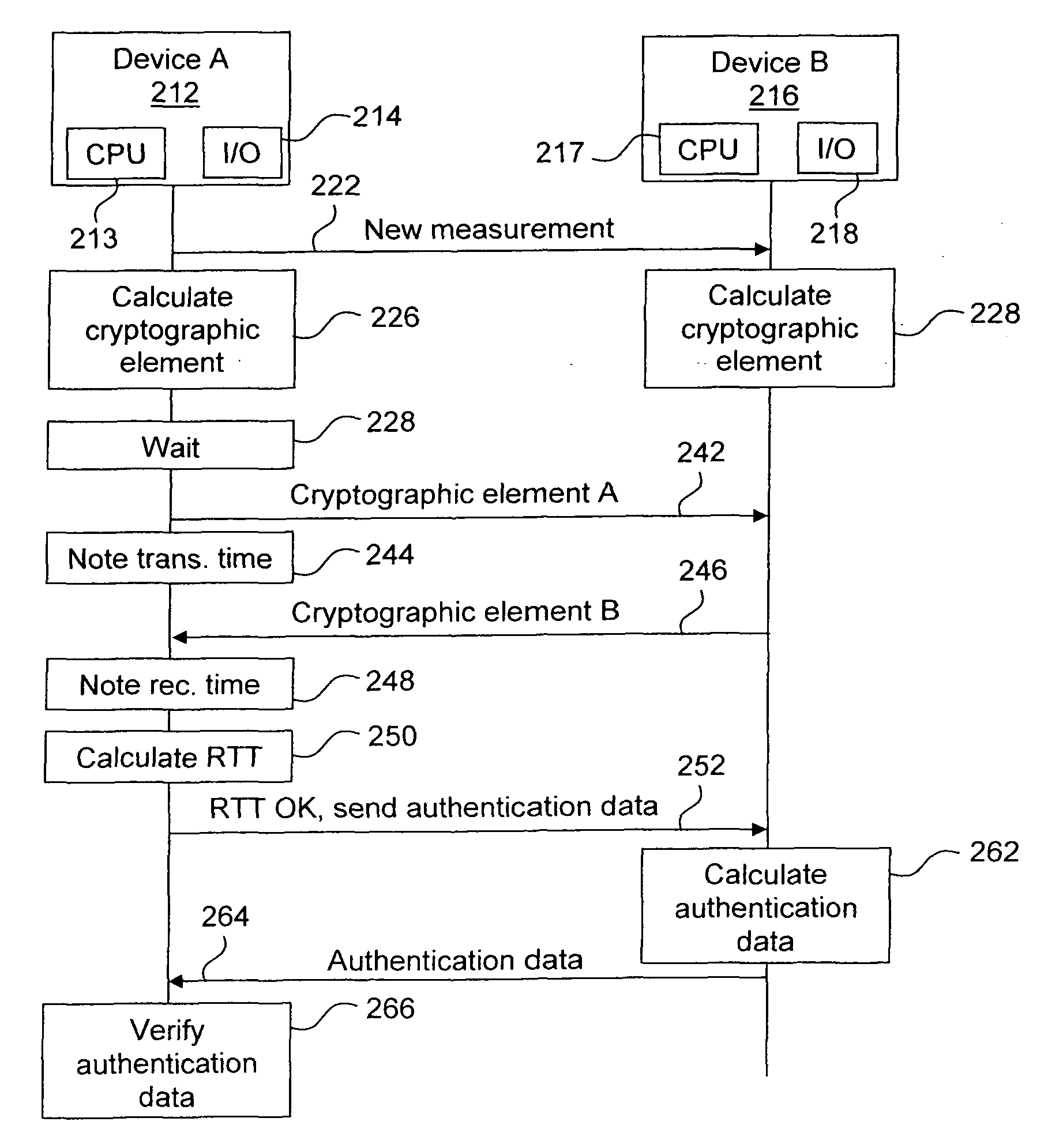
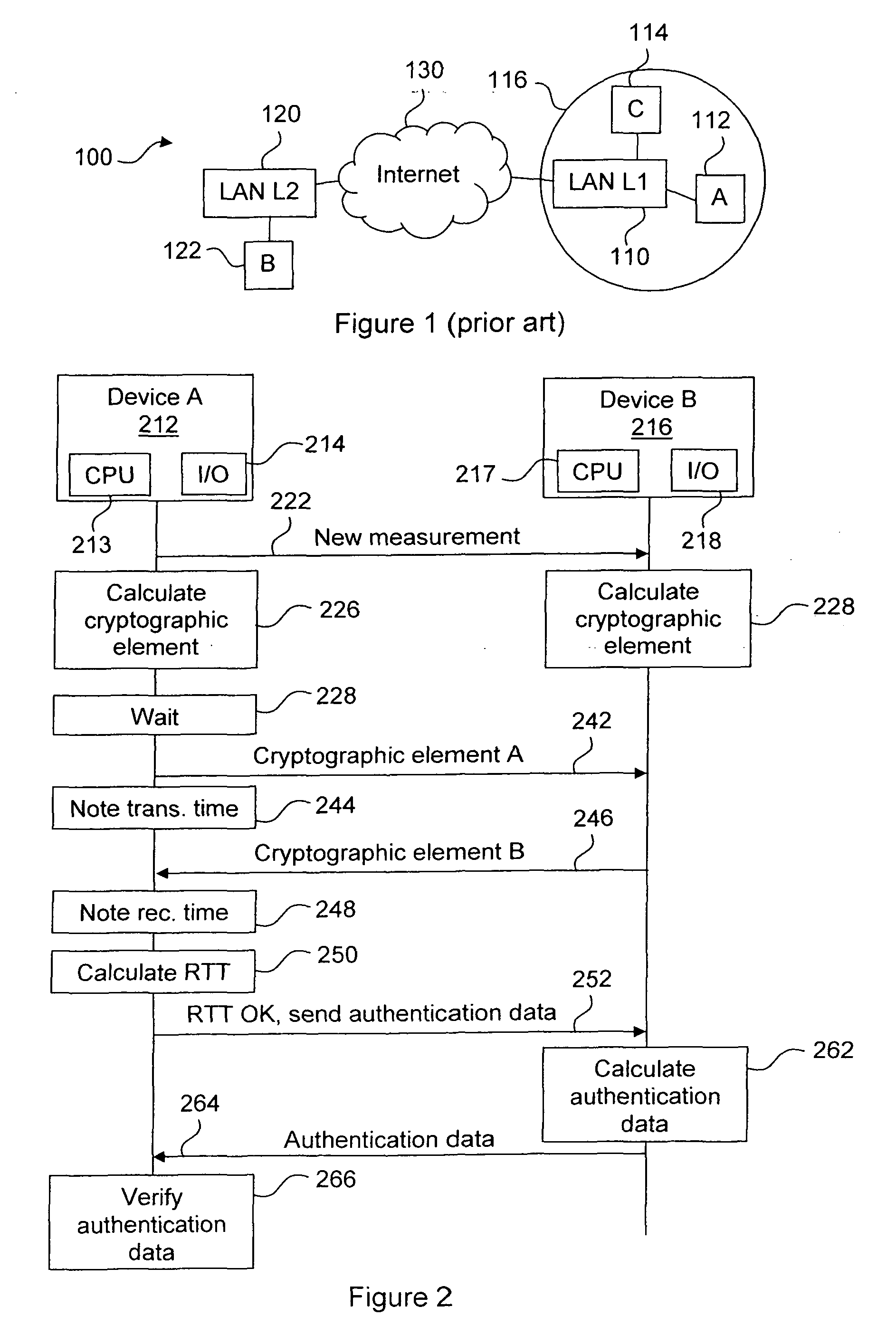
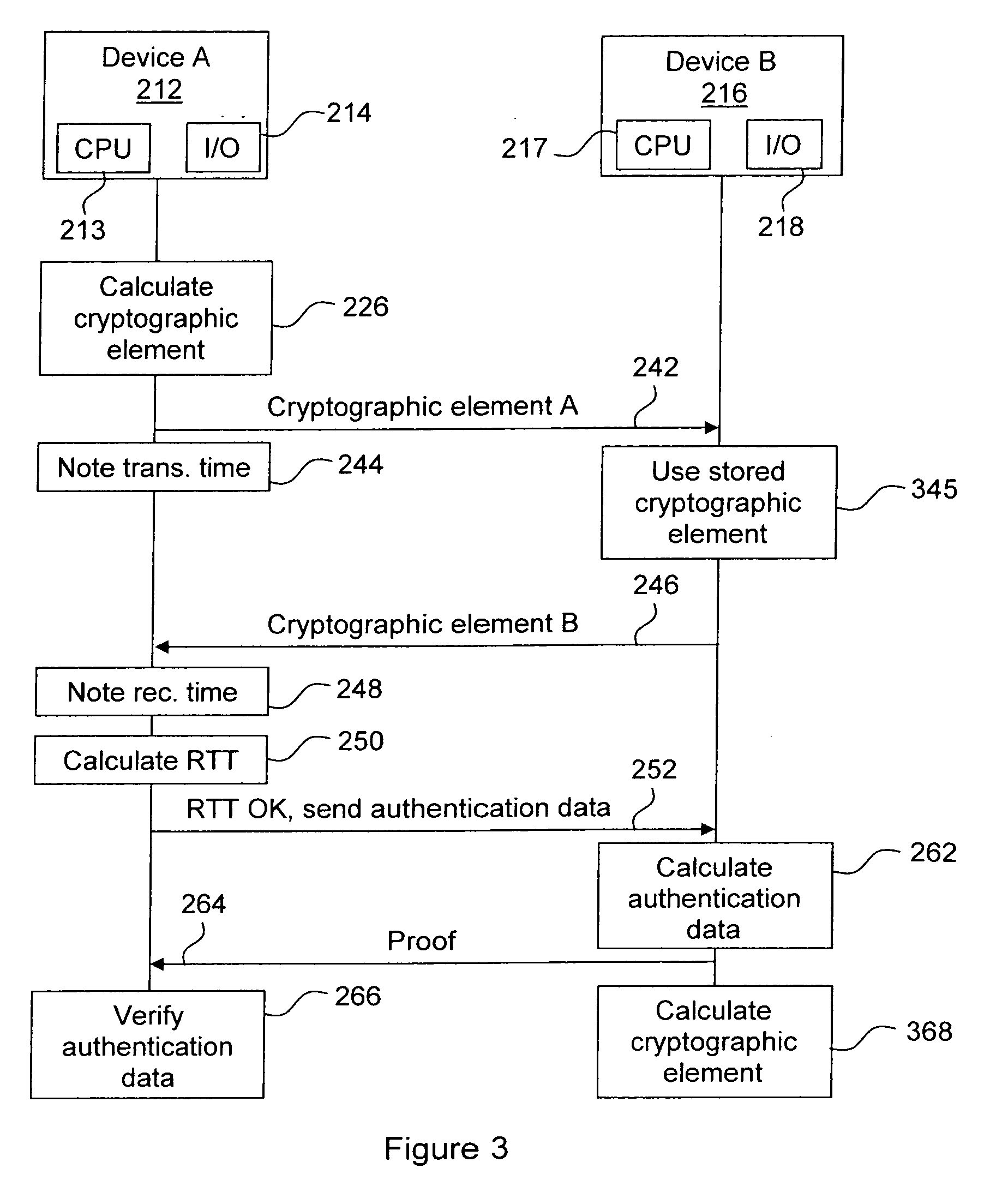
Method and Devices for Secure Measurements of Time-Based Distance Between Two Devices
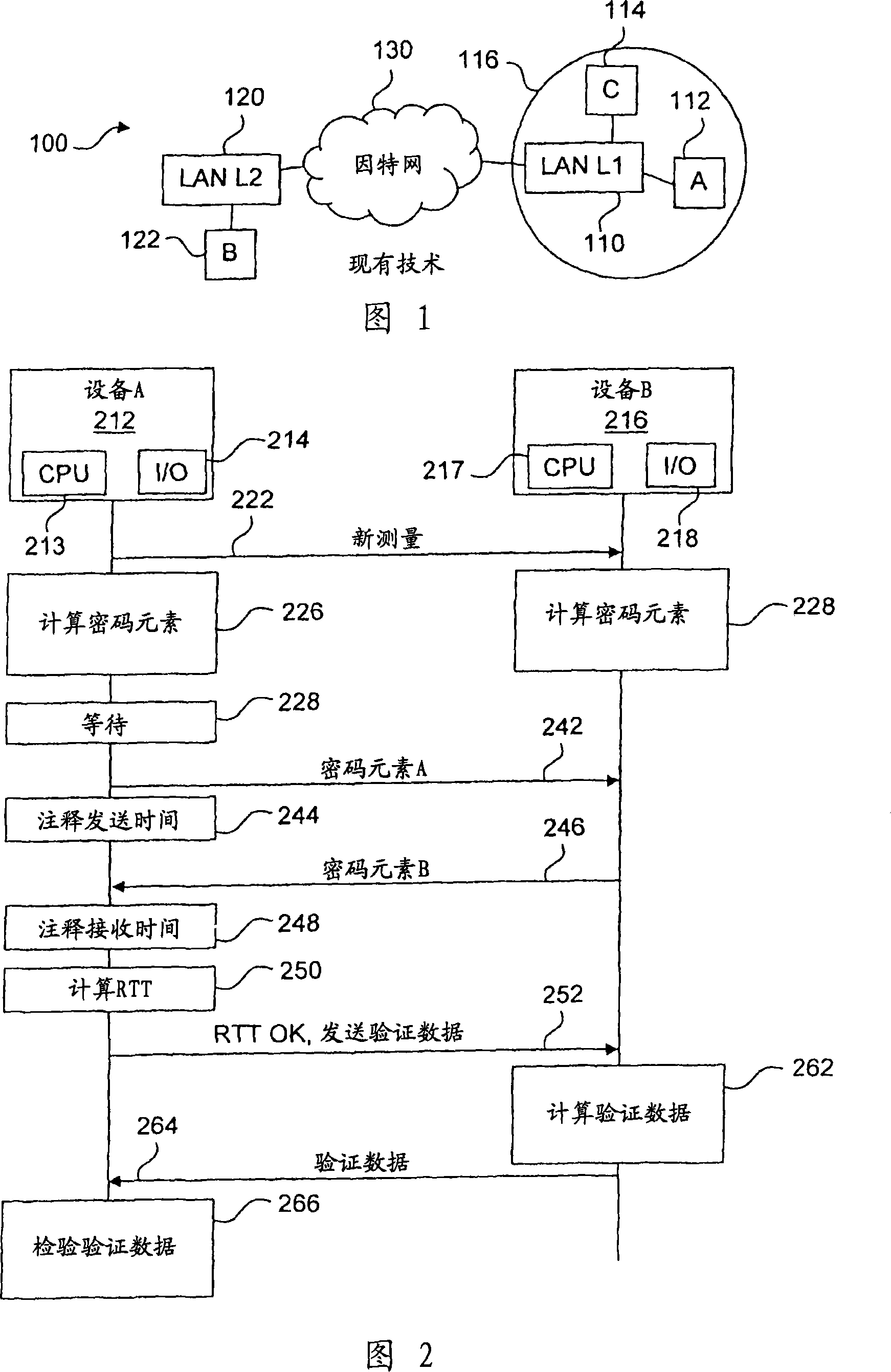
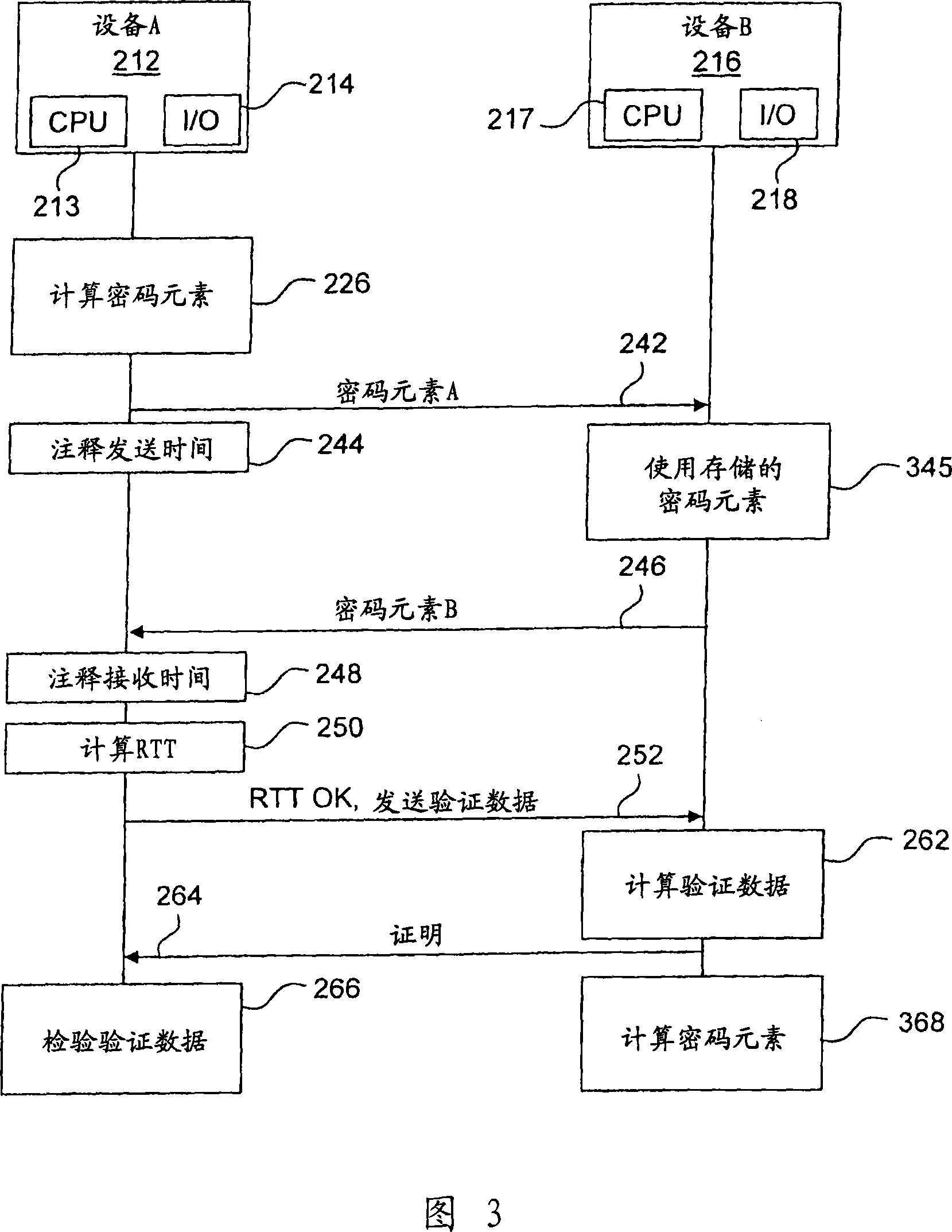
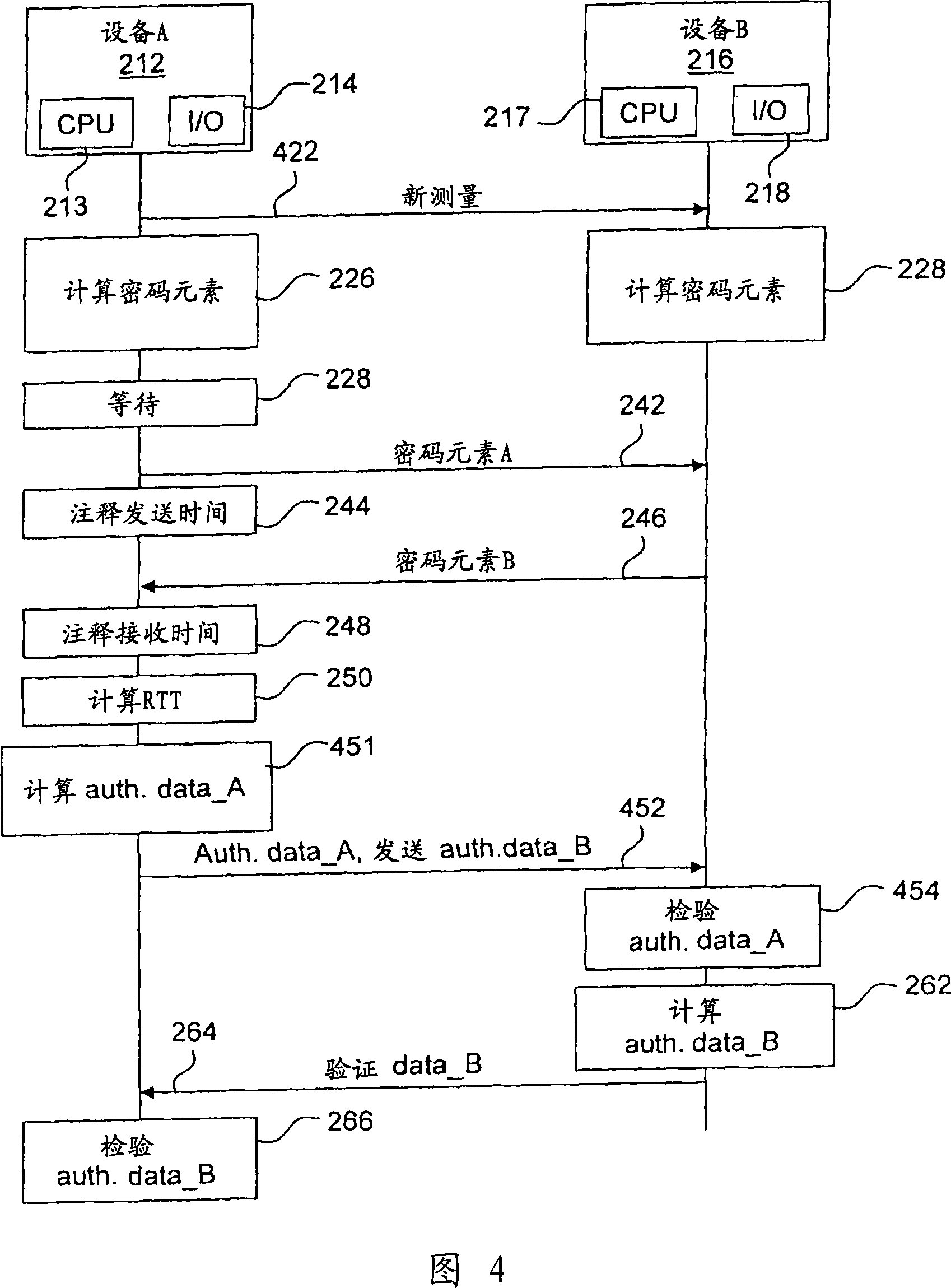
In order to provide a secure measurement of Round Trip Time (RTT), the calculation of RTT and the authentication data are separated. A device A sends a message to device B to start the method. Both devices generate a random number and device A waits for device B to finish. Device A sends its random number to B, which answers with its own random number, and device A calculates the RTT. If the RTT is below a certain limit, device A then requires authentication data, which is calculated by device B and sent to device A that verifies the authentication data. The RTT can thus be securely calculated regardless of the calculating resources of device B. Alternate embodiments, a system and devices are also provided.
Owner:THOMSON LICENSING SA
Pre-crash safety system
InactiveUS8248295B2Pedestrian/occupant safety arrangementAnti-collision systemsSecurity measurementRadar
Owner:TOYOTA JIDOSHA KK
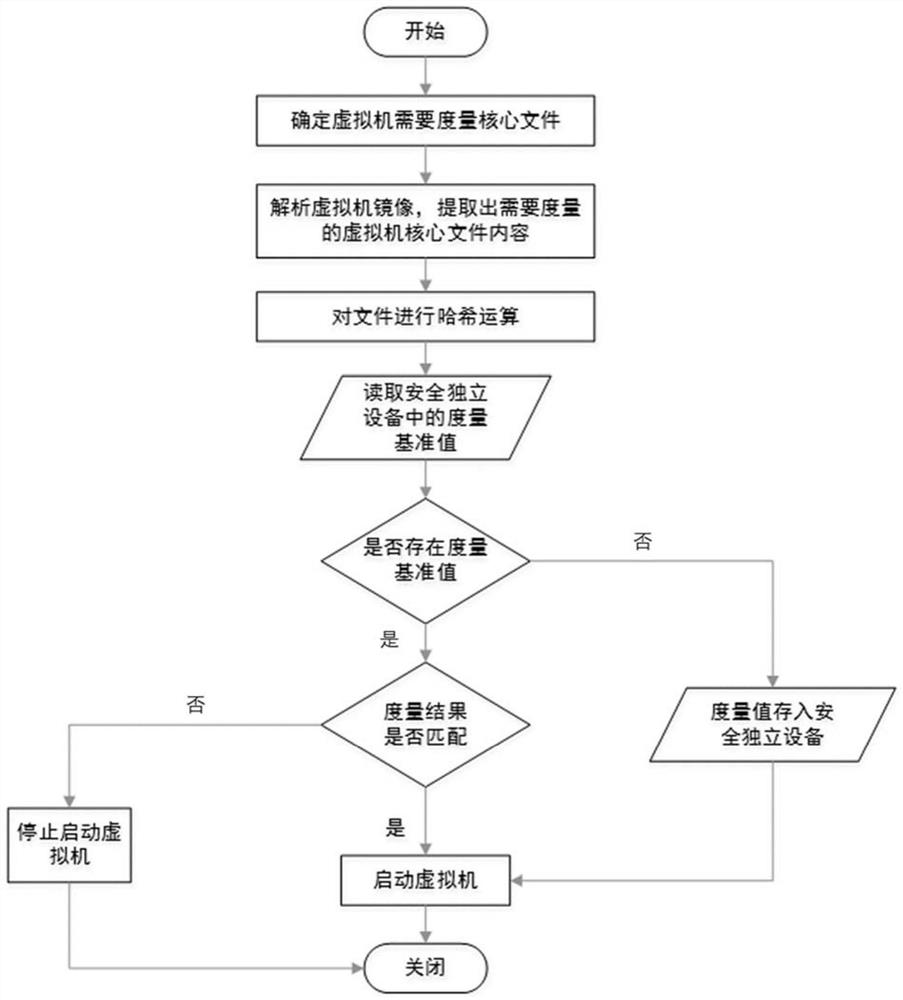
Virtual machine static measurement method and device based on built-in security architecture
ActiveCN111638936AImprove securityEnsure safetySoftware simulation/interpretation/emulationVirtualizationSecurity measurement
The invention relates to a virtual machine static measurement method and device based on a built-in safe architecture. The method comprises the steps of in the starting process of a physical host, enabling safe independent equipment to carry out safety measurement on a host machine system and virtualization software to ensure credibility of the host machine system and the virtualization software;enabling the host machine system and the virtualization software to determine a to-be-measured virtual machine core file; analyzing the virtual machine mirror image file, extracting the content of theto-be-measured virtual machine core file, performing security measurement on the content, and generating a measurement value; if judging that the virtual machine is started for the first time, indicating that the metric value serves as a reference value to be stored in the safe independent equipment, and the virtual machine is started; and if judging that the virtual machine is not started for the first time, verifying the metric value and a reference value in the safe independent equipment, cancelling starting of the virtual machine if verification fails, and starting the virtual machine ifverification succeeds. According to the invention, the extension of the static measurement mechanism of the virtual machine to the virtual machine can be realized, and the security of the virtual machine is enhanced.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
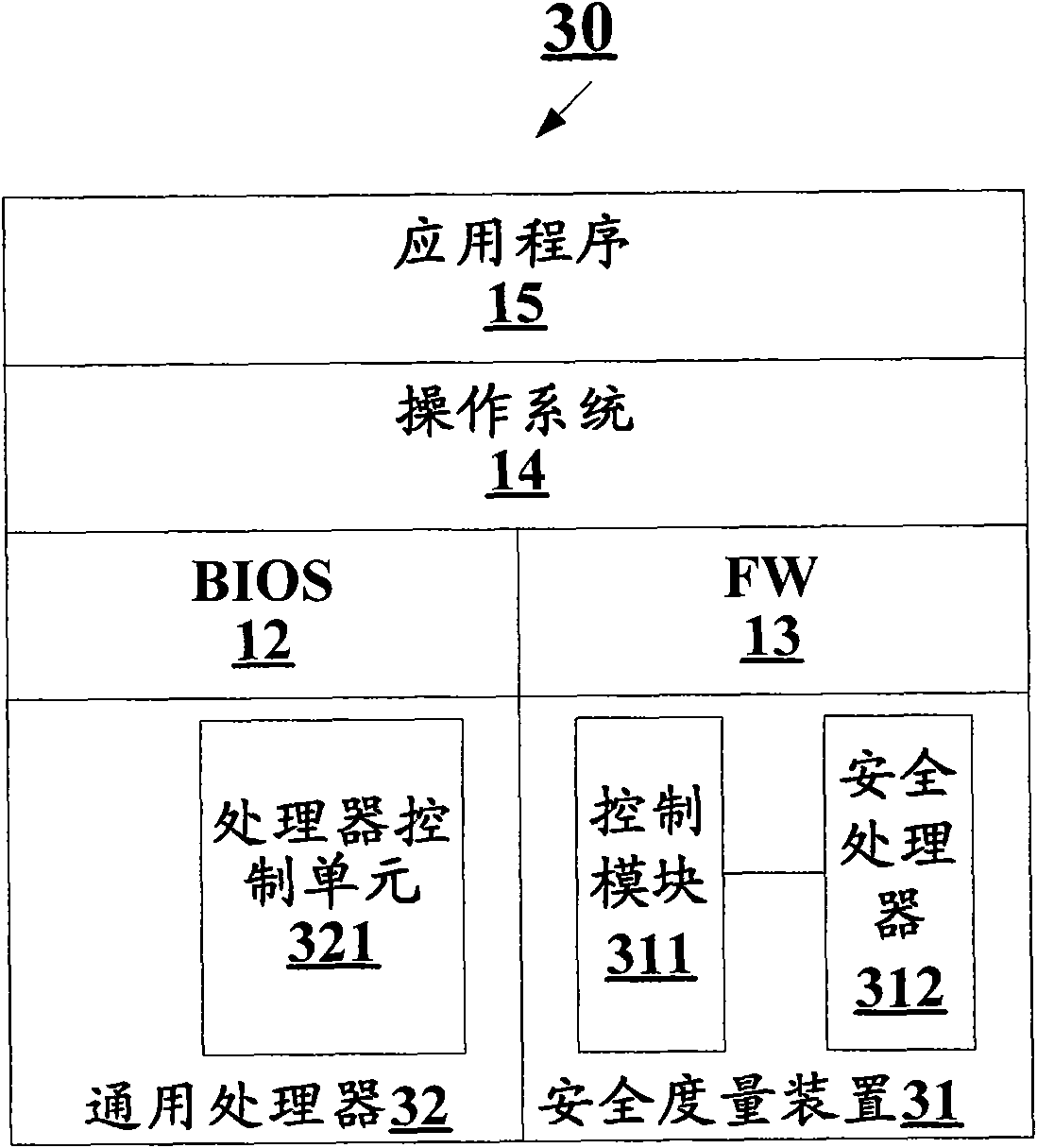
Dynamic security measure implementation method, security measurement device and application system
ActiveCN101996286AProtection securityMeet performance requirementsSoftware testing/debuggingPlatform integrity maintainanceComputer hardwareSecurity measurement
The invention discloses a dynamic security measure implementation method, a security measurement device and an application system, wherein the security measurement device comprises a control module and a security processor, wherein the control module is used for accessing system and / or software information and sending a measurement comparison instruction and the system and / or software informationto the security processor; the security processor is used for measuring the received system and / or software information according to the measurement comparison instruction from the control module, comparing the measured result obtained by measurement with a stored measurement reference value and returning the state of the compared result according to the compared result. According to the dynamic security measure implementation method, the security measurement device and the application system, whether the called system and / or software information is falsified is determined according to the comparison of the measured result and the measurement reference value, thereby finishing integrity detection before the system and / or software information is loaded to an application system.
Owner:北京多思技术服务有限公司
Method and devices for secure measurements of time-based distance between two devices
InactiveCN101204067AUser identity/authority verificationData switching networksSecurity measurementEngineering
In order to provide a secure measurement of Round Trip Time (RTT), the calculation of RTT and the authentication data are separated. A device A (212) sends a message (222) to device B (216) to start the method. Both devices generate (224; 226) a random number (Random_A, Random_B) and device A waits (228) for device B to finish. Device A sends (242) its random number to B, which answers (246) with its own random number, and device A calculates (250) the RTT. If the RTT is below a certain limit, device A then requires (252) authentication data, which is calculated (262) by device B and sent (264) to device A that verifies (266) the authentication data. The RTT can thus be securely calculated regardless of the calculating resources of device B. Alternate embodiments, a system and devices are also provided.
Owner:INTERDIGITAL CE PATENT HLDG
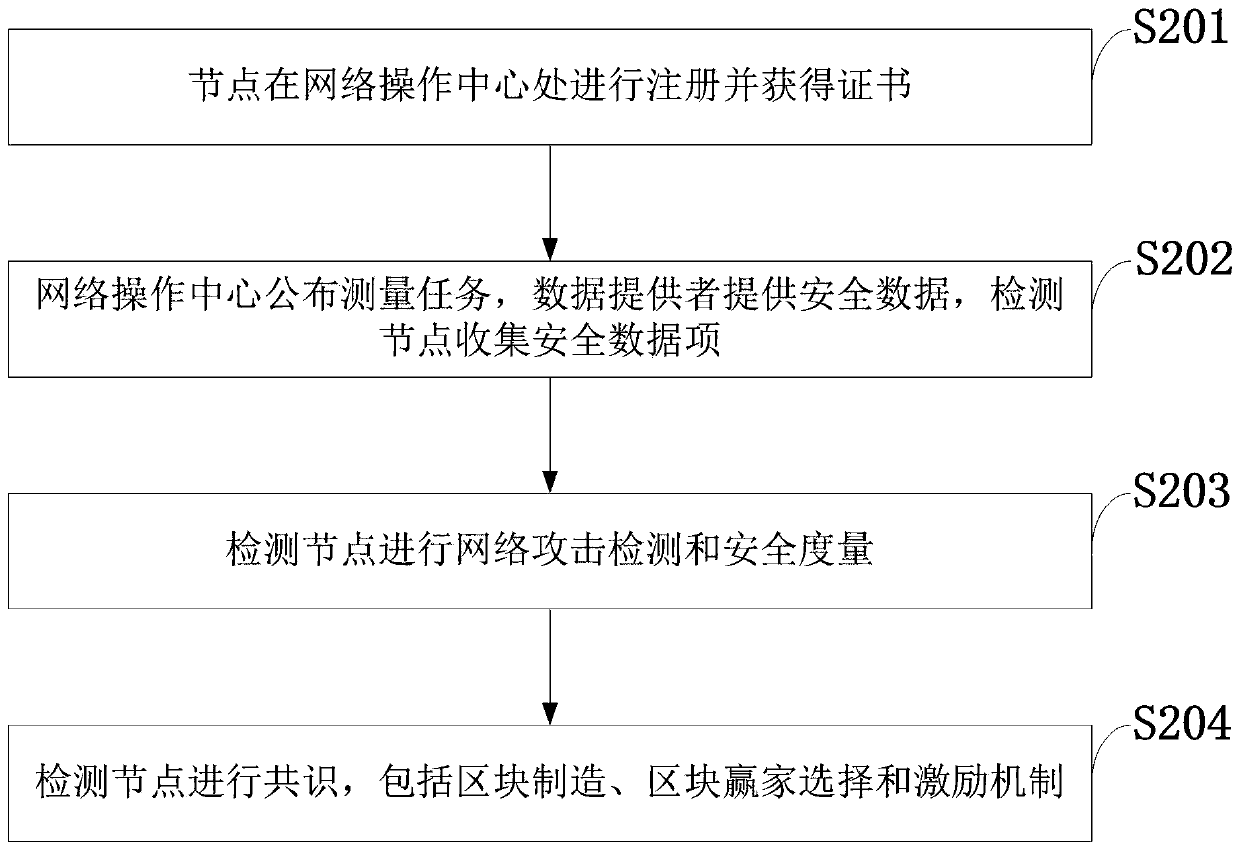
Distributed network attack detection and security measurement system and method based on block chain
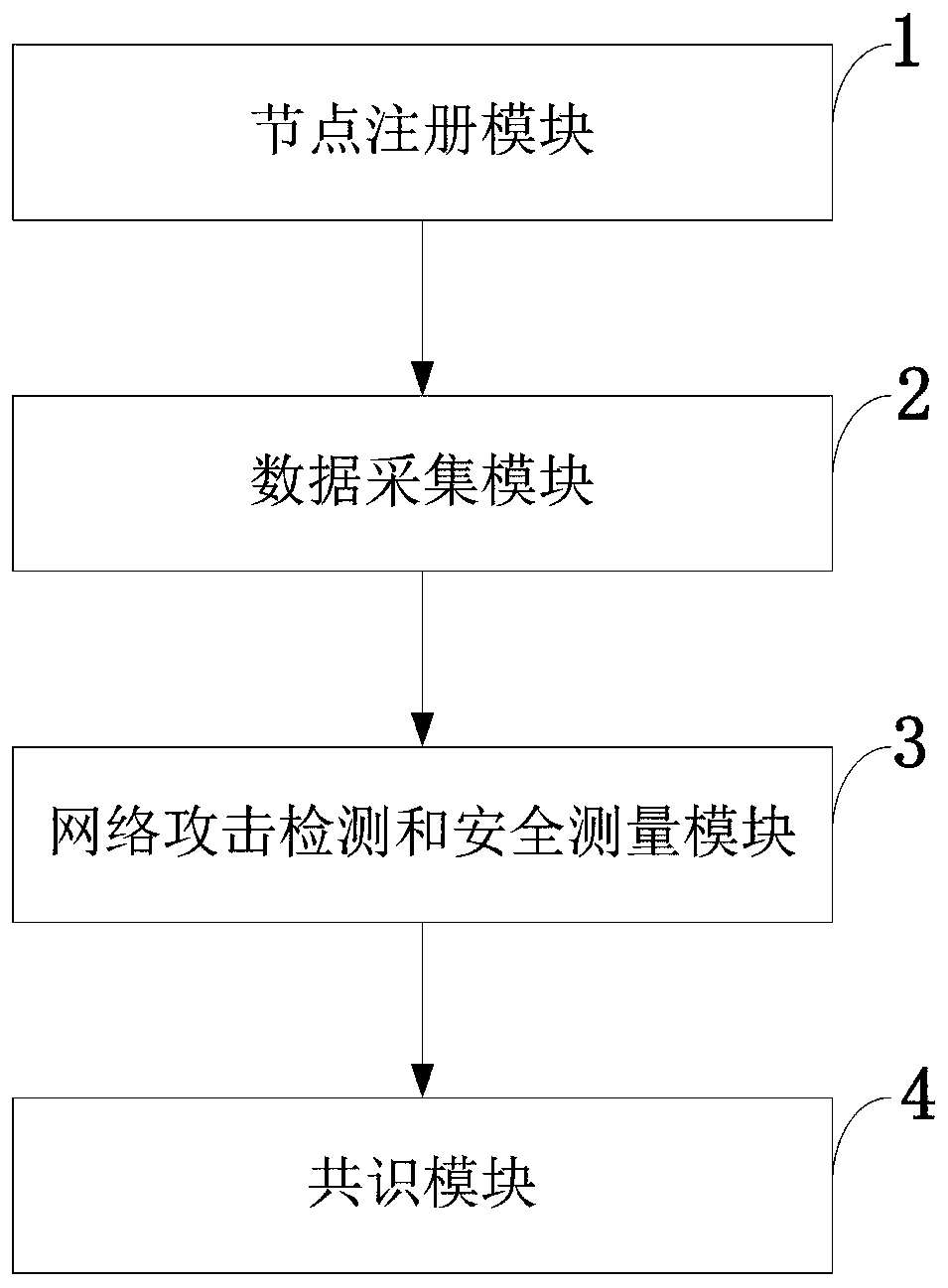
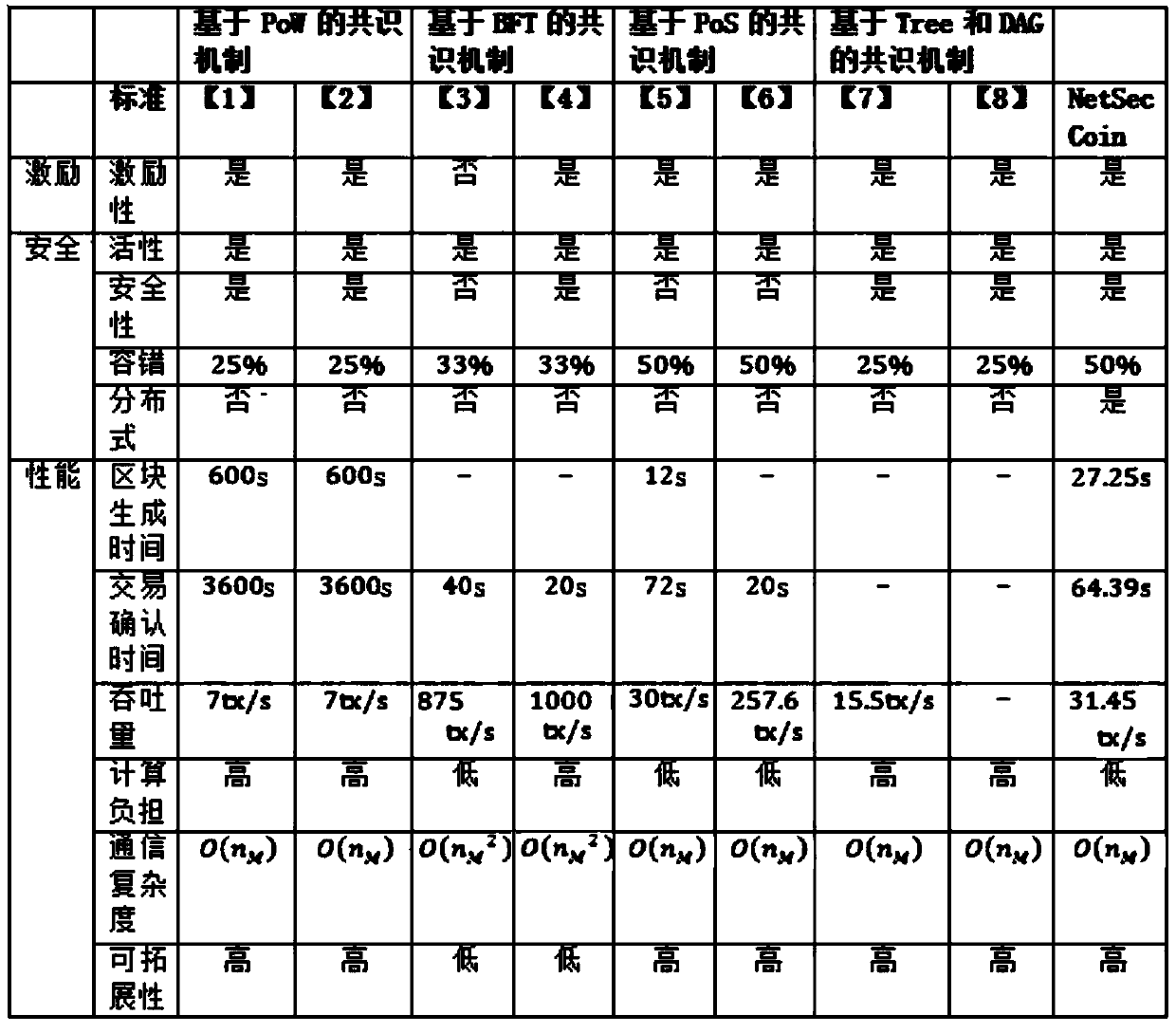
ActiveCN110120936AOvercome infeasibilityAvoid forksUser identity/authority verificationSecurity arrangementSecurity measurementData provider
The invention belongs to the technical field of wireless communication, and discloses a distributed network attack detection and security measurement system and method based on a block chain. Registering is performed at a network operation center and a certificate is obtained; a network operation center publishes a measurement task, a data provider provides security data, and a detection node collects security data items; the detection node performs network attack detection and security measurement; and a detection node manufactures a block, and finally consensus is performed. A network operation center is allowed to publish a measurement task, and a data provider provides security data; the detection node verifies the collected security data and carries out fused attack detection to obtain a detection result; and the detection nodes generate blocks, and finally consensus is achieved among the detection nodes. According to the invention, a data provider can be stimulated to provide security data, and detection nodes are stimulated to carry out fused attack detection and network security measurement; infeasibility of a single detection node is overcome, and bifurcation, low efficiency and centralization of the block chain are overcome.
Owner:XIDIAN UNIV
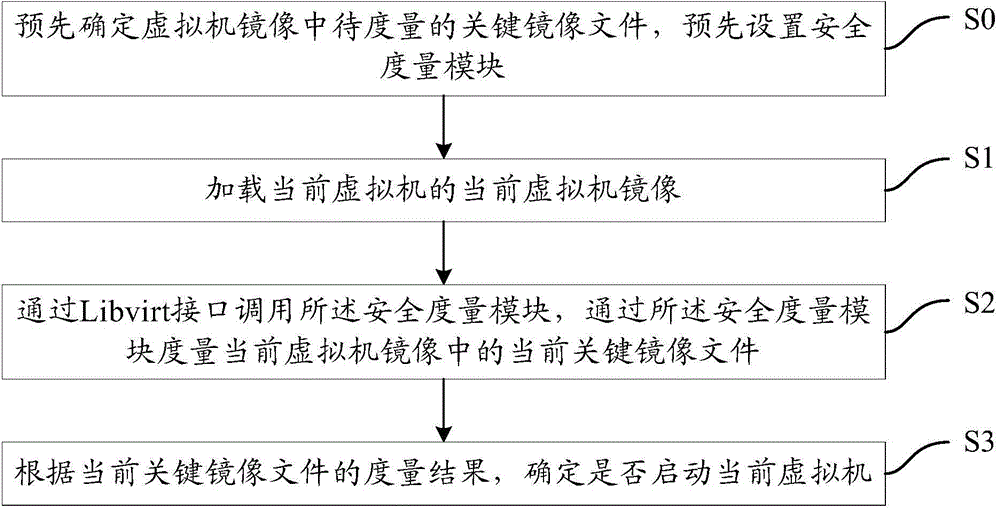
Virtual machine security protection method and apparatus
InactiveCN104866392AProtection securityPlatform integrity maintainanceRedundant operation error correctionSecurity measurementComputer module
The present invention provides a virtual machine security protection method and apparatus. The method comprises: pre-determining a key mirror file to be measured in a virtual machine mirror, and pre-configuring a security measurement module; and further comprises: S1, loading a current virtual mirror of a current virtual machine; S2, calling the security measurement module via a Libvirt interface, and measuring a current key mirror file in the current virtual machine mirror using the security measurement module; and S3, determining, according to a measurement result of the current mirror file, whether to enable the current virtual machine. The virtual machine security protection method and apparatus provided by the present invention can protect security of the virtual machine.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Secure time functionality for a wireless device
InactiveCN101444063AIncreased security time informationAccounting/billing servicesComputer security arrangementsTime informationCurrent meter
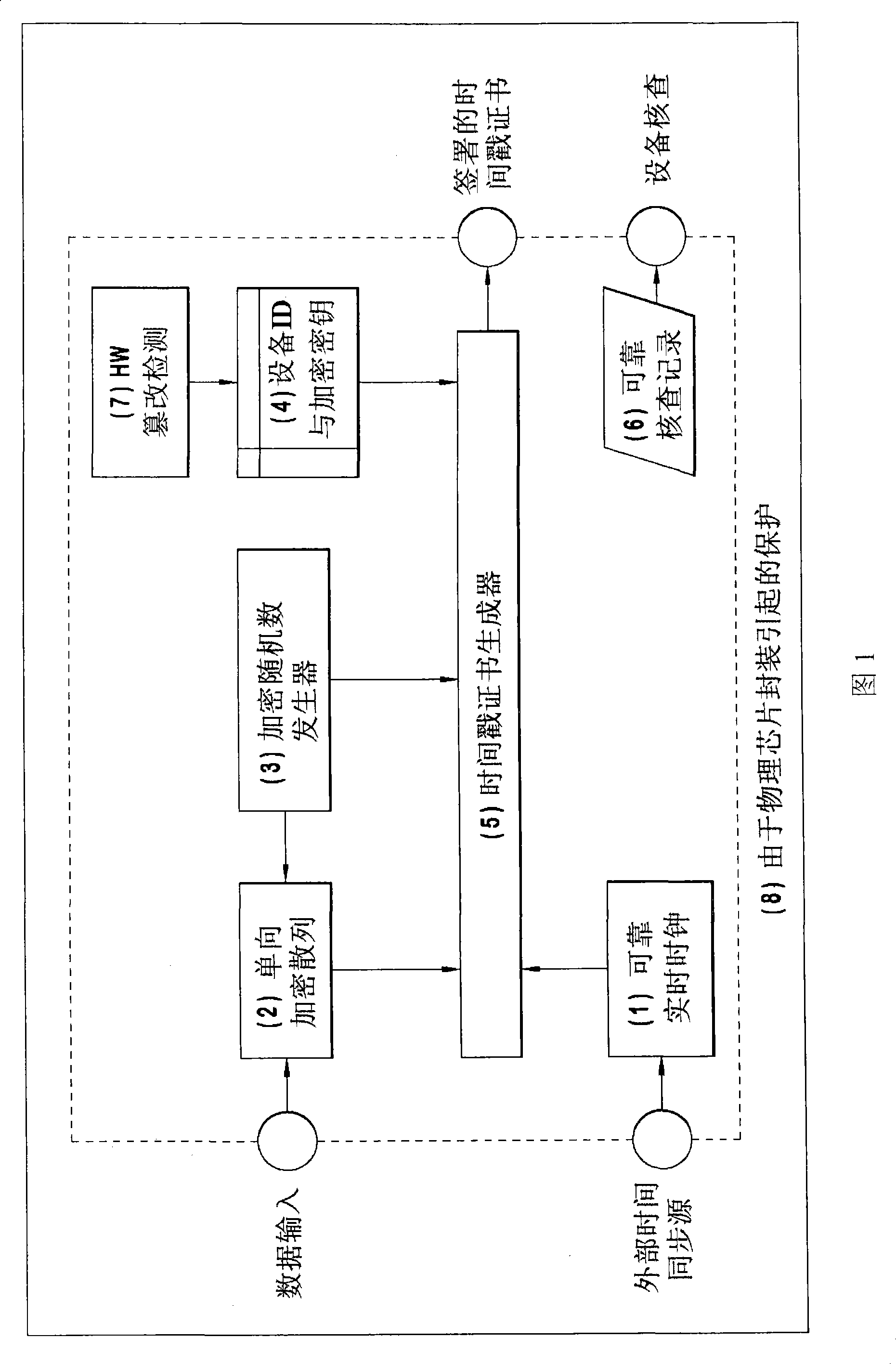
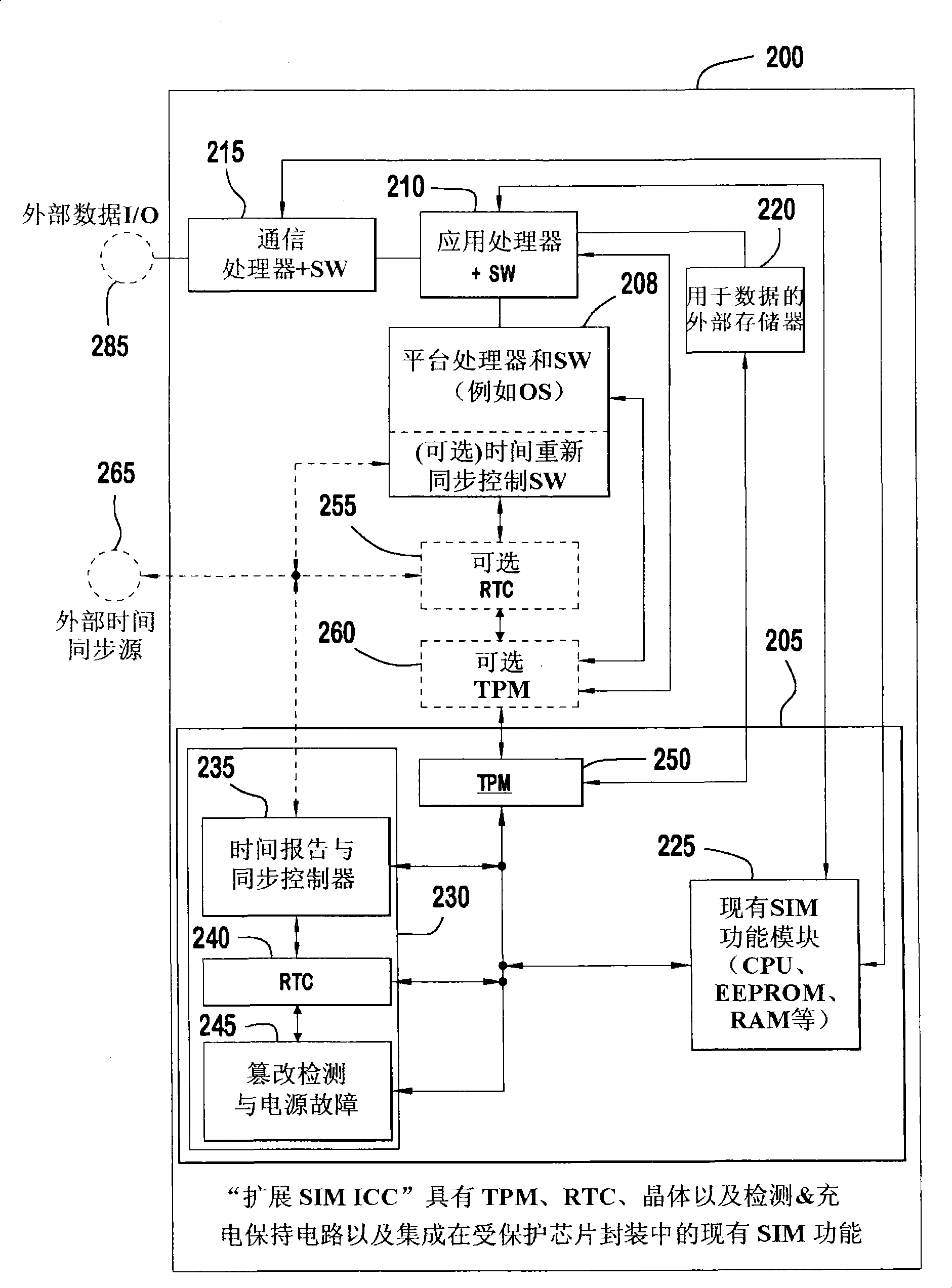
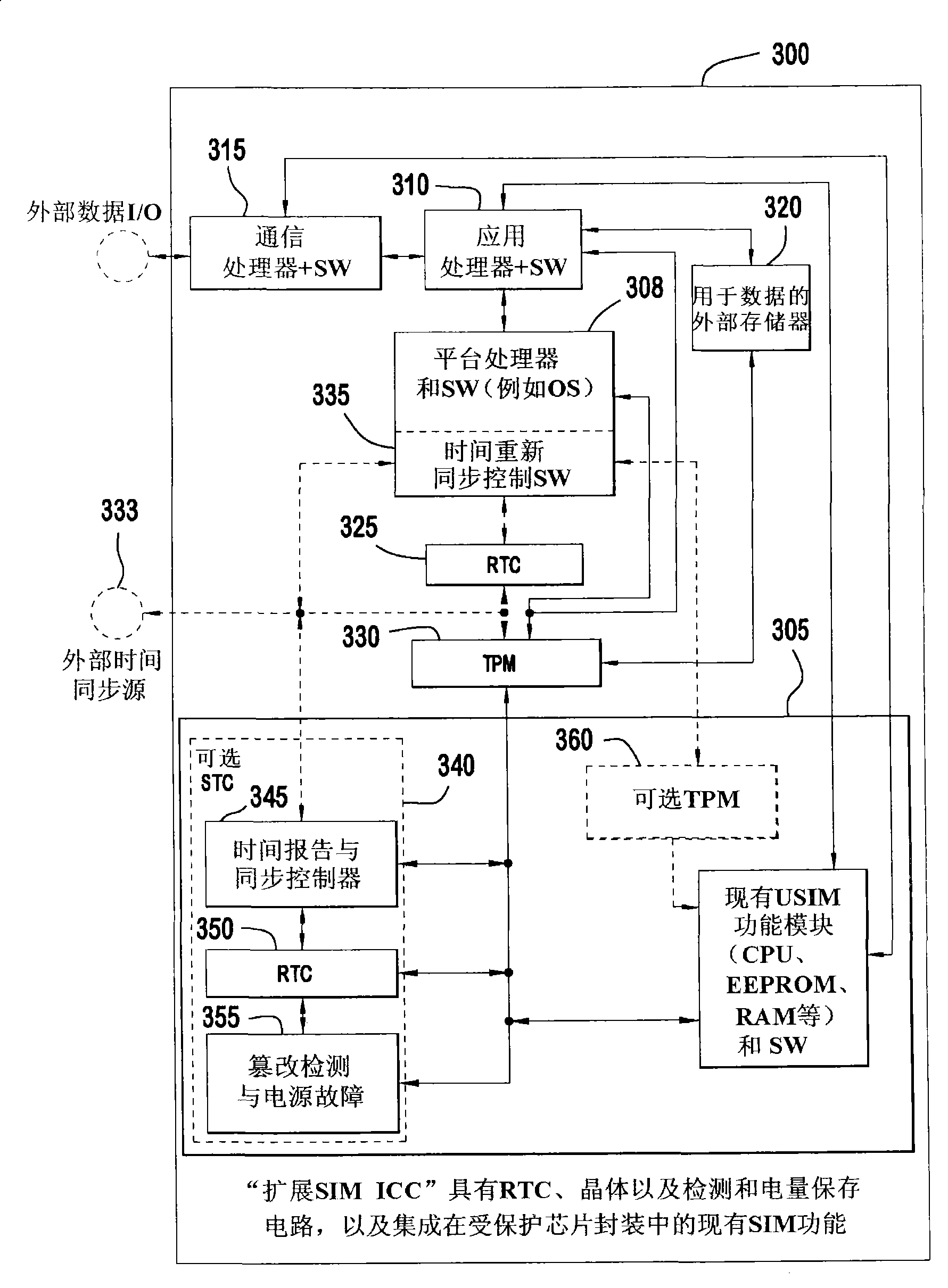
The present invention is related to a wireless transmit / receive unit (WTRU) for providing advanced security functions. The WTRU includes trusted platform module (TPM) for performing trusted computing operations; and a secure time component (STC) for providing a secure measurement of a current time. The STC and the TPM are integrated to provide accurate trusted time information to internal and external to the WTRU. The STC may be located on an expanded a subscriber identity module (SIM), on the WTRU platform, or two STCs may be used, one in each location. Similarly, the TPM may be located on an expanded SIM, on the WTRU platform, or two TPMs may be used, one in each location. Preferably, the STC will include a real time clock (RTC); a tamper detection and power failure unit; and a time report and sync controller.
Owner:INTERDIGITAL TECH CORP
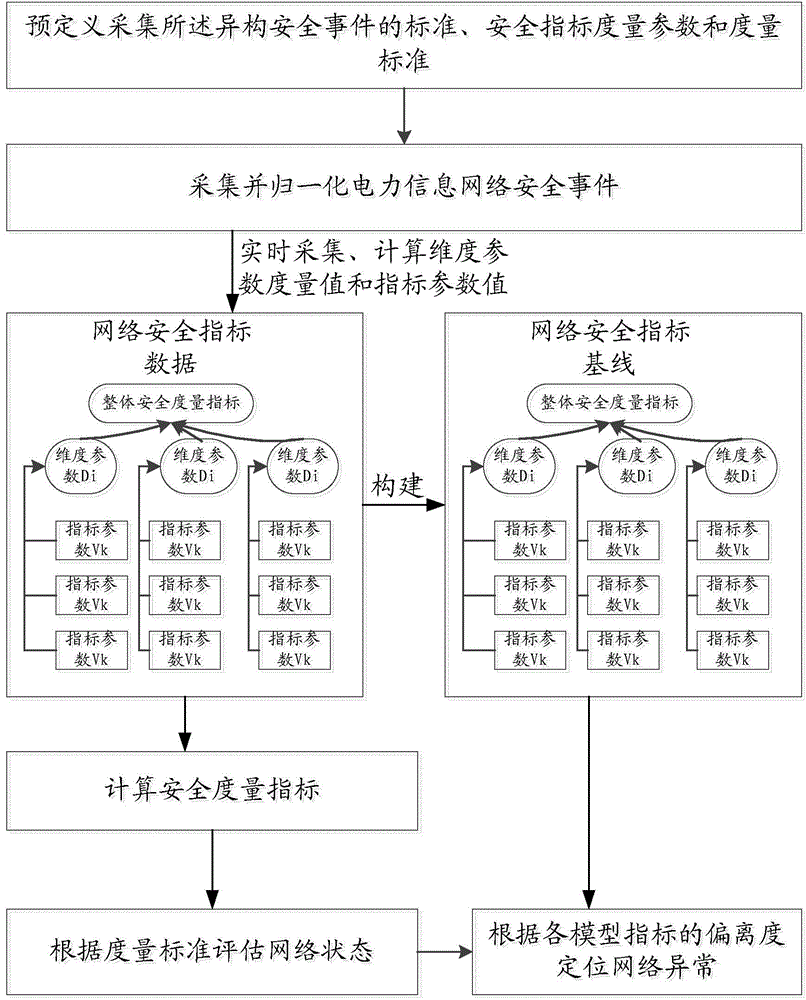
Indexed security measurement system based on power information network security event mining
The invention discloses indexed security measurement system and device based on power information network security event mining. The method and device are characterized in that the power information network heterogeneous security events are acquired on real time and normalized through a pre-defined template; the real-time data of index parameters Vk of the normalized standard safety events are acquired on real time, and the measurement value Ei of the dimension parameter Di and the whole network security measurement index H can be obtained according to the data. According to the method and device, the pre-defined security measurement strategy can be performed for adapting to complex network demand; an automatic, indexed and intelligent security measurement system is created based on the real-time characteristic and comprehensiveness of the security event data, and therefore, network security state and effectiveness can be accurately evaluated.
Owner:STATE GRID CORP OF CHINA +1
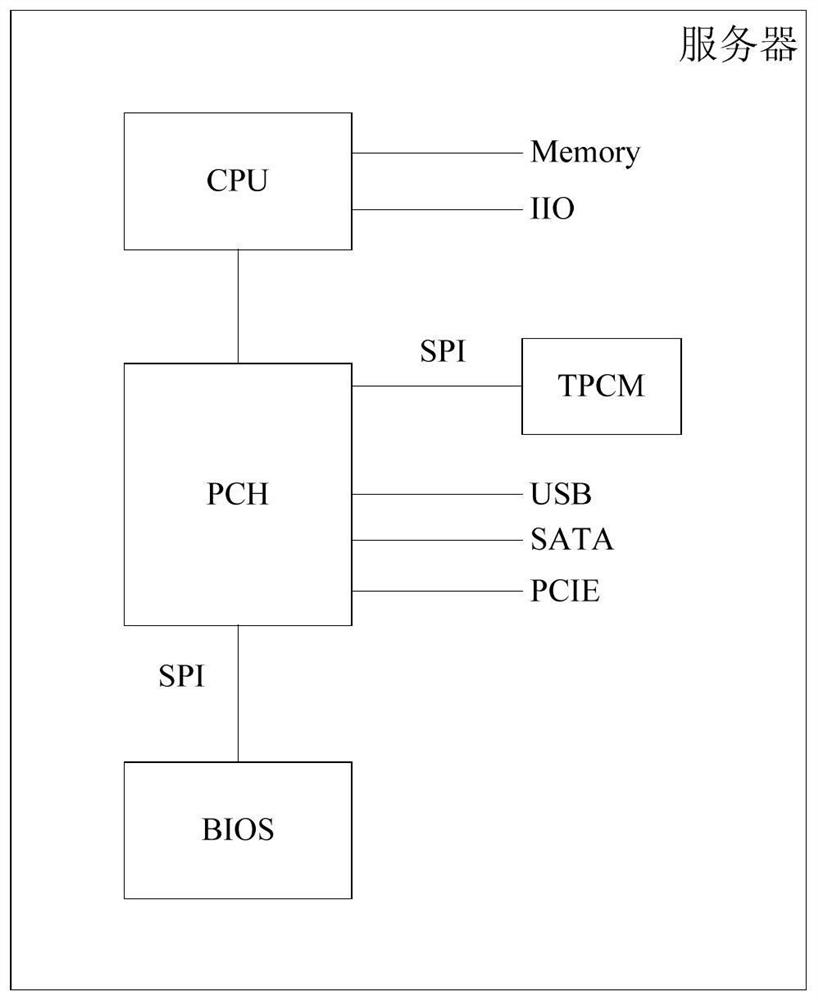
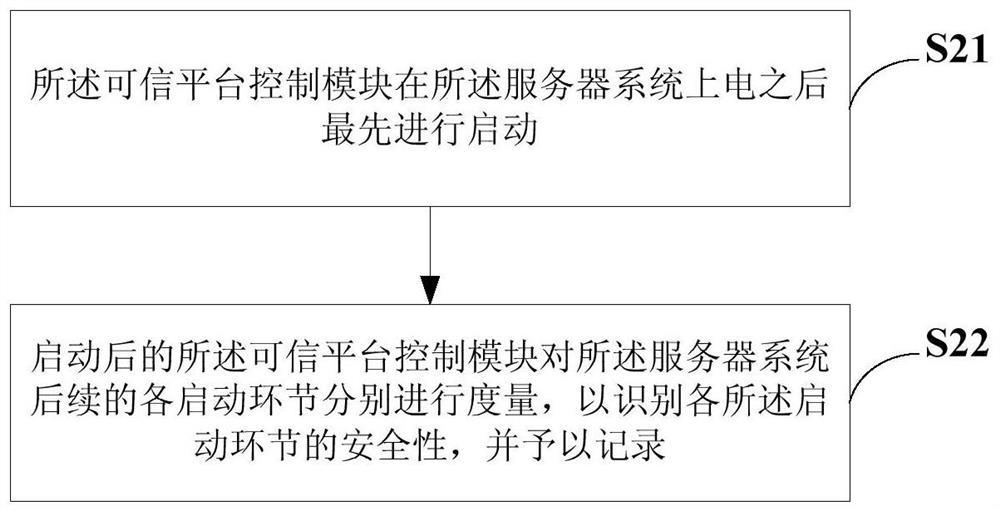
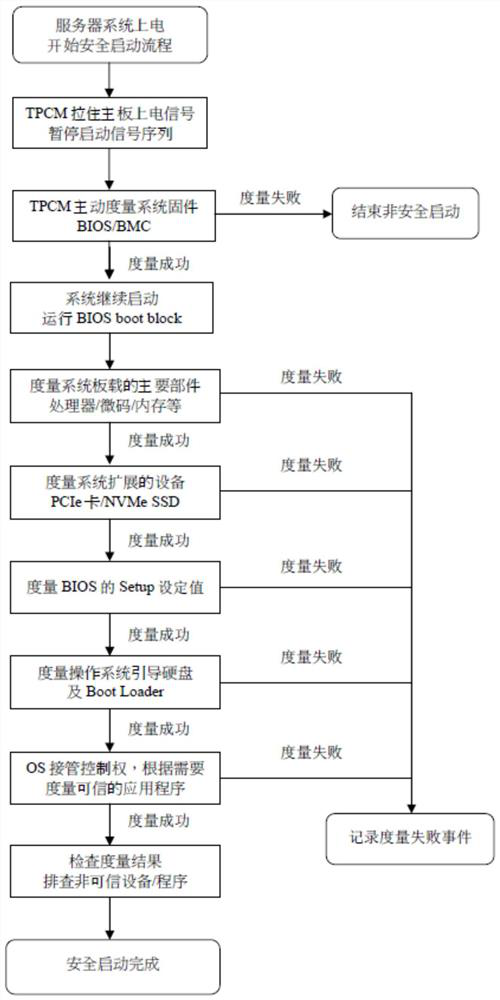
Security measurement method and security measurement device for server system startup, and server
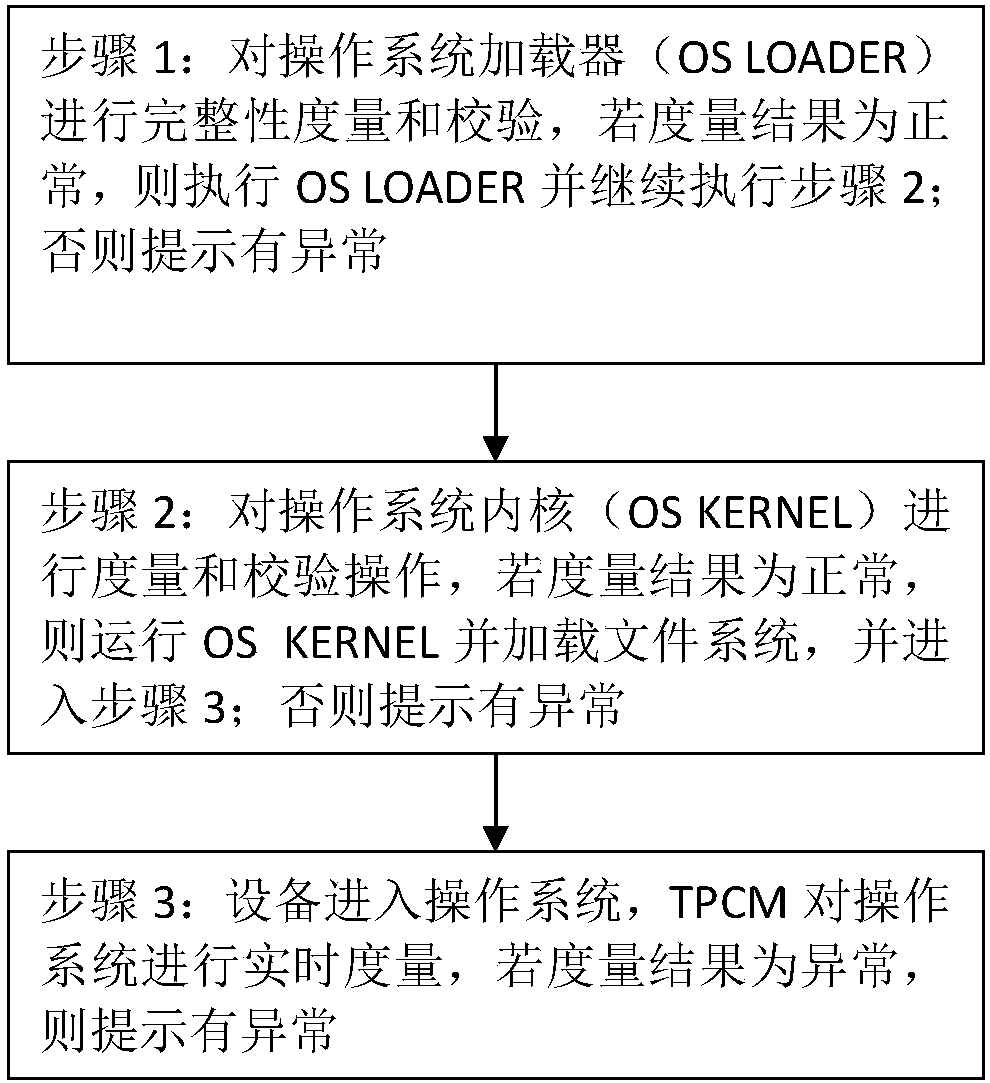
PendingCN111950014AImplement Active MetricsSecure bootError detection/correctionDigital data protectionSecurity measurementSoftware engineering
The invention provides a security measurement method and a security measurement device for server system startup, and a server. The security measurement method for server system startup is applied toa trusted platform control module of the server system. The method comprises the steps that the trusted platform control module is started firstly after the server system is powered on; and the started trusted platform control module measures each subsequent starting link of the server system so as to identify the security of each starting link and record the security. According to the invention,the trusted platform control module is adopted, so that the security of the server system startup is effectively improved.
Owner:INVENTEC PUDONG TECH CORPOARTION +1
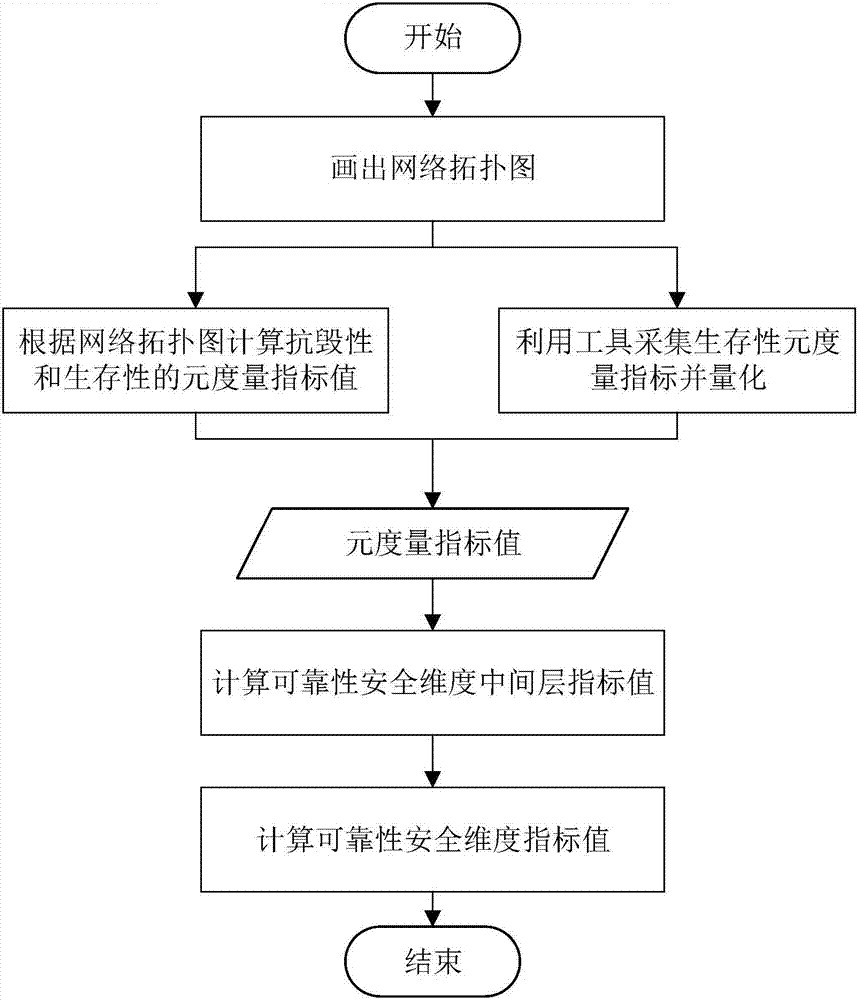
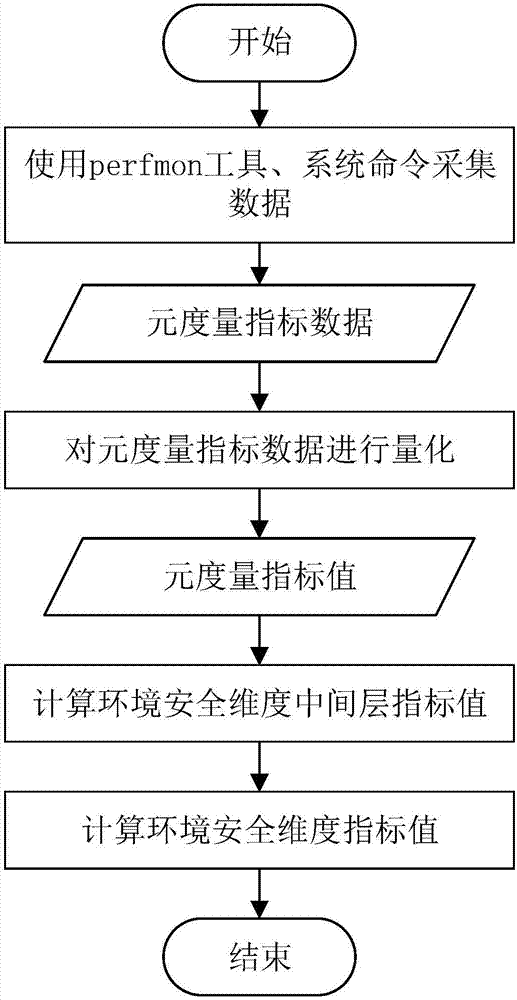
Multi-dimensional and multi-granularity network space security measurement method
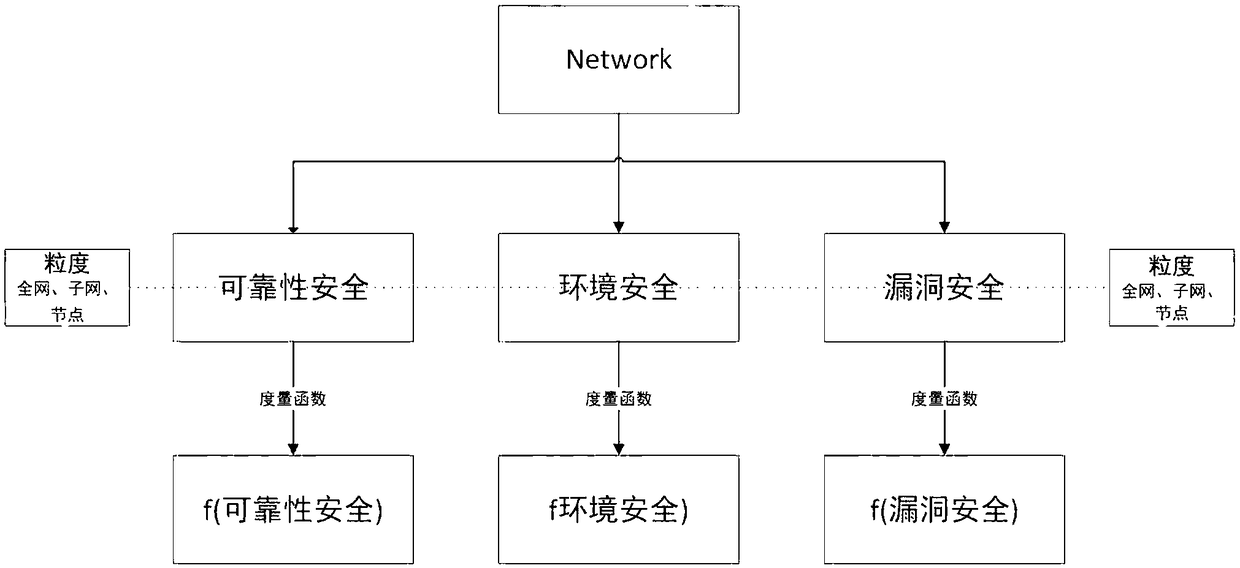
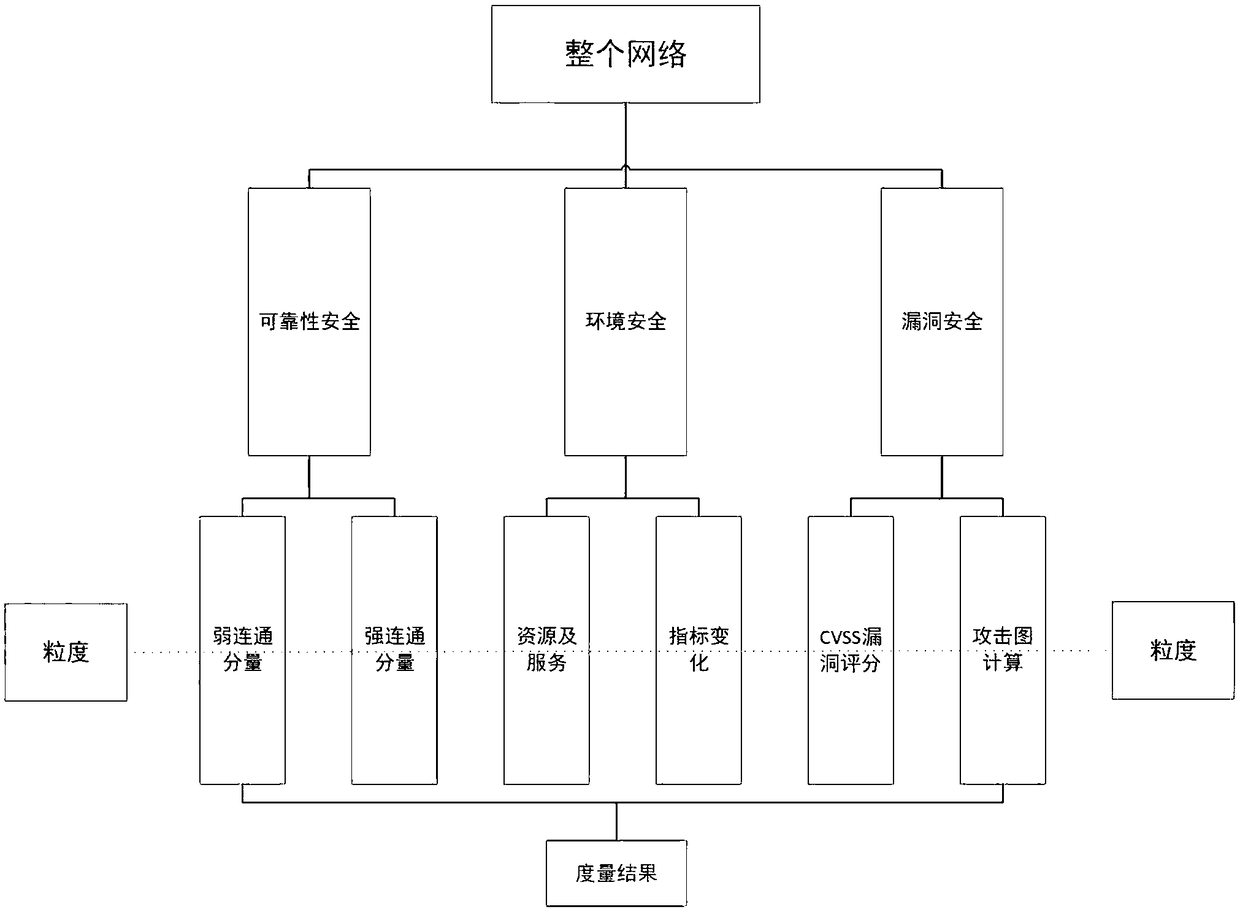
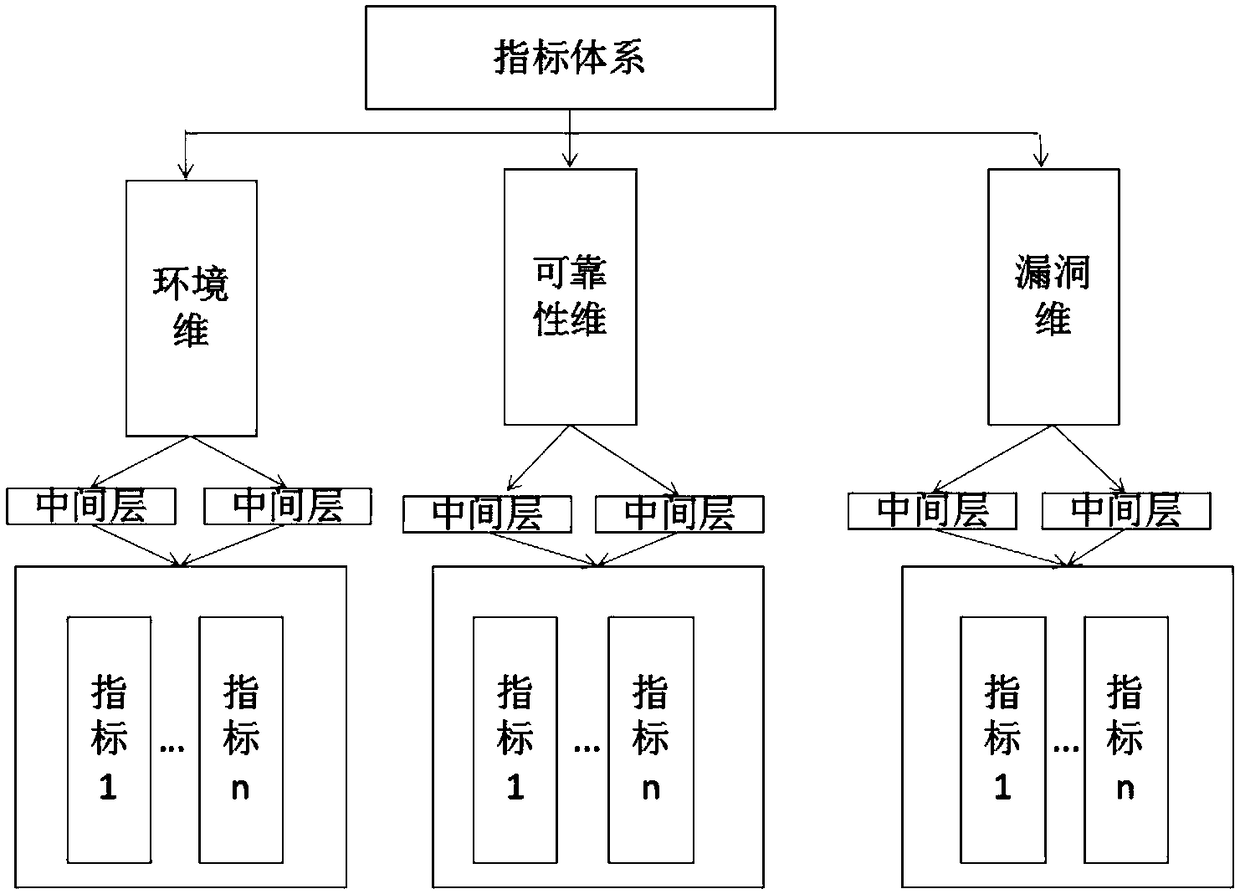
ActiveCN108769018AReduce complexityImprove accuracyTransmissionSecurity measurementEngineering principles
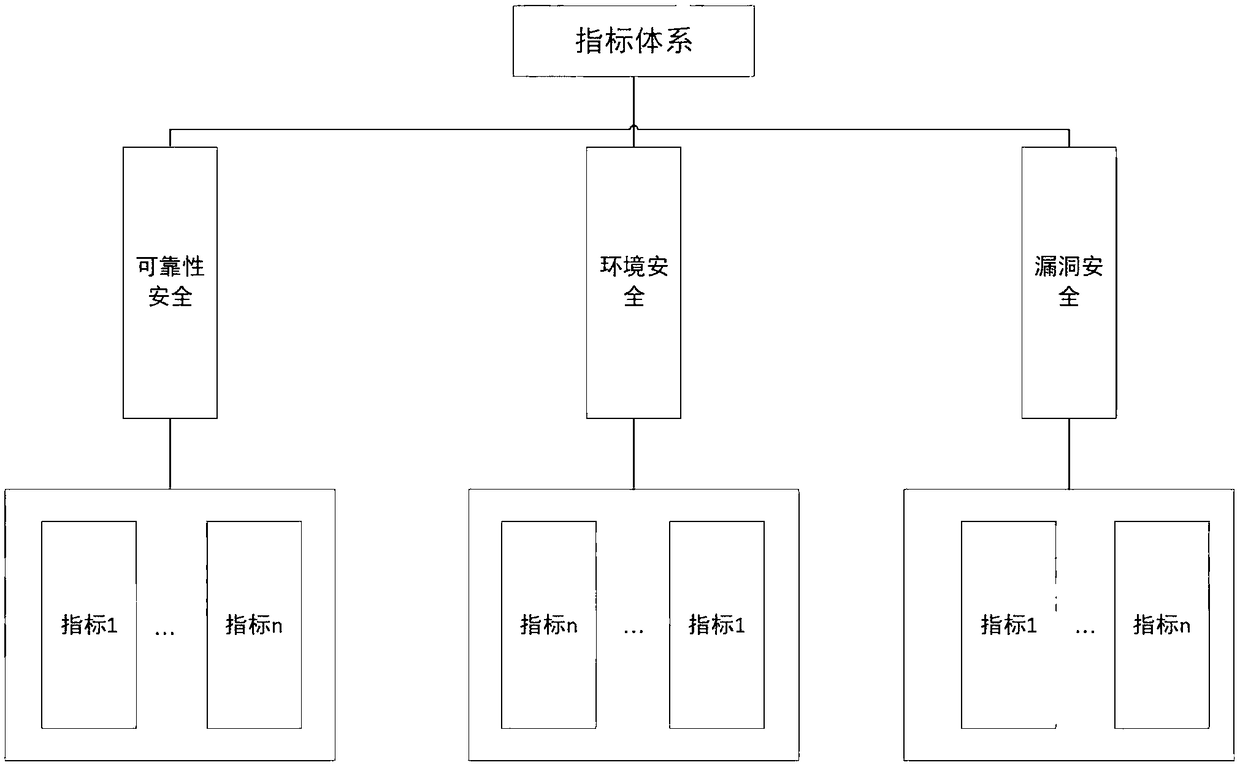
The invention discloses a multi-dimensional and multi-granularity network space security measurement method. The multi-dimensional and multi-granularity network space security measurement method comprises the following steps: dividing a network system into three hierarchies according to logical hierarchy, wherein the three hierarchies are reliability security, environment security and vulnerability security separately; extracting and selecting indexes in the network system according to the three hierarchies, and establishing a network space security index system by means of the system engineering principle and the analytic hierarchy process (AHP); performing dimensional division on each hierarchy based on the established network space security index system; wherein the reliability securityis measured by a weak connectivity dimension and a strong connectivity dimension, the environment security is measured by a network asset and service dimension and an asset index change dimension, and the vulnerability security is measured by a vulnerability dimension and an attack graph dimension; and adding the granularity on the basis of the hierarchy and dimension, and obtaining the measurement values of each hierarchy and each dimension within the specified range of the granularity, wherein the sum is the network space security measurement result. Using the multi-dimensional and multi-granularity network space security measurement method, the measurement results are more accurate and comprehensive.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Low-pressure gauge used for hazardous gas security measurement
The invention discloses a structure of low pressure gauge for the security measurement of dangerous gas, which is composed of a radiation source, a collector, an acceleration grid, a shell, an end cap, a stainless sheet, an insulating base, a flange base, a metal indium wire seal ring, a connecting bolt, a connecting screw, a ceramic lead wire and an electrode component. The structure utilizes the beta particles generated by the radiation source to ionize the gas molecules in a detected environment; the direct current voltage provided by the acceleration grid forms an electric field between the collector and the acceleration grid; the positive ions generated by ionization are finally collected on the collector via the electric field force to form a weak current signal of microampere level; when the detected environment pressure changes, the generated current signal changes too, and changes of the detected environment pressure and the current signal have linear proportional in low vacuum range, therefore, the current signal generated by the collector can be measured to measure low vacuum pressure. The low pressure gauge has simple structure, high measurement accuracy, small volume, explosion resistance and the application for the measurement in low temperature environment.
Owner:NO 510 INST THE FIFTH RES INST OFCHINA AEROSPAE SCI & TECH
Server credibility measuring method
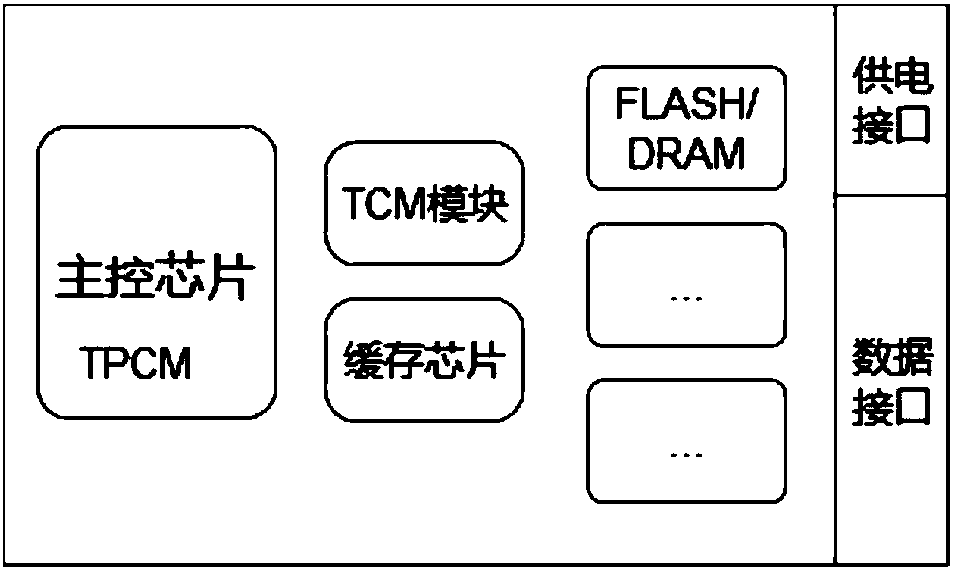
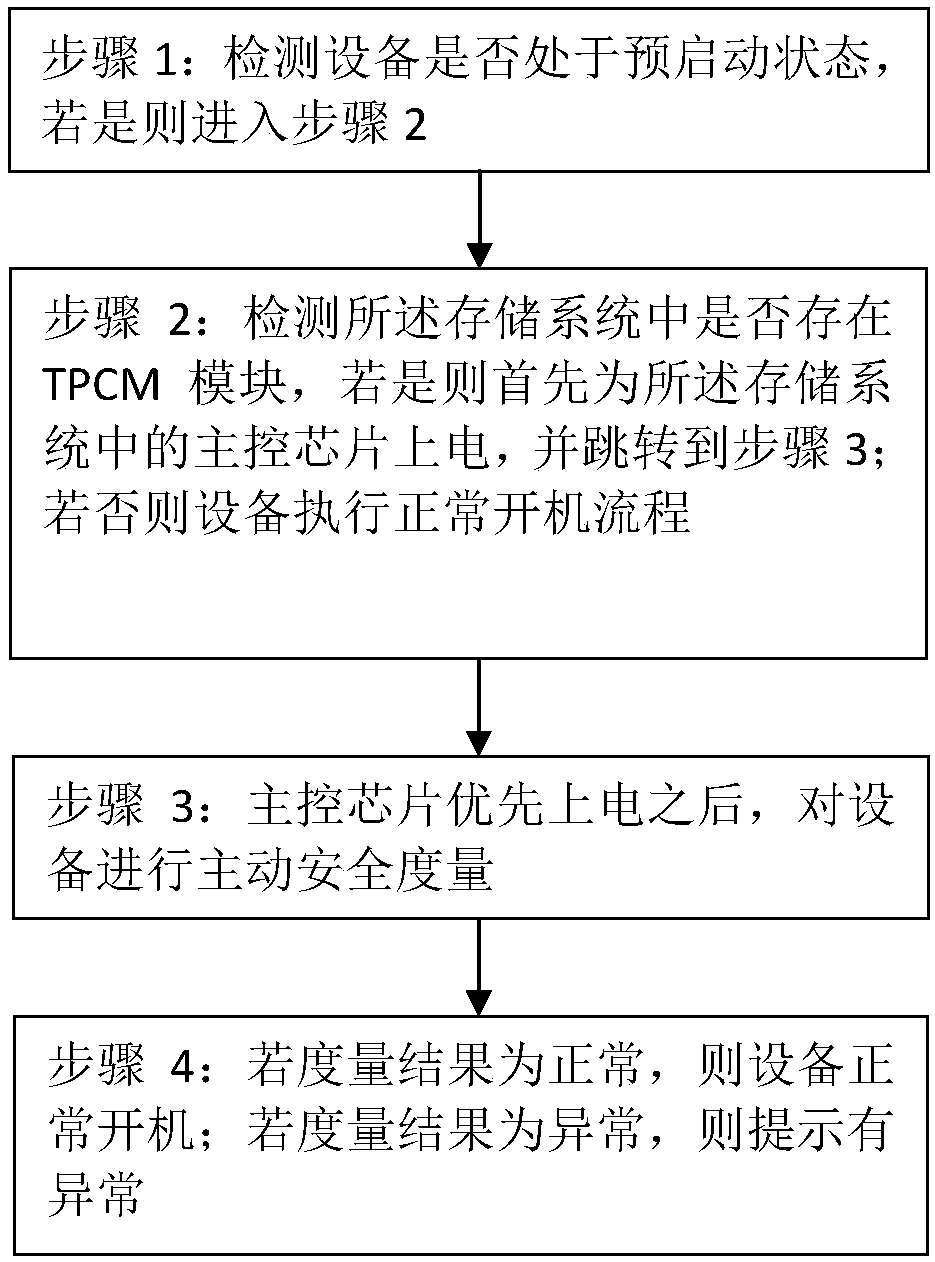
PendingCN110096393ALow costDetecting faulty hardware by power-on testHardware monitoringMultiplexingSecurity measurement
The invention discloses a server credibility measuring method. The method comprises the following steps of when the equipment is in a pre-starting state, and if it is detected that a TPCM module exists in a storage system, powering on a main control chip in a solid-state system firstly; then, carrying out the active security measurement on the firmware of the BIOS and the BMC; if the measurement results are all normal, starting the equipment normally, and if one measurement result is abnormal, not starting the equipment. According to the technical scheme provided by the invention, the multiplexing of the main control chip of the memory can be realized, and the TPCM security measurement function is realized by utilizing the main control chip, so that the cost of the trusted computing hardware is reduced, and the later product popularization is facilitated.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
Comprehensive security monitoring system for substation
InactiveCN105680565AReduce resource usageReduce occupancyCircuit arrangementsThermometers using physical/chemical changesEquipment temperatureEngineering
The invention relates to a comprehensive security monitoring system for a substation. The comprehensive security monitoring system comprises a perimeter security monitoring module, a running equipment temperature online monitoring module, a security measurement and control host and an information management module, wherein the perimeter security monitoring module comprises a first microprocessor and a laser fence; the laser fence is connected with the first microprocessor; the perimeter security monitoring module is used for detecting intrusion information in the perimeter of the substation; the running equipment temperature online monitoring module comprises a second microprocessor and a temperature measurement unit, which are connected with each other; the running equipment temperature online monitoring module is used for monitoring a real-time temperature of running equipment; the security measurement and control host is connected with the first microprocessor and the second microprocessor in a wireless communication manner and is used for receiving and processing the intrusion information and temperature information; and the information management module is connected with the security measurement and control host through an optical fiber network, and is used for receiving the information of the security measurement and control host and achieving information sharing. Compared with the prior art, the comprehensive security monitoring system has the advantages of being integrated in system, open in interface, convenient to maintain and the like.
Owner:SHANGHAI UNIVERSITY OF ELECTRIC POWER
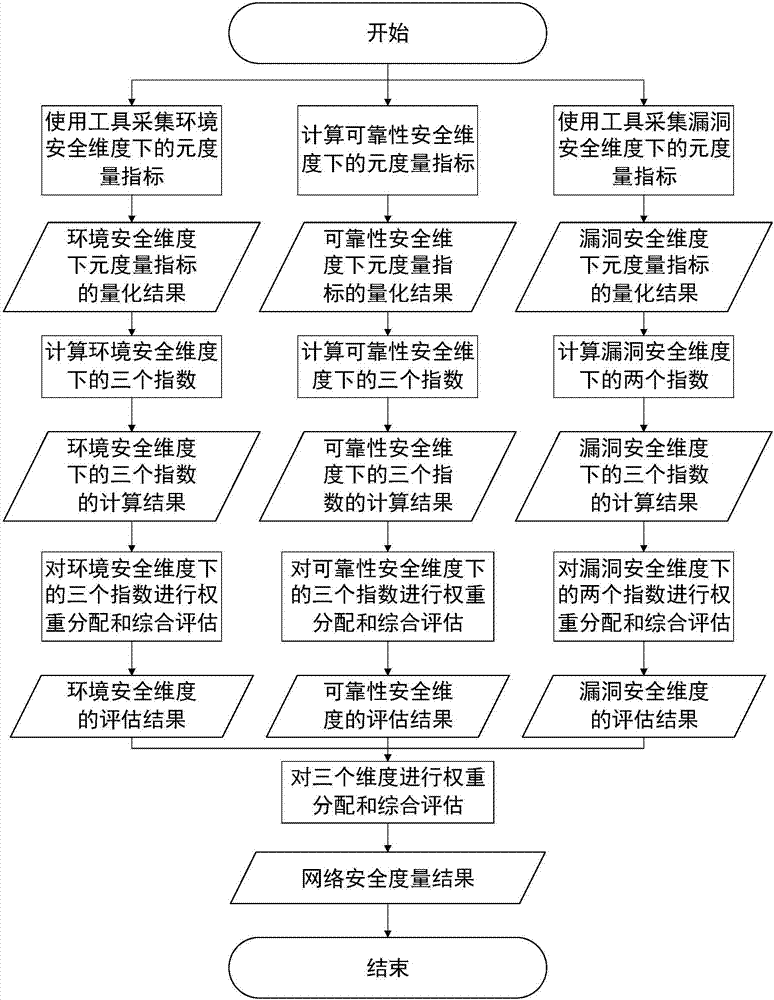
Multidimensional network security measurement method based on TOPSIS
ActiveCN107483487AEasy to collectEasy to quantifyData switching networksSecurity measurementDependability
The invention provides a multidimensional network security measurement method based on a TOPSIS. The method measures the network security from three dimensions, namely environmental security, vulnerability security and reliability security, selects a relevant metric index under each dimension and quantizes the index, and then evaluates the metric indexes under different dimensions in combination with a TOPSIS comprehensive evaluation method to obtain a network security measurement result, so as to find the defects in the network and improve the network security.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
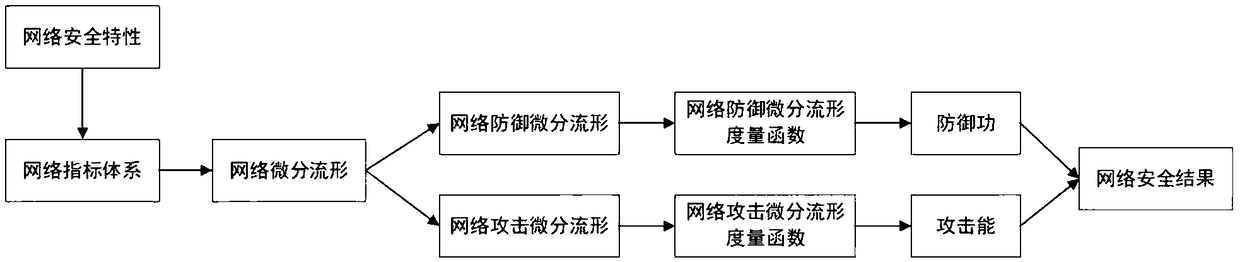
Network space security measurement method based on differential manifolds
ActiveCN108712436AComprehensive measurementDynamic changes can be quantifiedData switching networksSecurity measurementSecurity index
The invention discloses a network space security measurement method based on differential manifolds, which is more objective, more accurate and more comprehensive compared with other traditional network space security measurement and evaluation methods. The method comprises the following steps: firstly, establishing a network space security index system based on three dimensions, wherein the threedimensions comprise a reliability dimension, an environment dimension and a vulnerability dimension, which are considered from three aspects of hardware environment, software resources and vulnerabilities depending on which the network survive; constructing the established network space security index system into two differential manifolds of attack and defense by using a differential manifold construction method, wherein the network defense differential manifold is established according to the reliability dimension and the environment dimension, and the network attack differential manifold is established according to the vulnerability dimension; measuring the established two differential manifolds of network attack and defense by using a mathematical function to obtain the defense powerof the network defense differential manifold and the attack energy of the network attack differential manifold; and using the defense power and the attack energy as network space security measurementvalues.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Server hard disk security measurement method and device
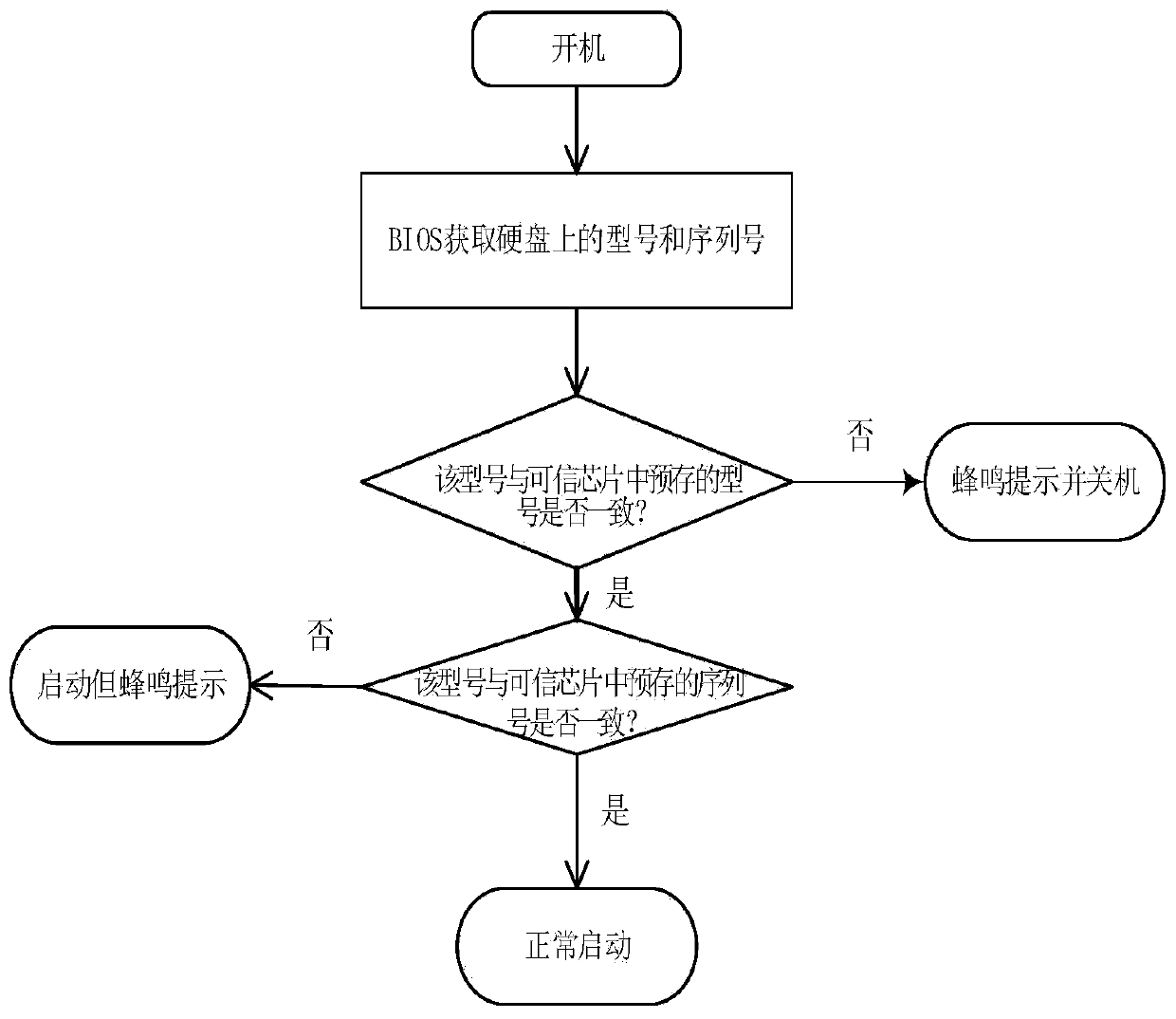
InactiveCN111291427ATimely alarmImplement the measurement functionHardware monitoringInternal/peripheral component protectionSecurity measurementSoftware engineering
The invention provides a server hard disk security measurement method and device. The method comprises the following steps: pre-storing identification information of related hard disks in a server ina trusted chip; in response to startup and electrification of the server, enabling the BIOS to acquire identification information of the hard disk and compare the acquired identification information with pre-stored identification information; and in response to the comparison failure, enabling the BIOS to control the server to stop starting and / or give an alarm. According to the invention, the hard disk on the computer can be timely alarmed after being replaced, and the method has good popularization and use values in the field of secrecy.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com