Systems and methods for using eye signals with secure mobile communications
An eye and user technology, applied in wireless communication, transmission systems, security devices, etc., can solve the problem of refusing to ensure the ability to use equipment to communicate, unable to refuse, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
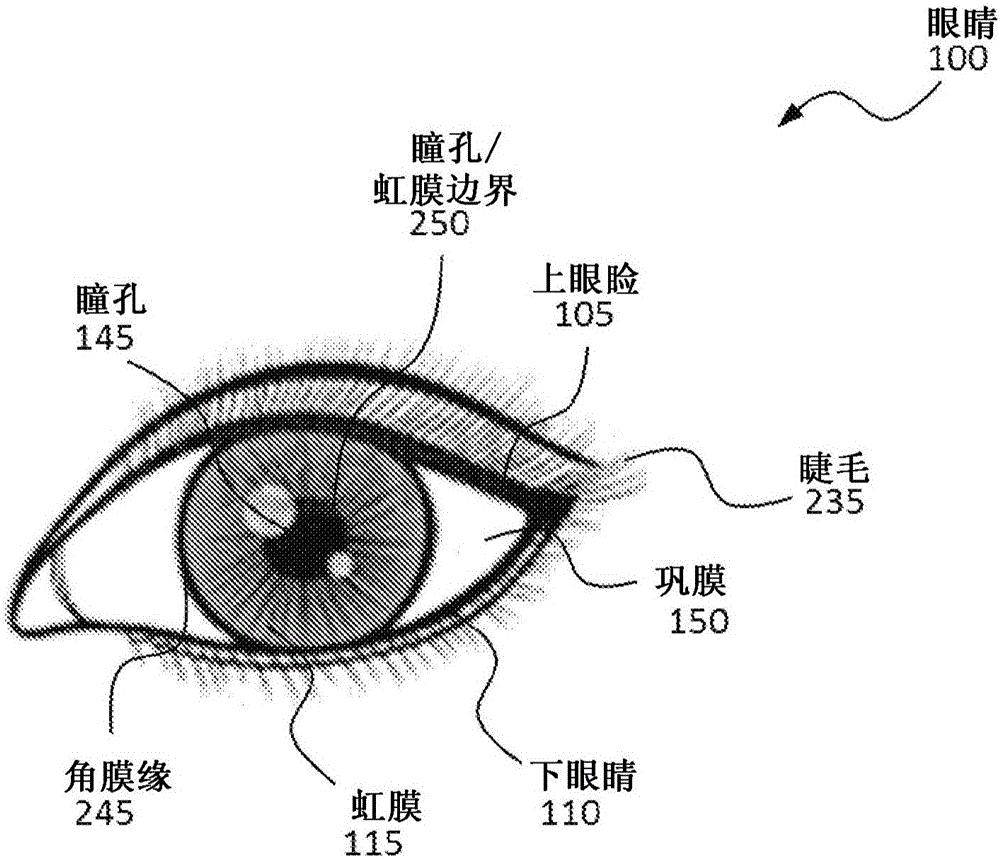
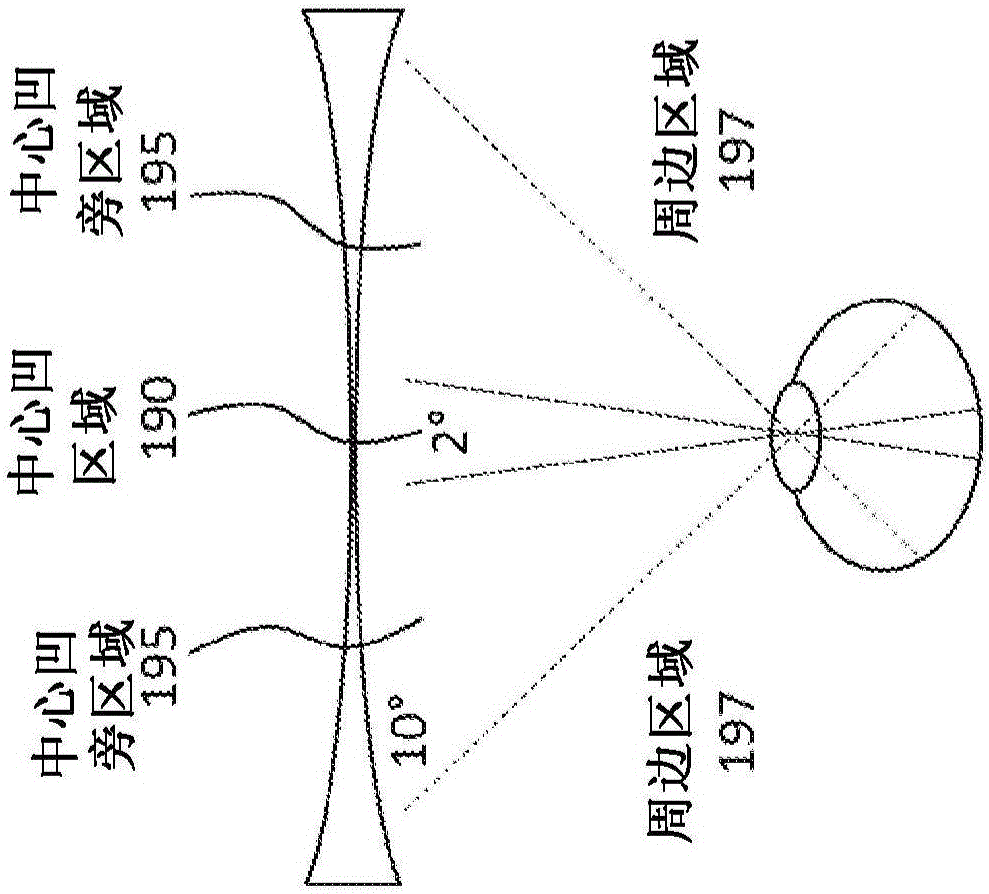
[0077] In the following description, and for purposes of explanation, numerous specific details are set forth in order to provide a thorough understanding of various aspects of the embodiments. However, it will be understood by those skilled in the relevant art that the devices, systems, and methods herein may be practiced without these specific details. It is to be understood that other embodiments may be utilized and structural and functional changes may be made without departing from the scope of the devices, systems, and methods herein. In other instances, known structures and devices are shown or discussed more generally in order to avoid obscuring the embodiments. In many cases, the description of an operation is sufficient to enable a human to implement the various forms, especially when the operation is implemented in software. It should be noted that there are many different and alternative configurations, devices and techniques in which the disclosed embodiments may...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com