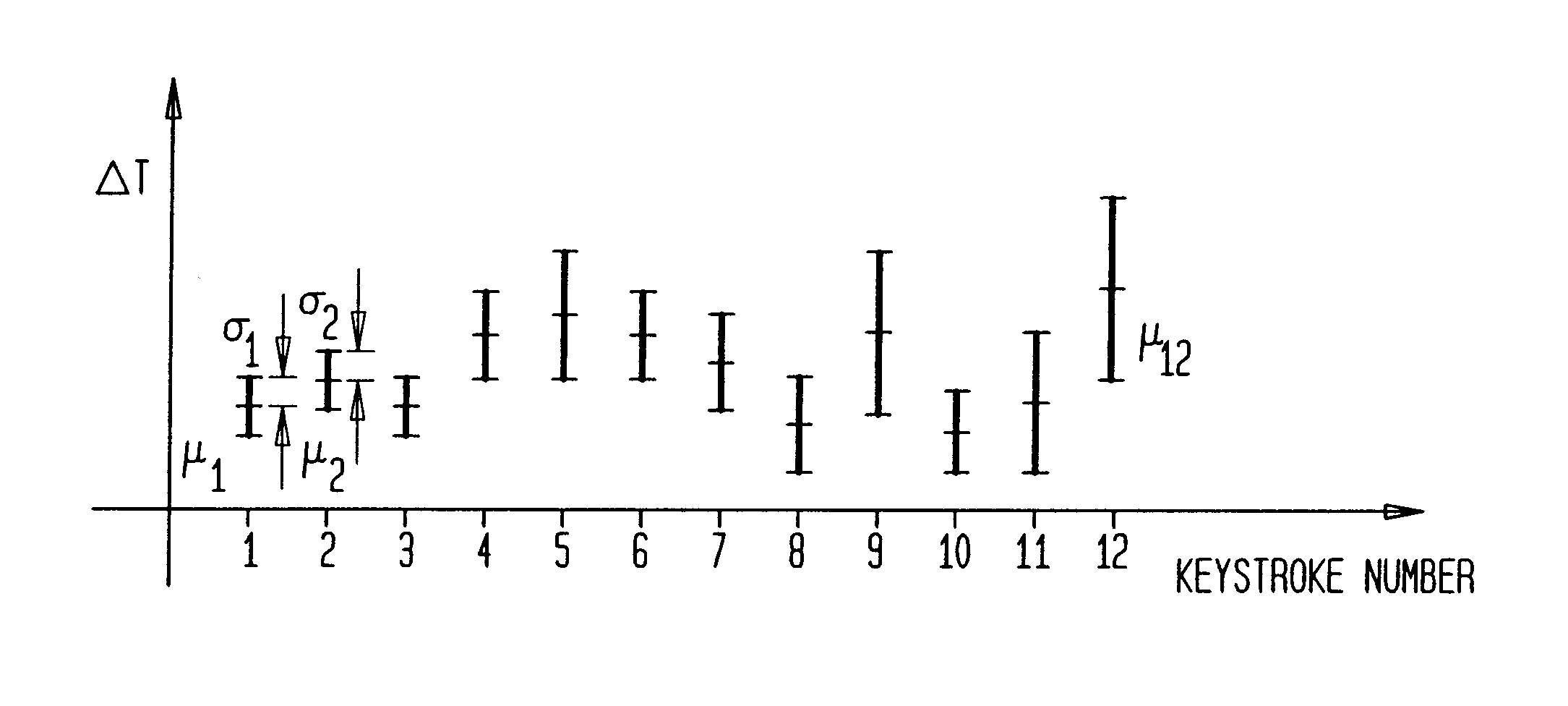Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
788 results about "Security Measure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security measures - measures taken as a precaution against theft or espionage or sabotage etc.; "military security has been stepped up since the recent uprising".
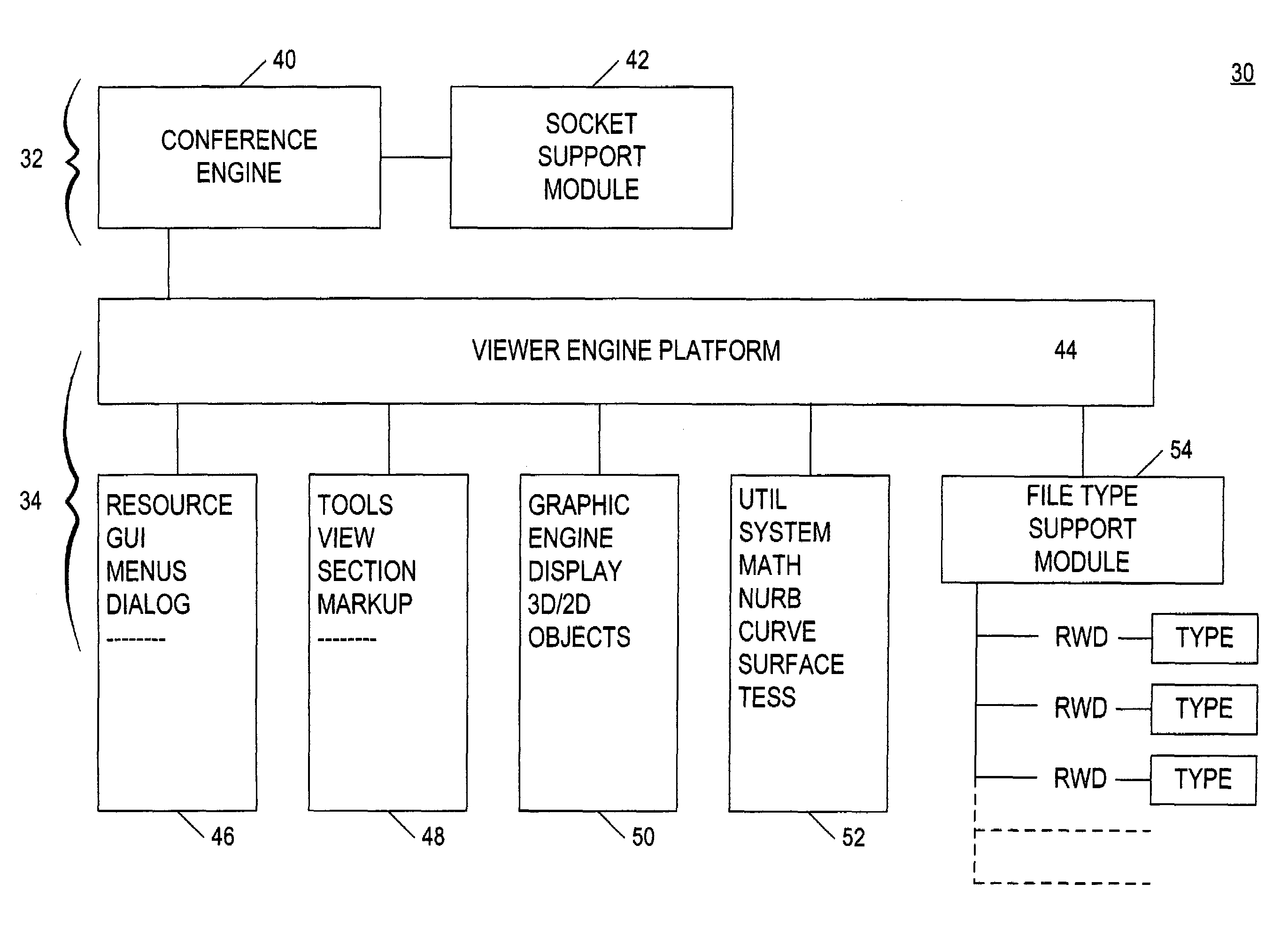
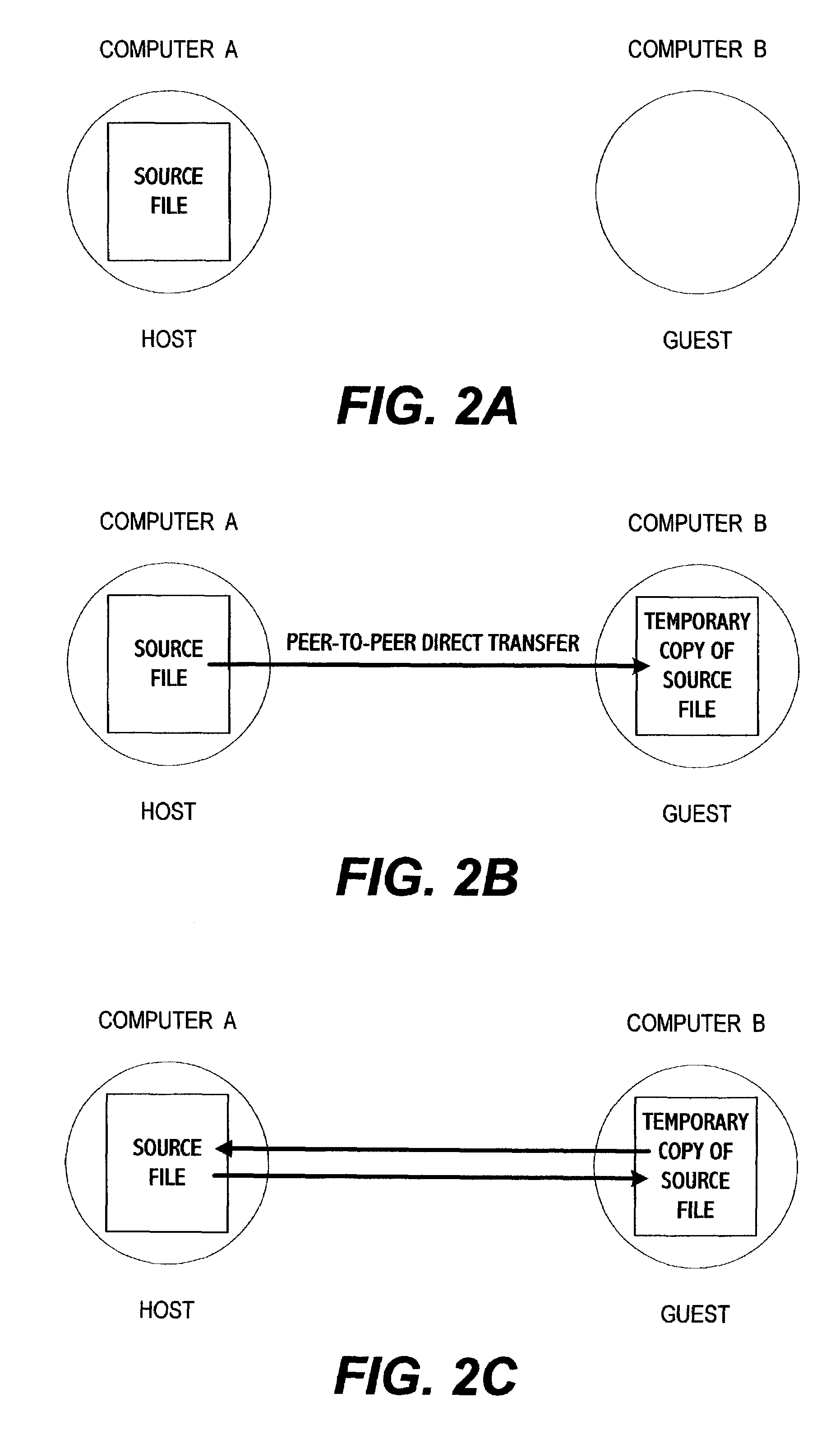
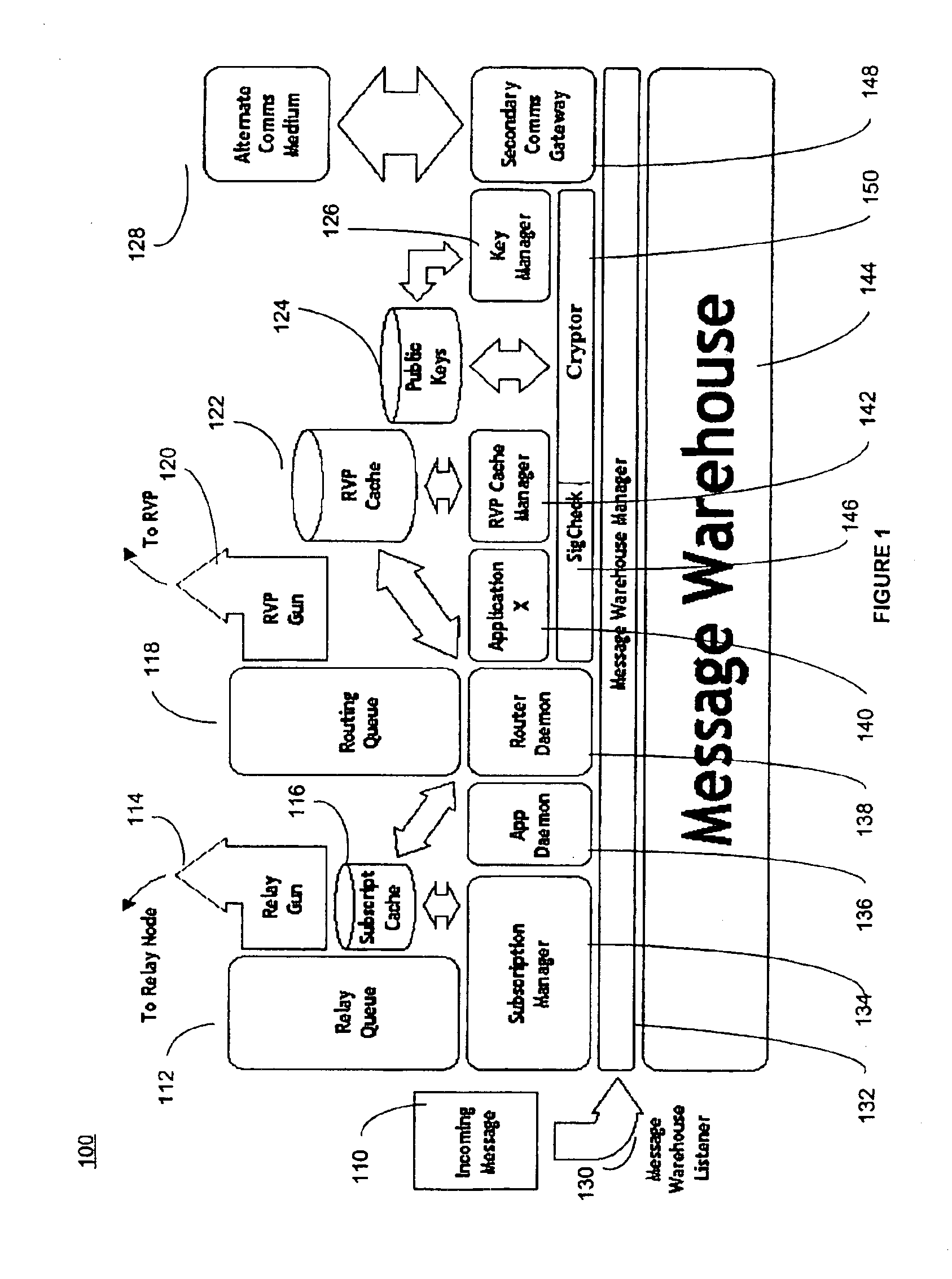
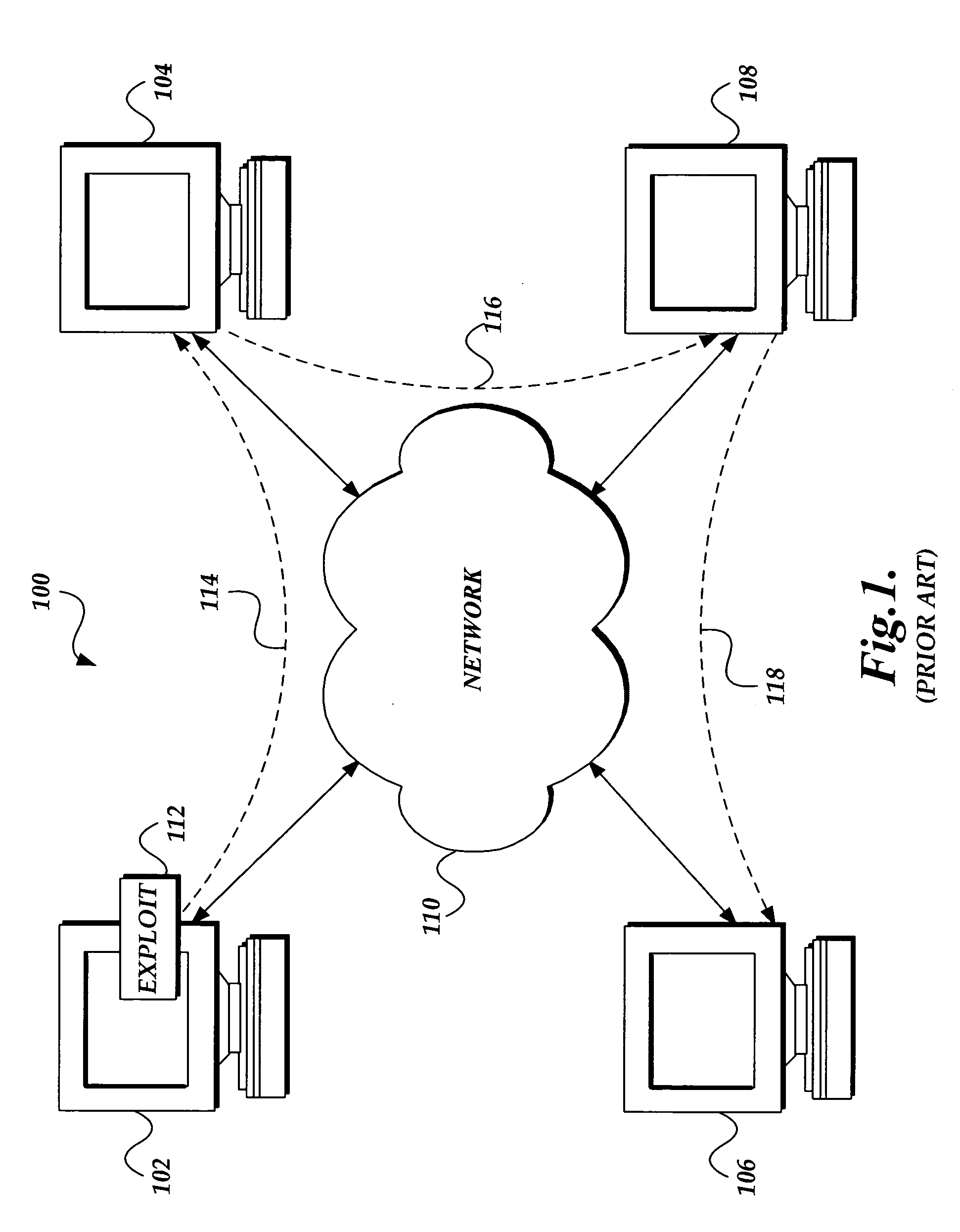
System for electronic file collaboration among multiple users using peer-to-peer network topology
InactiveUS7353252B1Avoid storage problemsMultiple digital computer combinationsOffice automationDocumentation procedurePrivate network
A system for electronic file collaboration among multiple users is implemented using command messages transmitted on dedicated network channels established between conference participants in a peer-to-peer architecture with total autonomy from a central server. The system employs owner-in-control methodology to allow direct transmission of copies of documents among participants by permission, and to prevent storage of copies of documents used in a conference by participants. Mark-ups, additions, and other actions occurring on a conference document can only be saved by the document owner. An advanced viewer engine is provided for reading, displaying and manipulating electronic data in texts, tables, vectors and 3D model formats, as well as common raster images. A proxy module allows data transmitted through IPFW routers or firewall devices with sufficient authentications and security measures.
Owner:SIGMA DESIGNS
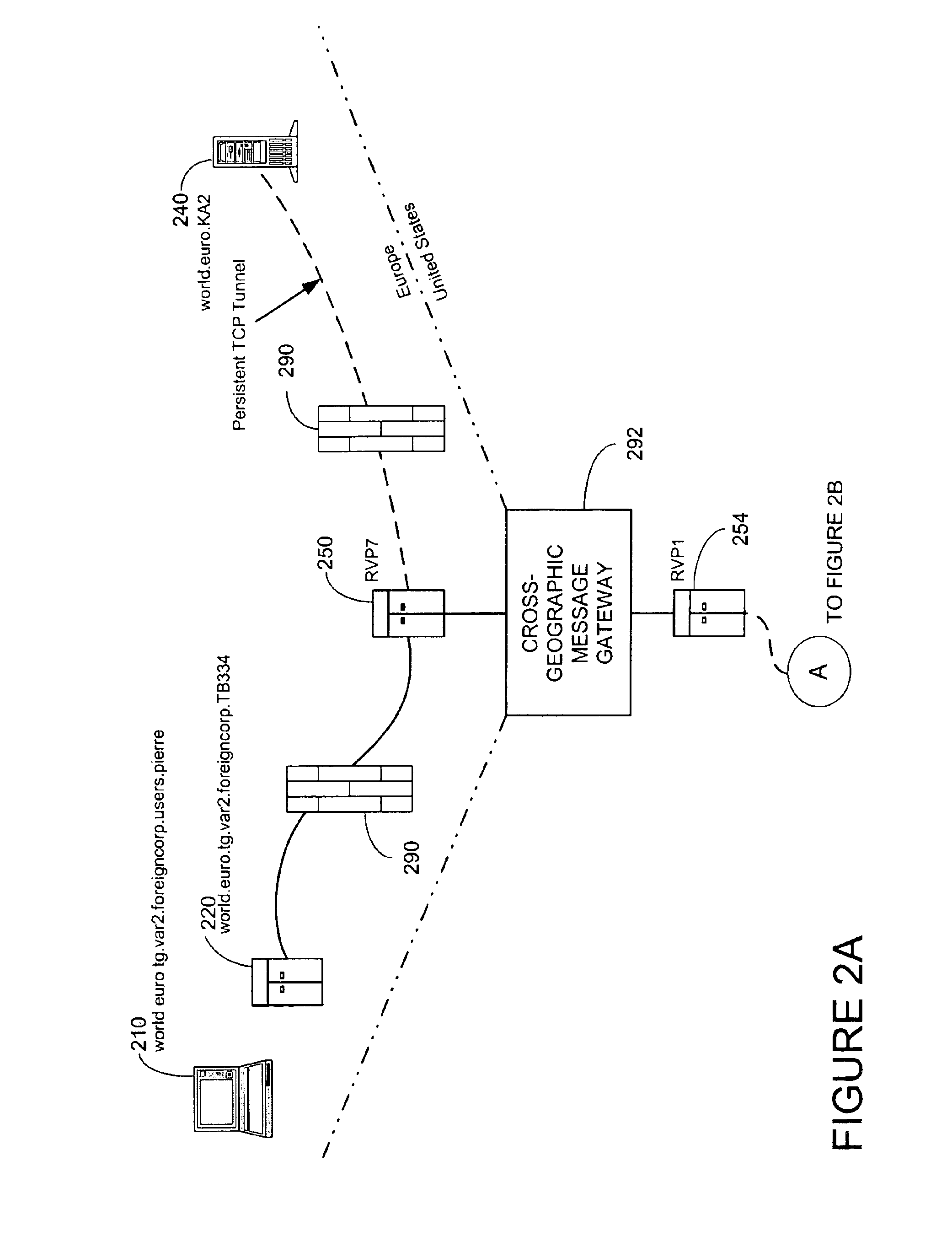
System and method for secure message-oriented network communications
InactiveUS6959393B2Minimize threatFacilitate and control accessKey distribution for secure communicationDigital data processing detailsSecurity MeasureNetwork communication
The present invention provides a message-oriented middleware solution for securely transmitting messages and files across public networks unencumbered by intervening network barriers implemented as security measures. It also provides a dynamic, dedicated, application level VPN solution that is facilitated by the message-oriented middleware. Standard encryption algorithms are used to minimize the threat of eavesdropping and an Open-Pull Protocol (OPP) that allows target nodes to pull and verify the credentials of requestors prior to the passing of any data. Messaging can be segregated into multiple and distinct missions that all share the same nodes. The security network's architecture is built to resist and automatically recover from poor, slow, and degrading communications channels. Peers are identifiable by hardware appliance, software agent, and personally identifiable sessions. The security network provides a dynamic, private transport for sensitive data over existing non-secure networks without the overhead and limited security associated with traditional VPN solutions.
Owner:THREATGUARD
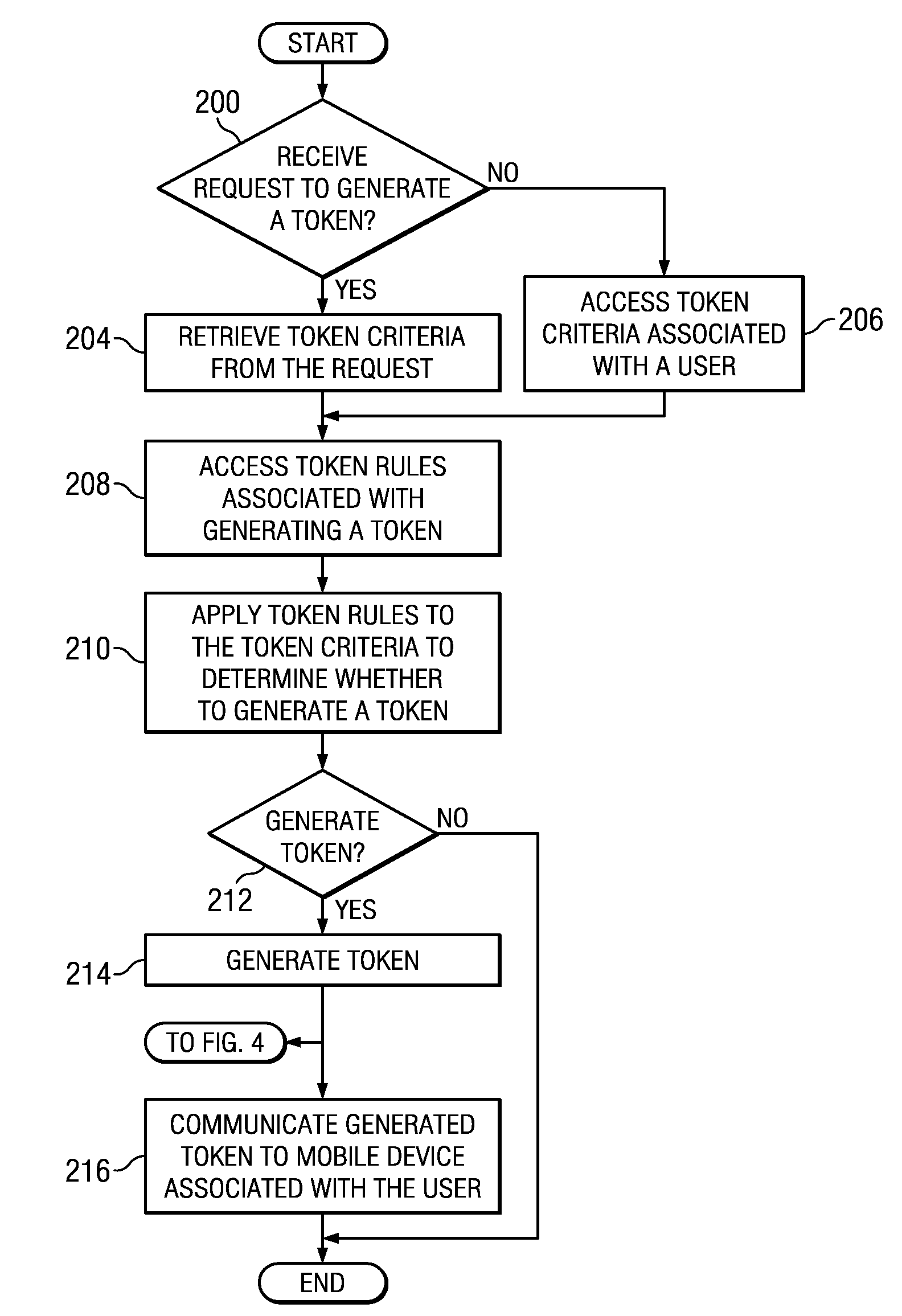
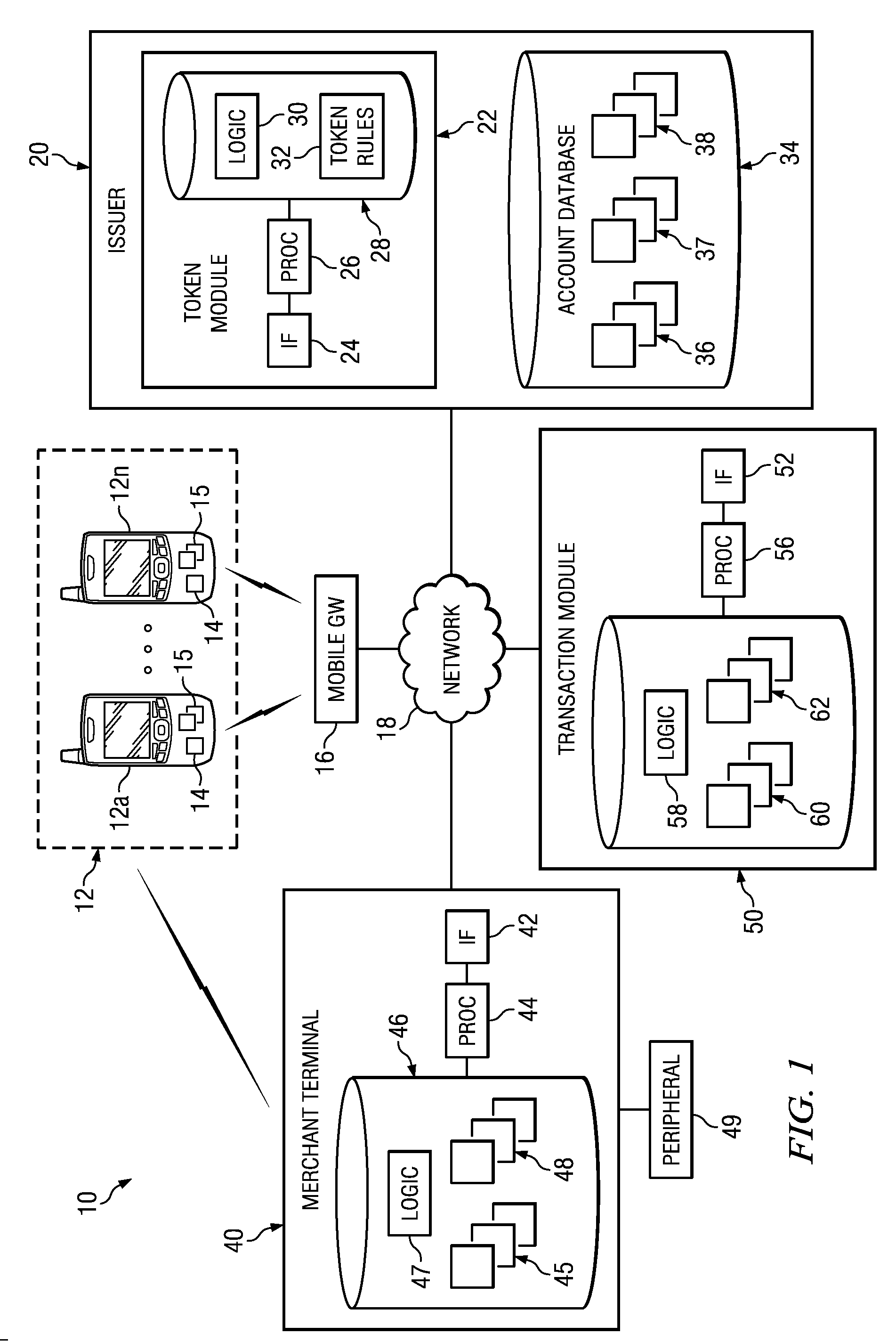
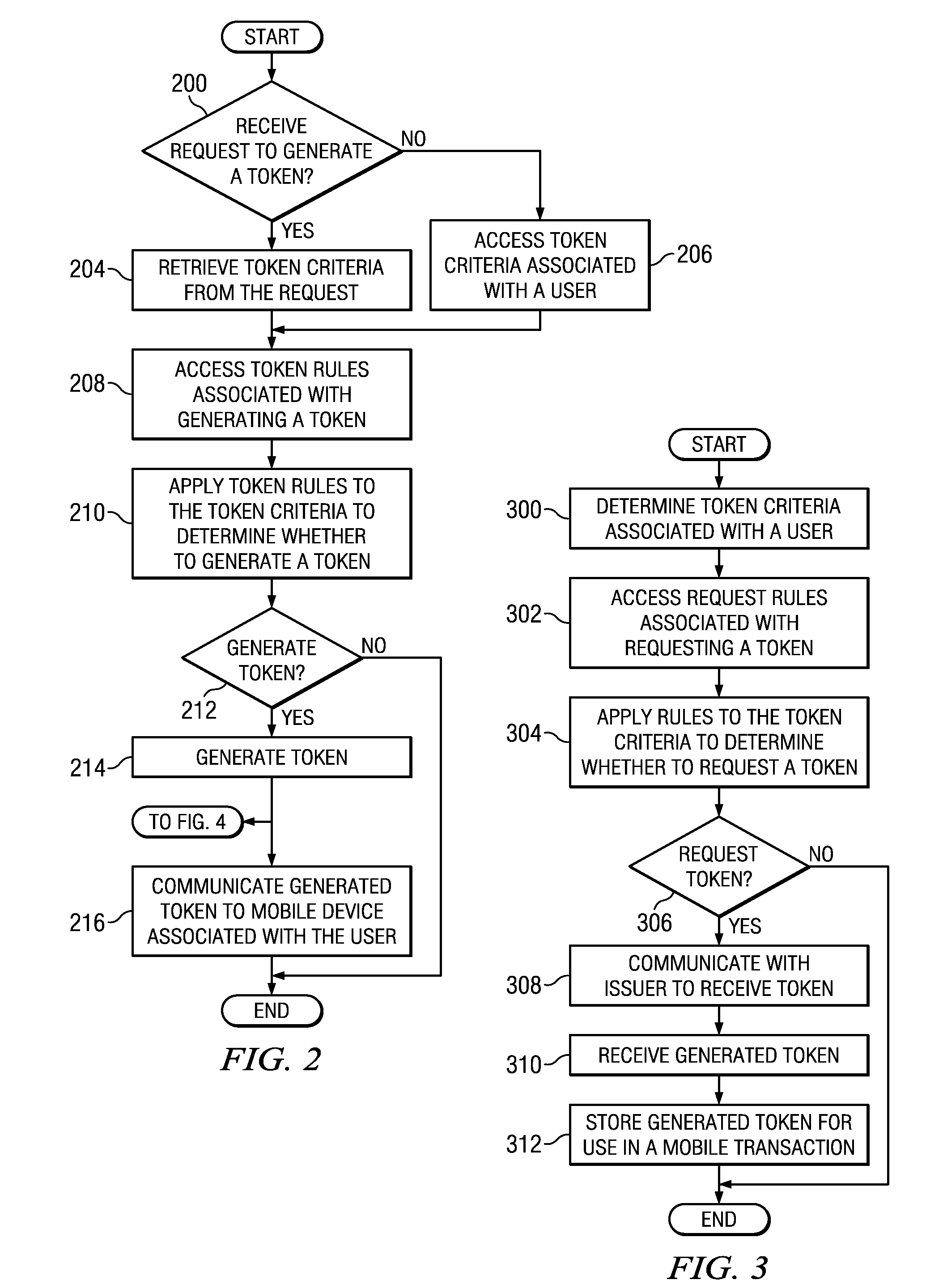
Implementing security measures for authorized tokens used in mobile transactions
ActiveUS20140025958A1Disadvantages can be reduced eliminatedTransactions be reduced eliminatedUnauthorized memory use protectionHardware monitoringSecurity MeasureMobile transaction
Security measures for tokens comprise storing security rules associated with a generated token in a memory. A processor, communicatively coupled to the memory, accesses the security rules associated with the generated token and determines whether to encrypt the generated token by applying at least a portion of the security rules to the generated token. The processor encrypts the generated token. An interface, communicatively coupled to the processor, communicates the encrypted token to a mobile device associated with a user.
Owner:BANK OF AMERICA CORP
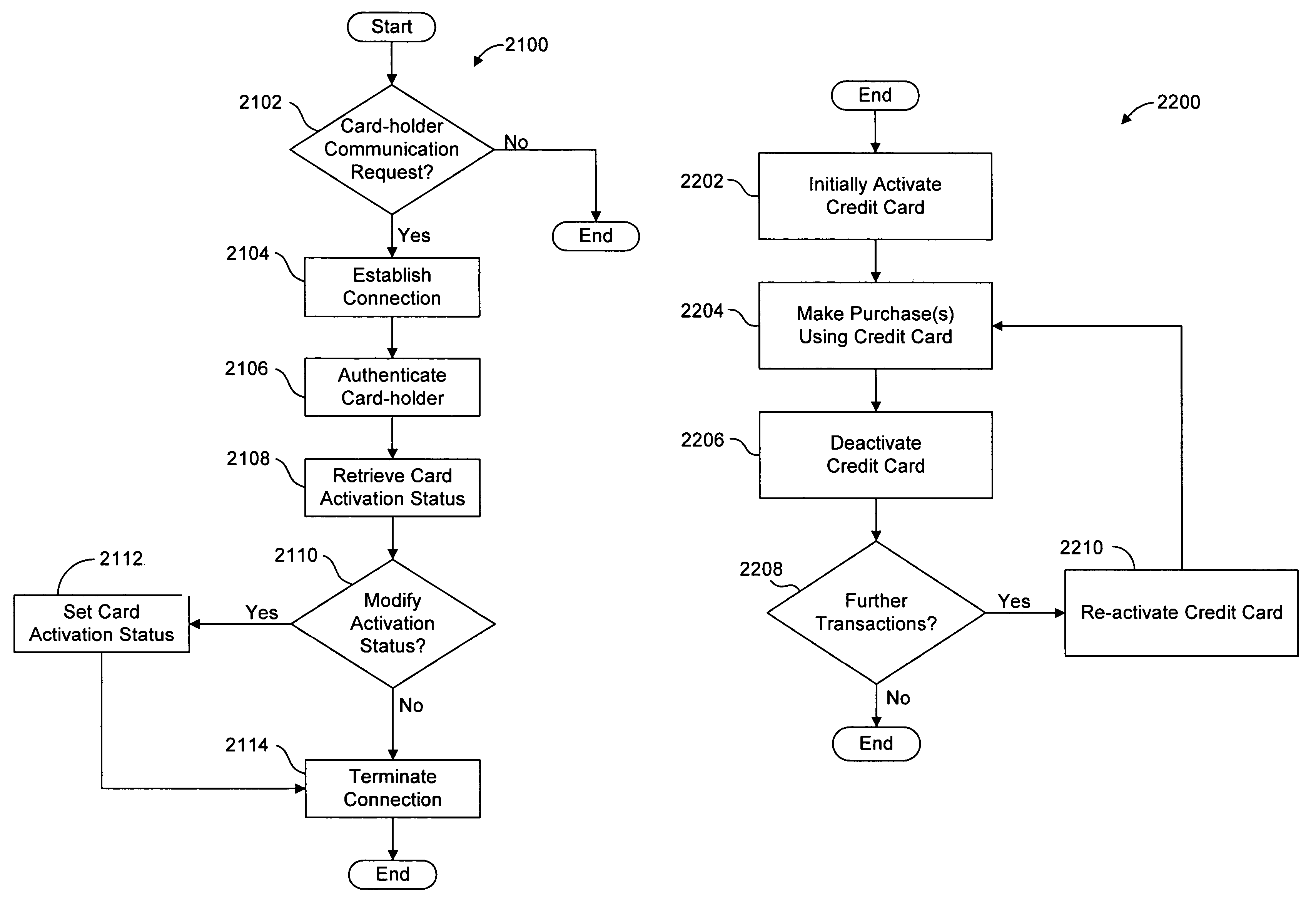
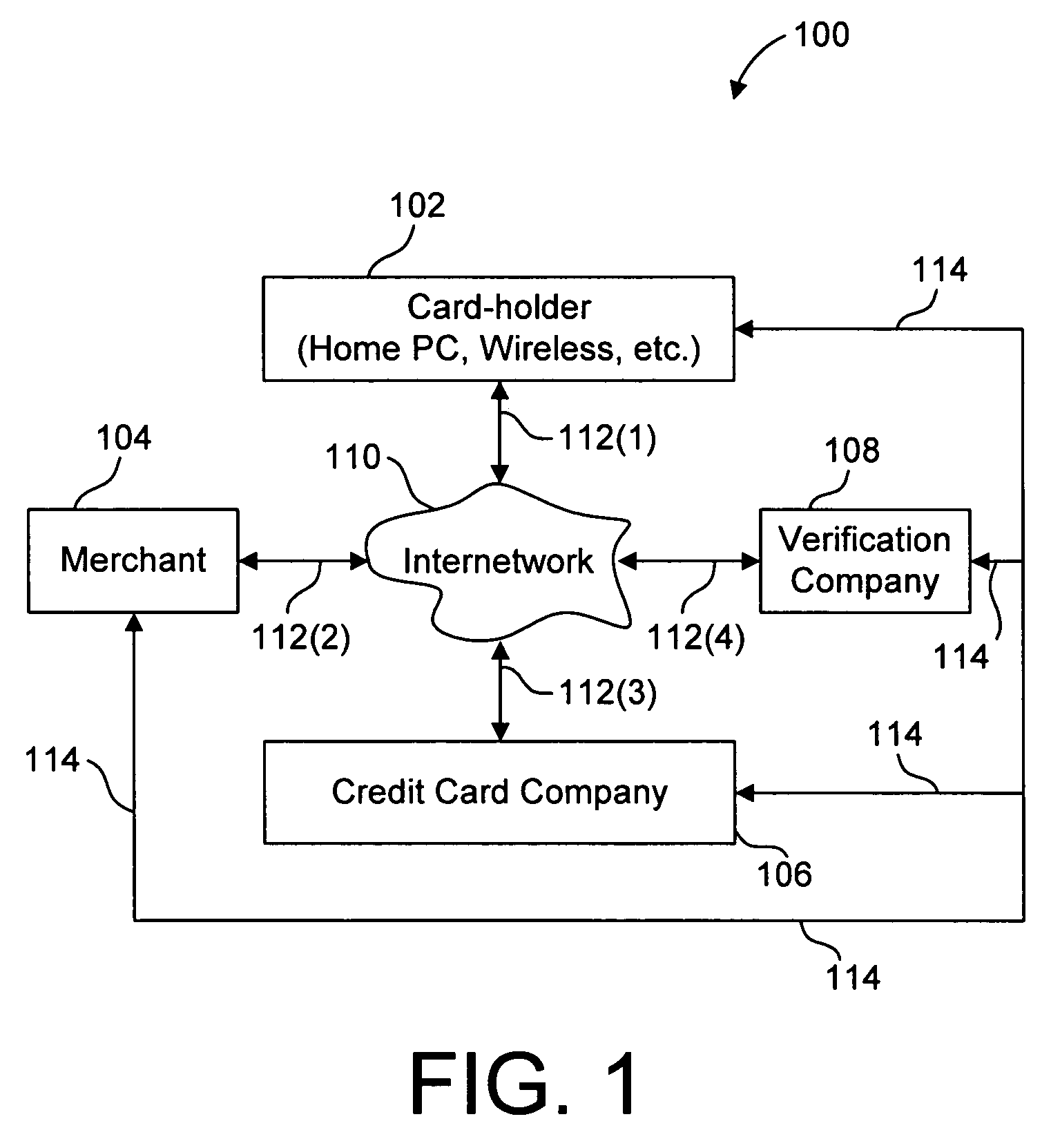
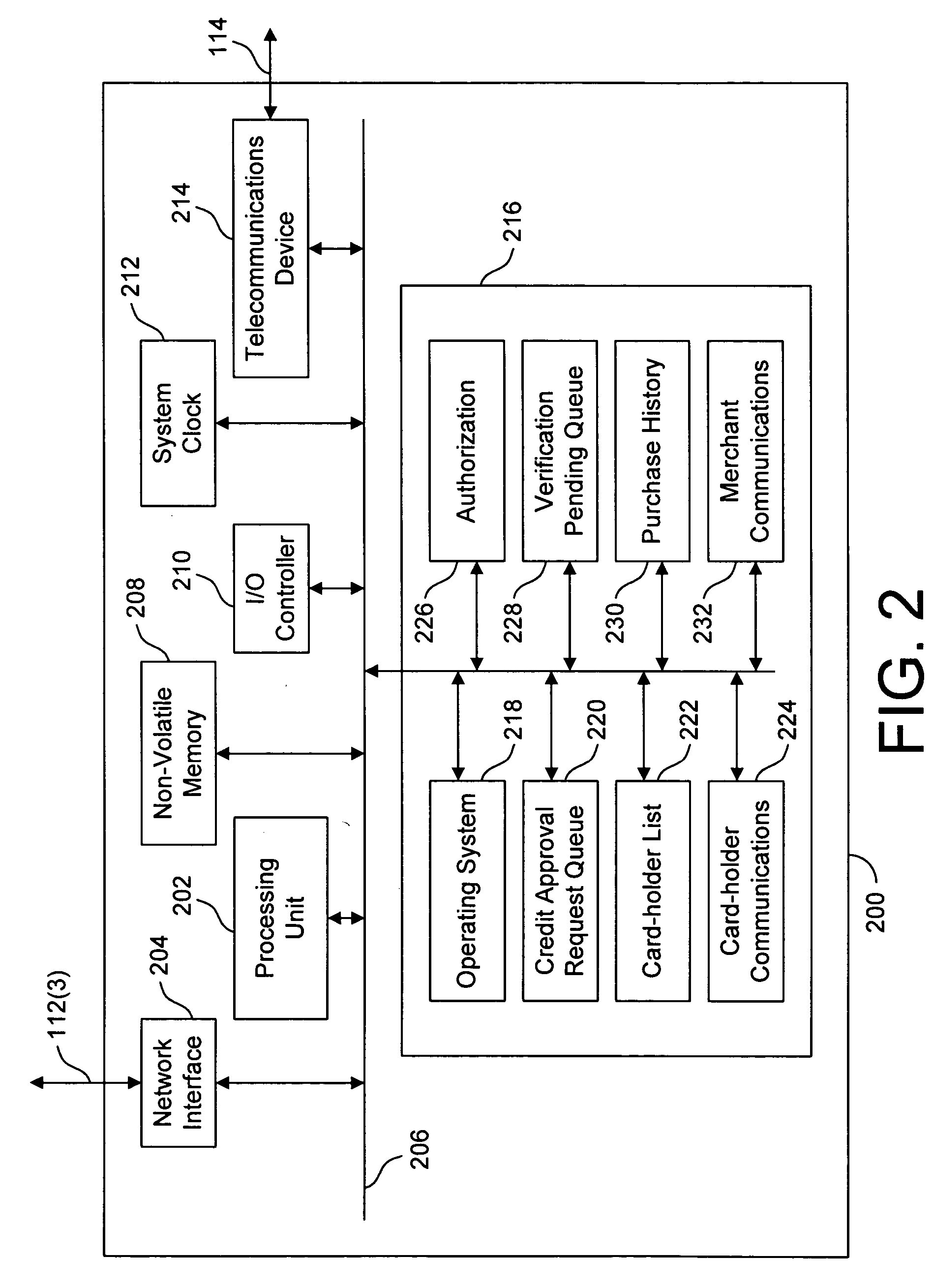
System and method for securing a credit account
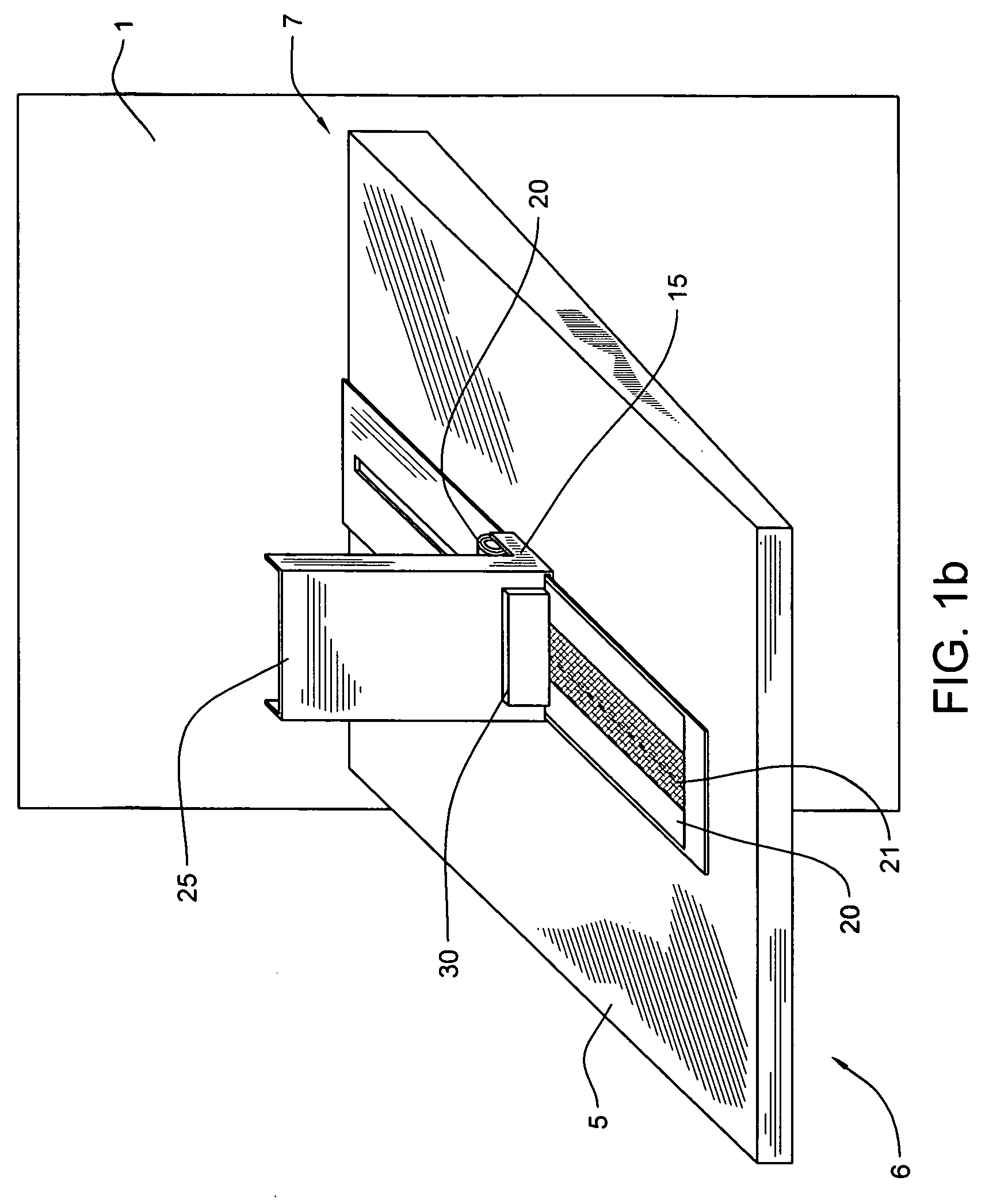
ActiveUS7264154B2Facilitates card-holder verificationEliminate needComplete banking machinesFinanceCredit cardSecurity Measure
Owner:HARRIS INTPROP LP
Method and apparatus for optimizing networking potential using a secured system for an online community
The present invention provides a method and apparatus for users to search networks, both their own network and their peers' networks, all under the umbrella of a “multiple level access” security system. The present invention has been designed to optimize networking capabilities among users in a comprehensive online community. Networking among such a secured environment will allow users an opportunity to enhance their networking potential by expanding their networks to their peers' and beyond. A user registers with the online community and personally adds individuals that they know to their personal networking database. While adding these peers to the networking database, the user grants a specific level of access to each individual. This security measure is devised to discourage solicitation from other unwanted online users. The levels of access give the user an opportunity to control the amount of personal information, including contacts that they make, available to their individual peers. Based on the level of access granted by the user, the peer may or may not be able to access the users information or the user's personal databases for potential networking. The level of access granted by two individuals need not be the same for each other.
Owner:MICROSOFT TECH LICENSING LLC
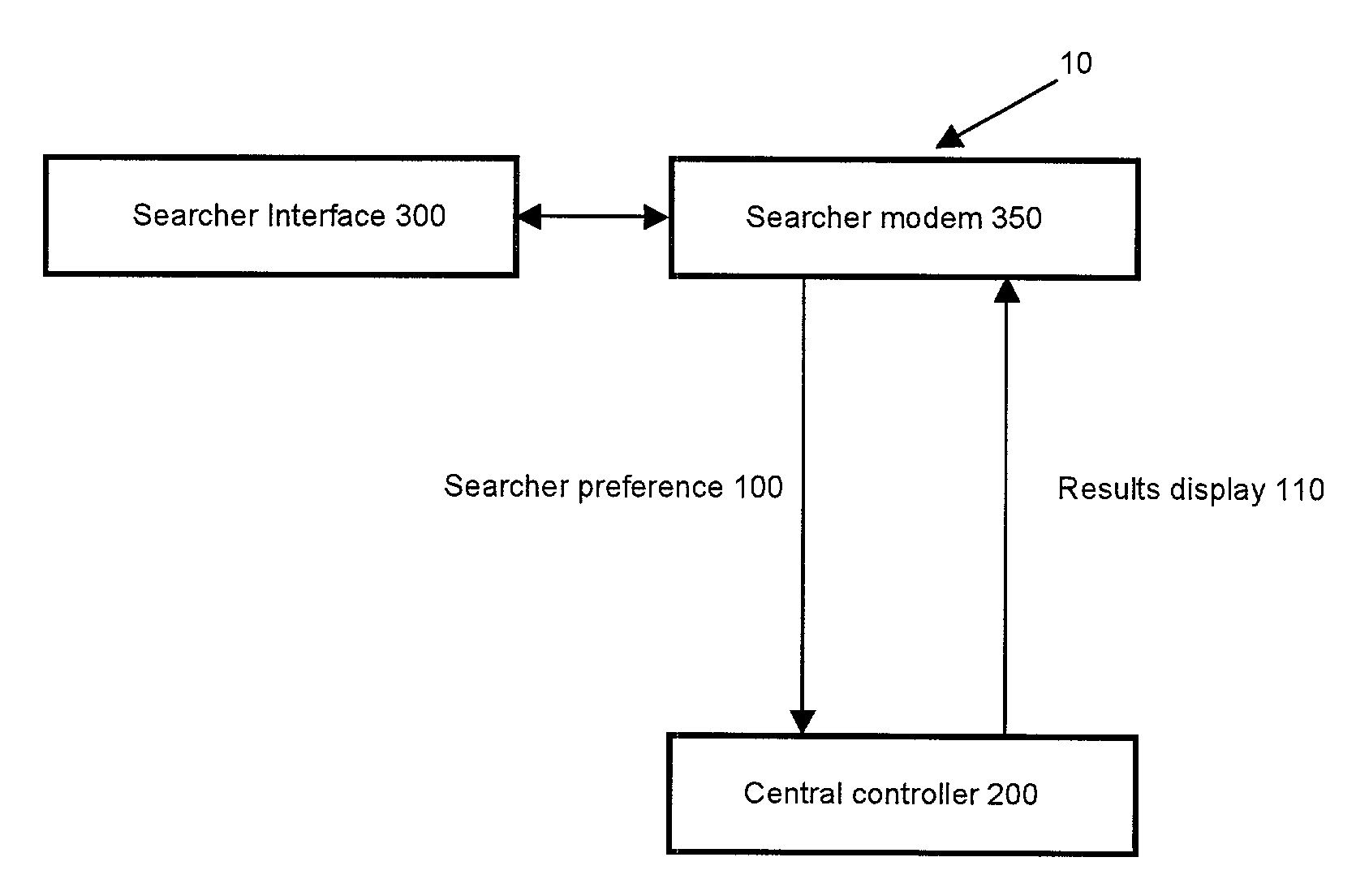
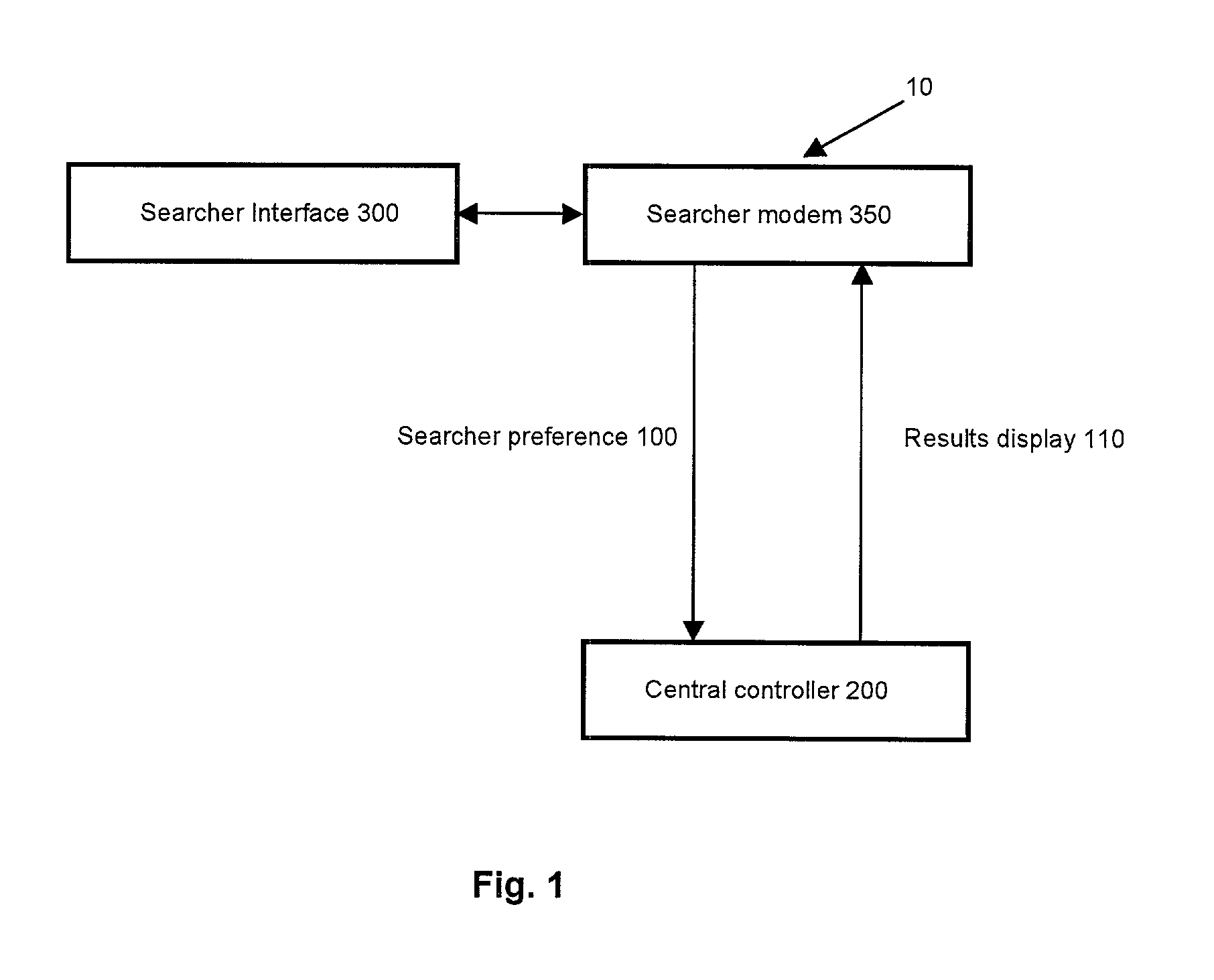
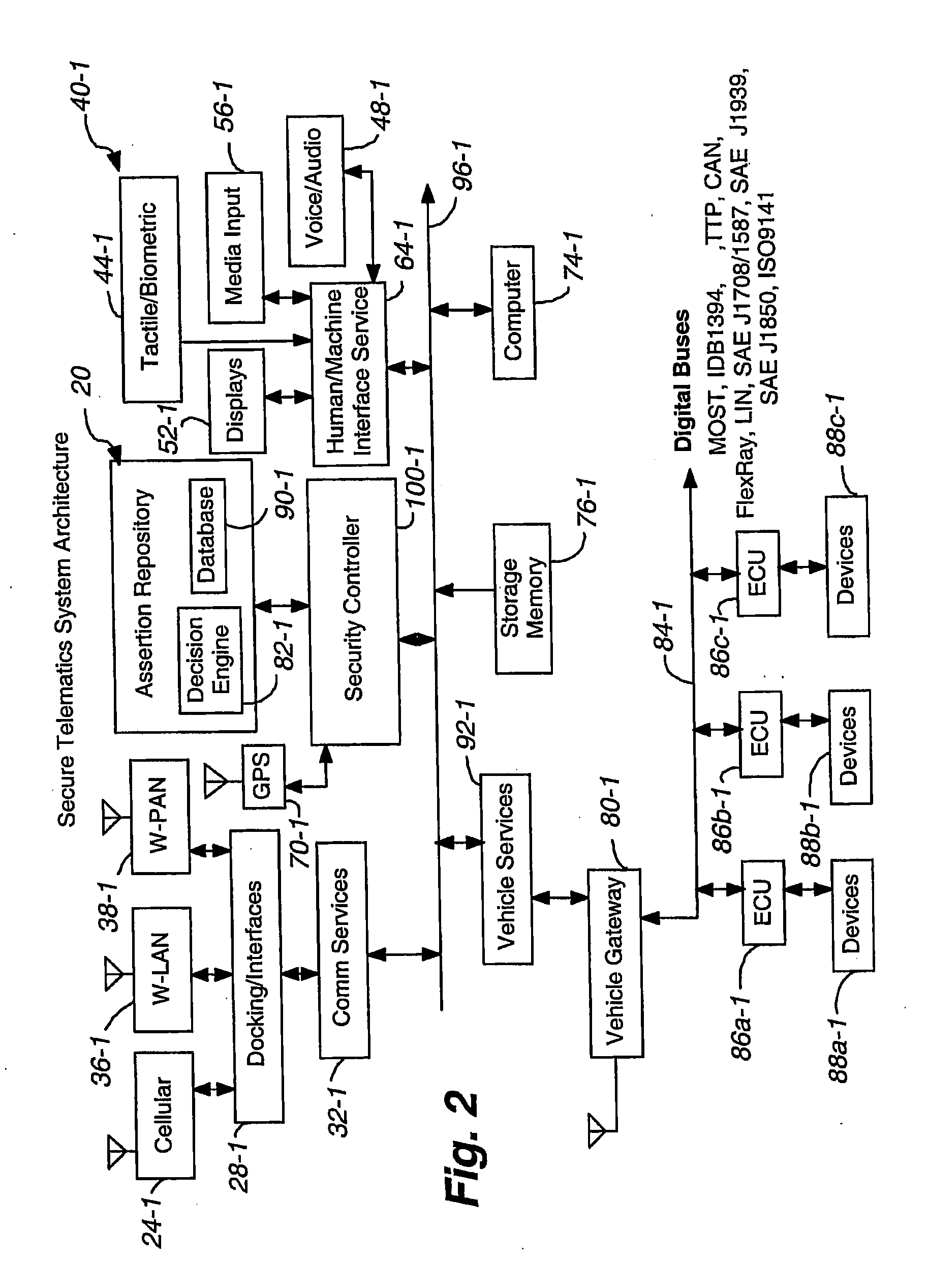
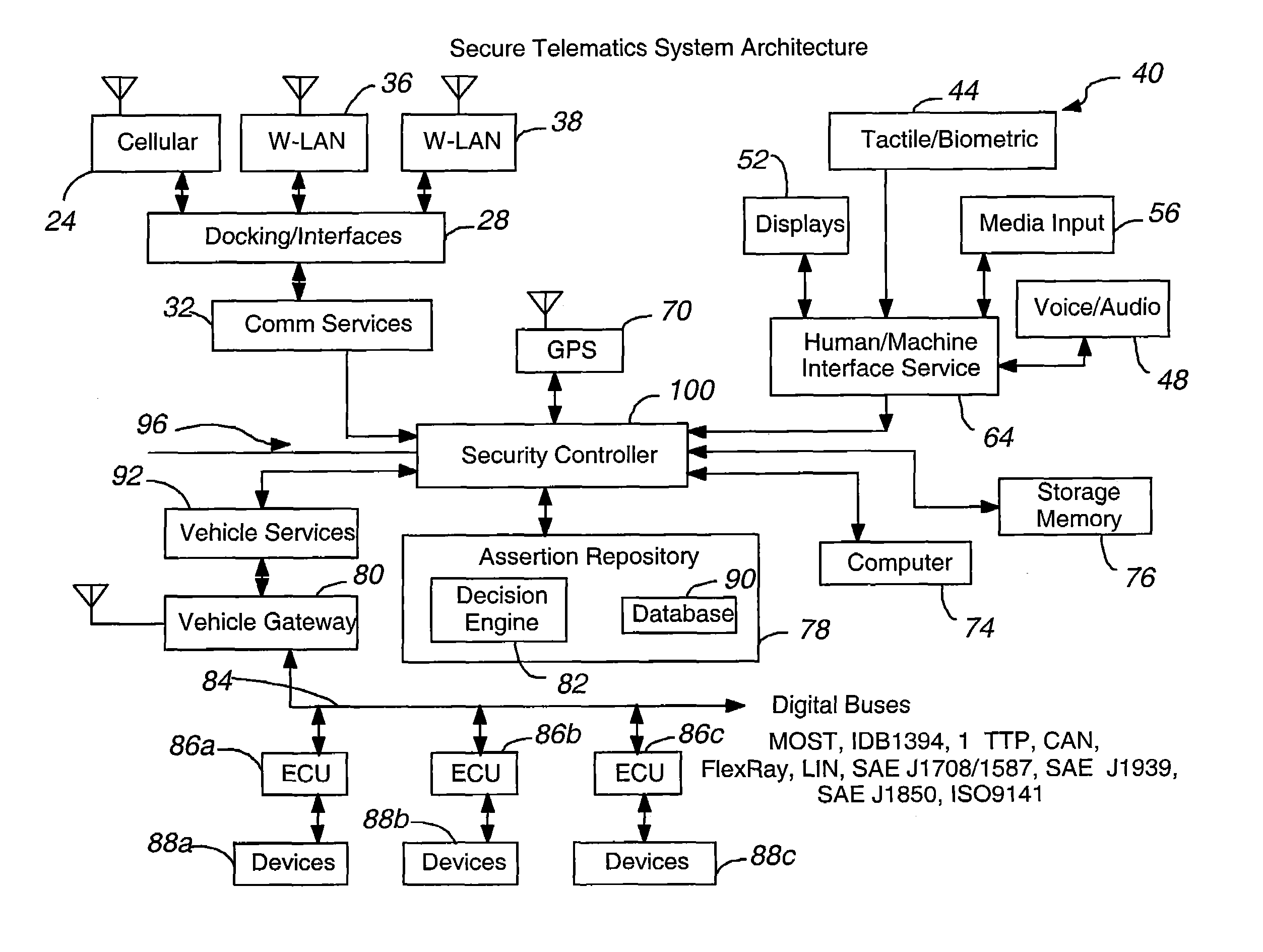
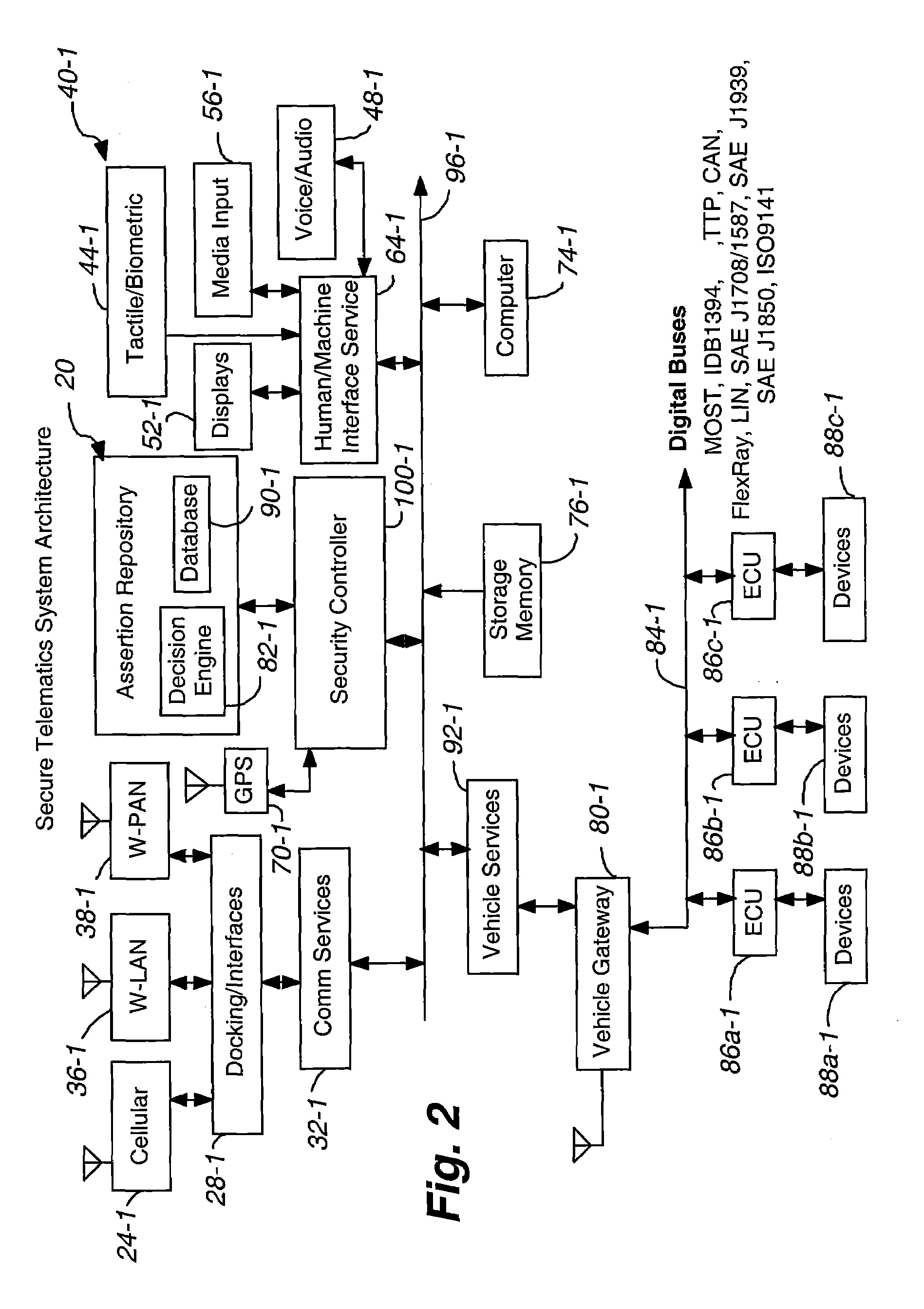
Secure telematics
InactiveUS20080148374A1Expands telematics usageImprove integrityVehicle testingRegistering/indicating working of vehiclesComputer networkService provision
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resources' security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
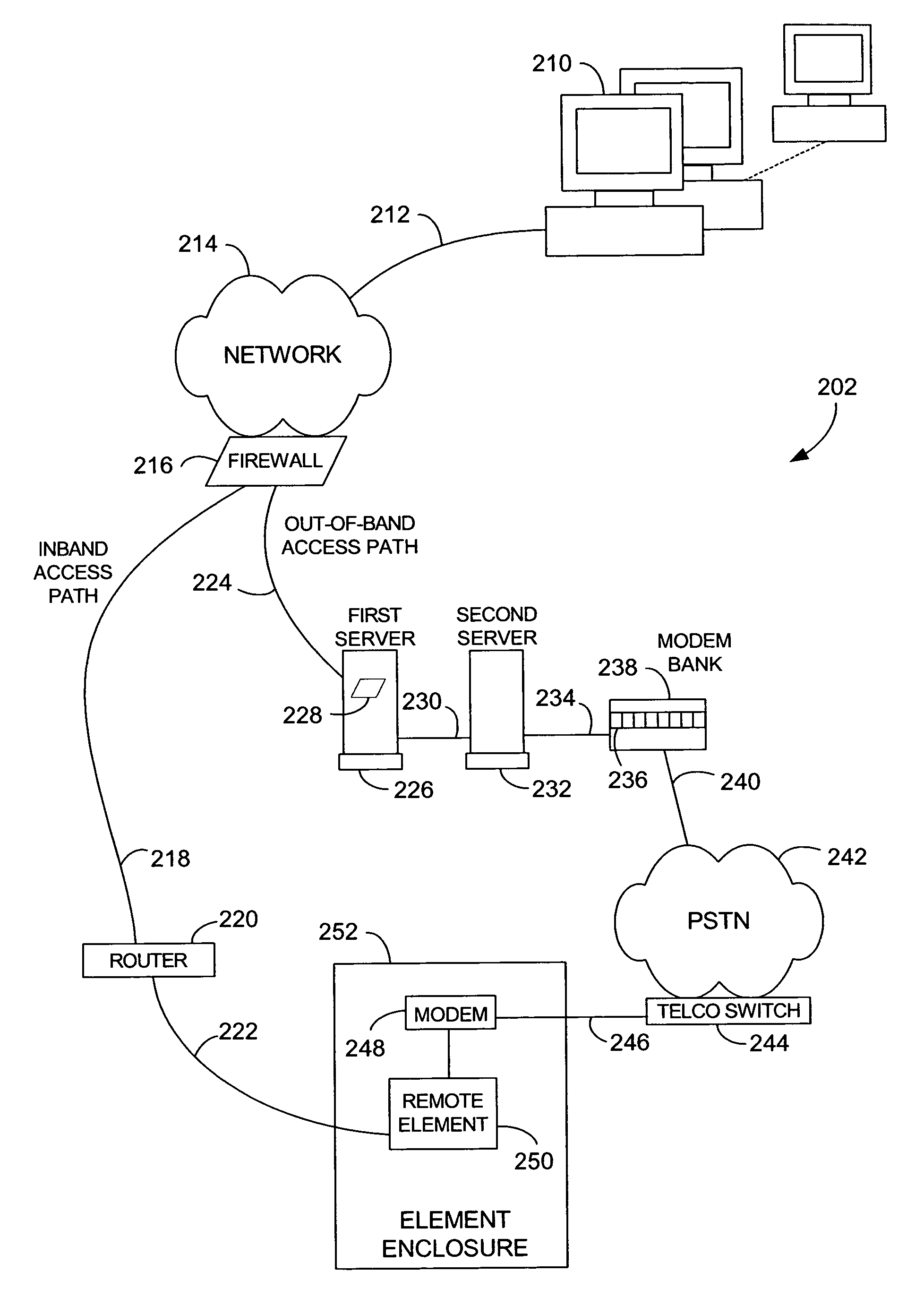
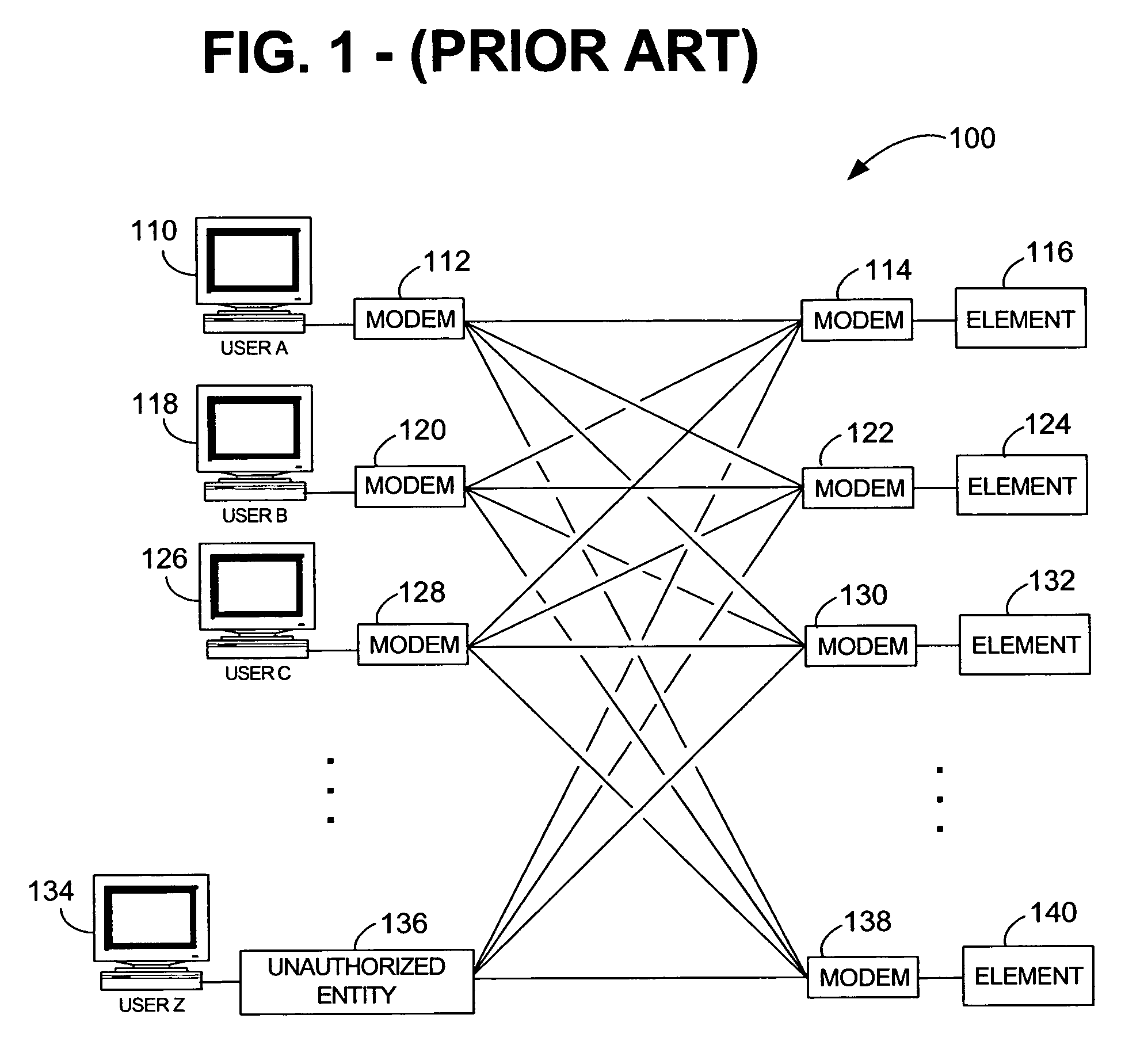
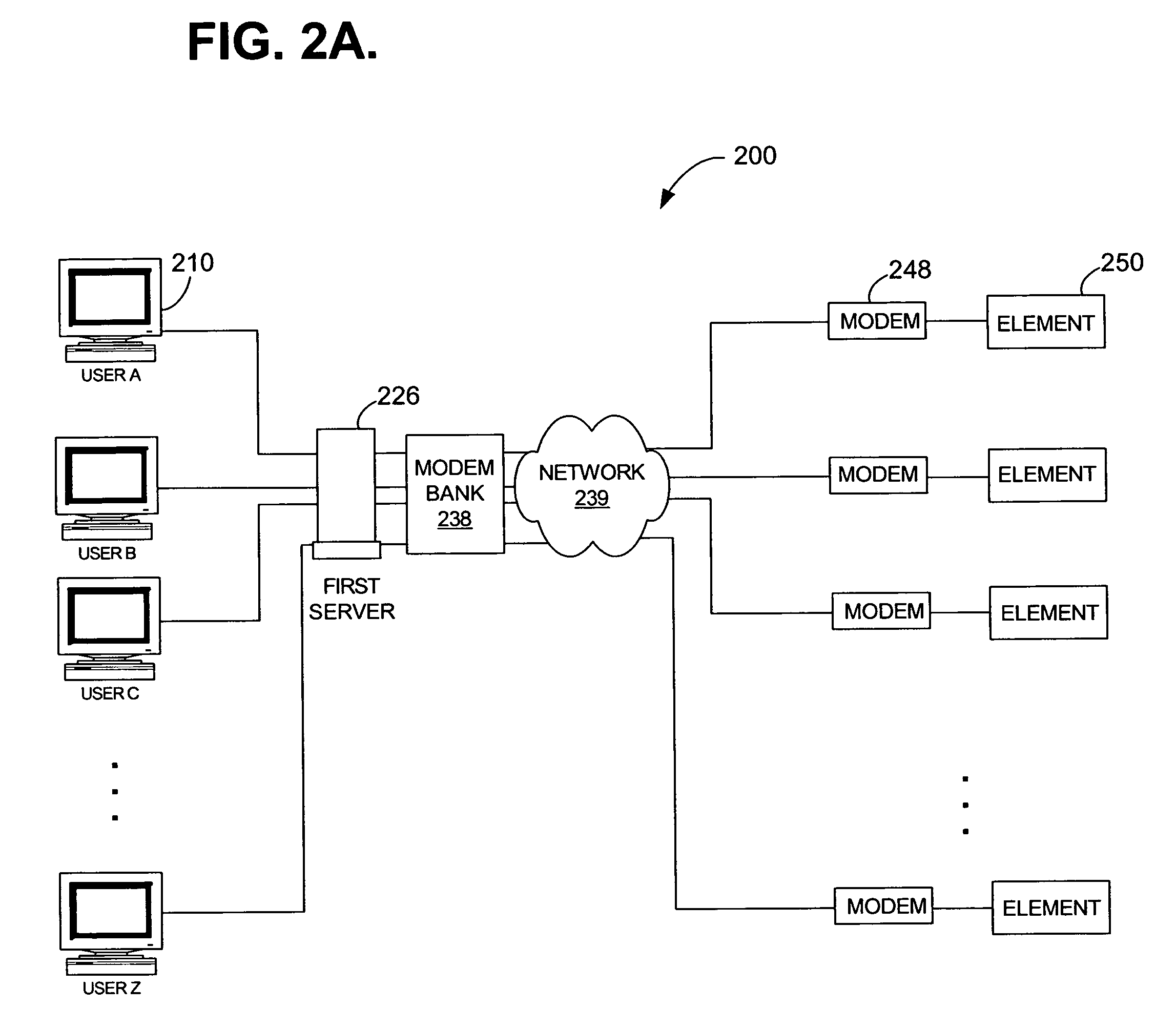
Method and system for providing secure, centralized access to remote elements
ActiveUS7640581B1Reduce overheadReduce eliminateMultiple digital computer combinationsProgram controlNetwork elementSecurity Measure
A system and method for establishing centralized, out-of-band access to remote network elements is provided. Status and other information can be securely retrieved from the remote elements. One or more servers observe and manage a plurality of remote elements using modem-to-modem communications between a modem bank and a remote modem. Requests are submitted through a central mediation point, thereby allowing central control of user profiles and a collection of security audit log information. One or more authentication mechanisms provide enforced security measures and trusted communication paths between a user and a remote element. Remote elements can be securely monitored and administered from a central location.
Owner:CENTURYLINK INTPROP
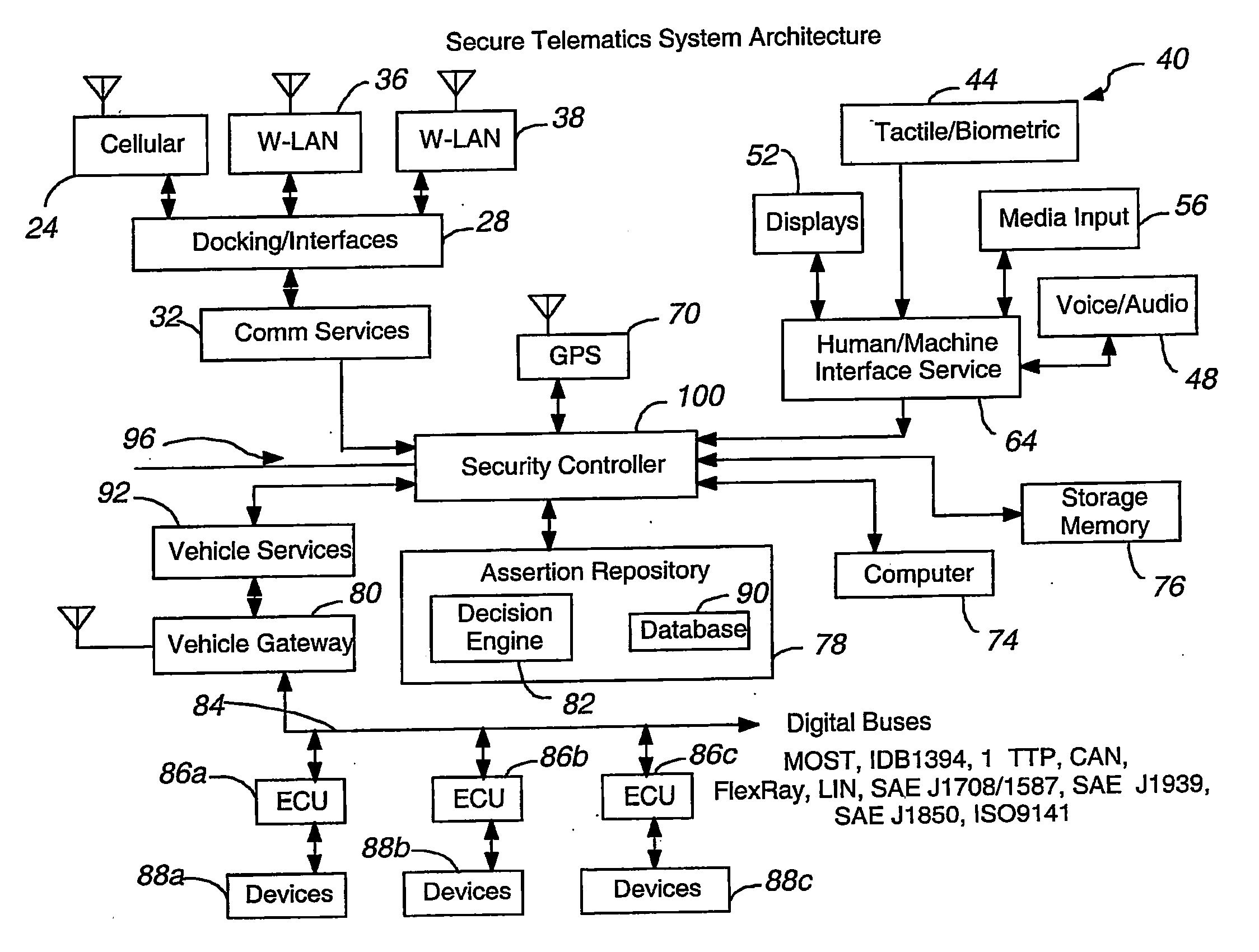
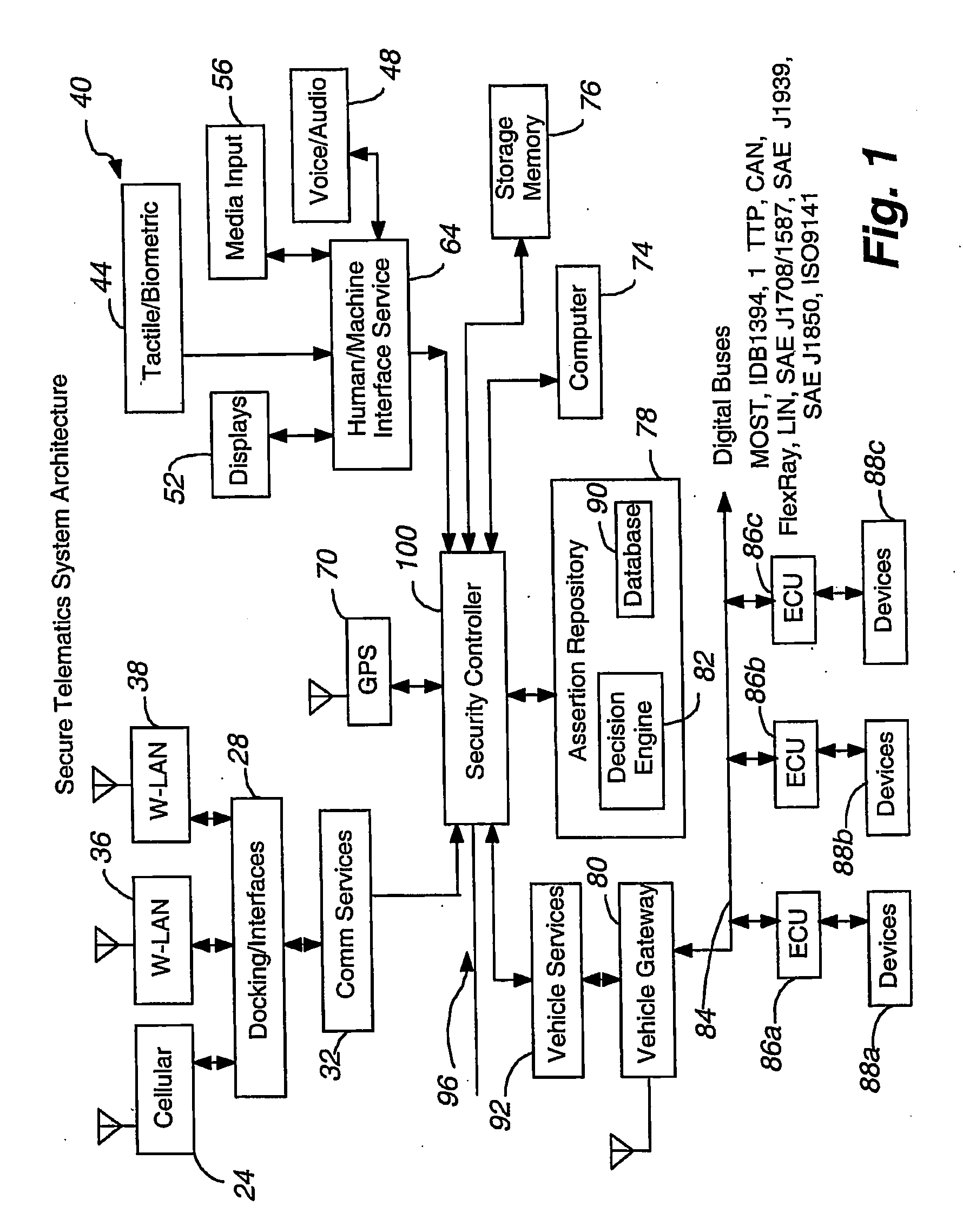
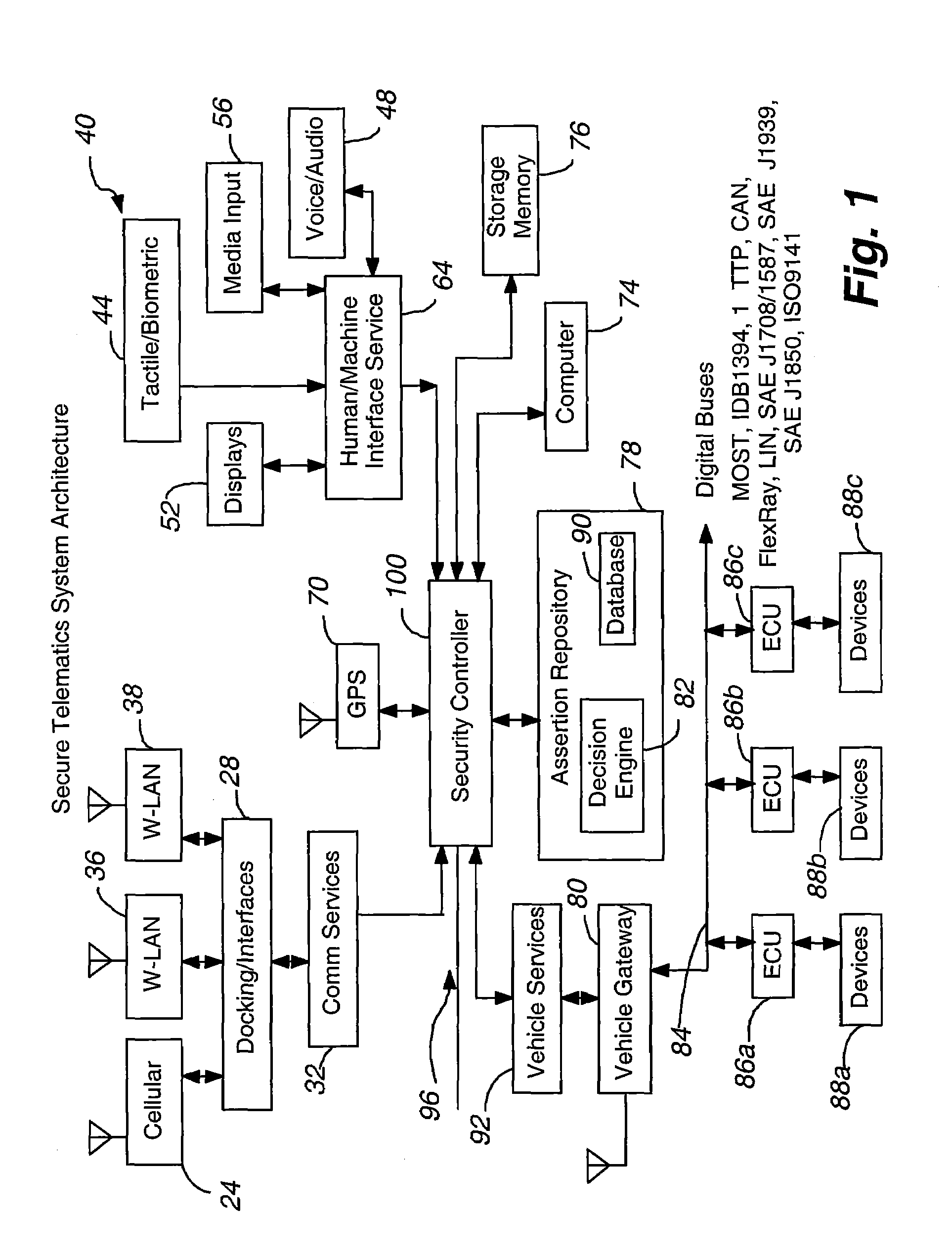
Secure telematics
ActiveUS7366892B2Expands telematics usageLow costUnauthorised/fraudulent call preventionRegistering/indicating working of vehiclesService provisionSecurity Measure
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resource'0 security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
Integrating operating systems and run-time systems
InactiveUS6546546B1Specific access rightsMemory adressing/allocation/relocationOperational systemApplication software
The Virtual Machine is viewed by many as inherently insecure despite all the efforts to improve its security. This invention provides methods, apparatus, and computer products to implement a system that provides operating system style protection for code. Although applicable to many language systems, the invention is described for a system employing the Java language. Hardware protection domains are used to separate Java classes, provide access control on cross domain method invocations, efficient data sharing between protection domains, and memory and CPU resource control. Apart from the performance impact, these security measures are all transparent to the Java programs, even when a subclass is in one domain and its superclass is in another, when they do not violate the policy. To reduce the performance impact, classes are grouped and shared between protection domains and map data lazily as it is being shared. The system has been implemented on top of the Paramecium operating system used as an example of an extensible operating system application.
Owner:IBM CORP
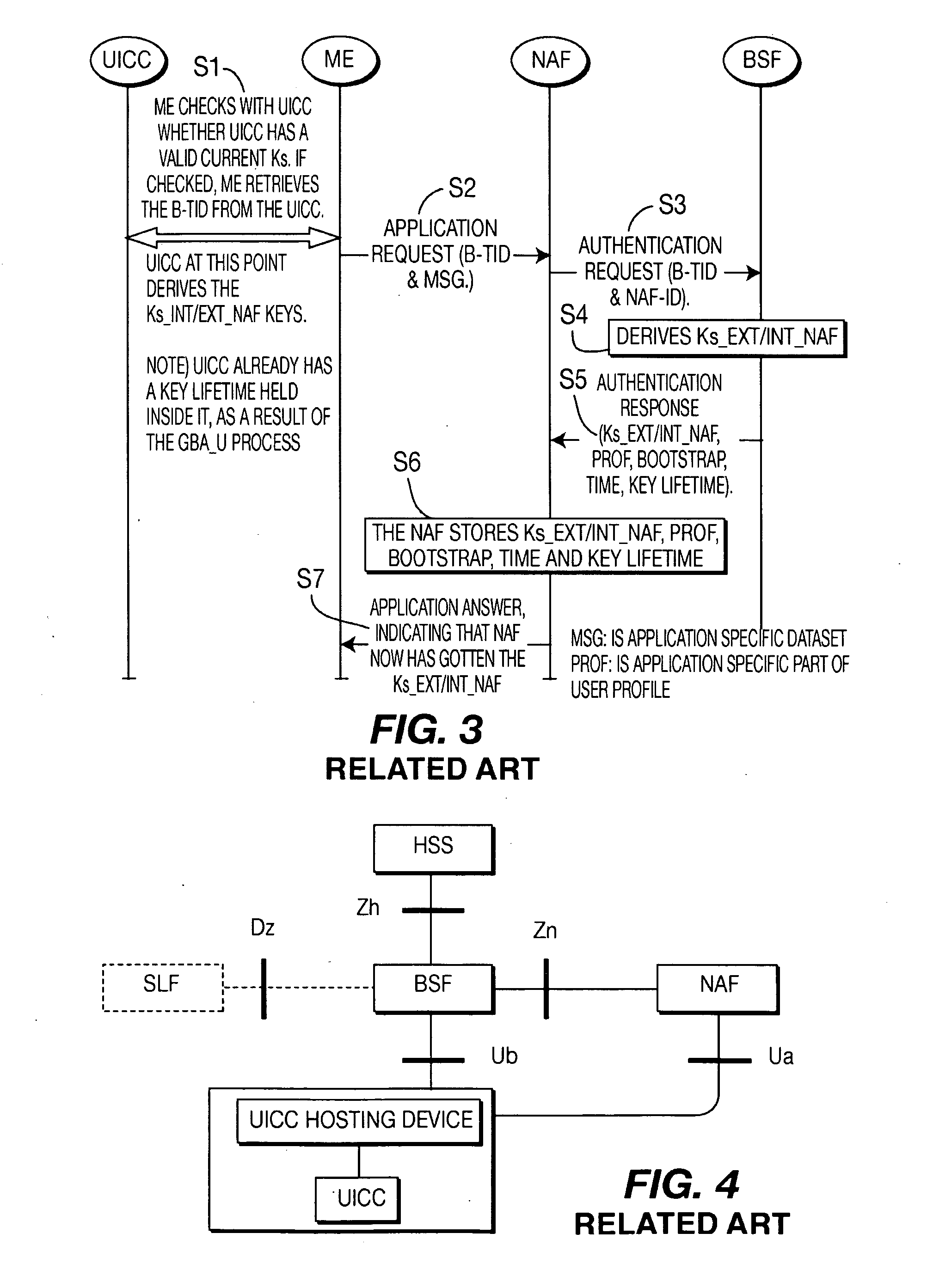
Techniques for secure channelization between uicc and a terminal
InactiveUS20090209232A1Improve integrityReduce needUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemThird generation
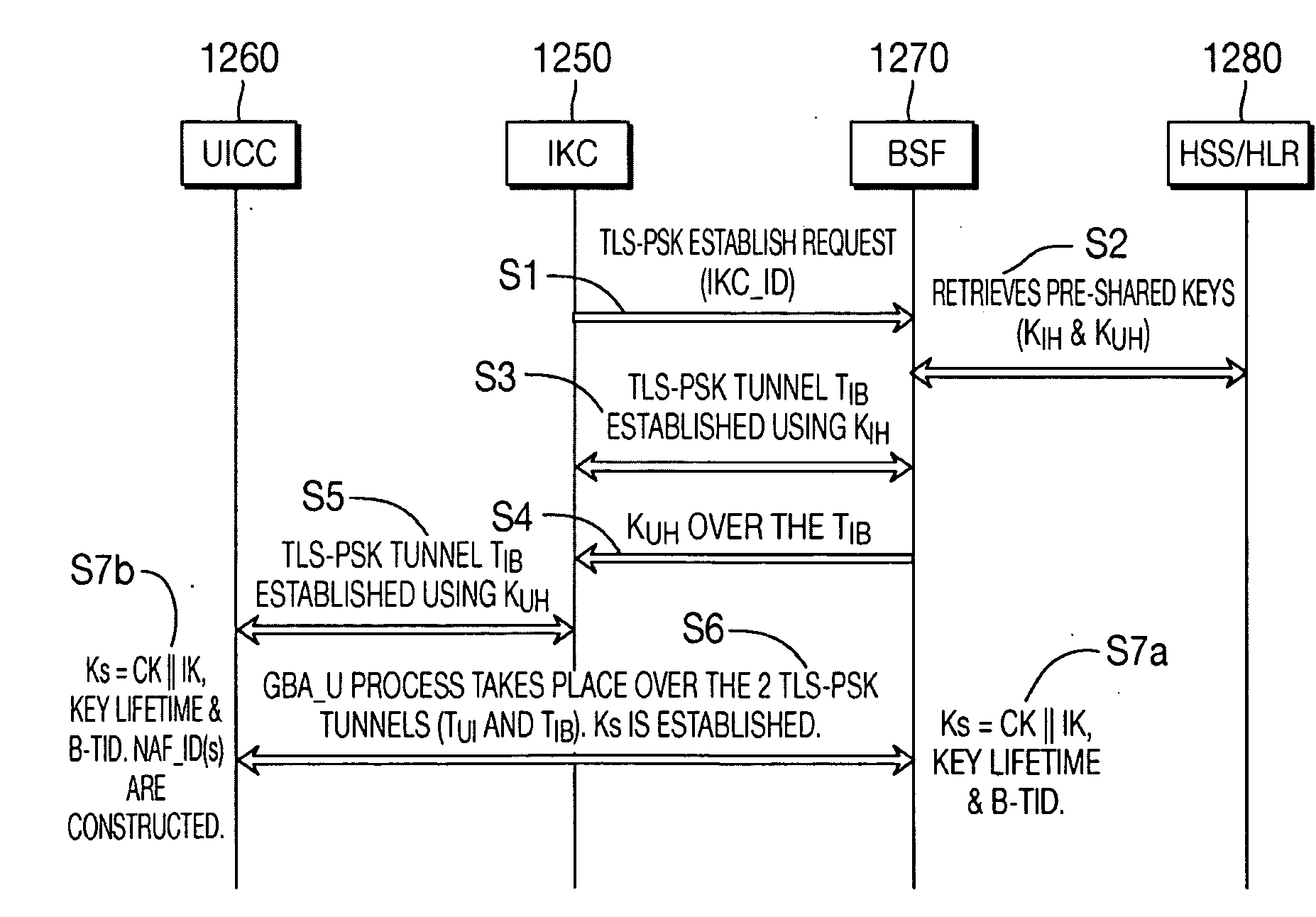
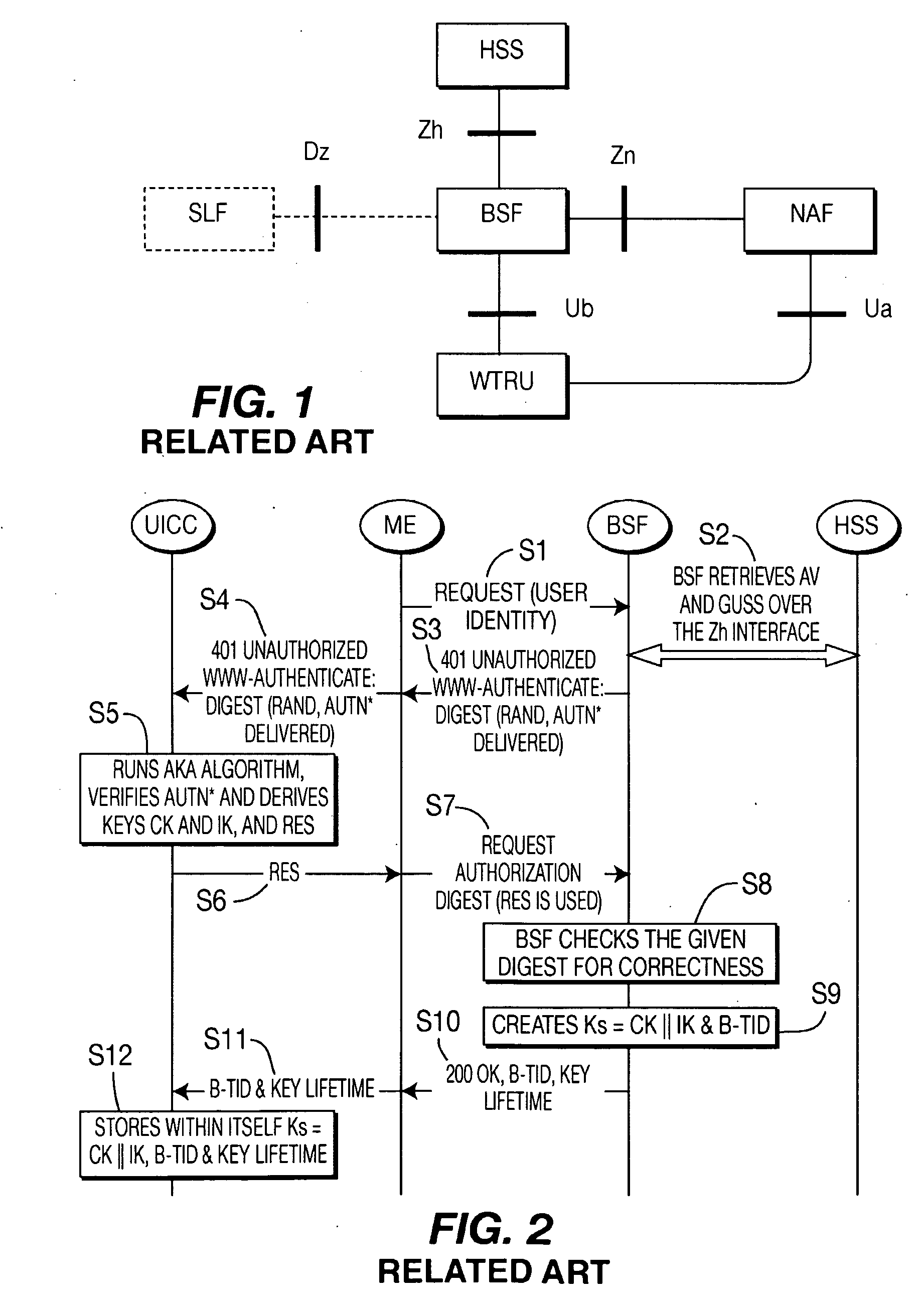
The present invention is related to a wireless communication system. 3G UMTS mobile phone systems rely on a protected smart card called the UMTS integrated circuit card (UICC) that provides UMTS subscriber identity module (USIM) applications as a basis or root of various security measures protecting the communication path between the 3G mobile terminal and the UMTS wireless network (or UTRAN). Disclosed is a method by which the UICC exchanges information with a terminal, such as an Internal Key Center (IKC 1250) and a Bootstrapping Server Function (BSF 1270) enables a procedure where multiple local keys specific to applications and Network Application Functions (NAFs) (Ks_local) are used for authentication and to encrypt and decrypt messages.
Owner:INTERDIGITAL TECH CORP
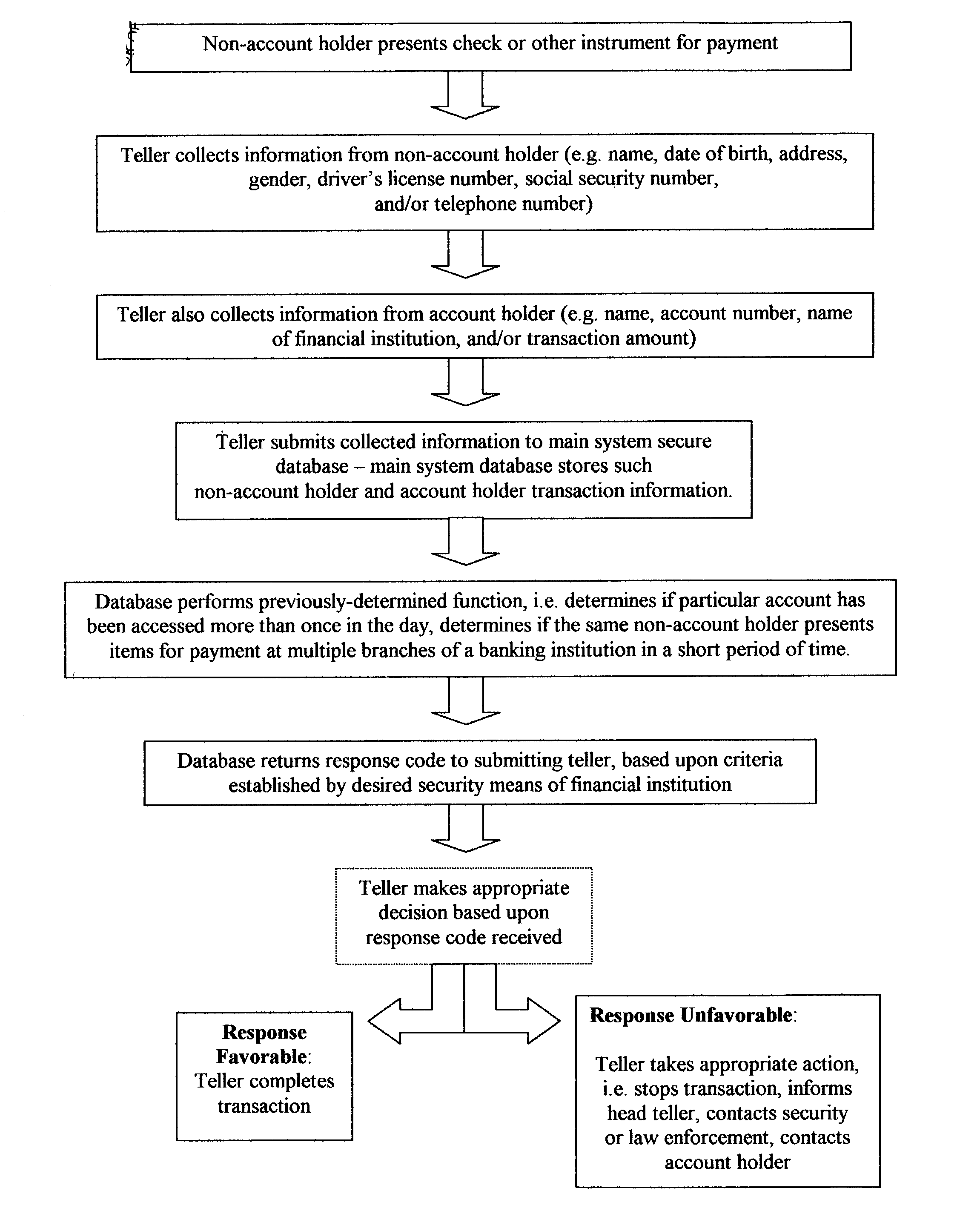
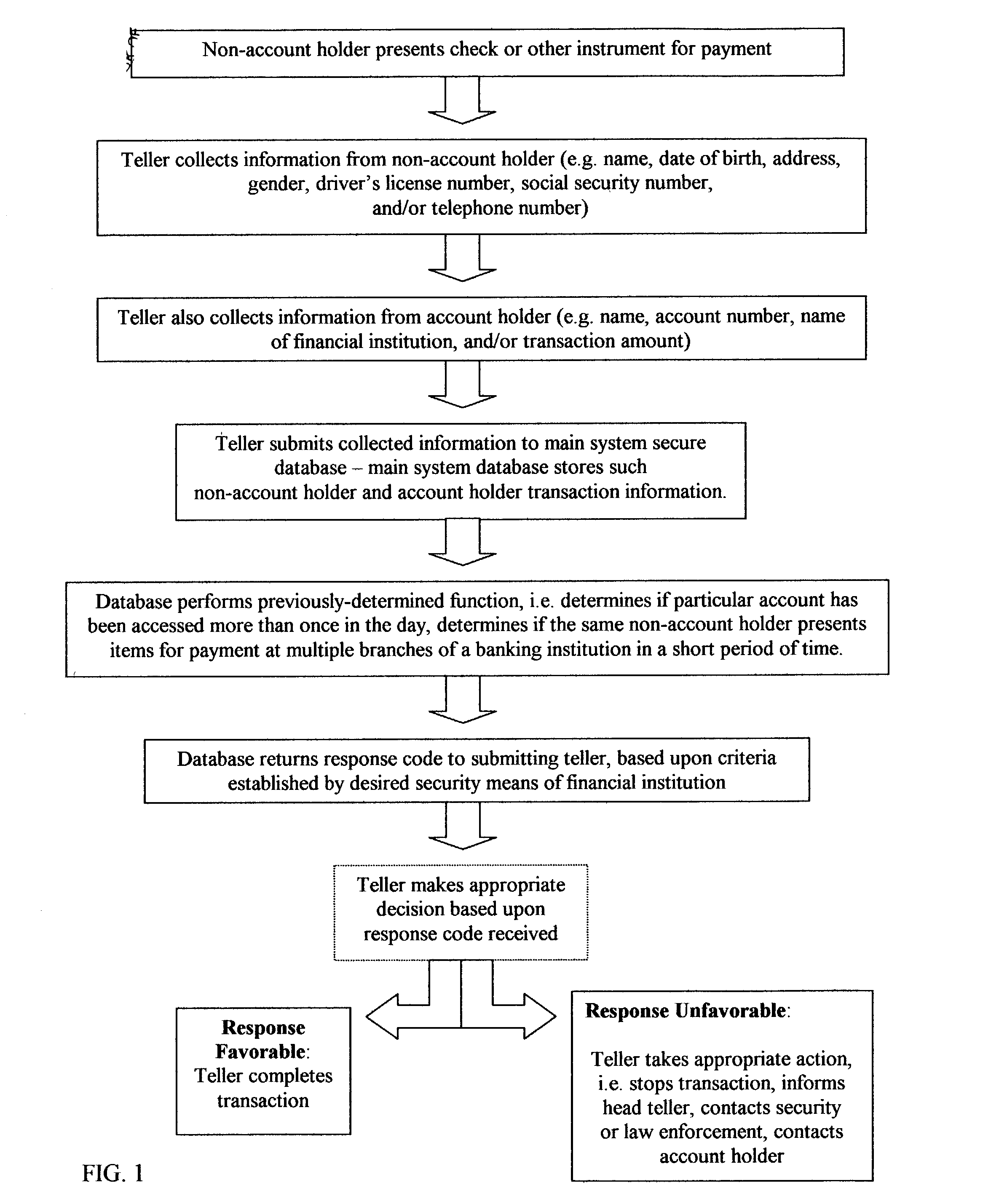
Fraud detection and security system for financial institutions
InactiveUS20030182214A1Limit losses to individual FIsAvoid checkingFinancePayment circuitsSocial Security numberCheque
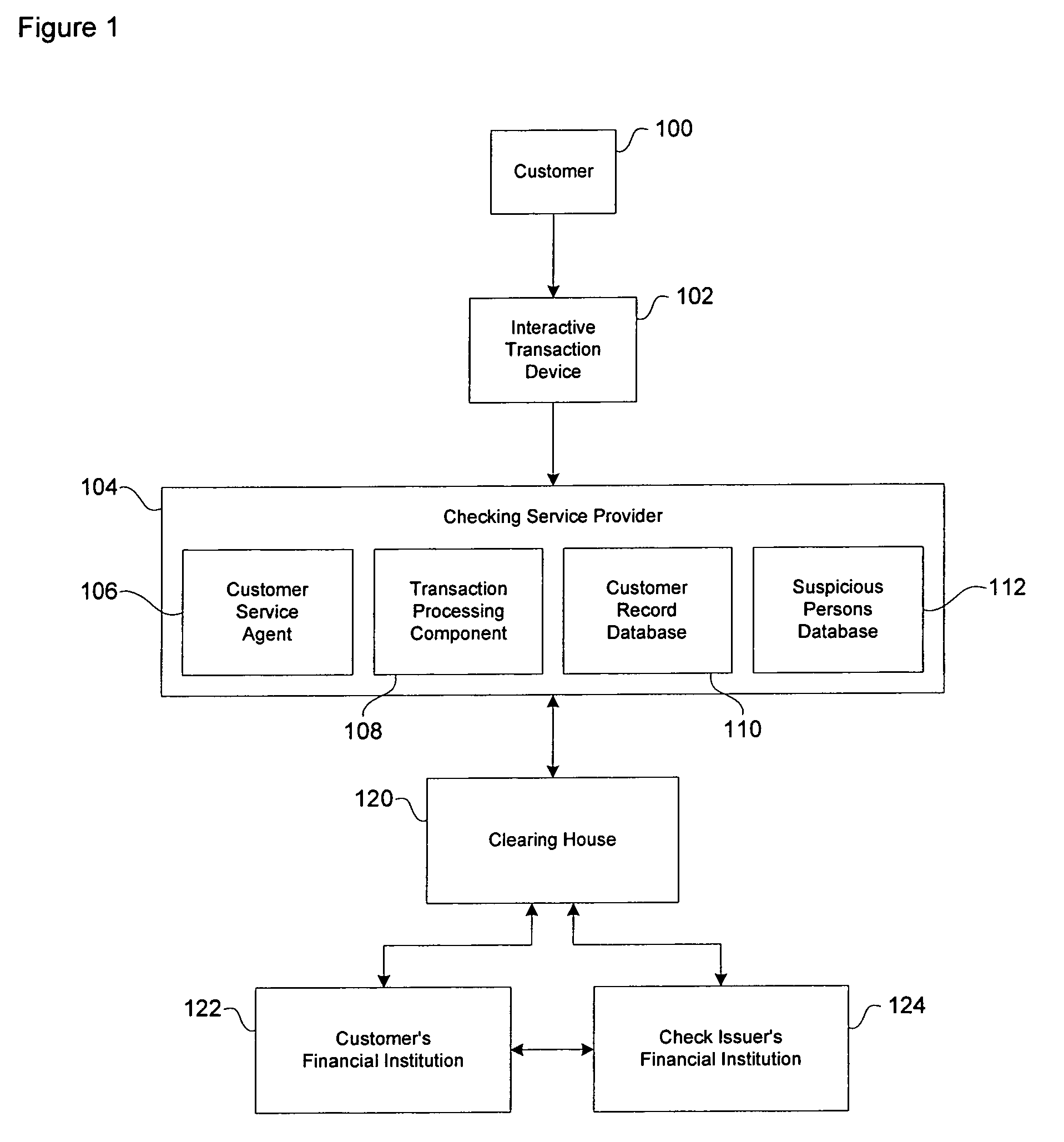
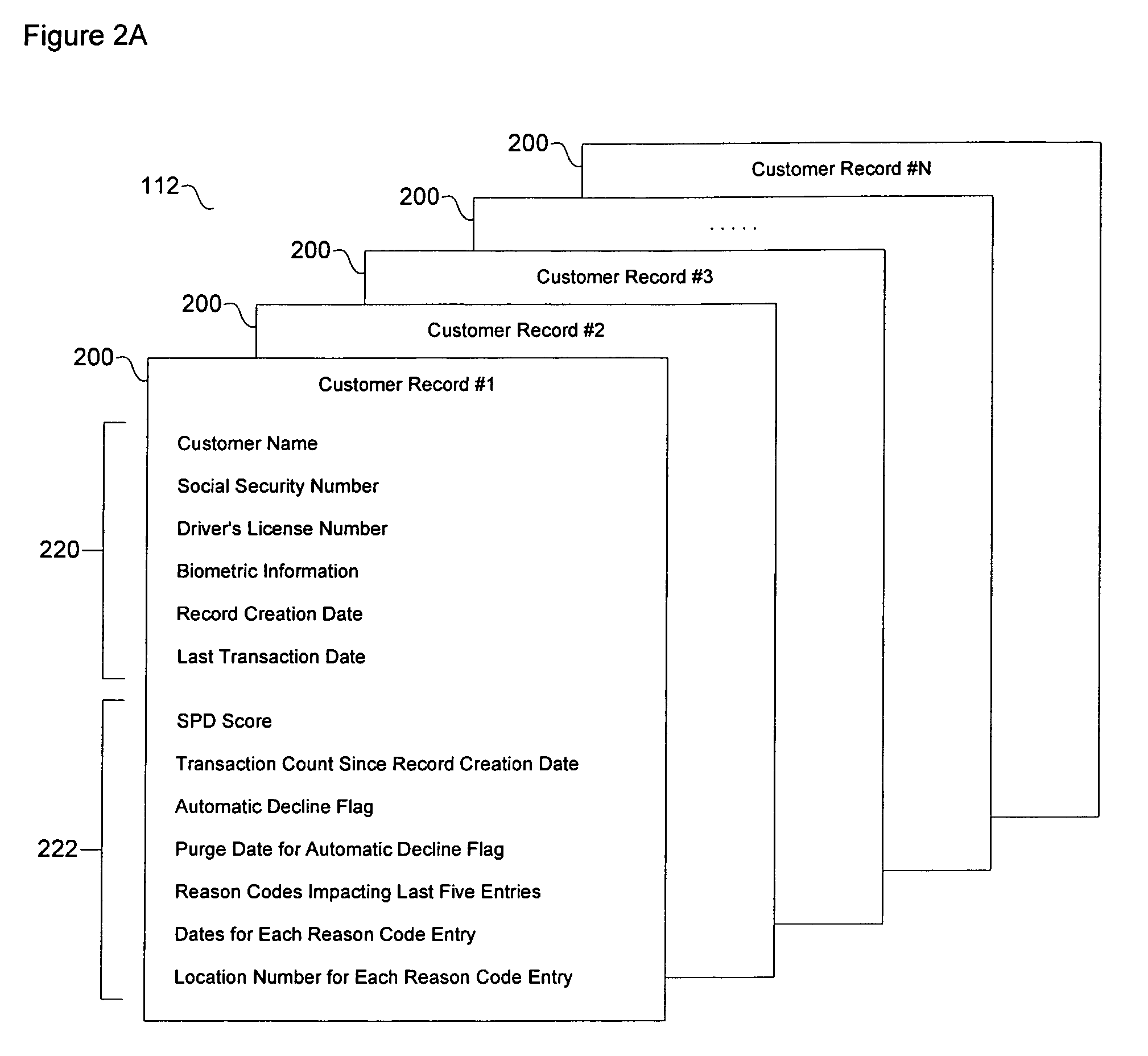
A fraud detection and security system for financial institutions utilizes a secure database of information relating to financial transactions of non-account holders who present checks and other instruments for payment. The system collects and tracks the frequency of particular aspects of the subject's behavior, and flags deviations from such norms for the purpose of indicating that fraudulent or criminal behavior may be occurring. At such time, the teller or other employee with whom the subject is dealing may stop the transaction, to the benefit of the financial institution and account holder. The system also allows for law enforcement to detect related transactions, or a string of criminal activity from the same perpetrator. In the preferred mode, the system includes a teller collecting information from the non-account holder, including name, date of birth, address, gender, driver's license number, social security number, and / or telephone number. At the time of the transaction, such data is submitted to the system database and the database returns a response code based upon criteria established by the financial institution's desired security measures, accomplished by installation of new software or by integration of a custom program. The system alerts tellers to suspicious activity, such as when a particular account is accessed more than once in a day, or when the same non-account holder presents items for payment at multiple branches of a banking institution in a short period of time.
Owner:TAYLOR MICHAEL K
System for inventory management
ActiveUS20050168345A1Electric signal transmission systemsHand manipulated computer devicesSecurity MeasurePurchasing
The present invention relates to a system for tracking product on a shelf. In an embodiment, an indicia strip is placed on a self coiling sheet, and a sensor is configured to read the indicia strip. The data on the indicia strip corresponds to the location of a pusher assembly. In an embodiment, a store computer can use the data regarding the location of the pusher assembly to determine the amount of inventory on the shelf. In an embodiment, the store computer can automatically order additional inventory based on the levels of inventory on the shelf. In an embodiment, a deviation from normal customer purchasing habits can be used to prompt security measures so as to reduce the possibility of product theft.
Owner:RTC IND
System for inventory management
ActiveUS7792711B2Electric signal transmission systemsHand manipulated computer devicesSecurity MeasurePurchasing
Owner:RTC IND
Suspicious persons database
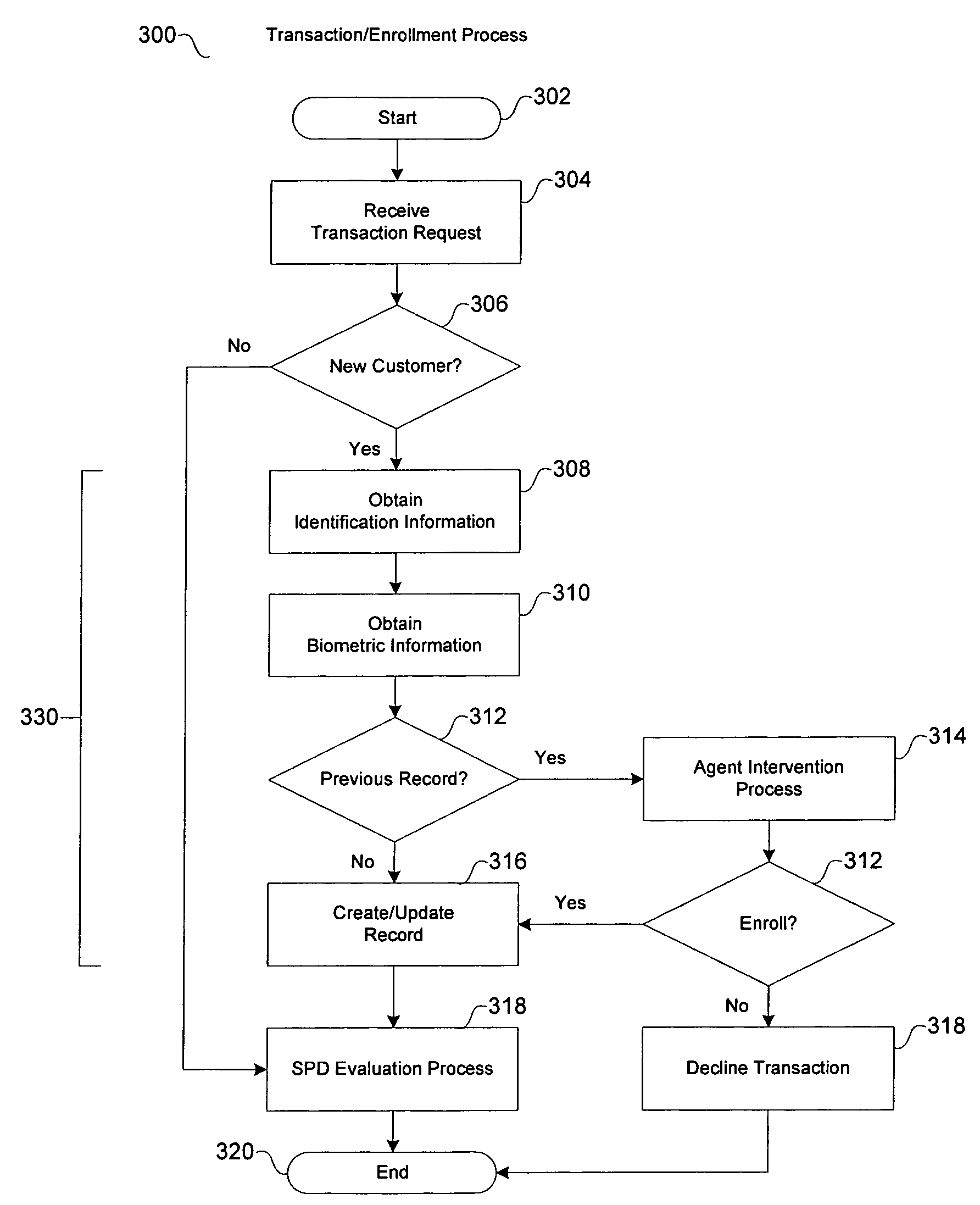
Most financial transactions involving check deposits and cashing at automatic teller machines are often associated with high risk. Although conventional security measures for many automatic teller machines record financial transactions, the recorded events are typically viewed after suspicious or criminal activity has already occurred. Therefore, a financial institution may not know in advance whether requested financial transactions are of suspicious or fraudulent intent. The present teachings relate to a method of scoring customers prior to authorization in a manner so as to identify suspicious behavior or suspicious activity. The method also relates to marking suspicious individuals by storing related transaction information, such as biometric data, in a database for purposes of verifying identification information and scoring the validity of future financial transactions.
Owner:FIRST DATA
Method and apparatus for achieving secure password access
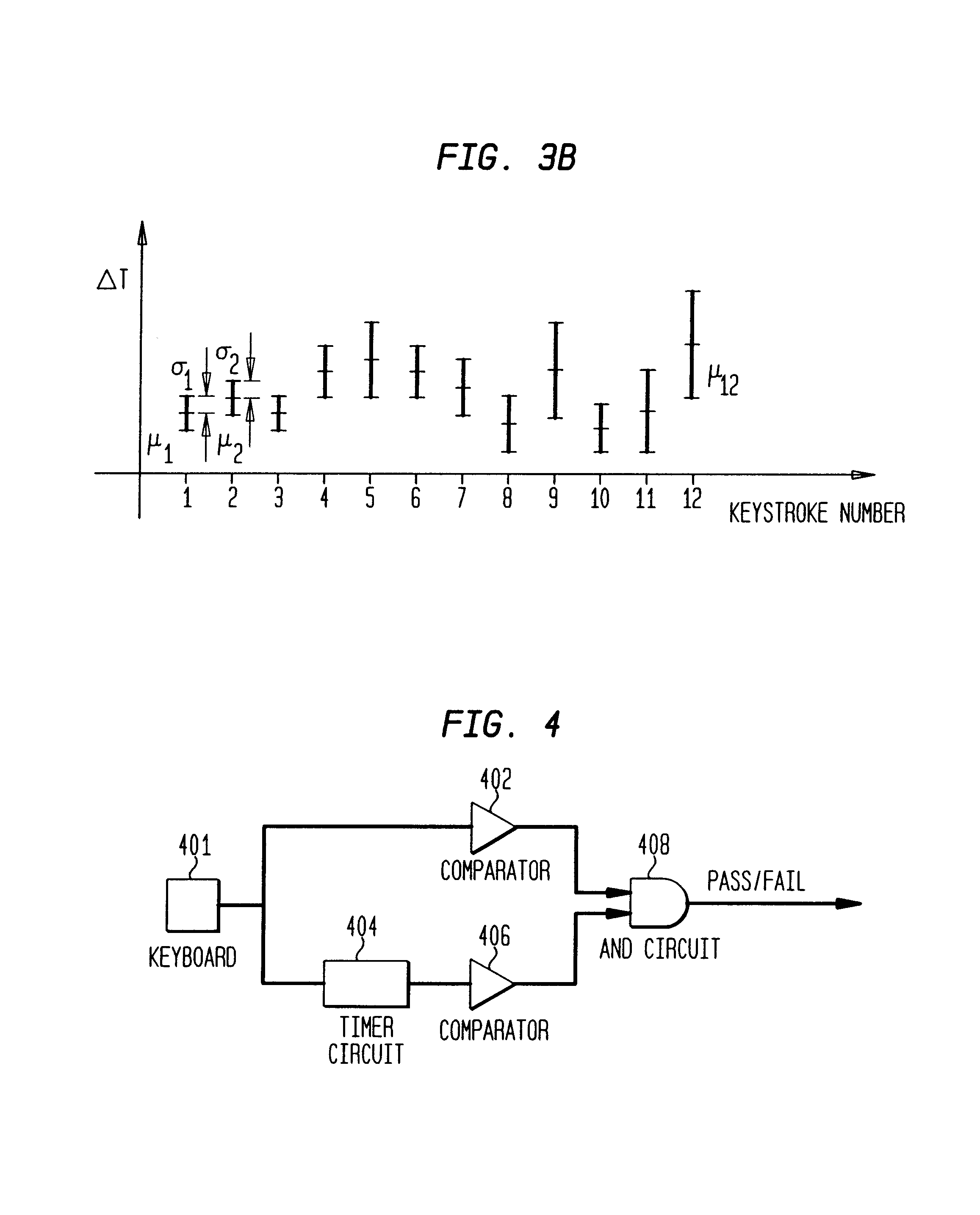
InactiveUS6895514B1Improve securityComplete security measuresDigital data processing detailsUser identity/authority verificationPasswordTyping
A method and apparatus for enhancing the security of password security systems. The authorization decision related to passwords is based not only on entry of the correct characters in the correct sequence but also on the keystroke sequence timing associated with the typing habits of an authorized user. The keystroke sequence timing provides an additional security measure to each password similar to signature or fingerprint systems. Particularly, each person has a unique typing style and this uniqueness is captured in the present invention as keystroke sequence timing and used as an additional recognition means.
Owner:GEMPLU
Network security device and method for protecting a computing device in a networked environment
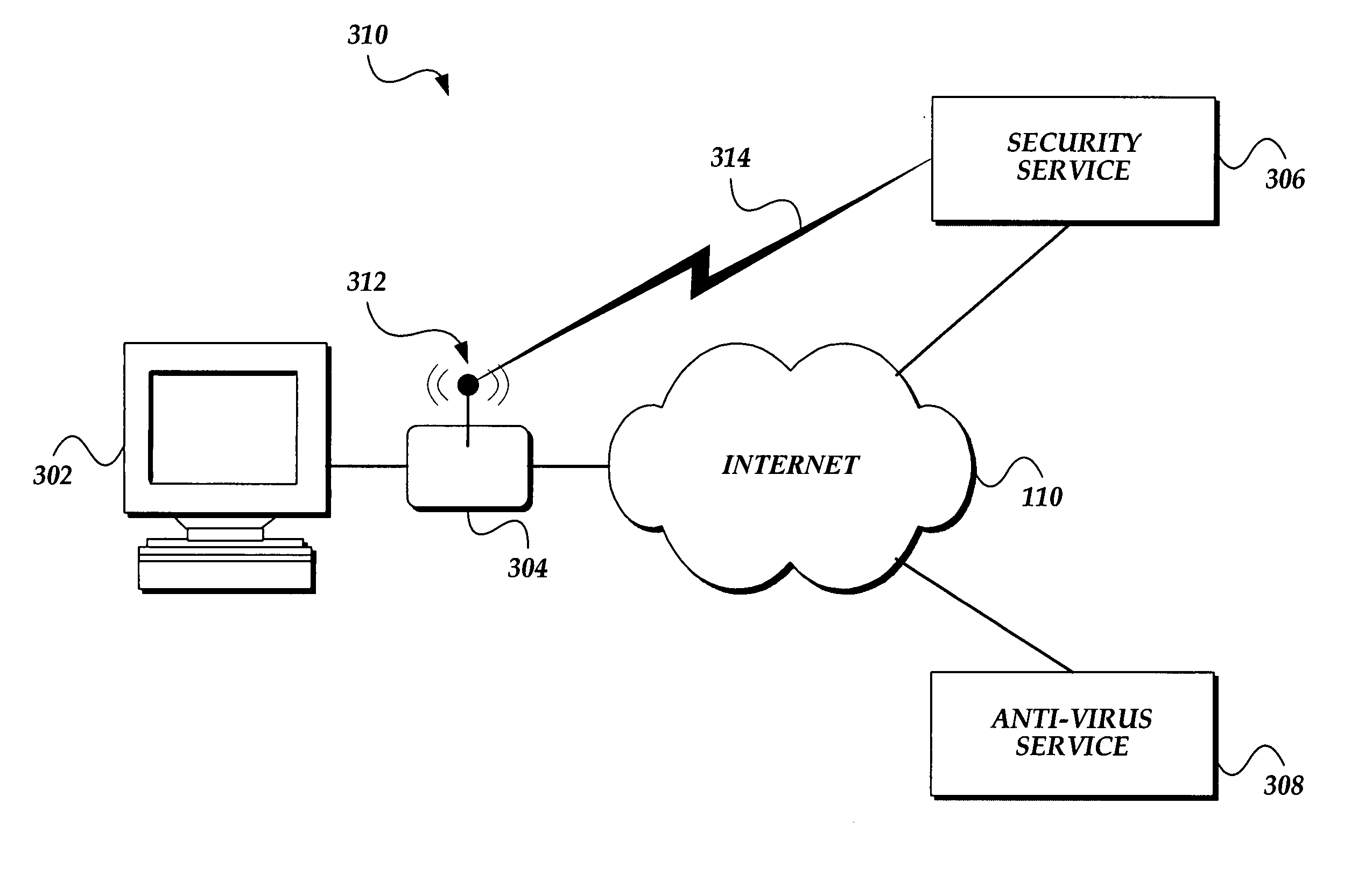
ActiveUS20060095965A1Memory loss protectionDetecting faulty computer hardwareNetwork activitySecurity Measure
A network security module for protecting computing devices connected to a communication network from security threats is presented. The network security module is interposed, either logically or physically, between the protected computer and the communication network. The network security module receives security information from a security service. The security information comprises security measures which, when enforced by the network security module, protect the computer from a security threat to the computer. The network security module implements the security measures by controlling the network activities between the protected computer and the network. The network security module also temporarily implements security patches until corresponding patches are installed onto the protected computer.
Owner:MICROSOFT TECH LICENSING LLC
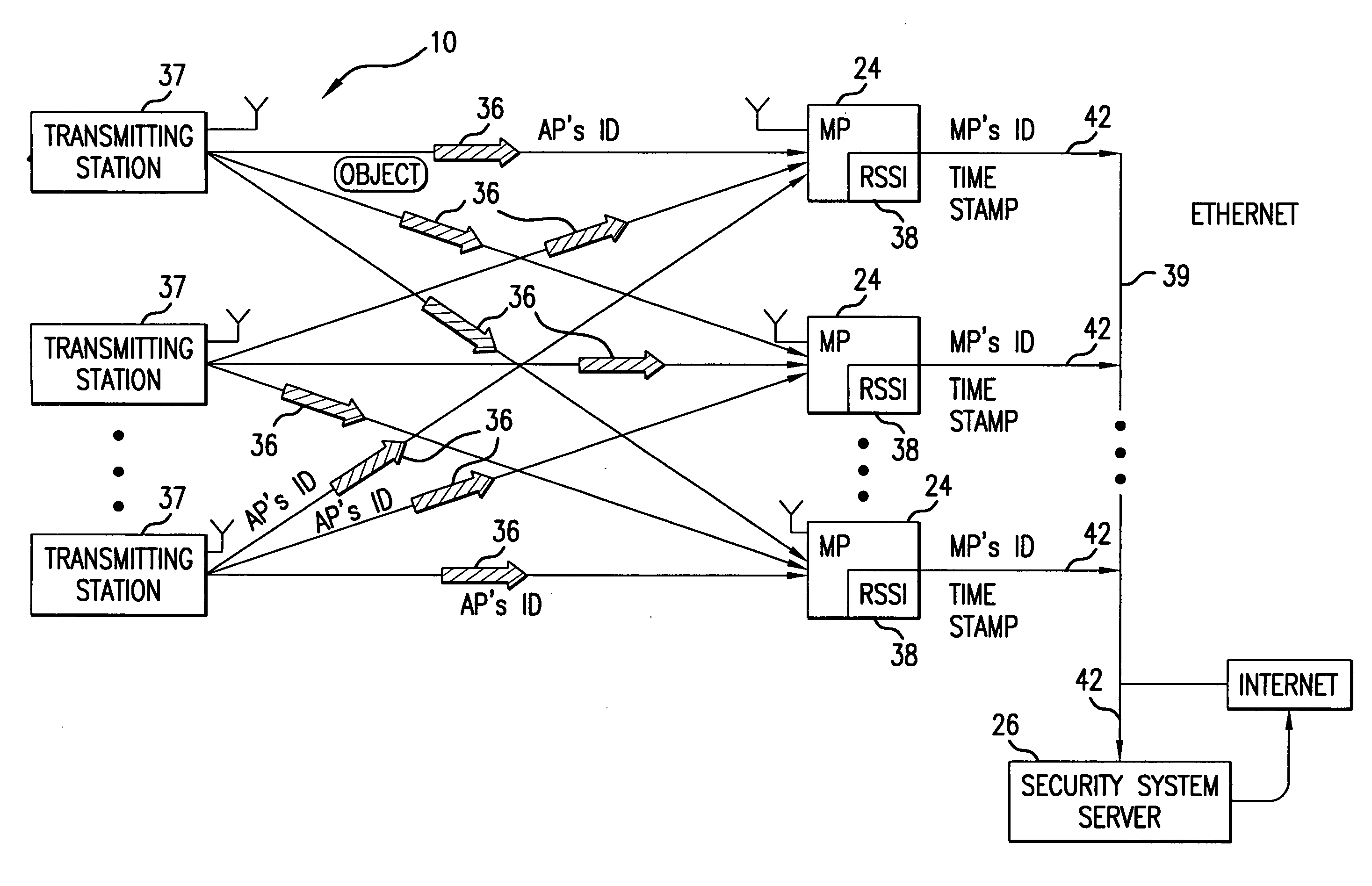
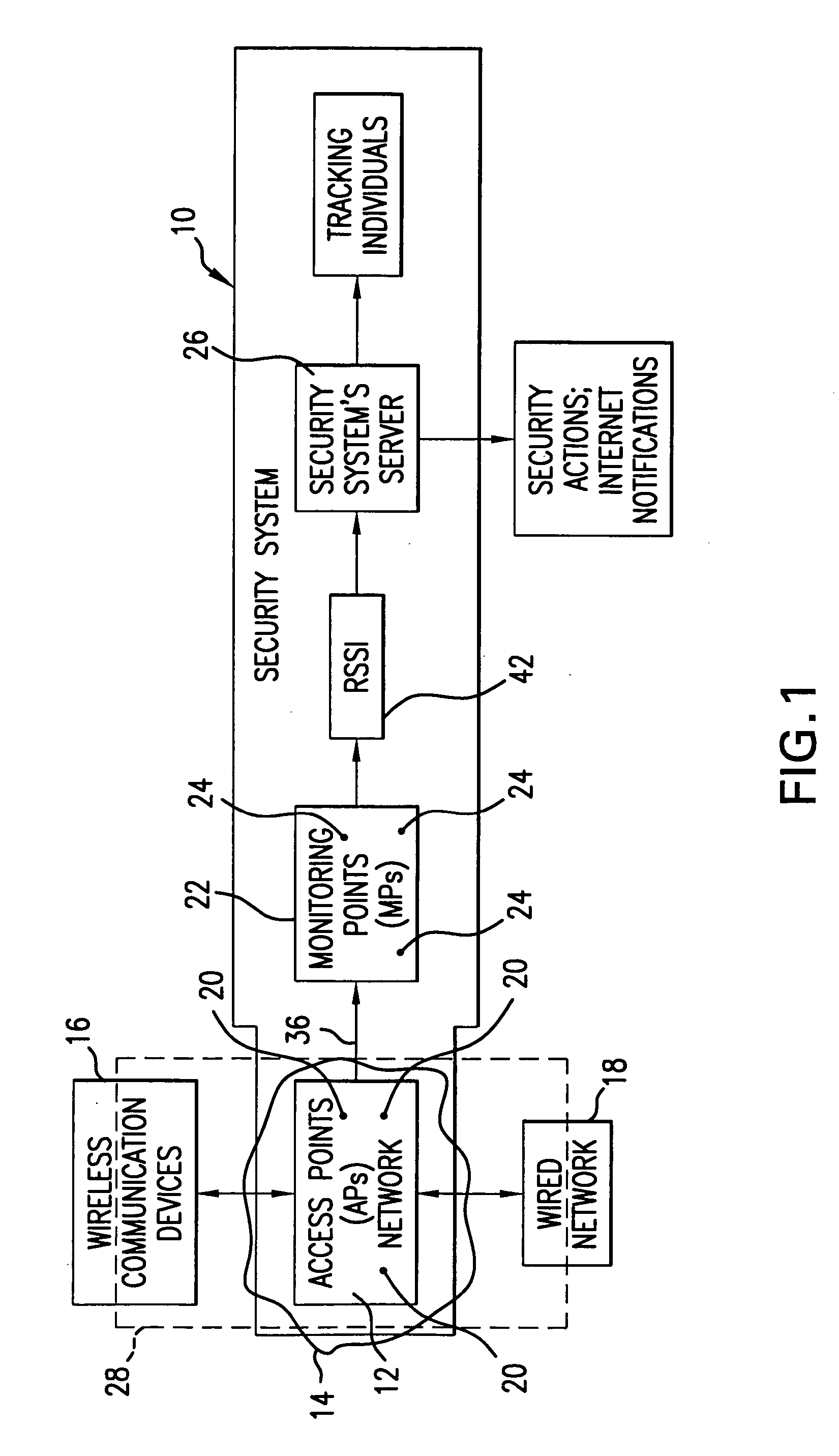
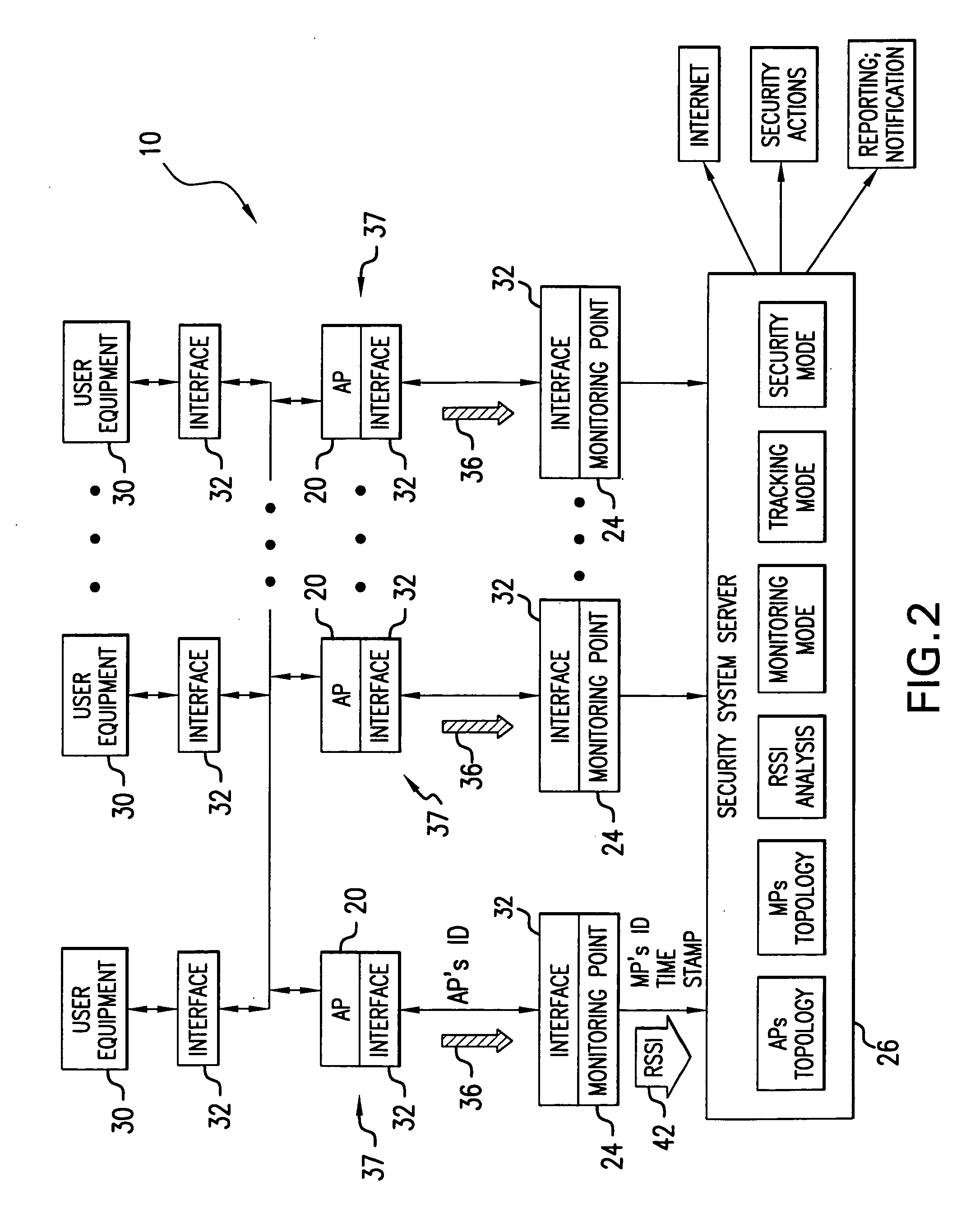
Method and system for providing physical security in an area of interest
InactiveUS20050055568A1Keep trackDigital data processing detailsHardware monitoringWi-FiPhysical security
A system for detecting the presence of an intruder in a protected area utilizes a received signal strength indicator (RSSI) value of signals broadcast from transmitting stations deployed in the protected area. The system includes monitoring points for receiving broadcast signals, measuring the RSSI values of the received signals, and transmitting the measured RSSI values to a security system server. The security system server analyzes the RSSI values, and initiates security measures when the physical security of the protected area is violated which is detected when the measured RSSI values deviate from a predetermined strength of the broadcast signals. The security system also has the ability to track objects in the protected area and keep track of their movement in real time and report such movement. The system may be based on a Wi-Fi infrastructure in the protected area.
Owner:UNIV OF MARYLAND
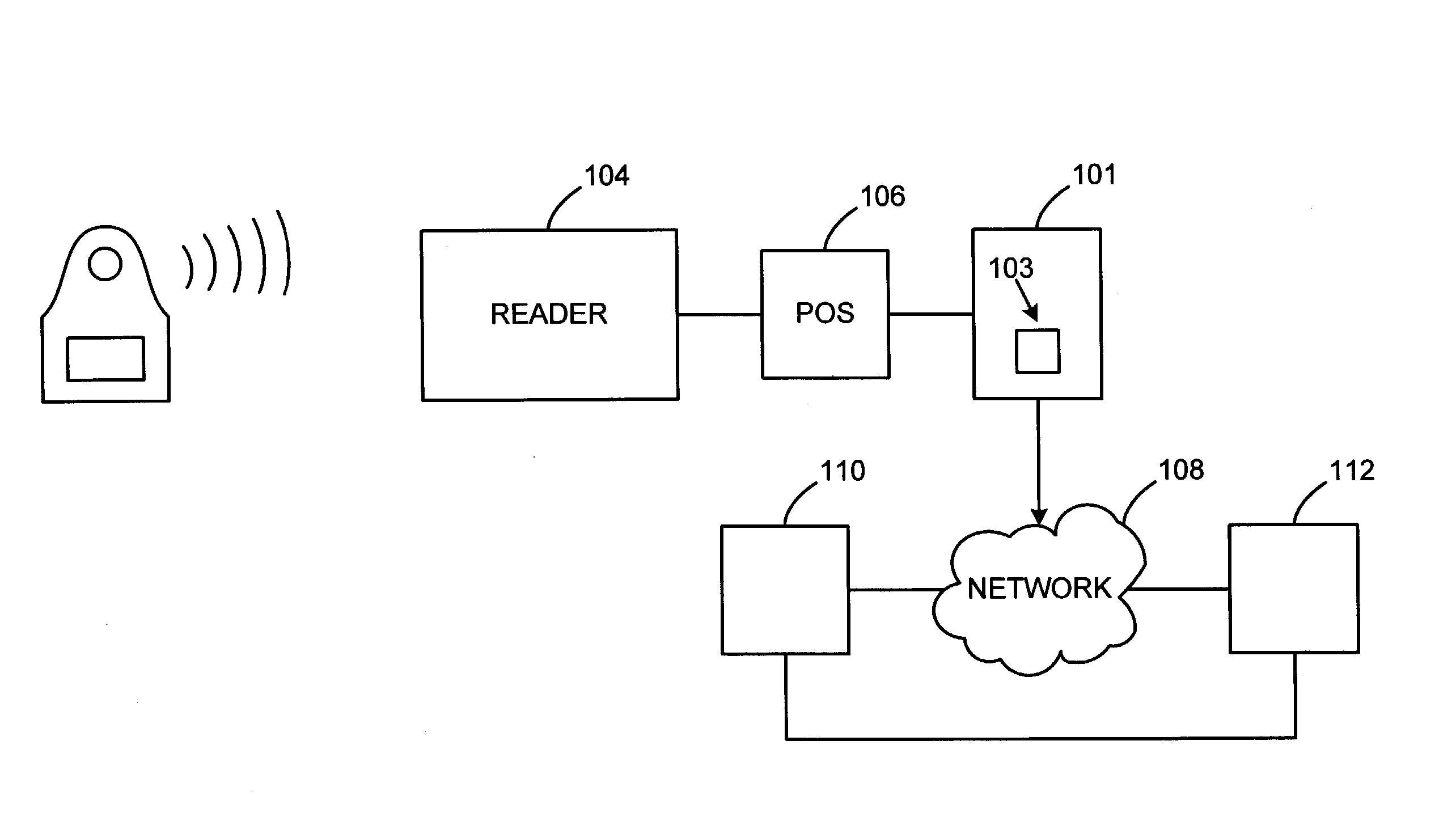
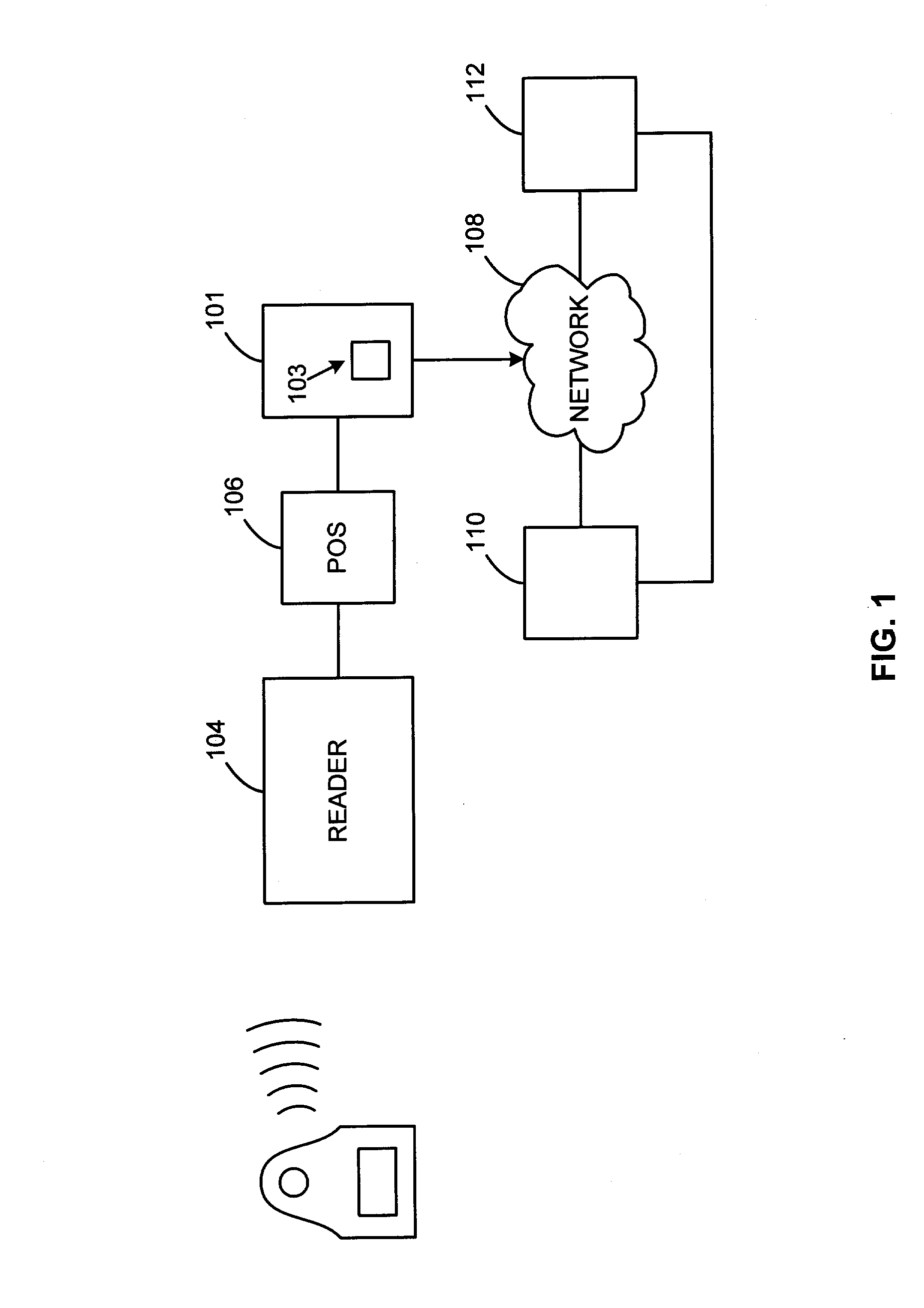
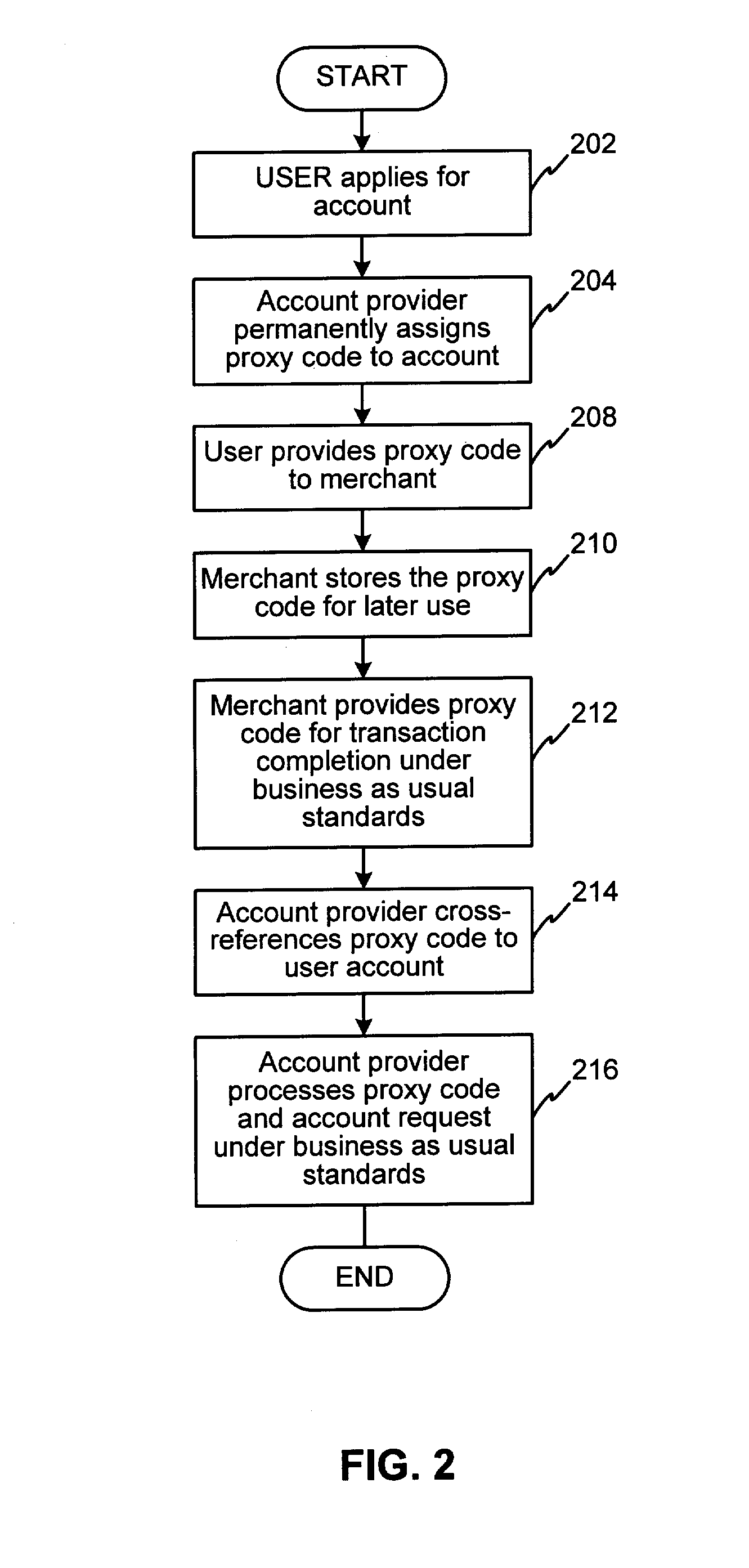
System and method for securing sensitive information during completion of a transaction
InactiveUS20050033686A1Electric signal transmission systemsDigital data processing detailsSecurity MeasureIdentification device
A system and method for securing a Radio Frequency (RF) transaction using a proxy code, which is permanently assigned to the RF identification device (RFID) transaction account number. An account issuer permanently assigns the proxy code to a transaction account correlated to the RFID transaction device. The proxy code is uploaded onto the transaction device for later use in completing a transaction request. During transaction completion, the proxy code is provided to a merchant system in lieu of any sensitive transaction account information. Since the proxy code is permanently assigned, the number need not be changed or updated once uploaded into a payment device or merchant system. Since the proxy code contains no sensitive information, the sensitive information related to the transaction account is secured from theft where the merchant system internal security measures may fail.
Owner:LIBERTY PEAK VENTURES LLC
System and method for unified threat management with a relational rules methodology
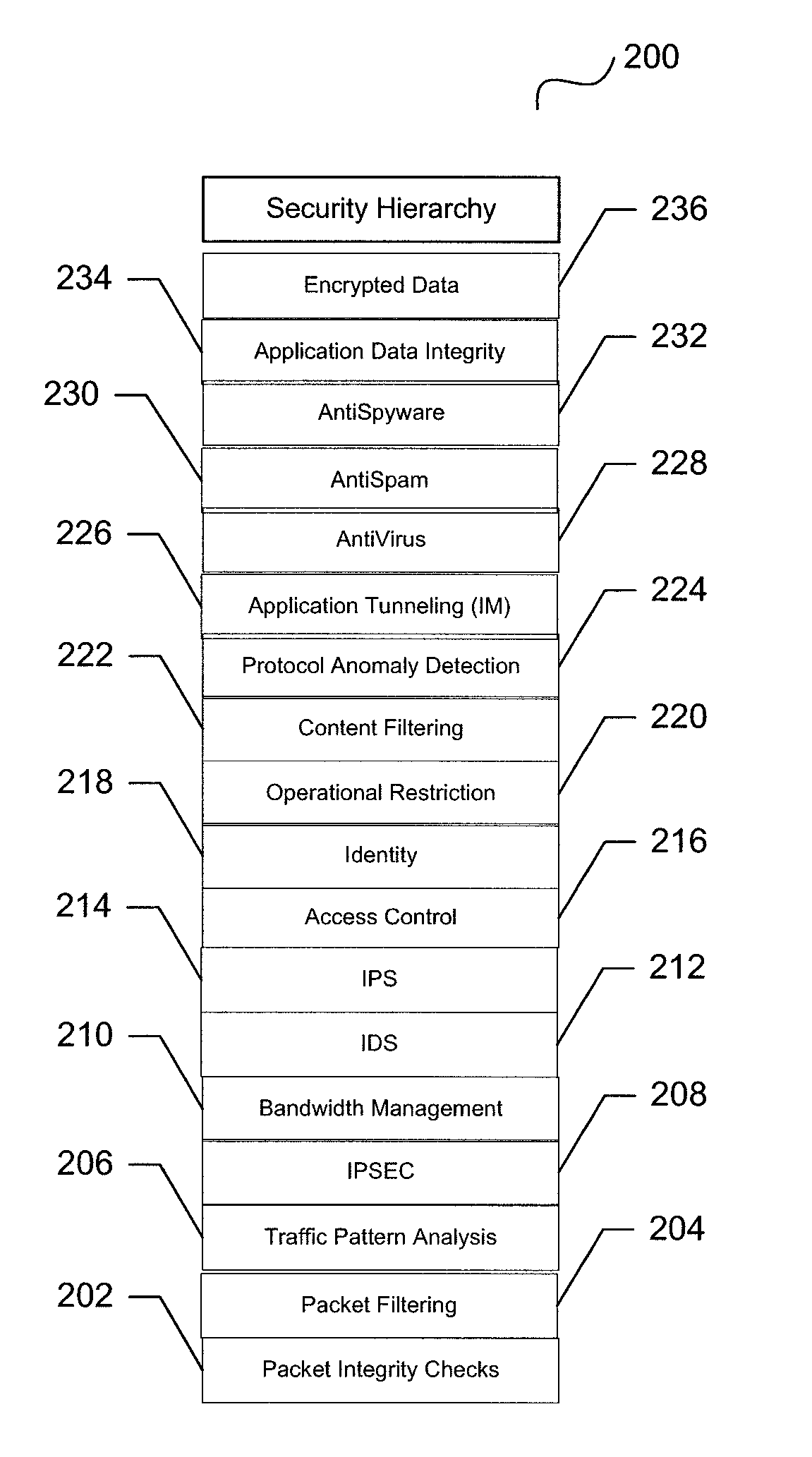
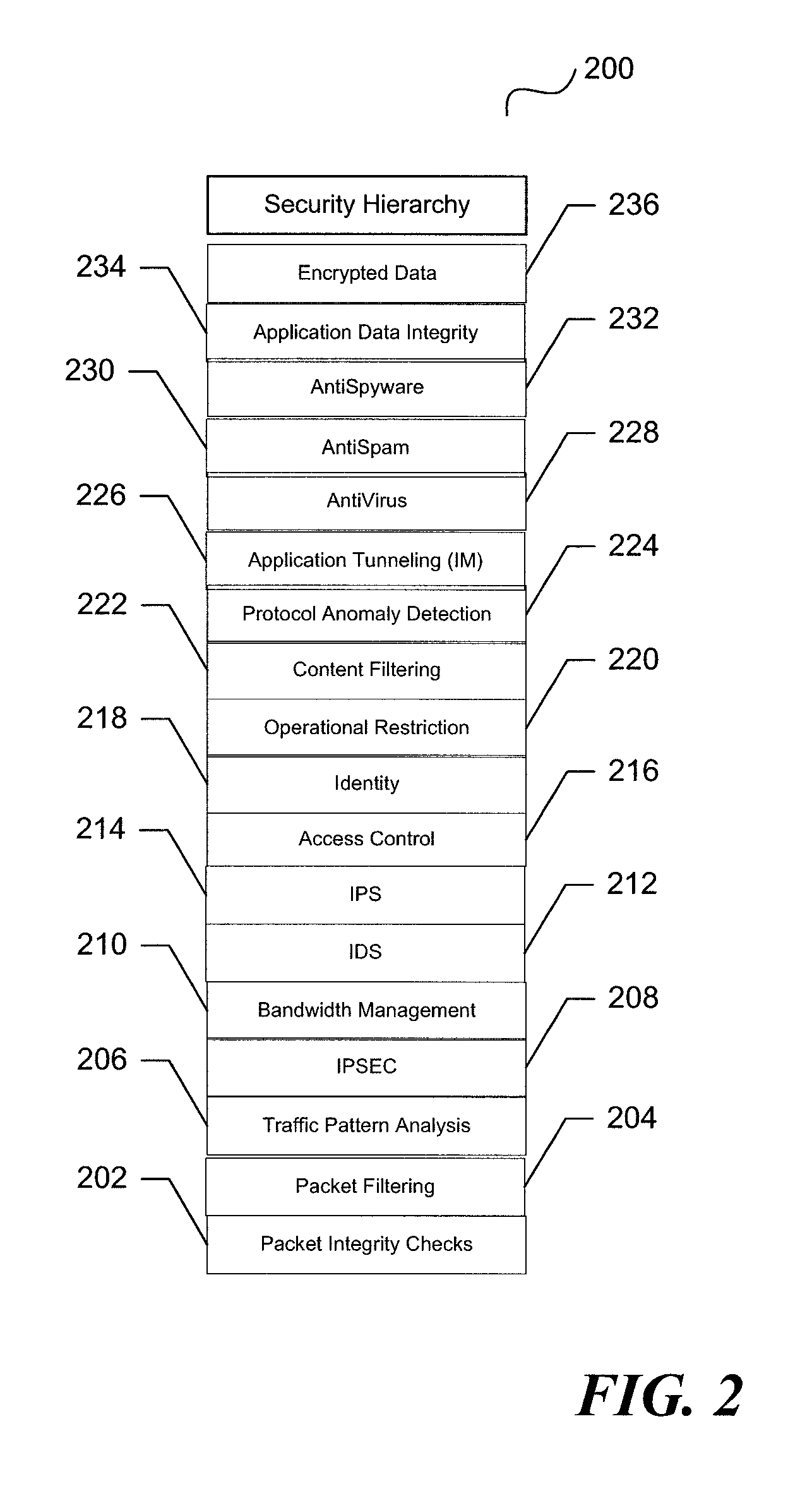
ActiveUS7735116B1Improve performanceImprove securityDigital data processing detailsUser identity/authority verificationSecurity measurementSecurity Measure
A unified threat management system is provided with a uniform relational rules model. The unified relational rules model provides for the sub-setting of rules and the ability to derive a result based partially from previous security measurements. The sharing of a security check from one security implementation to another using an object-oriented methodology is facilitated. Security policy is divided into specific security features that result in a security hierarchy. The security features may be considered to be listed sequentially, from bottom to top, and form a relationship with one another. These relationships are used to build a current security measure upon a previous security measure and may be used as a pre-cursor when marshalling data content to be validated.
Owner:CA TECH INC
Universal authorization and access control security measure for applications
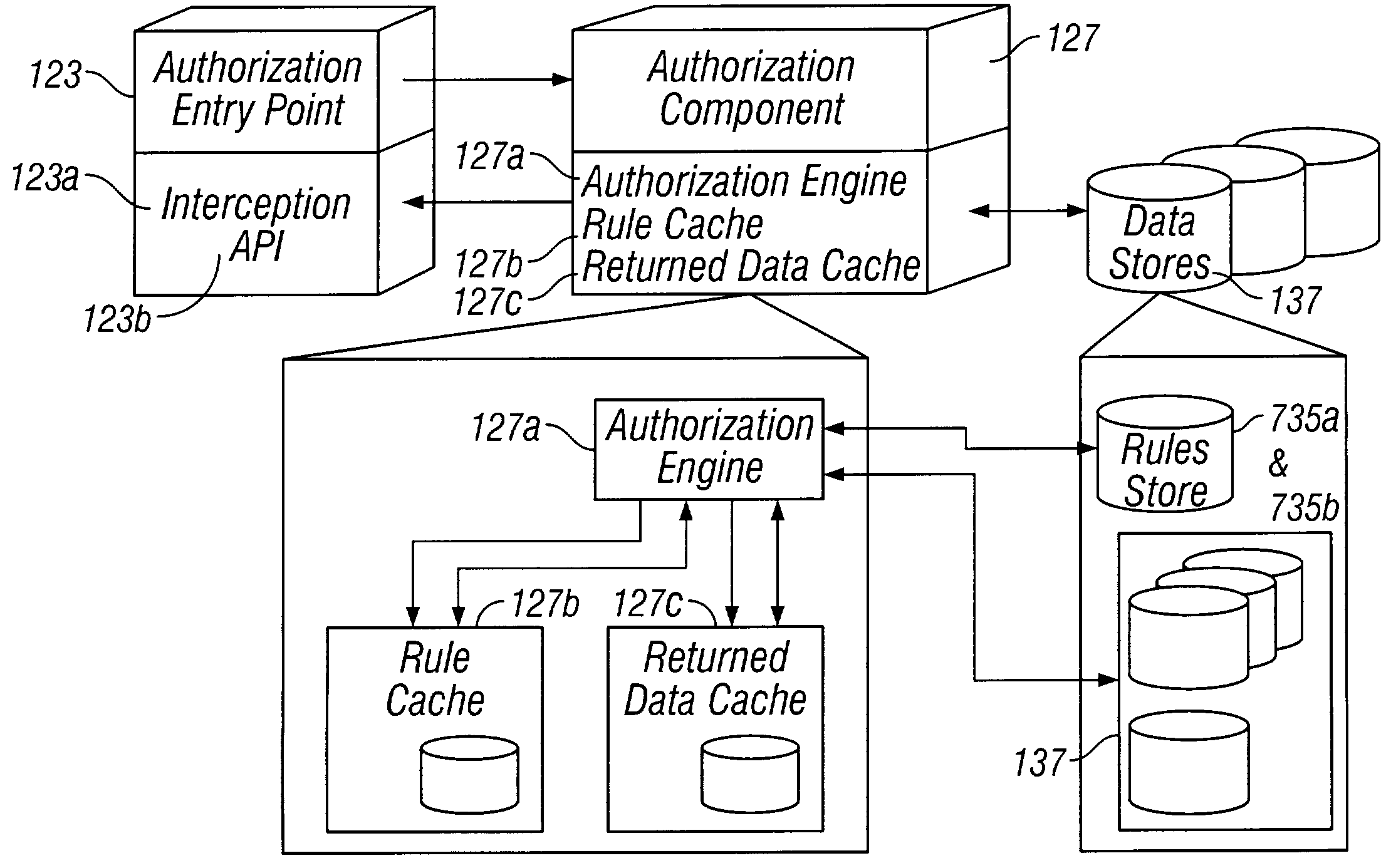
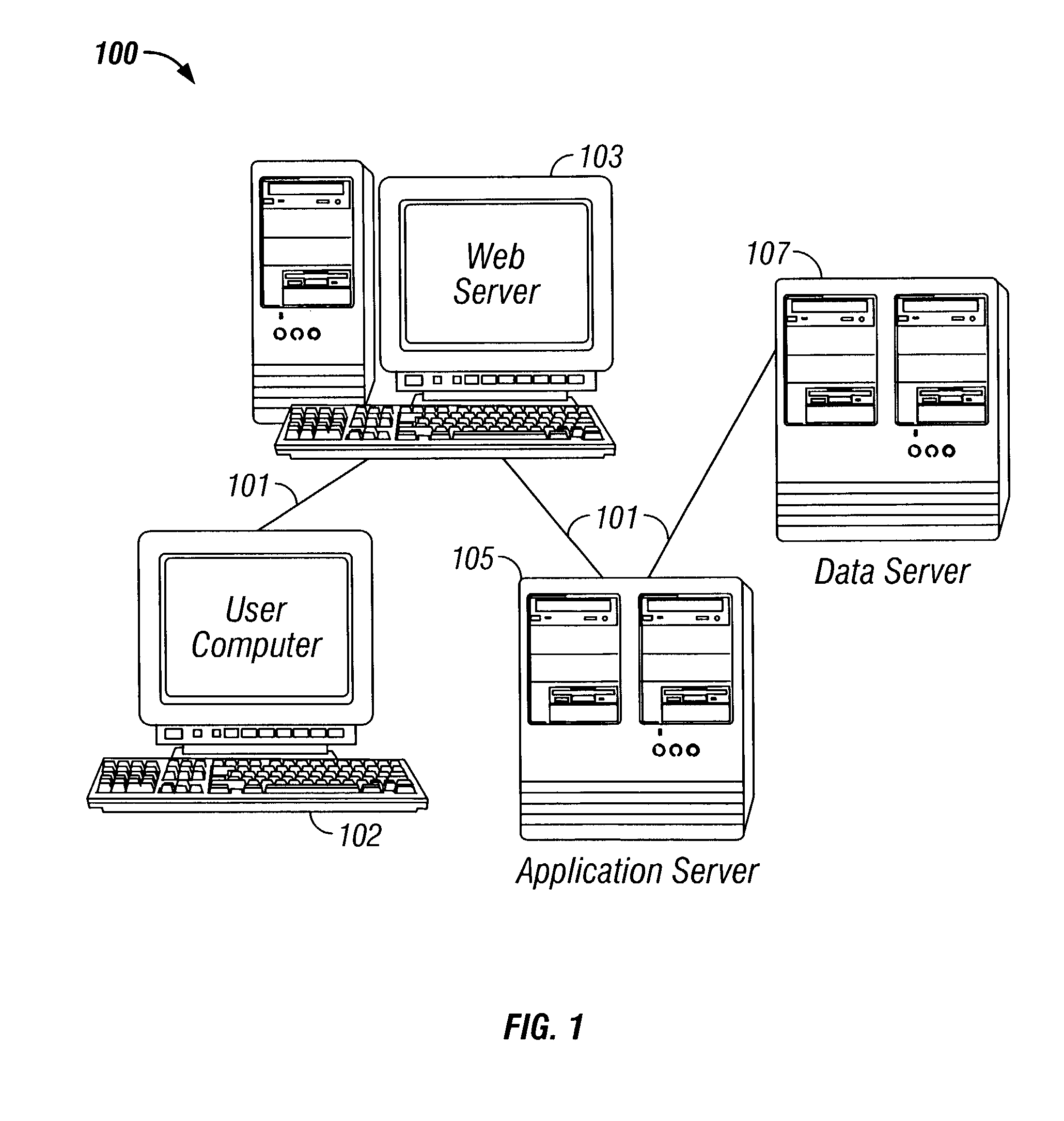
InactiveUS7865931B1Improve authorization response timeShort response timeDigital data processing detailsUser identity/authority verificationApplication serverWeb service
The invention provides a system that includes: a web server, an application server, and a data server all connected to each other. The system is intended to protect web based applications. A web server receives a request and transmits it as a message to the application server. When the application server receives the request, the application server extracts attributes of this request. The application server uses an authorization engine to determine if each attribute of the request is authorized by accessing the data server to compare each attribute of the request with at least one rule from a rules store. The rules store resides on the data server. If the attributes of the request meet the rules in the rules store, then the request is executed by the application server.
Owner:ACCENTURE GLOBAL SERVICES LTD
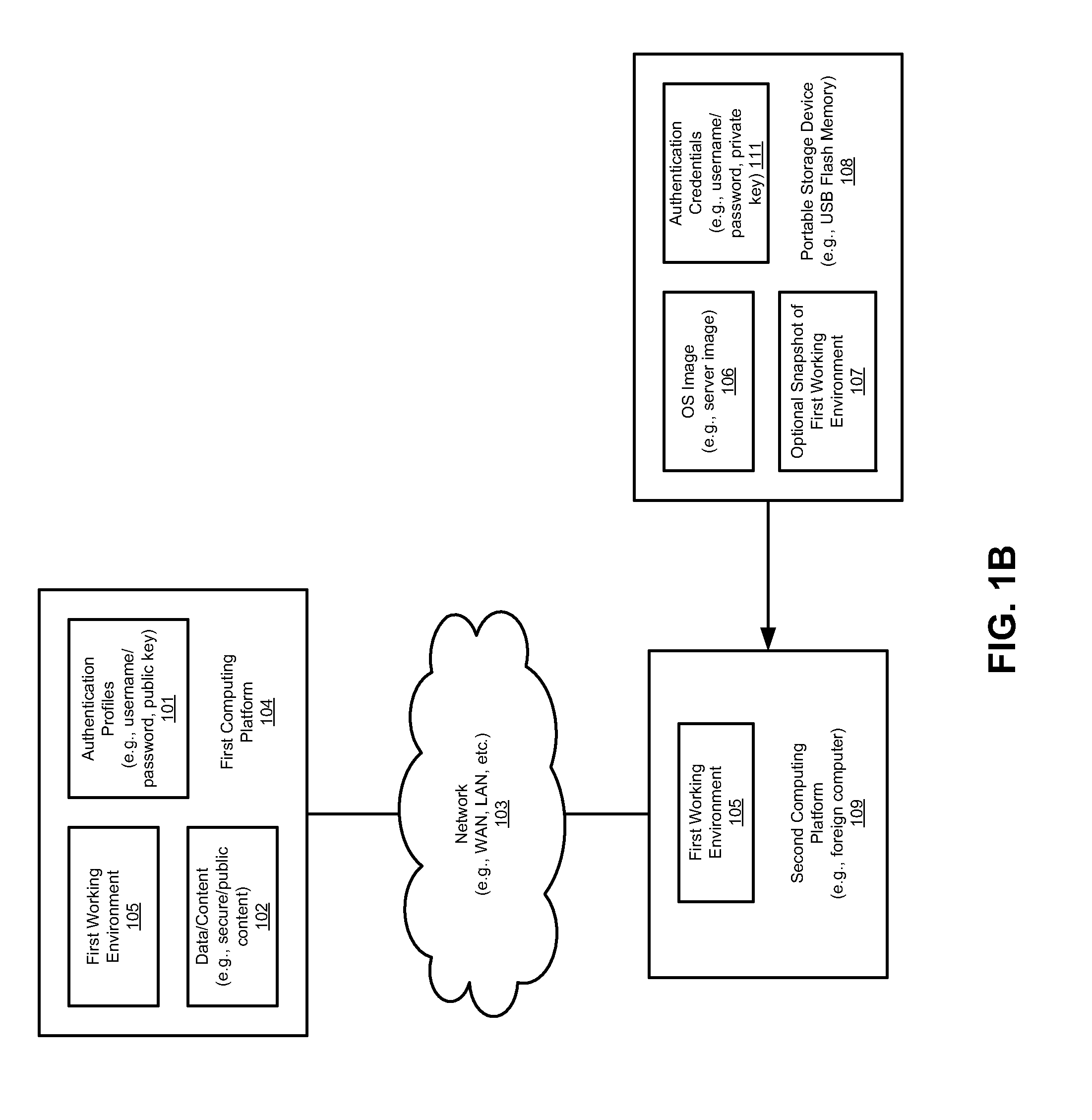
Portable USB device that boots a computer as a server with security measure
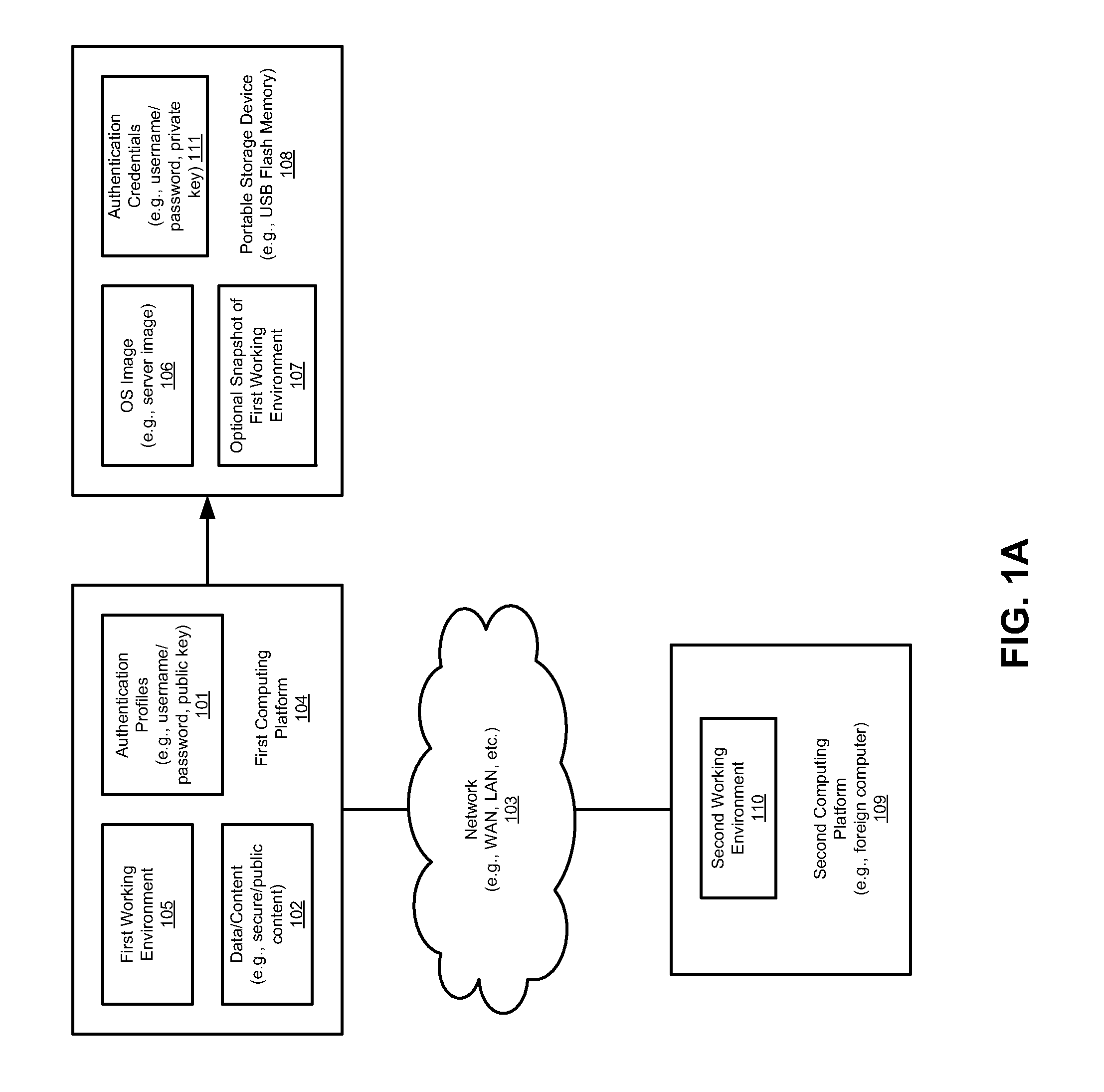
InactiveUS20080082813A1Public key for secure communicationUser identity/authority verificationWorking environmentSecurity Measure
Techniques for booting a host computer from a portable storage device with customized settings with secure measure are described herein. According to one embodiment, in response to detecting a portable storage device inserted into a first host computer, the portable storage device is authenticated using a private key stored within the portable storage device against a public key stored in a second host computer over a network. In response to a successful authentication, data representing a personal working environment associated with a user of the portable storage device is downloaded from the second host computer over the network. After reboot, the first host computer is configured using the obtained settings of the personal working environment, such that the user of the portable storage device can operate the second host computer in view of the personal working environment. Other methods and apparatuses are also described.
Owner:SUPER TALENT ELECTRONICS
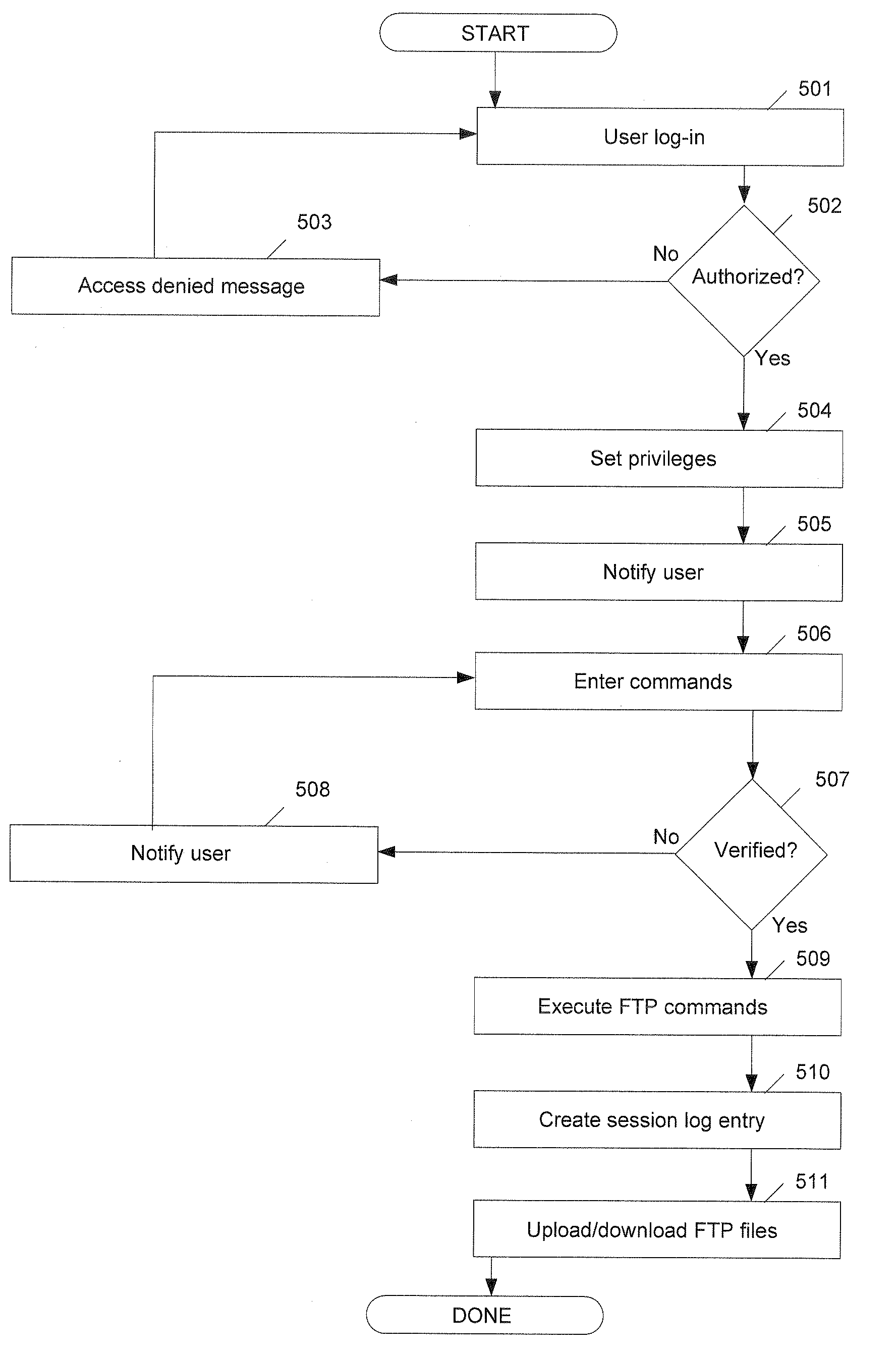
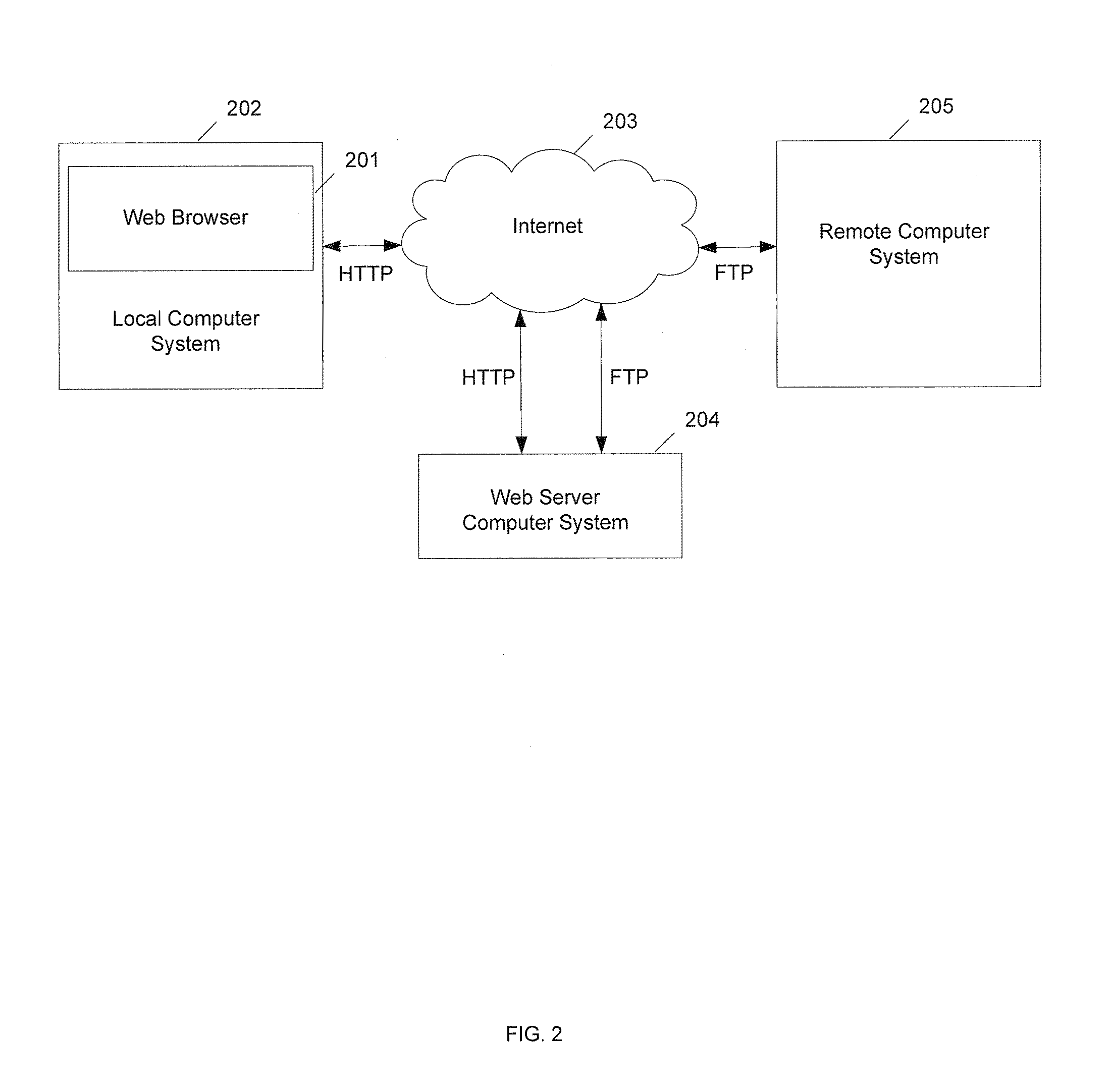
Remote computer system management through an FTP internet connection
InactiveUS7467211B1Multiple digital computer combinationsNetwork connectionsOperational systemSystems management
A method for remote computer systems management through an FTP Internet connection. A user operating on a remote client issues requests to the host server. These requests are first sent to an FTP server which enforces security measures. Upon authentication, the FTP server issues appropriate commands and then passes these commands on to the operation system of the host server through an FTP transfer. The commands perform standard features of the operation system which are not normally allowable by traditional FTP. Responses are sent back through the FTP server to the original requestor's remote client computer. A web-based management application may be used to provide an intuitive, user-friendly graphical user interface to be operated in conjunction with a web browser on the local client computer. The user submits requests through this web control panel to initiate operations to be executed on the remote operating system of the host server. These HTTP web requests are initially transmitted to a web server a which processes the HTTP requests and then submits the requests to the FTP server by establishing an IP connection. Likewise, responses sent back through the FTP server are passed on to the web server and reported to the user through HTML over HTTP to the original user's web browser for display.
Owner:CISCO TECH INC
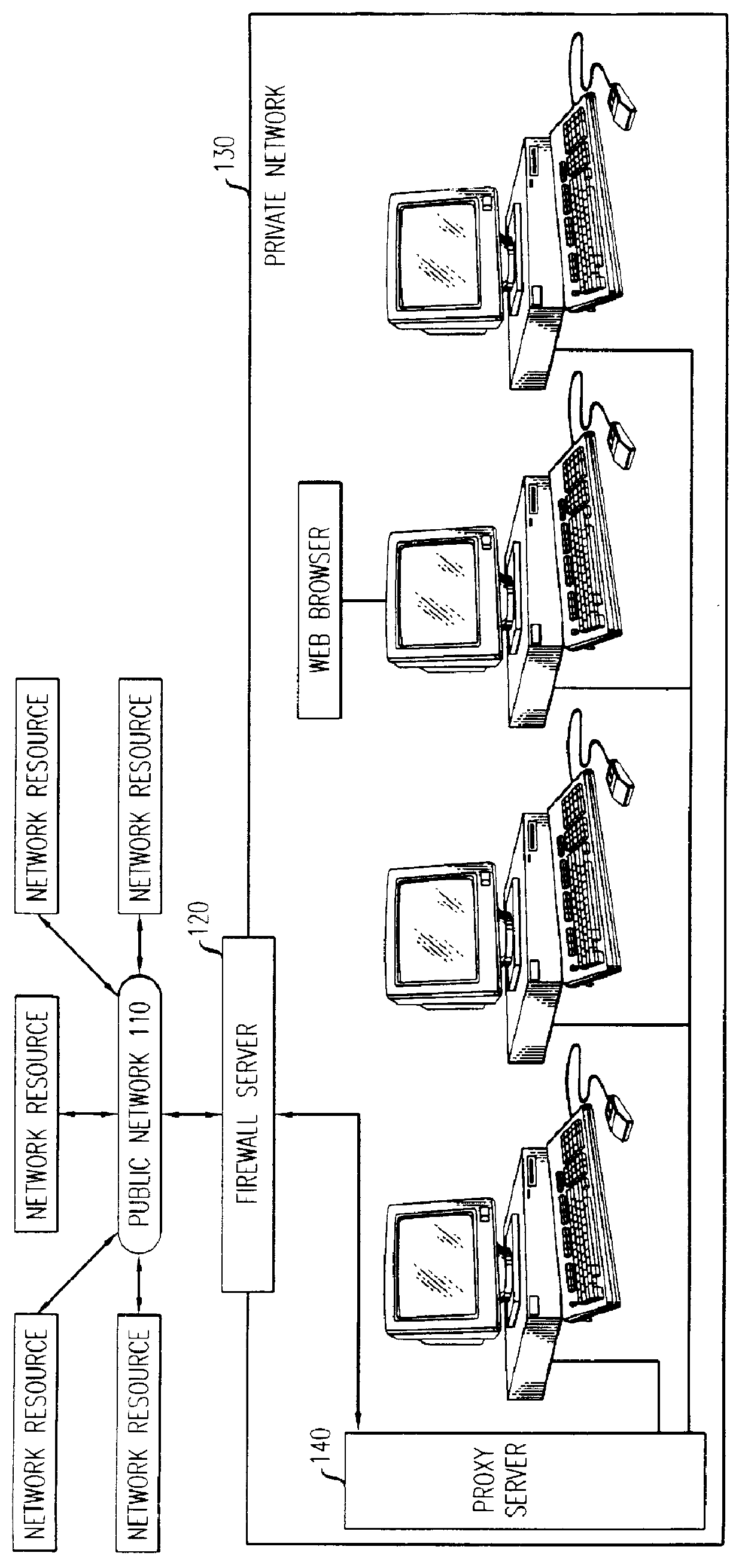
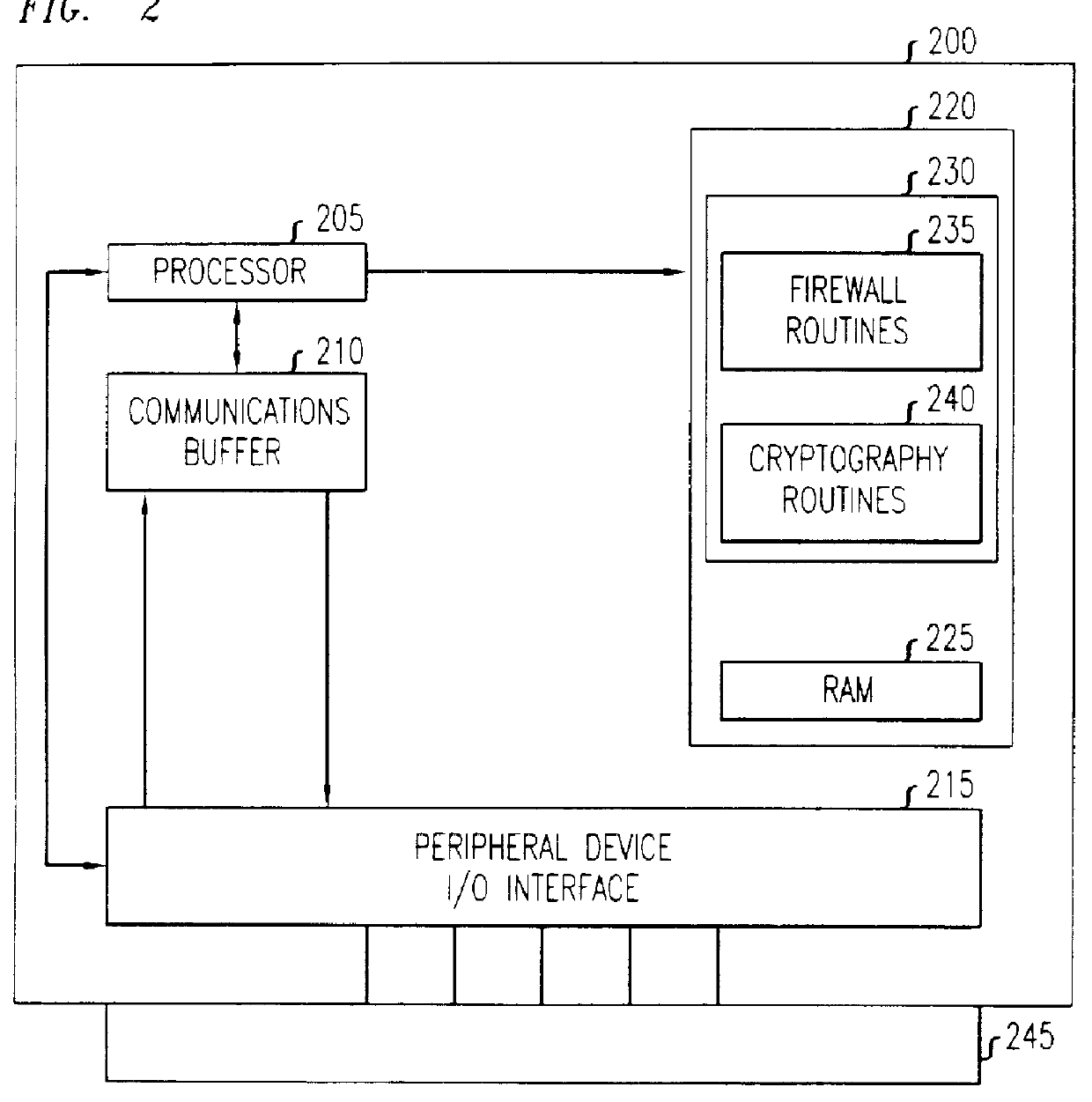
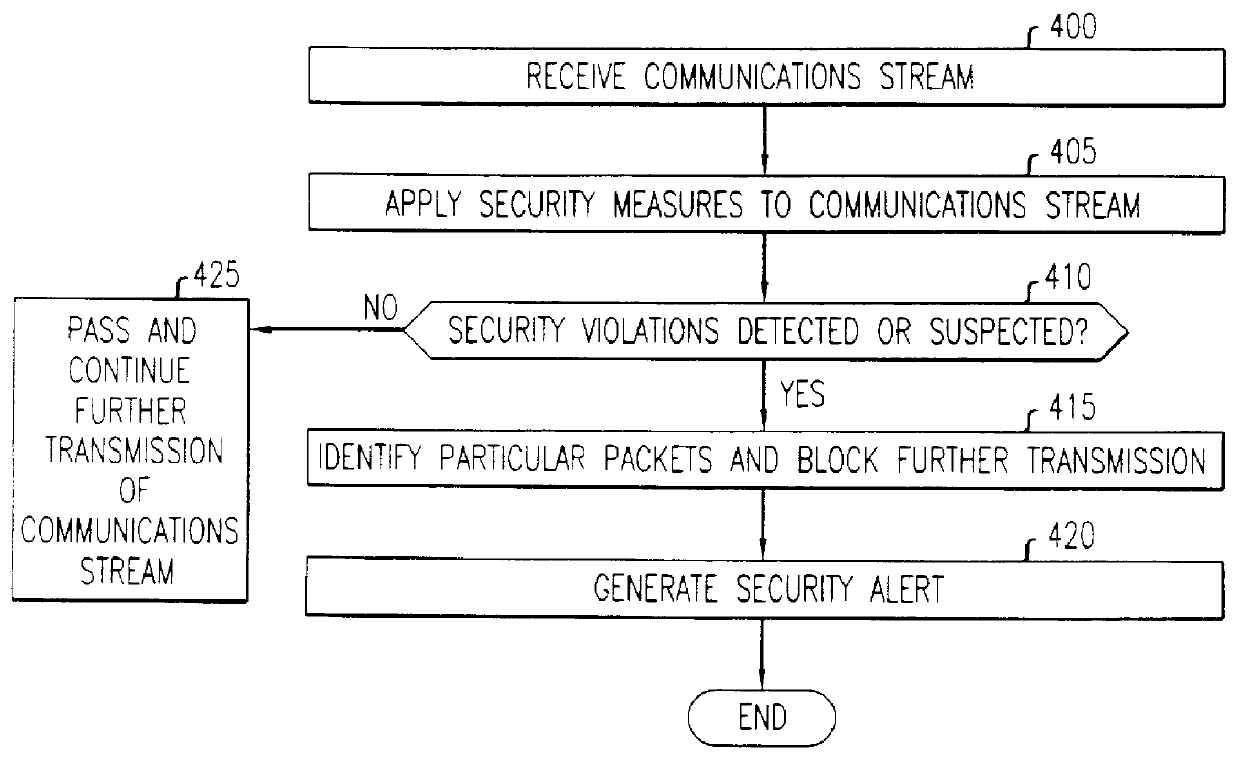
Firewall security method and apparatus
InactiveUSH1944H1Reduce riskUnauthorized memory use protectionMultiple digital computer combinationsSecurity MeasurePersonal computer
A technique for the delivering a client-based firewall. A firewall security device is configured for connecting to individual clients, e.g., personal computers, for providing firewall security measures directly to the client. The firewall security device is configured as a electronic dongle which is attached to an external communications port of the client, e.g., the parallel communications port. The incoming communications stream to the client from, e.g., public networks, is passed through the firewall security device. In this way, the firewall security device applies and delivers a set of standard network security measures thereby protecting the client from security breaches triggered by the communications stream received from the public network. Advantageously, the firewall is delivered directly by the client without intervention, use, or connection to a separate firewall server.
Owner:LUCENT TECH INC
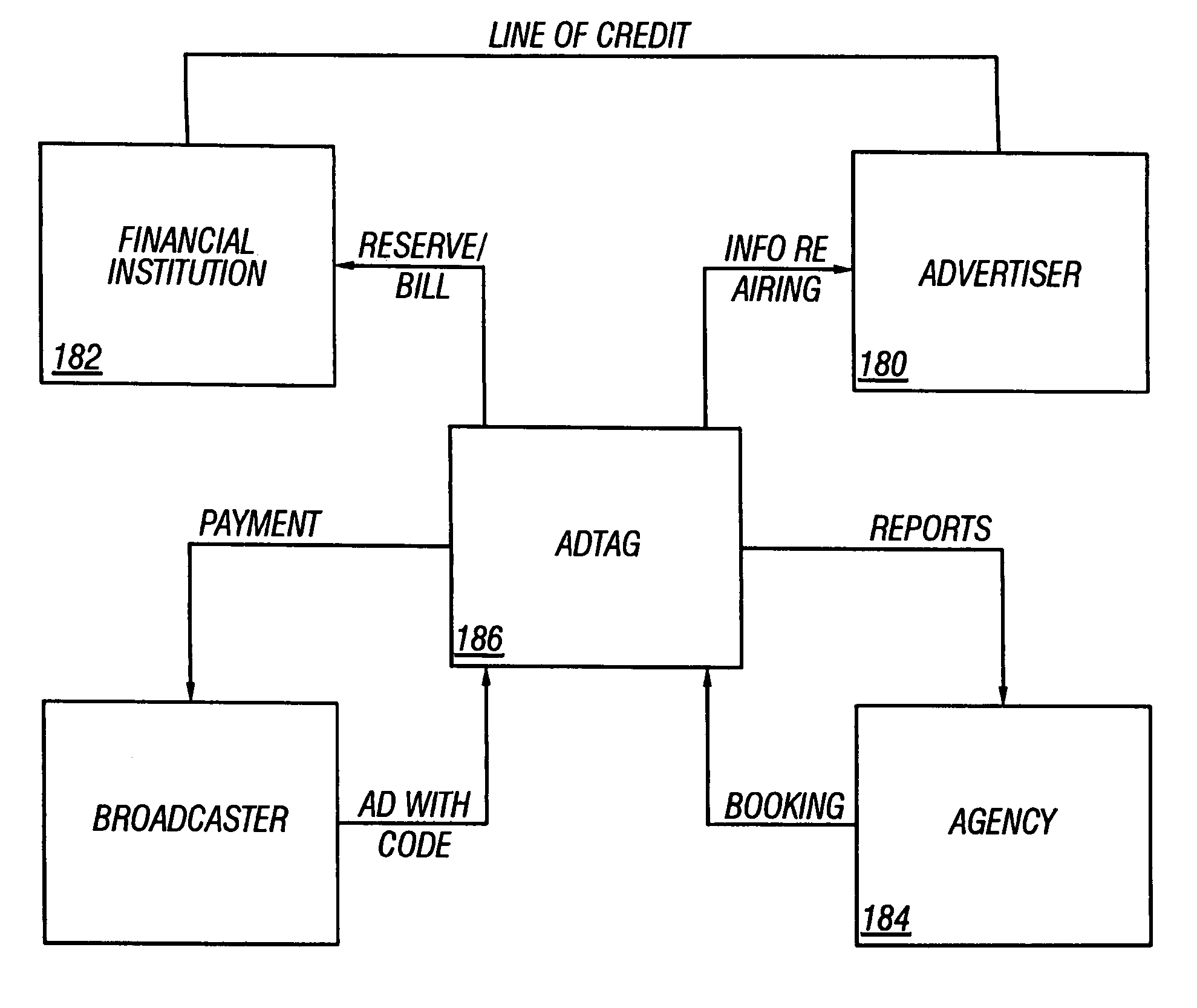
Television advertising automated billing system
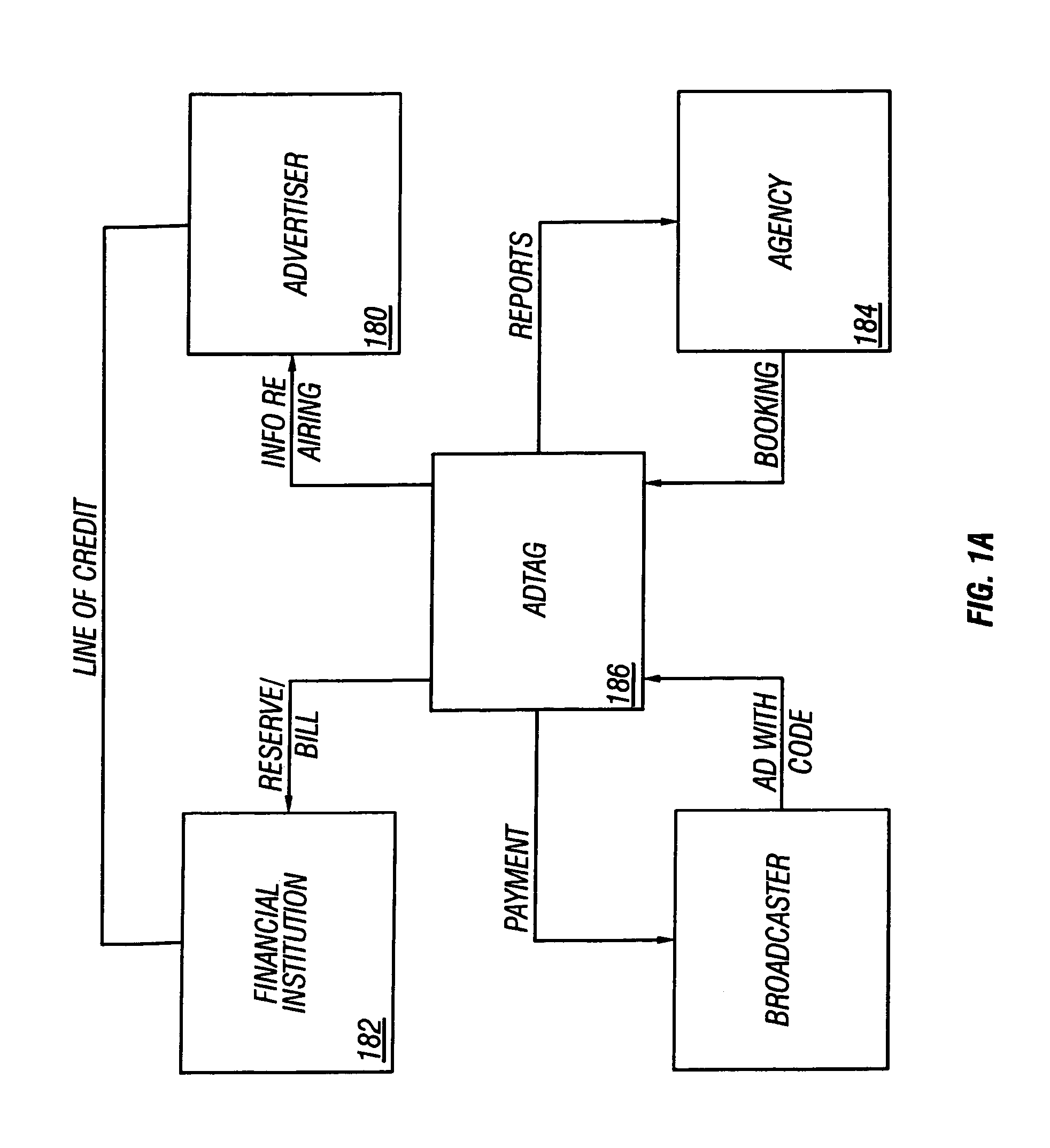
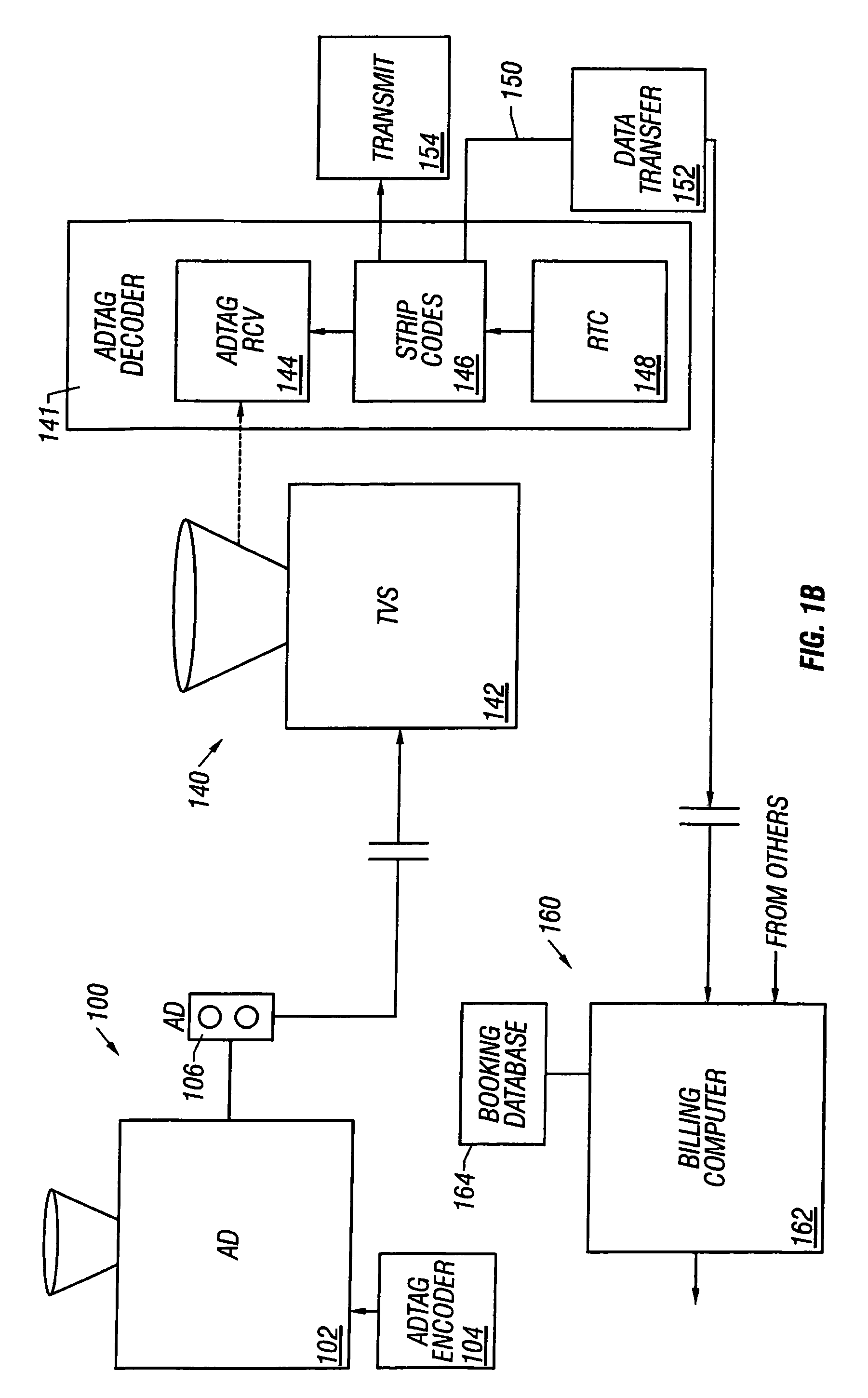
InactiveUS7039930B1Avoid possibilityAccurate accountingAdvertisementsPicture reproducers using cathode ray tubesPaymentClosed captioning
Advertising is marked with a code in a way which makes it difficult to fool the system. The advertising is marked with a code at the time the advertising is produced. Then, when the advertising is broadcast, the code on the advertising is analyzed. Different security measures can be used, including producing the code in the closed captioning so that many different people can see the code, or comparing codes in one part of the signal with a code in another part of the signal. Measures are taken to prevent the code from being used to detect commercials. According to another part of this system, a paradigm for a clearinghouse is disclosed in which the user signs up with the clearinghouse, obtains a line of credit, and the advertiser, the agency, and the ad producer also subscribe to the service. When the ad is actually aired, the payment can be automatically transferred.
Owner:CALIFORNIA INST OF TECH
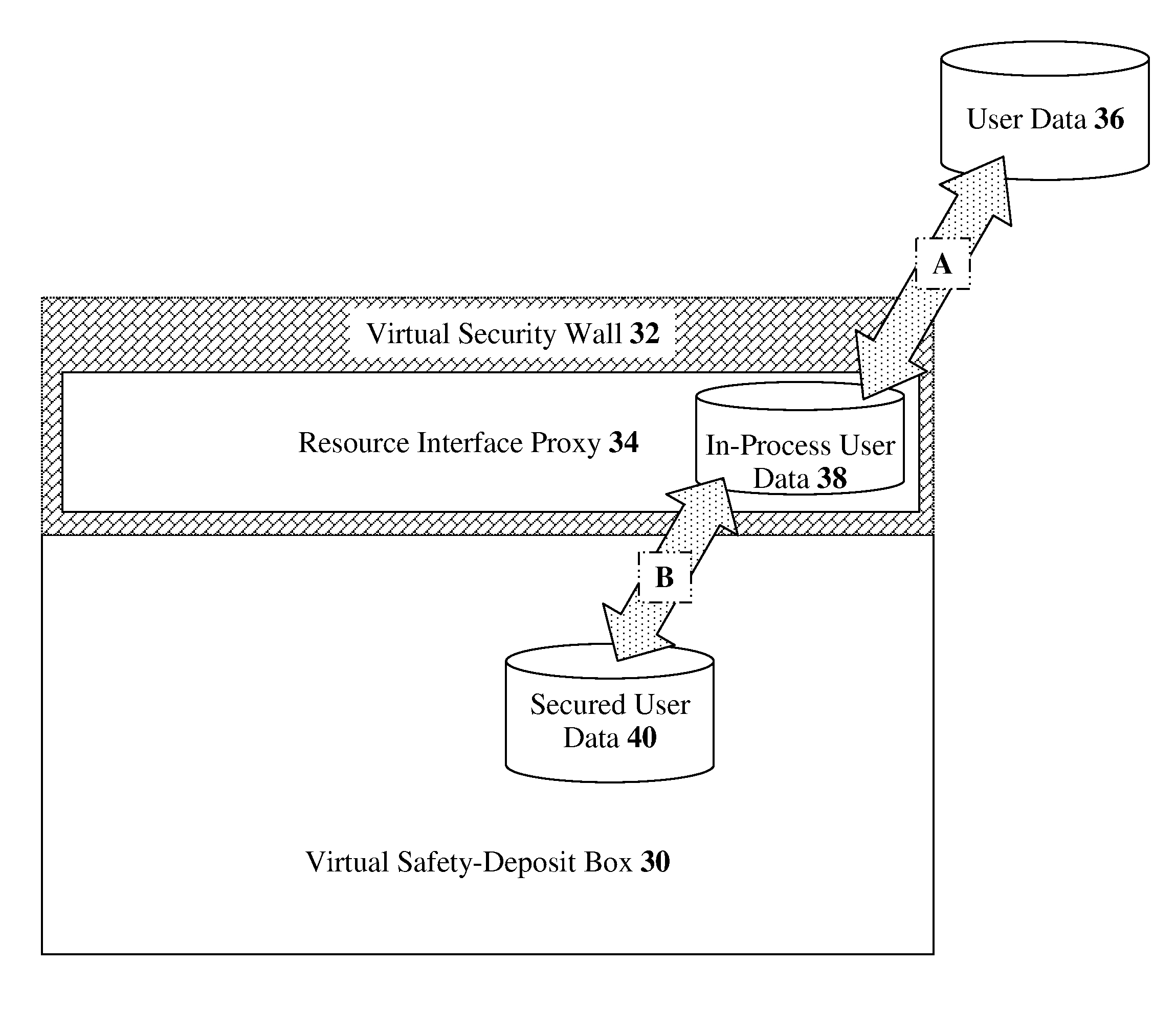
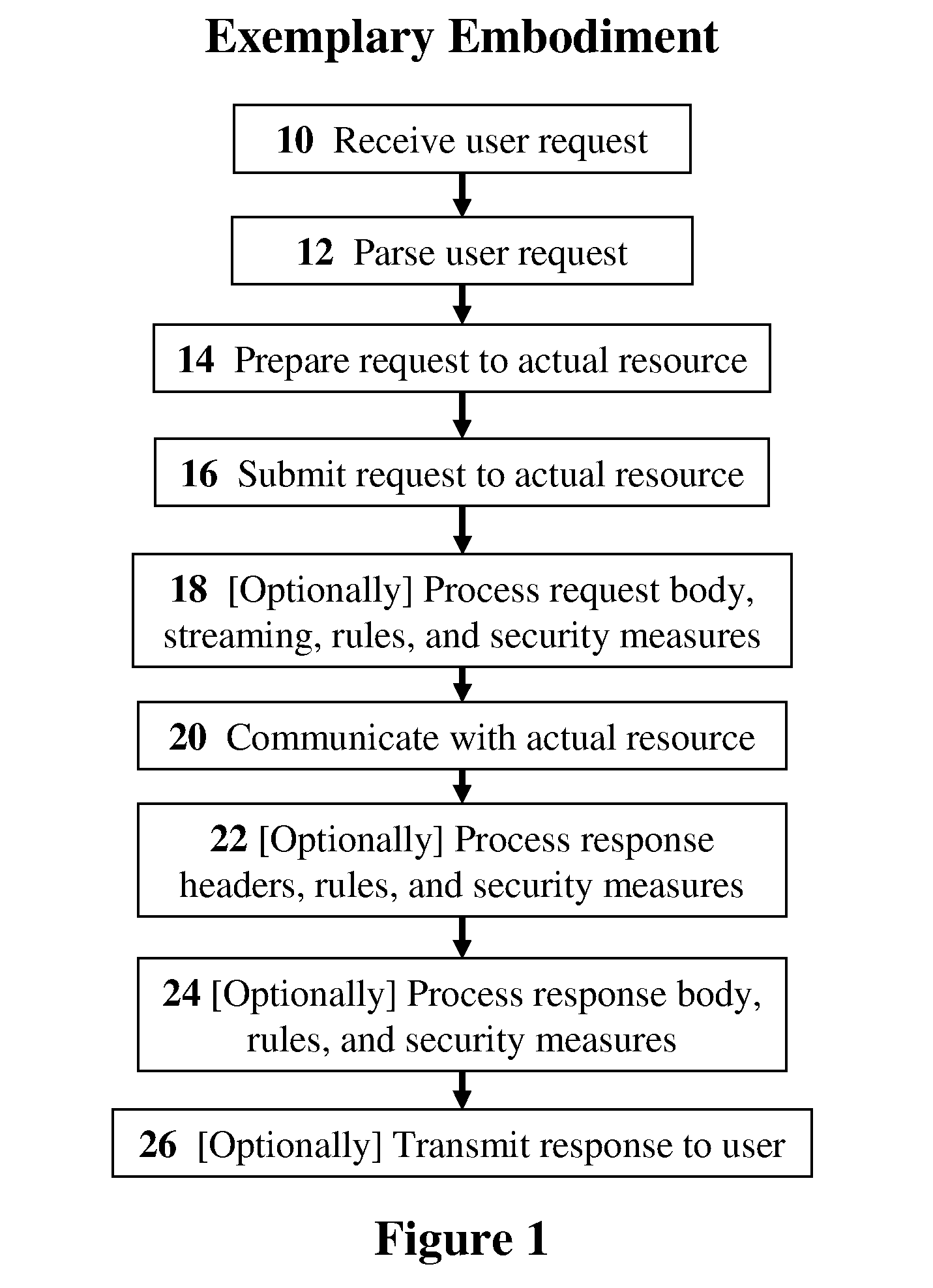
Methods, devices, and media for securely utilizing a non-secured, distributed, virtualized network resource with applications to cloud-computing security and management
InactiveUS20110072489A1Full securityFull controlDigital data protectionMultiple digital computer combinationsVirtualizationData stream
The present invention discloses methods, devices, and media for securely utilizing a non-secured, distributed, virtualized network resource with applications to cloud-computing security and management. Methods including the steps of: receiving, by a deployed security mechanism, a user request over a network; parsing the user request by the deployed security mechanism; preparing, including applying security measures, the user request to transmit to a computing-service resource; and submitting, by the deployed security mechanism, the user request to the computing-service resource. Methods further including the steps of: dividing an original data stream into a set of split data streams; applying a first invertible transformation function to the split data streams, which produces an intermediate set of data streams; and extracting a final set of data streams from the intermediate set by applying a selection rule which produces the final set, thereby transforming the original data stream into individually-unintelligible parts.
Owner:PORTICOR
ATM and POS terminal and method of use thereof
A method of providing money, goods, services or the like to an account-holder based on an account when the daily ATM limit set by a bank has been met, or when a debit or credit card PIN cannot be remembered. The process will enable one to access cash and items of value through either the ATM network or a point-of-sale network to thereby obtain cash or an item of value. If the account-holder has exceeded the ATM network limit, a processor may prompt the account-holder to determine if the account-holder would like to access the account through the point-of-sale network. The money or item of value will be disbursed to the account-holder at a third location, where precautionary security measures may be utilized to ensure that the person receiving the cash is indeed the proper account-holder.
Owner:EVERI PAYMENTS
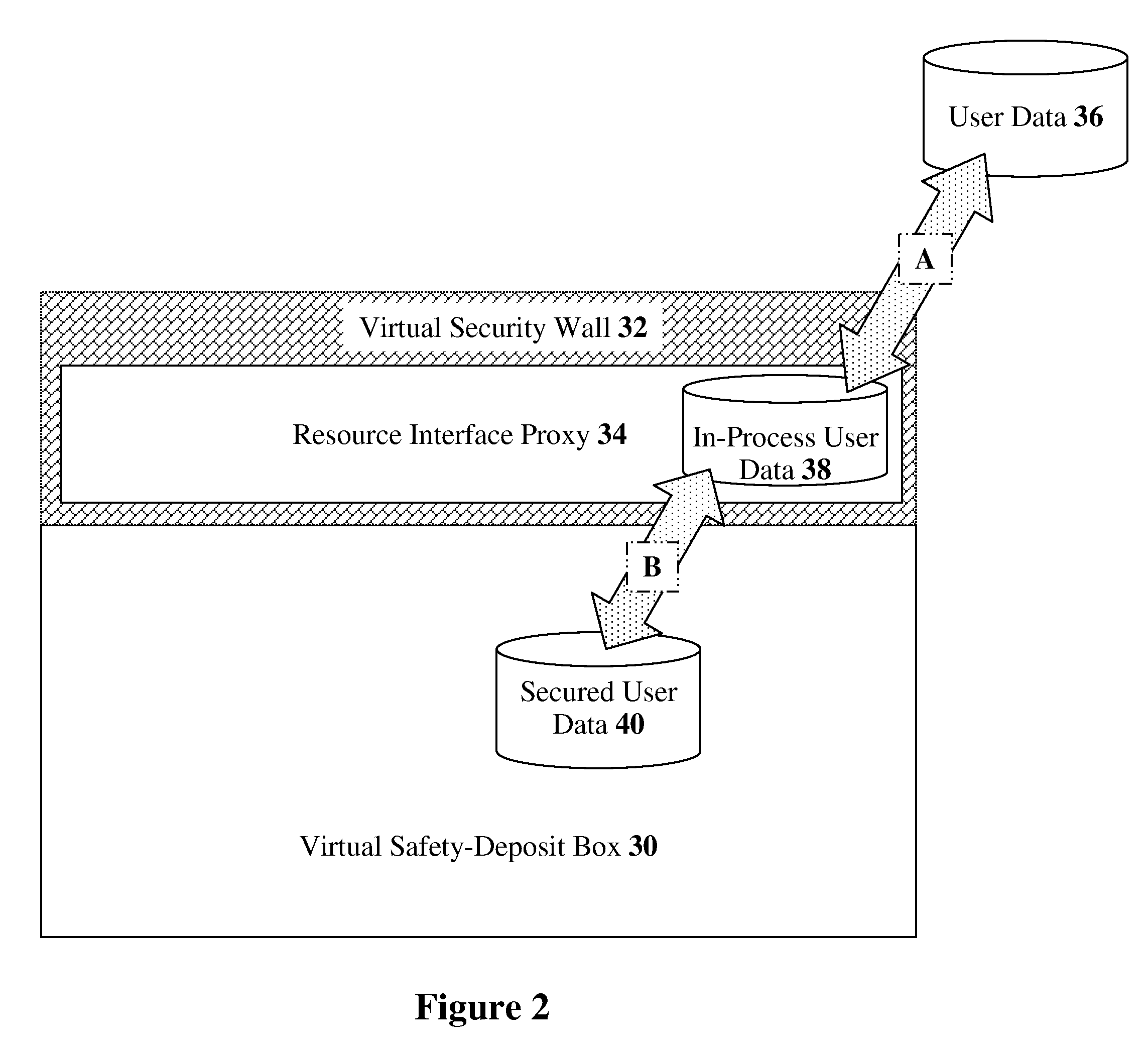
Annotation security to prevent the divulgence of sensitive information
InactiveUS20050038788A1Preventing divulgence of sensitive informationAvoid problemsComputer security arrangementsSpecial data processing applicationsInternet privacySecurity Measure
Methods, systems, and articles of manufacture that may be used to prevent sensitive information from being divulged in an annotation are provided. Upon creation, modification and / or retrieval of an annotation, a set of predefined security rules may be applied to the annotation, in an effort to detect sensitive information contained therein. Upon detecting sensitive information in an annotation, appropriate security measures may be taken, such as notifying a user creating, modifying, or retrieving the annotation (e.g., prompting the user to modify annotation to remove the sensitive information), preventing entry of the annotation, and / or notifying appropriate personnel in charge of security, such as a system administrator.
Owner:IBM CORP
System for collecting, storing, presenting and analyzing immunization data having remote stations in communication with a vaccine and disease database over a network
ActiveUS7908155B2Physical therapies and activitiesDigital data processing detailsData centerMobile station
A system is provided for collecting and storing immunization and disease data. Immunization mobile stations (IMSs) are provided with a software application to facilitate the collection of patient information such as biographical data, previous vaccination data, medical history, medications in use, occupation, administration of recent vaccination, disease symptoms and the like. IMSs synchronize the patient information with information stored in a database maintained at a data center that is accessible to different groups of personnel based on different privileges defined at the data center and security measures. Patients can access electronic patient records created by the IMSs, and stored at the IMSs and / or a local server and eventually at the data center, via telephone or computer (e.g., via web browser). IMSs can capture and store images of vaccination and disease symptom sites on patients. The database allows for vaccination and disease tracking and disease control. The IMSs can be provided with a vaccination recommendation engine to determine if a patient is eligible for a vaccination and electronic patient consent forms, and are programmable to track adverse events and create follow-up reports after a vaccine is administered.
Owner:BECTON DICKINSON & CO
Method and apparatus for preserving data in a system implementing Diffserv and IPsec protocol
InactiveUS7746781B1Reduce the possibilityTransmission systemsFrequency-division multiplex detailsTraffic capacityDifferentiated services
An improved method is described for providing Differentiated Services (Diffserv) traffic to a node in a network that implements a security method that discards duplicate packets received at the node. The method includes the step of identifying at least two service levels to be provided to received traffic and assigning separate sequential sequence numbers and different anti-replay bitmasks to each of the service levels. The anti-replay bitmask indicates the sequence numbers of packets that have been previously received at the node that should be compared against a received packet to determine whether a duplicate packet has been received. Such an arrangement reduces the possibility that traffic having lower priority is dropped as a security measure.
Owner:RPX CLEARINGHOUSE
Conditional utilization of private short-range wireless networks for service provision and mobility
ActiveUS20080008140A1Without depletionWithout securityError preventionFrequency-division multiplex detailsTelecommunicationsService provision
A system for managing the integration of a private short-range wireless network into a service / mobility domain. The private short-range wireless network may be converted into a semi-private short range wireless network by managing access to the network in accordance with rules defined by a home user. These rules allow a home user to define how visitors will be granted access to the semi-private short-range network when the user is at home or away. Restricted access may be enforced when the home user is present, and security measures may force the semi-private short-range wireless network to enter a safe mode when a condition is met.
Owner:NOKIA TECHNOLOGLES OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com