Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
34 results about "Superclass" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A taxonomic rank below subphylum and above class.
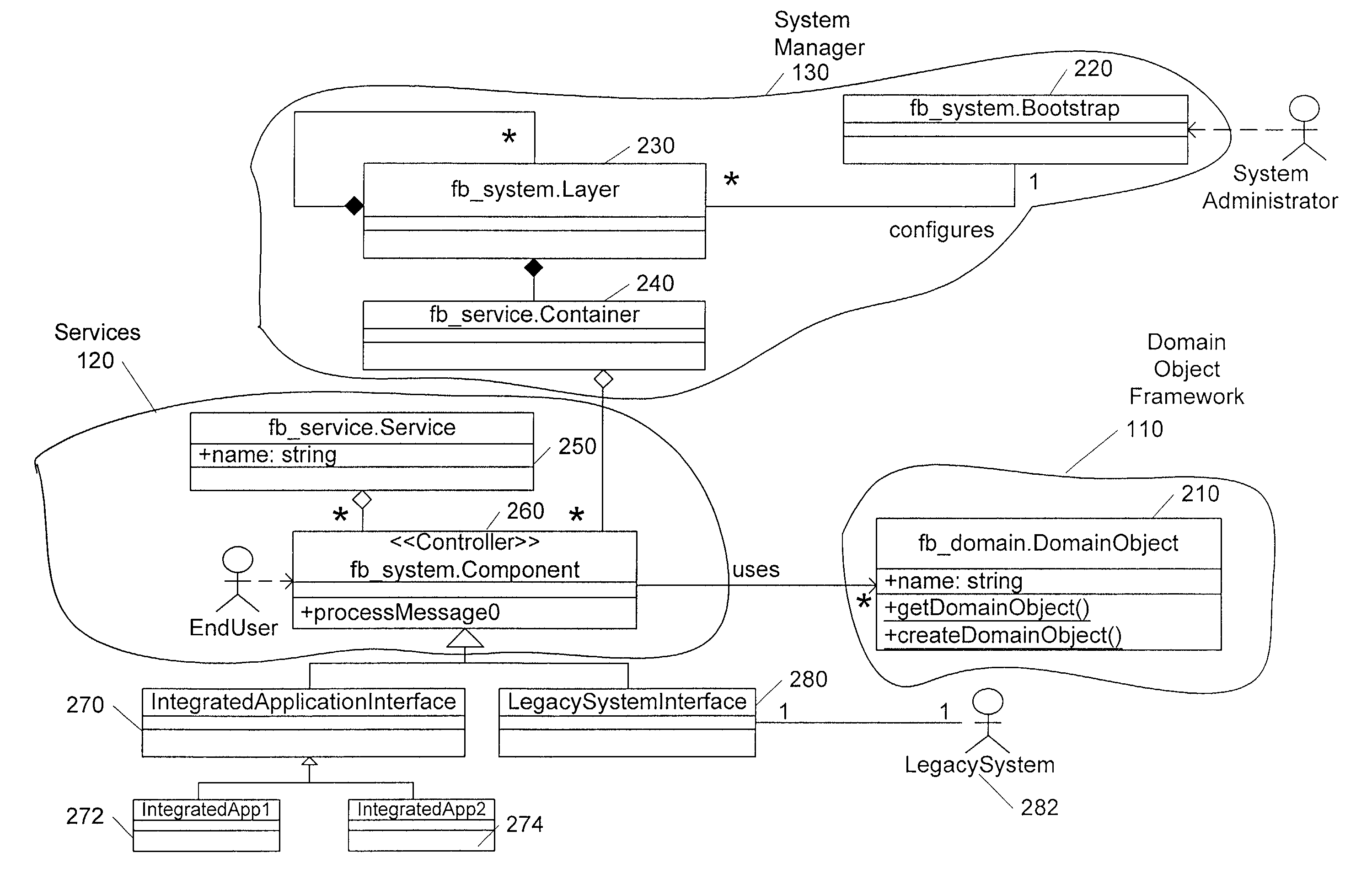
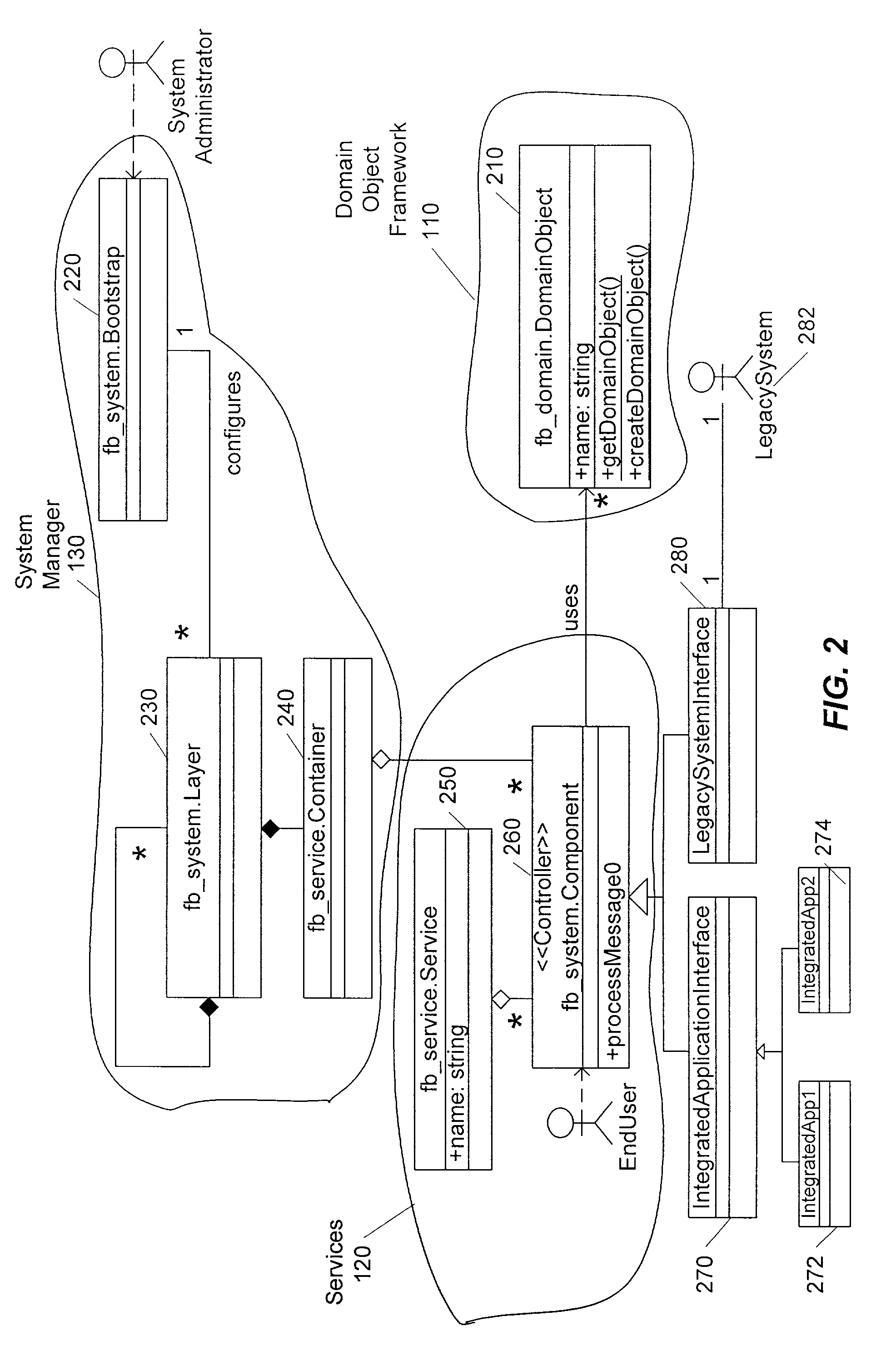
System for integrating data between a plurality of software applications in a factory environment
InactiveUS7047517B1Reduce complexityEasy to modifySpecific program execution arrangementsSpecial data processing applicationsService provisionSystems management
An architecture for integrating data between a plurality of software applications in a factory environment comprises a factory system and a domain application. The factory system comprises a domain object superclass and at least two first-level subclasses of the domain object superclass. An instantiation of one of the first-level subclasses corresponds to a domain object, which represents an item in a factory. The factory system also includes a service, which provides an operation related to the domain object. The service comprises at least one component, where each component is operable to perform the operation related to the domain object. The architecture also includes a domain application, which implements a component of the service of the factory system to perform the operation related to the domain object. The architecture can optionally include a system manager for managing hardware and software in the factory.
Owner:ADVANCED MICRO DEVICES INC
Integrating operating systems and run-time systems
InactiveUS6546546B1Specific access rightsMemory adressing/allocation/relocationOperational systemApplication software
The Virtual Machine is viewed by many as inherently insecure despite all the efforts to improve its security. This invention provides methods, apparatus, and computer products to implement a system that provides operating system style protection for code. Although applicable to many language systems, the invention is described for a system employing the Java language. Hardware protection domains are used to separate Java classes, provide access control on cross domain method invocations, efficient data sharing between protection domains, and memory and CPU resource control. Apart from the performance impact, these security measures are all transparent to the Java programs, even when a subclass is in one domain and its superclass is in another, when they do not violate the policy. To reduce the performance impact, classes are grouped and shared between protection domains and map data lazily as it is being shared. The system has been implemented on top of the Paramecium operating system used as an example of an extensible operating system application.
Owner:IBM CORP
System and method for enabling dynamic modifed class reloading in an application server environment
InactiveUS7882501B1Software engineeringMultiple digital computer combinationsApplication serverComputer science
System and method for enabling dynamic class reloading in an application server environment. A distinction is made between “versionable” and “non-versionable” classes. Versionable classes are classes that should be automatically reloaded when they are modified. The application server(s) may execute a background task that executes periodically to check for modified versionable classes. Users may specify class versionability by specifying a list of explicitly versionable classes, specifying a list of superclasses whose extending classes should be considered to be versionable, and specifying a list of interfaces whose implementing classes should be considered to be versionable. Once the background task discovers a modified versionable class, the background task may cause the class to be reloaded, e.g., by instantiating a new classloader and instructing the new classloader to reload the class. The background task may purge the reloaded class from any caches that the application server maintains.
Owner:ORACLE INT CORP
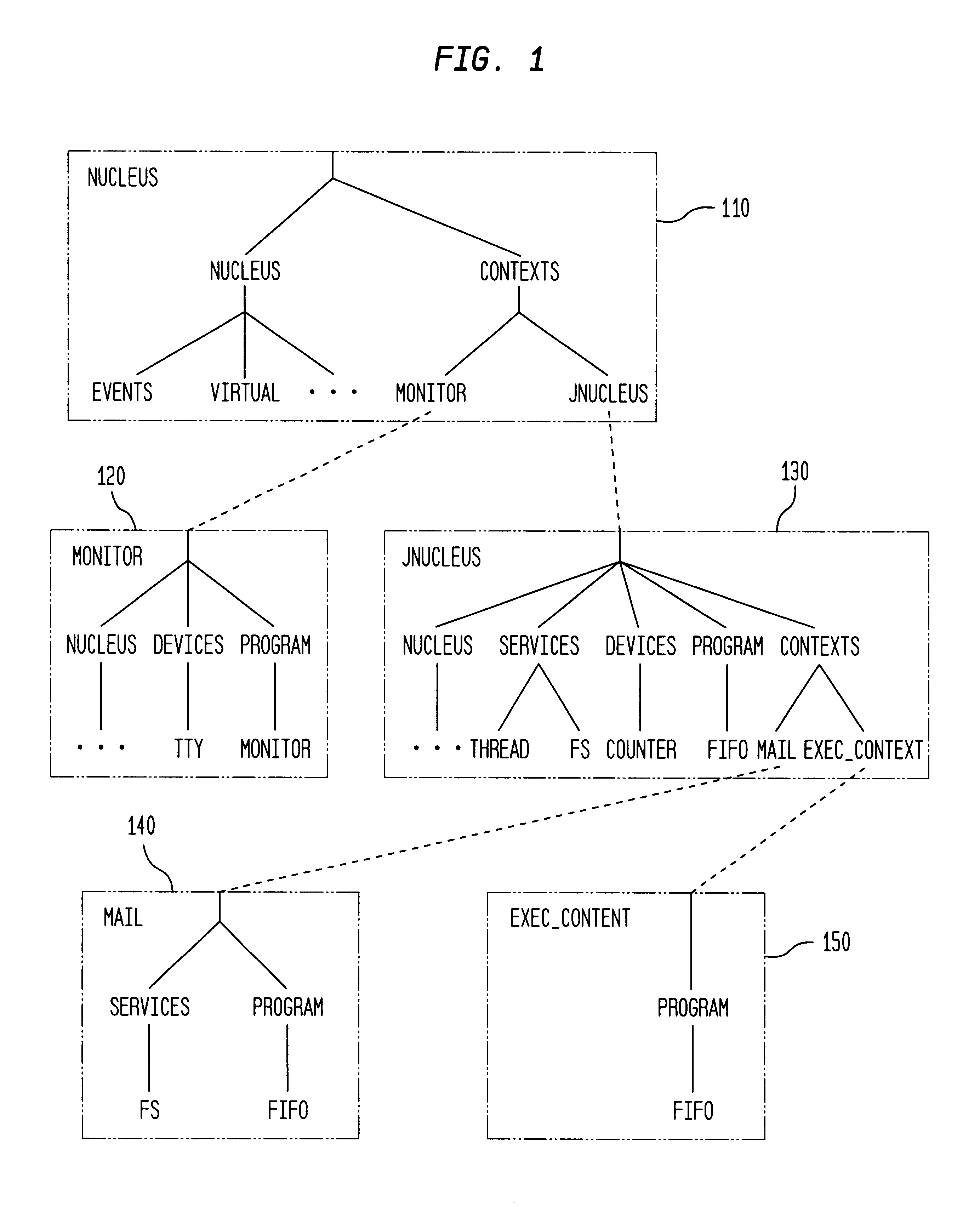
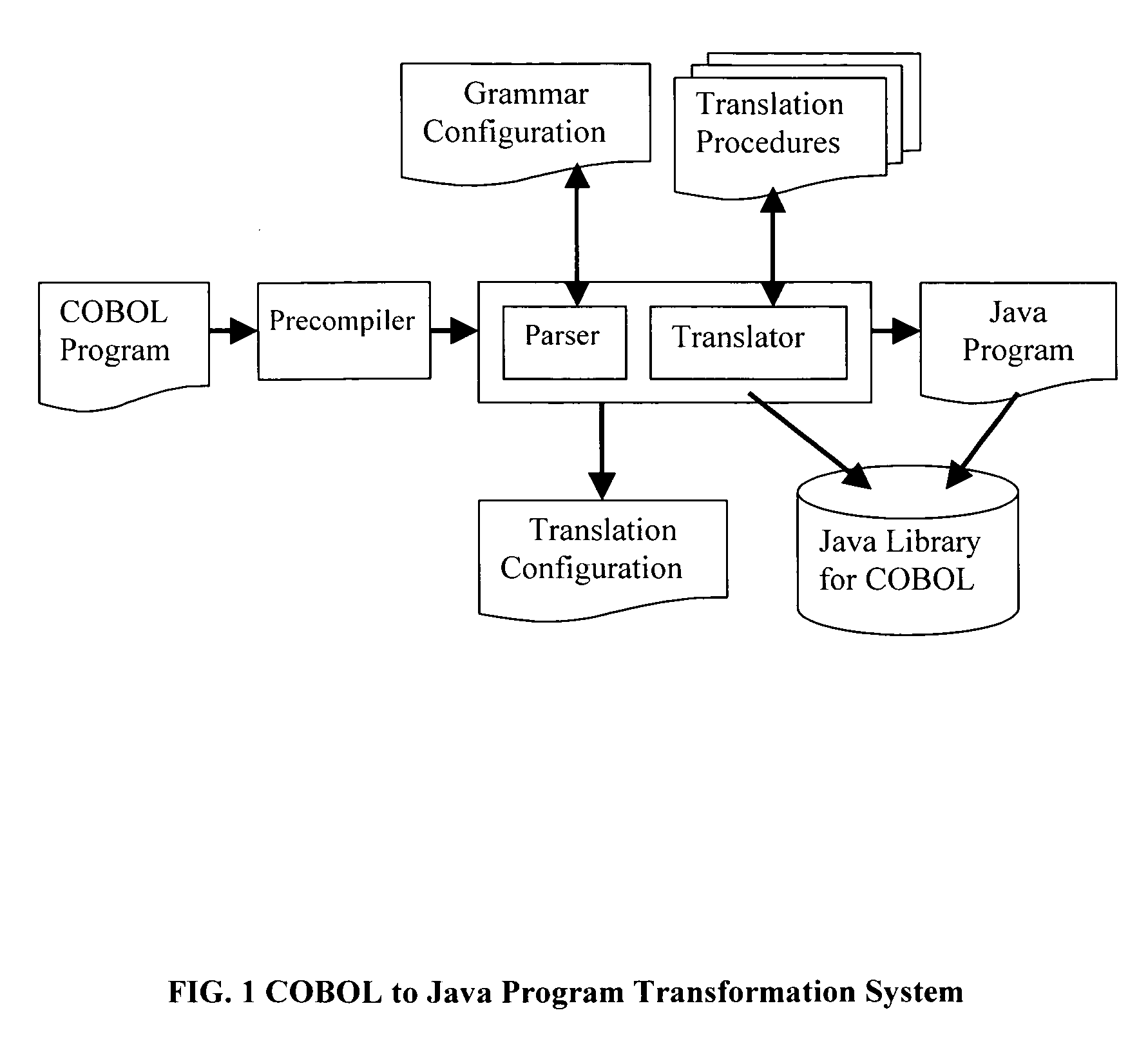
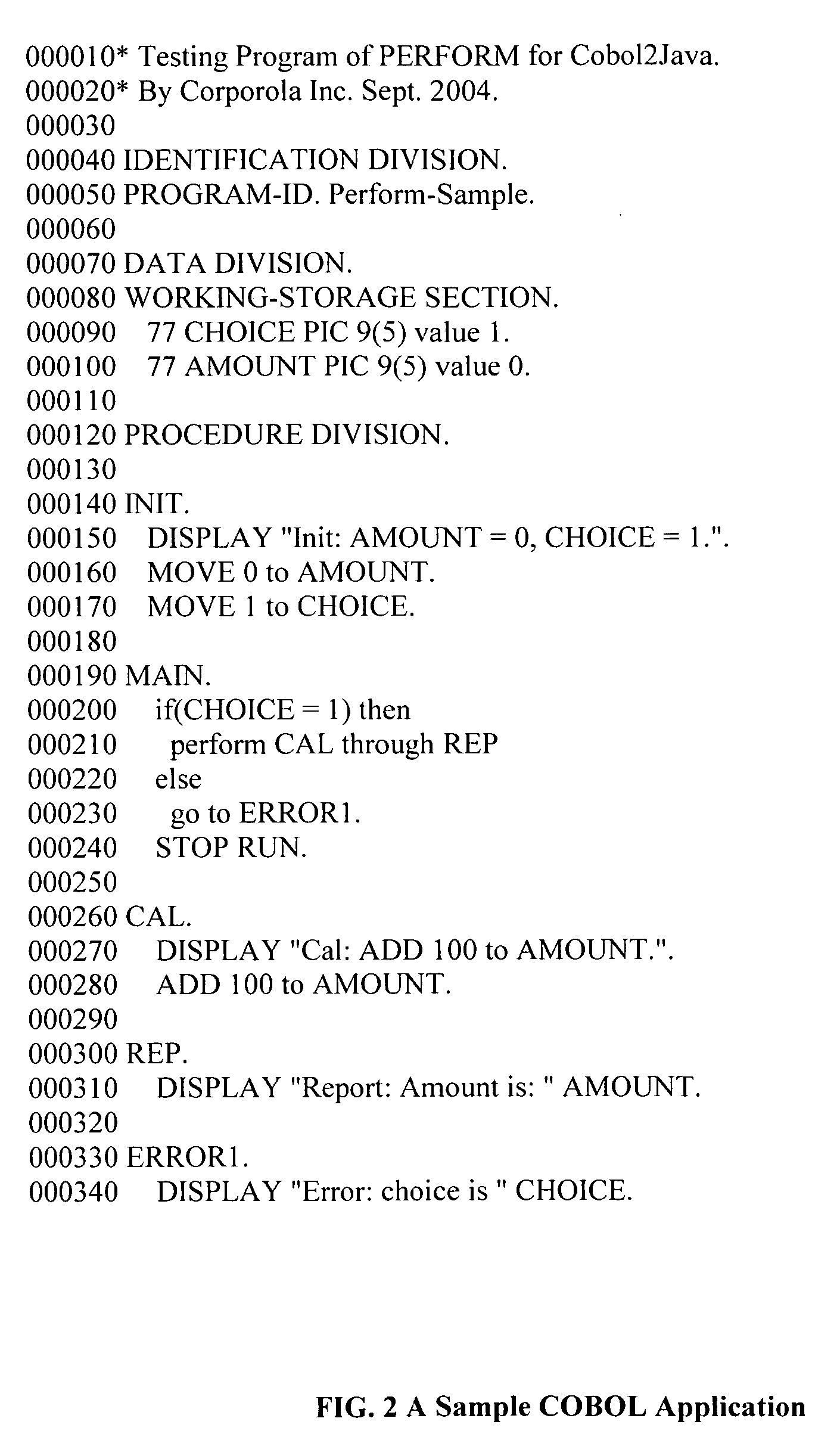
Method for program transformation and apparatus for COBOL to Java program transformation
InactiveUS20060031820A1Maintain maintainabilityImprove maintainabilityProgram controlMemory systemsTime complexityGoto
The present invention relates to a method for program transformation and an apparatus for COBOL to Java program transformation. The method consists of: (1) a new approach for statement-to-statement program transformation, facilitated by a predefined target language library, which keeps original comments, program control flow, functionality, and time complexity; (2) a new approach for goto statement elimination, which uses existing exception handling mechanism in target language and its implementation is hidden in a super class in a library; (3) a new extended BNF to distinguish different occurrences of the same term in a BNF production; (4) a new approach for embedded statement as a special marker statement and a comment, (5) in the description of the above, a program transformation specification language is defined to describe relationship between comments in two languages. (6) an apparatus, as the preferred embodiment of the method, is a COBOL to Java program transformation system Cobol2Java; a sample COBOL application and its Cobol2Java translation are given.
Owner:LI AIZHONG
Ontology-integration-position specifying apparatus, ontology-integration supporting method, and computer program product
InactiveUS7805451B2Digital data information retrievalDigital data processing detailsShortest distanceAssociation Class
Attribute mapping information is stored, in which a superclass of an associated class in an integration-source ontology already associated with an integration-destination ontology, an attribute of the superclass, and an integration destination attribute of a class in the integration destination are associated with each other. An integration target class in the integration source is specified to acquire an attribute of a superclass of the integration target class. An associated class having the shortest distance from the integration target class is specified, to specify an integration-destination-associated class associated with the specified associated class. An inheritance relation is followed from the integration-destination-associated class to specify a class having the integration destination attribute corresponding to the attribute in the mapping information as a position where the class associated with the integration target class is present.
Owner:KK TOSHIBA
System and method for dynamically processing declarative language instance data
InactiveUS7065742B1Software engineeringSpecial data processing applicationsSpatial managementObject code
A method and system for dynamically processing instance data are provided. A namespace manager obtains declarative language instance data including tags, attributes and values for generating user interface objects. The instance data refers to one or more modules registered with a namespace manager in which the modules include meta-data defining one or more class definitions in a class hierarchy. Each class definition defines one or more properties of the class and references to a superclass / subclass(es) for the class. Thereafter, the namespace manager validates the instance data according to the class hierarchy and generates object code for instantiating an object hierarchy having classes, properties and values corresponding to the instance data.
Owner:MICROSOFT TECH LICENSING LLC
System and Method for Automatic Invocation of Constructor Code for Superclasses
ActiveUS20130339926A1Programming languages/paradigmsSpecific program execution arrangementsSuperclassInheritance hierarchy
A system and method for automatic invocation of object initializers, or constructors, for superclasses featuring the ability to modify the contents of classes of existing applications at runtime, which includes adding new superclasses to the class inheritance hierarchy of the existing classes. The system redefines the content of classes of the existing classes and the new superclasses during the loading of the classes to additionally include code statements that invoke constructors of the redefined classes and the new superclasses. The invocation of the constructors at runtime performs the initialization of the objects.
Owner:ZEROTURNAROUND
Flexible object persistence framework using data cursor objects loaded from superclasses
InactiveUS6125364AFlexible approachData processing applicationsDigital data processing detailsObject storageData store
This system involves an object persistence framework for an object-oriented program which provides a persistent class, data storage class and a data cursor class, that permits specialized implementations of object storage and retrieval with heterogeneous permanent storage systems.
Owner:IBM CORP
Method and apparatus for rewriting bytecodes to minimize runtime checks
InactiveUS6978448B1Reduce in quantitySoftware engineeringSpecific program execution arrangementsComputerized systemSuperclass
Methods and apparatus for reducing the number of runtime checks performed during the execution of a virtual machine. According to one aspect of the present invention, a computer system includes a preloader, a compiler, and a virtual machine. The preloader is arranged to determine whether a bytecode makes an active reference to a class which requires an execution of a static initializer, and is also arranged to determine if the class has a superclass which requires the execution of the static initializer. The compiler is arranged to accept a source file generated by the preloader as input and to produce an object file, and the virtual machine is arranged to execute the object file.
Owner:ORACLE INT CORP
System to include multiple instances of data on a web page
Multiple instances of the same fields of data can be displayed or presented with user interface components on a web page. The web page may be presented on any number of processing devices, such as a computer, rich client, telephone, PDA, etc. A superclass manages an index corresponding to the number of instances and calls a subclass to obtain the index and then get and set the values of the data pertaining to the index. The user interface components may be JavaServer Faces components.
Owner:IBM CORP
Ontology-integration-position specifying apparatus, ontology-integration supporting method, and computer program product
InactiveUS20080082574A1Digital data information retrievalDigital data processing detailsShortest distanceAssociation Class
Attribute mapping information is stored, in which a superclass of an associated class in an integration-source ontology already associated with an integration-destination ontology, an attribute of the superclass, and an integration destination attribute of a class in the integration destination are associated with each other. An integration target class in the integration source is specified to acquire an attribute of a superclass of the integration target class. An associated class having the shortest distance from the integration target class is specified, to specify an integration-destination-associated class associated with the specified associated class. An inheritance relation is followed from the integration-destination-associated class to specify a class having the integration destination attribute corresponding to the attribute in the mapping information as a position where the class associated with the integration target class is present.
Owner:KK TOSHIBA
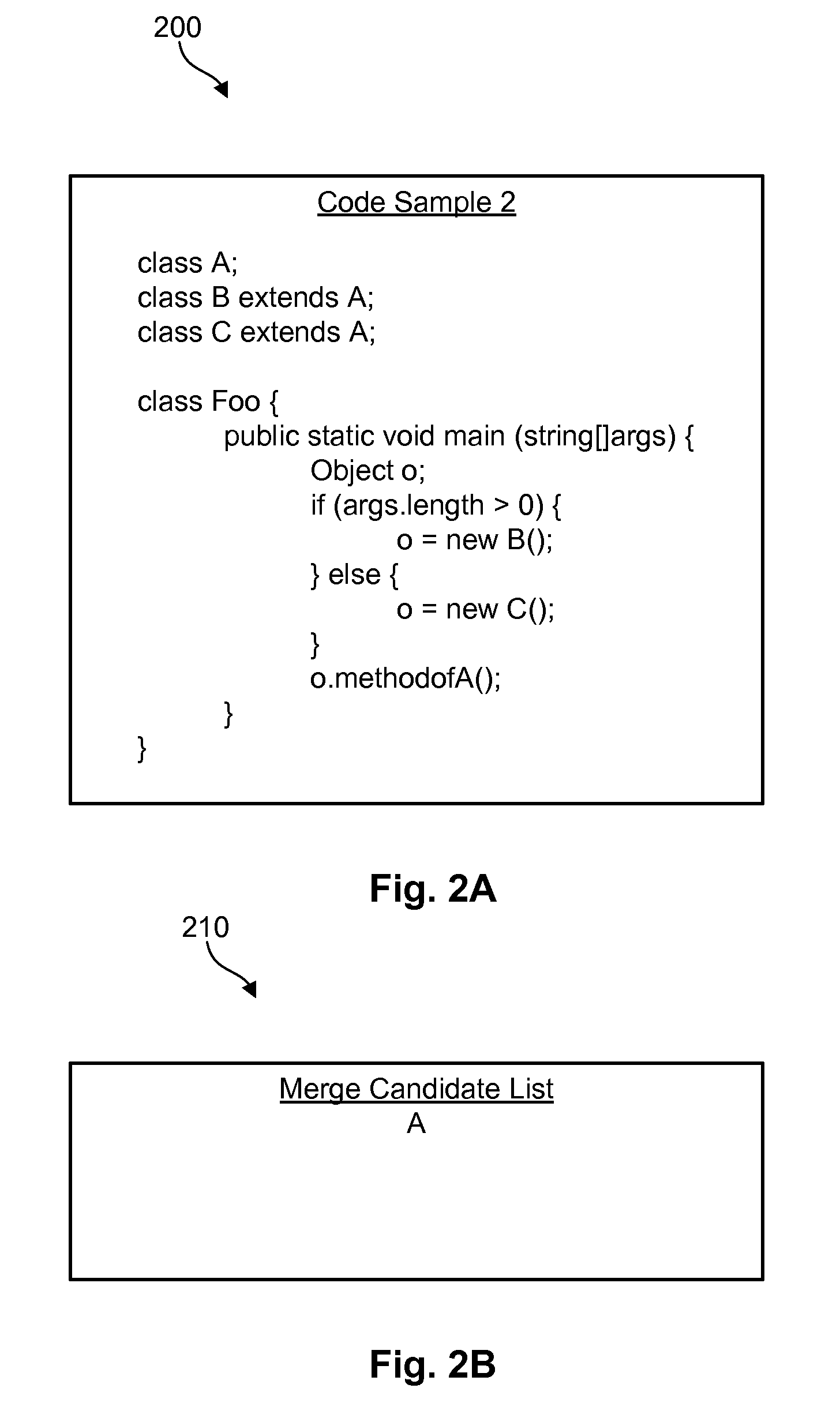
Type merging technique to reduce class loading during JAVA verfication
An apparatus, process, and computer program product to merge types in an object-oriented program is disclosed herein. In one embodiment, a process may include analyzing a method within an object-oriented program to identify merge candidates. These merge candidates may then be recorded in a merge candidate list. The process may further include identifying at least two code paths in the method that merge into a single code path and that operate on different types. The types in these code paths may then be merged to a nearest common superclass listed in the merge candidate list. In selected embodiments, the types may be merged to the java.lang.Object class in the event the merge candidate list is empty.
Owner:IBM CORP
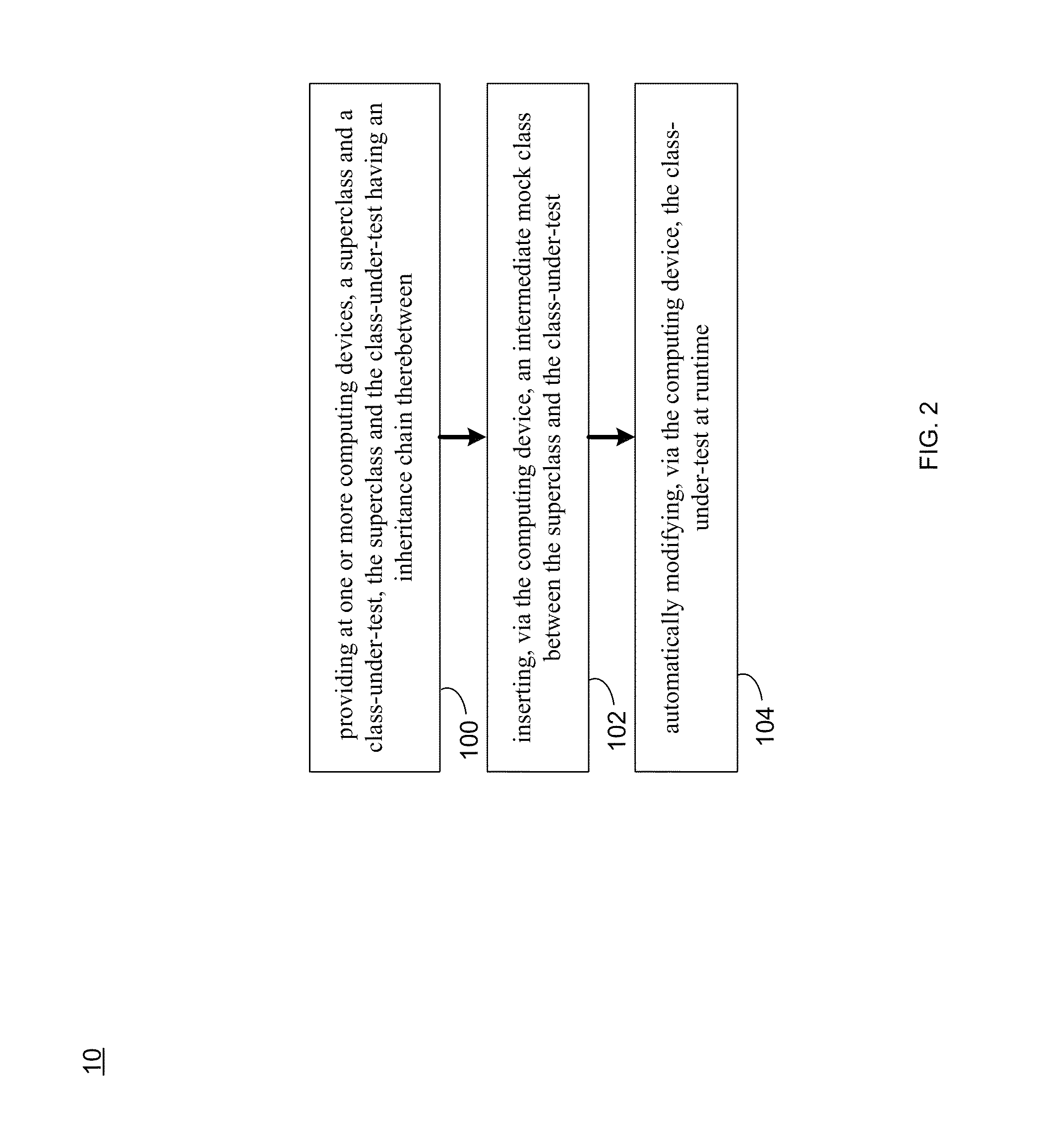
Automated testing process
ActiveUS20130007713A1Error detection/correctionSoftware engineeringAutomatic testingComputer science
A method, computer program product, and system for automating a test environment is provided. The method may include providing, at one or more computing devices, a superclass and a class-under-test, the superclass and the class-under-test having an inheritance chain therebetween. The method may further include inserting, via the computing device, an intermediate mock class between the superclass and the class-under-test. The method may also include automatically modifying, via the computing device, the class-under-test at runtime.
Owner:IBM CORP
Automated testing process
A method, computer program product, and system for automating a test environment is provided. The method may include providing, at one or more computing devices, a superclass and a class-under-test, the superclass and the class-under-test having an inheritance chain therebetween. The method may further include inserting, via the computing device, an intermediate mock class between the superclass and the class-under-test. The method may also include automatically modifying, via the computing device, the class-under-test at runtime.
Owner:IBM CORP
Client and method for database
ActiveUS20070276847A1Digital data information retrievalDigital data processing detailsDatabase serverClient-side
A client accepts 20 an input query, rewrites 22 the query and forwards 24 the query to a database server, which returns 26 results which are then rewritten 28. The database includes classes arranged hierarchically as superclasses and subclasses, and / or properties also arranged hierarchically as superproperties and subproperties. In embodiments, the query is rewritten 22 to replace each instance of each class and each property in the input query with the transitive closure of the respective class or property. The client allows inferencing whether or not this is supported by the database server.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
System and method for defining and using subclasses declaratively within markup
InactiveUS7120618B2Easy to learnDigital computer detailsNatural language data processingXMLHuman language
Described is a system, method, and data structure that enables an executable assembly associated with a subclass to be generated from a subclass definition within a markup document. In accordance with the invention, the subclass definition is written based on a schema. The schema may be XML-based. The schema includes a subclass tag for defining a name for the subclass. The name is associated with a type for an object that is instantiated when the executable assembly executes. The schema further includes one or more hints, such as for specifying a programming language to compile the subclass definition, for specifying a superclass from which the subclass derives, for specifying actions to perform when the object becomes instantiated, for creating an event definition and event handler for the subclass, and for specifying a property that becomes a member within the object when the object is instantiated.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for supporting object oriented programming class replacement
A method and system for accessing a home object in an object oriented programming (OOP) environment using a locator object capable of locating a home object for a class or a subclass. The locator object supports inheritance for itself, and is capable of locating a home for either an OOP superclass or subclass. By providing a mechanism for locating the home for either the superclass or subclass, preferably in a static manner, client code may be reused with subclasses without having to change code.
Owner:IBM CORP
Method and apparatus for finding terminal classes in a collection of programming language classes
ActiveUS7543272B1Easy to findDecompilation/disassemblyReverse engineeringSystems analysisComputer science
One embodiment of the present invention provides a system that facilitates finding terminal classes in a collection of programming language classes, wherein a terminal class is a class that is not extended by any other class. The system operates by receiving a collection of classes. The system then adds the classes to a map of the collection of classes, wherein keys to each class in the map include each class' superclass and the interfaces each class directly implements. Next, the system analyzes a given class in the map of the collection of classes to determine if the given class extends any other class in the collection of classes. If so, the system removes this extended class from the collection of classes. Finally, the system repeats the steps of analyzing classes and removing extended classes until all remaining classes in the collection of classes are terminal classes.
Owner:ORACLE INT CORP
Processing method for reverse inheritance modeling of data acquisition and processing system
InactiveCN103873297ARealize the reverse modeling processImprove access efficiencyData switching networksModel methodTelecommunications network
The invention relates to the technical field of modeling methods of data acquisition and processing systems for telecommunication network operation maintenance, in particular to a processing method for reverse inheritance modeling of a data acquisition and processing system. In the modeling process of the data acquisition and processing system, before a superclass model is established, a subclass model is firstly established. The subclass model is an abstract of measuring object instances with the same class characteristic of the data acquisition and processing system. When the superclass model is established, the superclass model reversely inherits the measuring object instances of the subclass model which is established before. By adopting the method provided by the invention, the abstraction and modeling processes of the superclass model are improved, the operation by users is facilitated, the access efficiency of measuring objects is improved, the complexity during modeling by the users is reduced, the abstraction and the generality of the superclass model are guaranteed to be high, the query and the representation of business data based on the superclass model are facilitated and the accuracy of the data is guaranteed.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
Automated testing process
InactiveUS20130007714A1Error detection/correctionSoftware engineeringAutomatic testingComputer science
A method, computer program product, and system for automating a test environment is provided. The method may include providing, at one or more computing devices, a superclass and a class-under-test, the superclass and the class-under-test having an inheritance chain therebetween. The method may further include inserting, via the computing device, an intermediate mock class between the superclass and the class-under-test. The method may also include automatically modifying, via the computing device, the class-under-test at runtime.
Owner:IBM CORP
Protecting object identity in a language with built-in synchronization objects
ActiveUS7458061B2Improve identityObject oriented databasesSpecific program execution arrangementsSuperclassHuman language
Methods and systems for protecting object identity in an object-oriented programming language. An object from a class for protecting object identity is instantiated in memory. The object includes a first method that determines whether two object values are equal, and a second method that overrides an identity method associated with a superclass of the object by invoking the first method, the identity method for determining the identity of two objects. The object is immediately locked in response to the instantiating, so that the identity of the locked object is protected from threads that attempt to synchronize on the locked object.
Owner:ORACLE INT CORP
Identification method of superclass of G-protein-coupled receptors and Web service system thereof
InactiveCN101609486AImprove classification accuracyRealize online prediction functionBiological neural network modelsSpecial data processing applicationsPattern recognitionG protein-coupled receptor
The invention relates to an identification method of superclass of G-protein-coupled receptors (GPCRs) and a Web service system thereof; in the method, first order signature modules of samples of the GPCRs are adopted to express the samples of the GPCRs; a discrete binary particle swarm algorithm is adopted to extract the effective characteristics of the samples of the GPCRs; an integrated classifier model based on a fuzzy neural network is adopted to complete the classification of the GPCRs. The invention has the characteristics of high classification precision, fast speed and the like. The Web service system comprises the following steps: loading an identification model by a predictor; inputting the G-protein-coupled receptors sequence submitted by a Web client into a data transmitter; outputting the predicted results of the GPCRs classification; returning to the Web client by a Servlet component, The invention can predict the classification of the G protein-coupled receptor based on a common Web user.
Owner:DONGHUA UNIV
Method for scaling fine-grained object recognition of consumer packaged goods
A method is provided for identifying consumer packaged goods (CPGs). The method comprises (a) identifying a set of objects as being a set of CPGs by applying a first level of object recognition to the set of objects, wherein said set of objects has N members, wherein N≥2, and wherein applying the first level of object recognition to the set of objects includes applying a first predefined set of criteria to the object; (b) for each of the N objects, (i) performing a second level of object recognition on the object by applying a second predefined set of criteria to the object, (ii) assigning the object to one of a plurality of predefined superclasses S=[Sl, . . . , Sj], wherein j≥2, based on the results of the second level of object recognition, (iii) applying a bounding box to the object, (iv) capturing an image of the object with an image capturing device, and (v) cropping the image to the bounding box, thereby yielding a cropped image of the object; and (c) for each object in each set SiεS, (i) performing a third level of object recognition on the cropped image of the object by applying a set of criteria Ci to the object, and (ii) assigning the object to one of a plurality of predefined subclasses B=[Bl, . . . , Bk], wherein k≥2, based on the results of the third level of object recognition.
Owner:PENSA SYST INC
Dialog item interface definition object
InactiveUS7712109B2Simple and powerful mannerOvercome disadvantagesMultiprogramming arrangementsExecution for user interfacesBase classSoftware engineering
An object-oriented item is used to define the behavior of an item in a dialog box in a windows environment. A class hierarchical library is established with a base class setting up initial definitions of instance variables and methods used to define the behavior of a customized item. An applications developer can create customized items for a dialog box by creating subclasses. The subclasses will inherit portions of the superclasses, and the developer will customize the items by overriding certain methods. The object, an instance of the class, is referenced by a resource associated with an application.
Owner:APPLE INC
Type merging technique to reduce class loading during Java verification
An apparatus, process, and computer program product to merge types in an object-oriented program is disclosed herein. In one embodiment, a process may include analyzing a method within an object-oriented program to identify merge candidates. These merge candidates may then be recorded in a merge candidate list. The process may further include identifying at least two code paths in the method that merge into a single code path and that operate on different types. The types in these code paths may then be merged to a nearest common superclass listed in the merge candidate list. In selected embodiments, the types may be merged to the java.lang.Object class in the event the merge candidate list is empty.
Owner:INT BUSINESS MASCH CORP
Type independent permission based access control
InactiveUS8387111B2Many applicationsWithout any changeDigital data processing detailsUnauthorized memory use protectionSemanticsMedia access control
A method and apparatus for type independent permission based access control are provided. The method and apparatus utilize object inheritance to provide a mechanism by which a large group of permissions may be assigned to a codesource without having to explicitly assign each individual permission to the codesource. A base permission, or superclass permission, is defined along with inherited, or subclass, permissions that fall below the base permission in a hierarchy of permissions. Having defined the permissions in such a hierarchy, a developer may assign a base permission to an installed class and thereby assign all of the inherited permissions of the base permission to the installed class. In this way, security providers need not know all the permission types defined in an application. In addition, security providers can seamlessly integrate with many applications without changing their access control and policy store semantics. Moreover, application providers' security enforcement is no dependent on the security provider defined permissions. The method and apparatus do not require any changes to the Java security manager and do not require changes to application code.
Owner:IBM CORP
System and method for automatic invocation of constructor code for superclasses
ActiveUS9639329B2Programming languages/paradigmsProgram loading/initiatingSuperclassInheritance hierarchy
A system and method for automatic invocation of object initializers, or constructors, for superclasses featuring the ability to modify the contents of classes of existing applications at runtime, which includes adding new superclasses to the class inheritance hierarchy of the existing classes. The system redefines the content of classes of the existing classes and the new superclasses during the loading of the classes to additionally include code statements that invoke constructors of the redefined classes and the new superclasses. The invocation of the constructors at runtime performs the initialization of the objects.
Owner:ZEROTURNAROUND
Identification method of superclass of G-protein-coupled receptors and Web service system thereof
InactiveCN101609486BImprove classification accuracyRealize online prediction functionBiological neural network modelsSpecial data processing applicationsPattern recognitionG protein-coupled receptor
The invention relates to an identification method of superclass of G-protein-coupled receptors (GPCRs) and a Web service system thereof; in the method, first order signature modules of samples of the GPCRs are adopted to express the samples of the GPCRs; a discrete binary particle swarm algorithm is adopted to extract the effective characteristics of the samples of the GPCRs; an integrated classifier model based on a fuzzy neural network is adopted to complete the classification of the GPCRs. The invention has the characteristics of high classification precision, fast speed and the like. The Web service system comprises the following steps: loading an identification model by a predictor; inputting the G-protein-coupled receptors sequence submitted by a Web client into a data transmitter; outputting the predicted results of the GPCRs classification; returning to the Web client by a Servlet component, The invention can predict the classification of the G protein-coupled receptor based on a common Web user.
Owner:DONGHUA UNIV
Refining hierarchies in object-oriented models
ActiveCN103679328AClass of ExcellenceNatural language translationSemantic analysisBusiness objectHuman language
A method and system for refining hierarchies in object-oriented models which comprise i) providing a business object model in the form of an object-oriented model having one or more members with multiple distinct verbalizations (synonyms); ii) identifying distinct verbalizations of a given business object model member; iii) reviewing existing rules of the business object model to produce mappings of the distinct verbalizations and any attributes or operations used in conjunction with the distinct verbalizations of members of the business object model; iv) analyzing the mappings to identify patterns of use of the distinct verbalizations; and vi) categorising a distinct verbalization as a superclass or subclass.
Owner:IBM CORP
Refinement of Hierarchies in Object-Oriented Models
InactiveCN103679328BClass of ExcellenceNatural language translationSemantic analysisTheoretical computer scienceEngineering
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com