Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
596results about "Decompilation/disassembly" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
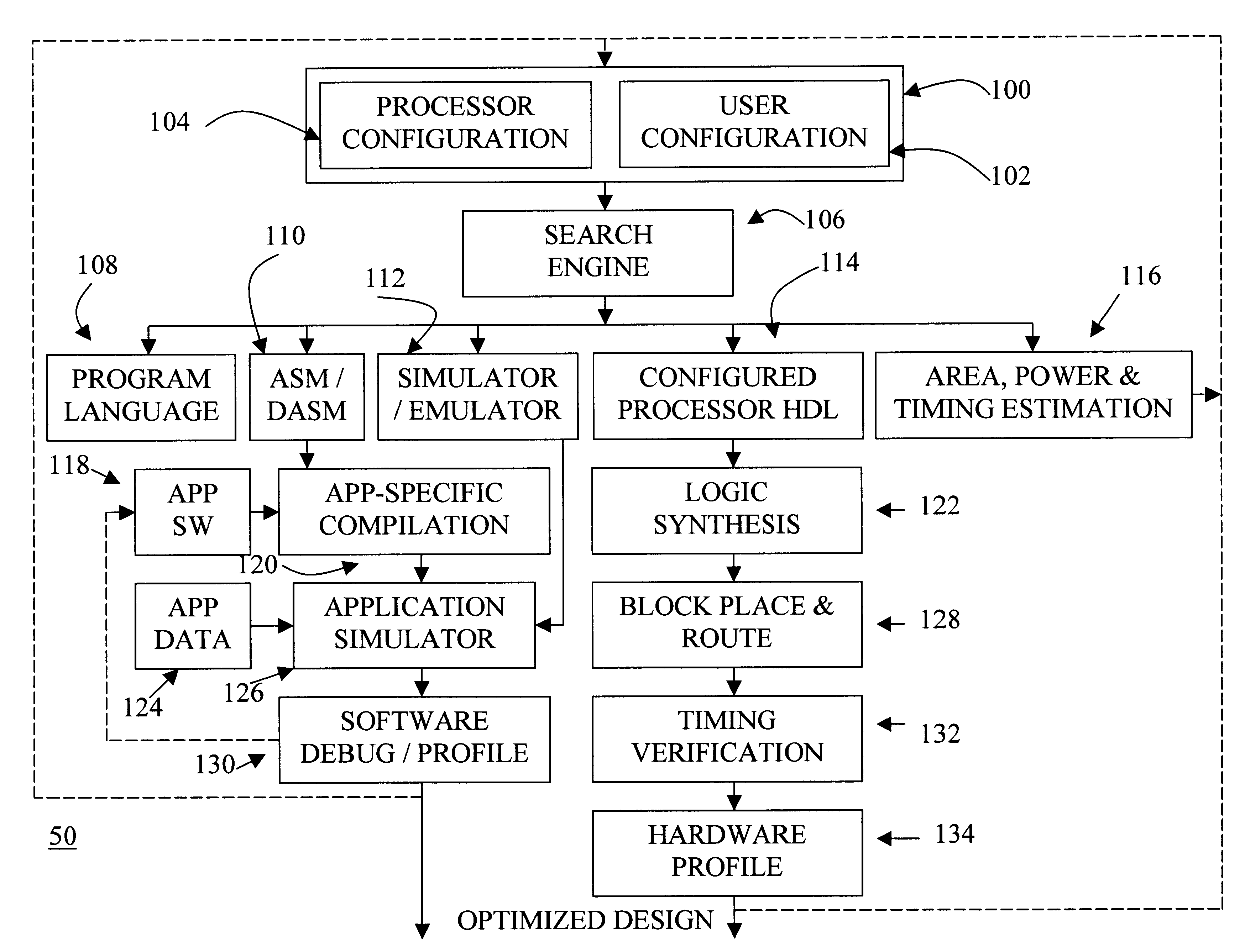
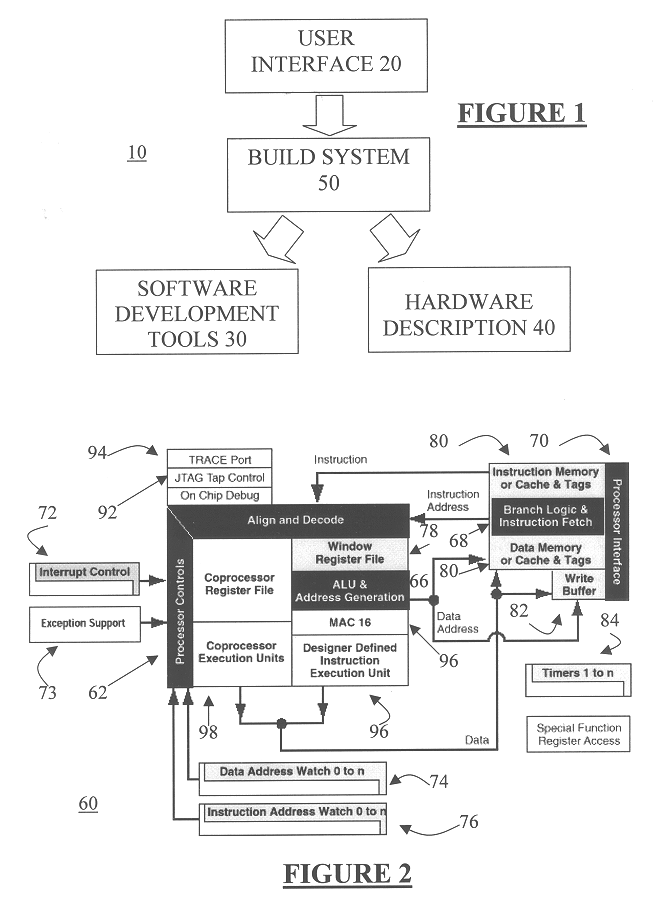
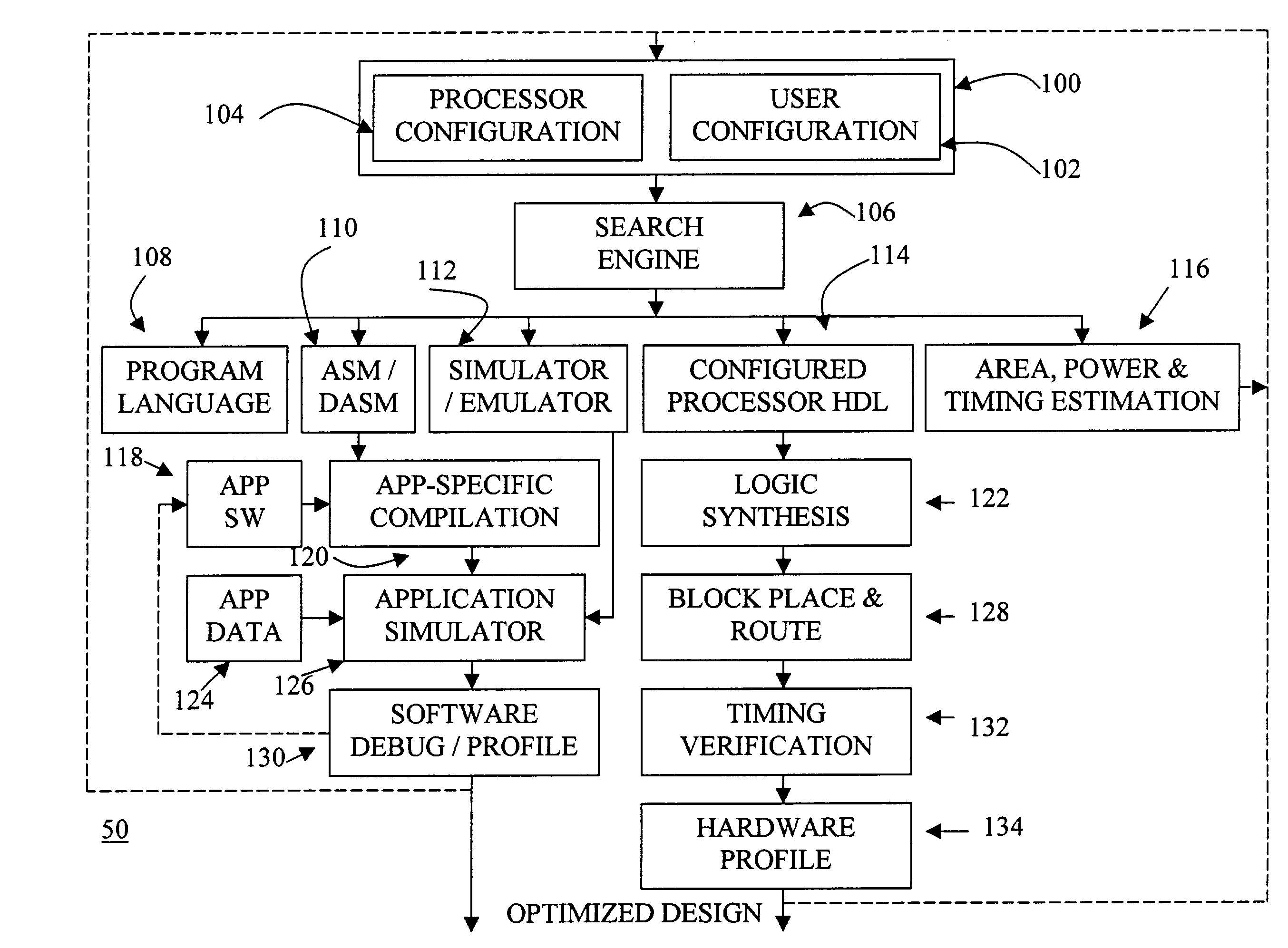
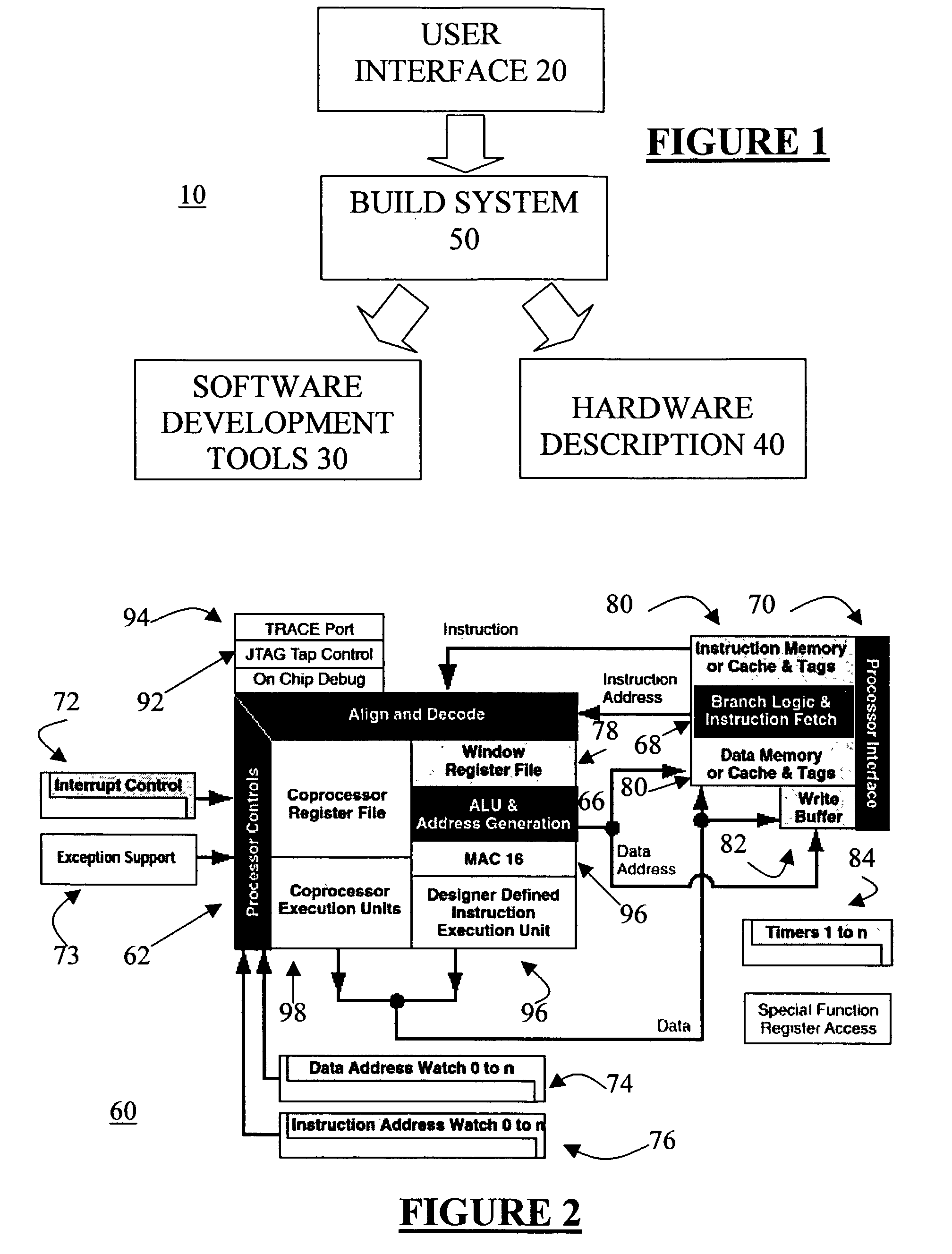
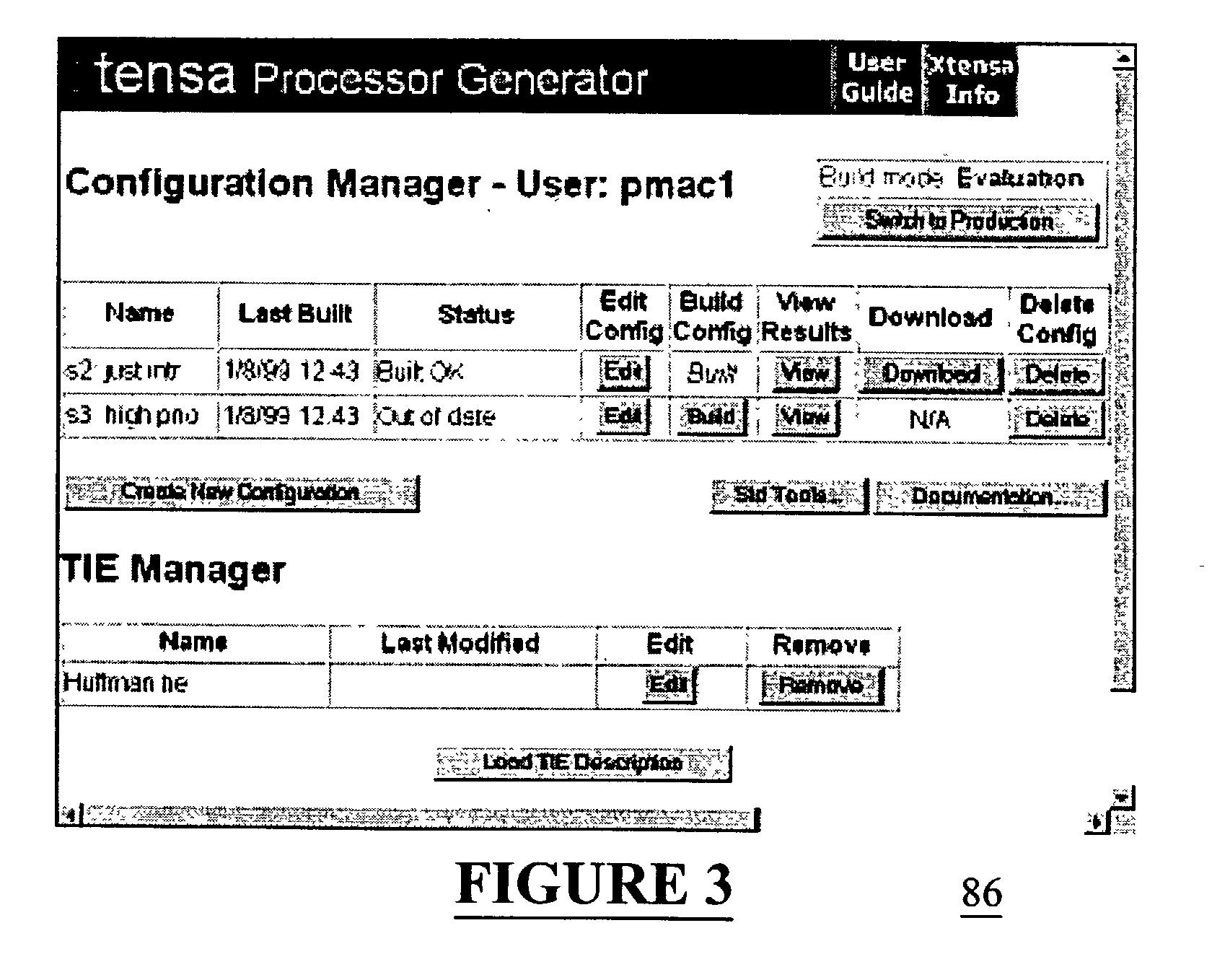
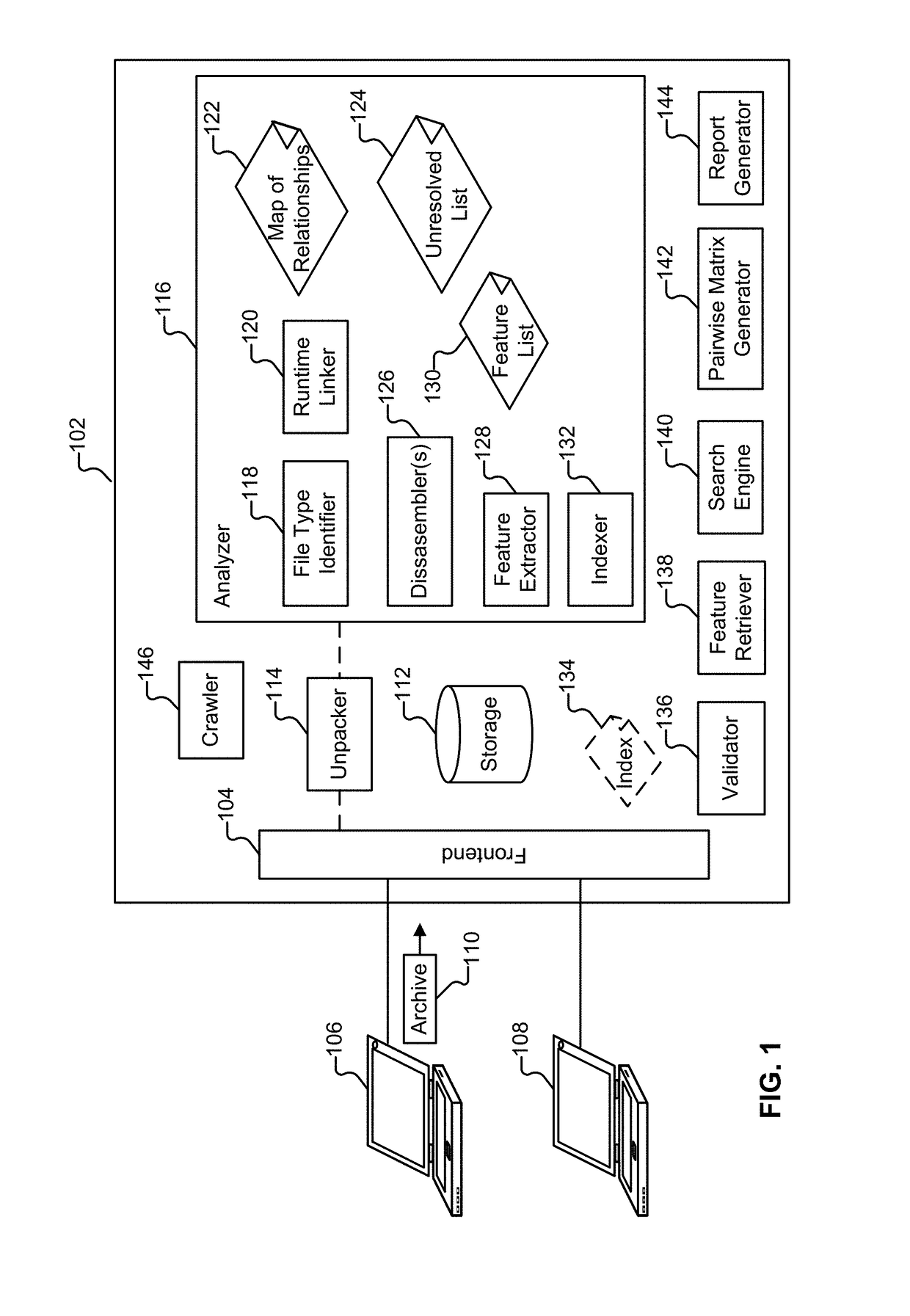
Automated processor generation system for designing a configurable processor and method for the same
InactiveUS6477683B1Decompilation/disassemblyCAD network environmentApplication softwareProcessor design
An automated processor design tool uses a description of customized processor instruction set extensions in a standardized language to develop a configurable definition of a target instruction set, a Hardware Description Language description of circuitry necessary to implement the instruction set, and development tools such as a compiler, assembler, debugger and simulator which can be used to develop applications for the processor and to verify it. Implementation of the processor circuitry can be optimized for various criteria such as area, power consumption, speed and the like. Once a processor configuration is developed, it can be tested and inputs to the system modified to iteratively optimize the processor implementation. By providing a constrained domain of extensions and optimizations, the process can be automated to a high degree, thereby facilitating fast and reliable development.
Owner:TENSILICA
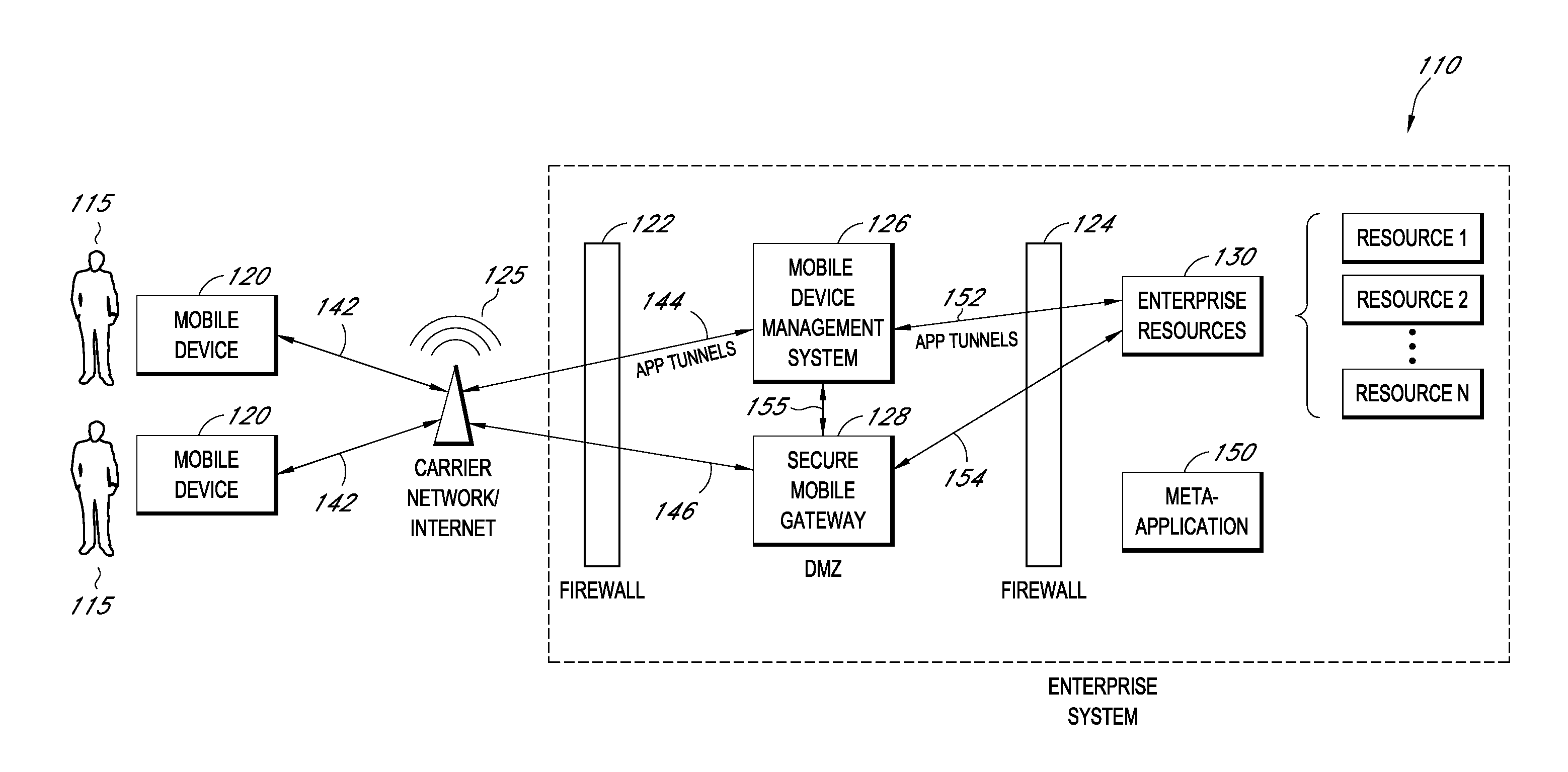
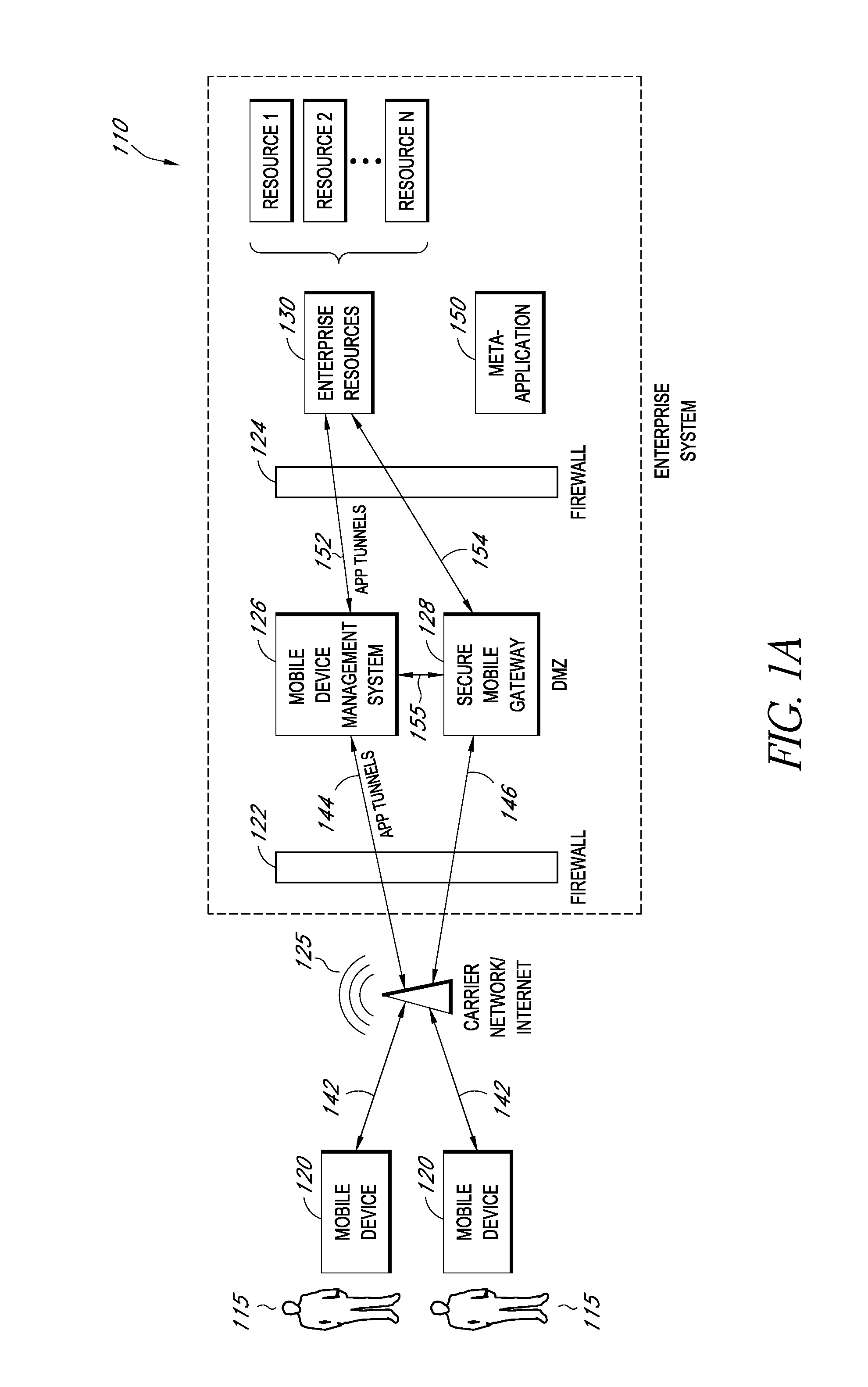
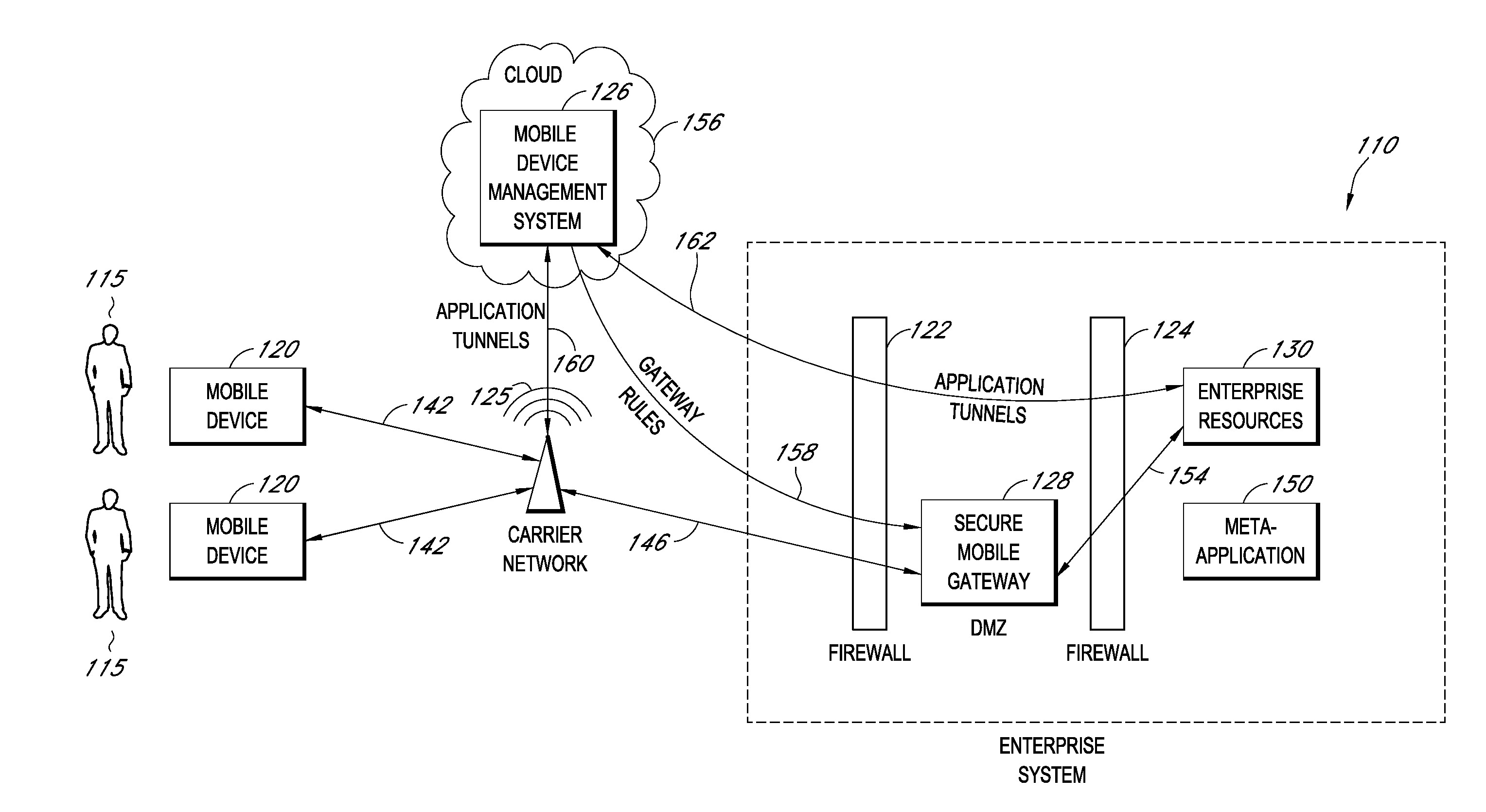
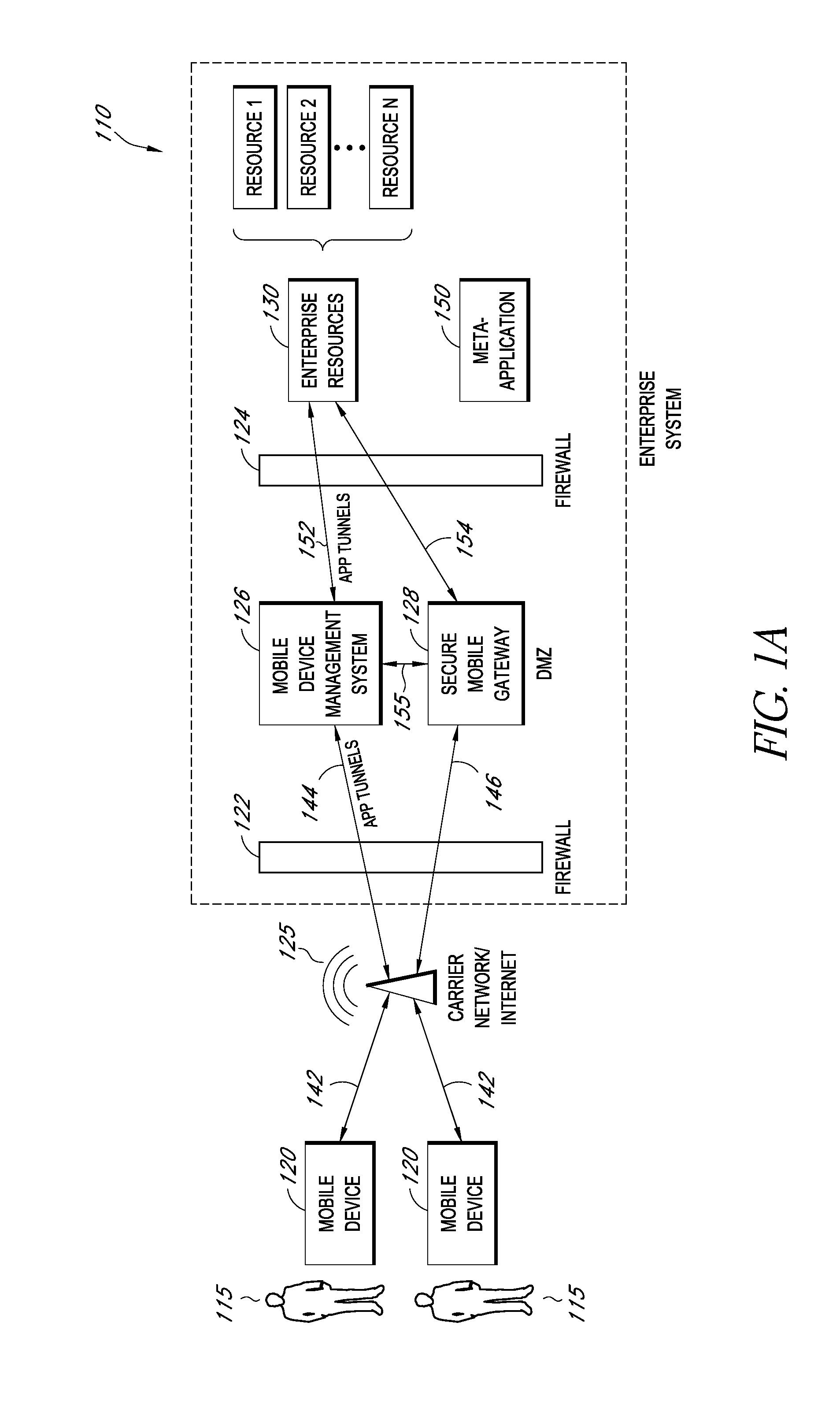
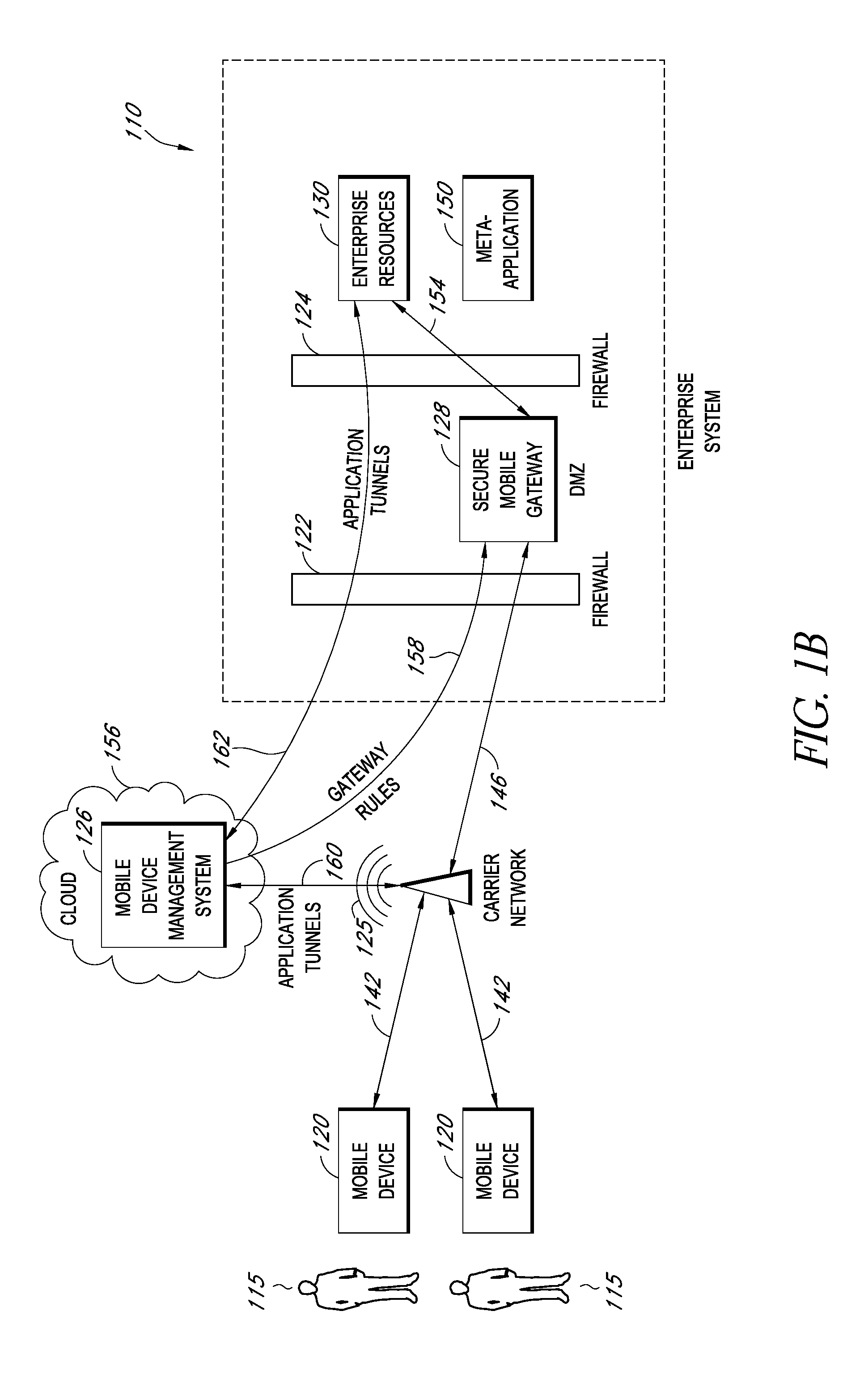
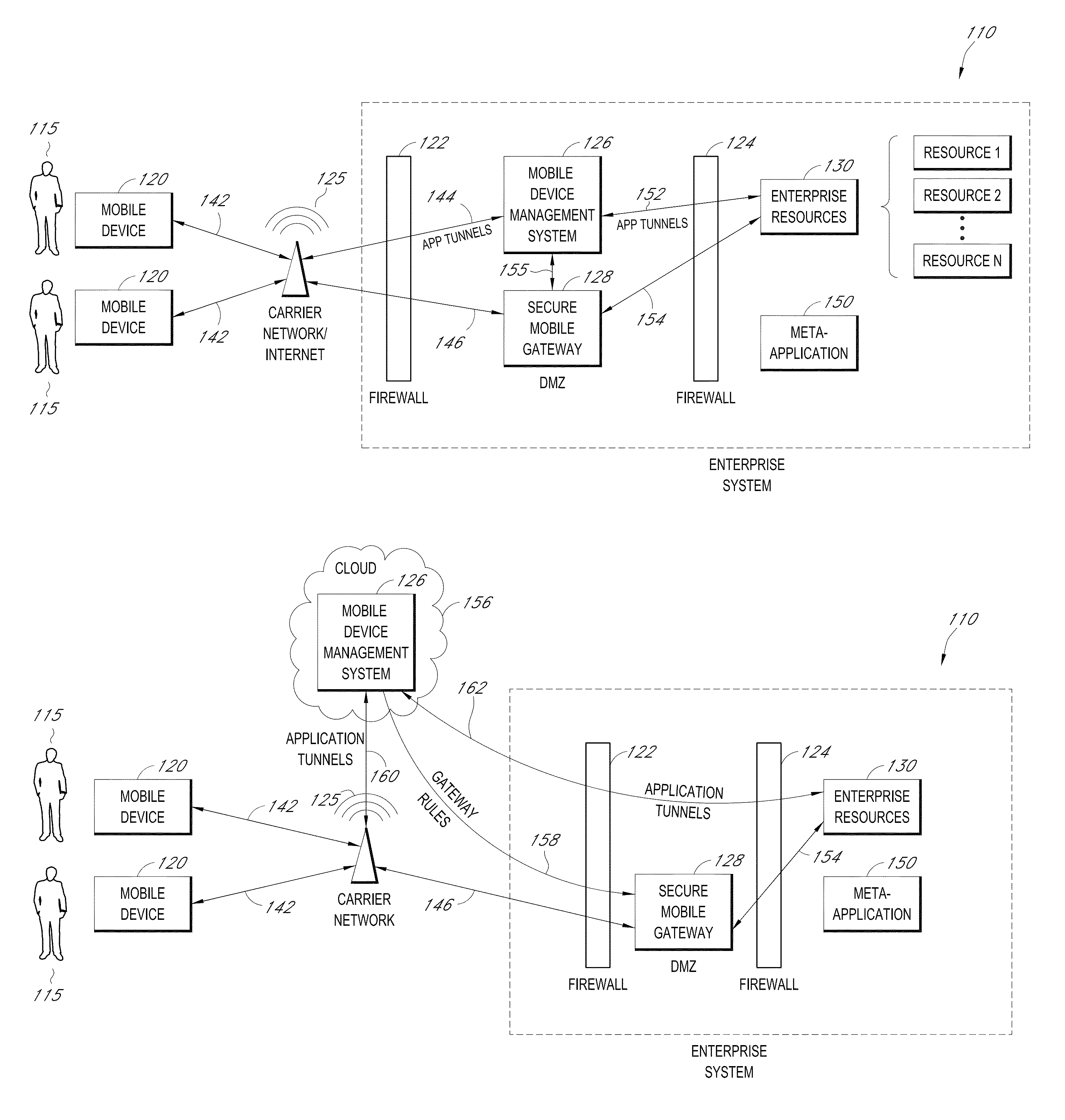
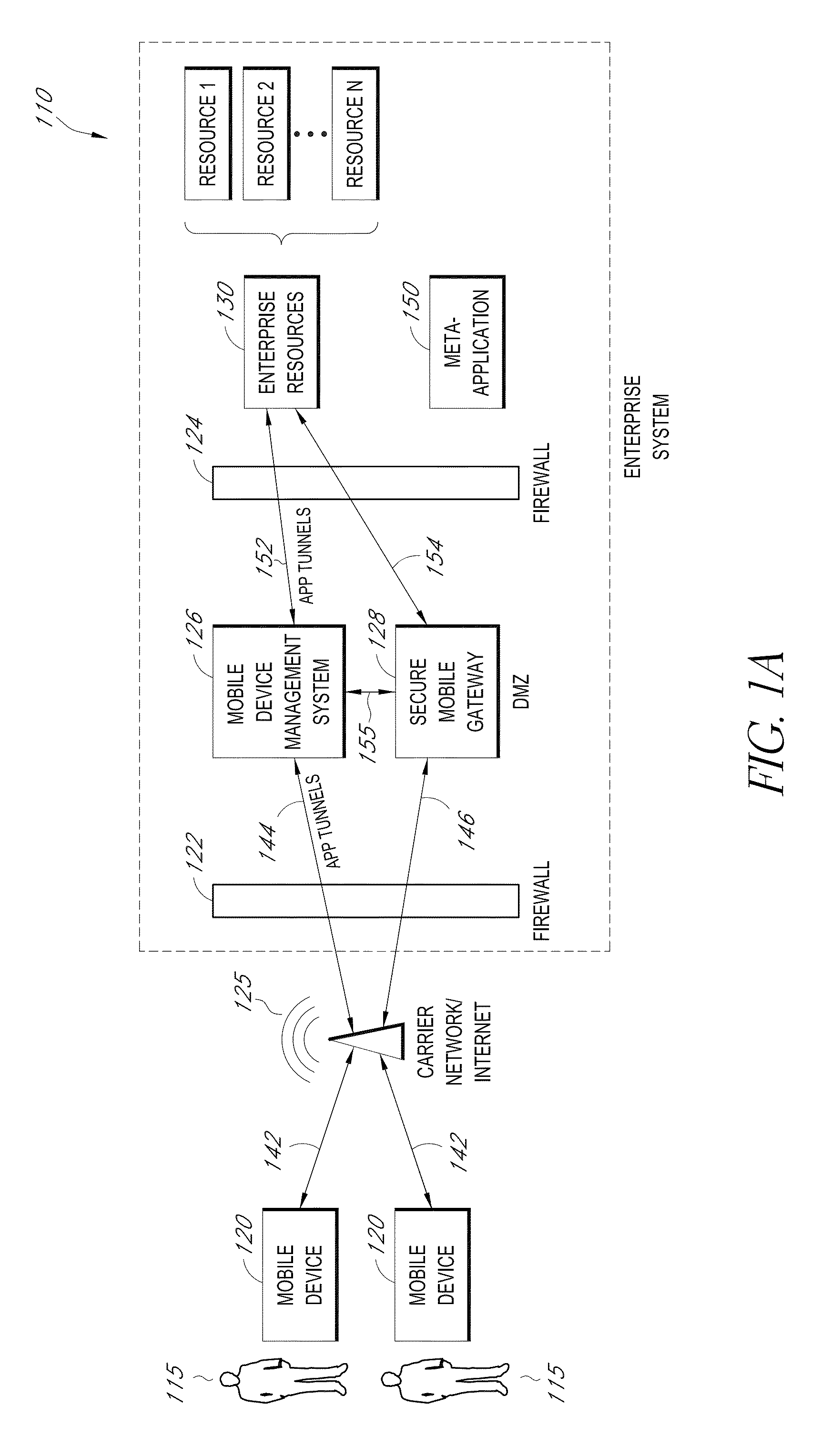
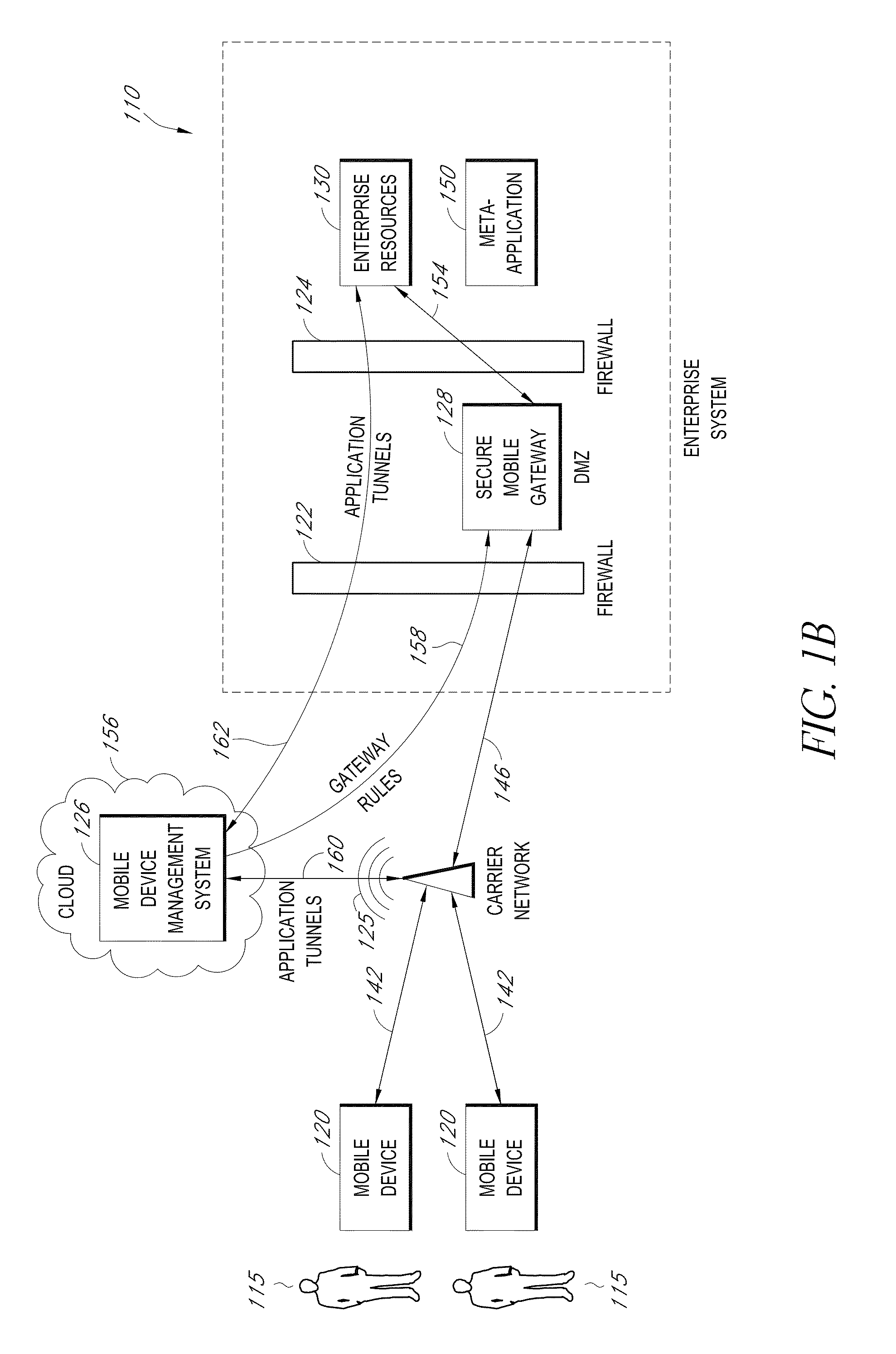
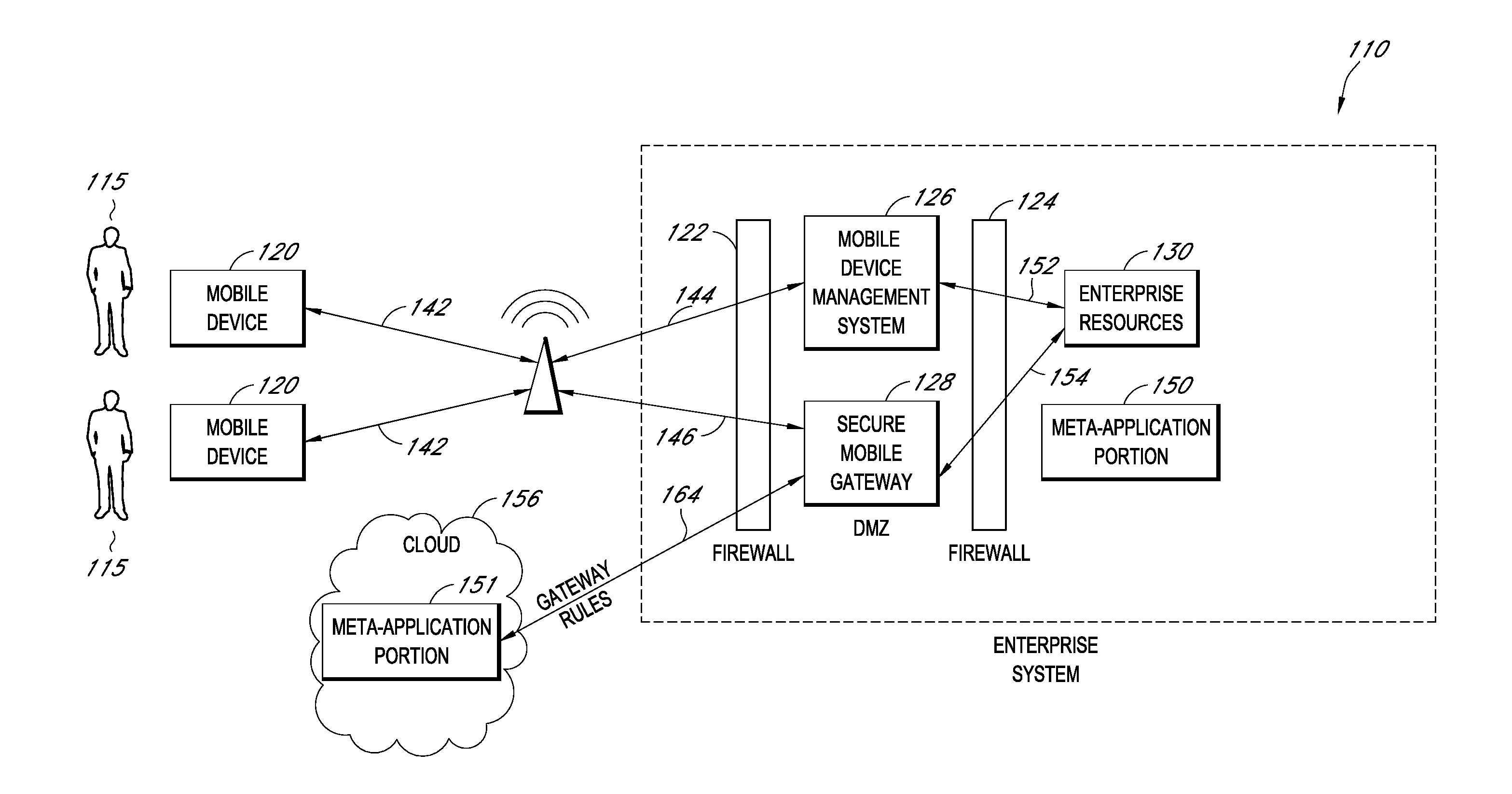
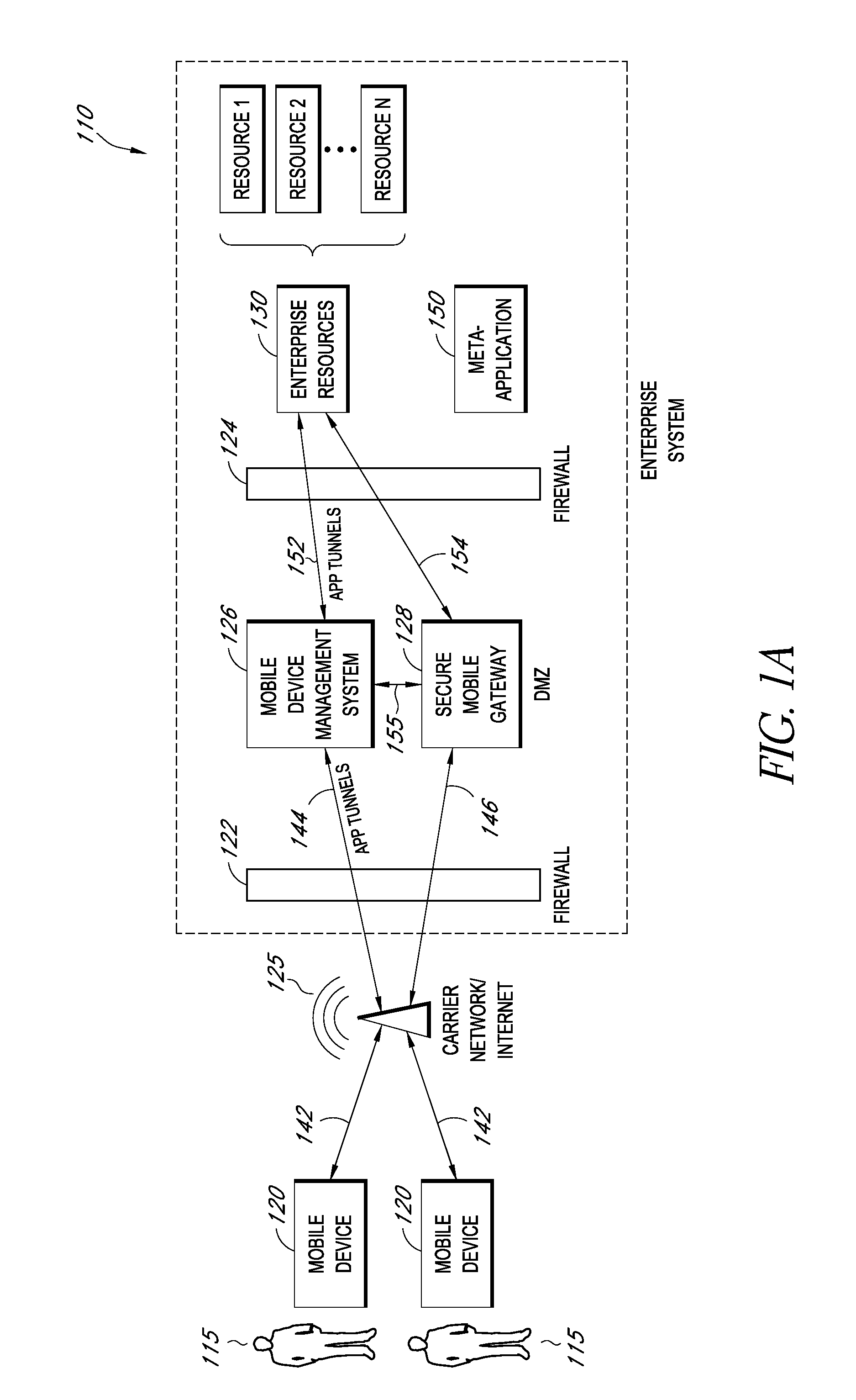
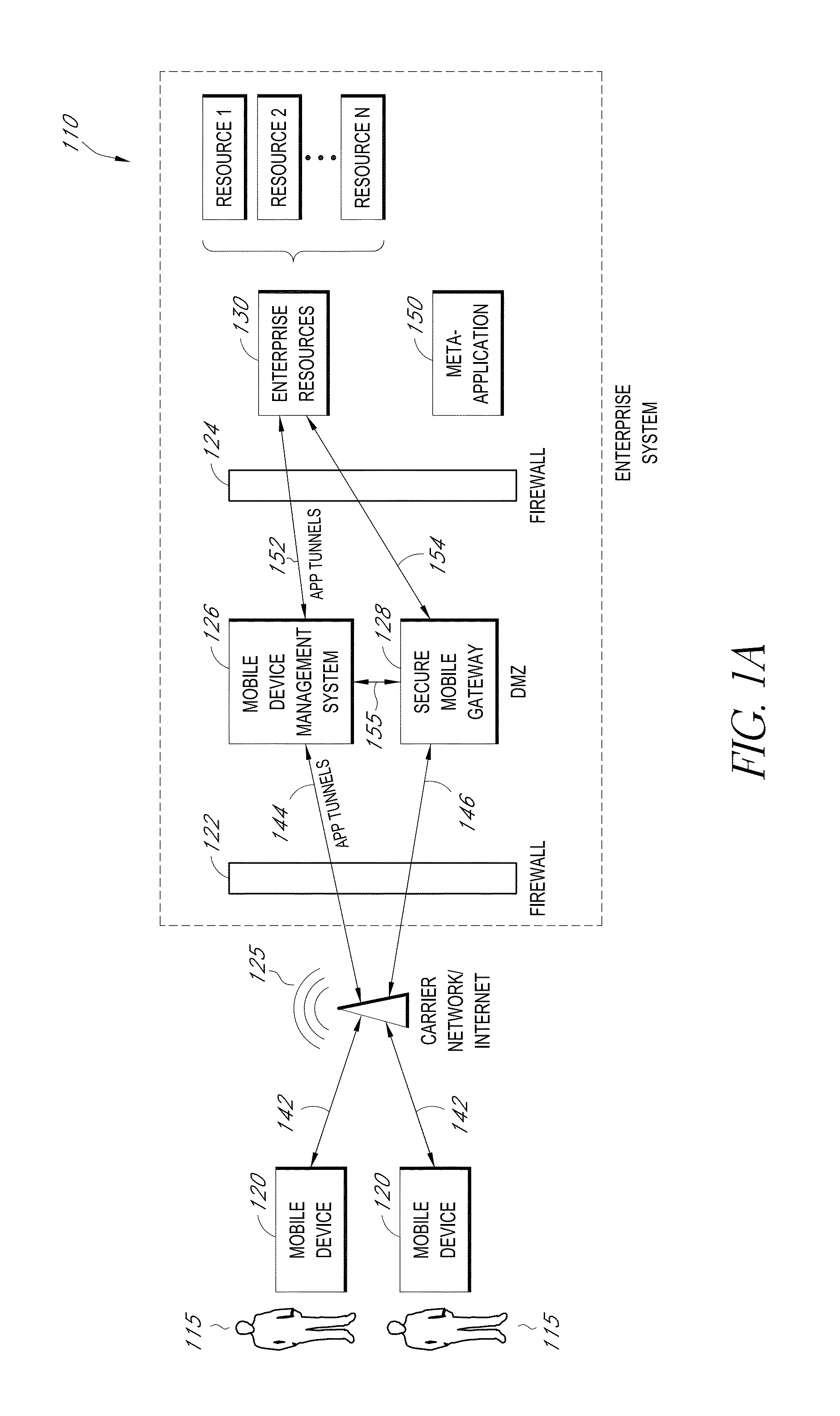
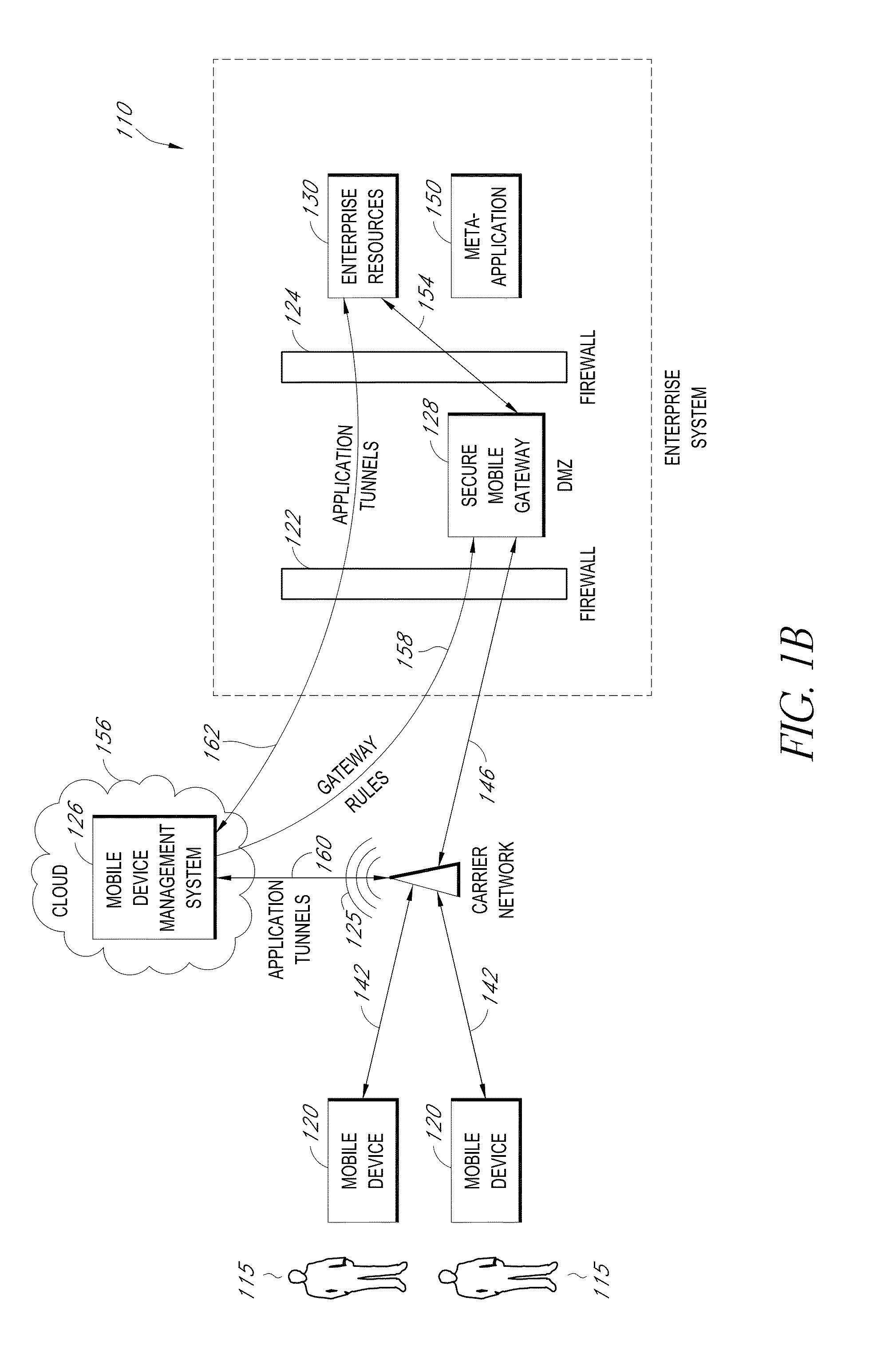
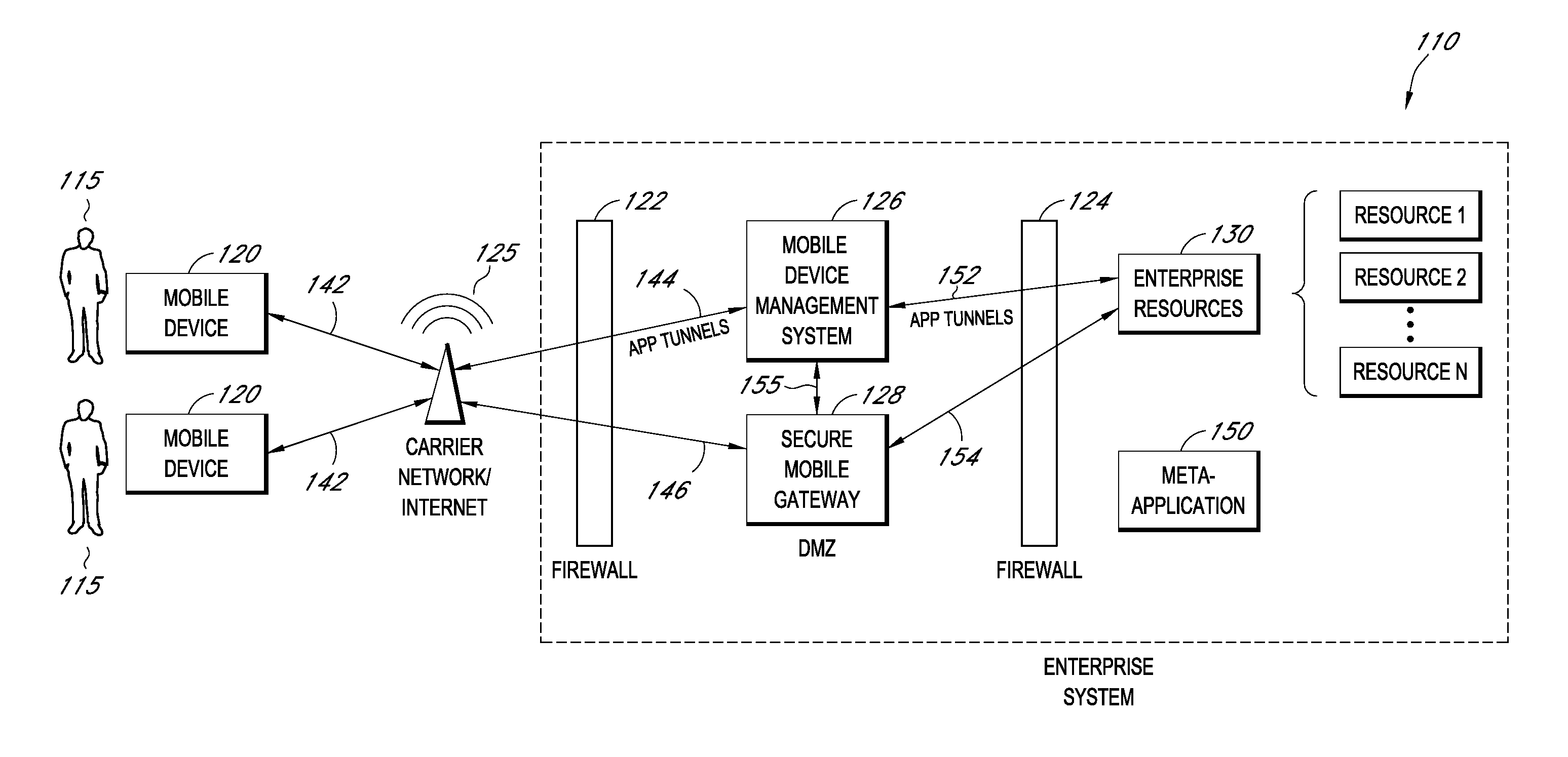
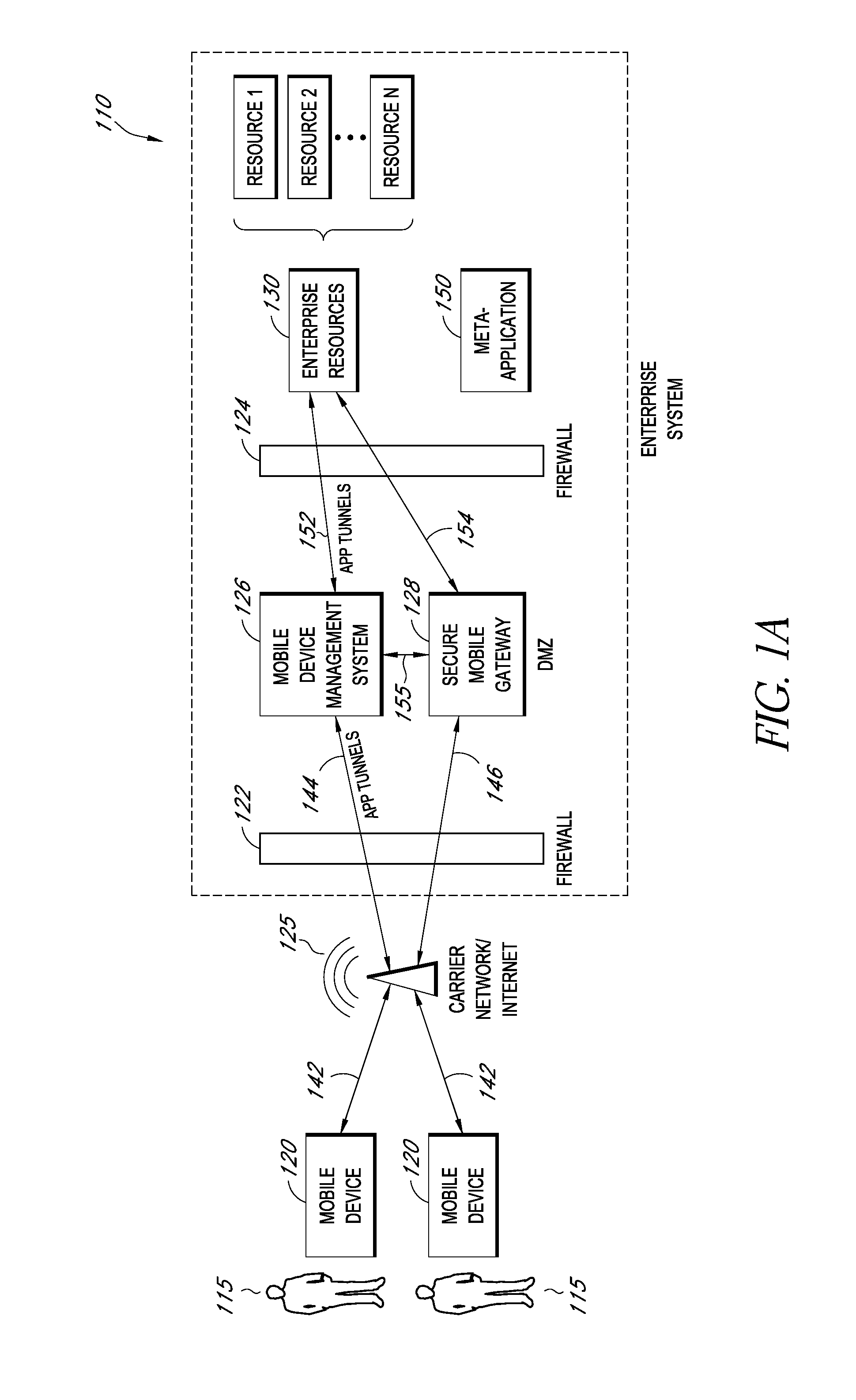
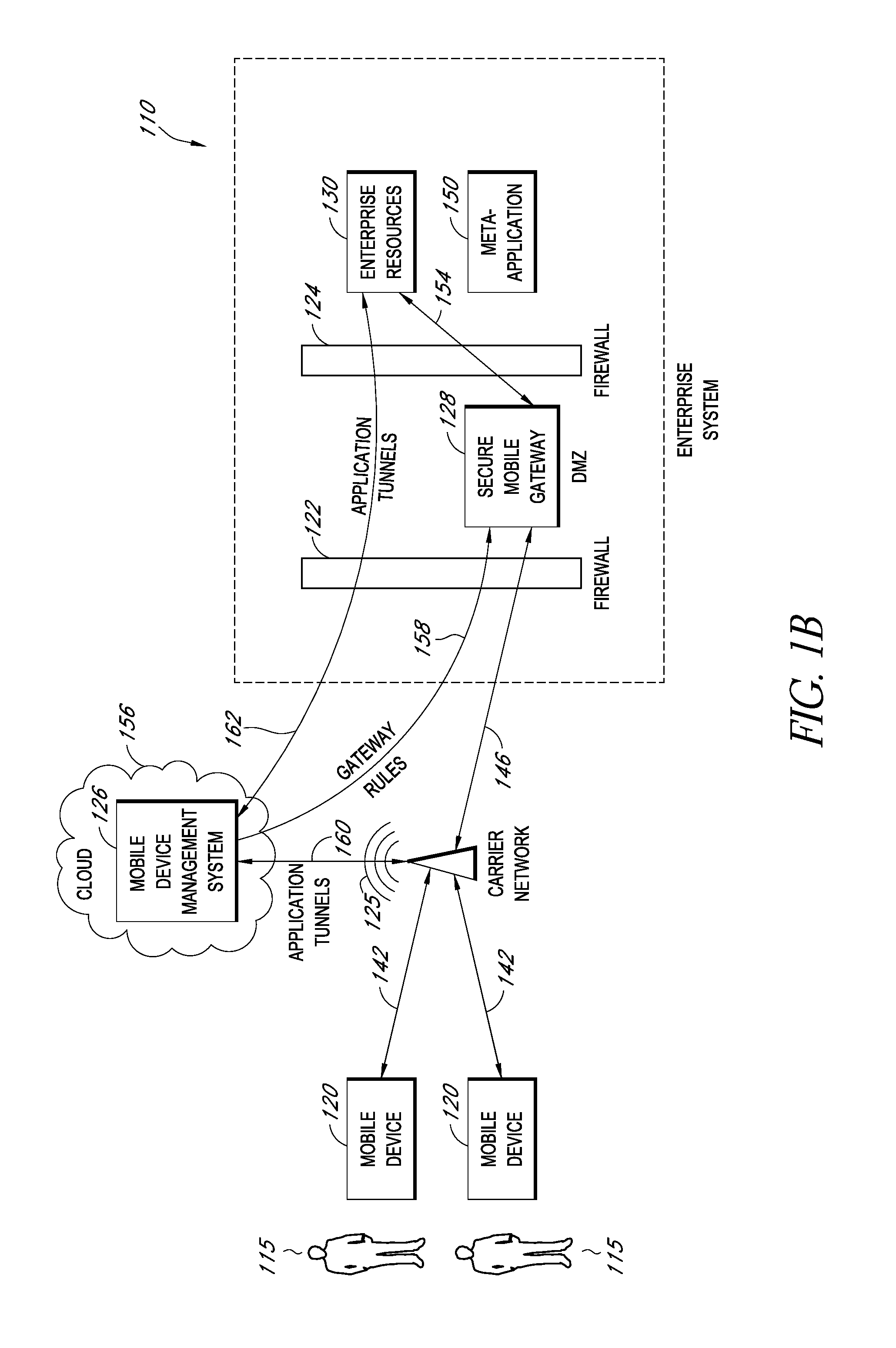
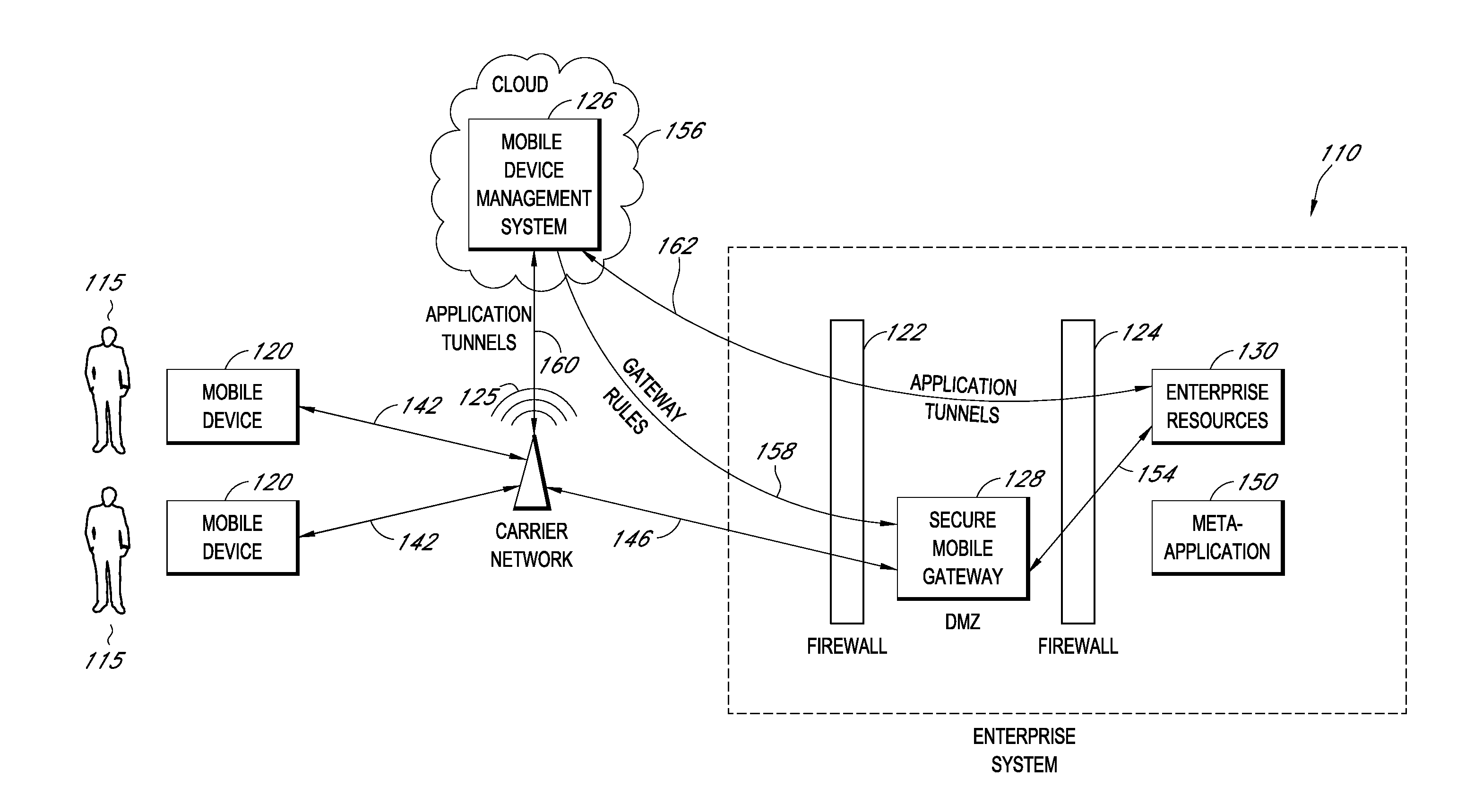
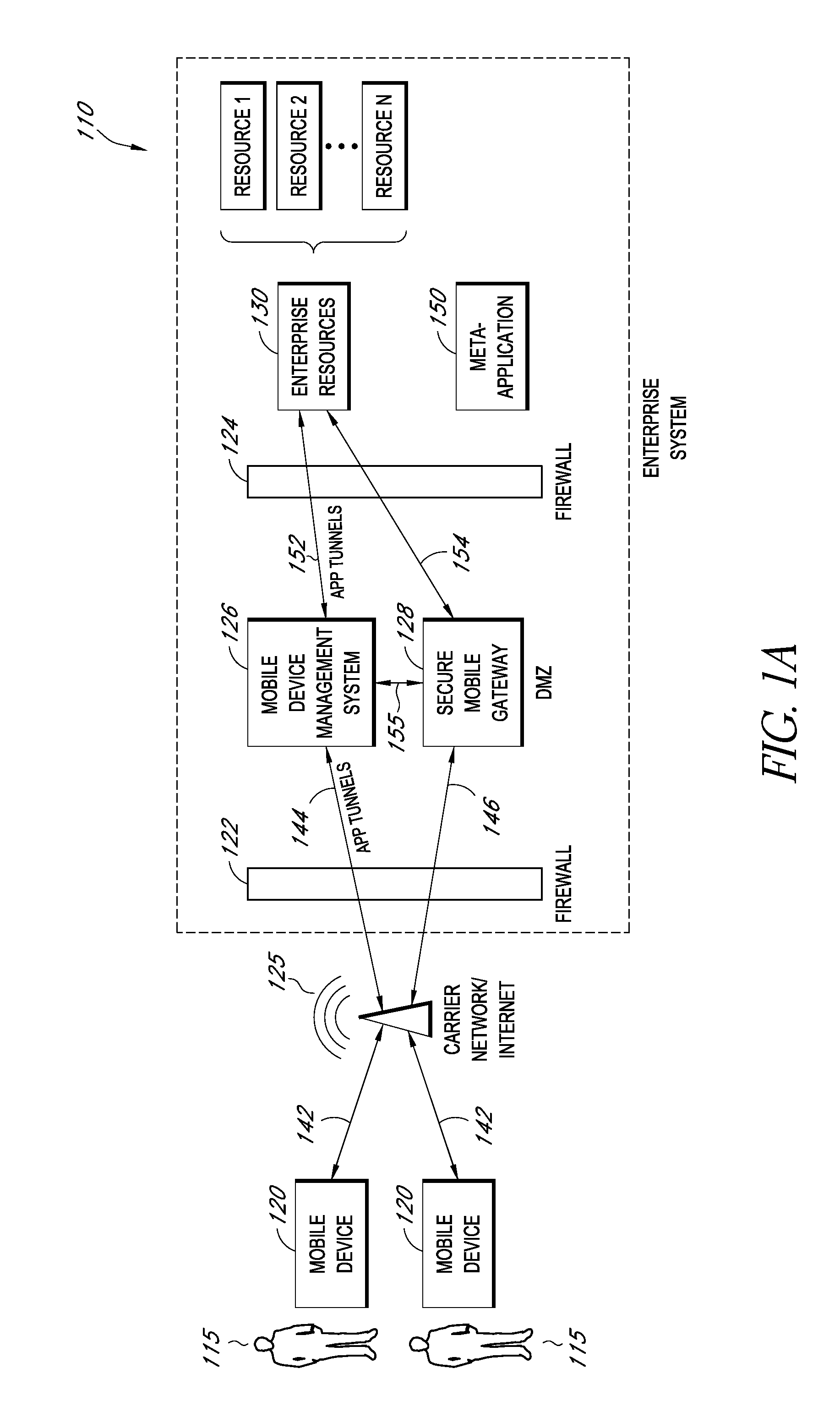
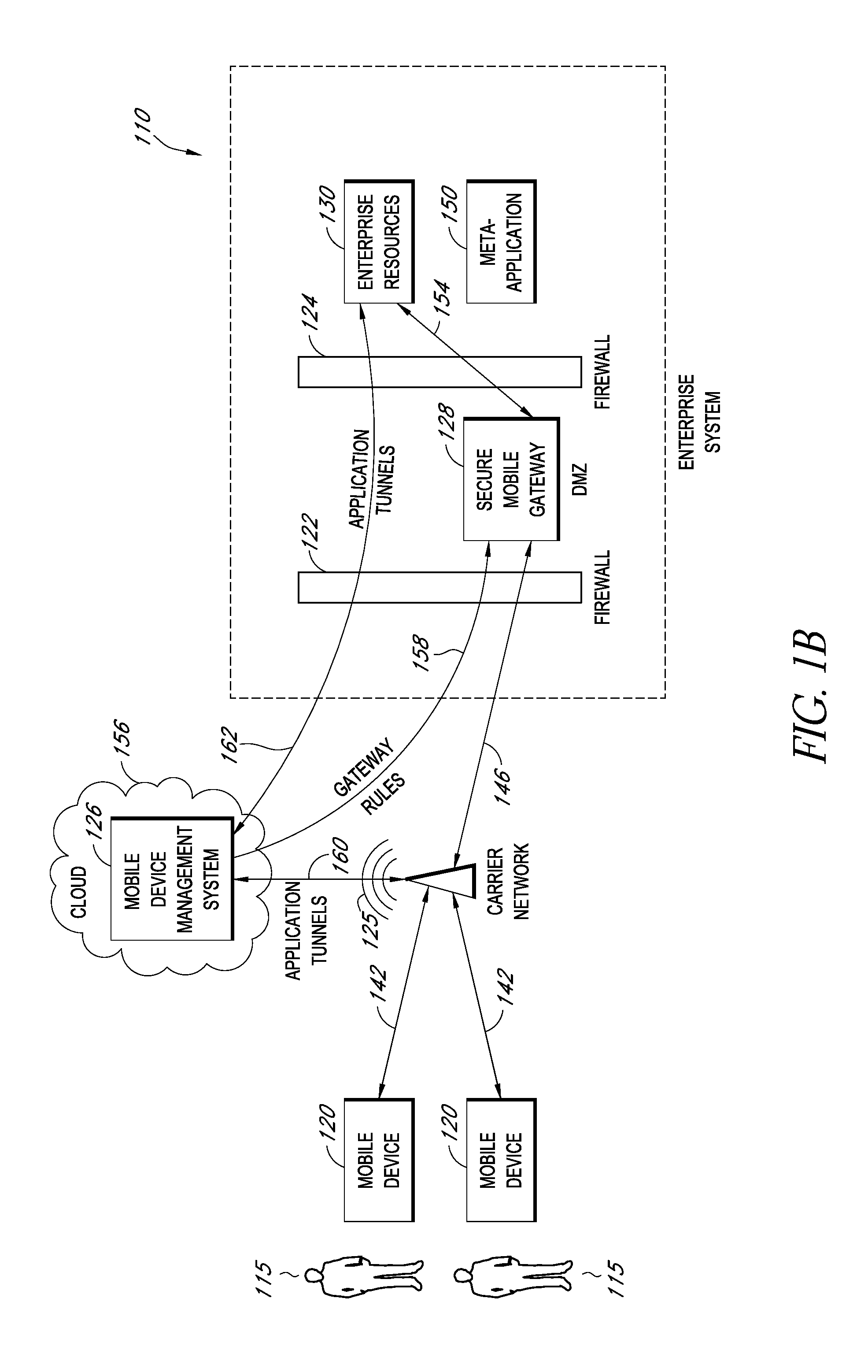
Secure container for protecting enterprise data on a mobile device
ActiveUS20140006347A1Digital data information retrievalDecompilation/disassemblyDocumentation procedureApplication server
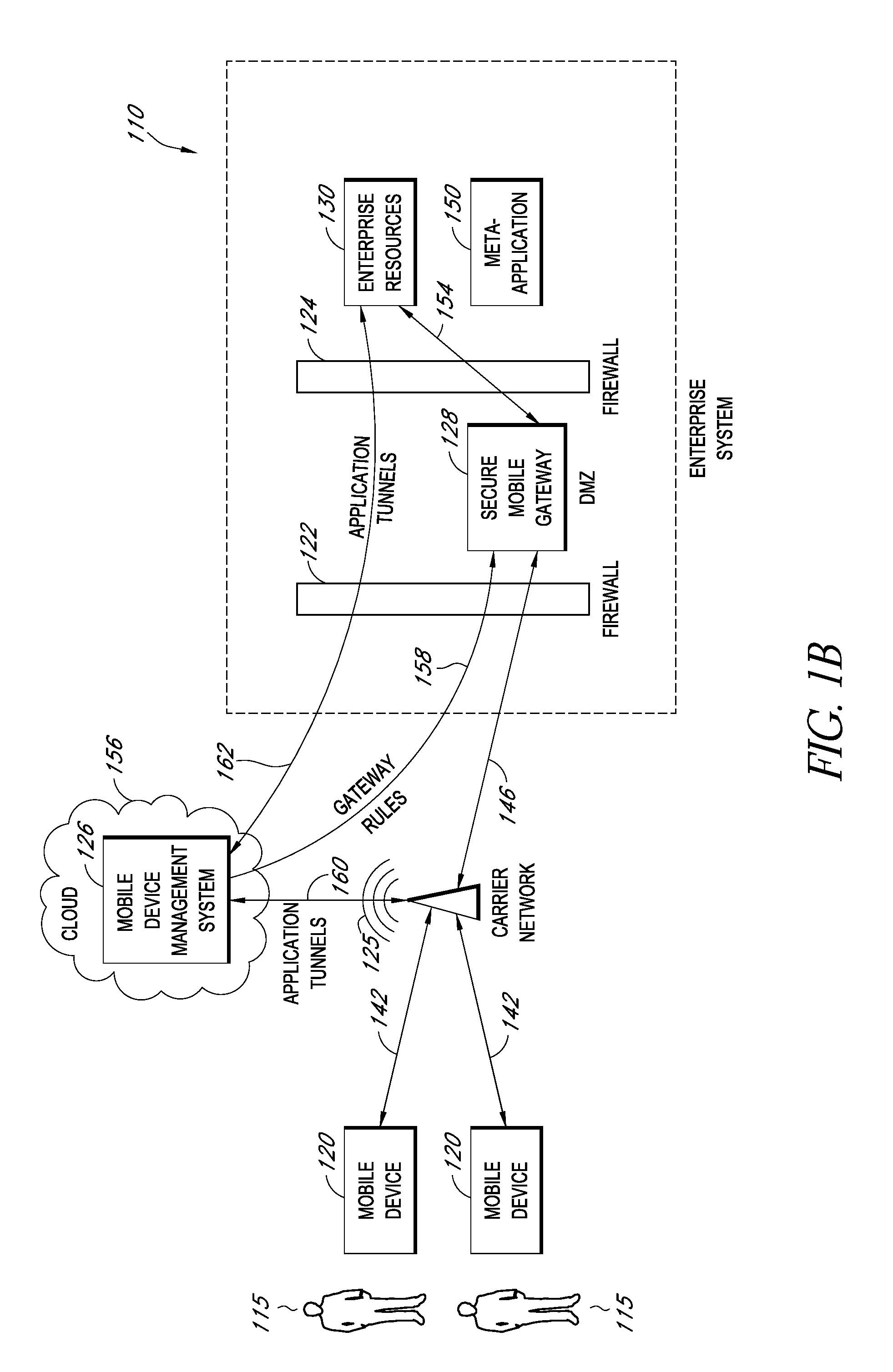
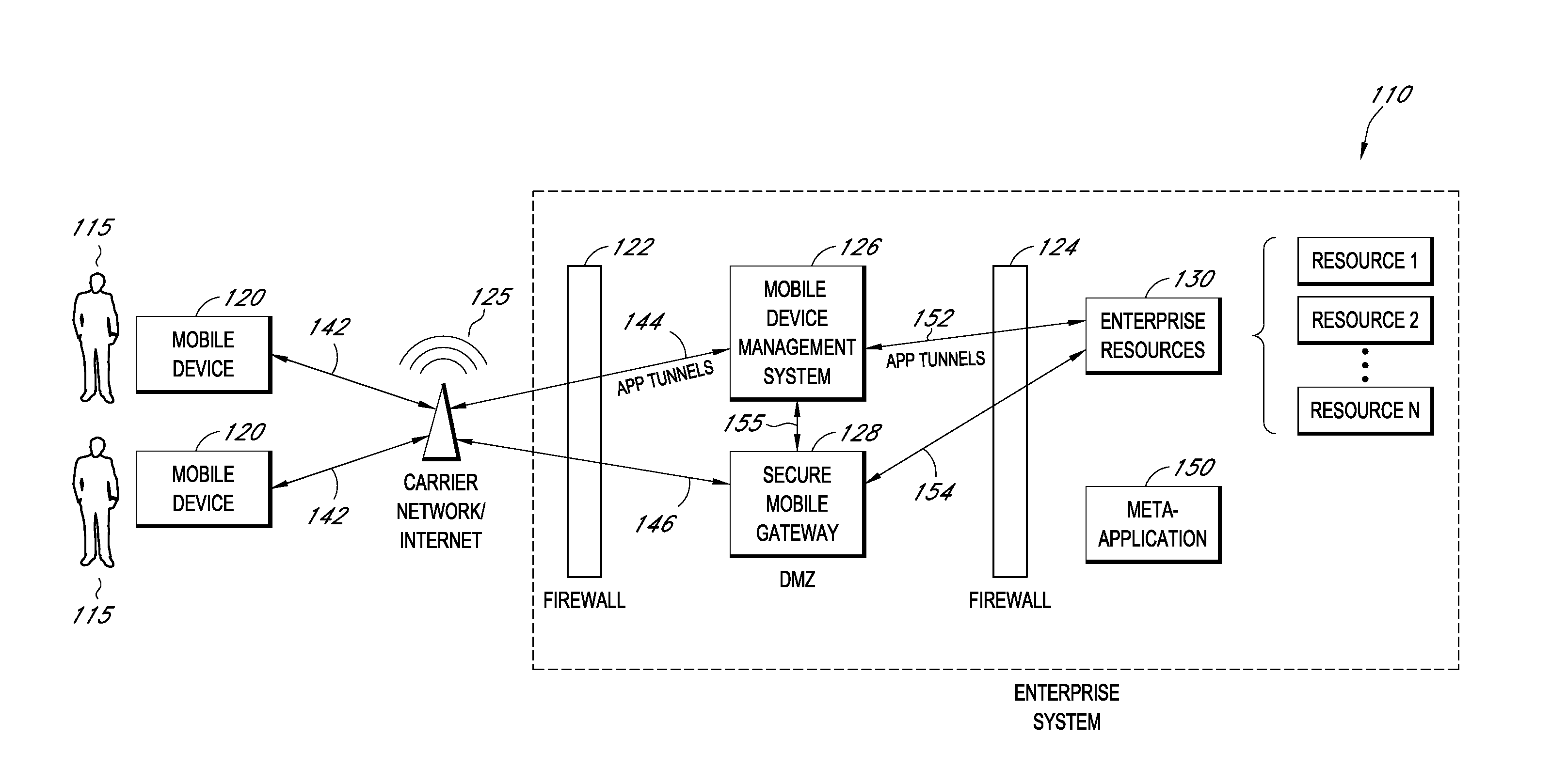
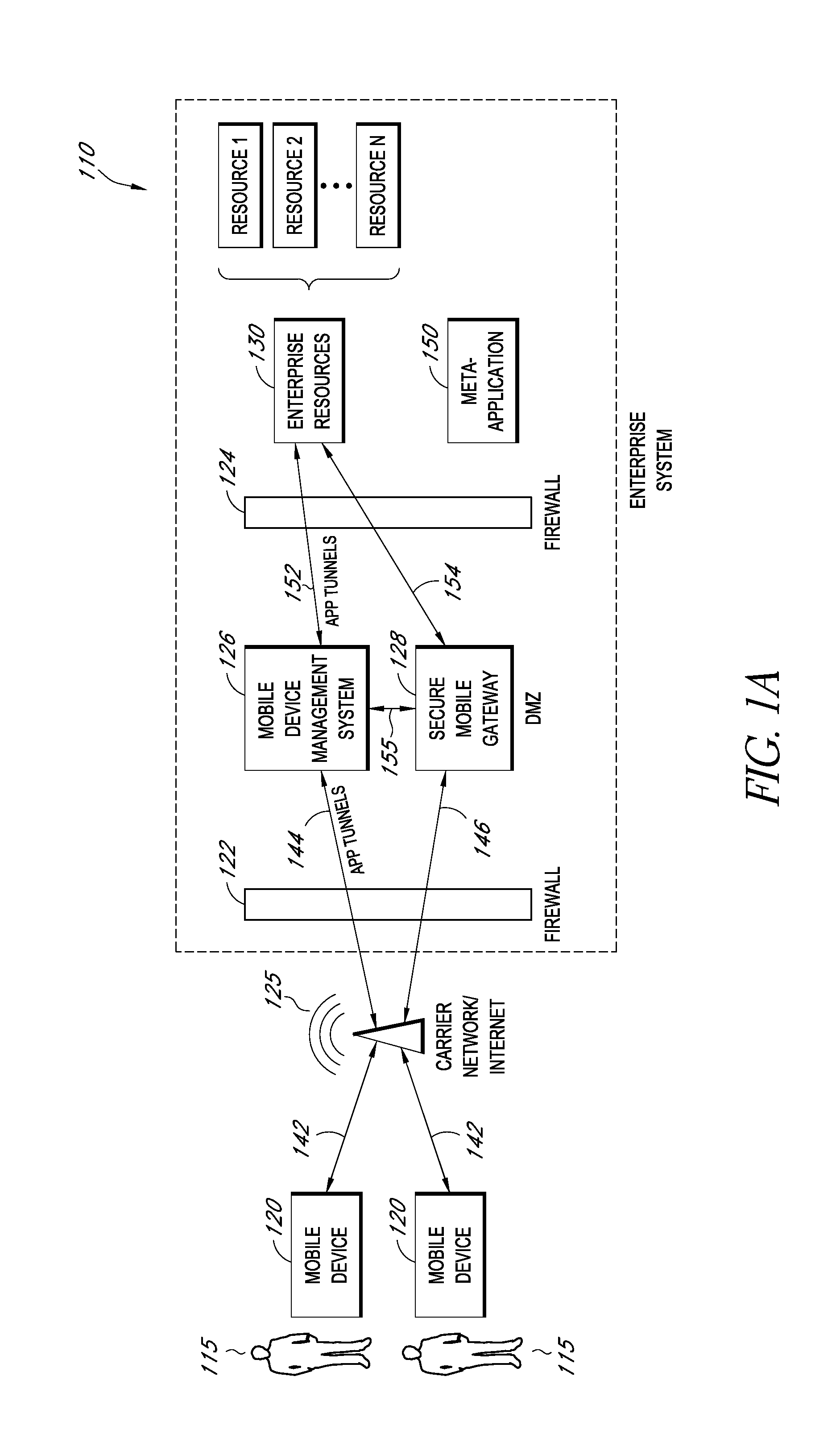
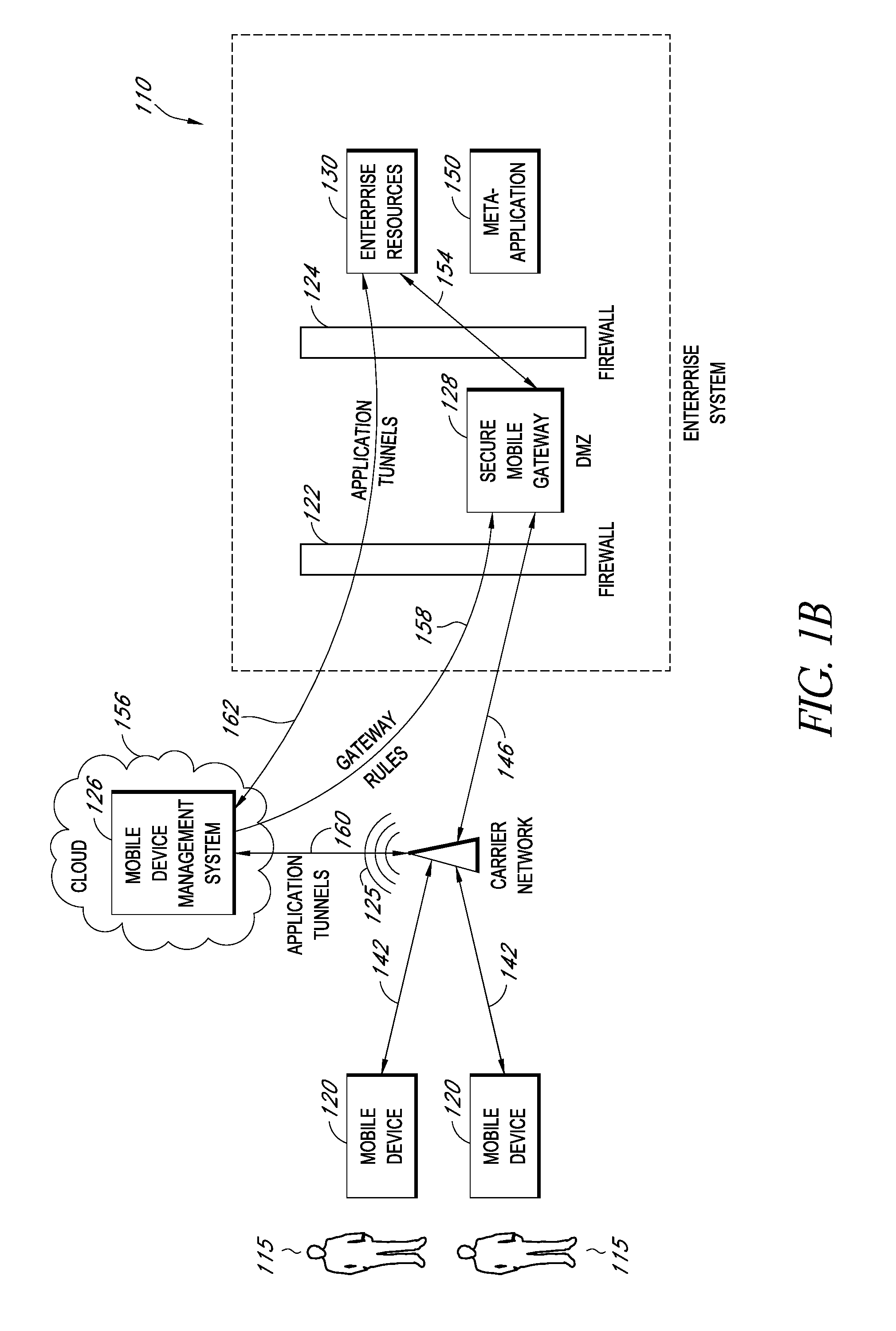
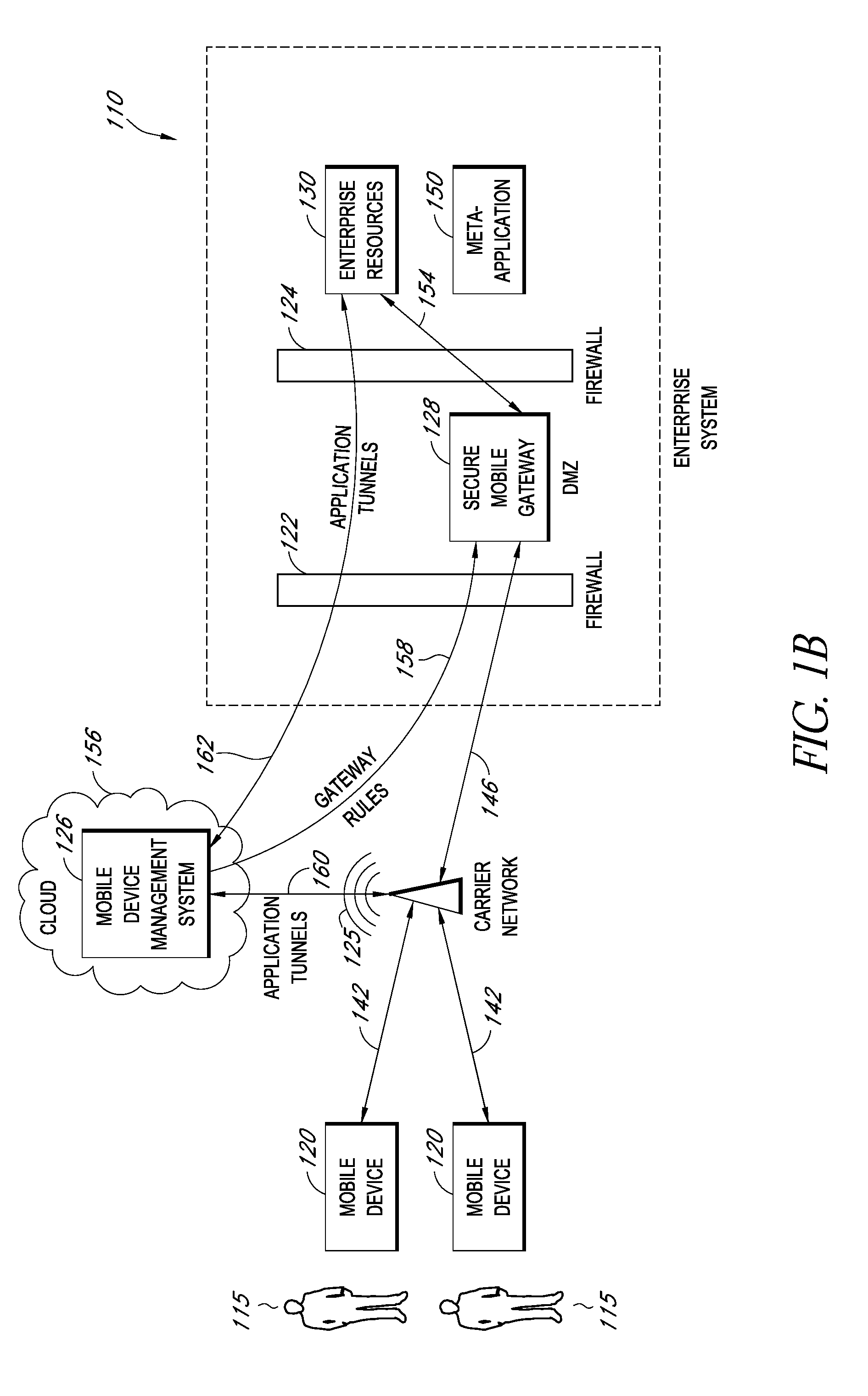
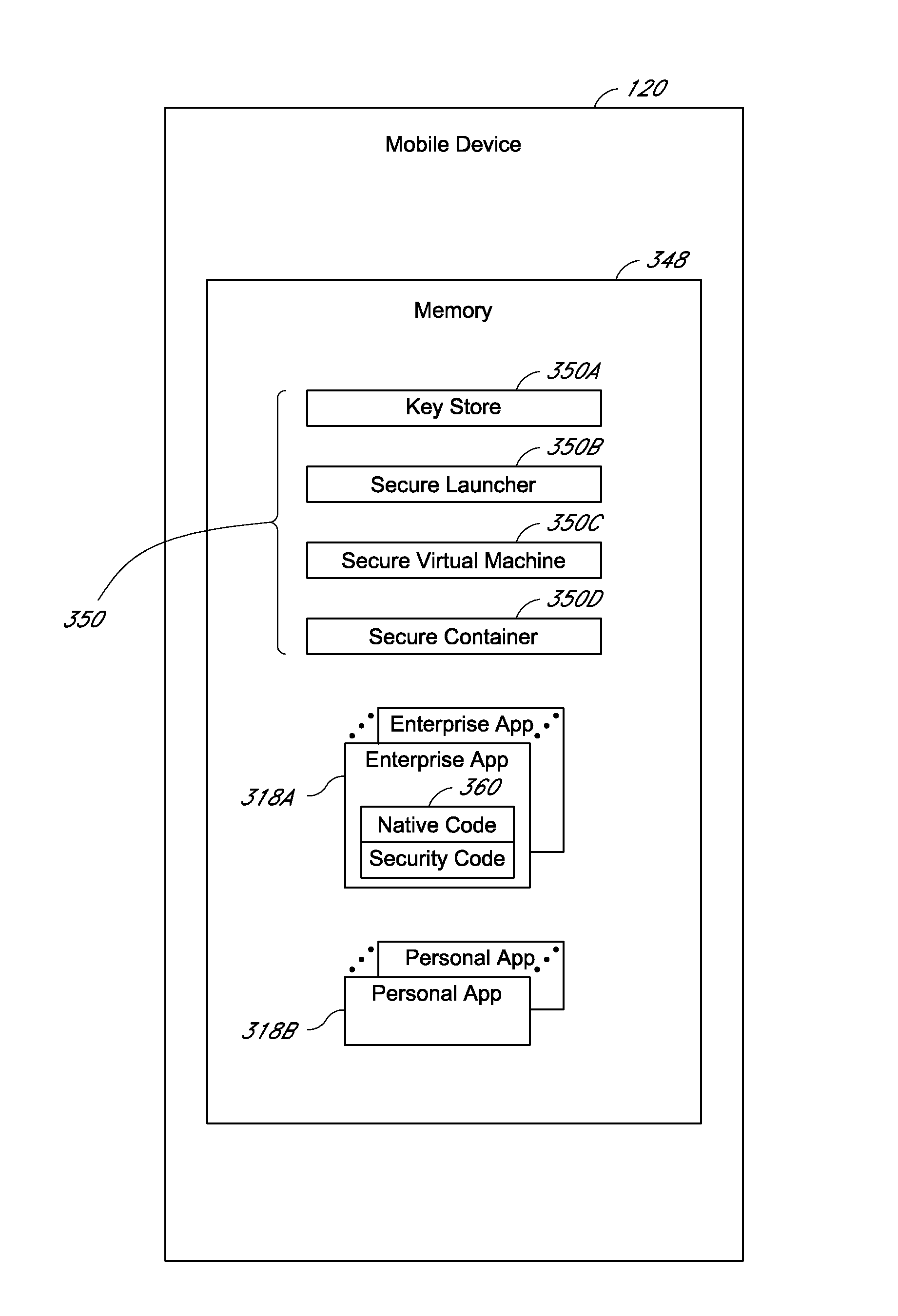
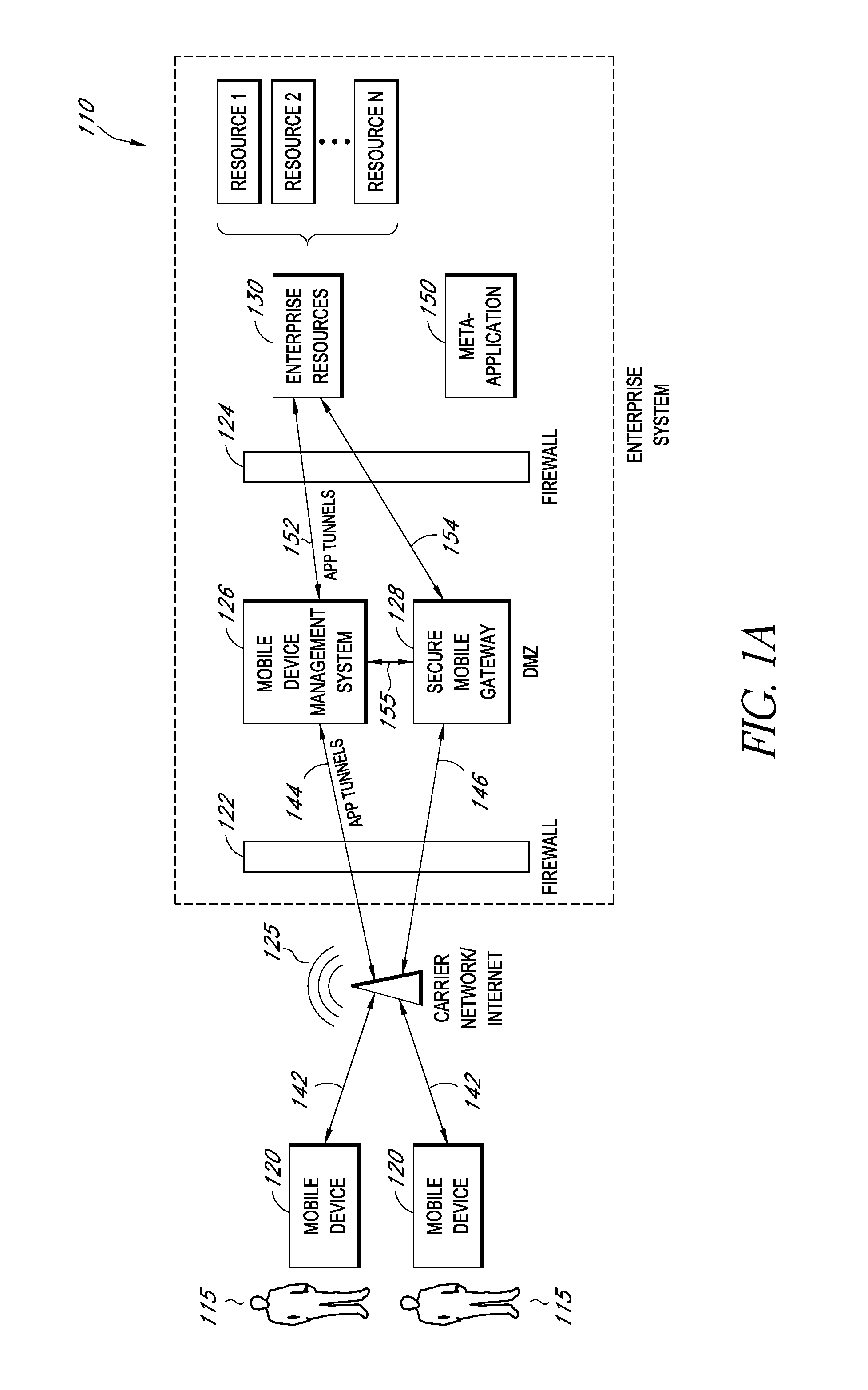
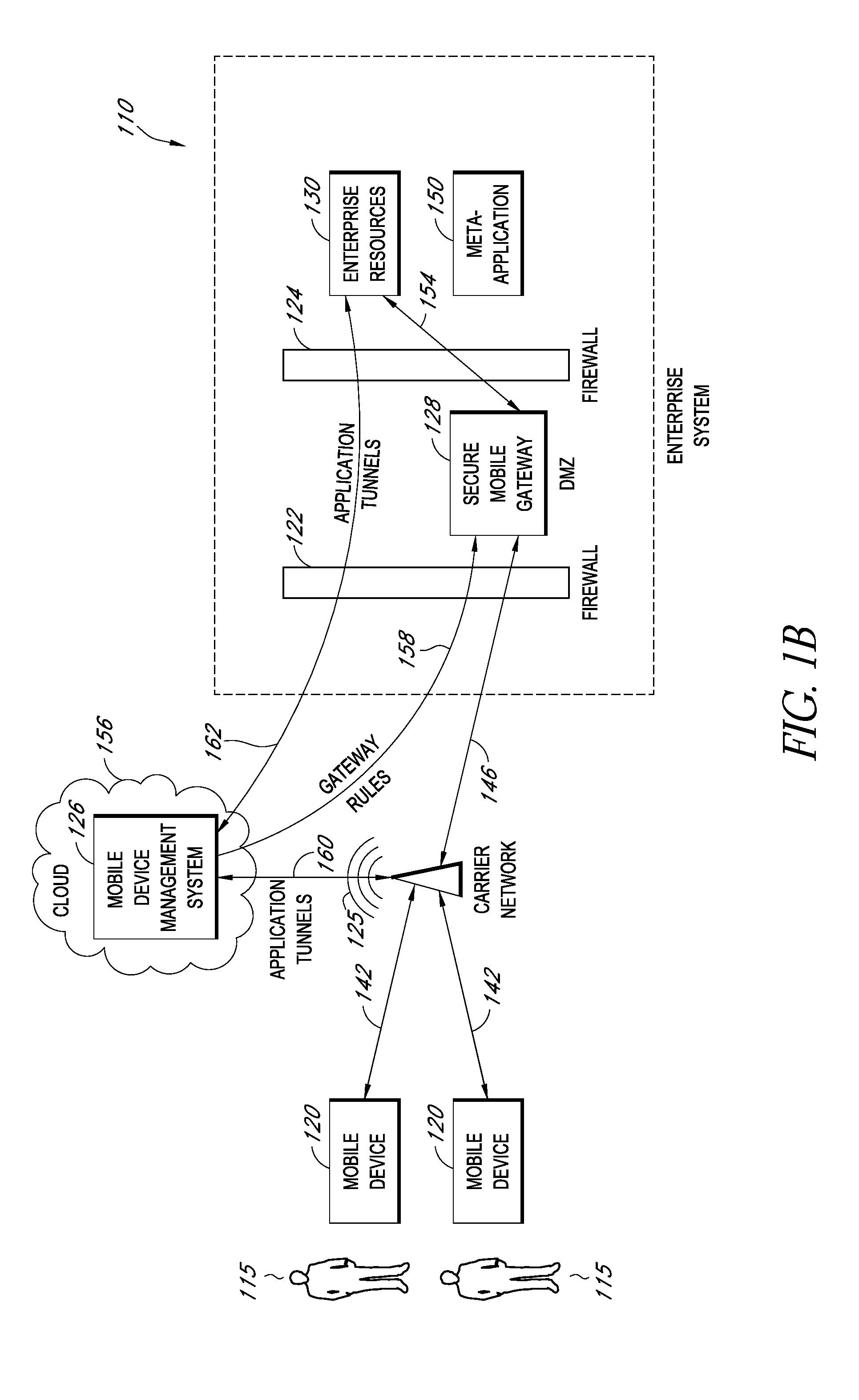
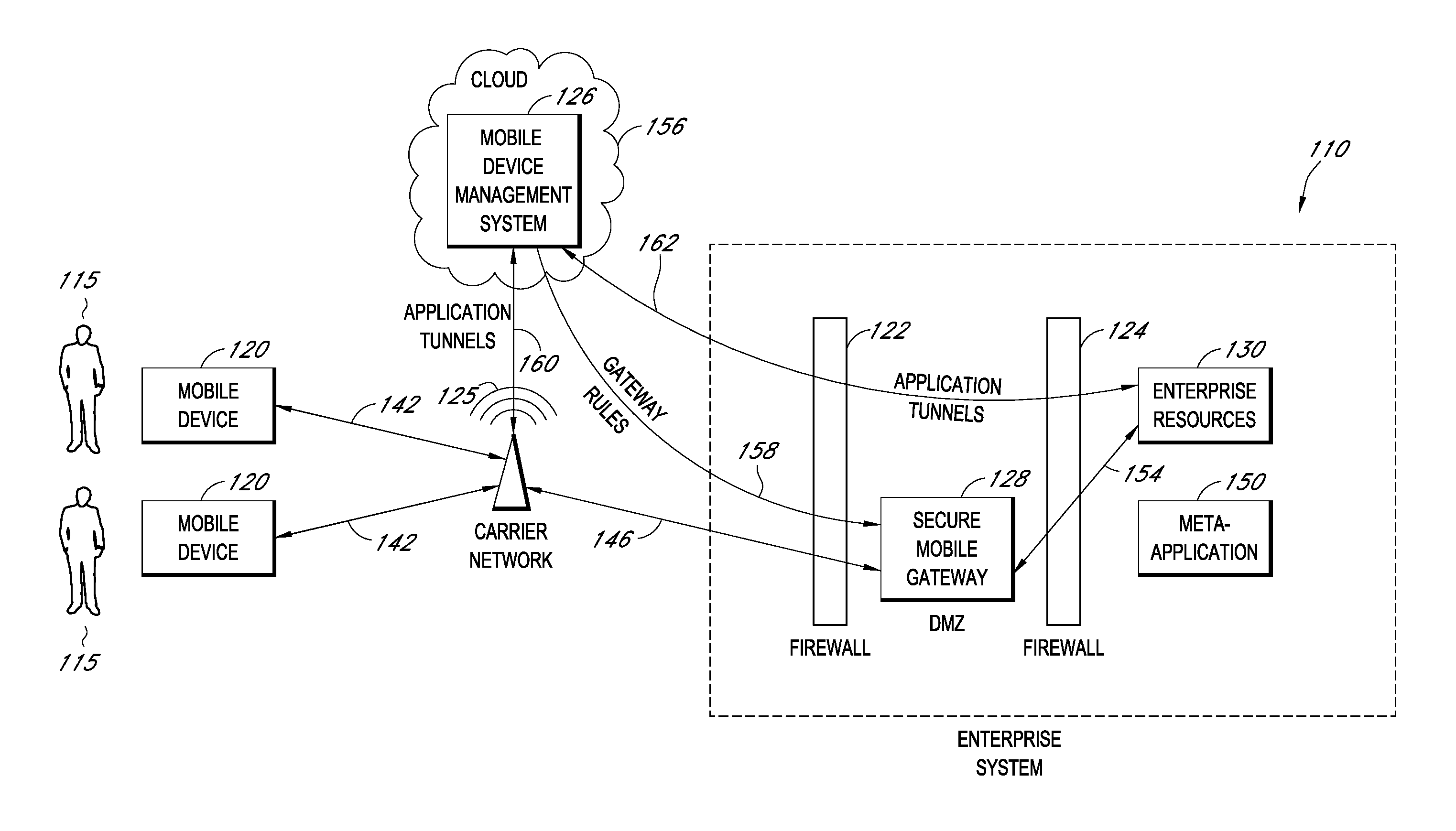
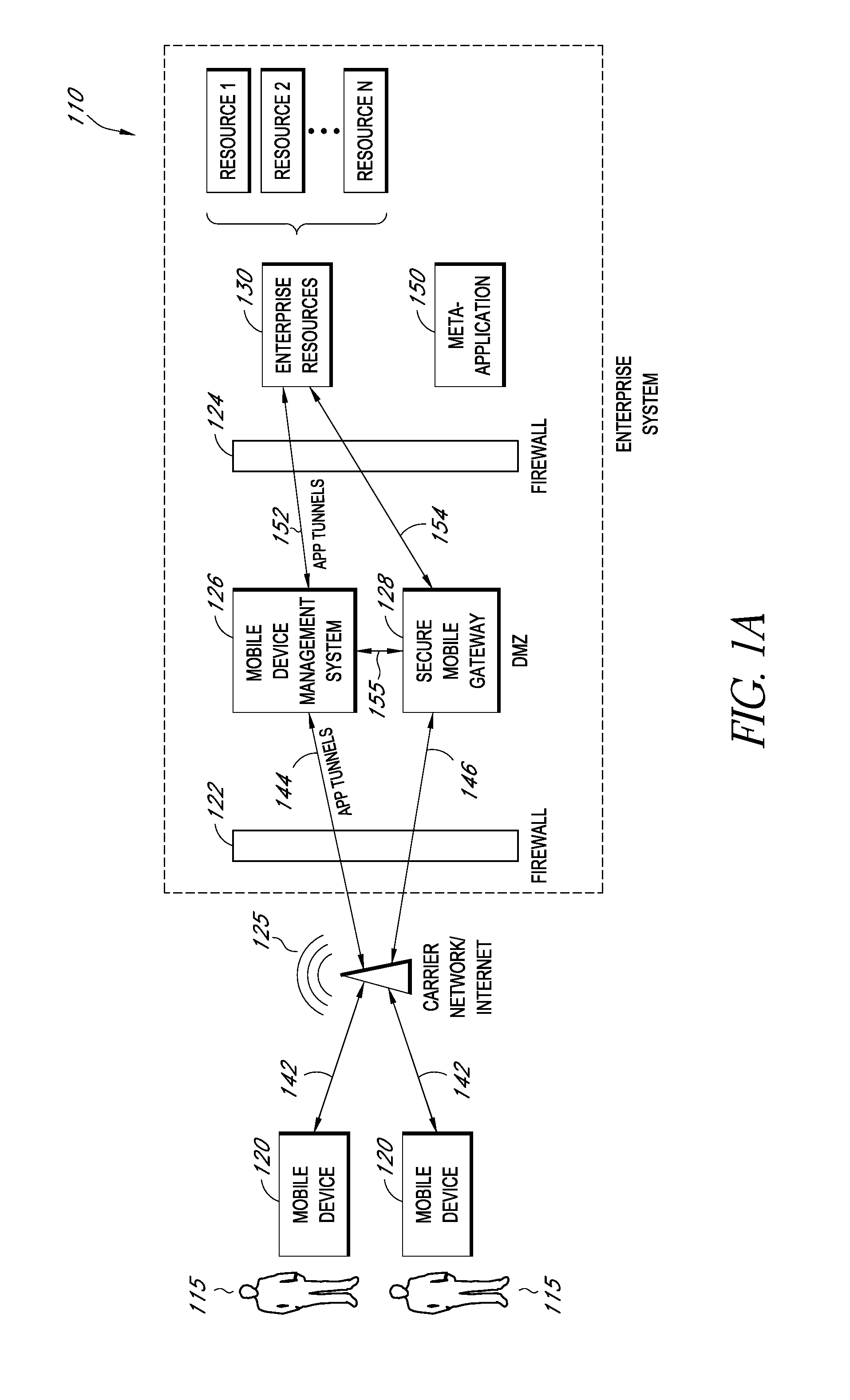
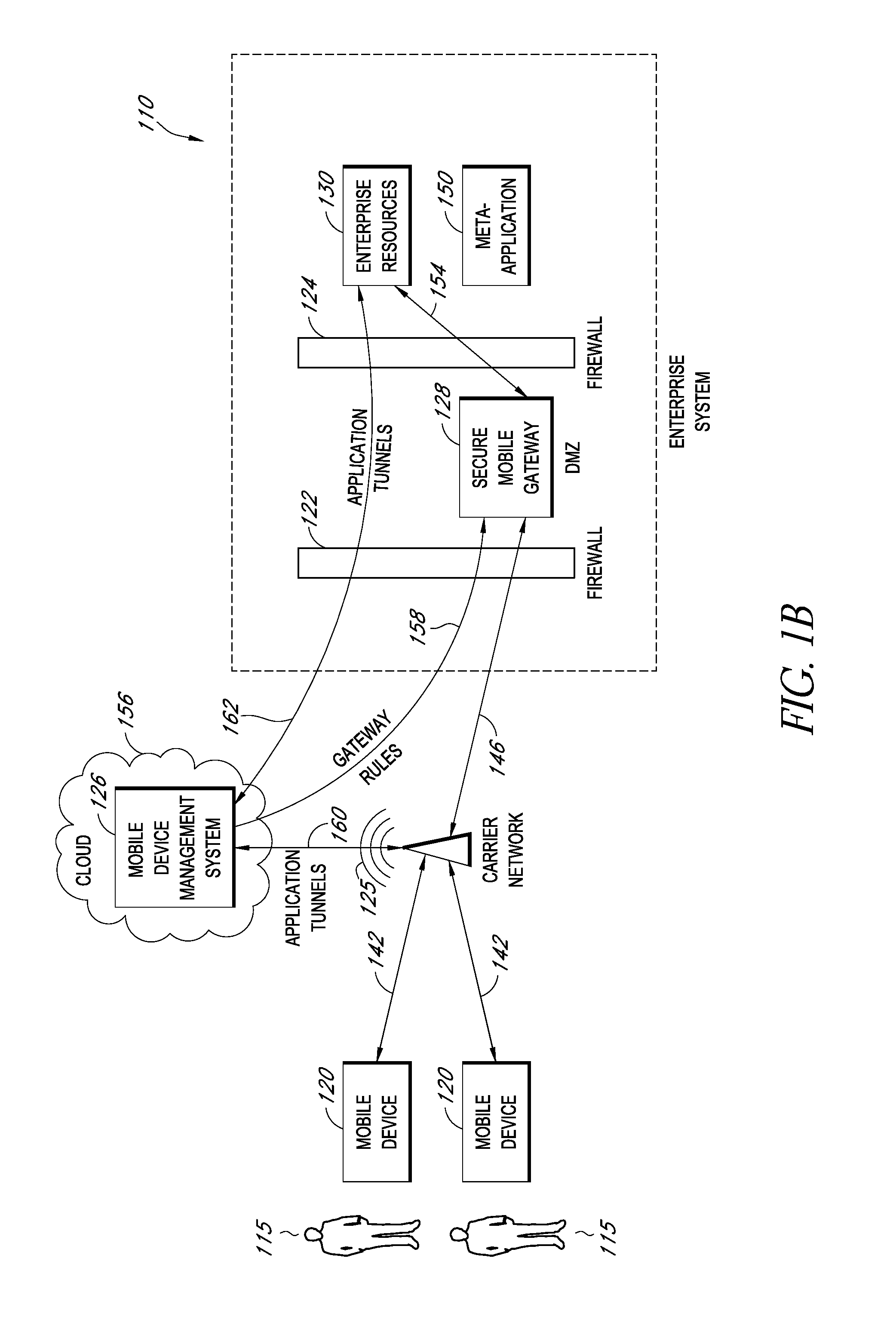
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Controlling mobile device access to enterprise resources
ActiveUS20140007183A1Decompilation/disassemblyDigital data protectionApplication serverEnterprise resource planning
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Gateway for controlling mobile device access to enterprise resources
ActiveUS20140007214A1Decompilation/disassemblyDigital data processing detailsApplication serverResource based
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Secure mobile browser for protecting enterprise data
ActiveUS8869235B2Decompilation/disassemblyDigital data information retrievalDocumentation procedureApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Secure mobile browser for protecting enterprise data
ActiveUS20140007182A1Decompilation/disassemblyDigital data protectionDocumentation procedureApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Modifying pre-existing mobile applications to implement enterprise security policies
ActiveUS20140007048A1Decompilation/disassemblyDigital data protectionApplication serverCorporate security
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Automated processor generation system for designing a configurable processor and method for the same
InactiveUS20030208723A1Decompilation/disassemblyGeneral purpose stored program computerApplication softwareProcessor design
An automated processor design tool uses a description of customized processor instruction set extensions in a standardized language to develop a configurable definition of a target instruction set, a Hardware Description Language description of circuitry necessary to implement the instruction set, and development tools such as a compiler, assembler, debugger and simulator which can be used to develop applications for the processor and to verify it. Implementation of the processor circuitry can be optimized for various criteria such as area, power consumption, speed and the like. Once a processor configuration is developed, it can be tested and inputs to the system modified to iteratively optimize the processor implementation. By providing a constrained domain of extensions and optimizations, the process can be automated to a high degree, thereby facilitating fast and reliable development.
Owner:TENSILICA
Software analysis framework
InactiveUS7051322B2Decompilation/disassemblySpecific program execution arrangementsSoftware analyticsScript analysis
Presently described is a decompilation method of operation and system for parsing executable code, identifying and recursively modeling data flows, identifying and recursively modeling control flow, and iteratively refining these models to provide a complete model at the nanocode level. The nanocode decompiler may be used to determine if flaws, security vulnerabilities, or general quality issues exist in the code. The nanocode decompiler outputs in a standardized, human-readable intermediate representation (IR) designed for automated or scripted analysis and reporting. Reports may take the form of a computer annotated and / or partially human annotated nanocode listing in the above-described IR. Annotations may include plain English statements regarding flaws and pointers to badly constructed data structures, unchecked buffers, malicious embedded code or “trap doors,” and the like. Annotations may be generated through a scripted analysis process or by means of an expert-enhanced, quasi-autonomous system.
Owner:VERACODE
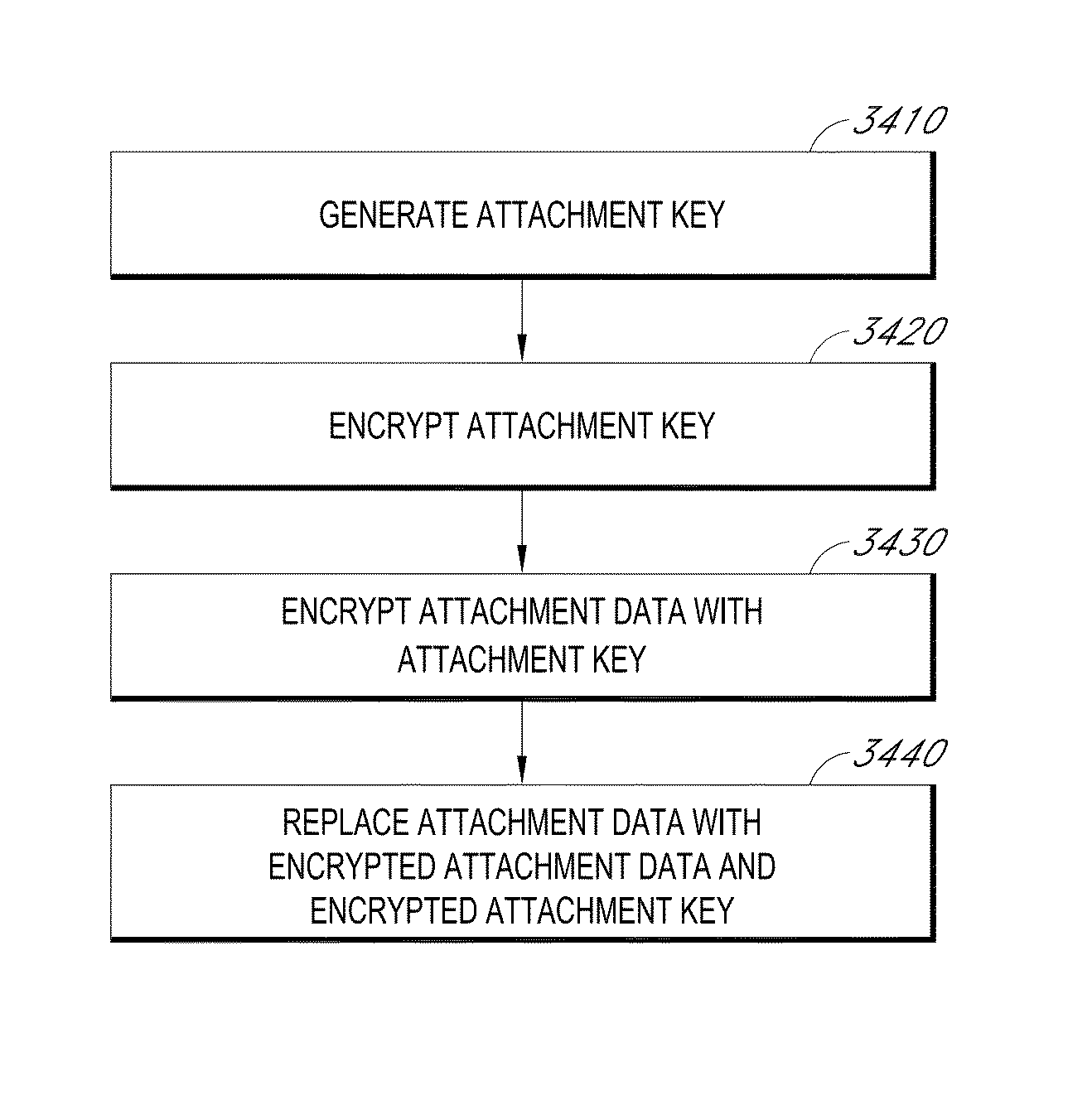
Protecting enterprise data through policy-based encryption of message attachments
ActiveUS8886925B2Decompilation/disassemblyDigital data information retrievalApplication serverPaper document
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
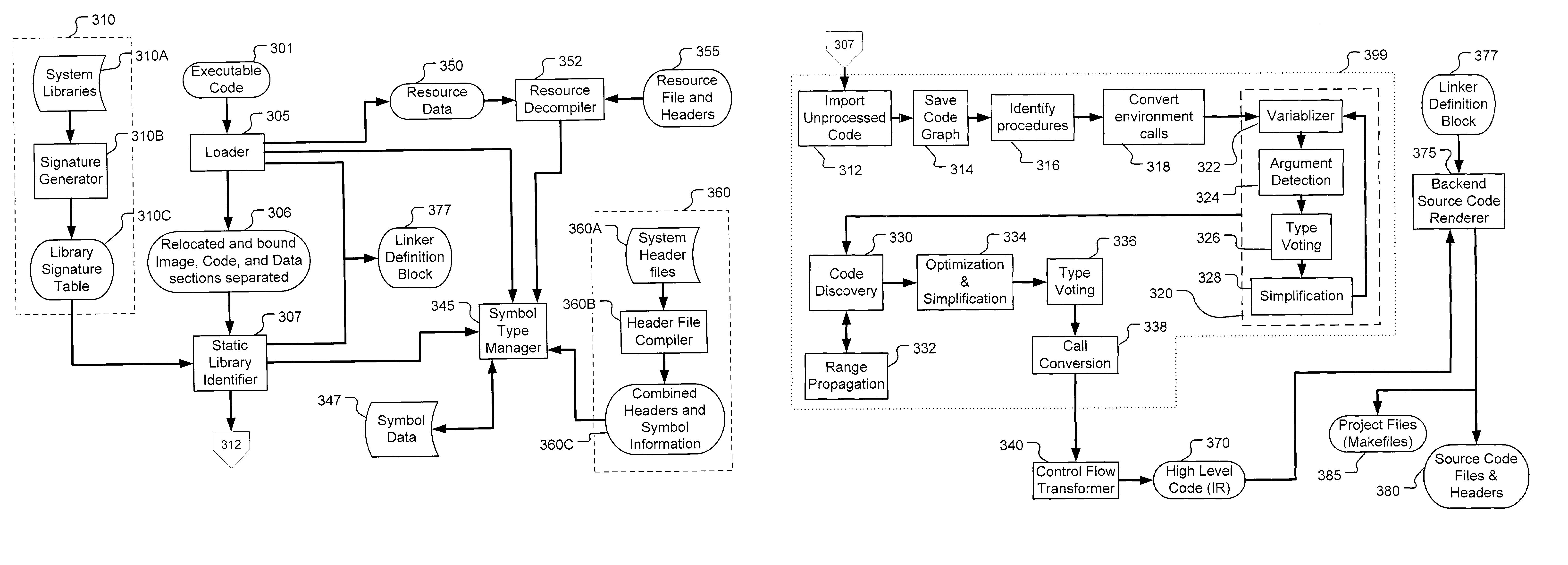
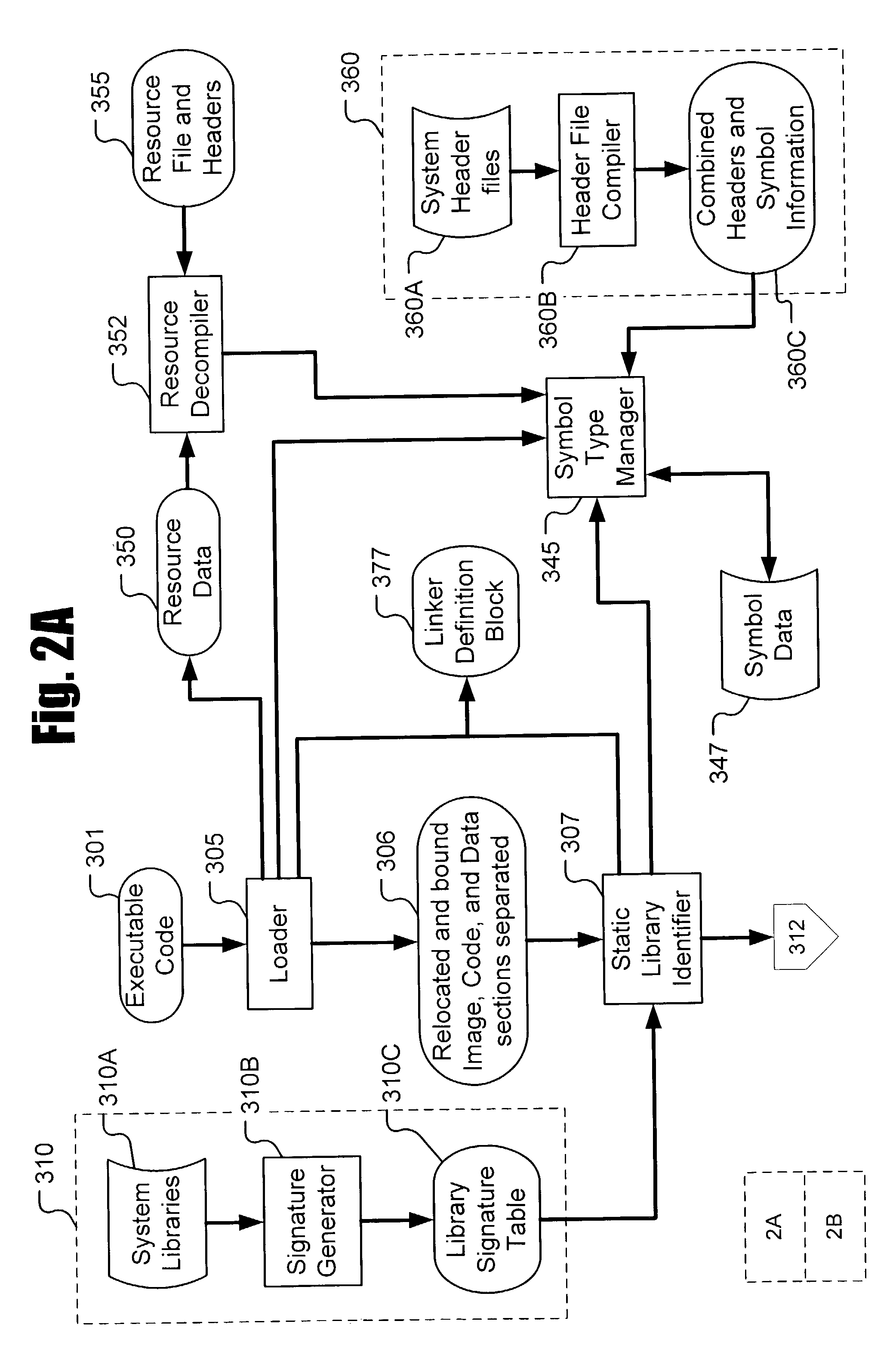
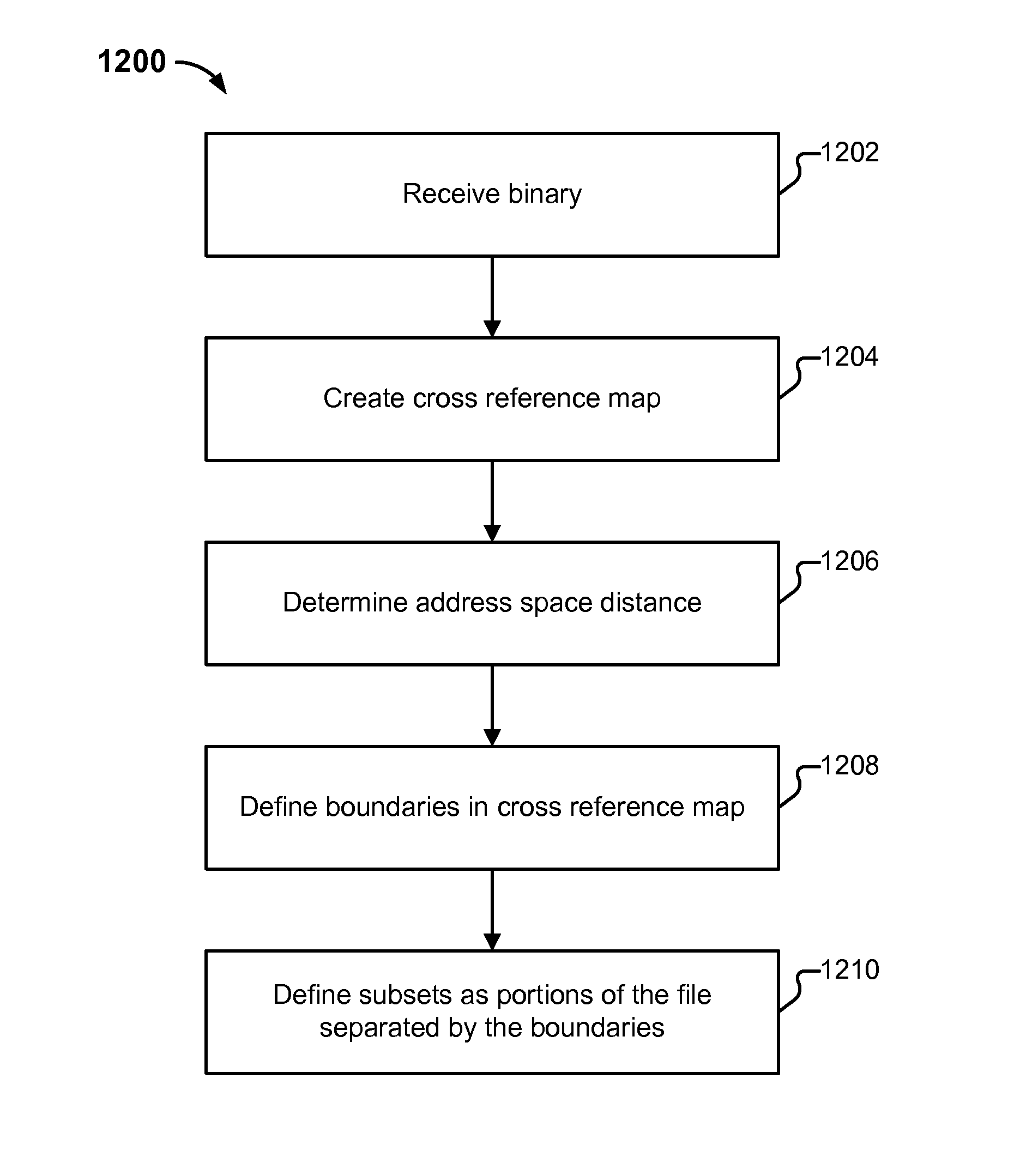
Recovering source code structure from program binaries
Recovering structure from binaries is disclosed. A binary file having components including a plurality of linker objects is received. A cross reference map of linker objects is created. The linker objects are associated based on calls. An address space distance for each call is determined. Boundaries are defined in the cross reference map based on the address space distance. Subsets are defined as portions of the file that are separated by the boundaries.
Owner:ORCHARD VALLEY MANAGEMENT LLC
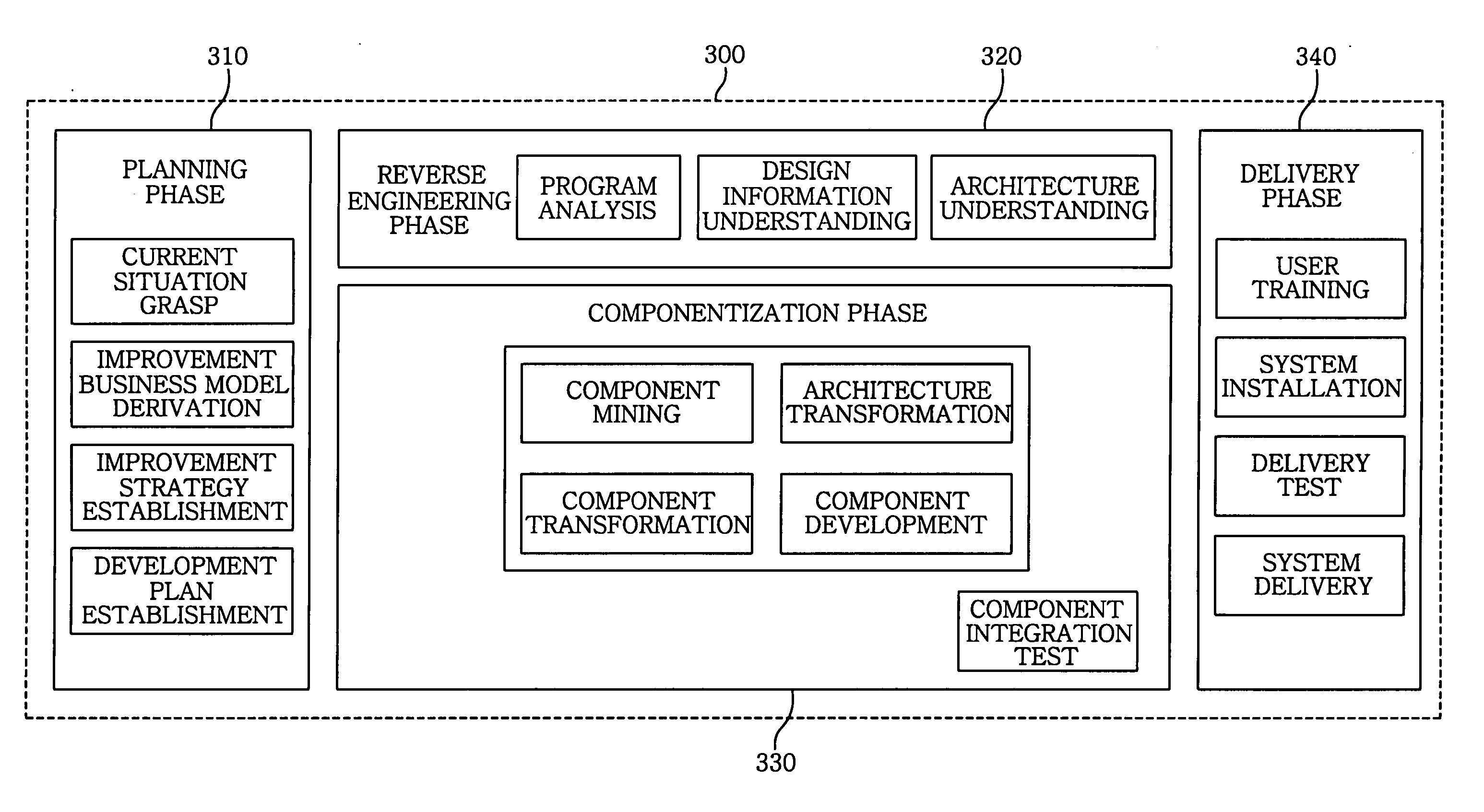
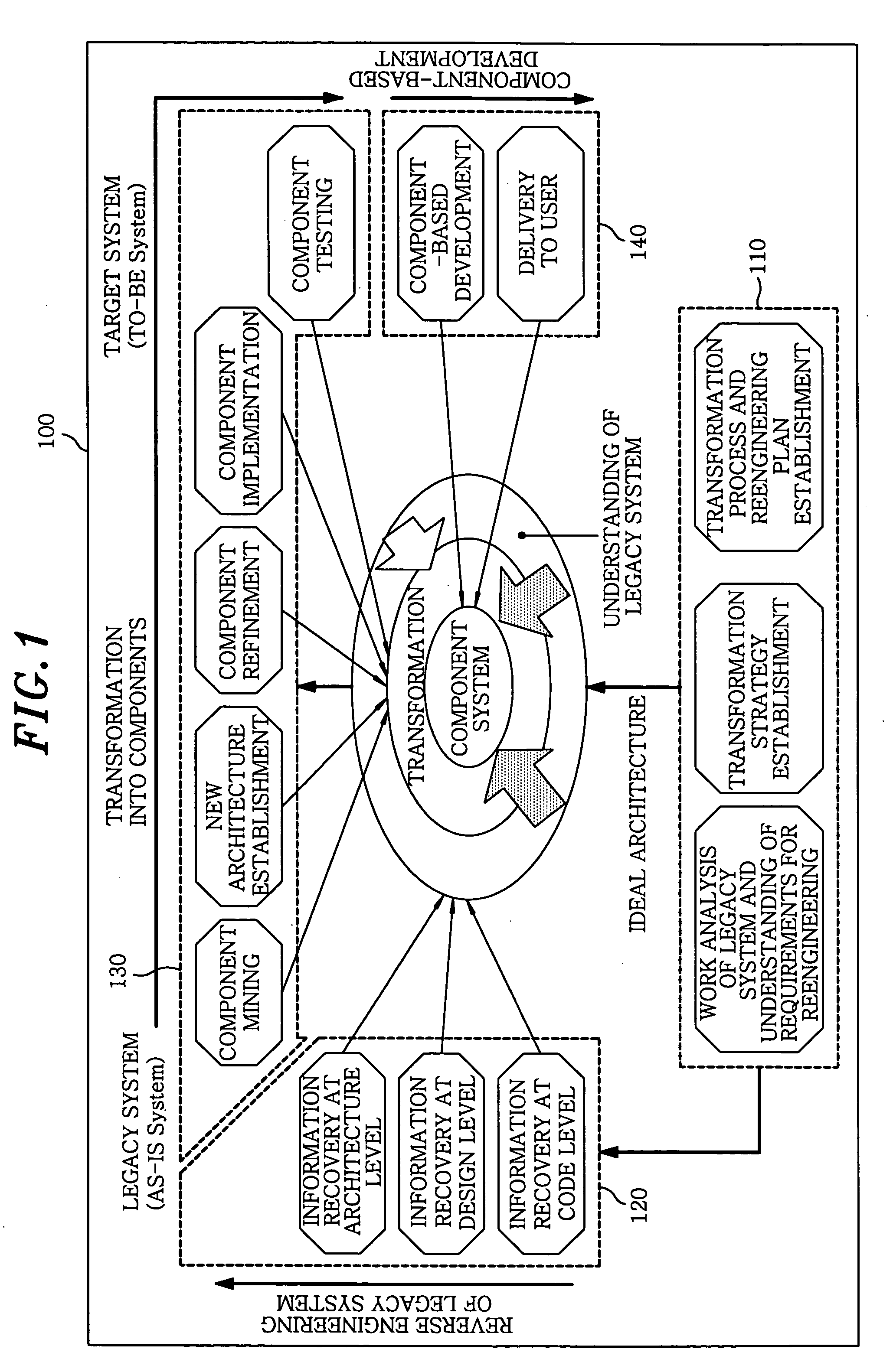
Componentization method for reengineering legacy system
InactiveUS20050138603A1Minimizing semantic differenceIncrease valueDecompilation/disassemblyReverse engineeringProduction rateSoftware engineering
The present invention proposes a Magic and Robust Methodology Integrated-Reengineering (MaRMI-RE), which is a reengineering methodology defining a process including procedures and techniques for a componentization of legacy systems and work products generated during the process. A continuous evolution model for the legacy systems proposed in the present invention enables the legacy systems to be systematically transformed into component systems capable of smoothly complying with new requirements, thus maximizing productivity and efficiency of the legacy systems with respect to potential business and system change requirements.
Owner:ELECTRONICS & TELECOMM RES INST
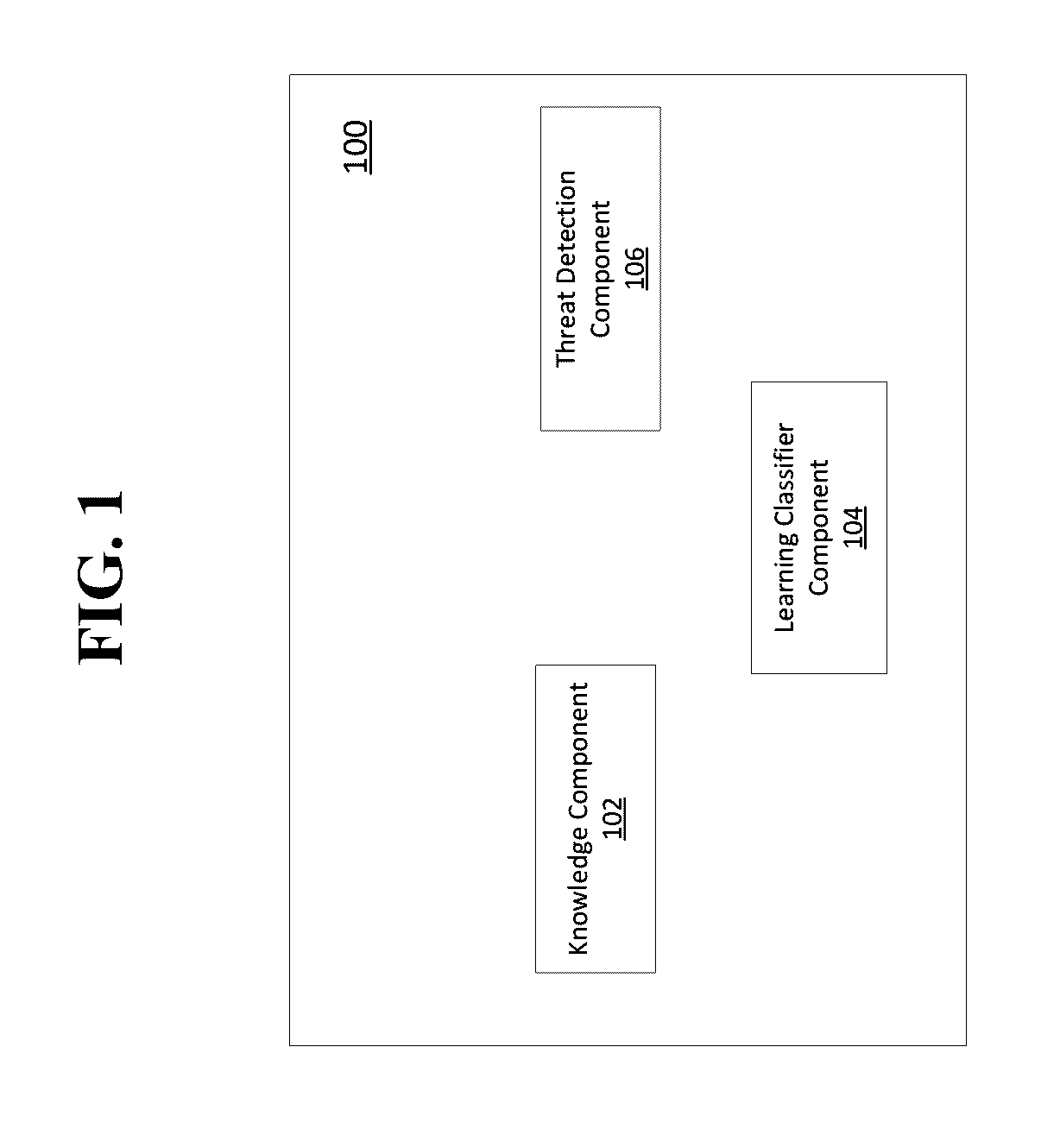
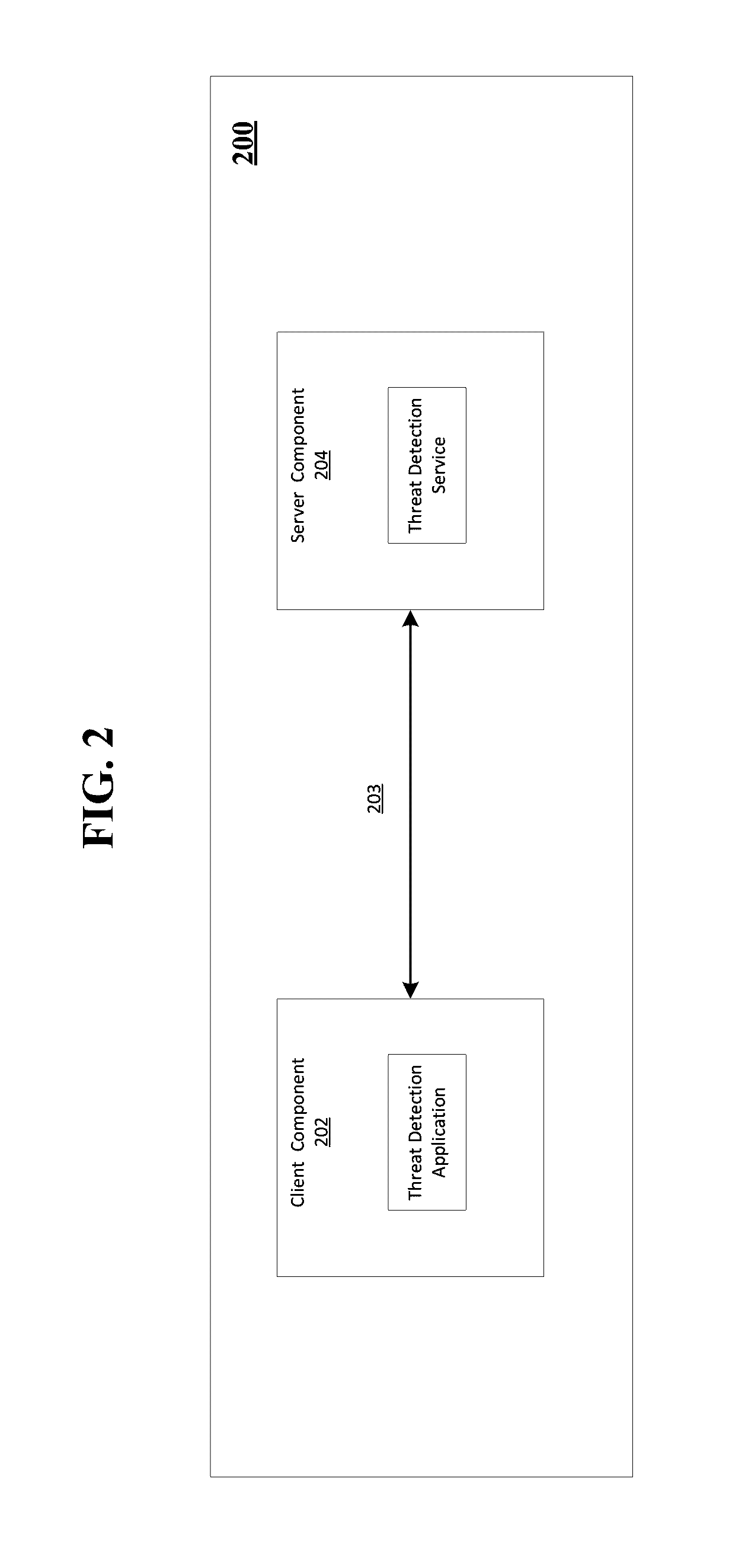
Automatic threat detection of executable files based on static data analysis
ActiveUS20160335435A1Preventing executionDecompilation/disassemblyKernel methodsStatic timing analysisAnalysis aspect
Aspects of the present disclosure relate to threat detection of executable files. A plurality of static data points may be extracted from an executable file without decrypting or unpacking the executable file. The executable file may then be analyzed without decrypting or unpacking the executable file. Analysis of the executable file may comprise applying a classifier to the plurality of extracted static data points. The classifier may be trained from data comprising known malicious executable files, known benign executable files and known unwanted executable files. Based upon analysis of the executable file, a determination can be made as to whether the executable file is harmful.
Owner:OPEN TEXT CORPORATION
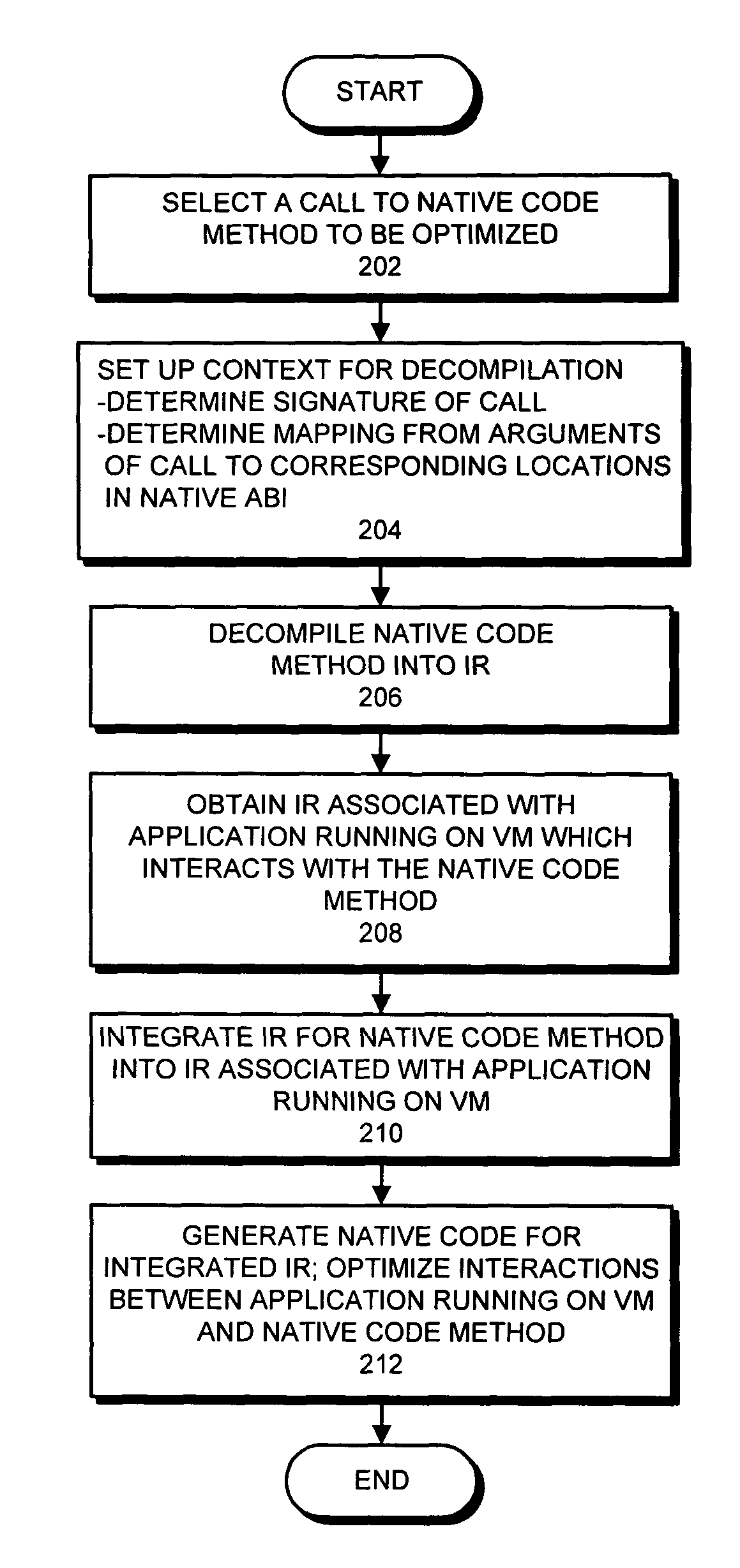
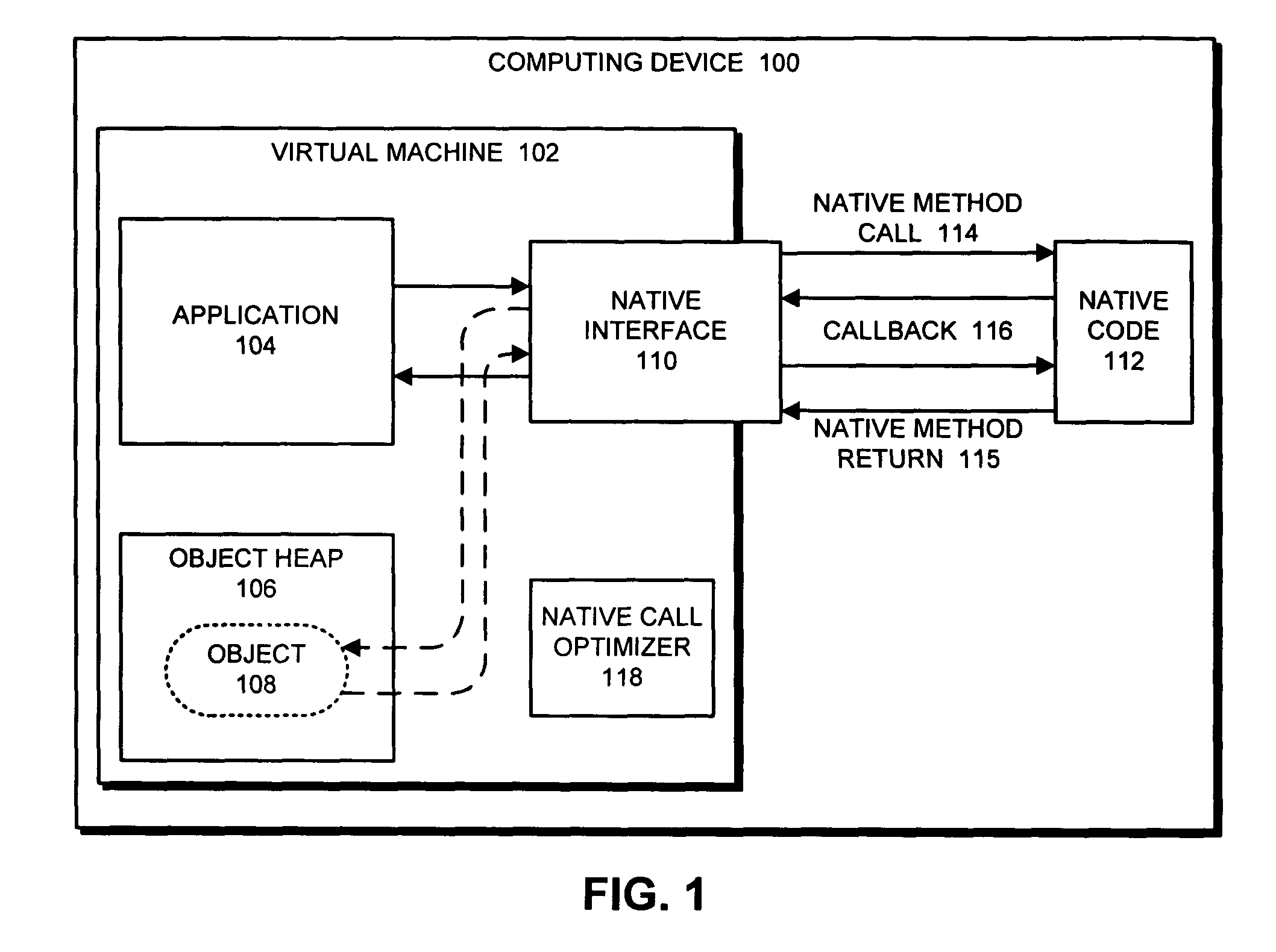
Reducing the overhead involved in executing native code in a virtual machine through binary reoptimization
ActiveUS7840951B1Reduce overheadEnhanced interactionDecompilation/disassemblyProgram controlApplication softwareIntermediate language
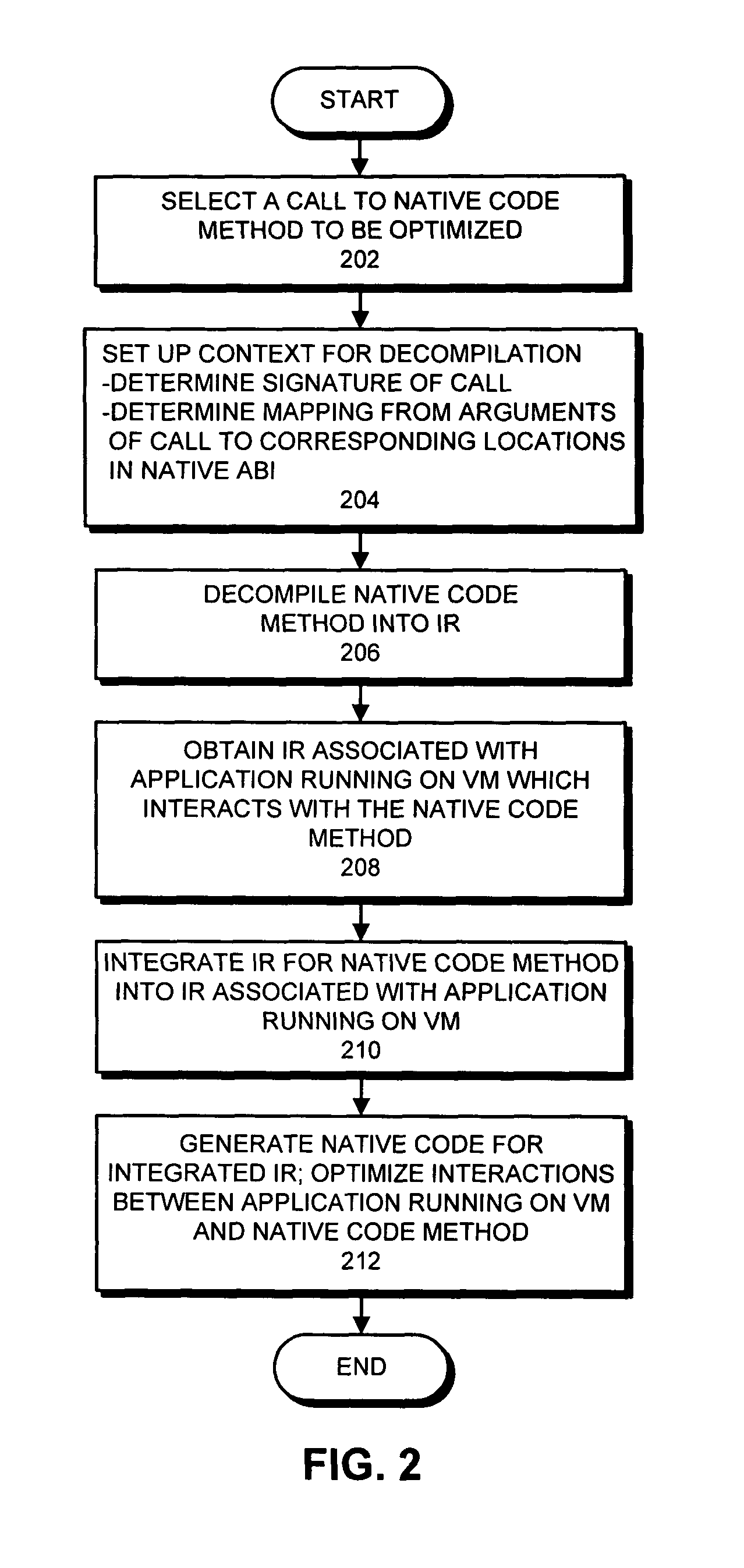
One embodiment of the present invention provides a system that reduces the overhead involved in executing a native code method in an application running on a virtual machine. During operation, the system selects a call to a native code method to be optimized within the virtual machine, decompiles at least part of the native code method into an intermediate representation, and obtains an intermediate representation associated with the application. Next, the system combines the intermediate representation for the native code method with the intermediate representation associated with the application running on the virtual machine to form a combined intermediate representation, and generates native code from the combined intermediate representation, wherein the native code generation process optimizes interactions between the application running on the virtual machine and the native code method. A variation on this embodiment involves optimizing callbacks by the native code method into the virtual machine.
Owner:ORACLE INT CORP
Protecting enterprise data through policy-based encryption of message attachments
ActiveUS20140006772A1Decompilation/disassemblyDigital data protectionDocumentation procedureApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
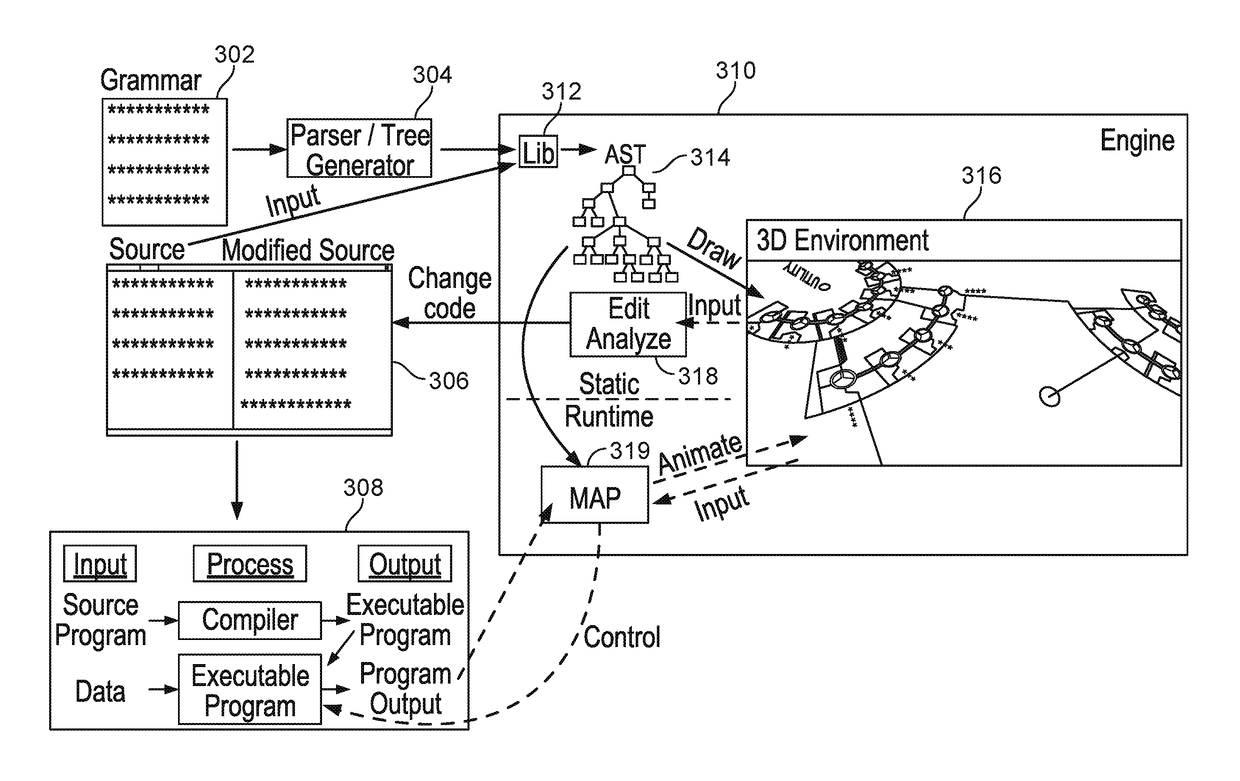
Visualizing the structure and execution of a program
A graphical representation of a set of graphical objects representing elements of a computer code is provided. The set of graphical objects includes a first graphical object and a second graphical object. The first graphical object represents a first element and the second graphical object represents a second element. The first graphical object appears higher in hierarchy than the second graphical object. The first element is higher in programming abstraction level than the second element. At least a portion of the graphical objects is animated to visualize an execution of the computer code.
Owner:PRIME SOFTWARE SYST INC
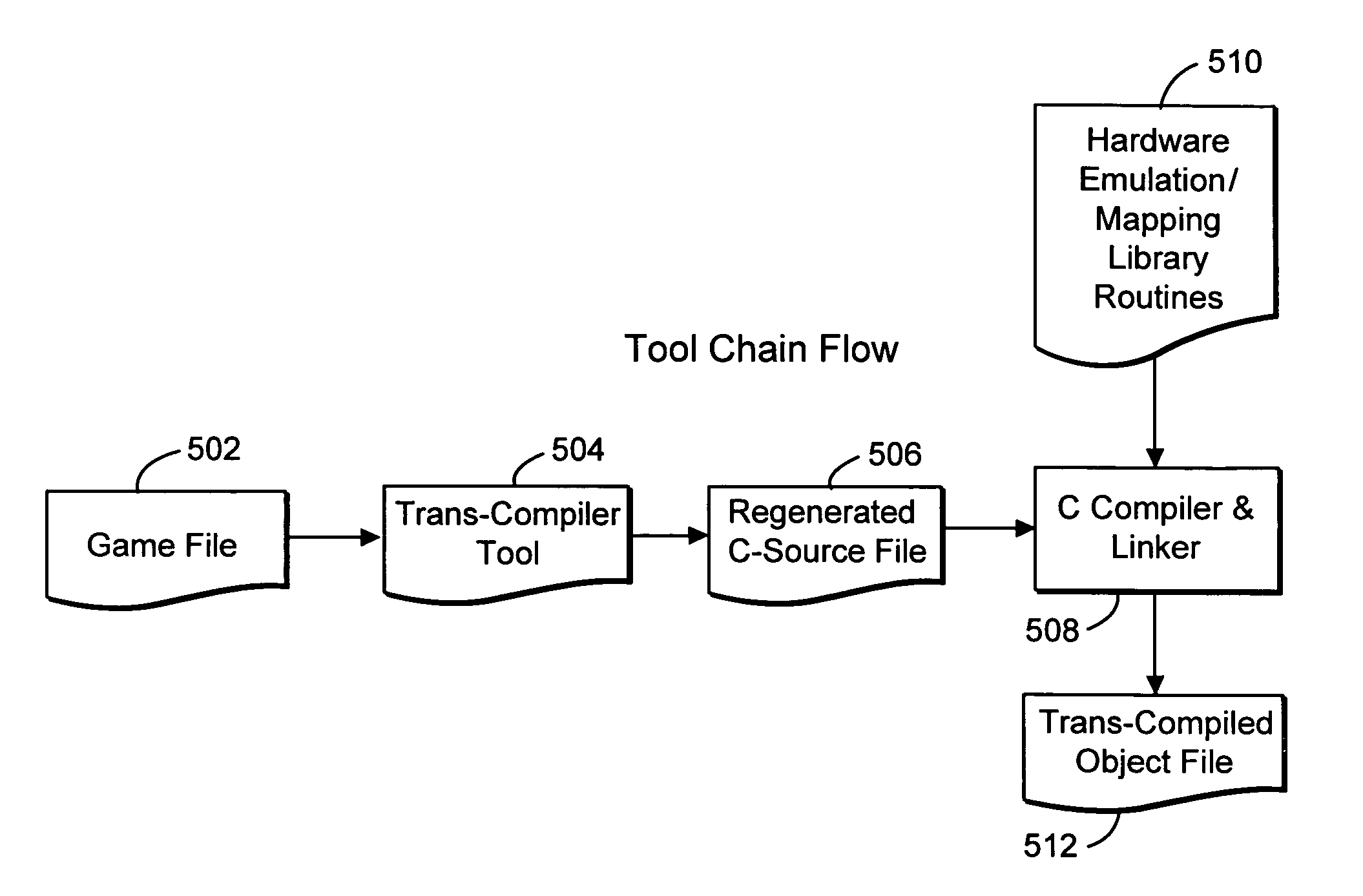
System and method for trans-compiling video games
ActiveUS7765539B1Low costImprove performanceDecompilation/disassemblyProgram code adaptionTheoretical computer scienceOrders of magnitude (speed)
A method of porting a video game or other application from one platform to another involves decompiling the game executable to develop source code in a high level programming language such as C. The (re)generated source code is re-linked using target native libraries to handle hardware functions (e.g., video, audio, etc.) for the target platform. The resulting “trans-compiled” executable is able to efficiently run on the target platform, potentially providing orders of magnitude speed performance boost over other traditional techniques.
Owner:NINTENDO CO LTD
Control Flow Integrity System and Method
ActiveUS20150135313A1Provide securityMaintaining system correctnessDecompilation/disassemblyMemory loss protectionParallel computingComputer software
Owner:RUNSAFE SECURITY INC
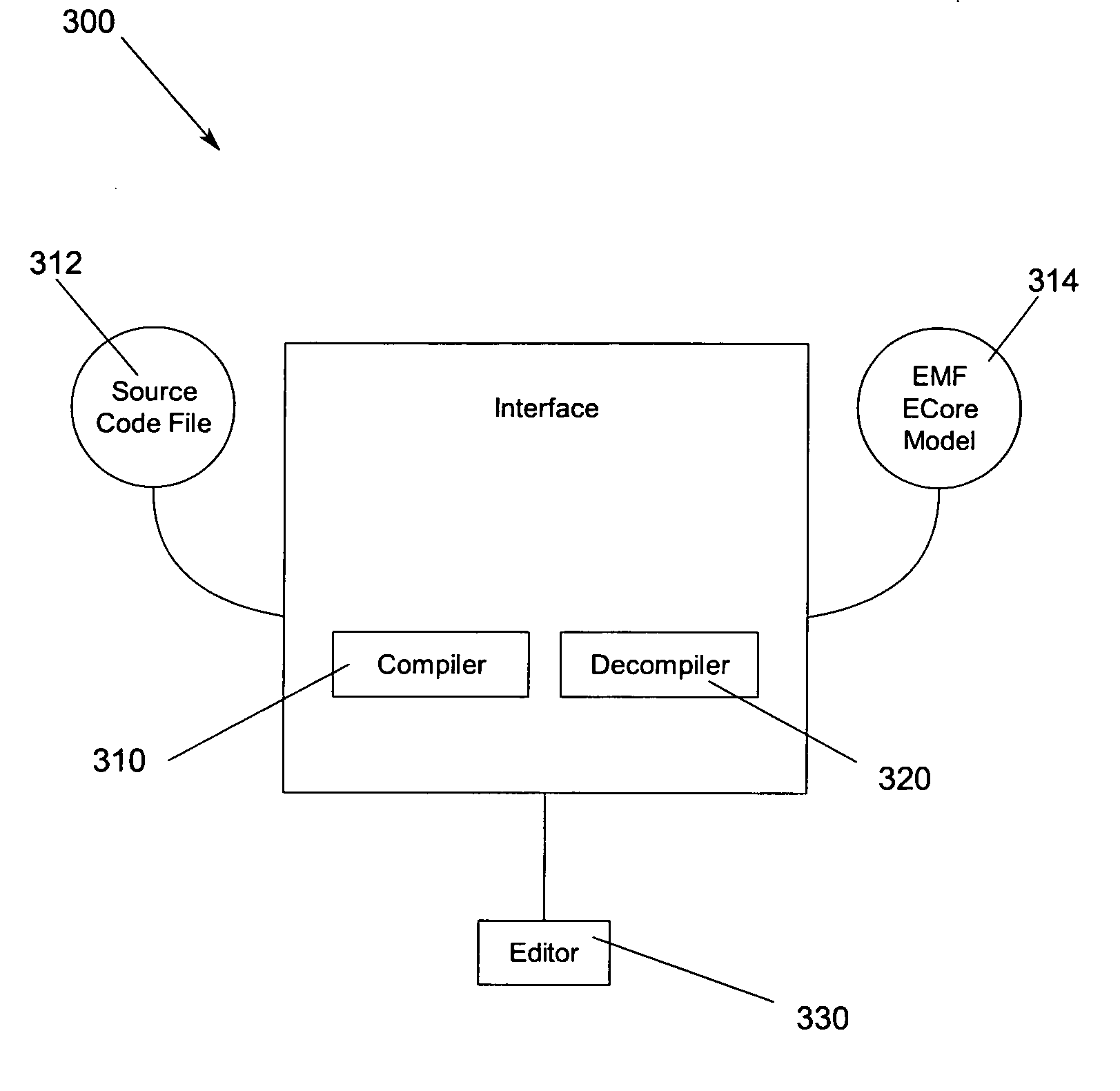
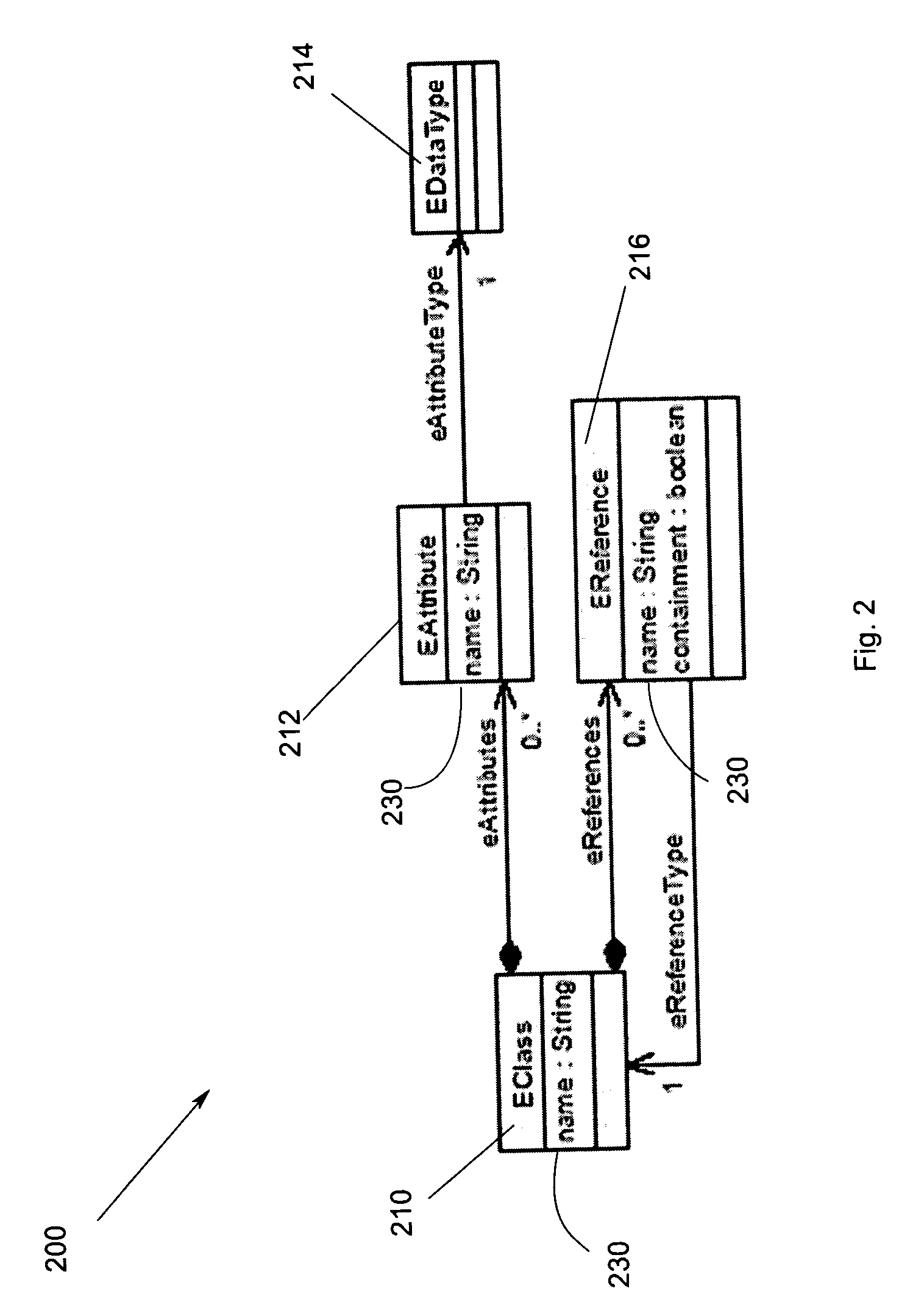
Method, apparatus and program storage device for representing eclipse modeling framework (EMF) ecore models in textual form
InactiveUS20070079299A1Decompilation/disassemblySpecific program execution arrangementsEclipseSource code
A method, apparatus and program storage device for representing software models in textual form. A representation of a computer program selected from a group comprising a model and source code representing a model is provided. A counterpart to the selected representation of the computer program is produced.
Owner:IBM CORP
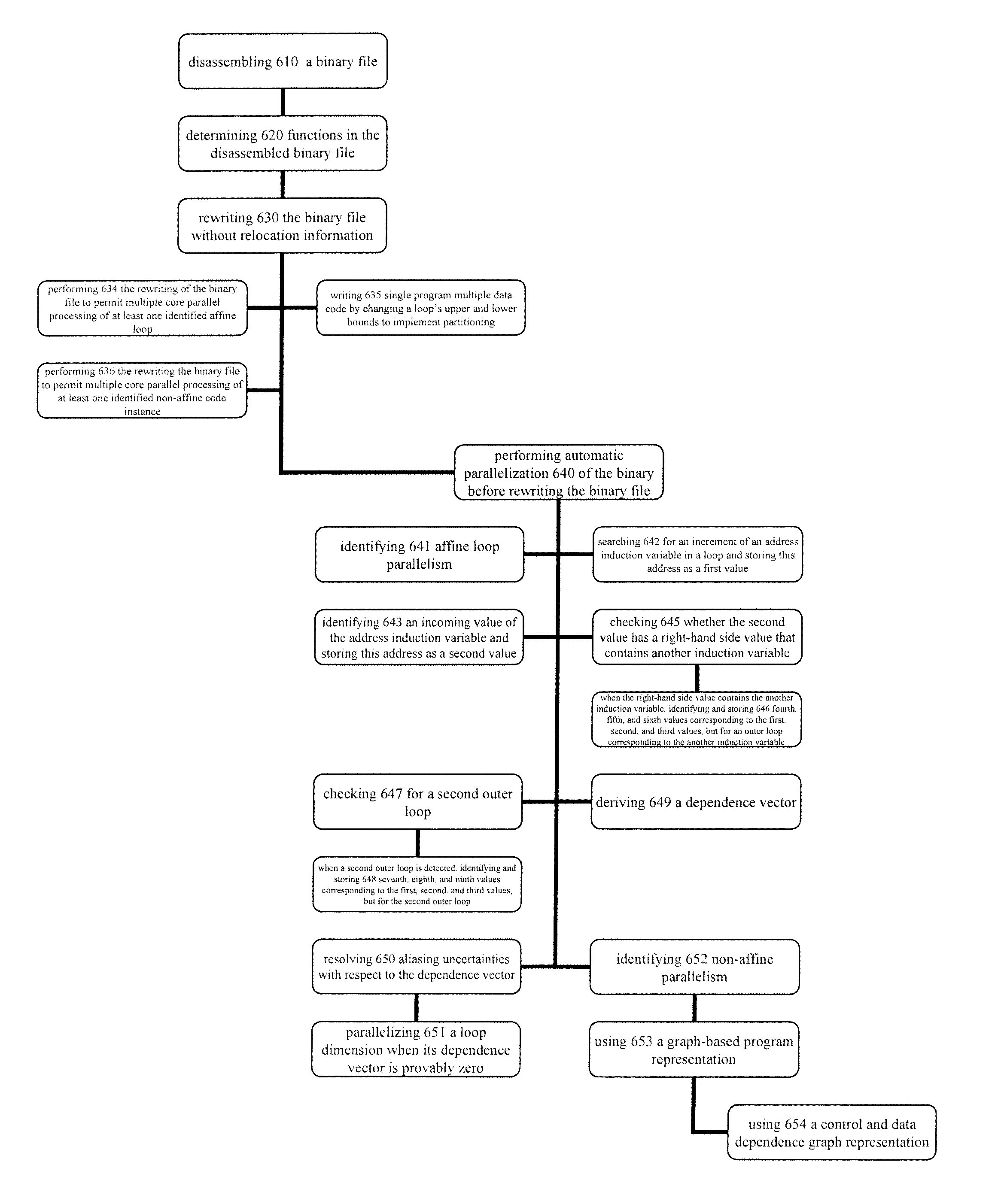
Automatic parallelization using binary rewriting
Binary rewriters that do not require relocation information and automatic parallelizers within binary rewriters are provided, as well as methods for performing binary rewriting and automatic parallelization. The method, in certain embodiments. includes disassembling a binary file and determining functions in the disassembled binary file. The method can further include rewriting the binary file without relying on relocation information or object files. Optionally, the method can further include performing automatic parallelization of the binary before rewriting the binary file.
Owner:UNIV OF MARYLAND
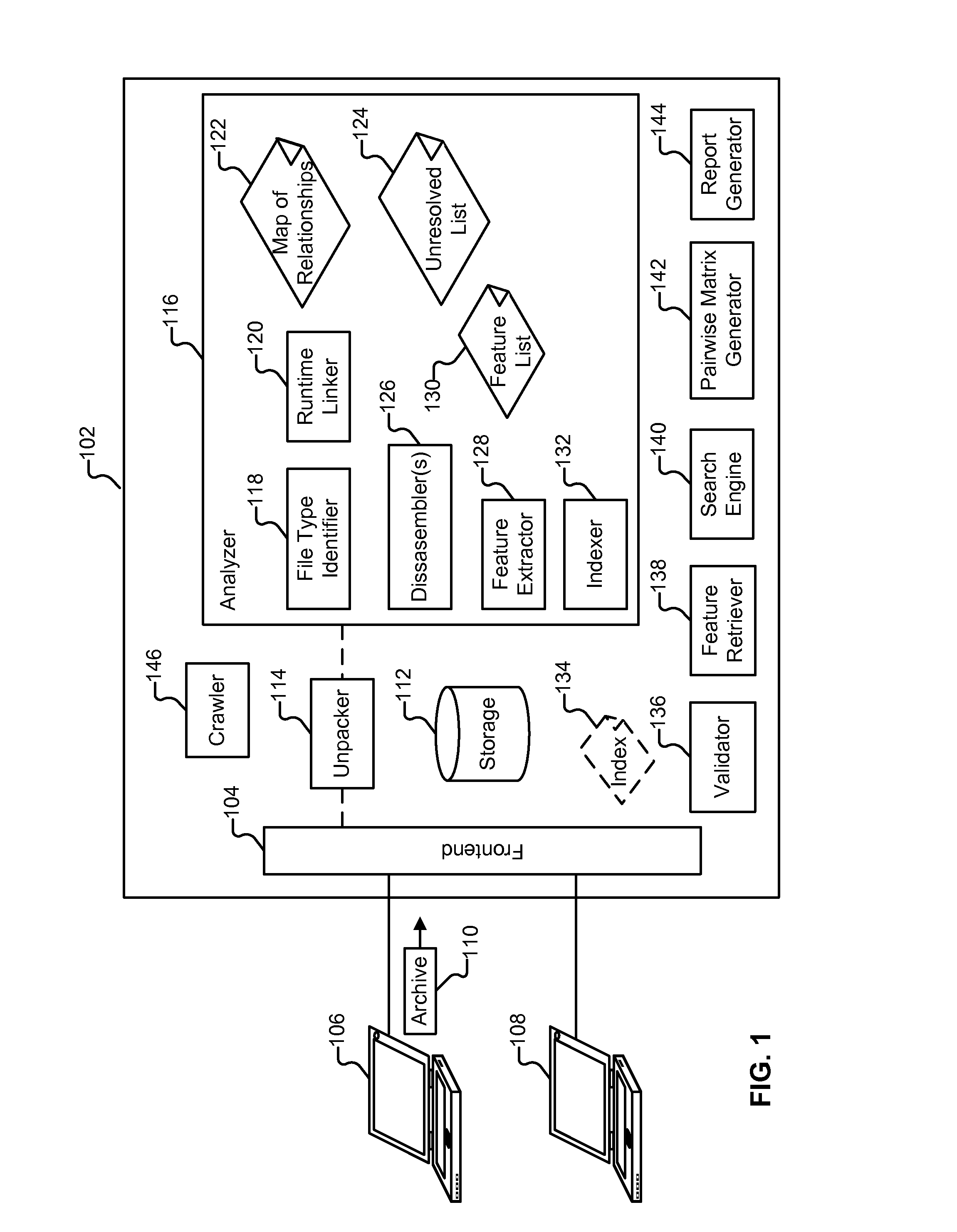
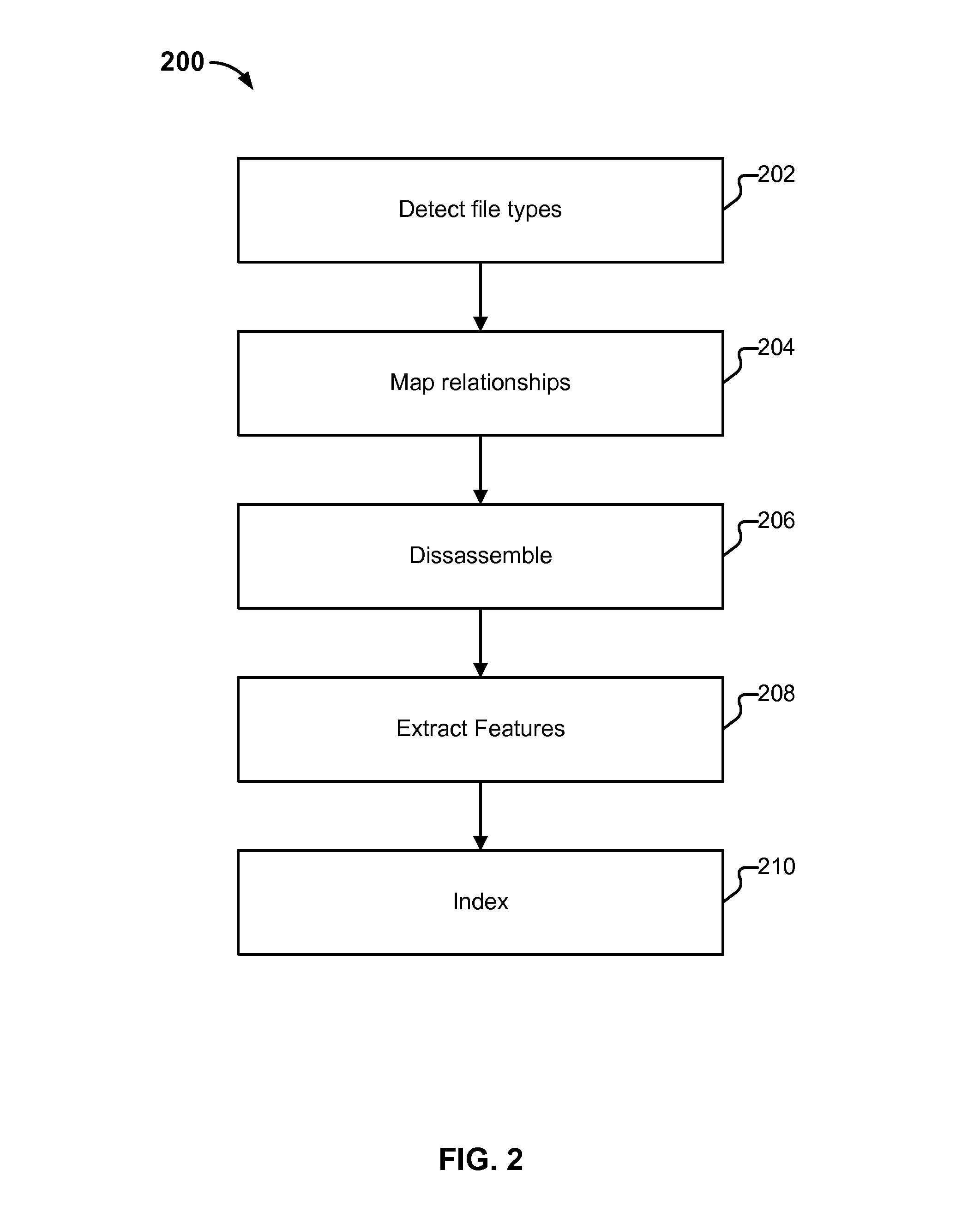
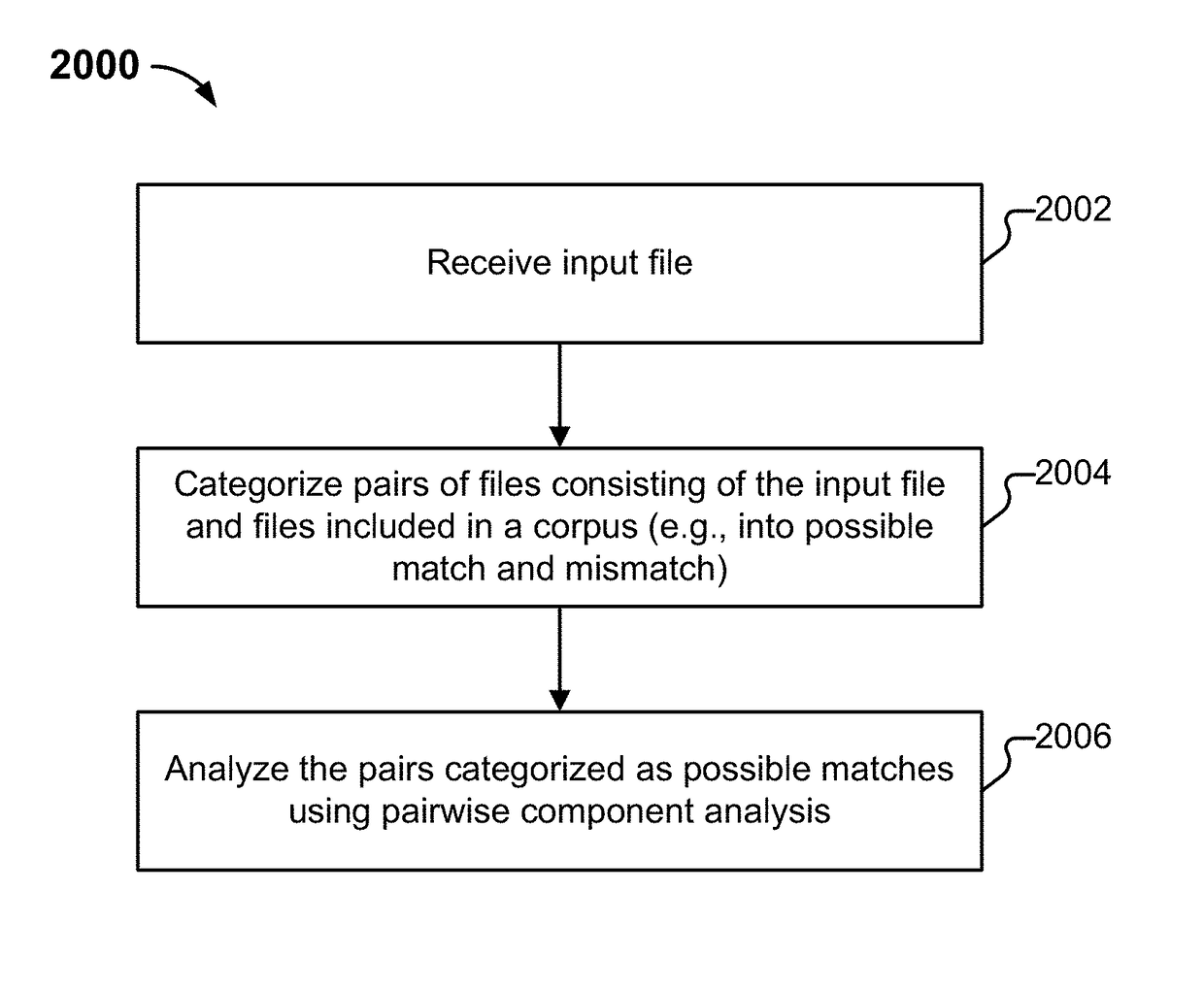
Software similarity searching
Similarity analysis of software is disclosed. An input file is received. Pairs of files that consist of the input file and files included in a corpus are categorized into one of a possible match and a mismatch. Those pairs classified as possible matches are analyzed using a pairwise component analysis.
Owner:ORCHARD VALLEY MANAGEMENT LLC
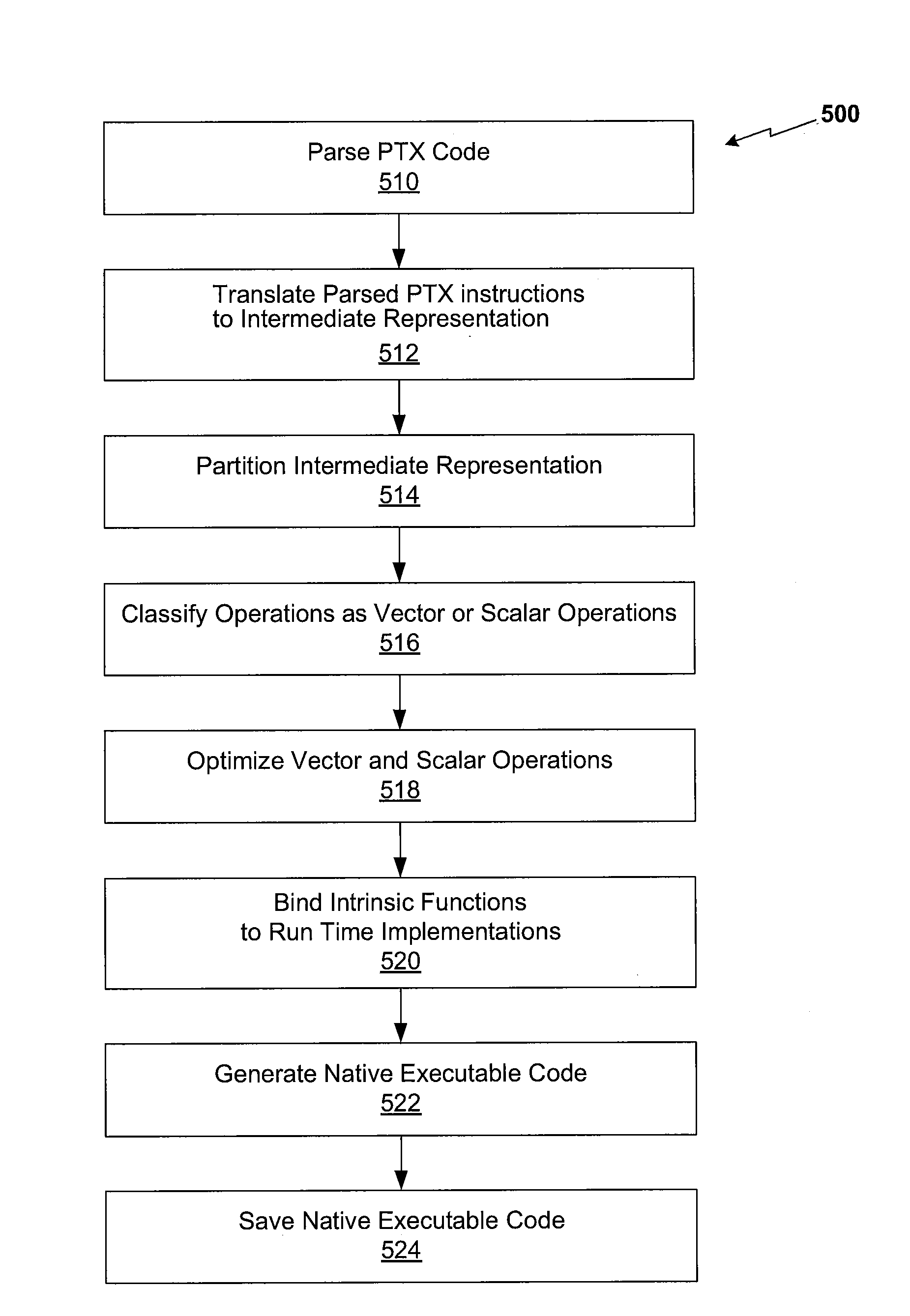
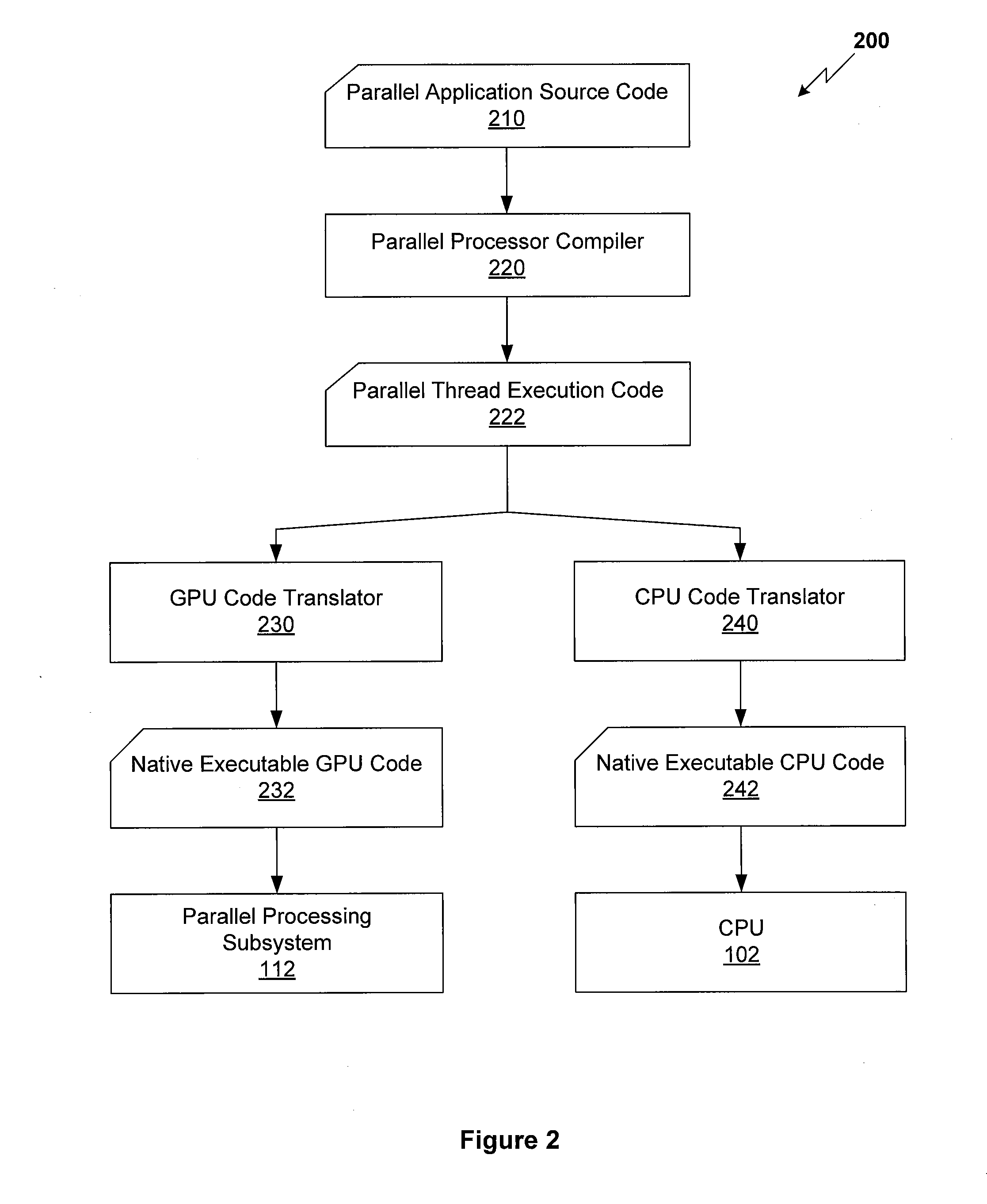
Method for compiling a parallel thread execution program for general execution
ActiveUS20130198494A1Efficiently and advantageously executedDecompilation/disassemblyDigital computer detailsGeneral purposeGraphics
A technique is disclosed for executing a compiled parallel application on a general purpose processor. The compiled parallel application comprises parallel thread execution code, which includes single-instruction multiple-data (SIMD) constructs, as well as references to intrinsic functions conventionally available in a graphics processing unit. The parallel thread execution code is transformed into an intermediate representation, which includes vector instruction constructs. The SIMD constructs are mapped to vector instructions available within the intermediate representation. Intrinsic functions are mapped to corresponding emulated runtime implementations. The technique advantageously enables parallel applications compiled for execution on a graphics processing unit to be executed on a general purpose central processing unit configured to support vector instructions.
Owner:NVIDIA CORP
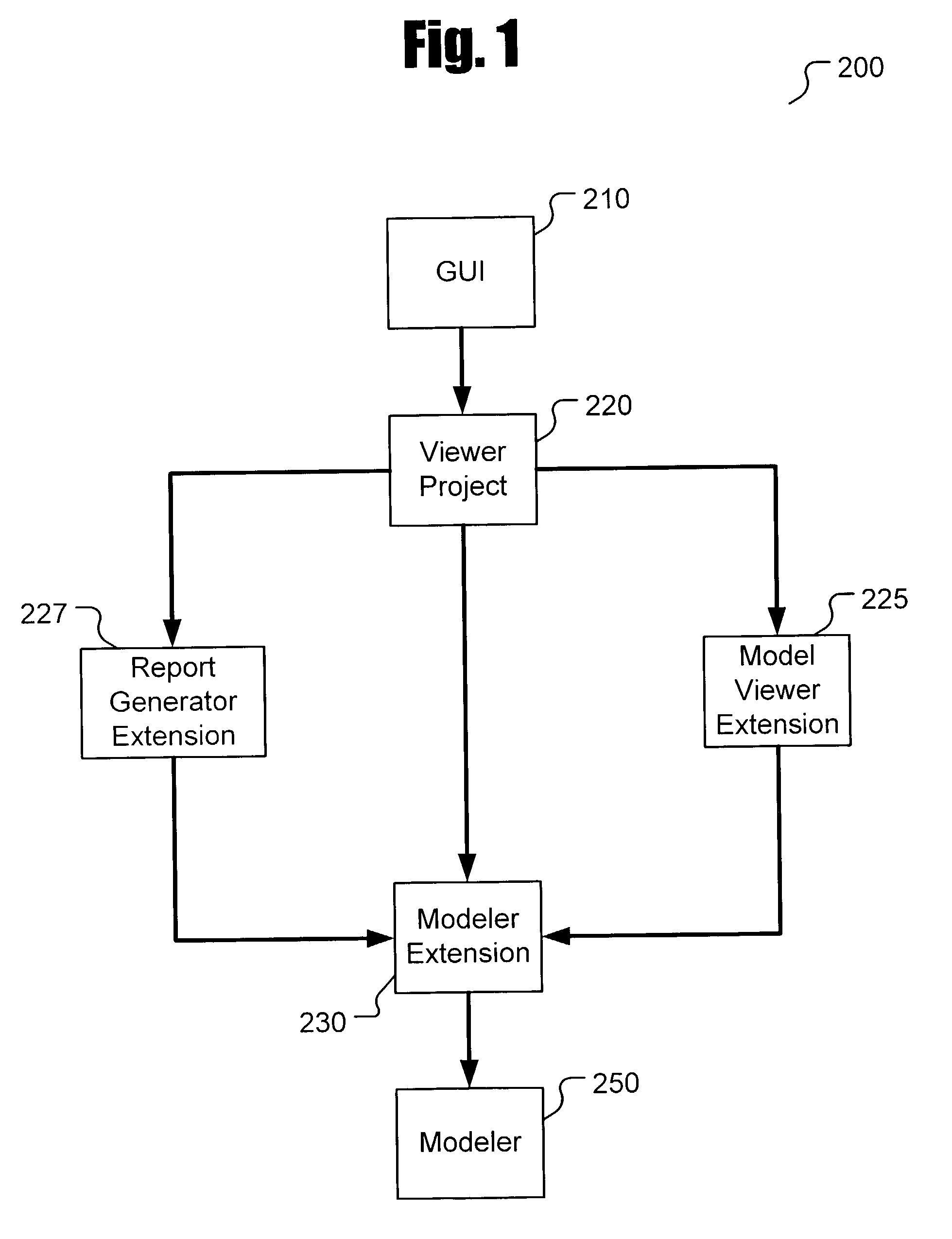
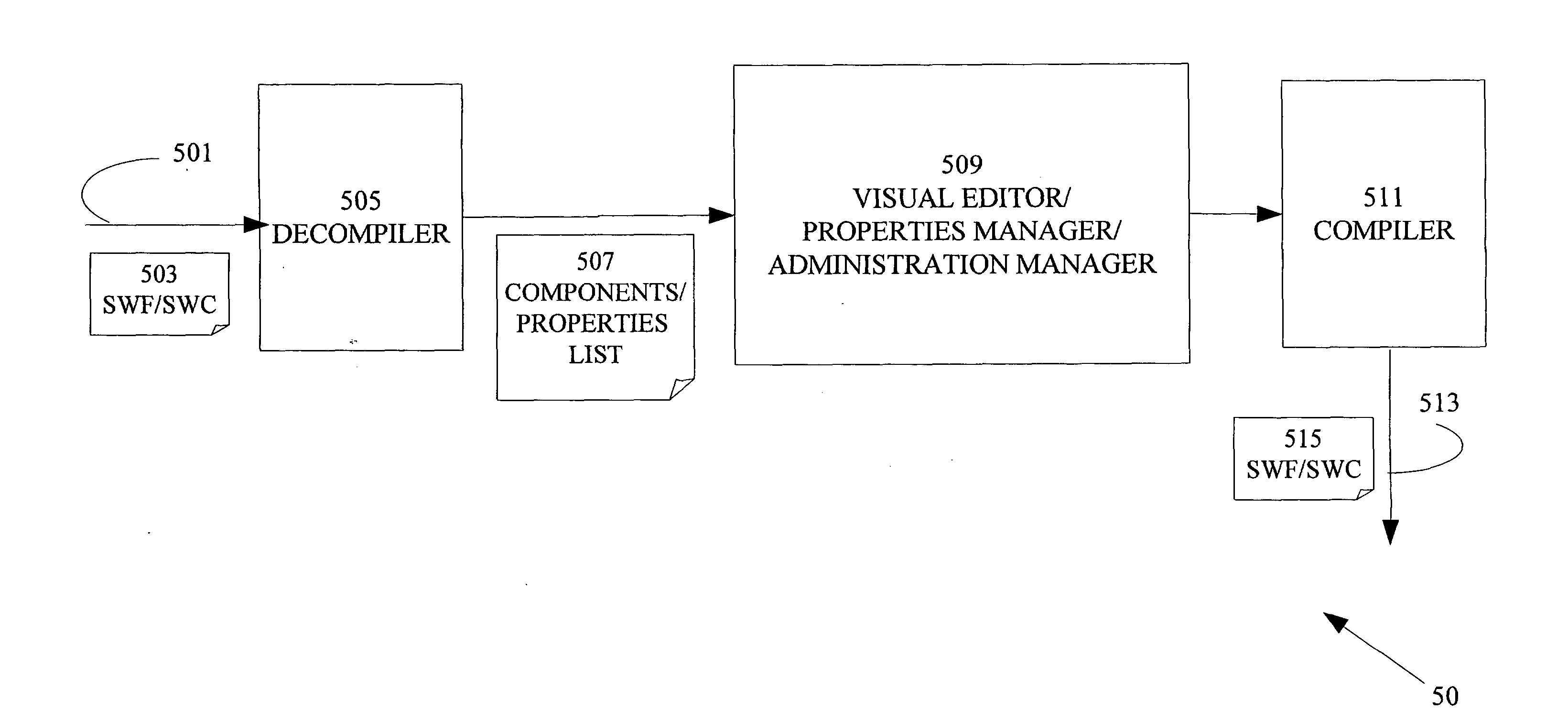
System and Method for Managing Content of Rich Media
InactiveUS20080215968A1Decompilation/disassemblyNatural language data processingReal time displayFile copying
A method for editing rich media content in a computerized device. The rich media content is stored in a static or binary file. The binary file is copied into storage operatively attached to the computerized device and decompiled and component s of the rich media content are extracted, (FIGS. 5&6). Properties of the components of the rich media content are presented and the properties are edited, (FIGS. 5&6). Preferably, during editing the modified rich media content is displayed in real time. An edited file including modified rich media content is stored preferably in lieu of the original binary file:
Owner:DYNAMIC FLASH
Rules based detection and correction of problems on mobile devices of enterprise users
ActiveUS20140007193A1Decompilation/disassemblyDigital data processing detailsDocumentation procedureApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Software analysis framework
InactiveUS20060253841A1Decompilation/disassemblySpecific program execution arrangementsSoftware analyticsScript analysis
Presently described is a decompilation method of operation and system for parsing executable code, identifying and recursively modeling data flows, identifying and recursively modeling control flow, and iteratively refining these models to provide a complete model at the nanocode level. The nanocode decompiler may be used to determine if flaws, security vulnerabilities, or general quality issues exist in the code. The nanocode decompiler outputs in a standardized, human-readable intermediate representation (IR) designed for automated or scripted analysis and reporting. Reports may take the form of a computer annotated and / or partially human annotated nanocode listing in the above-described IR. Annotations may include plain English statements regarding flaws and pointers to badly constructed data structures, unchecked buffers, malicious embedded code or “trap doors,” and the like. Annotations may be generated through a scripted analysis process or by means of an expert-enhanced, quasi-autonomous system.
Owner:VERACODE
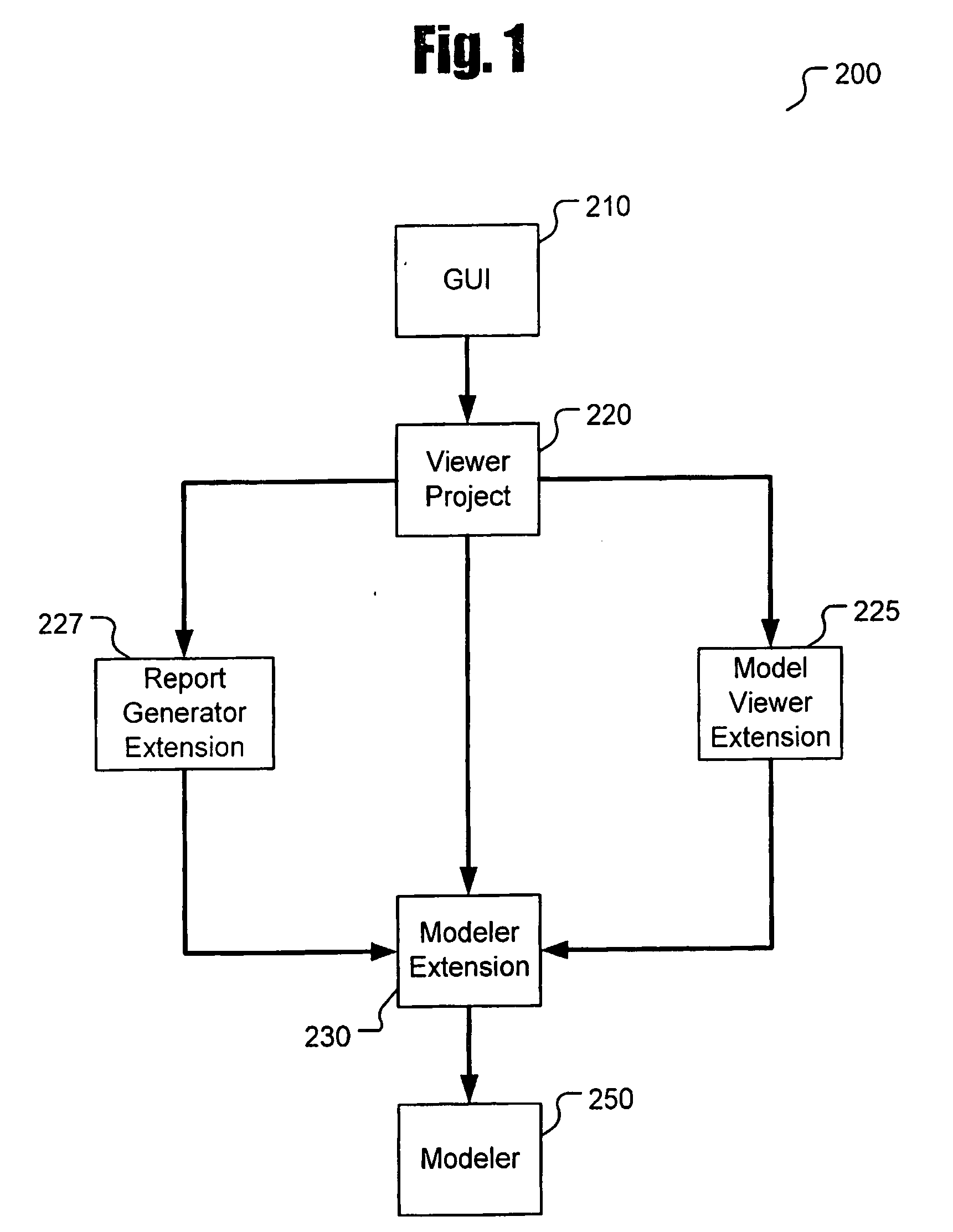
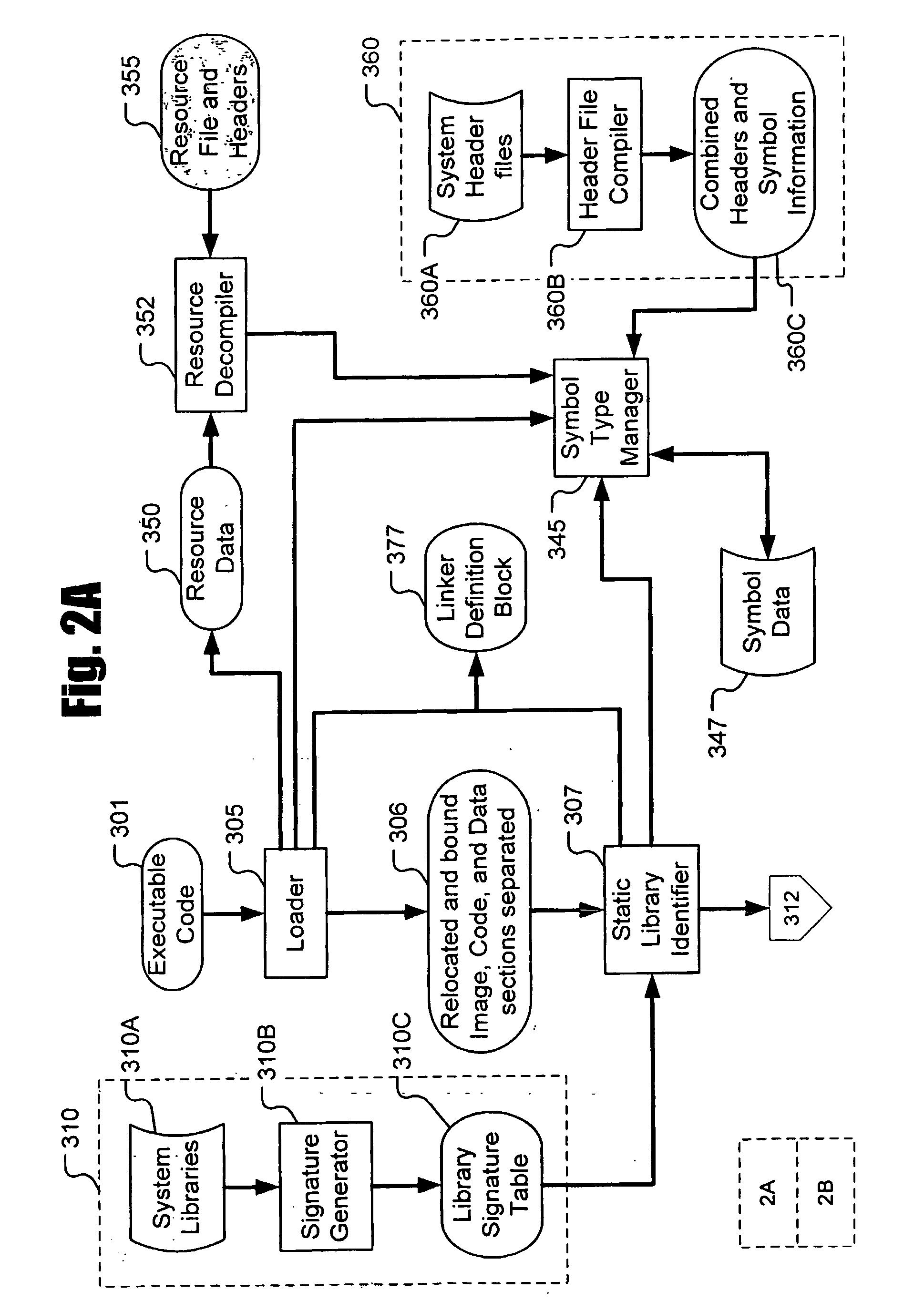
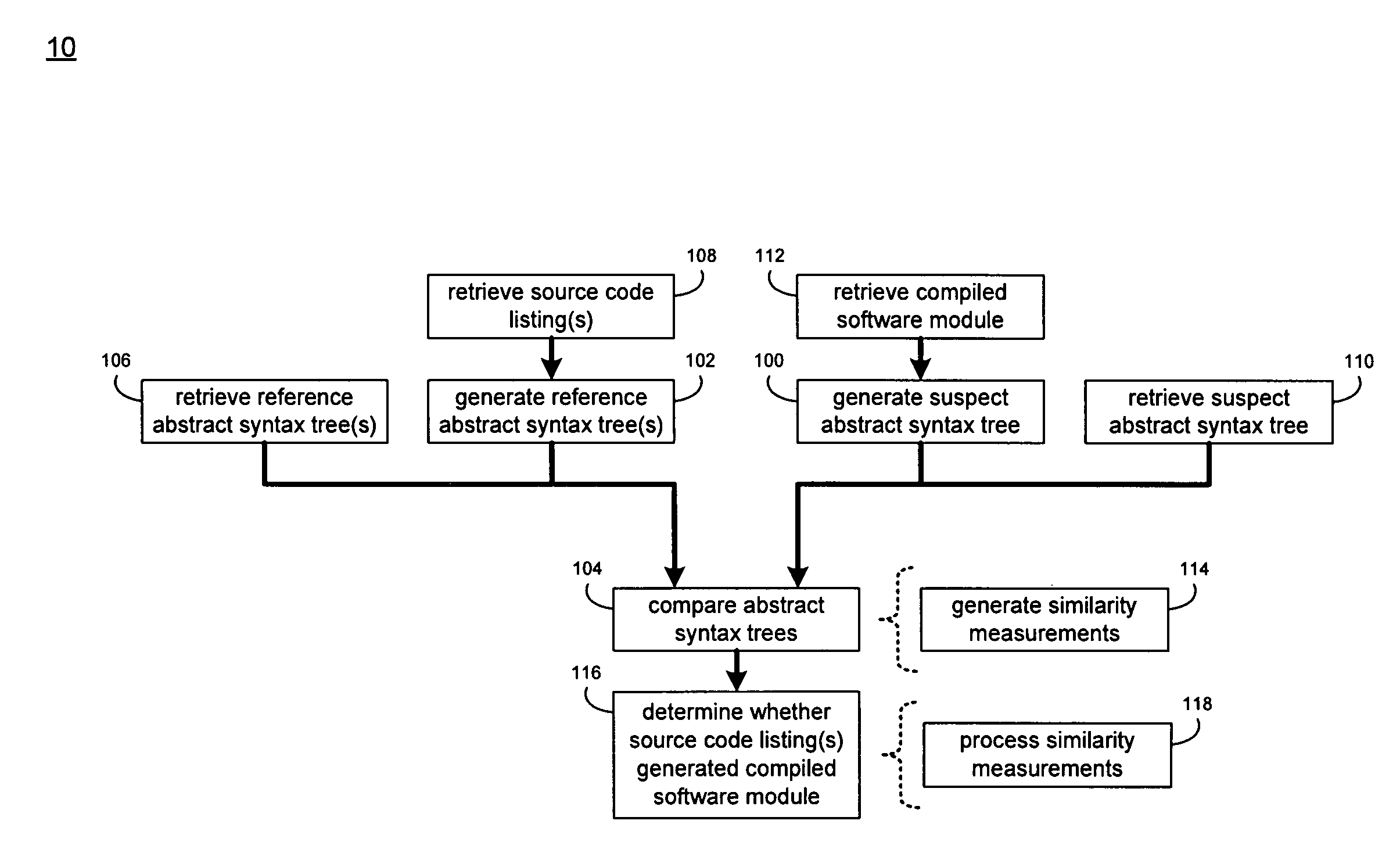
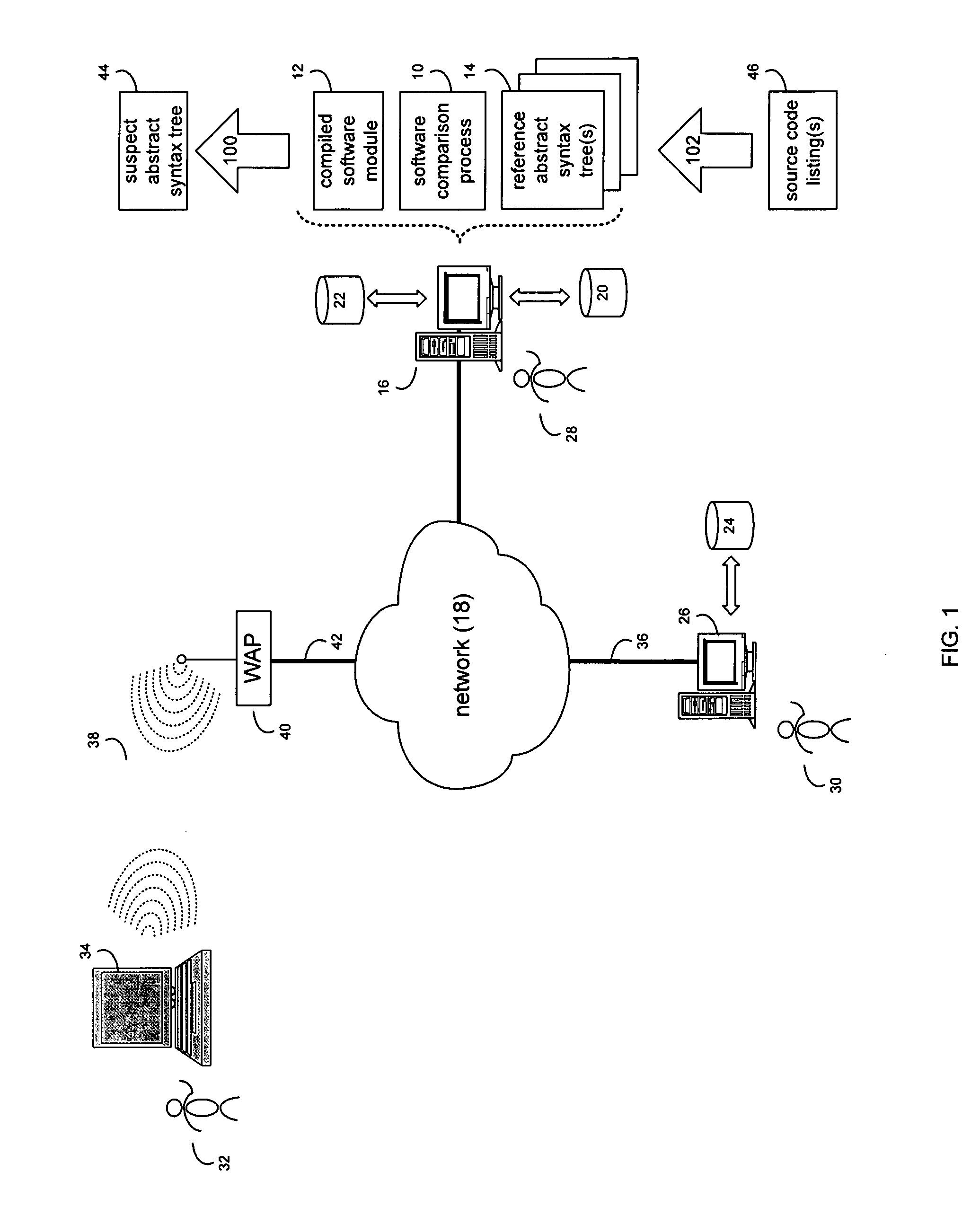
System and method for comparing partially decompiled software
InactiveUS20090172650A1Decompilation/disassemblyProgram controlTheoretical computer scienceAbstract syntax tree
A method and computer program product for generating a suspect abstract syntax tree by partially decompiling a compiled software module. The suspect abstract syntax tree is compared to one or more reference abstract syntax trees.
Owner:IBM CORP
Providing secure mobile device access to enterprise resources using application tunnels
ActiveUS20140007192A1Decompilation/disassemblyDigital data processing detailsApplication serverResource based
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC +1
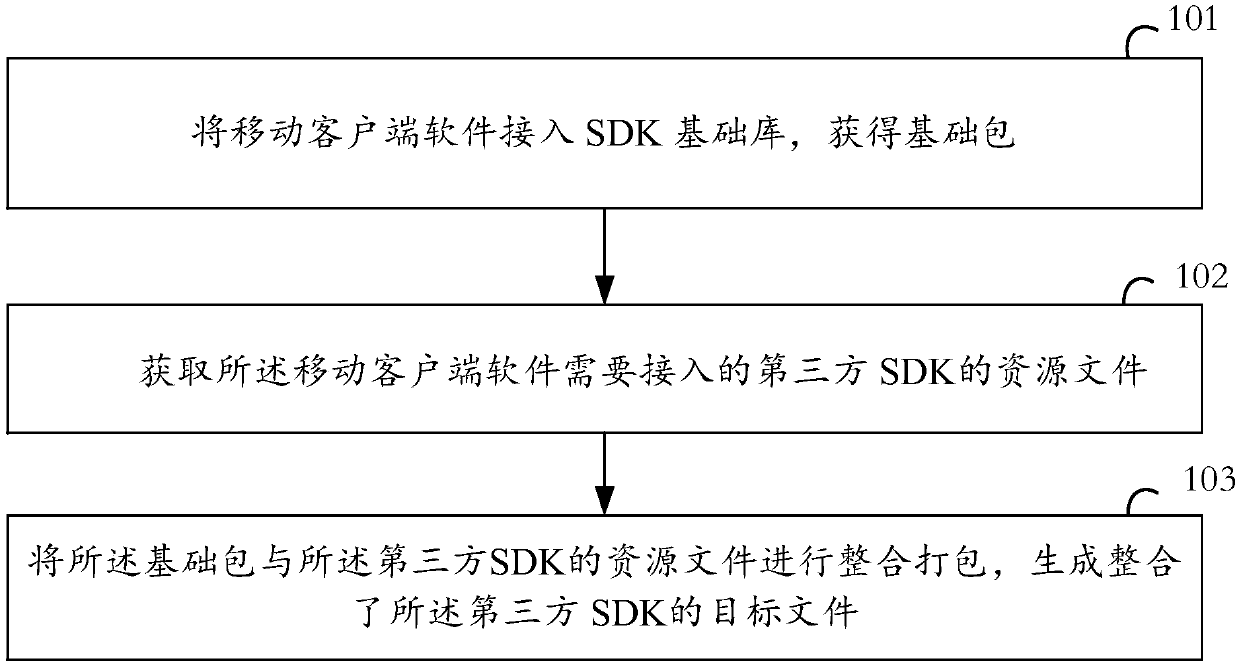
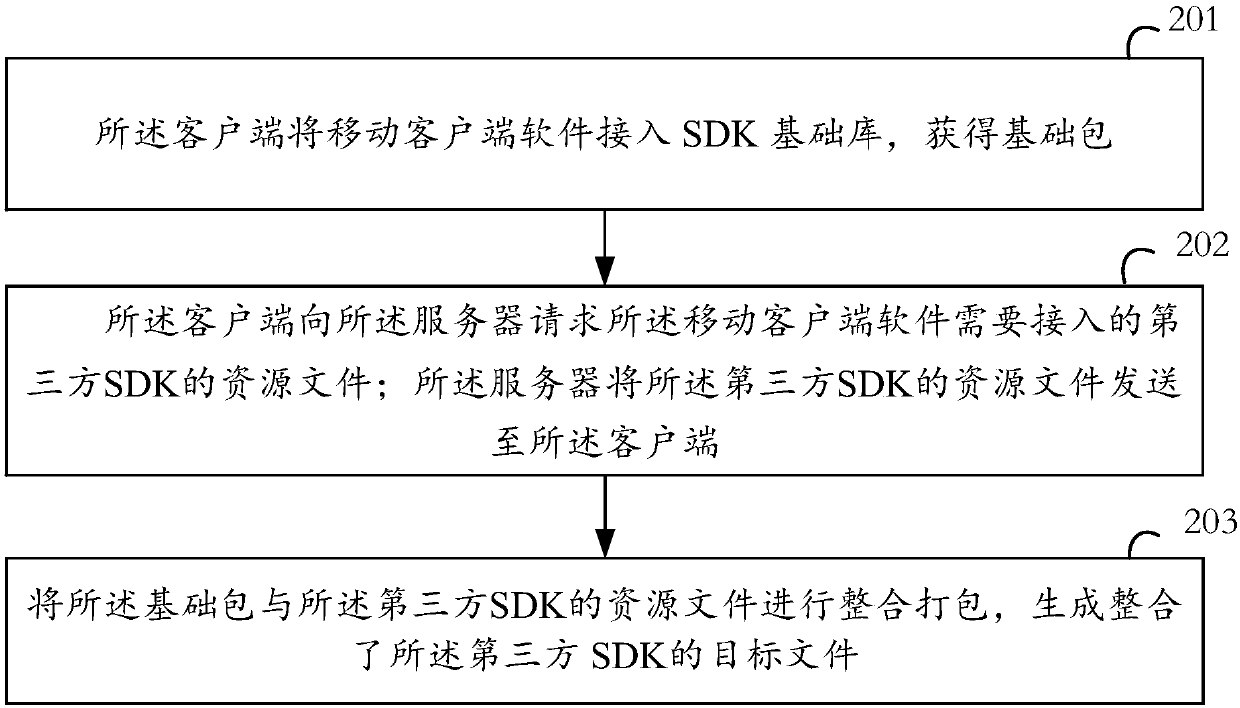
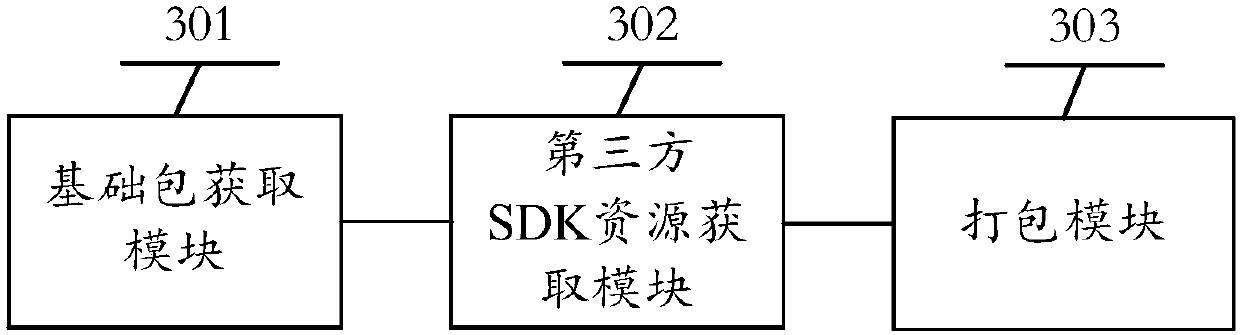
Software development kit (SDK) access method, client and SDK access system
InactiveCN107589947AEasy accessReduce labor costsDecompilation/disassemblyVersion controlSoftware development processThird party
The invention discloses a software development kit (SDK) access method, a client and an SDK access system, for solving the technical problem that in the prior art, the SDK access method is high in consumed labor cost and relatively long in access time. The method comprises the steps of connecting mobile client software to an SDK basic library to acquire a basic packet; acquiring a resource file ofa third-party SDK to which the mobile client software needs to be connected; integrating and packaging the basic library and the resource file of the third-party SDK to generate a target file integrating the third-party SDK. With the application of the SDK access method, the client and the system provides by the invention, the situation that the mobile client software quickly accesses the third-part SDK can be achieved, and labor cost can be saved.
Owner:成都极娱网络科技有限公司
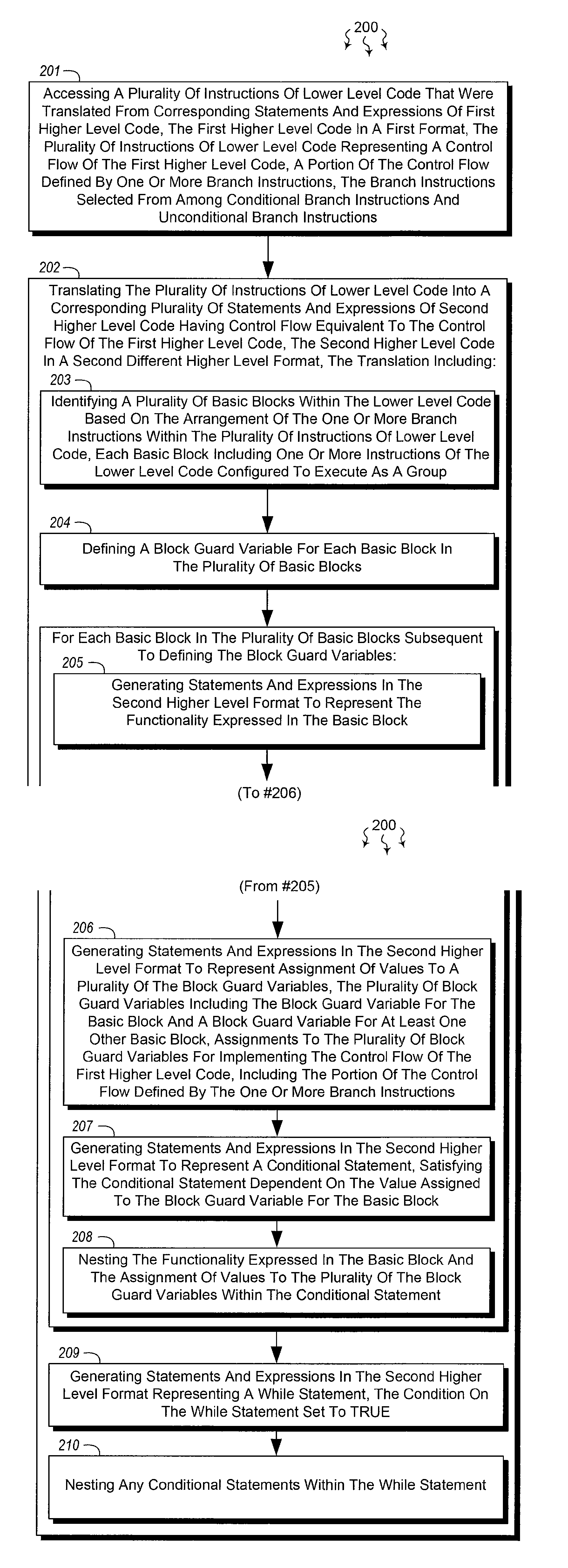
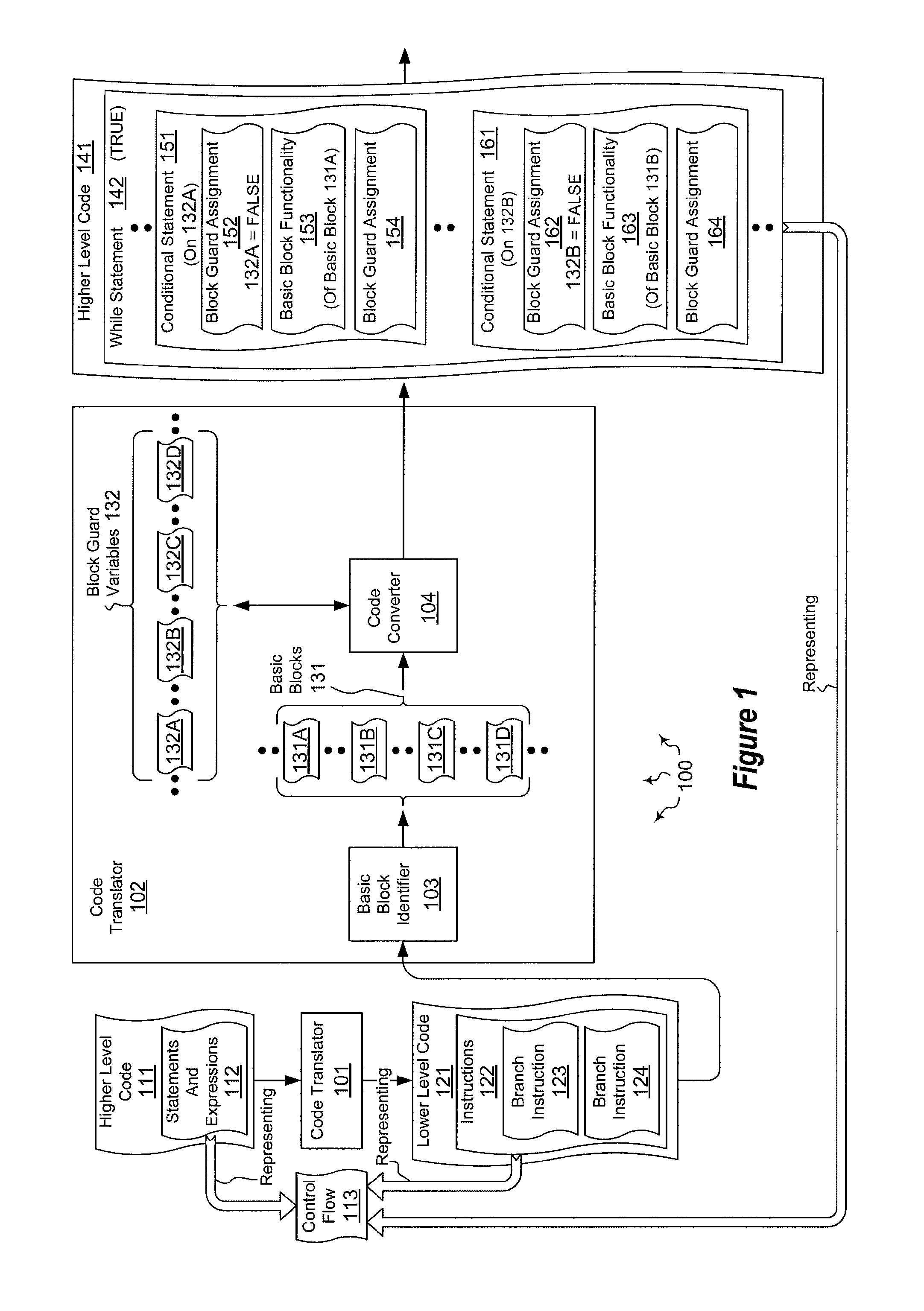
Reconstructing program control flow
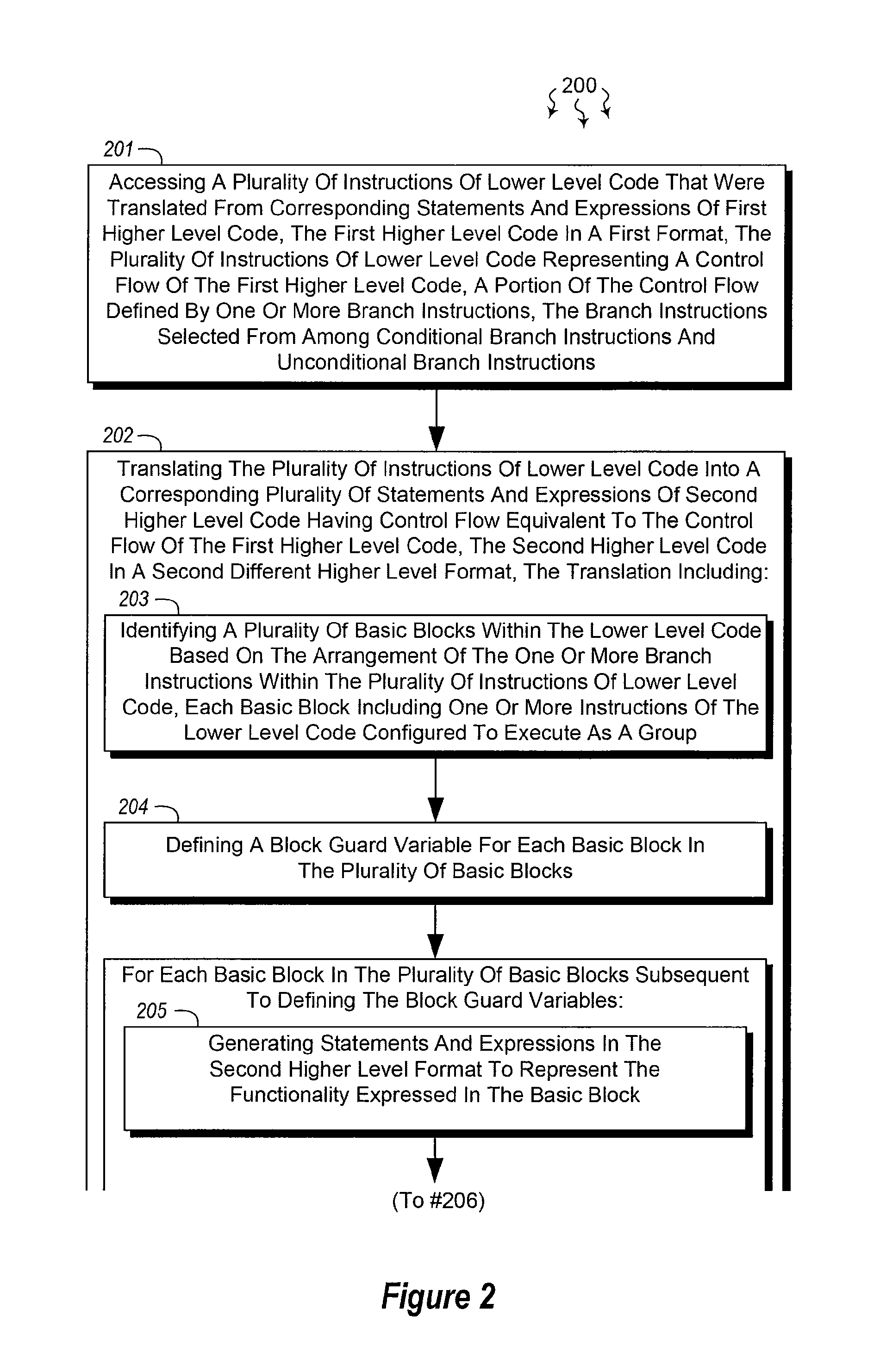
The present invention extends to methods, systems, and computer program products for reconstructing program control flow. Embodiments include implementing or morphing a control flow graph (“CFG”) into an arbitrary loop structure to reconstruct (preserve) control flow from original source code. Loop structures can be optimized and can adhere to target platform constraints. In some embodiments, C++ source code (a first higher level format) is translated into a CFG (a lower level format). The CFG is then translated into HLSL source code (a second different higher level format) for subsequent compilation into SLSL bytecode (that can then be executed at a Graphical Processing Unit (“GPU”)). The control flow from the C++ source code is preserved in the HLSL source code.
Owner:MICROSOFT TECH LICENSING LLC
Method and device for multi-core instruction-set simulation
InactiveUS20100269103A1Maintain accuracyReduce synchronization overheadDecompilation/disassemblyCAD circuit designData segmentParallel computing
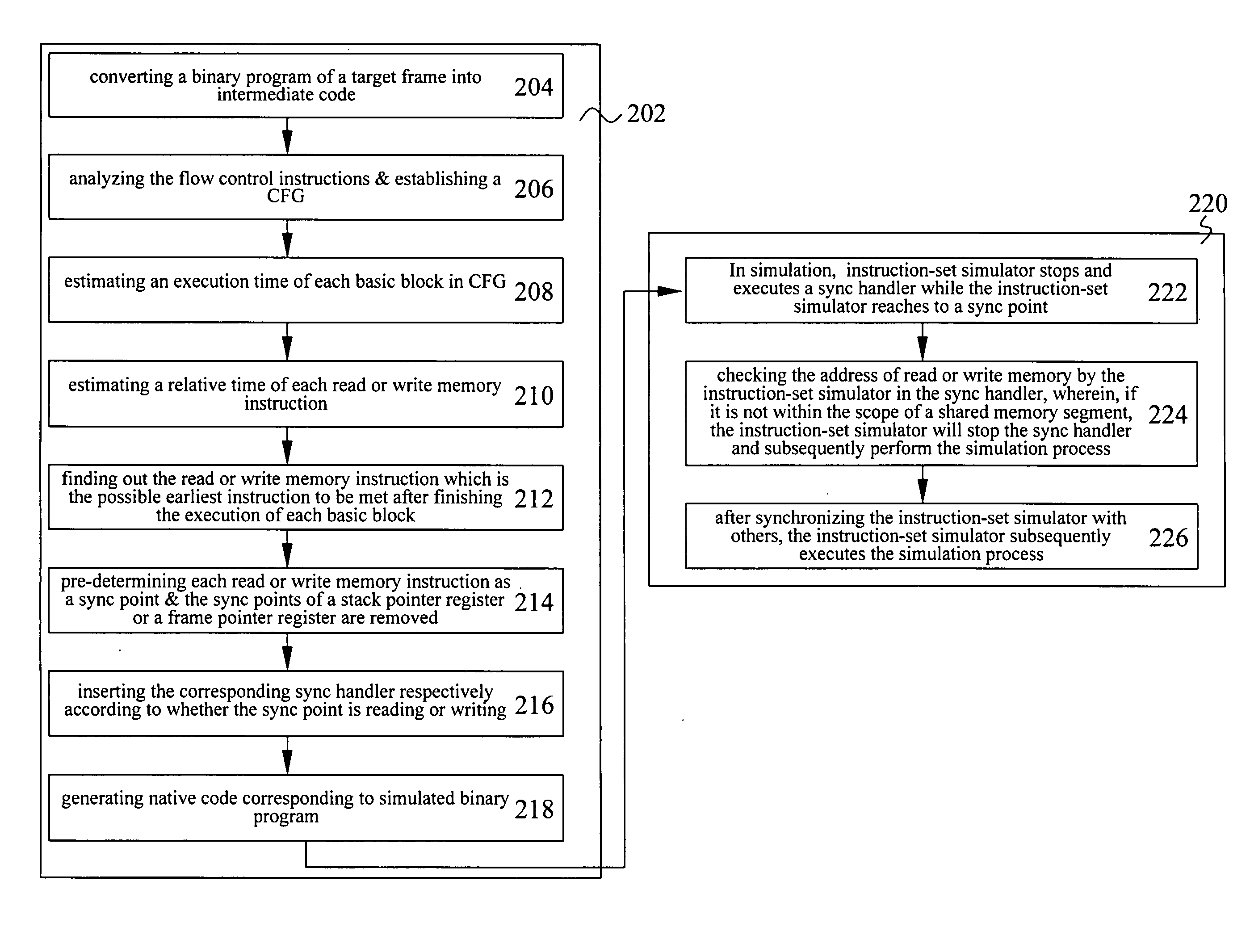
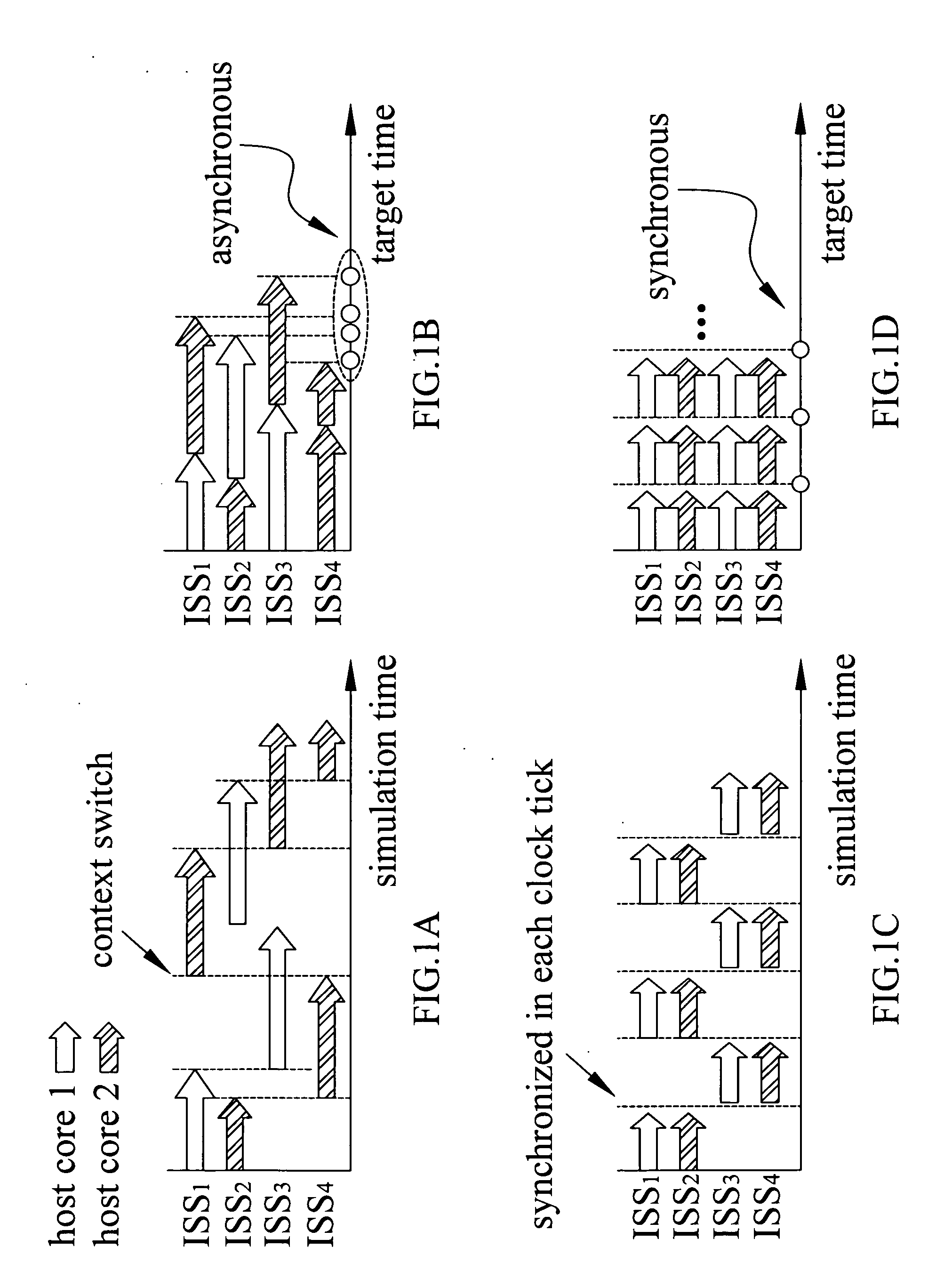
The present invention discloses a method for multi-core instruction-set simulation. The proposed method identifies the shared data segment and the dependency relationship between the different cores and thus effectively reduces the number of sync points and lowers the synchronization overhead, allowing multi-core instruction-set simulation to be performed more rapidly while ensuring that the simulation results are accurate. In addition, the present invention also discloses a device for multi-core instruction-set simulation.
Owner:NATIONAL TSING HUA UNIVERSITY
Popular searches
Software design Computer programmed simultaneously with data introduction Software simulation/interpretation/emulation Special data processing applications Memory systems Code compilation Platform integrity maintainance Location information based service Program/content distribution protection Security arrangement
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com