Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1272 results about "Static data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
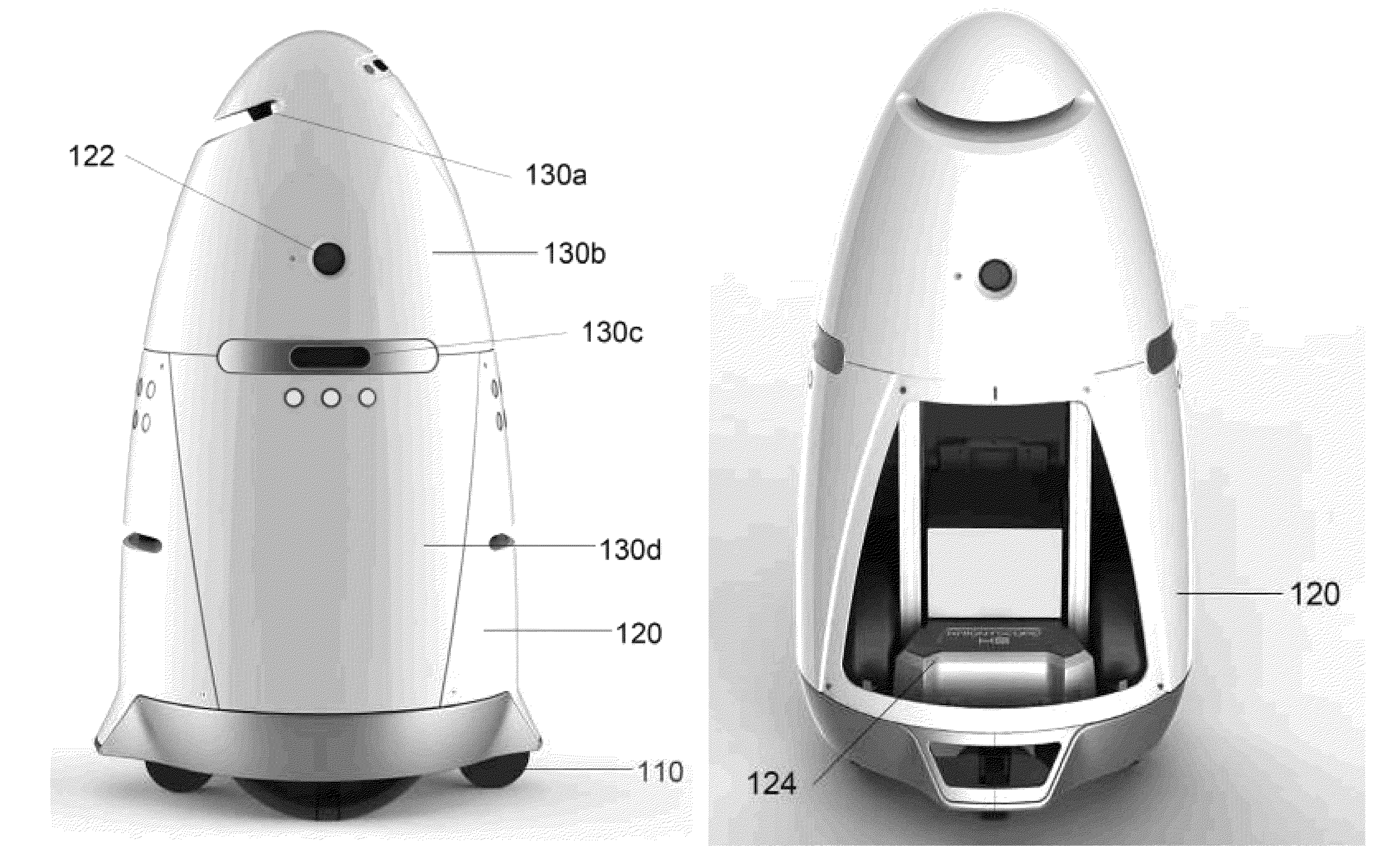
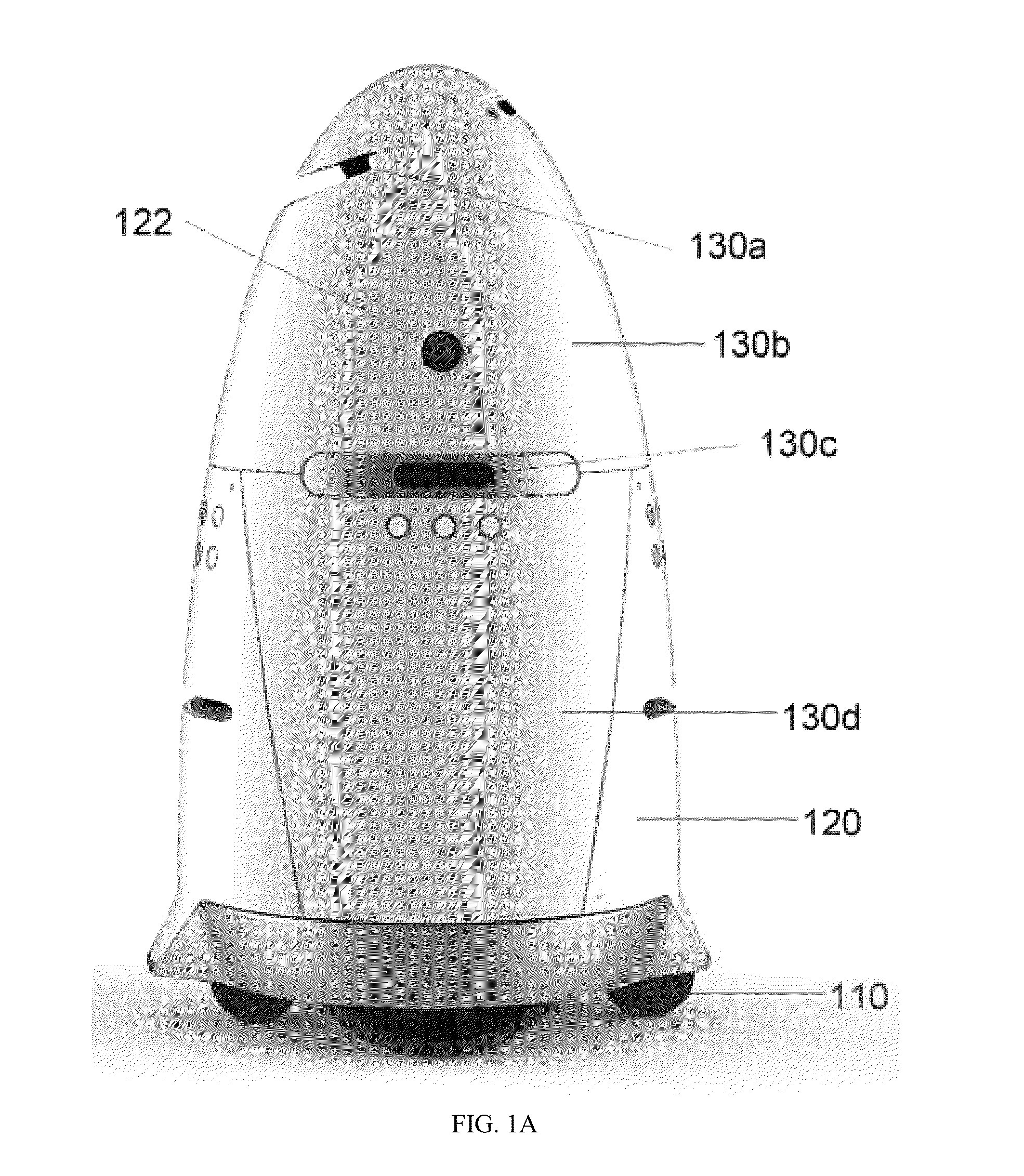
Autonomous data machines and systems
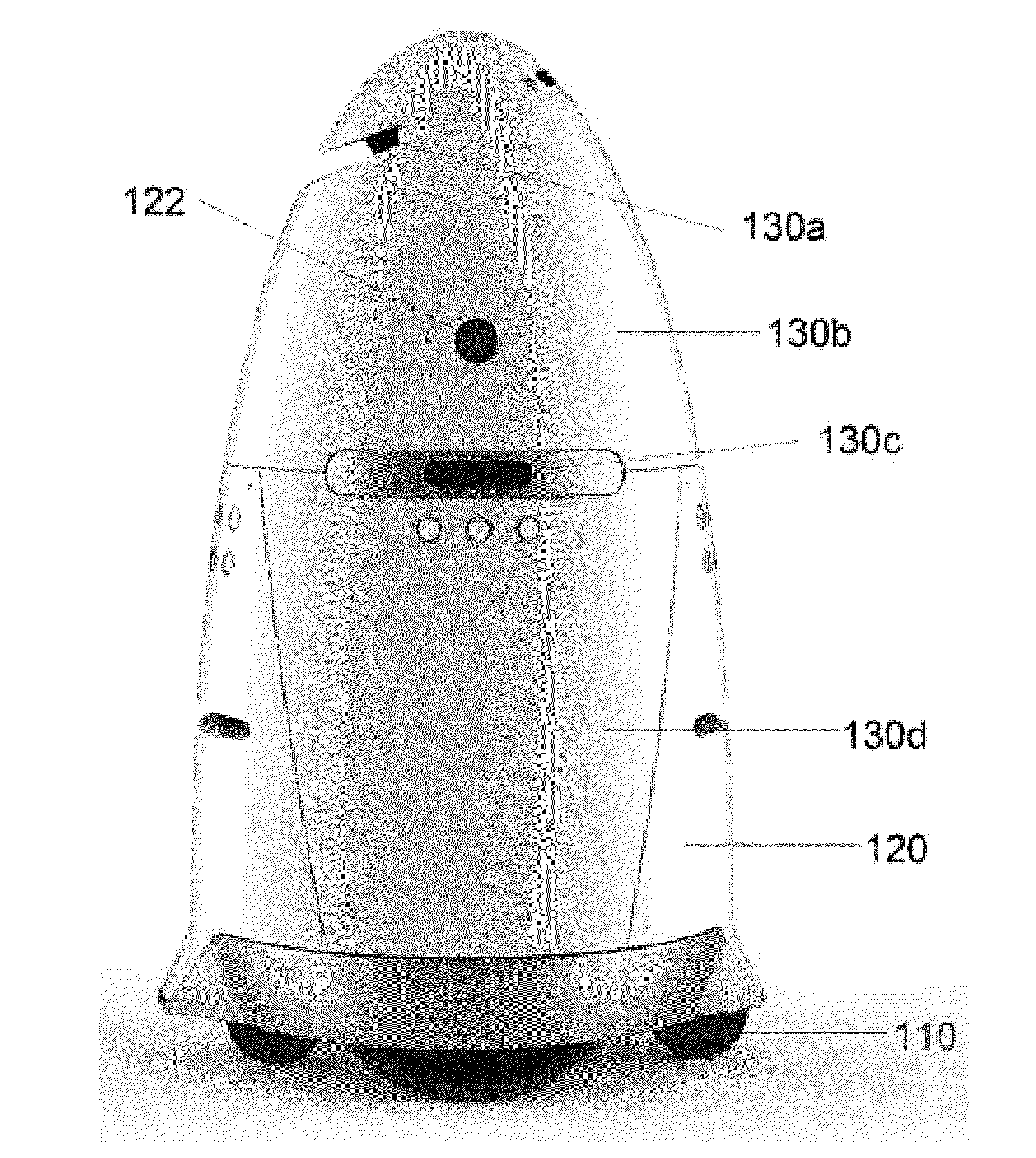
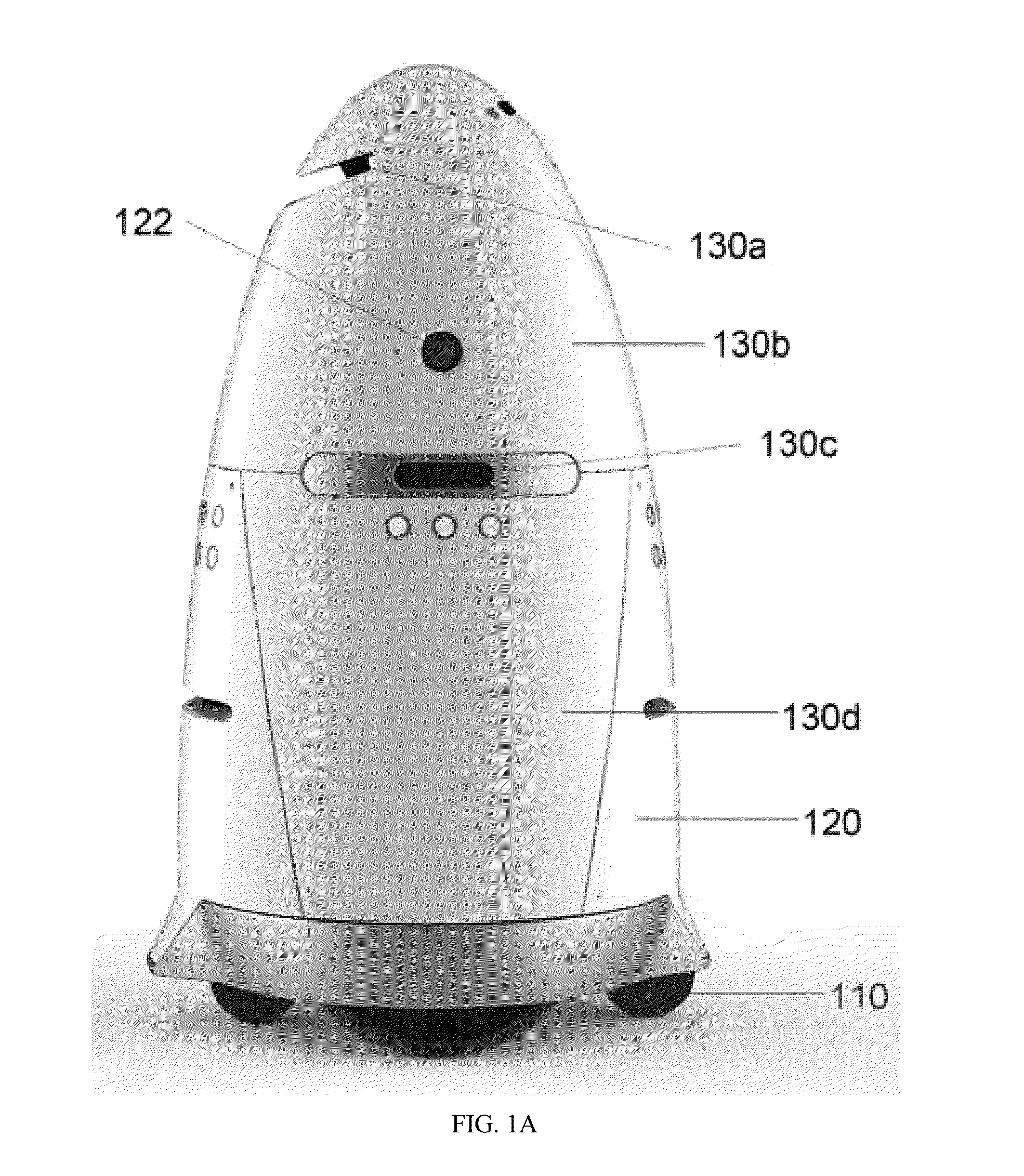
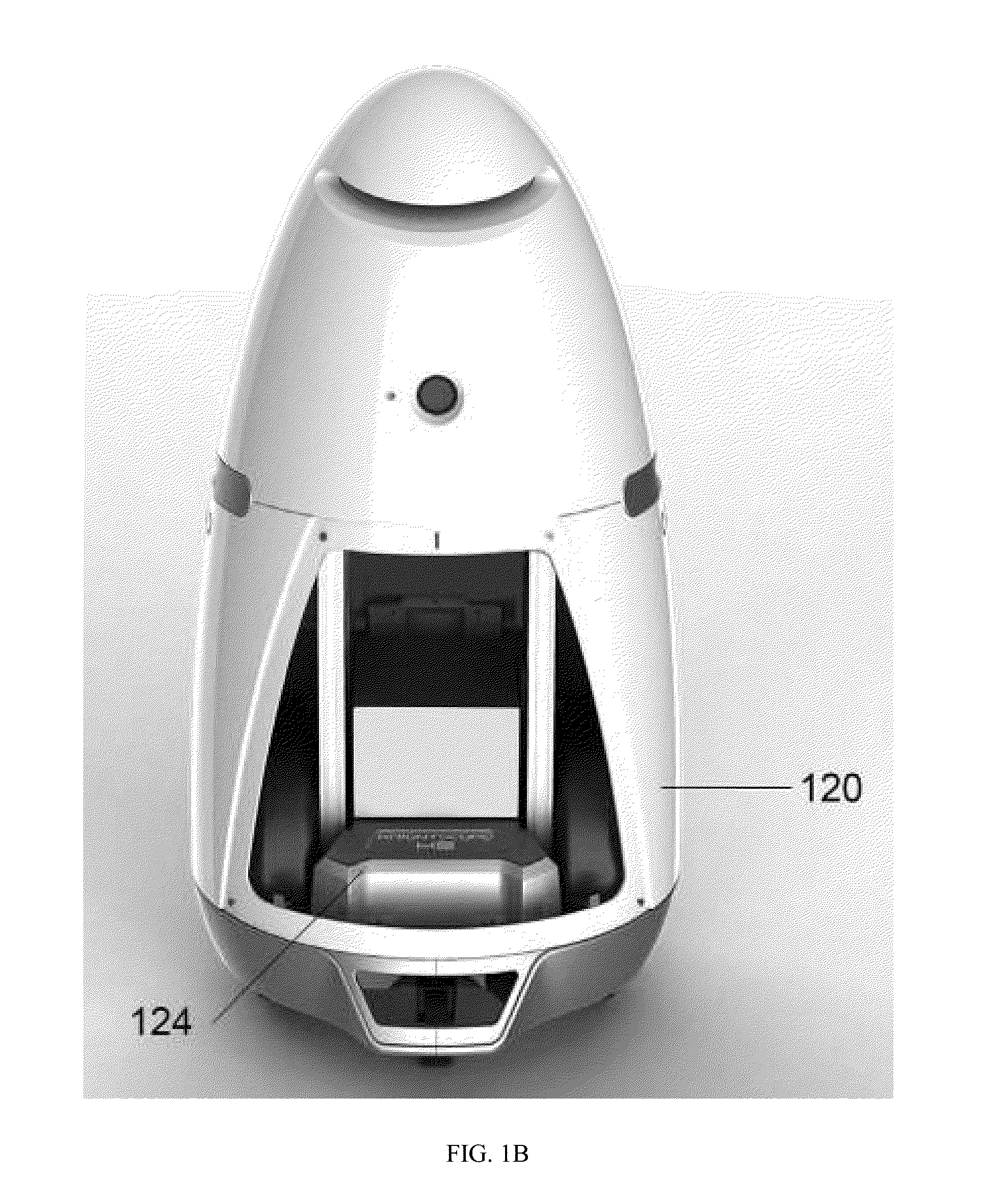
ActiveUS20150205298A1Reduce negative personalReduce economic impactAcoustic signal devicesPropulsion by batteries/cellsData sourceData mining
Autonomous data machines and systems may be provided, which may be deployed in an environment. The machines may roam within the environment and collect data with aid of one or more sensors. The data may be sent to a control center, which may optionally receive information from additional data sources, such as other on-site sensors, existing static data, or real-time social data. The control center may send instructions to the machines to perform one or more reaction based on the received information. The autonomous data machines may be capable of reacting autonomously to one or more detected condition. In some instances, the autonomous data machines may be employed for security or surveillance.
Owner:KNIGHTSCOPE
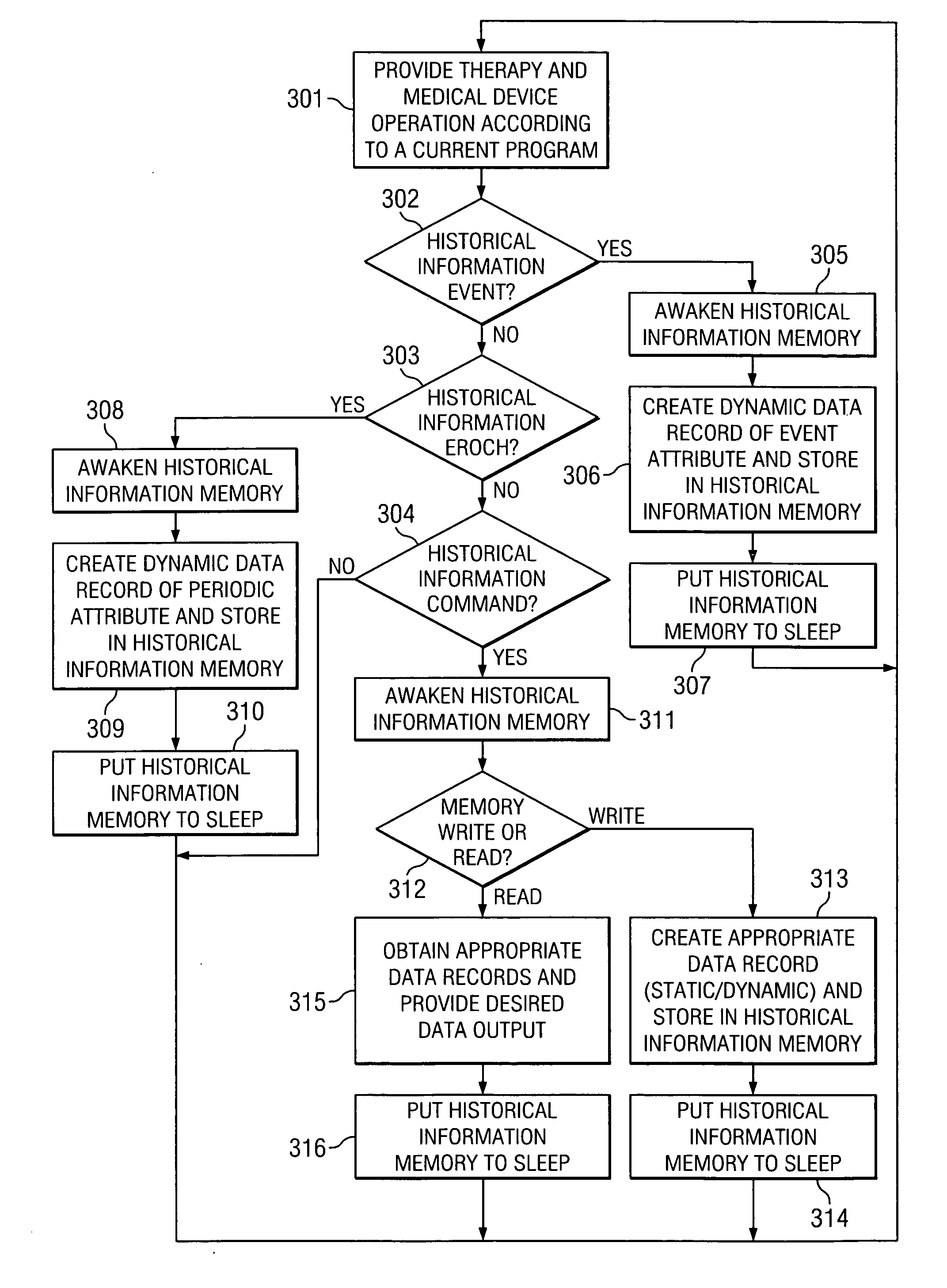
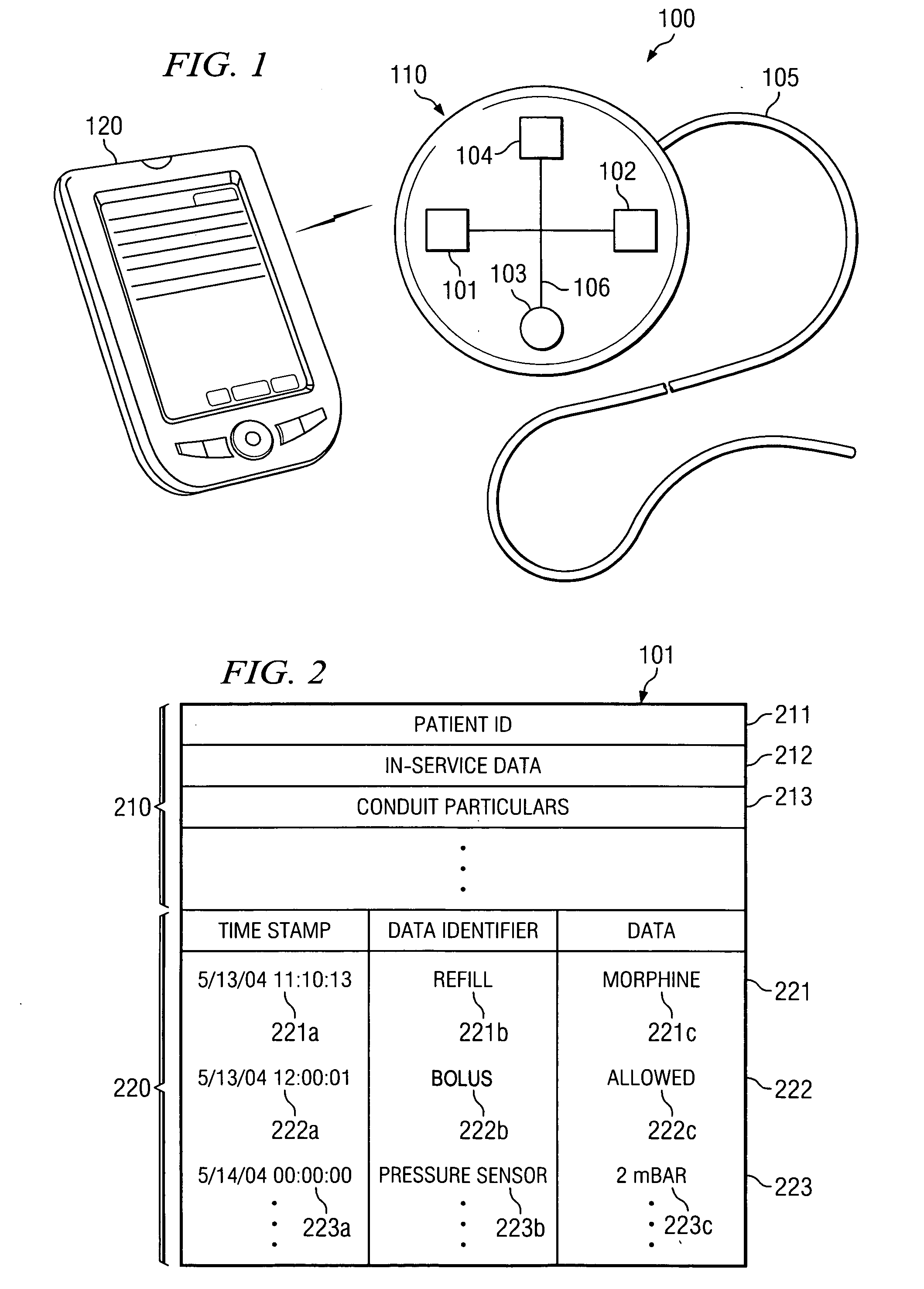
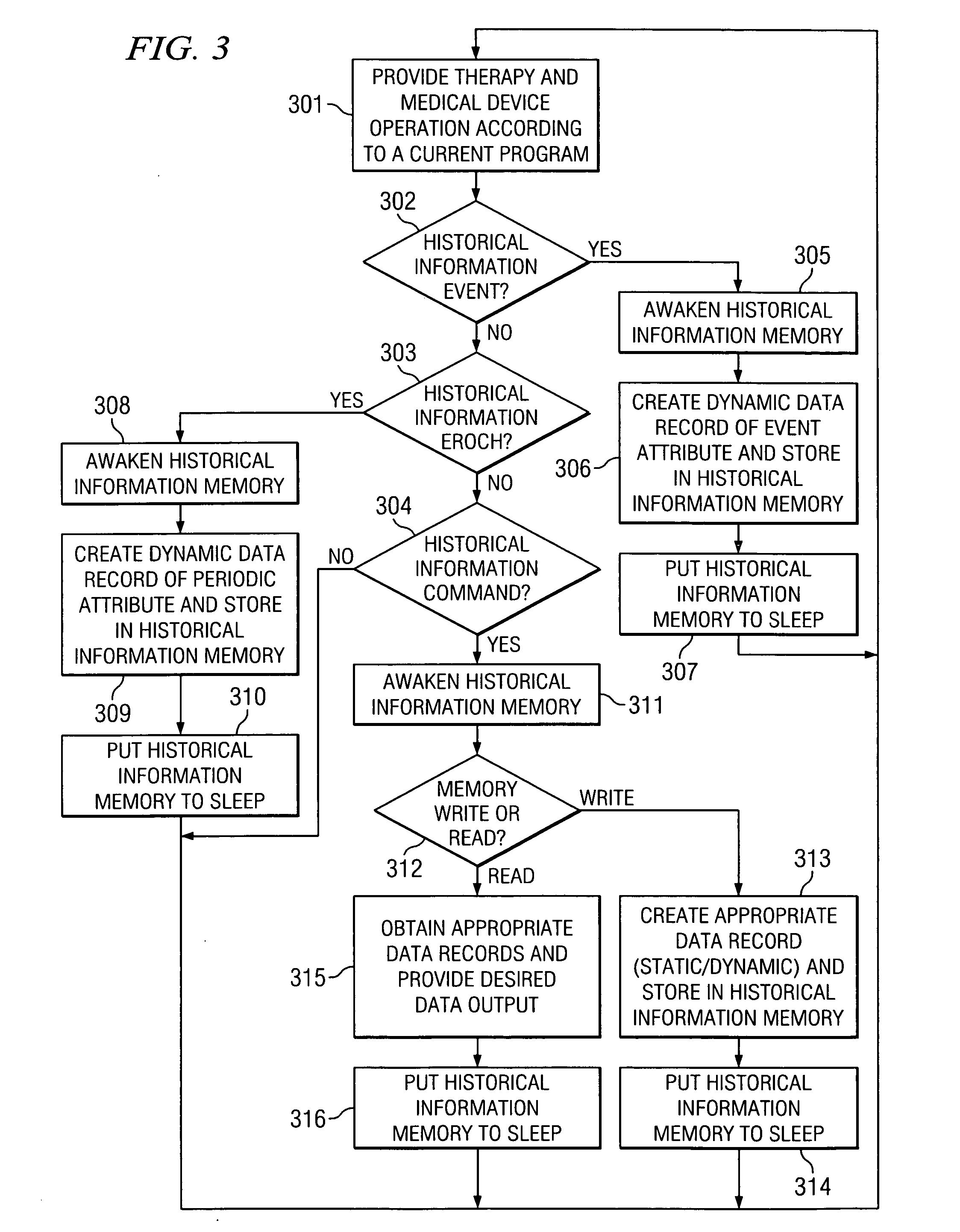
System and method of managing medical device historical data
ActiveUS20050283210A1Eliminates and mitigates issueImprove insightsLocal control/monitoringHeart defibrillatorsCardiac deviceDynamic data
Disclosed are systems and methods which provide management of historical information associated with a medical device, such as an implantable neurostimulation pulse generator, drug pump, cardiac device, hearing enhancement device, or vision enhancement device. Such management of historical information includes storage of historical information within an associated medical device. Historical information stored within a medical device may provide a complete summary of the use, configuration, and operation of the medical device, e.g., information spanning the entire in-service life of the medical device. Historical information for which management is provided may include both static data and dynamic data. The historical information may be used in configuring the medical device, analyzing the operation of the medical device, autonomously altering operation of the medical device, etcetera.
Owner:ADVANCED NEUROMODULATION SYST INC
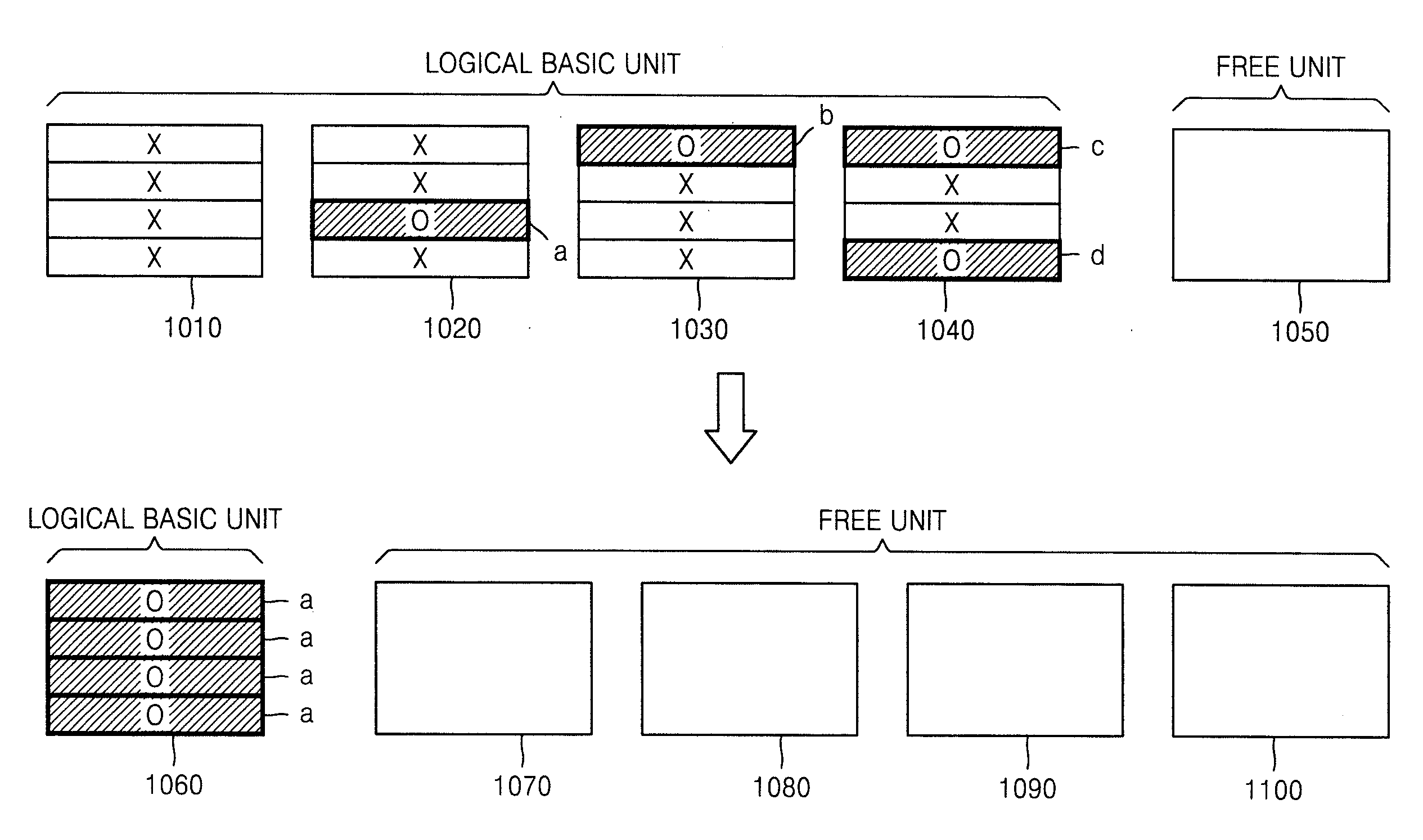
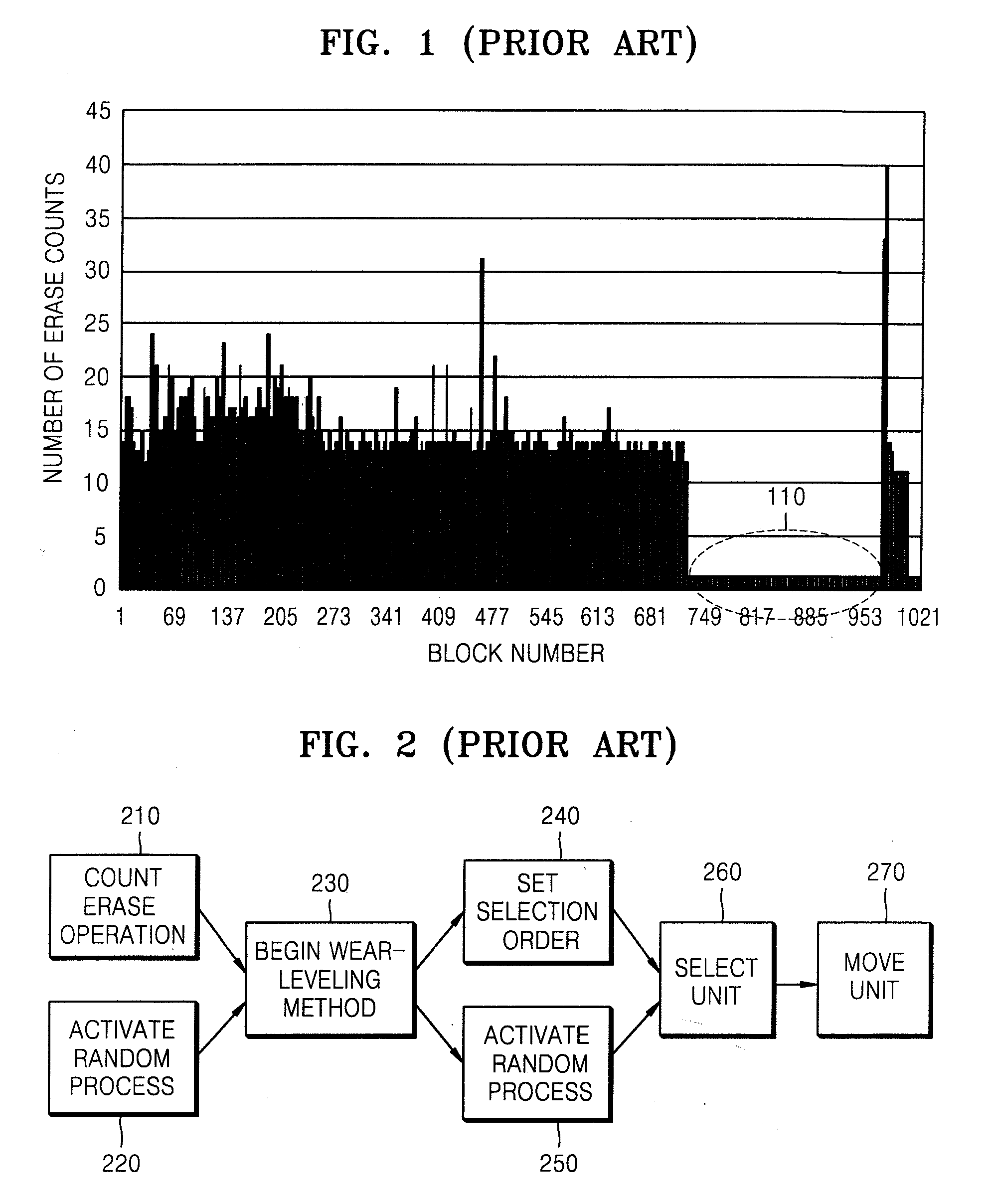
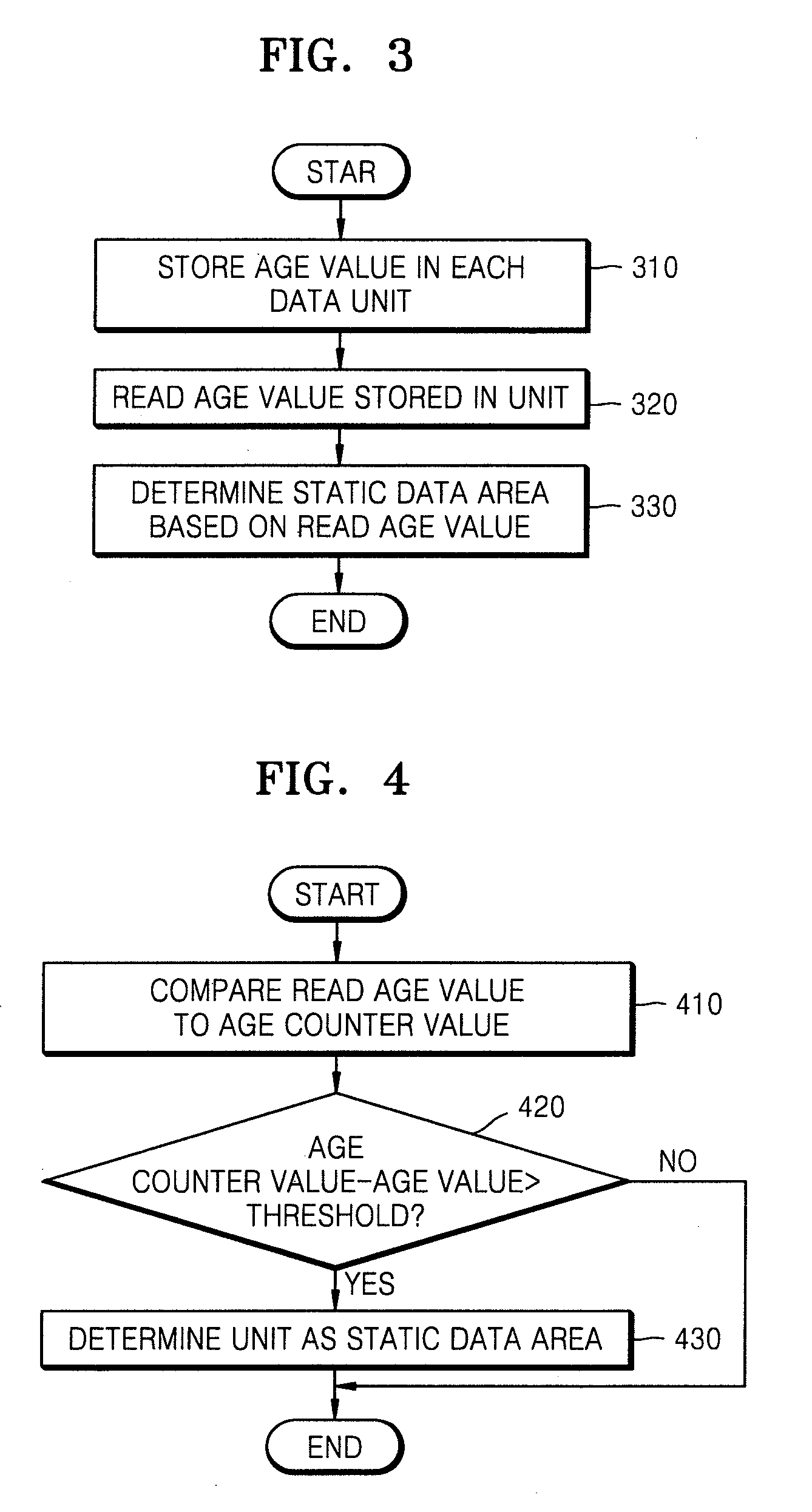
Method and apparatus for detecting static data area, wear-leveling, and merging data units in nonvolatile data storage device
ActiveUS20080147998A1Wear-leveling effectAccurate areaMemory architecture accessing/allocationRead-only memoriesLeveling effectAge values
Provided are a method and apparatus for wear-leveling of a nonvolatile data storage device, whereby a wear-leveling effect is maximized by storing an age value indicating a write time in each data unit of the nonvolatile data storage device and detecting a static data area based on age values. The method includes storing an age value indicating a write time in each unit assigned to write data therein, reading an age value stored in a unit, and determining a static data area based on the read age value. Accordingly, a static data area can be correctly detected without additional overhead, and a wear-leveling effect of the entire storage device can be increased by moving data to and from the static data area, thereby extending the lifespan of the storage device.
Owner:SAMSUNG ELECTRONICS CO LTD
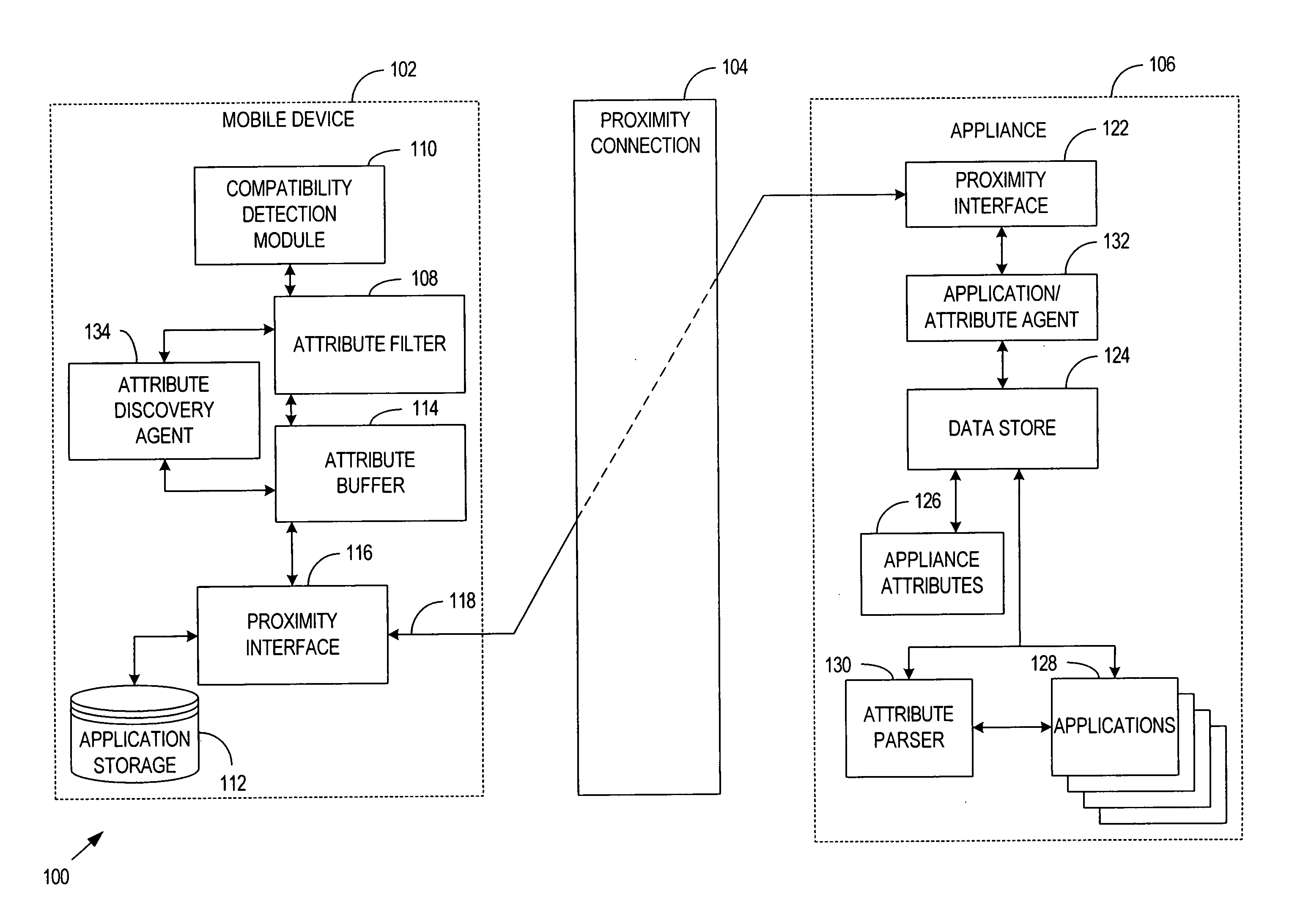
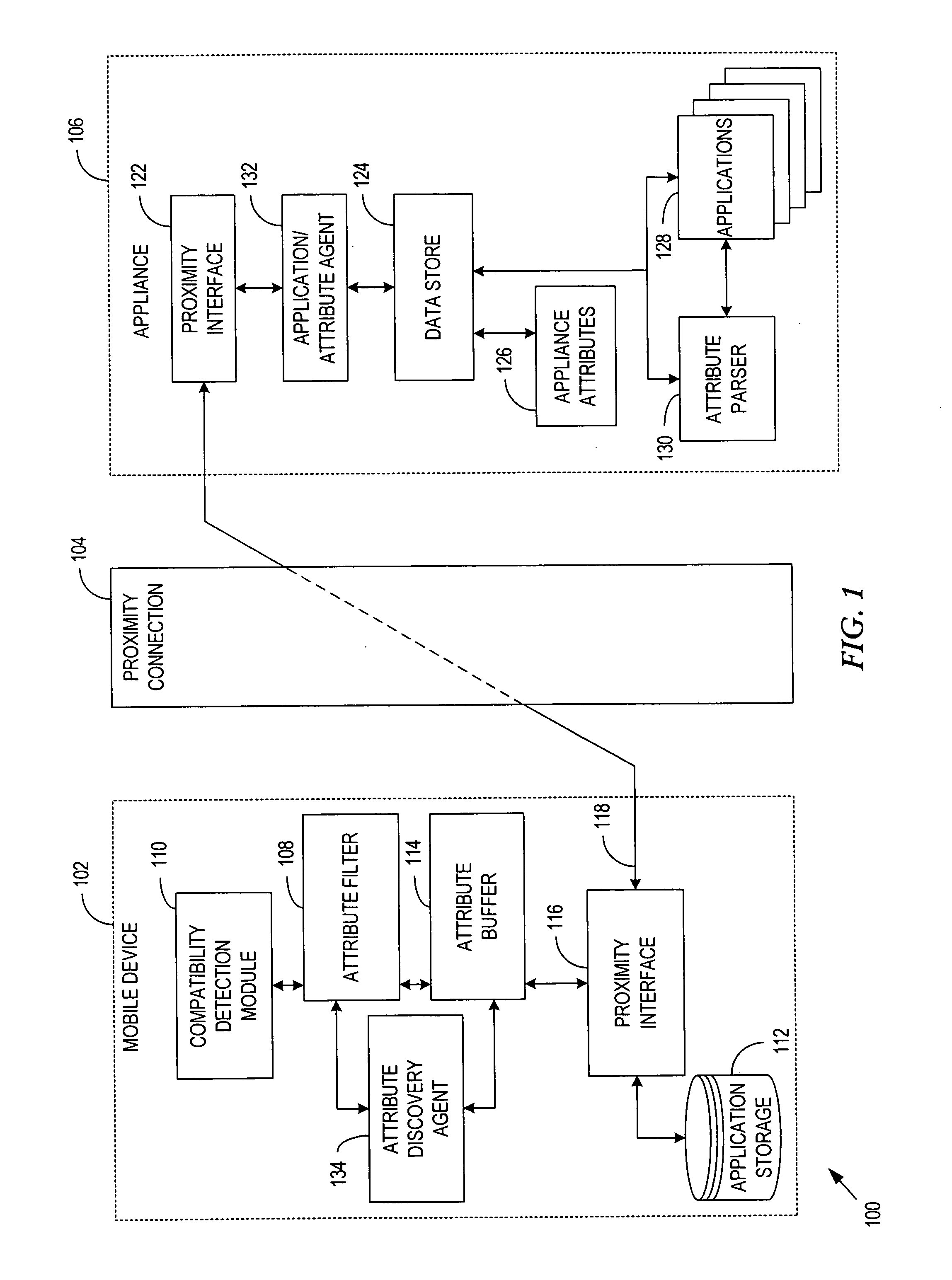
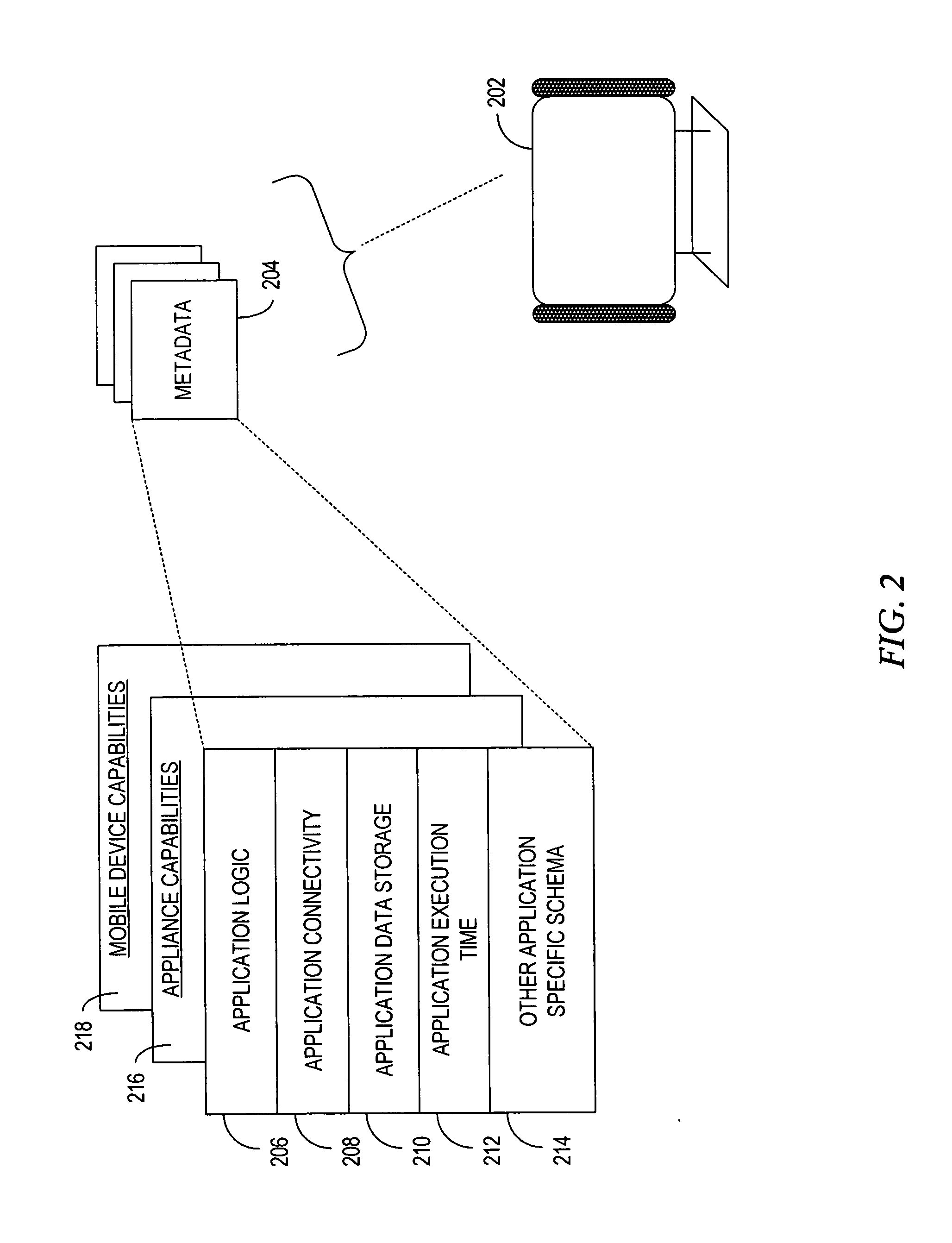
System, method and apparatus for data transfer between computing hosts
A system, method and apparatus to facilitate application and data transfer between a computation host acting as an application source and a computation host acting as an application target. Sufficient execution logic and static data exists between the two computation hosts and a third party interrogation device to allow a determination of the compatibility of applications resident within the source computation host and the application target, as well as the determination of the compatibility between the applications and the interrogation device itself. If compatibility exists, transfer of the applications between the computation hosts via the third party interrogation device is facilitated, whereby the interrogation device supplies temporary storage for the applications.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Database for executing policies for controlling devices on a network
InactiveUS6615218B2Data processing applicationsDigital data processing detailsDatabase triggerData store
A database that can store static and dynamic entries, wherein a static entry contains conventional static data, and a dynamic entry contains information specifying dynamic behavior to control devices on a network. In this database, the act of storing a dynamic entry in the database triggers control over devices on the network. More specifically, one embodiment of a database system according to the present invention includes a data storage medium for storing entries as well as an indexing structure for locating entries on the data storage medium. It also includes a storage mechanism for performing operations to store entries on the data storage medium. Encoded on the data storage medium are dynamic entries containing descriptions of dynamic behavior for the devices on the network. The database additionally includes an execution mechanism that, in response to a dynamic entry being stored on the data storage medium, commands the devices on the network to perform the dynamic behavior specified in the dynamic entry. In a variation on the above embodiment, the execution mechanism is configured to periodically monitor and control the devices on the network.
Owner:ORACLE INT CORP
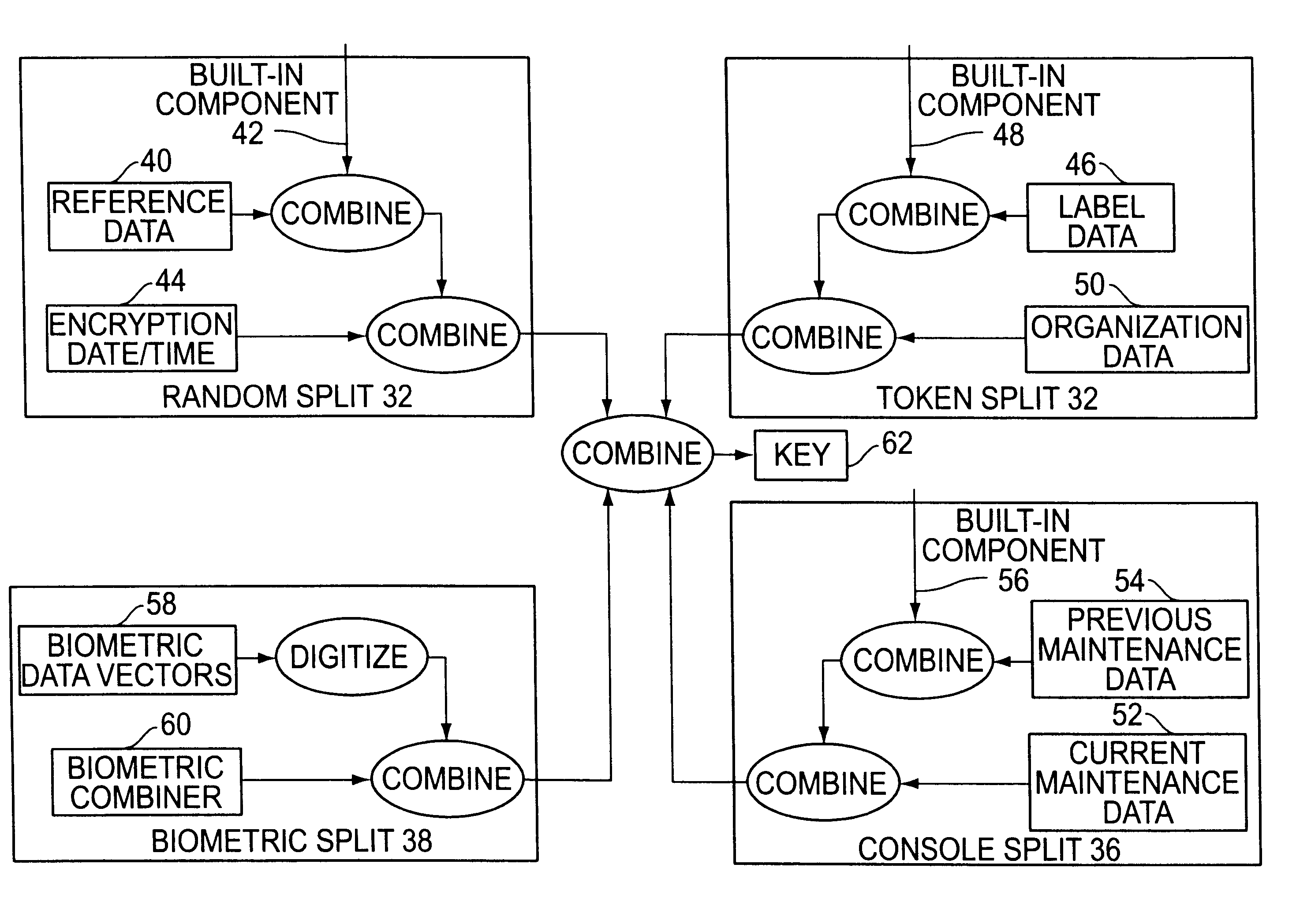
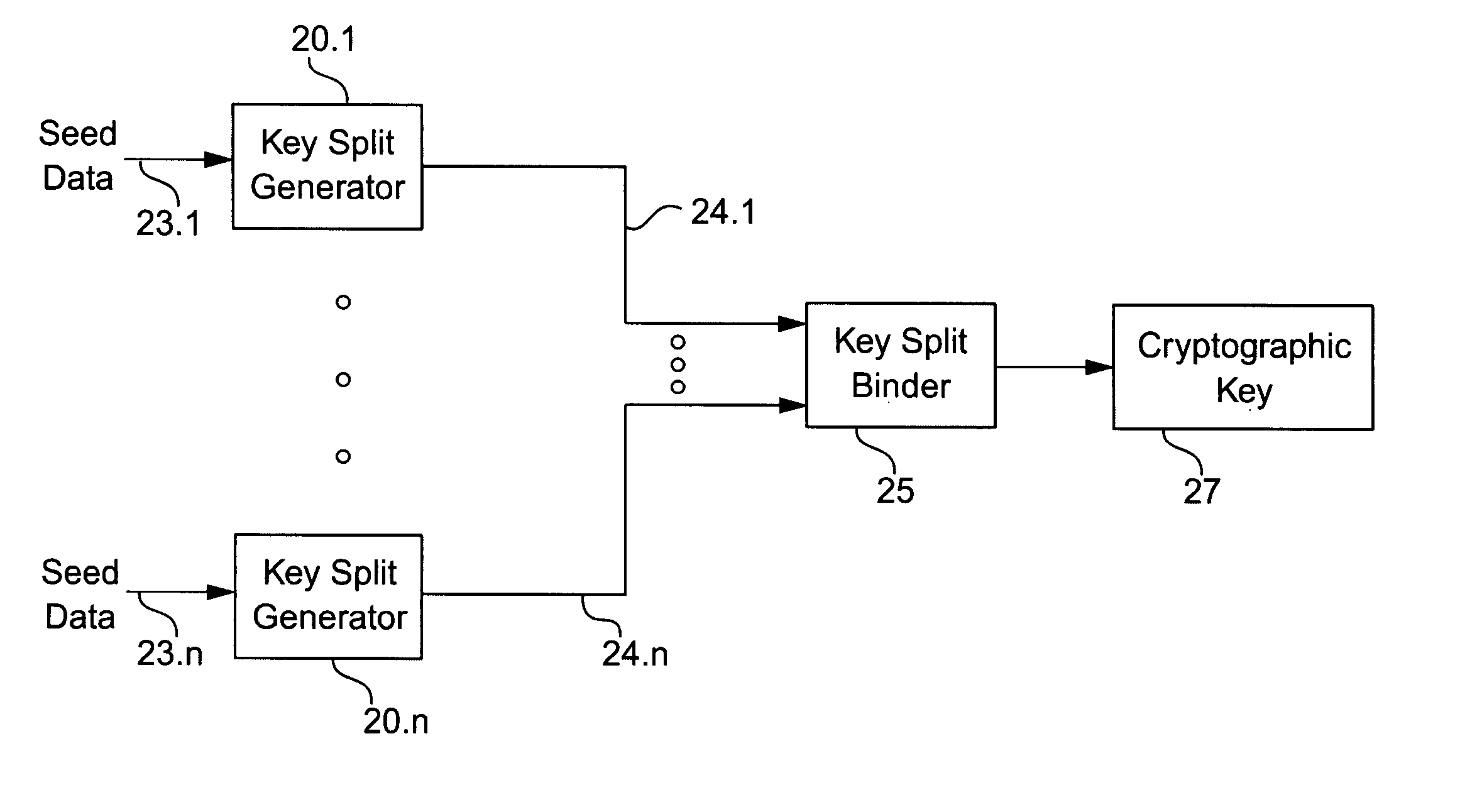
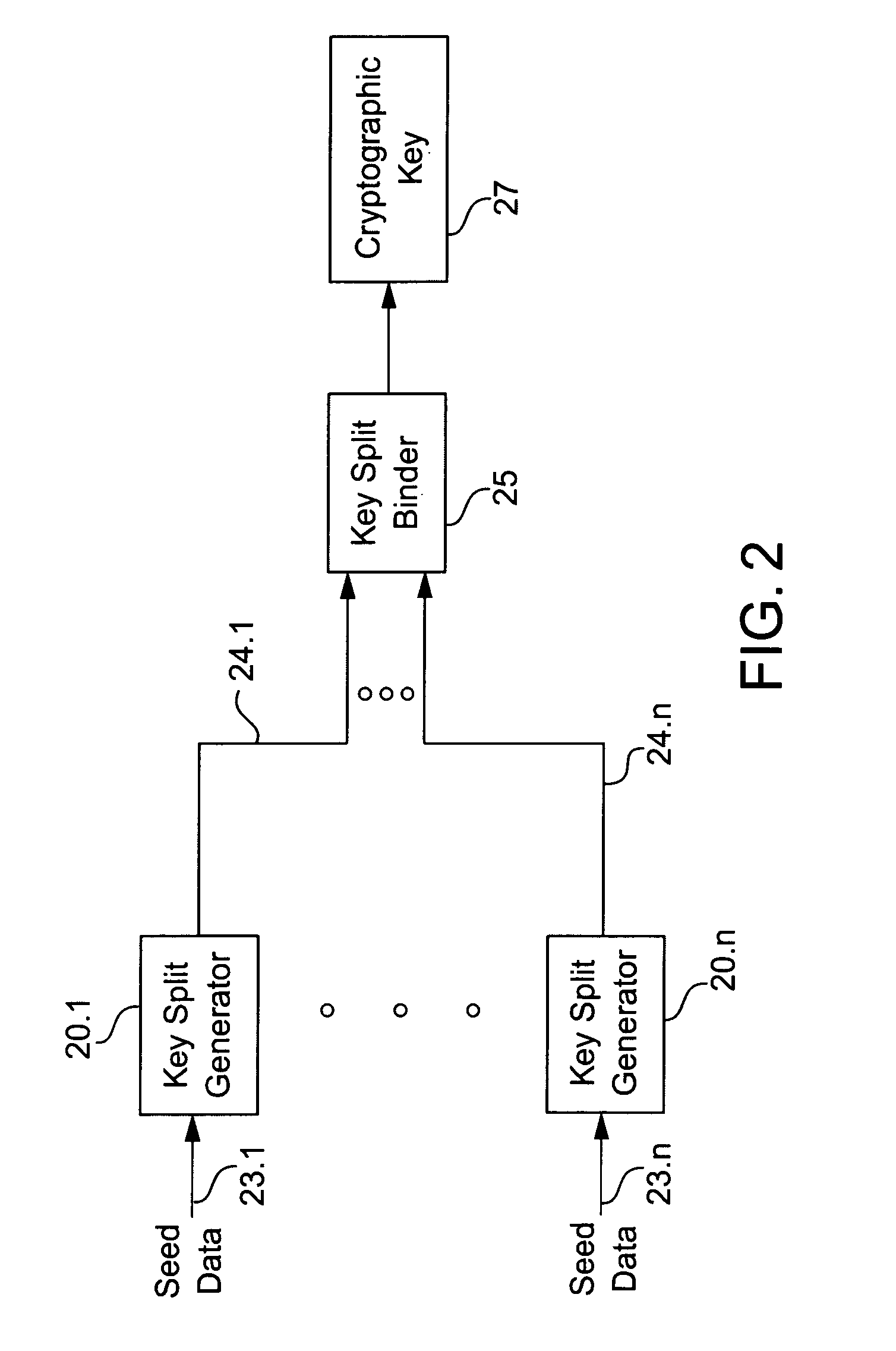
Cryptographic key split combiner
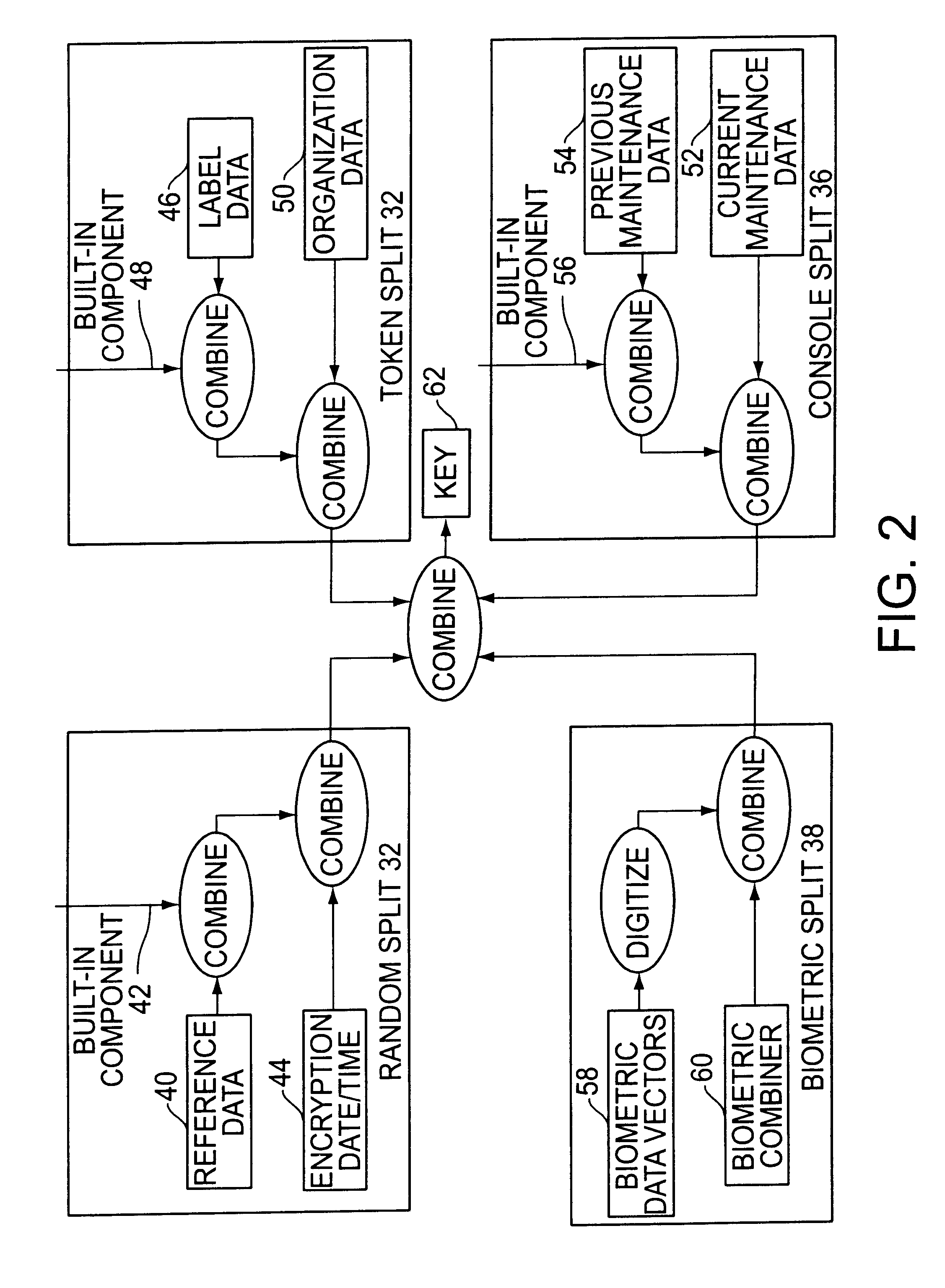
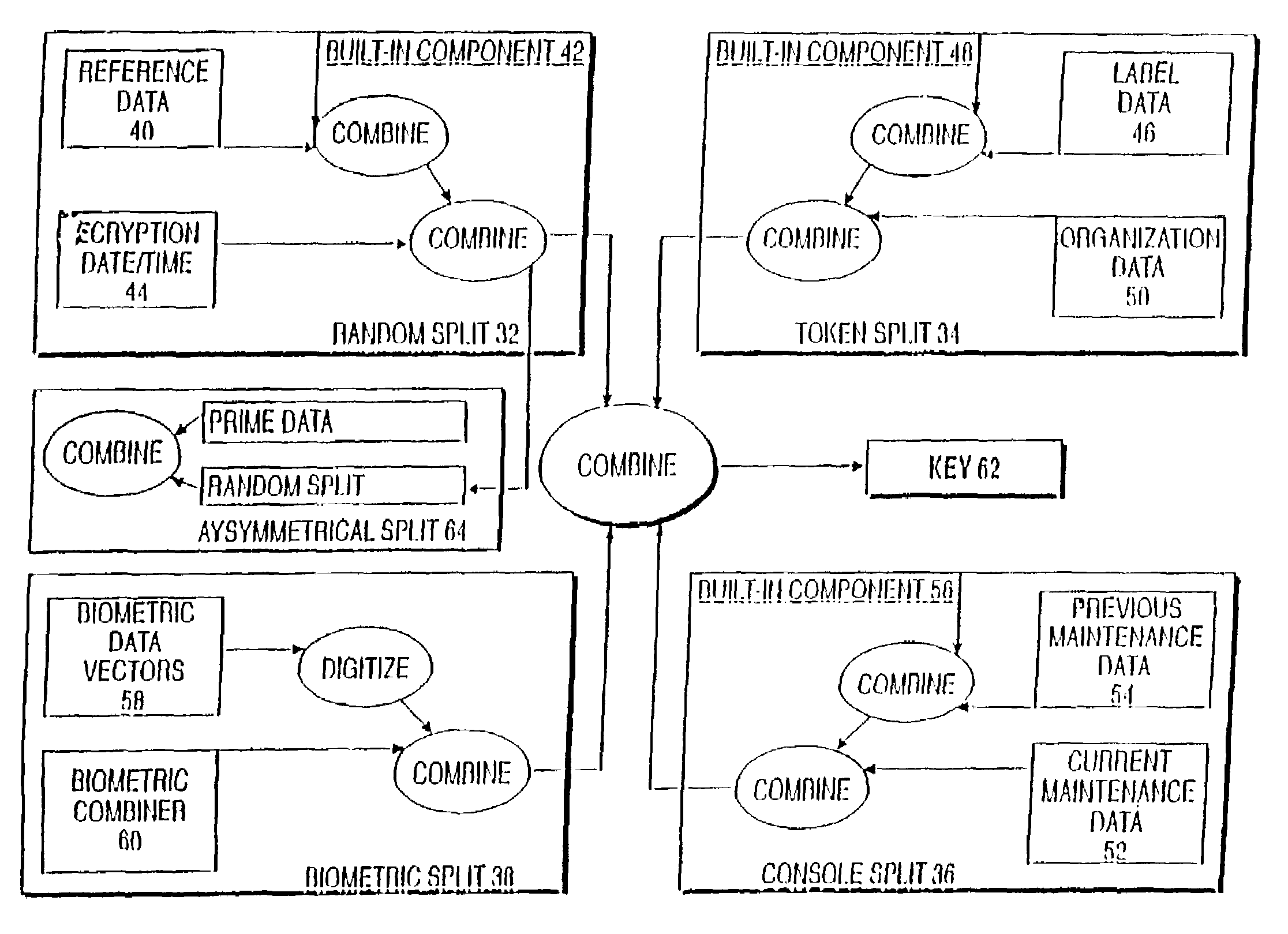
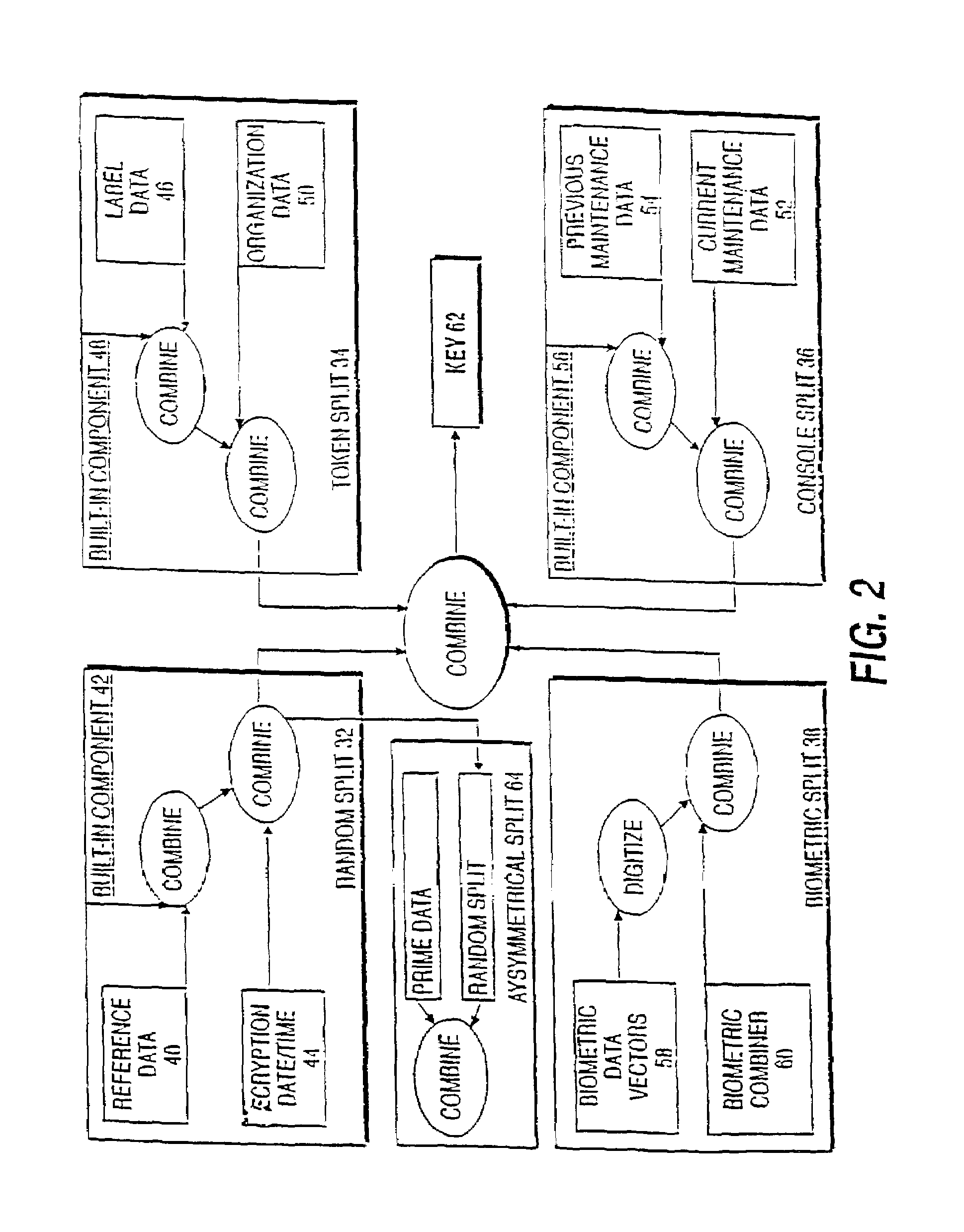
InactiveUS6542608B2Improve securityKey distribution for secure communicationSynchronising transmission/receiving encryption devicesBiometric dataLabeled data
A cryptographic key split combiner, which includes a number of key split generators for generating cryptographic key splits and a key split randomizer for randomizing the cryptographic key splits to produce a cryptographic key, and a process for forming cryptographic keys. Each of the key split generators generates key splits from seed data. The key split generators may include a random split generator for generating a random key split based on reference data. Other key split generators may include a token split generator for generating a token key split based on label data, a console split generator for generating a console key split based on maintenance data, and a biometric split generator for generating a biometric key split based on biometric data. All splits may further be based on static data, which may be updated, for example by modifying a prime number divisor of the static data. The label data may be read from a storage medium, and may include user authorization data. The resulting cryptographic key may be, for example, a stream of symbols, at least one symbol block, or a key matrix.
Owner:TECSEC
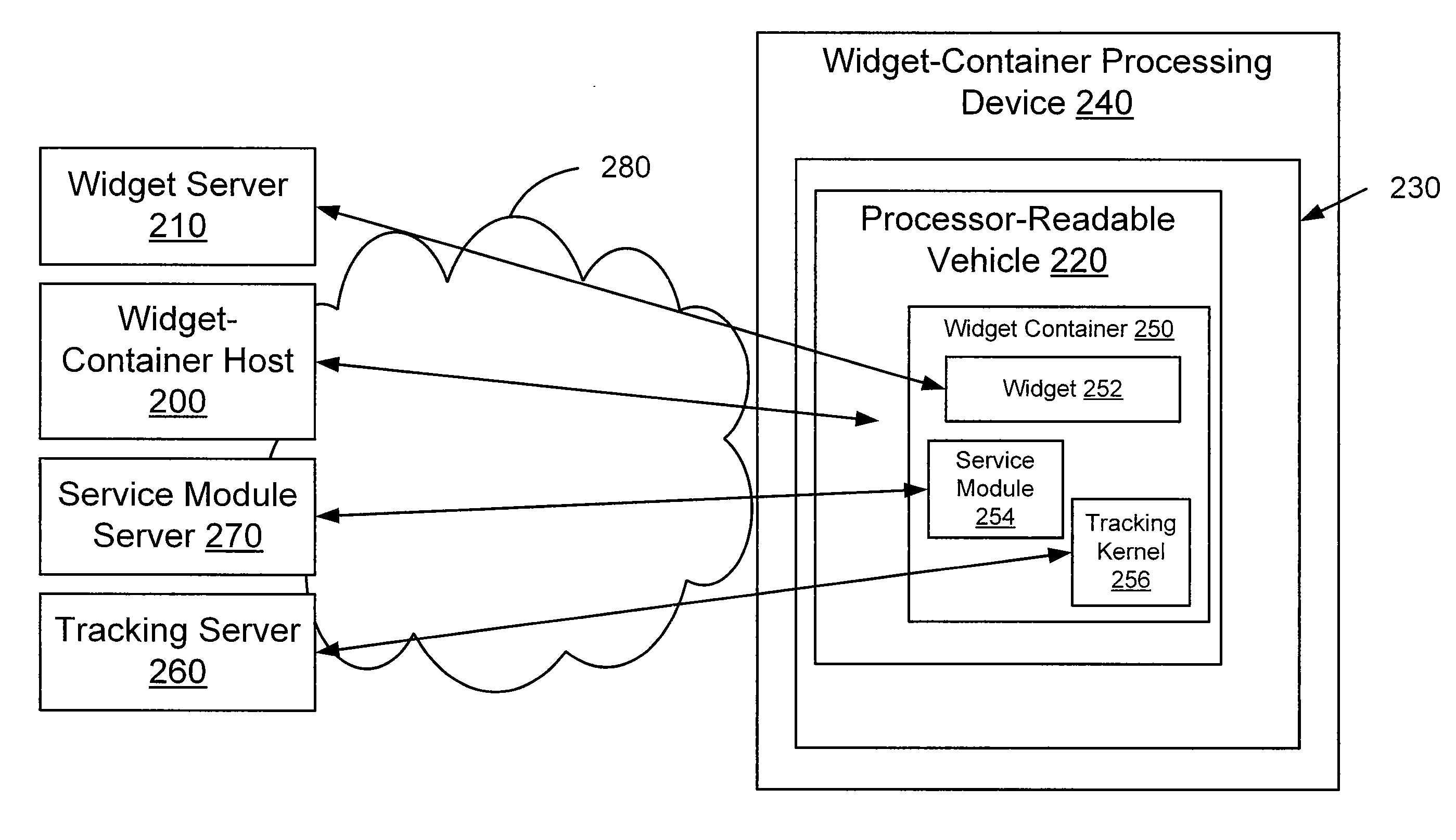
Method and Apparatus for Widget-Container Hosting and Generation
A method includes receiving at least one of a widget or a reference to a widget, where the widget can be at least one of a static data object, a media object, or a software object. At least a portion of a widget container, which is a procedural software framework containing a service module associated with the widget and the widget, is generated. The service module can be a pre-defined function associated with the widget container before the widget container is generated. The widget container can be configured to be executed at a widget-container processing device in response to a reference to the widget container being accessed from a processor-readable vehicle.
Owner:ORACLE INT CORP
Cryptographic key split binder for use with tagged data elements
InactiveUS7095852B2Weight increaseData can be securedKey distribution for secure communicationComputer hardwareBiometric data
A cryptographic key split binder includes key split generators that generate cryptographic key splits from seed data and a key split randomizer for randomizing cryptographic key splits to produce a cryptographic key, and a process for forming cryptographic keys. Key split generators can include a random split generator for generating a random key split based on reference data, a token split generator for generating a token key split based on label data, a console split generator for generating a console key split based on maintenance data or a biometric split generator for generating a biometric key split based on biometric data. Any key split can further be based on static data, which can be updated. Label data can be read from a storage medium, and can include user authorization data. A cryptographic key can be, for example, a stream of symbols, at least one symbol block, or a key matrix.
Owner:TECSEC
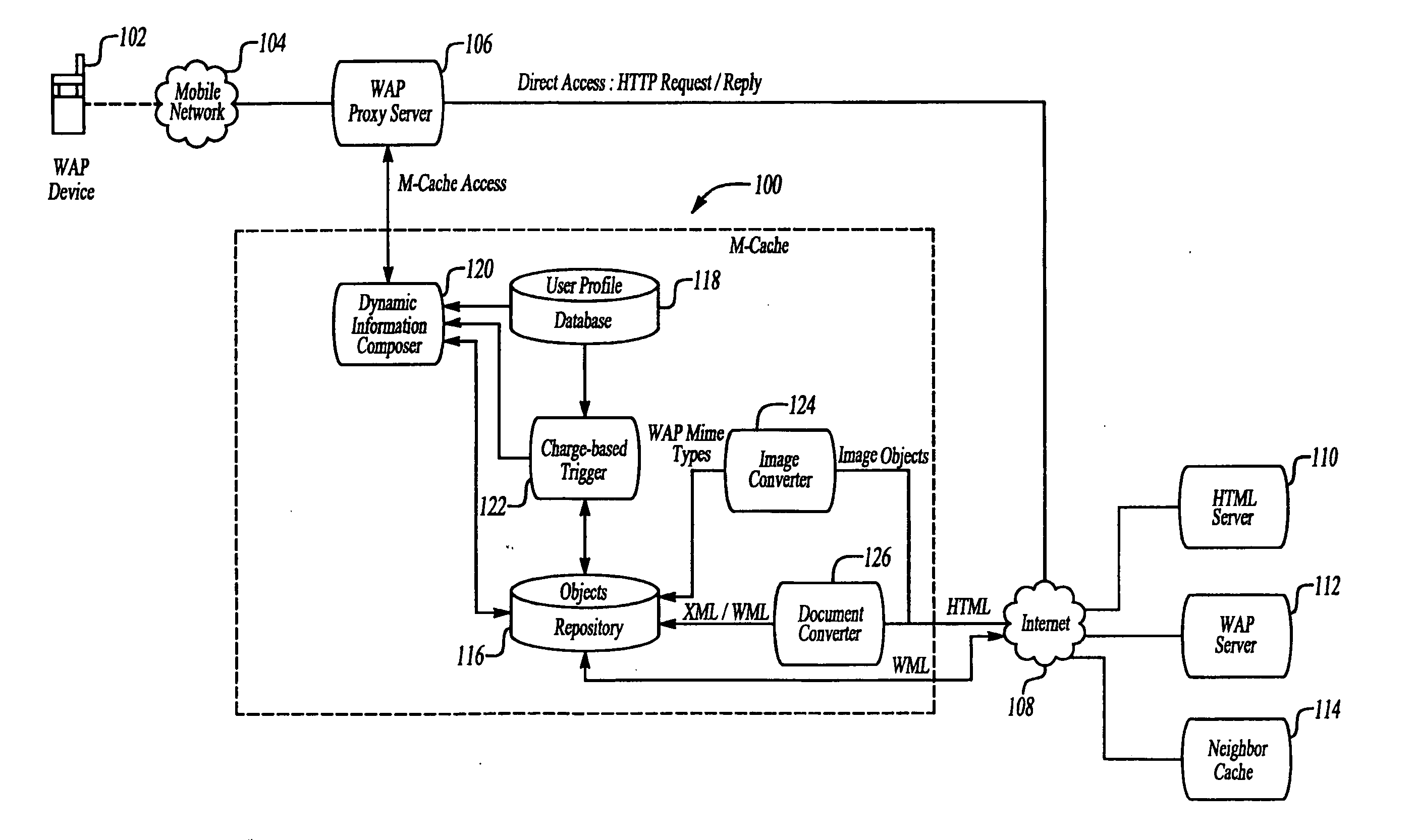
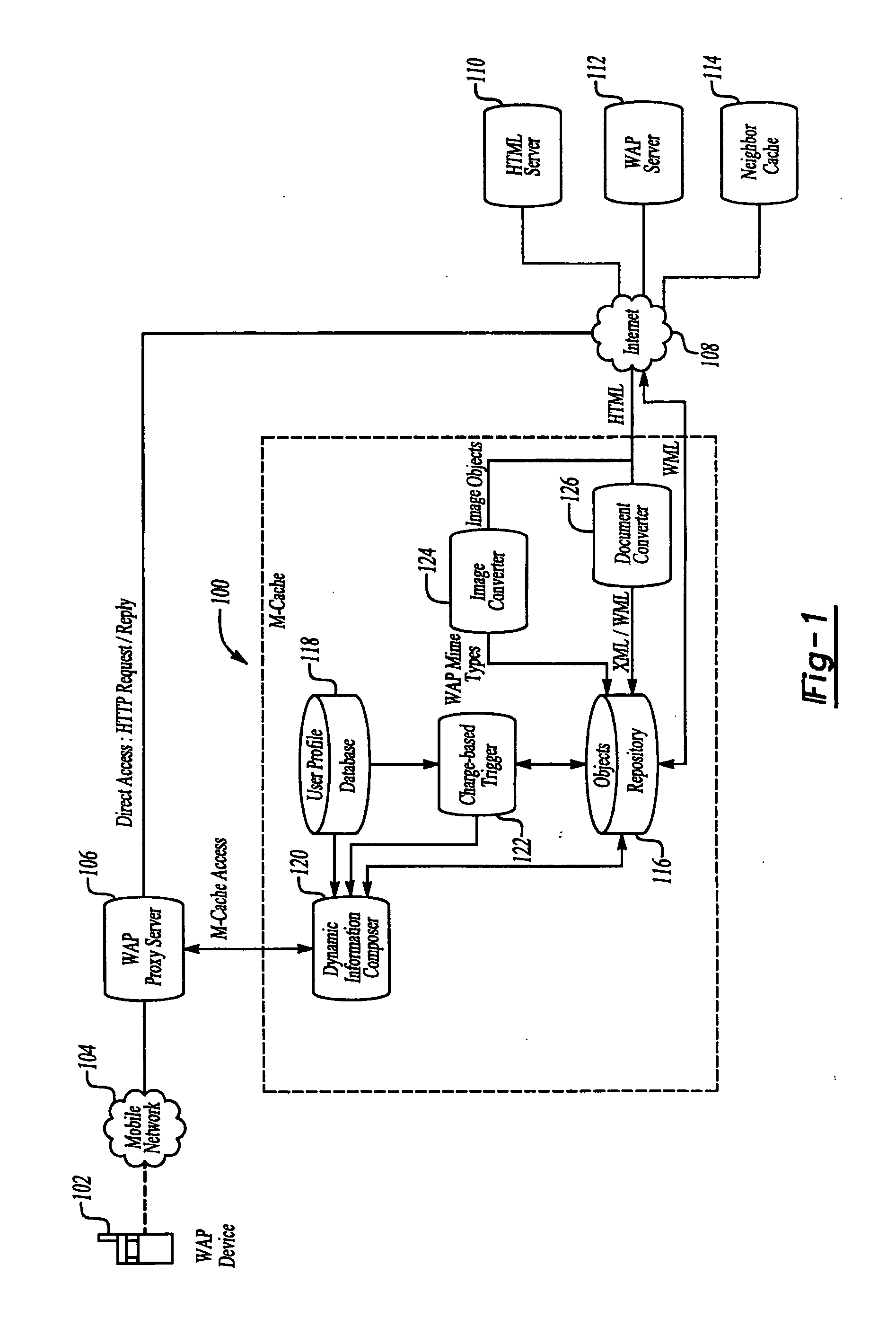
Mobile cache for dynamically composing user-specific information
InactiveUS20050210125A1Facilitate dynamic creationReduce traffic burdenMultiple digital computer combinationsTransmissionWireless Application ProtocolXML Base
A system and method for caching data in wireless application protocol (WAP) enabled services caches static data and facilitates dynamic creation of user-specific information to provide a customized output. The mobile cache generates the user-specific information in WML in real-time from cached information according to user-specified preferences. A change trigger triggers information delivery after a predetermined amount of cached information changes. The system may also include an image converter to ensure that image objects can be viewed easily on WAP-enabled devices having small display screens and a document converter to dynamically compose information from selected data based on XML-based content tagging.
Owner:UNWIRED BROADBAND INC
System And Method For Integration Of Streaming And Static Data
ActiveUS20090037514A1Rapid acquisitionRapid transformationTransmissionElectric digital data processingStreaming dataData source
The invention relates to integration of streaming data. The invention provides a means for integrating both high-throughput streaming and static content originating from multiple types and / or instances of data sources into discrete units of data. The invention provides integration of a wide variety of disparate streaming and static data sources as well as deployment of content in multiple protocols, either static or streaming or both. In the preferred embodiment, the invention provides a method and system for the insertion of domain-specific implementations of the JMS (Java Message System) messaging paradigm into a server-based JMS provider infrastructure. A Content Integration Framework provides access to Content Instances. The Content Integration Framework is used by Distribution Adapters that expose content from Content Instances cached in the system using a variety of protocols.
Owner:METAFLUENT
Autonomous data machines and systems
ActiveUS9329597B2Reduce negative personal and economic impactPromote safe buildingAcoustic signal devicesPropulsion by batteries/cellsData sourceData mining
Owner:KNIGHTSCOPE
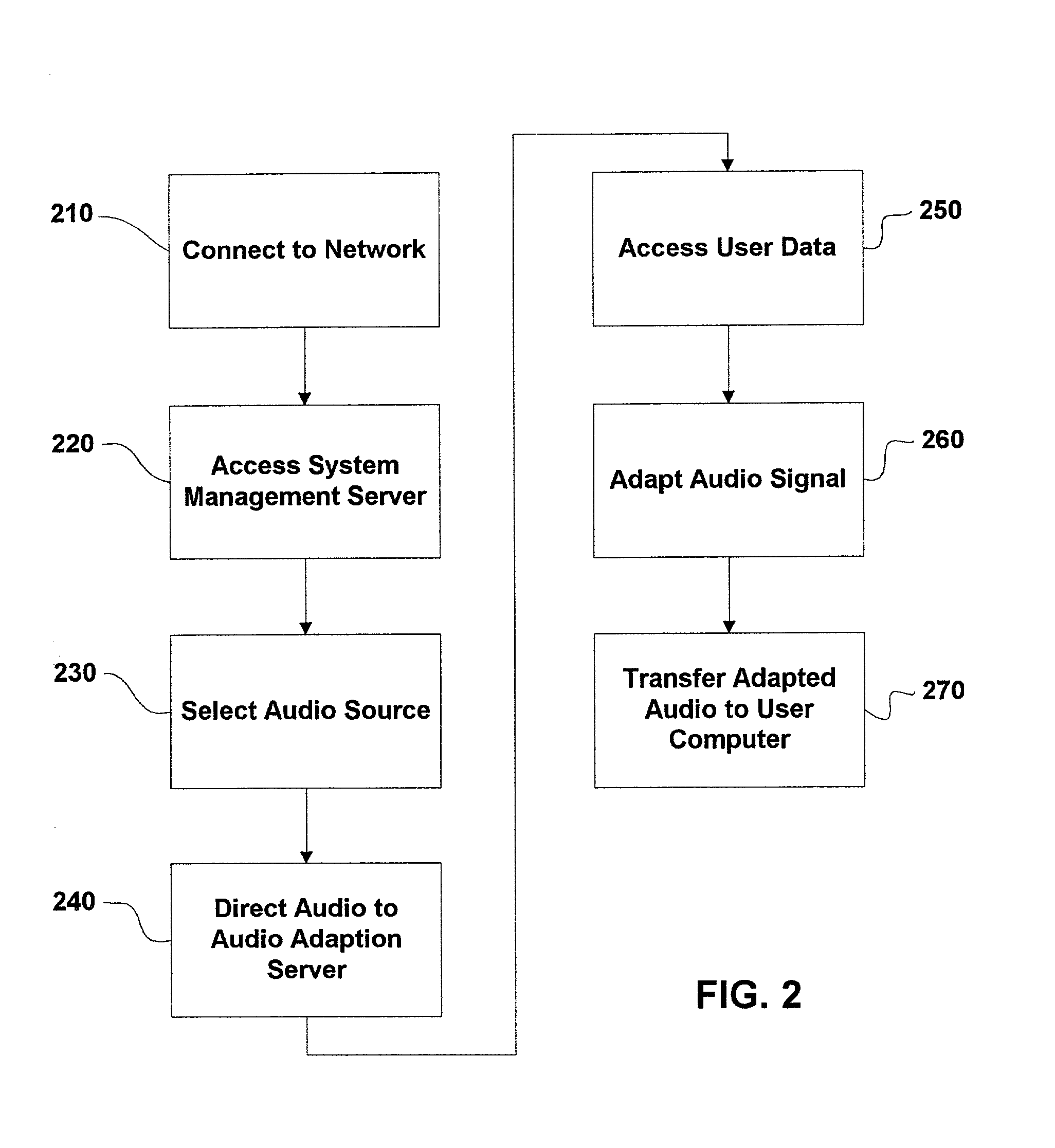
Adaptation of audio data files based on personal hearing profiles
InactiveUS20020068986A1Physical therapies and activitiesStereophonic circuit arrangementsDigital dataThe Internet
Methods and systems for high quality computer based adaptation of audio data are shown. Adaptation, delivery of audio data, and testing of user's hearing abilities can occur on computers or computer networks such as the Internet Adaptation can compensate for frequency dependent and audio masking impairments. The audio to be adapted can include real-time streaming digital data or static data files. Standard digital audio formats are supported.
Owner:SOUND ID +1
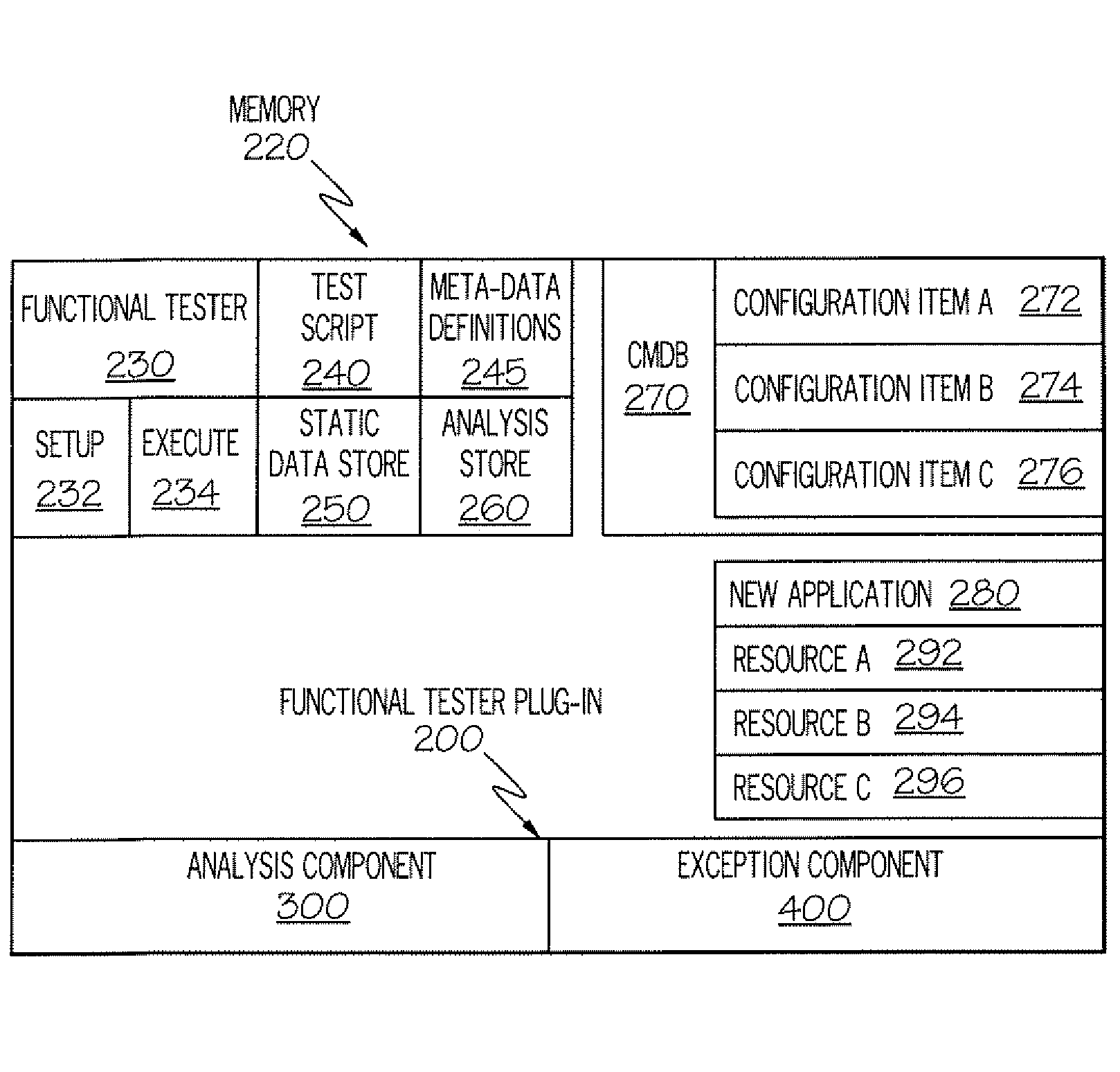
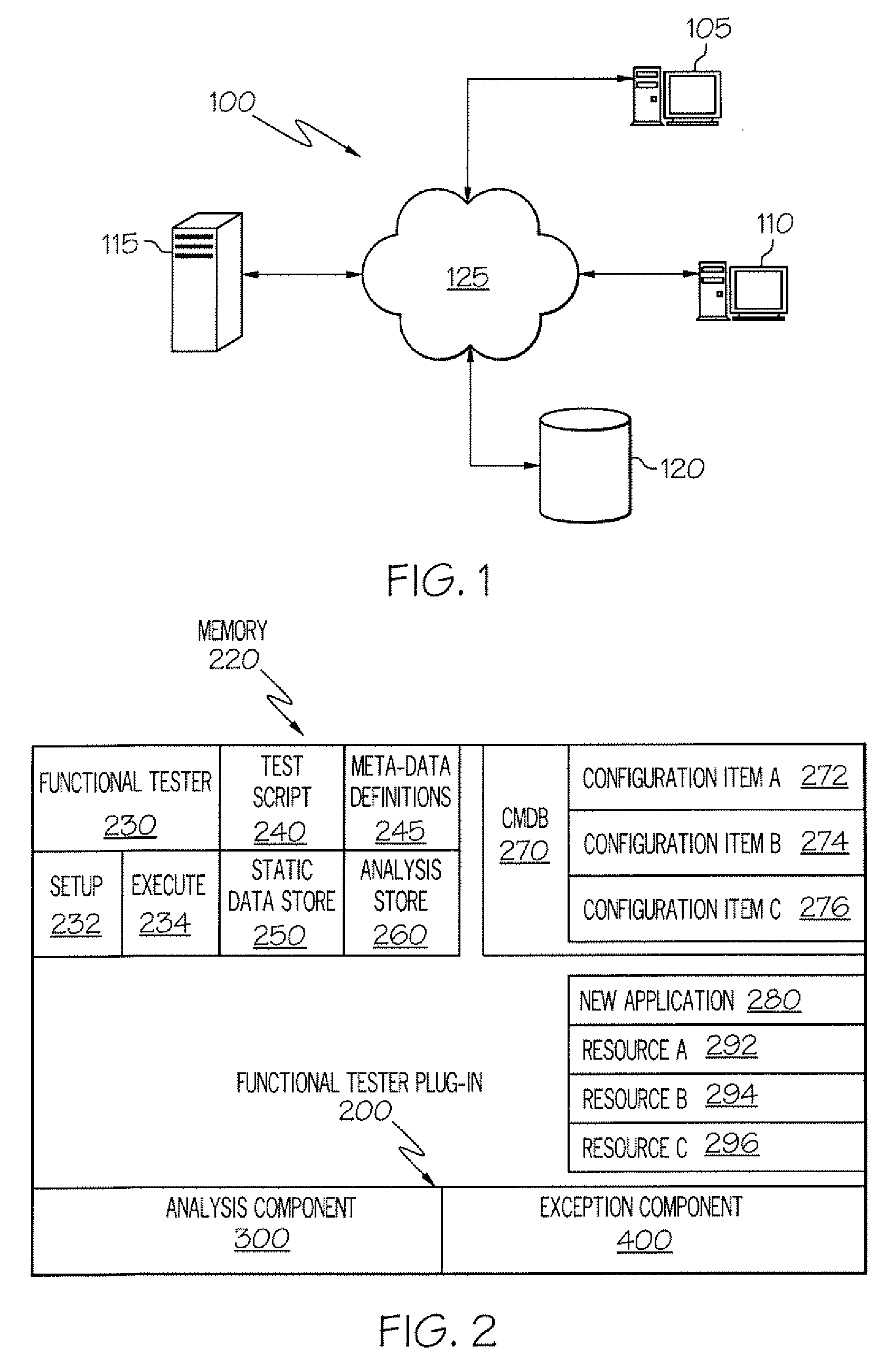
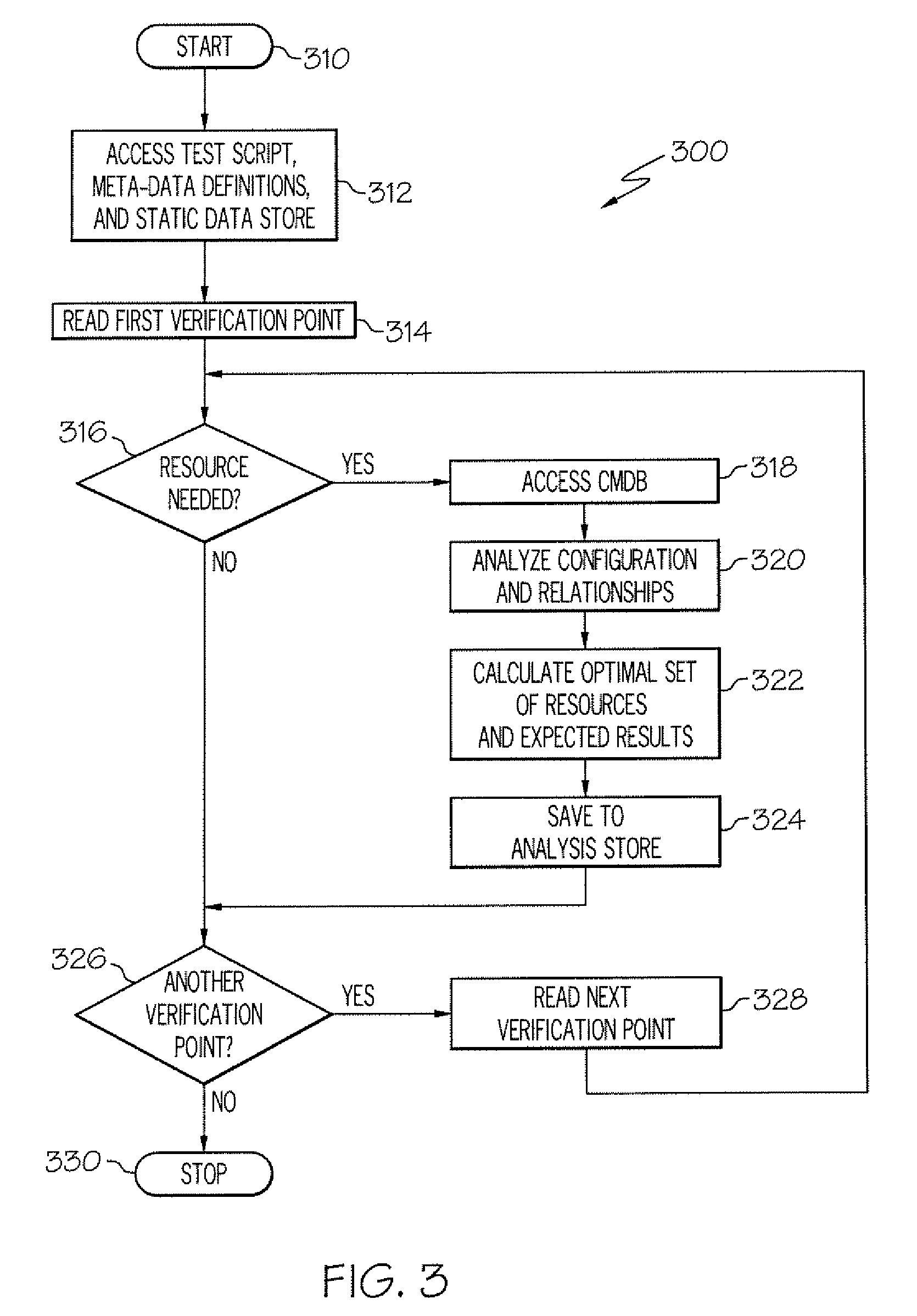
Method and Apparatus for Completing Functional Testing
InactiveUS20080276224A1Promote resultsError detection/correctionSoftware maintainance/managementFunctional testingTest script
The Functional Tester Plug-in (FTP) extracts information from a data base to enhance automated testing tools to accommodate changes to the computer environment and so that a simulation can be fully executed even if an exception occurs. The FTP accesses the test script and static data store created by a developer using the automated testing tool, wherein the test script and static data store indicate a first resource to be tested at a verification point and a first expected result. The FTP identifies the first resource used by the test script at a first verification point and accesses the data base. The FTP identifies the status and configuration of the first resource in the data base. The FTP calculates and optimal expected result based any changes in the status and configuration of the first resource. The FTP executes the test script using the optimal expected result based any changes in the status and configuration of the first resource.
Owner:IBM CORP
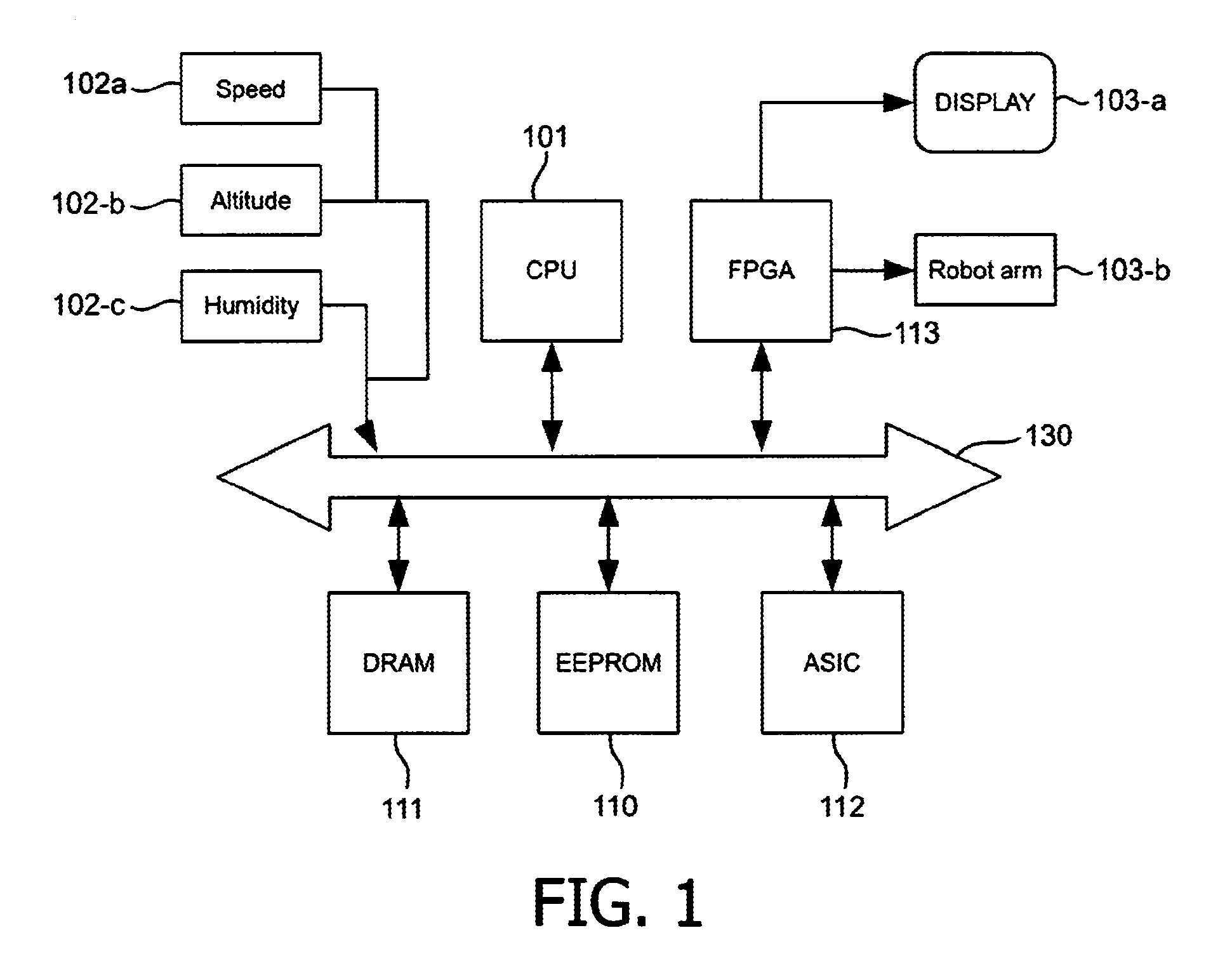
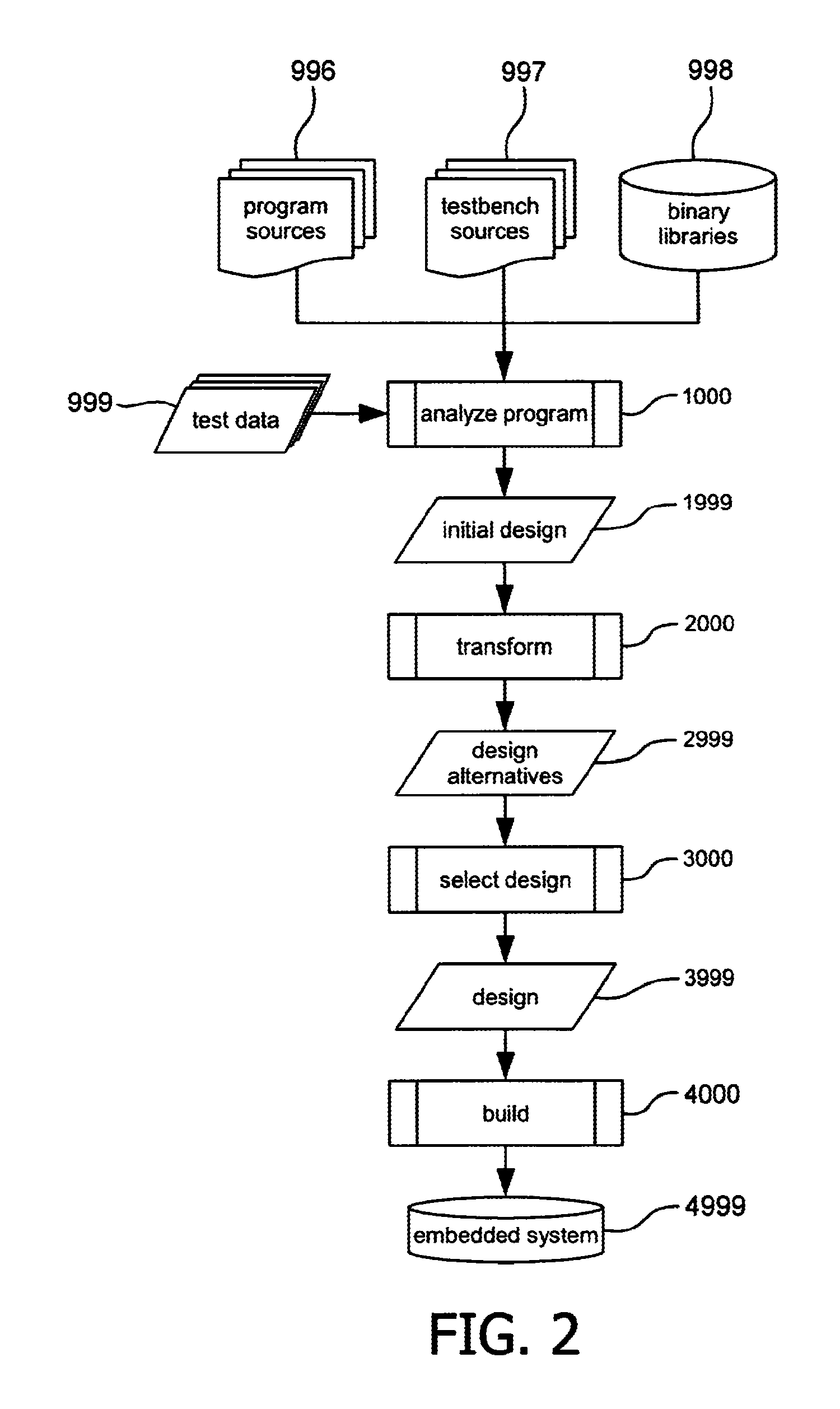
Embedded system development
InactiveUS20120144376A1Add partsLow costSoftware engineeringCAD circuit designTheoretical computer scienceDynamic data
A computer-implemented method of automatically generating an embedded system on the basis of an original computer program, comprising analyzing the original computer program, comprising a step of compiling the original computer program into an executable to obtain data flow graphs with static data dependencies and a step of executing the executable using test data to provide dynamic data dependencies as communication patterns between load and store operations of the original computer program, and a step of transforming the original computer program into an intermediary computer program that exhibits multi-threaded parallelism with inter-thread communication, which comprises identifying at least one static and / or dynamic data dependency that crosses a thread boundary and converting said data dependency into a buffered communication channel with read / write access.
Owner:VECTOR FABRICS BV
Method and file structures for managing data on a flash disk
ActiveUS7363420B2Input/output to record carriersMemory adressing/allocation/relocationDynamic dataMetadata
A method, apparatus and data structure for managing data in a memory device. The memory device is divided into two volumes. The first volume is intended for storing relatively static data, i.e. data which does not change or is not rewritten frequently. The second volume is intended for storing dynamic data, i.e. data which is changed or rewritten frequently. Each of the volumes is divided into a number of blocks, for example erase blocks, with each block being divided into sectors. In the dynamic volume, each of the erase blocks has one sector allocated for storing metadata, and the remaining sectors in the erase block are available for storing data, other than metadata. In the static volume, each of erase blocks can store more than one sector of metadata, in addition to data other than metadata. The metadata may be stored in consecutive sectors in the erase blocks. According to another aspect, the data structure is suitable for flash disk memory devices and flash disk memory devices used for multimedia applications.
Owner:AVAYA INC
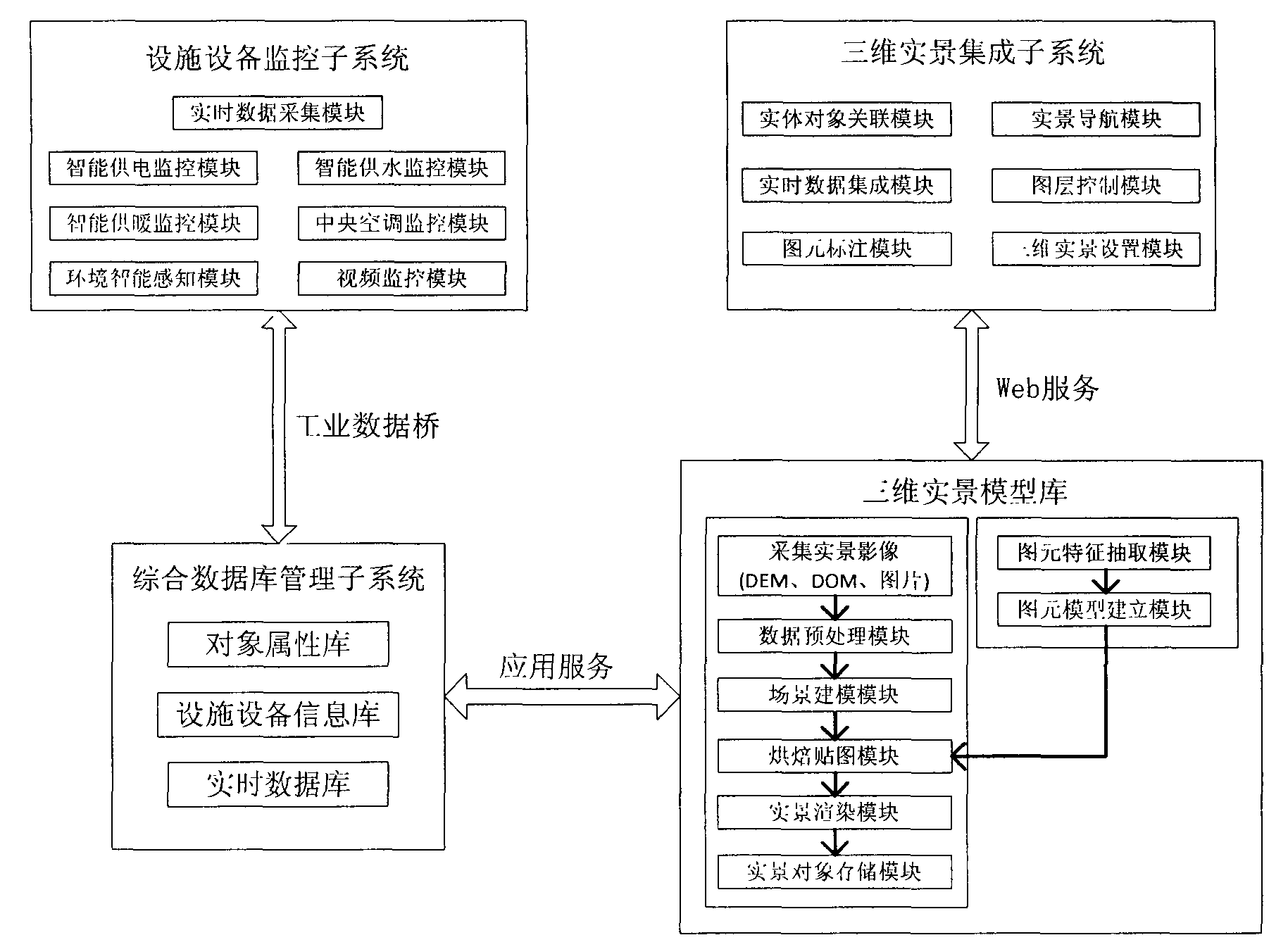
Equipment monitoring system based on three-dimensional real scenes and system integration method based on three-dimensional real scenes
InactiveCN103177391AChanges can be seen intuitivelyIncrease contentData processing applicationsSpecial data processing applicationsSystem integrationReal-time data
The invention discloses an equipment monitoring system based on three-dimensional real scenes and a system integration method based on three-dimensional real scenes. A database technology is fully utilized, and static data of a three-dimensional real scene model library is integrated and associated with dynamic data in an equipment monitoring subsystem to realize dynamism and instantaneity of three-dimensional real scene object information display; physical modeling is performed to smart equipment to form identifiable equipment three-dimensional pixel, feature information of the smart equipment is extracted to build a visual information data structure of the smart equipment; an industrial data bridge and an SOA (semiconductor optical amplifier) technology are utilized to integrate real-time date collected by the smart equipment to a three-dimensional real scene image so as to realize information display control and statistical analysis, accurate visualized dynamic information is provided for administrators in real time, and omnibearing monitoring requirements are met.
Owner:LOGISTICAL ENGINEERING UNIVERSITY OF PLA
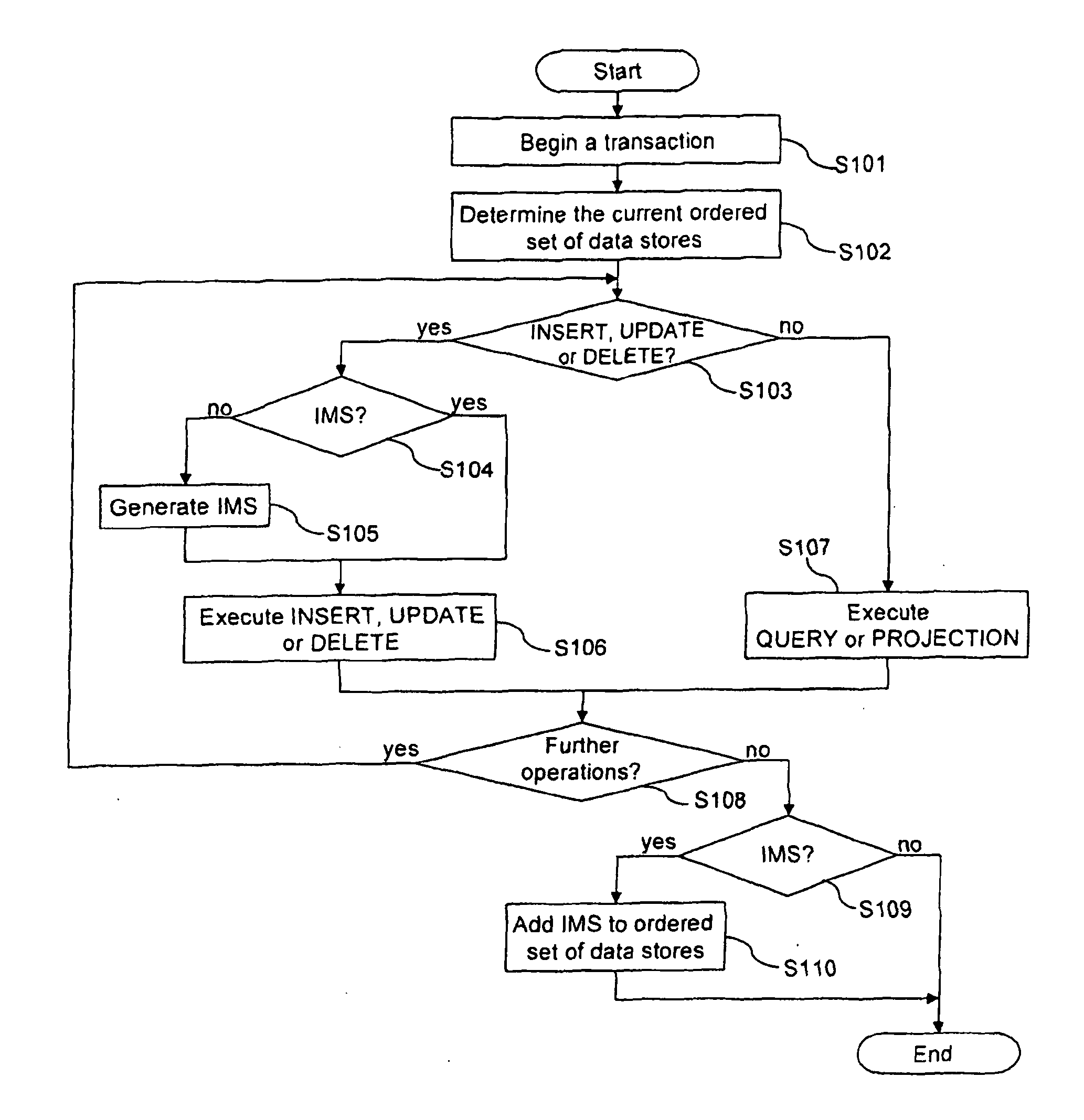
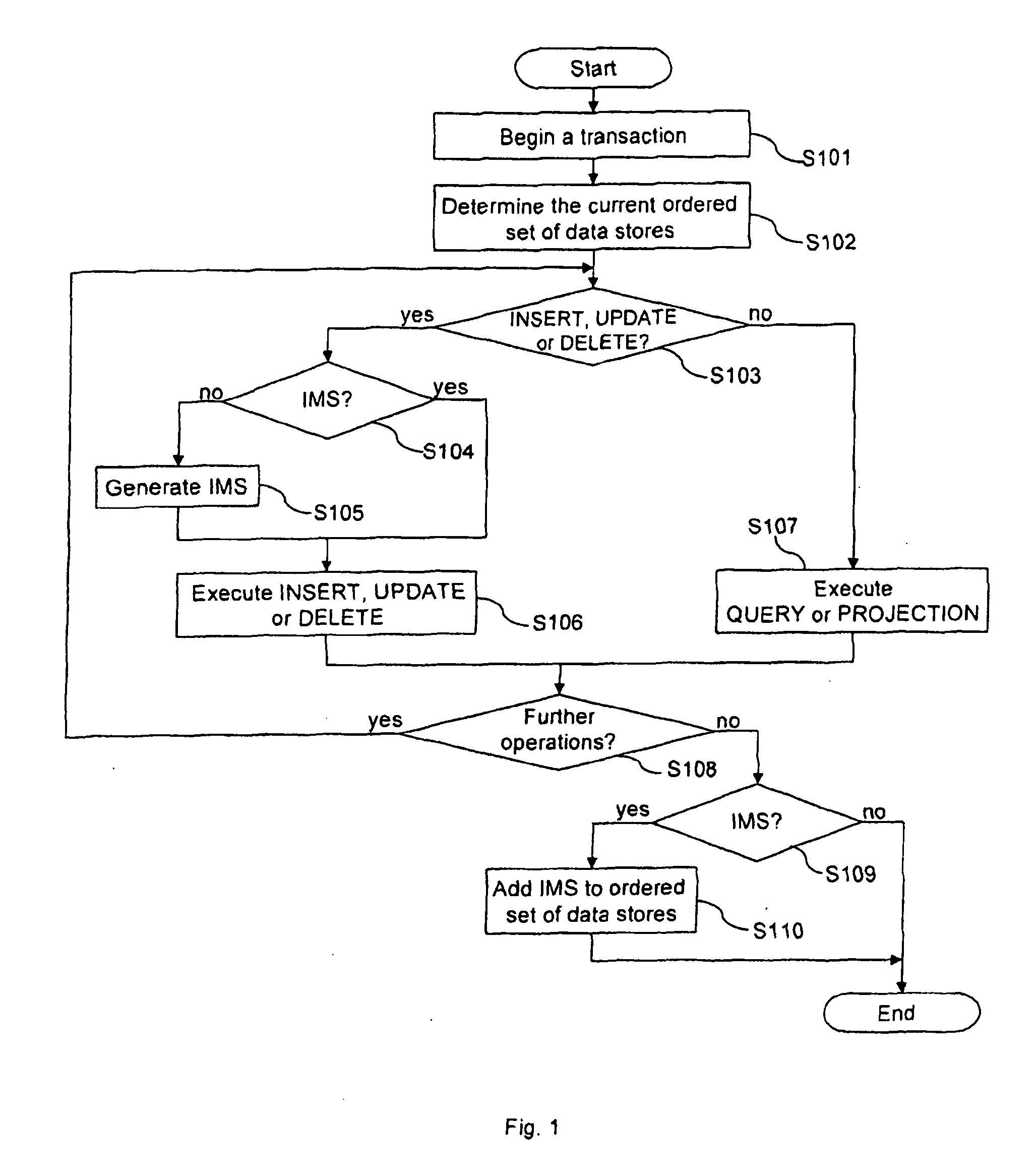
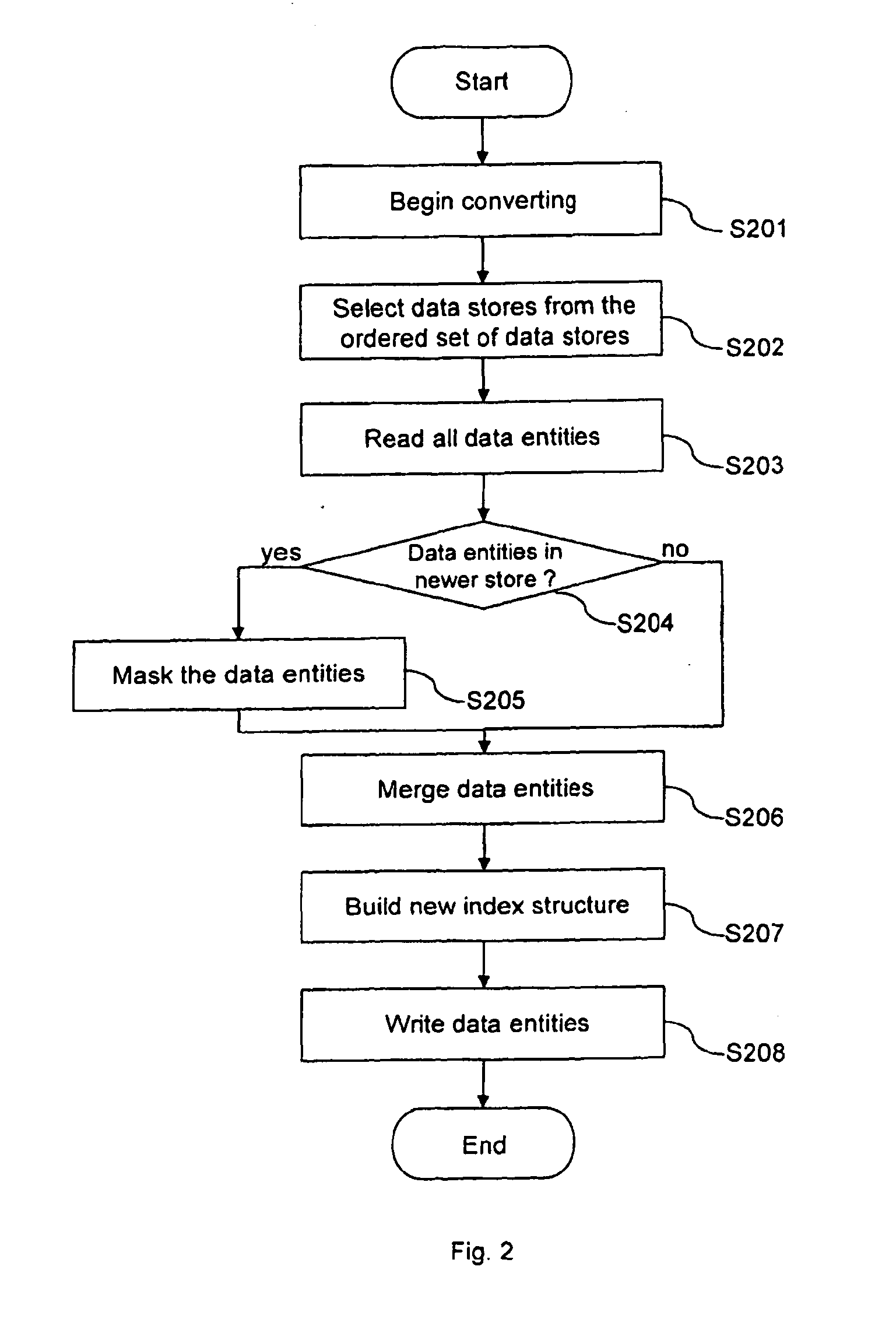
Method for performing transactions on data and a transactional database
ActiveUS20130110766A1Improve performanceLow costDigital data information retrievalDigital data processing detailsData storingOrder set
The present invention provides a method for performing transactions on data entities in a database and a transactional database. The database comprises an ordered set of data stores with at least one static data store, wherein said static data store uses an index structure based on a non-updatable representation of an ordered set of integers according to the principle of compressed inverted indices. The method allows to generate a modifiable data store when the performed transaction comprises an insert, update or delete operation, to execute operations of the transaction on the ordered set being present at the time when the transaction has been started and, if present, on the modifiable data store and to convert data stores to a new static data store, The insert, update or delete operation are executed on the modifiable data store which is the only data store modifiable for the transaction.
Owner:OPEN TEXT SA ULC
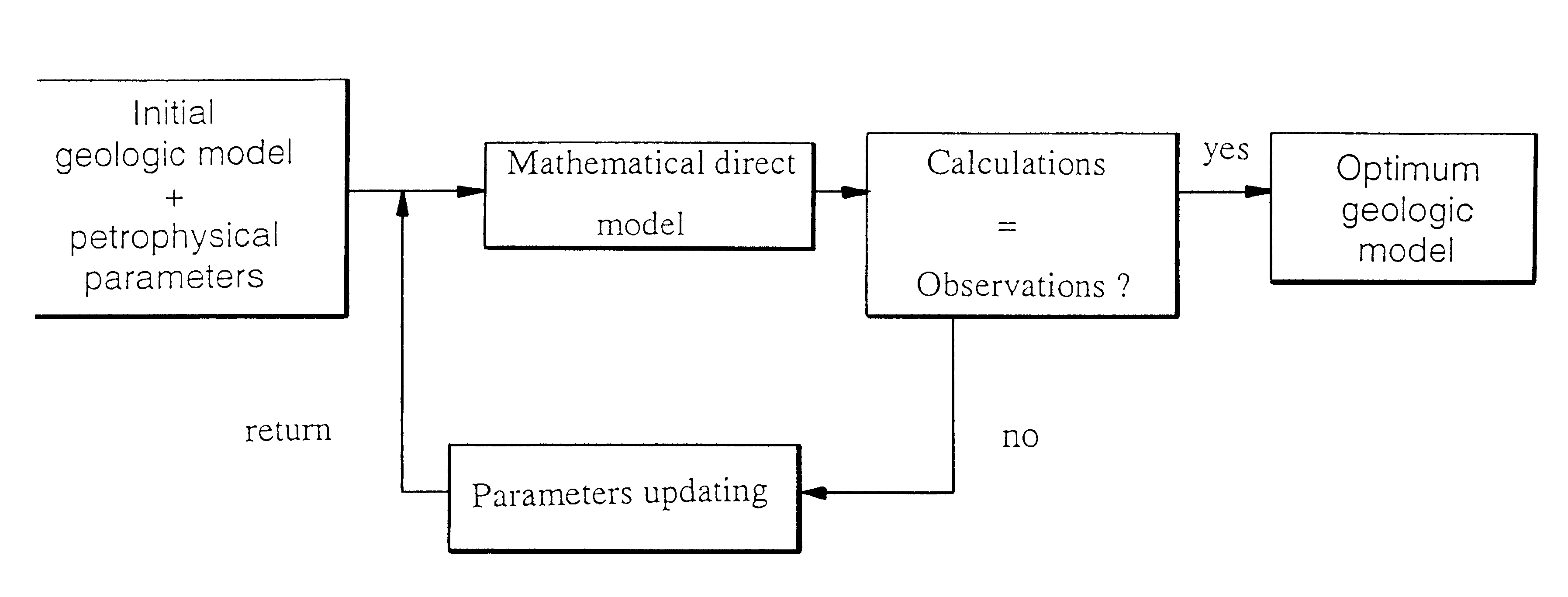
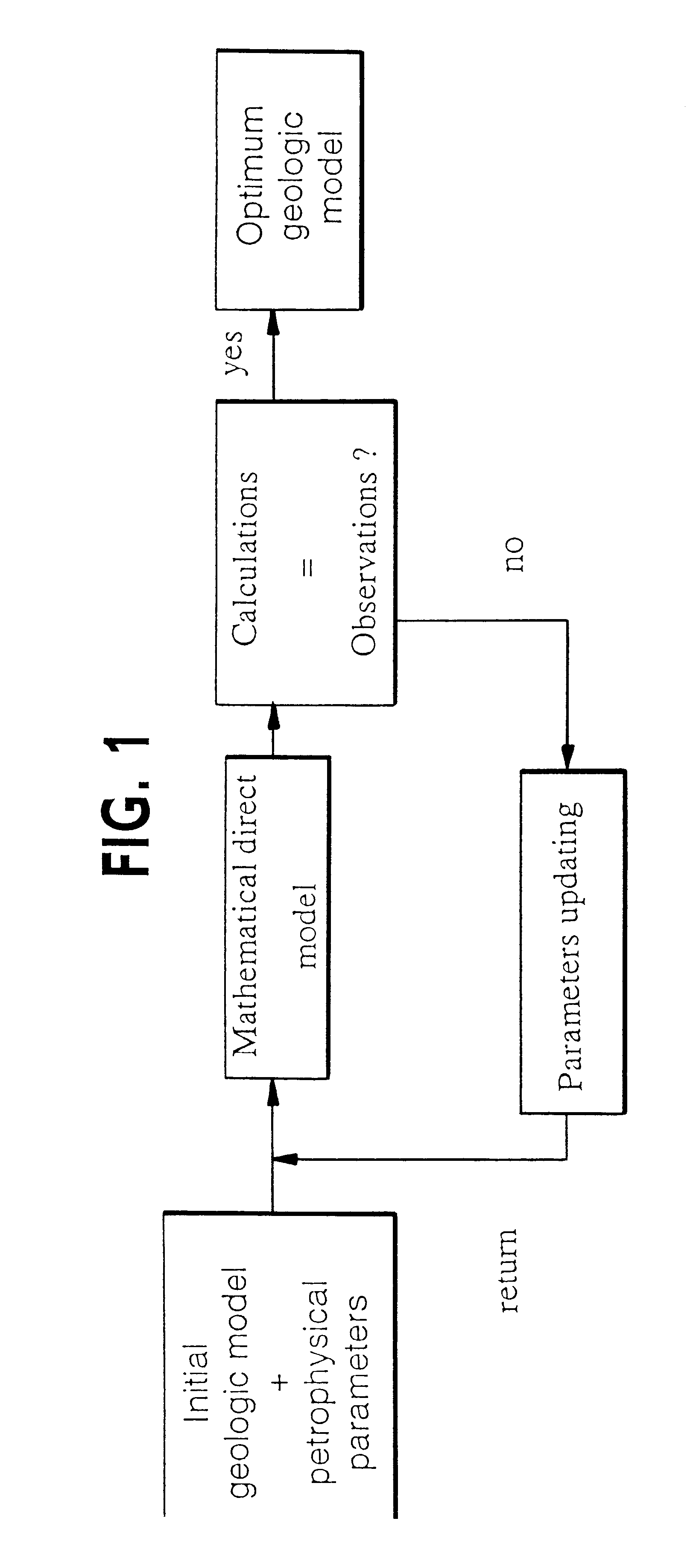
Method for forming a model of a geologic formation, constrained by dynamic and static data
InactiveUS6381543B1Electric/magnetic detection for well-loggingSeismic signal processingDynamic dataAcoustic impedance
Method for forming, by means of an inversion technique, a model of an underground zone, constrained by static data: data obtained by seismic exploration or measured in situ (logs), and by dynamic data: production measurement, well testing, etc. From an a priori selected meshed geologic model and from relations between parameters or physical quantities characteristic of the medium: acoustic impedance and cabsolute permeability for example, a simultaneous inversion of the two parameters is performed by minimizing a global cost function, which has the effect of considerably decreasing the number of possible solutions and of improving characterization of the underground zone. The method can be used notably for modelling hydrocarbon reservoirs, of zones likely to be used as gas, waste storage places, etc.
Owner:INST FR DU PETROLE
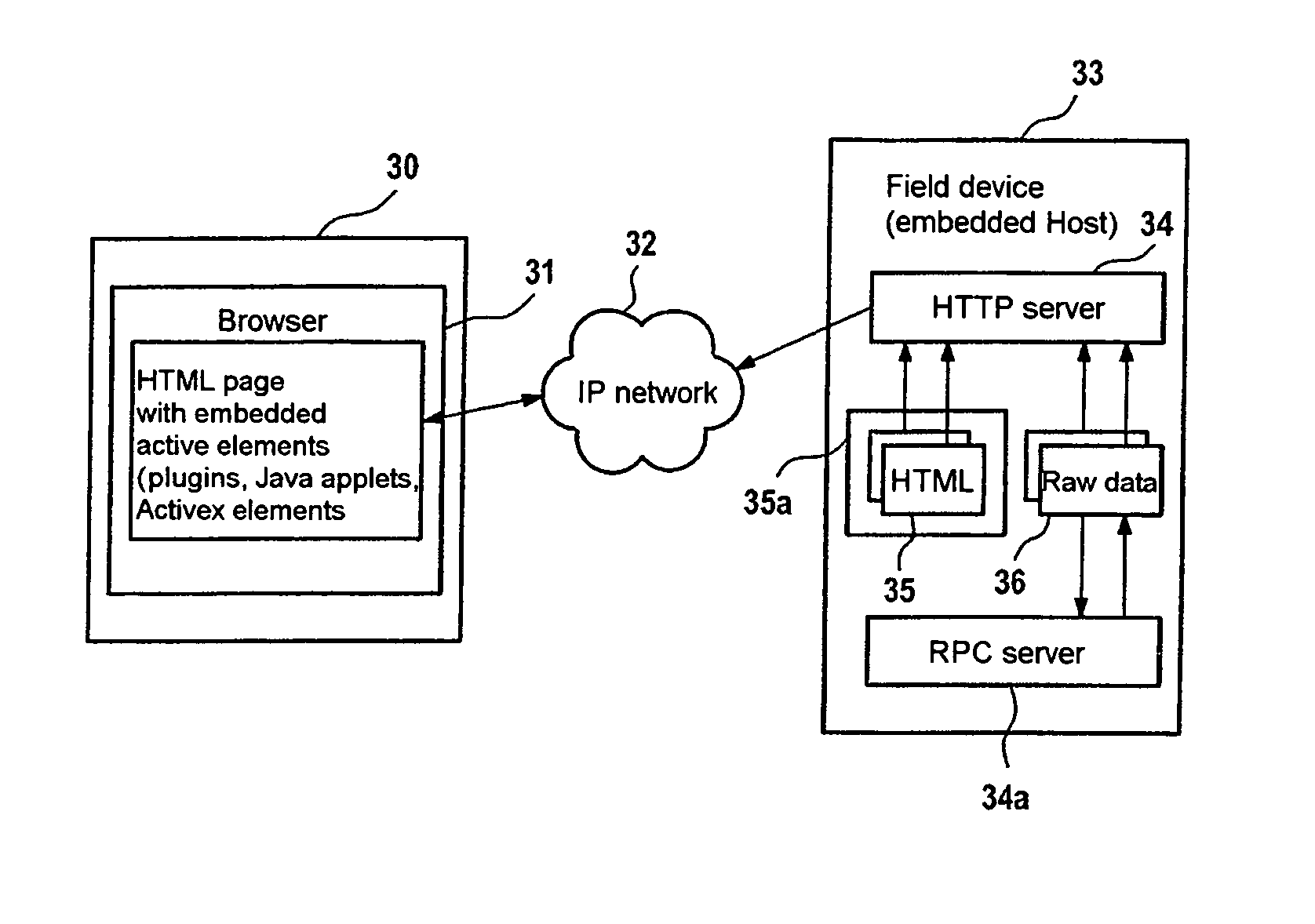
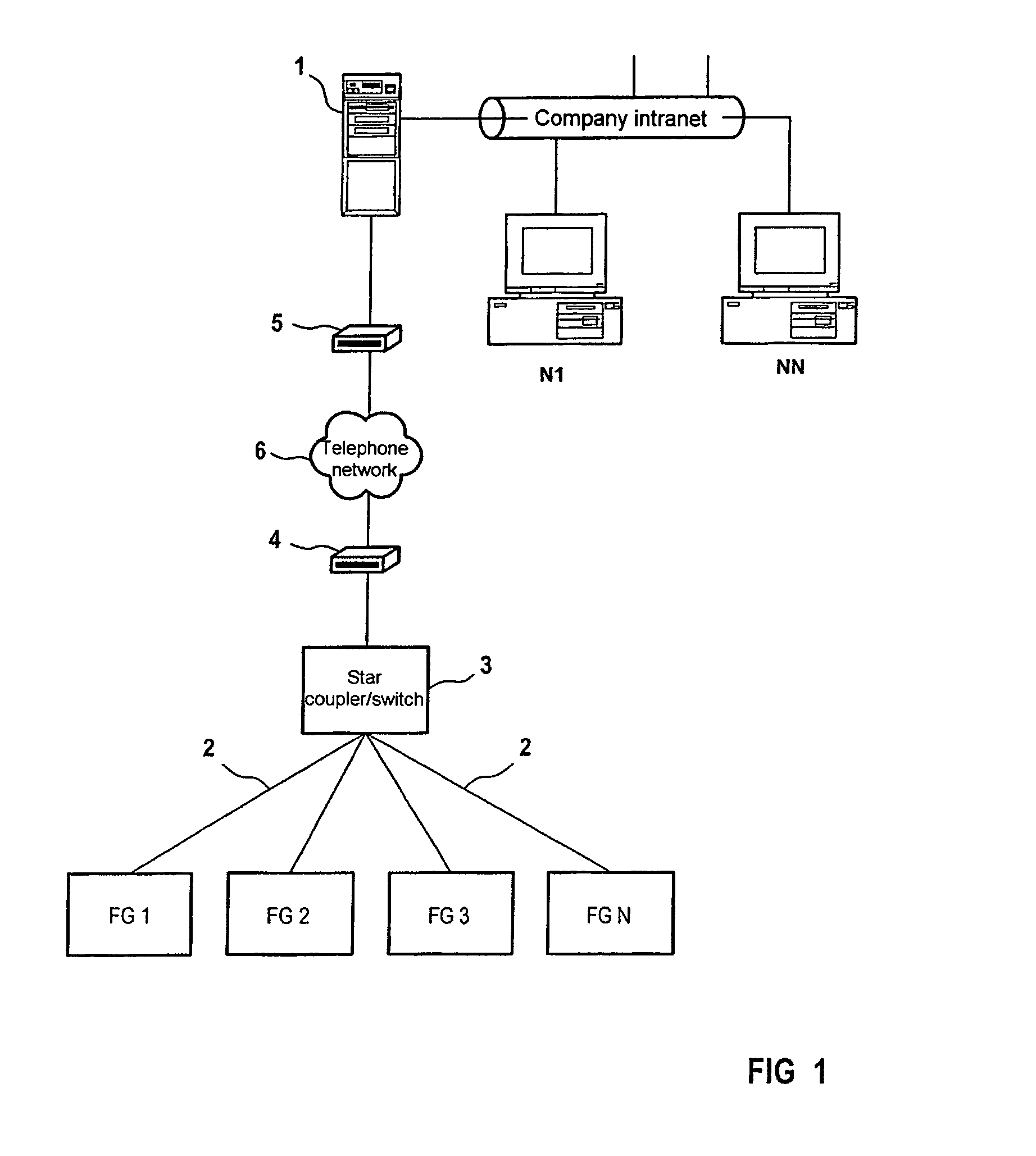
Method for operating and observing field devices
InactiveUS7072987B2Extends application optionImprove operational convenienceComputer controlSimulator controlData packUser device
The invention relates to a method for operating a proxy server device (1) connected to a field device (FG1–FGN), in addition to a proxy server device. The proxy server device can be connected to the field device and a user device (N1–NN) in order to respectively exchange electronic data in order to monitor and / or operate the field device. The electronic data consists of static data which is transmitted according to a first protocol standard and dynamic data which is transmitted according to a second protocol standard.
Owner:SIEMENS AG
Object oriented based, business class methodology for generating quasi-static web pages at periodic intervals
InactiveUS7171455B1Data processing applicationsDigital data information retrievalObject basedWeb service
A method for providing a requestor with access to dynamic data via quasi-static data requests, comprising the steps of defining a web page, the web page including at least one dynamic element, creating an executable digital code to be run on a computer and invoked at defined intervals by a scheduler component the executable code effective to create and storing a quasi-static copy of the defined web page, creating the scheduler component capable of invoking the executable code at predefined intervals, loading the executable code and the scheduler component onto a platform in connectivity with a web server and with one another, invoking execution of the scheduler component, and retrieving and returning the static copy of the defined web page in response to requests for the defined web page.
Owner:IBM CORP
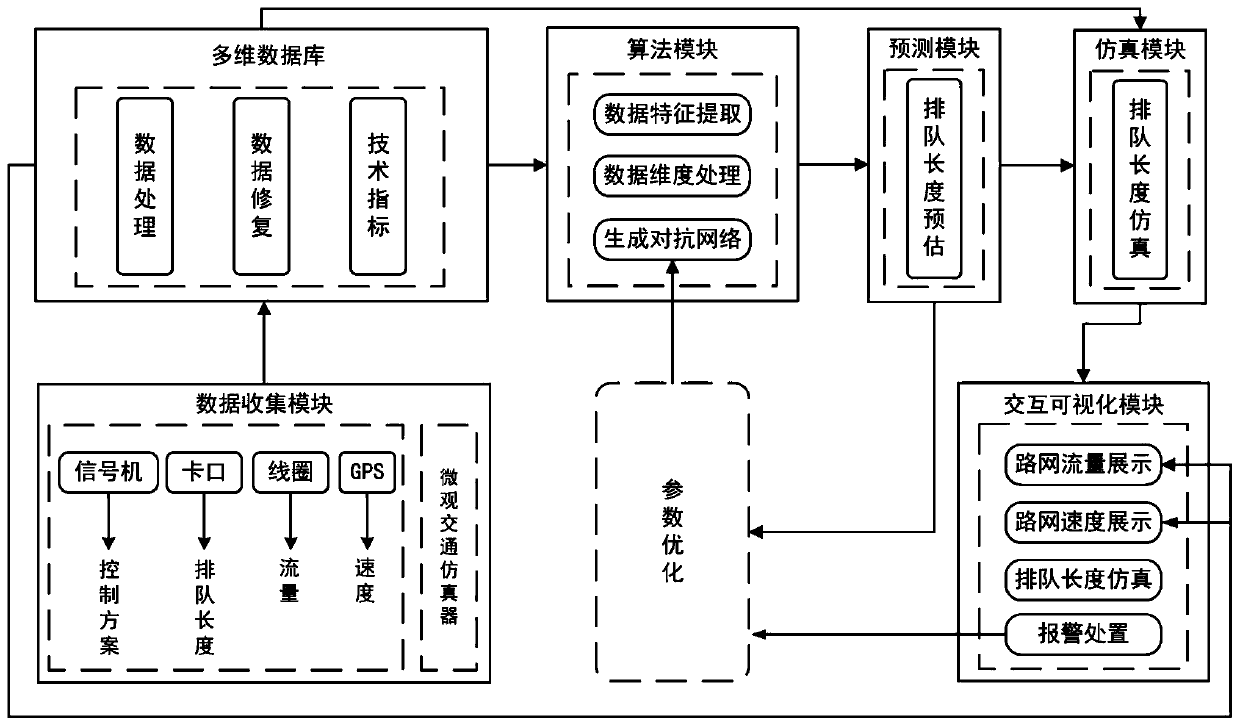
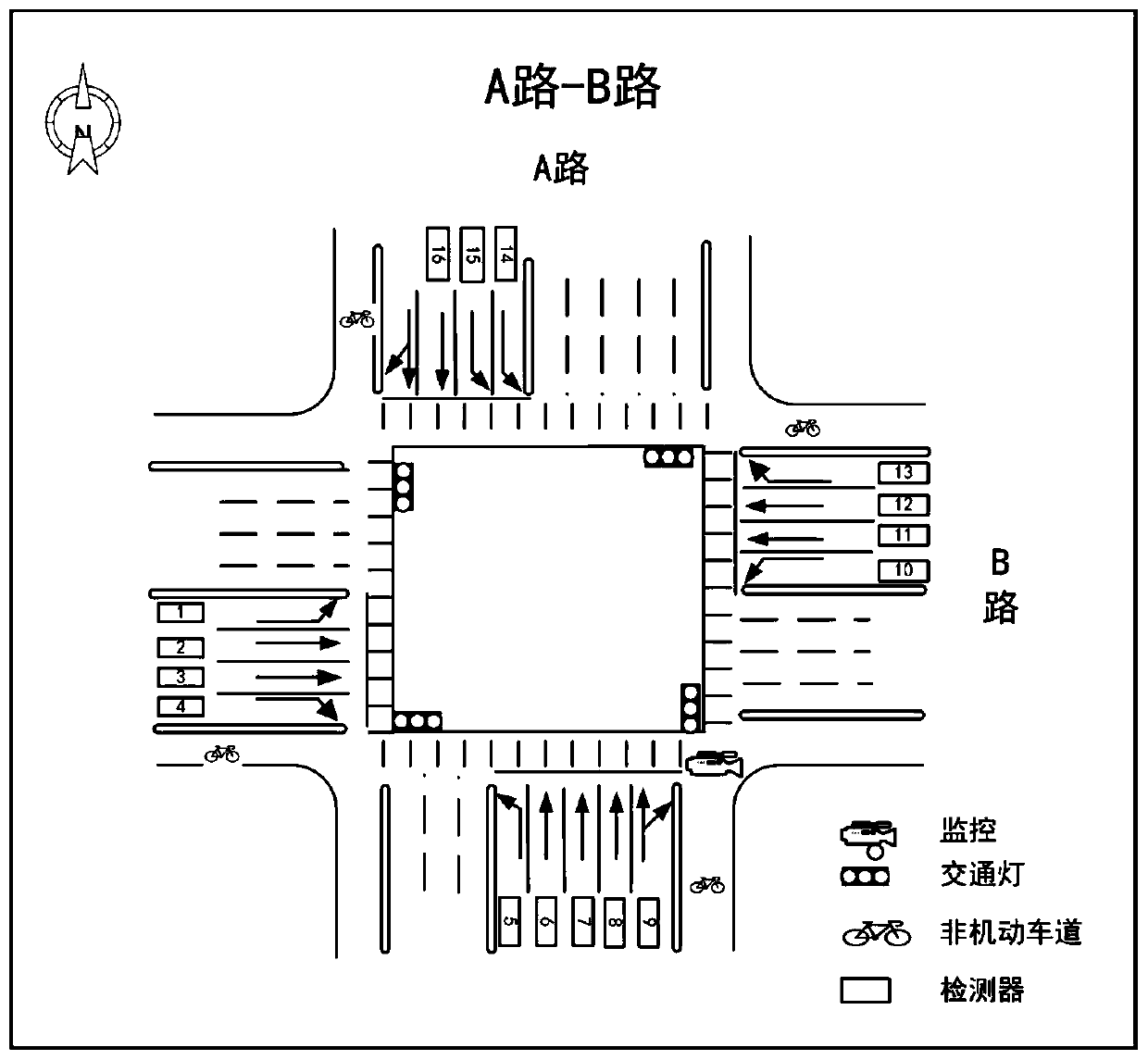
City-level intelligent traffic simulation system
ActiveCN110164128ASolve low work efficiencyDetection of traffic movementForecastingState predictionFeature extraction
The invention discloses a city-level intelligent traffic simulation system. With multi-source heterogeneous data as input, the vehicle queue length of each lane at an intersection can be predicted, the evolution of the vehicle queue length is further dynamically simulated, and the simulation system comprises a data collection module, a multidimensional database, an algorithm module, a traffic state prediction module, a traffic simulation derivation module and an interaction visualization module. In the data collection module, the collected data comprise traffic dynamic data and static data. The multidimensional database is used for receiving various traffic dynamic information in real time and storing road infrastructure configuration information. In the algorithm module, a generated confrontation network is used for data generation and state prediction on the vehicle queue length, and the processing process comprises data feature extraction, data dimension processing, confrontation network generation, and hyperparameter optimization. The vehicle queue length of each lane at the intersection can be predicted, and the evolution of the vehicle queue length is further dynamically simulated.
Owner:ENJOYOR COMPANY LIMITED
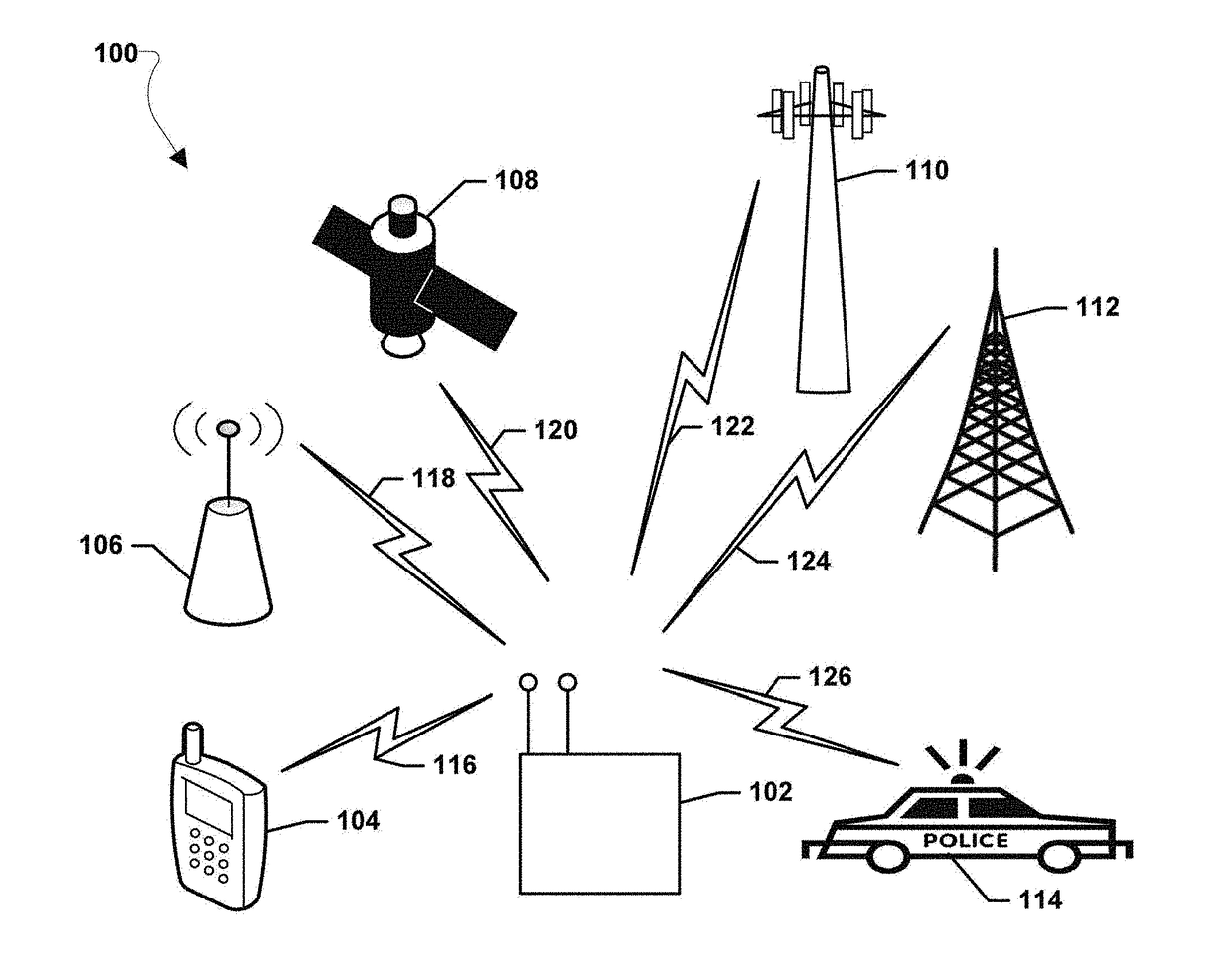
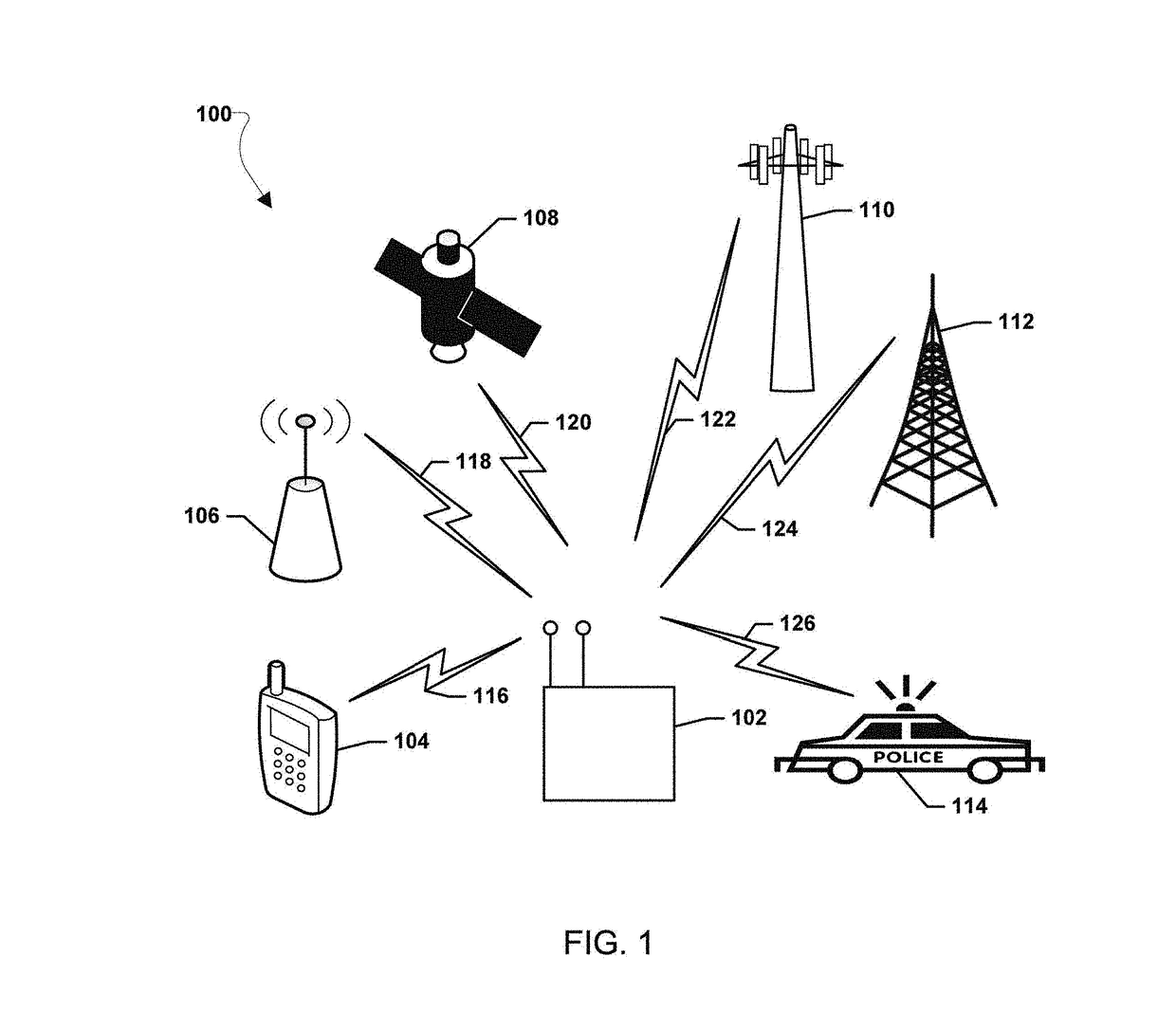
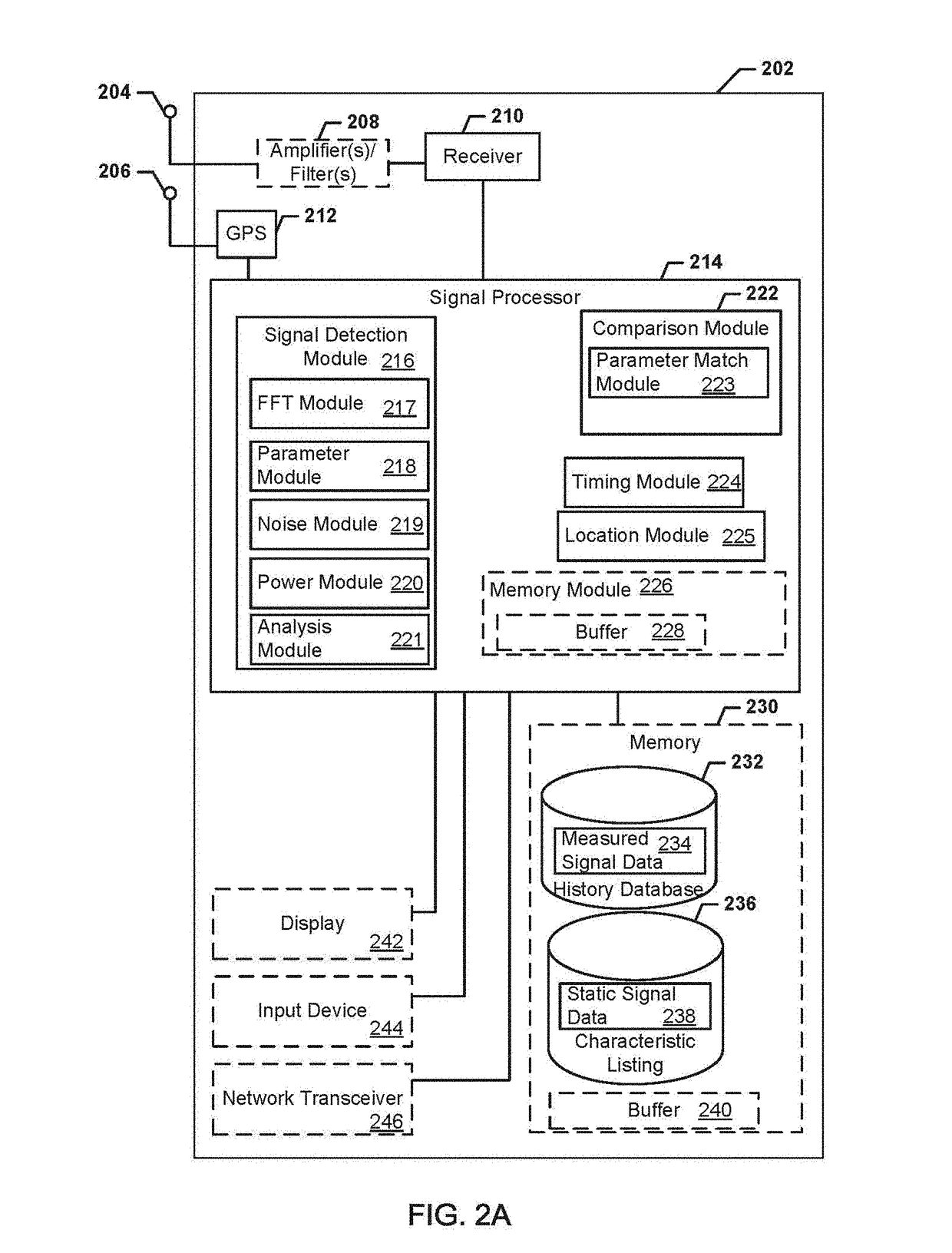
Systems, methods, and devices for electronic spectrum management for identifying signal-emitting devices
ActiveUS20170250766A1Receivers monitoringSpectral gaps assessmentFrequency spectrumSignal of interest
Apparatus and methods for identifying a wireless signal-emitting device are disclosed. The apparatus is configured to sense and measure wireless communication signals from signal-emitting devices in a spectrum. The apparatus is operable to automatically detect a signal of interest from the wireless signal-emitting device and create a signal profile of the signal of interest; compare the signal profile with stored device signal profiles for identification of the wireless signal-emitting device; and calculate signal degradation data for the signal of interest based on information associated with the signal of interest in a static database including noise figure parameters of a wireless signal-emitting device outputting the signal of interest. The signal profile of the signal of interest, profile comparison result, and signal degradation data are stored in the apparatus.
Owner:DIGITAL GLOBAL SYST INC
Voice and data encryption method using a cryptographic key split combiner
InactiveUS7095851B1Improve securityKey distribution for secure communicationUser identity/authority verificationMemory addressBiometric data
A cryptographic key split combiner, which includes a number of key split generators (42, 48, and 56) for generating cryptographic key splits (32, 34, 36, 38, and 64) and a key split randomizer for randomizing the cryptographic key splits to produce a cryptographic key (62), and a process for forming cryptographic keys. Each of the key split generators (42, 48 and 56) generates key splits (32, 34, 36, 38, and 64) from seed data (40, 44, 46, 50, 52, 54, 58, and 60). The key split generators may include a random split generator (42) for generating a random key split (32) based on reference data (40) and encryption date / time (44). Other key split generators may include a token split generator (48) for generating a token key split (34) based on label data (46) and organization data (50), a console split generator (56) for generating a console key split (36) based on current maintenance data (52) and previous maintenance data (54), and a biometric split generator for generating a biometric key split (38) based on biometric data (58). All splits may further be based on static data, which may be updated, for example by modifying a prime number divisor of the static data. The label data may be read from a storage medium, and may include user authorization data. The label data may be associated with label categories and subcategories of addresses, which are meaningful to a user who is specifying or determining the intended recipient(s) of the encrypted information or object. An array associated with a software component object may use key splits (32, 34, 36, 38, and 64) which determine which methods and properties are allowed and control access to the memory address for those allowed methods and properties. The resulting cryptographic key (62) may be, for example, a stream of symbols, at least one symbol block, or a key matrix.
Owner:TECSEC
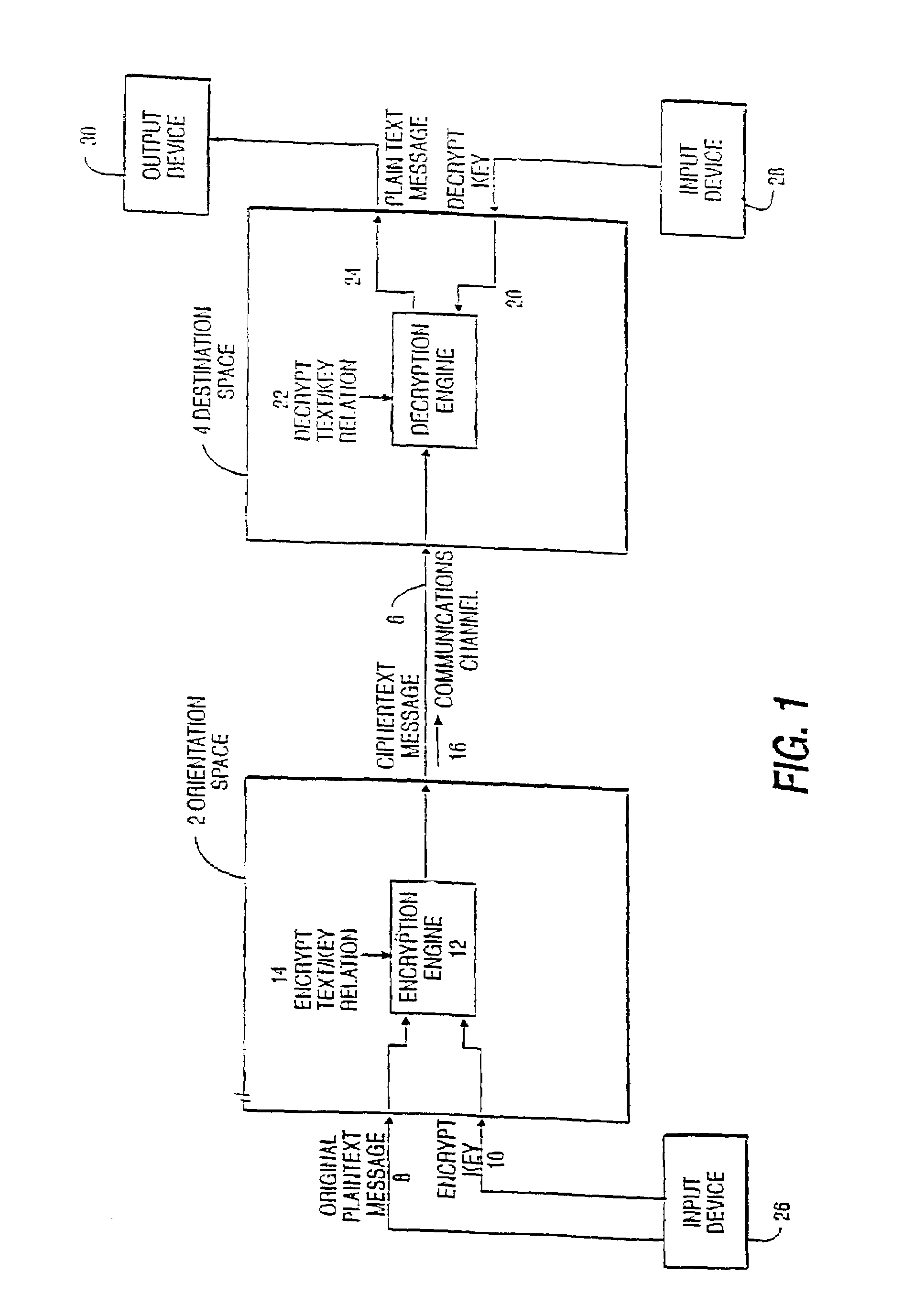
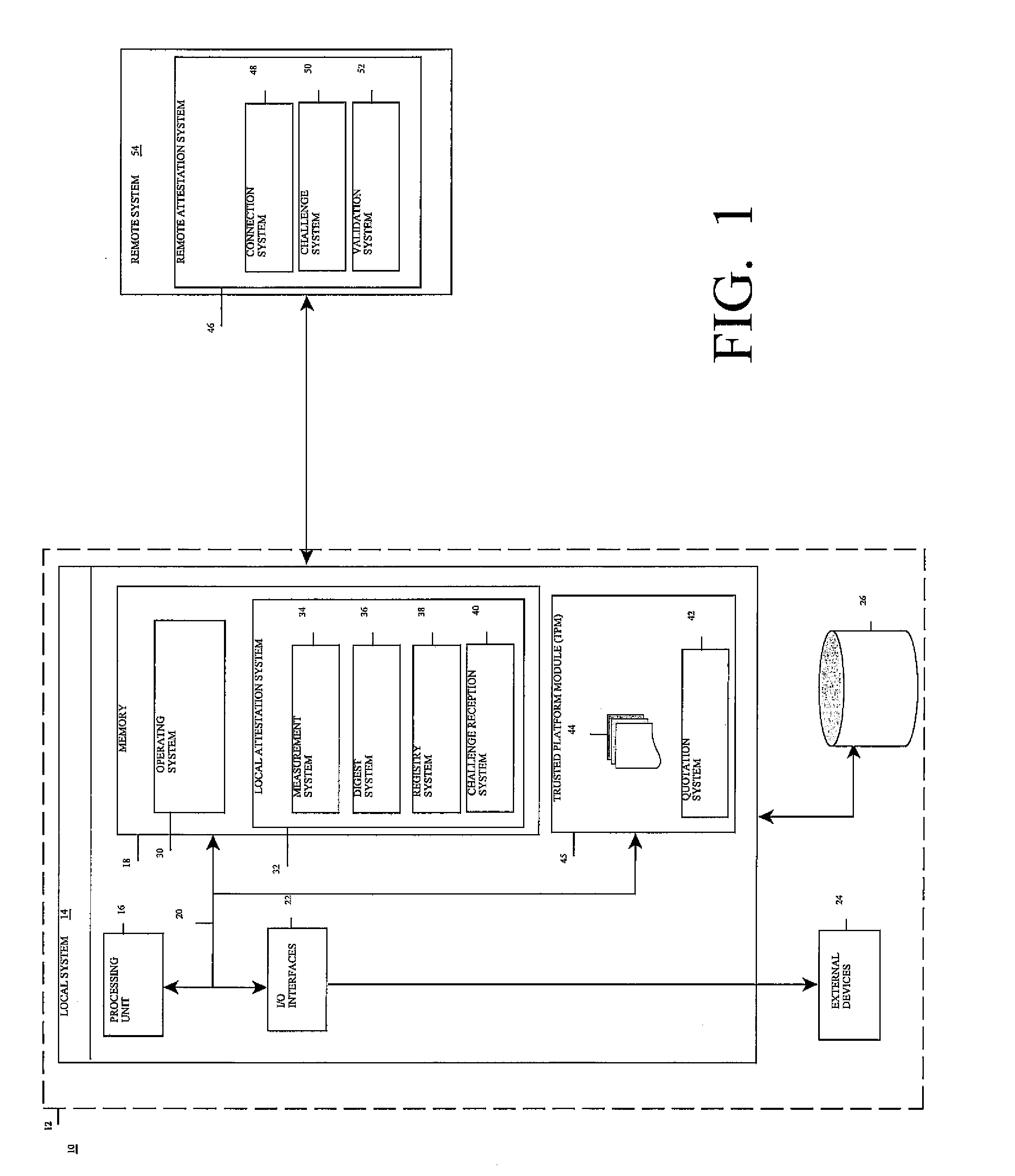
Method, system, and program product for remotely attesting to a state of a computer system
InactiveUS20080046752A1Secret communicationPlatform integrity maintainanceComputer hardwareRemote system
A method, system, and program product for remotely attesting to a state of computing system is provided. Specifically, the present invention allows a remote system to establish trust in the properties of the computer system. The properties to be trusted are expanded from the usual system software layers and related configuration files to novel types of data such as static data specific to the computer system, dynamic data determined at system startup, or dynamic data created as the computer system runs applications.
Owner:IBM CORP
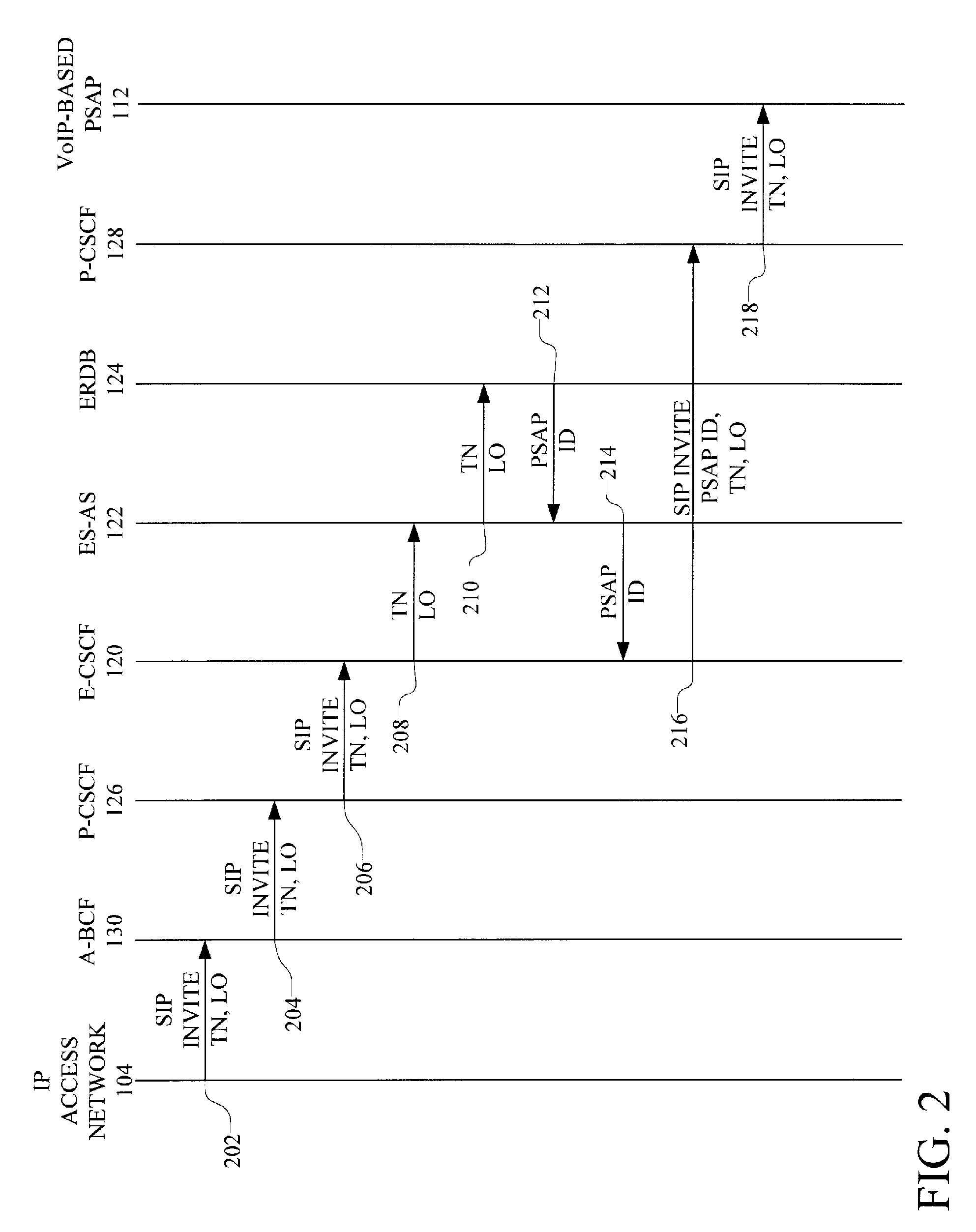
Emergency services call delivery from a legacy communications device to a VOIP psap
An Emergency Services Application Server (ES-AS) that obtains routing instructions for both VoIP-originated and non-VoIP-originated calls to emergency services numbers (e.g., 9-1-1). If the emergency request is a VoIP-originated call and includes a location object, the ES-AS queries its database using the location object to obtain routing information. If a location object is not provided, the ES-AS queries a location information server to obtain a location object. The ES-AS then uses the location object to query its database. If the call is originated by legacy user equipment, the ES-AS accesses a legacy automatic location information system to obtain location information and the associated PSAP. The ES-AS then queries its database with the returned information to refine routing information needed to route the call to the identified PSAP. The ES-AS includes a web services interface that allows a PSAP or authorized agency to change routing instructions dynamically, which overrides any static data in the ES-AS's routing database.
Owner:INTRADO LIFE & SAFETY INC
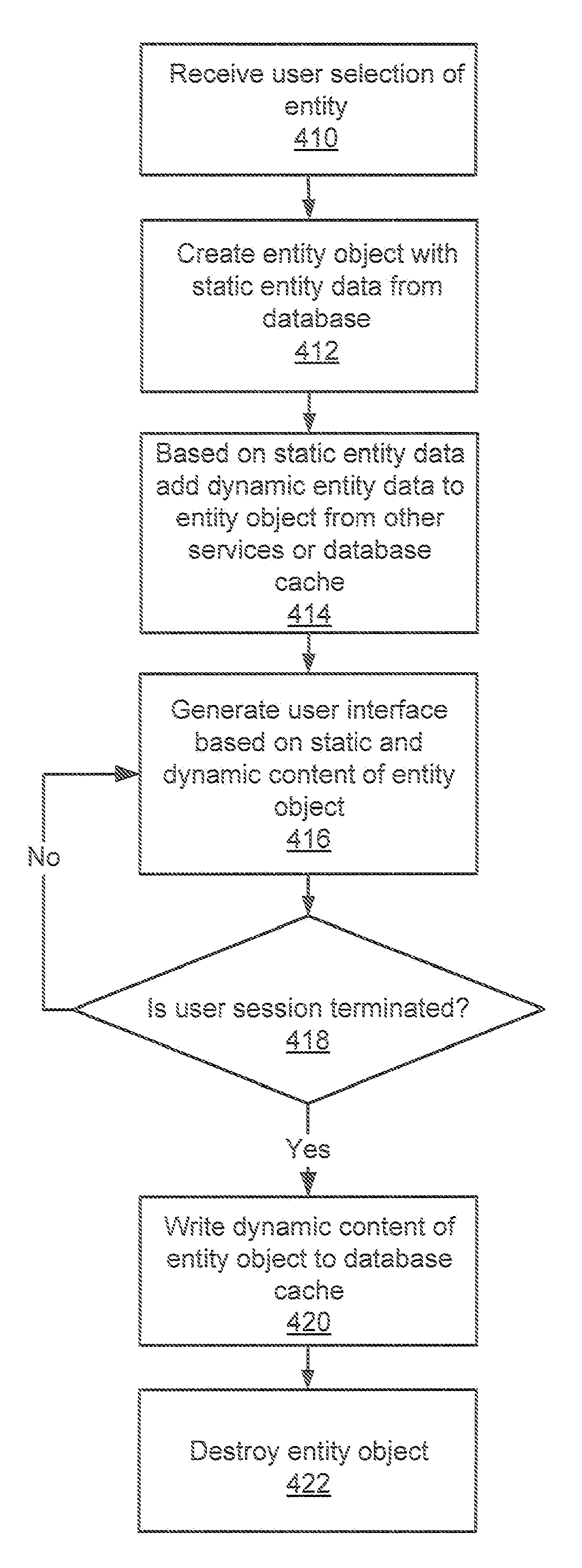
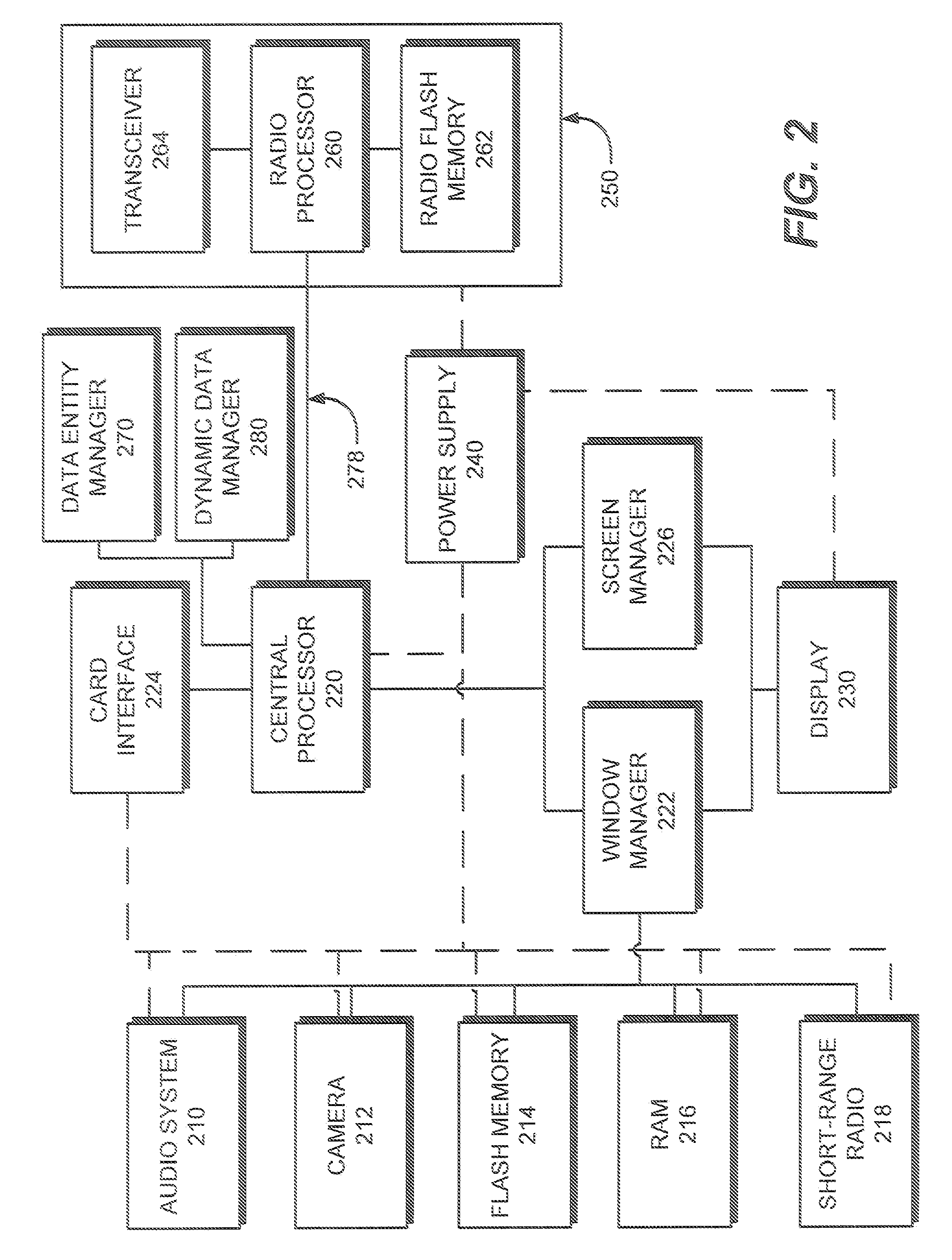
Integration of static and dynamic data for database entities and the unified presentation thereof
ActiveUS20090210441A1Database queryingDigital data processing detailsIntegrated databaseApplication software
A method is disclosed for presenting static and dynamic data corresponding to an entity within an application on a mobile device. An entity object is created as part of a data model within the application such that the entity object has a plurality of fields with the plurality of fields having static data corresponding to the entity. Based on the static data corresponding to the entity, dynamic data corresponding to the entity is received into the entity object from at least one of a plurality of applications executable within the mobile device. The static and dynamic data from the entity object corresponding to the entity is displayed simultaneously within a user interface of the application in a single presentation view.
Owner:QUALCOMM INC
Incremental real-time recording of tracked instruments in tubular organ structures inside the human body
InactiveUS8494612B2Improve recording accuracyGuaranteed accuracyUltrasonic/sonic/infrasonic diagnosticsSurgical navigation systemsHuman bodyAnatomical structures
Owner:DEUTES KREBSFORSCHUNGSZENT STIFTUNG DES OFFENTLICHEN RECHTS +1
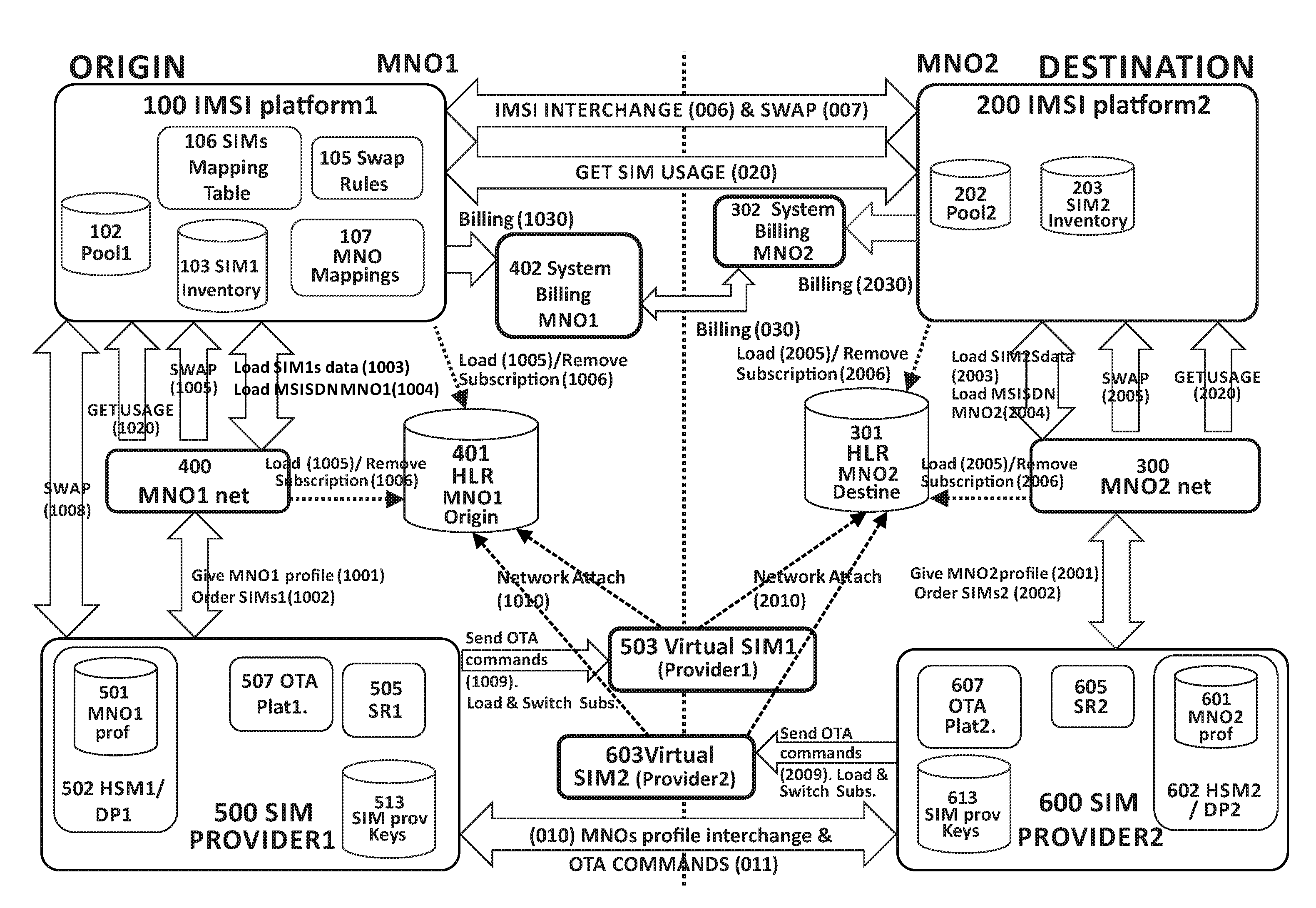
Method and System for Dynamic Managing of Subscriber Devices in Mobile Networks
ActiveUS20160183081A1Ensure safety and integrityStorage spaceAccounting/billing servicesSubstation equipmentDynamic dataMobile device
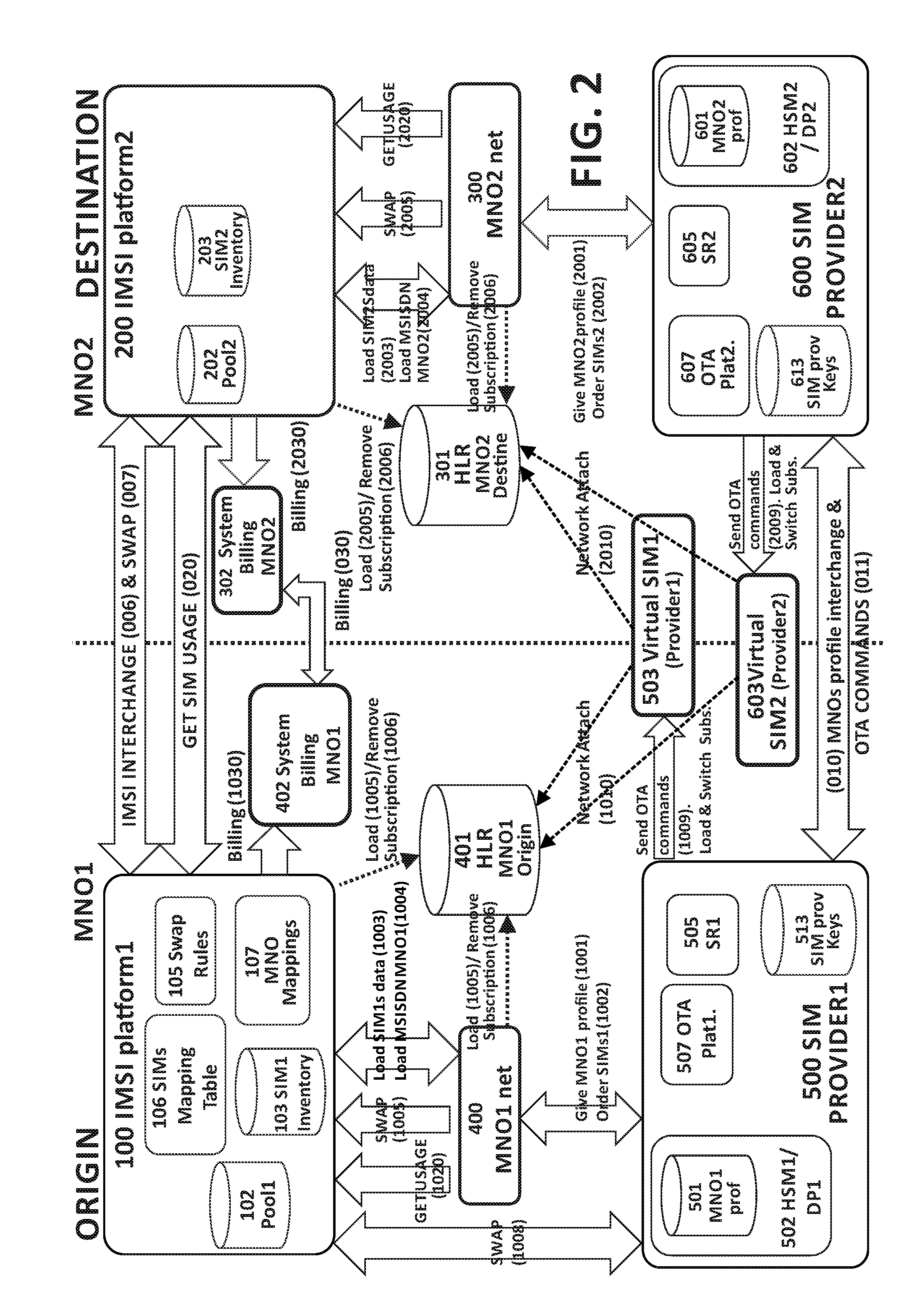
A system and method for managing subscriber mobile devices comprising:a home network (400) of a first mobile network operator (MNO1), in which data associated with at least one physical SIM of a subscriber device with an embedded SIM card (eUICC) is obtained, anda destination network (300) of a second mobile network operator (MNO2) which the device travels to, obtaining static data and dynamic data associated with at least one virtual SIM (503, 603) of the device.The dynamic data comprise a subscriber authentication key (Ki) and is obtained from a SIM provider platform (500, 600) on which the destination network (300) relies. The static data comprise IMSI / MSISDN identities and is stored in a pool (202) of the destination network (300).For a given virtual SIM, it is checked whether there is an association in a mapping table (106) of the first mobile network operator (MNO1) between the static data from the pool (202) and the physical SIM data from the home network (400).
Owner:TELEFONICA SA
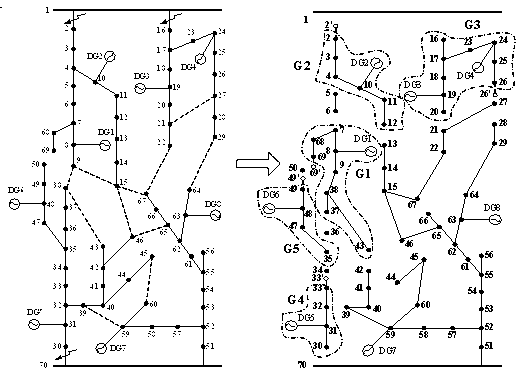
Optimization method of network variable structure with distributed type power supply distribution system
InactiveCN102868161AEasy to adjustSimple structureAc networks with different sources same frequencyNetwork variableSupply & distribution
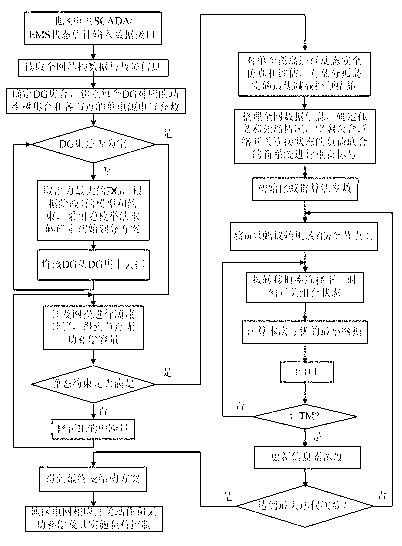
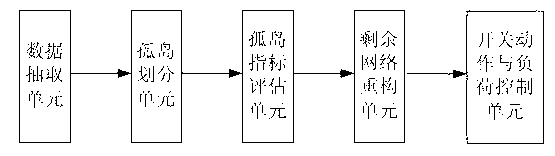
The invention discloses an optimization method of a network variable structure with a distributed type power supply distribution system. The optimization method includes that basic static data of electric power network structure parameters, distributed type power supply distribution, load capacity, faulty lines and the like are extracted, under the condition of present line fault, the basic static data are utilized to perform islanding scheme calculation and correction, survivability indexes constructed by the method are combined to perform an online evaluation for islanding network safe operation performances and implement immediate control measures, finally, on account of residual network structure data after final islanding electric power network division is performed, by means of an ant colony algorithm, a reconfiguration optimal computation is performed for residual network with minimum network loss as a target, and finally the electric power network structure with high safe operation level is obtained. On the basis of the developed algorism and function modules, the invention further provides a large-scale power distribution network intelligent optimization decision system based on multi-stage computation correction and survivability evaluation, according to the technical scheme, the division and reconstruction of the network with the generalized model distributed type power supply distribution system are achieved, and accurate reference of network structure adjustment, schedule and operation can be excellently provided for regional electric power network schedule staffs.
Owner:SICHUAN UNIV
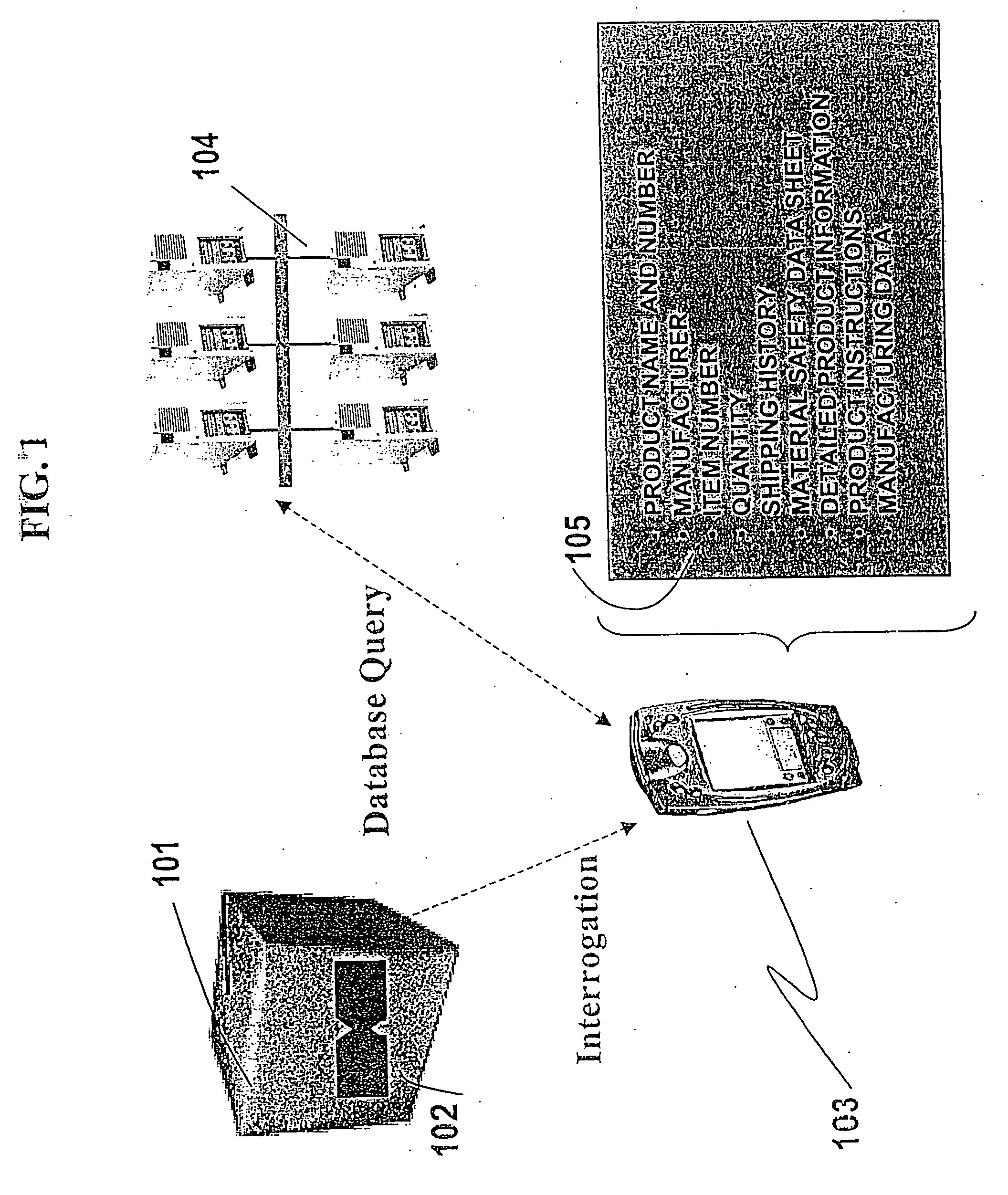
Materials handling, tracking and control system
A product information system comprises a product package, container or support having an RFID tag including data memory means for storing at least a unique digital identification code for the product and at least one remote storage access code, including a URL, for accessing additional dynamic and / or static data associated with the product which is stored outside the tag and container, the system being operative to retrieve the identification code and remote access code and to access the additional data via the Internet.
Owner:INT PAPER CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com