Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1480results about "Synchronising transmission/receiving encryption devices" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Encryption-Based Data Access Management
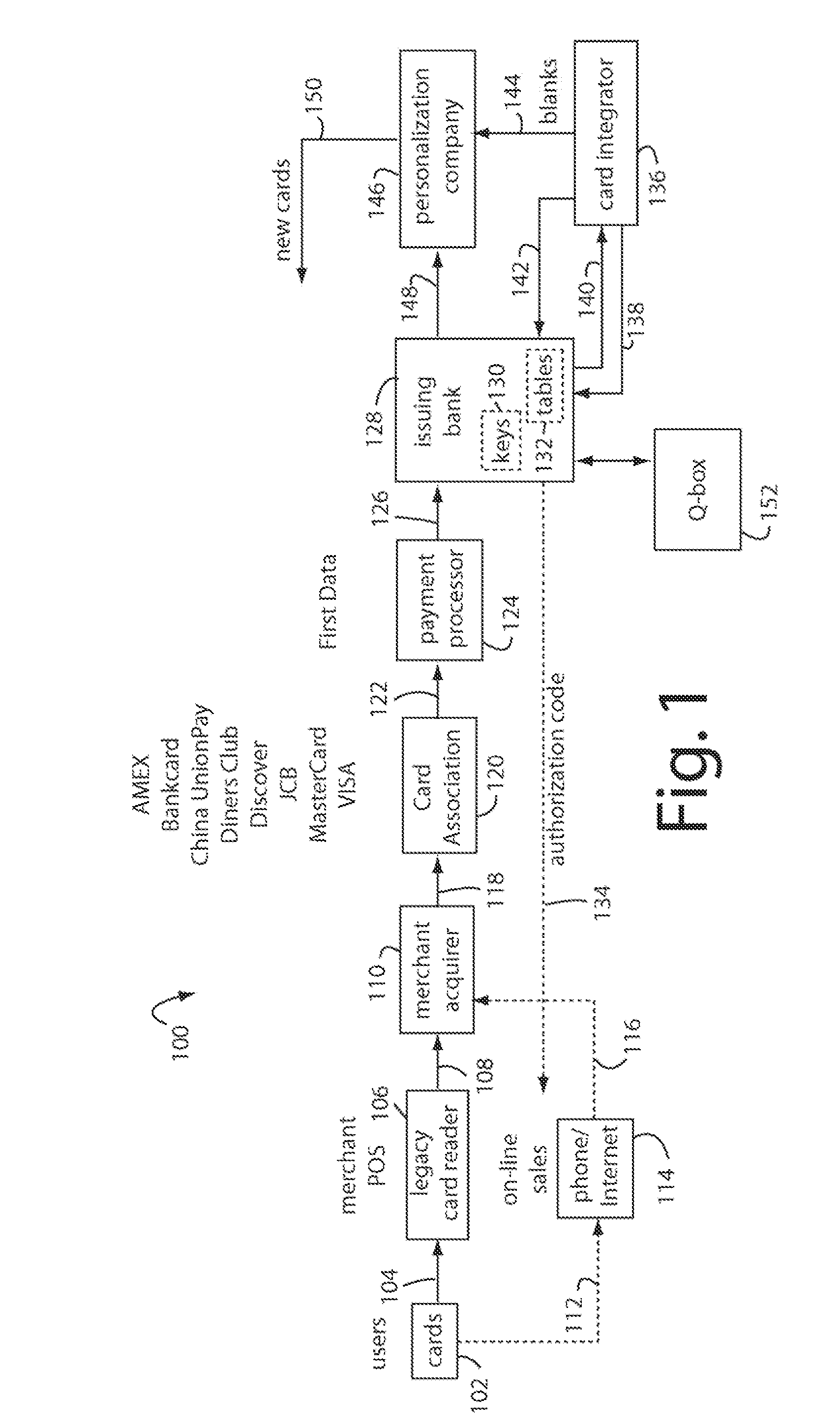
ActiveUS20140164774A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesKey serverData access
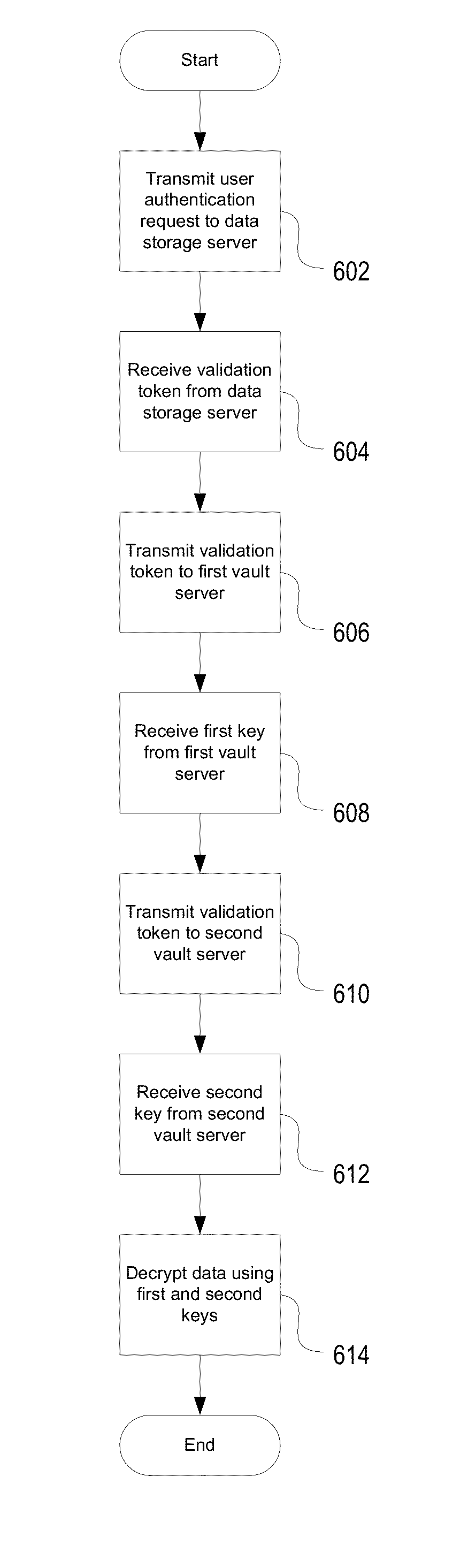
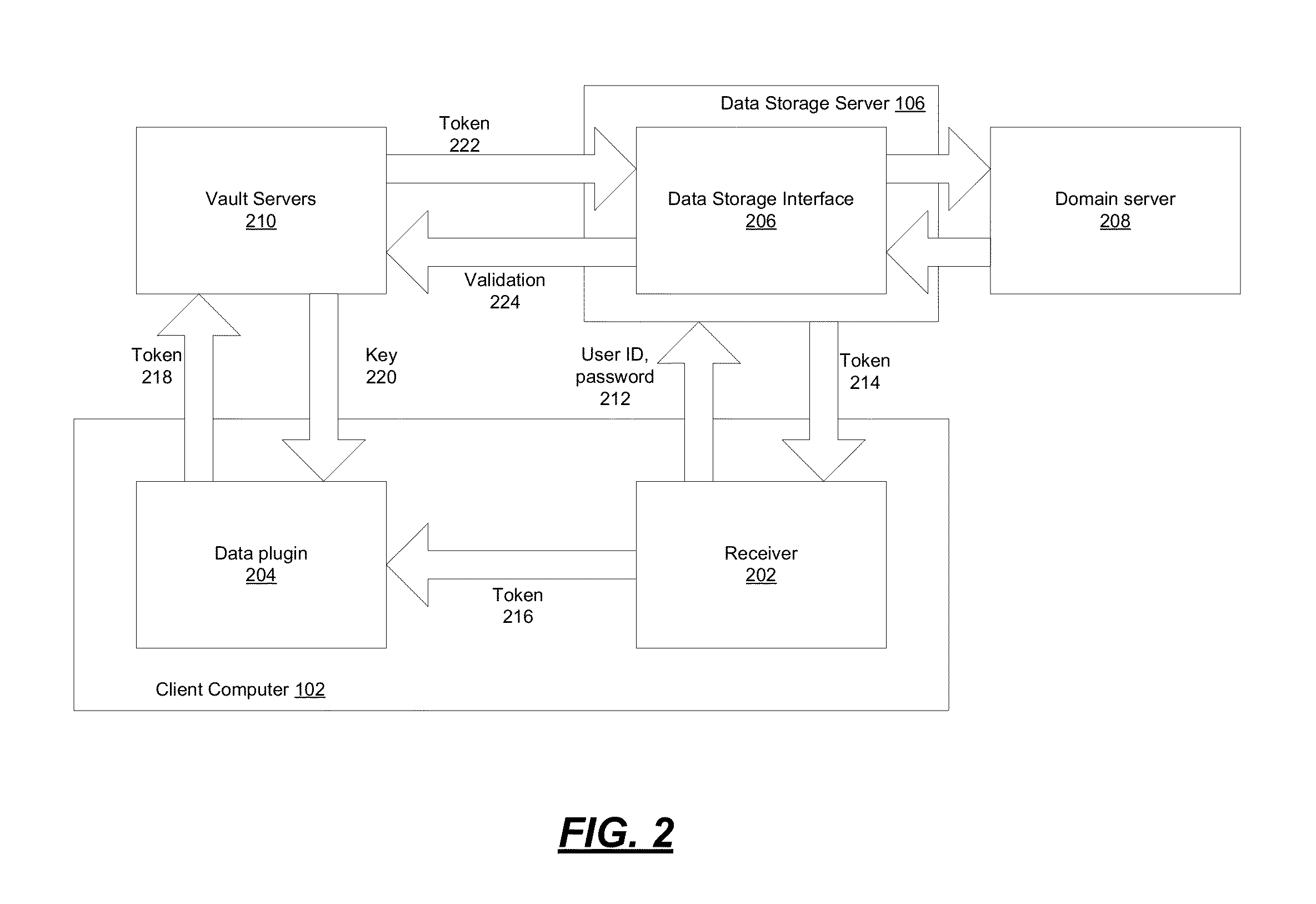
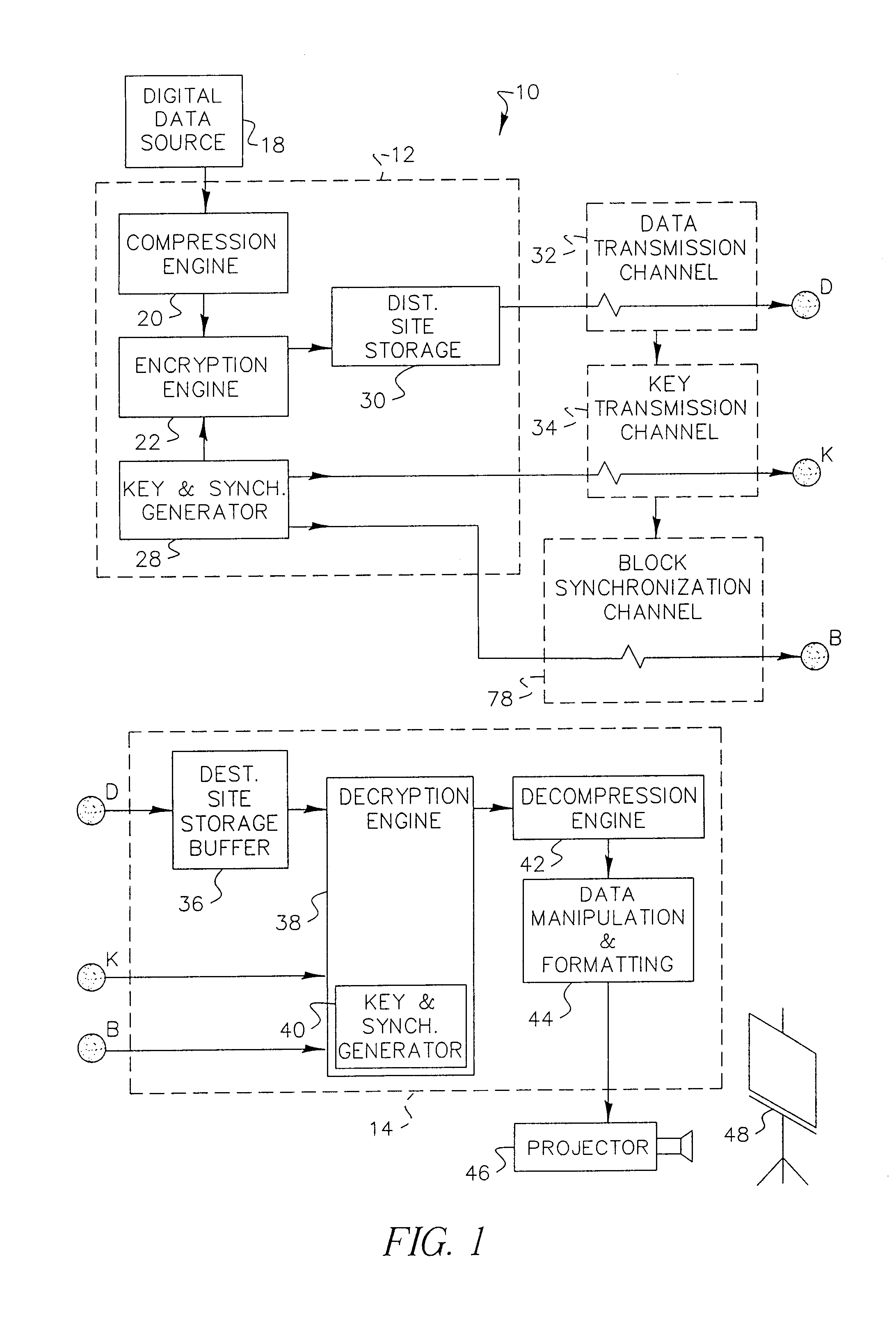
Encryption-based data access management may include a variety of processes. In one example, a device may transmit a user authentication request for decrypting encrypted data to a data storage server storing the encrypted data. The computing device may then receive a validation token associated with the user's authentication request, the validation token indicating that the user is authenticated to a domain. Subsequently, the computing device may transmit the validation token to a first key server different from the data storage server. Then, in response to transmitting the validation token the computing device may receive, from the first key server, a key required for decrypting the encrypted data. The device may then decrypt at least a portion of the encrypted data using the key.
Owner:CITRIX SYST INC
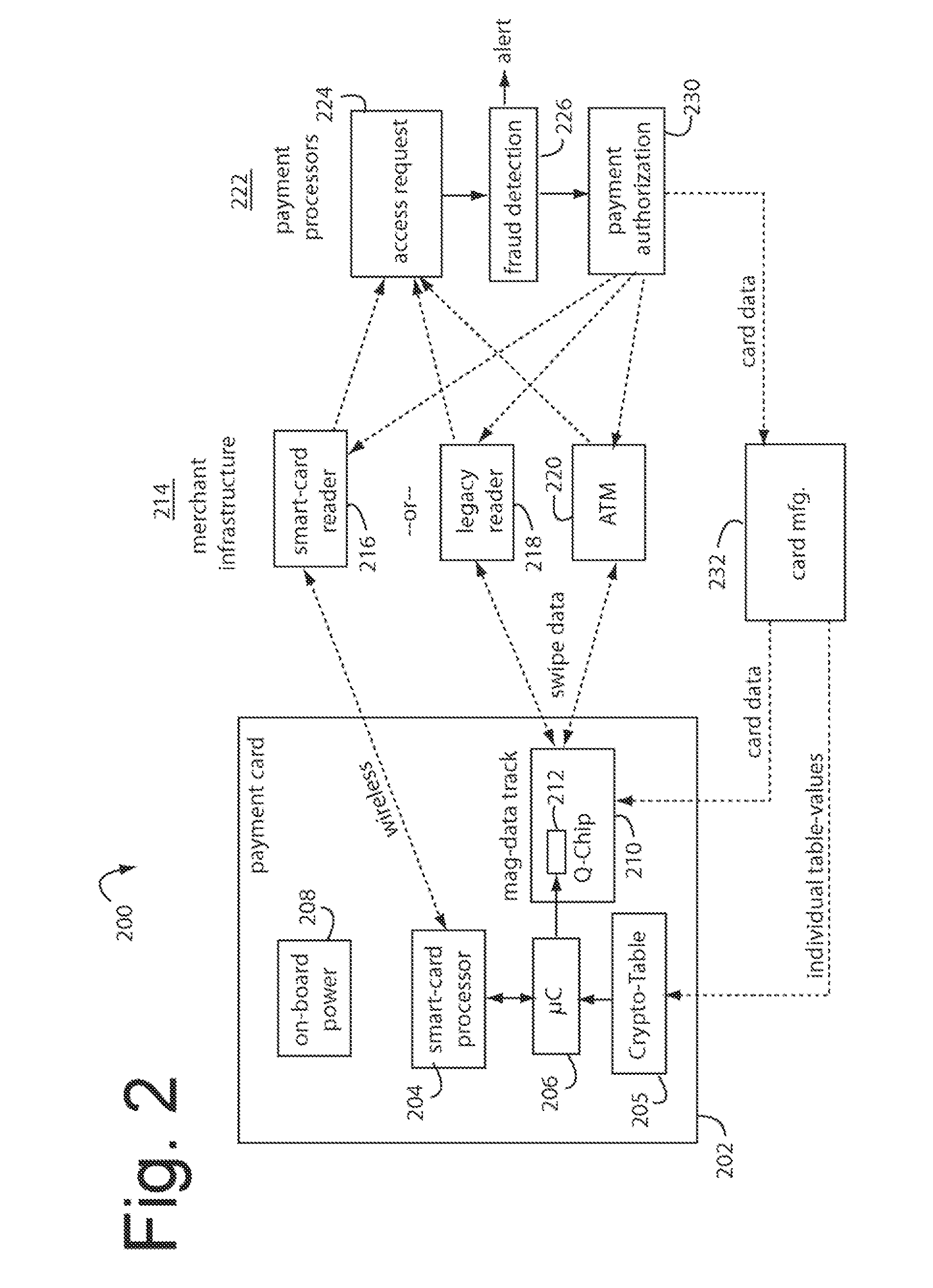
Financial transaction payment processor
InactiveUS20090006262A1Sufficient dataAcutation objectsSynchronising transmission/receiving encryption devicesPayment orderFinancial transaction
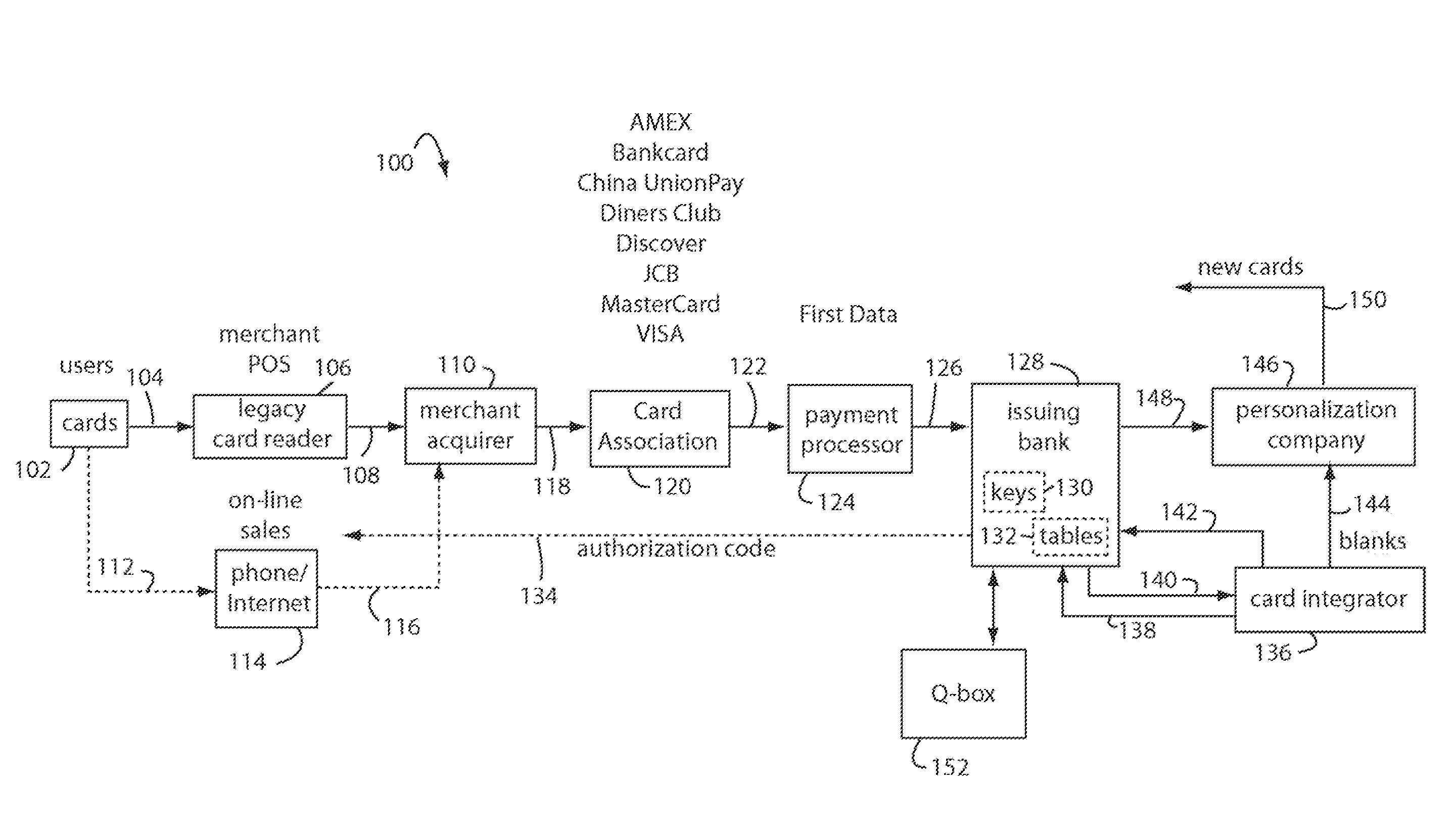
A financial transaction payment processor includes an account access request processor for receiving dynamic swipe data from a payment card through a merchant infrastructure. A fraud detection processor is connected to analyze a dynamic data obtained by the account access request processor that should agree with values pre-loaded in a Crypto-Table by a card manufacturer. A payment authorization processor is connected to receive a message from the fraud detection processor and to then forward a response to the merchant infrastructure.
Owner:FITBIT INC
Methods and system for managing intellectual property using a blockchain
InactiveUS20180285996A1Synchronising transmission/receiving encryption devicesData processing applicationsDashboardPayment
A system and methods for managing intellectual property using a blockchain are provided which may include one or more elements which forms a comprehensive foundation for an eco-system for innovation and intellectual property management. The elements may include: an intellectual property distributed ledger, an intellectual property digital policy server, non-binary trust models, automatic ontology induction, modifications to the blockchain “mining” and “proof of work” system, appstore for related applications, partial transparency transactionalized search engine, persistent and encapsulated software trust objects, licensing royalty smart contract with auditable payment tracking, micro-equity incentives, automated fraud detection intellectual property management dashboards, innovation workflow broker, innovation optimization tools, disruption mapping, and intelligent just-in-time learning. The system combines and integrates these functions to enable personal, intra-enterprise, inter-enterprise and extra-enterprise recordation, collaboration, searchability and its benefits, licensing and tracking of information regarding intellectual property over a networked distributed computing system.
Owner:FUTURELAB CONSULTING INC
Method for mapping at least two authentication devices to a user account using an authentication server
ActiveUS20180198614A1Improve securityReduce security risksSynchronising transmission/receiving encryption devicesUser identity/authority verificationSecure communicationAuthentication server
The invention provides a method for mapping at least two authentication devices to a user account using an authentication server, where each authentication device connects to the authentication server using a secured communication channel; their mapping to the user account is recorded on the authentication server, and, when a transfer of data between the authentication devices mapped to the user account occurs, the data is passed over from the first authentication device to the authentication server using a secured communication channel and from the authentication server to another authentication device mapped to the account of said user using a secured communication channel, where the aforesaid secured communication channel is created by the second authentication device. This procedure allows the use of a single personal local authentication factor for multiple authentication devices and increases the security of authentication of devices with authentication servers.
Owner:ADUCID
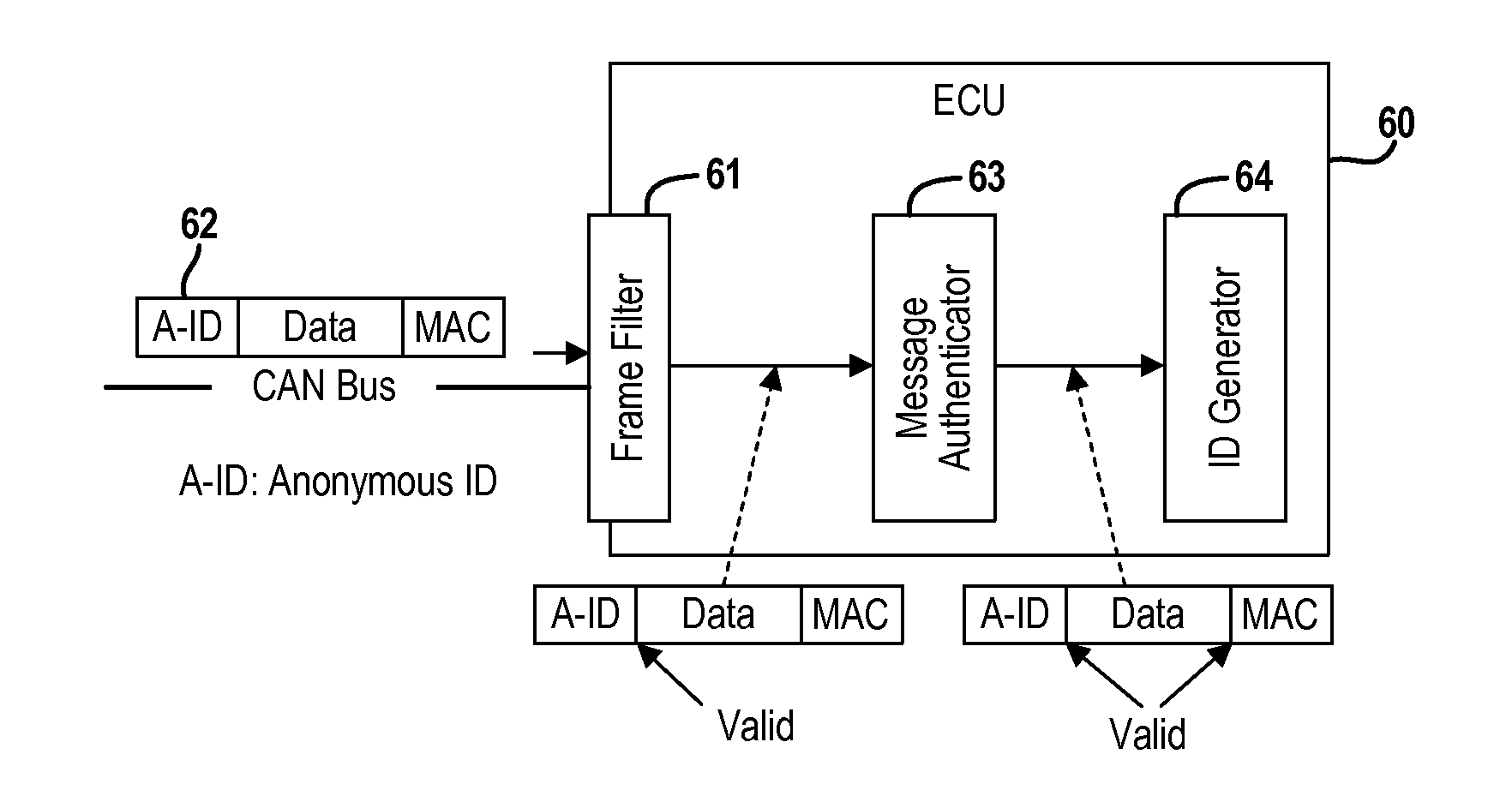
Real-Time Frame Authentication Using ID Anonymization In Automotive Networks
ActiveUS20150089236A1Reduce message authentication delay tmReduce delaysKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer networkData integrity
A real-time frame authentication protocol is presented for in-vehicle networks. A frame identifier is made anonymous to unauthorized entities but identifiable by the authorized entities. Anonymous identifiers are generated on a per-frame basis and embedded into each data frame transmitted by a sending ECU. Receiving ECUs use the anonymous identifiers to filter incoming data frames before verifying data integrity. Invalid data frame are filtered without requiring any additional run-time computations.
Owner:RGT UNIV OF MICHIGAN
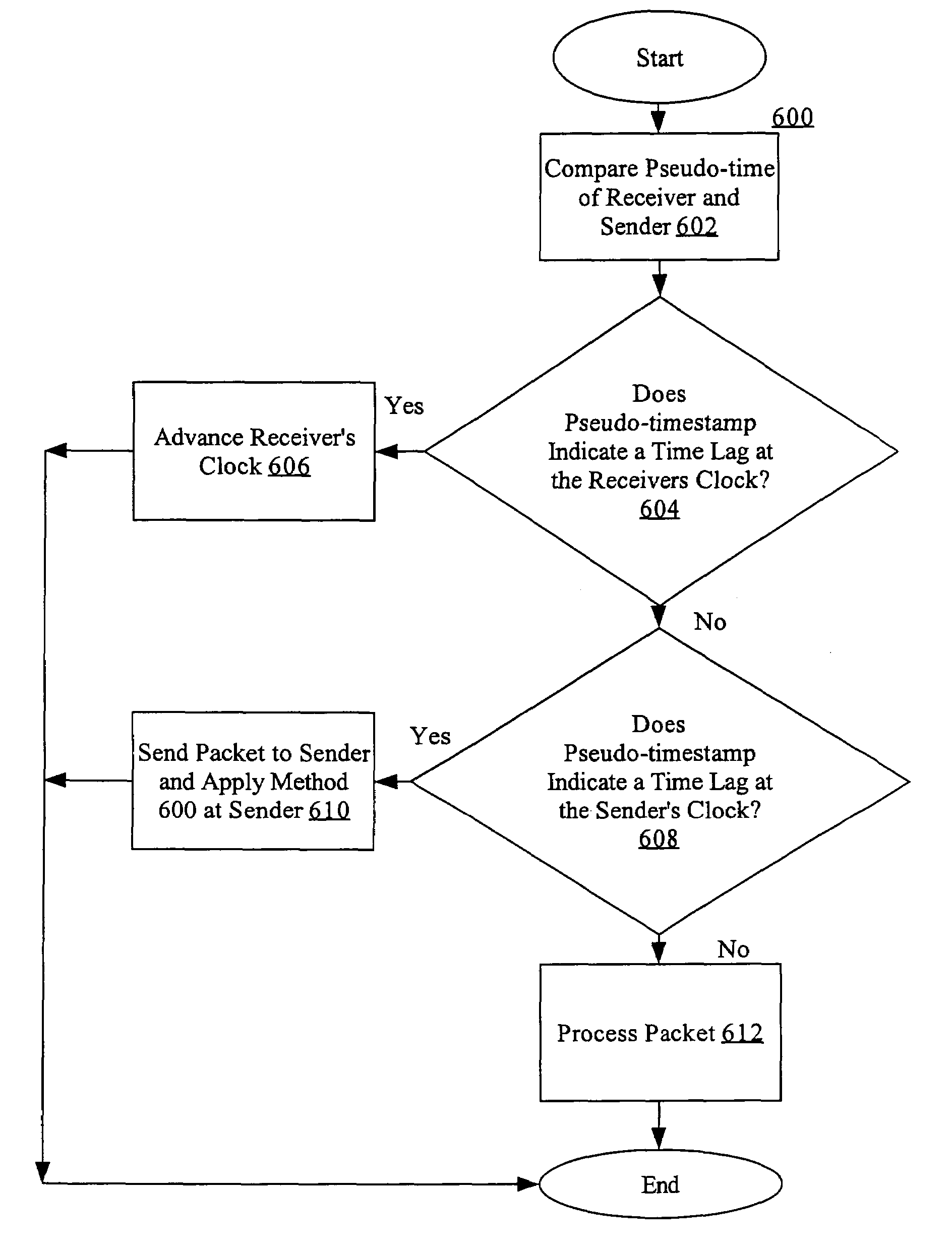
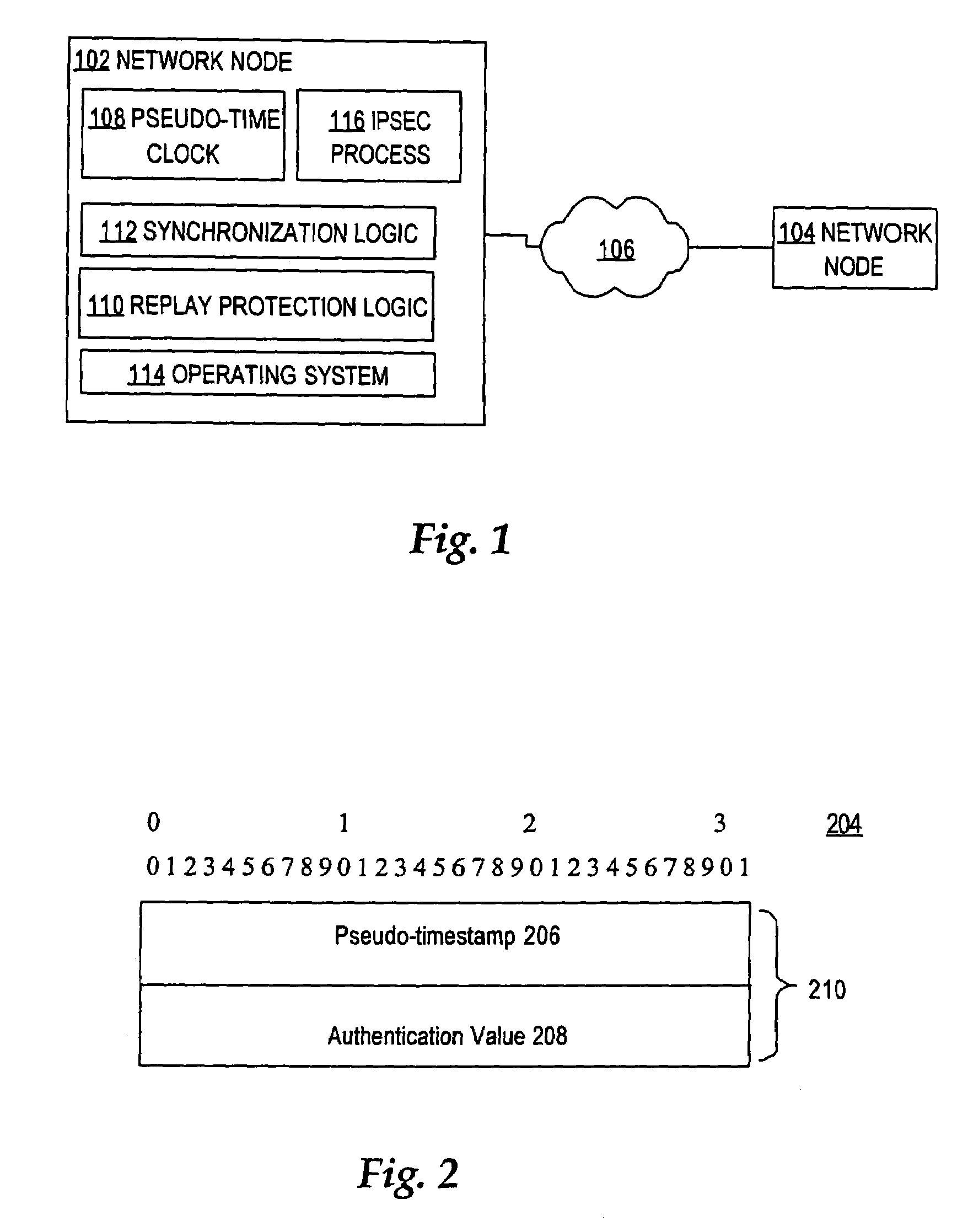
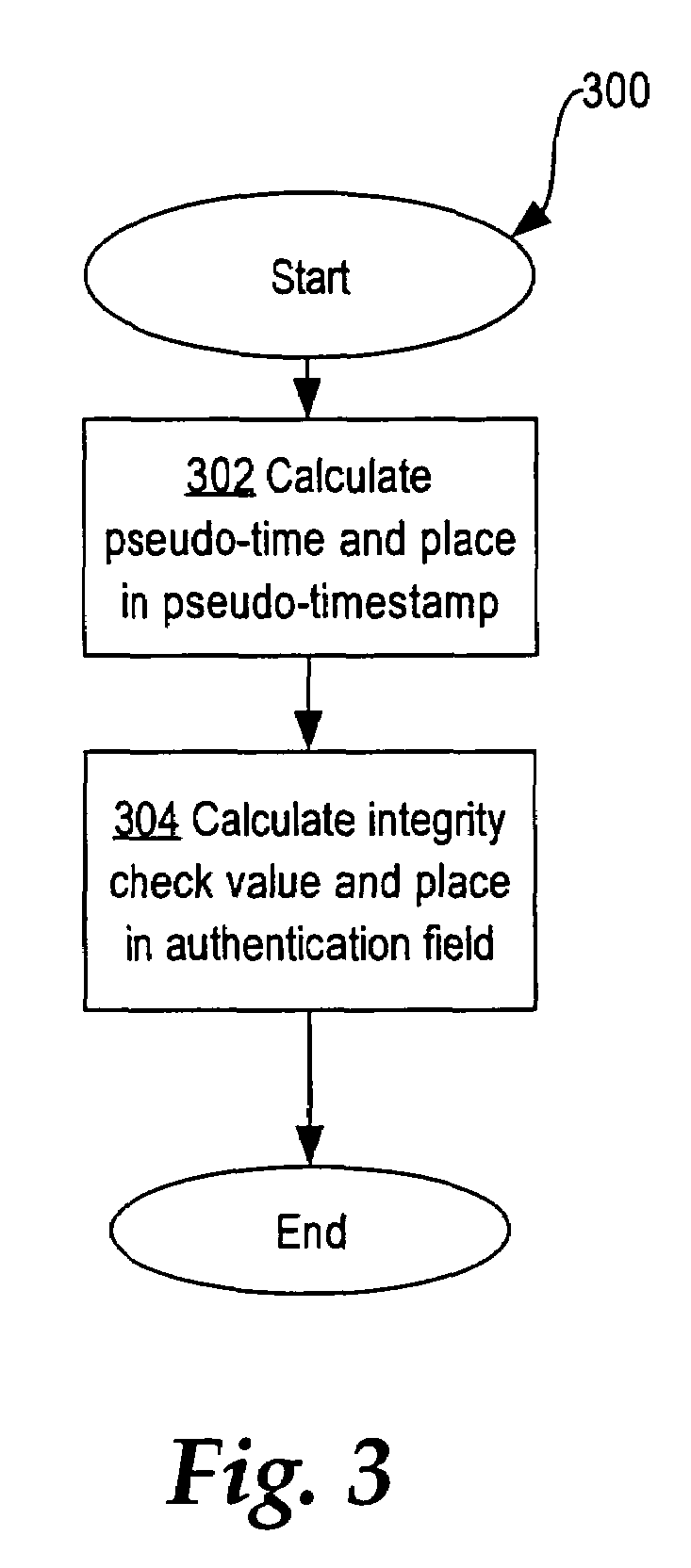
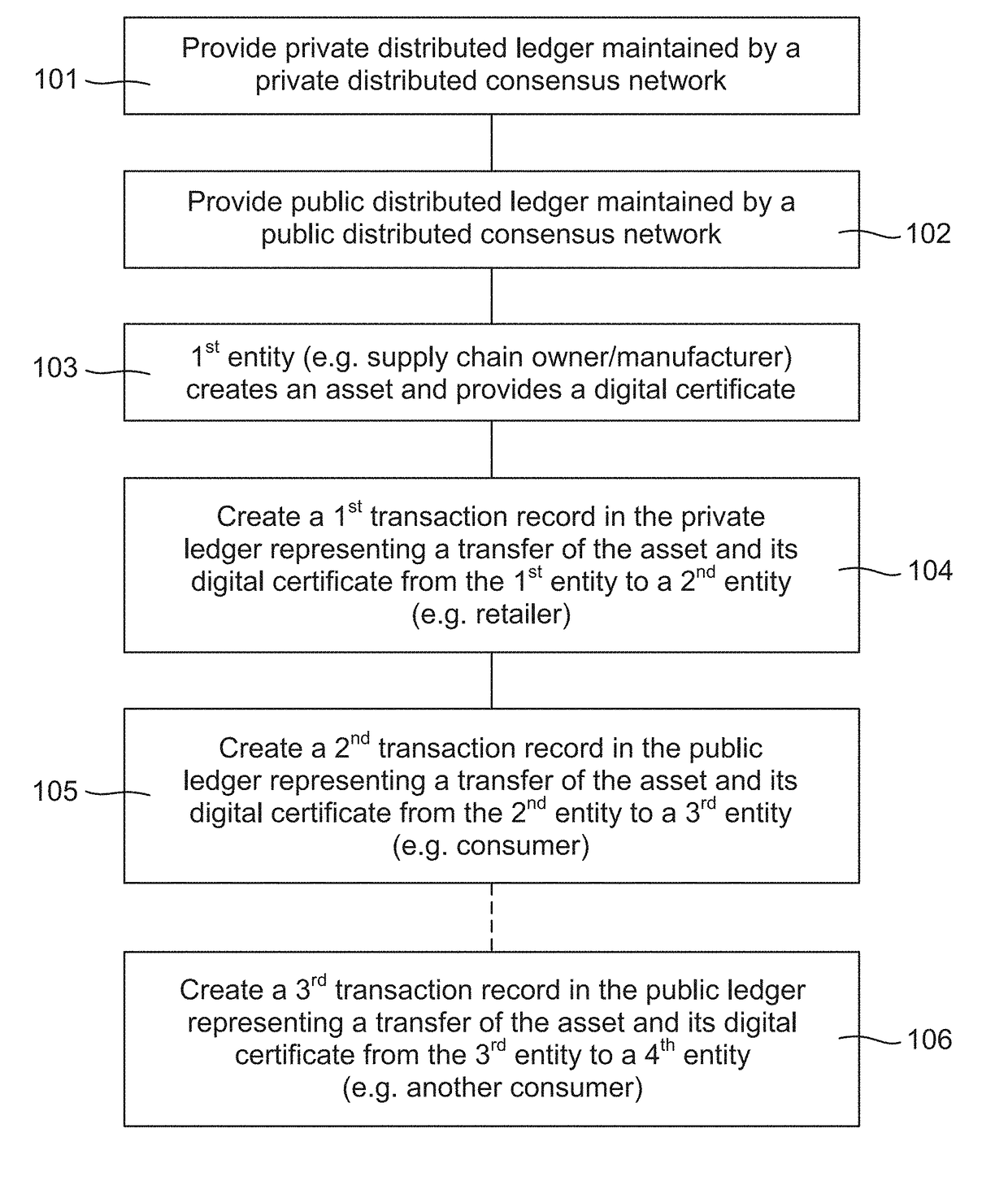
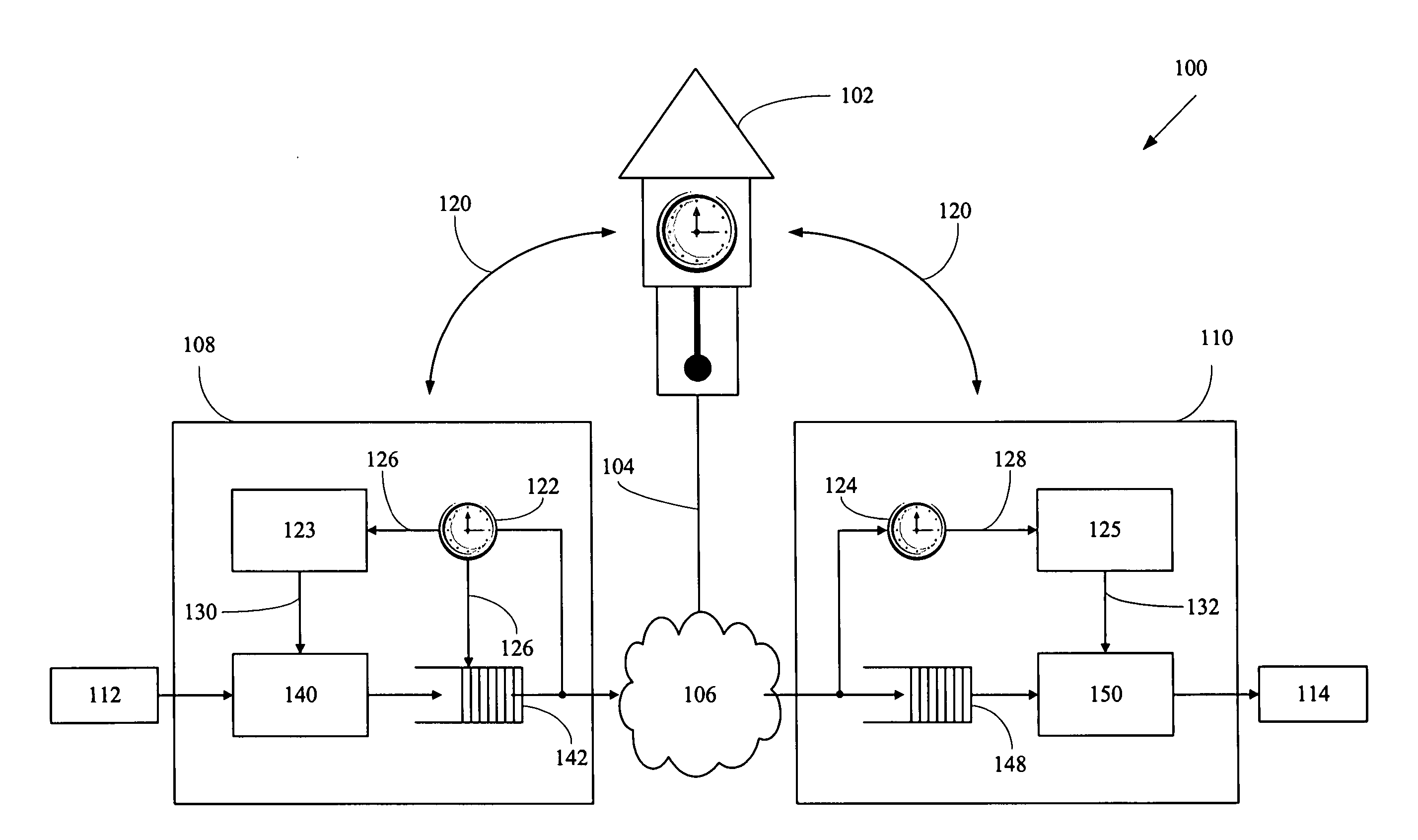
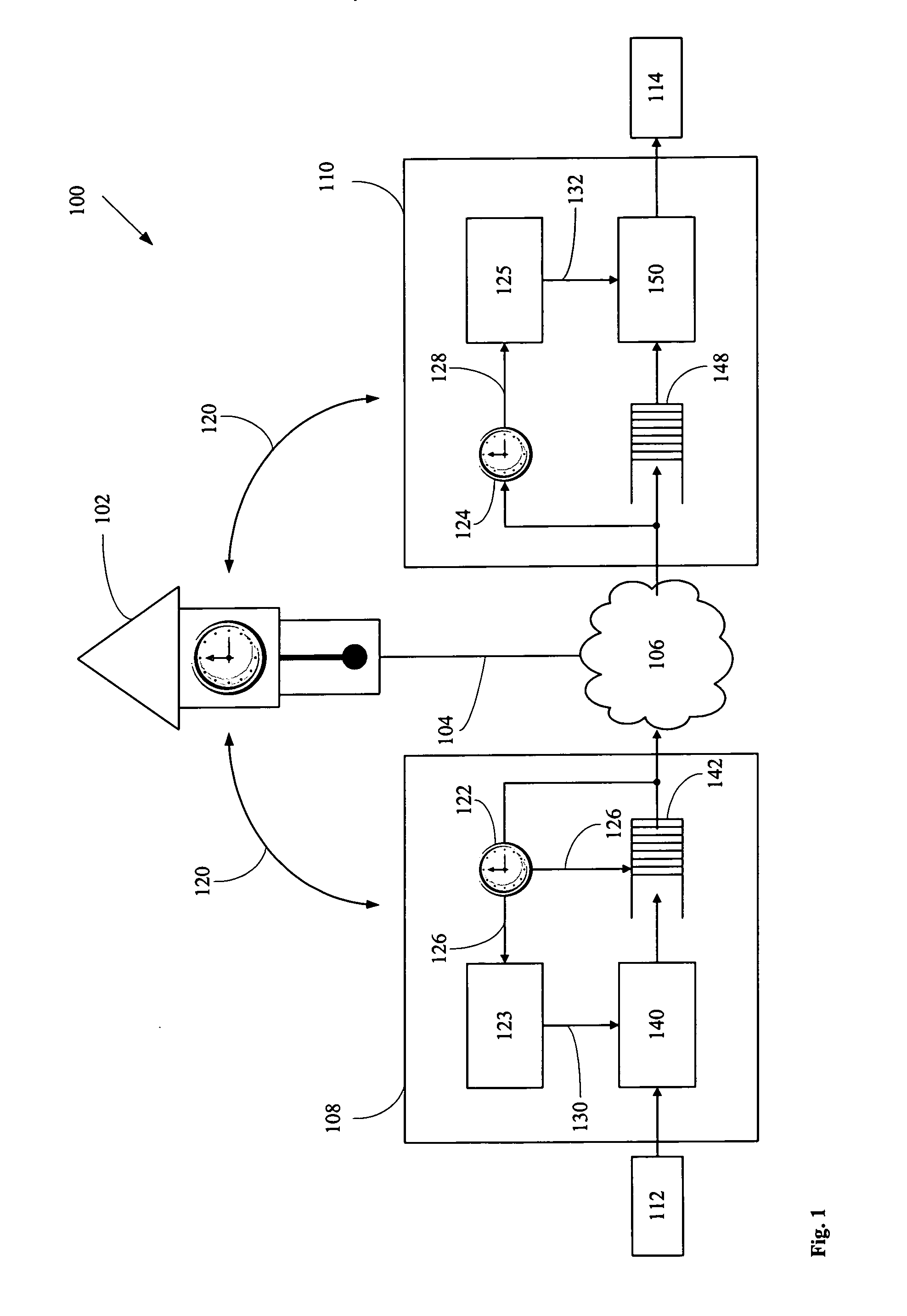
Method for self-synchronizing time between communicating networked systems using timestamps
ActiveUS7676679B2Synchronising transmission/receiving encryption devicesError detection/correctionTimestampNetworked system
Nodes in a network include a pseudo-timestamp in messages or packets, derived from local pseudo-time clocks. When a packet is received, a first time is determined representing when the packet was sent and a second time is determined representing when the packet was received. If the difference between the second time and the first time is greater than a predetermined amount, the packet is considered to be stale and is rejected, thereby deterring replay. Because each node maintains its own clock and time, to keep the clocks relatively synchronized, if a time associated with a timestamp of a received packet is later than a certain amount with respect to the time at the receiver, the receiver's clock is set ahead by an amount that expected to synchronize the receiver's and the sender's clocks. However, a receiver never sets its clock back, to deter attacks.
Owner:CISCO TECH INC
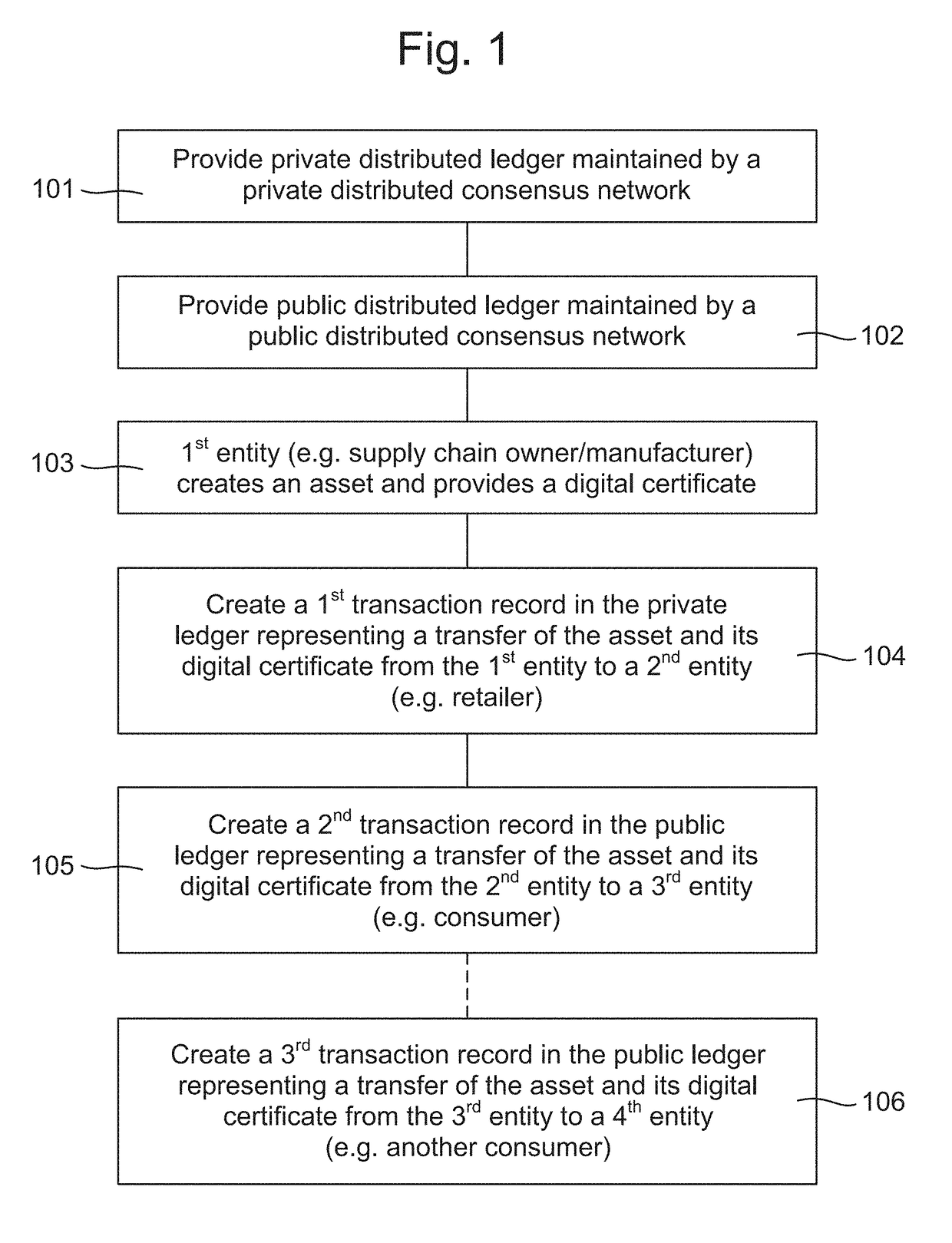
Methods and systems for processing assets
InactiveUS20170331896A1Improve securityRemoving reliance on a central authoritySynchronising transmission/receiving encryption devicesUser identity/authority verificationDistributed computingAuthentication
A computer-implemented method for processing an asset within a supply chain includes: providing a first distributed ledger maintained by nodes within a first distributed consensus network; providing a second distributed ledger maintained by nodes within a second distributed consensus network; creating the asset by a supply chain first entity associated with at least one node within the first network, and providing a digital certificate uniquely associated with the asset for authentication; creating a first transaction record in the first distributed ledger representing an asset transfer and its associated digital certificate from the first entity to a supply chain second entity associated with at least one node within the first network; and creating a second transaction record in the second distributed ledge representing an asset transfer and its associated digital certificate from the second entity to a supply chain third entity associated with at least one node within the second network.
Owner:DE LA RUE INT LTD
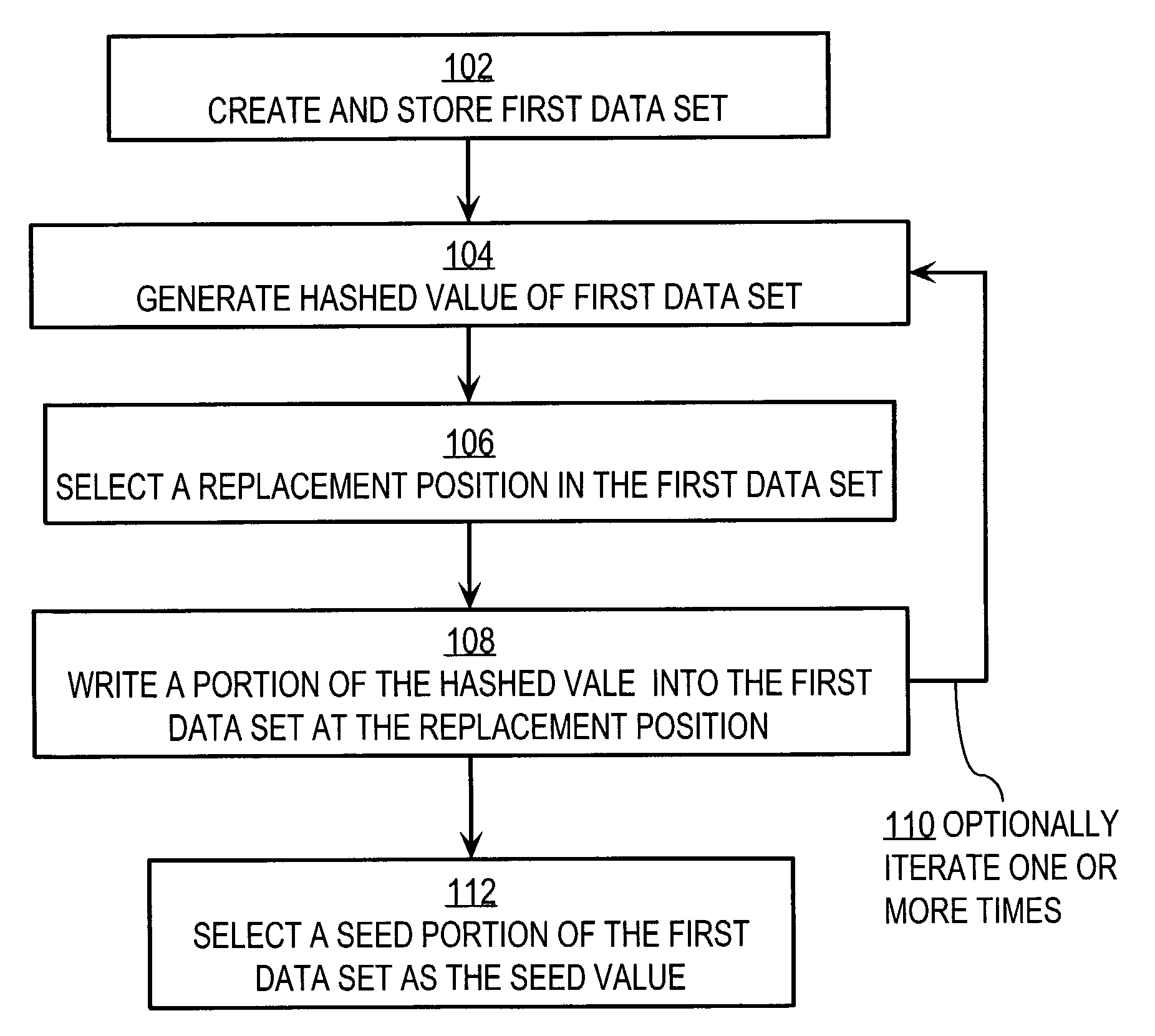
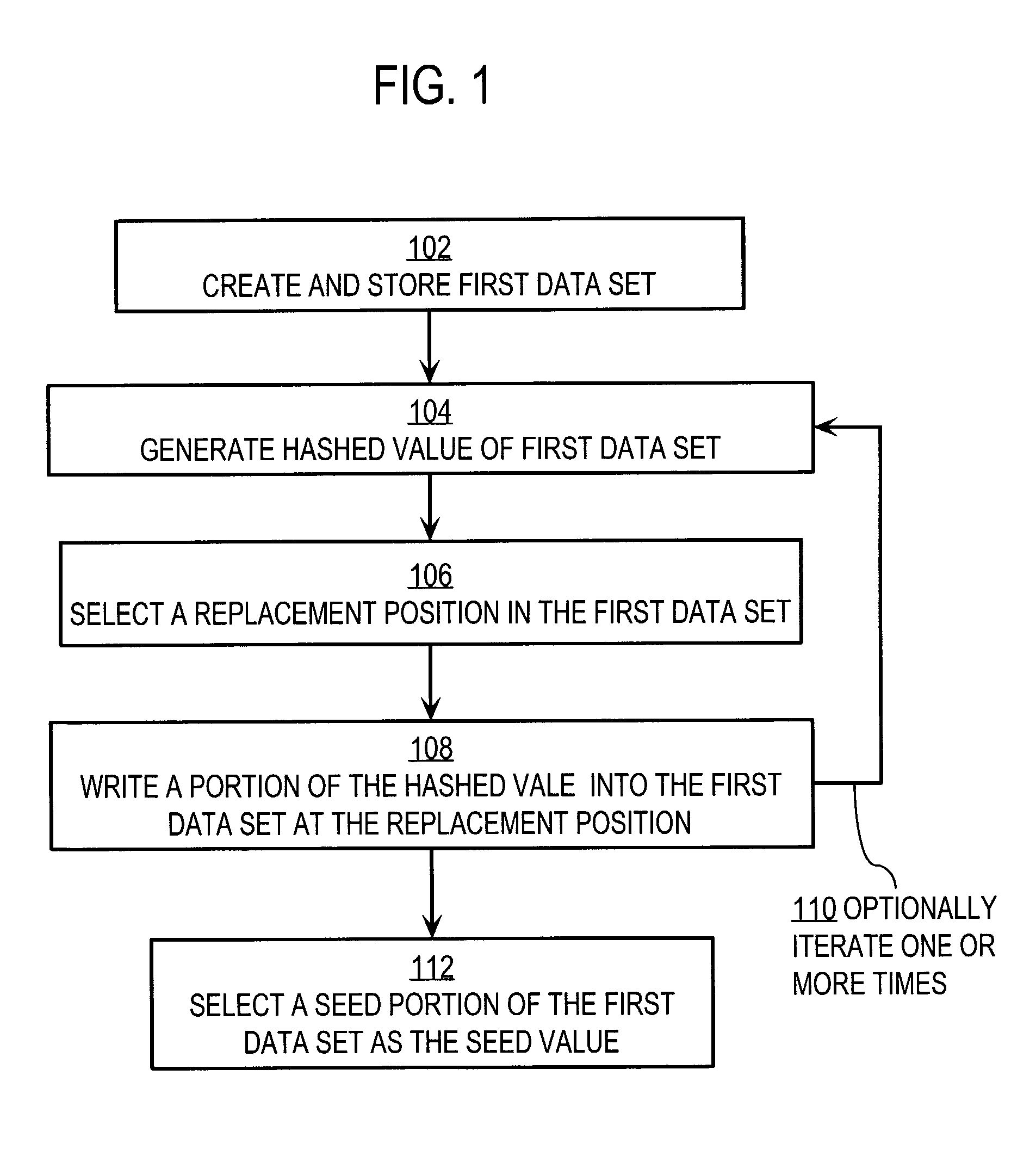
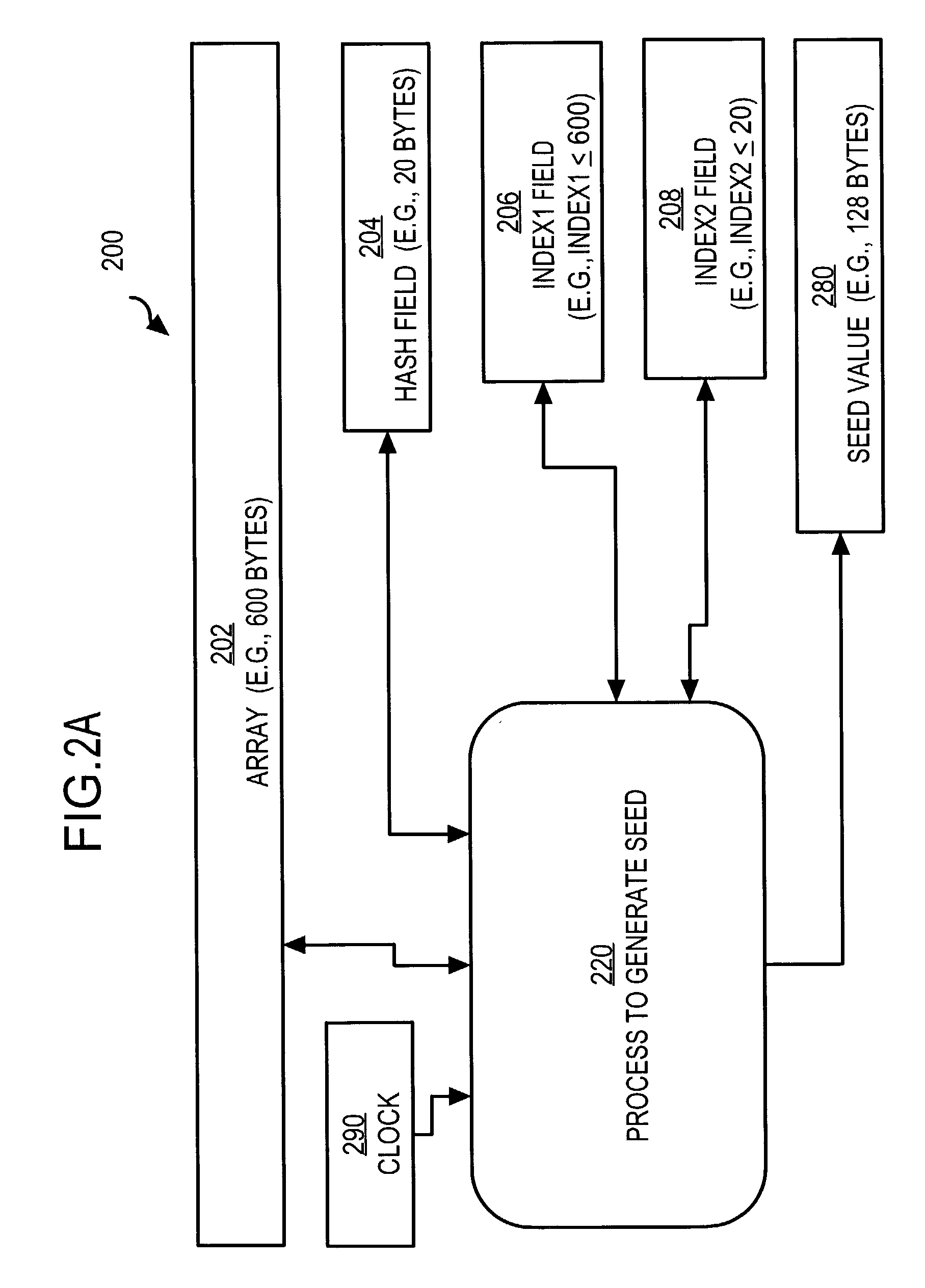
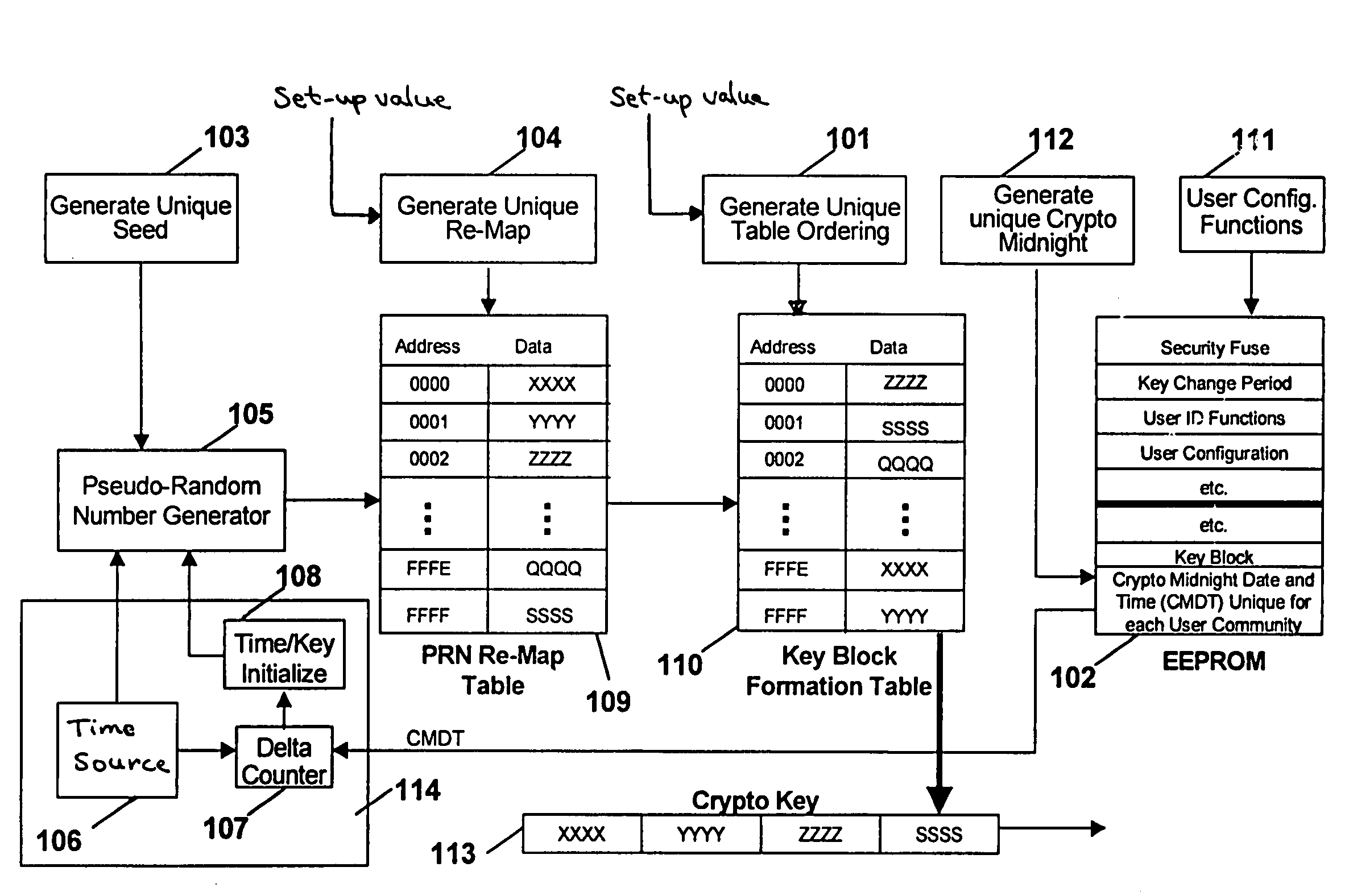
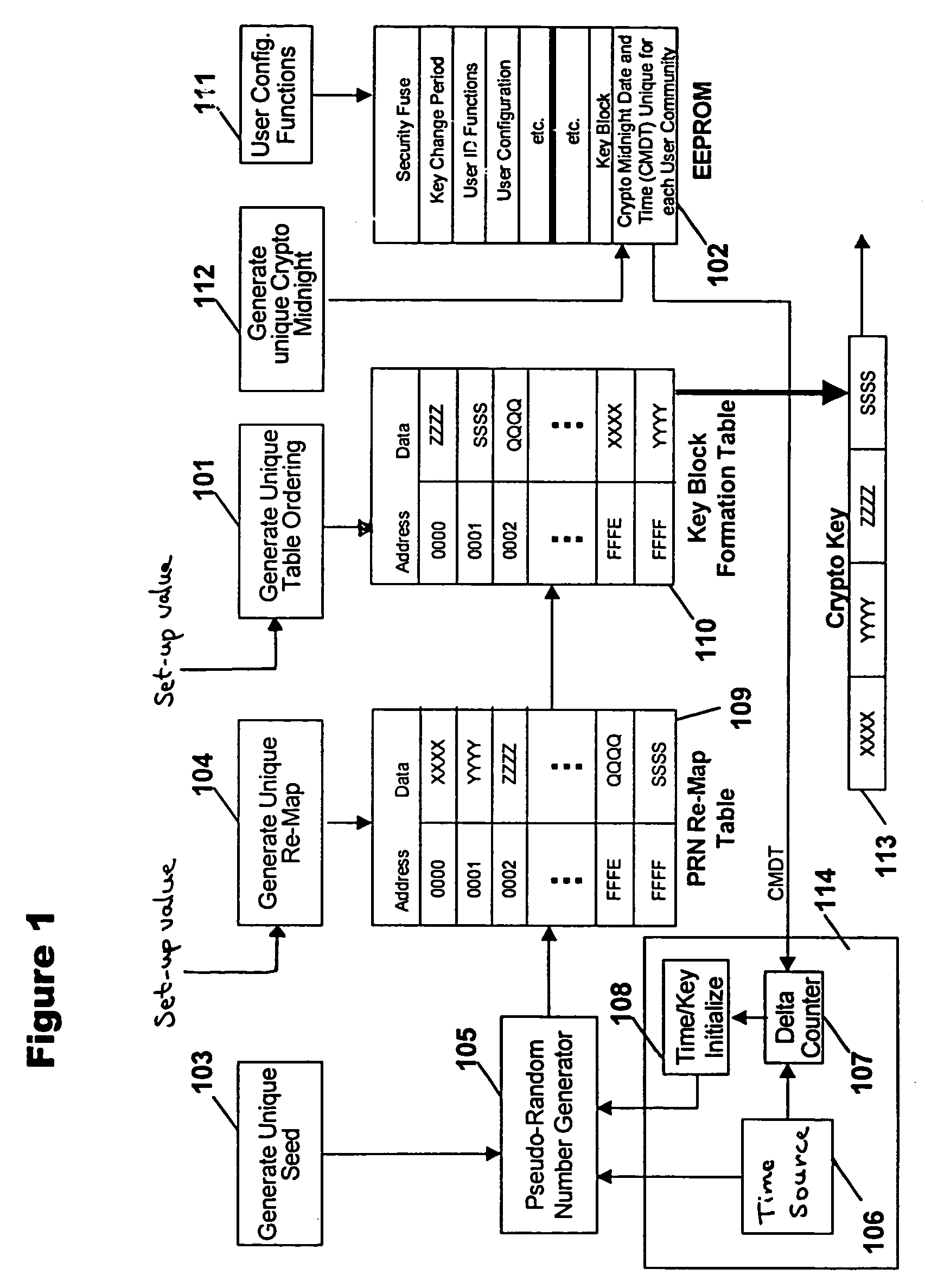
System and method for generating encryption seed values
ActiveUS7209561B1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesData setComputer science
A method for generating a seed value for use in symmetric encryption includes creating and storing a first data set and generating a hashed value based on the first data set. A replacement position in the first data set is selected, and at least a portion of the hashed value is written into the first data set at the replacement position. A seed portion of the first data set is selected as the seed value. By varying a number of iterations, a balance can be struck between performance (fewer iterations) and security (more iterations).
Owner:CYBERSOURCE CORP
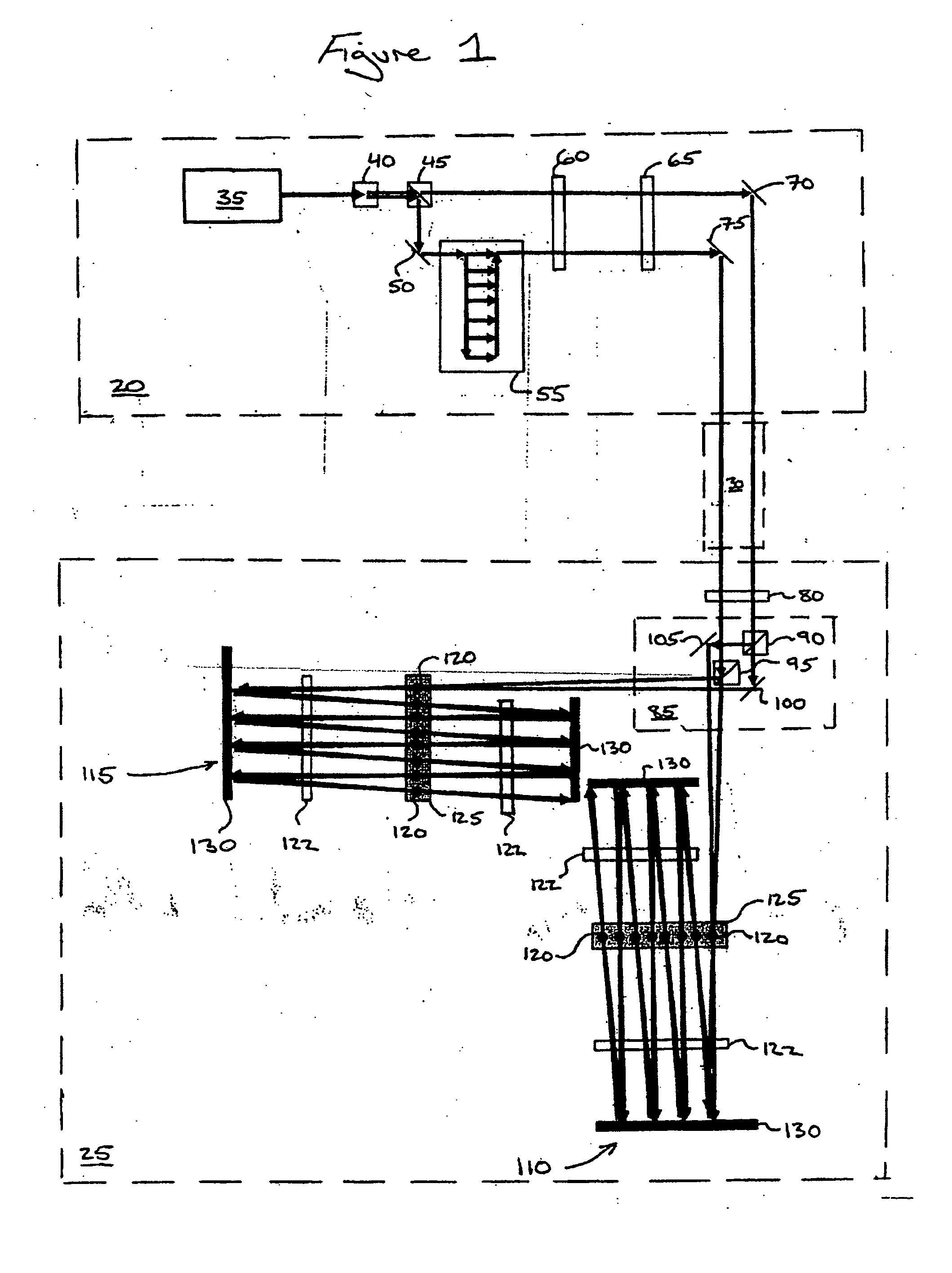
Encryption apparatus and method for synchronizing multiple encryption keys with a data stream
ActiveUS7242772B1Minimized in sizeImprove distributionKey distribution for secure communicationSynchronising transmission/receiving encryption devicesMultiple encryptionComputer hardware
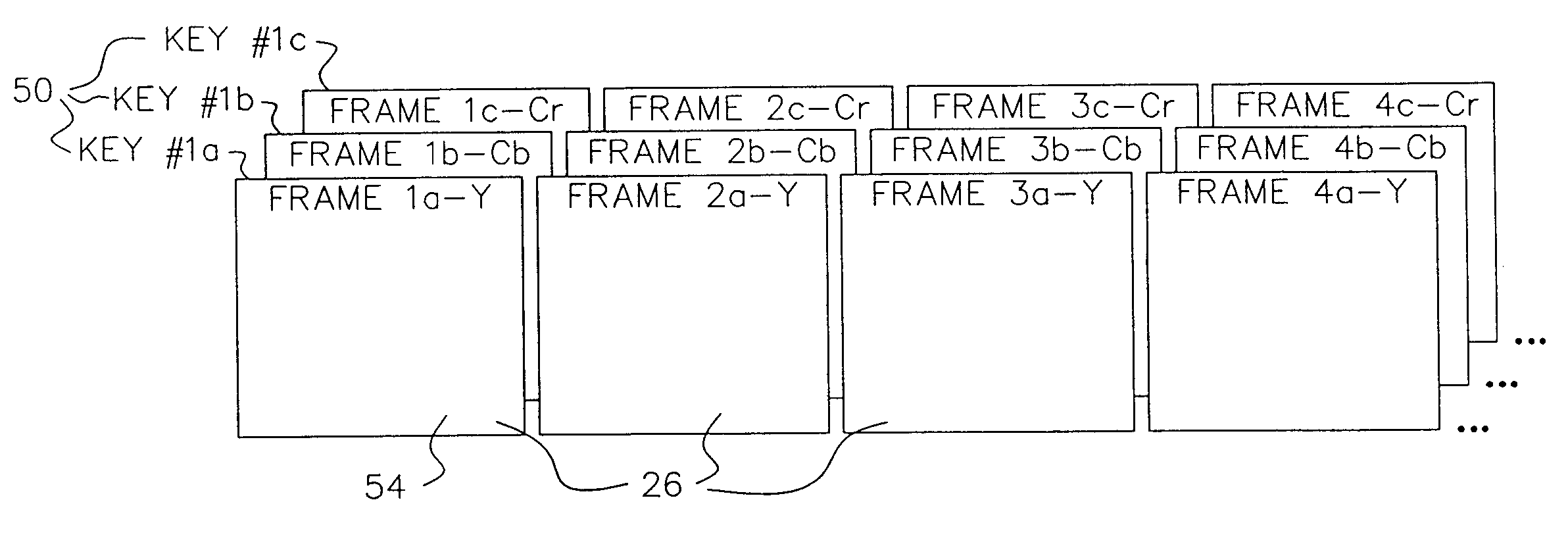
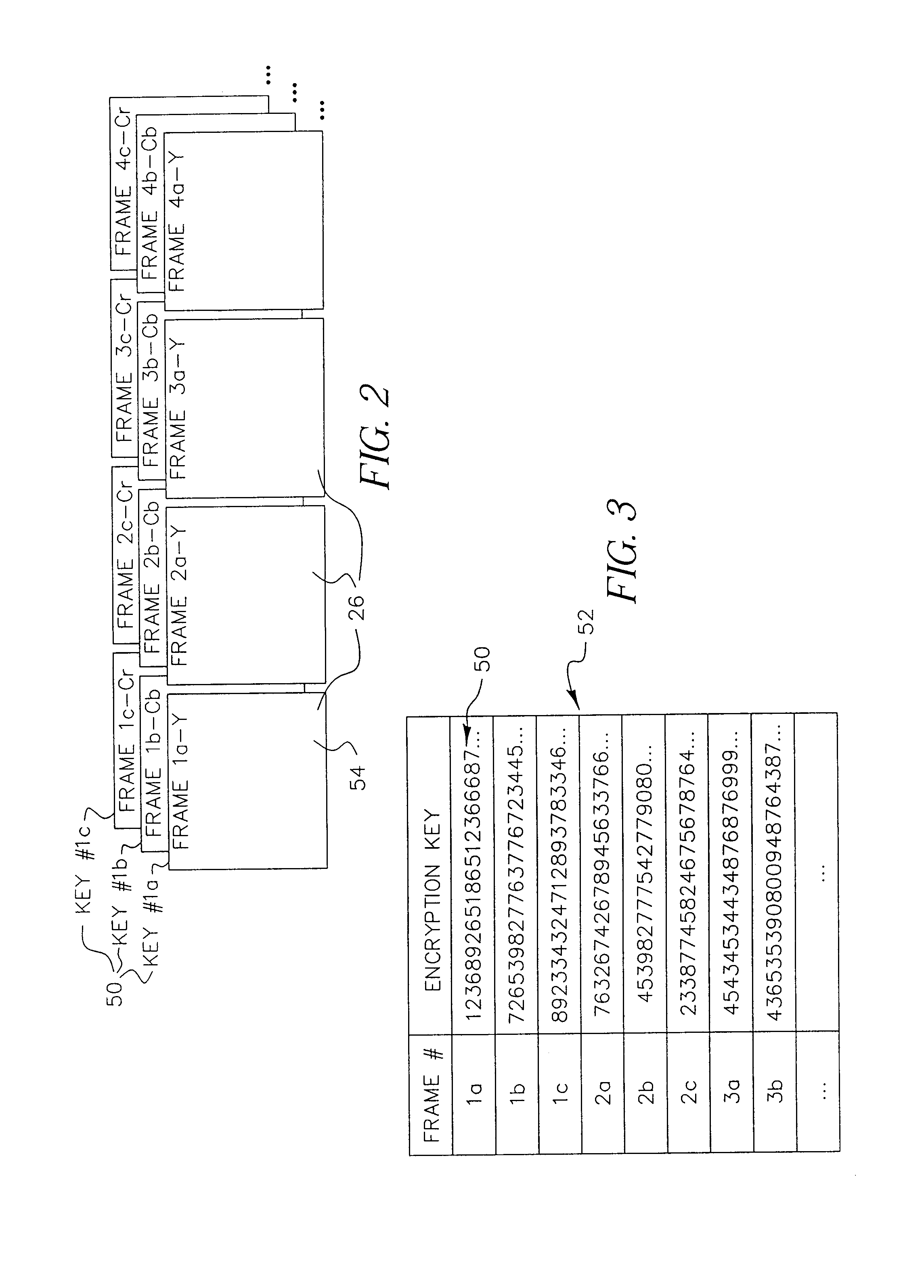
A data stream, such as a digital motion picture, is encrypted in units of one or more blocks, each block having an assigned encryption key. A plurality of encryption keys is assigned to the complete data stream, with a synchronization index provided to map each individual encryption key to its starting data block. Encryption keys and associated synchronization indices are provided separately from the data stream, using one or more additional data transfer mechanisms. An optional offset, randomly generated, allows variation in intervals between data blocks at which encryption by a specific encryption key can be performed.
Owner:MONUMENT PEAK VENTURES LLC
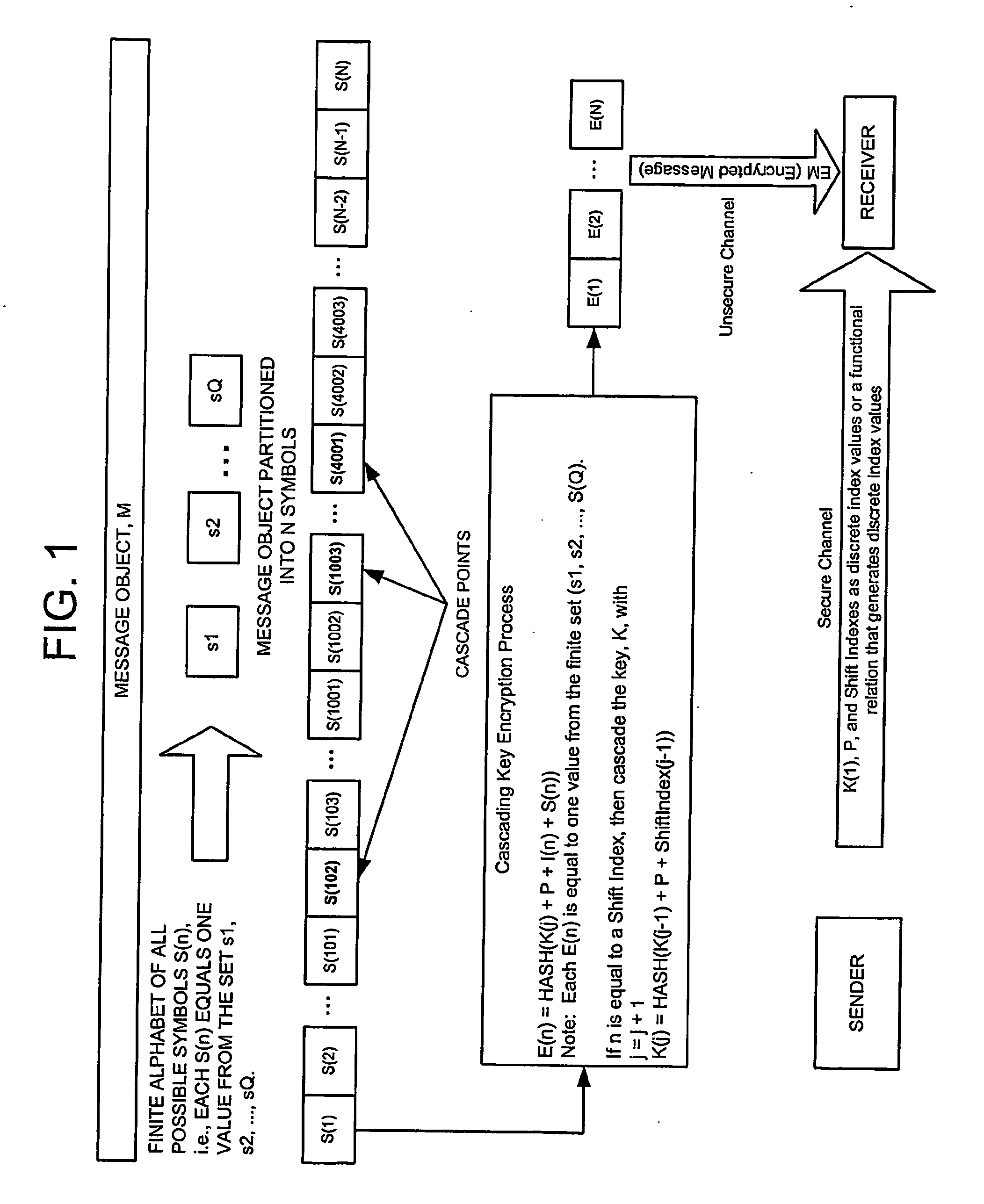
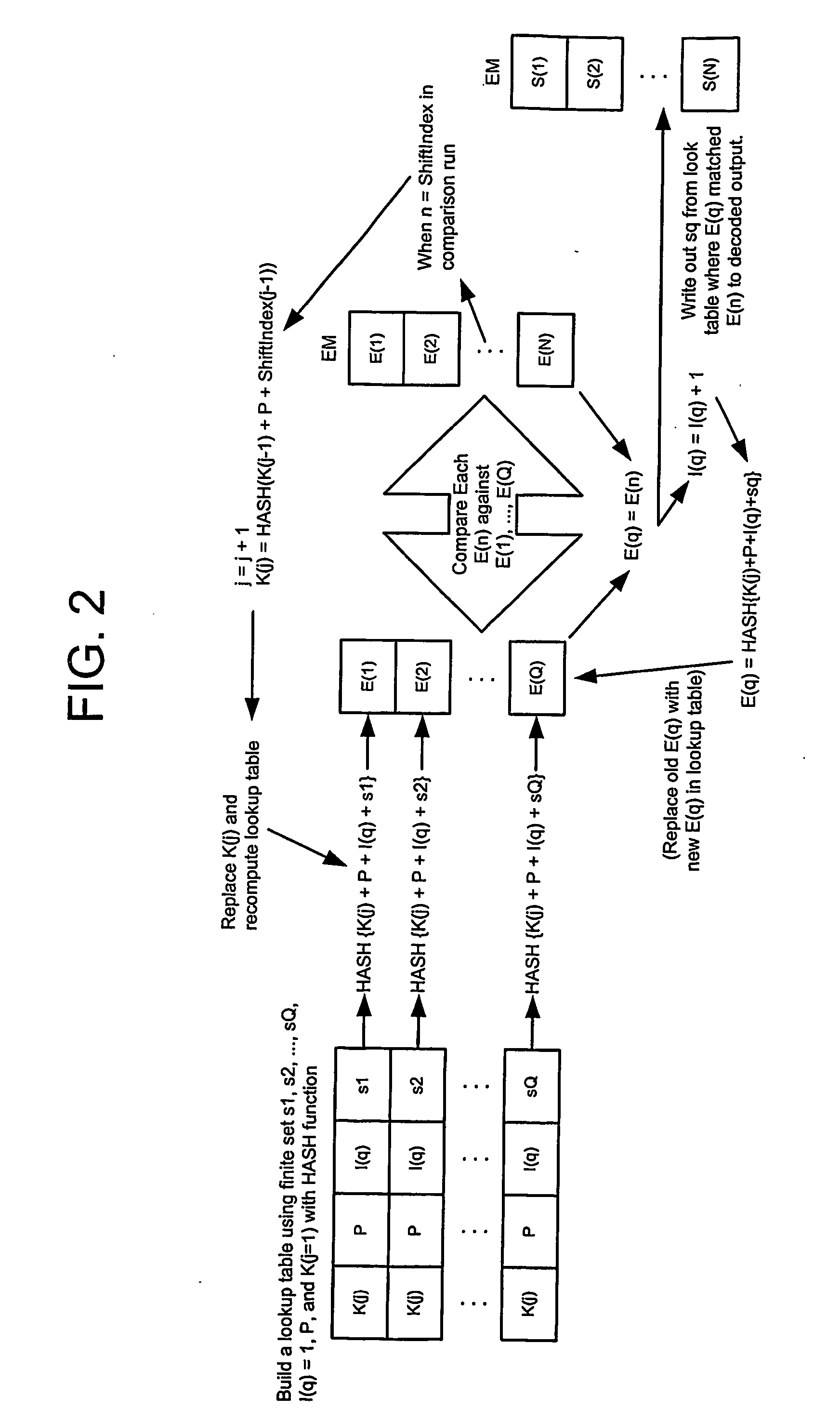
Cascading key encryption
InactiveUS20060265595A1Secure EncryptionSmall sizeKey distribution for secure communicationSynchronising transmission/receiving encryption devicesPasswordSecure transmission
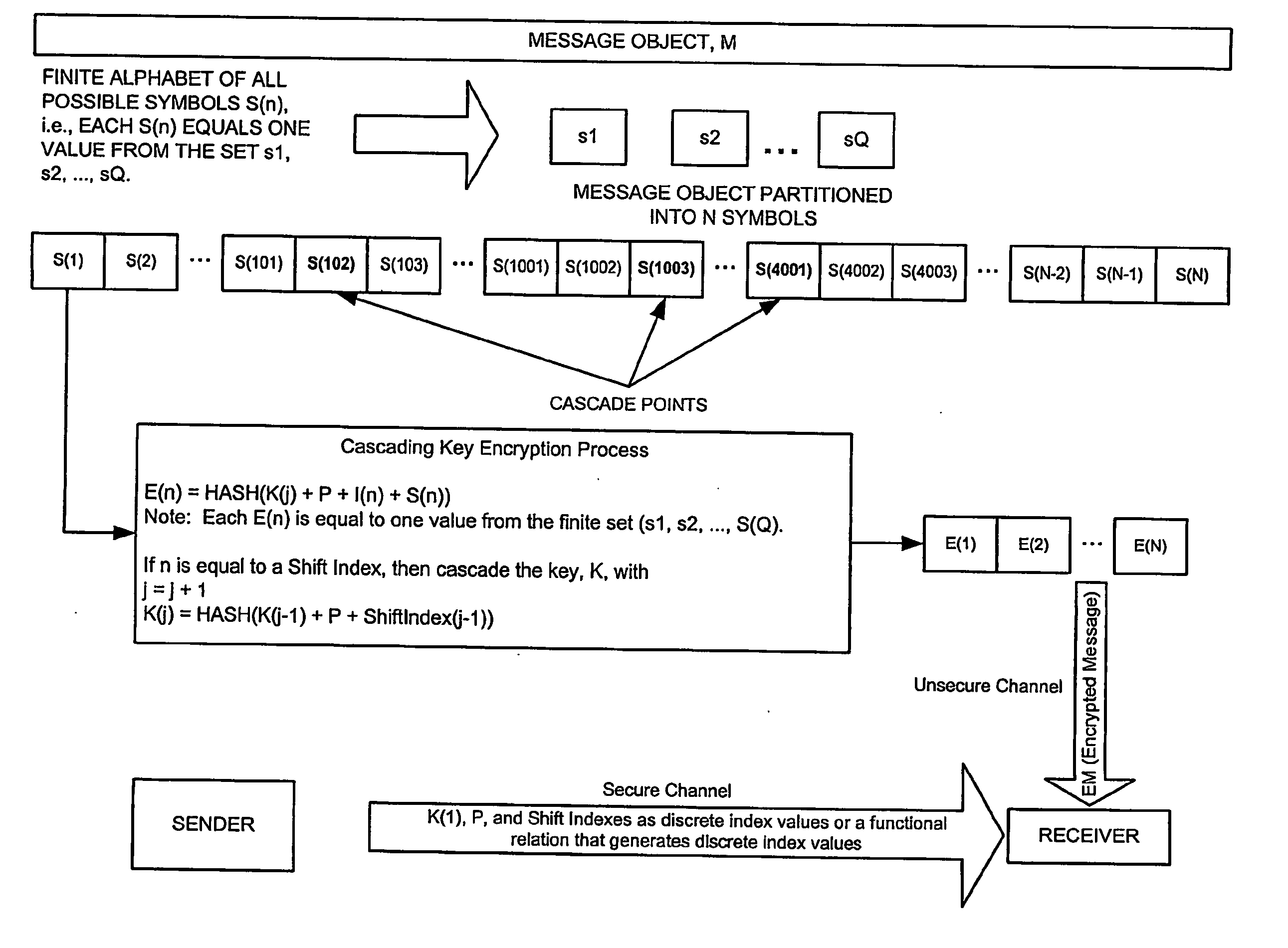
A method for securely transmitting data involves generating keys depending on previous keys and additional information, such as a password, in order to create a pseudo one-time pad. The data is encrypted using the pseudo one-time pad prior to transmission. Only the initial key and minimal additional data are transferred between the sender and receiver in order to synchronize the keys.
Owner:PATHFIRE
Method for transporting digital media
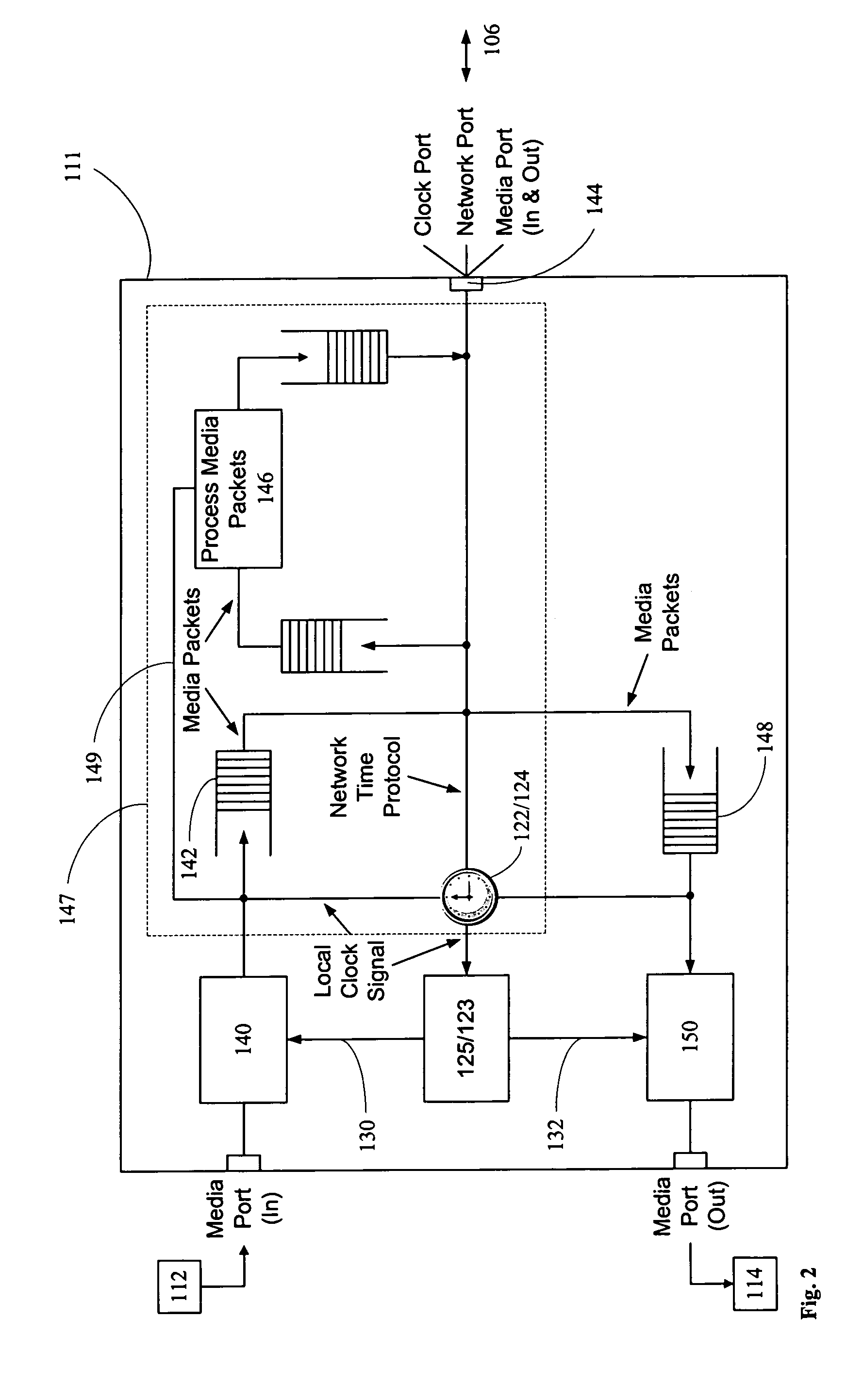
ActiveUS20060280182A1Low costSynchronising transmission/receiving encryption devicesTime-division multiplexTime ProtocolNetworked system
A networked system is provided for transporting digital media packets, such as audio and video. The network includes network devices interconnected to send and receive packets. Each network device can receive and transmit media signals from media devices. A master clock generates a system time signal that the network devices use, together with a network time protocol to generate a local clock signal synchronised to the system time signal for both rate and offset. The local clock signal governs both the rate and offset of the received or transmitted media signals. The system, which can be implemented using conventional network equipment enables media signals to be transported to meet quality and timing requirements for high quality audio and video reproduction.
Owner:AUDINATE HLDG PTY LTD
Method and system for encrypting and decrypting data using an external agent
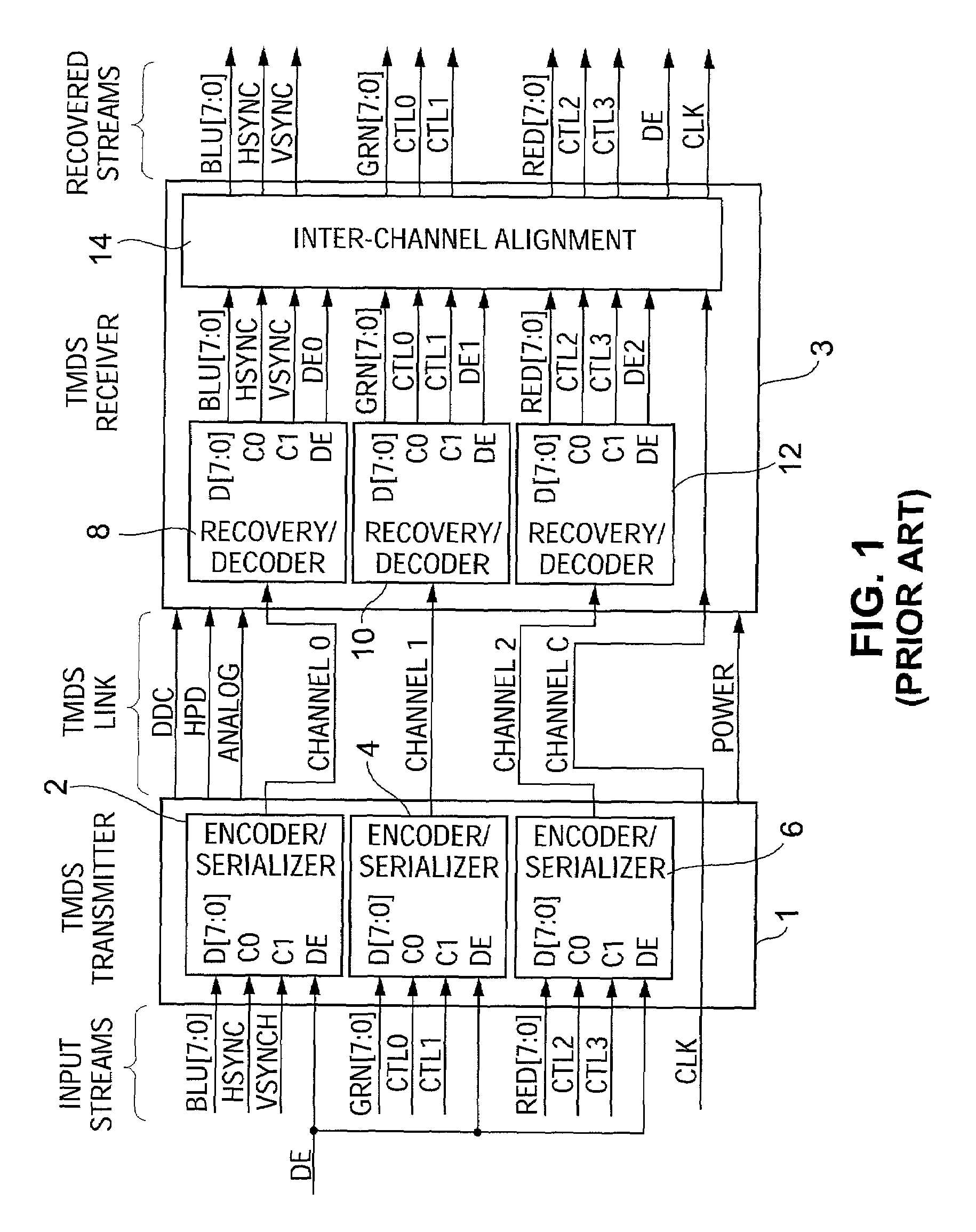
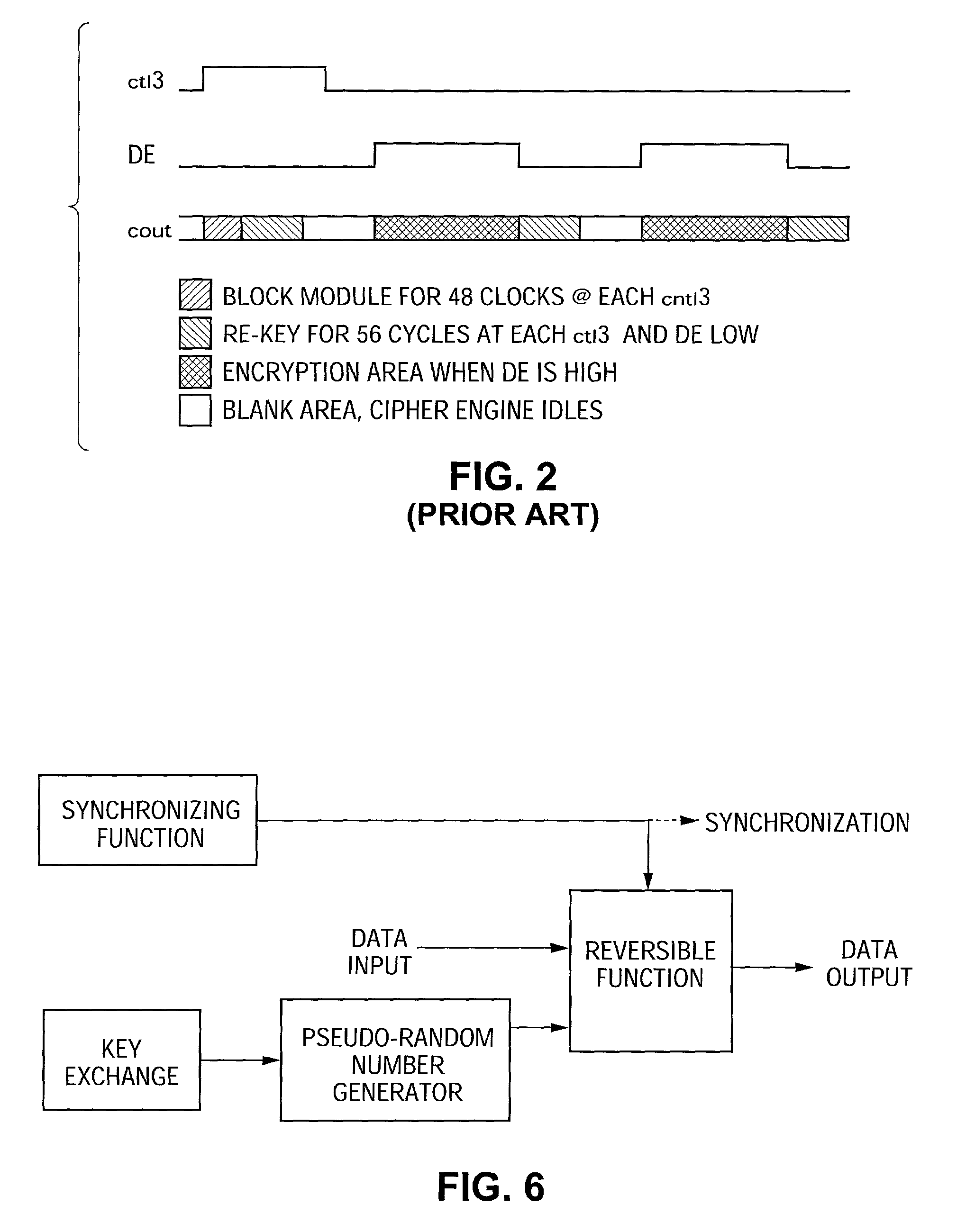
ActiveUS7242766B1Improve securitySynchronising transmission/receiving encryption devicesSecret communicationResponse processTelecommunications link
A communication system including a transmitter, a receiver, a communication link (for example, a TMDS-like link), and preferably also an external agent with which the transmitter and receiver can communicate, in which video data (or other data) are encrypted, the encrypted data are transmitted from the transmitter to the receiver, and the transmitted data are decrypted in the receiver, a transmitter and a receiver for use in such a system, a cipher engine for use in such a transmitter or receiver, a method for operating such a transmitter or receiver to encrypt or decrypt data, and a method for distributing keys to the transmitter and receiver. The receiver can be a player coupled to a downstream receiver by a TMDS-like link, and configured to re-encrypt the decrypted data (for example, using an AES or HDCP protocol) and send re-encrypted data over the link to the receiver. Optionally, the player is a repeater which translates the decrypted data from the transmitter, and then re-encrypts the translated data for transmission to the downstream receiver. The transmitter can itself be a player that receives and decrypts encrypted data from an upstream source. In preferred embodiments, the system implements a content protection protocol including a challenge-response procedure. After a new key is supplied to the receiver (and the same new key should have been supplied to the transmitter) and before the receiver can use the new key, the challenge-response procedure requires that the receiver validate the transmitter by verifying that the transmitter has proper knowledge of the new key.
Owner:LATTICE SEMICON CORP
Extending a secure key storage for transaction confirmation and cryptocurrency
PendingUS20190164156A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesInternet privacyEngineering
A system, apparatus, method, and machine readable medium are described for secure authentication. For example, one embodiment of a system comprises: an authenticator on a client device to securely store one or more private keys, at least one of the private keys usable to authenticate a block of a blockchain; and an attestation module of the authenticator or coupled to the authenticator, the attestation module to generate a signature using the block and the private key, the signature usable to attest to the authenticity of the block by a device having a public key corresponding to the private key.
Owner:NOK NOK LABS
Strong mutual authentication of devices
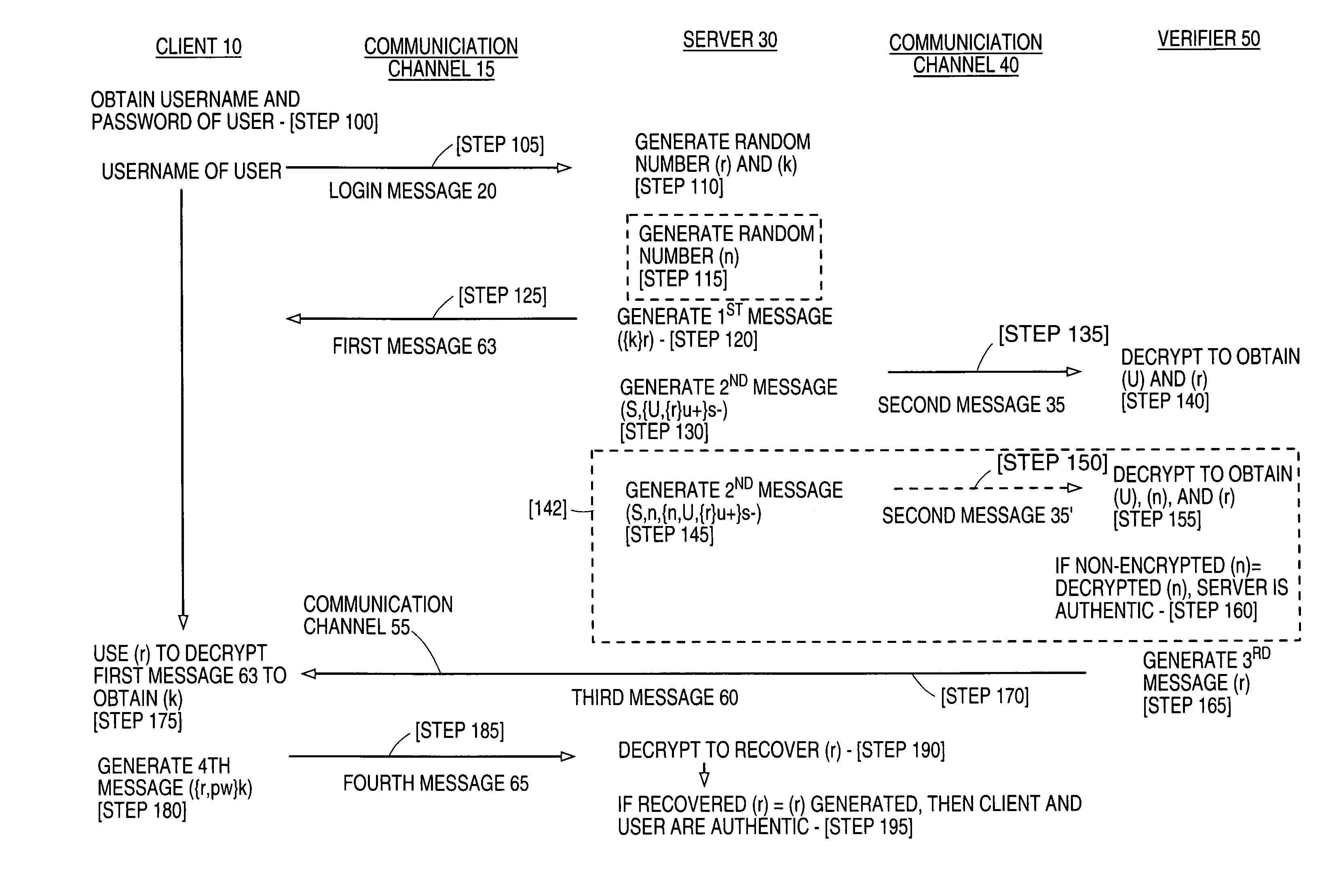
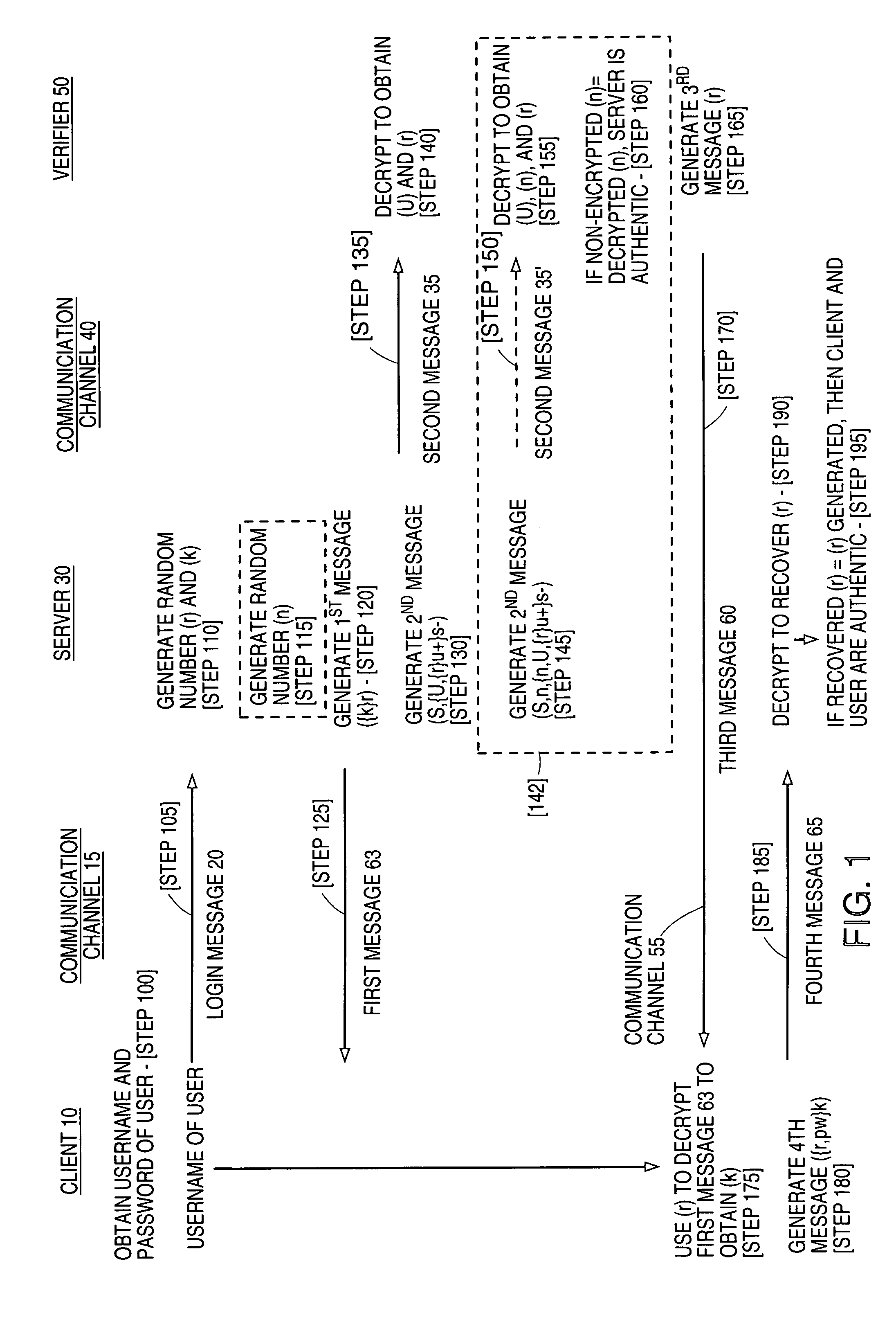
InactiveUS7020773B1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesCommunications systemClient-side
The present invention relates to a method for enabling strong mutual authentication between two computers in a communication system. A user from a client attempts to gain access to a server. The server transmits a first key encrypted by a second key to the client and a second key encrypted by a user's private key to a verifier. The verifier uses the user's login information to obtain the user's private key, which the verifier uses to obtain the second key. The verifier transmits the second key to the client and the client decrypts the first key with the second key. The client then transmits the second key encrypted by the first key to the server. If the received second key is the same as the generated second key, the client is authenticated to the server.
Owner:CITRIX SYST INC
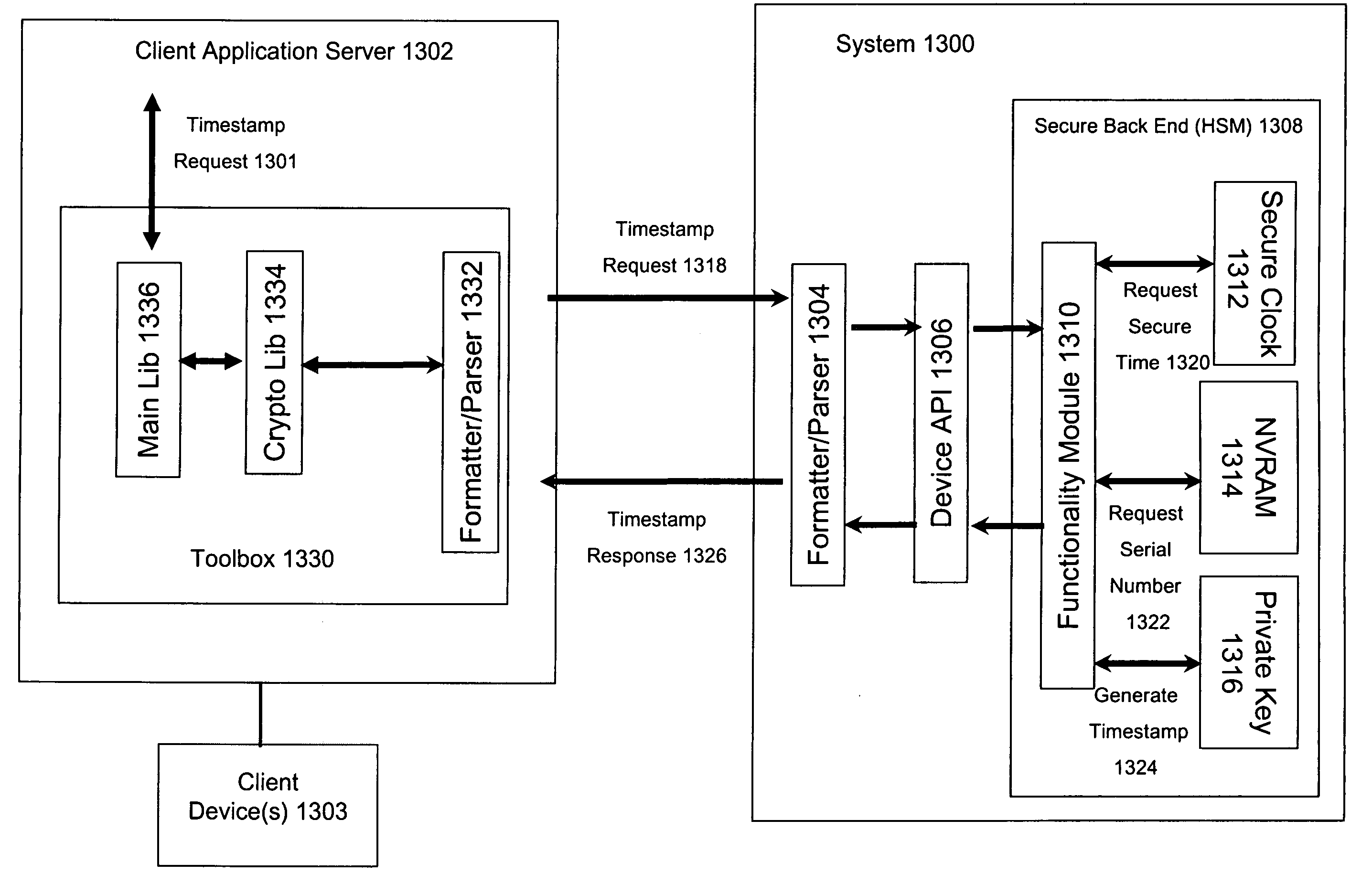
System and method for providing trusted time in content of digital data files
InactiveUS20050160272A1Synchronising transmission/receiving encryption devicesUser identity/authority verificationDigital dataReal-time clock
A personal computer (PC) system and methods for proving dates of digital data files, which are accessed, created, modified, received, or transmitted by the PC includes a trusted time source in a tamperproof environment, a first subsystem for saving the file at a moment in time, a second subsystem for retrieving from the trusted time source a date and a time corresponding to the moment in time, a third subsystem for appending the date and the time retrieved from the trusted time source to the saved file, a fourth subsystem for signing the saved file with the date and the time retrieved from the trusted time source appended thereto, a fifth subsystem means for hashing the signed file to produce a digest, a sixth subsystem for signing the digest with a key to produce a certificate, a seventh subsystem for appending the certificate to the saved file, and an eighth subsystem for saving the file with the certificate appended thereto. The trusted time source is a real time clock, which is not resettable, is independent of any system clock of the PC, and is installed locally relative to the PC.
Owner:TIME CERTAIN
Method and system for the processing of messages in a telecommunication system
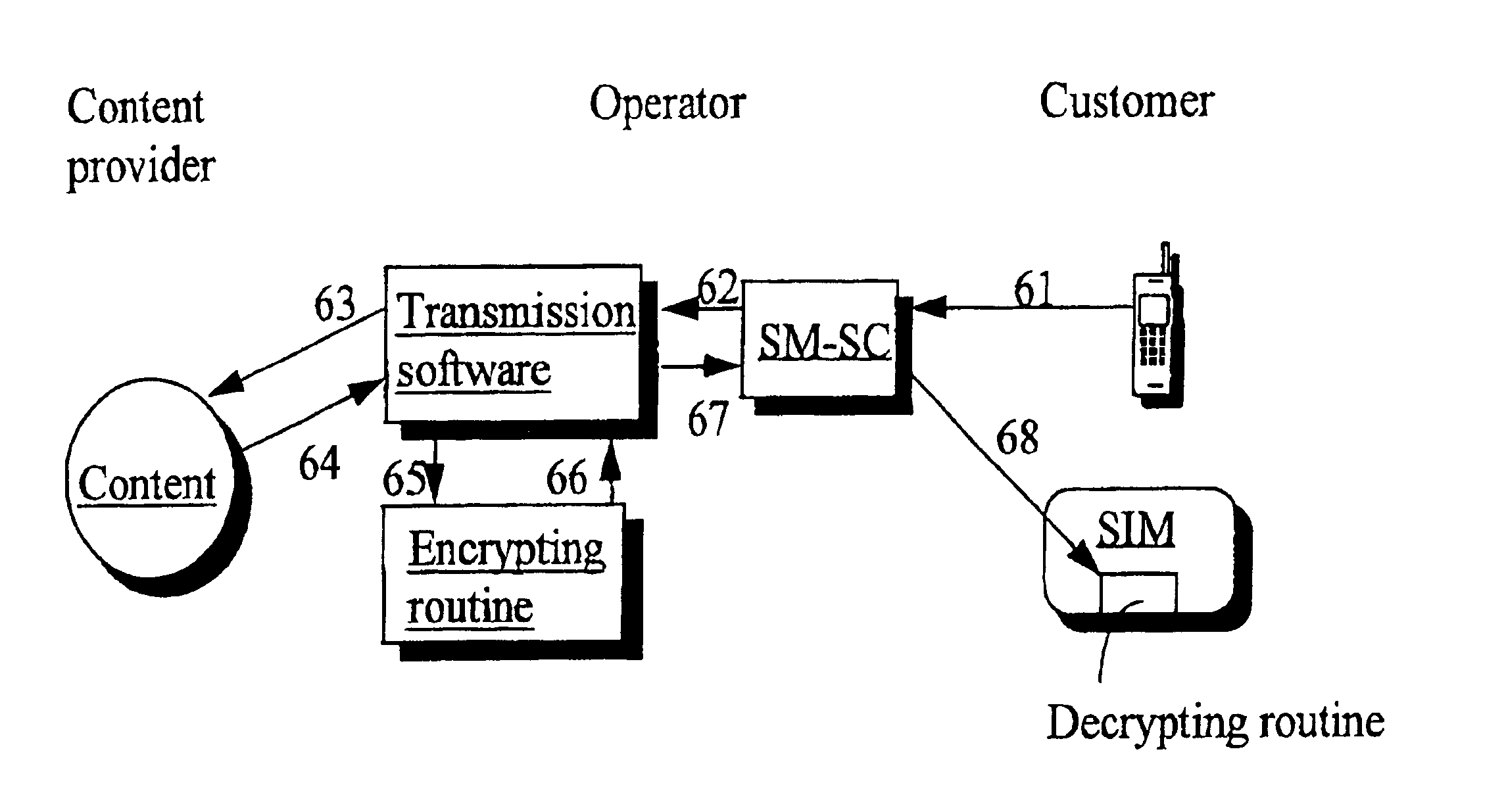
InactiveUS6925568B1Reliable identificationSynchronising transmission/receiving encryption devicesUnauthorized memory use protectionMobile stationGeographic area
A method and system for encrypting, in a telecommunication system, outgoing message traffic between mobile stations operating in accordance with current mobile communication standards and / or between a mobile station and a service provider, and for decrypting incoming message traffic, includes directing encrypted messages to and receiving encrypted messages from only those members of a limited closed receiver group that are located in a given geographic area.
Owner:SONERA
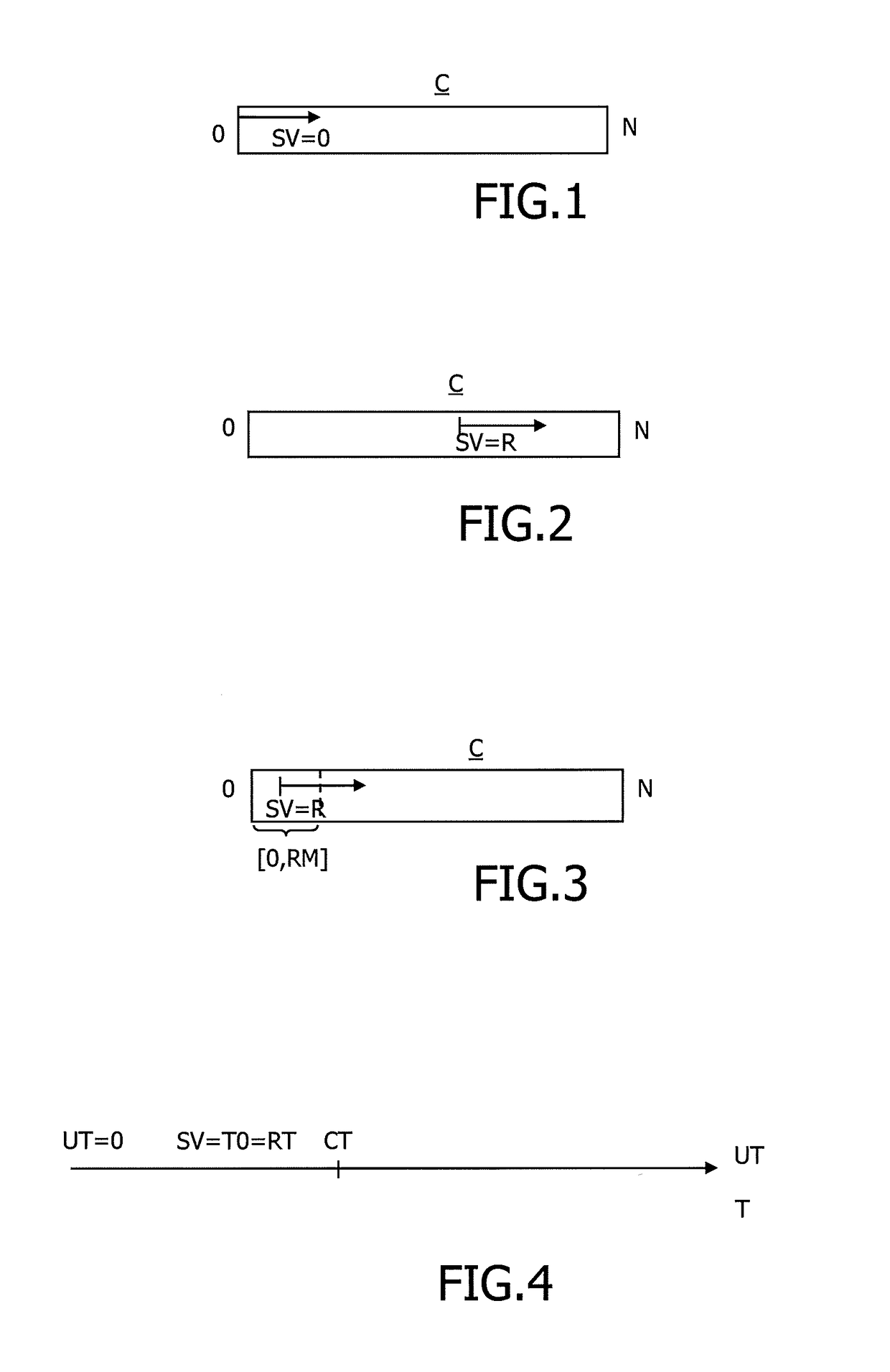
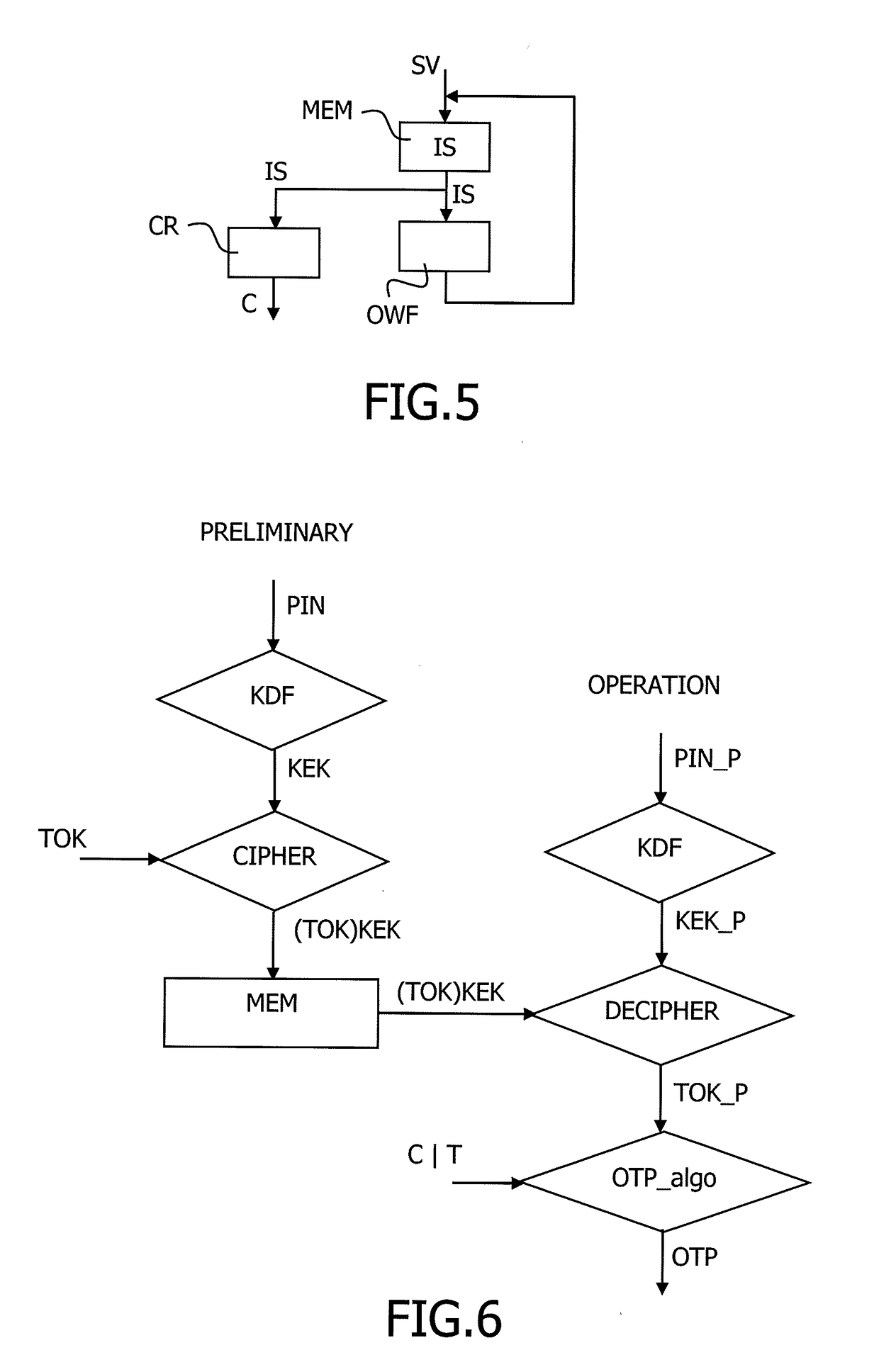
Method to manage a one time password key
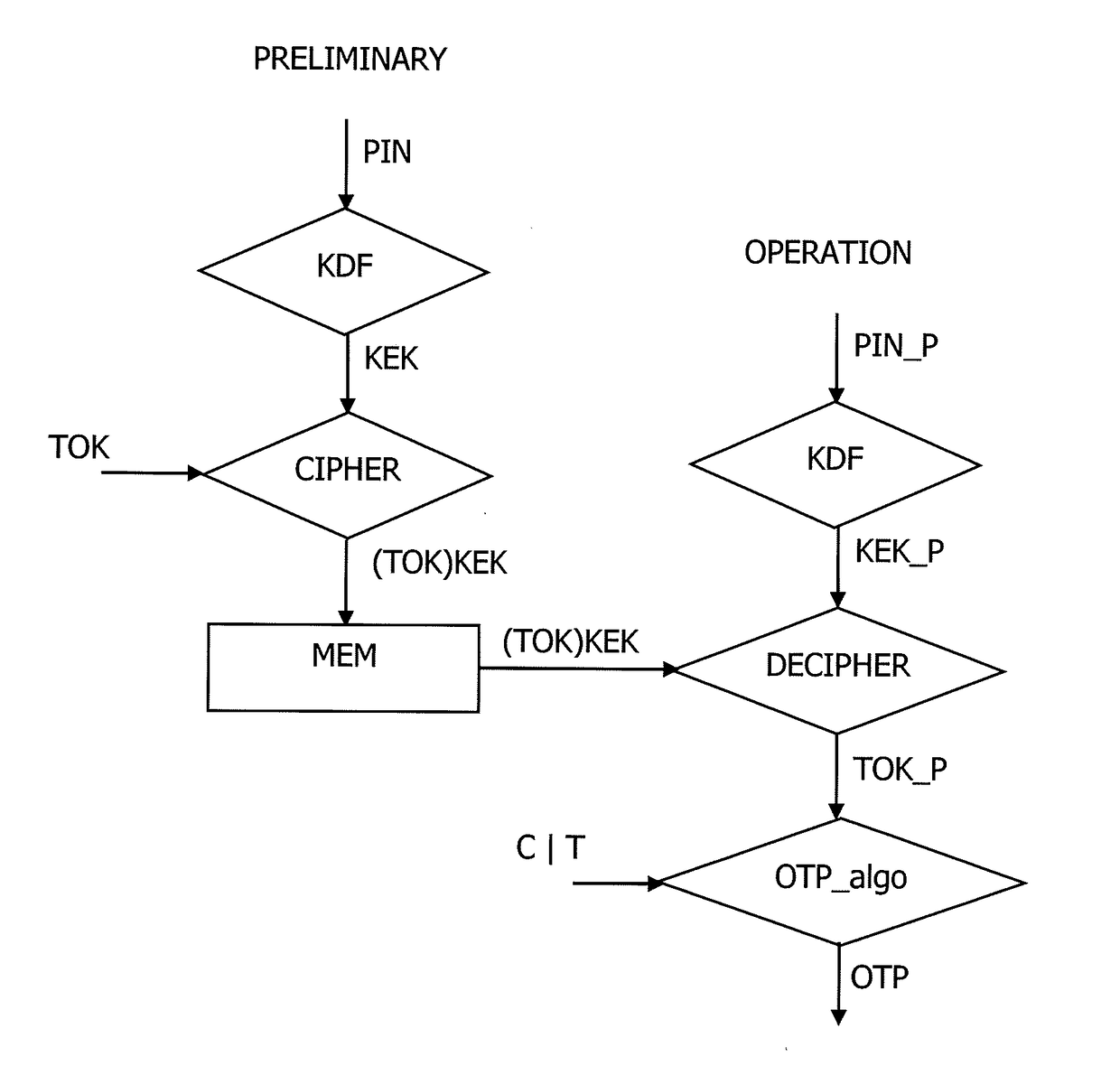
InactiveUS20170104739A1Synchronising transmission/receiving encryption devicesUser identity/authority verificationPersonal identification numberUser device
The present invention relates to a method to manage a One Time Password key, referenced OTP key, used in an OTP algorithm in a user device having access to an unsafe storage including the steps of retrieving a Personal Identification Number, named PIN, of a user of the user device, deriving a symmetric key from the PIN, encrypting the OTP key using the derived symmetric key, storing the encrypted OTP key in the unsafe storage, decrypting the OTP key using the derived symmetric key, and generating a next OTP key using an incremental parameter, wherein the start value of the incremental parameter of the OTP key generation is random.
Owner:GEMPLU
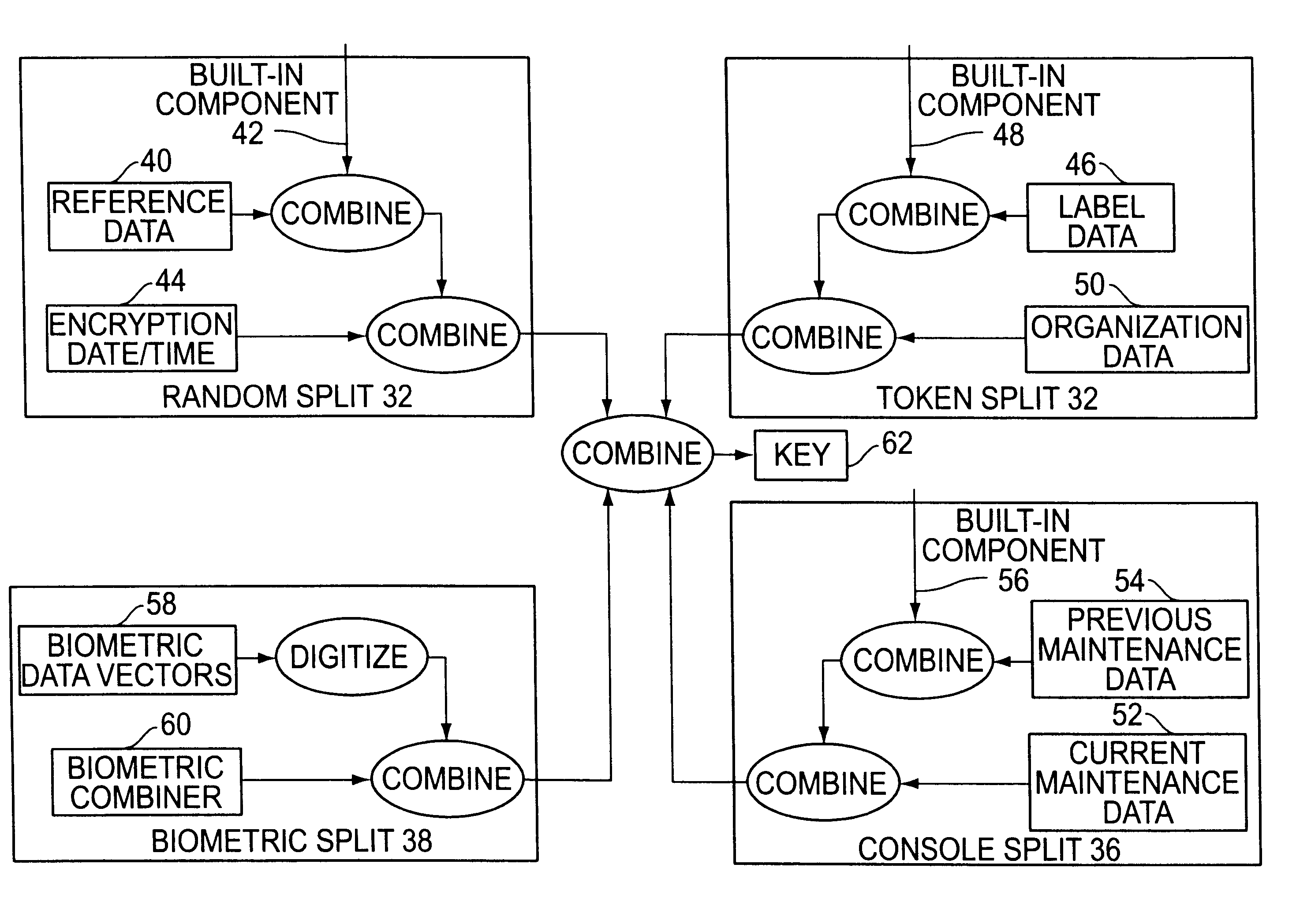
Cryptographic key split combiner
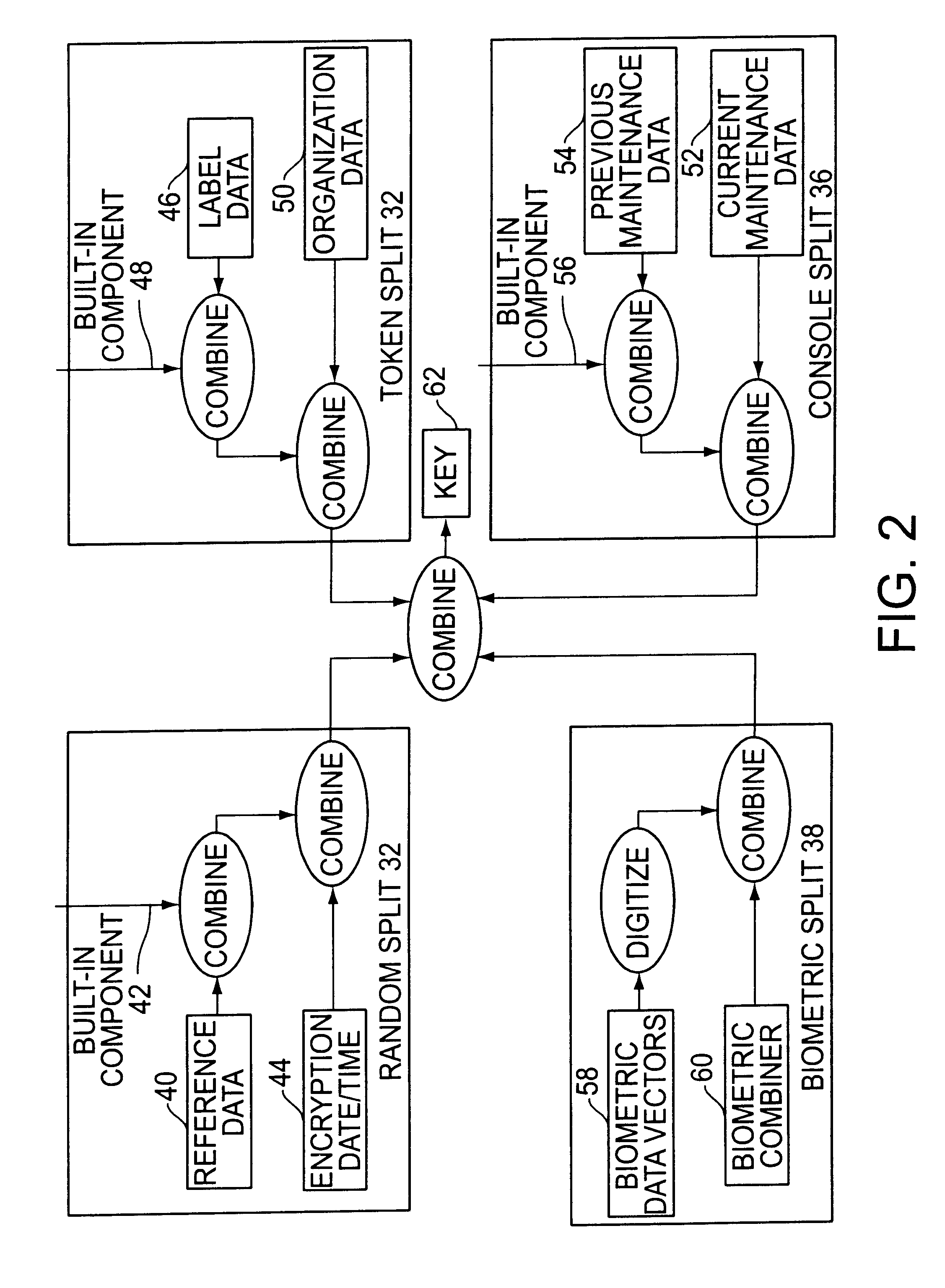
InactiveUS6542608B2Improve securityKey distribution for secure communicationSynchronising transmission/receiving encryption devicesBiometric dataLabeled data
A cryptographic key split combiner, which includes a number of key split generators for generating cryptographic key splits and a key split randomizer for randomizing the cryptographic key splits to produce a cryptographic key, and a process for forming cryptographic keys. Each of the key split generators generates key splits from seed data. The key split generators may include a random split generator for generating a random key split based on reference data. Other key split generators may include a token split generator for generating a token key split based on label data, a console split generator for generating a console key split based on maintenance data, and a biometric split generator for generating a biometric key split based on biometric data. All splits may further be based on static data, which may be updated, for example by modifying a prime number divisor of the static data. The label data may be read from a storage medium, and may include user authorization data. The resulting cryptographic key may be, for example, a stream of symbols, at least one symbol block, or a key matrix.
Owner:TECSEC
Digital readout method and apparatus
InactiveUS20100226495A1Television system detailsSynchronising transmission/receiving encryption devicesDetector arrayReadout integrated circuit
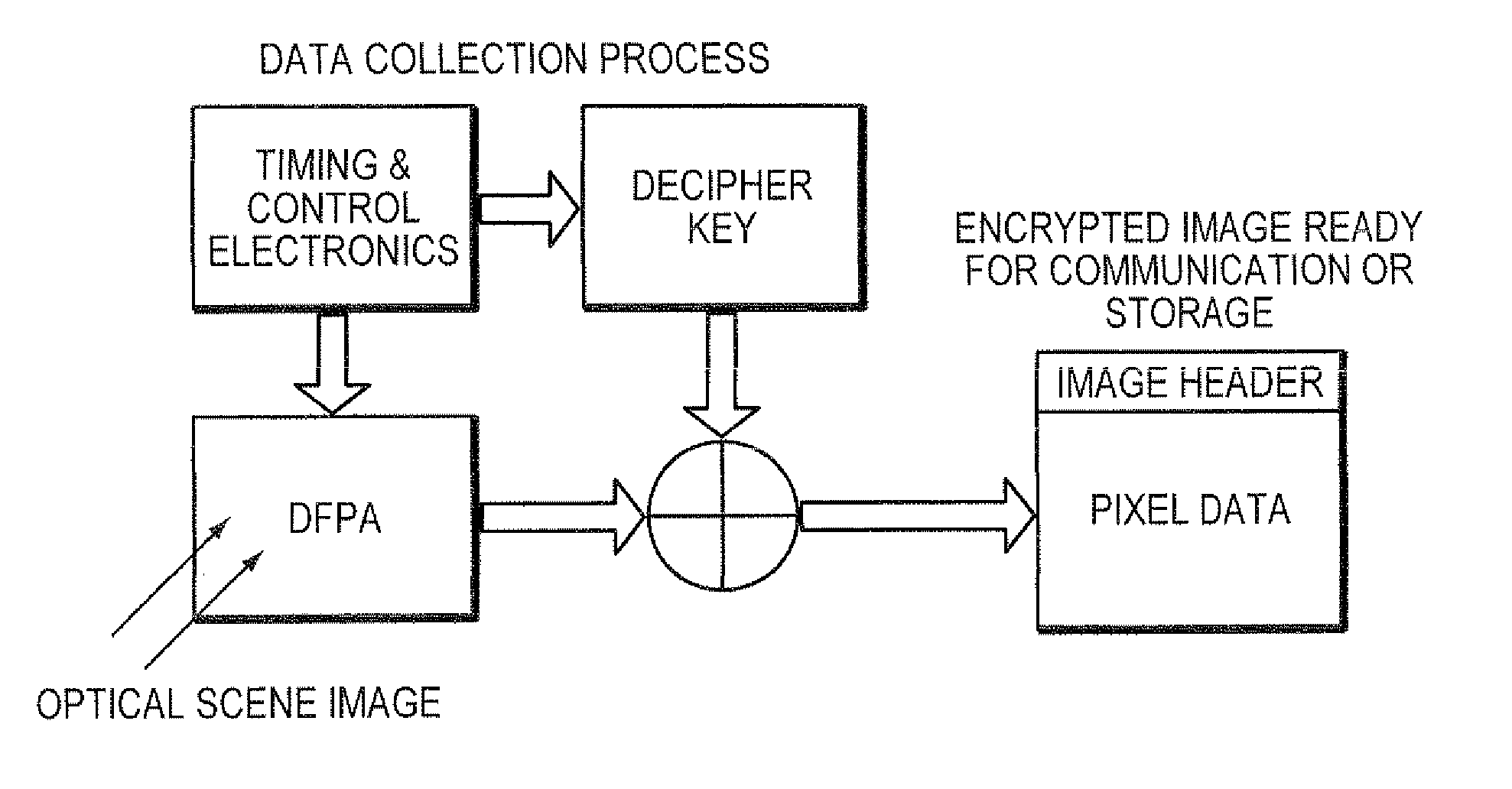
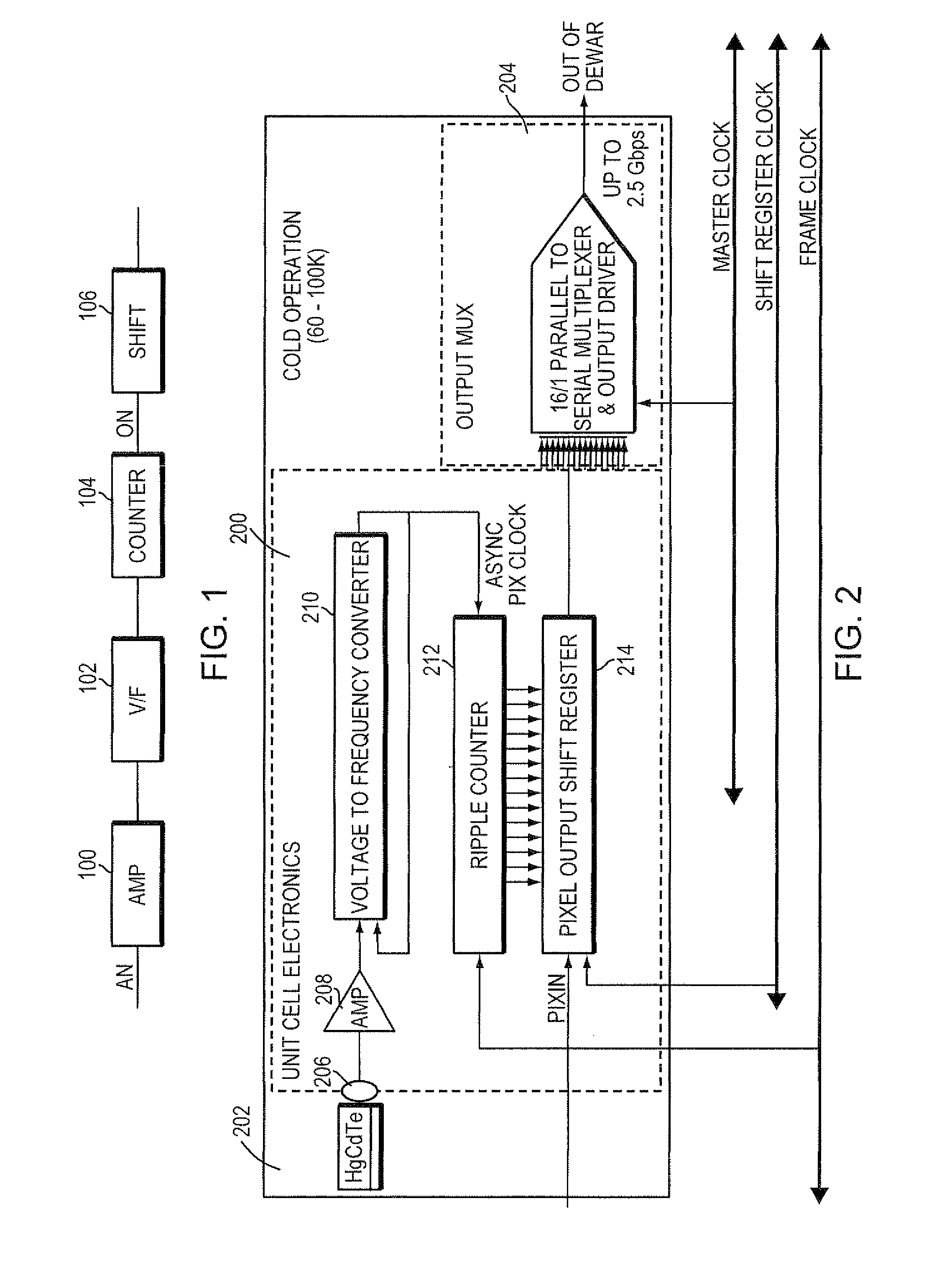
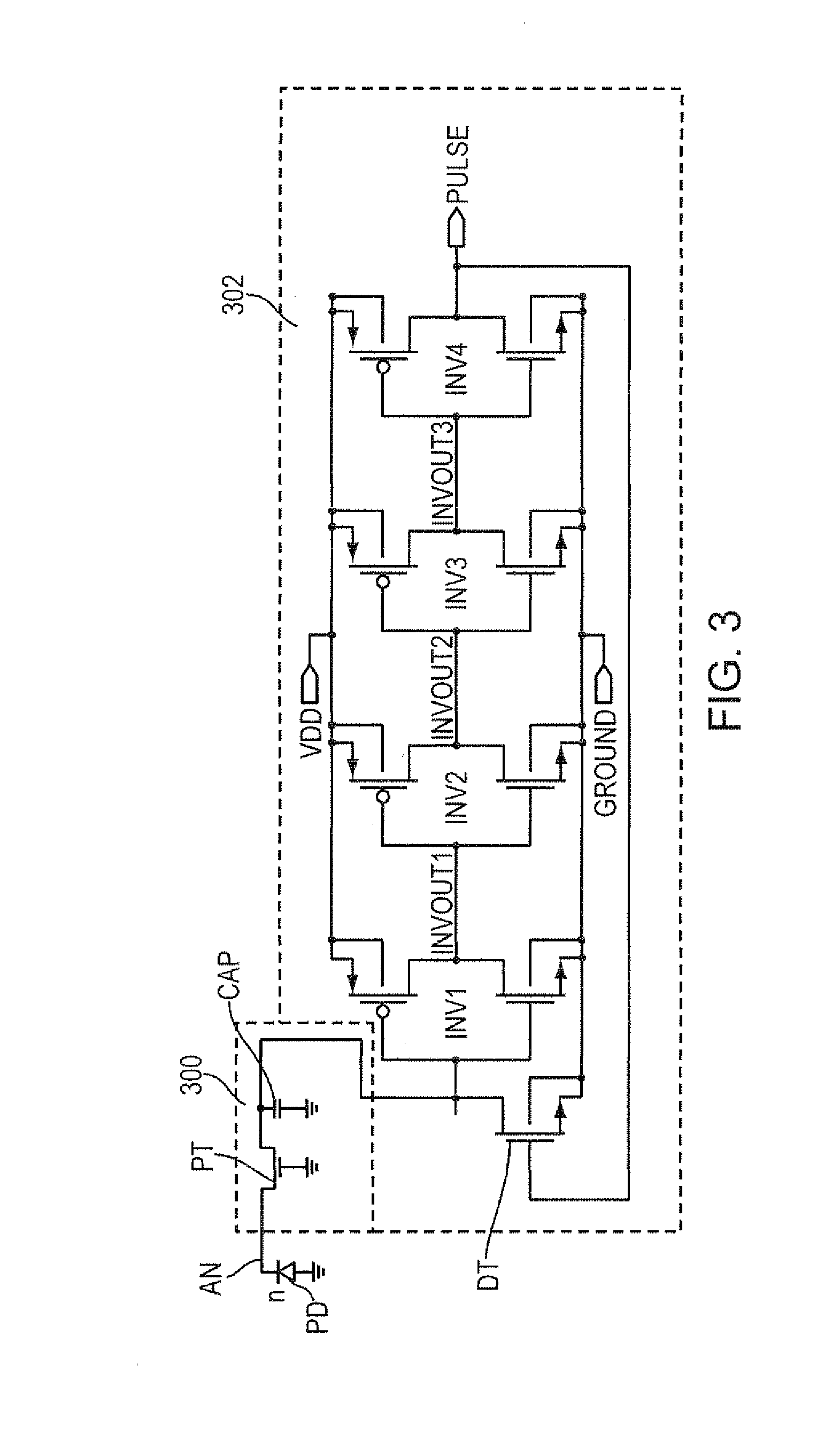
A digital focal plane array includes an all-digital readout integrated circuit in combination with a detector array. The readout circuit includes unit cell electronics, orthogonal transfer structures, and data handling structures. The unit cell electronics include an analog to digital converter. Orthogonal transfer structures enable the orthogonal transfer of data among the unit cells. Data handling structures may be configured to operate the digital focal plane array as a data encryptor / decipherer. Data encrypted and deciphered by the digital focal plane array need not be image data.
Owner:MASSACHUSETTS INST OF TECH
Computerized person-to-person payment system and method without use of currency
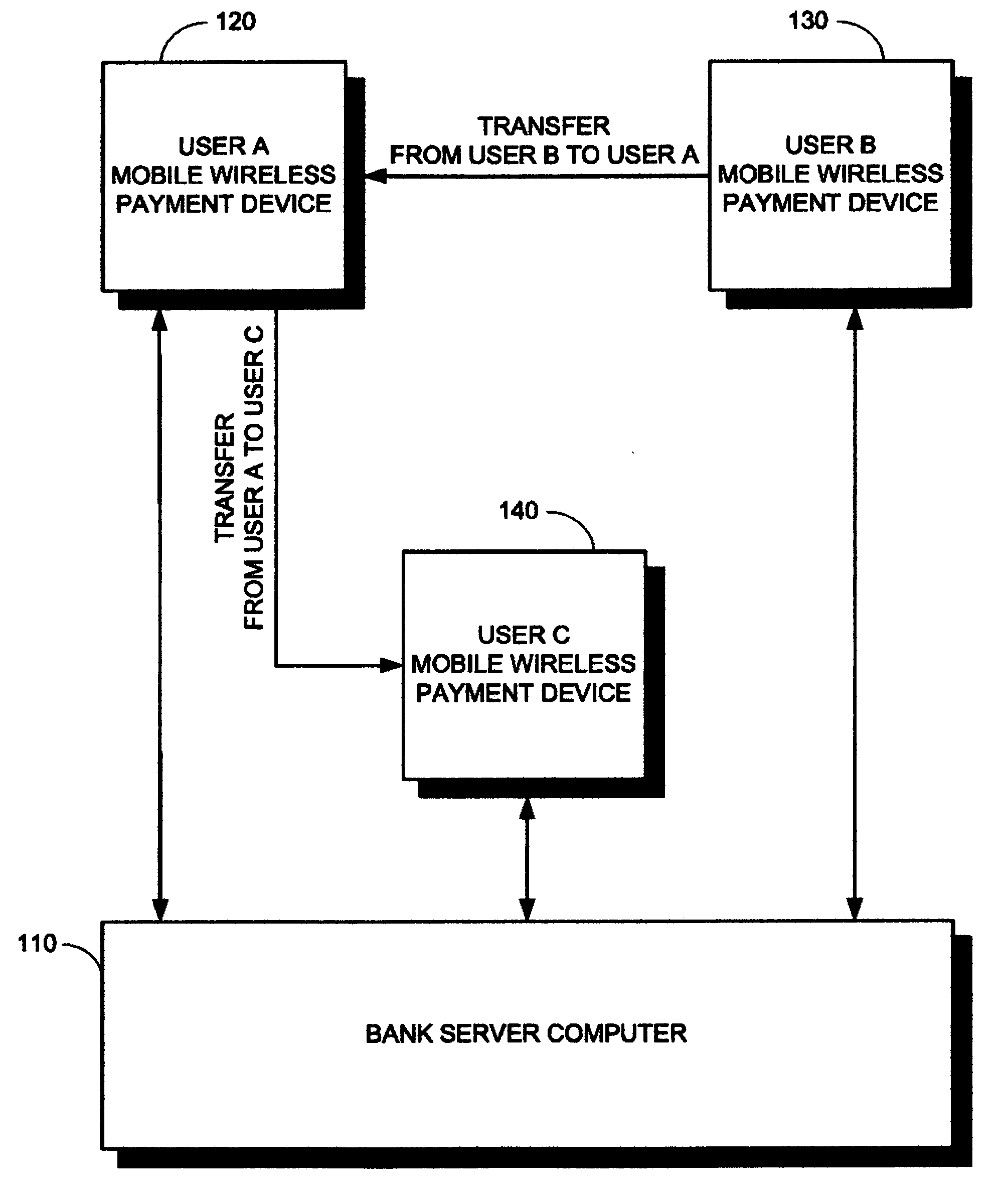
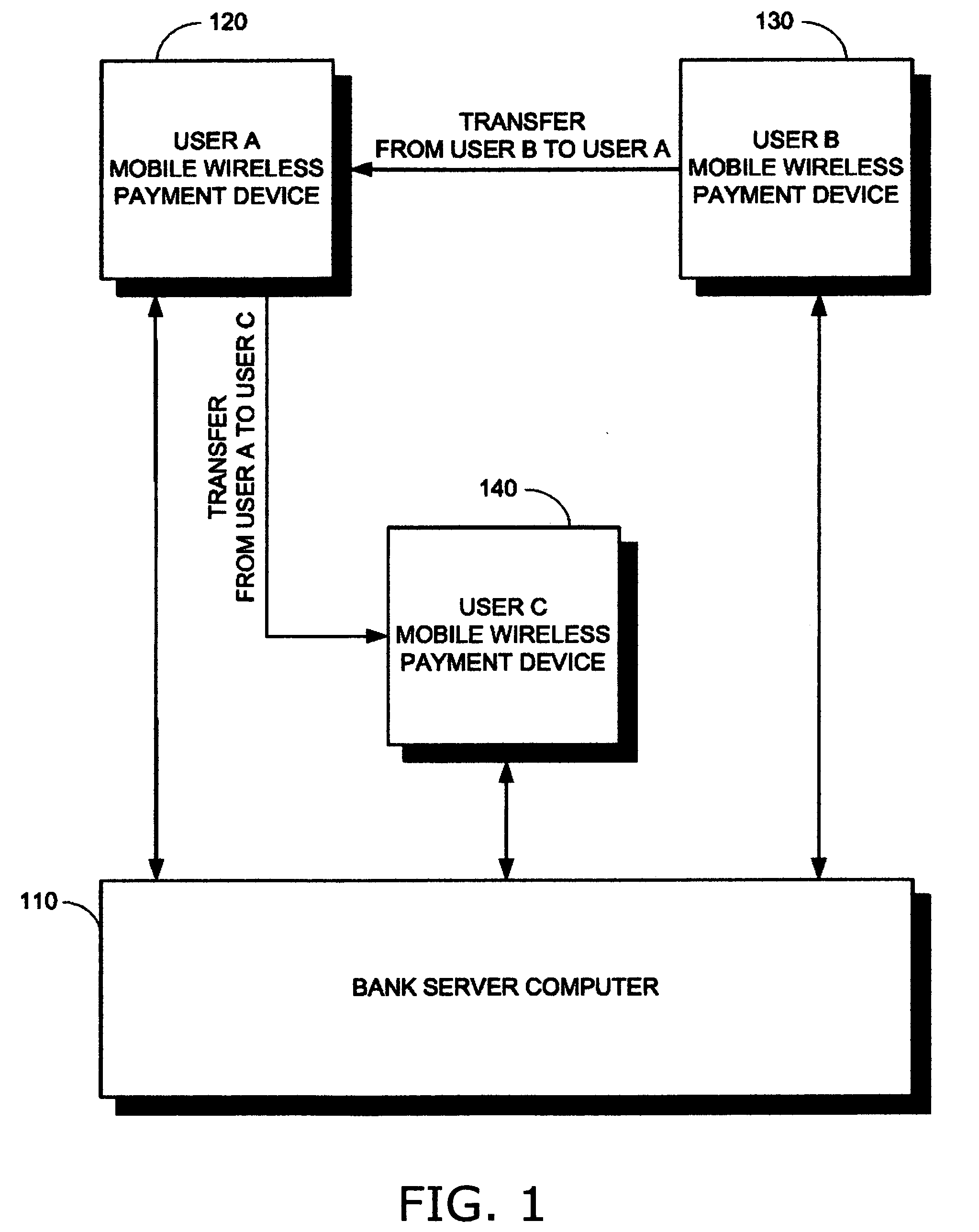
InactiveUS20080177668A1Maximum protection of privacyMaximum protectionSynchronising transmission/receiving encryption devicesFinanceBank accountClient-side
An electronic funds system, including a plurality of payment devices, each payment device including a payment application for (i) transferring funds to another payment device, (ii) receiving funds from another payment device, and (iii) synchronizing transactions with a bank server computer, a queue manager for queuing transactions for synchronization with the bank server computer, an encoder for encrypting transaction information, a proximity communication module for wirelessly communicating with another of the plurality of payment devices over a short range, a wireless communication module for communicating with a client computer and with the bank server computer over a long range, a plurality of client computers, each client computer including a payment device manager for (i) transmitting funds to a payment device, (ii) receiving funds from a payment device, and (iii) setting payment device parameters, and a wireless communication module for communicating with at least one of the plurality of payment devices and with a bank server computer over a long range, and at least one bank server computer, each bank server computer including an account manager for (i) managing at least one bank account associated with at least one of the payment devices, and (ii) processing transactions received from the plurality of payment devices, a decoder for decrypting encrypted transaction information, and a wireless communication module for communicating with the plurality of payment devices and with the plurality of client computers over a long range. A method and a computer-readable storage medium are also described and claimed.
Owner:DELEAN BRUNO
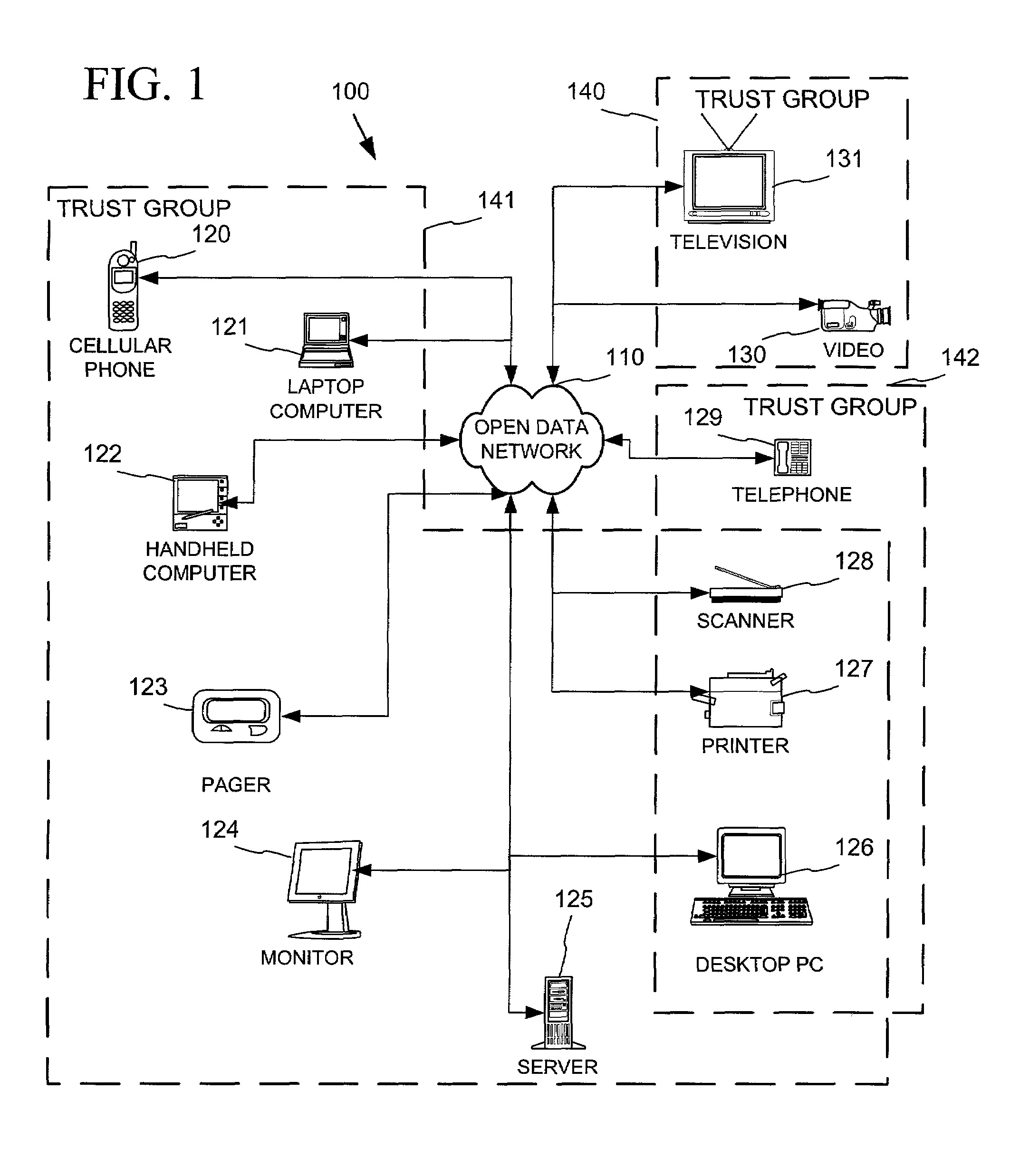
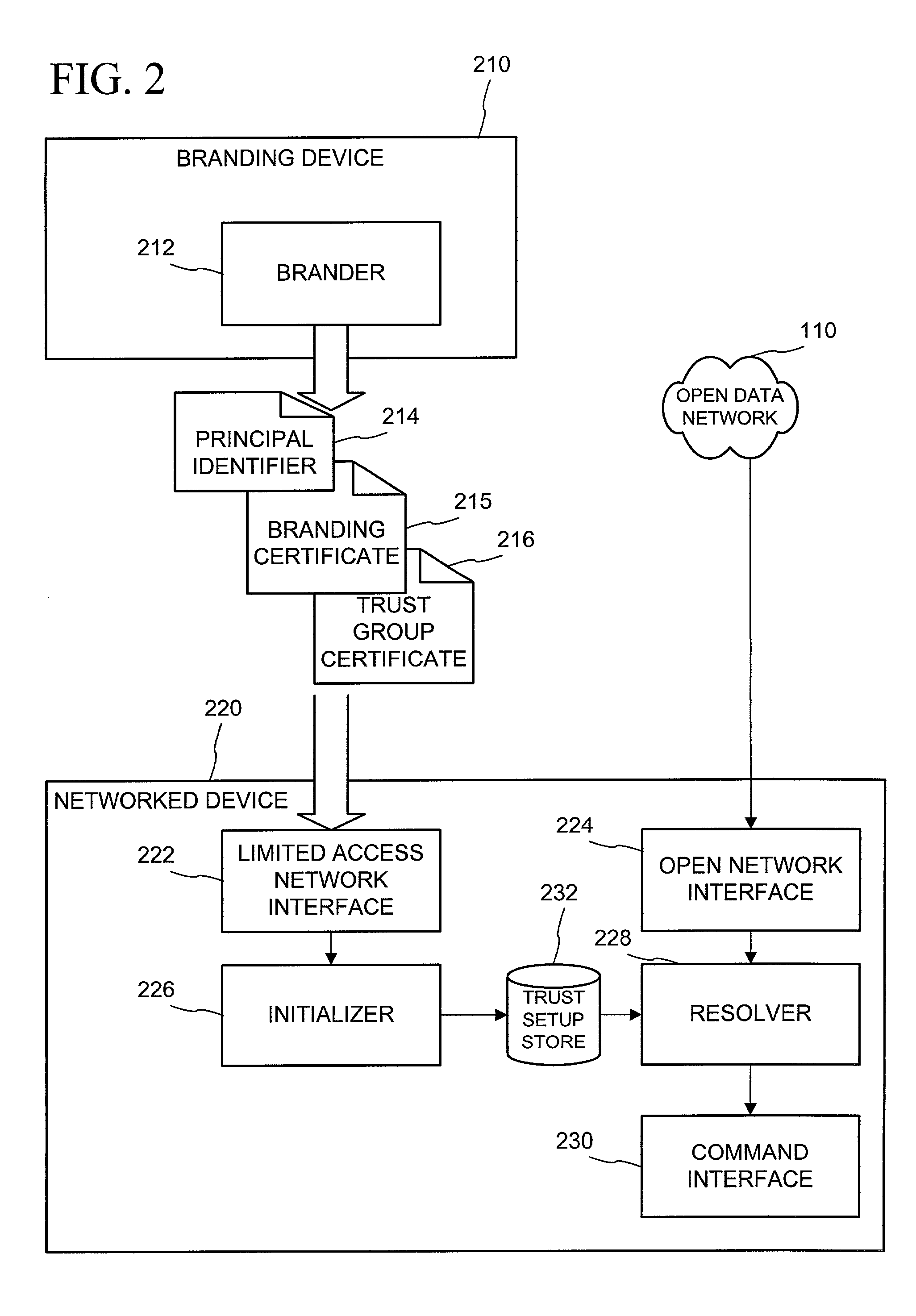
Networked device branding for secure interaction in trust webs on open networks
InactiveUS7500104B2CostSynchronising transmission/receiving encryption devicesDigital data processing detailsLimited accessNetwork media
A branding process provides a networked computing device with initial set up information, including a name, a public / private key pair, and a set of certificates the device will need to inter-operate with other devices in the trust group. A branding device conveys the initial set-up information to the networked computing device via a limited access network interface, or alternatively via a broadcast network media with the device enclosed in a wave guide and / or Faraday cage. The networked computing device can then use the set up information to verify that other devices on the network that seek to interact with the device are also members of the trust group, with which networked computing device can interact.
Owner:MICROSOFT TECH LICENSING LLC
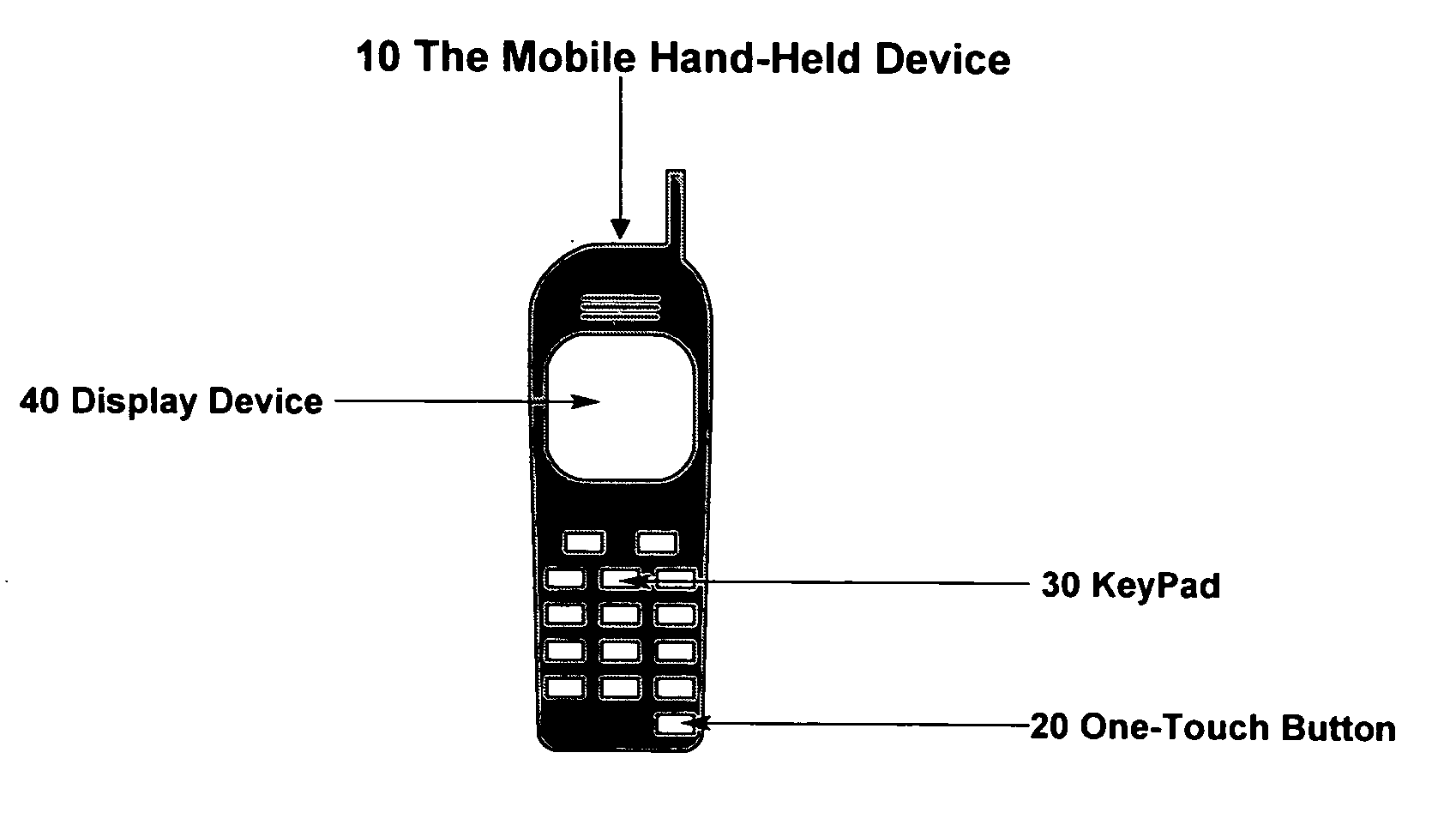
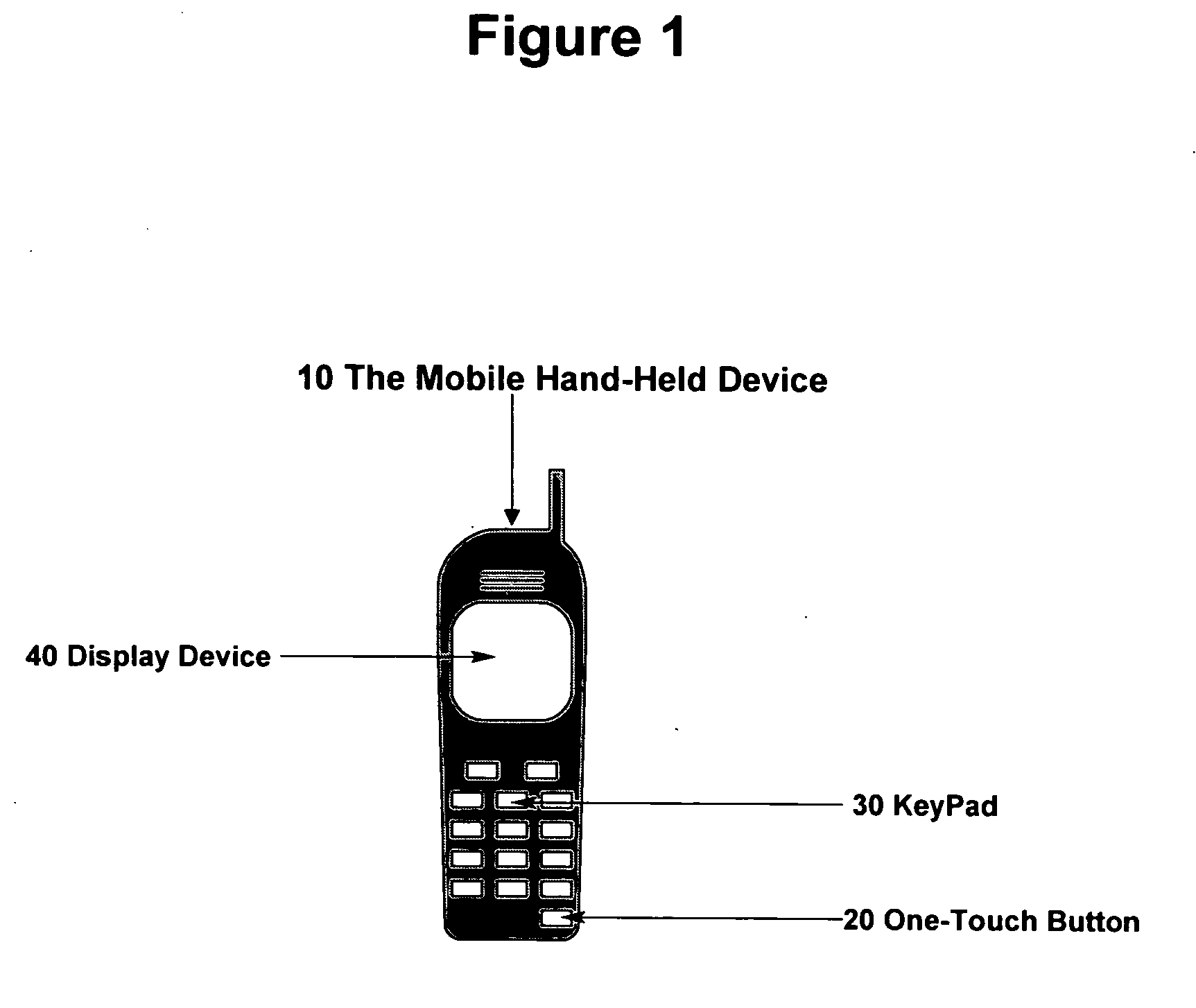
Method and apparatus for generating one-time password on hand-held mobile device
InactiveUS20060136739A1Easy to useSimple and easySynchronising transmission/receiving encryption devicesUnauthorised/fraudulent call preventionKey exchangeWeb service
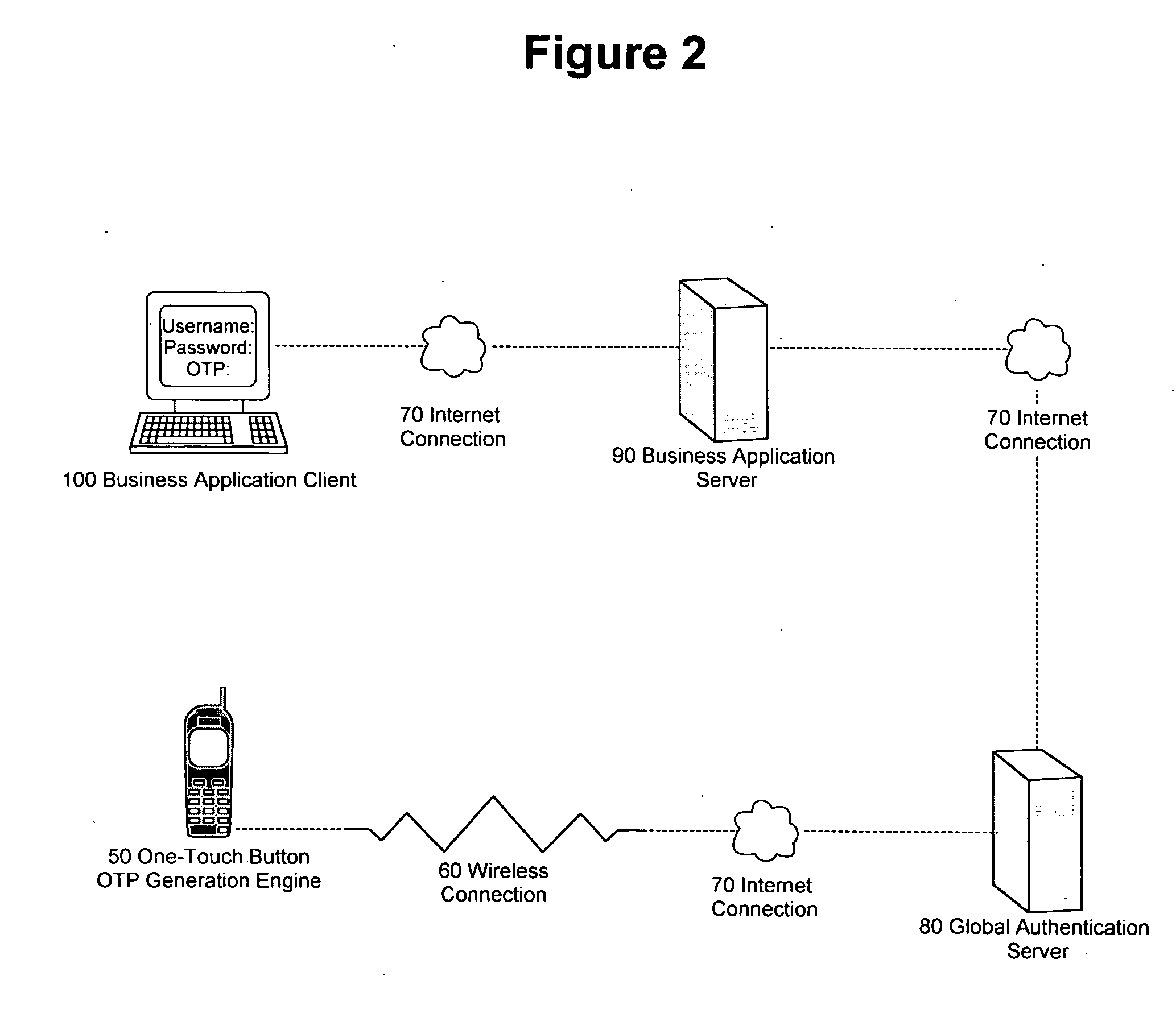
According to the invention, a system and an apparatus to use the One-Touch button on a mobile hand-held device to generate one time passwords (OTP) are disclosed. Components of this system comprise: a mobile hand-held device, a built-in One-Touch button on the mobile device, a Global Authentication Server, and an OTP Generation engine installed and ran on the mobile device. The mobile device user only needs to push the One-Touch button and an OTP is generated. The OTP is generated on the mobile device by the OTP generation engine after a secure key exchange process is performed between the remote Global Authentication Server and the mobile device. The mobile device is registered to use online web services that recognize the OTP through the Global Authentication Service. Online web services require that the user enter a combination of the user's known password and OTP for identity assurance. As a result of this invention, users will quickly adopt the two-factor authentication method as a central means to identify themselves.
Owner:BROCK CHRISTIAN +1
Network Security System
InactiveUS20090077379A1Limited accessSynchronising transmission/receiving encryption devicesUser identity/authority verificationComputer hardwareSecret share
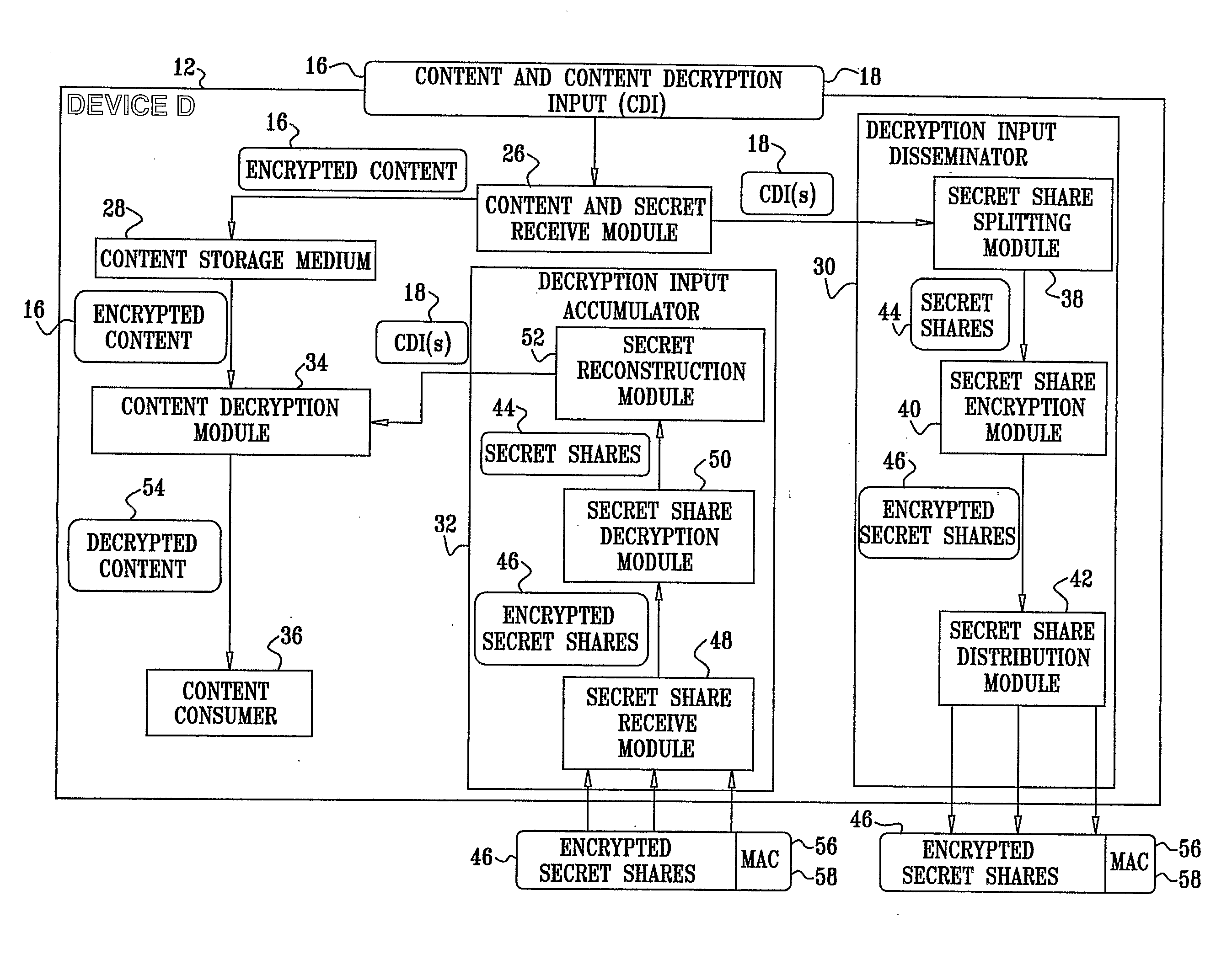
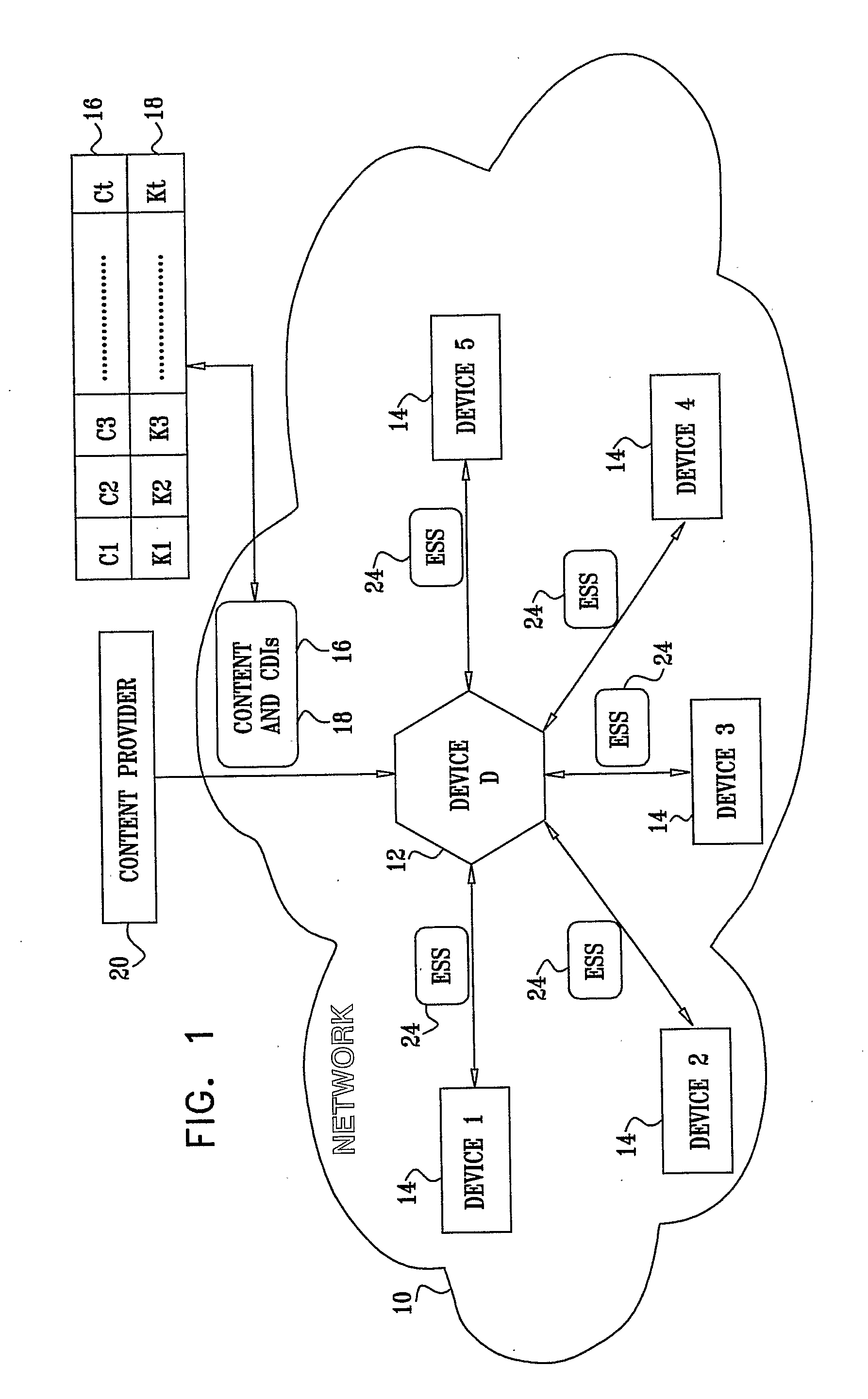
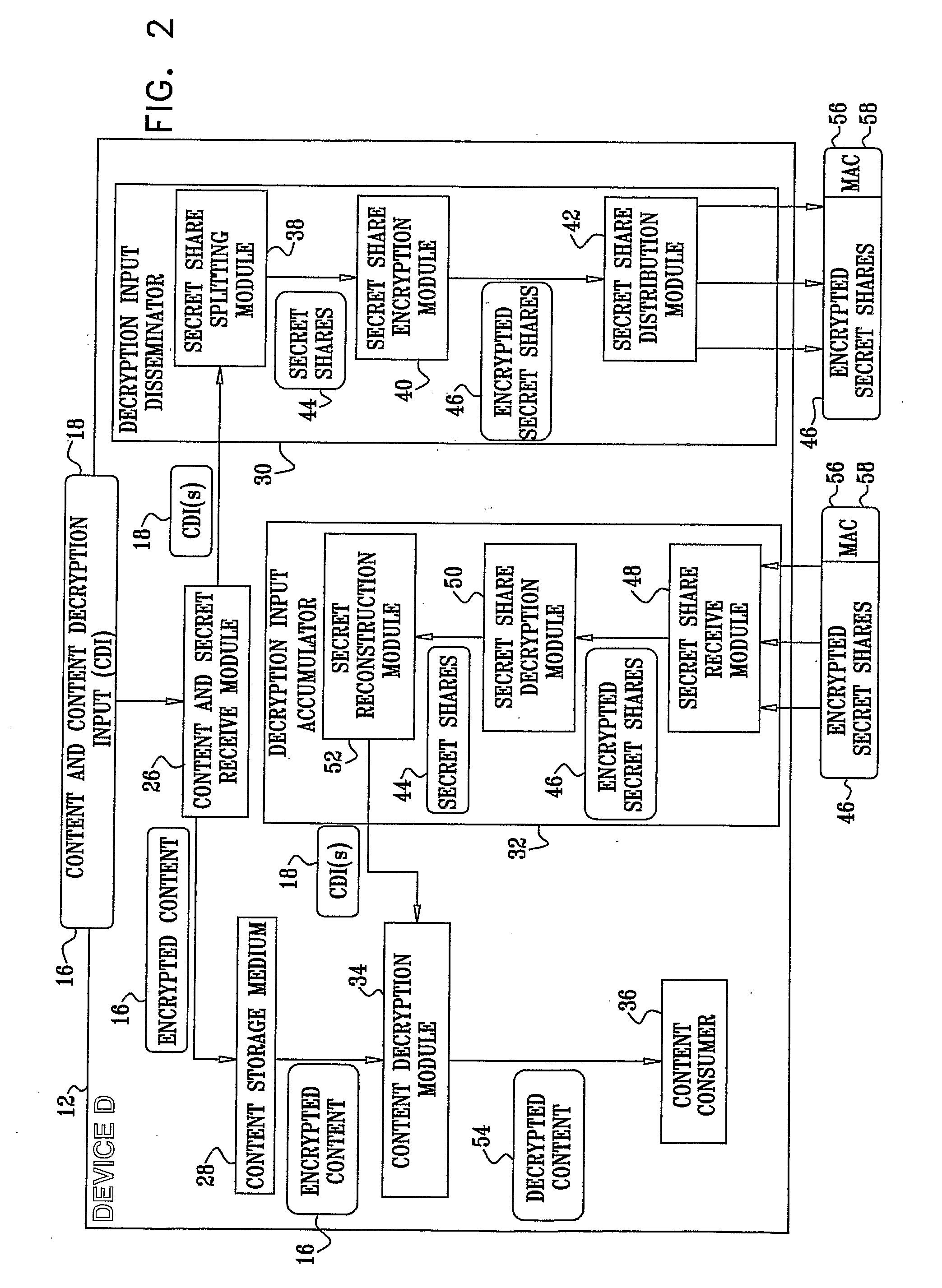
A system for restricting access to encrypted content stored in a consuming device (12) which is part of a network (10) including other devices (14), the system including a content storage medium to store the encrypted content, a secret-share distribution module to distribute secret-shares to the other devices (14), a secret-share receive module to receive the secret-shares from the other devices (14), a secret reconstruction module to form a content decryption input from the secret-shares received by the secret-share receive module, a content decryption module to receive the encrypted content from the content storage medium and the content decryption input from the secret reconstruction module and decrypt the encrypted content using the content decryption input thereby rendering decrypted content, and a content consumer to use the decrypted content, wherein the secret shares distributed to the other devices (14) are in an encrypted format for decryption by the consuming device (12) or the other devices (14).
Owner:CISCO TECH INC +1
Cryptographic communications using pseudo-randomly generated cryptography keys
InactiveUS7120696B1High strengthImprove securitySynchronising transmission/receiving encryption devicesRandom number generatorsSecure communicationCommunications system
An apparatus and method for generating pseudo-random cryptographic keys in a cryptographic communications system, whereby, given a common set of initializing configuration data, the pseudo-random cryptographic keys can be duplicatively generated by various independent pseudo-random key generators of the cryptographic communications system. In accordance with the preferred embodiment of the present invention, users of the communications system can each possess an independent pseudo-random key generator to securely communicate with other users also holding independent pseudo-random key generator that share the same initialization configuration data, no matter where the other users are located or whether the users are connected via wire or wireless communication network. The present invention facilitates secure communication without the need to transport decryption keys in advanced, thereby reducing the risk of the secure communication becoming compromised via interception of decryption keys.
Owner:STEALTHKEY
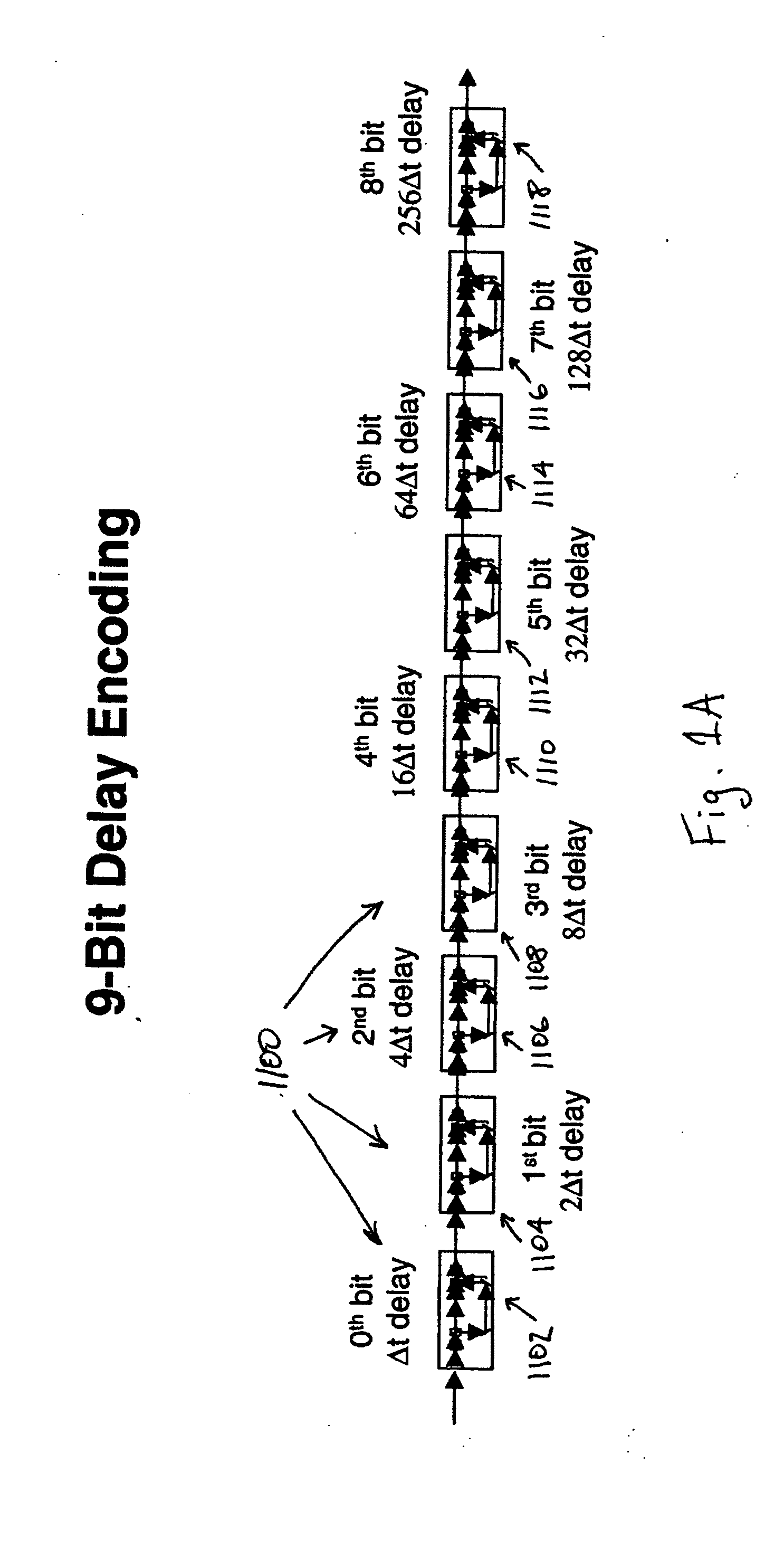
Secure quantum key distribution using entangled photons
InactiveUS20050135620A1High data rateImprove securityKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer hardwareData rate
A system and method of implementing quantum key distribution are provided that possess increased data rates and enhanced security. These increased data rates are provided through the use of biphotons. Through encoding bits of information on the intra-biphoton delay time and enabling separate polarization bases for each of the photons comprising each biphoton, the system and method increase data bandwidth available for quantum key distribution.
Owner:GENERAL DYNAMICS ADVANCED INFORMATION SYSTEMS
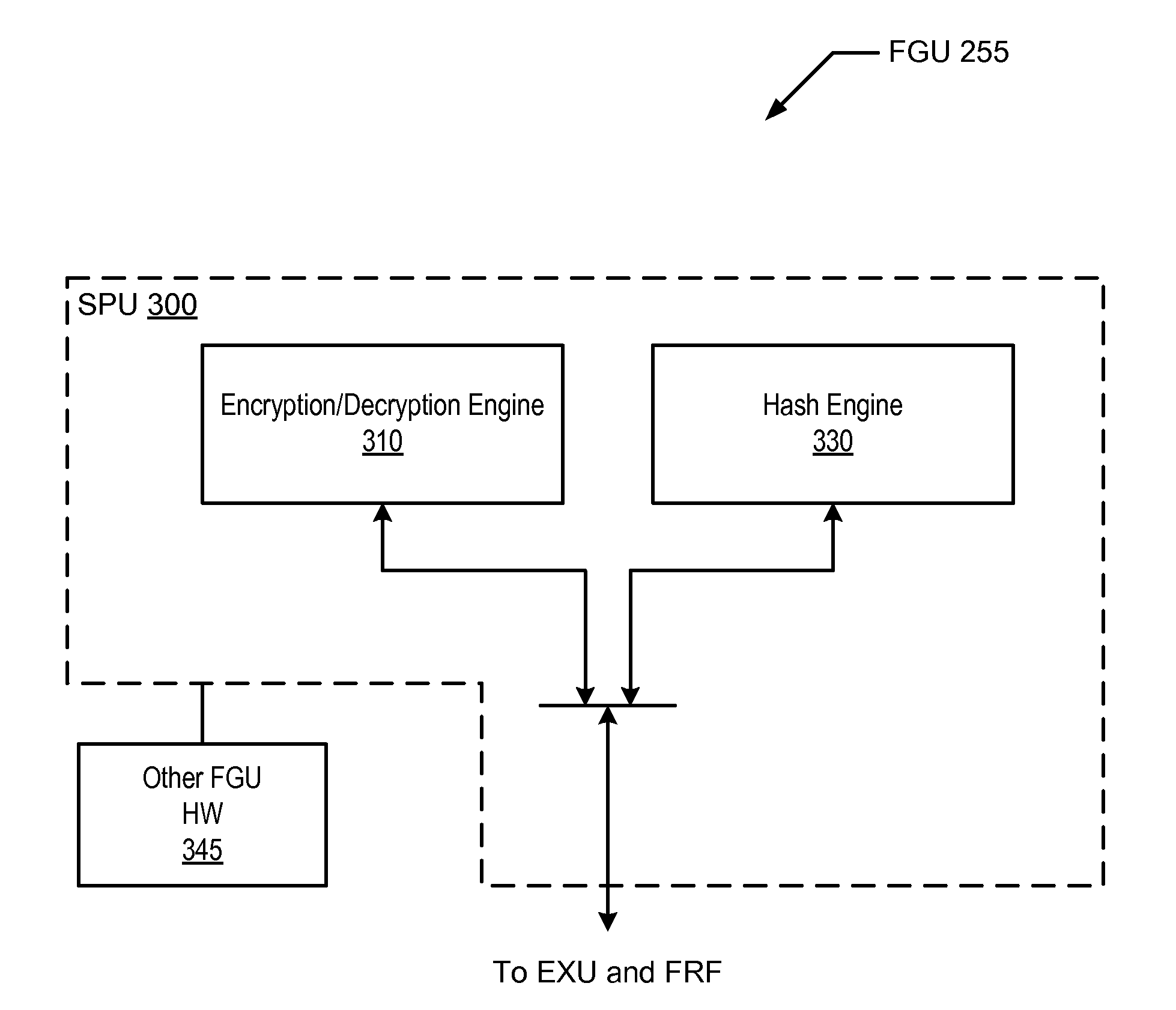
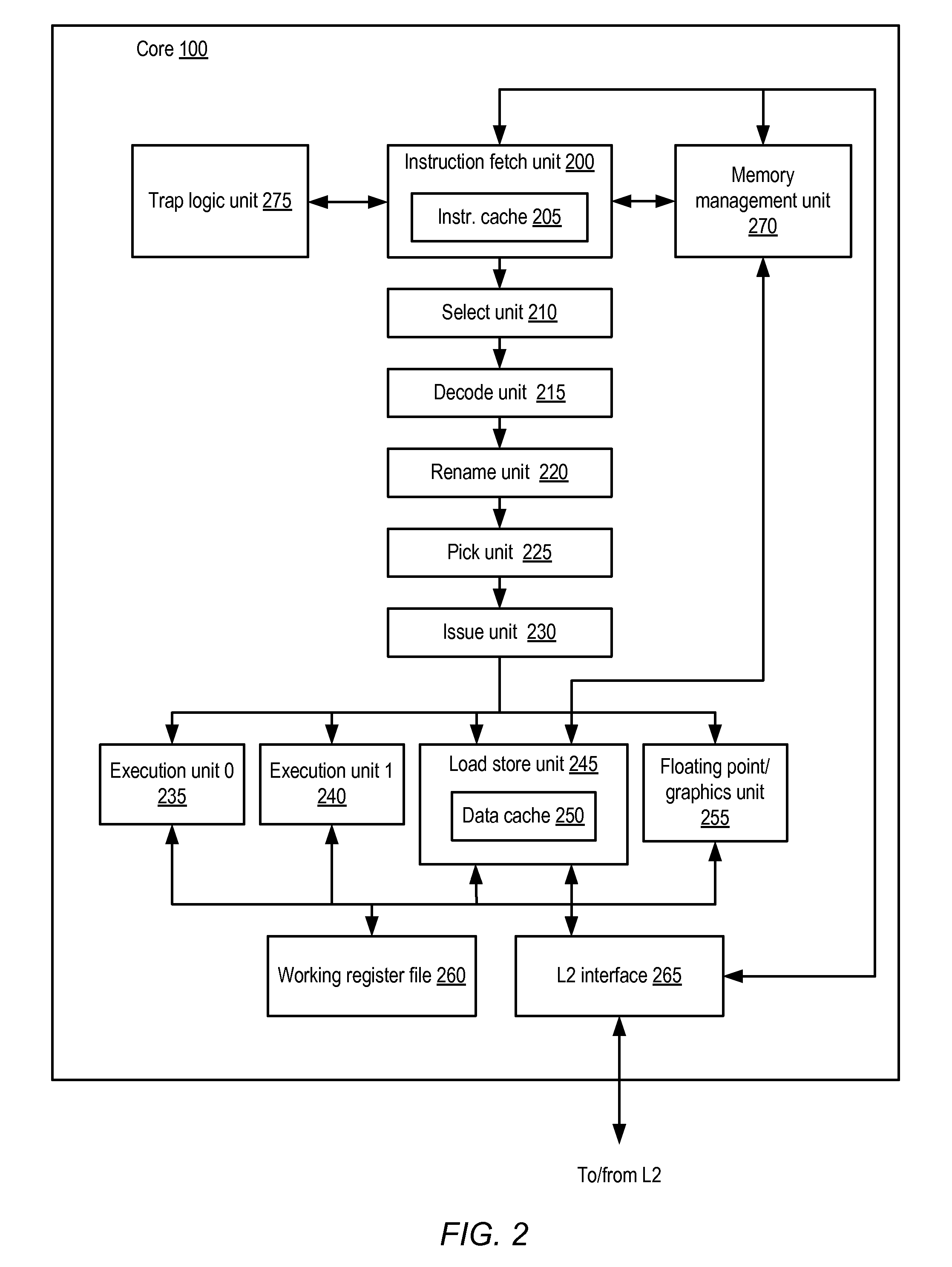
Processor and method for implementing instruction support for hash algorithms
ActiveUS20100250966A1Synchronising transmission/receiving encryption devicesDigital computer detailsComputer hardwareProcessor register
A processor including instruction support for implementing hash algorithms may issue, for execution, programmer-selectable hash instructions from a defined instruction set architecture (ISA). The processor may include a cryptographic unit that may receive instructions for execution. The instructions include hash instructions defined within the ISA. In addition, the hash instructions may be executable by the cryptographic unit to implement a hash that is compliant with one or more respective hash algorithm specifications. In response to receiving a particular hash instruction defined within the ISA, the cryptographic unit may retrieve a set of input data blocks from a predetermined set of architectural registers of the processor, and generate a hash value of the set of input data blocks according to a hash algorithm that corresponds to the particular hash instruction.
Owner:SUN MICROSYSTEMS INC
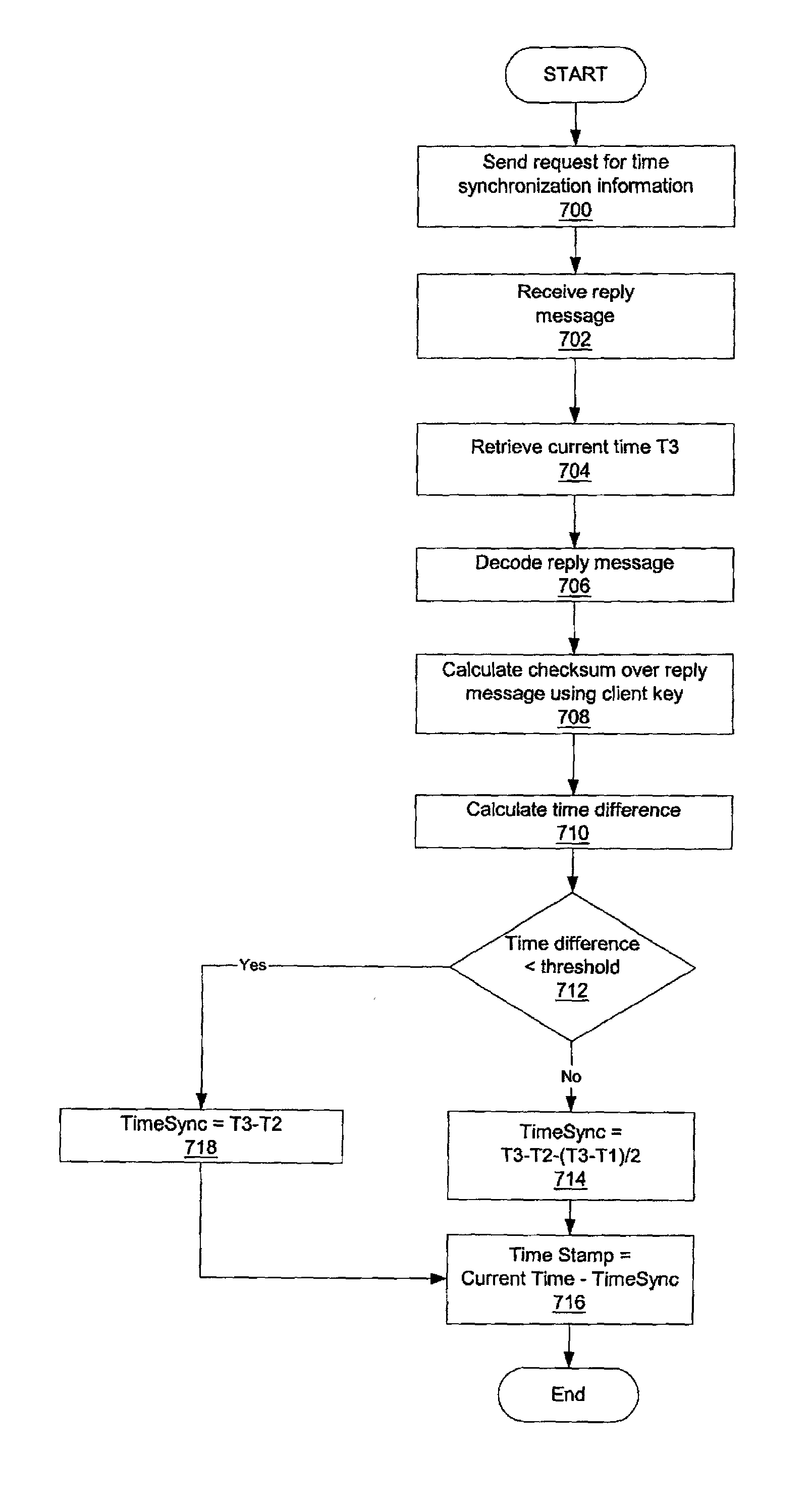
Method and apparatus for time synchronization in a network data processing system
InactiveUS20020078243A1Synchronising transmission/receiving encryption devicesUser identity/authority verificationData processing systemNetwork data
A method, apparatus, and computer implemented instructions for synchronizing time in a network data processing system. A request for time synchronization is received at a target data processing system. A current target time at the target data processing system is placed in a reply. The reply is sent to the source data processing system. A current source time from when the reply is received at the source data processing system is compared to the current target time to generate a comparison. A synchronization factor is generated using the comparison.
Owner:IBM CORP
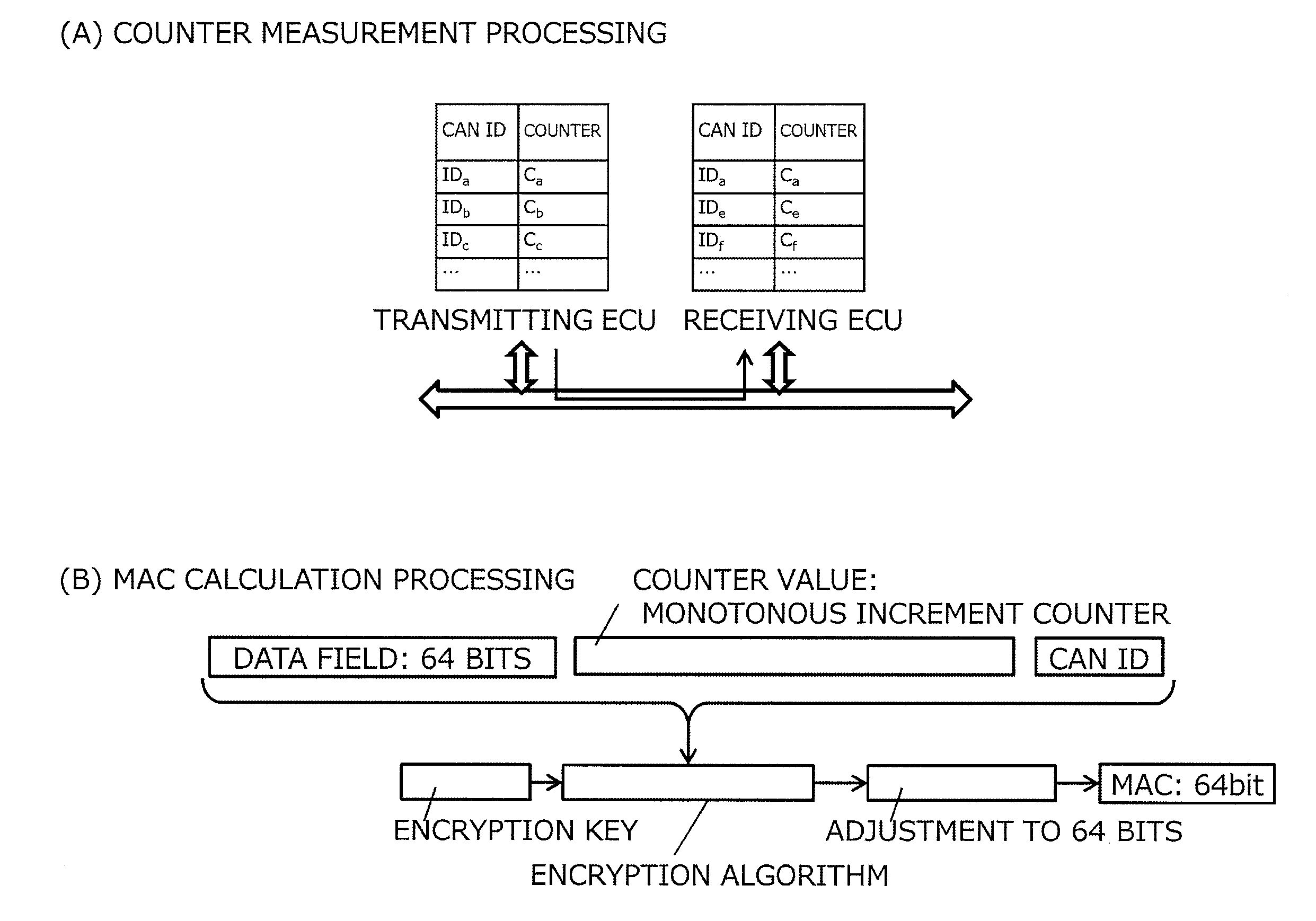
Message authentication method in communication system and communication system
ActiveUS20140310530A1Synchronising transmission/receiving encryption devicesUser identity/authority verificationComputer hardwareCommunications system
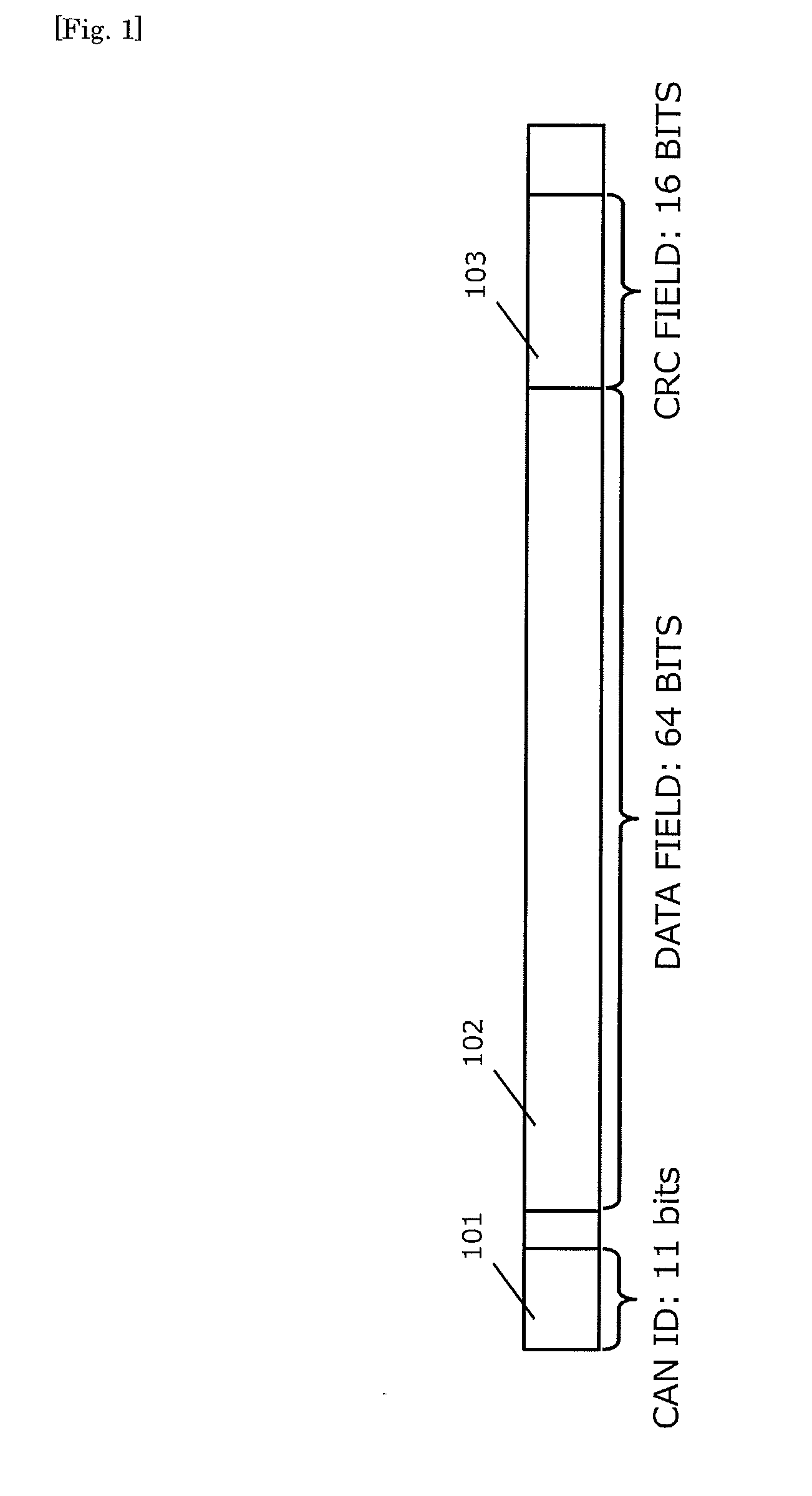
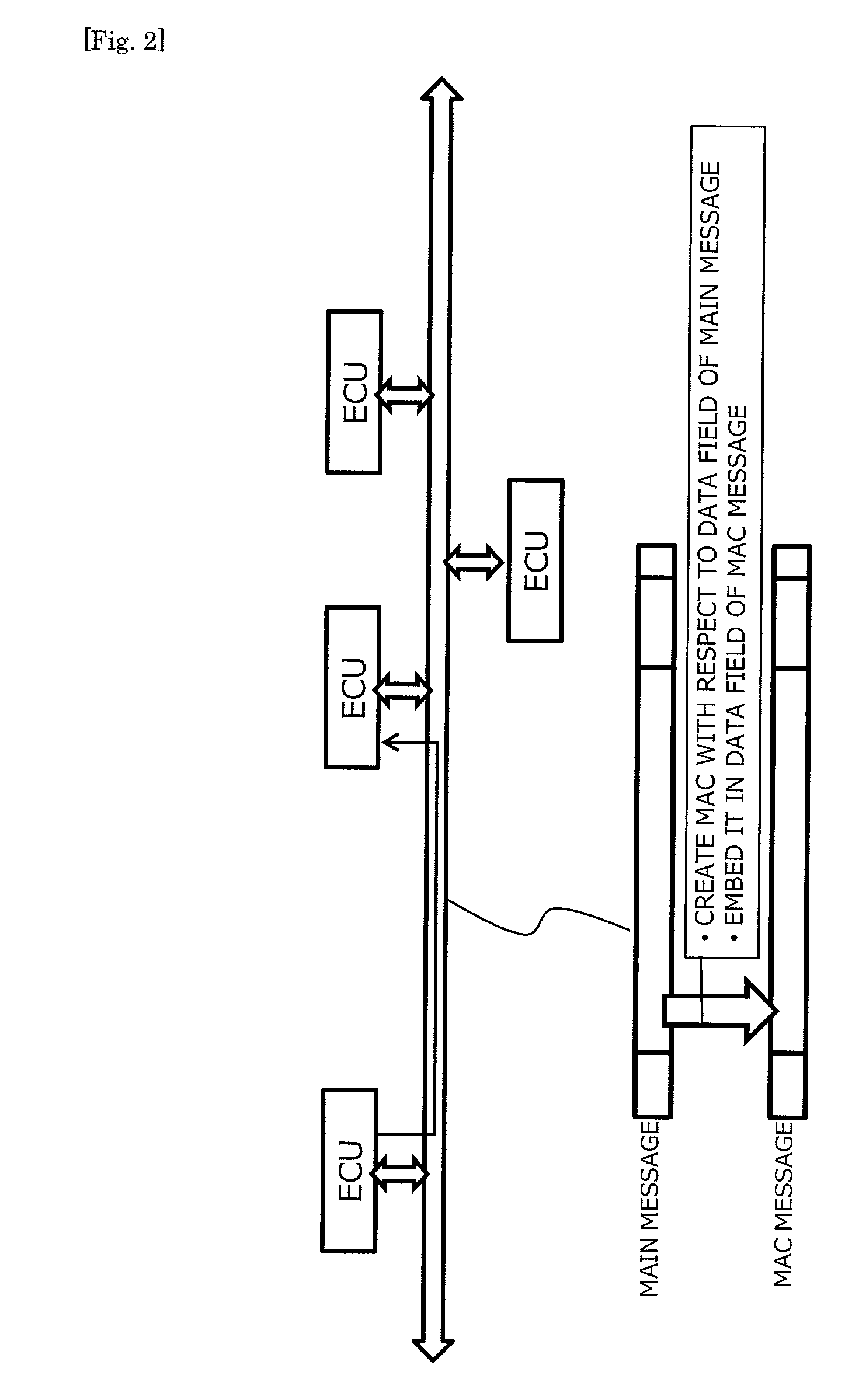
Each of ECUs counts the number of messages transmitted for each of CAN IDs. A transmission node that has transmitted a main message produces an MAC from a data field and the CAN ID in the main message and a counter value corresponding to the CAN ID, and transmits the MAC as an MAC message. A reception node that has received the main message produces an MAC from the data field and the CAN ID contained in the main message and the counter value corresponding to the CAN ID, and determines whether the MAC matches the MAC contained in the MAC message. By so doing, verification whether the main message is valid or not can be made. According to this configuration, message authentication by the MAC can be made without changing a CAN protocol.
Owner:TOYOTA JIDOSHA KK +1
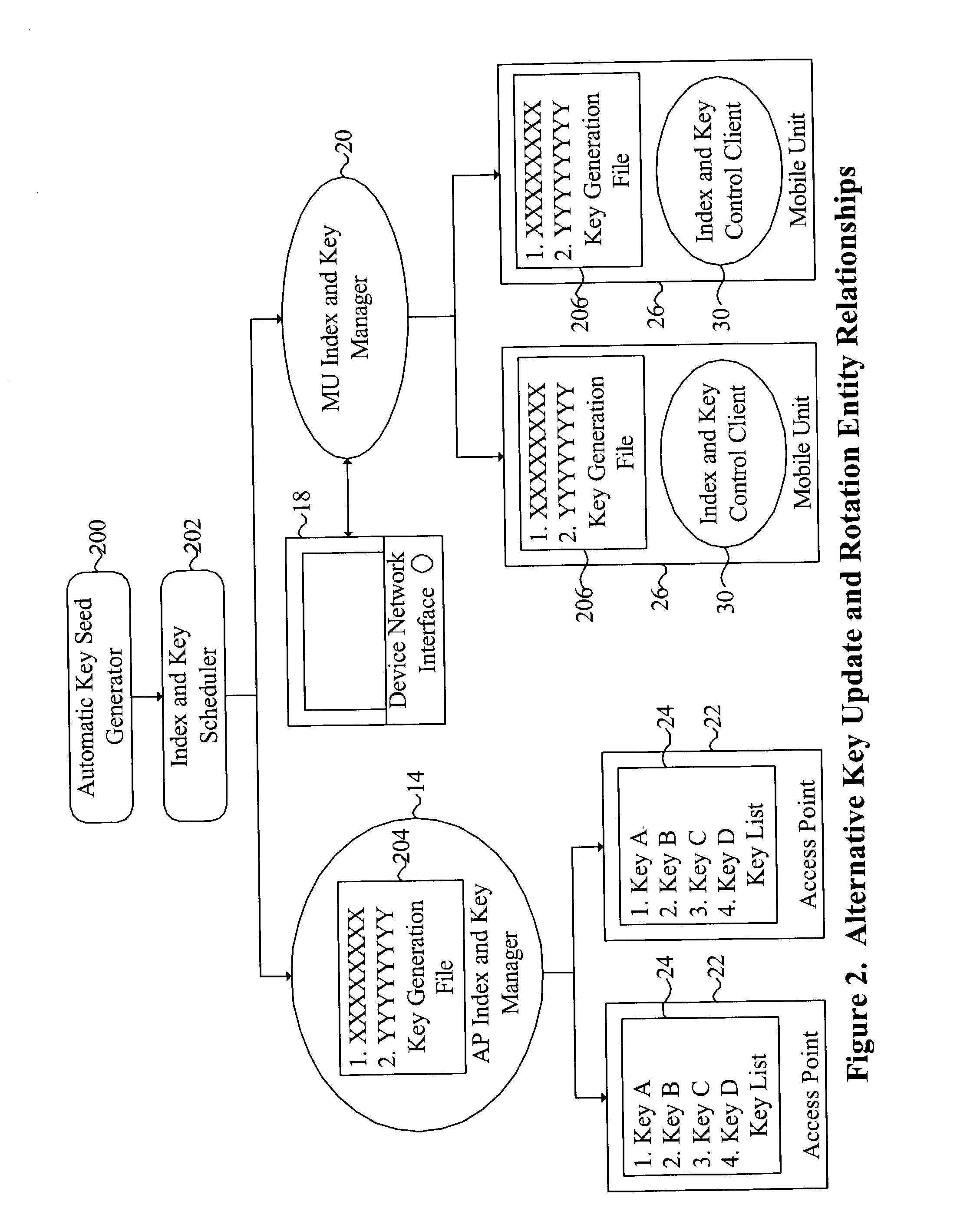
System and method for providing WLAN security through synchronized update and rotation of WEP keys
InactiveUS6965674B2Key distribution for secure communicationSynchronising transmission/receiving encryption devicesSecure communicationPeer-to-peer
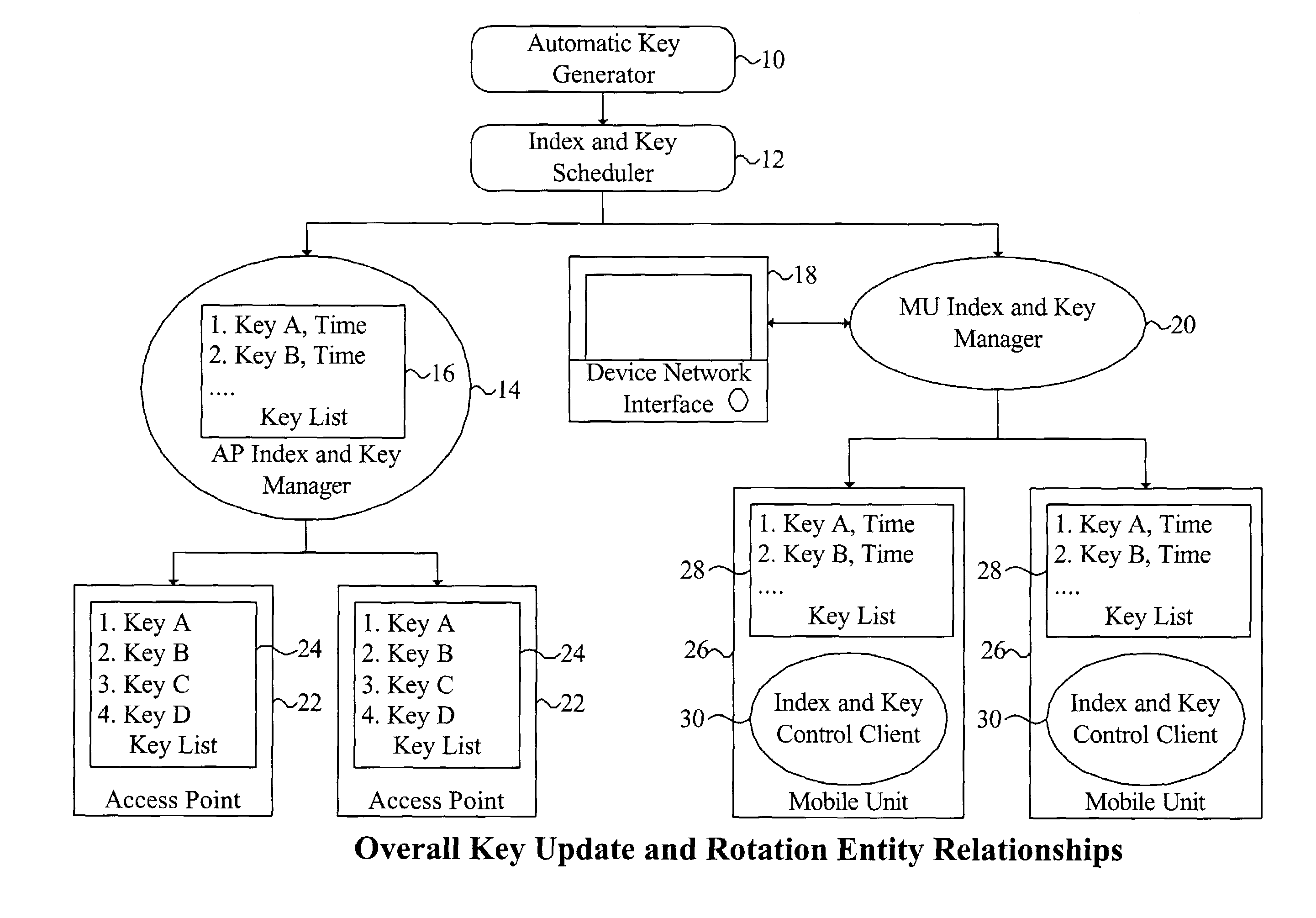
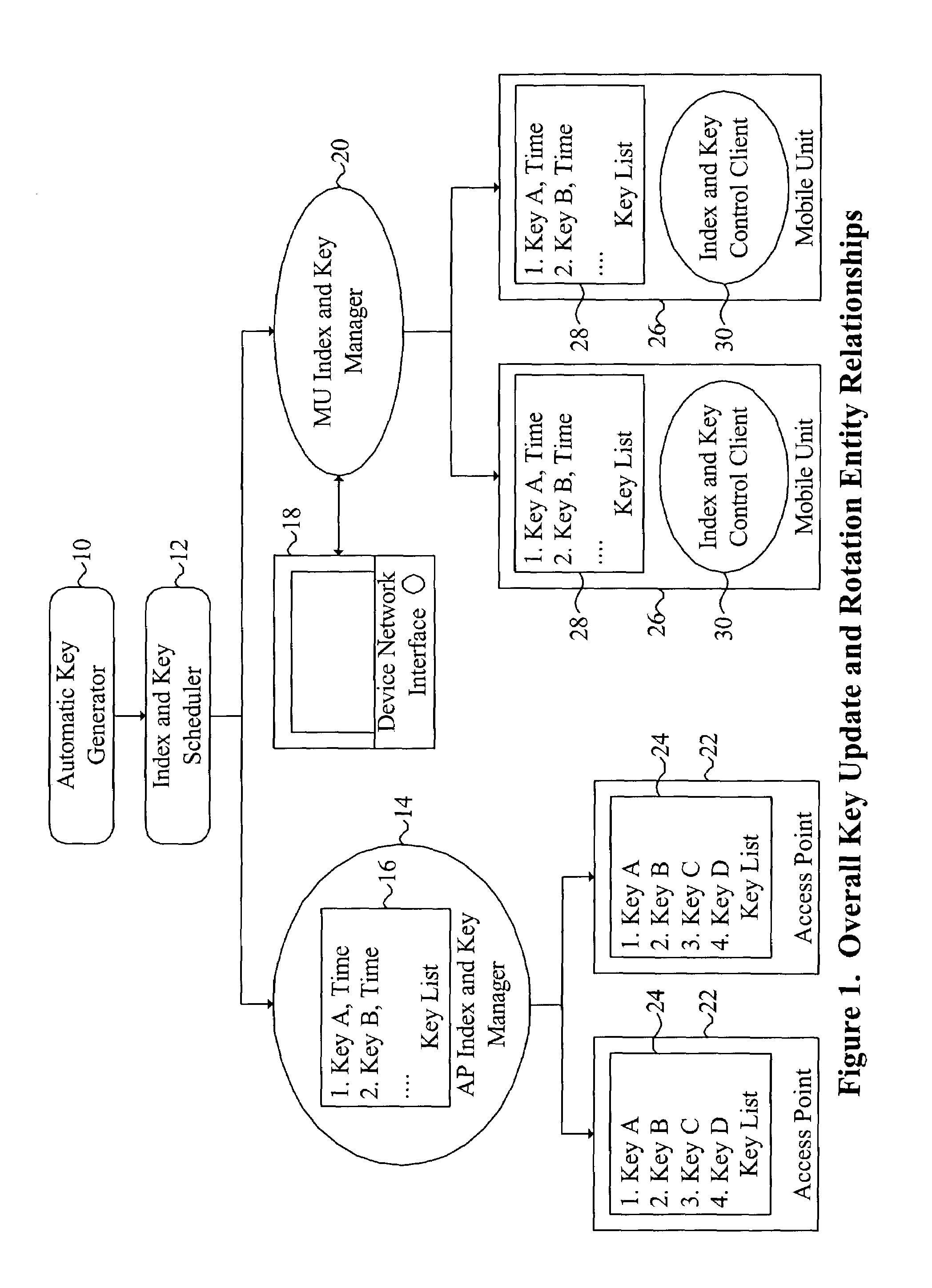
A system and method are disclosed that overcome deficiencies of prior art IEEE 802.11 WEP key management schemes. Preferred embodiments of the present system and method update WEP keys and rotate transmission key indices in a synchronized manner and on a frequent basis making it impractical for a hacker to gather sufficient network traffic using any one WEP key to decrypt that key and without disrupting communications. Preferred embodiments of the present system and method do not require changes in access point or mobile unit hardware, radio drivers, or firmware and are therefore compatible with existing or legacy network infrastructure or components. The disclosed system and method may be used to facilitate secure communications between one or more access points and one or more mobile units and / or groups of two or more mobile units engaging in peer-to-peer associations.
Owner:IVANTI INC
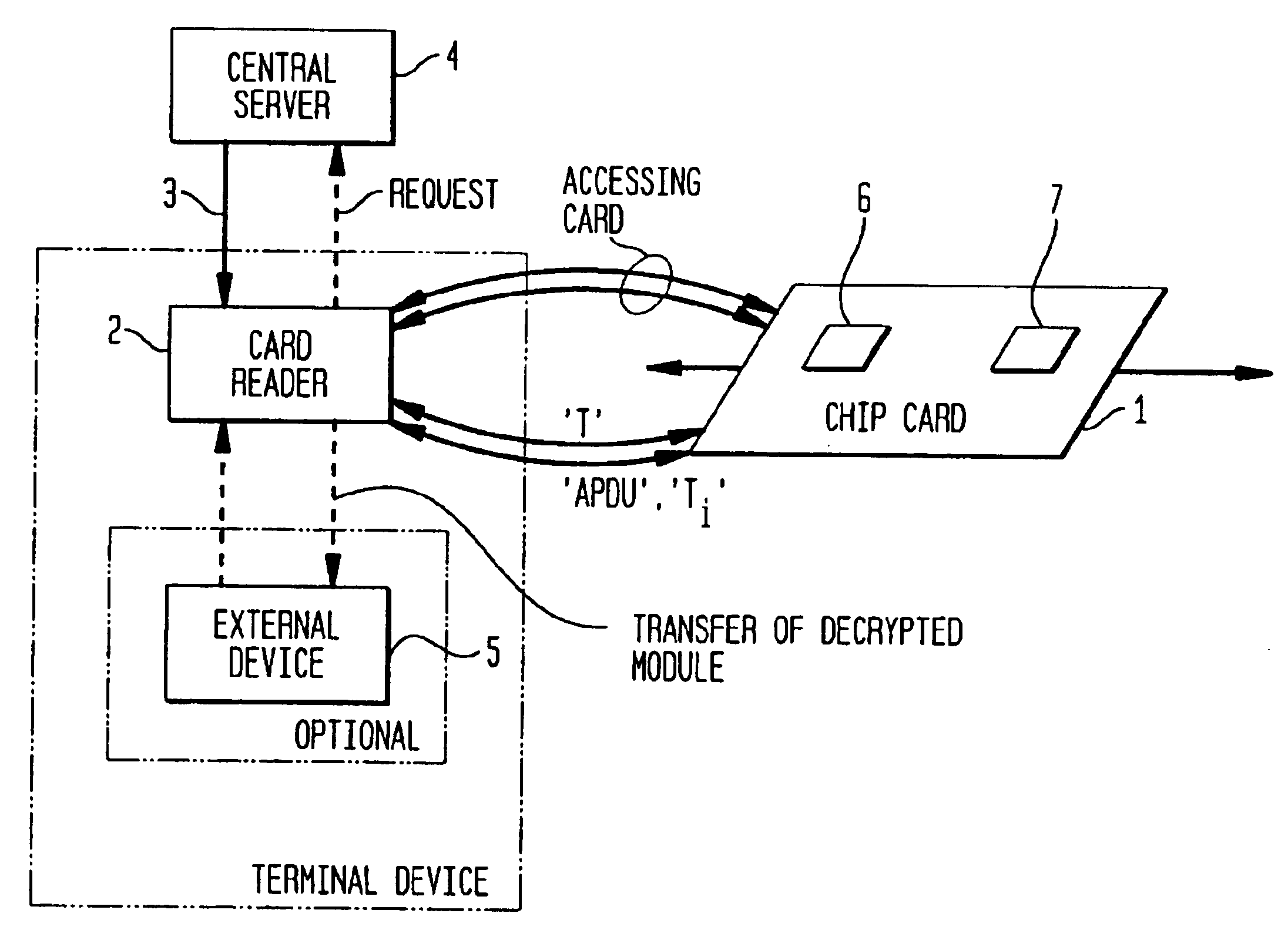
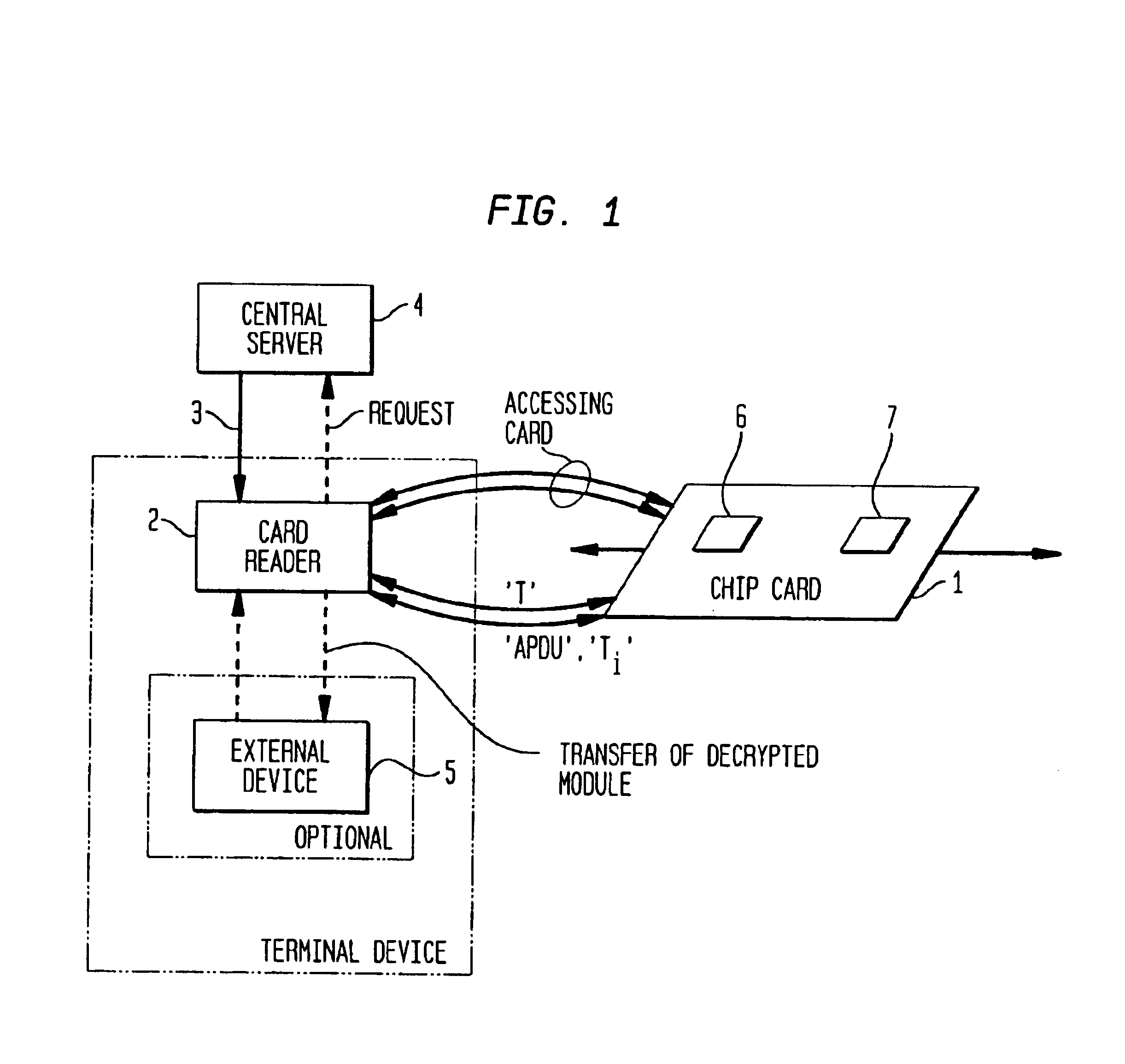
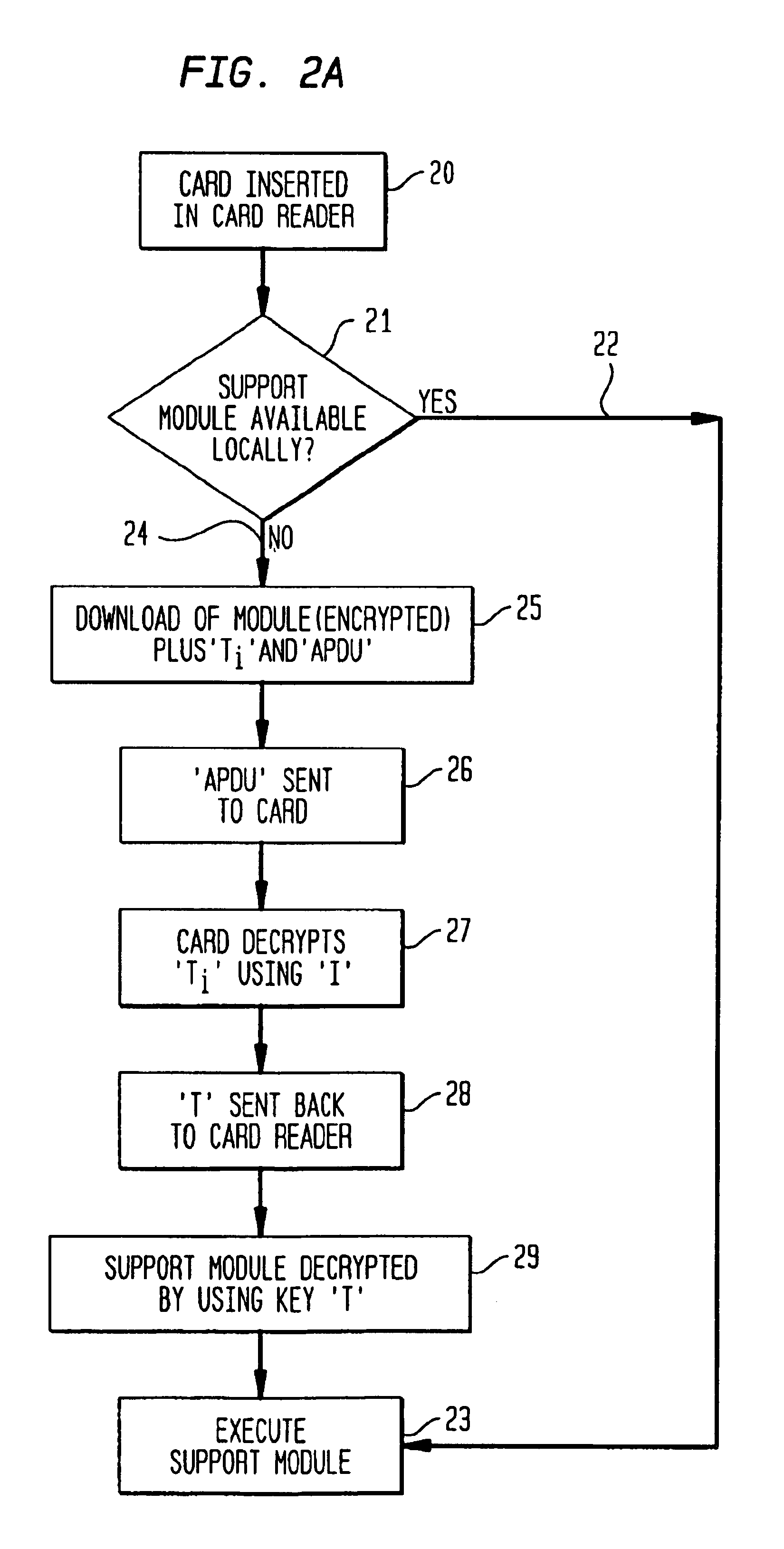
Method and system for securely handling information between two information processing devices
InactiveUS6892301B1Synchronising transmission/receiving encryption devicesDigital data processing detailsInformation processingTerminal equipment
Described is a mechanism for securely handling an information unit by a first information processing device (2), for instance a terminal device like a chip card reader, which interoperates with a second secure information processing device (1), for instance a portable device like a chip card, whereby the information unit is provided by an issuer. The information unit is provided from the issuer to the first device and encrypted by using a first key. The first key is also encrypted by using a second key. The second key is provided on the second secure device (1) and interconnecting the first and the second device enables to decrypt the first key by using the second key and then to decrypt the information unit by using the first key.
Owner:IBM CORP
Popular searches
Computer security arrangements Program control Special data processing applications Credit schemes Point-of-sale network systems Digital data information retrieval Encryption apparatus with shift registers/memories Digital data authentication Security arrangement Particular environment based services
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com