Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2595 results about "Secure transmission" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
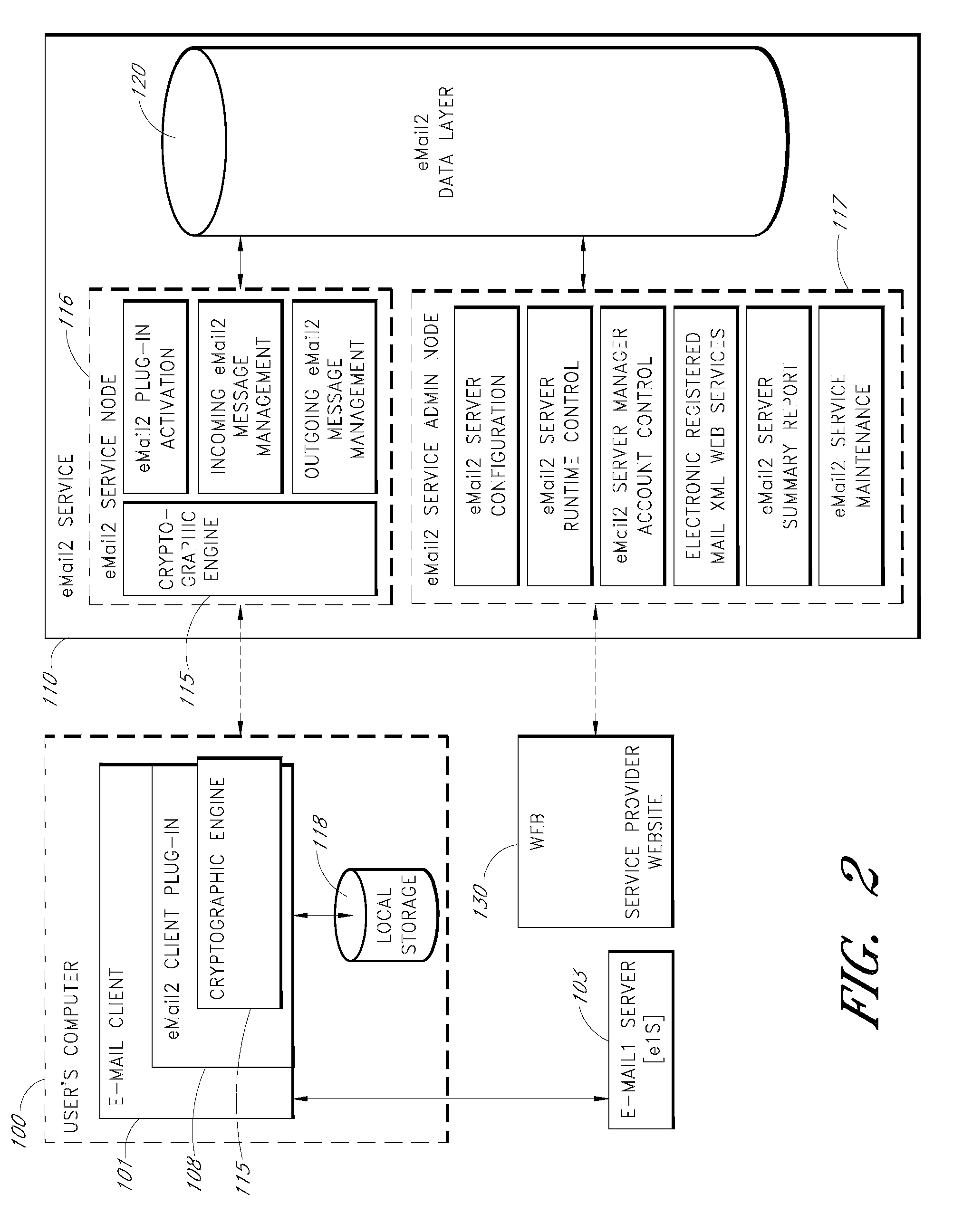
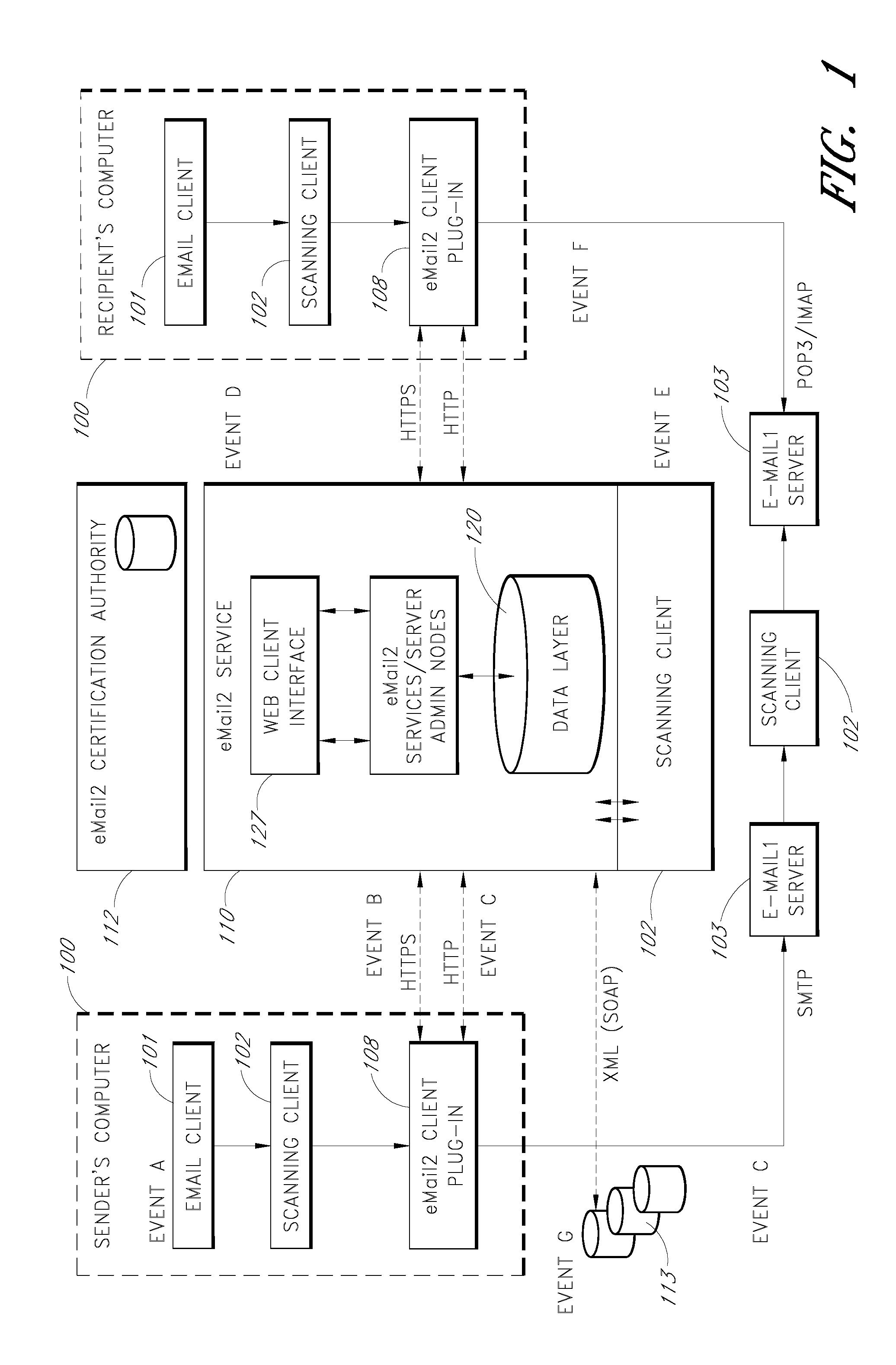
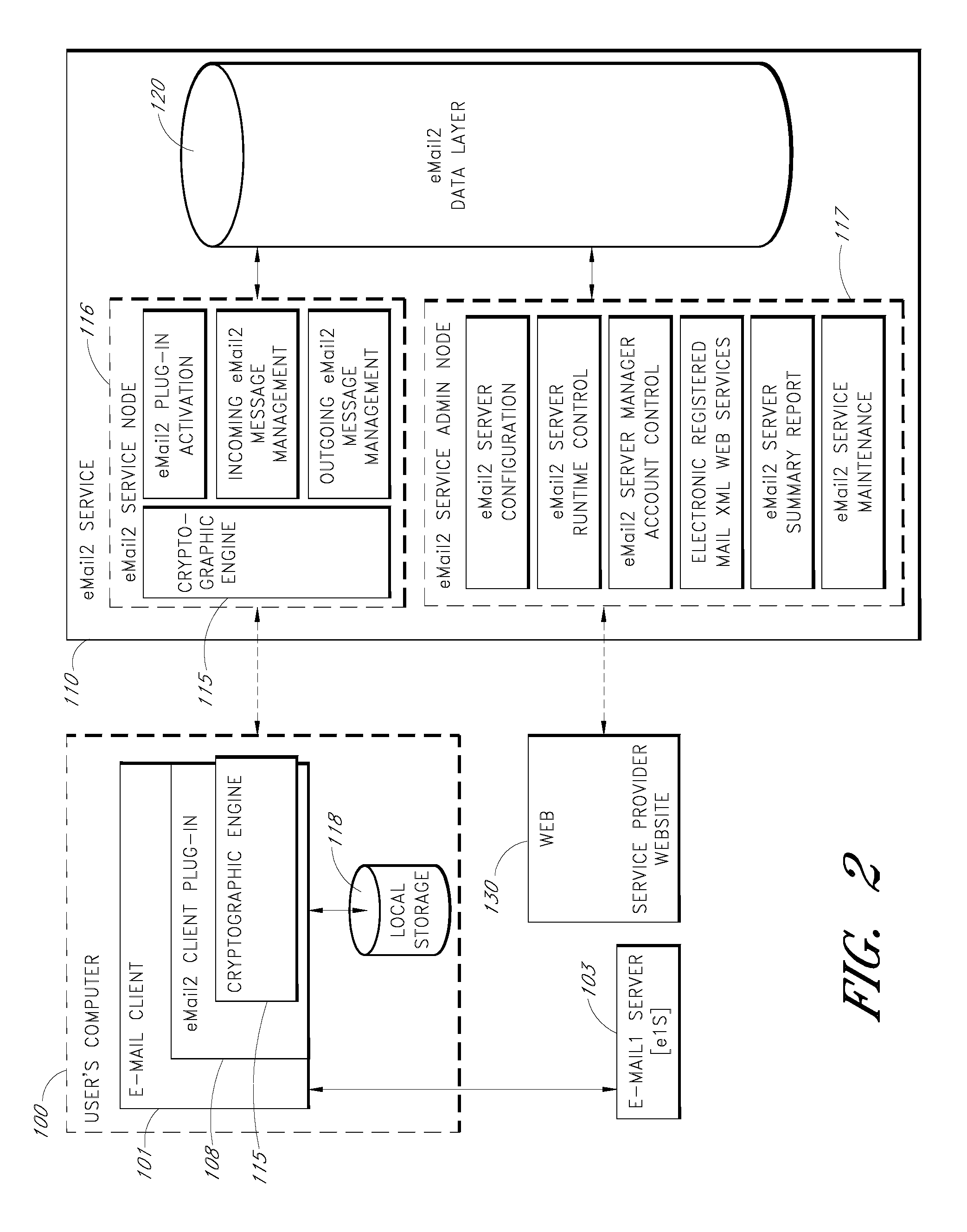
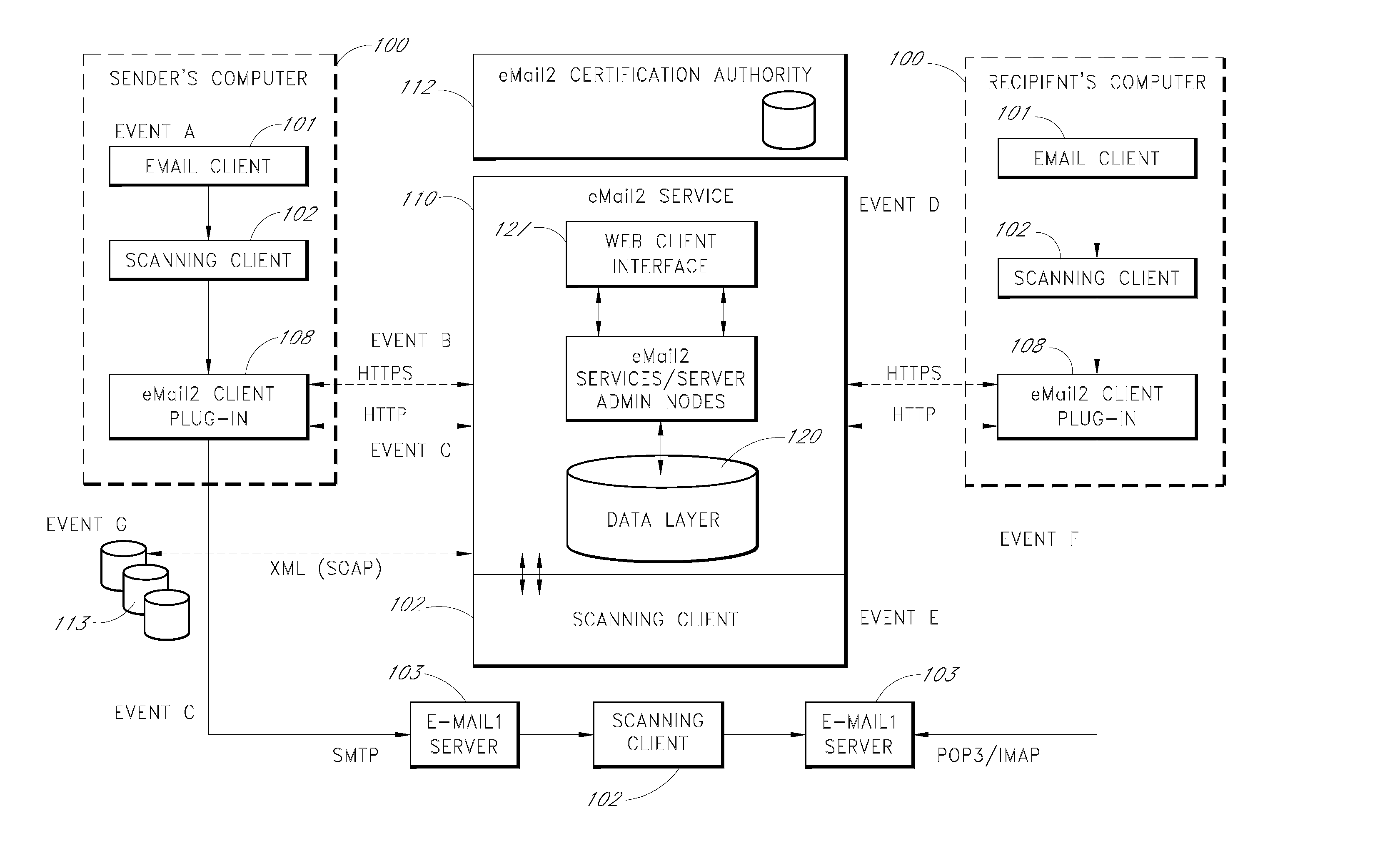
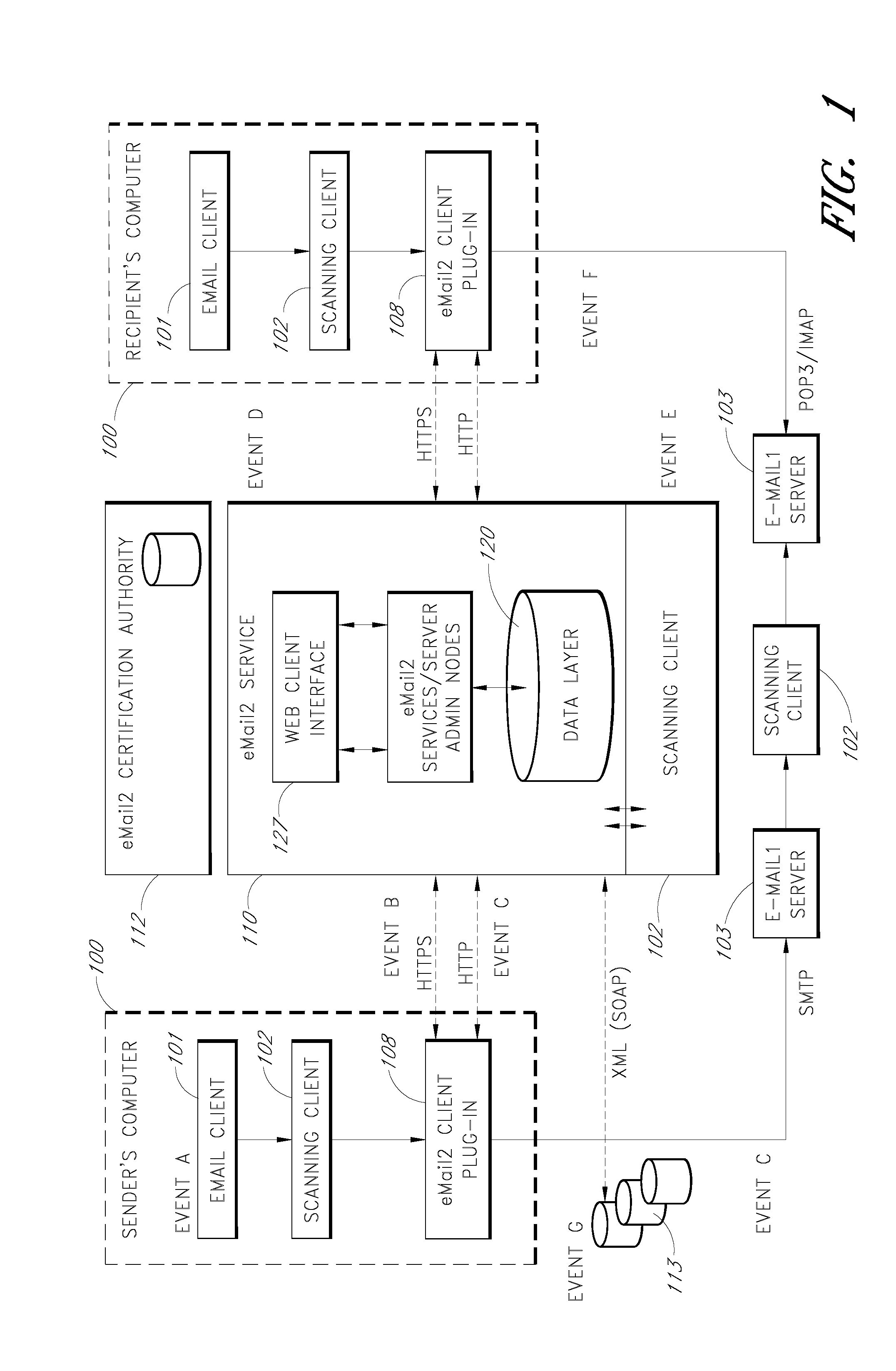
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. Many secure transmission methods require a type of encryption. The most common email encryption is called PKI. In order to open the encrypted file an exchange of keys is done.
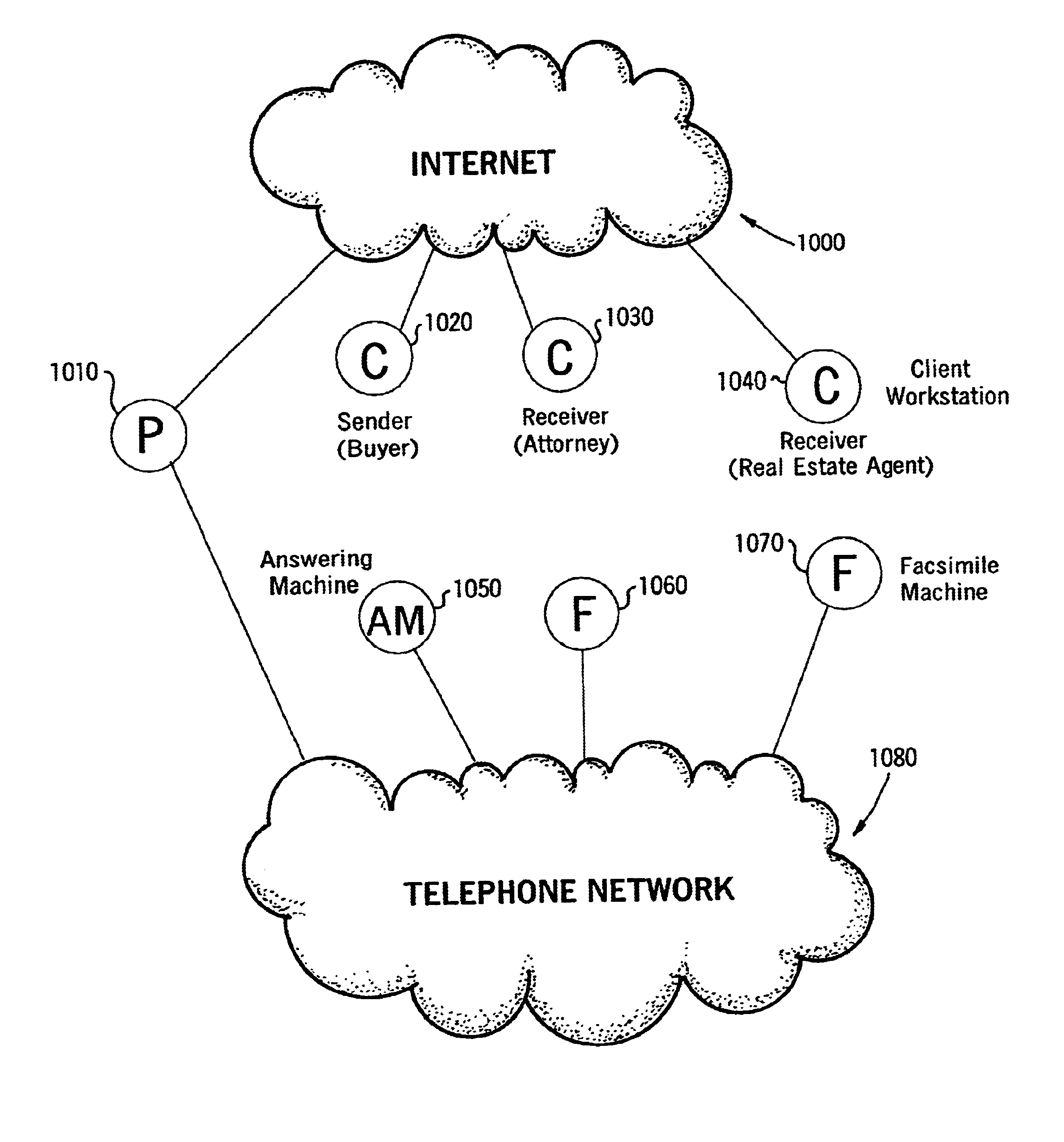
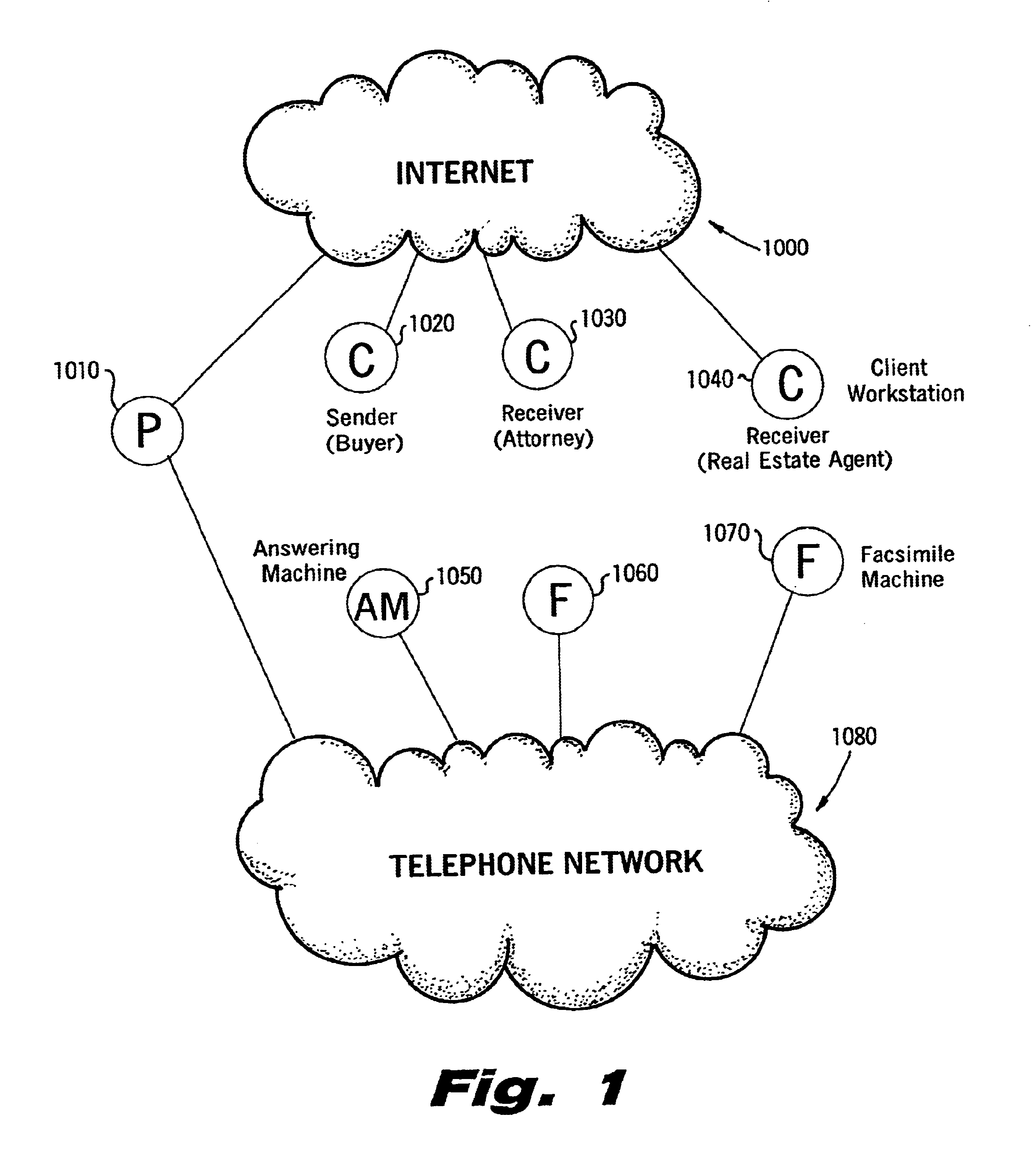
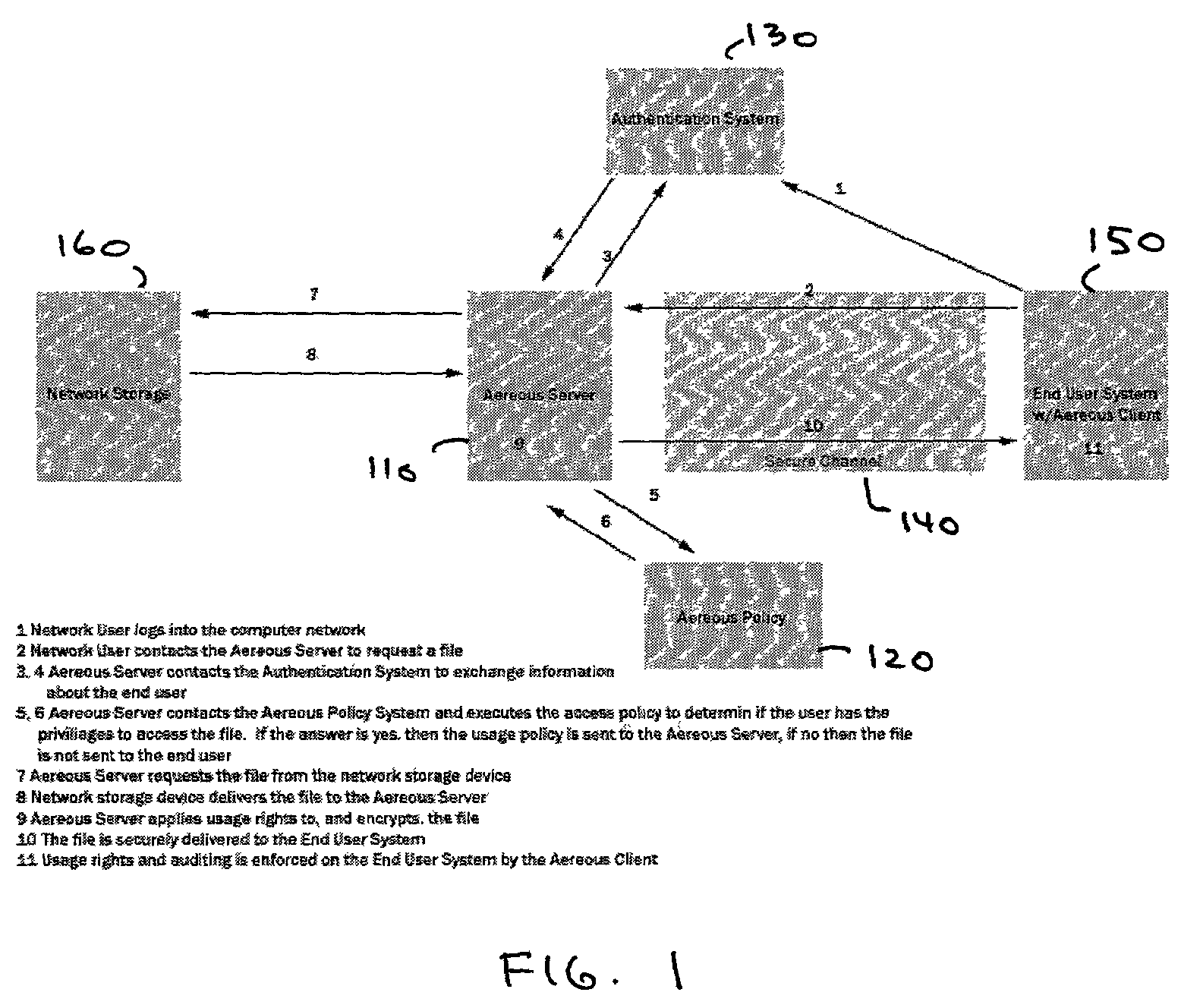
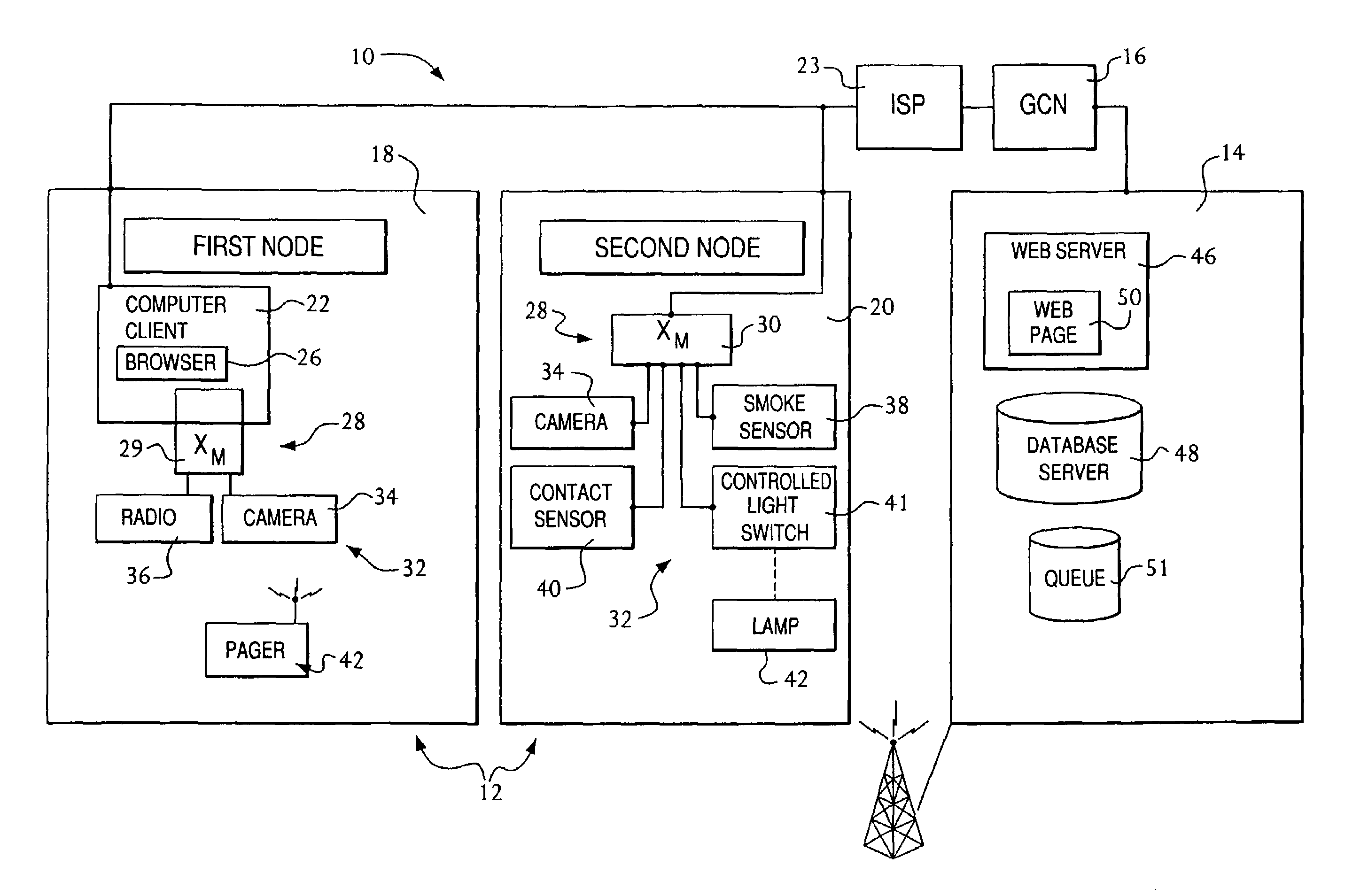
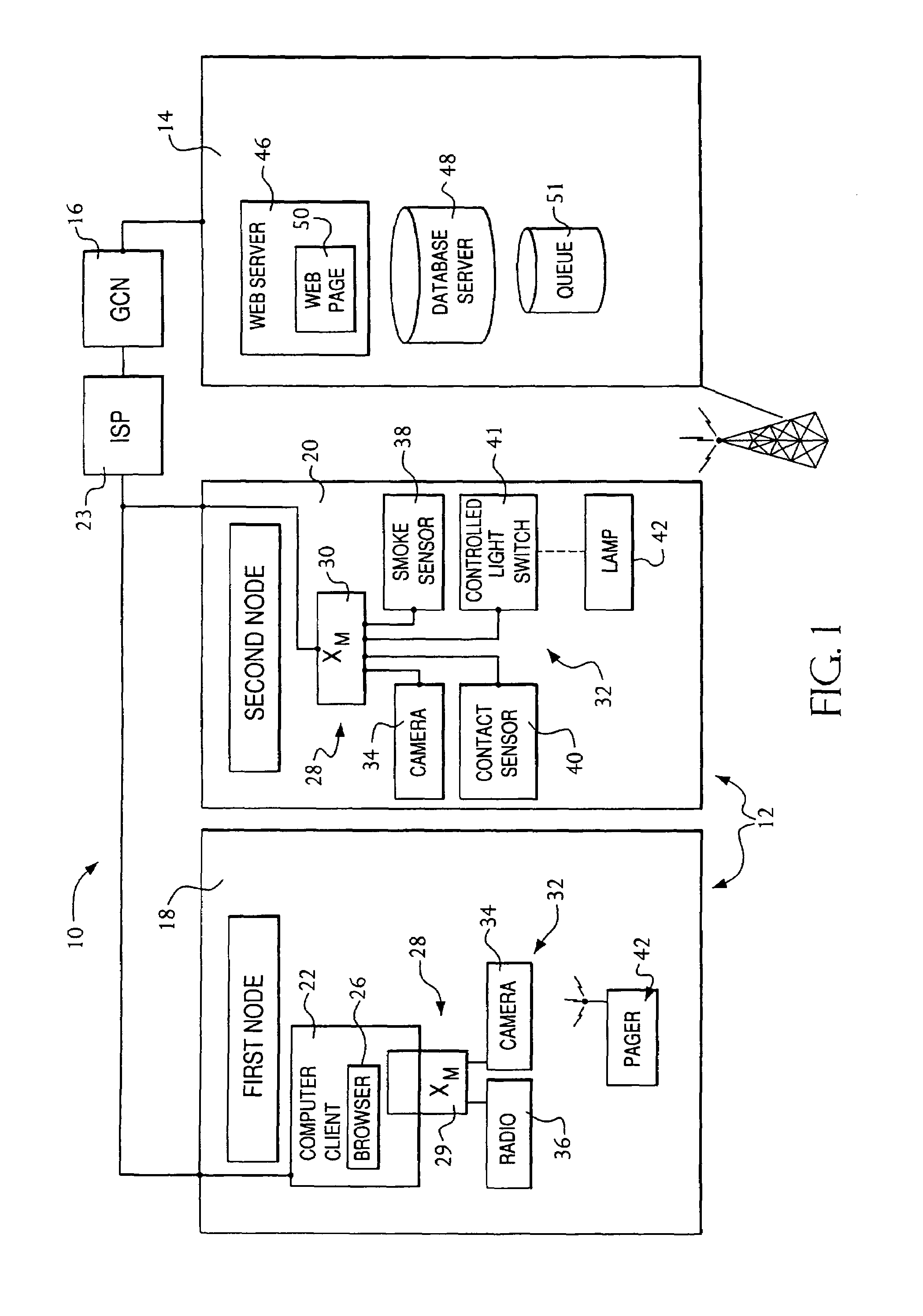
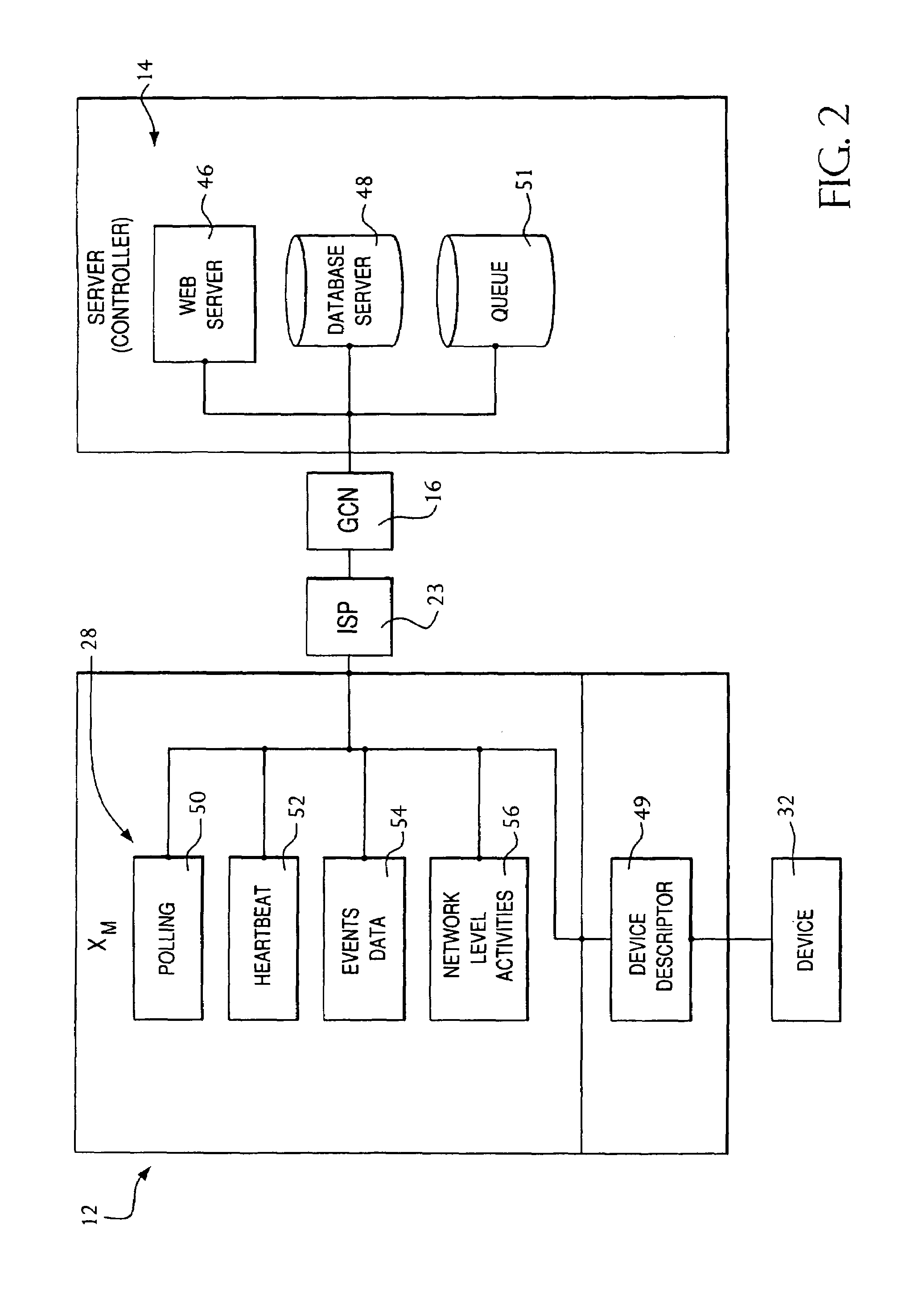
Sender- specified delivery customization
InactiveUS6643684B1Telephonic communicationMultiple digital computer combinationsSecure transmissionFacsimile
A system and method that enables a given sending user to specify a set of delivery policies and have them used for the electronic delivery of a given message, the message potentially having several heterogeneous parts (e.g., text and pictures) each of which is handled differently, and delivered to multiple heterogeneous devices (e.g., PCs, Smartphones, fax machines), and possibly to several distinct recipients. The factors with which a sender can qualify their delivery policies include: time / date, transmission cost; whether the transmission can be forwarded; receiving device capability; and network reliability, speed, and security transmission. Methods are also provided enabling a sender to specify that particular transmissions be redirected or copied, e.g., "send fax copy to my broker and my accountant." In one embodiment, the delivery policies may be specified using PICS.
Owner:SNAP INC
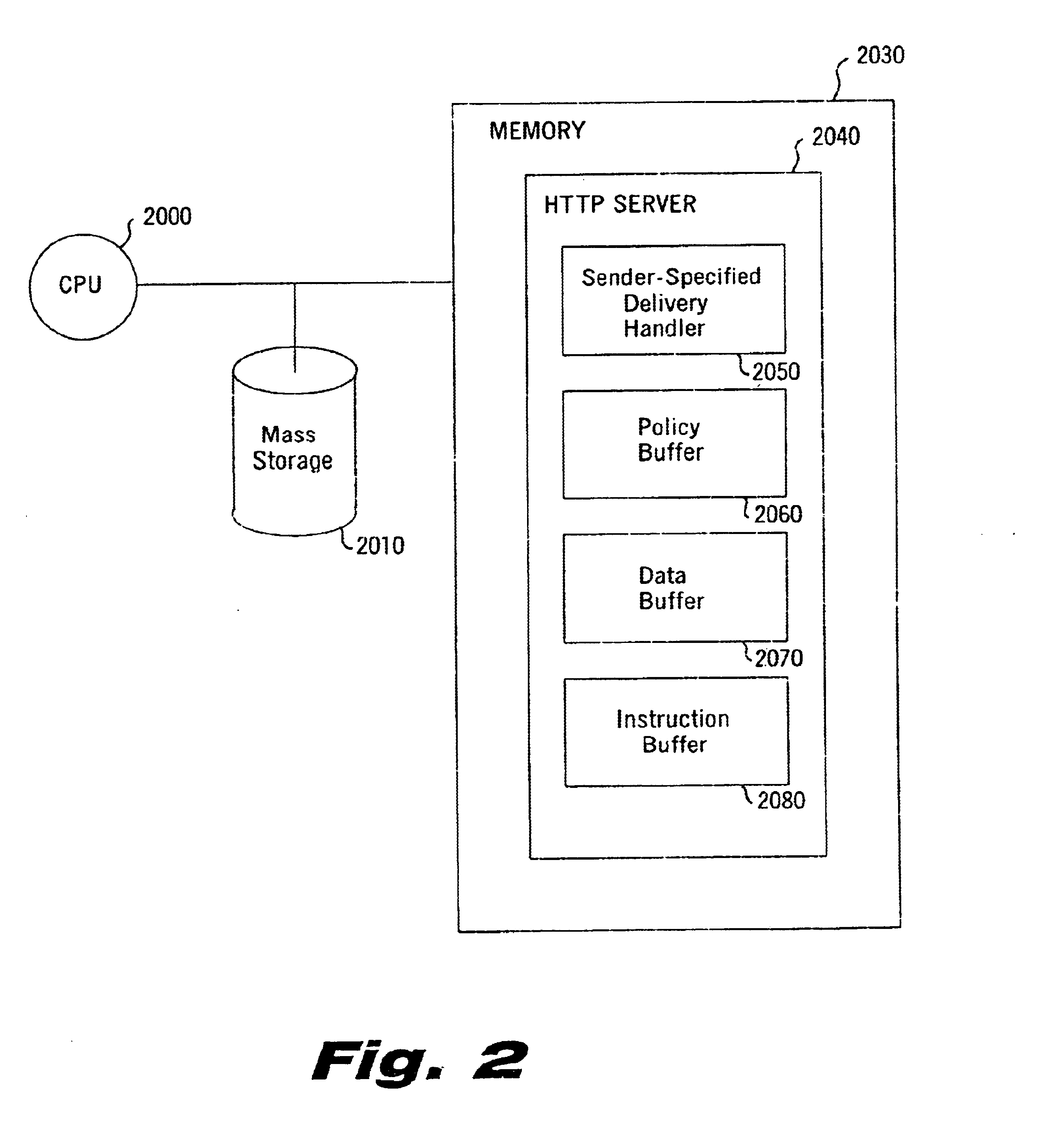
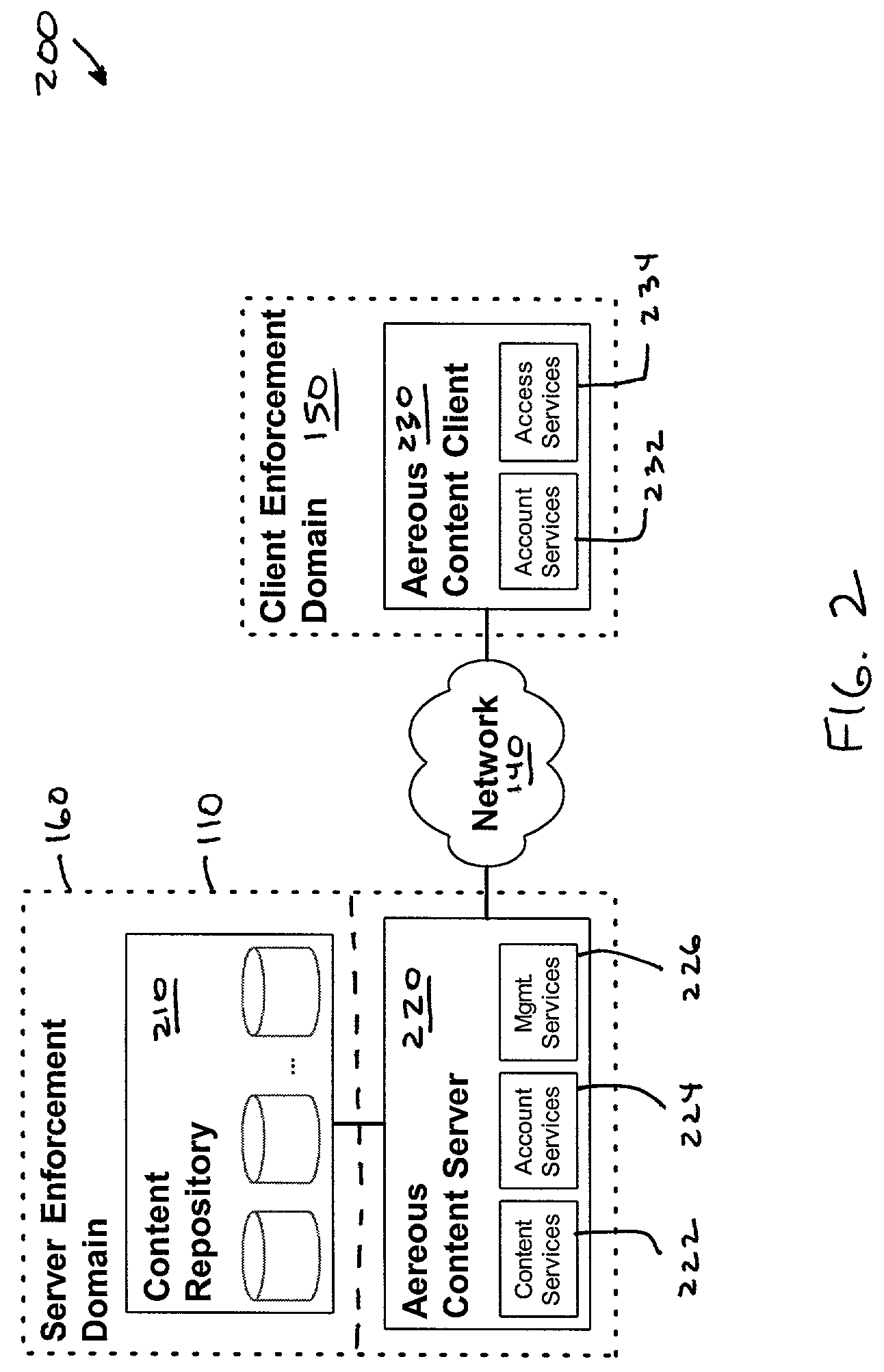
Dynamic file access control and management
InactiveUS7660902B2Improve securitySelectively accessedComputer security arrangementsMultiple digital computer combinationsDistributed File SystemFile system
A dynamic file access control and management system and method in accordance with the present invention may be a proxy file management system that includes one or more file system proxy servers that provide selective access and usage management to files available from one or more file systems or sources. The present invention may embody a secure transport protocol that tunnels distributed file systems, application independent usage controls connected to files on end-user computers, dynamically merging secondary content to a requested file, and applying bandwidth management to any of the foregoing. Embodied in the various implementations of the present invention is enhanced file security. Preferably, the proxy file management system is transparent to an end-user. A dynamic content management system may also be included that selectively adds content to requested files.
Owner:EMC IP HLDG CO LLC
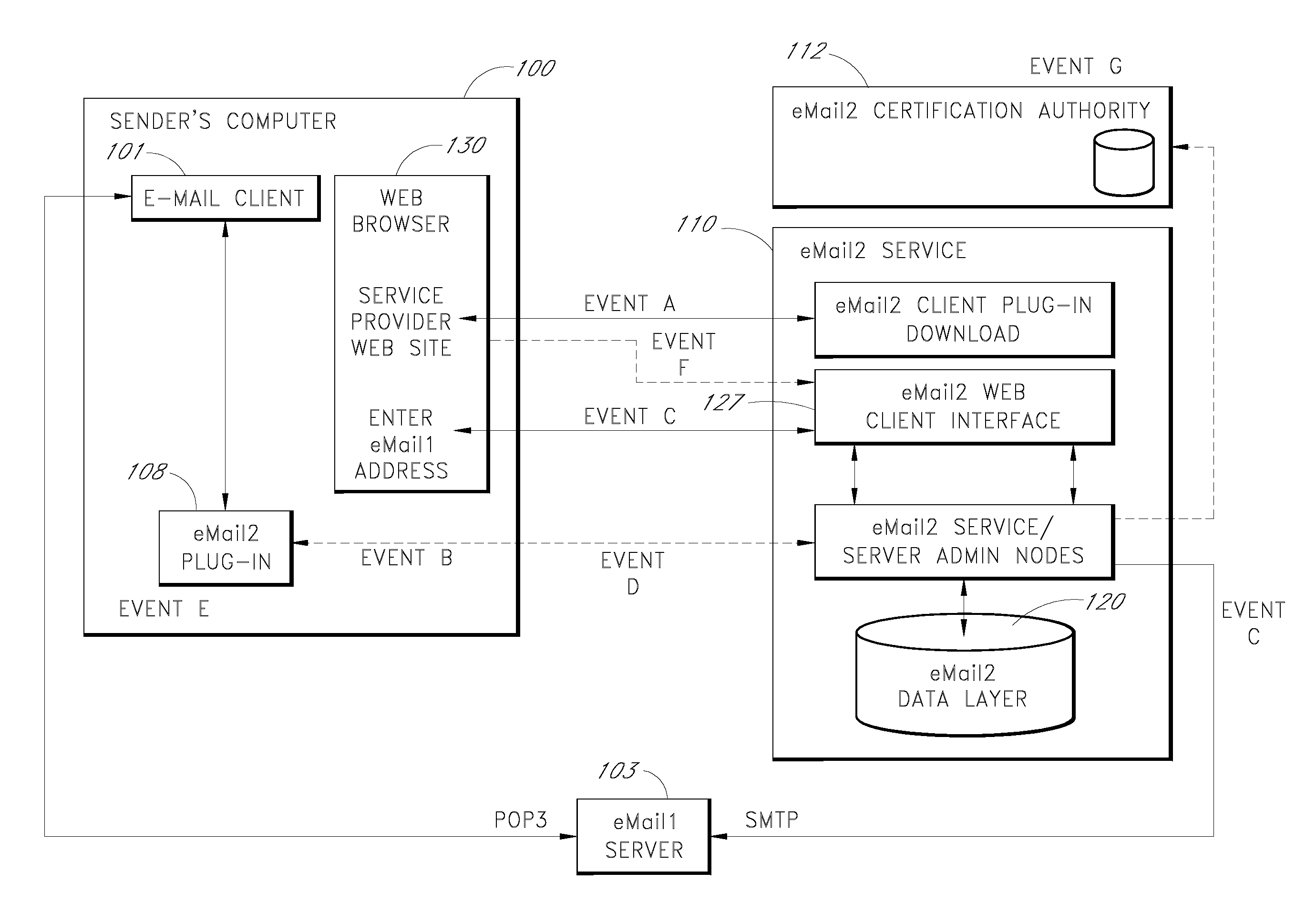
Secure electronic mail system
ActiveUS20070005713A1Easy to watchDigital data protectionMultiple digital computer combinationsEmail addressSecure transmission
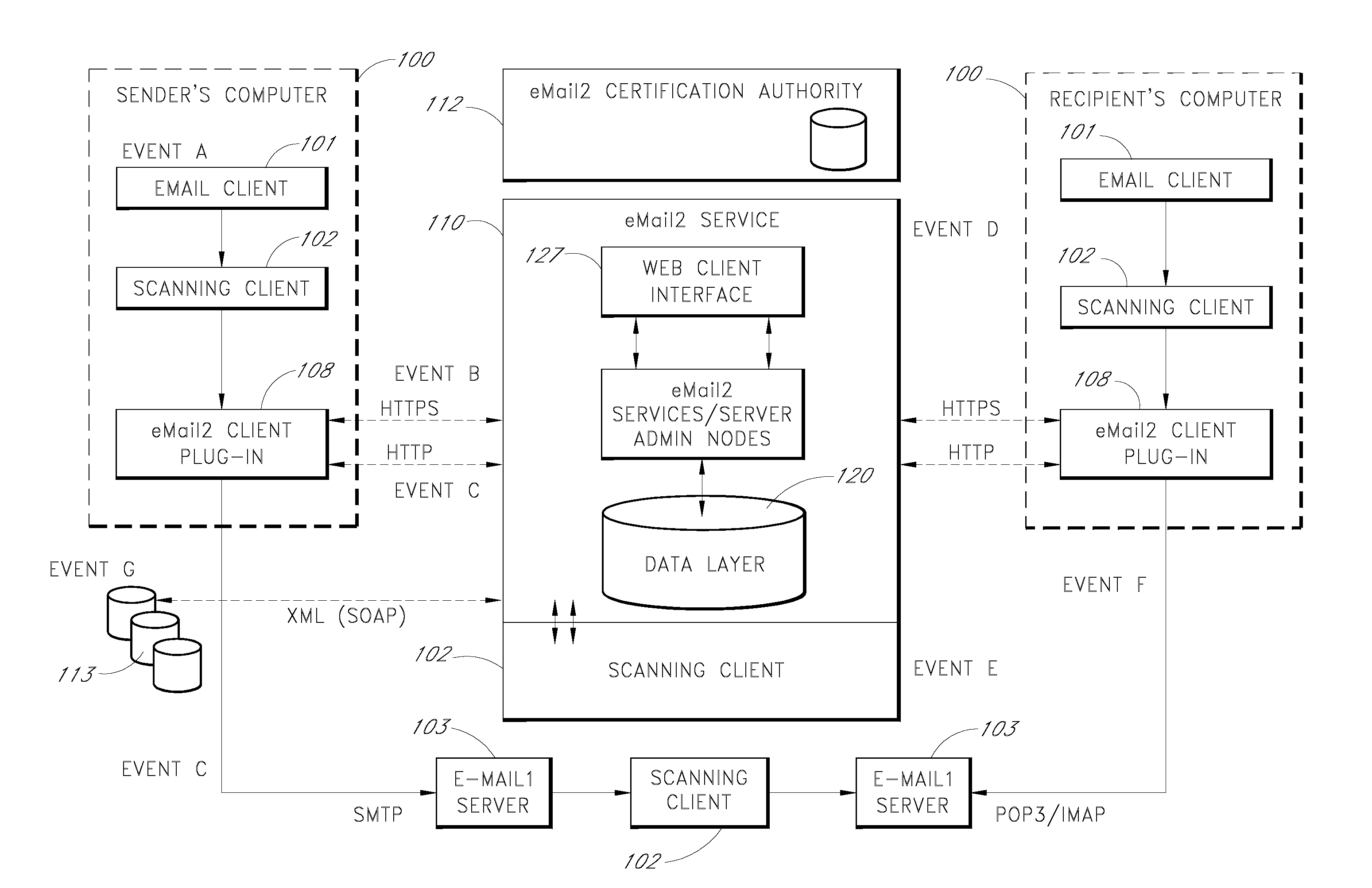
An e-mail system is disclosed that overcomes many deficiencies of, but is backward compatible with, existing e-mail systems. Embodiments of the system may include various features, including but not limited to: (1) secure transfer of e-mail messages, without the need for users to replace existing e-mail clients or to change e-mail addresses; (2) tracking of all actions performed in connection with an e-mail transmission; (3) the ability for a recipient to view information about an e-mail message, optionally including information about how other addressees have responded to it, before deciding whether to retrieve the e-mail message; (4) the aggregation of entire e-mail conversations into a single threaded view; (5) the ability to include both private and public messages in a single e-mail communication; (6) sender control over downstream actions performed in connection with an e-mail message; (7) flexible control over cryptographic methods used to encrypt emails messages for storage.
Owner:APPRIVER CANADA ULC
Methods and systems for secure transmission of information using a mobile device
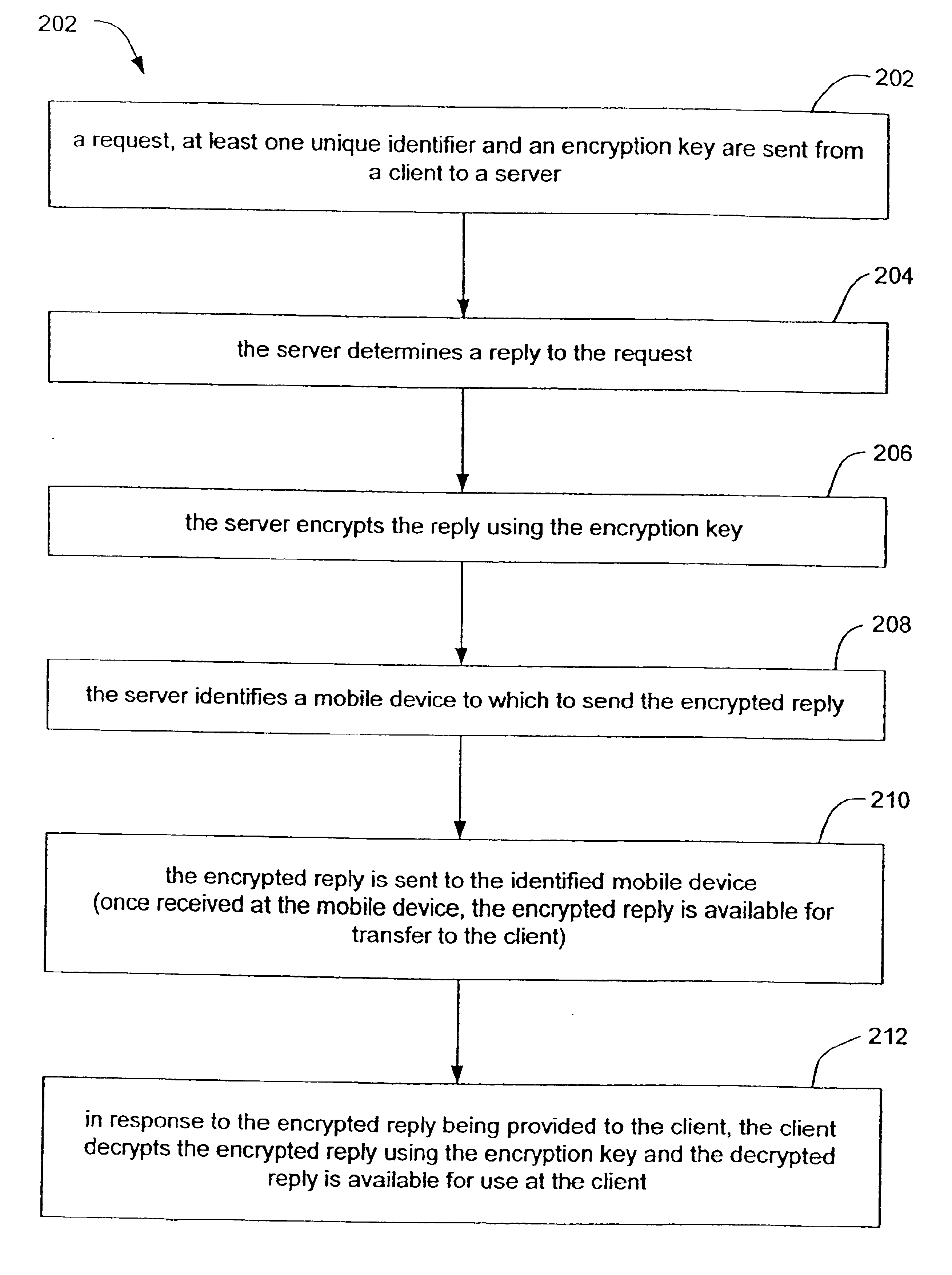
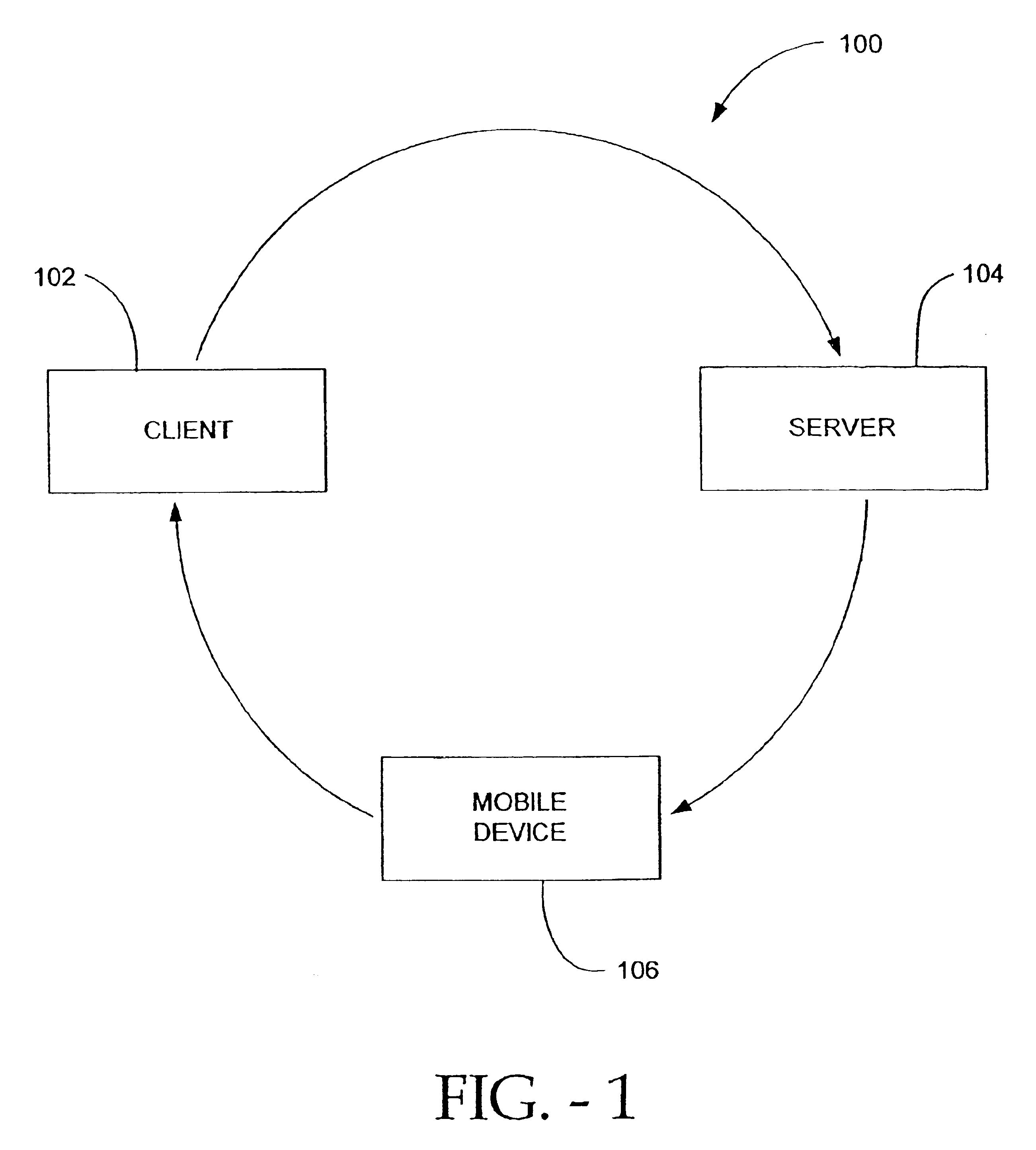
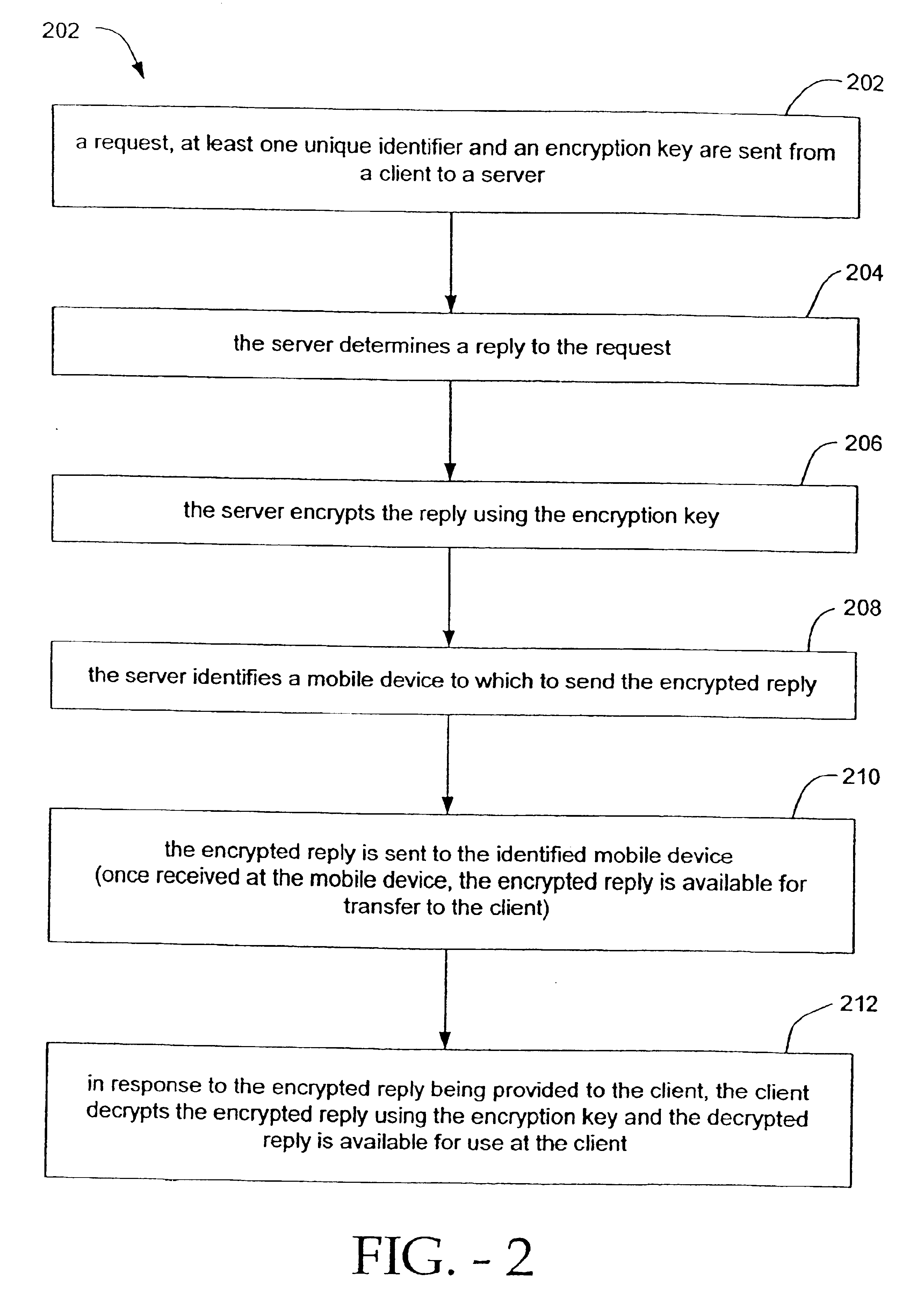
InactiveUS6880079B2Secure transmissionUser identity/authority verificationDigital data authenticationSecure transmissionUnique identifier
Methods and systems for secure transmission of information are provided. In accordance with a method of the present invention, a client sends to a server, a request, at least one unique identifier and an encryption key. The server generates a reply to the request and identifies a mobile device (based on the at least one unique identifier) to which to send the reply. The server also encrypts the reply, using the encryption key, to thereby produce an encrypted reply. The encrypted reply is then sent from the server to the mobile device (e.g., a mobile phone). Once received by the mobile device, the encrypted reply is available for transfer (automatically or manually) from the mobile device to the client. Once provided to the client, the client can decrypt the encrypted reply using the encryption key. The decrypted reply is then available for use at (e.g., by) the client.
Owner:ONESPAN NORTH AMERICA INC
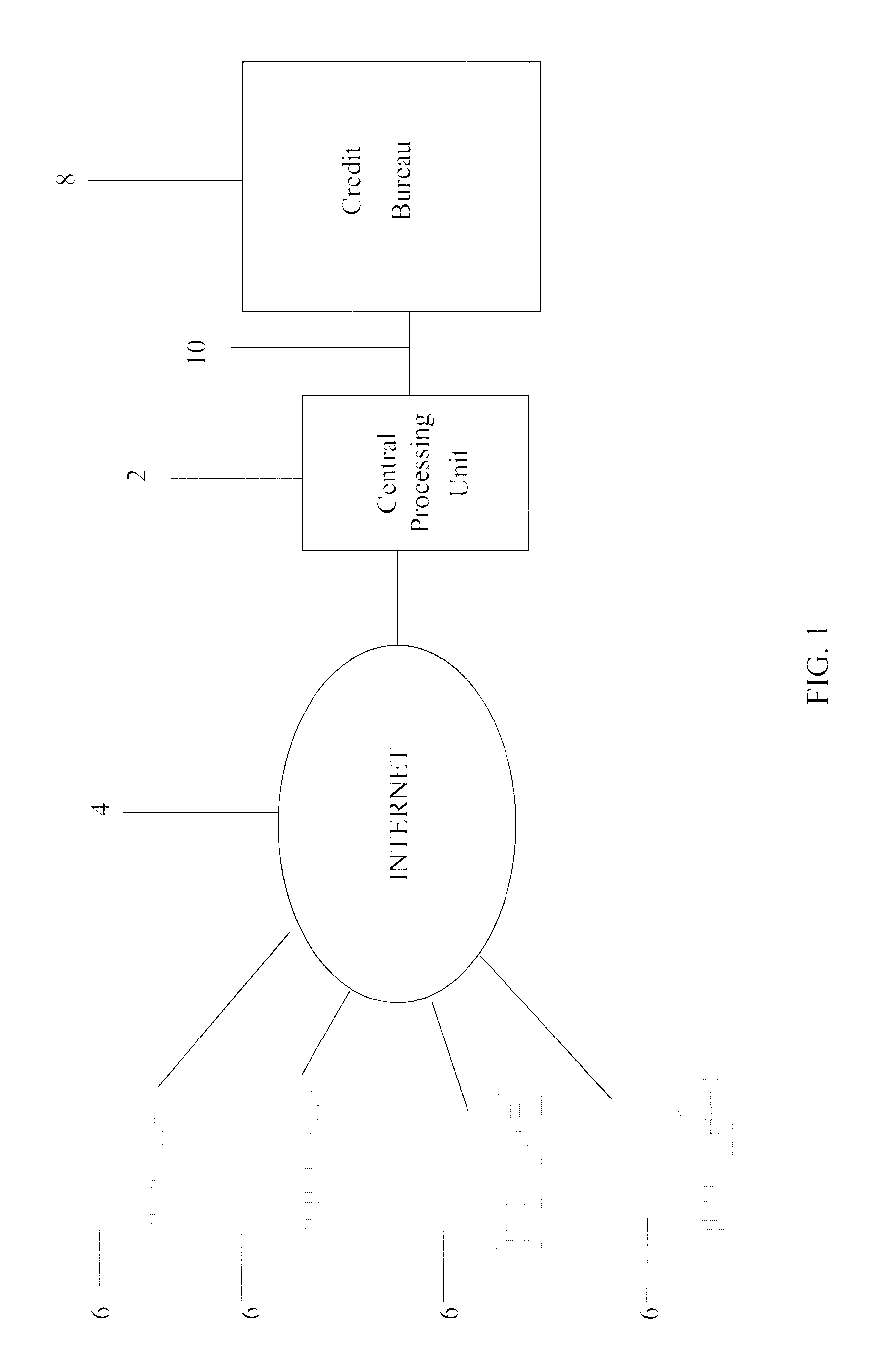
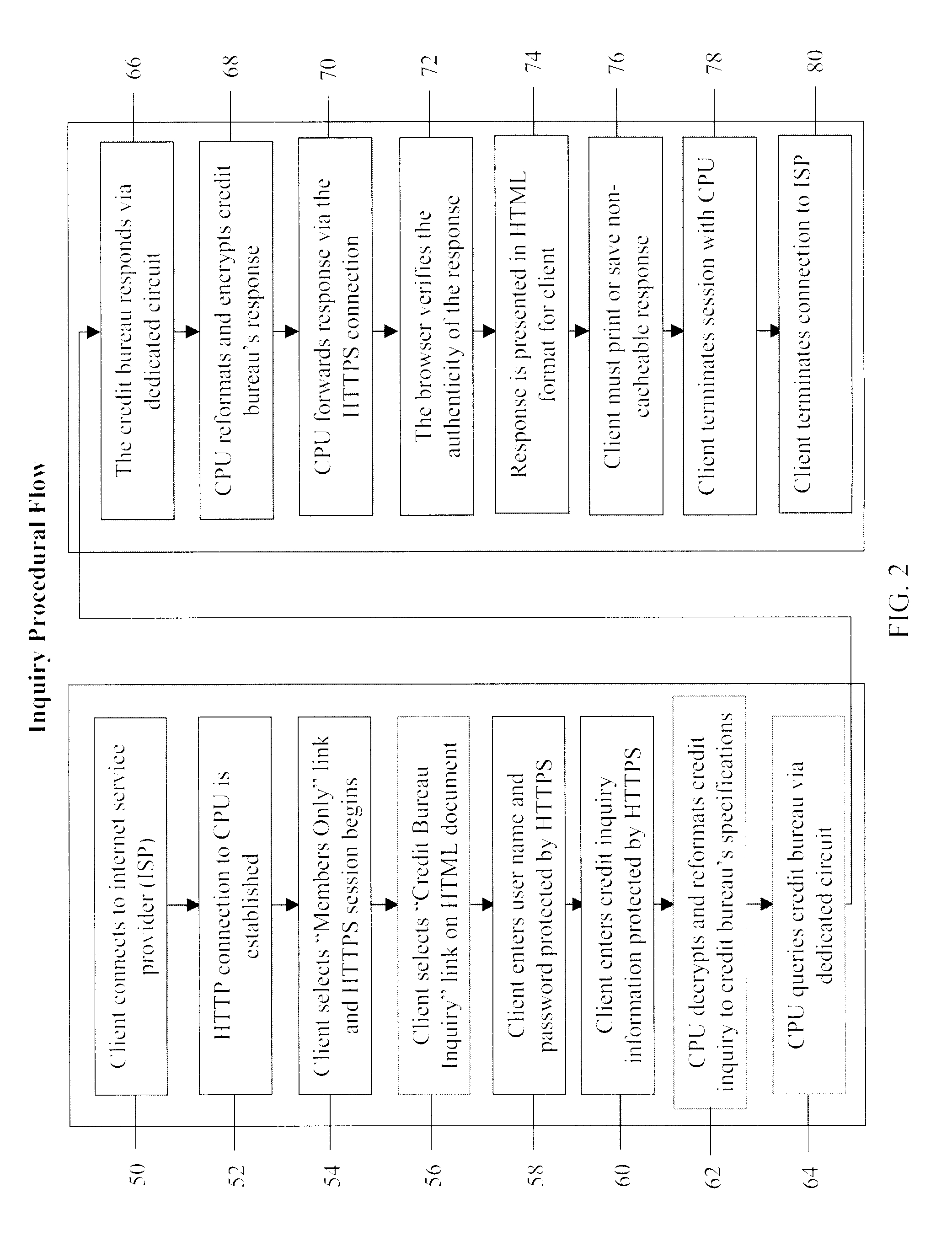
System and method for real-time electronic inquiry, delivery, and reporting of credit information
InactiveUS6988085B2More readable formatSecure transmissionComplete banking machinesFinanceWeb siteWeb browser
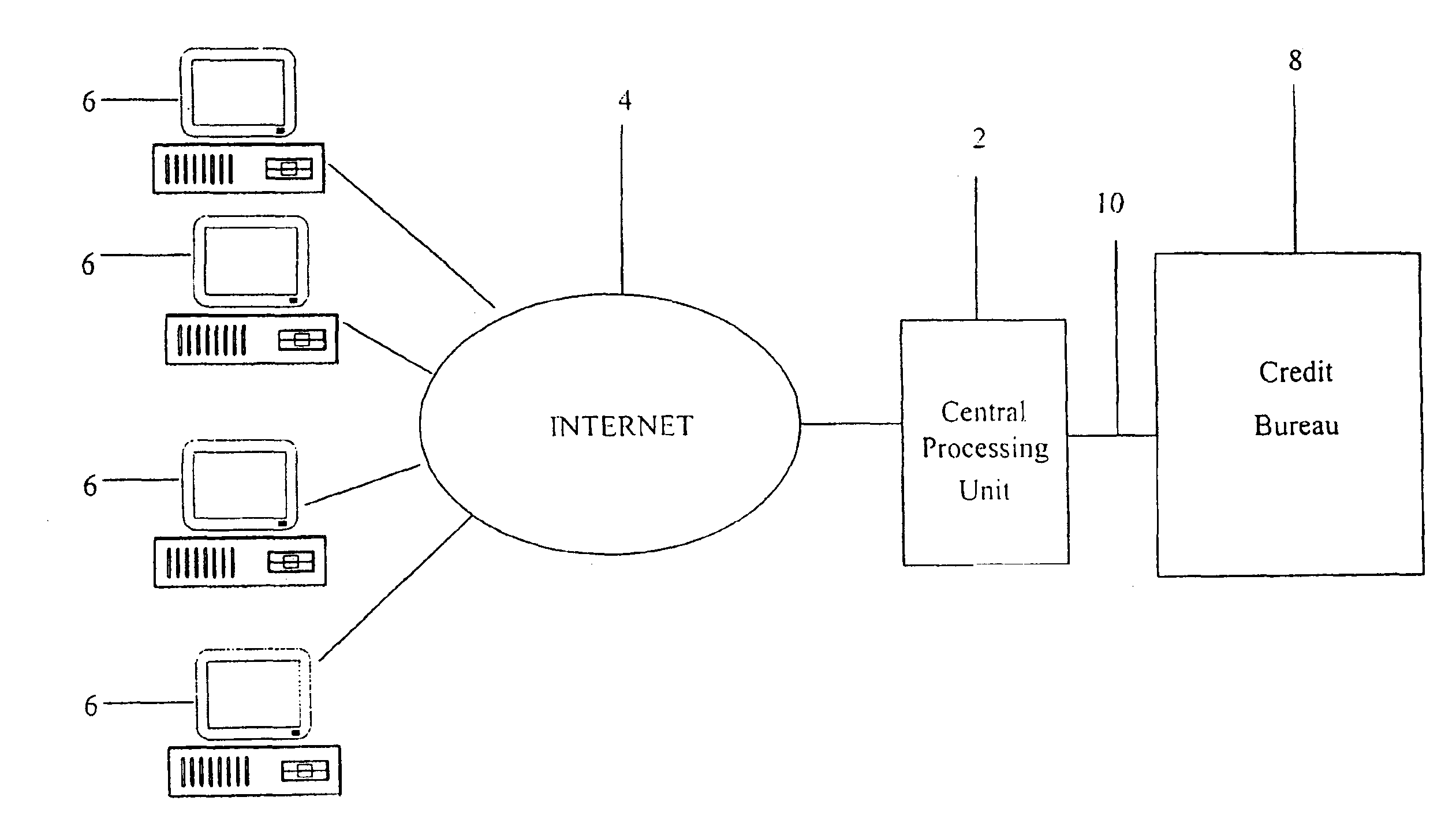
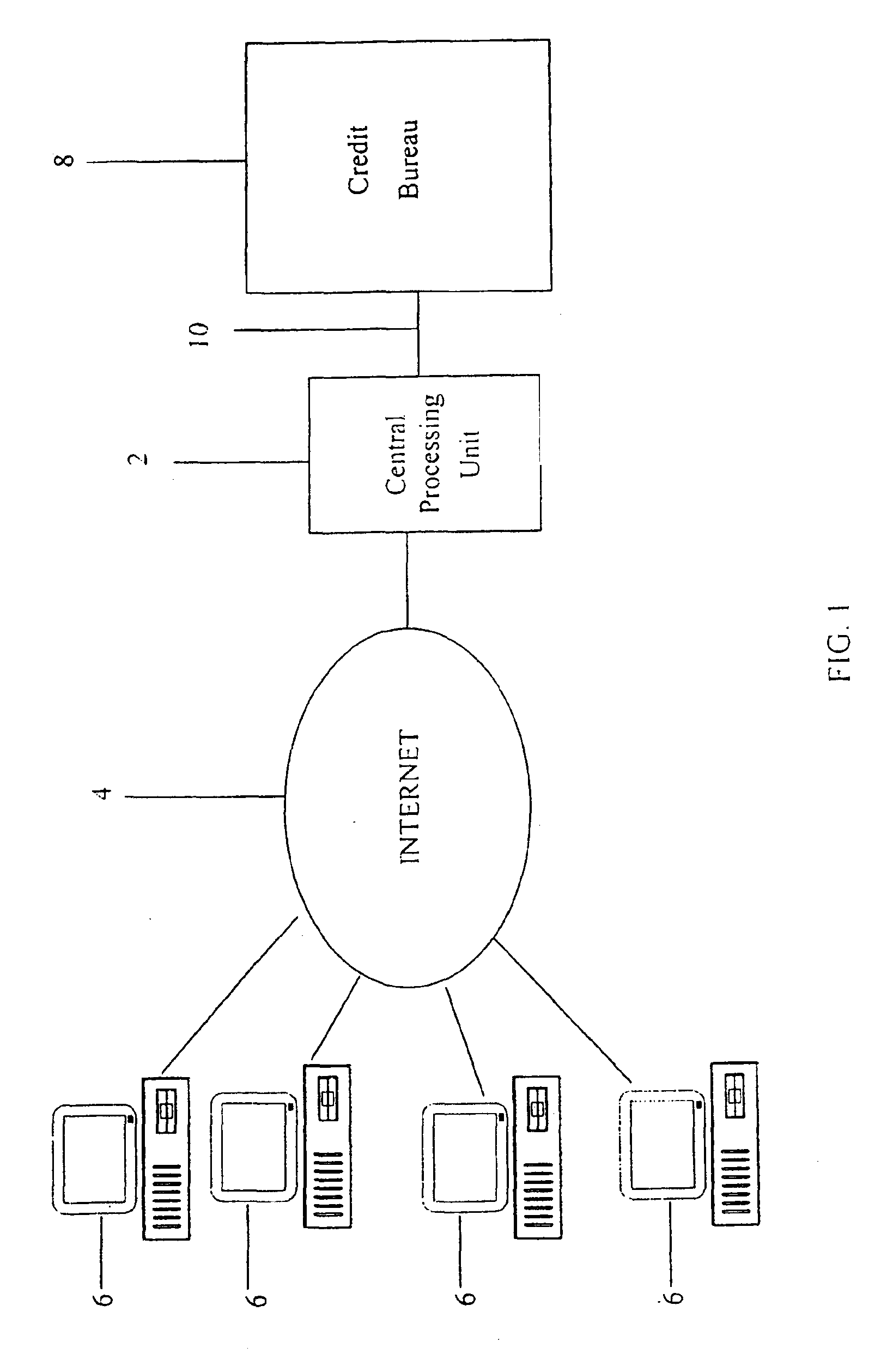
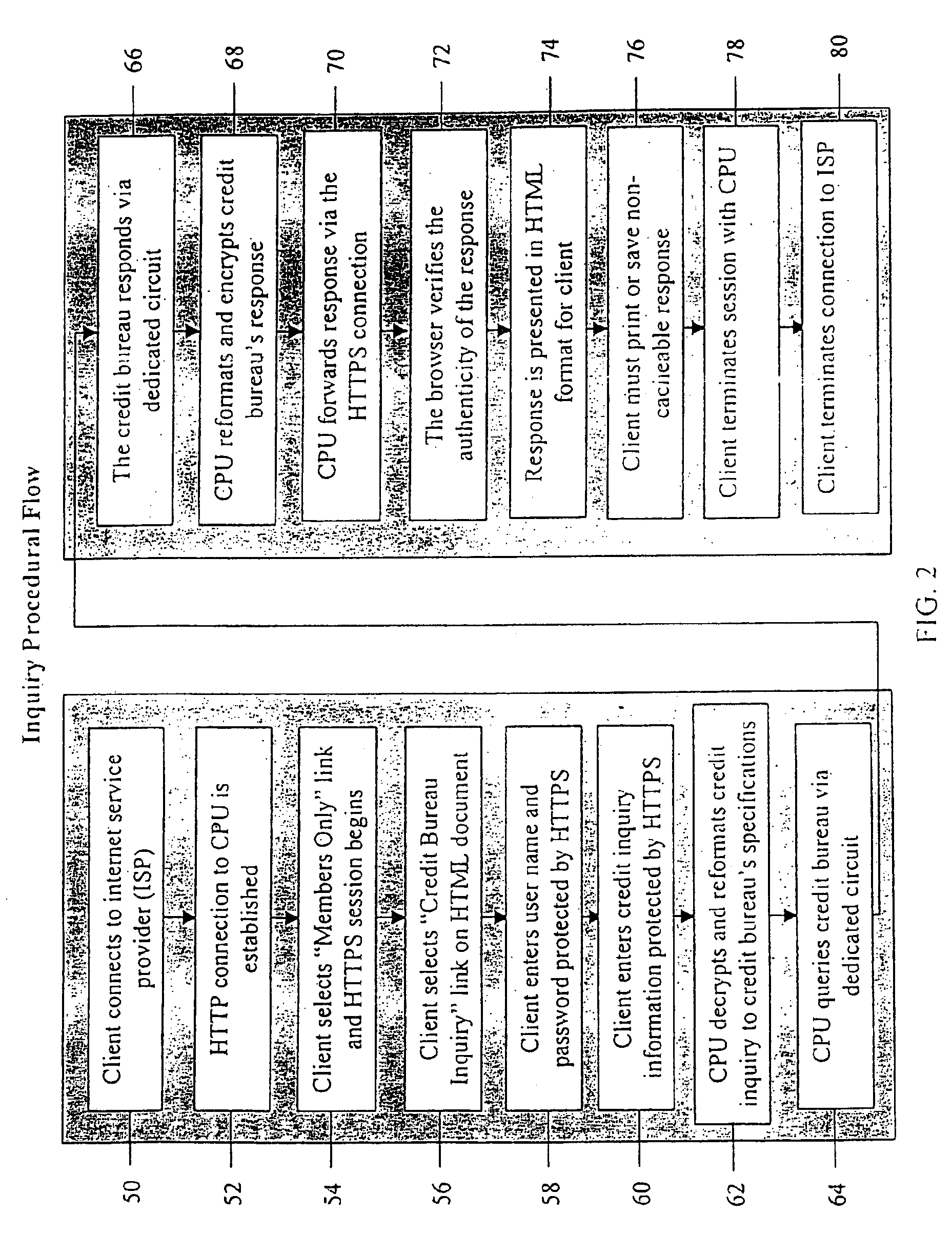
A system and method for providing electronic inquiry, delivery, and reporting of personal credit information to and from credit bureaus, preferably via the Internet. In the preferred embodiment, the system includes a web site that, by using a web browser, allows clients to request credit information from, or provide credit reports to, credit bureaus by entering certain data on pre-built forms in HTML format. The data is encrypted using means for secure transmission, such as a web browser with 128-bit secure socket layer (SSL) technology, then sent to a common gateway interface (CGI) application located on a web server. The CGI application decrypts and reformats the data to a standard format specified by the credit bureau. The CGI application initiates a query. Using a dedicated connection circuit to the credit bureau's computer, the CGI application reformats the response from the credit bureau to an HTML format and encrypts the data using the means for secure transmission. The HTML formatted data is then sent back to the client's computer over the Internet and displayed in the client's web browser in an easily read format.
Owner:F POSZAT HU
Access and control system for network-enabled devices
InactiveUS7120692B2Reduce computational overheadReduce communicationMultiple digital computer combinationsProgram controlControl systemSecure transmission
Owner:WESTERN DIGITAL TECH INC
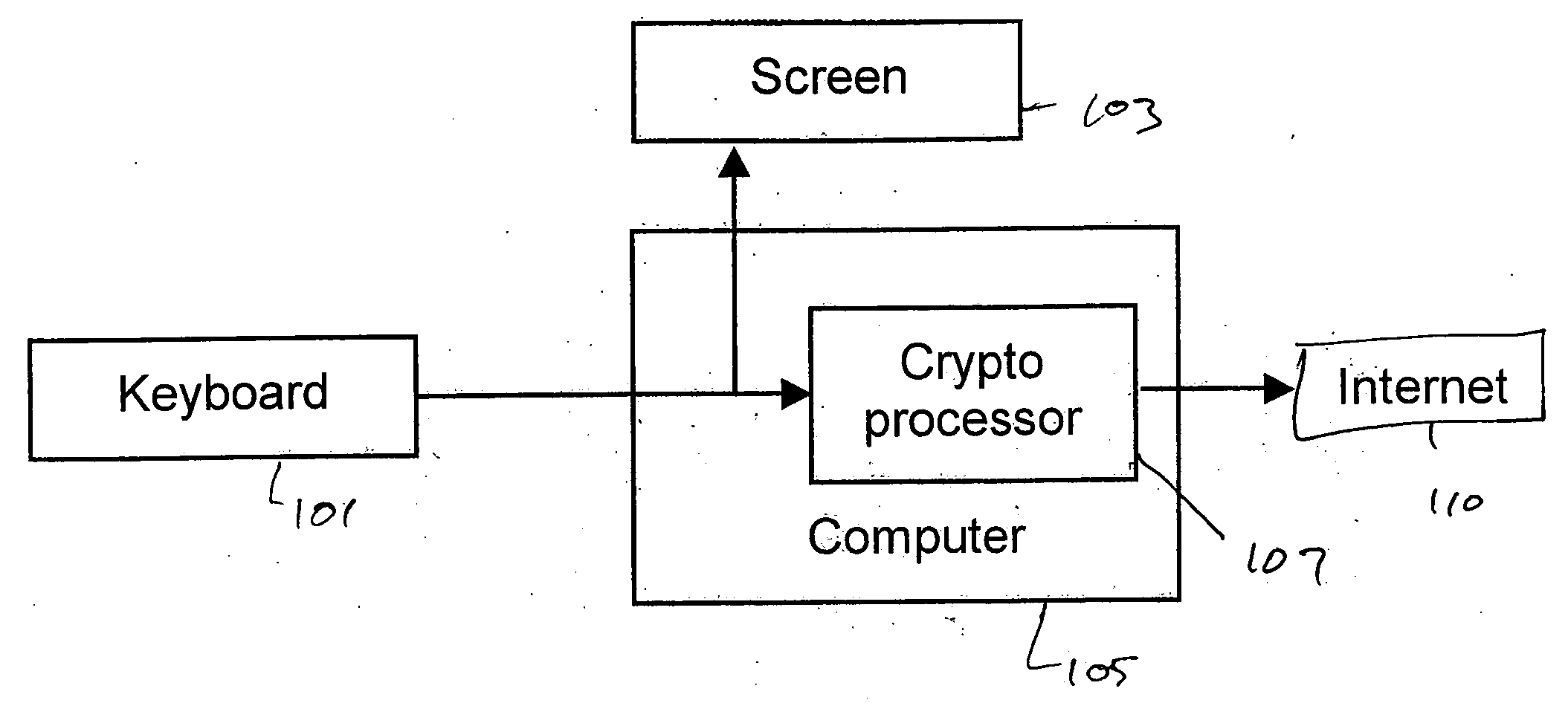
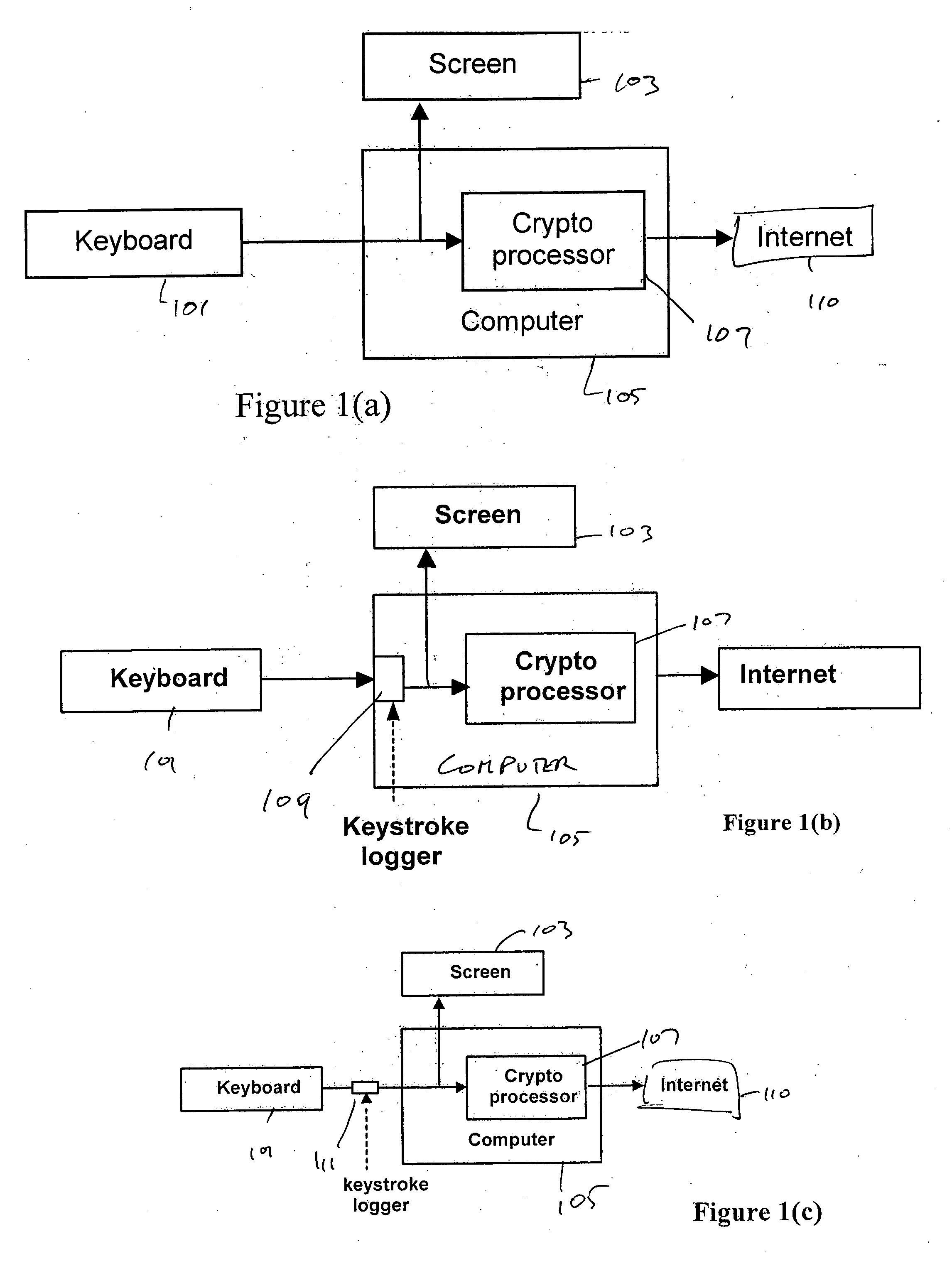
System and method for preventing identity theft using a secure computing device
ActiveUS20050071282A1Secure transmissionDigital data processing detailsMultiple digital computer combinationsSecure transmissionIdentity theft
A system and method for effecting secure transactions over a computer network in a manner designed to foil identity theft perpetrated from an untrusted computer. A connection from a client computer to the network wherein the client computer provides a user interface for a user, a connection from a server computer to the network, and a connection from a portable secure computing device to the network provides for secure transmission of private confidential user information from the user to a server. The private information is transmitted directly from the secure computing device to the server over the secure connection without possibility of capture on the computer with which the user is interacting.
Owner:GEMPLU
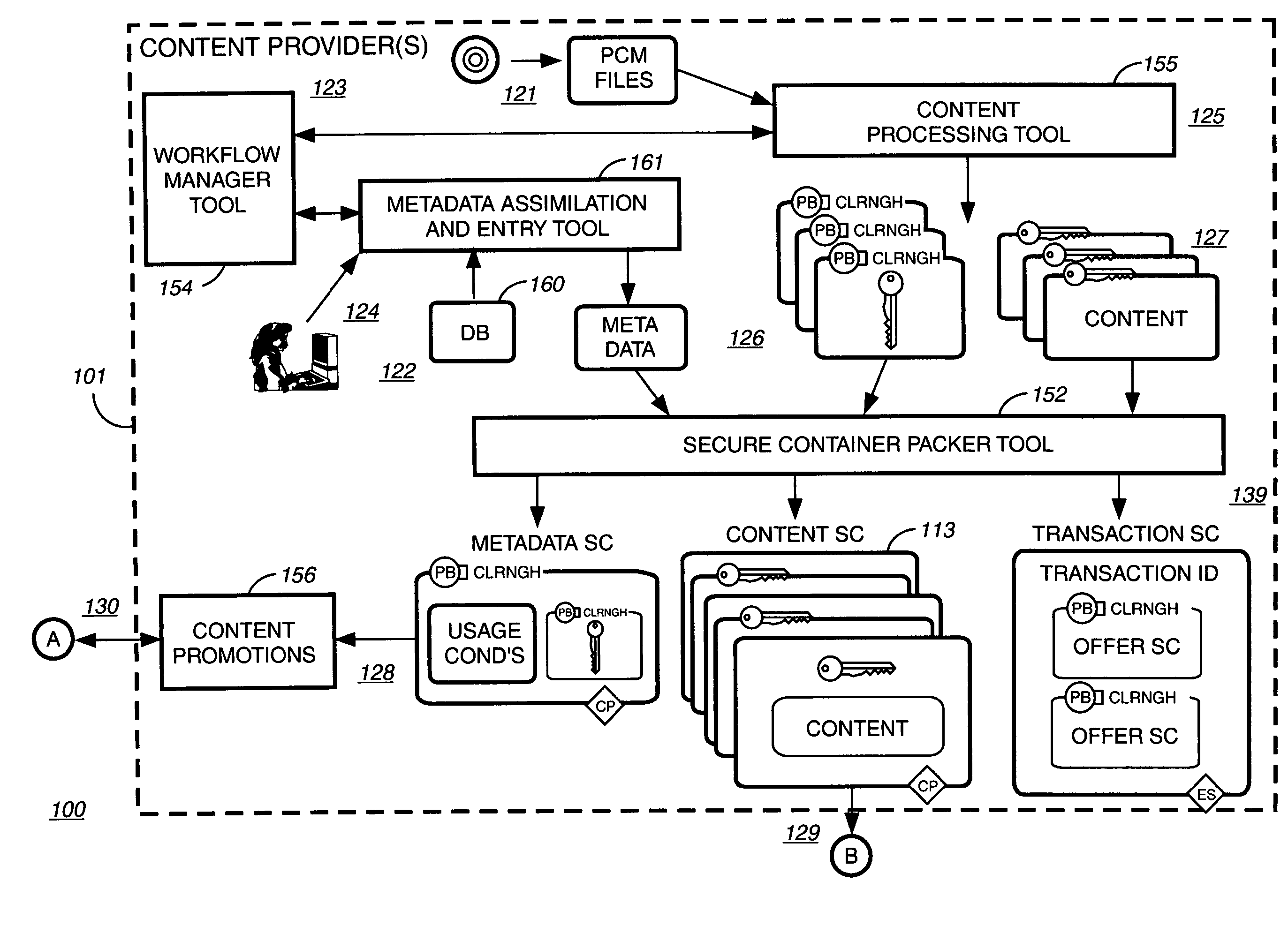
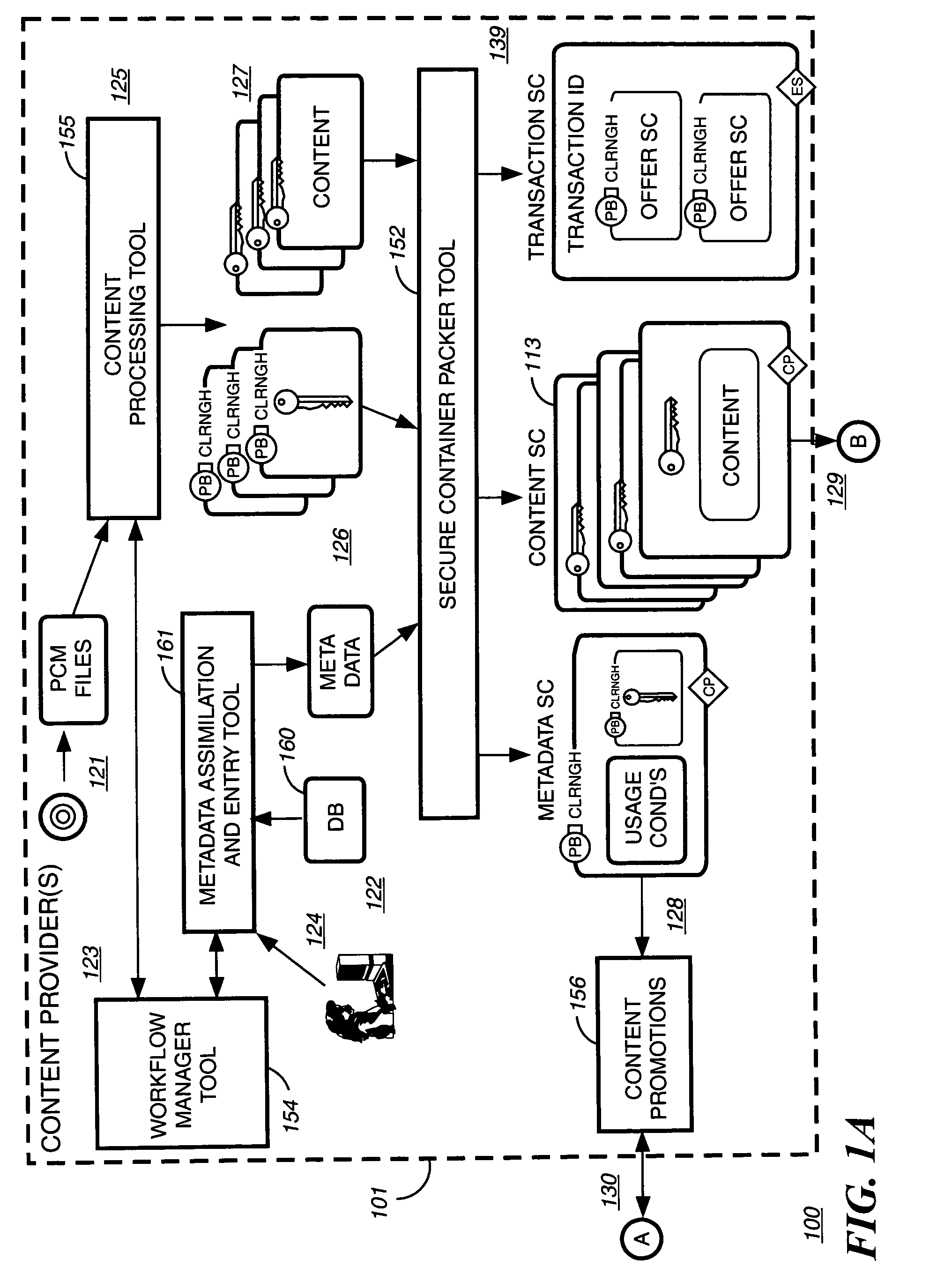
Super-distribution of protected digital content
InactiveUS20060095792A1Unauthorized memory use protectionHardware monitoringDigital contentSecure transmission
Super distribution of protected digital content is disclosed. According to one embodiment of the invention previously purchased encrypted digital content is received from a purchaser of the digital content. The purchaser of the previously purchased encrypted digital content is different from the recipient of the encrypted digital content. A secure transmission is established with an authorization authority for decrypting the content. A first decryption key for decrypting at least part of the previously purchased encrypted content as permitted by the authorization authority is received from the authorization authority. The at least part of the previously purchased encrypted content is decrypted as permitted by the authorization authority.
Owner:IBM CORP
Method for amortizing authentication overhead
InactiveUS7080046B1Payment architectureDigital data authenticationSecure transmissionData transmission
A method is disclosed for amortizing the authentication overhead of data transmissions. The method comprises establishing a first secure transmission of data between a transmitter and a receiver by transmitting at least one token to the receiver during the first secure transmission. There may be any number of senders and receivers, and any receivers may be a sender and vice versa. The method also comprises establishing at least one additional transmission of data between the sender and the receiver and transmitting the data and at least one token during the at least one additional transmission. In addition, the method compares the at least one token transmitted during the at least one additional transmission to the token transmitted during the first secure transmission to guarantee the authenticity of that at least one additional transmission.The method may also include transmitting a preselected number of tokens during the first secure transmission. The number of additional transmissions may or may not correspond to the preselected number of tokens. The at least one additional transmission may be conducted over an unsecure connection using open communication. The first secure transmission may be protected or encrypted.
Owner:AT&T DIGITAL LIFE
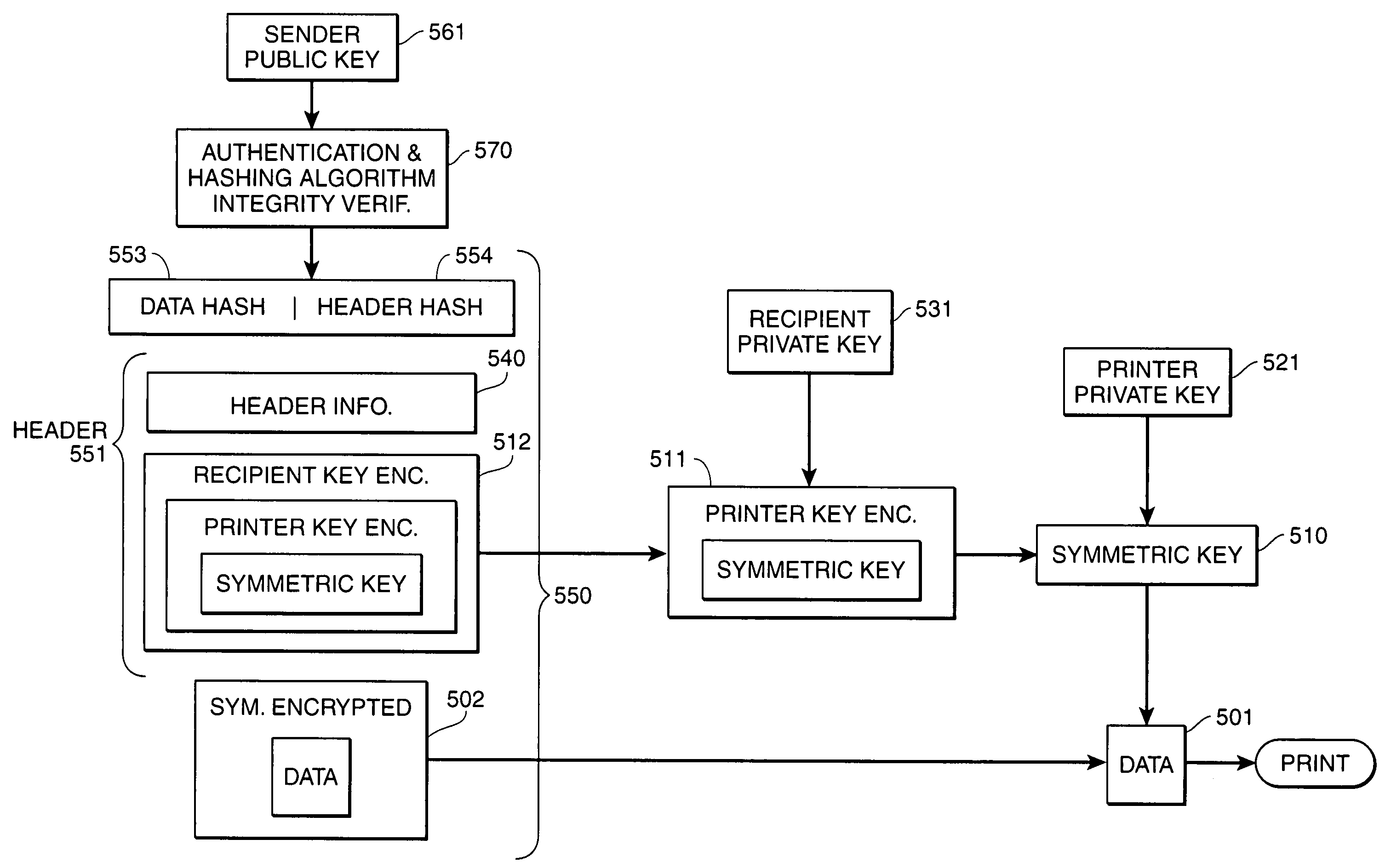
Targeted secure printing
InactiveUS7003667B1Key distribution for secure communicationDigital data processing detailsSecure transmissionOutput device
Secure transmission of data to an intended image output device, wherein the data can be used to generate an image at the intended image output device in the presence of an intended recipient. The data is encrypted using a first key. The first key is then encrypted using a second key and a third key. The second key is a public key of a first private key / public key pair, a private key of the first private key / public key pair being primarily in the sole possession of the intended image output device. The third key is a public key of a second private key / public key pair, a private key of the second private key / public key pair being primarily in the sole possession of the intended recipient of the image. The encrypted data and the twice-encrypted first key are transmitted to the intended image output device. The twice-encrypted first key is then decrypted by using the private keys of the second and first key pairs, respectively, which are primarily in the sole possession of the intended recipient device and the intended image output device, respectively. The data is then decrypted and printed at an image output device.
Owner:CANON KK
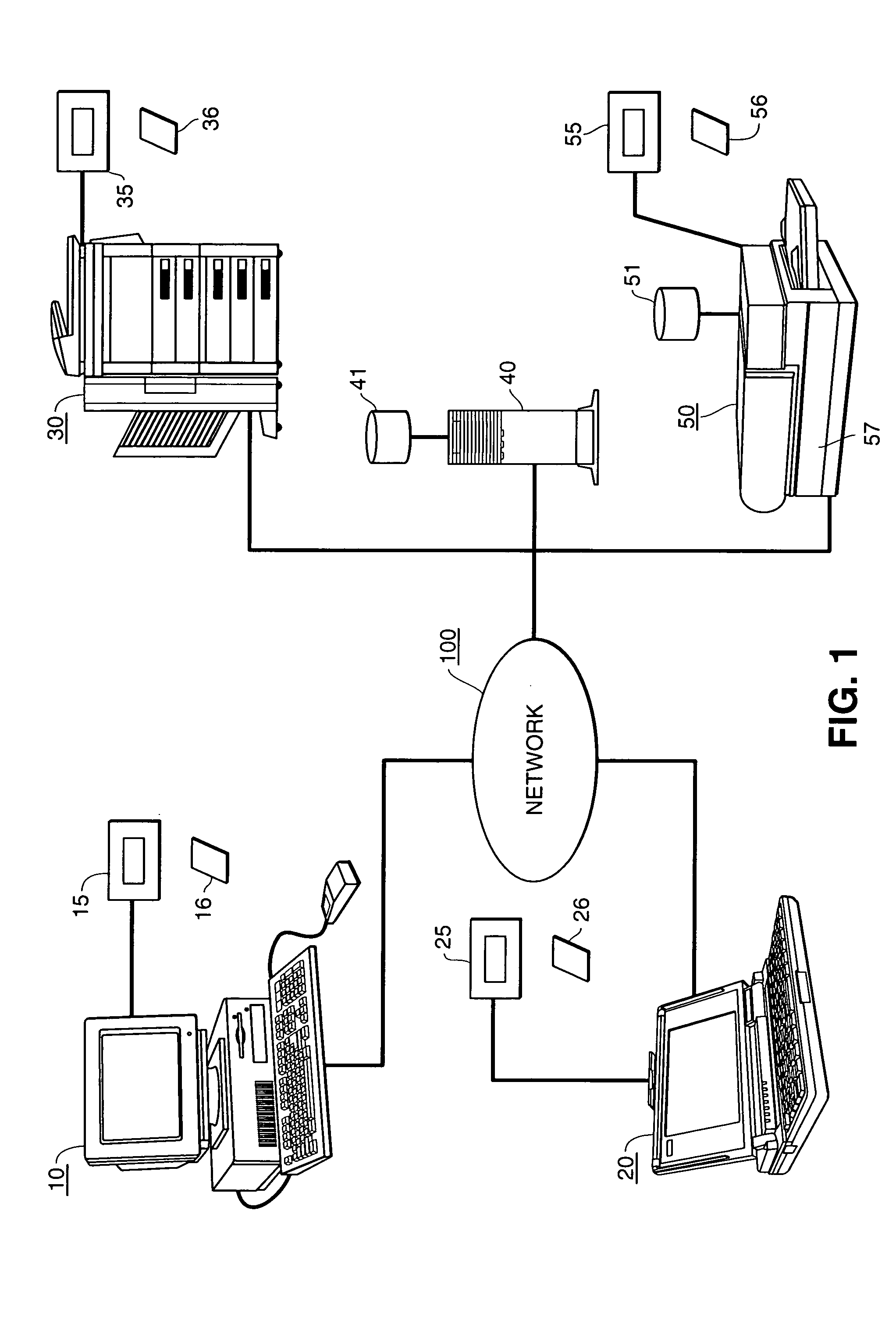
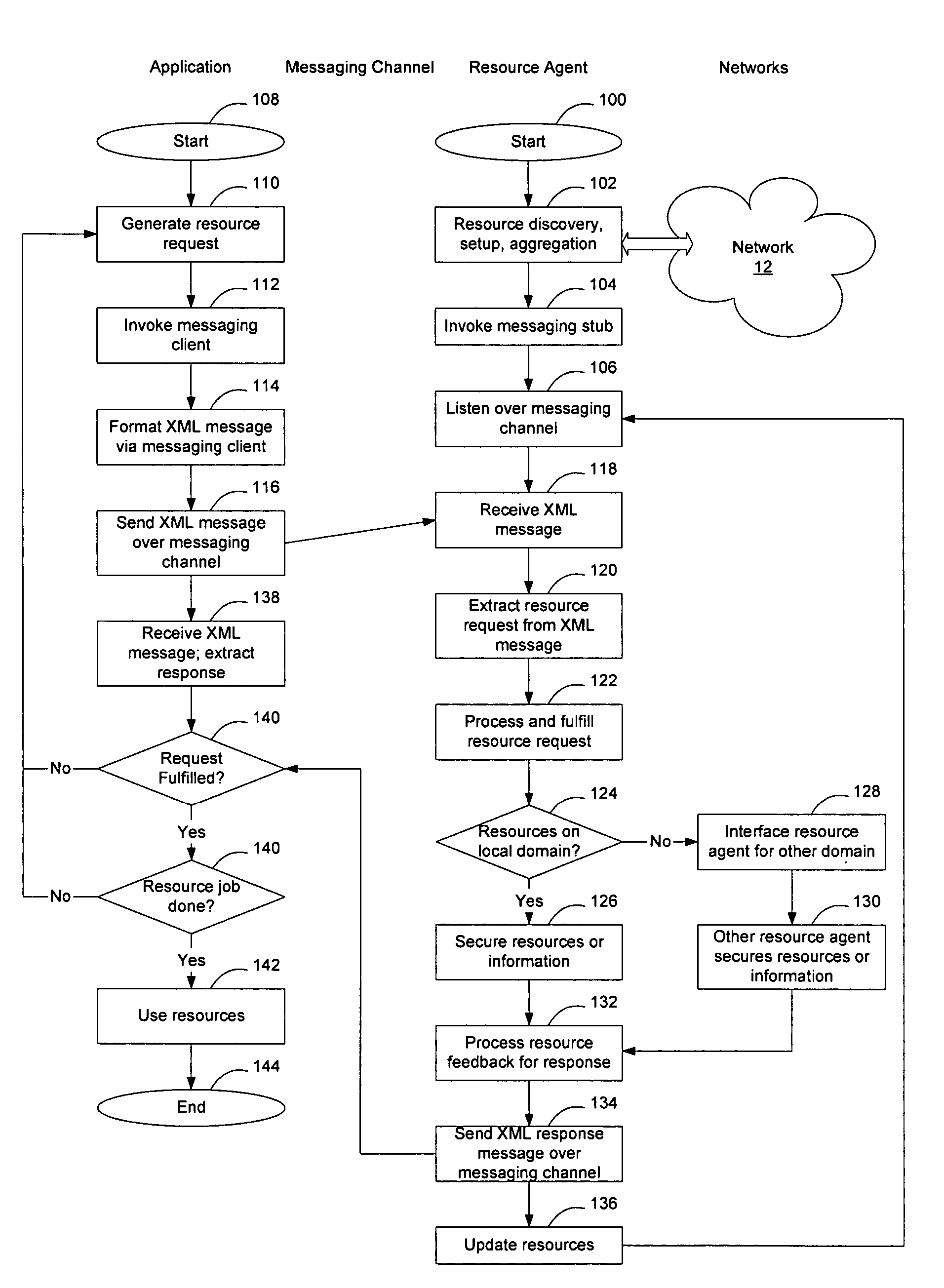
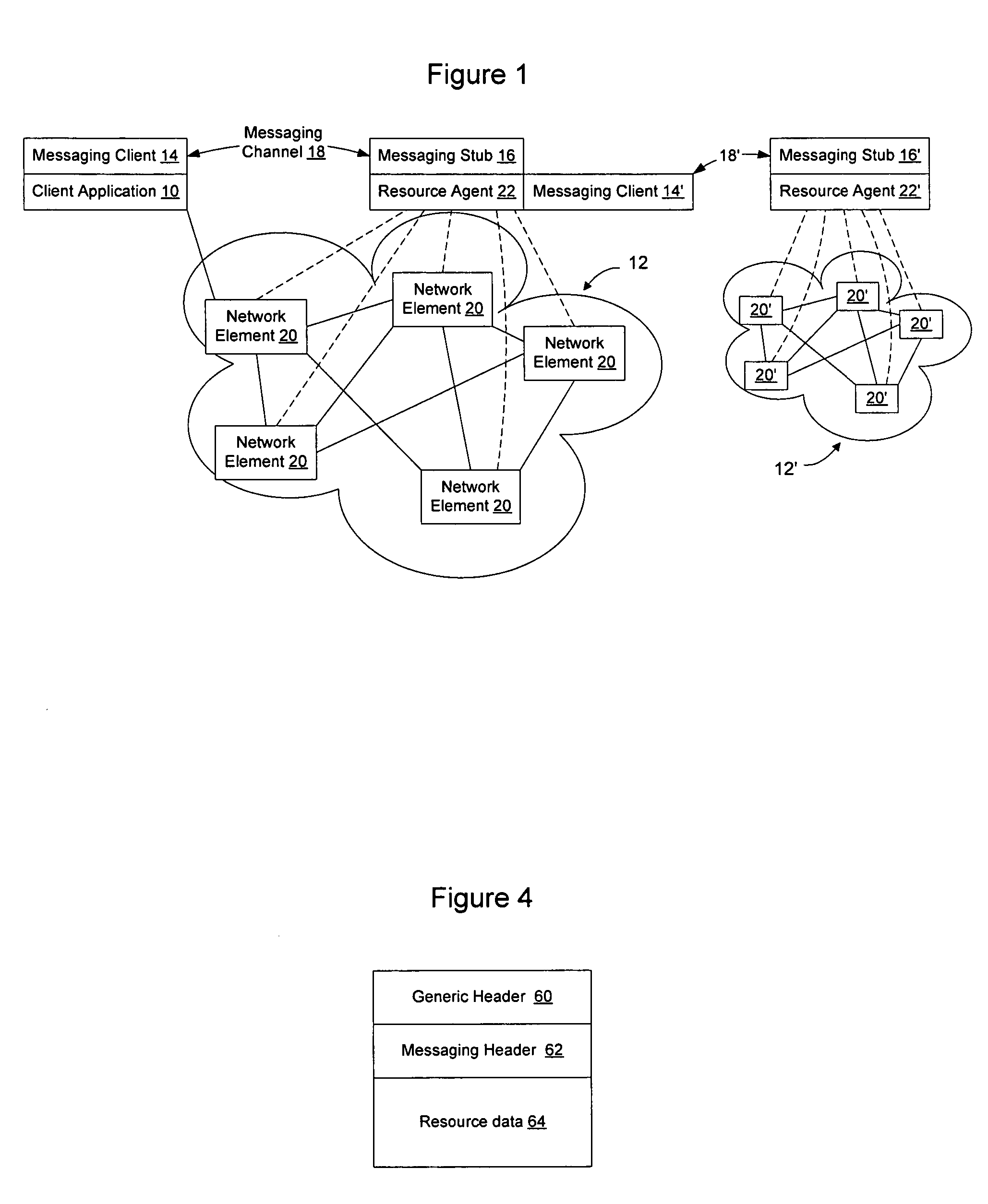
Extensible resource messaging between user applications and network elements in a communication network
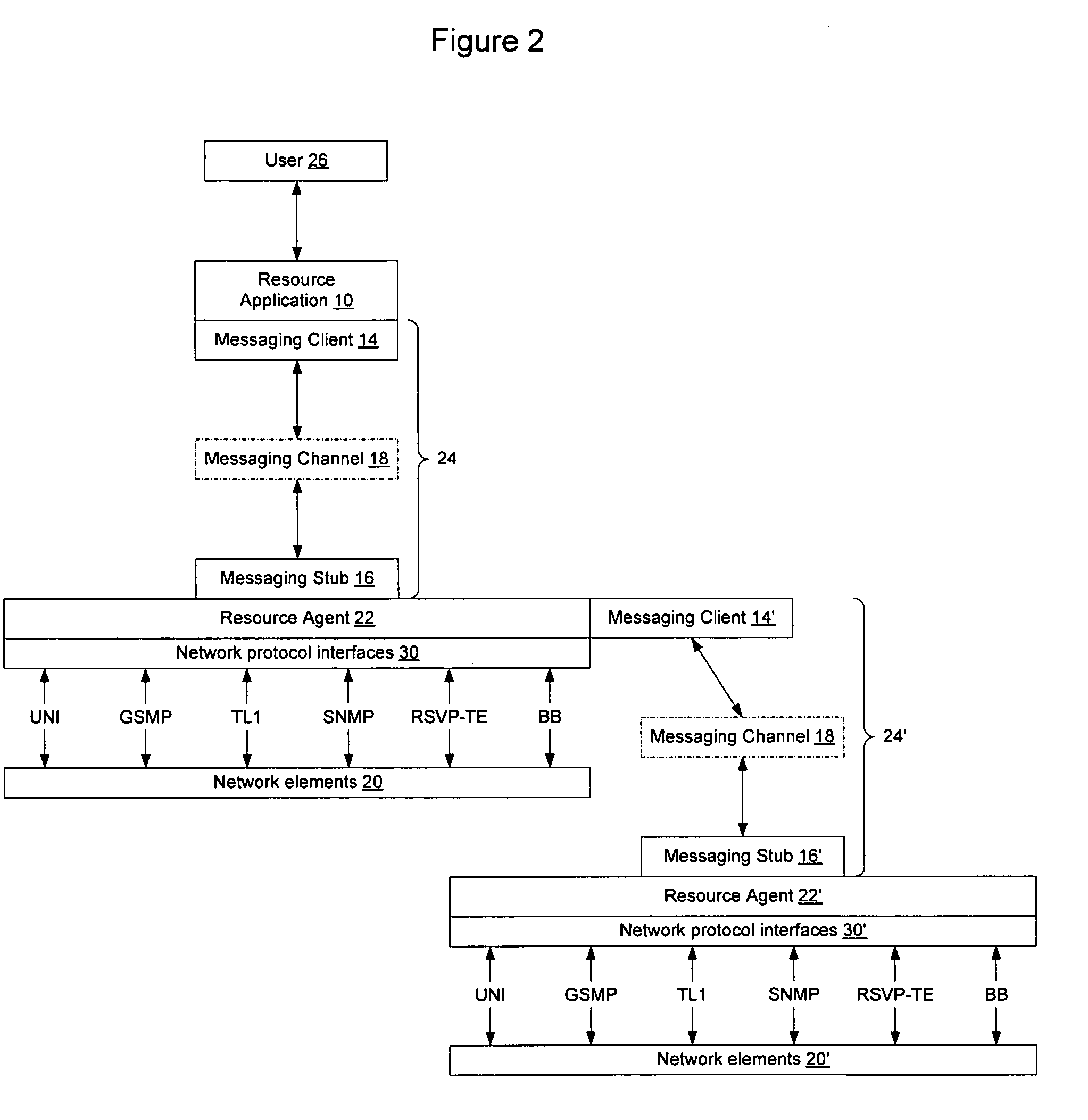
InactiveUS20060075042A1Easily use new network resourceAvoid resourcesMultiple digital computer combinationsTransmissionXML schemaMessage passing
Extensible resource messaging in a communication network is provided through creation of a flexible, extensible, and secure messaging environment. A client-server architecture may be implemented in which user applications employ messaging clients to send resource requests for network information, allocation and other operations and receive resource responses, and in which network elements, through resource agents, may use messaging servers to accept resource requests and return resource responses. Resource agents in different network domains may interact through the messaging environment and work together to fulfill resource requests. An XML-based messaging mechanism may be built with a defined message format that can provide flexible message contexts. Network resource semantics may be specified using XML schemas so that network resources are expressed as resource-specific XML elements and network updates can be implemented by updating the XML resource schemas. Secure enhancements may be realized by secure transport, message verification and other means.
Owner:NORTEL NETWORKS LTD
Secure network file access controller implementing access control and auditing
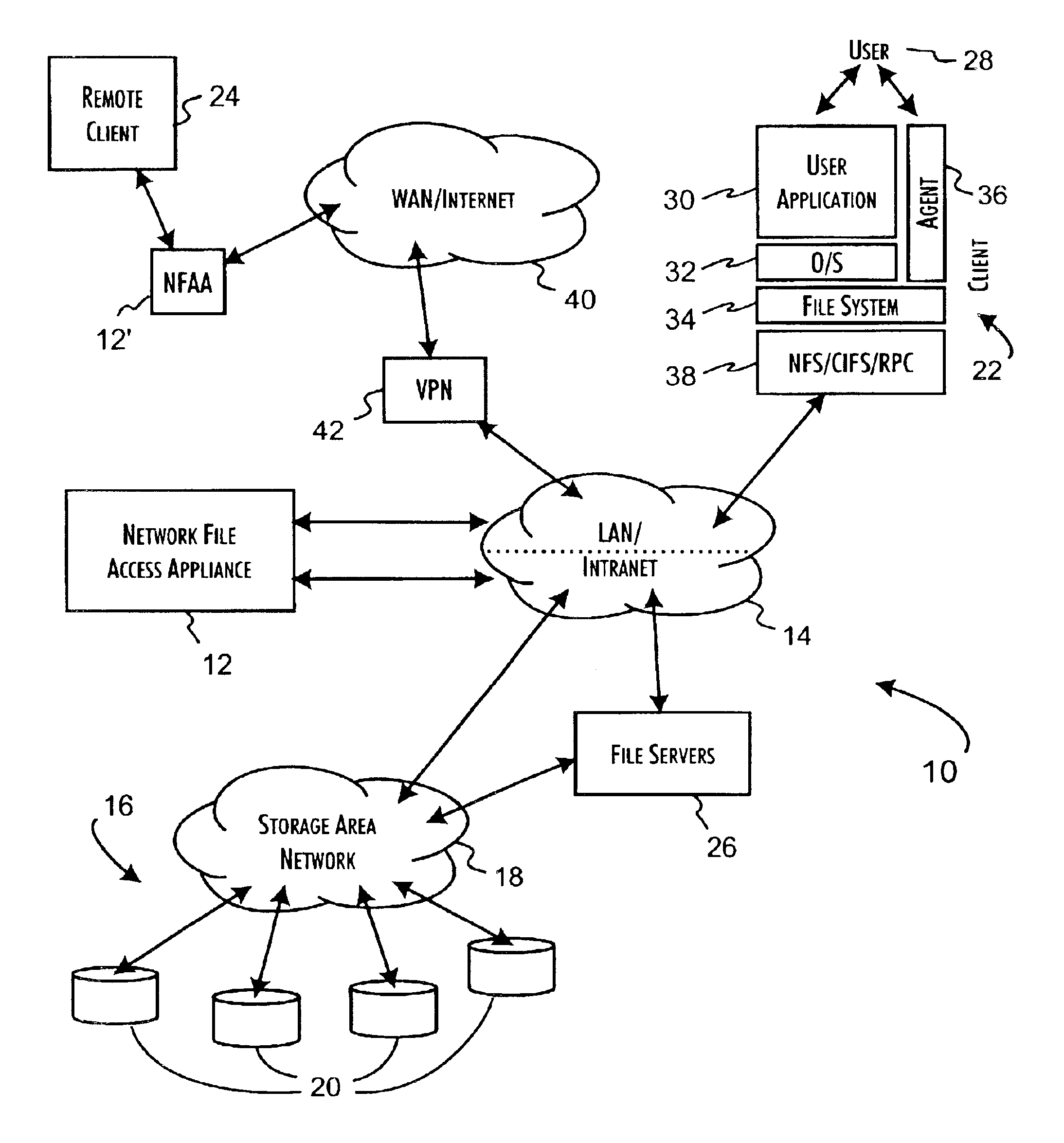
InactiveUS6931530B2Ensure integritySafe storageDigital data processing detailsUser identity/authority verificationReference mapSecure transmission
A network file access appliance operates as a secure portal for network file access operations between client computer systems and network storage resources. The file access appliance terminates network file access transactions, identified by packet information including client system, mount point, and file request identifiers, between client systems and mount points supported by the access controller. A policy parser determines, based on the packet information, to selectively initiate network file access transactions between the access controller and network storage resources to enable completion of selected network file access transactions directed from the clients to the network file access appliance. The network file access transactions directed to the network storage resources are modified counterparts of policy selected client network file access transactions modified to reference mapped network storage resource mount points and support the secure transfer and storage of network file data.
Owner:THALES DIS CPL USA INC
Adaptive method for amortizing authentication overhead
InactiveUS7085937B1Digital data processing detailsMultiple digital computer combinationsSecure transmissionSelf adaptive
A method is disclosed for amortizing the authentication overhead of data transmissions. The method comprises establishing a first secure transmission of data between a transmitter and a receiver by transmitting at least one token to the receiver during the first secure transmission. There may be any number of senders and receivers, and any receivers may be a sender and vice versa. The method also comprises establishing at least one additional transmission of data between the sender and the receiver and transmitting the data and at least one token during the at least one additional transmission. In addition, the method compares the at least one token transmitted during the at least one additional transmission to the token transmitted during the first secure transmission to guarantee the authenticity of that at least one additional transmission. The method may also include transmitting a preselected number of tokens during the first secure transmission. The number of additional transmissions may or may not correspond to the preselected number of tokens. The at least one additional transmission may be conducted over an unsecure connection using open communication. The first secure transmission may be protected or encrypted.
Owner:AT&T DIGITAL LIFE
System and method for providing secure internetwork services via an assured pipeline
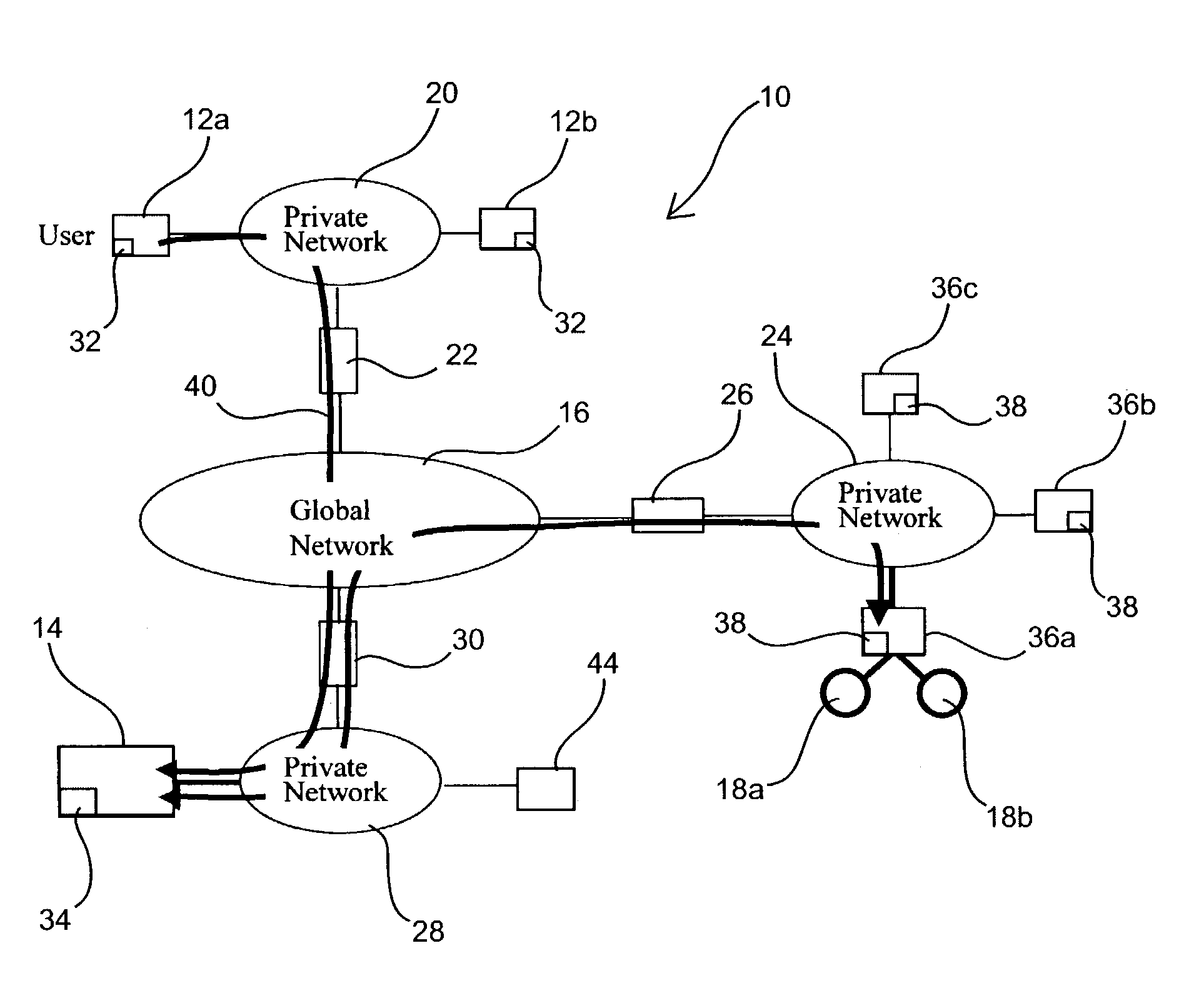
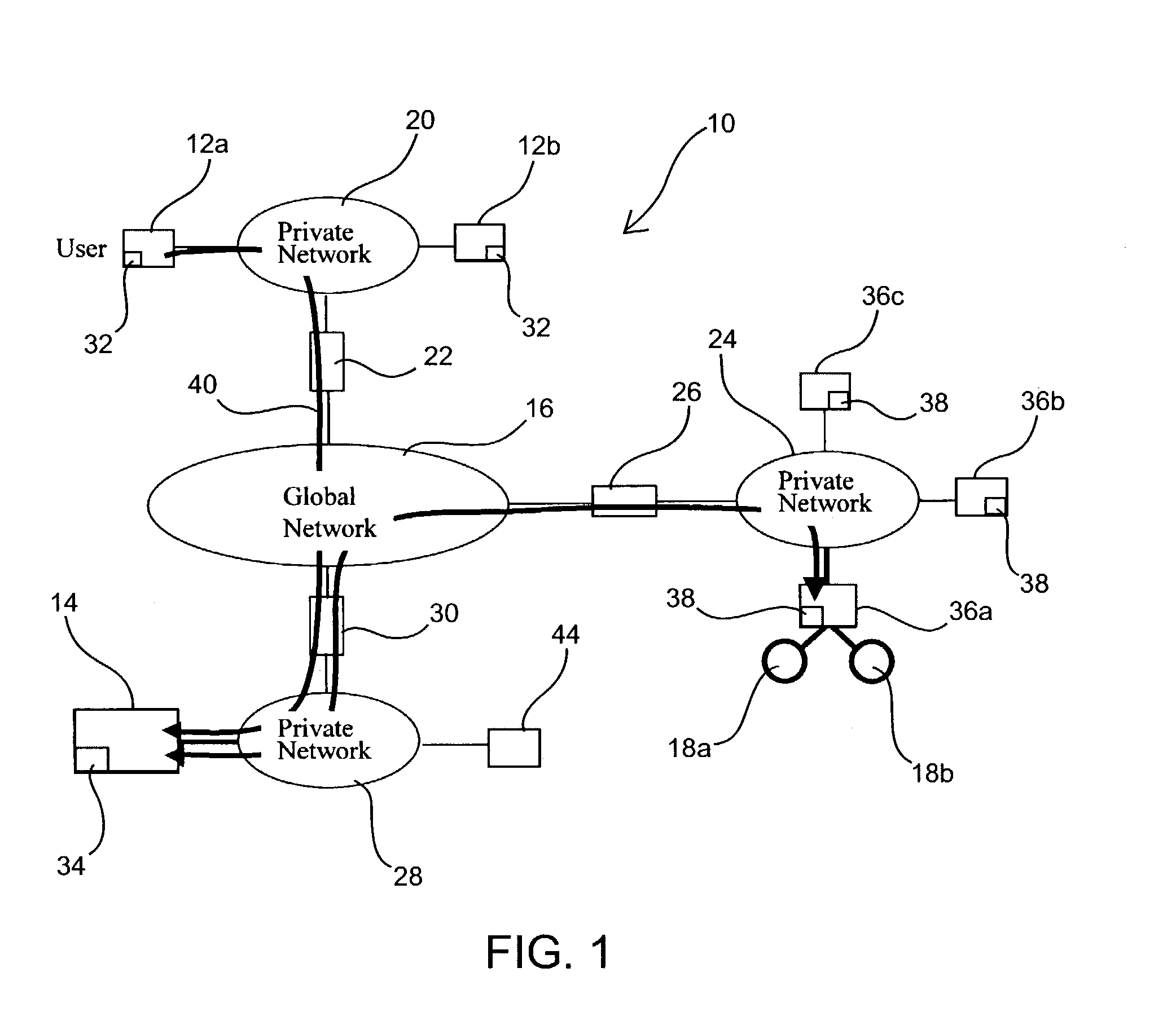
InactiveUS6772332B1Multiple digital computer combinationsPlatform integrity maintainanceSecure transmissionPrivate network
A system and method for the secure transfer of data between a workstation connected to a private network and a remote computer connected to an unsecured network. A secure computer is inserted into the private network to serve as the gateway to the unsecured network and a client subsystem is added to the workstation in order to control the transfer of data from the workstation to the secure computer. The secure computer includes a private network interface connected to the private network, an unsecured network interface connected to the unsecured network, wherein the unsecured network interface includes means for encrypting data to be transferred from the first workstation to the remote computer and a server function for transferring data between the private network interface and the unsecured network interface.
Owner:MCAFEE LLC
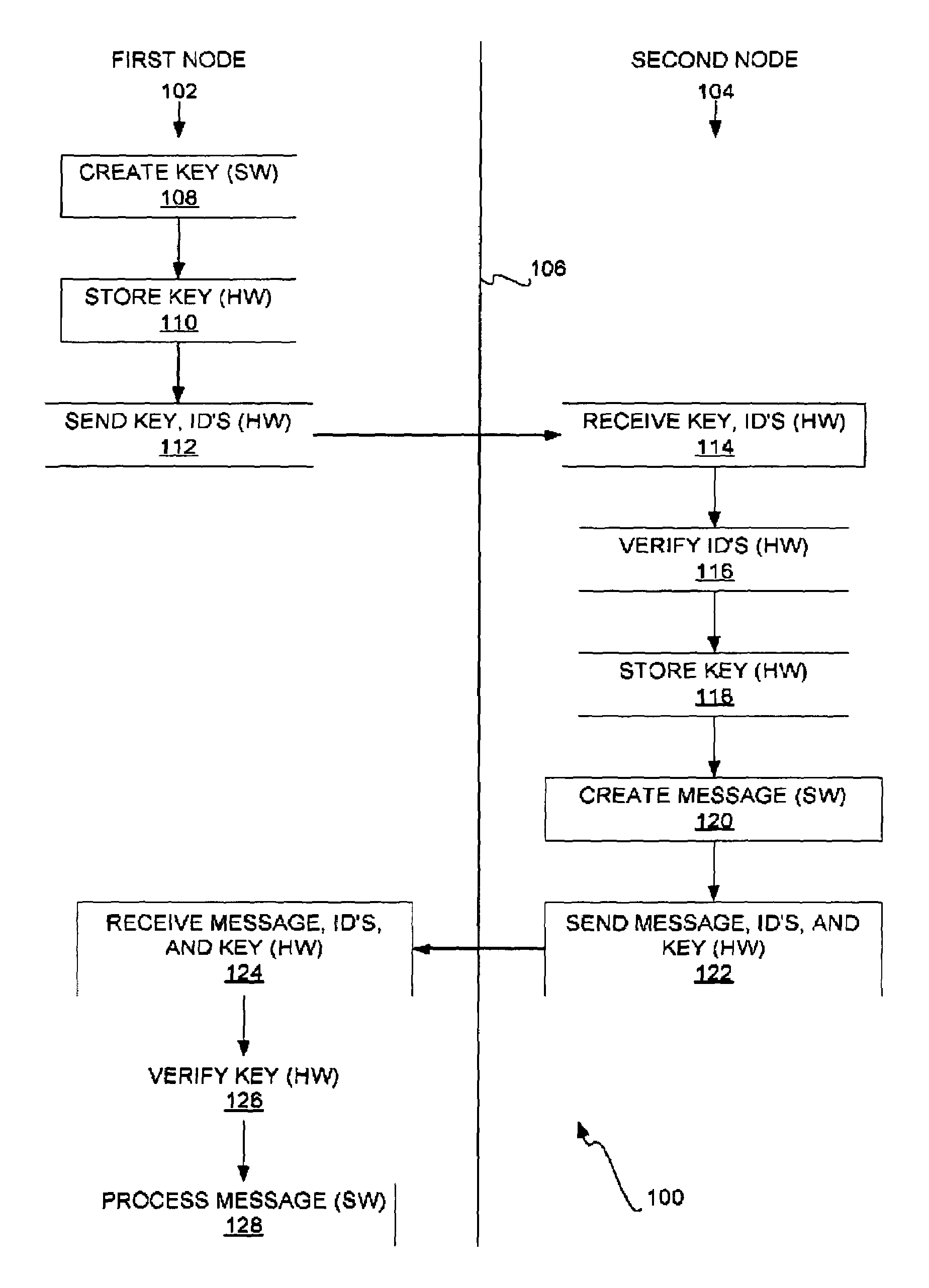
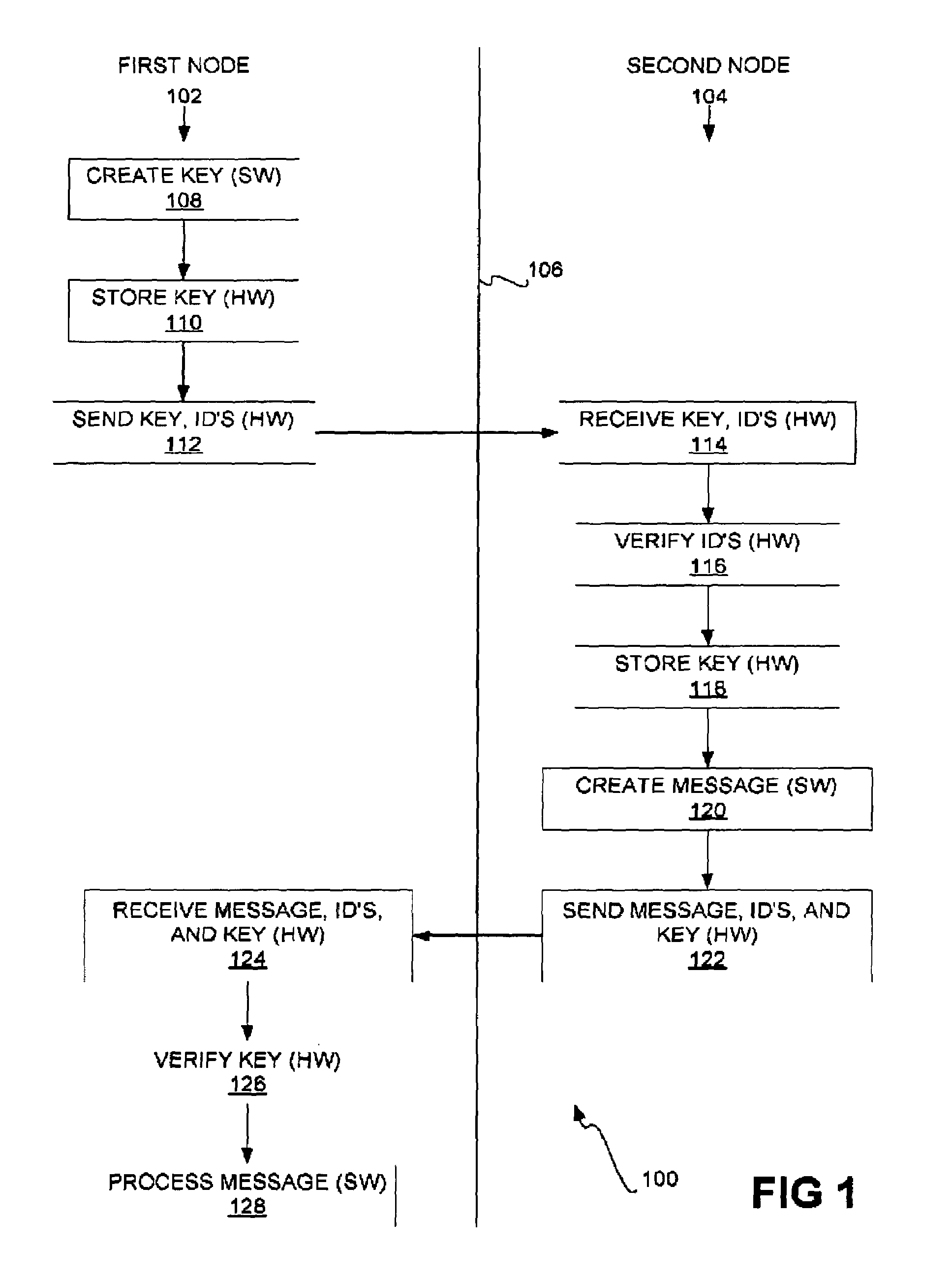
Secure inter-node communication
InactiveUS7231519B2Communication securityKey distribution for secure communicationDigital data processing detailsComputer hardwareSecure transmission
Secure inter-node communication is disclosed. The hardware of the first node sends a key, identification of the first node, and identification of a second node to hardware of the second node. The hardware of the second node receives the key and the identifications. The hardware of the second node verifies the identifications of the first and the second nodes, and stores the key. The key stored in the hardware of the first and the second nodes allows for a secure transmission channel from the software of the first node to software of the second node.
Owner:GOOGLE LLC
Data transfer and management system
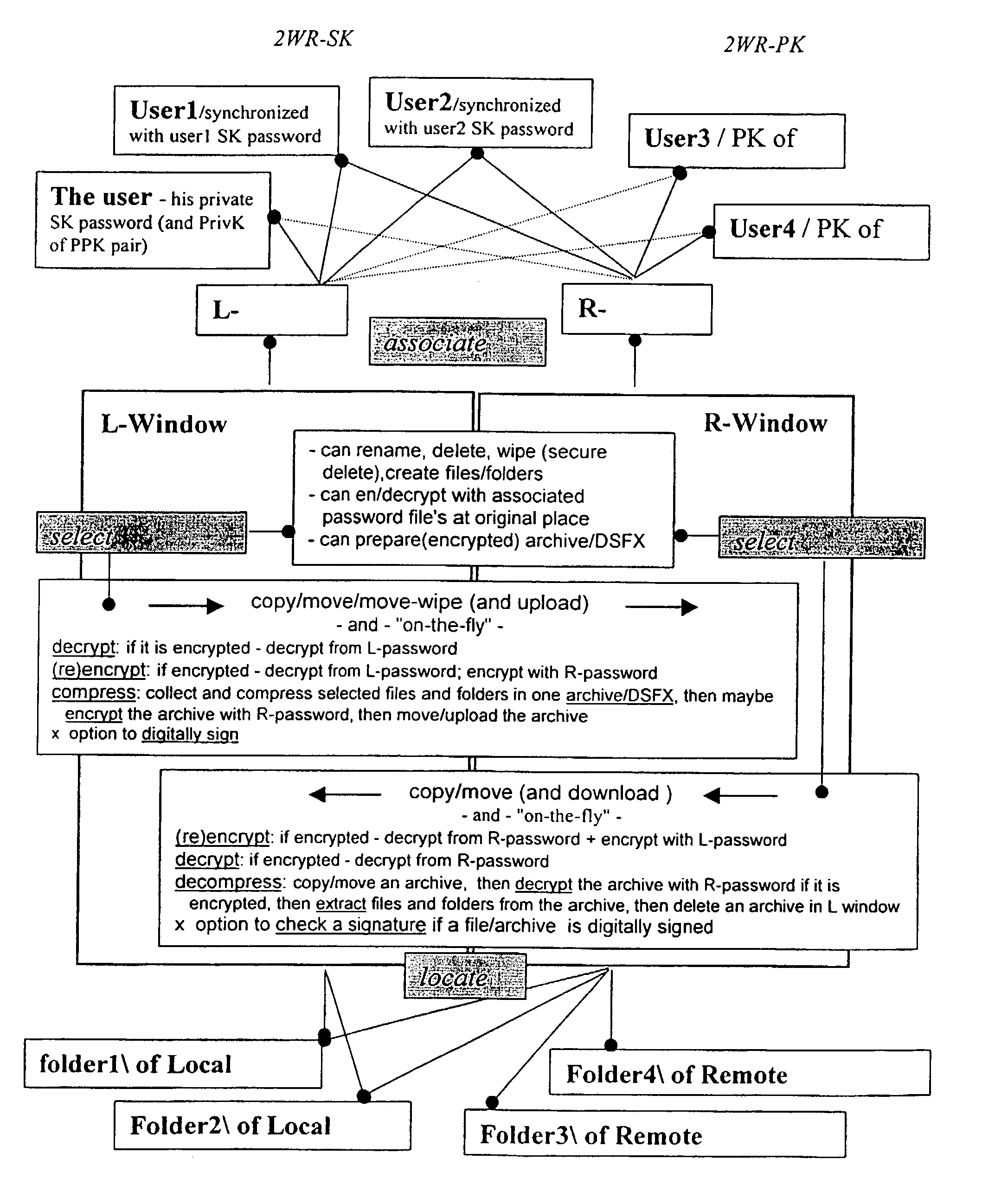
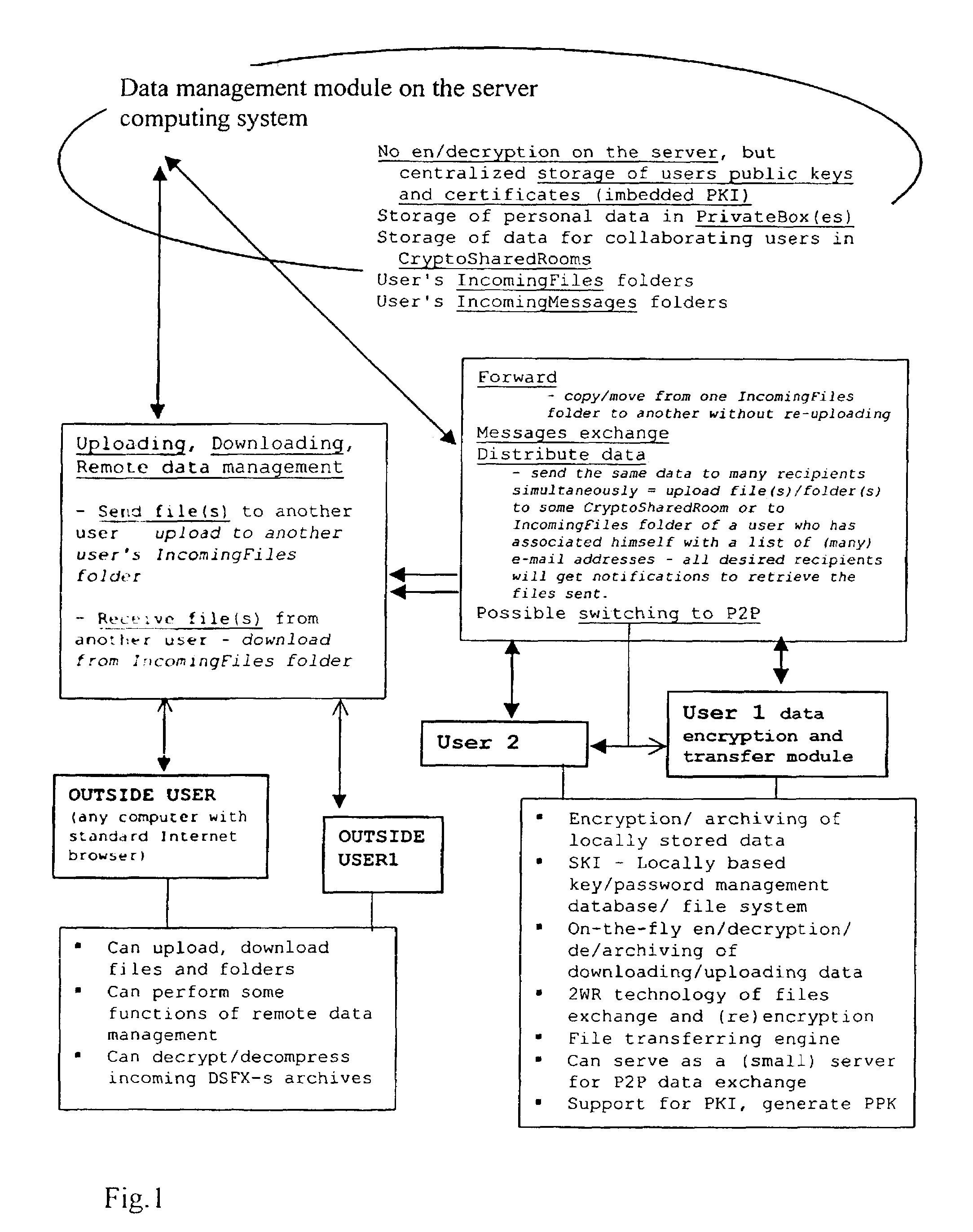
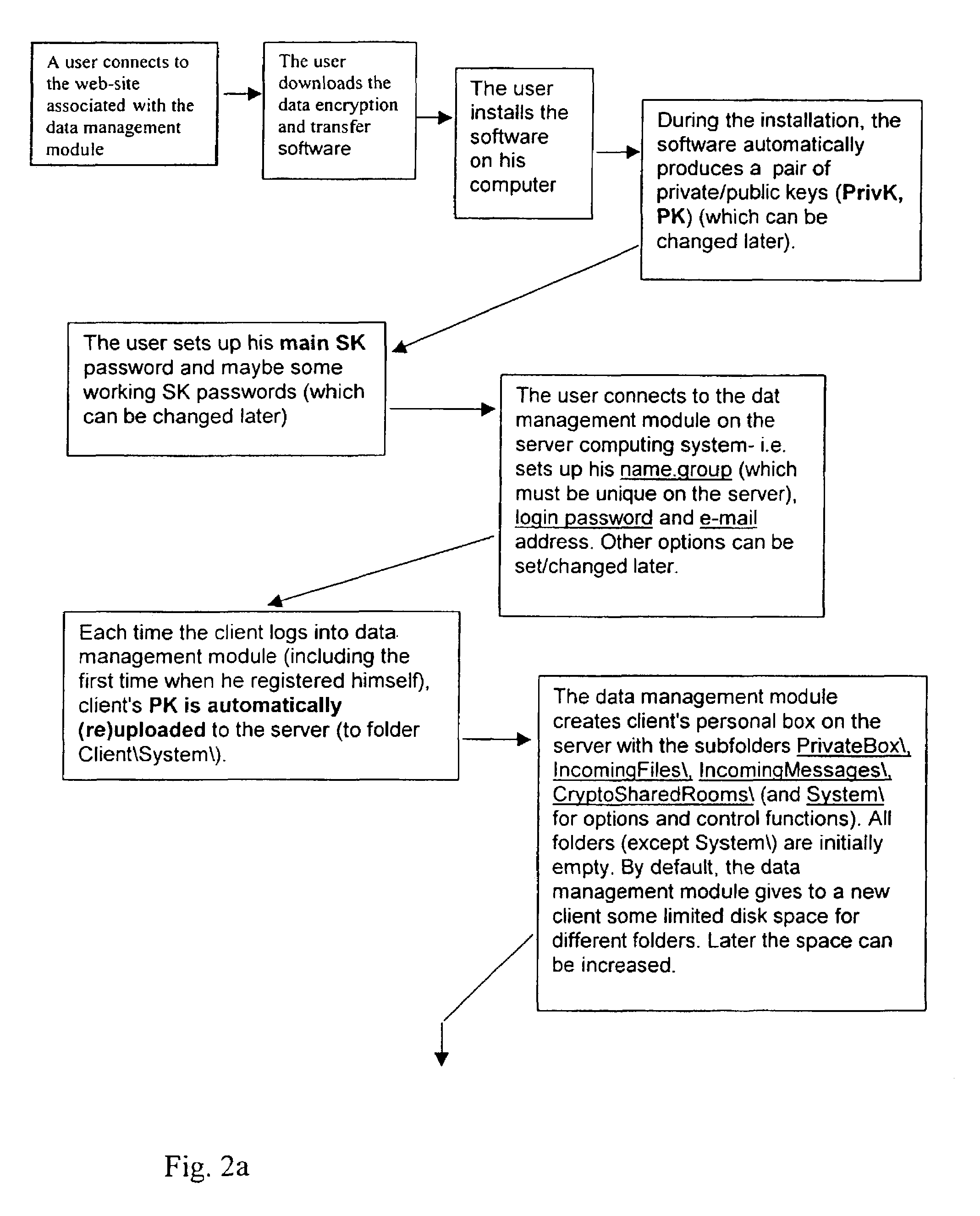
InactiveUS20030177422A1Easily and securely managedEasily downloadableReliability increasing modificationsError preventionMegabyteData file
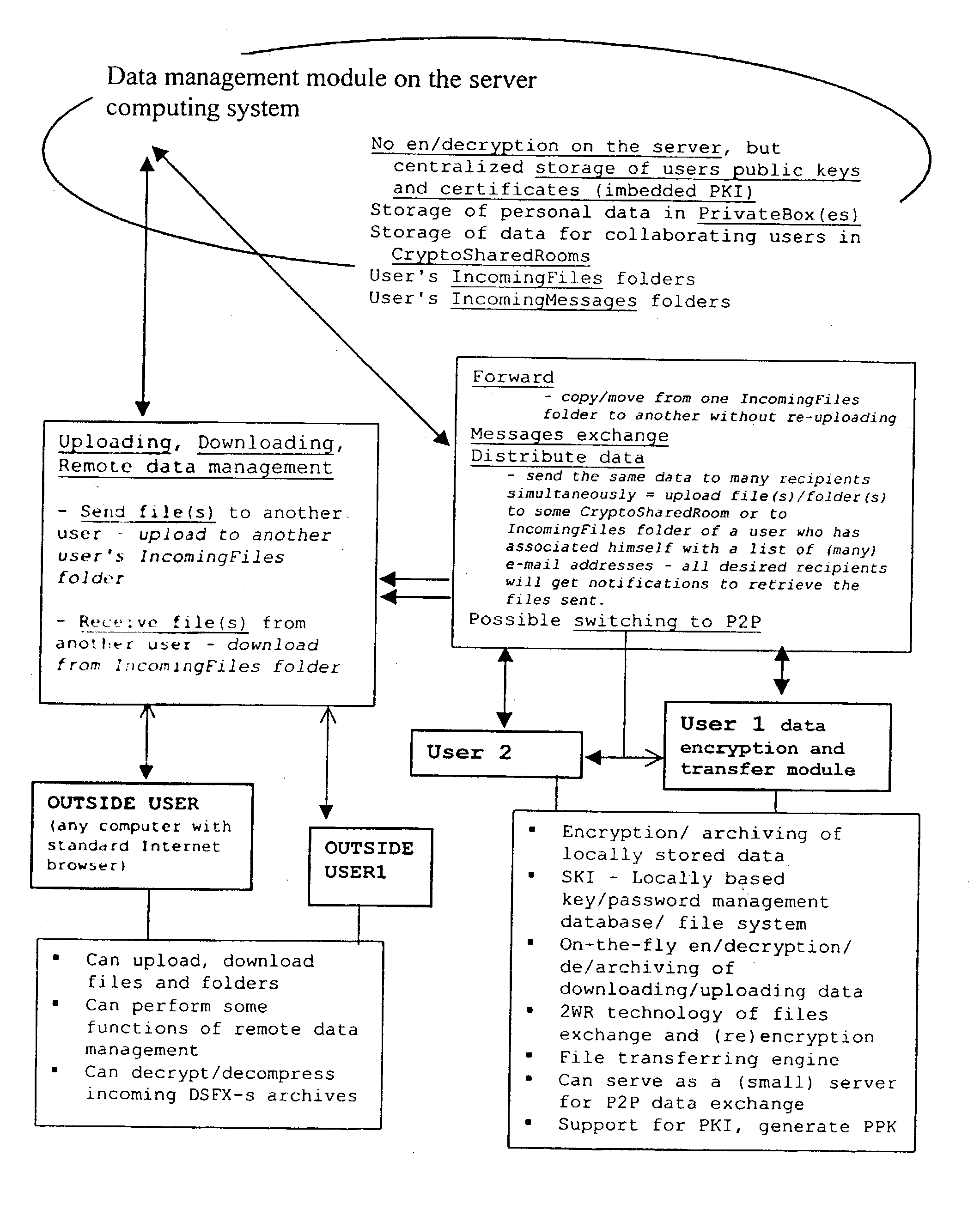
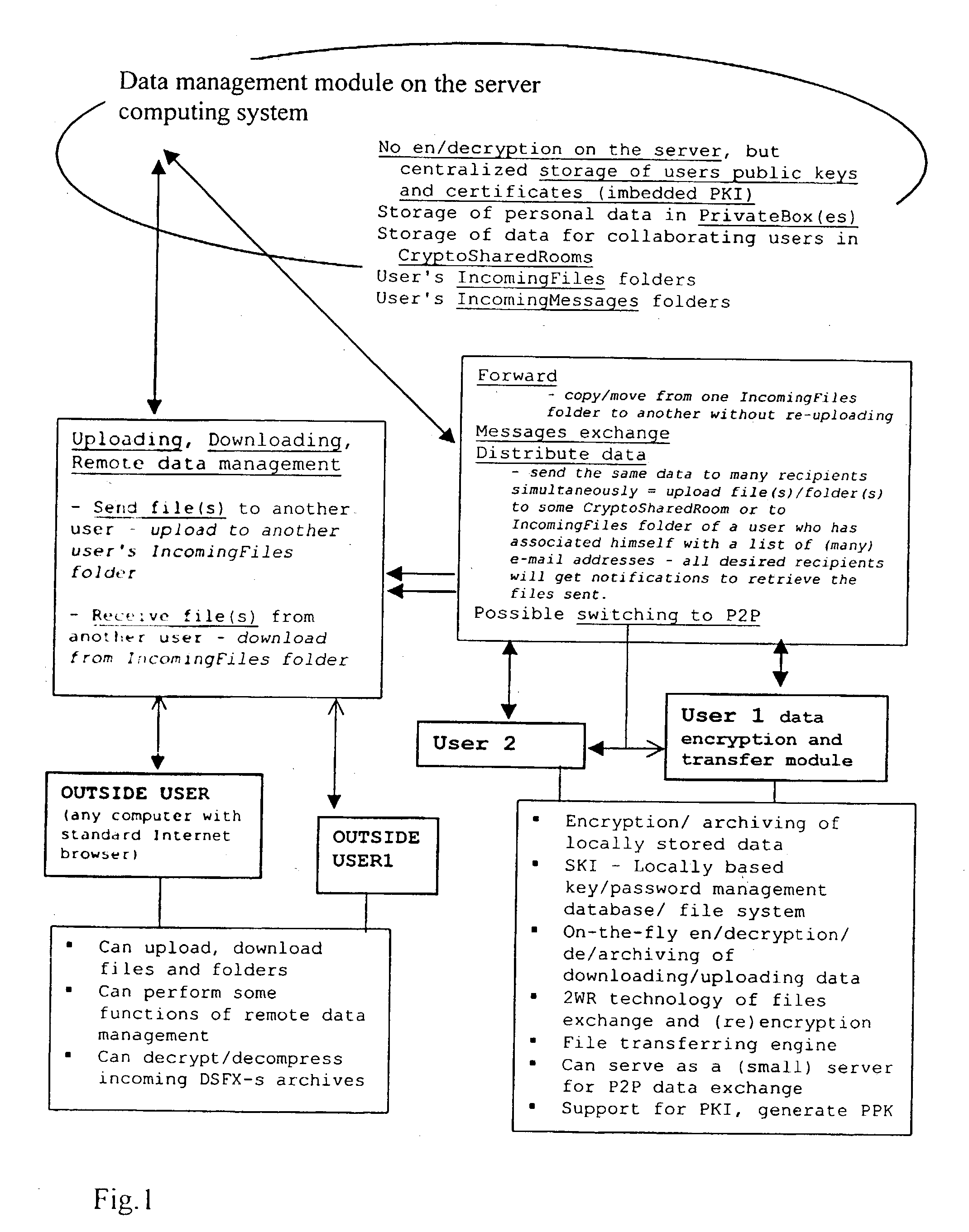
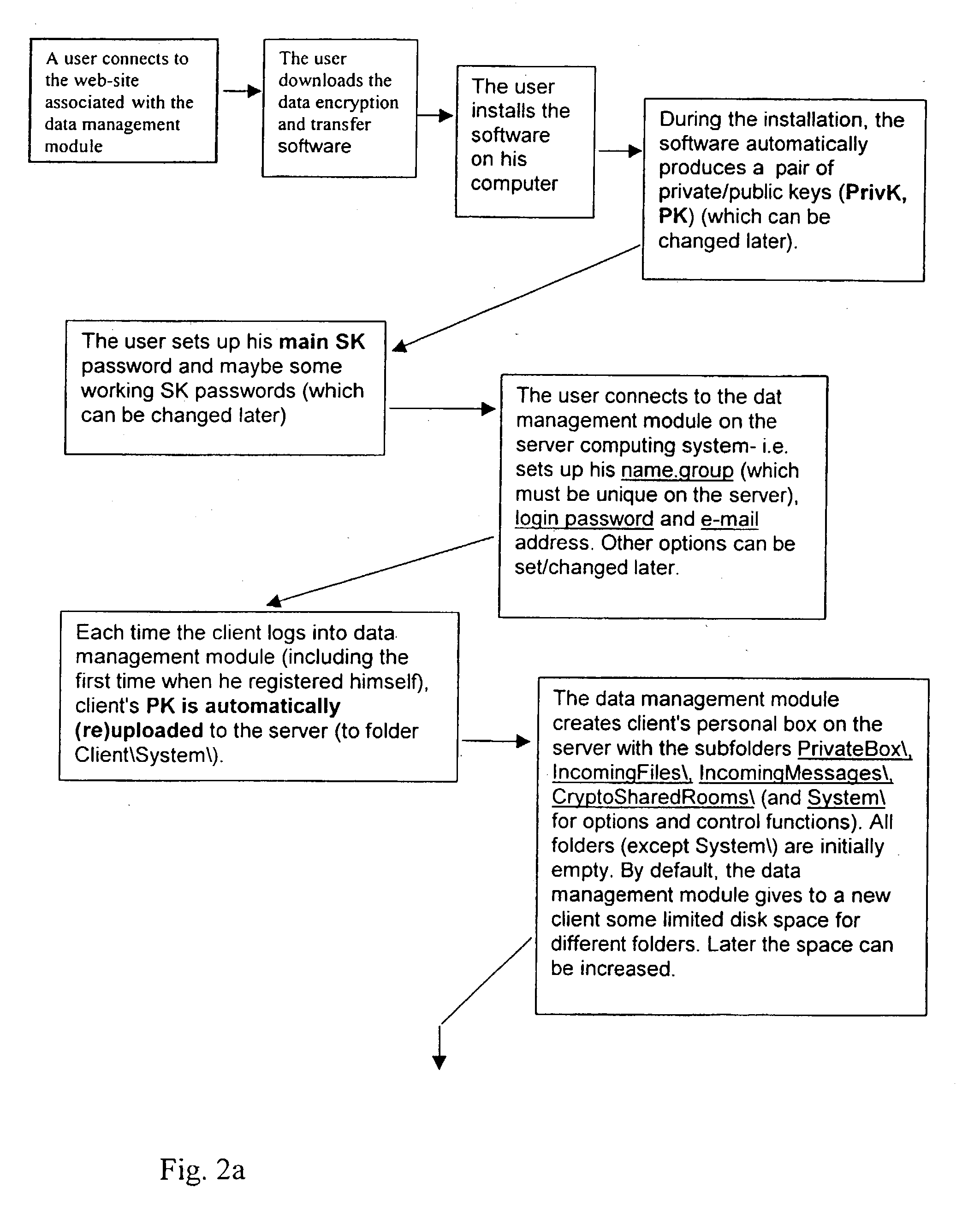
A system for the secure transfer of data and data management on the Internet has a data encryption and transfer module operable in a user computing system, a data management module operable in a server computing system, the transfer of data between the user and server computing systems being effected on the user computing system through use of the data encryption and transfer module, by moving the data to or from a first desktop window, associated with the user computing system, from or to a second desktop window, associated with the server computing system, each window being associated with a password, such that the step of moving the data from one window to the other causes the data to be encrypted / re-encrypted from one associated password to the other. The system also includes a password management module operable in the user computing system for managing the passwords, which are required to be used by a user of the system. The system uses symmetric key encryption coupled with file transfer protocol (FTP) data transfer and allows for the secure transfer of large data files of 100 megabytes or more.
Owner:HERBERT STREET TECH
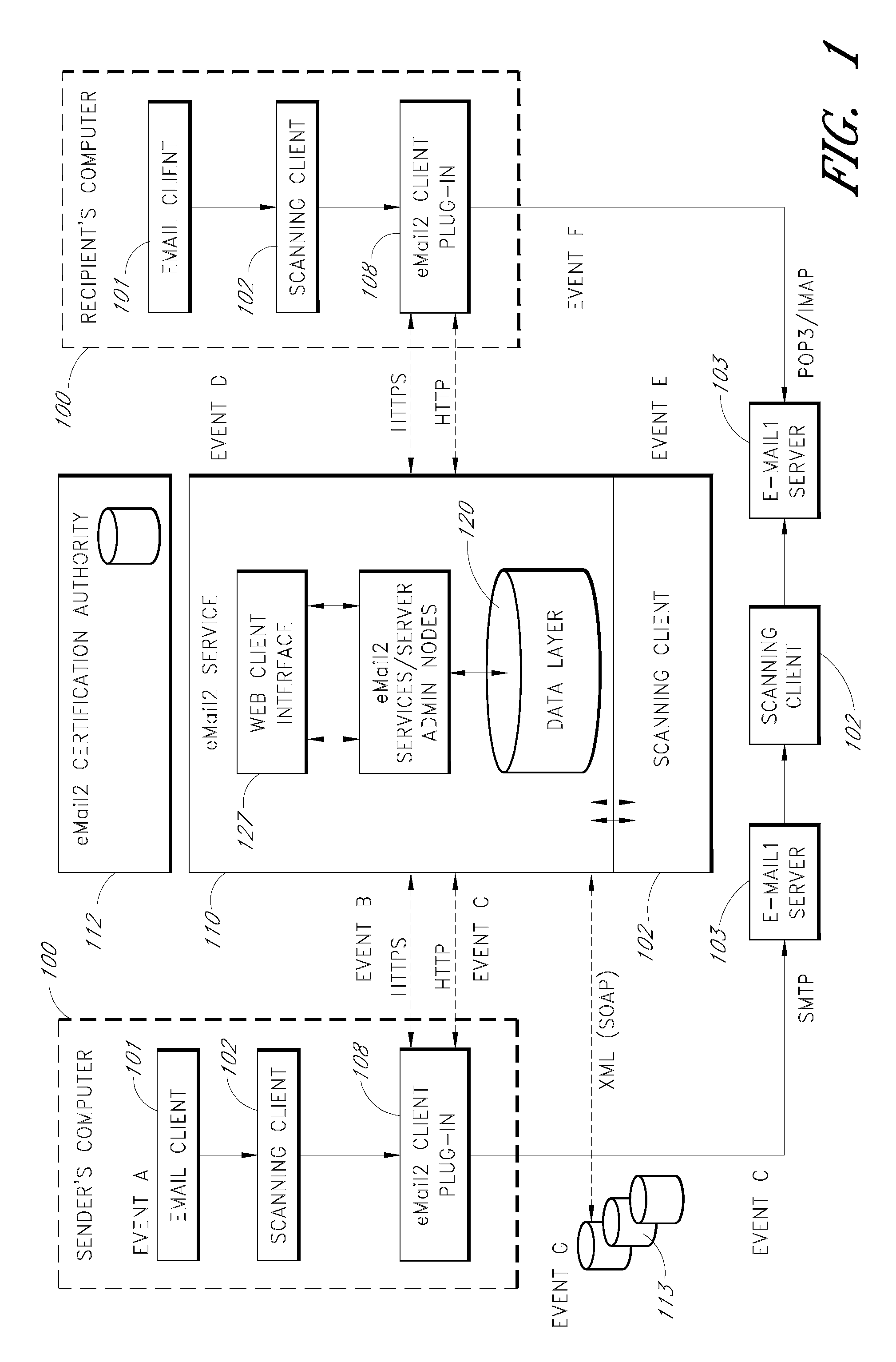
Electronic mail system with aggregation and integrated display of related messages
ActiveUS20070005715A1Easy to watchDigital data protectionMultiple digital computer combinationsEmail addressInternet privacy
An e-mail system is disclosed that overcomes many deficiencies of, but is backward compatible with, existing e-mail systems. Embodiments of the system may include various features, including but not limited to: (1) secure transfer of e-mail messages, without the need for users to replace existing e-mail clients or to change e-mail addresses; (2) tracking of all actions performed in connection with an e-mail transmission; (3) the ability for a recipient to view information about an e-mail message, optionally including information about how other addressees have responded to it, before deciding whether to retrieve the e-mail message; (4) the aggregation of entire e-mail conversations into a single threaded view; (5) the ability to include both private and public messages in a single e-mail communication; (6) sender control over downstream actions performed in connection with an e-mail message; (7) flexible control over cryptographic methods used to encrypt emails messages for storage.
Owner:APPRIVER CANADA ULC
Electronic mail system with pre-message-retrieval display of message metadata
ActiveUS20070005716A1Easy to watchDigital data protectionMultiple digital computer combinationsEmail addressSecure transmission
An e-mail system is disclosed that overcomes many deficiencies of, but is backward compatible with, existing e-mail systems. Embodiments of the system may include various features, including but not limited to: (1) secure transfer of e-mail messages, without the need for users to replace existing e-mail clients or to change e-mail addresses; (2) tracking of all actions performed in connection with an e-mail transmission; (3) the ability for a recipient to view information about an e-mail message, optionally including information about how other addressees have responded to it, before deciding whether to retrieve the e-mail message; (4) the aggregation of entire e-mail conversations into a single threaded view; (5) the ability to include both private and public messages in a single e-mail communication; (6) sender control over downstream actions performed in connection with an e-mail message; (7) flexible control over cryptographic methods used to encrypt emails messages for storage.
Owner:APPRIVER CANADA ULC
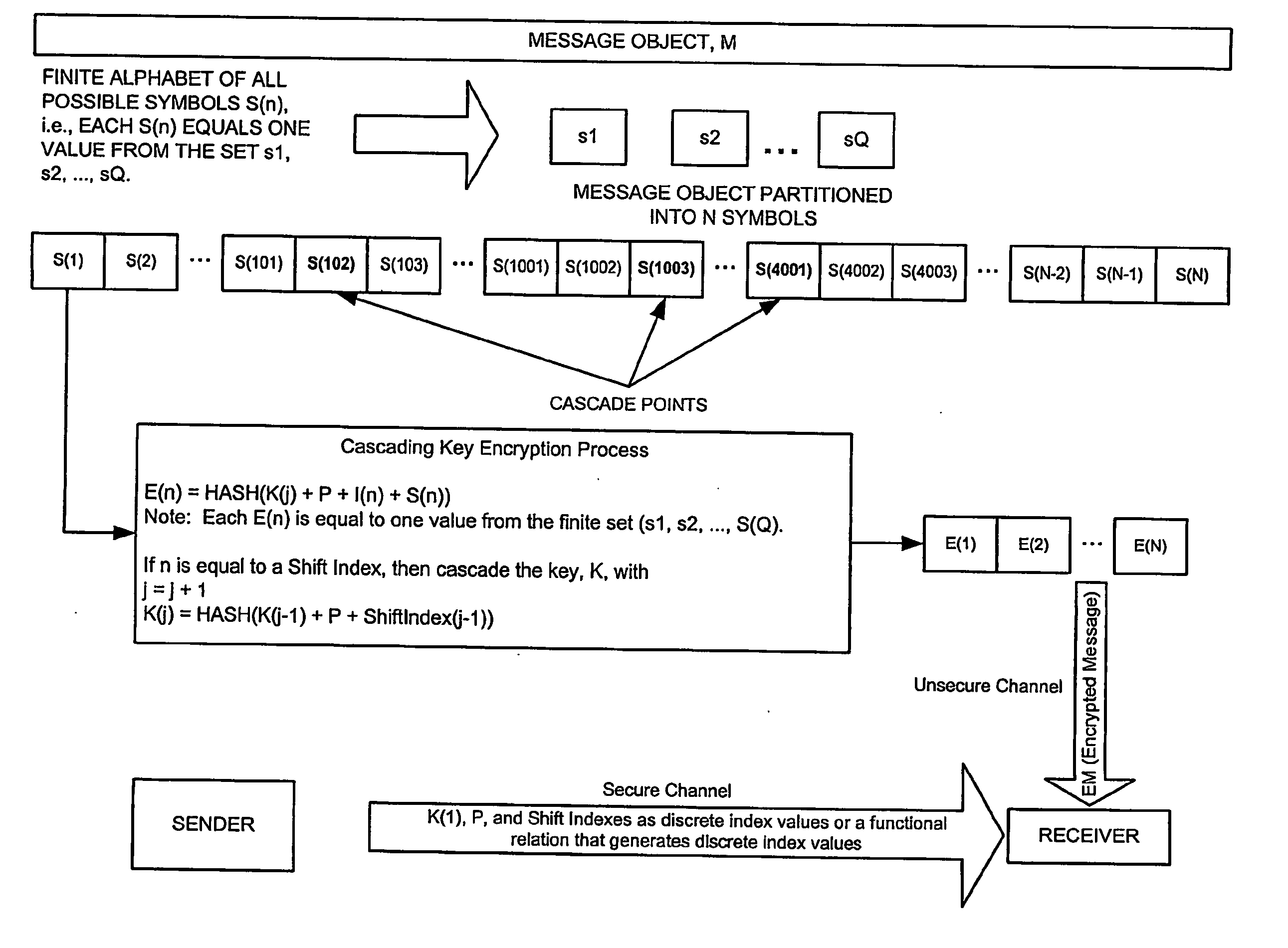
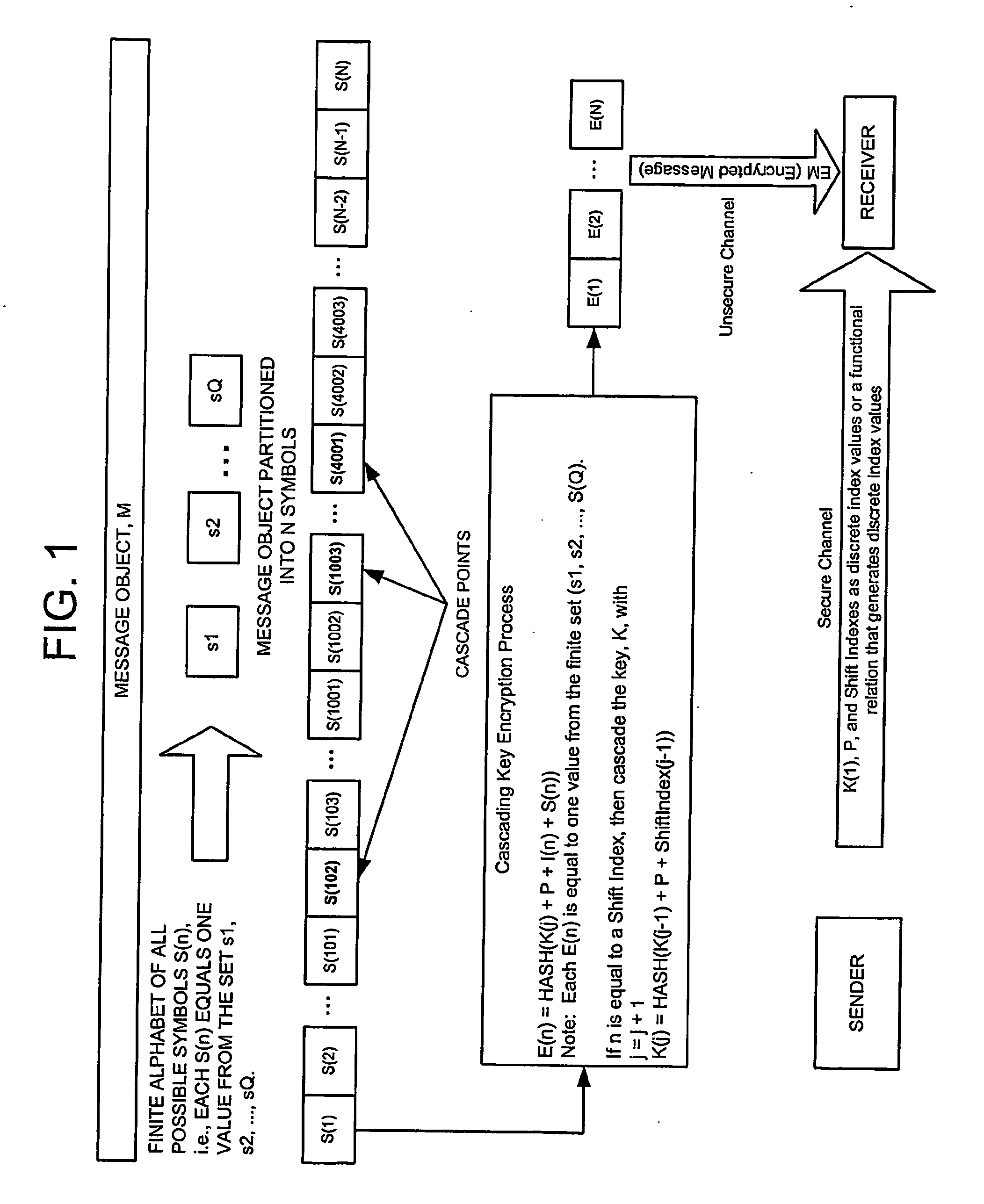
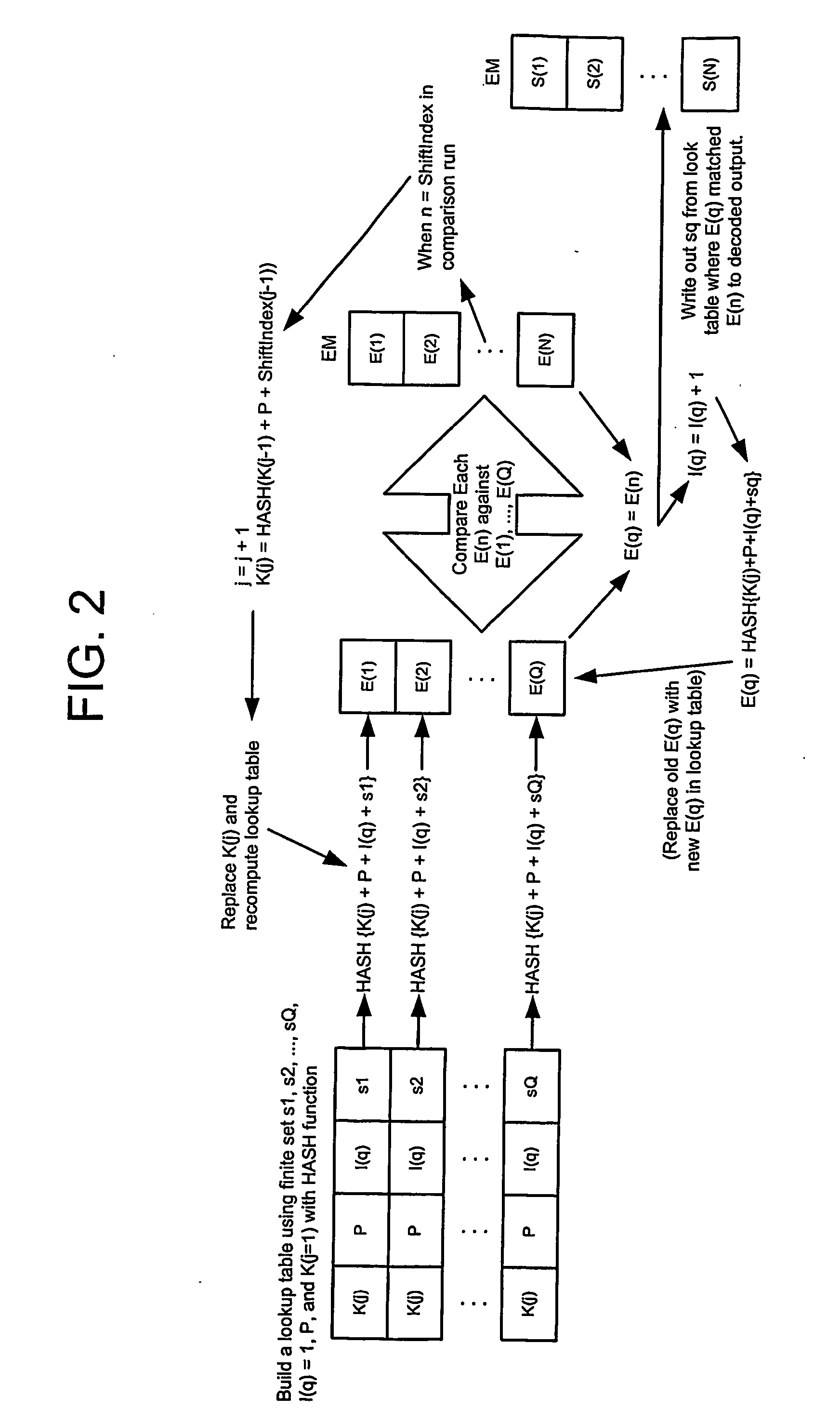
Cascading key encryption
InactiveUS20060265595A1Secure EncryptionSmall sizeKey distribution for secure communicationSynchronising transmission/receiving encryption devicesPasswordSecure transmission
A method for securely transmitting data involves generating keys depending on previous keys and additional information, such as a password, in order to create a pseudo one-time pad. The data is encrypted using the pseudo one-time pad prior to transmission. Only the initial key and minimal additional data are transferred between the sender and receiver in order to synchronize the keys.
Owner:PATHFIRE
Remote check deposit
InactiveUS20060242062A1Easy to optimizeConvenient truncationFinancePayment circuitsDocumentation procedureSubstitute check
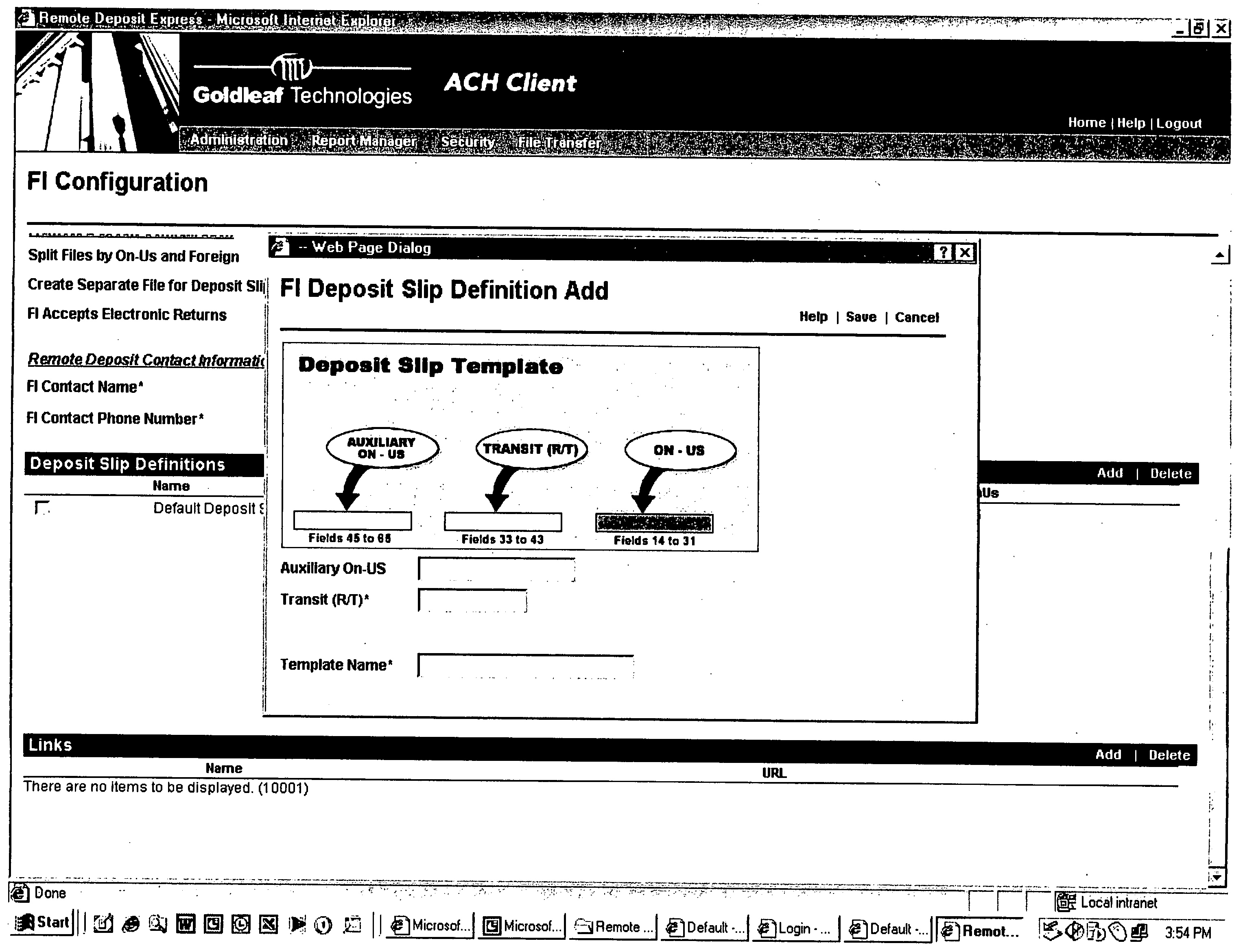
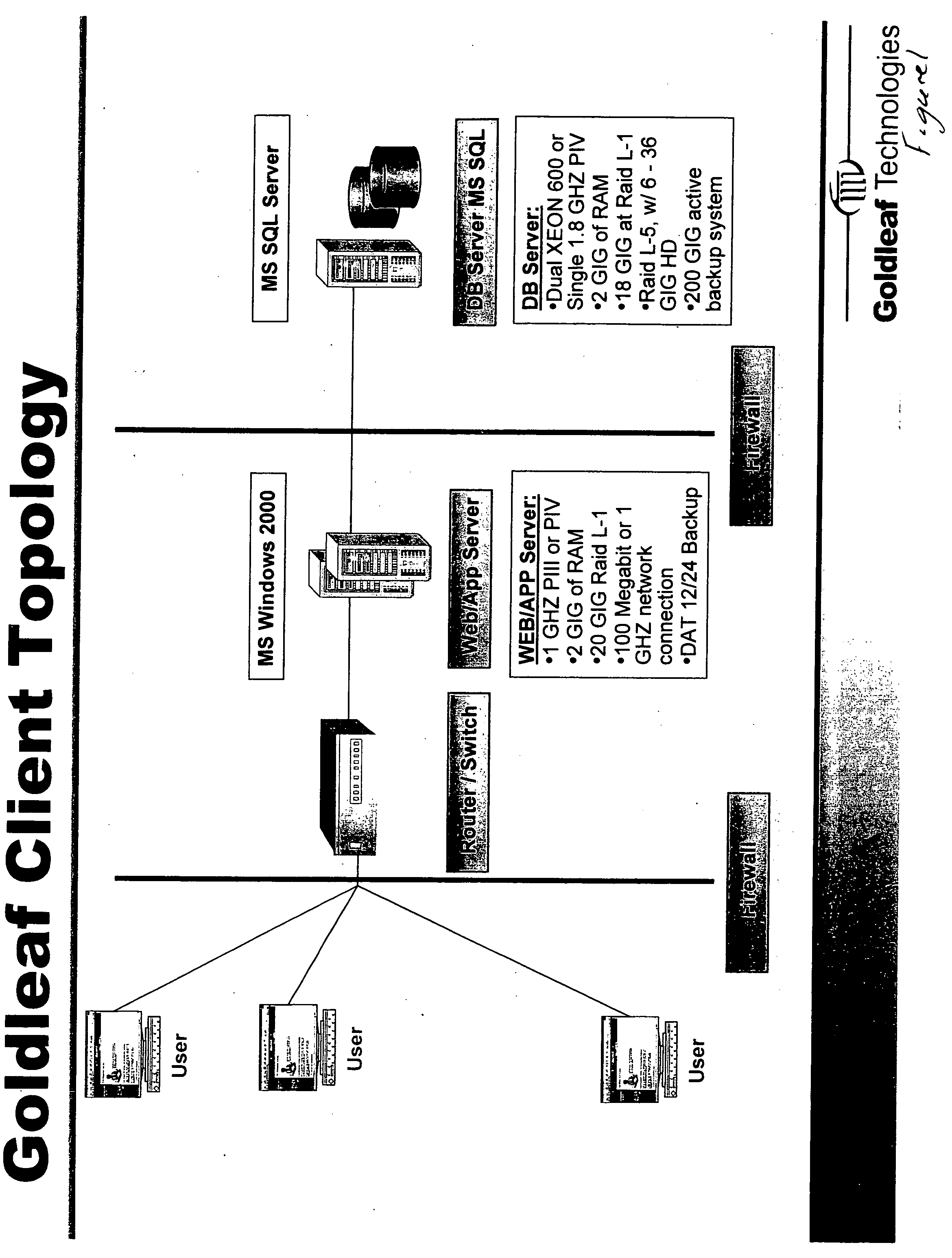
In accordance with the principles of the present invention, a system is provided for capturing a customer deposit at their place of business, converting the Magnetic Ink Character Recognition (MICR) data encoded documents into an image with an associated data file, and electronically transmit the data to a financial institution. The system allows the customer to scan each MICR encoded check that is to deposited with their financial institution, which captures financial institution routing information and customer account information. The associated image the physical check can be franked denoting the check has been electronically processed to avoid further processing. The resulting image and account data can then be processed by the financial institution. There are three options for encoding the amount: 1) the customer enters each amount after scanning the item prior to sending to the financial institution; 2) the financial institution enters the amount of each item after receiving the file from the customer; and 3) the amount field(s) are scanned and the amount is automatically entered. The system allows for both 1) online (Internet) capture of the MICR data and the associated image or 2) offline capture and the subsequent importing of the image and MICR data for transmission to the financial institution via the Internet. The financial institution can review the items captured online, and repair any item that is incorrect. The financial institution can use the system to print substitute checks that confirm to ANSI X9.90 for processing or deliver an electronic file in ANSI X9.37 format to any check processing system. The system includes secure transport over Internet connections for file transfer and dual control security to reduce fraudulent transactions from being initiated by the customer.
Owner:GOLDLEAF TECH
Data transmission of sensors
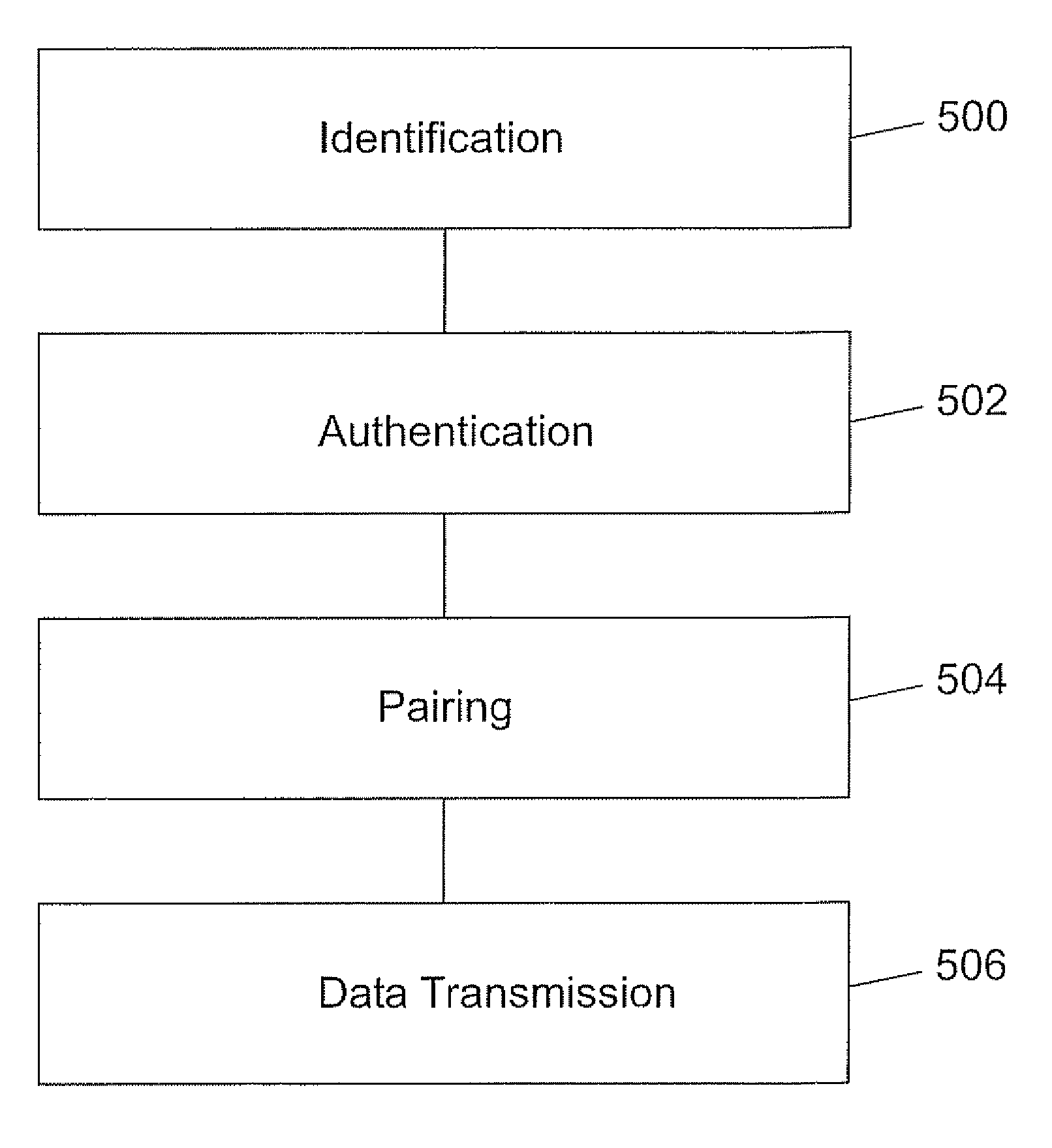
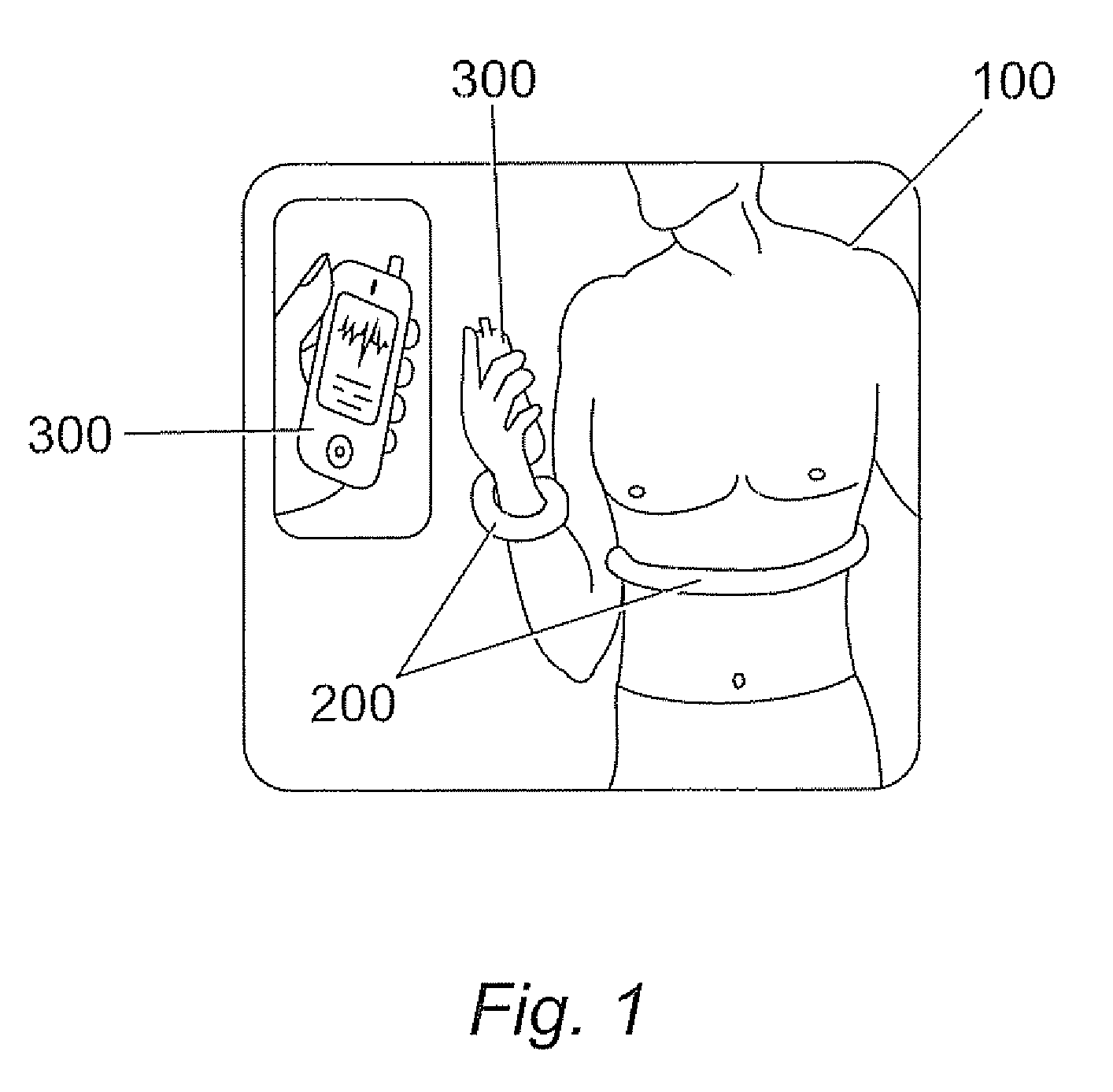
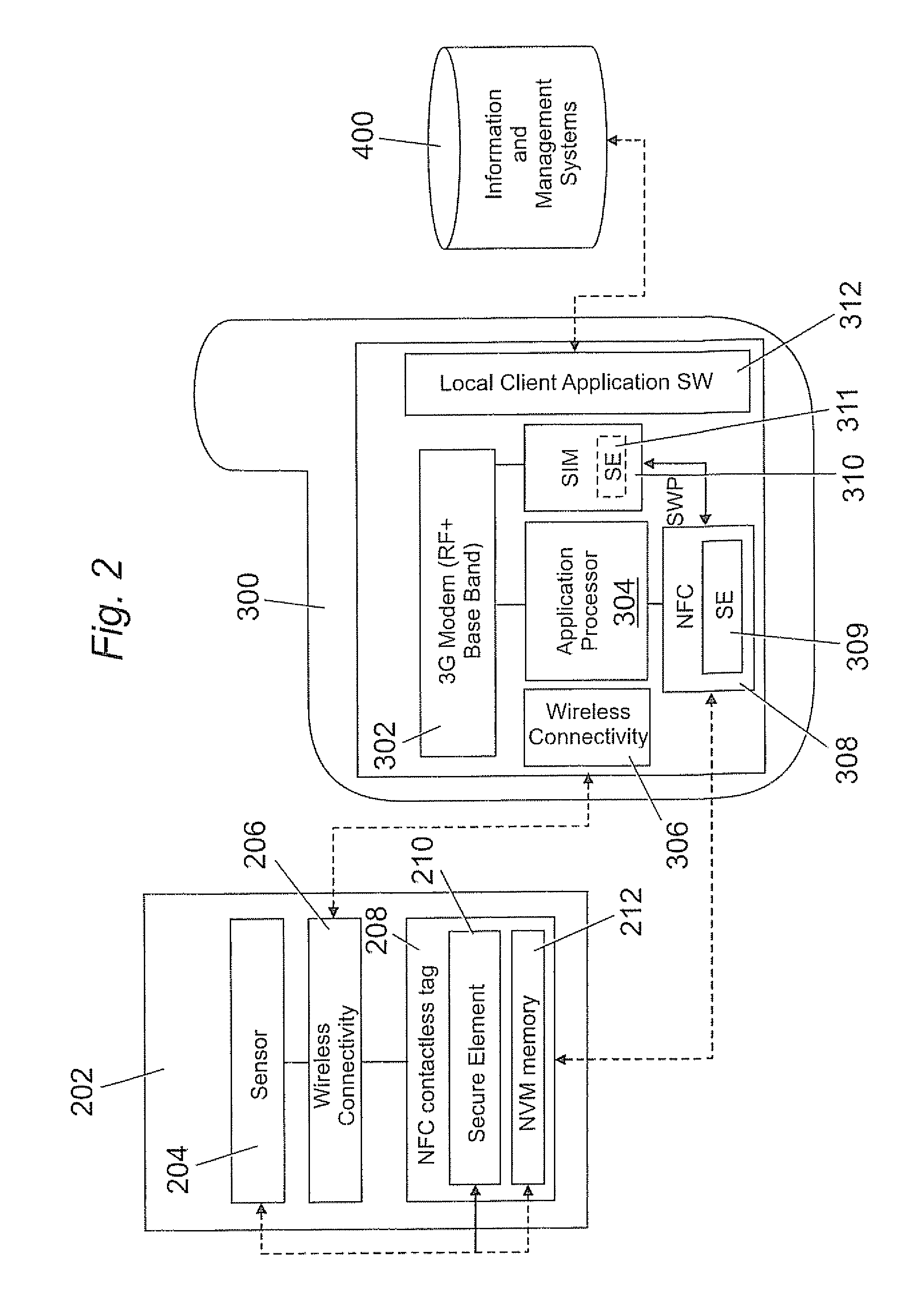
InactiveUS20100045425A1Secure transmissionElectric signal transmission systemsDigital data processing detailsSecure transmissionData transmission
A method for data transmission between a sensor module for measuring and storing data and a mobile device wherein the sensor module and the mobile device have identified each other and, wherein the sensor module comprises a first secure element capable of storing a first security key and the mobile device comprises a second secure element capable of storing a second security key characterized in that the method comprises the steps of an authentication step for carrying out a security process between the sensor module and the mobile device in order to authenticate the sensor module with the mobile device by means of comparing first and second security keys; a pairing step for establishing a communication between the sensor module and the mobile device in order to enable communication therebetween; a transmission step for establishing a secure transmission of data from the sensor module to the mobile device when comparison of the first and second security keys has resulted in authentication.
Owner:CHIVALLIER M LAURENT
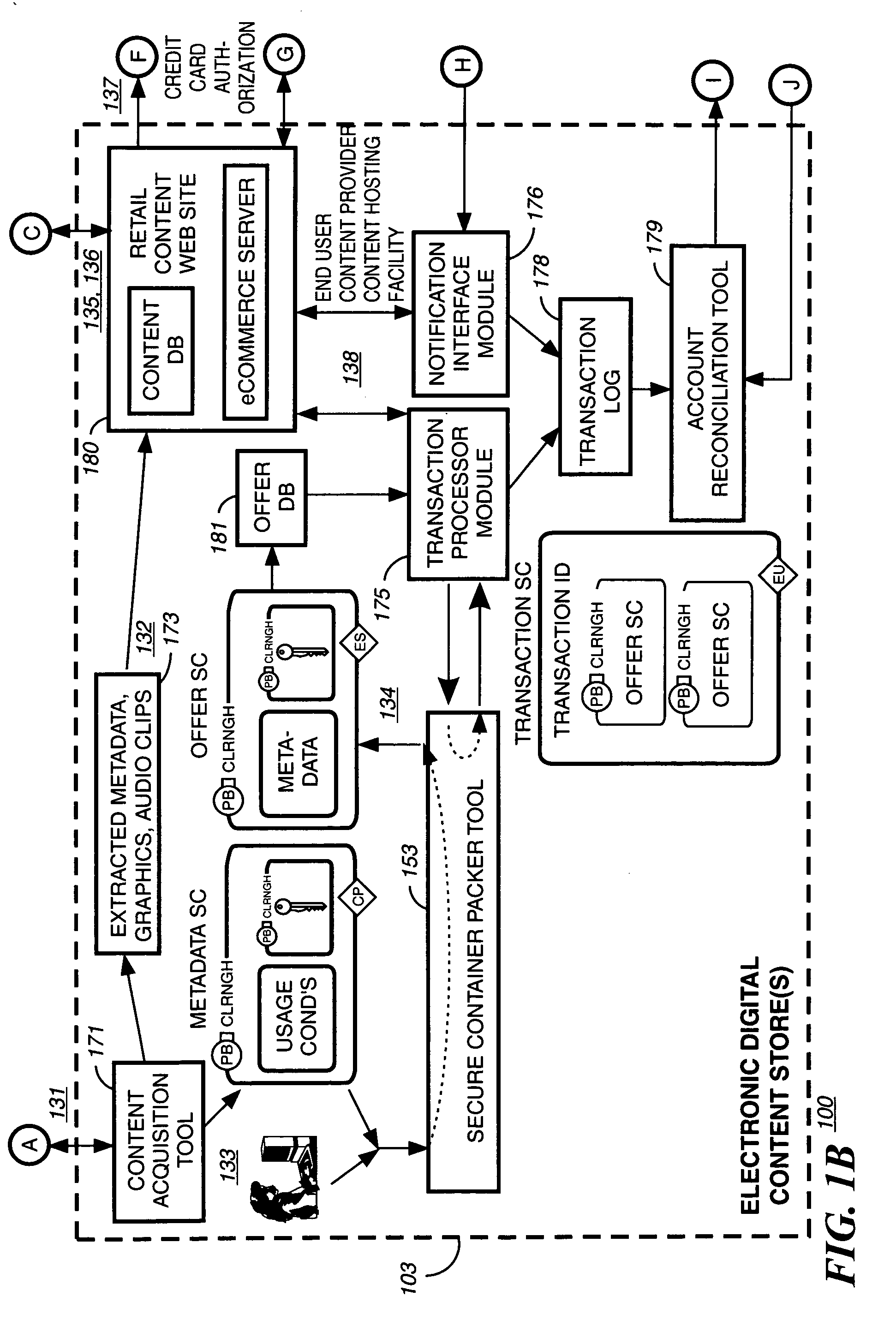
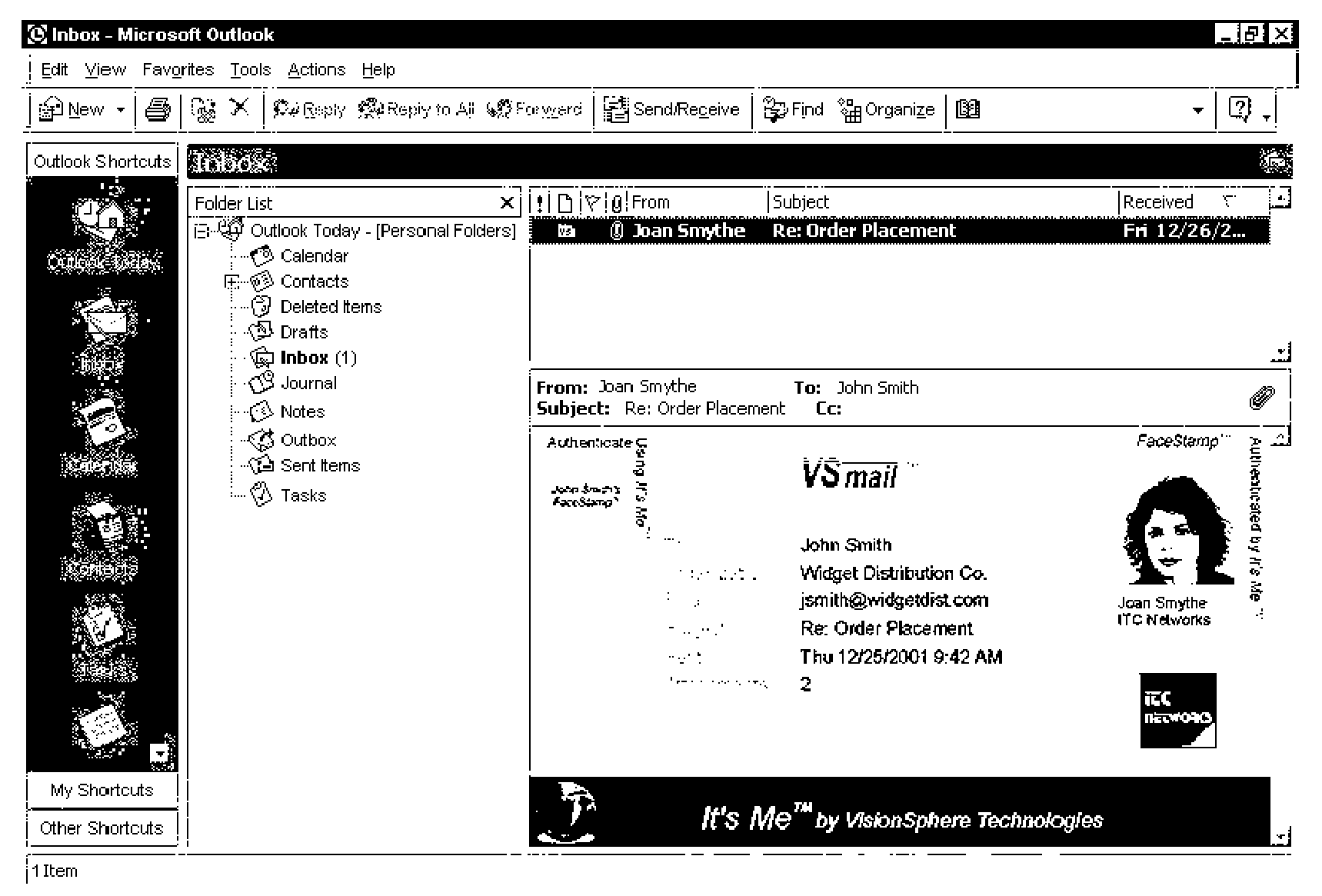
System for transmitting secure data between a sender and a recipient over a computer network using a virtual envelope and method for using the same
InactiveUS7117370B2Simple methodLimited accessElectric signal transmission systemsImage analysisNetworked Transport of RTCM via Internet ProtocolSecure transmission
A method for secure transmission of data, like e-mail and other secure documents, over a computer network includes the use of biometrics to verify that the sender of the data is confirmed as an individual authorized for secure access transmission of data over the network and by verifying that the recipient of the data is also an individual authorized to receive data by secure access transmission over the network. The methodology comprises creating a database containing the biometric templates of all individuals authorized for secure access transmission of data over the network and connecting the database to a data processor. The transmission of counterfeit messages is prevented by confirming the identity of the sender as an individual authorized for secure access transmission over the network by scanning a predetermined biometric of the sender, and comparing the biometric of the sender with the predetermined biometric of all individuals who are authorized for secure access transmission over the network. The recipient of a secure access message is not permitted to access the message until recipient's identity has been similarly confirmed as an individual authorized to receive messages secure access transmitted over the network. Once the recipient's identity is confirmed the message may be opened. The sender will receive confirmation by return electronic mail that the message has been opened by the authorized recipient.
Owner:KHAN SAL
Electronic mail system with functionality for senders to control actions performed by message recipients
ActiveUS20070005717A1Easy to watchDigital data protectionMultiple digital computer combinationsEmail addressInternet privacy
An e-mail system is disclosed that overcomes many deficiencies of, but is backward compatible with, existing e-mail systems. Embodiments of the system may include various features, including but not limited to: (1) secure transfer of e-mail messages, without the need for users to replace existing e-mail clients or to change e-mail addresses; (2) tracking of all actions performed in connection with an e-mail transmission; (3) the ability for a recipient to view information about an e-mail message, optionally including information about how other addressees have responded to it, before deciding whether to retrieve the e-mail message; (4) the aggregation of entire e-mail conversations into a single threaded view; (5) the ability to include both private and public messages in a single e-mail communication; (6) sender control over downstream actions performed in connection with an e-mail message; (7) flexible control over cryptographic methods used to encrypt emails messages for storage.
Owner:APPRIVER CANADA ULC
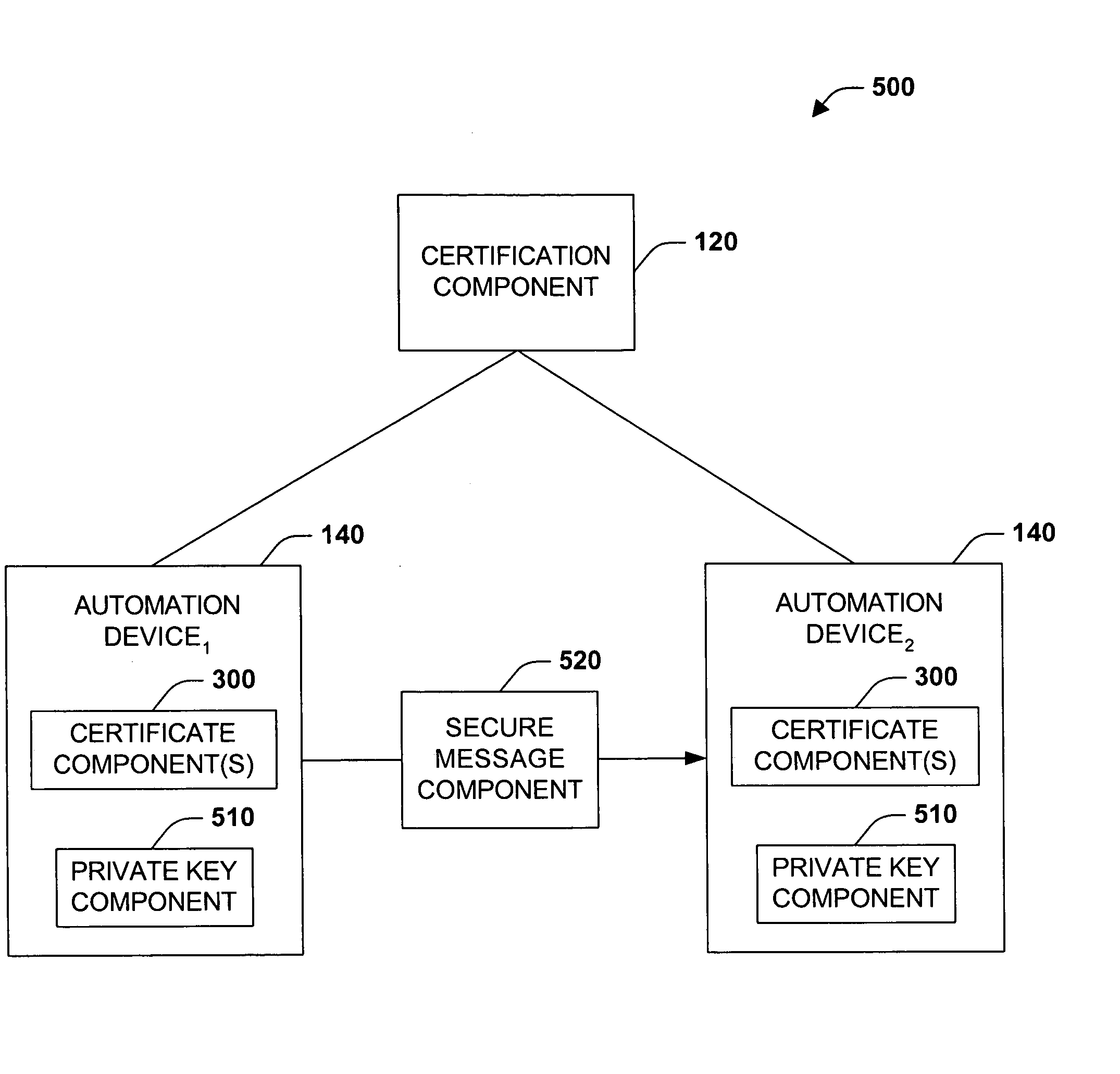
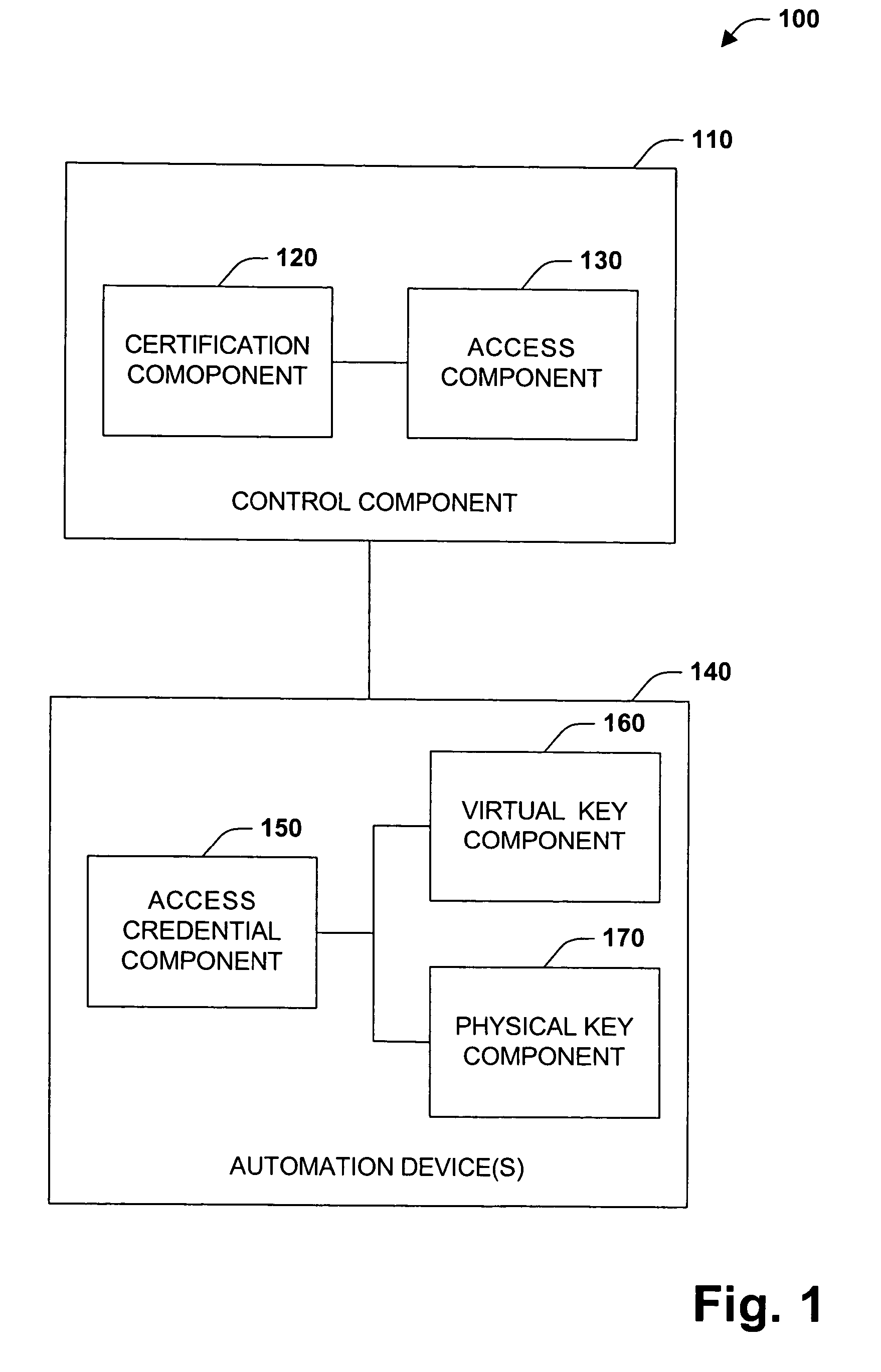
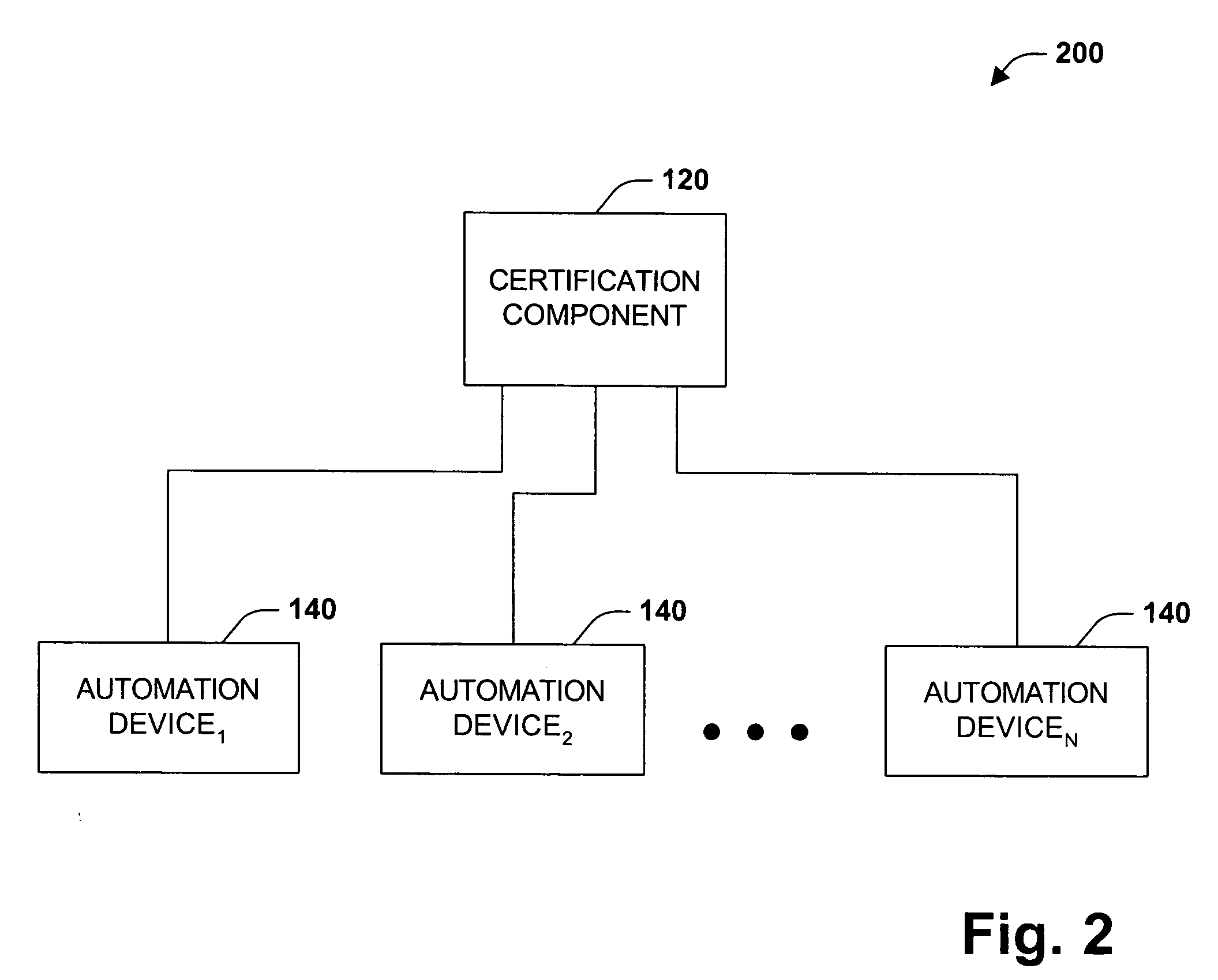
Digital rights management system and method
InactiveUS20050229004A1Improve securityCommunication securityProgramme controlComputer controlUser PrivilegeSecure transmission
The present invention concerns application of digital rights management to industrial automation devices including programmable logic controllers (PLCs), I / O devices, and communication adapters. Digital rights management involves a set of technologies for controlling and managing access to device objects and / or programs such as ladder logic programs. Access to automation device objects and / or programs can be managed by downloading rules of use that define user privileges with respect to automation devices and utilizing digital certificates, among other things, to verify the identity of a user desiring to interact with device programs, for example. Furthermore, the present invention provides for secure transmission of messages to and amongst automation devices utilizing public key cryptography associated with digital certificates.
Owner:ROCKWELL AUTOMATION TECH
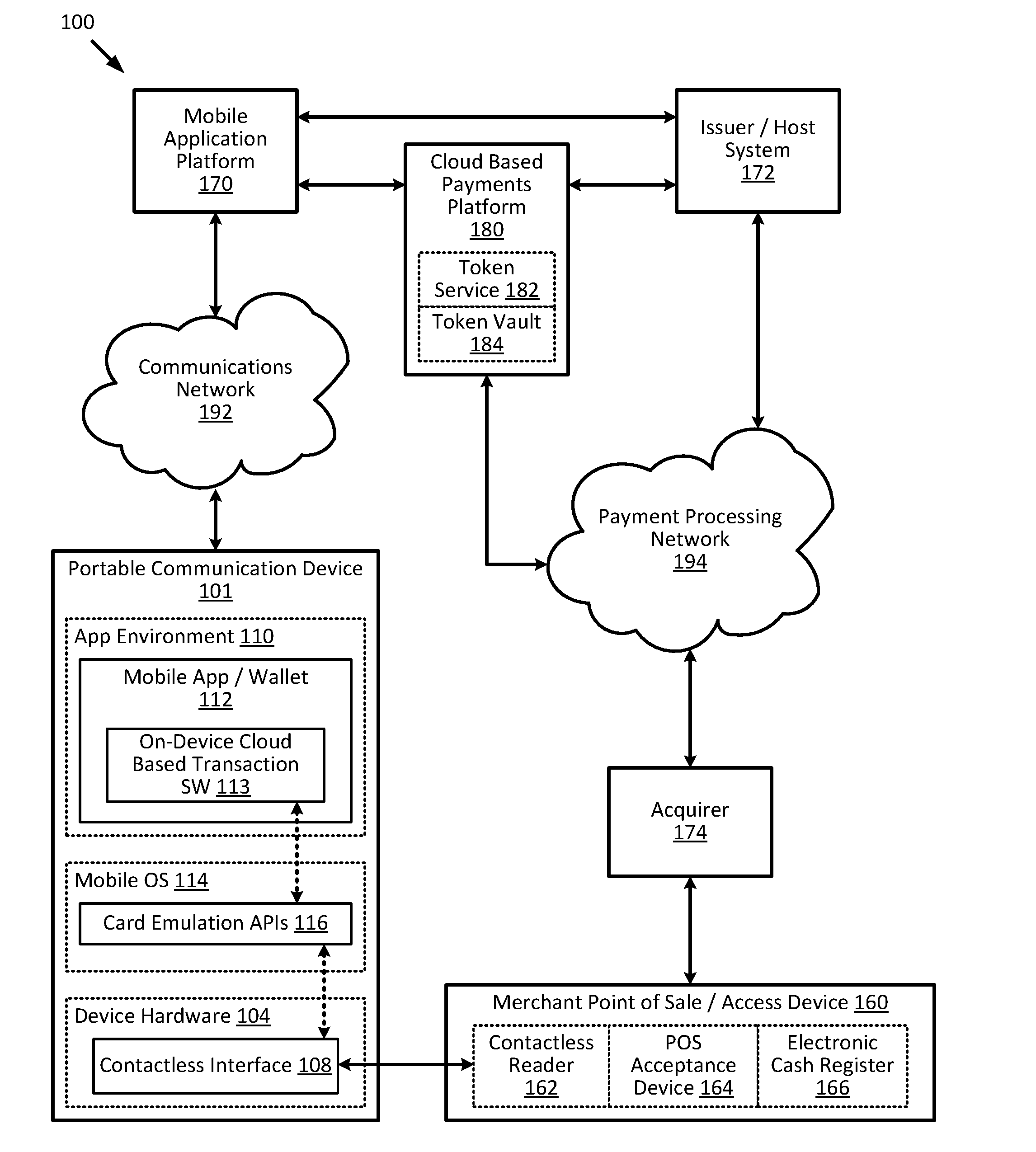
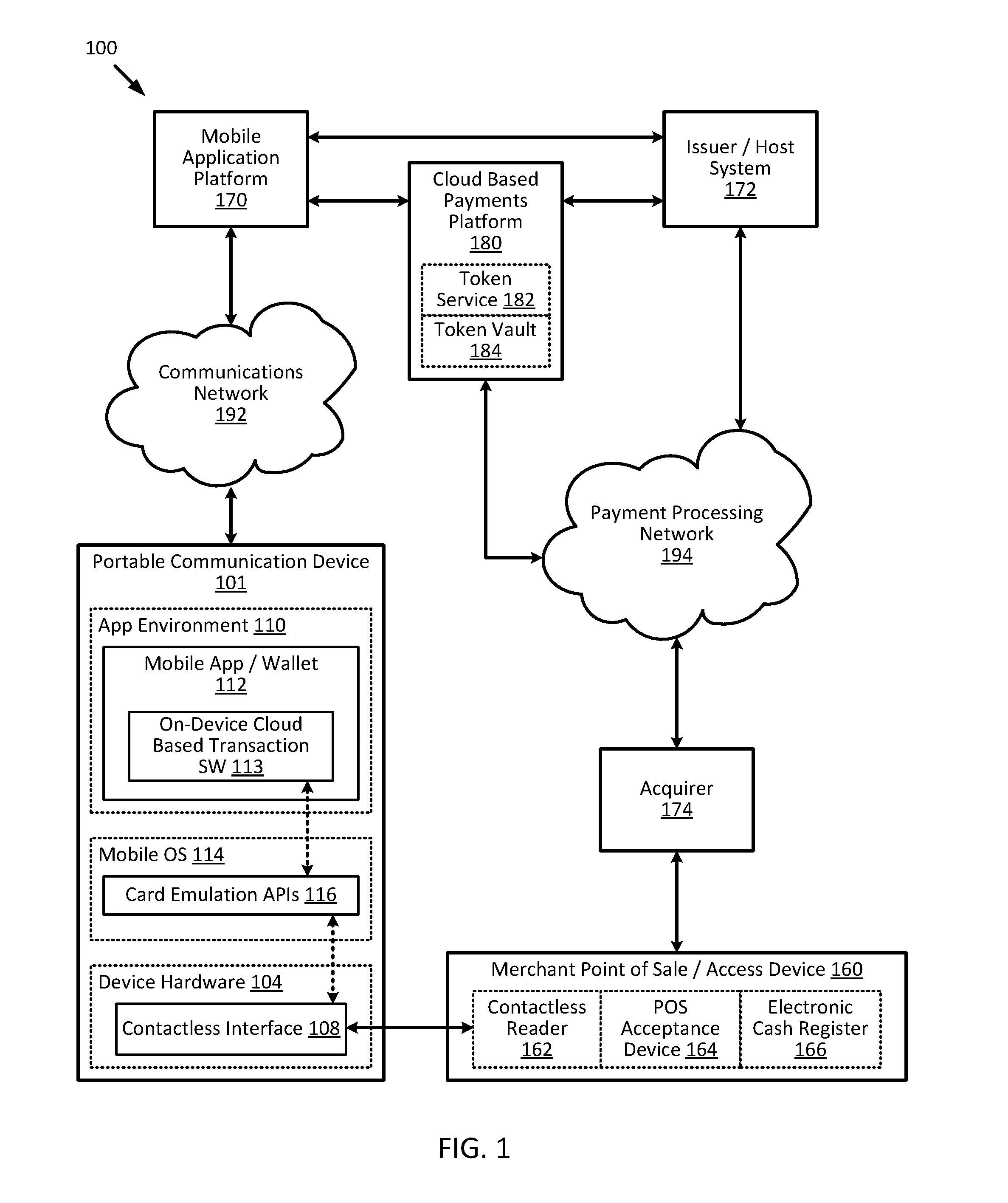
Cloud-based transactions with magnetic secure transmission
ActiveUS20160140545A1Improve securityLimited lifespanCryptography processingElectronic credentialsInternet privacySecure transmission
Owner:VISA INT SERVICE ASSOC
Network address translator and secure transfer device for interfacing networks
ActiveUS7283542B2Avoid less flexibilityReduce in quantityData switching by path configurationMultiple digital computer combinationsPrivate IPSecure transmission
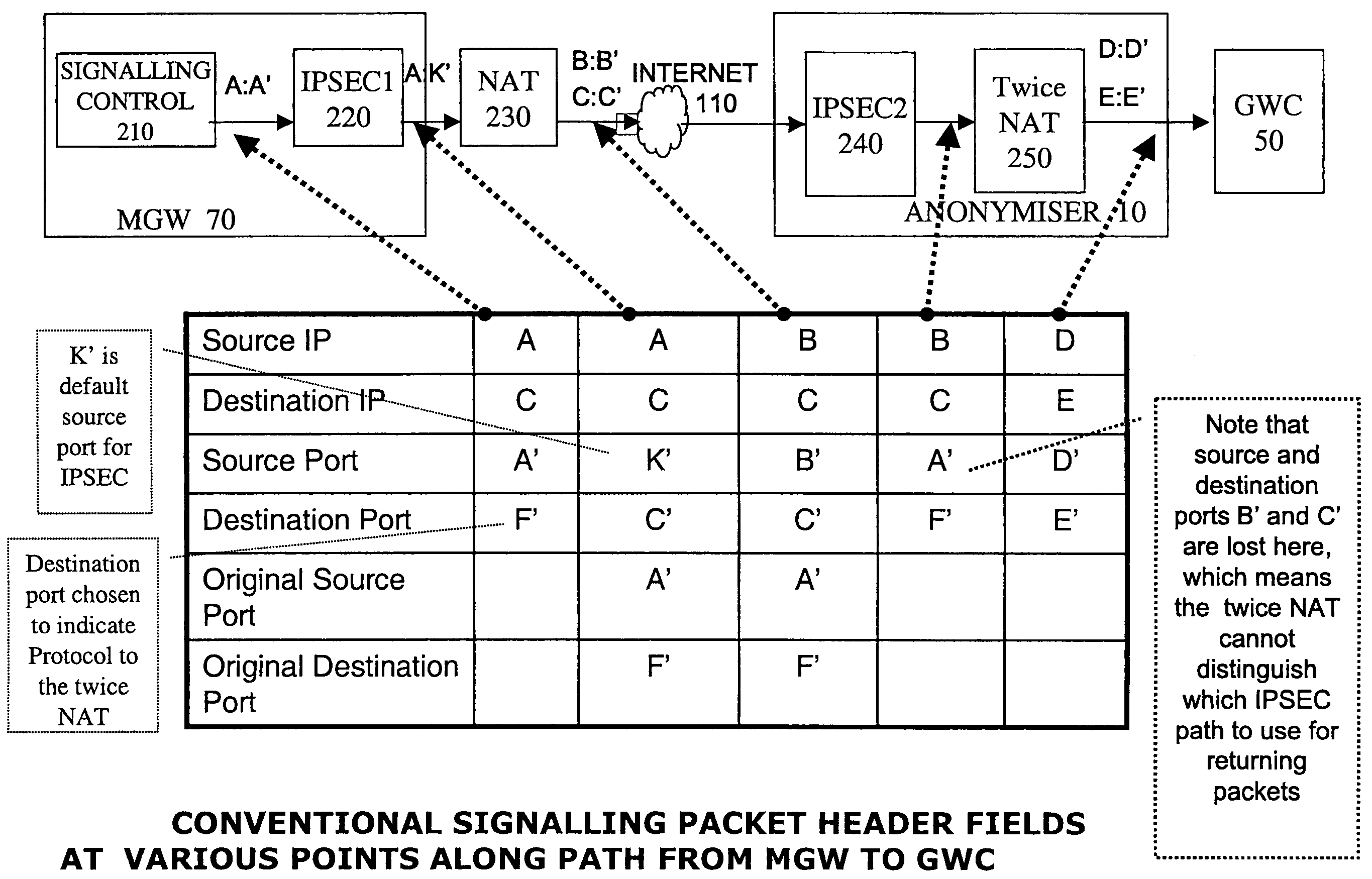
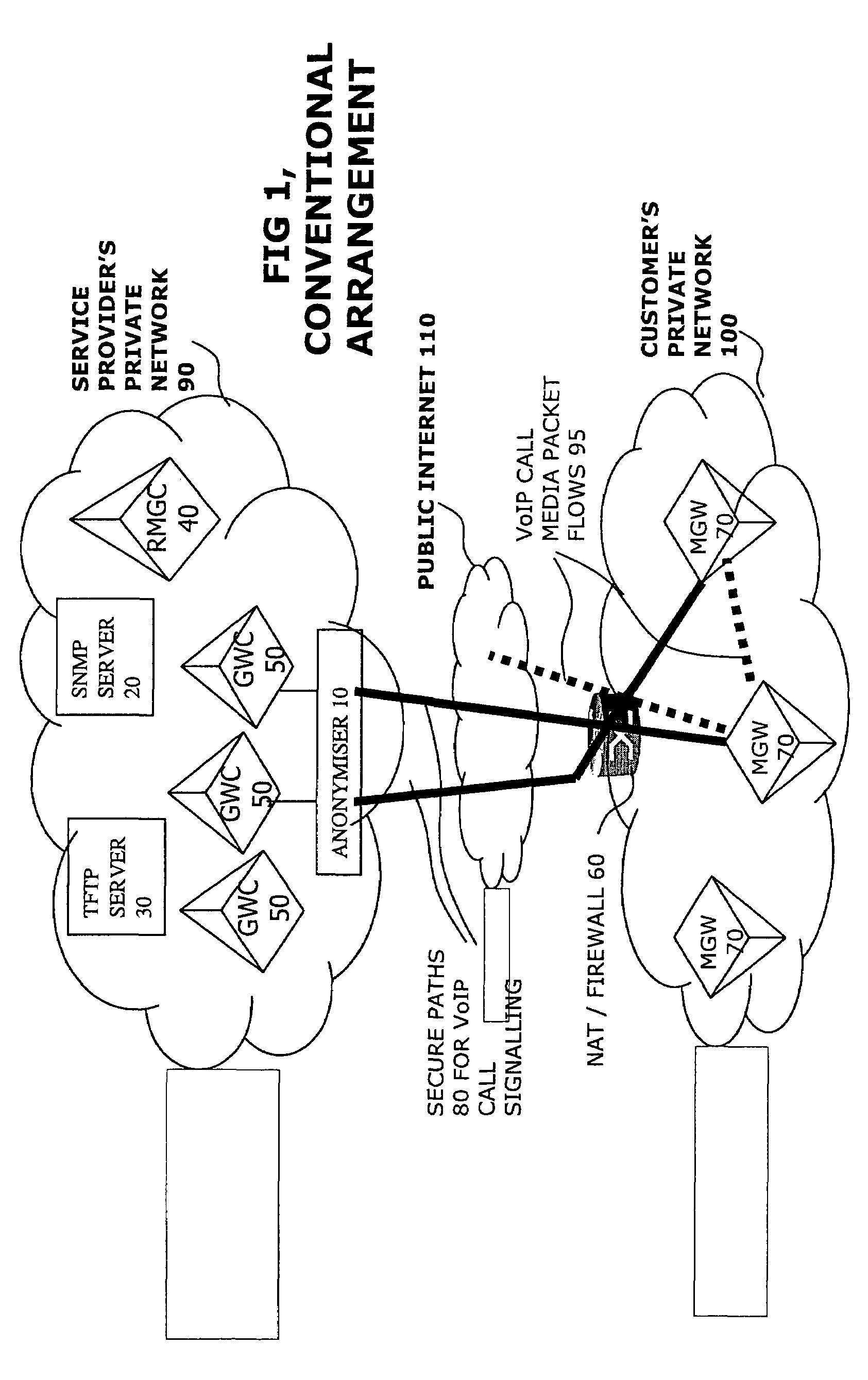
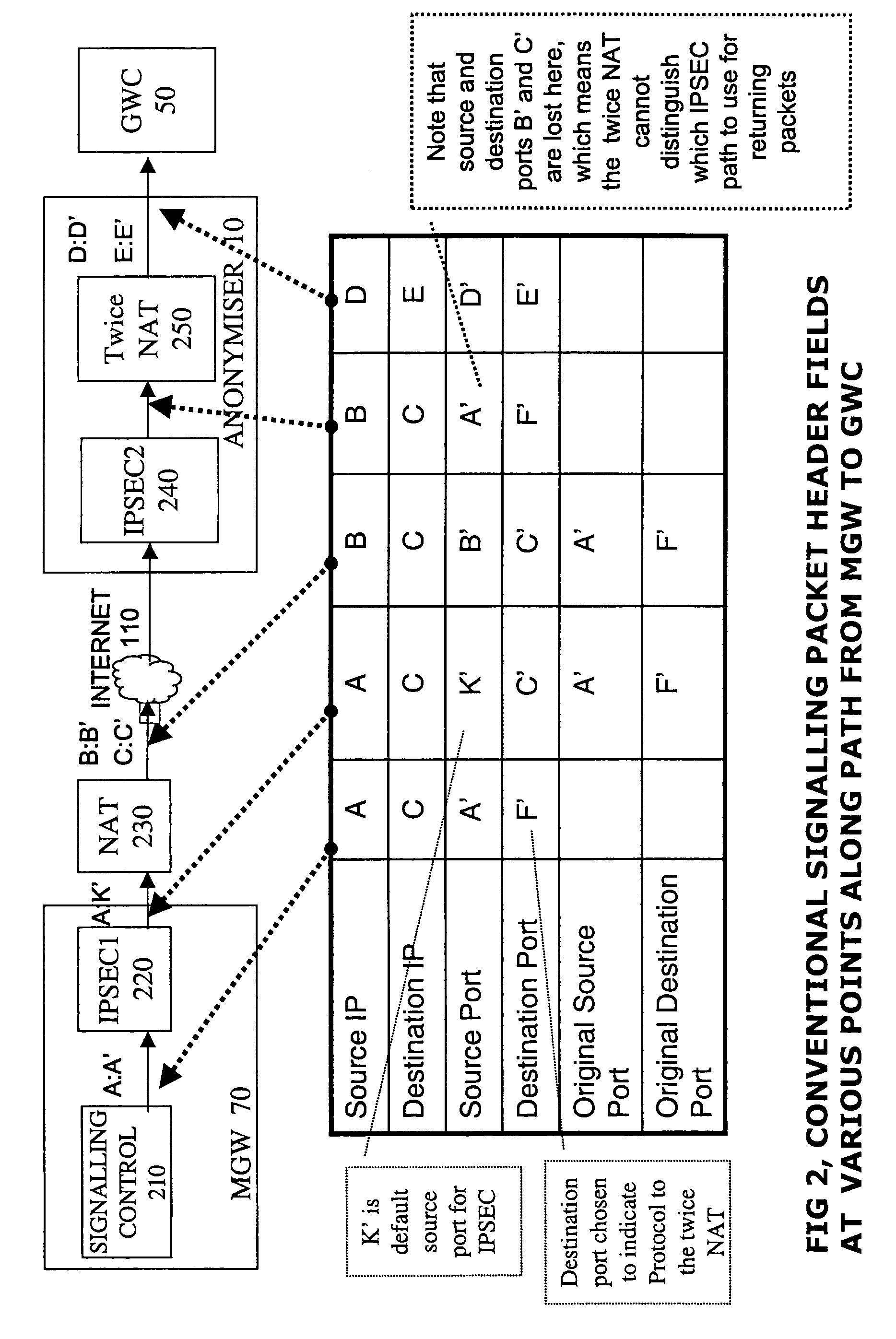
An interface for a private IP network interfaces flows of packets between gateway controllers and external media gateways. It has a network address translator and an IPsec device for maintaining secure paths to the external devices. A path identifier records which of the packet flows corresponds to which path. It is incorporated in the packet header, and means that the same interface can be used to couple many different external gateways, and interface them with many of the gateway controllers. Widespread deployment of such interfaces in anonymisers to achieve hiding of device addresses and network topology, as well as the reduction in use of expensive registered addresses is facilitated. By sending the path identifier in the packet, the IPsec device and the address translator can be loosely coupled devices, so standard readily available devices can be used.
Owner:GENBAND US LLC
Method and device for secure transmission of JPEG encoded images
ActiveUS20050281471A1Character and pattern recognitionColor television detailsCorrelation coefficientDigital data
A process for distributing digital still images according to a nominal format, where each image is broken into blocks and macroblocks that depend upon each other by correlation coefficients including analyzing contents of the still images to generate two parts: a) a primary contents in nominal format corresponding to the image as modified by substitution of certain correlation coefficients with coefficients that are of the same type, but which are random, and b) additional digital nature of any format, which includes substituted correlation coefficients and digital data that are likely to allow reconstruction of the modified image; transmitting separately the modified primary contents in real or deferred time and additional digital information in real time at a moment of viewing from a server towards recipient equipment; and calculating a synthesis of contents of the recipient equipment that is in nominal format as a function of the modified primary contents and the additional data.
Owner:OL SECURITY LIABILITY CO
Secure personal content server
InactiveUS7475246B1Risk minimizationPrevent access to informationDigital data processing detailsUser identity/authority verificationData setSecure transmission
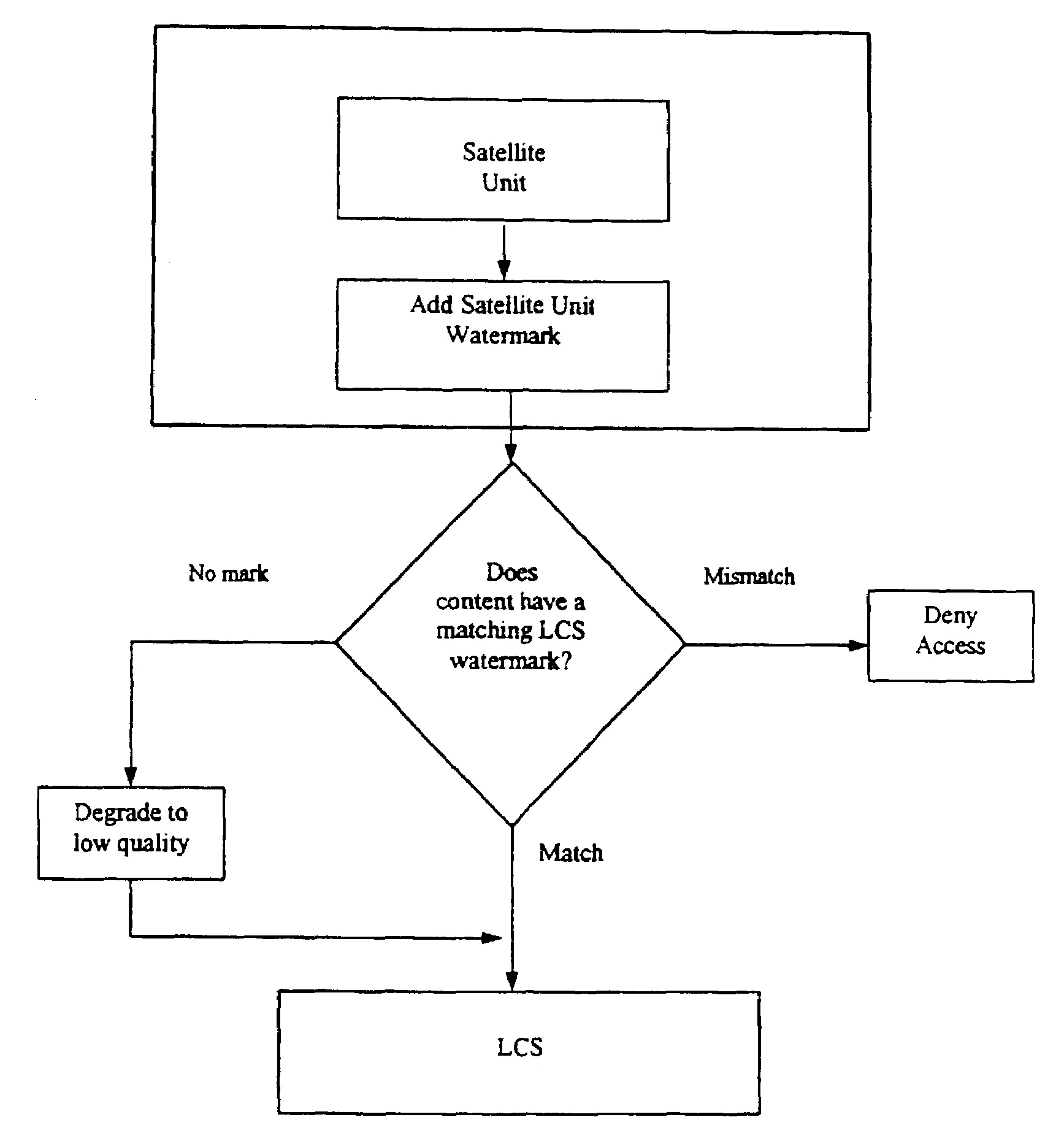
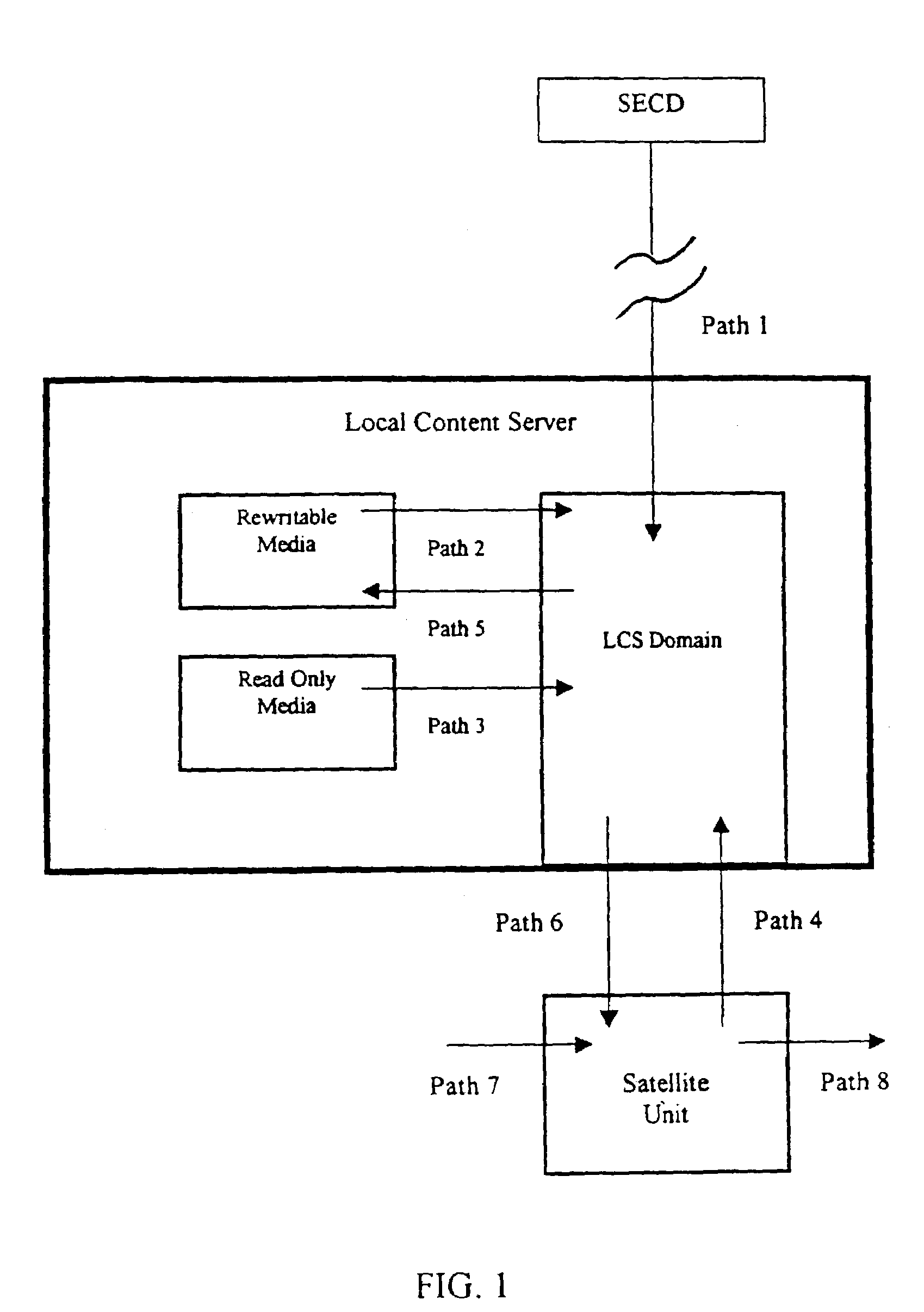
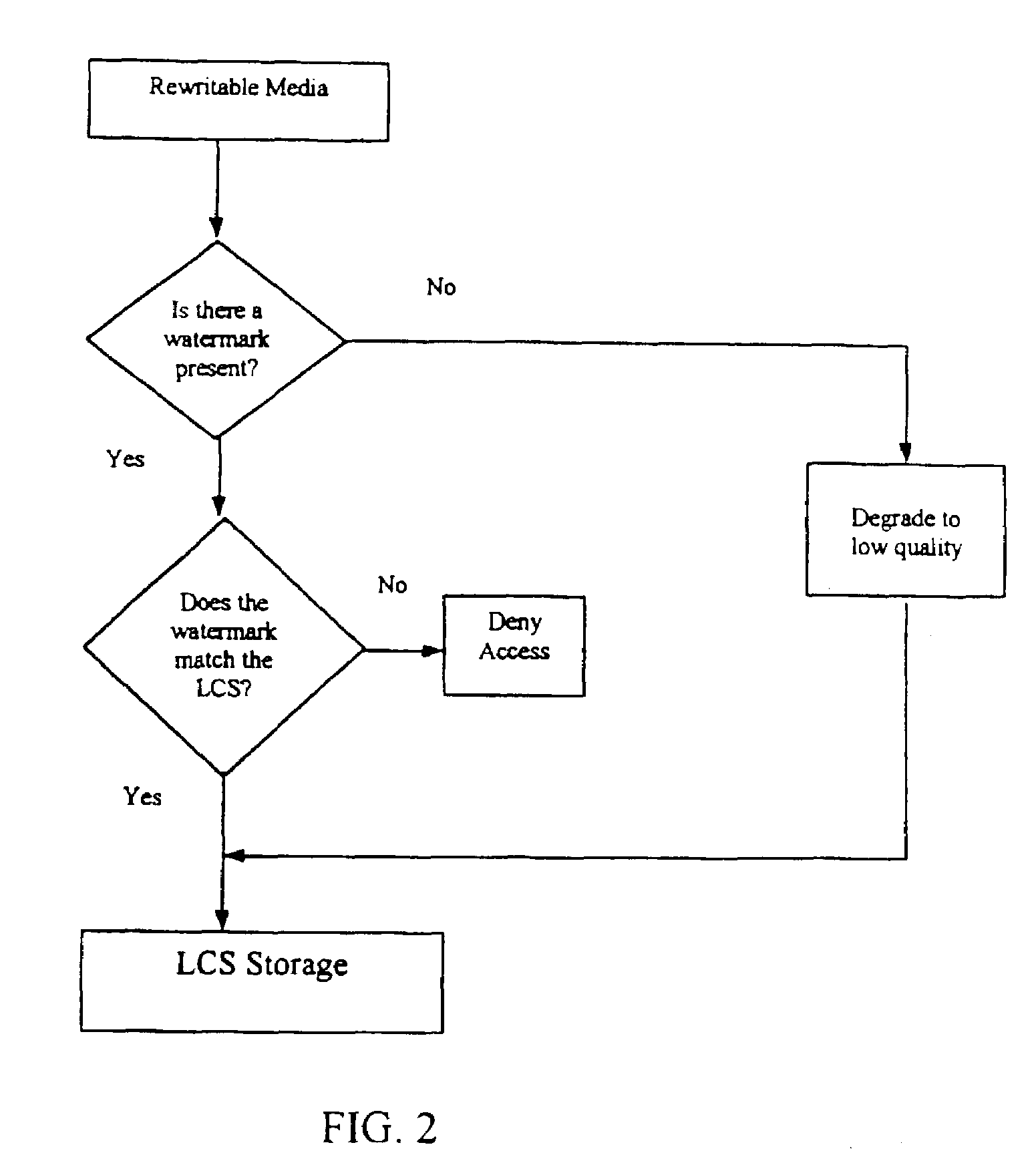
A local content server system (LCS) for creating a secure environment for digital content is disclosed, which system comprises: a communications port in communication for connecting the LCS via a network to at least one Secure Electronic Content Distributor (SECD), which SECD is capable of storing a plurality of data sets, is capable of receiving a request to transfer at least one content data set, and is capable of transmitting the at least one content data set in a secured transmission; a rewritable storage medium whereby content received from outside the LCS may be stored and retrieved; a domain processor that imposes rules and procedures for content being transferred between the LCS and devices outside the LCS, and a programmable address module which can be programmed with an identification code uniquely associated with the LCS. The LCS is provided with rules and procedures for accepting and transmitting content data. Optionally, the system may further comprise: an interface to permit the LCS to communicate with one or more Satellite Units (SU) which may be connected.
Owner:WISTARIA TRADING INC
System and method for real-time inquiry, delivery, and reporting of credit information
InactiveUS20030041031A1More readableSecure transmissionComplete banking machinesFinanceWeb siteWeb browser
<heading lvl="0">Abstract of Disclosure< / heading> A system and method for providing electronic inquiry, delivery, and reporting of personal credit information to and from credit bureaus, preferably via the Internet. In the preferred embodiment, the system includes a web site that, by using a web browser, allows clients to request credit information from, or provide credit reports to, credit bureaus by entering certain data on pre-built forms in HTML format. The data is encrypted using means for secure transmission, such as a web browser with 128-bit secure socket layer (SSL) technology, then sent to a common gateway interface (CGI) application located on a web server. The CGI application decrypts and reformats the data to a standard format specified by the credit bureau. The CGI application initiates a query. Using a dedicated connection circuit to the credit bureau's computer, the CGI application reformats the response from the credit bureau to an HTML format and encrypts the data using the means for secure transmission. The HTML formatted data is then sent back to the client's computer over the Internet and displayed in the client's web browser in an easily read format.
Owner:F POSZAT HU
Data transfer and management system
InactiveUS7406596B2Easy to manageEasily downloadableReliability increasing modificationsError preventionPasswordSecure transmission
A system for the secure transfer of data and data management on the Internet has a data encryption and transfer module operable in a user computing system, a data management module operable in a sewer computing system, the transfer of data between the user and the server computing systems being effected on the user computing system through use of the data encryption and transfer module, by moving the data to or from a first desktop window, associated with the user computing system, from or to a second desktop window, associated with the server computing system, each window being associated with a password, such that the step of moving the data from one window to the other causes the data to encrypted / re-encrypted from one associated password to the other.
Owner:HERBERT STREET TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com