Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
315 results about "Open communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In business, open communication (or open access to communication resources) is the ability of anyone, on equal conditions with a transparent relation between cost and pricing, to get access to and share communication resources on one level to provide value added services on another level in a layered communication system architecture. Simply put, Open access plans are to deregulate oligarchy of telecom operators in a bid to give consumers more choices for equipment, services and service vendors or carriers. It will also provide some breathing room for the controversial Net neutrality that has been the central issue between mobile carriers, like AT&T, Verizon and Sprint Nextel, and web media moguls, like eBay, Amazon.com and Google. True open communication is where employees are encouraged to share their thoughts and concerns, both good and bad, without the worry of retaliation from management when the feedback is bad.
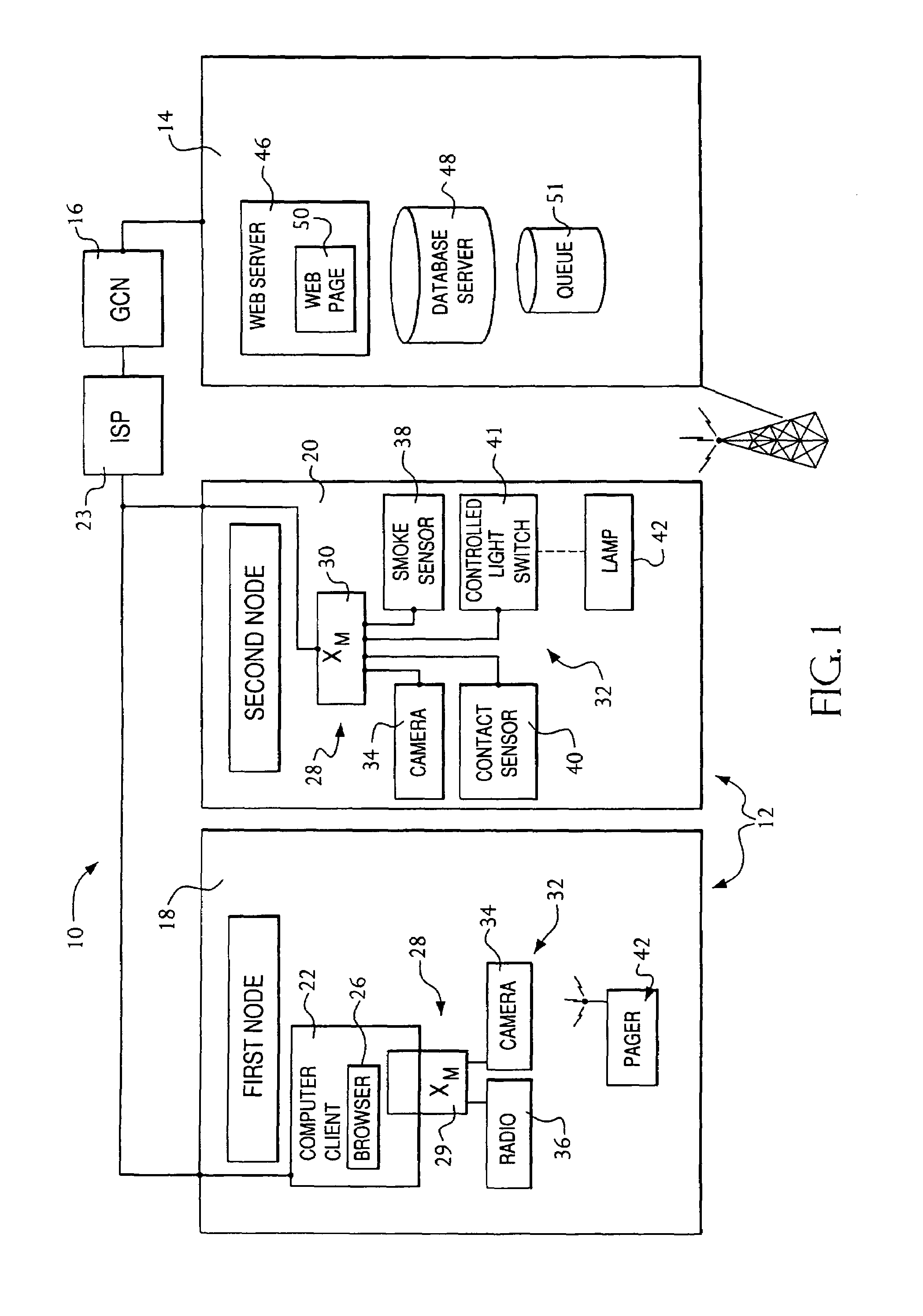
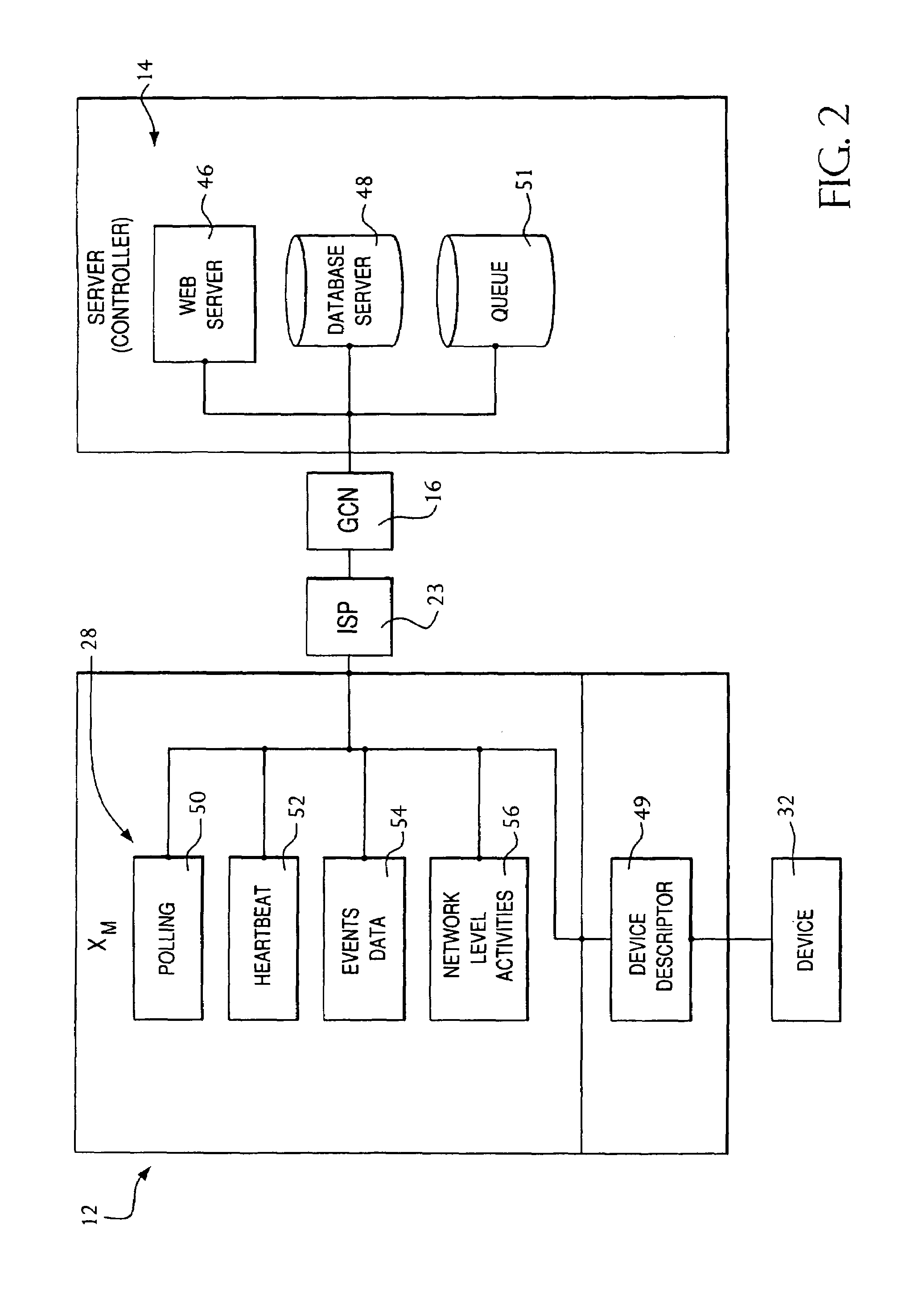
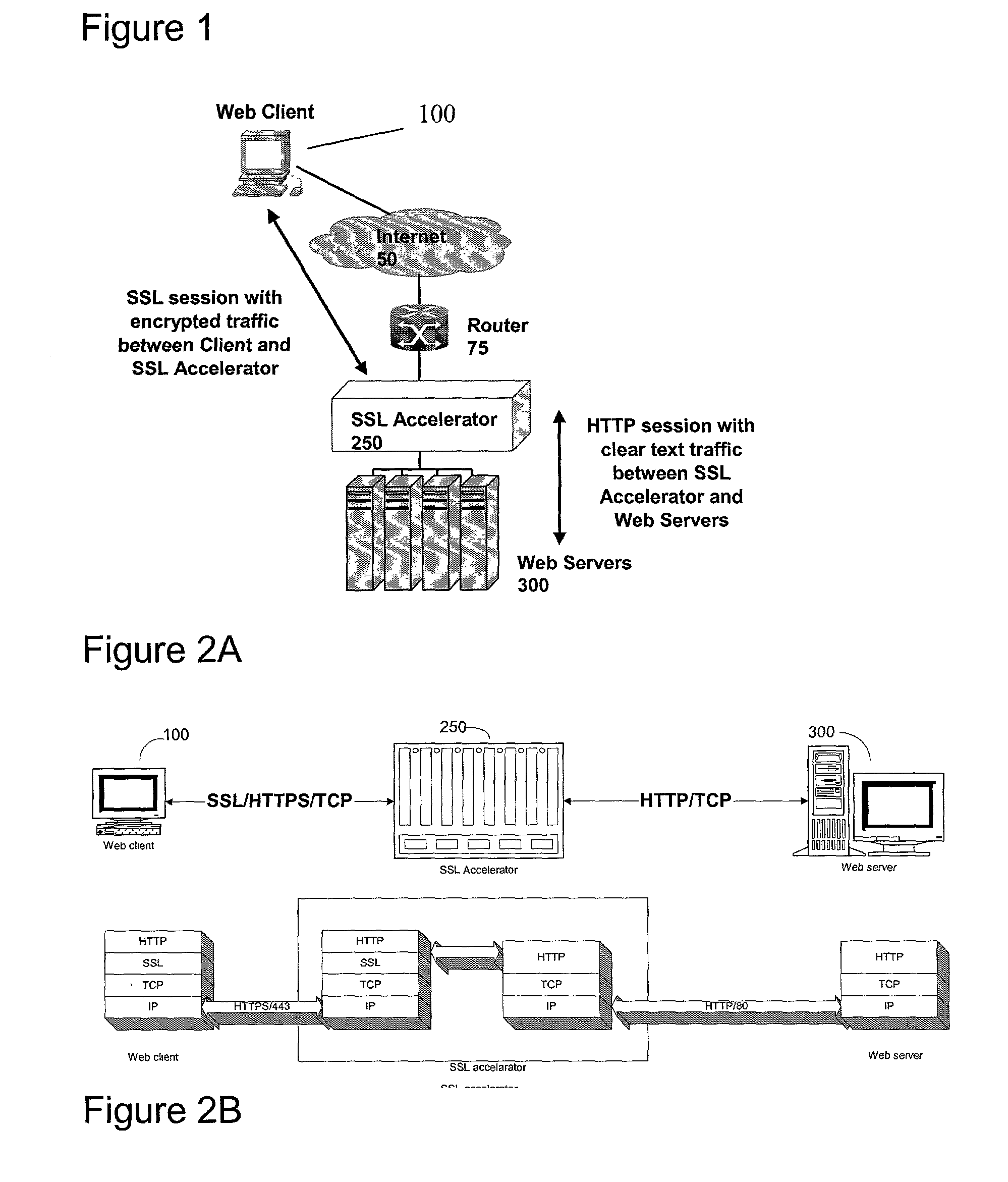
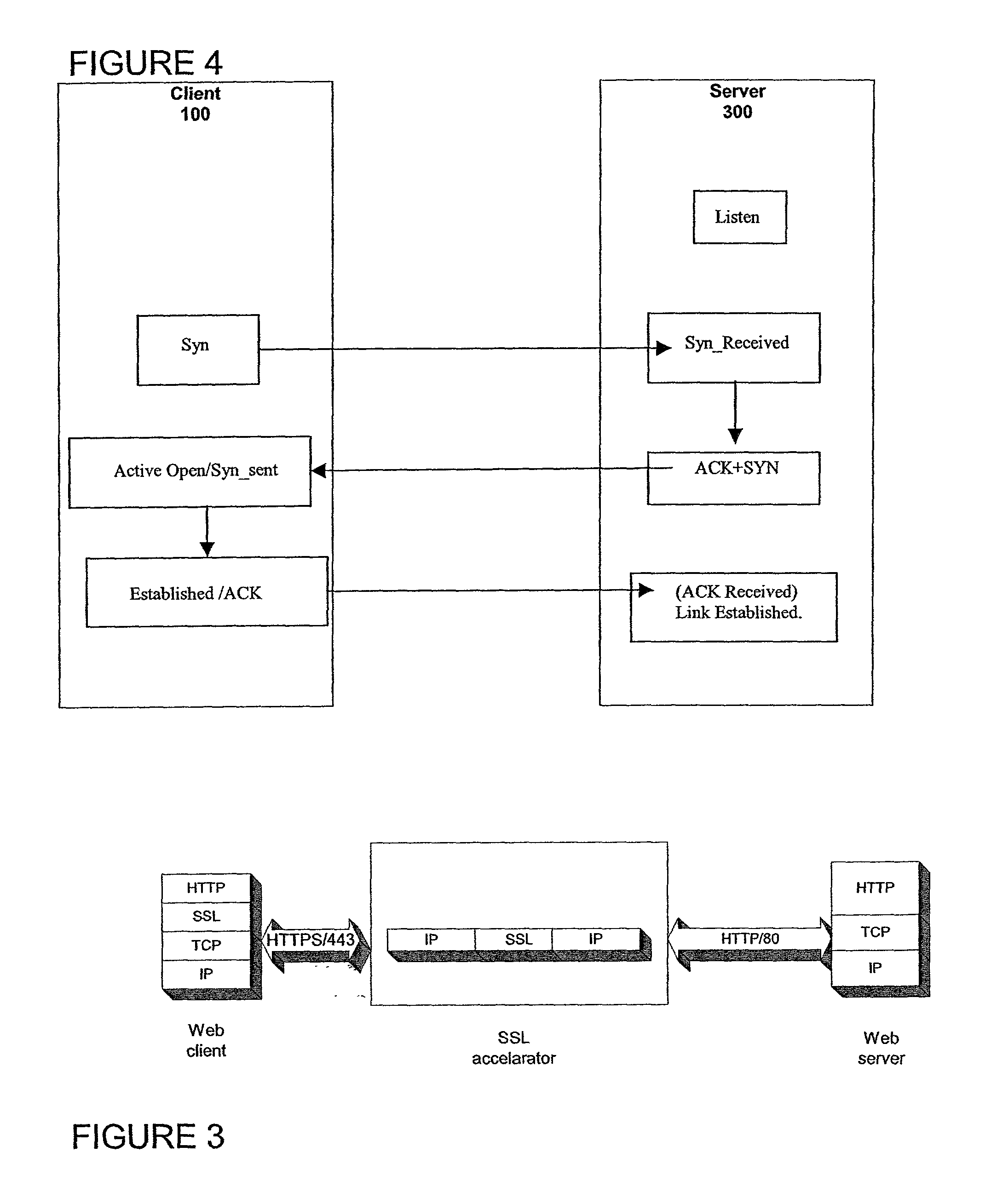
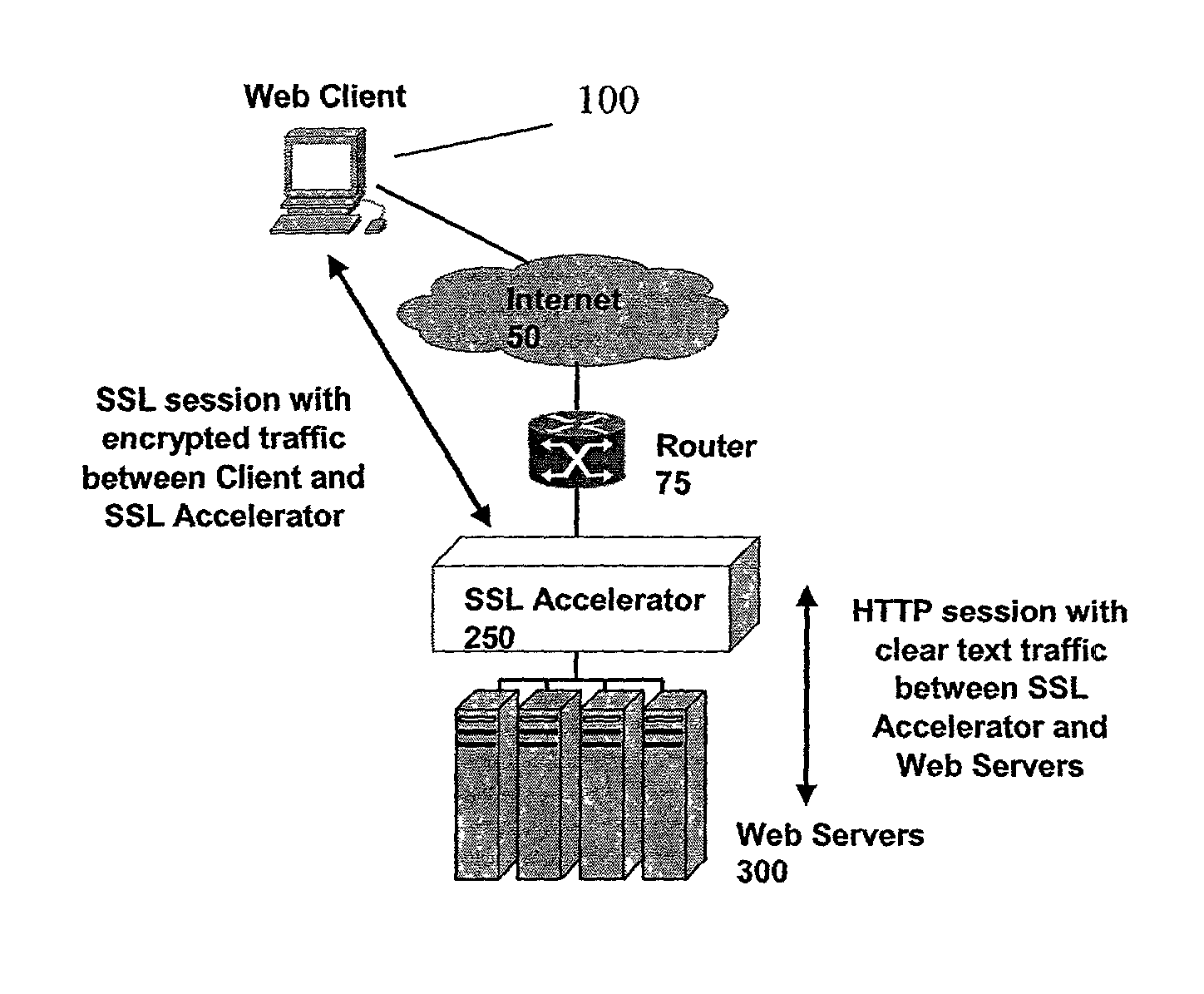
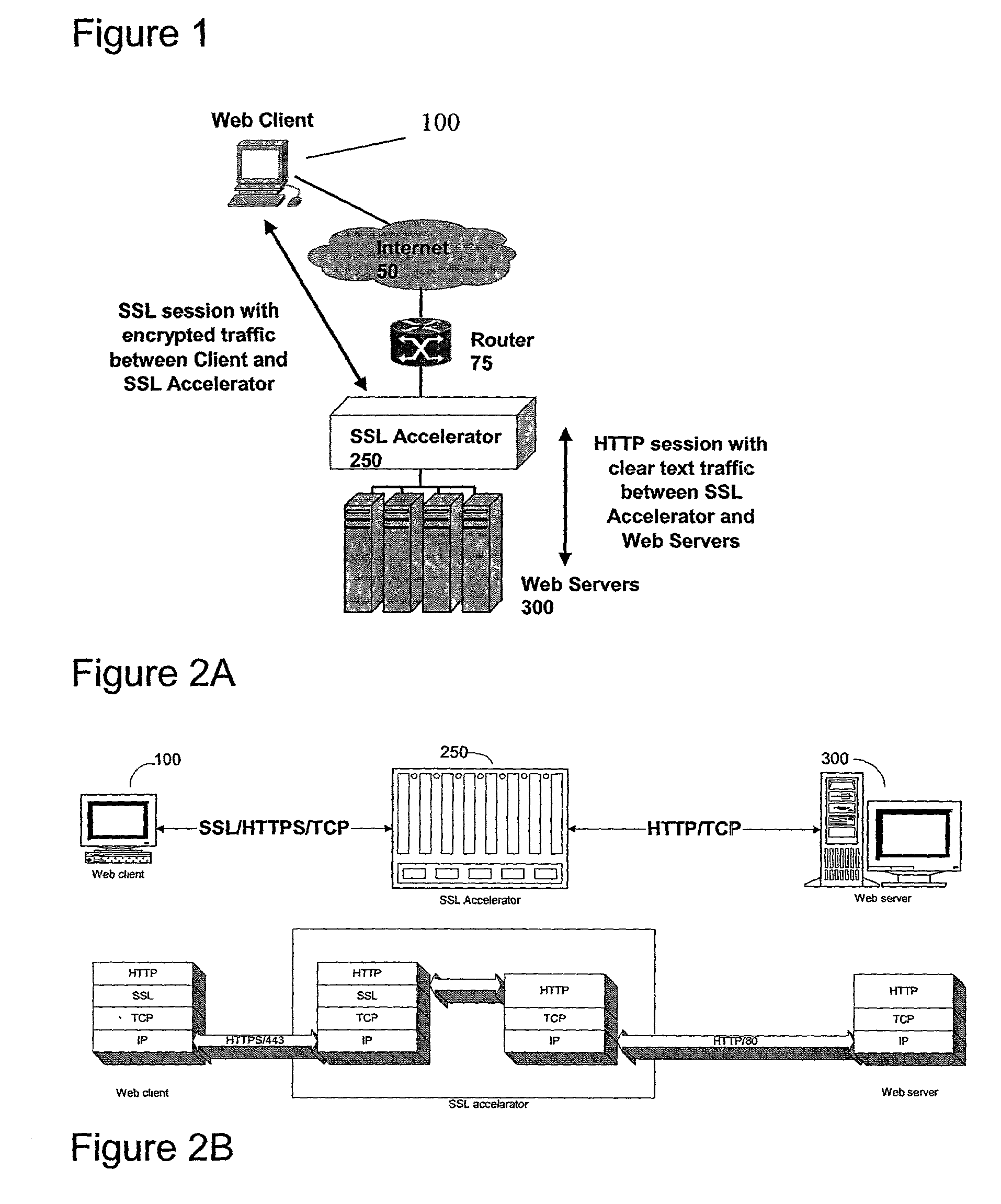
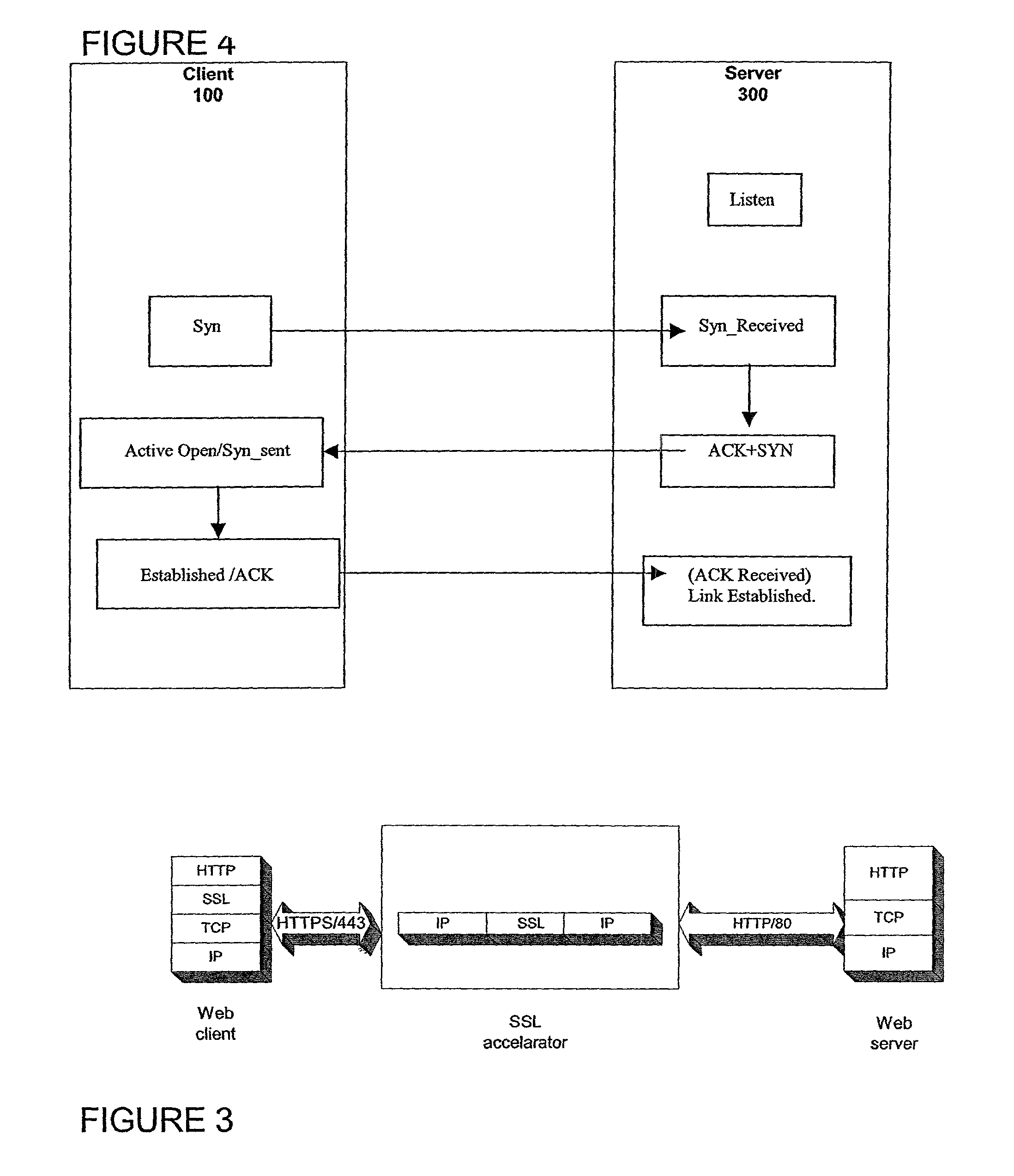
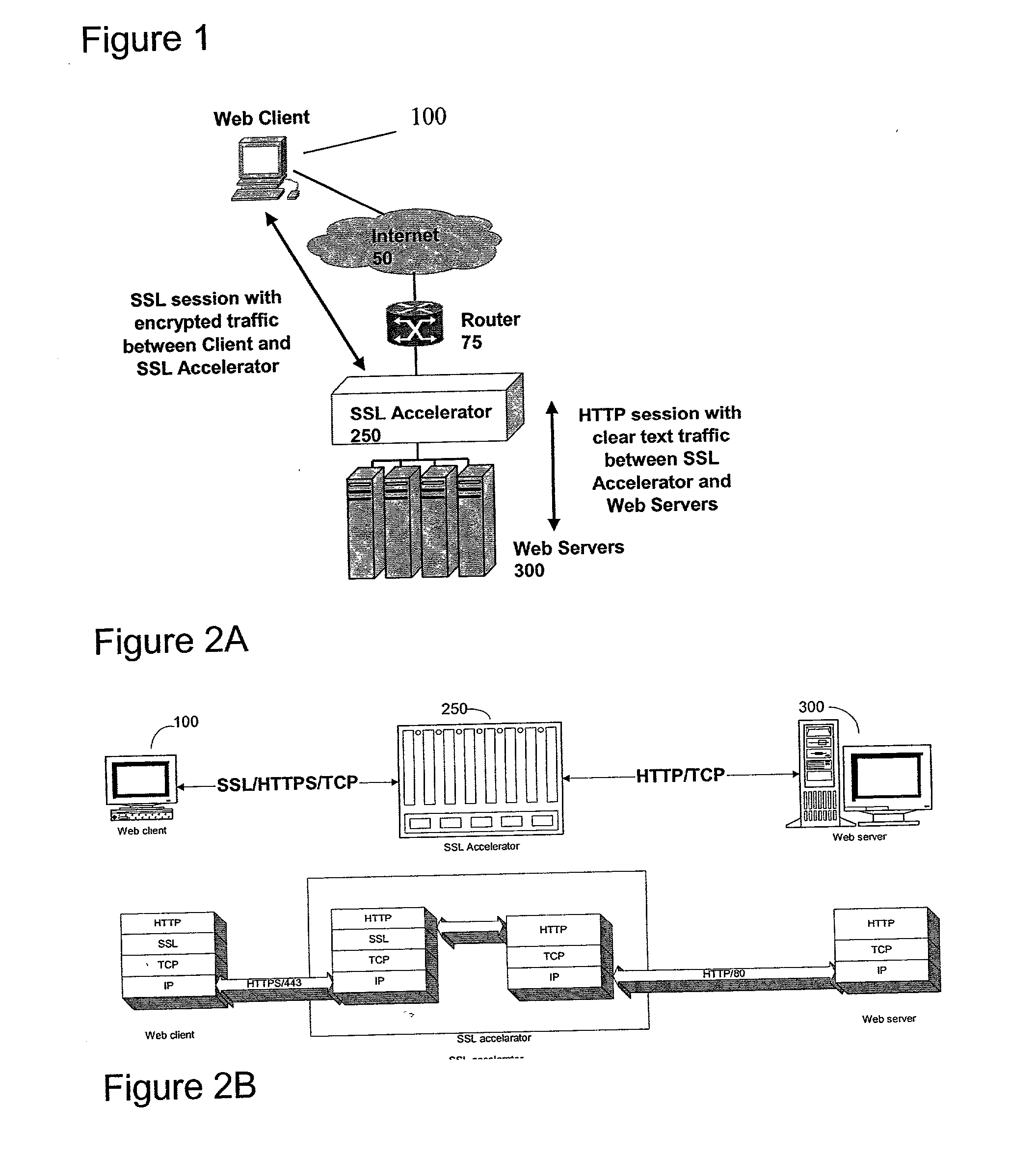
Secure sockets layer proxy architecture
ActiveUS20030014628A1Low hardware requirementsLower latencyError detection/correctionMultiple digital computer combinationsSecure communicationChannel coupling
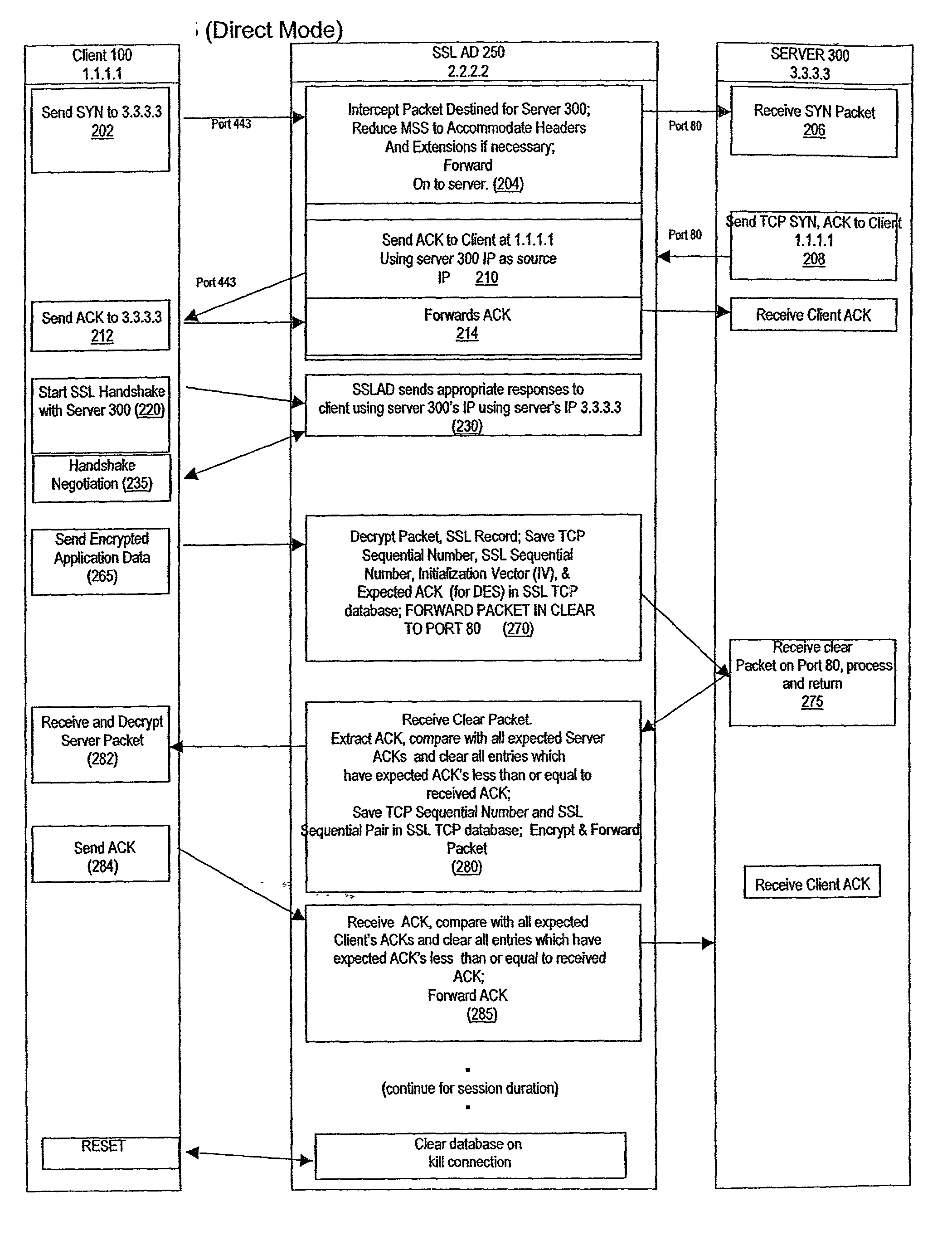
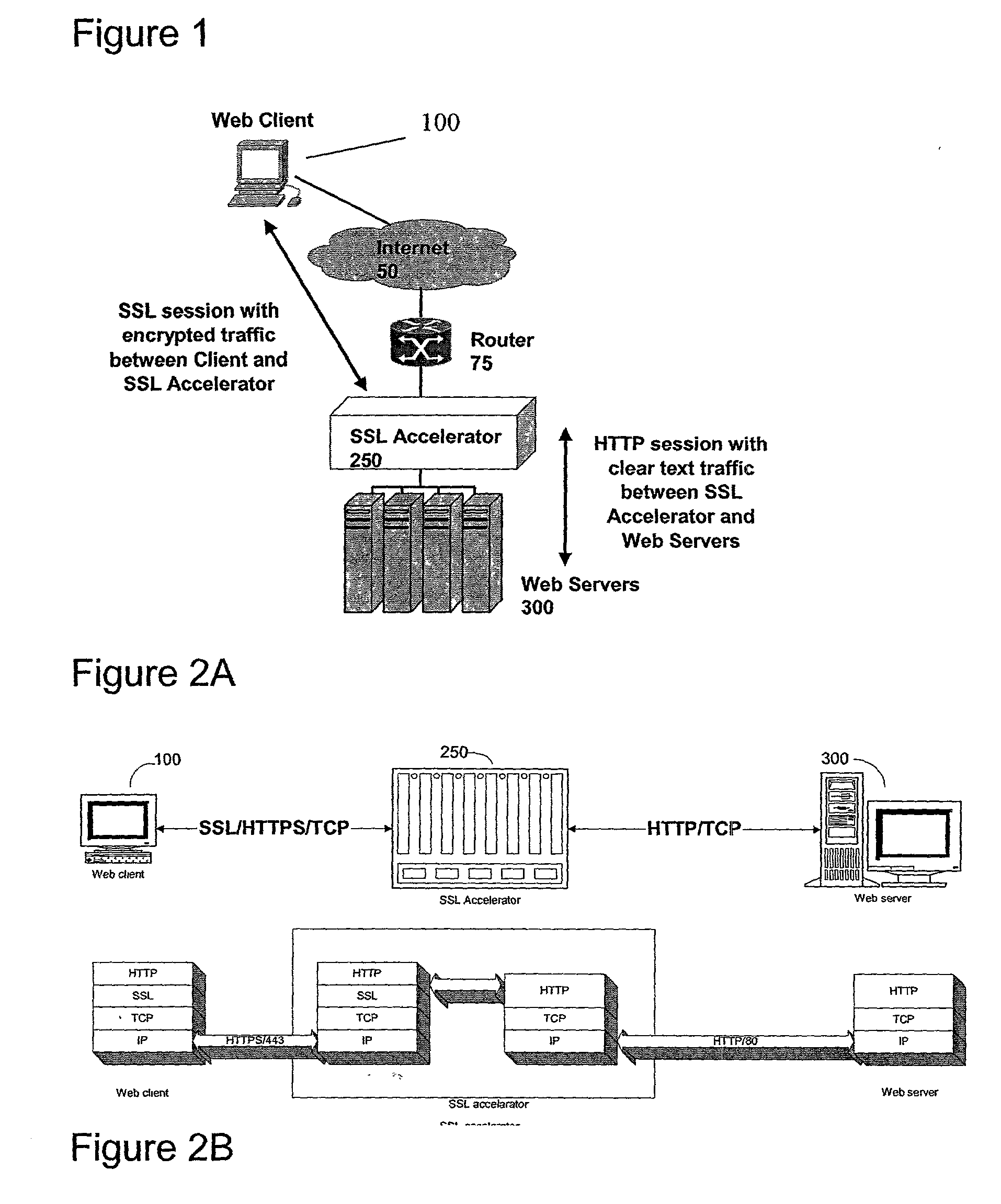
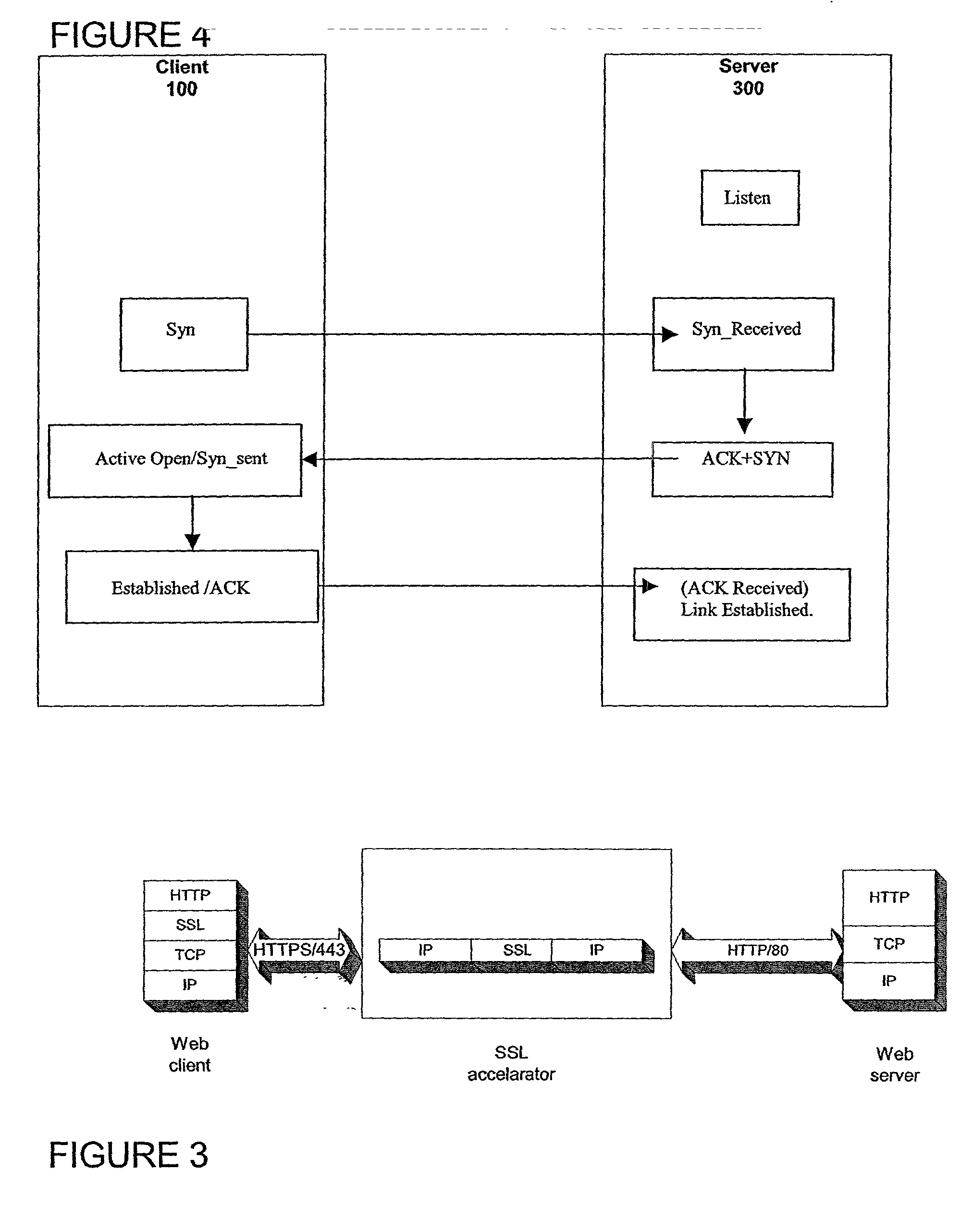
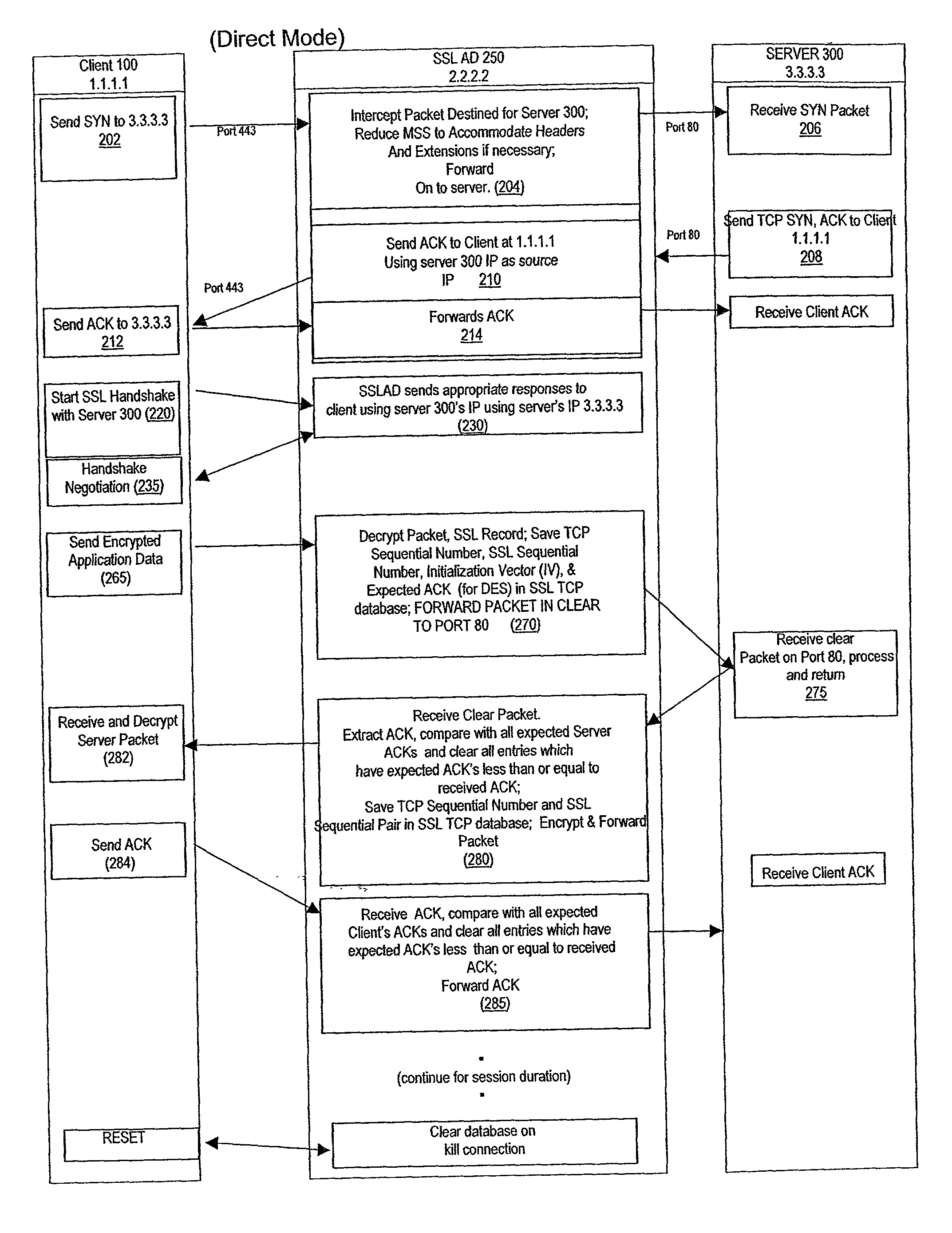
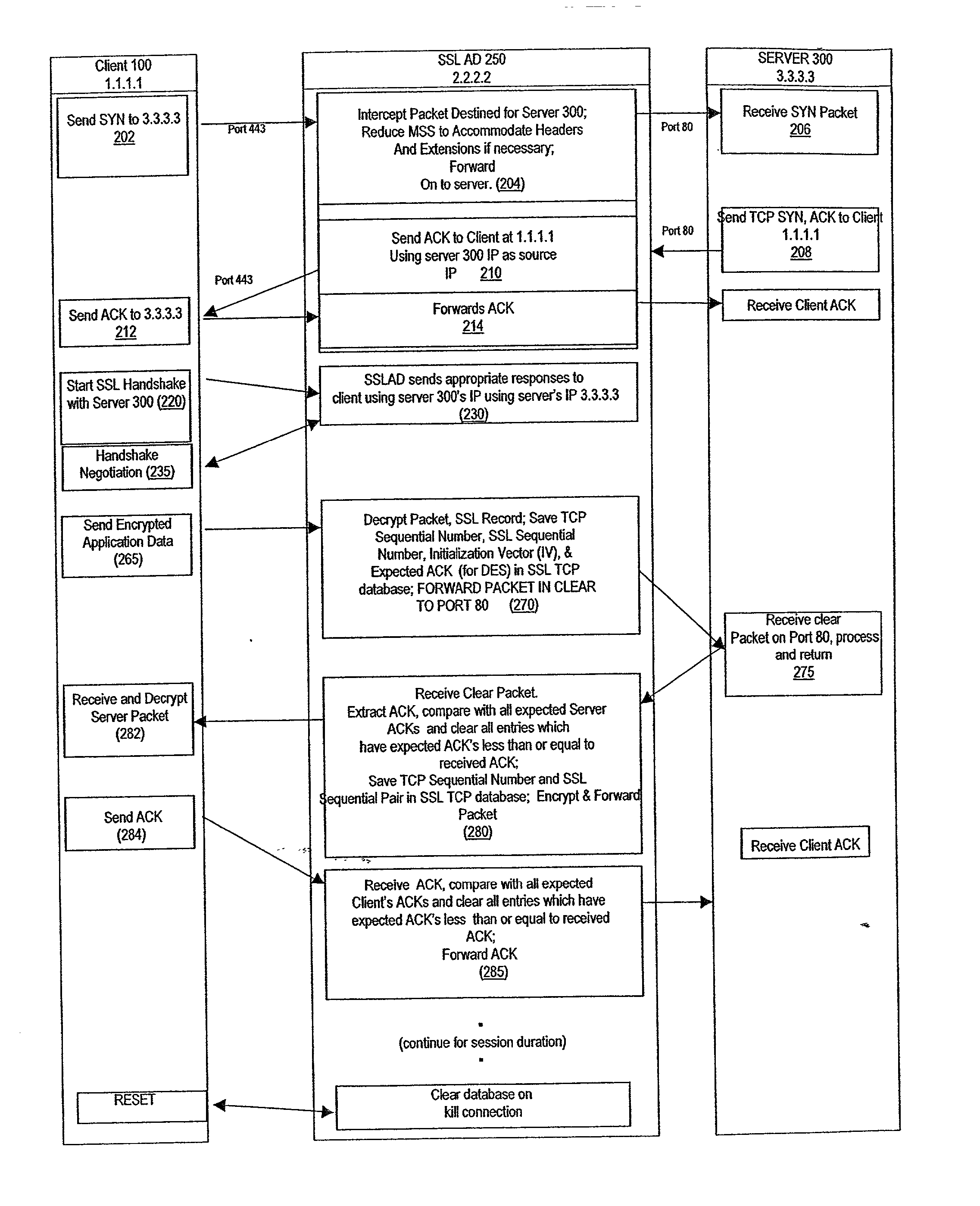
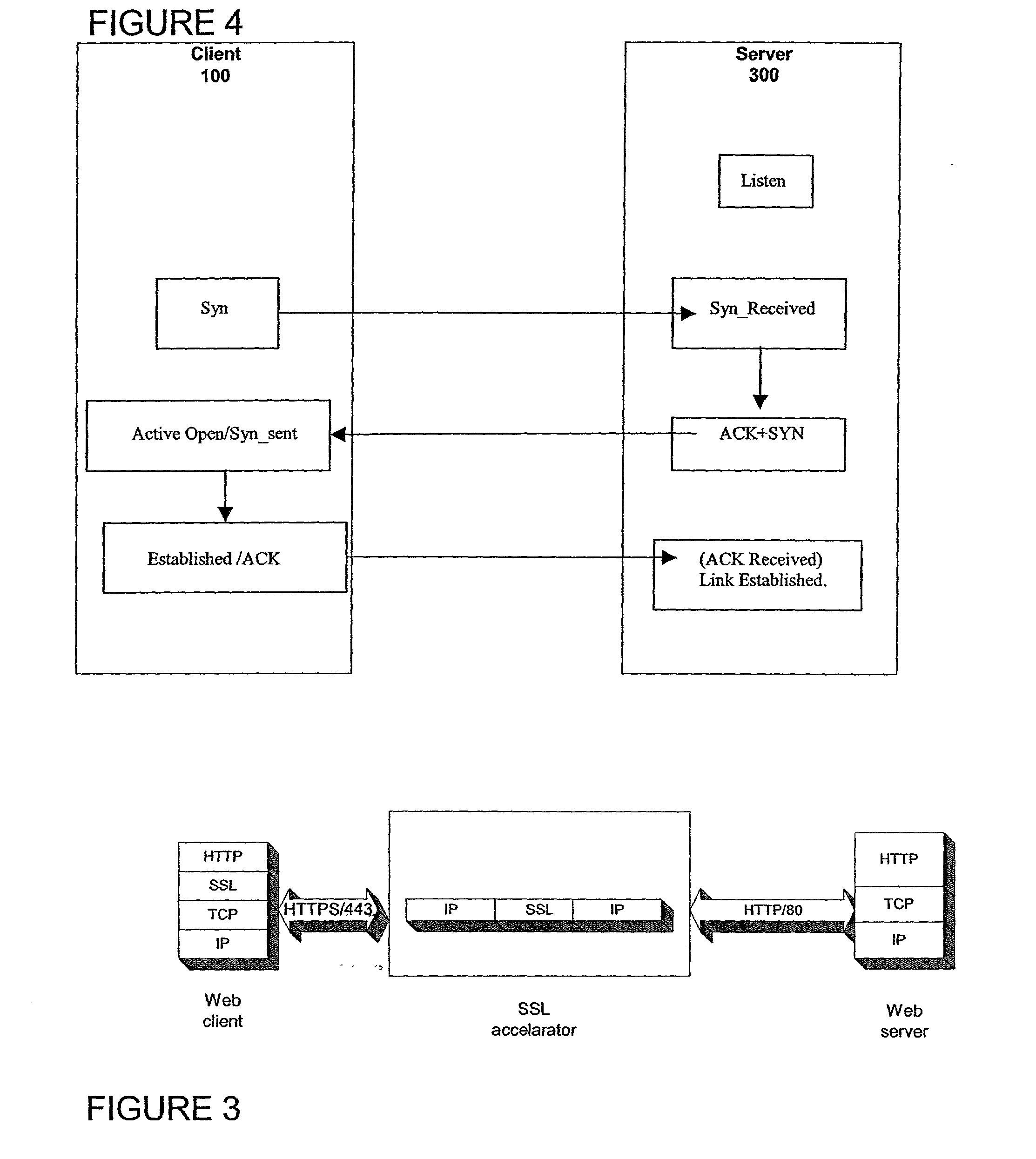
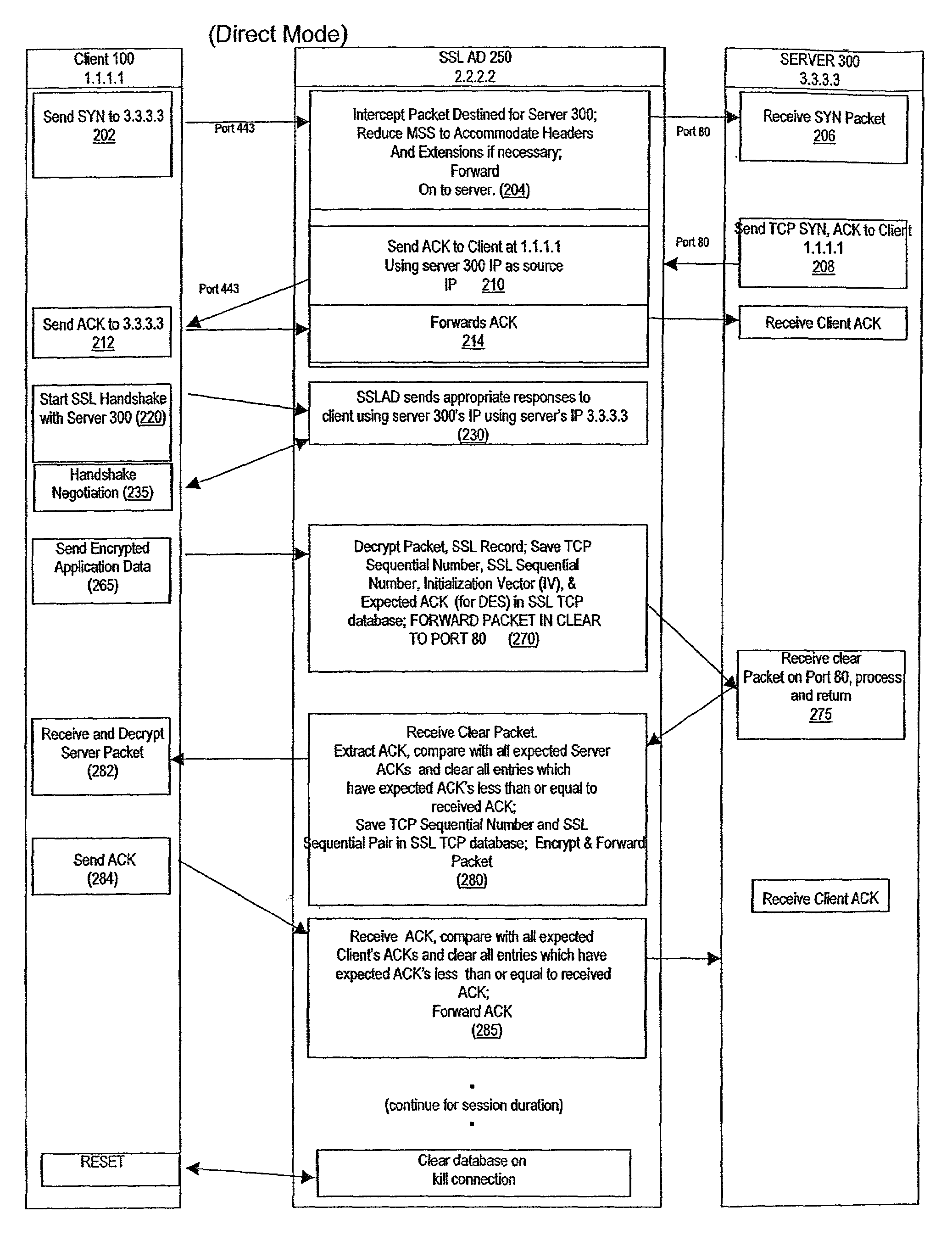
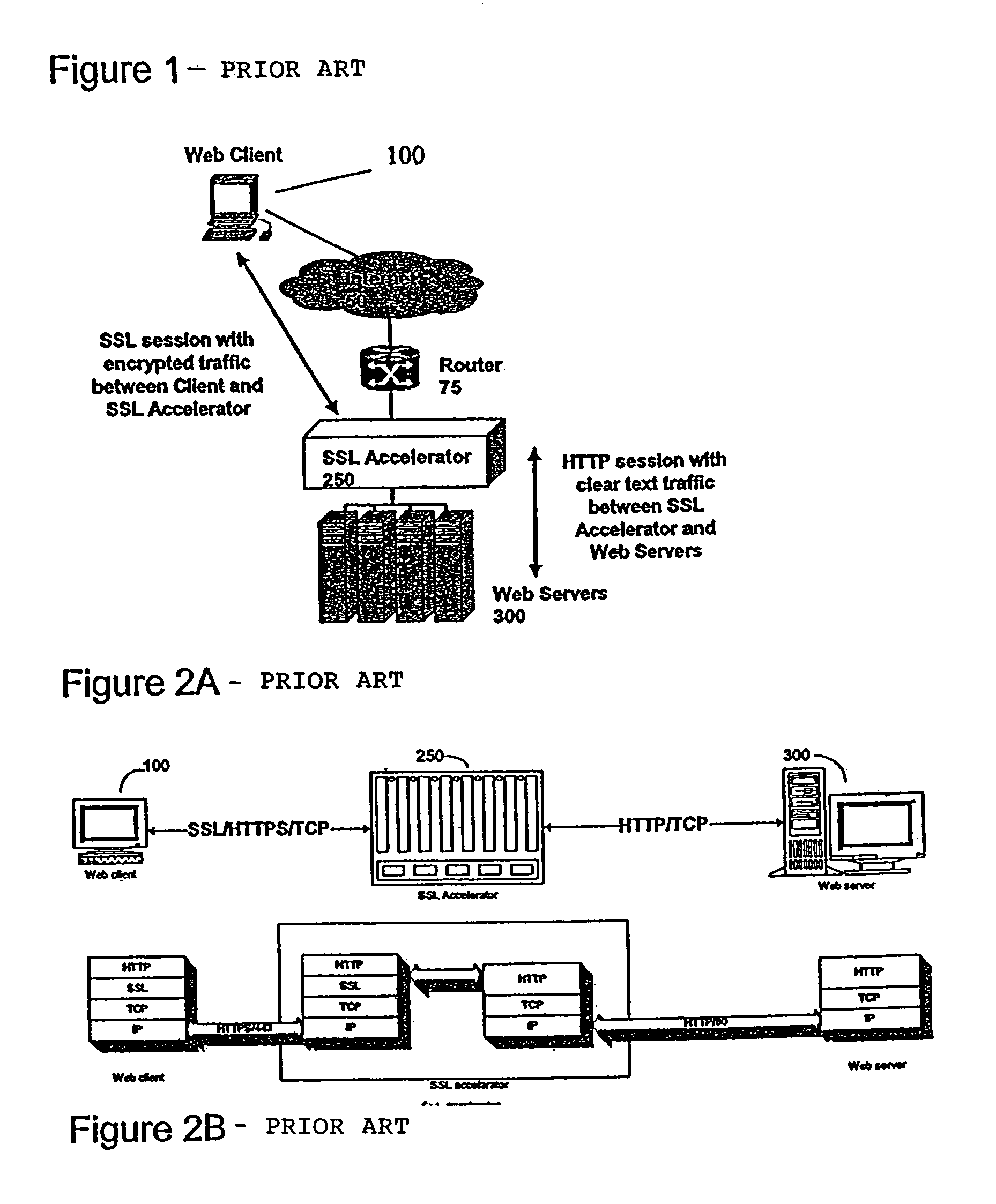
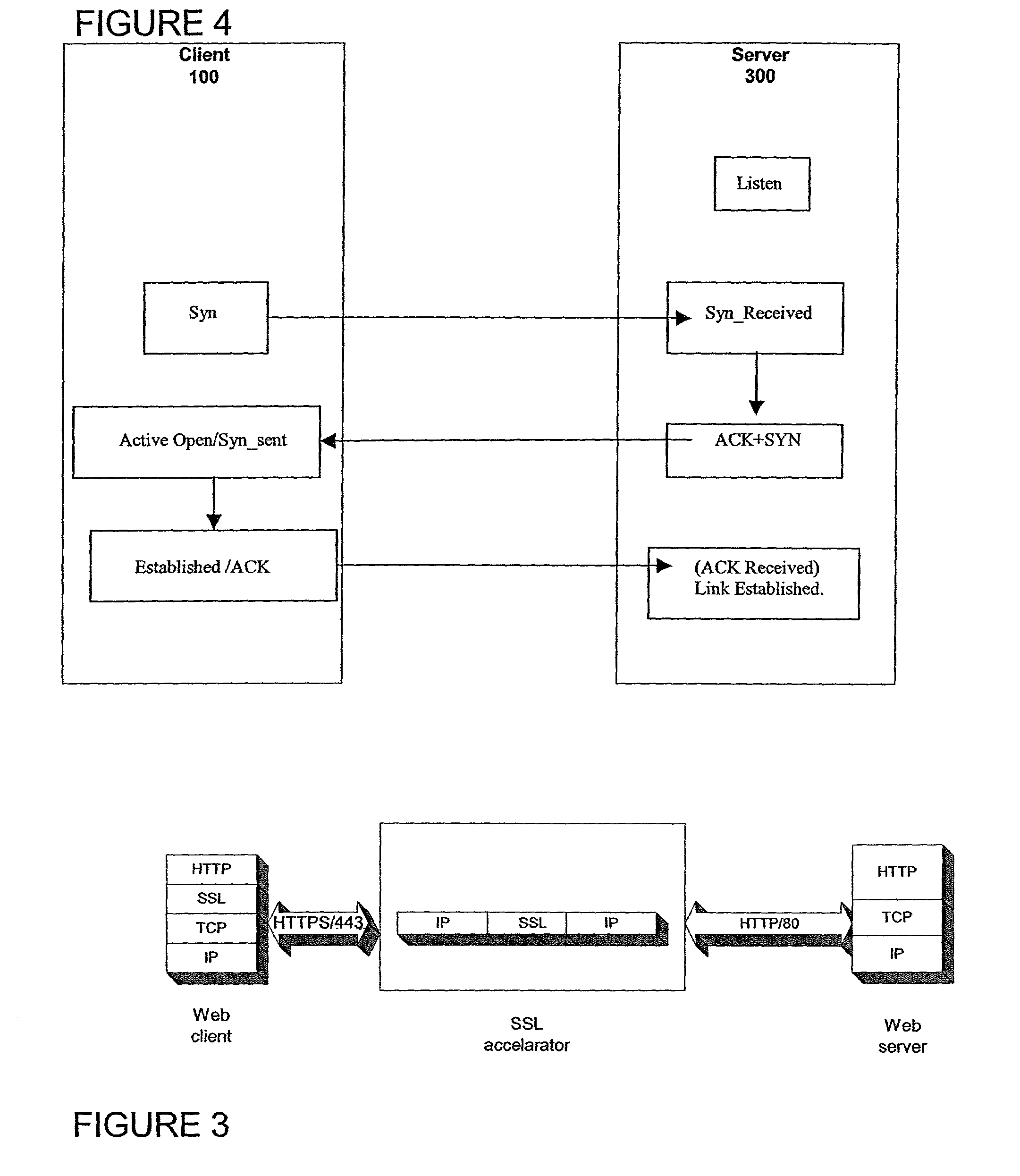
A method for secure communications between a client and one of a plurality of servers performed on an intermediary device coupled to the client and said plurality of servers. In one aspect, the method comprises: establishing an open communications session between the intermediary device and the client via an open network; negotiating a secure communications session with the client; establishing an open communications session with said one of said plurality of servers via a secure network; receiving encrypted data from the client via the secure communications session; decrypting encrypted application data; forwarding decrypted application data to the server via the secure network; receiving application data from the server via the secure network; encrypting the application data; and sending encrypted application data to the client. In a further aspect, an apparatus including a network interface communicating with the public network and the secure network at least one processor, programmable dynamic memory addressable by the processor, and a communications channel coupling the processor, memory and the network communications interface is provided. The apparatus further includes a proxy TCP communications engine, a proxy SSL communications engine, a server TCP communications engine; and a packet data encryption and decryption engine.
Owner:NEXSI SYST
Method for amortizing authentication overhead
InactiveUS7080046B1Payment architectureDigital data authenticationSecure transmissionData transmission
A method is disclosed for amortizing the authentication overhead of data transmissions. The method comprises establishing a first secure transmission of data between a transmitter and a receiver by transmitting at least one token to the receiver during the first secure transmission. There may be any number of senders and receivers, and any receivers may be a sender and vice versa. The method also comprises establishing at least one additional transmission of data between the sender and the receiver and transmitting the data and at least one token during the at least one additional transmission. In addition, the method compares the at least one token transmitted during the at least one additional transmission to the token transmitted during the first secure transmission to guarantee the authenticity of that at least one additional transmission.The method may also include transmitting a preselected number of tokens during the first secure transmission. The number of additional transmissions may or may not correspond to the preselected number of tokens. The at least one additional transmission may be conducted over an unsecure connection using open communication. The first secure transmission may be protected or encrypted.
Owner:AT&T DIGITAL LIFE
Secure sockets layer cut through architecture
ActiveUS20030014623A1Low hardware requirementsLower latencyDigital data processing detailsUser identity/authority verificationSecure communicationSession management
A method for secure communications between a client and a server. The method includes the steps of managing a communications negotiation between the client and the server; receiving encrypted data packets from the client; decrypting each encrypted packet data; forwarding unencrypted data packets to the server; receiving data packets from the server; encrypting the data packets from the server; and forwarding encrypted data packets to the client. In a further embodiment, an apparatus communicating with a client via a public network and communicating with one of a plurality of servers via a secure network is disclosed. The apparatus includes a network communications interface, at least one processor, programmable dynamic memory, and a communications channel coupling the processor, memory and network communications interface. In addition, the apparatus includes a client / server open communications session manager, a client secure communication session manager, a client / server secure communications session tracking database; and a data packet encryption and decryption engine.
Owner:NEXSI SYST
Adaptive method for amortizing authentication overhead
InactiveUS7085937B1Digital data processing detailsMultiple digital computer combinationsSecure transmissionSelf adaptive
A method is disclosed for amortizing the authentication overhead of data transmissions. The method comprises establishing a first secure transmission of data between a transmitter and a receiver by transmitting at least one token to the receiver during the first secure transmission. There may be any number of senders and receivers, and any receivers may be a sender and vice versa. The method also comprises establishing at least one additional transmission of data between the sender and the receiver and transmitting the data and at least one token during the at least one additional transmission. In addition, the method compares the at least one token transmitted during the at least one additional transmission to the token transmitted during the first secure transmission to guarantee the authenticity of that at least one additional transmission. The method may also include transmitting a preselected number of tokens during the first secure transmission. The number of additional transmissions may or may not correspond to the preselected number of tokens. The at least one additional transmission may be conducted over an unsecure connection using open communication. The first secure transmission may be protected or encrypted.
Owner:AT&T DIGITAL LIFE
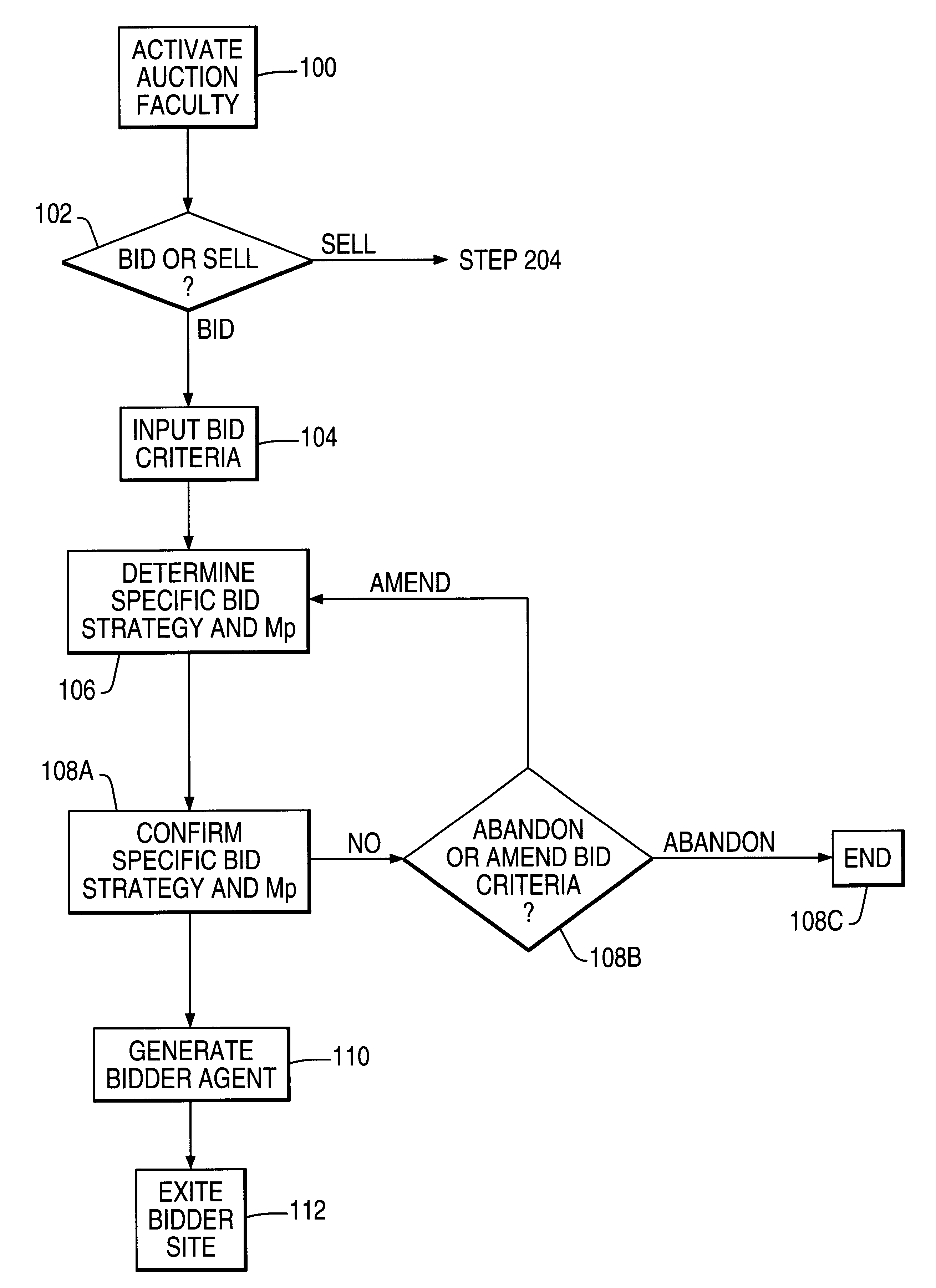
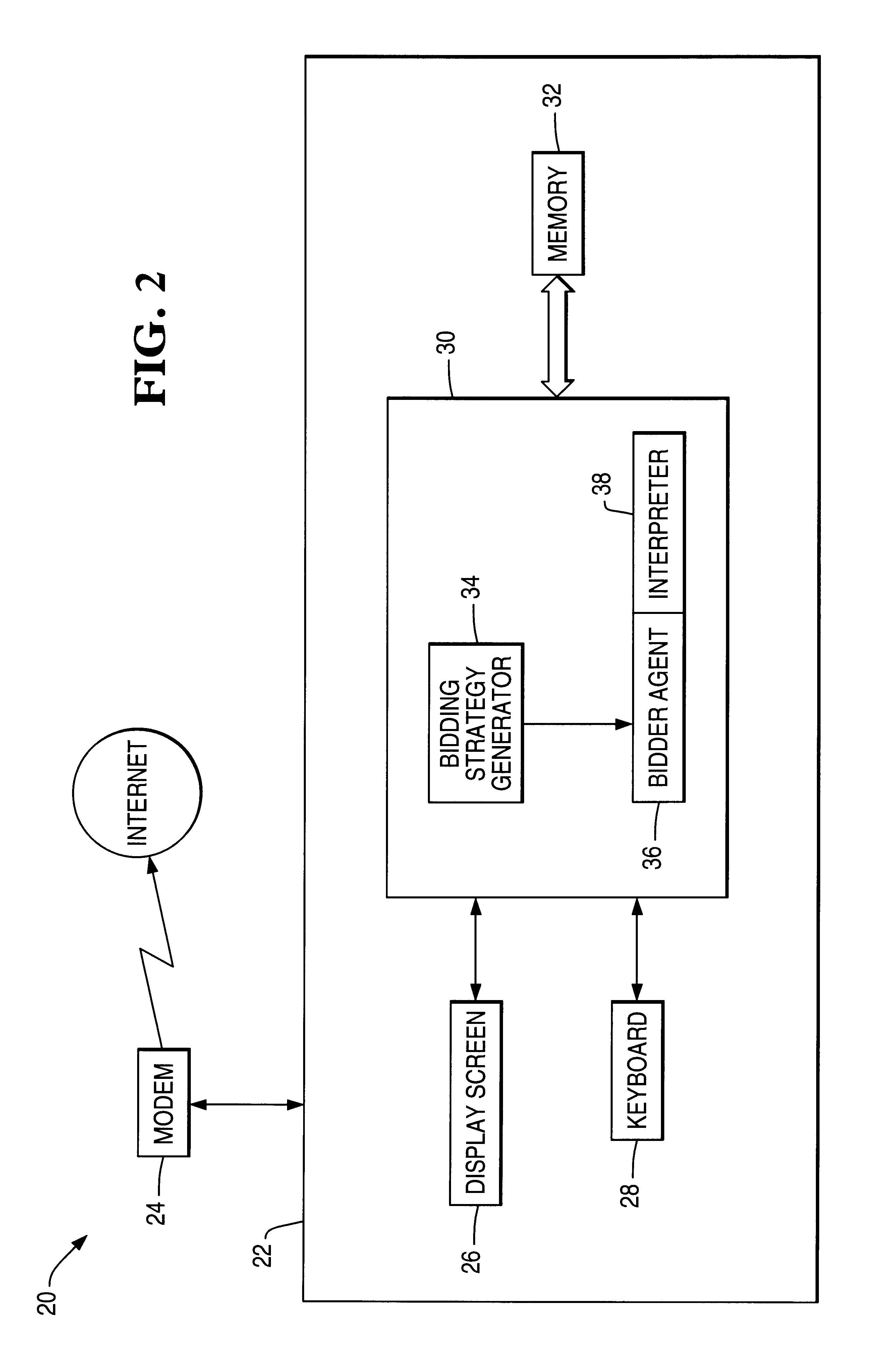
System and method for conducting an electronic auction over an open communications network
InactiveUS6871190B1Automate the processFinanceMultiple digital computer combinationsComputer scienceOpen communication
An interactive system conducts auctions over an open communications network. Remote bidder site(s) are interconnected with remote scum site(s). Data for desired merchandise to be acquired at an auction is entered and a bidding strategy is automatically generated at a remote bidder site. The generated bidding strategy is dien implemented at a remote seller site. Auction data relating to merchandise to be auctioned is entered and a selling strategy is generated on the basis of the auction data at the seller site. Thereafter, the generated selling strategy is implemented by interaction with bidding agent(s) at the seller site. During an auction at a seller site, the bidder and seller actions are controlled and synchronized.
Owner:HUAWEI TECH CO LTD
Secure sockets layer proxy architecture
InactiveUS7149892B2Reduce workloadEnhance layeringError detection/correctionMultiple digital computer combinationsSecure communicationChannel coupling
A method for secure communications between a client and one of a plurality of servers performed on an intermediary device coupled to the client and said plurality of servers. In one aspect, the method comprises: establishing an open communications session between the intermediary device and the client via an open network; negotiating a secure communications session with the client; establishing an open communications session with said one of said plurality of servers via a secure network; receiving encrypted data from the client via the secure communications session; decrypting encrypted application data; forwarding decrypted application data to the server via the secure network; receiving application data from the server via the secure network; encrypting the application data; and sending encrypted application data to the client. In a further aspect, an apparatus including a network interface communicating with the public network and the secure network at least one processor, programmable dynamic memory addressable by the processor, and a communications channel coupling the processor, memory and the network communications interface is provided. The apparatus further includes a proxy TCP communications engine, a proxy SSL communications engine, a server TCP communications engine; and a packet data encryption and decryption engine.
Owner:NEXSI SYST
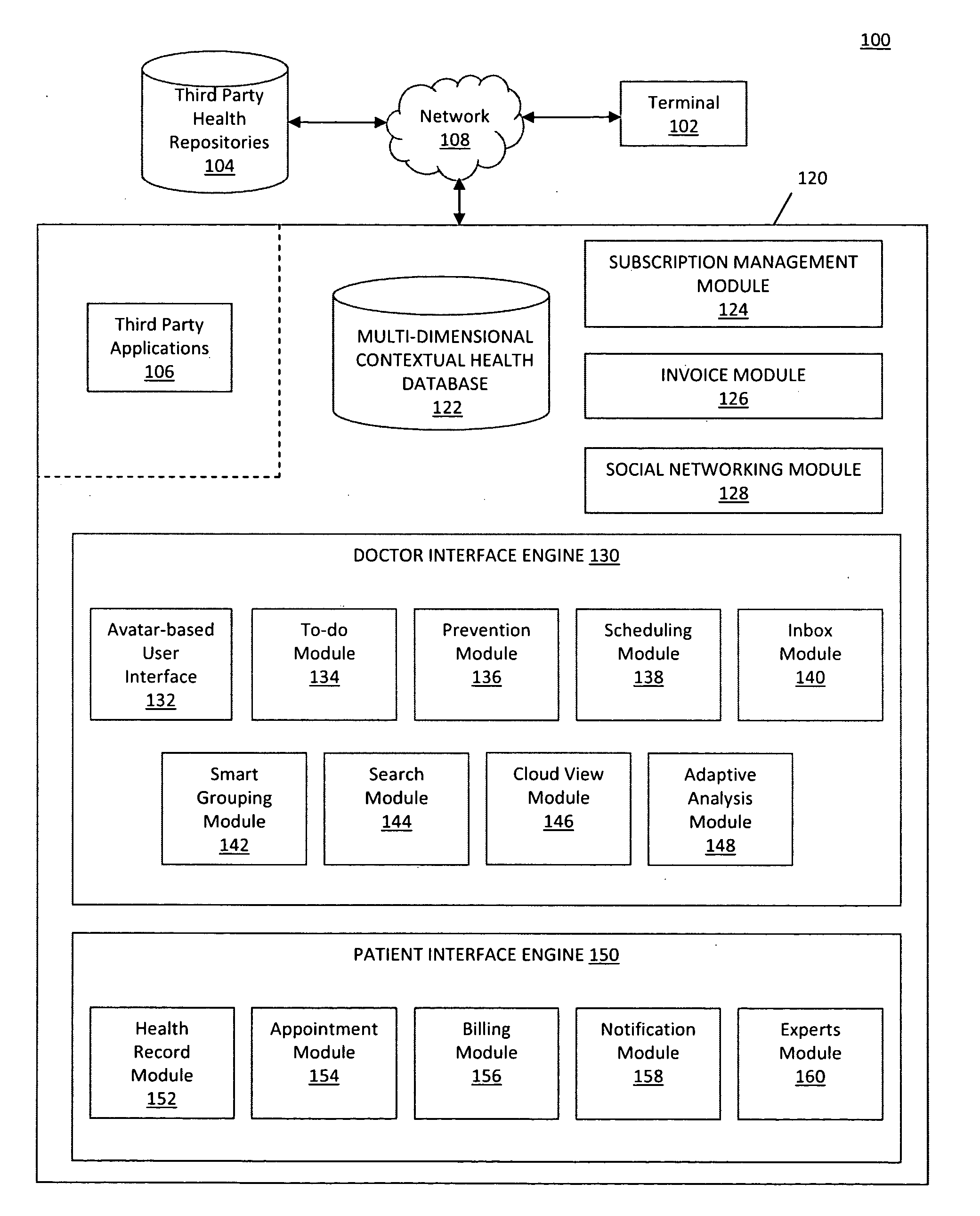
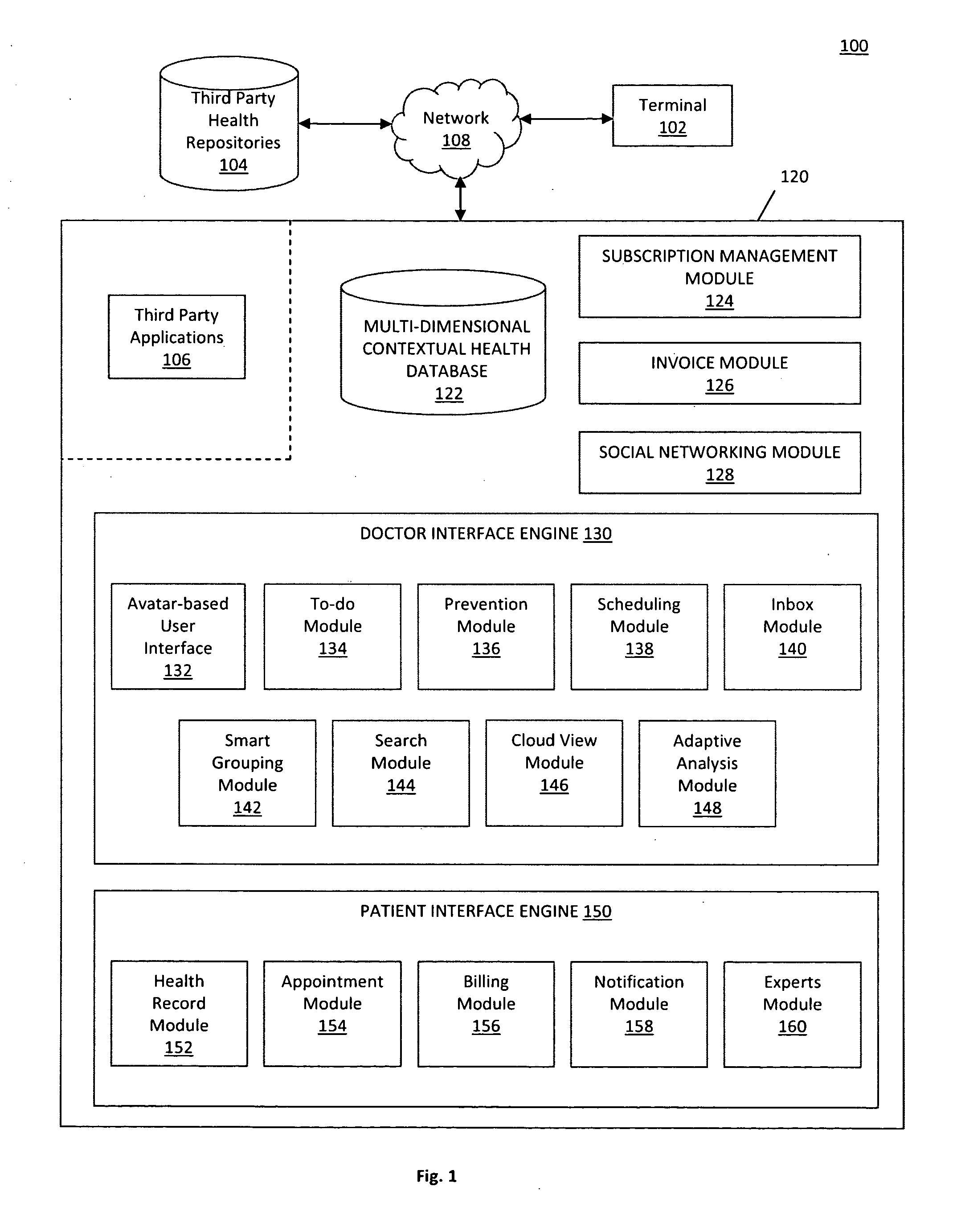
System and method for providing a multi-dimensional contextual platform for managing a medical practice
InactiveUS20100299155A1Improve medical experienceFacilitate communicationDrug and medicationsOffice automationPatient communicationMedical practice
A system and method is provided for generating a multi-dimensional contextual platform that may be used to manage, diagnose, and communicate with patients in a medical practice. In particular, the system may provide a website that may provide dynamic, avatar-based interfaces that include a doctor interface and a patient interface. A doctor may create a subscription with an operator of the website in order to find new patients and view patient health records across multiple dimensions. A patient may create a subscription with the operator to locate a doctor and maintain open communications with the doctor. Once subscribed, the doctor and patient may use the website to enhance the overall healthcare experience by using social networking aspects of the website to facilitate doctor and patient communication in real-time.
Owner:MYCA HEALTH
Bufferless secure sockets layer architecture
InactiveUS20030014625A1Minimization requirementsMore buffer memoryUser identity/authority verificationMultiple digital computer combinationsSecure communicationClient-side
A method for enabling secure communication between a client on an open network and a server apparatus on a secure network. The method is generally performed on a intermediary apparatus coupled to the secure network and the open network. The method includes the steps of negotiating a secure communications session with the client apparatus via the open network; negotiating an open communications session with the server via the secure network; receiving encrypted packet application data having a length greater than a packet length via multiple data packets; decrypting the encrypted packet application data in each data packet; forwarding decrypted, unauthenticated application data to the server via the secure network; and authenticating the decrypted packet data on receipt of a final packet of the segment.
Owner:NEXSI SYST
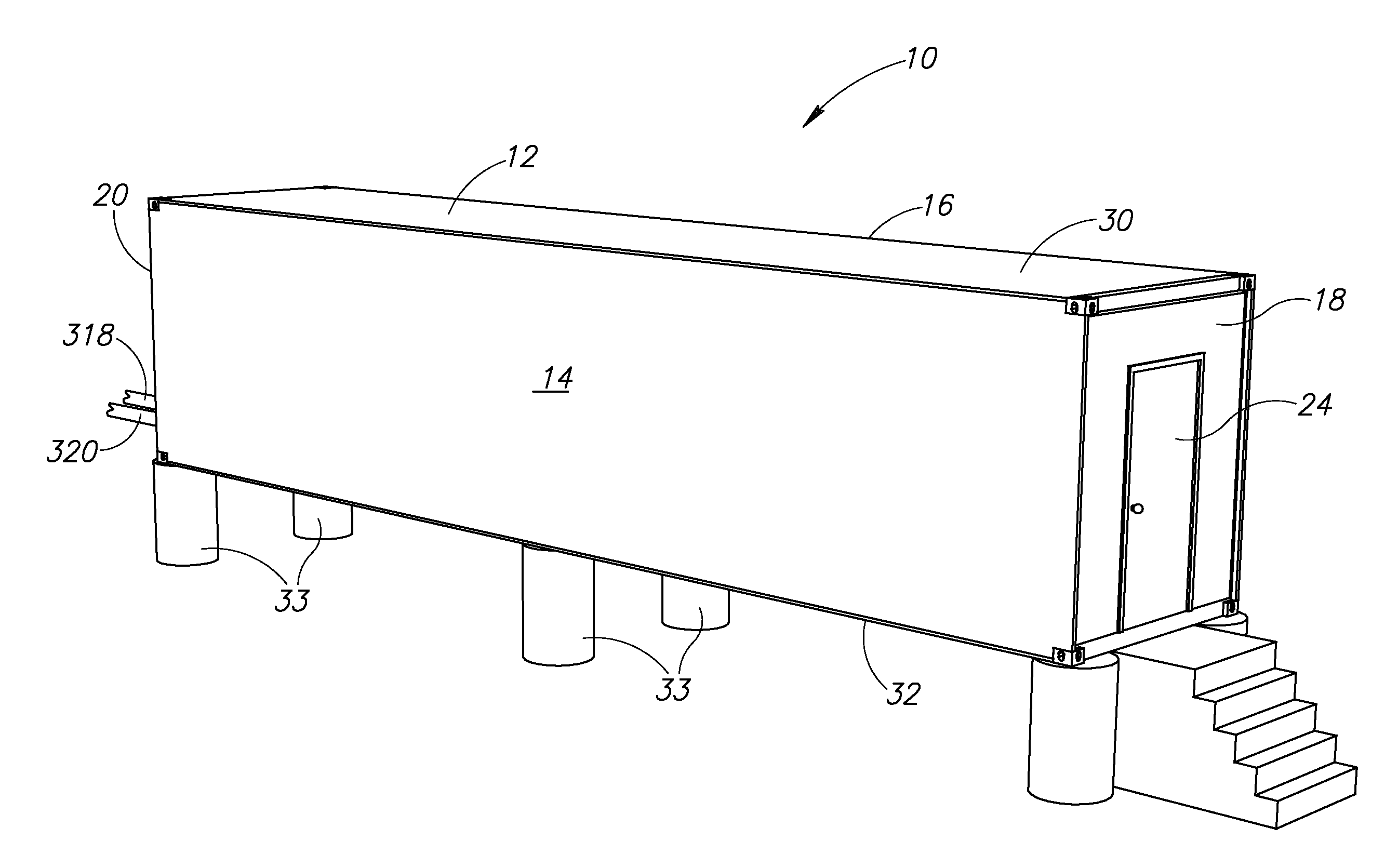
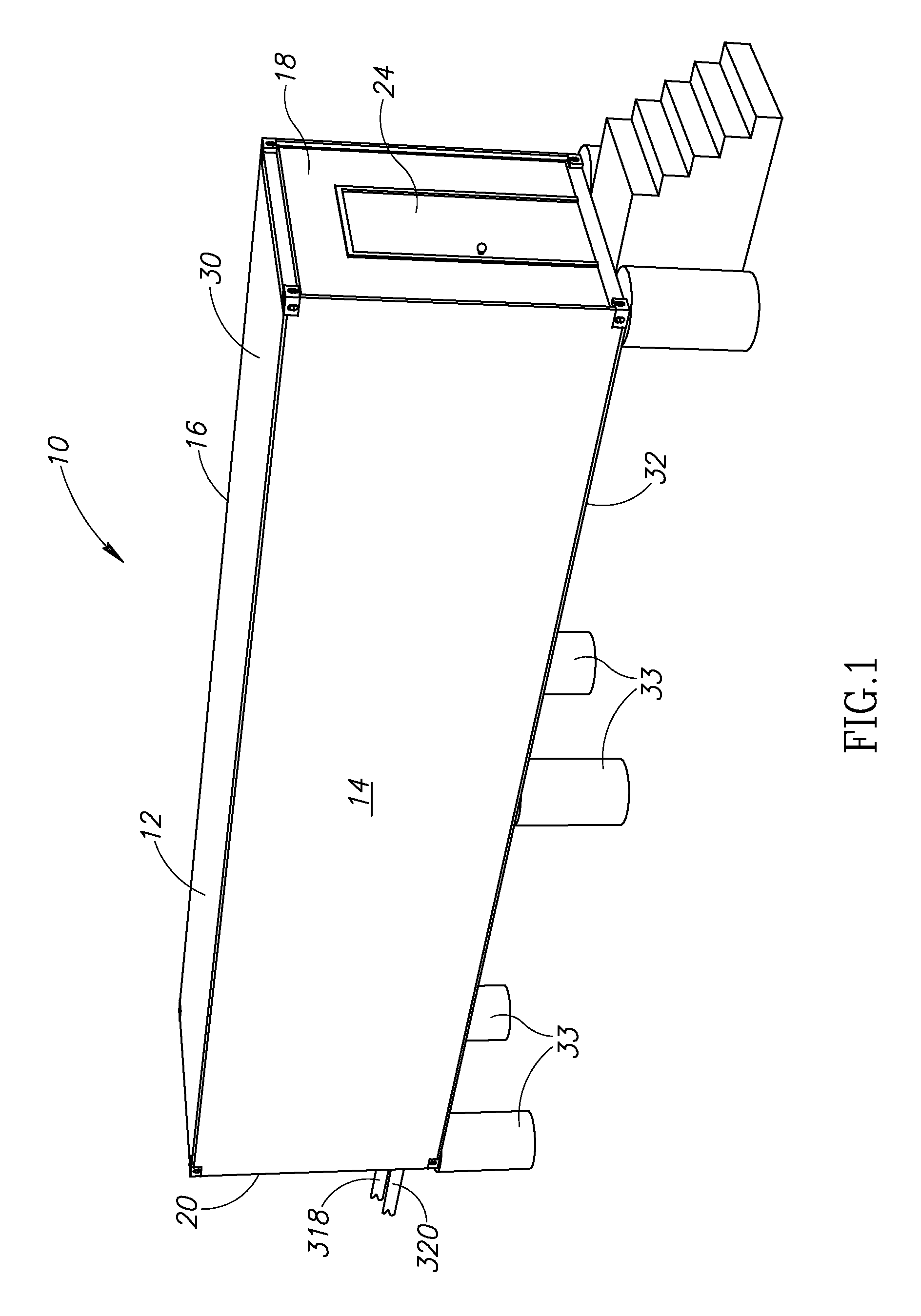
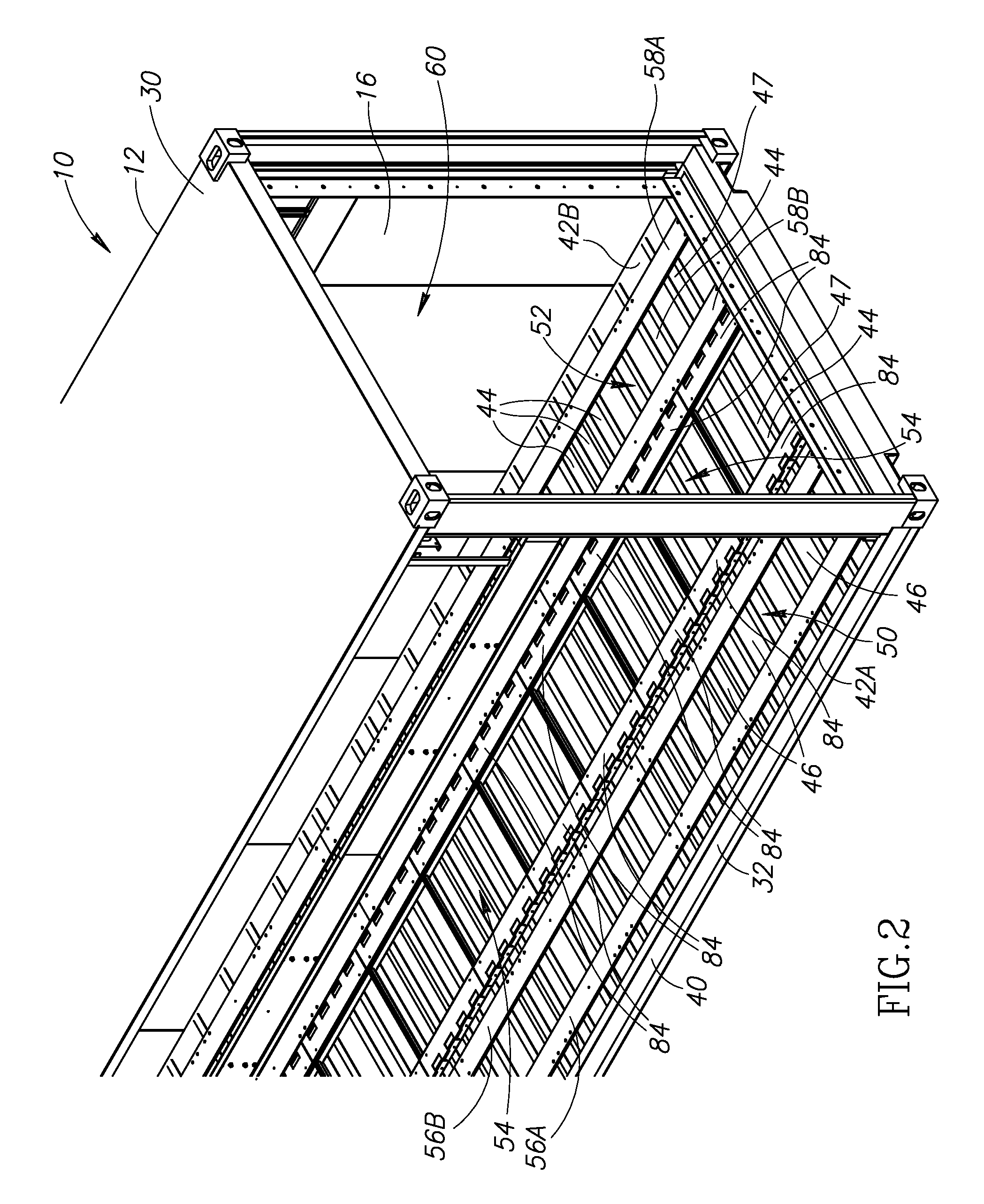
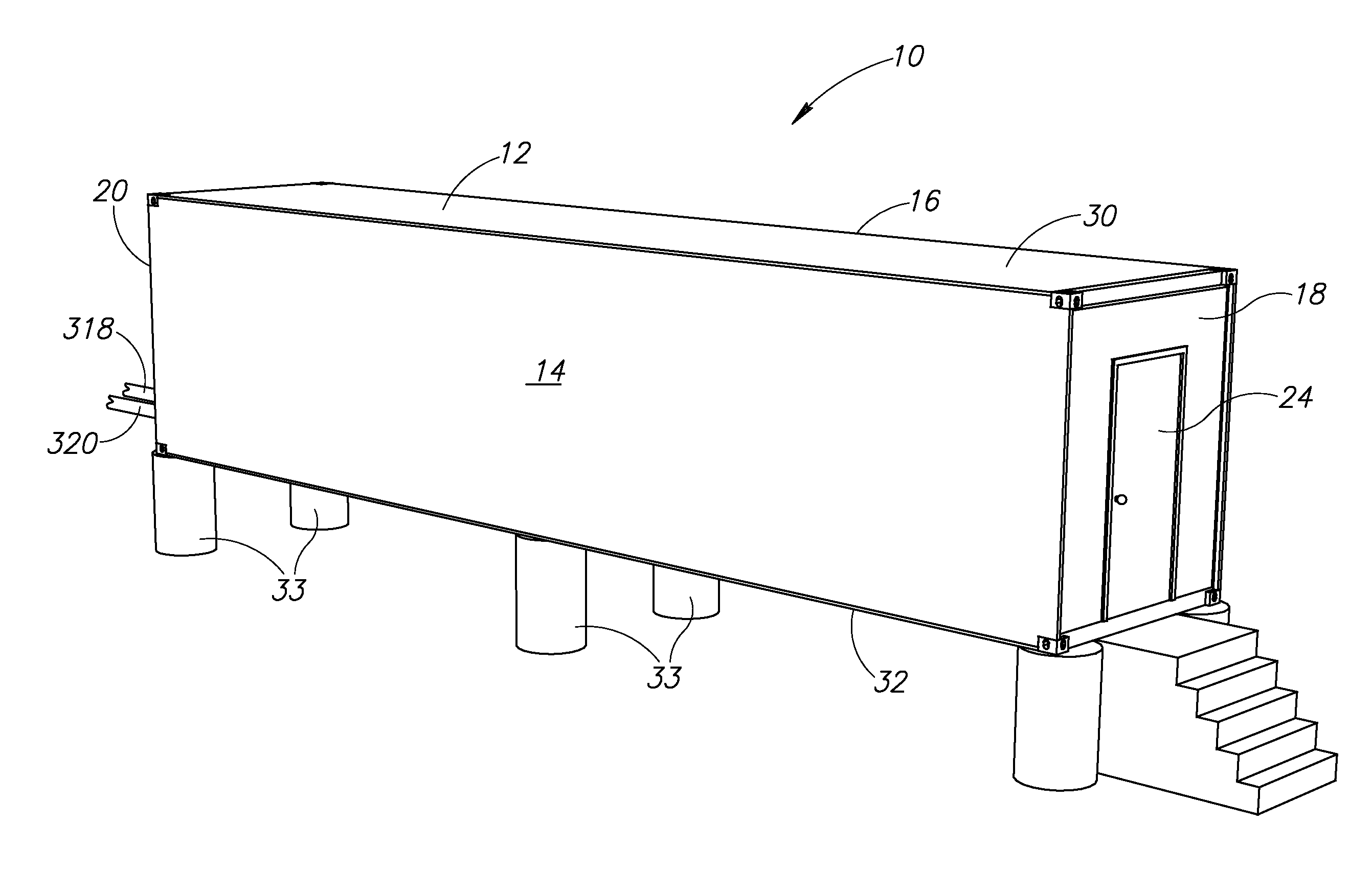
Data center
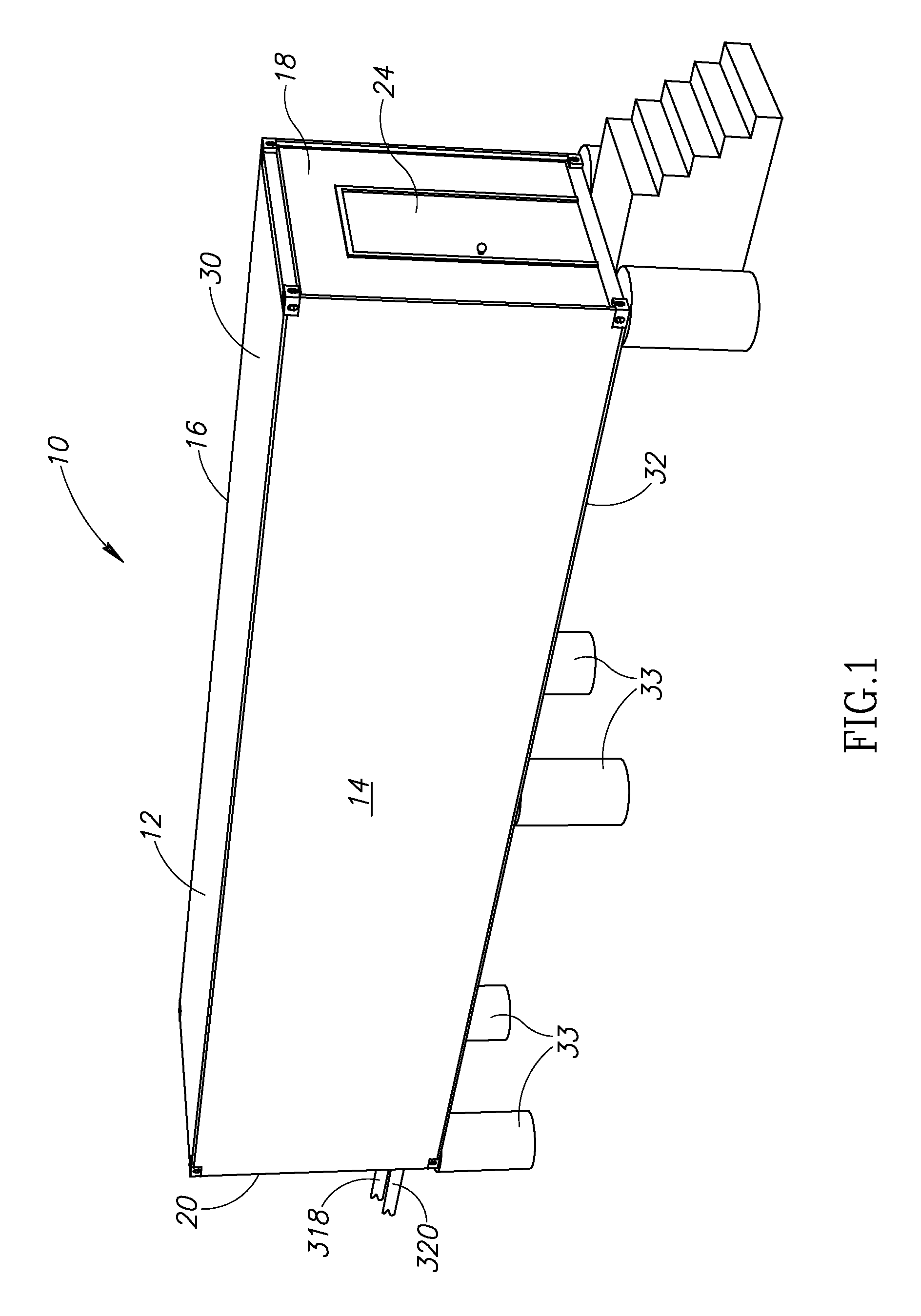
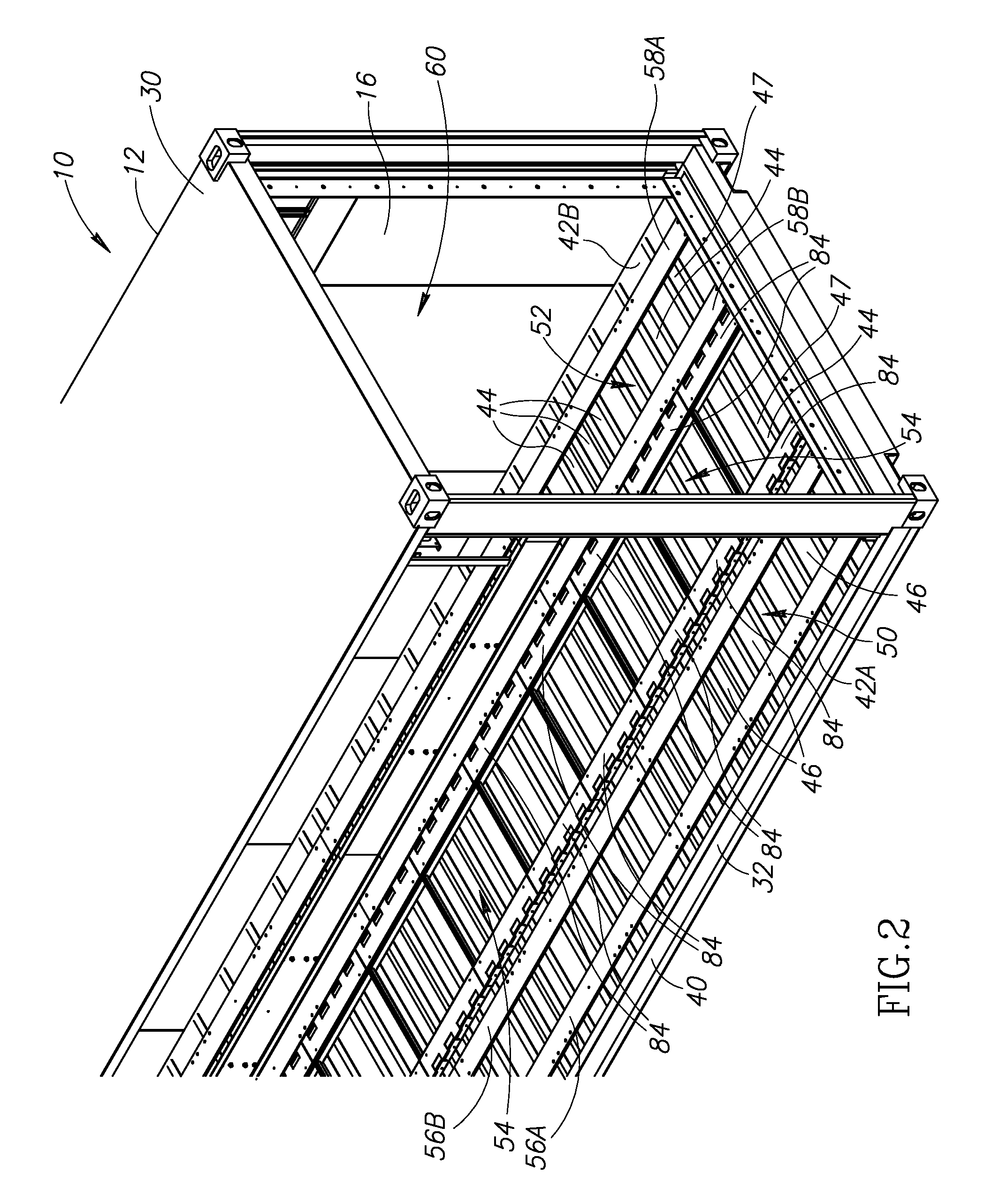
InactiveUS20100165565A1Electric signal transmission systemsMechanical apparatusData centerEngineering
A data center inside a shipping container having a lower plenum and an upper plenum in its interior. Heated air in the upper plenum exits therefrom into a plurality of heat exchangers adjacent thereto. Air cooled by the heat exchangers travels toward and enters the lower plenum. The data center includes a plurality of carriages each having an equipment receiving portion located between an open bottom portion in open communication with the lower plenum, and an open top portion in open communication with the upper plenum. Fans inside each of the carriages draw cooled air up from the lower plenum into the open bottom portion of the carriage, blow the cooled air up through the equipment receiving portion thereby cooling any computing equipment received therein, and vent the cooled air through the open top portion into the upper plenum.
Owner:CIRRASCALE
Data center
A data center inside a shipping container having a lower plenum and an upper plenum in its interior. Heated air in the upper plenum exits therefrom into a plurality of heat exchangers adjacent thereto. Air cooled by the heat exchangers travels toward and enters the lower plenum. The data center includes a plurality of carriages each having an equipment receiving portion located between an open bottom portion in open communication with the lower plenum, and an open top portion in open communication with the upper plenum. Fans inside each of the carriages draw cooled air up from the lower plenum into the open bottom portion of the carriage, blow the cooled air up through the equipment receiving portion thereby cooling any computing equipment received therein, and vent the cooled air through the open top portion into the upper plenum.
Owner:CIRRASCALE
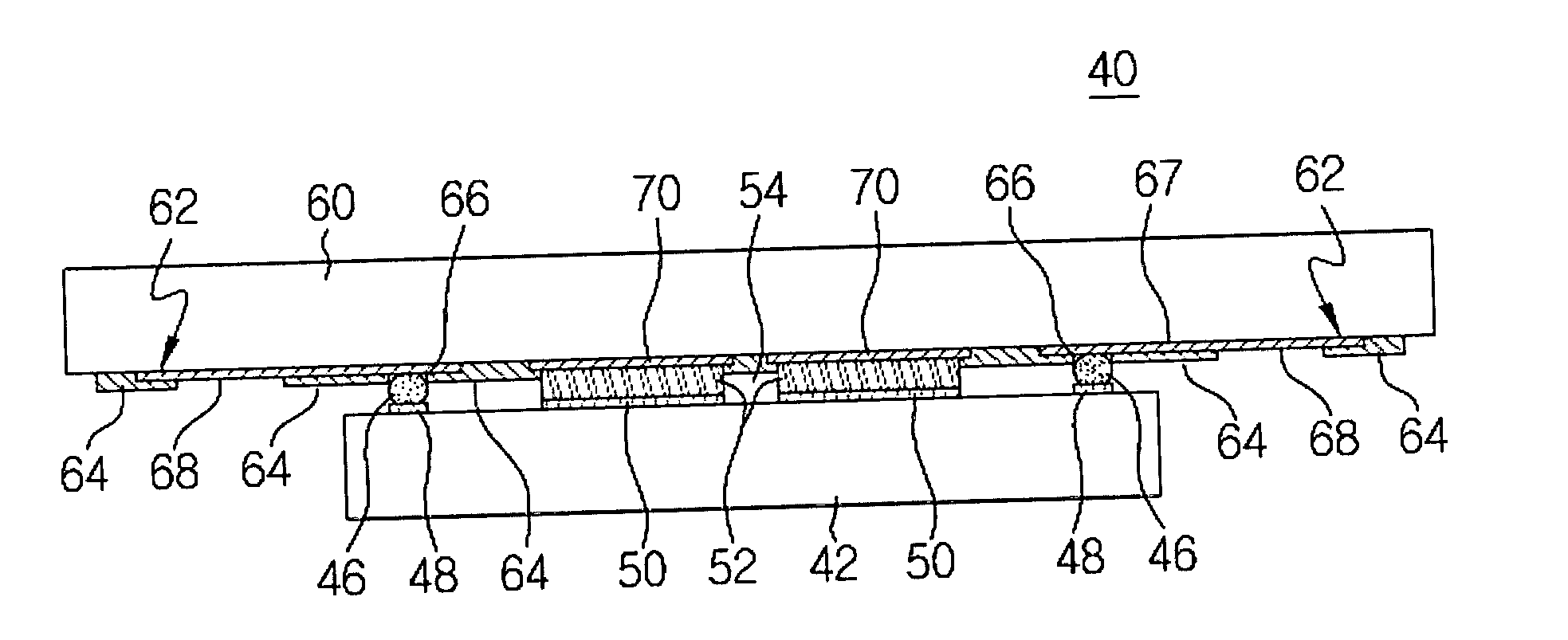
Electronic package for image sensor, and the packaging method thereof
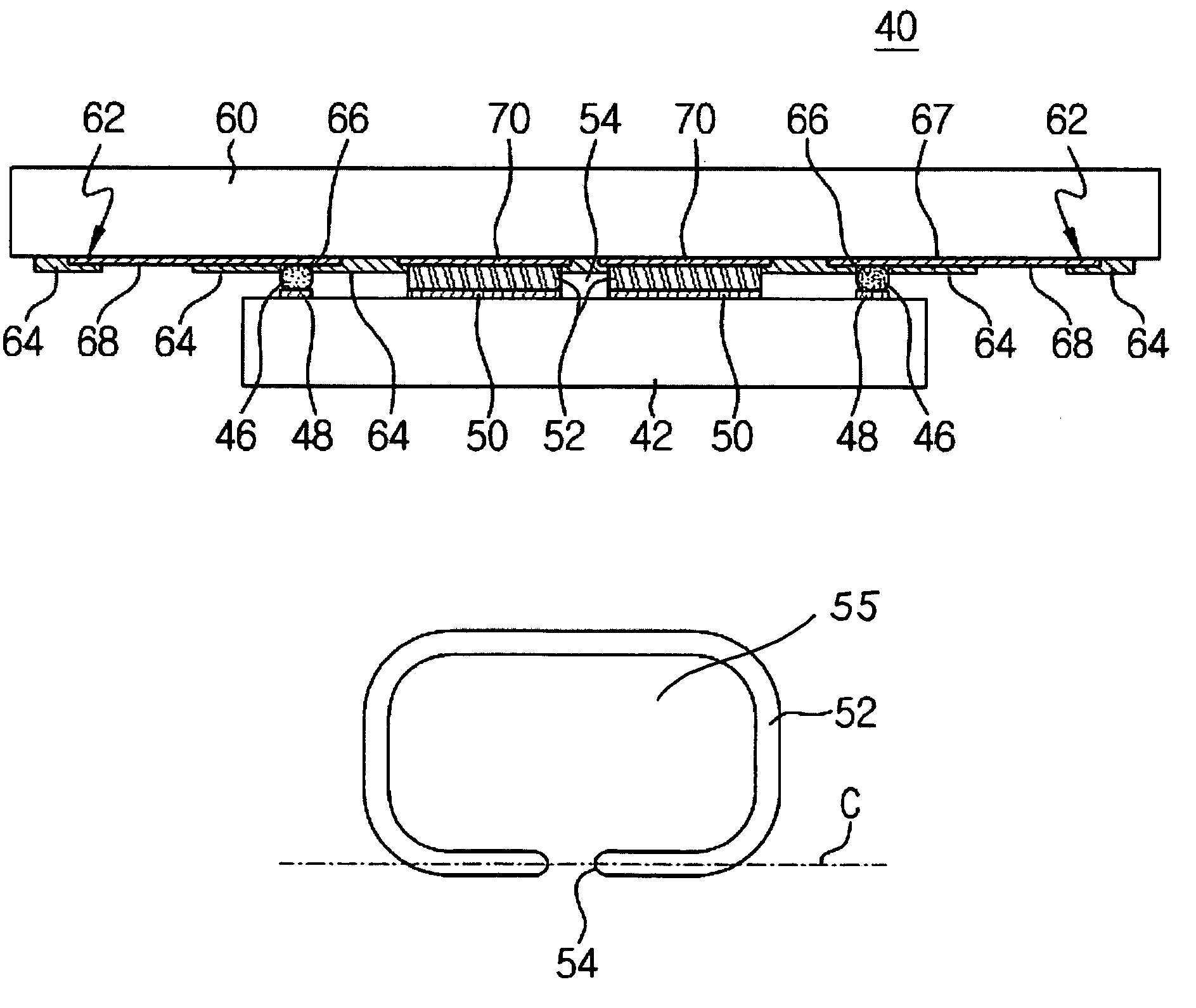
ActiveUS7141869B2Easy to useHighly cost-effective sealing techniqueSemiconductor/solid-state device detailsSolid-state devicesSemiconductor packageElectronic packages
A semiconductor device package and method for its fabrication are provided. The semiconductor device package generally includes at least one semiconductor die and a substrate coupled to the semiconductor die. The semiconductor die is provided with a front side defining a sealing area, and a first solder sealing ring pad formed on that front side. The substrate is provided with a front surface opposing the front side of the semiconductor die on which a second solder sealing ring pad is formed. A solder sealing ring structure is sandwiched between the first and second solder sealing pads of the substrate and semiconductor die, such that it extends peripherally about a substantial portion of the sealing area to substantially enclose thereat a cavity between the semiconductor die and the substrate. The solder sealing ring structure includes at least one venting portion defining against at least one of the substrate and semiconductor die an air vent in open communication with the cavity.
Owner:OPTOPAC
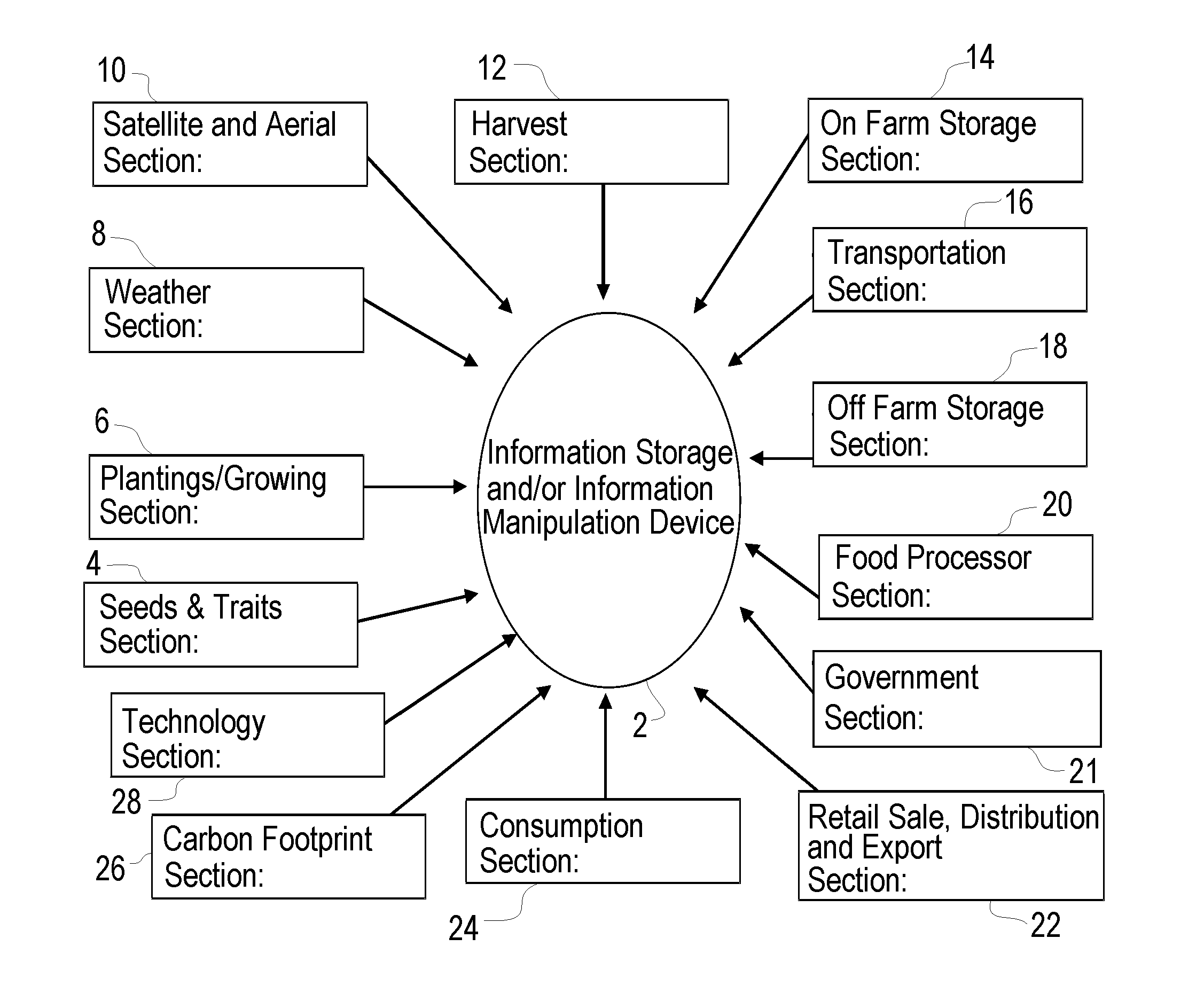
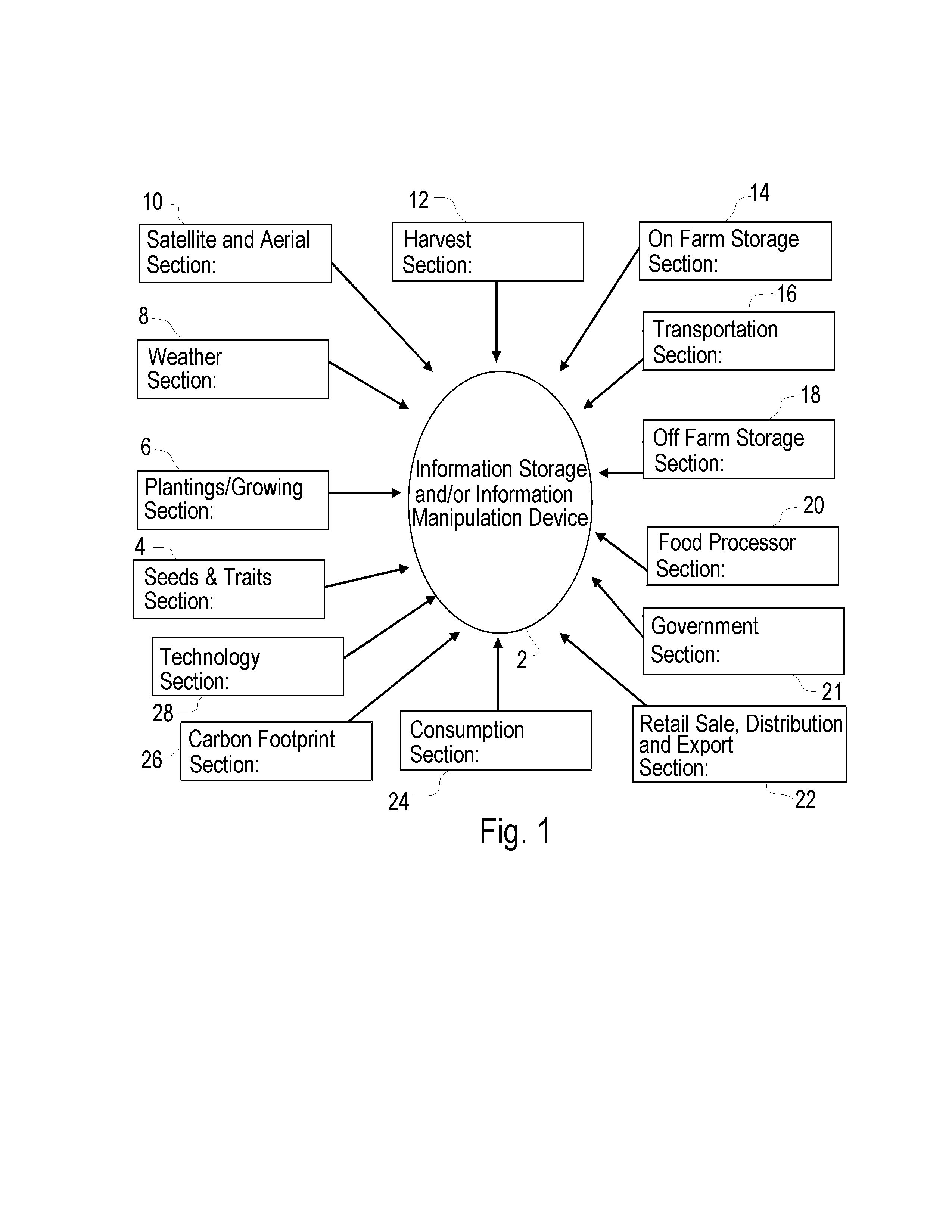
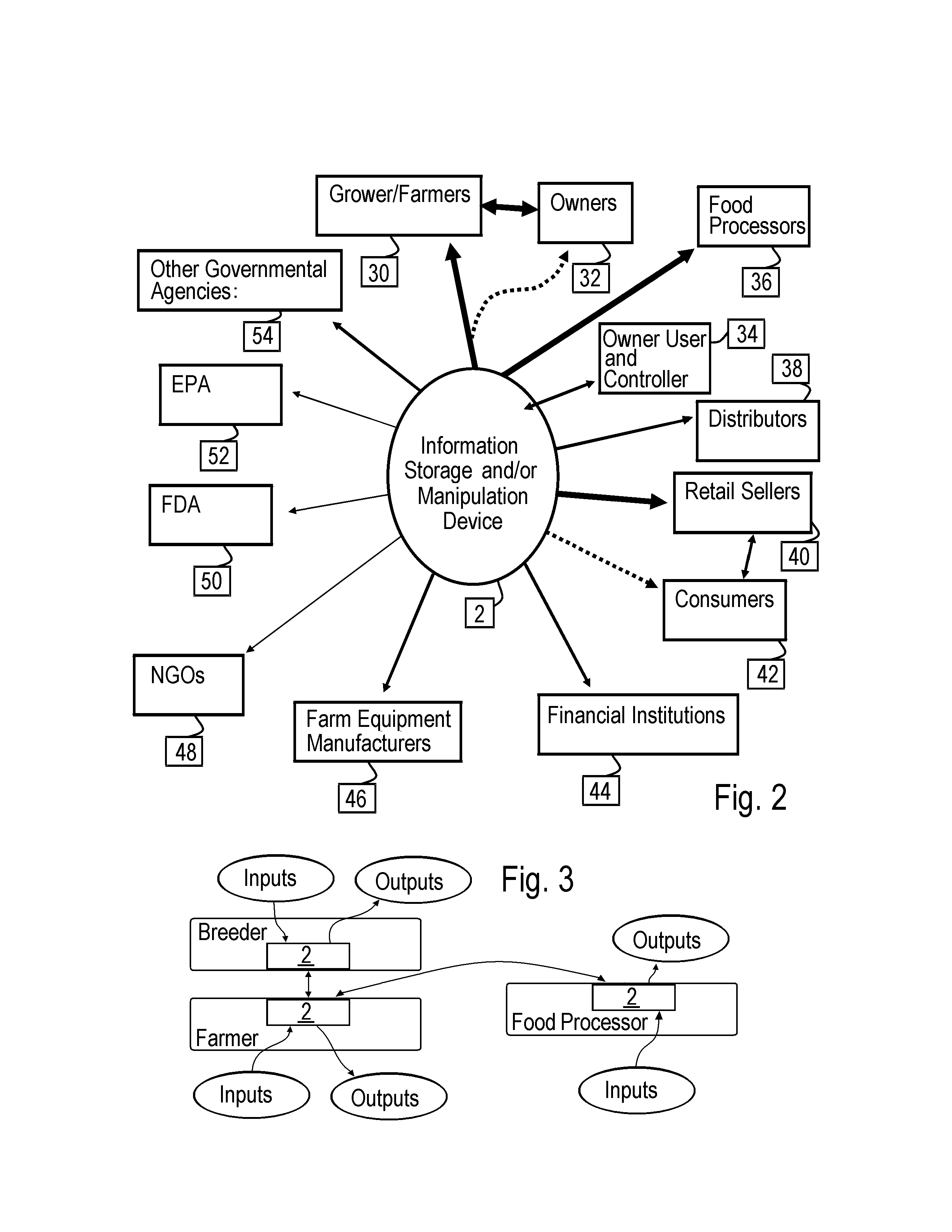
System and method of providing agricultural pedigree for agricultural products throughout production and distribution and use of the same for communication, real time decision making, predictive modeling, risk sharing and sustainable agriculture
A method for establishing an agricultural pedigree for agricultural products comprises the steps of: (a) Providing an open communication network accessible information storage device adapted to receive input of data relating to agricultural product production and distribution from multiple sources; (b) Inputting said data into said information storage device; (c) Storing and said data; and (d) Providing access to said data via the open communication network, wherein the information storage device is configured to be used as at least: (i) A tool for traceability of the agricultural products, (ii) A real time decision making tool, and (iii) A predictive modeling tool.
Owner:KLAVINS MARIS
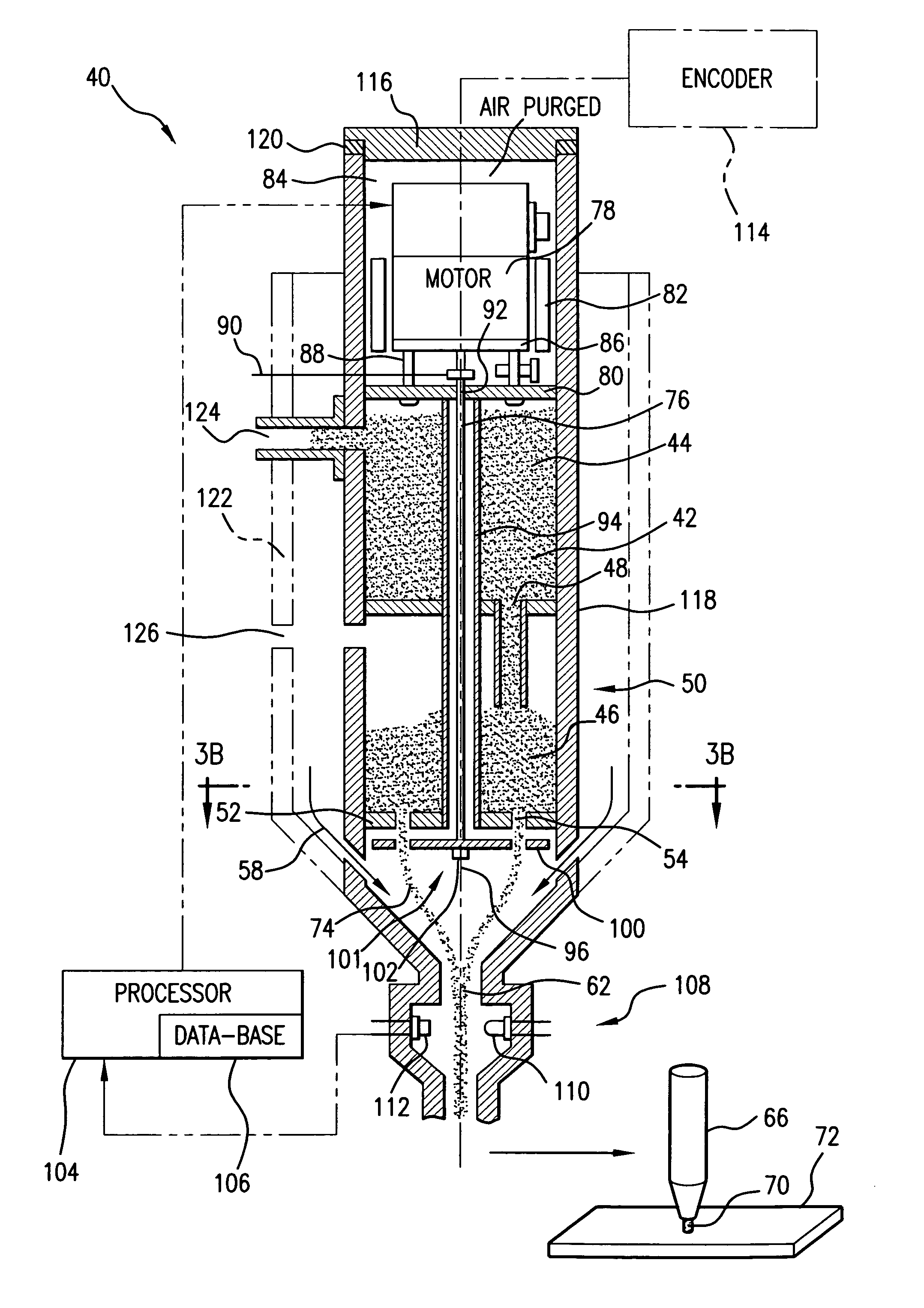
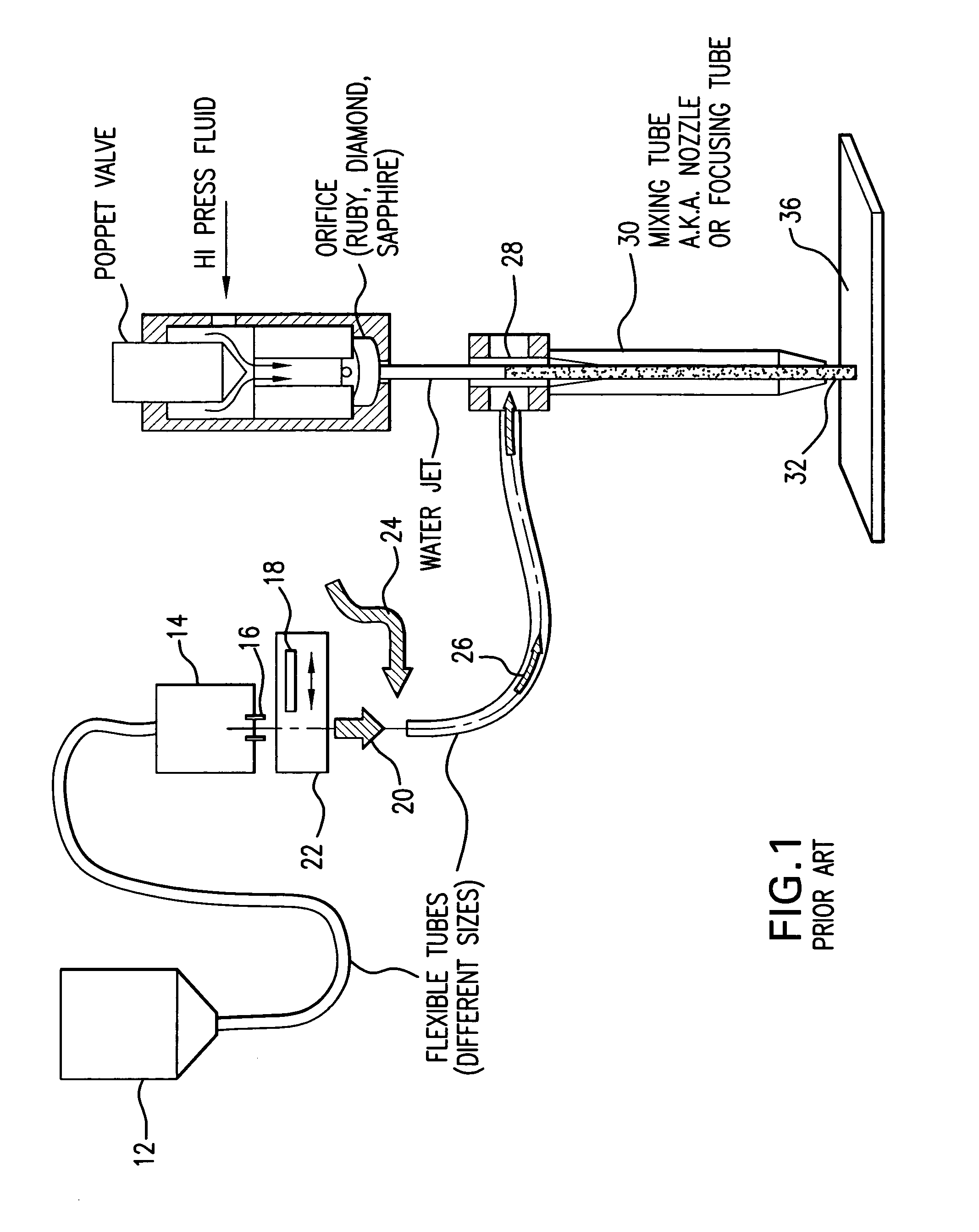
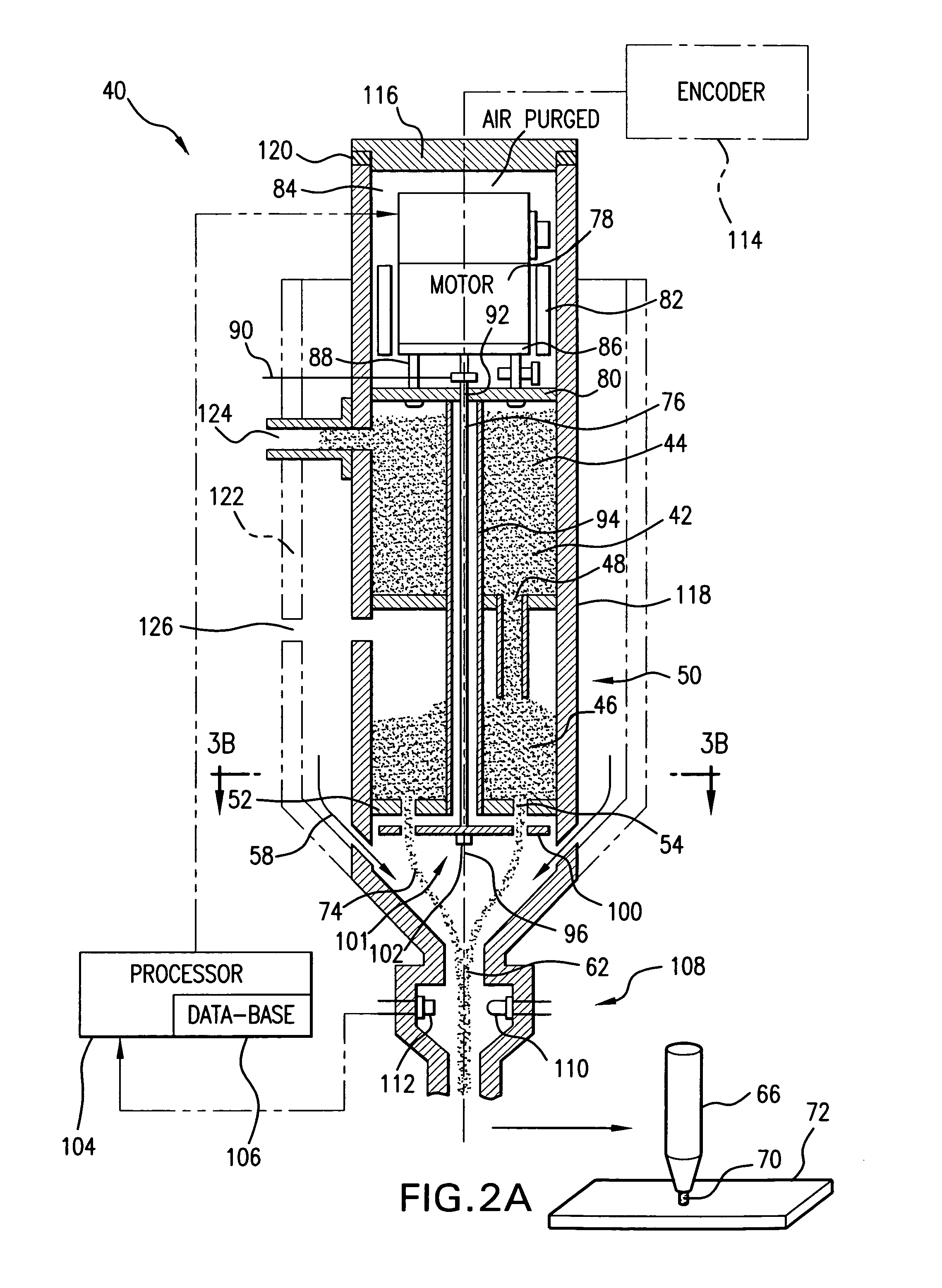
Variable rate dispensing system for abrasive material and method thereof
InactiveUS7040959B1Accurate and reliable yet efficientBlast gunsGrinding feed controlEngineeringActuator
An abrasive jet apparatus is provided which includes an abrasive dispenser defining a compartment for storing a granular abrasive material and at least one metering orifice disposed in open communication therewith for dispensing the granular abrasive material. The apparatus also includes a shutter assembly disposed adjacent the metering orifice, which includes a shutter member angularly displaceable between first and second positions relative to the metering orifice. The shutter member has formed therethrough at least one shutter opening which in the first position is substantially fully aligned with the metering orifice, and in the second position is substantially fully offset therefrom. The apparatus further includes a position actuator operatively coupled to the shutter mechanism for reversibly displacing the shutter member to the first and second positions and a plurality of intermediate positions therebetween for occluding a selective portion of the metering orifice. A flow rate of the abrasive material dispensed through said metering orifice is thereby maintained at a predetermined level.
Owner:LAI INT
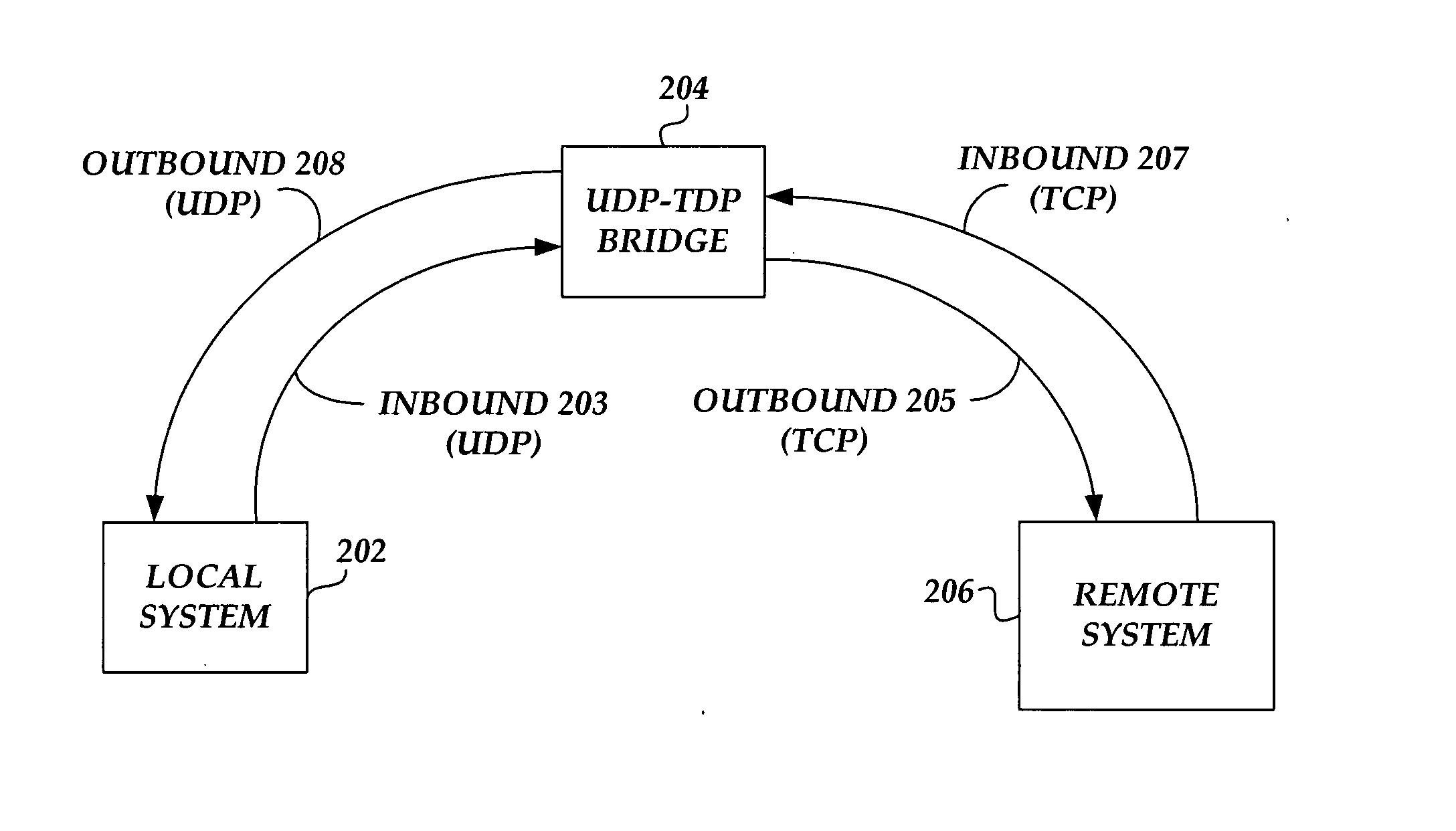
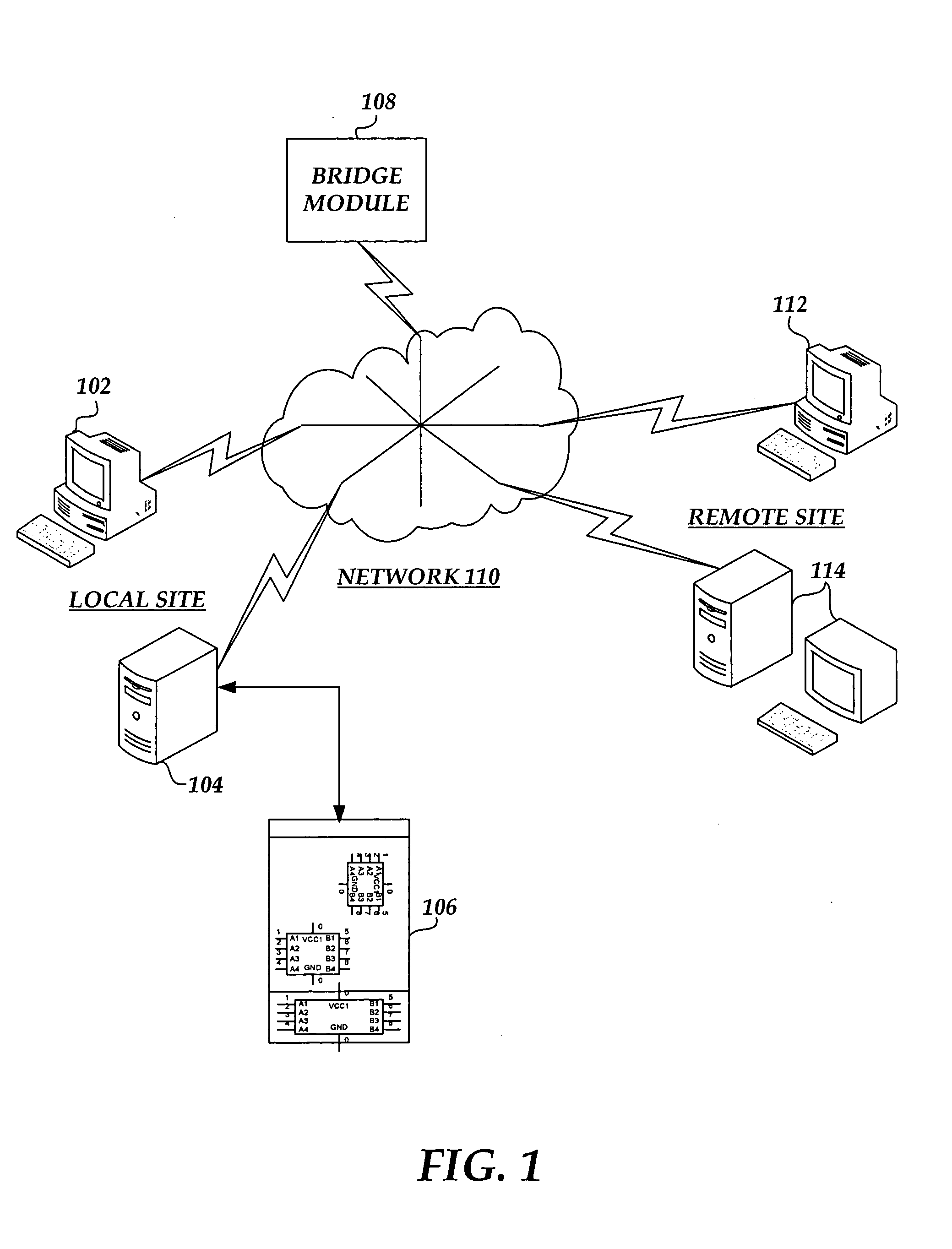
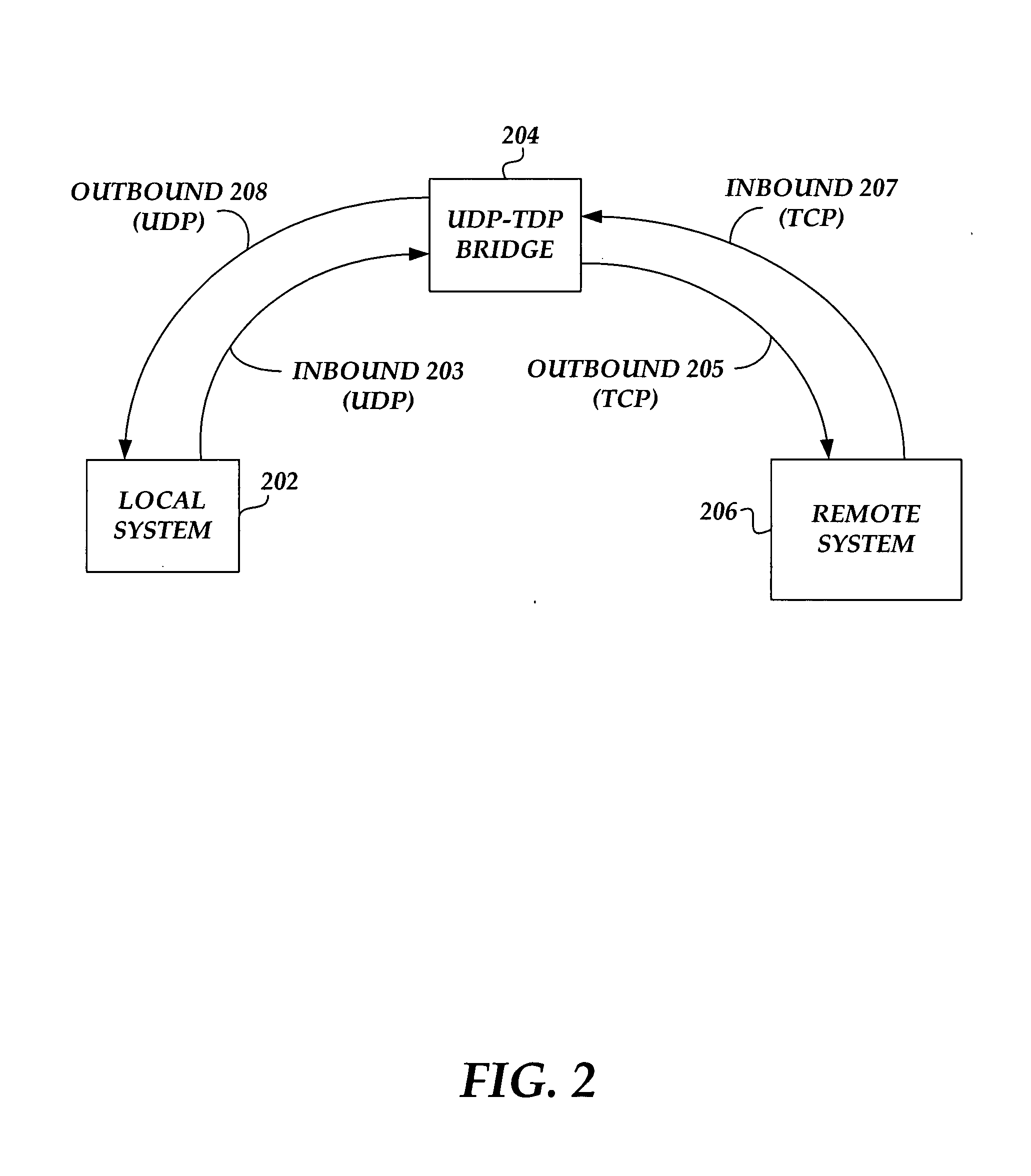
UDP to TCP bridge
A bridge module is bridging communications between computing systems using UDP (user datagram protocol) communication protocol and computing systems using TCP (transmission control protocol) communication protocol. Communications between the bridge and the computing system having UDP communication drivers are handled with the UDP protocol. Communications between the bridge and the computing system having TCP communication drivers are handled with TCP protocol. The UDP computing system, i.e. the computing system using UDP protocol, opens communications by performing a handshake routine with the bridge module. Once the UDP communication between the UDP computing system and the bridge module is established, the UDP computing system sends data packets to the bridge module. The bridge module converts these packets from UDP protocol to packets in TCP protocol and sends them to the TCP computing system, i.e. the computing system using TCP protocol. The TCP computing system can send data back to the UDP computing system by sending packets to the bridge module using the TCP protocol. The bridge module will convert the TCP data packets from the TCP computing system to data packets in UDP protocol and forward them on to the UDP computing system. One exemplary environment for the invention is console redirection from a computing system, that is running firmware such as BIOS, to a computing system that is running an operating system on top of BIOS.
Owner:AMERICAN MEGATRENDS
Method and apparatus for compounding medications
InactiveUS7748892B2Cosmetic preparationsShaking/oscillating/vibrating mixersEngineeringBULK ACTIVE INGREDIENT
Owner:MCCOY WILLIAM
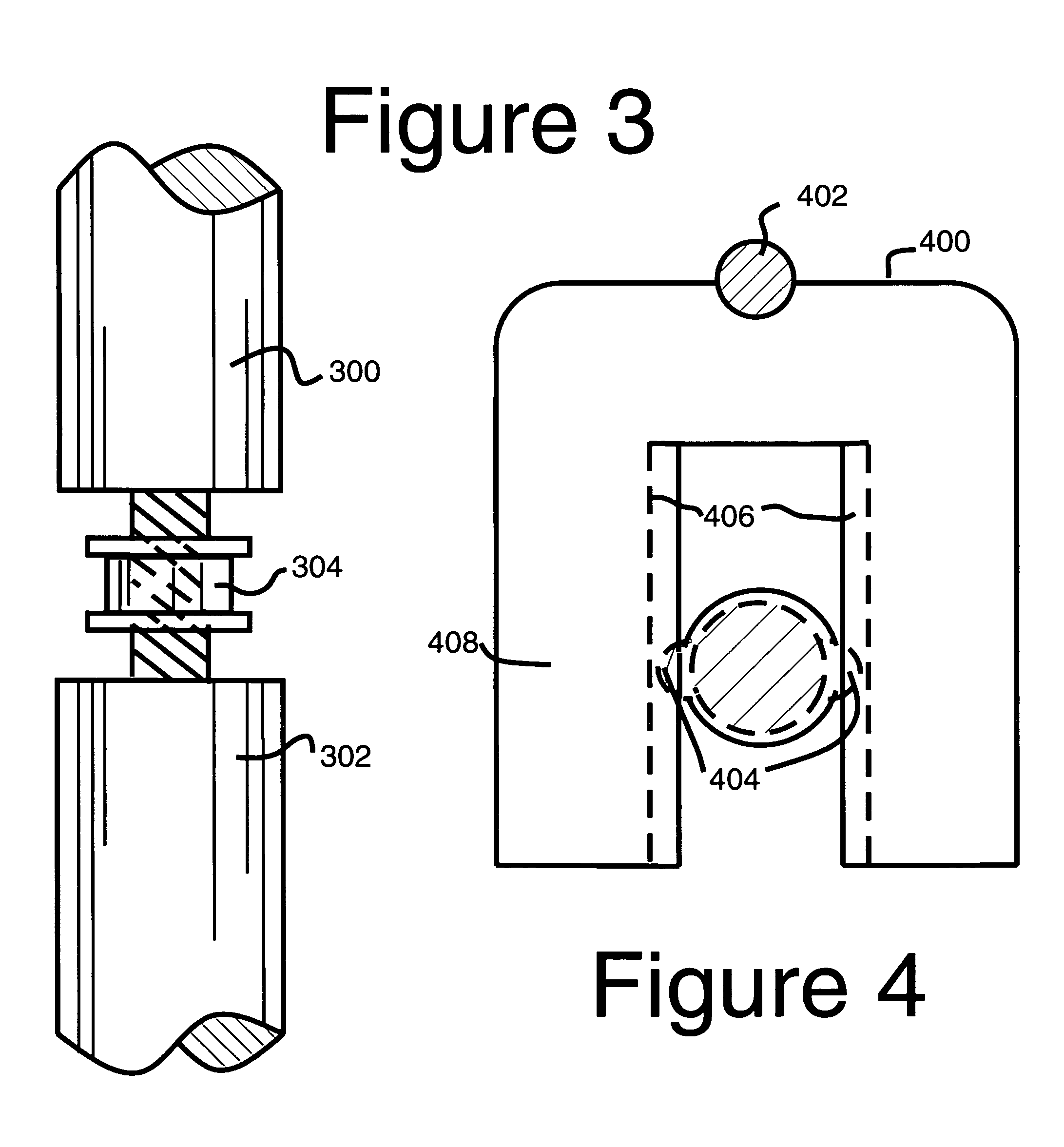
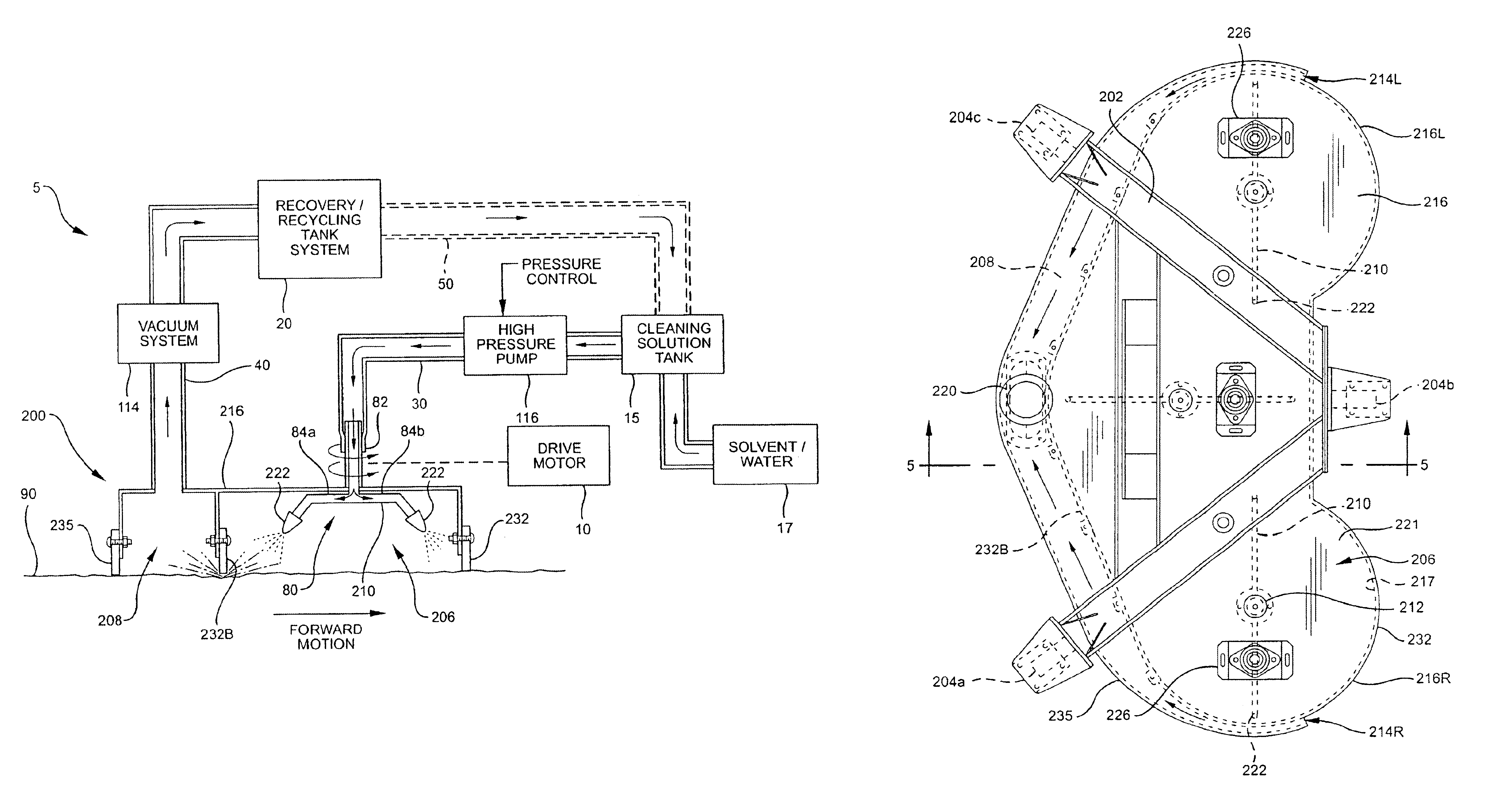
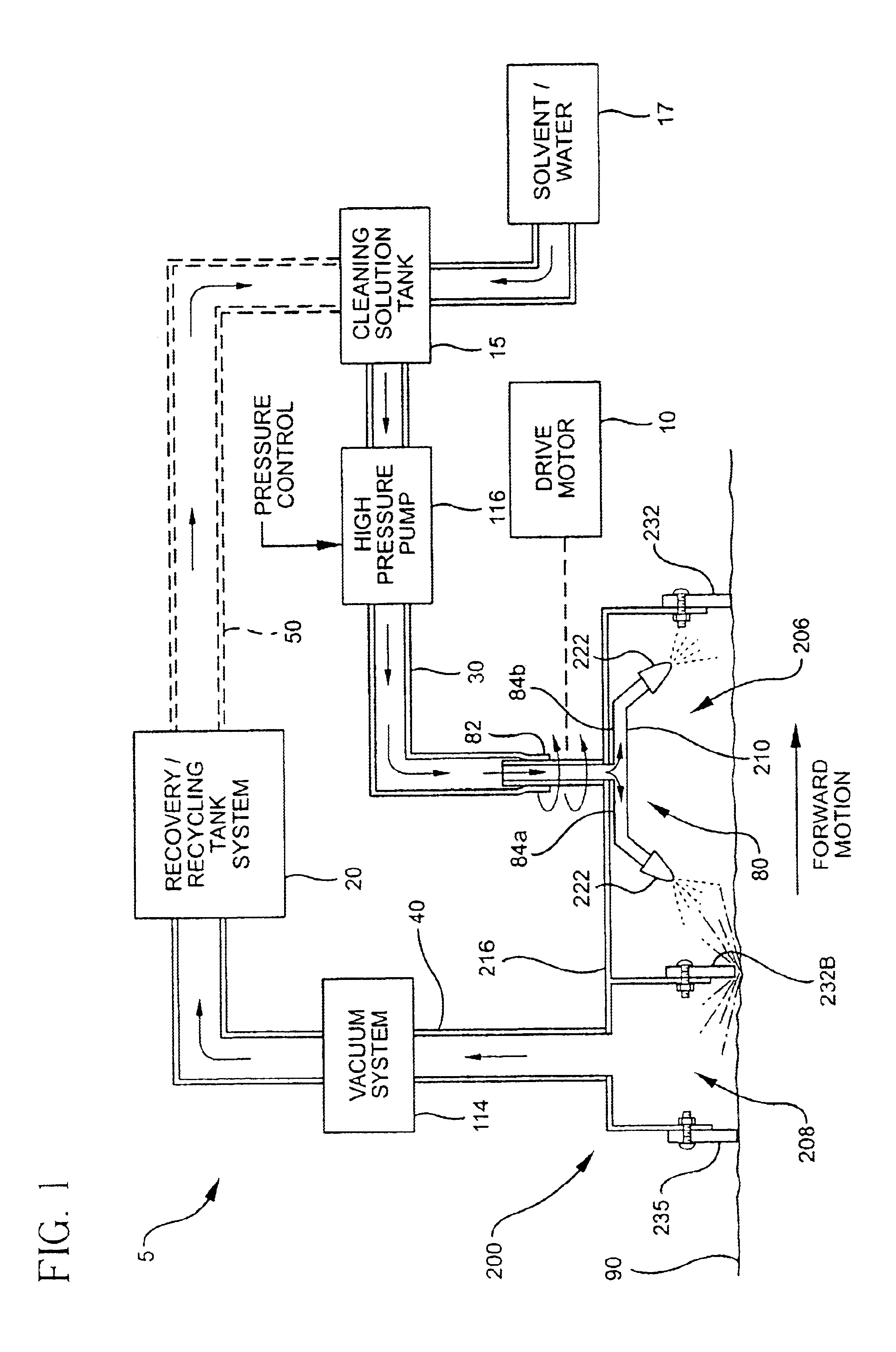
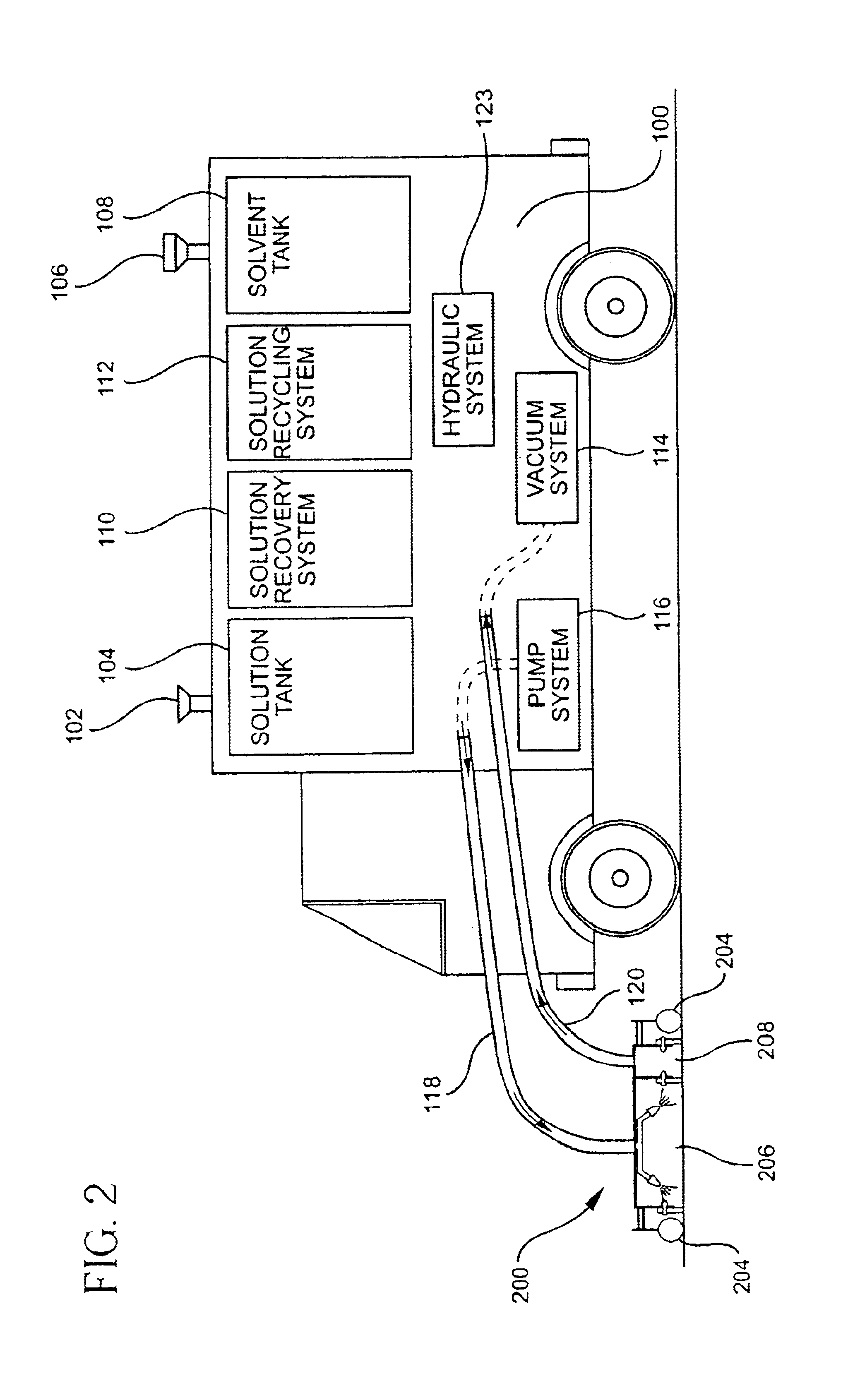
Brushless scrub head for surface maintenance
A device and method of use for cleaning a ground surface with pressurized cleaning solution is disclosed. The device includes a transportable deck having at least a first chamber and a second chamber, each first and second chamber being in open communication with the surface, said first chamber having a nozzle for directing a pressurized cleaning solution toward the ground surface, and said second chamber having a vacuum outlet for removing cleaning solution and debris from the surface. Additional embodiments of the present invention may include a solution recycling system for reusing recovered solution.
Owner:TENNANT COMPANY
Bufferless secure sockets layer architecture
InactiveUS7228412B2Reduce workloadEnhance layeringData taking preventionUser identity/authority verificationSecure communicationClient-side
A method for enabling secure communication between a client on an open network and a server apparatus on a secure network. The method is generally performed on a intermediary apparatus coupled to the secure network and the open network. The method includes the steps of negotiating a secure communications session with the client apparatus via the open network; negotiating an open communications session with the server via the secure network; receiving encrypted packet application data having a length greater than a packet length via multiple data packets; decrypting the encrypted packet application data in each data packet; forwarding decrypted, unauthenticated application data to the server via the secure network; and authenticating the decrypted packet data on receipt of a final packet of the segment.
Owner:NEXSI SYST
Method for communicating between a server and a client and corresponding client, server and system
ActiveUS20140040991A1Convenient for userDigital data processing detailsMultiple digital computer combinationsExpiration TimeTime segment
The invention relates to a method for communicating between a server and a client. The server and the client access at least one session extension key and / or a key associated with the session extension key, as an associated key. The server authorizes to extend an open communication session with the client until an expiration time only if the client sends to the server authentication data allowing the server to authenticate at least the client on a basis of the session extension key. The expiration time is a time at which the communication session is open completed by a predetermined extension time period. The invention also relates to corresponding client, server and system.
Owner:THALES DIS FRANCE SA
Identity management suite
InactiveUS20090126007A1OptimizationDigital data processing detailsUser identity/authority verificationOpen sourceIntegrated software
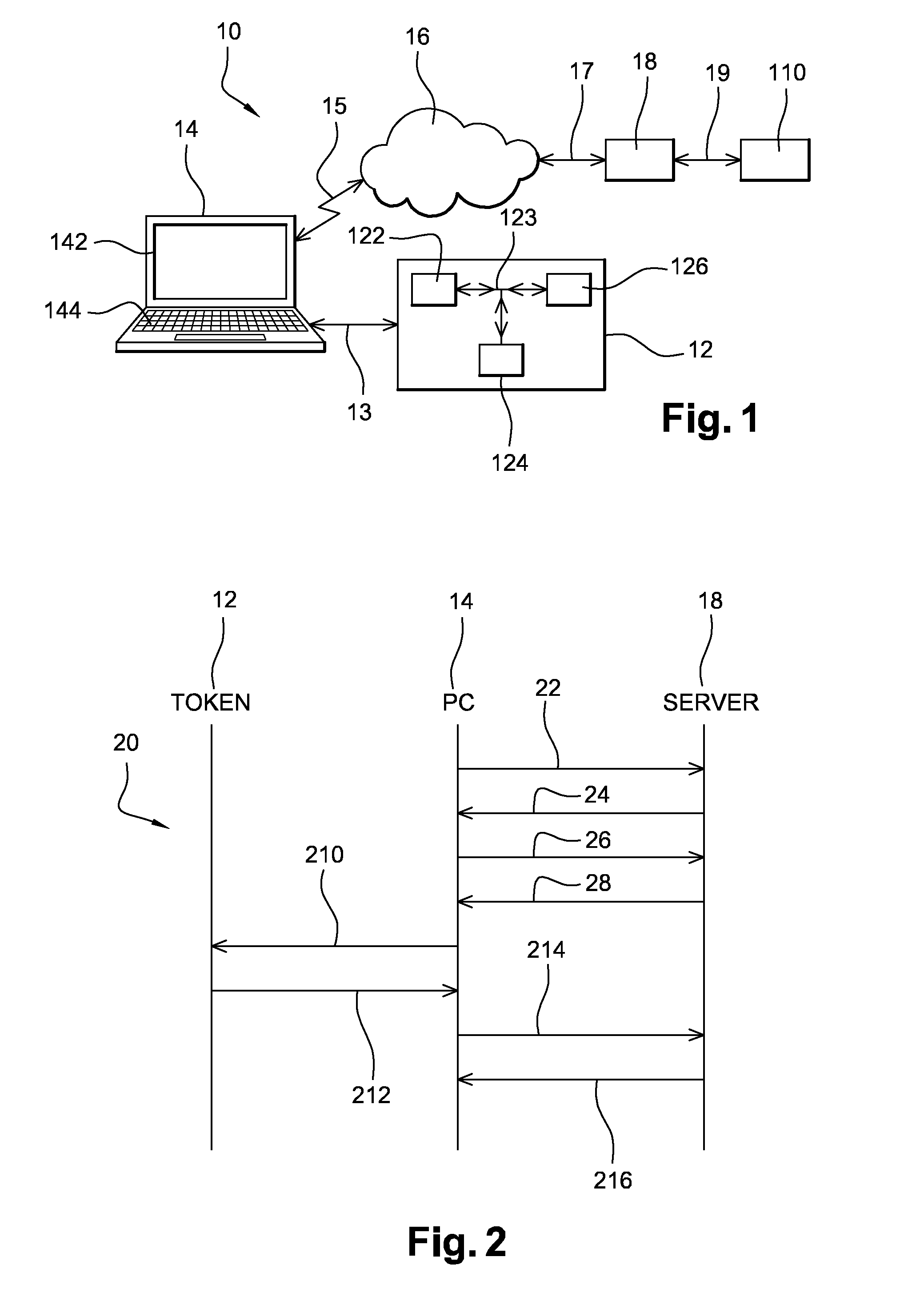
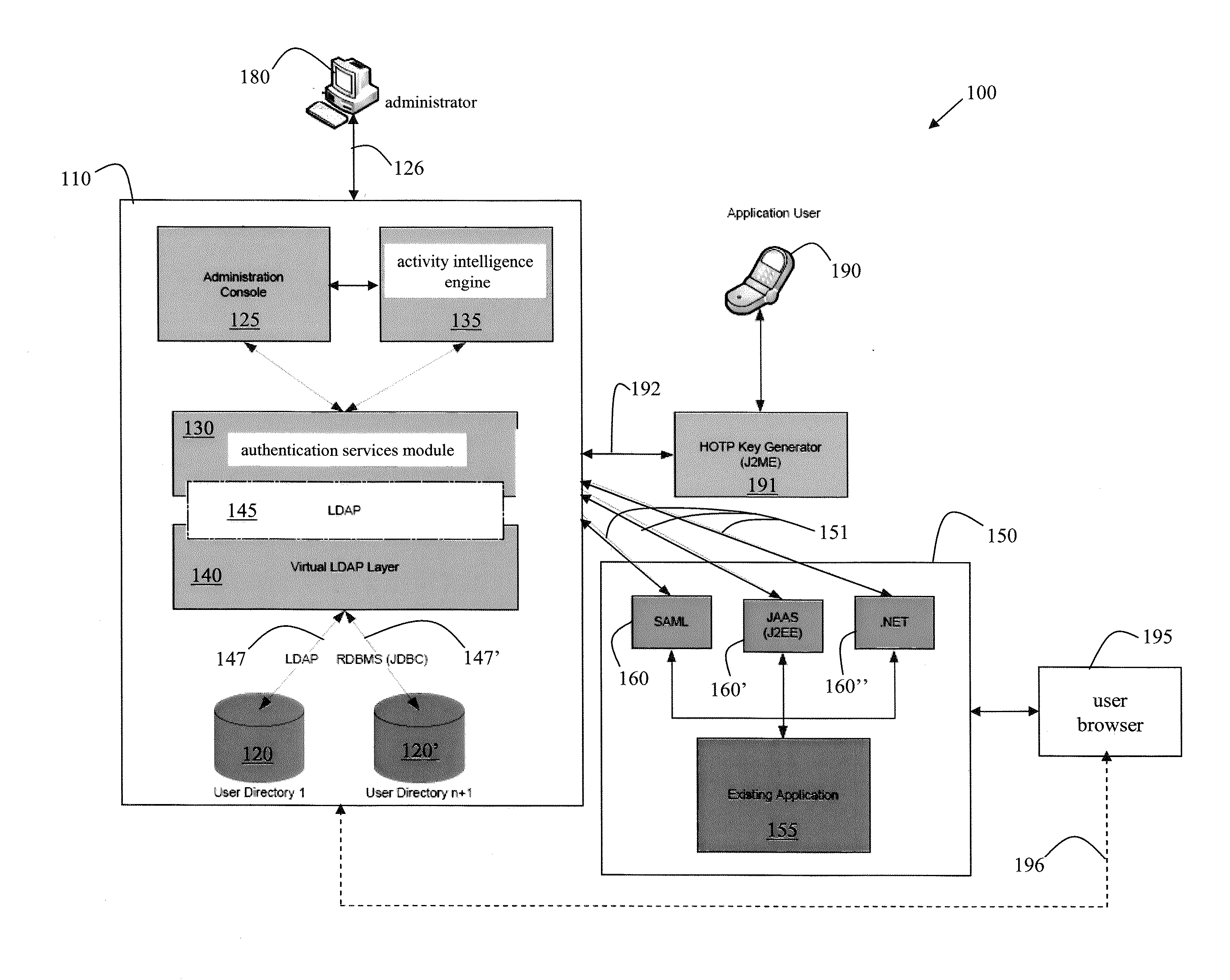
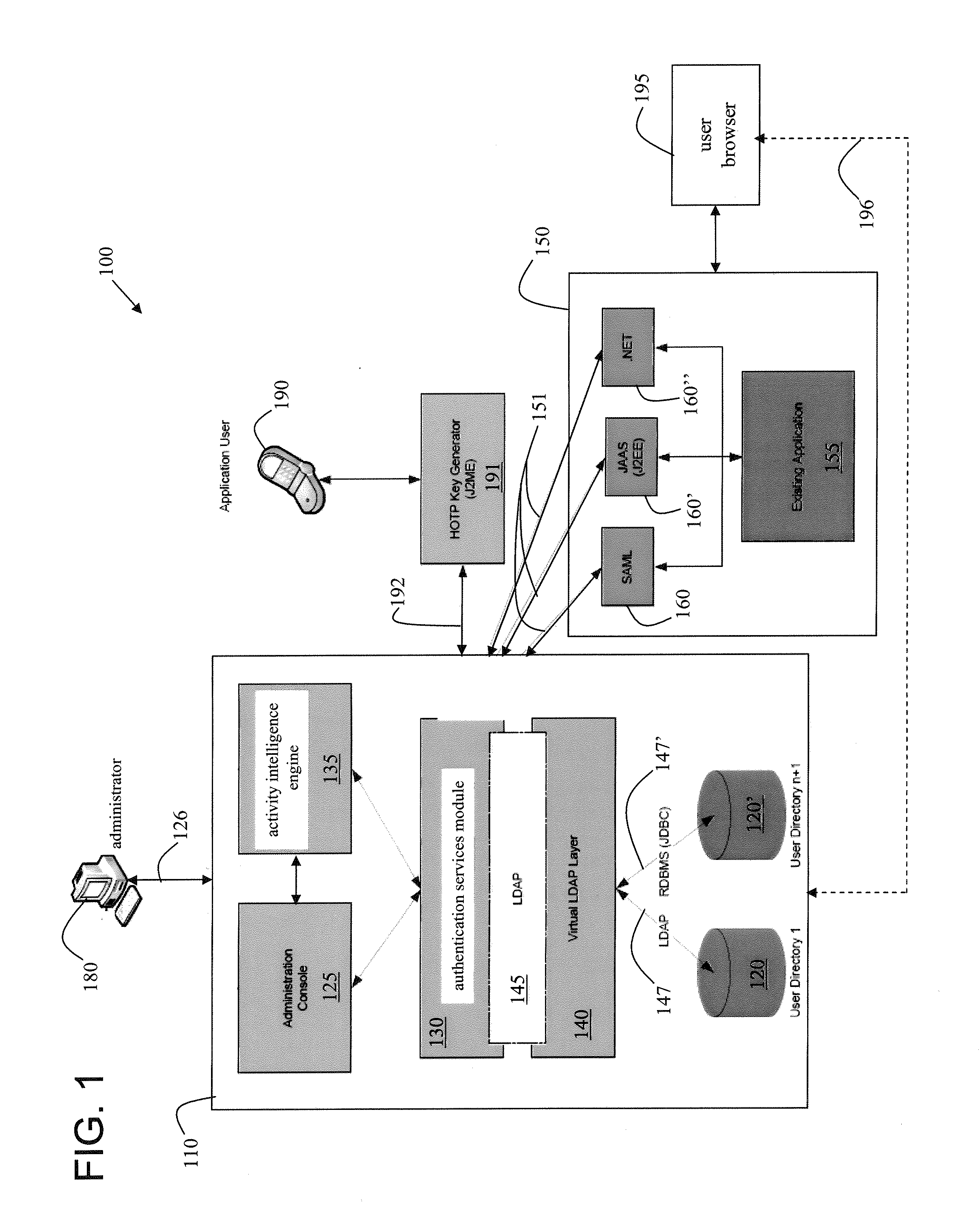
A server platform hosting an integrated software-based identity management suite used in a system for authenticating users with respect to a legacy application. The identity management suite includes an administration console for domain administration, an authentication services module for user authentication, an activity intelligence engine for monitoring user activity, an open-source-based virtual layer for mapping fields of a legacy user directory to fields within the server platform, and an internal interface using an open communication protocol adapted to provide communication between the open-source-based virtual layer and at least the authentication services module within the server platform.
Owner:AVANTIA
Services layer model for providing standards-based communications
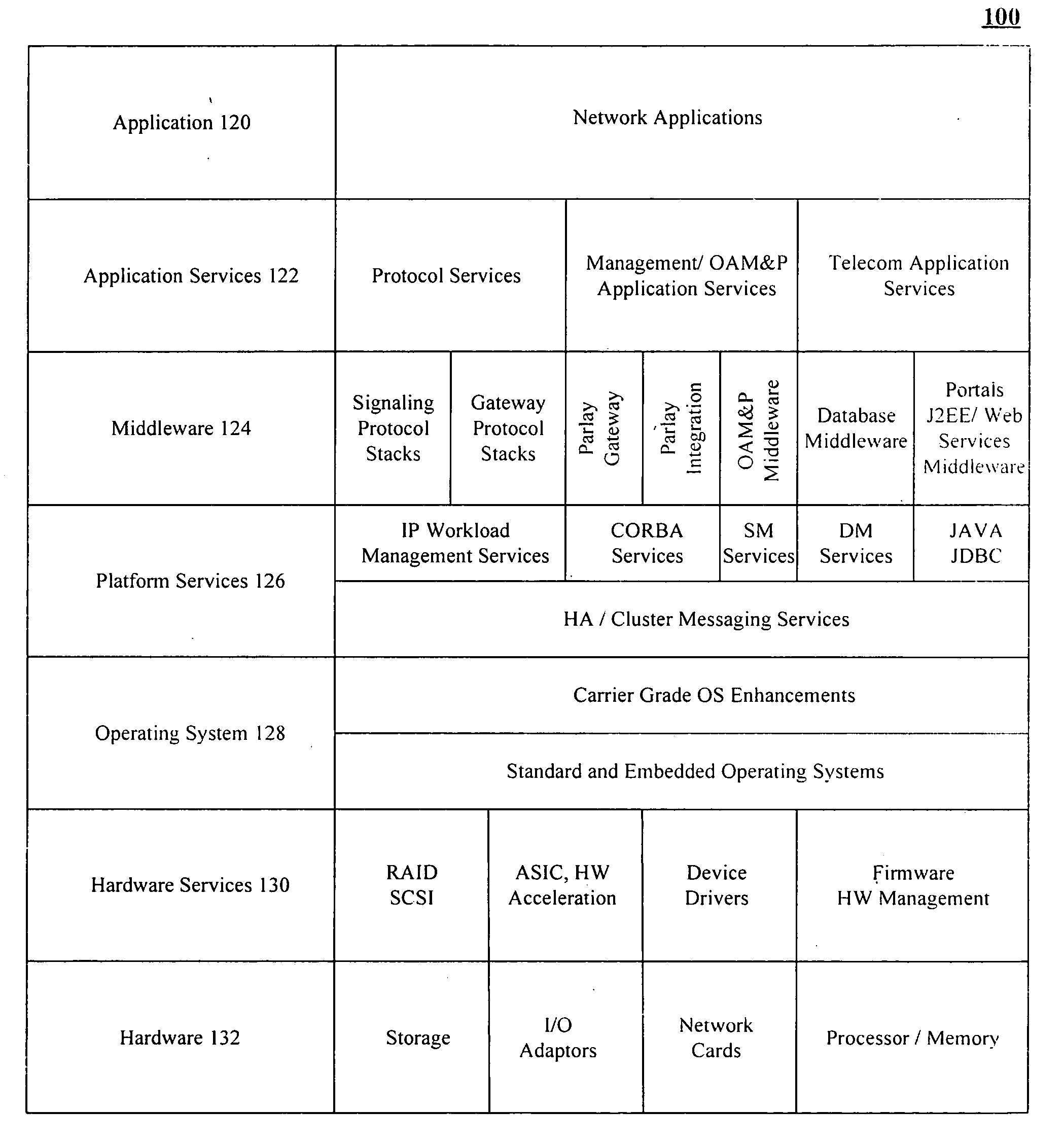
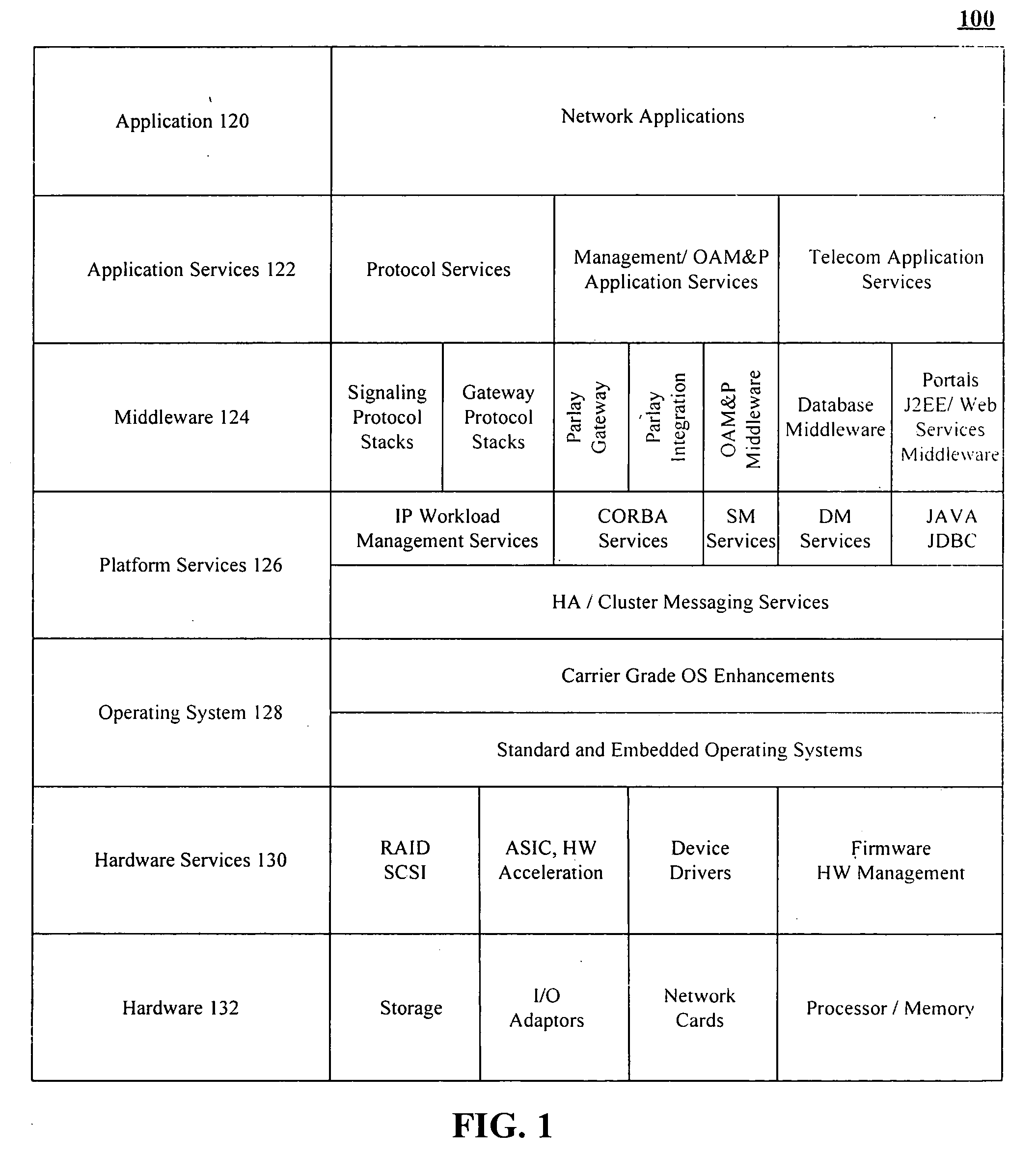
InactiveUS20050267979A1Eliminate gapsRemove overlapMultiple digital computer combinationsTransmissionOperational systemInterface layer
An open communications framework including an application layer that defines standards for applications, a middleware layer that defines standards for middleware, an operating system layer that defines standards for operating systems, and a hardware layer that defines standards for hardware. Interface layers based upon open-standards can be used to communicate data between the application layer and the middleware layer, between the middleware layer and the operating system layer, and between the operating system layer and the hardware layer.
Owner:LINKEDIN
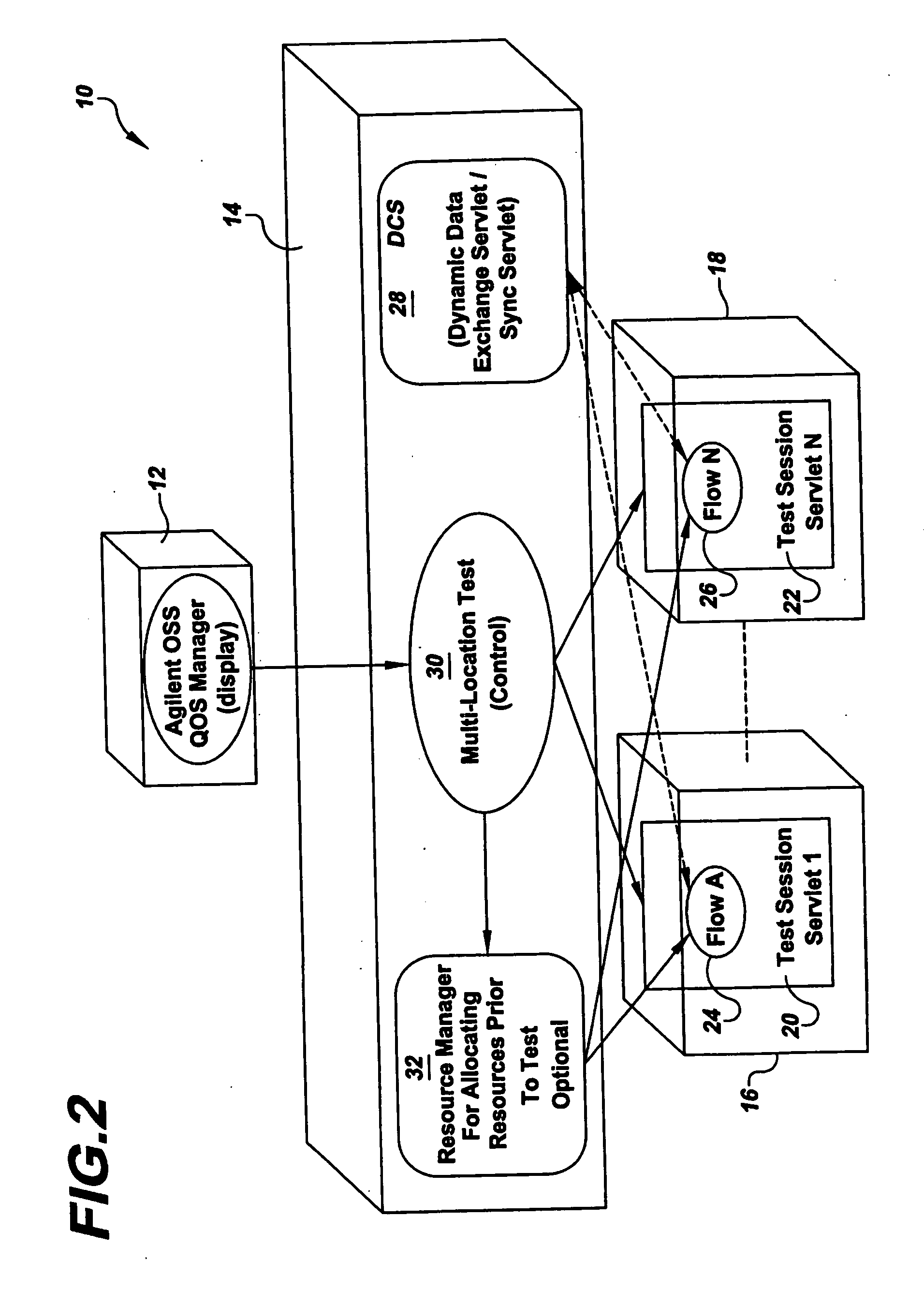
System for and method of multi-location test execution
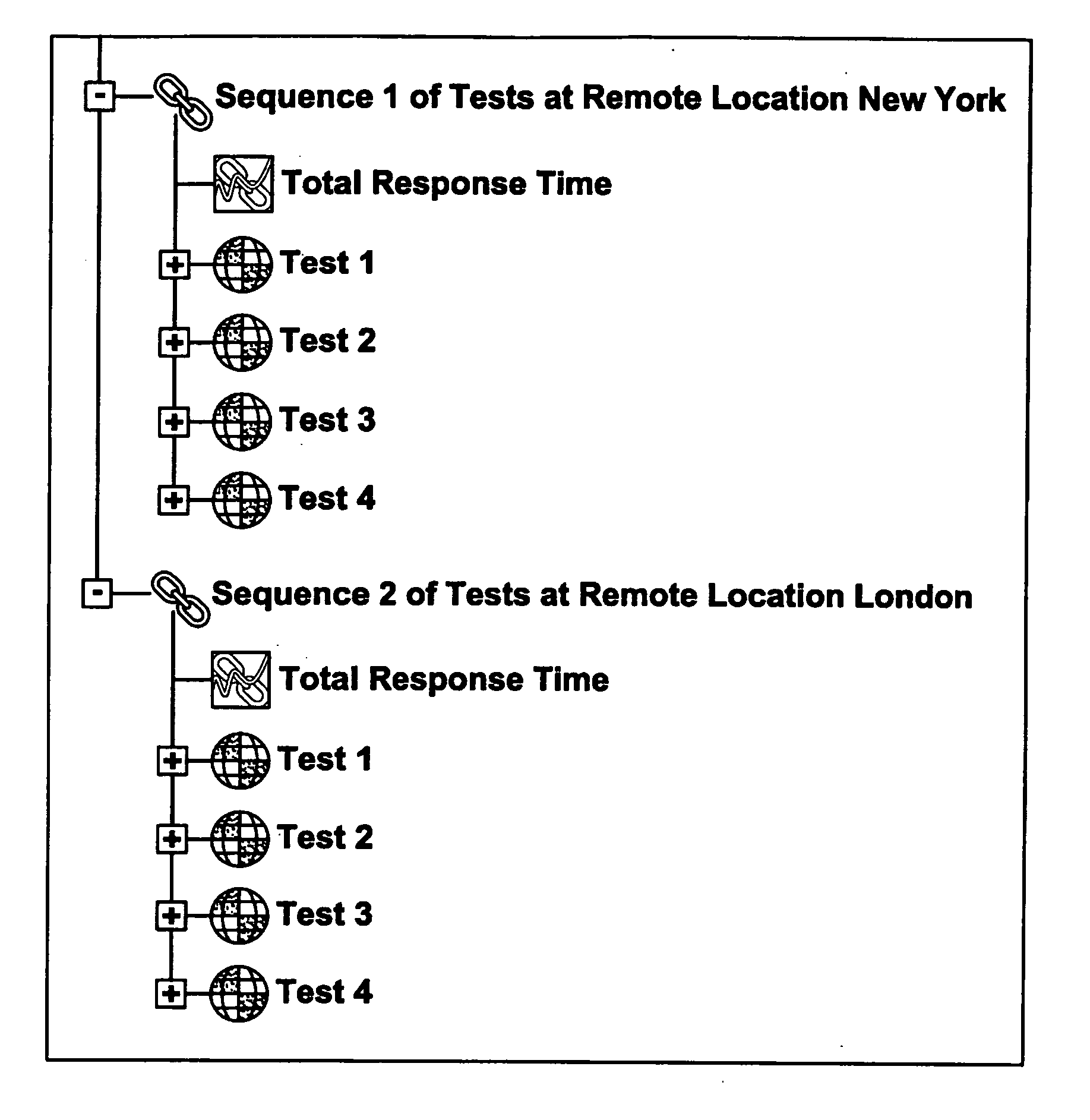
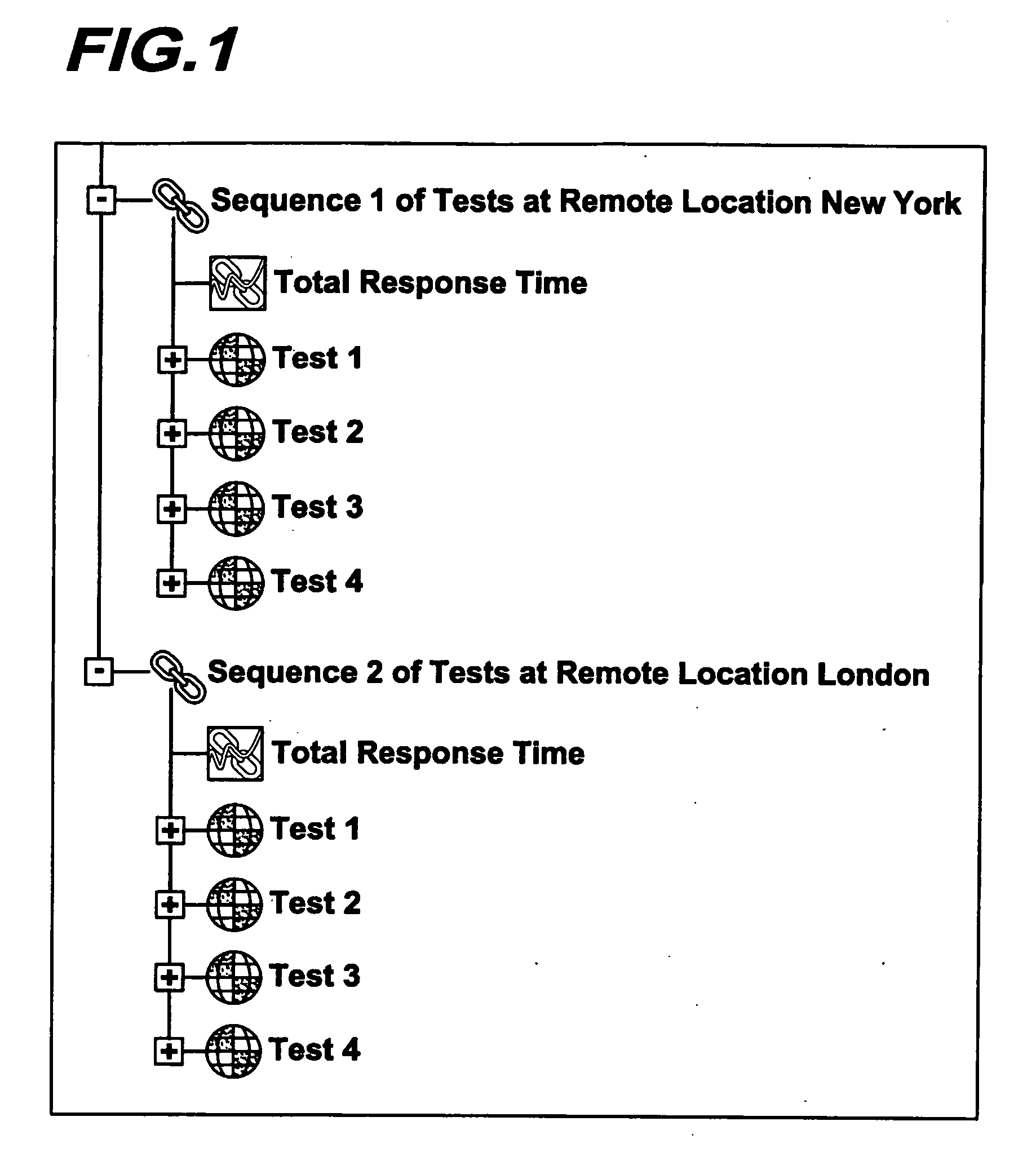
InactiveUS20070033441A1Easy to useAmplifier modifications to reduce noise influenceDigital computer detailsGraphicsTest execution
Methods, systems and computer program products for performing multi-location execution of tests between or among multi-sided test components in a wireless environment are described. Multiple flows are initiated substantially simultaneously and concurrently executed. A graphical representation of a multi-flow test is created that permits synchronization of the flows among agents at multiple remote locations. The graphical representation is converted into a textual representation in an open communication standard format, and information regarding each flow involved in the test is ascertained. The flows are substantially simultaneously initiated and concurrently executed with synchronization and dynamic data exchange components.
Owner:VIAVI SOLUTIONS INC
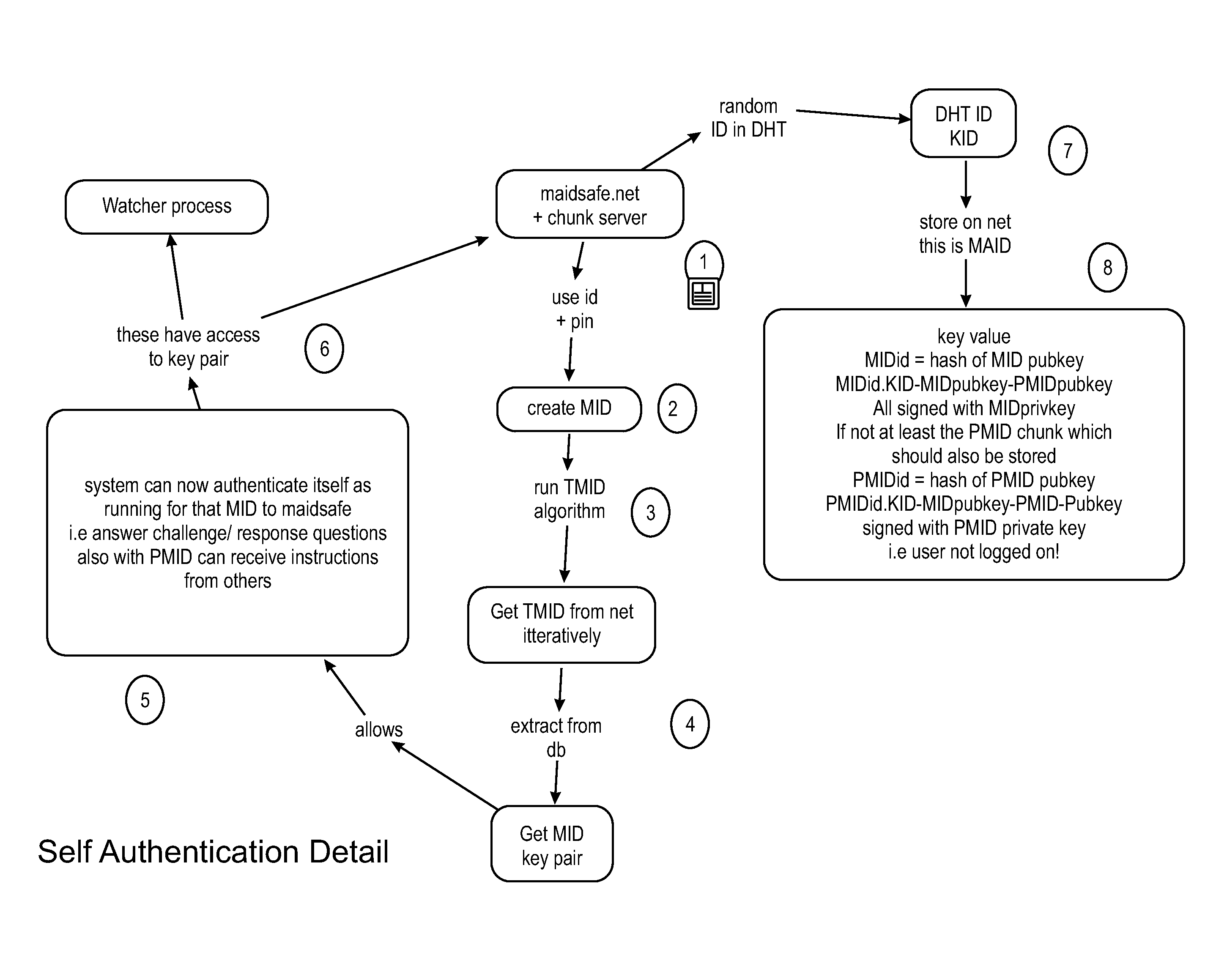
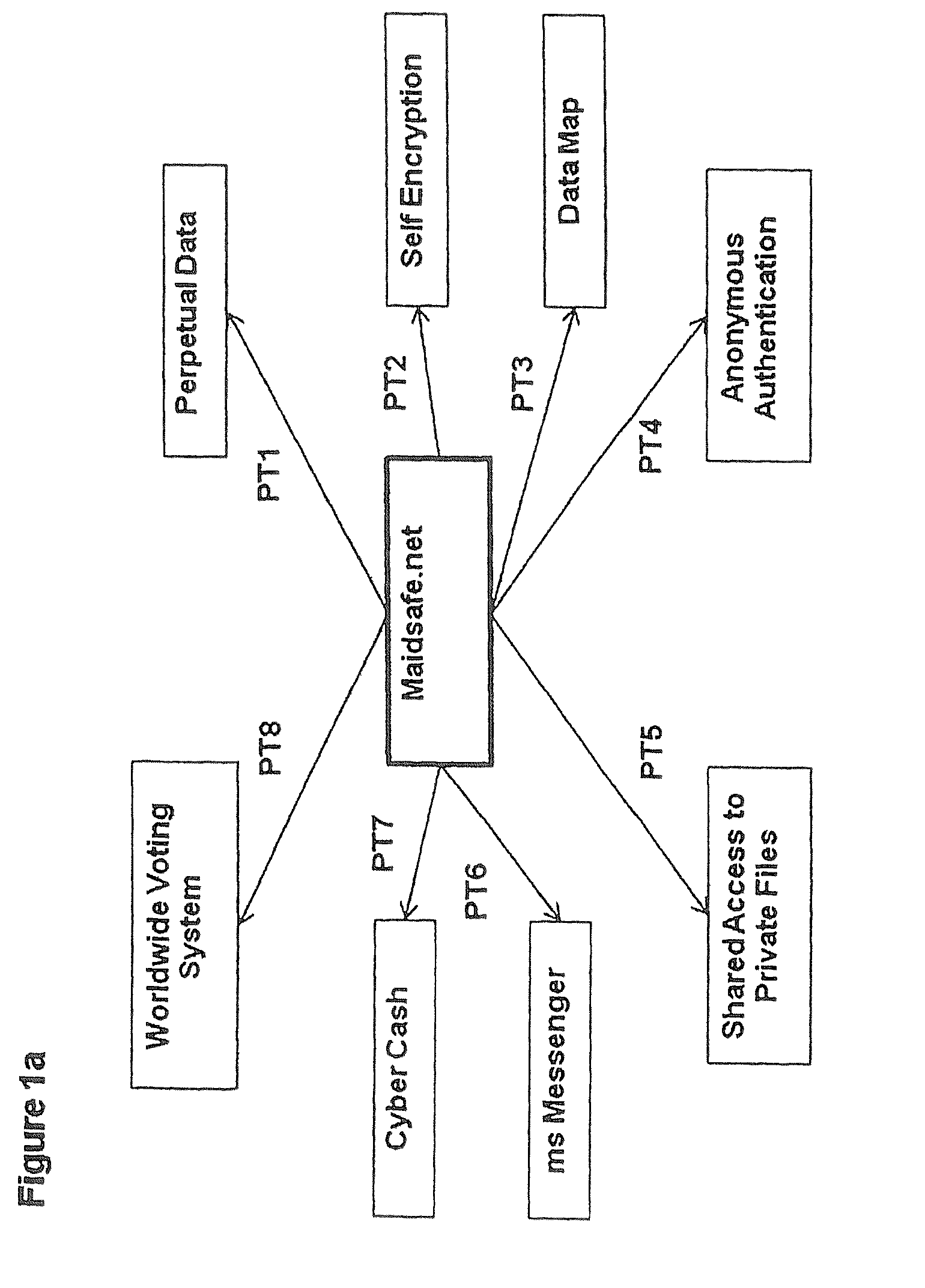
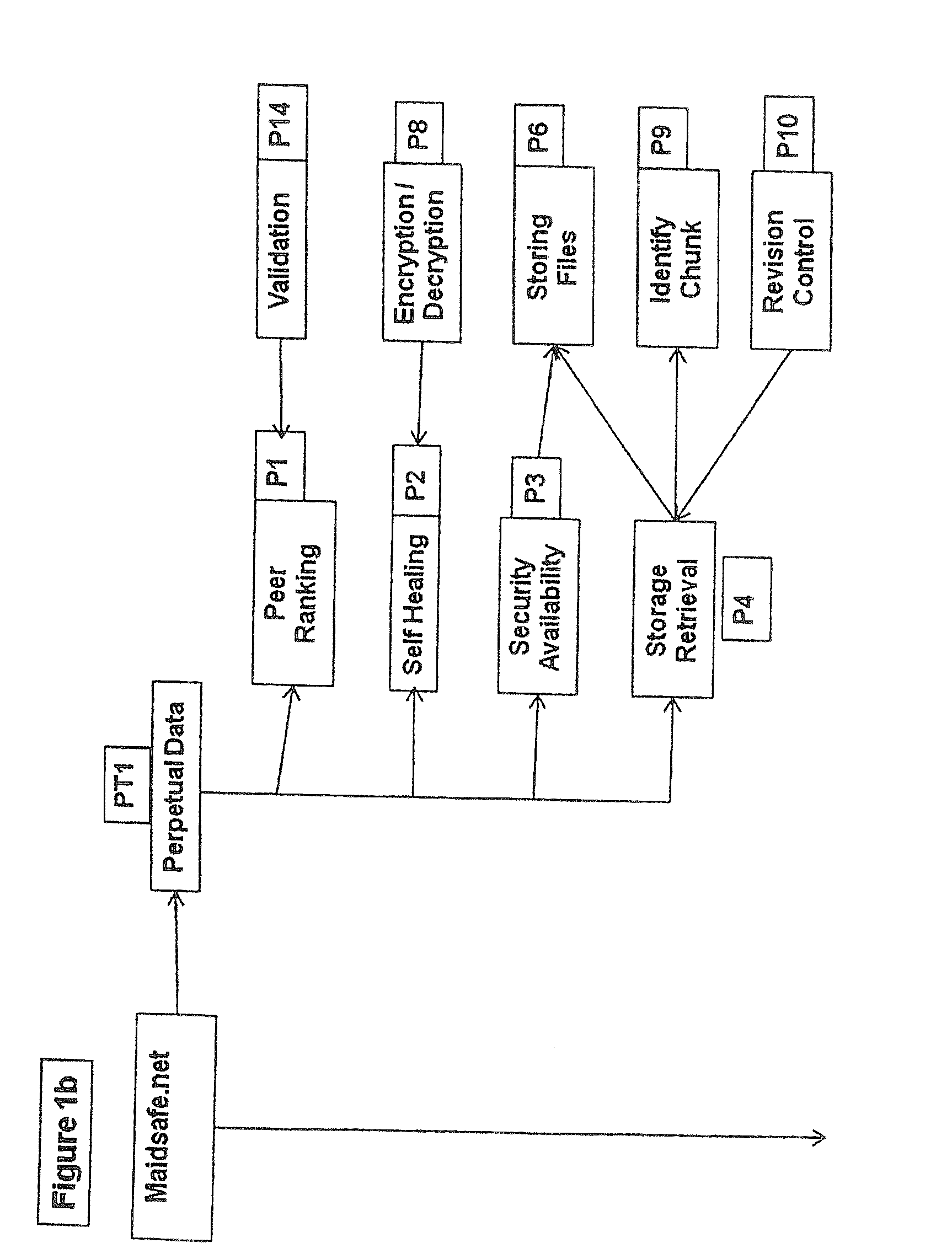
Self-encryption process
ActiveUS20120210120A1Maintain validityEasy to set upMultiple keys/algorithms usageDigital data protectionSecure communicationFree access
This invention is a network that is defined by its novel approach to privacy, security and freedom for its users. Privacy by allowing access anonymously, security by encrypting and obfuscating resources and freedom by allowing users to anonymously and irrefutably be seen as genuine individuals on the network and to communicate with other users with total security and to securely access resources that are both their own and those that are shared by others with them. The functional mechanisms that this invention provides will restore open communications and worry-free access in a manner that is very difficult to infect with viruses or cripple through denial of service attacks and spam messaging, plus, it will provide a foundation where vendor lock-in need not be an issue.
Owner:MAIDSAFE FOUND
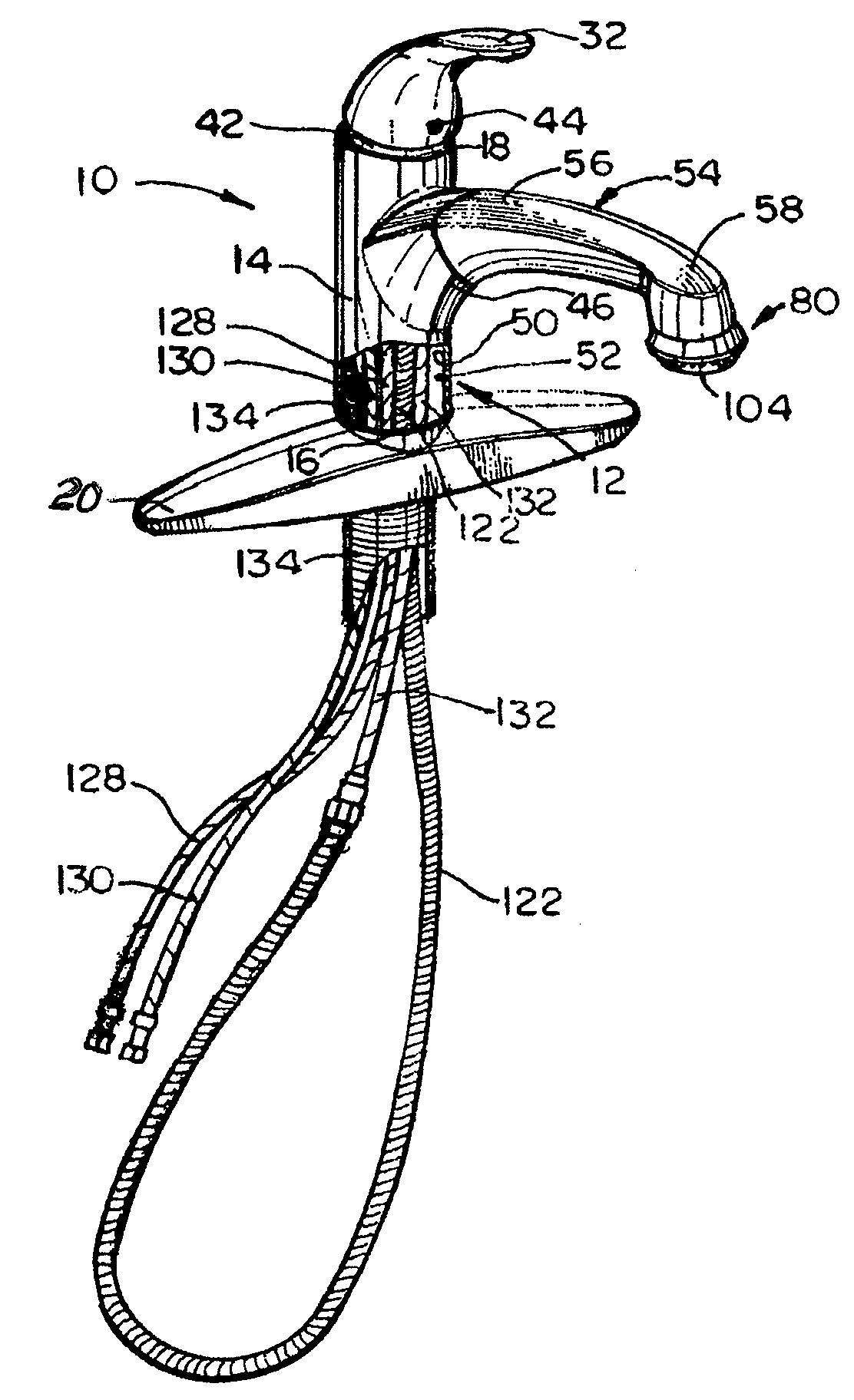
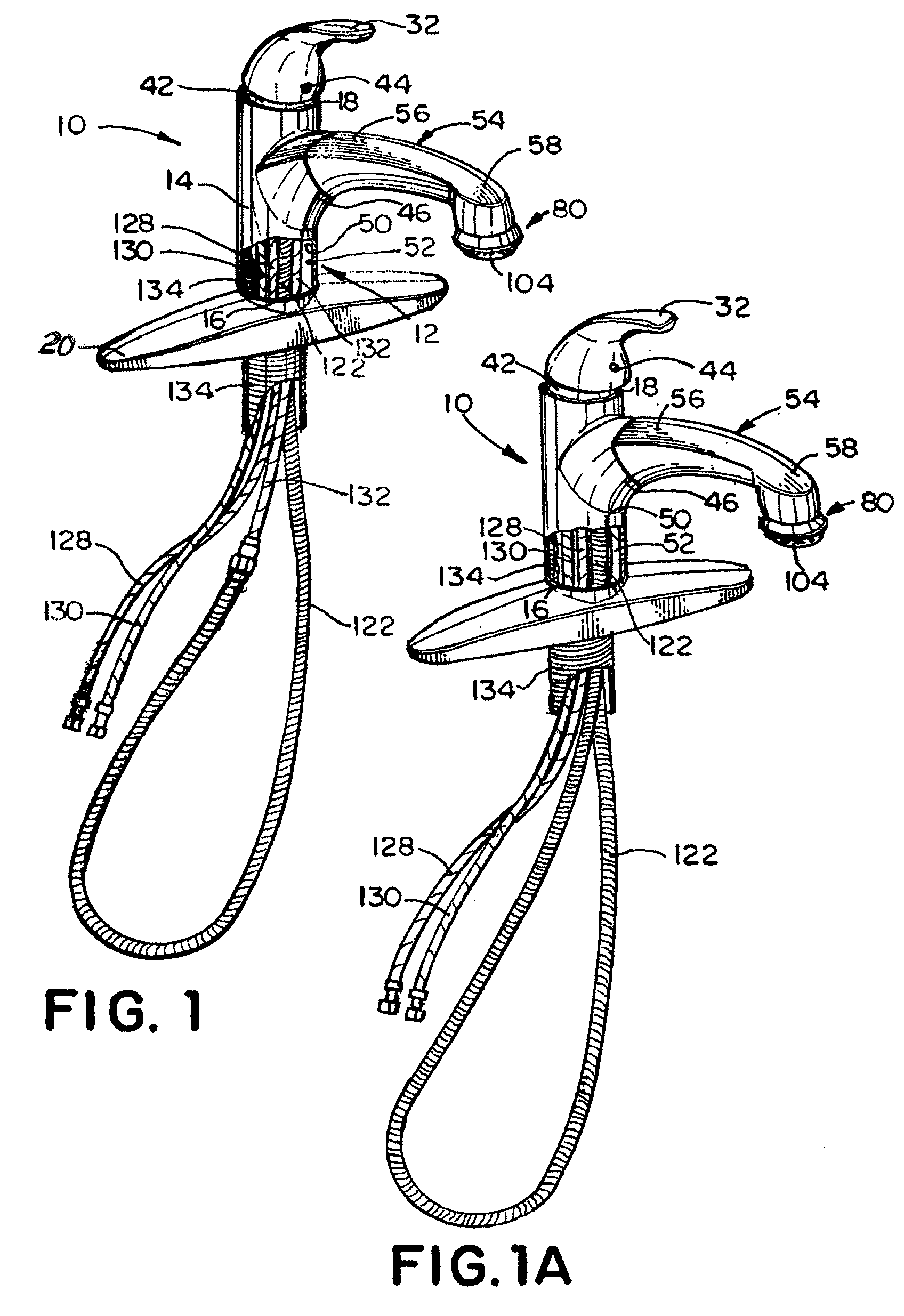
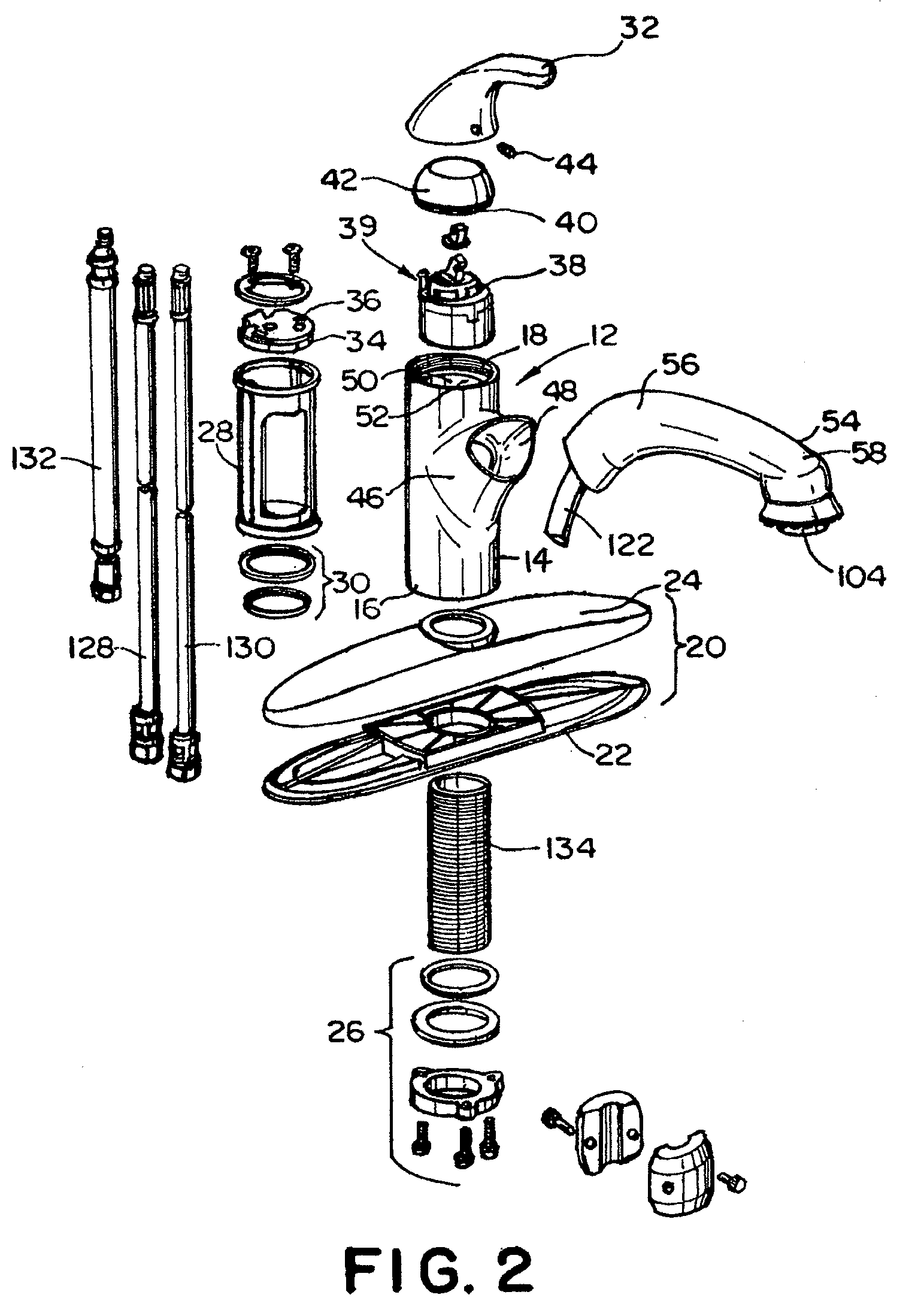
Faucet Having Pull-Out Spray Handle
The disclosure provides faucets, faucet assemblies and methods for delivering liquid through a faucet. The faucet includes a faucet body having a first open end configured for connection with a faucet base, a second open end for receiving a faucet handle, and a faucet body portion having an opening therein. The faucet body has an inner wall defining a passage extending therethrough. The faucet also includes a faucet handle and a spray handle having a first end section and a sprayer end section. The first end section is configured to be detachably connected to the faucet body portion, and the spray handle has an inner wall and a passage extending therethrough which is in open communication with the passage through the faucet body. The faucet also has a hose connection that can receive a hose for delivering liquid to the spray handle. The hose connection may be in the sprayer end section of the spray handle. The faucet may also include a mechanism for liquid flow control and / or a pull-down diverter in liquid communication with the hose connection for aerated or spray flow.
Owner:AS AMERICA
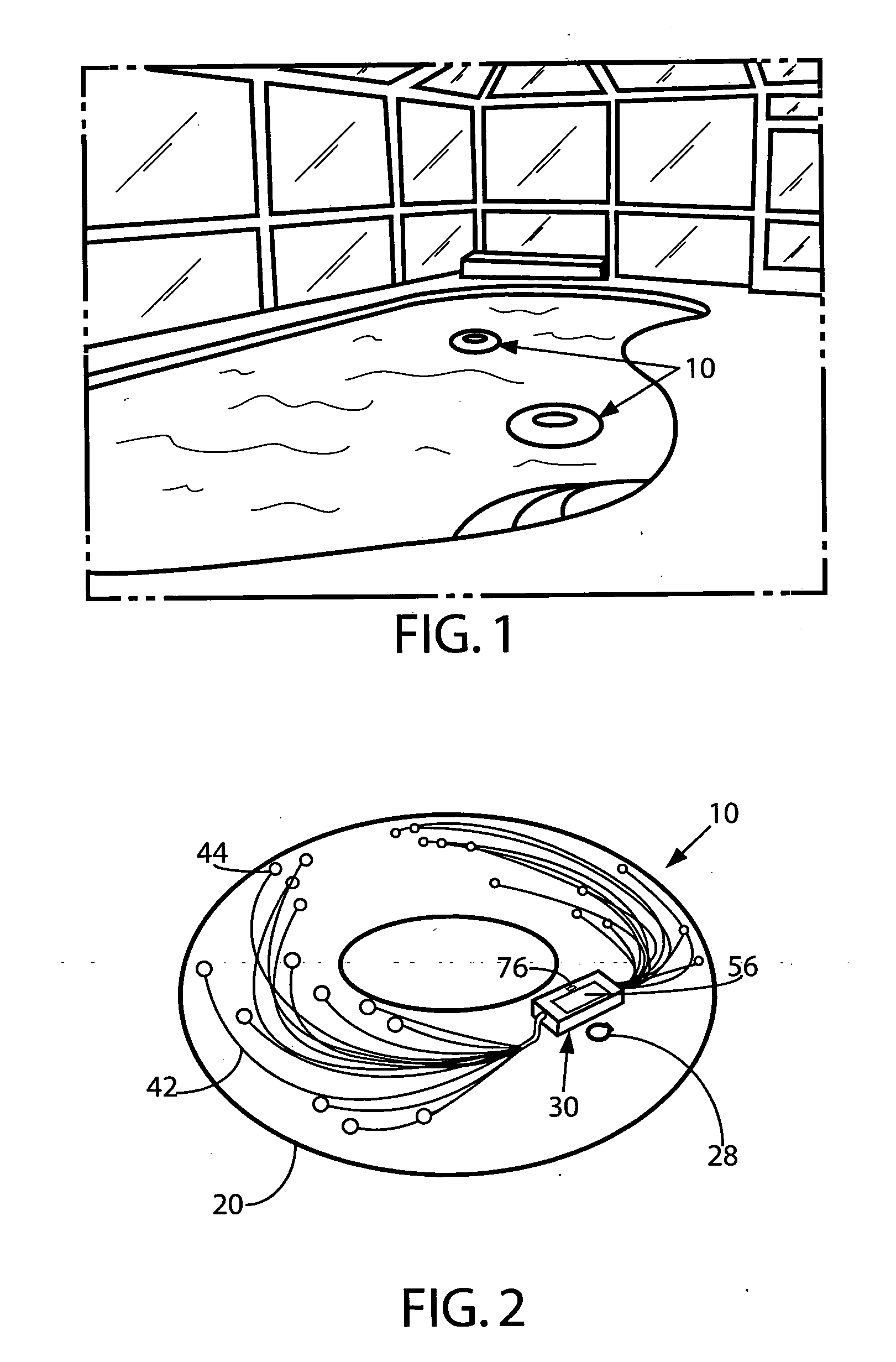
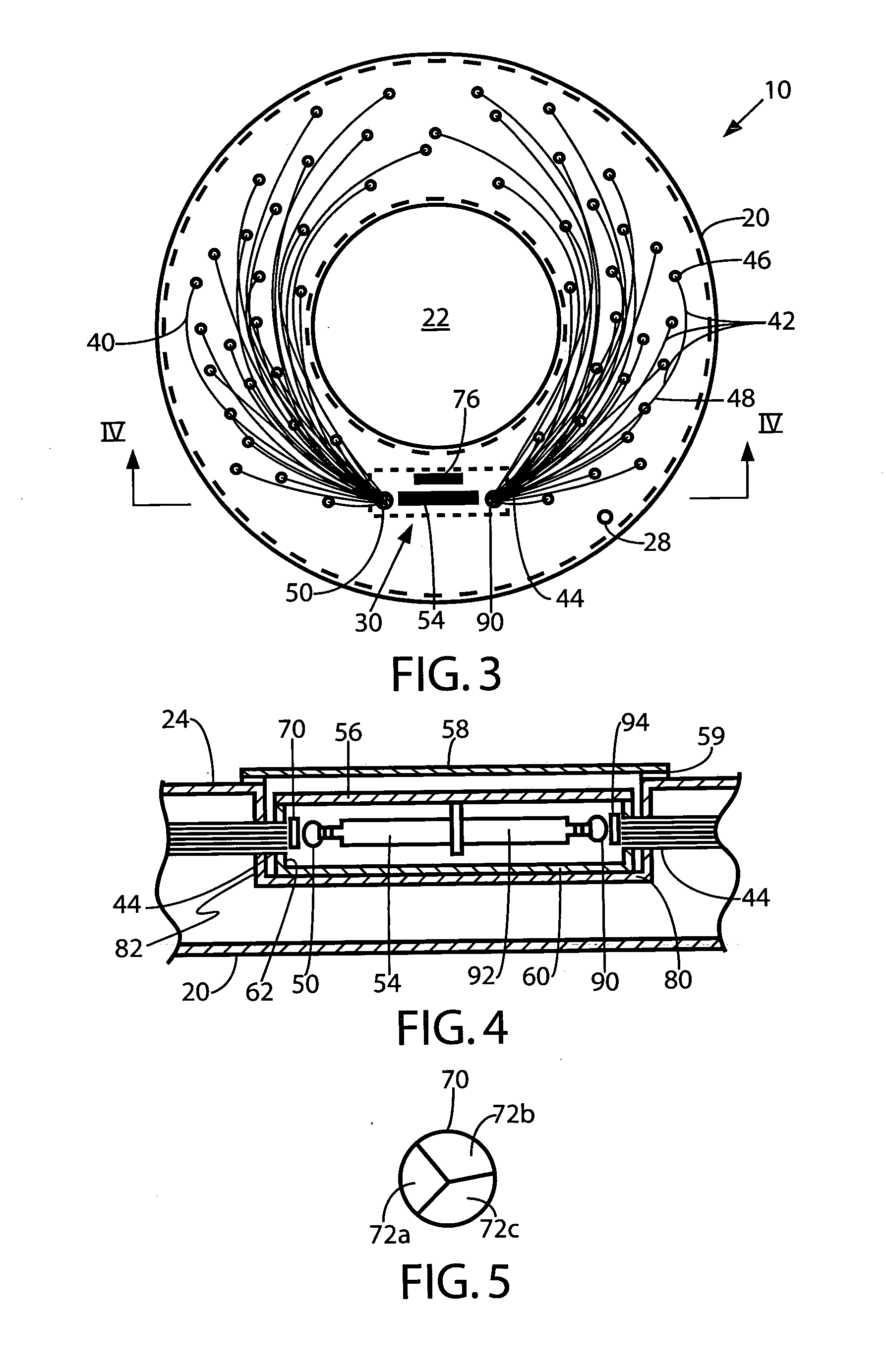
Light emitting flotation device
A flotation device includes a pocket formed within its hollow body in open communication with an exterior surface thereof and a hollow housing mounted in the pocket. Illuminatable fiber optic strands are disposed in a predetermined pattern within the hollow body each having a light receiving end thereof protruding into the pocket through a wall thereof in an air impermeable manner and further into the housing. An illumination source is mounted inside the housing in close proximity to the light receiving ends of the fiber optic strands and a power source is also disposed within the housing and operatively coupled to the illumination source. A multi-colored filter pane is mounted within the housing intermediate the illumination source and the receiving end of the each illuminatable fiber optic strand. A switch is provided and is manually operable by a user to operate the illumination source causing the strands to emit light.
Owner:MARCINKEWICZ DOROTHY J +1
Awning roll attachment with illumination and mist
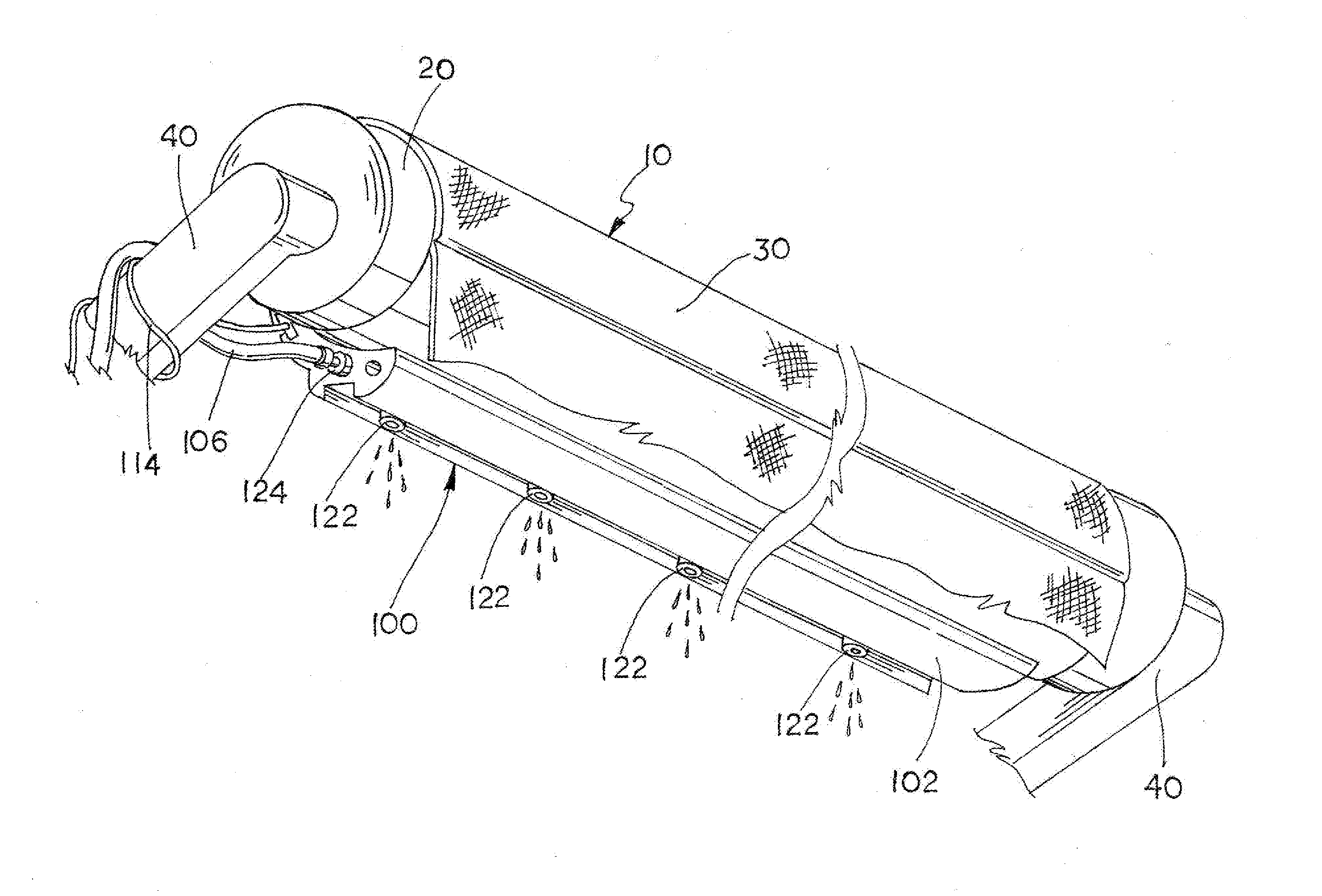
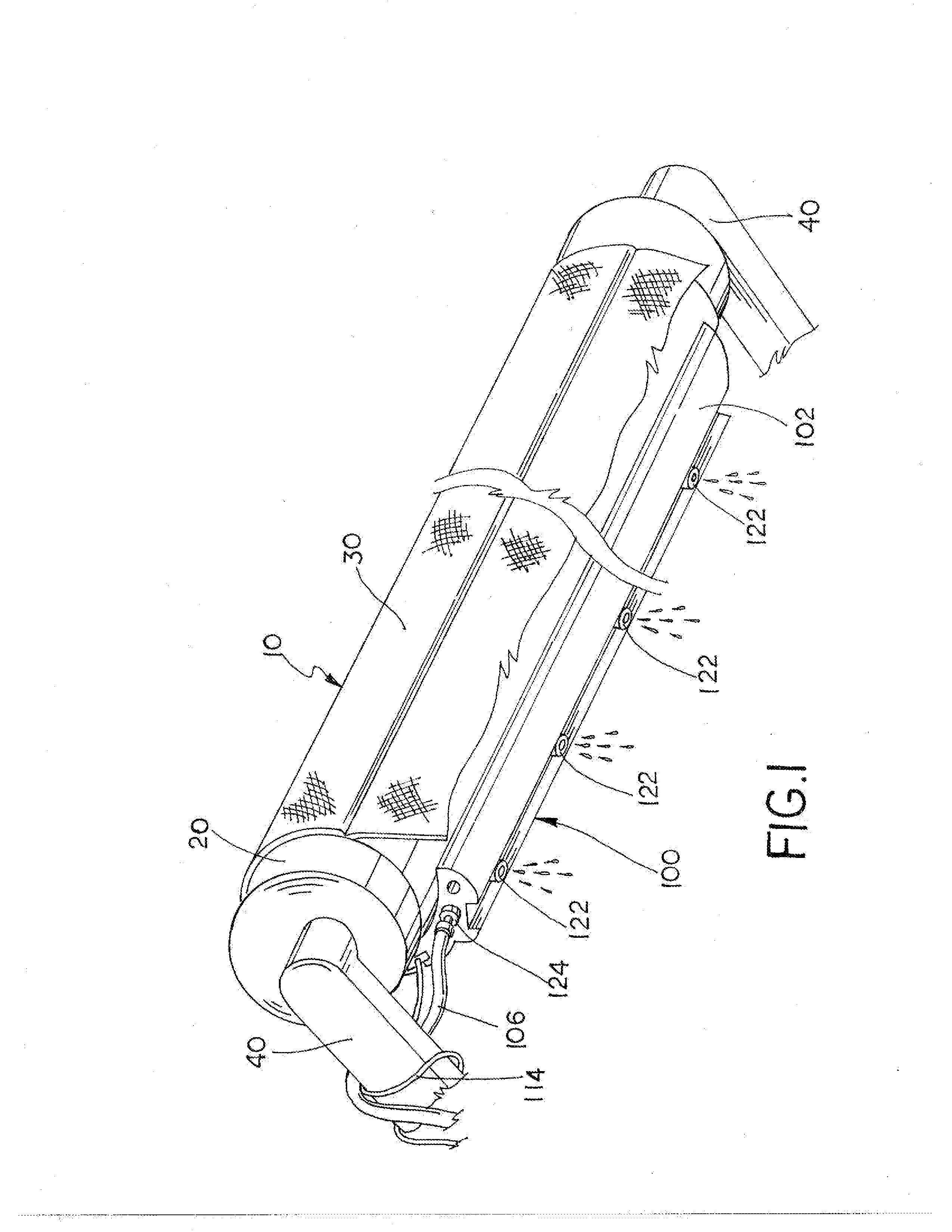
InactiveUS20130235558A1Clutter appearanceDetract from appearanceSunshadesDoor/window protective devicesLighting systemOpen communication
An awning roll attachment that mounts directly to the awning roll and includes an internal illumination system and misting system. The awning roll attachment is connected to a roll tube using a press fit connection. The illumination system includes a light strip that is seated or embedded within a longitudinal channel formed in the attachment body. The misting system includes a plurality of misting nozzles that are tapped into bores in the attachment body and are in open communication with an internal fluid passage formed in the attachment body that runs its entire length. A connection fitting is connected to the fluid passage at one end of the attachment body and an end plug closes the fluid passage at the opposite end of the attachment body.
Owner:ZHOU WEI
Method and apparatus for communicating data between two hosts
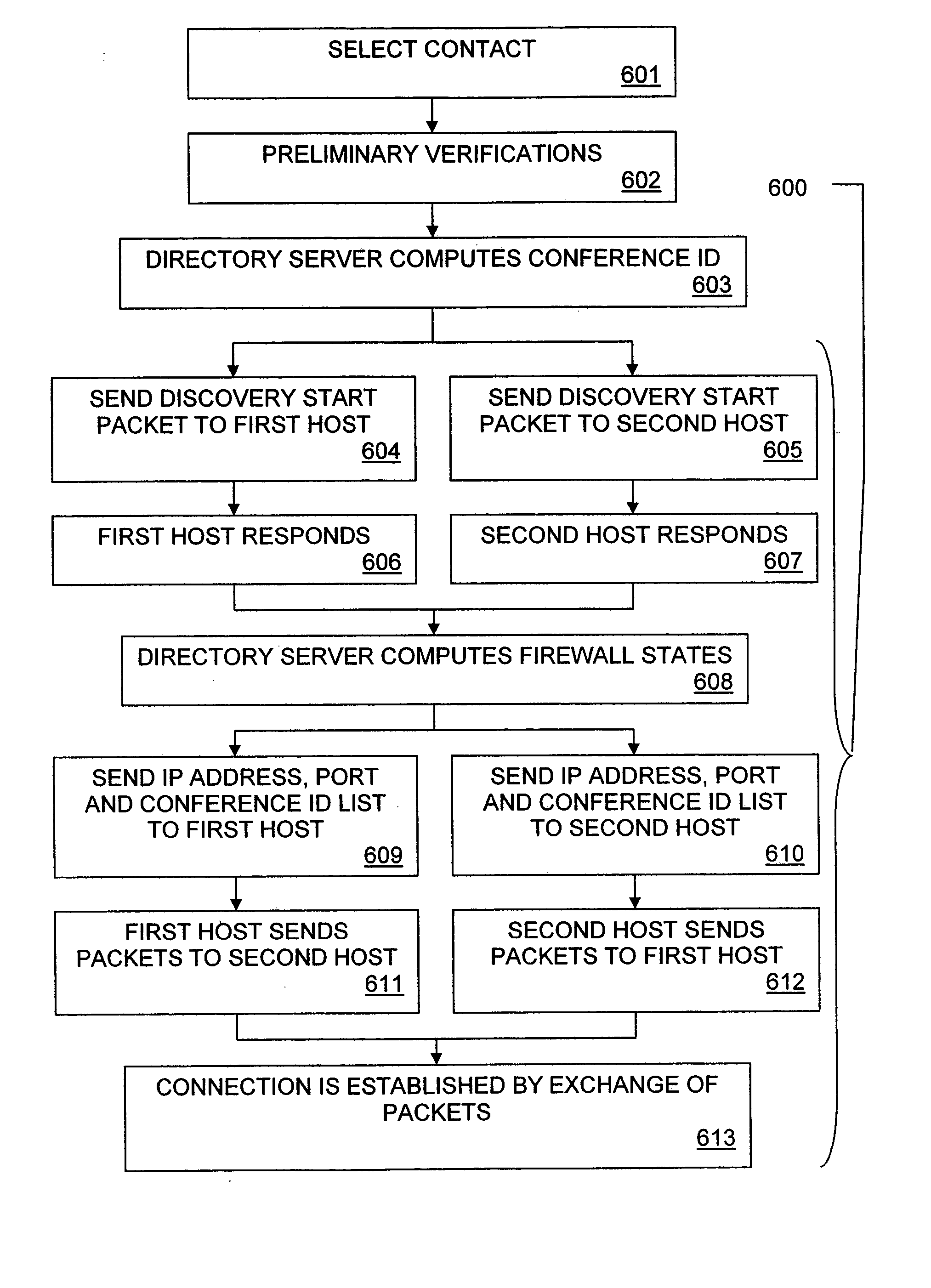
InactiveUS20050086358A1Lower latencyImprove performanceSpecial service provision for substationMultiplex system selection arrangementsOpen communicationNetwork security
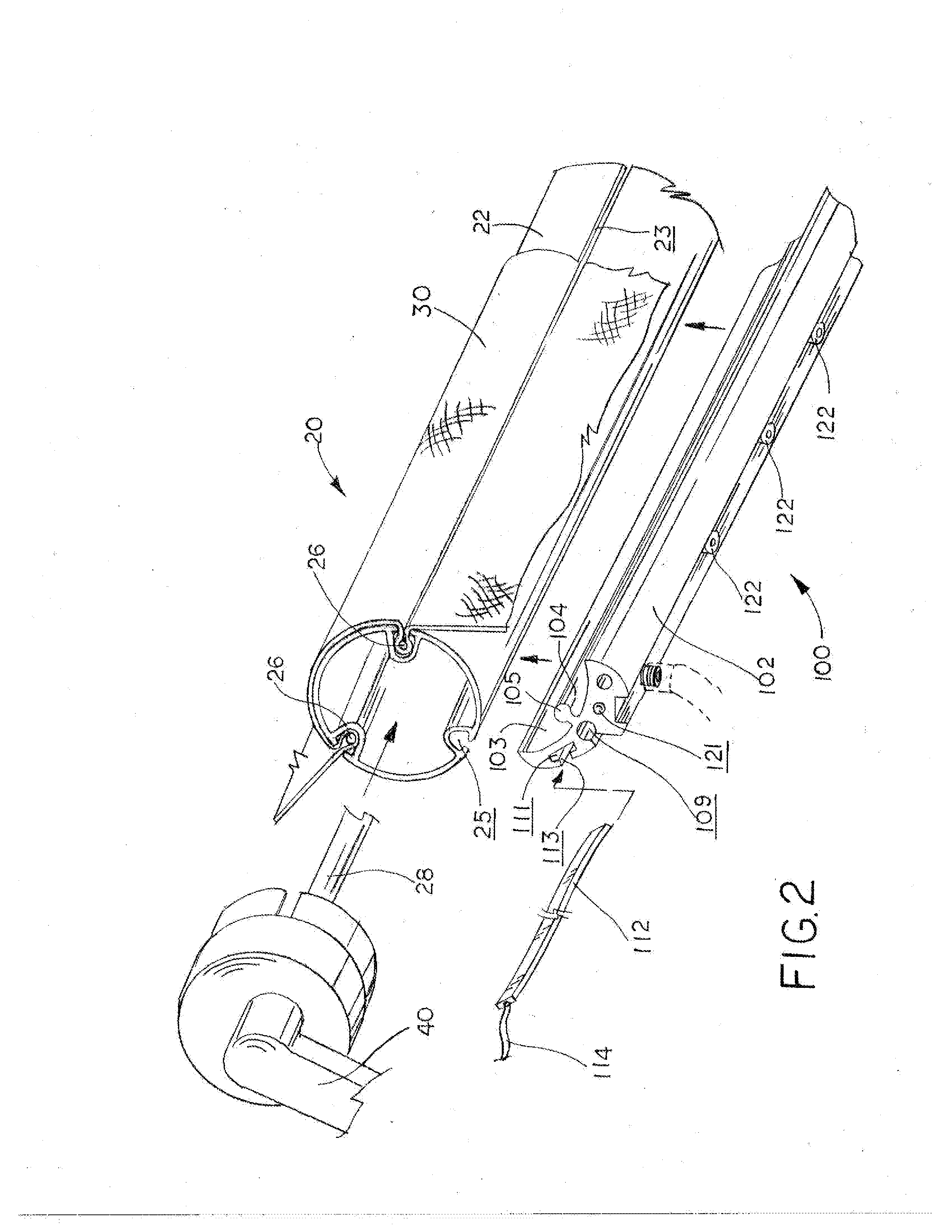
A method for communicating video data between at least a first host and a second host comprises: identifying, at a server, an address of the first host, to which the second host may communicate video data, and a sequence number expected by a network security system coupled between the first host and the server; and communicating, from the second host to the first host, video data using the address of the first host and the sequence number expected. The method may further comprise: identifying, at the server, an address of the second host, to which the first host may communicate video data, and a second sequence number expected by a network security system coupled between the second host and the server; and communicating, from the first host to the second host, video data using the address of the second host and the second expected sequence number. The second host may be adapted to perform the act of communicating without use of an intermediate server. The method may also further comprise communicating periodically, from the first host to the server, through the network security system, so as to maintain an open communication channel through the network security system to the first host at the address of the first host. The address of the first host may include address information and port information.
Owner:LOGITECH EURO SA
Multi-tiered safety control system and methods for online communities
InactiveUS20060253784A1Healthy balanceCost-effective to administerSpecial service provision for substationSpecial data processing applicationsAutomated algorithmControl system
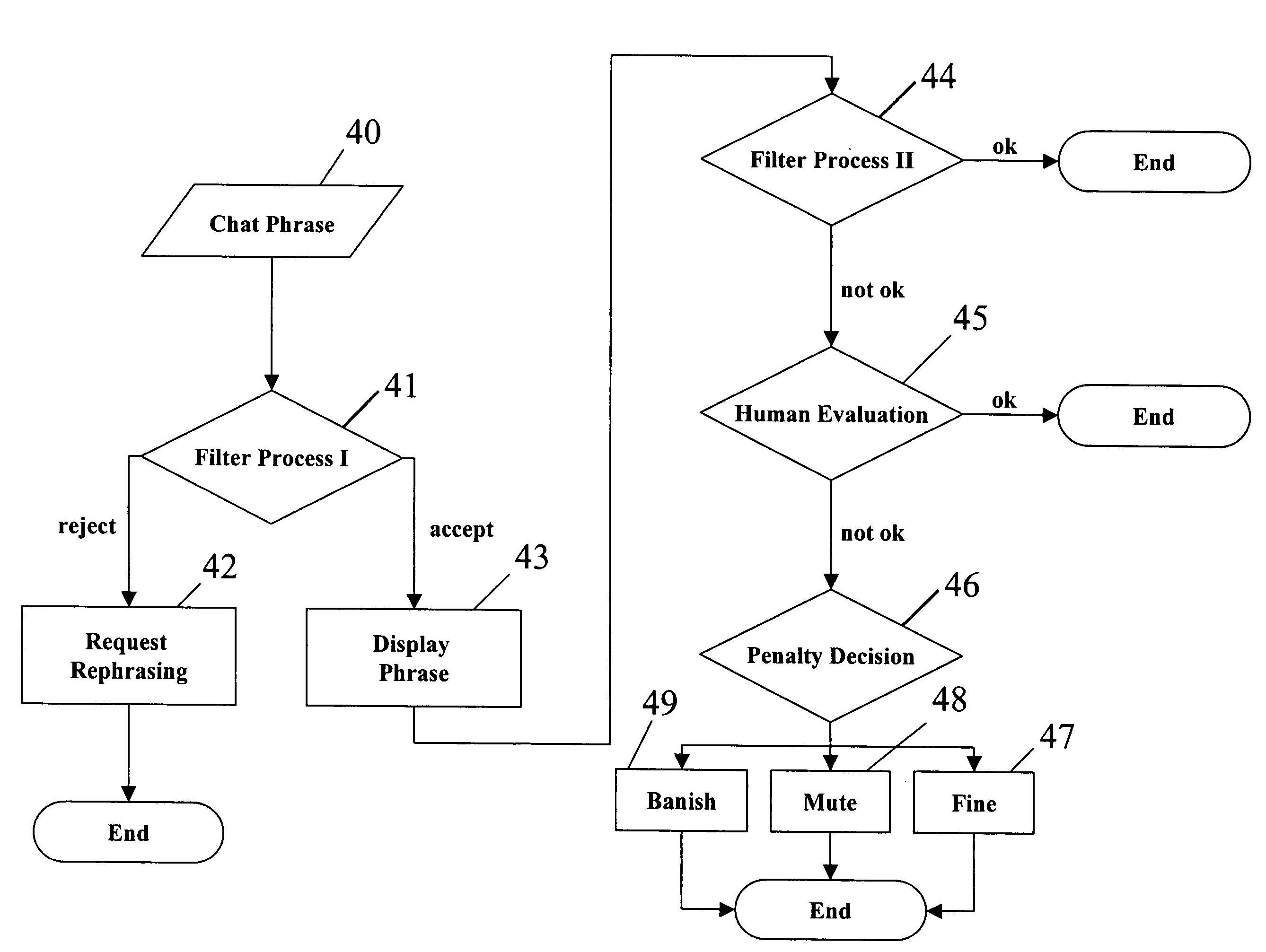
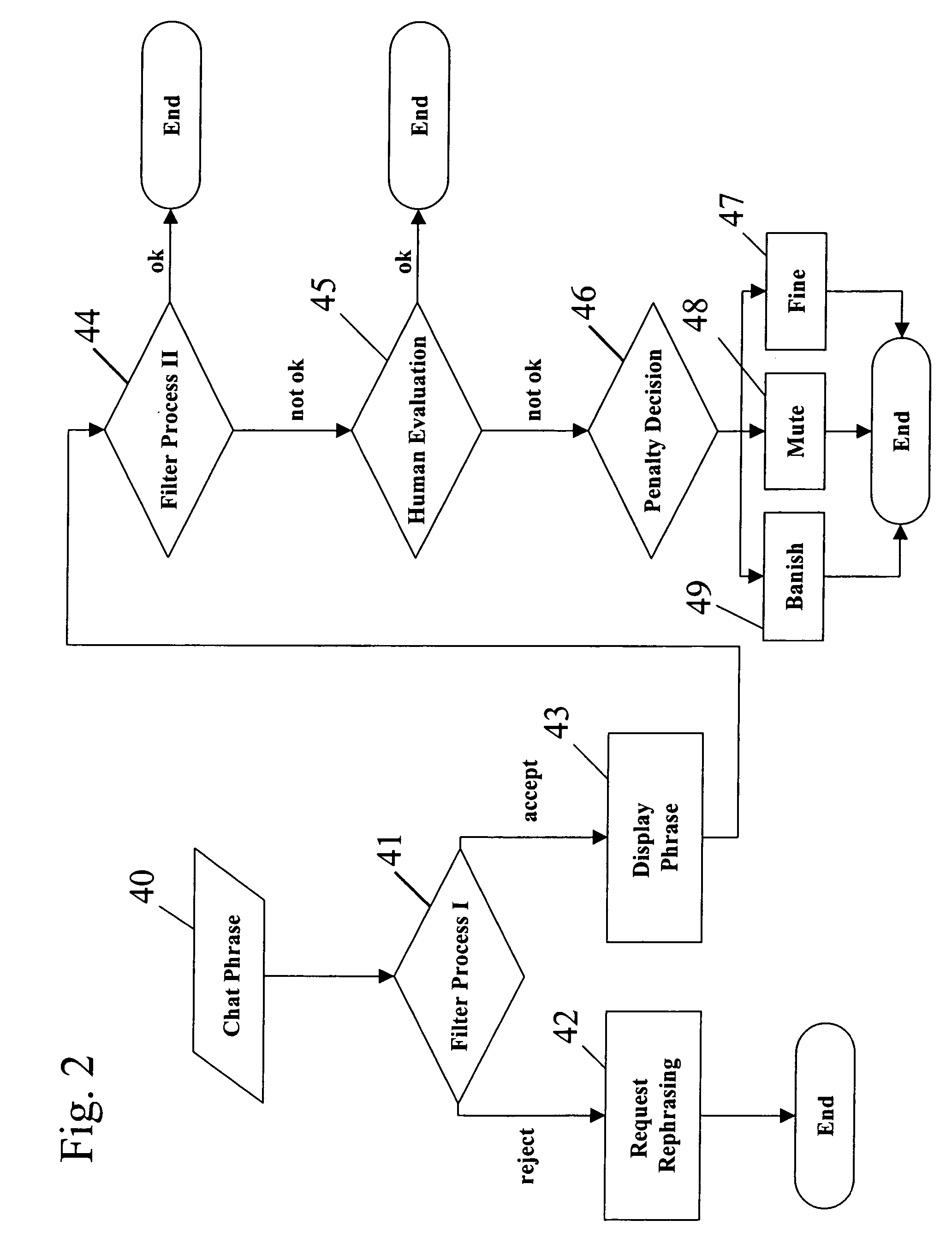
A system and method of maintaining community safety standards within an Internet community. A balance is achieved between open communication and costly supervision of an immersive online community by use of automated algorithms, human supervision and peer monitoring. An automated filtering process is used in conjunction with an evaluation and penalty process. The filter is enhanced over time. A peer-to-peer control and peer-to-administrator reporting scheme complete the system and methods to synergistically to maintain safety and set standards within the community.
Owner:NUMEDEON
Electronic package for image sensor, and the packaging method thereof
ActiveUS20060097335A1Simple and conveniently employedEasy to useSemiconductor/solid-state device detailsSolid-state devicesDevice materialSemiconductor
A semiconductor device package and method for its fabrication are provided. The semiconductor device package generally includes at least one semiconductor die and a substrate coupled to the semiconductor die. The semiconductor die is provided with a front side defining a sealing area, and a first solder sealing ring pad formed on that front side. The substrate is provided with a front surface opposing the front side of the semiconductor die on which a second solder sealing ring pad is formed. A solder sealing ring structure is sandwiched between the first and second solder sealing pads of the substrate and semiconductor die, such that it extends peripherally about a substantial portion of the sealing area to substantially enclose thereat a cavity between the semiconductor die and the substrate. The solder sealing ring structure includes at least one venting portion defining against at least one of the substrate and semiconductor die an air vent in open communication with the cavity.
Owner:OPTOPAC
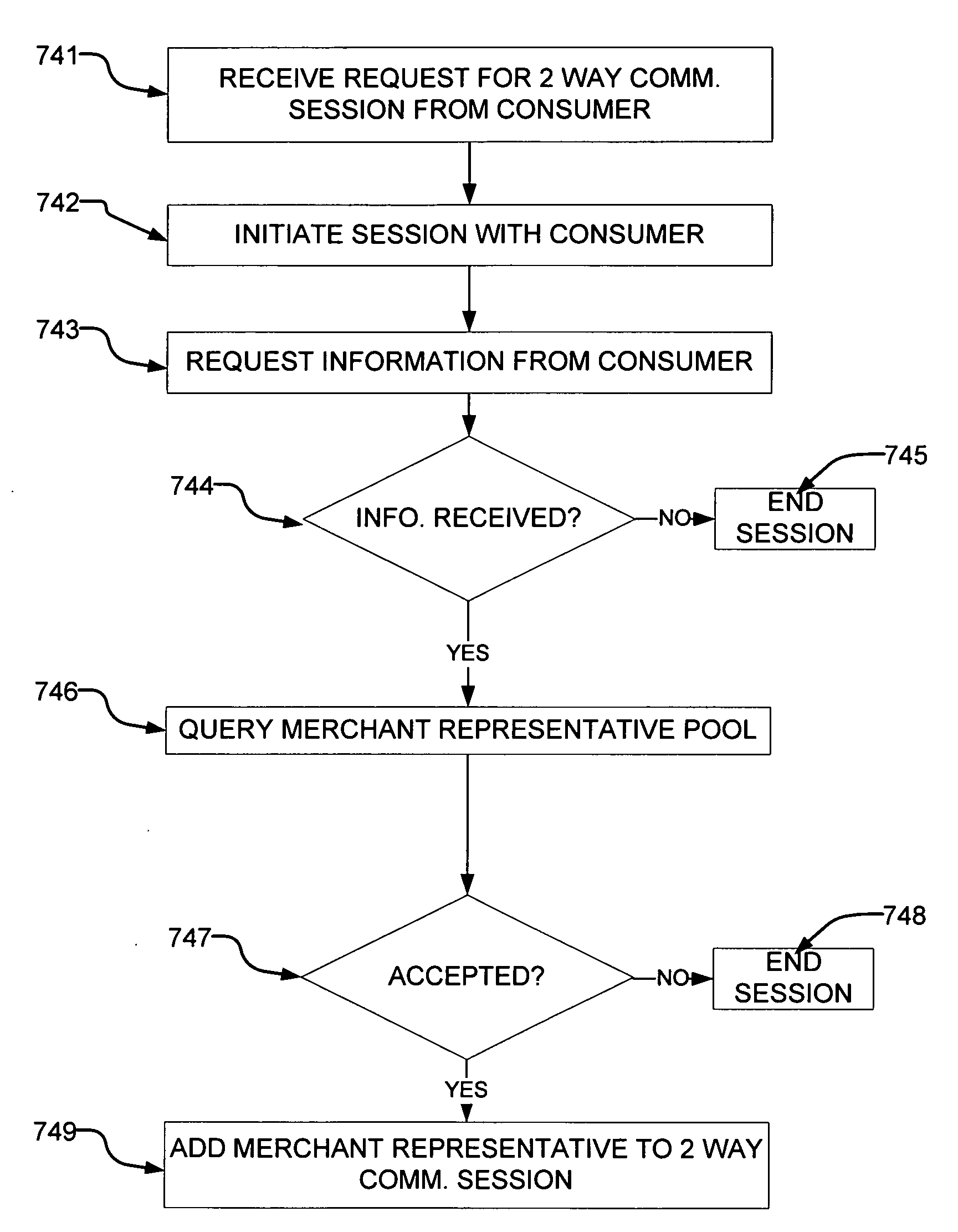
Presence optimized advertisement publishing system and methodology
A system and method are provided for publishing certain advertising information on-line. Presence indicators are incorporated into merchant advertisements published online. The presence indicators are preferably active hyper-links that are configured to allow a consumer to send a request to a merchant for initiation of a 2-way real time communications session. The system provides for adding one of a pool of merchant representatives to an opened communications session with the consumer. Advertisements may be selectively published or withheld from publication based upon the availability status of an associated merchant.
Owner:CONTACTATONCE LLC
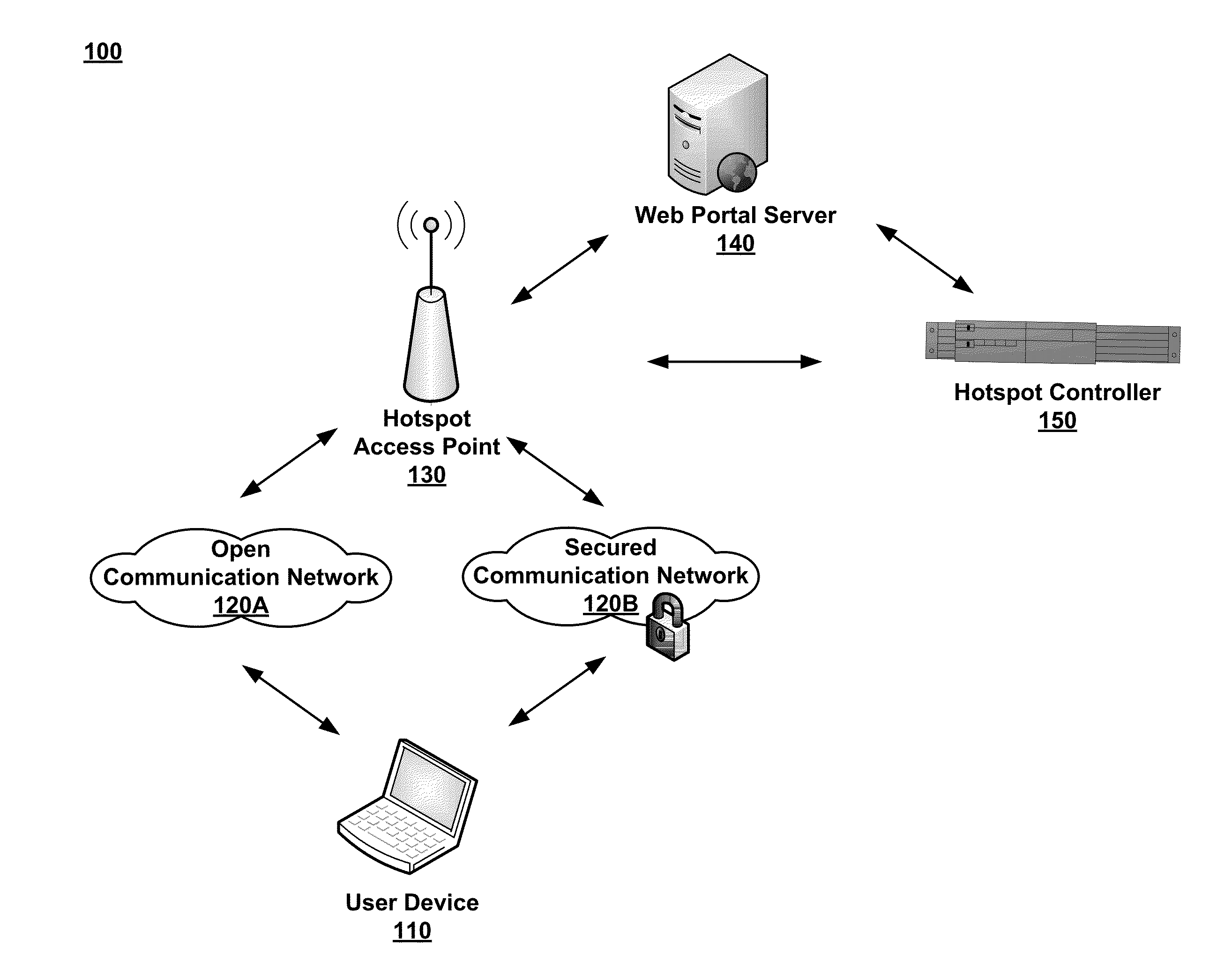
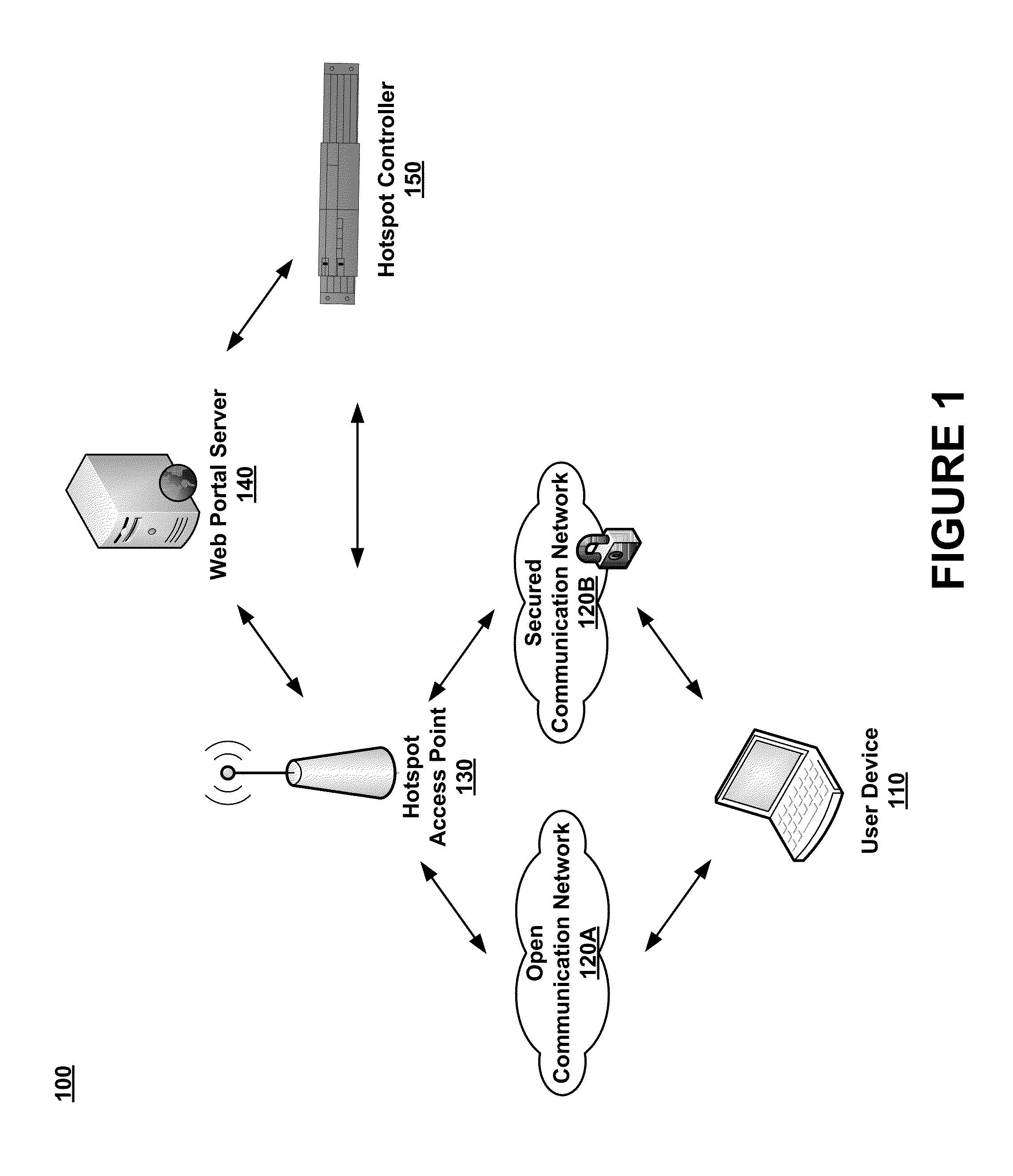
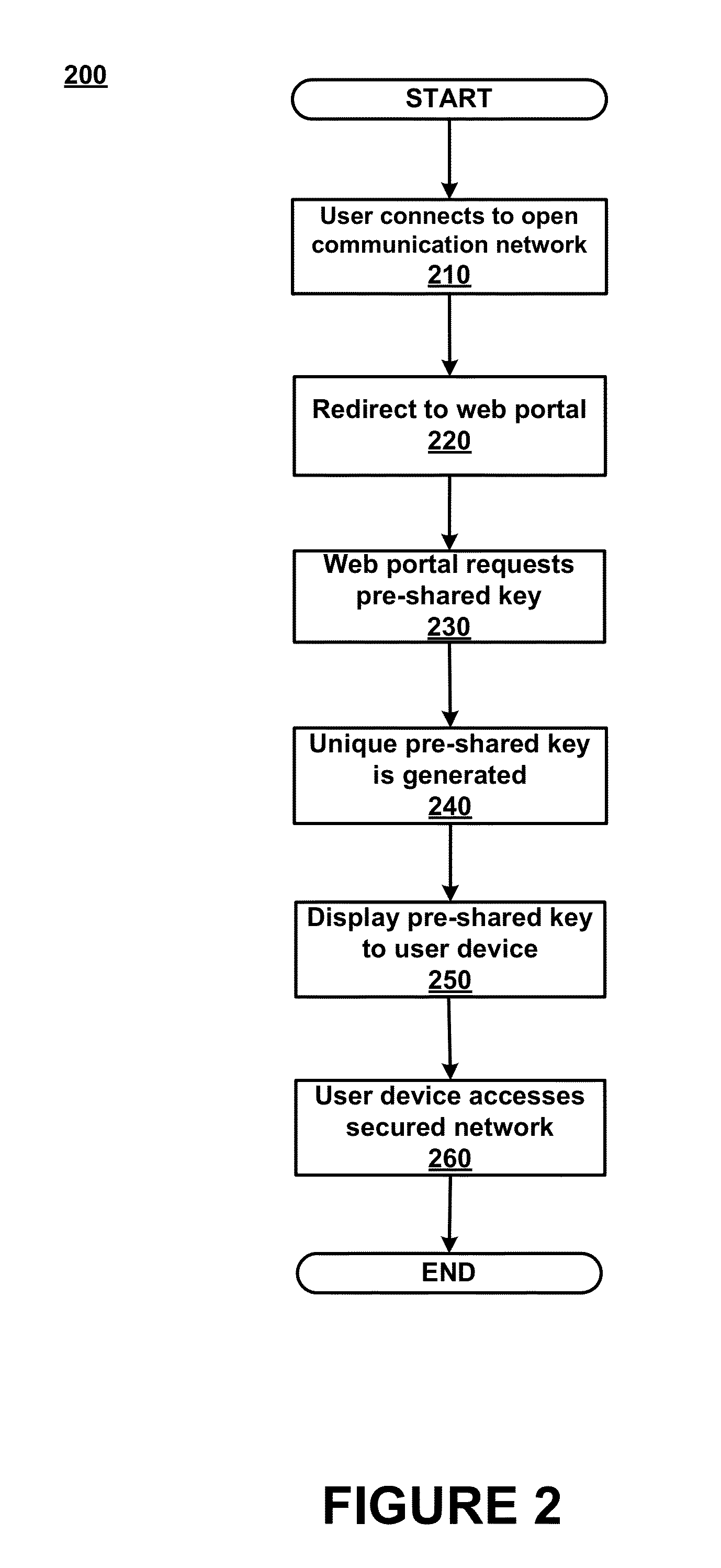
Dynamic PSK for Hotspots
ActiveUS20130212656A1Digital data processing detailsComputer security arrangementsComputer networkWeb page
Systems and methods for providing secured network access are provided. A user device located within range of a hotspot initiates a request sent via an open communication network associated with the hotspot. The request concerns secured network access at the hotspot by the user device. A unique pre-shared key is generated for the user device based on information in the received request and transmitted over the open communication network for display on a webpage accessible to the user device. The unique pre-shared key is stored in association with information regarding the user device. The user device may then use the unique pre-shared key in subsequent requests for secured network access.
Owner:ARRIS ENTERPRISES LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com