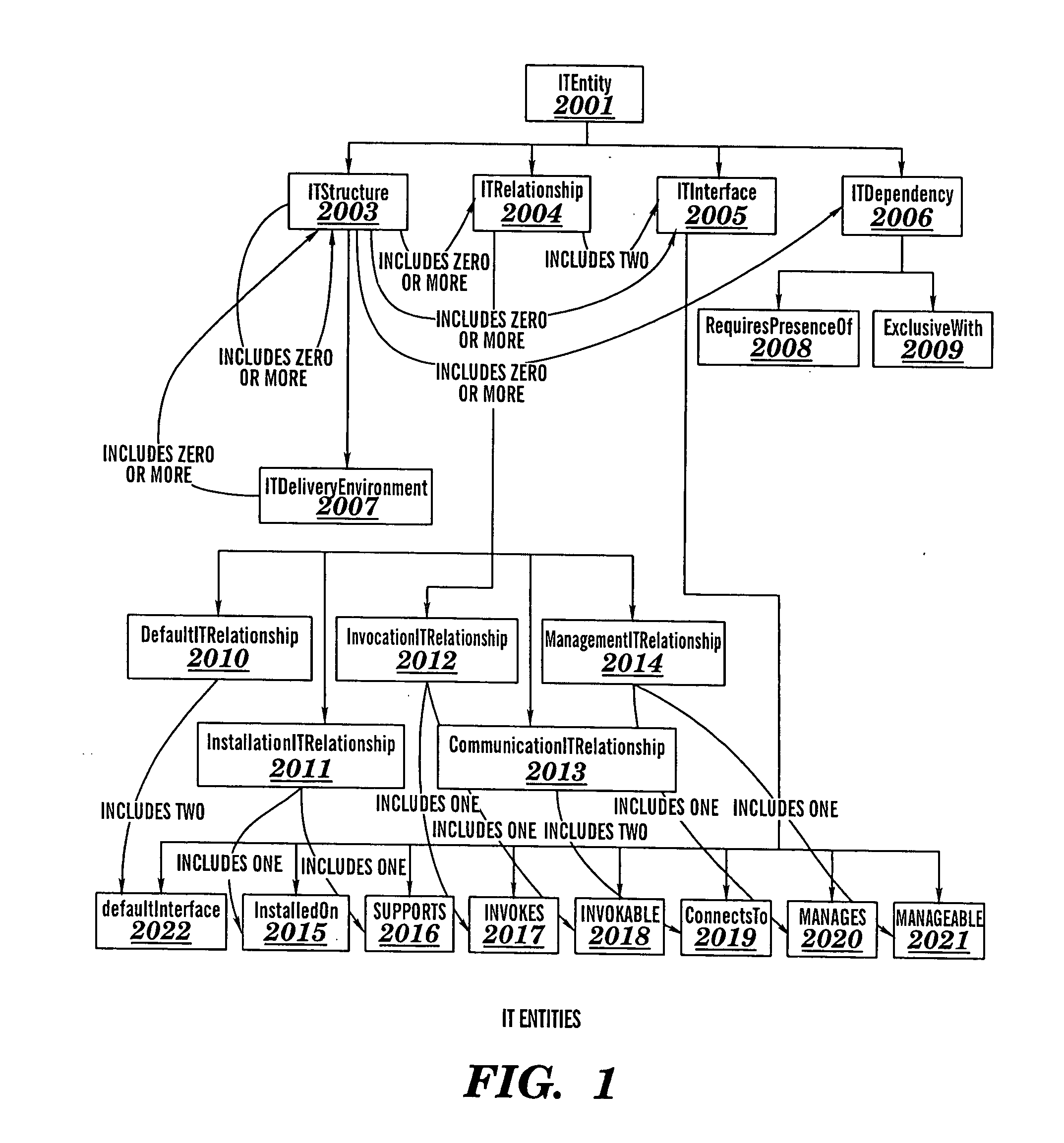
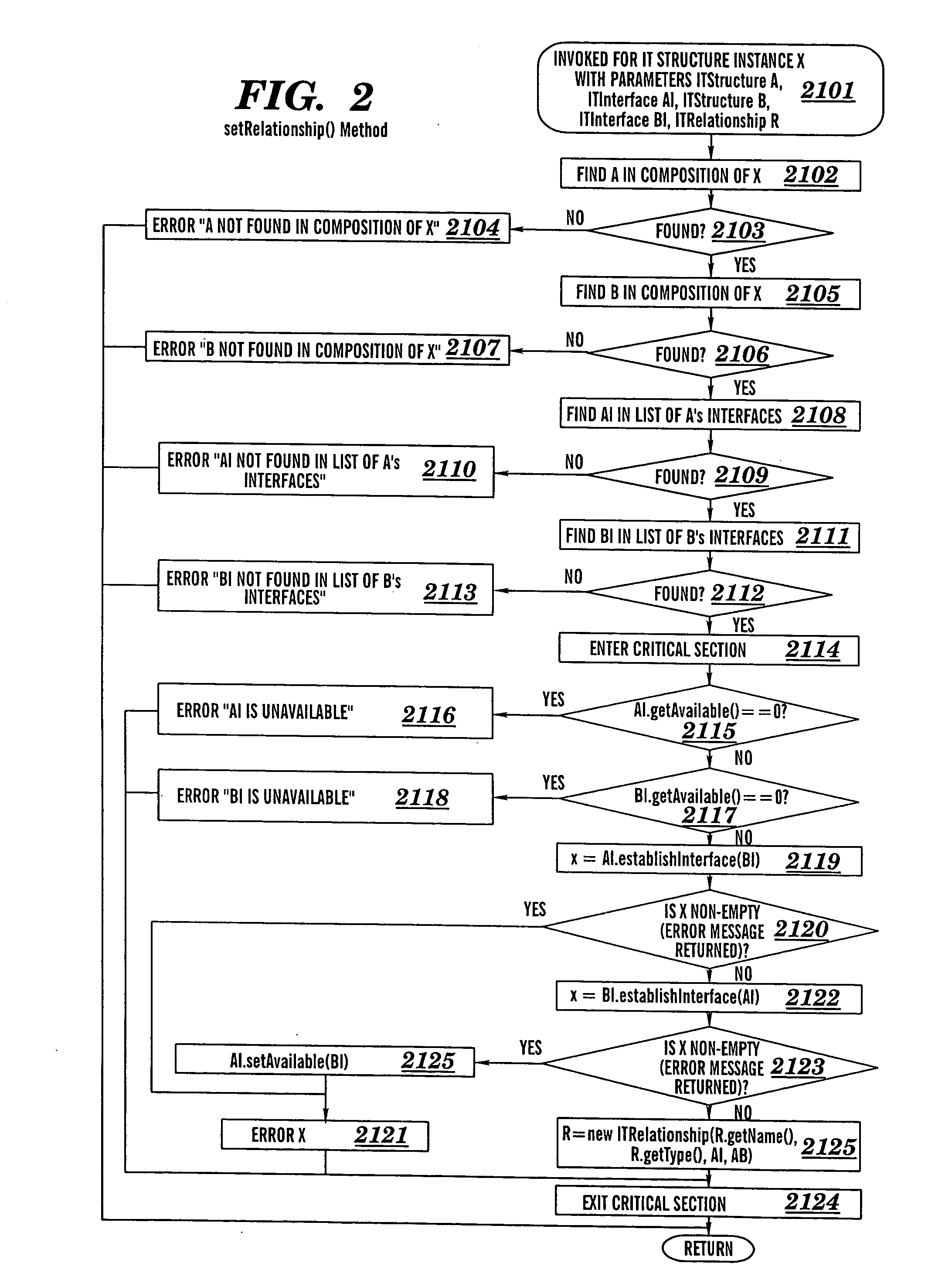
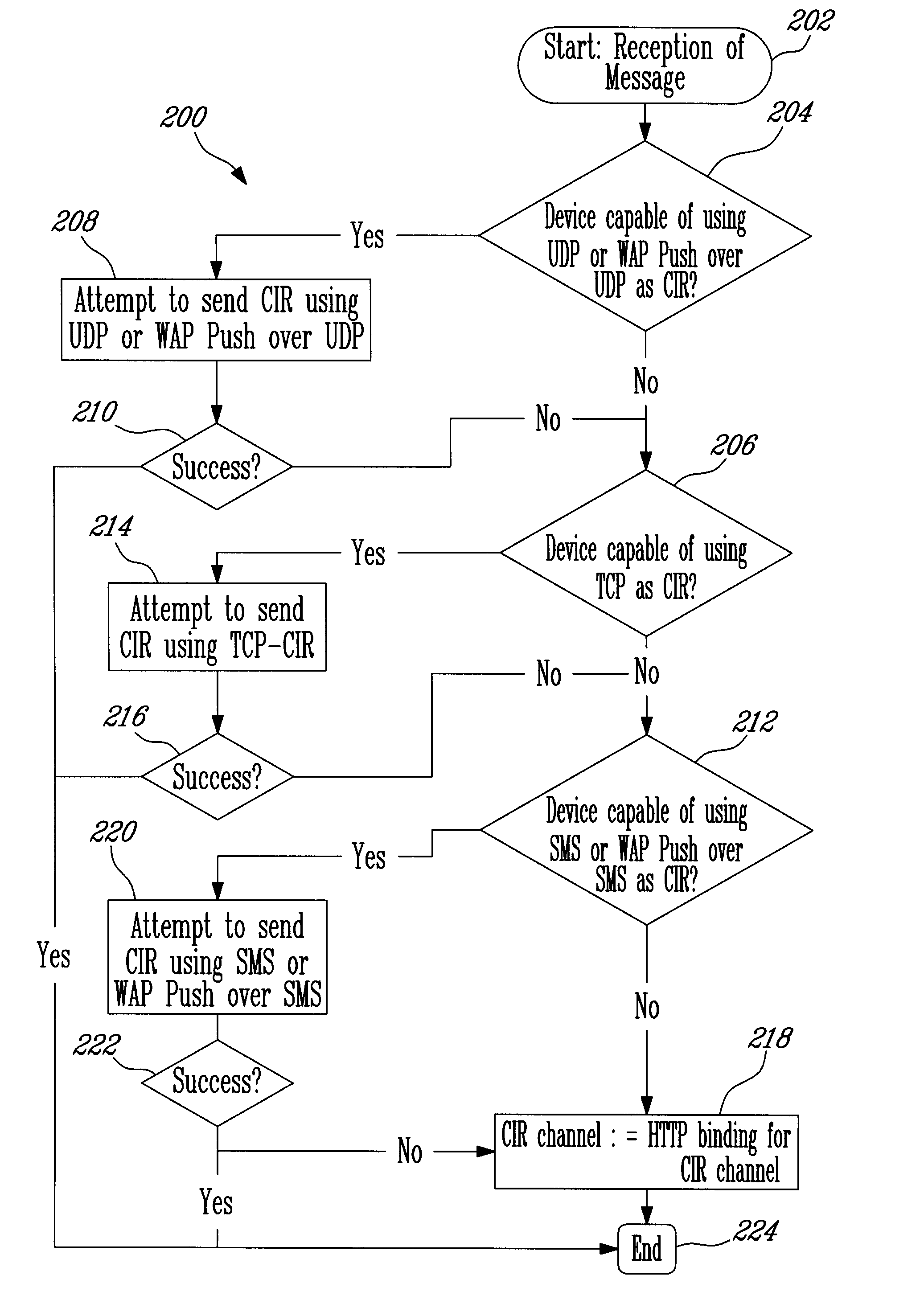
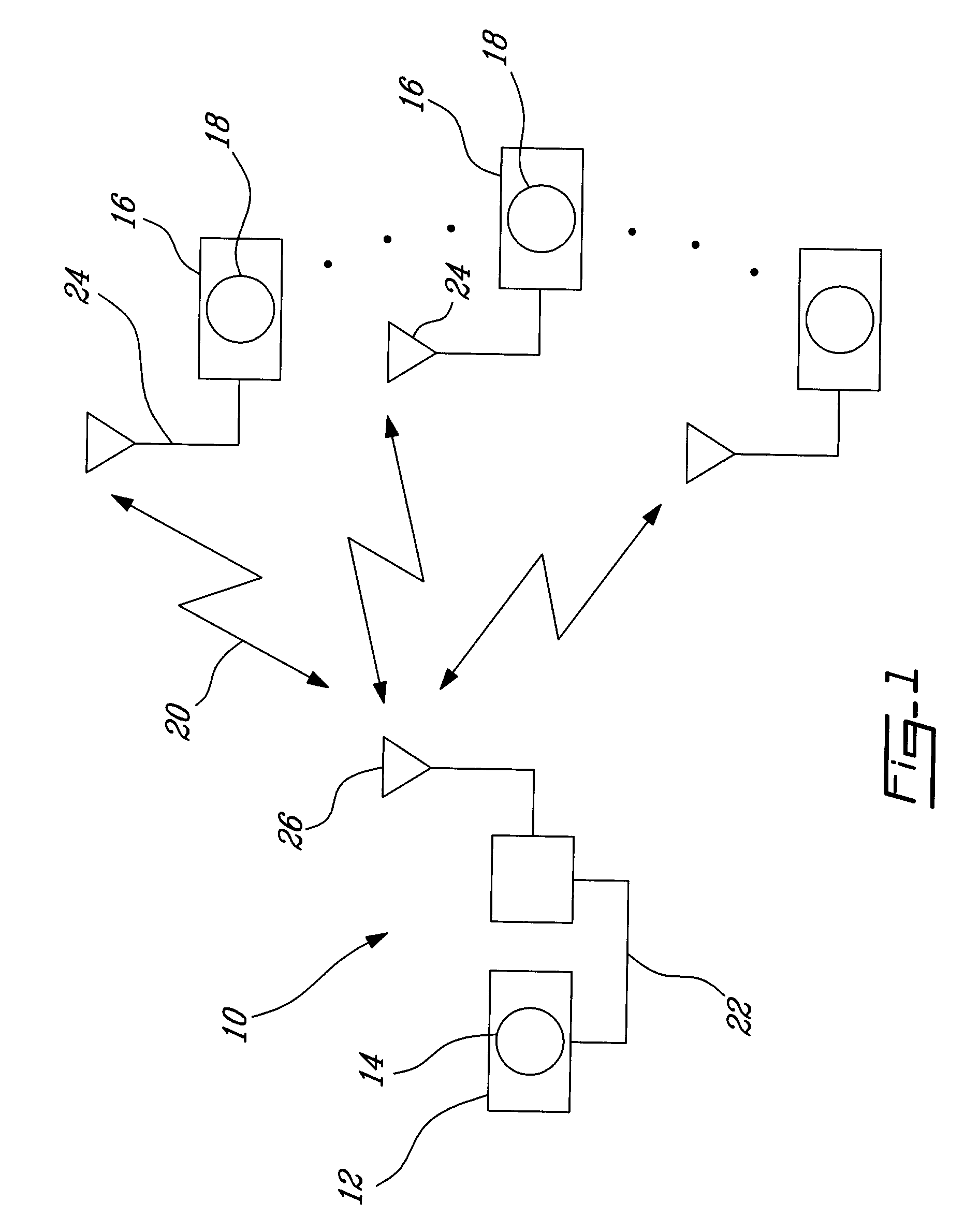
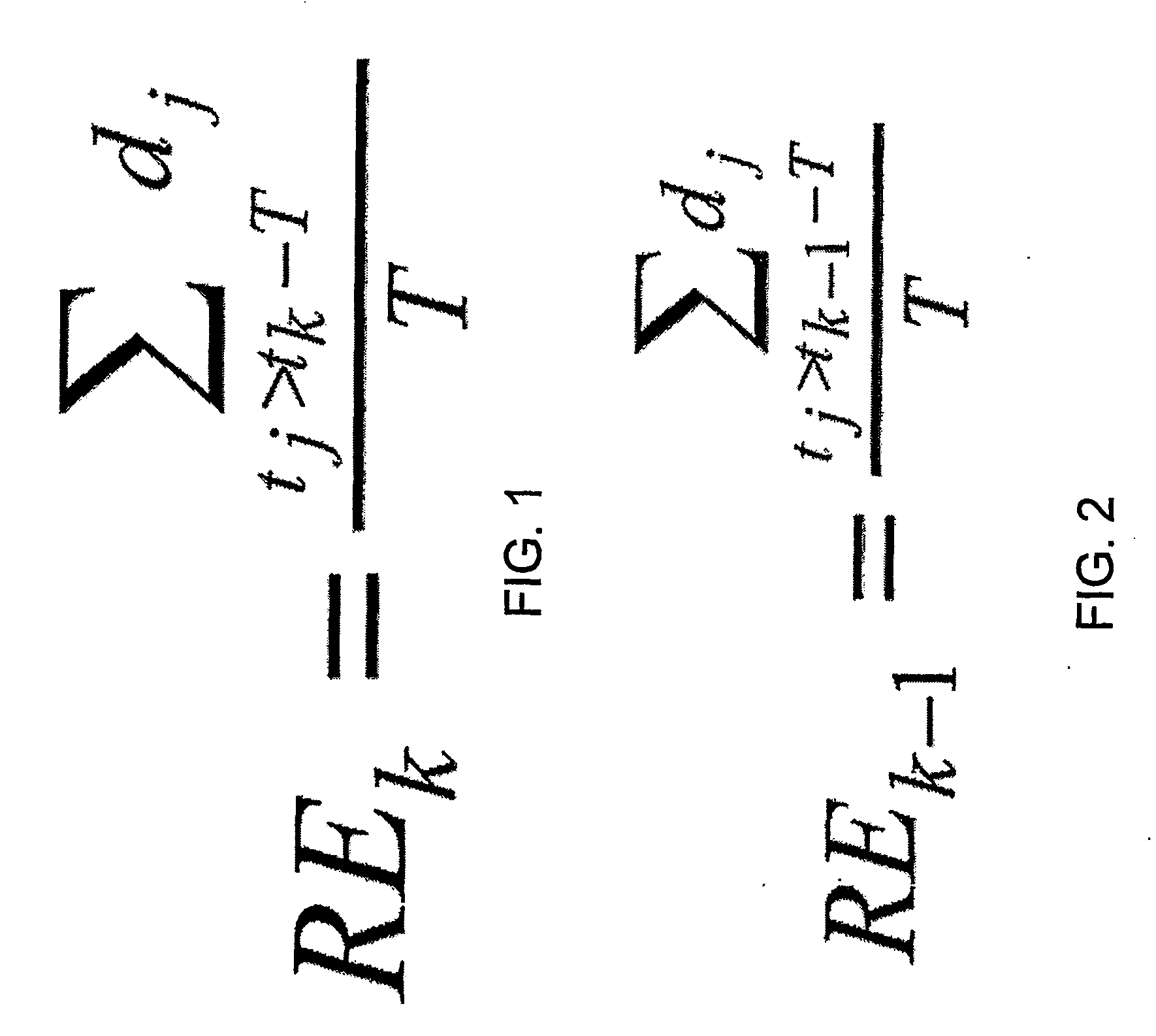Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2827 results about "Transmission Control Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
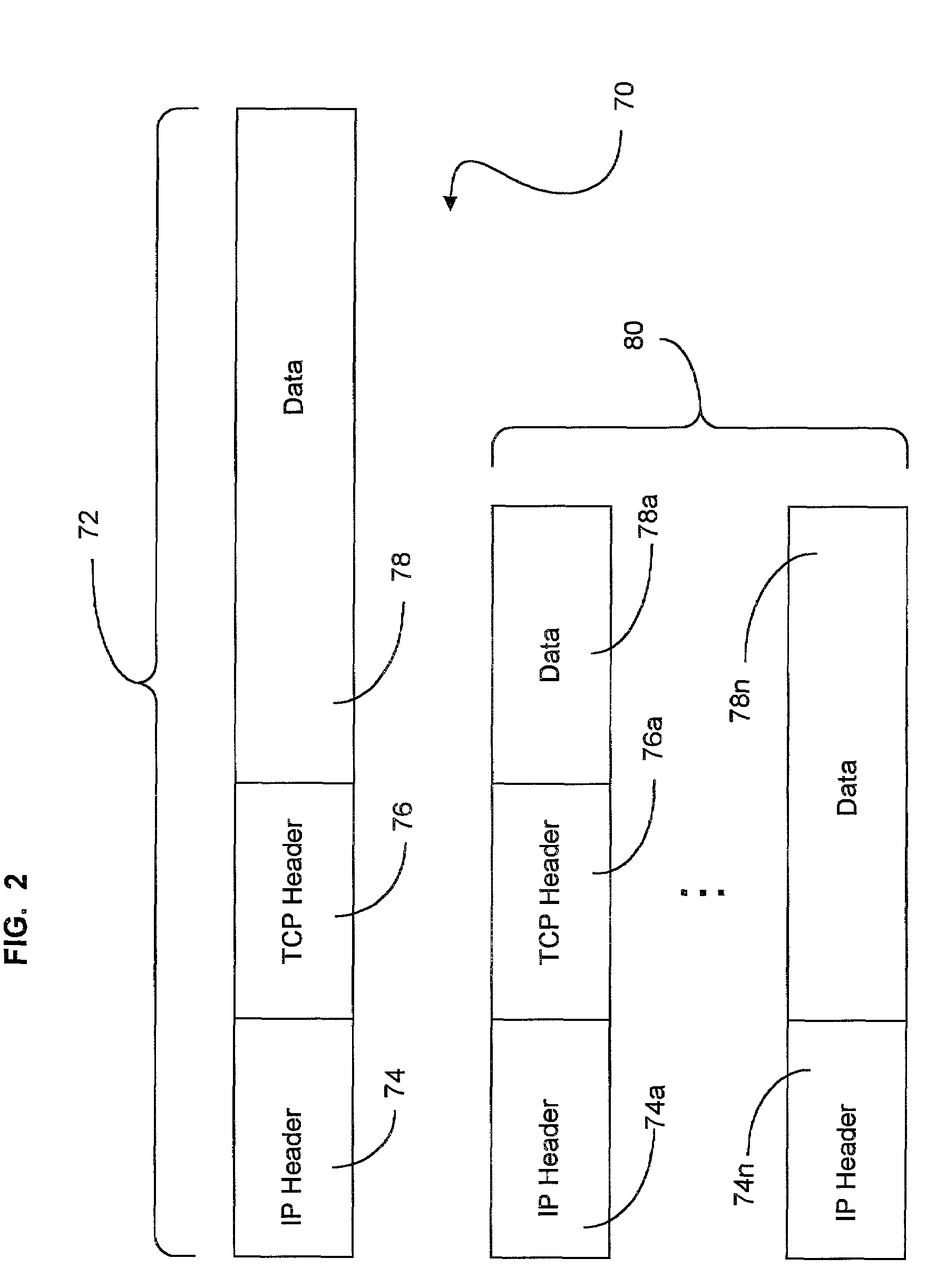
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered, and error-checked delivery of a stream of octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP. Applications that do not require reliable data stream service may use the User Datagram Protocol (UDP), which provides a connectionless datagram service that emphasizes reduced latency over reliability.
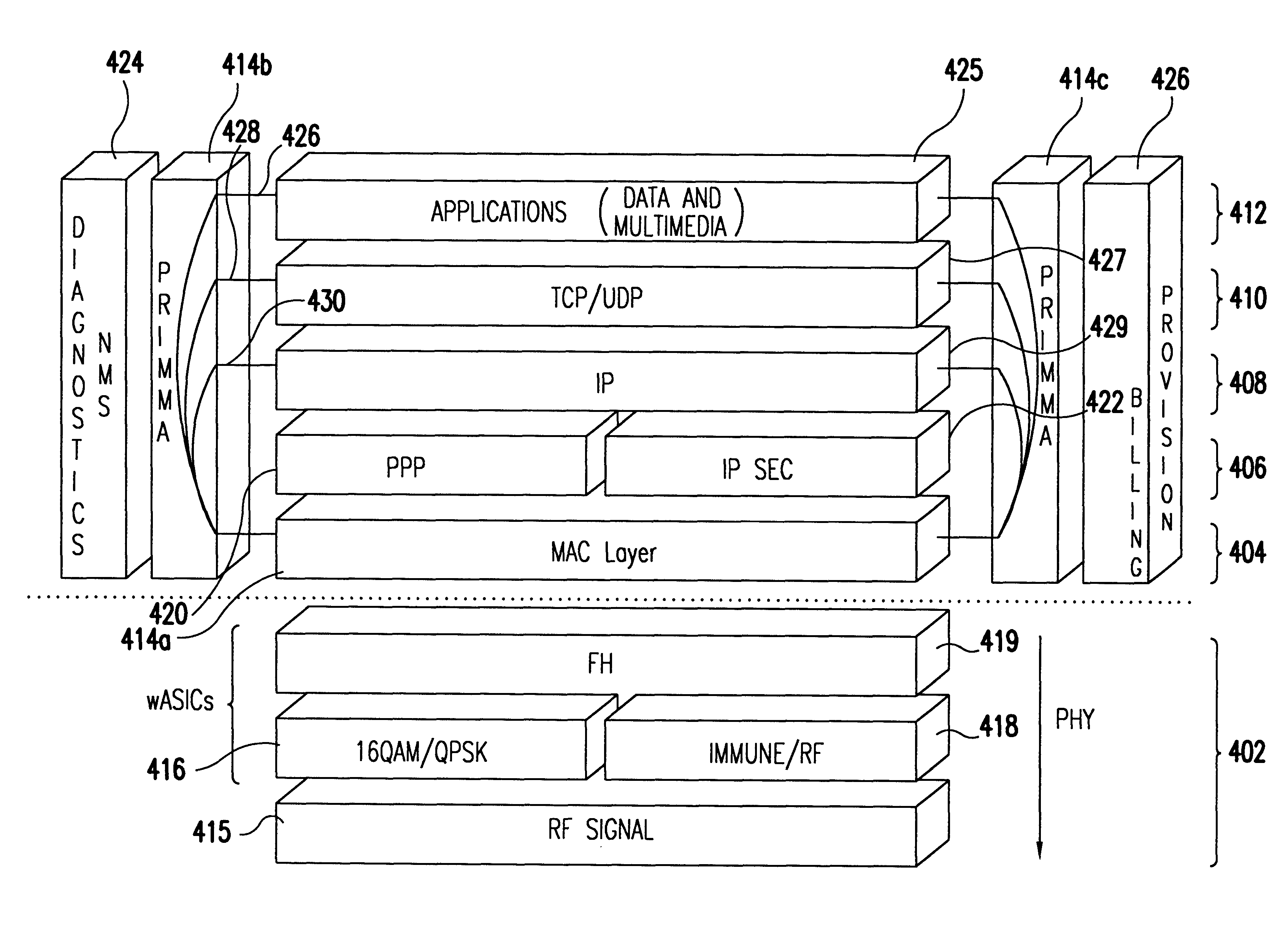
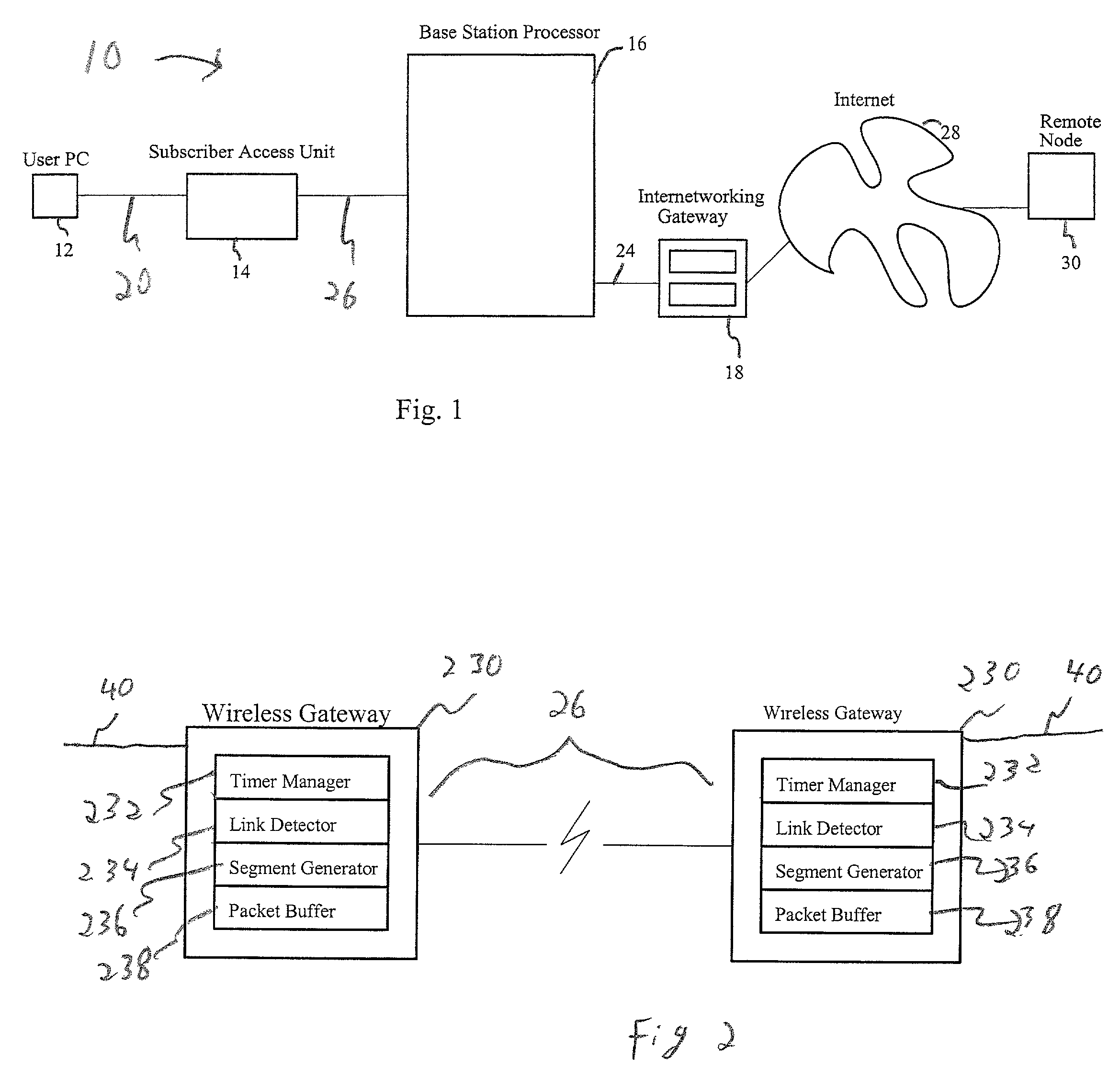
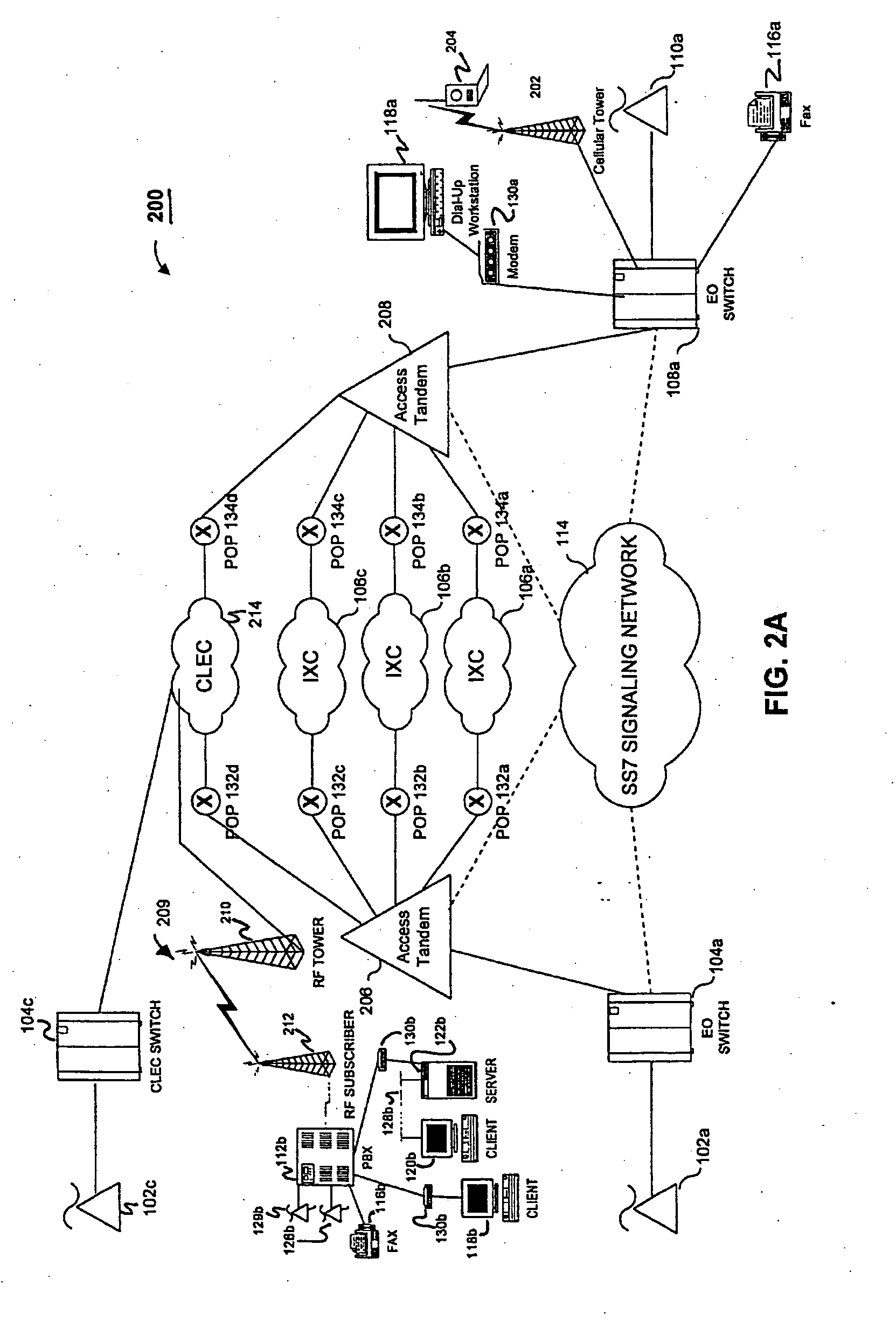
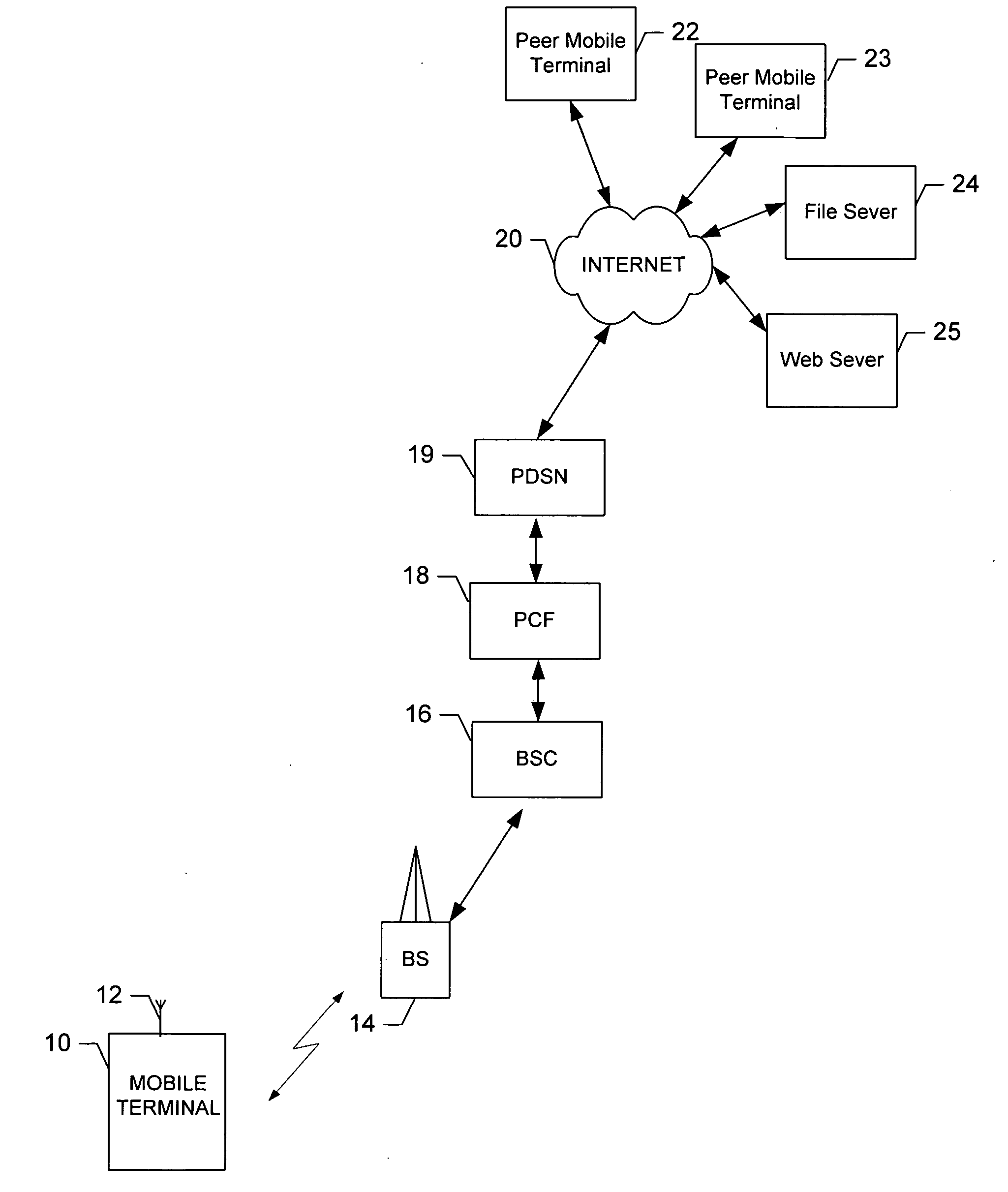
Transmission control protocol/internet protocol (TCP/IP) packet-centric wireless point to multi-point (PTMP) transmission system architecture
InactiveUS6862622B2Special service provision for substationError detection/prevention using signal quality detectorTransport systemWorkstation
A packet-centric wireless point to multi-point telecommunications system includes: a wireless base station communicating via a packet-centric protocol to a first data network; one or more host workstations communicating via the packet-centric protocol to the first data network; one or more subscriber customer premise equipment (CPE) stations coupled with the wireless base station over a shared bandwidth via the packet-centric protocol over a wireless medium; and one or more subscriber workstations coupled via the packet-centric protocol to each of the subscriber CPE stations over a second network. The packet-centric protocol can be transmission control protocol / internet protocol (TCP / IP). The packet-centric protocol can be a user datagram protocol / internet protocol (UDP / IP). The system can include a resource allocation means for allocating shared bandwidth among the subscriber CPE stations. The resource allocation is performed to optimize end-user quality of service (QoS). The wireless communication medium can include at least one of: a radio frequency (RF) communications medium; a cable communications medium; and a satellite communications medium. The wireless communication medium can further include a telecommunications access method including at least one of: a time division multiple access (TDMA) access method; a time division multiple access / time division duplex (TDMA / TDD) access method; a code division multiple access (CDMA) access method; and a frequency division multiple access (FDMA) access method.The first data network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN). The second network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN).
Owner:INTELLECTUAL VENTURES I LLC
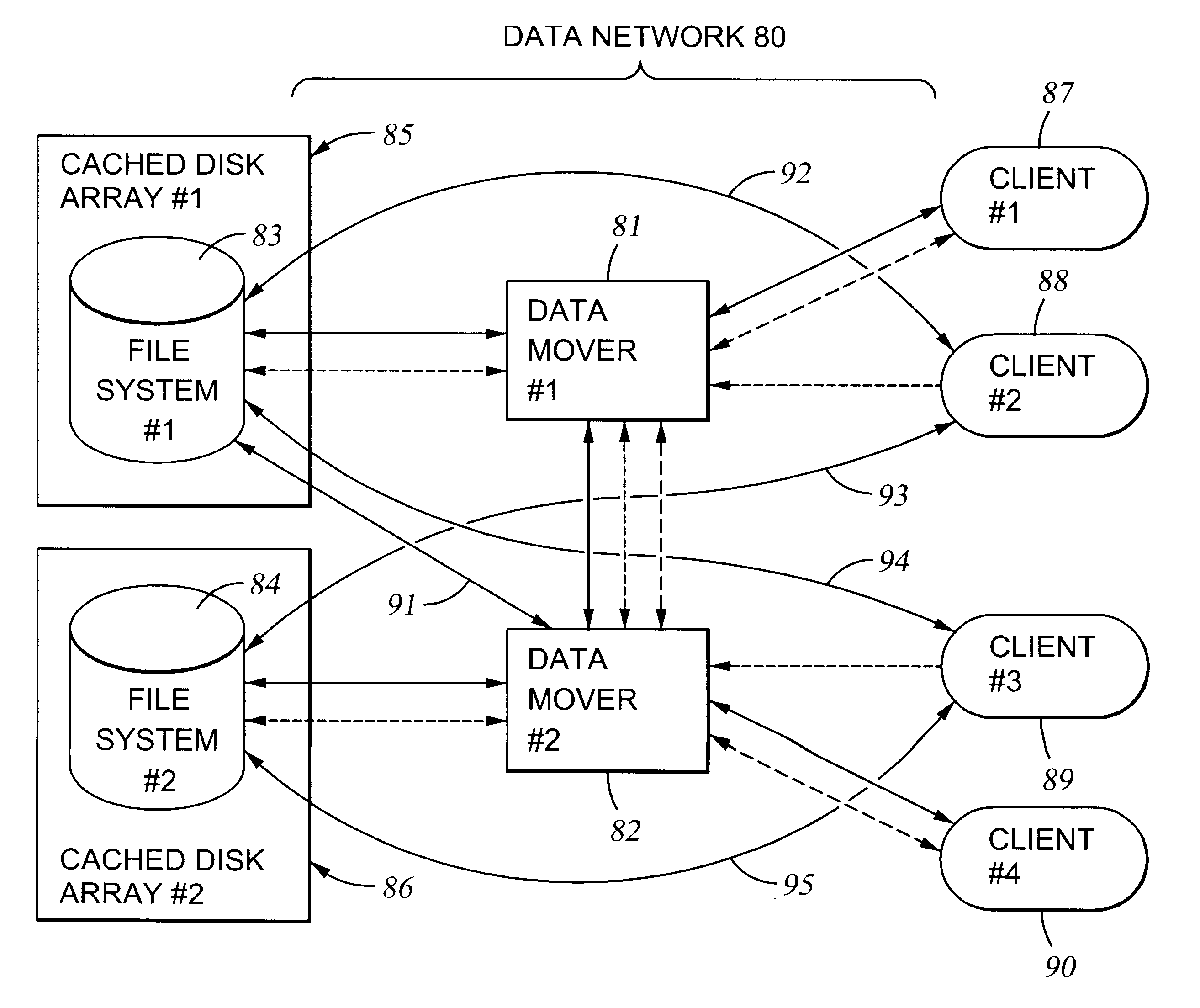
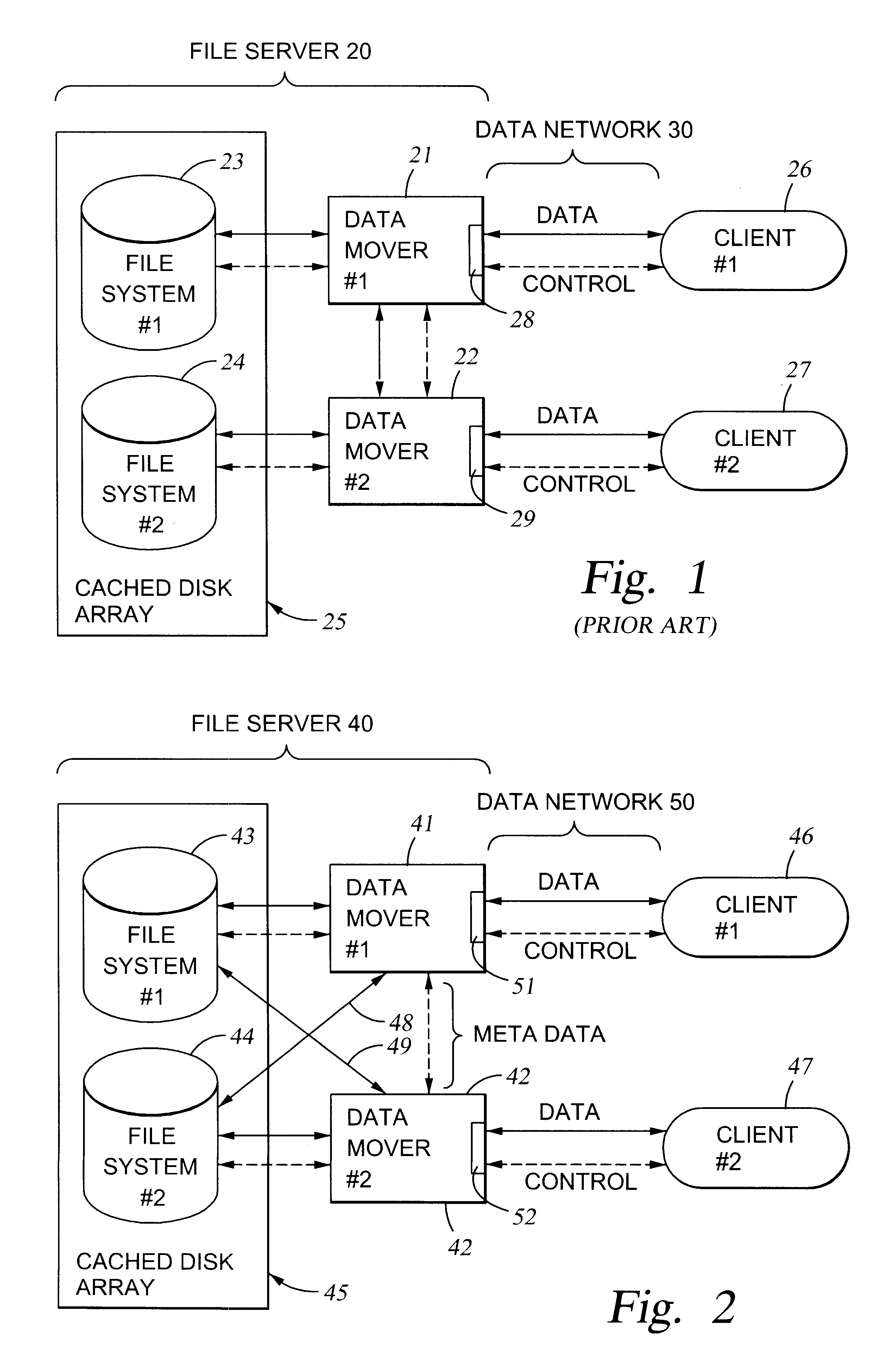
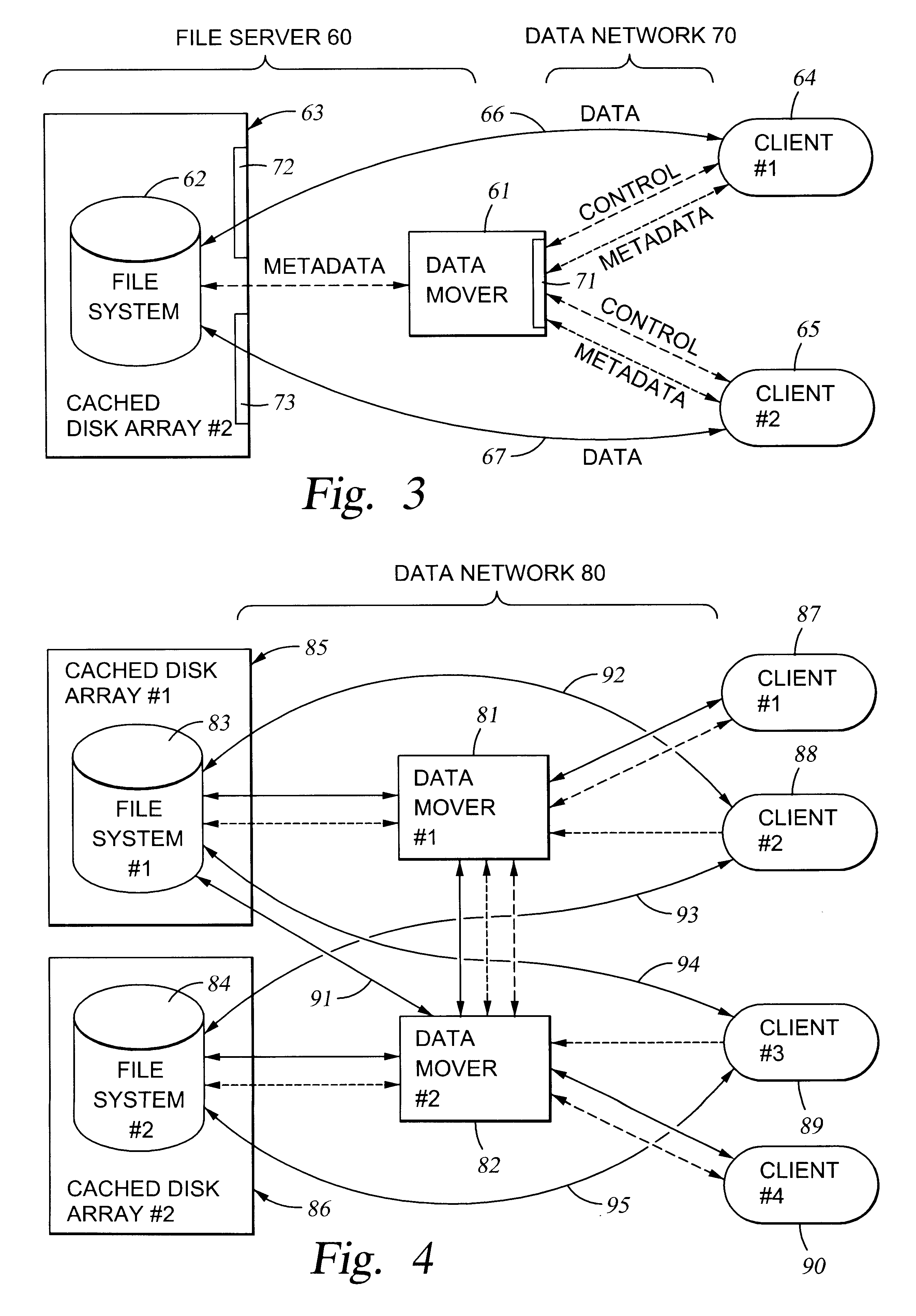
File server system using connection-oriented protocol and sharing data sets among data movers
InactiveUS6453354B1Digital data information retrievalMultiple digital computer combinationsMultiplexingData set
A first data mover computer services data access requests from a network client, and a second data mover computer is coupled to the first data mover computer for servicing data access requests from the first data mover computer. The first data mover computer uses a connection-oriented protocol to obtain client context information and to respond to a session setup request from the client by authenticating the client. Then the first data mover computer responds to a file system connection request from the client by forwarding the client context information and the file system connection request to the second data mover computer. Then the first data mover computer maintains a connection between the first data mover computer and the second data mover computer when the client accesses the file system and the first data mover computer passes file access requests from the client to the second data mover computer and returns responses to the file access requests from the second data mover computer to the client. In a preferred embodiment, the connection-oriented protocol is the Common Internet File System (CIFS) Protocol, and multiple clients share a Transmission Control Protocol (TCP) connection between the first data mover computer and the second data mover computer by allocation of virtual channels within the shared TCP connection and multiplexing of data packets of the virtual channels over the shared TCP connection.
Owner:EMC IP HLDG CO LLC
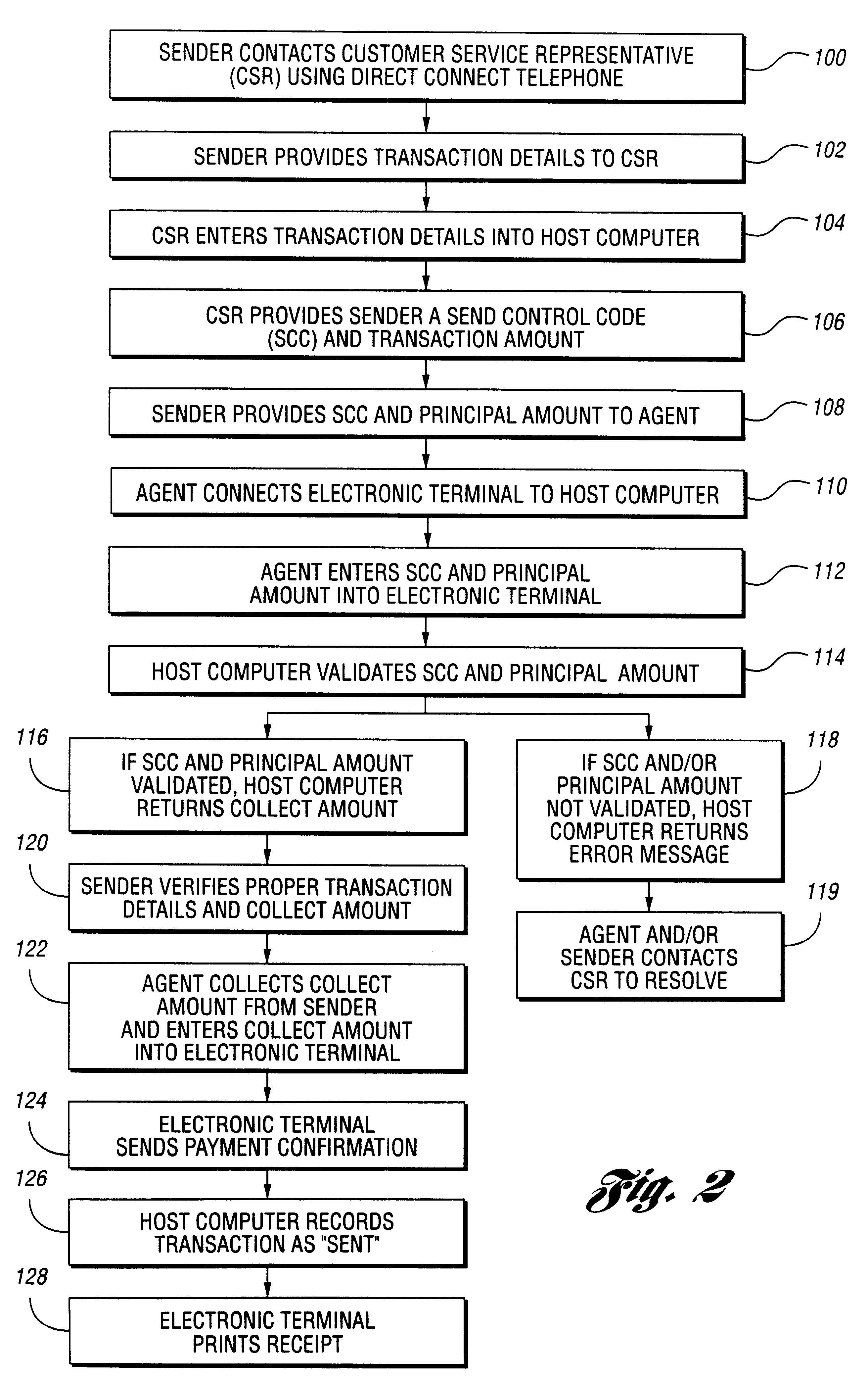
System and method for performing money transfer transaction using TCP/IP
InactiveUS6502747B1Low costShorten the timeComplete banking machinesFinanceInternet protocol suiteProtocol for Carrying Authentication for Network Access
A method of performing a money transfer transaction through a financial services institution includes receiving information regarding the transaction on a first computer of the financial services institution from a first electronic device using the Transmission Control Protocol / Internet Protocol suite (TCP / IP). The method may also include establishing a T1 connection between the first computer and the first electronic device. A system for performing a money transfer transaction using TCP / IP is also disclosed.
Owner:THE WESTERN UNION CO
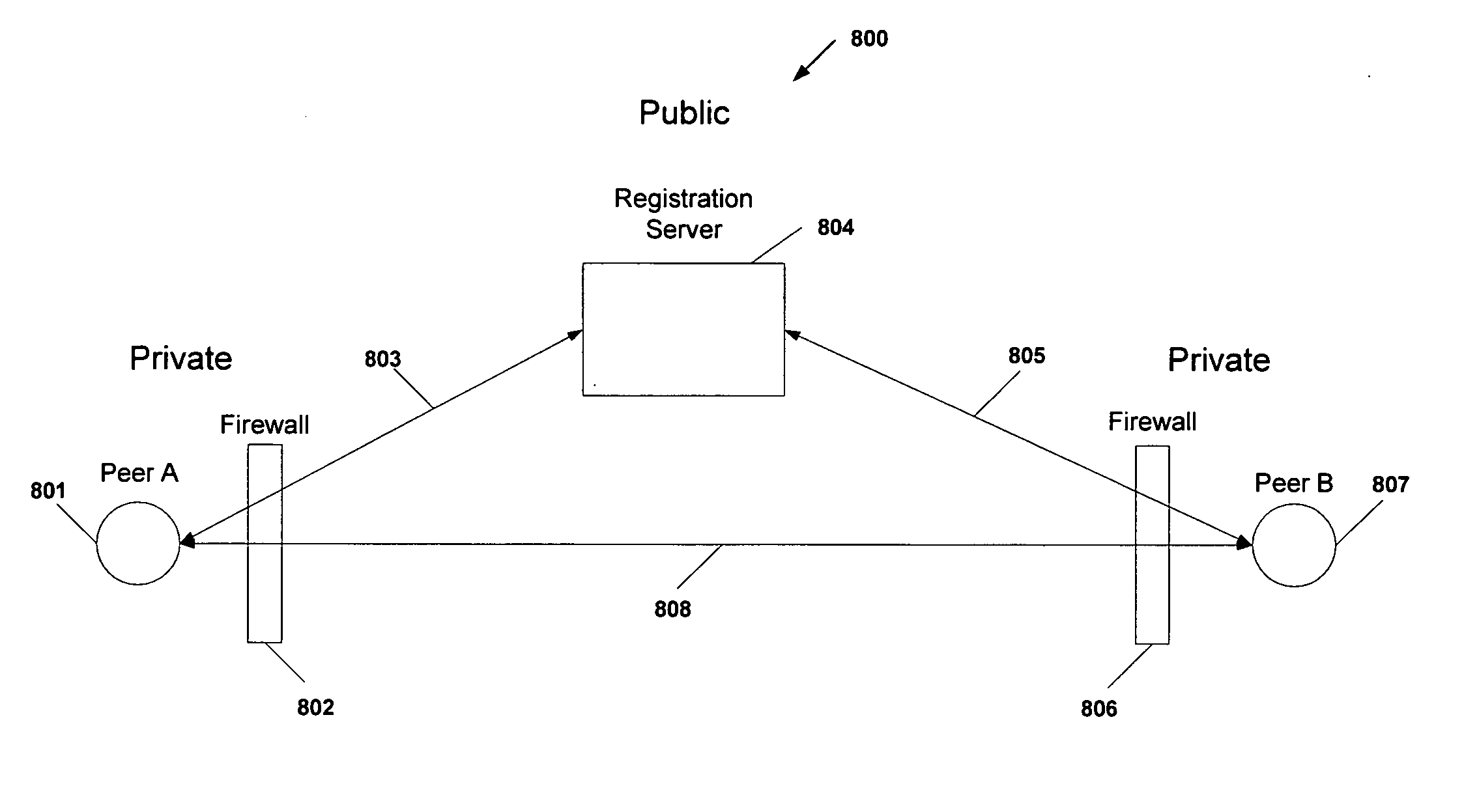
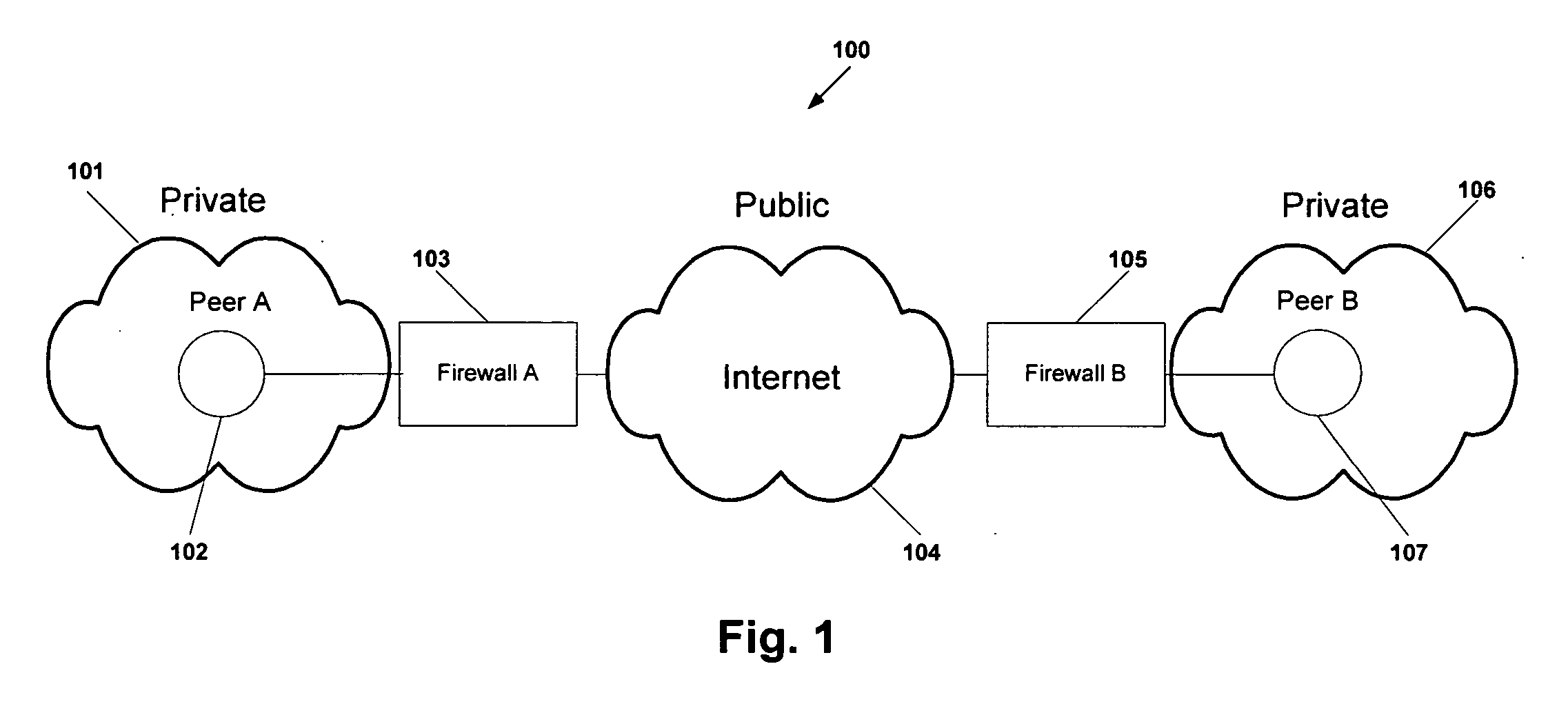
Protocol and system for firewall and NAT traversal for TCP connections
ActiveUS20060215684A1Time-division multiplexData switching by path configurationServer agentNAT traversal
Firewalls and network address translators (NAT) provide many advantages for client and the Internet itself, however, these devices break many existing transmission control protocol (TCP) / Internet Protocol (IP) applications, since they conceal the identity of IP clients (i.e., peers) and block transmission control protocol (TCP) call setup requests. Firewalls and NATs make it impossible for one TCP peer to discover another and establish a connection. Embodiments of this invention provides a system and a protocol to enable two TCP peers that exist behind one or more firewalls and NATs to automatically setup a true peer-to-peer TCP connection and exchange data without making changes to the firewall or NAT devices or existing TCP-based applications. In embodiments of this invention, the synchronization between the blind TCP peers is achieved using a system that consists of a registration server, an agent application, and a virtual network interface that together relay and replicate the control signals between the two TCP peers. In addition, embodiments of this invention are also used to traverse the NAT and establish a bi-directional peer-to-peer TCP connection in the firewall.
Owner:NETGEAR INC
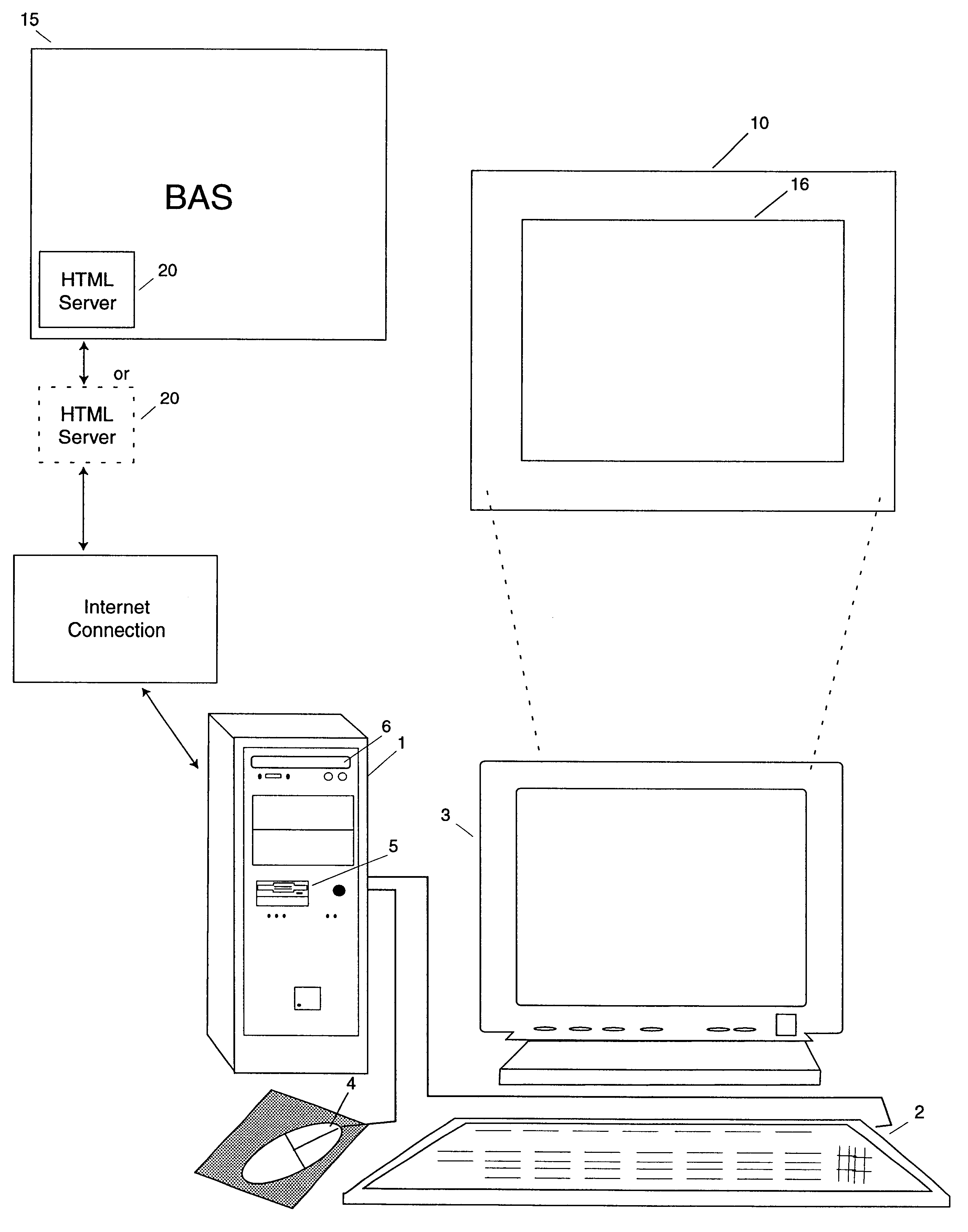
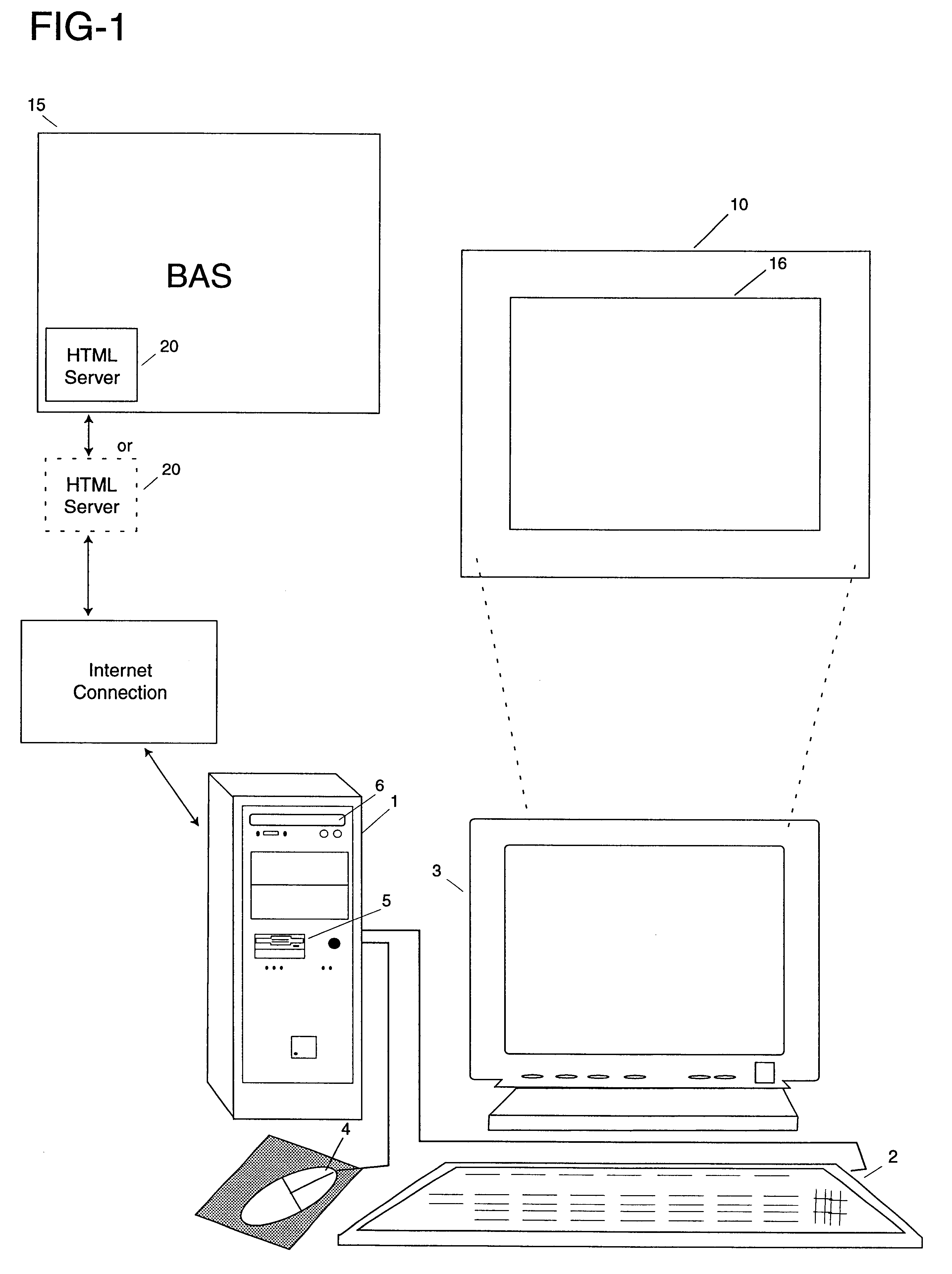
System for management of building automation systems through an HTML client program
Bi-directional communications via TCP ("Transmission Control Protocol") / IP ("Internet Protocol") between an HTML client program (i.e. "web browser") and the linked or embedded HTML server ("Hypertext Markup Language") of a Building Automation System ("BAS") are used to provide an authorized user with access to the interactive graphical panels of the BAS allowing the user to, for instance, monitor, control, configure and interact with the BAS or multiple BAS's.
Owner:TRIATEK HLDG
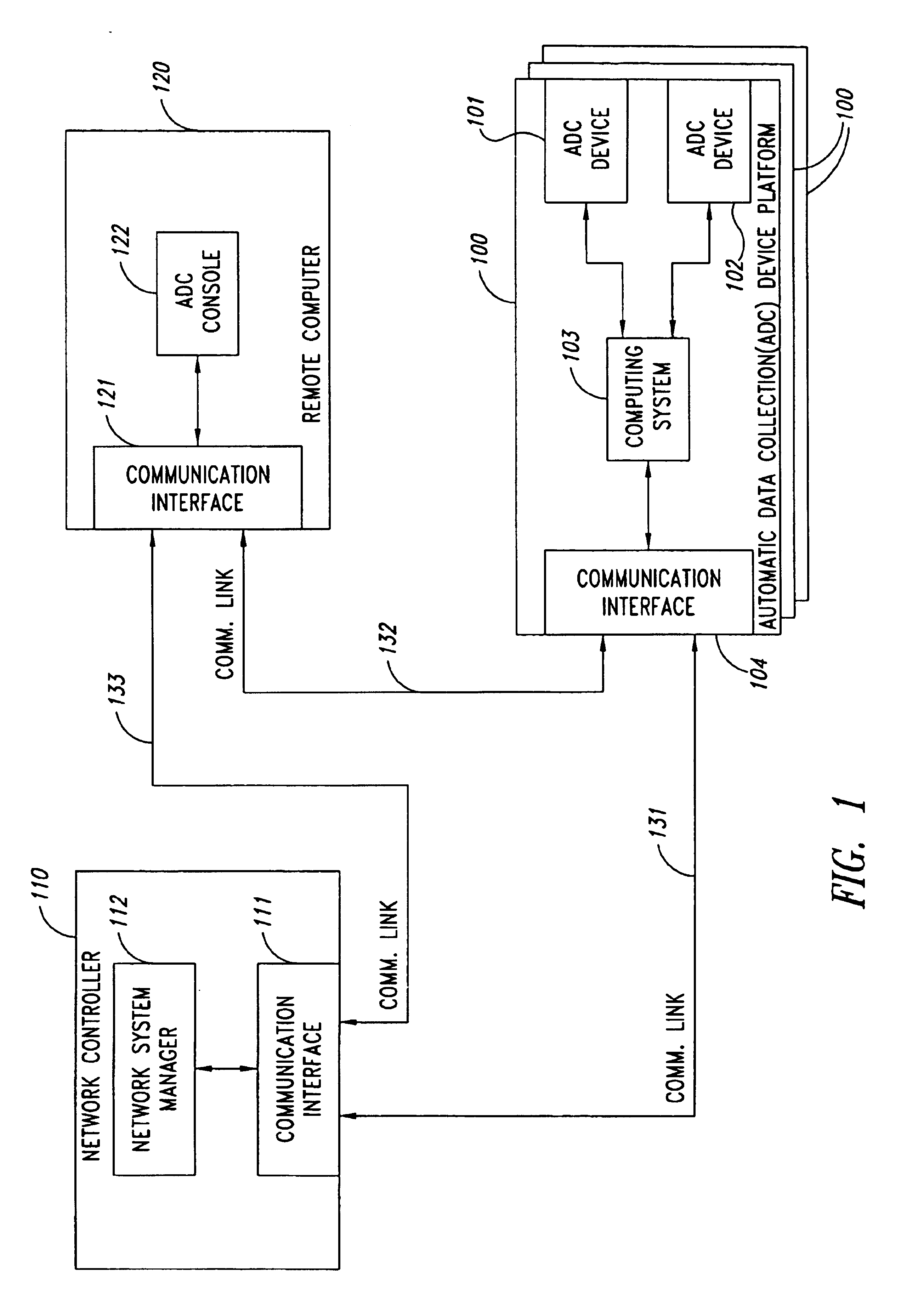
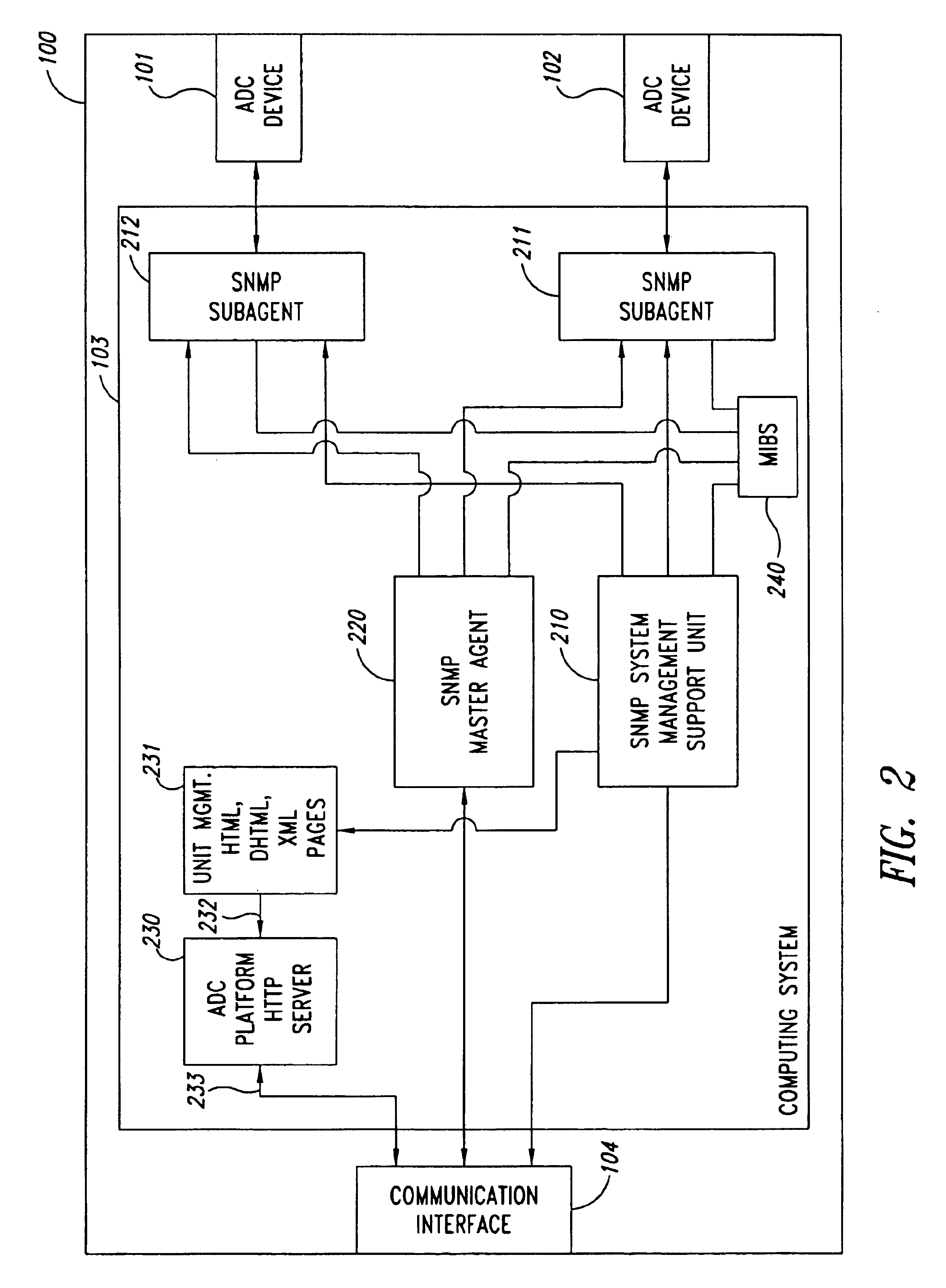
Remote anomaly diagnosis and reconfiguration of an automatic data collection device platform over a telecommunications network
InactiveUS6857013B2Detecting faulty hardware by remote testDigital computer detailsTelecommunications linkExtensible markup
Owner:INTERMEC IP CORP
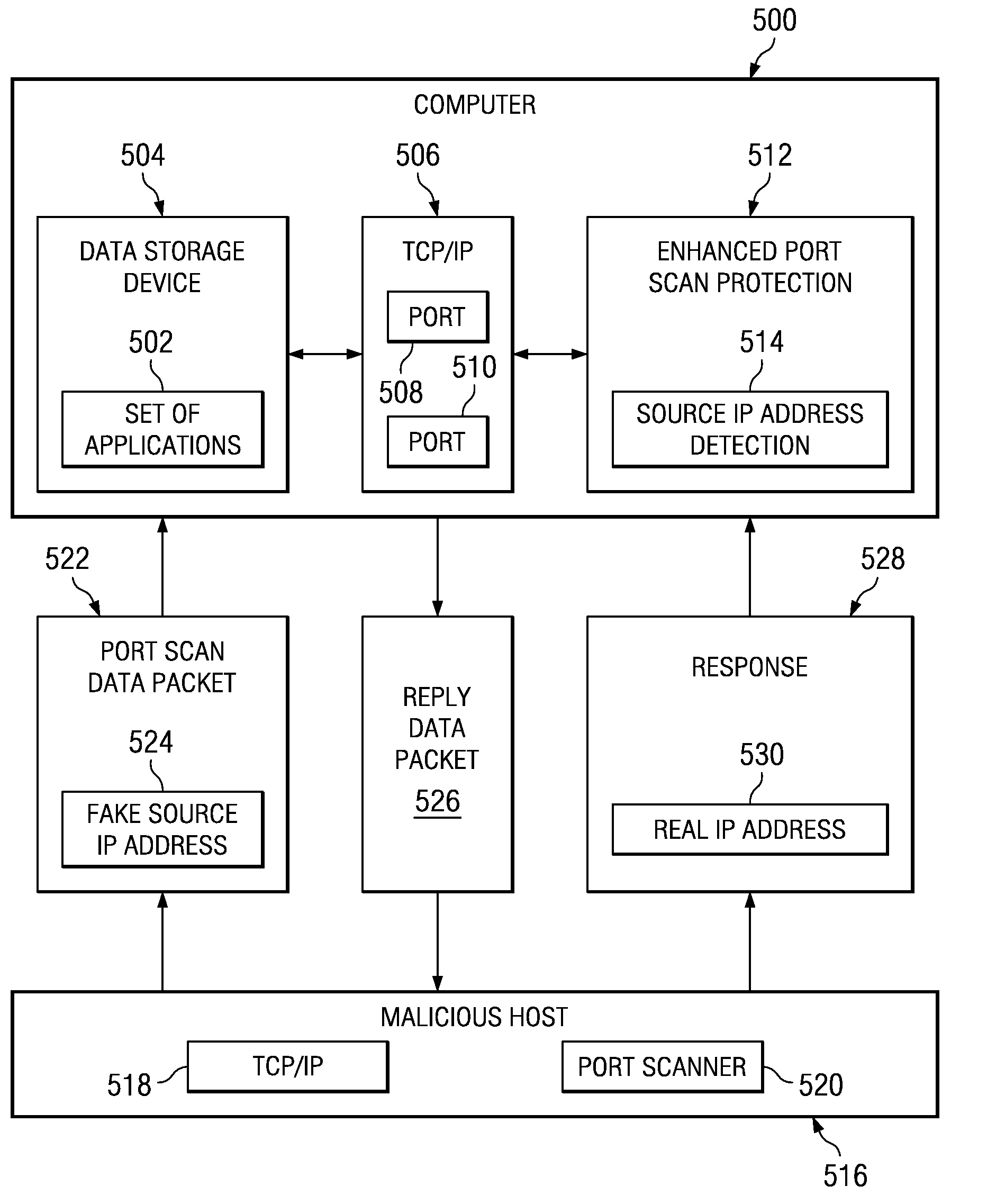
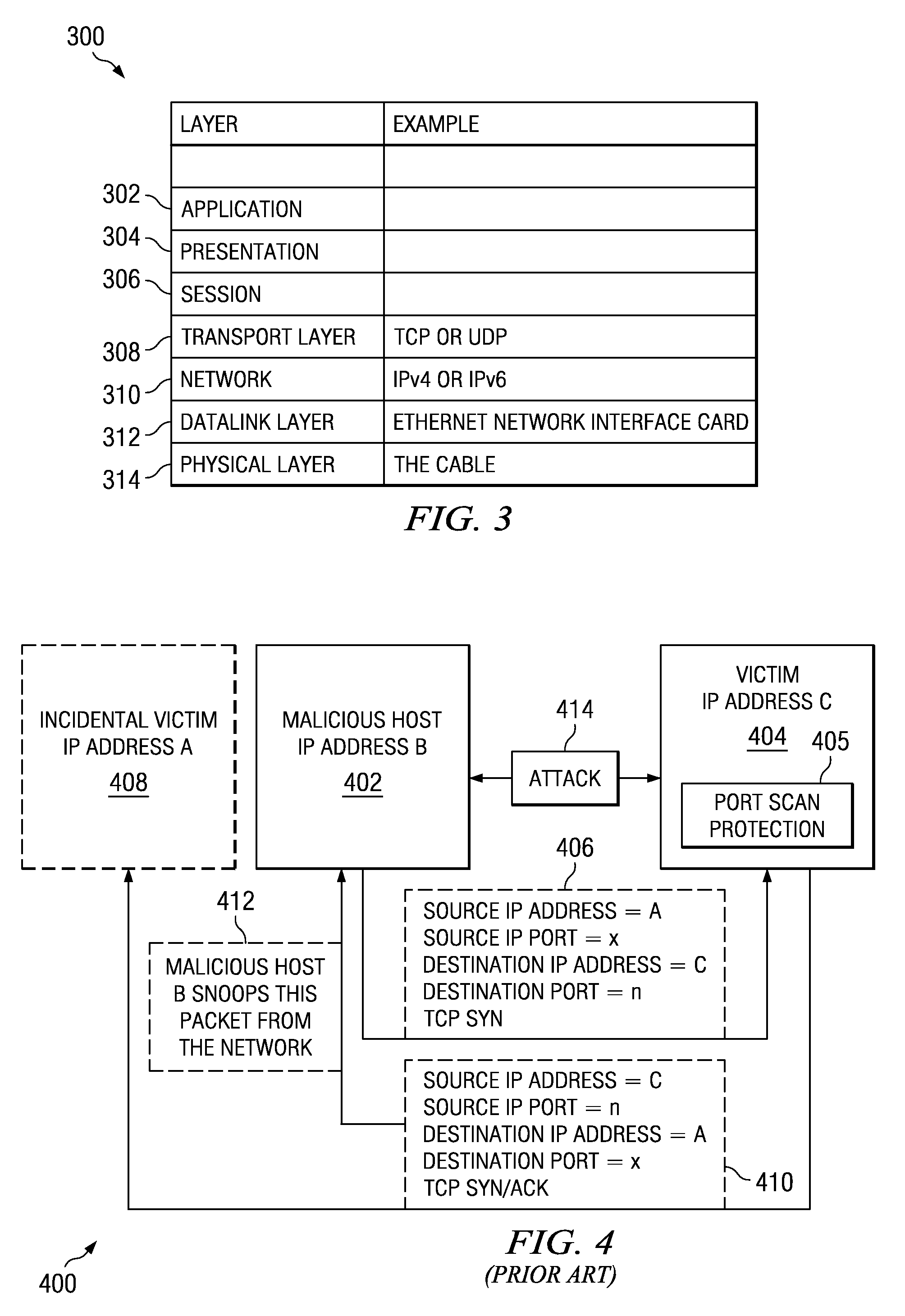
Method and apparatus for detecting port scans with fake source address
Owner:INT BUSINESS MASCH CORP
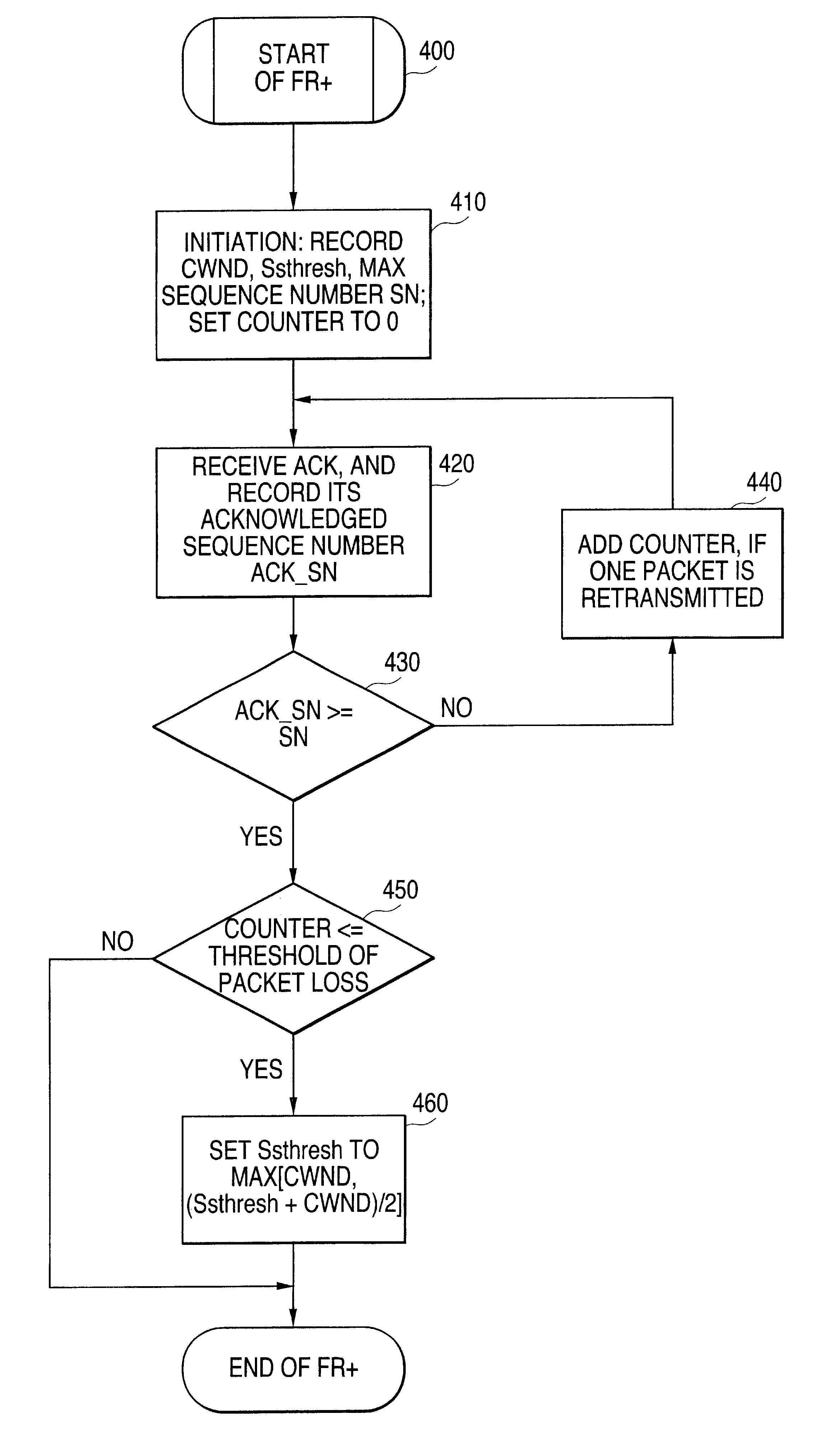
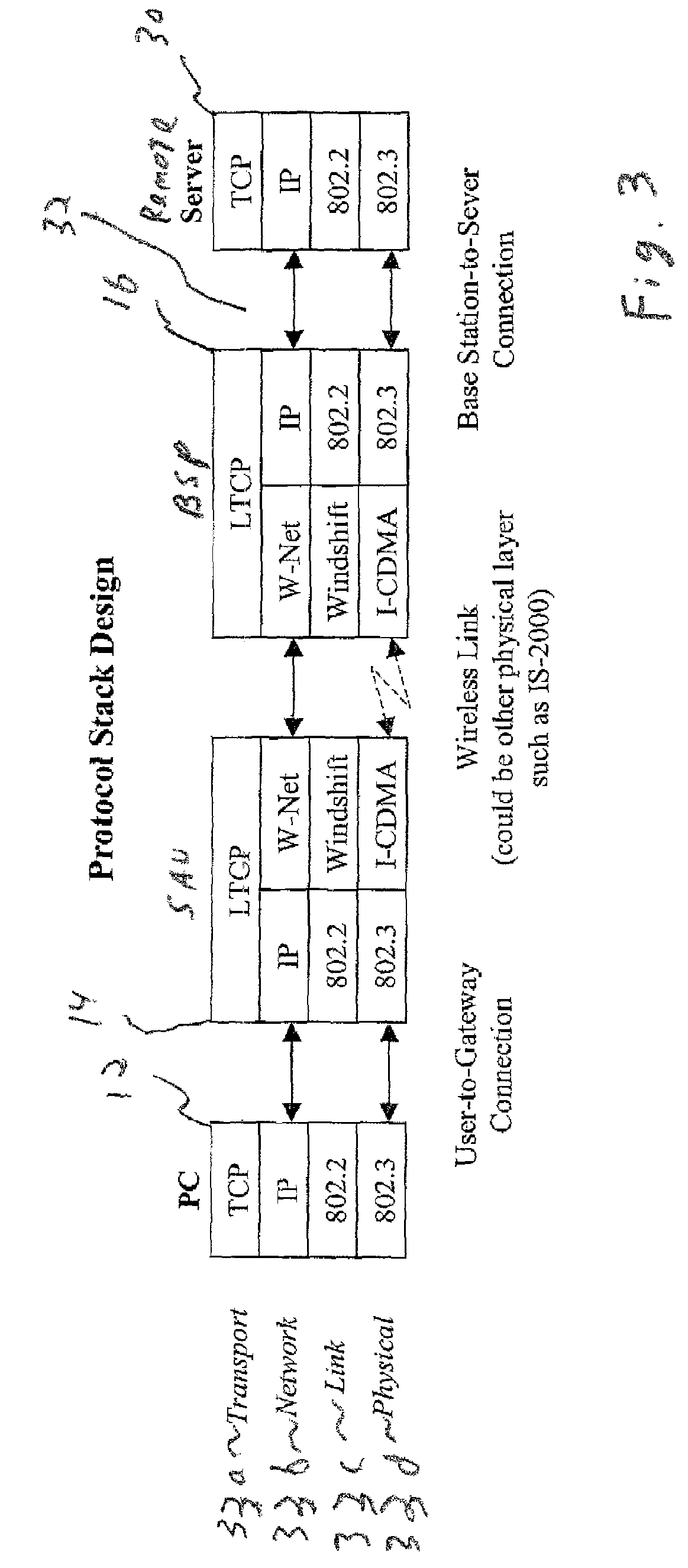
Performance enhancement of transmission control protocol (TCP) for wireless network applications
InactiveUS6757248B1Error prevention/detection by using return channelNetwork traffic/resource managementPerformance enhancementData stream
A new Fast Recovery Plus (FR+) mechanism, and associated method, for wireless and / or mobile network applications to control data flow and avoid network congestion in a TCP / IP packet-switched network.
Owner:NOKIA INTERNET COMM
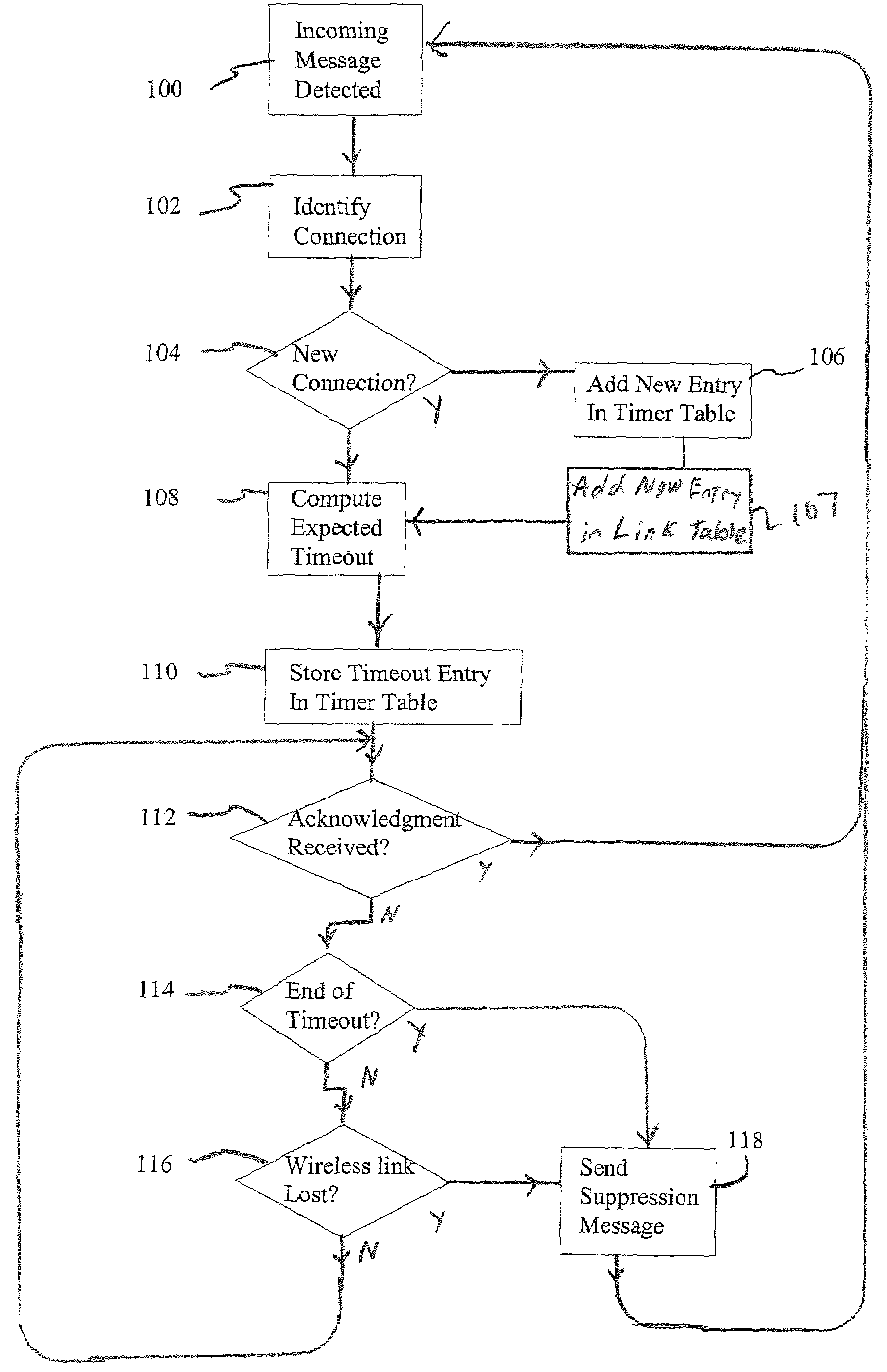
Link-aware transmission control protocol
InactiveUS7184401B2Reduction in message throughput caused by congestion control mechanisms is avoidedAvoid controlError prevention/detection by using return channelFrequency-division multiplex detailsSlow-startBiological activation
In a TCP / IP network, congestion control techniques such as slow start and congestion avoidance are employed. Such networks include wired and wireless links. However, normal operation of the wireless links exhibit different latencies than those exhibited over the wired link. The protocols employed in the wired network do not lend themselves well to efficient communication over wireless connections, and can cause slow start to be triggered. Determining when a sender will timeout due to non-receipt of an ACK, and intervening with a suppression message having an advertised window of zero to pause the user, are employed to prevent congestion control mechanisms such as slow start and congestion avoidance from activation
Owner:IPR LICENSING INC
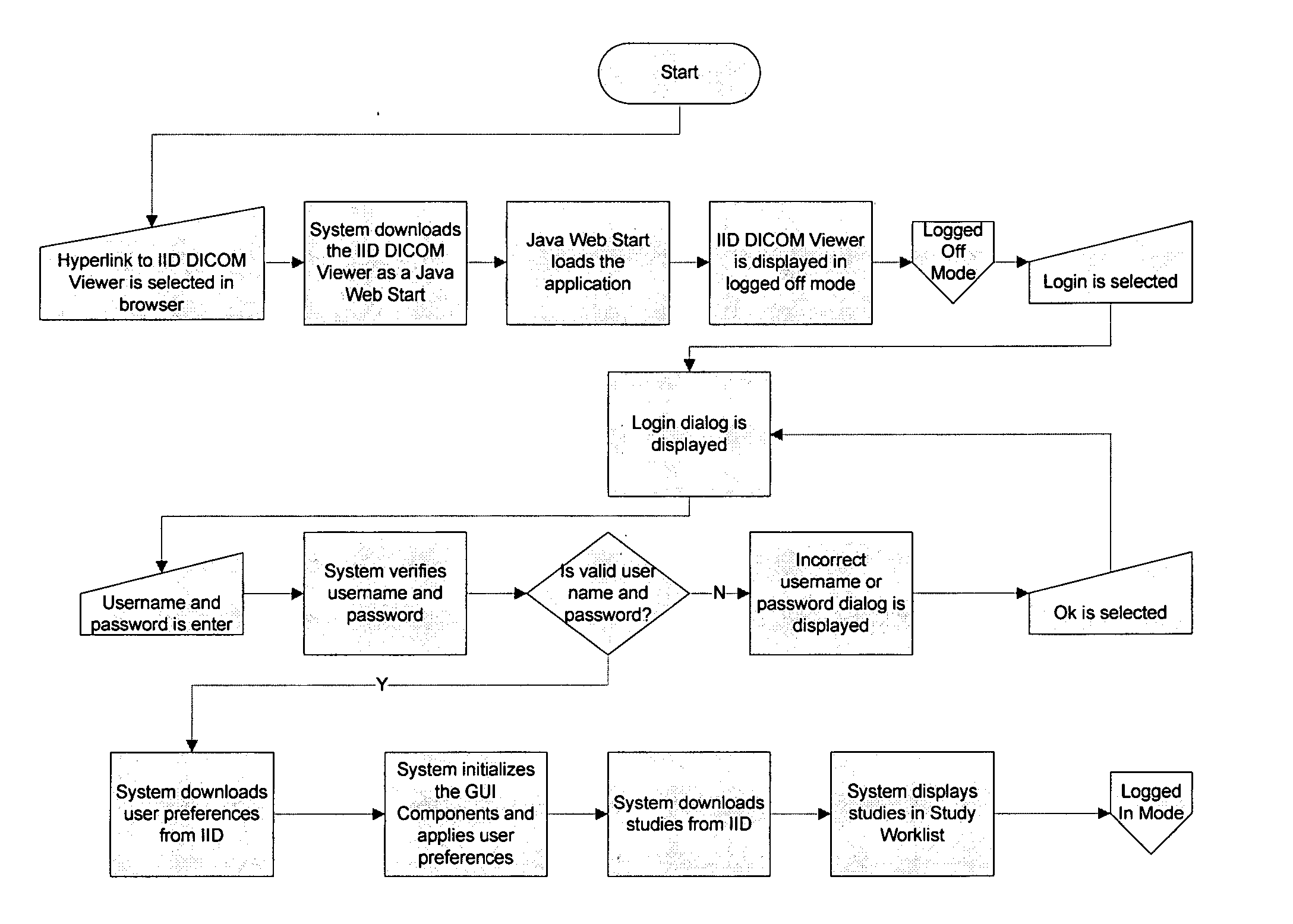
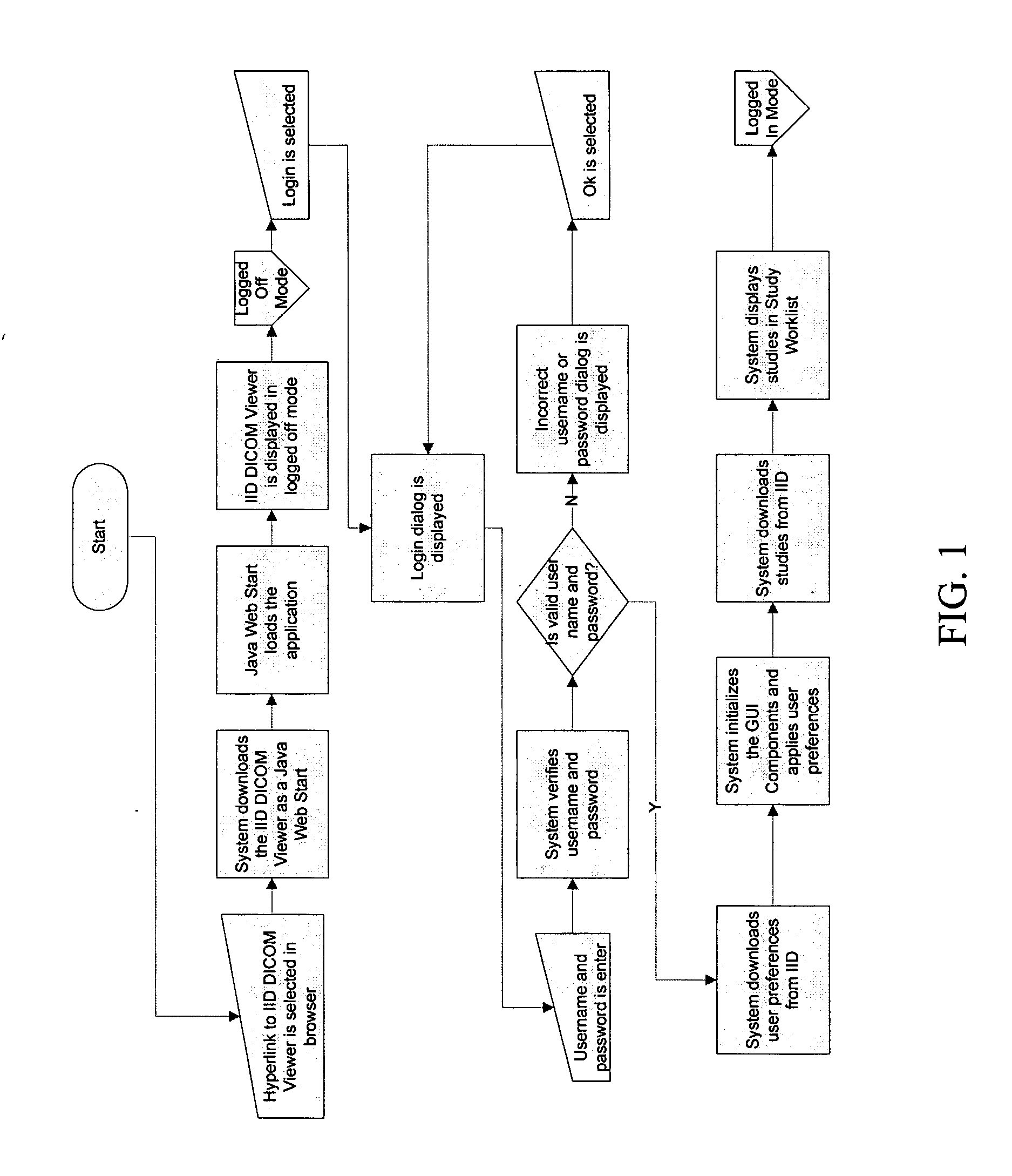
Methods and systems for providing data across a network
InactiveUS20060168338A1Digital data information retrievalDigital computer detailsDICOMRadiology studies
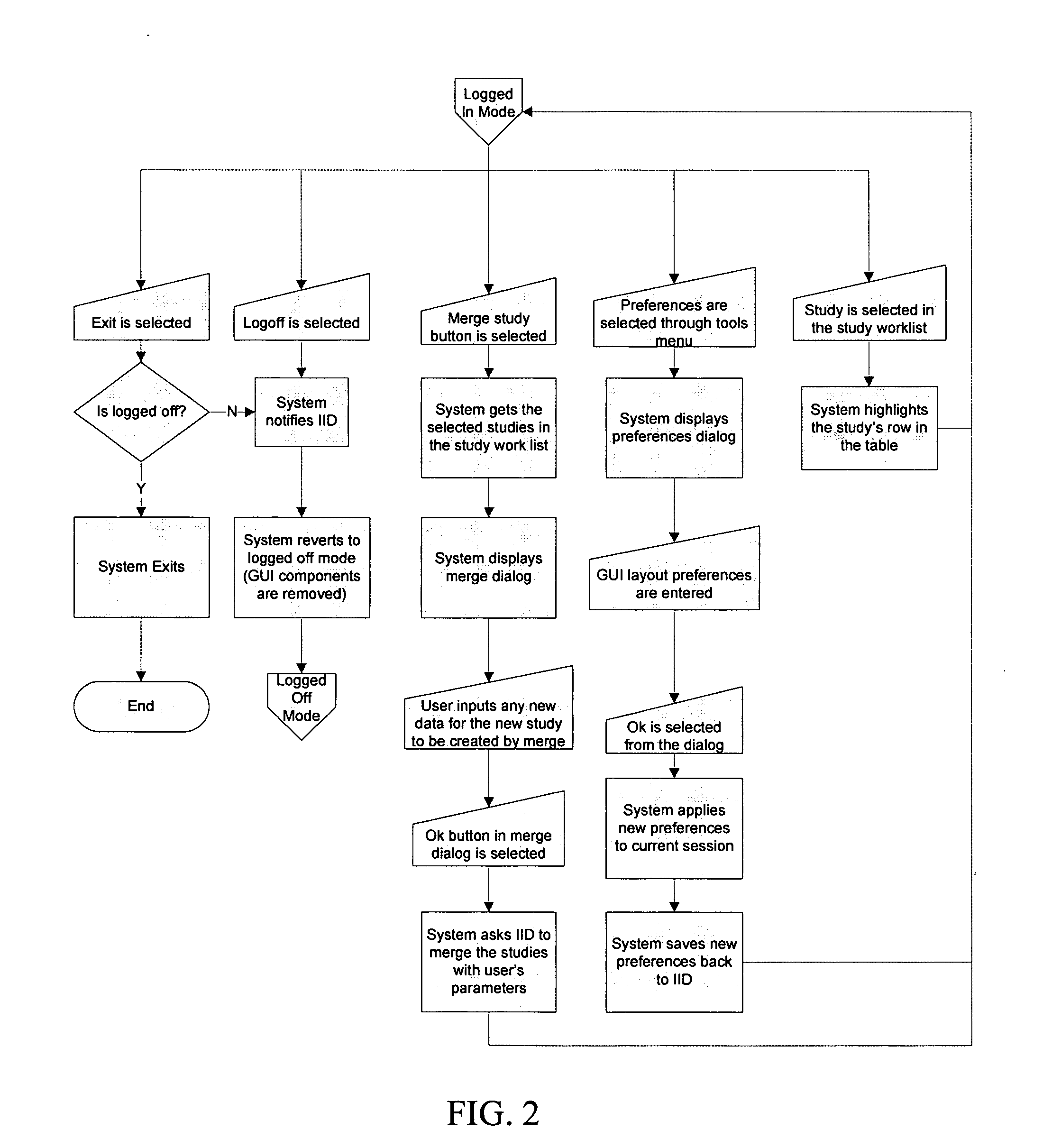
The present invention comprises systems, methods, and means for sending data across a network. Intelligent Image Distributions (IID) systems and methods are also disclosed. Systems, methods, and means for a HawkNet, a transmission control protocol, are likewise disclosed. A description of such systems handling DICOM radiology studies is presented along with a complete system for handling such studies.
Owner:NIGHTHAWK RADIOLOGY SERVICES
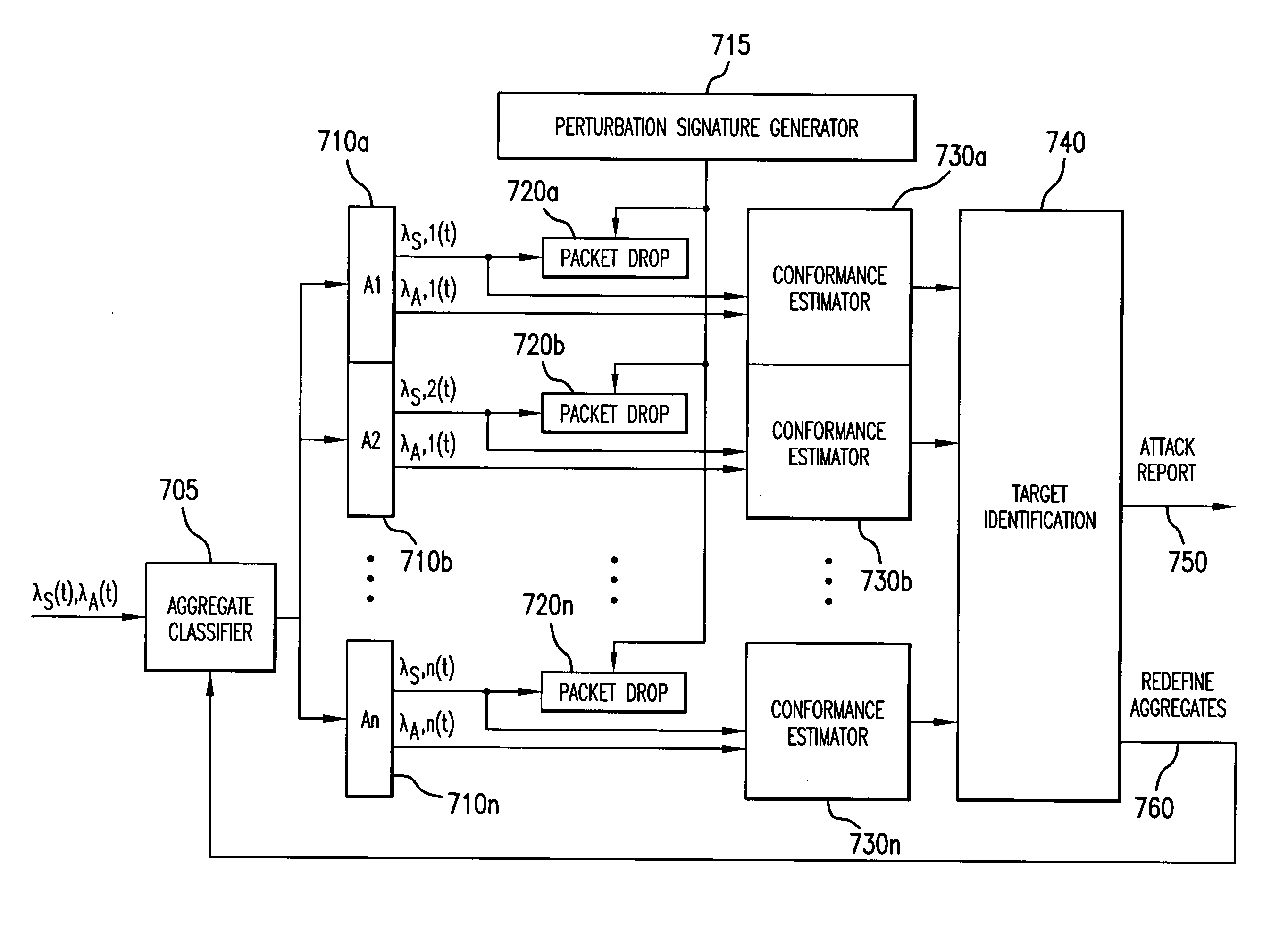
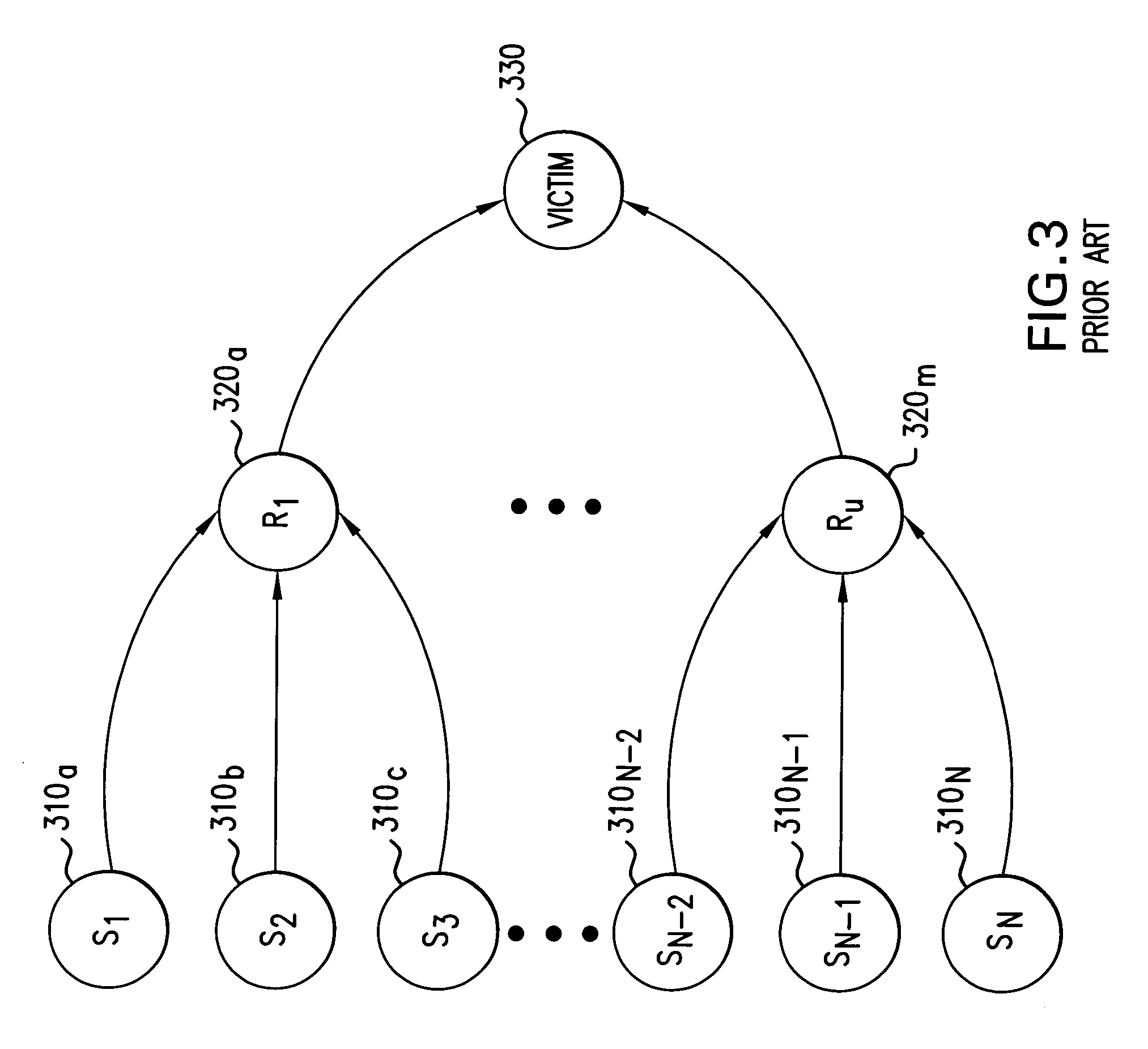
Detection of nonconforming network traffic flow aggregates for mitigating distributed denial of service attacks
An estimate of a portion of network traffic that is nonconforming to a communication transmission control protocol is used to signal that a distributed denial of service attack may be occurring. Traffic flows are aggregated and packets are intentionally dropped from the flow aggregate in accordance with an assigned perturbation signature. The flow aggregates are observed to determine if the rate of arrival of packets that have a one-to-one transmission correspondence with the dropped packets are similarly responsive to the perturbation signature. By assigning orthogonal perturbation signatures to different routers, multiple routers may perform the test on the aggregate and the results of the test will be correctly ascertained at each router. Nonconforming aggregates may be redefined to finer granularity to determine the node on the network that is under attack, which may then take mitigating action.
Owner:MARYLAND UNIV OF
Method and apparatus for improved data transmission
InactiveUS20070115814A1Bandwidth bottleneckMaximize qualityEnergy efficient ICTError prevention/detection by using return channelCombined usePublic network
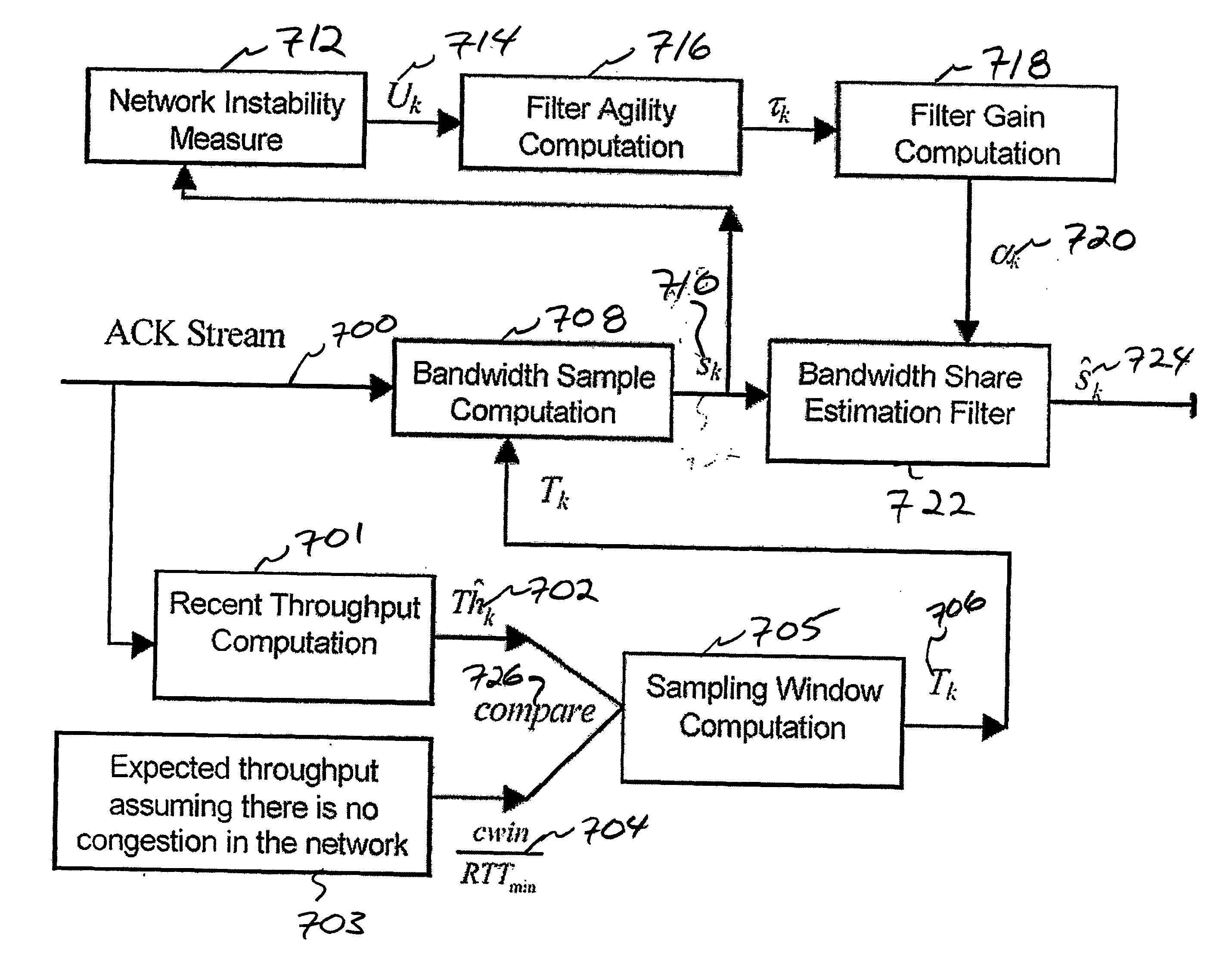
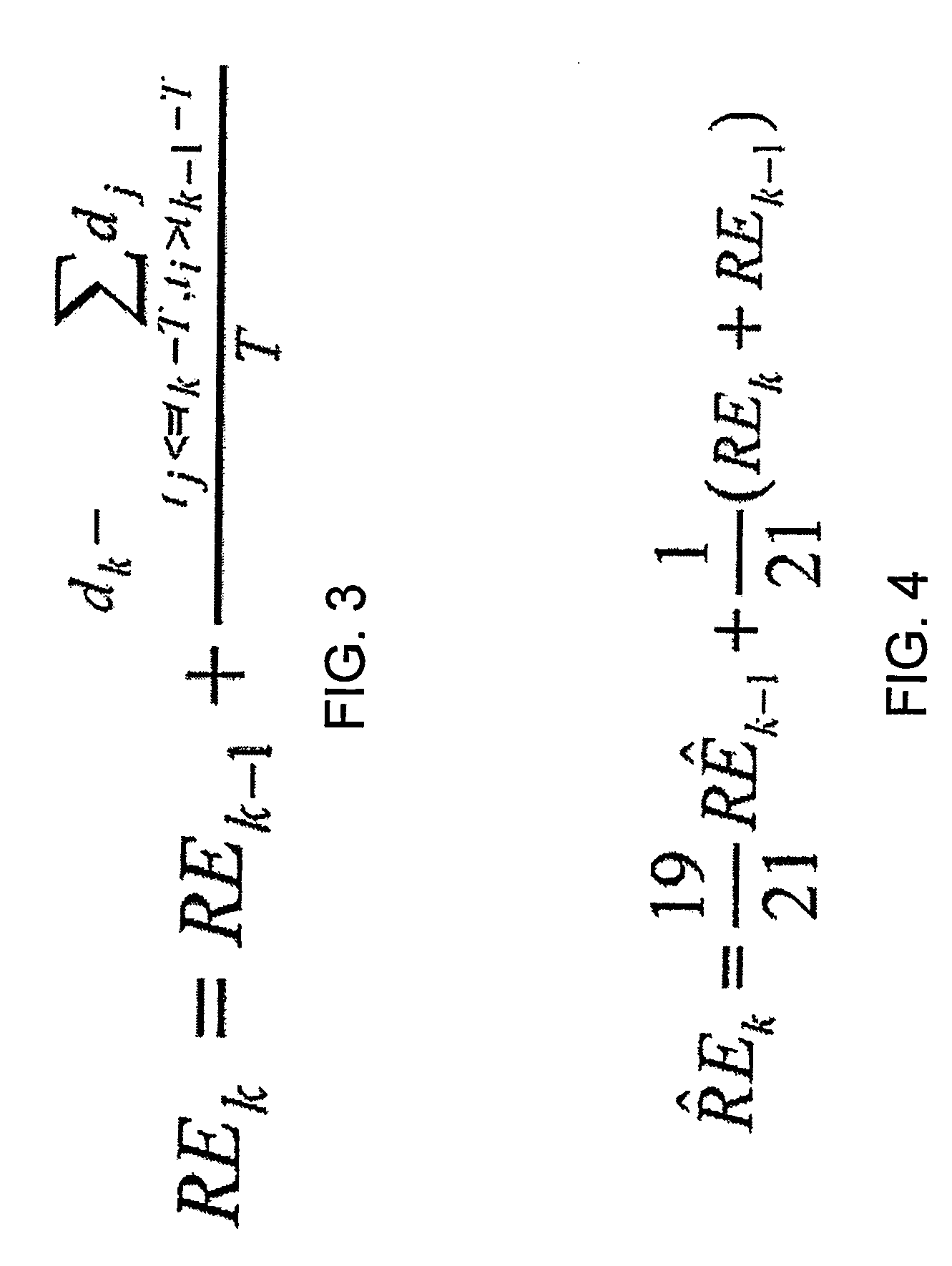
Methods and apparatuses for improved data transmission control protocols. Acknowledgment streams are used by a sender process to generate various estimates of eligible transmission rates that are fair to other processes competing for bandwidth across a common network. In addition, the acknowledgment streams are used in conjunction with various other standard transmission control protocol metrics to adapt a filter for use on the rate estimates. Additional improvements in throughput may no be had by measuring the overall capacity of the computer network using packet pair dispersion measurements and adaptive network probing. In addition, the methods may be adapted for both packet transmission and video streaming applications.
Owner:RGT UNIV OF CALIFORNIA
System and method for home automation using wireless control rf remocon module based on network
InactiveUS20060168618A1Reliable controlAppropriate performanceTelevision system detailsTelemetry/telecontrol selection arrangementsWireless controlRF module
Owner:CHOI DONG WOOK
Method and apparatus for class based transmission control of data connections based on real-time external feedback estimates obtained using messaging from a wireless network
InactiveUS6697378B1Network traffic/resource managementTime-division multiplexData connectionWireless mesh network
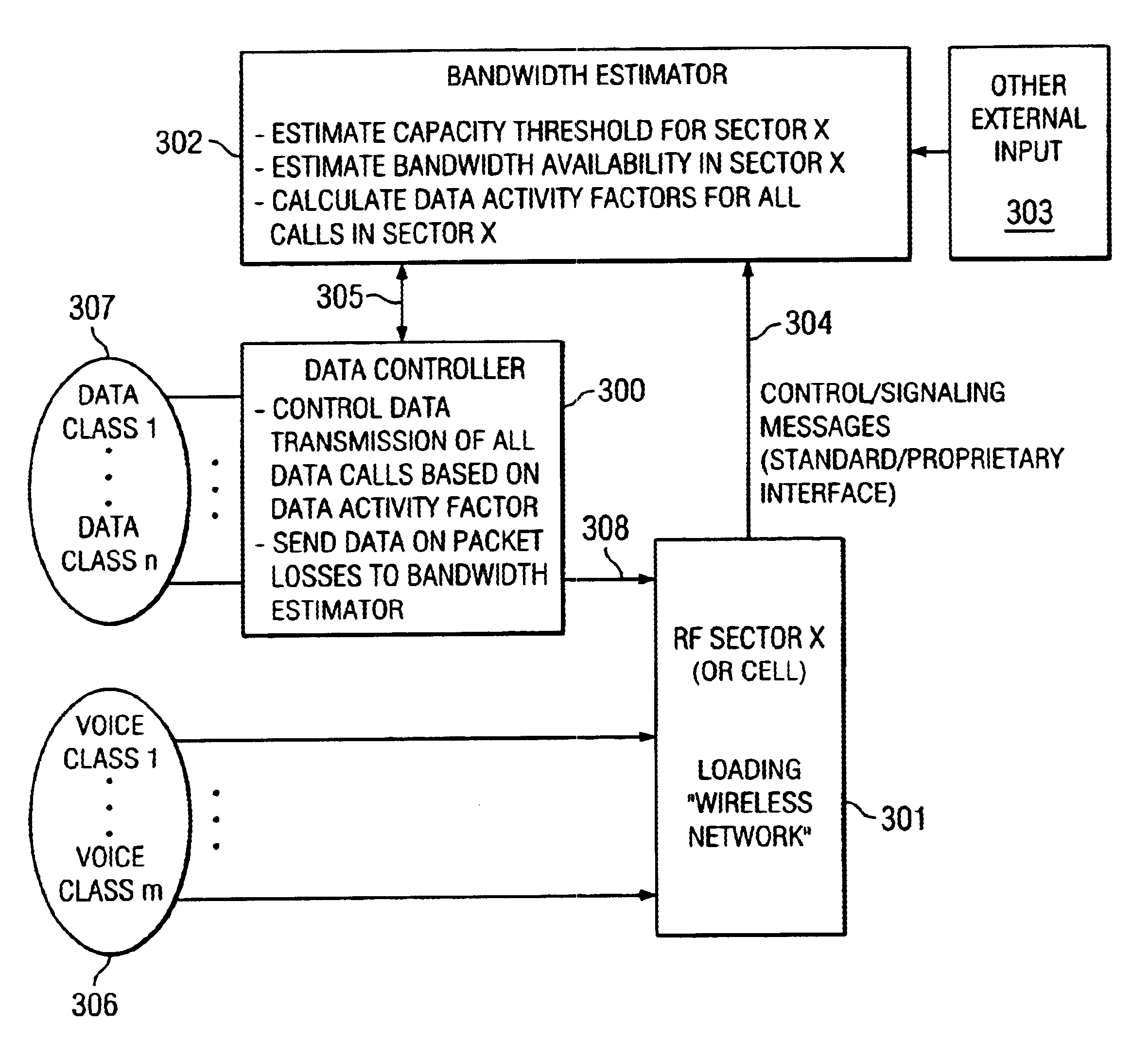
A system of wireless network with capabilities of transporting data packets, wherein the data transmission activity of each data connection is determined using the localized air interface capacity threshold and available bandwidth estimates obtained via the messages sent by the wireless network (FIG. 3). The system provides a unique and efficient way of providing control over data packet transmissions over a wireless network. The localized wireless network capacity threshold and available bandwidth estimates are obtained via use of empirical formulae and are improved upon via the use of messaging obtained from the wireless network by the Bandwidth Estimator (302) (FIG. 5 and 6). The data transmission activity factors of all data connections are determined by the Bandwidth Estimator using the localized capacity threshold and available bandwidth estimates, along with the priority / class of traffic of specific data calls (FIG. 7). The data transmission activity factors are implemented using the transmission window size update and local queuing by the Data Controller (300) (FIG. 8). Various implementations and interconnectivities of the Bandwidth Estimator and Data Controller functions are outlined (FIGS. 9-13).
Owner:CISCO TECH INC
Method and system for transmission control packet (TCP) segmentation offload
Certain aspects of the invention for packet segmentation and offload may comprise determining whether an identified packet is a large send offload packet (LSOP). If the identified packet is a LSOP, a selection may be made between a hardware process and a firmware process for handling the LSOP. The LSOP may then be processed by the selected hardware process or firmware process. At least a portion of protocol header information for a first segment of the LSOP may be stored and subsequently utilized for at least a header portion of a second segment of the LSOP. A payload corresponding to the second segment of the LSOP may be placed at a determined offset within a transmit buffer for the second segment. A header portion of the second segment may be updated based on at least a header portion of a previous segment.
Owner:AVAGO TECH INT SALES PTE LTD
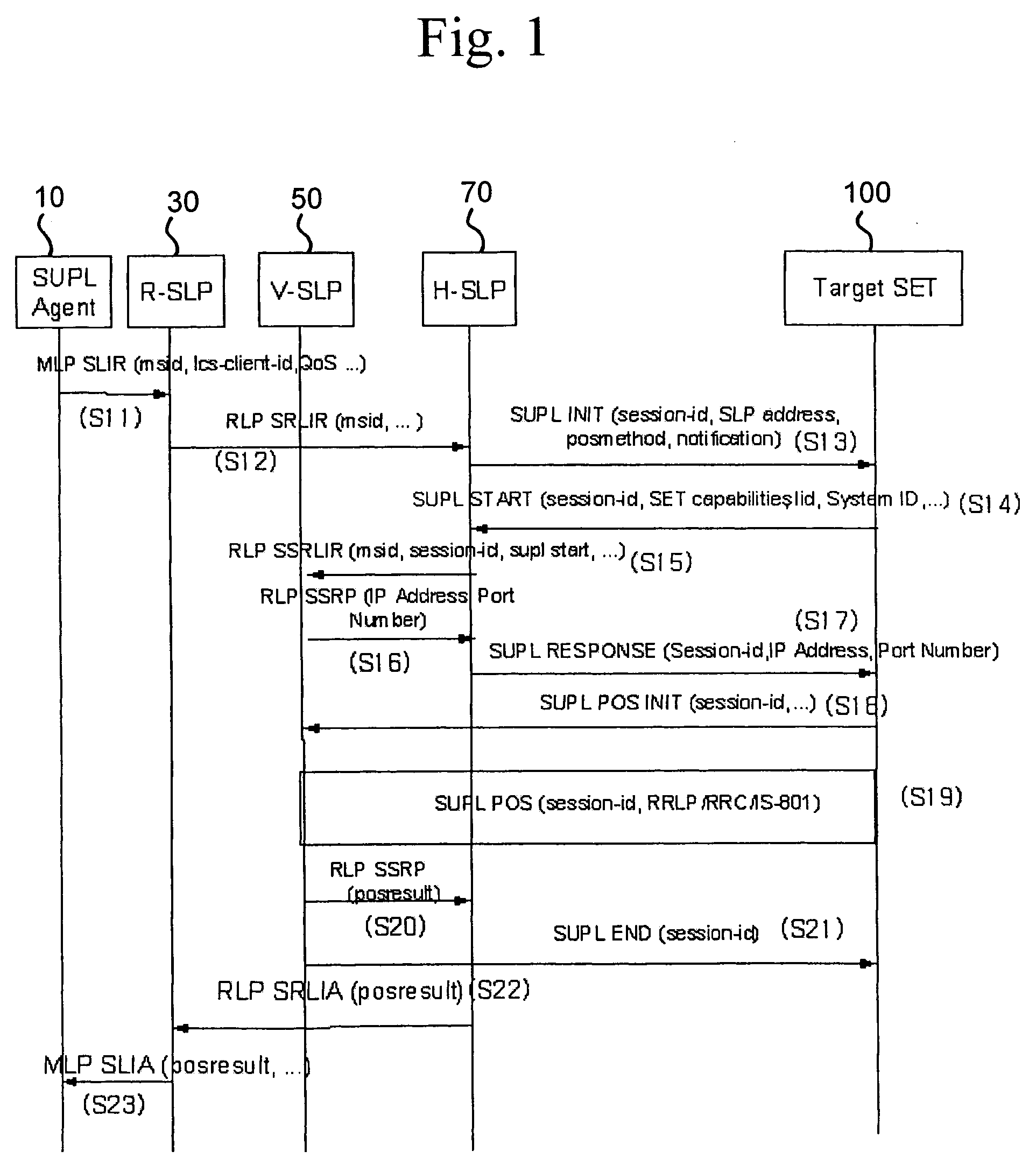
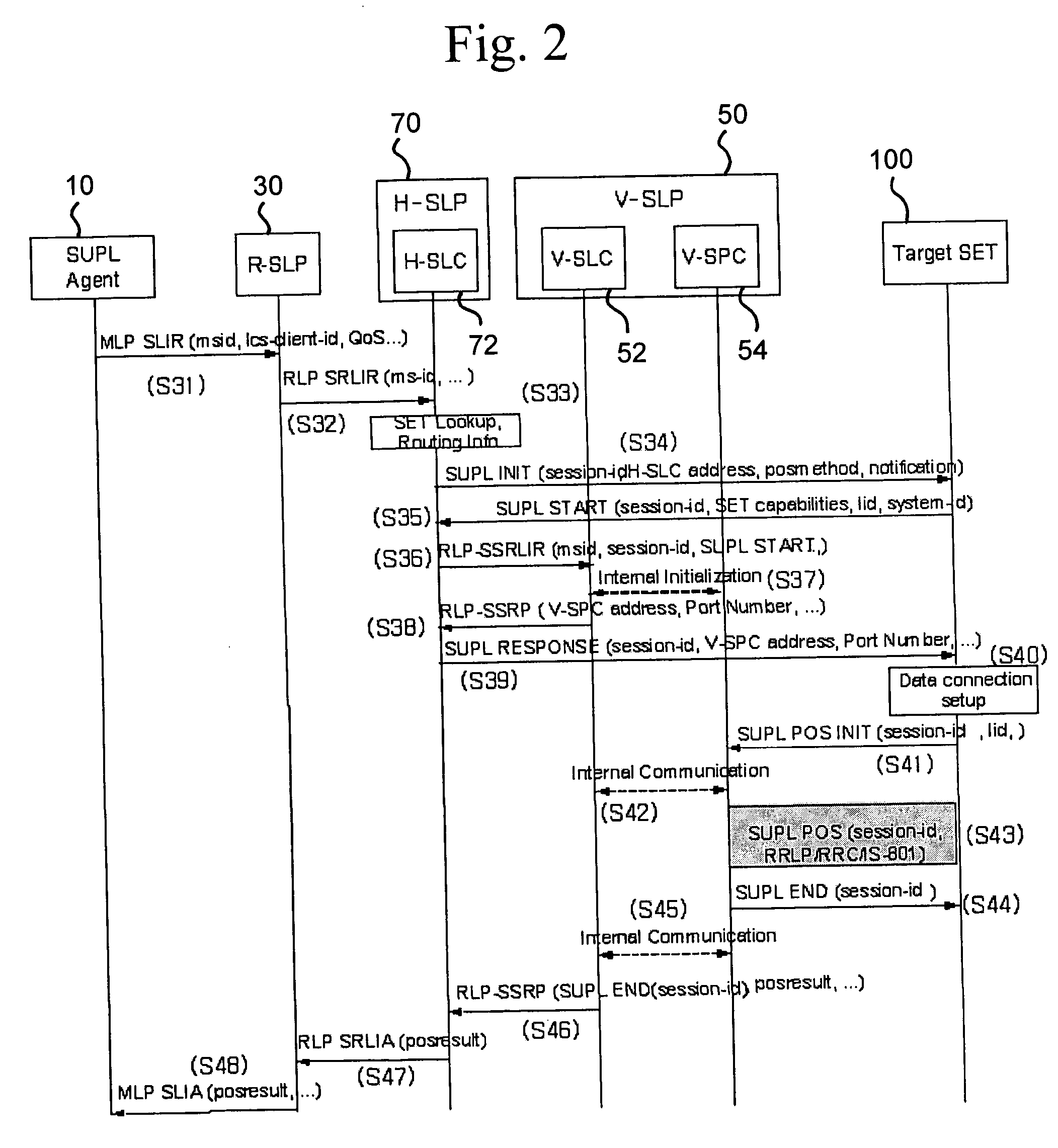
Roaming method and system in location information system
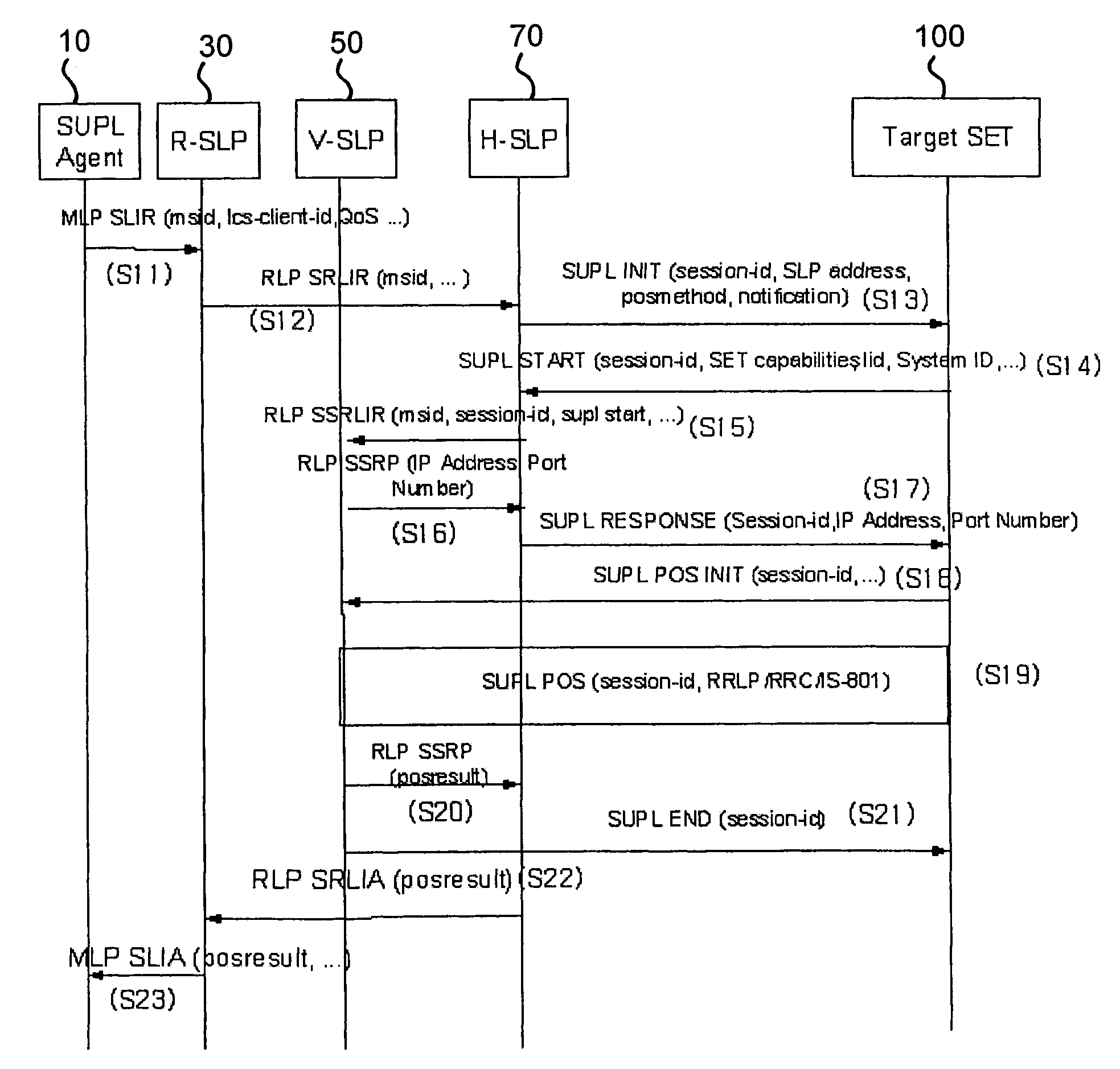
InactiveUS20060058042A1Reduce signaling burdenServices signallingConnection managementComputer networkSecure User Plane Location
A roaming method and system using a SUPL (Secure User Plane Location)-based location information system, are provided. According to an aspect of the present invention, the method can include the steps of establishing a transmission control protocol (TCP) connection between a target terminal and a visited network associated with the target terminal, if position information of the target terminal is requested; and obtaining, by the target terminal or a location server in the visited network, the position information of the target terminal, through the established TCP connection and without a TCP connection between the target terminal and a home network of the target terminal.
Owner:LG ELECTRONICS INC
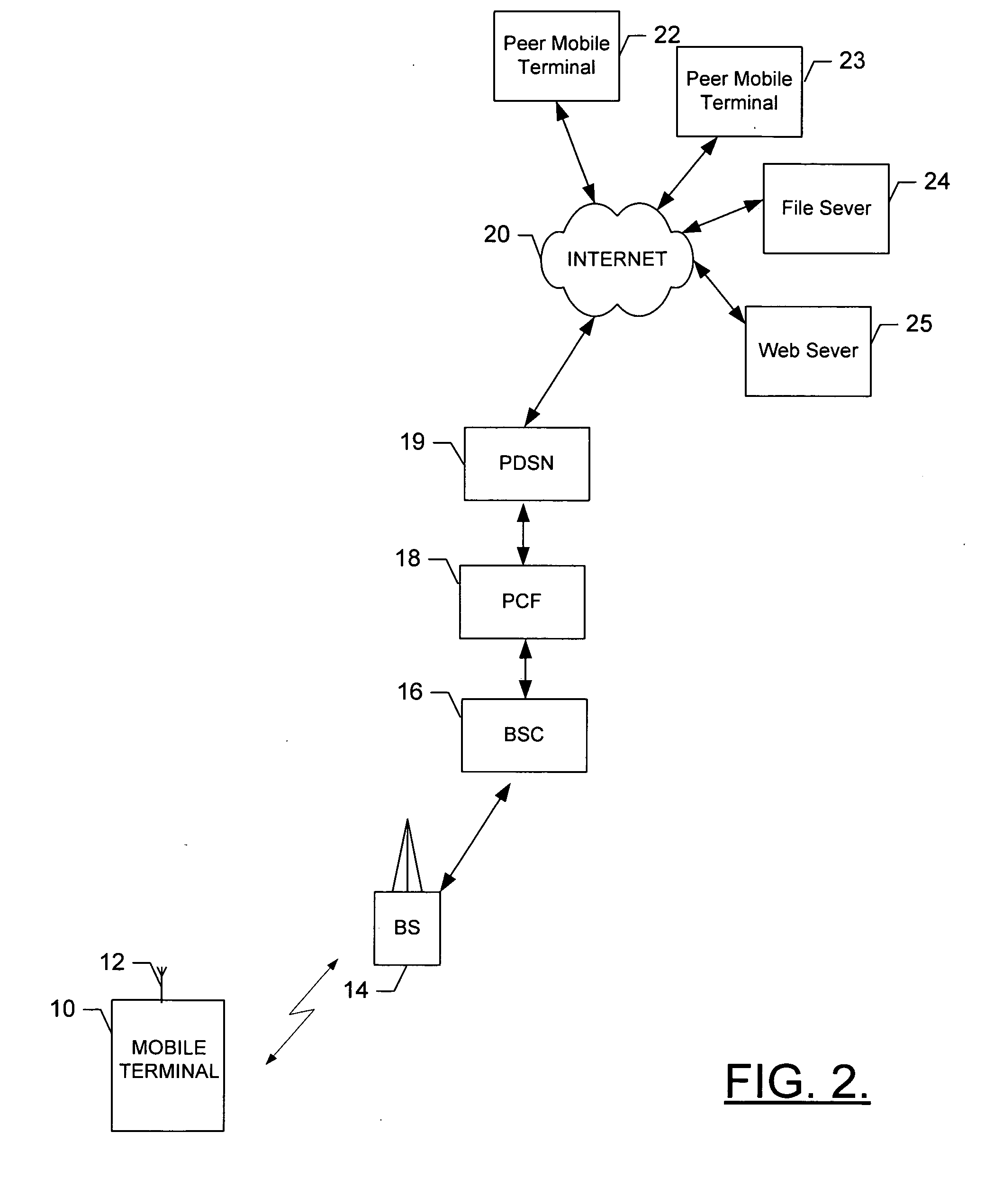
Transmission control protocol/internet protocol (TCP/IP) packet-centric wireless point to multi-point (PtMP) transmission system architecture
InactiveUS20050232193A1Special service provision for substationError detection/prevention using signal quality detectorQuality of serviceCode division multiple access
Owner:INTELLECTUAL VENTURES I LLC
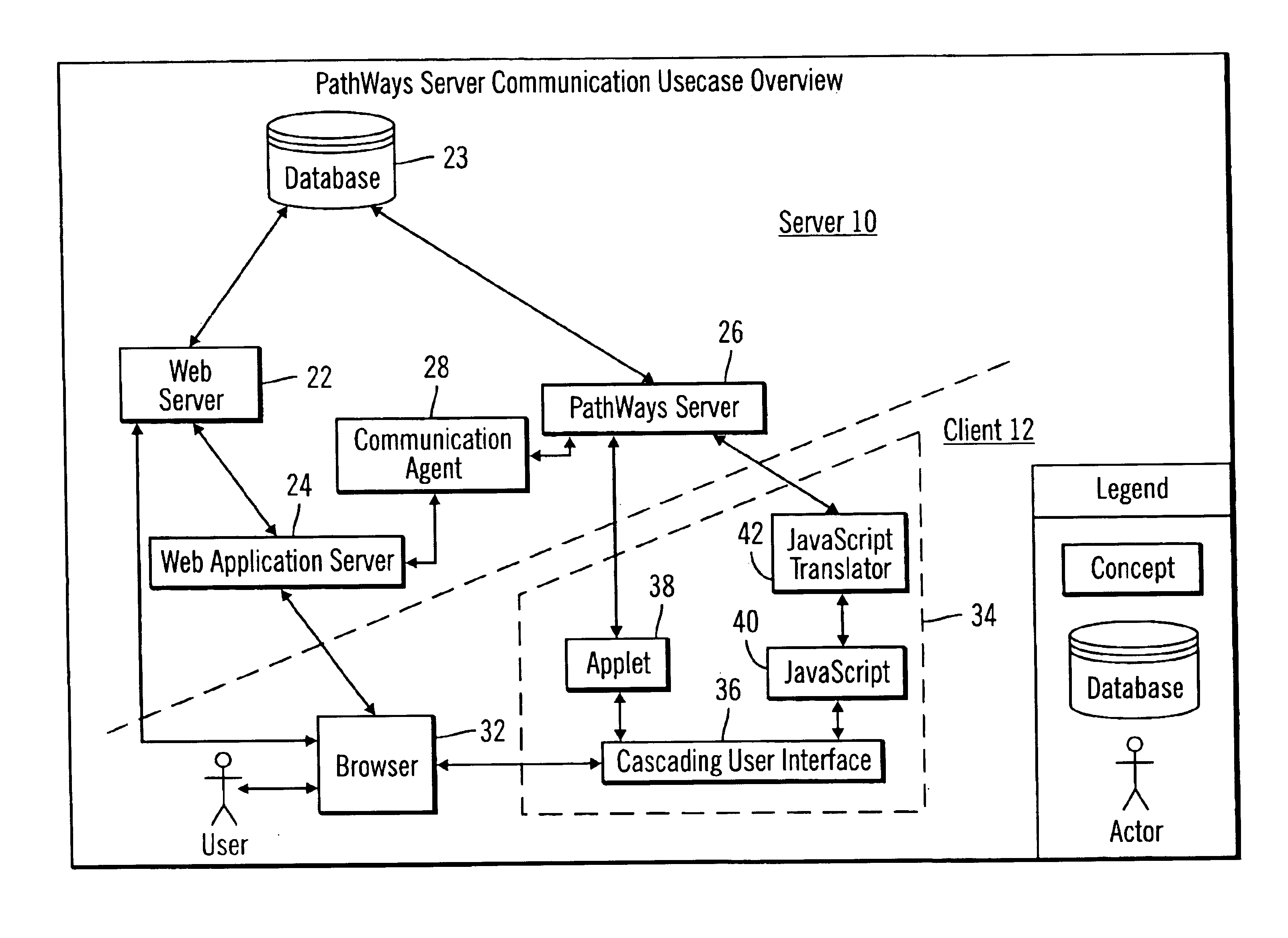
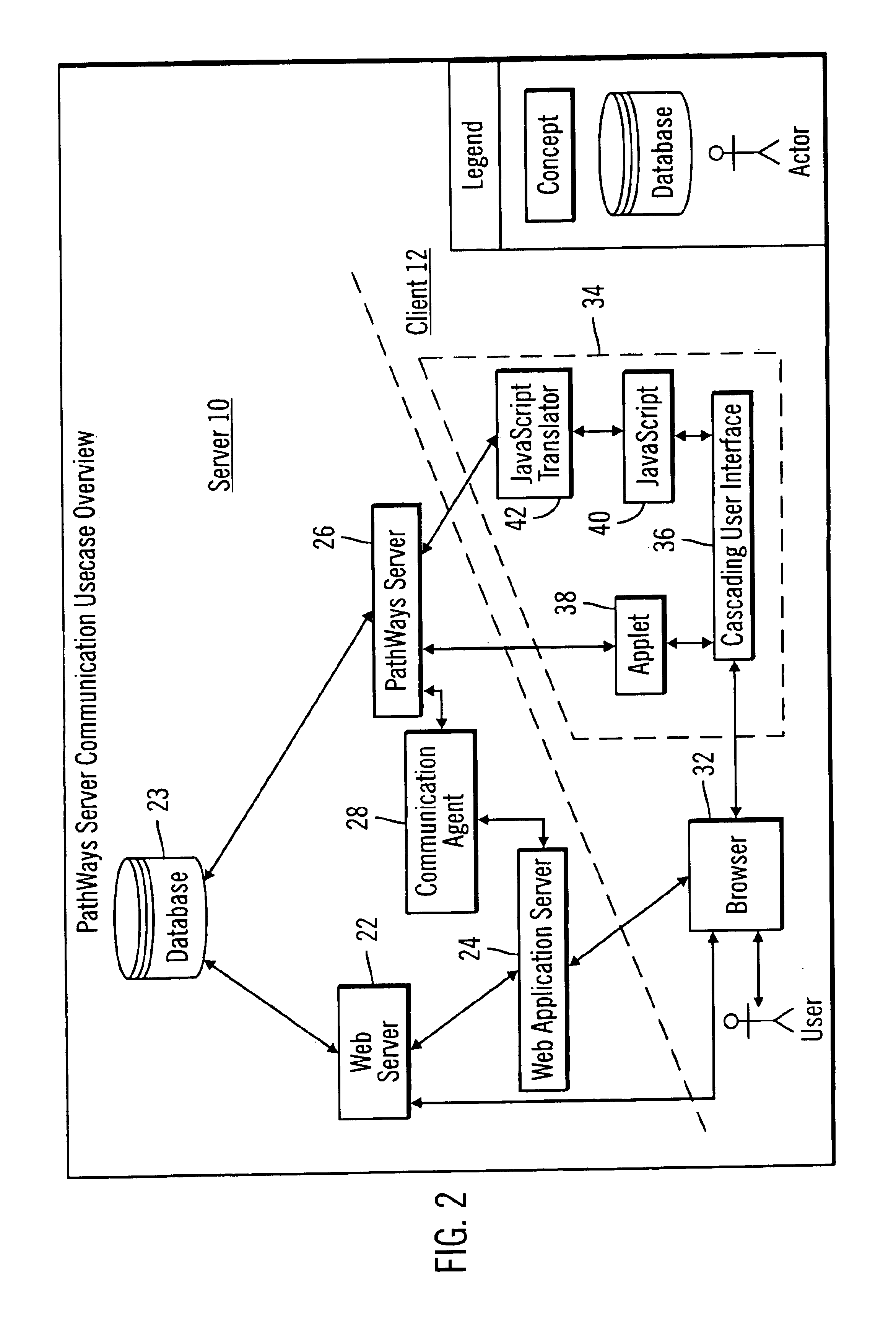
Web-based client/server communication channel with automated client-side channel endpoint feature detection and selection
A TCP / IP-based software application client / server communication channel construction mechanism is presented. The mechanism constructs a dedicated bi-directional data transmission for a single client / server session. The server software, running on a server host computer, provides session-based data services to one or more software clients. The client process supports one or more execution environments including: text-based scripting, Java or ActiveX components. The invoked code executing within the client computer detects the most attractive execution environment available within its execution environments, and uses the services of that execution environment client process to establish an optimal communication channel back to the server software process. Depending on the execution environment(s) available to the invoked code, the communication channel may be: (a) a content-independent, bi-directional transmission control protocol (TCP) connection, or (b) a content-dependent TCP connection, such as a TCP connection supporting only a single HTTP request / response pair.
Owner:PATH RELIABILITY
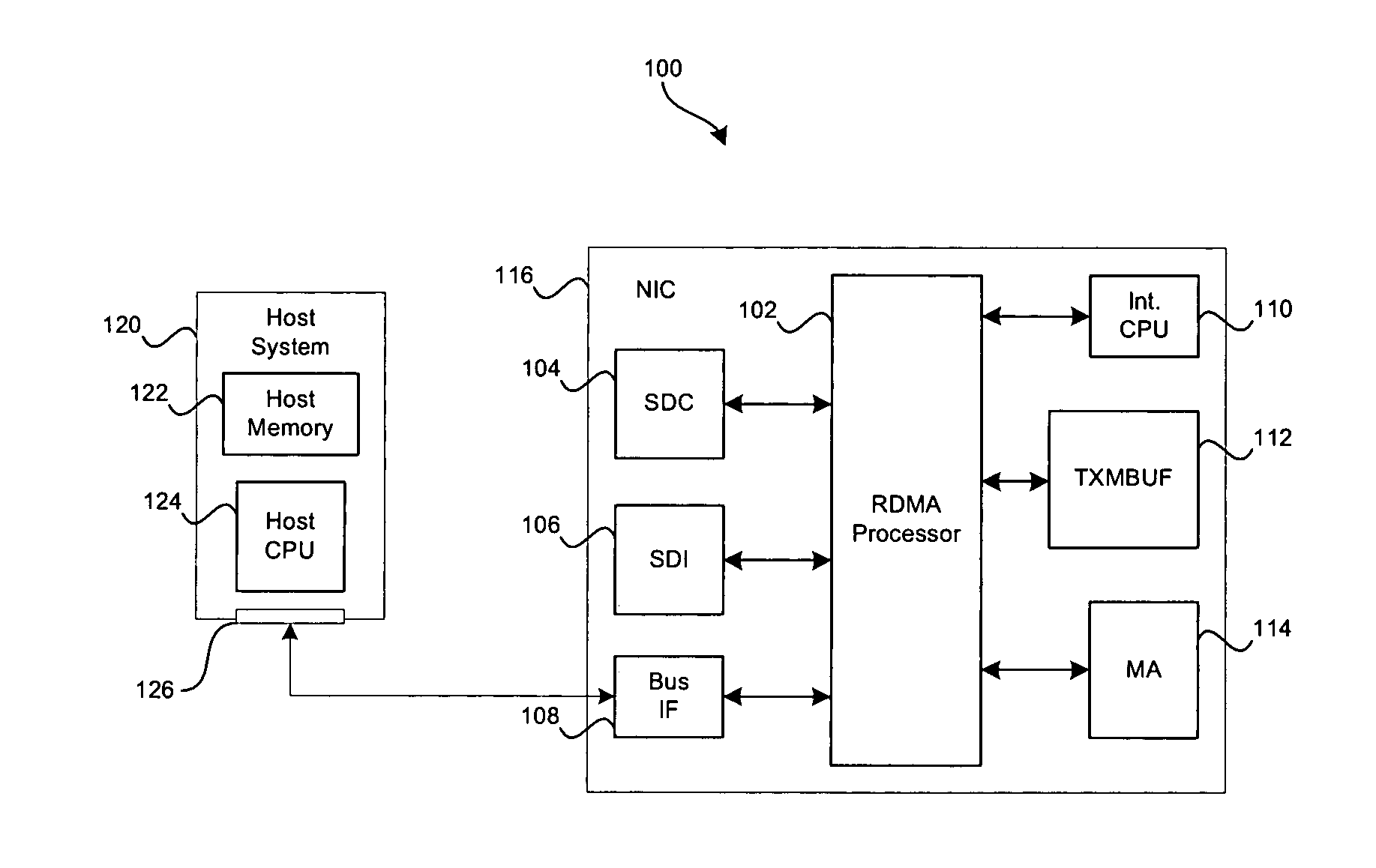
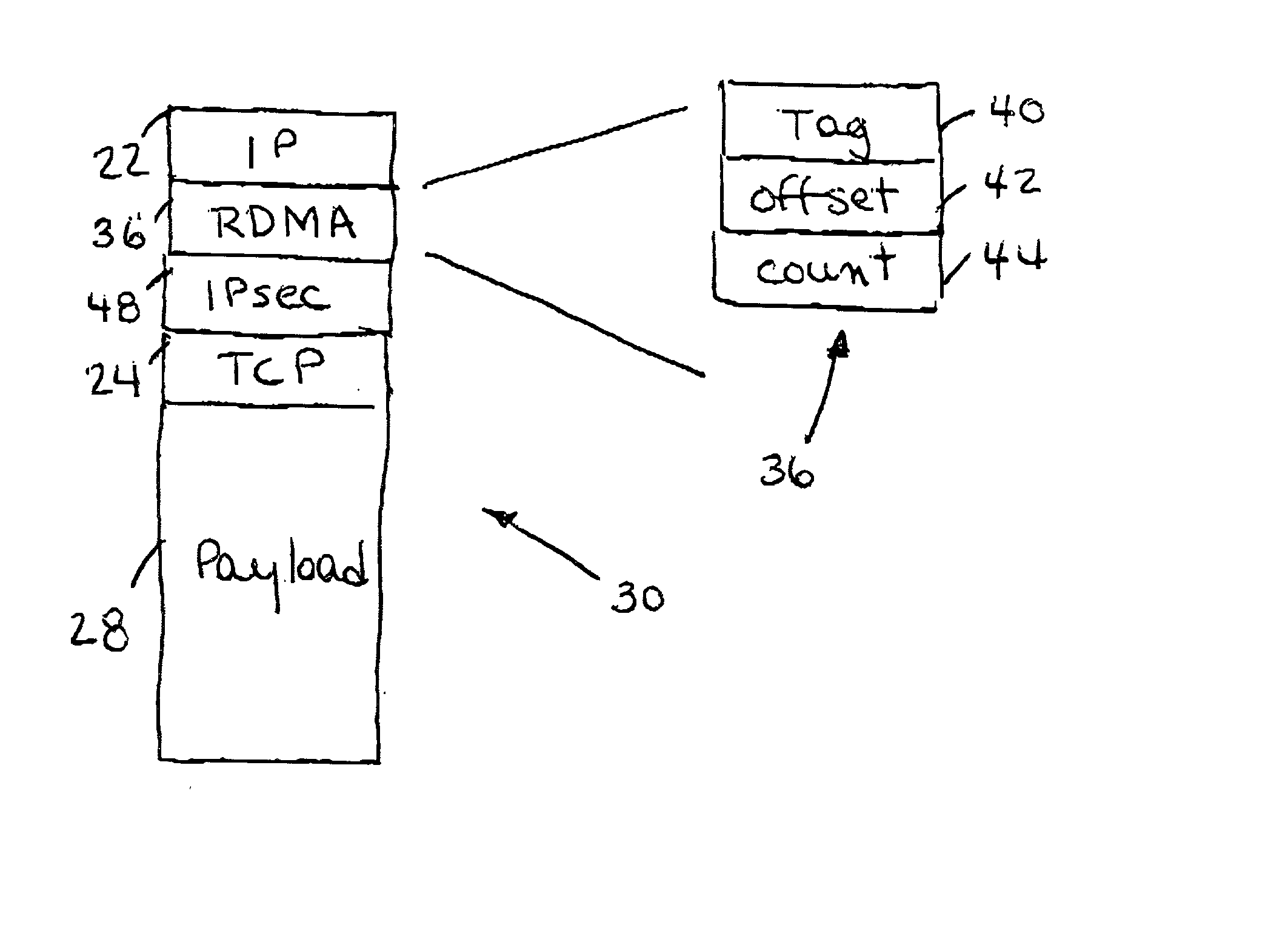
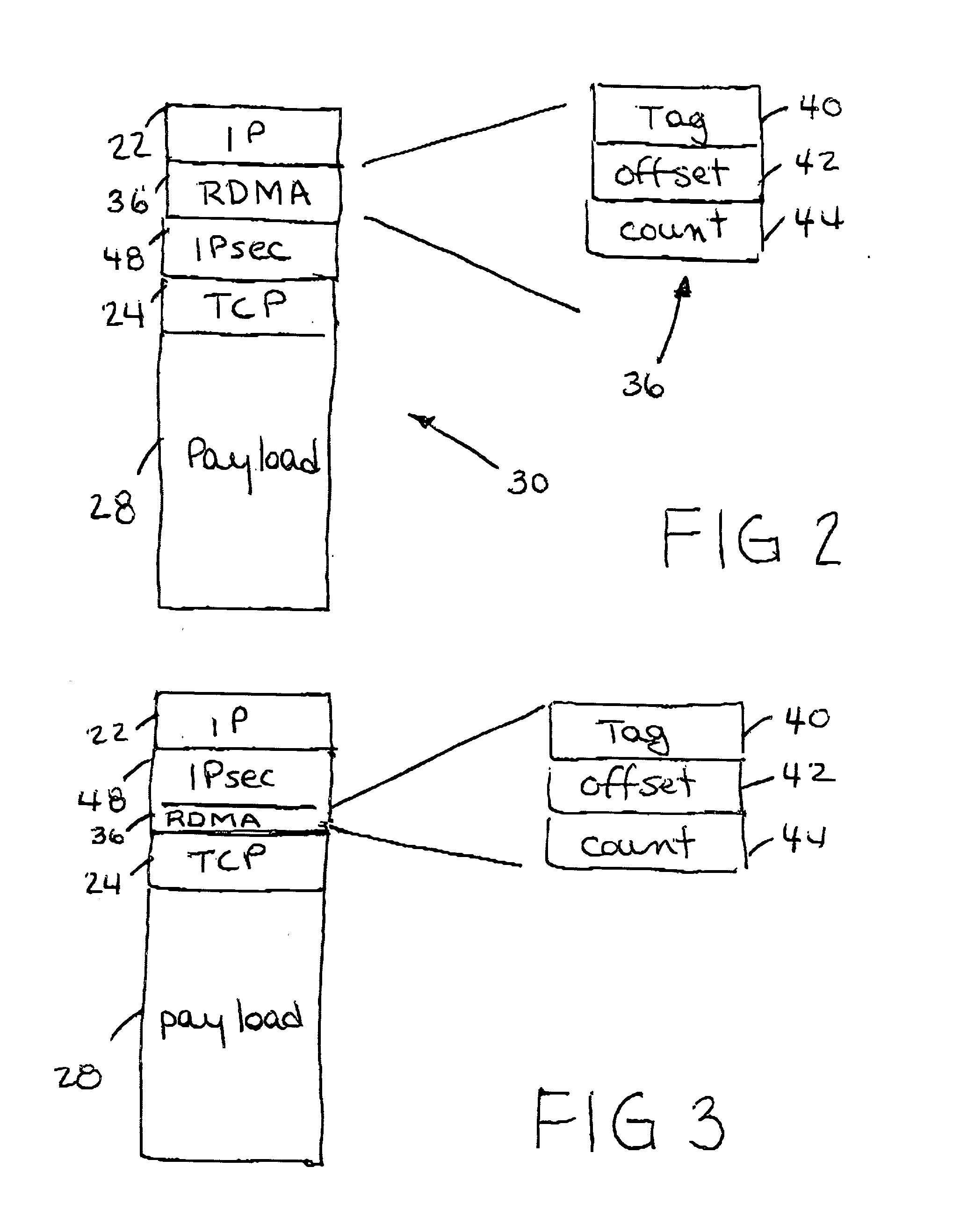
IP headers for remote direct memory access and upper level protocol framing
InactiveUS20020085562A1Time-division multiplexData switching by path configurationDirect memory accessRemote direct memory access
A data packet header including an internet protocol (IP) header, a remote direct memory access (RDMA) header, and a transmission control protocol (TCP) header, wherein the RDMA header is between the IP header and the TCP header.
Owner:IBM CORP
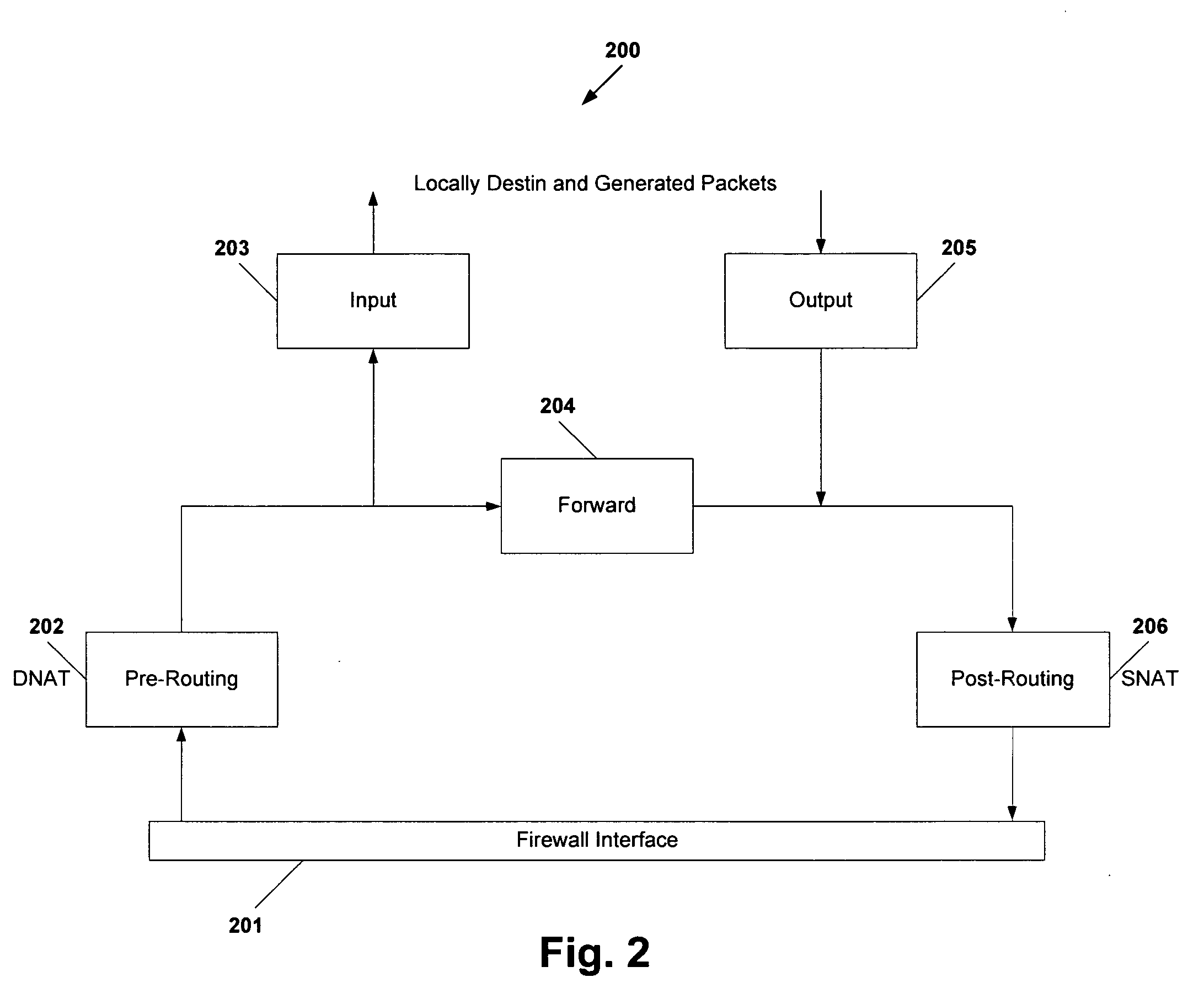
Automated generation of configuration elements of an information technology system
InactiveUS20060130133A1Low costReduce user effortMultiple digital computer combinationsProgram controlLoad SheddingClient-side
A firewall rule generation method, a load balancing rule generation method, and a wrapper generation method, for an Information Technology (IT) system, associated computer program products, and an associated processes for integrating computing infrastructure. The firewall rule generation method generates firewall rules allowing data transmission between a computer and a client, and subsequently assigns the firewall rules to firewalls of the IT system. The load balancing rule generation method assigns a load balancing mechanism to a load balanced group to which execution of an application is assigned, wherein the load balanced group has servers therein. For a client and computer having a communication protocol therebetween that is not allowed by a security policy, the wrapper generation method generates a communication protocol wrapper that opens a Transmission Control Protocol (TCP) connection between the client and the computer such that the TCP connection is allowed by the security policy.
Owner:KYNDRYL INC
Method and System for Communicating Message Notifications to Mobile Devices
ActiveUS20080263170A1Increase the number ofConnection managementMultiple digital computer combinationsCommunications systemMobile communication systems
There is disclosed a system and method for choosing between different Communication Initiation Request (CIR) channels in a mobile communications system when there are multiple CIR channels amongst which to choose. Additionally, there is disclosed a system and method for exploiting a Transmission Control Protocol (TCP) connection usage pattern that is characterized by periods of inactivity.
Owner:SYNCHRONICA
Method and transmitter for an efficient packet data transfer in a transmission protocol with repeat requests
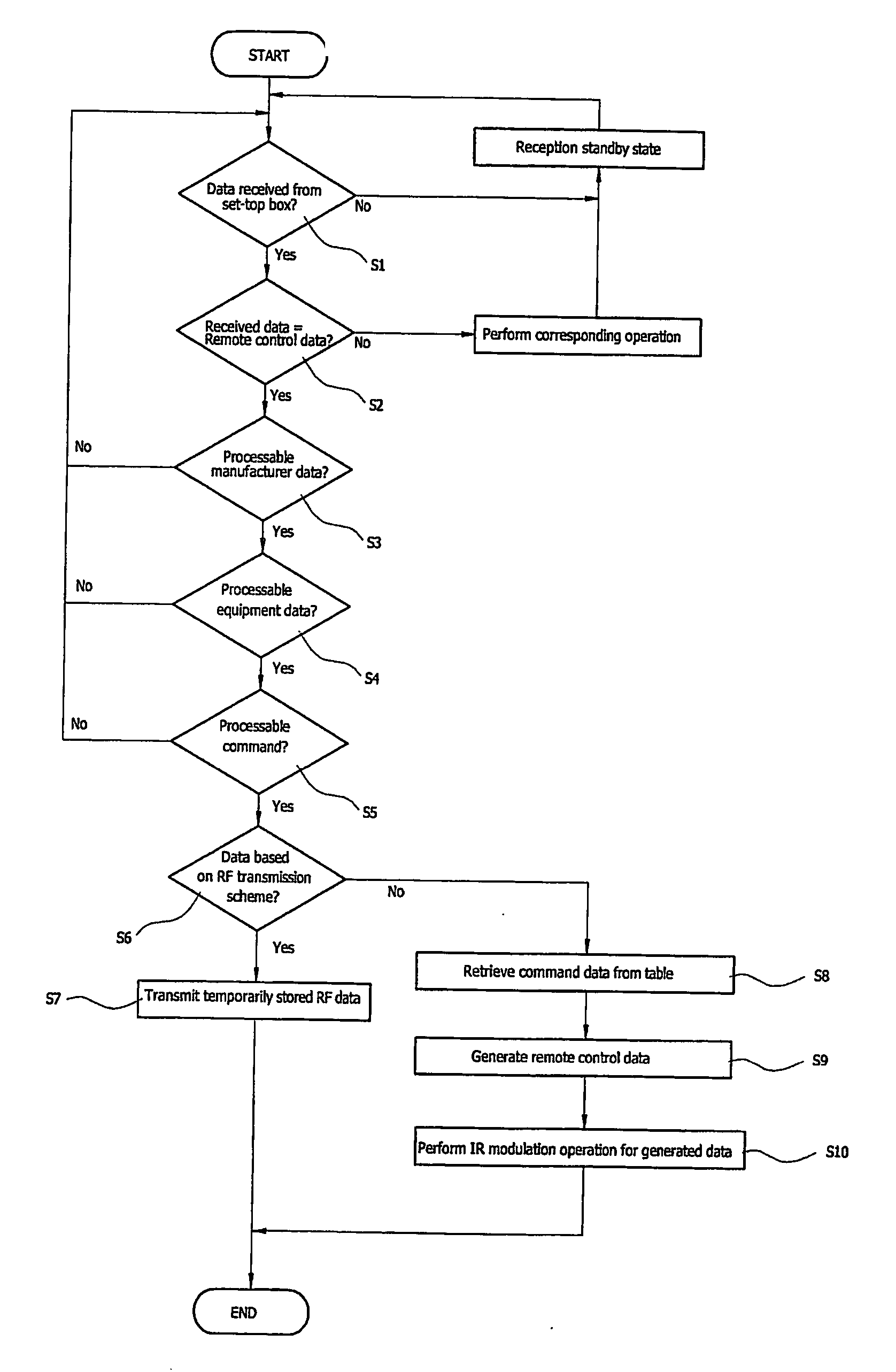
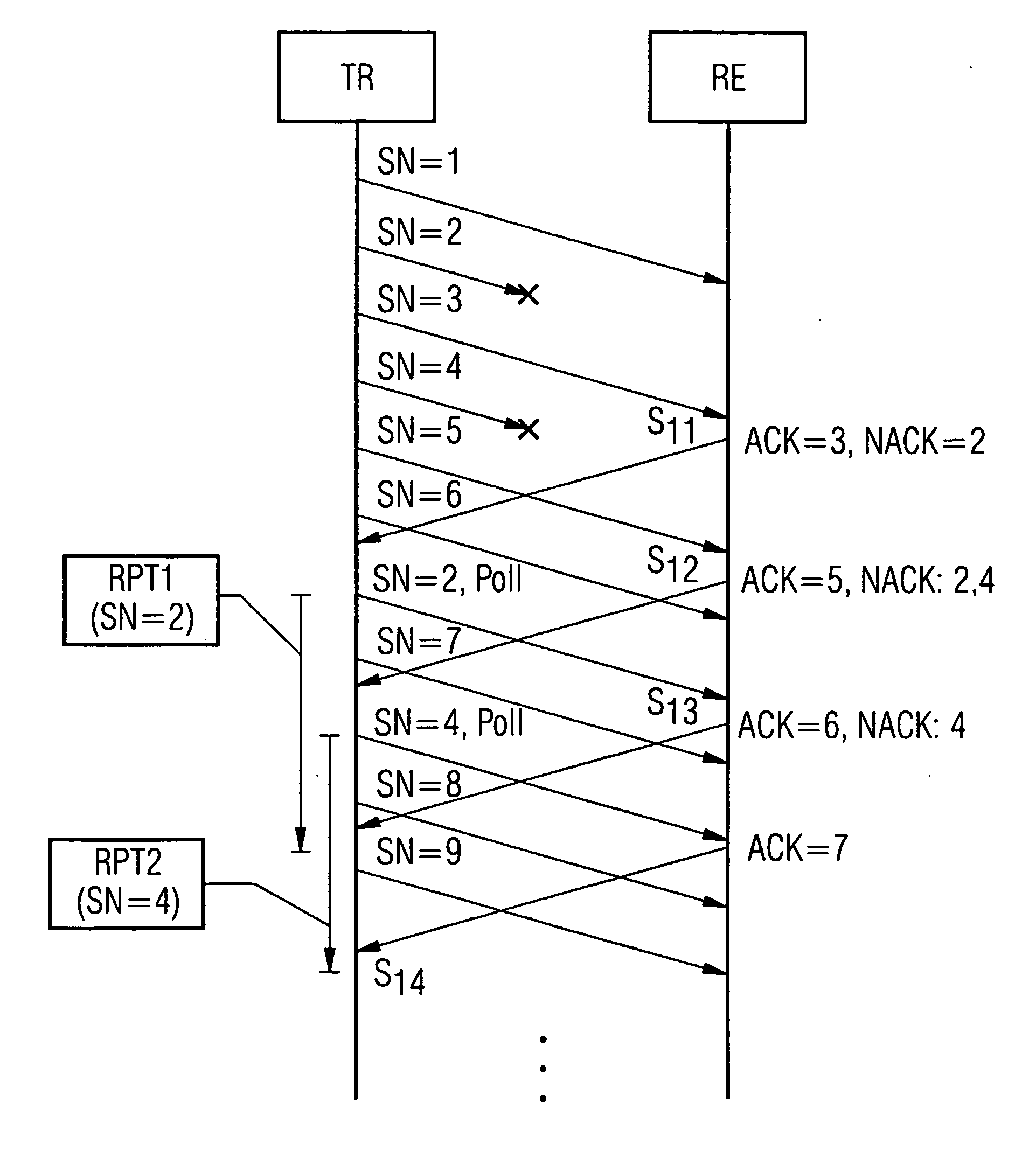
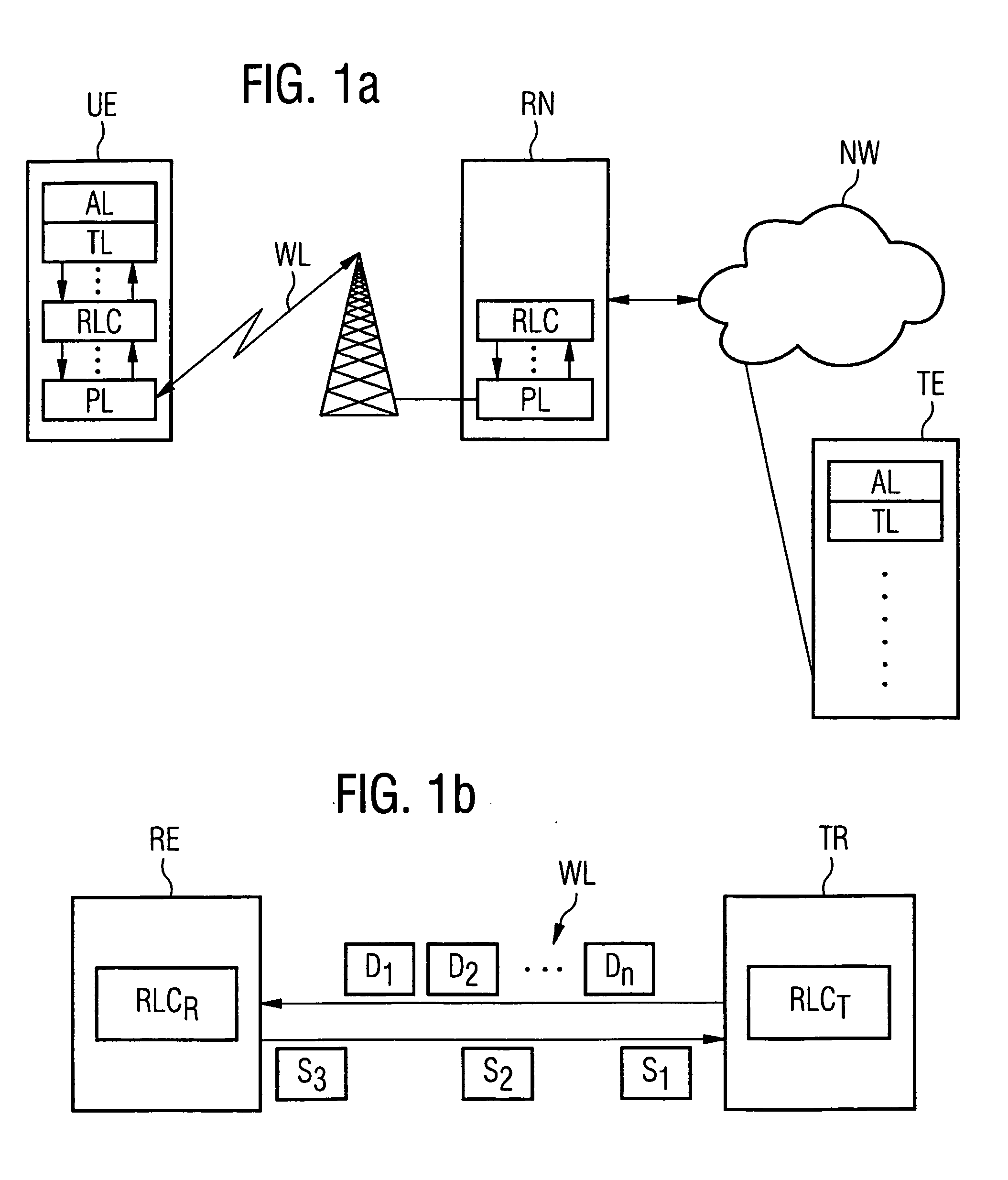
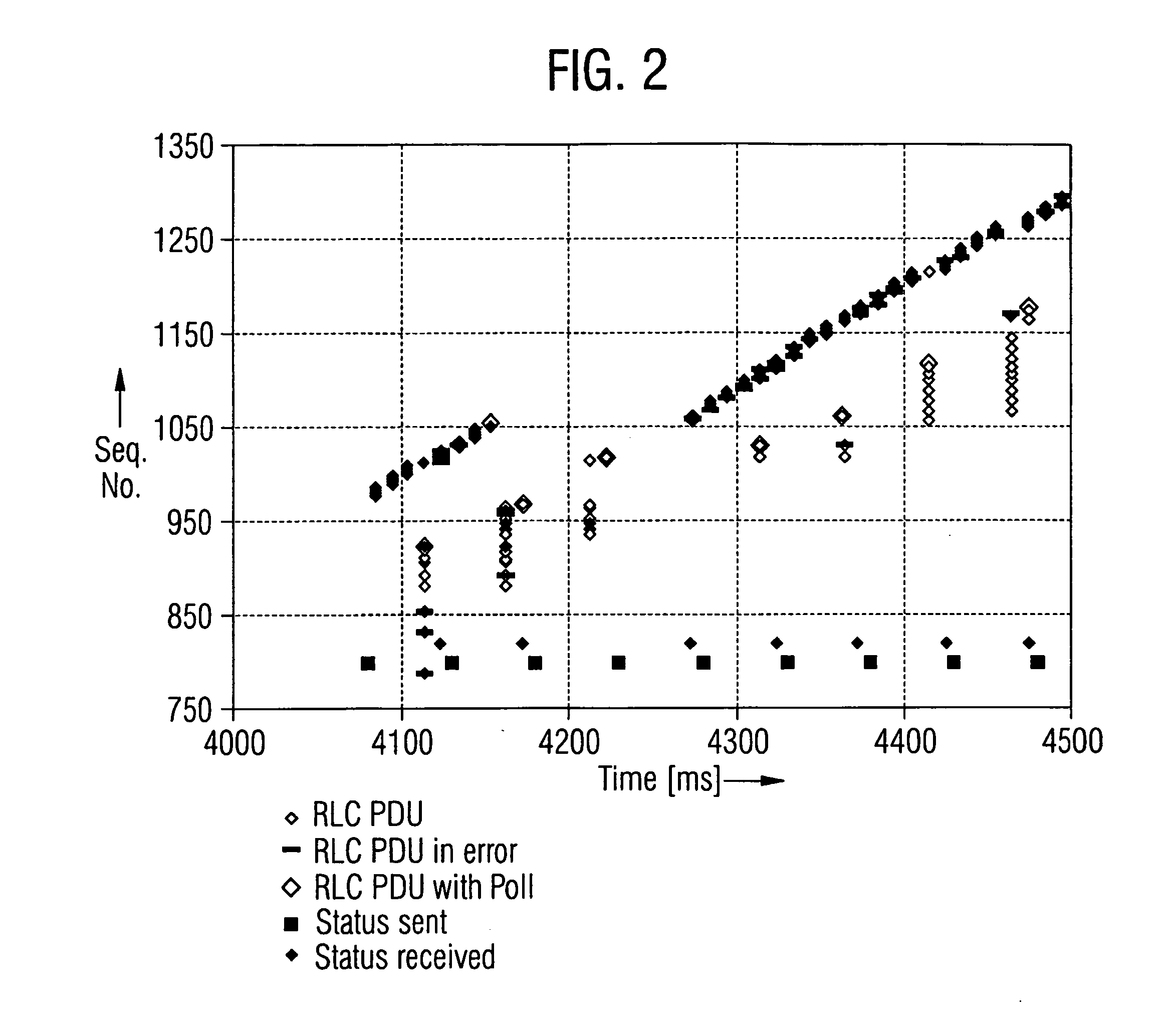
ActiveUS20040148396A1Spread the wordAvoid unnecessary multiple transmissionError prevention/detection by using return channelFrequency-division multiplex detailsTransmission protocolPacket data transmission
In a method for the transmission of data packets (D) from a transmitter (TR) to a receiver (RE) identification of transmitted data packets are stored. Defective data packets (D) are detected by the receiver (RE), status messages (S) which request defective data packets for retransmission are sent from the receiver (RE) to the transmitter (TR) and retransmissions of requested data packets are performed according to the status messages (S). The transmitter (TR) evaluates a first status message (S11) with an identification of at least one first requested data packet and retransmits the first data packet. The transmitter (TR) then initializes a timing unit according to the retransmission of the first data packet, wherein the timing unit or a threshold for the timing unit is attributable to the first data packet. When the transmitter evaluates a further status message (S12) and detects at least one further data packet that is requested for a retransmission, it selects the further data packet if the timing unit has reached the threshold or if the identification of the further data packet is different from the identification of the first data packets. Only the selected data packets are retransmitted. A transmitter and software programs embodying the invention are also described.
Owner:TELEFON AB LM ERICSSON (PUBL)
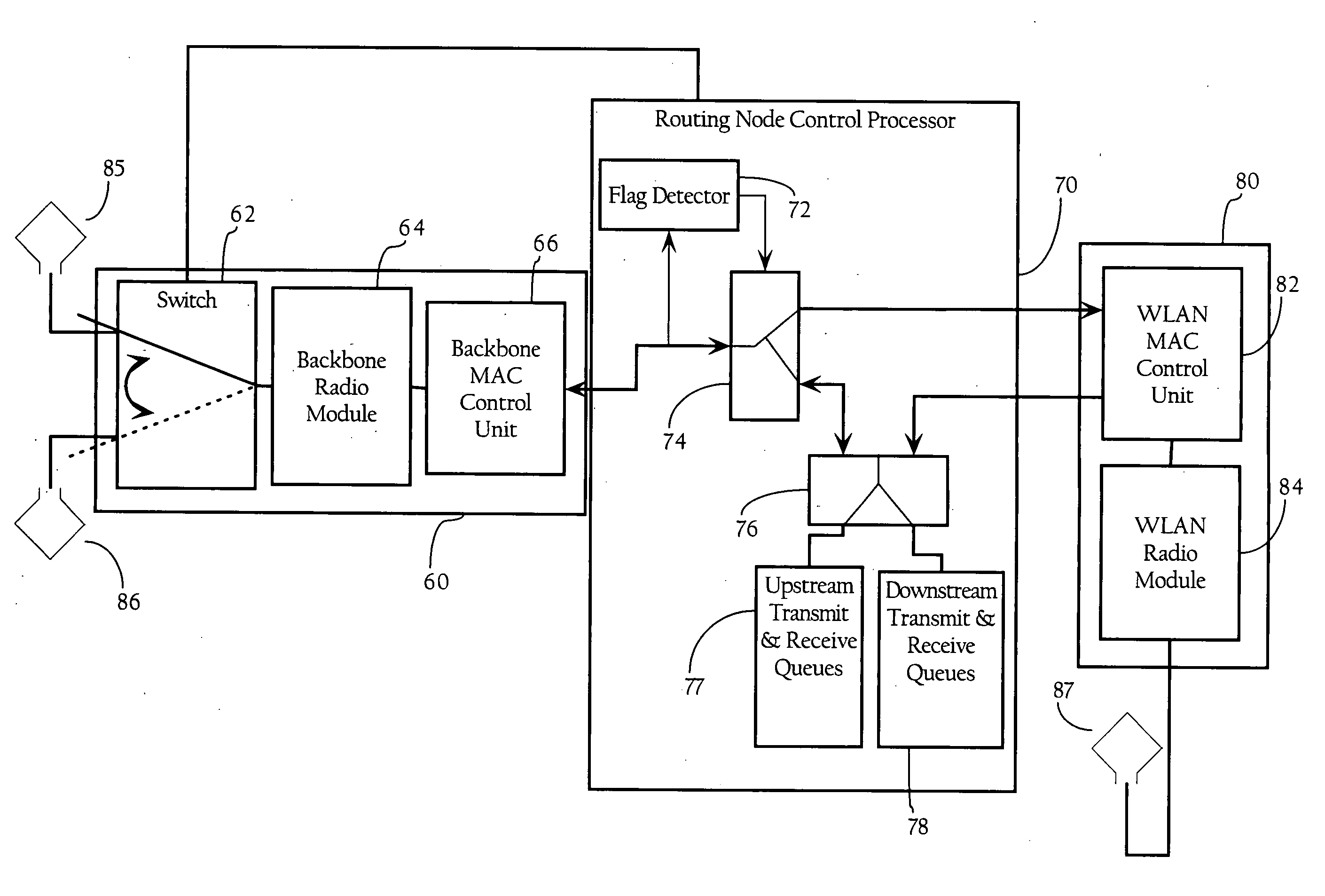
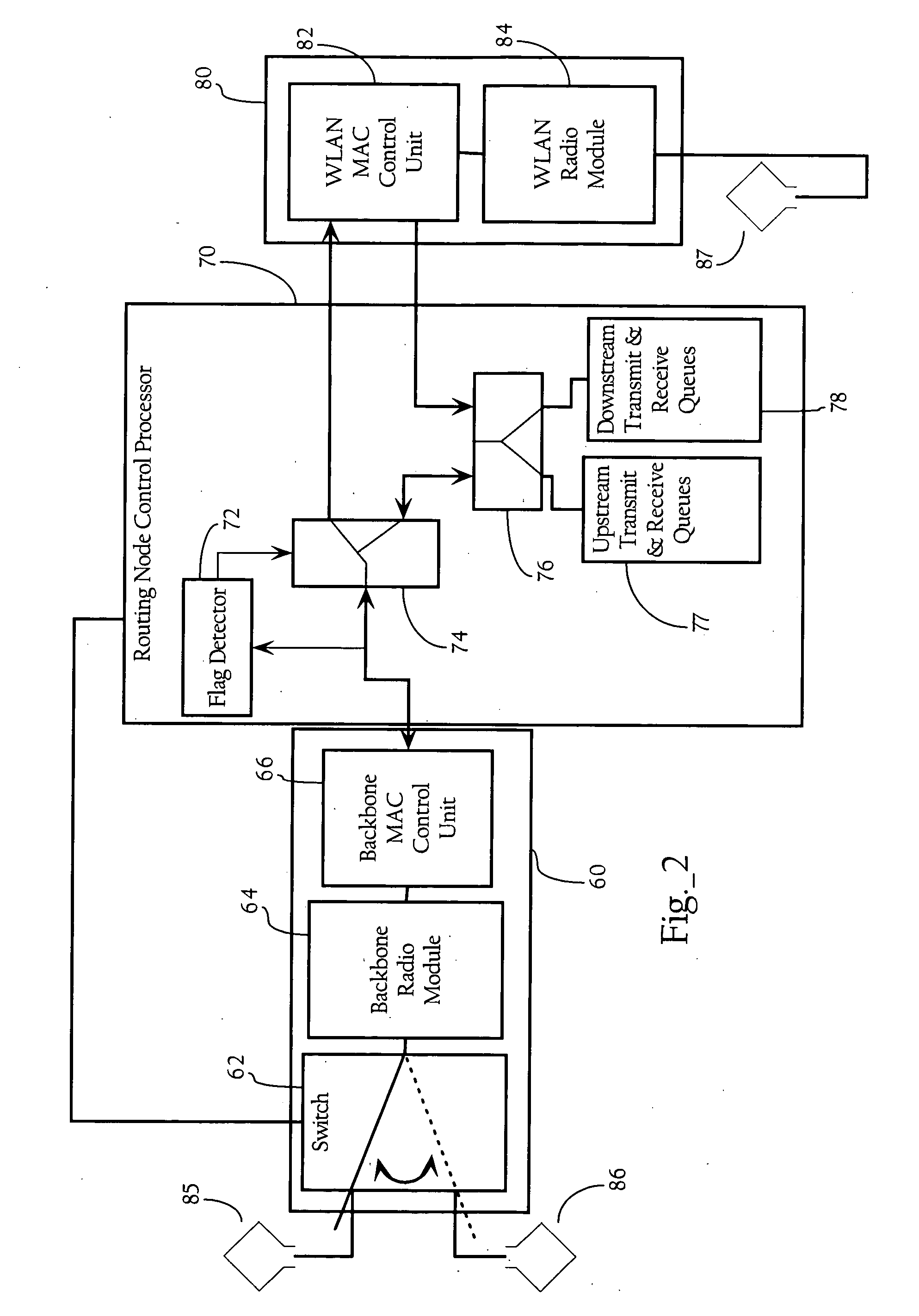
Dynamic modification of contention-based transmission control parameters achieving load balancing scheme in wireless mesh networks
ActiveUS20070206547A1Error preventionFrequency-division multiplex detailsWireless mesh networkMedia access
Methods, apparatuses and systems directed to facilitating load balancing and bandwidth allocation in wireless mesh networks. Generally, according to one implementation of the present invention, routing nodes implement a contention-based media access mechanism and self-allocate bandwidth within a wireless mesh network by dynamically modifying one or more contention-based transmission control parameters. The routing nodes determine a hop count and adjust one or more contention parameters based at least in part on the hop count.
Owner:CISCO TECH INC
Window flow control with common time reference
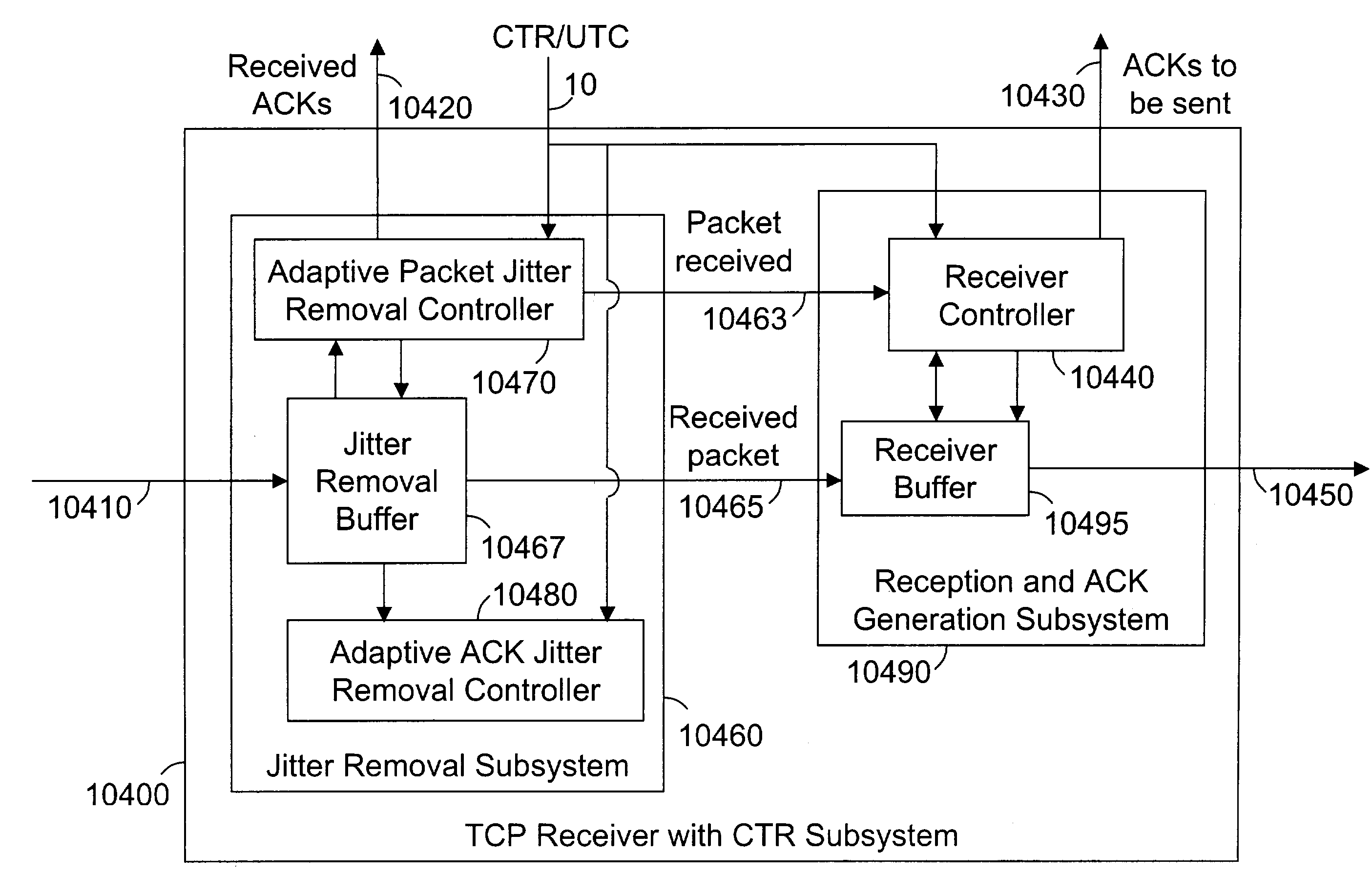
ActiveUS7307989B2Restrict levelData processing applicationsTime-division multiplexSlide windowData transmission
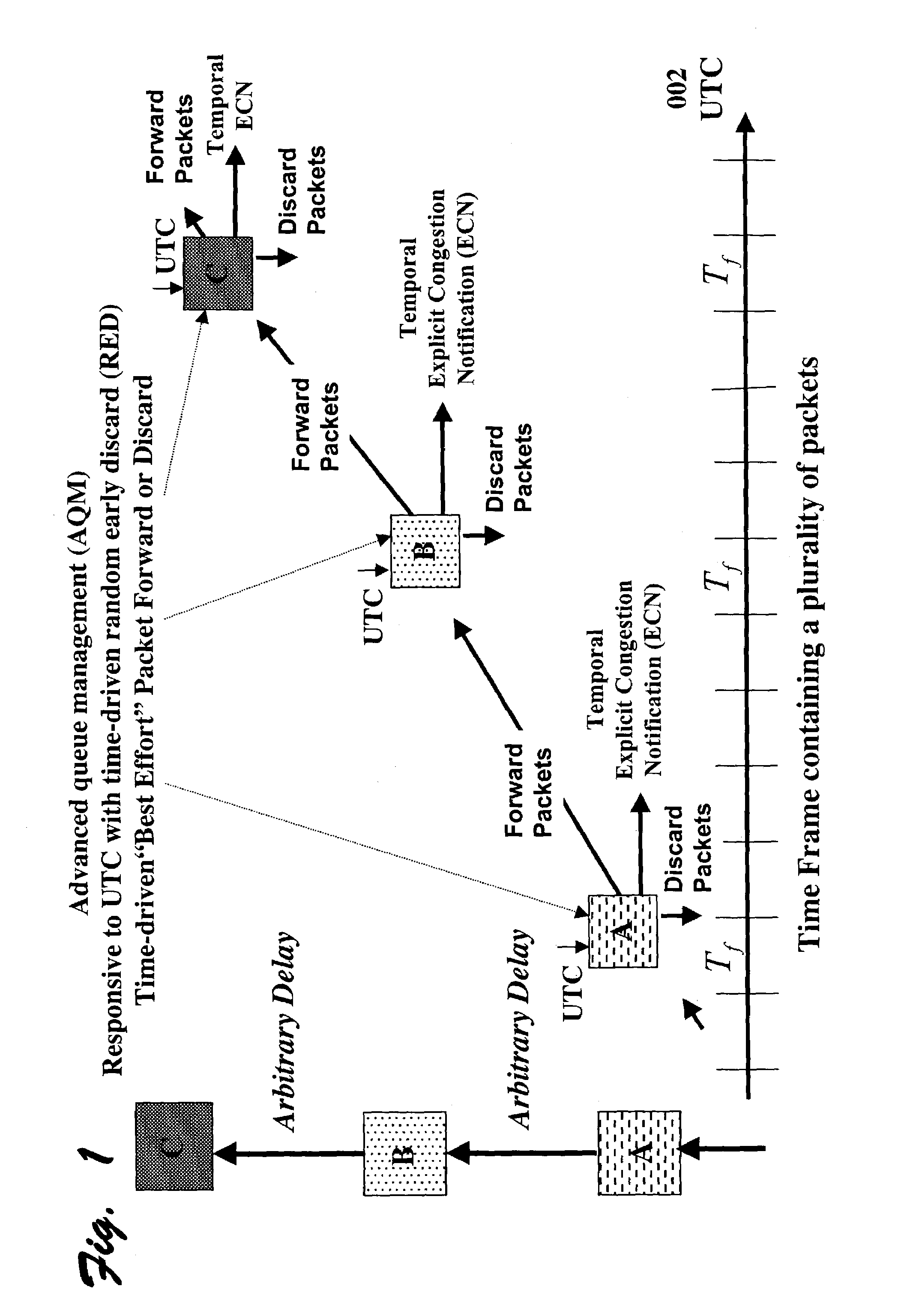
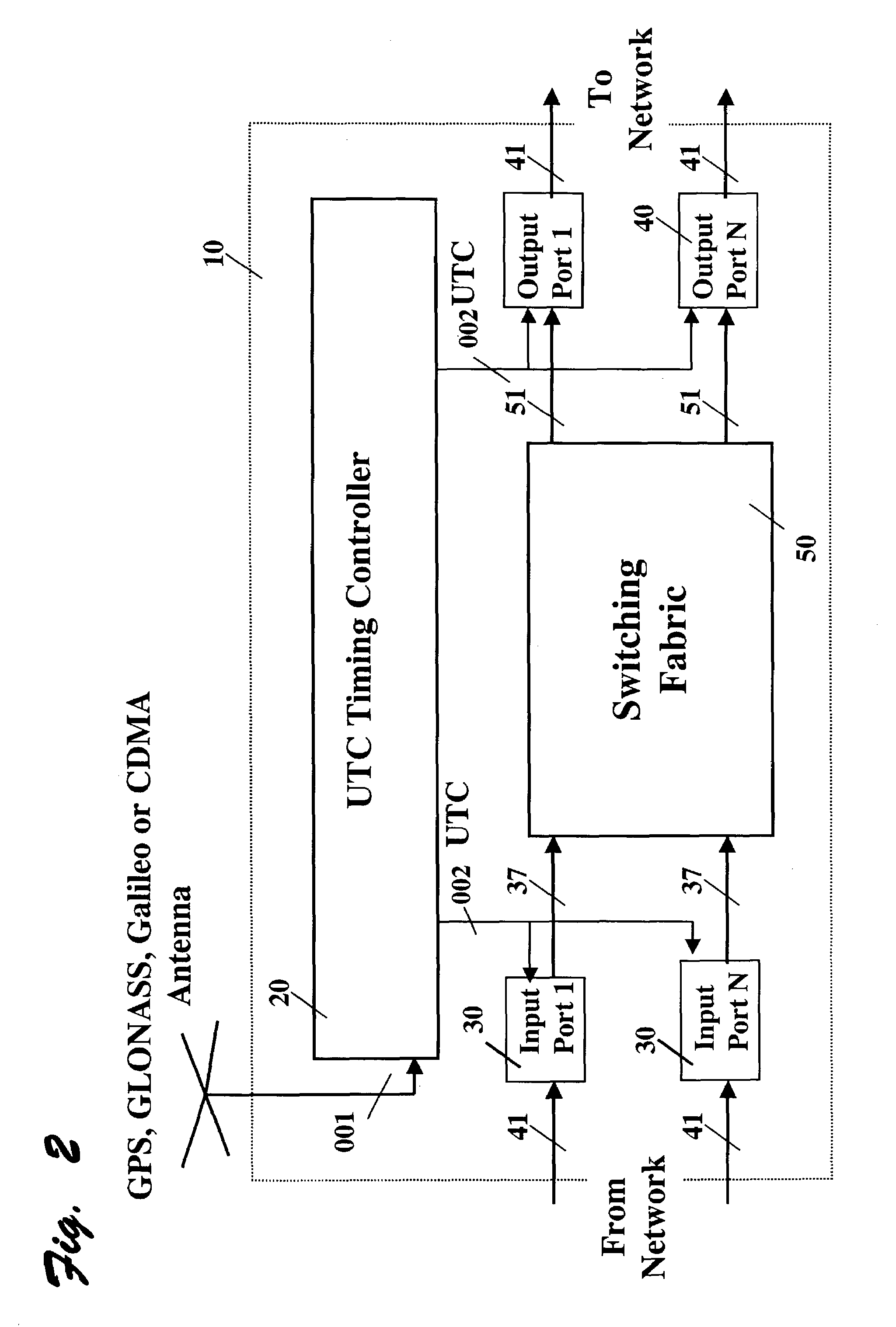
This invention relates generally to a method and apparatus for timely forwarding, discarding, and delivering data packets over the network and to their destination nodes and the optimization of data transfer throughput through the network. The timely forwarding and discarding are possible thanks to the standard global common time reference (CTR) that is known as UTC (Coordinated Universal Time). UTC is available from GPS (Global Positioning System), Galileo, and GLONASS (Global Navigation Satellite System). Data transfer throughput optimization is pursued by taking advantage of the timely forwarding and discarding properties to improve the data packets transfer flow control mechanisms, such as the sliding window re-sizing algorithm implemented by the widely deployed Transmission Control Protocol (TCP).
Owner:ATTESTWAVE LLC
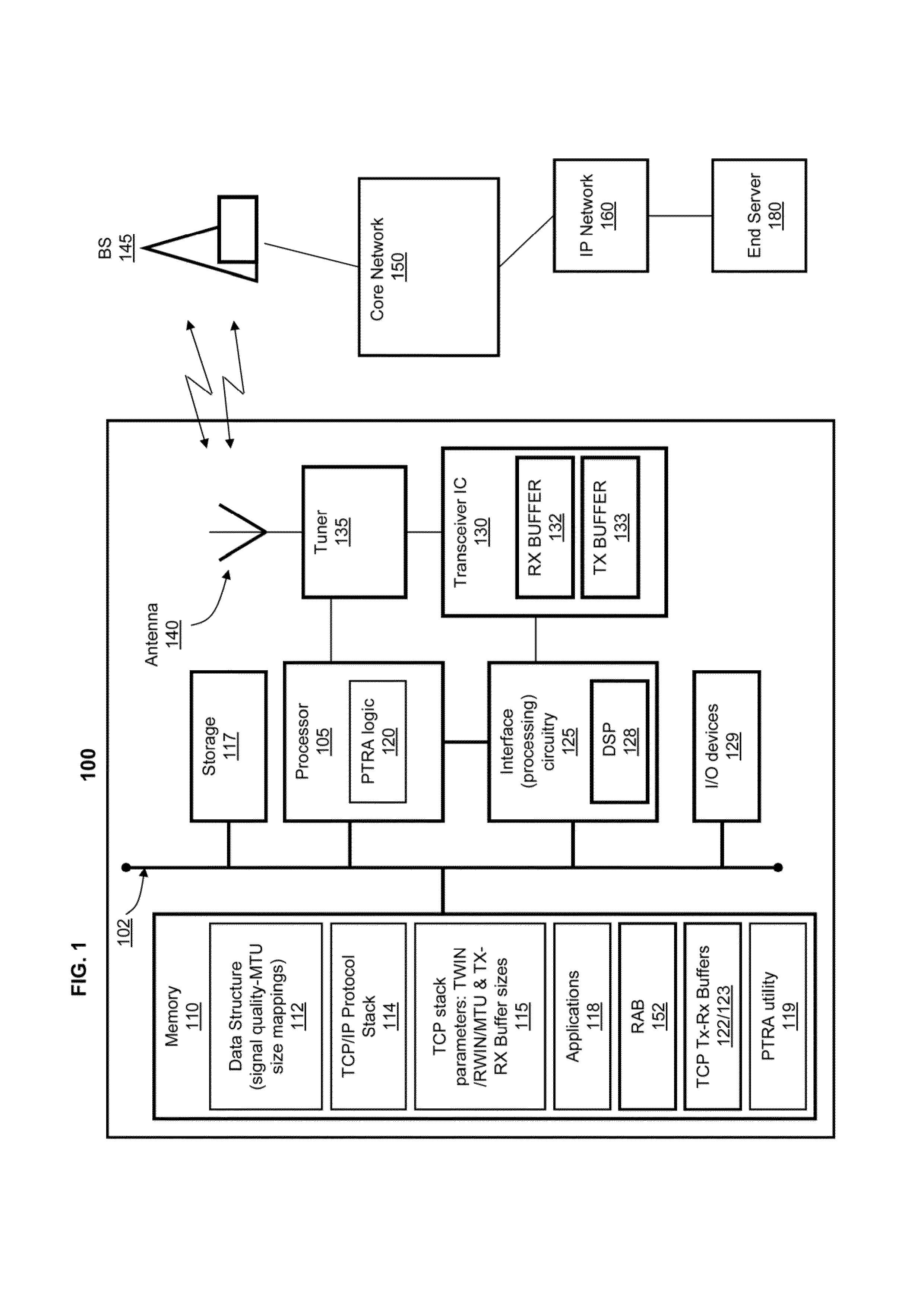
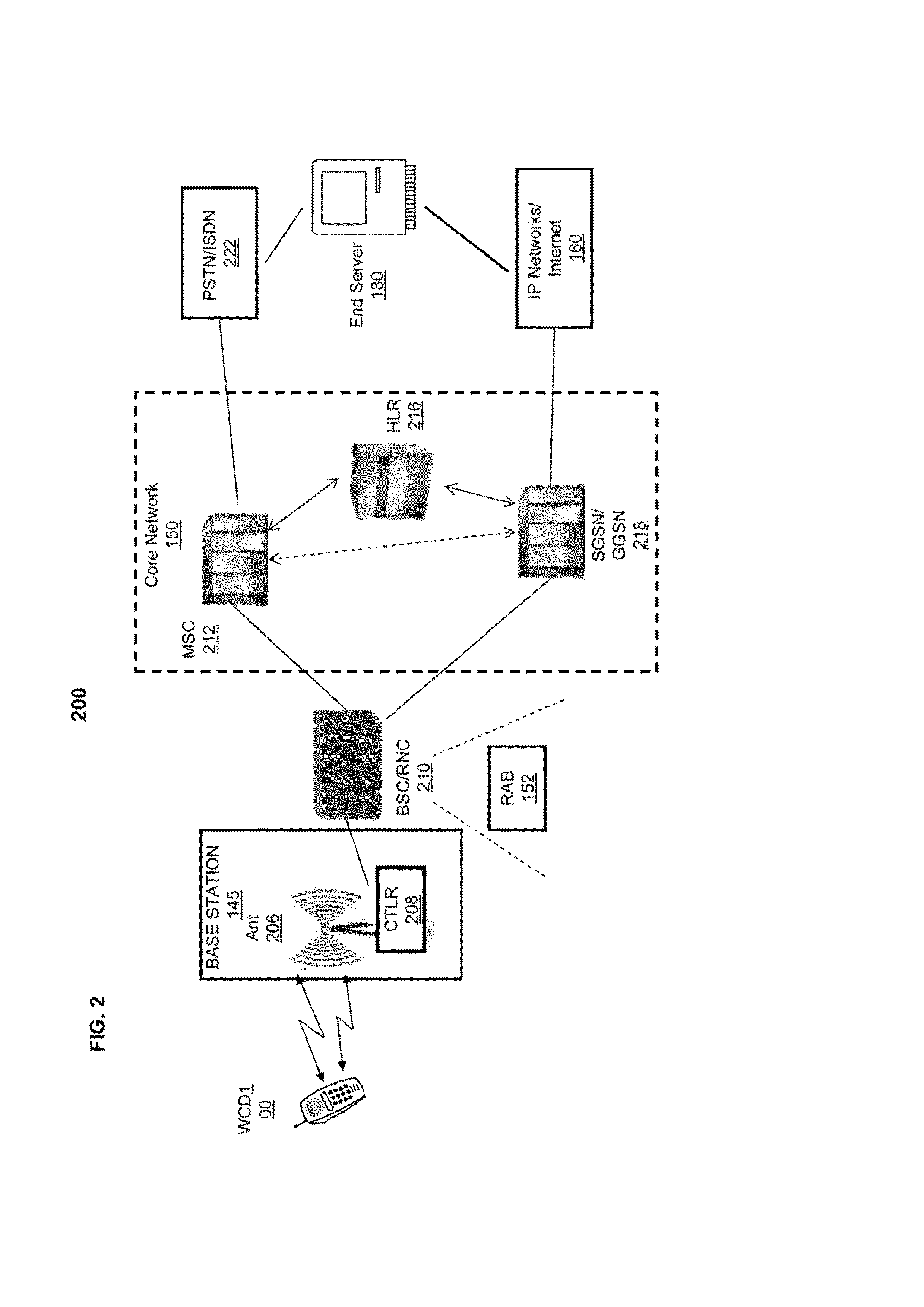
Dynamic TCP layer optimization for real-time field performance
ActiveUS20130176854A1Error preventionFrequency-division multiplex detailsTerminal serverTelecommunications link
A method and system that mitigates data session degradation over a radio link connection with an end server by allocating resources at a wireless communication device based on real-time radio frequency (RF) channel conditions. A performance tracking and resource allocation (PTRA) logic monitors radio access bearer (RAB) configuration and radio link quality for communication links between the WCD and the end server. The PTRA logic sets a maximum transmission unit (MTU) size parameter to a pre-established size associated with the measured radio link quality. In response to detecting a change in the RAB configuration, the PTRA logic performs a real-time round trip time (RTT) measurement utilizing individual RTTs associated with packet segments transmitted at a lower protocol layer. In addition, the PTRA logic modifies at least one of a transmission control protocol (TCP) receive window (RWIN) and a TCP transmit window (TWIN) using the real-time RTT measurements and RAB configuration.
Owner:GOOGLE TECH HLDG LLC
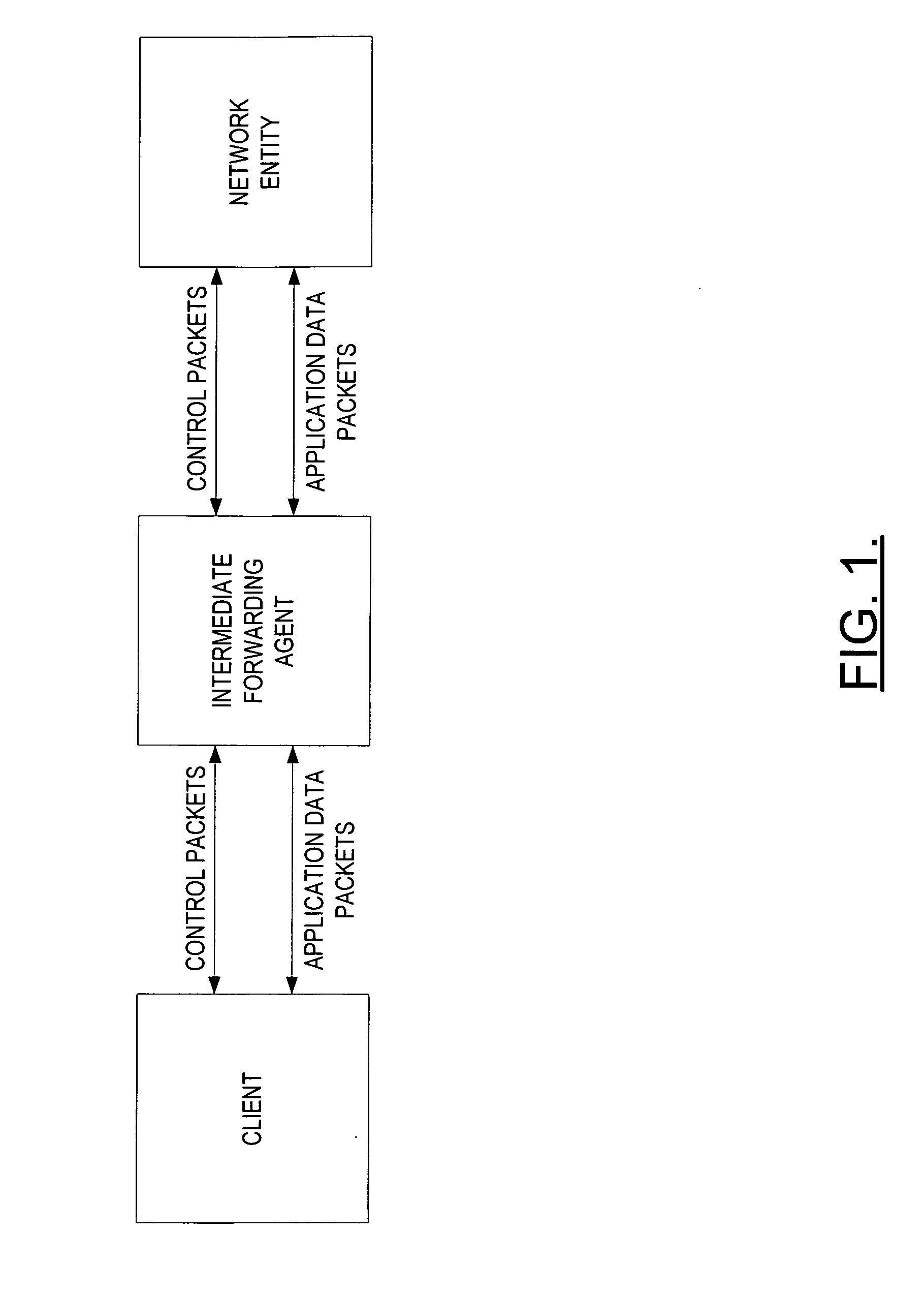
Prioritized control packet delivery for transmission control protocol (TCP)
InactiveUS20070091900A1Raise priorityFaster packet queue processing timeNetwork traffic/resource managementTime-division multiplexLink flowNetsniff-ng
A method is provided for transmitting data, wherein control packets are given priority with respect to application data packets. In general, this is accomplished by establishing a separate, distinct link flow over which only control packets (e.g., TCP control packets) will be transmitted. A higher priority is associated with this link flow. In addition, the reliability of control packets sent over the dedicated link flow can be improved upon by increasing the number of retransmissions associated with the control packets and / or decreasing the window of time before the retransmissions are sent. A system, mobile terminal, network entity, and computer program product for implementing the method are also provided.
Owner:NOKIA SOLUTIONS & NETWORKS OY
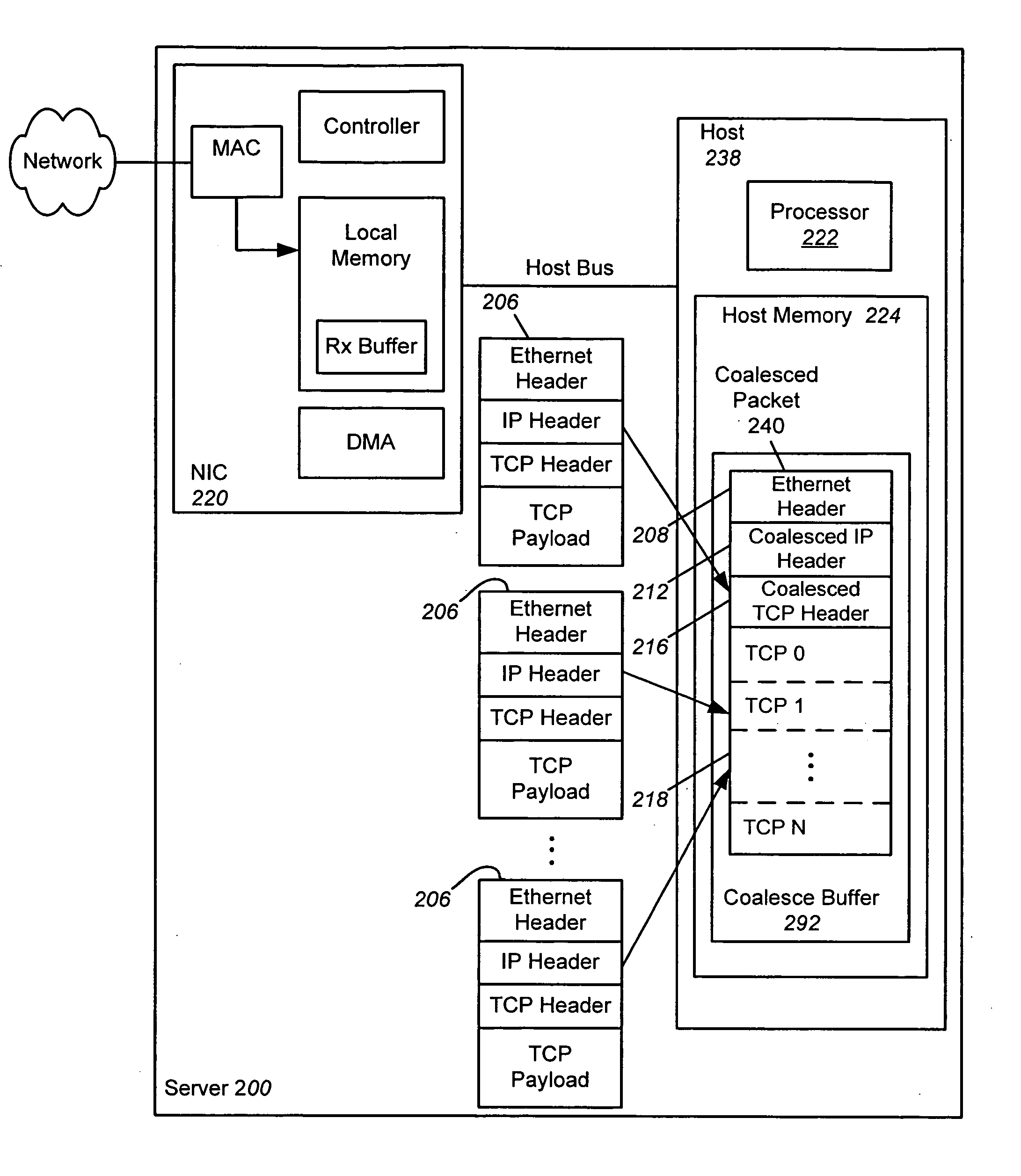
Receive coalescing and automatic acknowledge in network interface controller
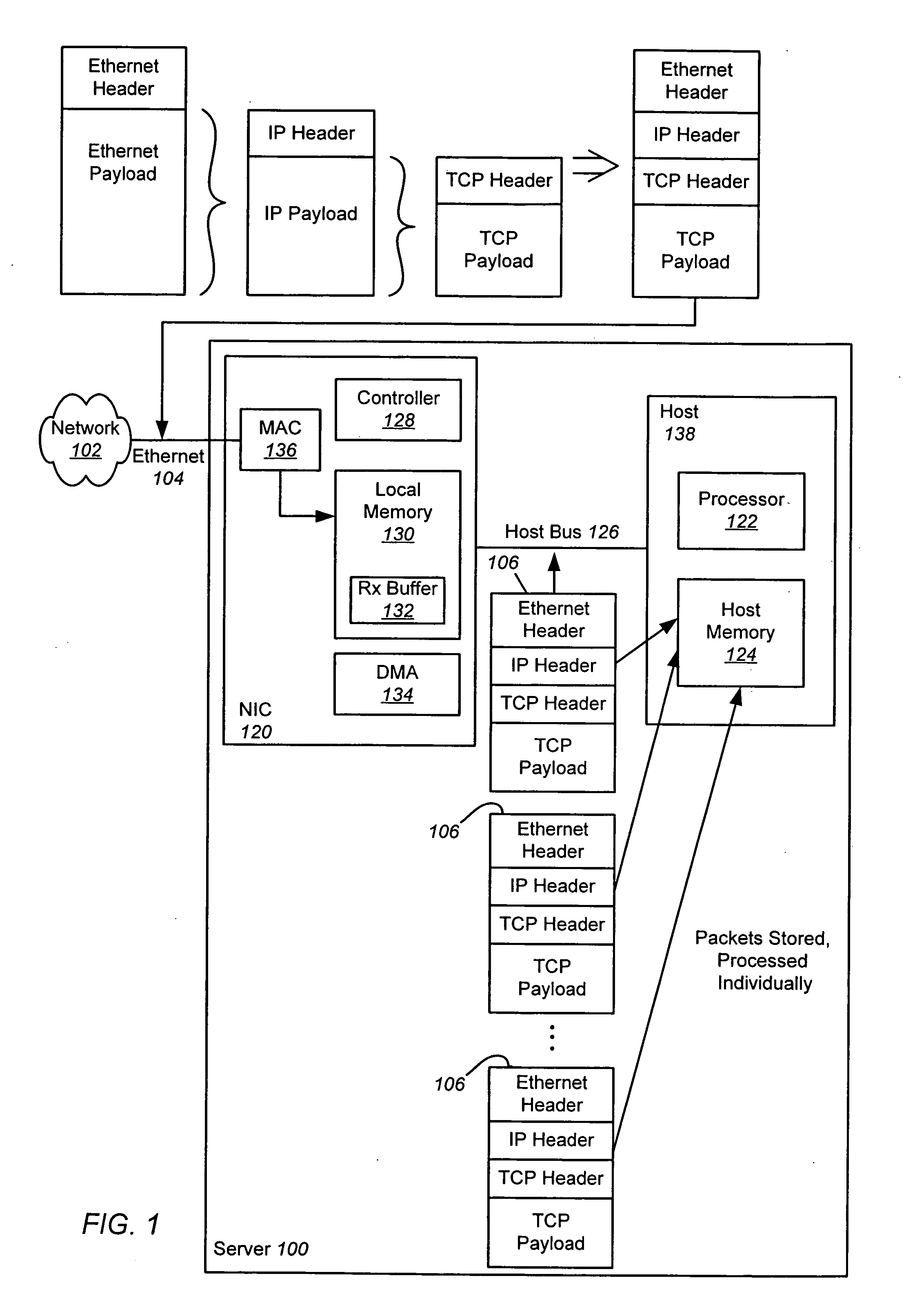
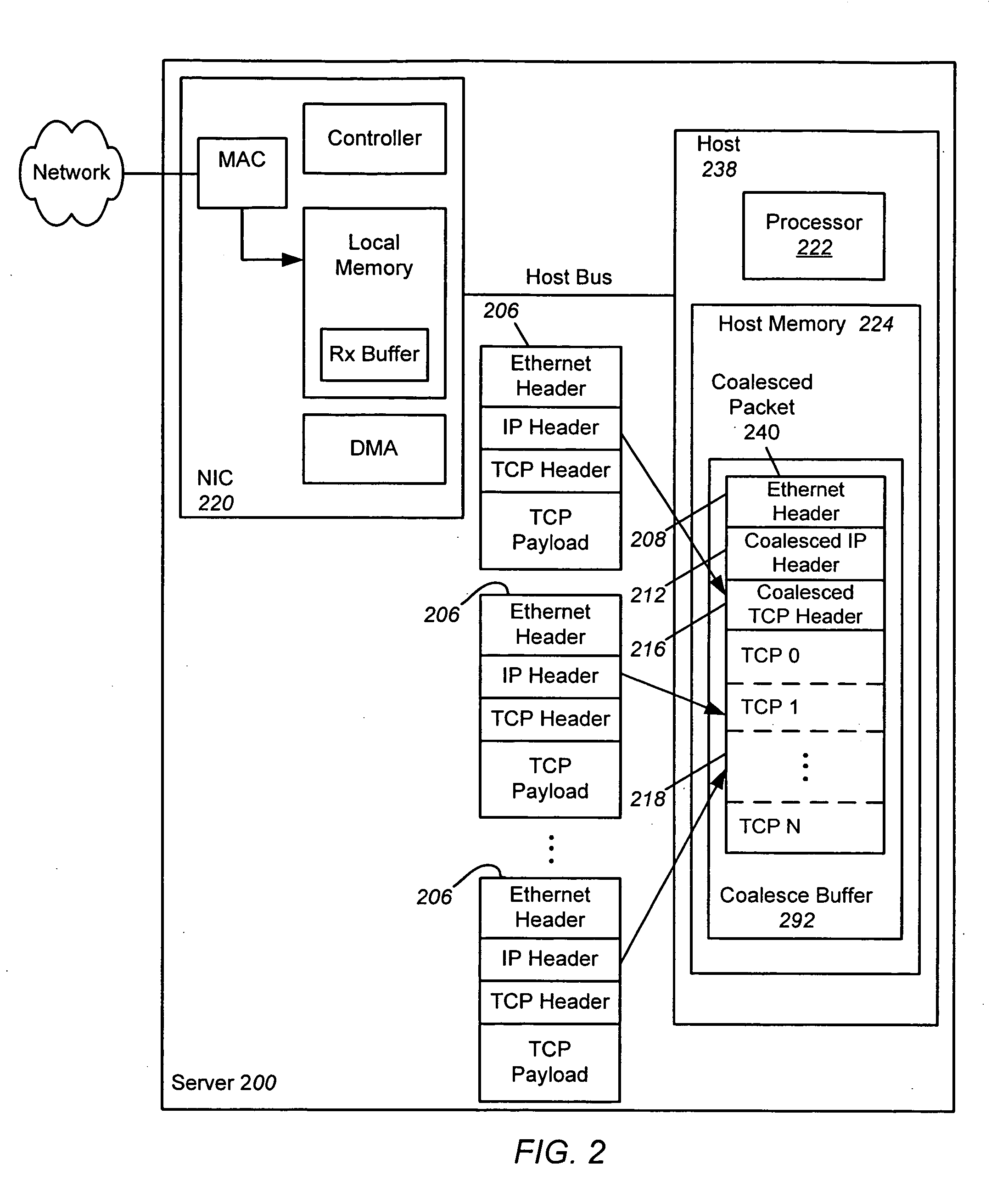
ActiveUS20070064737A1Reduce computational overheadImprove network performanceTime-division multiplexTransmissionHost memoryInternet Protocol
An apparatus and method is disclosed for reducing the computational overhead incurred by a host processor during packet processing and improving network performance by adding additional functionality to a Network Interface Controller (NIC). Under certain circumstances the NIC coalesces multiple receive packets into a single coalesced packet stored within a coalesce buffer in host memory. The coalesced packet includes an Ethernet header, a coalesced Internet Protocol (IP) header, a coalesced Transmission Control Protocol (TCP) header, and a coalesced TCP payload containing the TCP payloads of the multiple receive packets. By coalescing received packets into fewer larger coalesced packets within the host memory, the host software needed to process a receive packet will be invoked less often, meaning that less processor overhead is incurred in the host.
Owner:AVAGO TECH INT SALES PTE LTD
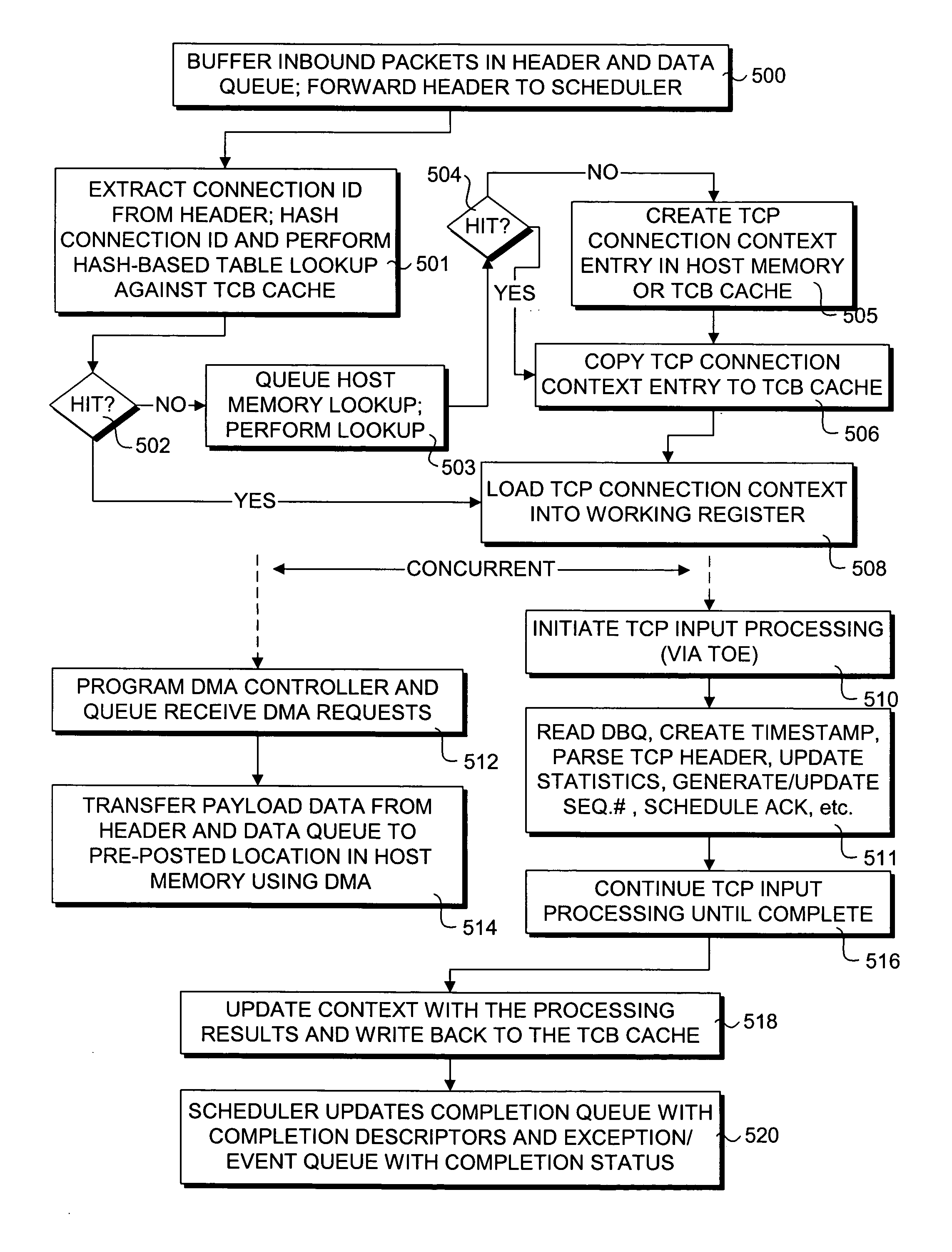
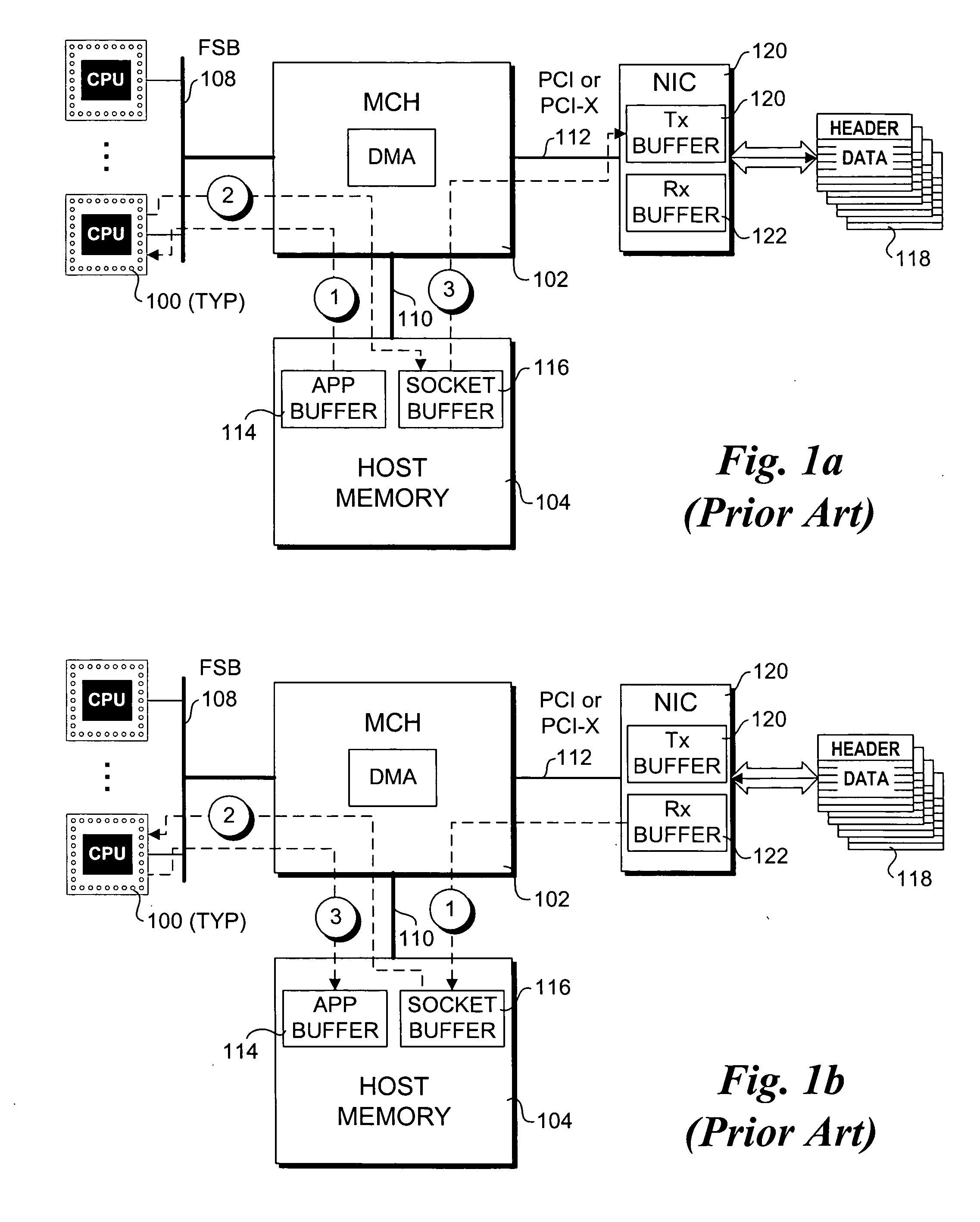
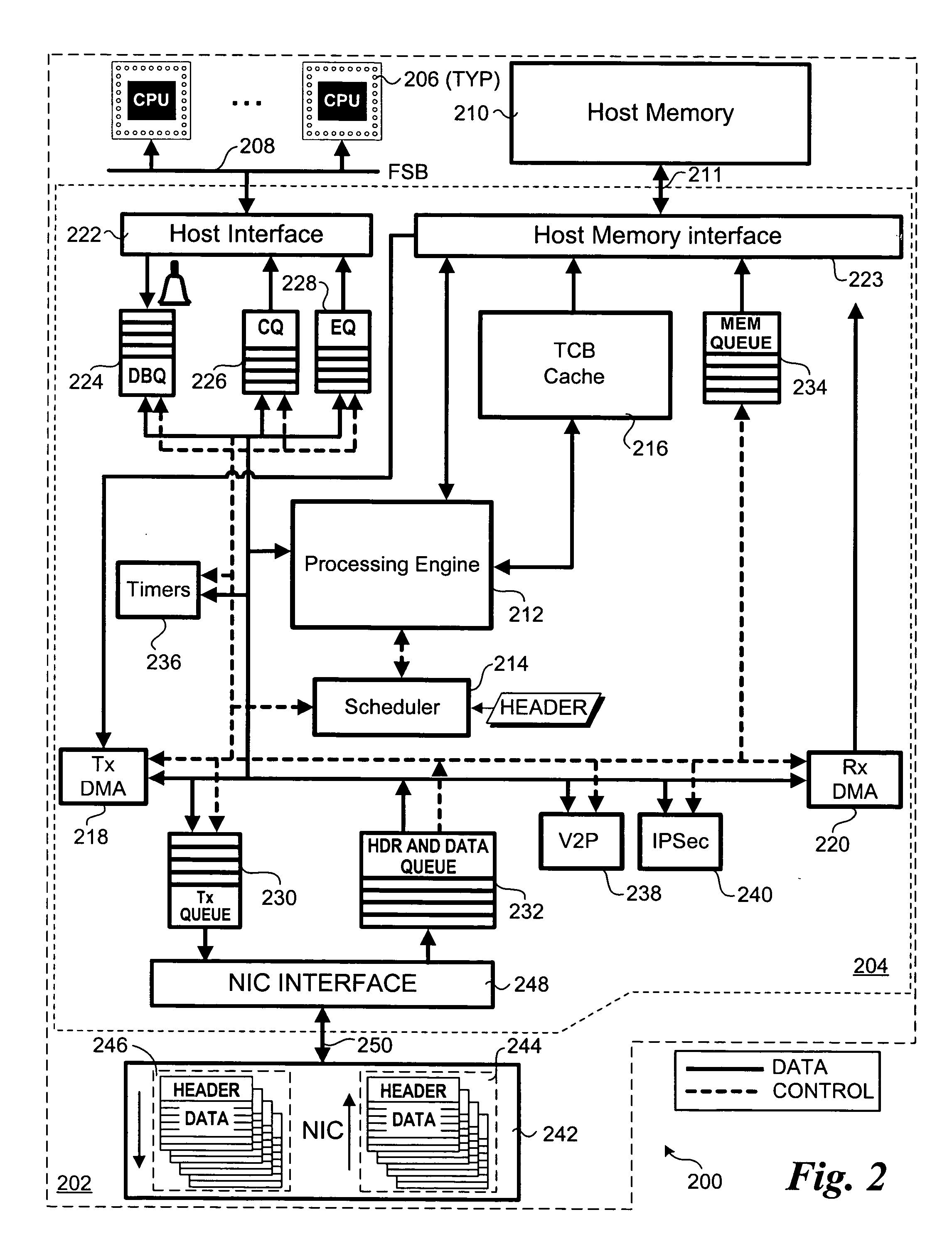
Hardware-based multi-threading for packet processing
Methods and apparatus for processing transmission control protocol (TCP) packets using hardware-based multi-threading techniques. Inbound and outbound TCP packet are processed using a multi-threaded TCP offload engine (TOE). The TOE includes an execution core comprising a processing engine, a scheduler, an on-chip cache, a host memory interface, a host interface, and a network interface controller (NIC) interface. In one embodiment, the TOE is embodied as a memory controller hub (MCH) component of a platform chipset. The TOE may further include an integrated direct memory access (DMA) controller, or the DMA controller may be embodied as separate circuitry on the MCH. In one embodiment, inbound packets are queued in an input buffer, the headers are provided to the scheduler, and the scheduler arbitrates thread execution on the processing engine. Concurrently, DMA payload data transfers are queued and asynchronously performed in a manner that hides memory latencies. In one embodiment, the technique can process typical-size TCP packets at 10 Gbps or greater line speeds.
Owner:TAHOE RES LTD
TCP proxy providing application layer modifications
ActiveUS7277963B2Multiple digital computer combinationsElectric digital data processingData segmentData stream
The invention disclosed is a Transmission Control Protocol (TCP) transport handler for a network intermediary. The handler examines all segments in a TCP / IP data stream between two nodes The handler maintains a list of changes made by an application module to a data segment within a data stream and utilizes that list to ensure that the sequence numbers for both receiver and transmitter refer to the same segments of data. The list of changes is also used to reapply changes to retransmitted packets. Data segments are not acknowledged until the receiver acknowledges a segment, eliminating the requirement of buffering data segments.
Owner:SANDVINE CORP
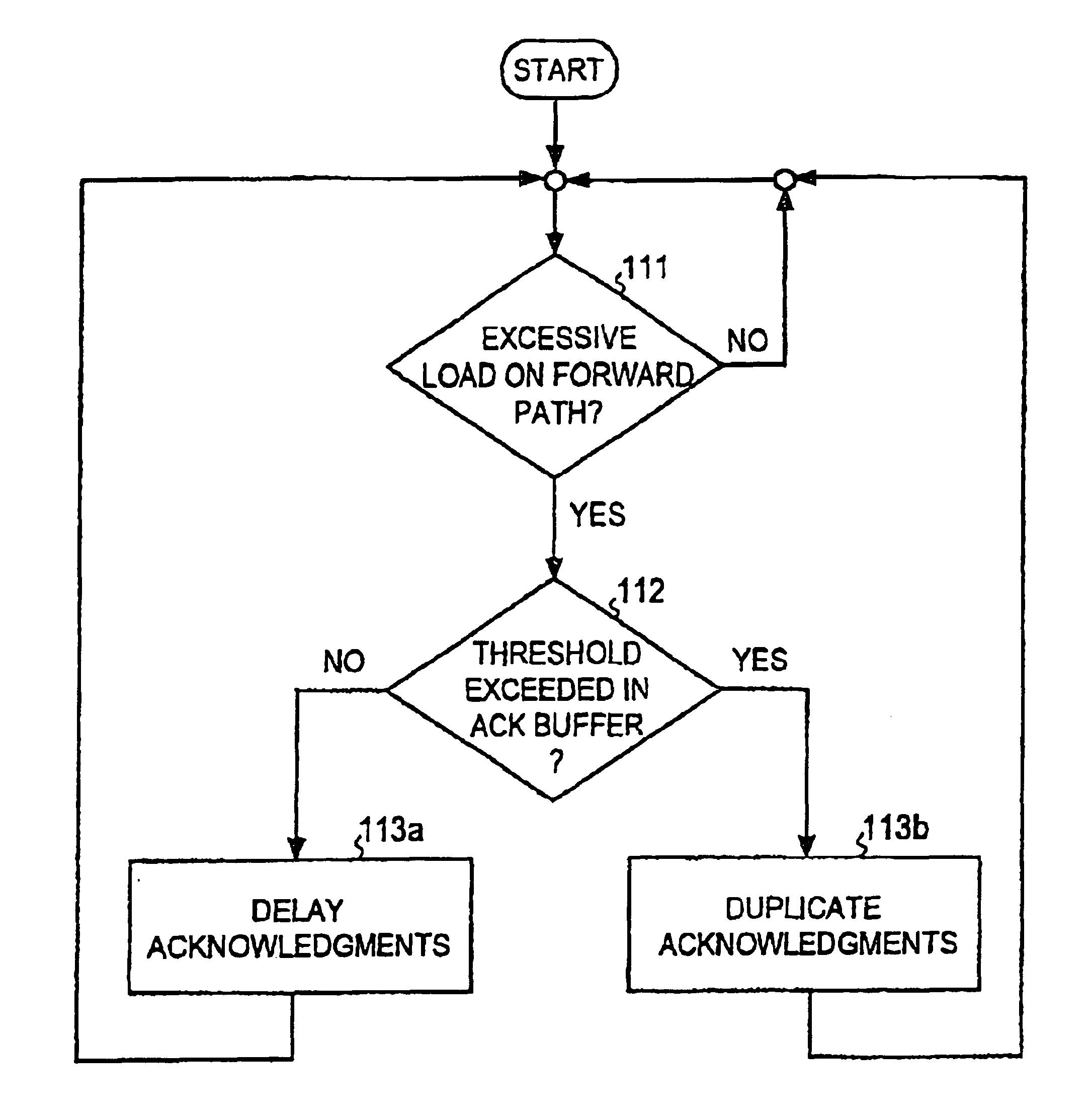
Congestion and overload control in a packet switched network
InactiveUS6882624B1Firmly connectedImprove performanceError preventionTransmission systemsTransport layerOverload control
The invention relates to a method for controlling overload in a packet switched network, especially in a network where Transmission Control Protocol (TCP) is used as the transport layer protocol. In order to inform the traffic source at a very early stage that the network is getting overloaded or congested, duplicate acknowledgments are transmitted towards the traffic source when the measured load level exceeds a predetermined threshold.
Owner:WSOU INVESTMENTS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com