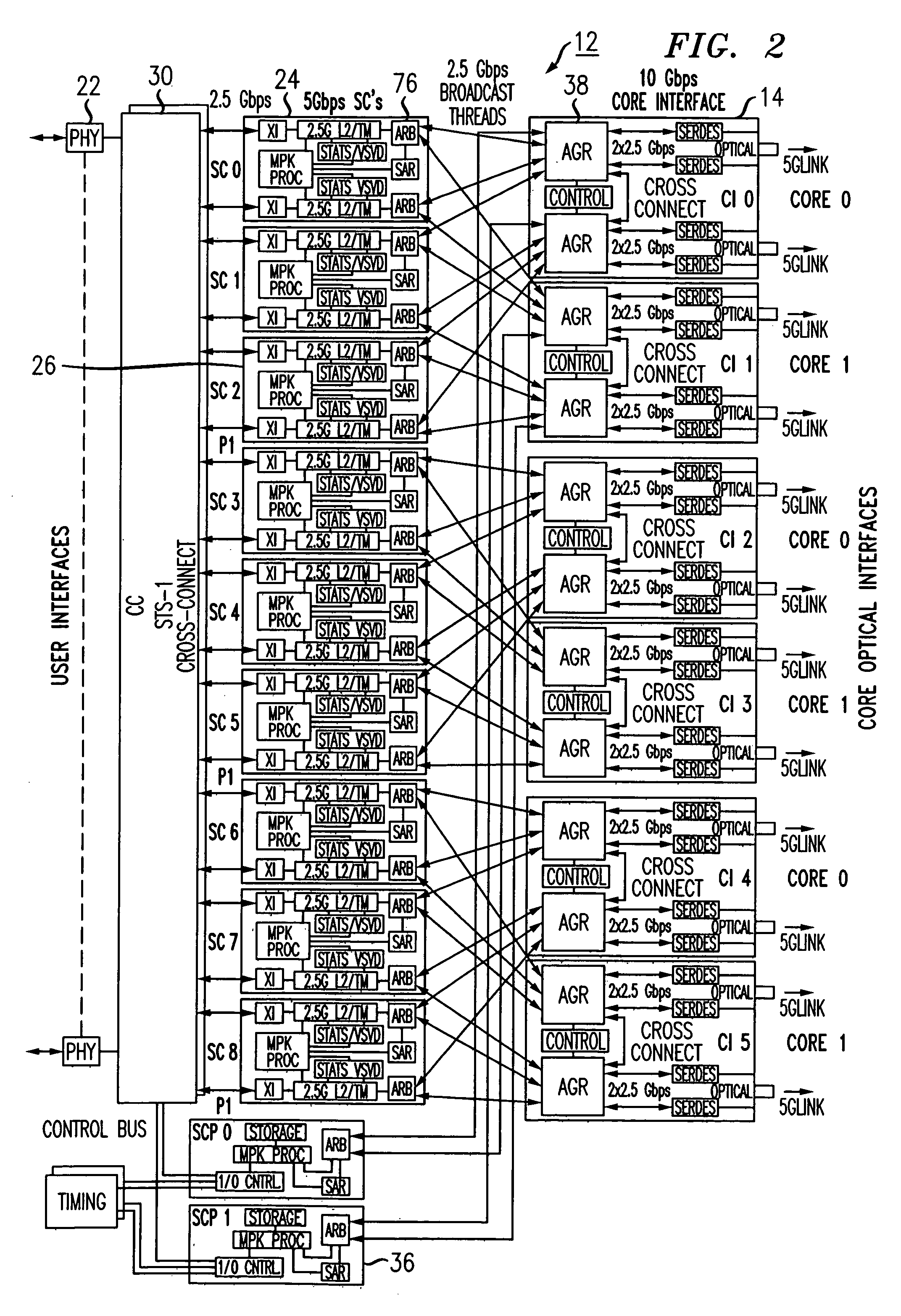
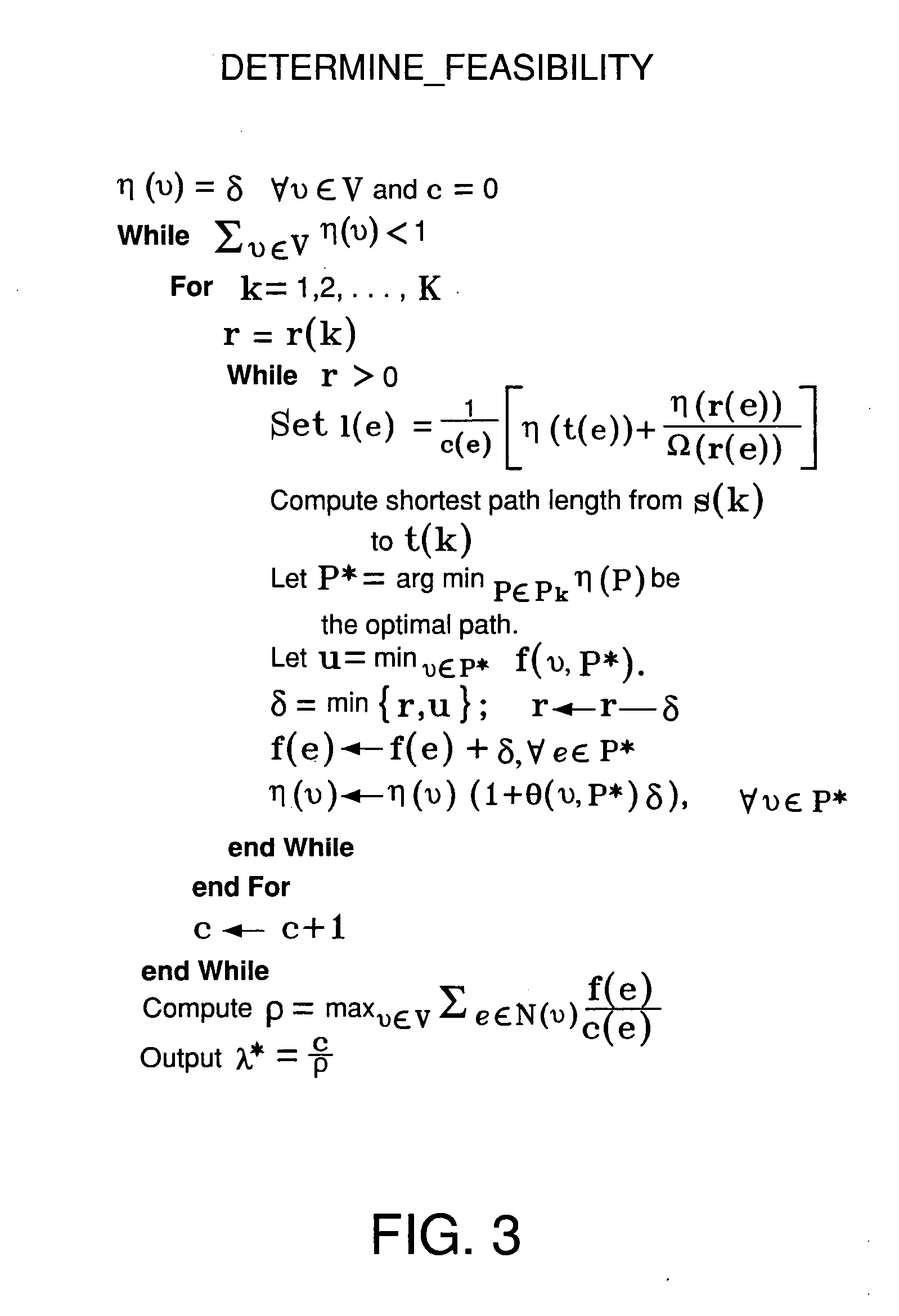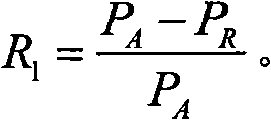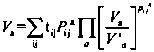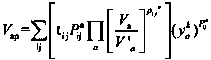Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
83 results about "Link flow" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
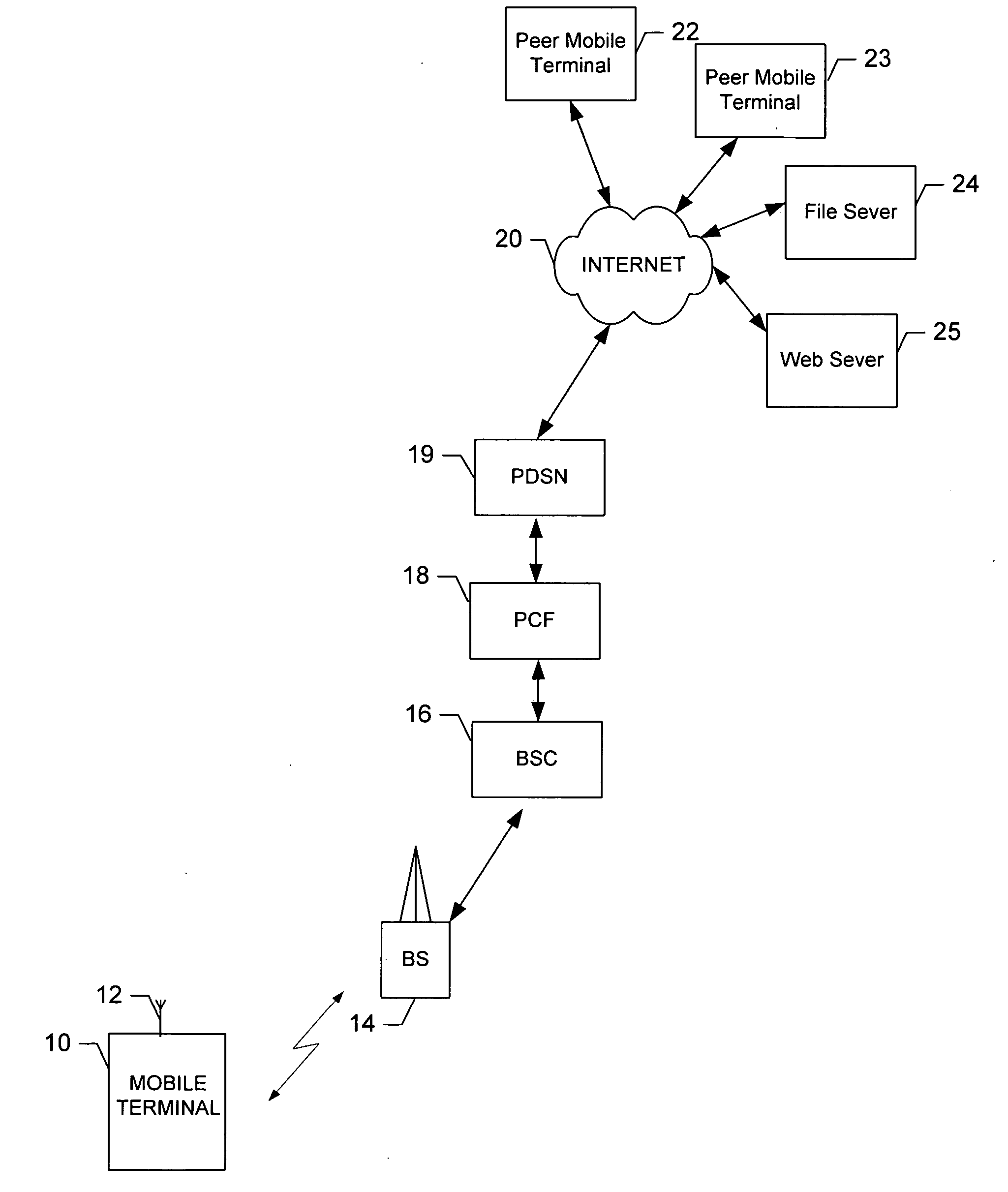
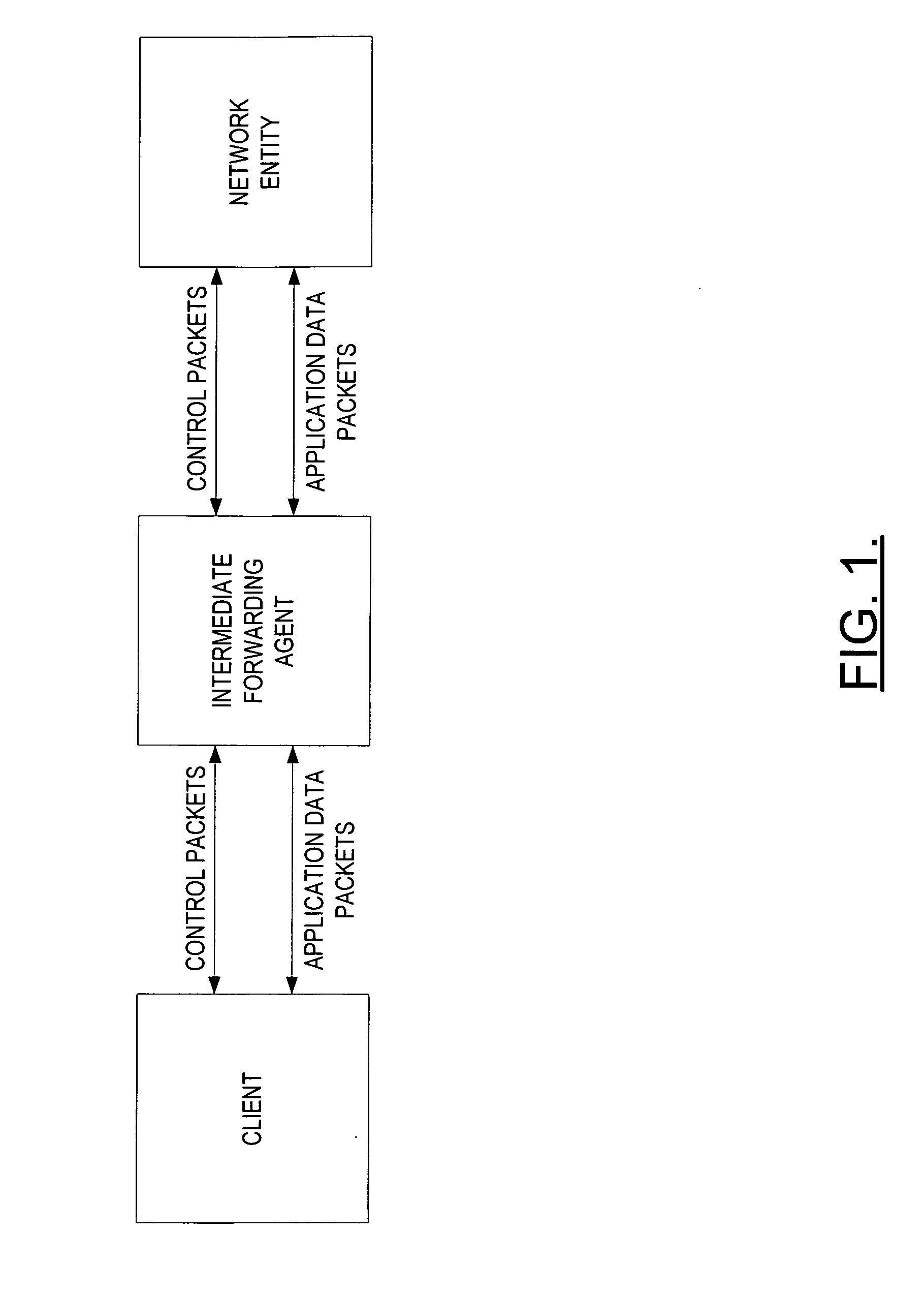
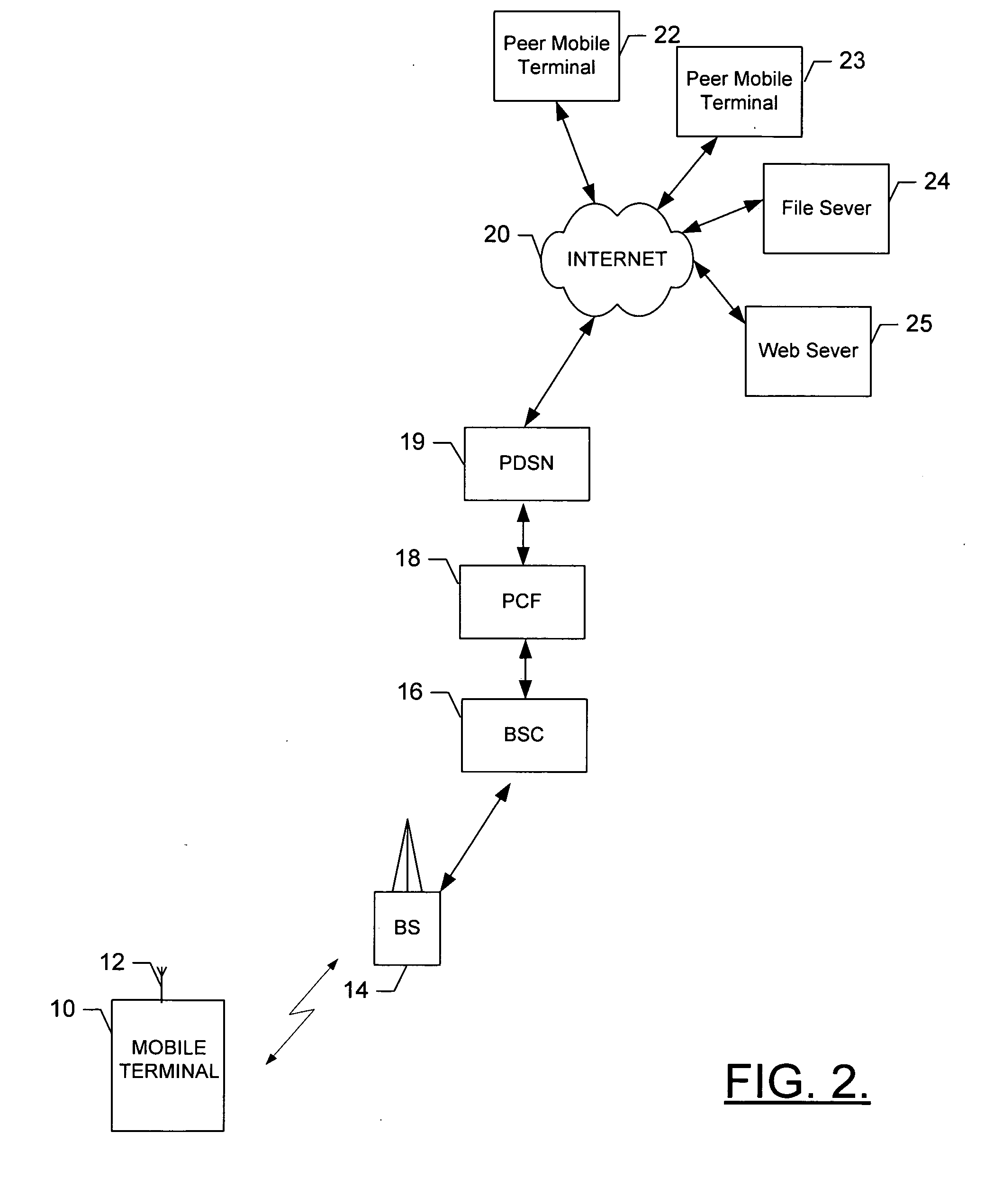
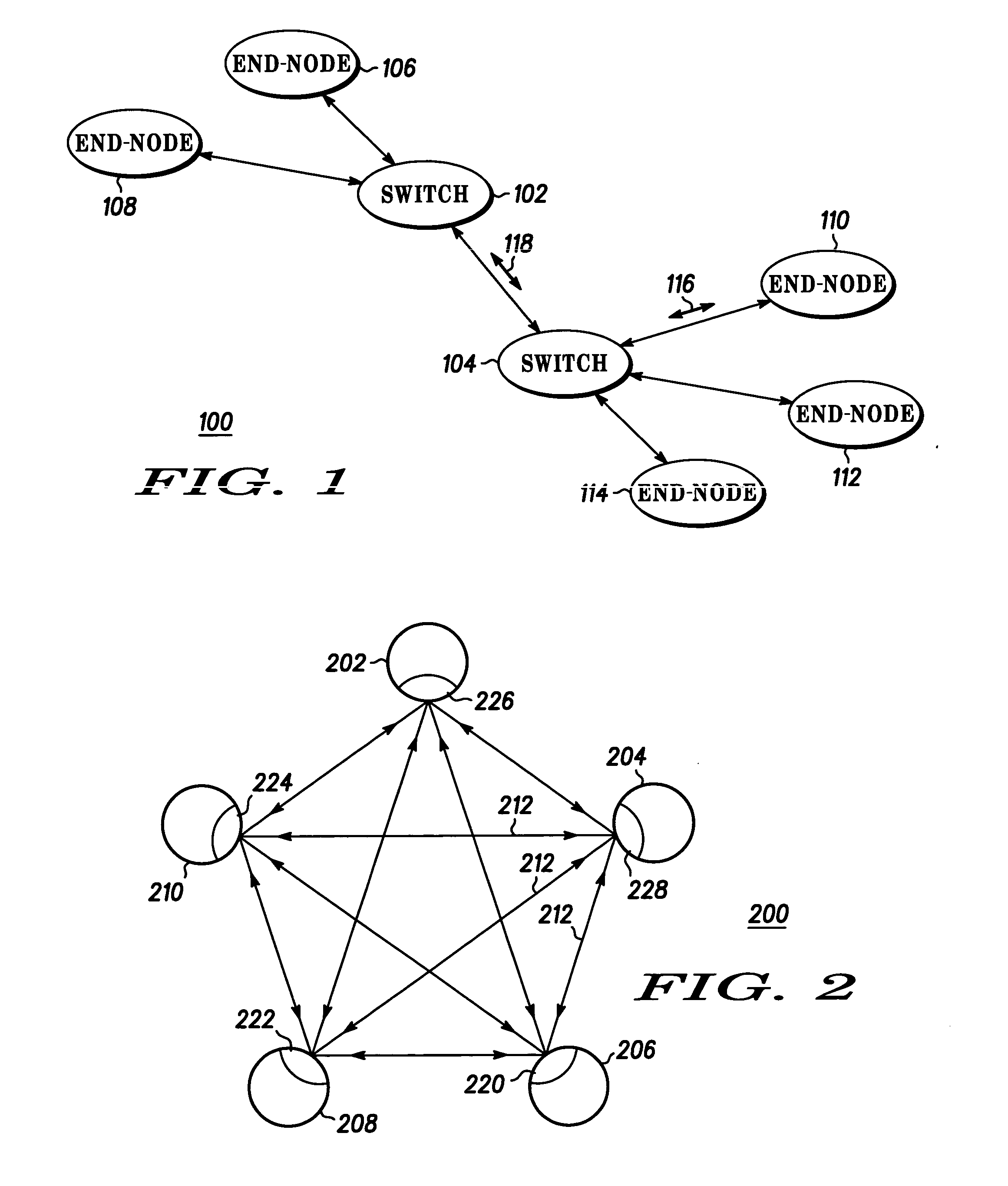
Prioritized control packet delivery for transmission control protocol (TCP)
InactiveUS20070091900A1Raise priorityFaster packet queue processing timeNetwork traffic/resource managementTime-division multiplexLink flowNetsniff-ng
A method is provided for transmitting data, wherein control packets are given priority with respect to application data packets. In general, this is accomplished by establishing a separate, distinct link flow over which only control packets (e.g., TCP control packets) will be transmitted. A higher priority is associated with this link flow. In addition, the reliability of control packets sent over the dedicated link flow can be improved upon by increasing the number of retransmissions associated with the control packets and / or decreasing the window of time before the retransmissions are sent. A system, mobile terminal, network entity, and computer program product for implementing the method are also provided.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Characterizing achievable flow rates in multi-hop mesh networks with orthogonal channels
InactiveUS20070025364A1Time-division multiplexData switching by path configurationMultiple edgesEdge coloring
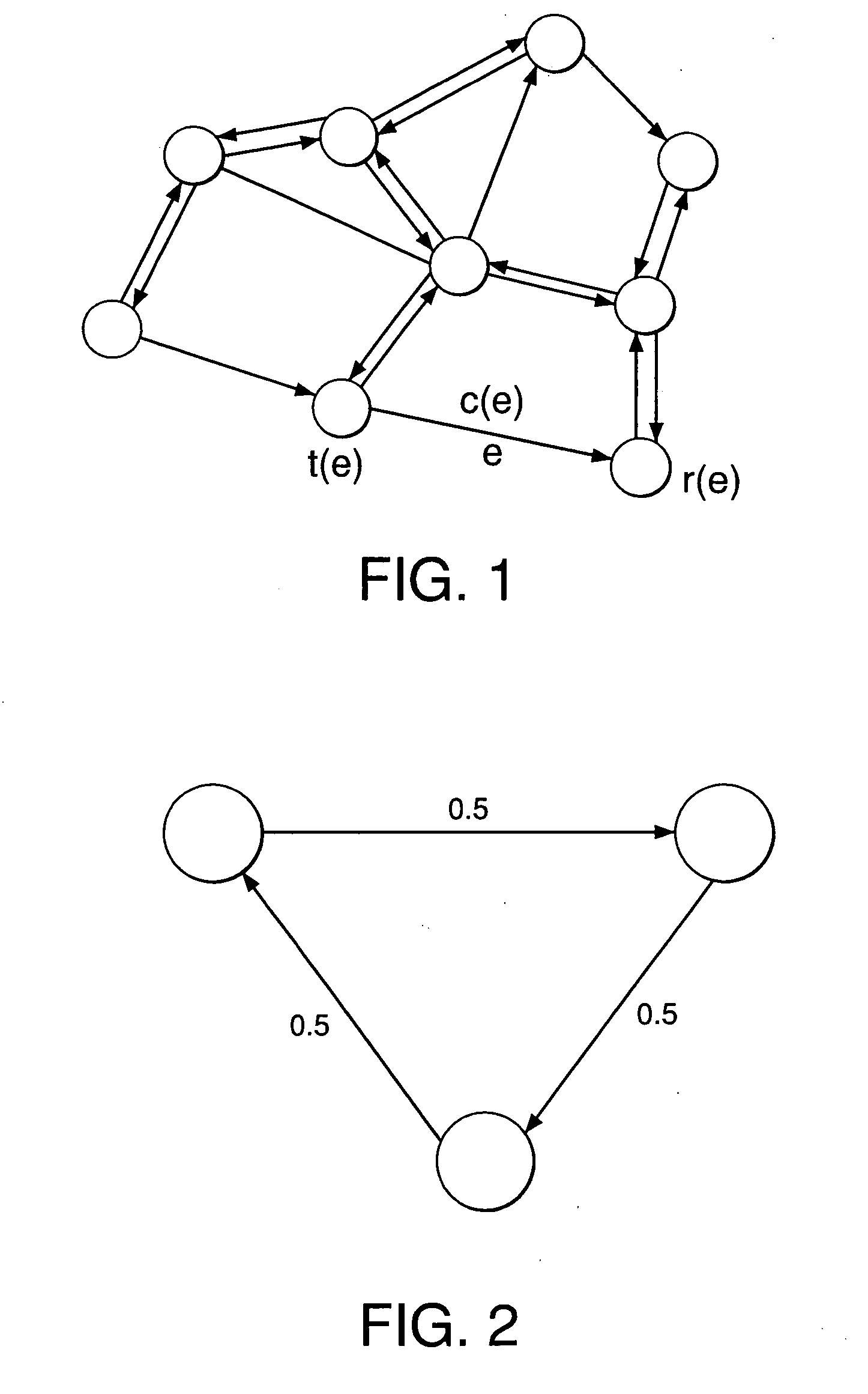
A method of routing data from a source node to a destination node in a multi-hop network of nodes interconnected by links comprises: (a) determining that a link-flow vector satisfies one or more necessary scheduling conditions for achievability, wherein the link-flow vector represents a set of flows to be routed on one or more links from the source node to the destination node; (b) generating a scheduling multi-graph for the network, wherein the scheduling multi-graph comprises a graph having at least one pair of nodes with multiple edges therebetween; (c) deriving one or more sufficient scheduling conditions for achievability of the link-flow vector by edge-coloring the scheduling multi-graph; (d) solving a linear optimization problem over the one or more necessary scheduling conditions to obtain an upper bound on the achievability of the link-flow vector; (e) generating, based on the scheduling multi-graph, a solution comprising a set of routes and an associated schedule for achieving the link-flow vector, the solution being a lower bound on the achievability of the link-flow vector; and (f) implementing a routing method using the set of routes and the associated schedule to route the link-flow vector from the source node to the destination node. At least one node v of the network is adapted to receive transmissions from a specified plurality Ω(v) of other nodes, and at least one of the scheduling conditions depends on Ω(v).
Owner:ALCATEL-LUCENT USA INC +1
System and method for regulating message flow in a digital data network
InactiveUS7283471B2Fairness among all virtual circuits for buffer resourcesStop transmissionError preventionFrequency-division multiplex detailsDigital dataPathPing
A system includes a plurality of computers interconnected by a network including one or more switching nodes. The computers transfer messages over virtual circuits established thereamong. A computer, as a source computer for one or more virtual circuit(s), schedules transmission of messages on a round-robin basis as among the virtual circuits for which it is source computer. Each switching node which forms part of a path for respective virtual circuits also forwards messages for virtual circuits in a round-robin manner, and, a computer, as a destination computer for one or more virtual circuit(s), schedules processing of received messages in a round-robin manner. Round-robin transmission, forwarding and processing at the destination provides a degree of fairness in message transmission as among the virtual circuits established over the network. In addition, messages are transmitted in one or more cells, with the round-robin transmission being on a cell basis, so as to reduce delays which may occur for short messages if a long messages were transmitted in full for one virtual circuit before beginning transmission of a short message for another virtual circuit. For each virtual circuit, the destination computer and each switching node along the path for the virtual circuit can generate a virtual circuit flow control message for transmission to the source computer to temporarily limit transmission over the virtual circuit if the amount of resources being taken up by messages for the virtual circuit exceeds predetermined thresholds, further providing fairness as among the virtual circuits. In addition, each switching node or computer can generate link flow control messages for transmission to neighboring devices in the network to temporarily limit transmission thereto if the amount of resources taken up by all virtual circuits exceeds predetermined thresholds, so as to reduce the likelihood of message loss.
Owner:AVAGO TECH INT SALES PTE LTD
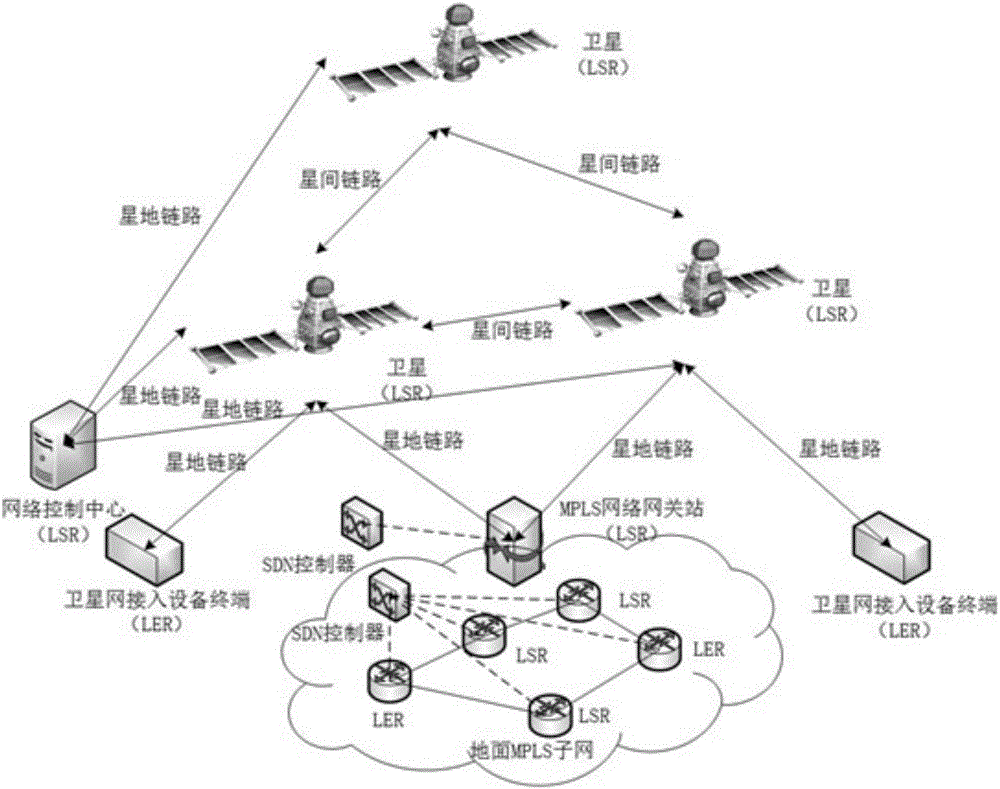
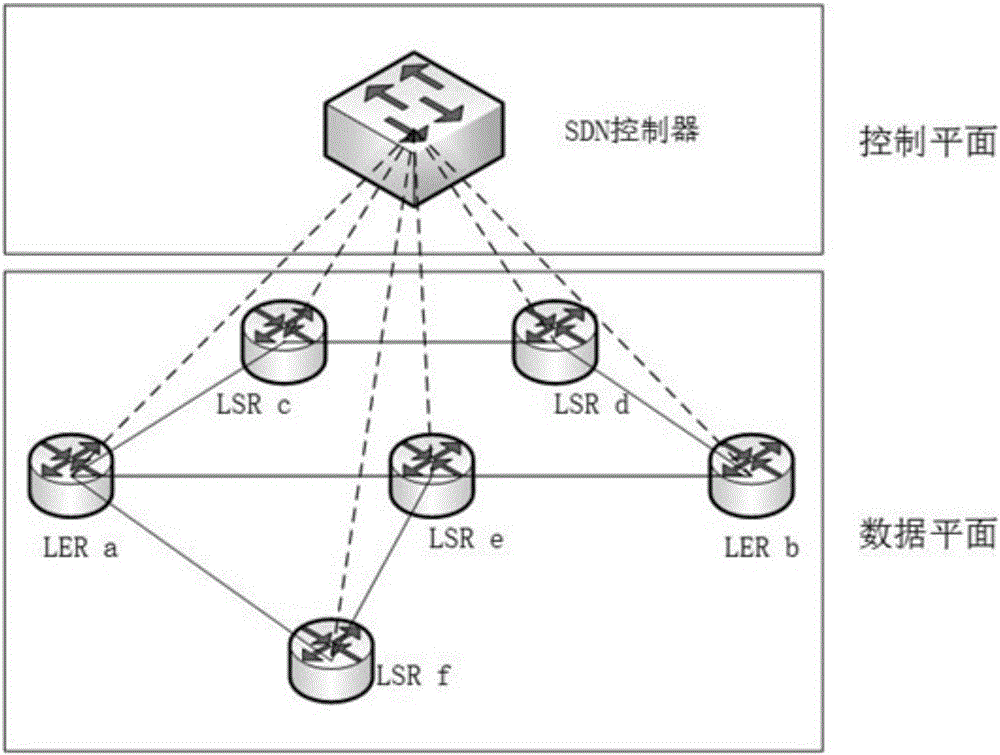
Satellite MPLS (multi-protocol label switching) network flow rate balancing method based on SDN (software defined network) controller
ActiveCN106789658AImprove service qualityImprove instabilityRadio transmissionData switching networksResource utilizationMulti protocol
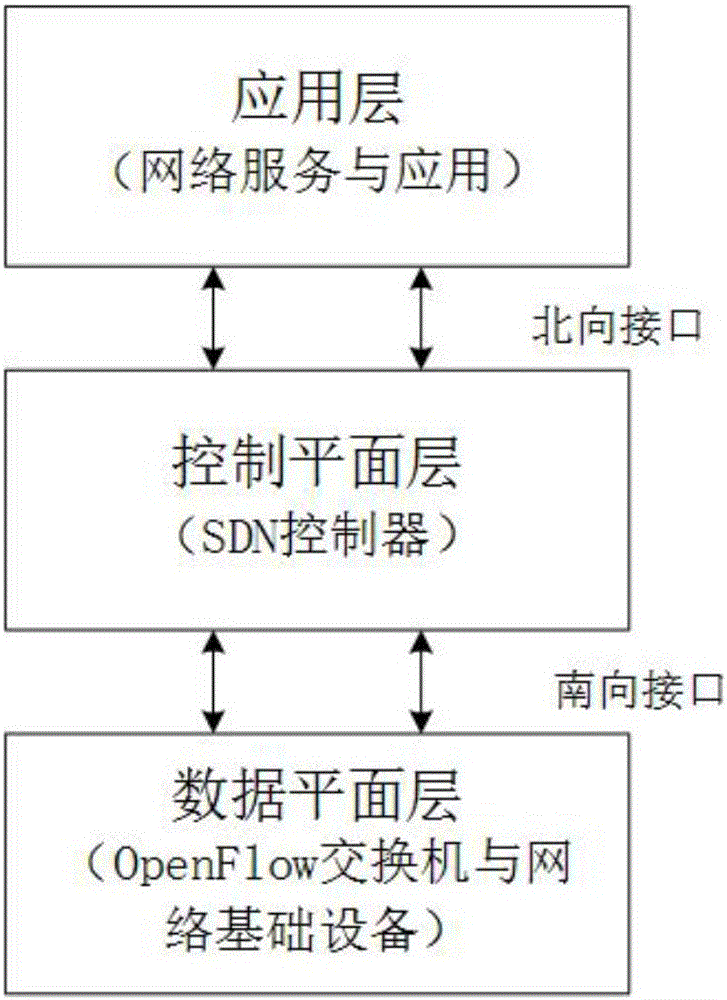
The invention discloses a satellite MPLS (multi-protocol label switching) network flow rate balancing method based on an SDN (software defined network) controller. An SDN controller is put on a network edge; the control plane of network equipment is separated from the data plane; the functions of the control plane are concentrated onto a special controller, so that the equipment complexity in the network is reduced. The data plane and the control plane are decoupled, and an SDN obtains great flexibility, so that the network has the characteristics of high expandability, easy maintenance, programmable performance and open performance. According to the method, the SDN controller peripherally collects network topology and network state information from a router / interchanger in a data plane through an OpenFlow protocol of a southbound interface; through calculation, the available bandwidth condition of each link is obtained, so that whether the path jam occurs or not is judged; whether the flow rate dispatching is needed or not is judged; the goal of collecting and analyzing the whole network flow rate distribution condition in real time is achieved; the link flow rate is reasonably deployed, so that the flexible control of the network flow rate is realized; in addition, the bandwidth resource utilization rate can be better improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
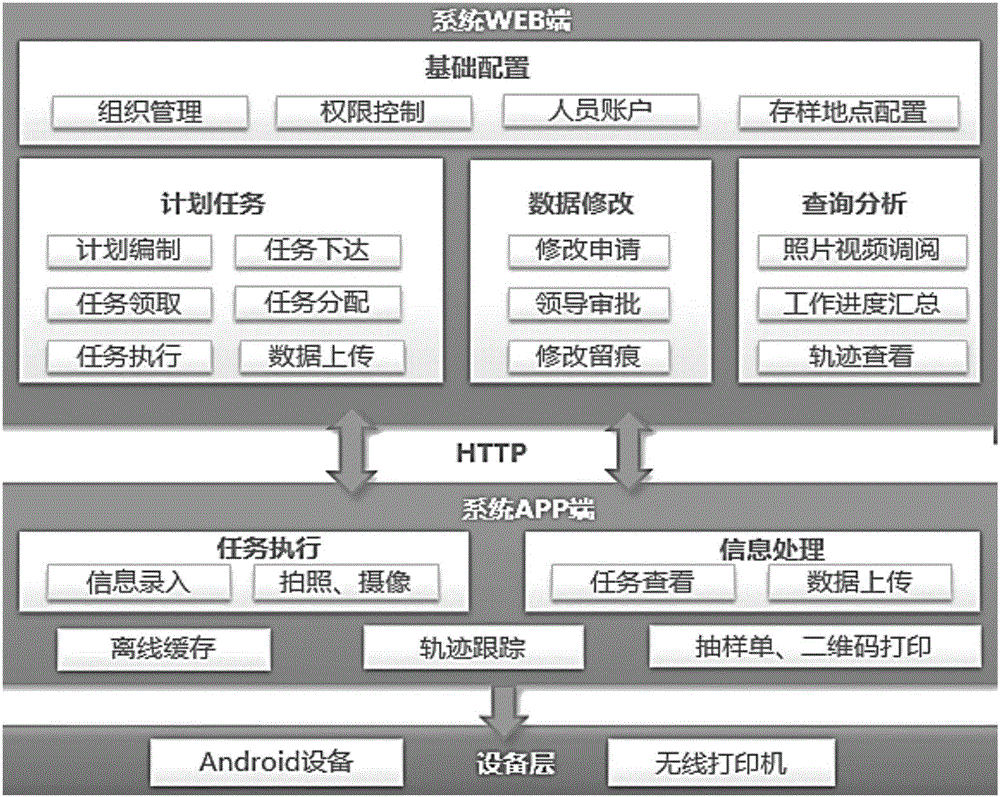
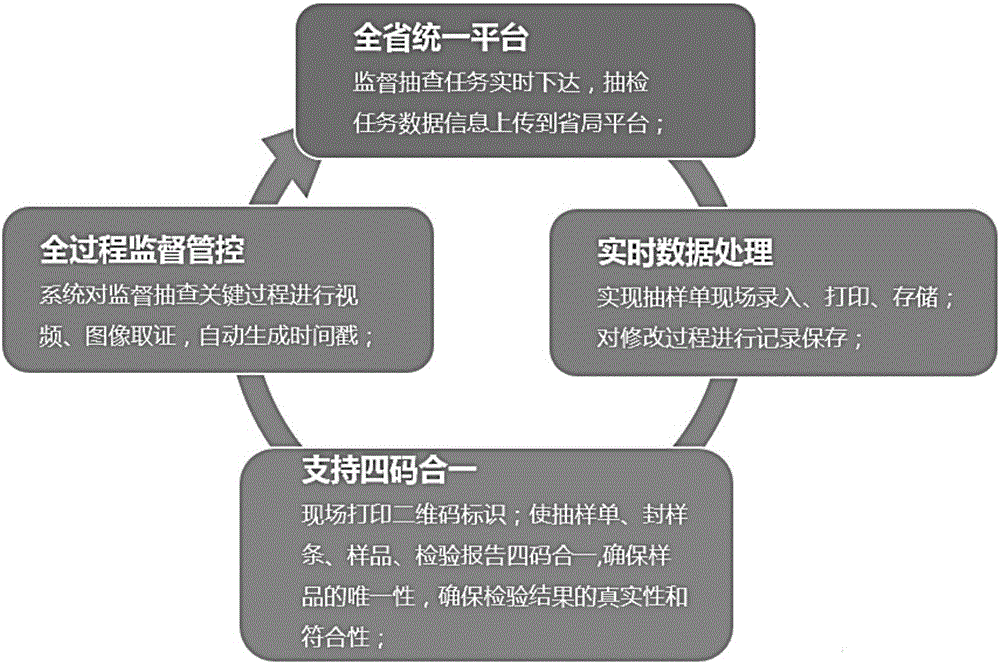
Quality random inspection execution process supervision system
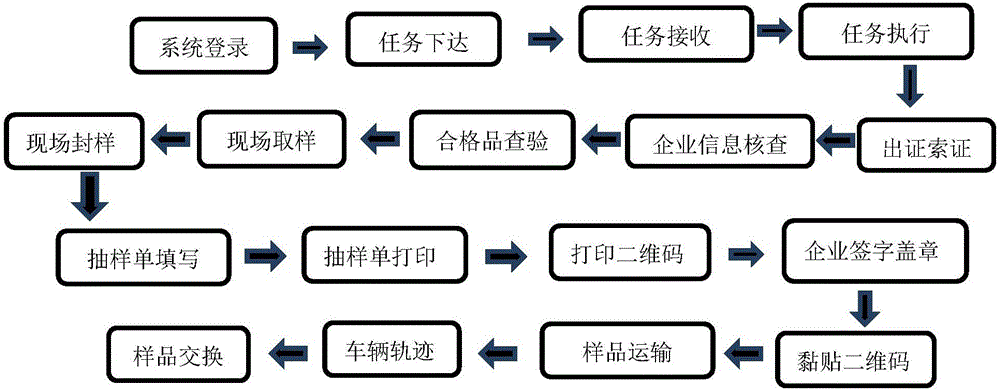
InactiveCN106408173ARaise the level of innovation and developmentSatisfies the requirement of "inverting the burden of proof" for the administrative act of evidence fixationResourcesCommerceTTEthernetNetwork connection
The invention relates to a quality random inspection execution process supervision system. With a B / S architecture adopted, a supervisor monitors and manages an execution process through adopting mobile Internet technologies and by means of a supervision server, namely, a supervision port, which is constructed through a browser, a server or the like, and a mobile phone or special execution terminal used by field execution staff, such as a mobile phone equipped with special application software; the supervision server of the system is provided with a recording database and a random inspection process supervision module; the execution terminal is in network connection with the supervision port so as to carry out sampling / sample purchase planning, task reception, download and information inputting of various steps of a random inspection execution process; the information acquisition of the solidified flow of the random inspection execution process can be obtained through the solidified sampling / sample purchase link flow module of the execution terminal; and the field random inspection staff carries out random inspection process execution and stores information and evidences of each step through using the application of the mobile phone or special execution terminal application.
Owner:邱霓 +1
Fast flow control methods for communication networks
InactiveUS7221653B2Reduce distractionsMaximize capacityError preventionNetwork traffic/resource managementTraffic capacityLink data
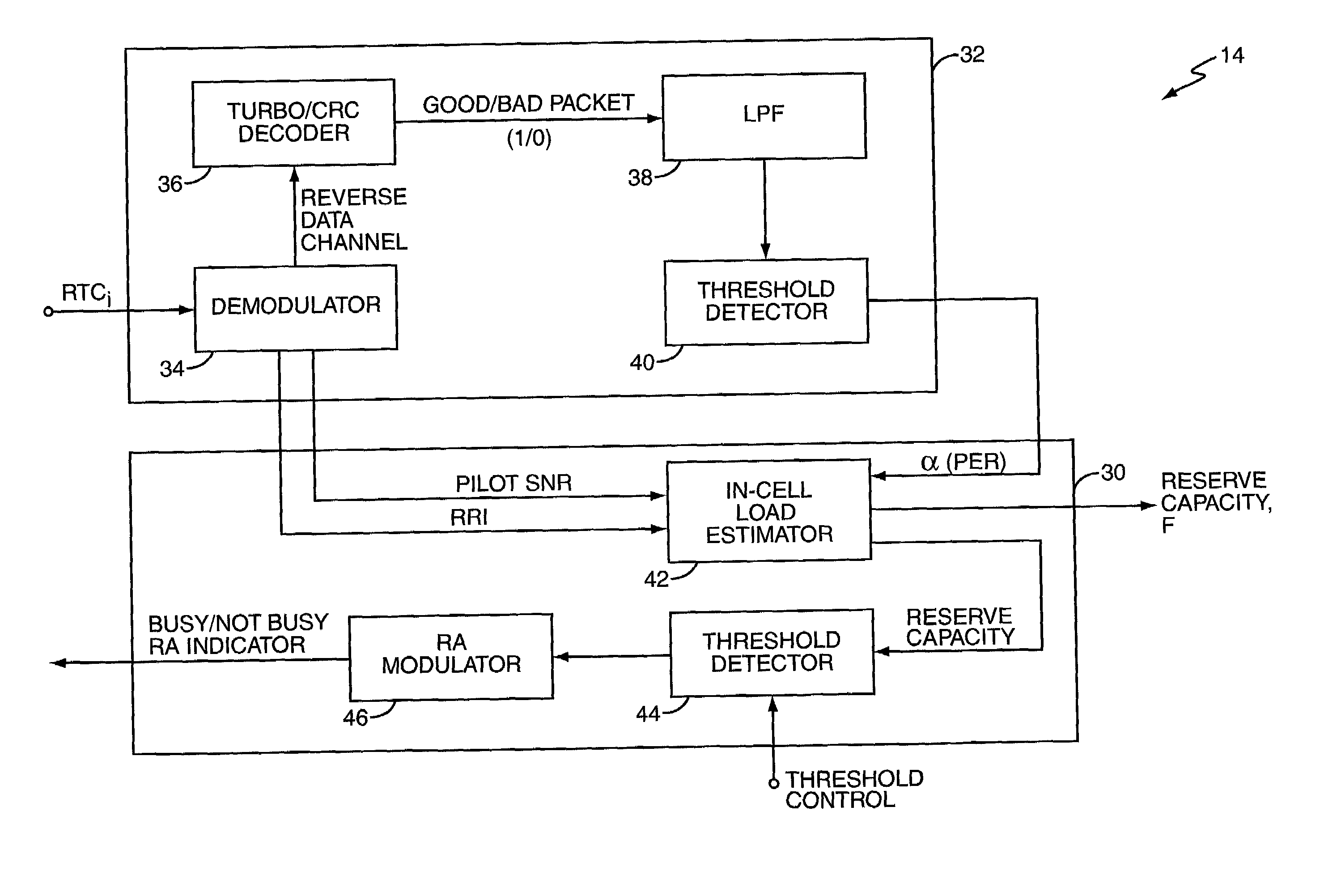
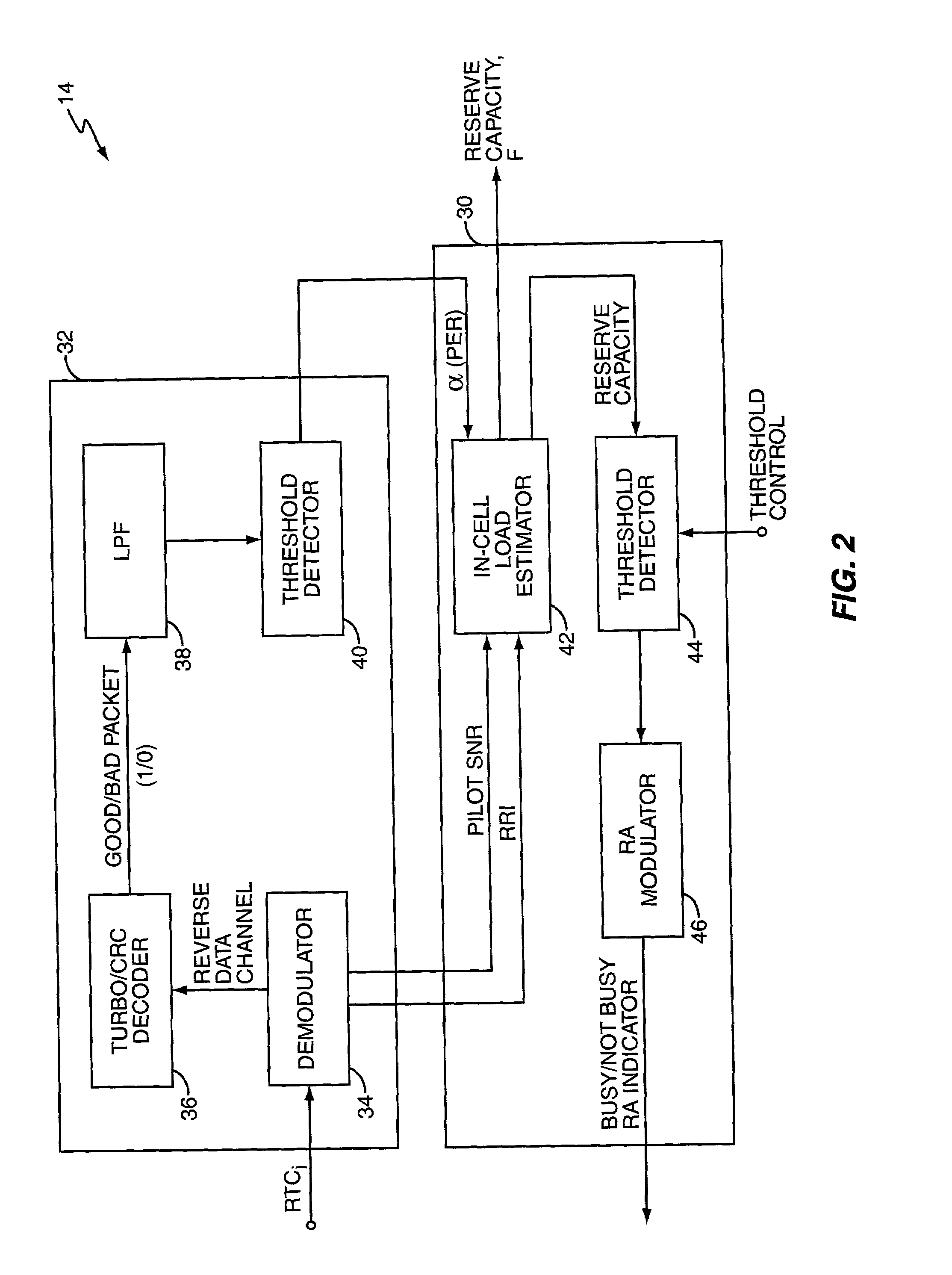
Reverse link flow control in a high data rate network determines current reverse link data channel rates for access terminals served by a network sector to identify corresponding defined channel gains, which are used to rapidly and reliably estimate total sector interference on the reverse link. Total sector interference indicates reverse link capacity utilization, and when remaining capacity approaches a defined threshold, the sector sets an activity indicator to a busy state indicating reverse link congestion. This action causes at least some access terminals to reduce their reverse link data channel rate. Interference calculation techniques preferably involve baseband digital processing using defined channel gains, permitting rapid evaluation of reverse link capacity and quick, reliable activity indicator updating, which increases reverse link capacity utilization. These techniques may be applied to inter-sector control, wherein the reverse activity indicator status for one sector depends on interference in one or more other sectors.
Owner:OPTIS WIRELESS TECH LLC
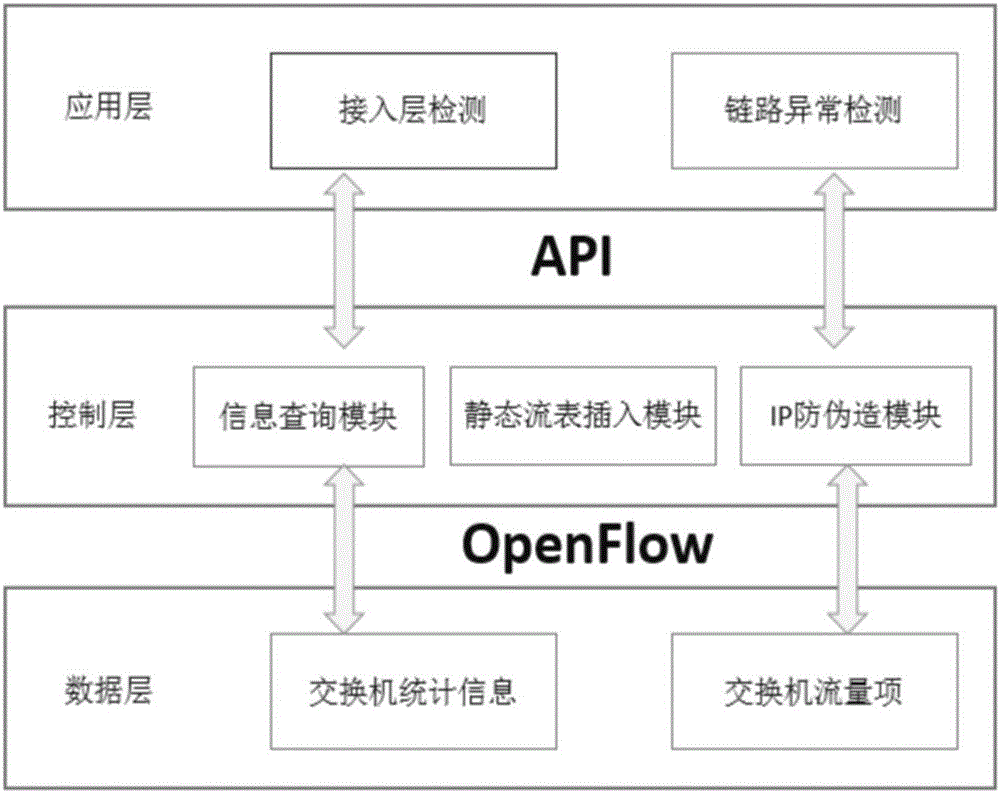
Network anomaly flow detection and defense system based on SDN (software defined networking)
The invention provides a network anomaly flow detection and defense system based on SDN (software defined networking). The SDN is quite different from a traditional network for detecting anomaly flow, a traditional detection method is enabled to be inapplicable, and with the application of the thought of separating a network control plane and a data plane, a new solution is provided for research and development of novel network applications and treatment of network security problems by the SDN. Based on the characteristics of centralized control and the like of an SDN structure, real-time flow monitoring is realized at the attack source, a multi-defense system is formed by adopting source IP anti-counterfeiting, access layer anomaly detection and link flow anomaly detection, anomaly flow is gradually filtered, and detection and defense for network layer DDoS (distributed denial of service) attacks at the source end are realized.
Owner:BEIJING UNIV OF TECH
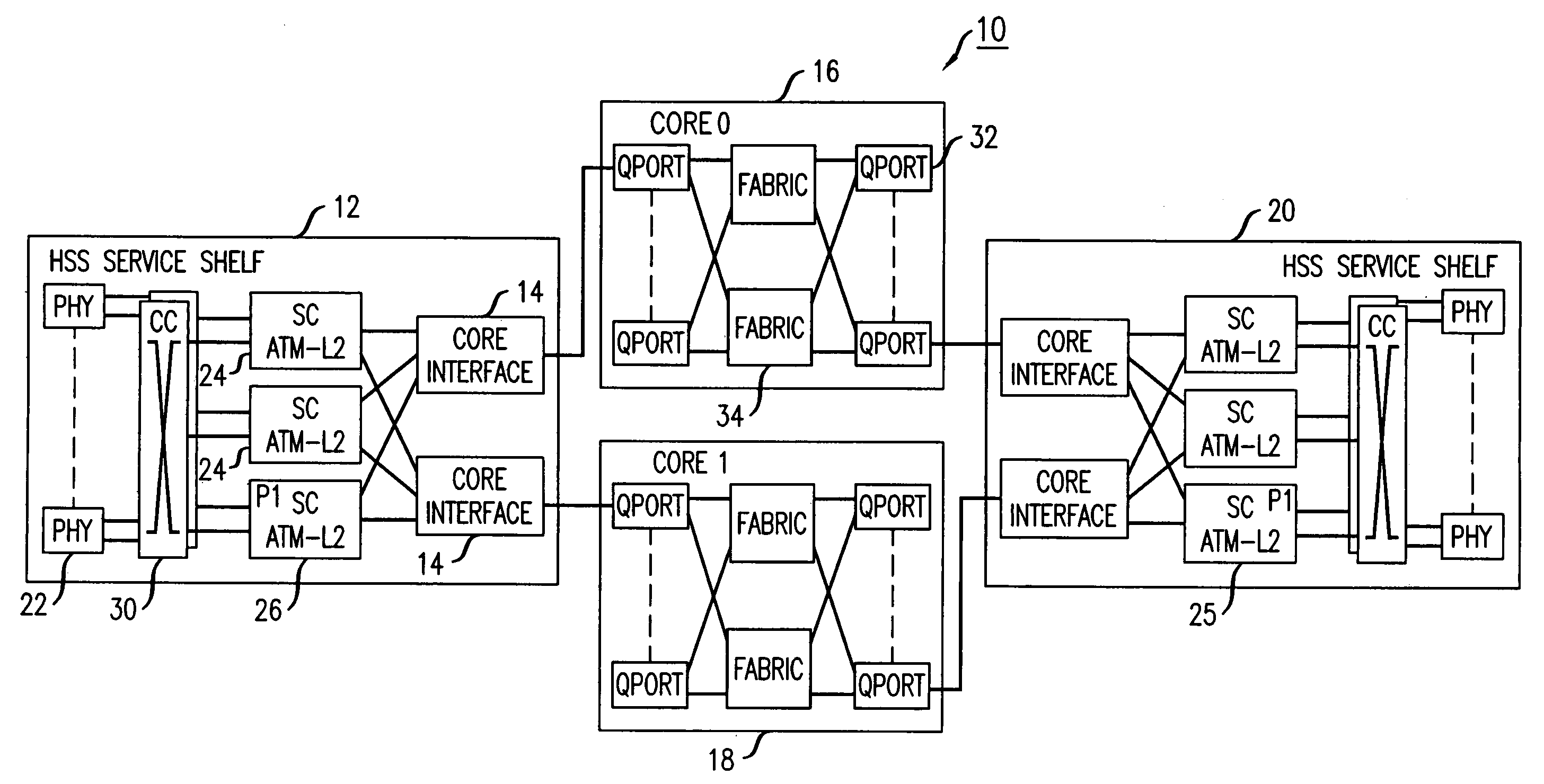
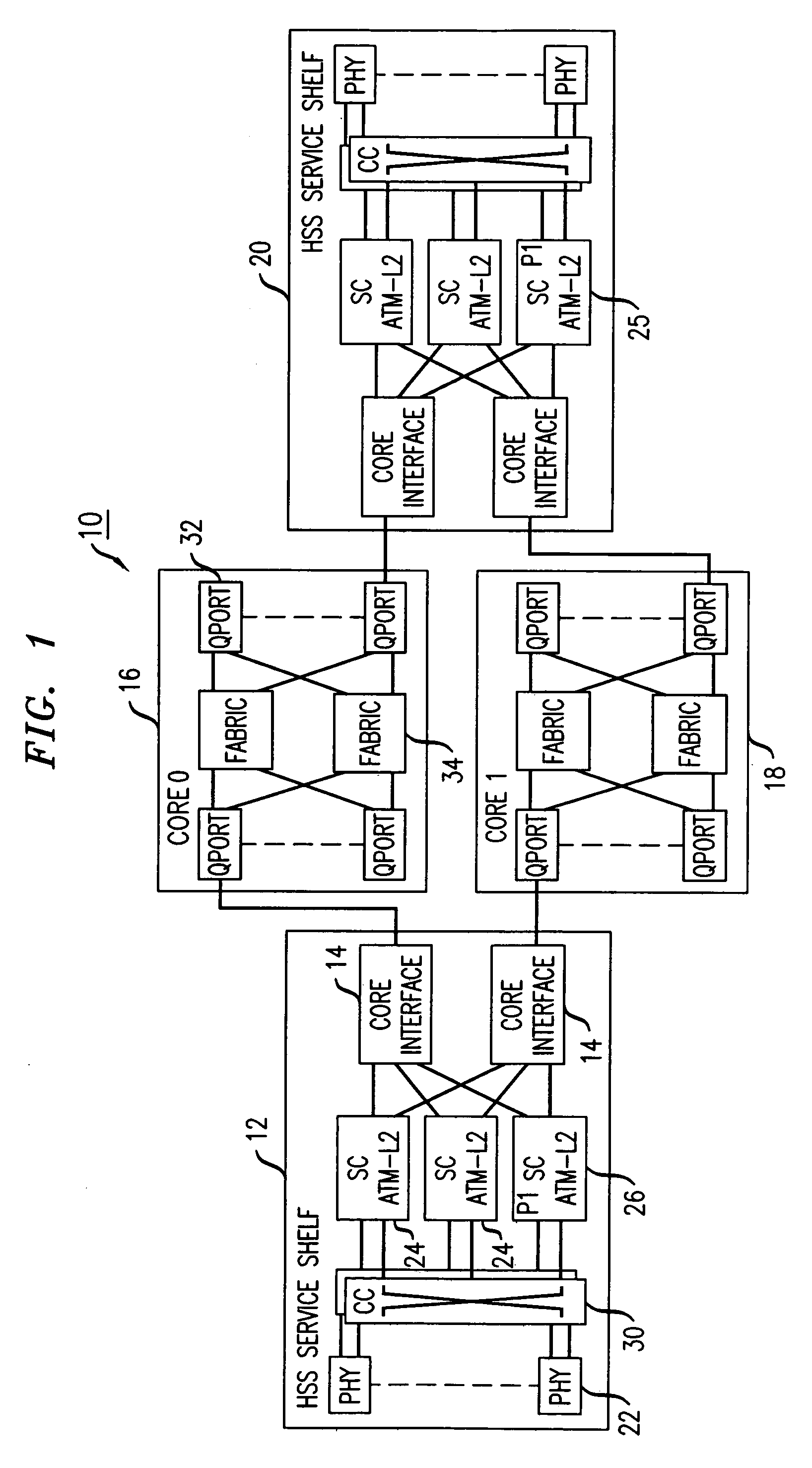
Apparatus and method for flow path based fault detection and service restoration in a packet based switching system
A methodology is provided for fault detection and service restoration in a multiservice switch on a per flow basis. An ingress source transmits the same data over each of two redundant cores. An egress receiver selects on a per flow bass which core to utilize. Bi-directional flows are not necessarily grouped together. The basic approach to fault detection is to assume that the two cores are not in lock step, but that the shelves are continually monitoring link flows for control path data as well as user data. The path monitoring is accomplished using a combination of arbiter and aggregator functions found in the service shelves and core interface cards, respectively. The arbiter transmits link test cells to both cores on a per flow basis, wherein the link test cells traverse and are monitored by respective aggregators to and from each core. When an egress arbiter determines that a flow is bad, it initiates a switch to the alternative source core, from which the flow would continue.
Owner:LUCENT TECH INC
Characterizing the capacity region in multi-channel, multi-radio mesh networks
InactiveUS20070147248A1Error preventionFrequency-division multiplex detailsOptimization problemLink flow
A method of characterizing a capacity region in a multi-channel, multi-radio mesh network of nodes interconnected by links. The method includes: (a) modeling the network by determining one or more link-flow feasibility constraints; (b) obtaining a feasible upper-capacity bound by solving an optimization problem using the one or more link-flow feasibility constraints as necessary conditions; and (c) using an algorithm adapted to provide a feasible lower-capacity bound by (i) receiving the solution to the optimization problem as input, (ii) allocating channels to links to meet a demand vector that satisfies the one or more link-flow feasibility constraints, and (iii) scheduling flows along the allocated channels. The upper- and lower-capacity bounds define the capacity region.
Owner:ALCATEL-LUCENT USA INC +1
Increment deployment SDN network-based method for defending link flooding attack
The invention relates to an increment deployment SDN network-based method for defending a link flooding attack. A node upgrade algorithm is utilized to pick out routers that need to be upgraded into software-defined network function nodes and the routers are upgraded; when congestion occurs in a network, a congestion link is positioned through the software-defined network function nodes deployed in the network; congestion link information of the whole network is collected, and on this basis, whether current network congestion forms a link flooding attack is judged; and if the link flooding attach is formed, global flow engineering is started to balance flow of the whole network, otherwise, the congestion link is relieved through backup of a path. According to the increment deployment SDN network-based method for defending a link flooding attack, in a traditional network, a small quantity of nodes are upgraded into software-defined network function nodes, the link flooding attack is detected, a link group that is attacked is positioned, and link flow of the whole network is balanced through centralized control flow engineering, so that the root of a link flooding attack is eliminated, thereby effectively defending the link flooding attack.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
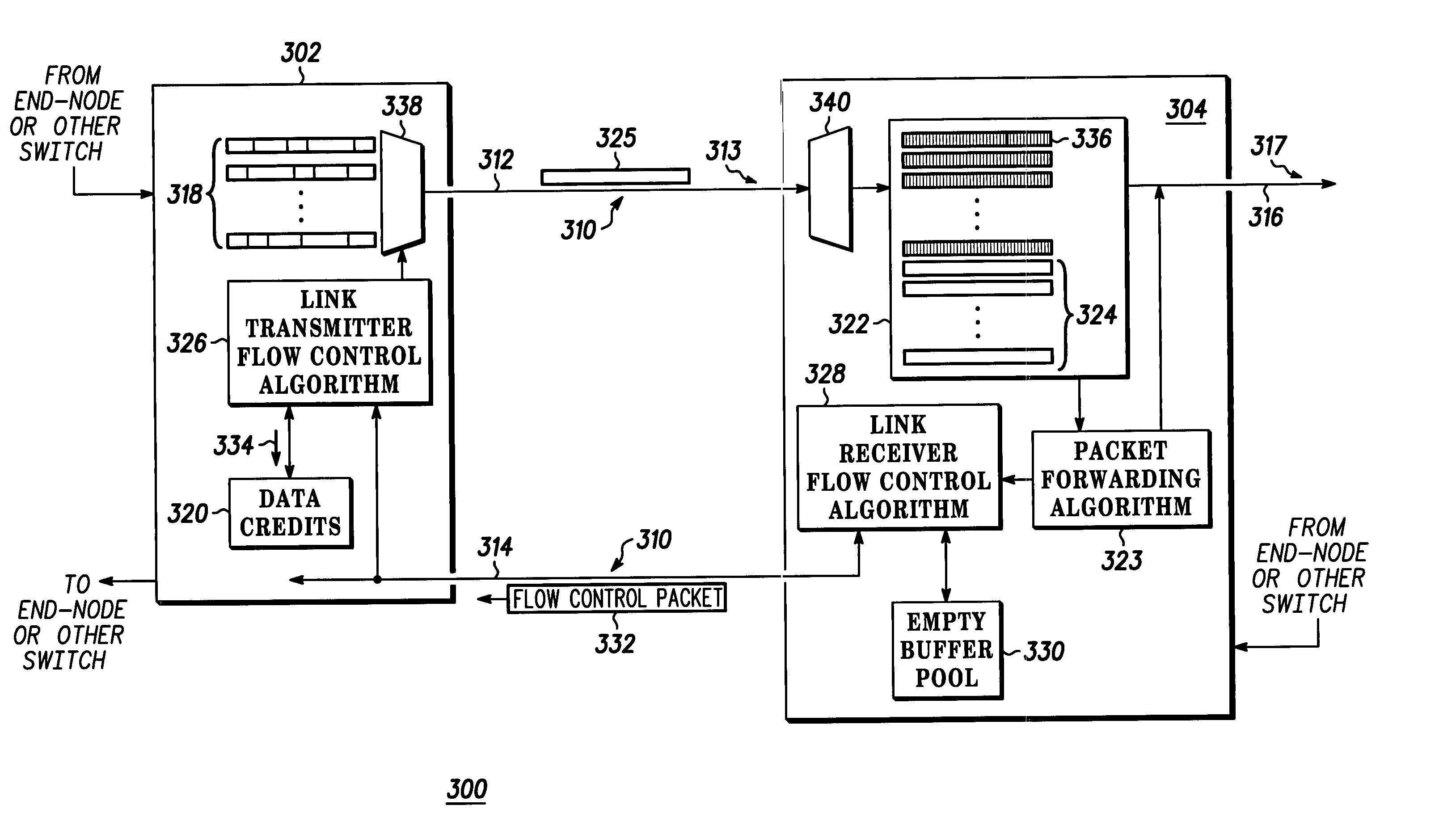
Method of transmitter oriented link flow control
InactiveUS20050063308A1Error preventionFrequency-division multiplex detailsTraffic capacityLink flow
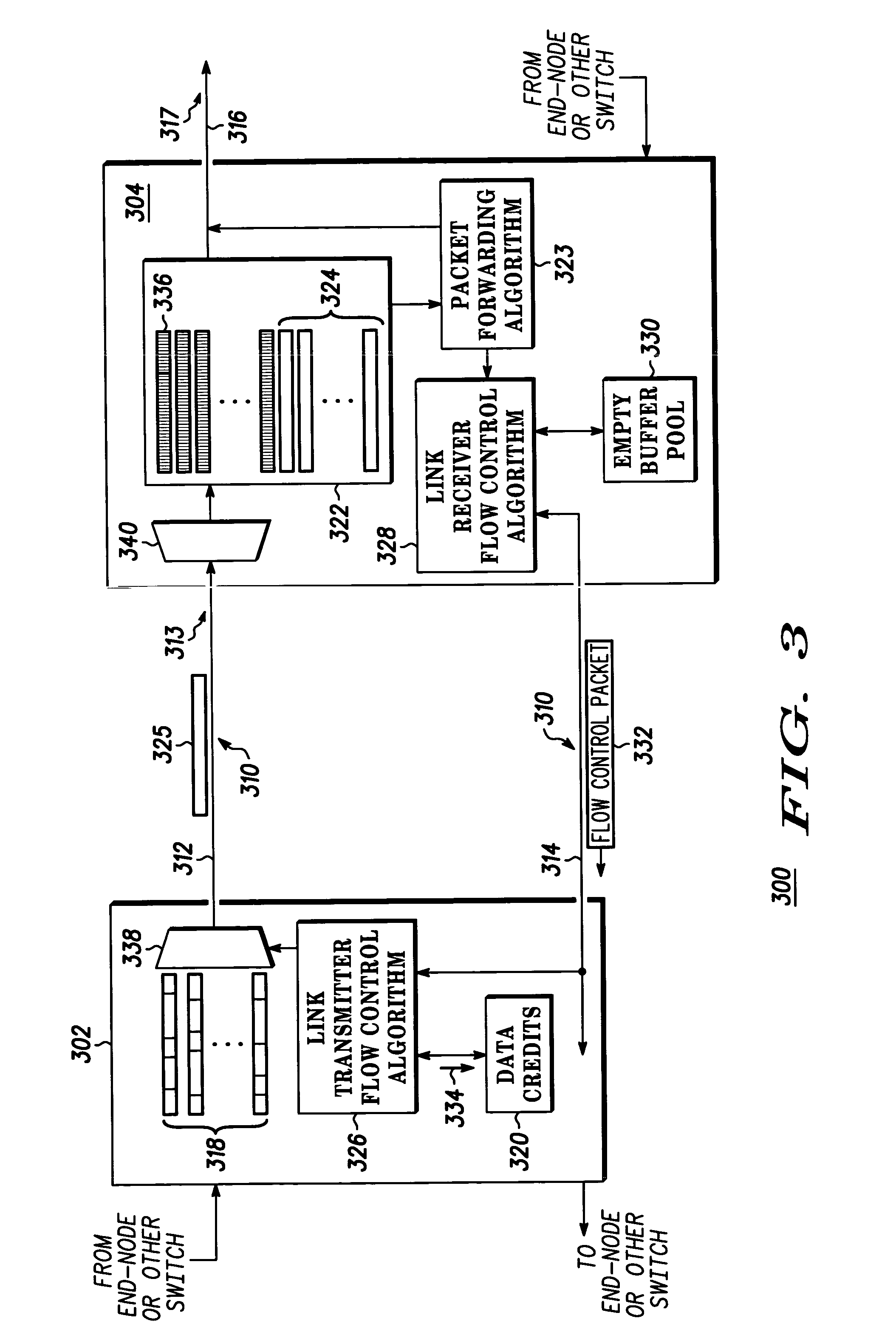
A method includes a link receiver (304) providing a plurality of data credits (320) to a link transmitter (302) and the link transmitter transmitting a packet (325) to the link receiver, where the link transmitter takes the packet from one of a plurality of logical channels (318), and where the link transmitter selects from which of the plurality of channels to draw the packet. The link receiver transmits a flow control packet (332) to the link transmitter to add additional data credits (334) to the plurality of data credits, where the link transmitter selects to which of the plurality of logical channels to allocate the additional data credits. A plurality of receiver buffers (322) are placed into a free buffer pool (330) as the packet is transmitting out of the plurality of receiver buffers, where the free buffer pool corresponds to additional data credits. The link receiver transmitting the flow control packet to the link transmitter on the reverse link (314) if the free buffer pool contains additional data credits and the reverse link is idle.
Owner:EMERSON NETWORK POWER EMBEDDED COMPUTING
Crossroad dynamic turning proportion two-step prediction method based on double Bayes
ActiveCN103927891ALarge local errorHigh precisionControlling traffic signalsSpecial data processing applicationsDesign improvementControl system
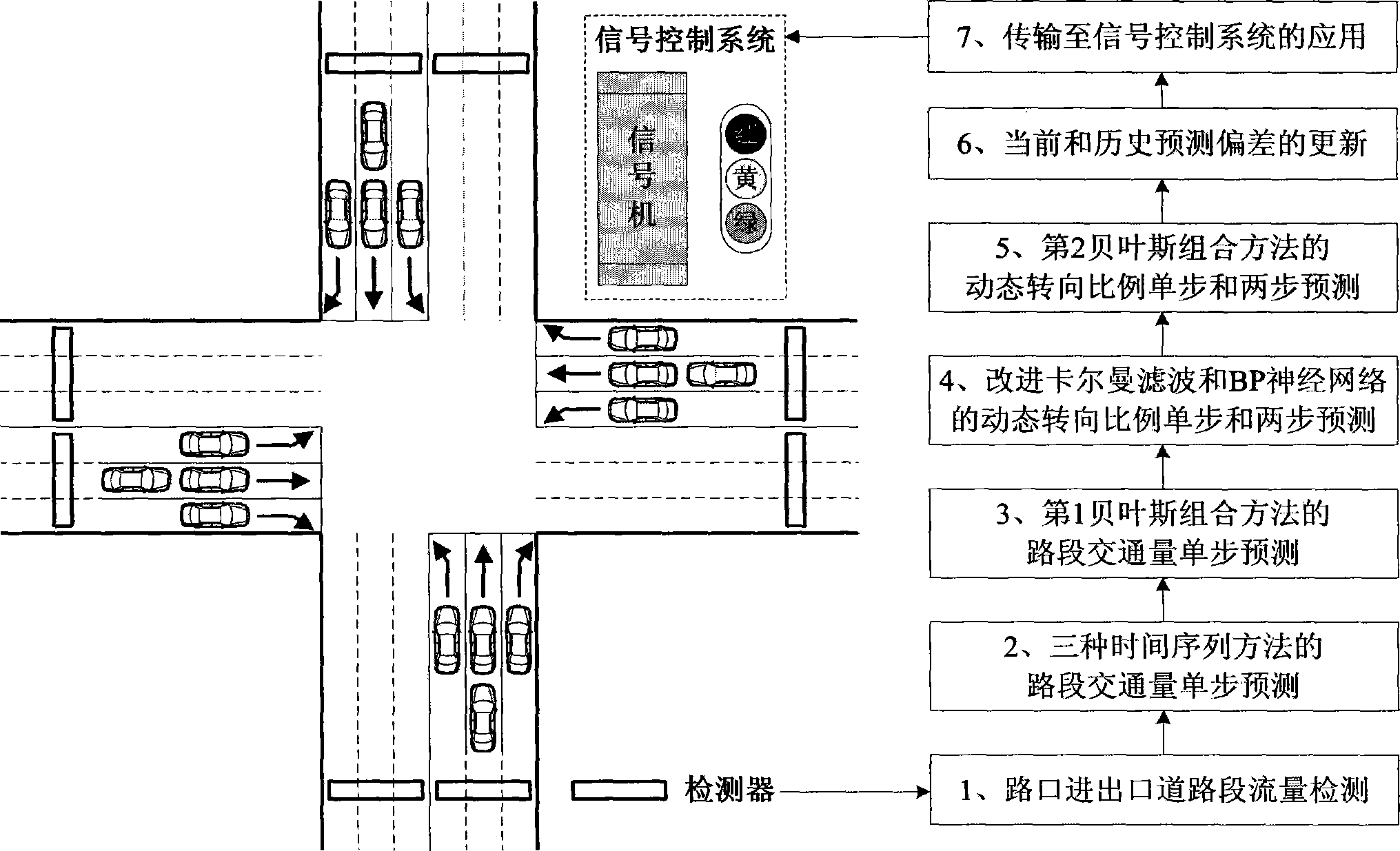
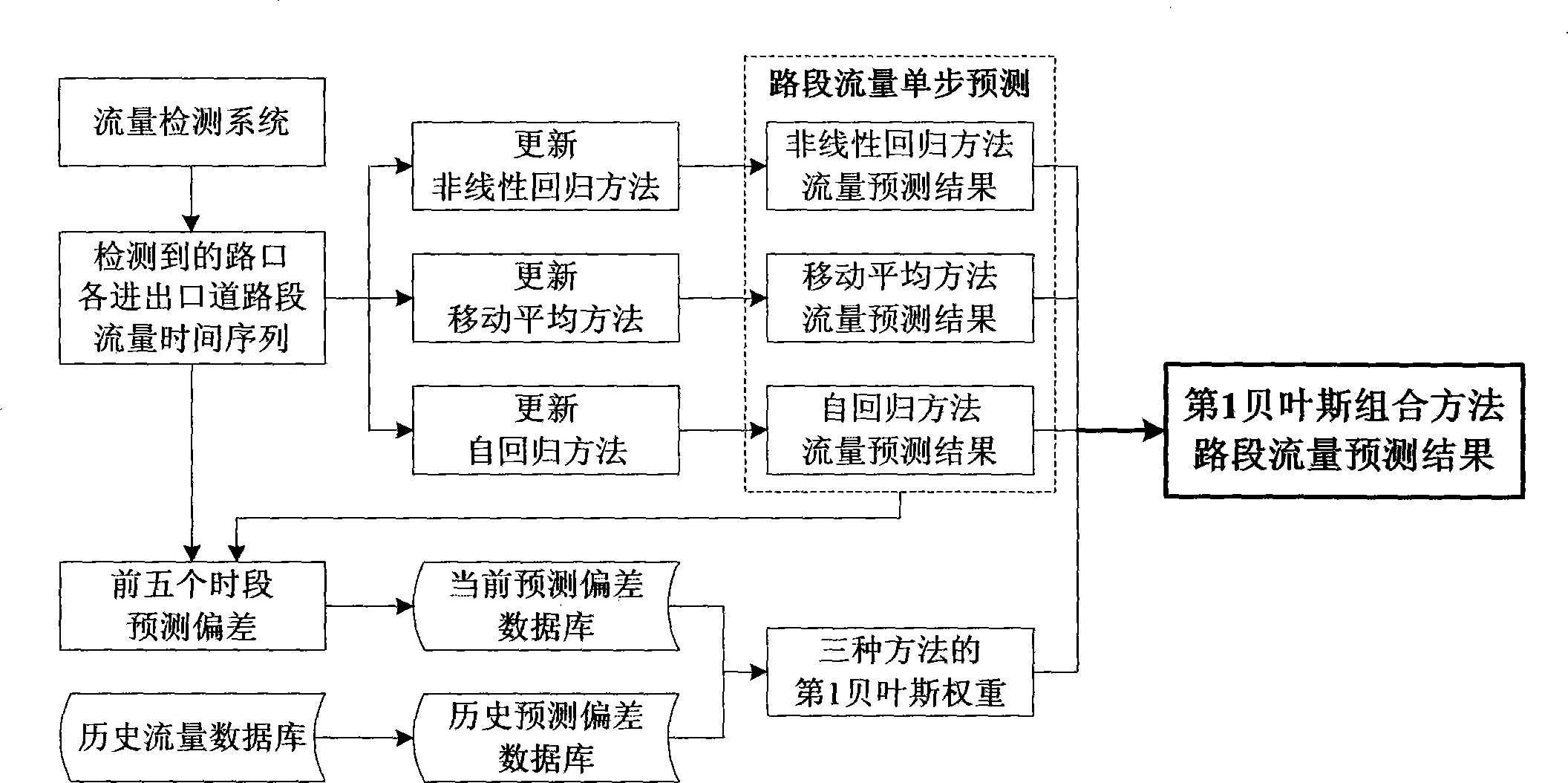
The invention discloses a crossroad dynamic turning proportion two-step prediction method based on double Bayes. According to the crossroad dynamic turning proportion two-step prediction method, a first Bayes combination method is designed by means of link flow detected by entries and exits at a crossroad and with combination of history flow data to predicate entry and exist flow in the next time period, an improved Kalman filtering algorithm and an improved counterpropagation neural network algorithm are designed based on the entry and exist flow in the next time period to predicate dynamic turning proportion of the next first time period and the next second time period, a second Bayes combination method is designed under the conditions that predication errors are corrected through history turning proportion data to calibrate and update weight dynamically, and dynamic turning proportion one-step and two-step prediction values of double Bayes combination methods can be obtained. By means of the existing method, dynamic turning proportion one-step value can be obtained only, and the existing method has advantages and disadvantages in precise and efficiency. The crossroad dynamic turning proportion two-step prediction method comprehensively has the advantages of all methods, avoids local overhigh deviation, is high in precision, and can obtain one-step and two-step prediction values simultaneously and provide basis supporting for an intelligent traffic control system.
Owner:BEIJING UNIVERSITY OF CIVIL ENGINEERING AND ARCHITECTURE
Positive feedback ethernet link flow control for promoting lossless ethernet
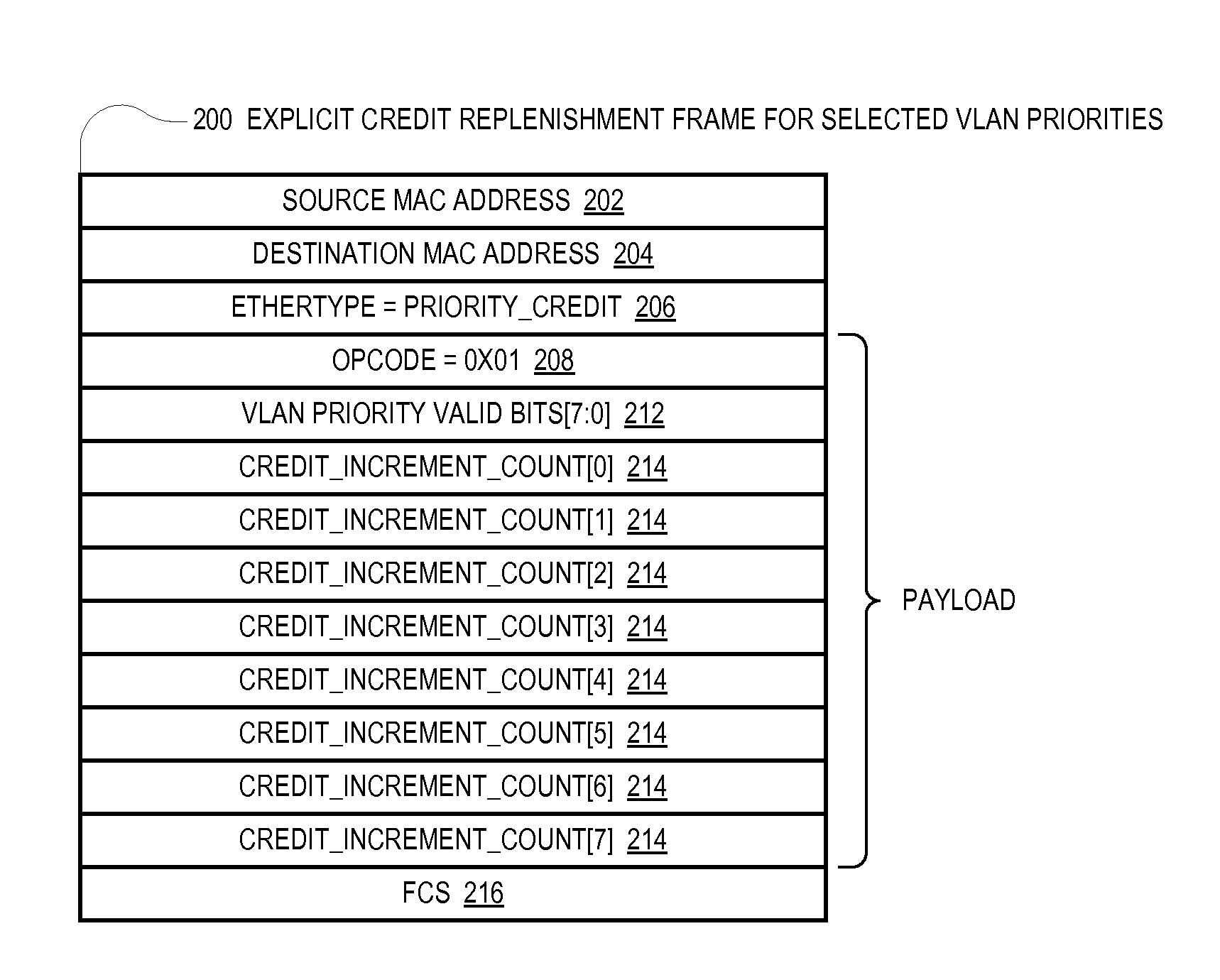
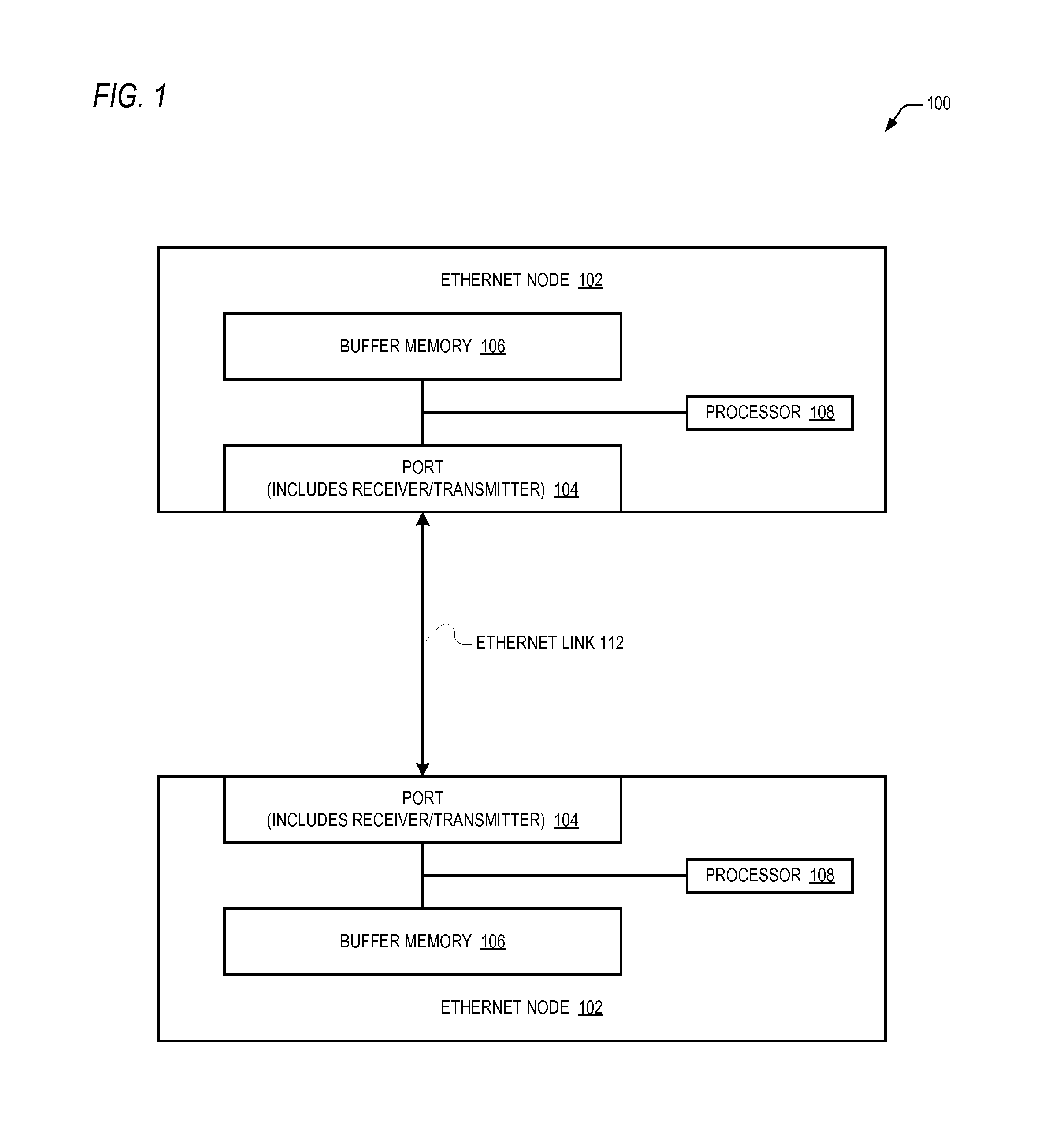
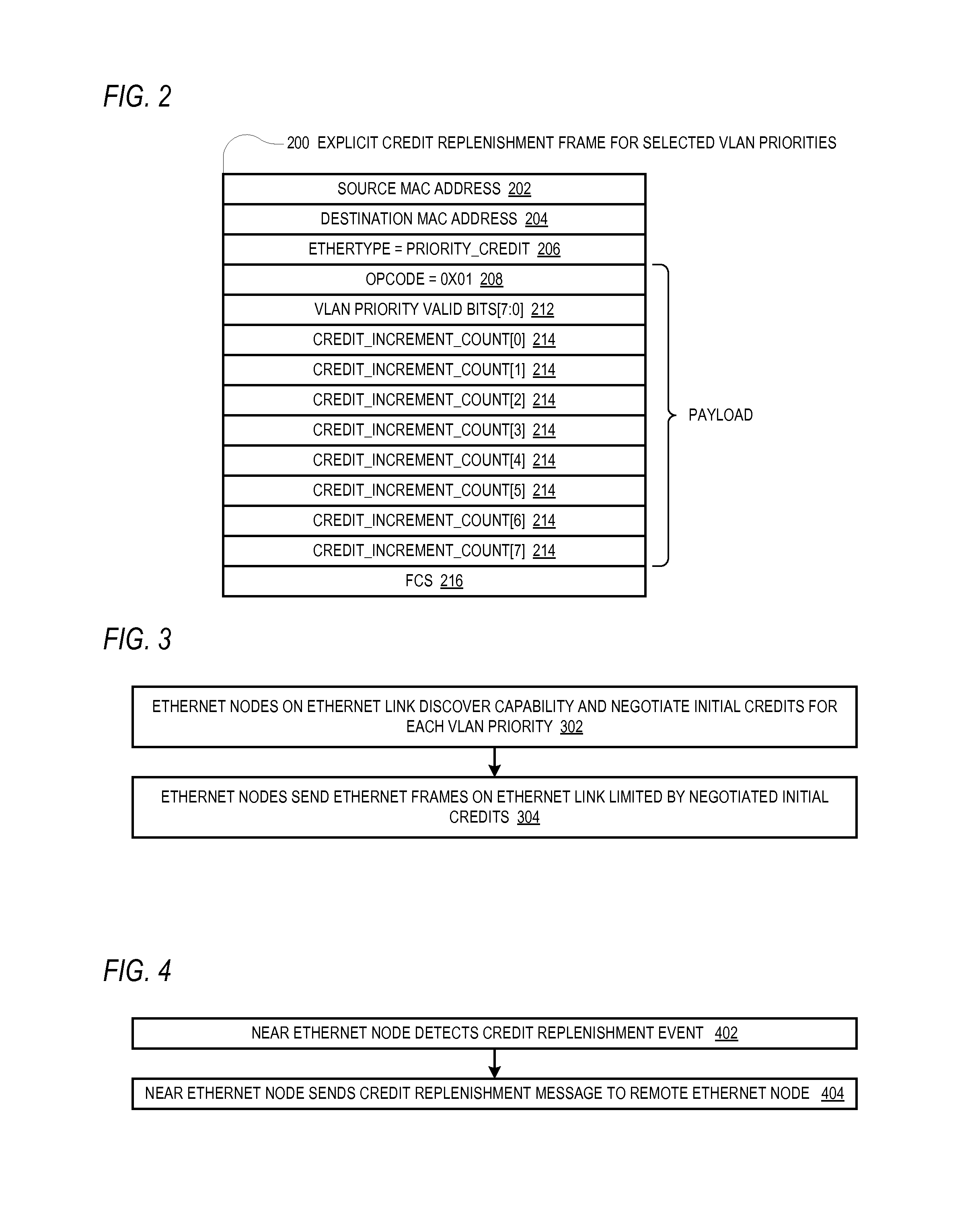
An Ethernet node includes a receiver and transmitter for coupling to an Ethernet link for transceiving Ethernet frames with a remote Ethernet node at a remote end of the Ethernet link. The Ethernet node sends to the remote Ethernet node credit information that enables the remote Ethernet node to know an amount of Ethernet frames the remote Ethernet node is allowed to send to the Ethernet node. The credit information may be specified on a VLAN priority basis and may be included in a header piggy-backed on a host Ethernet frame or may be included in an explicit frame. The credit information may incrementally replenish credits or may specify an absolute credit amount and may be sent in response to processing frames, detection of a frame error, receipt of a request from the remote node or other events.
Owner:AVAGO TECH INT SALES PTE LTD
Method and apparatus for adjusting link velocity
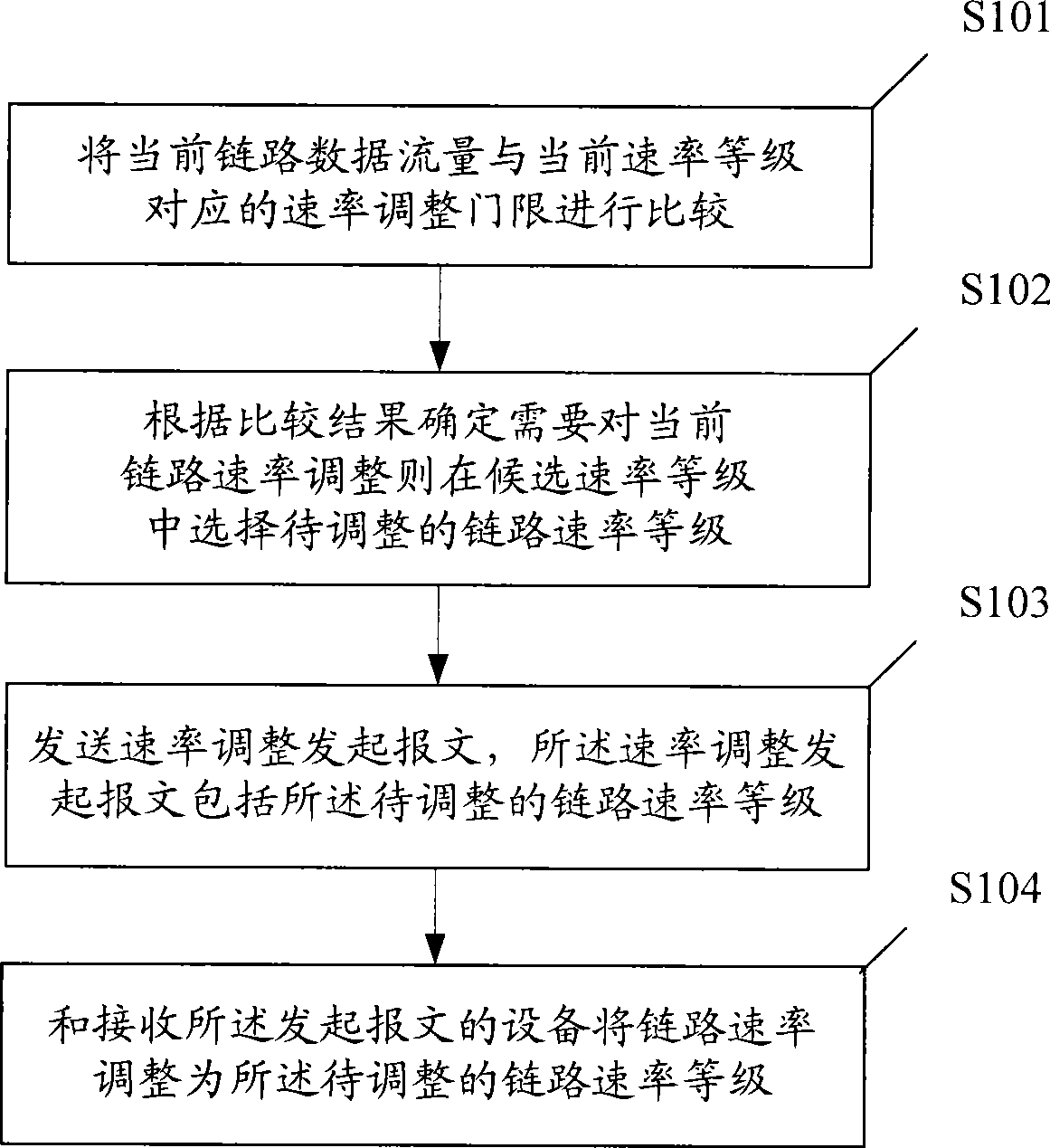
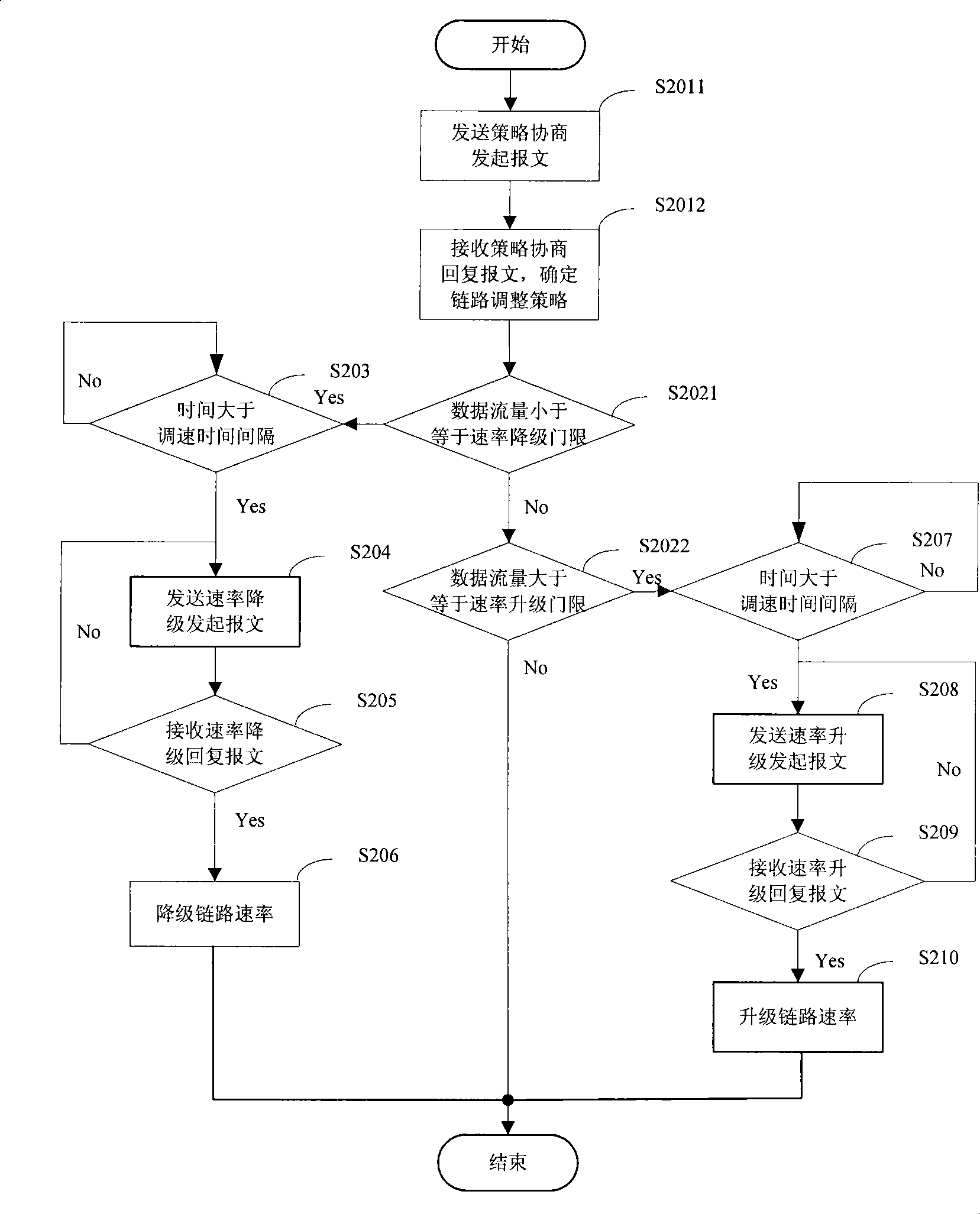
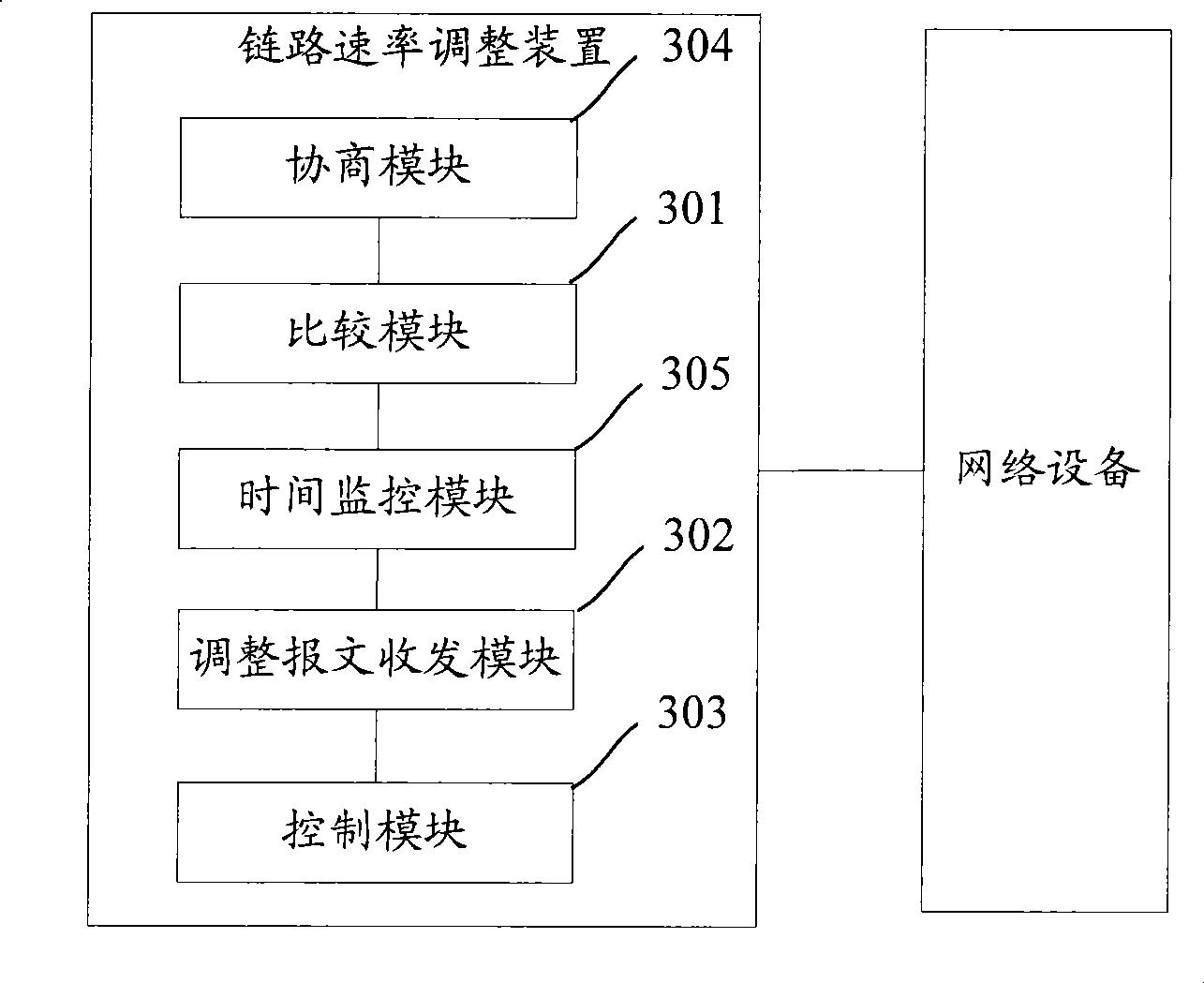
InactiveCN101510847ATo achieve the purpose of energy savingError preventionData switching networksSelf adaptiveLink flow
The embodiment of the invention discloses a link speed regulation method and a device thereof, wherein the link speed regulation method comprises the following steps: the current link flow is compared with a speed regulation threshold corresponding to a current speed grade; if determination is made that the current link speed needs regulation according to a comparison result, a link speed grade to be regulated is selected from alternate speed grades and a speed regulation starting message which comprises the link speed grade to be regulated is transmitted; and a device receiving the starting message regulates the link speed to the link speed grade to be regulated. The technical proposal compares the current link data flow with the speed regulation threshold corresponding to the current speed grade, selects the link speed grade to be regulated, and regulates the link speed to the link speed grade to be regulated so as to cause the link speed to carry out self-adapted regulation on the base of data flow, thus realizing the purpose of saving energy.
Owner:HUAWEI TECH CO LTD
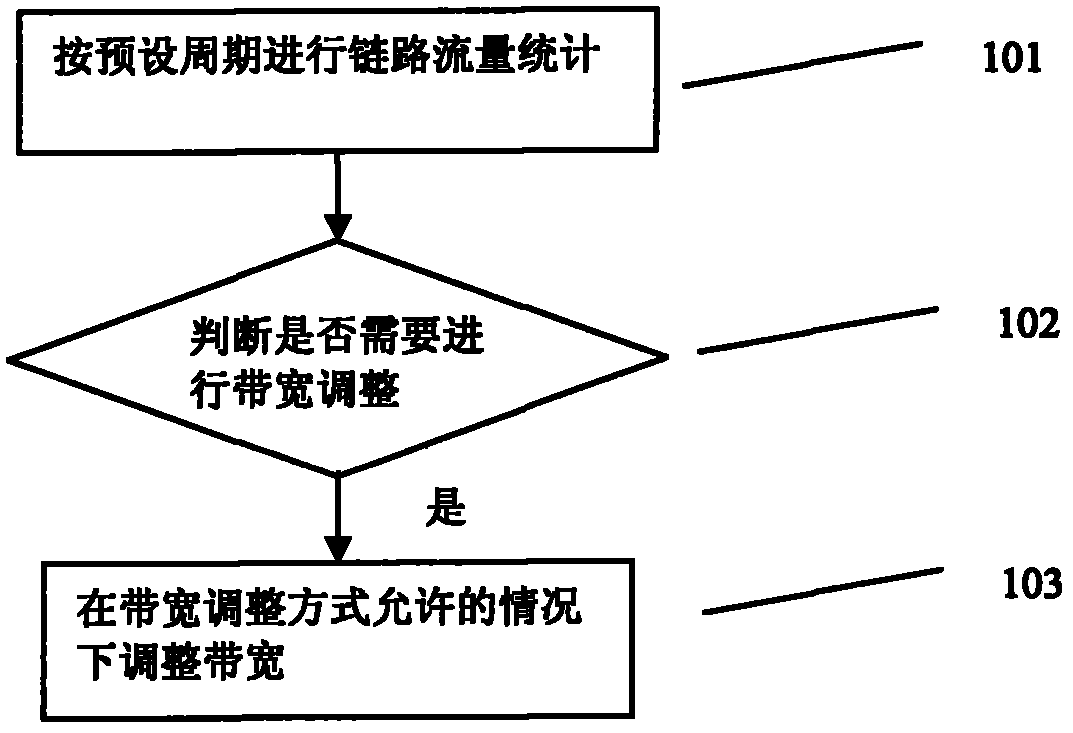
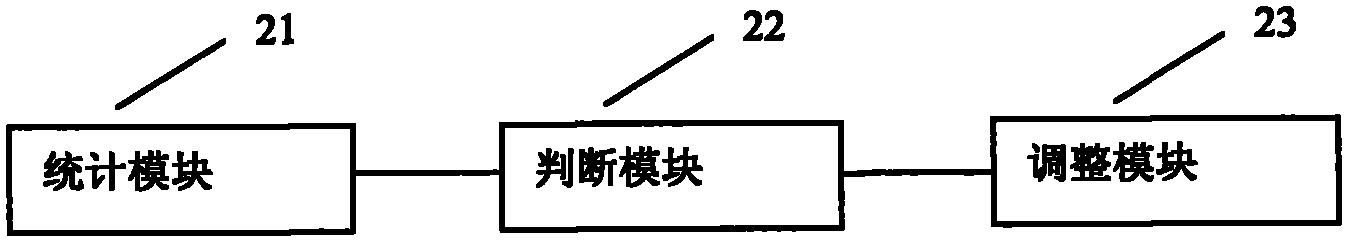
Method and device for adjusting link bandwidth
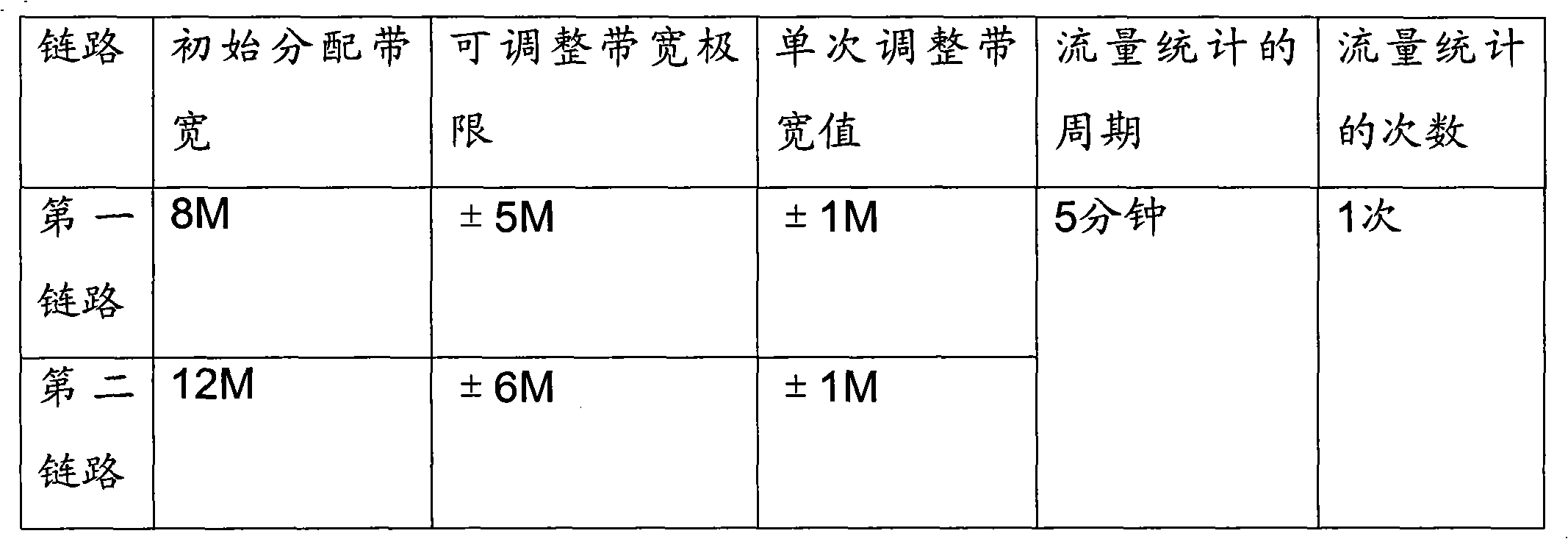
InactiveCN102158391AAllocation Dynamic AdjustmentData switching networksTraffic capacityPrivate network
The embodiment of the invention relates to a method and a device for adjusting link bandwidth. Links adopt two single-board spanning load sharing links in a virtual private network and comprise a first link and a second link. The method comprises the steps of performing link flow statistics on the first link and the second link according to a preset period, judging whether the first link and / or the second link are / is required to be subject to bandwidth adjustment according to results of the link flow statistics, and adjusting the bandwidth of the first link and / or the second link when the bandwidth adjusting method is allowed if the bandwidth adjustment is required. By adopting the scheme, the bandwidth distribution proportion of each link shared by each load on a VPN (Virtual Private Network) HQoS network side can be controlled according to the practical demand of an operator, and bandwidth distribution can be dynamically adjusted according to the requirement of communication equipment, so that the method has more flexibility.
Owner:BEIJING HUAWEI DIGITAL TECH
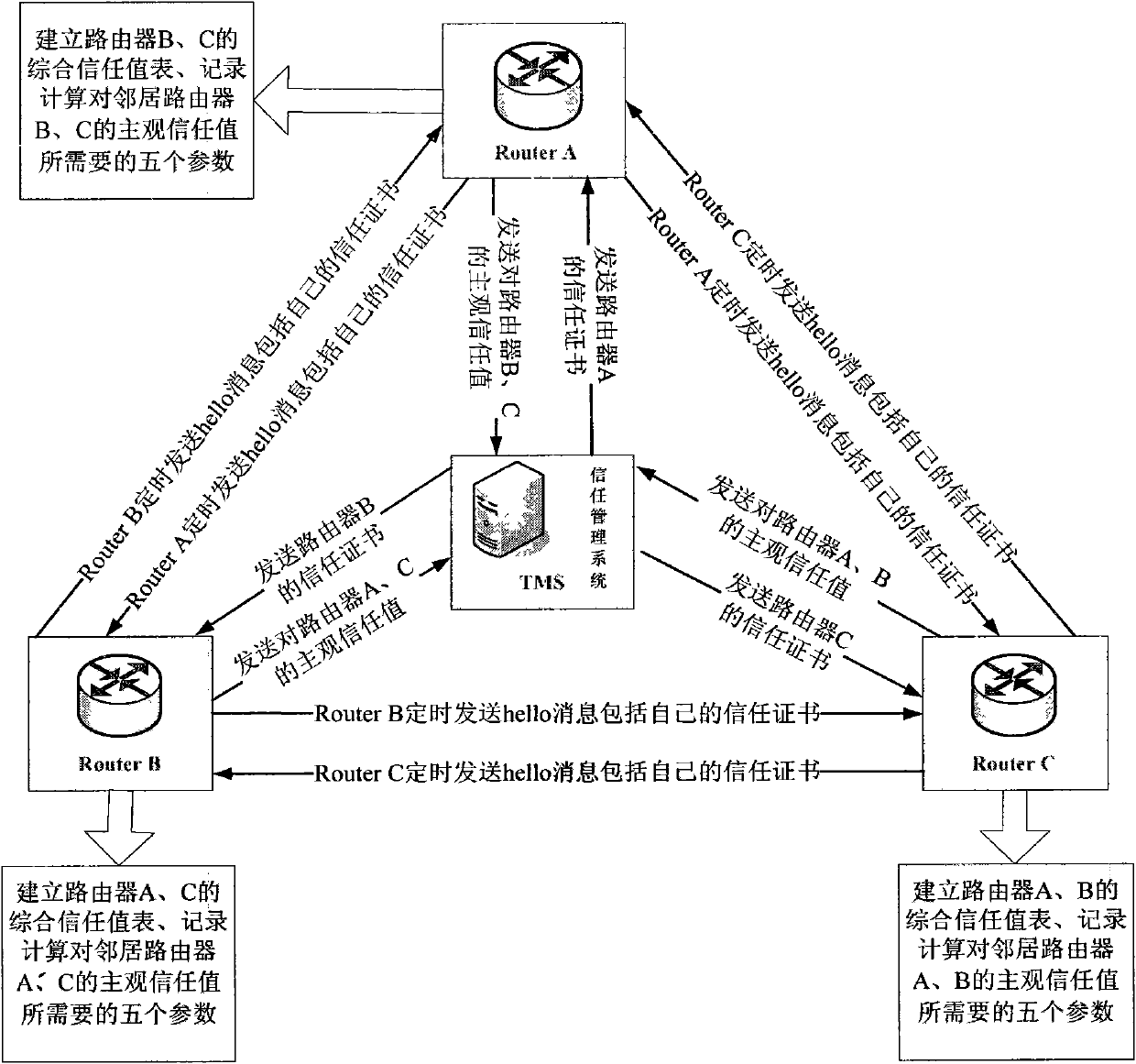
Trust management system based trusted reconstructing method of IP routing protocol
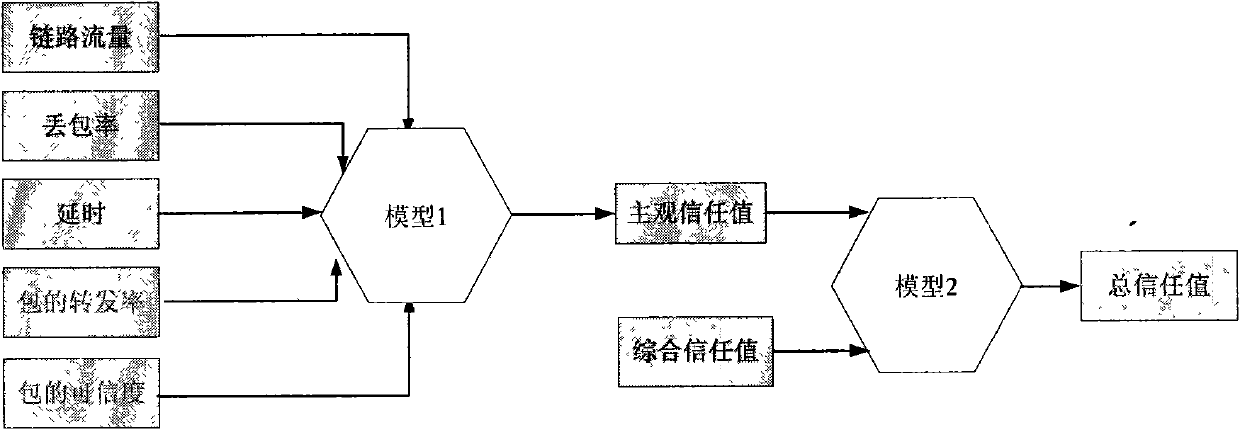
The invention discloses a trust management system based trusted reconstructing method of an Open Shortest Path First (OSPF) routing protocol, which comprises the following steps of: (1) before each router is added into a network, registering to the trust management system, and sending corresponding trust certificates to the routers by the trust management system, the trust certificates including comprehensive trust values of the routers and each being calculated according to safe parameters and configuration parameters of the routers and all the subjective trust value of the neighbor router to the routers by the trust management system; (2) transferring the trust certificates among the routers through hello information, wherein an adjacency relation is not established for the router without the trust certificate, all the routers in the network are ensured to have own trust certificates; (3) each router calculating the subjective trust value of the neighbor router based on network real time parameters including link flow, packet loss probability, retardation, transmission rate of the packet and reliability of the packet, during an interactive work with the neighbor router, calculating a total trust value of the neighbor router by using the comprehensive trust value and the subjective trust value of the neighbor router, and modifying a metric field of a link-state announcement Router_LSA packet as the total trust value and synchronizing a link-state data base;(4) modifying a Dijkstra algorithm, using a reciprocal of the total trust value between the routers as the parameter for the arithmetic computation, selecting the router with higher trust value to generate a shortest path tree, and forming a trust routing list; (5) periodically reporting the subjective trust value of the neighbor routers to the trust management system by each router, simultaneously obtaining the parameter required for computing the subjective trust value, updating the trust certificate of each router at fixed time, and eliminating the router with the overdue trust certificate out of the network to maintain the topological structure of the whole network.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Route protection converting method and device
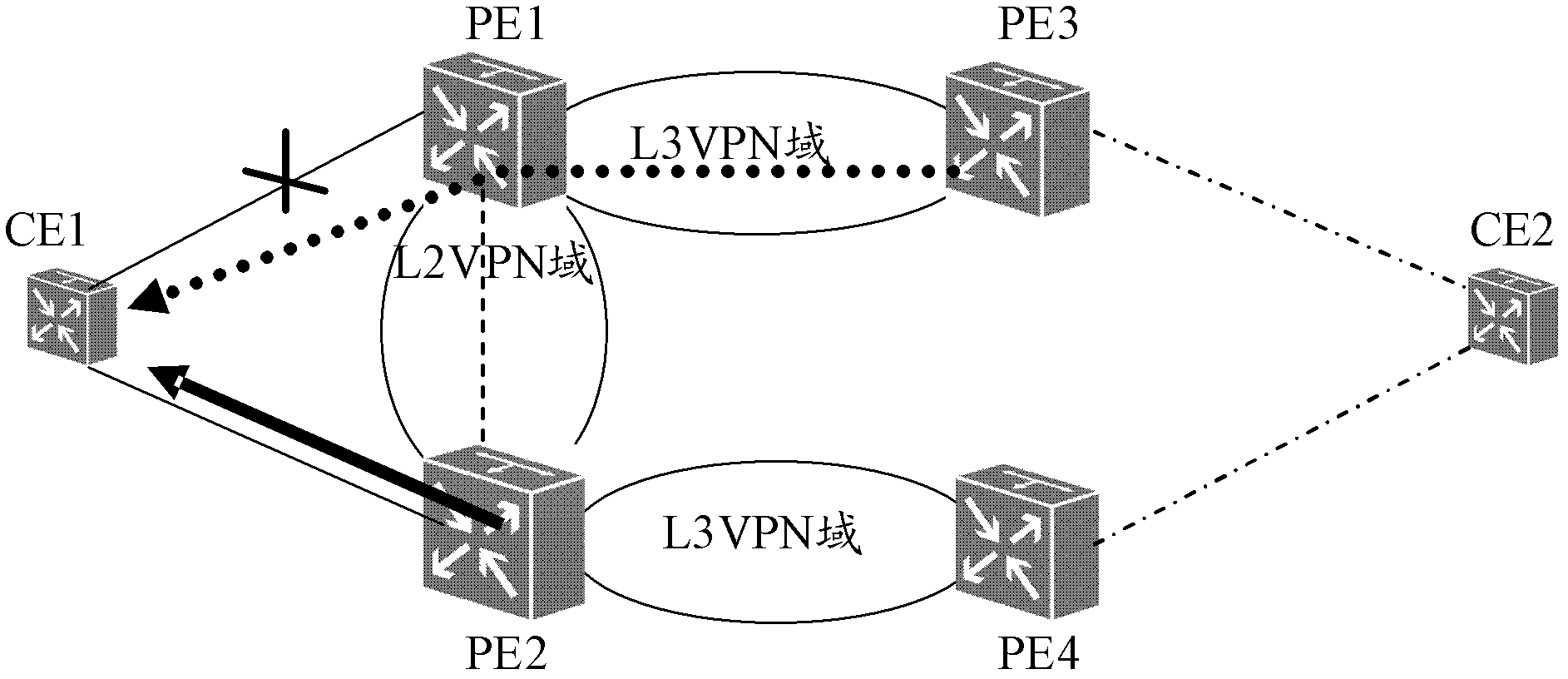
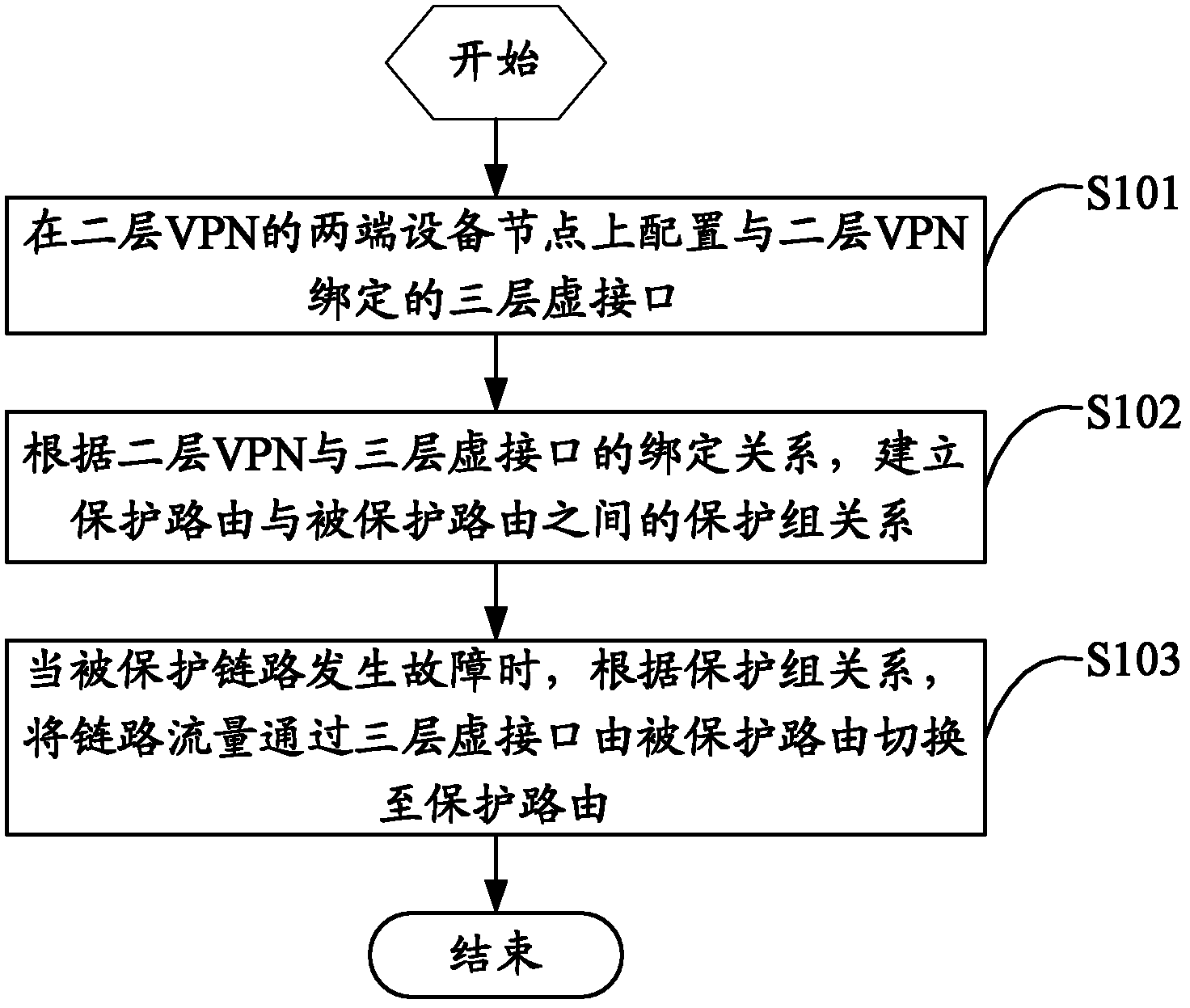
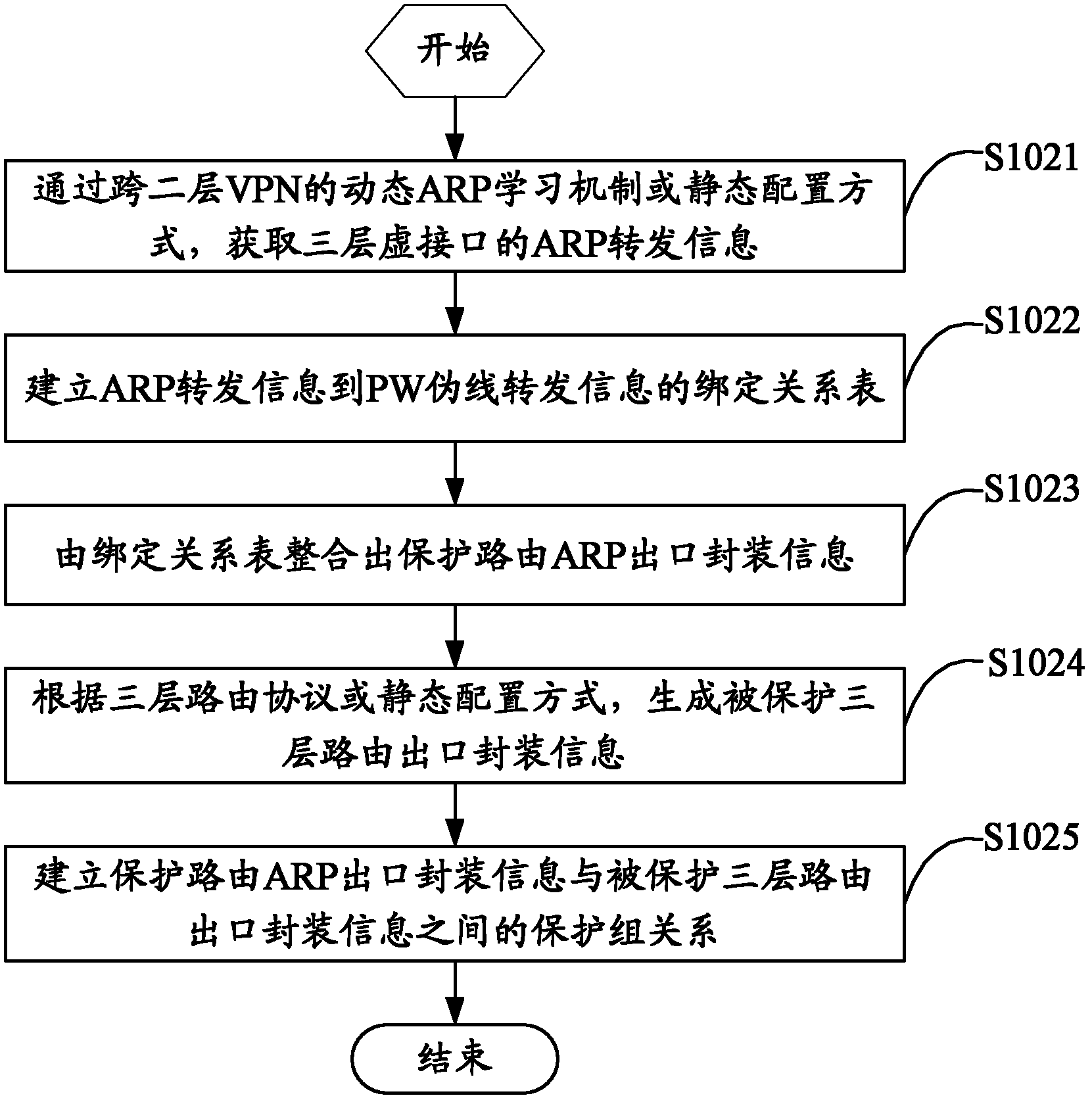
ActiveCN102611618AReduce complexityAchieve protectionNetworks interconnectionAddress Resolution ProtocolDirect memory access
The invention relates to a route protection converting method and device. The route protection converting method comprises the following steps of: configuring a three-layer virtual interface bound with a two-layer VPN (Virtual Private Network) on device nodes of two ends of the two-layer VPN; establishing a protection group relation between a protection route and a protected route according to the binding relation of the two-layer VPN and the three-layer virtual interface; and converting a link flow rate from the protected route to the protection route through the three-layer virtual interface according to the protection group relation when a protected link has failure. According to the route protection converting method disclosed by the invention, through the three-layer virtual interface ARP (Address Resolution Protocol) protection policy, without changing an original network topology and two / three-layer domain partition, the protection of an over two-layer network domain on a three-layer network domain route is realized, a problem of flow interruption of the three-layer route at the two / three-layer network connection caused by DOWN (Direct Memory Access Controller) is solved, and additional devices and a hardware lookup operation do not need to be additionally arranged; and in addition, the expandability of a network structure is improved, the network complexity is reduced and the maintenance cost is saved when conversion performances are ensured.
Owner:ZTE CORP
Network slice virtual resource allocation method, system and device
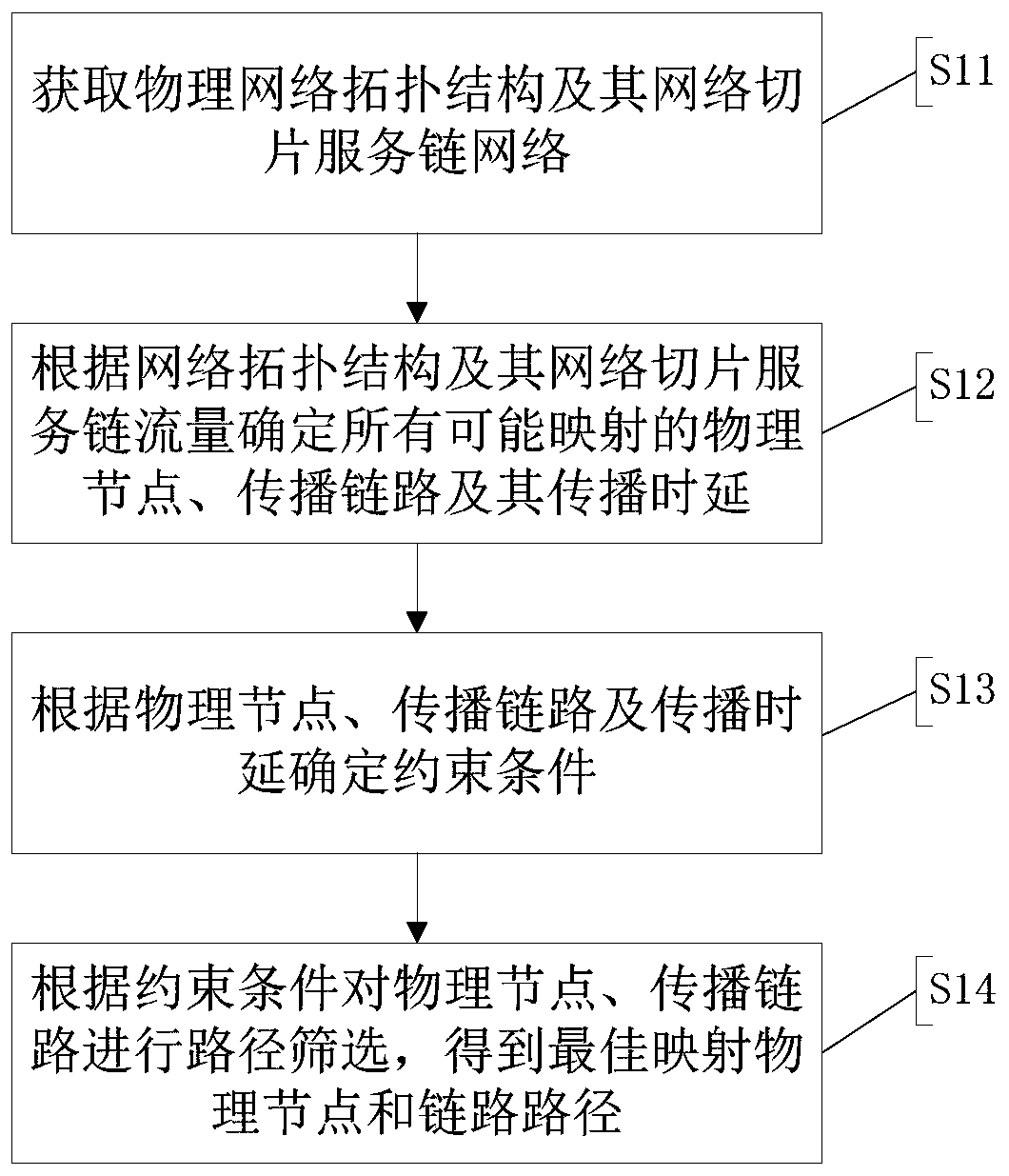
InactiveCN110768837AReduce consumptionEvenly distributedData switching networksPropagation delayPathPing
The invention provides a network slice virtual resource allocation method, system and device. The method comprises the following steps: acquiring a physical network topology structure and a network slice service chain network thereof; determining all possible mapped physical nodes, propagation links and propagation time delay thereof according to the network topology structure and the network slice service link flow thereof; and determining a constraint condition according to the physical node, the propagation link and the propagation delay, and performing path screening on the physical node and the propagation link according to the constraint condition to obtain an optimal mapping physical node and an optimal mapping link path. By implementing the method and the device, the network communication capacity limitation and the ultra-low time delay performance requirement limitation are comprehensively considered, so that the time delay of network communication transmission can be reducedand the network slice virtual resources can be allocated under the condition of the maximum network communication capacity.
Owner:BEIJING UNIV OF POSTS & TELECOMM +3
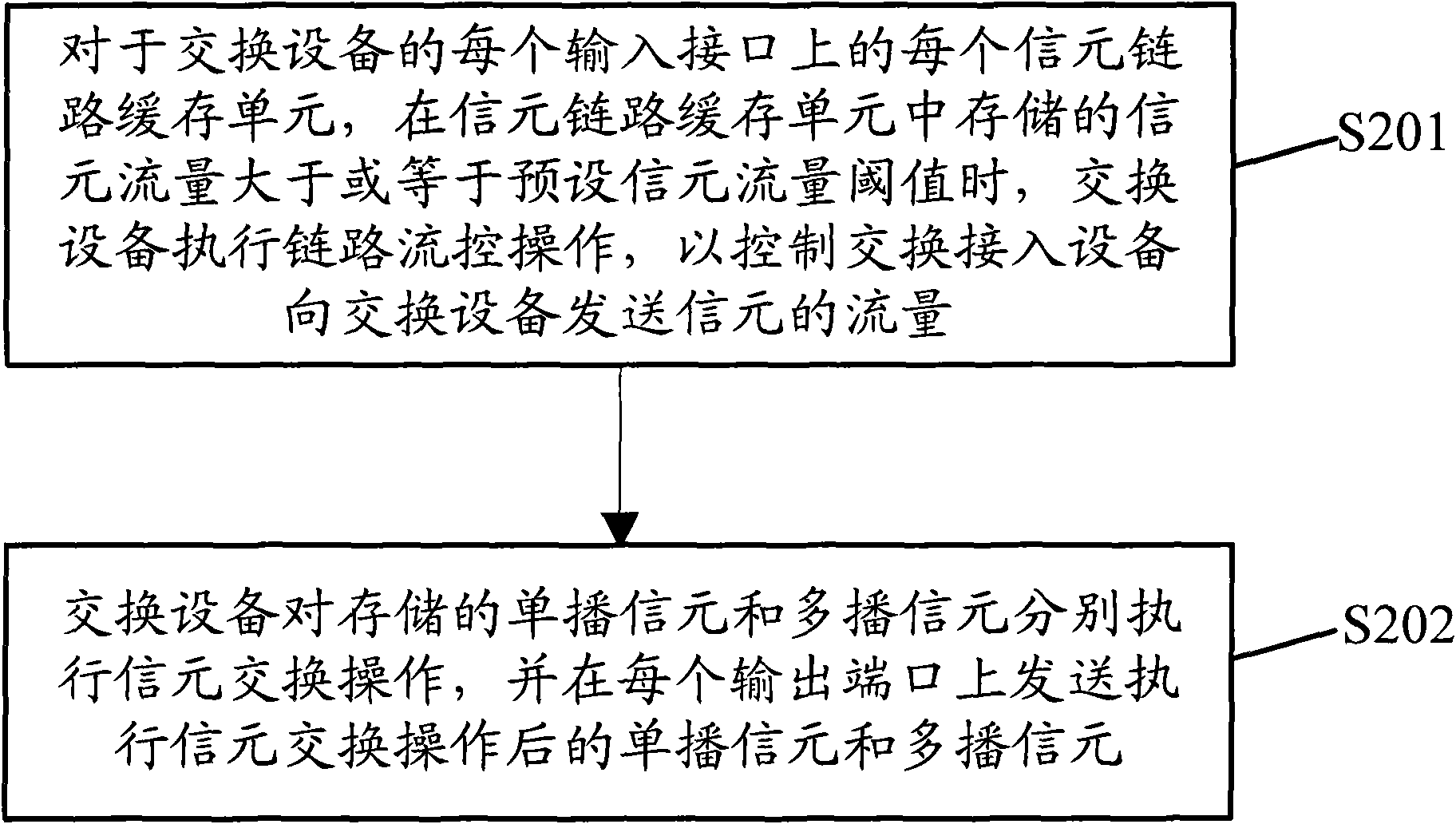
Method and system for cell dispatching
ActiveCN102111327AAvoid accumulationAvoid mutual congestionData switching networksComputer networkData interchange
The invention discloses a method and a system for cell dispatching. The method comprises the following steps: for each cell link cache unit on each input interface of switching equipment, when flow rate of cells stored in the cell link cache unit is larger than or equal to the preset threshold of cell flow, the switching equipment performs link flow control operation to uplink switched access equipment, so as to control the switched access equipment to send cell flow to the switching equipment. The cell link cache unit comprises a unicast cell link cache unit for storing unicast cells and a multicast cell link cache unit for storing multicast cells. The switching equipment executes cell switching operation to the stored unicast and multicast cells, and sends the unicast and multicast cells which have received cell switching operation at each output port. By adopting the invention, congestion between unicast operation and multicast operation is avoided, the data switching efficiency is improved, and the system resource is saved.
Owner:SANECHIPS TECH CO LTD
Link state detection method, device and system
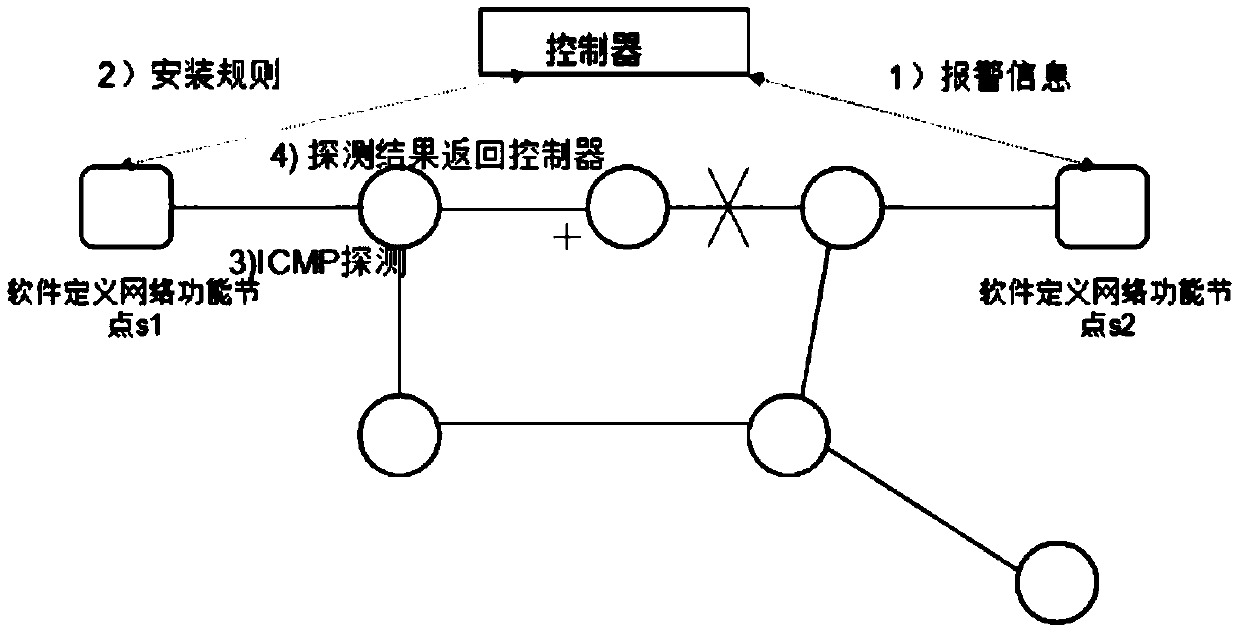
InactiveCN105812201AImprove efficiencyReduce in quantityData switching networksHigh level techniquesLink flowComputer science
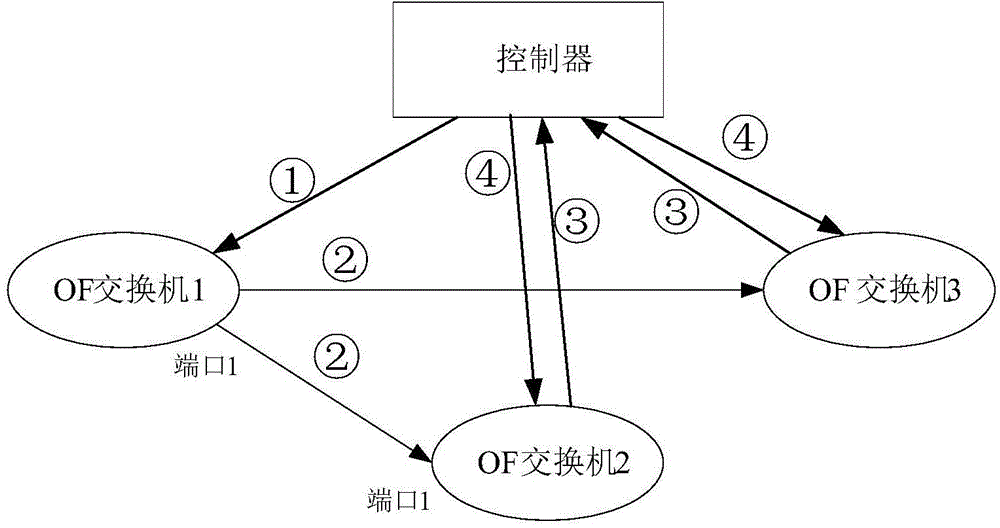
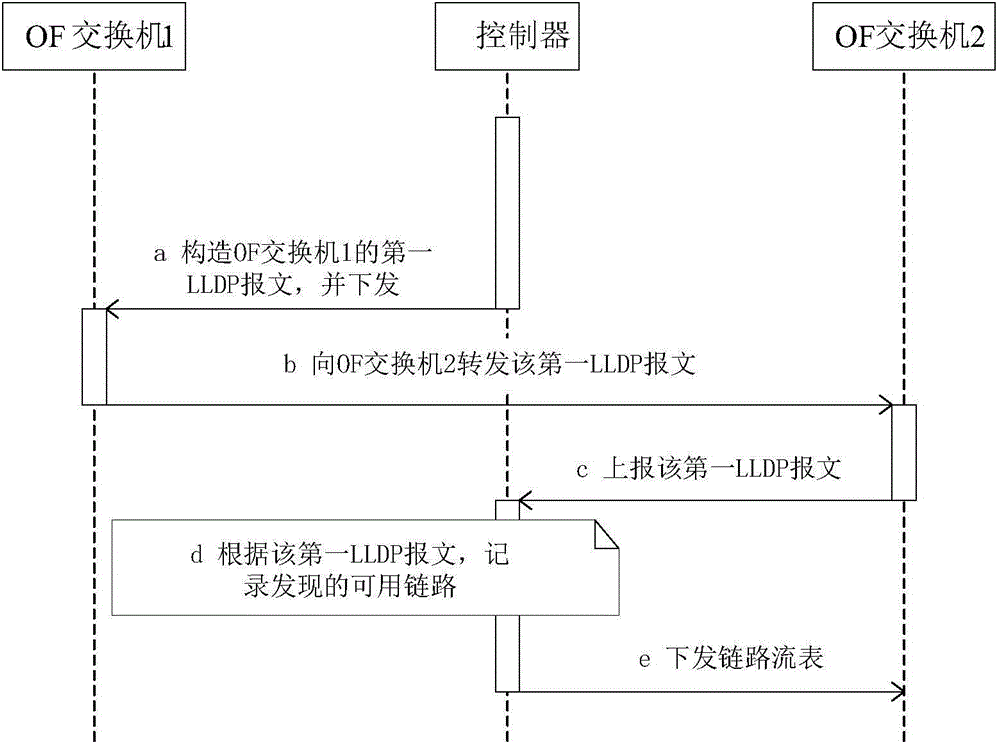
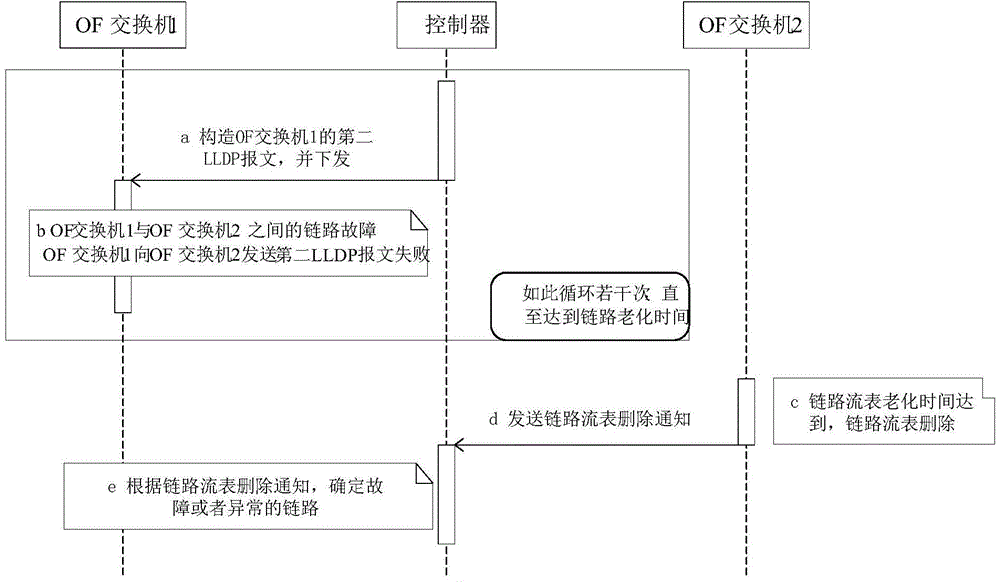
An embodiment of the invention provides a link state detection method, device and system that are applied to a software definition network SDN and used for reducing state detection messages of a link between a controller and a switch machine. After the controller discovers a usable link, the controller sends a link flow table to the switch machine, and the link flow table is used for instructing the switch machine to discarding messages, used for detecting the state of the usable link, forwarded by other switch machines via the usable link.
Owner:HUAWEI TECH CO LTD
Multilink accessing and flow load dispatching managing method
InactiveCN101867521AImprove smoothnessReduce access latencyData switching networksTraffic capacityAccess time
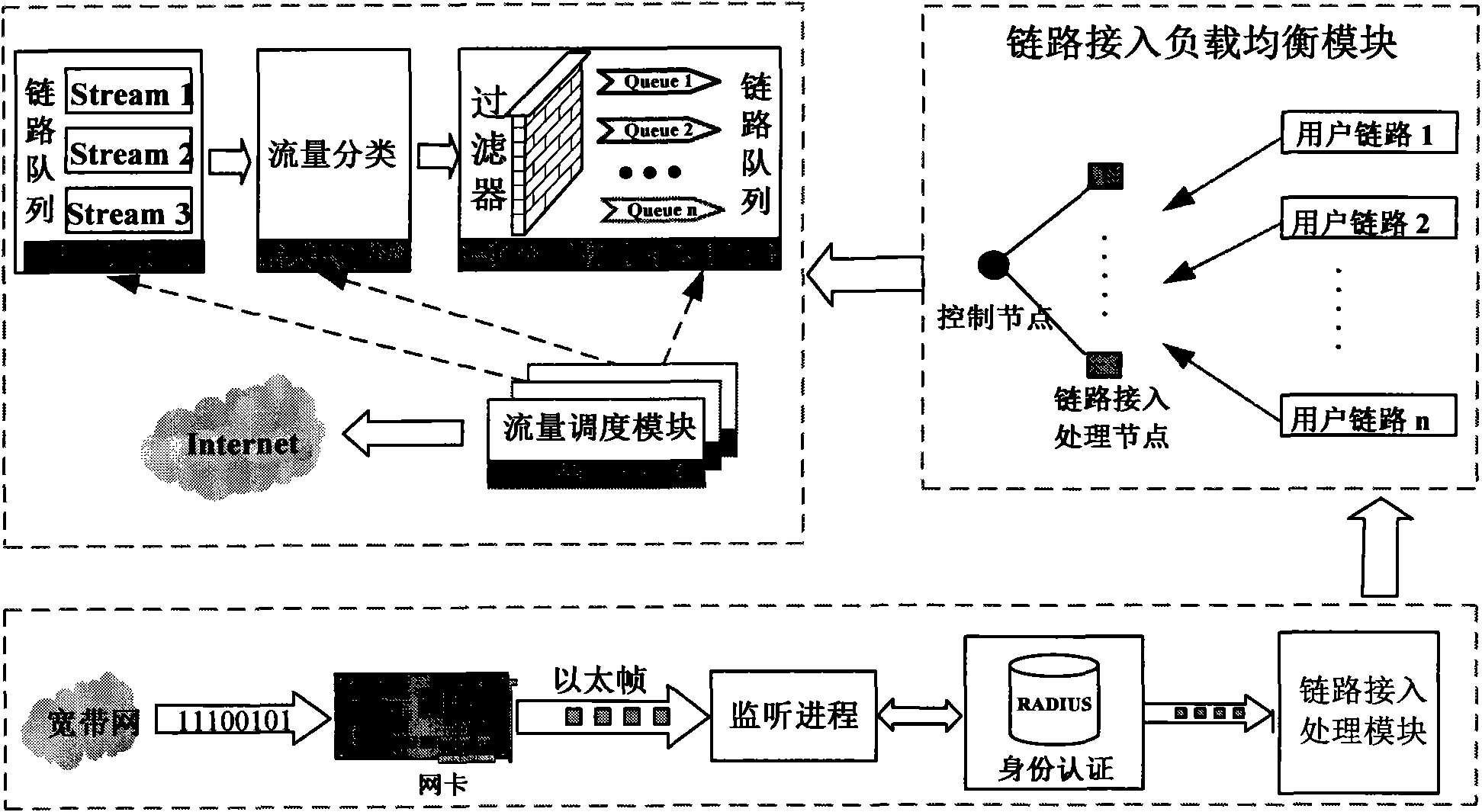
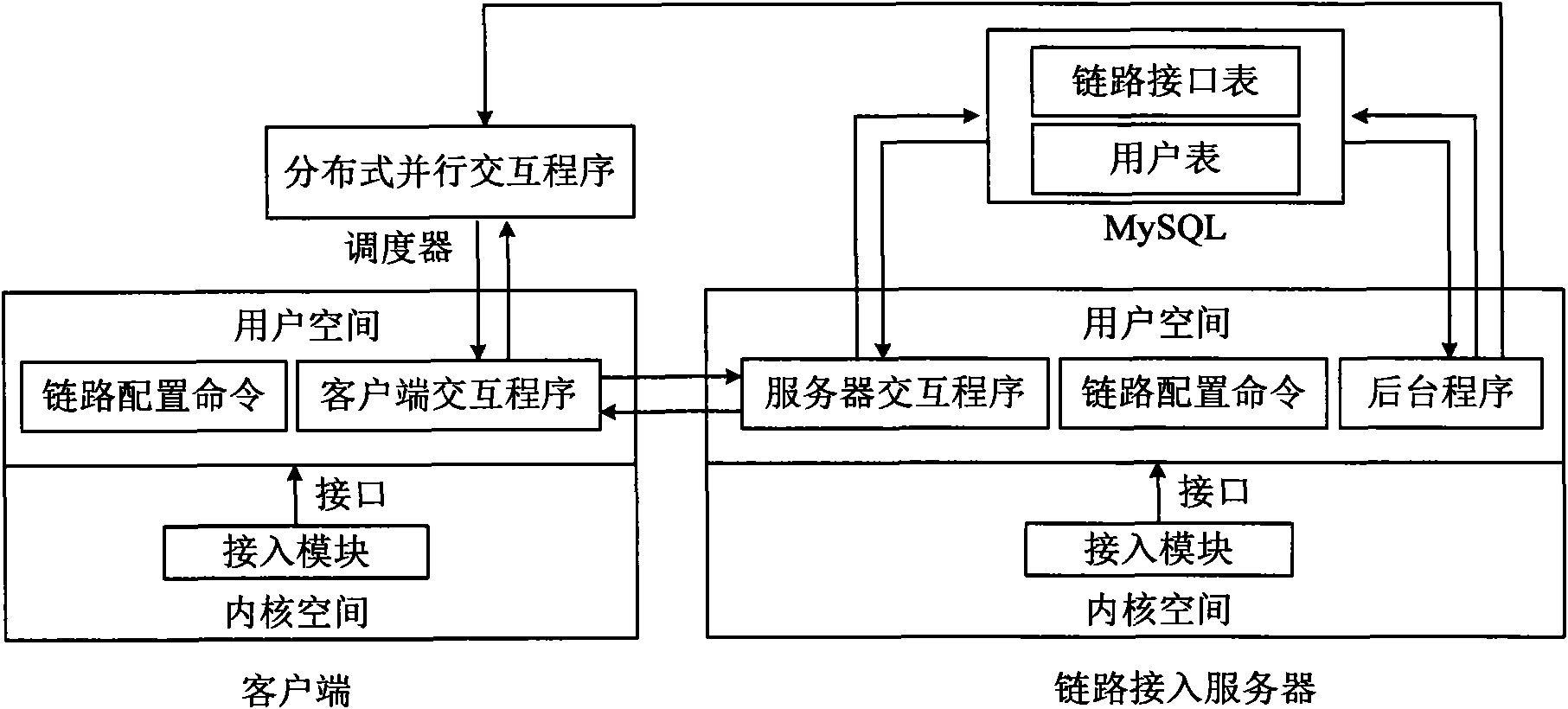
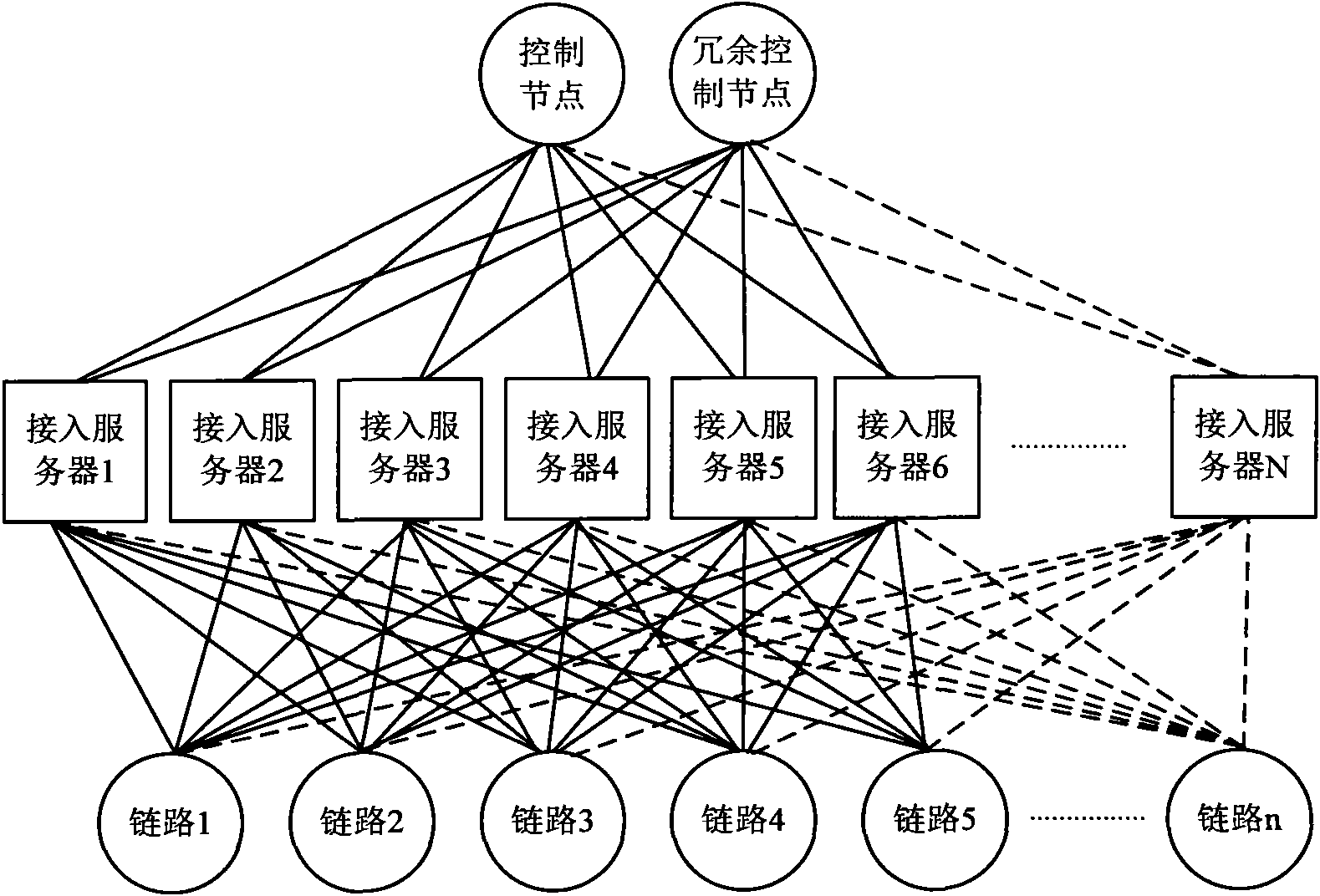
The invention provides a network multilink accessing and flow load dispatching managing method. The method combinatively comprises the following steps that: 1) a link accessing module de-encapsulates a received packet and provides an interface to upper application; 2) a link accessing and load balancing module parallelizes the user link accessing and flow dispatching management in a distributing way; and 3) a link flow controlling module controls the flow. The method is realized by the link accessing module, the link accessing and load balancing module and the ink flow controlling module. The method supports large-scale link accessing, can effectively reduce the link access time delay of data, improves the smoothness of the flow of the link and the use ratio of the whole bandwidth of the system, and is suitable for controlling the flow of the accessed link of high-performance wide band.
Owner:郭小雪
Scheduling method of network-on-chip router based on network information
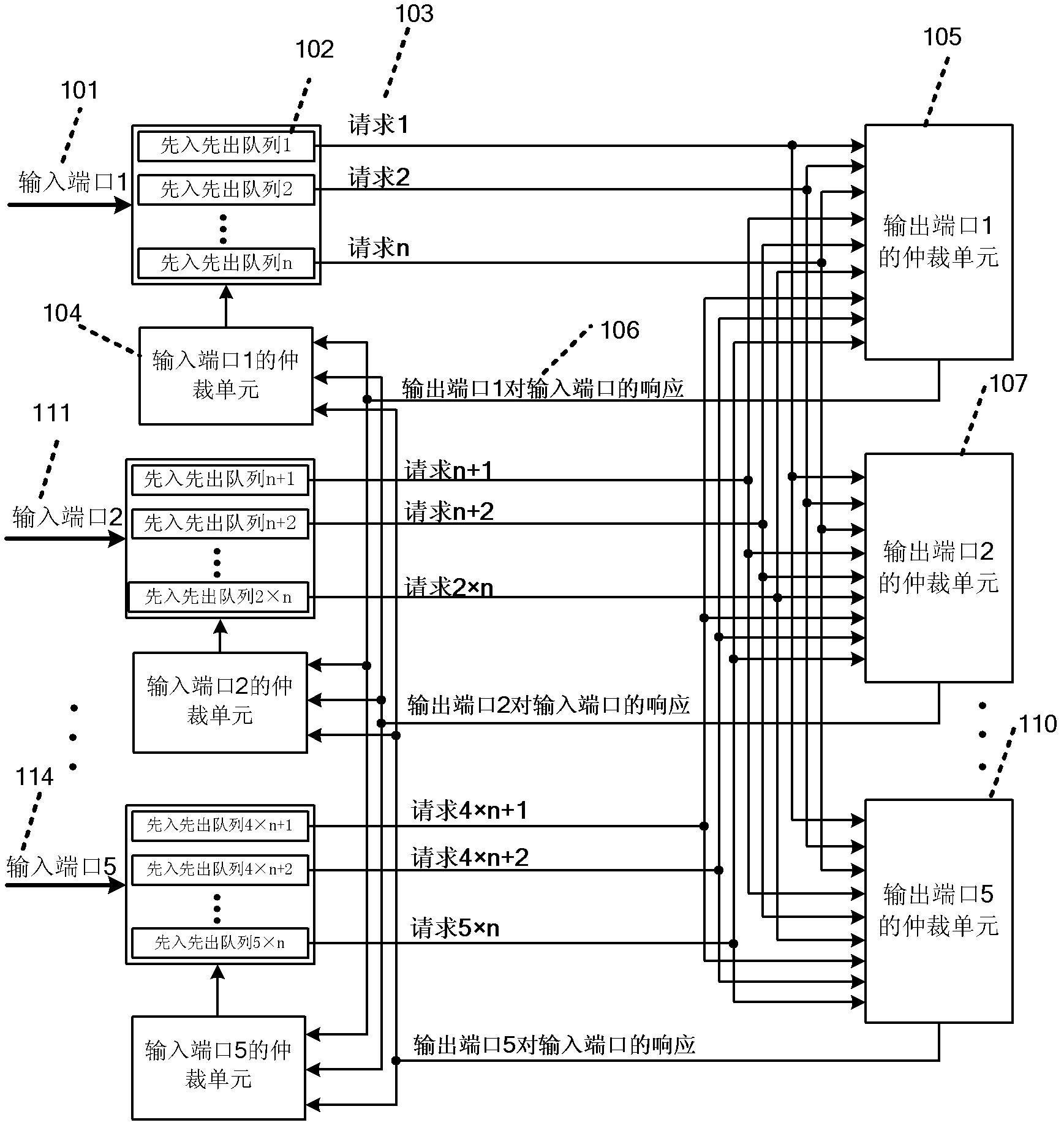
InactiveCN102546417AReduce latencyMitigate situations where multiple router nodes are blockedData switching networksNetworks on chipLink flow
The invention discloses a scheduling method of a network-on-chip router based on network information, and mainly solves the problem that the router has limited buffer space and longer grouping time so as to seriously block a network. The scheduling method is finished through two stages as follows: at the first stage, an input arbitration unit selects an input queue as a response queue according to the three parameters, namely hop count from a source node to a destination node, the hop count from a current node to the destination node and lock virtual channel number of a local input port; and at the second stage, an output arbitration unit selects according to the three parameters, namely, the lock virtual channel number of an output link, the hop count from the source node to the destination node and the hop count from the current node to the destination node, and a best transmission path is selected between an input port and an output port grouped on the network-on-chip router through the scheduling of two stages. The scheduling method provided by the invention has the advantages of low time delay, high throughput and balanced grouping link flow, and can optimize distribution of an inner path of the network-on-chip router.
Owner:陕西光电子先导院科技有限公司
Method for controlling up-link flow
ActiveCN1984067APrevent overflowAvoid packet lossNetwork traffic/resource managementData switching networksNetwork packetComputer science
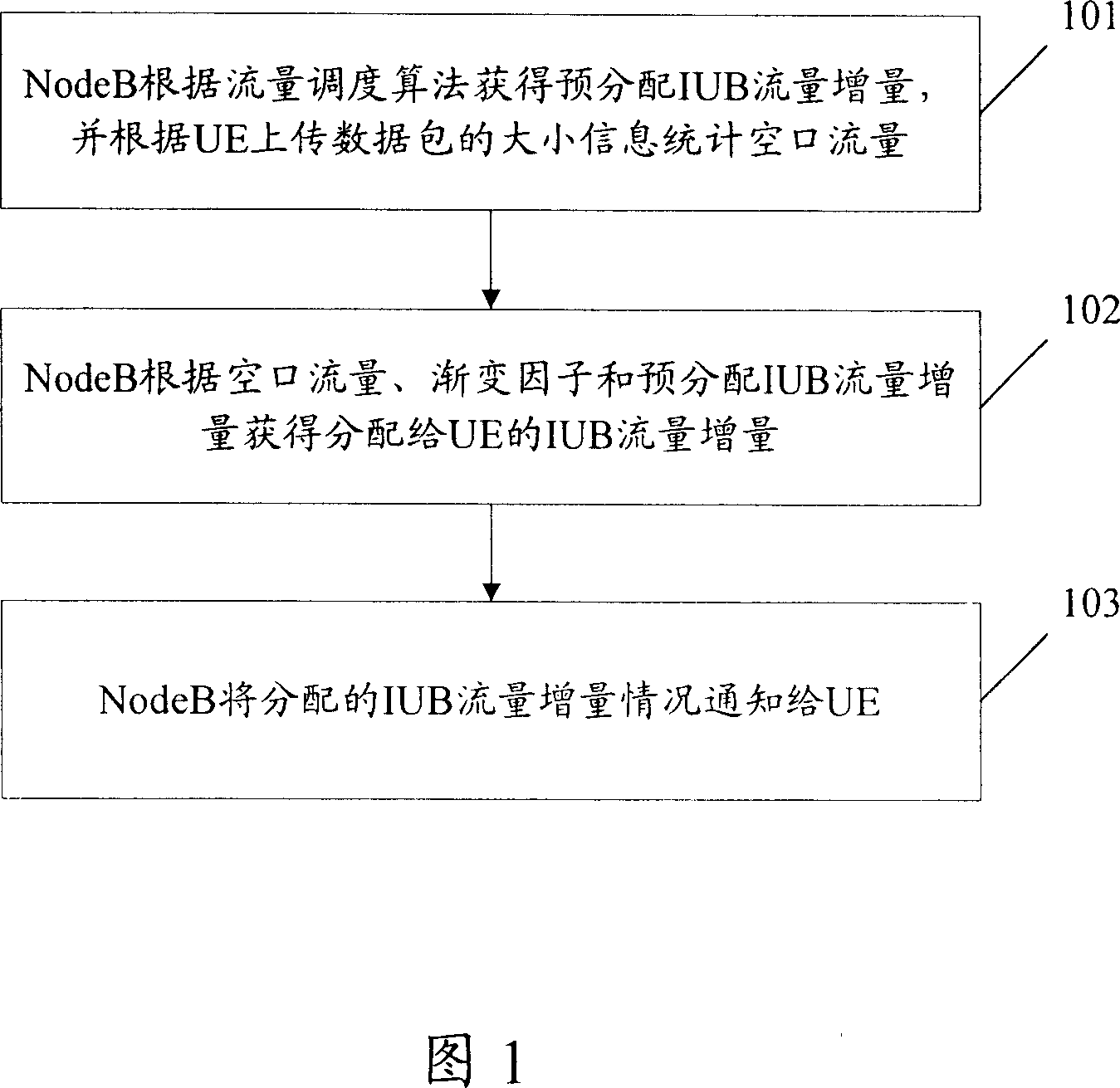
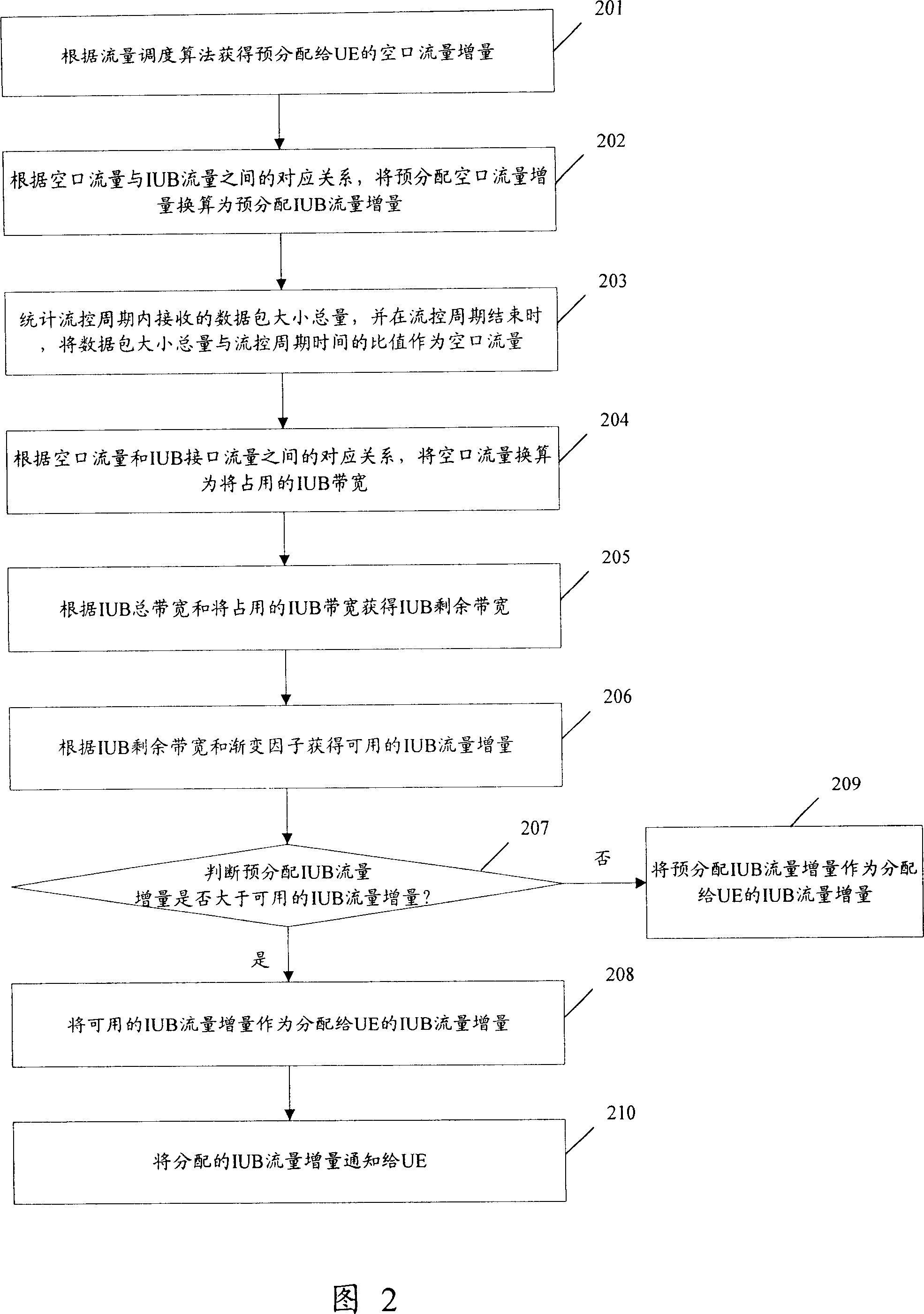
The invention provides a of ascending flow control method, the key lies in that the establishment of a gradual factor, take the product of IUB residual flow of base stations nodes (NodeB) and gradual factor as a control to distribute IUB flow incremental value to user equipment (UE). NodeB first obtain the predistribute IUB flow incremental value according to the flow scheduling algorithm, and calculate the empty flux according to size information of data packet the UE uploaded; NodeB obtains the IUB flow incremental value distribute to UE according to empty flow, gradual factor and predistribute IUB flow incremental value, finally notice to UE the distributed IUB incremental flow value. Use the scheme of this invention can gradually release the remaining IUB flow resources, control the distribution of IUB incremental flow value to UE, balance empty flow and IUB flux, prevent obstruction of IUB interface and overflows the cache phenomenon.
Owner:XFUSION DIGITAL TECH CO LTD
Neural network-based low amplitude network flow anomaly detection method
InactiveCN102075383AAvoid the impact of the detection stepGood for concealing traffic anomaliesError preventionData switching networksNerve networkAlgorithm
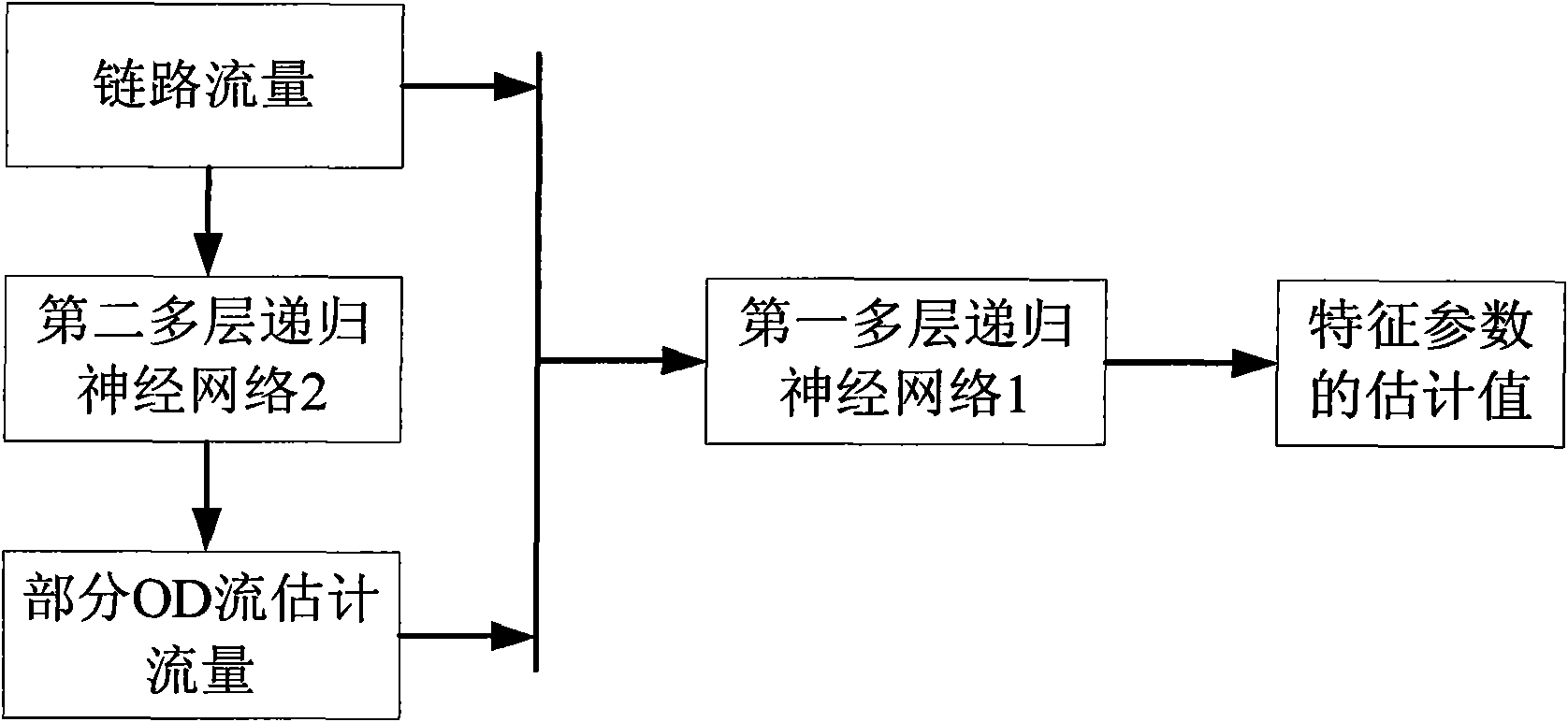
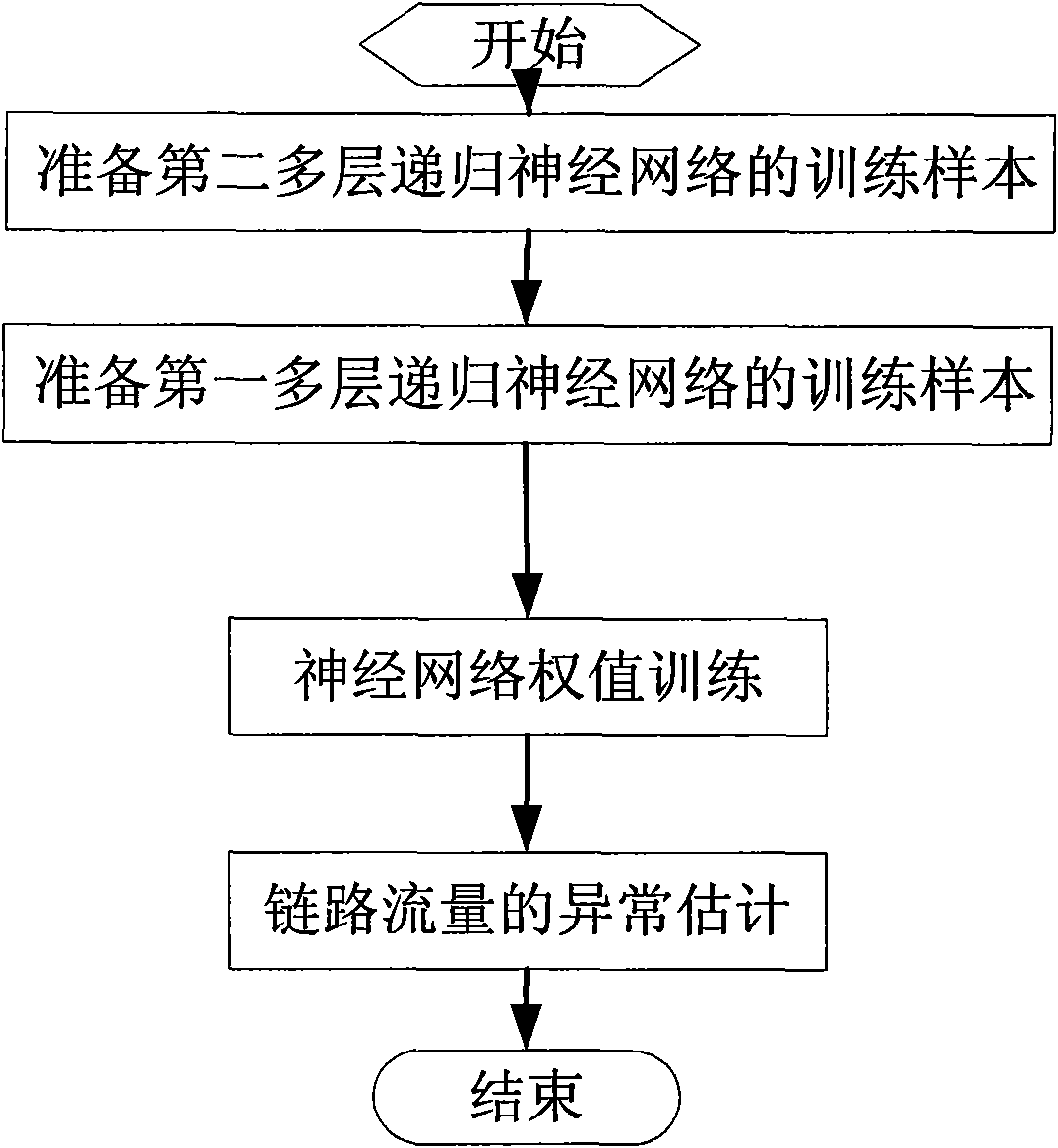
The invention discloses a neural network-based low amplitude network flow anomaly detection method. In the method, a neural network module comprises a second multilayer recurrent neural network and a first multilayer recurrent neural network, the input of the second multilayer recurrent neural network is directly measurable link flow, and the output of the second multilayer recurrent neural network is the estimated flow of part of origin-destination (OD) flow; and the input of the first multilayer recurrent neural network is the link flow and the estimated flow of the part of OD flow, which is output by the second multilayer recurrent neural network and serves as supplementary constraint input, and the output of the first multilayer recurrent neural network is the estimated value of a characteristic parameter. In the invention, the step of inversion from a link to the OD flow is skipped, so the influences of errors generated in a prediction process on a detection step are avoided effectively, and the real-time prediction of the OD flow correlation at next moment can be provided. When the method is used, the detection of hidden flow anomaly is easier, the detection process does not completely rely on the estimation from the link to the OD flow any more, the problem that the inversion error influences the detection is solved, and the frame allows for estimation from link flow to multiple OD flow characteristic parameters.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
Fluid apparatus unit structure
ActiveUS20100163125A1Shorten the length of the flow pathShorten the lengthEngine sealsFluid pressure sealed jointsCompound (substance)Engineering
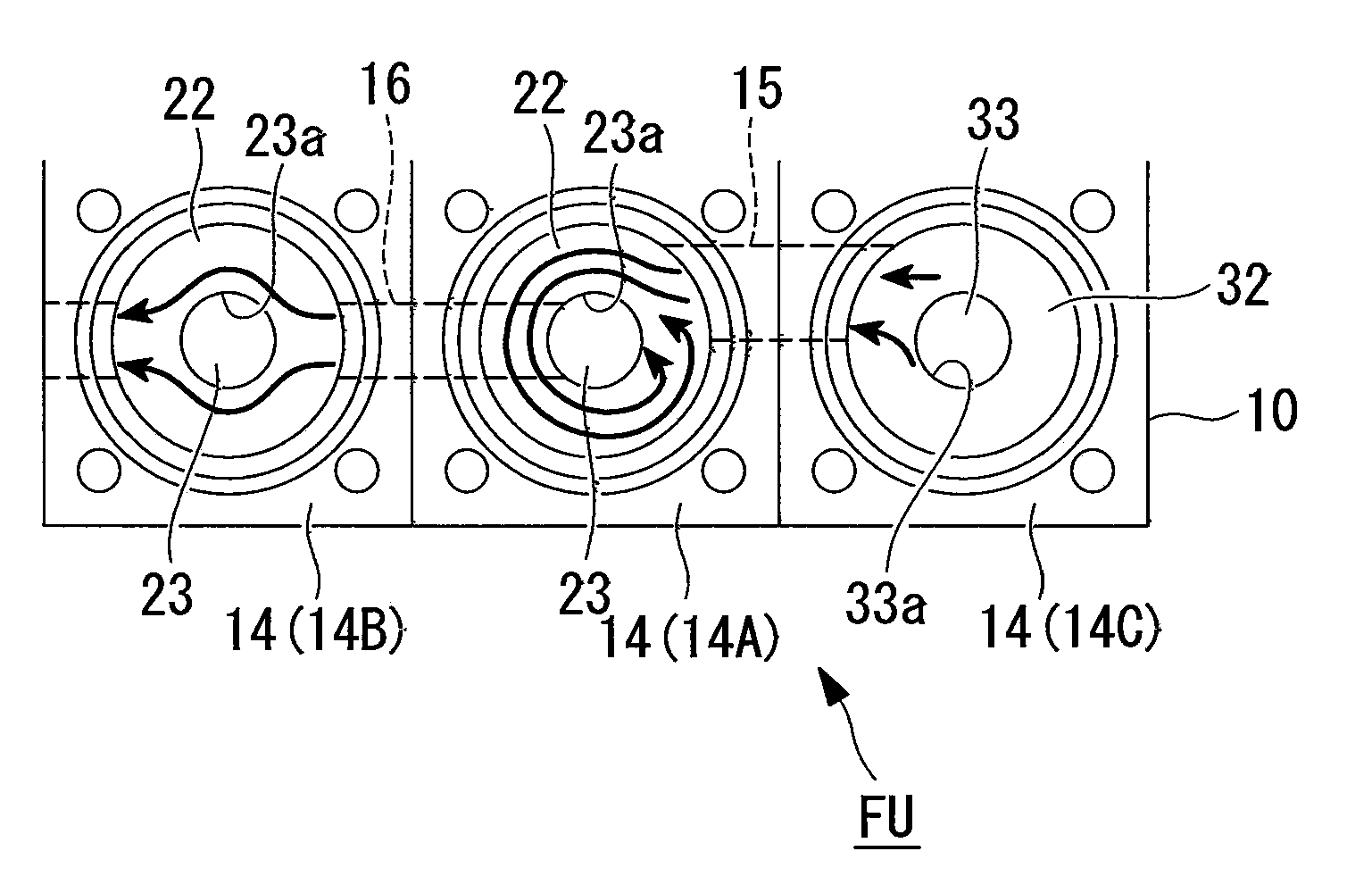
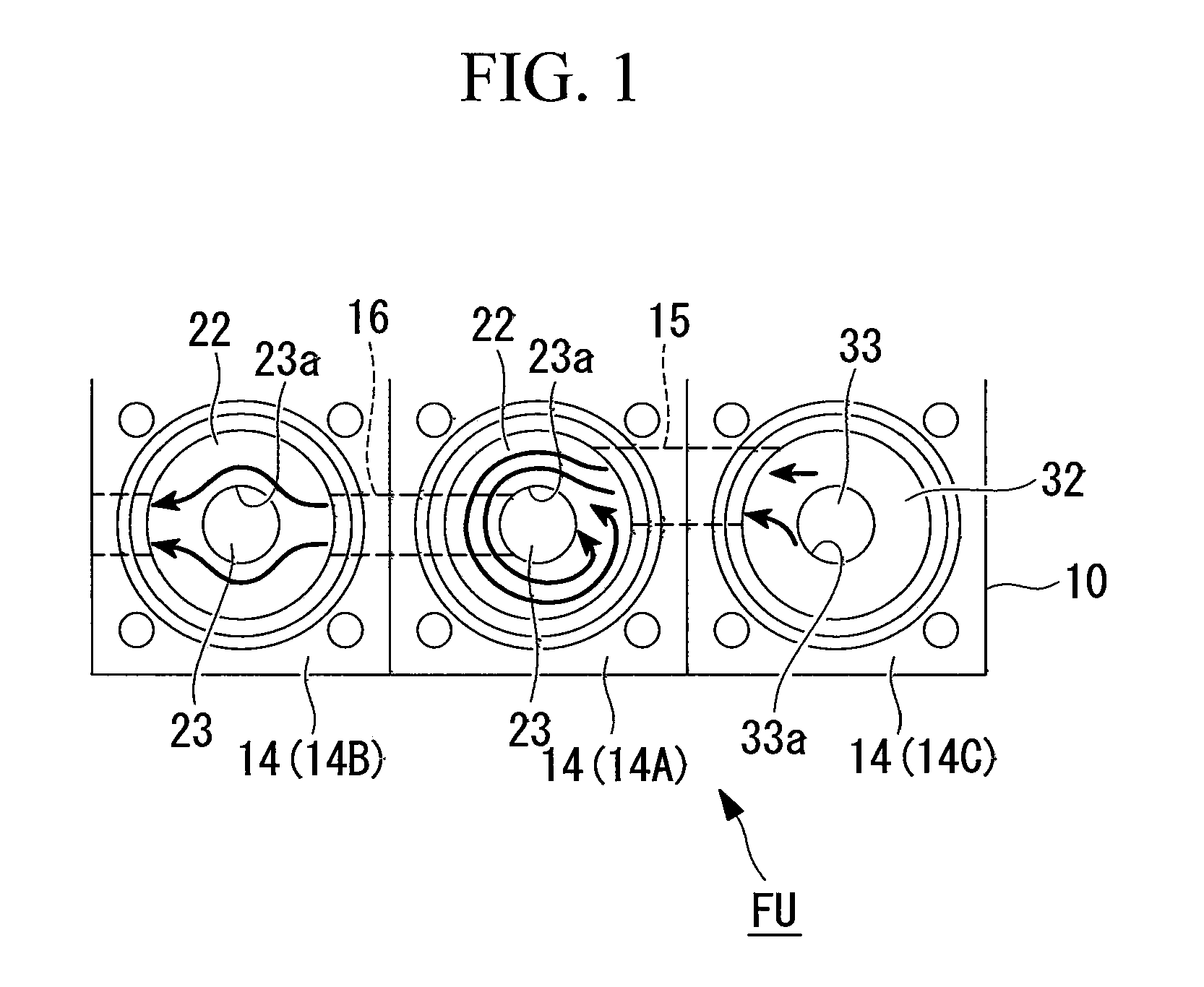
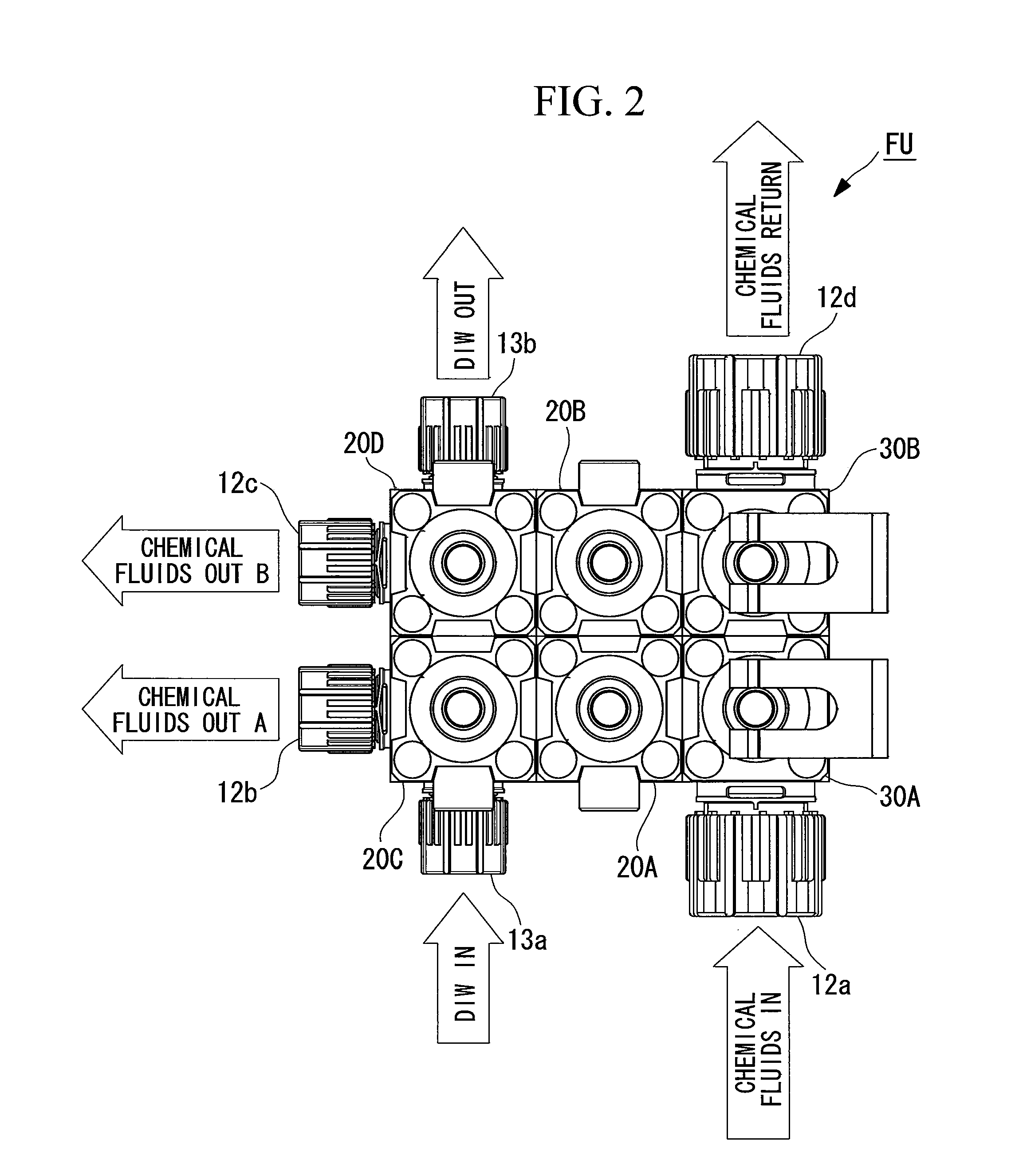
A fluid apparatus unit structure is provided that can be applied to a use in which a chemical fluid is removed as necessary while chemical fluid circulation and water circulation are being carried out, a fluid such as a chemical fluid does not readily solidify therein, and the fluid apparatus unit structure is compact. In the fluid apparatus unit structure (FU) that groups together and integrates plural fluid apparatus components that are connected via a flow path into a base member (10), a linked flow path (15), which links an adjacent air pressure control valve (20A) and a manual control valve (30A) that form a first chemical fluid discharge path that carries out chemical fluid circulation, is offset from the axial center of the fluid apparatus components.
Owner:SURPASS IND
Direct link establishment method and related equipment
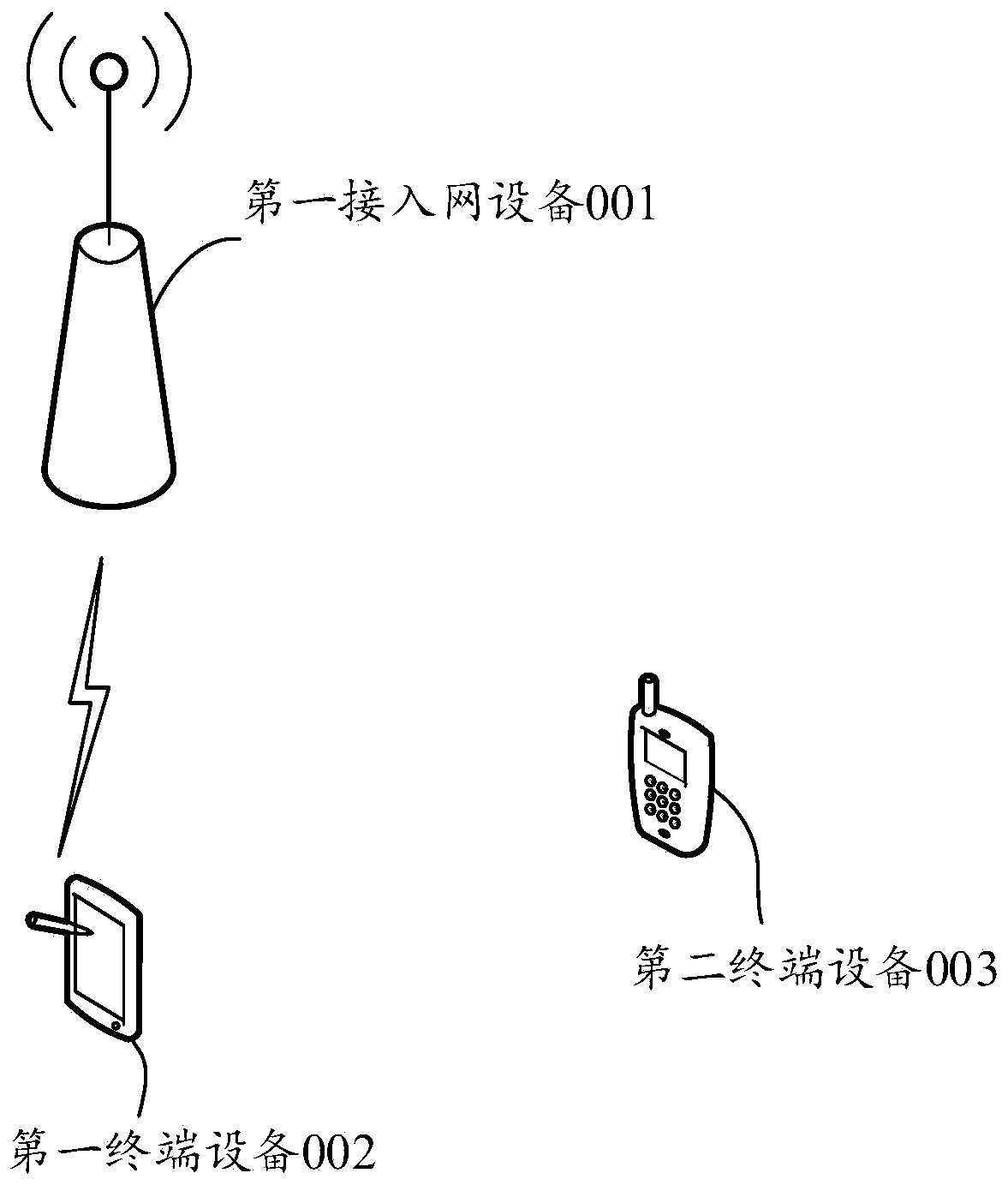
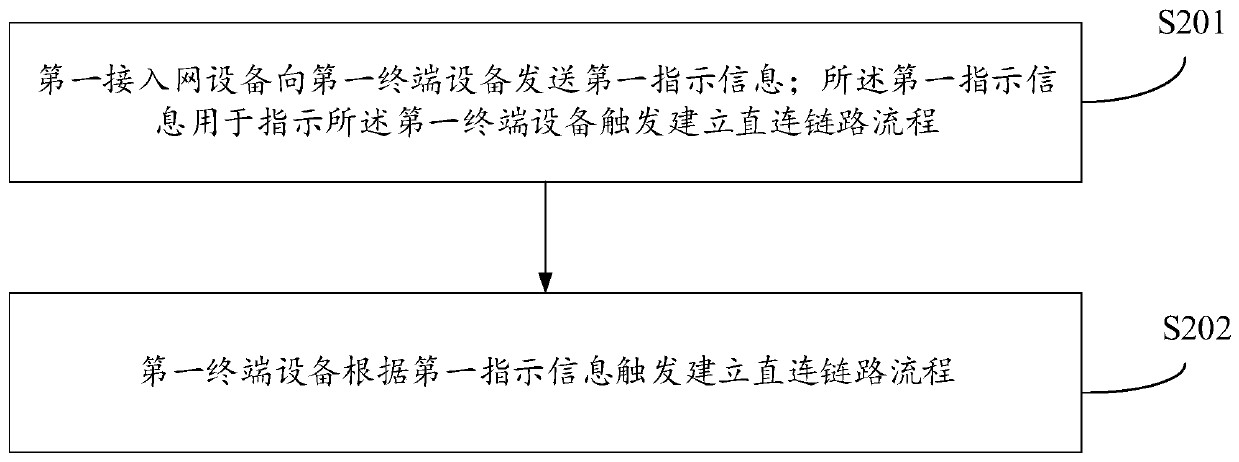
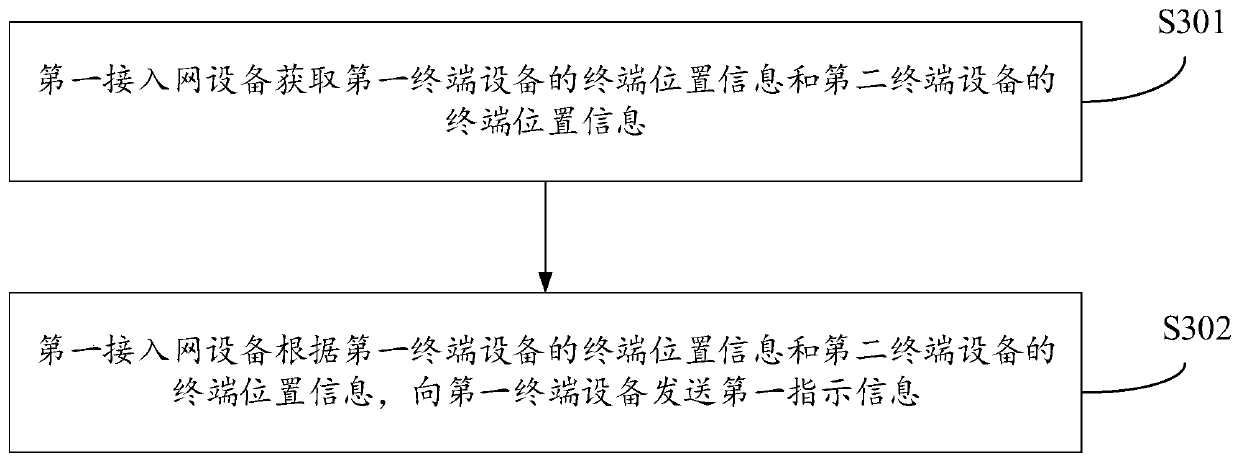
ActiveCN111314881ASave powerSave wireless resourcesPower managementParticular environment based servicesAccess networkTerminal equipment
The embodiment of the invention discloses a direct link establishment method and related equipment. The method comprises the following steps: first access network equipment sends first indication information to first terminal equipment, wherein the first indication information is used for indicating the first terminal device to trigger establishment of a direct connection link flow. According to the invention, the electric quantity of the terminal equipment and wireless network resources can be saved.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
Road OD data reconstruction method
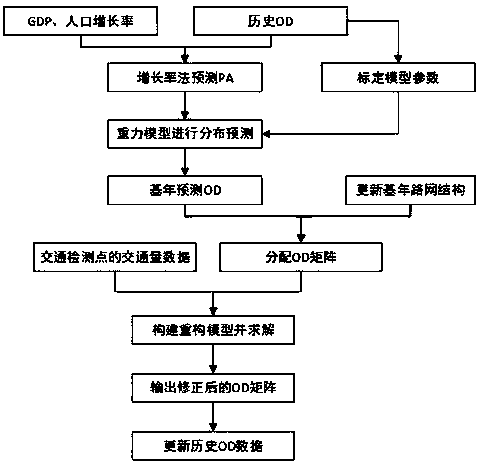
InactiveCN108446810AAvoid repetitionIncreased level of precisionForecastingDistribution matrixTraffic capacity
Provided is a road OD data reconstruction method. The method comprises: OD reconstruction basic data demand analysis, a priori OD matrix, a link flow distribution matrix obtained by traffic distribution, and link counting data obtained by traffic detection points being the OD reconstruction basic data; OD reconstruction model and algorithm, using a checking method of an inspection region and a maximum entropy principle as theoretical basis of model establishment, and using the predicted priori matrix, an updated distribution model, and link counting data of the traffic detection points as basic data, to establish a base year OD process model and provide a corresponding solution algorithm. The method corrects the predicted OD through traffic flow data obtained by simple traffic detection equipment or observation stations, to obtain brand new base year OD data, and realize OD reconstruction based on checking and a prediction model. The method provides real-time dynamic traffic basic datafor transportation planning, construction and management, improves traffic construction and management informationization level, provides basis for traffic detection point layout.
Owner:SOUTHEAST UNIV
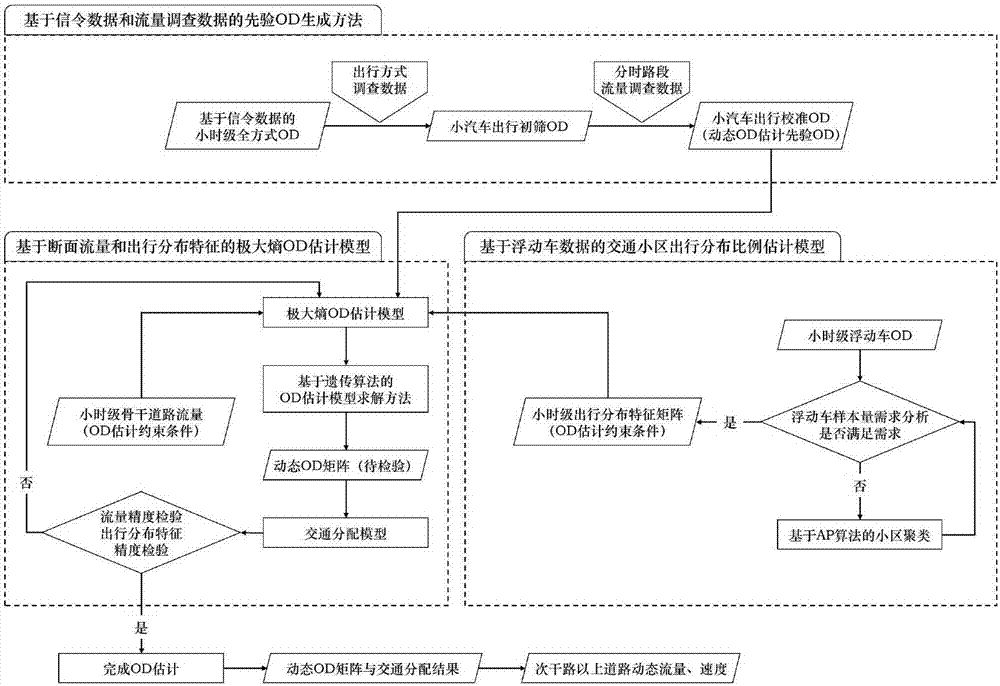
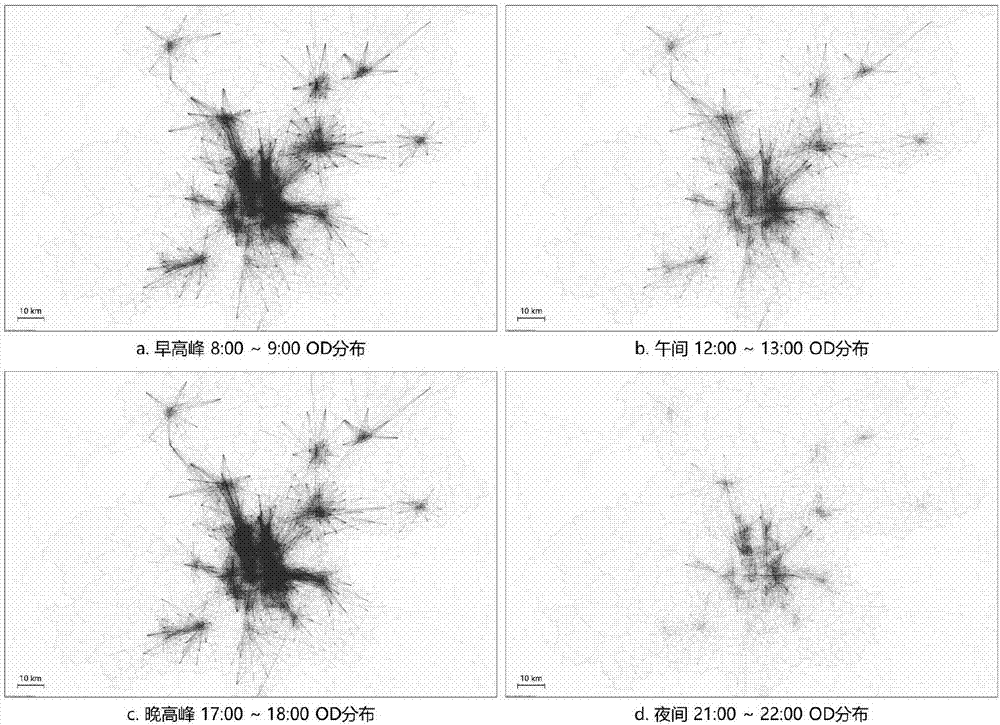
Car OD extraction method based on signaling and floating car data
ActiveCN106875686ARealization of dynamic OD estimationSolve the problem that the dynamic prior OD is difficult to obtainDetection of traffic movementDistribution characteristicSimulation
The invention discloses a car OD extraction method based on a signaling and floating car data, and belongs to the technical field of transportation. In view of the problem that there is no dynamic priori OD for the existing dynamic OD estimation, the invention provides a dynamic priori OD acquisition method based on mobile phone signaling data and traffic investigation data. In view of the problem that the traffic flow observed in the dynamic OD process is of limited coverage and insufficient constraints, the invention provides travel distribution characteristic constraints based on floating car data, and provides travel distribution characteristic calculation methods under different sample sizes. In order to bring both link flow constraints and travel distribution characteristic constraints into the OD estimation process, the invention builds a maximum entropy OD estimation model based on double constraints, and provides a solution. The problem that it is difficult to acquire dynamic priori OD in the existing dynamic OD estimation can be solved. Adequate constraints can be provided under the condition of existing data in order to realize car dynamic OD estimation.
Owner:BEIJING UNIV OF TECH
Self-evolvable logic fabric
InactiveUS20130258905A1Reduce probabilityMaximize flowData switching by path configurationMultiple digital computer combinationsDigital dataParallel computing
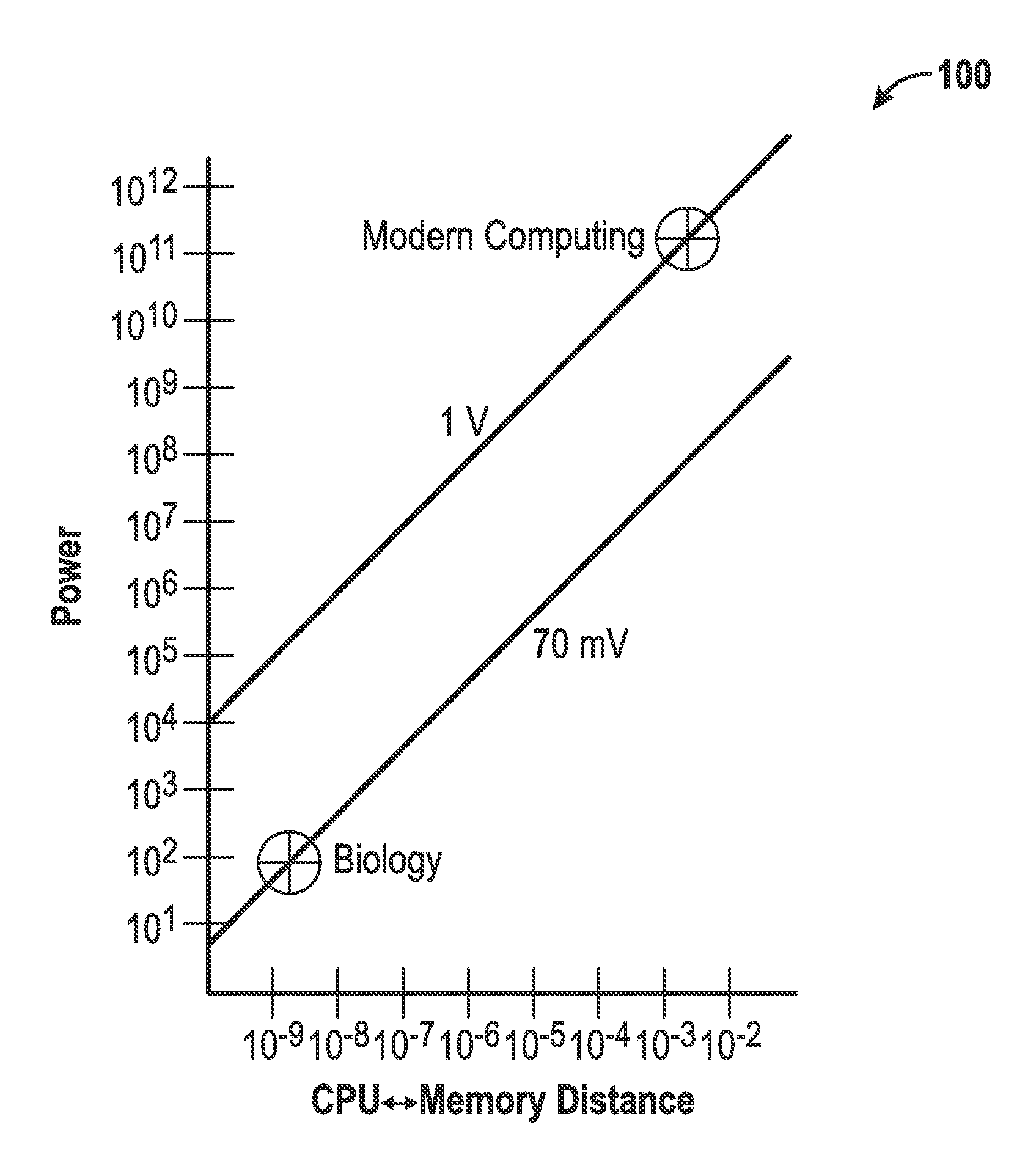
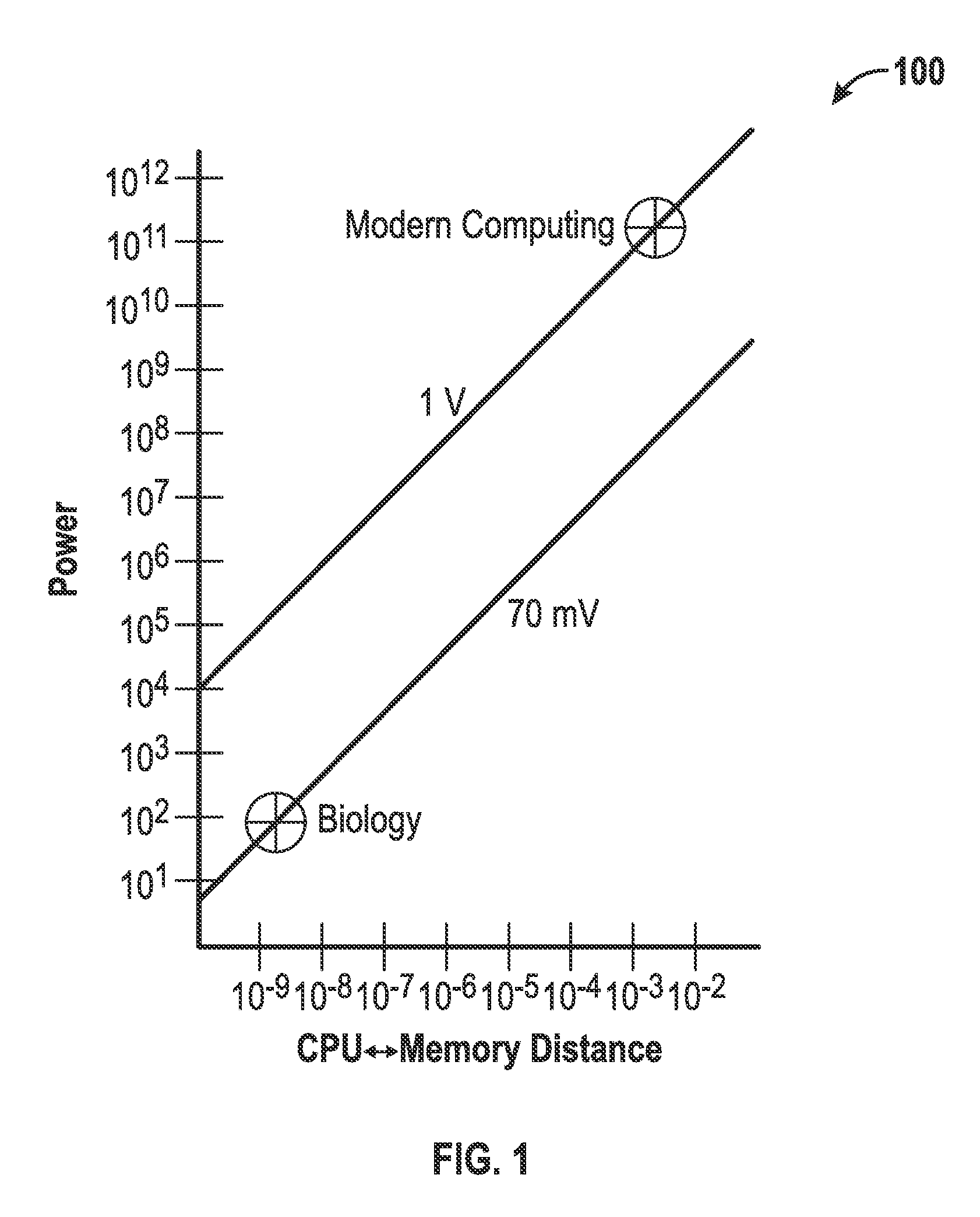
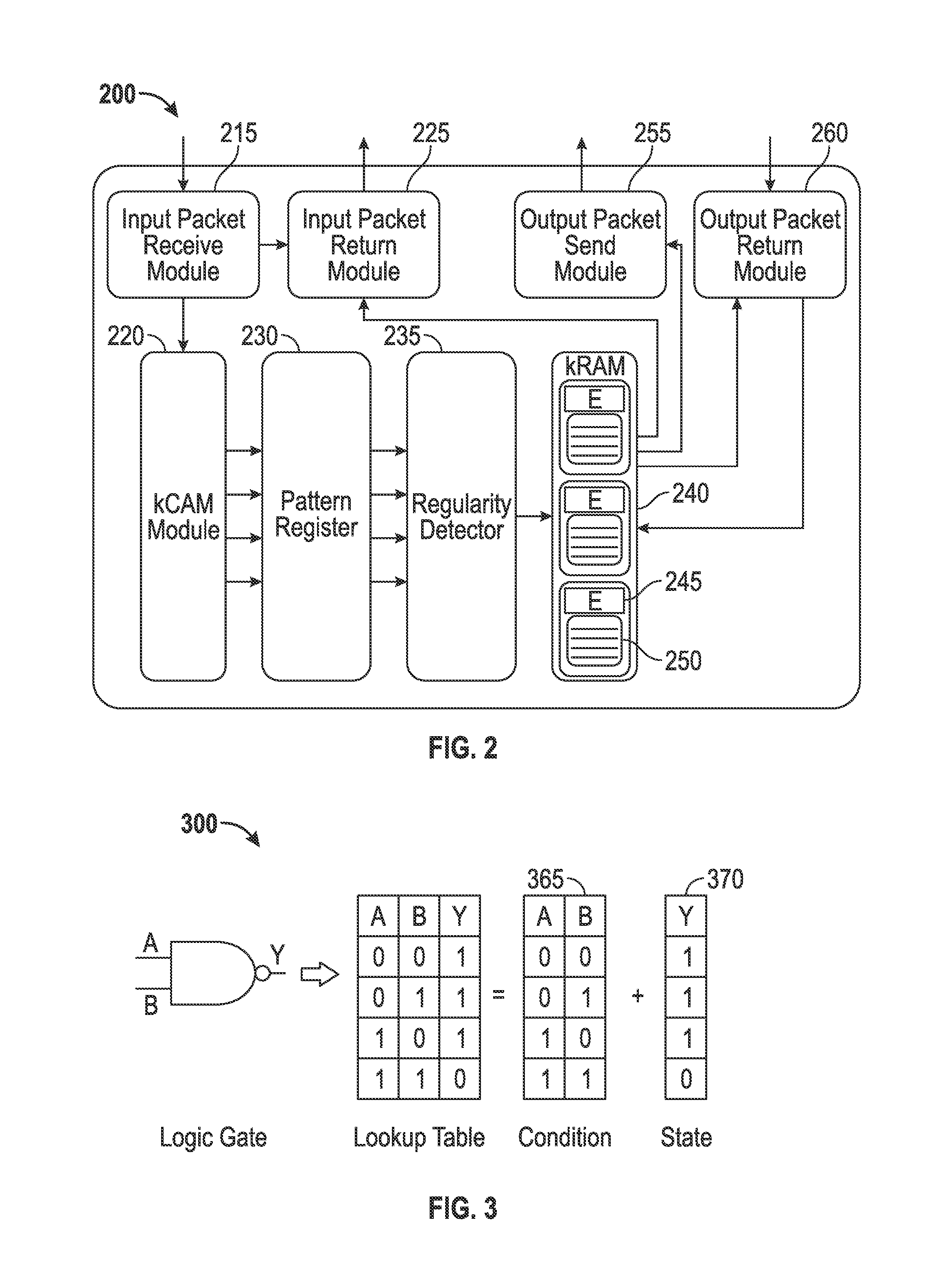
Methods and systems for achieving self-organized growth of a logic pathway. A number of hardware modules that represents a core can be configured and communicated via a packet routing architecture. Each core includes a plurality of sub-modules that interact dynamically to a growth algorithm. A flow network can be created between a sensor input and a prediction of a desired sensor input and a link can be formed between a regularity within a core and another core via a link-flow-selection process. A digital data packet can be transmitted between the cores for communicating activation of the regularity and to exchange energy. Such physically-self organized circuit fabric system interacts dynamically to a growth algorithm that takes the input to produce a desired output and continuously self-repair and / or heal if damaged.
Owner:KNOWM TECH
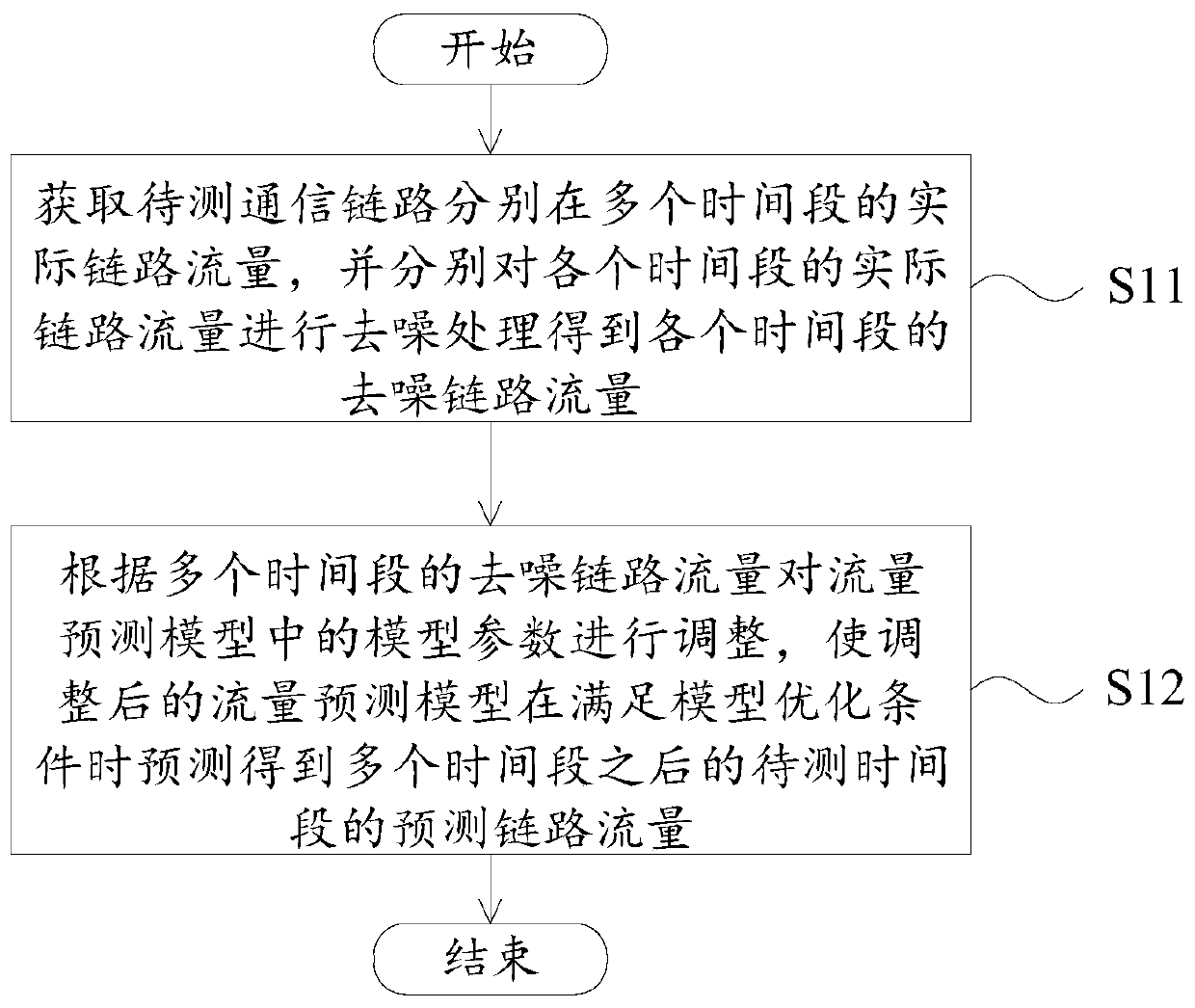
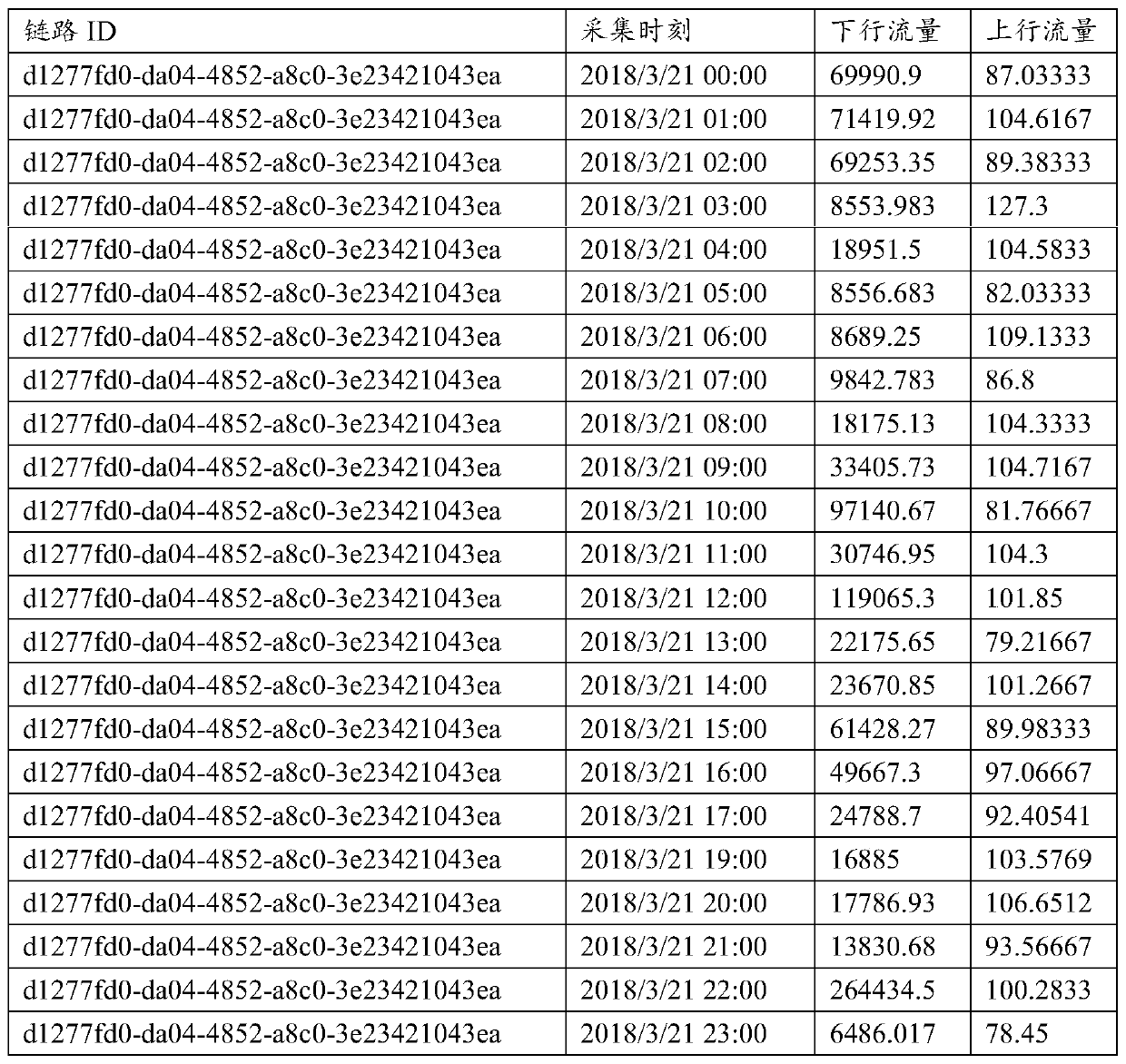
Link traffic prediction method and device, and electronic equipment
ActiveCN110351123AIn line with historical trendsReal-time online trainingData switching networksTraffic predictionTelecommunications link
The embodiment of the invention provides a link flow prediction method and a device, and electronic equipment. The method comprises the following steps: firstly, performing de-noising on actual link traffic of a communication link to be tested in a plurality of time periods to obtain de-noised link traffic; and adjusting model parameters in the flow prediction model according to the denoised linkflow of the multiple time periods, so that the adjusted flow prediction model predicts the predicted link flow of the to-be-measured time period after the multiple time periods when meeting model optimization conditions. Therefore, the accuracy of the prediction result is improved.
Owner:NEW H3C BIG DATA TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com