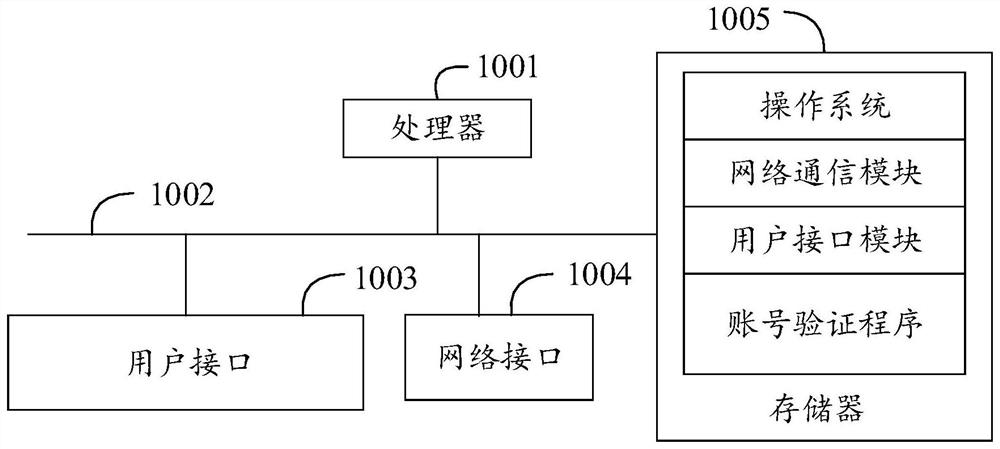
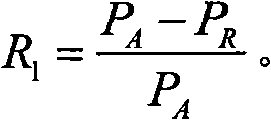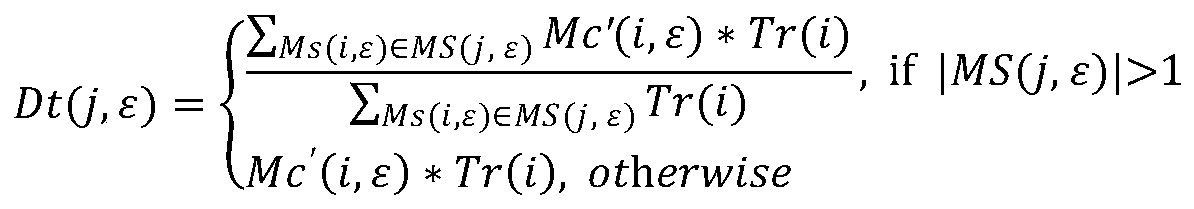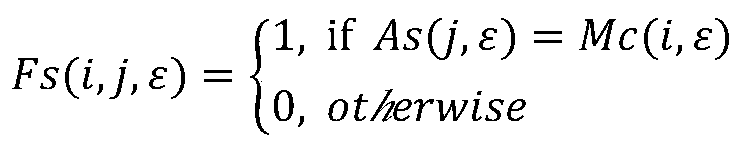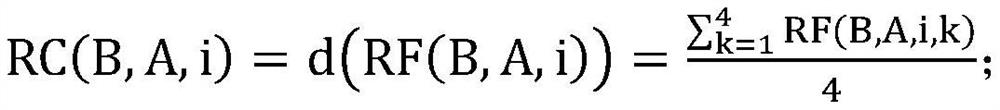Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
51 results about "Trust certificate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
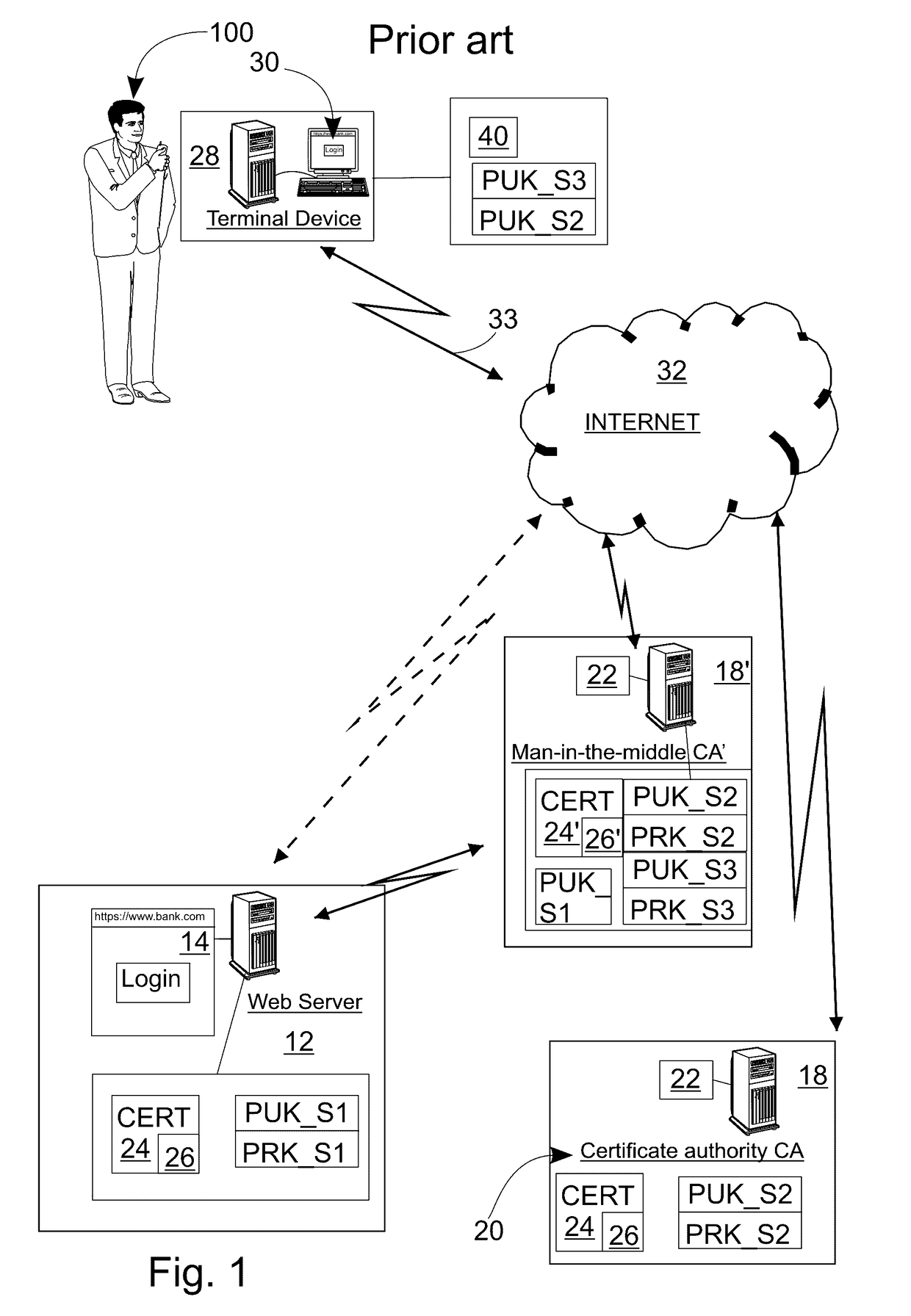
In finance, a trust certificate is a corporate bond backed by other securities, usually a parent corporation borrowing against securities of its subsidiaries.
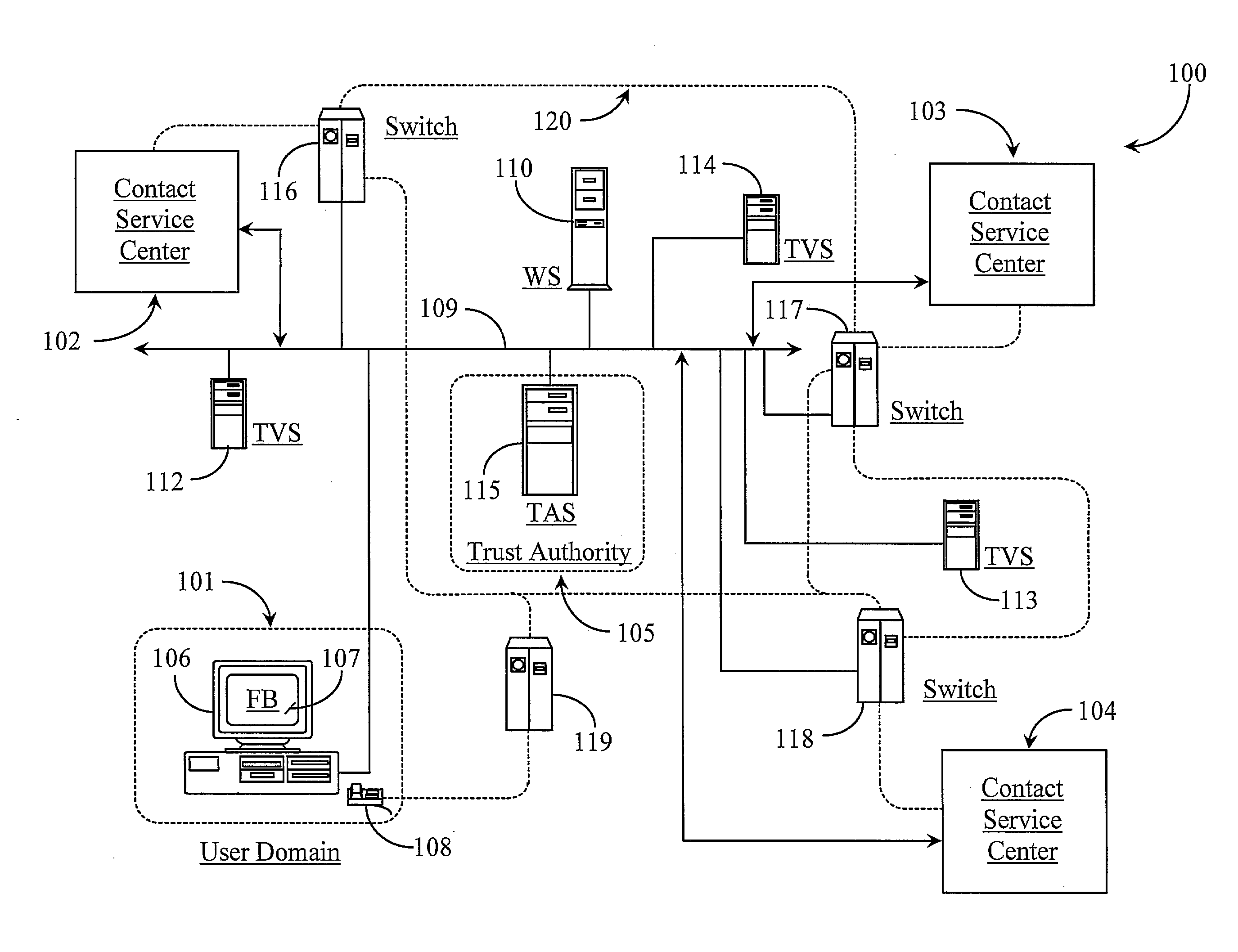
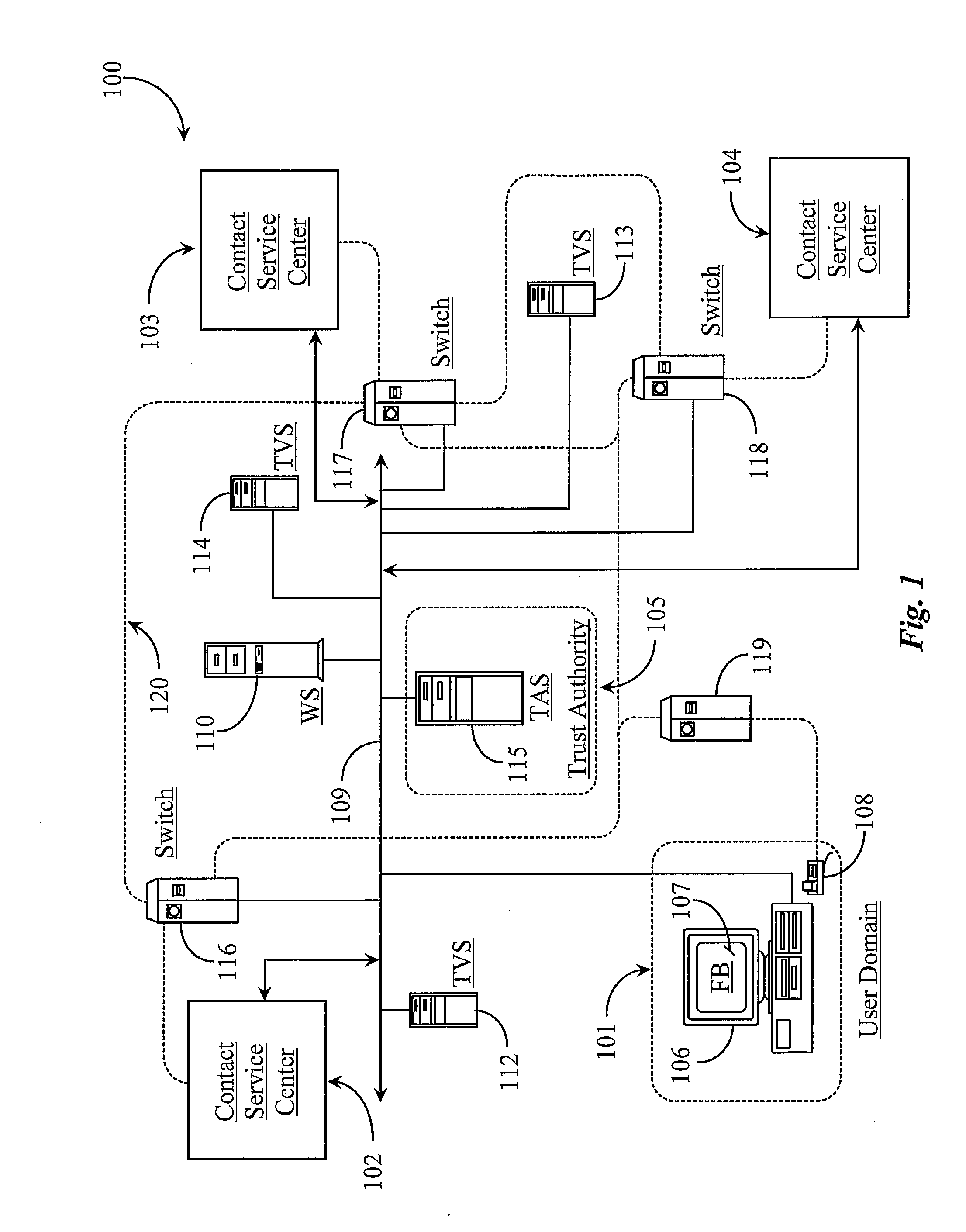
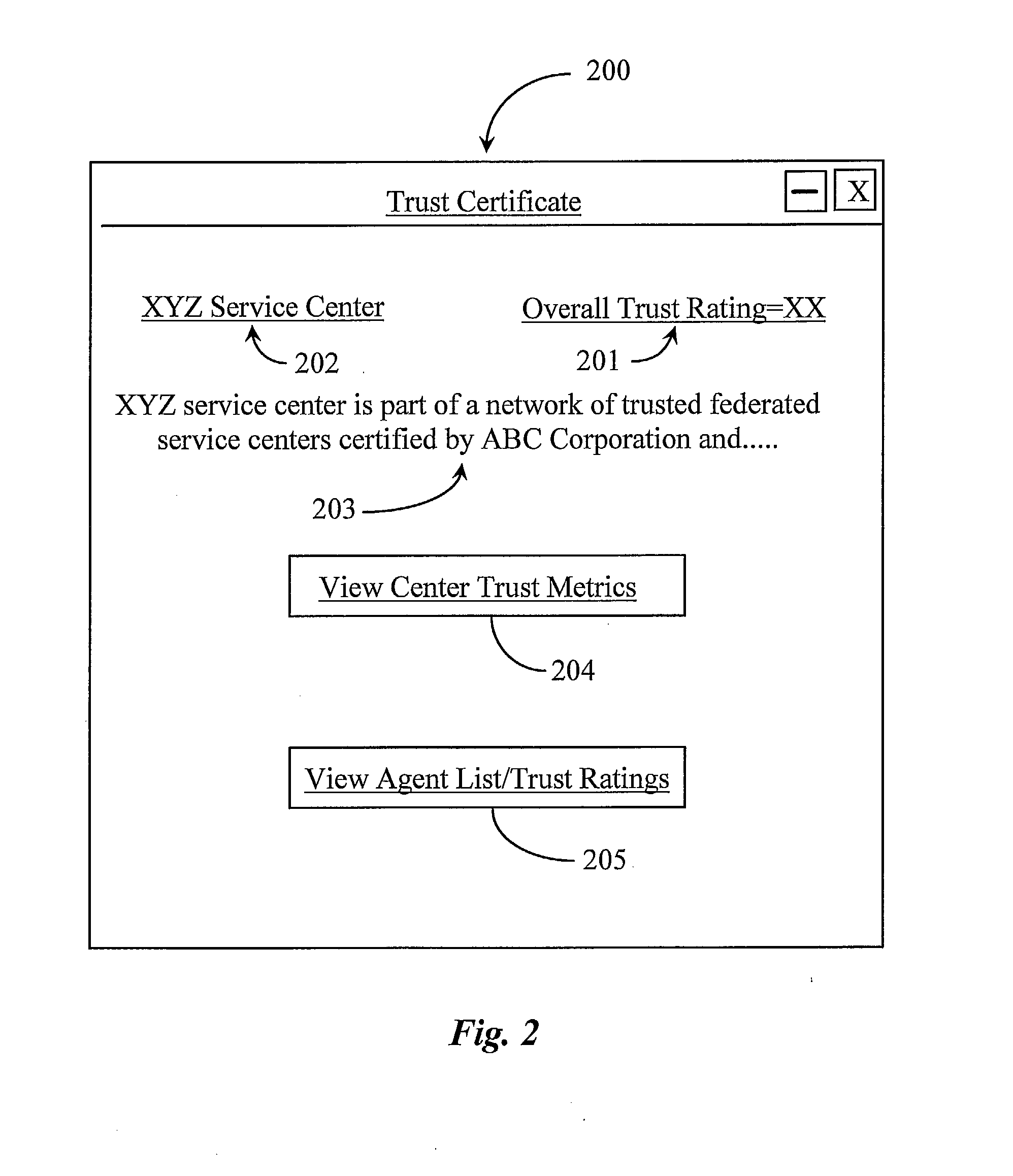
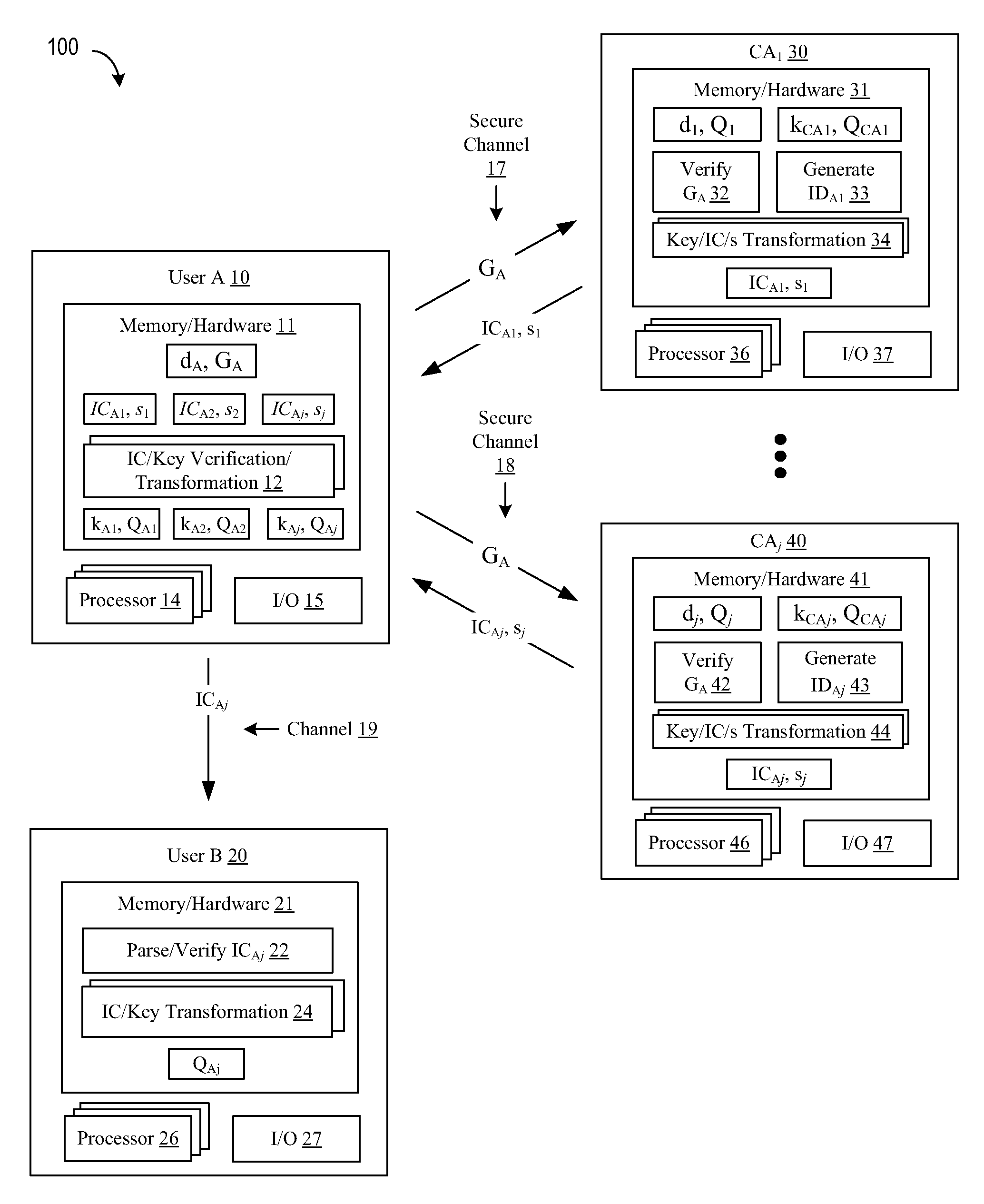
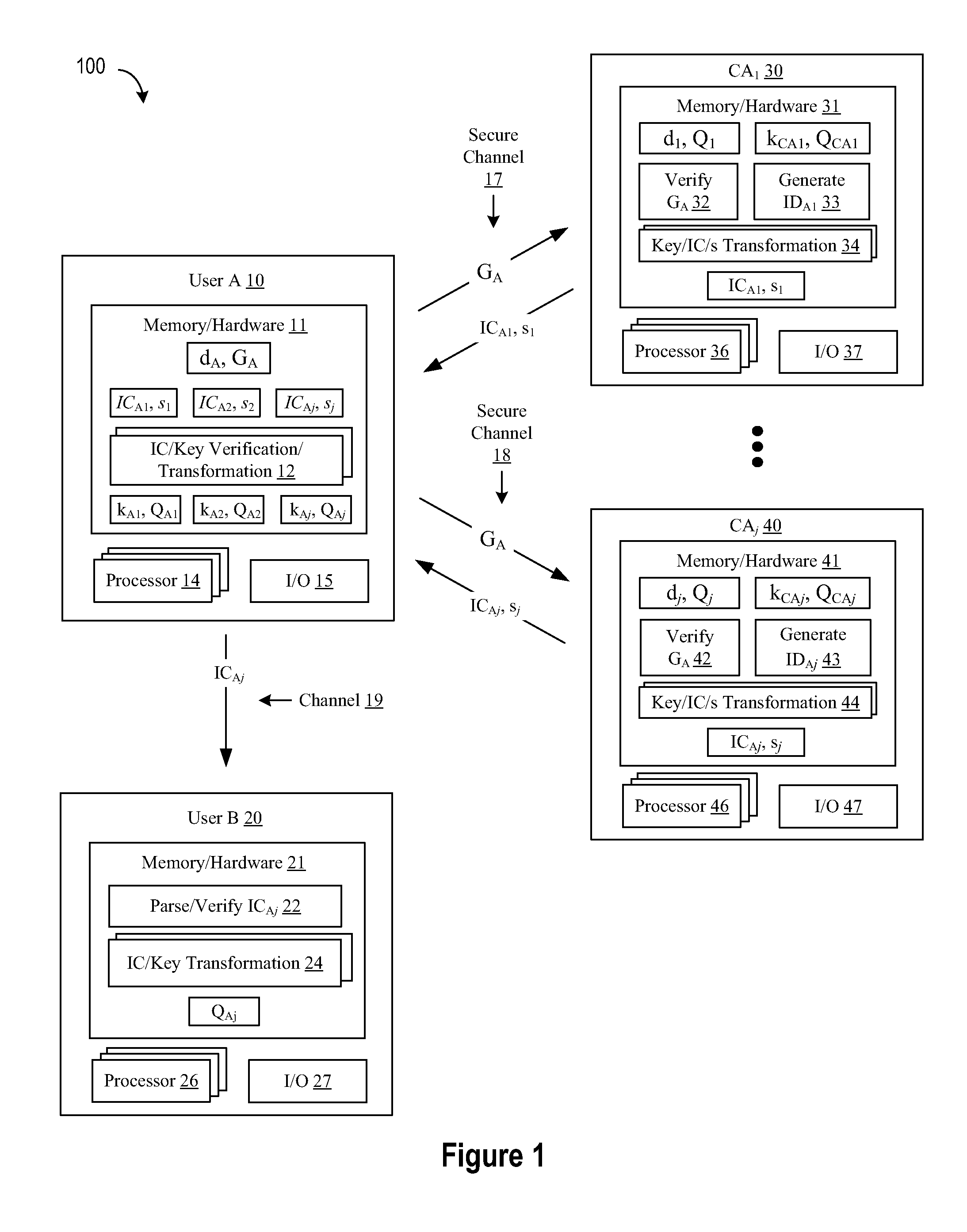
Method and System for Establishing and Managing Trust Metrics for Service Providers in a Federated Service Provider Network
InactiveUS20090172776A1Digital data processing detailsTelevision conference systemsCommunication interfaceCommunication endpoint
A system for issuing, validating, and managing trust between two or more entities authenticated to operate in a federated network includes one or more servers for issuing trust certificates based on one or more trust metrics, and one or more servers for validating issued trust certificates. Entities operating through a communications interface may be issued trust certificates pursuant to evaluation relative to certain trust metrics, the certificates accompanying communications between entities the certificates subject to validation at communication end points of interaction.
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC
Certificating vehicle public key with vehicle attributes
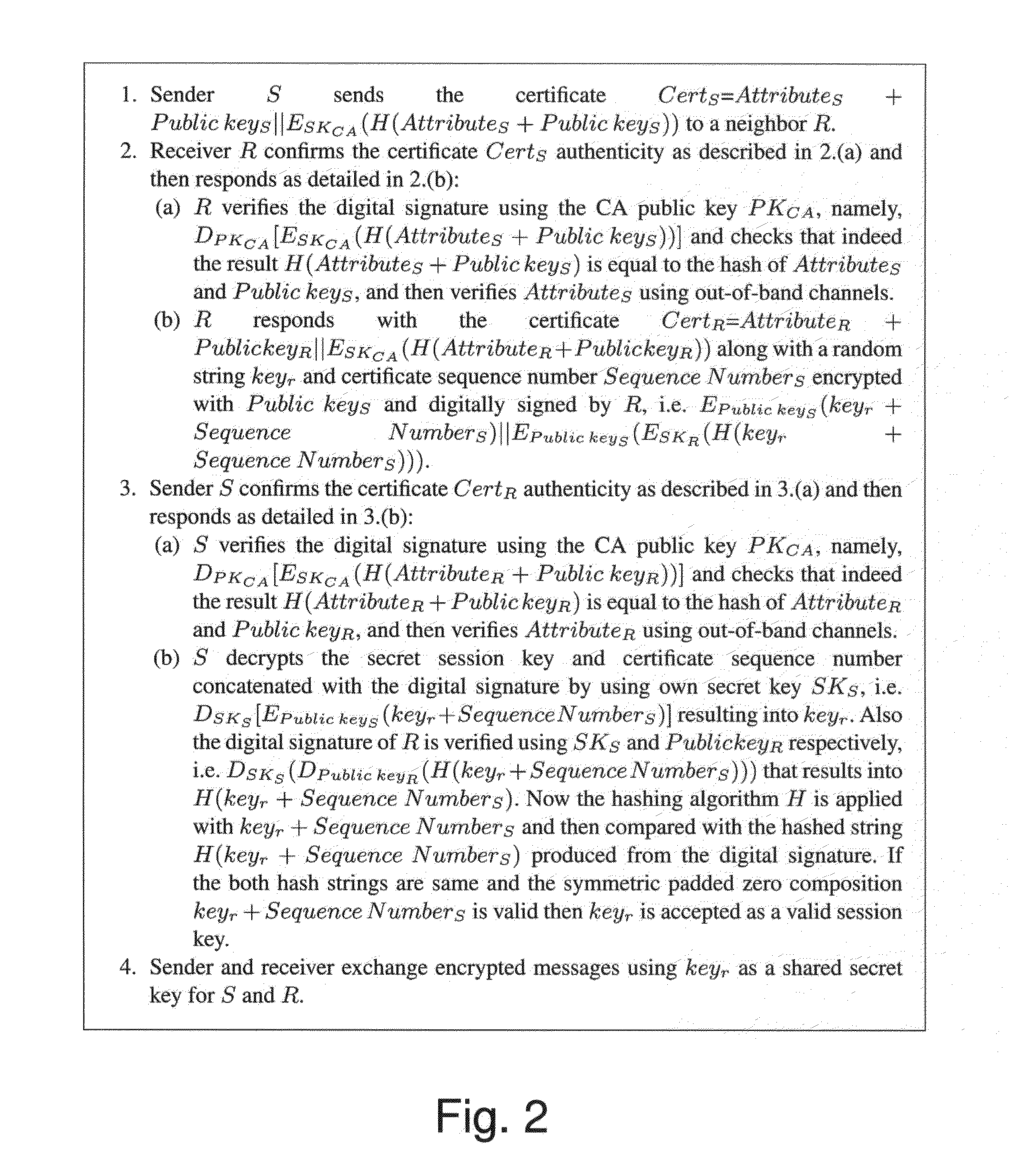
ActiveUS20150052352A1Public key for secure communicationUser identity/authority verificationImaging processingDigital signature
A method for providing secure connection between vehicles over channels of a wireless communication network, according to which, a first unique pair of digitally signed public key and private key is provided to each vehicle, along with additional vehicle-related data including a visually static collection of attributes of the vehicle. A unique certificate number is generated for each vehicle and monolithic data consisting of the public key, the certificate number and the attributes is signed by a trusted certificate generating authority. Prior to wireless communication between a first vehicle and a second vehicle, a verification step is performed during which the first vehicle sends its unique certificate number to a second vehicle over a communication channel; the second vehicle verifies the authenticity of received unique certificate number of the first vehicle and attributes by a camera that captures attributes which are visible, using image processing means. If the attributes are verified successfully, the second vehicle sends its unique certificate number to the first vehicle over a communication channel, along with a secret session key, which is valid for the current session only. Then the first vehicle verifies the authenticity of received unique certificate number of the second vehicle and attributes by a camera that captures attributes of the second vehicle which are visible, using signal processing means and both vehicles are allowed to securely exchange message or data using the secret session key.
Owner:DOLEV SHLOMI +3
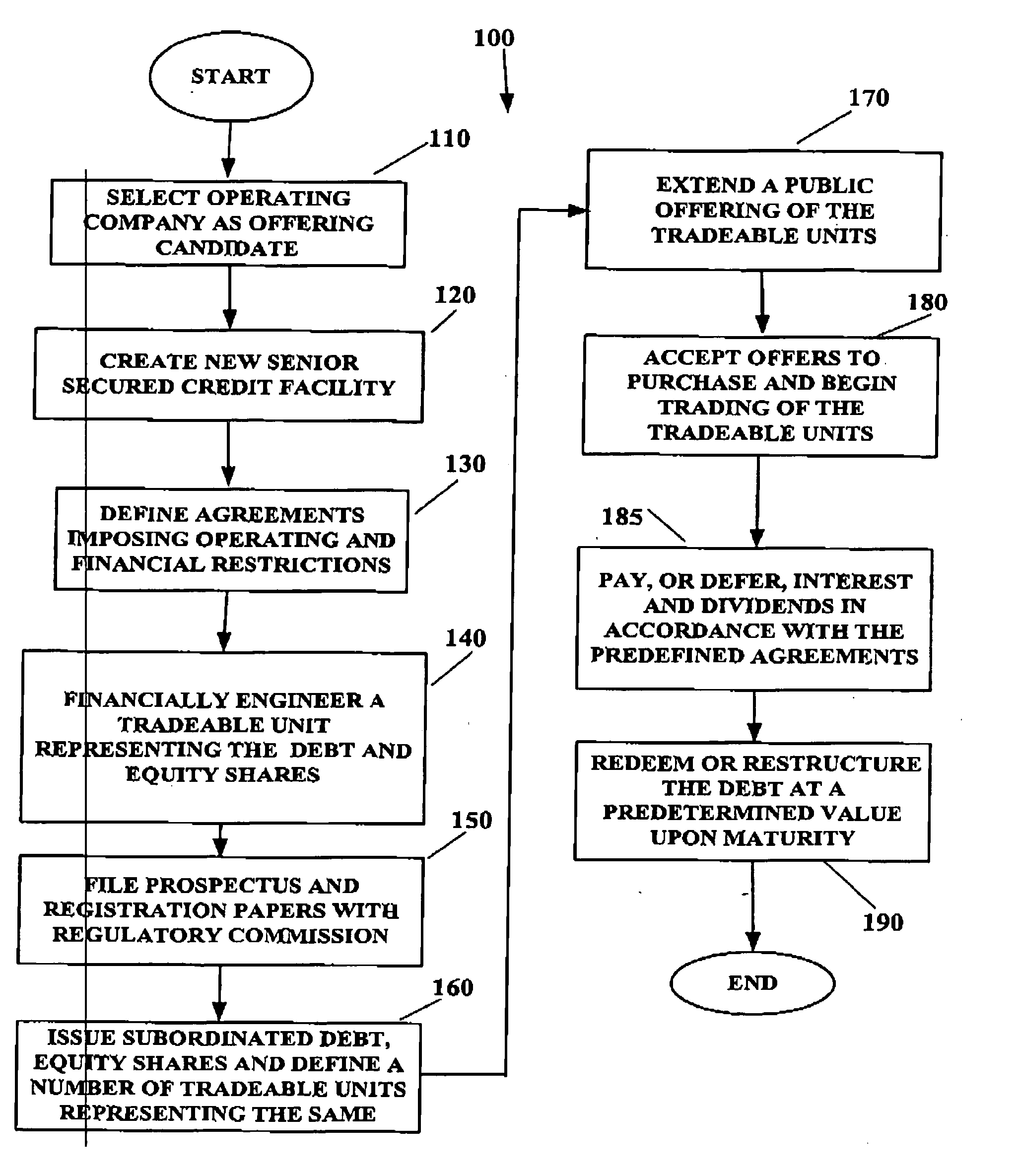
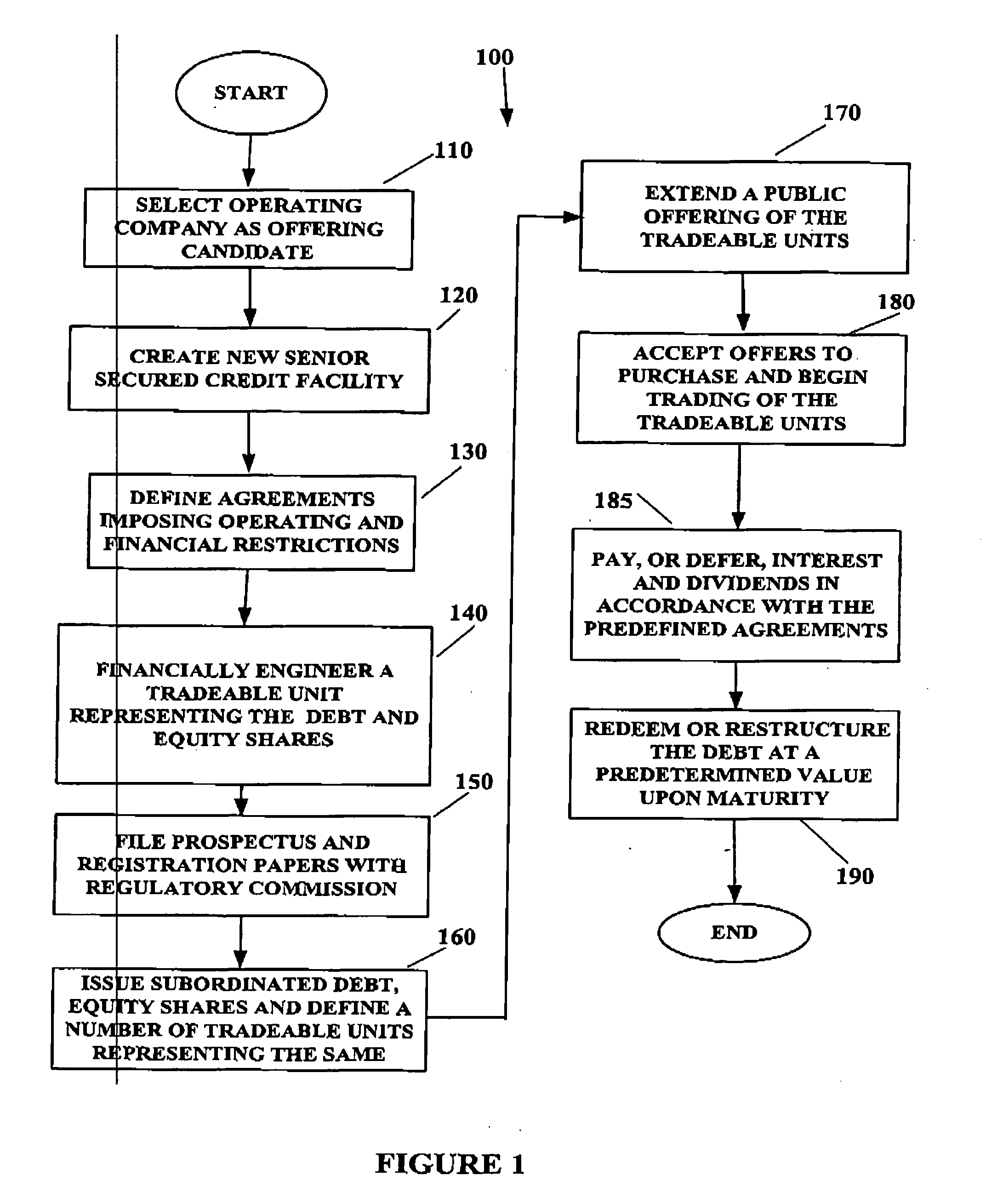
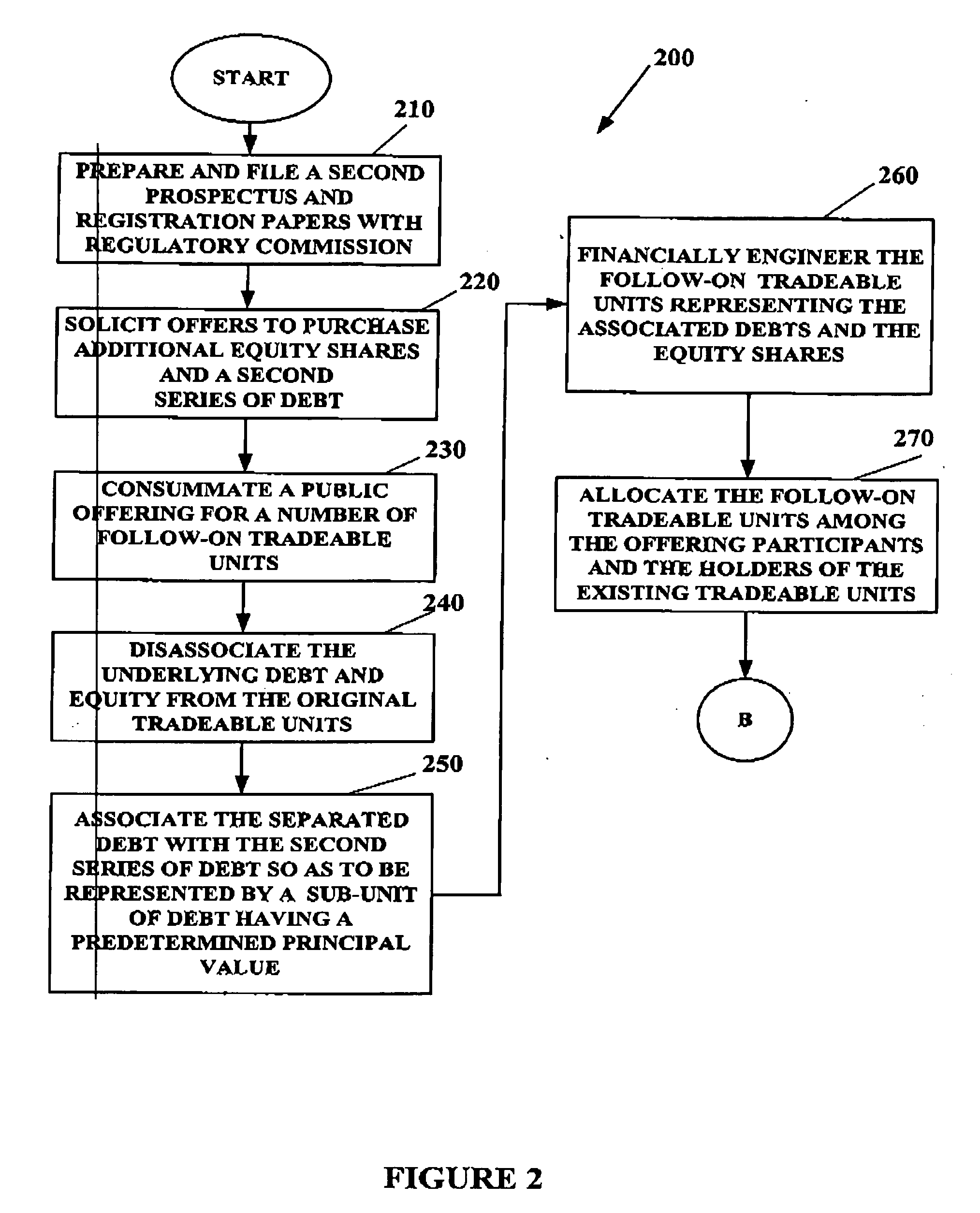
System and method for creating tradeable financial units
InactiveUS20050203818A9FinanceSpecial data processing applicationsTrust certificateFinancial transaction
An article suitable for trade as a unit in a financial offering by a company, representing in a predetermined ratio both equity and debt, while providing direct ownership of the equity and debt. The debt is interest bearing at a particular rate until a particular maturity date. An article suitable for trade as a unit in a subsequent offering further includes a second debt, which is interest bearing at the same particular rate until the same particular maturity date as the first debt. A software reference can associate the equity and debt(s) of the unit to a unique number that is suitable for facilitating the clearing and settlement of purchases and sales. The unit provides direct ownership of the equity and debt without an intervening holding entity or the need for trust certificates. Methods establishing such units and for decomposing them are described.
Owner:CIBC WORLD MARKETS
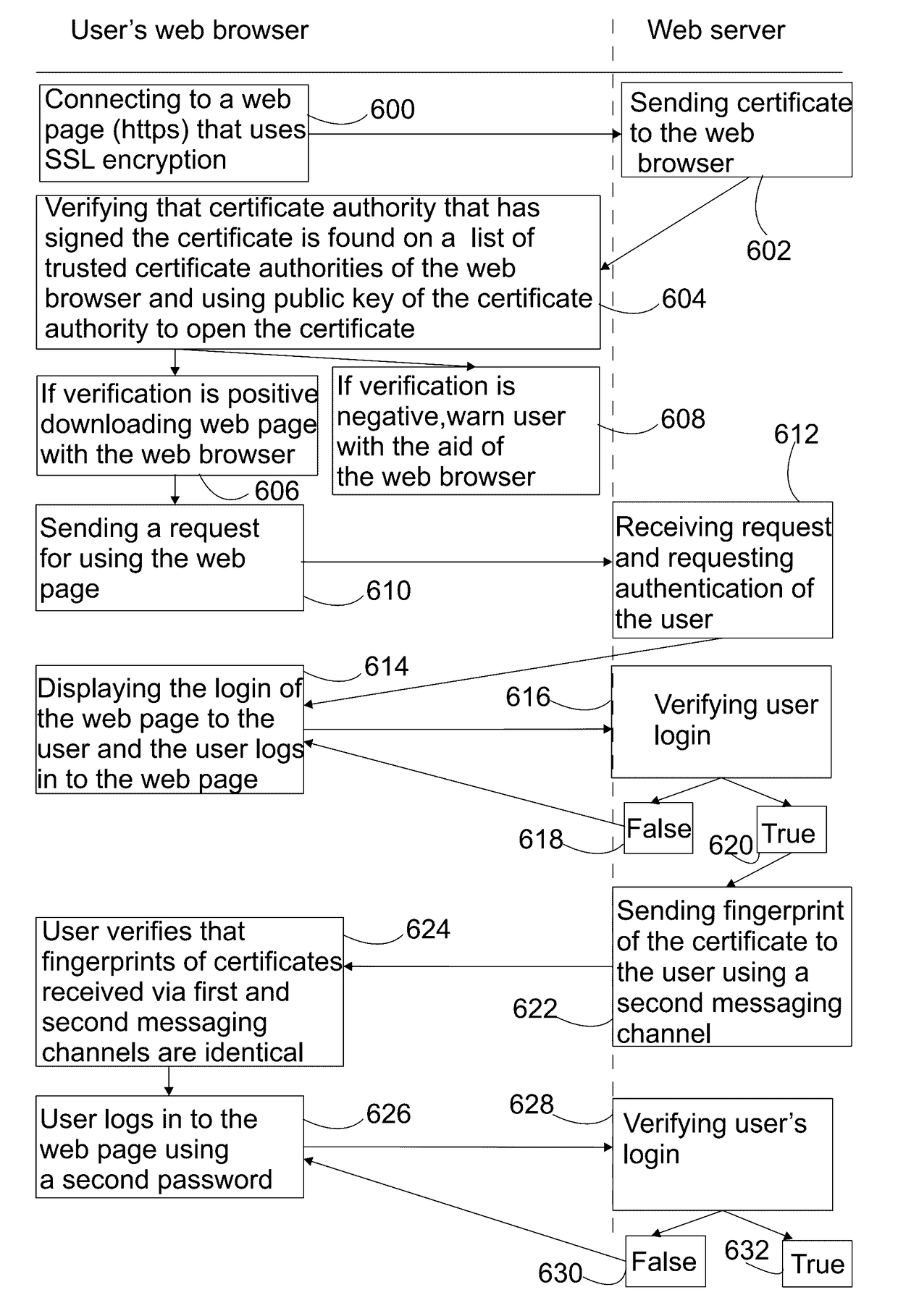
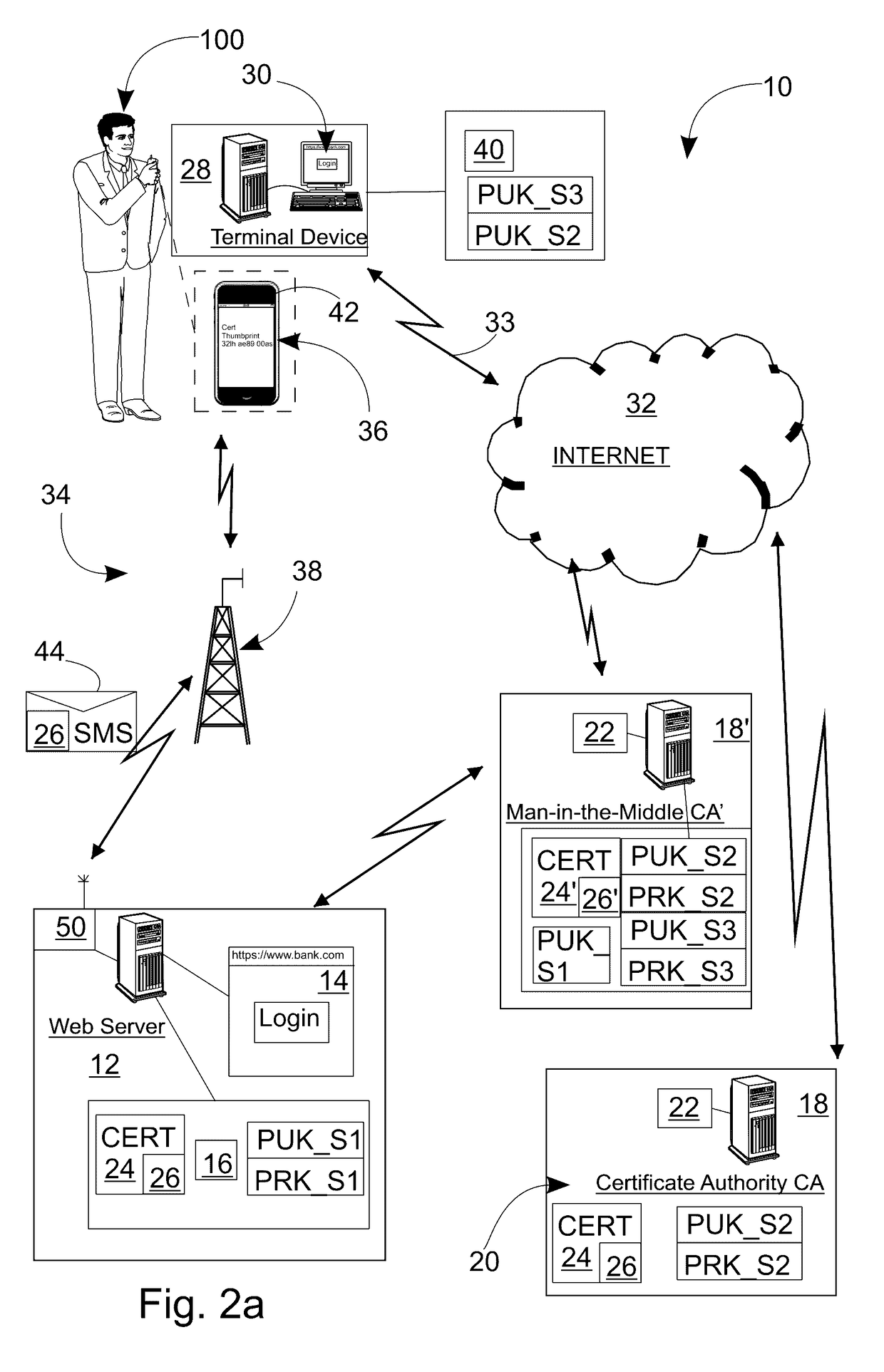
Method and a system for verifying the authenticity of a certificate in a web browser using the ssl/tls protocol in an encrypted internet connection to an https website
ActiveUS20170118029A1User identity/authority verificationPublic key infrastructure trust modelsWeb browserWeb service
A method for verifying the authenticity of a certificate in a web browser using an SSL / TLS protocol in an encrypted Internet connection to an HTTPS website includes establishing an encrypted connection to the HTTPS website using the web browser on a user's terminal device. A certificate including a public key of the HTTPS website and signed by a trusted certificate authority is sent to the user's web browser from the web server using the Internet connection. The certificate authority that signed the certificate is compared against the list of trusted certificate authorities. The certificate authority is verified as being included in the list. The thumbprint of the certificate is sent as an additional security check key using a second messaging channel, external to the Internet connection between HTTPS website and web browser of the user's terminal device, and the contact data in the customer register. The additional security check key is compared with the thumbprint received by the web.
Owner:ONLINE SOLUTIONS OY
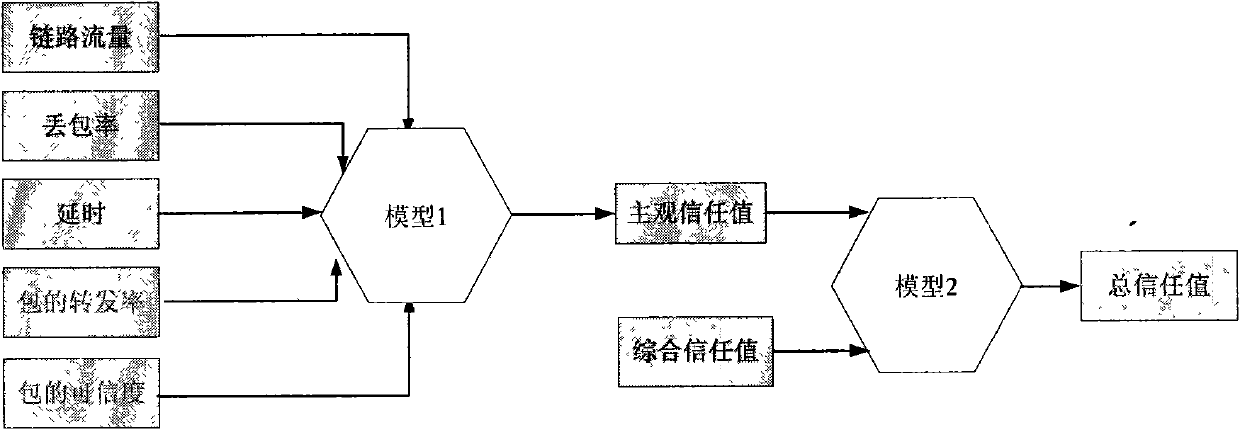
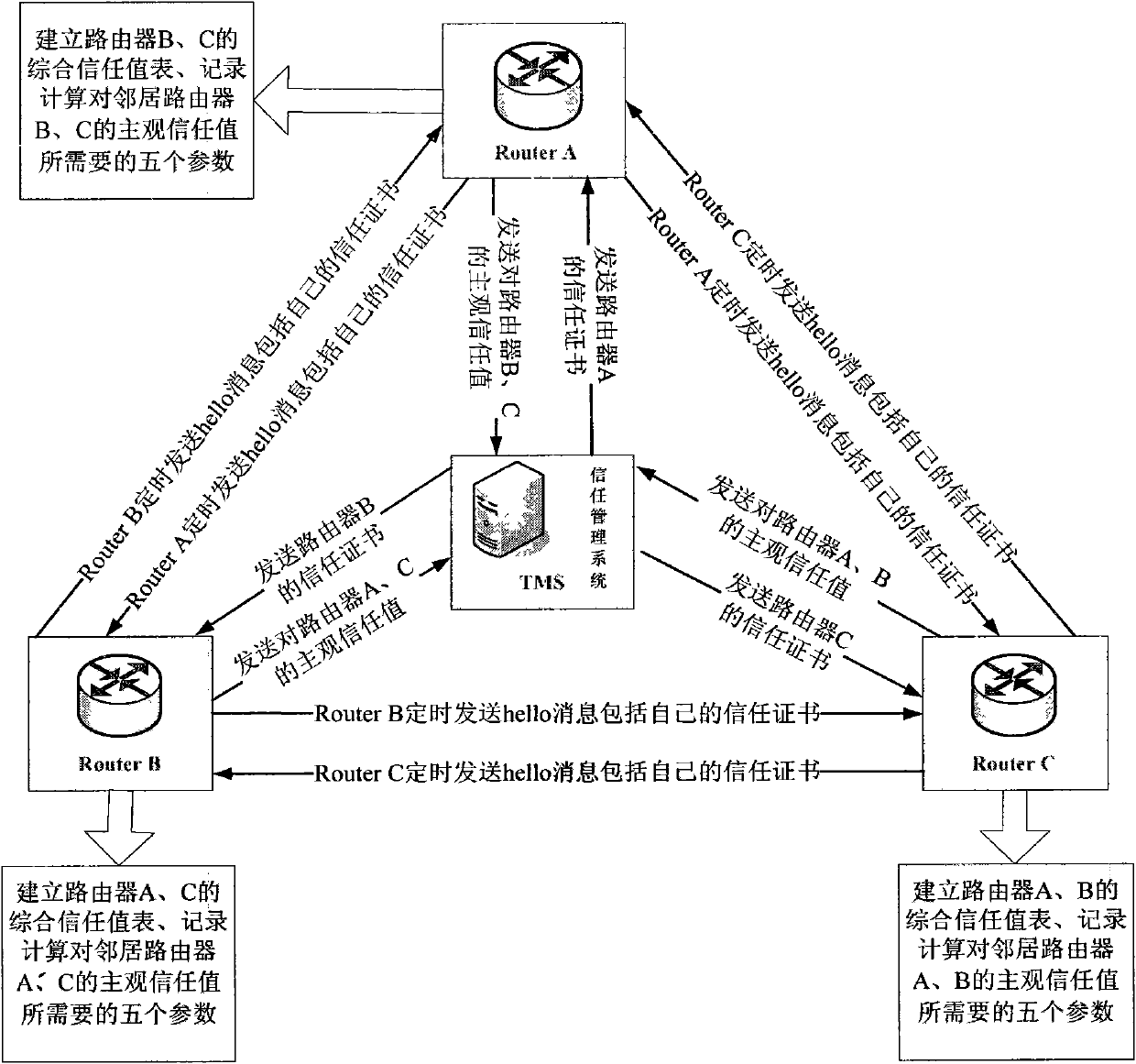
Trust management system based trusted reconstructing method of IP routing protocol
The invention discloses a trust management system based trusted reconstructing method of an Open Shortest Path First (OSPF) routing protocol, which comprises the following steps of: (1) before each router is added into a network, registering to the trust management system, and sending corresponding trust certificates to the routers by the trust management system, the trust certificates including comprehensive trust values of the routers and each being calculated according to safe parameters and configuration parameters of the routers and all the subjective trust value of the neighbor router to the routers by the trust management system; (2) transferring the trust certificates among the routers through hello information, wherein an adjacency relation is not established for the router without the trust certificate, all the routers in the network are ensured to have own trust certificates; (3) each router calculating the subjective trust value of the neighbor router based on network real time parameters including link flow, packet loss probability, retardation, transmission rate of the packet and reliability of the packet, during an interactive work with the neighbor router, calculating a total trust value of the neighbor router by using the comprehensive trust value and the subjective trust value of the neighbor router, and modifying a metric field of a link-state announcement Router_LSA packet as the total trust value and synchronizing a link-state data base;(4) modifying a Dijkstra algorithm, using a reciprocal of the total trust value between the routers as the parameter for the arithmetic computation, selecting the router with higher trust value to generate a shortest path tree, and forming a trust routing list; (5) periodically reporting the subjective trust value of the neighbor routers to the trust management system by each router, simultaneously obtaining the parameter required for computing the subjective trust value, updating the trust certificate of each router at fixed time, and eliminating the router with the overdue trust certificate out of the network to maintain the topological structure of the whole network.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Computer implemented method and a computer system to prevent security problems in the use of digital certificates in code signing and a computer program product thereof
ActiveUS20150156024A1Process safetyUser identity/authority verificationComputer security arrangementsSoftware distributionSoftware engineering
A computer implemented method including a software distributor signing via a first server at least one software file using a digital certificate with a digital signature and at least one user via a computing device acquiring a copy of the signed software file. The digital certificate to be used is previously recorded in a second server in communication with the first server, the digital certificate to be recorded being provided by the software distributor upon a registration of the latter in the second server and including information obtained from a trust certificate chain associated to the digital certificate when performing the registration. The second server generates, upon a request made by the software distributor, a hashstamp of the signed software file.
Owner:TELEFONICA CYBERSECURITY TECH SL
Message reliability evaluation method for aggregation of two trust evaluations in car networking
ActiveCN109195162AThe assessment results are accurateFast evaluationUser identity/authority verificationLocation information based serviceDynamic featureTrustworthiness
The present invention discloses a message reliability evaluation method for aggregation of two trust evaluations in car networking. A trust center is configured to maintain trust information of vehicles, and the vehicles require the newest trust certificates themselves at a fixed period, message publishers carry the newest trust certificates when sending the messages to prove the trustworthiness themselves; a message receiver extracts the trust certificates and integrally considers the message of the plurality of message publishers to determine the reliability after receiving each message, generate one trust feedback for each message publisher and send the trust feedbacks to the trust center, and then the trust center updates the trust feedbacks and locally store the trust feedbacks. The message reliability evaluation method for aggregation of two trust evaluations in car networking can effectively aggregate the two trust evaluations with no need for requiring the trust center by the message receivers in real time so that the evaluation result is more accurate and the evaluation speed is faster, the condition that the vehicles cannot be connected with the trust center in a short time can be compatible, and the message reliability evaluation method for aggregation of two trust evaluations in car networking more accord with the high dynamic features of the car networking.
Owner:JINAN UNIVERSITY
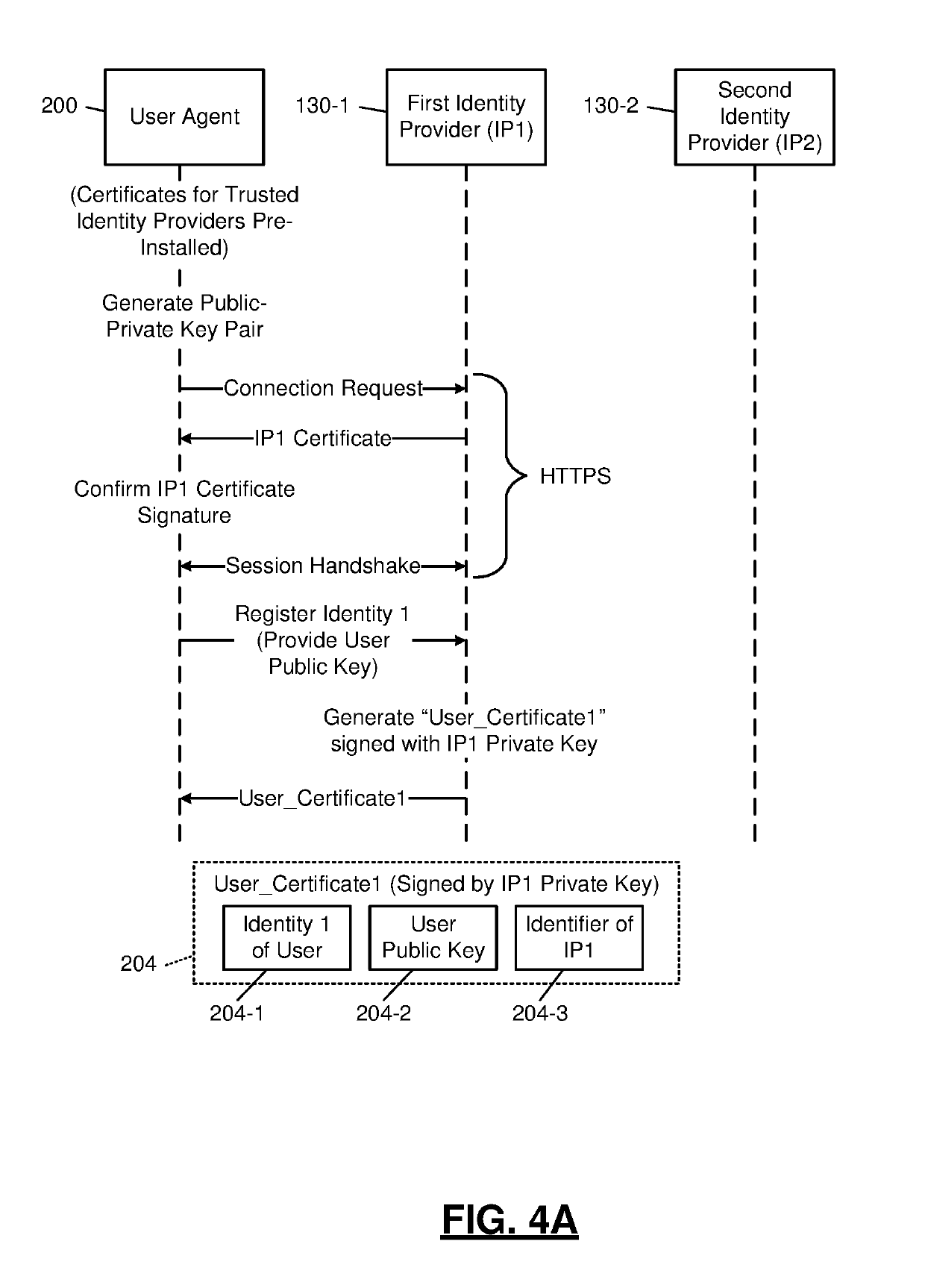
Identity-Based Certificate Authority System Architecture
ActiveUS20190260594A1Public key for secure communicationUser identity/authority verificationWeb serviceIdentity provider
A system includes a processor and a computer-readable medium storing instructions for execution. The instructions include generating a cryptographic pair of user public and private keys for a user. The instructions include registering an identity of the user with an identity provider, transmitting the user public key, and receiving a user certificate from the identity provider. The instructions include signing a trust certificate for a web server, including an address and a public key of the web server, with the user private key. The instructions include, in response to an access request from the user specifying a second web server: obtaining a second trust certificate from the second web server; and establishing a connection with the second web server in response to successful verification of a signature of the second trust certificate using a public key corresponding to a trusted contact of the user.
Owner:MICROSOFT TECH LICENSING LLC
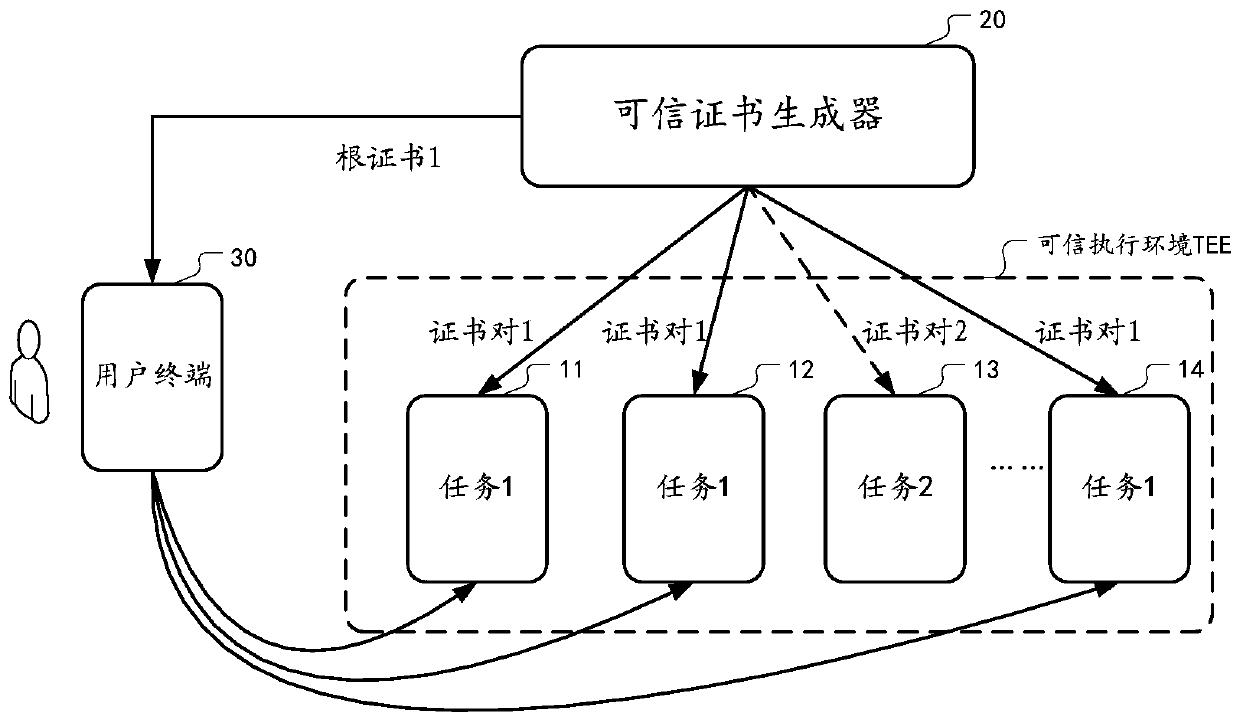
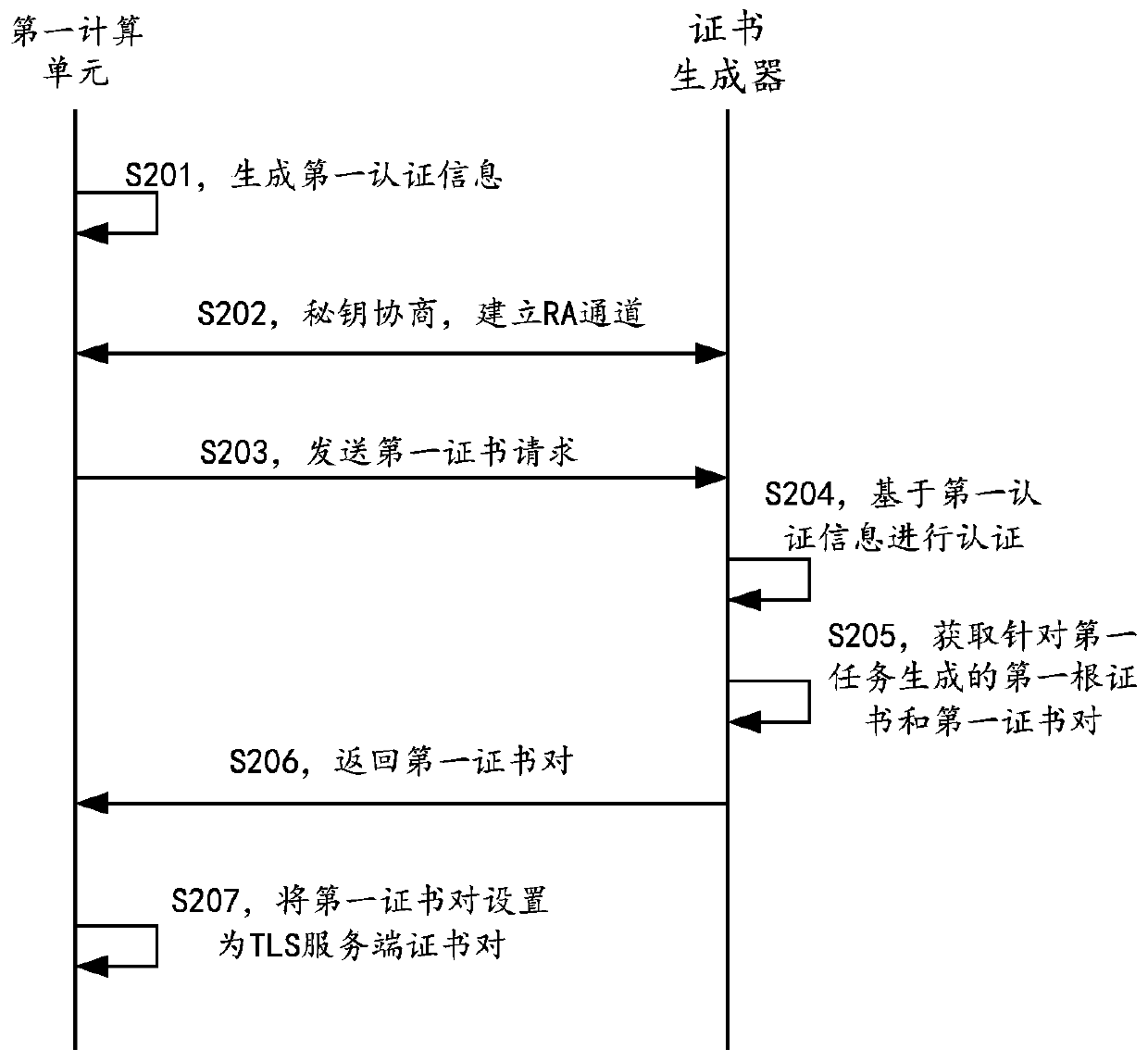
Method and device for providing high-availability computing service through certificate issuing
ActiveCN110677240AEase of Computing ServicesAchieve securityKey distribution for secure communicationUser identity/authority verificationRoot certificateSecure communication
The embodiment of the invention provides a method and device for providing a high-availability service by signing and issuing a certificate. According to the scheme, a trusted certificate generator distinguishes different calculation tasks through code hash, a certificate chain and a private key are generated for one code hash, the certificate chain comprises a public key certificate and a corresponding root certificate, and the public key certificate is matched with the private key to form a certificate pair. And then, the trusted certificate generator distributes the certificate pair to eachauthenticated trusted computing unit which runs the computing task corresponding to the code hash. And on the other hand, the trusted certificate generator distributes the root certificate in the certificate chain to the user terminal requesting the computing task. Thus, a user terminal having a root certificate and a trusted computing unit having a corresponding certificate pair can communicatesecurely by means of a TLS protocol.
Owner:ADVANCED NEW TECH CO LTD
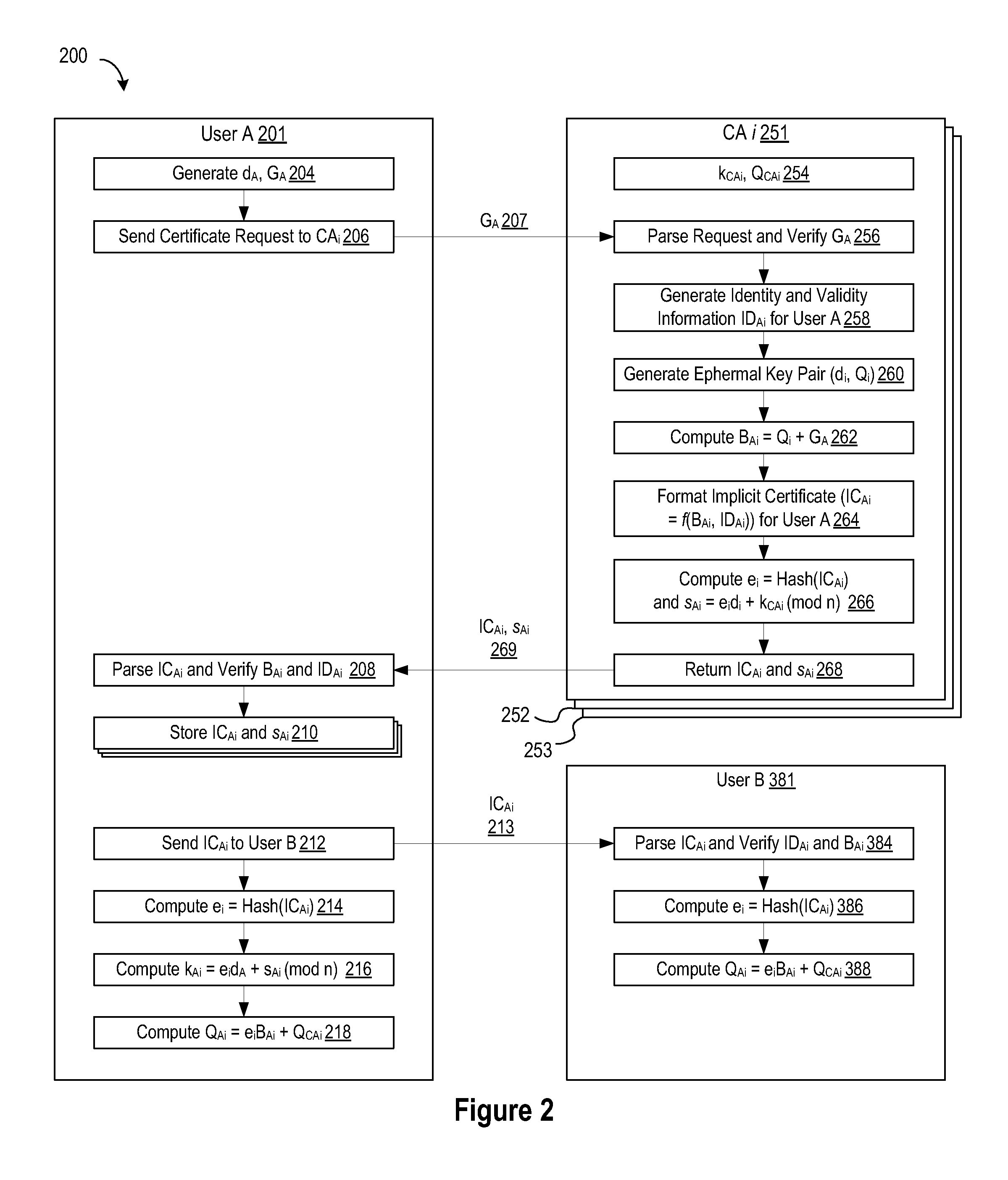
Using a single certificate request to generate credentials with multiple ECQV certificates
ActiveUS8701169B2Key distribution for secure communicationDigital data processing detailsCommunications systemInternet privacy
Owner:MALIKIE INNOVATIONS LTD
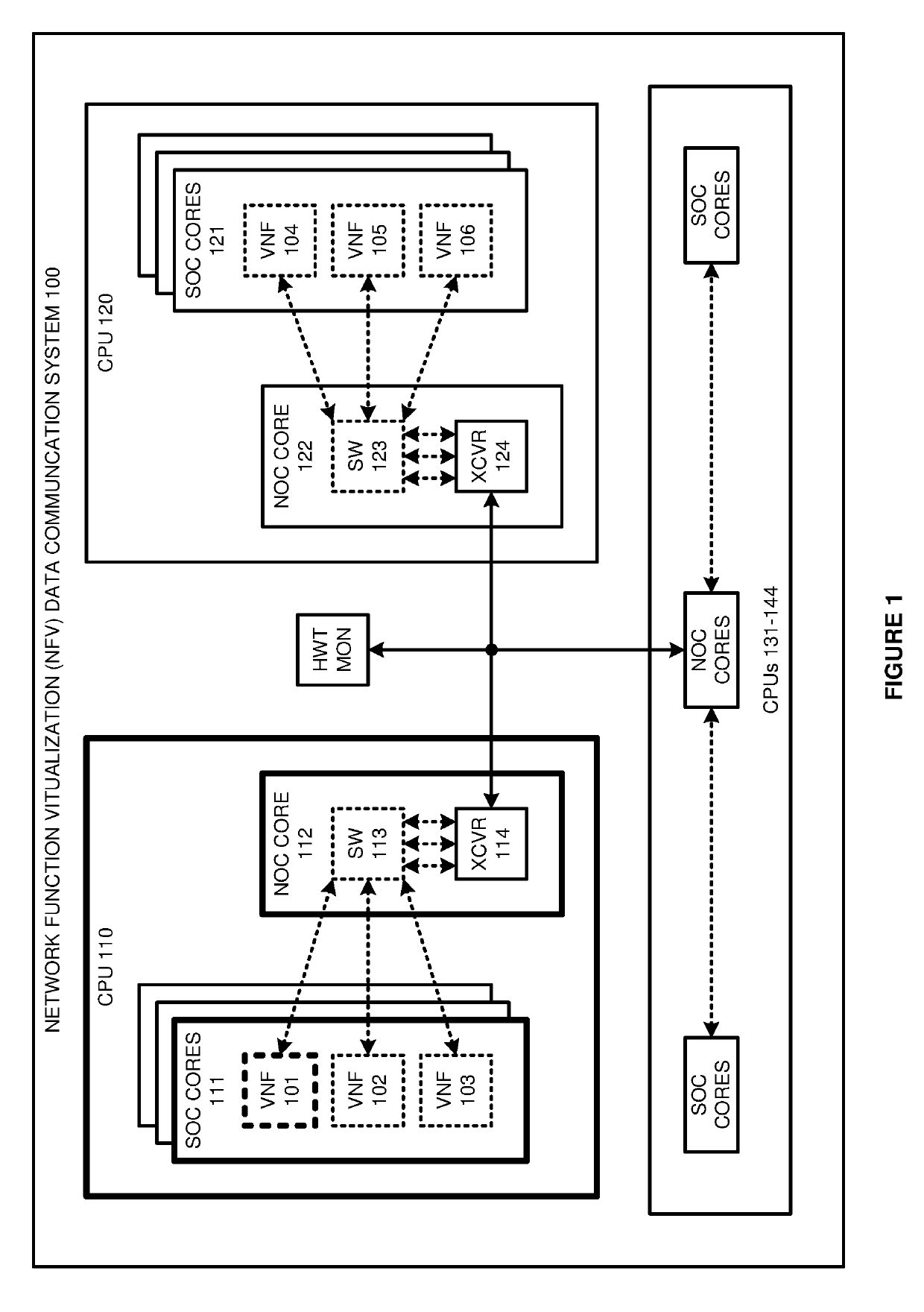
Hardware-trusted network function virtualization (NFV) data communications
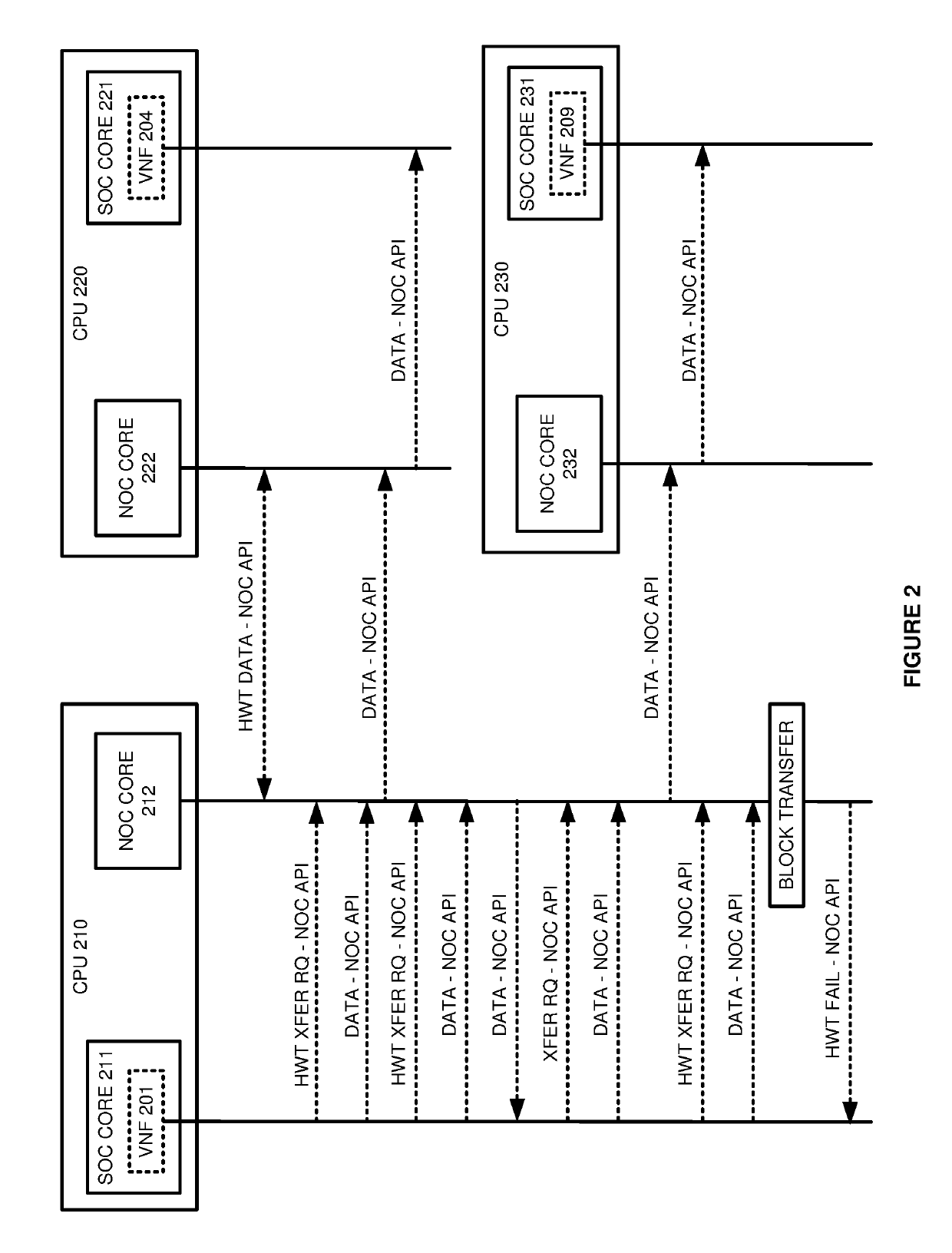
ActiveUS20190258796A1Interprogram communicationDigital data protectionApplication programming interfaceApplication software
A Network Function Virtualization (NFV) Central Processing Unit (CPU) comprises a network core and a system core. The network core receives and validating hardware trust certificates from external circuitry that obtains the hardware trust certificates using a read-only hardware trust identifier that is physically-embedded in the external circuitry. The system core executing an NFV Virtual Network Function Component (VNFC) and generating VNFC data for the external circuitry. The system core calls an Application Programming Interface (API) for a hardware trusted communication with the external circuitry and transfers the VNFC data to the network core. In response to the API call, the network core transfers the VNFC data to the external circuitry when the network core successfully validates the hardware trust certificates from the external circuitry. The network core blocks the user data when the network core did not successfully validate the hardware trust certificates from the external circuitry.
Owner:T MOBILE INNOVATIONS LLC
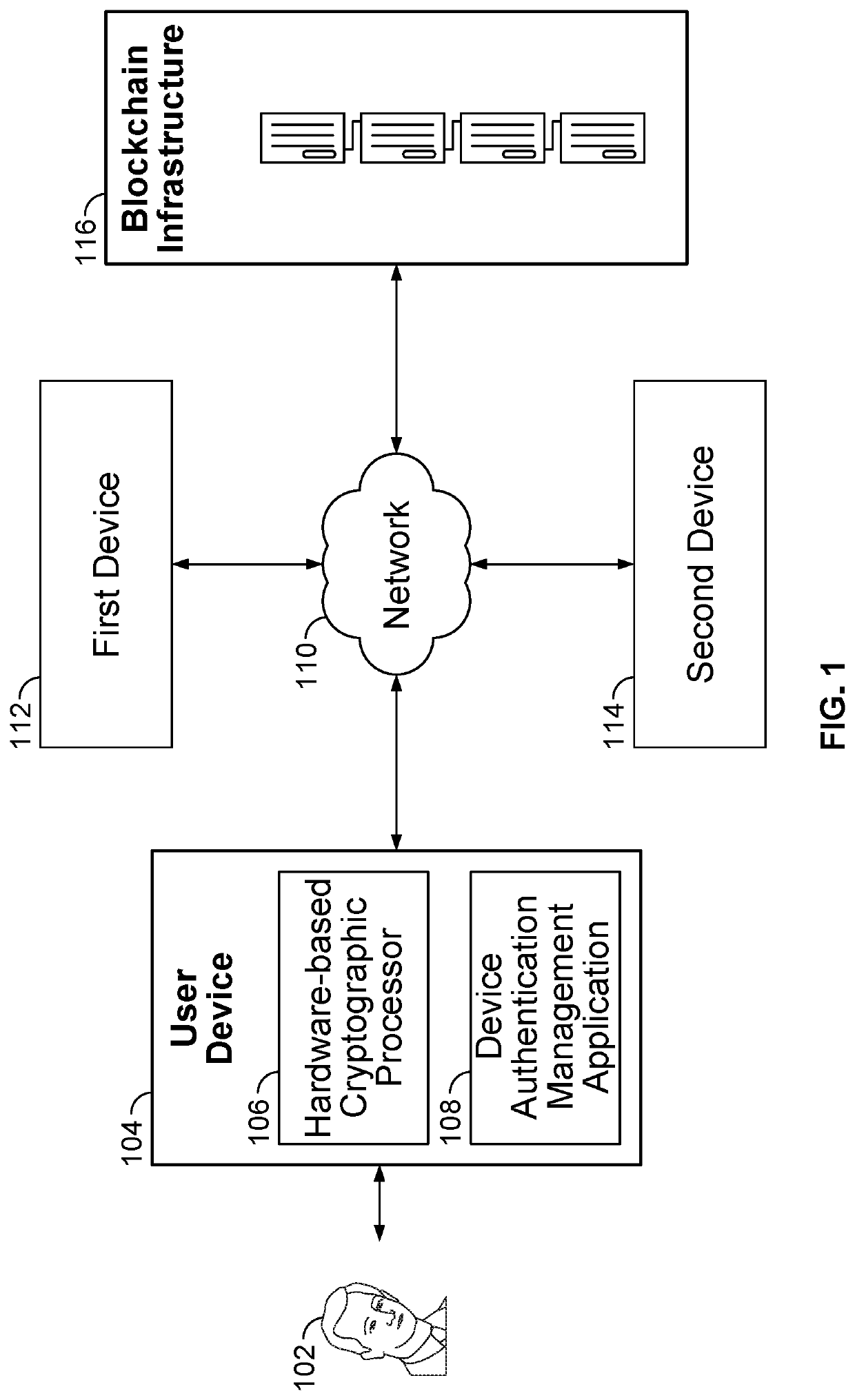
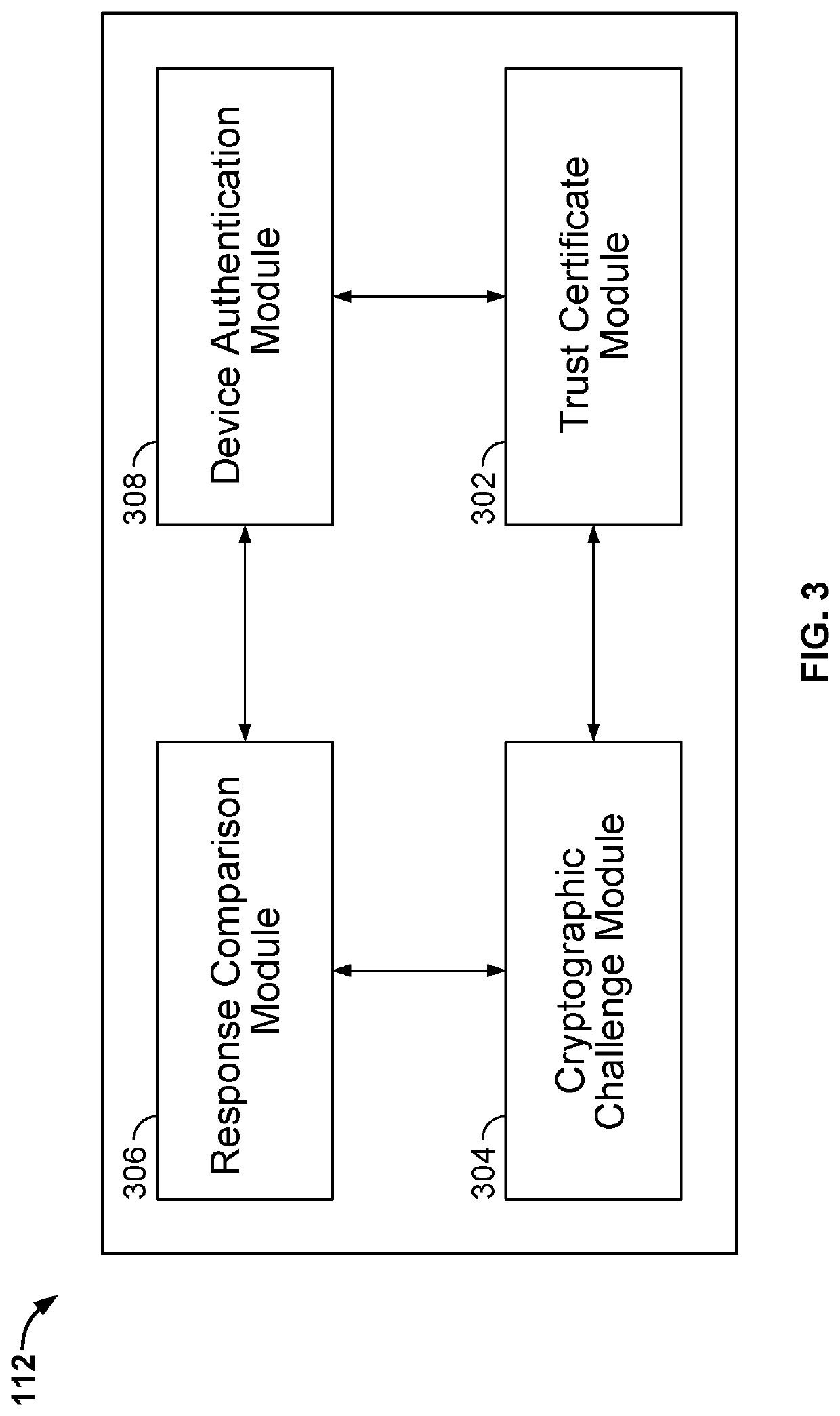
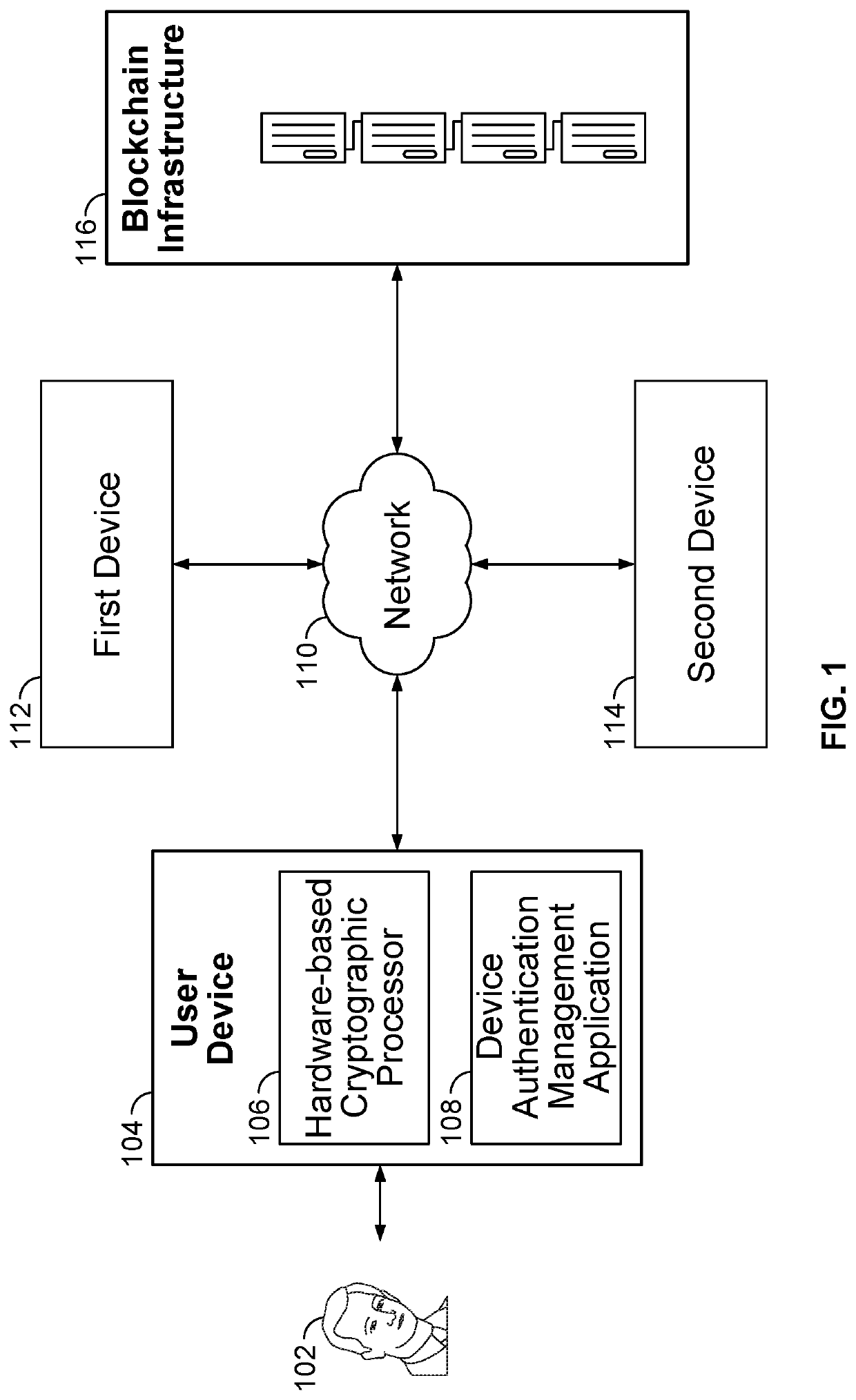
System and method for blockchain-based device authentication based on a cryptographic challenge
ActiveUS10715312B2Multiple keys/algorithms usageEncryption apparatus with shift registers/memoriesUser deviceInternet privacy
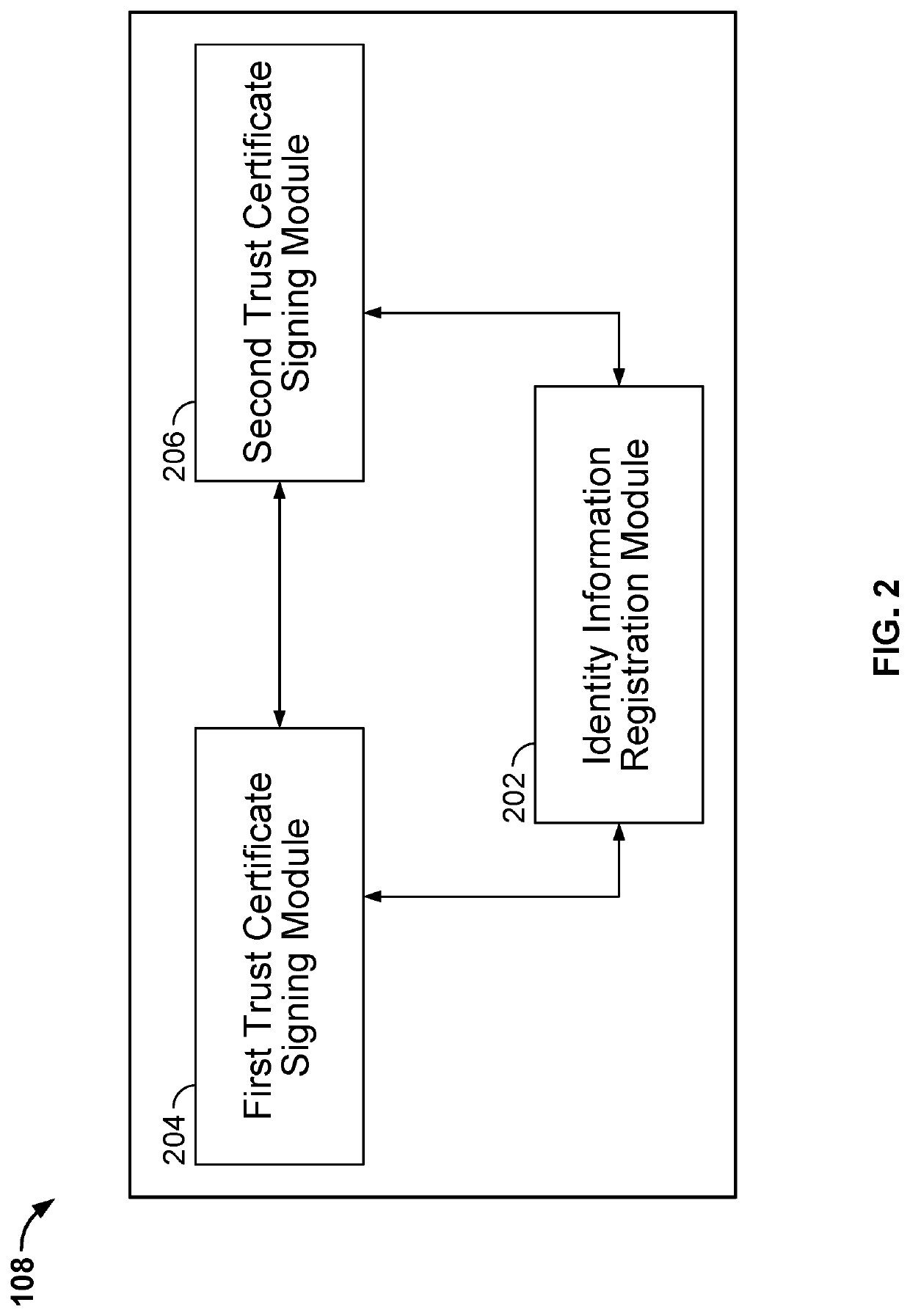
Blockchain-based device authentication by a user device to enable a second device is disclosed to perform an action on a first device on behalf of a user linked to the user device, based on a command received from the second device. Authentication includes the steps of: (i) obtaining an indentity information associated with an identity document of the user; (ii) storing the identity information, and a set of credentials, with a blockchain to link the identity information with the set of credentials for the user; (iii) signing a first trust certificate by a user private key on the blockchain to obtain a first signed trust certificate; and (iv) signing a second trust certificate by the user private key on the blockchain to obtain a second signed trust certificate.
Owner:WORKDAY INC
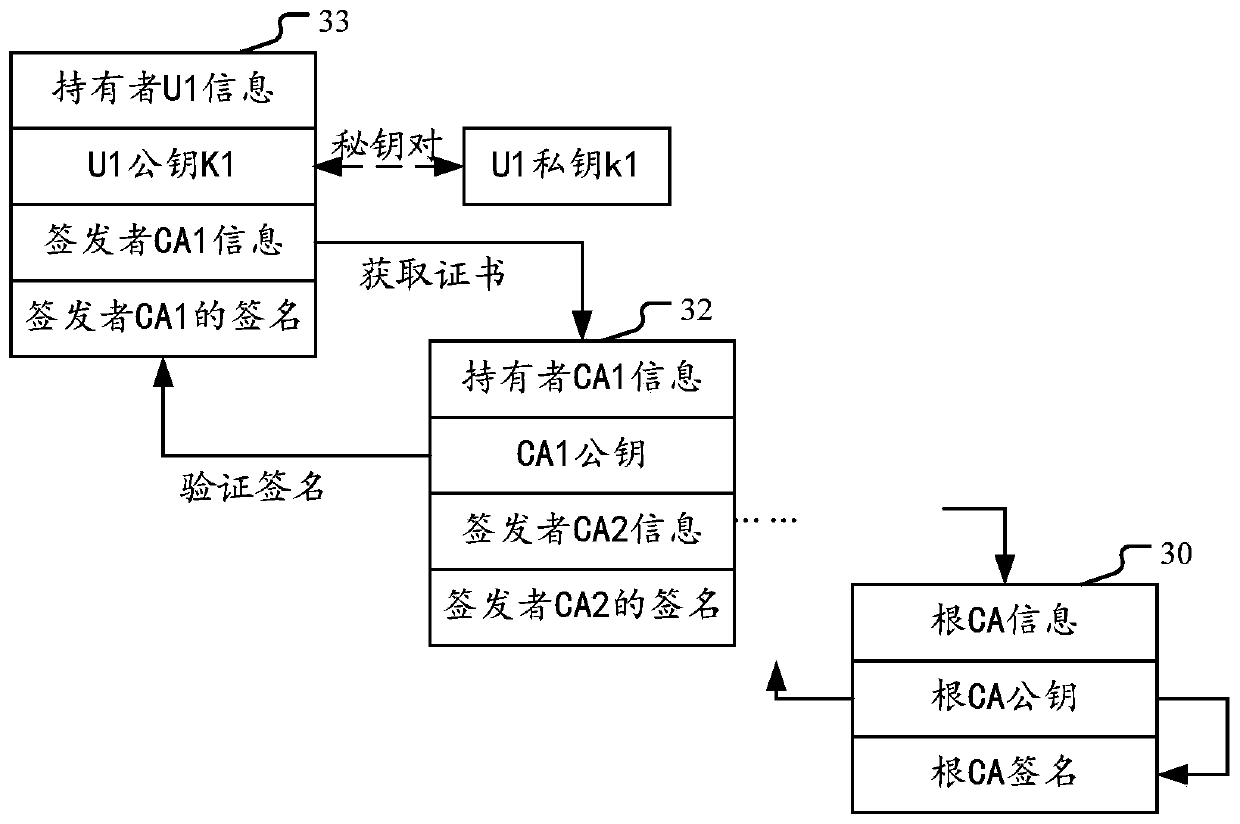
PKI certificate cross-domain authentication method based on blockchain
ActiveCN113672942AImprove real-time performanceImprove securityDigital data protectionRoot certificateInternet privacy
The invention discloses a PKI certificate cross-domain authentication method based on a blockchain. The method comprises the following steps: when a user initiates a cross-domain access request through a client end, a certificate is shown to an authentication server; the authentication server initiates a request to the blockchain for verifying whether each certificate in a certificate chain is revoked or not according to attribute fields of the shown certificate; a smart contract searches whether each certificate is valid in a BCRL (blockchain certificate revocation list), obtains a whole certificate chain, verifies whether the certificate chain is valid step by step from a root-of-trust certificate of a relying party, and signs and issues a user access token if each certificate is not revoked and the certificate chain verification is passed. Through the method provided by the invention, a complex topological structure in cross authentication is solved, a certificate chain trust path can be quickly constructed based on a multi-node tampering-free trust anchor of the blockchain, and the security of PKI certificate cross-domain authentication is improved.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
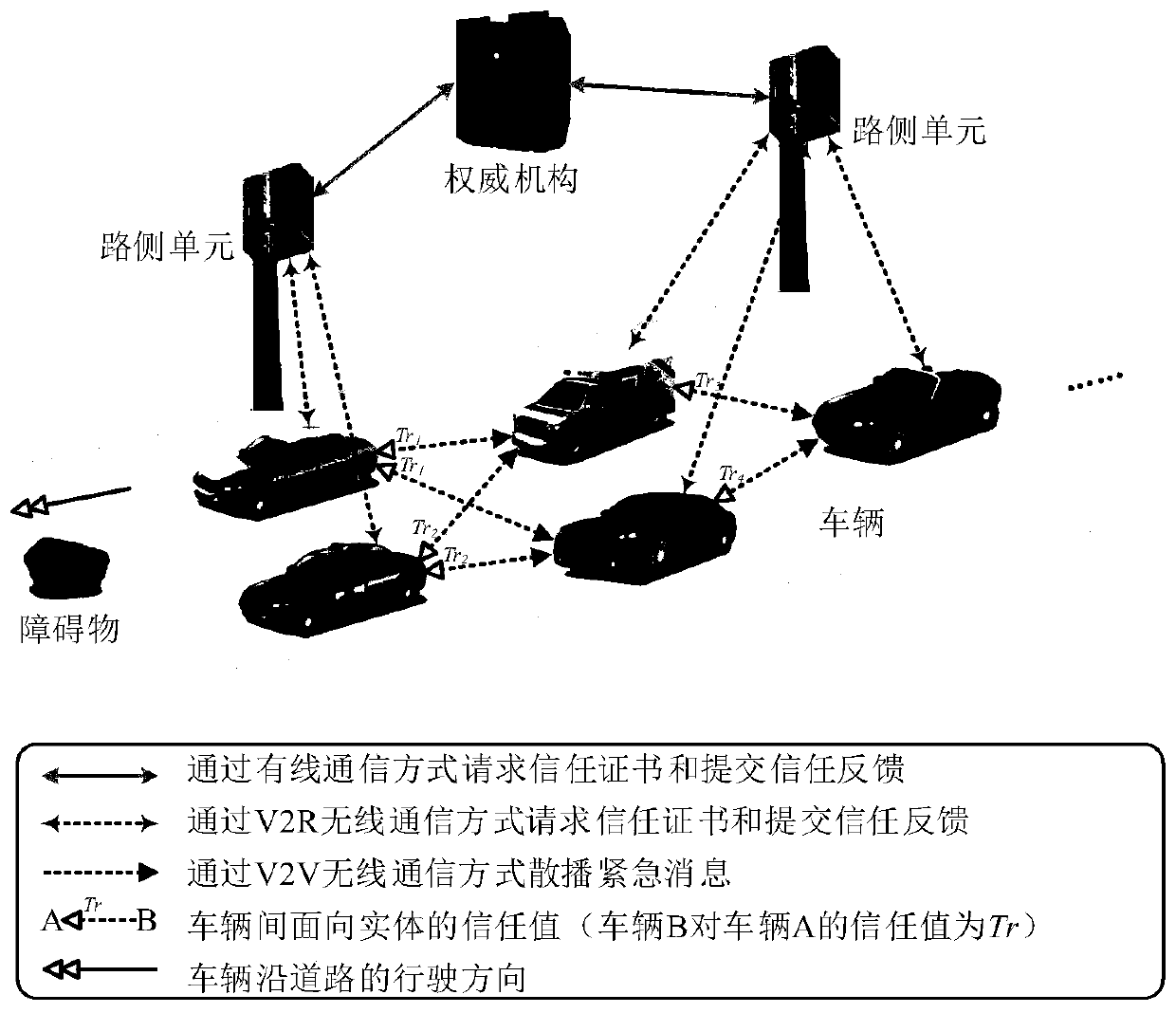
Emergency message spreading method and system based on trust cascading in Internet of Vehicles
InactiveCN111093189AThe assessment results are accurateActively and honestly participateParticular environment based servicesVehicle infrastructure communicationCommunication interfaceEvaluation result
The invention discloses an emergency message spreading method and system based on trust cascading in the Internet of Vehicles, and the system comprises an authority mechanism, a road side unit, and avehicle. The authority mechanism is responsible for providing registration and revocation services for the vehicle, and storing and updating the trust information of the vehicle. The road side unit provides a communication interface for the vehicle and the authority mechanism; the vehicle-mounted unit is installed on a vehicle and can communicate with the adjacent road side unit and other vehicles. When an emergency event occurs, an emergency message can be spread among nearby vehicles in a trust cascade manner, in which an entity-oriented trust value (which can be evaluated and updated by a trust certificate and included in the trust certificate) is used as an important weight; according to the method and system, the entity-oriented trust value is efficiently applied to data-oriented trust evaluation, and compared with an existing message spreading mode, the evaluation result is more accurate and has a good incentive mechanism, error tolerance, compatibility and robustness.
Owner:JINAN UNIVERSITY
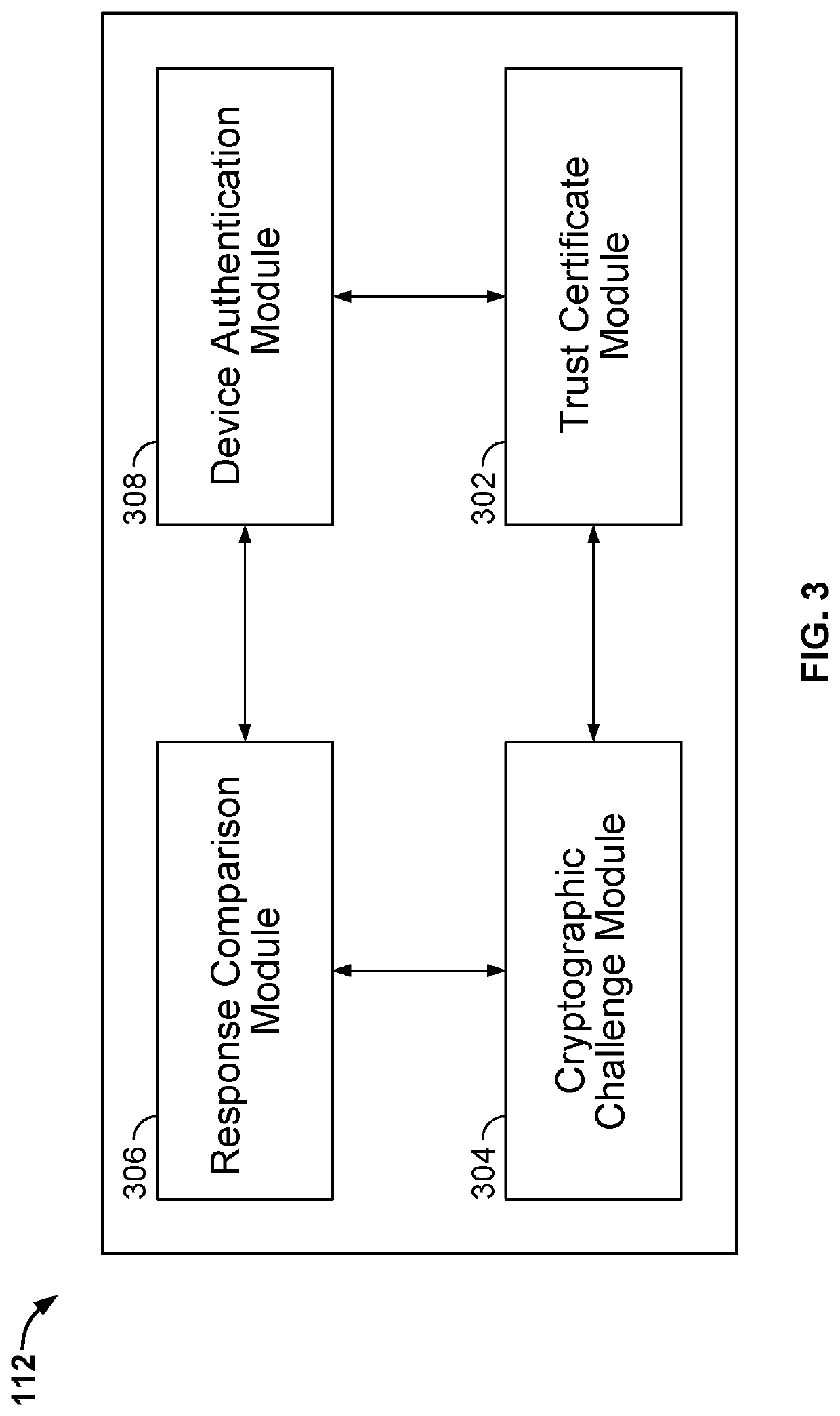
System and method for blockchain-based device authentication based on a cryptographic challenge
ActiveUS20200322131A1Multiple keys/algorithms usageEncryption apparatus with shift registers/memoriesTrust certificateEngineering
A system for blockchain-based authentication comprises an interface and a processor configured to (i) receive, by a first device, a command from a second device, where the first device is associated with a first trust certificate, (ii) receive a second trust certificate from the second device, (iii) communicate a cryptographic challenge using a public key of the second device to the second device, (iv) receive a response to the cryptographic challenge from the second device, (v) check whether the response matches with a predetermined correct response or not, and (vi) authenticate the second device and execute the commend received from the second device only if the response matches with the predetermined correct response.
Owner:WORKDAY INC
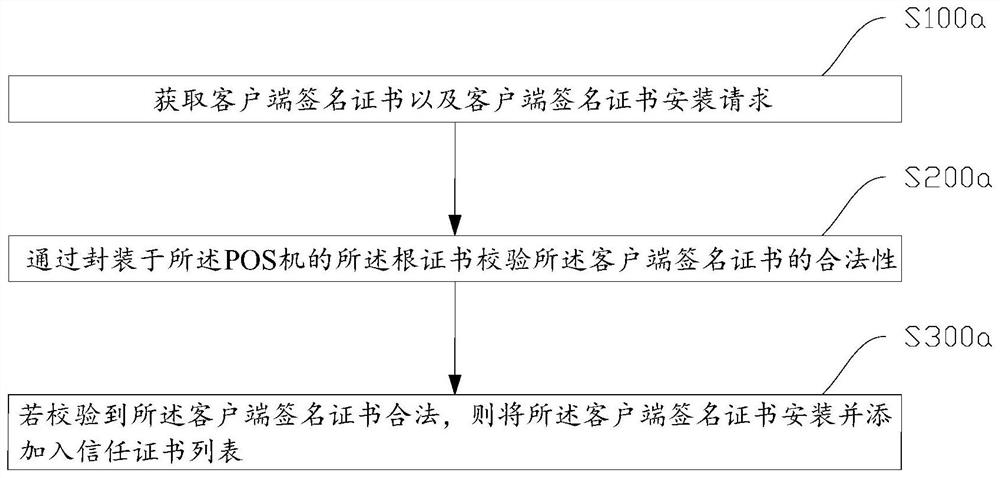
Security verification method and device for APK signature information and POS machine
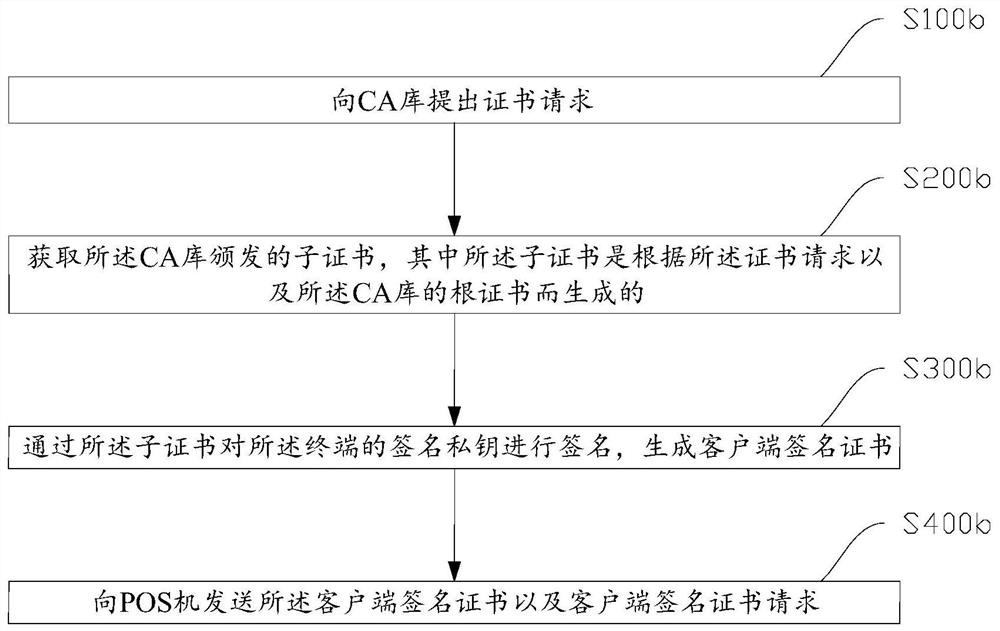
ActiveCN112134711APrevent tamperingEnsure safetyUser identity/authority verificationCash registersTrust certificateEngineering
The invention provides a security verification method for APK signature information, which is applied to a POS machine, and a root certificate of a CA library is packaged on the POS machine. The method comprises the following steps of: obtaining a client signature certificate and a client signature certificate installation request; verifying the legality of the client signature certificate throughthe root certificate packaged in the POS machine, a legal client signature certificate being obtained by a sub-certificate signature private key corresponding to the root certificate; and if it is verified that the client signature certificate is legal, installing the client signature certificate and adding the client signature certificate into a trust certificate list.
Owner:深圳市捷诚技术服务有限公司
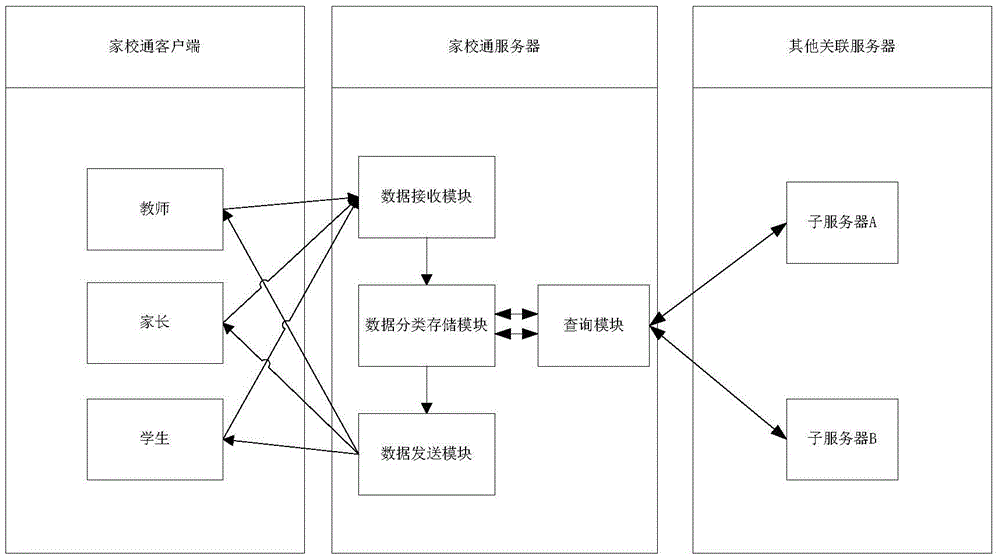
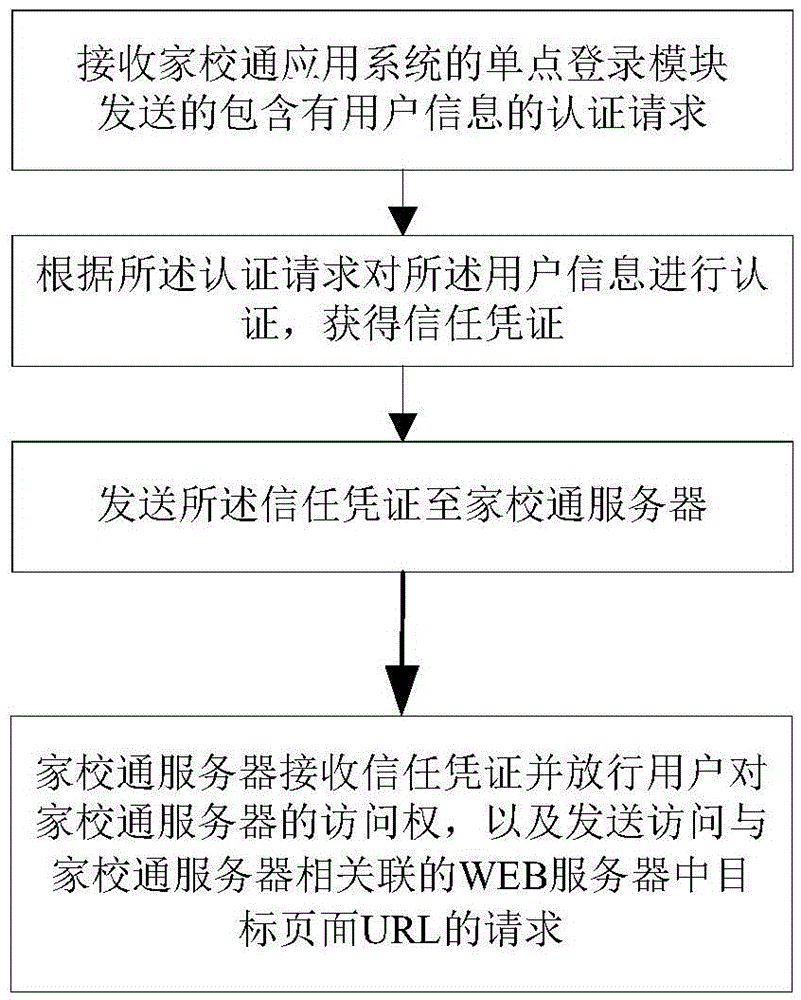
Single sign-on method for families-school connection application system and device thereof
InactiveCN106850513AImplement single sign-on technologySolve the problem of registering multiple accountsData processing applicationsTransmissionWeb serviceMultiple platform
The invention discloses a single sign-on method for a families-school connection application system and a device thereof. The method comprises the following steps: receiving an authentication request which is sent by a single sign-on module of the families-school connection application system and contains the user information; authenticating the user information according to the authentication request to obtain a trust certificate, and sending the trust certificate to a families-school connection server; ensuring that the families-school connection server receives the trust certificate and releases the access right of the user to the families-school connection server; and ensuring that the families-school connection server sends a request of accessing a target page URL in a WEB server which is associated with the families-school connection server, and the WEB server receives the request and transmits the target page URL to the families-school connection server. According to the single sign-on method and the device disclosed by the invention, the sign-on of multiple platforms can be achieved through single sign-on by using the single sign-on technique, and the data access authority after sign-on can be improved; the families-school connection server opens the interface to the families-school connection application system, and thus the data source approach of the families-school connection client can be expanded, the data volume can be increased, and the pressure of the families-school connection server can also be reduced.
Owner:浪潮数字(山东)科技有限公司
Authentication method and system
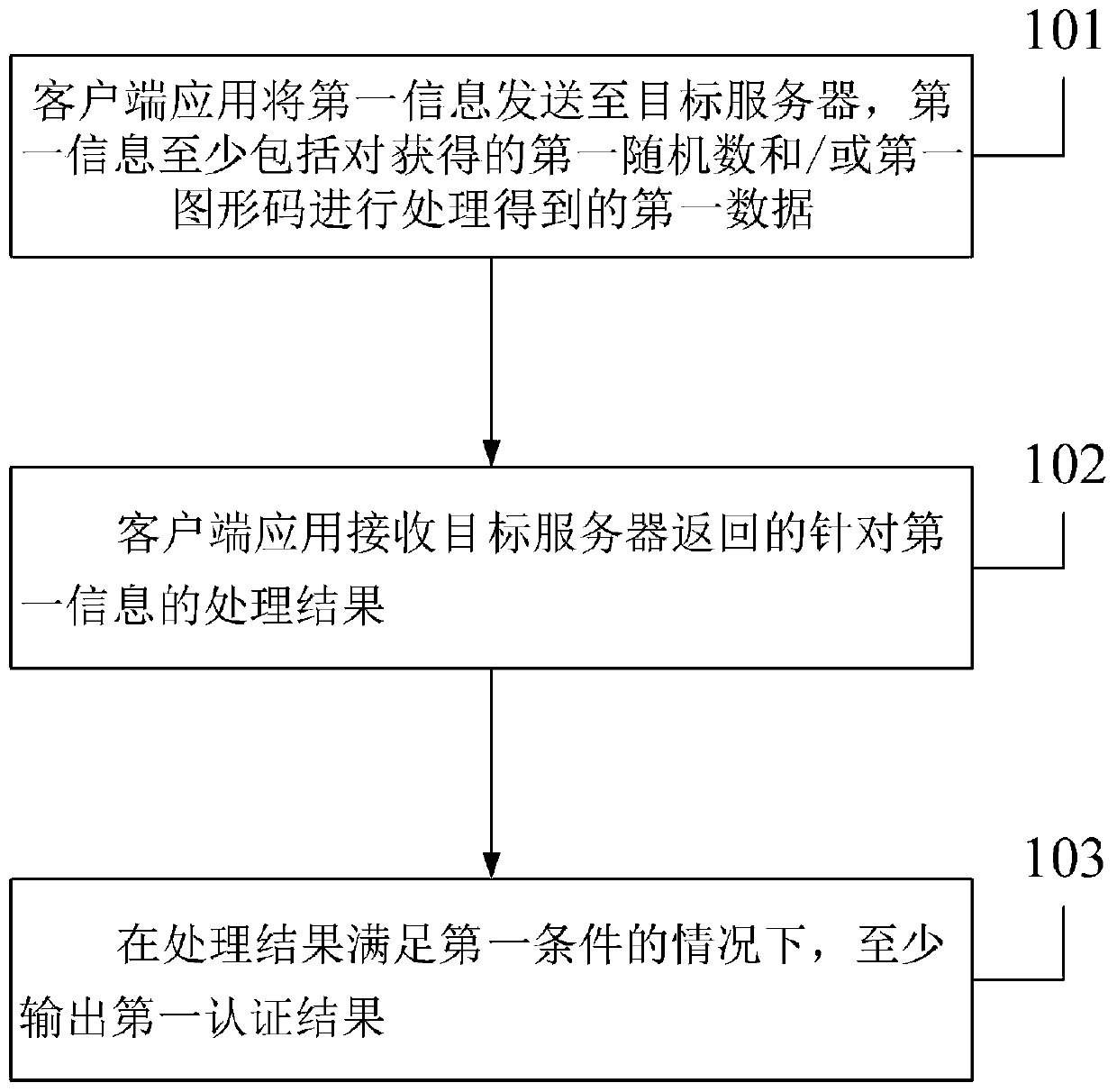
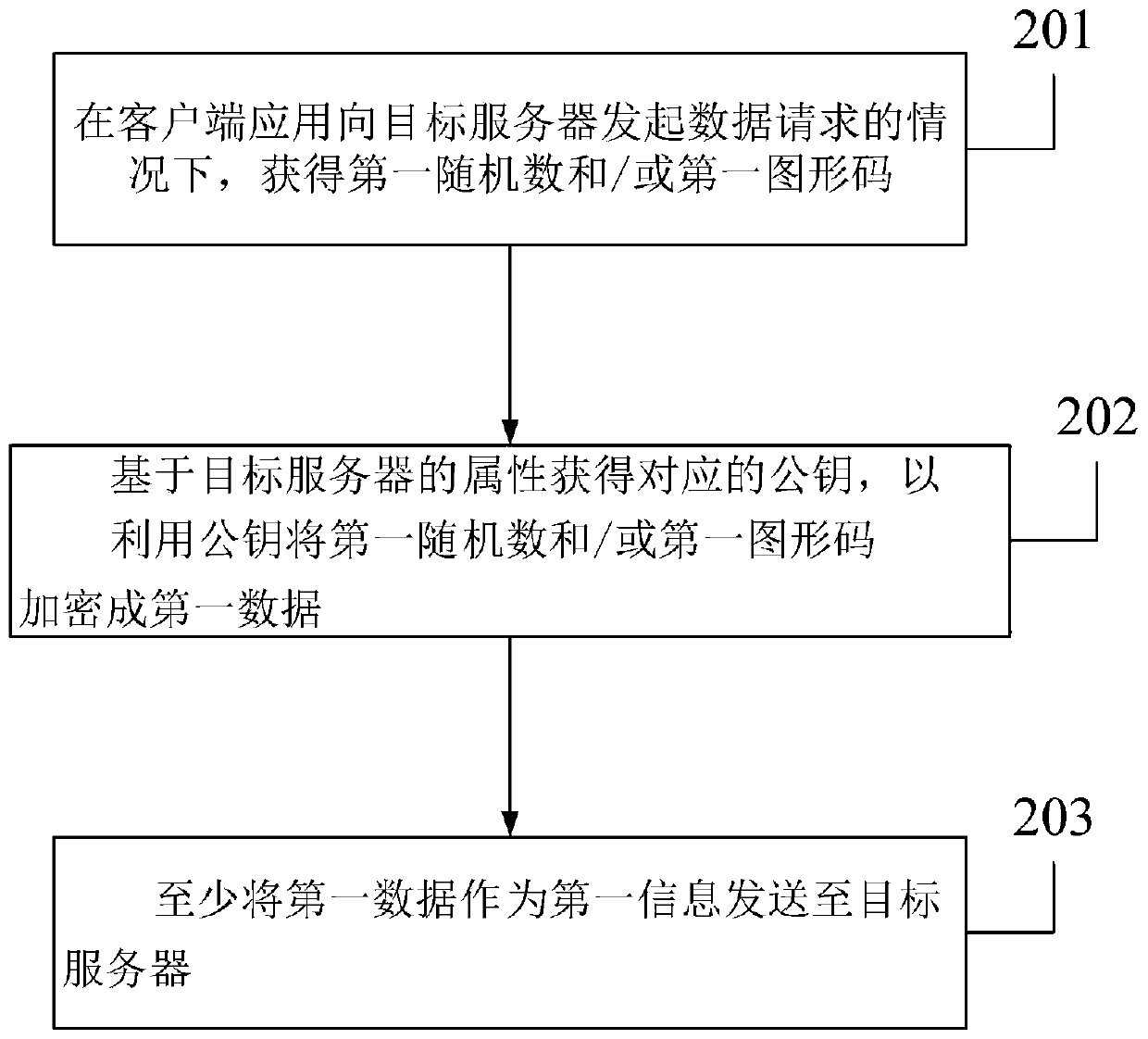
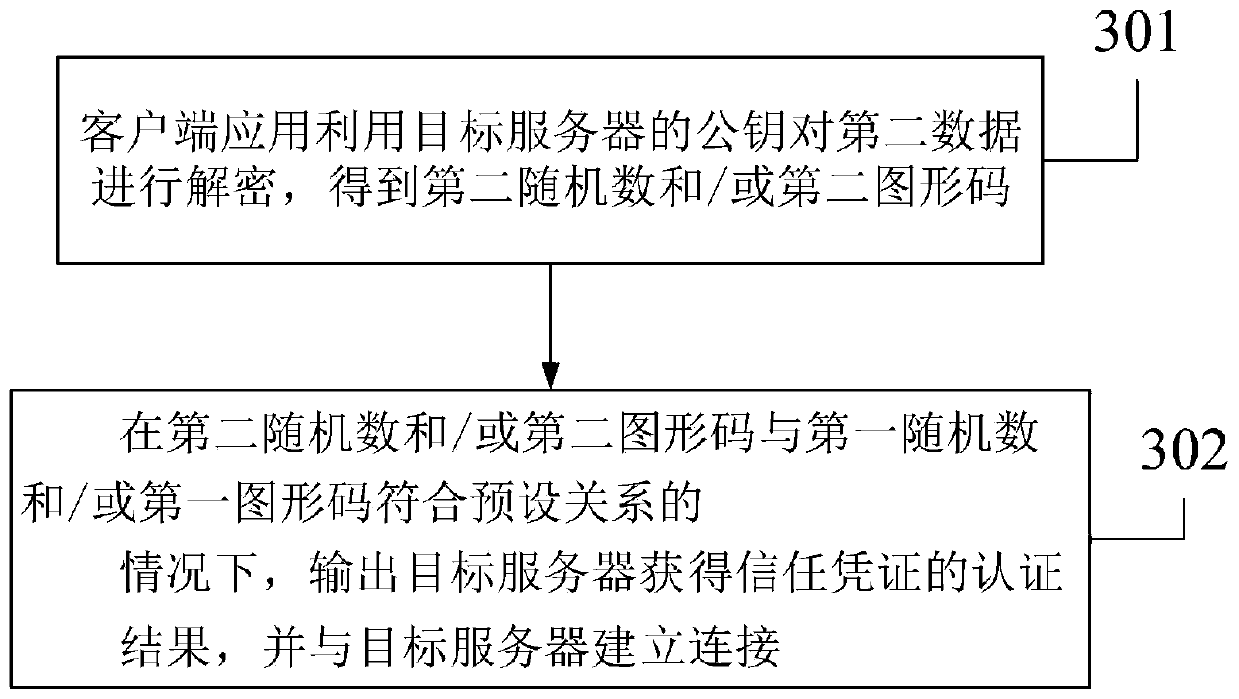
InactiveCN111181722AReduce usageImprove connection securityKey distribution for secure communicationGraphicsBusiness enterprise
The embodiment of the invention discloses an authentication method and system, and the method comprises the steps that a client application transmits first information to a target server, wherein thefirst information at least comprises first data obtained through the processing of an obtained first random number and / or a first graphic code; the client application receives a processing result forthe first information returned by the target server; under the condition that the processing result meets a first condition, the client application at least outputs a first authentication result, wherein the mode of processing the first random number and / or the first graphic code by the client application is at least related to the attribute of the target server, and the first authentication result represents that the target server obtains a trust certificate. According to the authentication method and system provided by the embodiment of the invention, identity authentication is carried out by sending the encrypted random number and / or graphic code to the server, so that the problem that the enterprise client cannot be normally used after the certificate is modified by software is avoided, and the connection security and stability of the client and the server are improved.
Owner:LENOVO (BEIJING) LTD
Method of establishing the trustworthiness level of participant in communication connection
InactiveCN1203640CLow communication requirementsReduce communication costsKey distribution for secure communicationUser identity/authority verificationInternet privacyTrust certificate
Owner:TREND MICRO INC
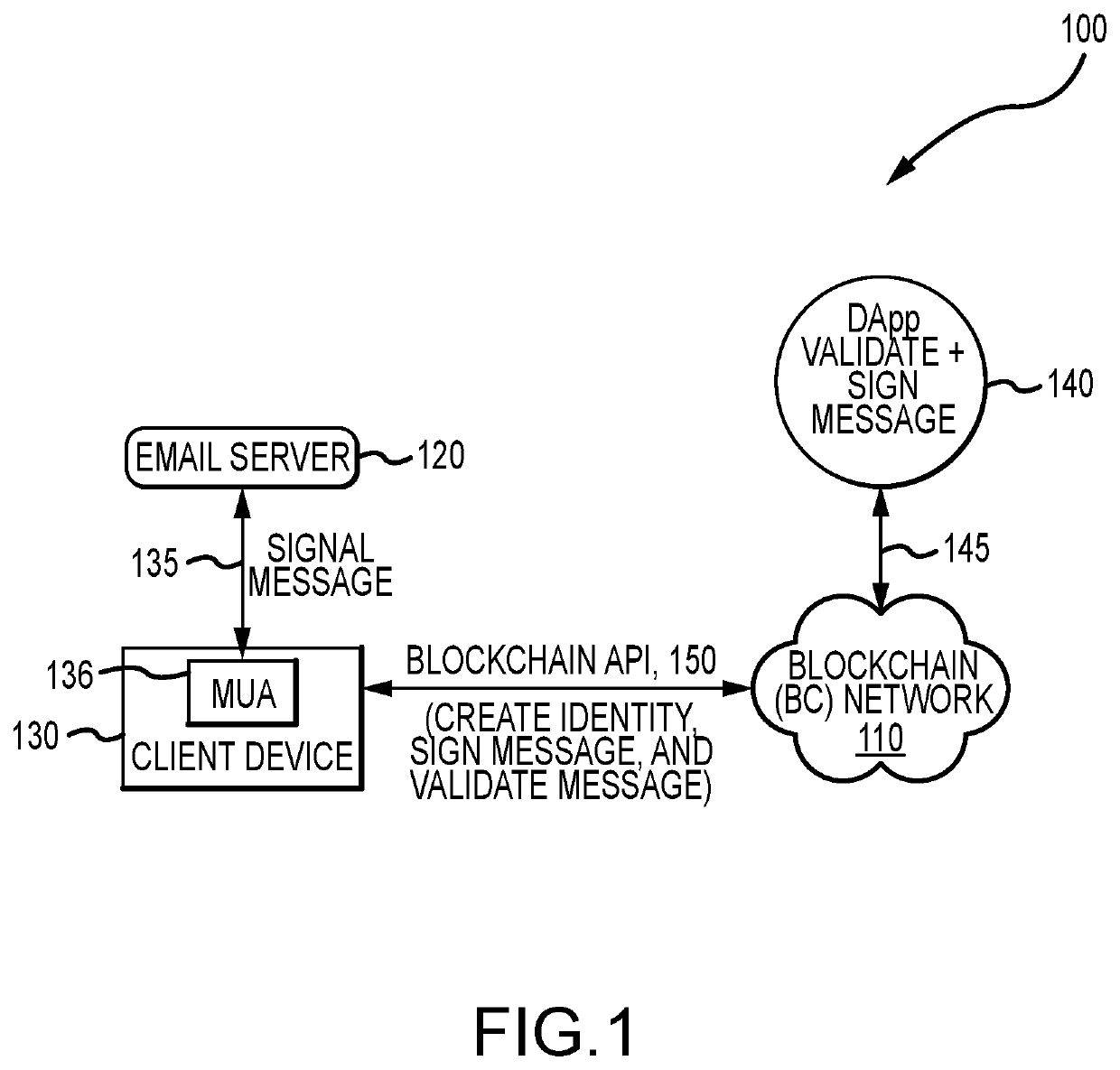
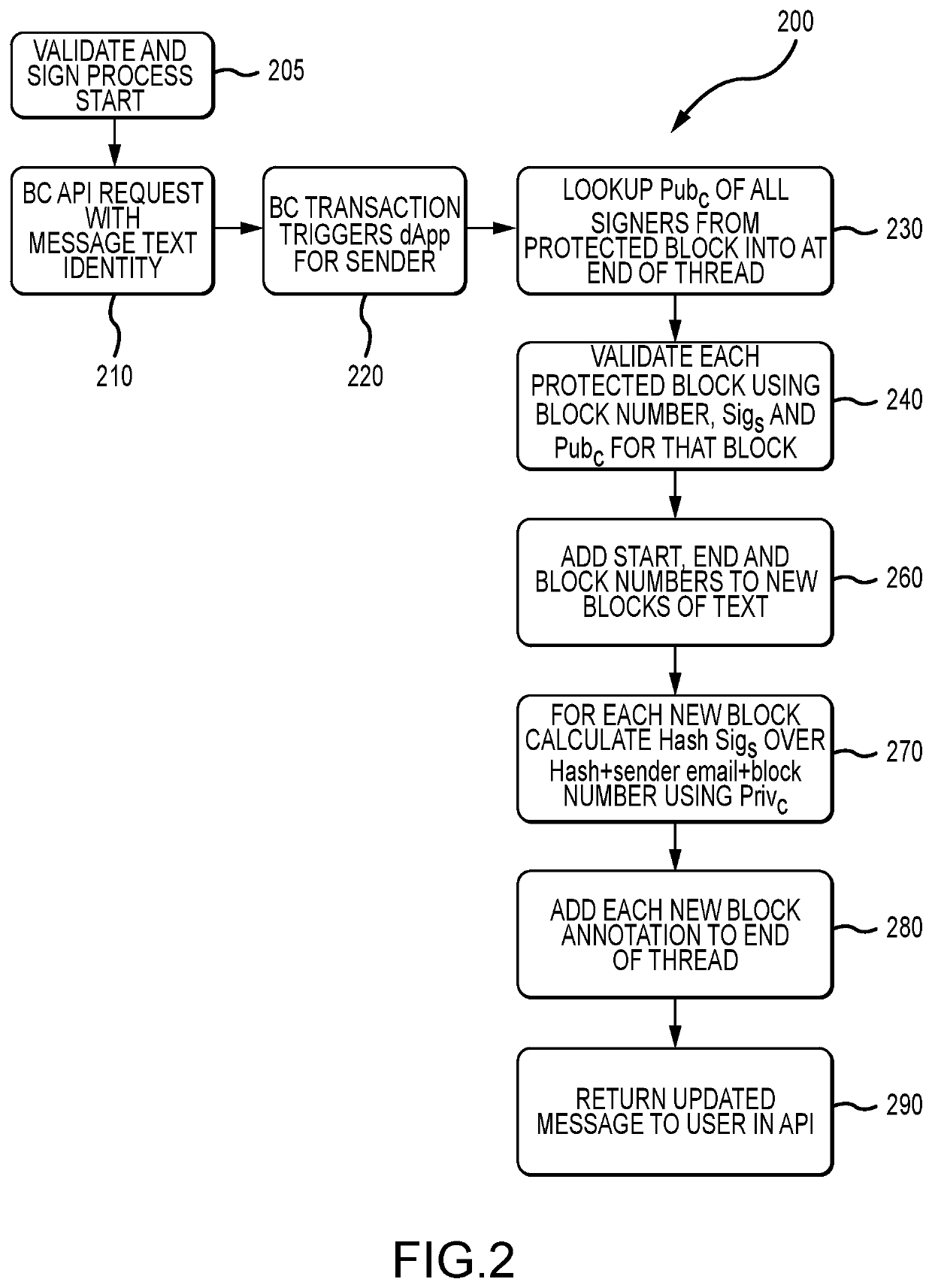
Blockchain-driven certification of iterative electronic communications
PendingUS20220150202A1Key distribution for secure communicationUser identity/authority verificationCommunications systemSystem verification
A communication system configured to provide blockchain-driven certification of iterative electronic communications such as e-mail-based communications. The system provides blockchain-driven certification by storing the hash of an e-mail thread in a blockchain each time the message or its elements are modified. This allows the system to verify whether or not the thread has been tampered with since it was last modified, when the last verified message was added to the thread. The system creates a baseline that is used towards creating trust certificates ensuring the recipients of such iterative electronic communications that the message has not been breached during its iterations that are shared between two or more parties, e.g., communications participants including senders and recipients.
Owner:MITEL
Distributed trust management system and method for obtaining distributed credential chain
InactiveCN1791115AEnhanced description abilityIncrease flexibilityTransmissionInternet privacySystems management
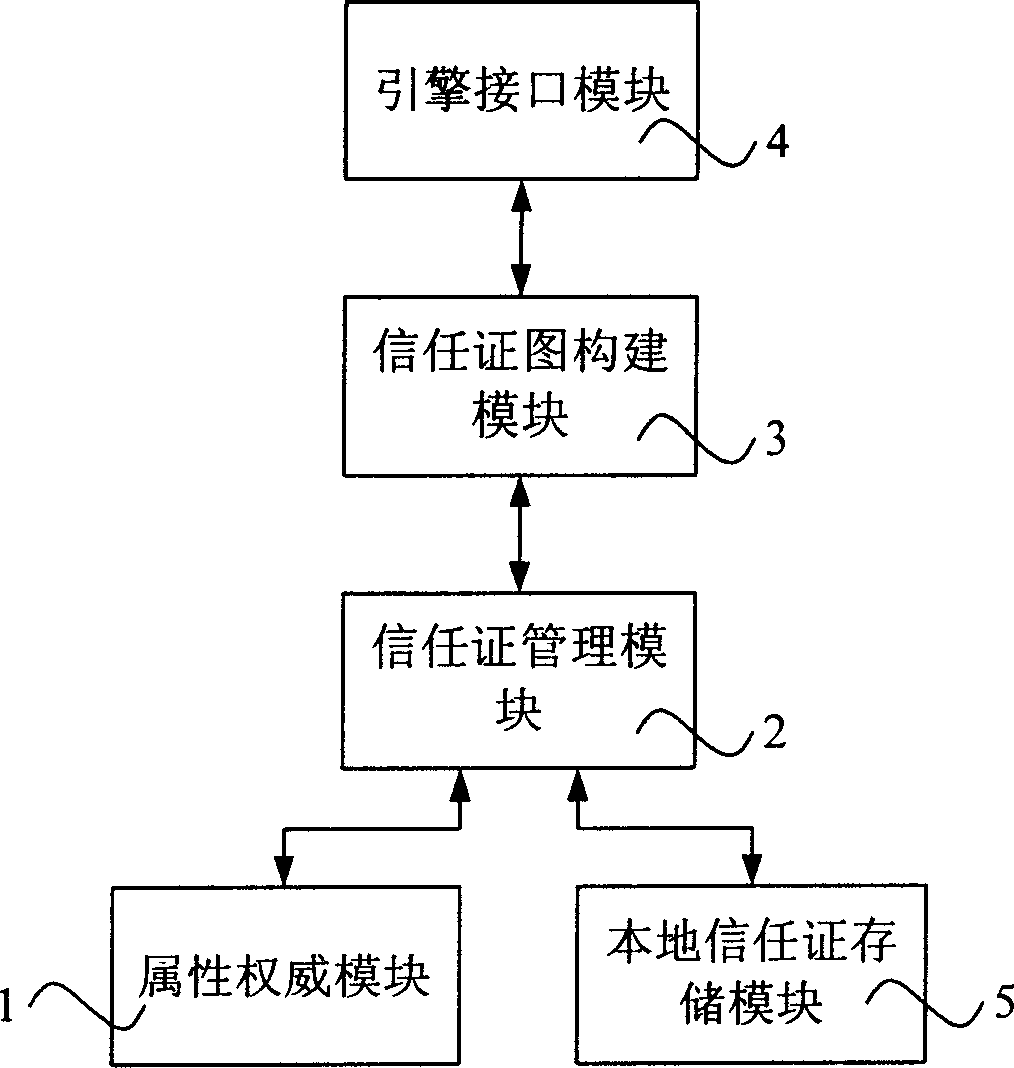
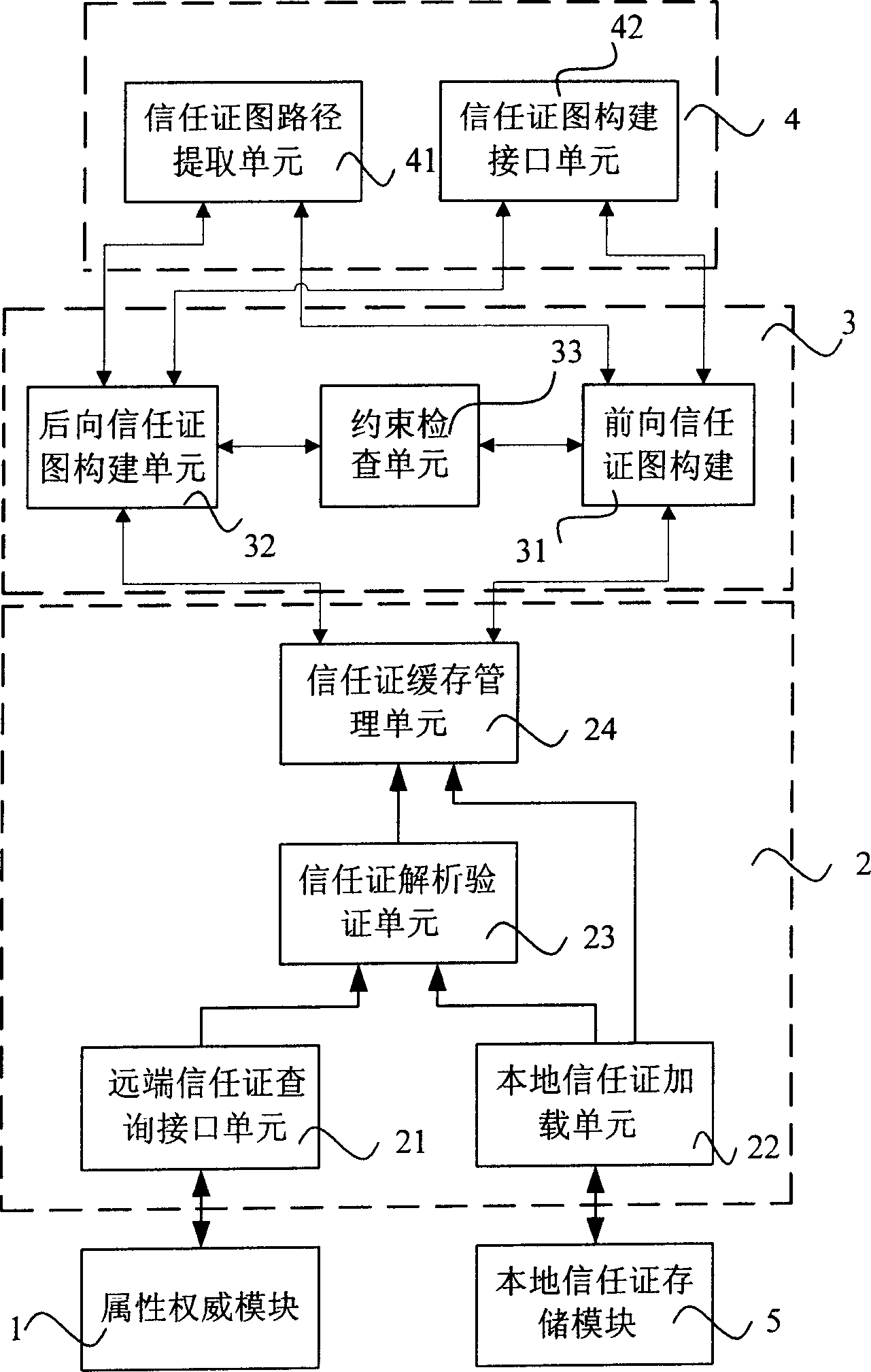
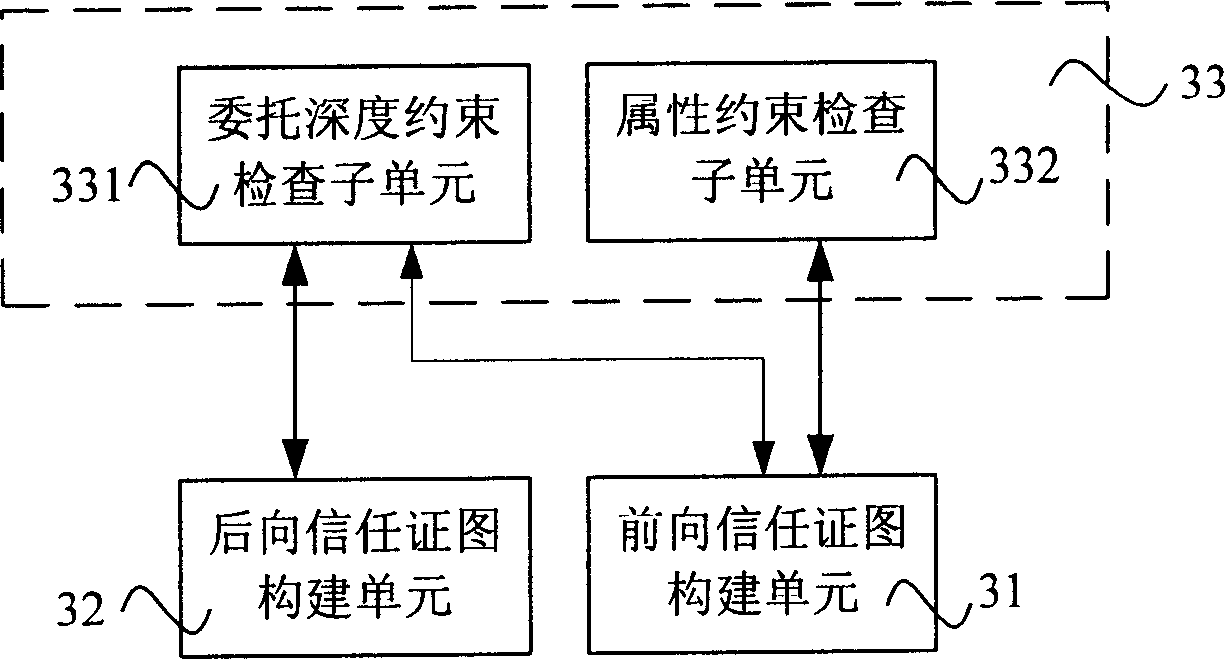
The invention relates to a distributed trust management system, which comprises: connected by turns, an attribute authorization module, a trust certificate management module, a trust certificate chart construction module, an engine interface module, and local trust certificate storage module. It also relates to a method to acquire distributed trust certificate link: receiving find request for trust certificate link; constructing trust certificate chart; extracting all paths of appointed nodes to output. This invention adds depth and attribute constrain to RTML, and improves algorithm efficiency and system performance.
Owner:BEIHANG UNIV
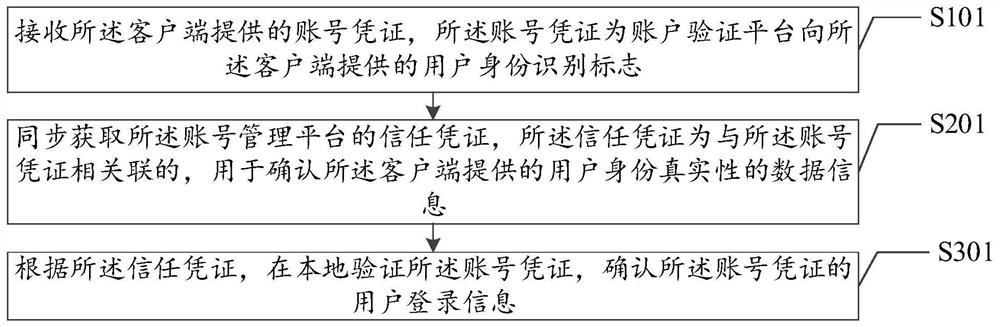
Account verification method and device, system and computer readable storage medium
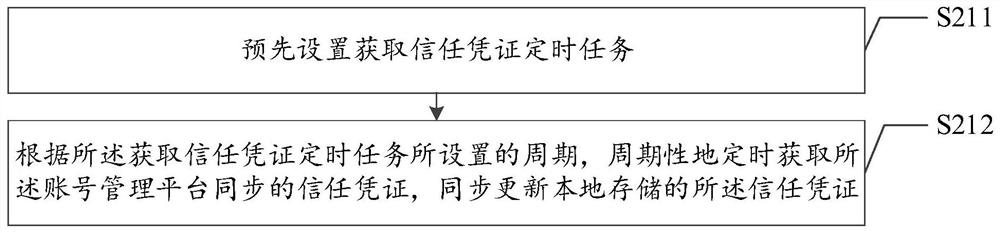
PendingCN112417401AImprove verification success rateImprove user experienceDigital data authenticationComputer securityTrust certificate
The invention discloses an account identification method and device, a system and a readable storage medium, and is applied to the field of the Internet, and the account identification method comprises the following steps: receiving an account certificate sent by a client, wherein the account certificate is a unique identity identification mark which is provided by an account management platform for the client and reflects user login information; synchronously obtaining a trust voucher of the account management platform, wherein the trust voucher is data information associated with the accountvoucher and used for confirming the authenticity of the user identity provided by the client; and locally verifying the account certificate according to the trust certificate, and confirming user login information of the account certificate. Compared with the prior art, the account verification method provided by the invention effectively improves the account verification success rate, shortens the response time of responding to the client request, and optimizes the use experience of the user.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD +1
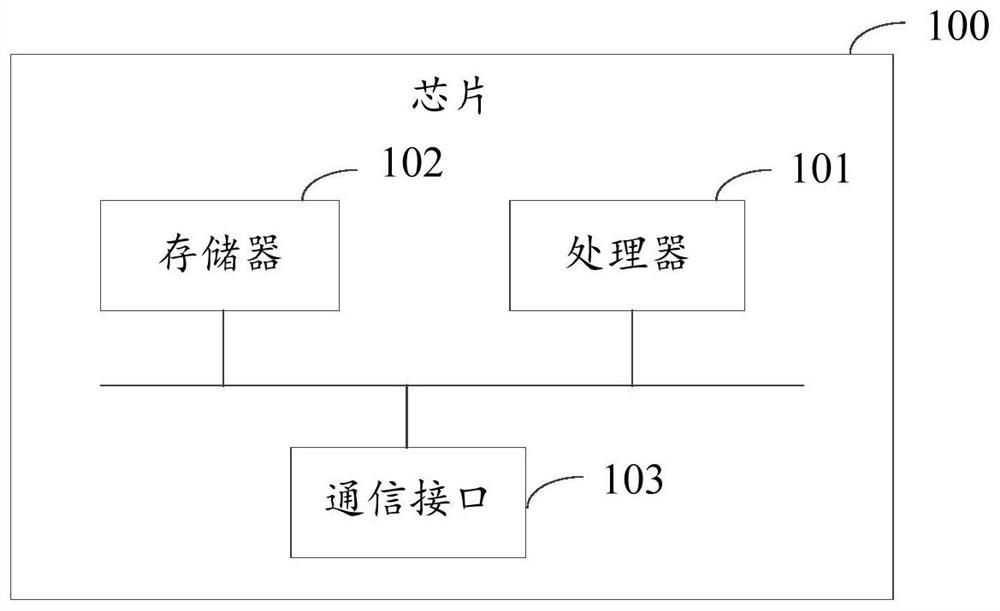
Information processing method and device, chip, terminal and electronic device
PendingCN112367173AAvoid security issuesTimely updateUser identity/authority verificationInformation processingComputer network
The invention provides an information processing method and device, a chip, a terminal and an electronic device. The method comprises the steps of receiving a certificate, wherein the certificate comprises a certificate number; and when it is determined that the certificate number exists in a pre-stored trusted certificate number, updating a pre-stored historical certificate including the certificate number by using the certificate. After the certificate is received, the pre-stored historical certificate with the same certificate number as the certificate is updated by using the certificate, so that the pre-stored certificate is updated in time, and the information security problem caused by the fact that the stored certificate is not updated all the time is avoided; and meanwhile, the problem of signature verification failure due to the fact that the stored certificate is not updated in time is solved.
Owner:SUMAVISION TECH CO LTD
Ue onboarding and provisioning using one way authentication
An apparatus and system for onboarding based on UE default manufacturer credentials are described. A UE sends default manufacturer credentials and an indication to proceed with restricted onboarding to an onboarding non-public network (O-SNPN). An Onboarding Server validates the authenticity of the UE based on the manufacturer credentials and sends a certificate. The UE is provisioned with a set of roots of trust certificate information to use to authenticate the certificate using one way authentication. After authentication, the UE receives network credentials and performs mutual authentication to register with a NPN while being authenticated by a home network. The UE identity is indicated as anonymous in response to an indication by the O-SNPN for subscriber identifier privacy.
Owner:INTEL CORP
Method and System for Trusted Evidence Storage Based on Scalable Distributed Query System
ActiveCN110956463BAddress regulatory issuesReduce loadPayment protocolsHigh level techniquesBalancing networkNetworked system
The present invention provides a method and system for trusted certificate storage based on an extensible distributed query system, which is applied to a P2P network system, where the P2P network system includes multiple nodes; The acyclic graph ledger structure cooperates with the nRW consensus mechanism to solve the supervision problem in the process of large-scale sharing and exchange; for the above-mentioned non-scalability problem in the deposit process, the embodiment of the present invention also adopts the method of optimizing the number of hops. The number of hops of message transmission optimizes the P2P network system, and constructs a P2P network system with a relatively balanced network, so that the processing operation of the query result is evenly distributed to all nodes in the network, and the output degree is dynamically adjusted according to the computing power of the node. The size of the query will not have a great impact on the query delay under the premise of ensuring load balancing, which ensures the scalability of the system.
Owner:PEKING UNIV
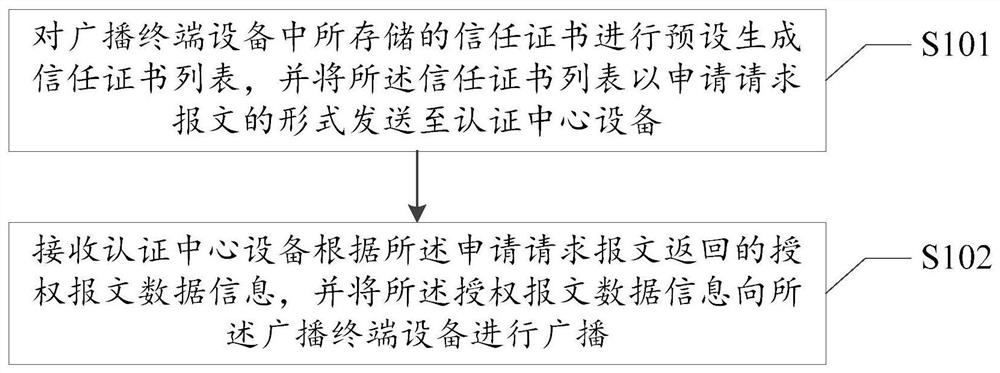
Digital certificate lightweight transmission method and system thereof
ActiveCN111988291AIncrease storage capacitySimplify business processesUser identity/authority verificationDigital data protectionRoot certificateDigital signature
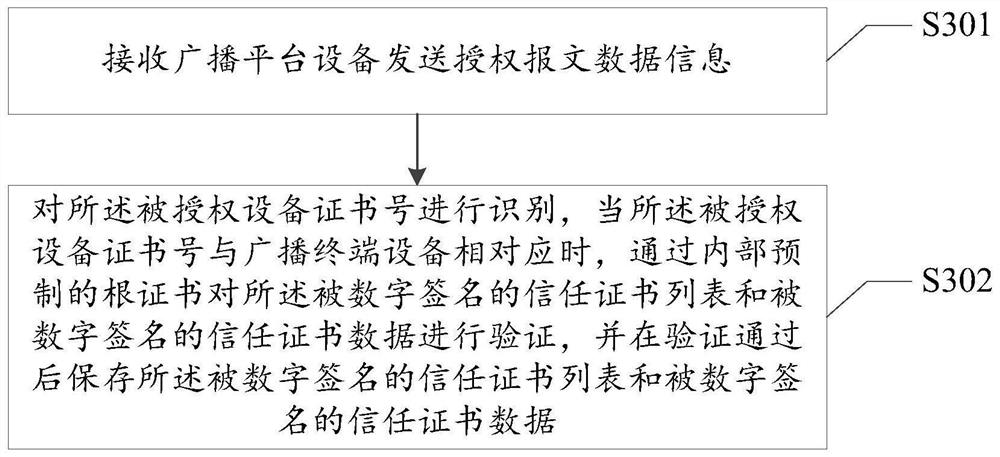
The invention provides a digital certificate lightweight transmission method. The method comprises the following steps: presetting trust certificates stored in a broadcast terminal device to generatea trust certificate list, and sending the trust certificate list to an authentication center device in the form of an application request message; receiving authorization message data information returned by the authentication center equipment according to the application request message, broadcasting on the broadcast terminal equipment; and the broadcast terminal device identifies the certificatenumber of the authorized broadcast terminal device, and when the certificate number of the authorized broadcast terminal device corresponds to the broadcast terminal device, the broadcast terminal device verifies the digitally signed trust certificate list and the digitally signed trust certificate data according to a preset root certificate and stores the verified trust certificate list and thedigitally signed trust certificate data. Through a lightweight digital certificate protocol, the problems of limited storage capacity of broadcast terminal equipment and broadcast and television network transmission are solved, and the mode that the validity of the digital certificate can be verified only by depending on OCSP and LDAP services is simplified in a safe white list mode.
Owner:BEIJING JN TASS TECH
Certificate switching method and device
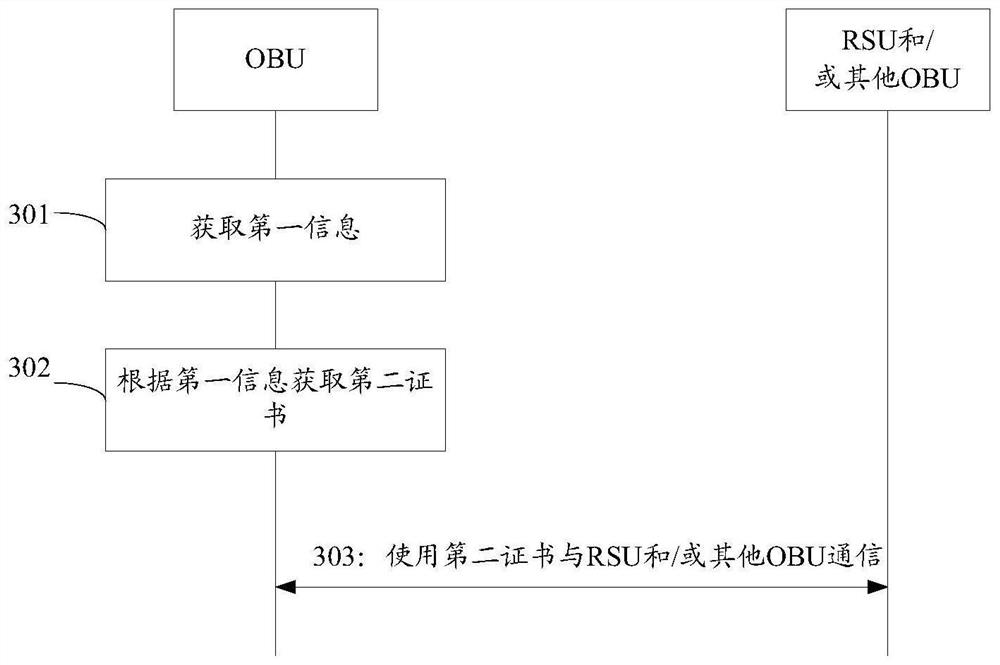
ActiveCN113472541AKey distribution for secure communicationUser identity/authority verificationIn vehicleTrust certificate
The embodiment of the invention provides a certificate switching method and device, relates to the field of wireless communication, and can solve the problem that when a sender and a receiver use certificates issued by different public key infrastructure systems, the sender and the receiver cannot communicate due to the fact that the legality of the certificates of the sender and the receiver cannot be verified. The method comprises the steps: a vehicle-mounted unit acquiring first information, the first information being used by the vehicle-mounted unit to determine to switch a first certificate to a trusted certificate in a second network, the first certificate being a trusted certificate in a first network; the vehicle-mounted unit obtains a second certificate according to the first information, and the second certificate is a trusted certificate in the second network; and the vehicle-mounted unit uses the second certificate to communicate with a road side unit and / or other vehicle-mounted units.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Electronic certificate generation method, payment method and server
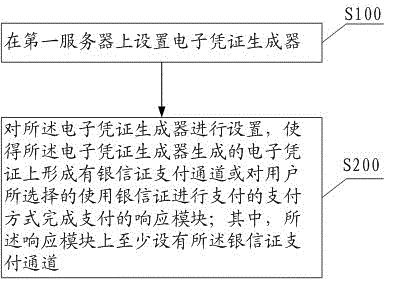
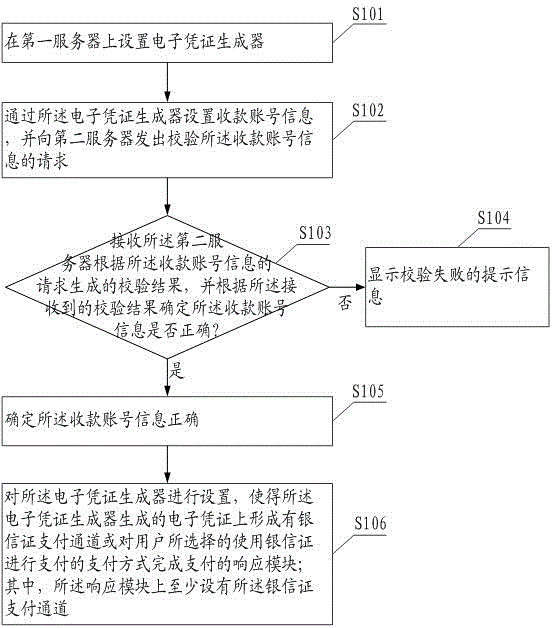
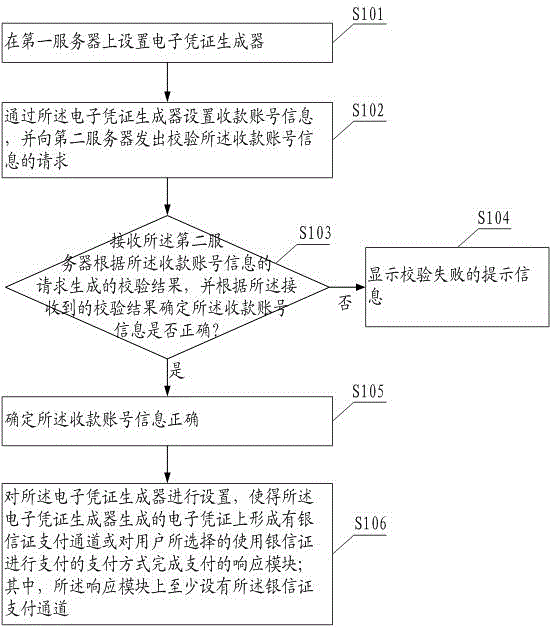
InactiveCN106886896AWith convenient function of online shoppingMeet online shopping needsElectronic credentialsPaymentComputer science
The invention provides an electronic certificate generation method, and the method comprises the steps: arranging an electronic certificate generator on a first server; setting the electronic certificate generator, and forming a bank trust certificate payment channel on an electronic certificate generated by the electronic certificate generator or a response module which complete the payment in a payment mode that a user selects a bank trust certificate for payment. The response module is at least provided with the bank trust certificate payment channel. According to the embodiment of the invention, the generated electronic certificate cooperates with the bank trust certificate for use. The method achieves a function of convenient online shopping, can meet the online shopping demands of a user and also can achieve the credit and fund safety in online transaction.
Owner:SHENZHEN CIFPAY NETWORK BANK TECH
A lightweight trust assessment method for Internet of Vehicles
ActiveCN109347852BShorten the timeReduce bandwidth consumptionUser identity/authority verificationData switching networksComputer networkDigital signature
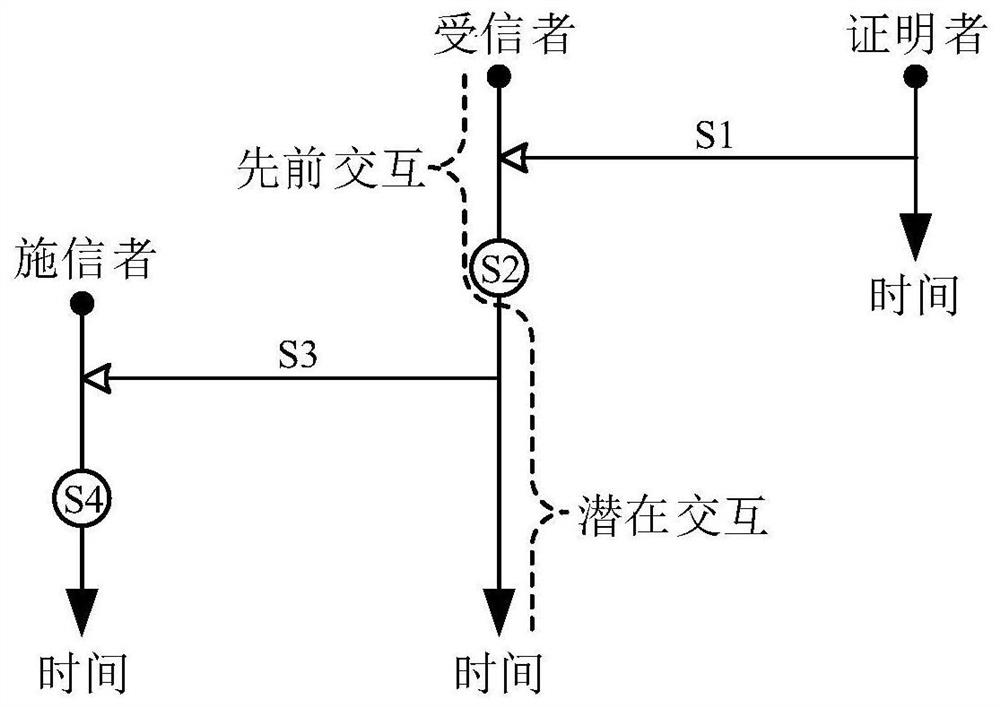
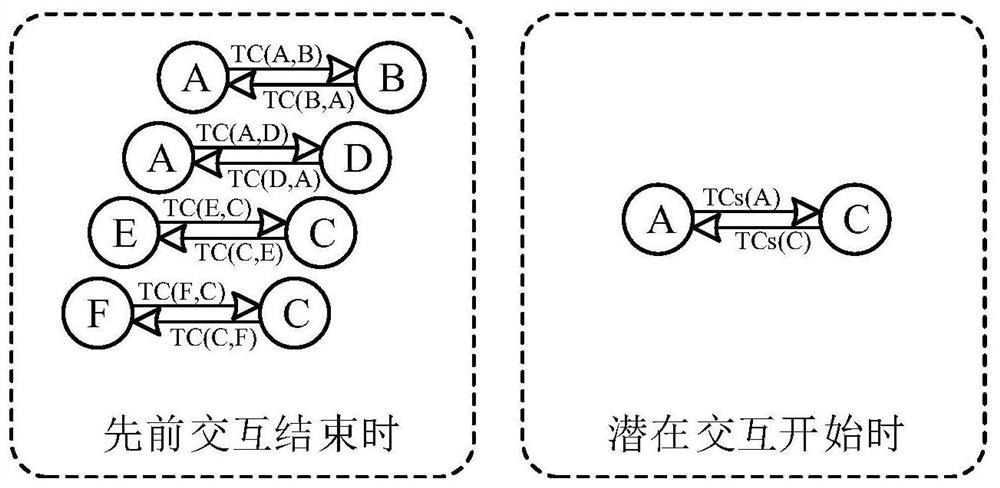
The invention discloses a lightweight Internet of vehicles trust evaluation method. The method specifically comprises the following steps that: S1, when previous interaction between nodes is finished,two interaction sides generate trust certificates including own digital signatures for the opposite side according to interaction experience, and transmit the trust certificates to the opposite side;S2, the two interaction sides verify signature information after receiving new trust certificates, and update local storage in order to save most favorable eta trust certificates at most, wherein (eta is an element of a set Z<+>) is a system parameter; S3, at the start of potential interaction, two potential interaction sides transmit locally-stored trust certificates to the opposite side in order to prove own trustworthiness; and S4, the two potential interaction sides verify the authenticity of the trust certificates through digital signature information, export the trust value of the opposite side, and determine whether to agree to interact with the opposite side or not, wherein the interaction is implemented only when the two sides agree to interact. The lightweight Internet of vehicles trust evaluation method is independent of a trust center and a roadside unit, and conforms to the large scale and distribution features of the Internet of vehicles more.
Owner:JINAN UNIVERSITY
Consensus method and device for blockchain system based on non-negotiation random lottery
ActiveCN108269090BEnsure safetyImprove the real-time performance of transactionsPayment protocolsTrust certificateEngineering
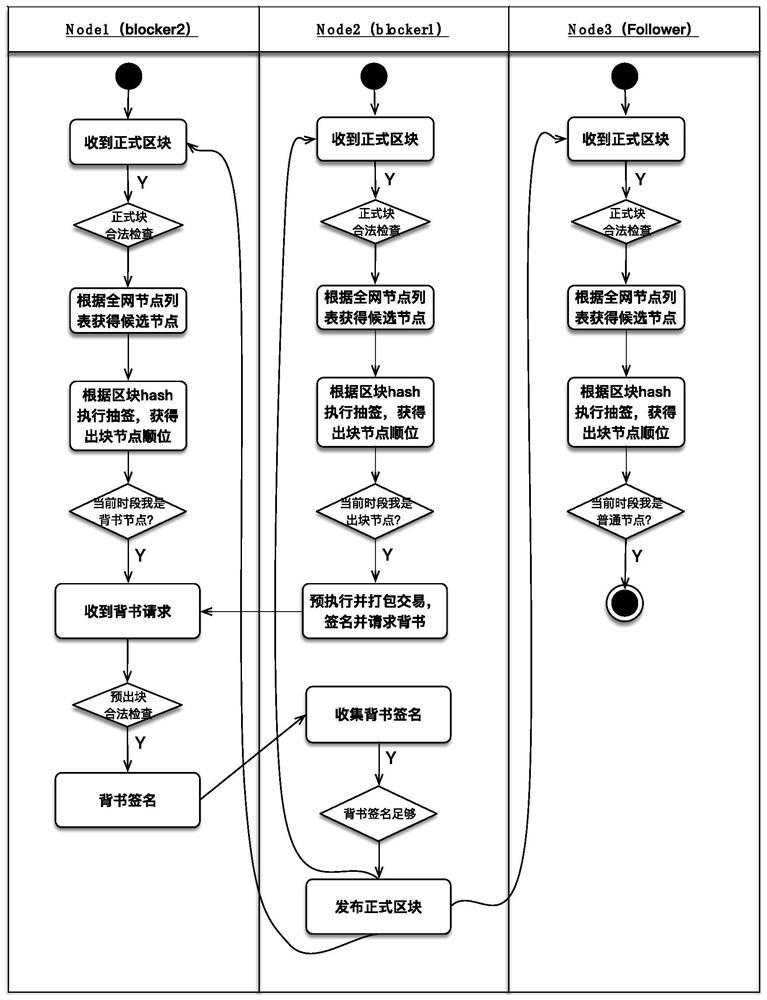
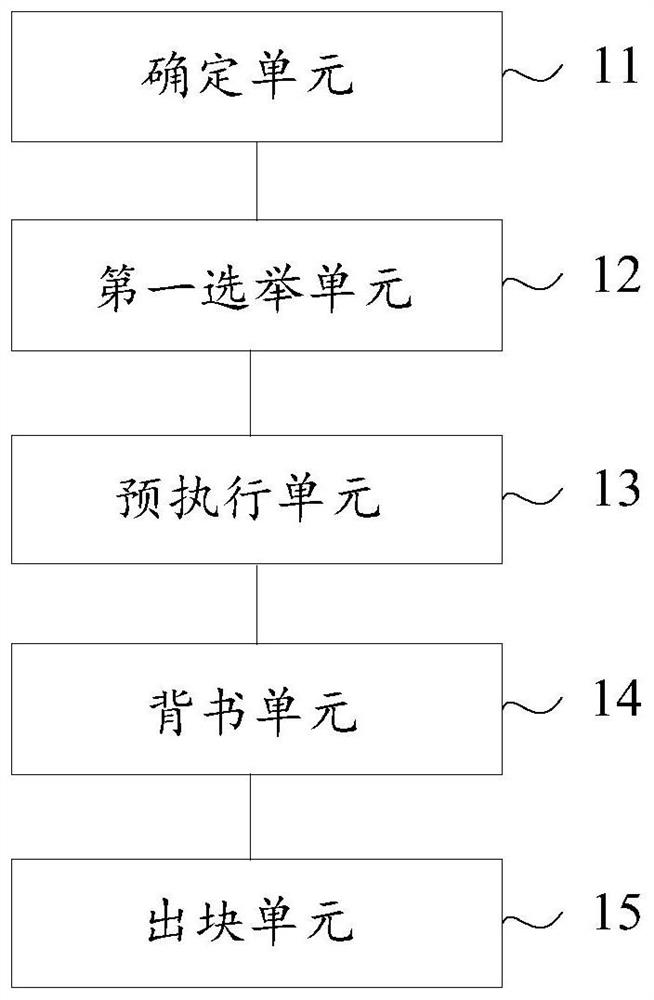
The present invention provides a consensus method and device for a block chain system based on non-negotiation random lottery. The method includes: after receiving a legal block, determining the currently qualified nodes according to the trust certificate list of the whole network; performing non-negotiation random draw on the currently qualified nodes to obtain a sequence of nodes arranged in order, the The sequence determines the only block-producing node that is eligible to produce a block at each specific period of time that follows. In each subsequent specific period of time, the block-producing node sends the pre-produced block and collects the endorsement; after the endorsement node receives the endorsement request, it checks the legitimacy of the pre-produced block and signs the legal pre-produced block; After more than 50% of the endorsement signatures, the endorsement signatures are added to the pre-produced block to form a formal block and broadcast to the entire network. The present invention can prevent malicious nodes from manipulating lottery results and ensure the security of blockchain operation; Real-time transaction of the system.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com