Certificate switching method and device
A certificate and communication device technology, applied in security devices, secure communication devices, user identity/authority verification, etc., can solve problems such as inability to verify the validity of certificates and inability to communicate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
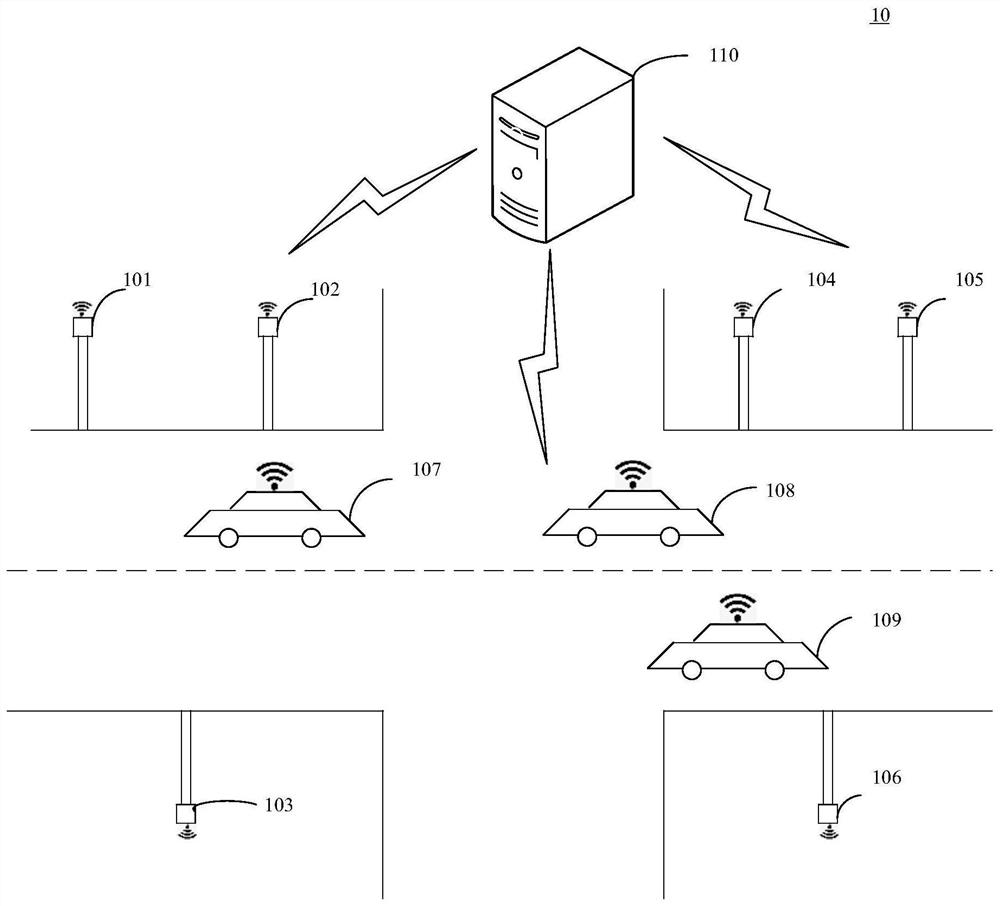
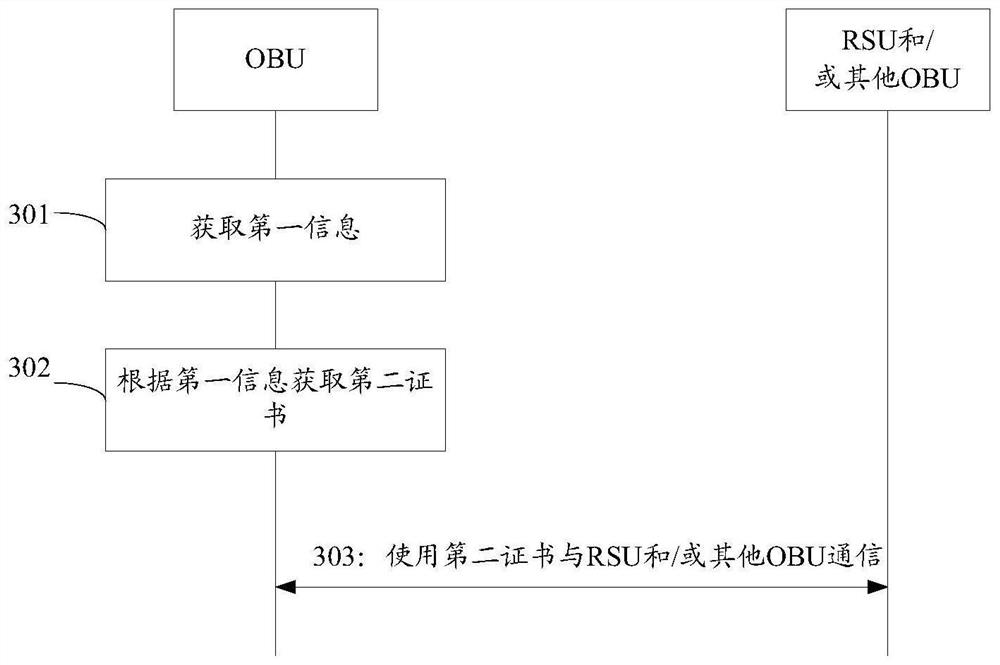
[0126] It can be understood that the information included in the above first request is different, therefore, the process for the server to obtain the second certificate according to the first request is different. The process for the server to obtain the second certificate according to the first request can refer to the following example 1, example 2 and example 3:
[0127] Example 1, when the first request includes the information of the second network, the first public key and the registration certificate of the OBU, the server determines the first AA in the second network according to the information of the second network, and sends the first certificate to the first AA Request information, and receive first certificate response information from the first AA.
[0128] Wherein, the first certificate request information may be used to request the second certificate, the first certificate request information may include the first public key and the registration certificate of...
example 2
[0130] Example 2, when the first request includes the information of the second network, the first public key and the second public key, the server determines the first EA and the second AA in the second network according to the information of the second network, and the server sends the first The EA sends the second certificate request information and receives the second certificate response information from the first EA, and the server sends the third certificate request information to the second AA and receives the third certificate response information from the second AA.
[0131] Wherein, the second certificate request information may be used to request the registration certificate of the OBU, and the second certificate request information may include the identifier of the OBU and the second public key. The second certificate response information may include the registration certificate of the OBU. The third certificate request information may be used to request the secon...
example 3
[0133] Example 3, when the first request includes the information of the second network and the registration certificate of the OBU, the server stores or presets a public key seed, and the server determines the third AA in the second network according to the information of the second network, and according to the key Derivation algorithm (for example, butterfly key expansion mechanism (butterfly key expansion, BKE)) and the public key seed to obtain the public key of the second certificate, the server sends the fourth certificate request information to the third AA, and receives the request information from the third AA The fourth certificate response message.
[0134] Wherein, the fourth certificate request information may be used to request the second certificate, and the fourth certificate request information may include the registration certificate of the OBU and the public key of the second certificate. The fourth certificate response information may include the second ce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com