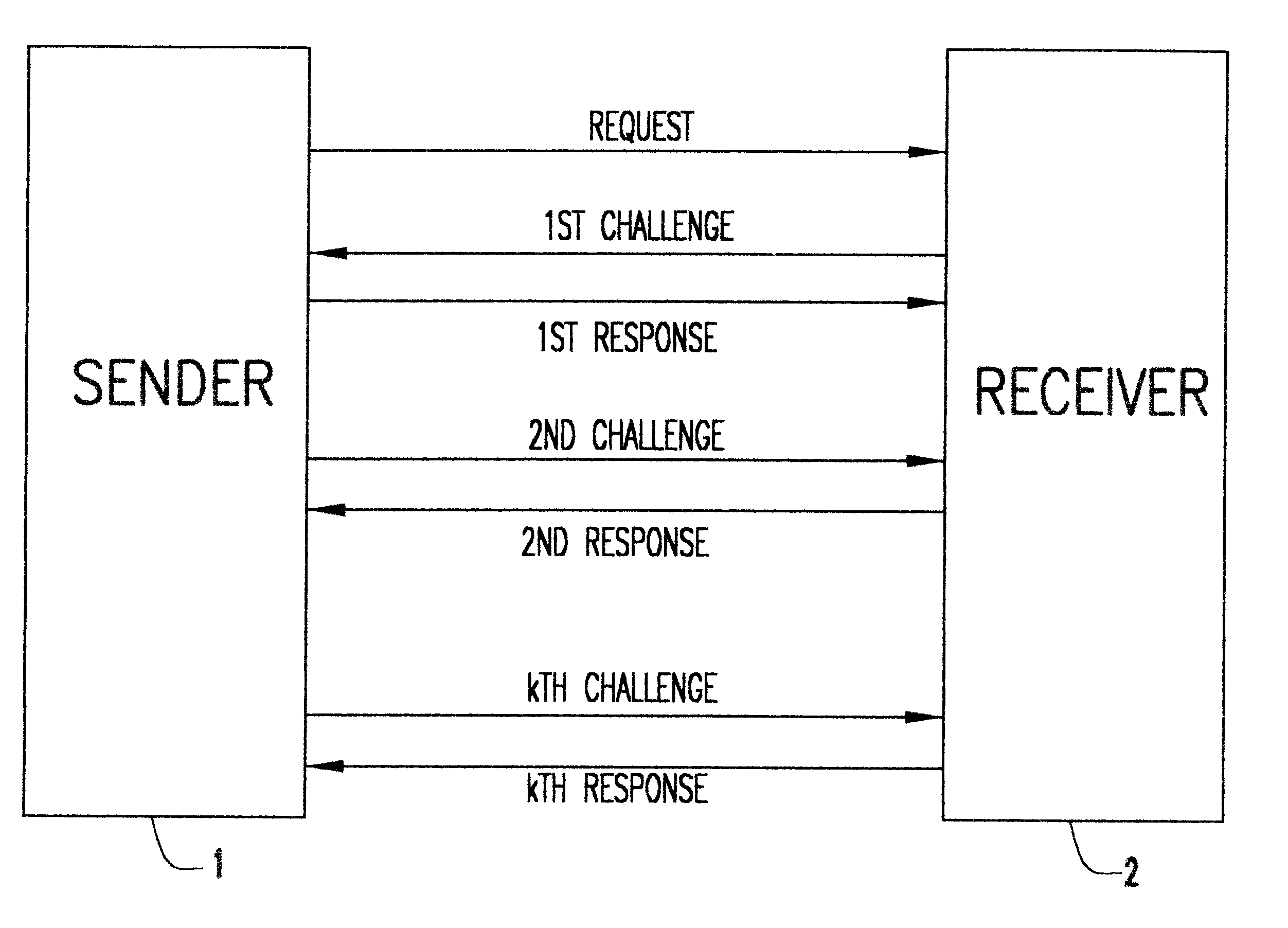
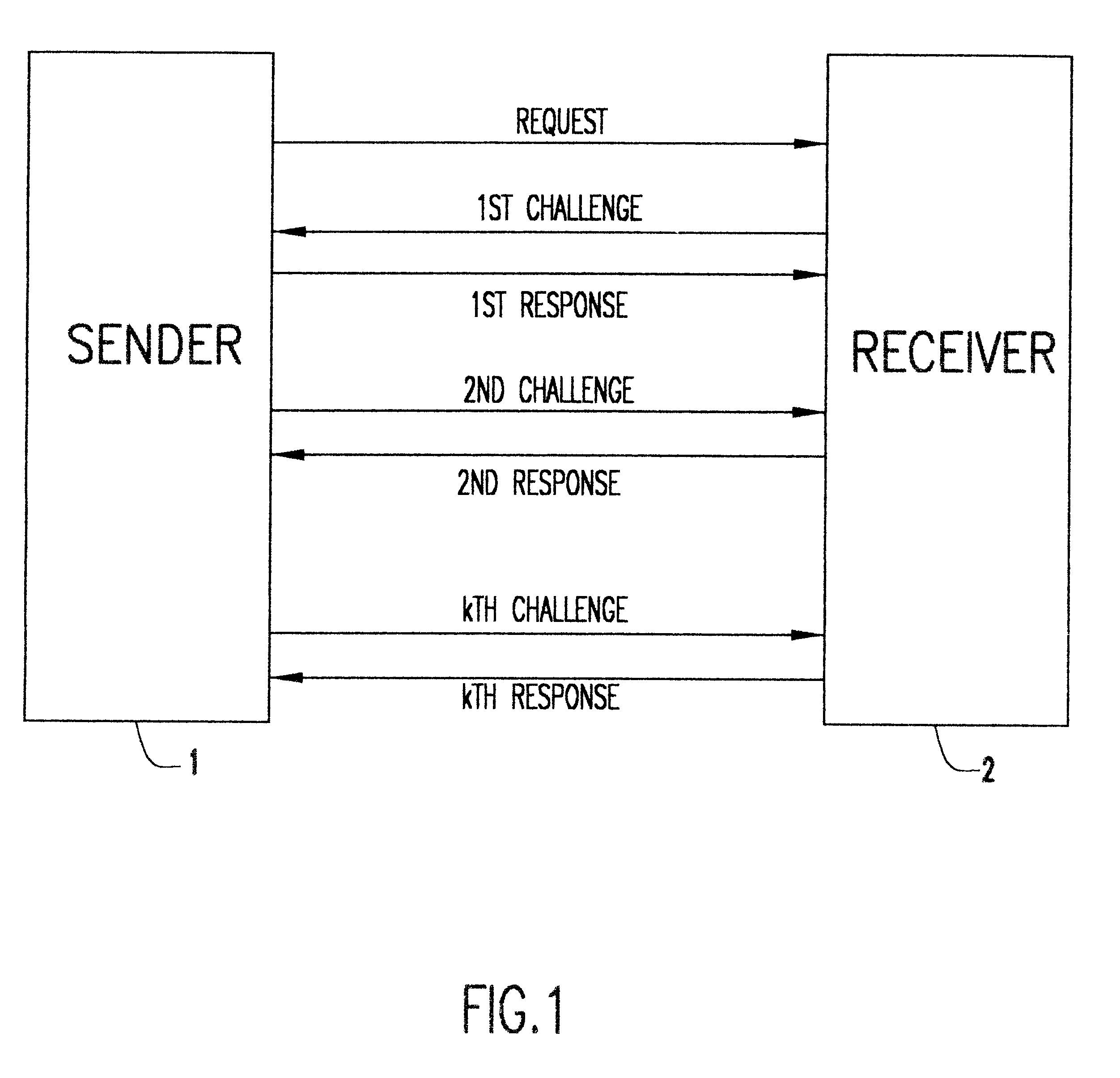
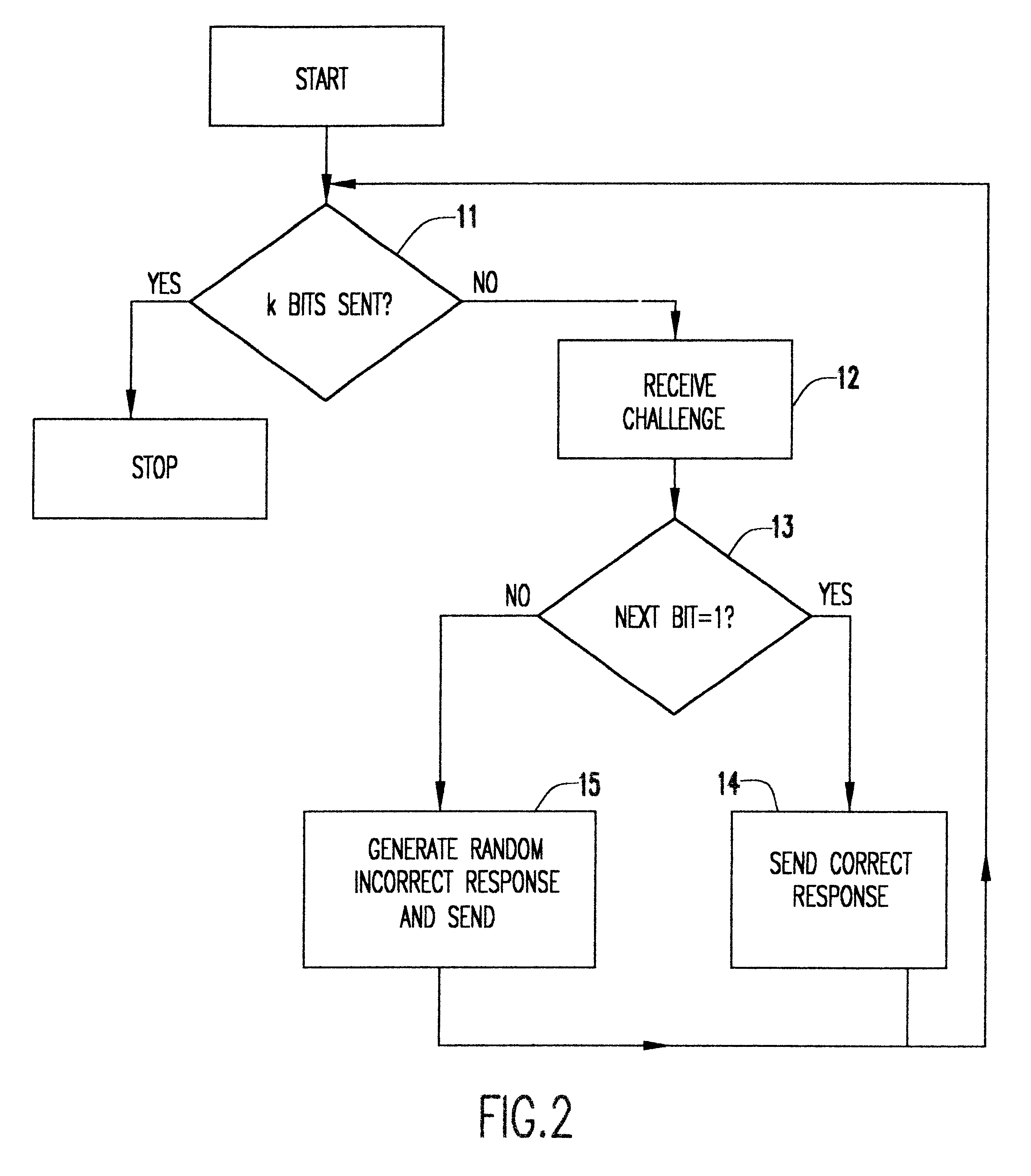
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
255 results about "Correct response" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
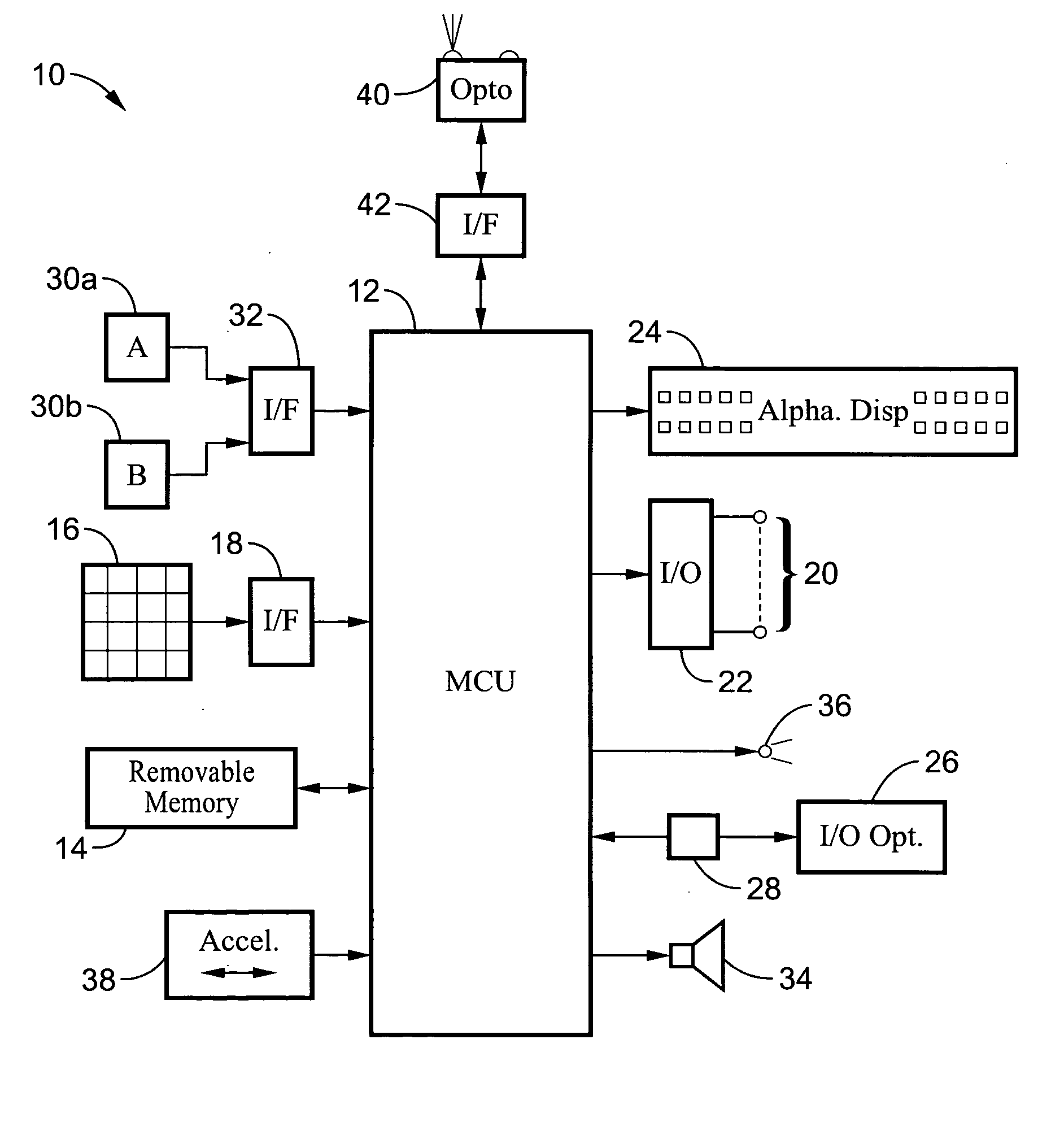
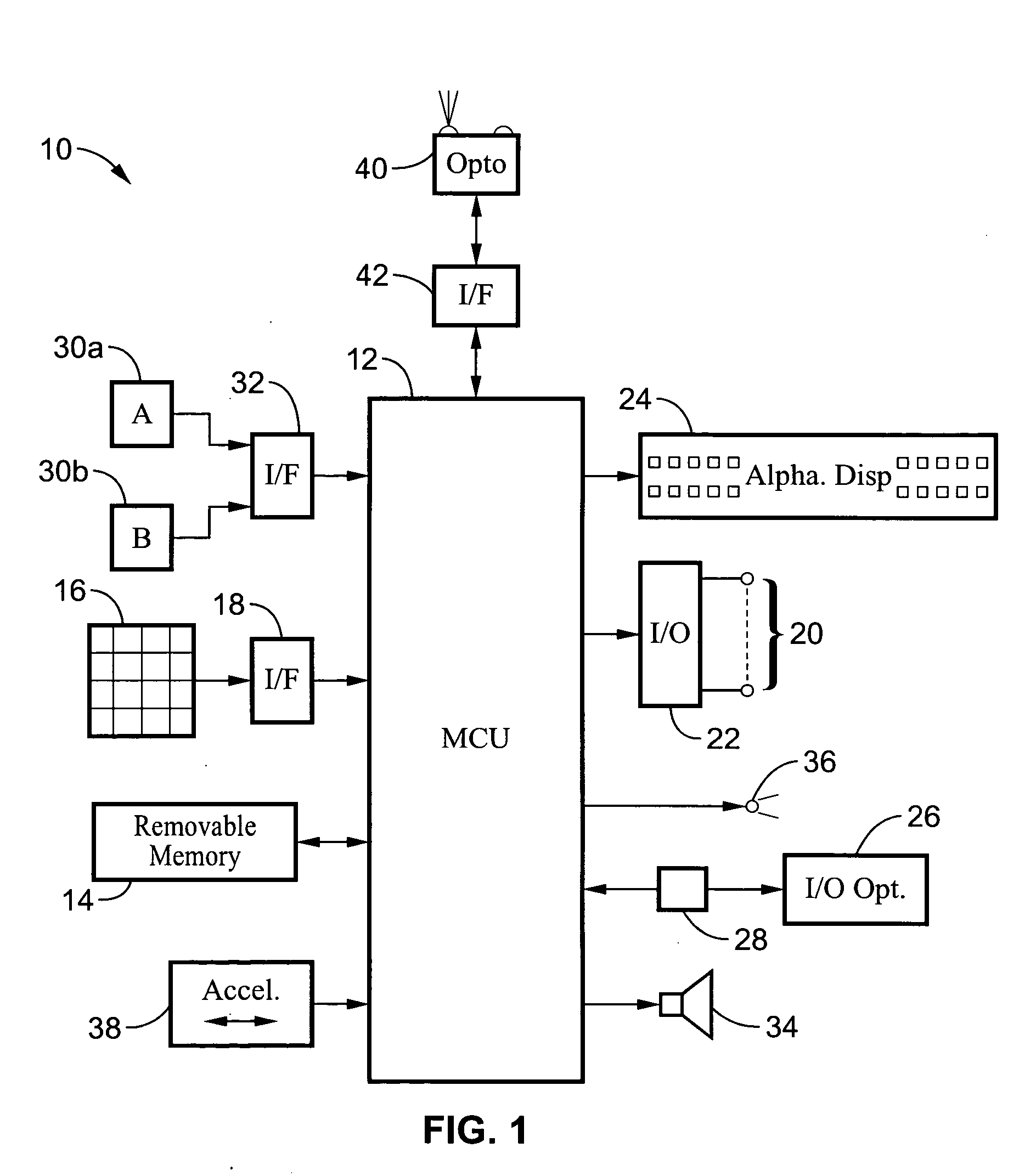
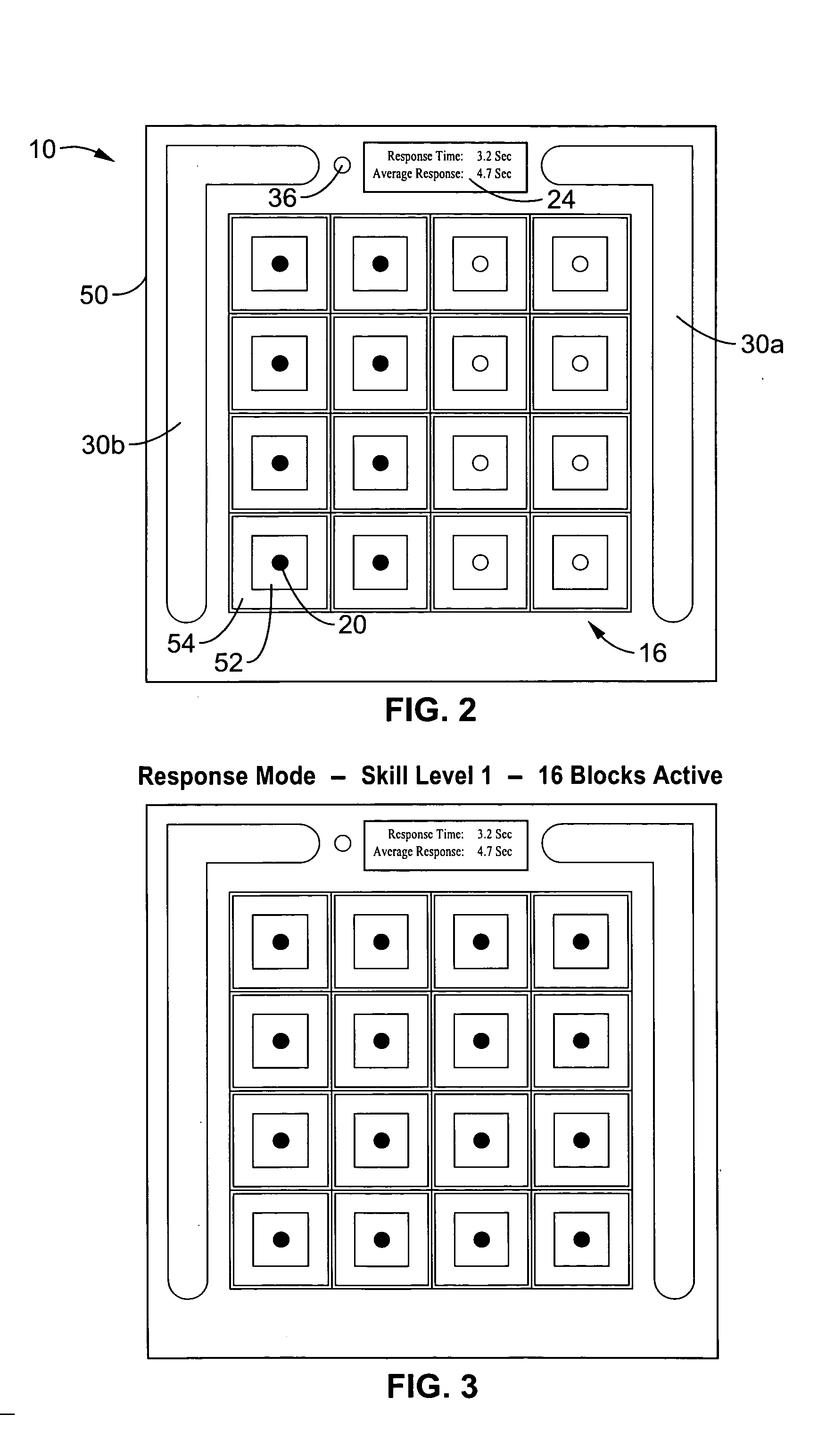
Method and apparatus for automated training of language learning skills
A computer program for execution on a computing device is provided to cross-train students in language development skills such as letter-word correspondence, word recognition, vocabulary, and sentence and paragraph comprehension. A set of programs provide an adaptive methodology for training a student in decoding (semantic, syntactic, phonological, and morphological relationships), knowledge of rhymes, synonyms, antonyms, and homophones, spelling, letter-word correspondences, sentence comprehension, grammatical comprehension, working memory, vocabulary, paragraph comprehension, and improved reading comprehension. In each program, students are presented with an animated scene that poses a question, and a set of answers. The set of answers contain a correct response, and a number of incorrect responses or foils. The student advances to more complex levels by satisfying predetermined correct thresholds. Through repetition and intensity, the student's language skills are developed.
Owner:SCI LEARNING
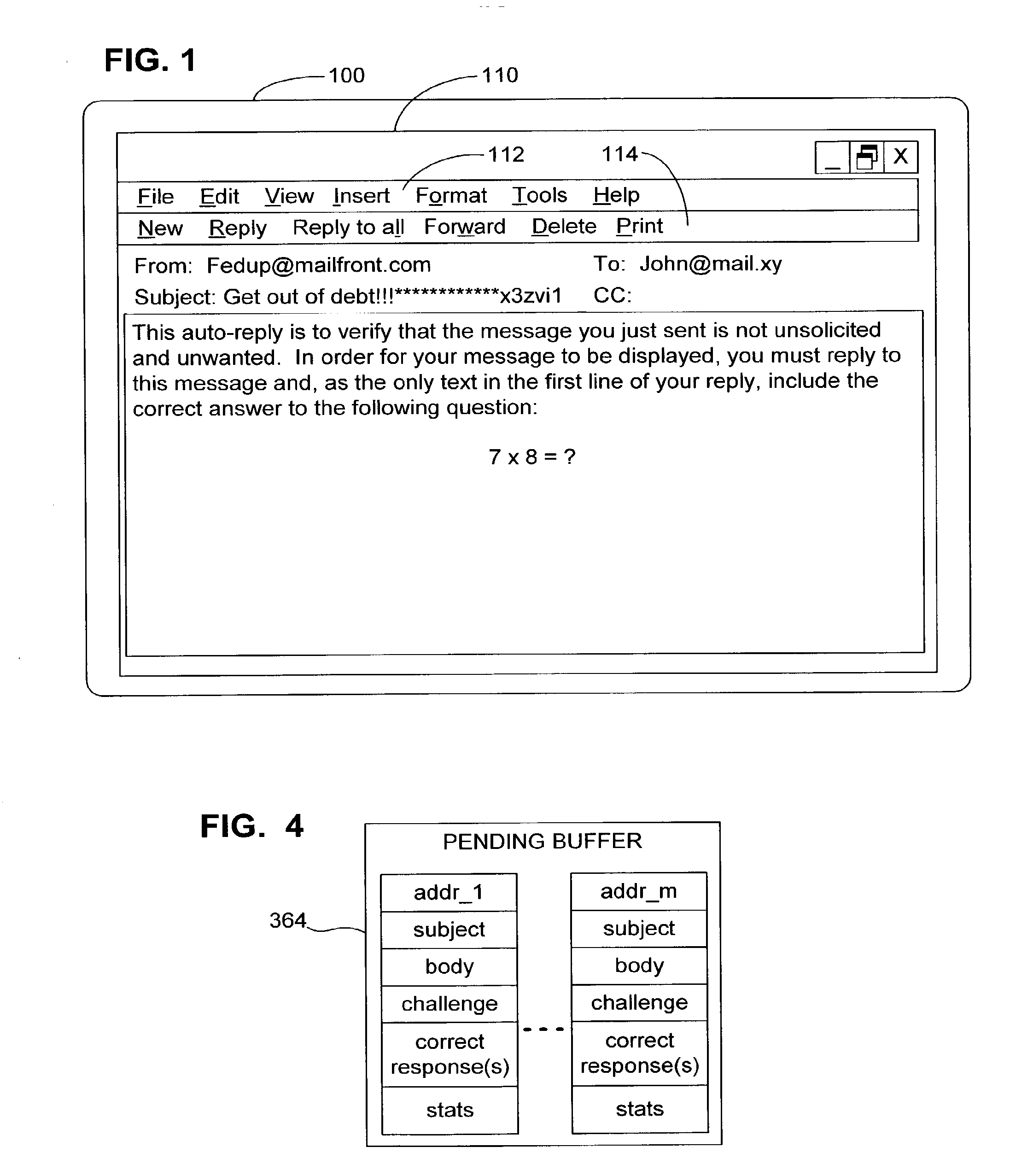
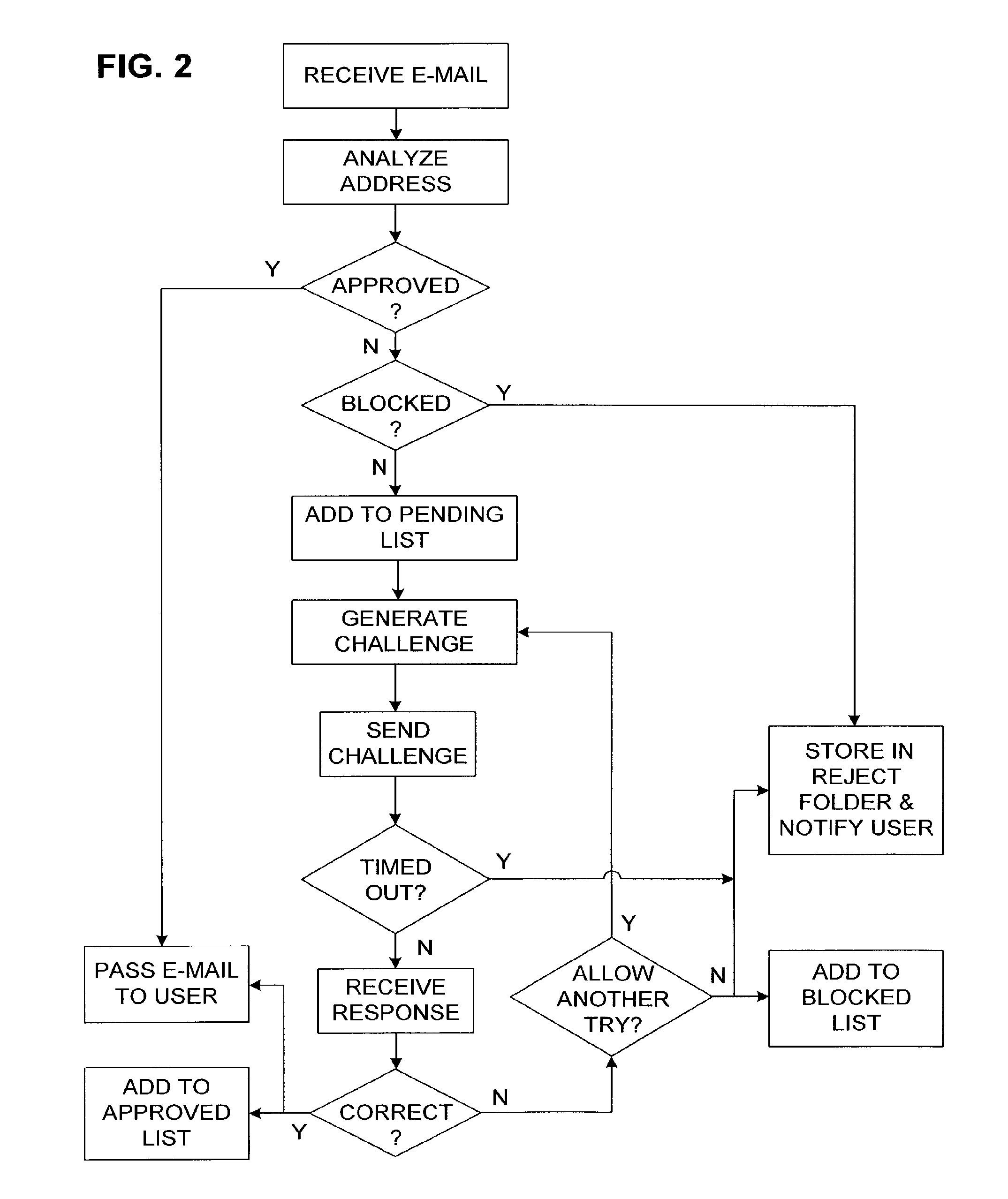
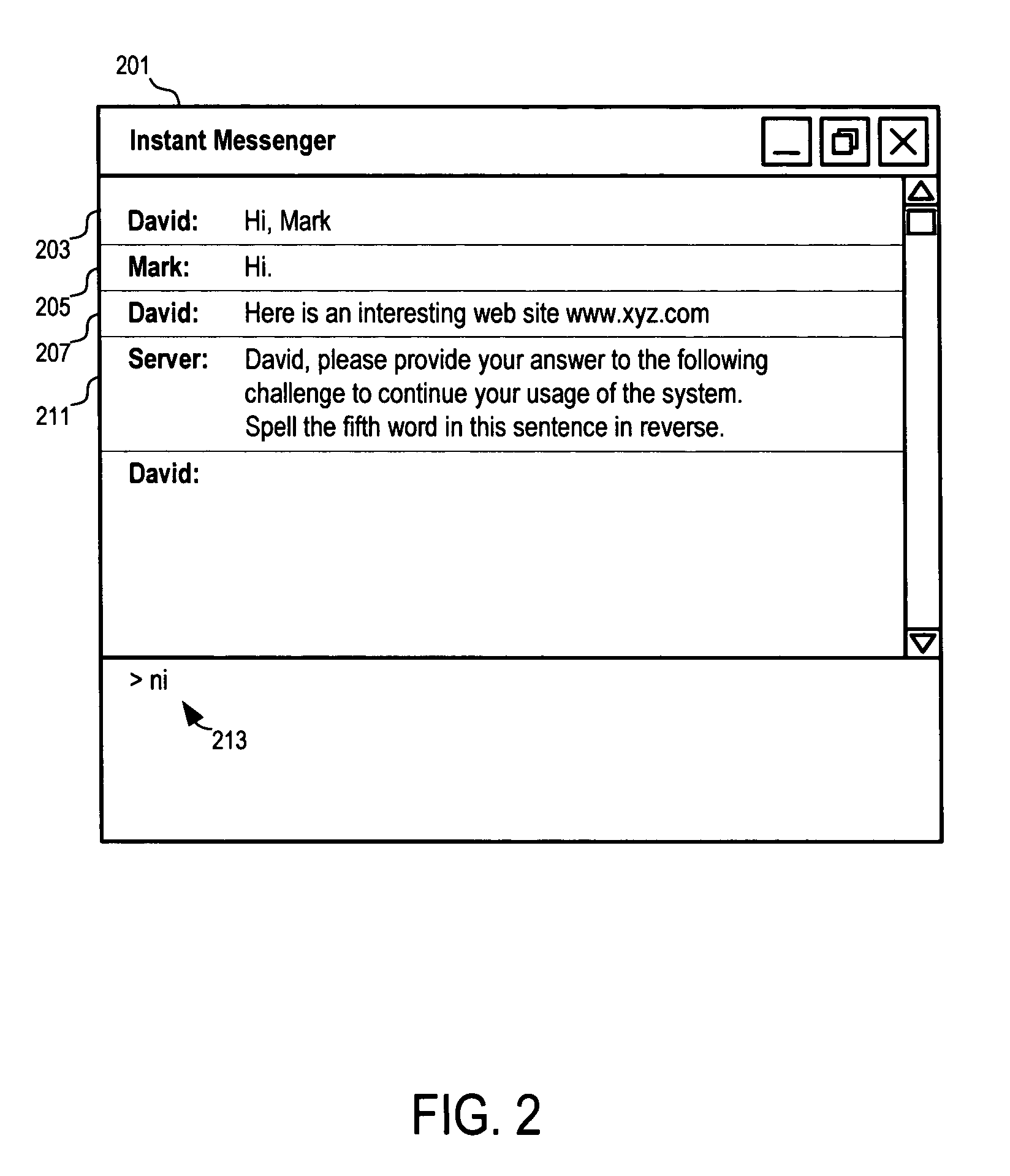
Active E-mail Filter with Challenge-Response
InactiveUS20080168145A1Accurate answerMultiple digital computer combinationsOffice automationCorrect responseChallenge response
Owner:QUEST SOFTWARE INC
Prevention of unauthorized scripts
ActiveUS7606915B1Improved script preventionEasy to solveDigital data processing detailsMultiple digital computer combinationsComputer hardwareCorrect response
Methods and system of preventing unauthorized scripting. The invention includes providing one or more tests to a user for distinguishing the user from a machine when the user requests access to the server. By storing information on a correct solution to the test in a block of data and sending the block of data together with the test, the invention provides stateless operation. Moreover, maintaining a database of previously used correct responses prevents replay attacks. The invention also includes providing combinations of alternative tests, such as visually altered textual character strings, audible character strings, and computational puzzles. Other aspects of the invention are directed to computer-readable media for use with the methods and system.
Owner:MICROSOFT TECH LICENSING LLC
User-centric authentication system and method
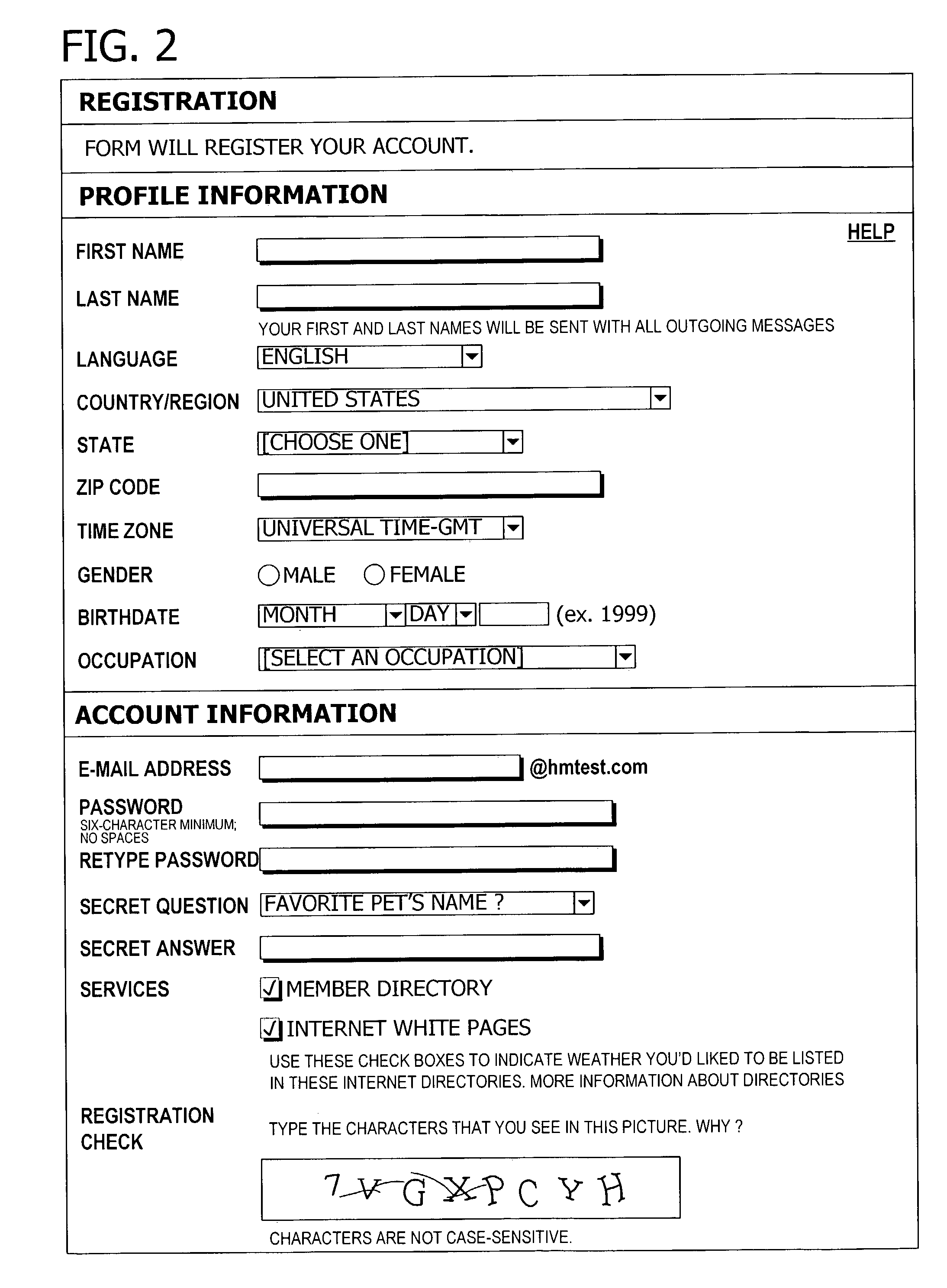
ActiveUS20090037983A1Difficult to answerGood degreeDigital data processing detailsAnalogue secracy/subscription systemsComputer resourcesCorrect response
A system for authenticating a user in a network. The authentication system includes a computer resource having secure data, an authentication computing system providing dynamic authentication of a user accessing the computer resource, and a user communication device for communicating between the user and the computer resource. The computing system presents a challenge for which a specified response is required based upon a pre-determined function. Access is then granted by the computing system upon providing the correct response to the presented challenge by the user.
Owner:CHIRUVOLU GIRISH
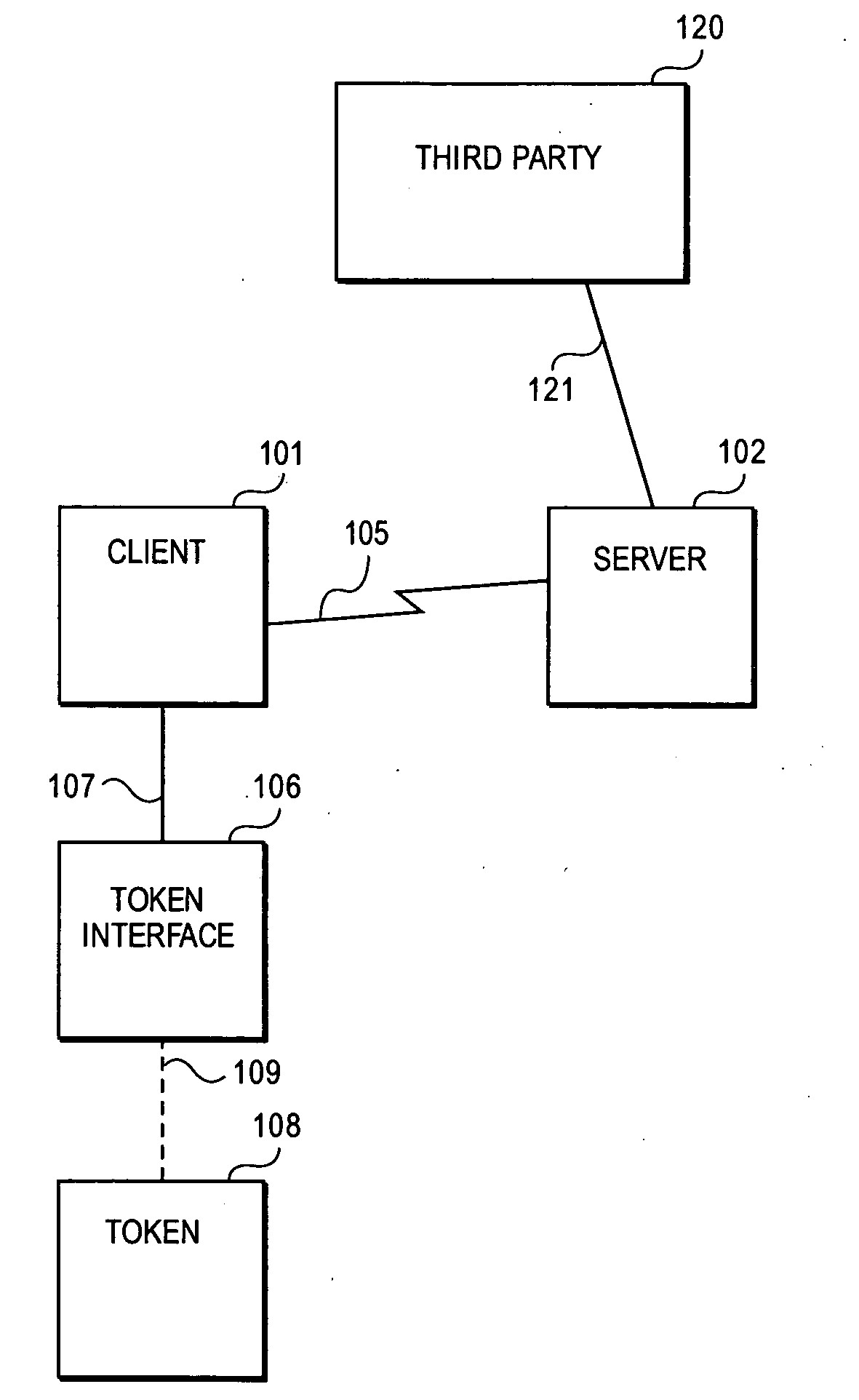
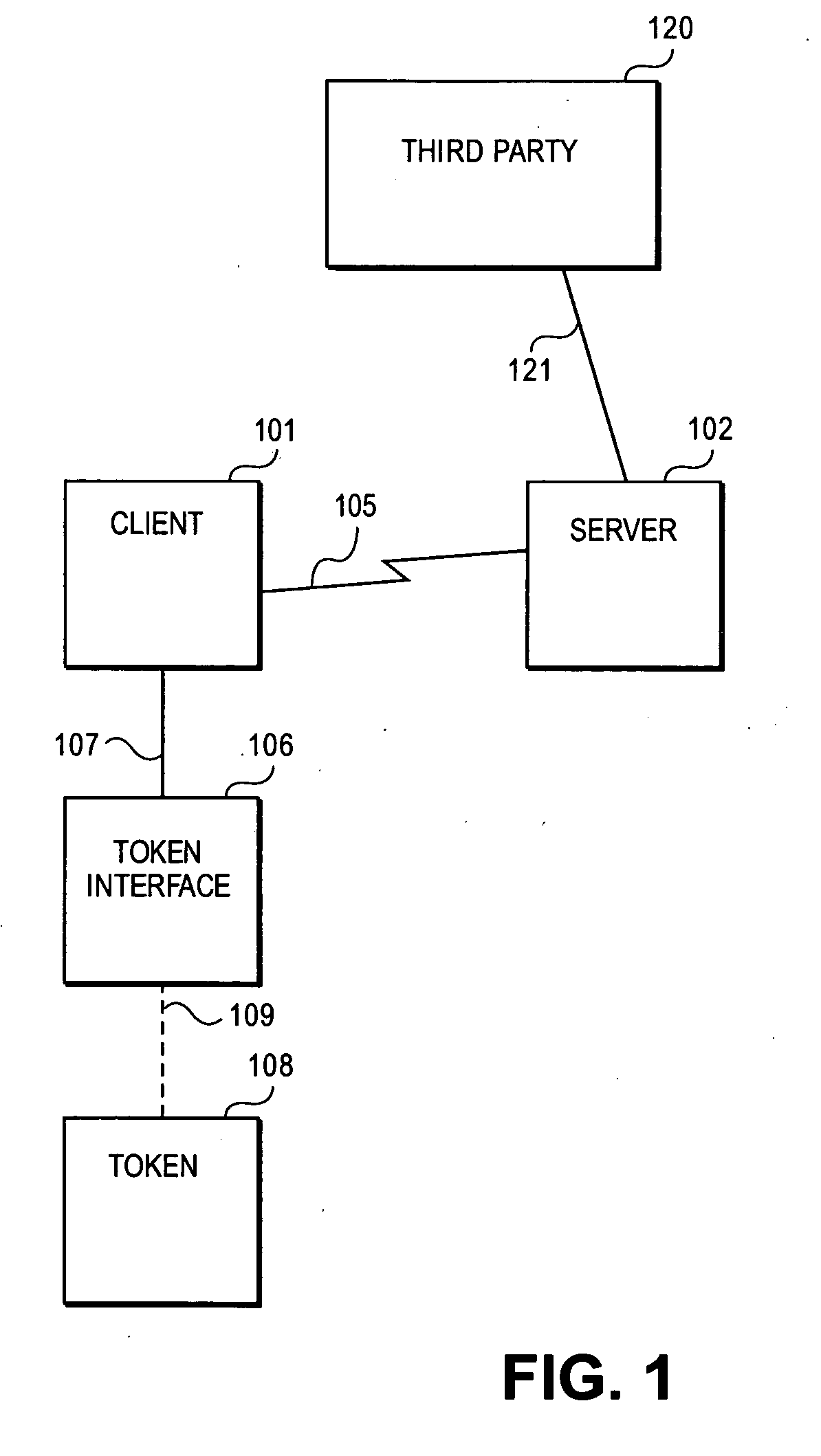
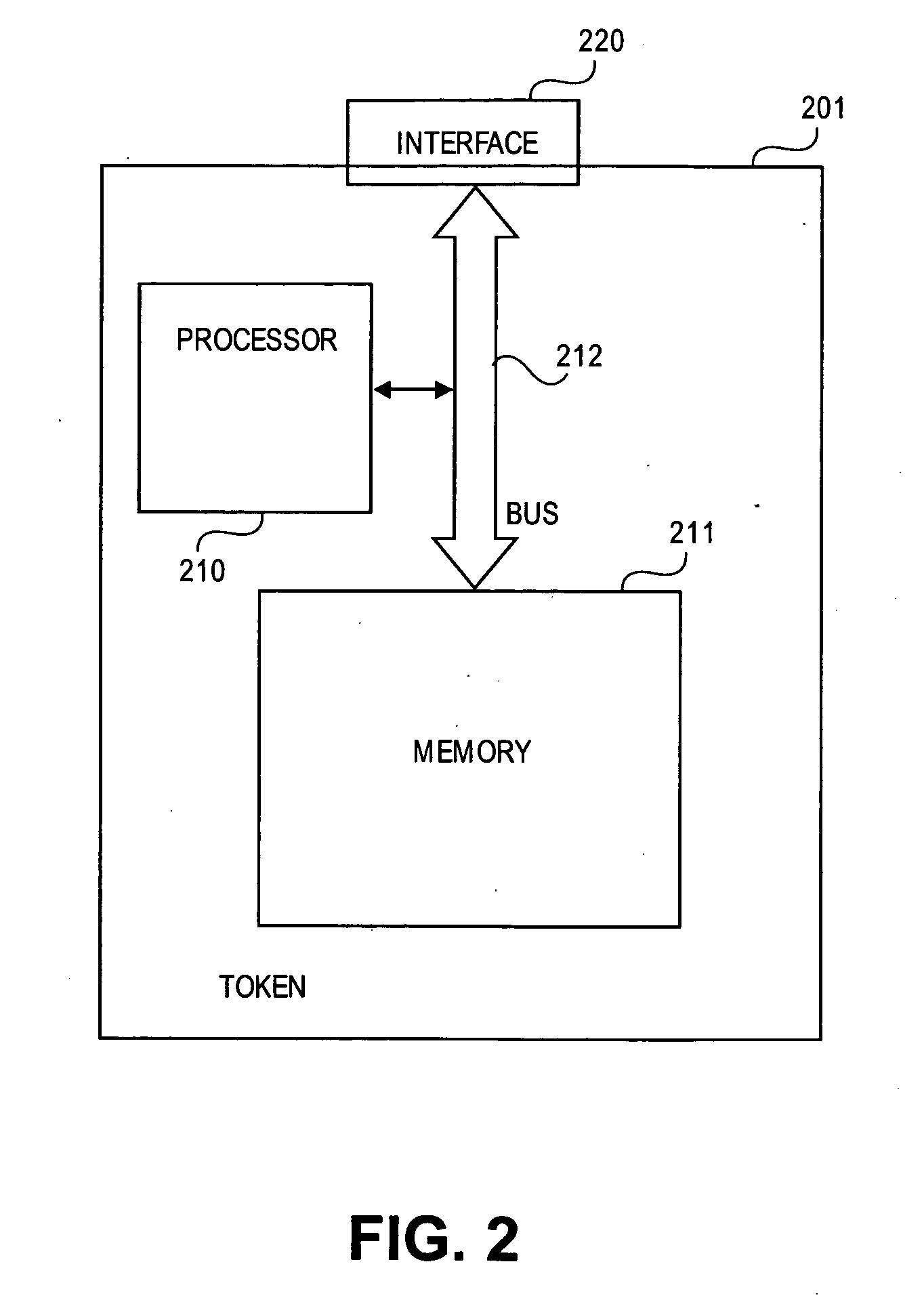
Methods and systems for remote password reset using an authentication credential managed by a third party
ActiveUS20080046982A1Digital data processing detailsUser identity/authority verificationThird partyPassword
Embodiments of the present invention provide a secure remote password reset capability. In some embodiments, an exemplary method provides a remote reset of a password associated with a token in a computer system having a security server. A token-based authentication process is activated by connecting the token to the security server. A server-based authentication process is initiated in the security server by activating a password reset process in a security client. The server-based authentication process communicates with the token-based authentication process over a secure channel. An authentication credential is managed by a third party agent that supplies a query and the authentication credential as a correct response to the query to the security server. A prompt provided by the password reset process collects the authentication credential and a new password. After the authentication credential is validated mutually authentication is performed between the security server and the token. The token is updated with the new password based on a successful result of the mutual authentication.
Owner:RED HAT
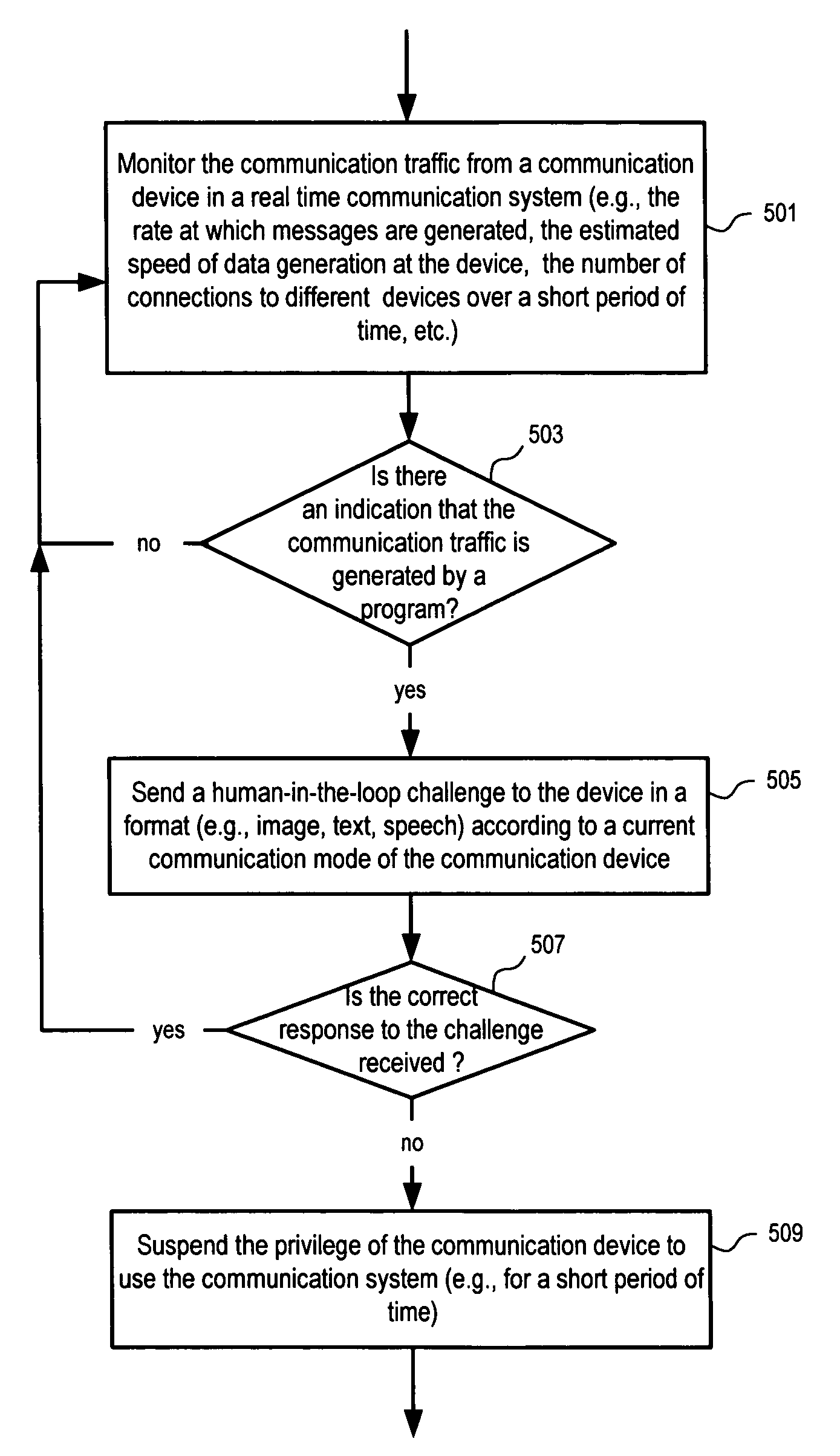
Methods and apparatuses for presenting challenges to tell humans and computers apart
ActiveUS7945952B1Memory loss protectionDigital data processing detailsCommunications systemVoice communication
Methods and apparatuses to tell humans and machines apart. In one embodiment, automated determination of whether a human or machine is at the other end of a communication channel is based on whether the correct response to a challenge / question is received from the other end of the communication channel. The challenge is provided in a non-image format, such as a text based questions or a sound clip, to prevent abuses of the communication system by computer software robots. The communication system may be primarily for text and / or voice communications, or be such that the rendering image-based challenges can cause significant disruption in normal flow of usage. In one example, the challenge includes deliberately generated random misspelling. In one example, the challenge is context sensitive, factual based, and / or instructive of an operation in a natural language to obtain a result.
Owner:GOOGLE LLC
Selective treatment of messages based on junk rating
InactiveUS20050204005A1Mitigate accidentalMitigate unintentional exposureMultiple digital computer combinationsData switching networksUser inputSpamming
The present invention provides a unique system and method that mitigates viewing potentially offensive or spam-like content such as in a preview pane. In particular the system and / or method involve assigning a junk score to a message and then determining an appropriate treatment of the message based on its junk score. Messages with junk scores that exceed a challenge threshold can be hidden from a message listing such as in the user's inbox while a challenge is sent to the message sender. Upon receiving a validated and correct response from the sender, the message can be released or revealed to the user in the user's inbox. Content associated with messages with junk scores that exceed a blocking threshold can be blocked from view in a preview pane. Explicit user input can be required to unblock the content.
Owner:MICROSOFT TECH LICENSING LLC
Keyless encryption of messages using challenge response
InactiveUS6535980B1Key distribution for secure communicationUser identity/authority verificationComputer hardwareSecure transmission
A method of keyless encryption of messages allows secure transmission of data where data security is not available for some technical or legal reason. The method of data transfer uses a challenge response in which a correct response to a challenge is used to transmit the value "1", while a deliberately false response is made to transmit the value "0". Any message can be transmitted as a binary string using successive applications of this method.
Owner:IBM CORP
Novel response game systems and method
Novel response games provide members of a World community opportunities to receive response points and subsequent prizes, awards, fortune, and fame for correctly responding to and / or controlling various elements of interactive promotions, productions, and products with respect to all genres of existing and future / innovative / interactive publications, radio, music, Television (e.g., talent shows, game shows, award shows, reality, sitcom, drama, etc.) film (e.g. feature, animated, documentary, etc.), video games, politics, and manufacturing. Most notably novel response games compel and empower viewers to take part in Television promotions, productions, and programs. Correct responses are generally determined by a Television producer's and SPONSOR'S targeted viewers (e.g. a designated response game point controller). Players receiving a highest response point total for a plurality of response sessions are identified as highly in-sync with a response point controller (e.g. producer's and sponsor's targeted viewers) and qualify to be selected to star on Television as viewer / controller representatives. While starring on Television viewer / controller representatives are presented with various producer's and sponsor's business element options associated with a future Television promotion, production, and program provided. The representatives are shown evaluating each business element and selecting a number of most suitable elements to become future response game elements. The producer's and sponsor's elements selected by the viewer / controller representatives are determined by the representatives to be the most suitable elements for viewers to respond to during a future response game. After all, who could be more qualified to represent viewers than those proven to be most in-sync with viewers?Novel response games are designed to utilize producer and sponsor provided elements as response game elements relating to the producer's and sponsor's interactive promotions, productions, and end products. In essence a response games is intended to be wrapped around all genres of media promotions, productions, and products.
Owner:PATCHEN JEFFERY ALLEN
Interactive neural training device
InactiveUS7452336B2Easy to useNot easy to damageElectrotherapyPerson identificationTouch PerceptionHand movements
Owner:INTERACTIVE NEURO TECH
Methods of temporal knowledge-based gaming
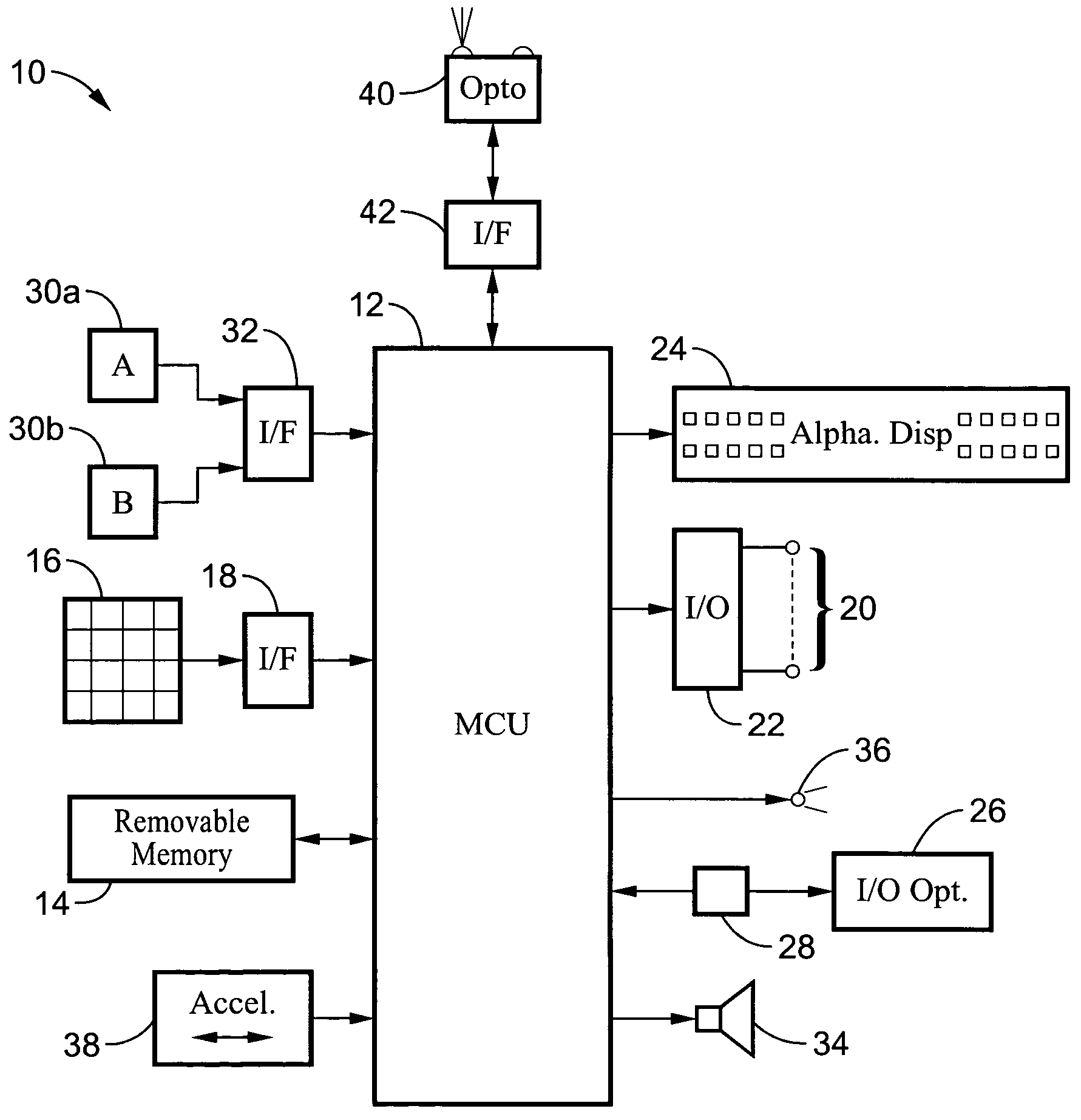
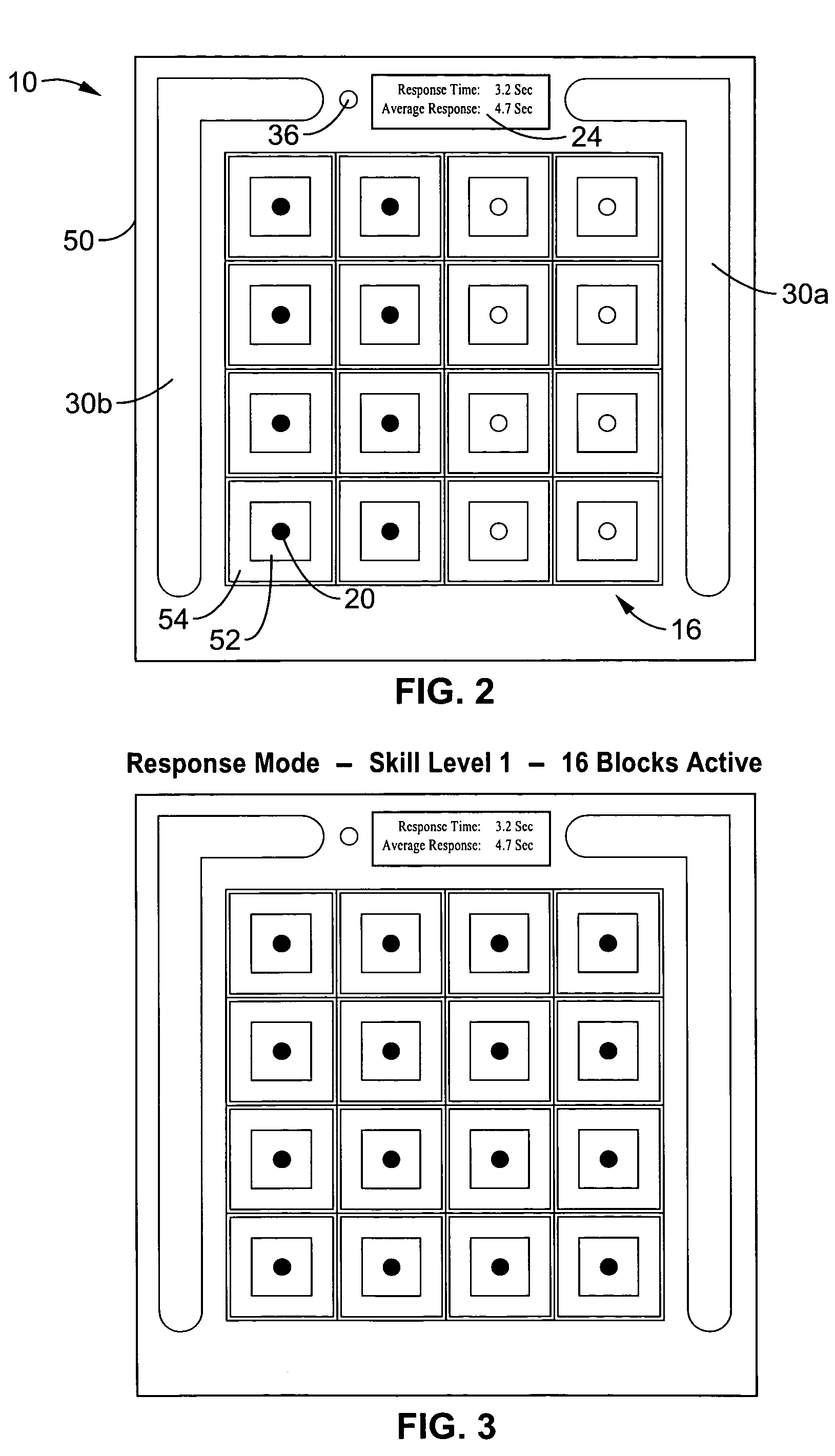
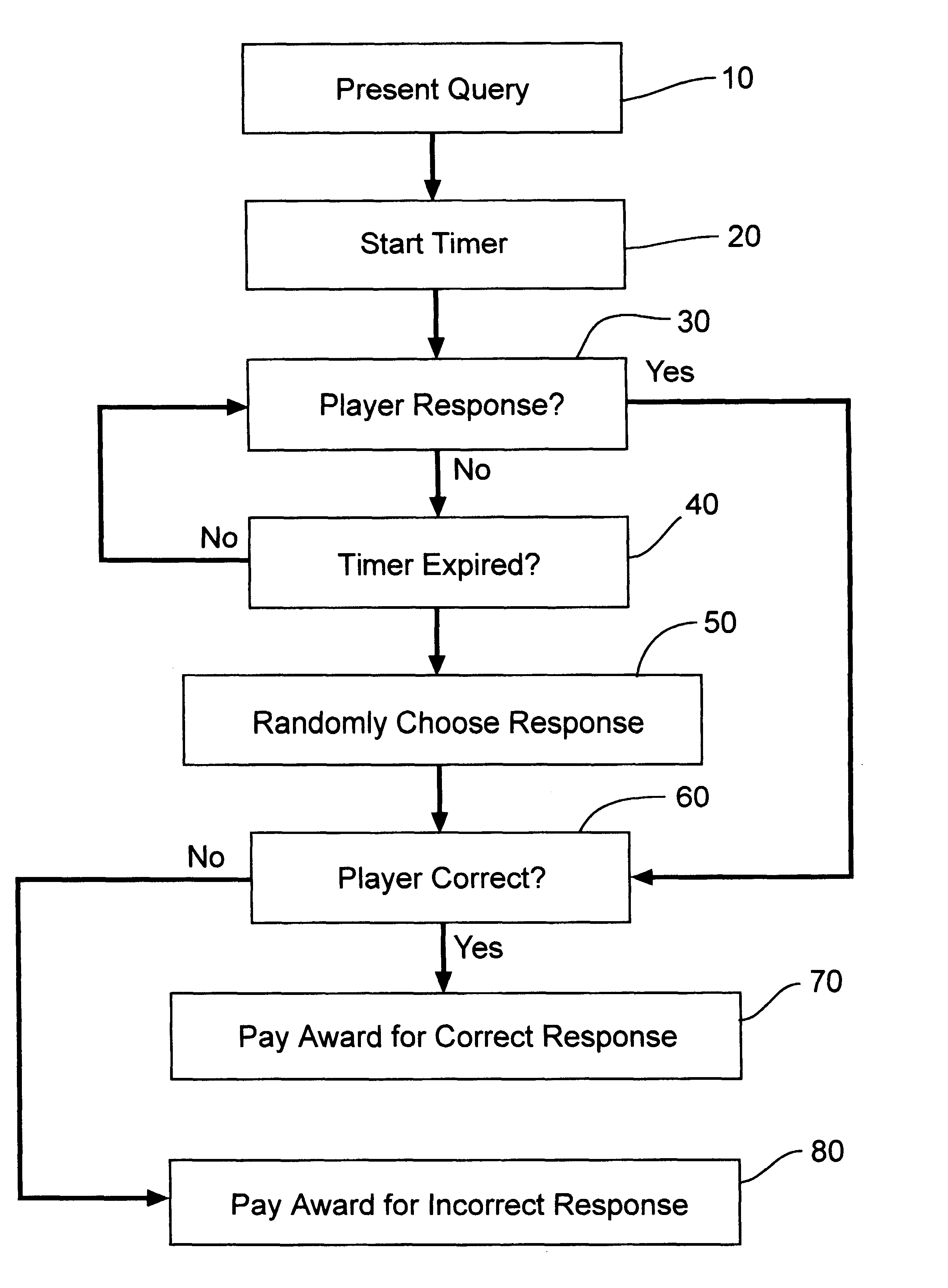
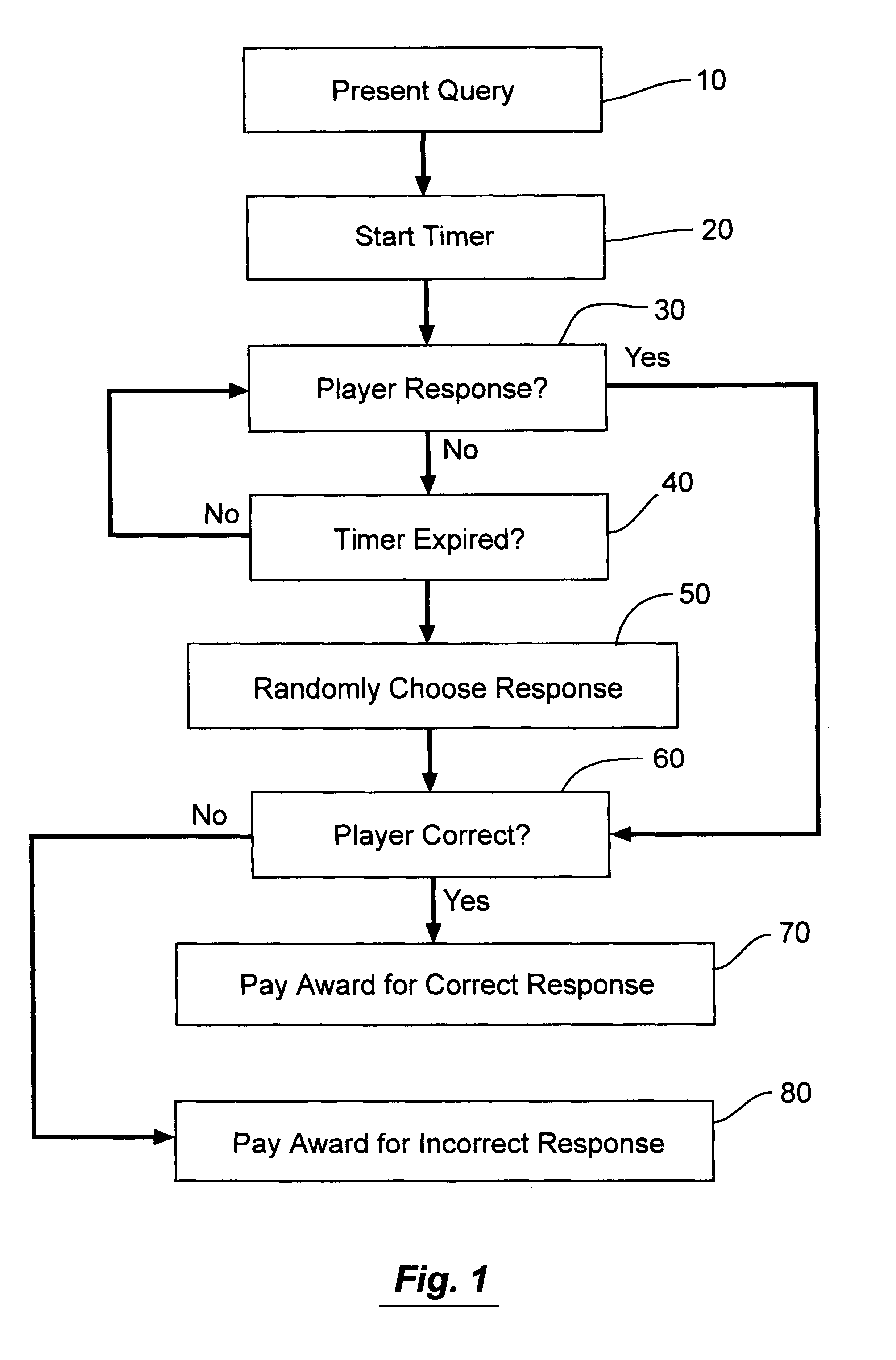
InactiveUS6752717B2Board gamesApparatus for meter-controlled dispensingCorrect responseKnowledge base
Providing, in a casino game, a time period for a player to provide a response to a query presented in the casino game or in a bonus game to the casino game. Paying a higher award for a correct response and a lower award for an incorrect response when the player answers within the time period. When no response is received, randomly choosing a response and paying the player based on the correctness of the response.
Owner:PROGRESSIVE GAMING INT +1
Epidemic preventing and controlling system for detecting and searching people with abnormal temperatures
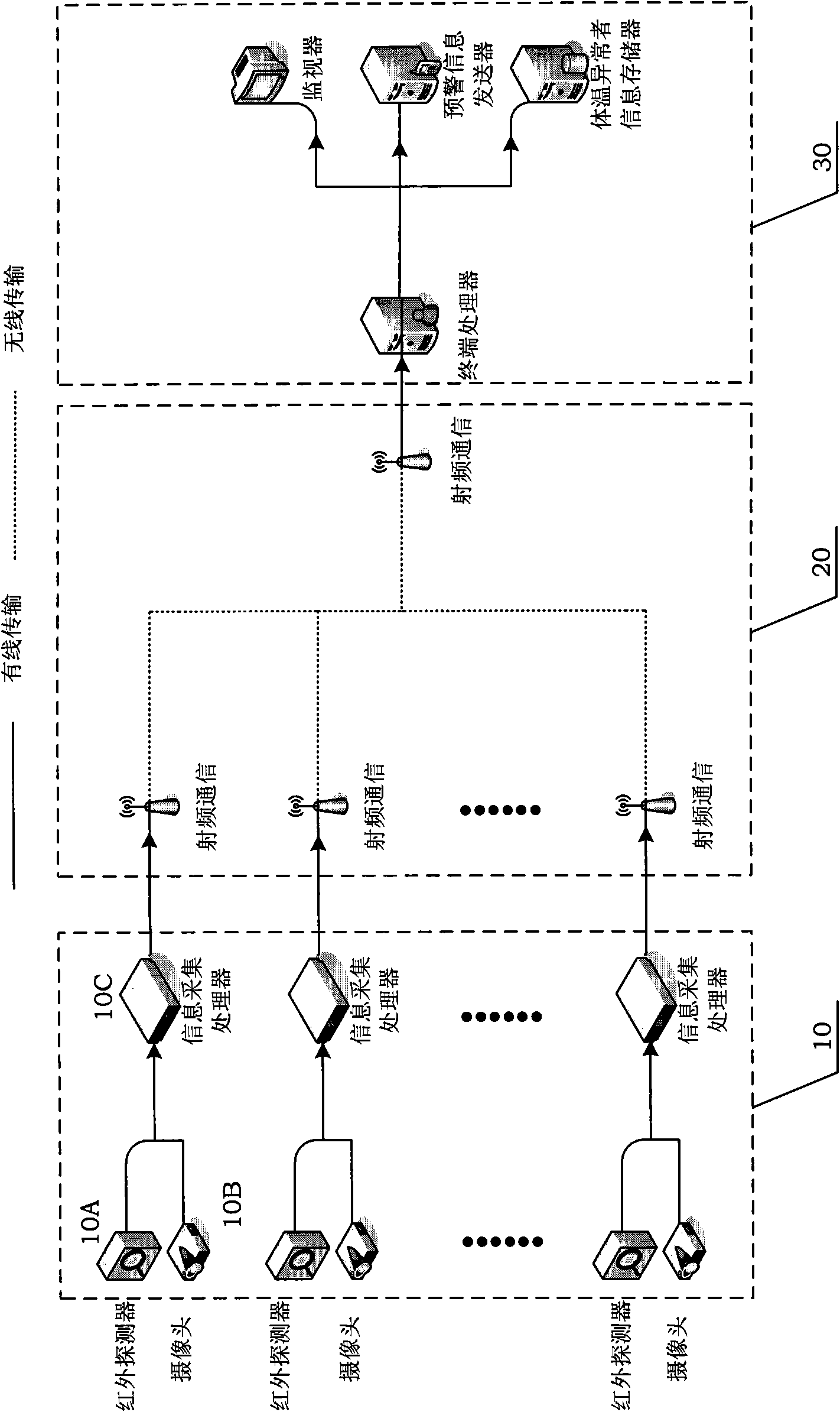
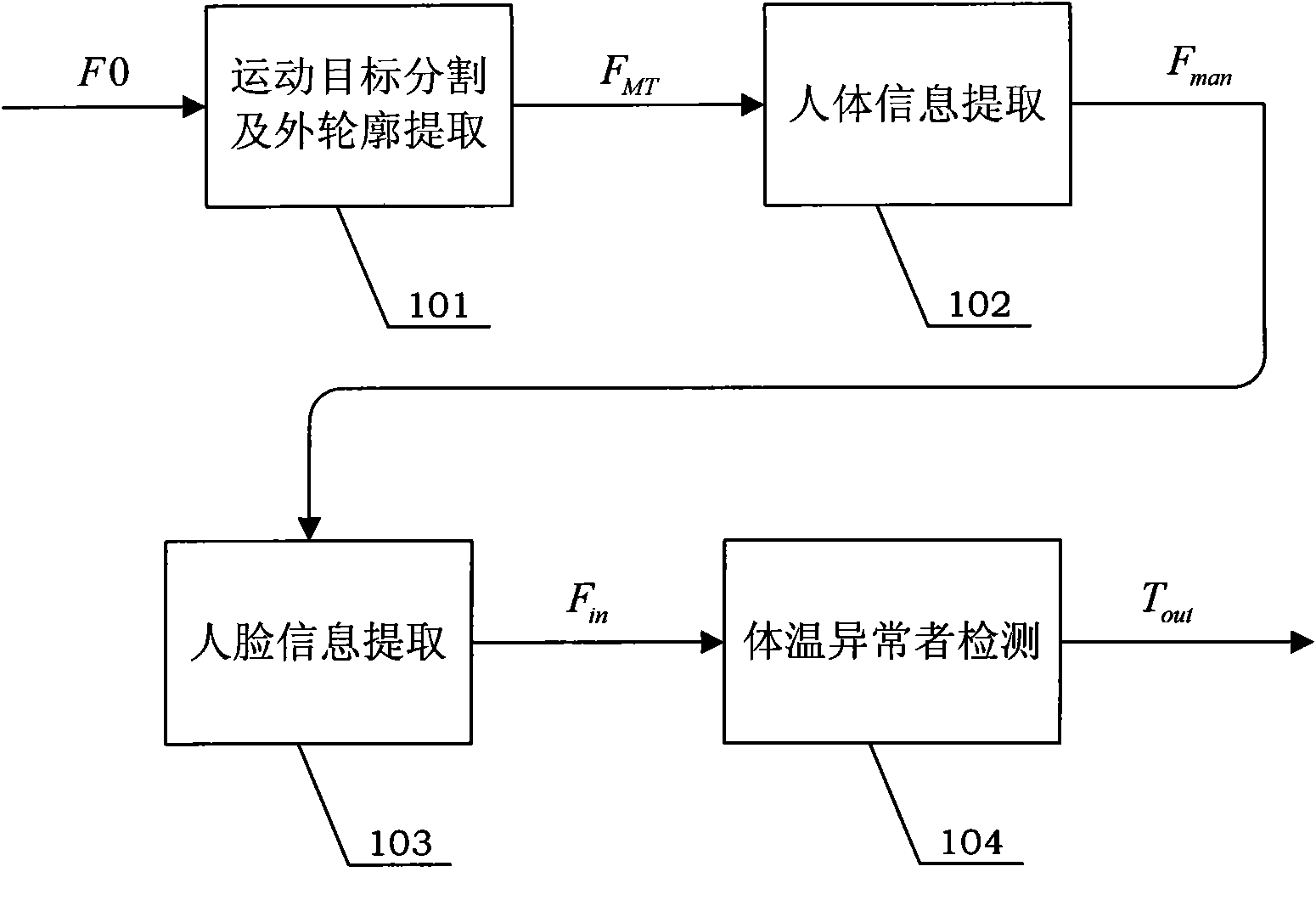
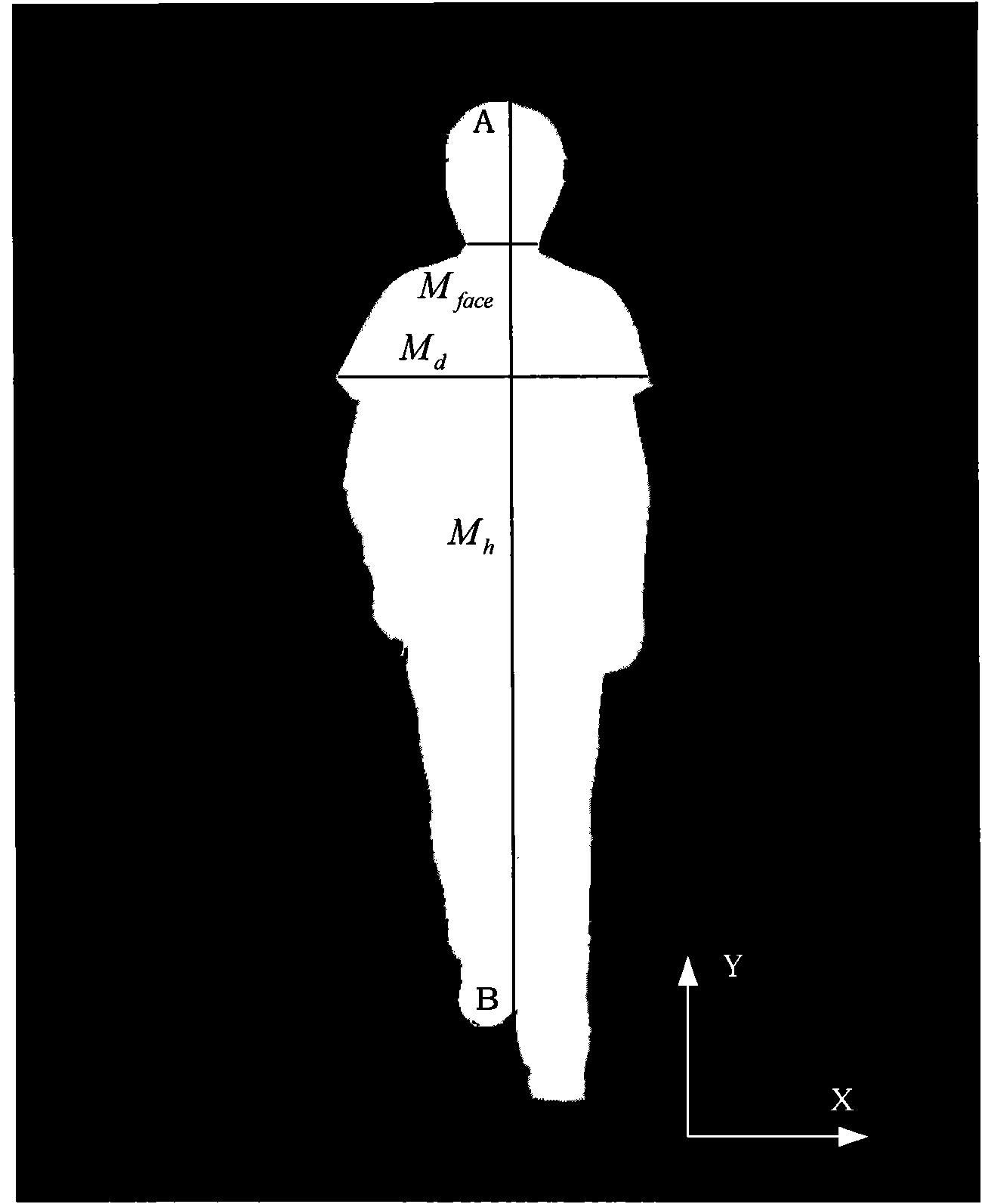
InactiveCN101999888APay attention to the epidemic situation in real timeEffective prevention and control informationDiagnostic recording/measuringSensorsScheduling instructionsComputer module
The invention discloses an epidemic preventing and controlling system for detecting and searching people with abnormal temperatures. The system comprises an information acquisition processing module, a communication processing module and a terminal processing module. The information acquisition processing module consists of an infrared detector, a camera and an information acquisition processor, wherein the infrared detector is used for acquiring face temperature information; the camera is used for acquiring face video information; and the information acquisition processor is used to perform motion target division and profile extraction on the face temperature information and the face video information so as to obtain information of people with abnormal temperatures. The communication processing module is used for transmitting the information of the people with the abnormal temperatures to the terminal processing module. The terminal processing module performs real-time dynamic searching of the people with abnormal temperatures in a monitored area and can send scheduling instruction information for giving an epidemic prompt and tracking people and the like. The system of the invention can monitor and recognize the people with abnormal temperatures in the monitored area and accordingly make a correct response and give good warning for coming epidemics, so that even epidemics outbreak, the people with abnormal temperatures can be found at first time and the epidemic preventing efficiency is improved as high as possible.
Owner:BEIHANG UNIV
Interactive neural training device
InactiveUS20050065452A1Easy to useNot easy to damageElectrotherapyPerson identificationTouch PerceptionHand movements
An apparatus and method for rehabilitating patients and assessing tactile skills in response to visual stimuli generated from a portable neural training device. The device generates a visual output to elicit tactile response (hand movement) from the patient. The device preferably automatically adjusts the difficulty of a session in response to demonstrated patient skill level (i.e. combination of correct responses, speed, and accuracy of responses). The invention evaluates and challenges the patient to control tactile response, overcome visual perception difficulties, or practice simple multi-tasking or reasoning skills. The invention also provides information which is valuable to those administering the rehabilitation program or assessing patient skill and / or progress. By way of example the neural training device is described with an embodiment having discrete fixed keys and an embodiment utilizing a touch sensitive display screen.
Owner:INTERACTIVE NEURO TECH
Method and device for transmitting response message
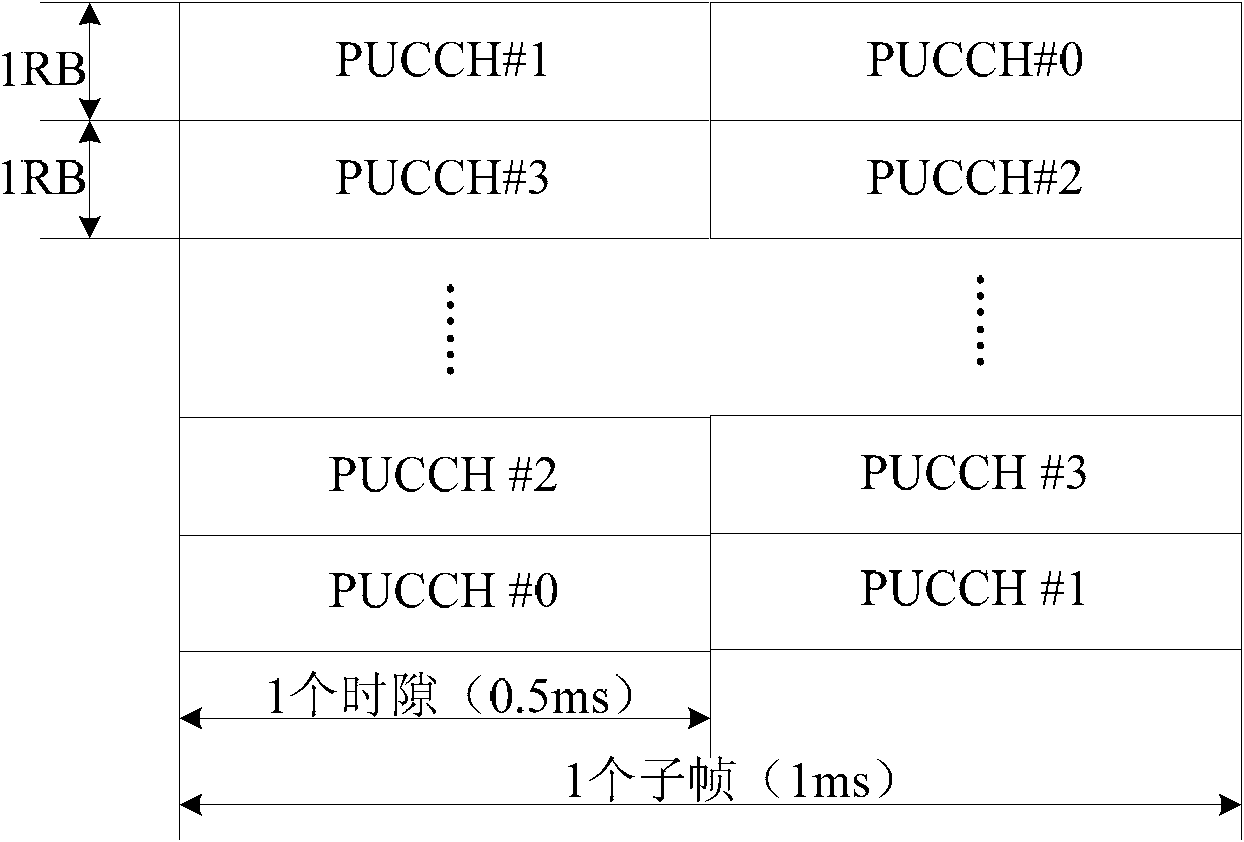
InactiveCN101989898ASolve the problem that the sending of reply message cannot be completedImprove performanceError prevention/detection by using return channelControl channelCorrect response
The invention provides method and device for transmitting a response message. The method comprises the steps that: the type of a current system is determined when a terminal needs to transmit a response message, wherein the response message can be a correct response message ACK or a wrong response message NACK; the type of the system comprises a frequency division duplex FDD system and a time division duplex TDD system; the terminal determines the feedback mode of the response message, wherein the feedback mode consists of a channel selection mode and a physical uplink control channel PUCCH format 3; and the terminal can determine the PUCCH resource of the response message according to the type of the system and the feedback mode, and then transmits the response message by using the determined PUCCH resource. By the method and the device, the problem that a UE (user equipment) can not transmit the response message in some cases is overcome, and the performance of the system is improved.
Owner:ZTE CORP
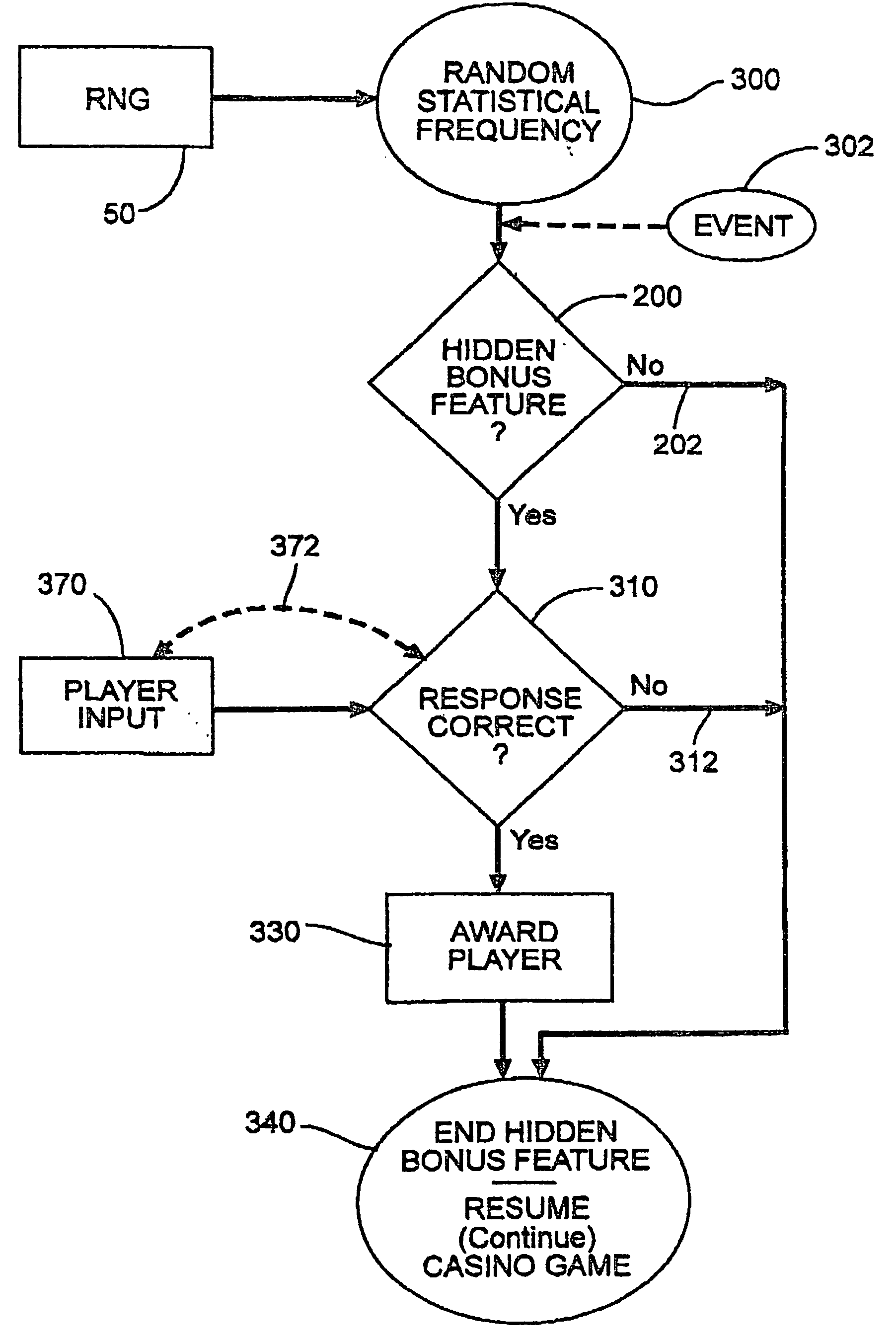
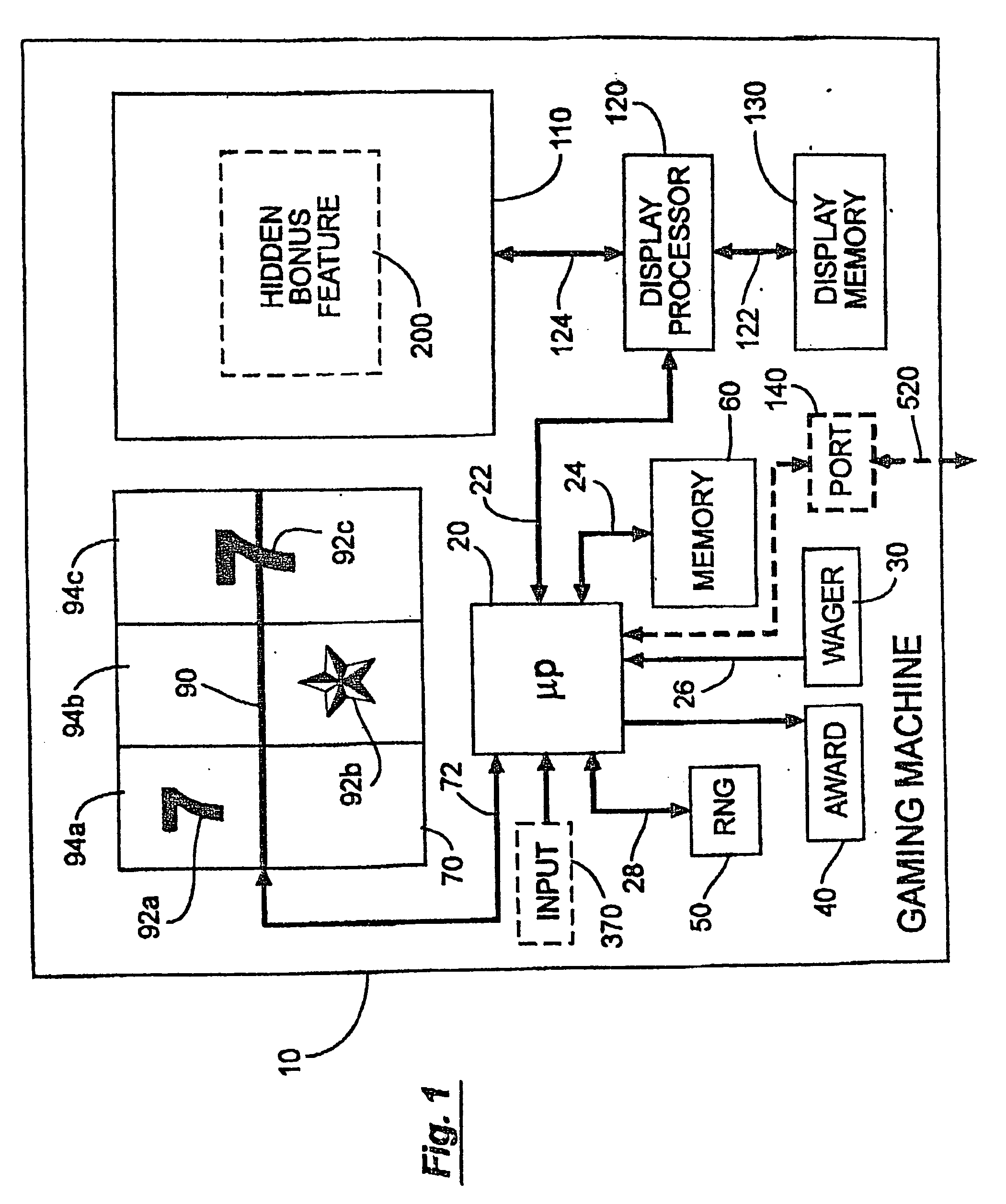
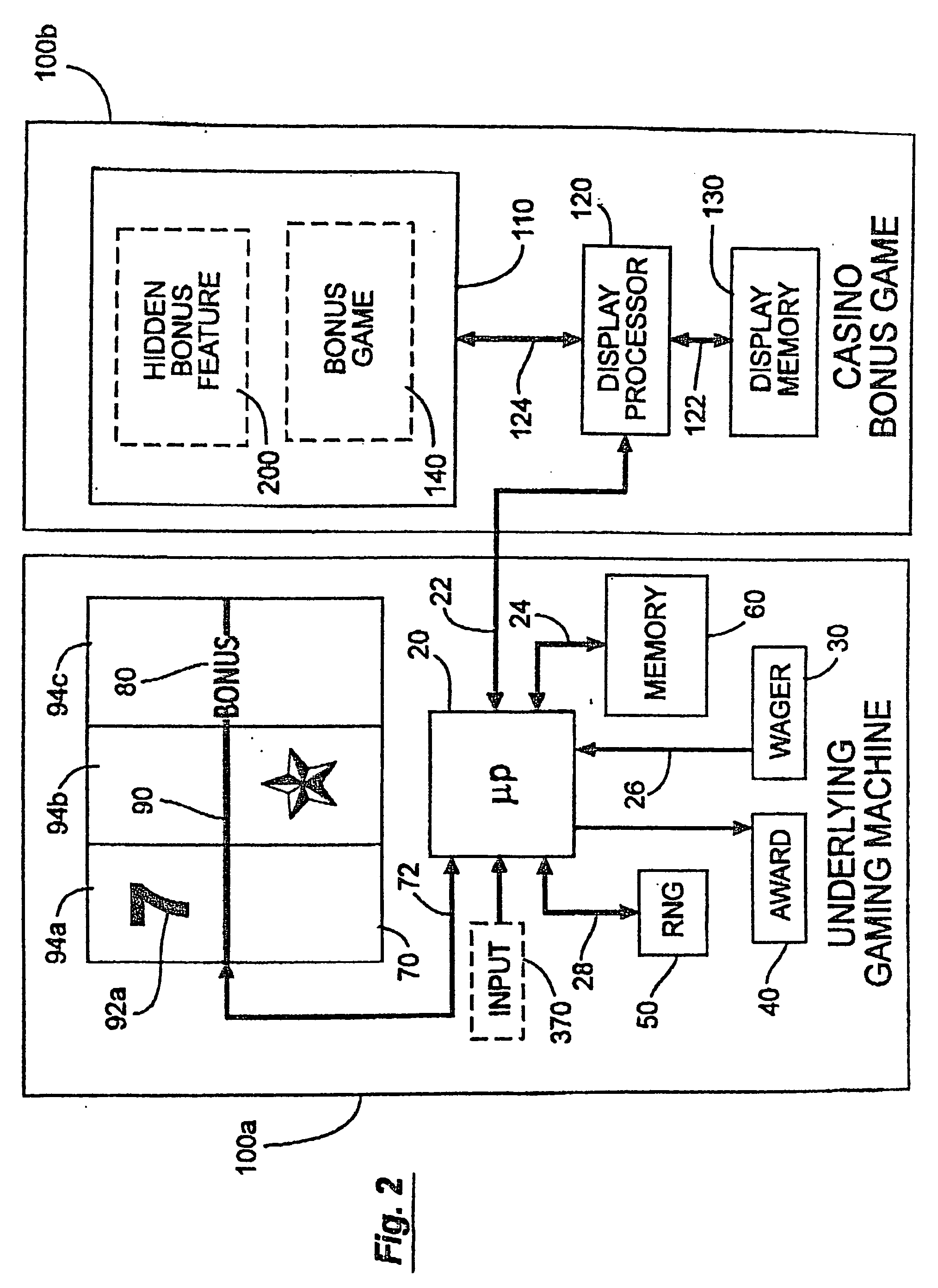
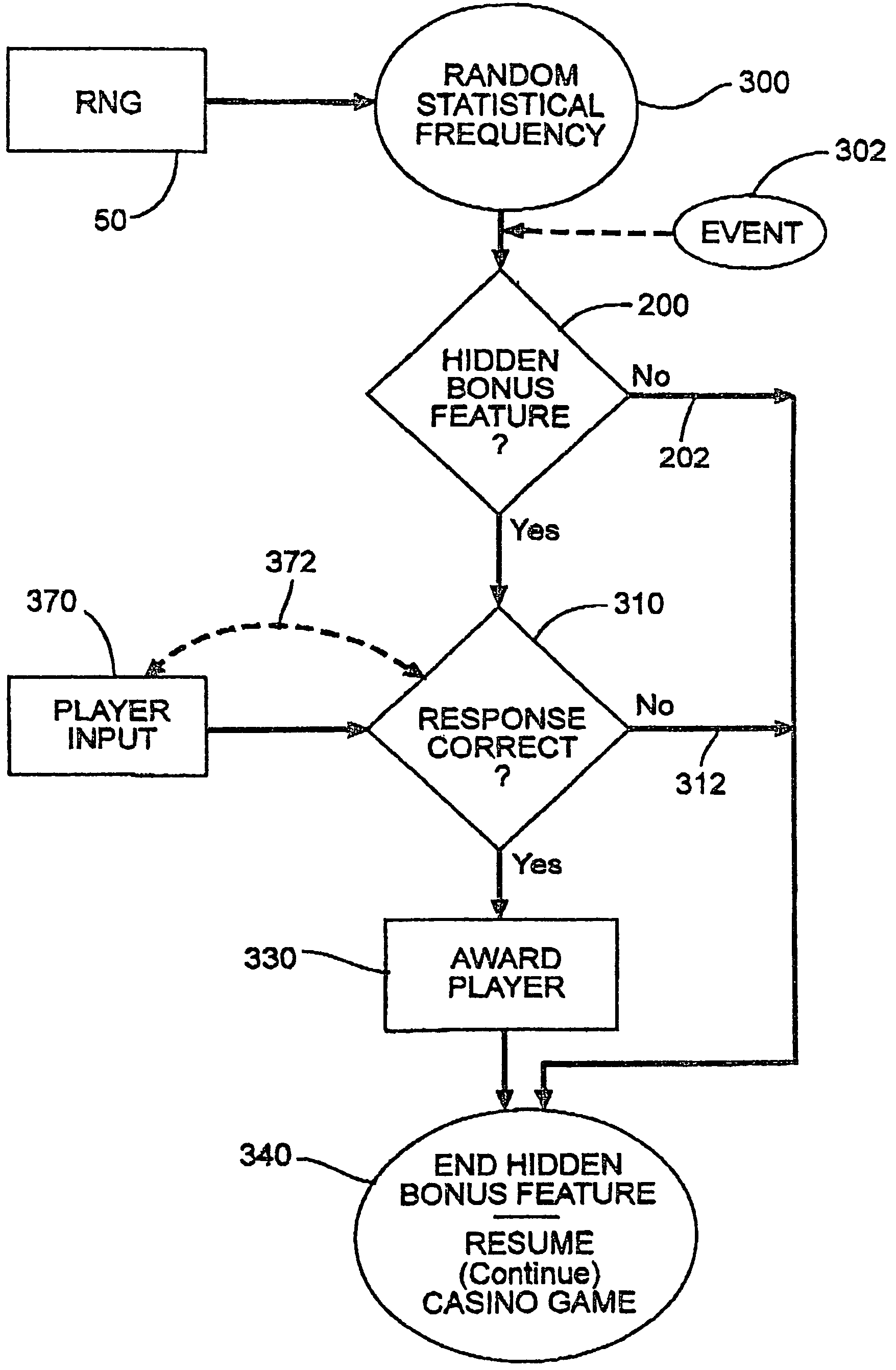
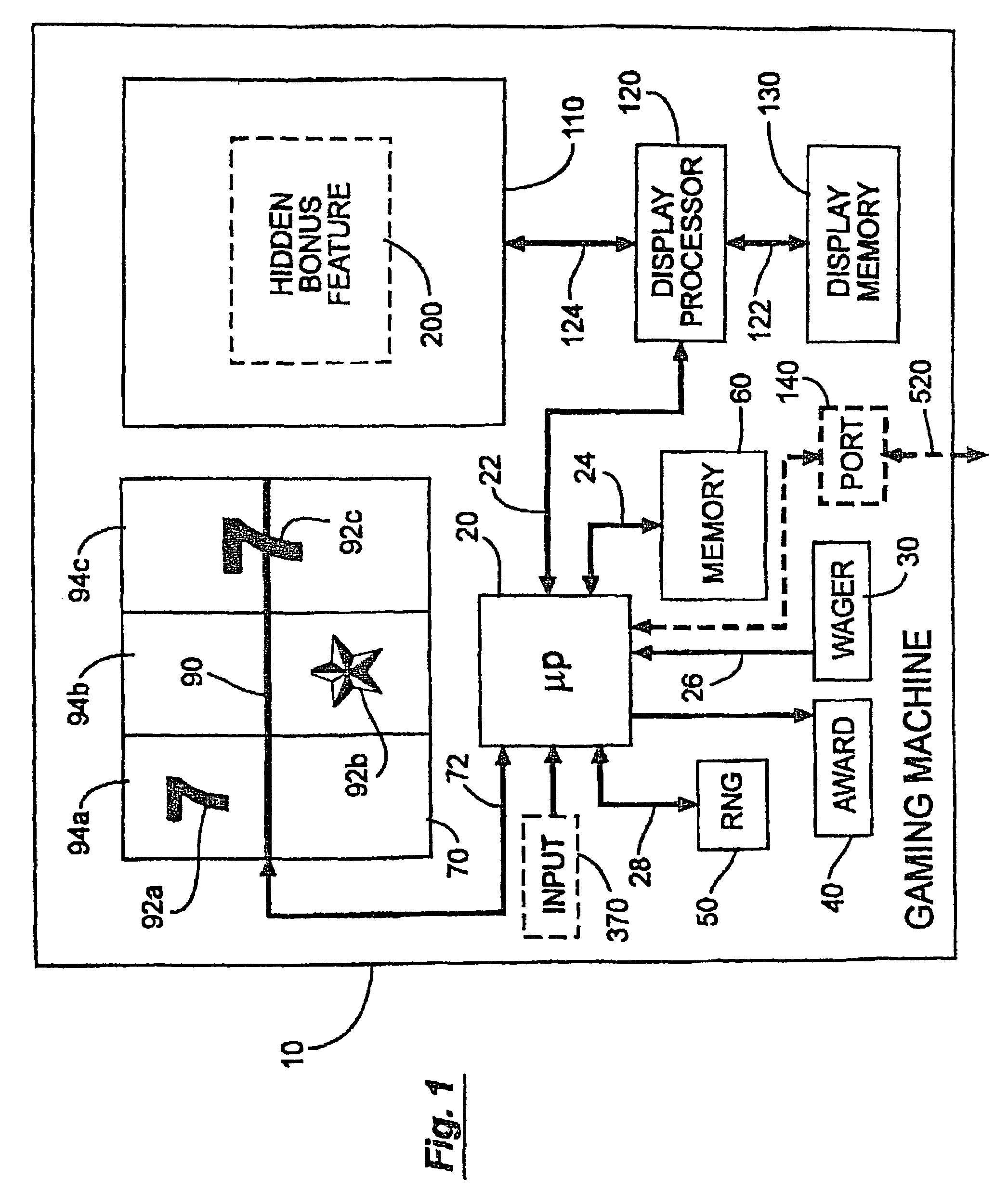
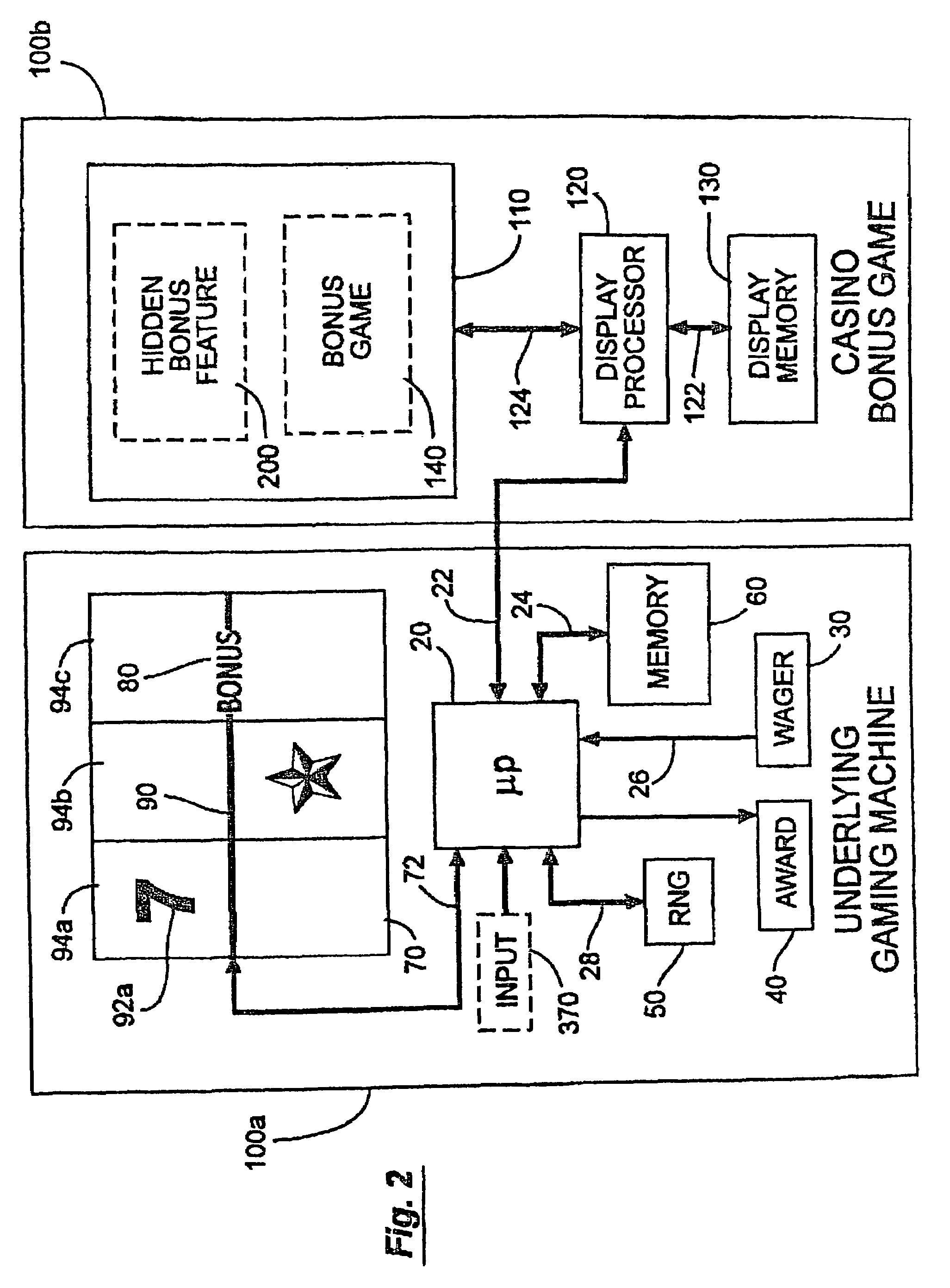
Casino game with hidden bonus feature
InactiveUS20050282619A1Board gamesApparatus for meter-controlled dispensingCorrect responseArtificial intelligence
During play of a casino game a hidden bonus feature unknown to the player occurs as no separate indicator is activated. The occurrence of the hidden bonus feature may be at a random statistical frequency or other event. When the player inputs a correct response to the hidden bonus feature, the player receives an additional award. If a correct response is not received or if the hidden bonus feature is ignored, the player does not receive any further award. The hidden bonus feature does not affect the outcome of the play of the casino game.
Owner:PROGRESSIVE GAMING INT +1
System and method for strong access control to a network
ActiveUS7310813B2Digital data processing detailsAnalogue secracy/subscription systemsCorrect responseData storing
A system and method for strong access control to a network is provided. An access control server and authentication device are provided for controlling access to a network. The access controlled by the access control server may include network protocols, network resources, and electronic devices that may be coupled to the network. Network resources may include data stored on the network. The access control server may grant access to the network to a user based upon a correct response received from an authentication device assigned to the user. The user may be able to access only selected data that may be determined by an access level assigned to the authentication device. Upon authentication, the authentication device must remain active to maintain a network session. The authentication device becomes inactive when it is deactivated, uncoupled from the network, or in any mode in which the device cannot produce a response to the access control server. The network session ends when it is determined that the authentication device is inactive.
Owner:AUTHENEX
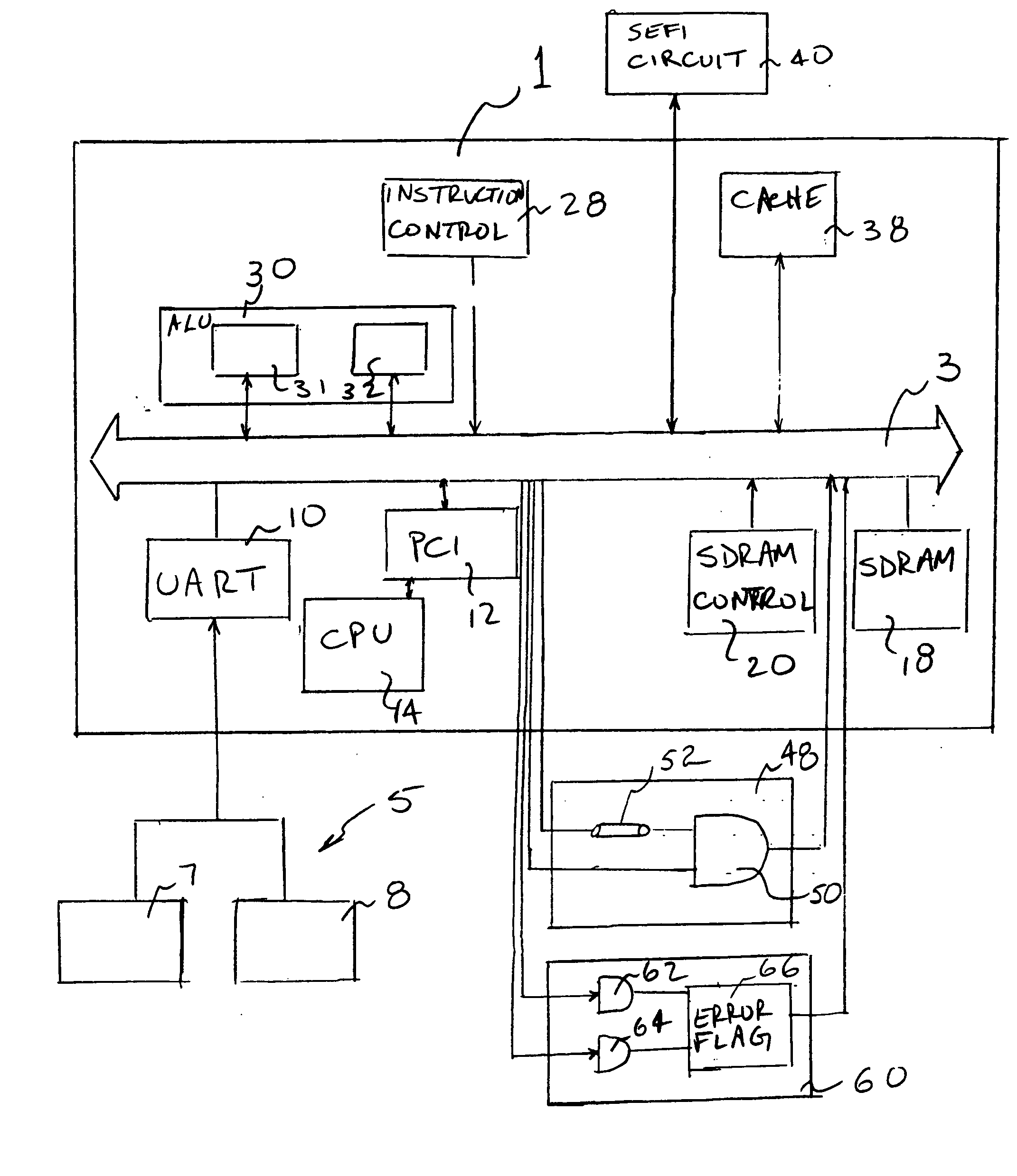
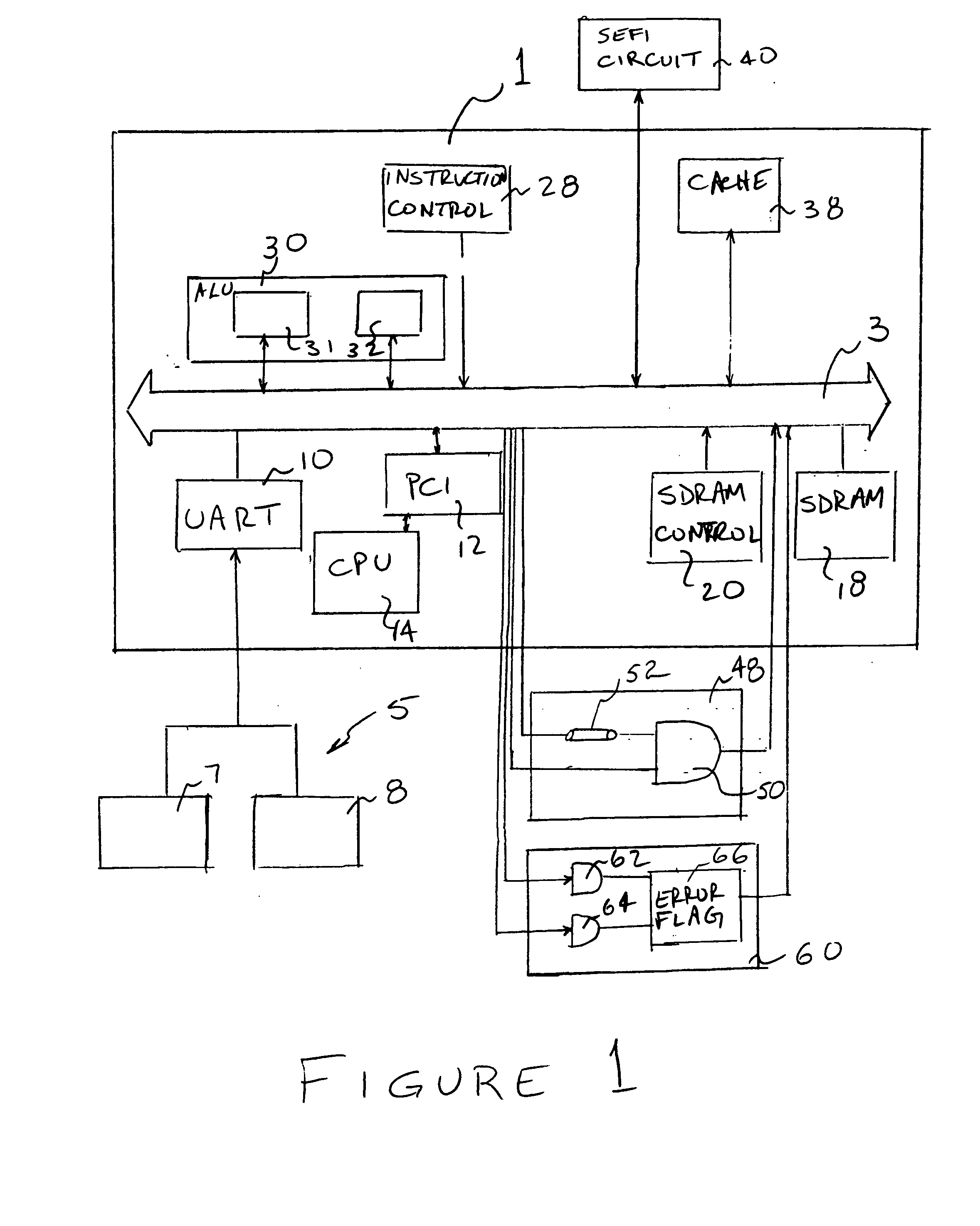
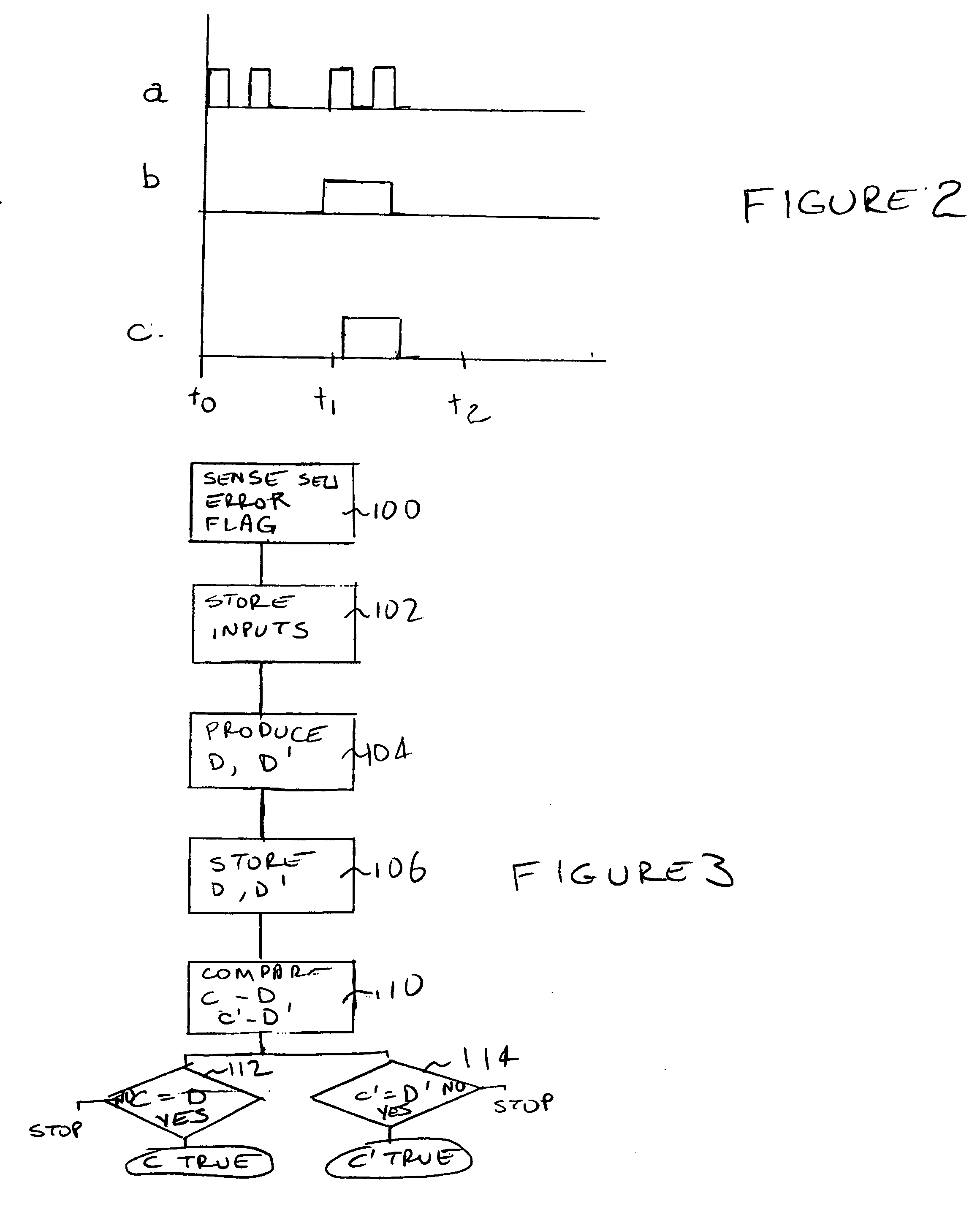
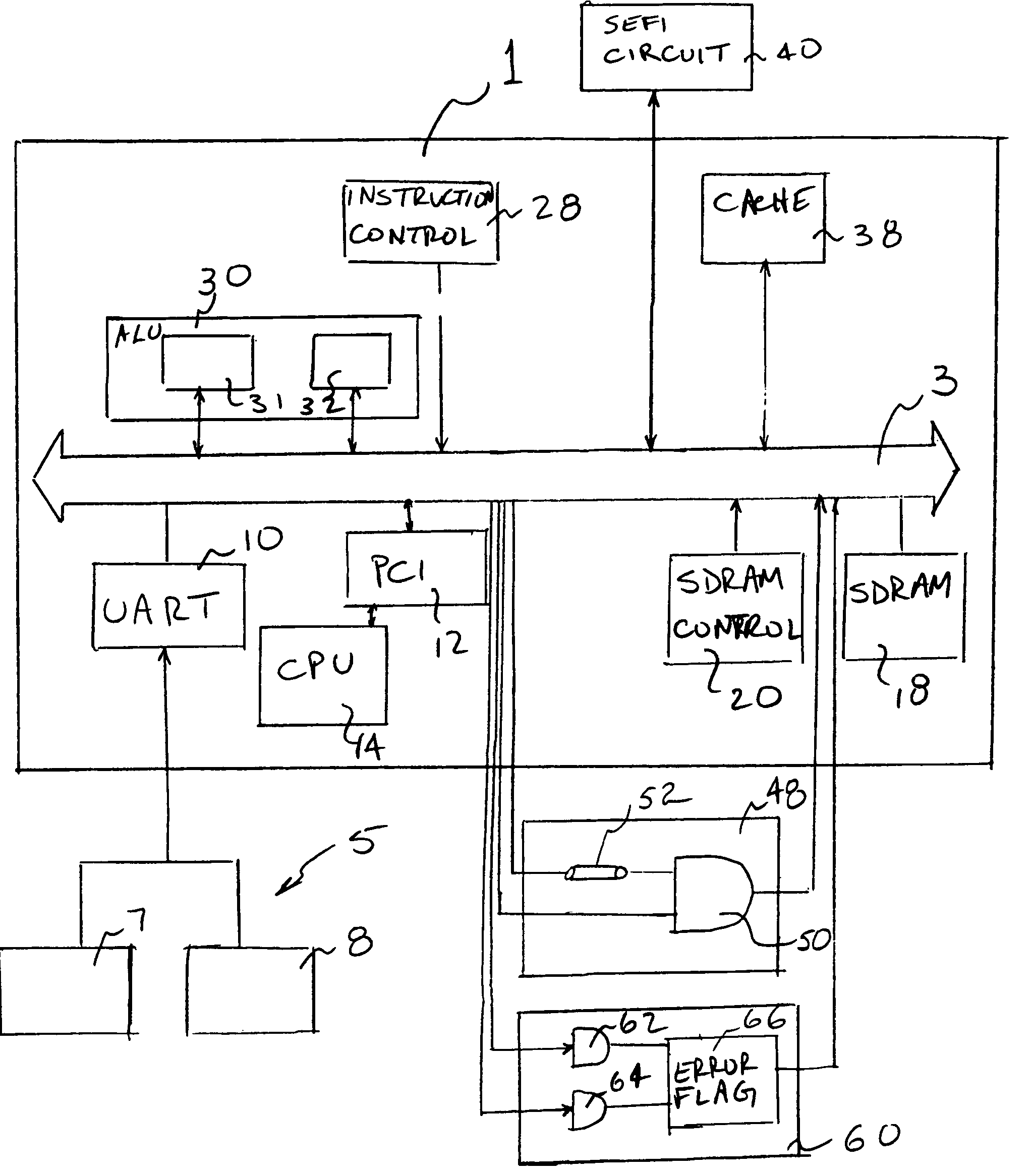
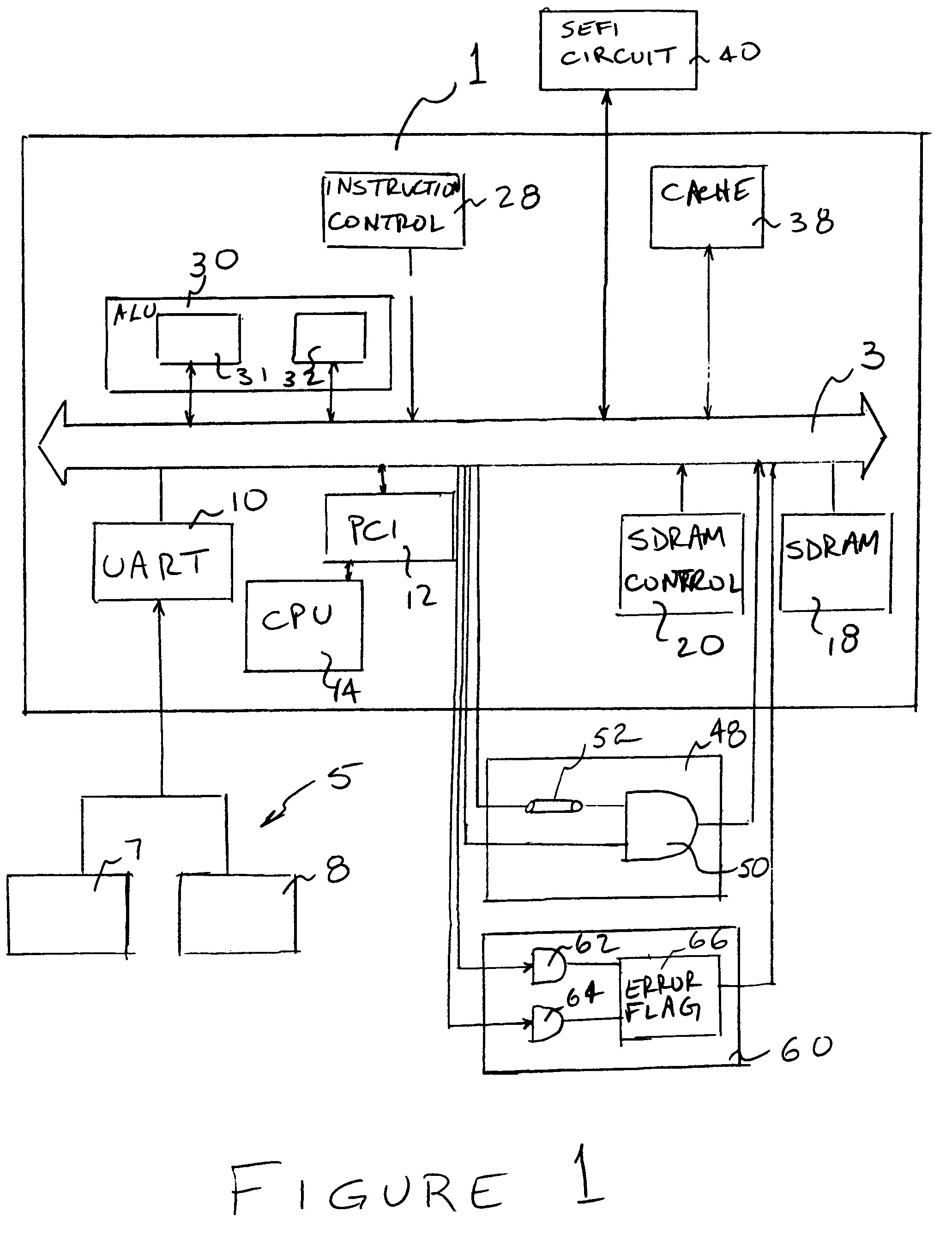
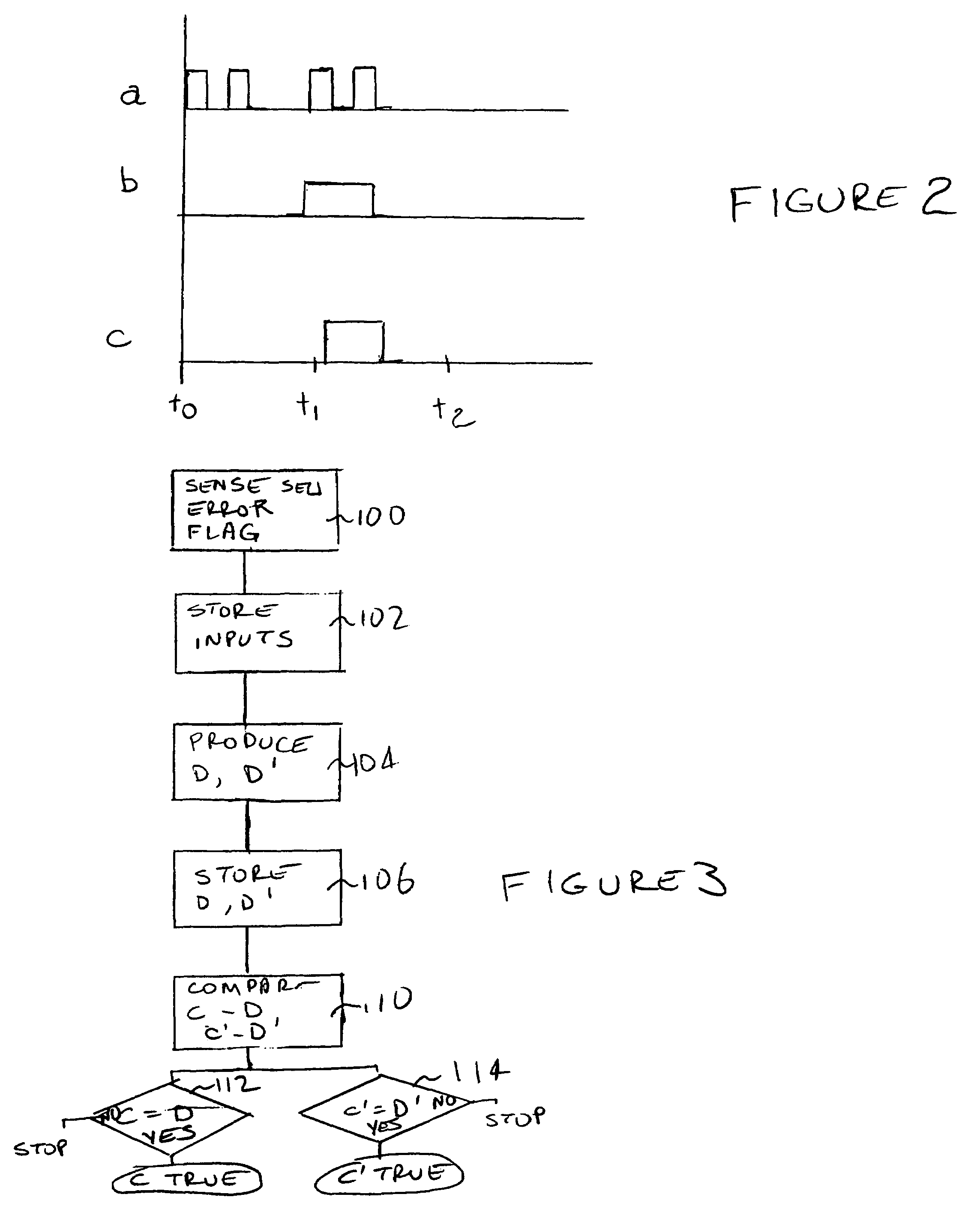
SEU and SEFI fault tolerant computer
A non-hardened processor is made fault tolerant to SEUs and SEFIs. A processor is provided utilizing time redundancy to detect and respond to SEUs. Comparison circuitry is provided in a radiation hardened module to provide special redundancy with the need to run additional processors. Additionally, a hardened SEFI circuit is provided to periodically send a signal to the process which, in the case of a processor not in the SEFI state, initiates production by the processor of a “correct” response. If the correct response is not received within a particular time window, the SEFI circuit initiates progressively severe actions until a reset is achieved.
Owner:SPACE MICRO A CORP OF DELAWARE
Method for awarding a player responding to a hidden bonus game feature that interrupts casino game play
InactiveUS7247096B2Board gamesApparatus for meter-controlled dispensingCorrect responseArtificial intelligence
Owner:PROGRESSIVE GAMING INT +1
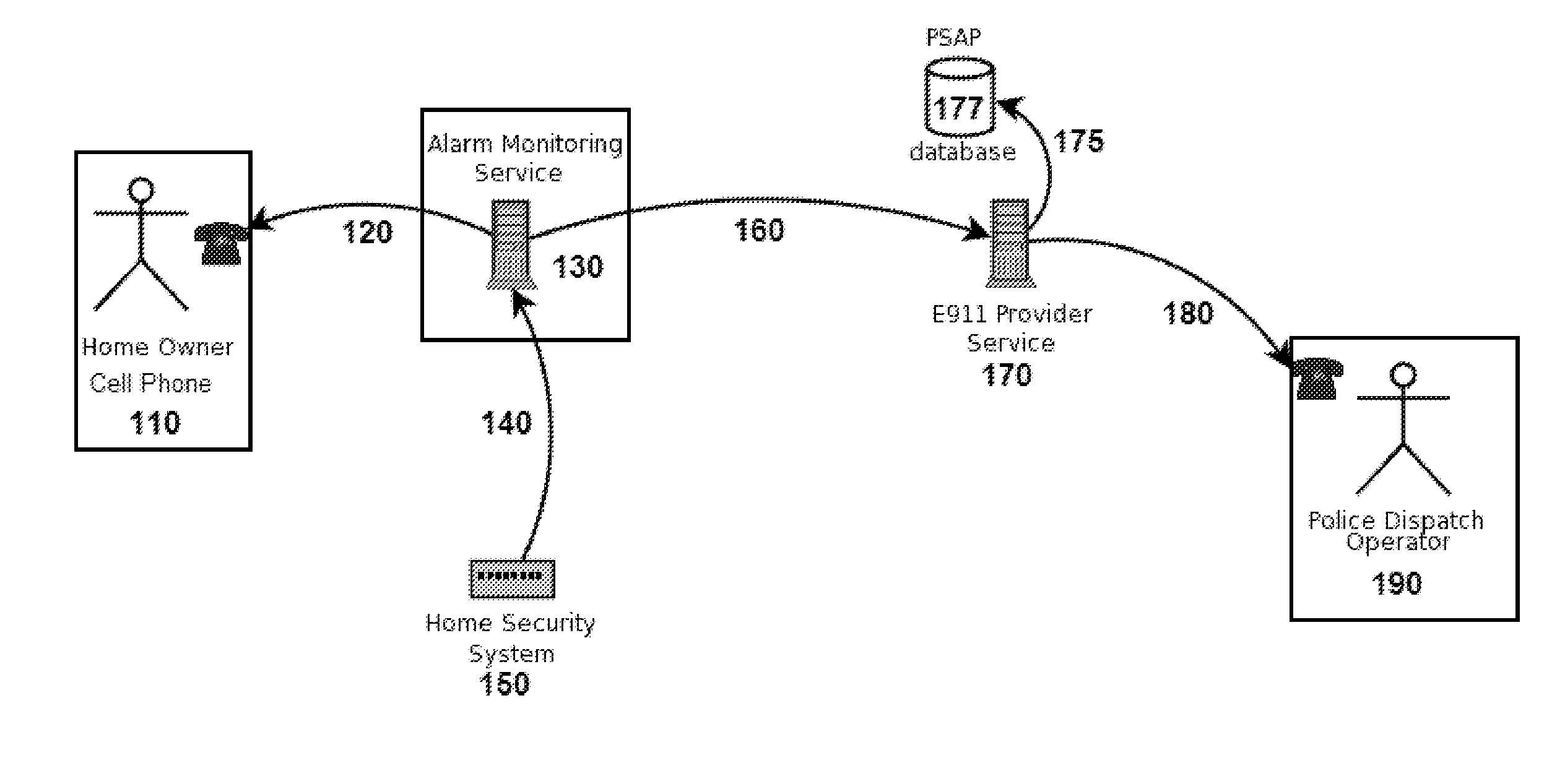
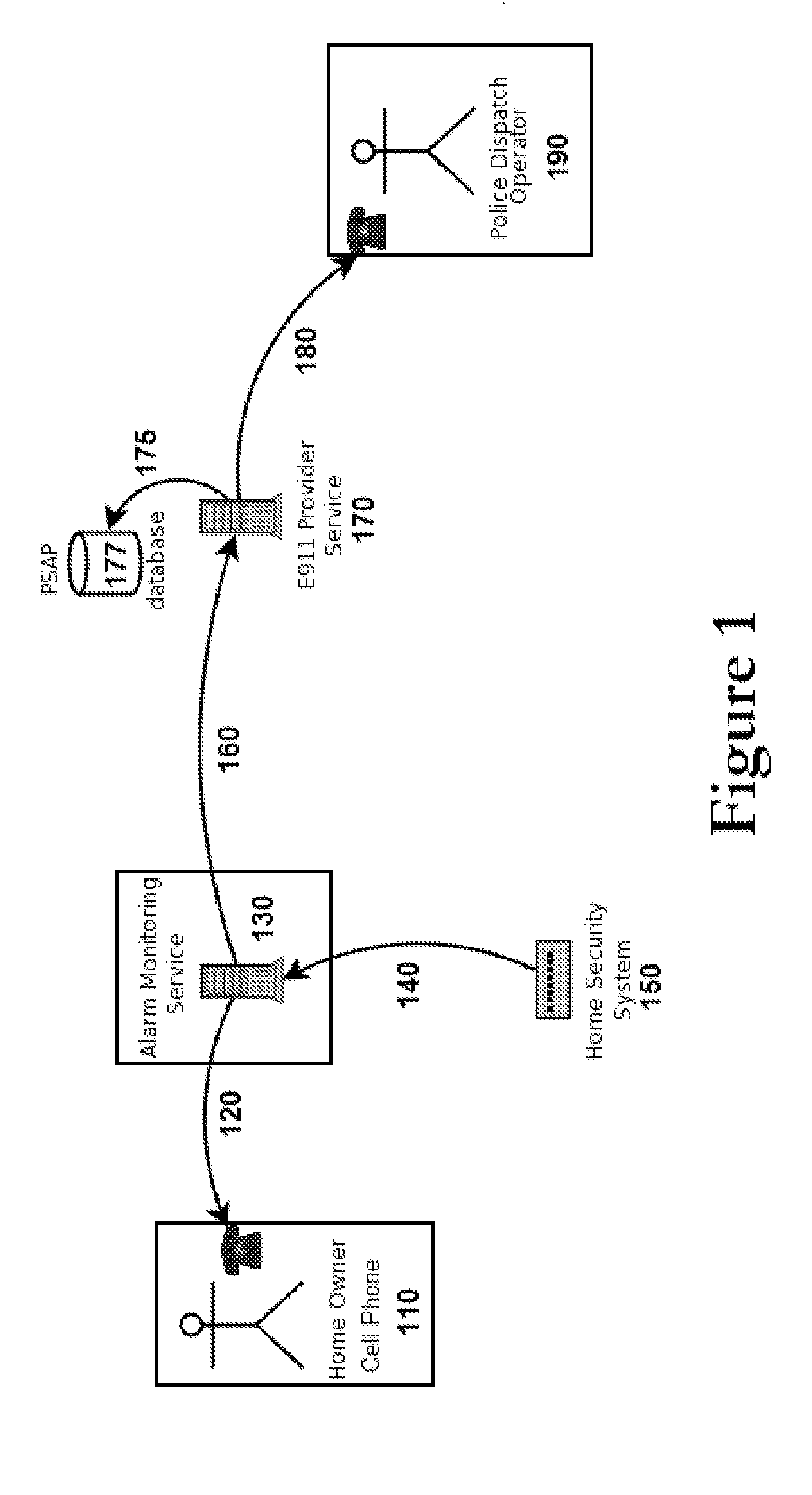
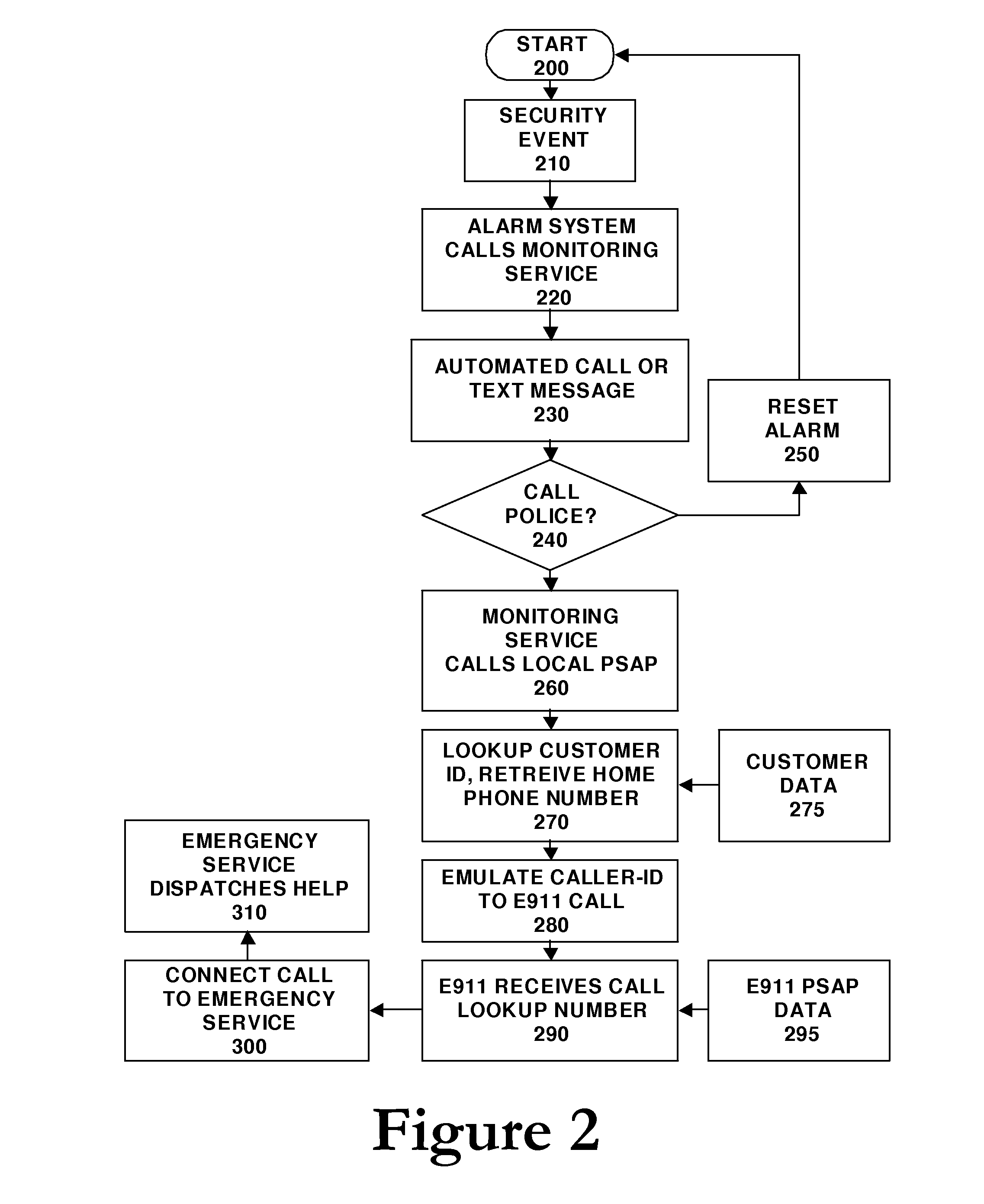
Enhanced 911 notification for internet enabled alarm system
ActiveUS20080118039A1For direct connectionTelephonic communicationNetwork connectionsThe InternetEngineering
The present invention allows an alarm monitoring service to ally with a PSAP provider to allow our customers to direct connect to the 911 center responsible for their home, but no matter where the customer calls from. When an alarm monitoring company or middleware provider's automatic notification function calls the customer to report an alarm, the customer can connect directly to the local 911 even when traveling, if needed. The alarm monitoring company contacts the customer if an alarm event occurs and offers the customer the opportunity to connect with the 911 call center for their home. If the customer indicates they want to call 911, the call is routed to the correct PSAP center, with the customers home Caller ID number emulated for the call. In this manner, the PSAP center can determine, from the emulated Caller ID data, the correct response agency that is local to the customer's home.
Owner:NUMEREX CORP
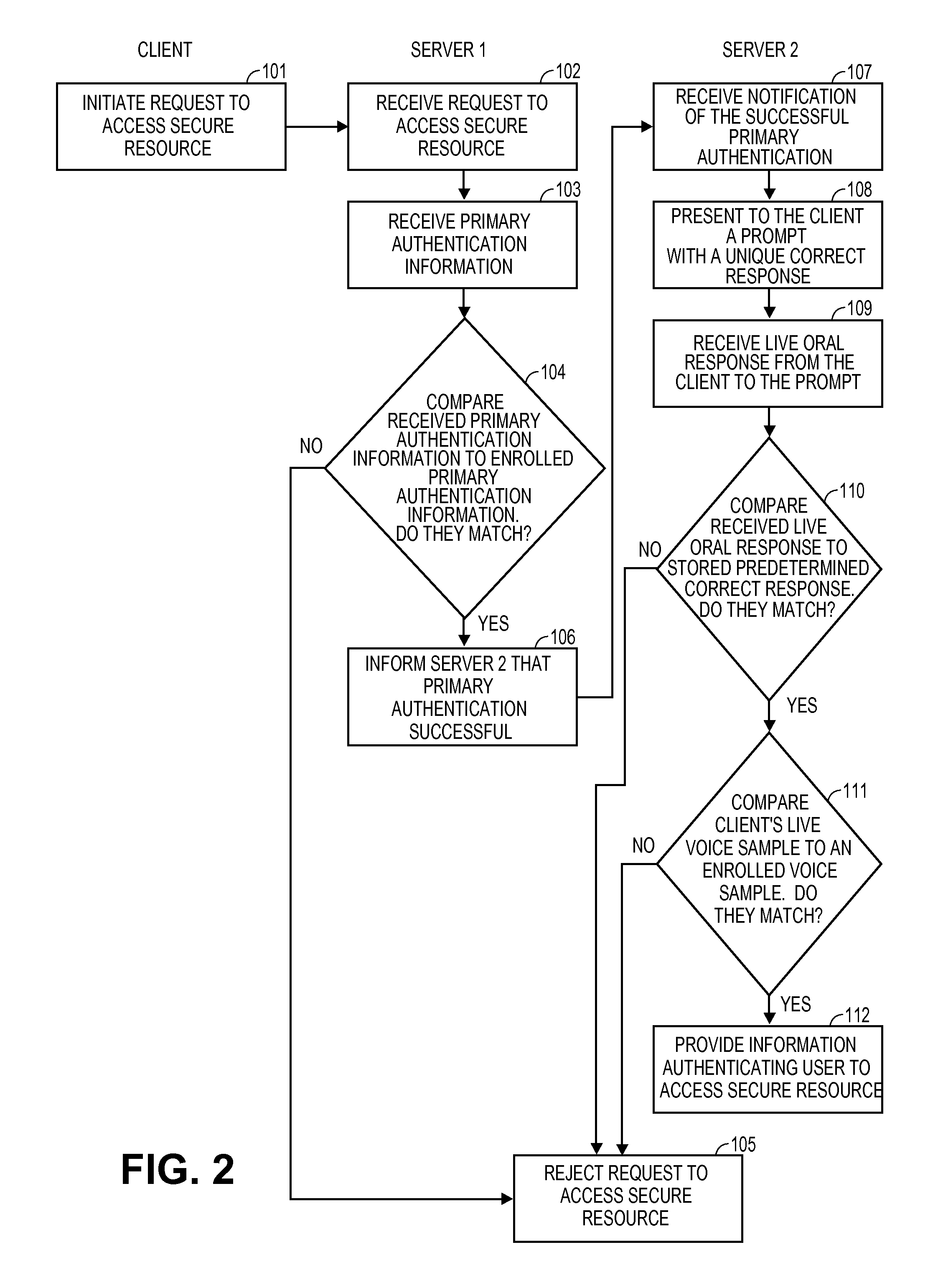
Computer program, method, and system for voice authentication of a user to access a secure resource
InactiveUS20120253810A1Prevent imitationDigital data authenticationSpeech recognitionLive voiceCorrect response
Authenticating a purported user attempting to access a secure resource includes enrolling a user's voice sample by requiring the user to orally speak preselected enrollment utterances, generating prompts and respective predetermined correct responses where each question has only one correct response, presenting a prompt to the user in real time, and analyzing the user's real time live response to determine if the live response matches the predetermined correct response and if voice characteristics of the user's live voice sample match characteristics of the enrolled voice sample.
Owner:PHONEFACTOR
Secure cloud service construction method and device based on mimic defense
InactiveCN107454082AGuaranteed to provide the correctEnhanced endogenous securityTransmissionResource poolGuideline
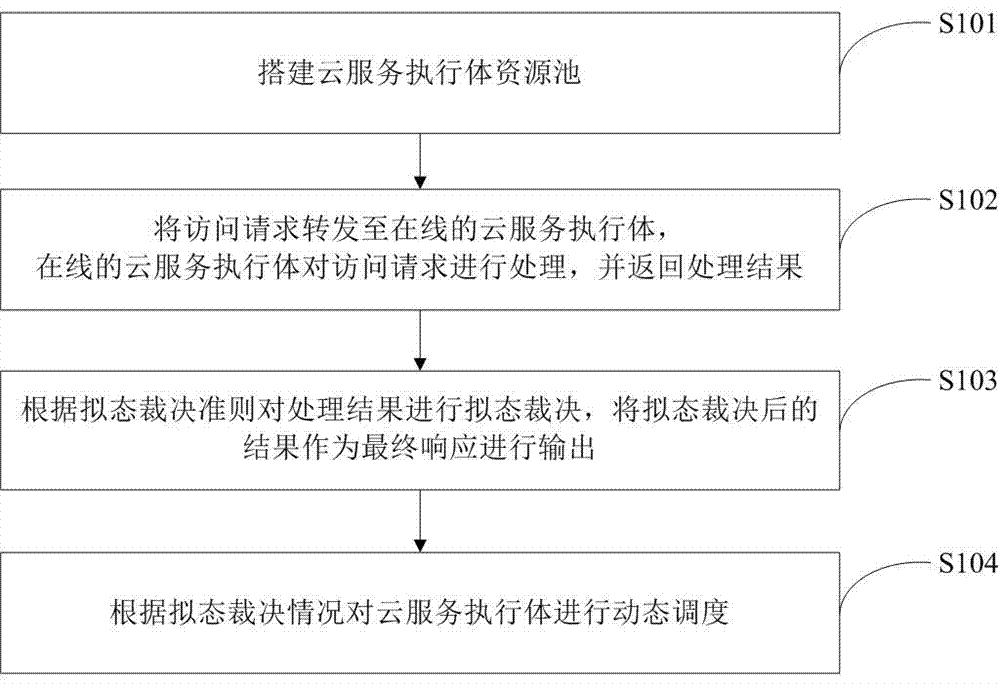
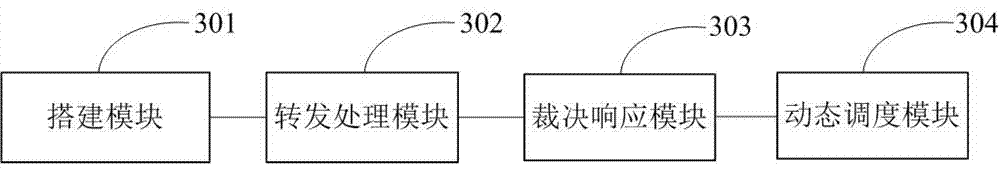
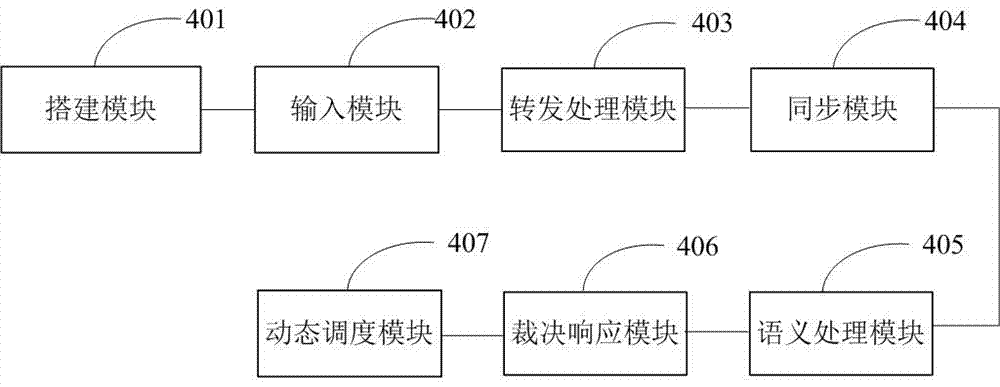
The invention belongs to the technical field of network space security, and especially relates to a secure cloud service construction method and device based on mimic defense. The secure cloud service construction method based on mimic defense includes the following steps: a cloud service executor resource pool is built; an access request is forwarded to online cloud service executors, and the online cloud service executors process the access request and return processing results; the processing results are decided in a mimic way according to the mimic decision criterion, and the results after mimic decision are output as final response; and the cloud service executors are scheduled dynamically according to the mimic decision condition. A secure cloud service construction device based on mimic defense includes a building module, a forwarding and processing module, a decision response module, and a dynamic scheduling module. The invention provides a secure cloud service construction method and device based on mimic defense in order to solve security problems brought by the dependence on a single cloud service, to improve the reliability and security of cloud services, and to ensure correct response to an access request.
Owner:THE PLA INFORMATION ENG UNIV
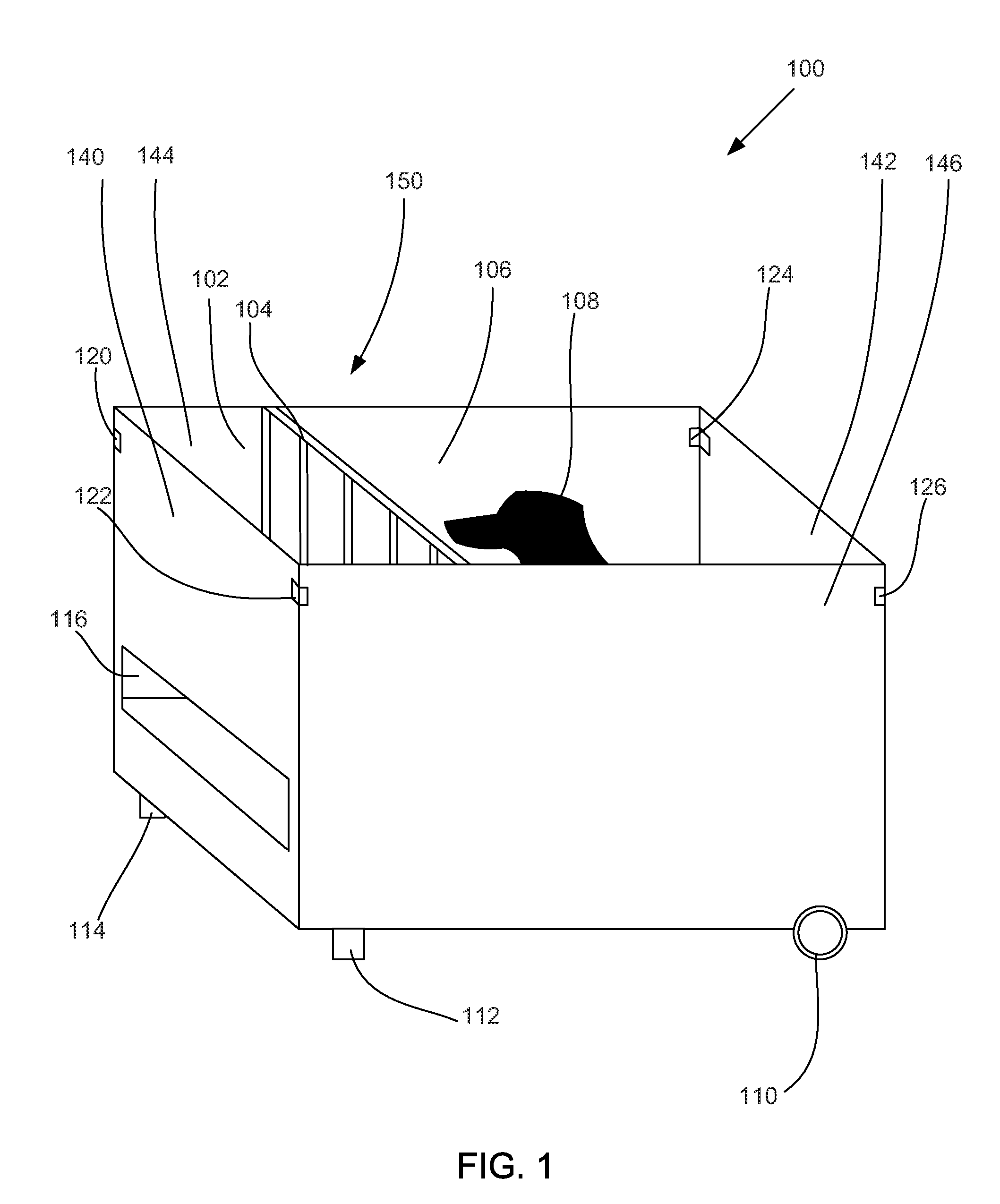
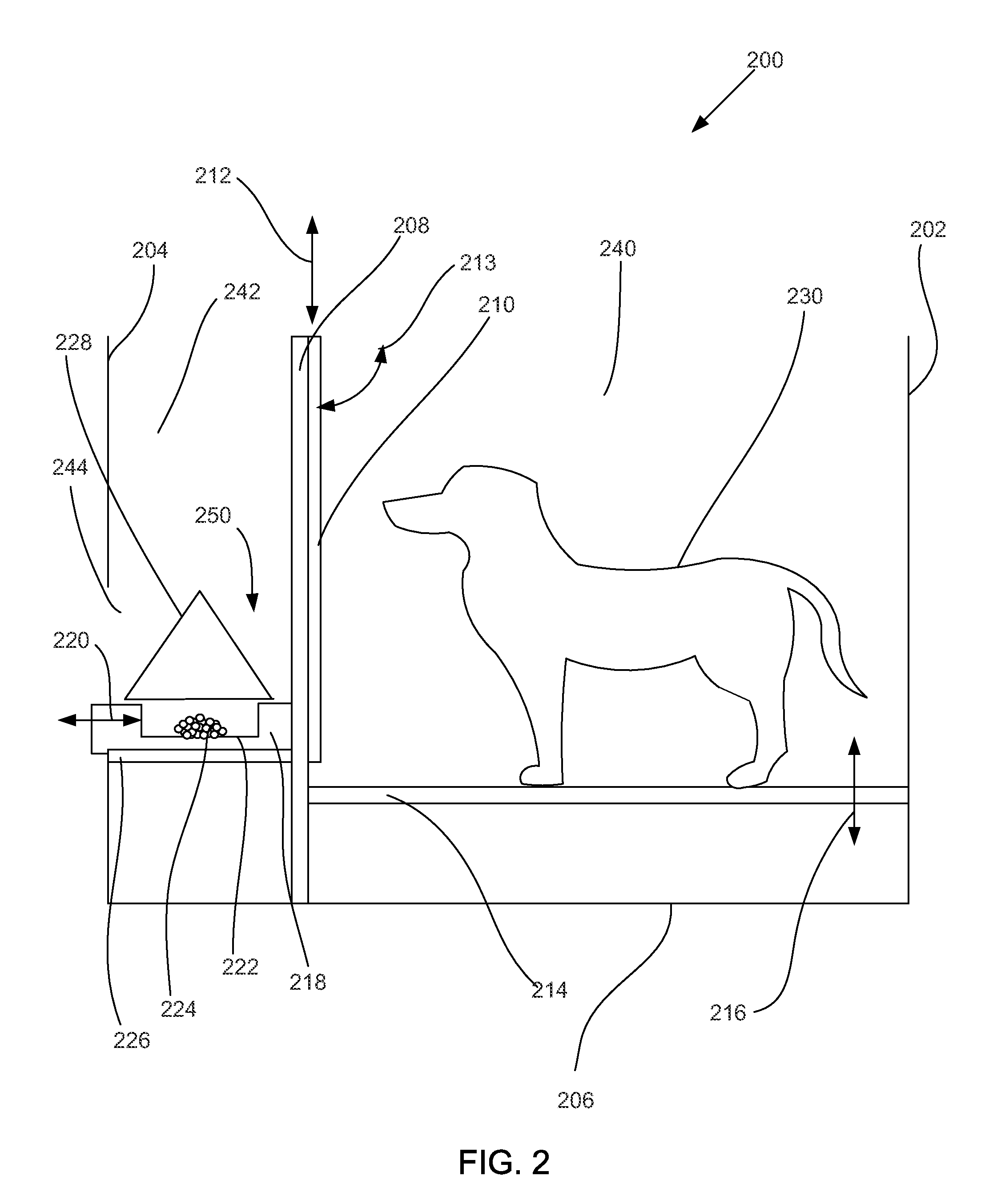
System and method for cognitive assessment and training of an animal
InactiveUS20120077159A1Stabilization of cognitive performanceAnimal housingElectrical appliancesCorrect responseAnimal subject
An apparatus and method for cognitive assessment and training of an animal subject. A subject is placed in a testing environment, such as a subject chamber of a cognitive assessment and training apparatus. At least one cognitive assessment and training session comprising a plurality of trials is performed. In a trial, a trial assembly is prepared at a first level. The trial assembly includes at least one stimuli and a reward, where a target stimuli of the at least one stimuli is associated with the reward. The subject is allowed access to the stimuli. When a correct response is determined from the subject, the subject is allowed to access a reward associated with the correct response. The subject is advanced to trials at a next level when a learning criterion is reached. At least one cognitive assessment score is generated based on the plurality of trials and the at least one cognitive assessment and training session.
Owner:CANCOG TECH
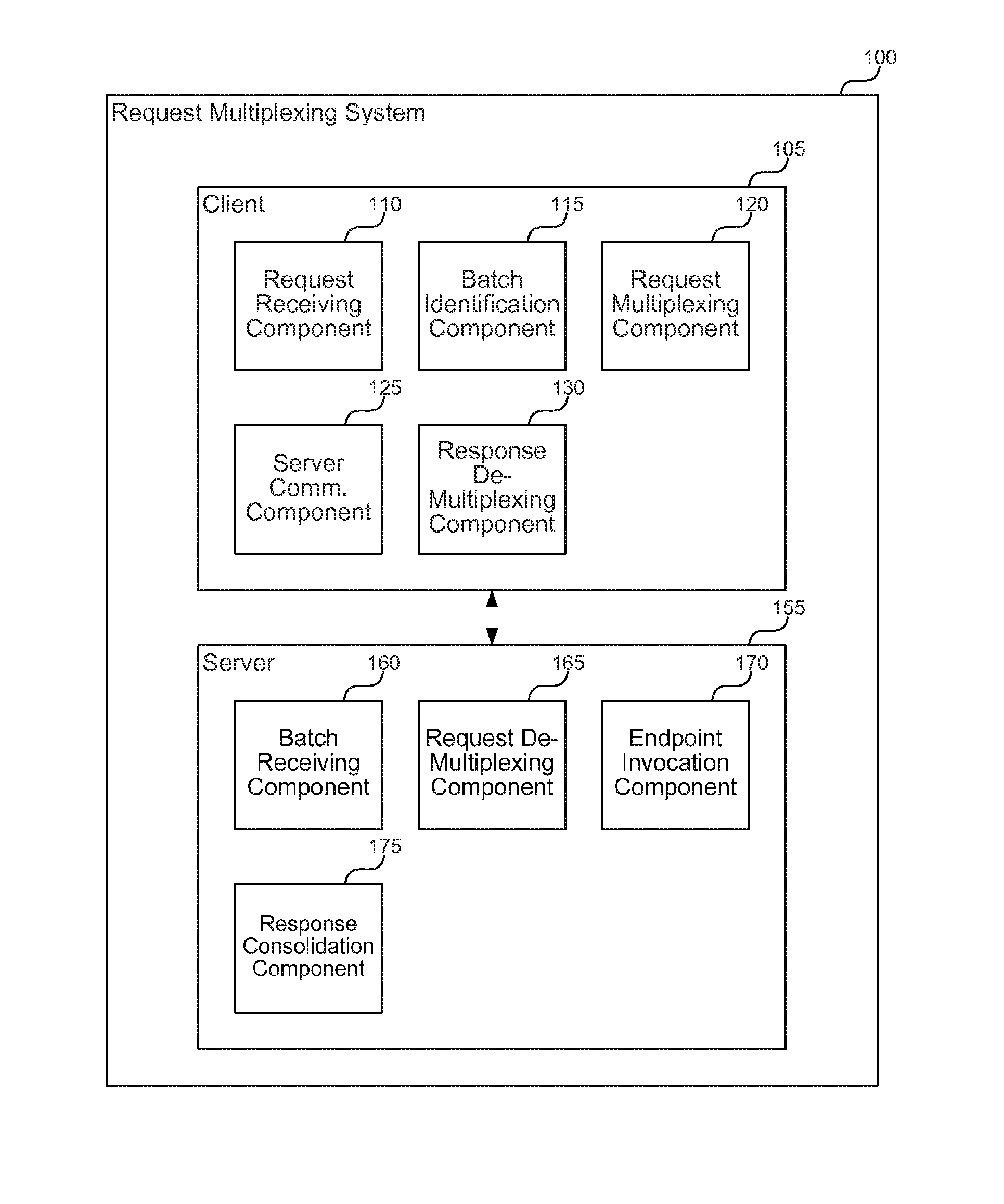
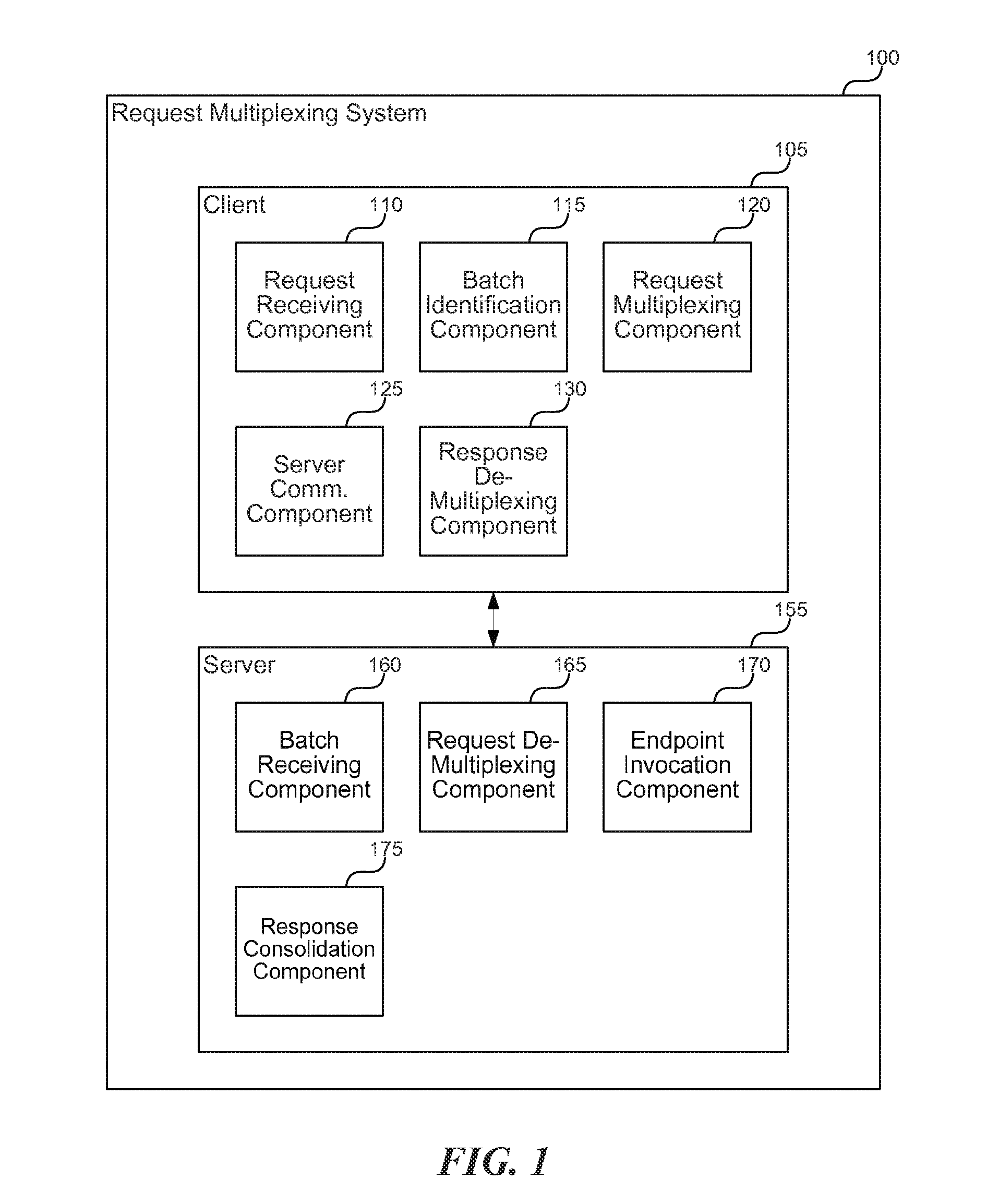
Multiplexing web requests for improved performance
ActiveUS20140101235A1Digital data processing detailsNatural language data processingMultiplexingClient-side
A request multiplexing system is described herein that takes multiple asynchronous requests from a client to multiple server endpoints and multiplexes the requests at the client into a single request to a new server endpoint. The new endpoint demultiplexes the requests at the server, calls the pre-existing separate endpoints to get the correct response for each request, combines the responses into a single multiplexed response, and returns the combined response to the client. On the client side, the response data is split up and handed to the appropriate handlers. From the components' points of view and those of the endpoints on the server, the requests occur just as they originally may. However, new logic on both the client and the server has packaged and unpackaged requests and responses appropriately to accomplish without component modification what formerly involved extensive coordination between developers of various components.
Owner:REDFIN CORP
SEU and SEFI fault tolerant computer
A non-hardened processor is made fault tolerant to SEUs and SEFIs. A processor is provided utilizing time redundancy to detect and respond to SEUs. Comparison circuitry is provided in a radiation hardened module to provide special redundancy with the need to run additional processors. Additionally, a hardened SEFI circuit is provided to periodically send a signal to the process which, in the case of a processor not in the SEFI state, initiates production by the processor of a “correct” response. If the correct response is not received within a particular time window, the SEFI circuit initiates progressively severe actions until a reset is achieved.
Owner:SPACE MICRO A CORP OF DELAWARE
Predictive customer service environment
ActiveUS20140012626A1Improve accuracyFacilitate customer interactionArtificial lifeAutomatic exchangesCorrect responseDatabase
A mechanism for facilitating customer interactions within a customer service environment provides prompt and accurate answers to customer questions. A smart chat facility for use in a customer service environment to predict a customer problem examines a customer chat transcript to identify customer statements that set forth a customer issue and, responsive to this, can route the customer to an agent, an appropriate FAQ, or can implement a problem specific widget in the customer UI. Customer queries are matched with most correct responses and accumulated knowledge is used to predict a best response to future customer queries. The iterative system thus learns from each customer interaction and can adapt to customer responses over time to improve the accuracy of problem prediction.
Owner:24 7 AI INC
Automatic identification method of electric power meter on RS-485 bus
InactiveCN101969429AReduce workloadLow technical requirementsData switching networksElectric power systemCorrect response
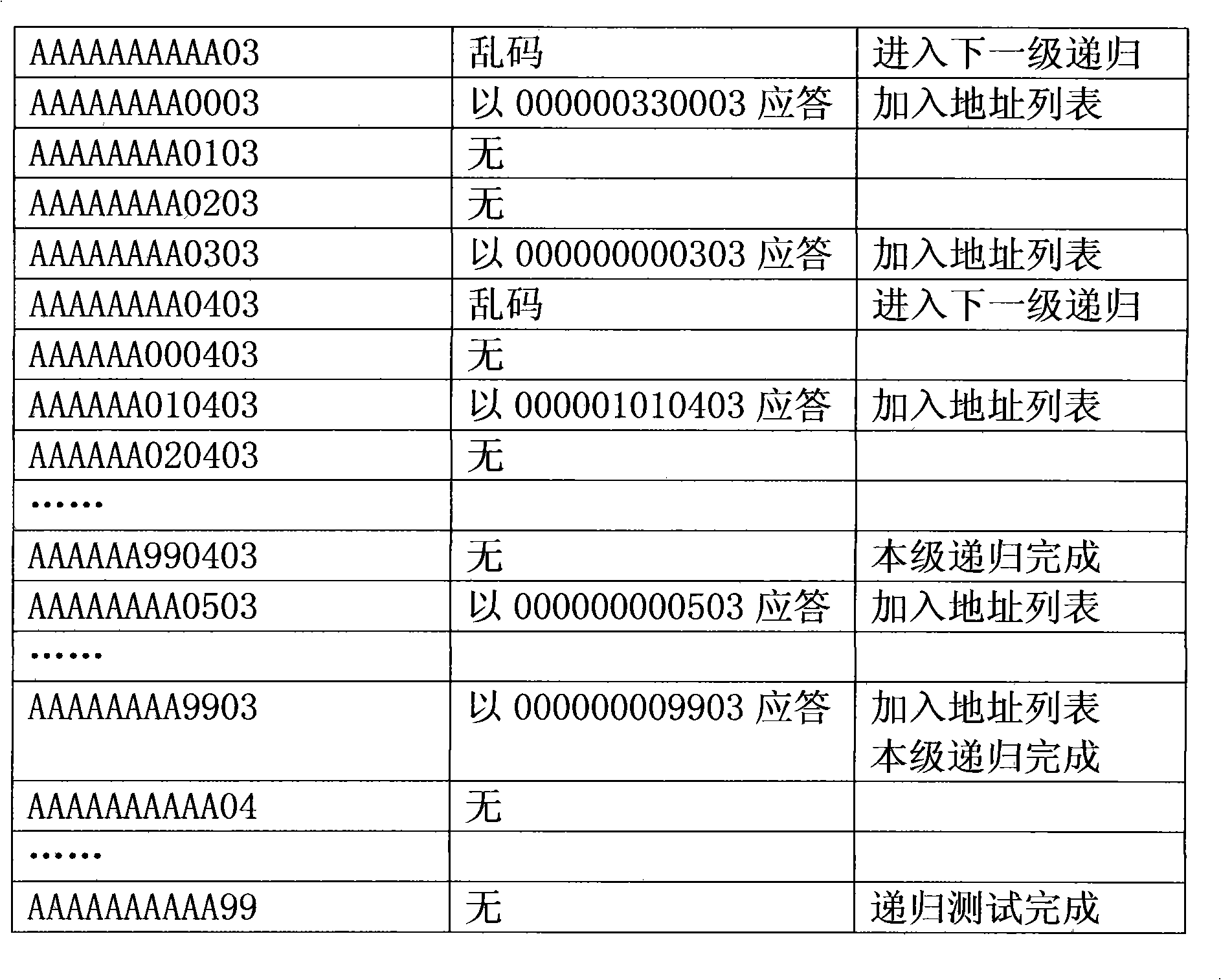
The invention discloses an automatic identification method of an electric power meter on RS-485 bus, wherein different protocols and communication rates are used for the following operations: firstly using broadcast address to distribute a reading meter order by a collecting apparatus; then if no response received, no electric power meter in match condition exists; if correct response is received, acquiring a meter address from a response message to be added into a meter address list of the collecting apparatus; if a messy code response which is not matched with the response format in the protocol is received, a plurality of electric power meters in match condition exist, taking AAAAAAAAAAAA as initiation meter address, and entering recursive query test; and after the test completes, converging to obtain a group of electric power meter address, protocol and communication rate list. The application of the identification method can save corresponding artificial maintaining work.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD SHAOXING POWER SUPPLY CO +1
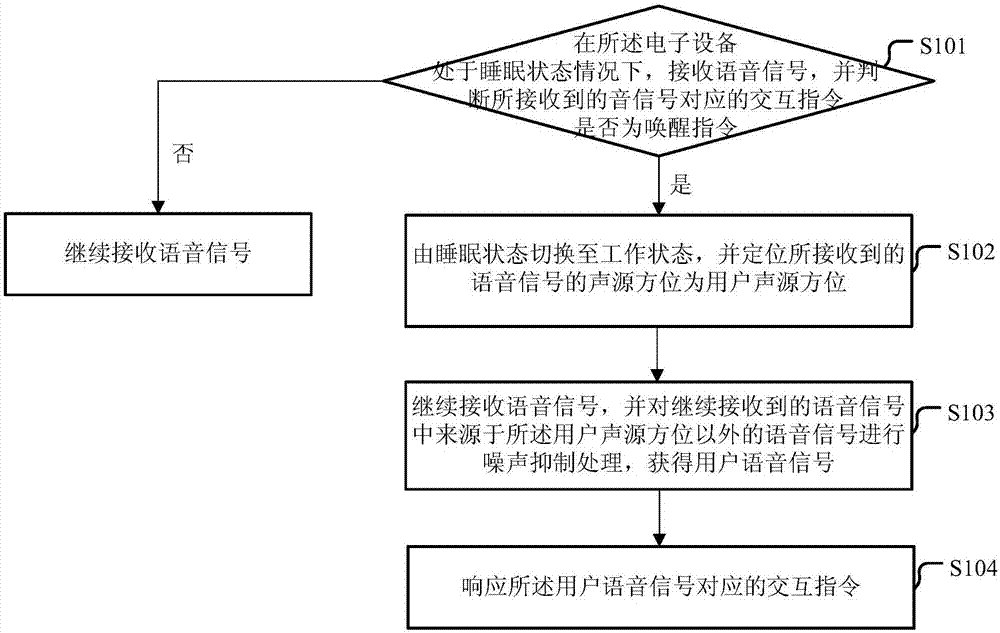
Speech signal processing method, apparatus and electronic device
The embodiments of the present invention disclose a speech signal processing method, a speech signal processing apparatus and an electronic device. The method comprises the following steps that: when the electronic device is under a sleep state, speech signals are received, whether an interaction instruction corresponding to the received speech signals is a wake-up instruction is judged; if the interaction instruction corresponding to the received speech signals is a wake-up instruction, the sleep state is switched to a working state, and the sound source direction of the received speech signals is positioned as a user sound source direction; speech signals are further received, noise suppression processing is performed on speech signals in the further received speech signals, wherein the speech signals in the further received speech signals do not come from the user sound source direction, so that user speech signals are obtained; and an interaction instruction corresponding to the user speech signals is responded. According to the speech signal processing method, the speech signal processing apparatus and the electronic device of the invention, the electronic device performs noise suppression processing on the speech signals in the further received speech signals which do not come from the user sound source direction, so that the obtained user speech signals are speech signals emitted by a user in the user sound source direction, and therefore, a correct response can be made, and user experience can be improved.
Owner:BEIJING ORION STAR TECH CO LTD
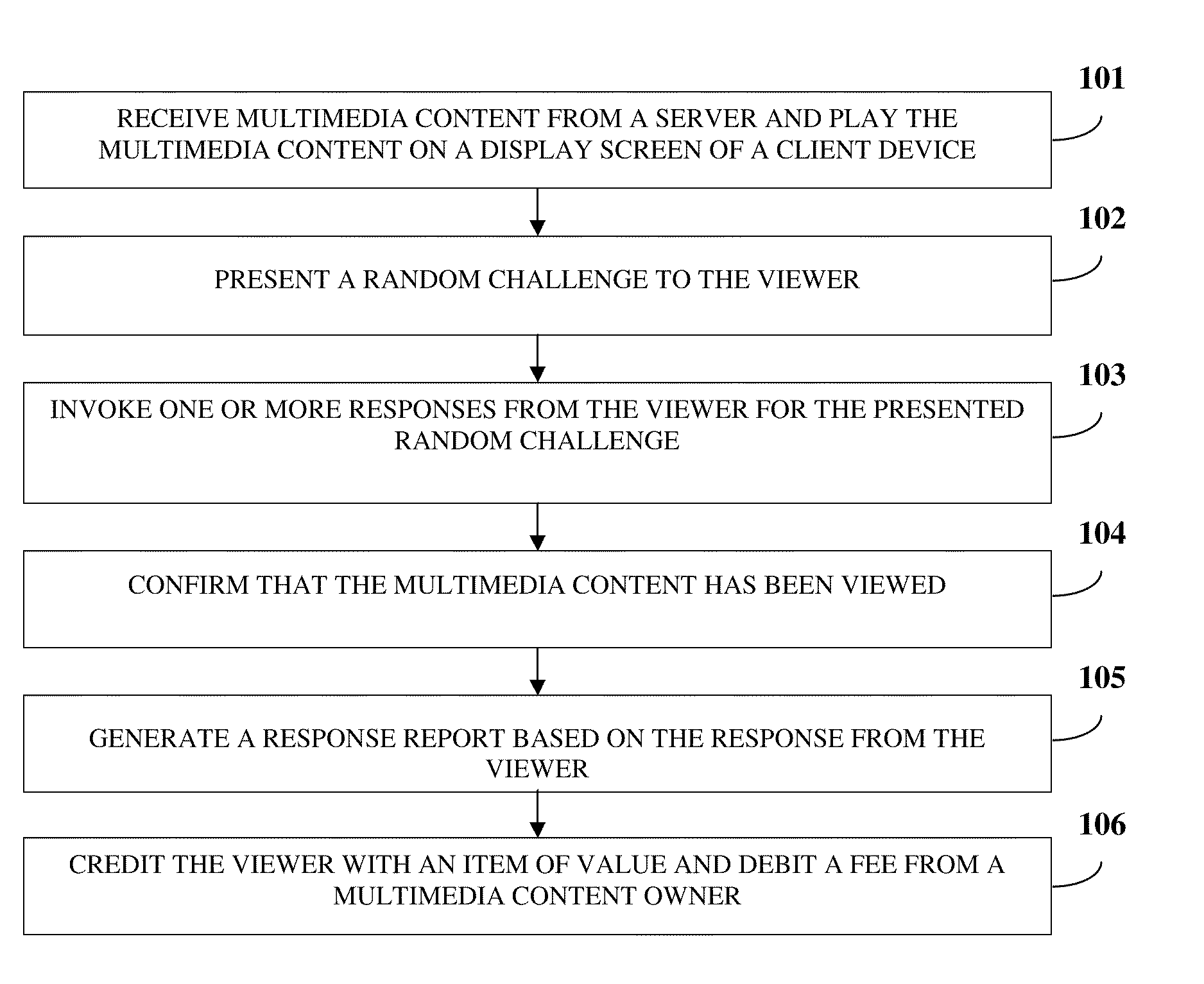
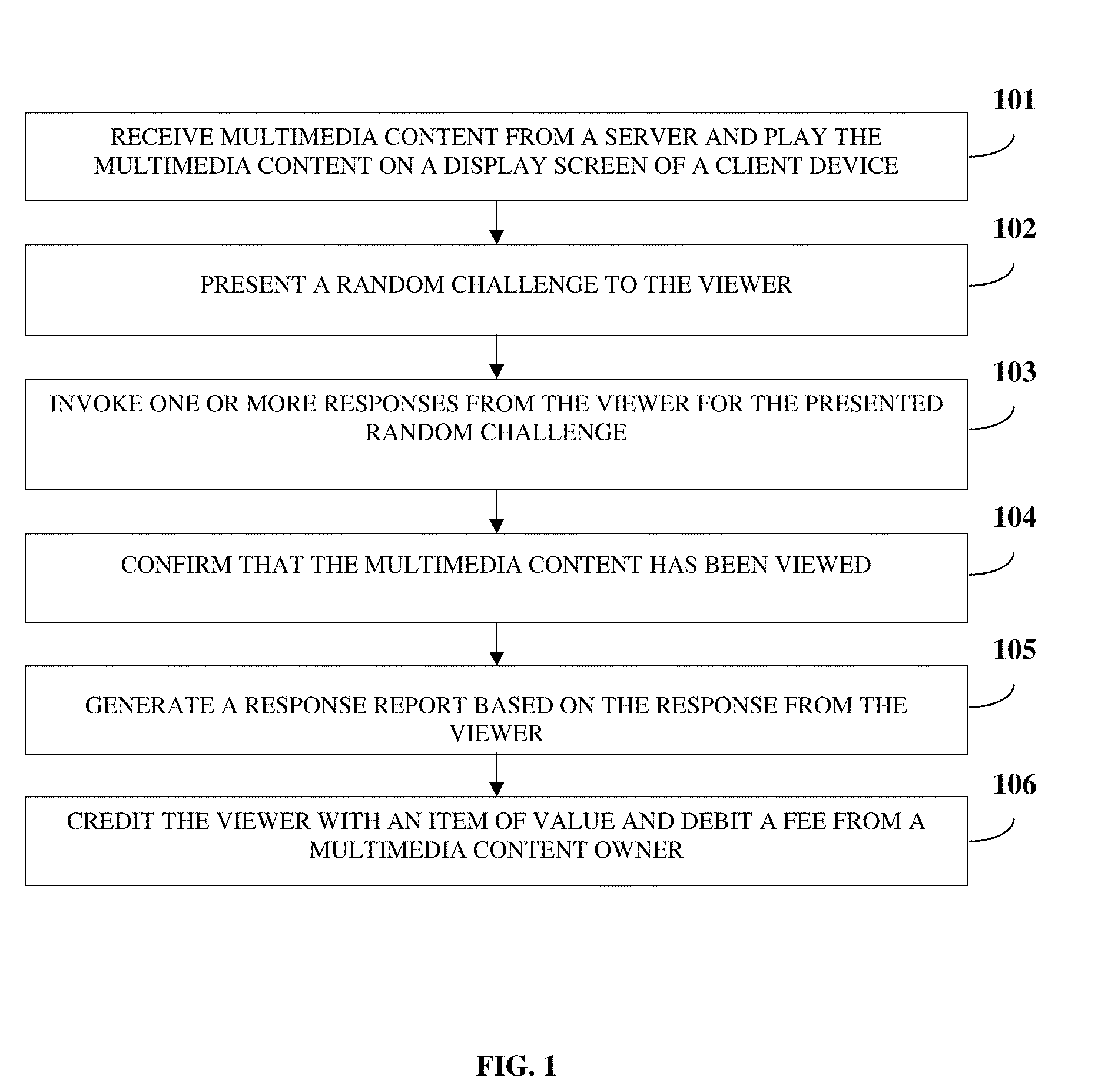
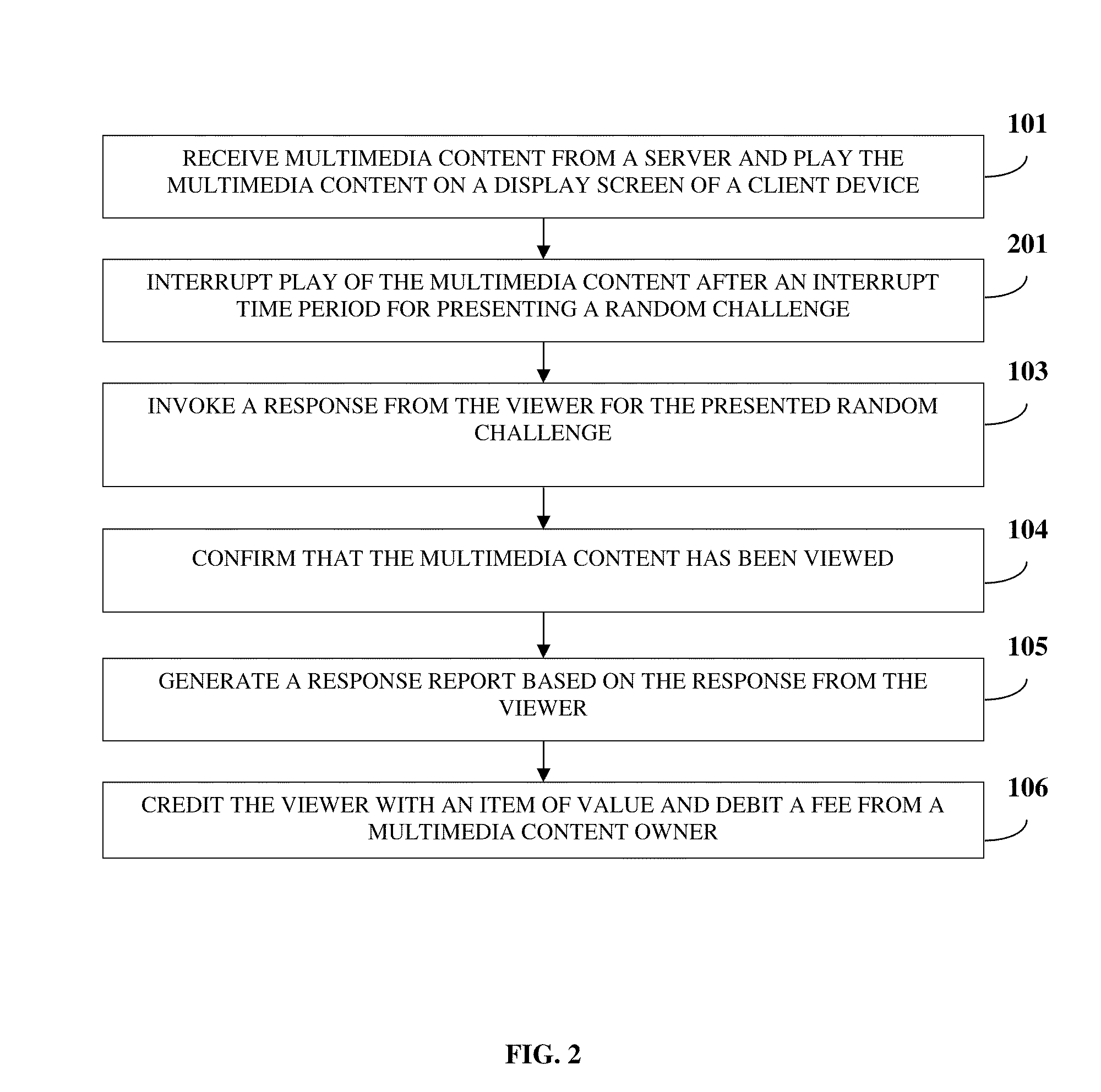
Multimedia Content Viewing Confirmation
InactiveUS20100058376A1Broadcast transmission systemsAnalogue secracy/subscription systemsClient-sideCorrect response
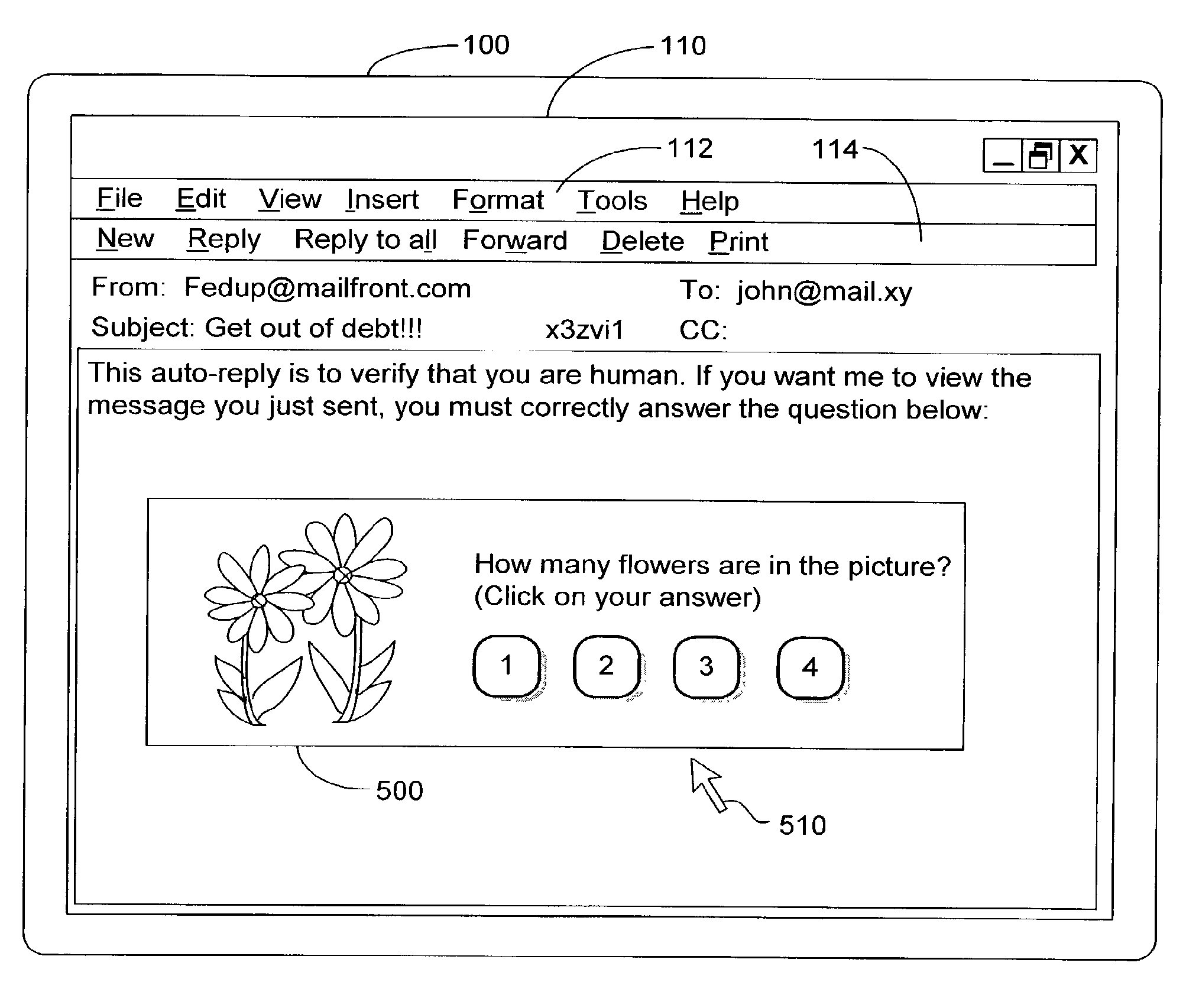
Disclosed herein is a computer implemented method and system for confirming that a viewer viewed multimedia content on a client device. A multimedia content owner uploads multimedia content on a server. The client device receives the multimedia content from the server and plays the multimedia content on a display screen of the client device. A random challenge is presented to the viewer by overlaying the random challenge on the multimedia content. A response for the presented random challenge is invoked from the viewer. A correct or partially correct response from the viewer confirms that the multimedia content has been viewed by the viewer. A response report is generated based on the response from the viewer. The viewer is credited with an item of value and the multimedia content owner is debited a fee, if the response report confirms the multimedia content was viewed by the viewer.
Owner:ADGENESIS HLDG LLC
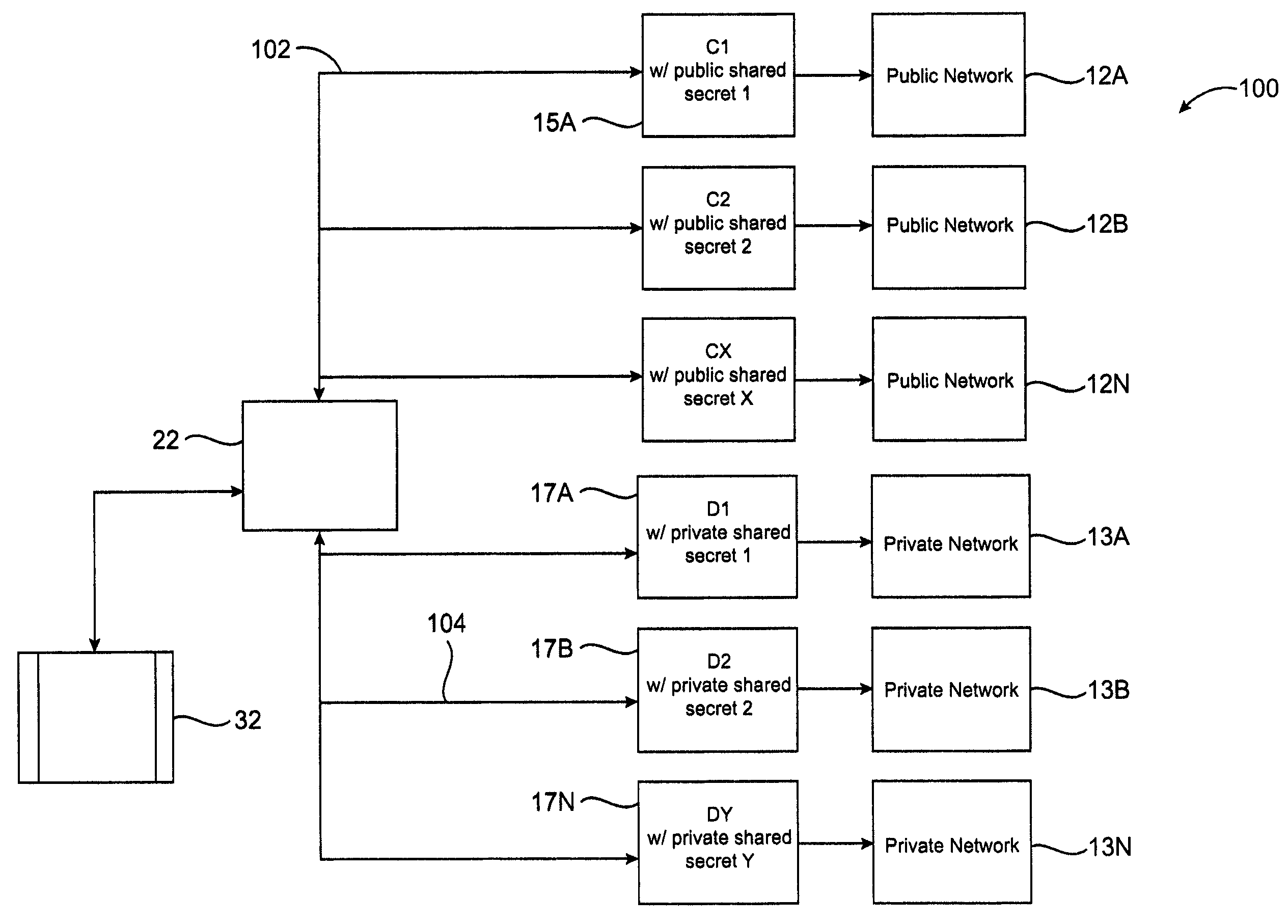
System and method for controlling access to multiple public networks and for controlling access to multiple private networks
InactiveUS7334255B2Digital data processing detailsUser identity/authority verificationPrivate networkCorrect response
A system and method for controlling access to multiple public networks and for controlling access to multiple private networks is provided. Authentication is used with unique public shared secrets and unique private shared secrets to control access to the networks. The invention includes a user device for communicating with at least a public network and / or a private network. The device may be capable of accessing multiple networks through one or more private networks with multiple access control servers. The user device must provide a correct response to each access control server, before access to the network may be granted. The device generates a one-time password, or response, to gain access to a controlled network server. The response generated by the device is matched to a response generated by an access control server that may have generated a challenge that prompted the response. If the two responses match, the device is authenticated and a user of the device is granted access to the network server.
Owner:AUTHENEX
Retractable truck step with wireless door sensor
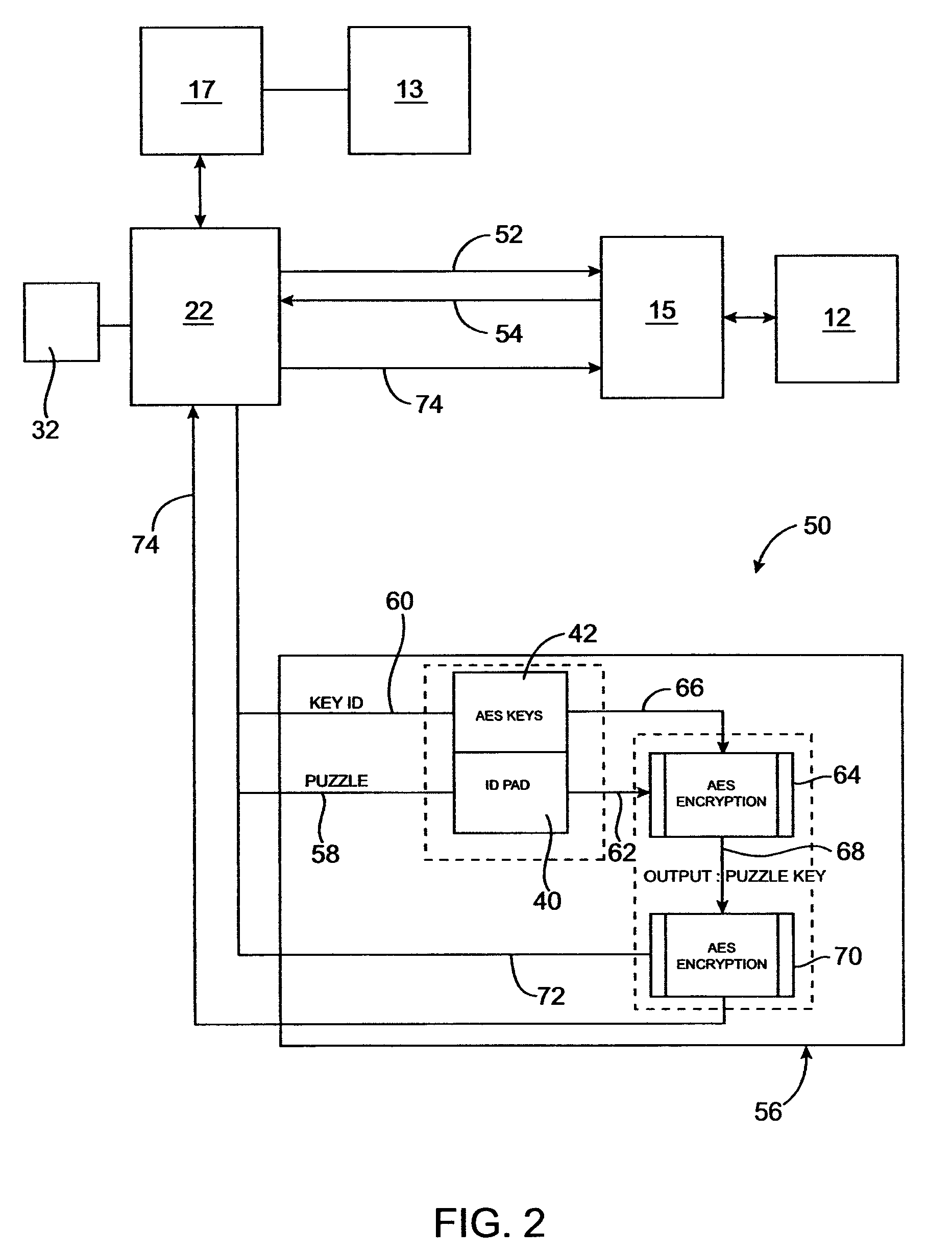
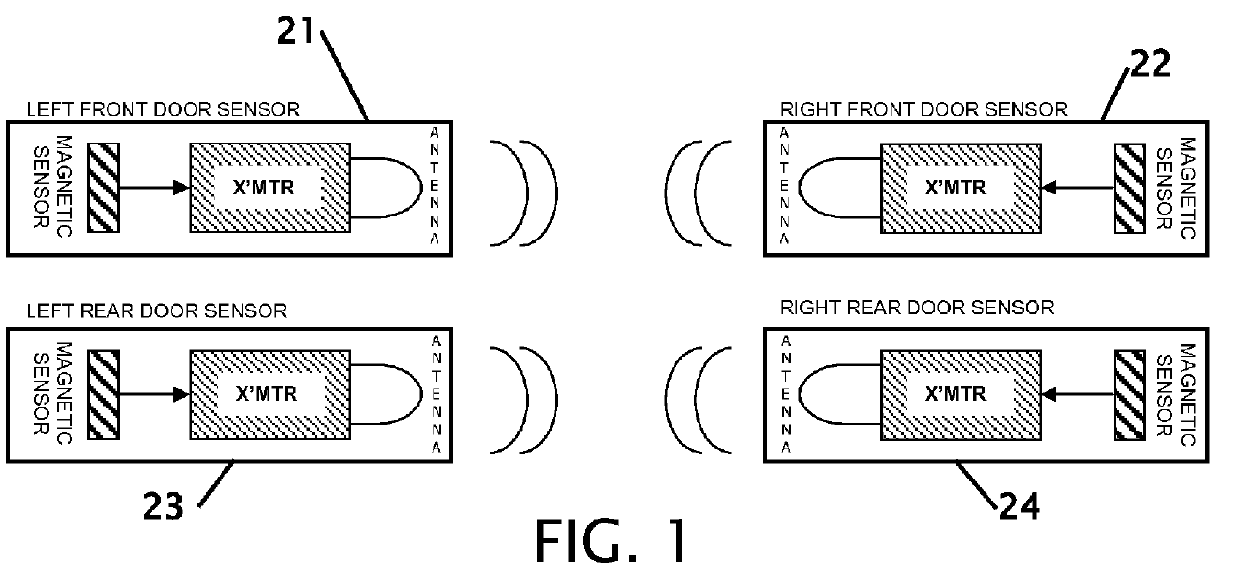
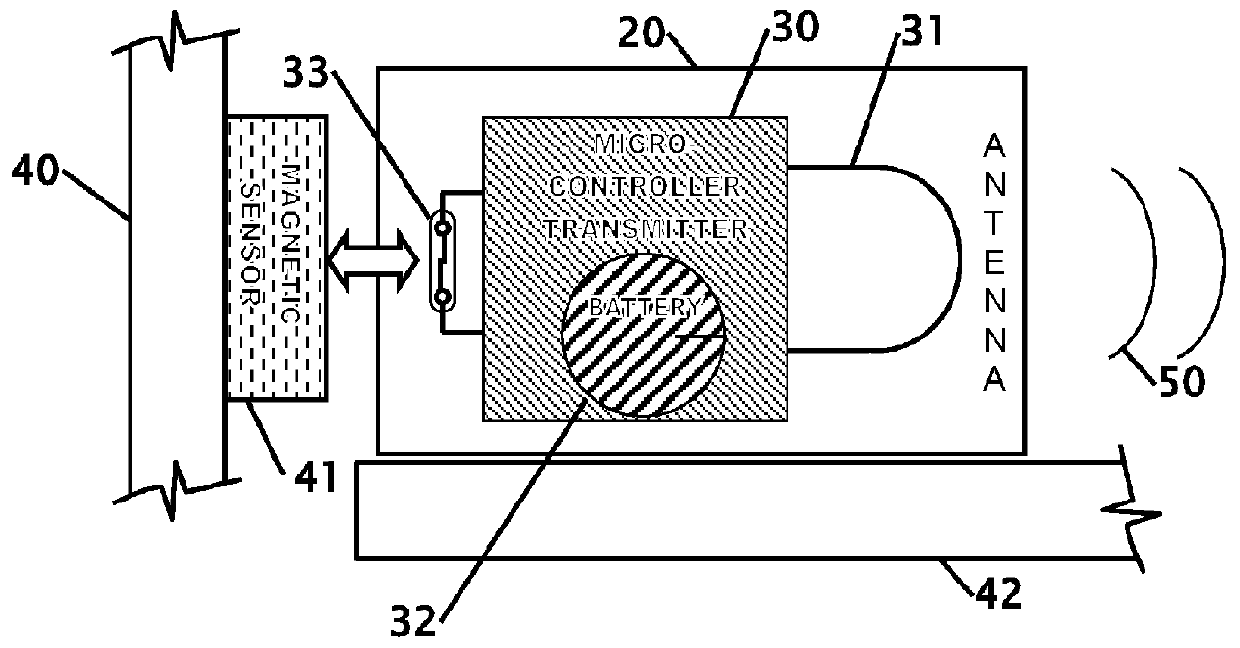
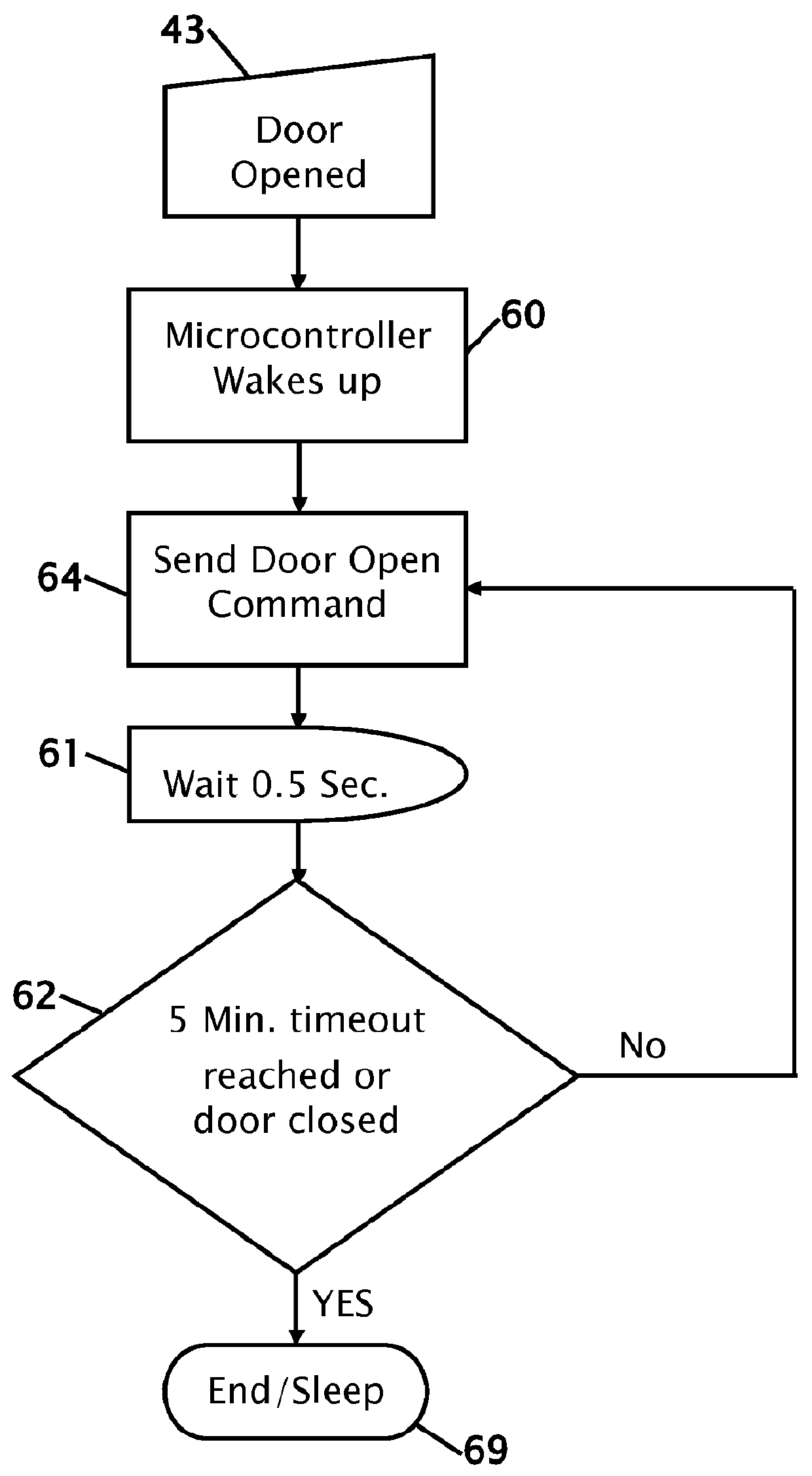
InactiveUS20120139206A1Easy to installReduce power consumptionSteps arrangementMagnetic/electric field switchesCorrect responseJamb
Improvements using a wireless door sensor in each door to eliminate modifying a vehicle wiring and simplify installation of a retractable step and controller for the step. Up to four magnetic door sensors / transmitter are mounted on the edge of each door jamb. A magnet is mounted in the door jamb in proximity to the transmitter's magnetic sensor when the door is closed. The transmitter operates in a sleep mode until the sensor state changes. Upon door movement the transmitter sends an open status message to a receiver where the message data is stored and the controller determines the correct responses. If a door on either side is open the receiver engages the appropriate step motor and lowers the step. The step remains lowered until the receiver stops receiving messages indicating a door is closed or the transmitter on an open door has timed out ceasing transmissions.
Owner:MAY RICHARD P
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com