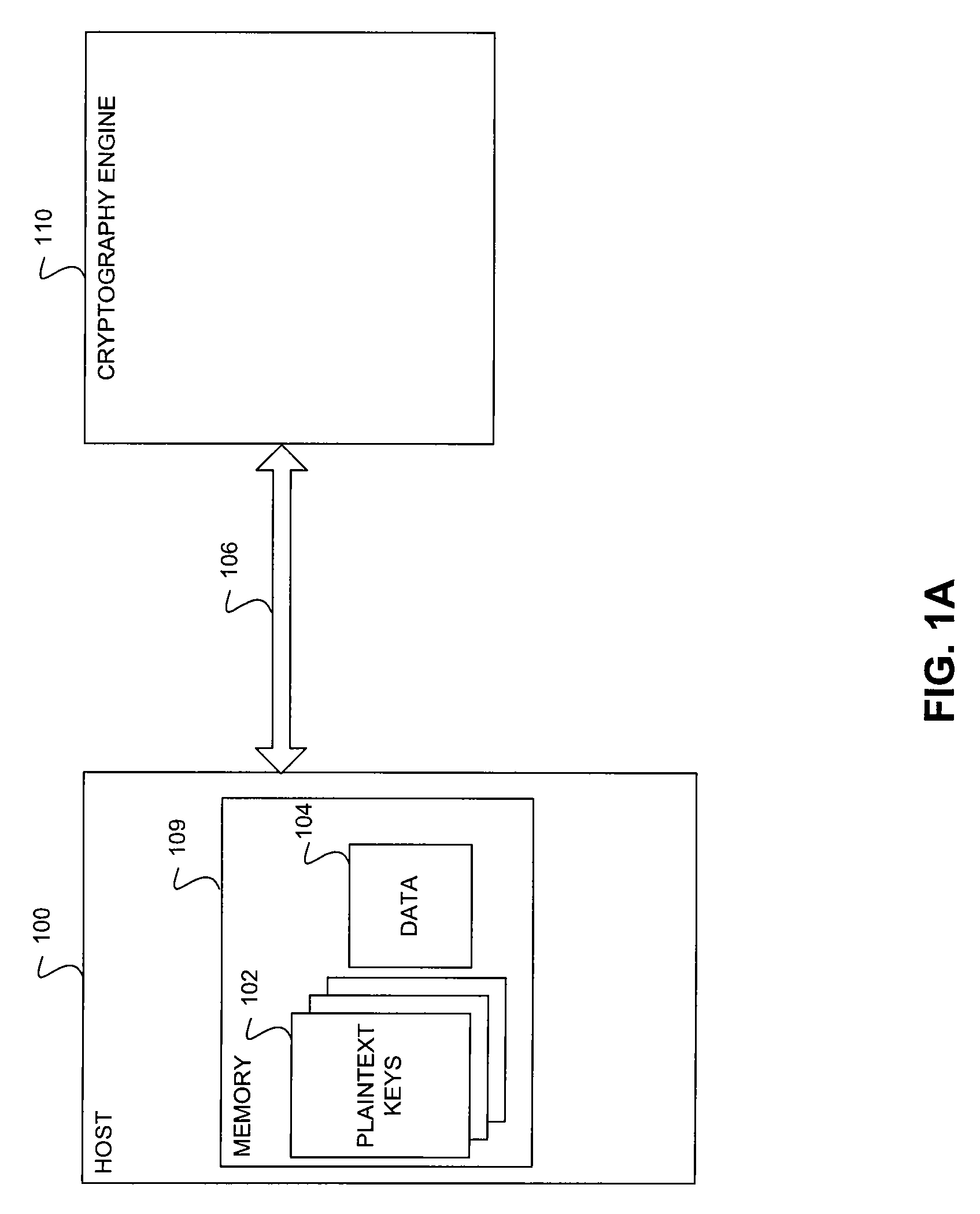
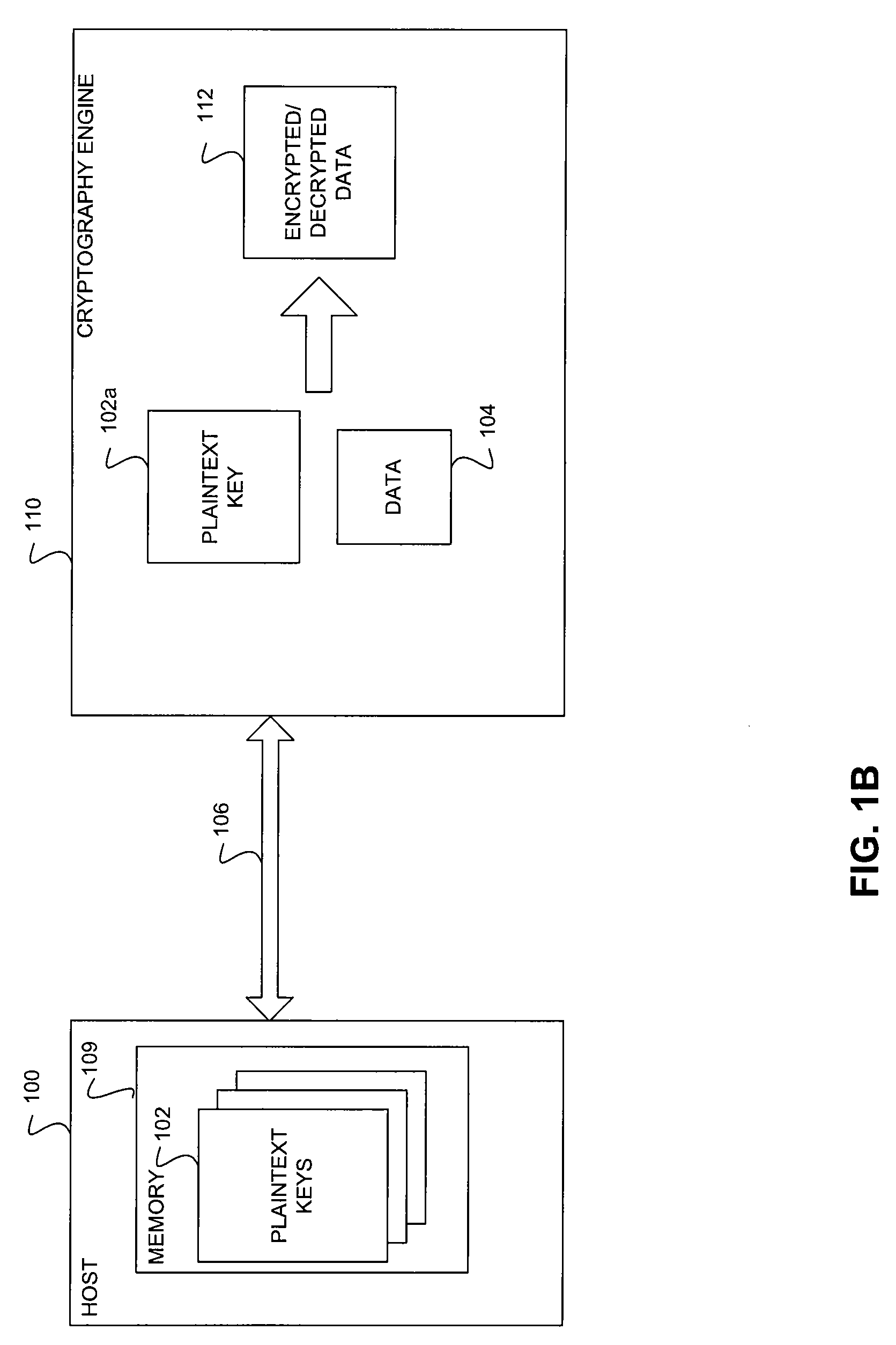
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
919 results about "Secure channel" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
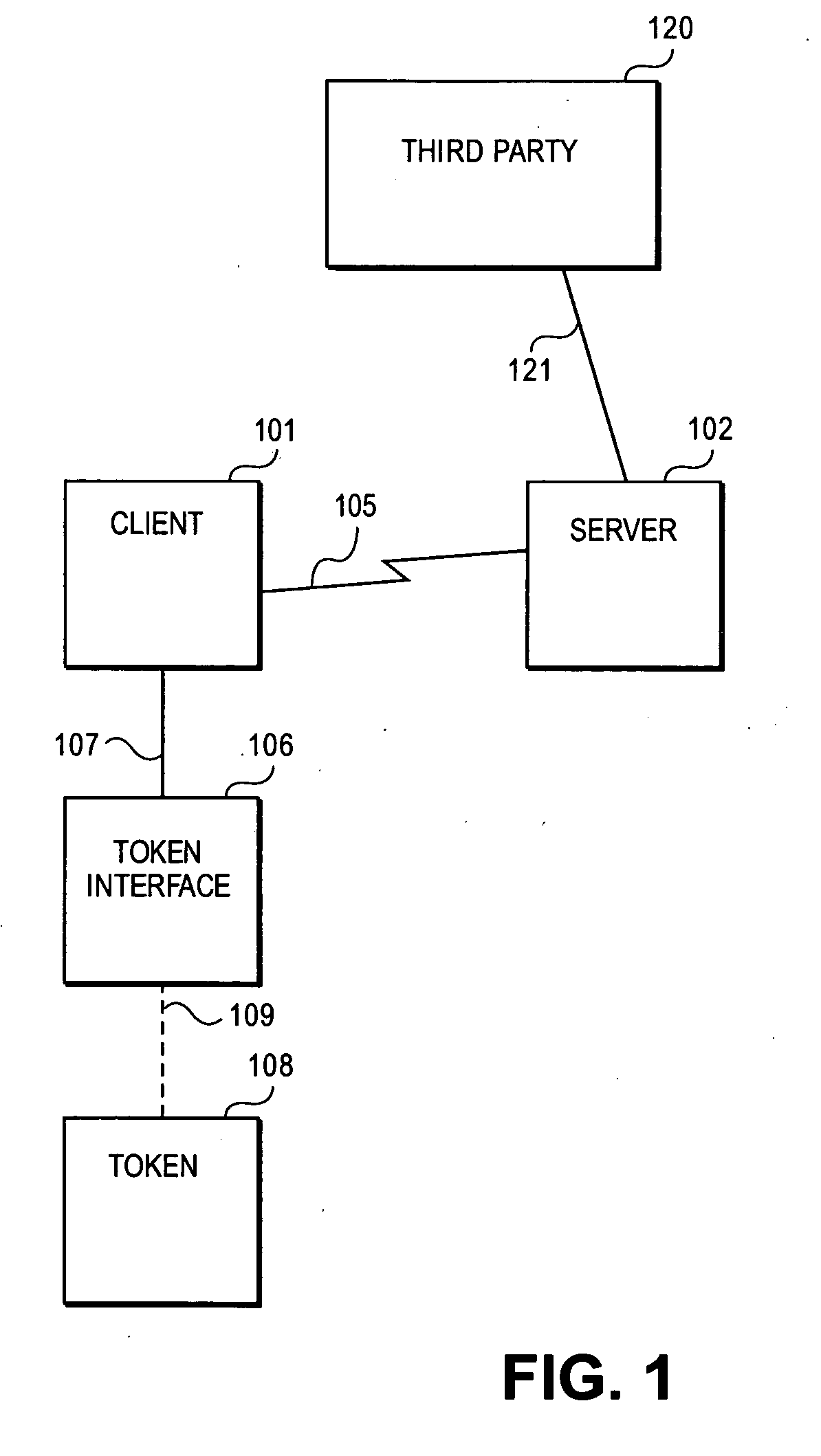
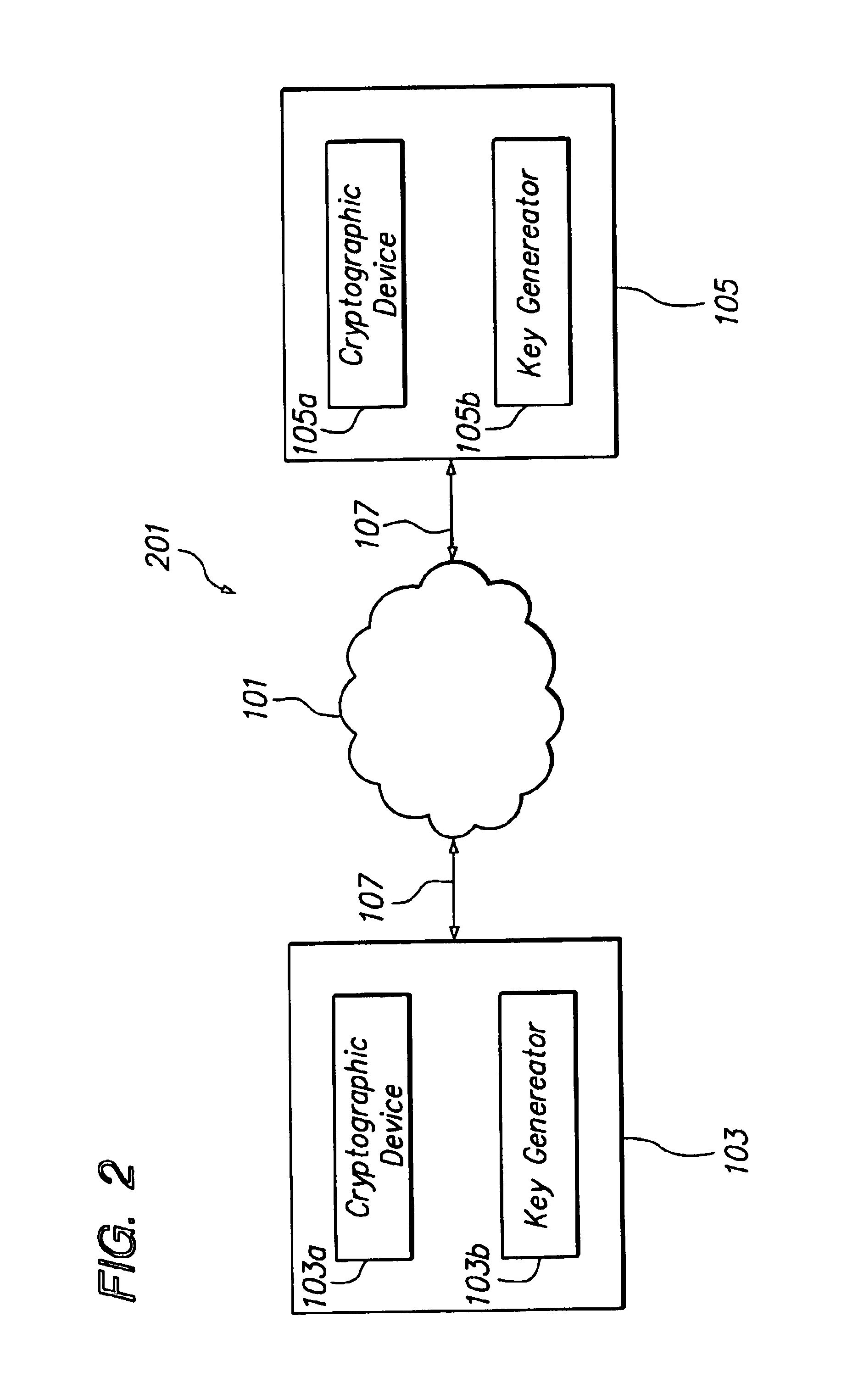
In cryptography, a secure channel is a way of transferring data that is resistant to overhearing and tampering. A confidential channel is a way of transferring data that is resistant to overhearing (i.e., reading the content), but not necessarily resistant to tampering. An authentic channel is a way of transferring data that is resistant to tampering but not necessarily resistant to overhearing.
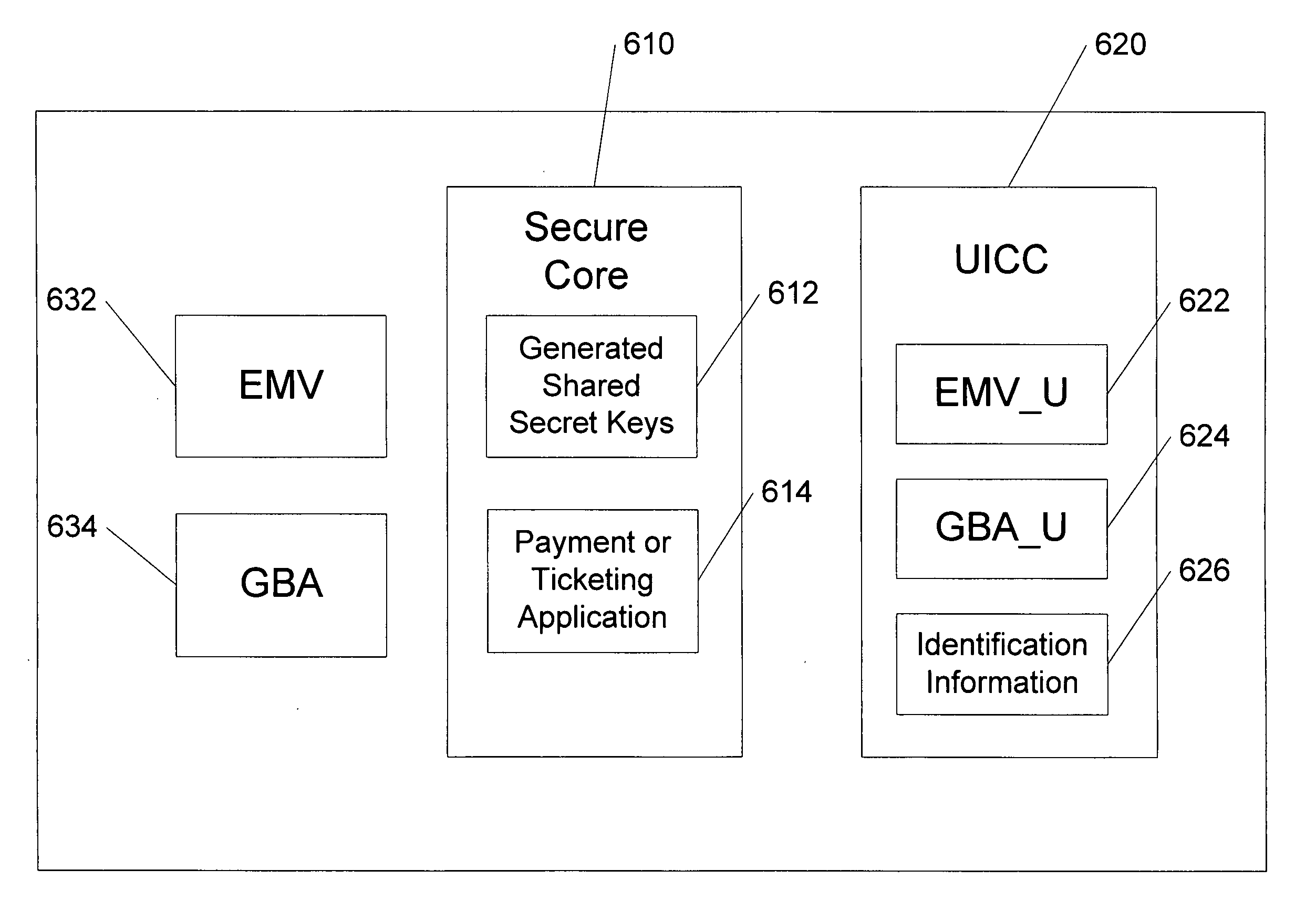
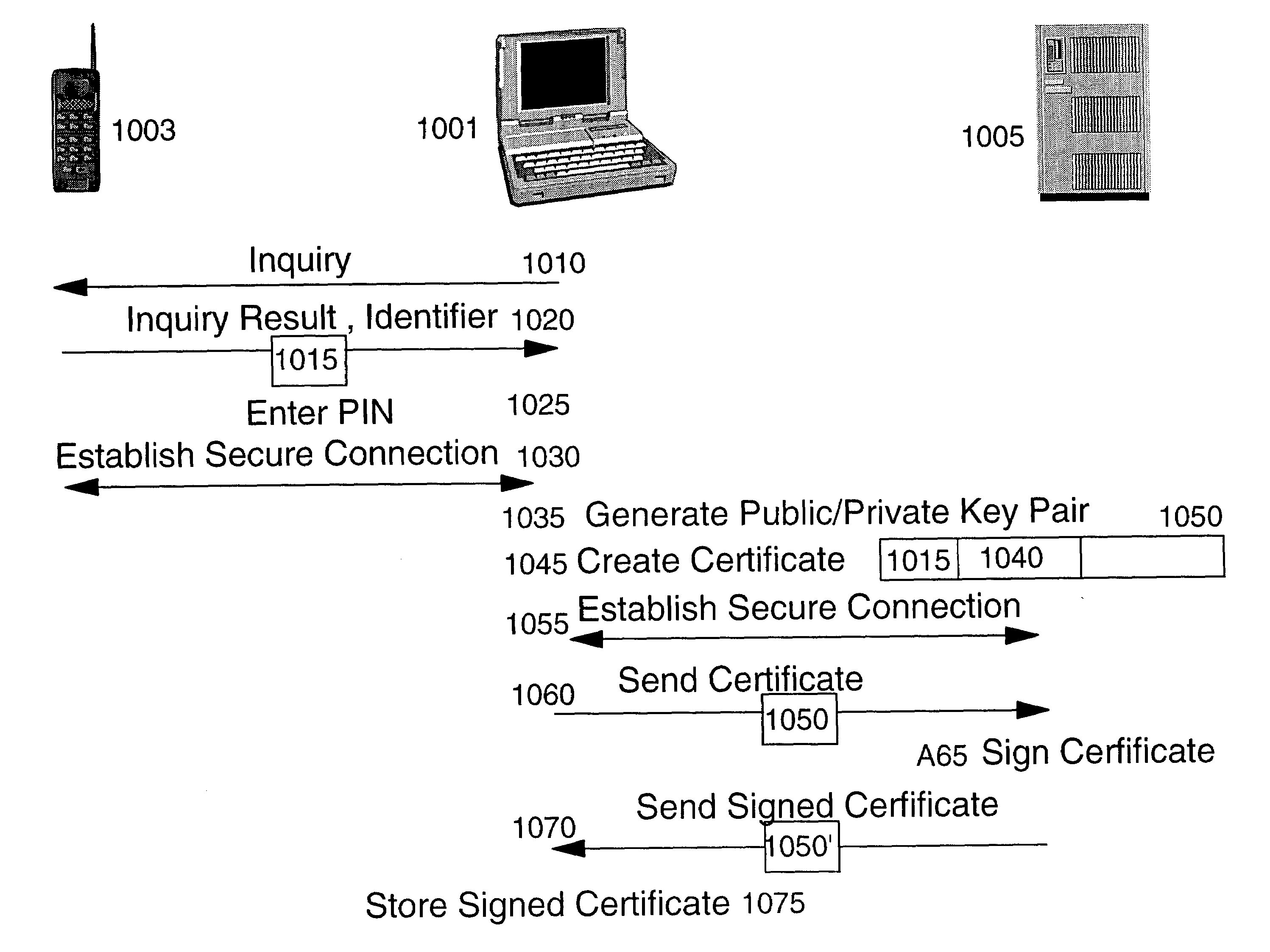
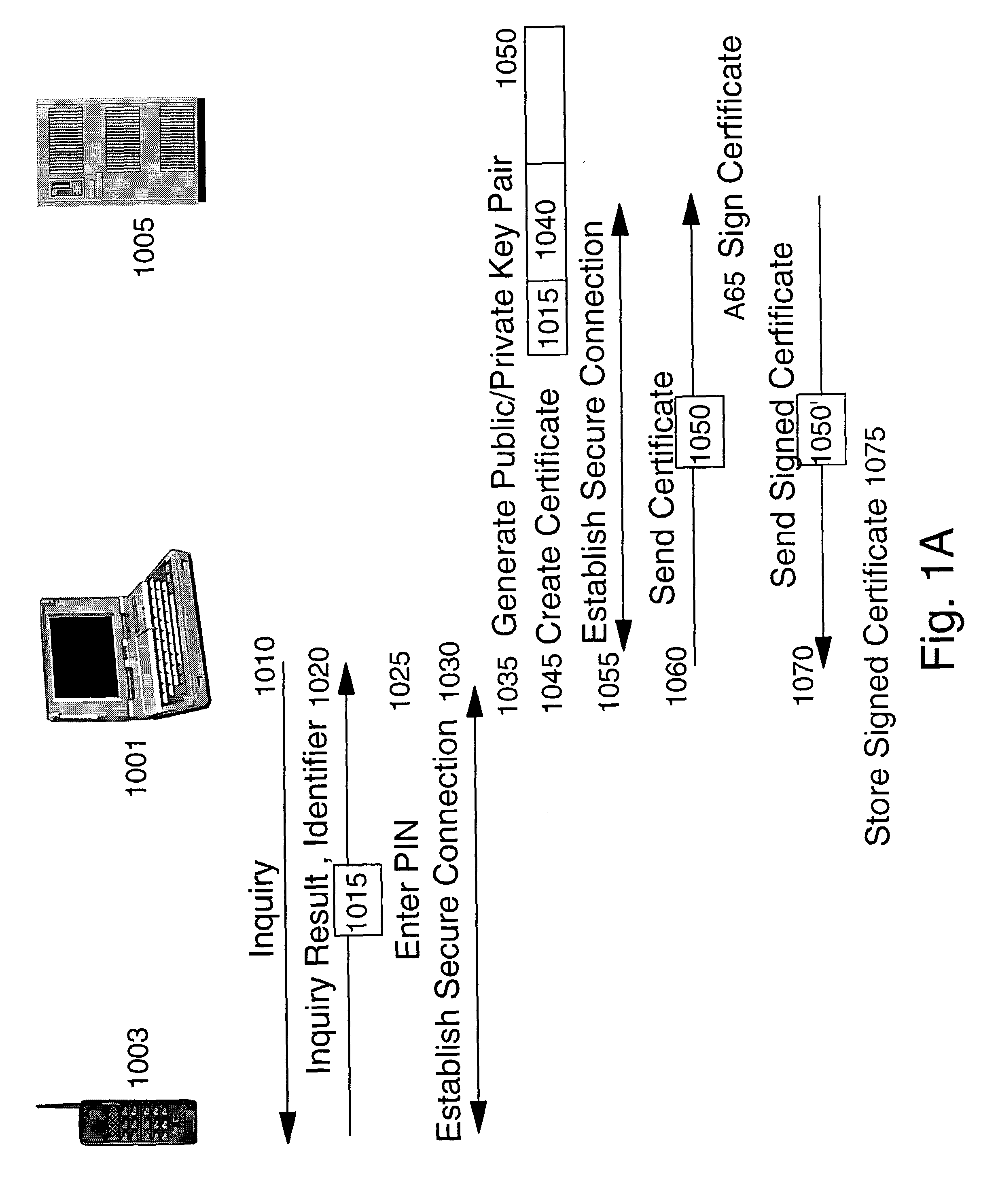
Methods, system and mobile device capable of enabling credit card personalization using a wireless network
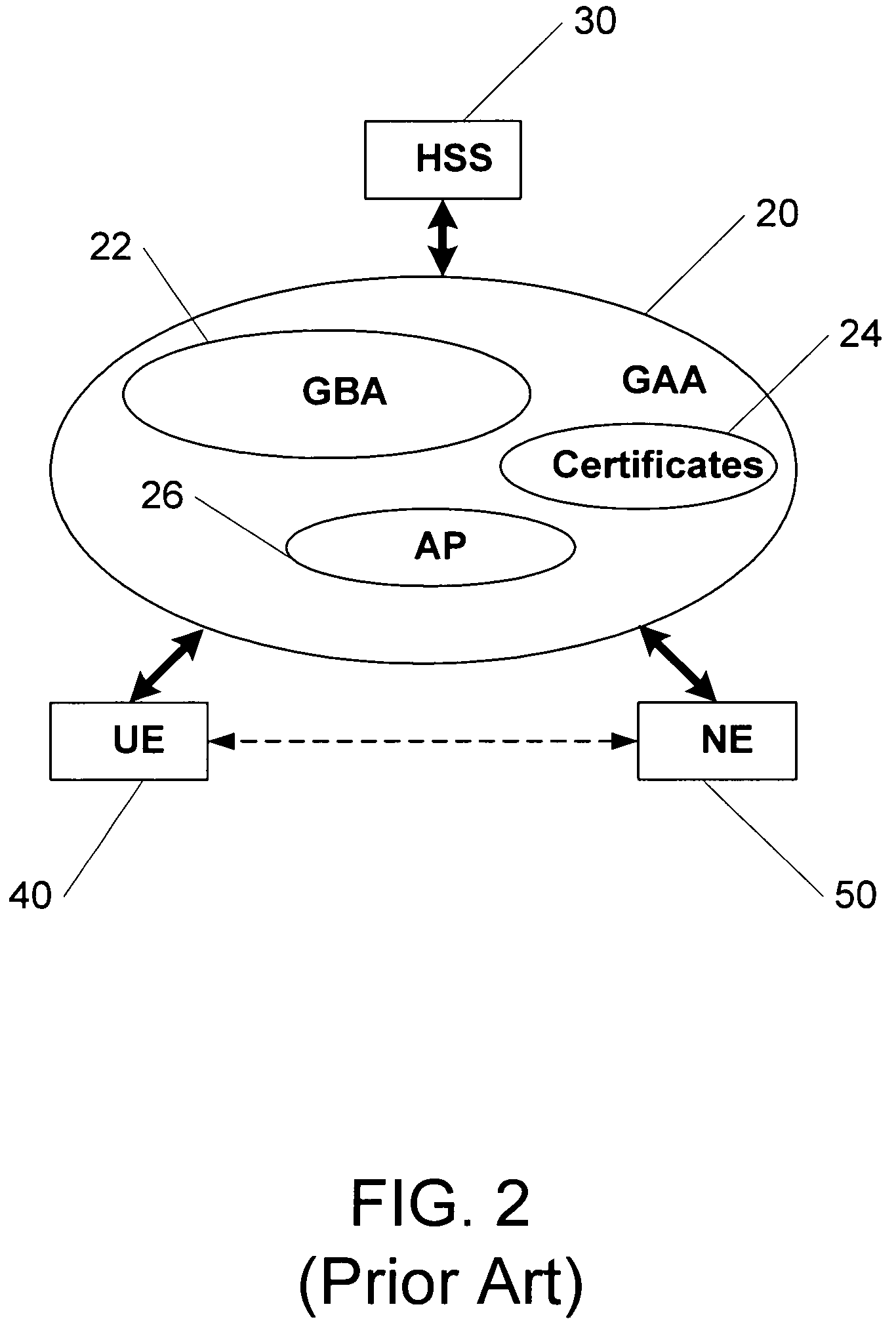
Methods of creating a secure channel over which credit card personalization data can be transmitted over the air (OTA) are provided. In particular, Generic Authentication Architecture (GAA) may be used to establish a secure communication channel between the user equipment (UE) and a personalization application server or bureau acting as a network application function (NAF) server. An user equipment, personalization application service (e.g., a NAF server), a system embodying a personalization application server and an user equipment, and a computer program product are also provided for creating a secure channel, such as via GAA, over which credit card personalization data can be transmitted OTA.
Owner:NOKIA TECHNOLOGLES OY
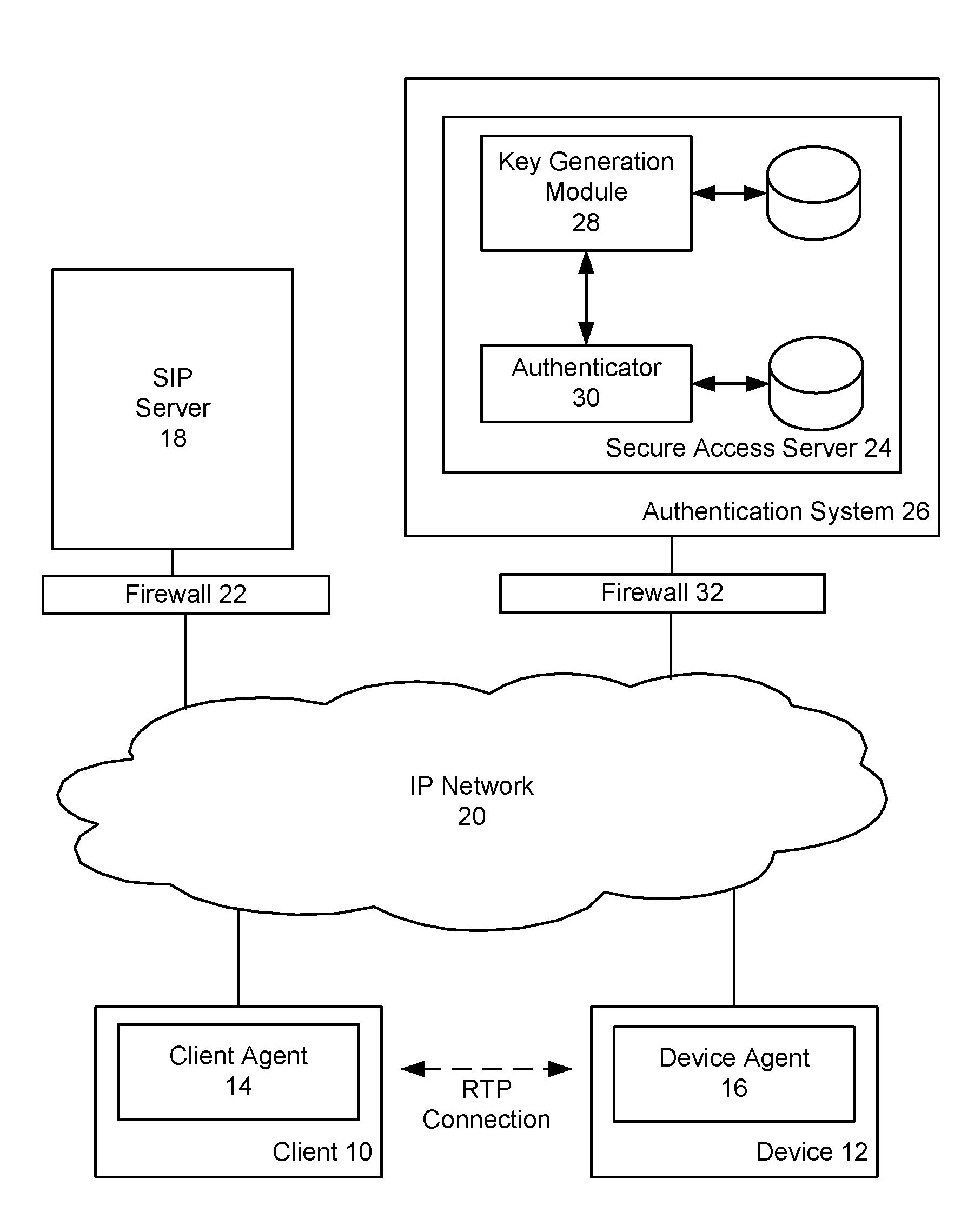
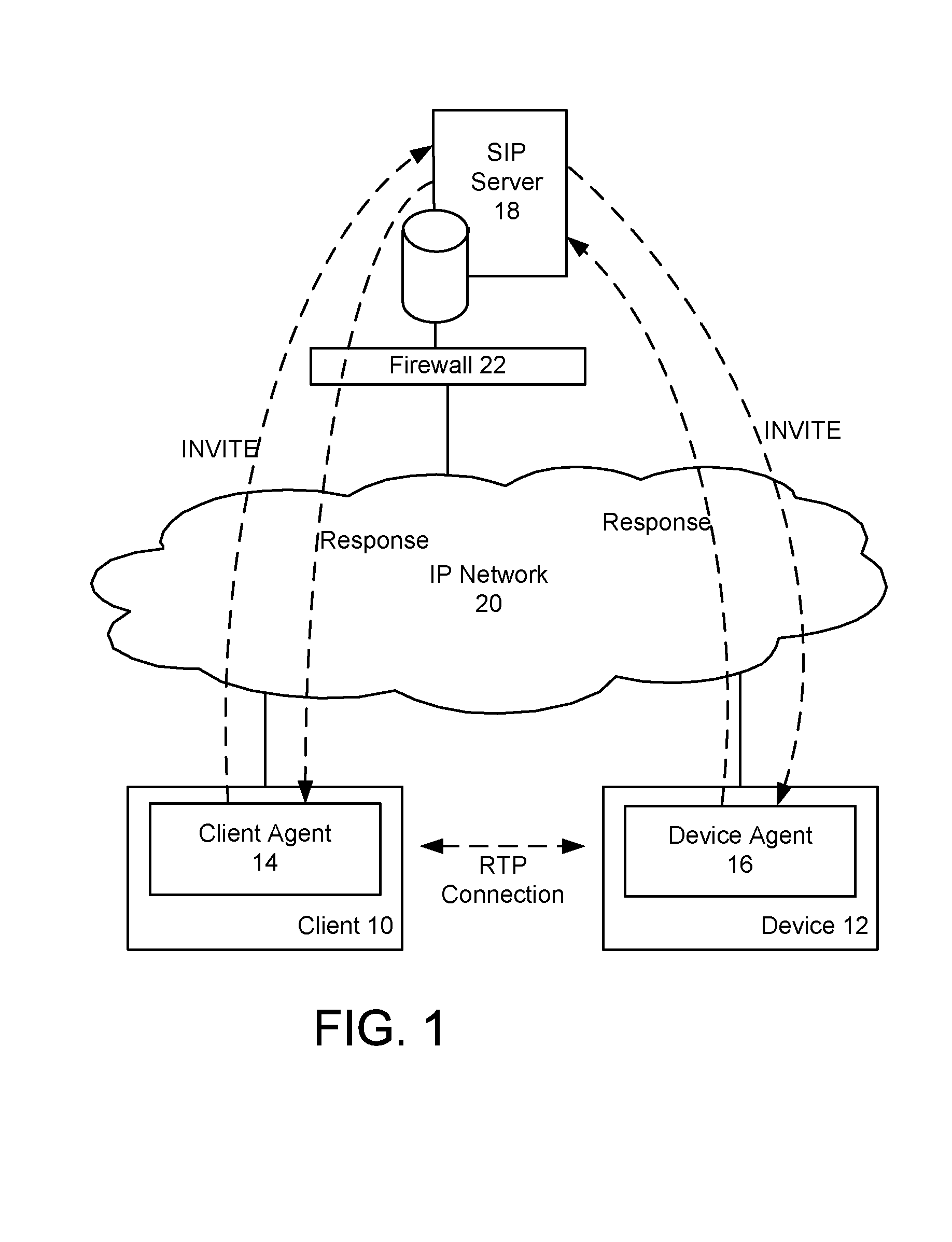
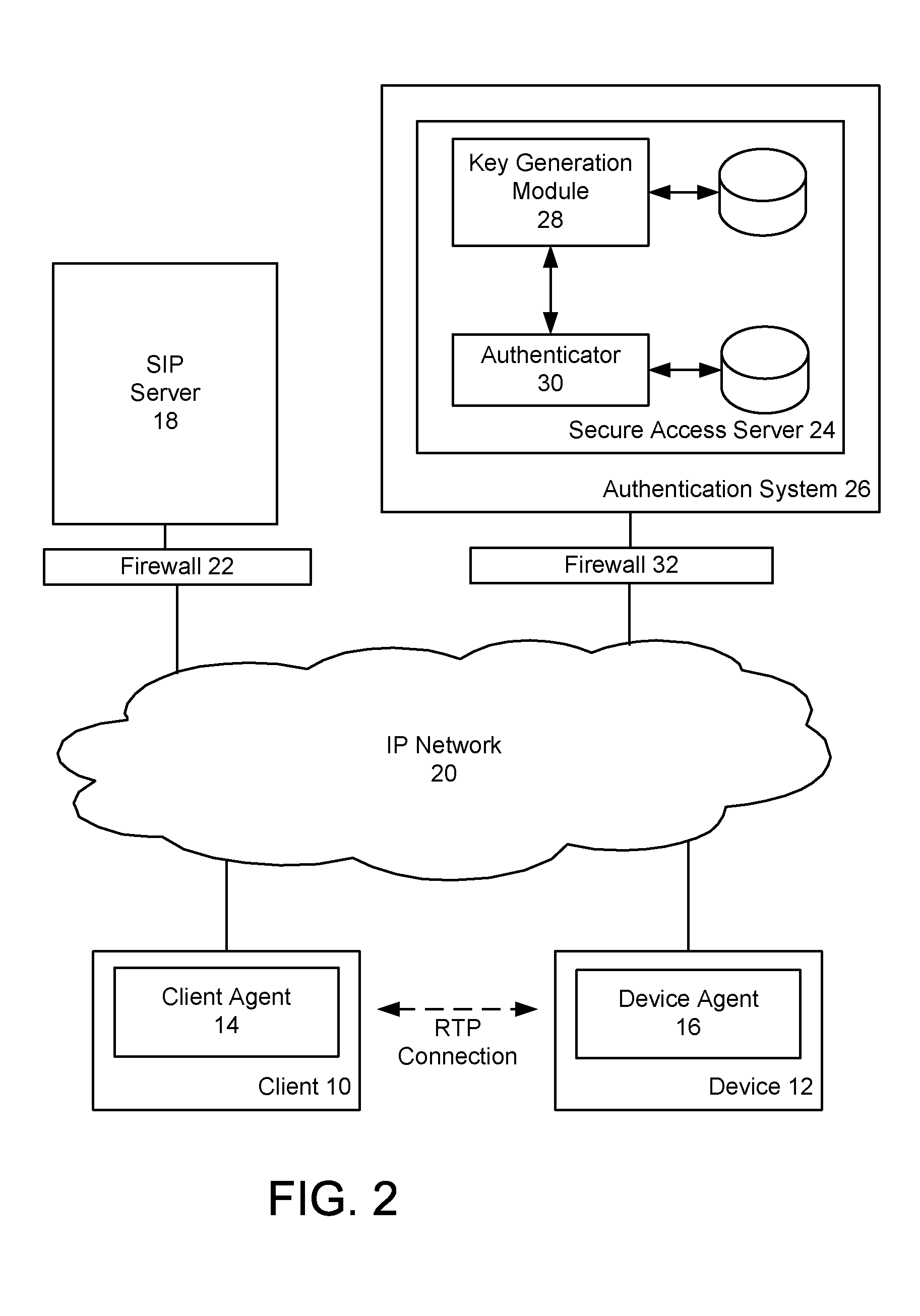
Device authentication and secure channel management for peer-to-peer initiated communications
ActiveUS20080235511A1Multiple keys/algorithms usageUser identity/authority verificationKey exchangeSignaling protocol
A method and system for providing secure access to a device initiating communications using a peer-to-peer signaling protocol, such as a SIP or H.323. In a device registration phase, the device contacts a secure access server, and authenticates to the secure access server by providing an identification, such as its factory ID. The secure access server then issues a device ID and private key to the authenticated device. A client can then initiate a further communication session and be authenticated by the secure access server. The secure access server returns the device identification and the device's public key to the client. The client and device can then perform a symmetrical key exchange for their current communication session, and can communicate with appropriate encryption. The device's private key can be set to expire after one or more uses.
Owner:BCE
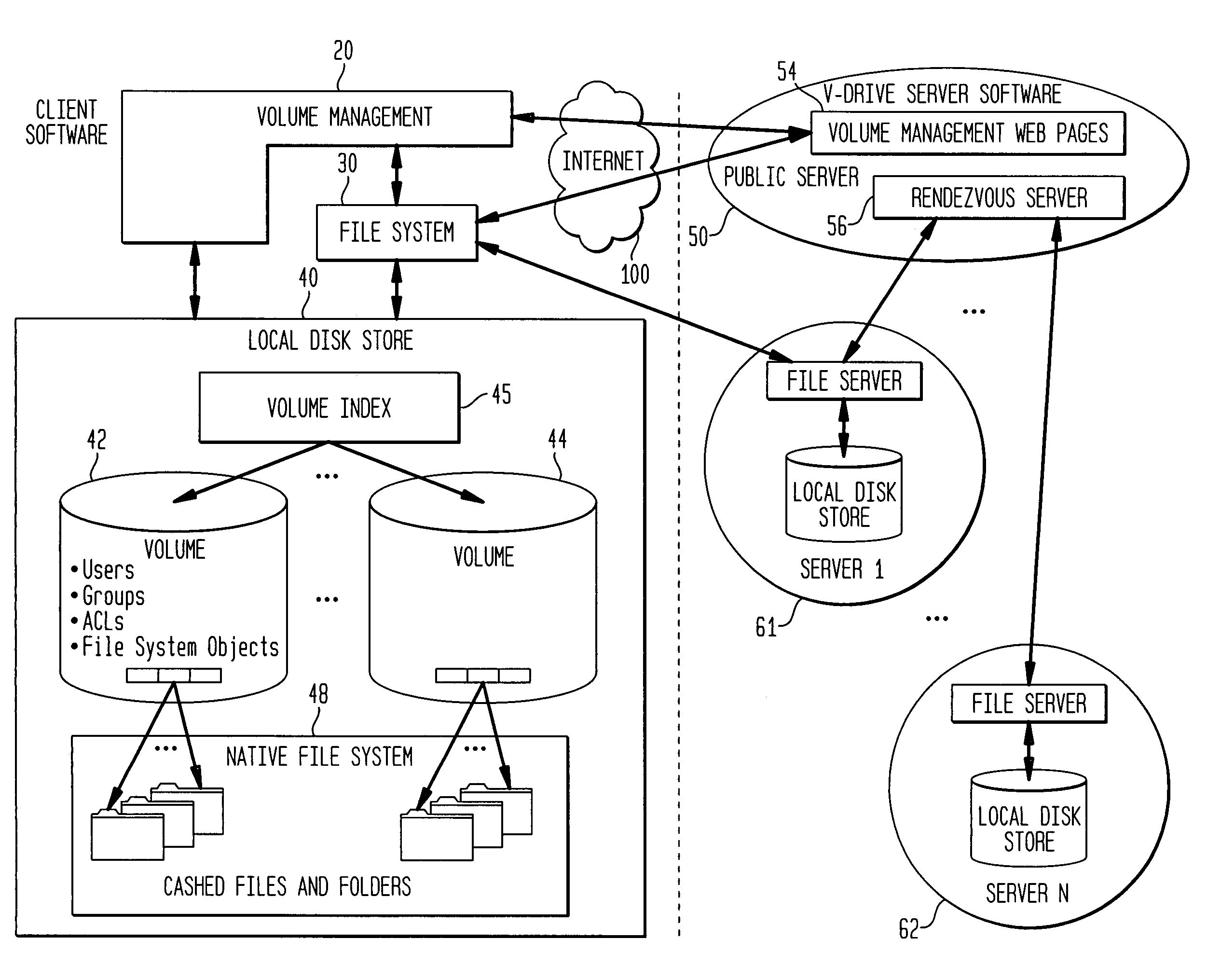
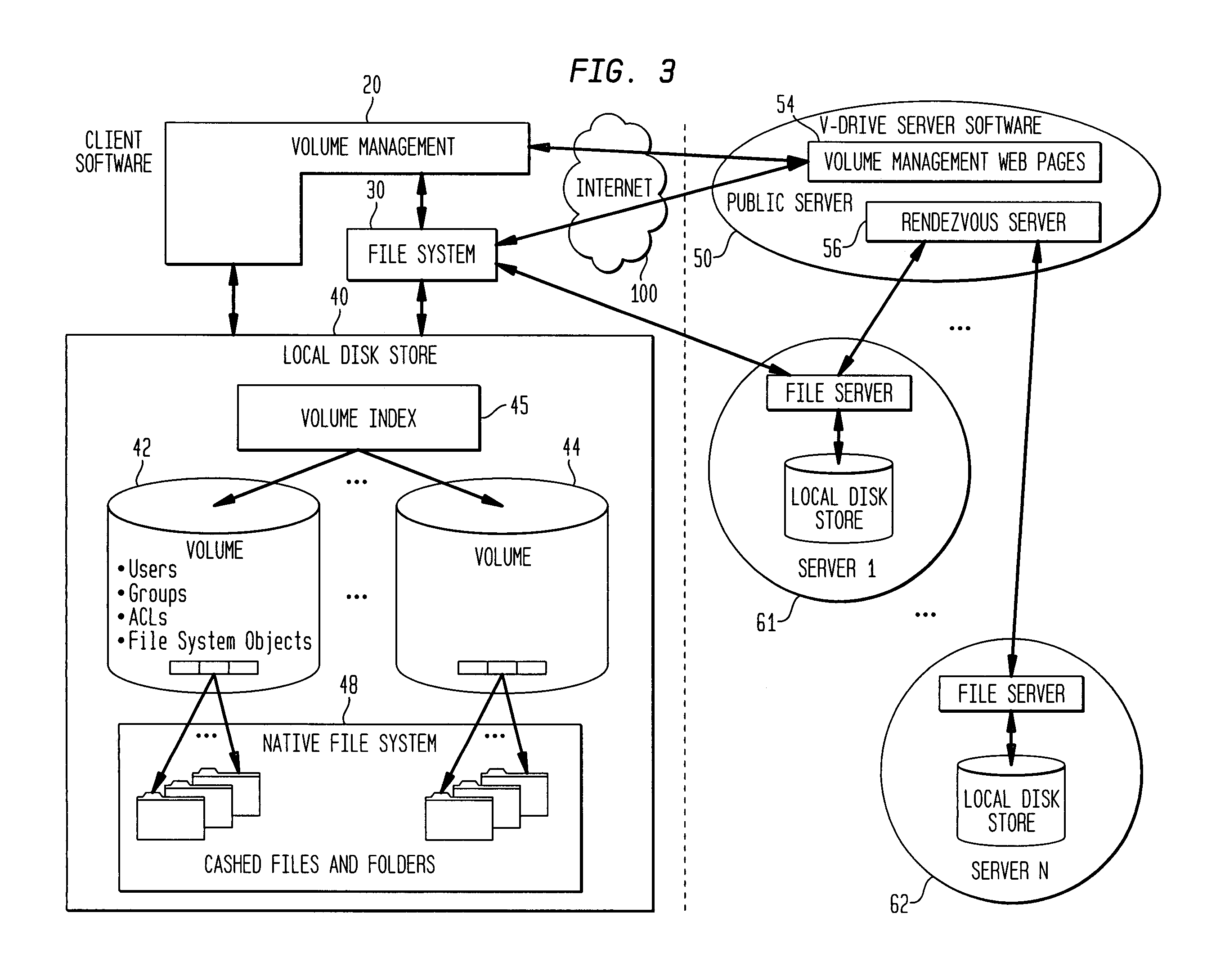
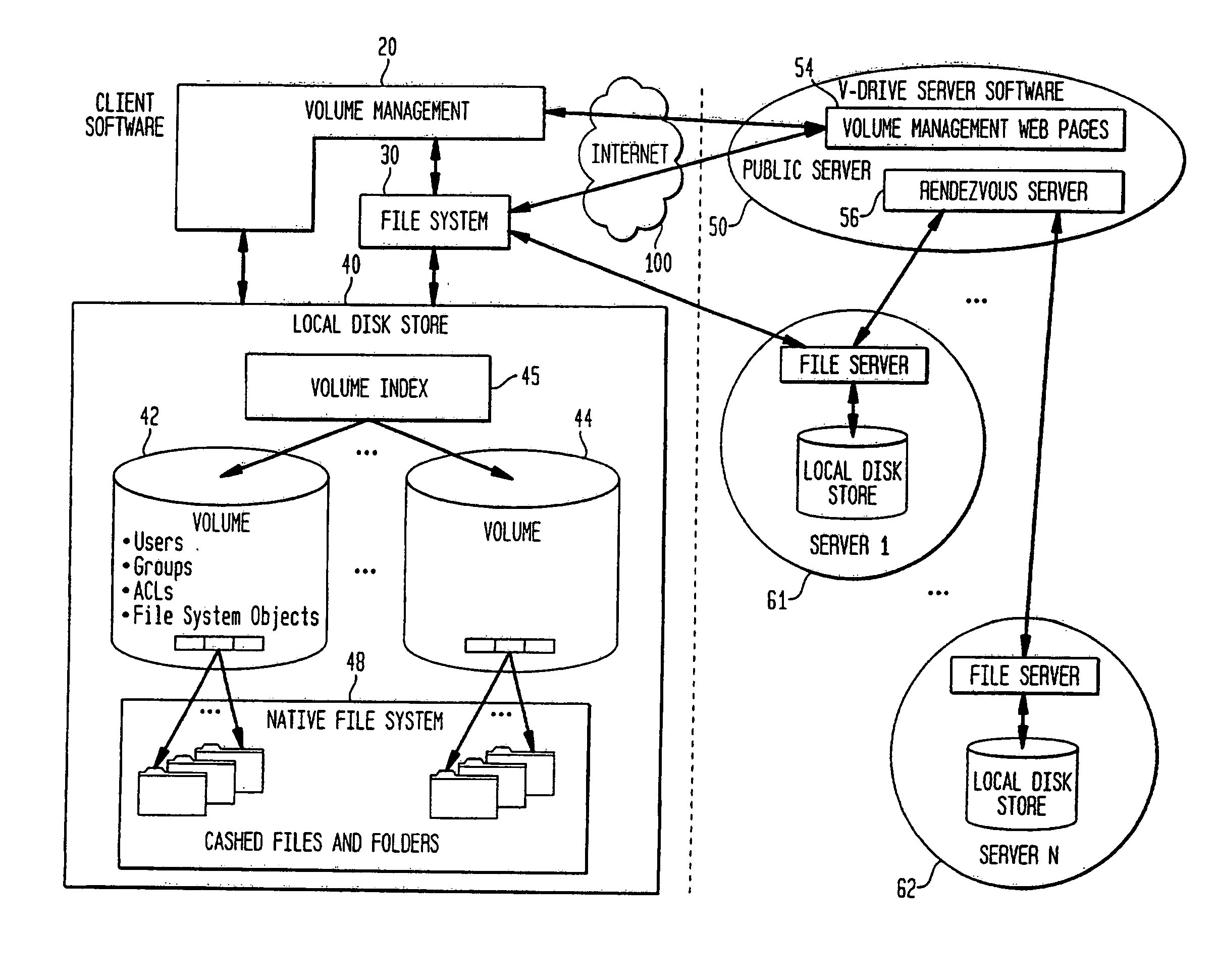
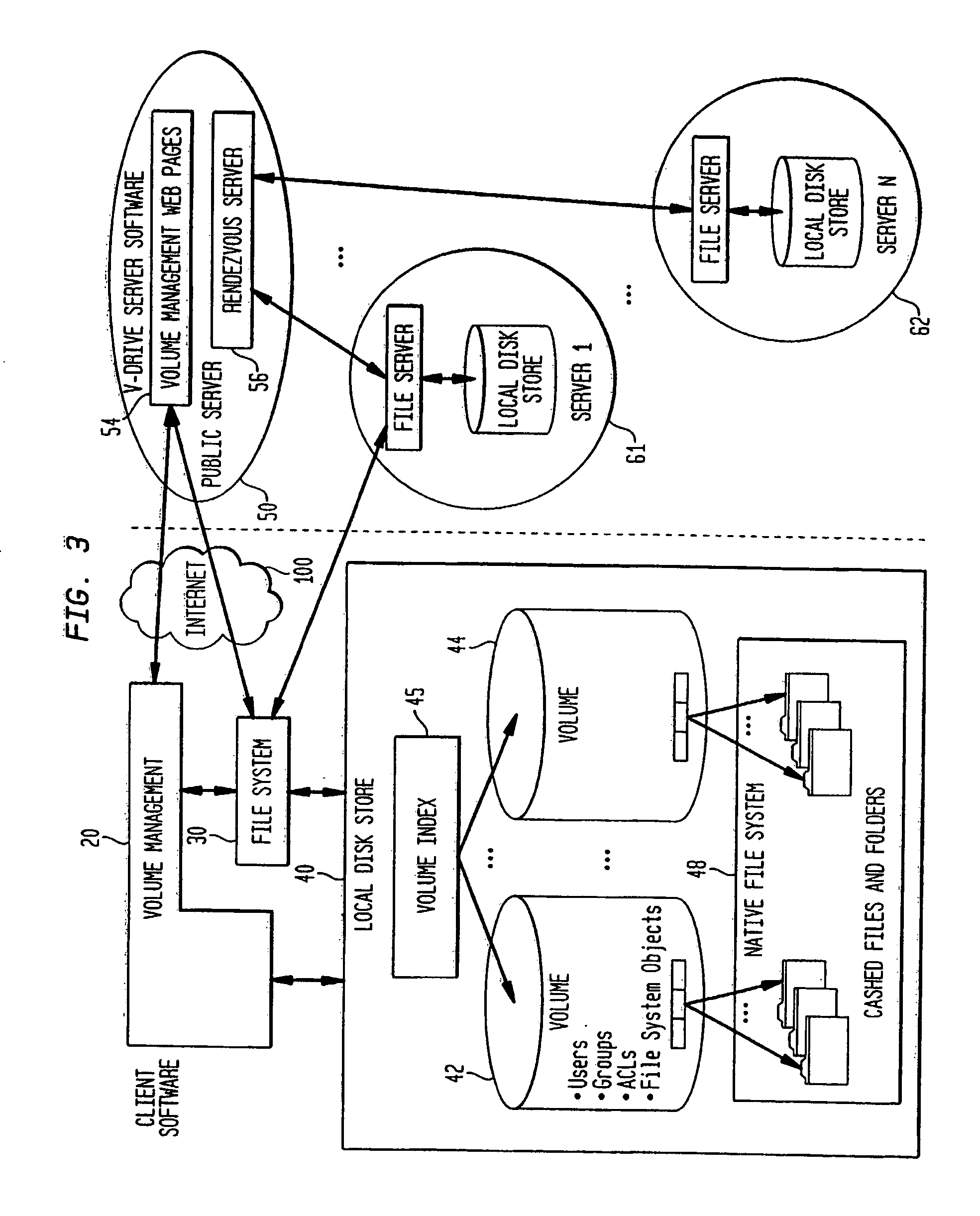
Internet-based shared file service with native PC client access and semantics and distributed access control
InactiveUS7136903B1Web data retrievalPublic key for secure communicationWide area networkAccess control
A multi-user file storage service and system enable each user of a pre-subscribed user group to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Additionally, an encrypted key is transferred from the file server node to a particular client node via a secure channel. The encrypted key uses an encryption function and a decryption function not known locally at the remote file server. Furthermore, both privileged access control rights and file sharing mode access control to a particular file of the group of files are delegated to one or more distributed nodes other than the remote file server node which provides the data.
Owner:GOOGLE LLC
Internet-based shared file service with native PC client access and semantics and distributed version control
InactiveUS20060129627A1Multiple digital computer combinationsTransmissionOperational systemWide area network
A multi-user file storage service and system enable each user of a pre-subscribed user group to operate an arbitrary client node at an arbitrary geographic location, to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node in communication with the remote file server node via the wide area network. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Illustratively, the integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Thus, all native operating system application programming interfaces operate as if all multi-user applications accessing the files function as if the remote server and client nodes were on the same local area network. Illustratively, an interface is provided for adapting file access one of the client nodes. The interface designates at the client node each accessible file of the group as stored on a virtual storage device. The interface enables access to the designated files in a fashion which is indistinguishable, by users of, and applications executing at, the client node, with access to one or more files stored on a physical storage device that is locally present at the client node. Illustratively, an encrypted key is transferred from the remote file server node to one of the client nodes via a secure channel. The key is encrypted using an encryption function not known locally at the remote file server node. The transferred key is decrypted at the client node. The key is used at the client node to decrypt information of the files downloaded from the remote file server node or to encrypt information of the files prior to uploading for storage at the remote file server node. Access control to a particular one of the files of the group can be delegated to an access control node.
Owner:GOOGLE LLC
Method and apparatus for efficiently initializing mobile wireless devices
InactiveUS6980660B1Efficient administrationEliminating inflexibilityKey distribution for secure communicationDigital data processing detailsSecure communicationUnique identifier
A method and system for enabling wireless devices distributed throughout an enterprise to be efficiently initialized for secure communications. The method and system utilize well known public key cryptography and machine unique identifiers to establish a secure channel and initialize the wireless devices.
Owner:IBM CORP
Methods, system and mobile device capable of enabling credit card personalization using a wireless network
Methods of creating a secure channel over which credit card personalization data can be transmitted over the air (OTA) are provided. In particular, Generic Authentication Architecture (GAA) may be used to establish a secure communication channel between the user equipment (UE) and a personalization application server or bureau acting as a network application function (NAF) server. An user equipment, personalization application service (e.g., a NAF server), a system embodying a personalization application server and an user equipment, and a computer program product are also provided for creating a secure channel, such as via GAA, over which credit card personalization data can be transmitted OTA.
Owner:NOKIA TECH OY
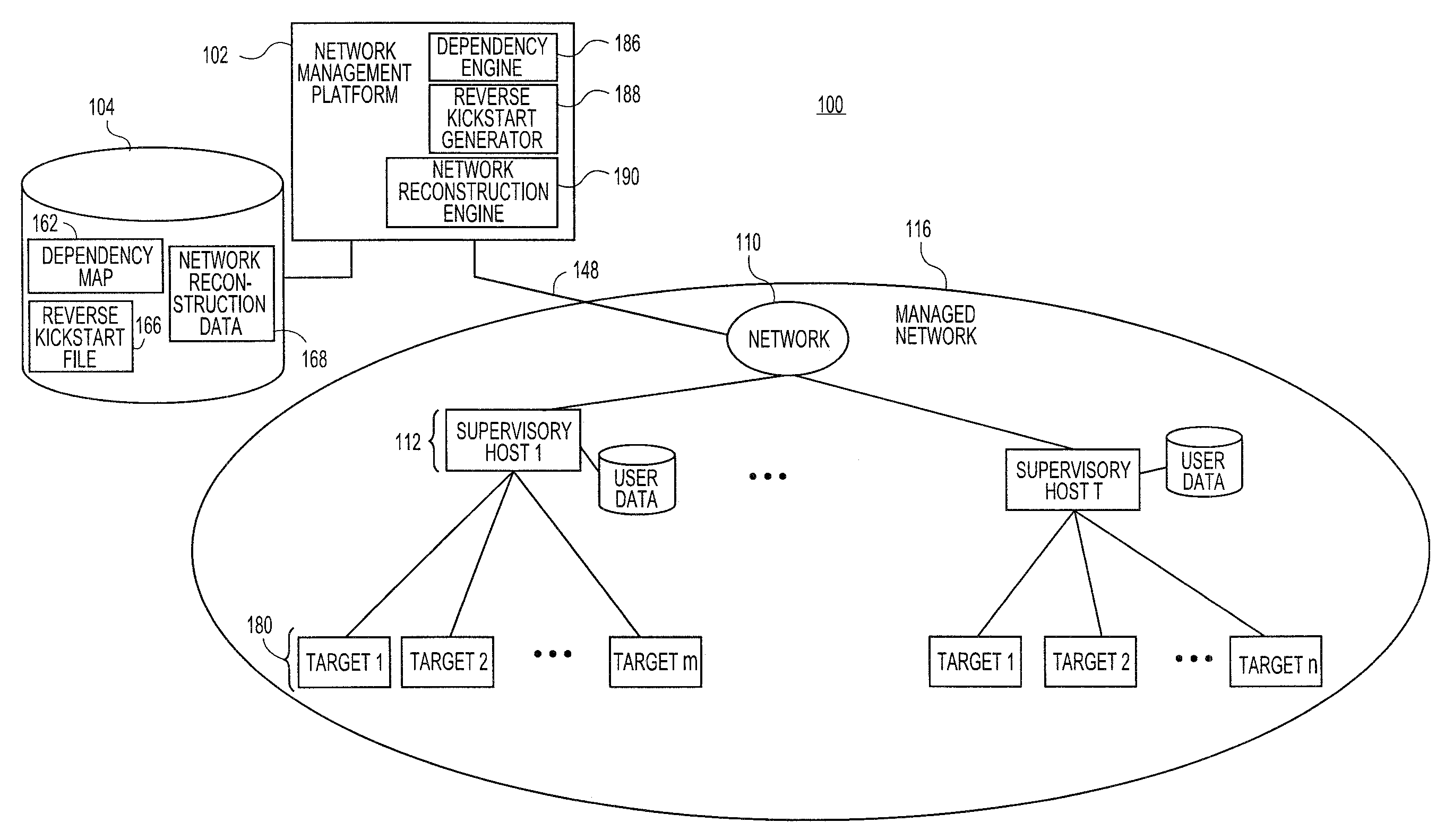
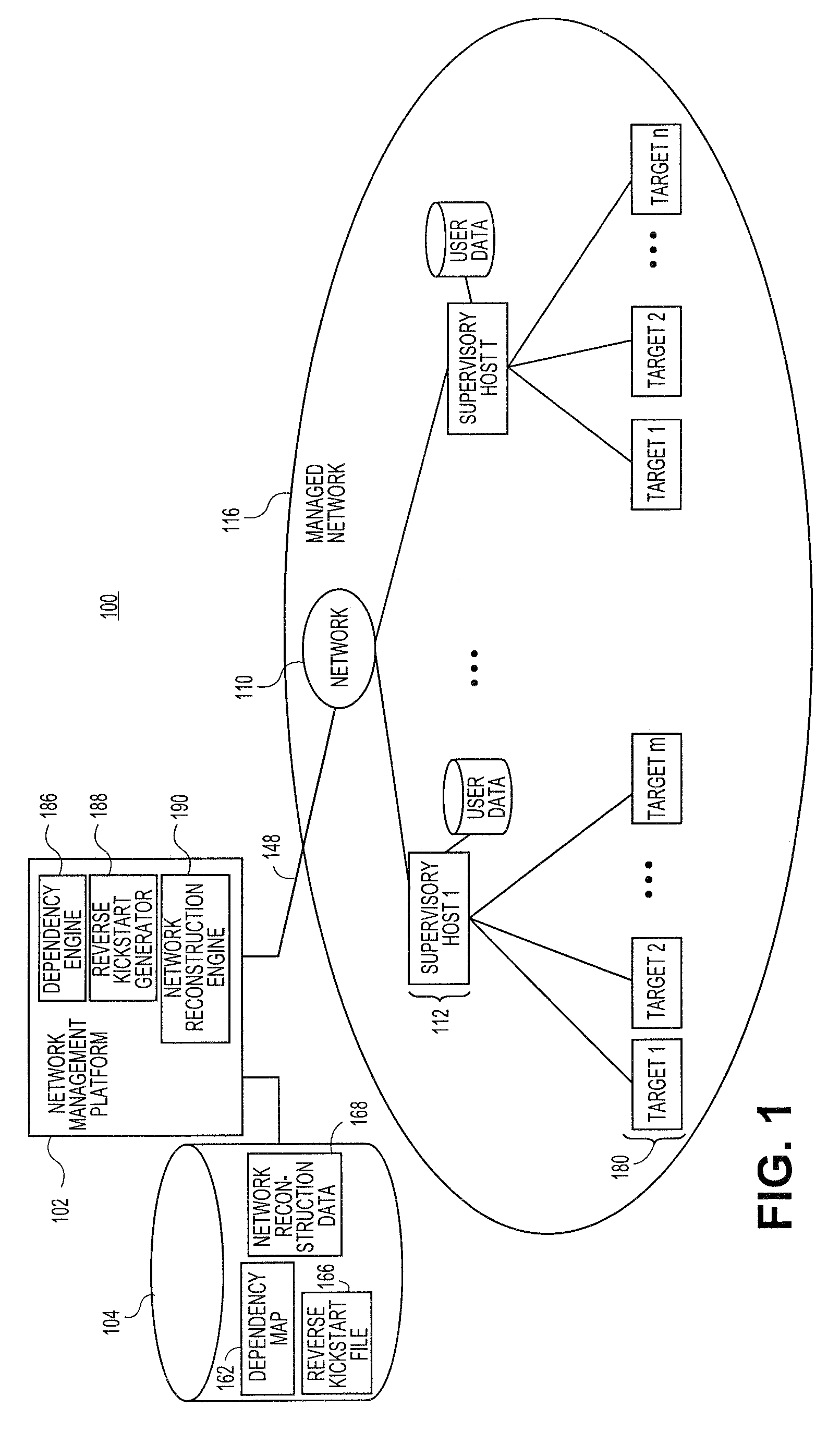
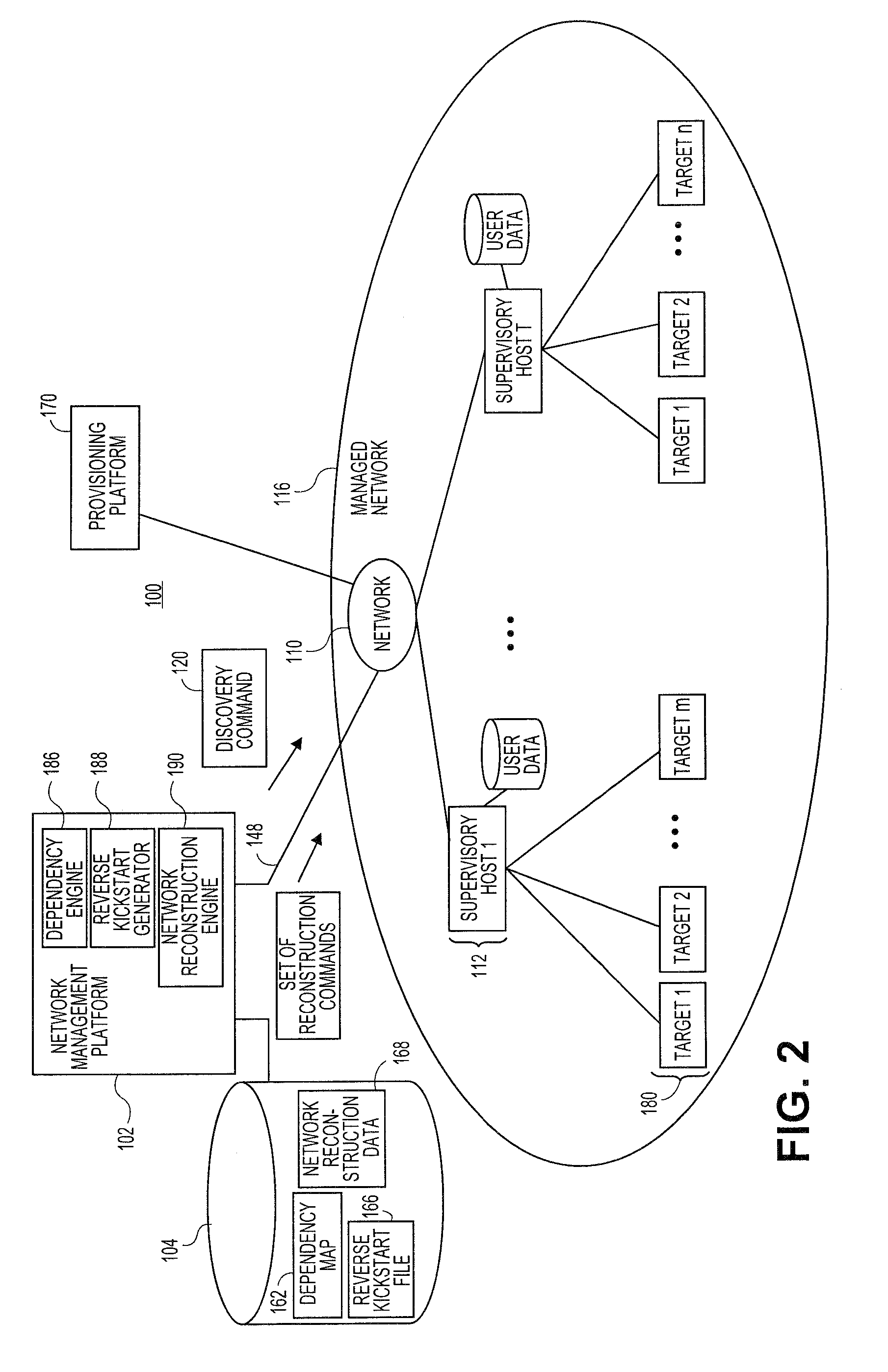
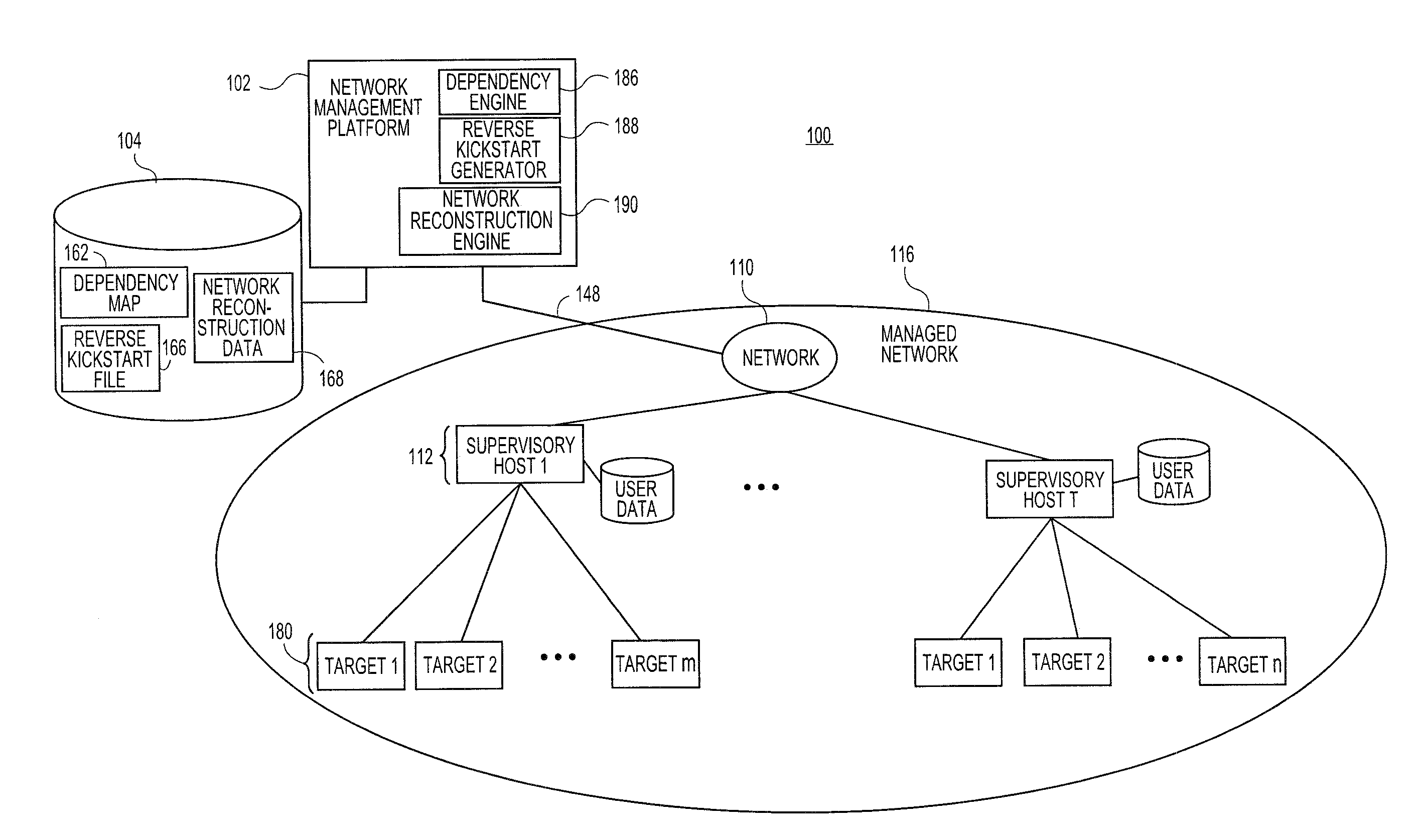
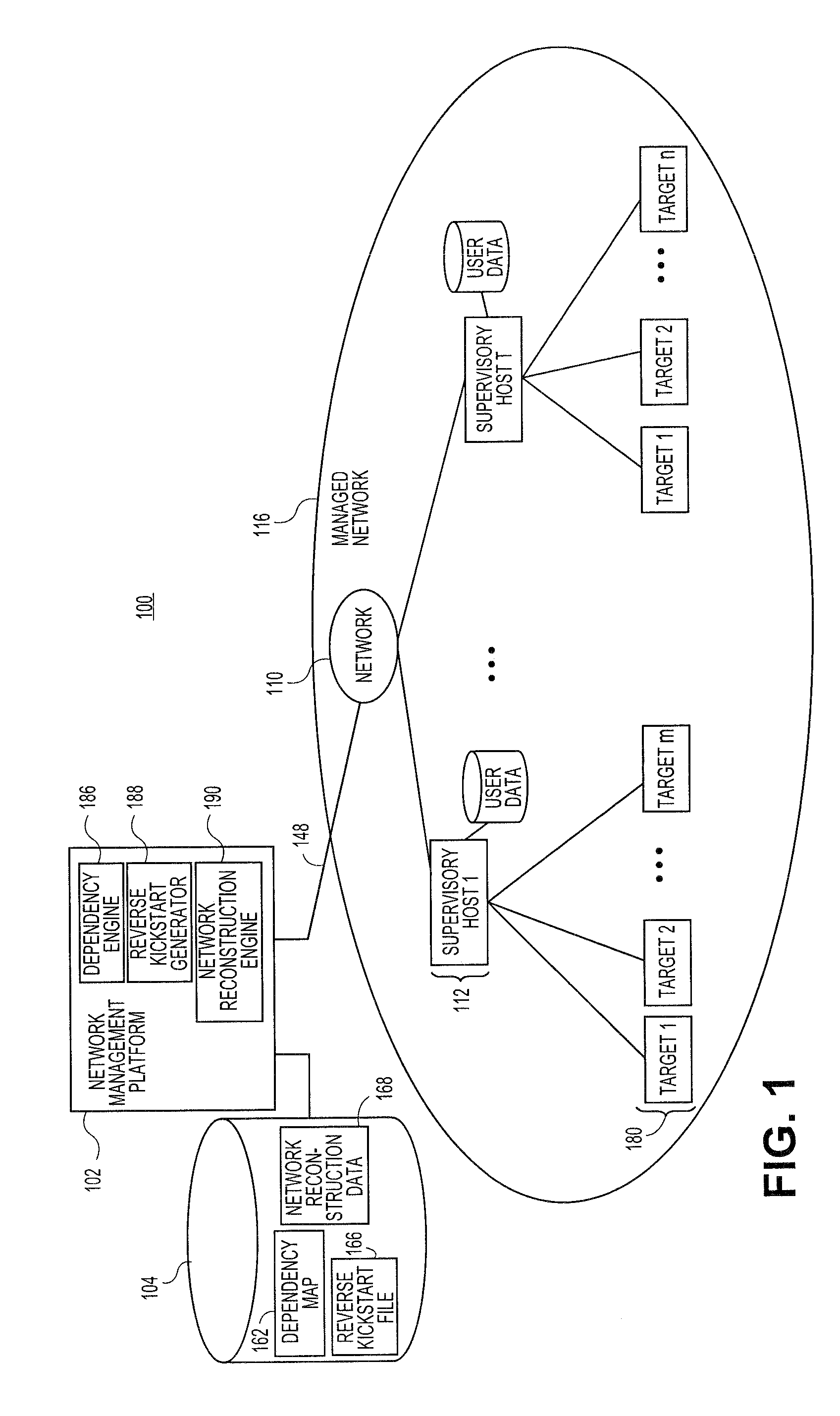
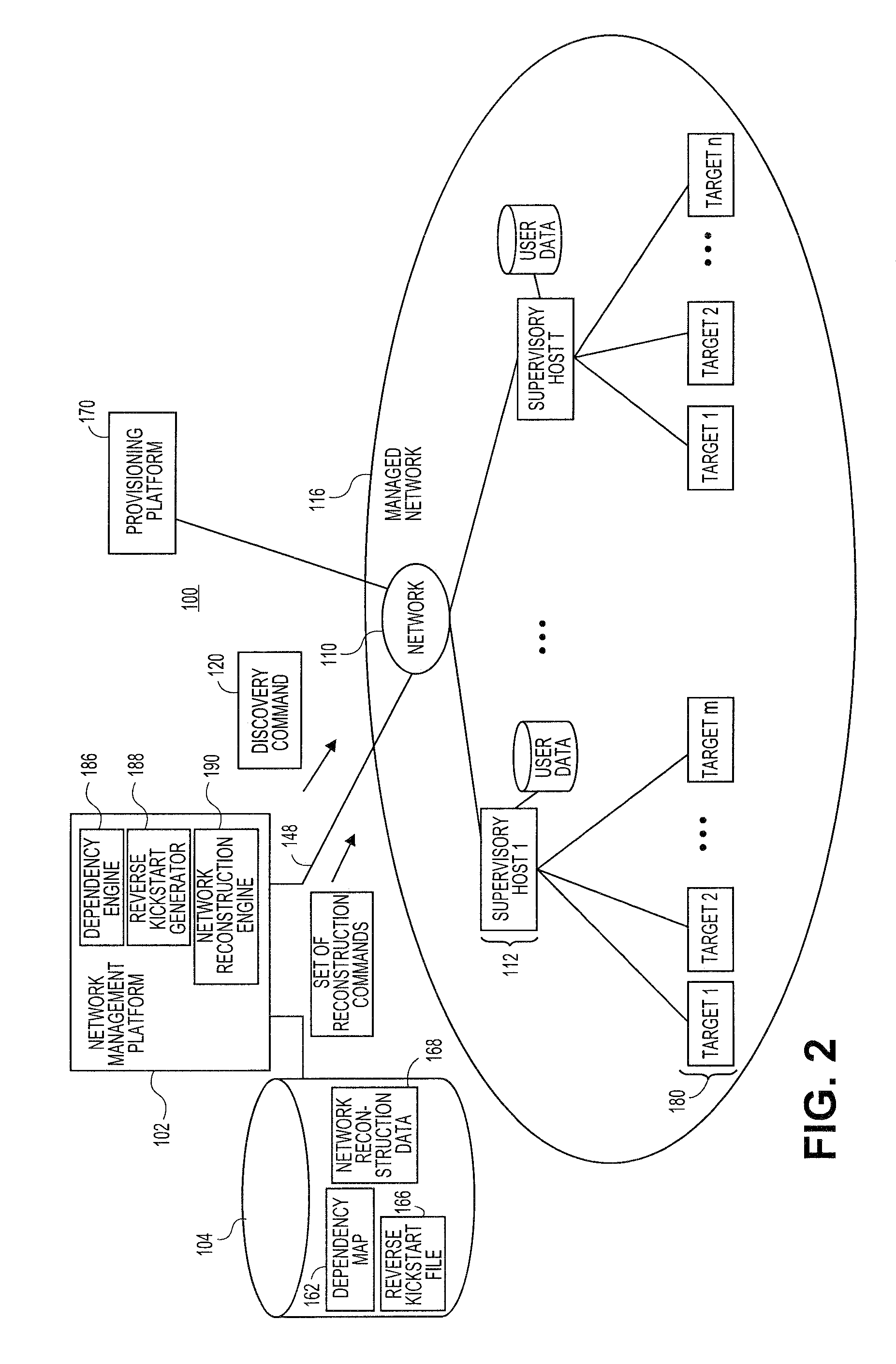
Systems and methods for automatically generating system restoration order for network recovery
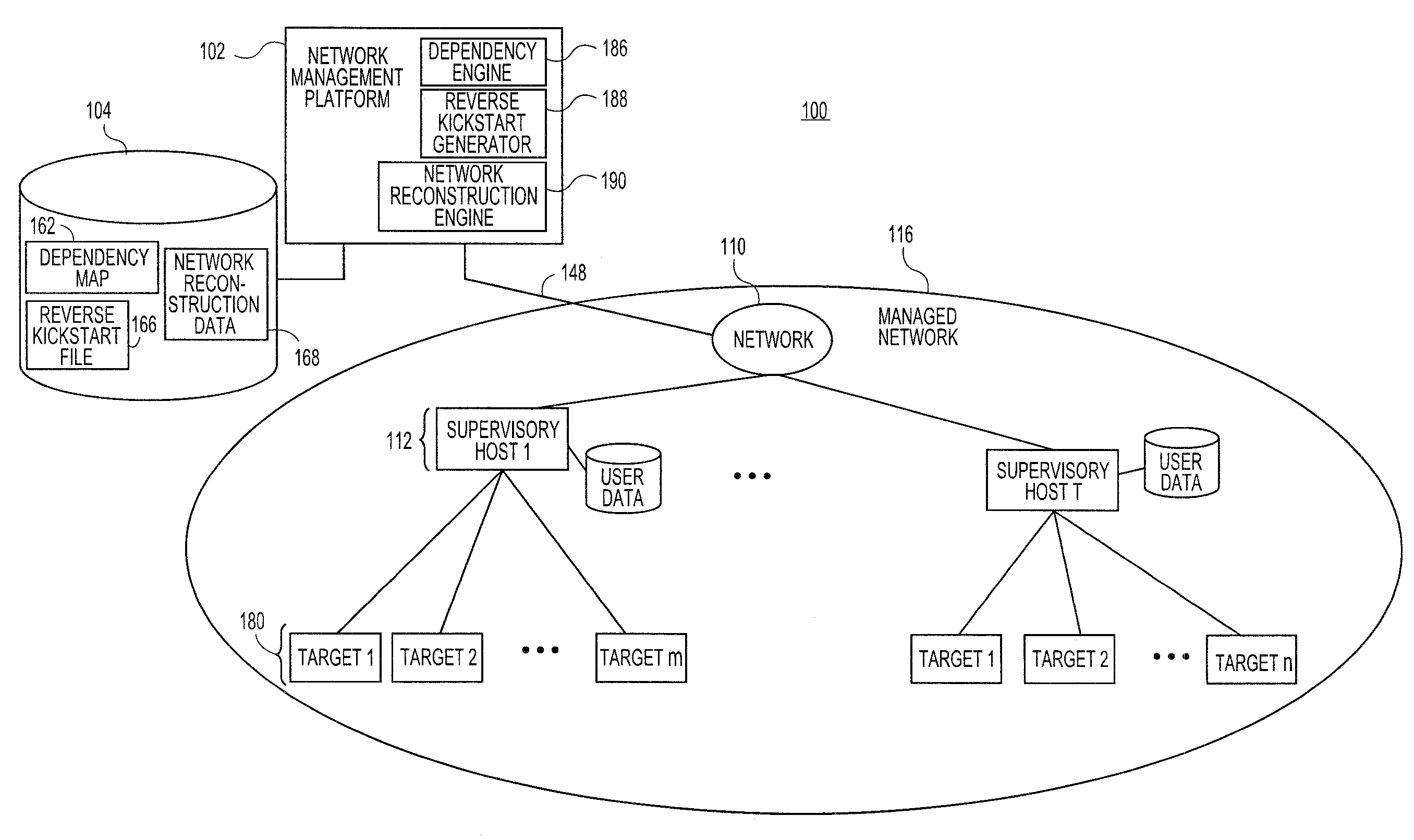
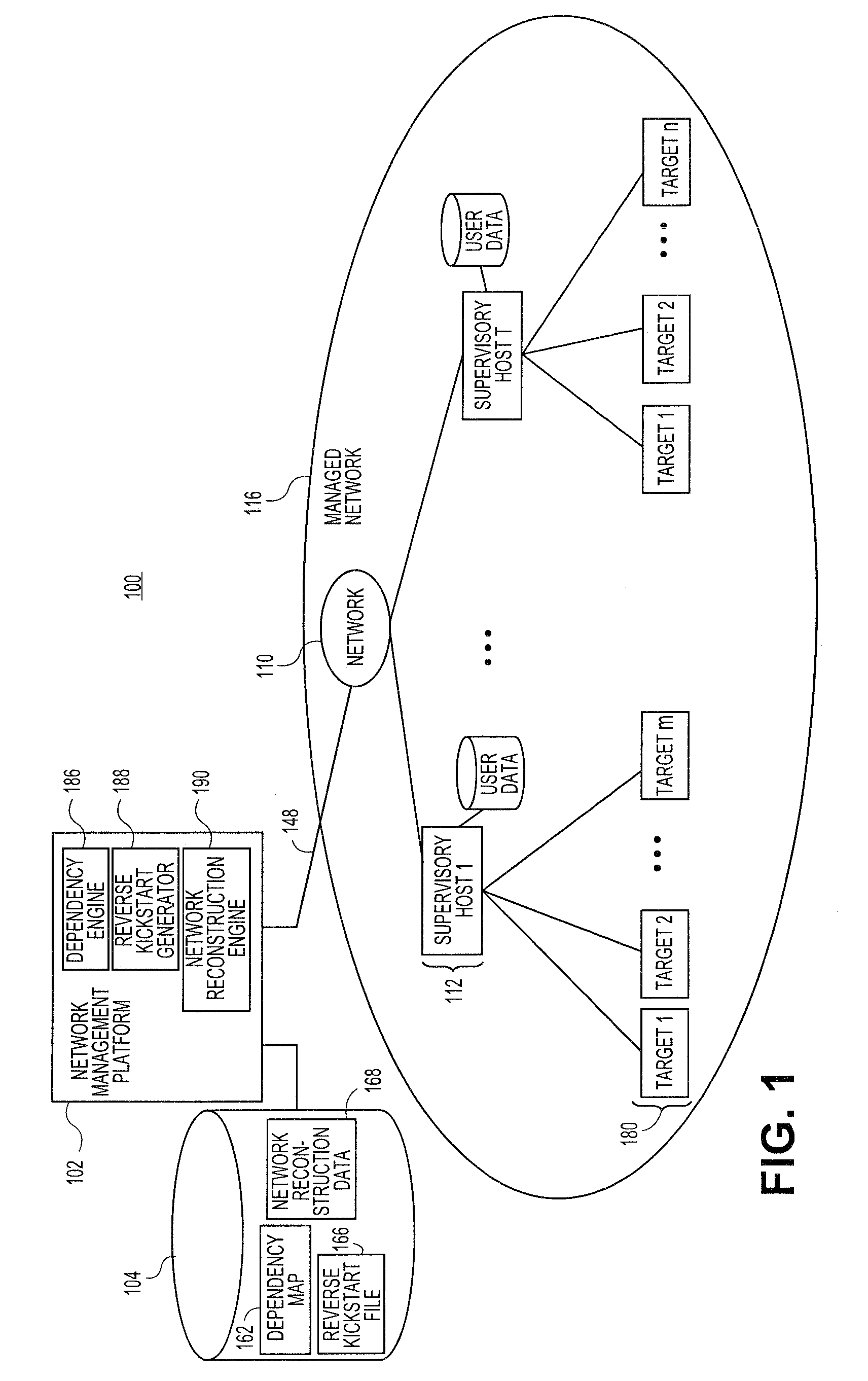
Embodiments relate to systems and methods for automatically generating a system restoration order for network recovery. A set of managed machines, such as personal computers or servers, can be managed by a network management platform communicating with the machines via a secure channel. The network management platform can access a dependency map indicating a required order for restoration of machines or nodes on a network. The network management platform likewise access a reverse kickstart file for each machine to be automatically restored in order to ensure proper functioning of the network, and extract a current configuration of that machine for purposes of restoring the overall network.
Owner:RED HAT
System and method for secure relayed communications from an implantable medical device
ActiveUS9215075B1Good security mechanismLarge block sizePhysical therapies and activitiesDrug and medicationsSecure communicationMedical equipment
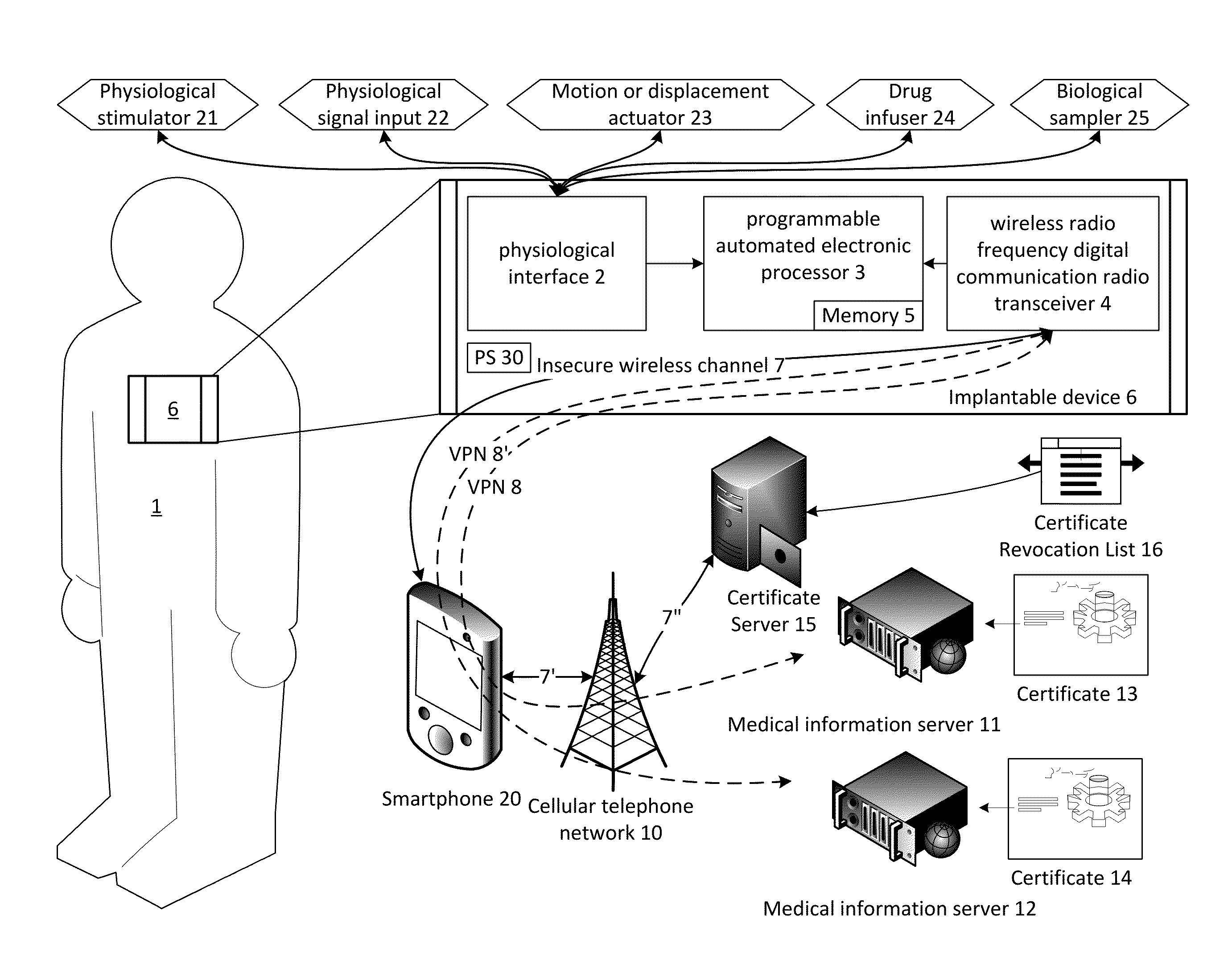
The present invention provides systems and methods for supporting encrypted communications with a medical device, such as an implantable device, through a relay device to a remote server, and may employ cloud computing technologies. An implantable medical device is generally constrained to employ a low power transceiver, which supports short distance digital communications. A relay device, such as a smartphone or WiFi access point, acts as a conduit for the communications to the internet or other network, which need not be private or secure. The medical device supports encrypted secure communications, such as a virtual private network technology. The medical device negotiates a secure channel through a smartphone or router, for example, which provides application support for the communication, but may be isolated from the content.
Owner:POLTORAK TECH
Methods and systems for remote password reset using an authentication credential managed by a third party
ActiveUS20080046982A1Digital data processing detailsUser identity/authority verificationThird partyPassword
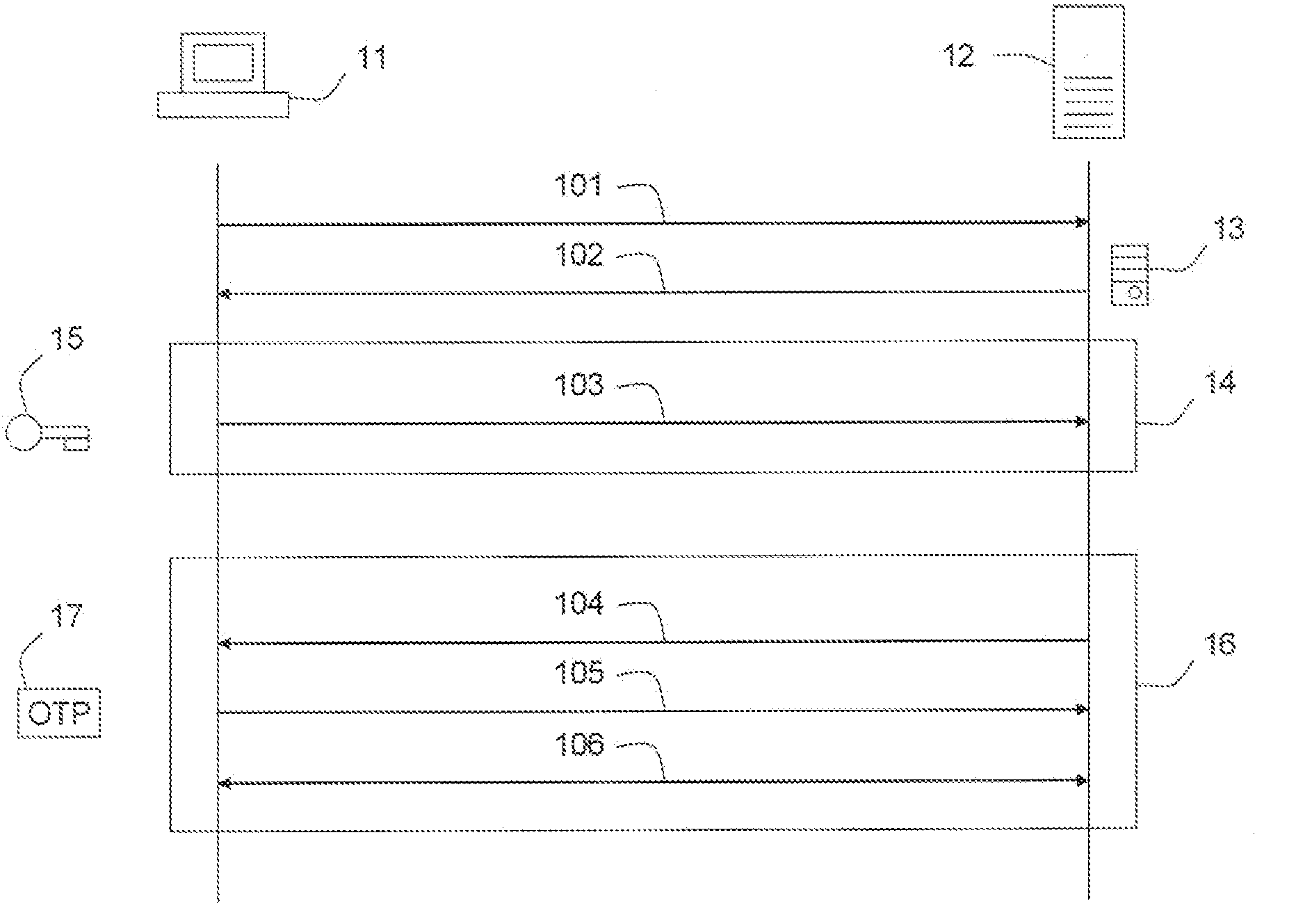
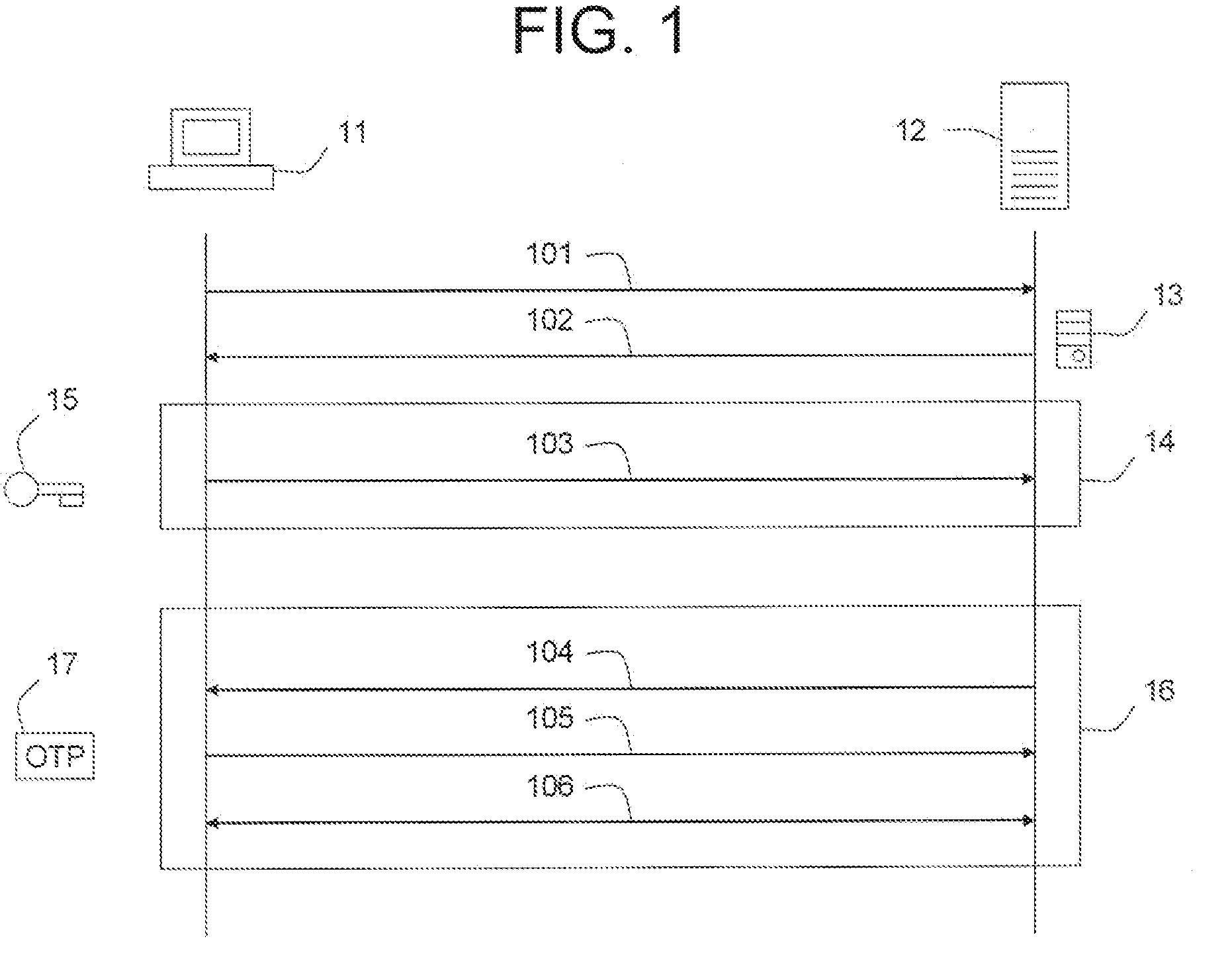
Embodiments of the present invention provide a secure remote password reset capability. In some embodiments, an exemplary method provides a remote reset of a password associated with a token in a computer system having a security server. A token-based authentication process is activated by connecting the token to the security server. A server-based authentication process is initiated in the security server by activating a password reset process in a security client. The server-based authentication process communicates with the token-based authentication process over a secure channel. An authentication credential is managed by a third party agent that supplies a query and the authentication credential as a correct response to the query to the security server. A prompt provided by the password reset process collects the authentication credential and a new password. After the authentication credential is validated mutually authentication is performed between the security server and the token. The token is updated with the new password based on a successful result of the mutual authentication.
Owner:RED HAT
Method for server-side detection of man-in-the-middle attacks
InactiveUS20090210712A1User identity/authority verificationMan-in-the-middle attackNetwork Communication Protocols
Problem The combination of a tendency towards permissivity when verifying certificate authenticity and the use of in-band client authentication opens up an opportunity for attackers to mount man-in-the-middle attacks on SSL connections.Solution The invention exposes any discrepancy between the intended recipient of the client credential and the actual recipient of the client credential by cryptographically including parameters that are uniquely linked to the channel (i.e., the communication session, as characterized by the parameters of the protocols that are being used), preferably the channel end points, in the calculation of the client credential. This links the process that provides the secure channel (e.g., the SSL protocol session) to the process that provides the authentication credential (e.g., the OTP token operation), thus exposing any attack that would break up the client-server channel. This is achieved without the requirement for an additional encrypted tunnel and allowing the continued use of existing components such as existing browsers.
Owner:VASCO DATA SECURITY INTERNATIONAL
Secure and efficient offloading of network policies to network interface cards
ActiveUS8856518B2Multiple digital computer combinationsData switching networksVirtualizationProtocol for Carrying Authentication for Network Access
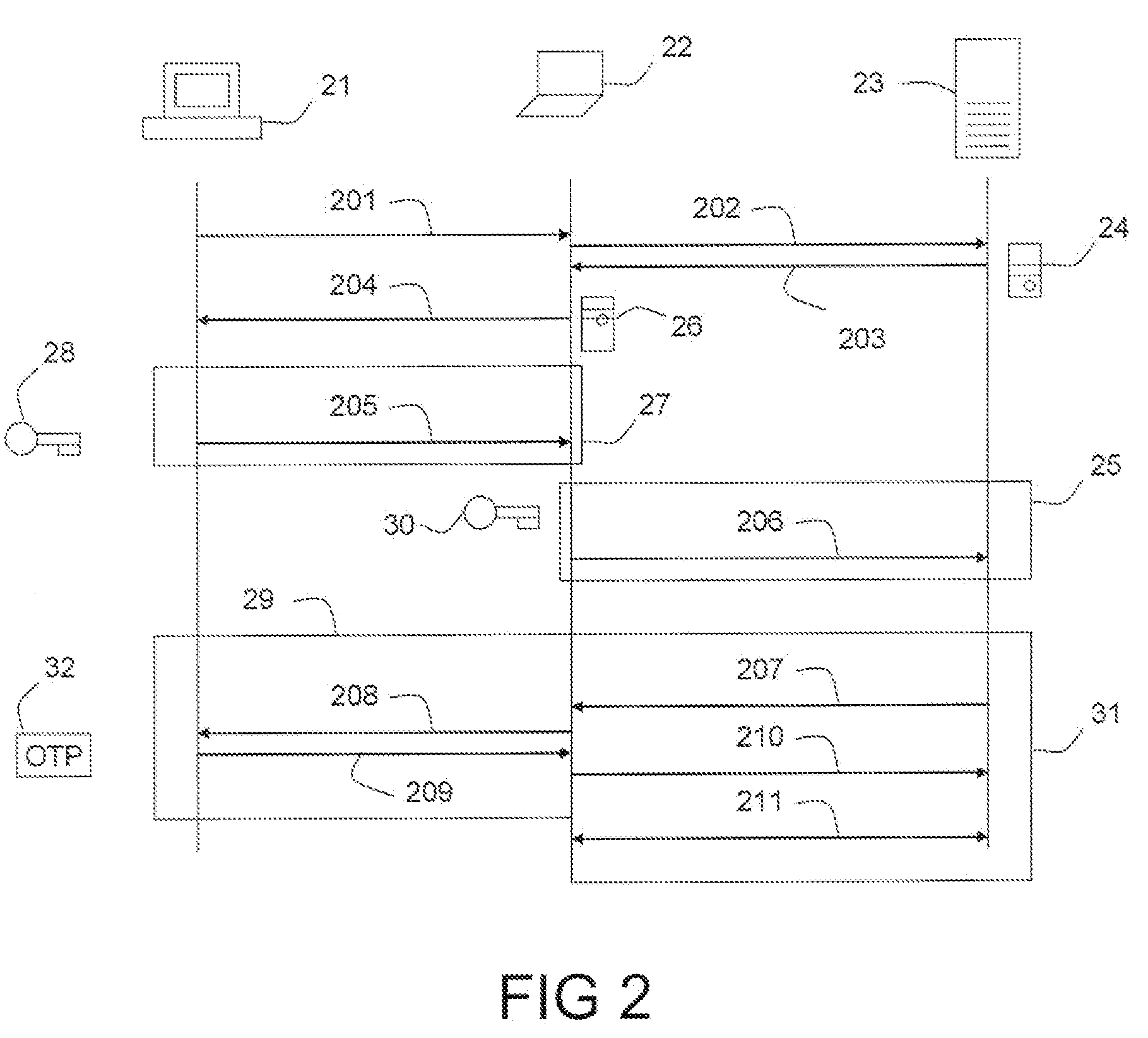
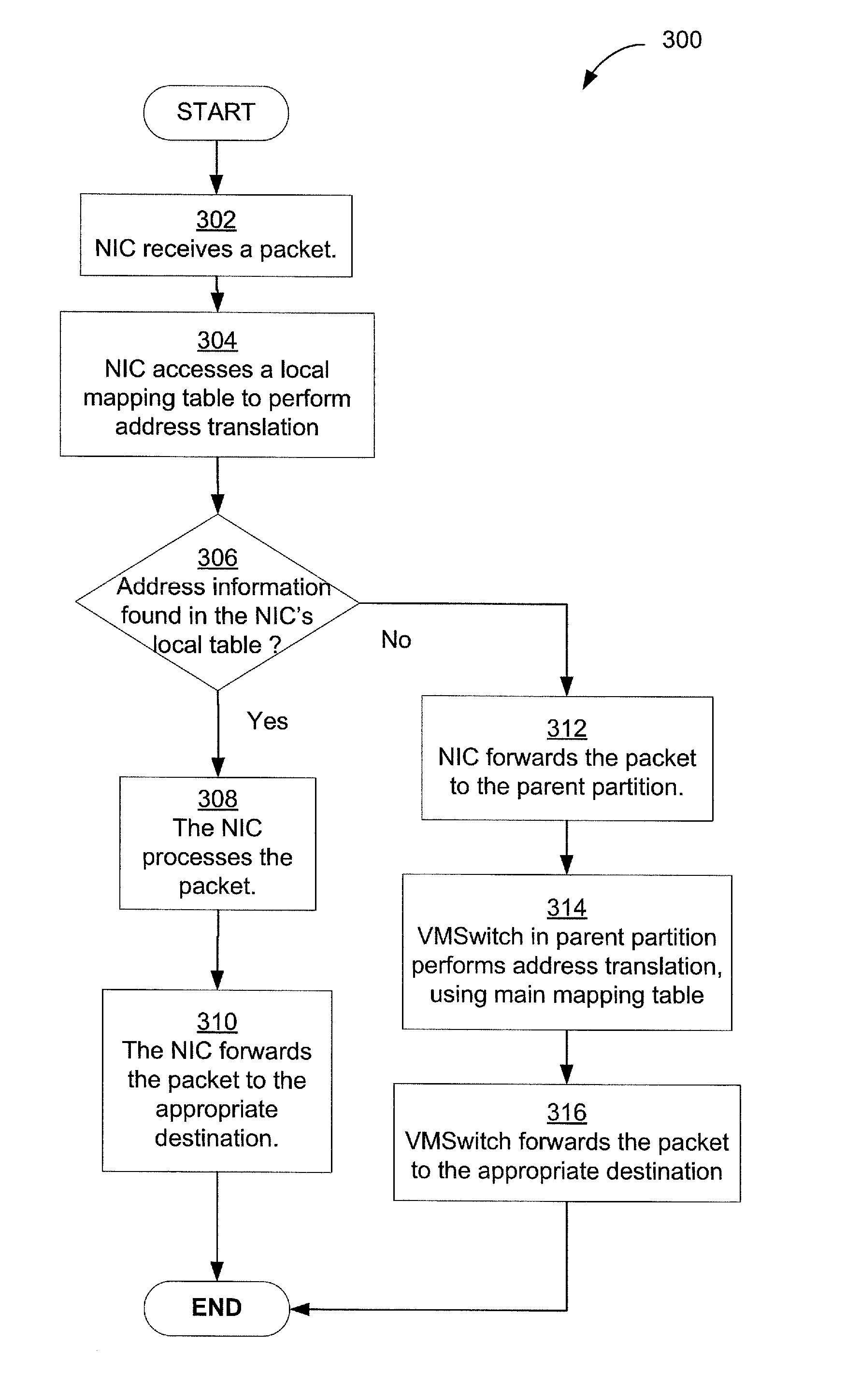
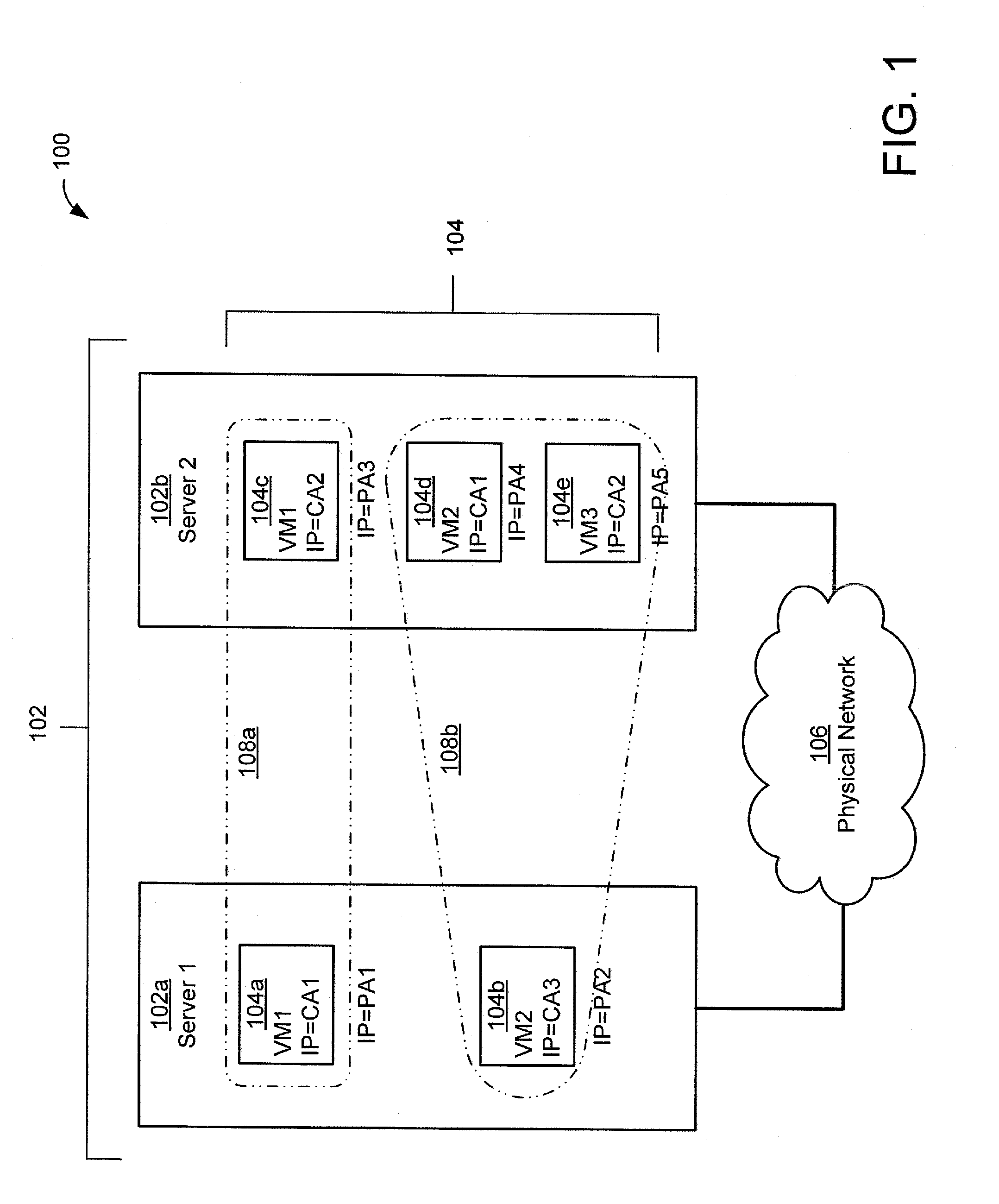
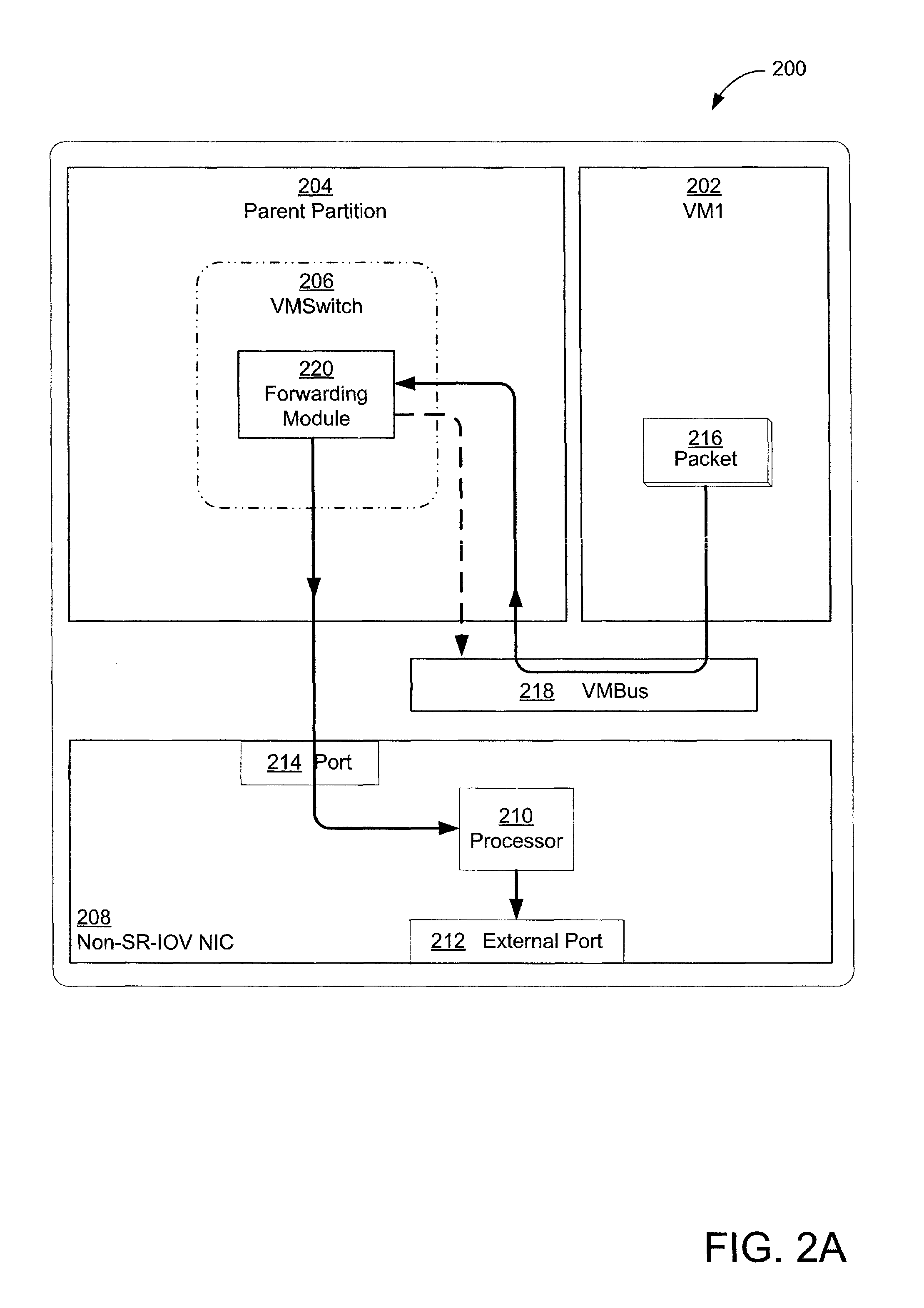
Techniques for efficient and secure implementation of network policies in a network interface controller (NIC) in a host computing device operating a virtualized computing environment. In some embodiments, the NIC may process and forward packets directly to their destinations, bypassing a parent partition of the host computing device. In particular, in some embodiments, the NIC may store network policy information to process and forward packets directly to a virtual machine (VM). If the NIC is unable to process a packet, then the NIC may forward the packet to the parent partition. In some embodiments, the NIC may use an encapsulation protocol to transmit address information in packet headers. In some embodiments, this address information may be communicated by the MC to the parent partition via a secure channel. The NIC may also obtain, and decrypt, encrypted addresses from the VMs for routing packets, bypassing the parent partition.
Owner:MICROSOFT TECH LICENSING LLC
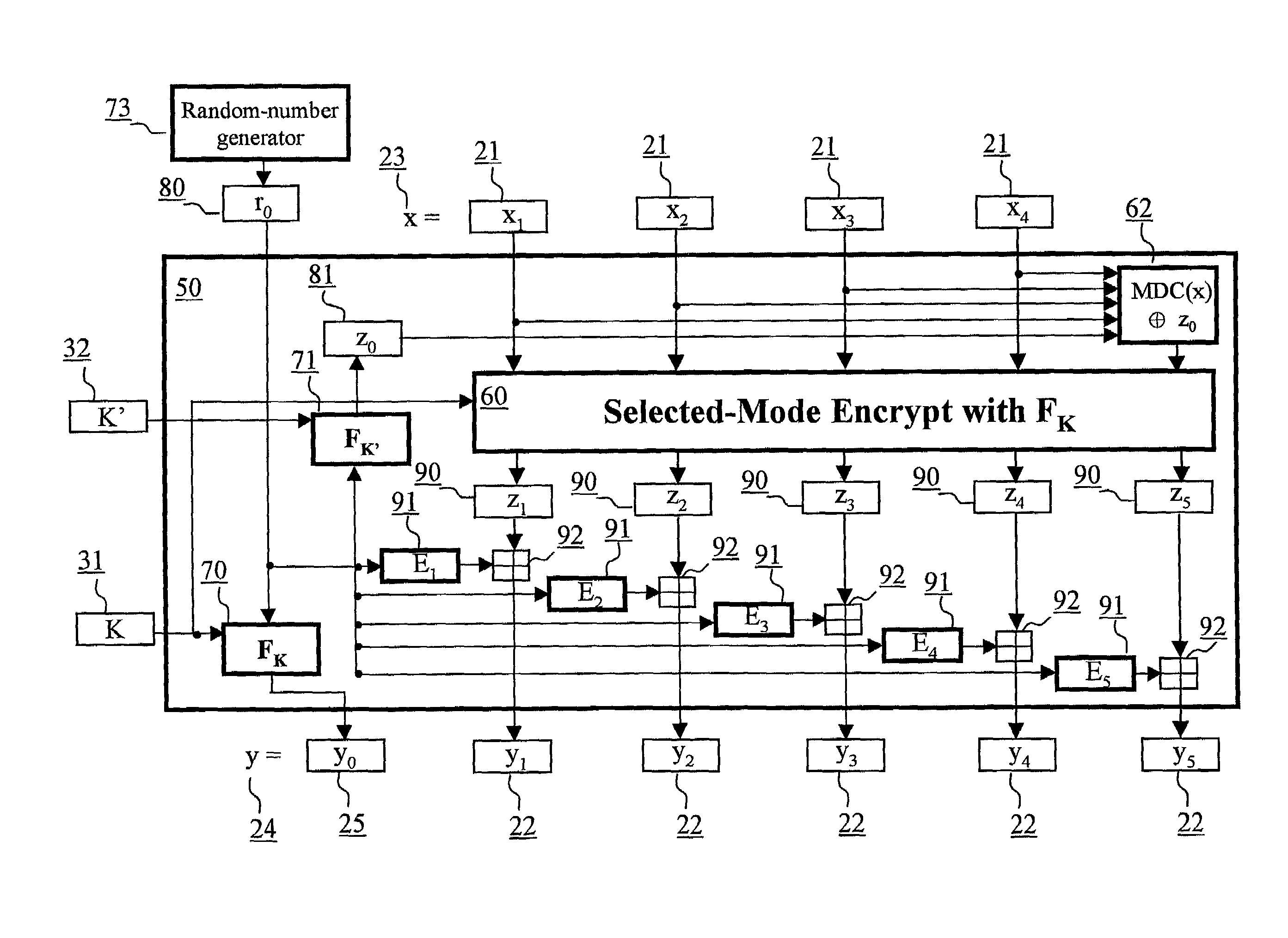
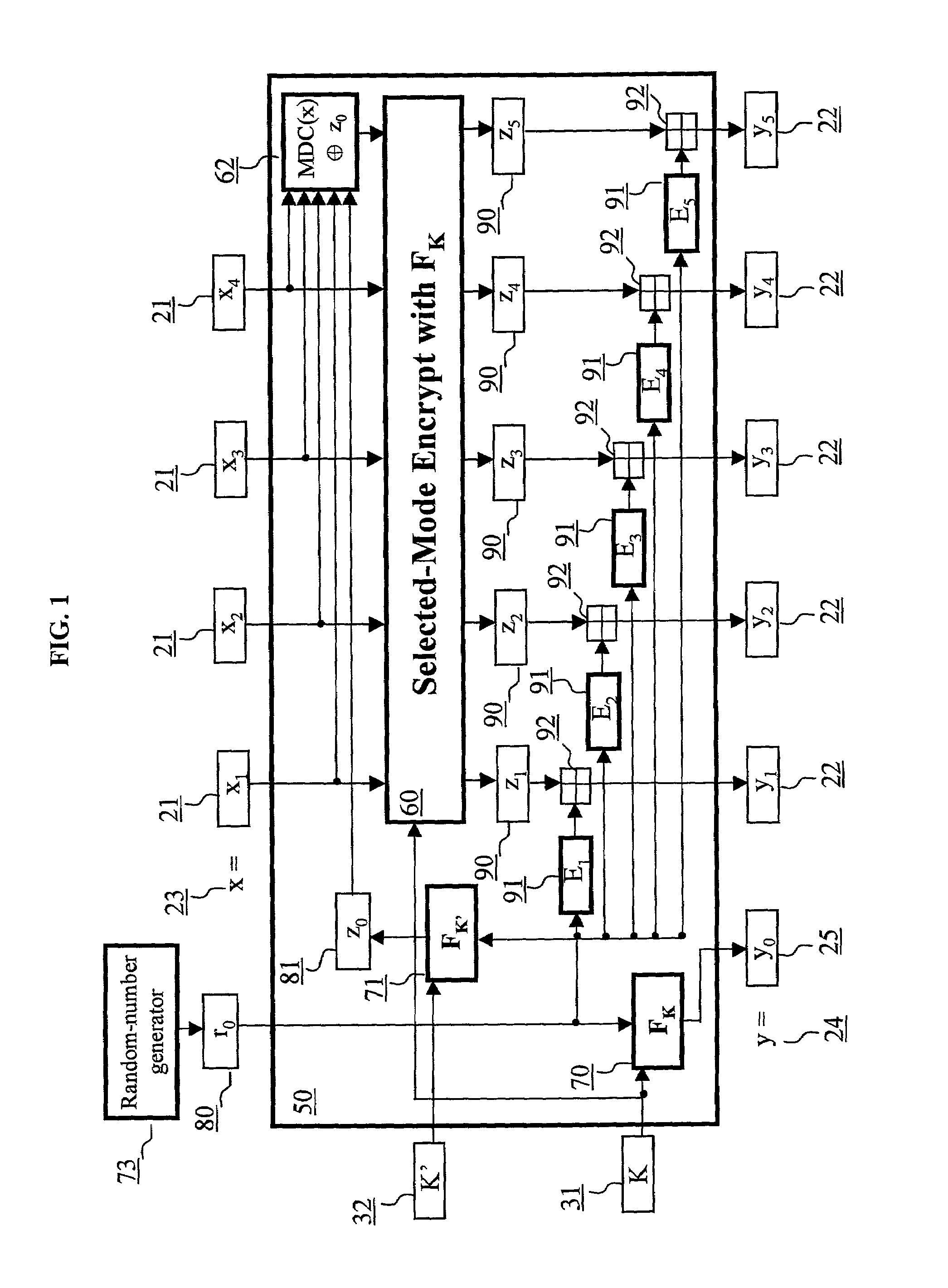
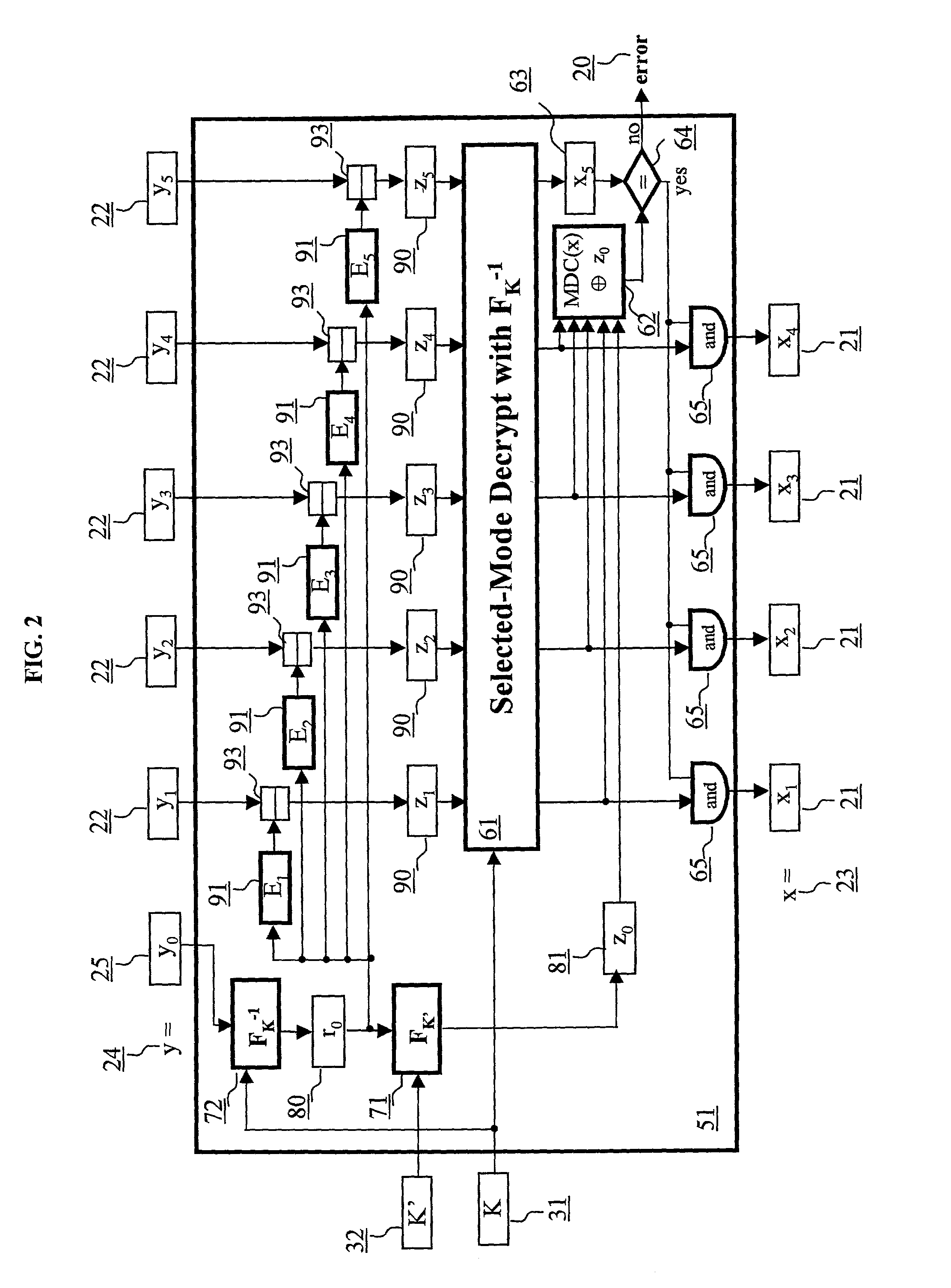
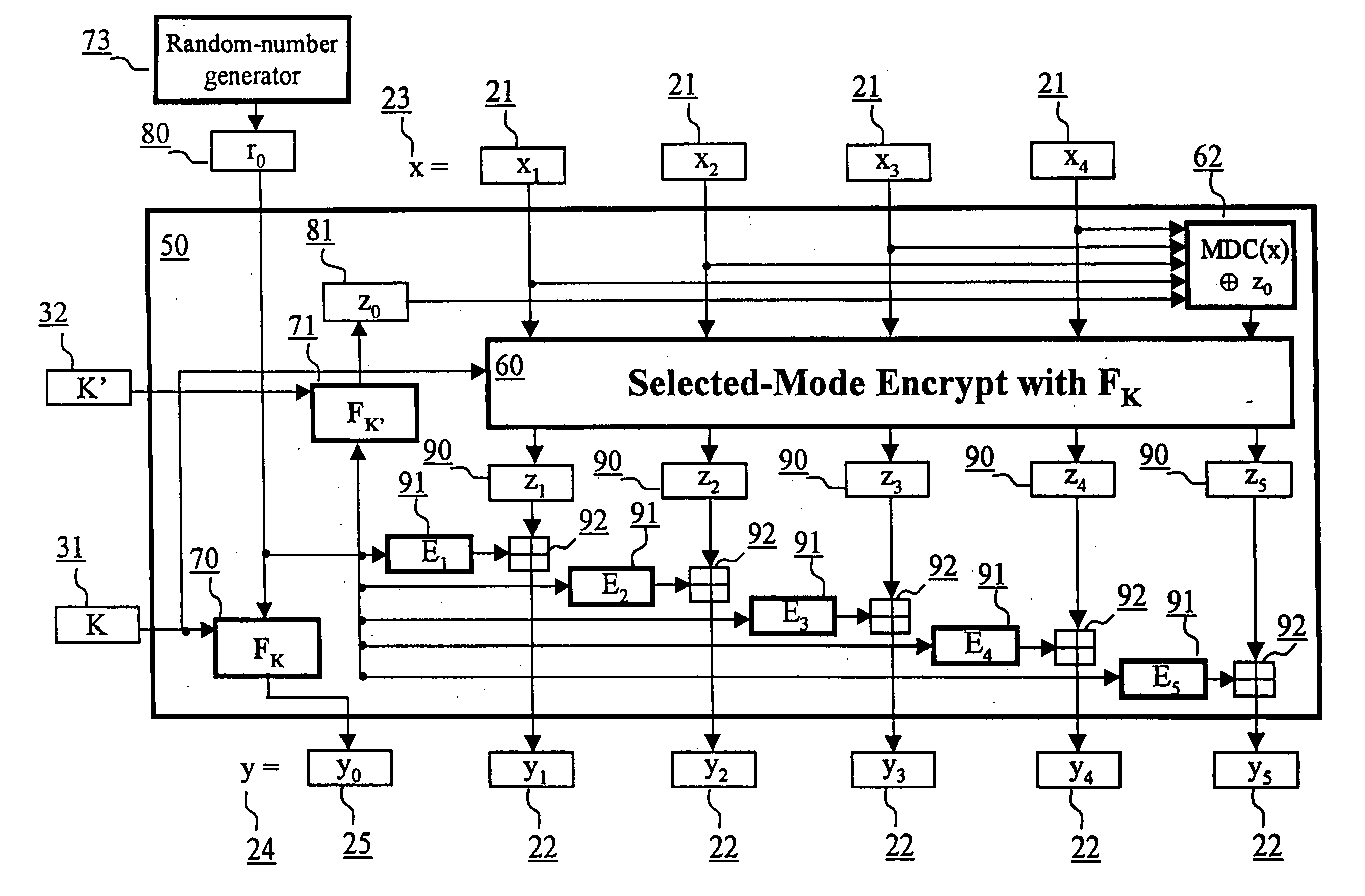
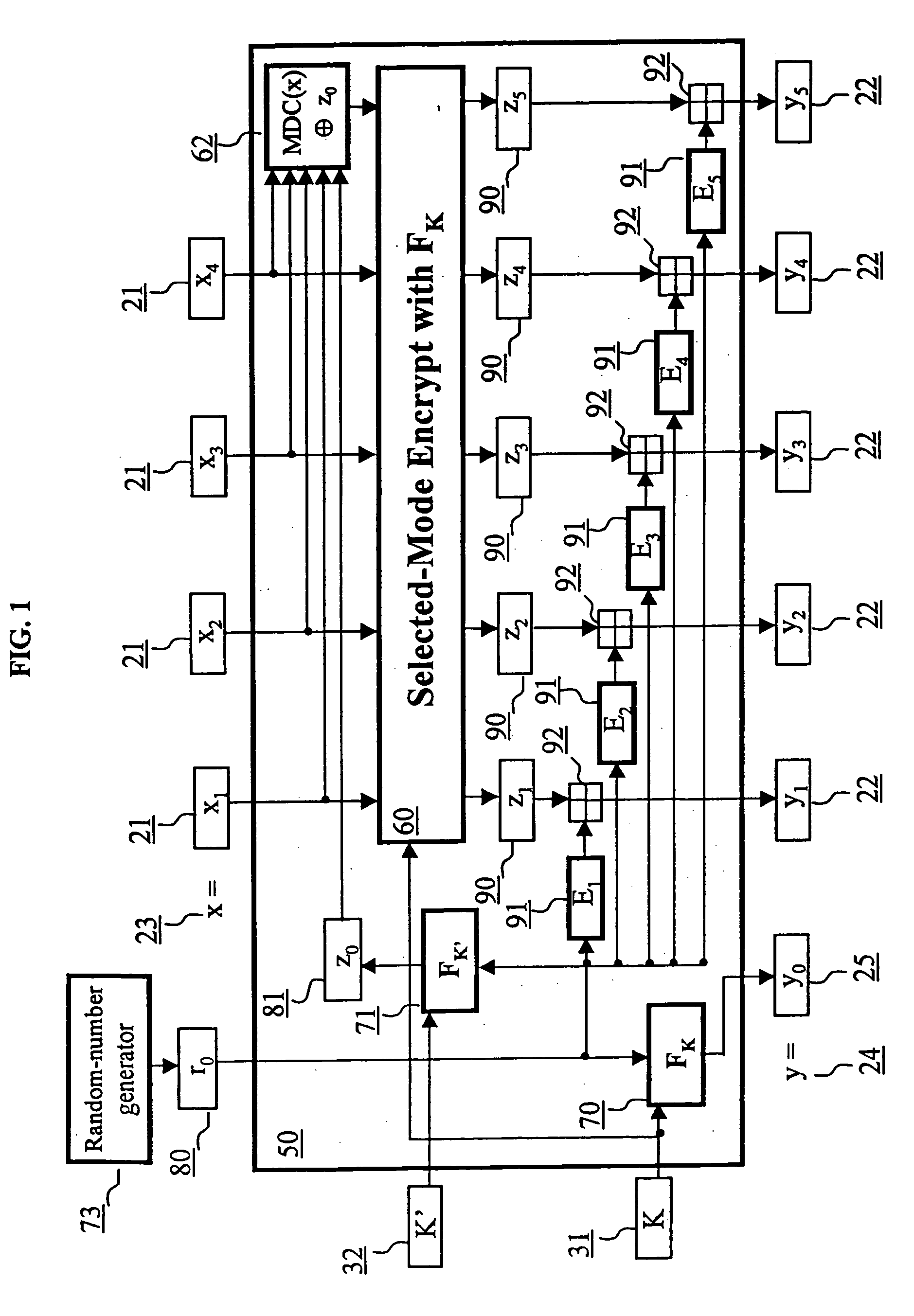
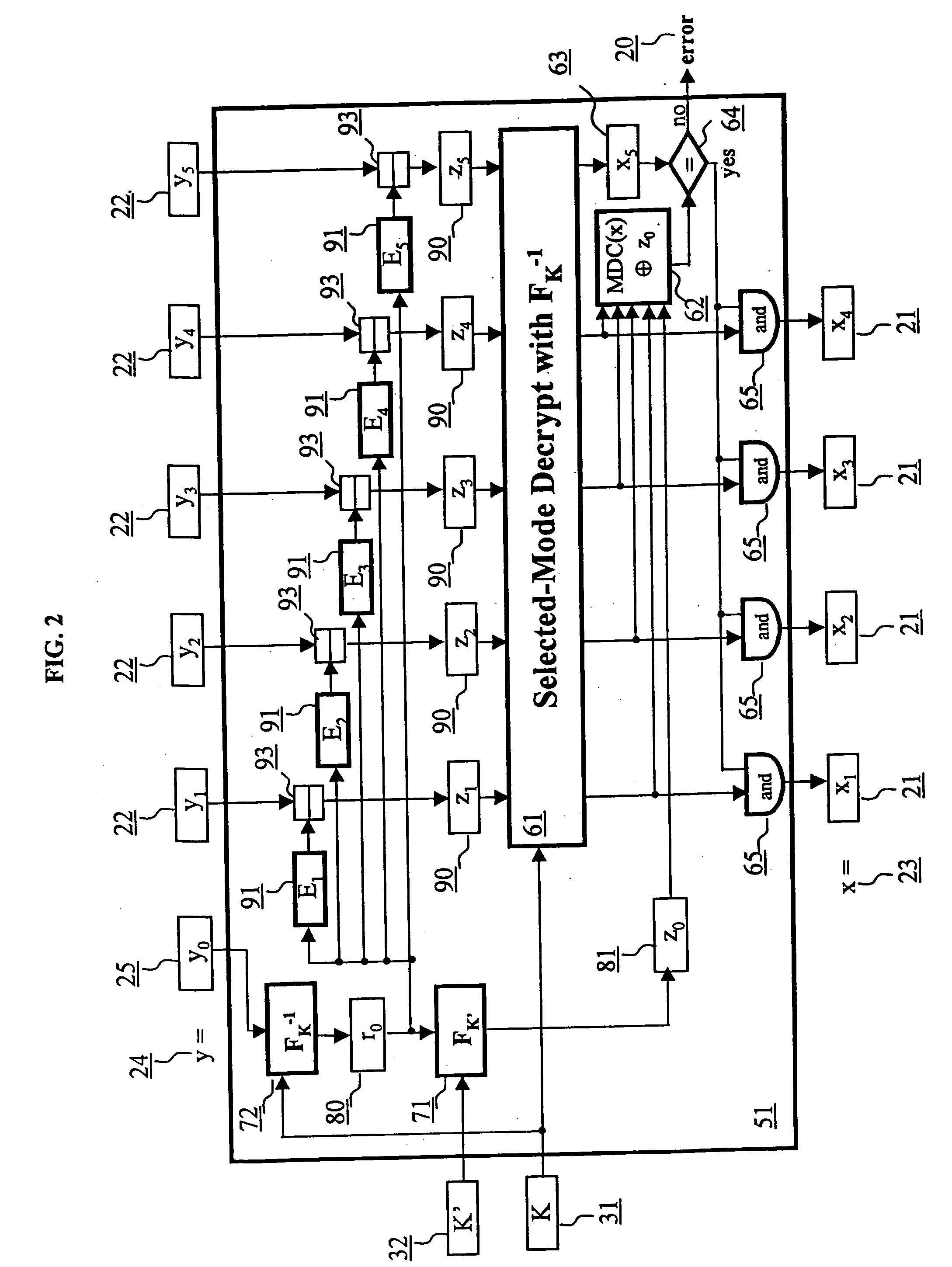
Block encryption method and schemes for data confidentiality and integrity protection
ActiveUS6973187B2Encryption apparatus with shift registers/memoriesUser identity/authority verificationPower applicationComputer hardware
A block encryption method and schemes (modes of operation) that provide both data confidentiality and integrity with a single cryptographic primitive and a single processing pass over the input plaintext string by using a non-cryptographic Manipulation Detection Code function for secure data communication over insecure channels and for secure data storage on insecure media. The present invention allows, in a further aspect, software and hardware implementations, and use in high-performance and low-power applications, and low-power, low-cost hardware devices. The block encryption method and schemes of this invention allow, in yet a further aspect, encryption and decryption in parallel or pipelined manners in addition to sequential operation. In a yet further aspect, the block encryption method and schemes of this invention are suitable for real-time applications.
Owner:VDG
Secure Channel For Image Transmission
ActiveUS20080301441A1Prevent tamperingMemory loss protectionError detection/correctionWeb browserCheque
Systems, devices, and methods for establishing a secure session for the transmission of data from an input device to a remote server device is disclosed. The input device may be an electronic check scanner attached to a banking customer's home personal computer. The customer may visit a bank's Internet website using the web browser or other application on their personal computer, and then submit scanned images of check to the bank. The bank, however, to ensure security and prevent fraud, may wish to establish a secure session between the devices and components in the system before the image data may be scanned and transmitted.
Owner:BANK OF AMERICA CORP
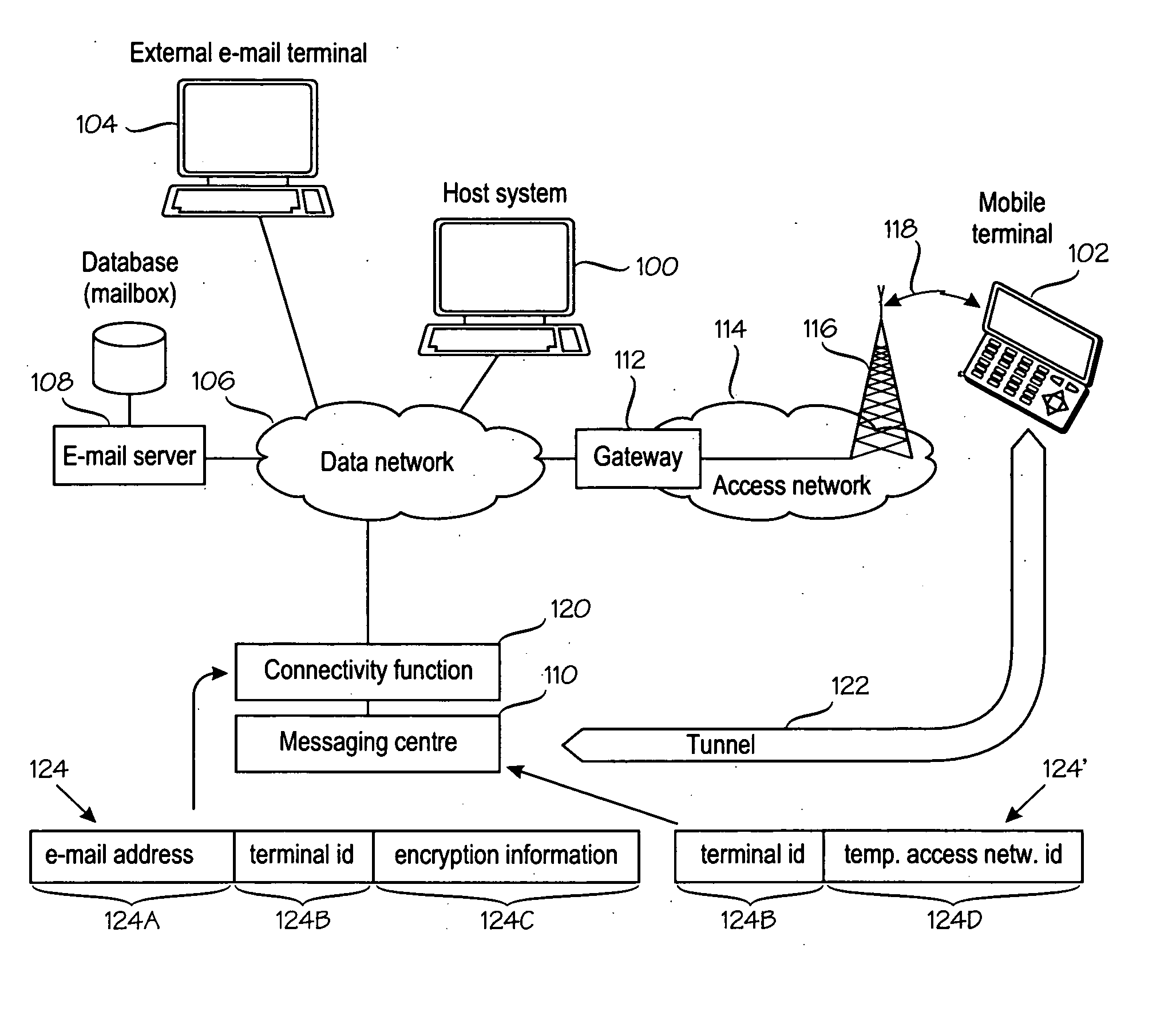
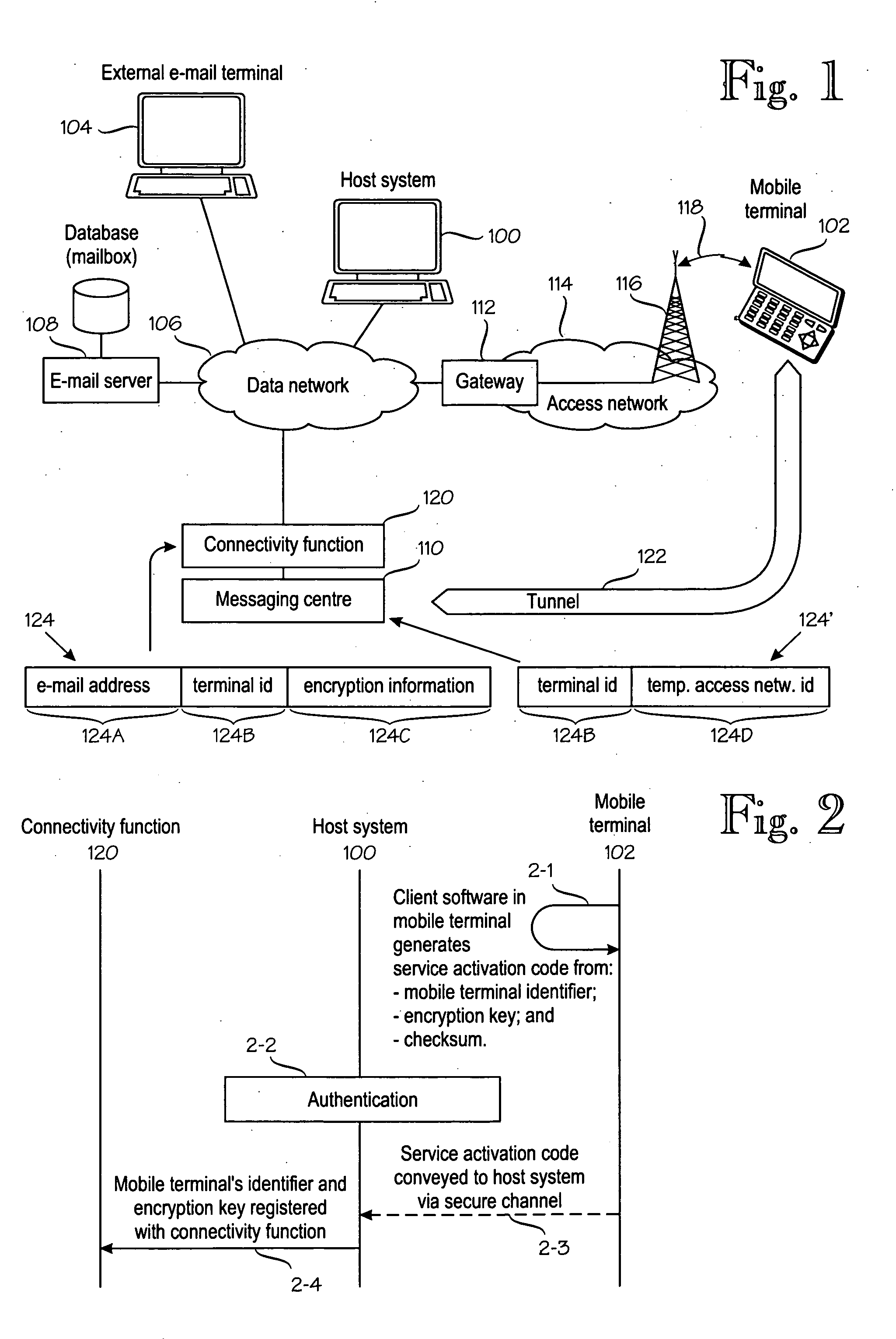
Data security in a mobile e-mail service
A method for conveying e-mail traffic between an e-mail server (108) and a mobile terminal (102) which has an e-mail address (122A) under the e-mail server and permanent terminal identity (122B) and a temporary identity (122D) in an access network (114). A connectivity function (600) is operationally coupled to the e-mail server (108) and the access network (114). The connectivity function (120) encrypts e-mail traffic to the mobile terminal and decrypt e-mail traffic from the mobile terminal, by using encryption information (122C). The mobile terminal generates (2-1) a service activation code which comprises an identifier (124D) of the mobile terminal, encryption information (122C) and checksum information. The service activation code is conveyed (2-3, 2-4) via a secure channel (2-3) to an authenticating terminal (100), from which the identifier (124D) of the mobile terminal and the encryption information (122C) are conveyed to the connectivity function (600).
Owner:SEVEN NETWORKS INC
Block encryption method and schemes for data confidentiality and integrity protection
InactiveUS20060056623A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationPower applicationComputer hardware
Owner:VDG
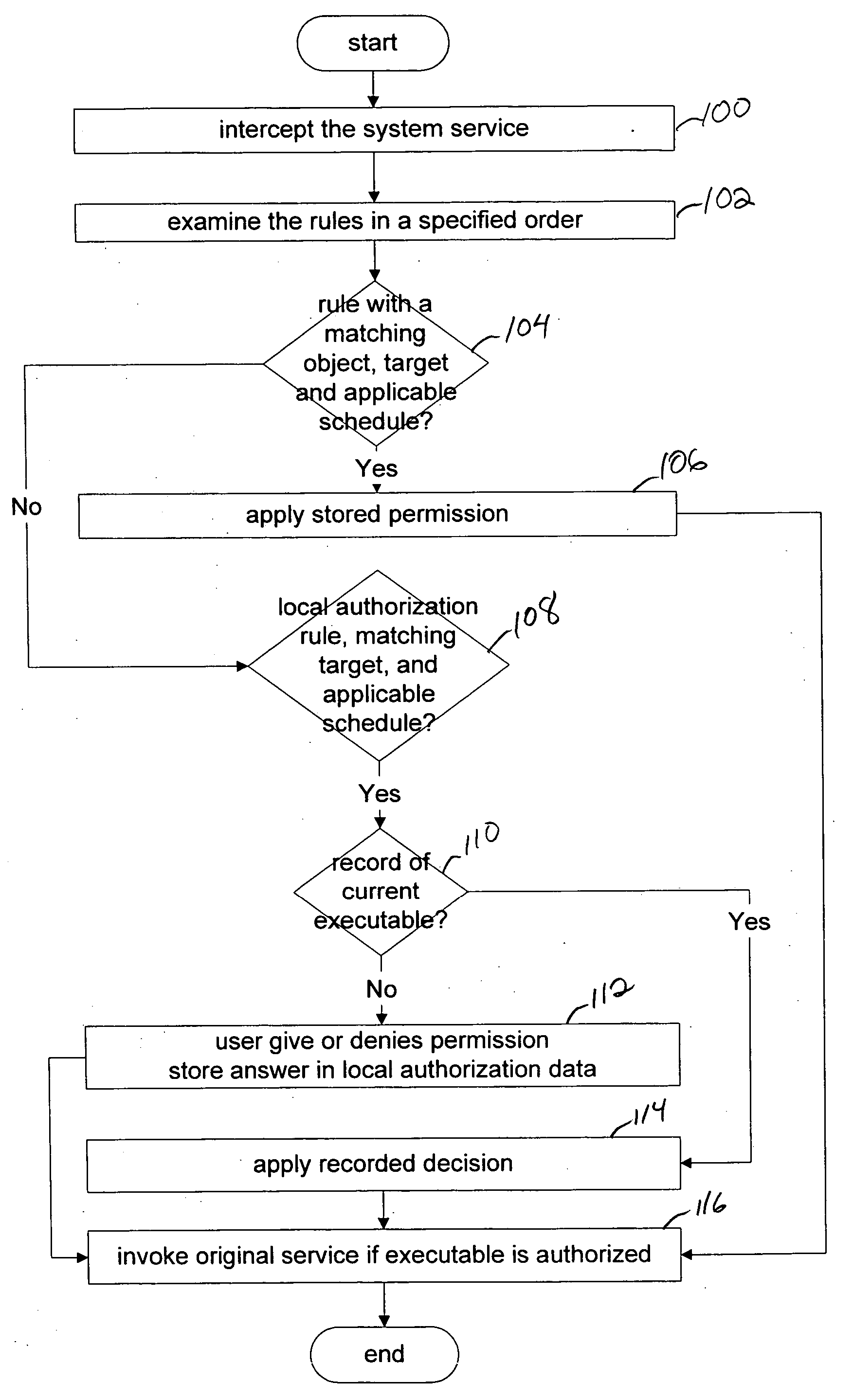
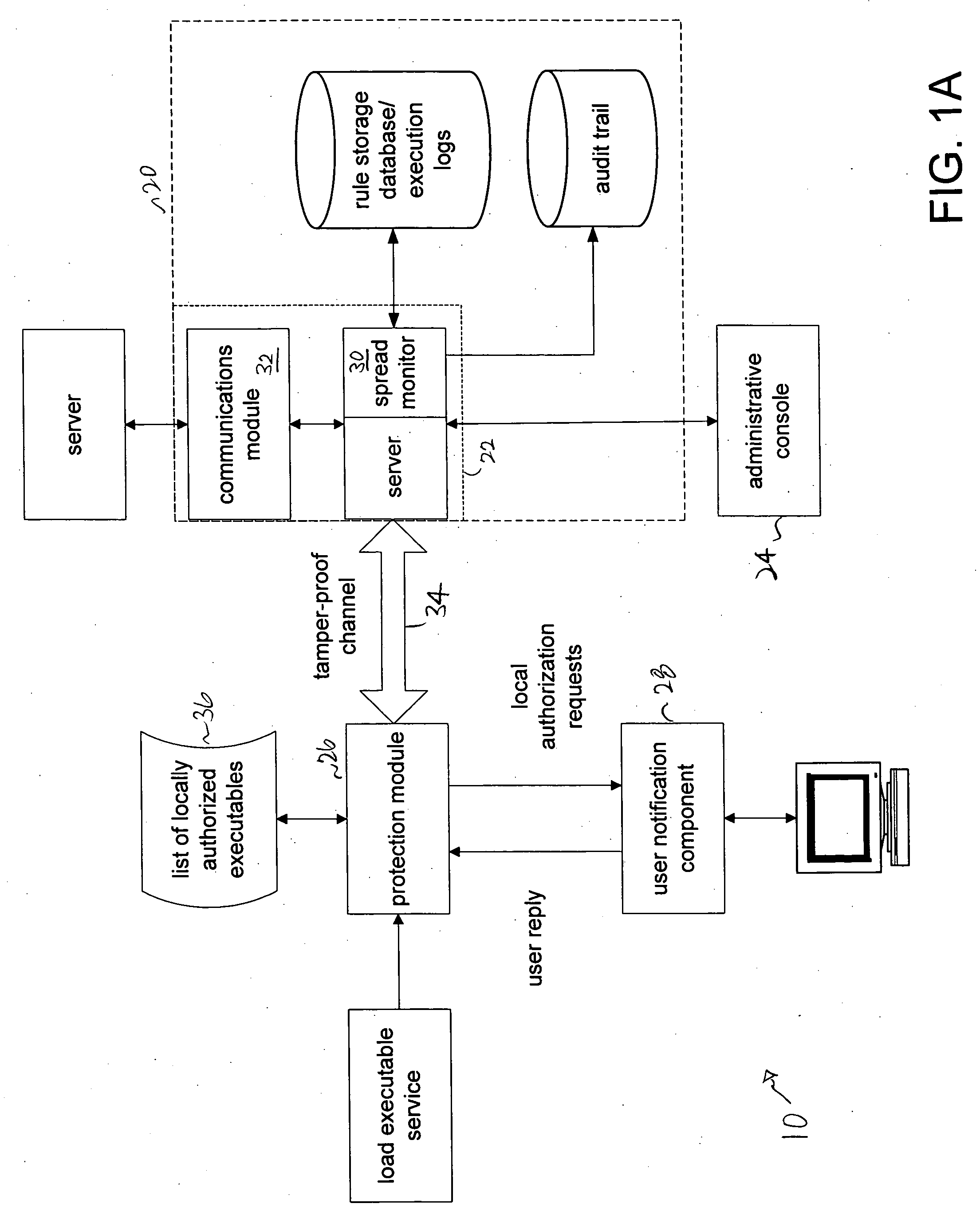
On-line centralized and local authorization of executable files
ActiveUS20050262558A1Reduce in quantityMemory loss protectionDigital data processing detailsComputerized systemAuthorization
Owner:IVANTI INC
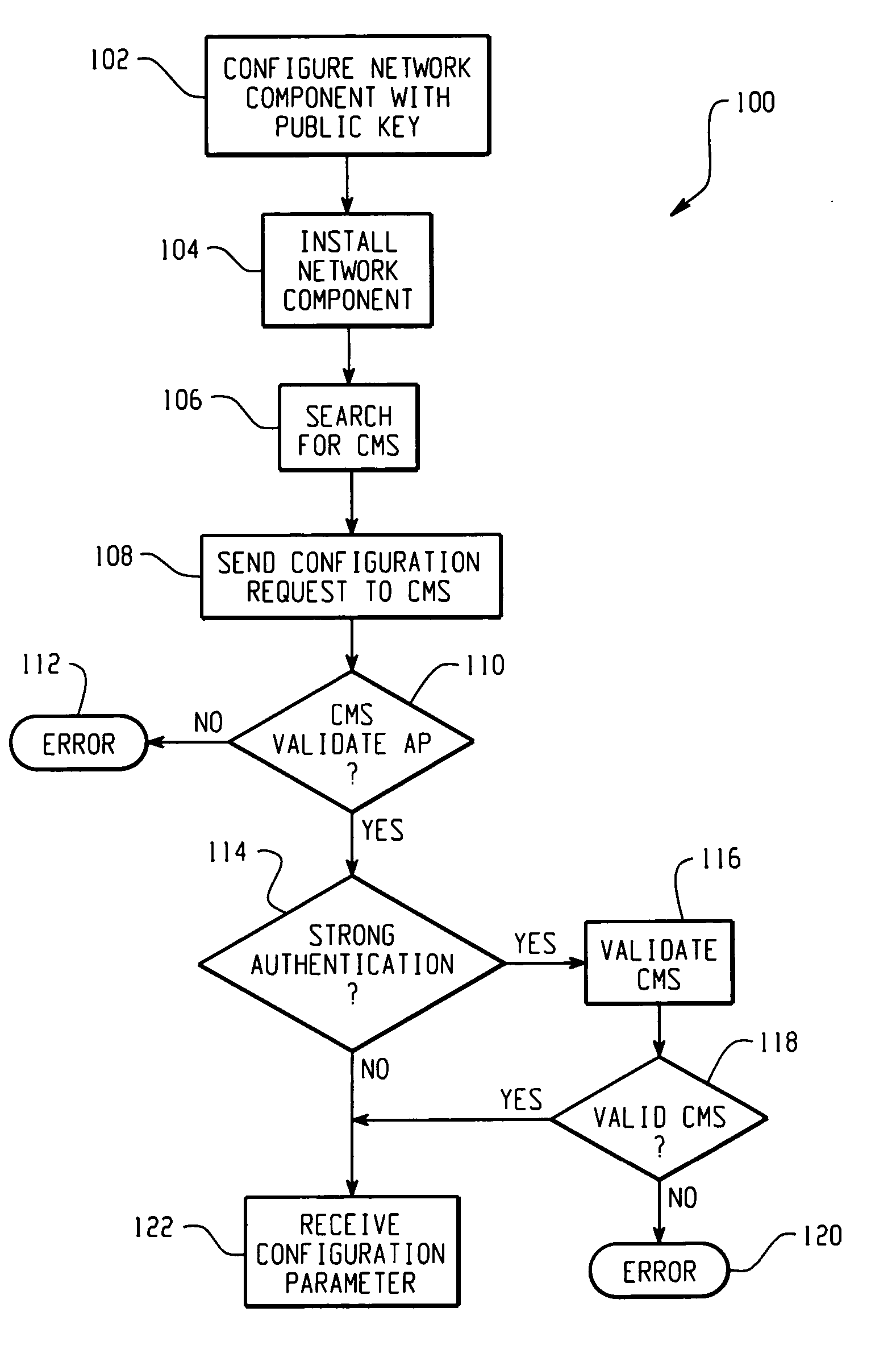
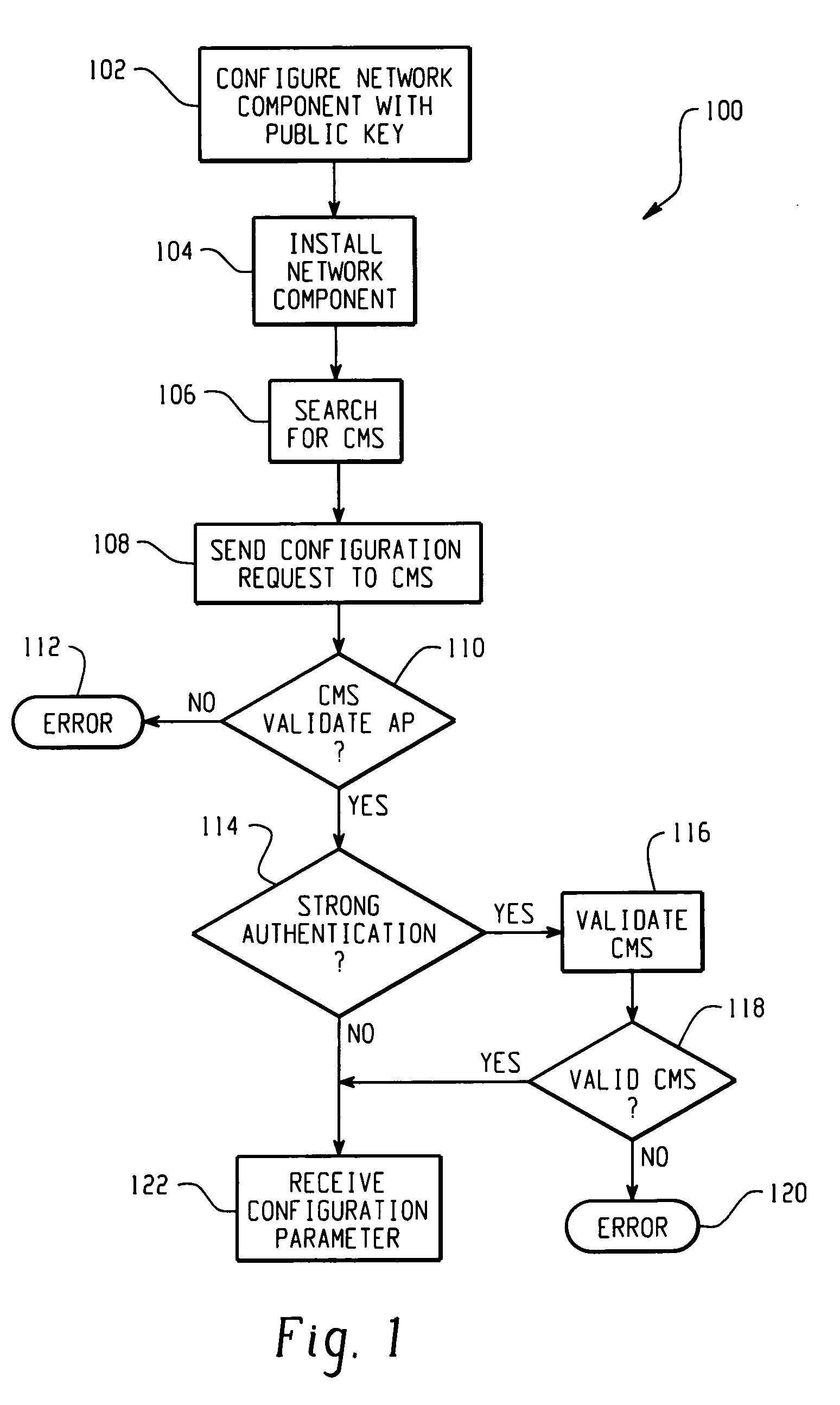
Method for securely and automatically configuring access points
ActiveUS20060114839A1Network traffic/resource managementData switching by path configurationTrust relationshipSecure channel
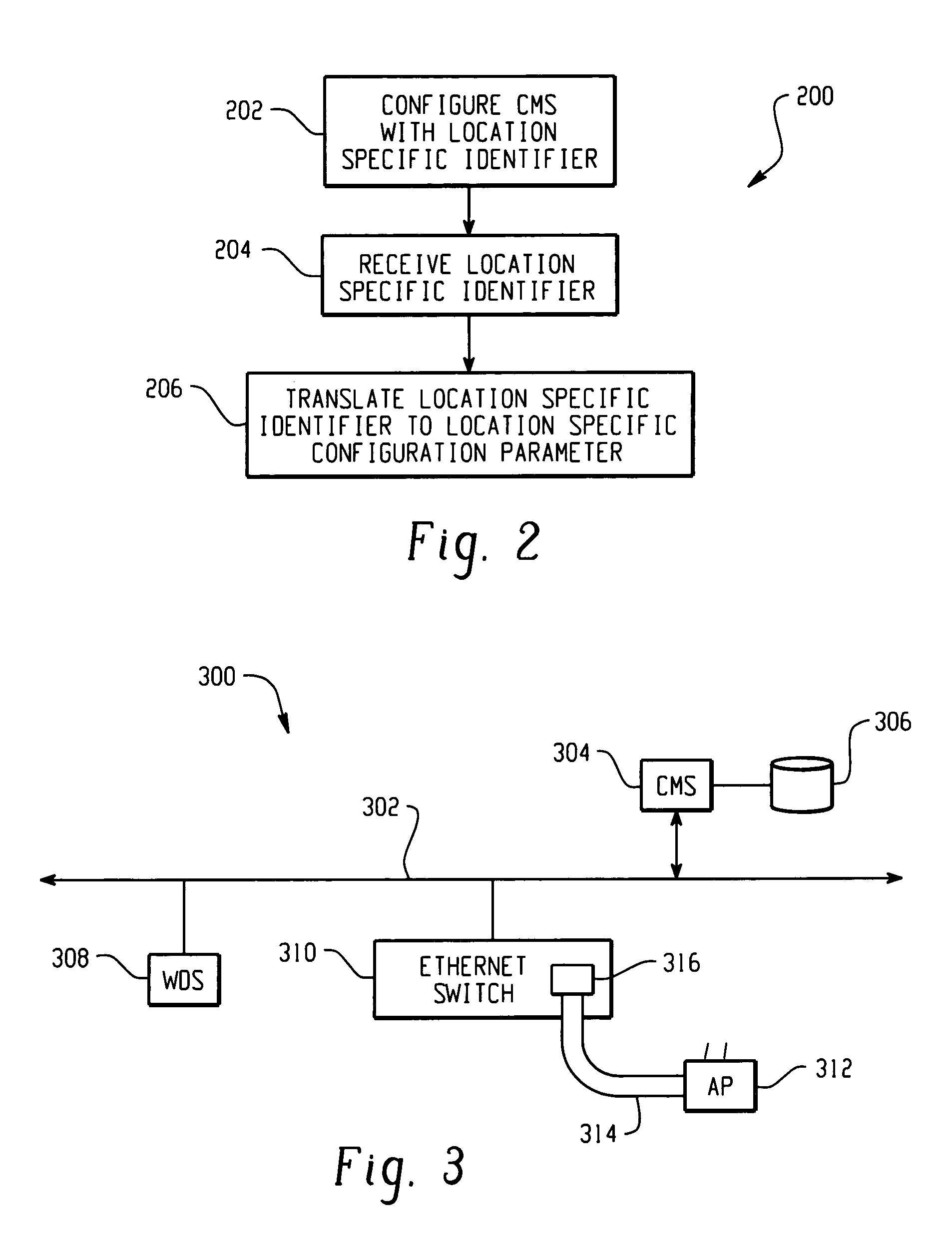
The present invention is contemplates an automatic, secure AP configuration protocol. Public / private keys and public key (PK) methods are used to automatically establish a mutual trust relationship and a secure channel between an AP and at least one configuration server. An AP automatically forwards a location identifier to the configuration server, and the configuration server delivers common, AP specific, and location specific configuration parameters to the AP.
Owner:CISCO TECH INC
Method to support secure network booting using quantum cryptography and quantum key distribution
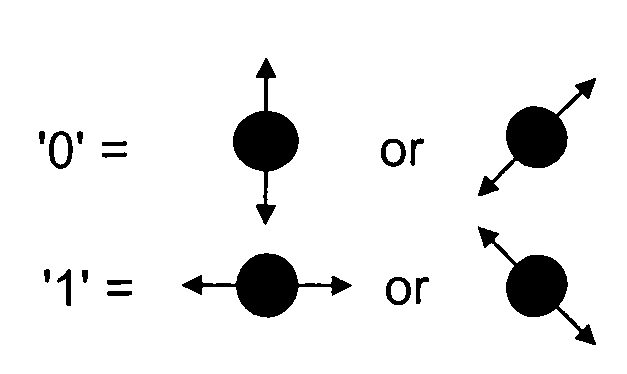
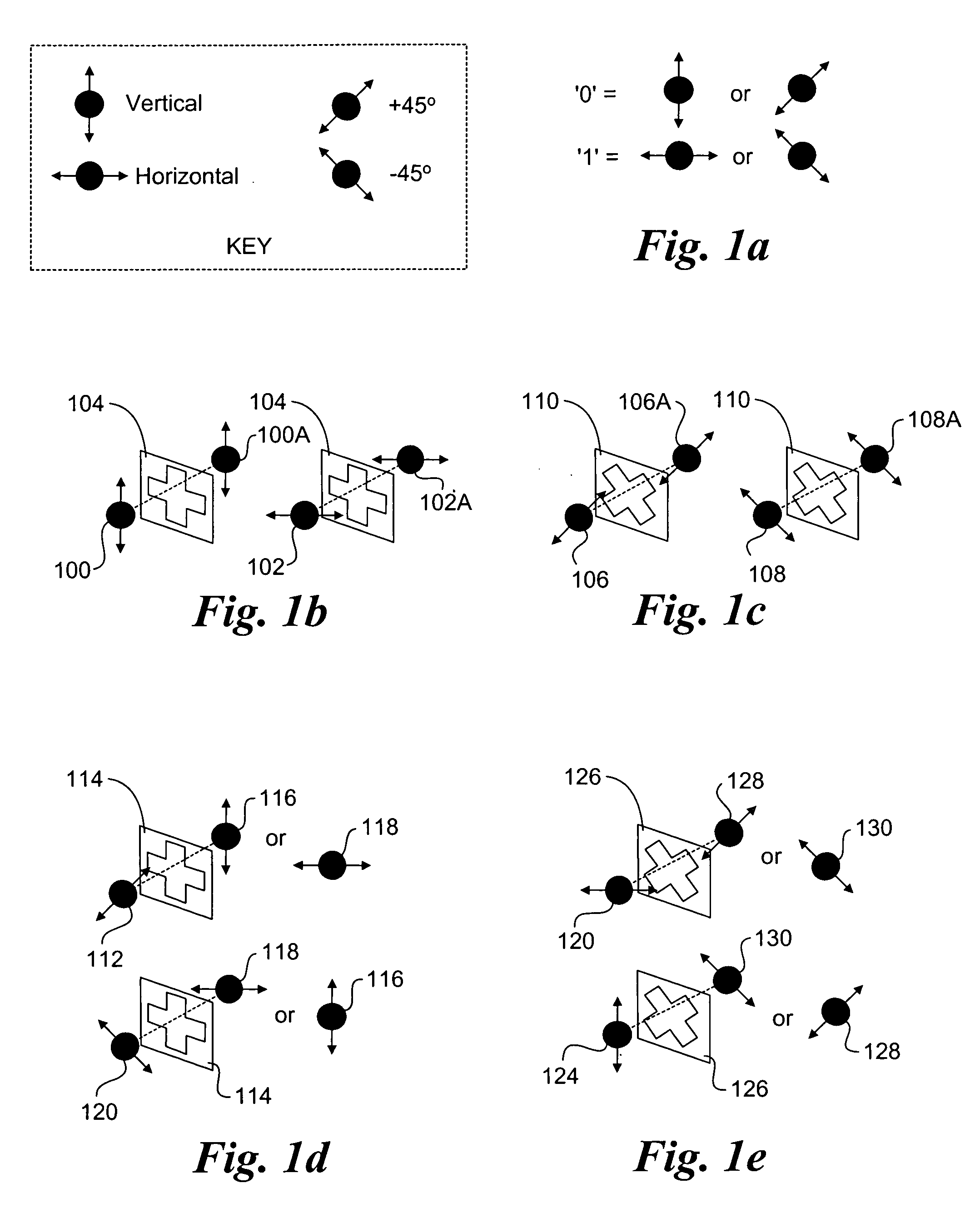
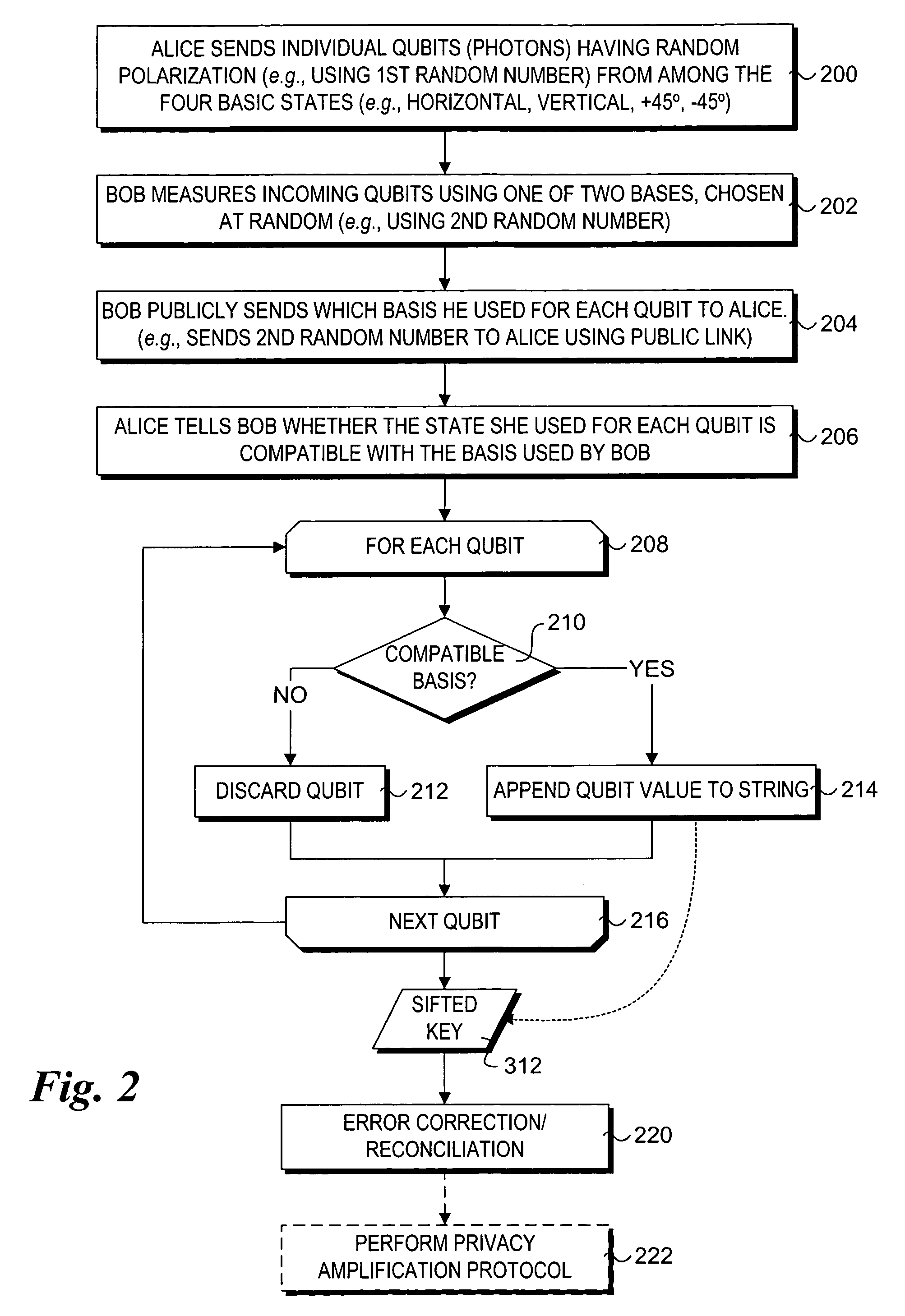
A method and system to support secure booting and configuration. The mechanism employs an optical link comprising a quantum channel that is used to send data encoded as quantum bits (qubits) via respective photons. Qubits encoded using a first random basis at the client and are sent to the boot server, which processes the qubits using a second random basis to extract the encoded data. A public channel is used to send data indicative of the second random basis to the client. A symmetric quantum key is then derived a both the client and the boot server using a comparison of the random basis' and the original and extracted data. The scheme enables the presence of an eavesdropper to be detected on the quantum channel. A DHCP message exchange is employed to obtain a network address, and, optionally, be provided with a network address for one or more boot servers. A boot image request is made to the boot server by the client, and a subsequent boot image is downloaded via a secure channel facilitated by the symmetric quantum key.
Owner:INTEL CORP
Systems and methods for automatic discovery of network software relationships
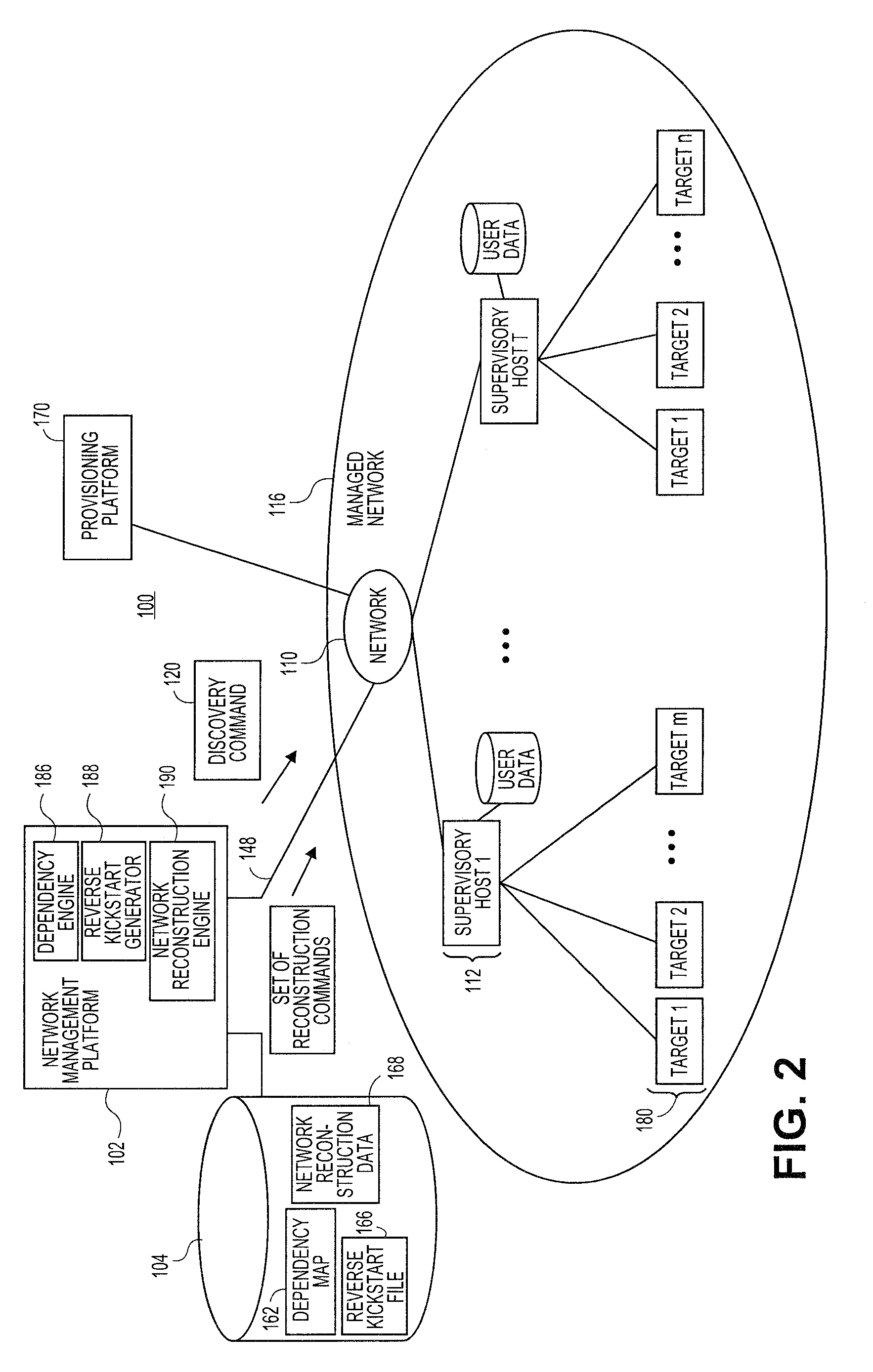
Embodiments relate to systems and methods for automatic discovery of network software relationships. A set of managed machines, such as personal computers or servers, can be managed by a network management platform communicating with the machines via a secure channel. The network management platform can issue a set of discovery commands interrogating nodes of the network to report software or services which they consume. The network management platform can build a dependency map encoding the dependency or other relationships between nodes in the managed network based on their use of software resources. Network restorations can therefore be conducted in a rational order, maintaining stability in the restored nodes and network.
Owner:RED HAT
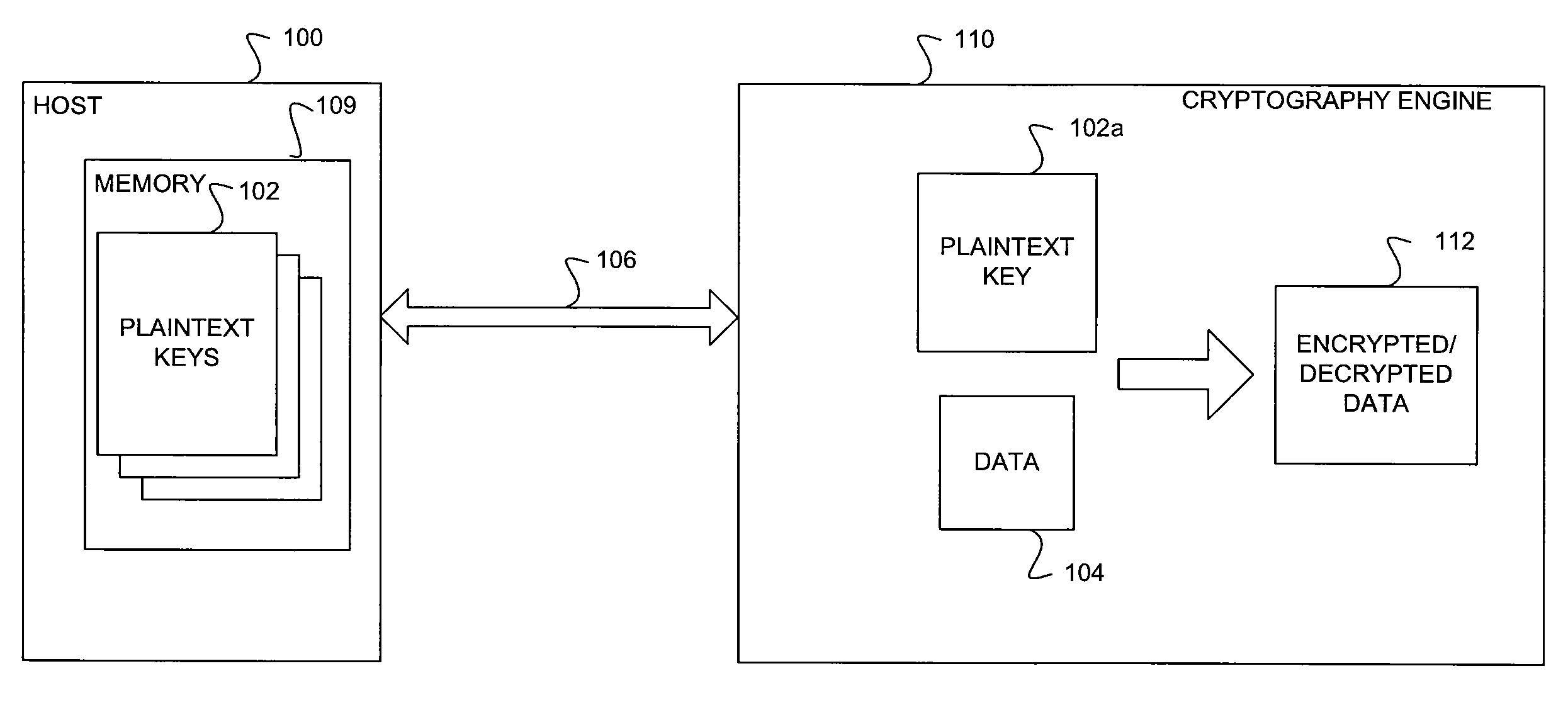
Scalable and Secure Key Management For Cryptographic Data Processing
ActiveUS20100254537A1Key distribution for secure communicationDigital data processing detailsGeneral purposePlaintext
A method and system for secure and scalable key management for cryptographic processing of data is described herein. In the method, a General Purpose Cryptographic Engine (GPE) receives key material via a secure channel from a key server and stores the received Key encryption keys (KEKs) and / or plain text keys in a secure key cache. When a request is received from a host to cryptographically process a block of data, the requesting entity is authenticated using an authentication tag included in the request. The GPE retrieves a plaintext key or generate a plaintext using a KEK if the authentication is successful, cryptographically processes the data using the plaintext key and transmits the processed data. The system includes a key server that securely provides encrypted keys and / or key handles to a host and key encryption keys and / or plaintext keys to the GPE.
Owner:AVAGO TECH INT SALES PTE LTD
Establishing a new shared secret key over a broadcast channel for a multicast group based on an old shared secret key
InactiveUS6941457B1Key distribution for secure communicationSecret communicationBroadcast channelsComputer science
An optimized approach for arriving at a shared secret key in a dynamically changing multicast or broadcast group environment is disclosed. In one aspect of the invention, a method is provided for communicating through a secure channel between members of a dynamically changing multicast group connected over an insecure network. The method provides that a first shared secret key for establishing a first multicast group is computed that includes a set of one or more first members. Based on the first shared secret key, a first multicast group exchange key is also generated. Upon receiving a first user exchange key from a first user requesting entry into the first multicast group, a second secret key, based on the first user exchange key and the first shared secret key is computed. The first multicast group exchange key is sent to the first user and used by the first user to generate the same second shared secret key. Through the use of the second shared secret key a second multicast group is established whose members include the first user and the set of one or more first members of the first multicast group as the second shared secret key provides a first secure channel for communicating between members of the second multicast group over the insecure network.
Owner:CISCO TECH INC
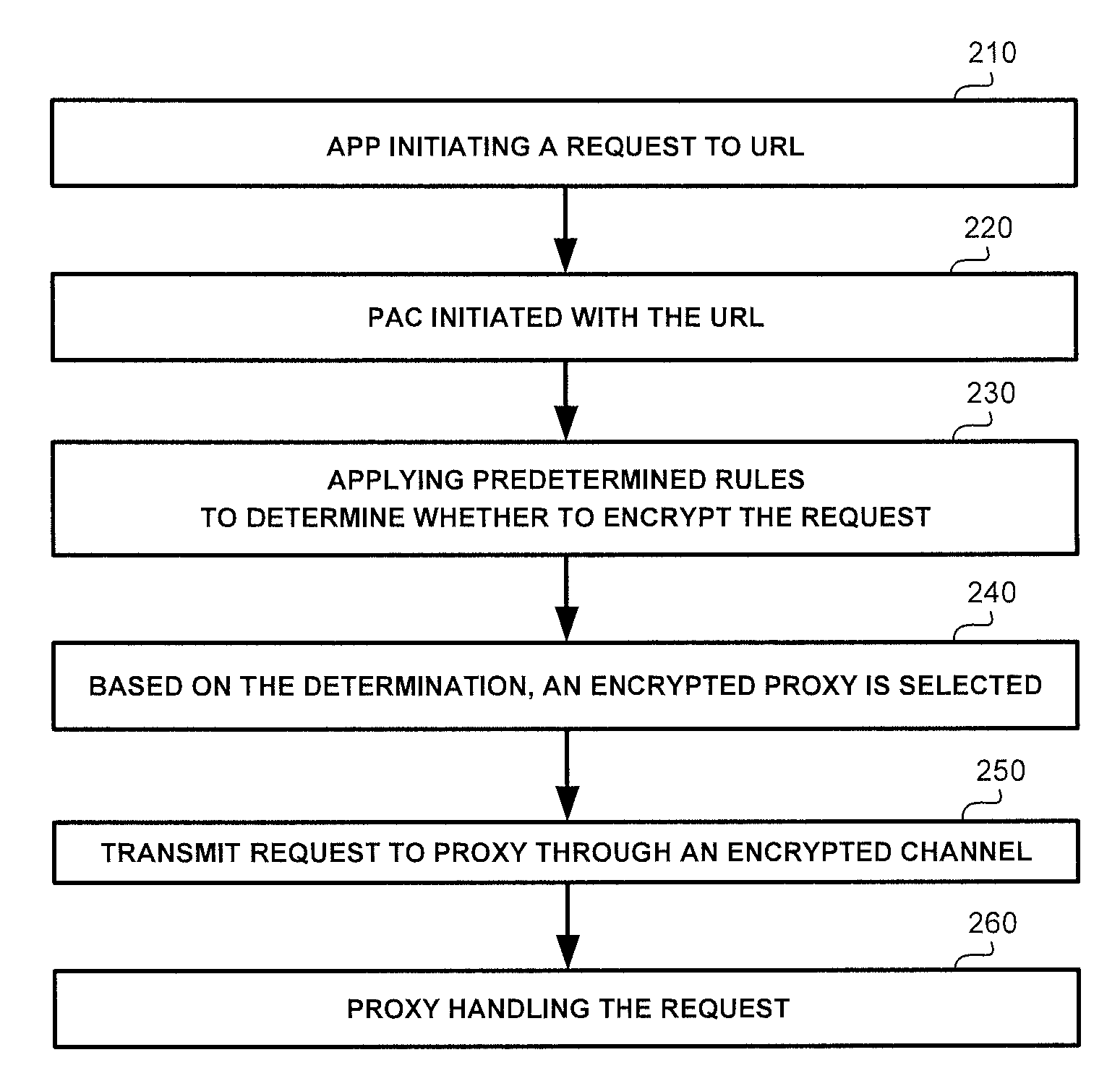
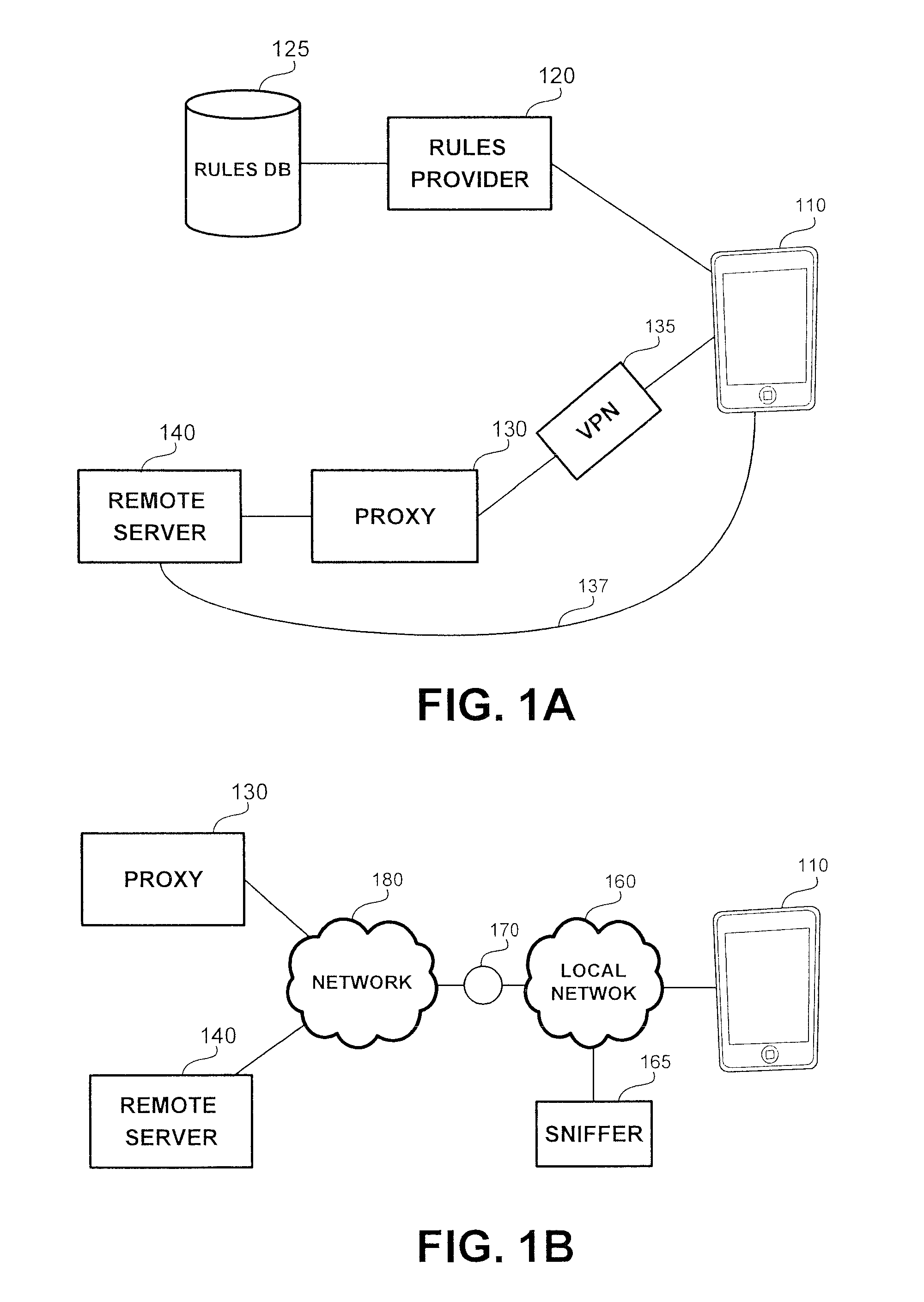
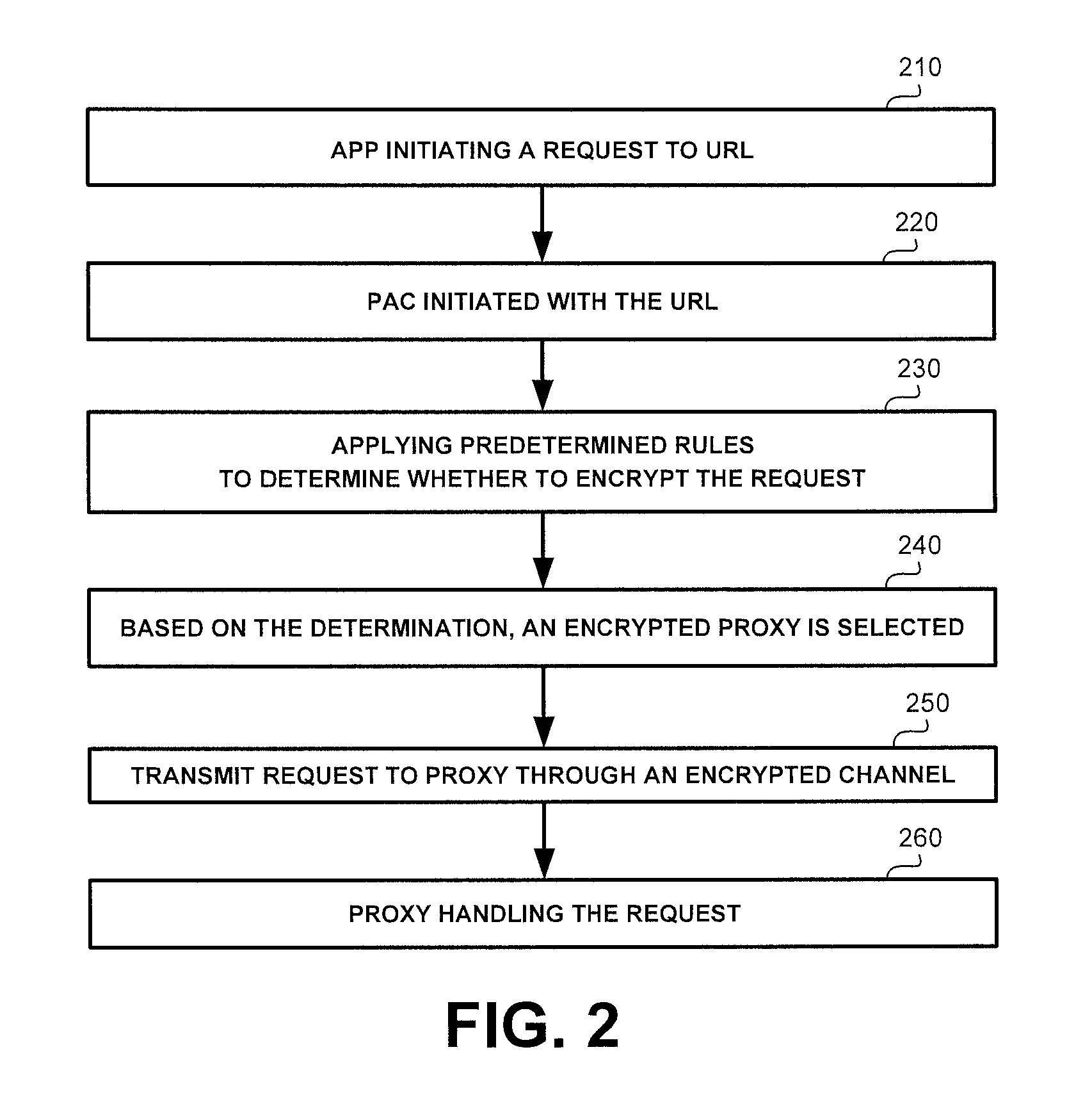
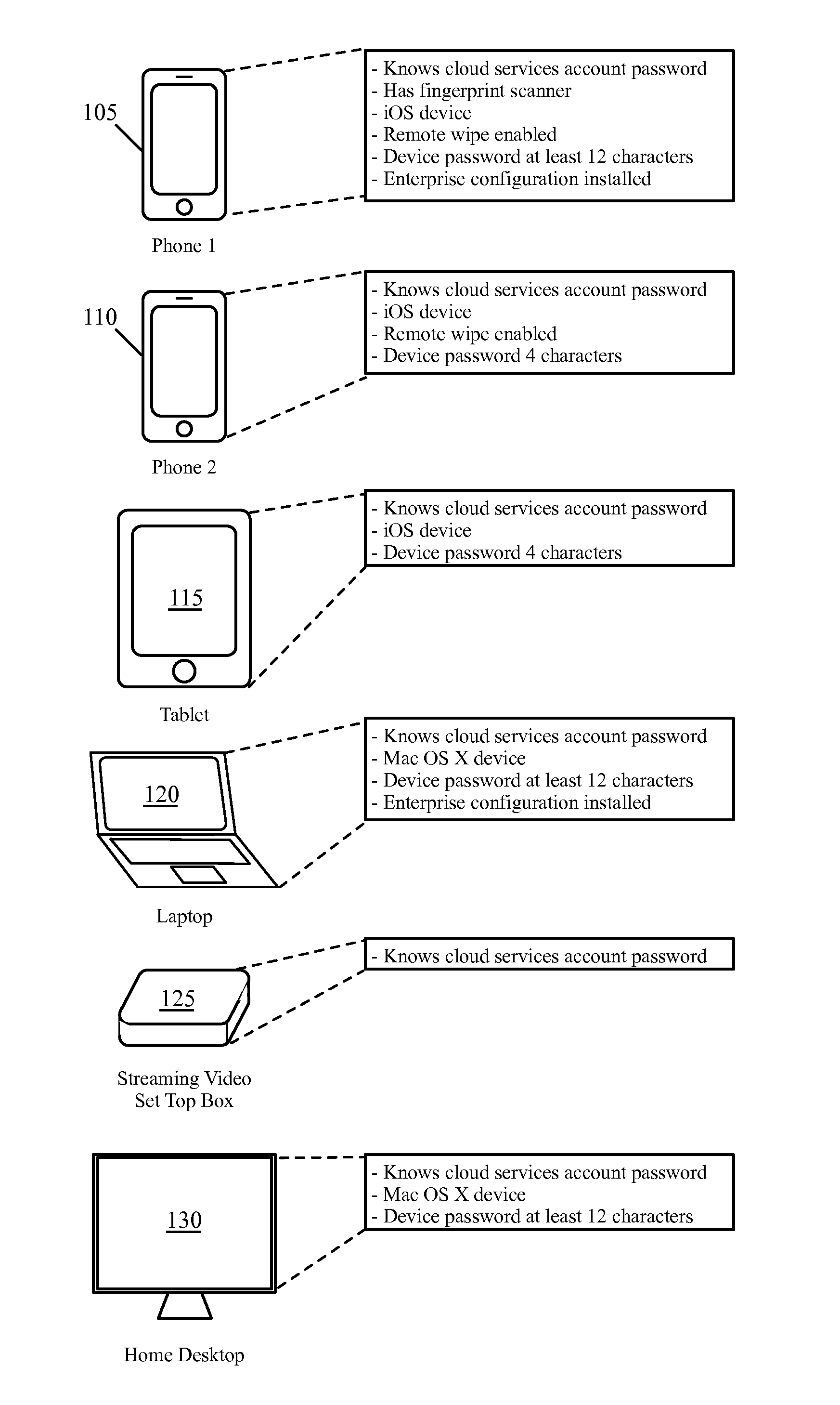
Selective encryption in mobile devices
A method, product and system for selective encryption in a mobile device. The method comprising: selectively encrypting requests issued by the mobile device, wherein said selectively encrypting comprises: obtaining a request issued by an application executed by the mobile device, the request having one or more characteristics, the request has a destination; determining, based on the one or more characteristics, whether to encrypt the request; and in response to a determination to encrypt the request, re-routing the request to be transmitted to the destination through a secure channel; whereby the request is encrypted regardless of the destination being a priori associated with the secure channel.
Owner:CA TECH INC
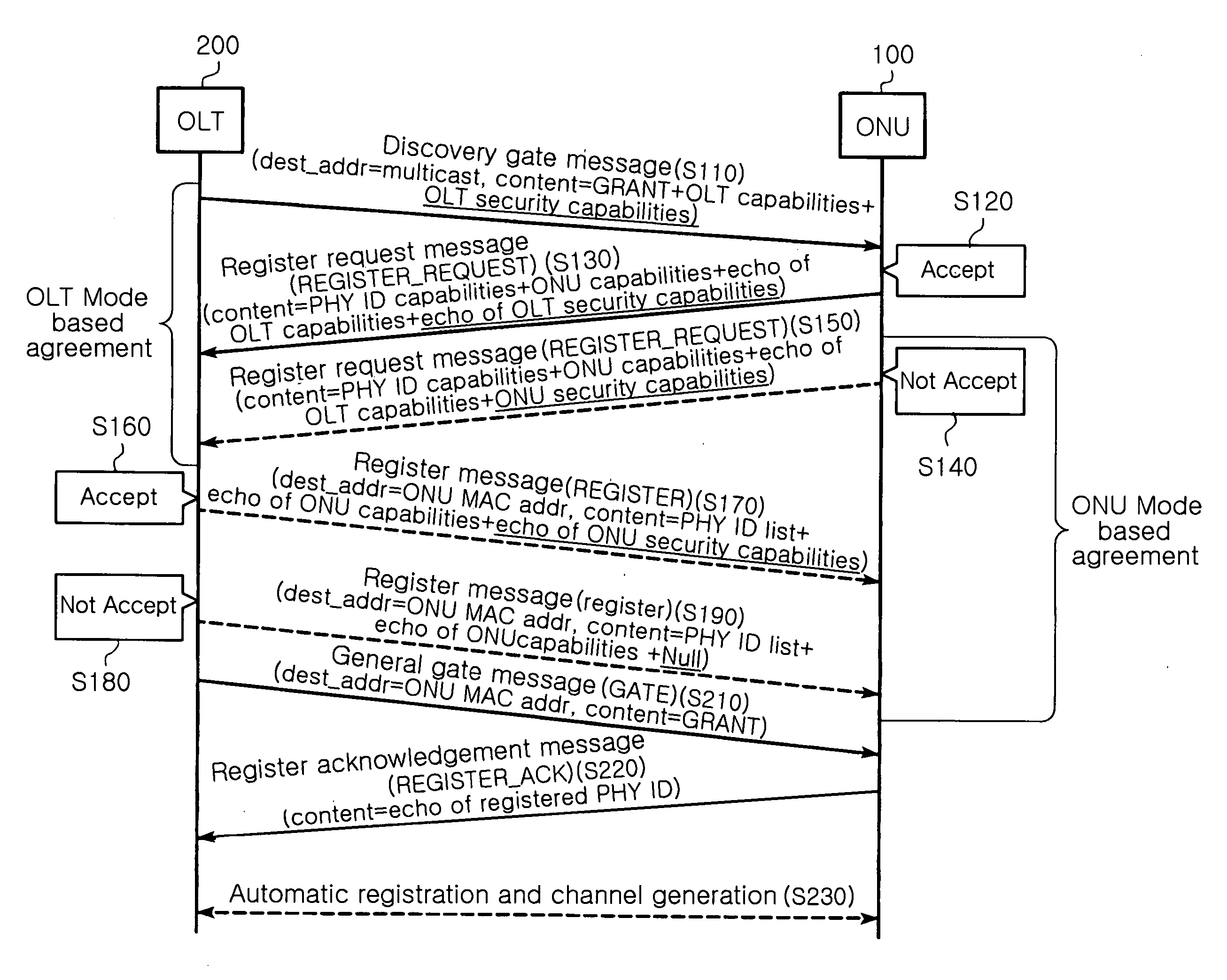
Method for setting security channel based on MPCP between OLT and ONUs in EPON, and MPCP message structure for controlling frame transmission
ActiveUS20070133800A1Efficiently provideMultiplex system selection arrangementsPublic key for secure communicationMessage structureKey distribution
Provided is a method for setting a security channel between an OLT and at least one ONU in an EPON. In detail, a channel is generated by which the OLT makes a reciprocal security capability agreement with the ONU that wants to set a security channel in a discovery interval and then automatically registers the ONU with the security capability agreement. The security channel is set by which the OLT distributes an encryption key for the security with the ONU completed with the security capability agreement. A renewal point of the encryption key is shared by transmitting a message indicative of a time to change the encryption key between the OLT and the ONU both completed with the encryption key distribution.
Owner:ELECTRONICS & TELECOMM RES INST
Synchronization And Verification Groups Among Related Devices
ActiveUS20160349999A1Protection attackInput/output to record carriersBroadcast service distributionDistributed computingSecure channel
Some embodiments provide a method for a first device to synchronize a set of data items with a second device. The method receives a request to synchronize the set of data items stored on the first device with the second device. The method determines a subset of the synchronization data items stored on the first device that belong to at least one synchronization sub-group in which the second device participates. Participation in at least one of the synchronization sub-groups is defined based on membership in at least one verification sub-group. The first and second devices are part of a set of related devices with several different verification sub-groups. The method sends only the subset of the synchronization data items that belong to at least one synchronization sub-group in which the second device participates to the second device using a secure channel.
Owner:APPLE INC
Systems and methods for generating reverse installation file for network restoration
Embodiments relate to systems and methods for generating a reverse installation file for network restoration. A set of managed machines, such as personal computers or servers, can be managed by a network management engine communicating with the machines via a secure channel. The network management engine can scan the managed network for kickstart, or provisioning answer files, that were used to install software to network nodes at a prior time. The network management engine can access the original kickstart file, and update that file to reflect a current state of the associated machine by inserting user-supplied updates, storage configuration updates, security credentials, and / or other data. Upon a crash or other malfunction of the associated machine, the network management platform can access the reverse kickstart file and generate a restoration of that node to a current state from the reverse kickstart data.
Owner:RED HAT
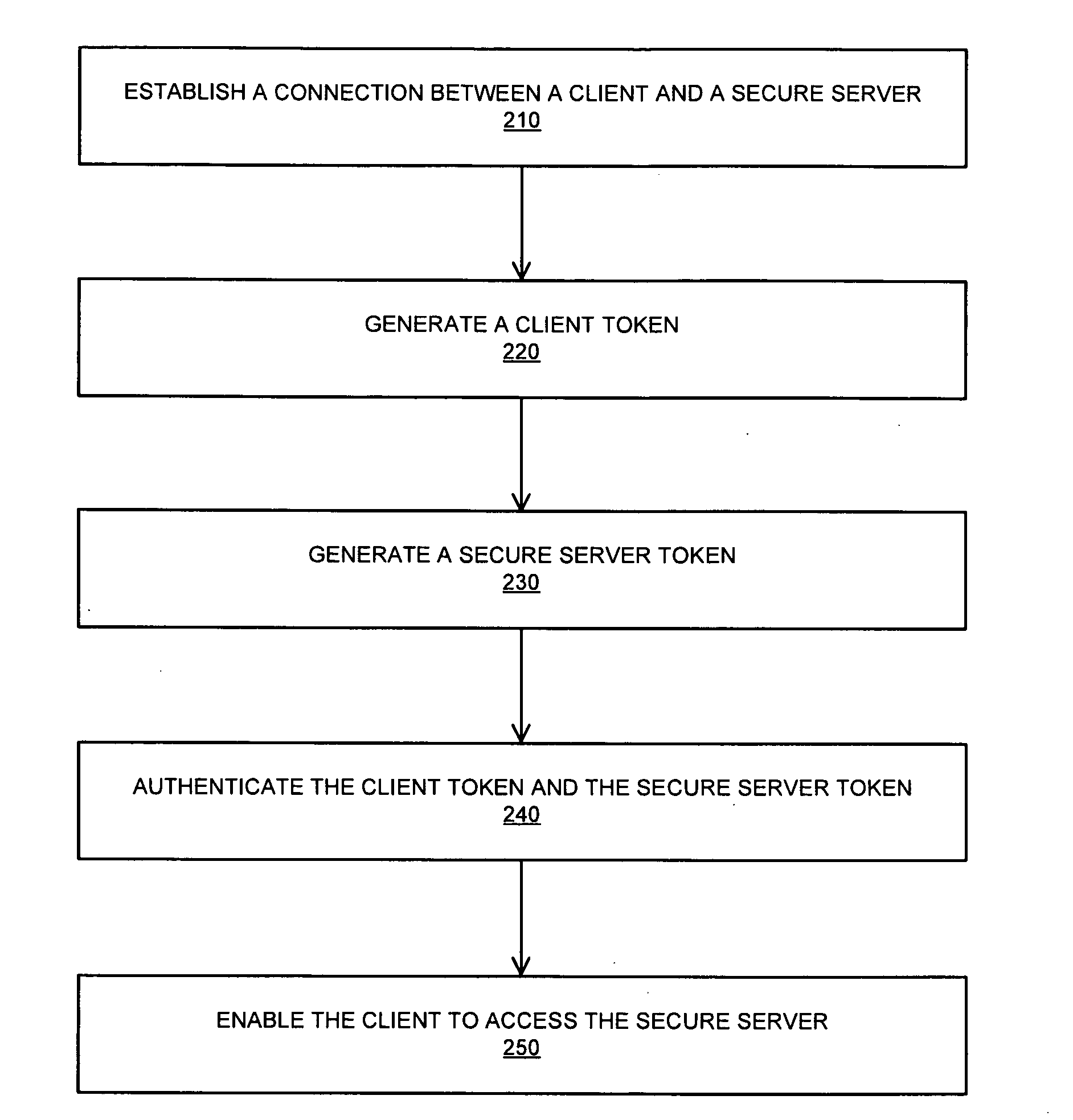
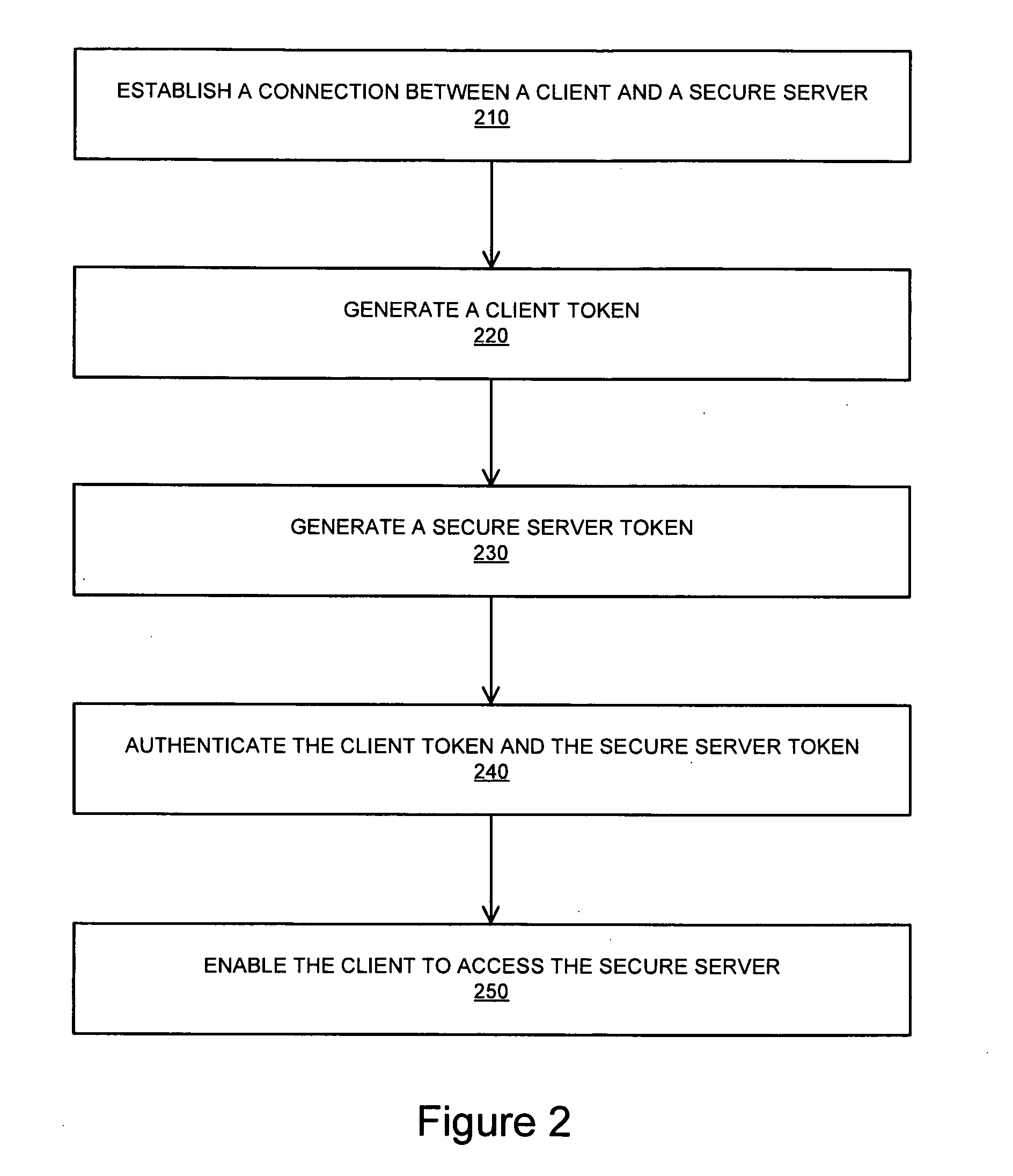
Systems and methods for establishing a secure communication channel using a browser component
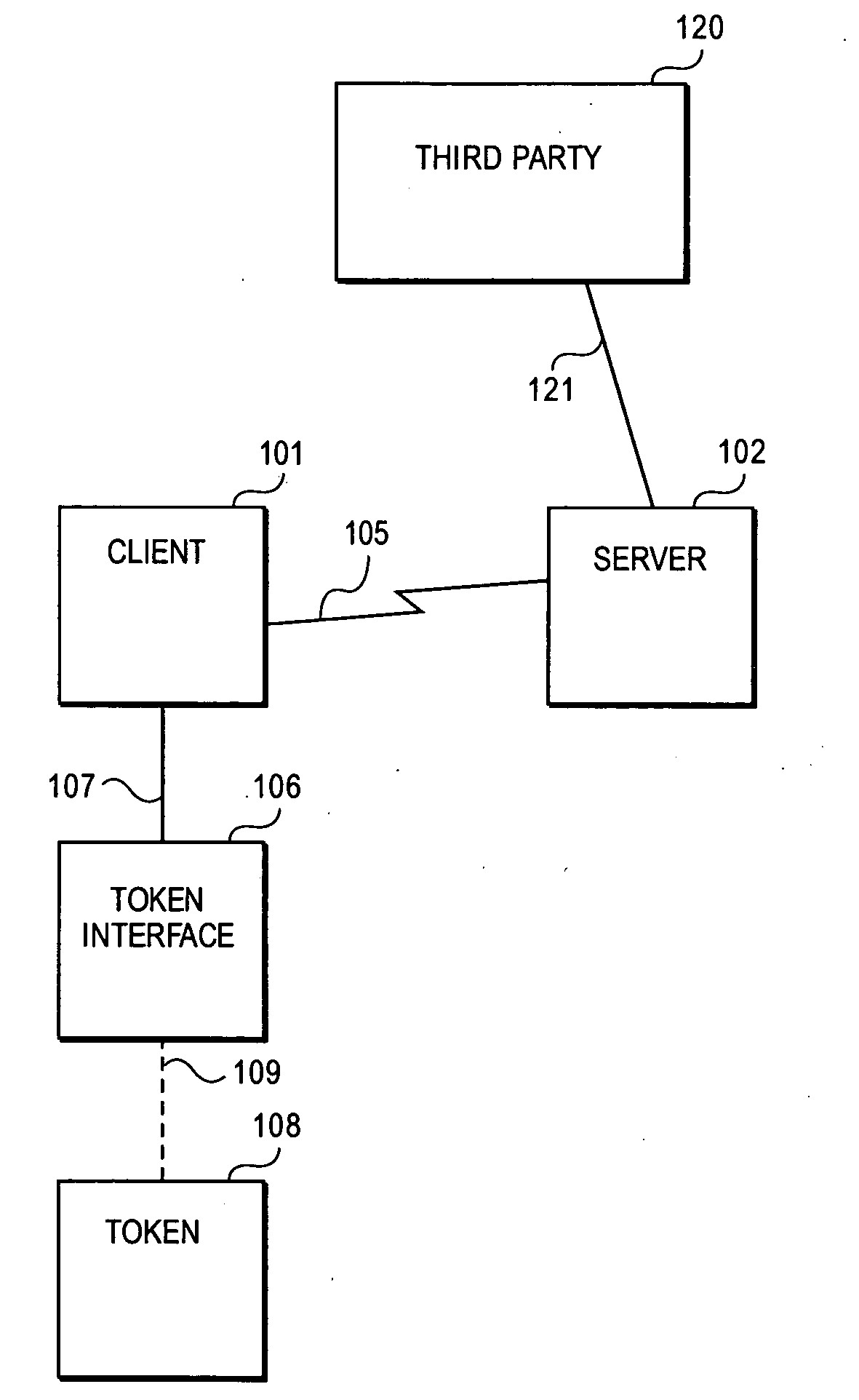
InactiveUS20100318802A1Digital data processing detailsUser identity/authority verificationClient-sideSecure communication channel
A system for providing a secure channel for communication comprises a client comprising a browser, a secure server and a browser component installed on the client that enables a user to establish a connection with the secure server, the browser component configured to generate a first token. The secure server is configured to generate a second token, and wherein the client is provided with access to the secure server upon verification of the first token and the second token.
Owner:BALAKRISHNAN AJIT
Method and apparatus for distributing and updating group controllers over a wide area network using a tree structure
InactiveUS6901510B1Reduces the workload on the group controllerSpecial service provision for substationKey distribution for secure communicationBinary treeWide area network
Apparatus and computer-readable media are disclosed for establishing secure multicast communication among multiple multicast proxy service nodes of domains of a replicated directory service that spans a wide area network. Domains are organized in a logical tree. Each domain has a logical tree that organizes the multicast proxy service nodes, a group manager at the root node, a multicast key distribution center, multicast service agent, directory service agent and key distribution center. Multicast proxy service nodes store a group session key and a private key. Replication of the directory performs key distribution. A multicast group member joins or leaves the group by publishing message. The local key distribution center and multicast service agent obtain the publisher's identity from a local directory service agent. Based on the identity, a secure channel is established with the directory service agent in the group member's domain. Keys of the binary tree branch that contains the joining or leaving node are updated, and an updated group session key and a new private key are received.
Owner:CISCO TECH INC
Key management technique for establishing a secure channel
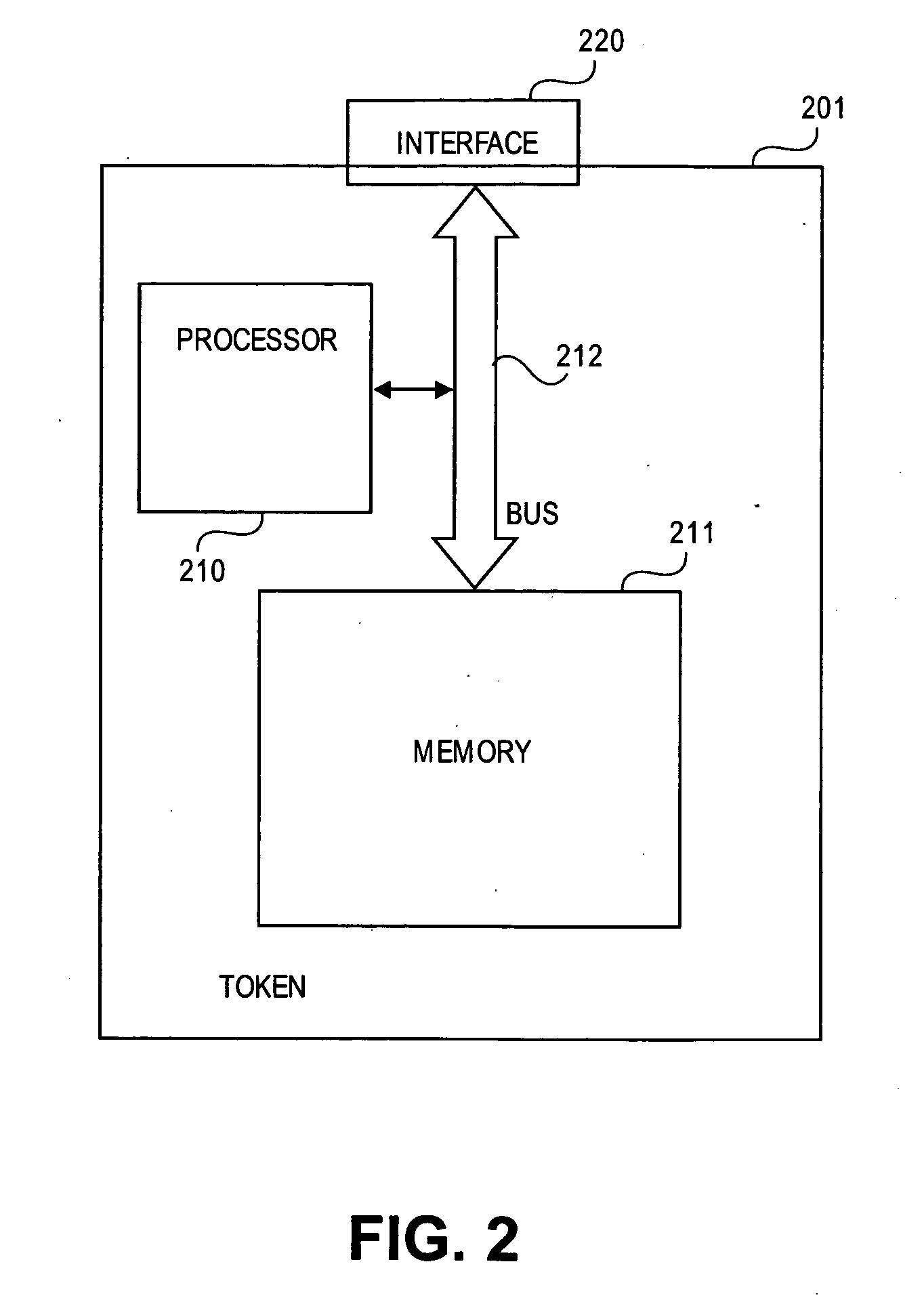
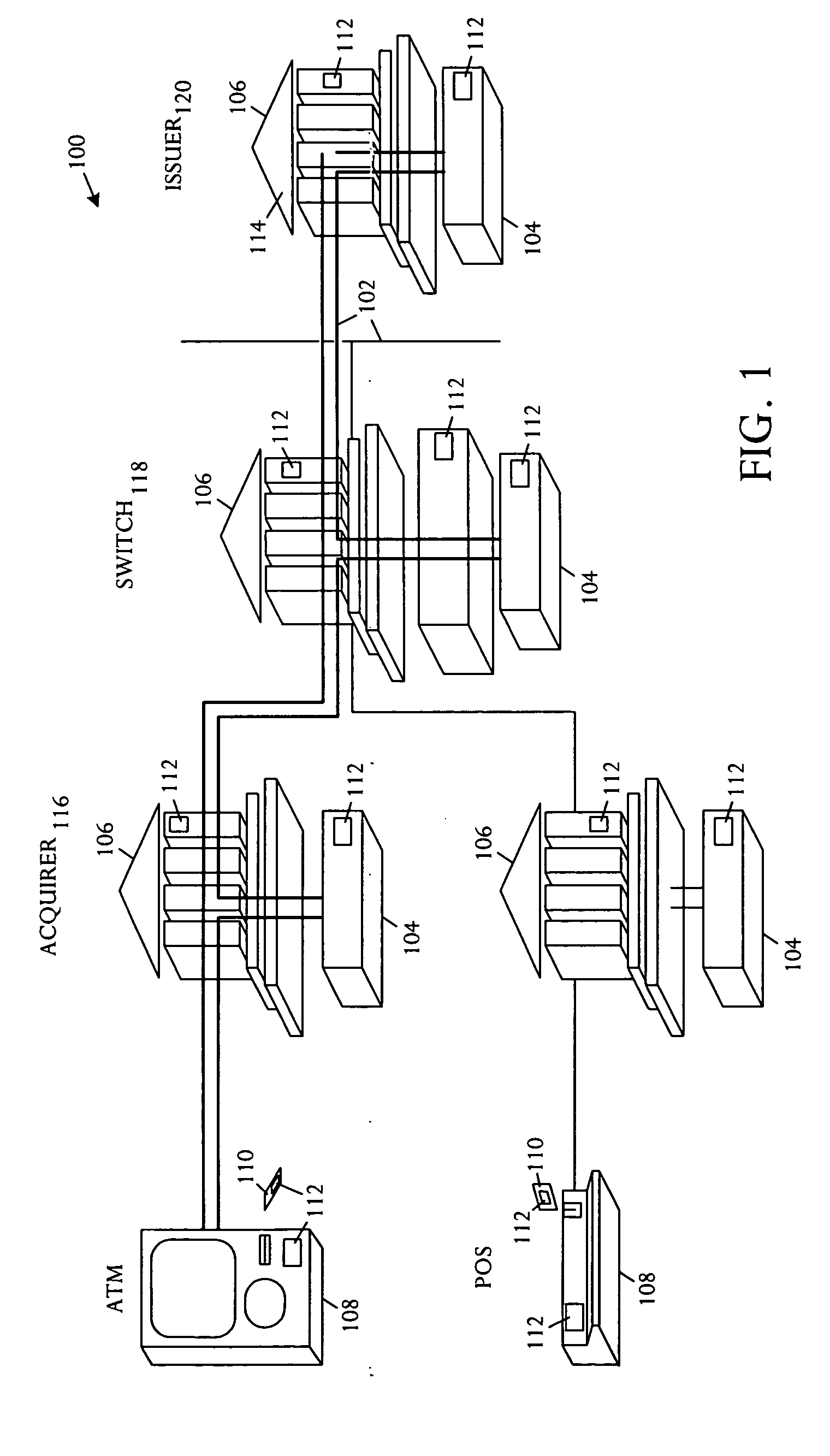
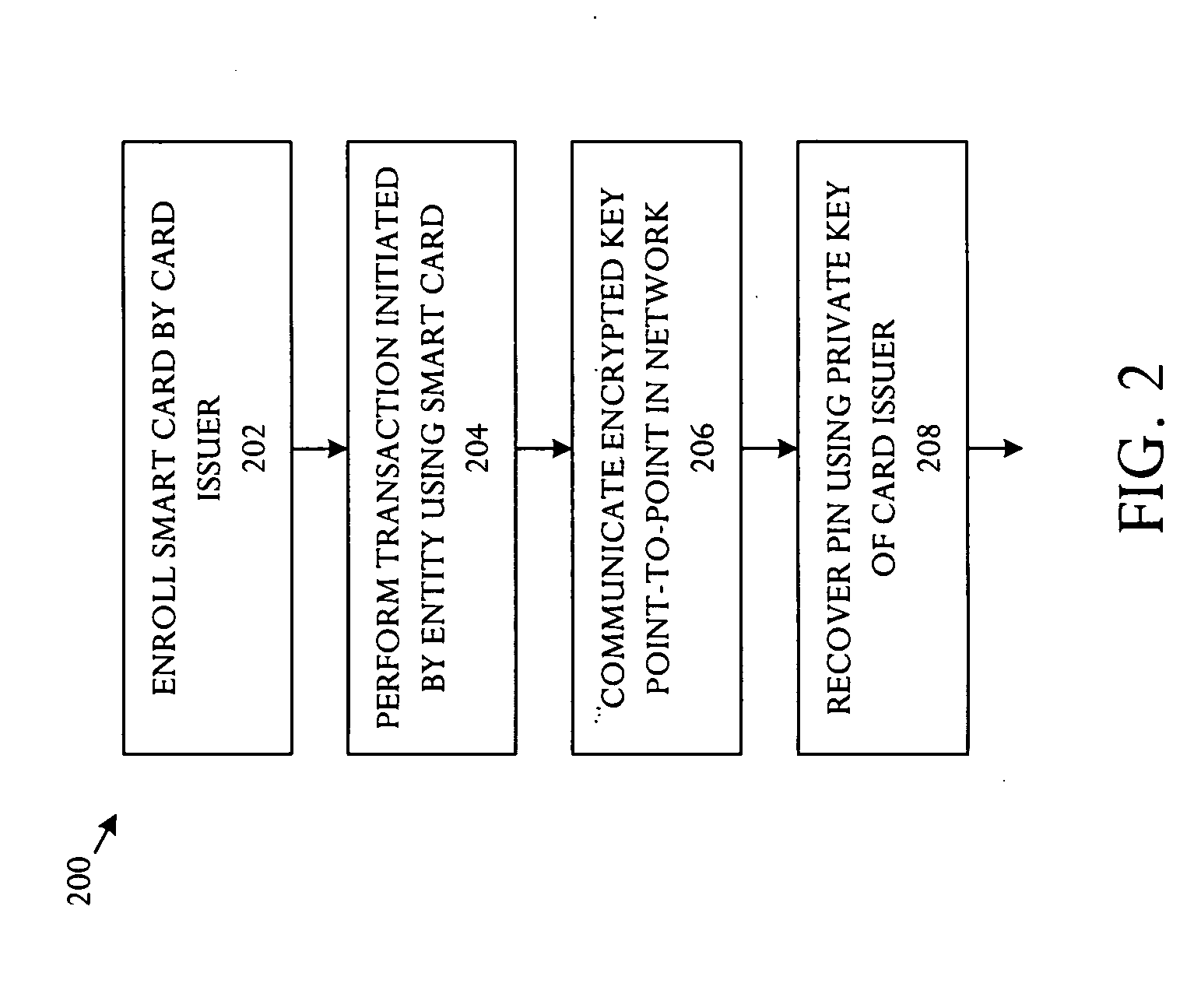
InactiveUS20050172137A1Eliminate operationKey distribution for secure communicationPublic key for secure communicationSmart cardFinancial transaction
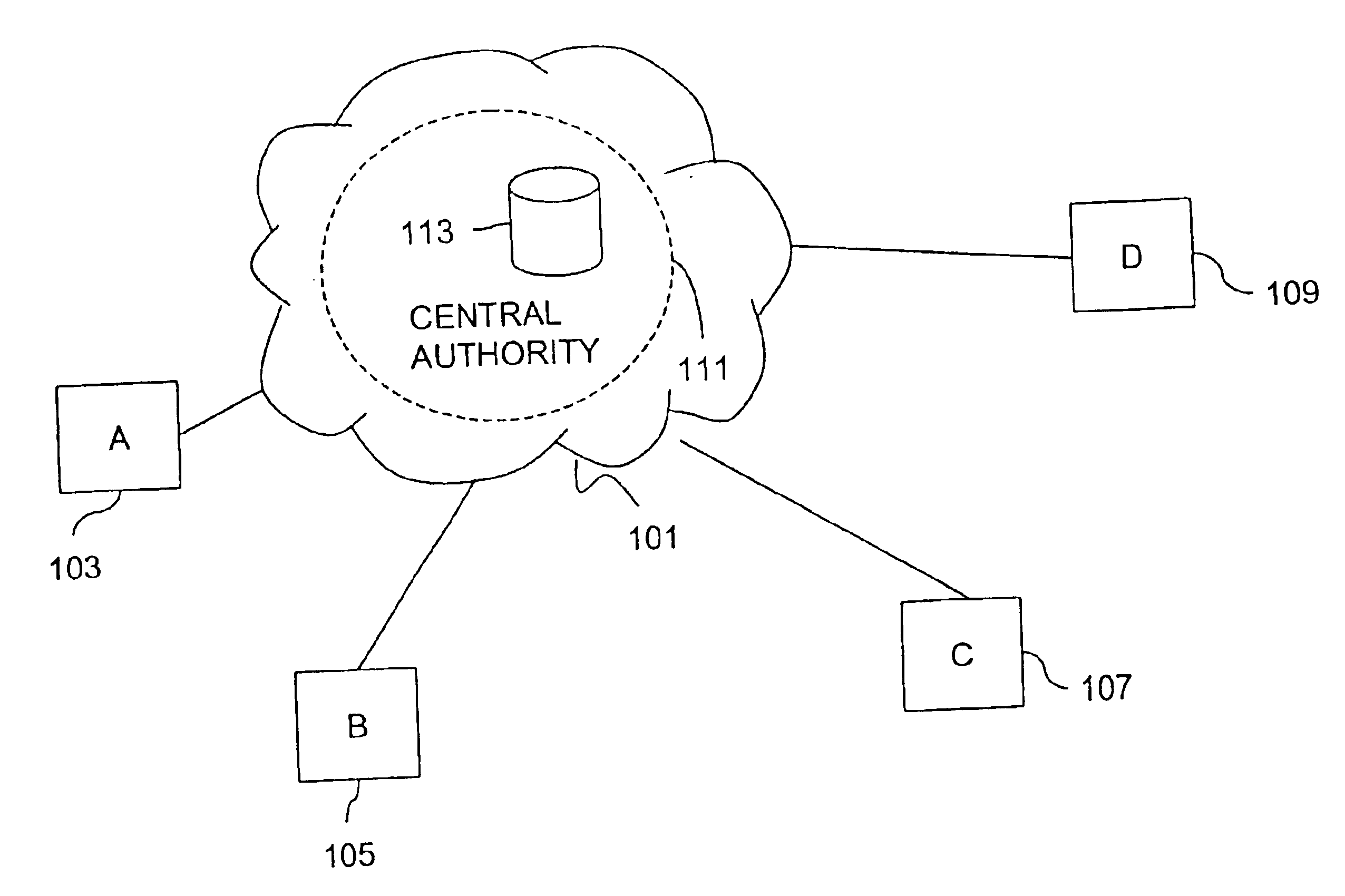
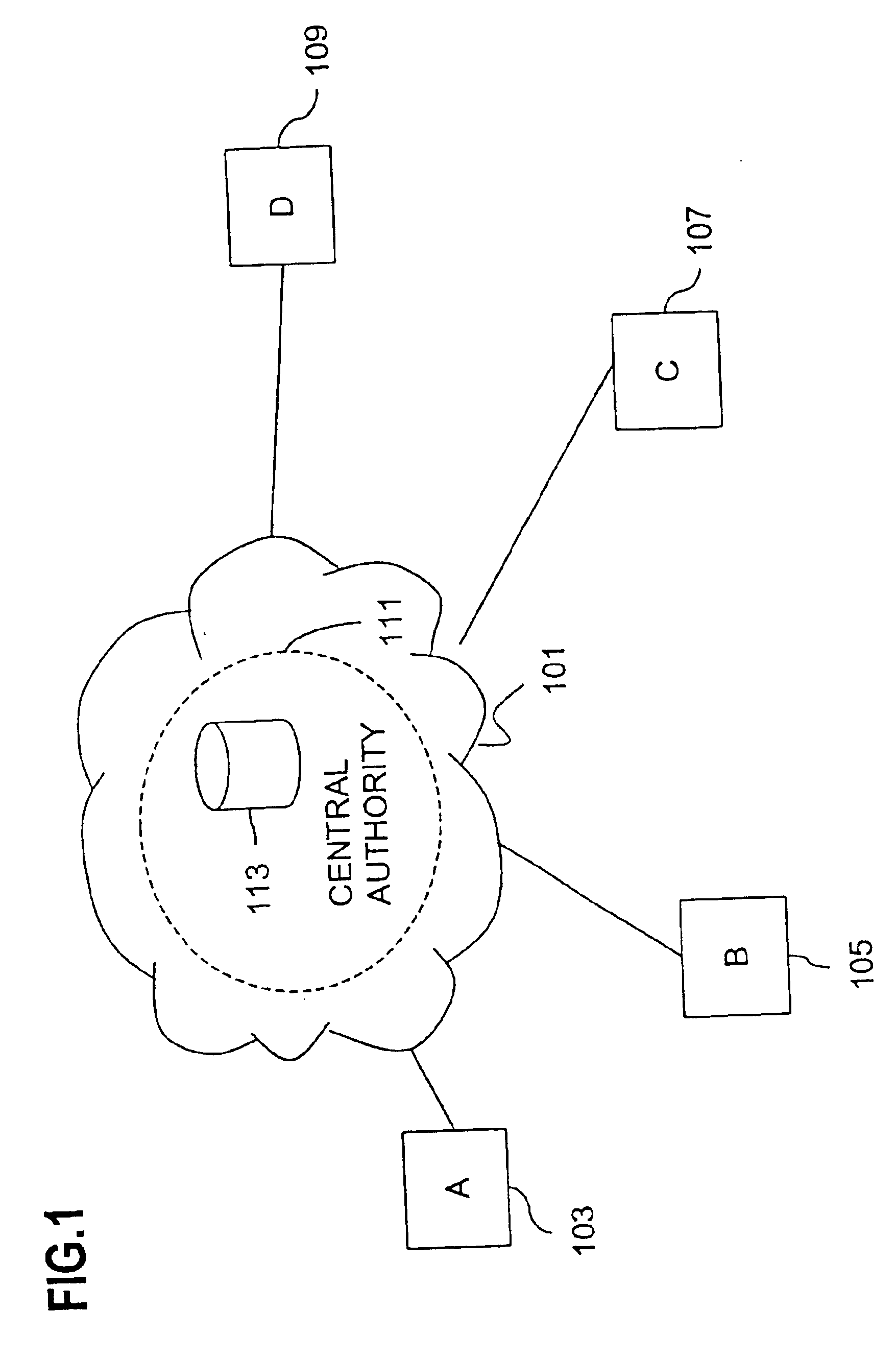
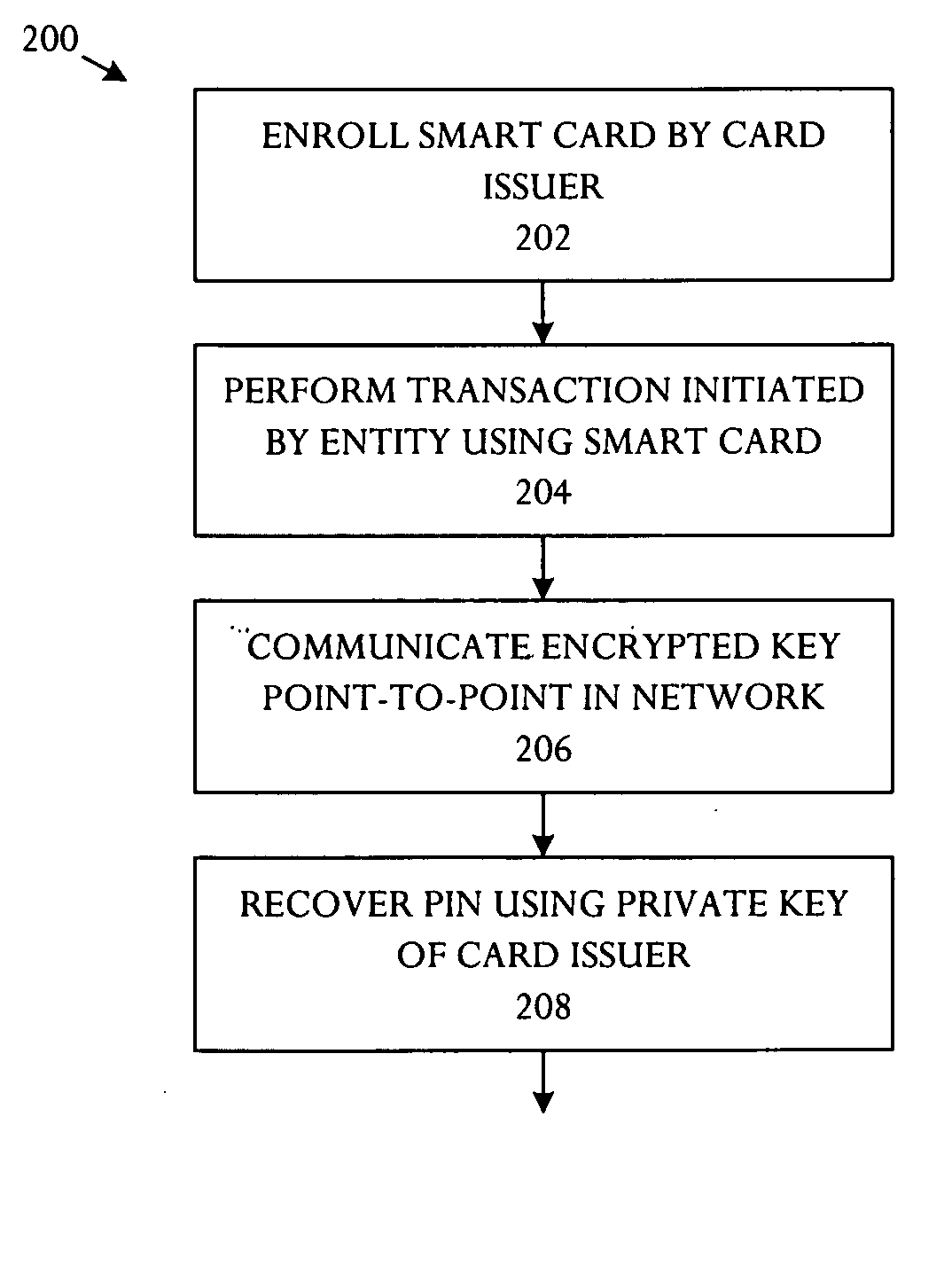
A key management technique establishes a secure channel through an indeterminate number of nodes in a network. The technique comprises enrolling a smart card with a unique key per smart card. The unique key is derived from a private key that is assigned and distinctive to systems and a card base of a card issuer. An enrolled smart card contains a stored public entity-identifier and the secret unique key. The technique further comprises transacting at a point of entry to the network. The transaction creates a PIN encryption key derived from the smart card unique key and a transaction identifier that uniquely identifies the point of entry and transaction sequence number. The technique also comprises communicating the PIN encryption key point-to-point in encrypted form through a plurality of nodes in the network, and recovering the PIN at a card issuer server from the PIN encryption key using the card issuer private key.
Owner:MICRO FOCUS LLC
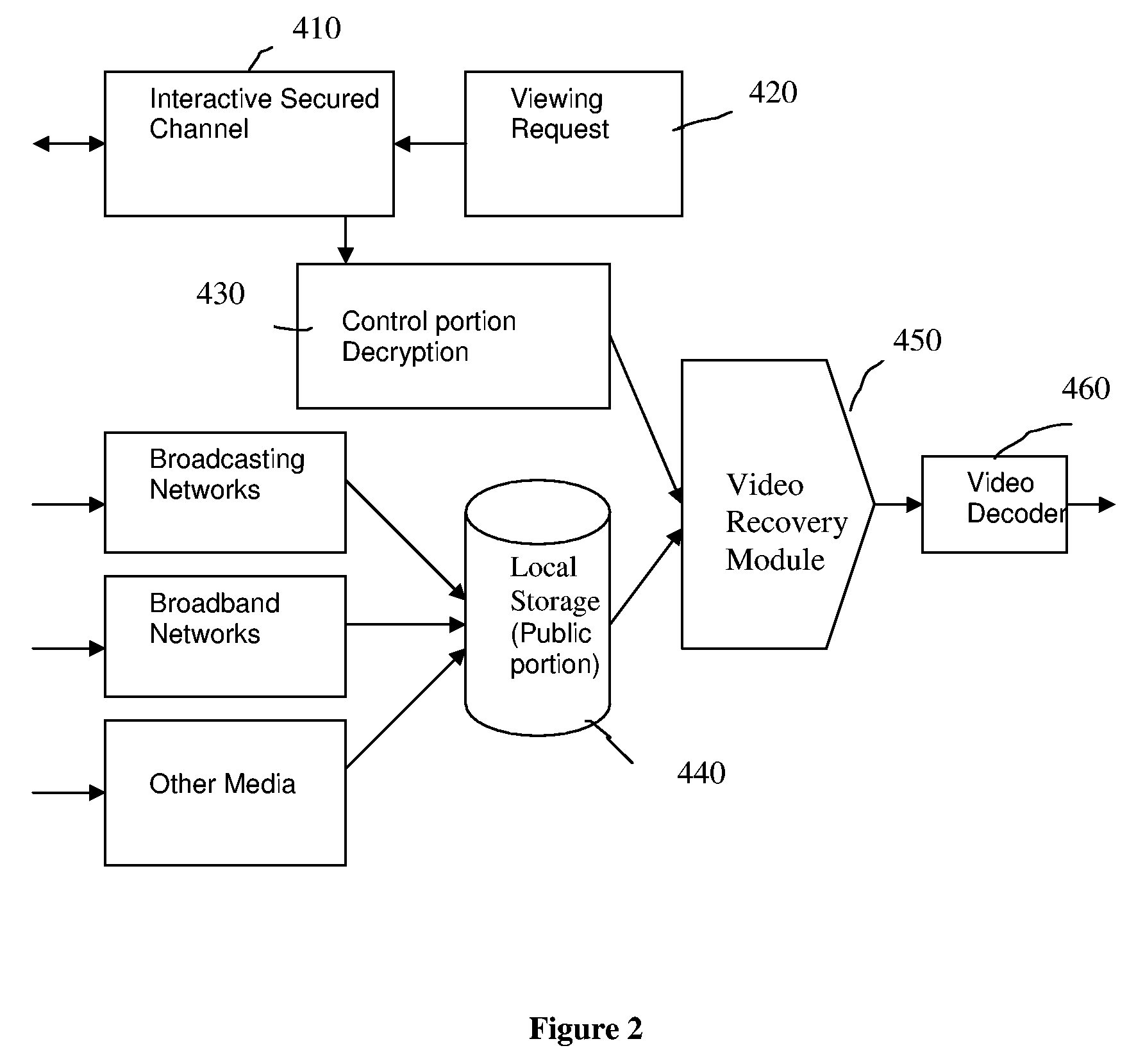
Method and Apparatus for Content Protection and Copyright Management in Digital Video Distribution
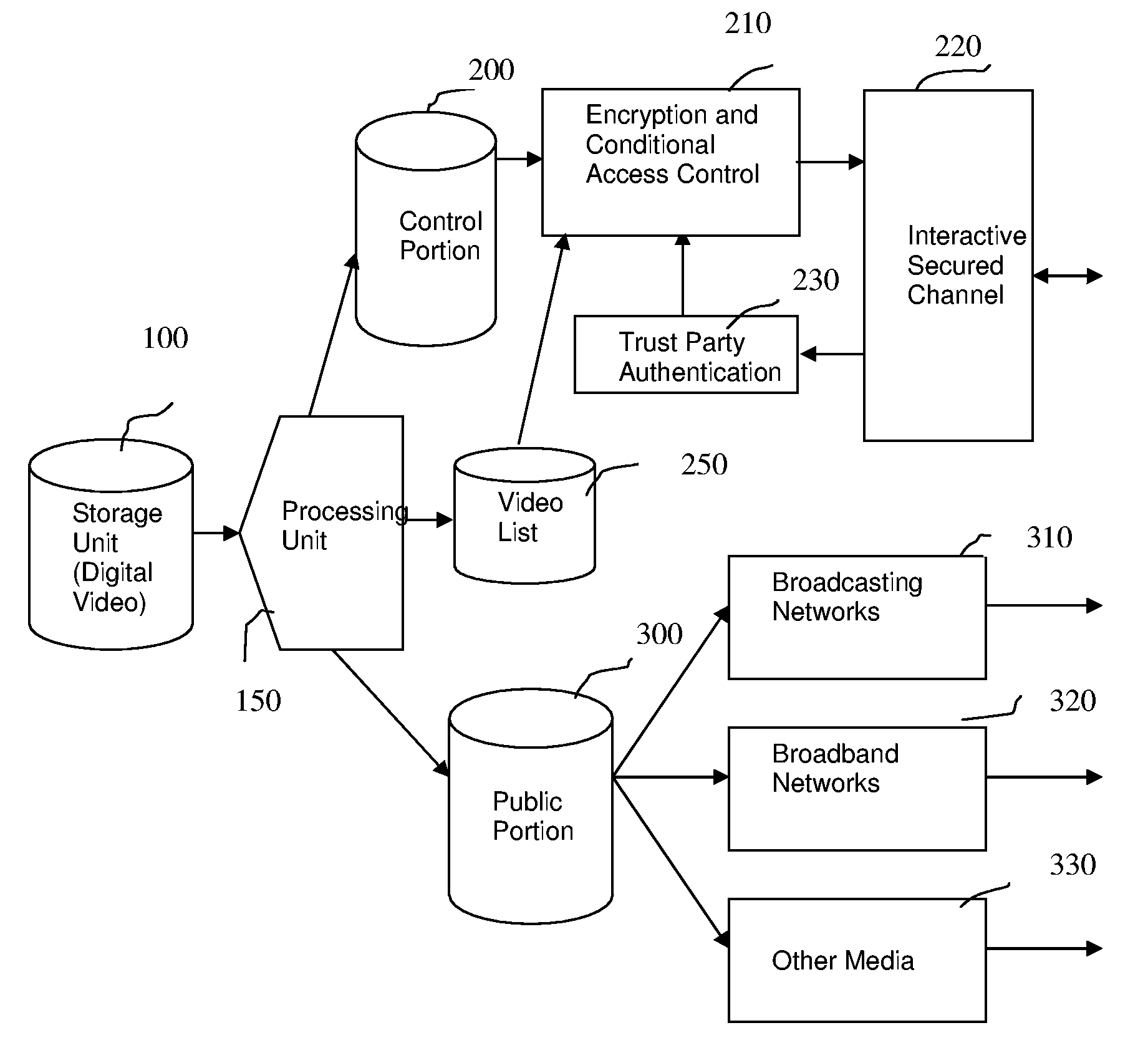
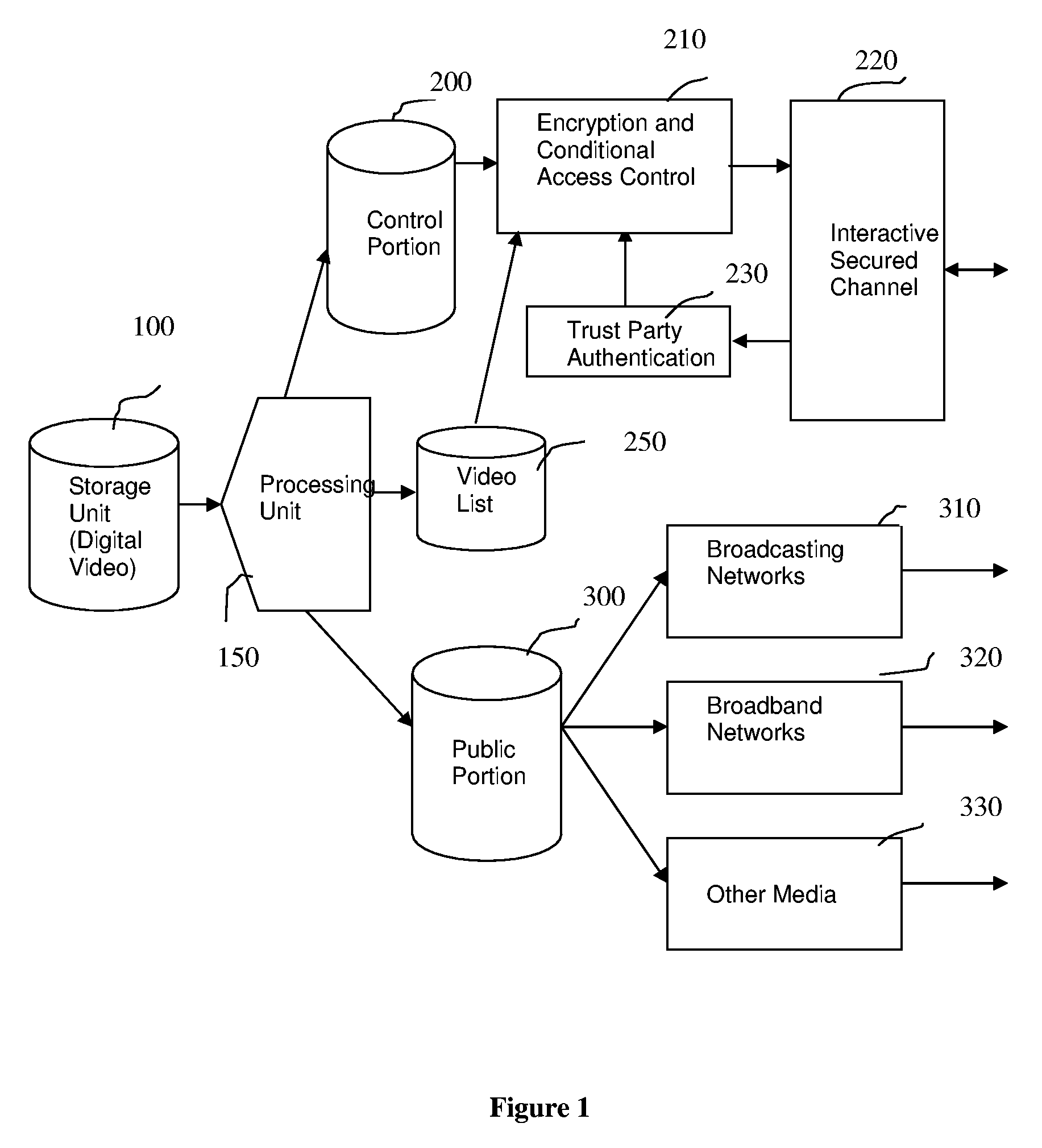
InactiveUS20060190403A1Effective copyright managementEfficient managementData processing applicationsTelevision systemsDigital videoComputer graphics (images)
This patent presents a method, apparatus and system for content protection and copyright management in digital video distribution over packet-based networks. The system consists of a distribution server and its agents. The distribution server first divides a digital video into parts and then processes them into public and control portions. The public and control portions are constructed in such a way that the public portion consists of the majority of the digital video while the control portion consists of only a small fraction of the video and other crucial information for restoring the video to its original format. The public portion is freely distributed without much restriction. In the absence of the control portion, the public portion cannot be decoded for video displaying. Thus, the control portion is delivered to an agent at a premise of authorized subscribers or viewers via a packet-based interactive secured channel at the time of restoring the full-length video content for displaying. An agent, which maintains the interactive secured channel with the distribution server, combines both public and control portions of a digital video back into its original format for displaying.
Owner:VIX TECHNOLOGY
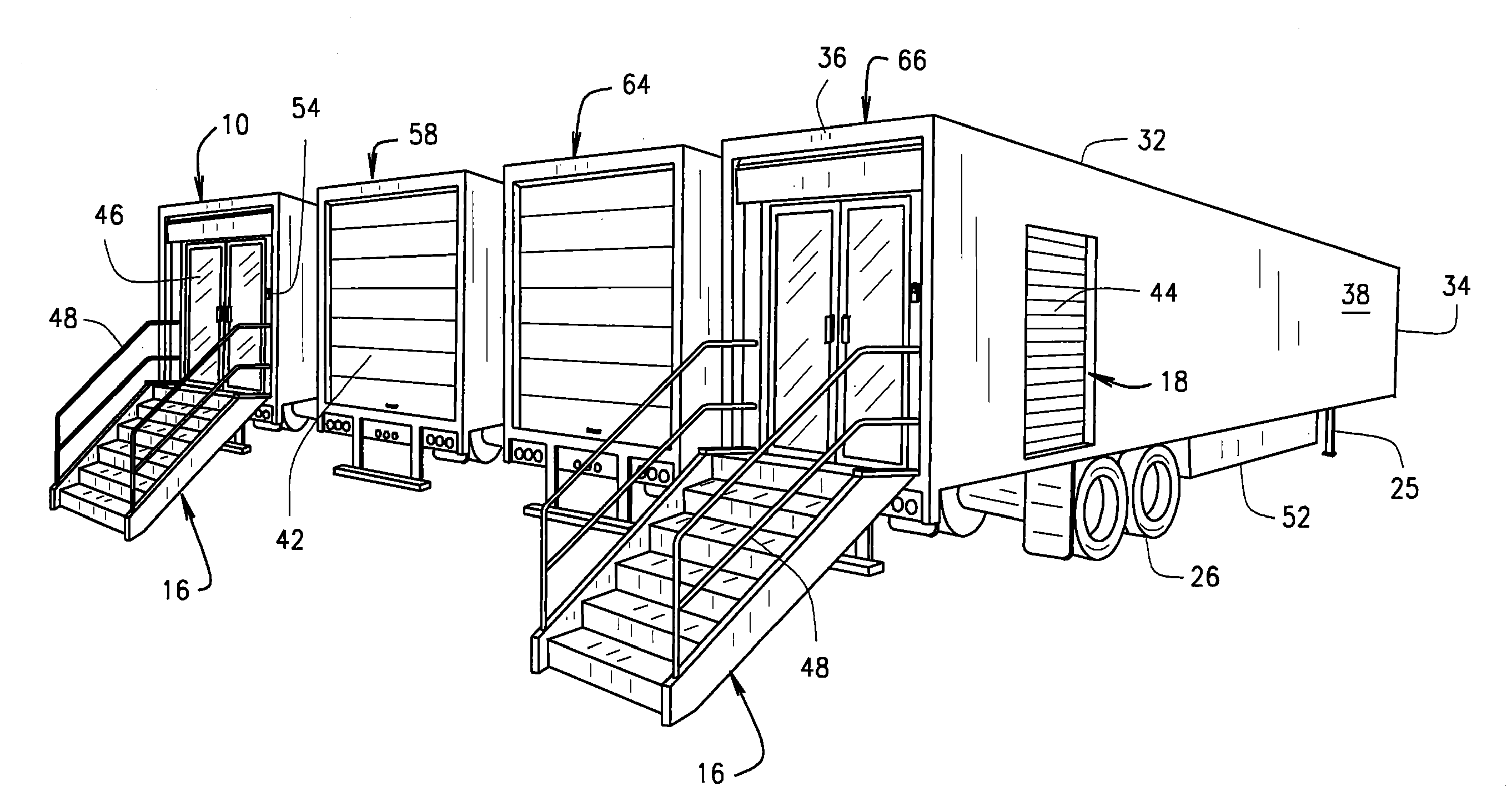
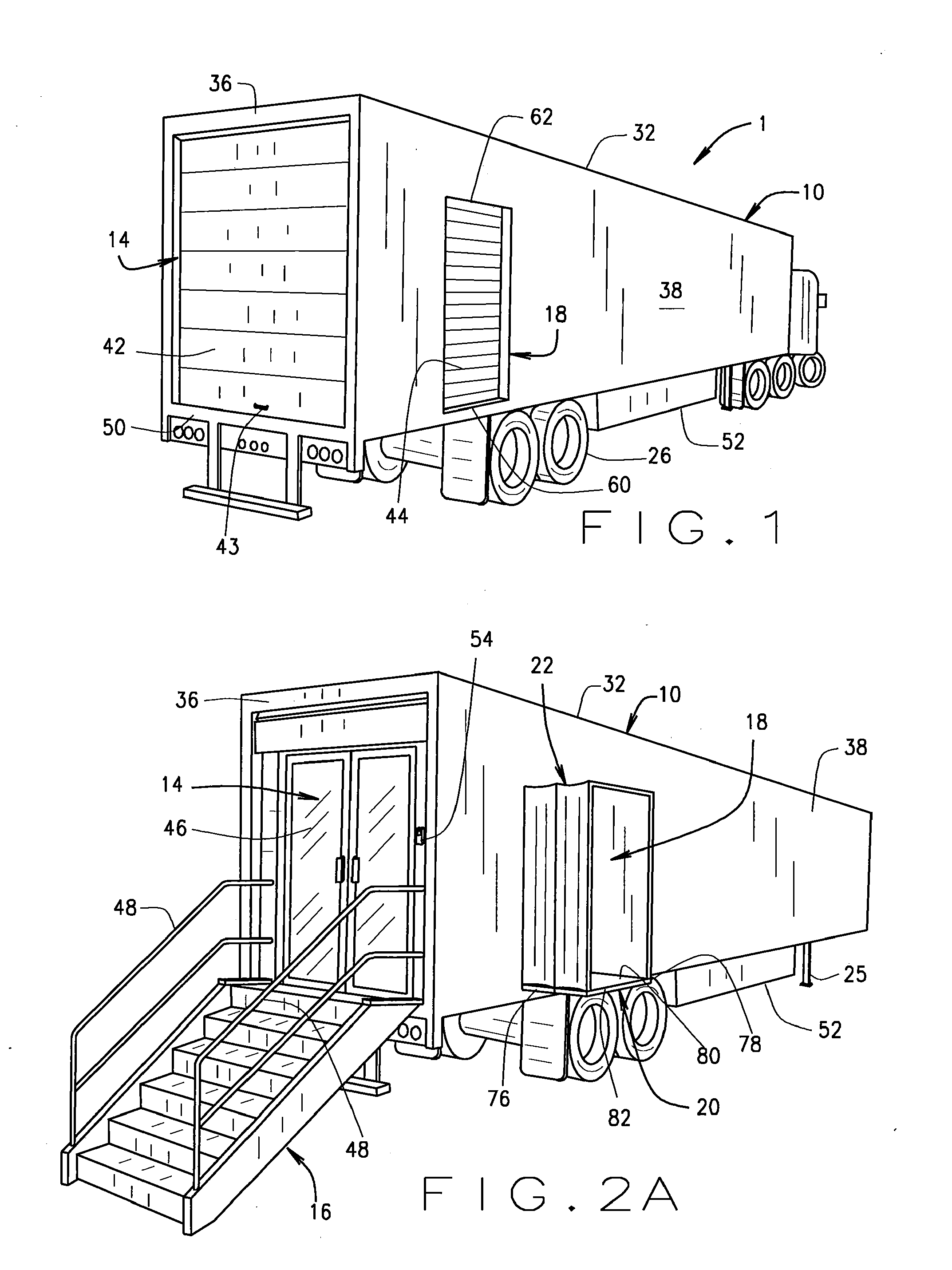
Mobile retail store structure with inventory system
ActiveUS20110313811A1Reduce interior noiseImprove ventilationHand manipulated computer devicesTents/canopiesTelecommunicationsComputer module
A mobile retail store structure transportable to a plurality of different locations includes a trailer construction configured both exteriorly and interiorly for housing a plurality of storage bins wherein products and / or parts can be stored. Each trailer is a self-sufficient module which includes doors at one end of the trailer unit for entry and exit thereto, portable stairs for providing access to the entry doors, opposed side doors and associated walkways for allowing coupling to additional similarly constructed trailers, extendable canopies for providing a secure passageway between the respective coupled trailers, and a generator / HVAC system for providing heating, cooling and electrical power to each trailer unit. In one embodiment, a terminal is provided to allow a user to either browse electronically various items for selection and / or sale, or access a self-service check-out station to complete a transaction. A plurality of terminals can be coupled to communicate with a master server terminal over a wired / wireless network.
Owner:SENCORPWHITE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com