Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5106results about "Data resetting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
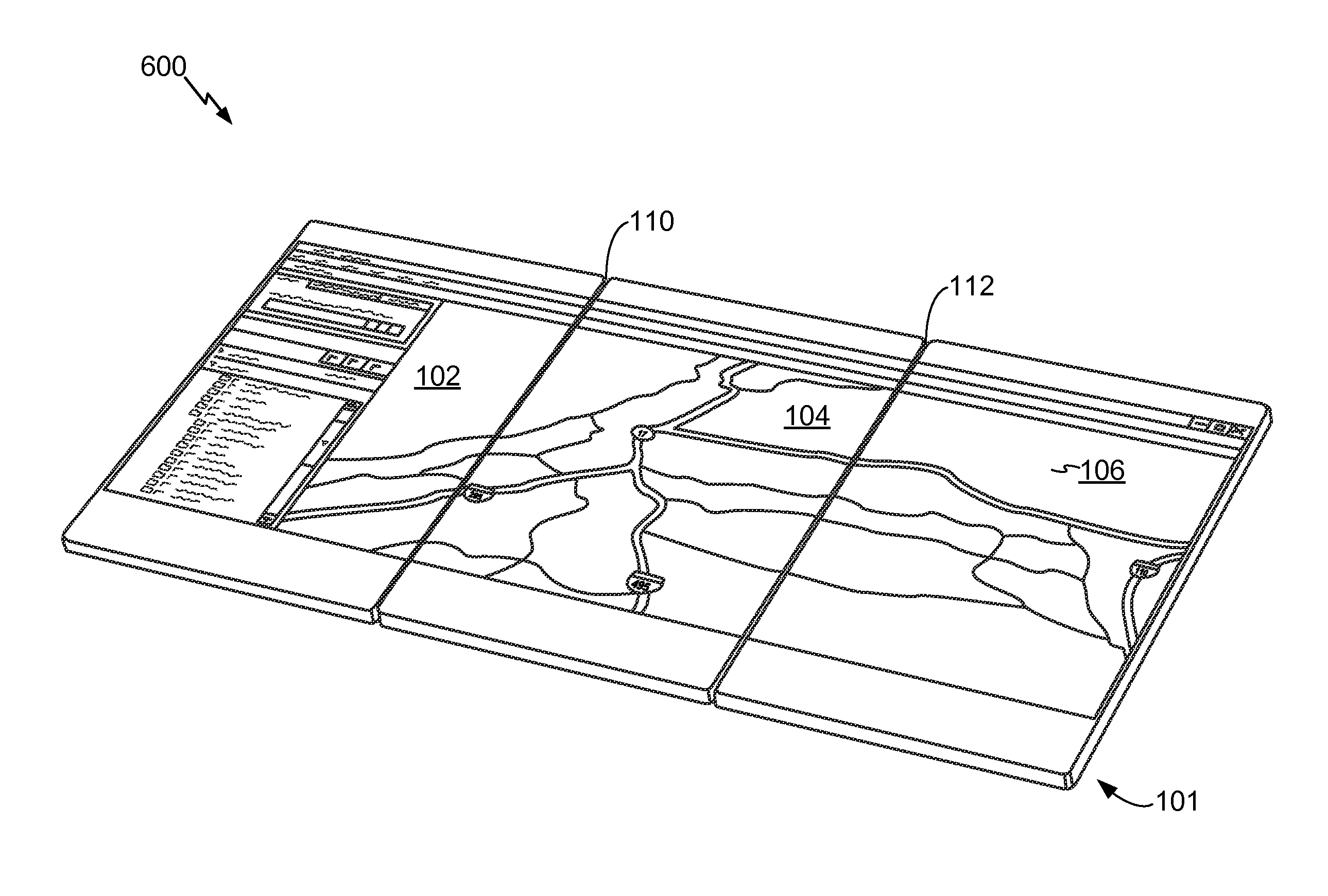
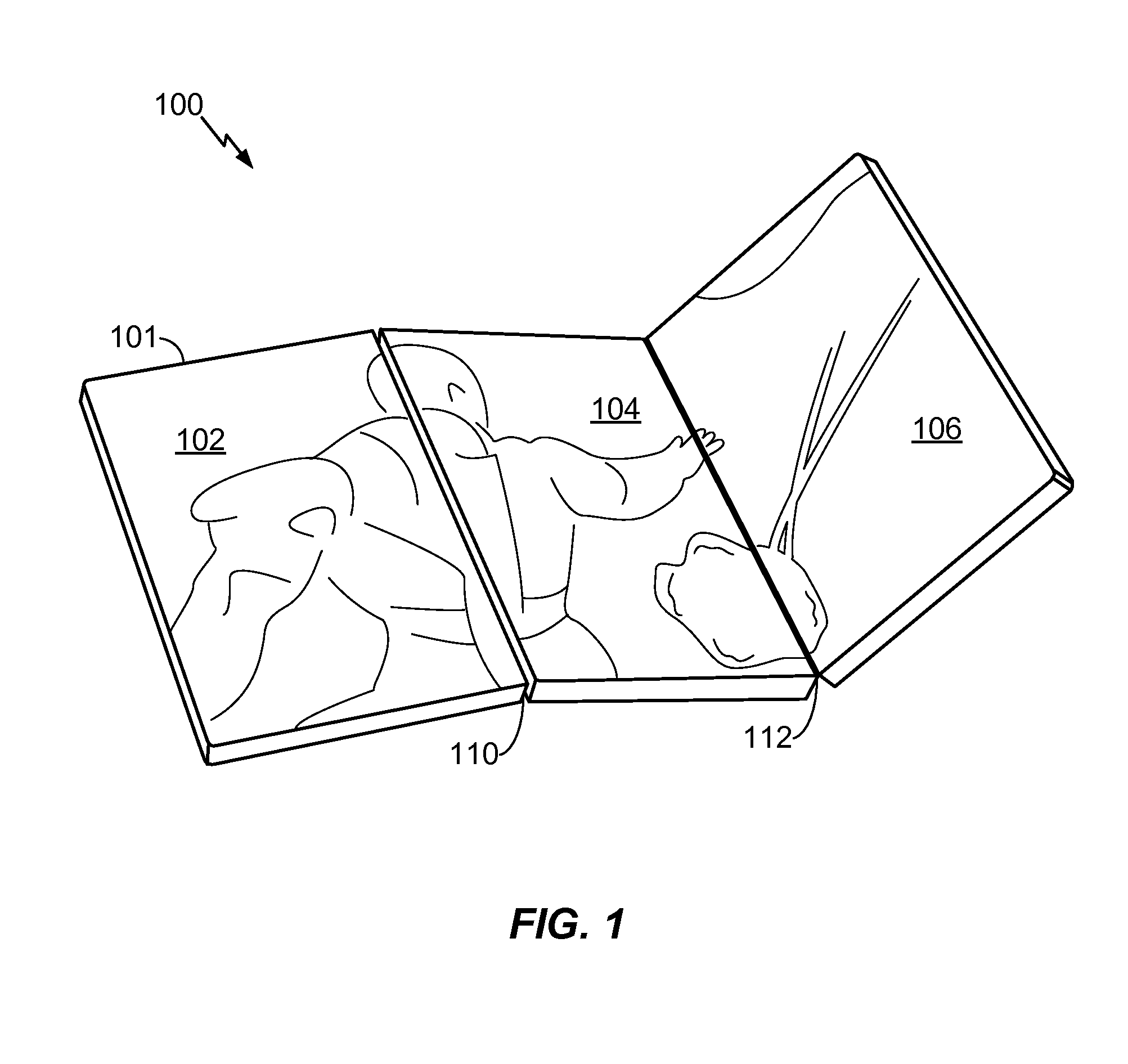
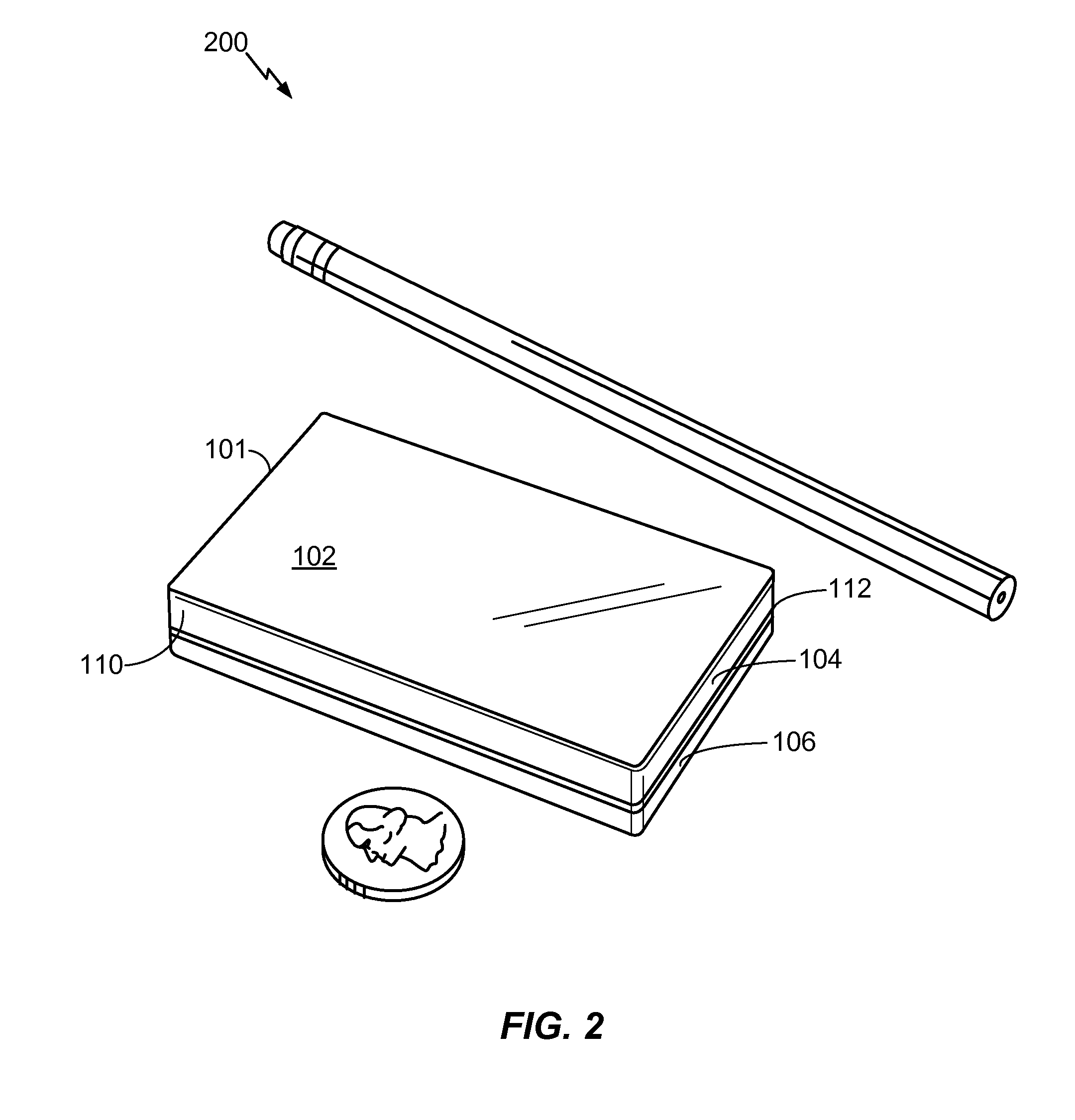
Multi-fold mobile device with configurable interface
ActiveUS20100064244A1Large screen sizeSmall sizeDevices with multiple display unitsDevices with sensorGraphicsGraphical user interface
A multi-fold mobile device with a configurable interface is disclosed. In a particular embodiment, a method includes detecting a hardware configuration change from a first configuration to a second configuration at an electronic device that includes at least a first panel having a first display surface and a second panel having a second display surface. The hardware configuration change includes a change in a relative orientation of the first display panel to the second display panel. The method also includes automatically modifying a graphical user interface displayed at the first display surface and the second display surface at least partially based on the second configuration.
Owner:QUALCOMM INC
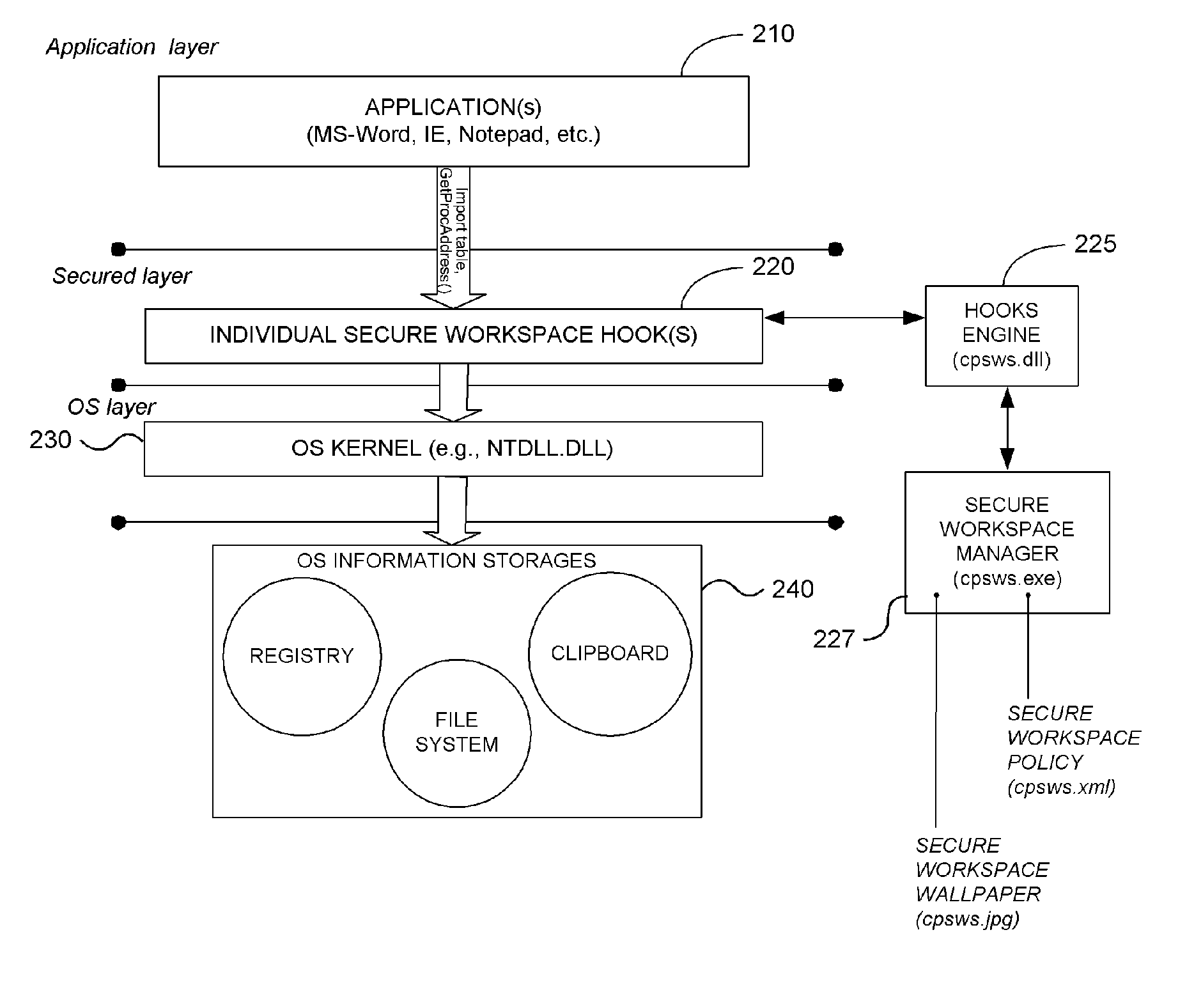
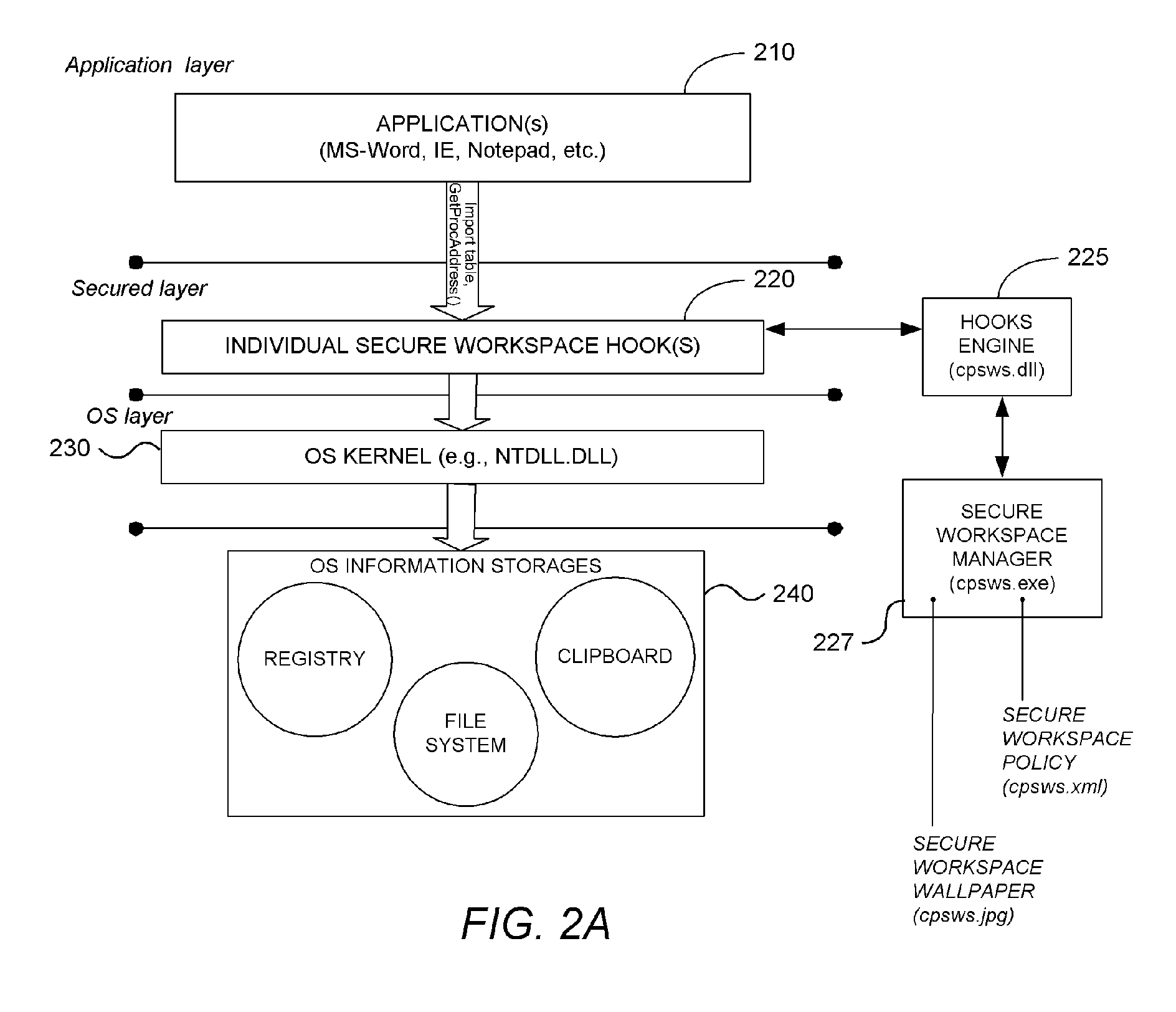
System and Methodology Providing Secure Workspace Environment
ActiveUS20070101435A1Avoid violationsUser identity/authority verificationAnalogue secracy/subscription systemsOperational systemWorkspace
System and methodology providing a secure workspace environment is described. In one embodiment, for example, in a computer system, a method is described for creating a secured workspace within an existing operating system for allowing users to run applications in a secured manner, the method comprises steps of: creating a policy for configuring the secured workspace, the policy specifying how information created during operation of the applications may be accessed; hooking particular functions of the operating system in order to obtain control over the information created during operation of the applications; during operation of the applications, encrypting the information to prevent unauthorized access; in response to a request for access to the information, determining whether the request complies with the policy; and if the request complies with the policy, satisfying the request by providing access to a decrypted copy of the information.
Owner:CHECK POINT SOFTWARE TECH INC
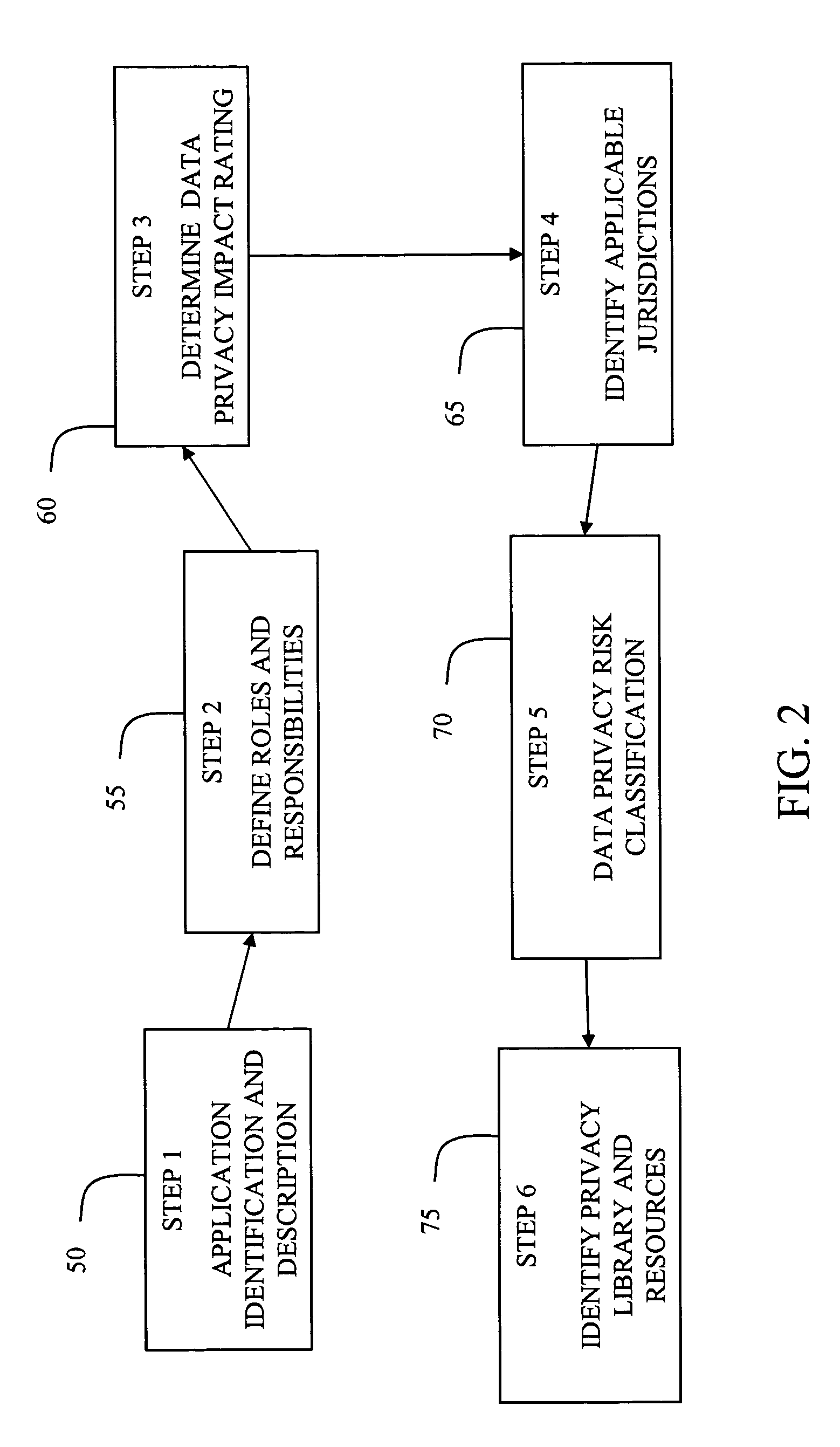
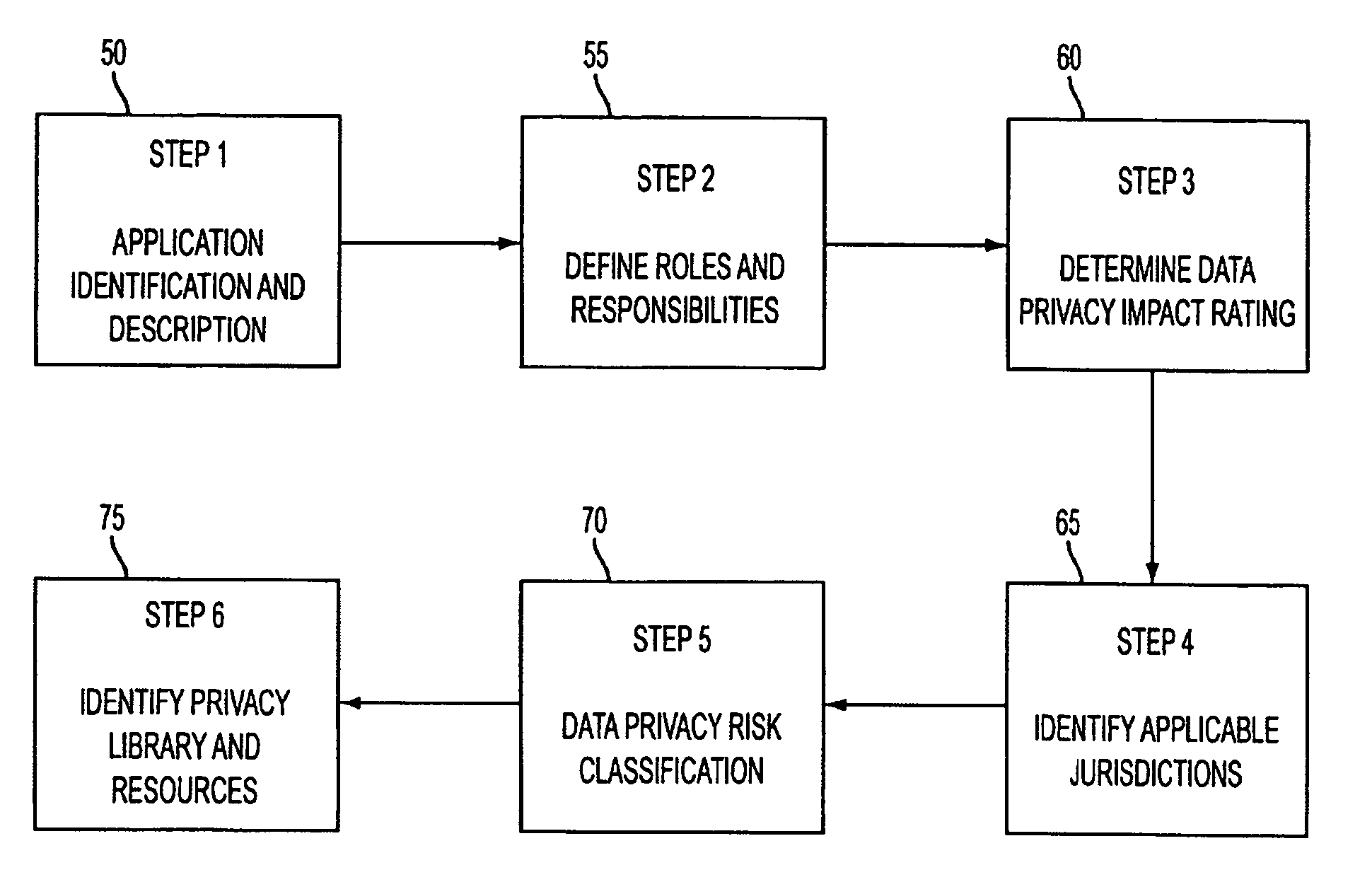
System and method for managing data privacy
ActiveUS7234065B2Easy to manageSpeed up the processUser identity/authority verificationUnauthorized memory use protectionInternet privacyKey issues
A system and method for assessing the risk associated with the protection of data privacy by software application. A decision engine is provided to assess monitor and manage key issues around the risk management of data privacy. The system creates a core repository that manages, monitors and measures the data privacy assessments of applications across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager responsible for the application). The responses are tracked in order to evaluate the progress of the assessment and the status of the applications with respect to compliance with the enterprise's data privacy policies and procedures as well as the regulations and laws of the jurisdictions in which the application is operated. Once a questionnaire has been completed, the application is given ratings both with respect to the data privacy impact of the application and the application's compliance with the data privacy requirements. If a risk exists, a plan for reducing the risk or bringing the application into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be acknowledged through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
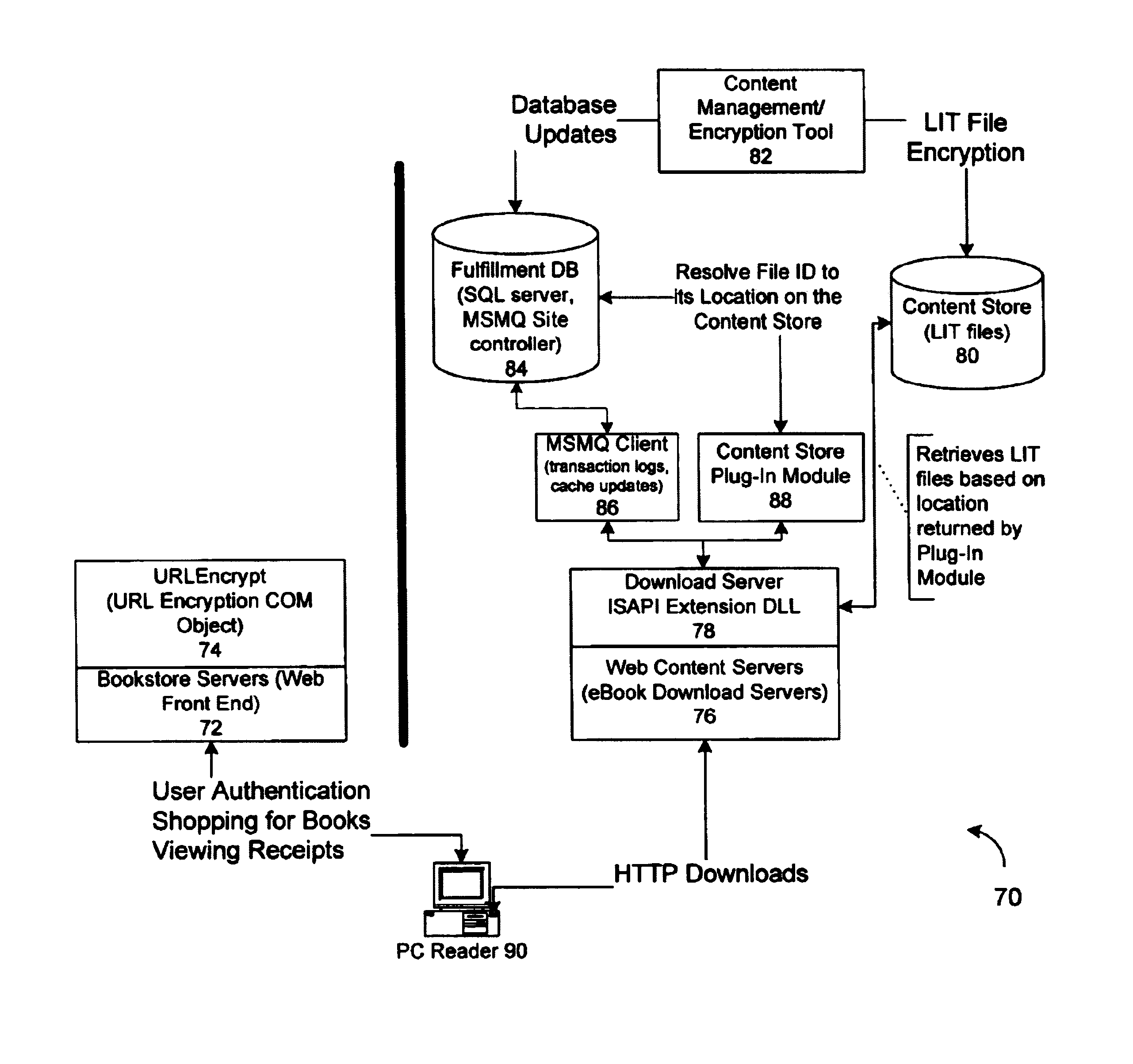
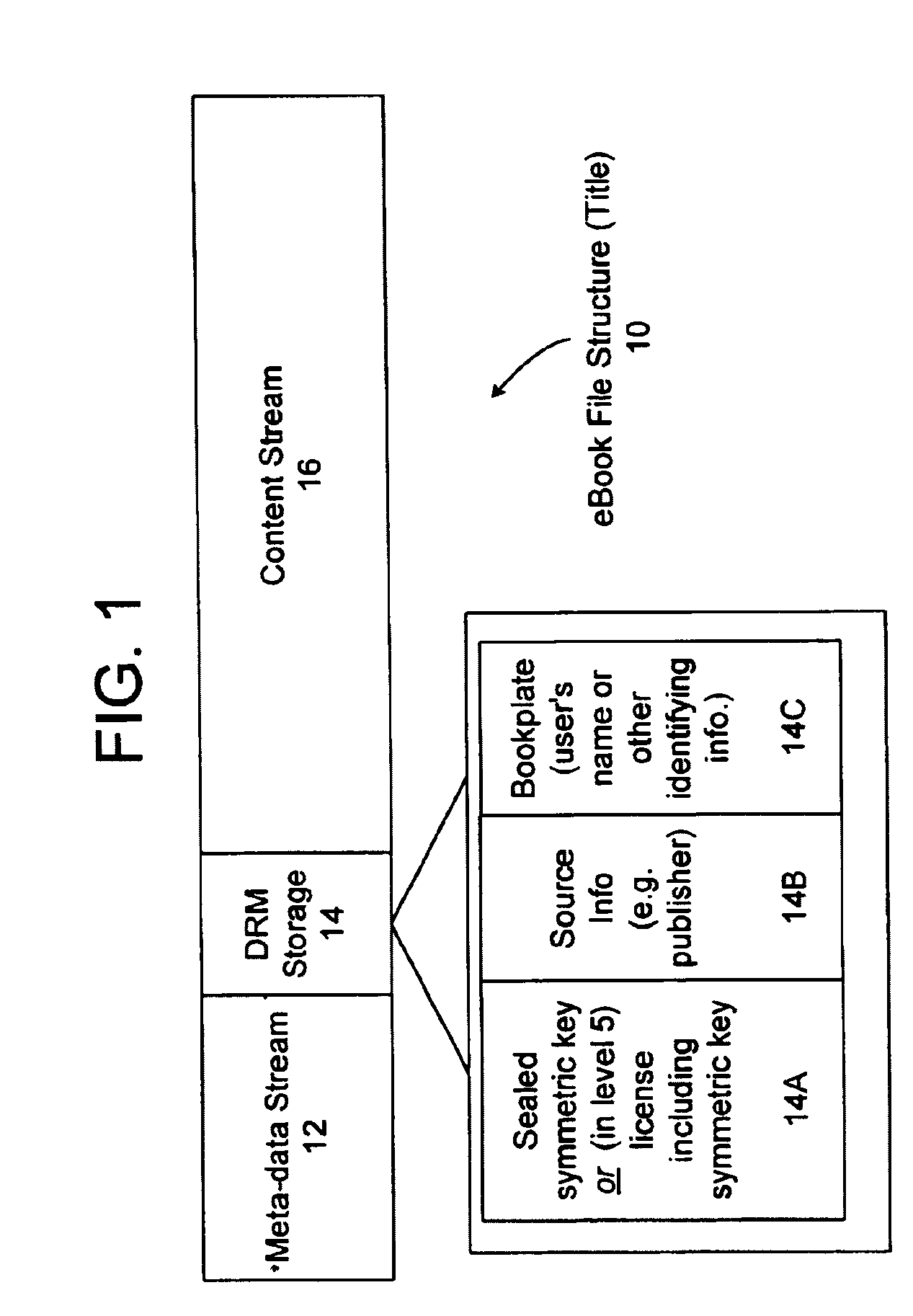
Server for an electronic distribution system and method of operating same
ActiveUS7047411B1Preventing unchecked proliferationKey distribution for secure communicationUser identity/authority verificationStore and forwardDigital rights management system
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content items, the retail site transmits to the purchase a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon the following the link, the fulfillment site downloads the ordered content to the consumer preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enable those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
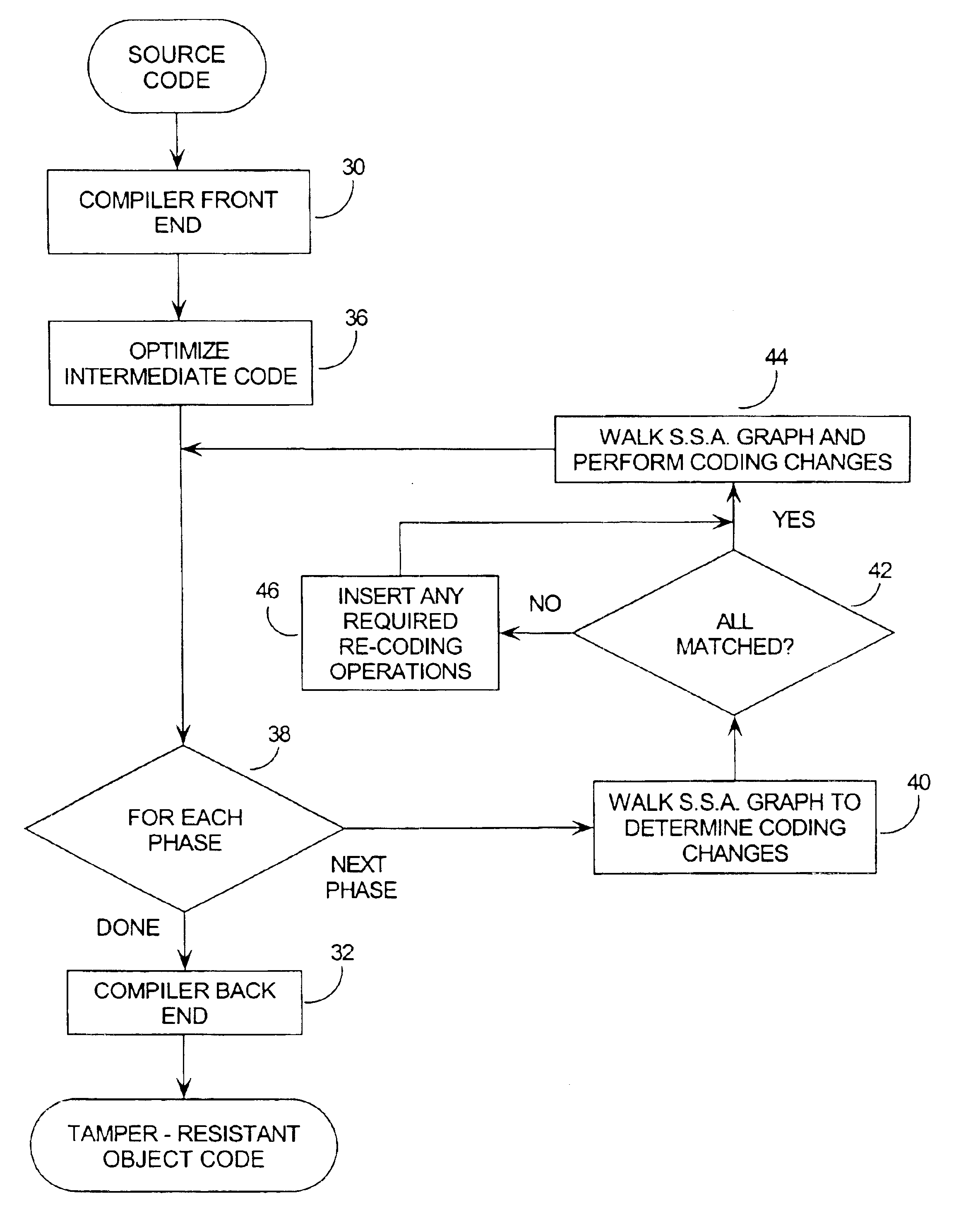
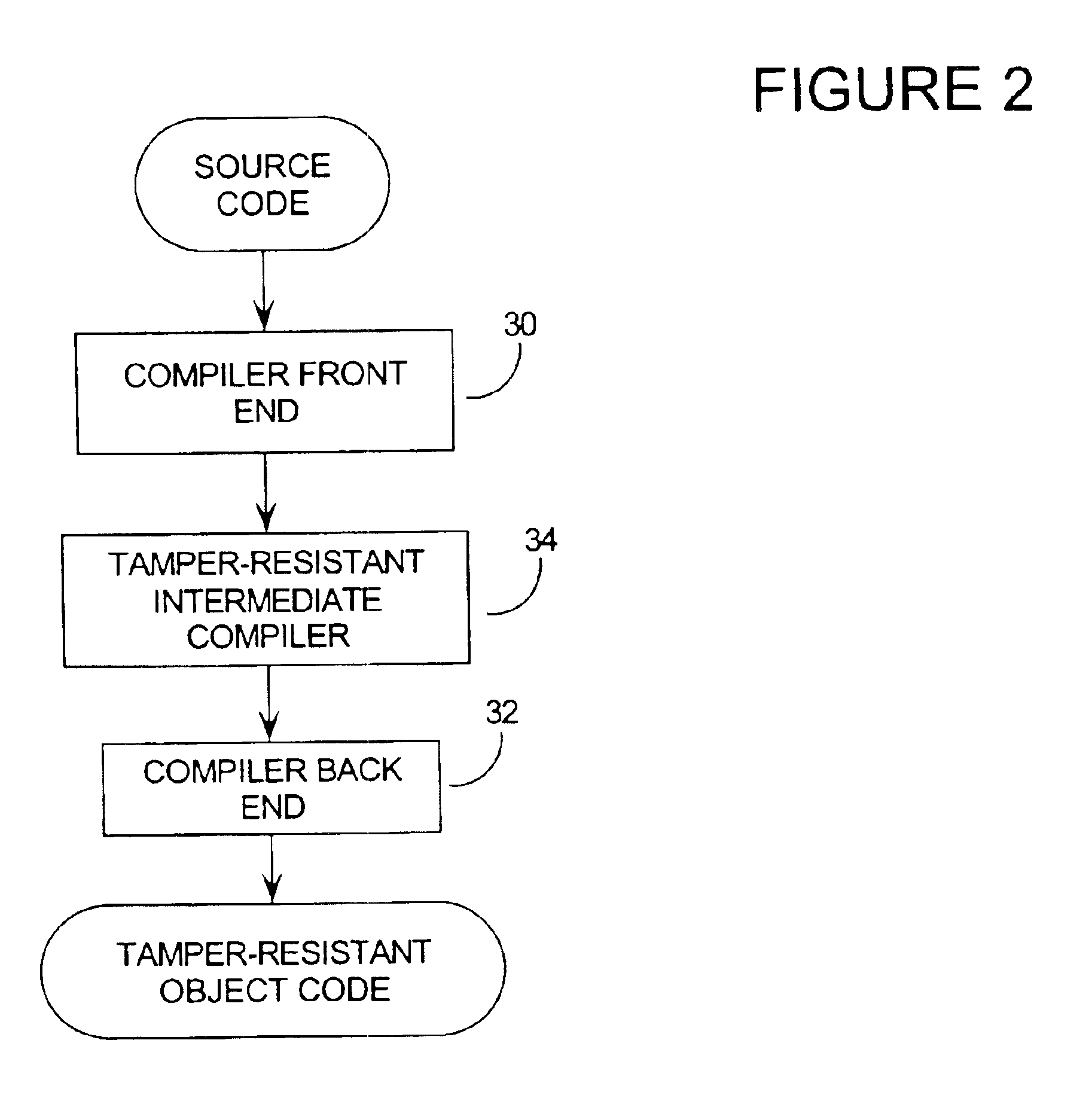
Tamper resistant software encoding
InactiveUS6842862B2Improvement in tamper-resistanceIncreased complexityMemory loss protectionUnauthorized memory use protectionTamper resistancePassword
The present invention relates generally to computer software, and more specifically, to a method and system of making computer software resistant to tampering and reverse-engineering. “Tampering” occurs when an attacker makes unauthorized changes to a computer software program such as overcoming password access, copy protection or timeout algorithms. Broadly speaking, the method of the invention is to increase the tamper-resistance and obscurity of computer software code by transforming the data flow of the computer software so that the observable operation is dissociated from the intent of the original software code. This way, the attacker can not understand and decode the data flow by observing the execution of the code. A number of techniques for performing the invention are given, including encoding software arguments using polynomials, prime number residues, converting variables to new sets of boolean variables, and defining variables on a new n-dimensional vector space.
Owner:IRDETO ACCESS
System and method for managing data privacy
InactiveUS20070283171A1Easy to manageSpeed up the processUnauthorized memory use protectionHardware monitoringInternet privacyKey issues
A system and method for assessing the risk associated with the protection of data privacy by software application. A decision engine is provided to assess monitor and manage key issues around the risk management of data privacy. The system creates a core repository that manages, monitors and measures the data privacy assessments of applications across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager responsible for the application). The responses are tracked in order to evaluate the progress of the assessment and the status of the applications with respect to compliance with the enterprise's data privacy policies and procedures as well as the regulations and laws of the jurisdictions in which the application is operated. Once a questionnaire has been completed, the application is given ratings both with respect to the data privacy impact of the application and the application's compliance with the data privacy requirements. If a risk exists, a plan for reducing the risk or bringing the application into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be acknowledged through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
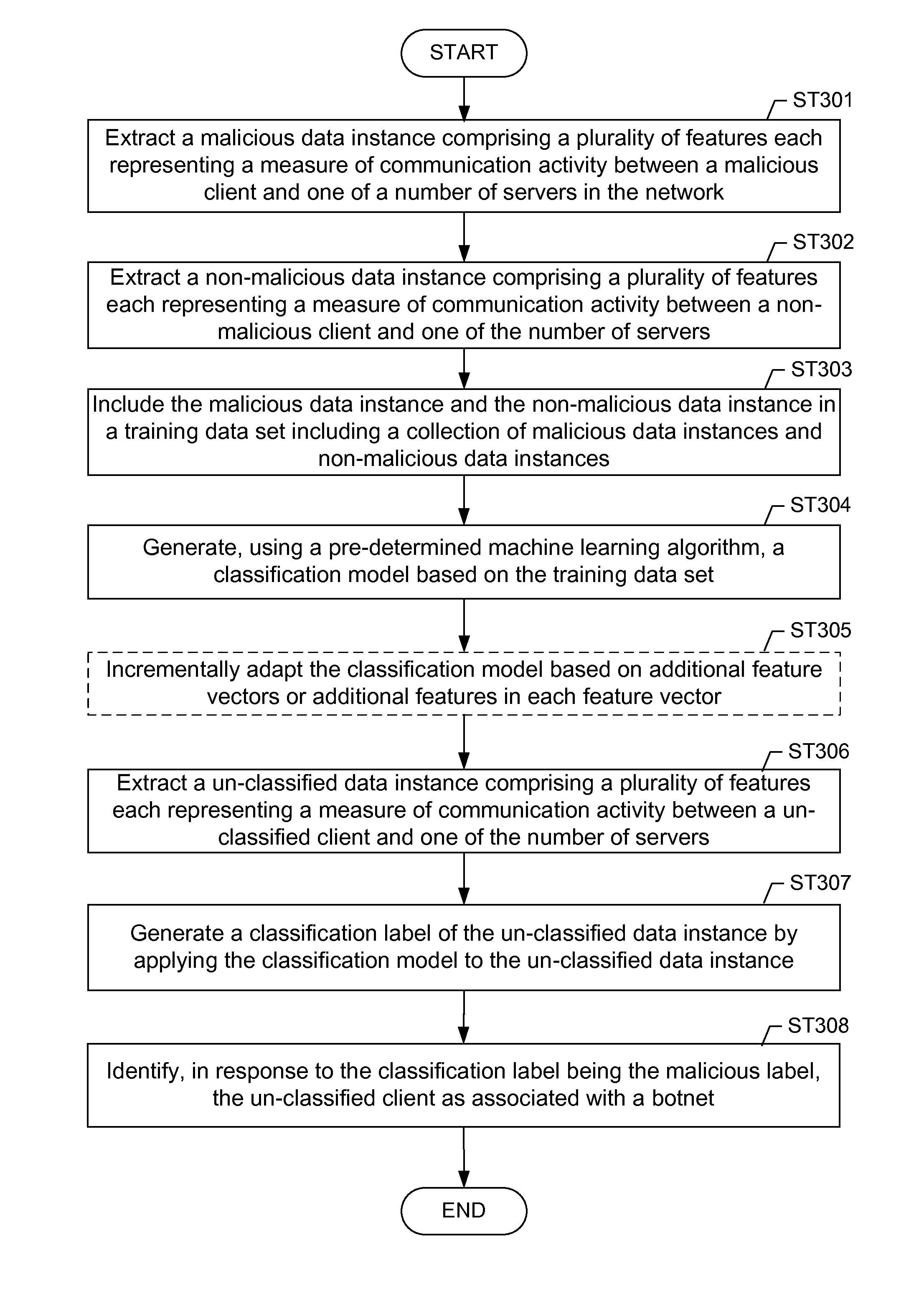
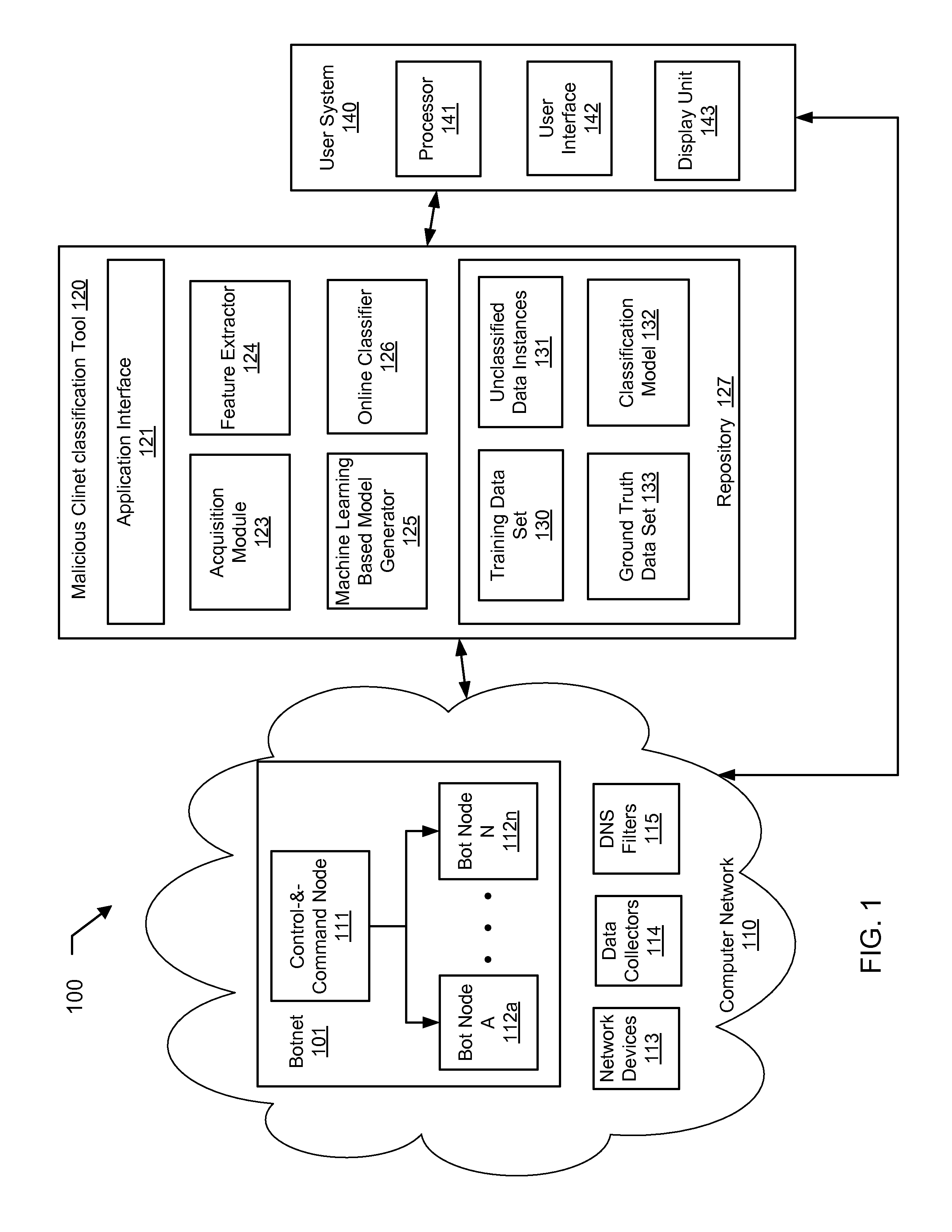
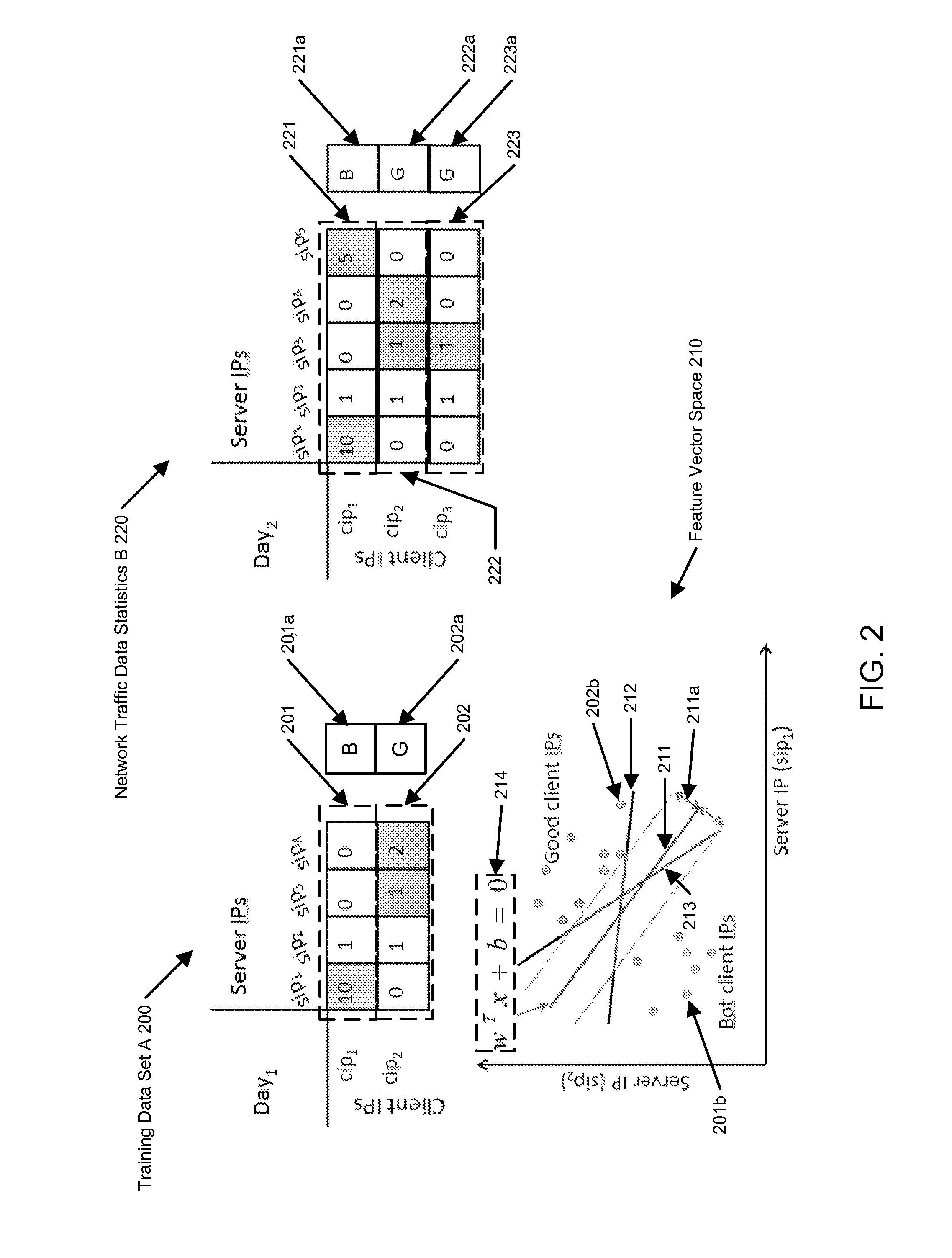
Machine learning based botnet detection with dynamic adaptation
Embodiments of the invention address the problem of detecting bots in network traffic based on a classification model learned during a training phase using machine learning algorithms based on features extracted from network data associated with either known malicious or known non-malicious client and applying the learned classification model to features extracted in real-time from current network data. The features represent communication activities between the known malicious or known non-malicious client and a number of servers in the network.
Owner:THE BOEING CO
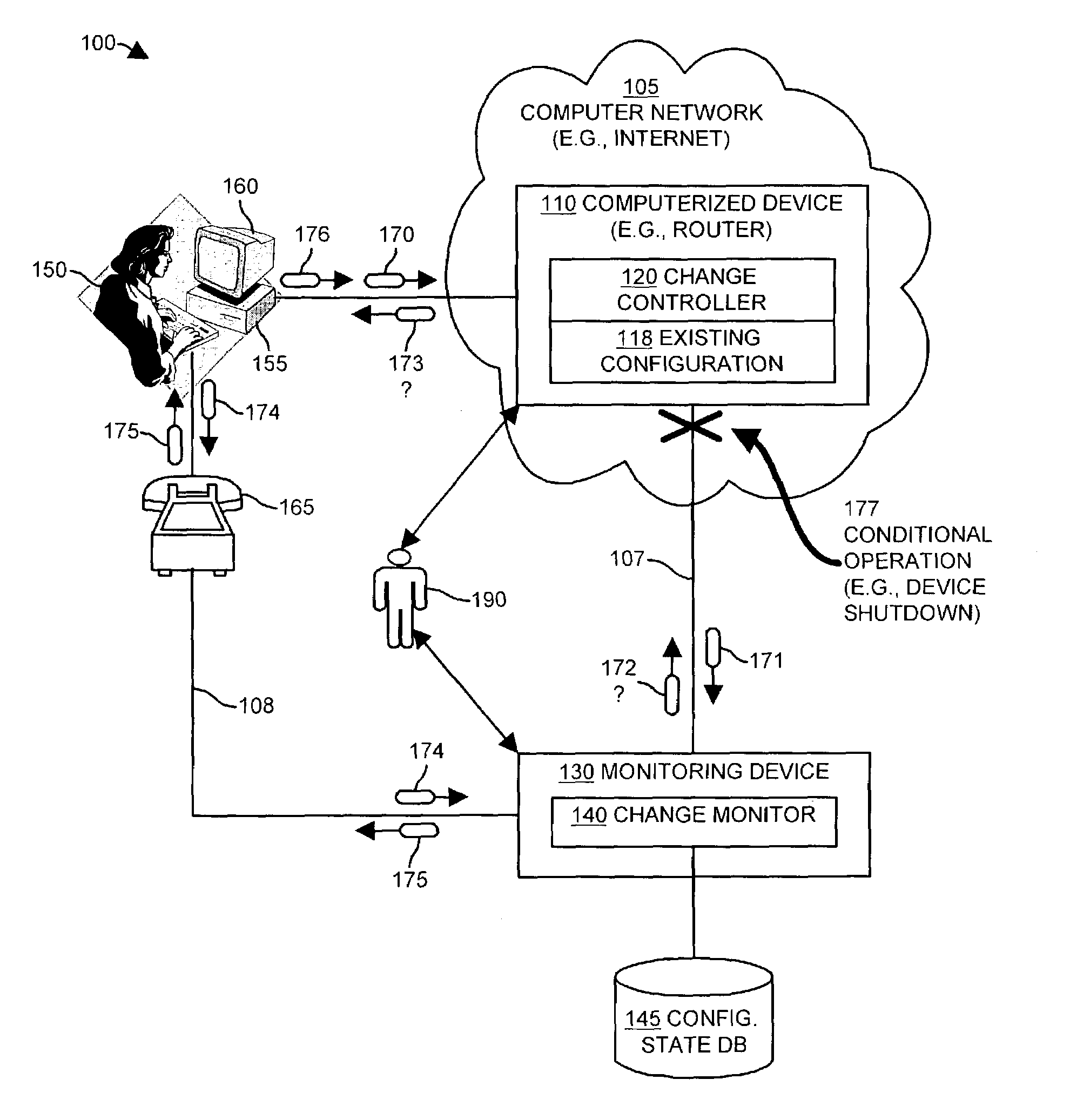
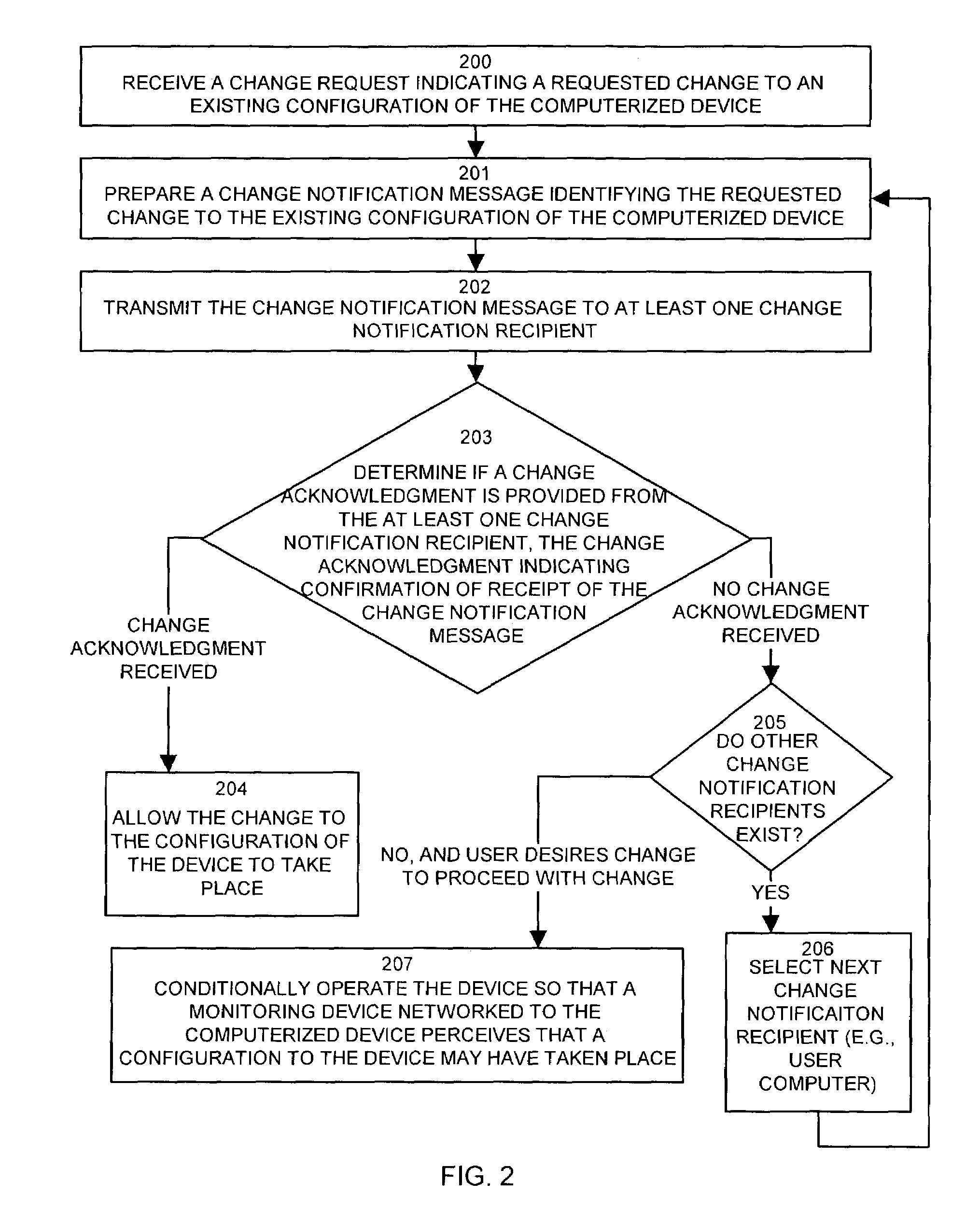
Methods and apparatus for auditing and tracking changes to an existing configuration of a computerized device
InactiveUS7024548B1Maliciously compromisedOvercome deficienciesMemory loss protectionError detection/correctionNotification ReceiverChange control
A change controller application, process and system tracks modification to a configuration of a computerized device by receiving a change request indicating a requested change to an existing configuration of the computerized device and preparing a change notification message identifying the requested change to the existing configuration of the computerized device. The change controller transmits the change notification message to at least one change notification recipient and determines if a change acknowledgement is provided in response. If a change acknowledgement is provided from a change notification recipient that indicates confirmation of receipt of the change notification message, the system allows the requested change to the configuration of the computerized device to take place. If the change acknowledgement is not provided from a change notification recipient, the system conditionally operates the computerized device so that a monitoring device networked to the computerized device perceives that a configuration change to the computerized device may have taken place.
Owner:CISCO TECH INC
Method of time multiplexing a programmable logic device
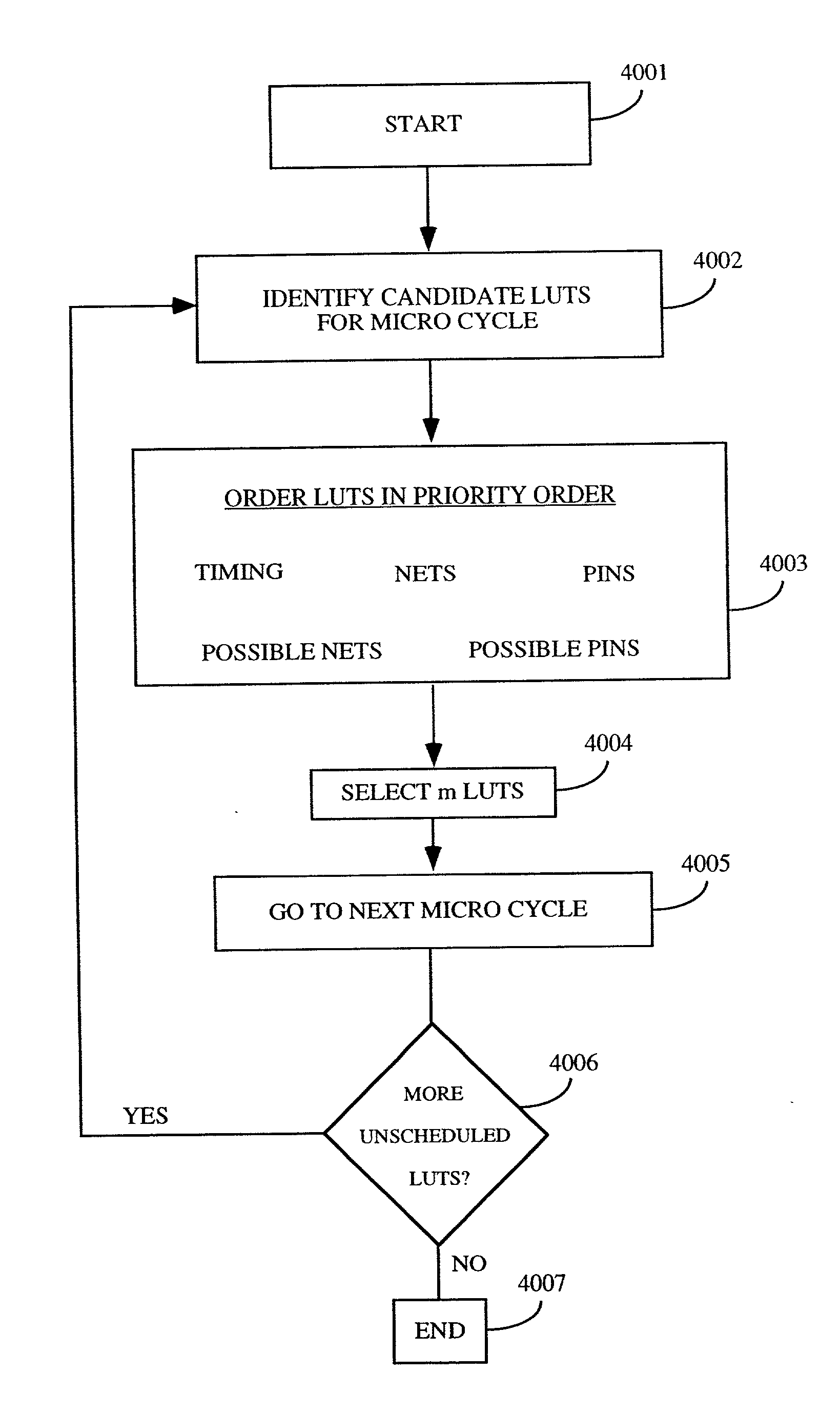
InactiveUS20020010853A1Reduce in quantityEasy to reuseDigital computer detailsData resettingProgrammable logic deviceLogic element
A programmable logic device (PLD) comprises at least one configurable element, and a plurality of programmable logic elements for configuring the configurable element(s). Alternatively, a PLD comprises an interconnect structure and a plurality of programmable logic elements for configuring the interconnect structure. In either embodiment, at least one of the programmable logic elements includes N memory cells. A predetermined one of the N memory cells forms part of a memory slice, wherein at least a portion of each slice of the programmable logic device is allocated to either configuration data or user data memory. Typically, one memory slice provides one configuration of the programmable logic device. In accordance with one embodiment, a memory access port is coupled between at least one of the N memory cells and either one configurable element or the interconnect, thereby facilitating loading of new configuration data into other memory slices during the one configuration. The new configuration data may include off-chip or on-chip data. The present invention typically allocates at least one slice to user data memory and includes means for disabling access to at least one of the N memory cells.
Owner:XILINX INC
Method and arrangement for implementing IPSEC policy management using filter code
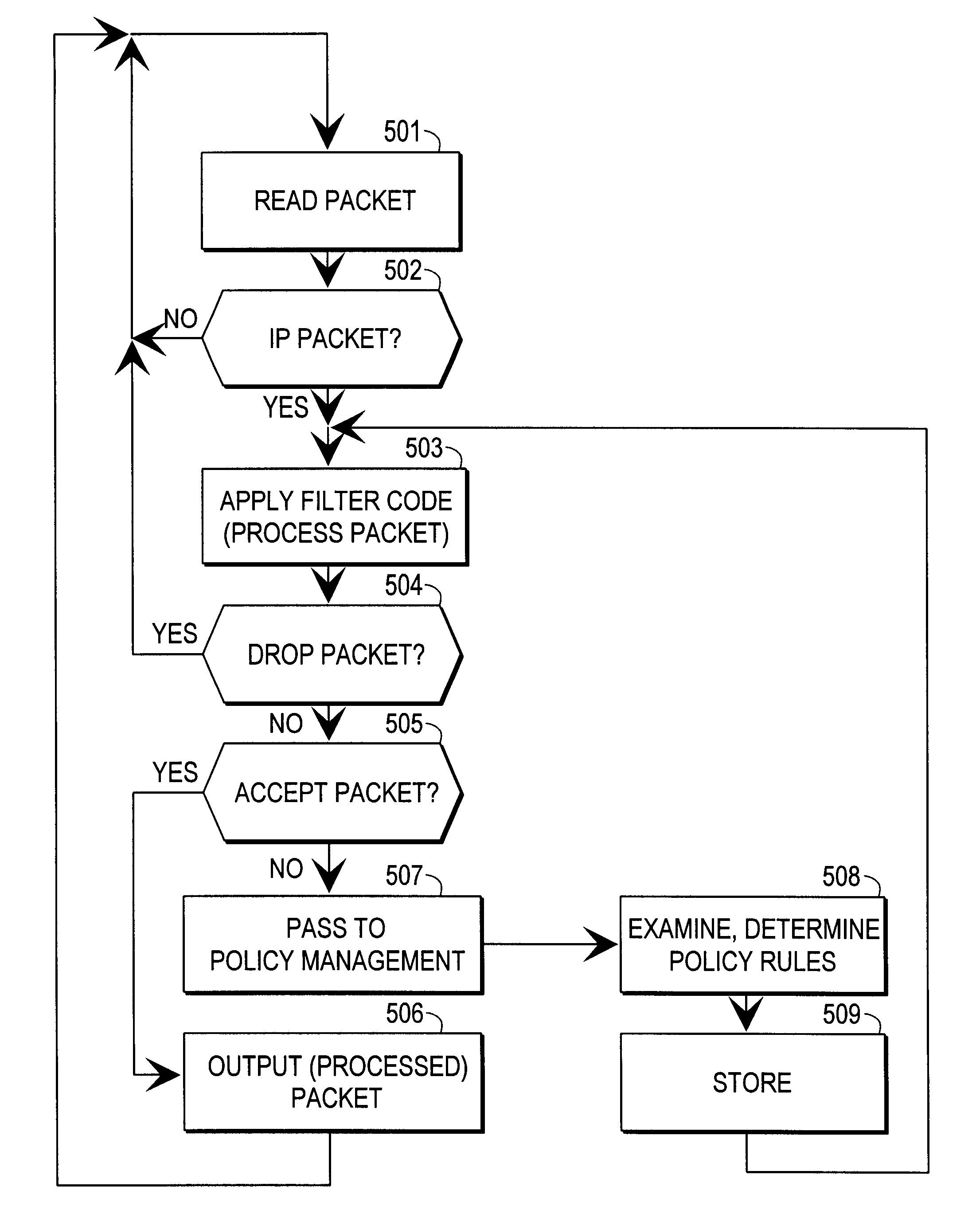
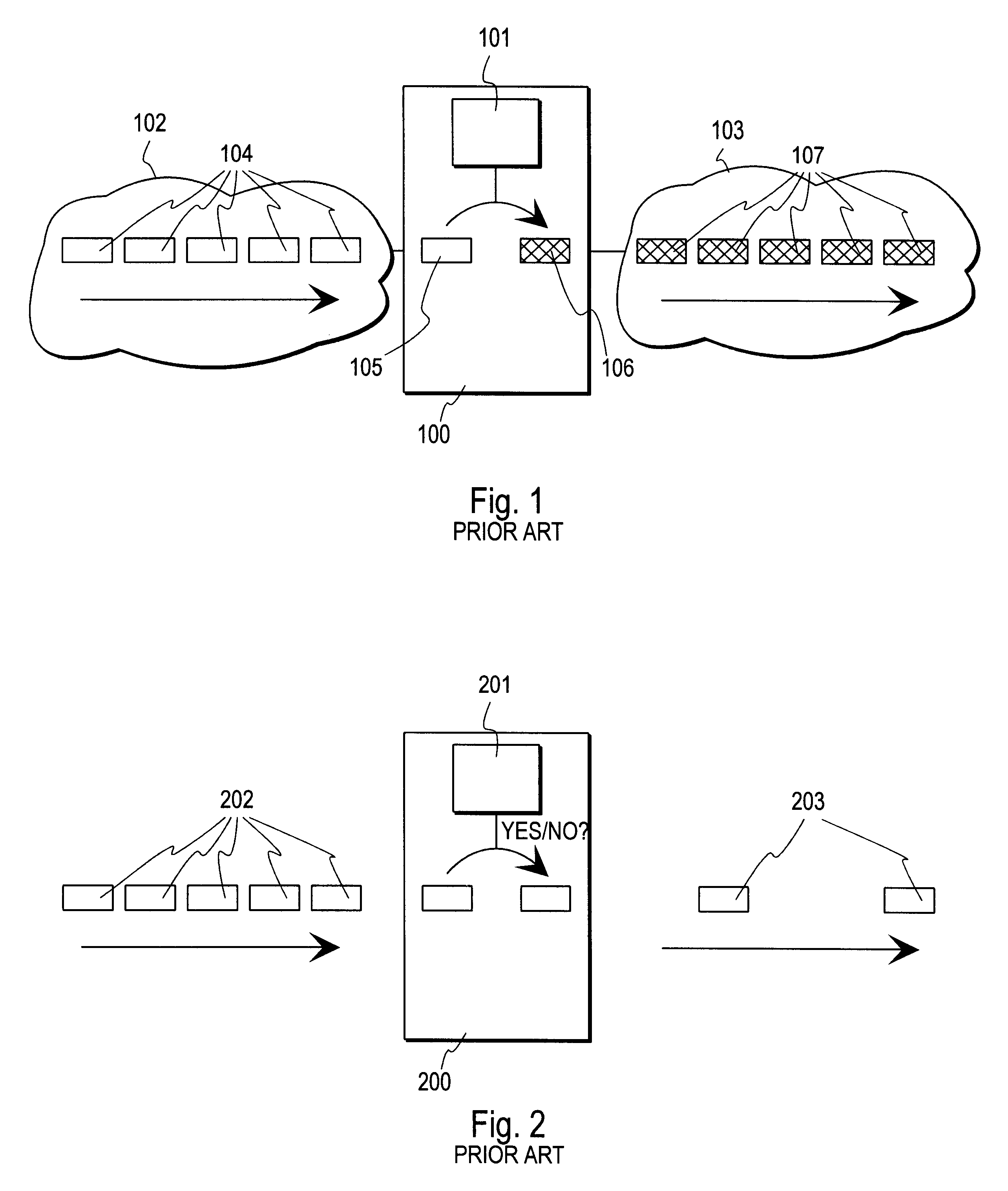
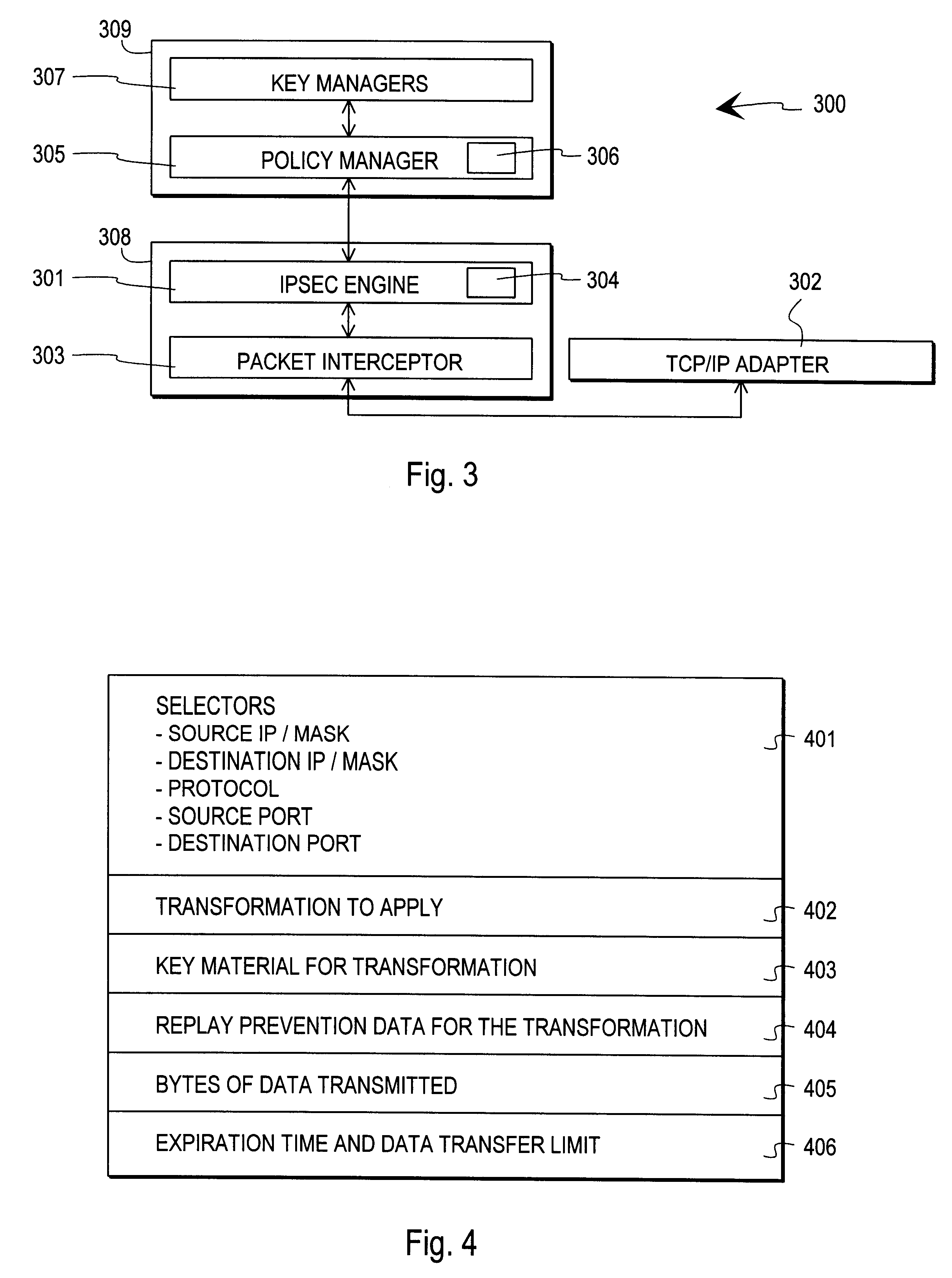
InactiveUS6253321B1User identity/authority verificationData resettingData processing systemComputer network
A data processing system implements a security protocol based on processing data in packets. The data processing system comprises processing packets for storing filter code and processing data packets according to stored filter code, and a policy managing function for generating filter code and communicating generated filter code for packet processing. The packet processing function is arranged to examine, whether the stored filter code is applicable for processing a certain packet. If the stored filter code is not applicable for the processing of a packet, the packet is communicated to the policy managing function, which generates filter code applicable for the processing of the packet and communicates the generated filter code for packet processing.
Owner:TECTIA
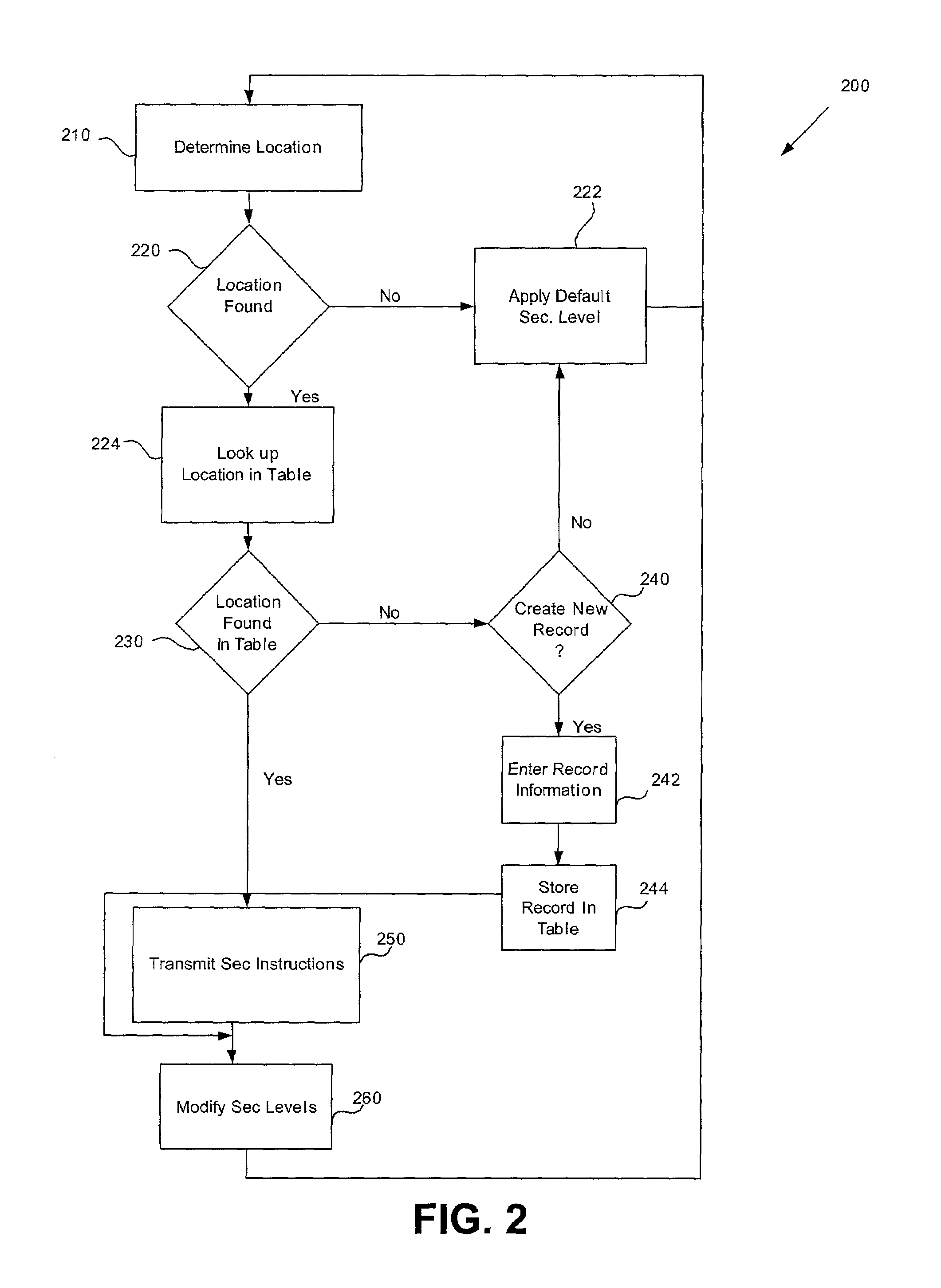
Location based security modification system and method
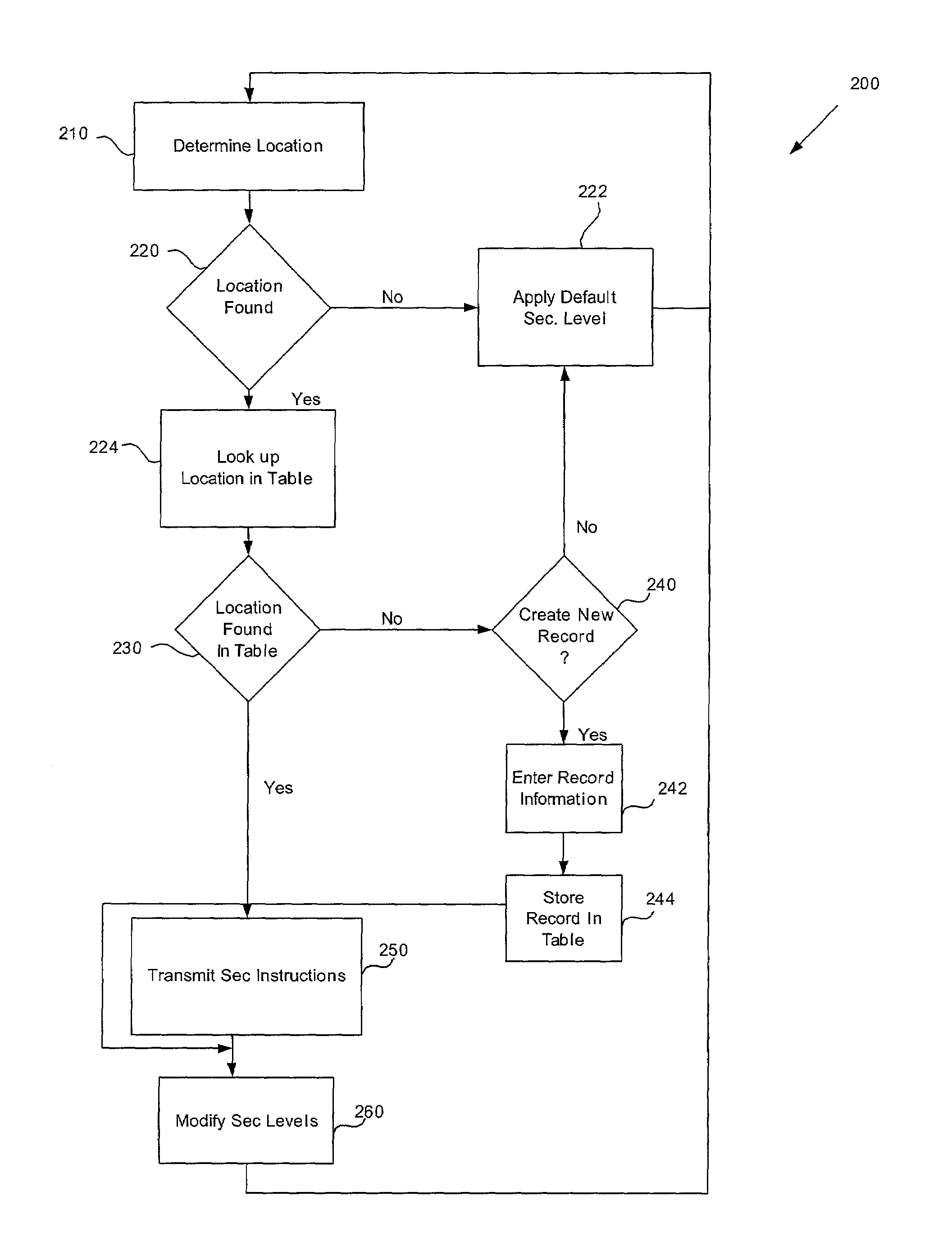
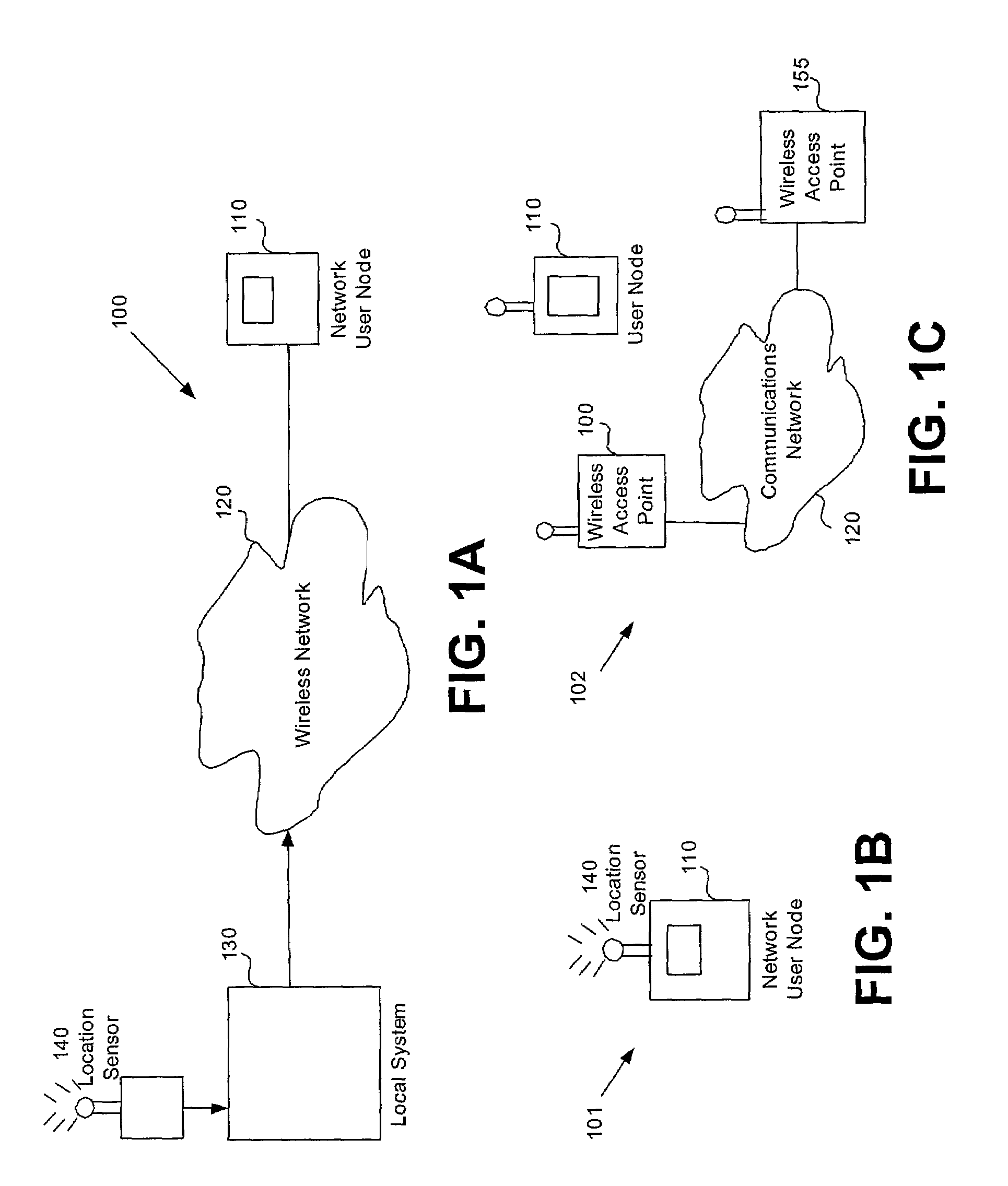
ActiveUS7591020B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSingle levelSecurity level
A method or system for providing a level of data security dependent on the location of the user of a wireless device is disclosed. One exemplary embodiment relates to a method of adjusting security for a network user node in communication with a network based upon the location of the node. The method is performed by determining the location of a network user node, selecting a single level of security from a group of more than two security levels based on the determined location, and modifying the security protection for the network user node based upon the selected level of security.
Owner:QUALCOMM INC
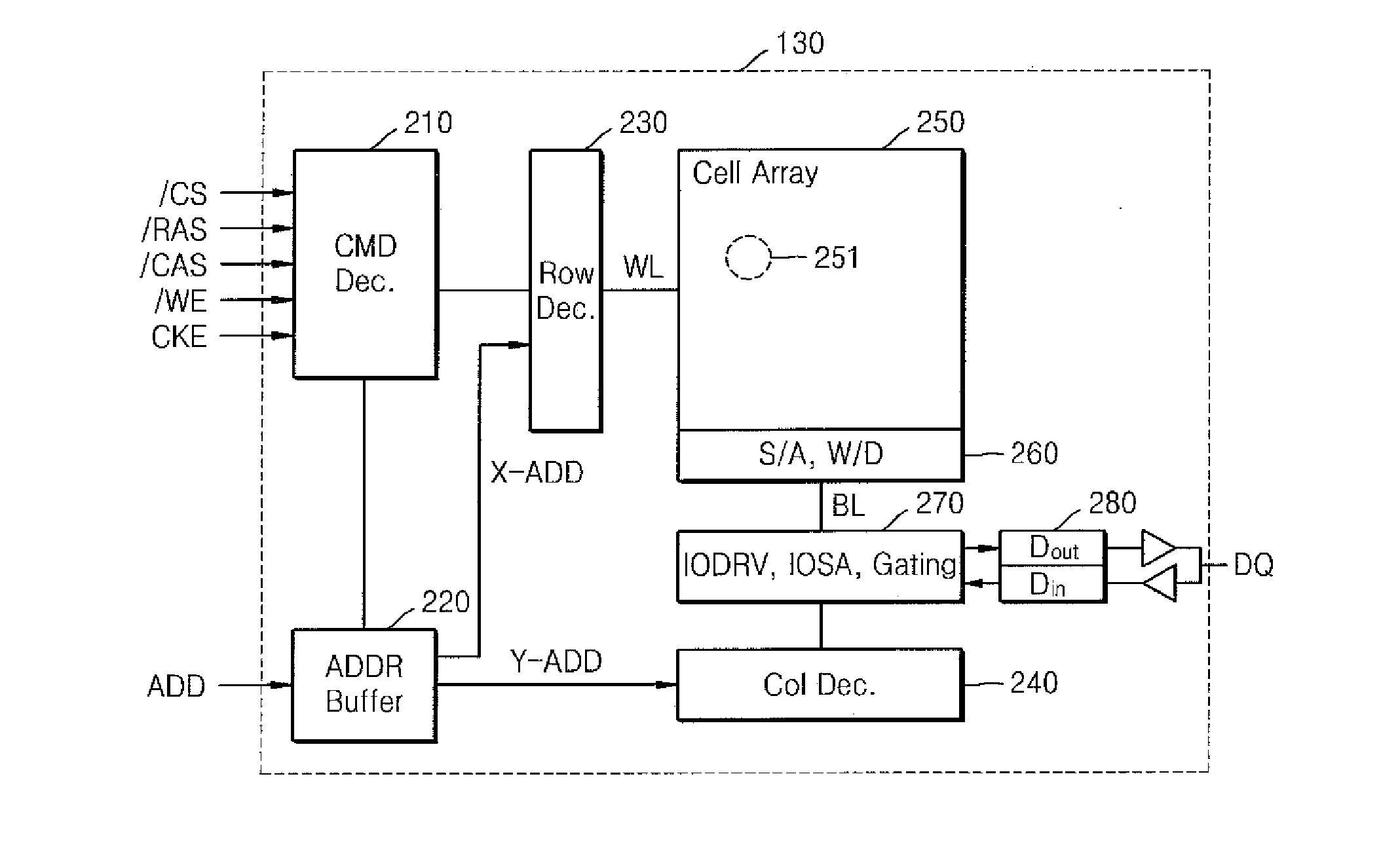
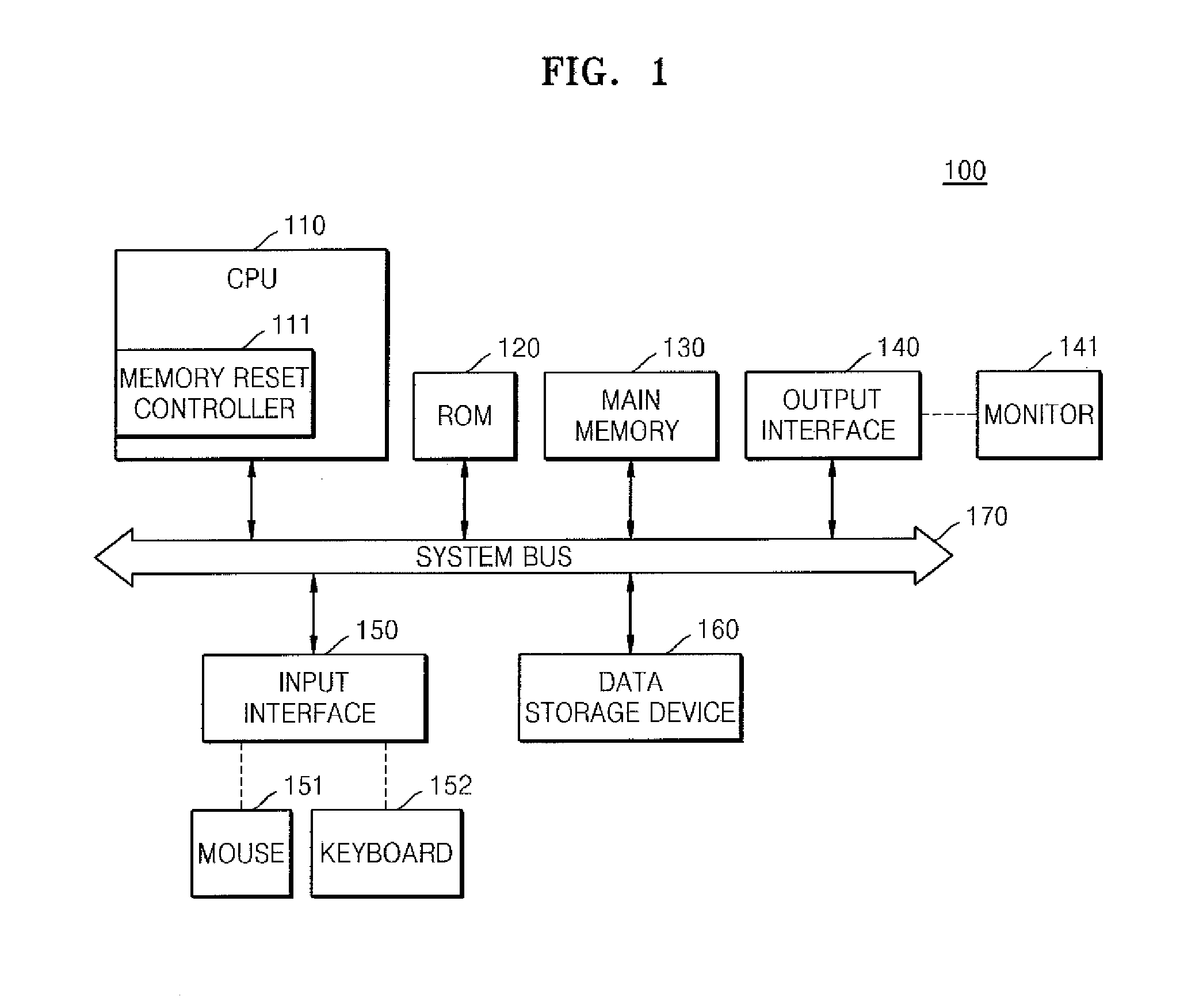
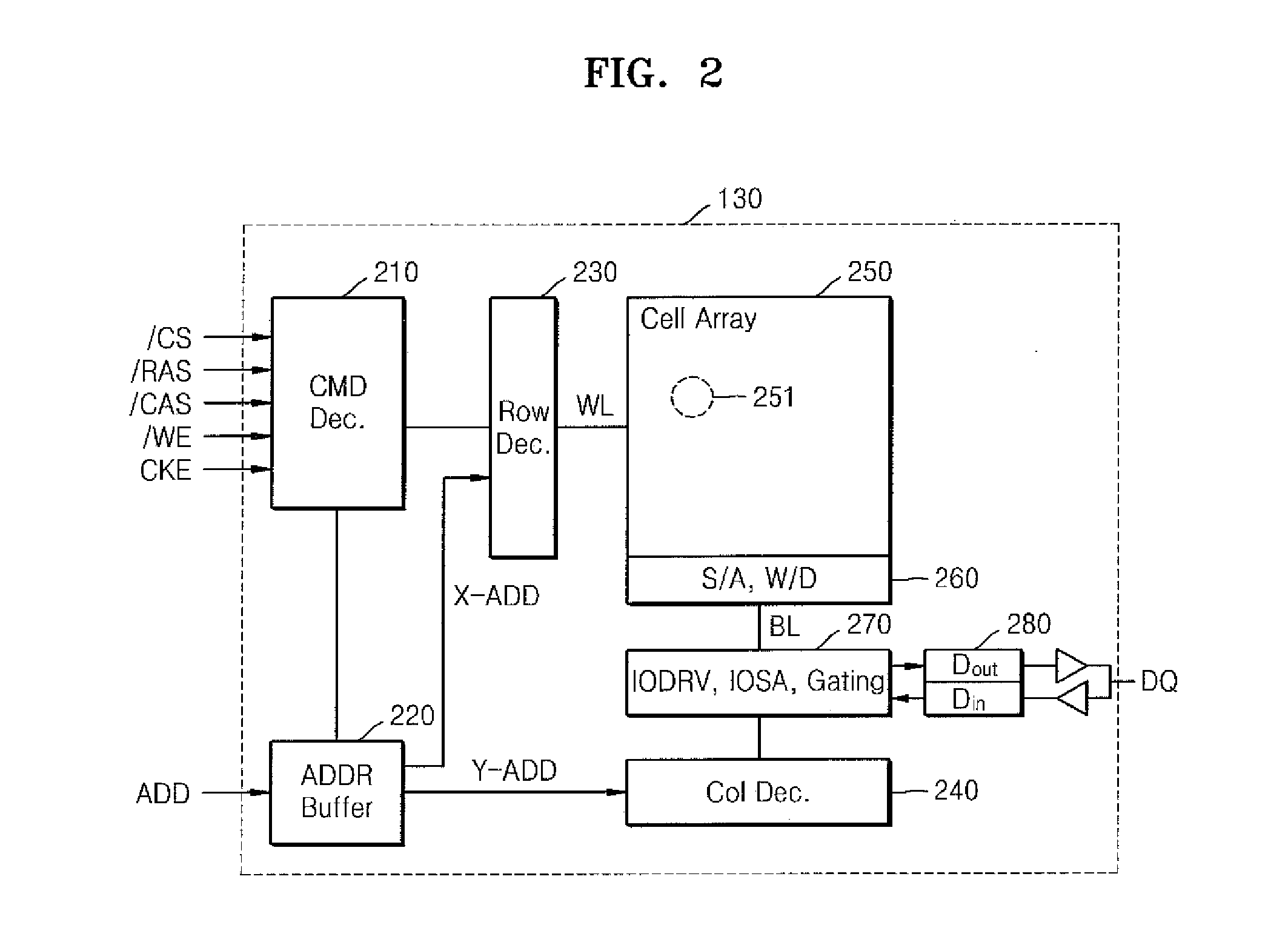
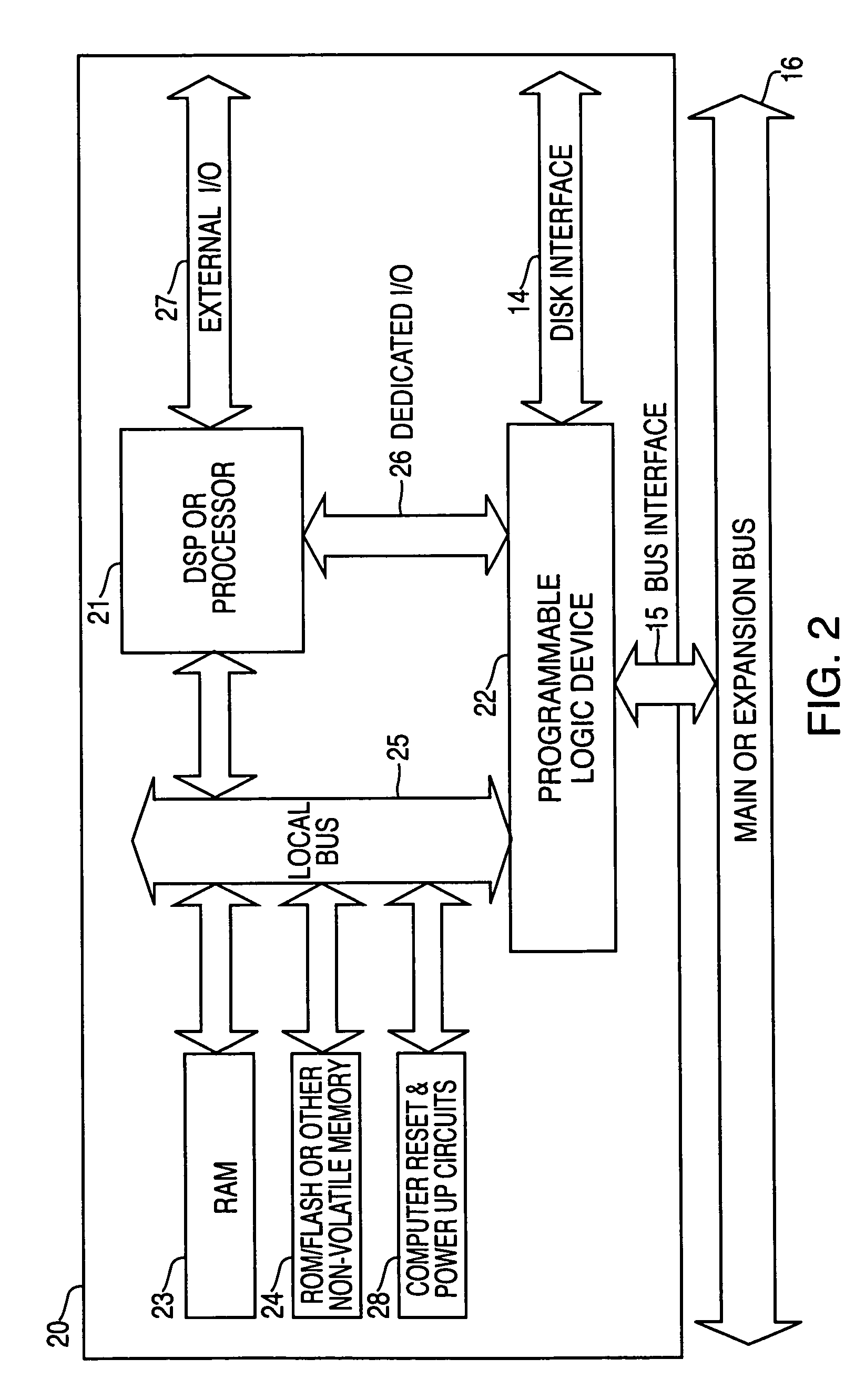
Computer system having non-volatile memory and method of operating the computer system
A computer system includes a central processing unit (CPU), a main memory including a non-volatile memory, and a memory reset controller controlling the main memory. If a memory reset command is input from outside, while the computer system is powered on / off, the memory reset controller deletes data stored in the main memory.
Owner:SAMSUNG ELECTRONICS CO LTD
Authenticated secure printing
InactiveUS6862583B1Guaranteed normal transmissionKey distribution for secure communicationUser identity/authority verificationComputer hardwareMultiple image
Authorized printout of an image corresponding to print data received at a print node from a network. The authorized printout comprises encrypting print data by a print node and storing the encrypted print data without printout, receiving authentication of an intended recipient to print the print data, and decrypting the encrypted print data by the print node and printing the decrypted print data by an image forming device, responsive to receipt of authentication in the receiving step. The print node may be the image forming device itself or a gateway to multiple image forming devices. The print node encrypts the print data with either a symmetric key or an asymmetric key.
Owner:CANON KK
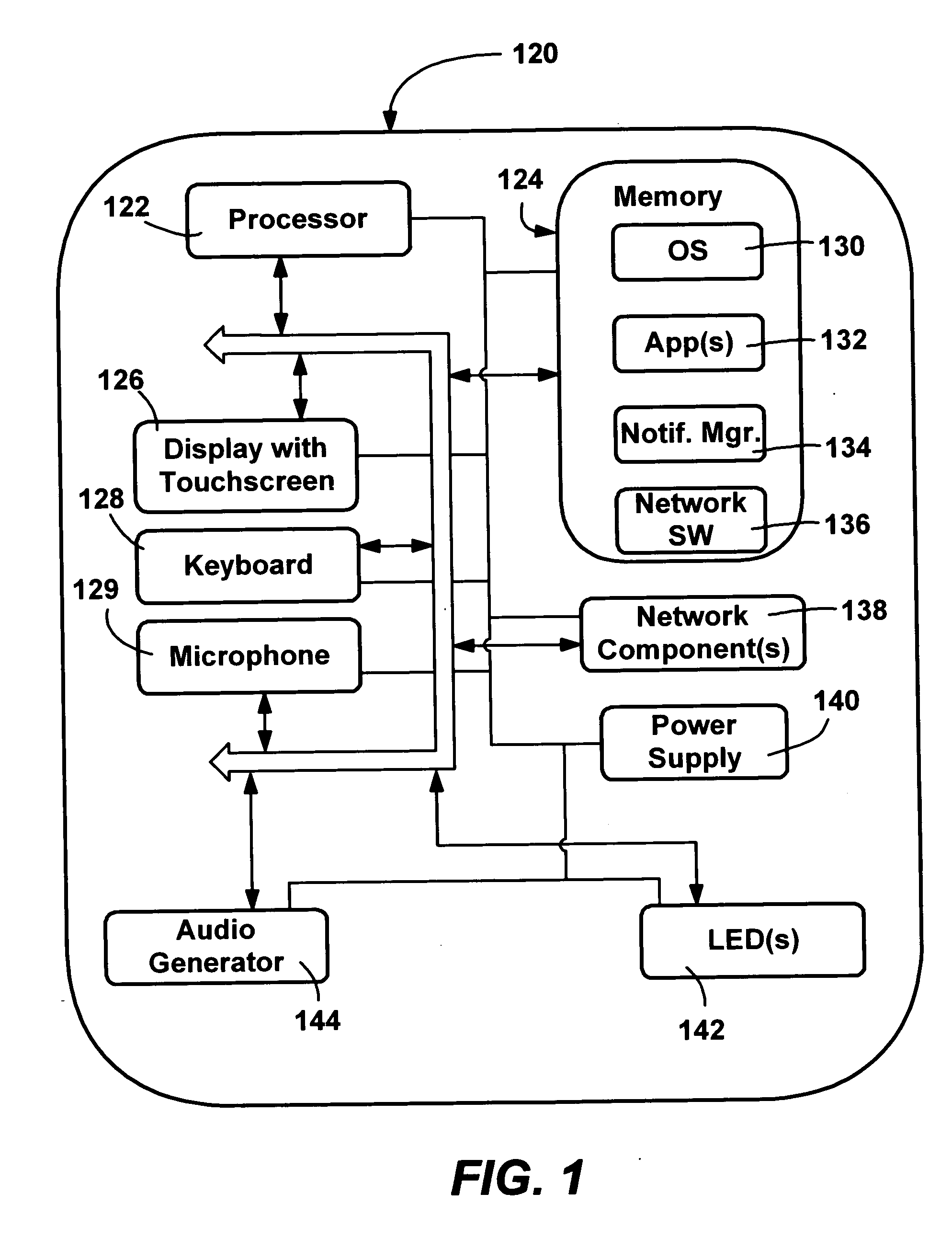
System, device, and method for providing personalized services in a communication system
InactiveUS7483964B1Near-field transmissionData resettingCommunications systemPersonalization service
A system, device, and method for providing personalized services in a communication system detects physical presence of a user and provides personalized services to the user based upon the physical presence of the user. The user is typically identified to some degree, and user-specific information is obtained based upon the identity of the user. The user-specific information is used to provide the personalized services to the user.
Owner:RPX CLEARINGHOUSE
Systems and methods for accelerated loading of operating systems and application programs
InactiveUS7181608B2Easy loadingBroaden applicationInput/output to record carriersCode conversionOperational systemComputerized system
Systems and methods are provided for accelerated loading of operating system and application programs upon system boot or application launch. In one aspect, a method for providing accelerated loading of an operating system includes maintaining a list of boot data used for booting a computer system, preloading the boot data upon initialization of the computer system, and servicing requests for boot data from the computer system using the preloaded boot data. The boot data may comprise program code associated with an operating system of the computer system, an application program, and a combination thereof. The boot data is retrieved from a boot device and stored in a cache memory device. The boot data is stored in a compressed format on the boot device and the preloaded boot data is decompressed prior to transmitting the preloaded boot data to the requesting system.
Owner:REALTIME DATA
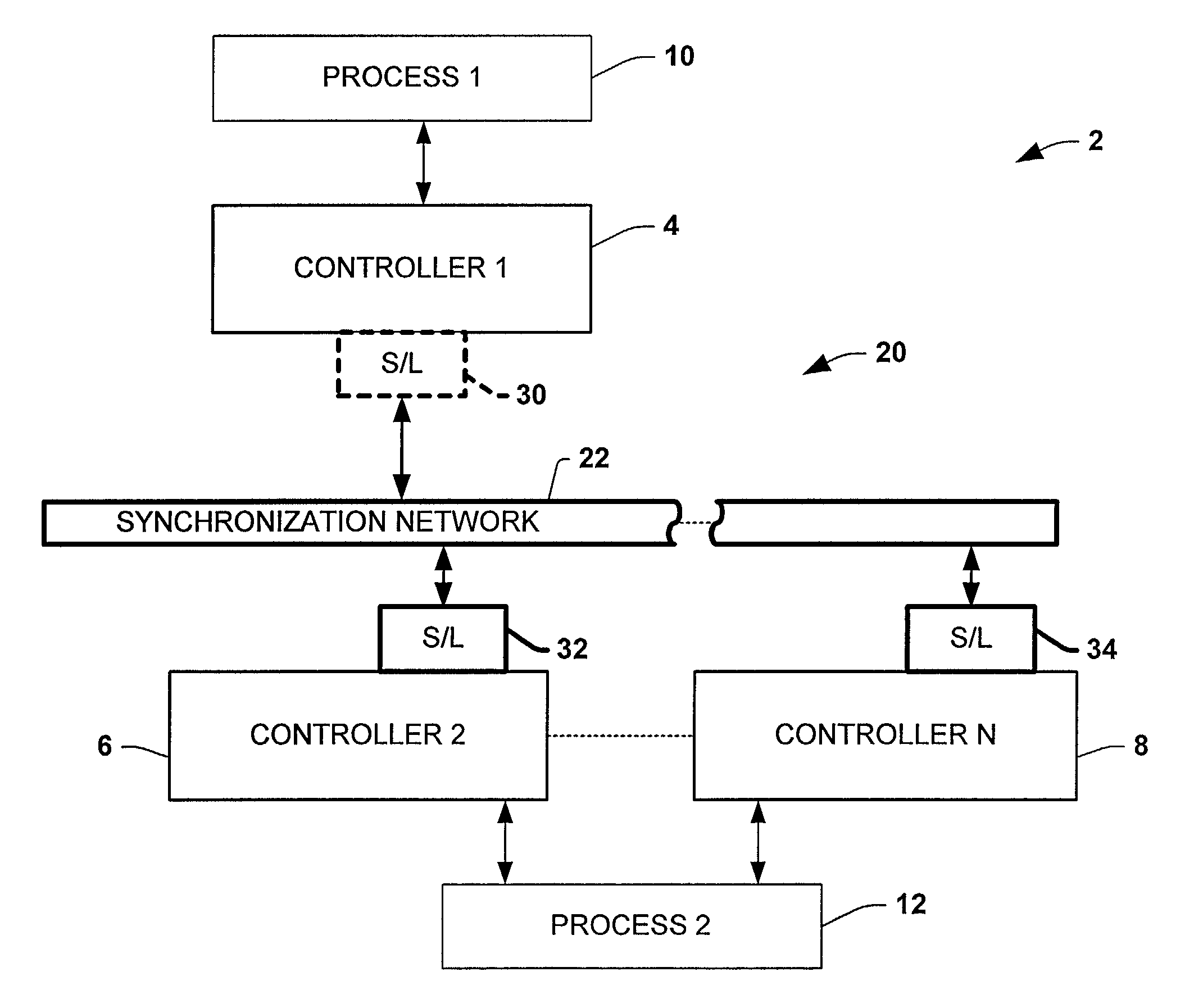
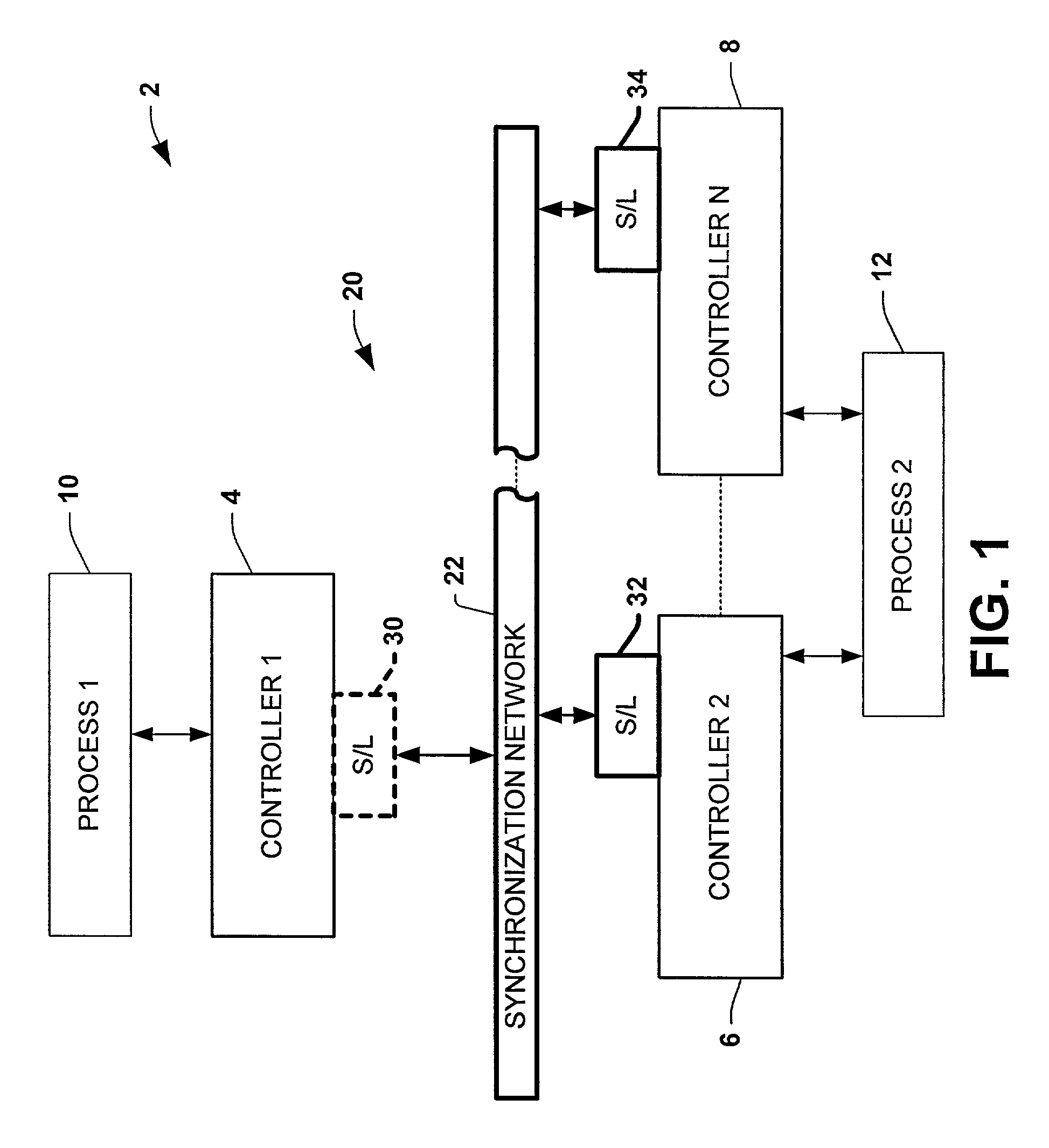
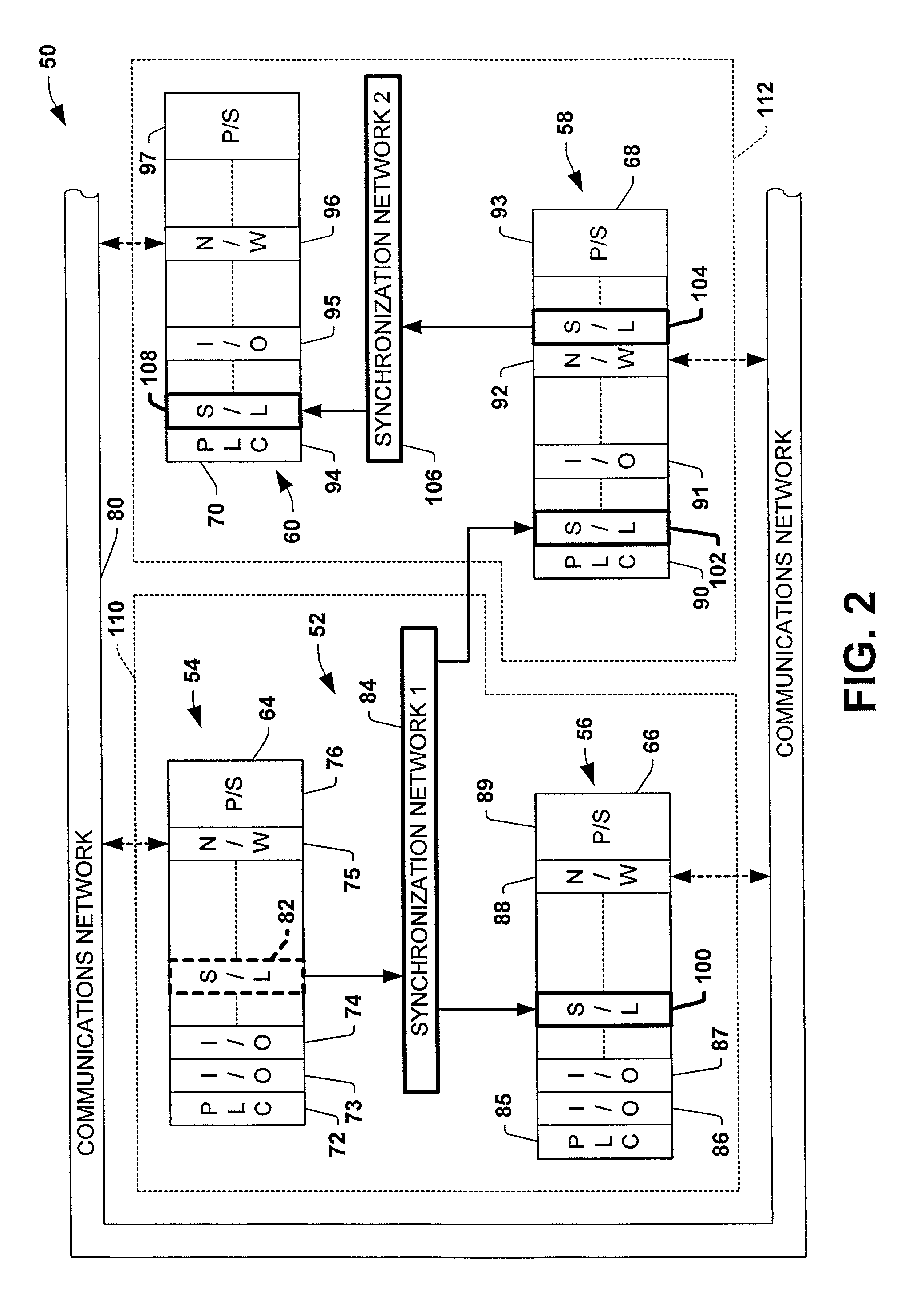
Protocol and method for multi-chassis configurable time synchronization
ActiveUS7007106B1Data representation error detection/correctionCode conversionSynchronous controlControl system
Systems and methods are disclosed for time synchronization of operations in a control system. Synchronization networks and devices are provided for transferring synchronization information between controllers in a distributed or localized control system, which is employed in order to allow operation of such controllers to be synchronized with respect to time. Also disclosed are synchronization protocols and hardware apparatus employed in synchronizing control operations in a control system.
Owner:ROCKWELL TECH
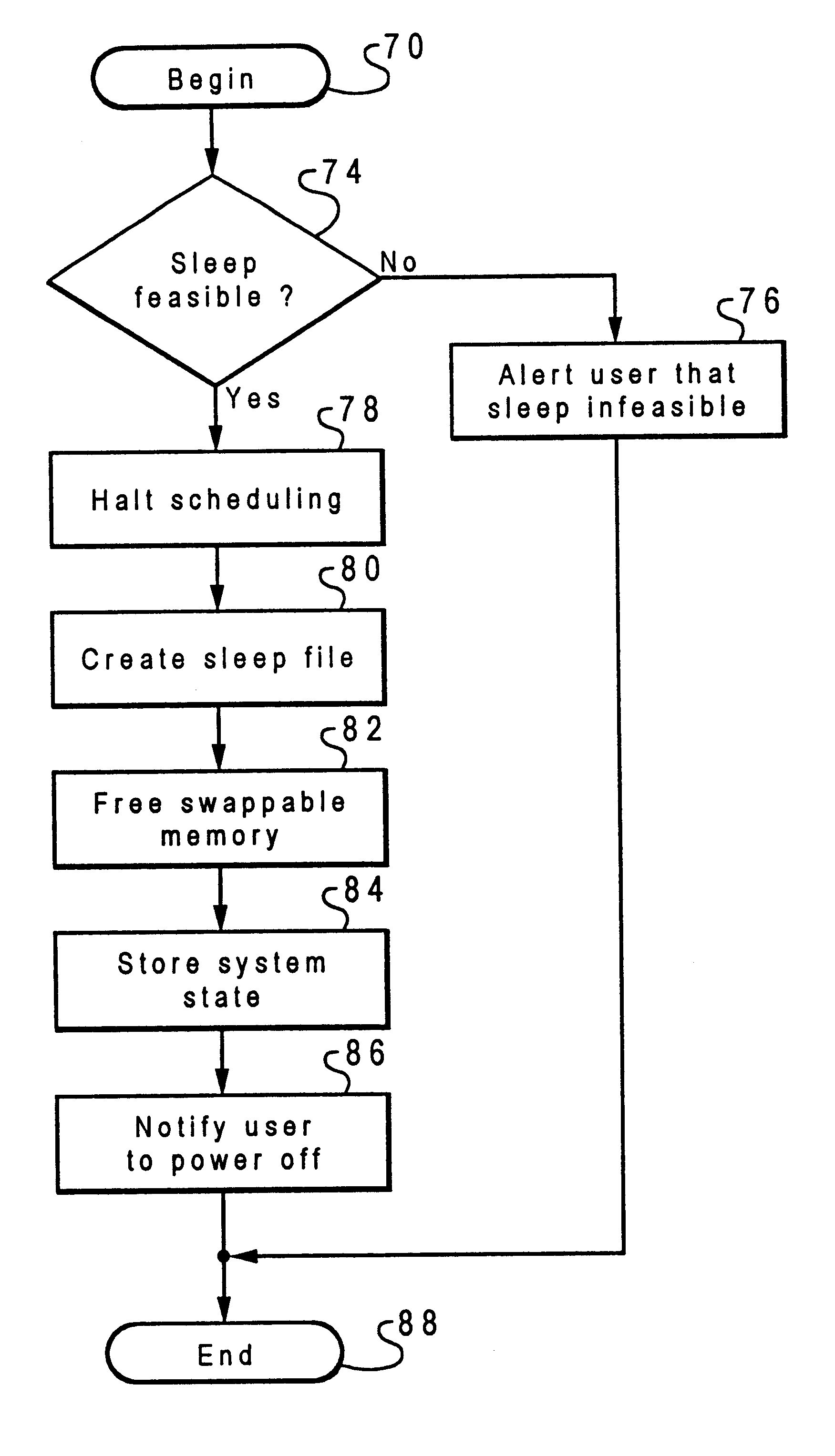
Method and system for efficiently saving the operating state of a data processing system
InactiveUS6393584B1Saving and restoring operating stateEnergy efficient ICTDigital computer detailsData processing systemMass storage
A method and system are disclosed for efficiently storing an operating state of a data processing system having a volatile memory within a nonvolatile mass storage device. In response to a selected input, a determination is made whether storing the operating state of the data processing system is possible. If storing the operating state is possible, scheduling of tasks to be performed by the data processing system is halted. Data not required for operation of the data processing system is then removed from the volatile memory. The operating state of the data processing system is stored within the nonvolatile mass storage device, thereby enabling the operating state of the data processing system to be efficiently restored. Thereafter, power is removed from the data processing system. In response to restoring power to the data processing system, a determination is made whether the operating state of the data processing system is stored within the nonvolatile mass storage device. In response to a determination that the operating state of the data processing system is stored within the nonvolatile mass storage device, the operating state of the data processing system is loaded from the nonvolatile mass storage device, thereby restoring the operating state of the data processing system.
Owner:IBM CORP
Network security and fraud detection system and method
ActiveUS7272728B2Avoid connectionAccess is deniedUser identity/authority verificationUnauthorized memory use protectionNetwork security policyNetwork service
A system and method to detect and prevent fraud in a system is provided. The system may uniquely identify physical devices connecting to a network, register unique devices, track end-user logins, associate end-user accounts with specific devices, and share information with multiple network service providers is described.
Owner:IOVATION
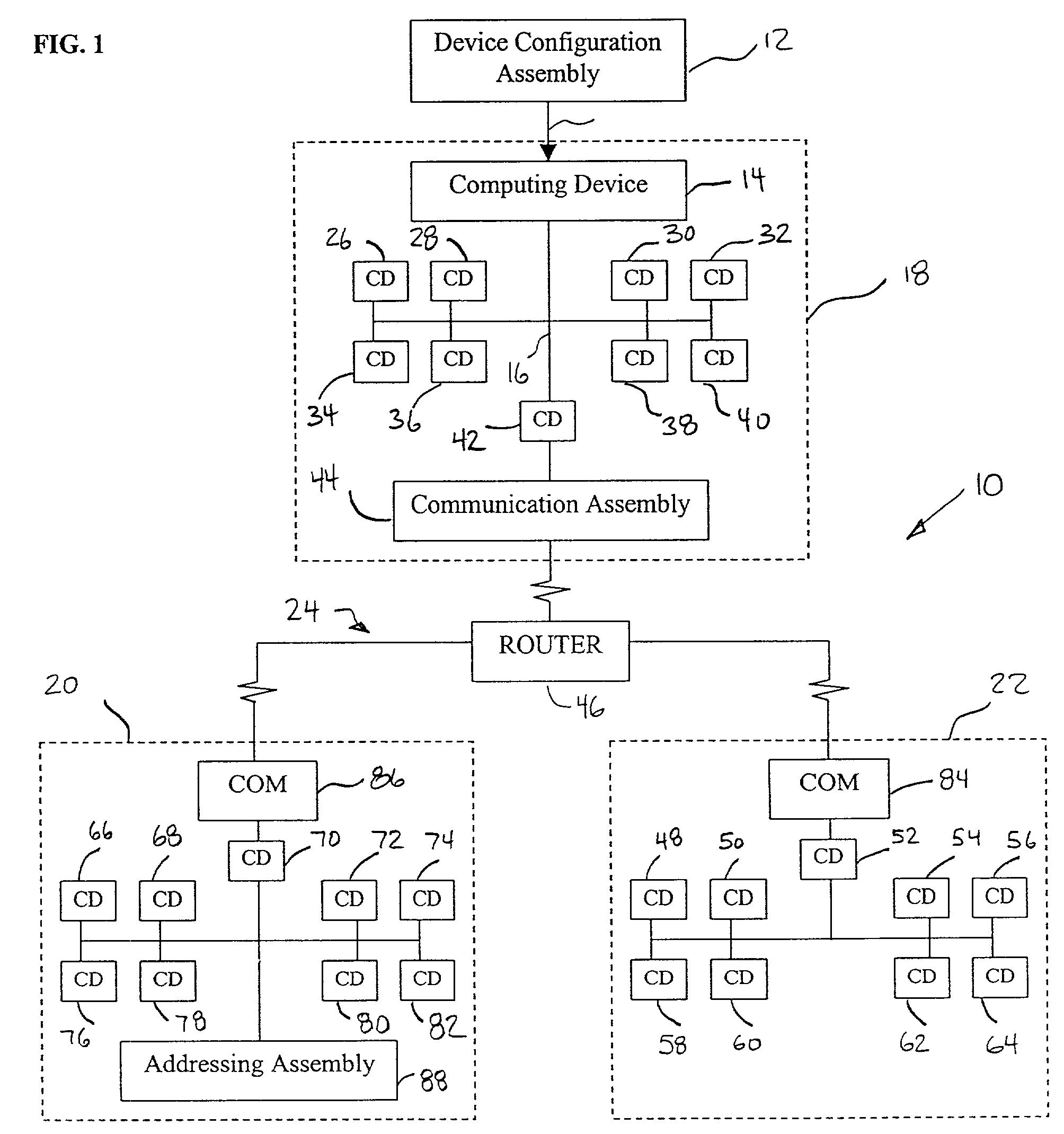
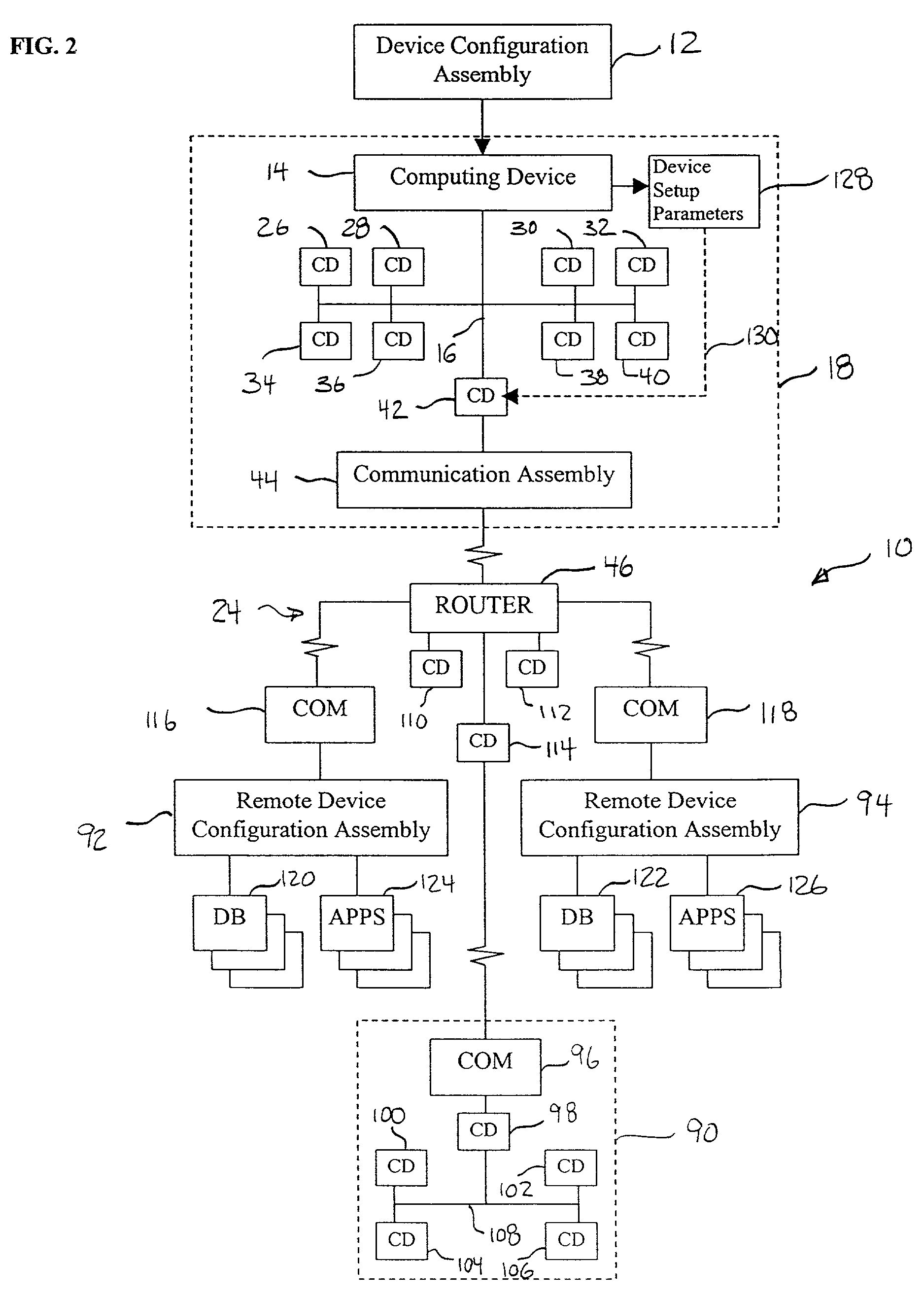
System and method for remote discovery and configuration of a network device
A technique for remotely configuring a computing device via a network. A device configuration system is provided to determine a network address of the computing device, to identify the computing device, and to facilitate network configuration of the computing device. The device configuration system also may include a remote interface and a remote device information system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
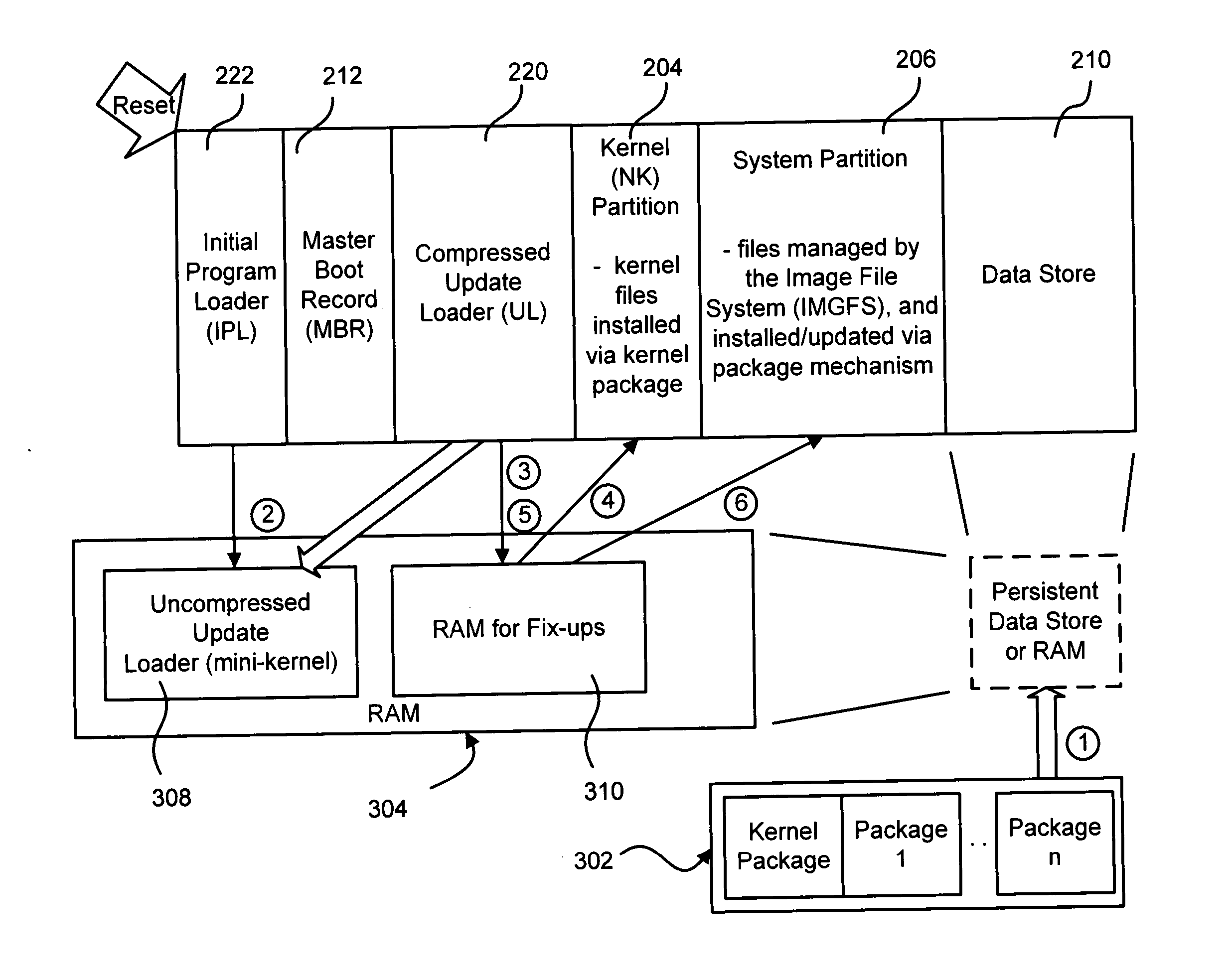
Applying custom software image updates to non-volatile storage in a failsafe manner
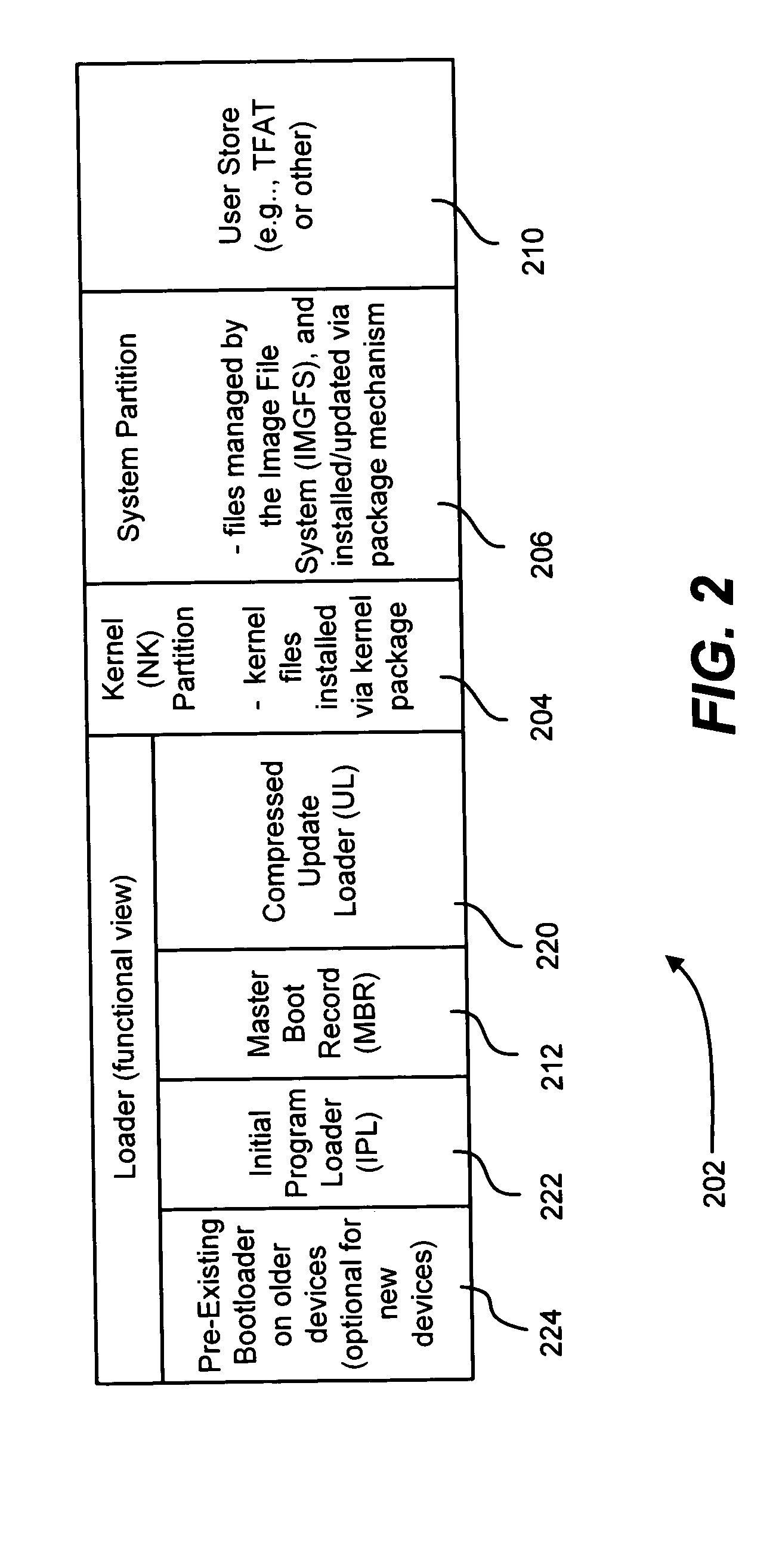
Described is a system and method in which software updates in the form of self-contained, secure entities are applied to an embedded device's non-volatile storage in a failsafe manner. Various types of software updates may be applied, and updates may contain executable code and / or data. Following a reboot, an initial program loader determines an update mode, and if updating, boots to a special update loader. The update loader processes update packages to apply the updates. Kernel partition, system partition and reserve section updates may be updated with entire files or binary difference files, with failure handling mechanisms are provided for each type of update. Updates may be simulated before committing them. Updates may be relocated in memory as appropriate for a device.
Owner:MICROSOFT TECH LICENSING LLC
Method for self-synchronizing time between communicating networked systems using timestamps
ActiveUS7676679B2Synchronising transmission/receiving encryption devicesError detection/correctionTimestampNetworked system
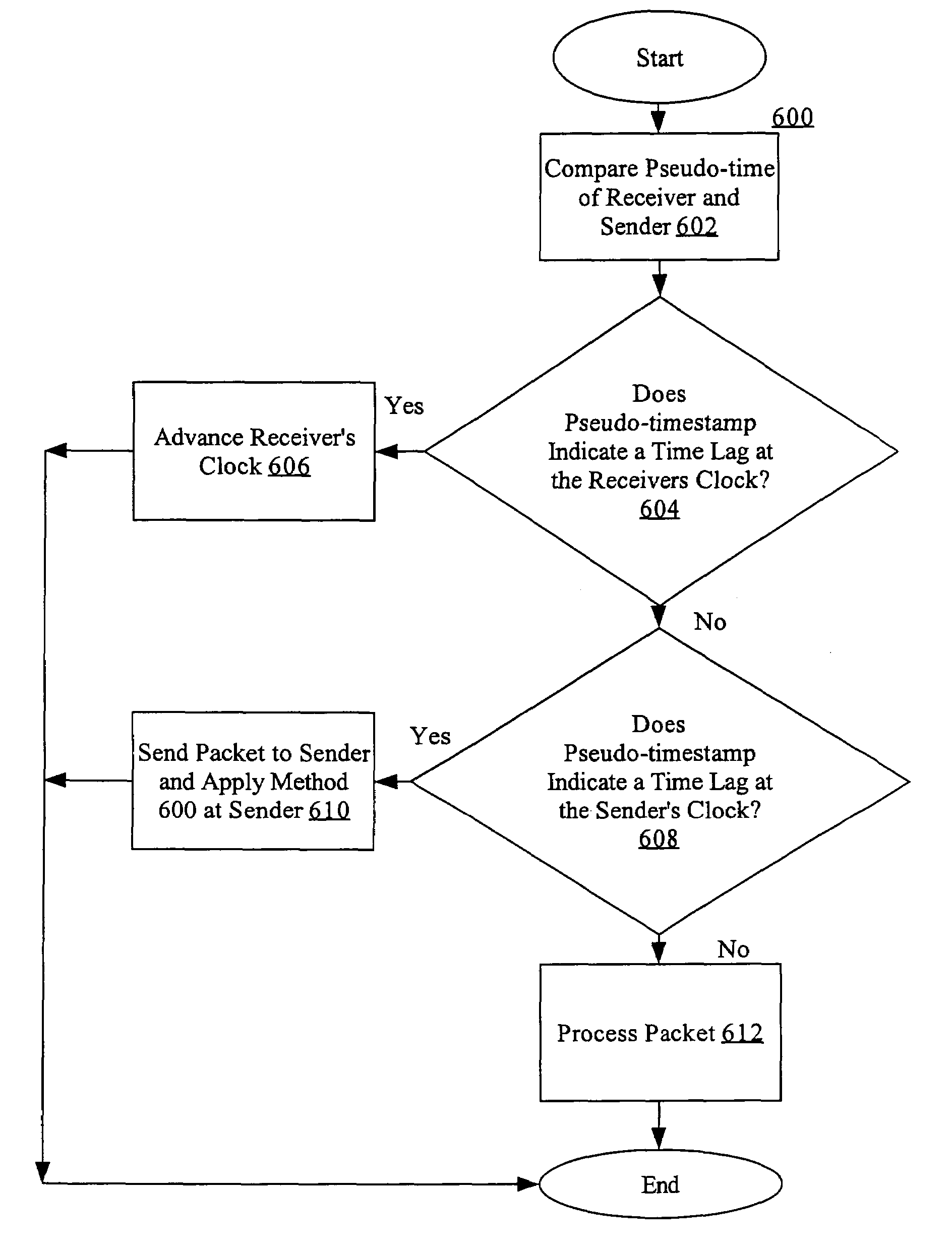
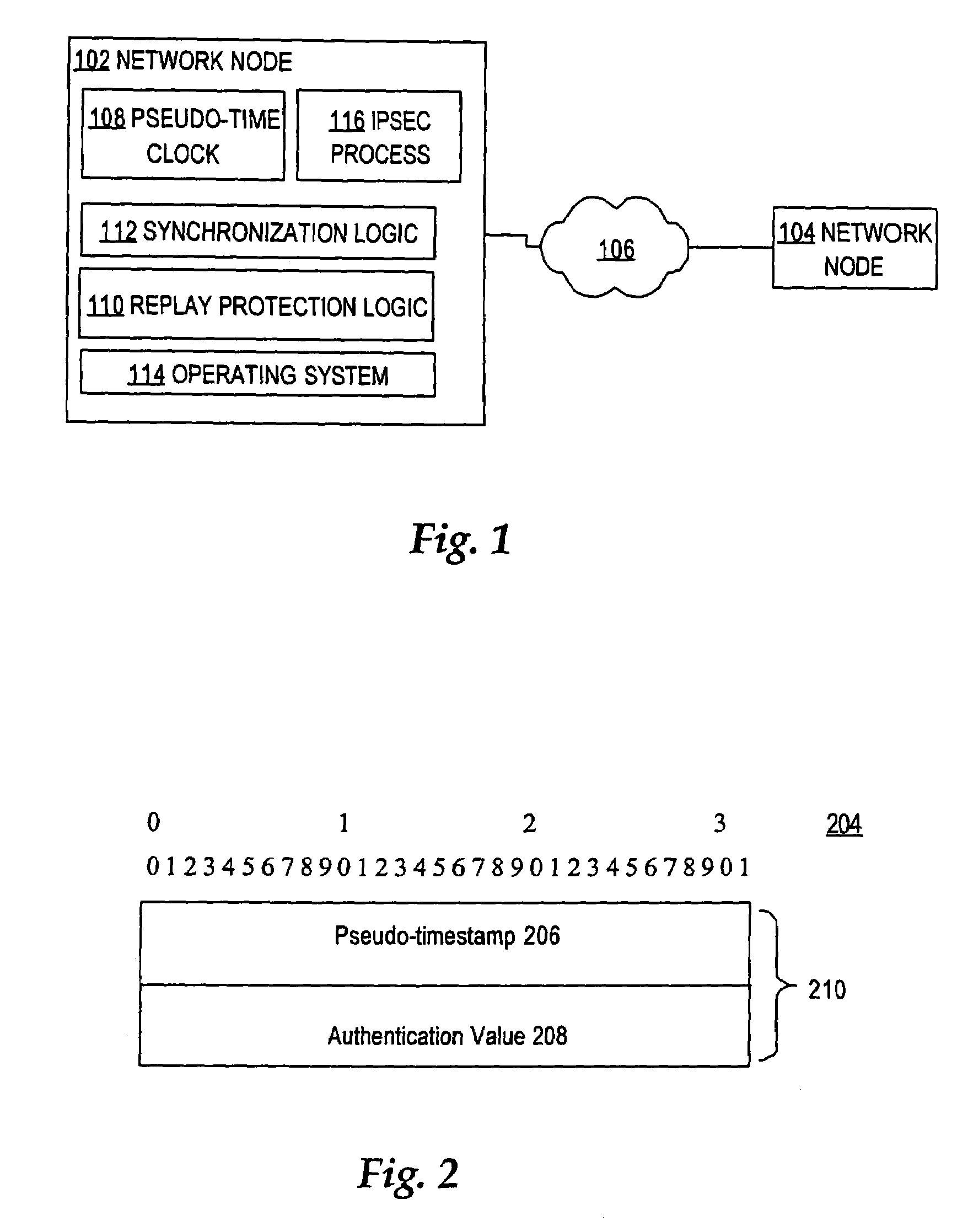
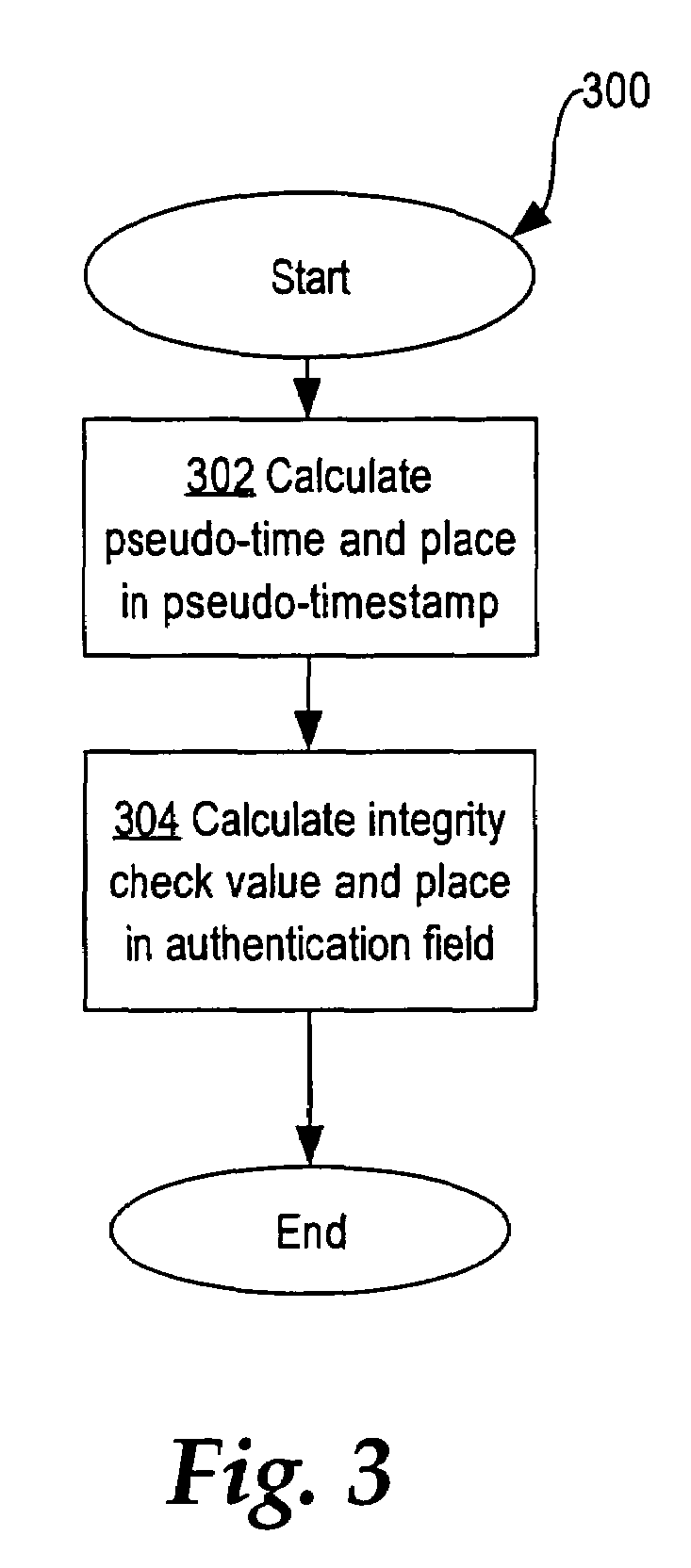
Nodes in a network include a pseudo-timestamp in messages or packets, derived from local pseudo-time clocks. When a packet is received, a first time is determined representing when the packet was sent and a second time is determined representing when the packet was received. If the difference between the second time and the first time is greater than a predetermined amount, the packet is considered to be stale and is rejected, thereby deterring replay. Because each node maintains its own clock and time, to keep the clocks relatively synchronized, if a time associated with a timestamp of a received packet is later than a certain amount with respect to the time at the receiver, the receiver's clock is set ahead by an amount that expected to synchronize the receiver's and the sender's clocks. However, a receiver never sets its clock back, to deter attacks.
Owner:CISCO TECH INC
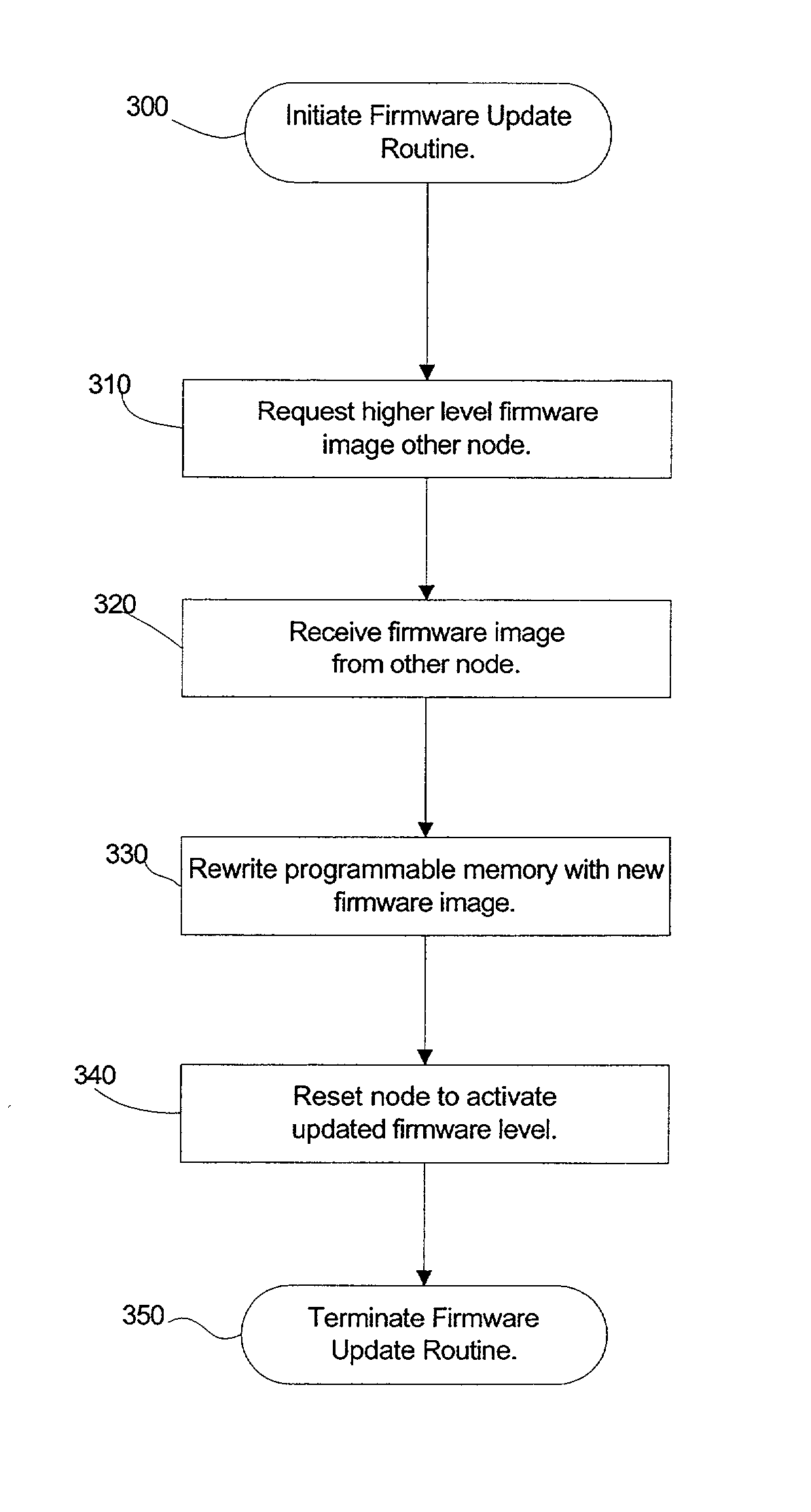
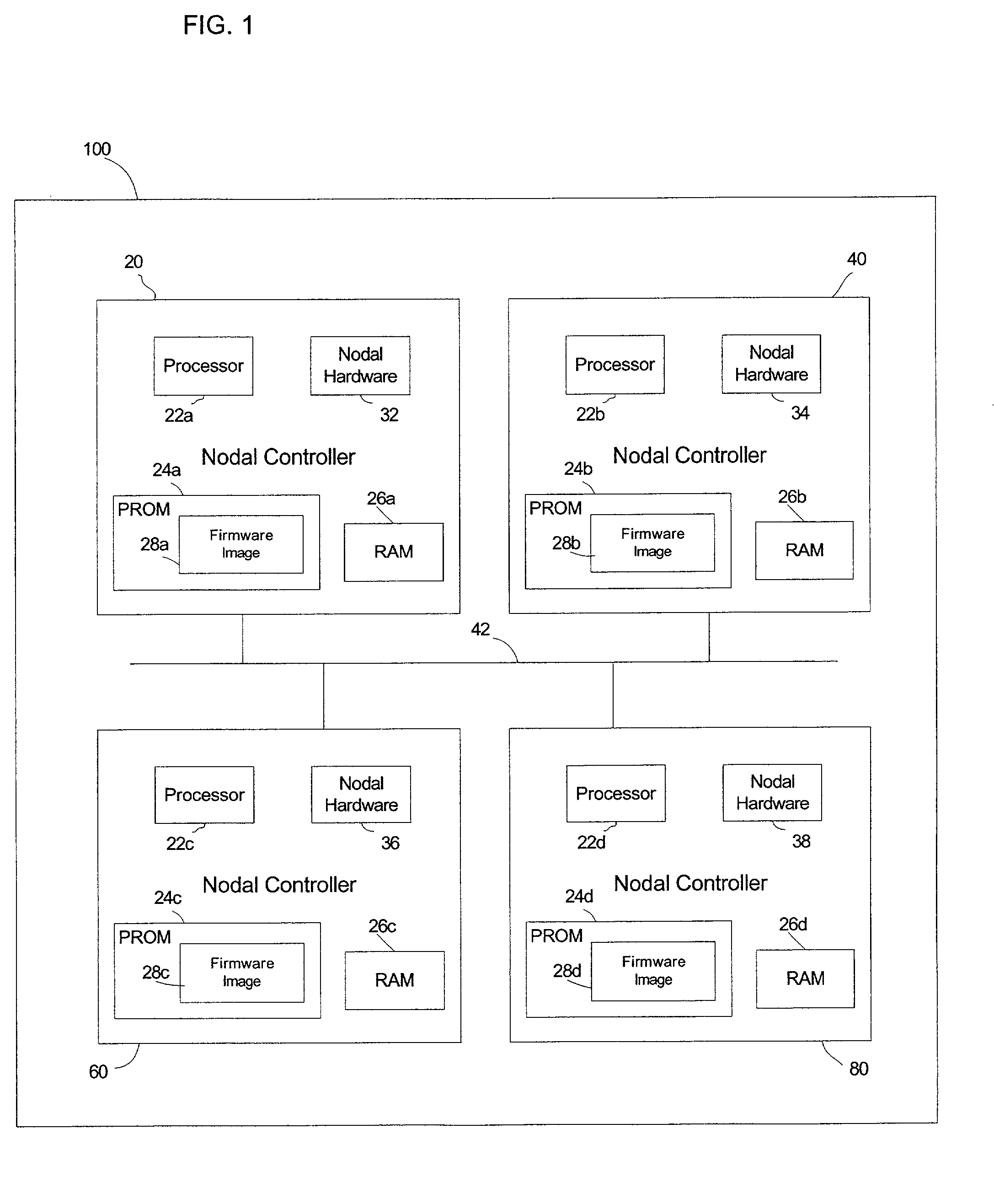
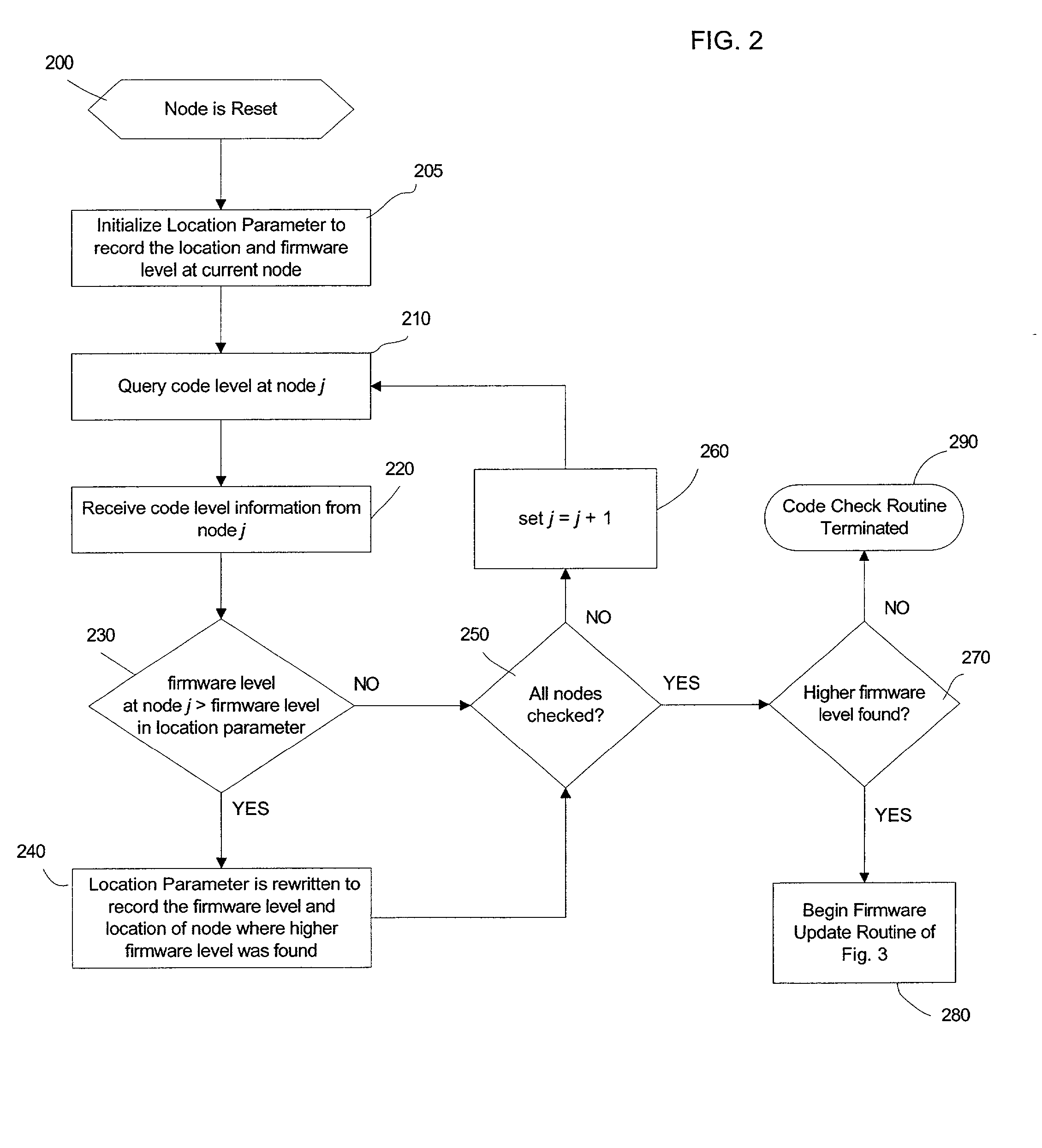
Automatic firmware update of processor nodes
InactiveUS20020091807A1Raise the possibilityAvoid incompatibilitiesDigital computer detailsData resettingCommunication interfaceProcessor node
Provided is a method, system, and program for updating the firmware in a nodal system. The nodal system includes at least two nodes, wherein each node includes a processing unit and a memory including code. The nodes communicate over a communication interface. At least one querying node transmits a request to at least one queried node in the nodal system for a level of the code at the node over the communication interface. At least one node receives a response from the queried node receiving the request indicating the level of code at the queried node over the communication interface. The node receiving the response determines whether at least one queried node has a higher code level.
Owner:IBM CORP
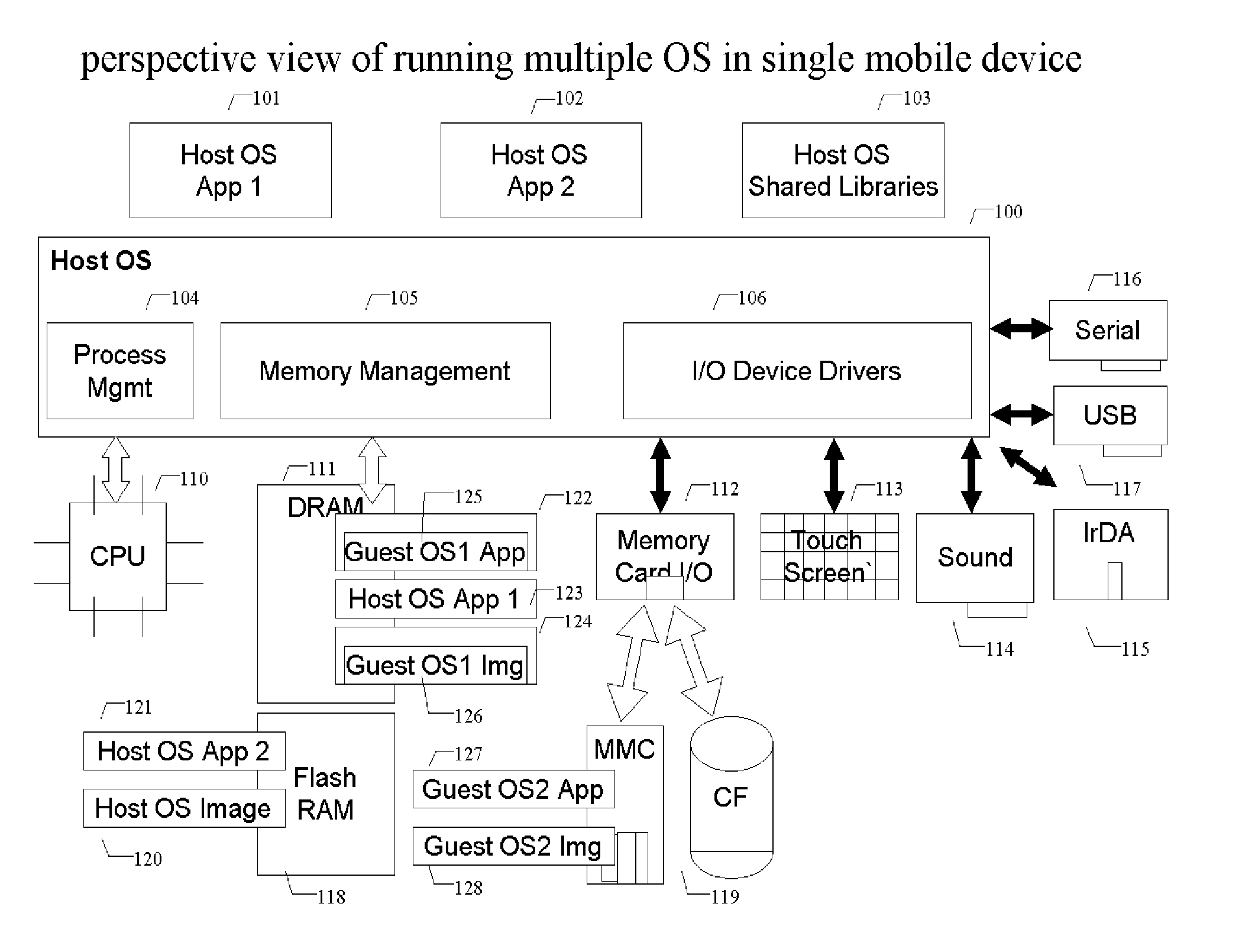
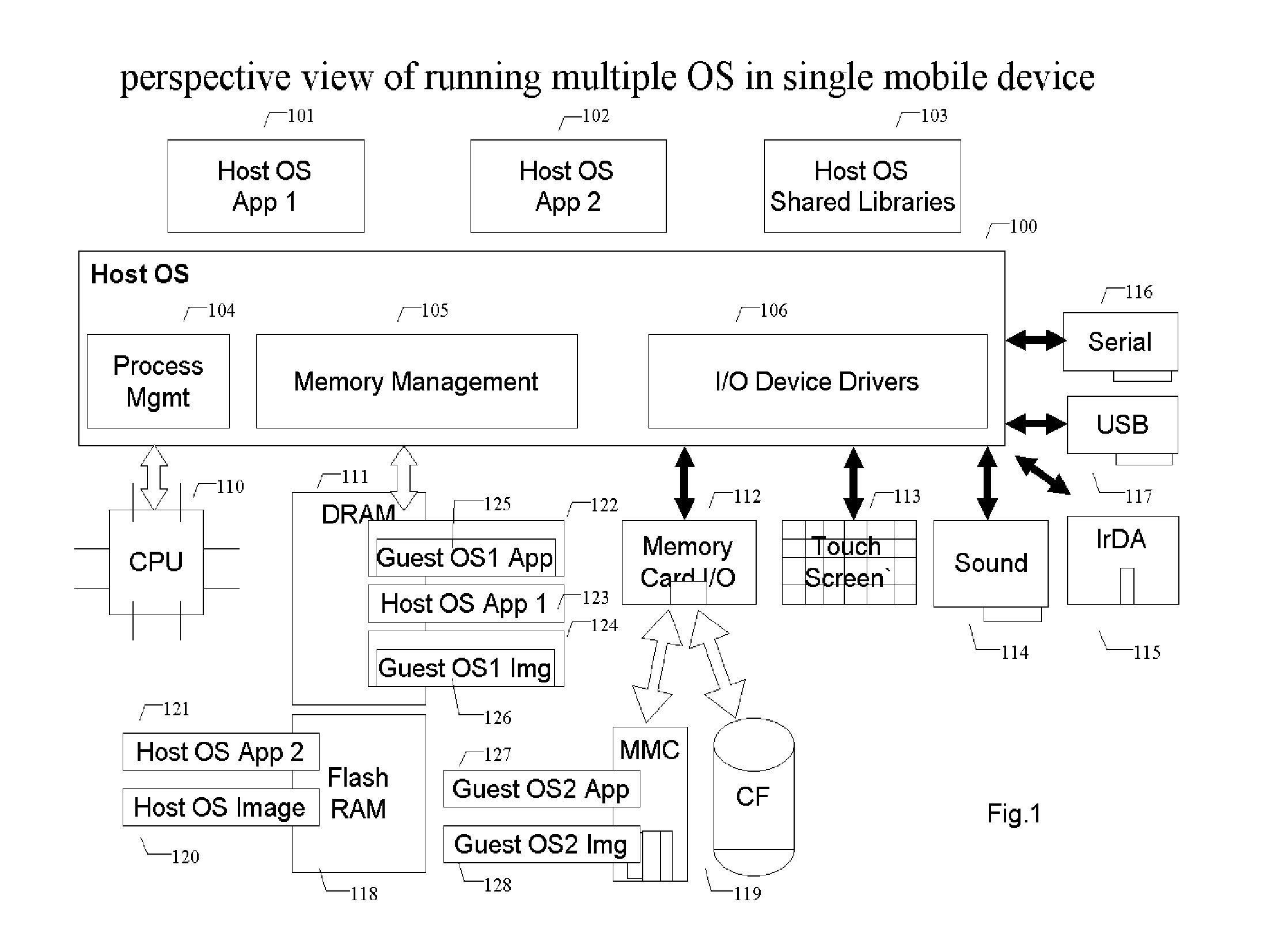
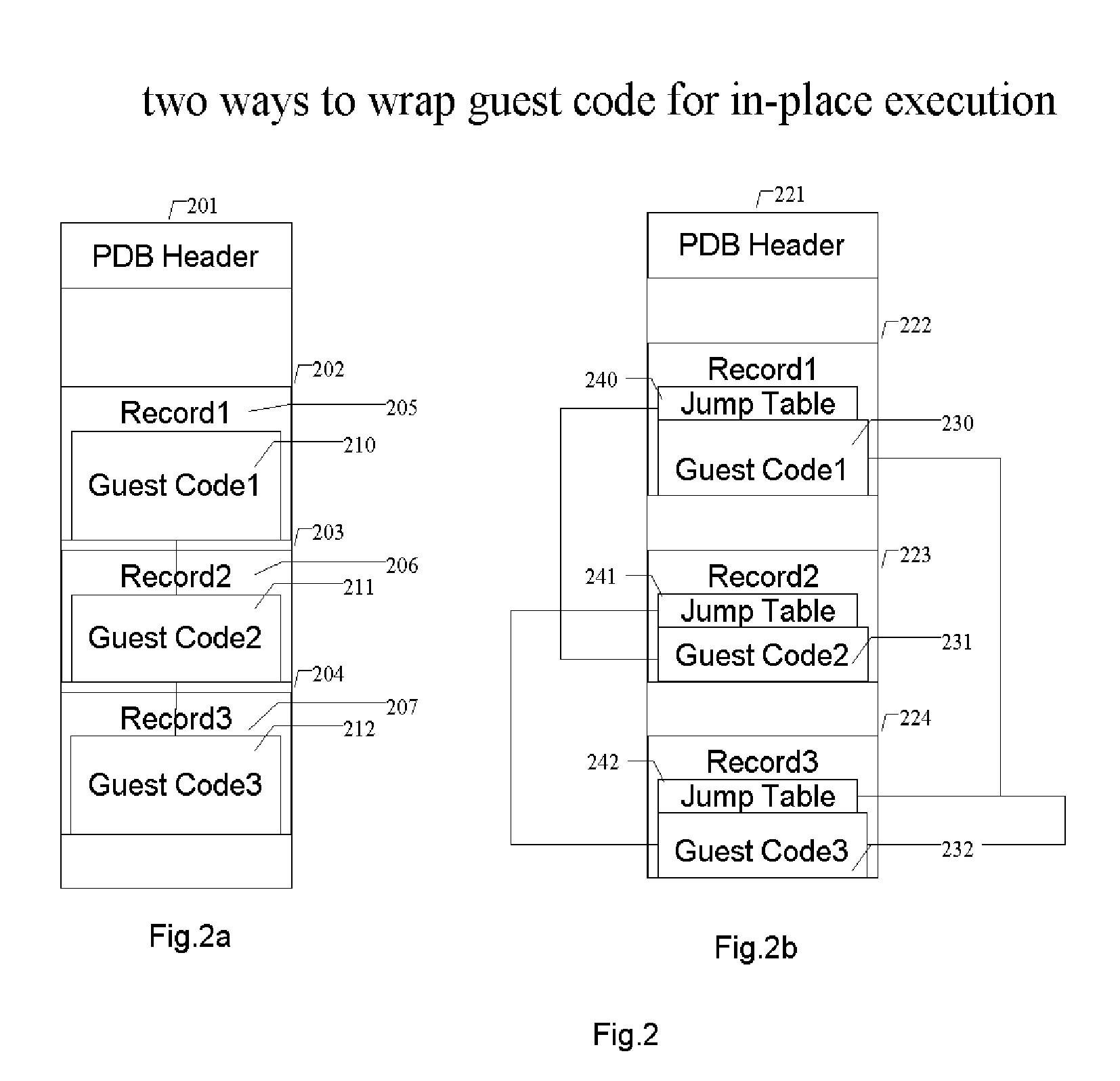
Methods and systems for running multiple operating systems in a single mobile device
ActiveUS20060010314A1Reduce memory usageError detection/correctionDigital computer detailsOperational systemEngineering
Methods and systems for running multiple operating systems in a single embedded or mobile device (include PDA, cellular phone and other devices) are disclosed. The invention allows a mobile device that normally can only run a single operating system to run another operating system while preserving the state and data of the original operating system. Guest OS is packaged into special format recognizable by the host OS that still can be executed in place by the system. The Methods include: •Change the memory protection bits for the original OS; •Fake a reduced physical memory space for guest OS; •Use special memory device driver to claim memories of host OS; •Backup whole image of the current OS and data to external memory card.
Owner:INTELLECTUAL VENTURES HOLDING 81 LLC
Reconfigurable computer architecture using programmable logic devices
A method and system for computing using reconfigurable computer architecture utilizing logic devices is disclosed. The computing may be accomplished by configuring a first programmable logic unit as a system controller. The system controller directs the implementation of an algorithm in a second one of the programmable logic units concurrently with reconfirguring a third one of the programmable logic units. In another aspect, the computing system may include a pair of independent, bi-directional busses each of which is arranged to electrically interconnect the system controller and the plurality of programmable logic devices. With this arrangement, a first bus may be used to reconfigure a selected one of the programmable logic devices as directed by the system controller while the second bus is used by an operational one of the programmable logic devices.
Owner:ALTERA CORP
System and method for installing an auditable secure network
InactiveUS6918038B1Short timeImprove securityMemory loss protectionError detection/correctionStationPassword
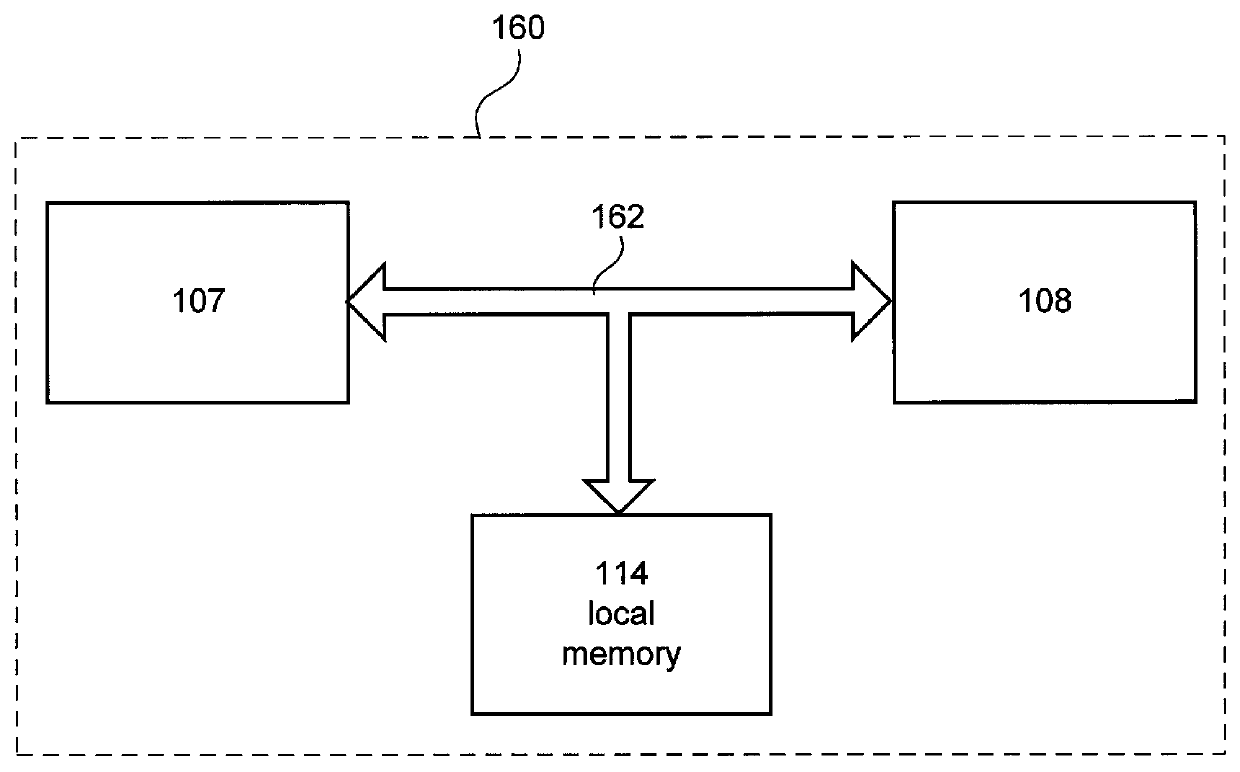
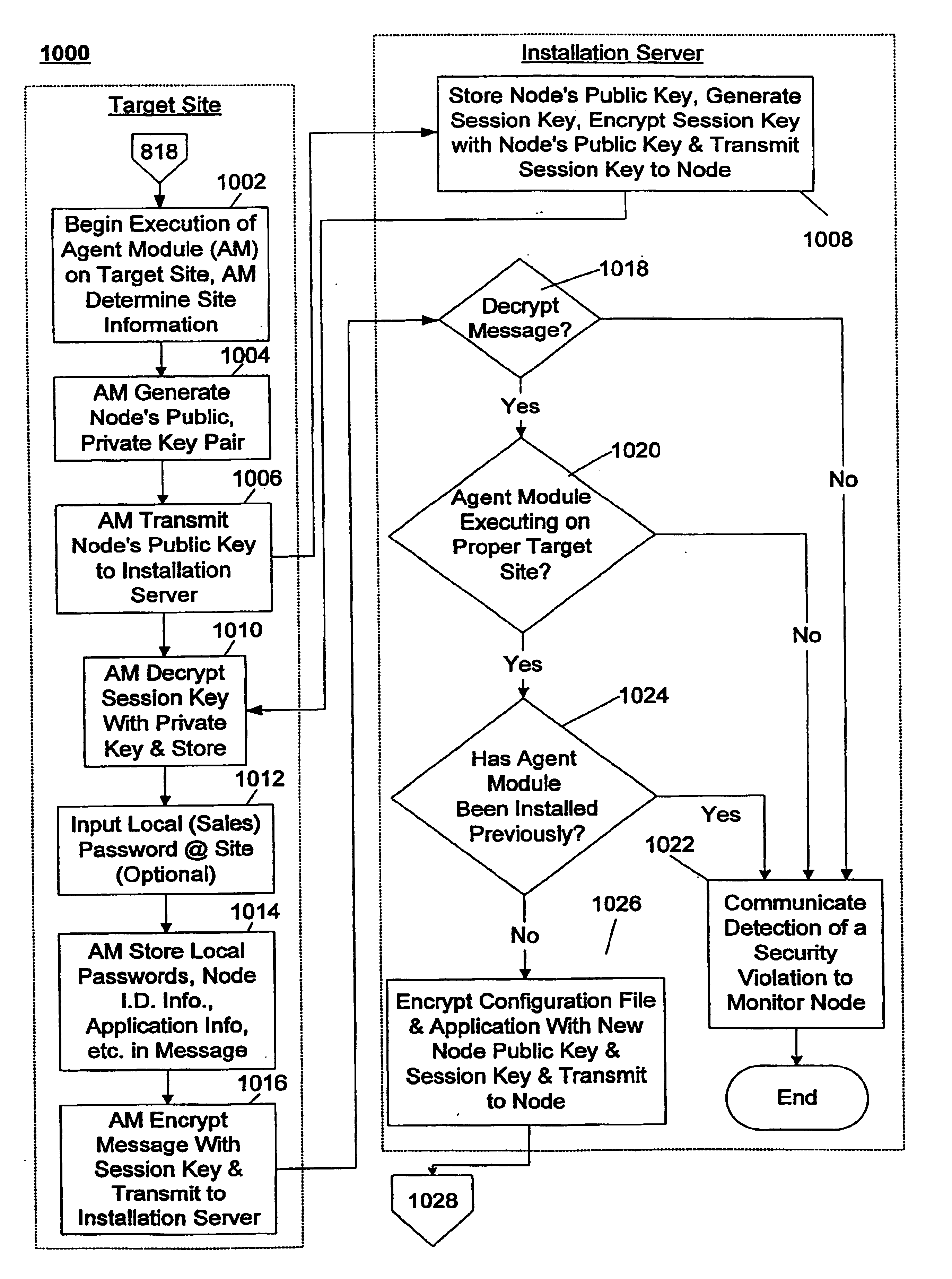
A system and method for generating and remotely installing a private secure and auditable network is provided. Node identification, link, and application information is input into a template. A generator generates components using the information in the template and the components are remotely installed using an installation server. The components include agent modules which are each installed at predetermined target site and establish communication with the installation server to facilitate the download of other components, including application software and configuration files. Each node can only be installed once and is specific to a predetermined target site. For each link, a unique pair of keys is generated in a form which is not human readable, each key corresponds to a different direction of communication over the link. Data transmitted between nodes is encrypted using public-private key pairs. At least one monitor node manages the security of the network, strobes keys, and may take nodes out of the network in the event of a security violation. In such a case, one or more nodes, or the entire network, may be regenerated and installed anew. Throughout the generation and installation a plurality of verifications, authorizations, and password entries may be required by independent groups to arrive at the network. Preferably, the installation is audited by several groups, and the overall operation may be audited by a second monitor node to detect the presence of an interposed “pirate” node.
Owner:ANGEL SECURE NETWORKS
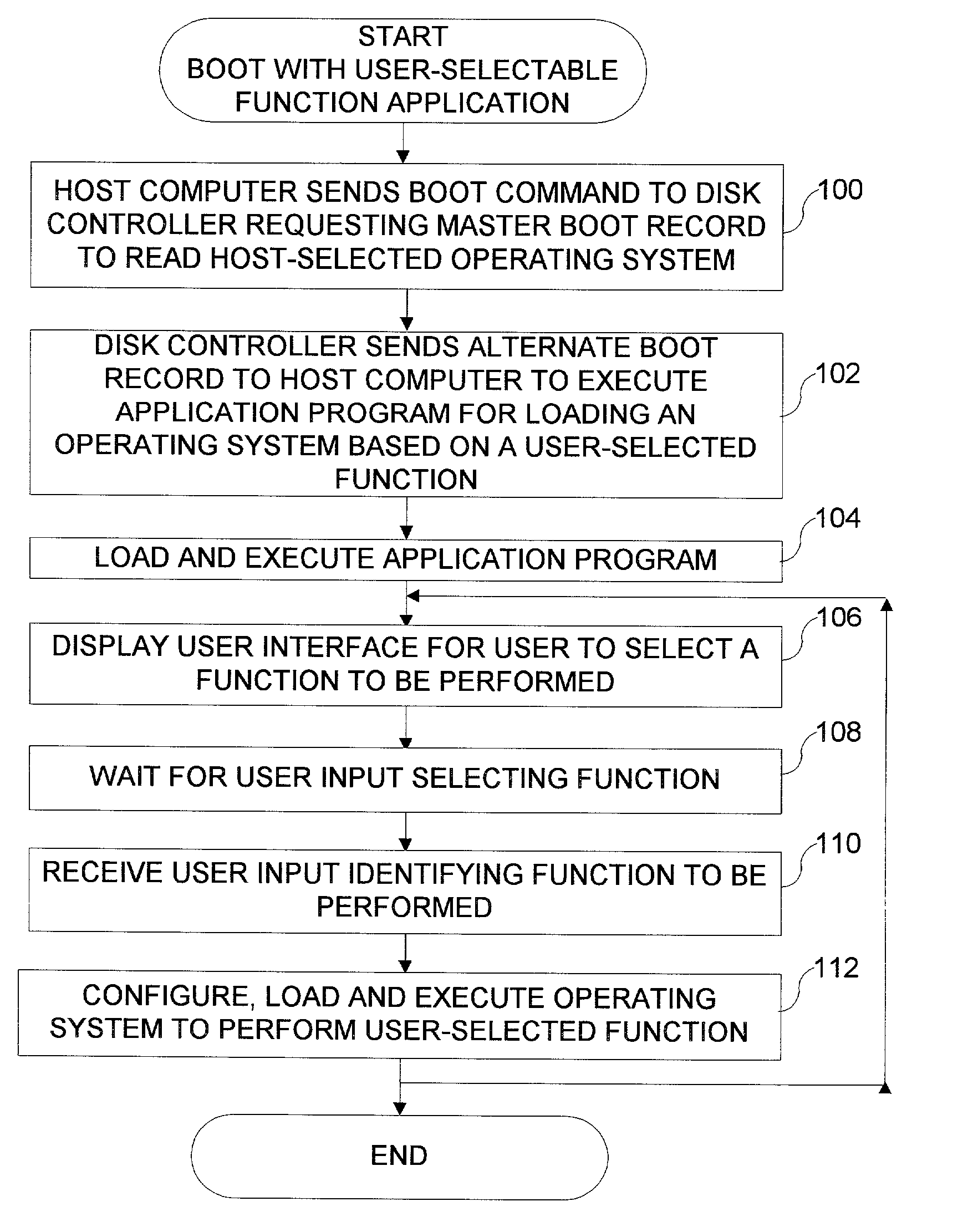
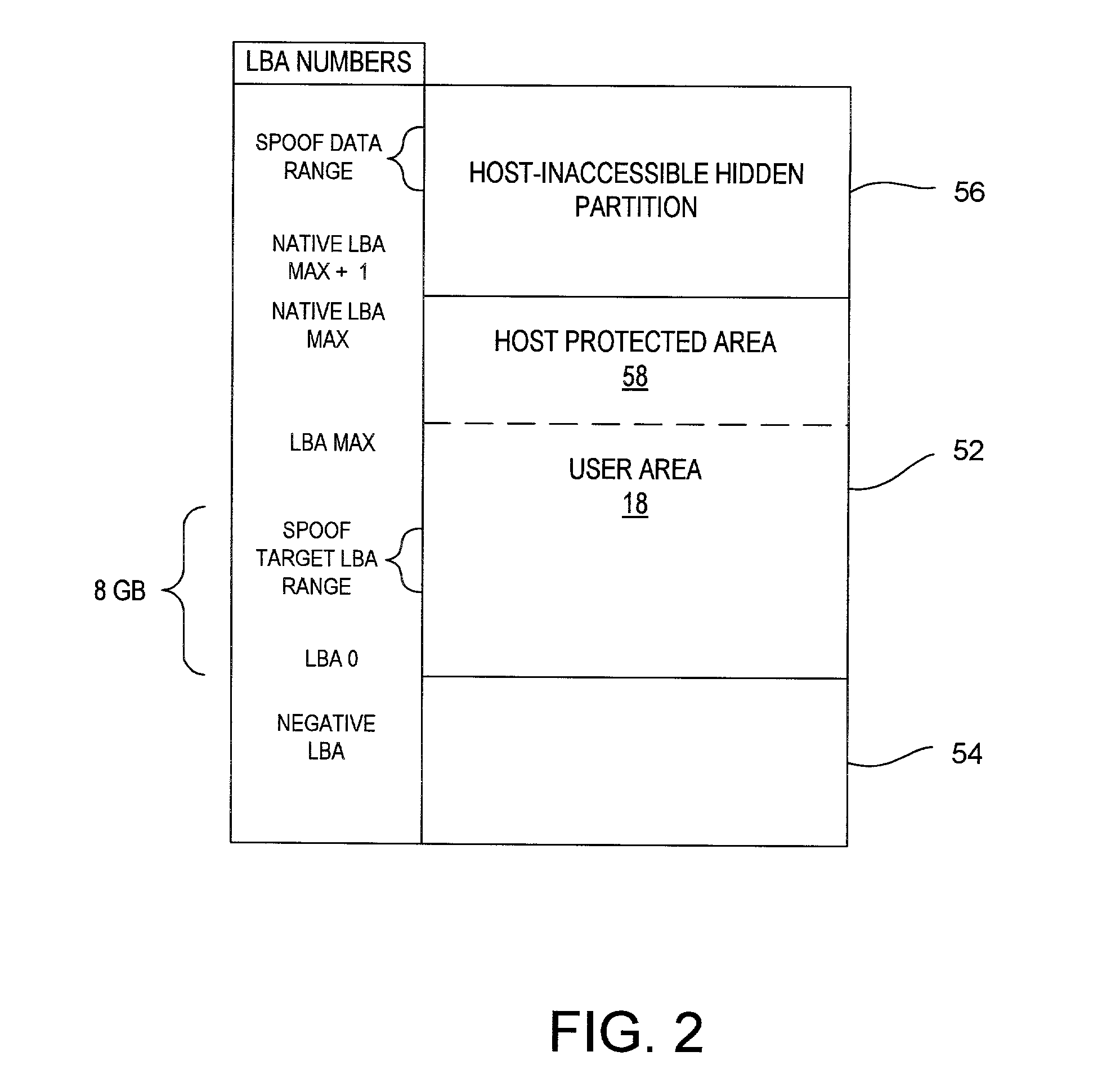
Disk drive having a protected partition configured to load an operating system for performing a user-selected function
A system for configuring, loading and executing an operating system for performing a user-selected function is disclosed. The system includes a disk drive including: a host-accessible user partition; a host-inaccessible hidden partition independent of the host-accessible user partition; and a disk controller. The user partition includes: a user partition address range; a host-selected operating system; and a host-selected master boot record. The host-inaccessible hidden partition includes: a hidden partition address range outside the user partition address range; an application program for allowing a user to select a function to perform and configuring, loading and executing an operating system to perform the selected function; and a drive-selected boot record for loading and executing the application program that allows the user to select a function and configures, loads and executes an operating system for performing the function.
Owner:WESTERN DIGITAL TECH INC
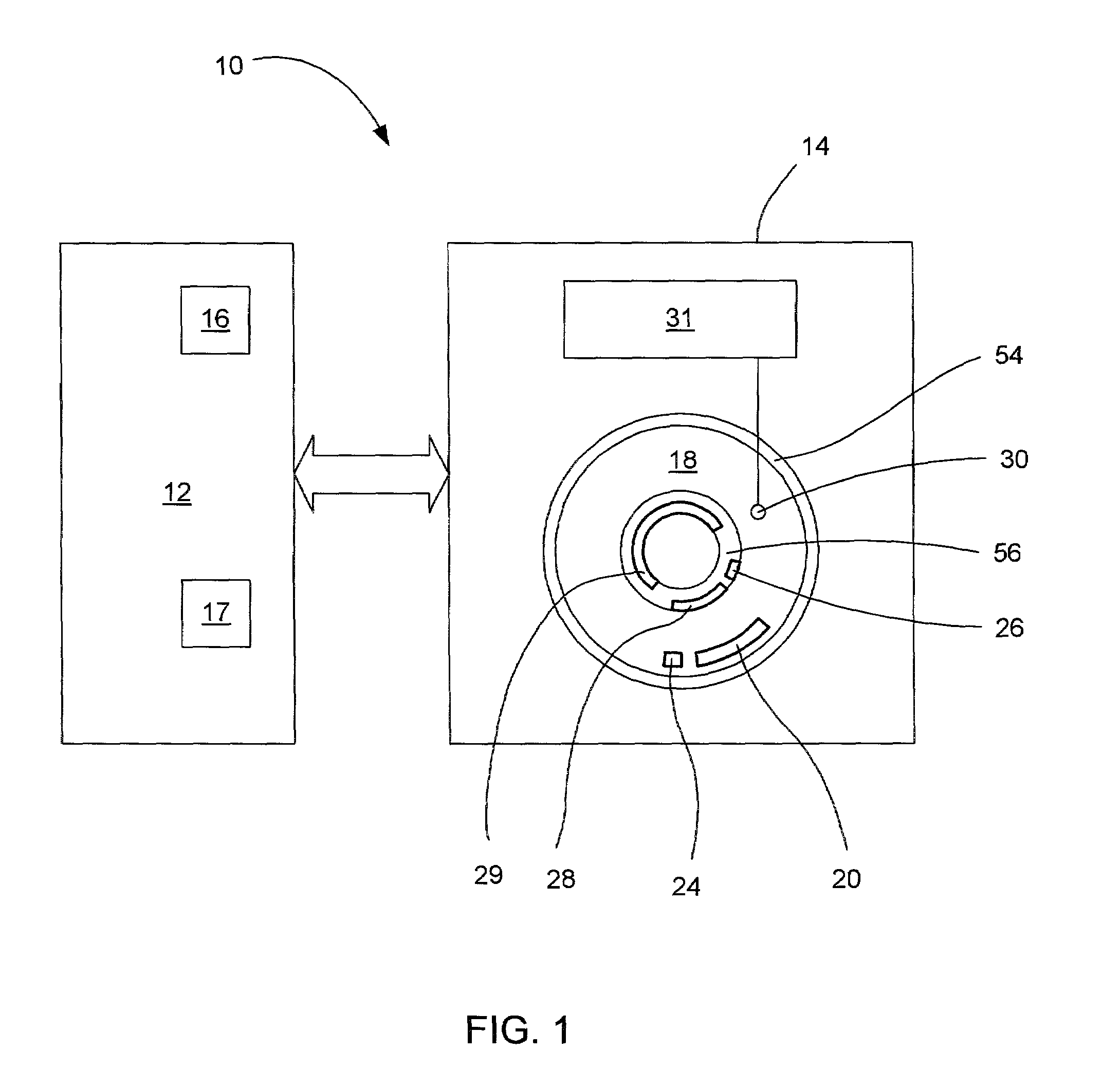
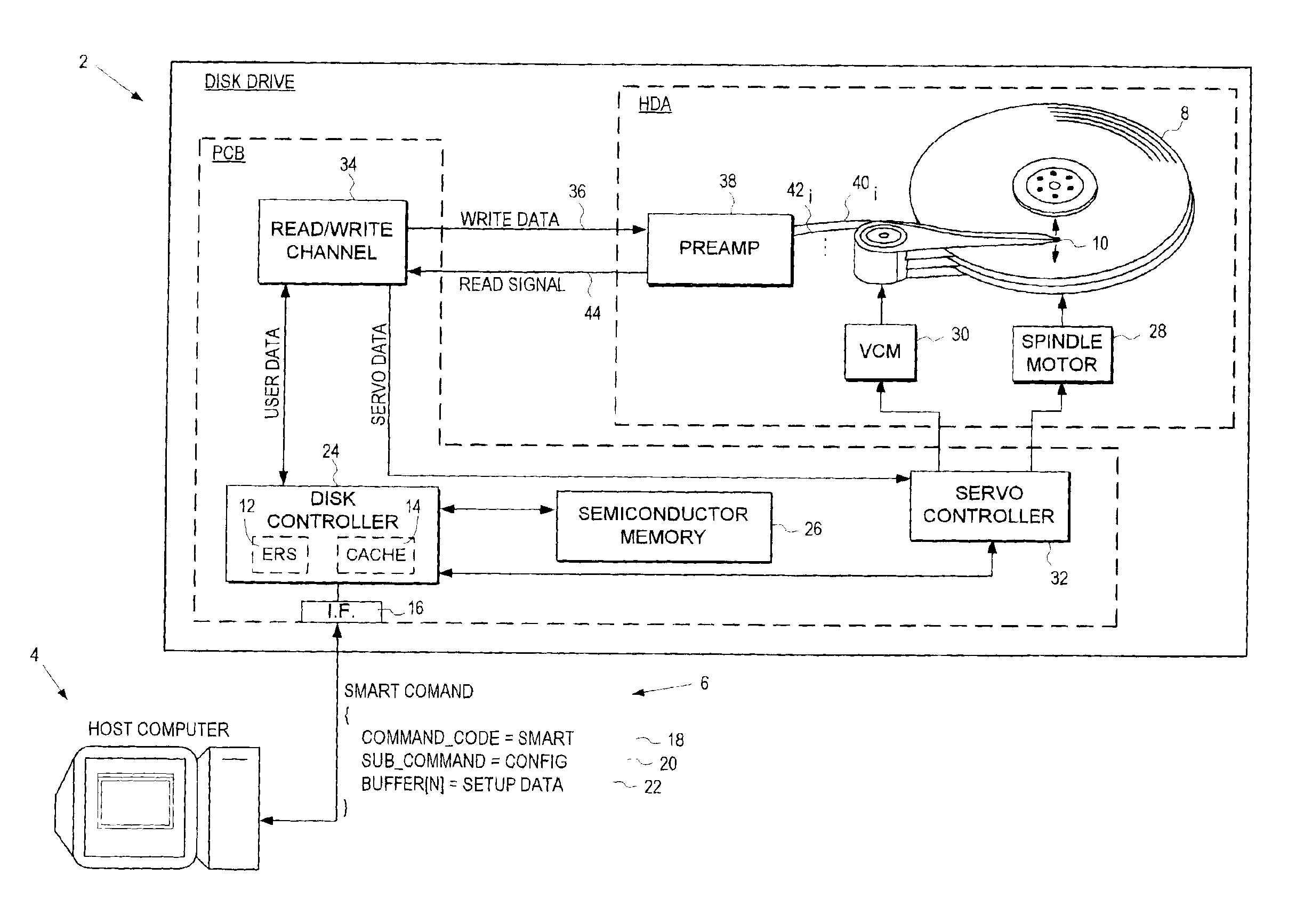
Disk drive for receiving setup data in a self monitoring analysis and reporting technology (SMART) command
InactiveUS6895500B1Digital computer detailsRecord information storageComputer hardwareData transmission
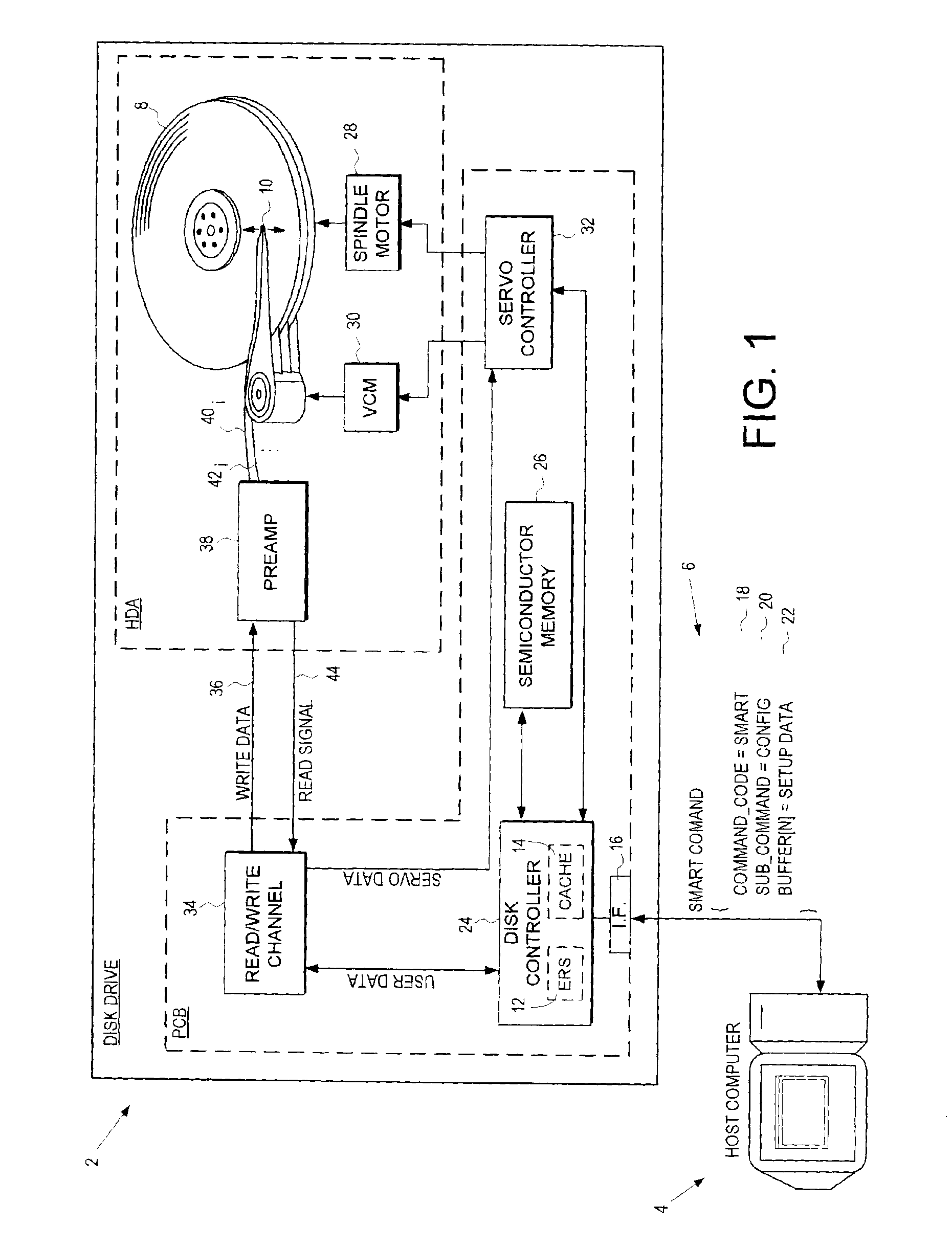
A disk drive is disclosed for receiving a Self Monitoring Analysis and Reporting Technology (SMART) command from a host computer. The disk drive comprises a plurality of configuration parameters stored in a non-volatile manner for configuring at least one system when the disk drive is powered on. The SMART command comprises a command code comprising a predetermined value for identifying the command code as a SMART command and a sub command comprising one of a plurality of predetermine values identifying one of a plurality of SMART commands selected from the group consisting of enabling SMART diagnostics, reading diagnostic data, and transmitting setup data to the disk drive. The SMART command further comprises setup data for modifying the configuration parameters.
Owner:WESTERN DIGITAL TECH INC
Policy based provisioning of network device resources
InactiveUS7062642B1Reduce administrative workloadProgram control using wired connectionsData resettingQuality of serviceData transmission
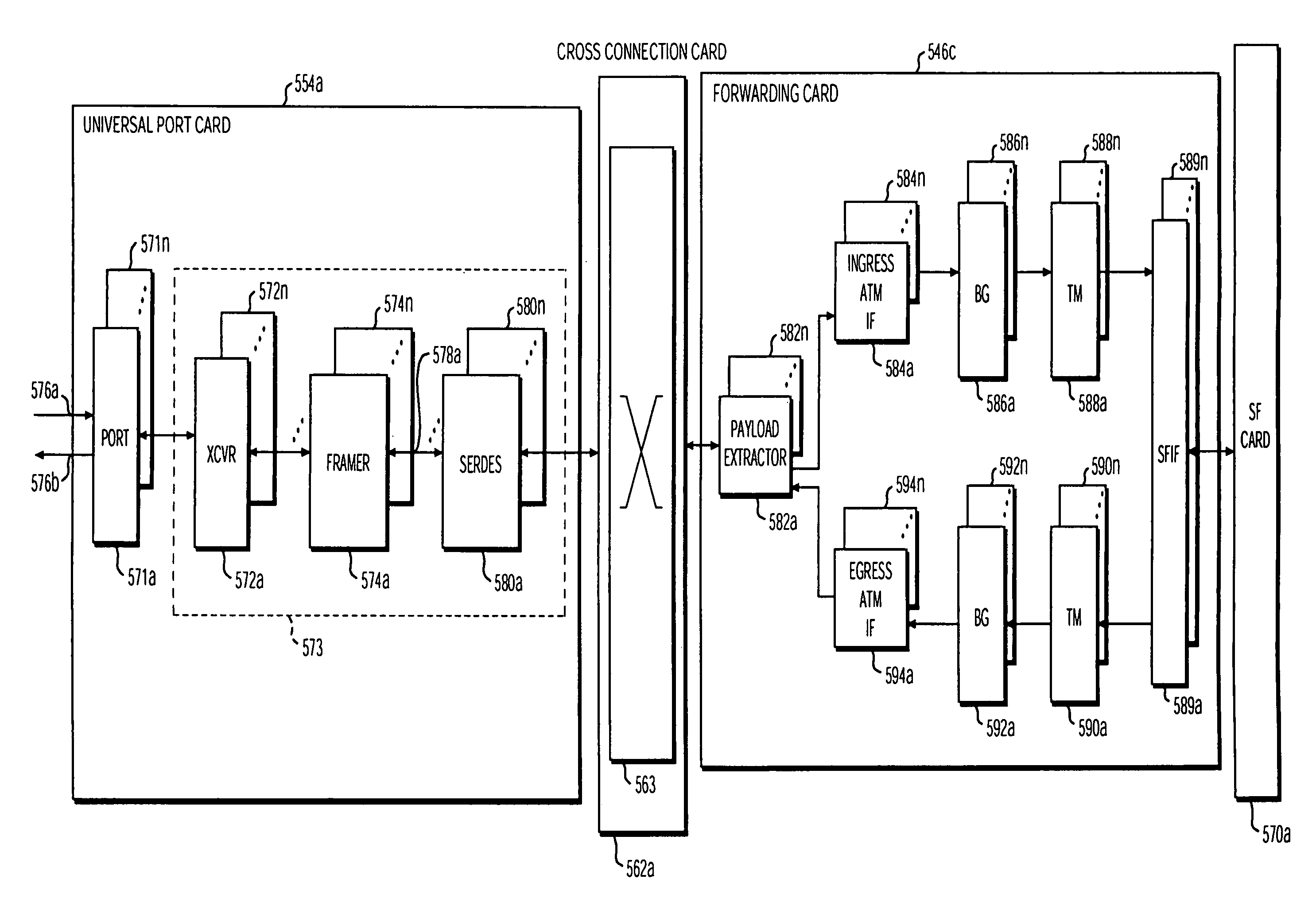
Methods are disclosed for establishing a path for data transmissions in a system having a plurality of possible paths by creating a configuration database and establishing internal connection paths based upon a configuration policy and the configuration database. The configuration policy can be based on available system resources and needs at a given time. In one embodiment, one or more tables are initiated in the configuration database to provide connection information to the system. For example, a path table and a service endpoint table can be employed to establishing a partial record in the configuration database whenever a user connects to a particular port on a universal port card in the system. The method can further include periodically polling records in the path table and transmitting data from the partial records to a policy provisioning manager (PPM). The PPM then implements a connection policy by comparing one or more of the new path characteristics, to the available forwarding card resources in the quadrant containing the universal port card port and path. The path characteristics can include the protocol, the desired number of time slots, the desired number of virtual circuits, and any virtual circuit scheduling restrictions. The PPM can also take other factors into consideration, including quality of service, for example, redundancy requirements or dedicated resource requirements, and balancing resource usage (i.e., load balancing) evenly within a quadrant.
Owner:CIENA
Networked digital video recording system with copy protection and random access playback
ActiveUS7231516B1Effective positioningHigh rateTelevision system detailsData resettingDigital videoDigital recording
In a multimedia recording and playback network for receiving from a content server a service package of multimedia content, the network including a media server in communication with the content server, a method of securely transmitting a master encryption key from the content server to the media server, including the steps downloading a service package certificate from the content server to the media server, authenticating, in the media server, the received service package certificate, the content server providing to the media server a key server certificate, a public key of the content server, and a client certificate request, the media server authenticating the key server certificate, providing to the content server, upon authentication of the key server certificate by the media server, a client certificate including a challenge signature, and a public key of the media server, the content server authenticating the client certificate including the challenge signature received from the media server, the media server requesting the master encryption key from the content server, and the content server responding by transmitting the master encryption key to media server.
Owner:GOOGLE TECH HLDG LLC
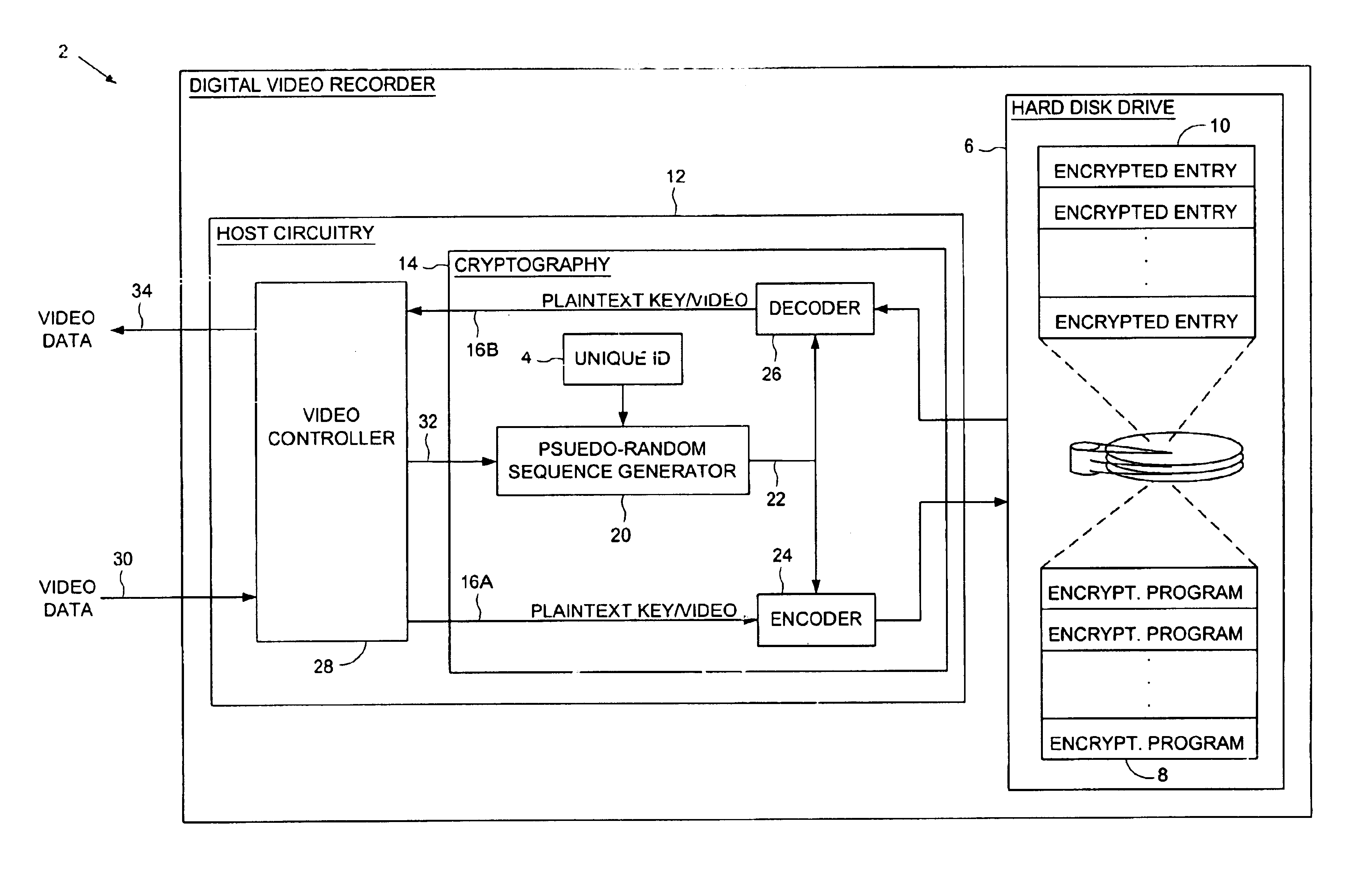
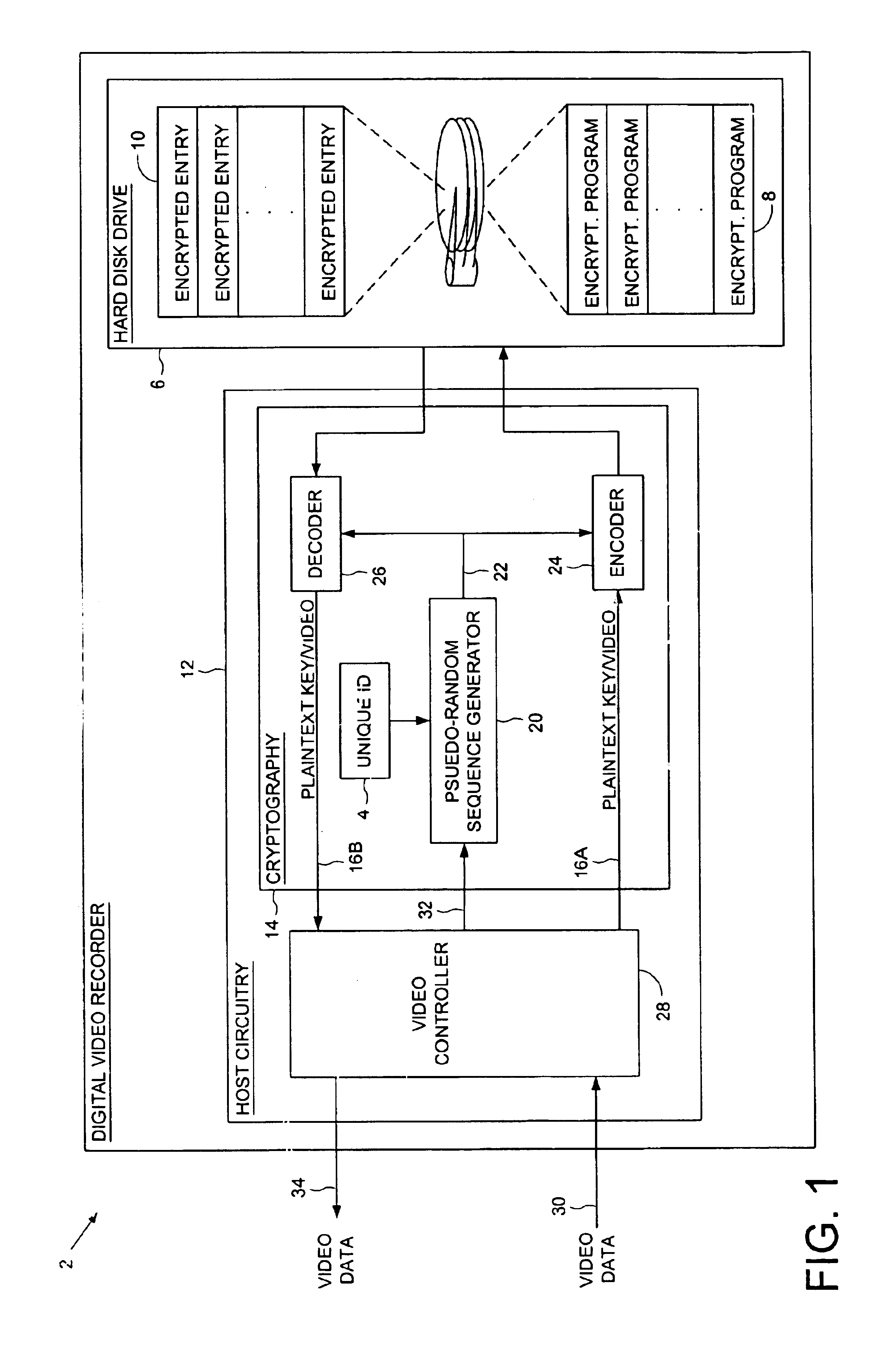
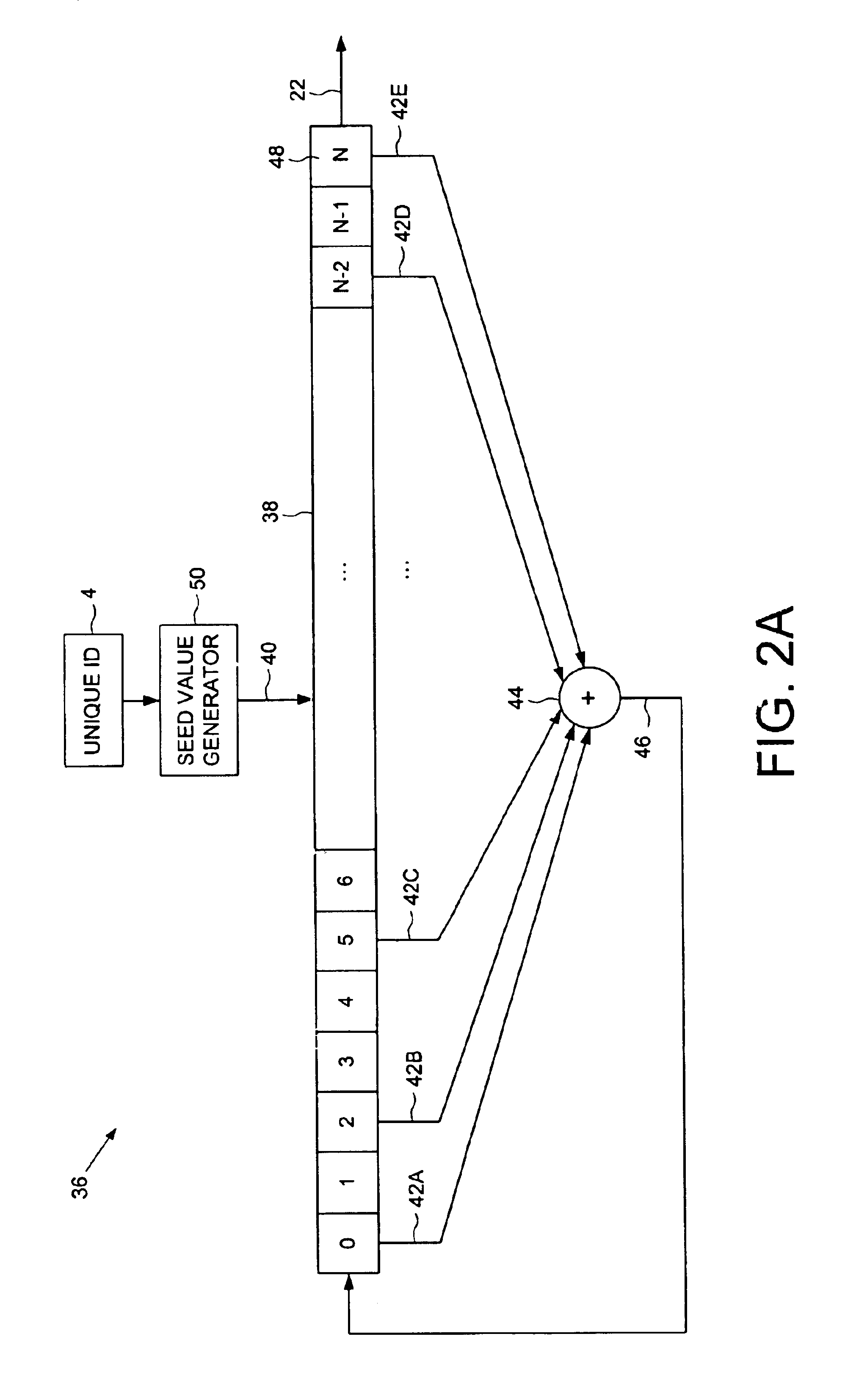
Digital video recorder employing a file system encrypted using a pseudo-random sequence generated from a unique ID
A digital video recorder (DVR) is disclosed comprising a unique ID, a hard disk drive (HDD) for storing a plurality of encrypted video programs and an encrypted file system, the encrypted file system comprising a plurality of encrypted file system entries for decrypting the plurality of video programs. The DVR further comprises host circuitry for interfacing with the HDD, the host circuitry comprising a cryptography facility for encrypting plaintext file system entries into the encrypted file system entries stored on the HDD, and for decrypting the encrypted file system entries read from the HDD into plaintext file system entries. The cryptography facility comprises a pseudo-random sequence generator, responsive to the unique ID, for generating a pseudo-random sequence. The cryptography facility further comprises an encoder for combining the pseudo-random sequence with the plaintext file system entries to generate the encrypted file system entries stored on the HDD, and a decoder for combining the pseudo-random sequence with the encrypted file system entries read from the HDD to generate the plaintext file system entries.
Owner:KEEN PERSONAL MEDIA +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com