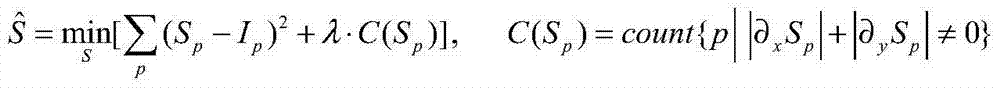Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1633results about How to "Reduce memory usage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
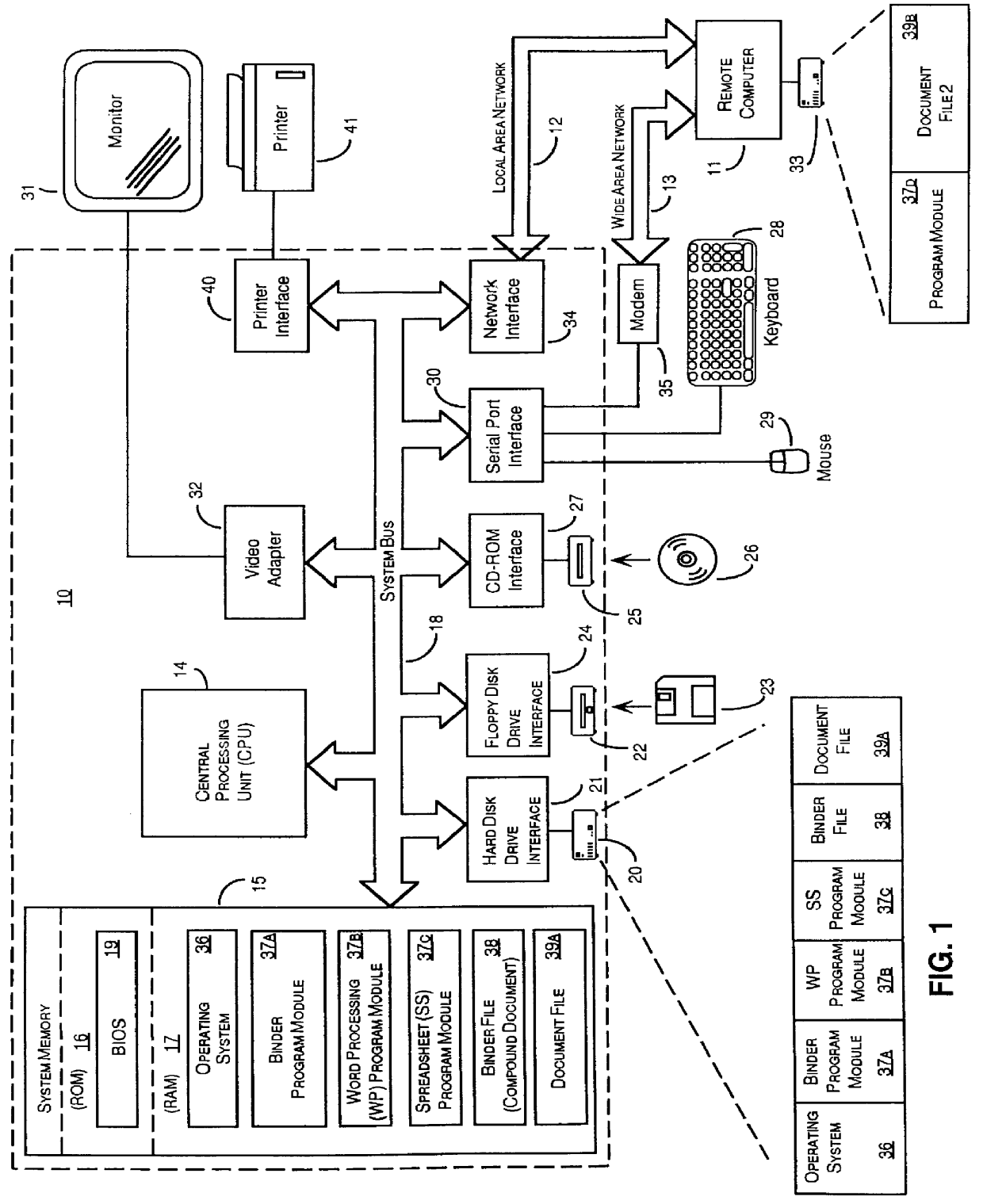
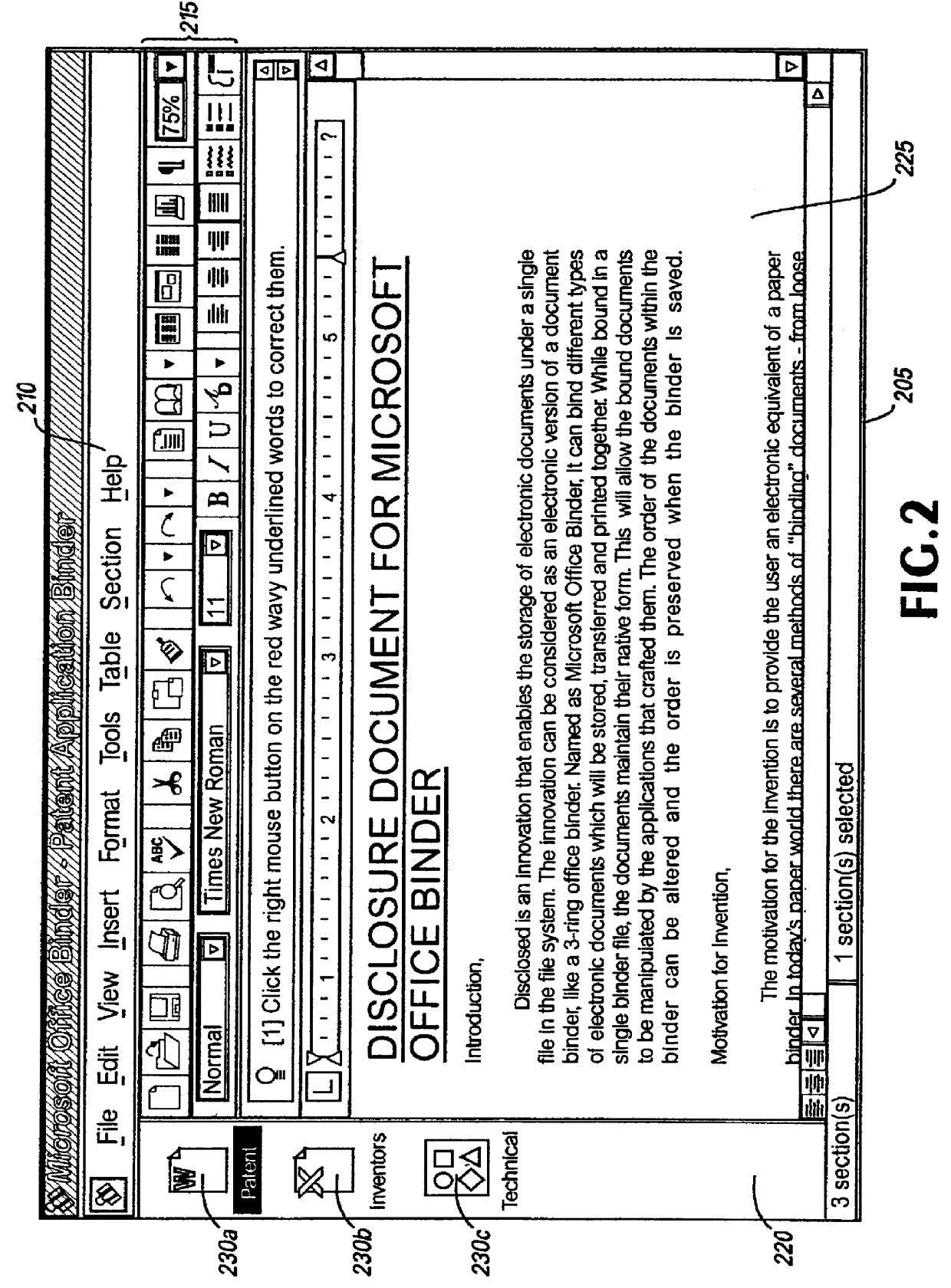
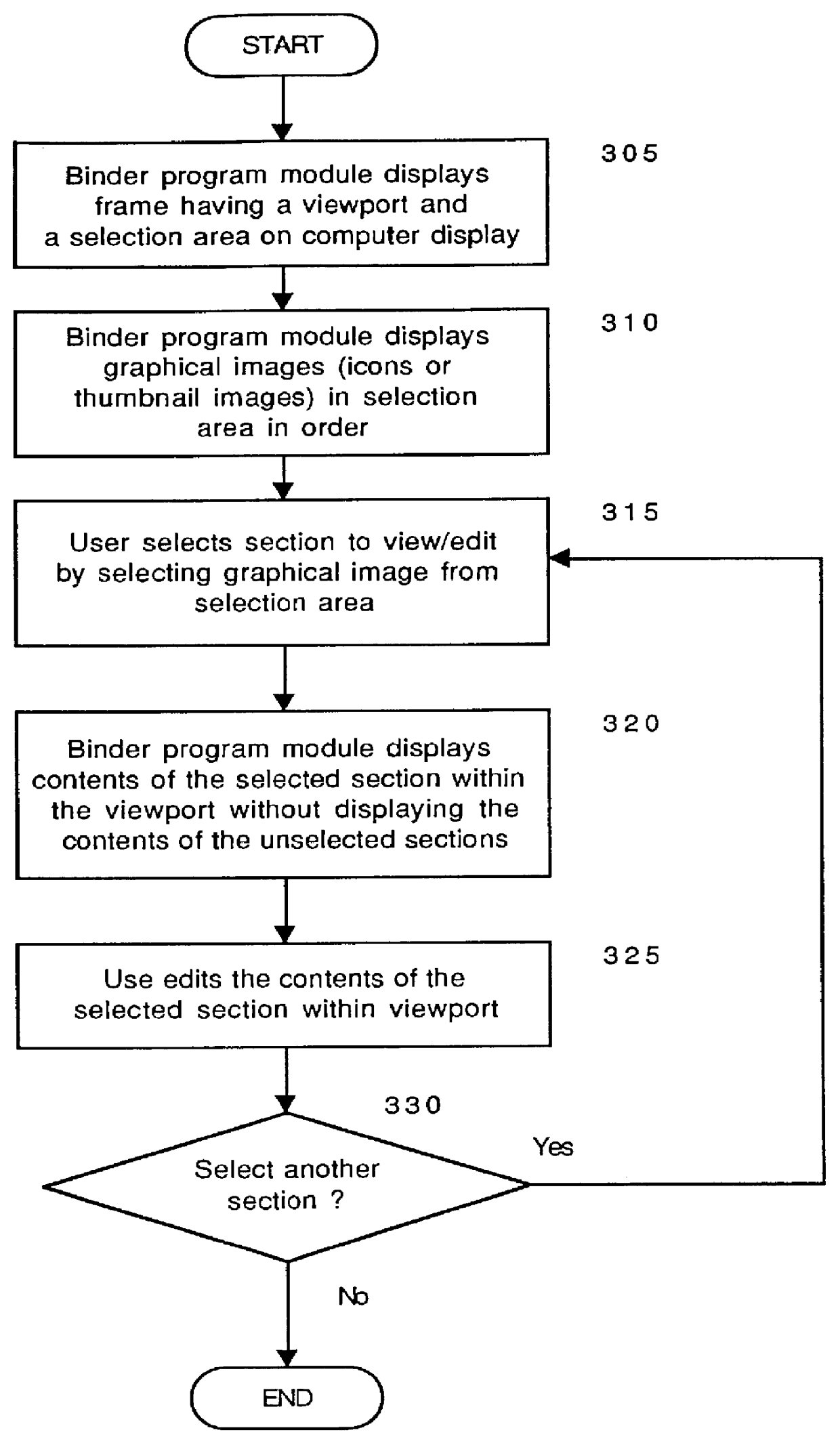
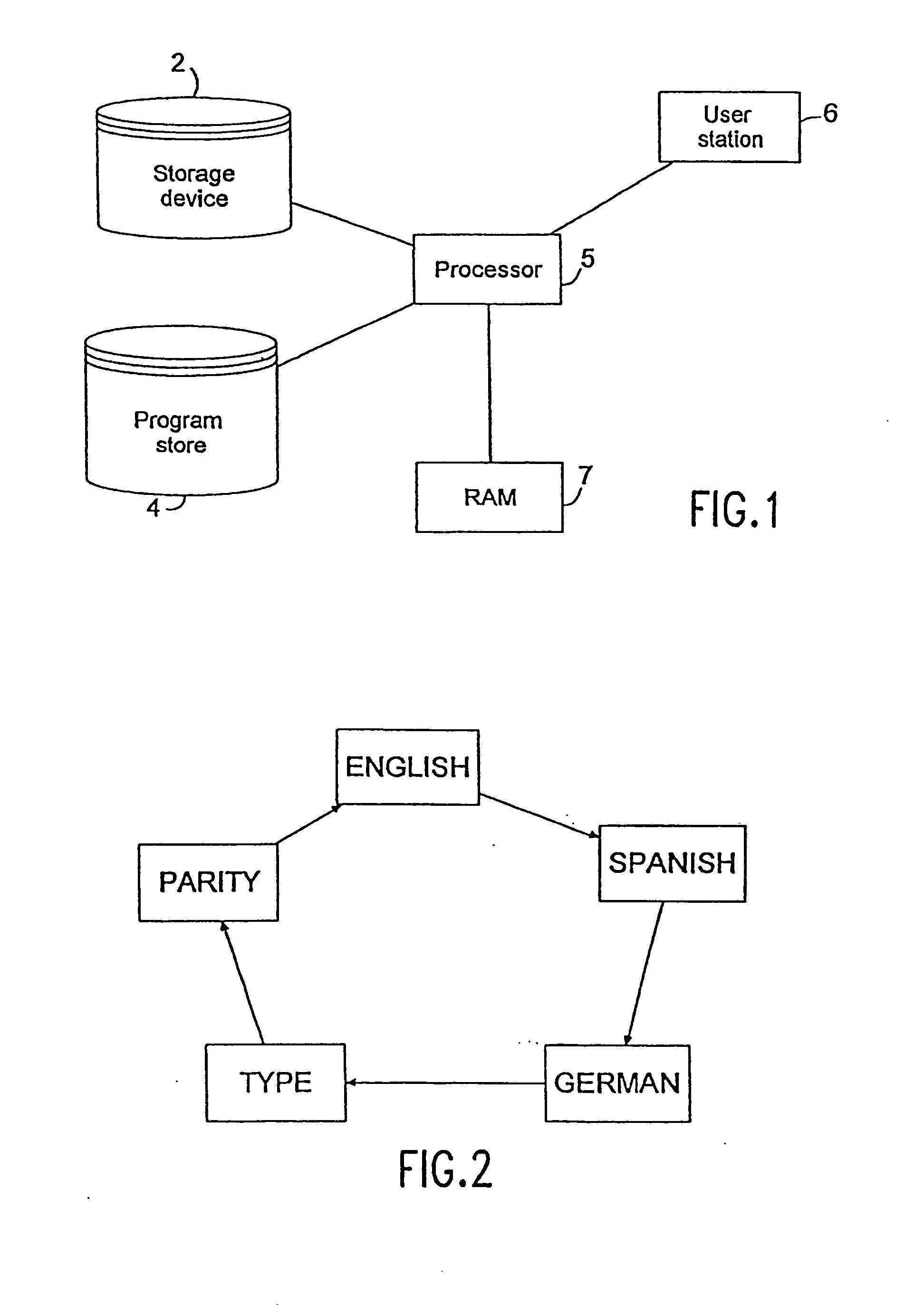
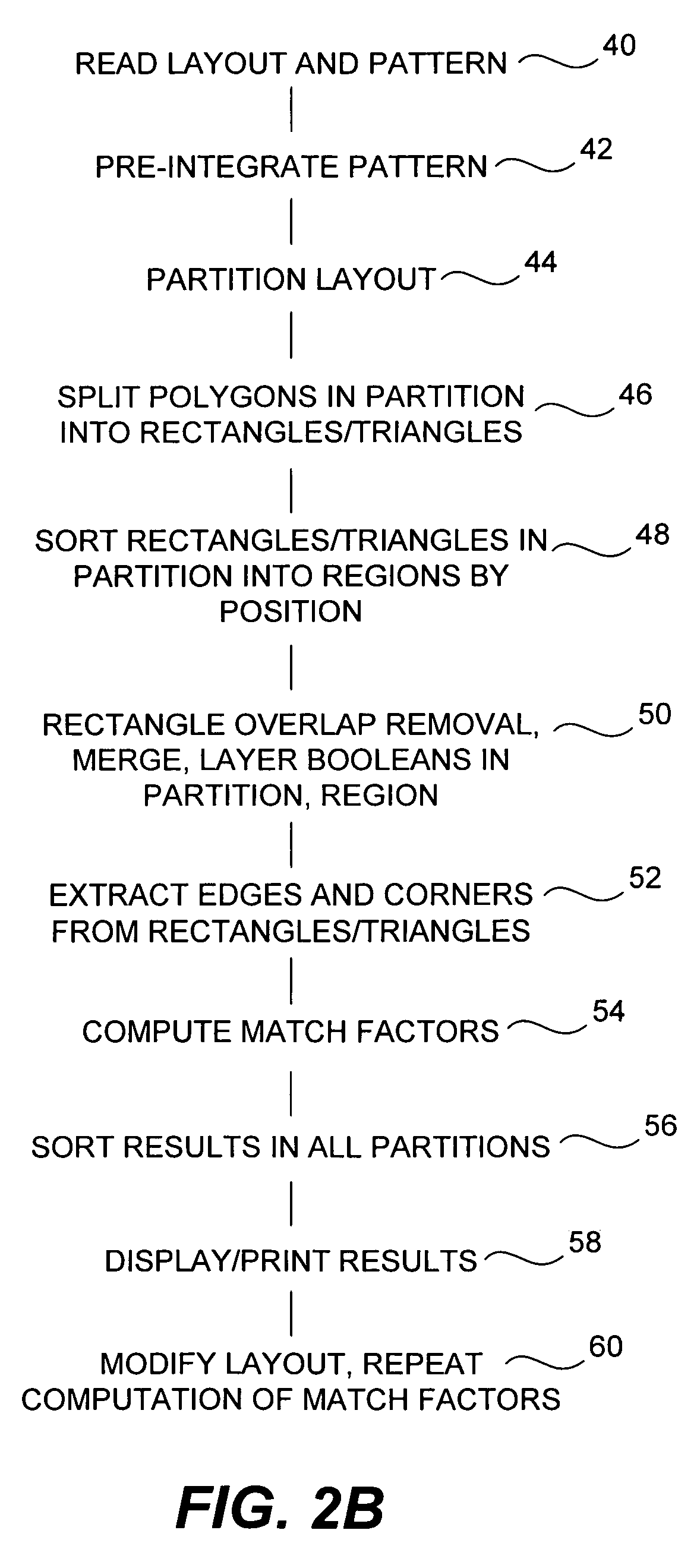
System and method for storing, viewing, editing, and processing ordered sections having different file formats
InactiveUS6026416AImprove practicalityReduce memory usageSpecial data processing applicationsDocument management systemsGraphicsApplication software
Ordered binder document sections having different file formats stored within a binder file. The binder file maintains the order of binder document sections and the native file format of each section. The ordered sections can be viewed and edited through a viewport of a frame displayed by a binder program module. By selecting graphical images displayed in a selection area of the frame the content of a binder document section can be viewed and edited without viewing the content of other binder document sections. The graphical images can be icons or graphical images derived from the content of sections called thumbnail images. A thumbnail image can be derived from either the first page or from multiple pages of an individual section. The binder program module can also dispatch the underlying application program modules that created each binder document section to print, spell check, and grammar check the binder document sections as a single data processing task. In this manner, selected sections of a binder document can be printed as a single consecutively printed document without having other print jobs interrupting or intervening between printed sections of the binder document.
Owner:MICROSOFT TECH LICENSING LLC
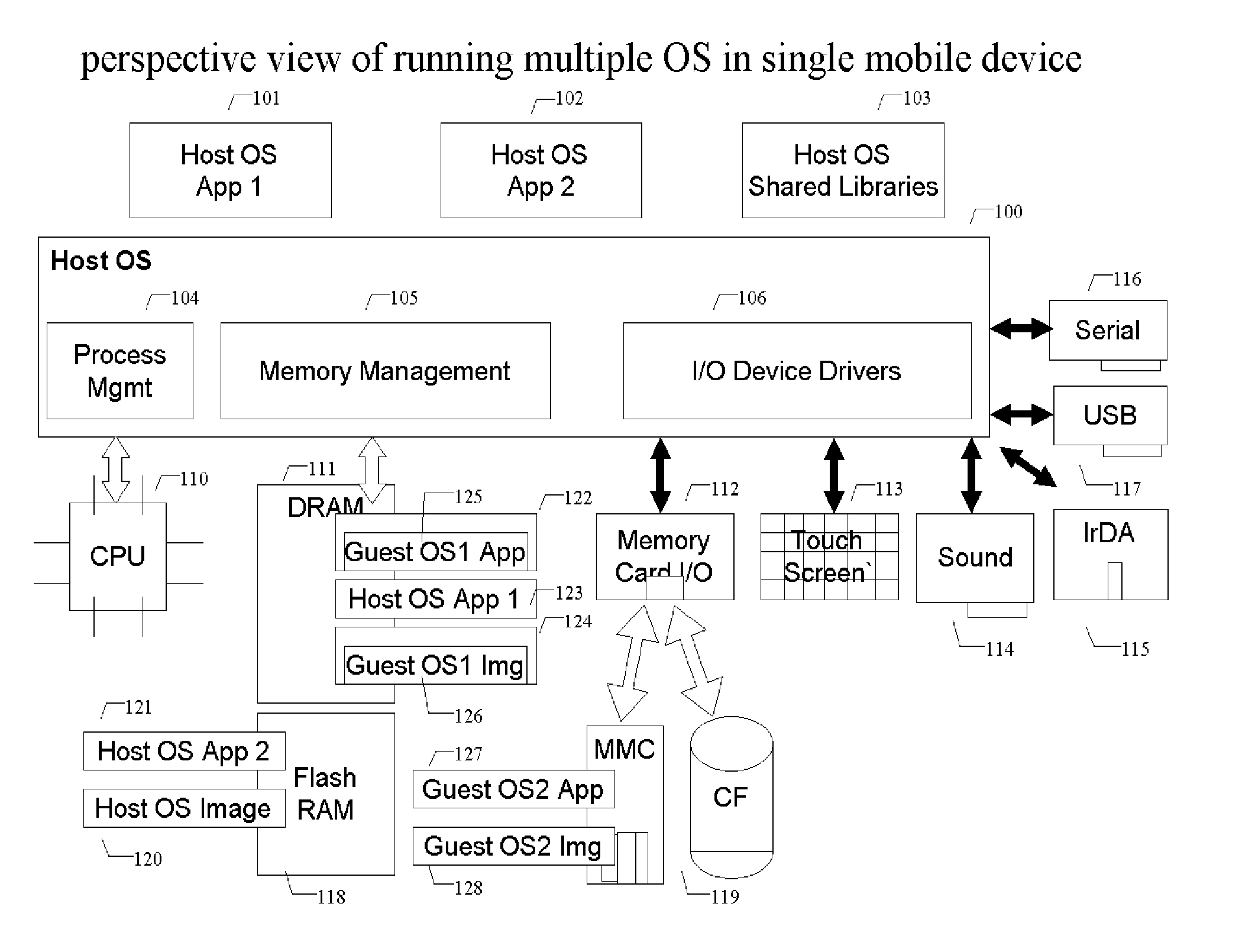
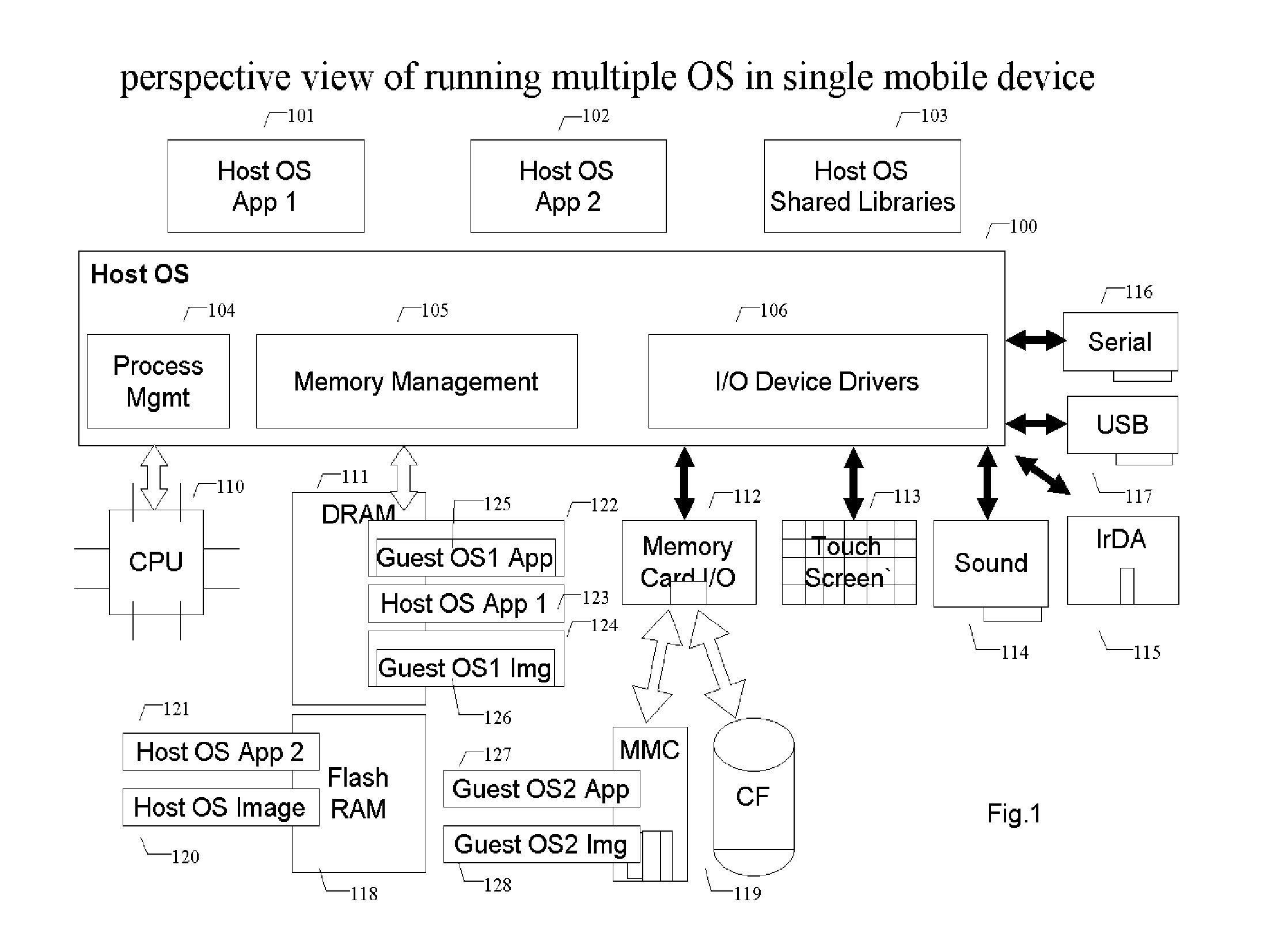
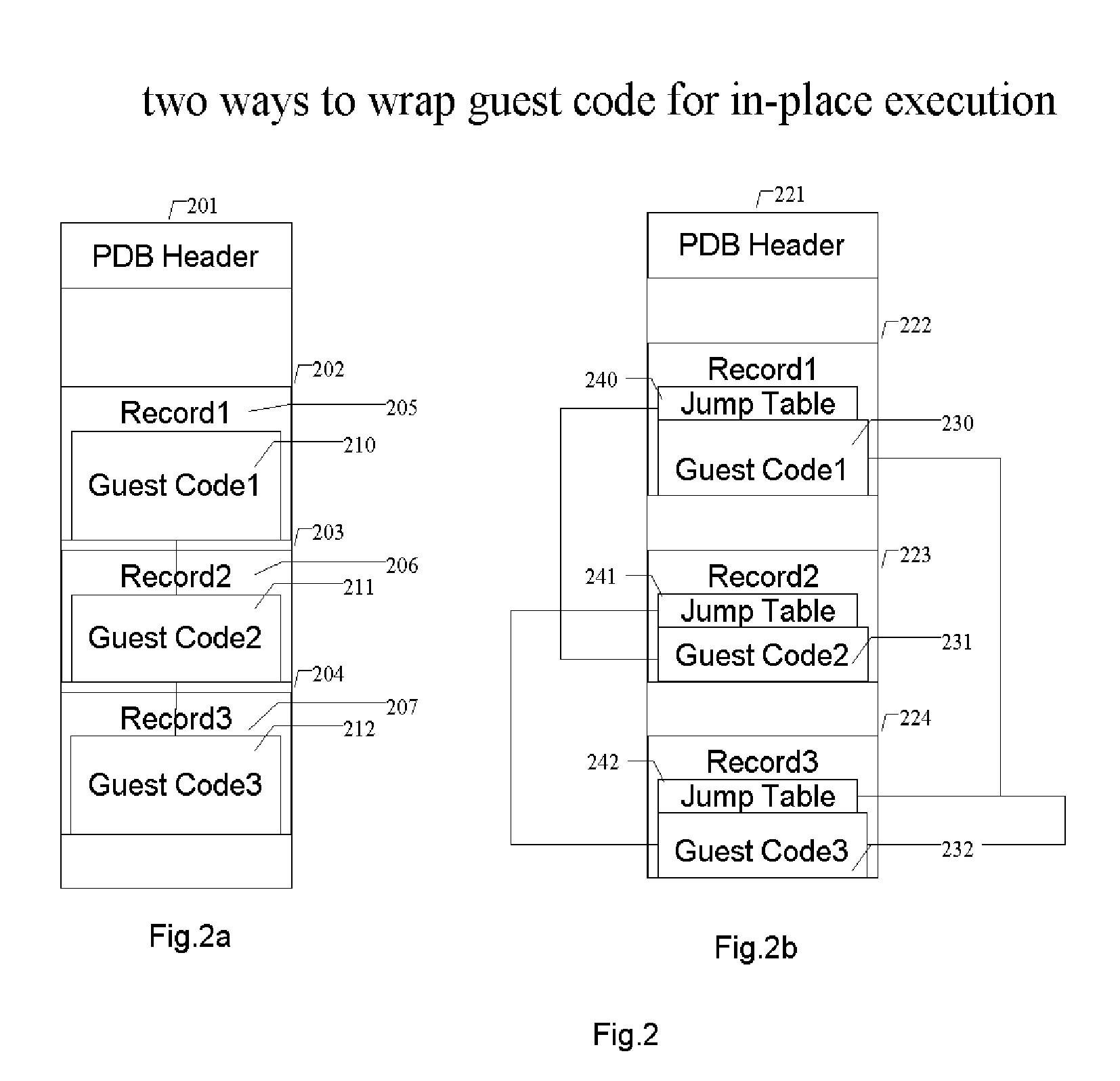
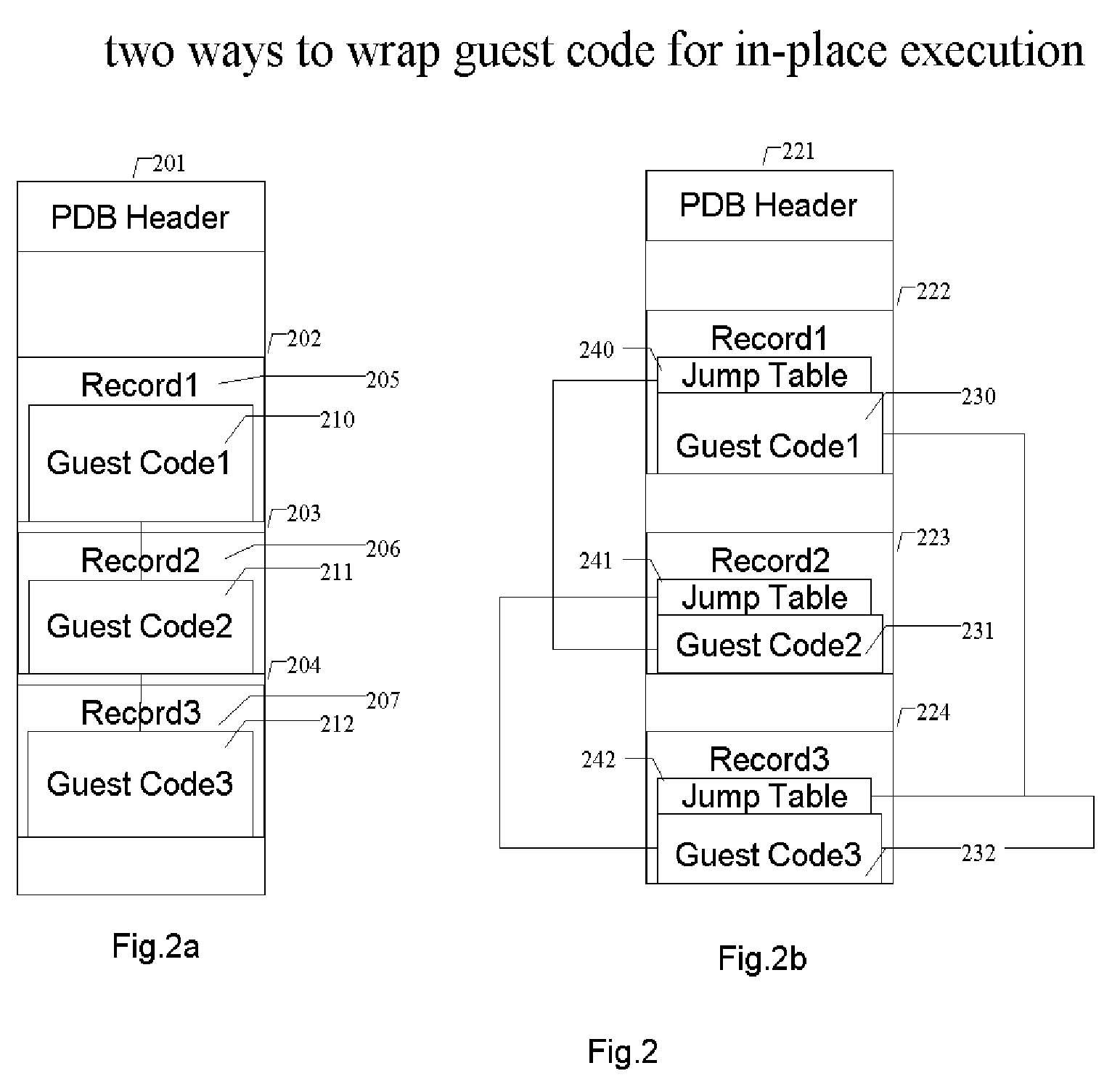
Methods and systems for running multiple operating systems in a single mobile device
ActiveUS20060010314A1Reduce memory usageError detection/correctionDigital computer detailsOperational systemEngineering
Methods and systems for running multiple operating systems in a single embedded or mobile device (include PDA, cellular phone and other devices) are disclosed. The invention allows a mobile device that normally can only run a single operating system to run another operating system while preserving the state and data of the original operating system. Guest OS is packaged into special format recognizable by the host OS that still can be executed in place by the system. The Methods include: •Change the memory protection bits for the original OS; •Fake a reduced physical memory space for guest OS; •Use special memory device driver to claim memories of host OS; •Backup whole image of the current OS and data to external memory card.
Owner:INTELLECTUAL VENTURES HOLDING 81 LLC
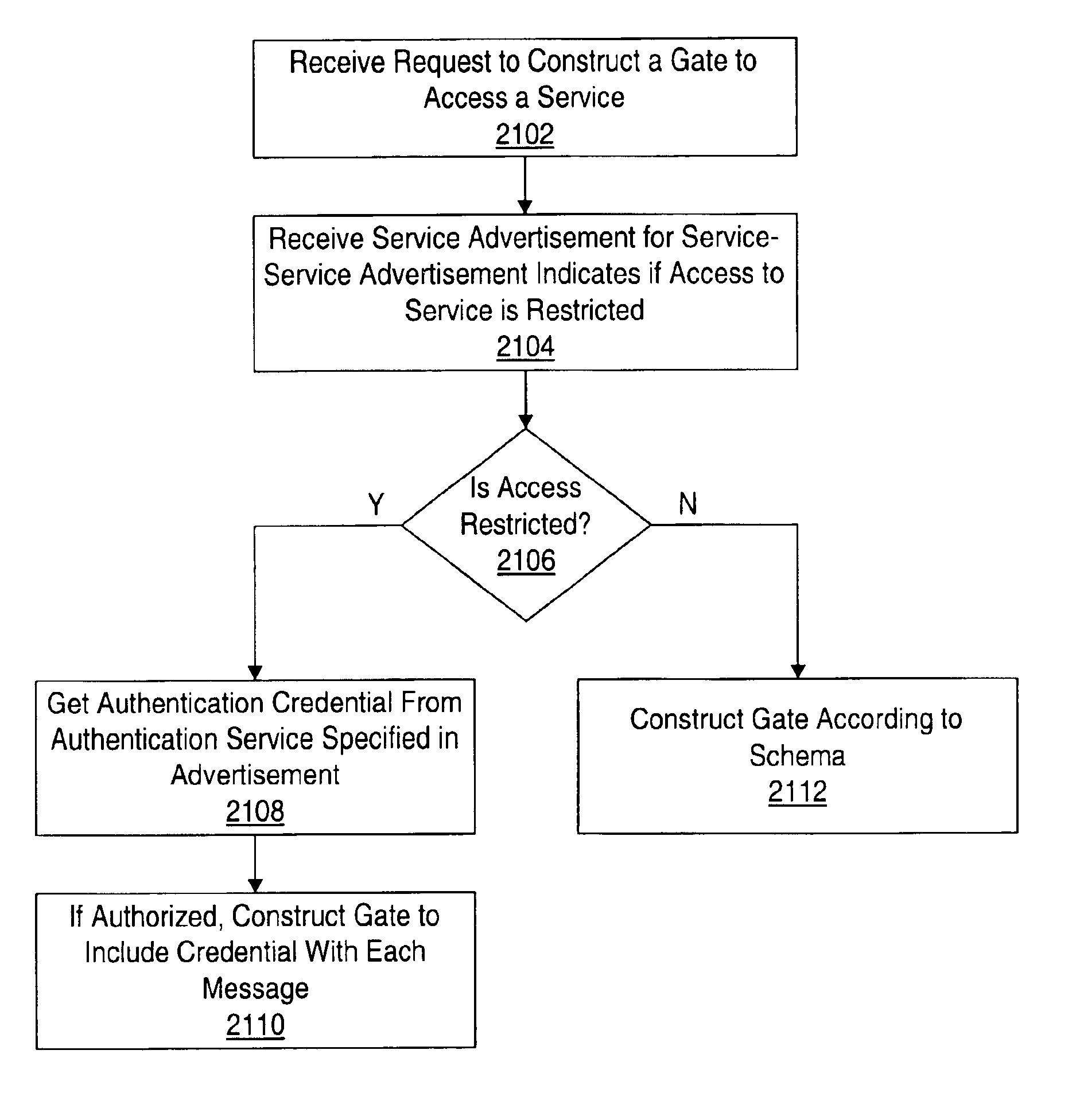
Efficient construction of message endpoints
InactiveUS7072967B1Easy constructionAvoid constructionMemory loss protectionError detection/correctionXML schemaDistributed Computing Environment
In a distributed computing environment, a message gate may be the message endpoint for a client or service. A message gate may provide a secure message endpoint that sends and receives type-safe messages. Devices may have a gate factory (e.g. message endpoint constructor) that is trusted code on the device for generating gates based on XML message descriptions. In one embodiment, the gate factory may construct a gate from the XML schema of the service, a URI for the service, and an authentication credential. Access to some services may be unrestricted. For such services, a gate may be constructed without an authentication credential, saving the overhead of running an authentication service and incorporating an authentication credential. Gate construction may also be optimized for certain clients that do not desire to perform checking of messages against a service's XML schema. If verification is not desired, a client may avoid or may chose to avoid building (e.g. by a gate factory) some or all of the gate code that checks the messages against the XML schema. Also, the building of a gate may be made lightweight by appropriate reuse or sharing of pieces used to construct other gates. Devices may maintain a cache of gates to avoid constructing them each time the same service is run.
Owner:ORACLE INT CORP
Facilitating processing within computing environments supporting pageable guests
ActiveUS20070016904A1Overcomes shortcomingEnhanced advantageMultiprogramming arrangementsSoftware simulation/interpretation/emulationPagingHost memory
Processing within a computing environment that supports pageable guests is facilitated. Processing is facilitated in many ways, including, but not limited to, associating guest and host state information with guest blocks of storage; maintaining the state information in control blocks in host memory; enabling the changing of states; and using the state information in management decisions. In one particular example, the guest state includes an indication of usefulness and importance of memory contents to the guest, and the host state reflects the ease of access to memory contents. The host and guest state information is used in managing memory of the host and / or guests.
Owner:IBM CORP
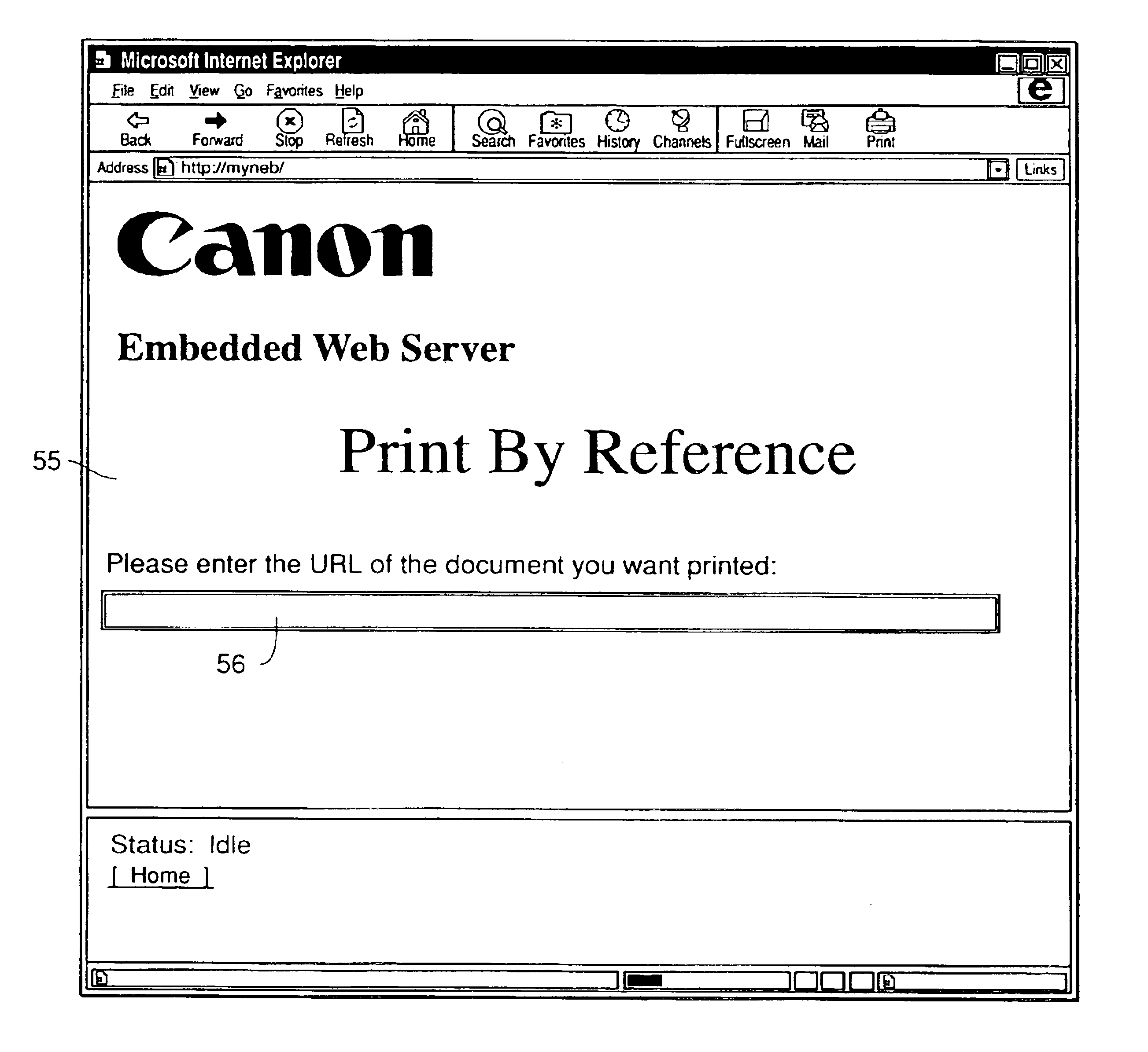
System for retrieving and printing network documents
InactiveUS6938202B1Precise positioningReduce memory usageDigital data processing detailsWeb printingWeb browserWeb service
A method for providing print-by-reference functionality includes providing a web page from a printer's embedded web server to a web browser, receiving a URL entered into the provided web page, retrieving a printable document corresponding to the URL, and printing the retrieved document.
Owner:CANON KK
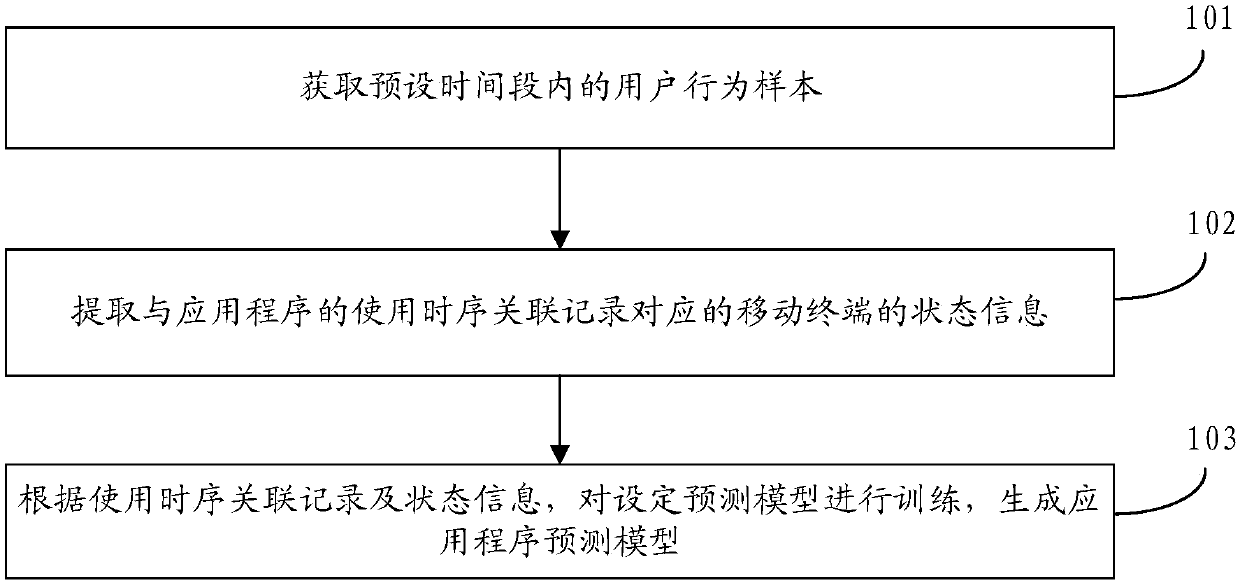
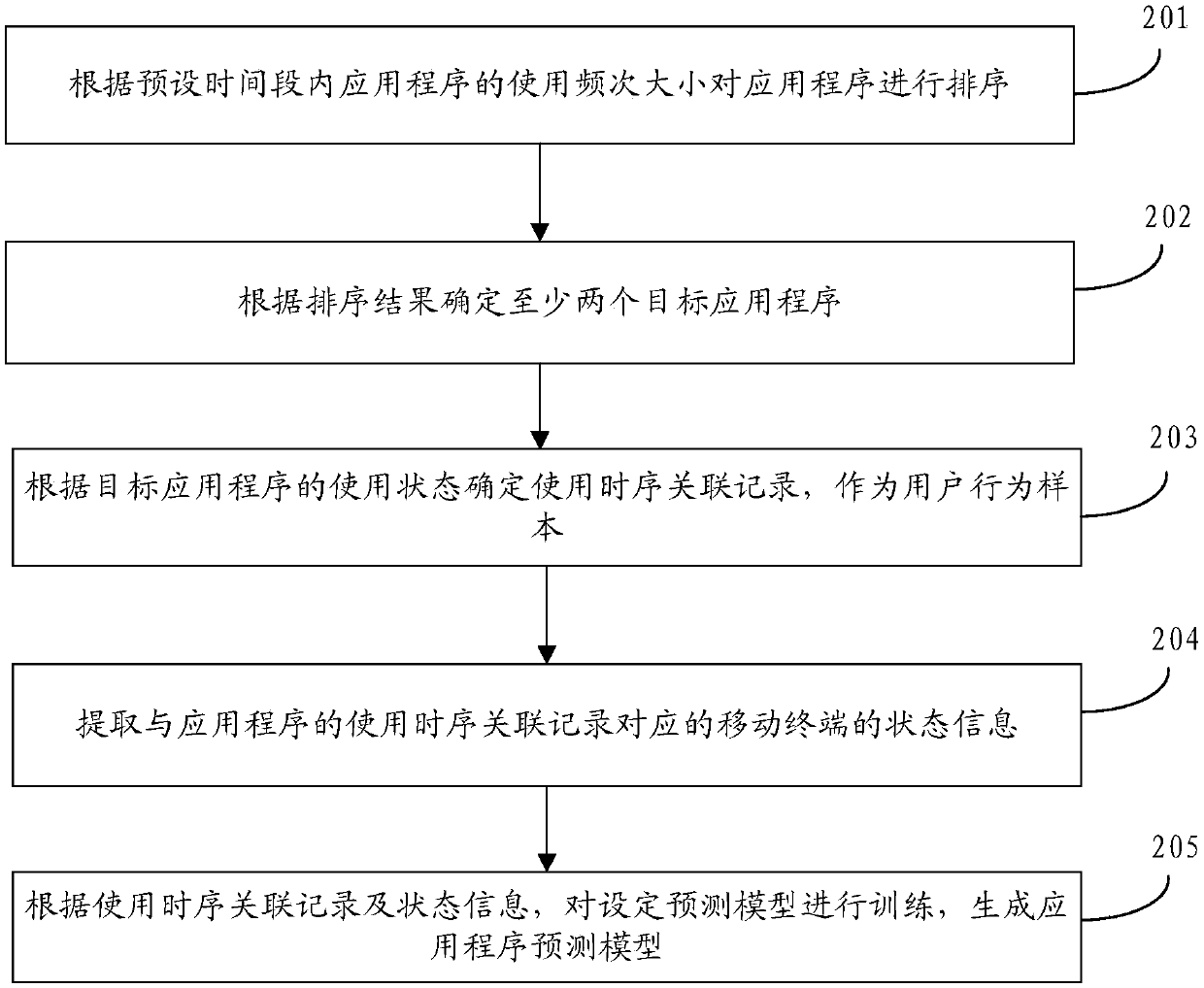
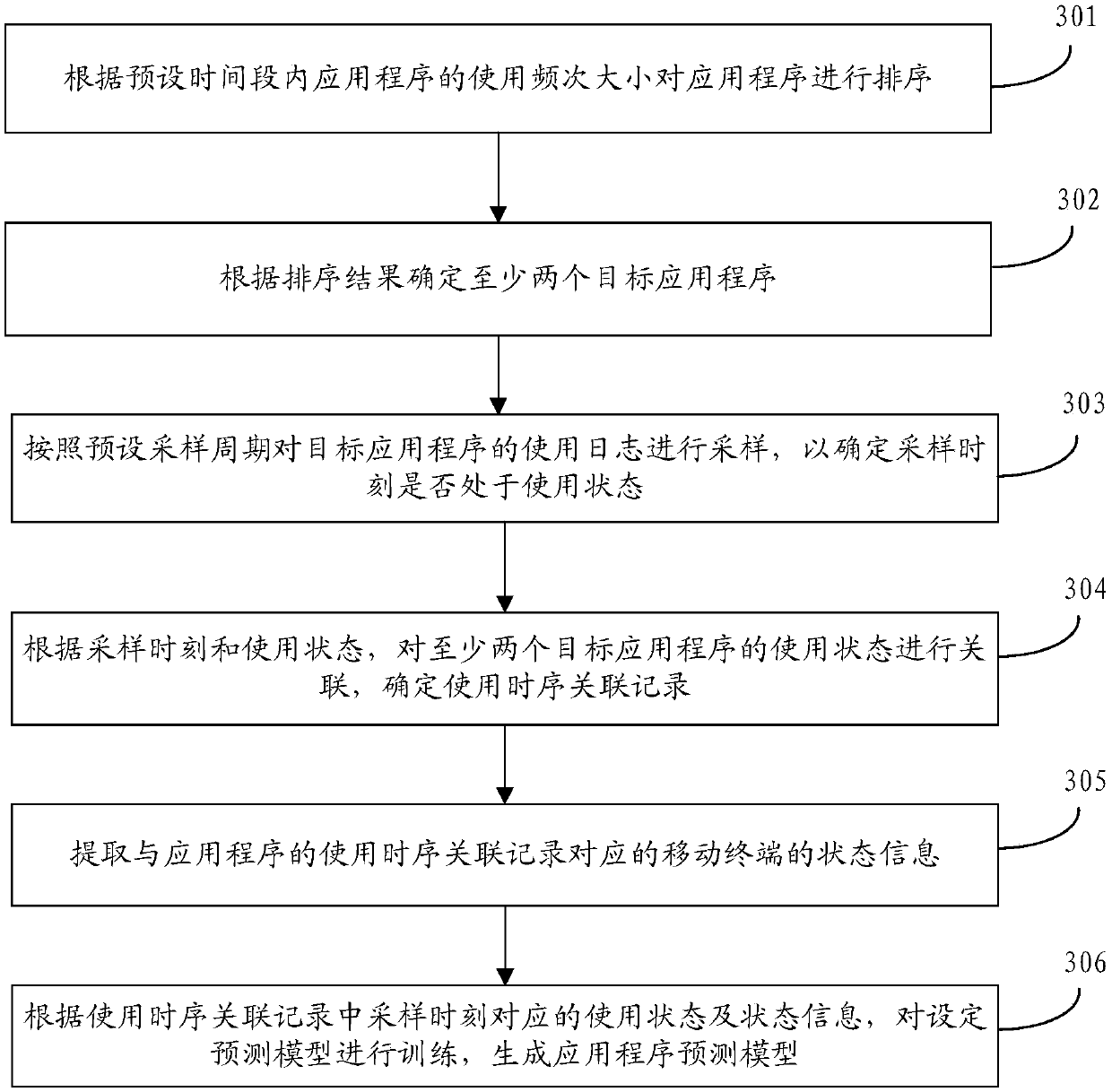
Forecasting model building, pre-loading method of application program, device, medium and terminal
ActiveCN107783801AReduce power consumptionReduce memory usageProgram loading/initiatingMachine learningBusiness forecastingTerminal system
The embodiment of the application discloses a forecasting model building and pre-loading method of an application program, a device, a medium and a terminal. The forecasting model building method of the application program includes steps of acquiring a user behavior sample in a preset time section, wherein the user behavior sample comprises use time sequence association records of two applicationprograms; extracting state information of the corresponding terminal of the use time sequence association records of the application programs; training a set forecasting model according to the use time sequence association records and the state information, and generating the forecasting model of the application program. Through adopting the technical scheme, the use time sequence association records of the application programs and corresponding terminal state information can be really reflected through sufficient use, the pre-loading mechanism of the application program is optimized, and theforecasting accuracy of the application program to be started is effectively improved; moreover, the power consumption and the memory share rate of the terminal system are further reduced.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
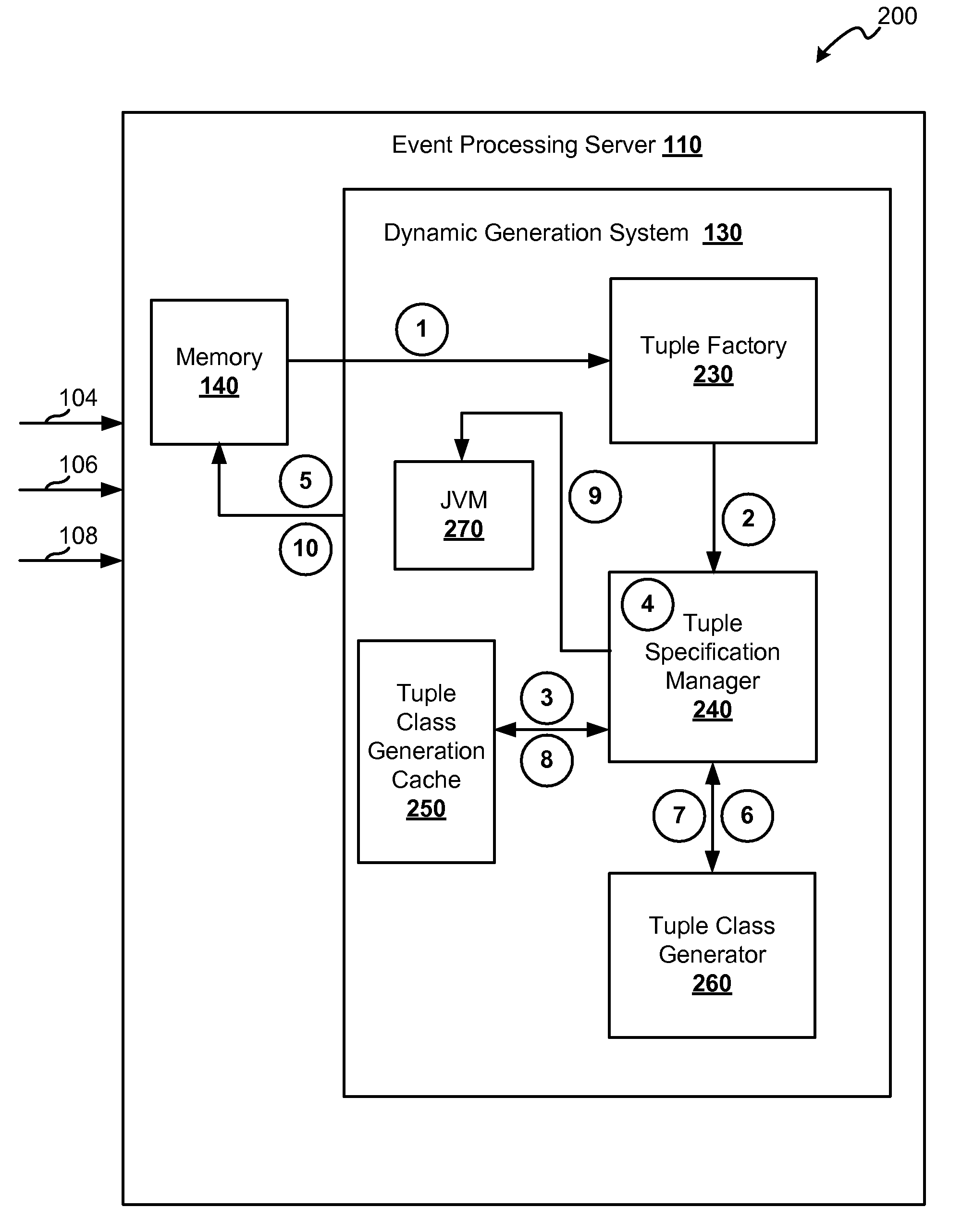
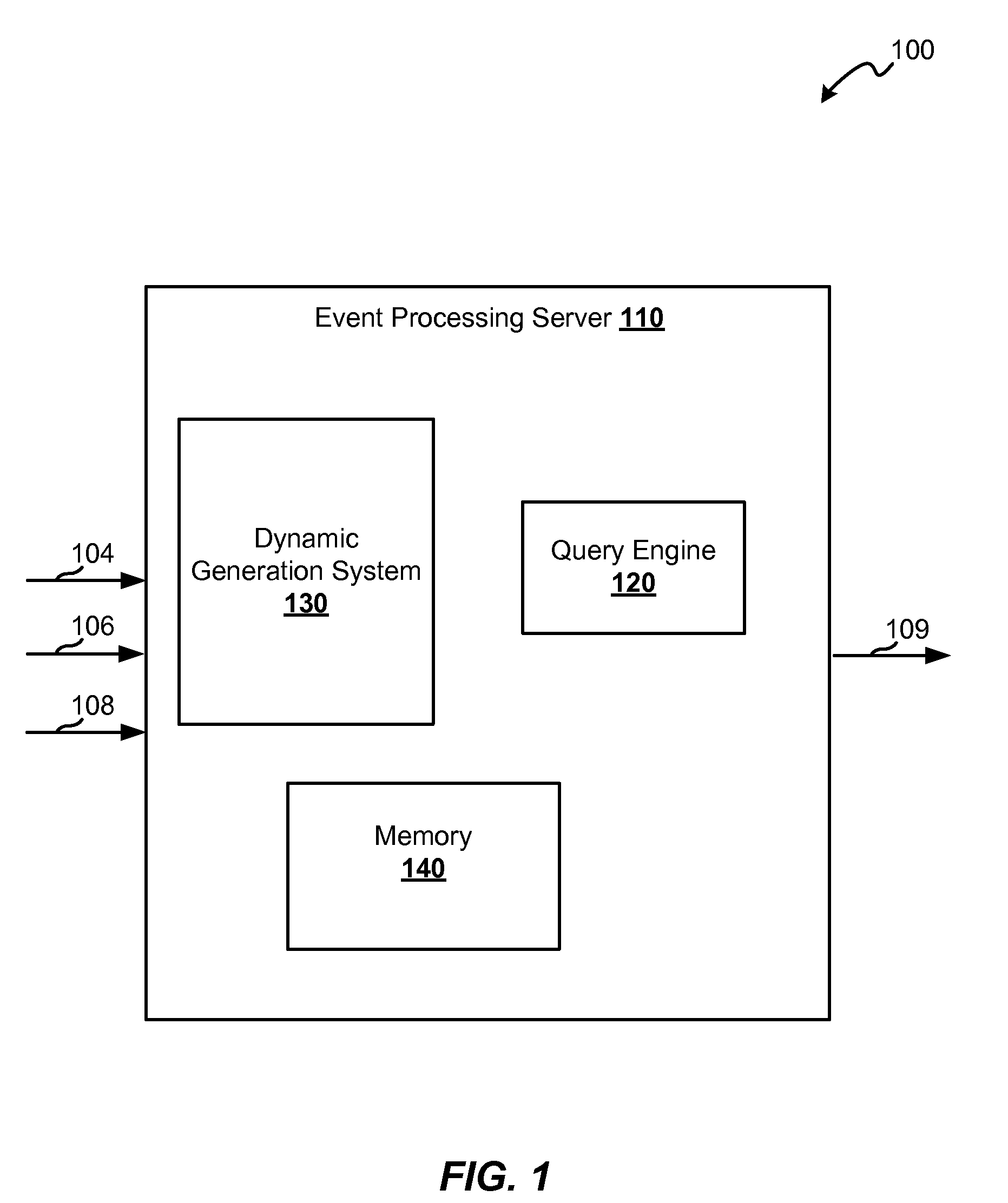
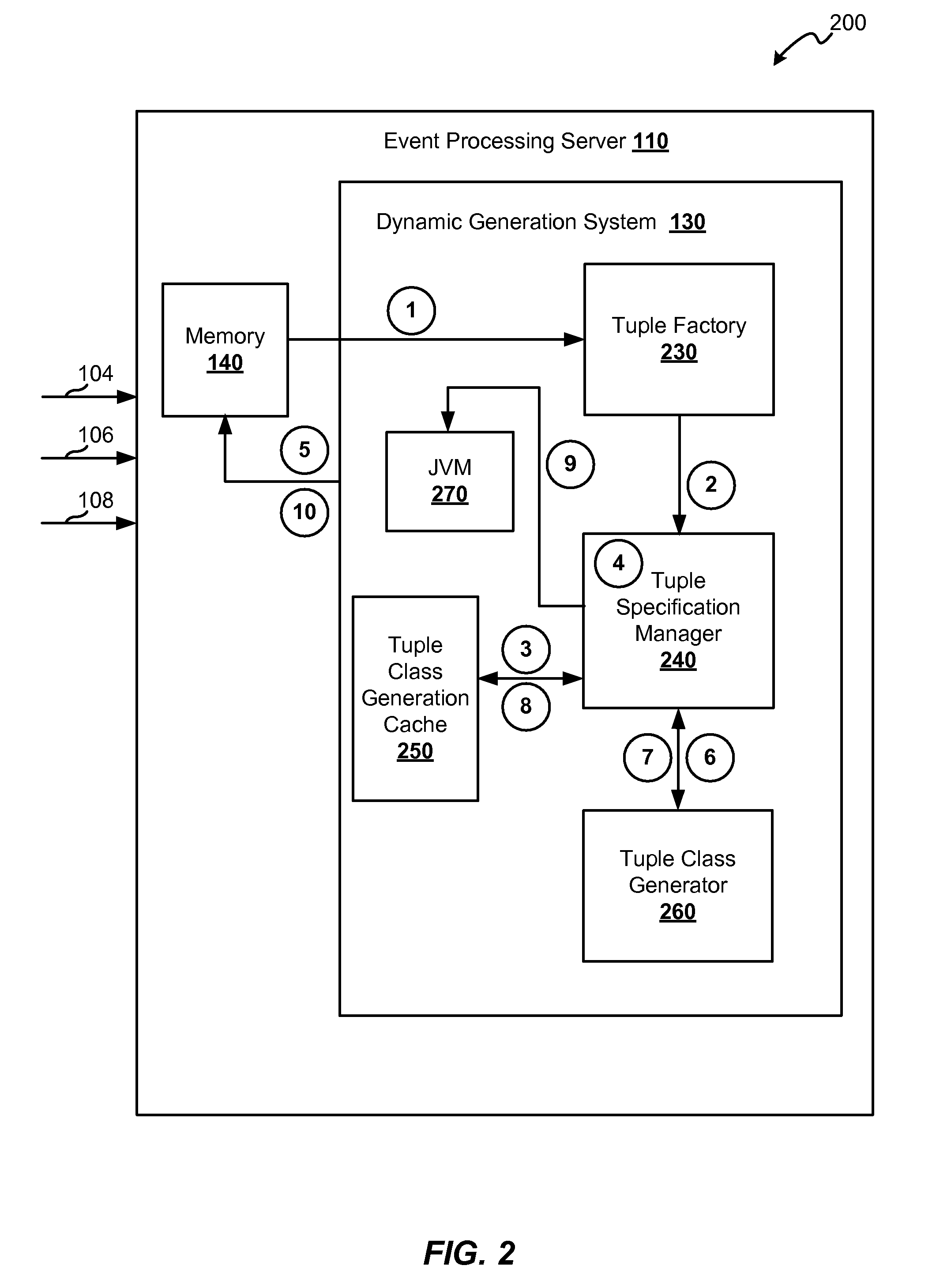
Framework for dynamically generating tuple and page classes
ActiveUS20100223606A1Reduce memoryImprove performanceSpecific program execution arrangementsMemory systemsData streamObject based
Techniques for reducing the memory used for processing events received in a data stream are provided. This may be achieved by reducing the memory required for storing tuples. A method for processing a data stream includes receiving a tuple and determining a tuple specification that defines a layout of the tuple. The layout identifies one or more data types that are included in the tuple. A tuple class corresponding to the tuple specification may be determined. A tuple object based on the tuple class is instantiated, and during runtime of the processing system. The tuple object is stored in a memory.
Owner:ORACLE INT CORP
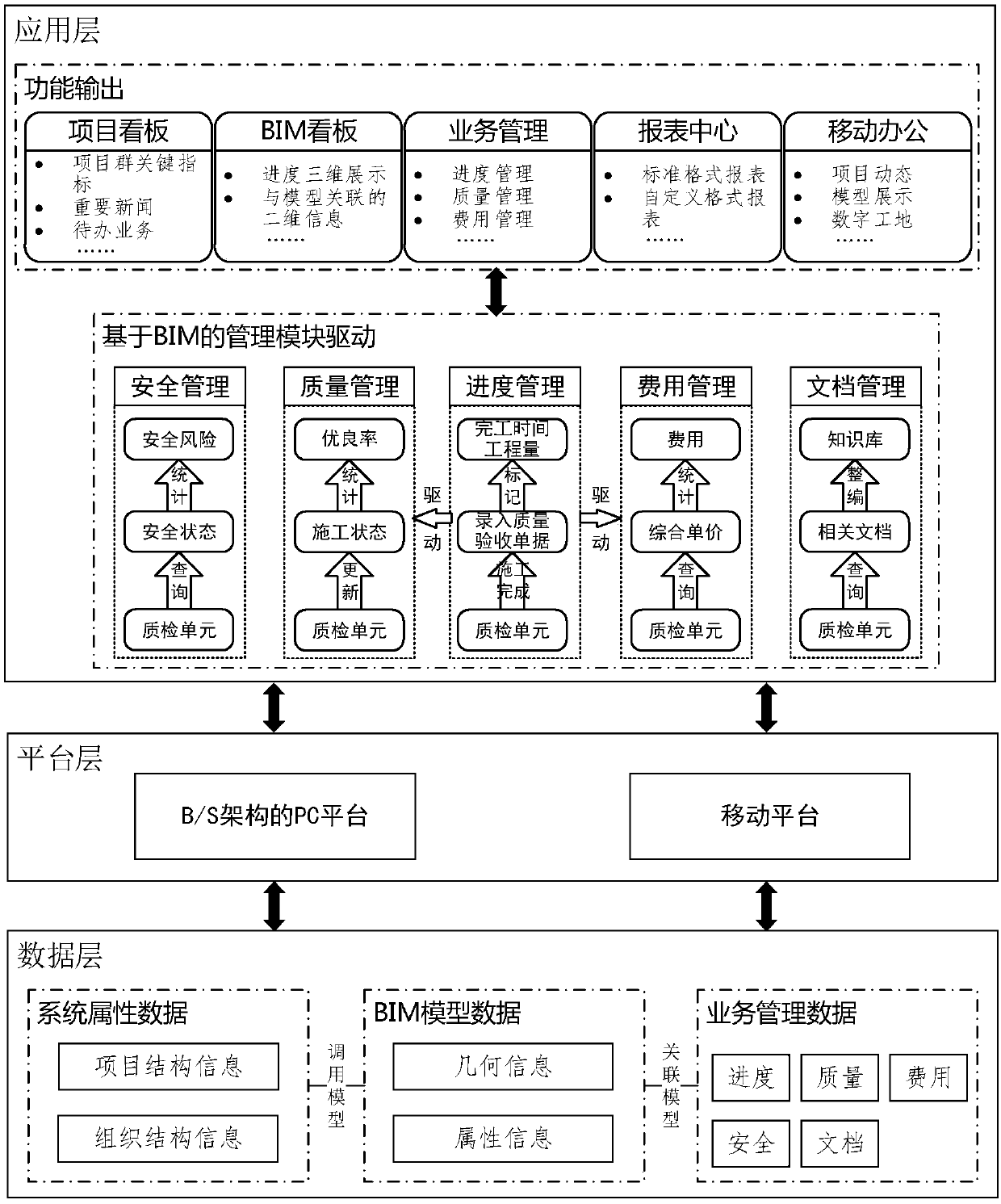
Digital management system and method for project construction processes
ActiveCN107622355AImprove acquisitionImprove circulation speedOffice automationResourcesBusiness managementProtocol Application
The invention discloses a digital management system for project construction processes. The system comprises a data layer, a platform layer and application layers, wherein the data layer comprises a BIM construction module which is created via a division principle of a construction quality management unit; the data layer comprises system attribute data, BIM model data and business management data;the platform layer consists of a B / S architecture-adopted PC platform and a mobile platform; the PC platform application layer consists of a project board module, a BIM board module, a business management module and a statement center module; a business management module comprises a progress management module, a quality management module, a safety management module, an expense management module and a document management module; and a mobile platform application layer is a mobile office layer which consists of a project dynamic module, a model display module and a digital construction site module. The system has the advantage of improving the management precision and efficiency of project construction processes.
Owner:CHANGJIANG SURVEY PLANNING DESIGN & RES
Methods and systems for running multiple operating systems in a single mobile device
ActiveUS7424601B2Reduce memory usageError detection/correctionDigital computer detailsExternal storageOperational system
Methods and systems for running multiple operating systems in a single embedded or mobile device (include PDA, cellular phone and other devices) are disclosed. The invention allows a mobile device that normally can only run a single operating system to run another operating system while preserving the state and data of the original operating system. Guest OS is packaged into special format recognizable by the host OS that still can be executed in place by the system. The Methods include: Change the memory protection bits for the original OS; Fake a reduced physical memory space for guest OS; Use special memory device driver to claim memories of host OS; Backup whole image of the current OS and data to external memory card.
Owner:INTELLECTUAL VENTURES HOLDING 81 LLC
Value-instance connectivity computer-implemented database
InactiveUS20080059412A1Reduce memory usageShorten the timeMulti-dimensional databasesSpecial data processing applicationsMulti dimensional dataData value
A computer-implemented database and method providing an efficient, ordered reduced space representation of multi-dimensional data. The data values for each attribute are stored in a manner that provides an advantage in, for example, space usage and / or speed of access, such as in condensed form and / or sort order. Instances of each data value for an attribute are identified by instance elements, each of which is associated with one data value. Connectivity information is provided for each instance element that uniquely associates each instance element with a specific instance of a data value for another attribute. In accordance with one aspect of the invention, low cardinality fields (attributes) may be combined into a single field (referred to as a “combined field”) having values representing the various combinations of the original fields. In accordance with another aspect of the invention, the data values for several fields may be stored in a single value list (referred to as a “union column”). Still another aspect of the invention is to apply redundancy elimination techniques, utilizing in some cases union columns, possibly together with combined fields, in order to reduce the space needed to store the database.
Owner:TARIN STEPHEN A
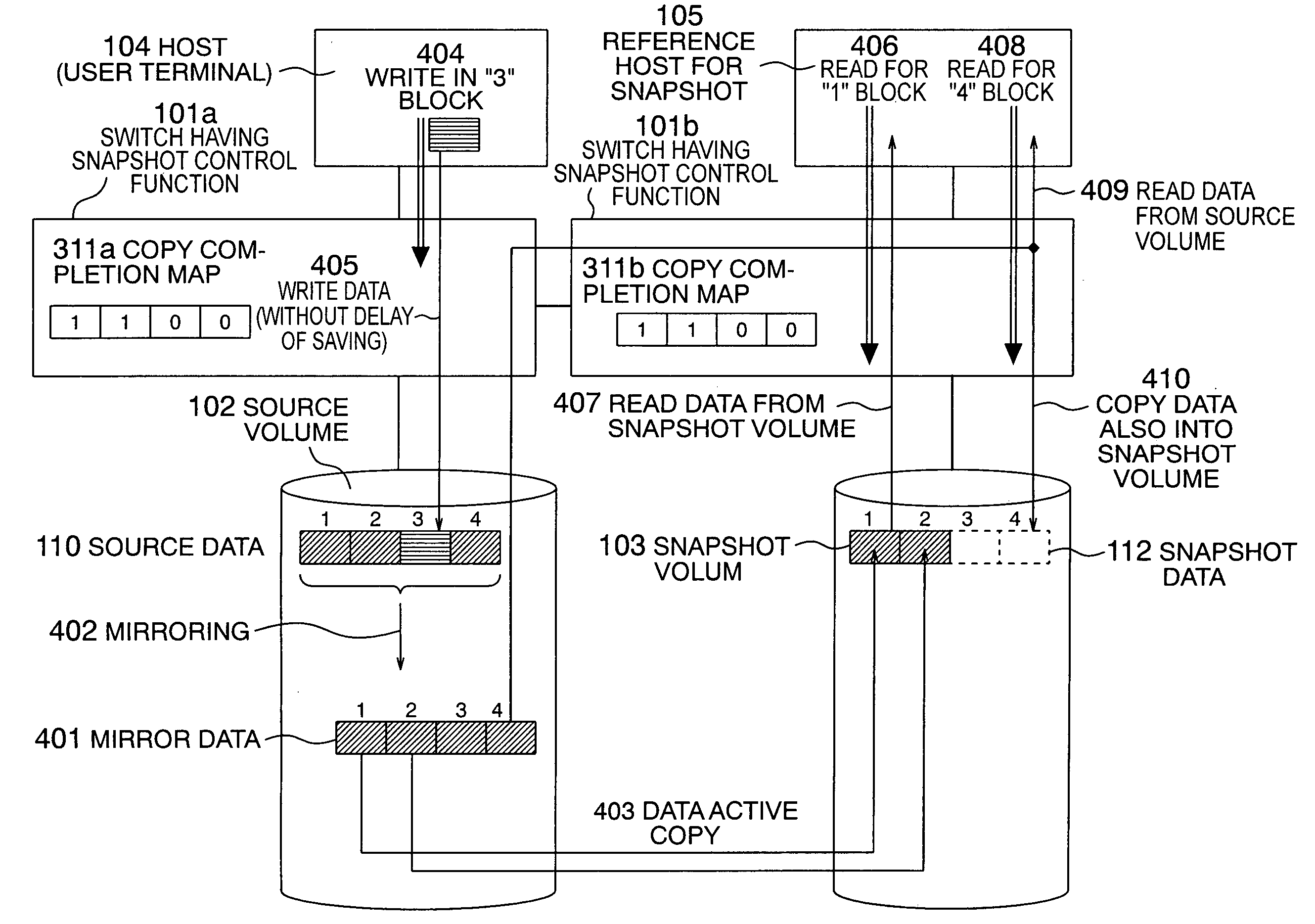
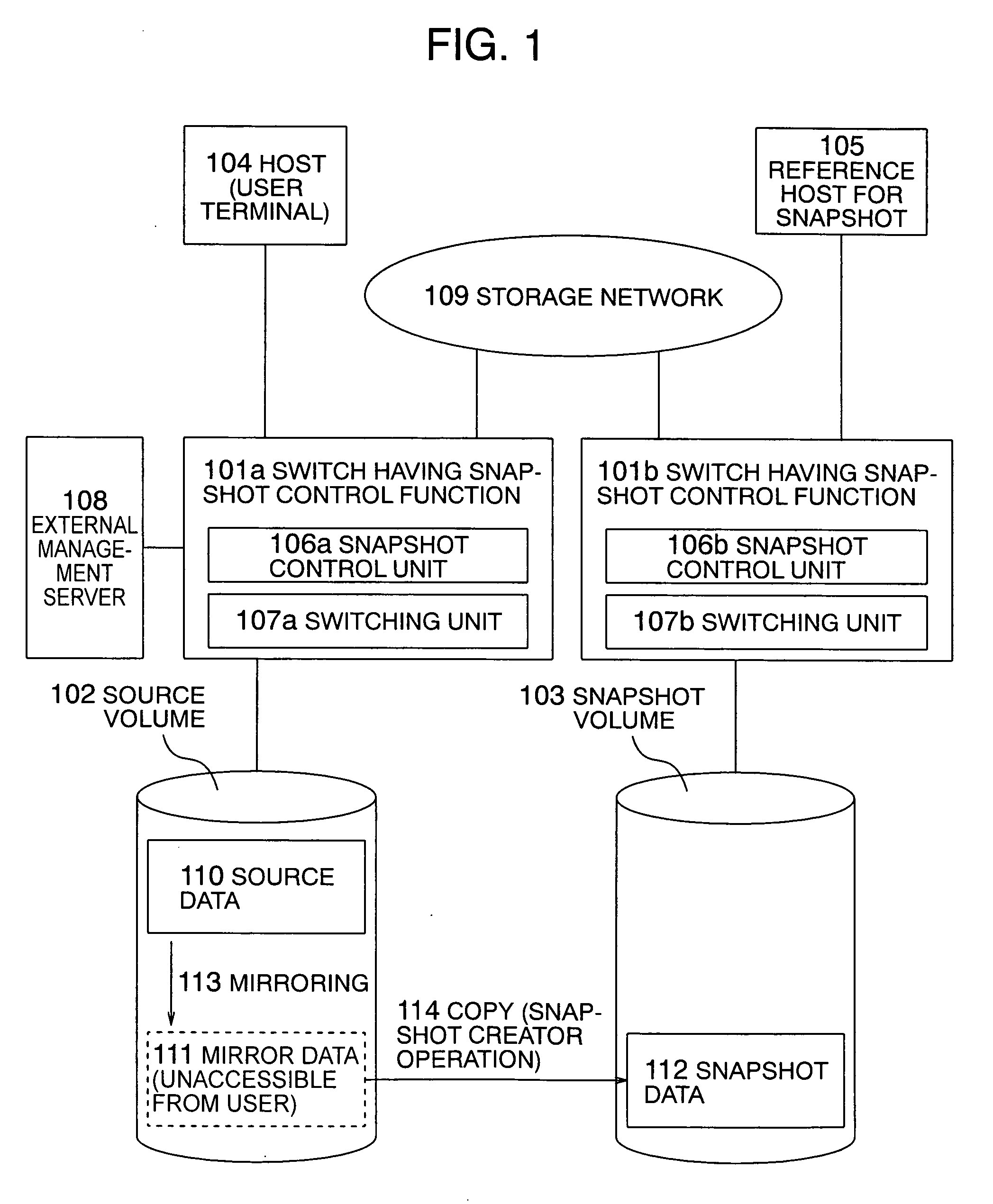
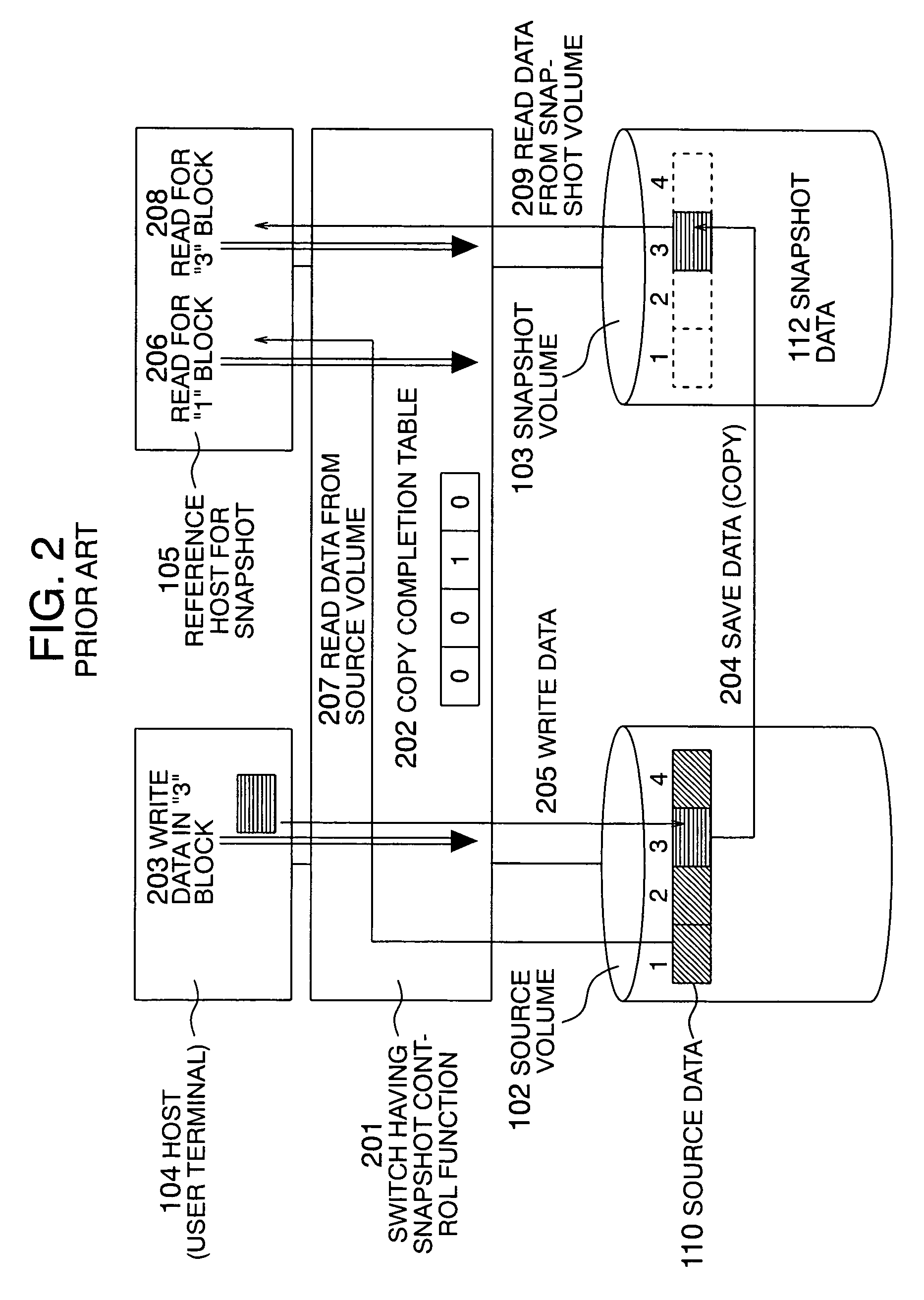
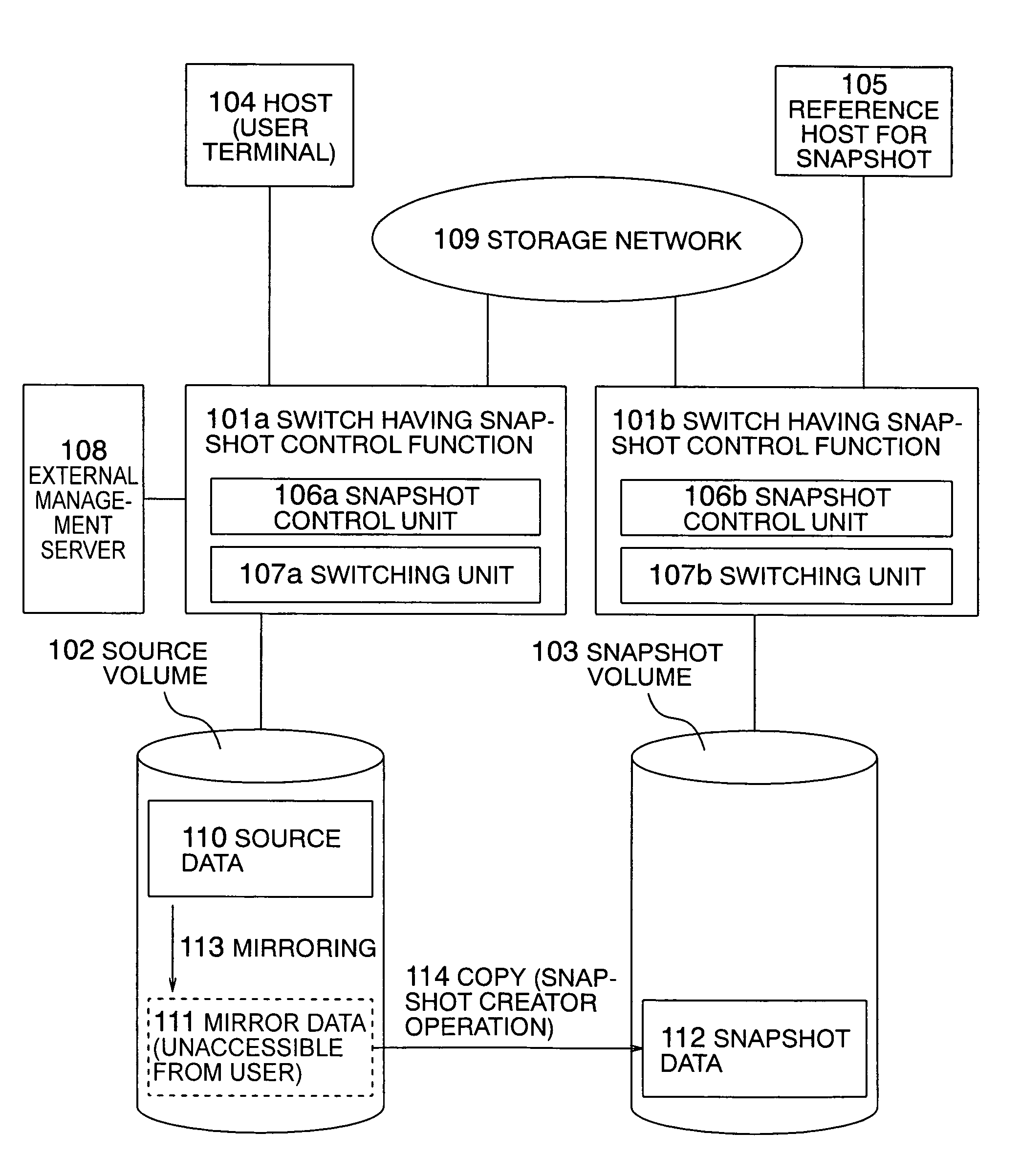
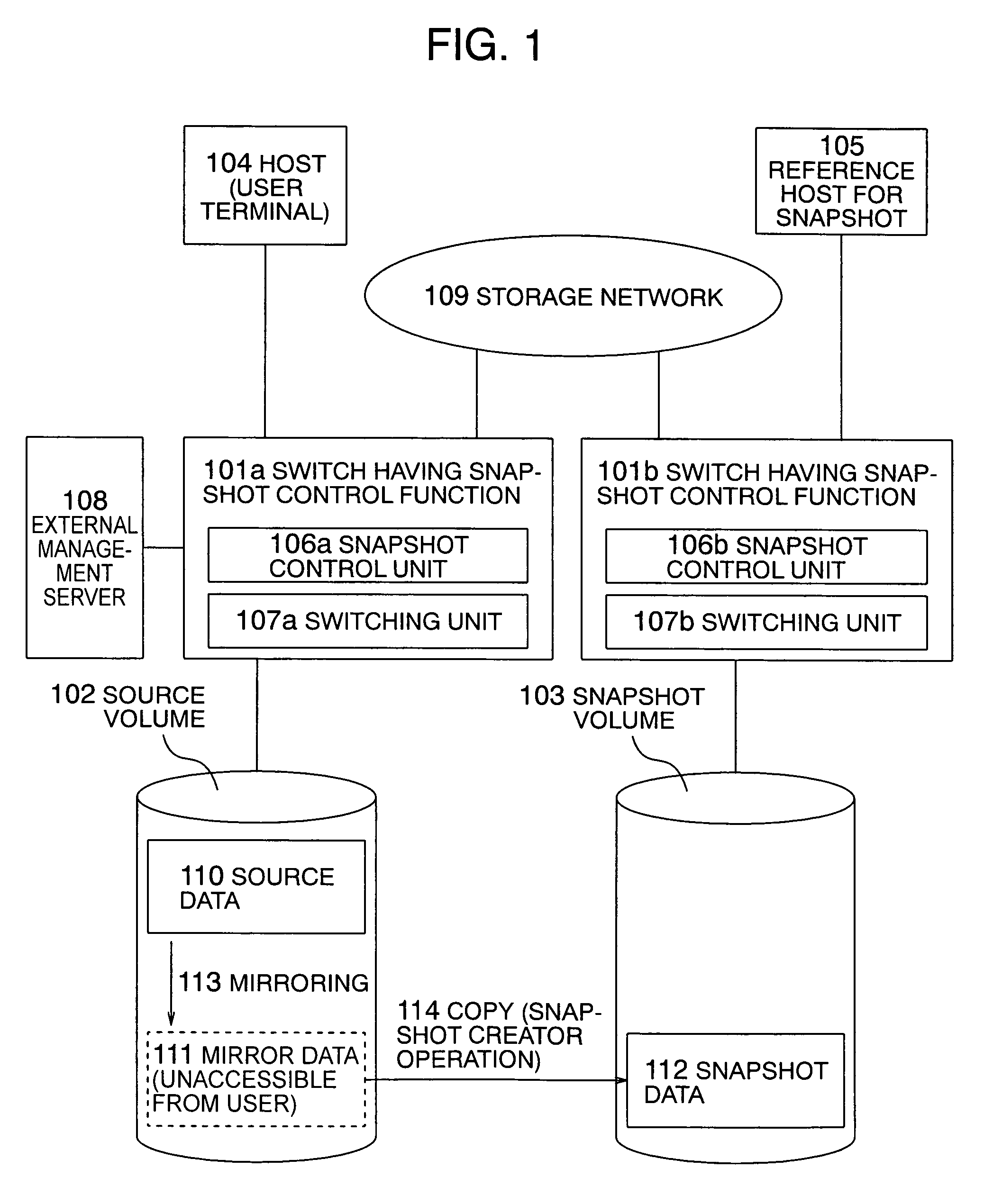
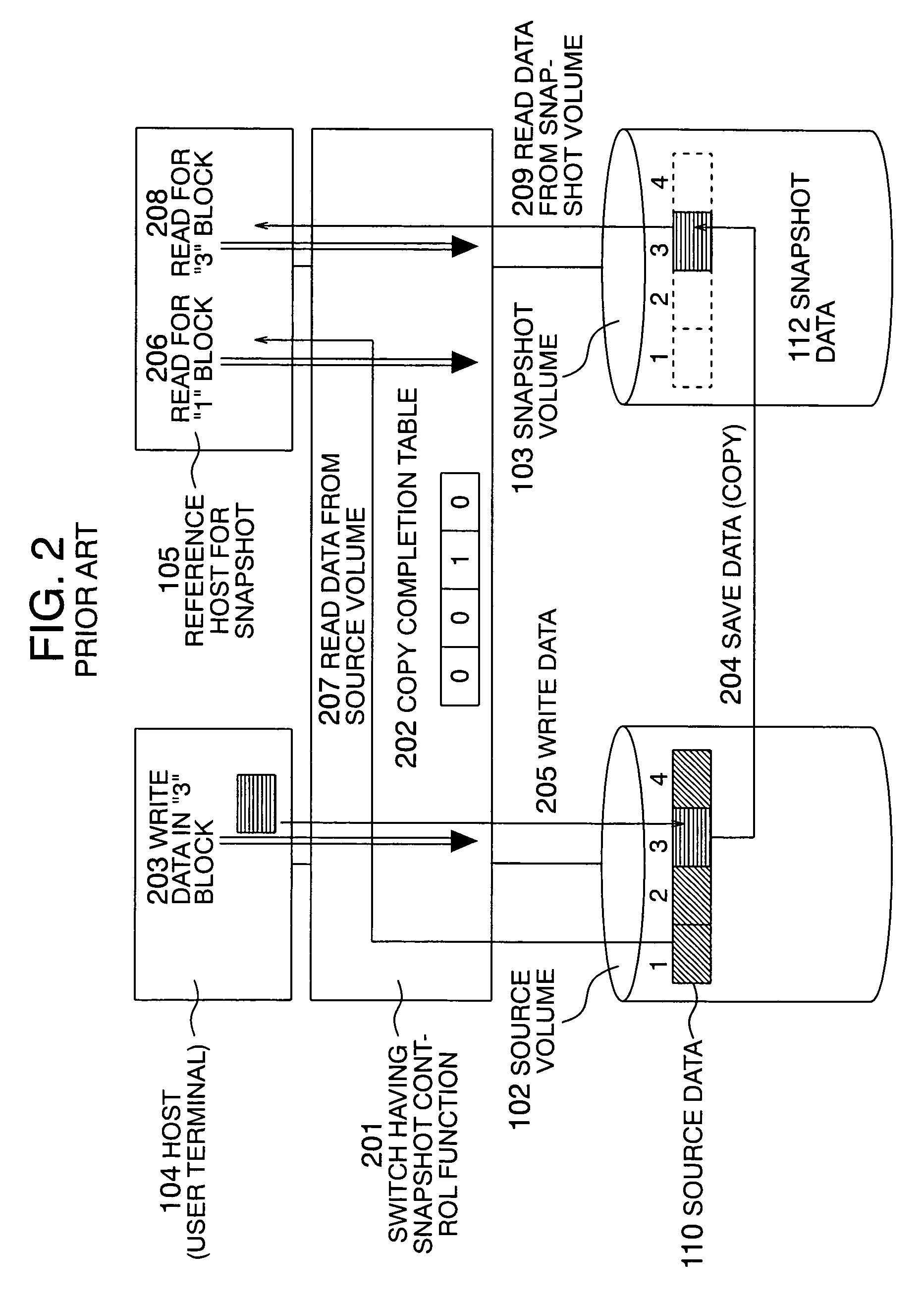
Method for acquiring snapshot
InactiveUS20050138312A1Reduce memory usageInput/output to record carriersMemory loss protectionTerm memoryMirror image
In a storage switch to control a snapshot operation in the file unit, the delay in the writing operation of a host due to a data saving operation is prevented. In a snapshot acquiring method, the memory usage in a switch is reduced to create a snapshot. The storage switch includes a function to create a snapshot of a file. To prevent occurrence of delay due to the data saving operation, a mirror of source data as a snapshot target is kept in a source volume in any situation or according to a predetermined condition with synchronization established between the mirror and the source data. In the creation of the snapshot, the mirror data is used. By creating the mirror data in sequential positions in the source volume, the positional correspondence between the source side and the snapshot side is simplified.
Owner:HITACHI LTD
Method for acquiring snapshot
InactiveUS7325110B2Reduce memory usageInput/output to record carriersMemory loss protectionOperating systemSource data
Owner:HITACHI LTD
Extended finite state automata and systems and methods for recognizing patterns using extended finite state automata
Deterministic finite automata (DFAs) are popular solutions to deep packet inspection because they are fast and DFAs corresponding to multiple signatures are combinable into a single DFA. Combining such DFAs causes an explosive increase in memory usage. Extended finite automata (XFAs) are an alternative to DFAs that avoids state-space explosion problems. XFAs extend DFAs with a few bytes of “scratch memory” used to store bits and other data structures that record progress. Simple programs associated with automaton states and / or transitions manipulate this scratch memory. XFAs are deterministic in their operation, are equivalent to DFAs in expressiveness, and require no custom hardware support. Fully functional prototype XFA implementations show that, for most signature sets, XFAs are at least 10,000 times smaller than the DFA matching all signatures. XFAs are 10 times smaller and 5 times faster or 5 times smaller and 20 times faster than systems using multiple DFAs.
Owner:WISCONSIN ALUMNI RES FOUND
Unmanned aerial vehicle trajectory planning method based on EB-RRT
InactiveCN107085437AFast convergenceReduce traversal timeNavigational calculation instrumentsComplex mathematical operationsTrajectory planningInsertion point
Owner:ZHEJIANG UNIV OF TECH
System and method for distributing route selection in an implementation of a routing protocol
ActiveUS7023808B2Reduce memory usageOvercome disadvantagesError preventionTransmission systemsPathPingData pack
Owner:CISCO TECH INC
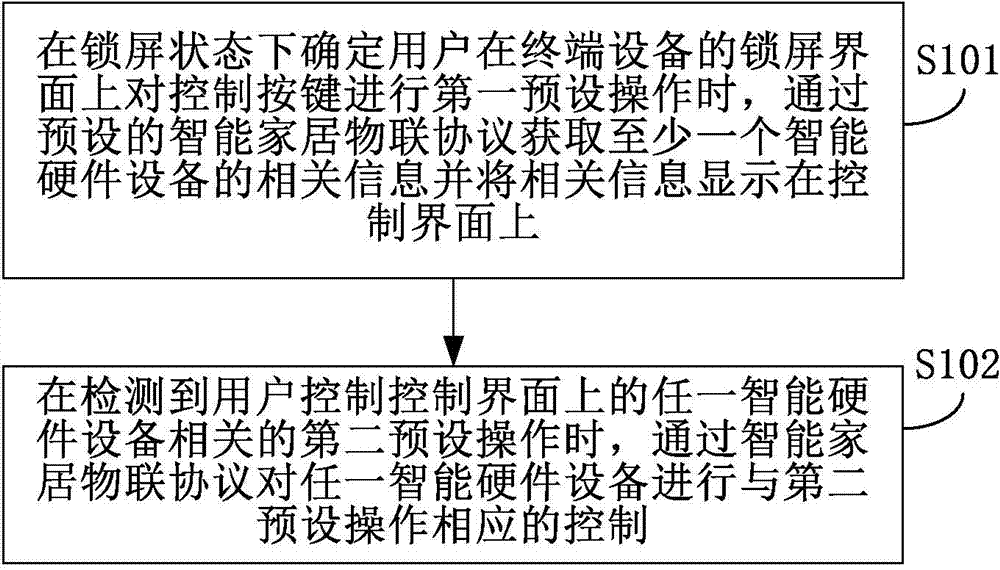
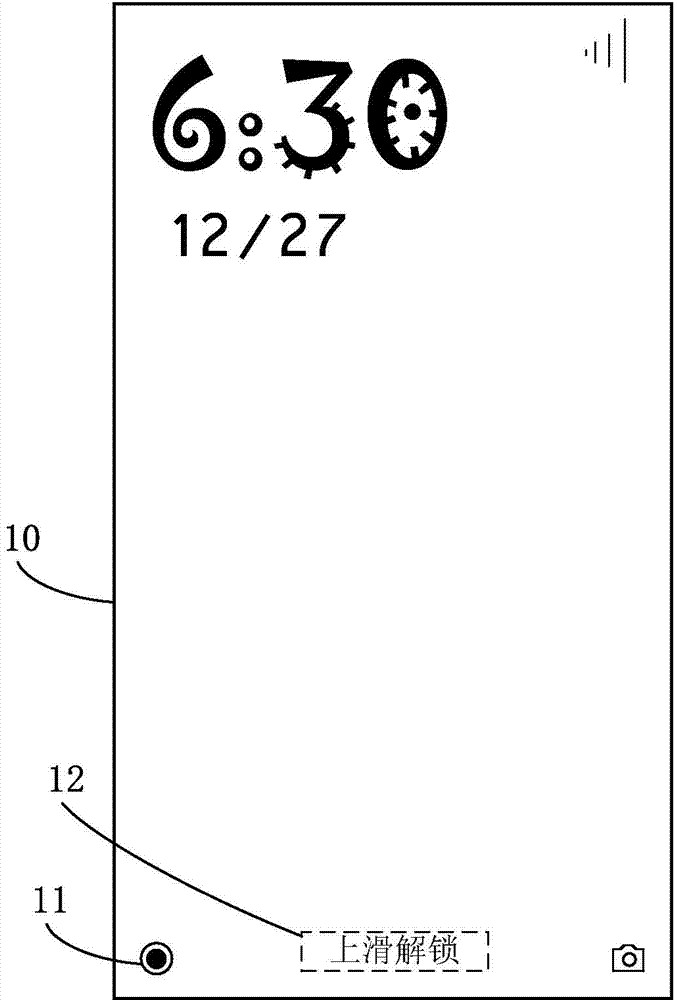
Intelligent hardware device control achieving method and device
ActiveCN104503688AReduce memory usageReduce battery consumptionProgramme controlComputer controlRelevant informationTerminal equipment
The invention relates to an intelligent hardware device control achieving method and device which aims at simplifying control operation of a user on an intelligent hardware device. The method includes acquiring relevant information of at least one intelligent hardware device through the preset intelligent home thing network protocol when determining that the user conducts first preset operation on a control key on a lock screen interface of a terminal device in the lock screen state and displaying the relevant information on the control interface; conducting controlling corresponding to second preset operation on the intelligent hardware device through the intelligent home thing network protocol when detecting that the user controls the second preset operation relevant to any intelligent hardware device on the control interface. By means of the method and device, the shortcoming that the user unlocks the terminal device and then enters the corresponding intelligent hardware applications to control the intelligent hardware device is overcome, the control operation process of the intelligent hardware device is simplified, and the intelligent hardware device can be controlled conveniently in the lock screen state of the terminal device.
Owner:XIAOMI INC
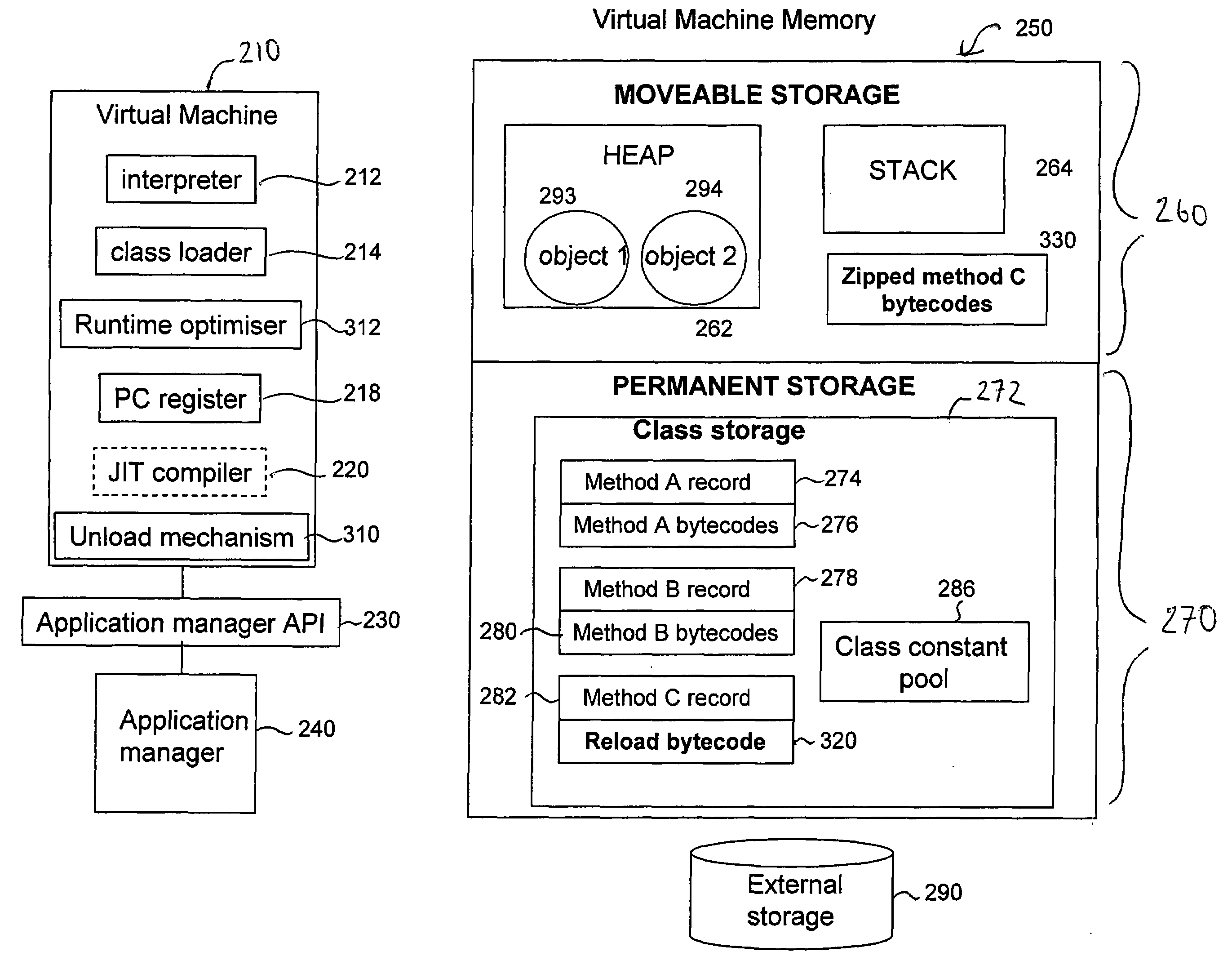
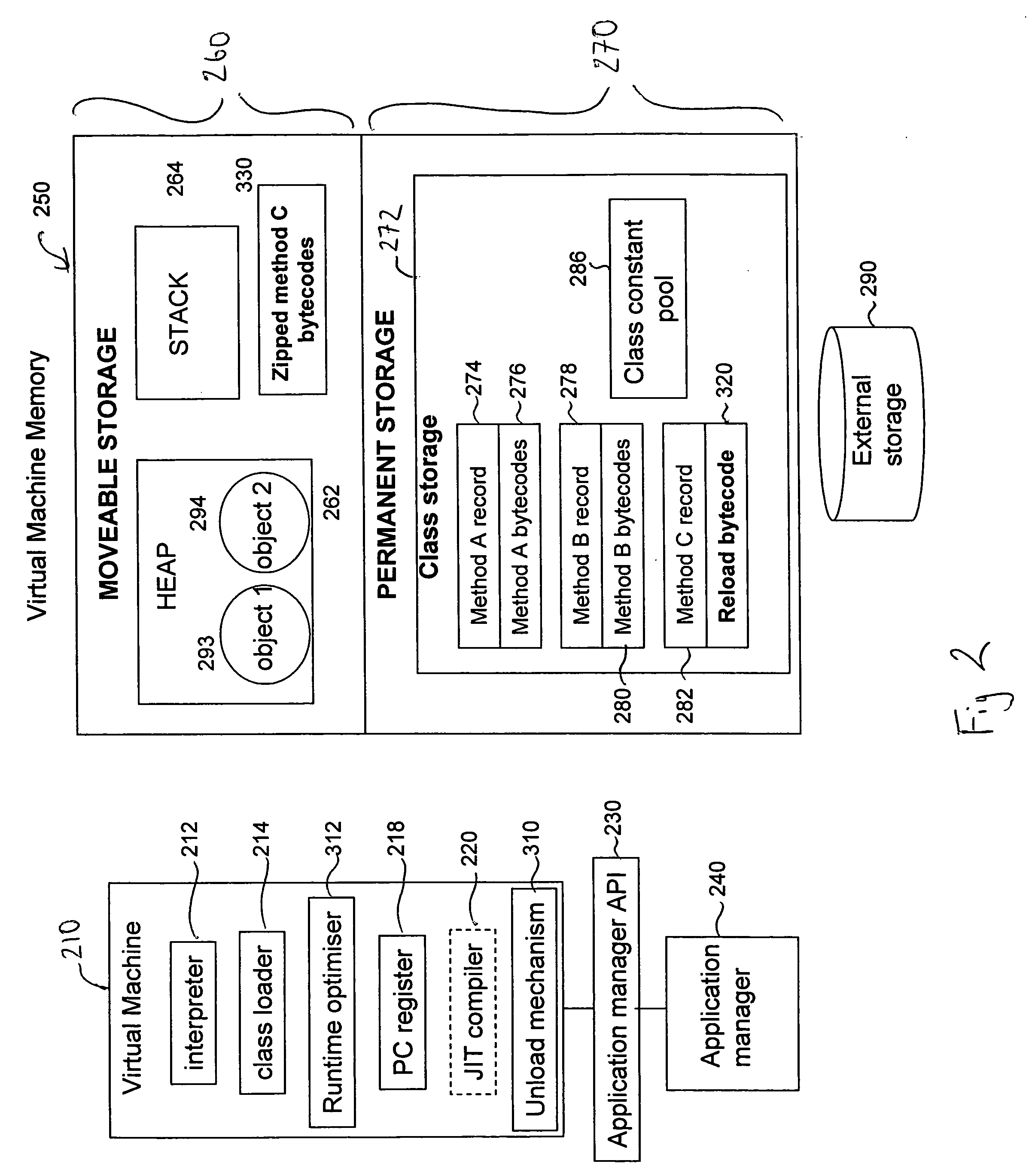
Reducing memory usage of a data processing task performed using a virtual machine
ActiveUS20090204963A1Affect performance of processReduce impactSoftware simulation/interpretation/emulationSpecial data processing applicationsVirtual machineProgram code
A method of performing a processing task in a data processing apparatus is provided that reduces memory usage of the processing task. According to this method a Virtual Machine performs the steps of accessing platform-neutral program code in a function repository, executing the processing task on the Virtual Machine and analysing at a current execution point on a function-by-function basis which functions in the function repository are inactive functions. The Virtual Machine performs software-based unloading from the function repository of at least a portion of platform-neutral program code corresponding to one or more inactive functions. A corresponding virtual machine and data processing apparatus are also provided.
Owner:ARM LTD
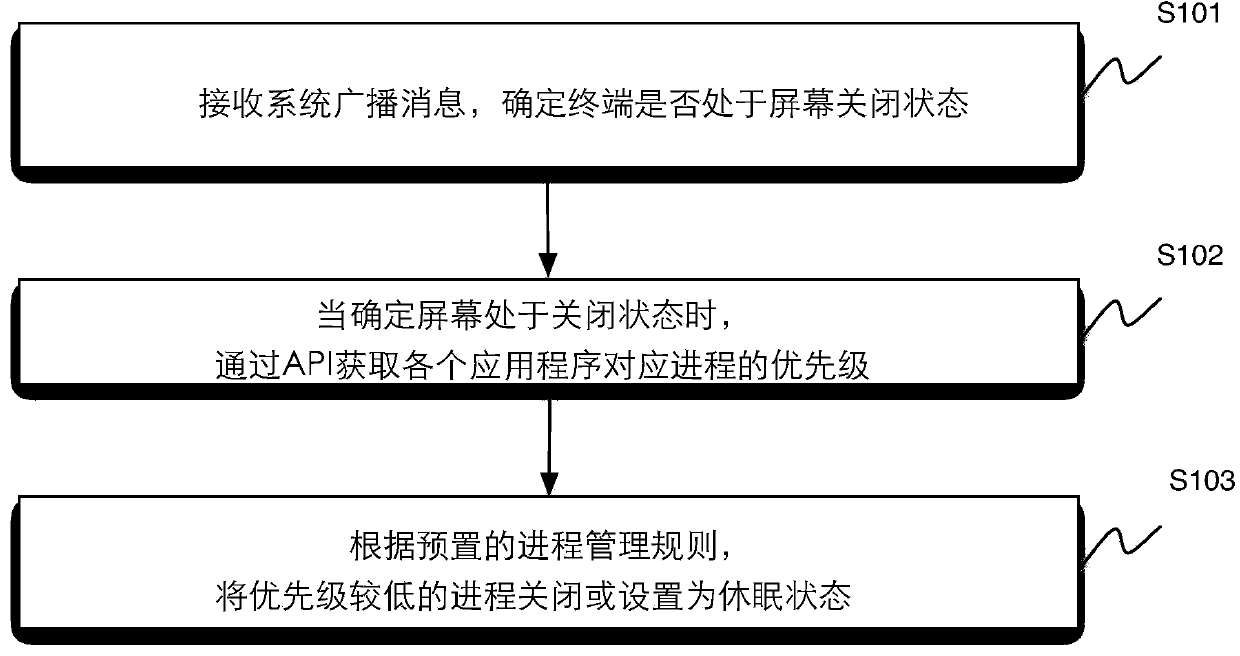
Method and device for managing application program processes
ActiveCN104199669AReduce memory usageReduce battery consumptionPower supply for data processingSpecific program execution arrangementsInternal memorySleep state
The invention discloses a method and device for managing application program processes. The method includes: a receiving system broadcasts a message to determine whether the screen of a terminal is closed or not; when the screen is closed, the process identification of each application program is traversed through an application program calling interface so as to find the process importance index of each application process, and the process priority of each application program is determined according to the process importance index; the processes with low priority are closed or set into a sleep state according to preset process managing rules. The method has the advantages that the processes with low priority are closed or set into the sleep state according to the priority of the processes, the processes with low priority are set into sleep preferably after screen locking, and accordingly internal memory space is saved, and power consumption is reduced.
Owner:BEIJING QIHOO TECH CO LTD
Method of locating areas in an image such as a photo mask layout that are sensitive to residual processing effects
InactiveUS7155698B1Lower matching requirementsReduce memory usageImage enhancementImage analysisPattern recognitionComputer graphics (images)
Owner:RGT UNIV OF CALIFORNIA
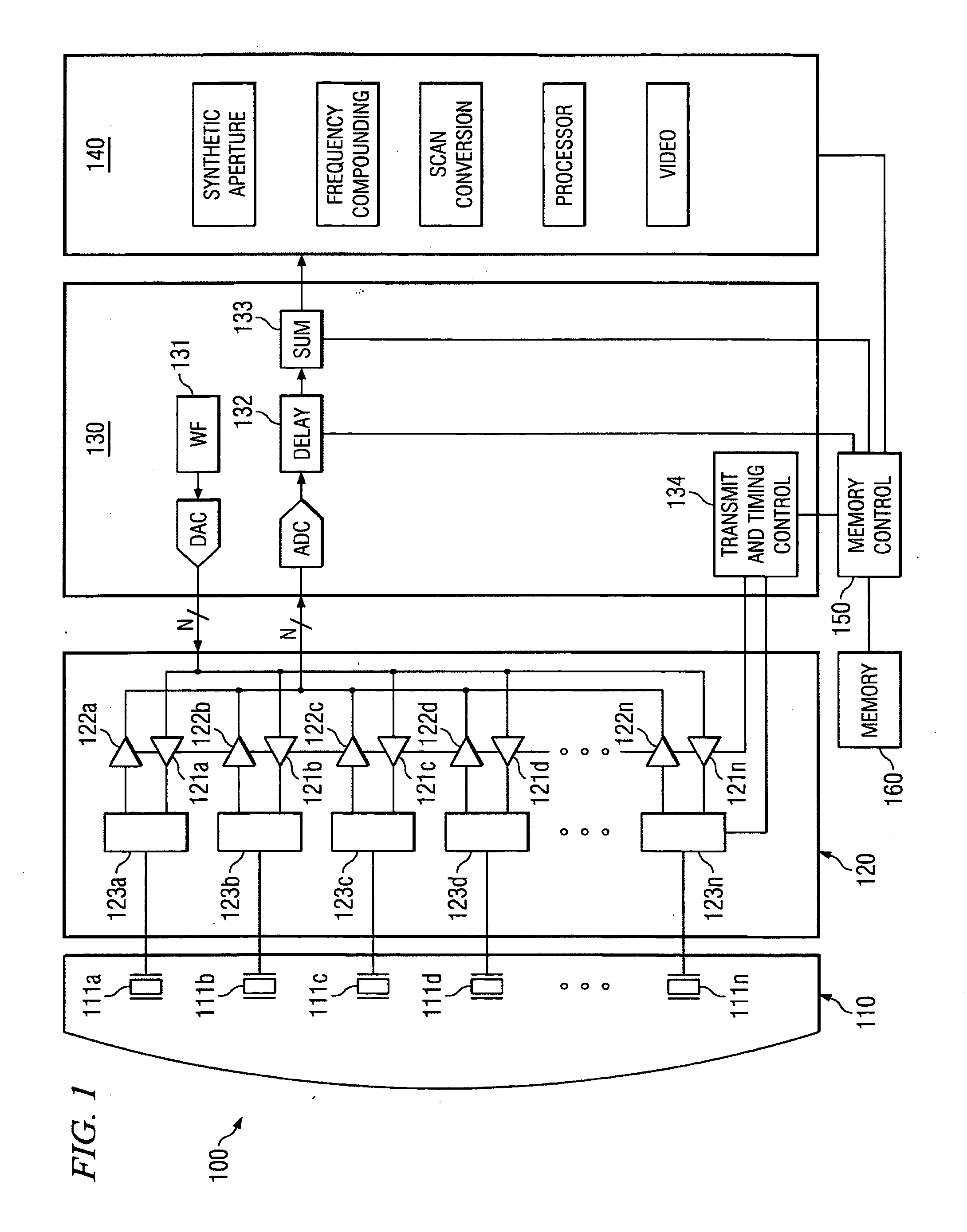
Systems and methods for ultrasound beam forming data control
ActiveUS20120195161A1Reduce memory usageImprove data transfer rateSound producing devicesPhotographyData controlSonification
Disclosed are systems and methods which efficiently control storage of and / or access to data which includes repetitive data or data which is used by different modes, processes, etcetera. Embodiments provide control for storage of and / or access to large amounts of data used in ultrasound system beam forming for image generation using a hierarchy of sequencers for controlling storage of and / or access to data. A frame sequencer may provide control at a frame level while an address sequencer is implemented to provide control at a data access level.
Owner:FUJIFILM SONOSITE
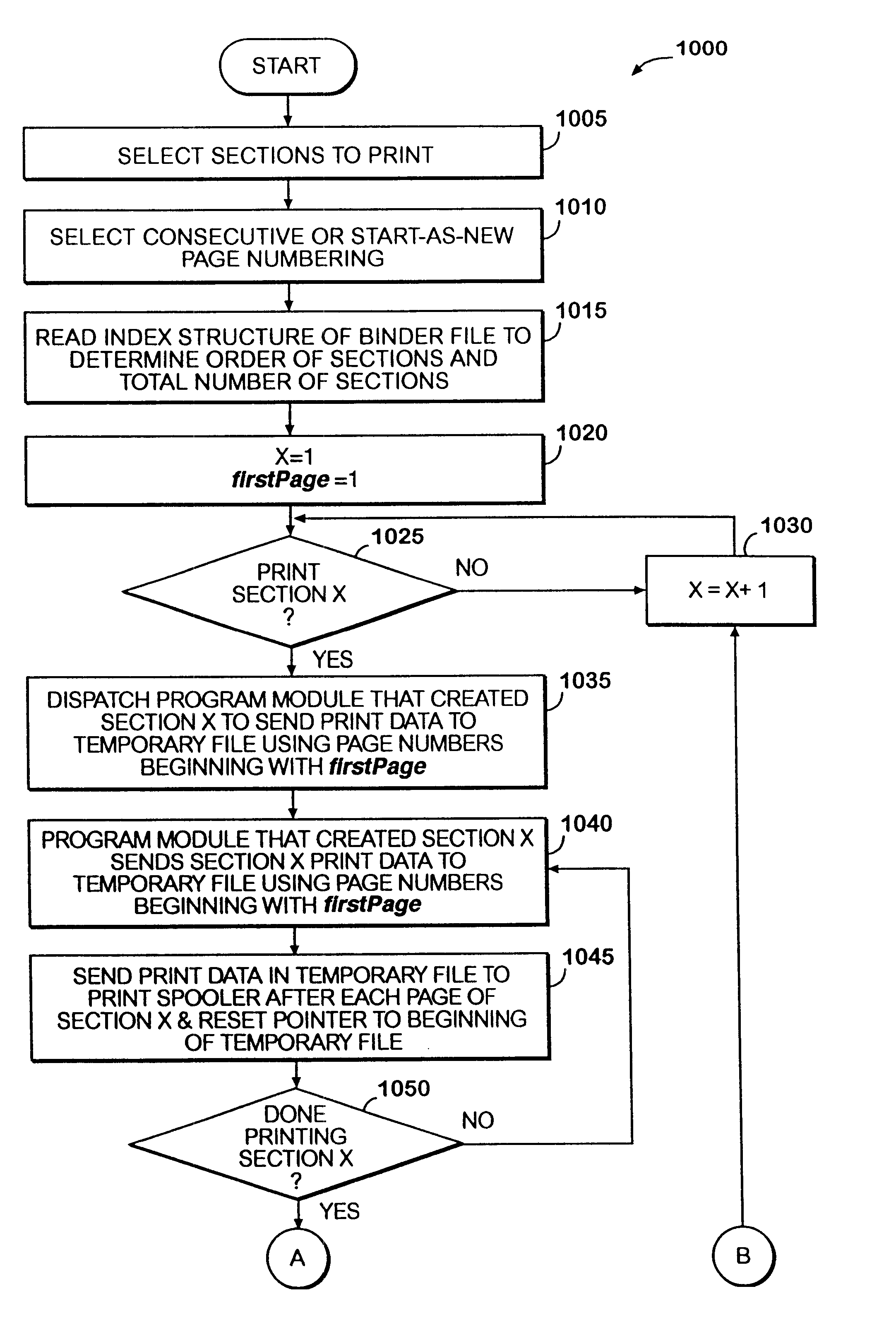
System and method for printing ordered sections having different file formats
InactiveUS6393441B1Reduce memory usageWaste memory resourceSpecial data processing applicationsDocument management systemsDocumentationDocument section
Ordered binder document sections having different file formats stored within a binder file. The binder file maintains the order of binder document sections and the native file format of each section. The binder program module can dispatch the underlying application program modules that created each binder document section to print the binder document sections as a single uninterrupted print job. In this manner, selected sections of a binder document can be printed as a single consecutively printed document without having other print jobs interrupting or intervening between printed sections of the binder document.
Owner:MICROSOFT TECH LICENSING LLC
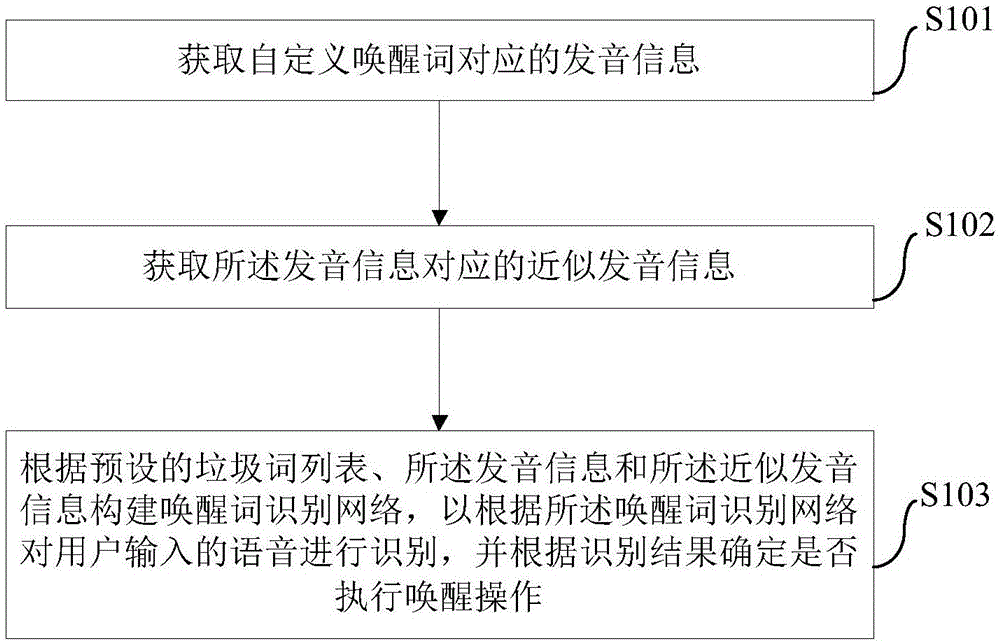
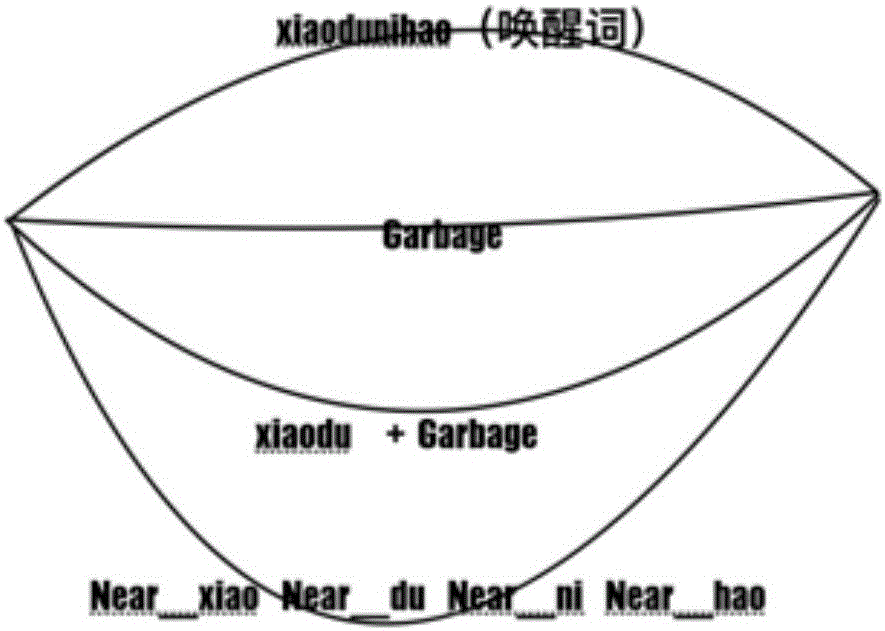
Voice wakeup method and voice wakeup device based on artificial intelligence
ActiveCN106611597AEasy to spread outReduce occupancySpeech recognitionSpeech synthesisMemory footprintWord list
The invention proposes a voice wakeup method and a voice wakeup device based on artificial intelligence. The voice wakeup method comprises the following steps: acquiring pronunciation information corresponding to a custom wakeup word; acquiring approximate pronunciation information corresponding to the pronunciation information; and building a wakeup word recognition network according to a preset spam word list, the pronunciation information and the approximate pronunciation information so as to recognize voice input by a user according to the wakeup word recognition network and determine whether or not need to perform a wakeup operation according to the recognition result. According to the embodiments of the invention, a wakeup word recognition network can be built dynamically for different custom wakeup, so that the accuracy of wakeup is enhanced effectively, the rate of false alarm is reduced, and the wakeup efficiency is improved. The device has smaller memory footprint and low power consumption.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
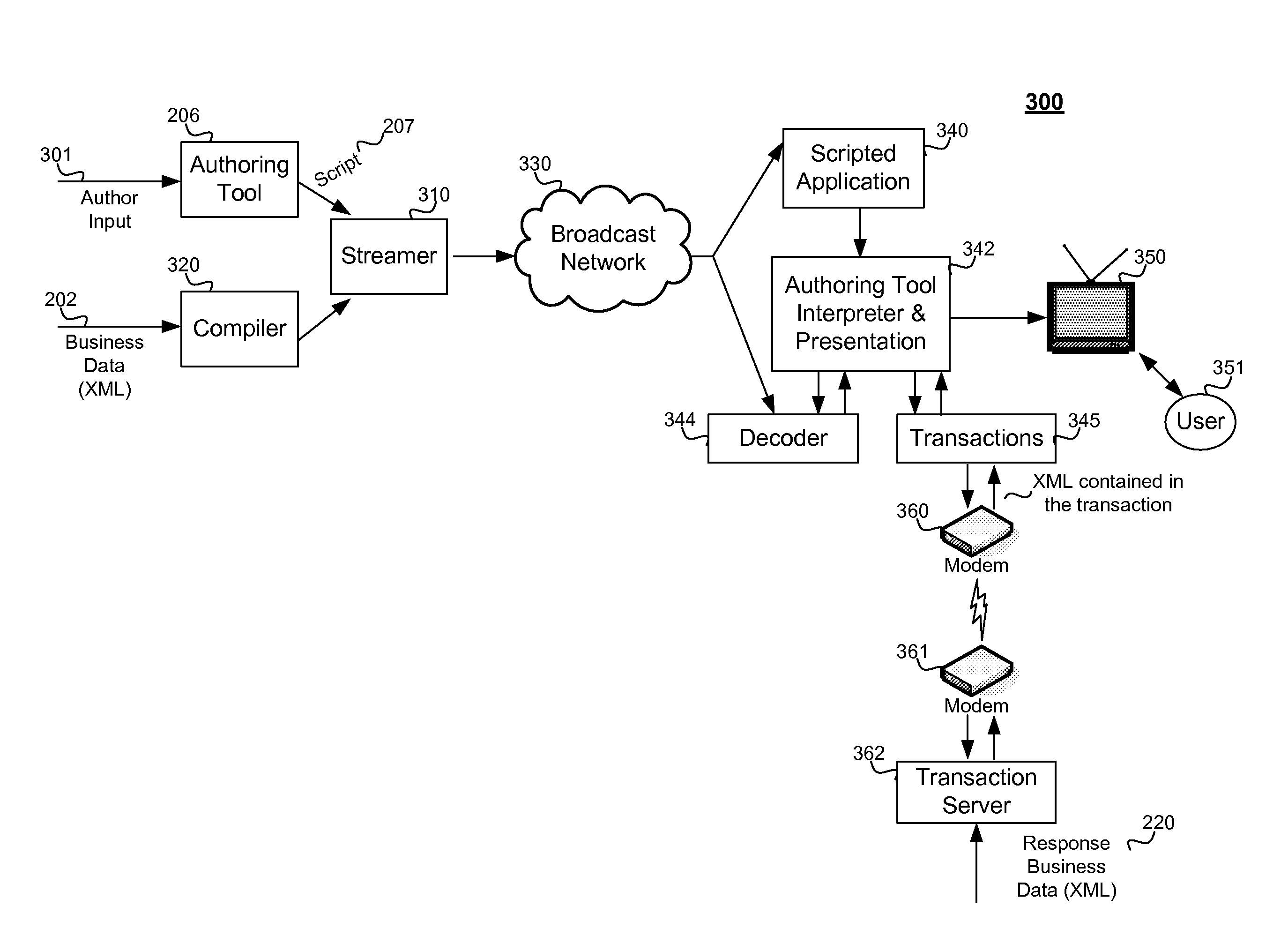
Interactive media presentation system for presenting business data over a digital television network
ActiveUS7516468B1Improve access speedReduce memory usageTelevision system detailsColor television detailsMemory footprintApplication software
The method includes steps for creating and updating an interactive television application, which includes business data and other interactive and dynamic data which changes frequently over time. The interactive television application and data is transmitted over a television broadcast network, and the method includes steps for presenting the data to the user. Business data is compiled into a binary form, the business data for example comprising descriptions of products. A description of an interactive application is generated using an authoring tool. The authoring tool allows a creative designer to create page layouts and use simple script to specify how to respond to user interactions. The compiled business data and the script are streamed to a receiver for generating video information for a user's television, wherein the receiver uses the script to access the compiled business data and generate a presentation of the data for the user. The receiver can be a set-top box for use with a cable television provider, a terrestrial television provider or a satellite television provider. The business data can be compatible with a version of XML (extensible markup language). The business data can be referenced within script created using an authoring tool without the instances of the business data being present at the time of authoring. The compiling can be configured to improve the access speed of the receiver to the business data and to reduce a memory footprint of the business data on the receiver. The business data can be updated and recompiled without requiring the application to be re-authored manually.
Owner:ORACLE INT CORP
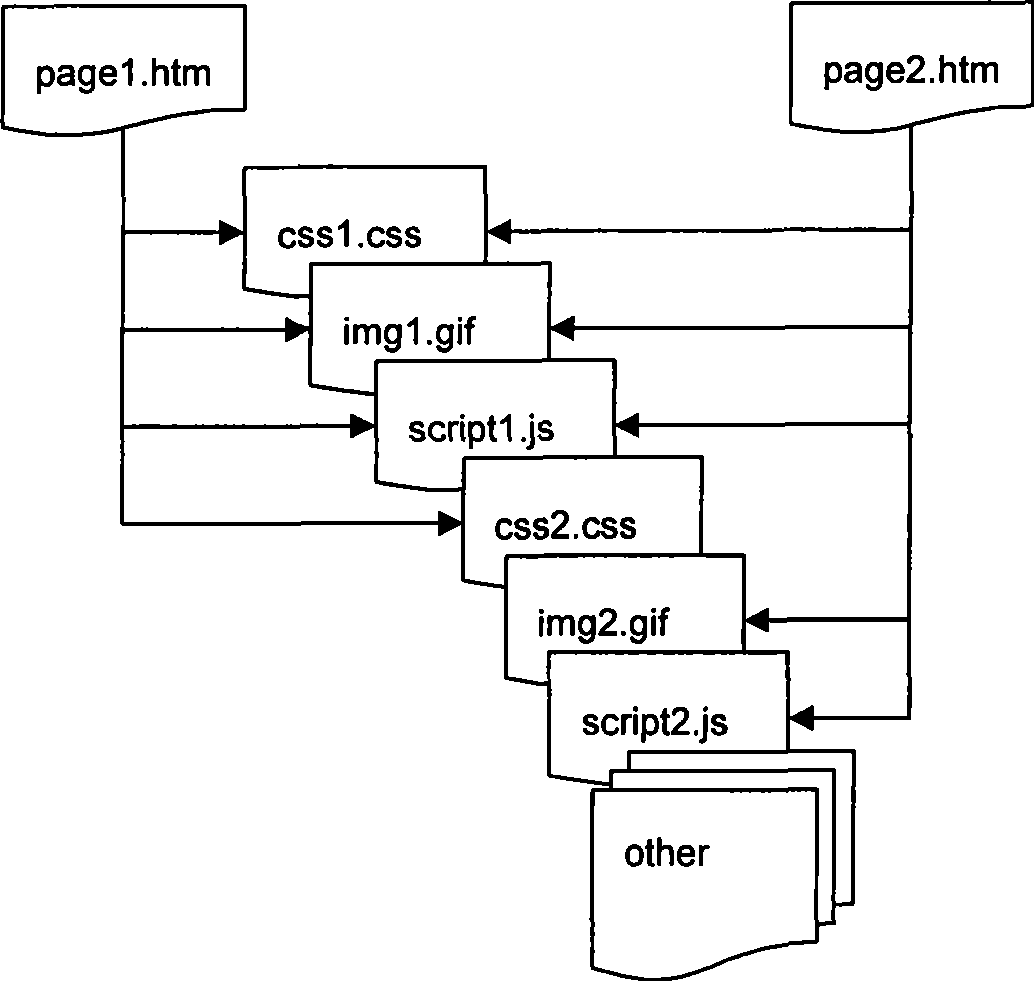
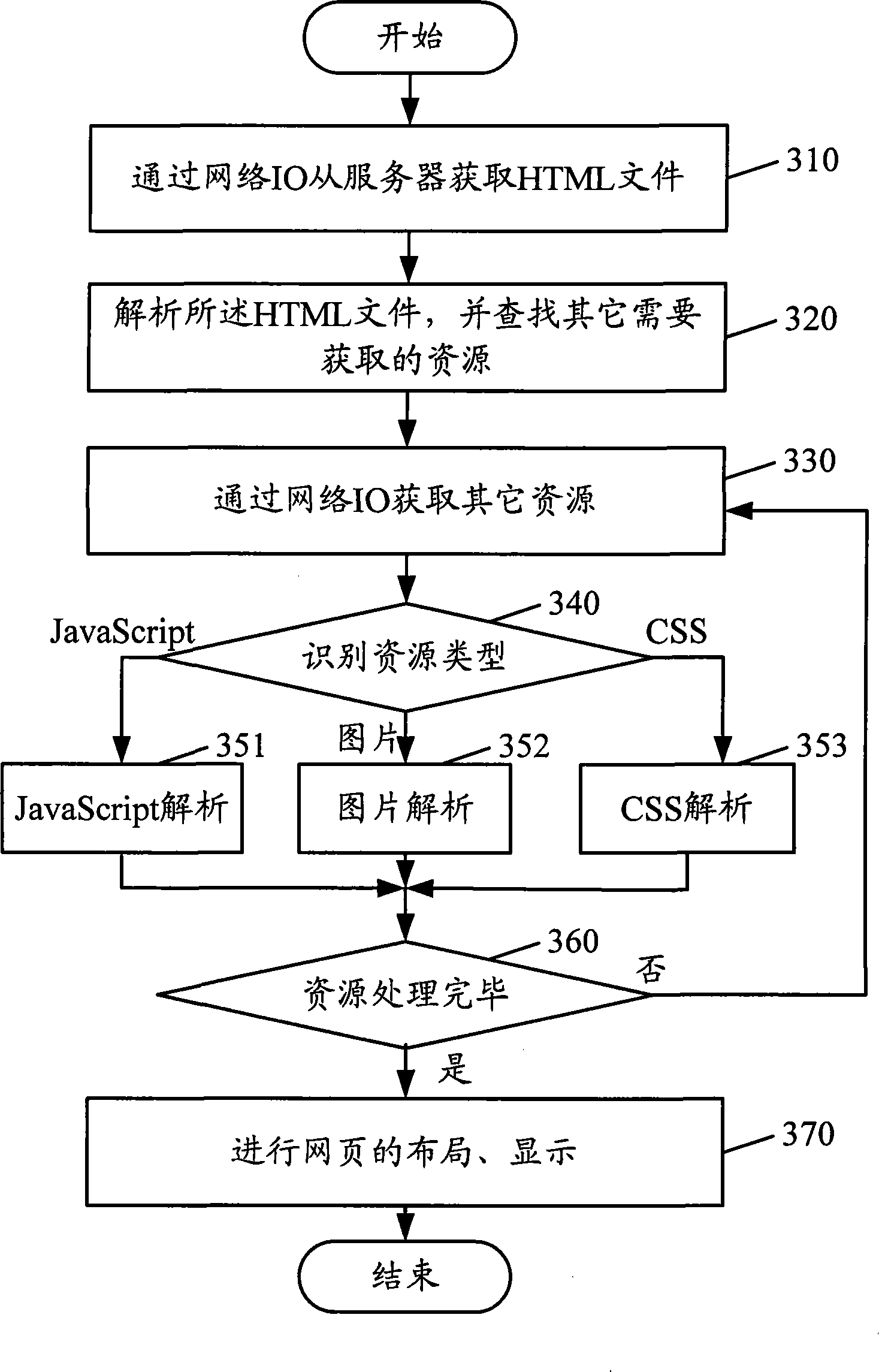
Web page loading method and device
InactiveCN101382958AAvoid reparsingImprove loading timeWebsite content managementSpecial data processing applicationsMemory footprintWeb page
The embodiment of the invention discloses a webpage loading method and a webpage loading device. The method includes the following steps: whether resource analysis data corresponding to resources to be loaded exists is judged and the resource analysis data is directly loaded if so; otherwise, the original resource to be loaded is requested and analyzed to generate resource analysis data corresponding to the original resource to be loaded and the resource analysis data is loaded. Via the share of the resource analysis data after analysis, the re-analysis of shared resource is avoided, thereby saving loading time, improving loading speed and reducing the memory footprint.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
Constructing control flows graphs of binary executable programs at post-link time
InactiveUS7207038B2Clarifies overall structureReduce memory usageSoftware engineeringSoftware simulation/interpretation/emulationControl flowBasic block
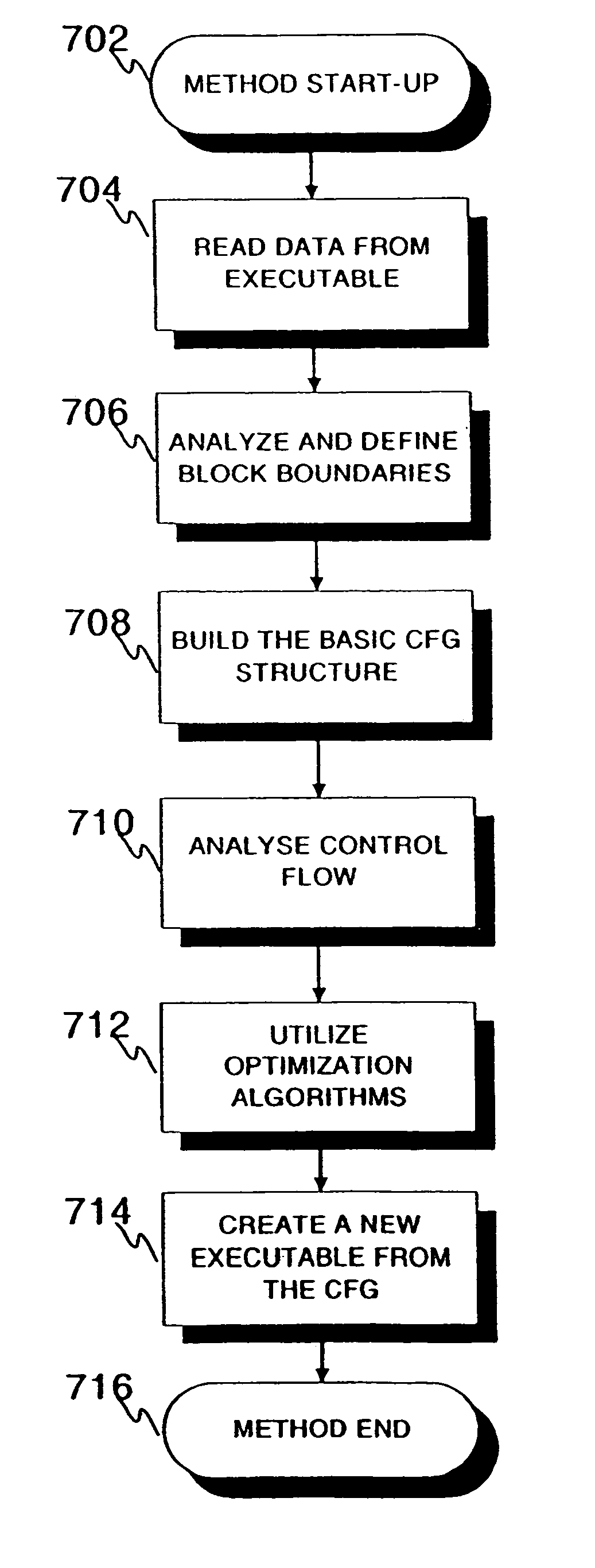
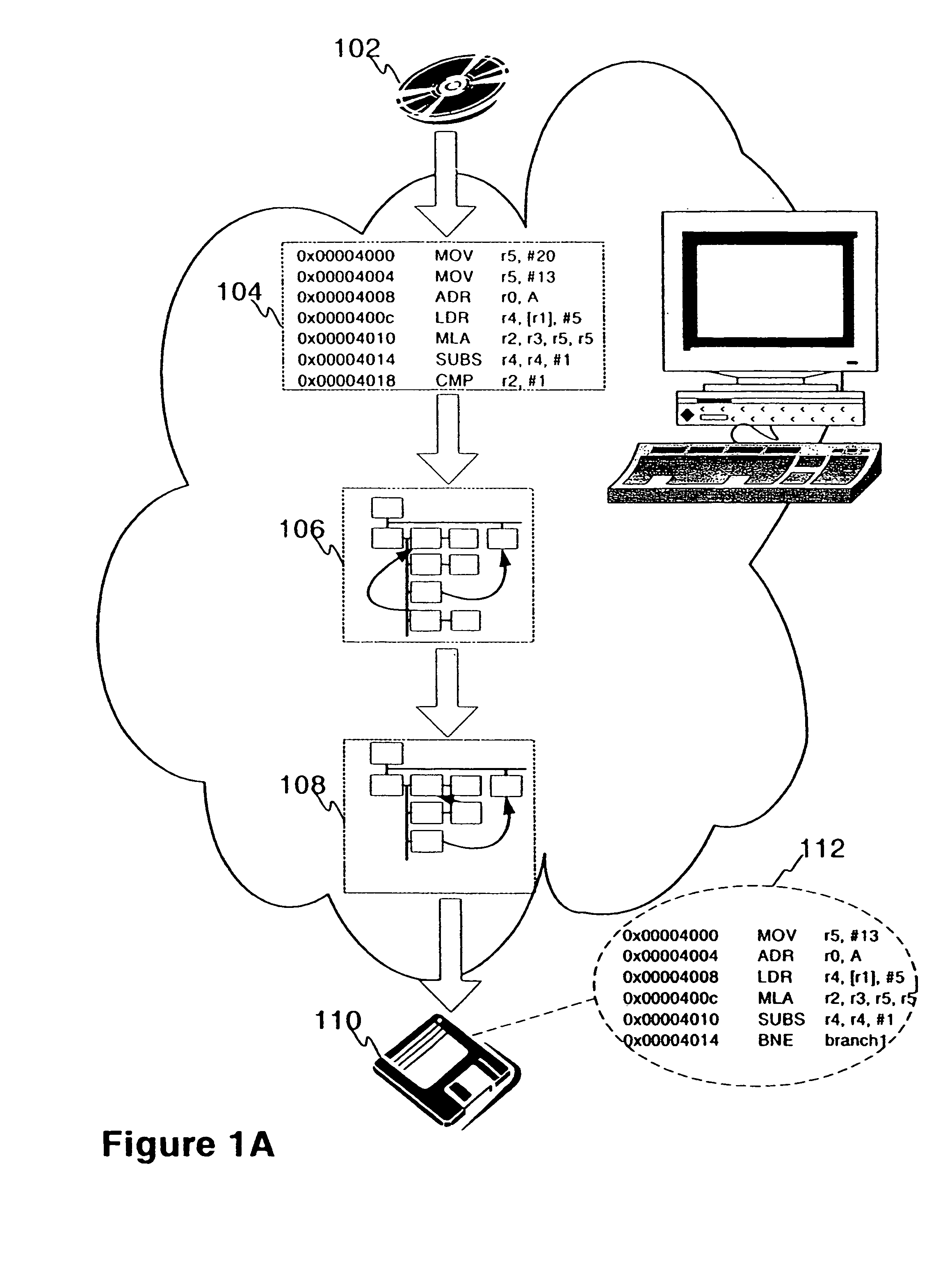
A method and a system for constructing a control flow graph (CFG, 106) from an executable computer program (104). The solution detects data intermixed with instructions and instruction set changes. The method includes the steps of defining block leader types specifying basic block boundaries in the program (104), building a CFG structure (106) according to the basic blocks found in the program, and adding control flow and addressing information to the CFG (106) by propagating through the basic blocks and internals thereof. The CFG (106) may be then optimised (108) and a compacted executable (112) created as a result.
Owner:NOKIA CORP
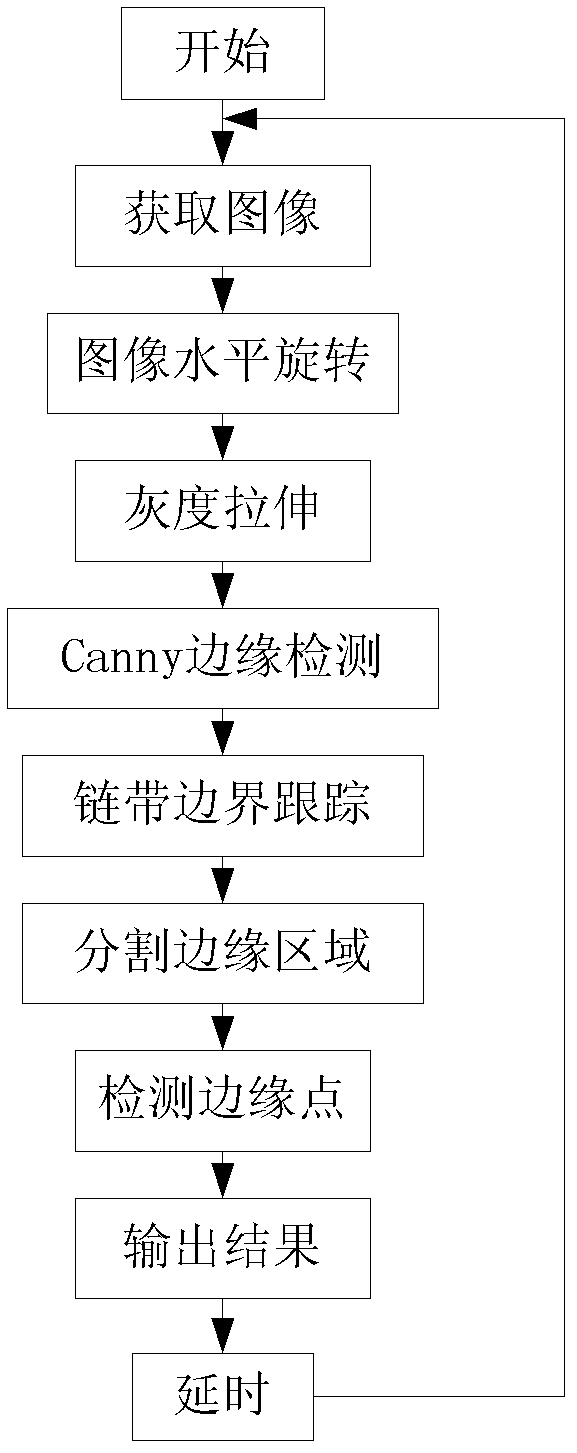
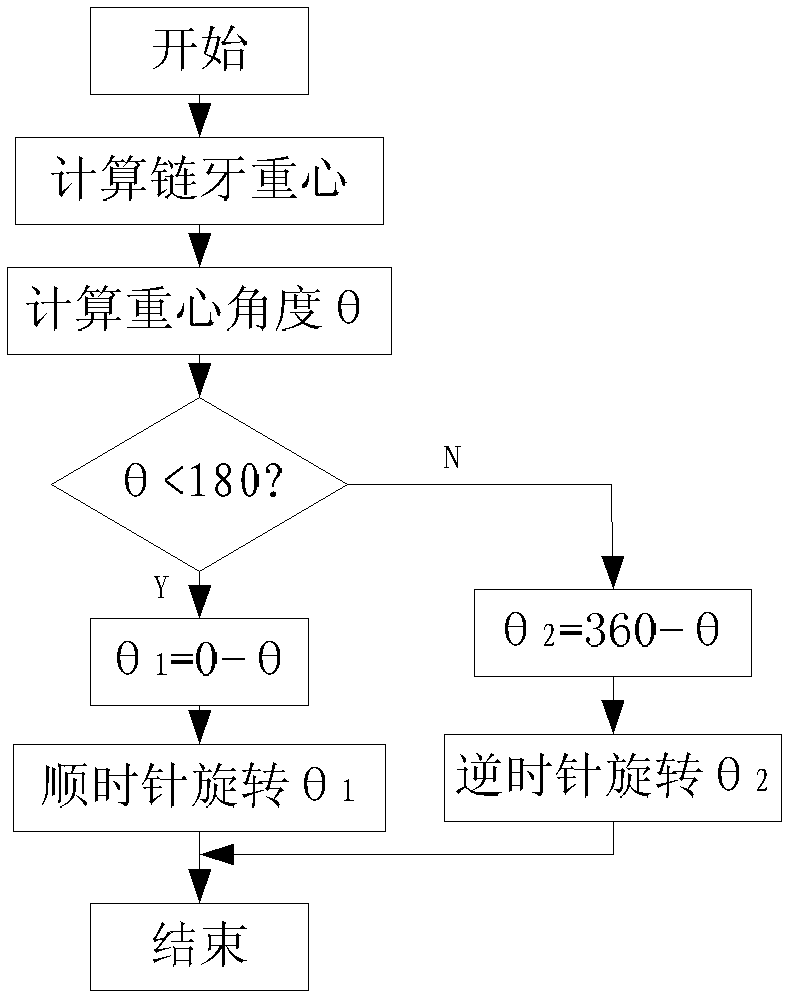
Method for detecting defects of chain belts of zipper on basis of digital image processing
InactiveCN102495069AReduce complexityReduce difficultyOptically investigating flaws/contaminationDigital signal processingControl system
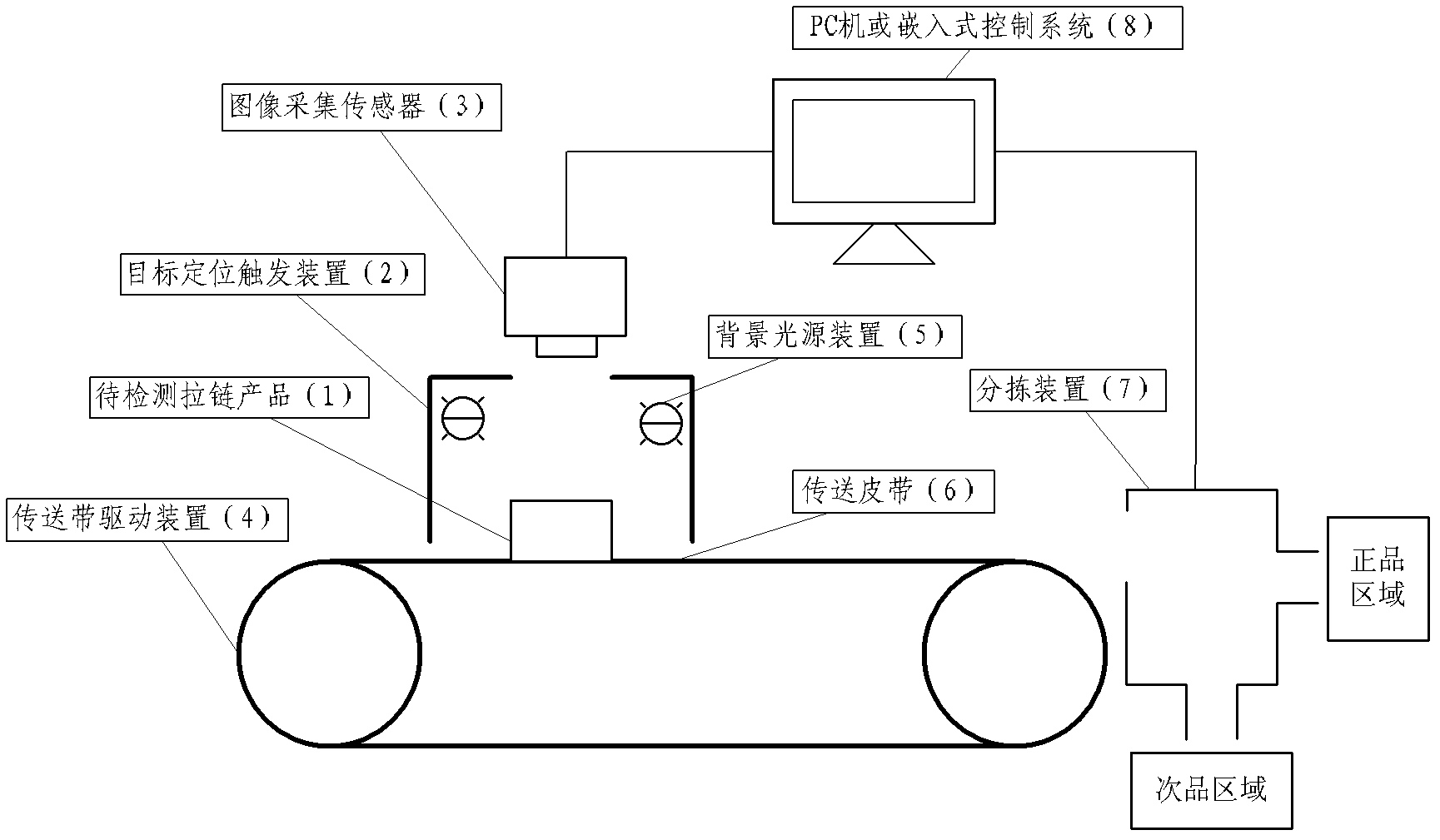
The invention relates to a method for detecting the defects of chain belts of a zipper on the basis of digital image processing, belonging to a novel technology in the technical field of appearance quality inspection of zippers in the hardware industry. According to the method, a detection device consisting of a target positioning and triggering device, an image acquisition sensor, a conveyor belt driving device, a background light source device, a feed belt, a sorting device and a PC (Personal Computer) machine or an embedded control system is utilized to carry out detection; and a zipper product to be detected is fed into a feed belt platform of the detection device and is then fed to a detection region under the drive of the driving device, then the zipper product is subjected to target positioning by the target positioning and triggering device, a chain belt digital image of the zipper is acquired by the image acquisition sensor, the image is transmitted to the PC machine or the embedded control system, the target image is processed by the PC machine or the embedded control system, and whether a chain belt region of the zipper has the defects is compared and judged according to a processing result and the judgment standard. The method has the characteristics of simple detection process, high detection speed, high detection accuracy and the like.
Owner:广东辉丰科技股份有限公司
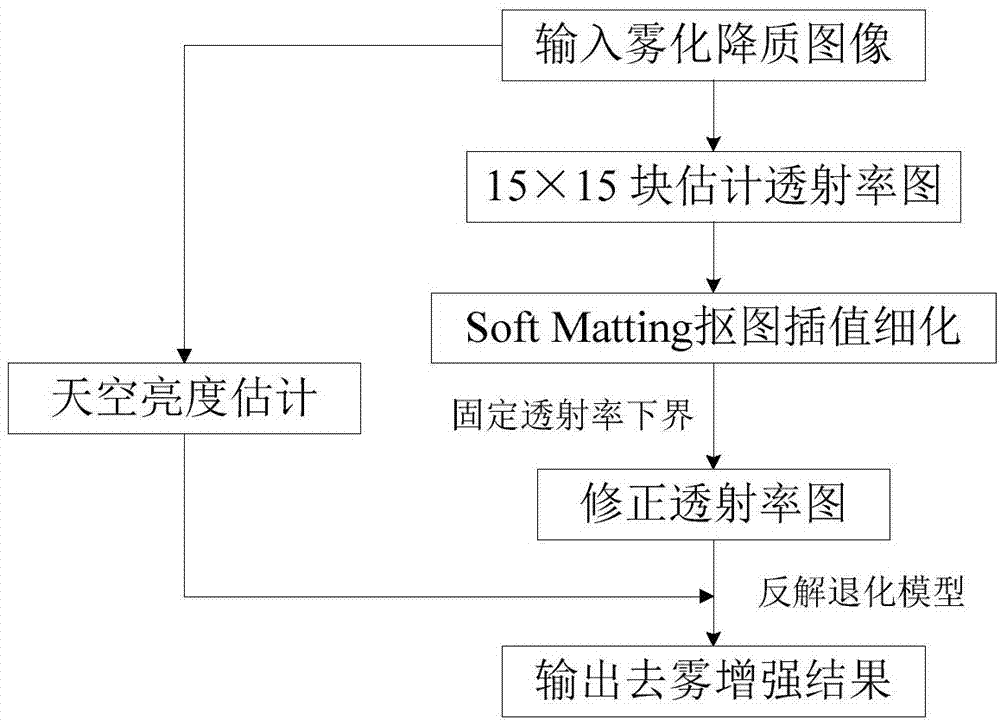
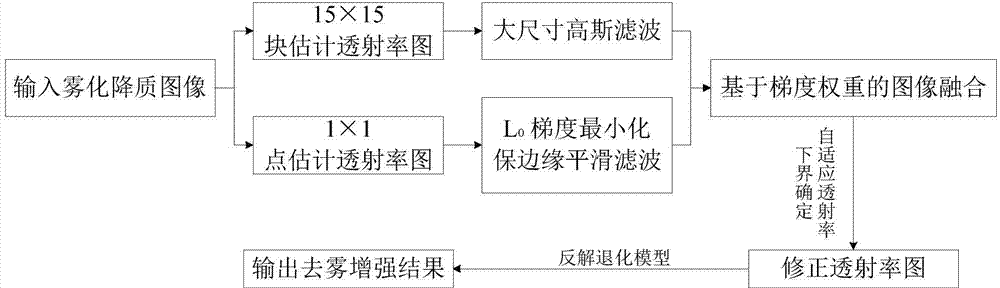
Dark channel prior image dehazing method based on multiscale fusion
ActiveCN103942758ASuppress false edgesTransmittance images are accurateImage enhancementTransmittanceSky brightness
The invention discloses a dark channel prior image dehazing method based on multiscale fusion. The dark channel prior image dehazing method based on multiscale fusion comprises the steps that (1) minimum value filter is conducted on a fog-degraded image through a color channel with a neighborhood size of 1*1 and a color channel with a neighborhood size of 15*15, so that corresponding dark channel images are obtained, and an estimated point transmissivity graph and an estimated block transmissivity graph are calculated based on the dark channel images; (2) edge image smoothness protection based on L0 gradient minimization is conducted on the estimated point transmissivity graph; (3) large-size Gaussian filter is conducted on the estimated block transmissivity graph; (4) with a normalized gradient magnitude as the weight, the estimated point transmissivity graph and the estimated block transmissivity graph are fused to enable a corrected transmissivity graph to be obtained; (5) the lower bound of the transmissivity is estimated based on median filtering; (6) the sky brightness is estimated by means of a 15*15 dark channel image; (7) inverse solution is conducted on a fog-degraded model, and a dehazing result is output. The dark channel prior image dehazing method based on multiscale fusion has the advantages that the dehazing capacity is high, the complexity is low, the image dehazing quality and the image dehazing efficiency can be improved.
Owner:NAT UNIV OF DEFENSE TECH
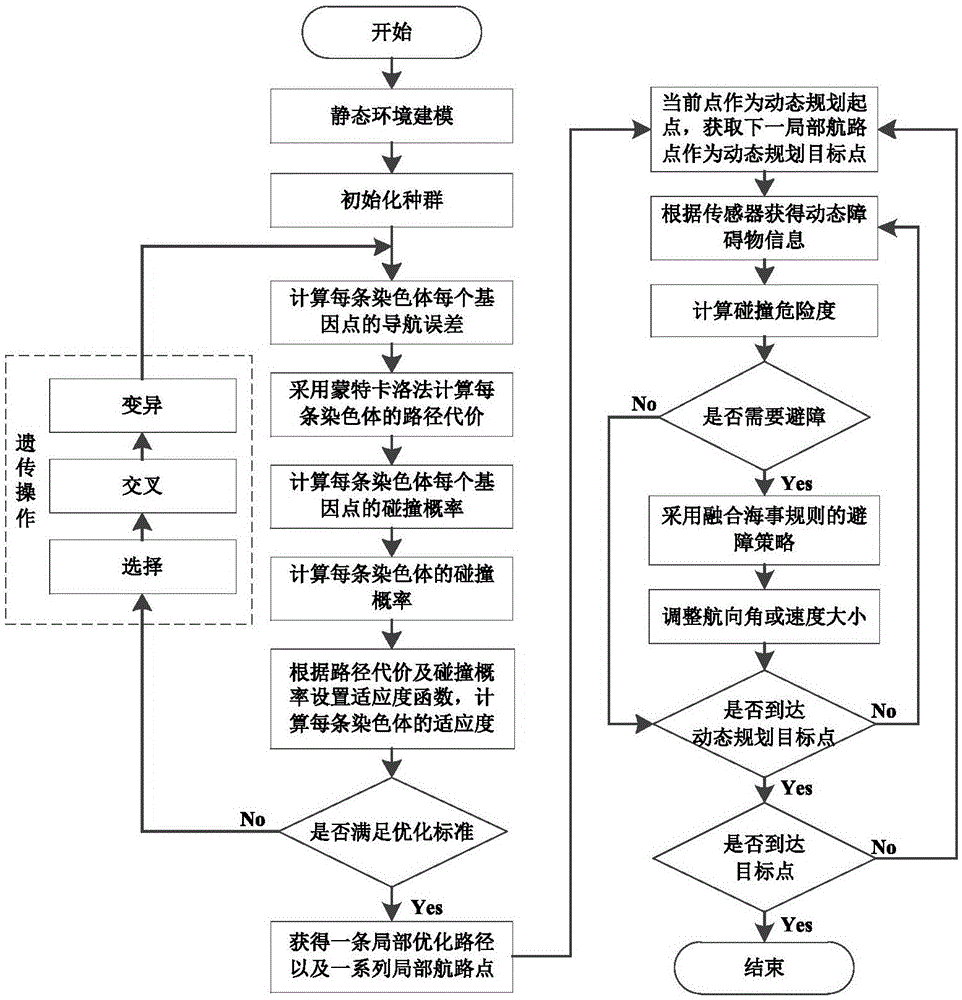
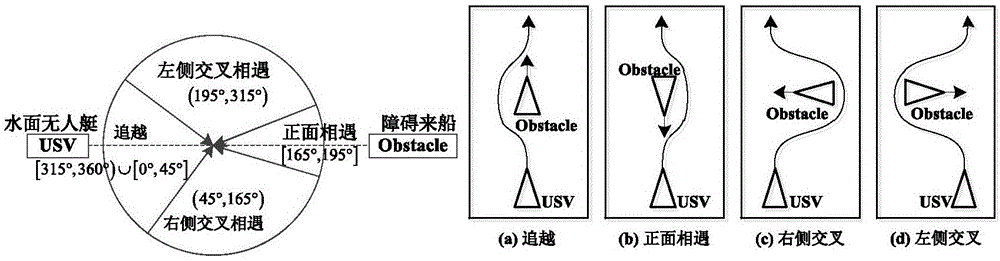
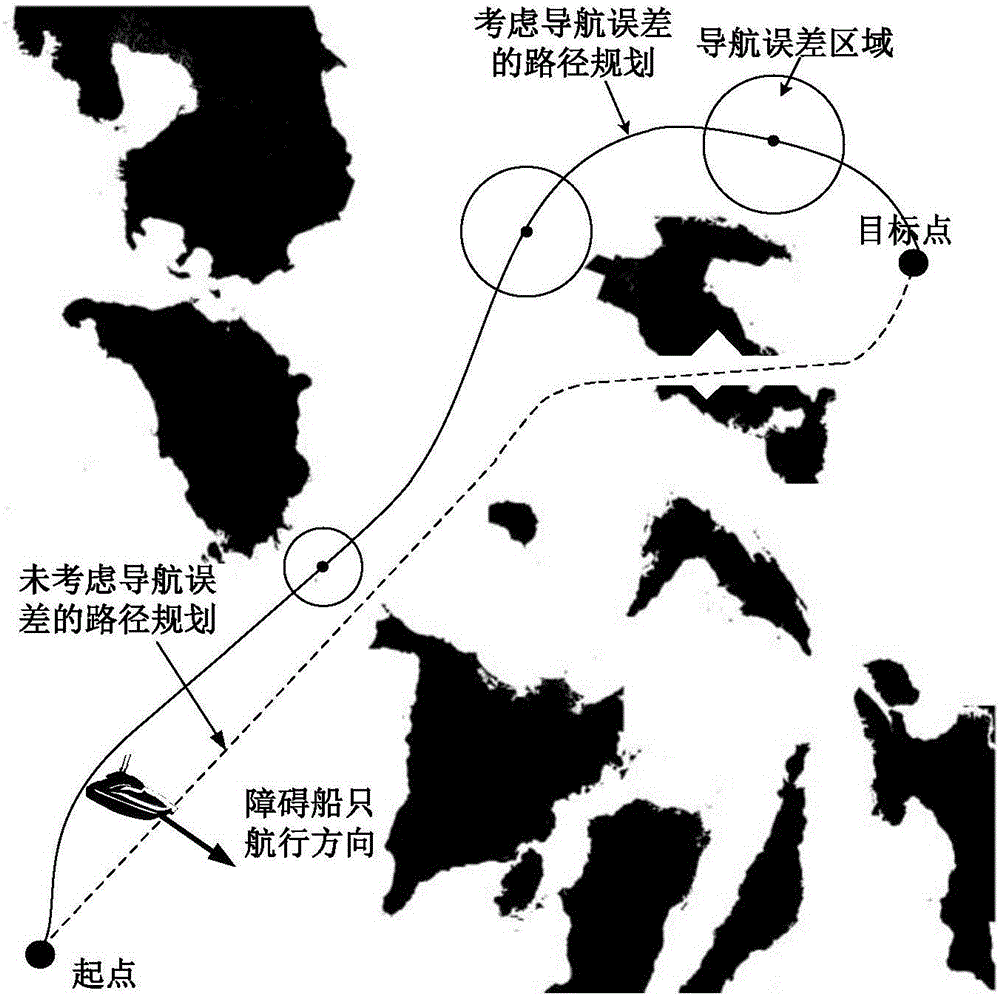
Water unmanned ship local hierarchical path planning method based on navigation error constraint
ActiveCN106845716AShort no-touch pathEnsure safetyForecastingGenetic algorithmsPlanning approachGenetic algorithm
The invention discloses a water unmanned ship local hierarchical path planning method based on the navigation error constraint. The method mainly includes the steps of local static path planning based on the navigation error constraint and combined with a genetic algorithm; local dynamic path planning fused with the maritime affair rule. The hierarchical thinking is adopted, local path planning is divided into two levels of static path planning and dynamic path planning, the static barrier avoiding problem is solved, and the dynamic barrier avoiding problem is also solved. According to static path planning based on the navigation error constraint and combined with the genetic algorithm, adverse influences of navigation errors on path selection are reduced, and the safety of path planning is improved; according to dynamic path planning based on the marine affair rule, the dynamics constraint of a water unmanned ship is considered, and the feasibility of path planning is improved.
Owner:SOUTHEAST UNIV
Increasing buffer locality during multiple table access operations
InactiveUS8010766B2Reducing disk access costEasy to integrateDigital data information retrievalSpecial data processing applicationsInformation processingInformation handling system
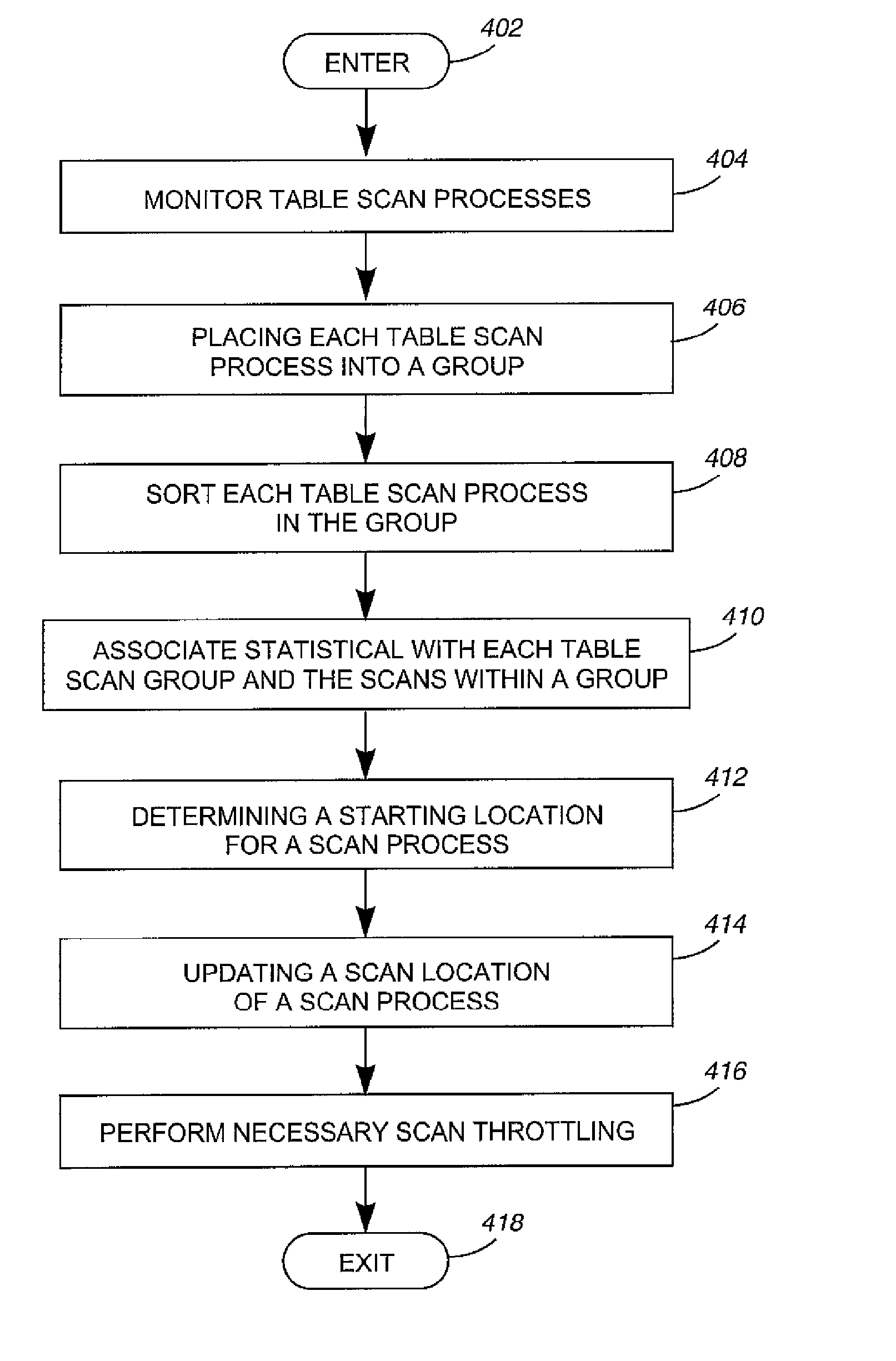
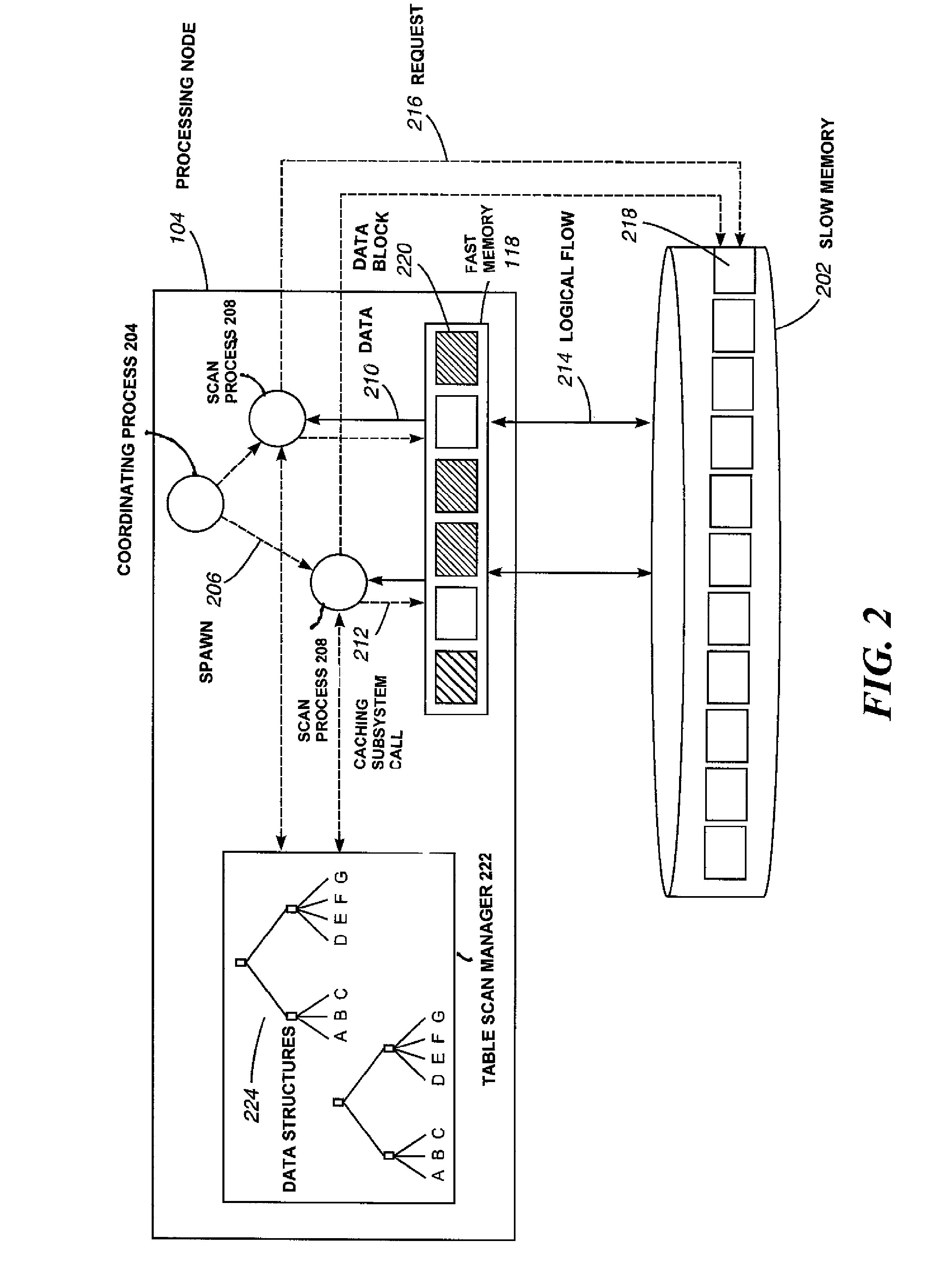
Disclosed are a method, information processing system, and computer readable medium for managing table scan processes. The method includes monitoring a plurality of storage medium table scan processes. Each storage medium table scan process in the plurality of storage medium table scan processes is placed into a plurality of scan groups based on storage medium pages to be scanned by each of the storage medium table scan processes. Each storage medium table scan process in a scan group can share data within a storage medium page.
Owner:IBM CORP
Key point positioning method and terminal
ActiveCN105512627AHigh precisionReduce processing difficultyCharacter and pattern recognitionComputer terminalFace perception
The embodiment of the invention discloses a key point positioning method and a terminal. The method comprises the steps of detecting a target object as a face image during the collecting process of the target object; generating a target detecting region on the face image of the i frame for human face recognition and location according to a preset configuration and annotating the target detecting region, wherein i is larger than or equal to 1; when i is larger than 1, estimating the key point information of a human face based on the face image of the i frame according to the similarity matching strategy between a previous frame and the current frame so as to obtain the category of the human face for the face image of the i frame; according to the category of the human face for the face image of the i frame, determining a first initial shape out of a plurality of preset candidate initial shapes; and calculating the position of an initial face key point in the face image of the i frame according to the target detecting region and the first initial shape.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com