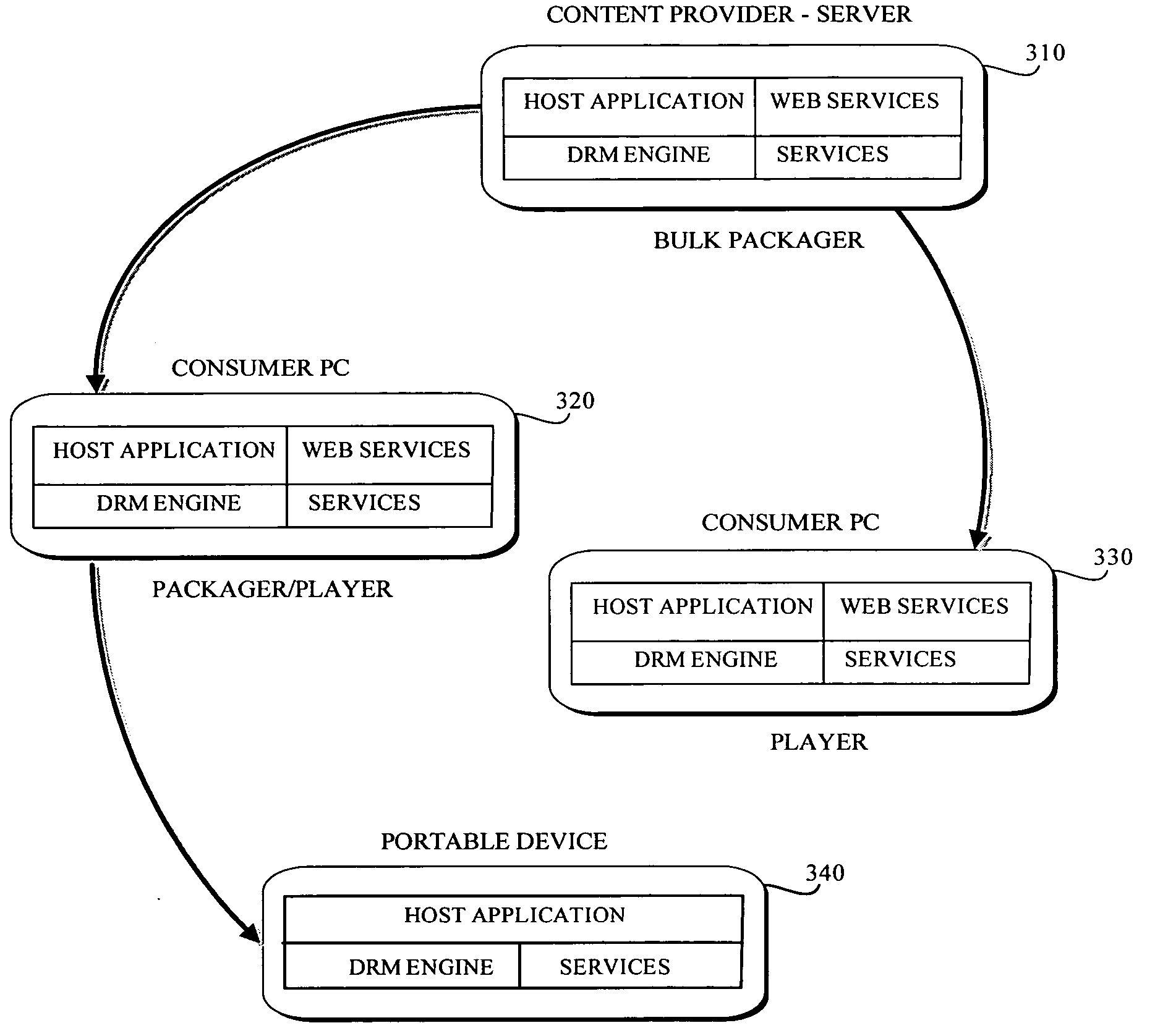
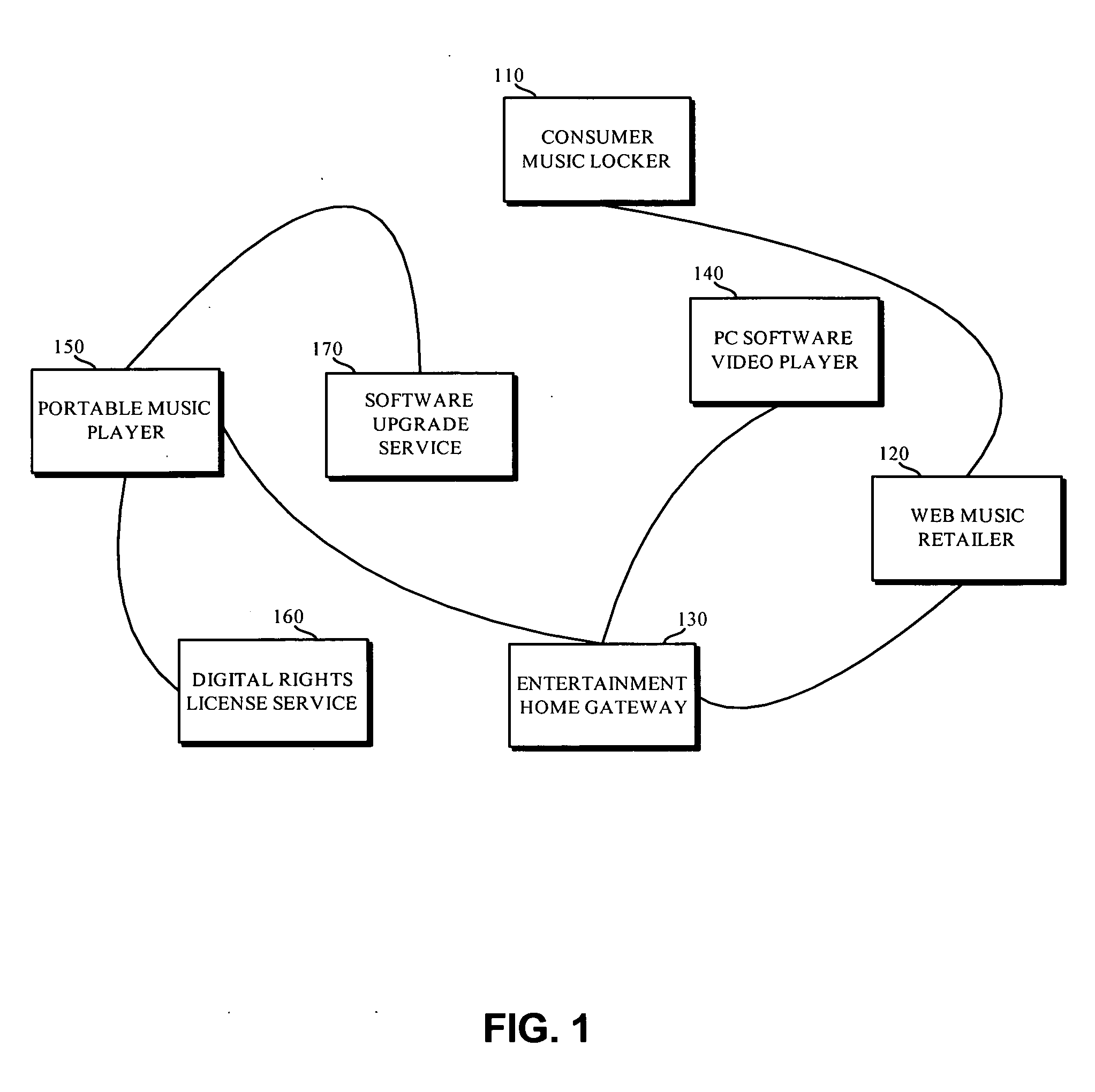
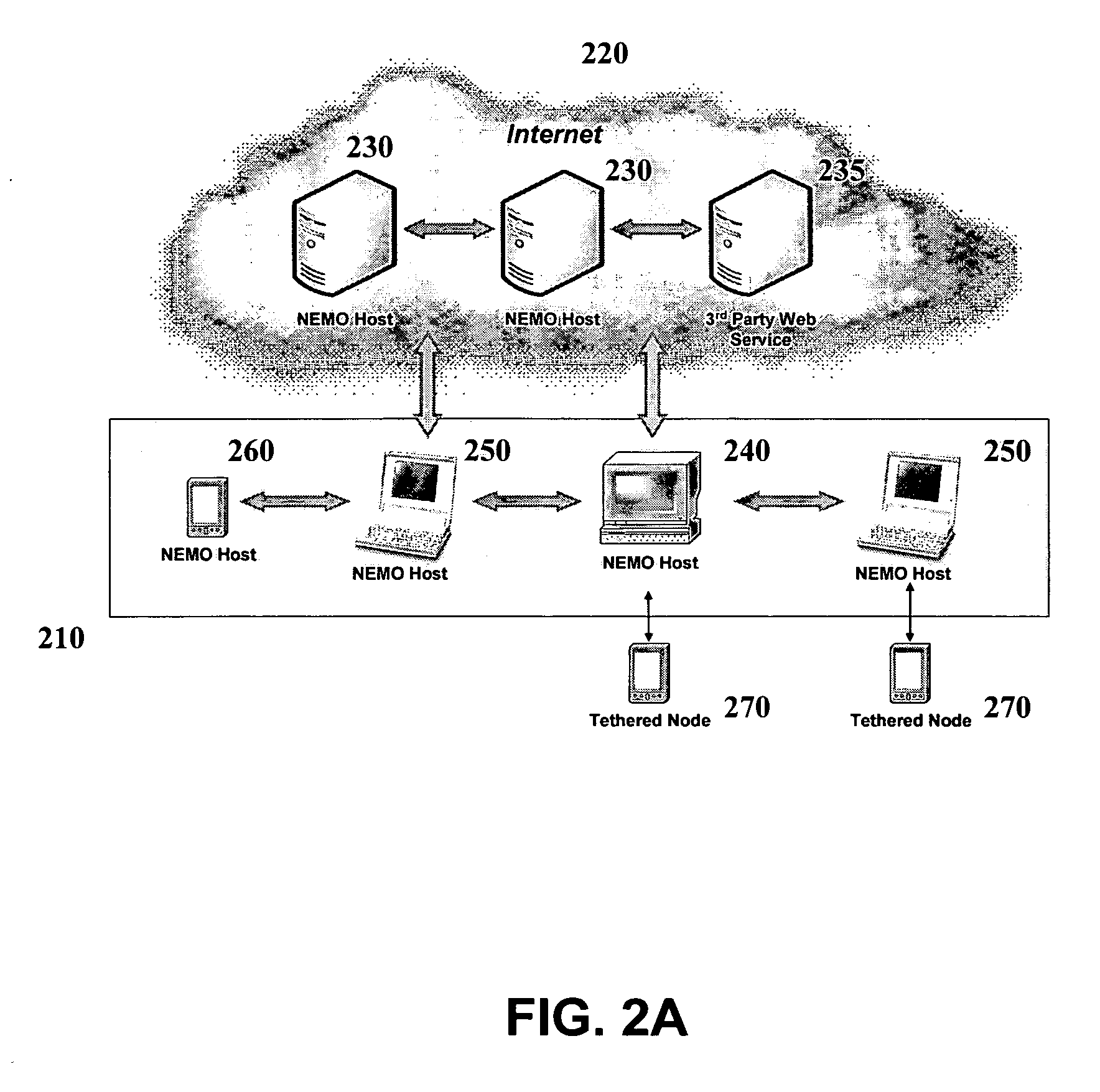
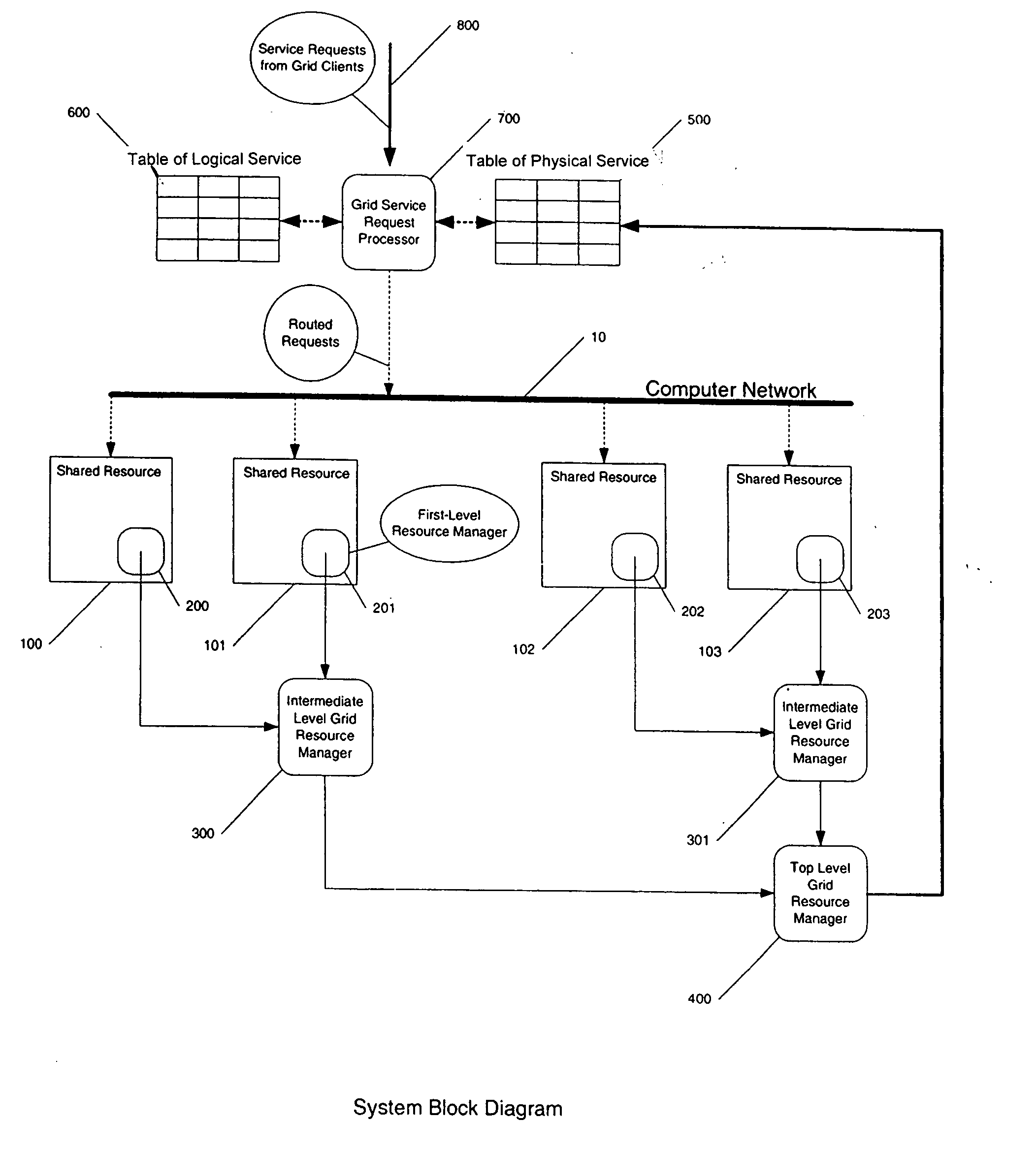
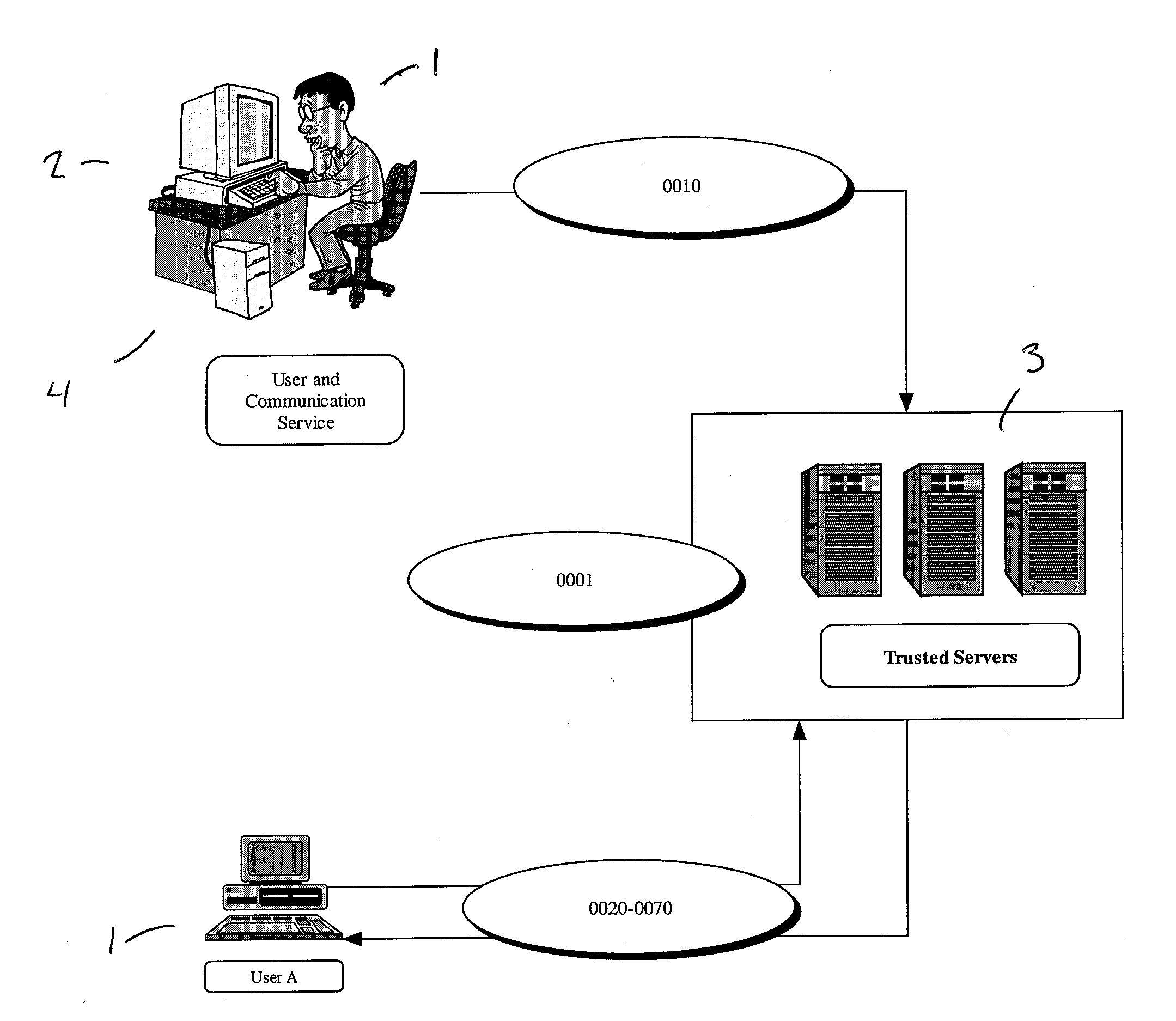
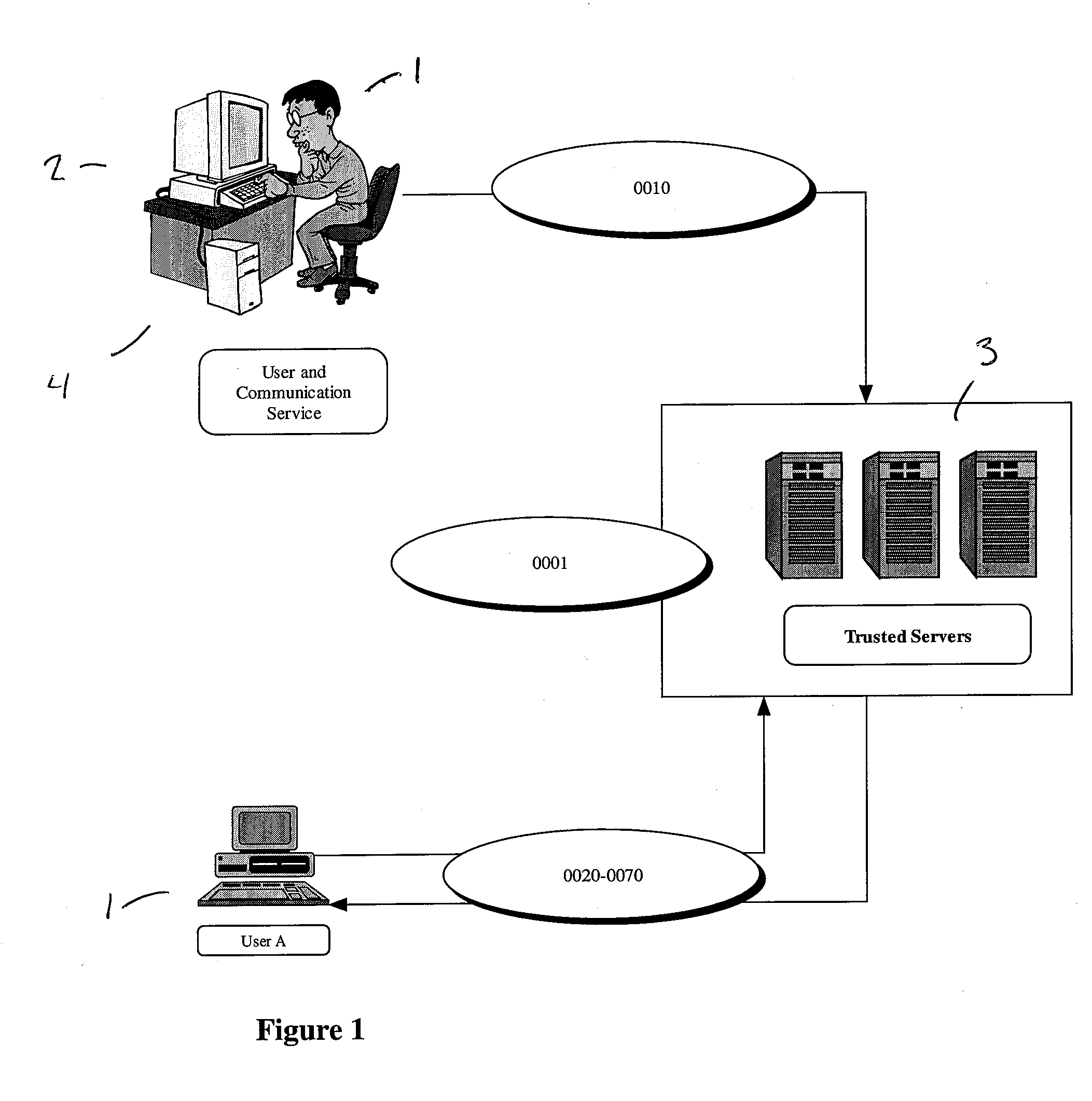
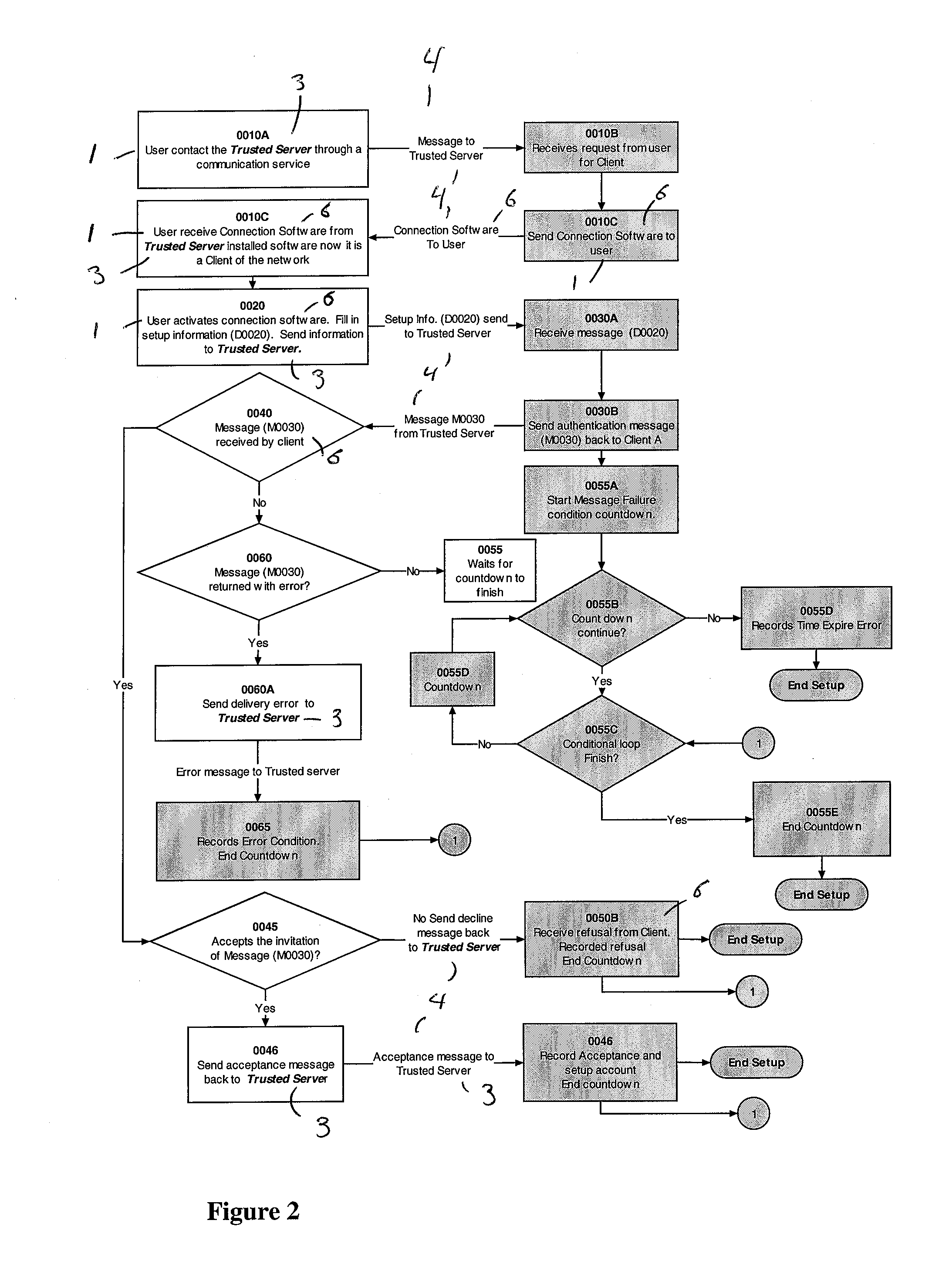
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2408 results about "Shared resource" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, a shared resource, or network share, is a computer resource made available from one host to other hosts on a computer network. It is a device or piece of information on a computer that can be remotely accessed from another computer, typically via a local area network or an enterprise intranet, transparently as if it were a resource in the local machine. Network sharing is made possible by inter-process communication over the network.
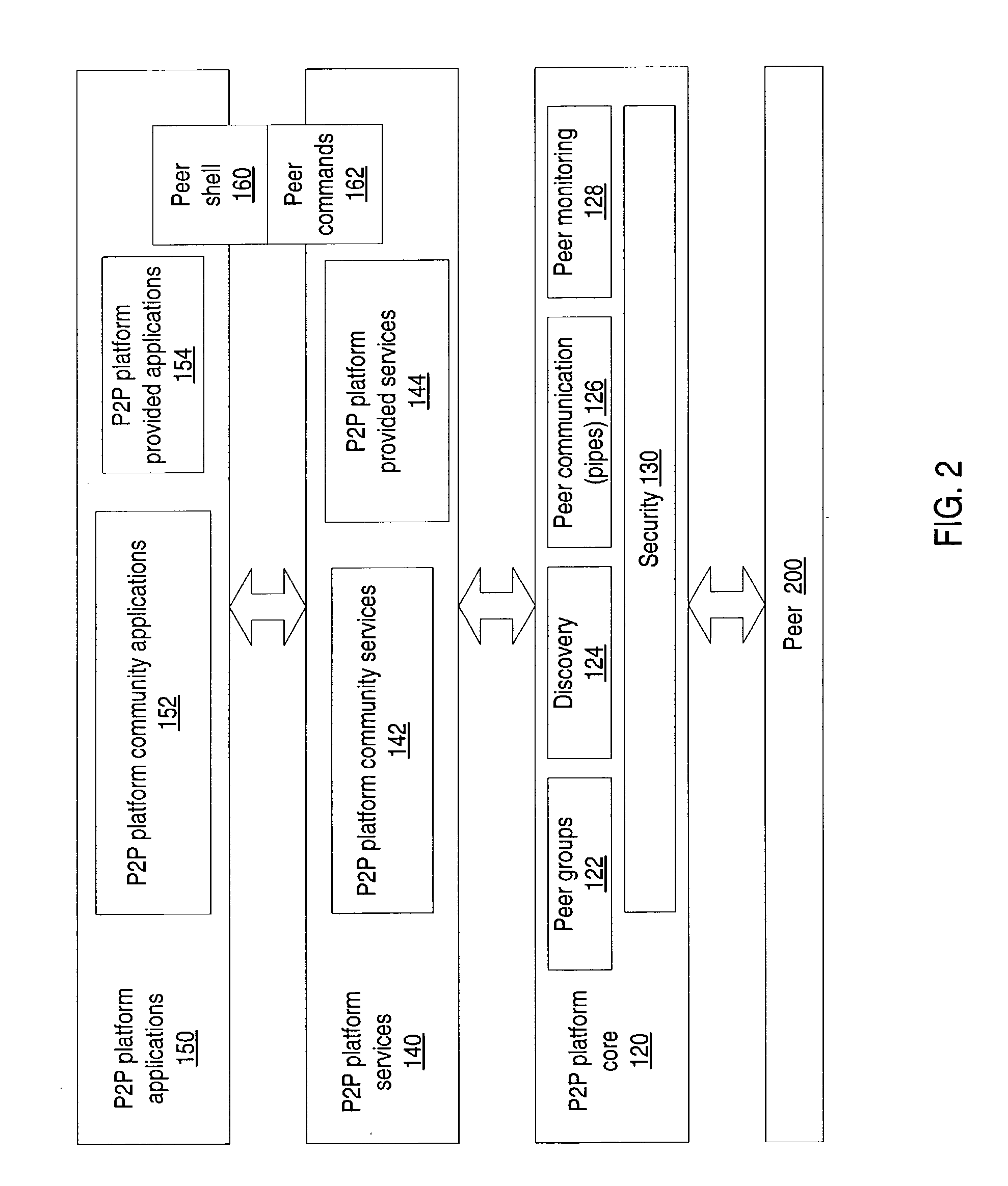
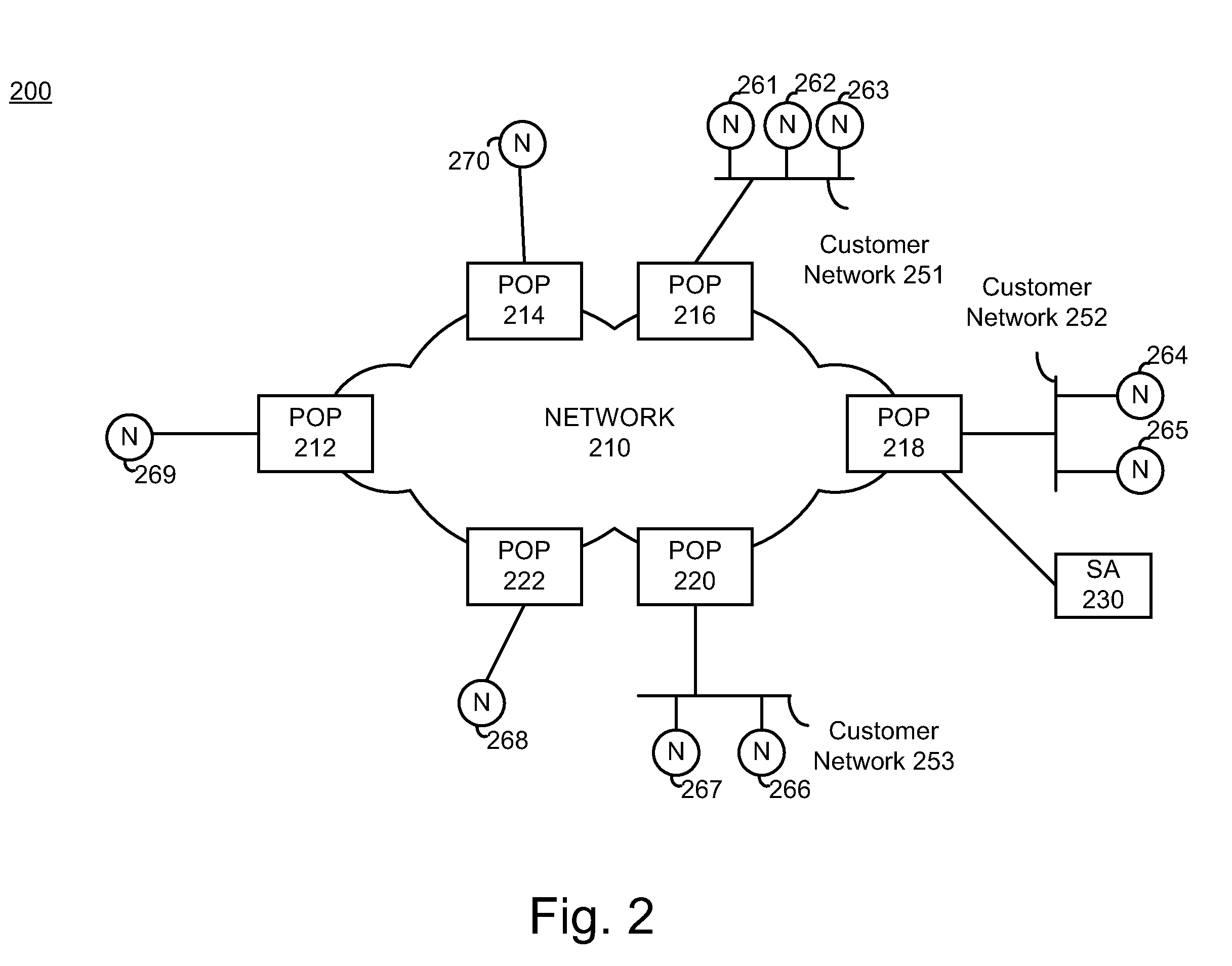
Interoperable systems and methods for peer-to-peer service orchestration
InactiveUS20050027871A1Facilitating commercial exchangeIncrease flexibilityWeb data indexingCryptography processingOperational systemWeb service
Systems and methods are described for performing policy-managed, peer-to-peer service orchestration in a manner that supports the formation of self-organizing service networks that enable rich media experiences. In one embodiment, services are distributed across peer-to-peer communicating nodes, and each node provides message routing and orchestration using a message pump and workflow collator. Distributed policy management of service interfaces helps to provide trust and security, supporting commercial exchange of value. Peer-to-peer messaging and workflow collation allow services to be dynamically created from a heterogeneous set of primitive services. The shared resources are services of many different types, using different service interface bindings beyond those typically supported in a web service deployments built on UDDI, SOAP, and WSDL. In a preferred embodiment, a media services framework is provided that enables nodes to find one another, interact, exchange value, and cooperate across tiers of networks from WANs to PANs.
Owner:INTERTRUST TECH CORP
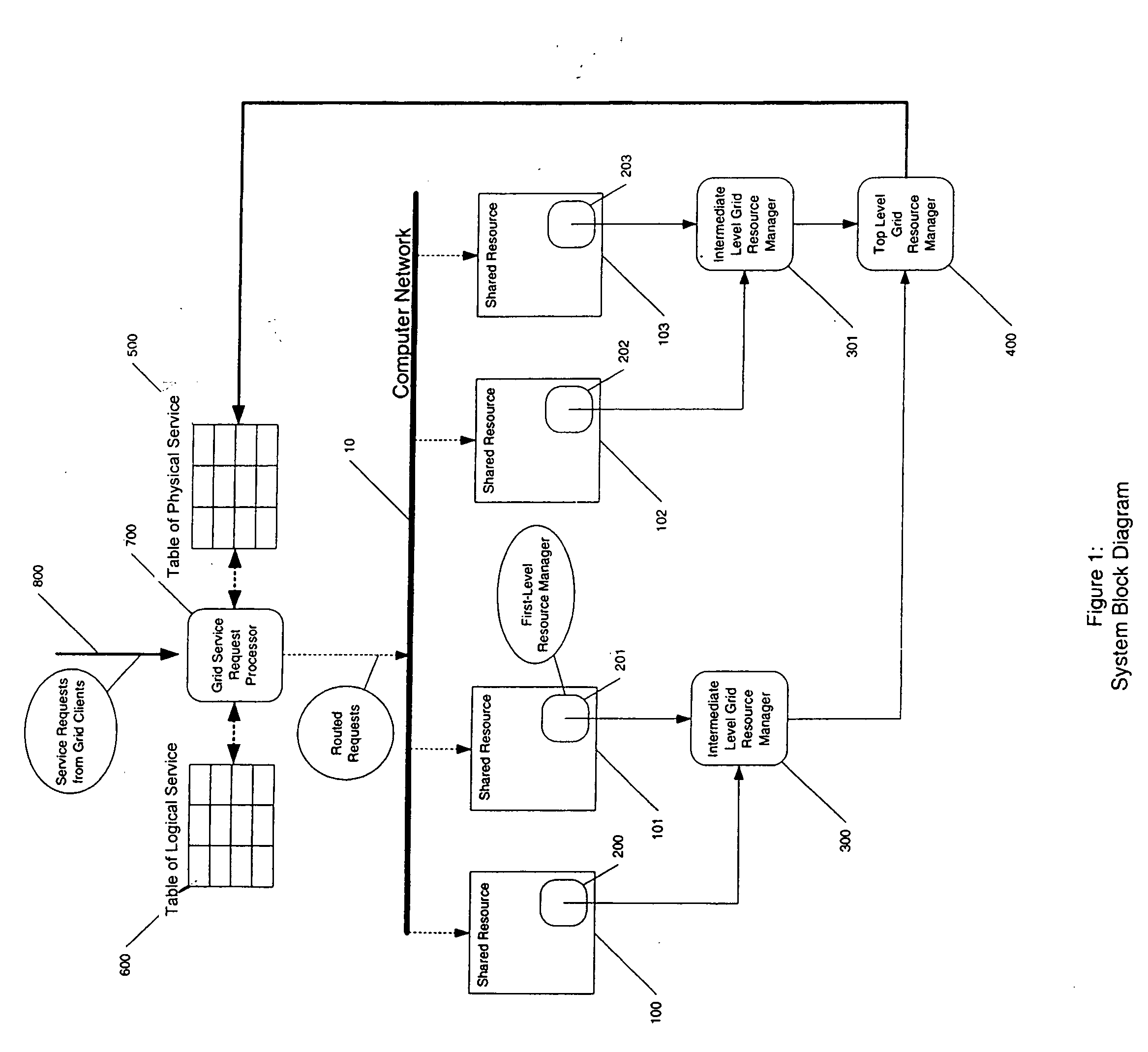
Policy-based hierarchical management of shared resources in a grid environment
InactiveUS20060294238A1Facilitates efficient means for routingDigital computer detailsProgram controlService guaranteeClient-side
The invention relates to controlling the participation and performance management of a distributed set of resources in a grid environment. The control is achieved by forecasting the behavior of a group of shared resources, their availability and quality of their performance in the presence of external policies governing their usage, and deciding the suitability of their participation in a grid computation. The system also provides services to grid clients with certain minimum levels of service guarantees using resources with uncertainties in their service potentials.
Owner:IBM CORP
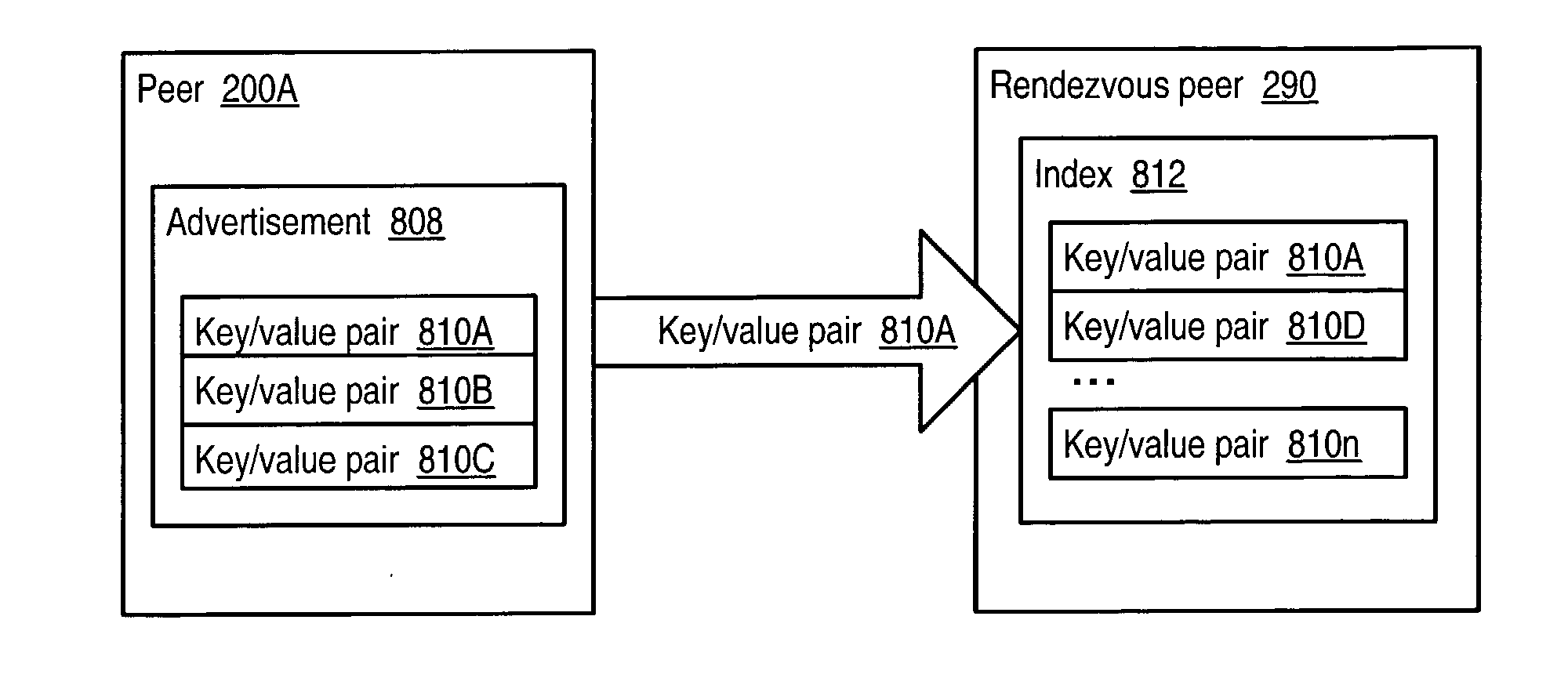
Decentralized peer-to-peer advertisement
Embodiments of a shared resource distributed index mechanism that peers in a peer-to-peer network may utilize to distribute index entries corresponding to resources to indexes of shared resources among one or more other peers. These indexes may be used to direct queries to peers where the queries are most likely to be answered. When a query is received by a rendezvous peer including one or more indexes, contents of the query may be "looked up" in the index to find matches. The results of the lookup may include information on one or peer(s) that may hold advertisement(s) to the resource requested by the query. The query may then be forwarded to one or more peers that may hold the advertisement for the resource. Embodiments may provide "loosely-coupled" distribution of index entries for use in querying for resources in the peer-to-peer network.
Owner:ORACLE INT CORP
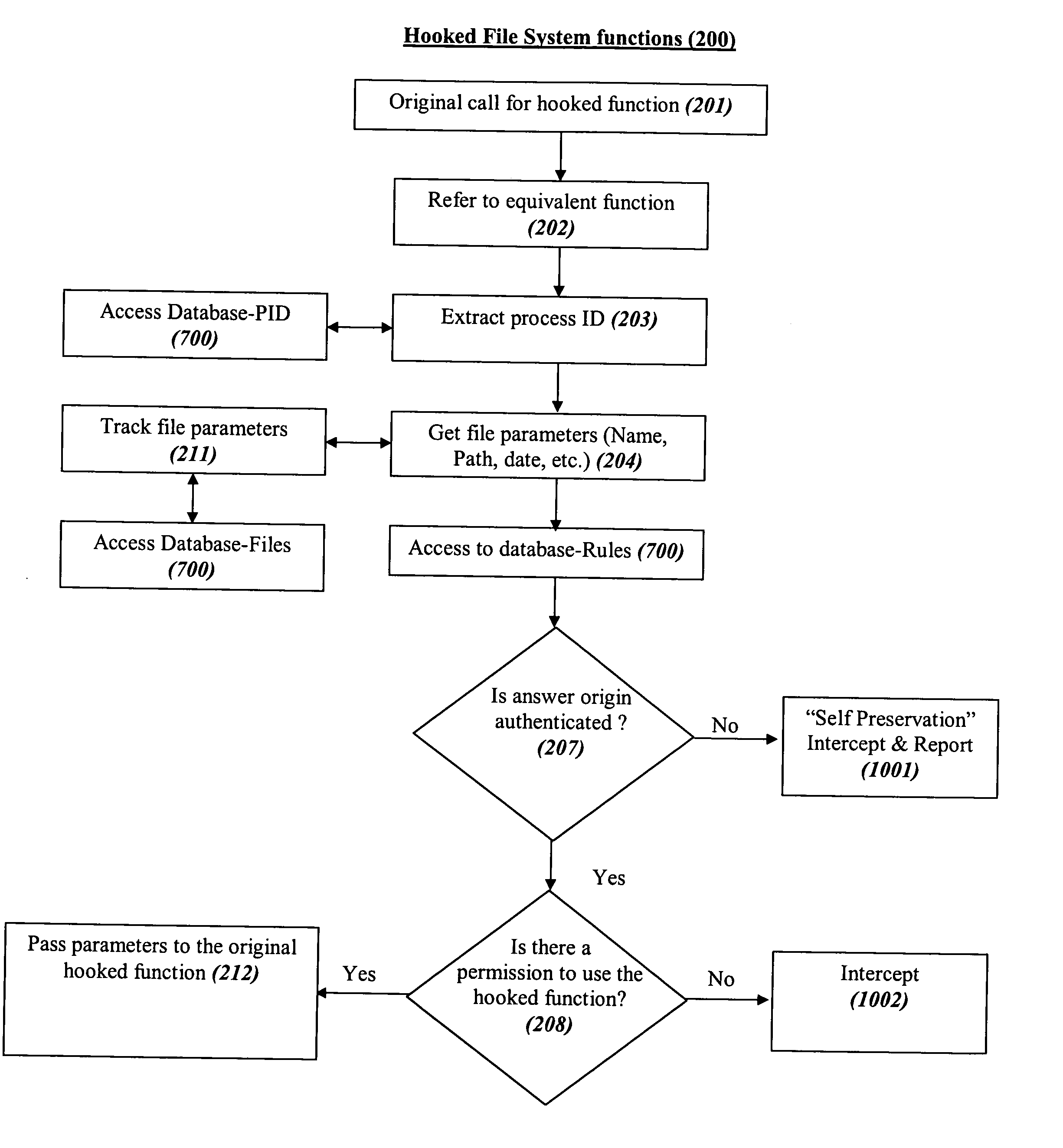
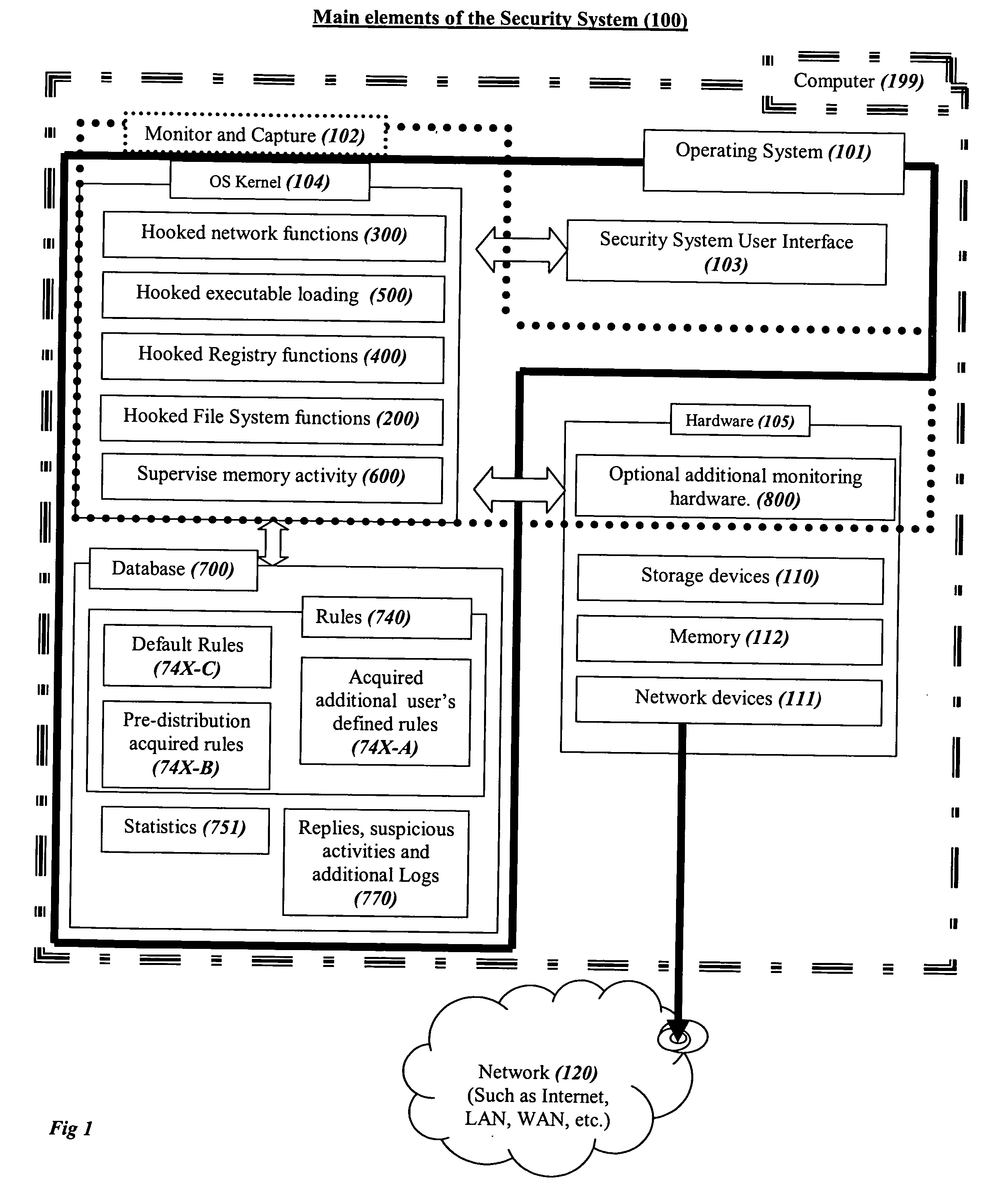
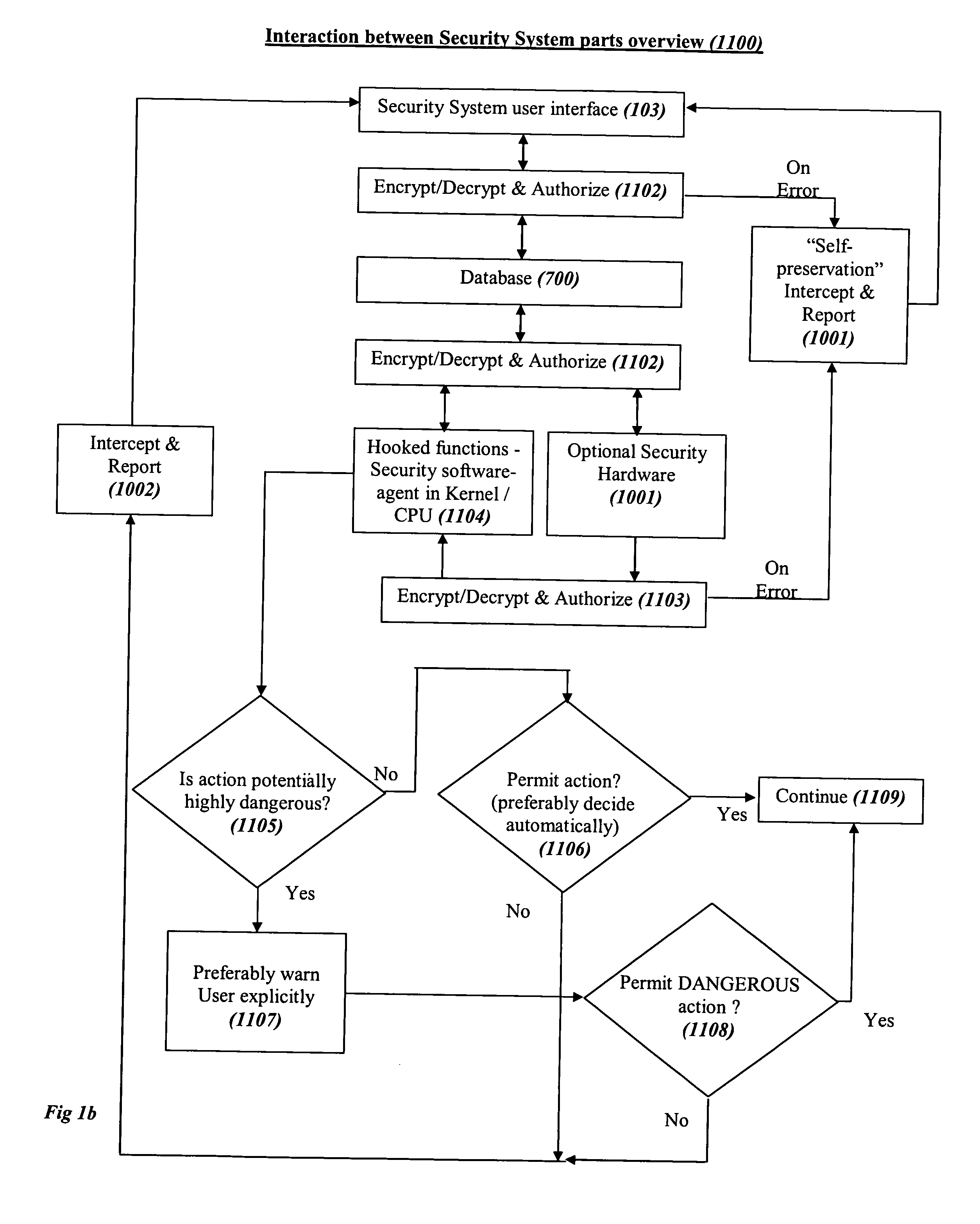
System and method for comprehensive general electric protection for computers against malicious programs that may steal information and/or cause damages
ActiveUS20050120242A1Reduce chanceDigital data processing detailsMultiple digital computer combinationsFree accessOperational system
In the prior art of computer security by default programs are allowed to do whatever they like to other programs or to their data files or to critical files of the operating system, which is as absurd as letting a guest in a hotel bother other guests as he pleases, steal their property or copy it or destroy it, or have free access to the hotel's management resources. The present concept is based on automatic segregation between programs. This is preferably done by creating automatically an unlimited number of Virtual Environments (VEs) with virtual sharing of resources, so that the programs in each VE think that they are alone on the computer, and (unless explicitly allowed by the user) any changes that they think they made in virtually shared resources are in reality only made in their own VE, while the user preferably has an integrated view of the computer.
Owner:BARHON MAYER BATYA
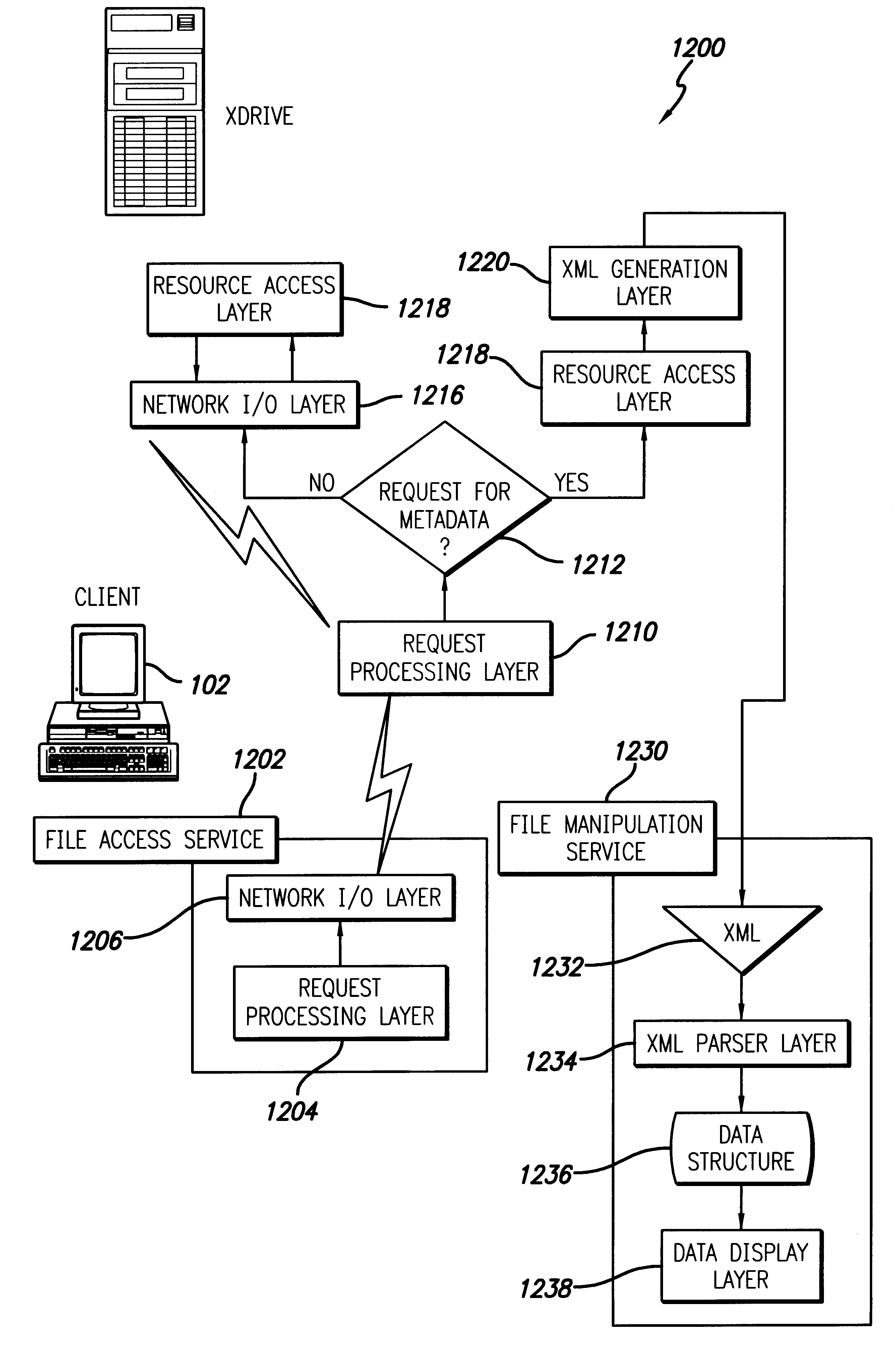
Shared internet storage resource, user interface system, and method
InactiveUS6351776B1Easy to understandData processing applicationsWeb data indexingData streamWeb service
The Shared Internet Storage Resource provides Internet-based file storage, retrieval, access, control, and manipulation for a user. Additionally, an easy-to-use user interface is provided both for a browser or stand-alone application. The entire method provides means by which users can establish, use, and maintain files on the Internet in a manner remote from their local computers yet in a manner that is similar to the file manipulation used on their local computers. A high capacity or other storage system is attached to the Internet via an optional internal network that also serves to generate and direct metadata regarding the stored files. A web server using a CGI, Java(R)-based, or other interface transmits and retrieves TCP / IP packets or other Internet information through a load balancer / firewall by using XML to wrap the data packets. File instructions may be transmitted over the Internet to the Shared Resource System. The user's account may be password protected so that only the user may access his or her files. On the user's side, a stand-alone client application or JavaScript object interpreted through a browser provide two means by which the XML or other markup language data stream may be received and put to use by the user. Internet-to-Internet file transfers may be effected by directly downloading to the user's account space.
Owner:TIME WARNER
System and method for simplified resource sharing
ActiveUS20100082784A1Digital computer detailsData switching networksComputer hardwareShared resource
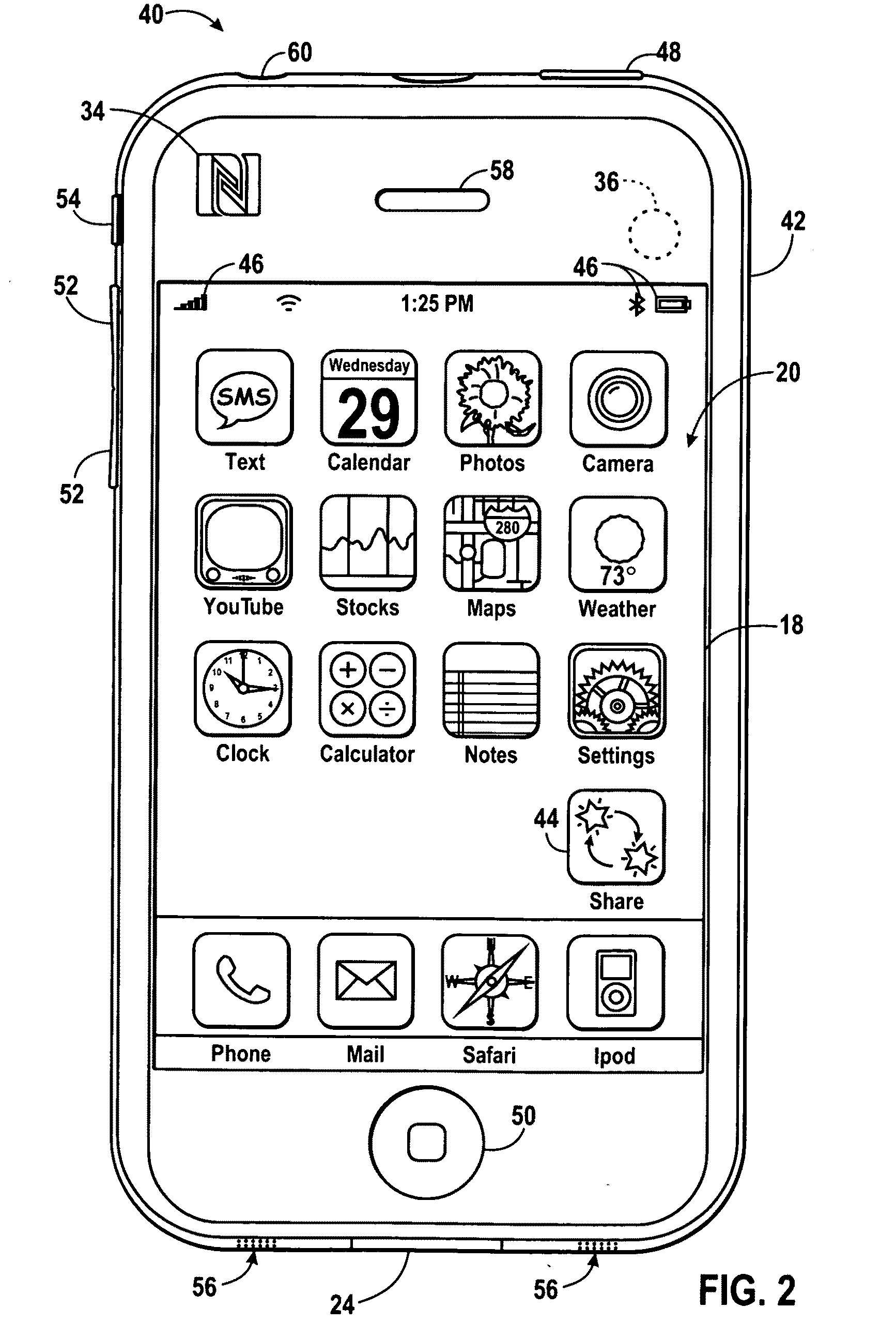
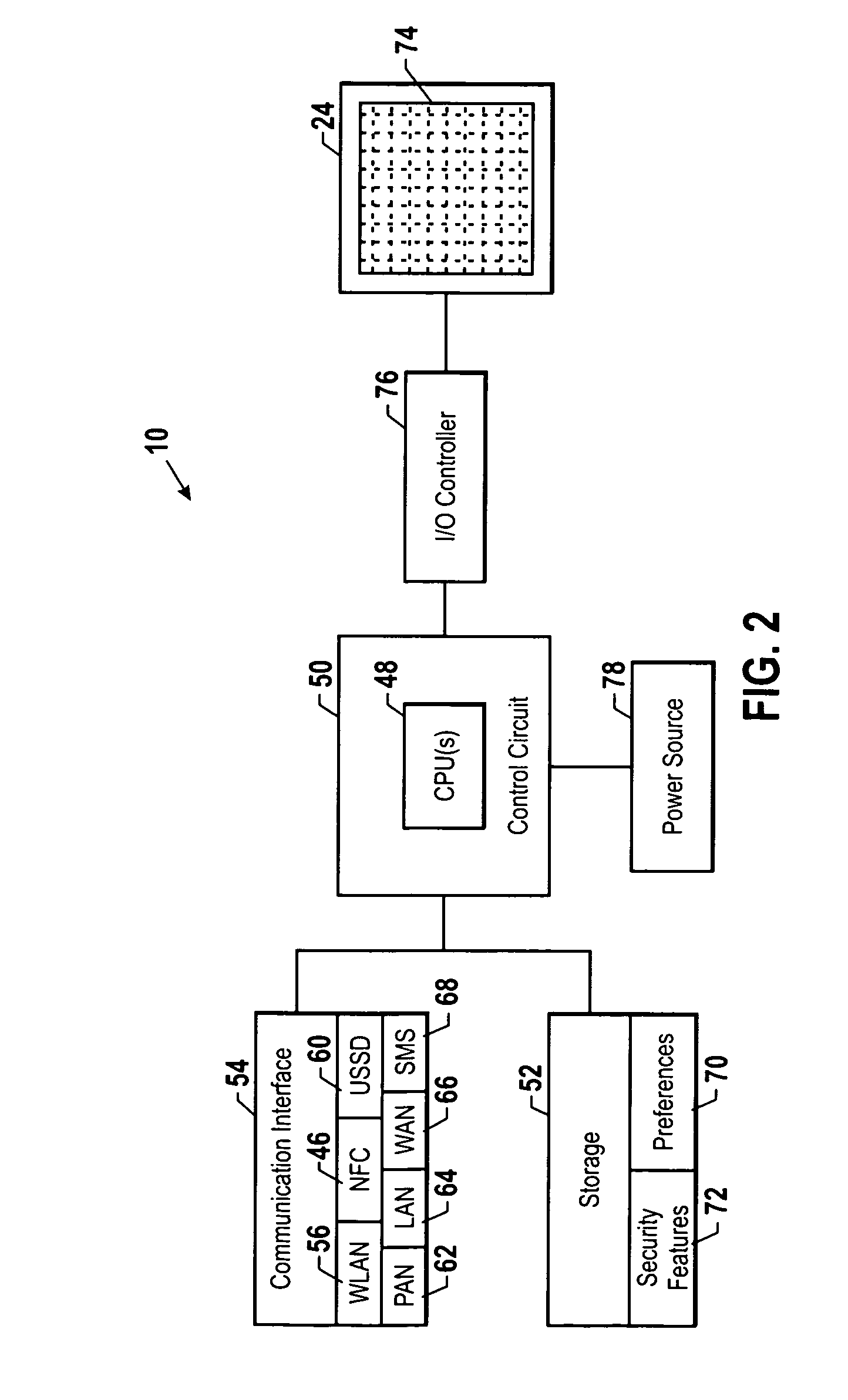
Systems, methods, and devices for simplified resource-sharing with electronic devices are provided. For example, a method for using at least one resource of a variety of electronic devices from another electronic device may include receiving resource-sharing information associated with a resource-sharing electronic device via near field communication, determining a resource-sharing scheme for using the resources of the resource-sharing electronic device based on the resource-sharing information, and sharing at least one resource of the resource-sharing electronic device using the determined resource-sharing scheme. The resource-sharing information may be received from a near field communication interface of the resource-sharing electronic device or from a radio frequency identification tag associated with the resource-sharing electronic device.
Owner:APPLE INC
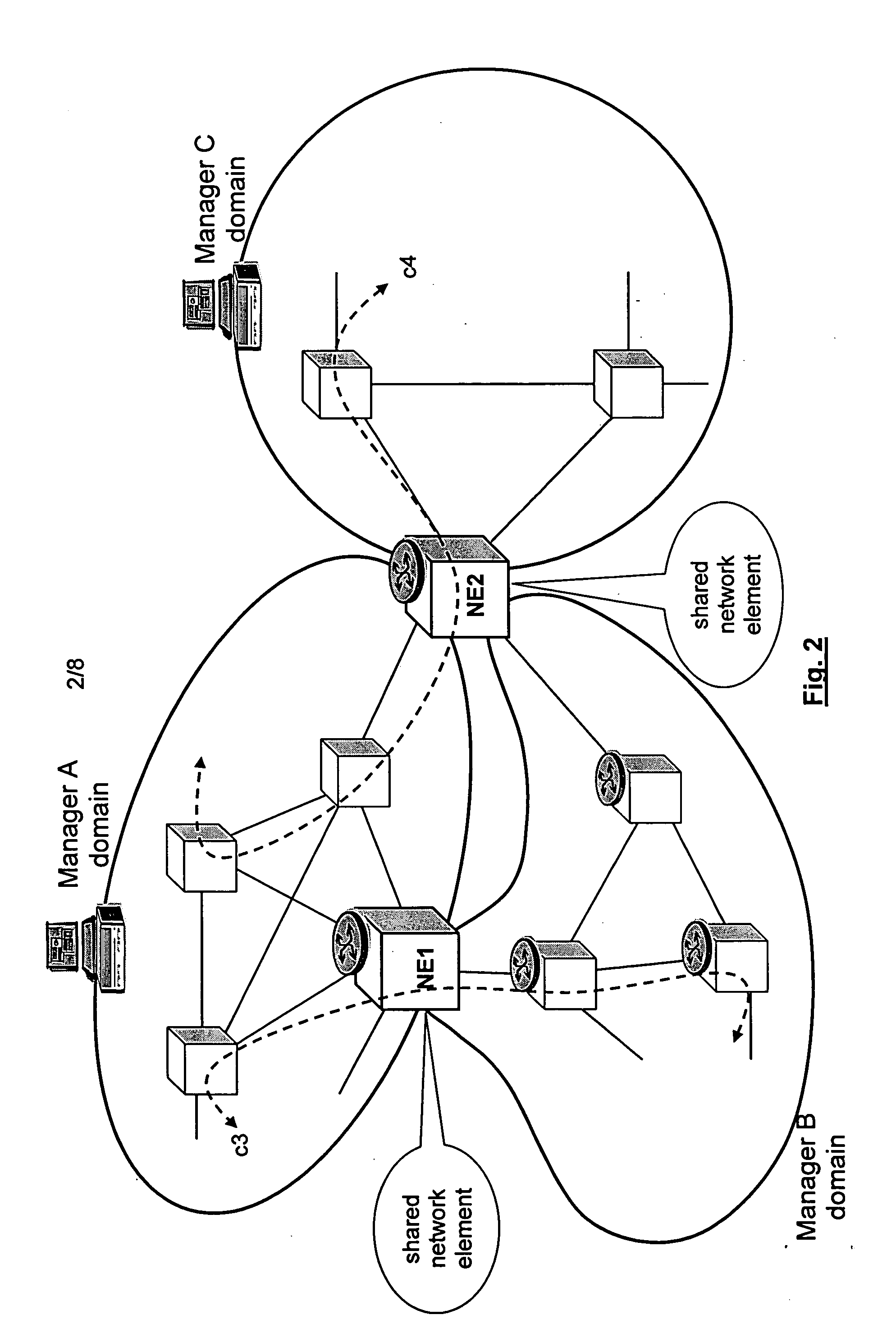
Shared resources in a multi manager environment
ActiveUS20060026225A1Reduce network element performanceMultiple digital computer combinationsTransmissionInformation repositoryManagement information base
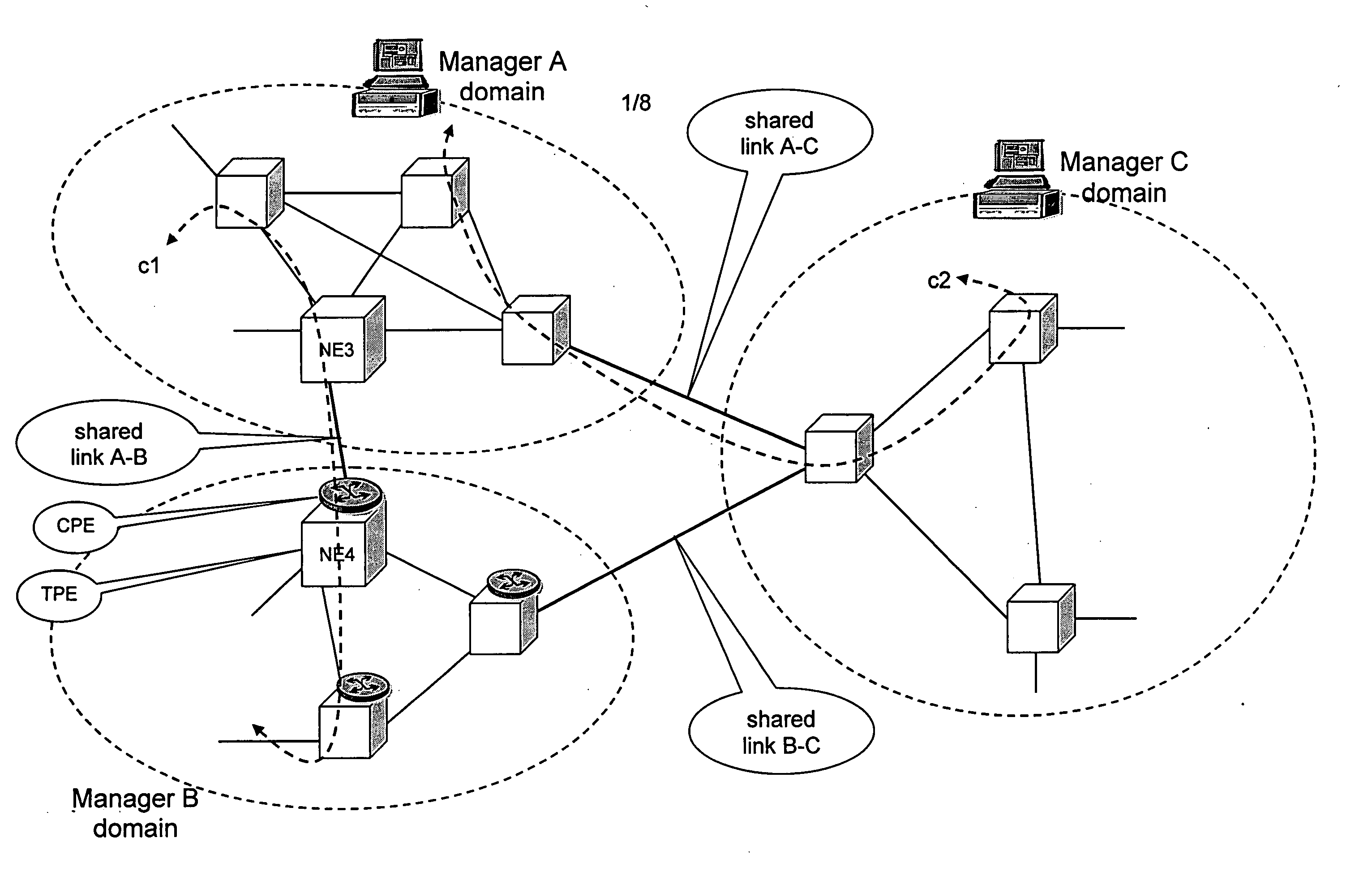
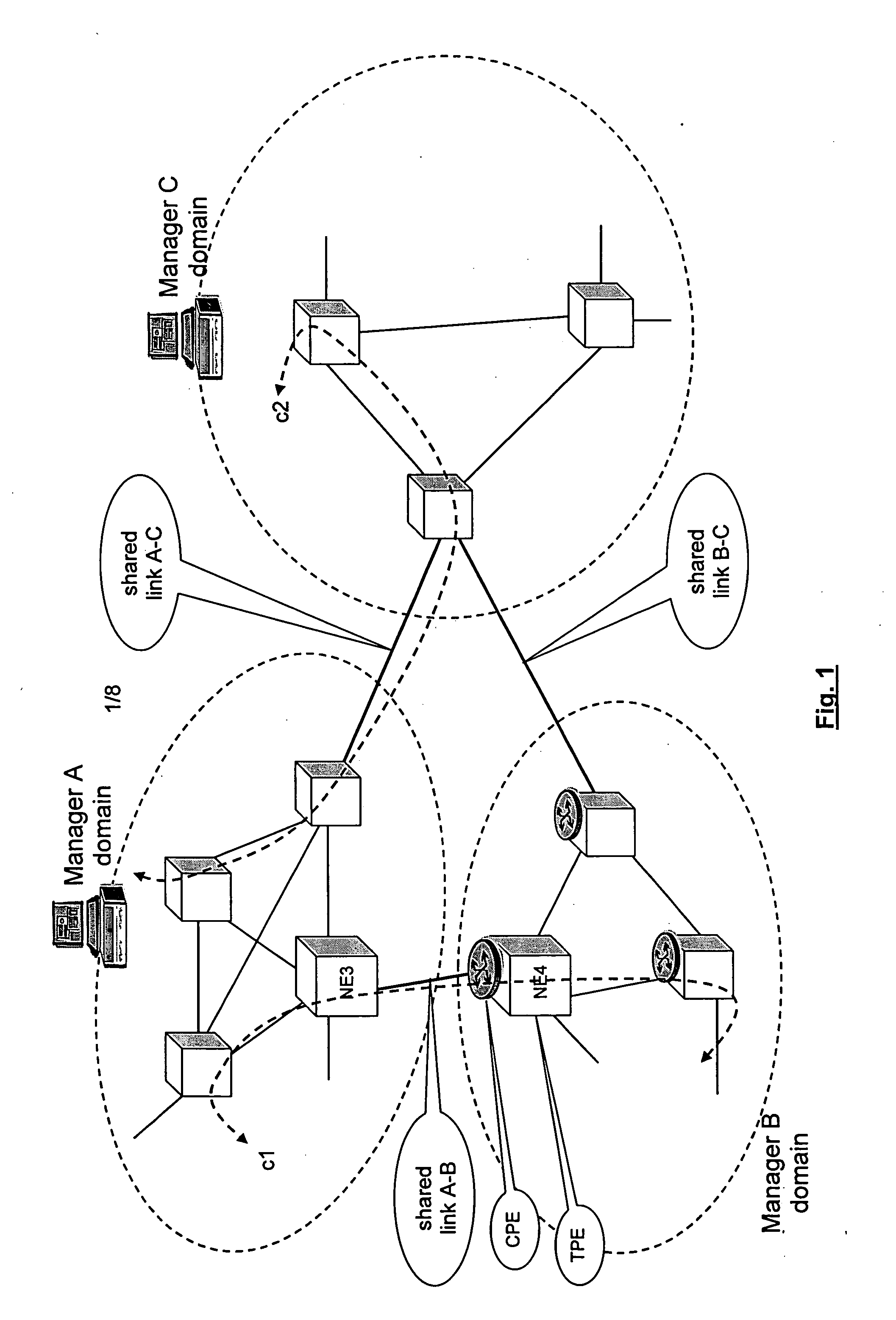
A method is described for controlling a shared resource for interconnecting two or more network domains being controlled by different Managers. Multiple Managers control the shared resource for the configuration of a segment of a connection between two different domains and the Managers cooperate in order to control dynamically the shared resource. Different network domains can be connected by a network element or by a link between different network elements belonging to the different network domains. In the first case the shared resource is a connection matrix of the network element, in the second case the shared resource includes the connection matrixes of the different network elements and the link between the network elements. A shared connection matrix includes some connection points for performing the cross-connections within the matrix: some connection points are controlled by one Manager, other connection points are controlled by another Manager and some shared connection points are controlled by both Managers. Multiple Managers control the shared resource by reading and writing information stored into a management information base, according to an explicit or implicit mode, or alternatevely by transmitting messages in the network directly between the Managers, according to a signalling protocol.
Owner:ALCATEL LUCENT SAS
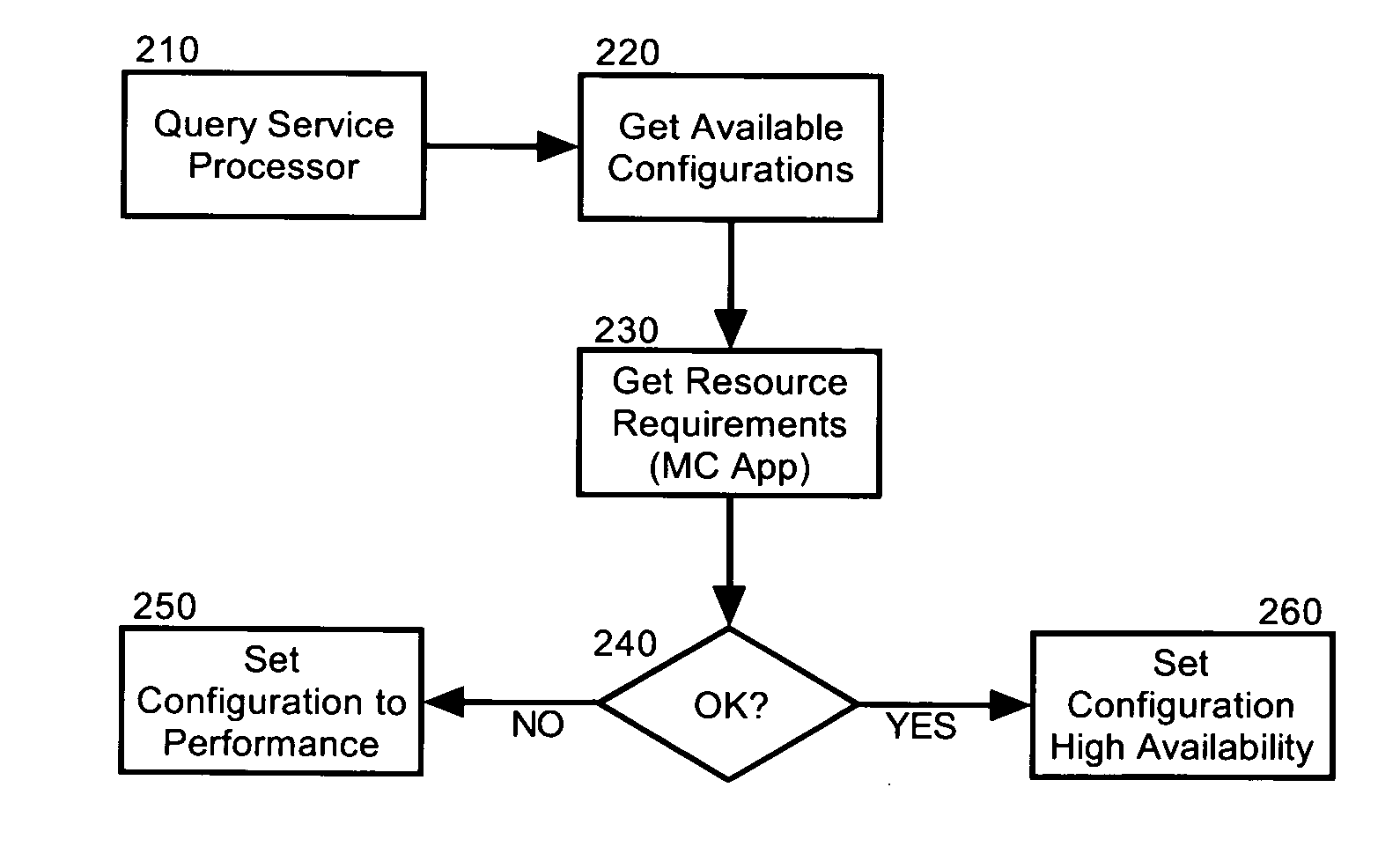
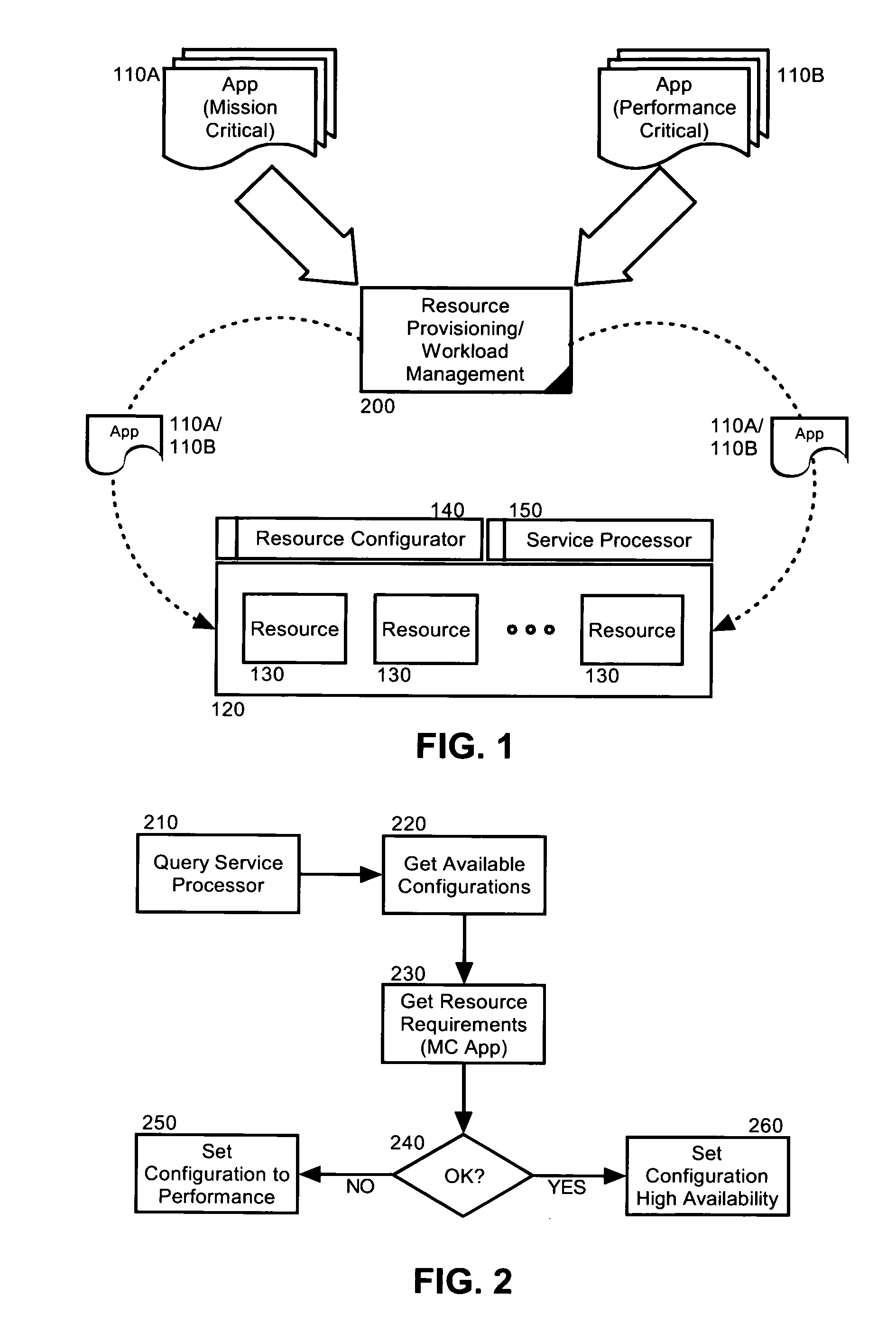
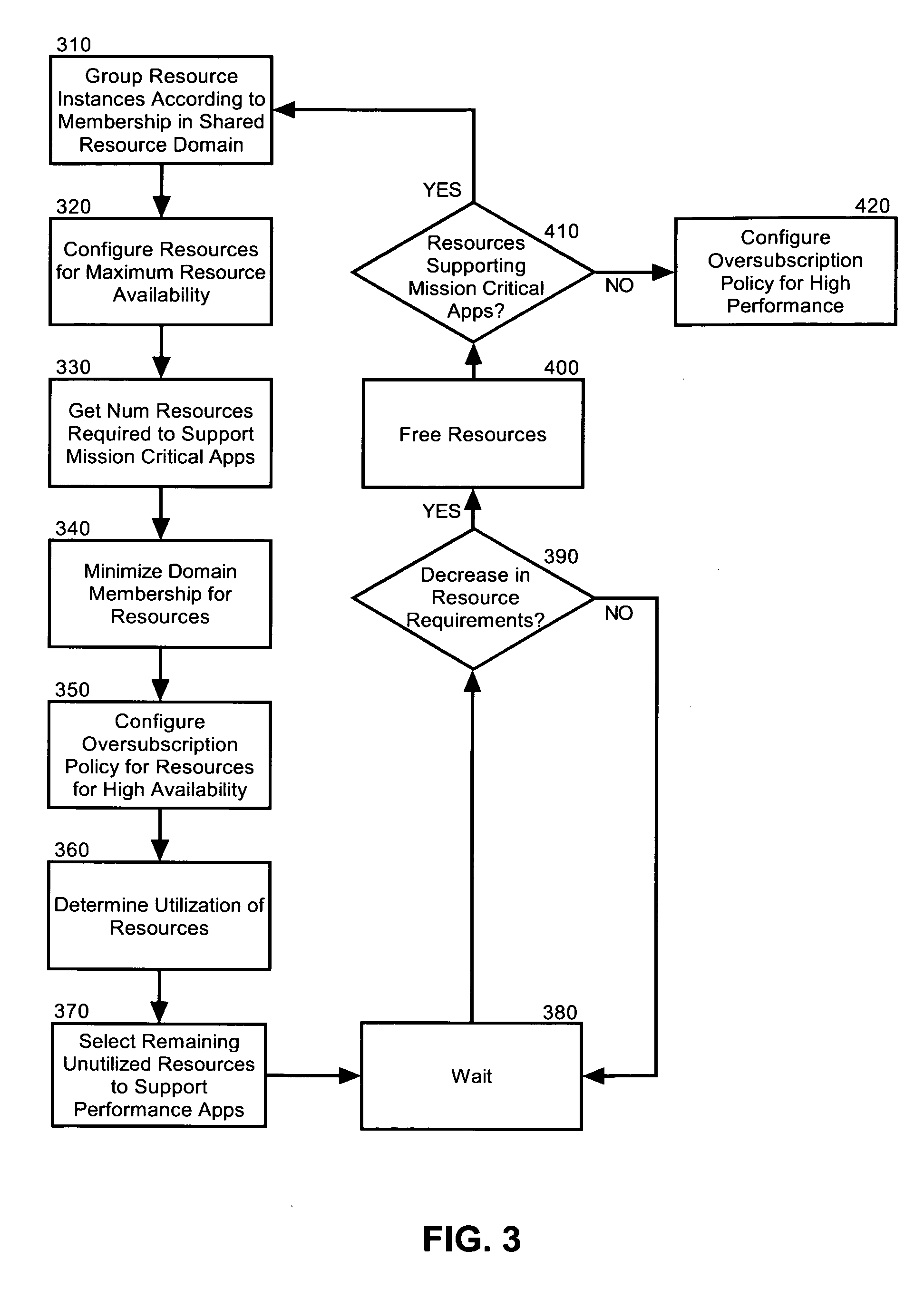
Dynamic resource allocation for disparate application performance requirements
InactiveUS20070198982A1Multiprogramming arrangementsMemory systemsResource poolData processing system
Embodiments of the invention address deficiencies of the art in respect to dynamic computing resource allocation, and provide a method, system and computer program product for dynamic resource allocation for disparate application performance requirements. In one embodiment of the invention, a resource allocation data processing system can include a shared resource pool including resources and a resource configurator coupled to the shared resource pool. The system further can include a service processor coupled to the resource configurator, wherein the service processor can include an application programming interface (API) exposing methods for commanding the resource configurator to configure the resources in the shared resource pool.
Owner:LENOVO ENTERPRISE SOLUTIONS SINGAPORE
System and method for creating a secure trusted social network
InactiveUS20060259957A1FinanceDigital data processing detailsInternet privacyElectronic communication
A system for a plurality of users to share resources with access, control and configuration based on pre-defined relationships of trust between the users of the system. A computer-based authority provides the services of authentication, identification and verification of each user within network. Processes are described that leads to the formation of an electronic community, which facilitates electronic communication and transactions in a defined manner.
Owner:TAM CHUNG +2
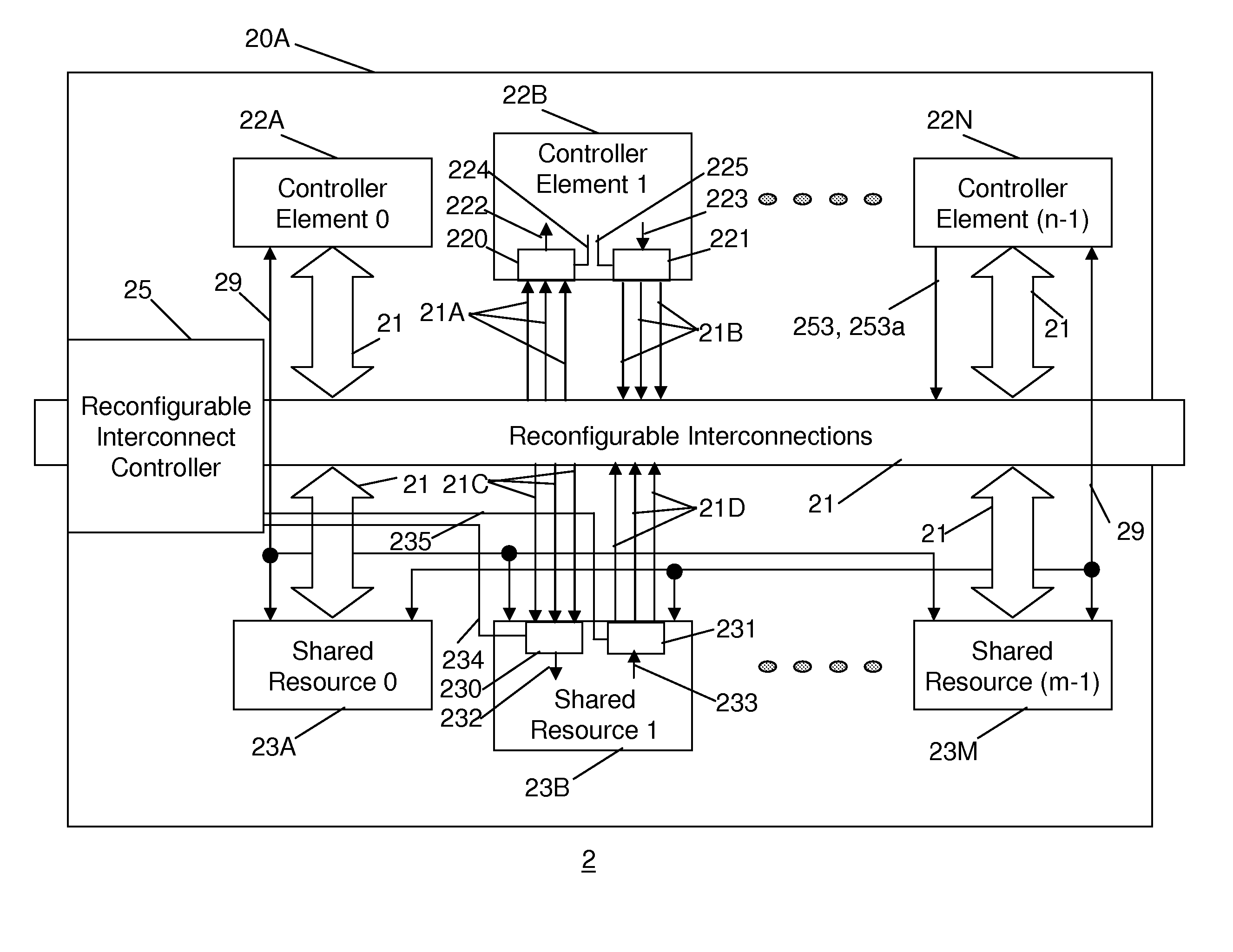
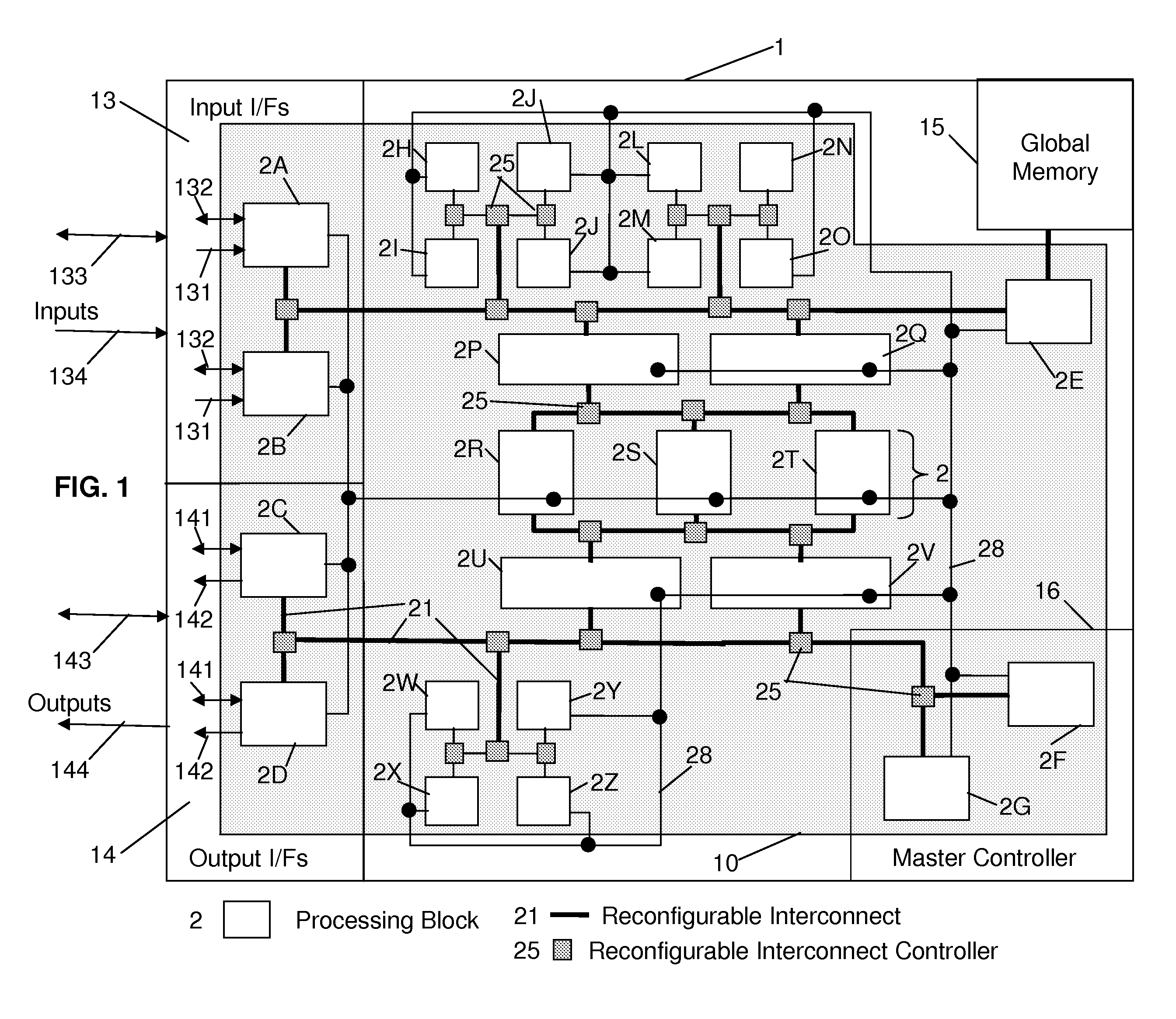
Reconfigurable integrated circuit
InactiveUS20070143577A1Energy efficient ICTArchitecture with single central processing unitNon real timeResource block
A reconfigurable integrated circuit is provided wherein the available hardware resources can be optimised for a particular application. Dynamically reconfiguring (in both real-time and non real-time) the available resources and sharing a plurality of processing elements with a plurality of controller elements achieve this. In a preferred embodiment the integrated circuit includes a plurality of processing blocks, which interface to a reconfigurable interconnection means. A processing block has two forms, namely a shared resource block and a dedicated resource block. Each processing block consists of one or a plurality of controller elements and a plurality of processing elements. The controller element and processing element generally comprise diverse rigid coarse and fine grained circuits and are interconnected through dedicated and reconfigurable interconnect. The processing blocks can be configured as a hierarchy of blocks and or fractal architecture.
Owner:AKYA HLDG
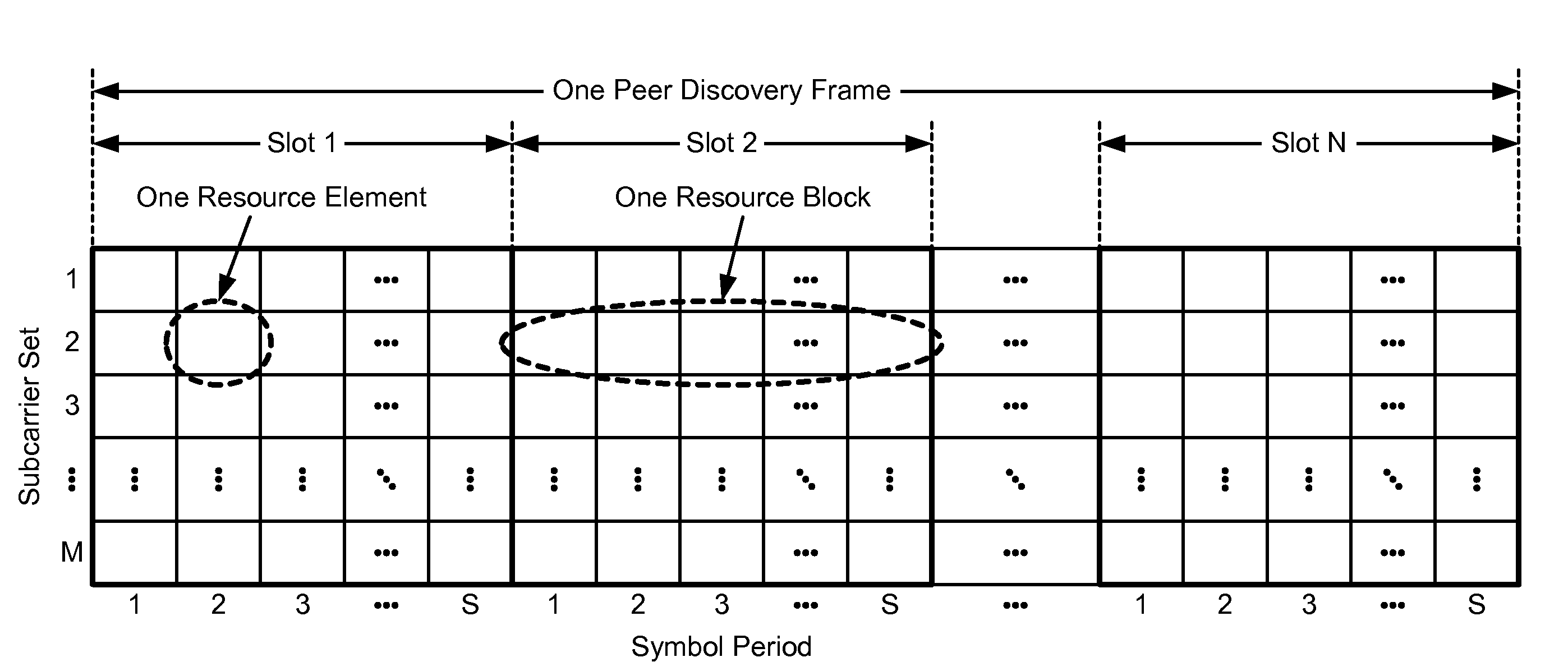
Transmission with collision detection and mitigation for wireless communication
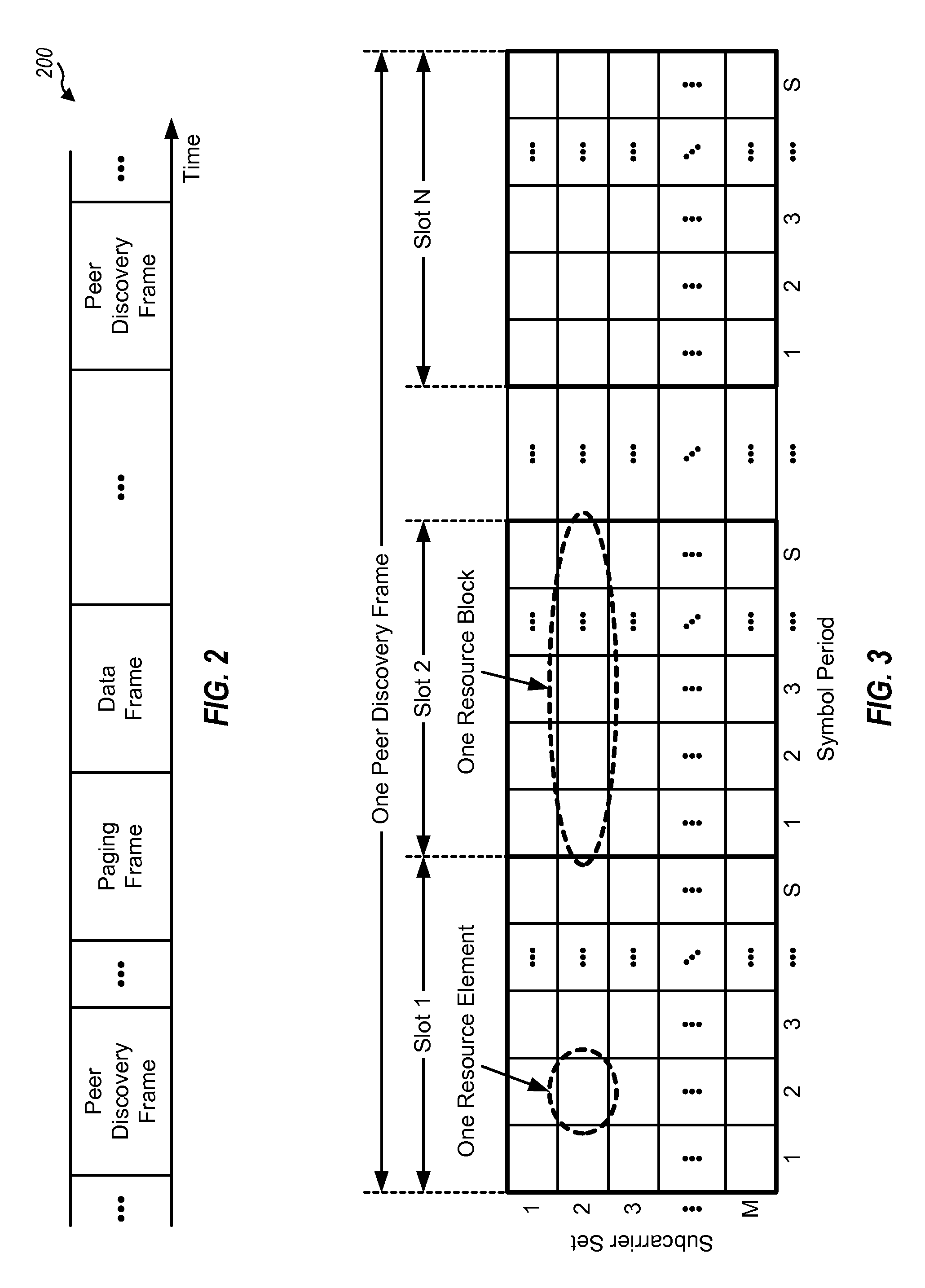
ActiveUS20100202400A1Improve interferenceWireless commuication servicesNetwork data managementTelecommunicationsResource element
Techniques for transmitting signals on shared resources in a manner to detect and / or combat collision are described. In an aspect, a terminal may transmit a signal on a subset of resource elements in a resource block, and at least one null resource element with no signal may be used to detect for collision of the signal. In another aspect, different terminals may simultaneously transmit their signals on different subsets of resource elements in a resource block. These different subsets of resource elements may be pseudo-randomly selected to randomize interference. In one design, a terminal may determine a resource block to use for transmission of a signal, select a subset of the resource elements in the resource block, and transmit the signal on the selected resource elements, e.g., to at least one other terminal for peer-to-peer communication. The signal may be a peer discovery signal, a paging signal, etc.
Owner:QUALCOMM INC
Personal message service with enhanced text to speech synthesis
InactiveUS7027568B1Distribution costReduce manufacturing costAutomatic call-answering/message-recording/conversation-recordingAutomatic exchangesShort Message ServiceTerminal equipment
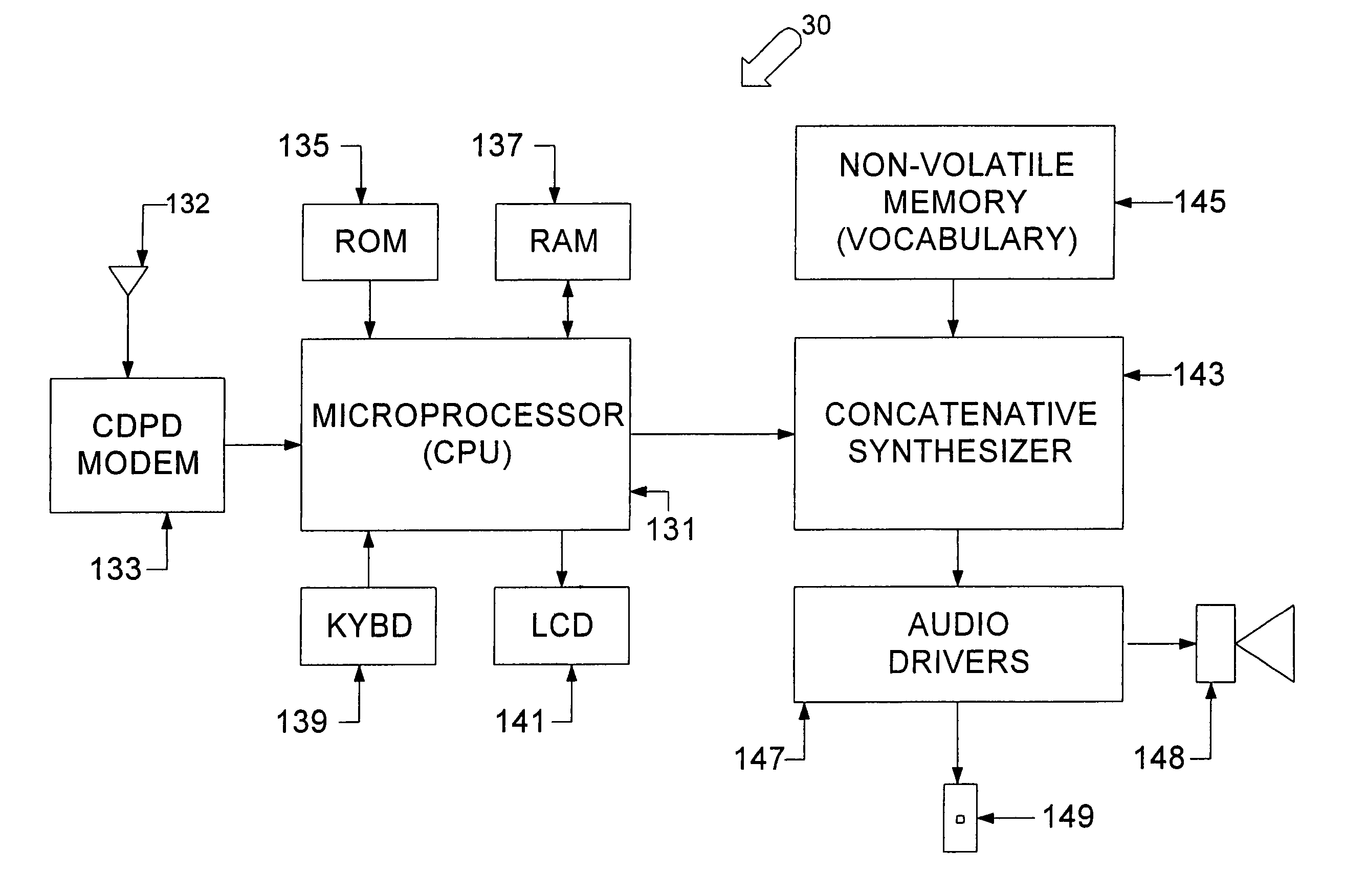
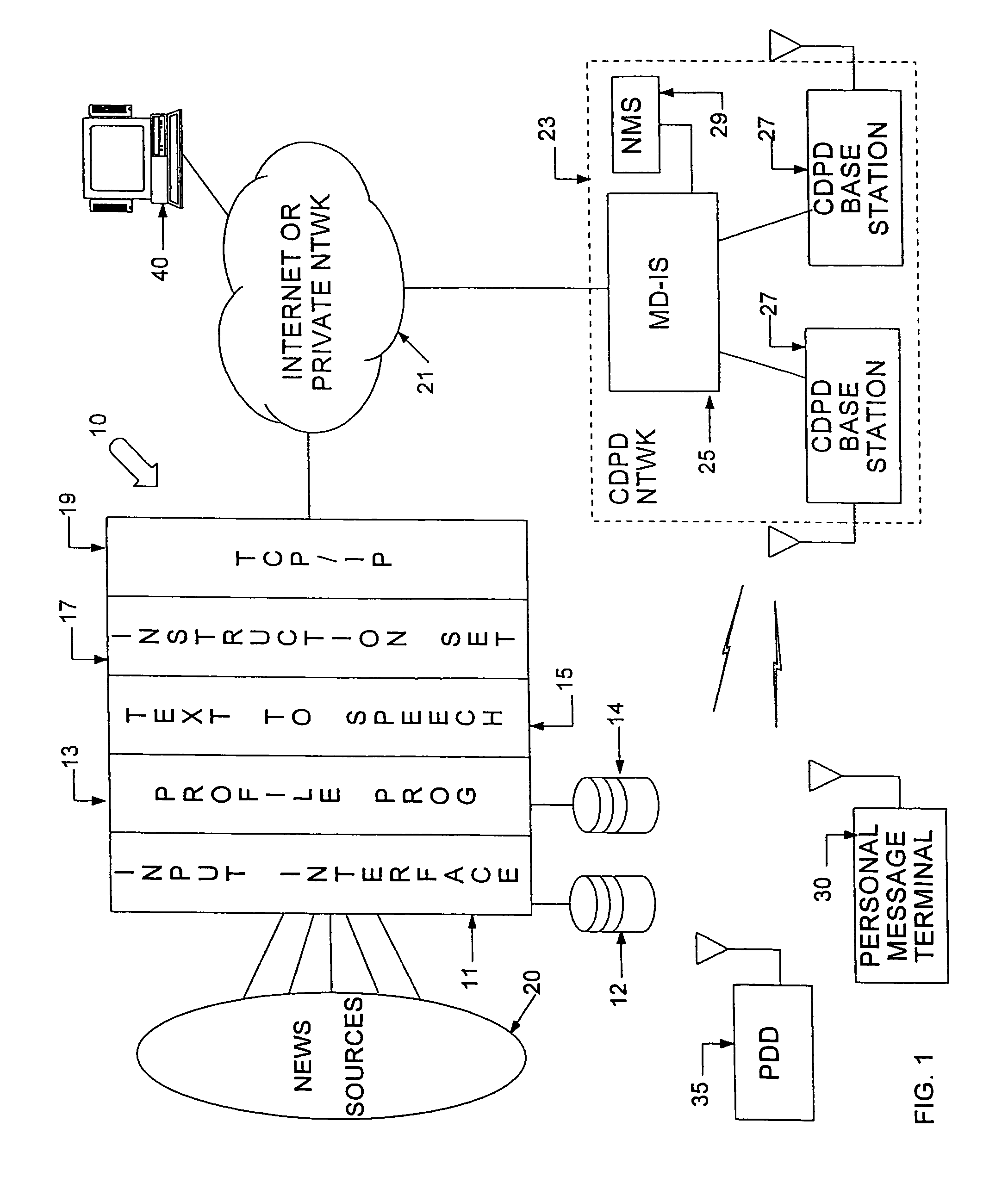
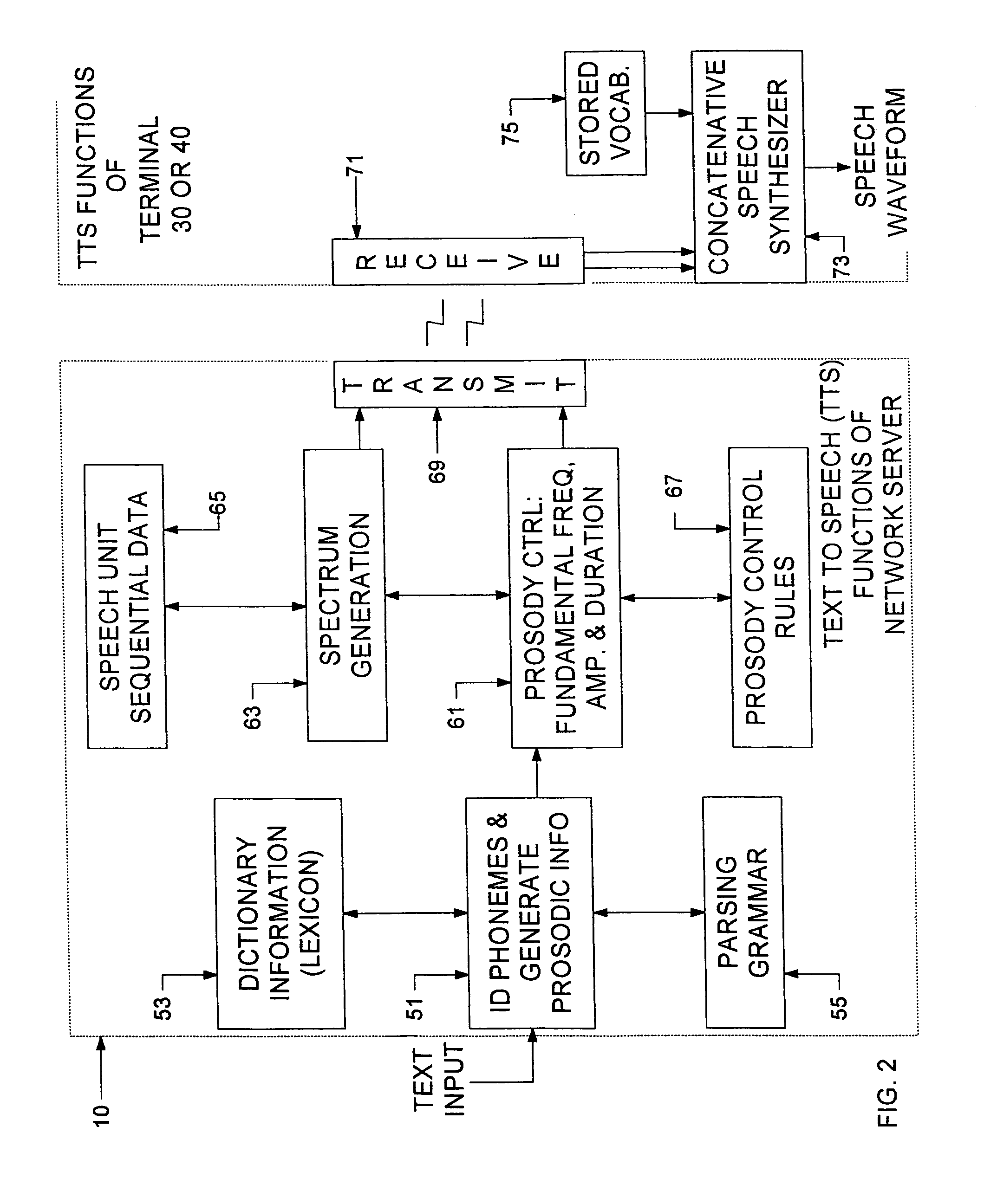
A server in a network gathers textual information, such as news items, E-mail and the like. From that information, the server develops or identifies messages for use by individual subscribers. The same server that accumulates the text messages or another server in the network converts the textual information in each message to a sequence of speech synthesizer instructions. The converted messages, containing the sequences of speech synthesizer instructions, are transmitted to each identified subscriber's terminal device. A synthesizer in the terminal generates an audio waveform signal, representing the speech information, in response to the instructions. In the preferred embodiment, the terminals utilize concatenative type speech synthesizers, each of which has an associated vocabulary of stored fundamental sound samples. The instructions identify the sound samples, in order. The instructions also provide parameters for controlling characteristics of the signal generated during waveform synthesis for each sound sample in each sequence. For example, the instructions may specify the pitch, duration, amplitude, attack envelope and decay envelope for each sample. The division of the text to speech synthesis processing between the server and the terminals places the cost of the front end processing in the server, which is a shared resource. As a result, the hardware and software of the terminal may be relatively simple and inexpensive. Also, it is possible to upgrade the quality of the synthesis by upgrading the server software, without modifying the terminals.
Owner:GOOGLE LLC
Shared Internet storage resource, user interface system, and method
InactiveUS20100185614A1Promote activeDigital data processing detailsMultiple digital computer combinationsData streamWeb service
The Shared Internet Storage Resource provides Internet-based file storage, retrieval, access, control, and manipulation for a user. Additionally, an easy-to-use user interface is provided both for a browser or stand-alone application. The entire method provides means by which users can establish, use, and maintain files on the Internet in a manner remote from their local computers yet in a manner that is similar to the file manipulation used on their local computers. A high capacity or other storage system is attached to the Internet via an optional internal network that also serves to generate and direct metadata regarding the stored files. A web server using a CGI, Java®-based, or other interface transmits and retrieves TCP / IP packets or other Internet information through a load balancer / firewall by using XML to wrap the data packets. File instructions may be transmitted over the Internet to the Shared Resource System. The user's account may be password protected so that only the user may access his or her files. On the user's side, a stand-alone client application or JavaScript object interpreted through a browser provide two means by which the XML or other markup language data stream may be received and put to use by the user. Internet-to-Internet file transfers may be effected by directly downloading to the user's account space.
Owner:OBRIEN BRETT +3
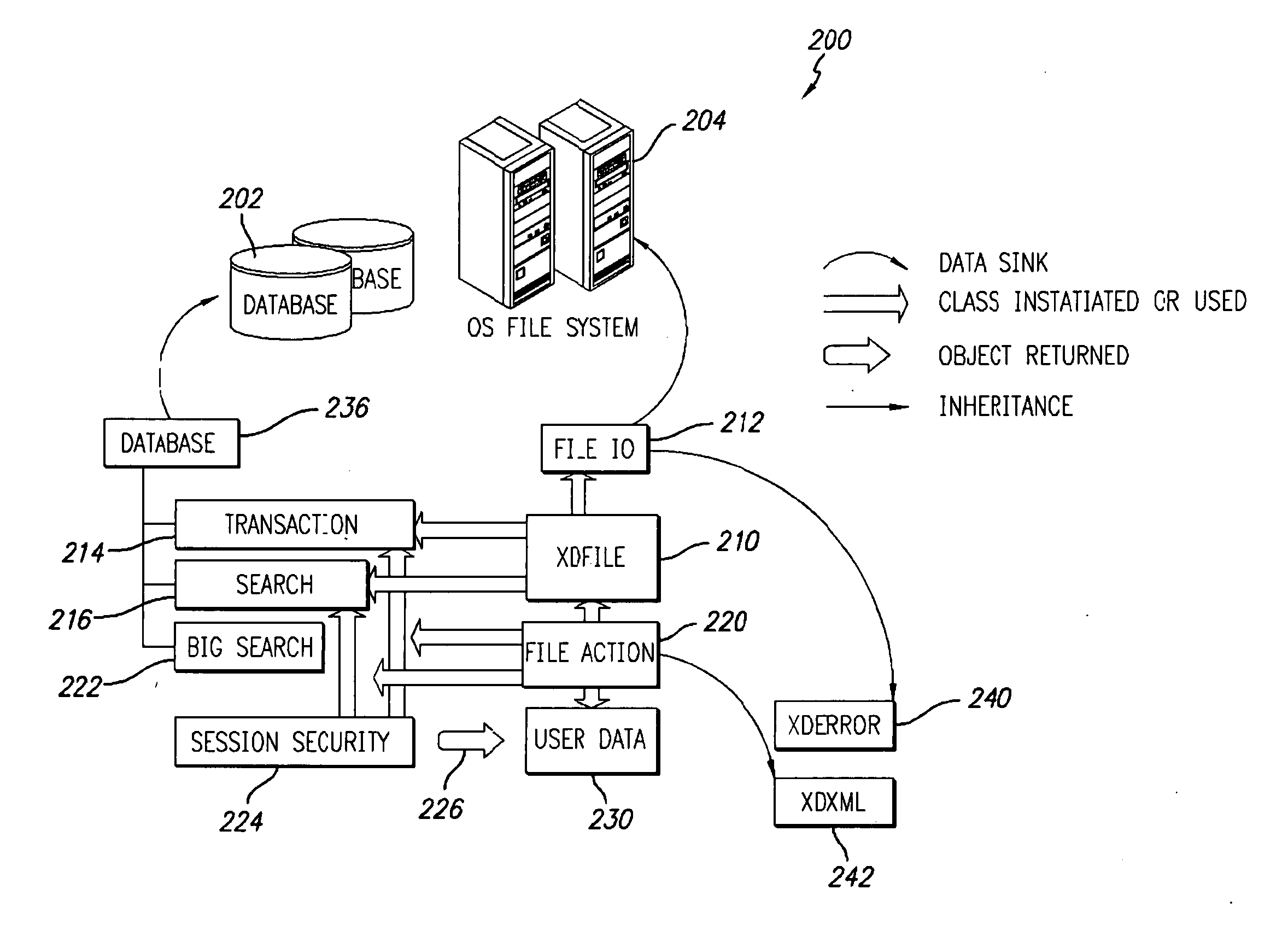
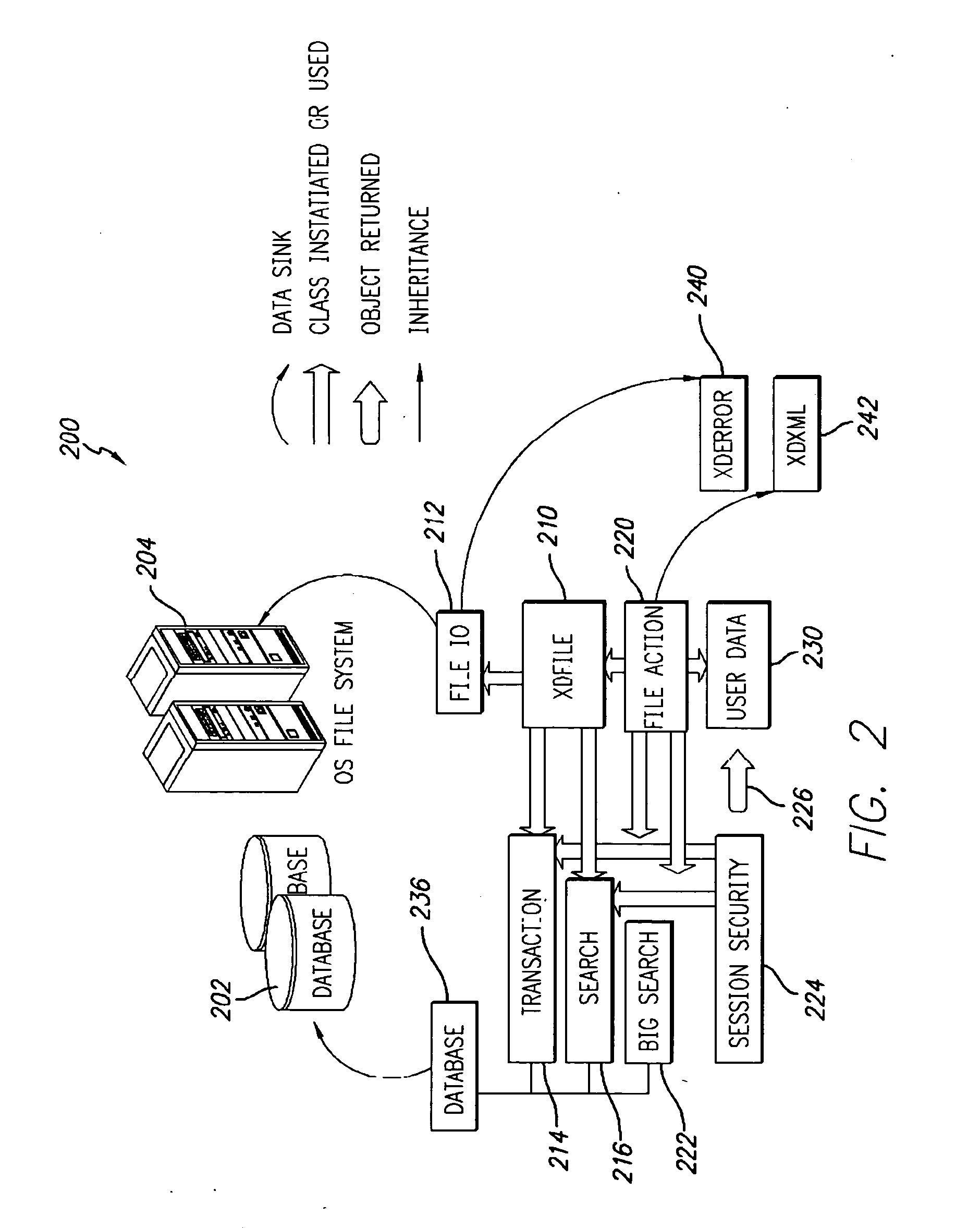
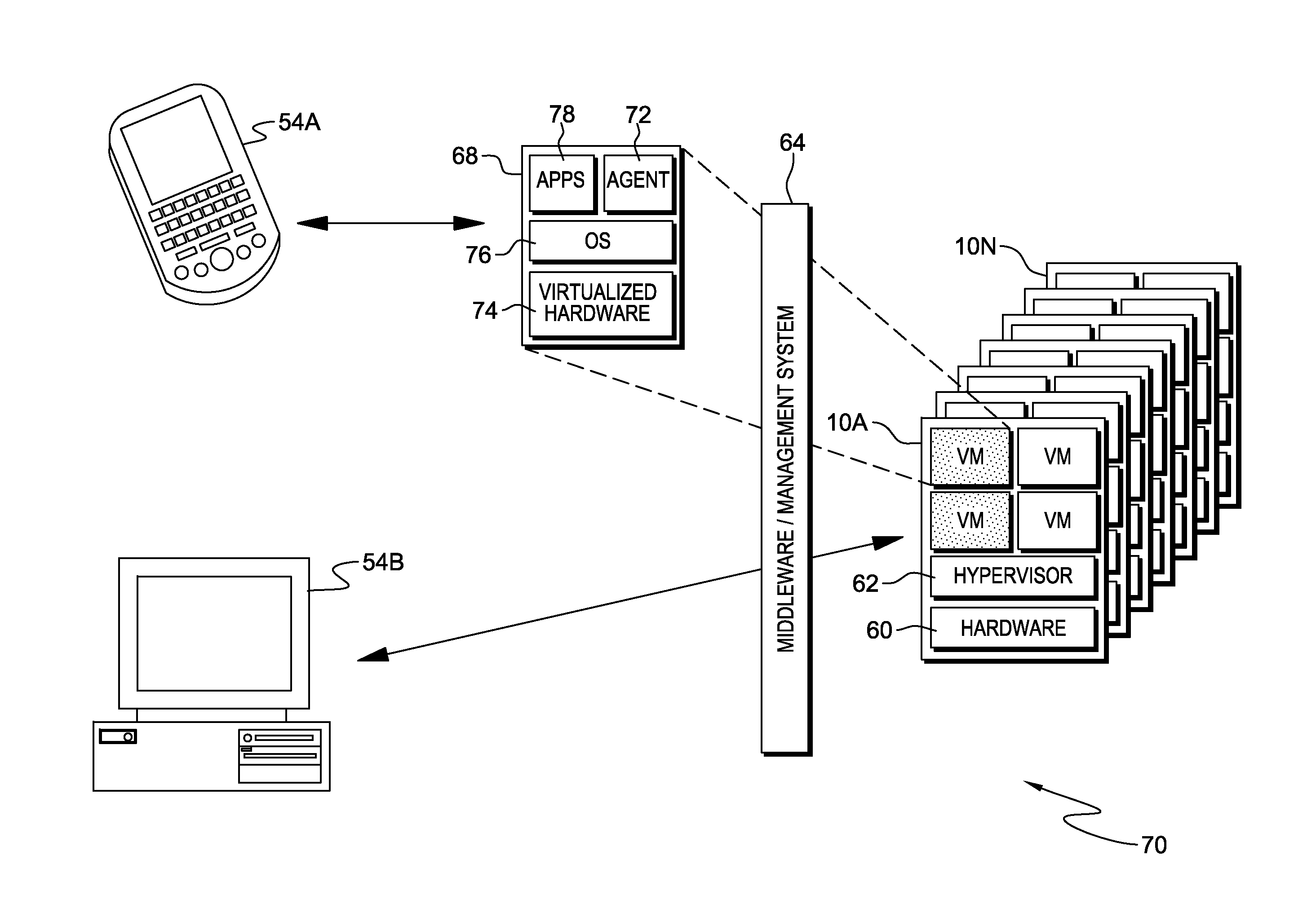
Open platform architecture for shared resource access management
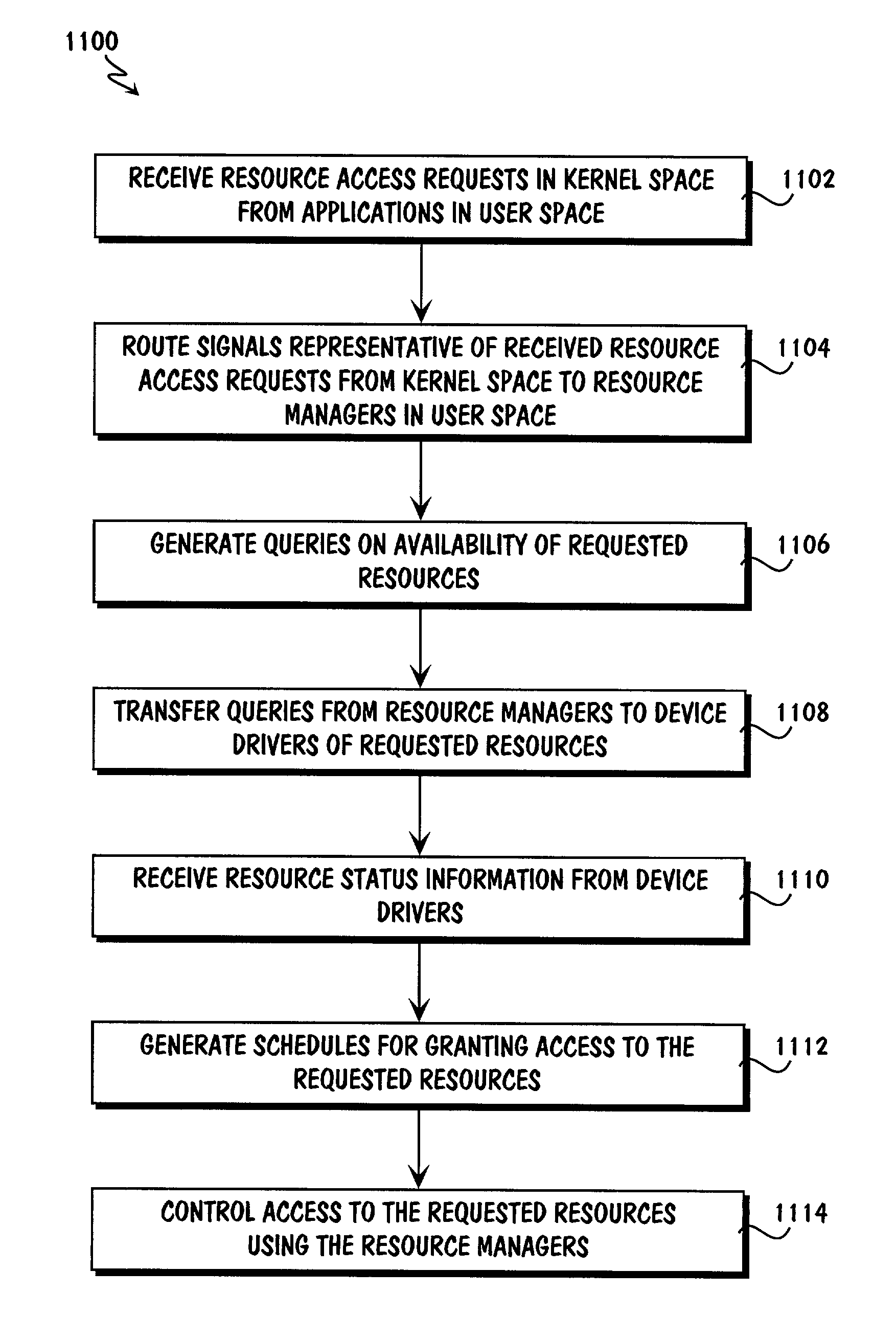
An open platform architecture and methods for shared resource access management are provided. A redirection module in kernel space receives requests for access to resources from applications in user space. The redirection module routes signals representative of the received requests to a device driver interface in user space. Components of the device driver interface include resource management modules and device drivers that correspond to available resources. The resource management modules generate queries to the device drivers regarding availability of the requested resources. Upon receipt of resource status information from the device drivers, components of the device driver interface generate schedules for granting access to the requested resources. Further, the device driver interface components control access to the resources in accordance with the generated schedules including issuing responses to the requesting applications and the device drivers of the requested resources.
Owner:WI LAN INC
Method and system for managing time division multiplexing (TDM) timeslots in a network switch
InactiveUS20030026287A1Time-division multiplexRadio transmissionStatistical time division multiplexingFibre Channel
A system and method for managing the allocation of Time Division Multiplexing (TDM) timeslots in a network switch. The network switch may use a TDM cycle comprising multiple timeslots to manage shared resources and to schedule data ingress and egress through the ports of the current configuration, wherein each port is assigned one or more timeslots. The network switch may be reprogrammed to support one of multiple timeslot assignment schemes for one of multiple port configurations. The network switch may support configurations with varying numbers of ports, e.g. 8- and 16-port configurations. A network switch may also support configurations where two or more ports are combined to form one port, for example, a 2 Gbs Fibre Channel port. To meet the requirements of the various configurations, the timeslot assignment scheme may be reprogrammed to meet the scheduling requirements of each of the possible port configurations.
Owner:BROCADE COMMUNICATIONS SYSTEMS
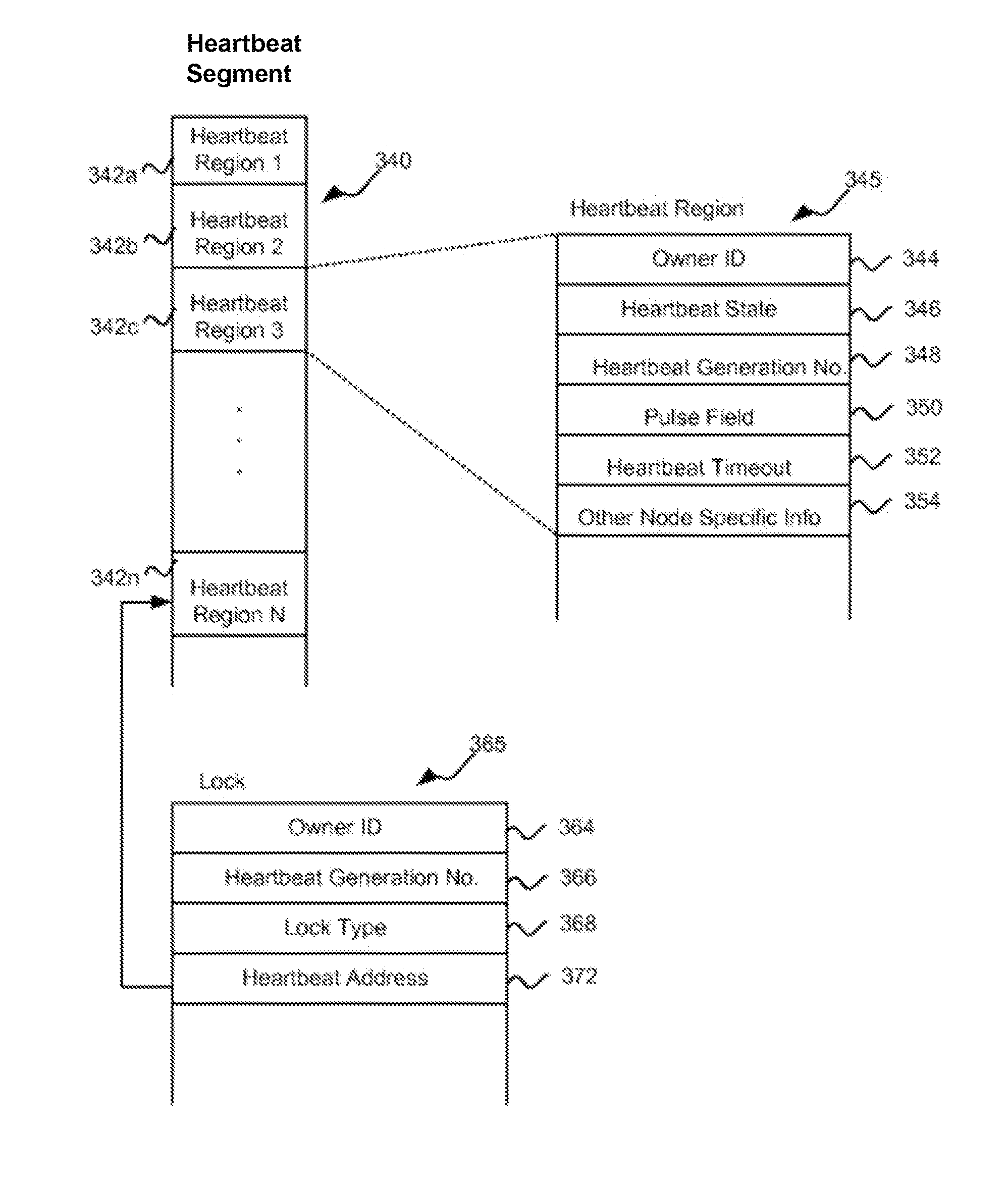
Associating heartbeat data with access to shared resources of a computer system
ActiveUS8560747B1Maintained efficiently and reliablyUnauthorized memory use protectionProgram controlVirtualizationTimestamp
A method, system and program code for implementing distributed locks to be maintained through the use of on disk heartbeats. An instance of a node need only maintain a single heartbeat for all locks associated with the node and all of its processes. The node updates its heartbeat by accessing common storage, either virtual or physical, and updating a timestamp value in its heartbeat within a predetermined time interval, otherwise the heartbeat becomes stale. Expired heartbeats can be cleared or broken to allow redistribution of any locks associated therewith. The inventive technique may be implemented in a traditional computer environment or in a fully or partially virtualized environment and requires no use of an IP network or a separate network based lock manager.
Owner:VMWARE INC
Agent framework for mobile devices
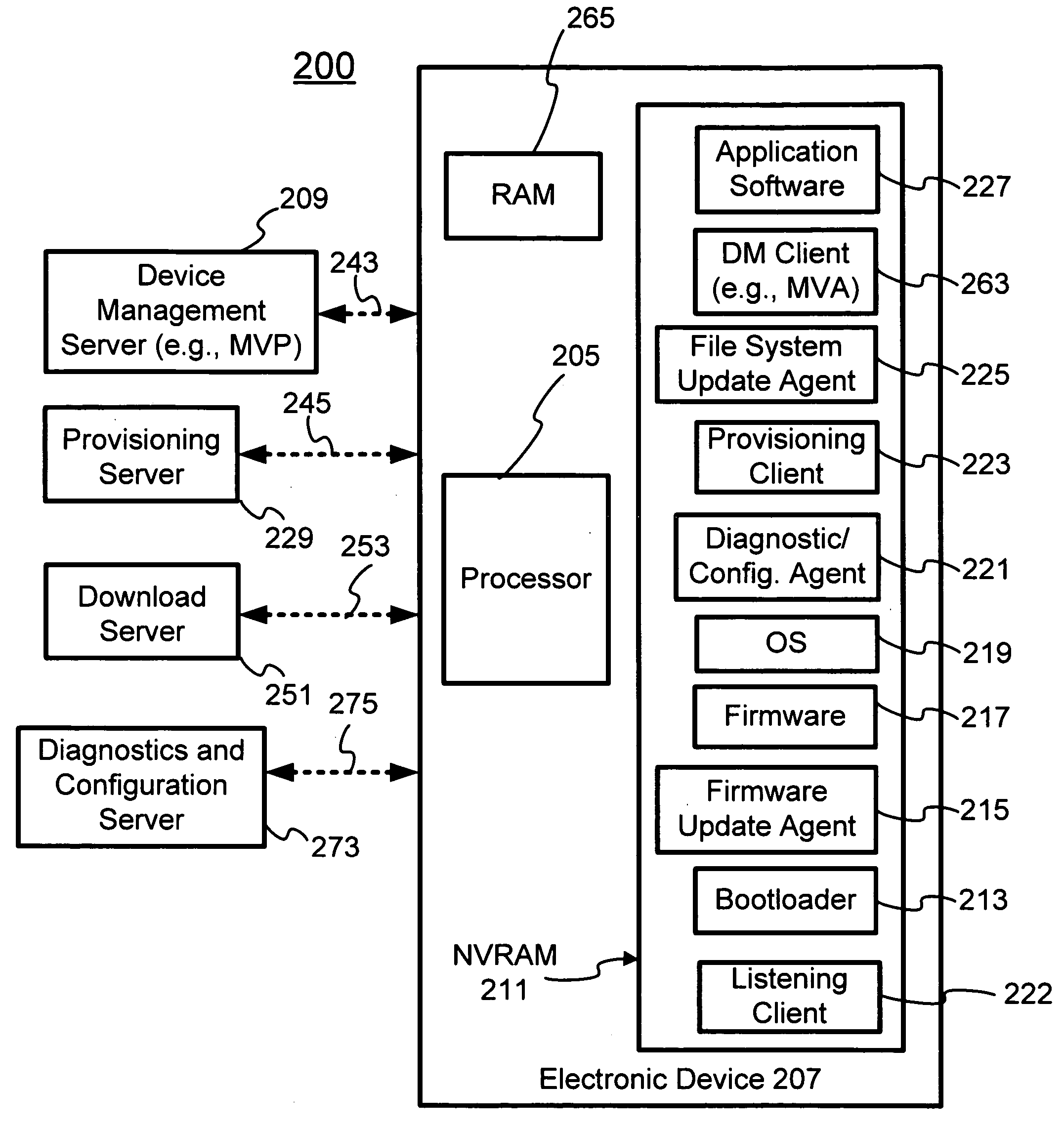
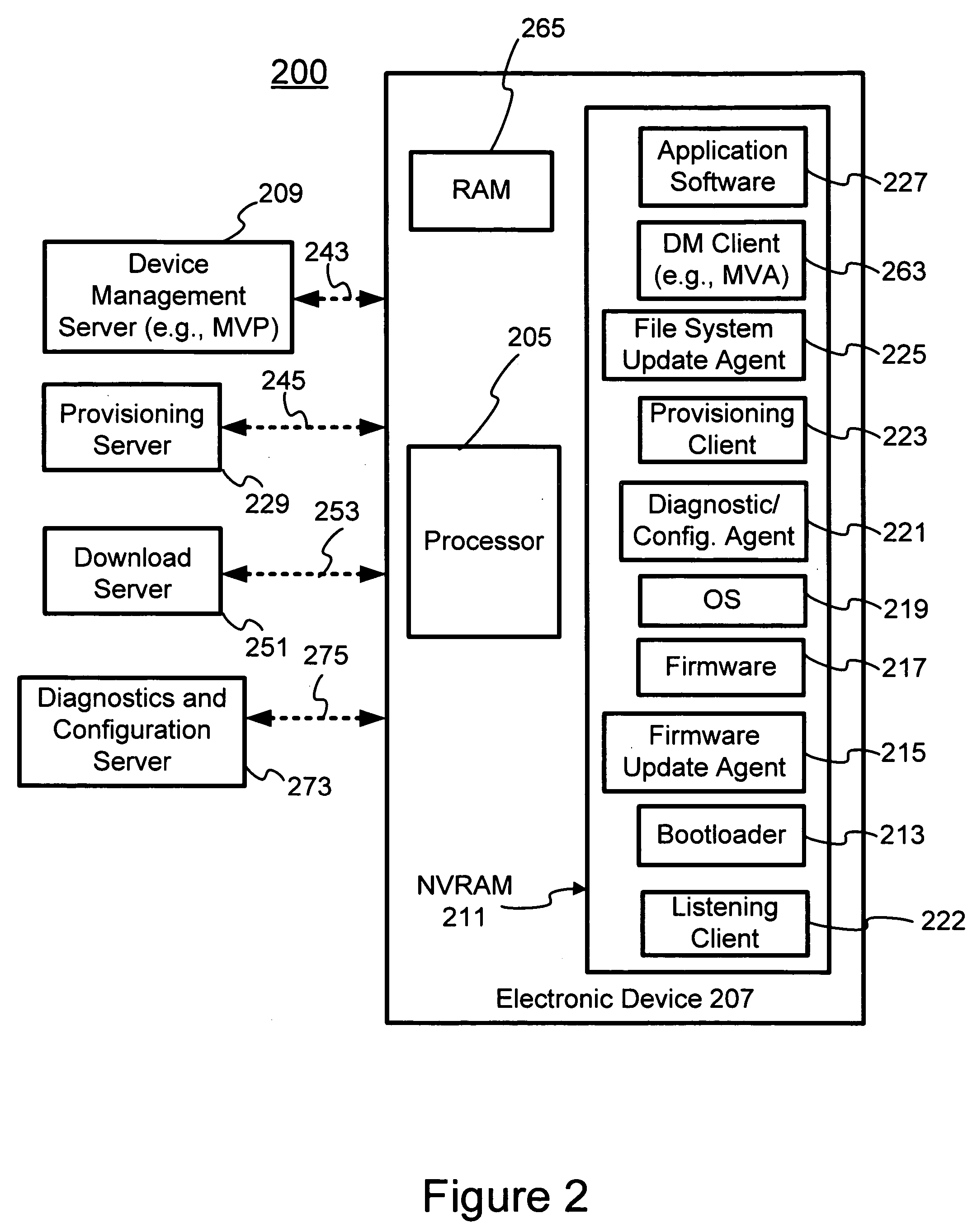
Herein described is an agent support framework used in a mobile communication device. The agent support framework provides a set of commonly used features that may be used by various client applications. The client applications may comprise one or more diagnostic / configuration agents that are used in monitoring device status, performing problem diagnosis, and obtaining configuration information from the mobile electronic device. Should a firmware or file system update be required, one or more update agents may be used to download one or more data files. The set of commonly used features provides shared resources to the various client applications. New client applications may be easily designed based on the set of commonly used features. The integration of new agents and / or clients to the agent support framework is facilitated by the ability of the agent support framework to provide shared resources when necessary.
Owner:HEWLETT PACKARD DEV CO LP
Resource allocation in virtual routers
InactiveUS20110016215A1Digital computer detailsData switching networksShared resourceResource allocation
A router system implements a plurality of virtual routers. Various combinations of resources may be shared by the router system when implementing the virtual routers. In one embodiment, the particular combination of resources to share when implementing the virtual router is user programmable.
Owner:VERIZON PATENT & LICENSING INC
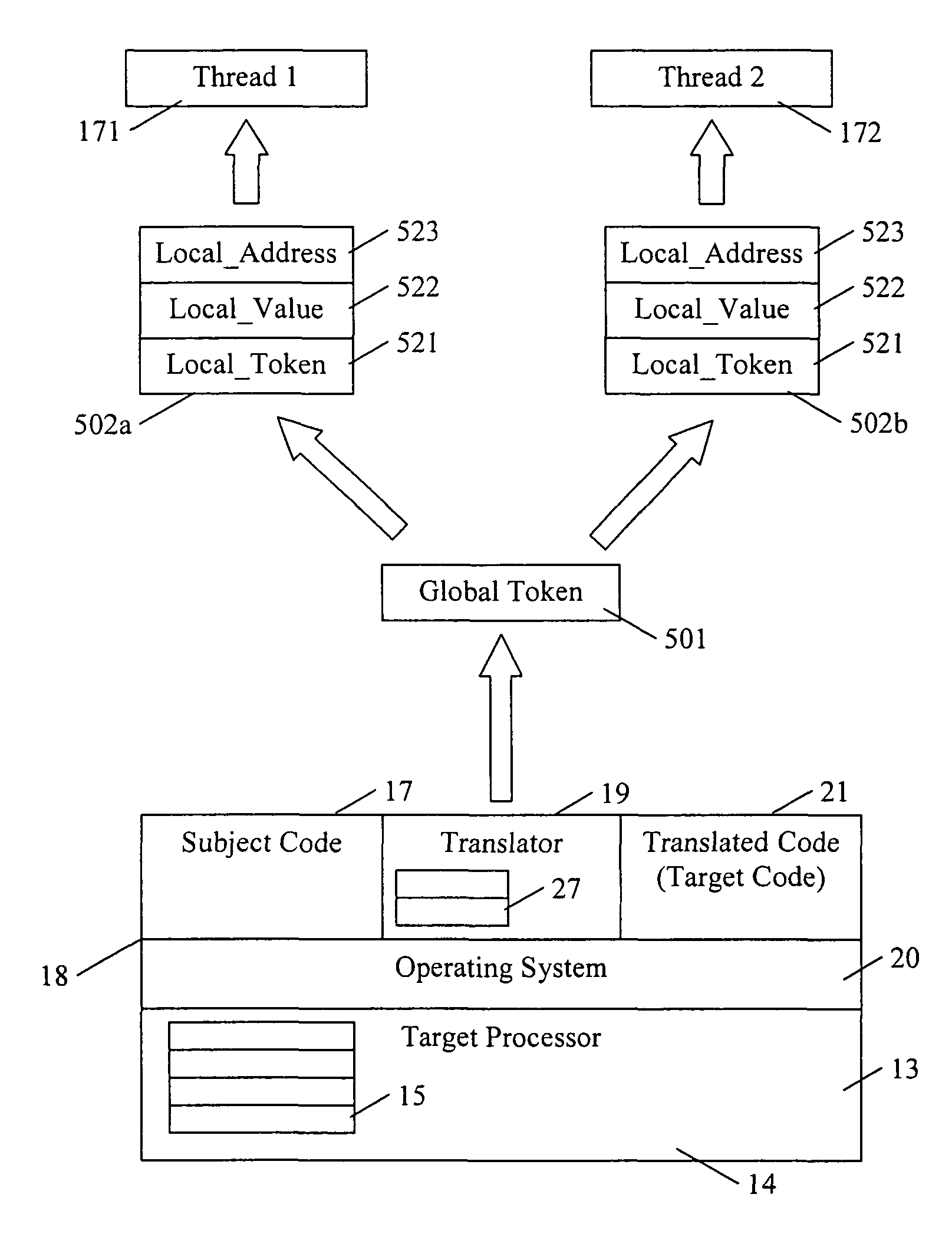
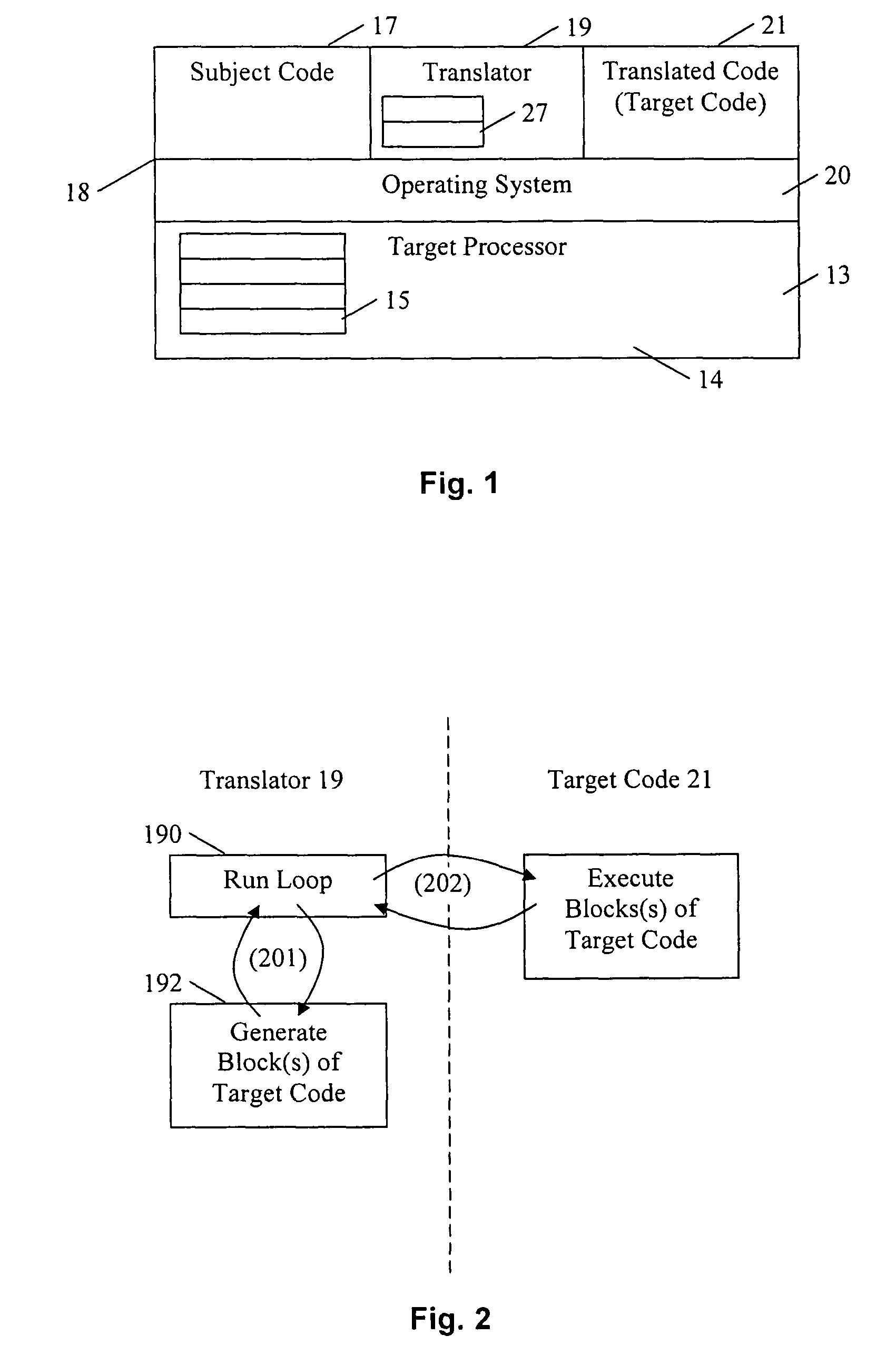
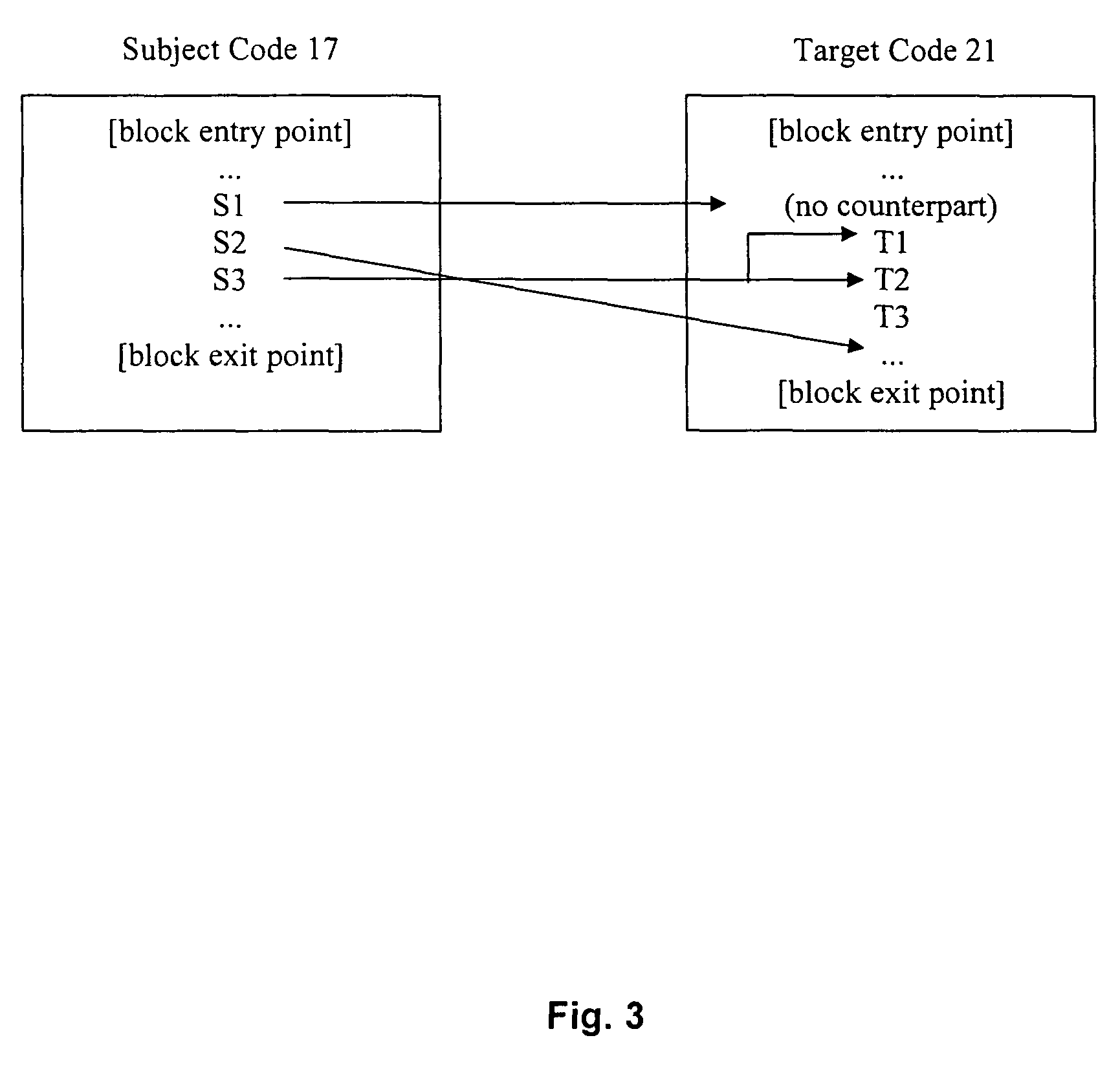
Converting program code with access coordination for a shared memory
A dynamic binary translator 19 converts a subject program 17 into target code 21 on a target processor 13. For a multi-threaded subject environment, the translator 19 provides a global token 501 common to each thread 171, 172, and one or more sets of local data 502, which together are employed to coordinate access to a memory 18 as a shared resource. Adjusting the global token 501 allows the local datastructures 502a,b in each thread to detect potential interference with the shared resource 18.
Owner:IBM CORP
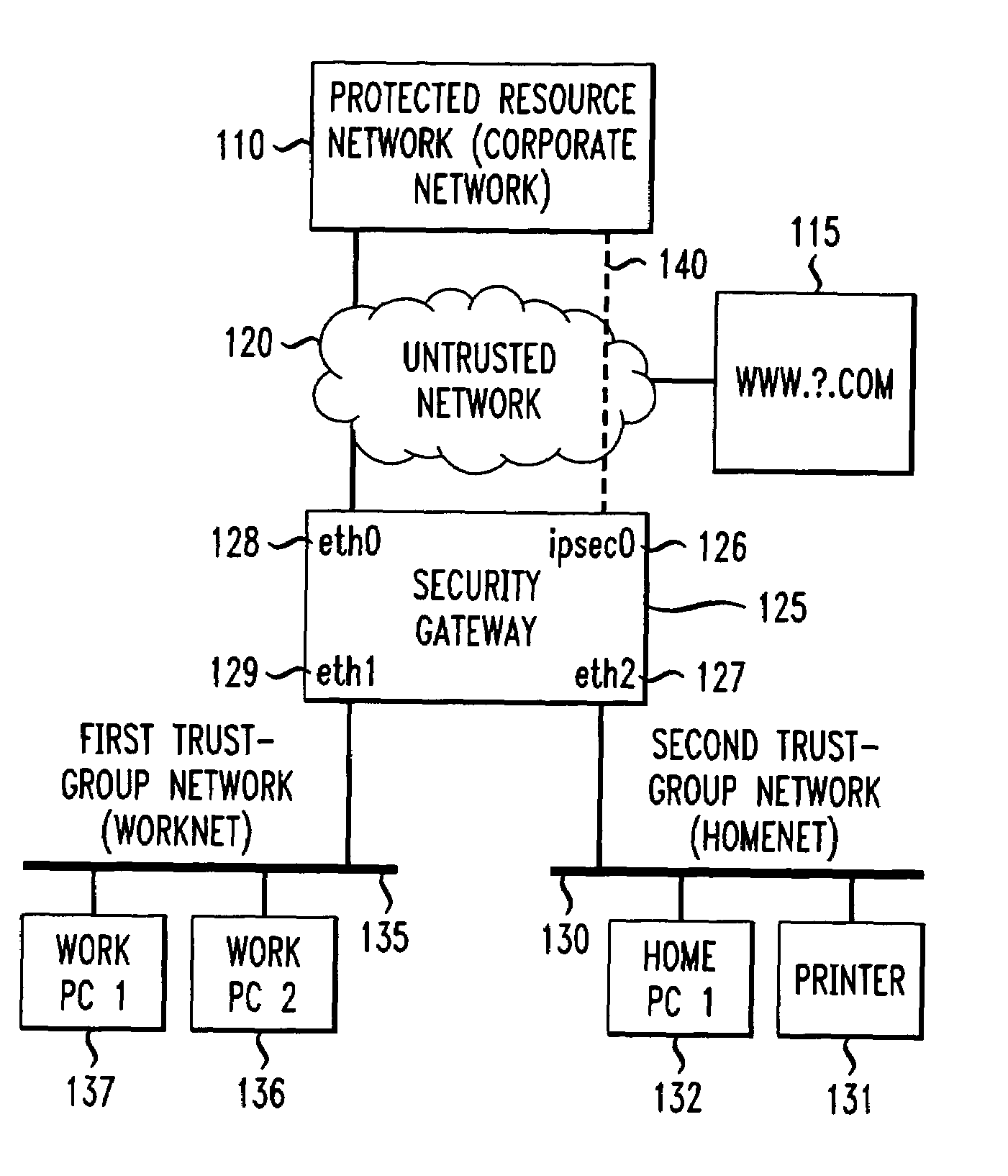
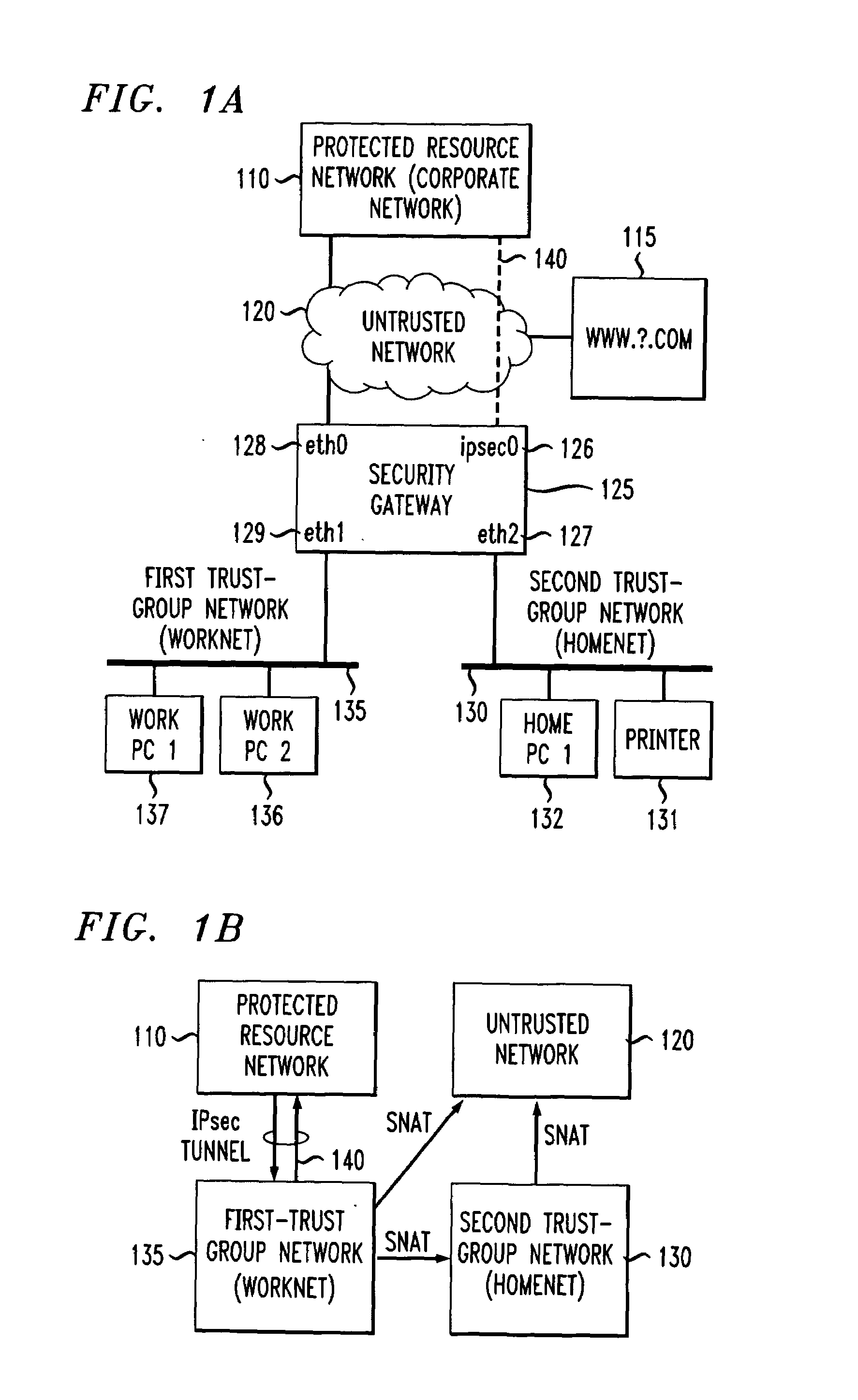
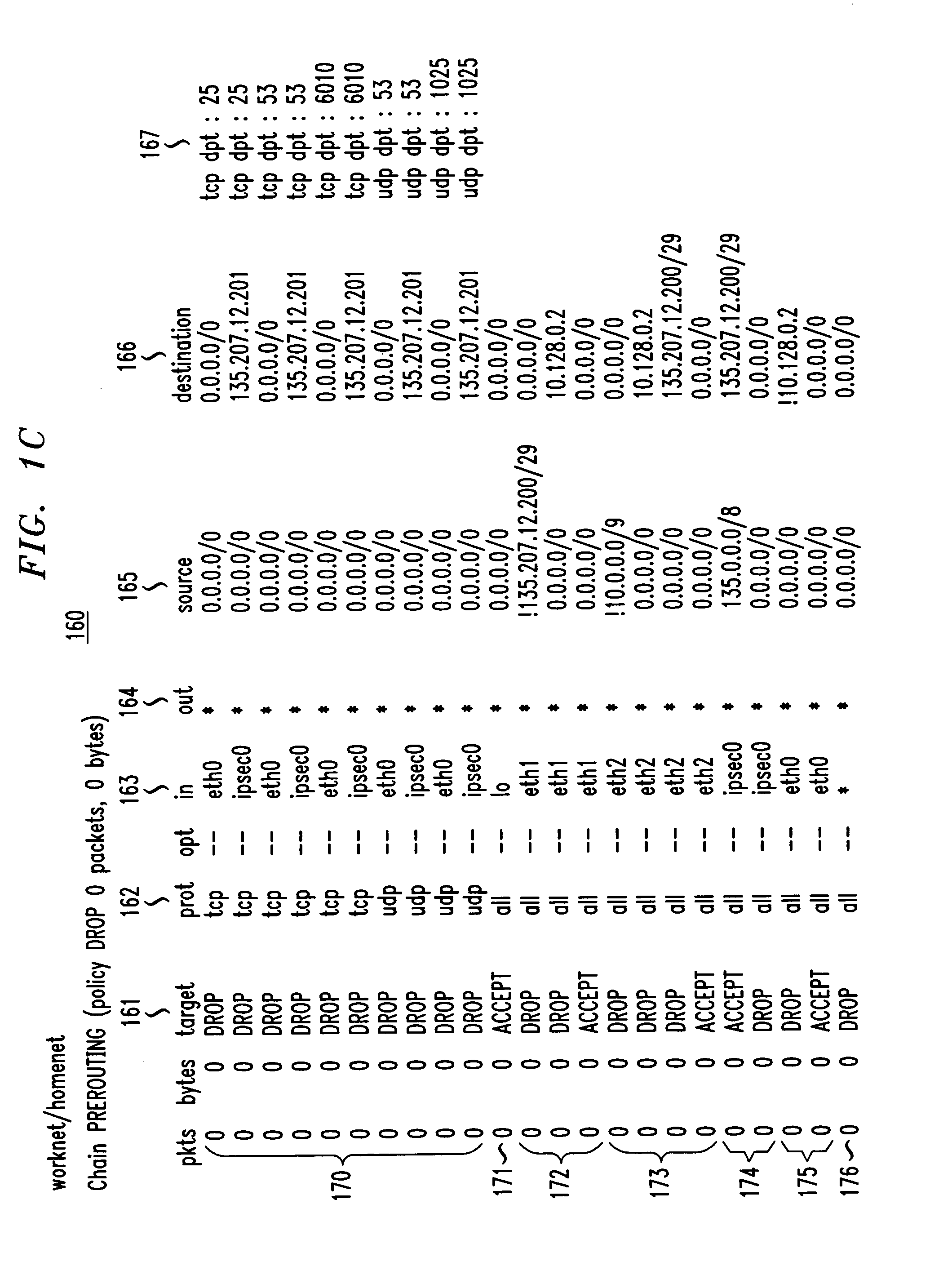
Method and apparatus for securely connecting a plurality of trust-group networks, a protected resource network and an untrusted network
InactiveUS7131141B1Improve securityMultiple digital computer combinationsProgram controlPrivate networkIp address
A security gateway provides a secure connection among one or more networks and a protected resource network. One of the local networks may be connected to the remote private network via a VPN IPsec tunnel. The networks may be local networks that share resources without compromising the security of the protected resource network. The local networks may have access to an untrusted network such as the Internet, sharing a single connection through the security gateway. Dynamic source network address translation is used to permit access from the network connected to the protected resource network to other, less trusted networks while concealing the actual IP addresses of hosts within that network.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
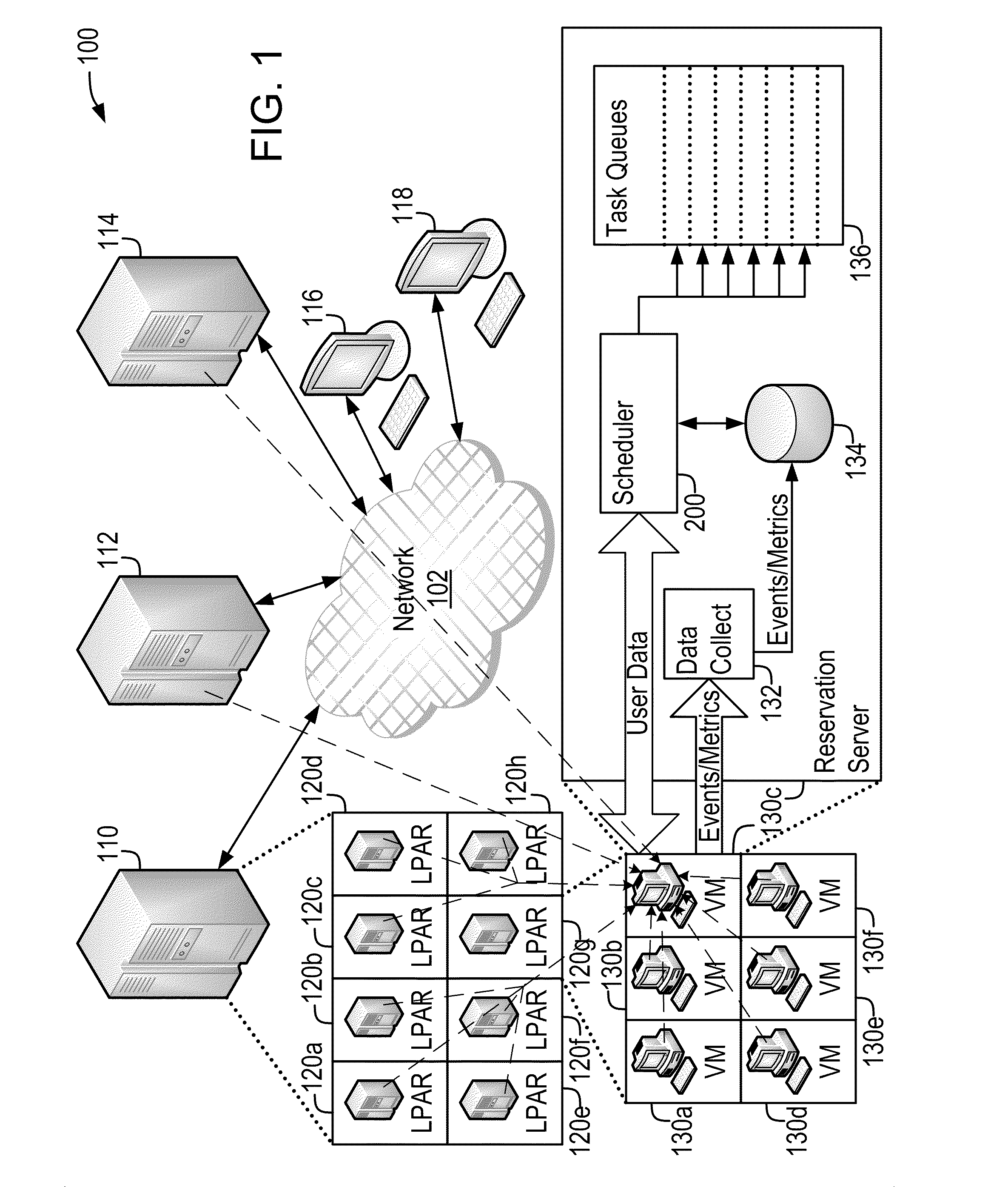
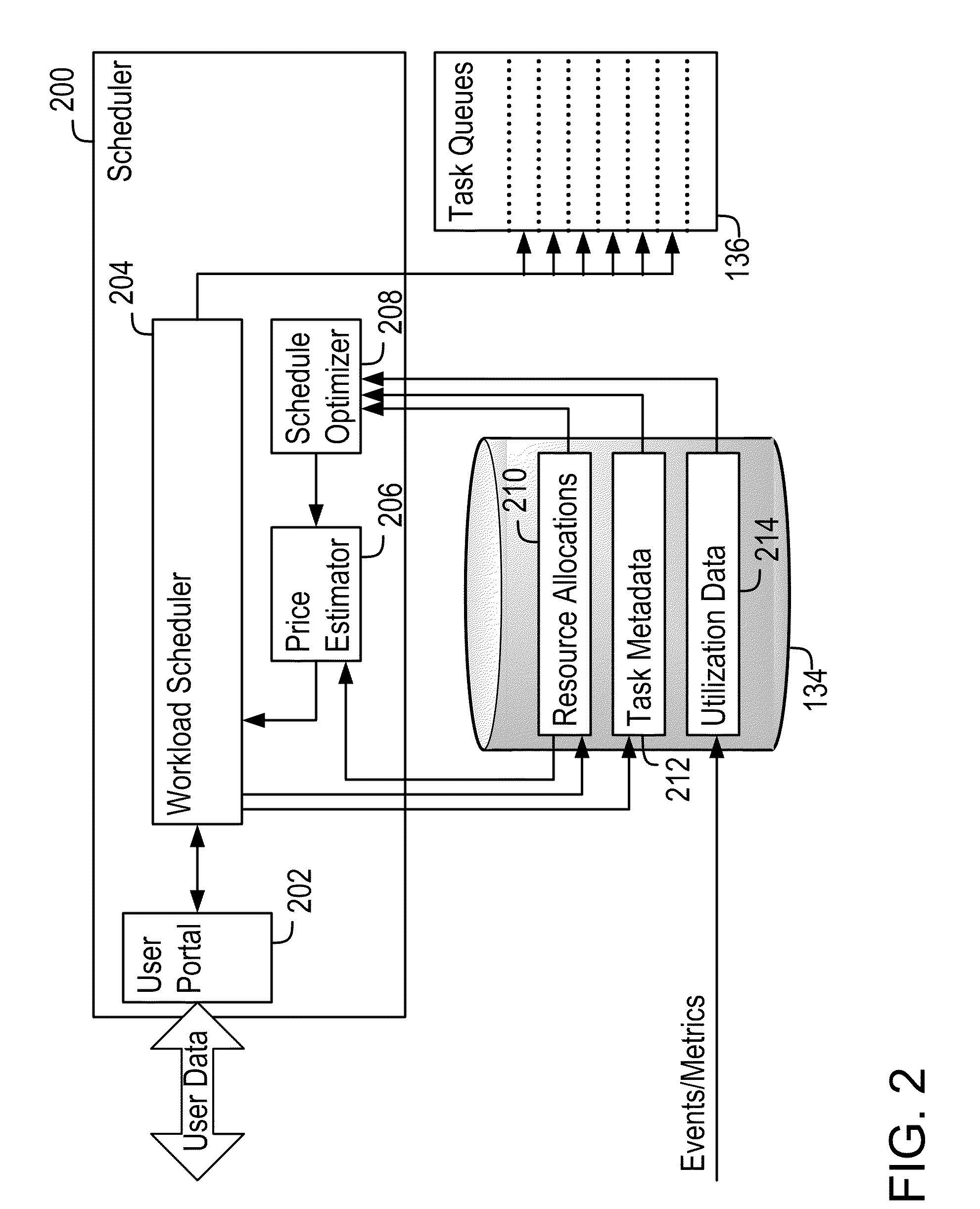
Demand-Driven Workload Scheduling Optimization on Shared Computing Resources
InactiveUS20110154353A1Low costHinder taskResource allocationMemory systemsTime scheduleProgram planning
Systems and methods implementing a demand-driven workload scheduling optimization of shared resources used to execute tasks submitted to a computer system are disclosed. Some embodiments include a method for demand-driven computer system resource optimization that includes receiving a request to execute a task (said request including the task's required execution time and resource requirements), selecting a prospective execution schedule meeting the required execution time and a computer system resource meeting the resource requirement, determining (in response to the request) a task execution price for using the computer system resource according to the prospective execution schedule, and scheduling the task to execute using the computer system resource according to the prospective execution schedule if the price is accepted. The price varies as a function of availability of the computer system resource at times corresponding to the prospective execution schedule, said availability being measured at the time the price is determined.
Owner:BMC SOFTWARE
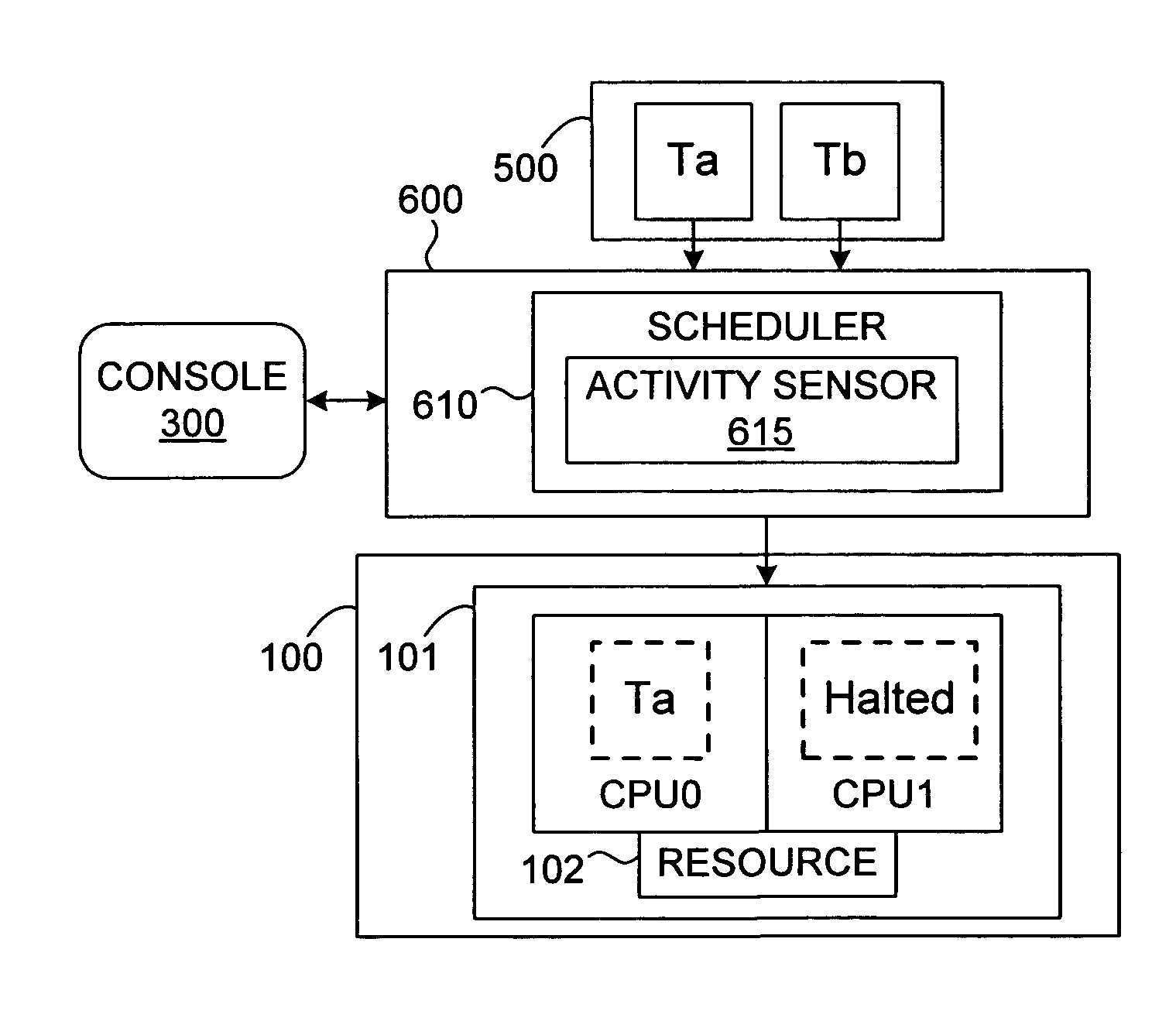
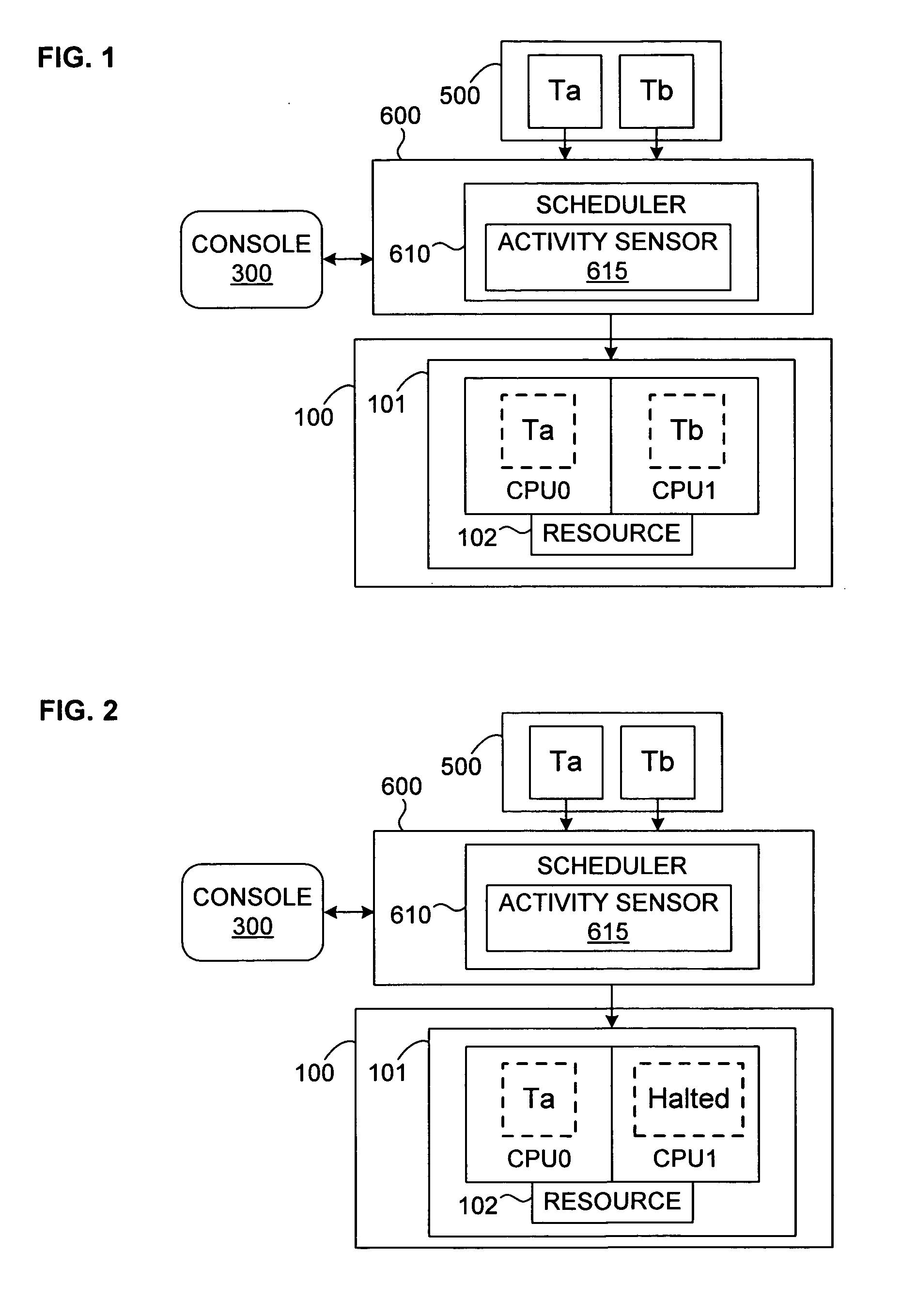
Mechanism for scheduling execution of threads for fair resource allocation in a multi-threaded and/or multi-core processing system
ActiveUS7707578B1Digital computer detailsMultiprogramming arrangementsThread schedulingShared resource
A thread scheduling mechanism is provided that flexibly enforces performance isolation of multiple threads to alleviate the effect of anti-cooperative execution behavior with respect to a shared resource, for example, hoarding a cache or pipeline, using the hardware capabilities of simultaneous multi-threaded (SMT) or multi-core processors. Given a plurality of threads running on at least two processors in at least one functional processor group, the occurrence of a rescheduling condition indicating anti-cooperative execution behavior is sensed, and, if present, at least one of the threads is rescheduled such that the first and second threads no longer execute in the same functional processor group at the same time.
Owner:VMWARE INC
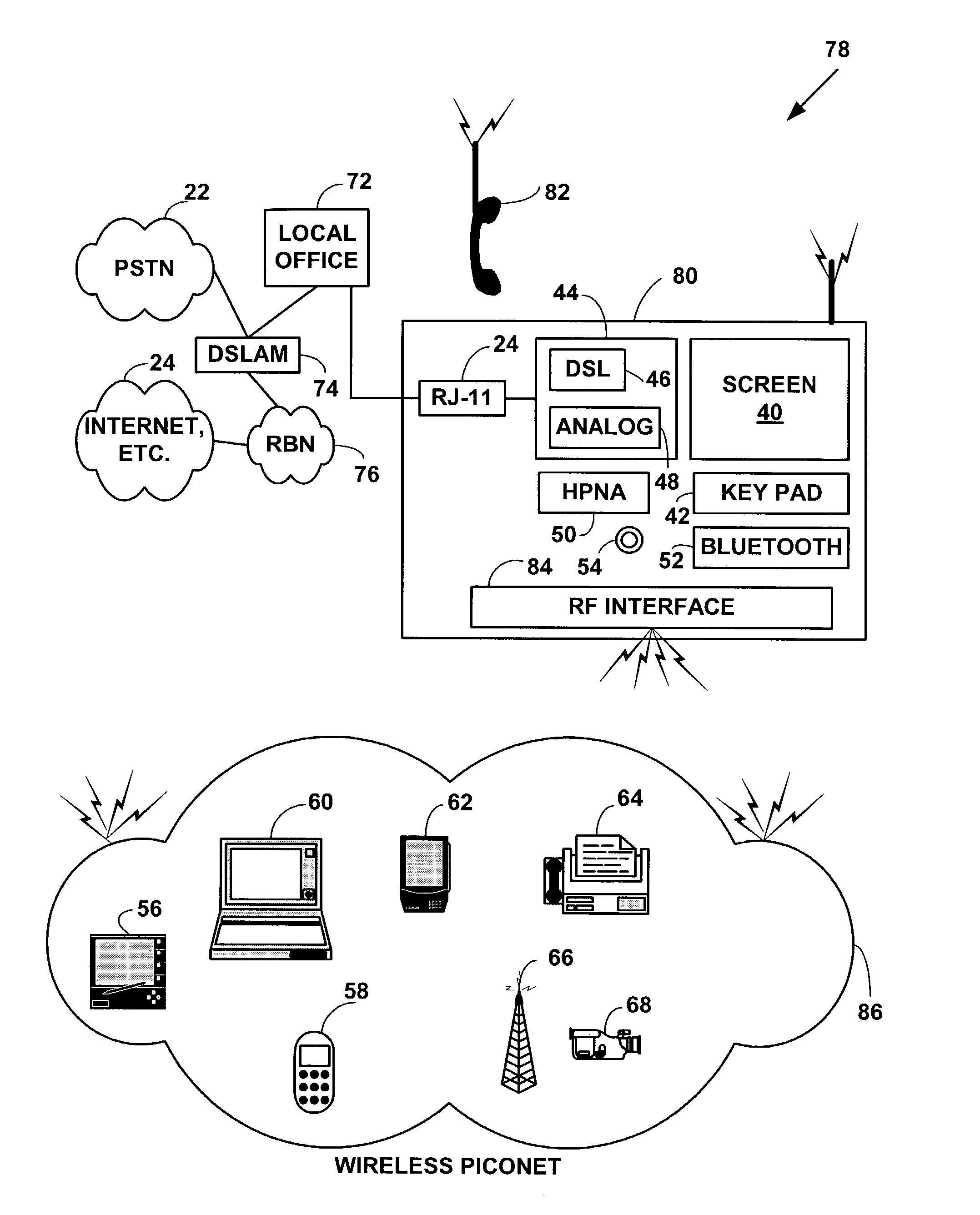
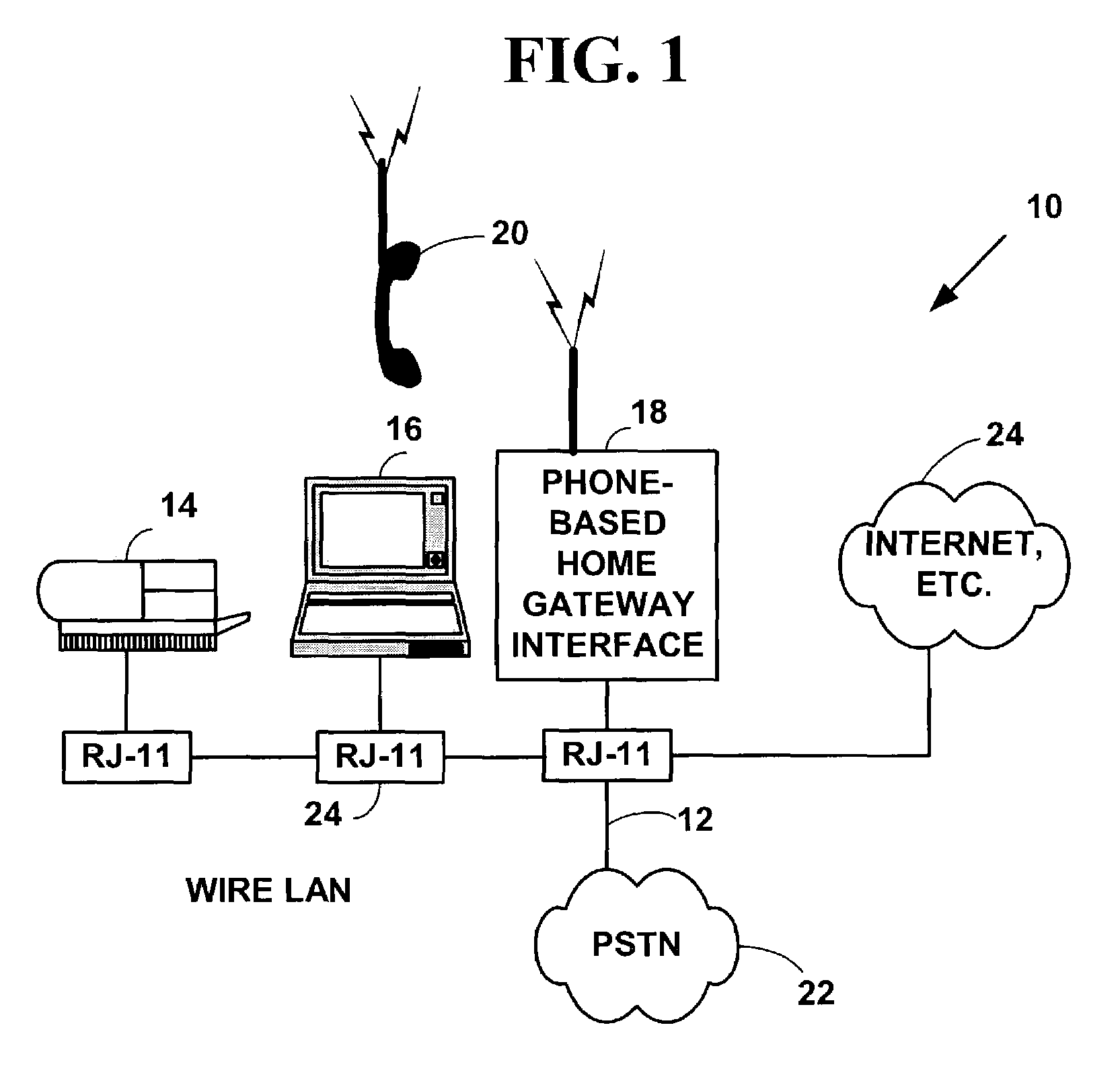
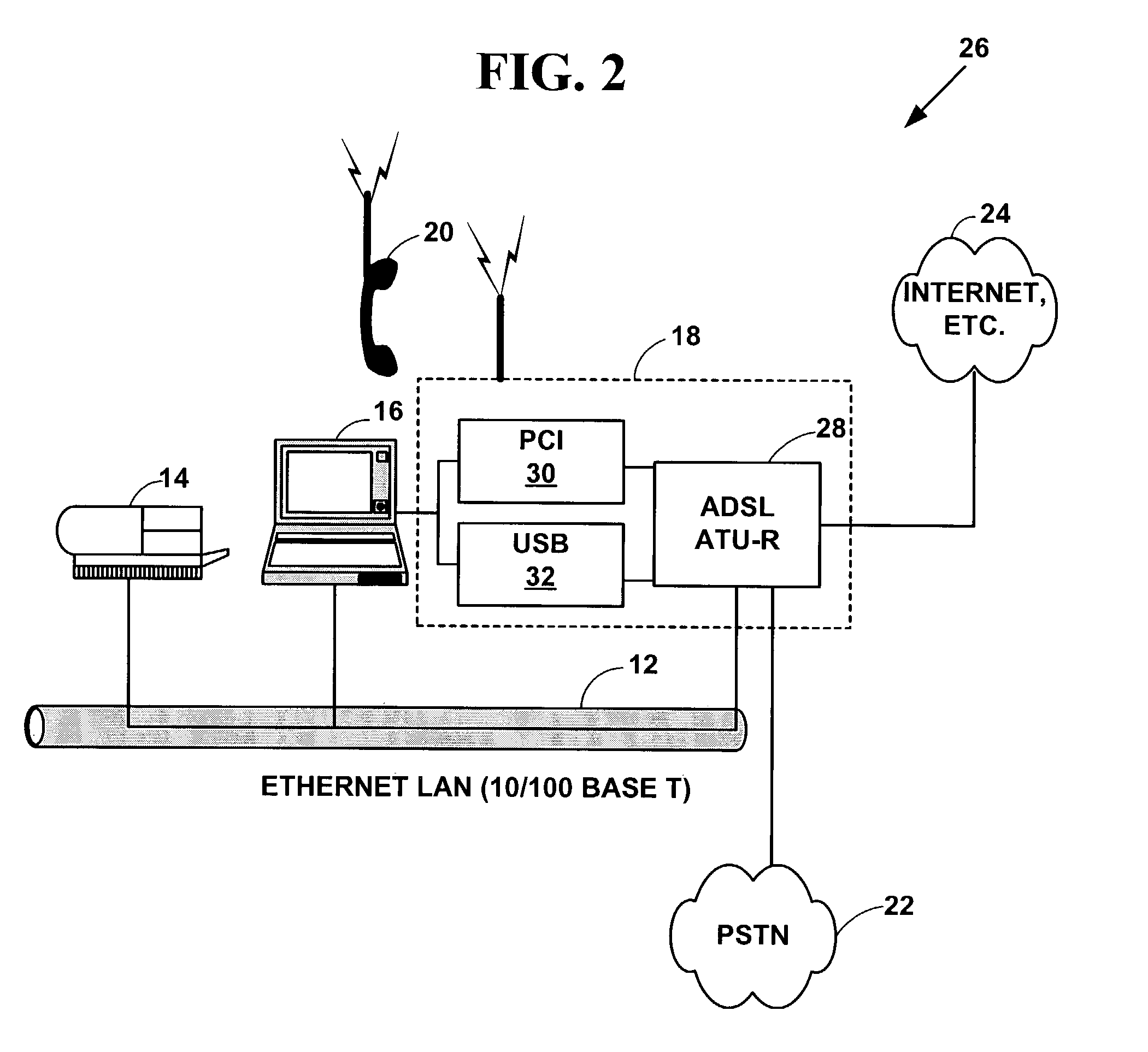
Broadband communications access device
InactiveUS7257106B2Network traffic/resource managementTime-division multiplexCable telephonyShared resource
An integrated phone-based home gateway system. The integrated phone-based home gateway system is a multi-function wireless and wired networking, wireless and wired telephony, broadband, gateway device. It provides automatic wireless and wired broadband initialization, configuration and service provisioning, gateway, routing and bridging functionality, wireless and wired data and telephony functionality and allows resource sharing among multiple wireless and wired devices.
Owner:ZHIGU HLDG
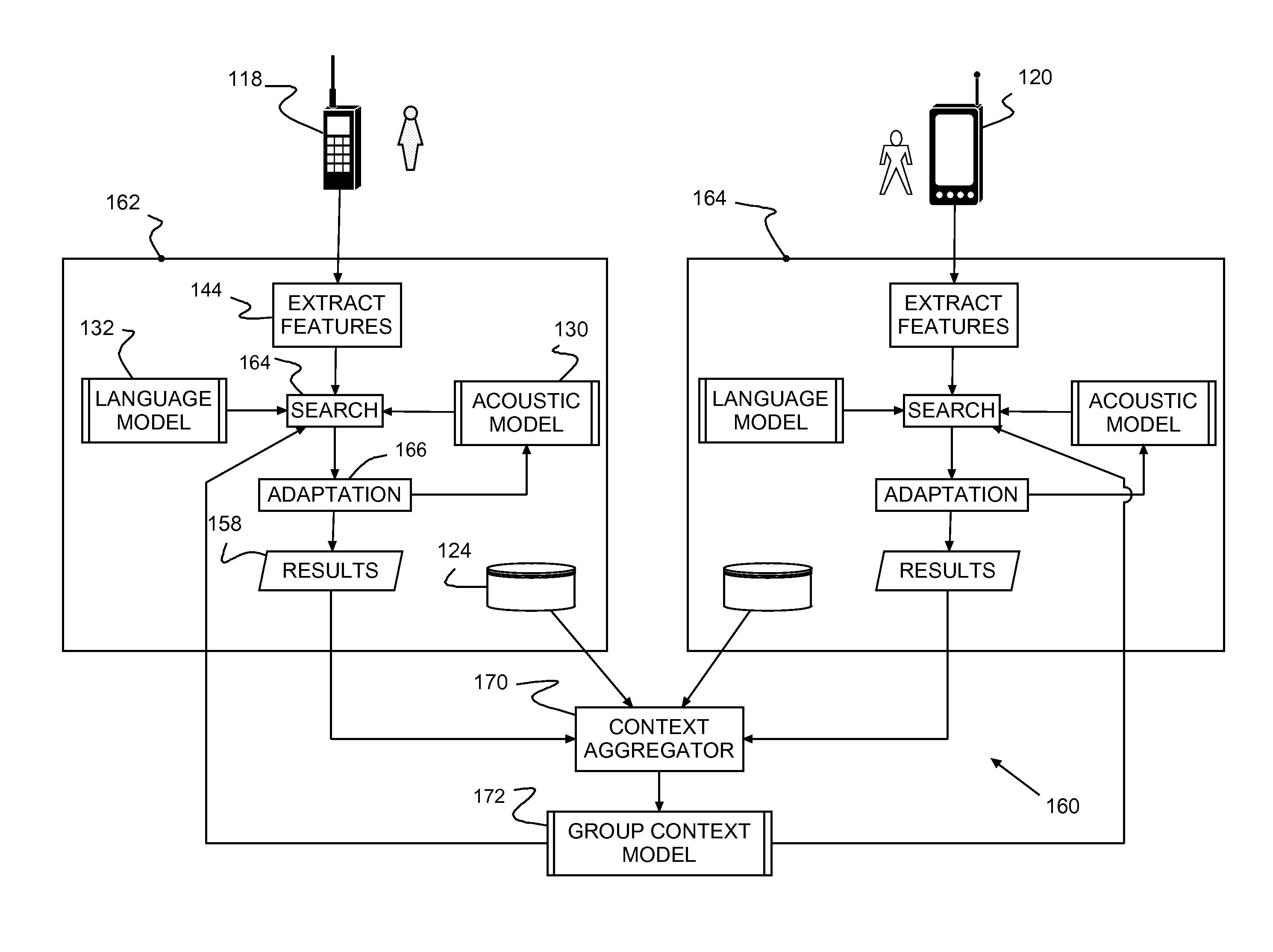
System, method and program product for providing automatic speech recognition (ASR) in a shared resource environment
InactiveUS9043208B2Improve speech recognition performanceLeveling precisionSpeech recognitionContext modelAmbiguity
A speech recognition system, method of recognizing speech and a computer program product therefor. A client device identified with a context for an associated user selectively streams audio to a provider computer, e.g., a cloud computer. Speech recognition receives streaming audio, maps utterances to specific textual candidates and determines a likelihood of a correct match for each mapped textual candidate. A context model selectively winnows candidate to resolve recognition ambiguity according to context whenever multiple textual candidates are recognized as potential matches for the same mapped utterance. Matches are used to update the context model, which may be used for multiple users in the same context.
Owner:INT BUSINESS MASCH CORP
Coordinating persistent status information with multiple file servers
InactiveUS6119244APrevent mutual attempt at takeoverMemory loss protectionDigital computer detailsMessage flowEngineering
The invention provides a storage system, and a method for operating a storage system, that provides for relatively rapid and reliable takeover among a plurality of independent file servers. Each file server maintains a reliable communication path to the others. Each file server maintains its own state in reliable memory. Each file server regularly confirms the state of the other file servers. Each file server labels messages on the redundant communication paths, so as to allow other file servers to combine the redundant communication paths into a single ordered stream of messages. Each file server maintains its own state in its persistent memory and compares that state with the ordered stream of messages, so as to determine whether other file servers have progressed beyond the file server's own last known state. Each file server uses the shared resources (such as magnetic disks) themselves as part of the redundant communication paths, so as to prevent mutual attempts at takeover of resources when each file server believes the other to have failed. Each file server provides a status report to the others when recovering from an error, so as to prevent the possibility of multiple file servers each repeatedly failing and attempting to seize the resources of the others.
Owner:NETWORK APPLIANCE INC
Peer-to-peer host station
A method and system is disclosed for allowing the sharing of one or more system resources between multiple devices. In one embodiment, a requesting device transmits a resource access request to a target device using a near-field communication (NFC) protocol. The target device responds by using the NFC connection to return a listing of resources available for sharing to the requesting device. The requesting device may select one or more of the available resources and establish an appropriate connection to access the selected resource or resources. In one embodiment, the requesting device may lack external network connectivity capabilities while the target device includes wi-fi connectivity as a shared resource. Accordingly, the requesting device may access external network of the target device via the target as a conduit.
Owner:APPLE INC
System and method for distribution of resources for an I/O virtualized (IOV) adapter and management of the adapter through an iov management partition
ActiveUS20090144731A1Multiprogramming arrangementsSoftware simulation/interpretation/emulationClient-sideShared resource
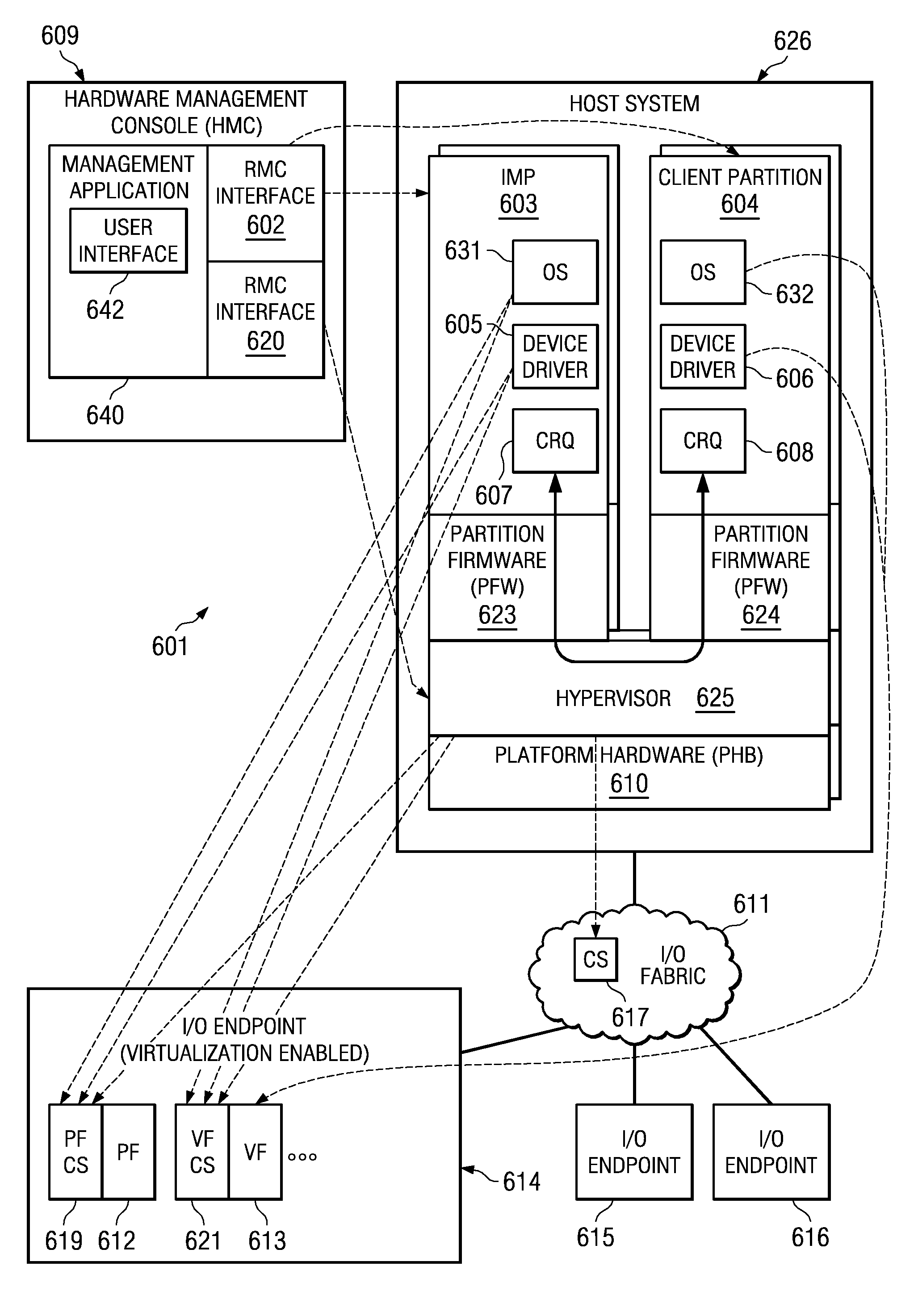
The system and method address the situation where an input / output (I / O) fabric is shared by more than one logical partition (LPAR) and where each LPAR can share with the other LPARs an I / O adapter (IOA). In particular, each LPAR is assigned its own separate address space to access a virtual function (VF) assigned to it such that each LPAR's perception is that it has its own independent IOA. Each VF may be shared across multiple LPARs. Facilities are provided for management of the shared resources of the IOA via a Physical Function (PF) of the IOA by assignment of that PF to an I / O Virtualization Management Partition (IMP). The code running in the IMP acts as a virtual intermediary to the VFs for fully managing the VF error handling, VF reset, and configuration operations. The IMP also acts as an interface to the PF for accessing common VF functionality. Furthermore, the functions of resource assignment and management relative to the VFs and the client partitions that use those VFs, which might normally be done by an entity like a hypervisor, are implemented by this IMP.
Owner:IBM CORP
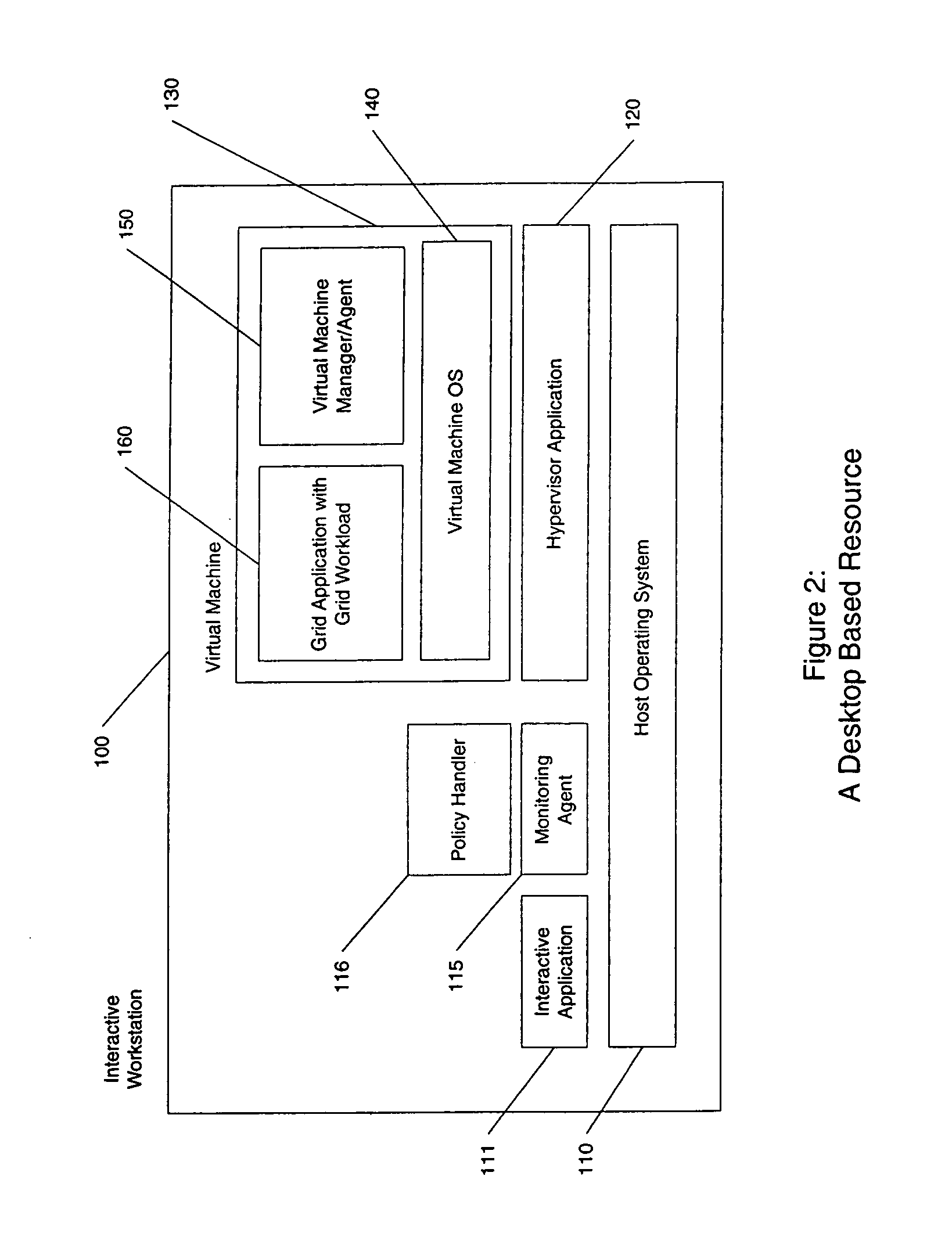
Shared resource service provisioning using a virtual machine manager
InactiveUS20100153945A1Avoid confictDigital computer detailsMultiprogramming arrangementsData processing systemCompletion time
A virtual machine manager (VMM) enables provisioning of services to multiple clients via a single data processing system configured as multiple virtual machines. The VMM performs several management functions, including: configuring / assigning each virtual machine (VM) for / to a specific, single client; scheduling the time and order for completing client services via the assigned client VM; instantiating a client VM at a scheduled time and triggering the execution of services tasks required for completing the specific client services on the client VM; monitoring and recording historical information about the actual completion times of services on a client VM; and updating a scheduling order for sequential instantiating of the multiple client VMs and corresponding client services, based on one or more of (i) pre-established time preferences, (ii) priority considerations, and (iii) historical data related to actual completion times of client services at a client VM.
Owner:IBM CORP
System, method and program product for optimizing virtual machine placement and configuration
ActiveUS20130080619A1Reduced shared resource energy consumptionReduce energy consumptionEnergy efficient ICTDigital computer detailsClient-sideMessage passing
A shared resource system, method of optimizing resource allocation in real time and computer program products therefor. At least one client device includes an optimization agent monitoring resource usage and selectively suggesting changes to resource configuration for the client device. A management system, e.g., in a cloud environment selectively makes resource capacity available to client devices and adjusts resource capacity available to client devices in response to the optimization agent. Client devices and provider computers connect over a network. The client devices and provider computer pass messages to each other over the network.
Owner:IBM CORP
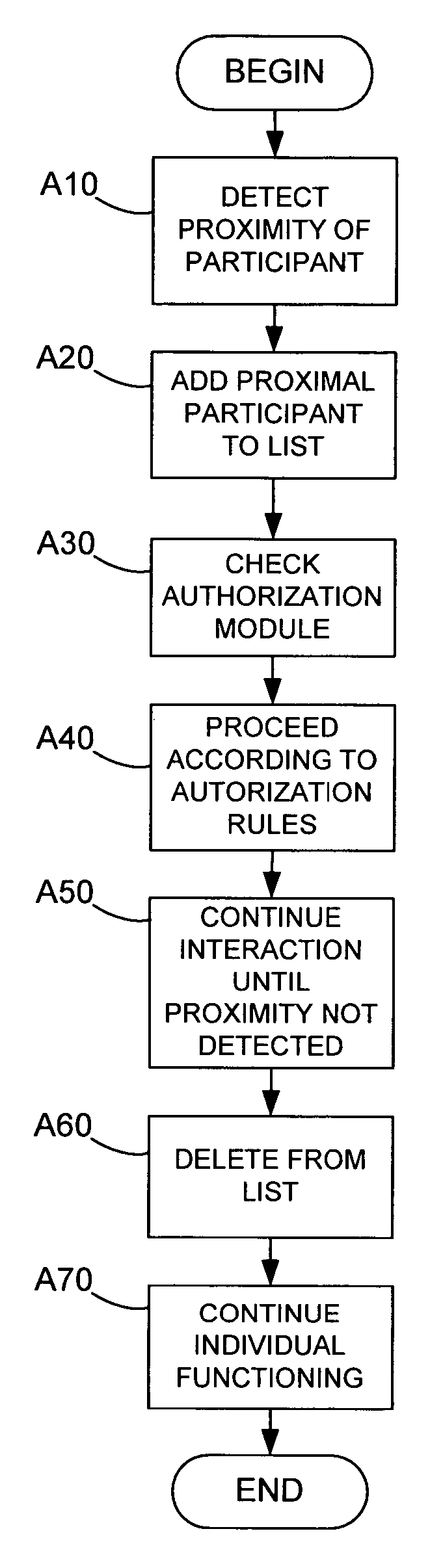
System and method for sharing information based on proximity
ActiveUS20050138576A1Facilitate resource sharingEnhanced interactionDigital data processing detailsDigital computer detailsComputer scienceAuthorization
A method and system are provided for facilitating interaction between a device and a device environment. The system may include a detection module for automatically detecting proximity of a participant within the device environment. The system may additionally include a user-configurable authorization module for authorizing the device to adjust a device user interface in a pre-determined manner in response to the detection of the participant. The system may also provide for sharing resources among multiple participating devices, wherein each of the multiple participating devices has a device specific set of application resources. The system may additionally include a configurable resource regulation mechanism for making the device specific application resources from the second participating device available to the first participating device.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com