Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
103 results about "Lock manager" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
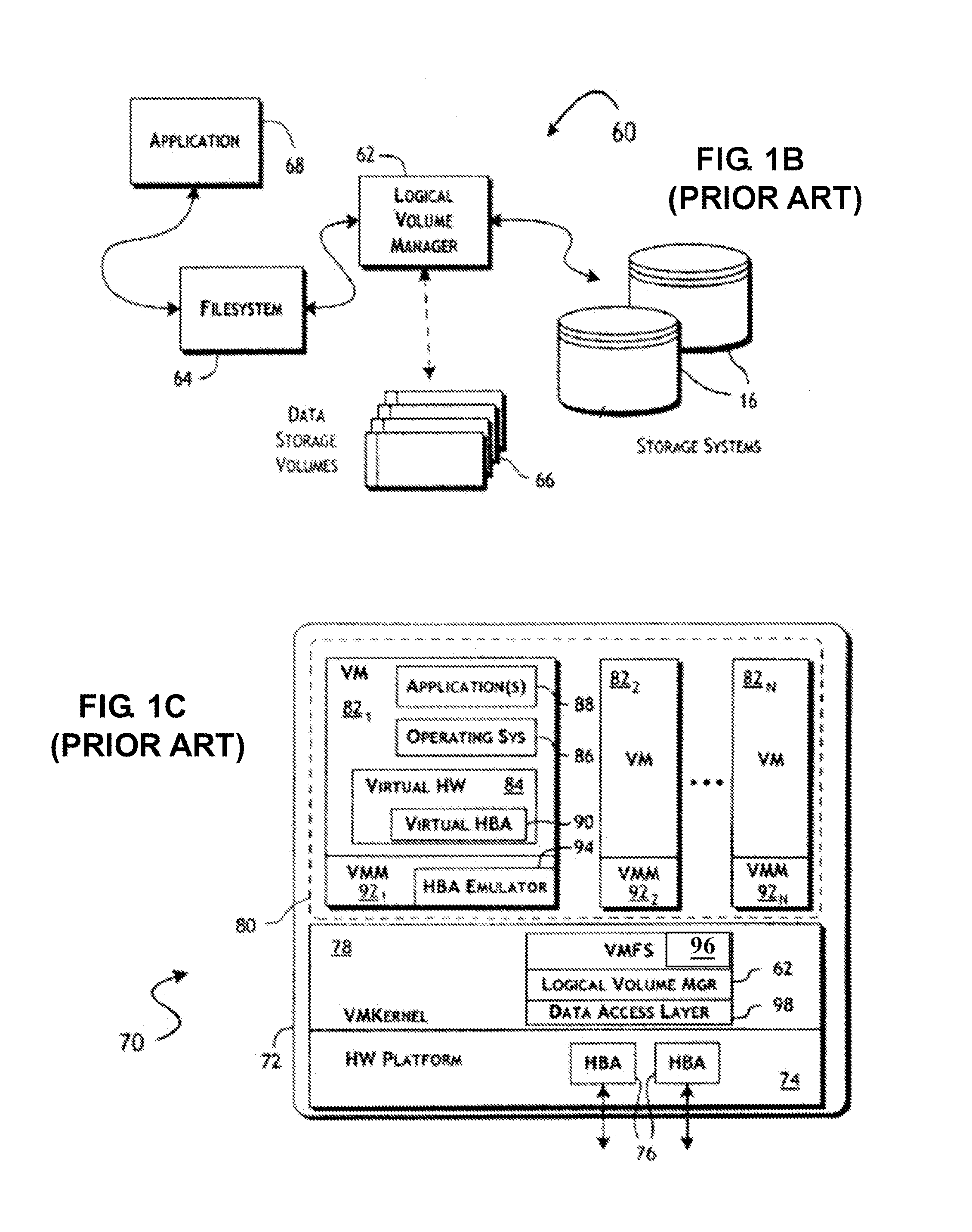
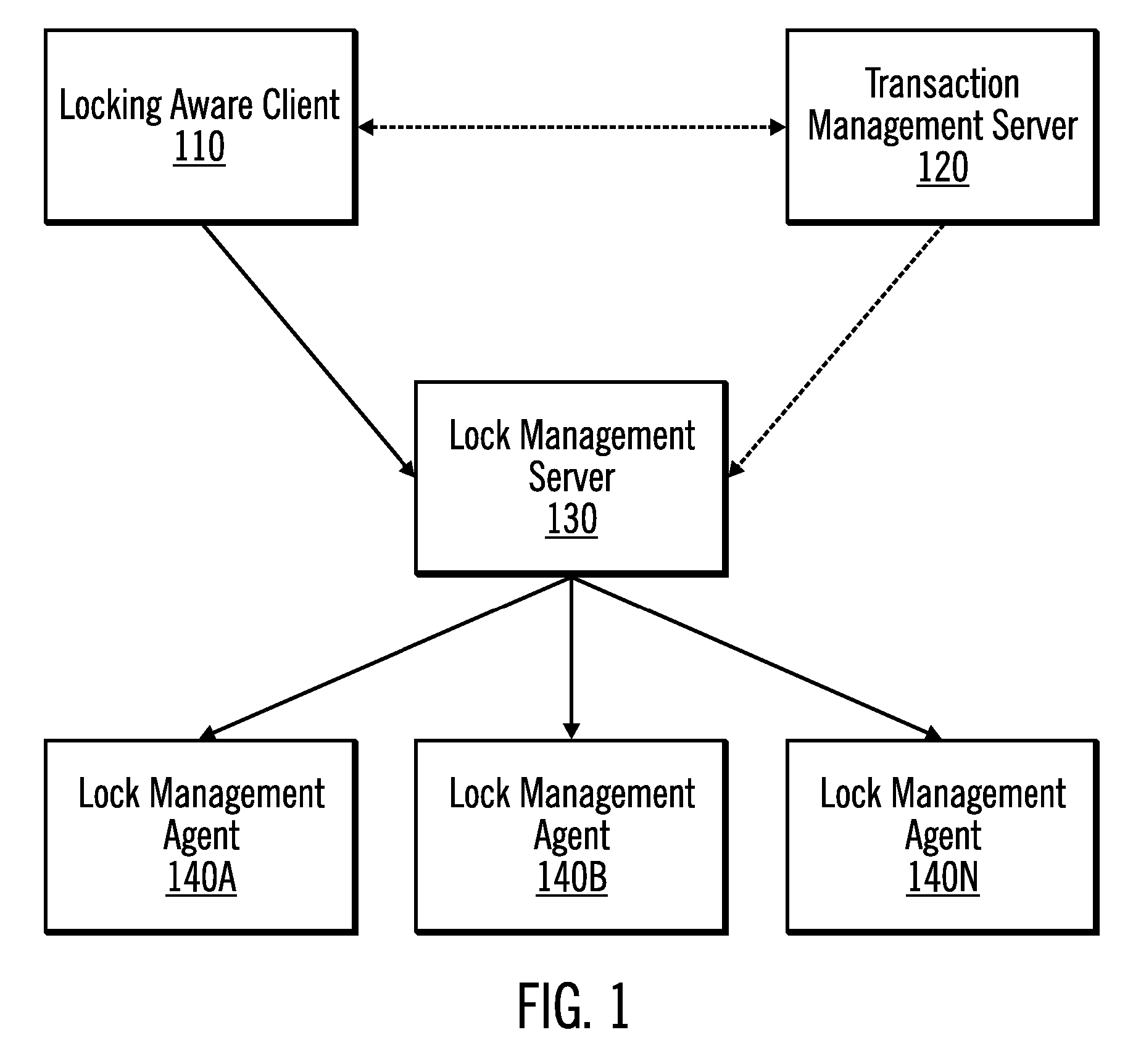
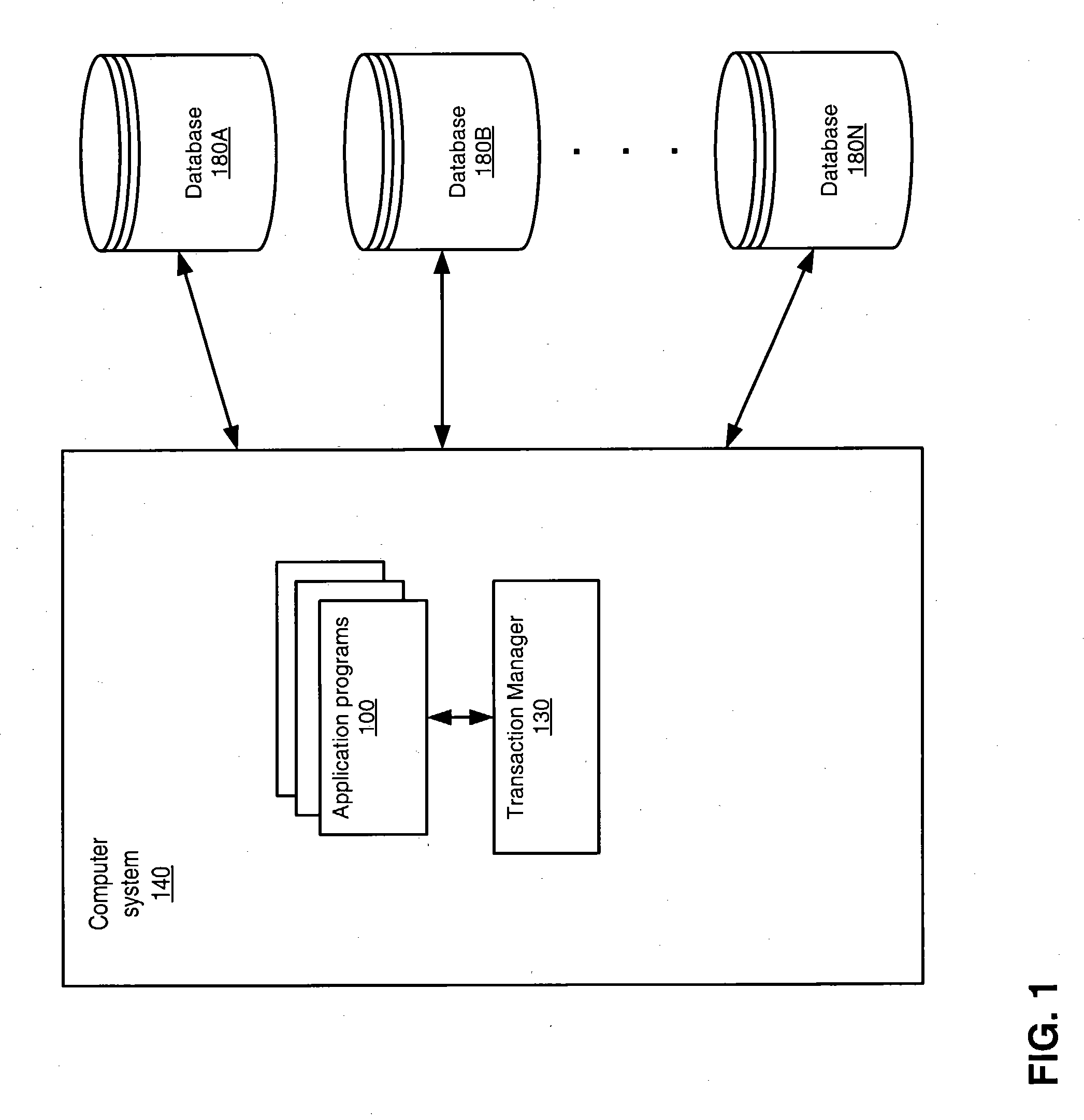
Method and apparatus providing optimistic locking of shared computer resources
InactiveUS6850938B1Digital data information retrievalData processing applicationsComputer resourcesLock manager
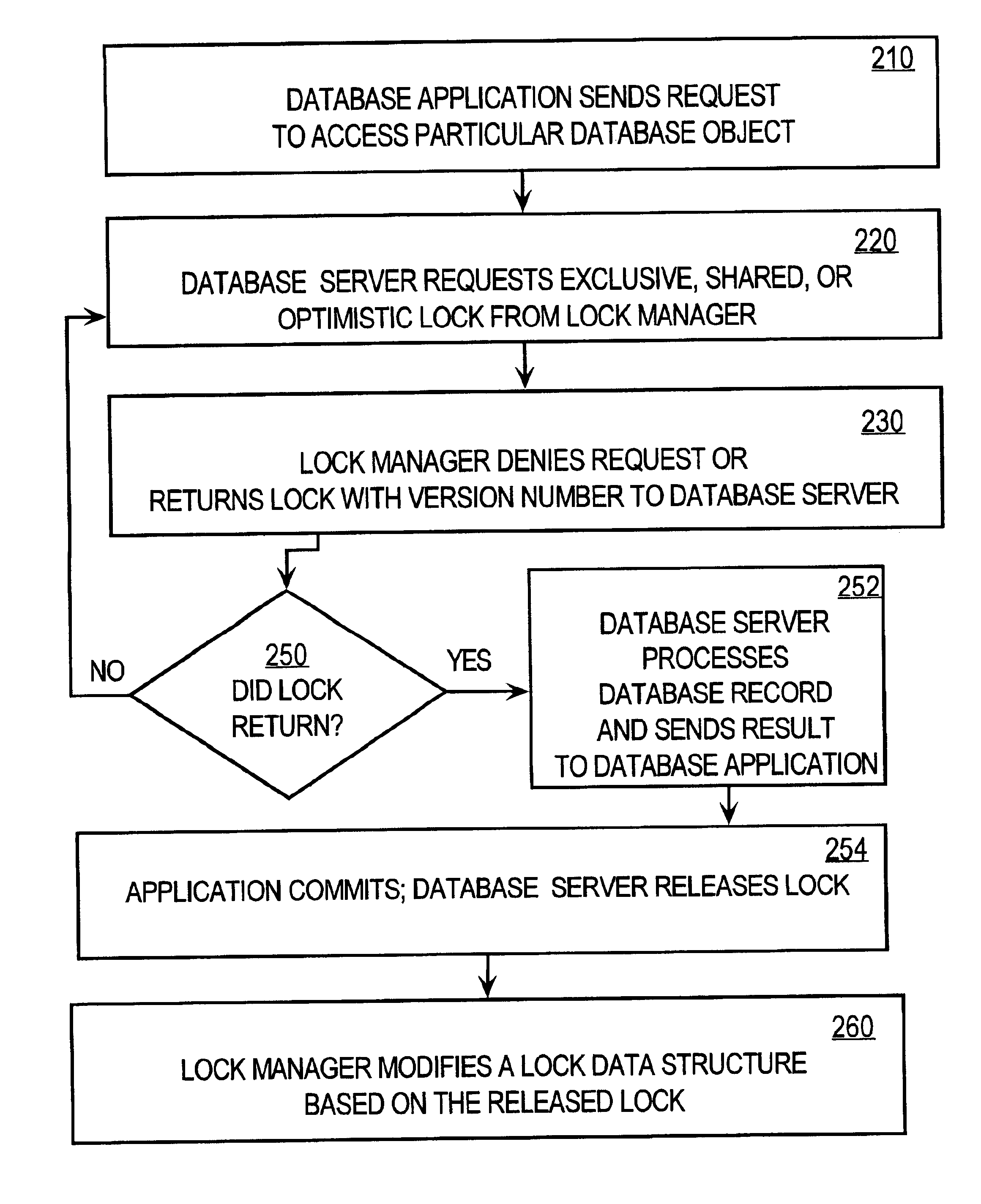
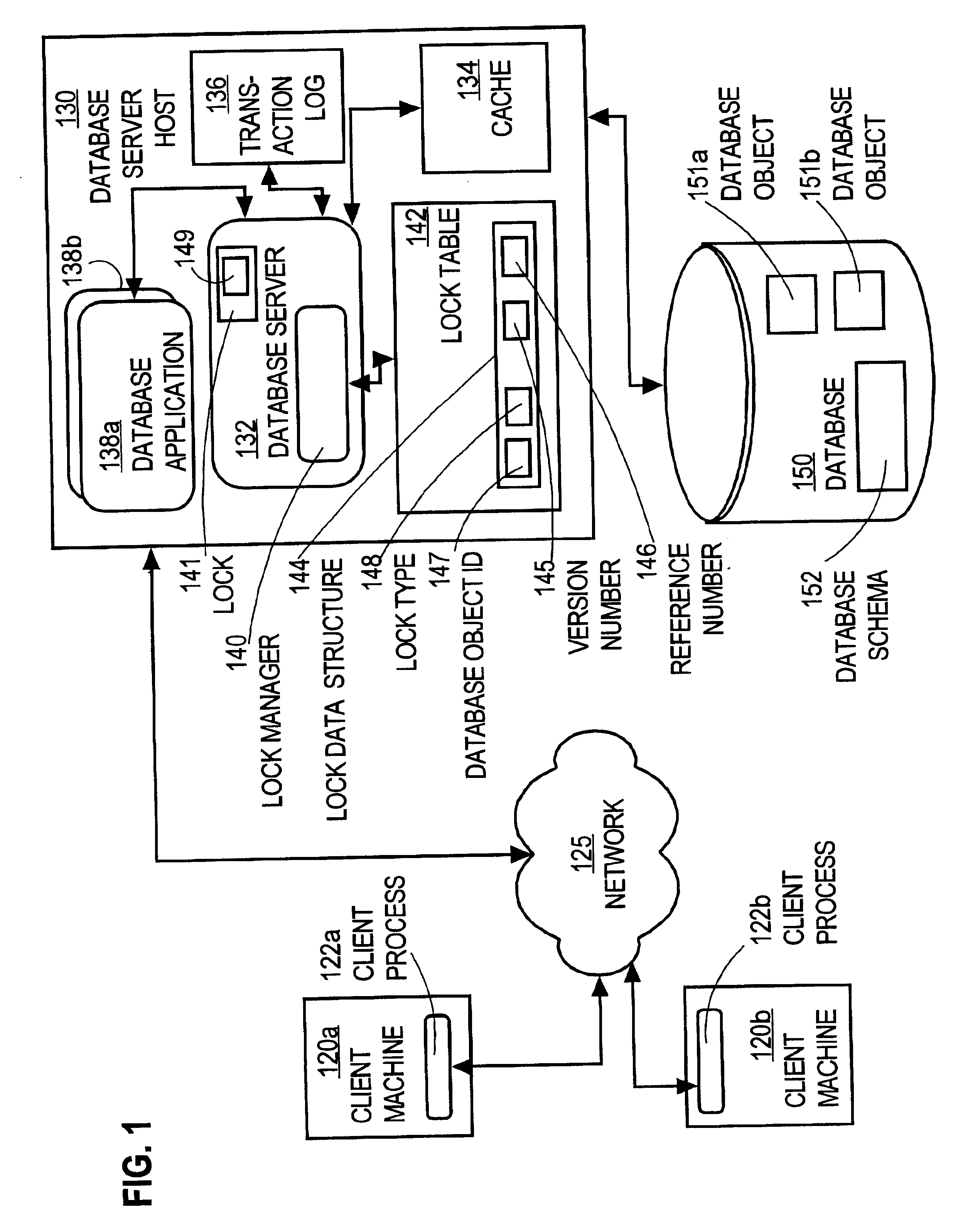
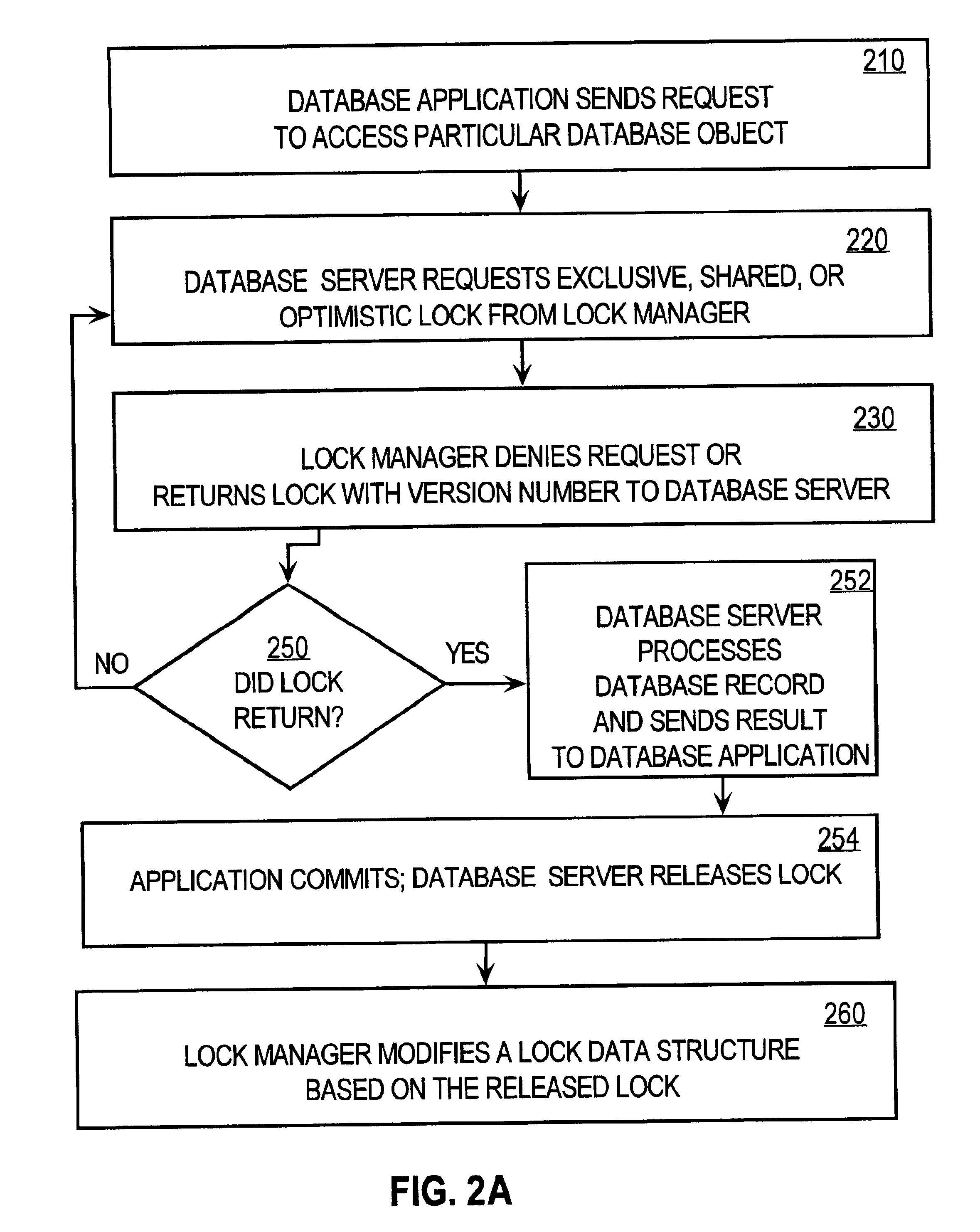
Techniques for concurrent access to a resource object, such as a database, include generating a lock data structure for a particular resource object. The lock data structure includes data values for a resource object identification, a lock type, and a version number. The version number is related to a number of changes to the resource object since the lock data structure was generated. A request is received from a requesting process. The request is for a requested lock type for access to the particular resource object. It is determined whether to grant the request based on the requested lock type and the lock type in the lock data structure. By carrying a lock version number in a lock data structure managed by a lock manager, improved optimistic locking is provided in a database. In particular, the approach enables introduction of optimistic locking to a legacy database without requiring burdensome changes to a database table schema.
Owner:CISCO TECH INC
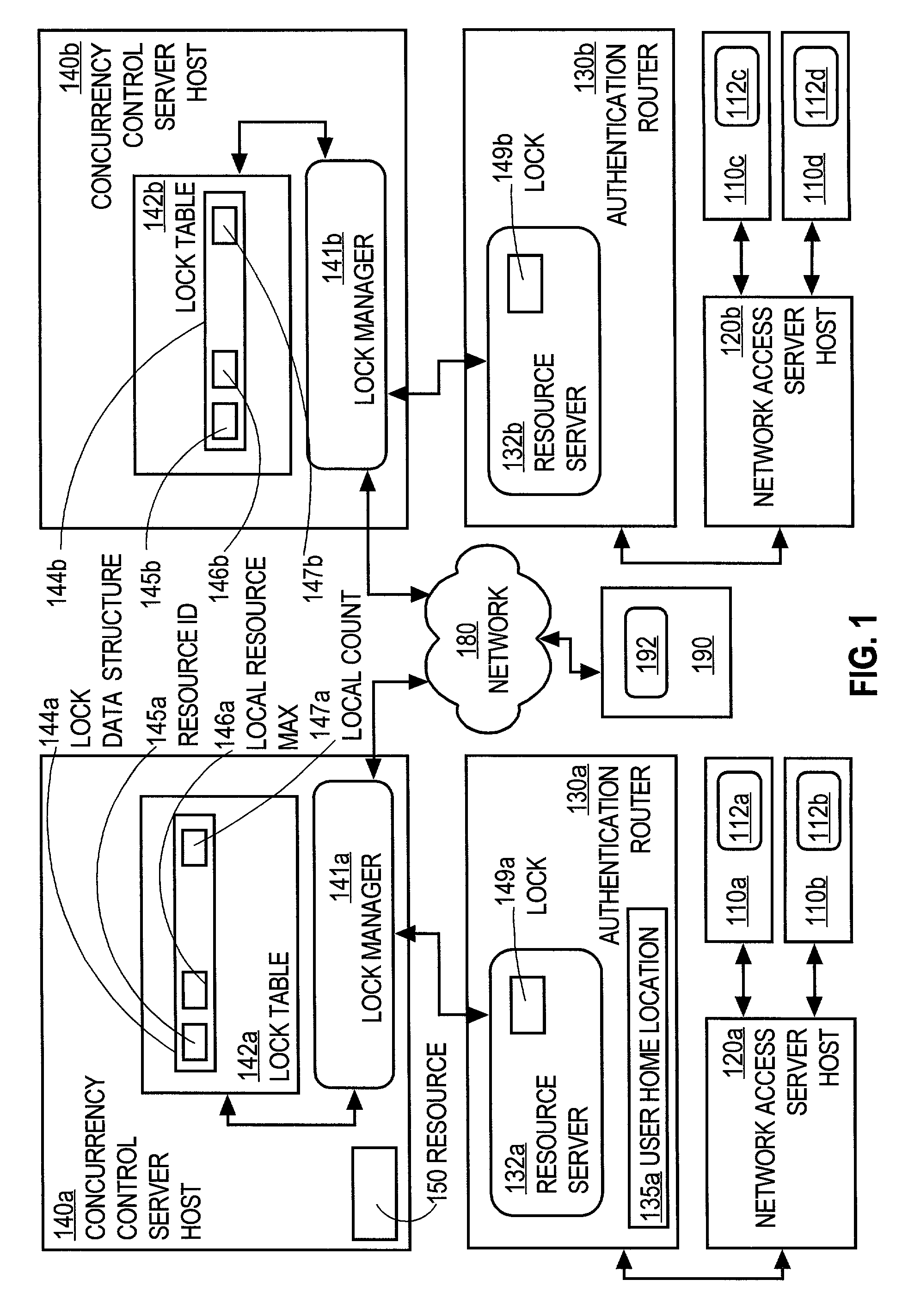
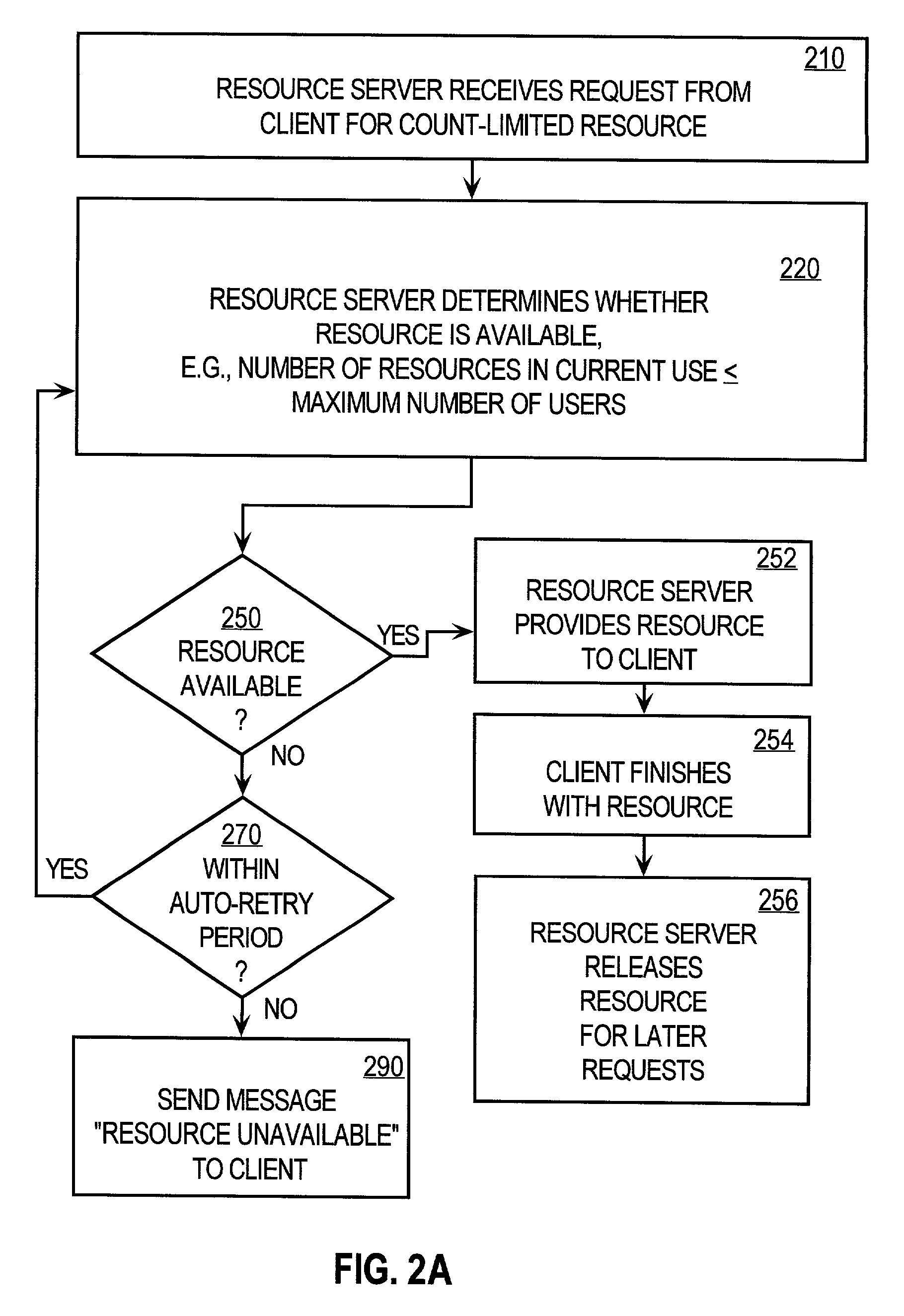
Controlling access of concurrent users of computer resources in a distributed system using an improved semaphore counting approach
ActiveUS7328263B1Data processing applicationsUnauthorized memory use protectionLimited resourcesComputer resources
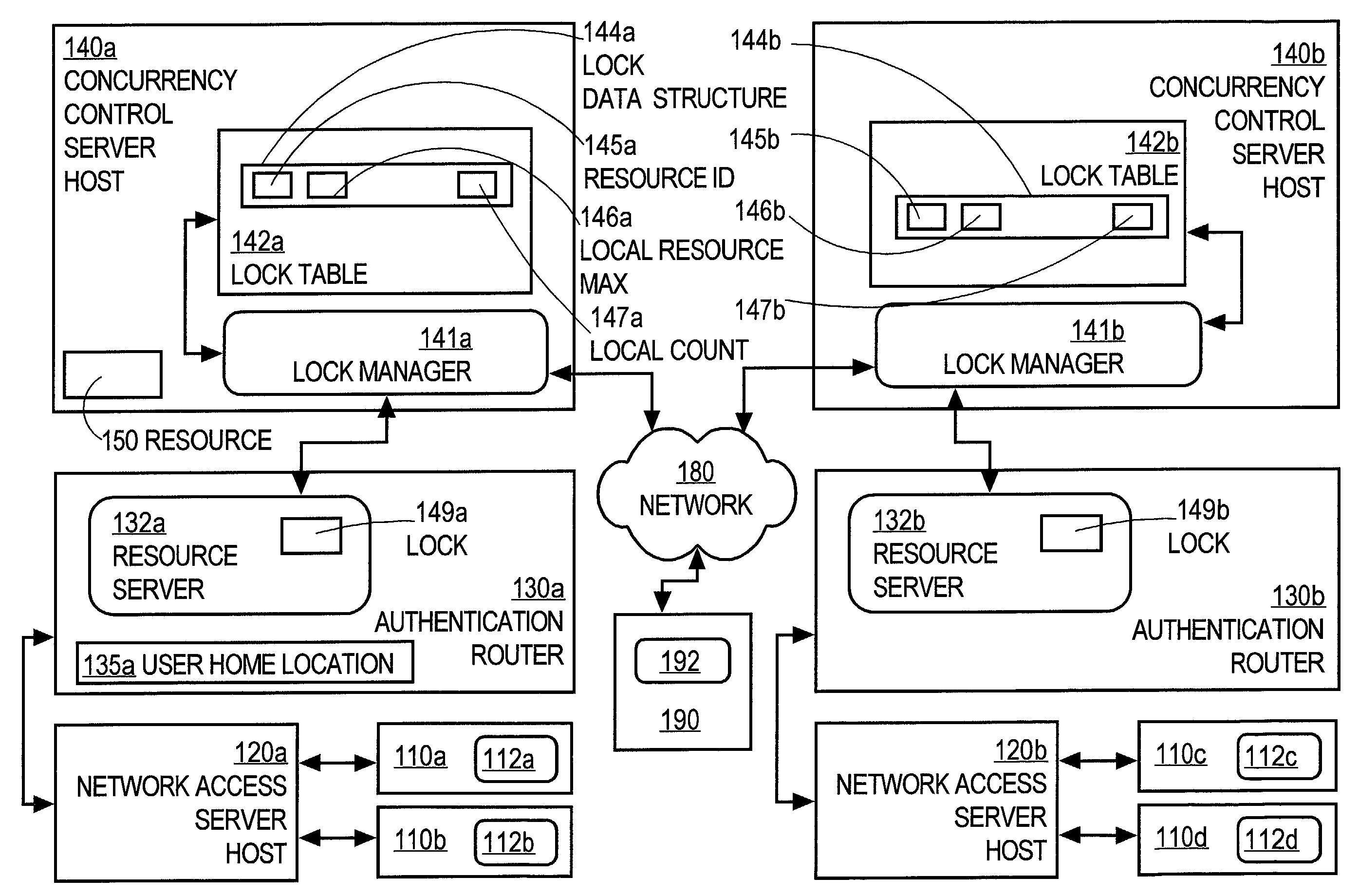
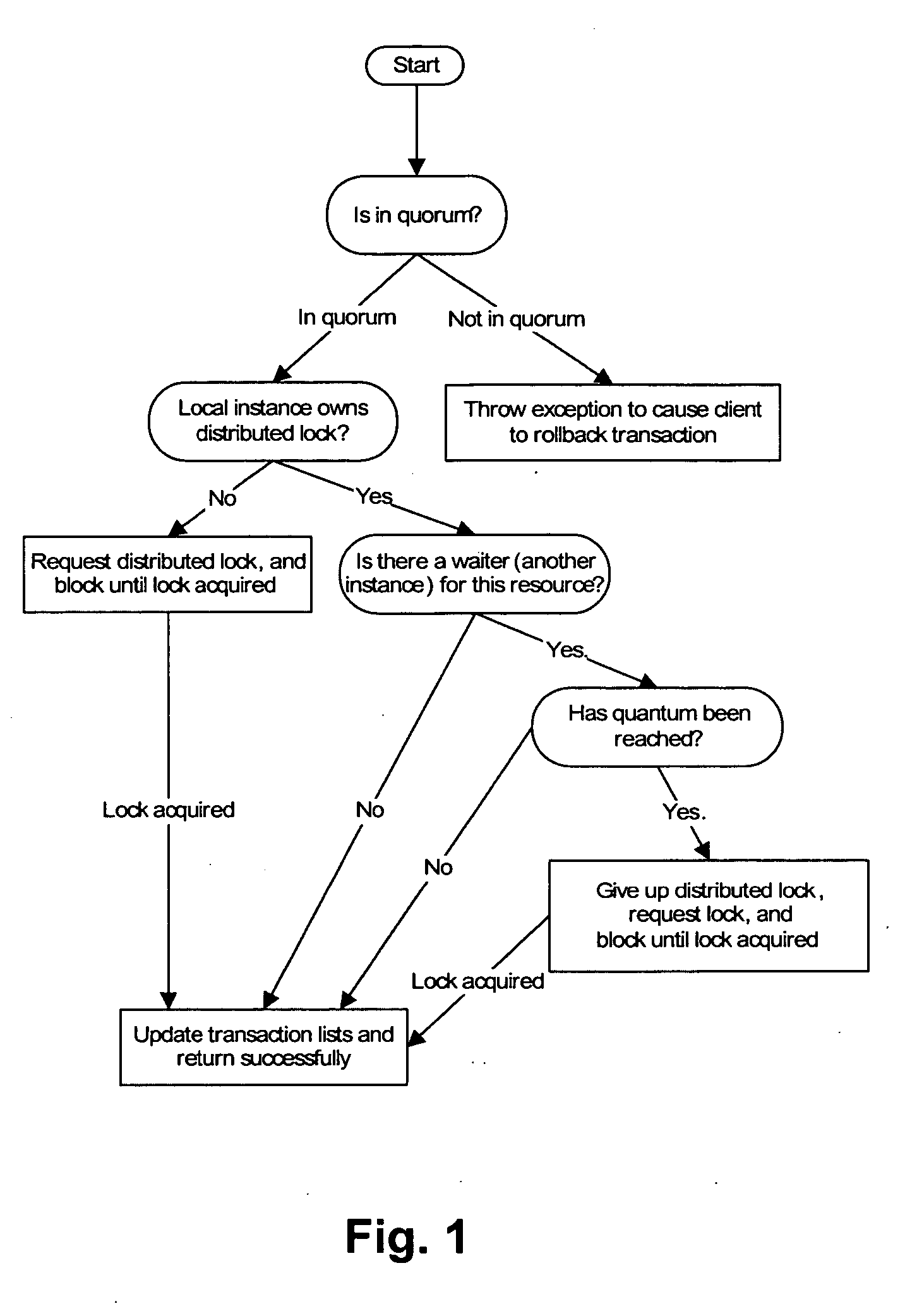
A method of controlling concurrent users of a distributed resource on a network is disclosed. In one aspect, there are one or more local lock managers executing on corresponding hosts and cooperating as a distributed lock manager. The resource is limited to a maximum number of concurrent users. A user identification for each user is associated with one host. In response to a request associated with a particular user associated with a first host, a lock is requested from a first local lock manager process executing on the first host. A related method of handling a request for a count-limited resource includes receiving a request from a client process for the computer resource. If it is determined that the request exceeds a maximum count for the resource, then it is determined whether a current time is within a retry time period of the client's first request. If it is determined the current time is within the retry time period, then it is automatically determined again whether the request exceeds the maximum count for the resource. If it is determined that the request does not exceed the maximum count, then the resource is provided to the client process.
Owner:CISCO TECH INC
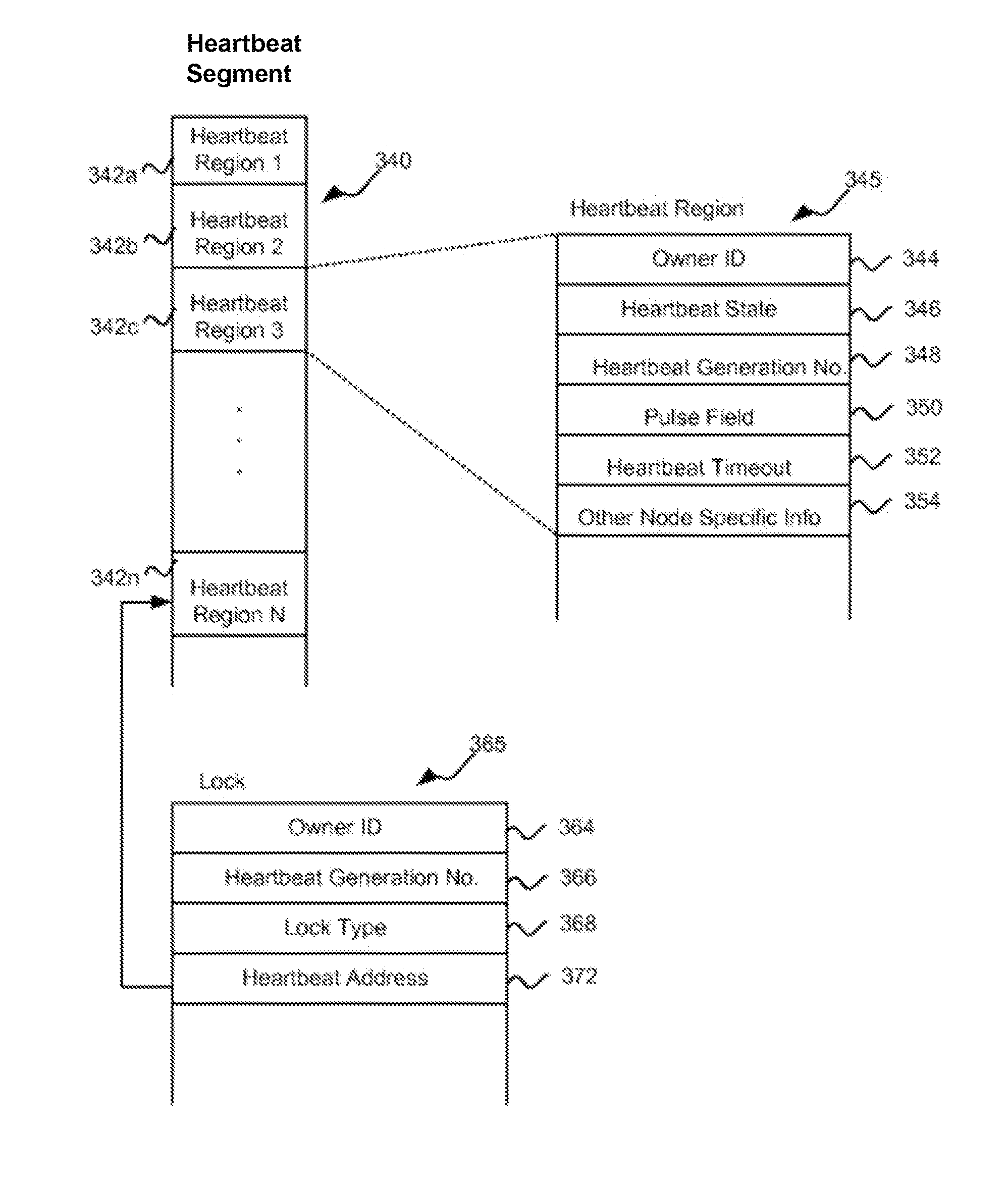
Associating heartbeat data with access to shared resources of a computer system
ActiveUS8560747B1Maintained efficiently and reliablyUnauthorized memory use protectionProgram controlVirtualizationTimestamp
A method, system and program code for implementing distributed locks to be maintained through the use of on disk heartbeats. An instance of a node need only maintain a single heartbeat for all locks associated with the node and all of its processes. The node updates its heartbeat by accessing common storage, either virtual or physical, and updating a timestamp value in its heartbeat within a predetermined time interval, otherwise the heartbeat becomes stale. Expired heartbeats can be cleared or broken to allow redistribution of any locks associated therewith. The inventive technique may be implemented in a traditional computer environment or in a fully or partially virtualized environment and requires no use of an IP network or a separate network based lock manager.
Owner:VMWARE INC
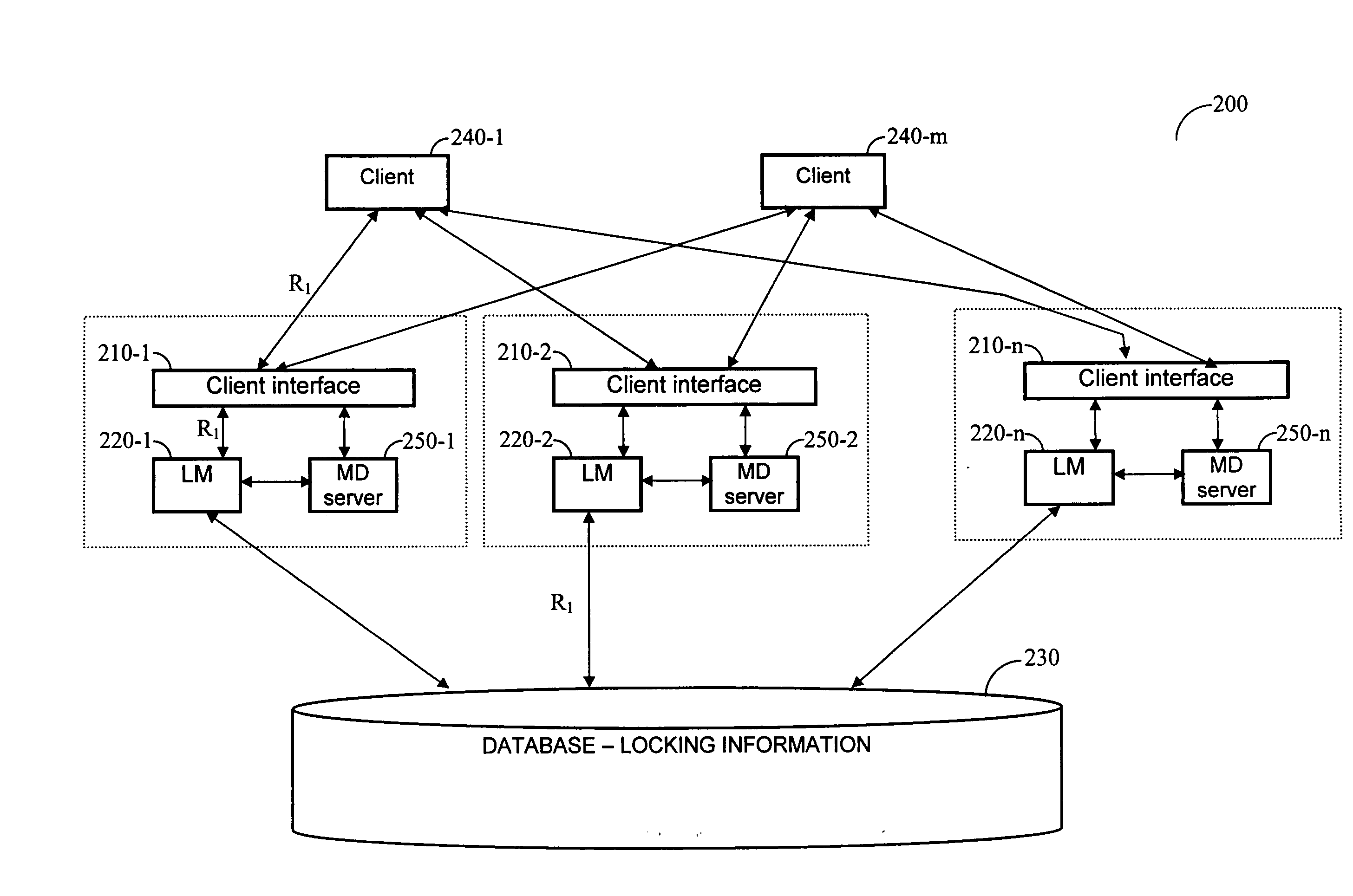
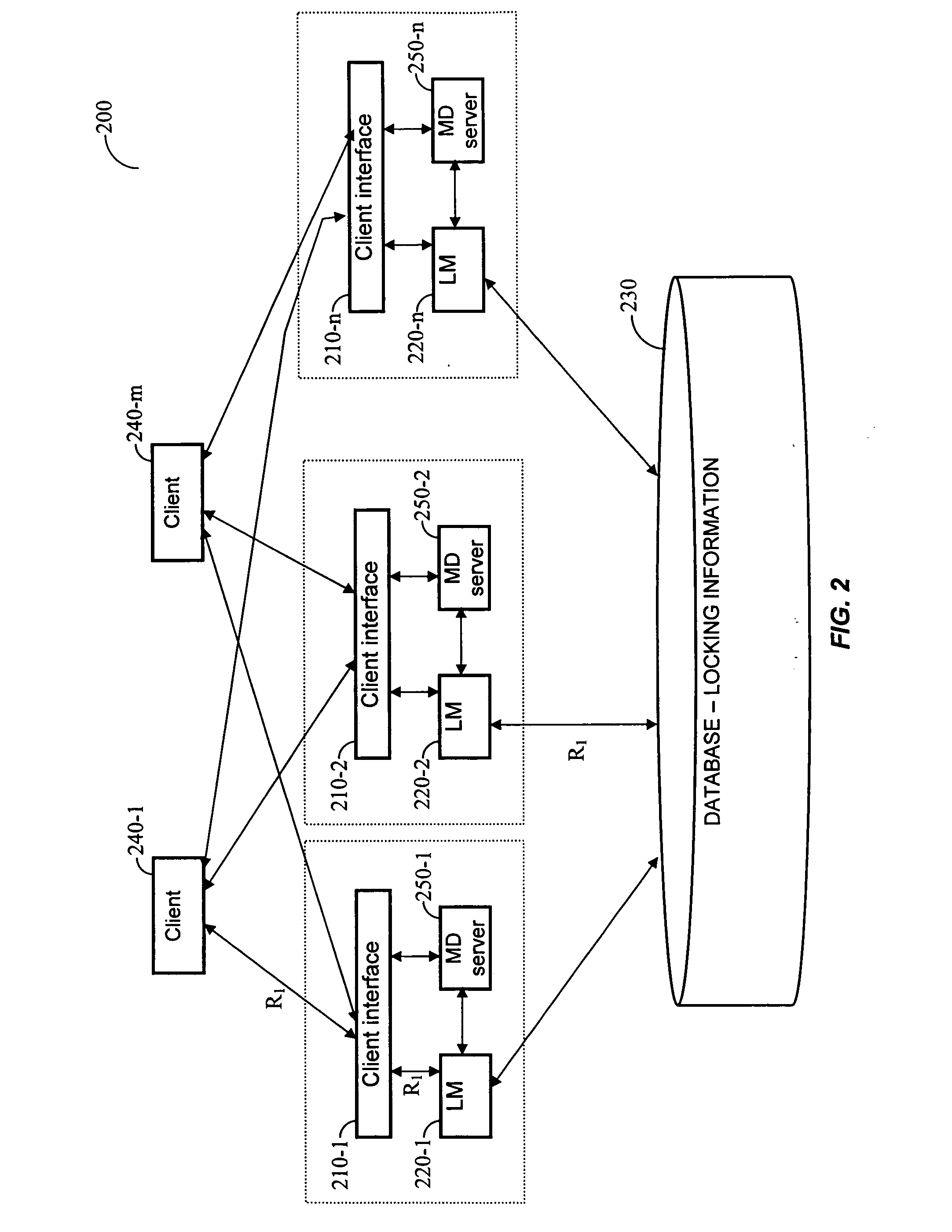
Method for managing lock resources in a distributed storage system
InactiveUS20050289143A1Digital data information retrievalMultiple digital computer combinationsFile systemLock manager
A method and a distributed locking system for the management of lock resources in a distributed files system having several lock managers, each managing lock resources in its respective domain. Each lock manager maintains a registry lock file that comprises of a list of all locked files and a list of lock requests. The registry lock files of all lock managers in the distributed locking system are saved in a central database. Furthermore, the system enables concurrent locking operations of different file sharing protocols on the same file system resources.
Owner:DELL GLOBAL - SINGAPORE BRANCH +1
Multi-protocol lock manager
ActiveUS7313557B1Data processing applicationsDigital data information retrievalLock managerSemantics
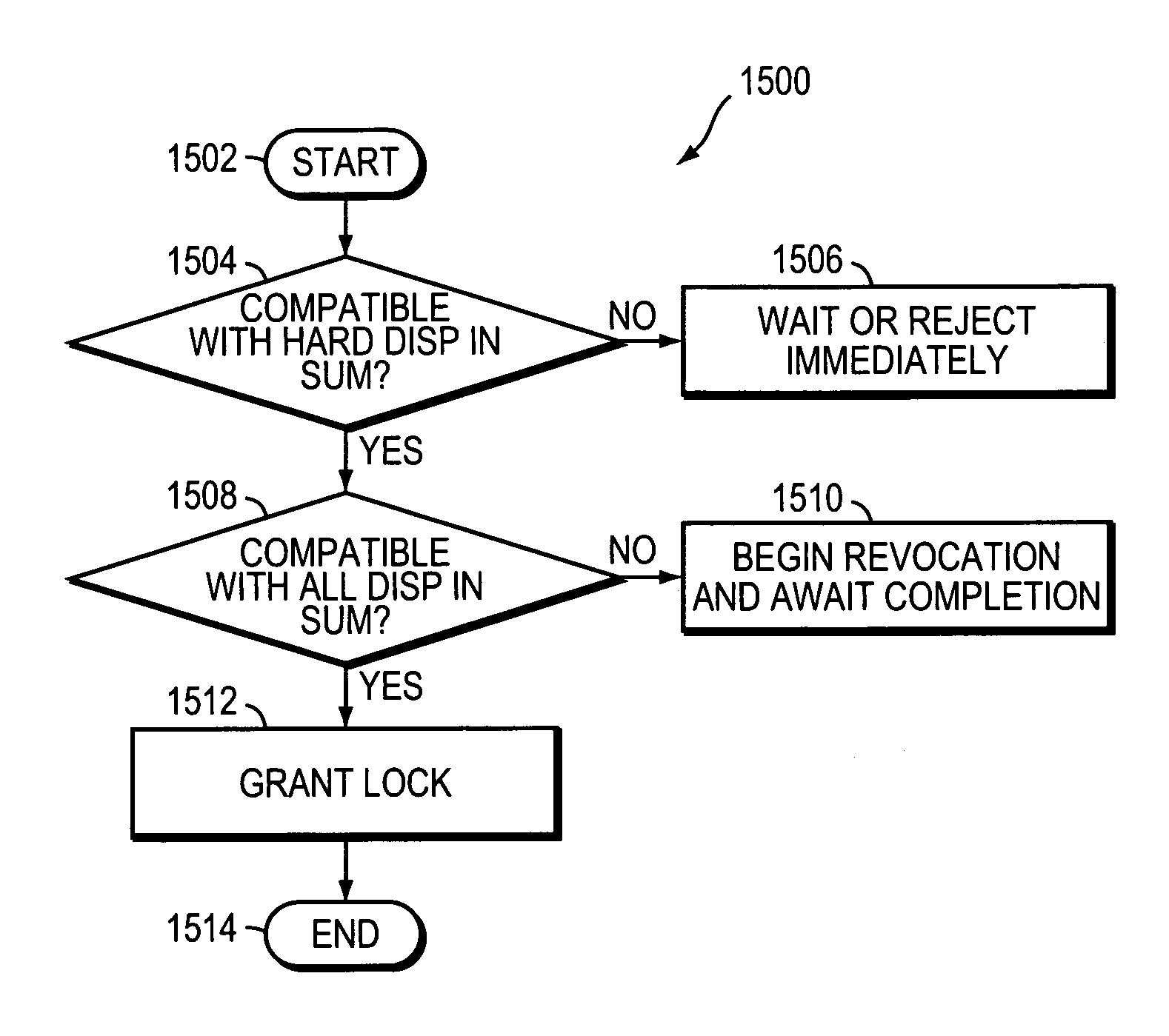
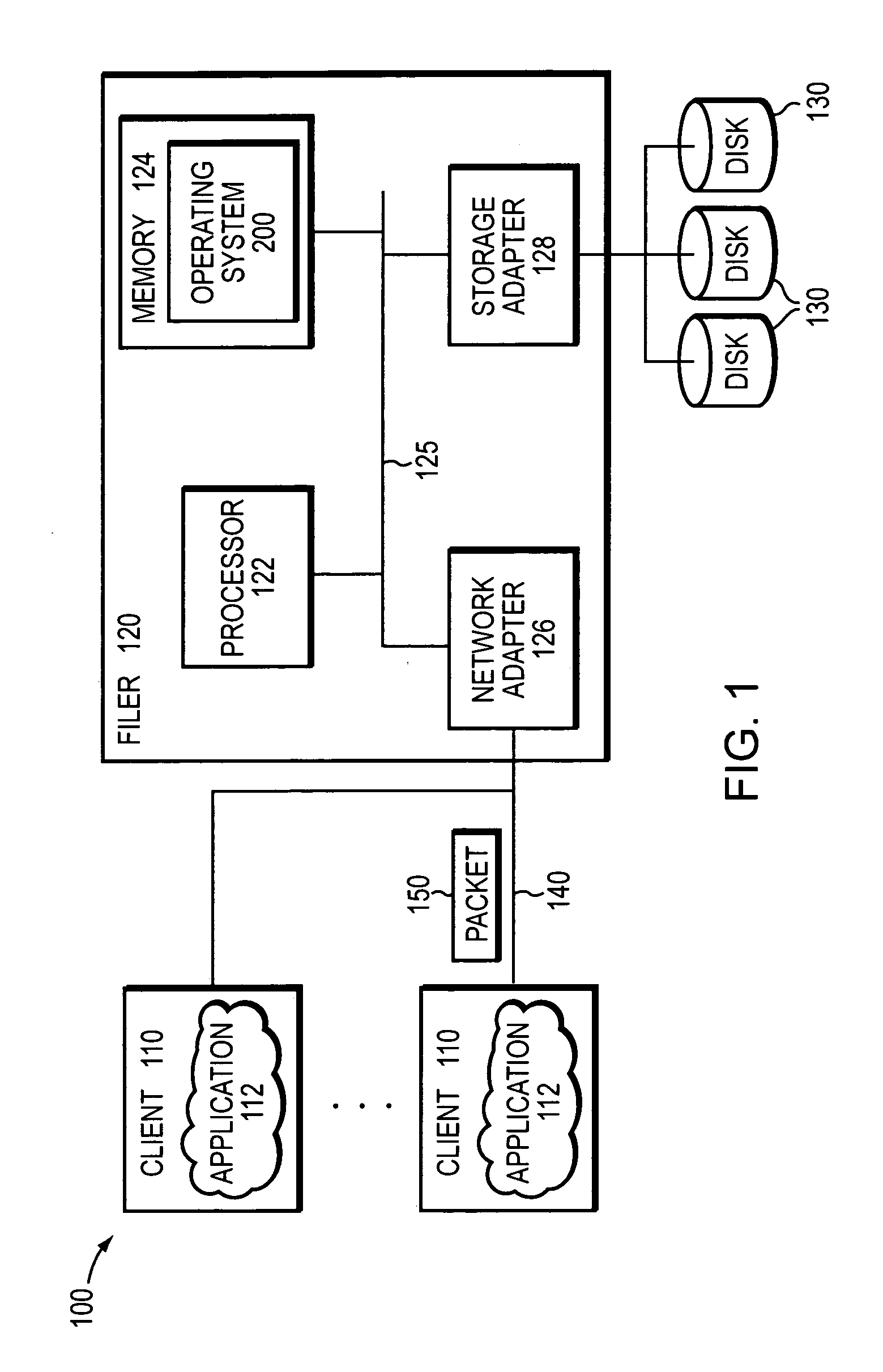
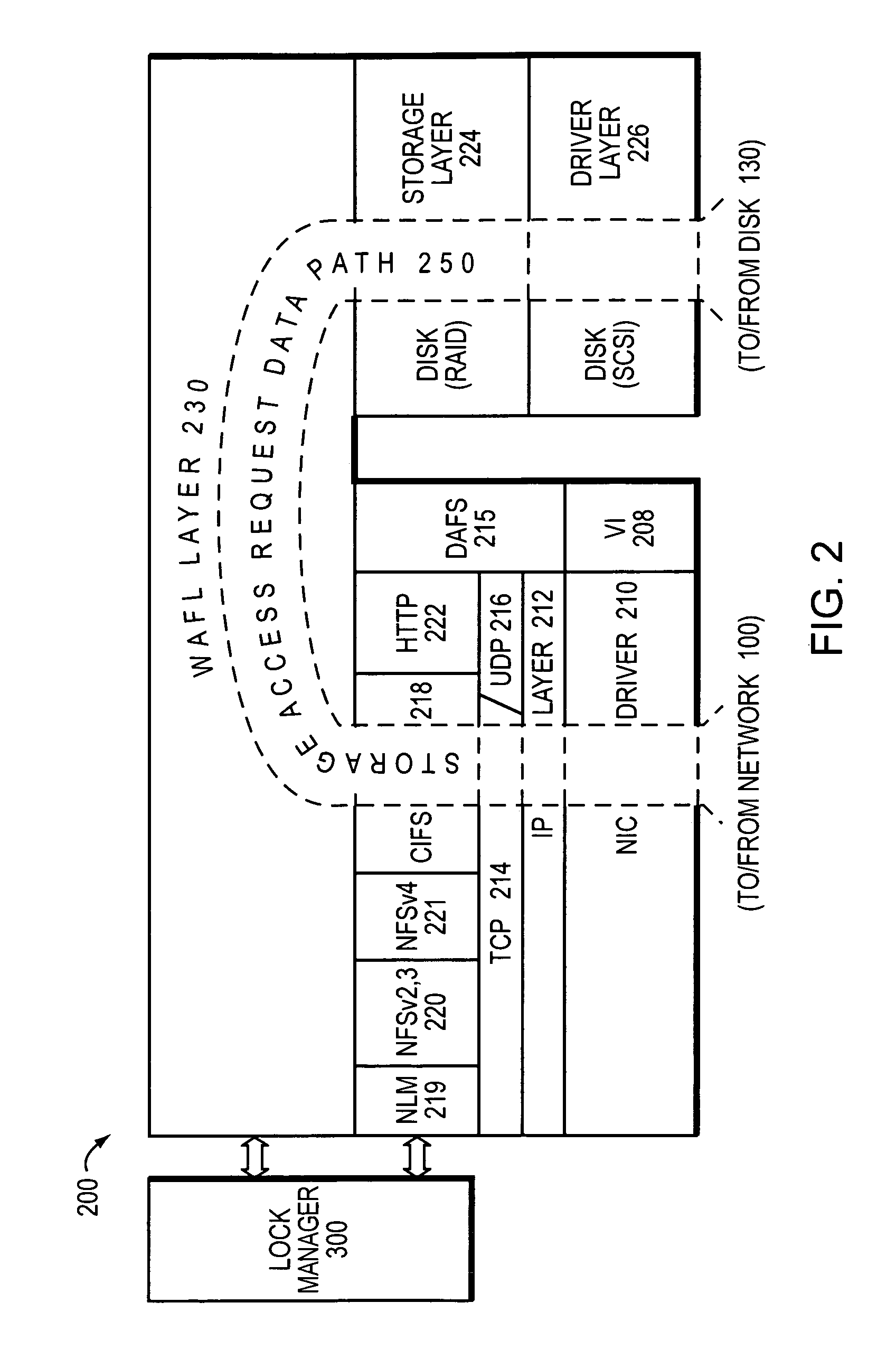
A multi-protocol lock manager efficiently manages granting, revoking and releasing of various types of locks on files or regions of files located on a file server, such as a filer. The various locks are associated with multiple different file access protocols, each having its own semantics. The multi-protocol lock manager allows the filer to take appropriate actions with respect to locking requests and other file access operations, while ensuring that the actions taken are always consistent with semantic requirements for each lock, as established by the associated file access protocol.
Owner:NETWORK APPLIANCE INC
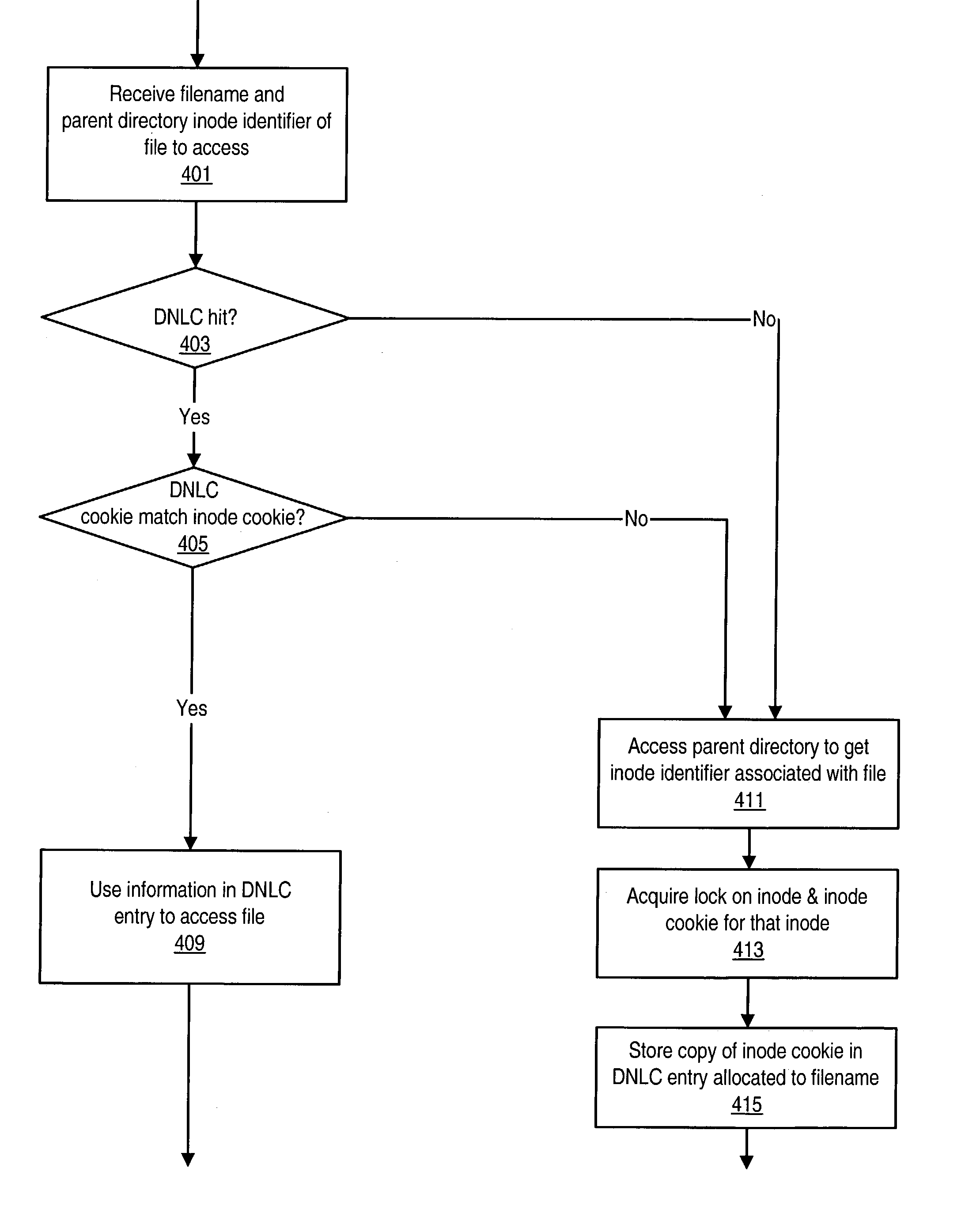
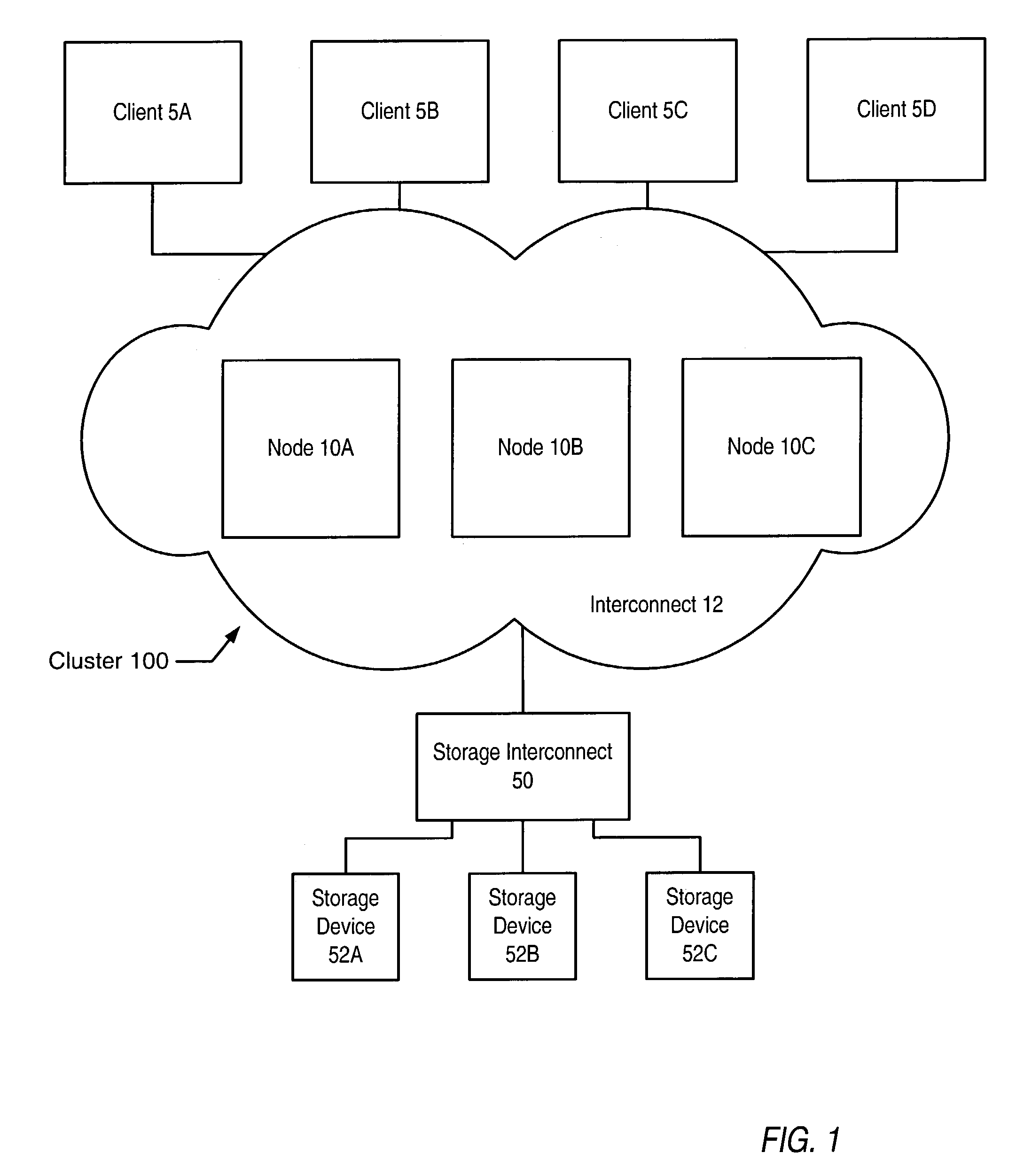
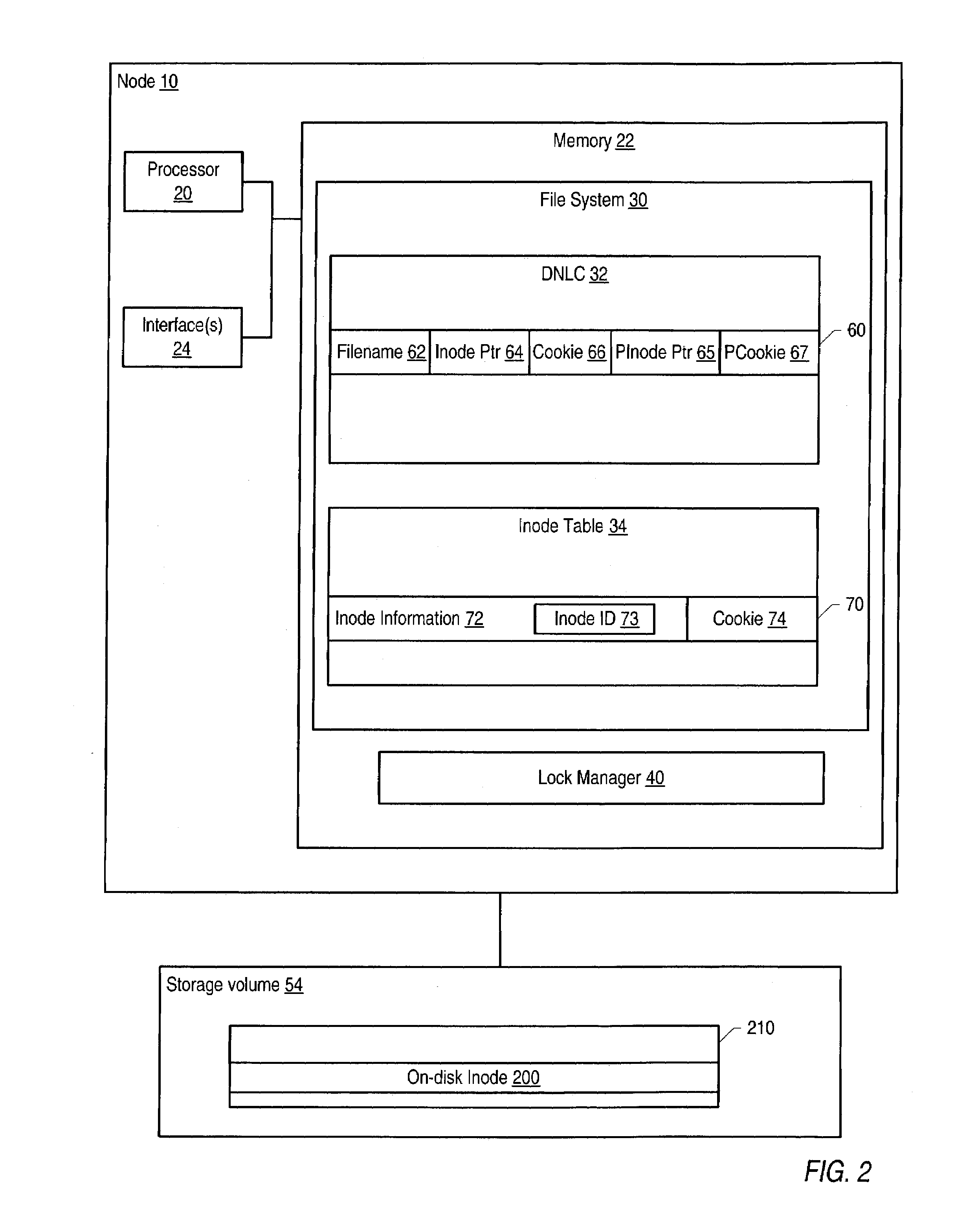
Cookie-based directory name lookup cache for a cluster file system
ActiveUS7103616B1Data processing applicationsDigital data information retrievalLock managerFile system
A method may involve: a node included in a cluster looking up a file in a metadata name cache; in response to a miss for the file in the metadata name cache, the node creating a metadata name cache entry for the file in the metadata name cache, where the metadata name cache entry includes a copy of a cookie associated with metadata allocated to the file; in response to a lock on the metadata changing state for the node, the node modifying the cookie associated with the metadata, where the lock changes state for the node in response to a request to a global lock manager for the lock on the metadata; and comparing the copy of the cookie stored in the metadata name cache entry to a current value of the cookie associated with the metadata to determine if the metadata name cache entry is valid.
Owner:SYMANTEC OPERATING CORP
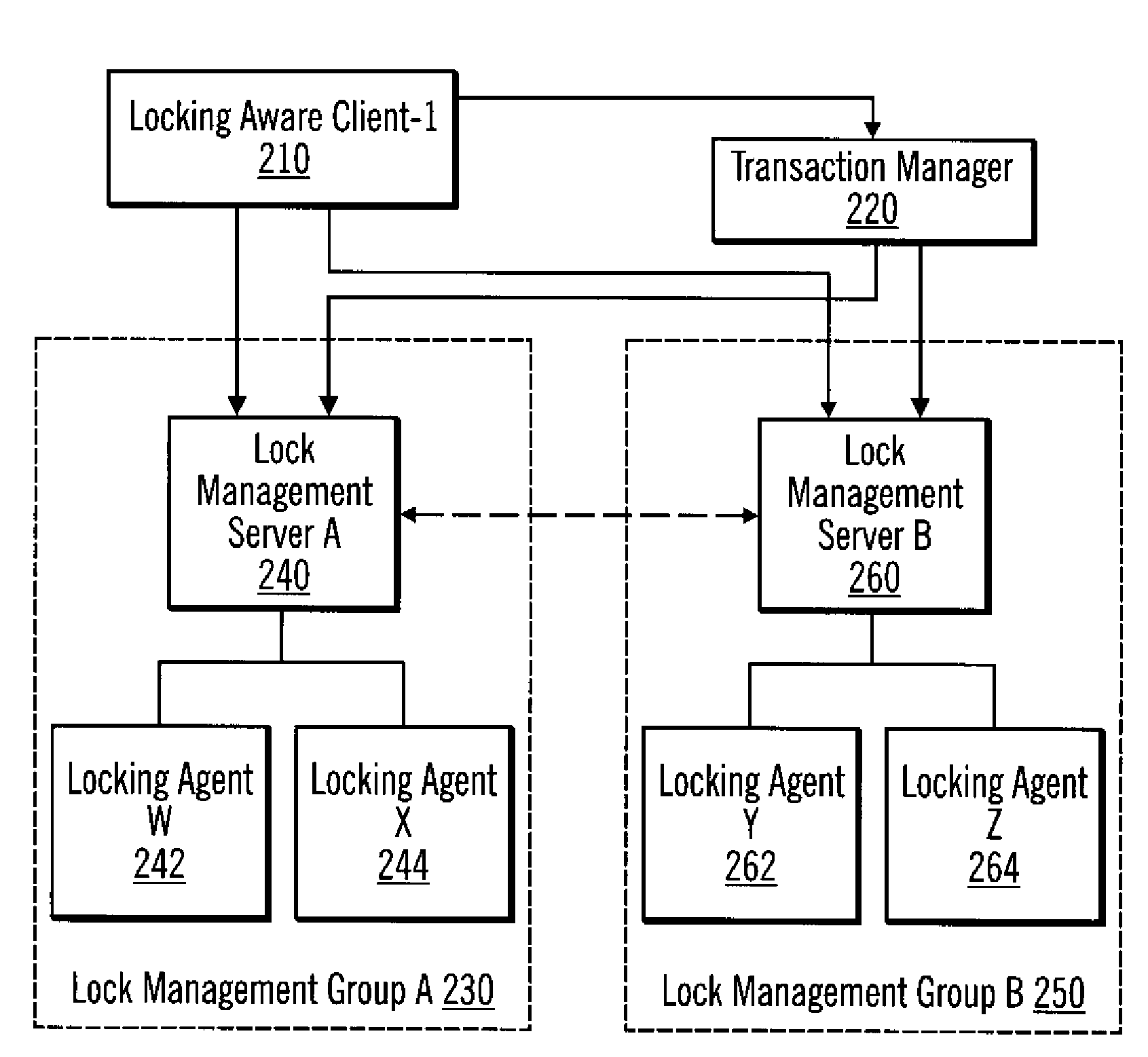
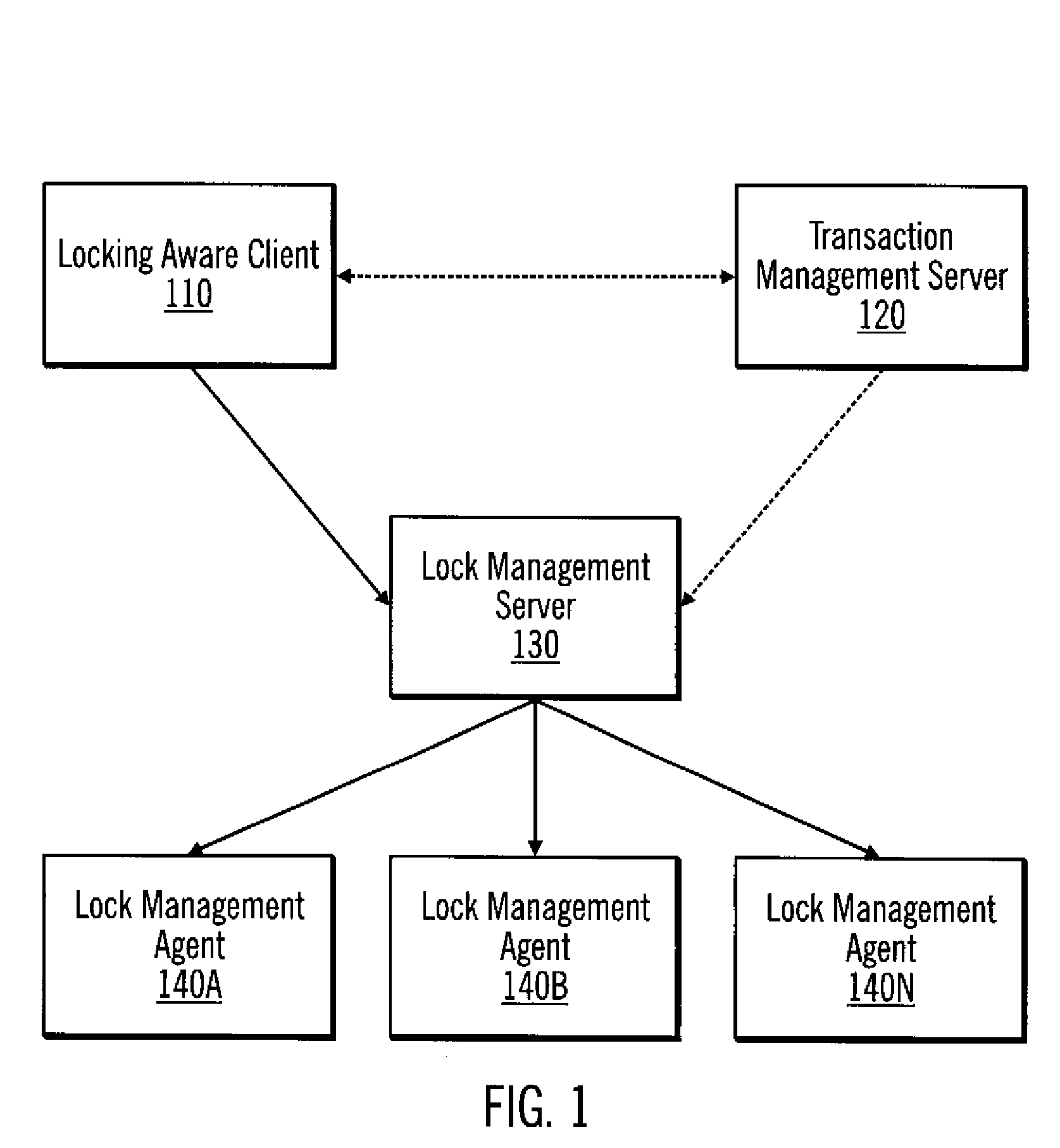
Method, system, and program for lock and transaction management
InactiveUS7289992B2Data processing applicationsProgram synchronisationTransaction managementLock manager
Disclosed is a method, system, and program for transaction management. An indication is received that a transaction is beginning. An operation identifier for the transaction is generated. Actions are logged for the transaction identified by the operation identifier, wherein the actions include requests, corresponding reverse requests, and locks granted.Also disclosed is a method, system, and program for locking management. A command is received that specifies an operation identifier. It is determined whether the command is associated with a transaction using the operation identifier. If it is determined that the command is associated with a transaction, operating at a transaction level of locking.Further disclosed is a method, system, and program for lock management. Under control of a lock manager, (i) lock request queuing is performed, (ii) heartbeat functions are performed, and (iii) state information is maintained.
Owner:IBM CORP
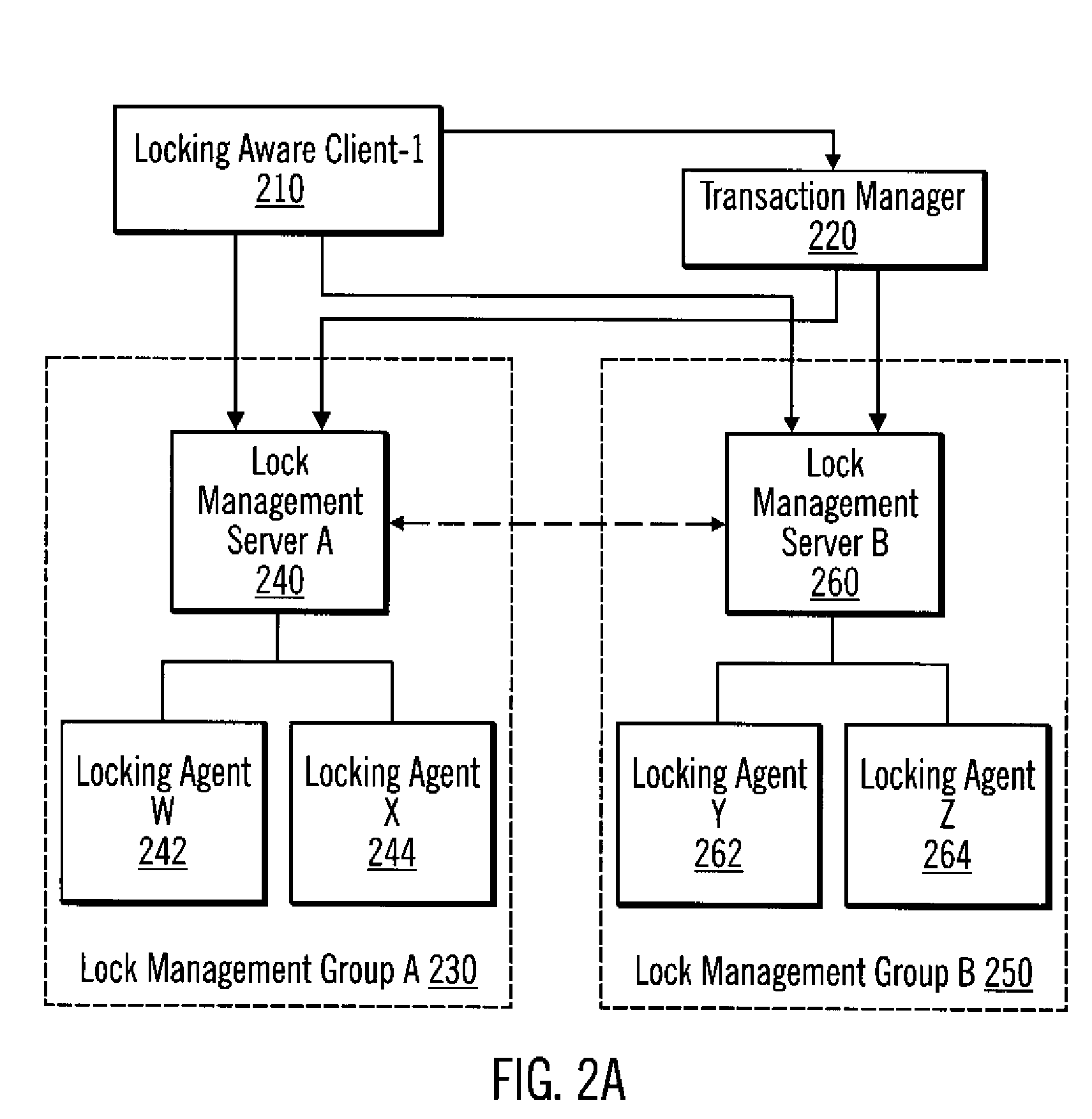
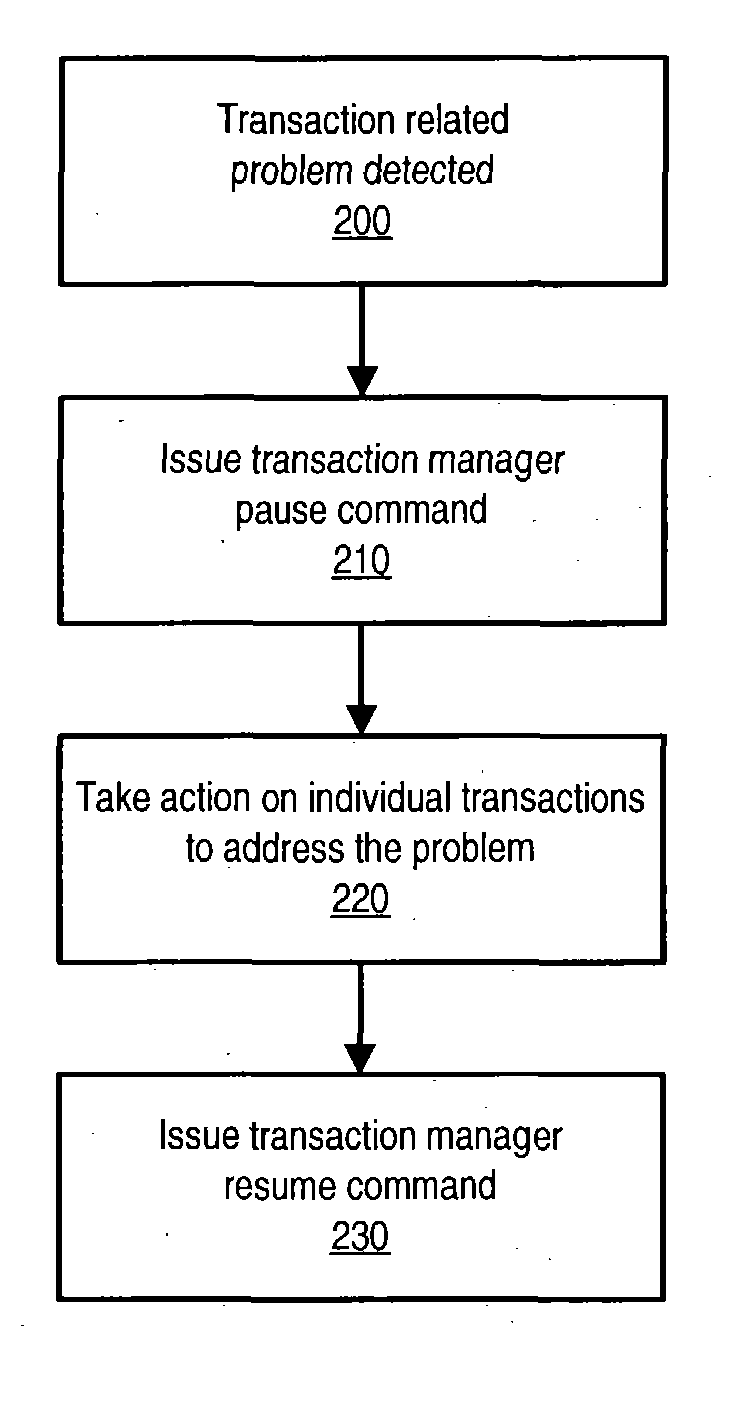
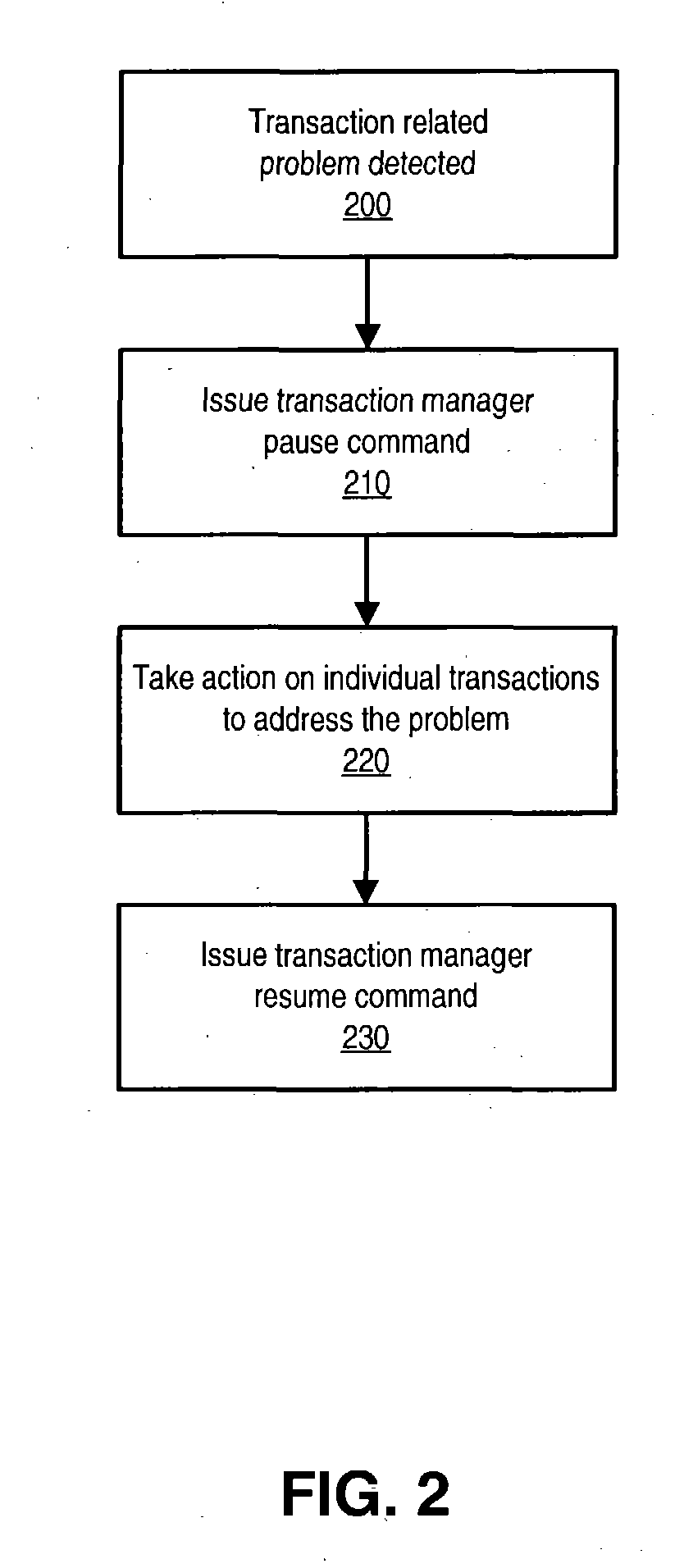
Read/write lock transaction manager freezing
ActiveUS20050015353A1Digital data processing detailsSpecial data processing applicationsLock managerComputer science
A transaction manager may be paused so that transactions managed by the transaction manager are prevented from making transactional state changes. When all transactions being coordinated by a transaction manager are paused, the transaction manager may be said to be paused or frozen. While the transaction manager is paused, the transactions that the transaction manager is supporting may not be allowed to complete. A transaction manager may be configured to obtain permission from a transaction freeze manager in order to transition the state of a transaction. The transaction freeze manager may function as a read / write lock manager controlling locks on a transaction freeze object. In servicing a transaction state transition request, the transaction freeze manager may grant the transaction manager a read lock on the transaction freeze object. In servicing a transaction manager pause request, the transaction freeze manager may grant an administrative entity a write lock on the transaction freeze object.
Owner:ORACLE INT CORP
Methods and systems for migrating network resources to improve network utilization
ActiveUS20090193122A1Improve network utilizationReduced and minimized amountDigital computer detailsProgram controlTraffic capacityLock manager
A method and system are disclosed for migrating network resources to improve network utilization, for use in a multi-node network wherein nodes of the network share network resources. The method comprises the steps of identifying a group of nodes that share one of the network resources, and identifying one of the nodes satisfying a specified condition based on at least one defined access latency metric. The shared resource is moved to the identified one of the nodes to reduce overall access latency to access the shared resource by said group of nodes. One embodiment of the invention provides a method and system to synchronize tasks in a distributed computation using network attached devices (NADs). A second embodiment of the invention provides a method and system to reduce lock latency and network traffic by migrating lock managers to coupling facility locations closest to nodes seeking resource access.
Owner:IBM CORP
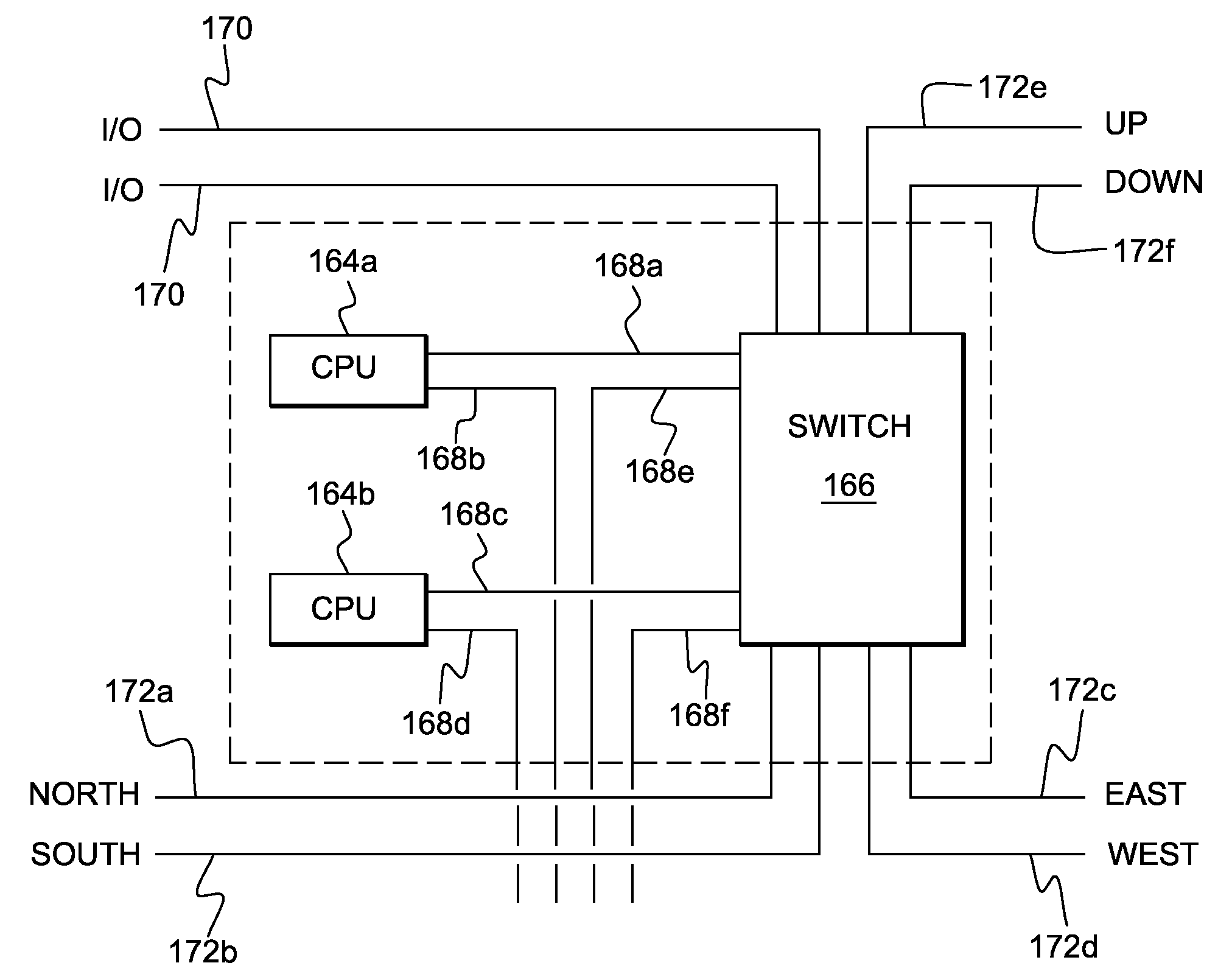
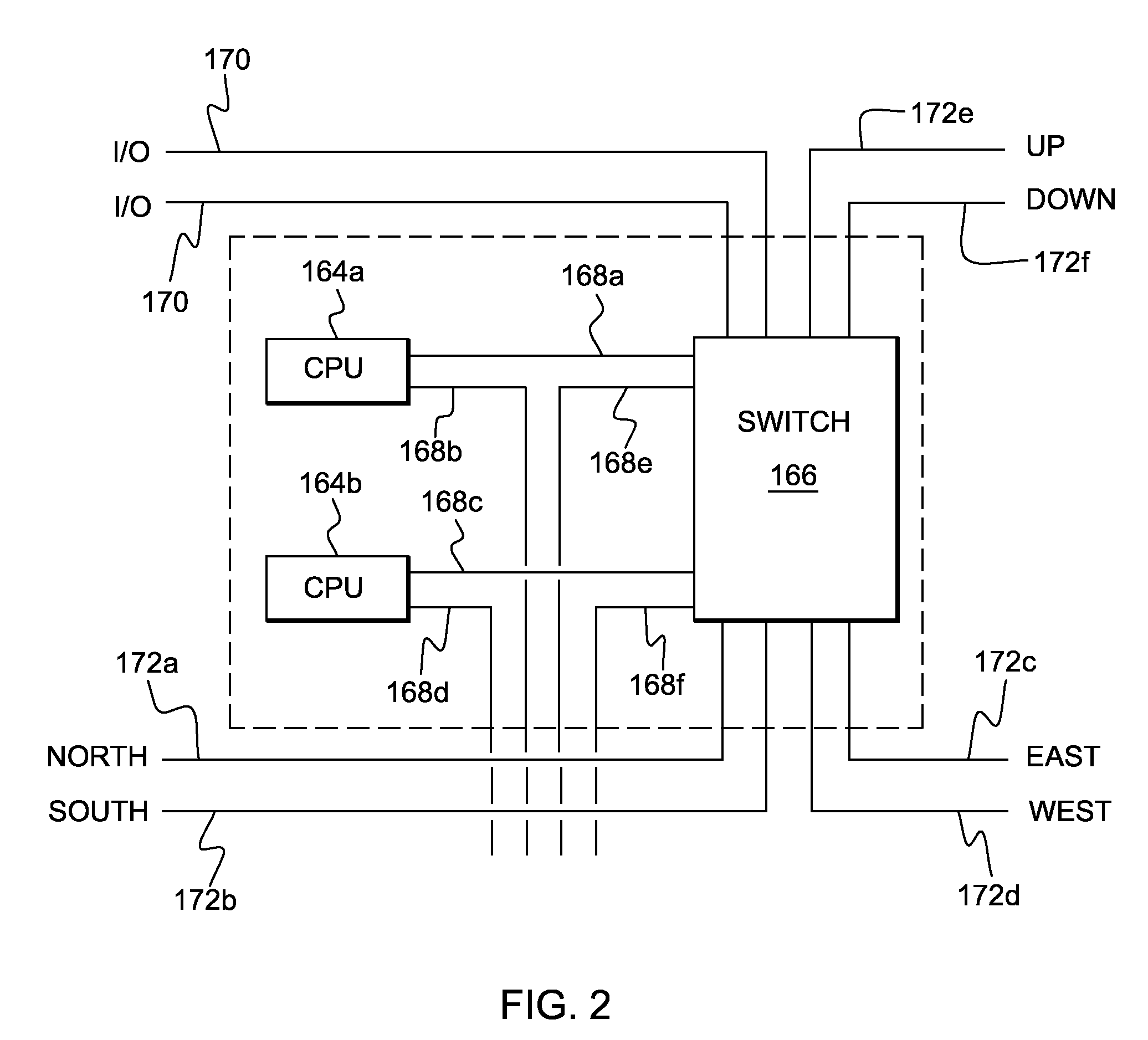
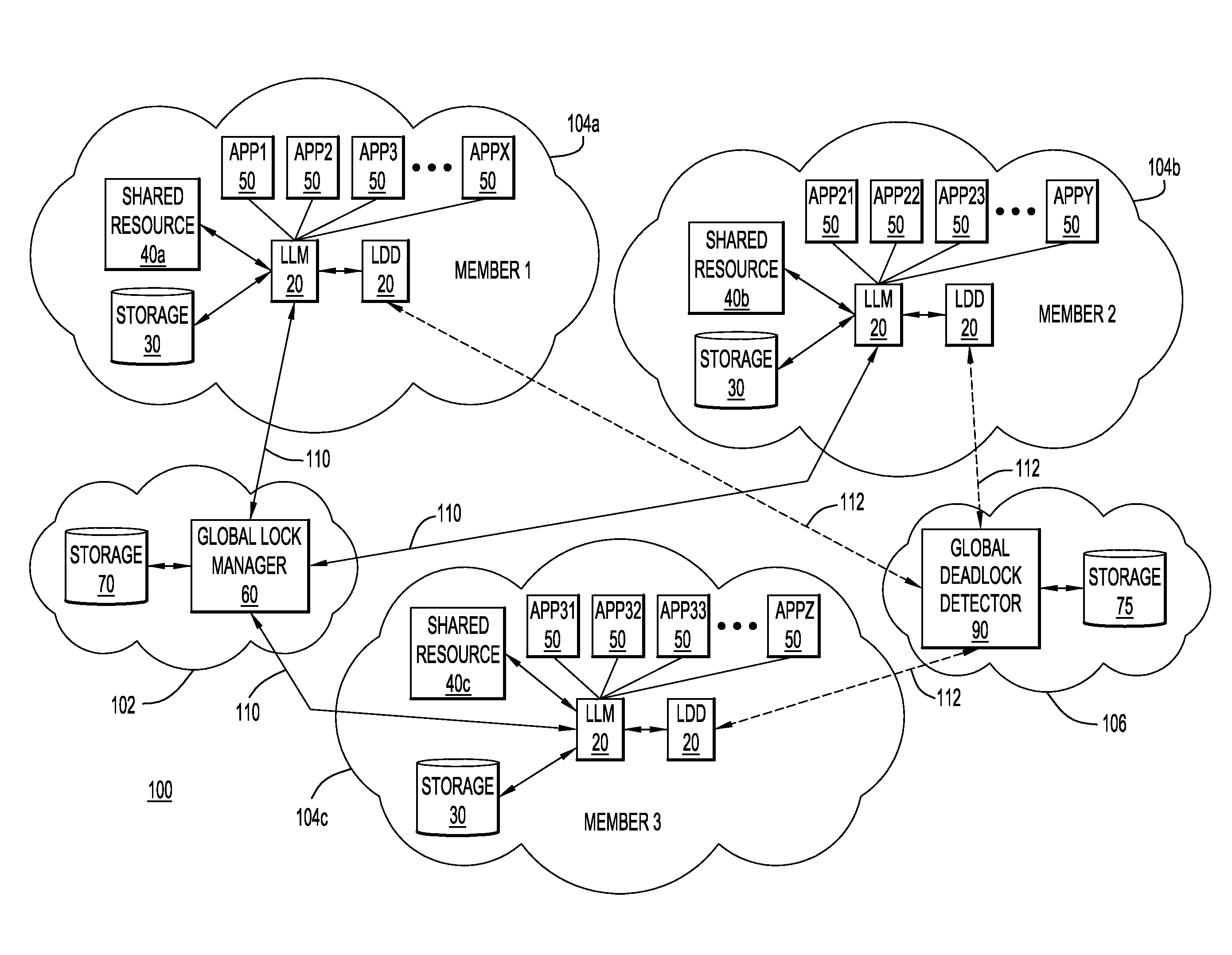
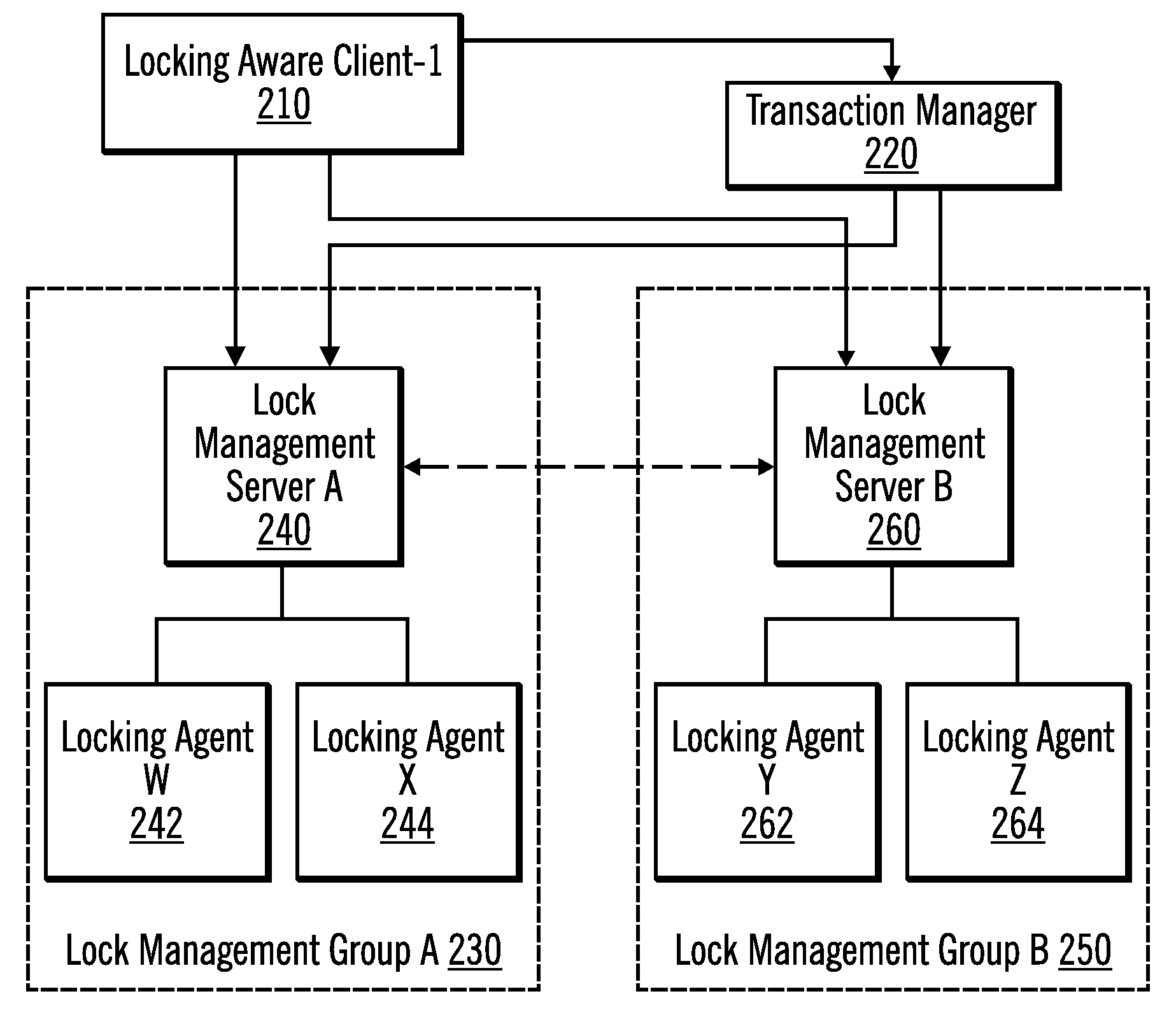
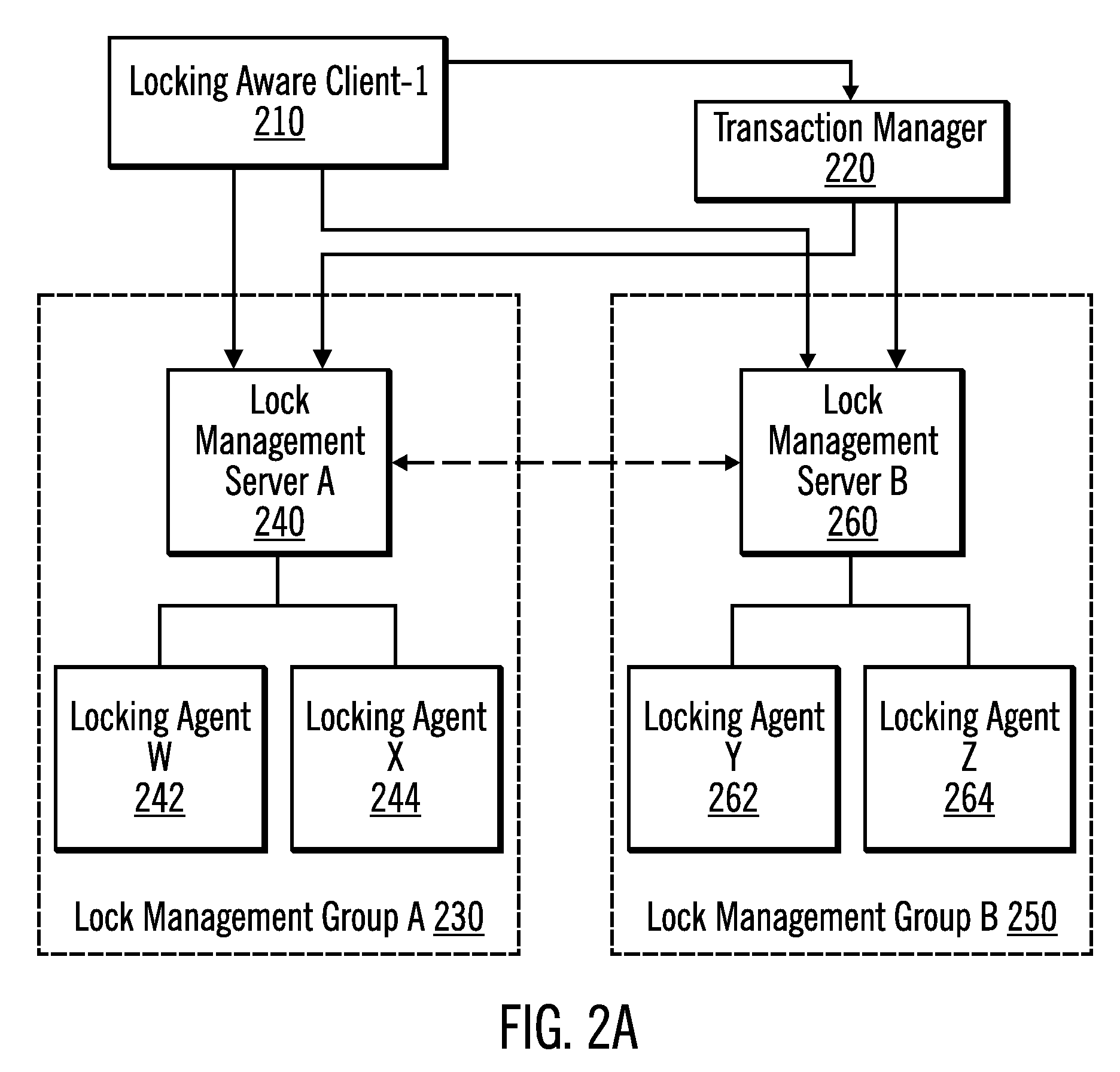
Two-Level Management of Locks on Shared Resources
InactiveUS20120089735A1Digital data information retrievalDigital computer detailsLock managerData system
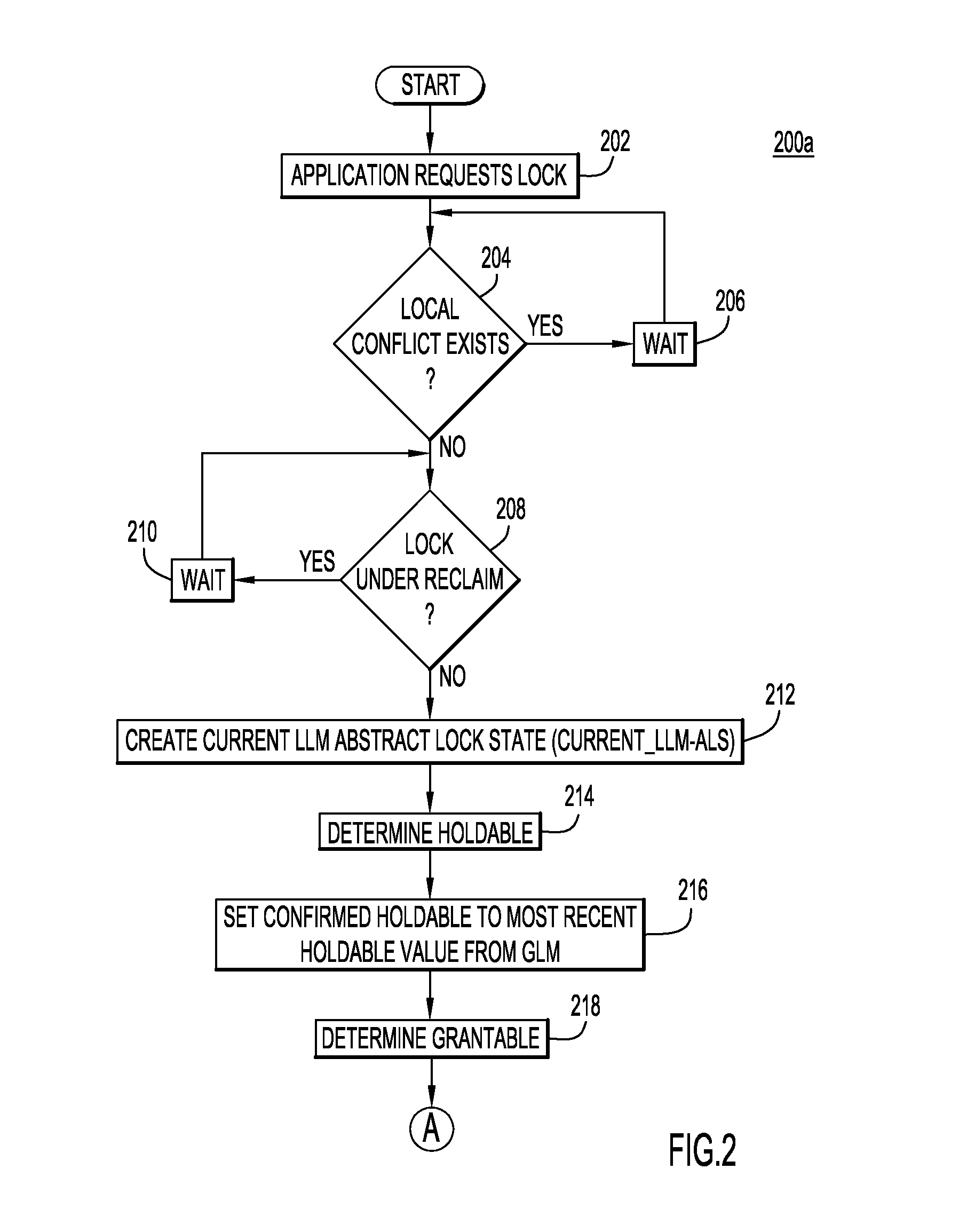
In a shared data system comprising one or more primary nodes and a plurality of secondary nodes, global lock manager on a primary node manages locks for shared resources by exchanging an abstract lock state with local lock managers on the secondary nodes. The abstract lock state includes a particular representation of all of the applications on the nodes that are requesting or are granted locks. The exchange of these particular lock states instead of individual requests improves performance by increasing concurrency and reducing off-machine communication. A global deadlock detector on a node detects and resolves global deadlocks, in conjunction with local deadlock detectors on the secondary nodes.
Owner:IBM CORP
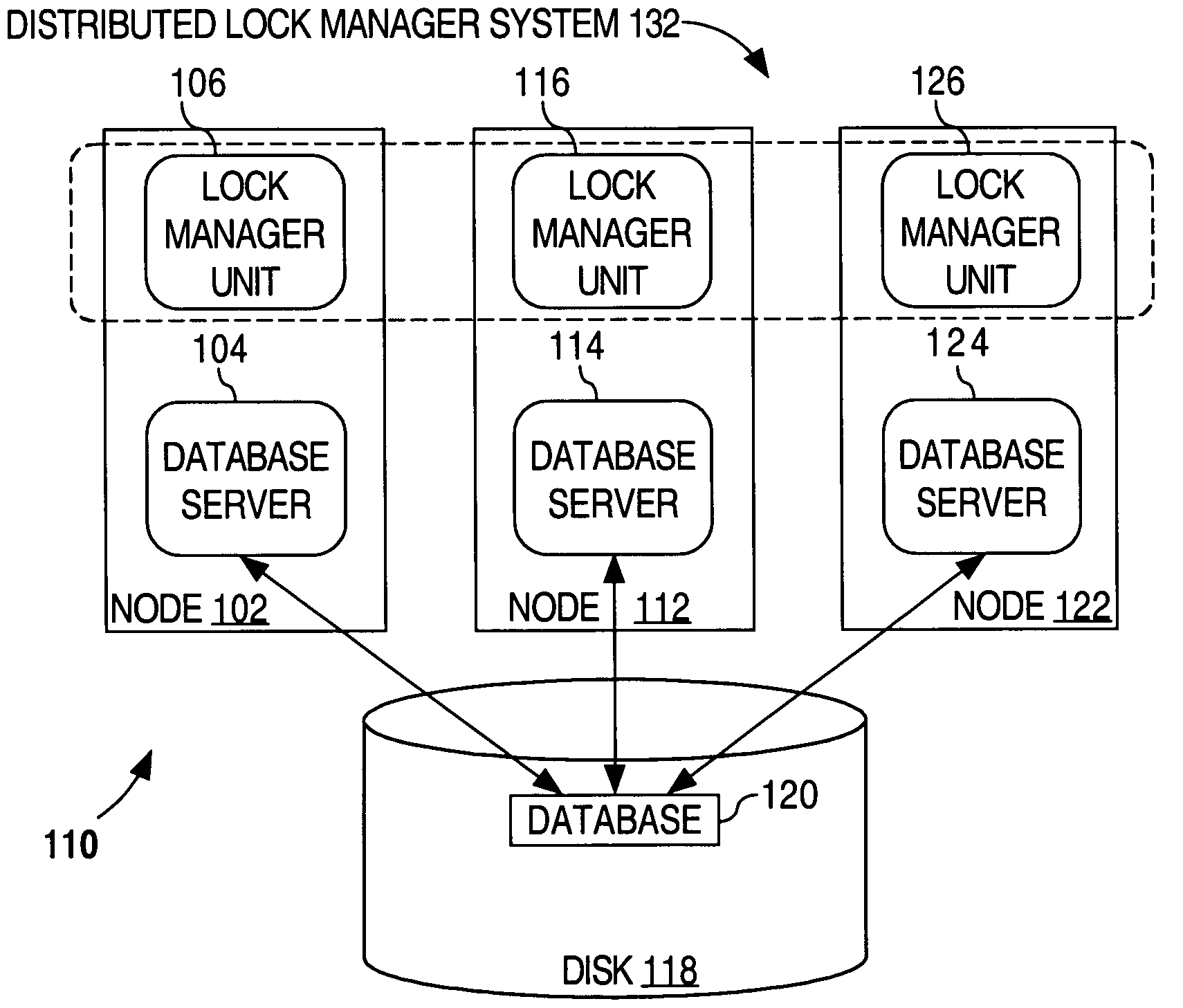
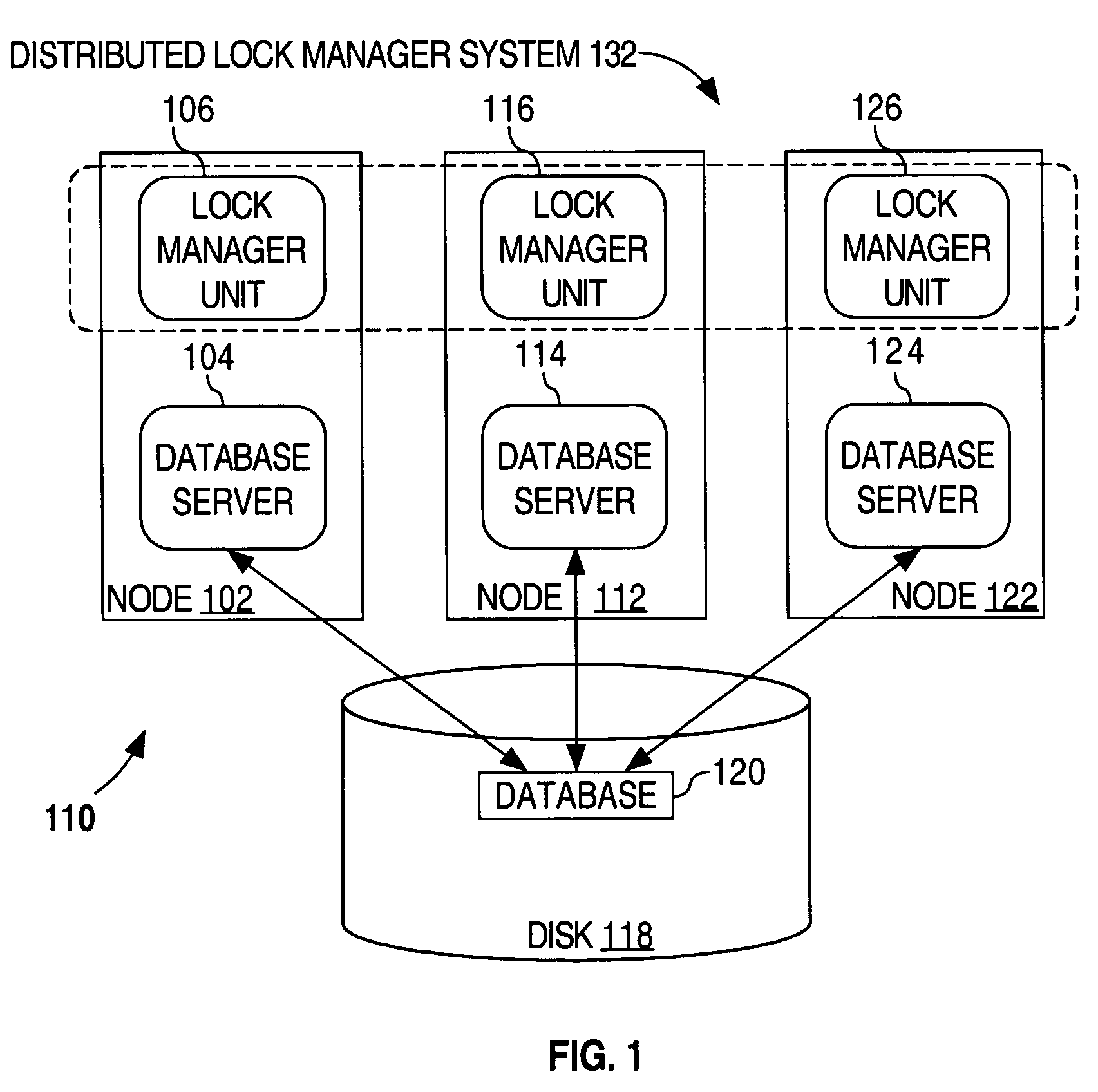
Fault tolerant distributed lock management
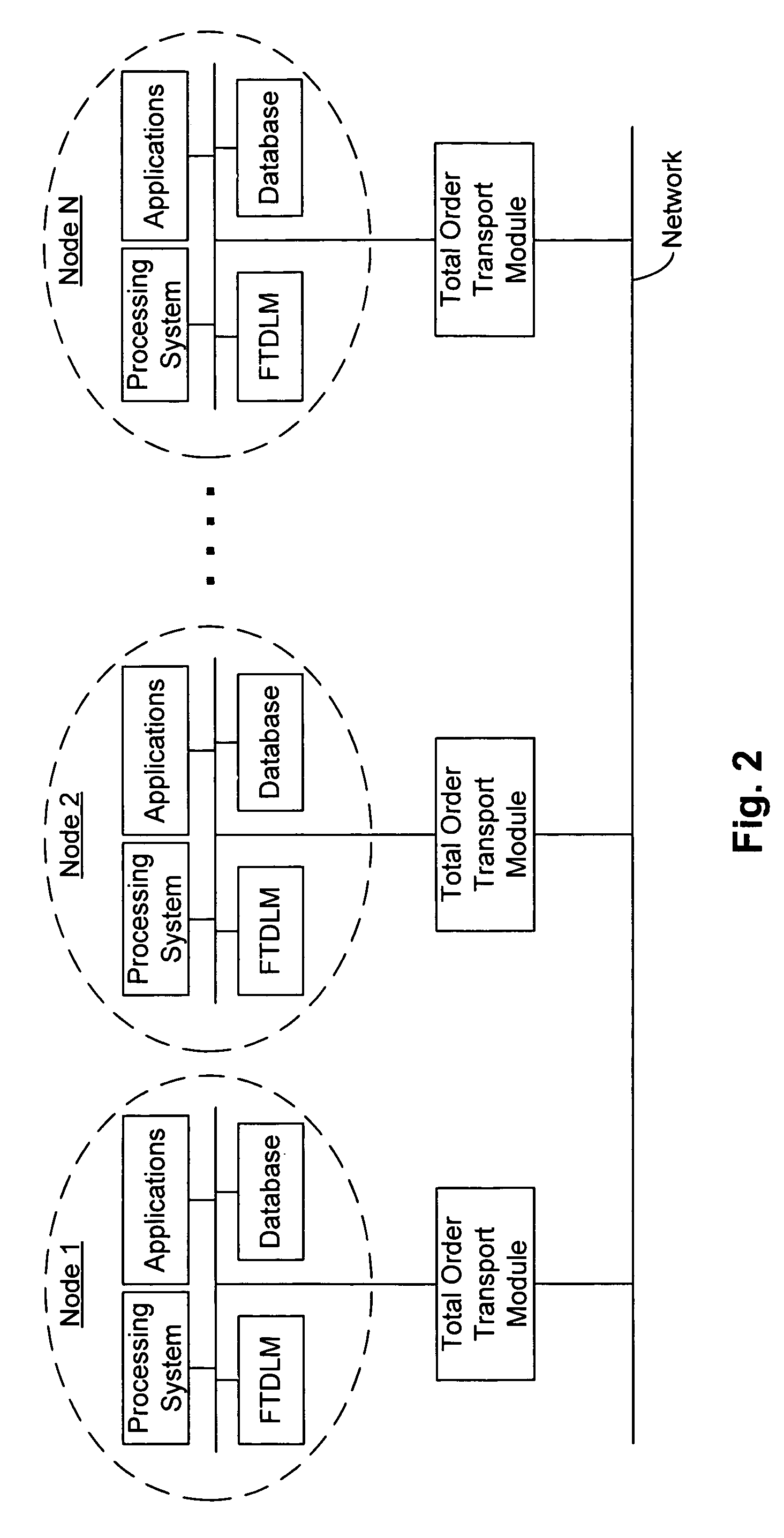
ActiveUS20060253856A1Maintain data consistencyError detection/correctionMultiprogramming arrangementsLock managerProtocol for Carrying Authentication for Network Access
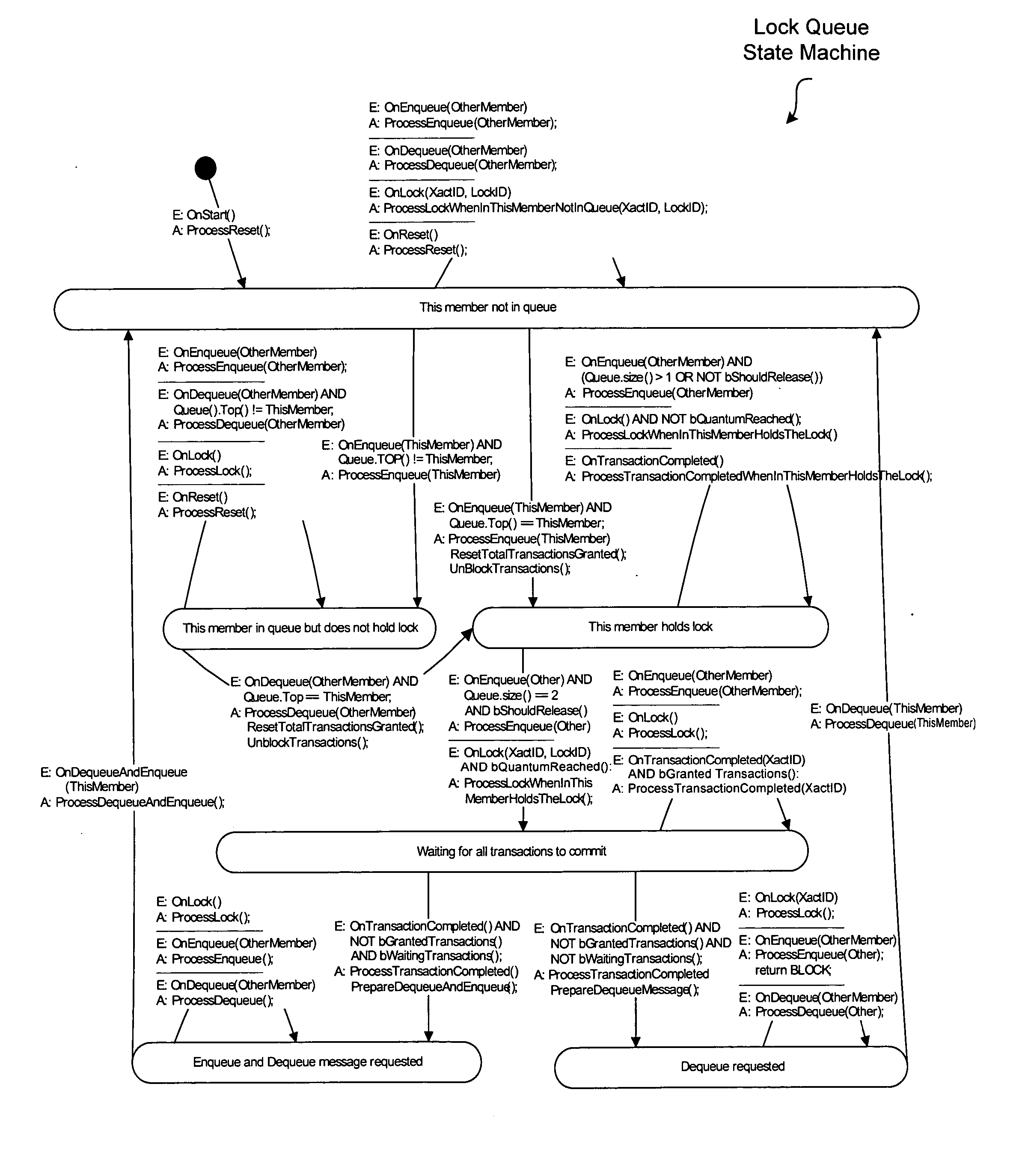
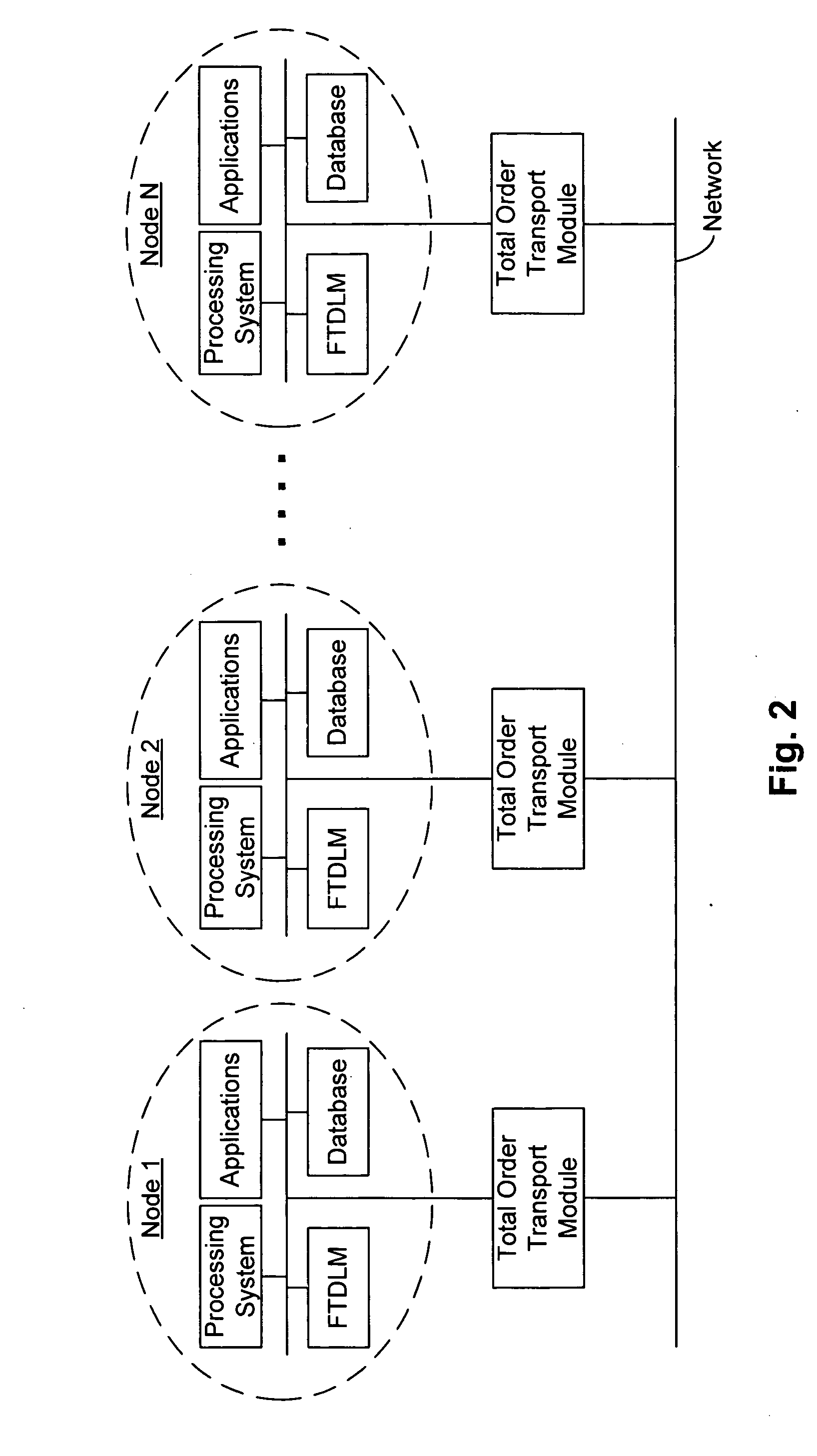
Distributed transaction and lock management techniques are disclosed that manage and regulate access to distributed data. A lock manager module is provided for regulating access to resources by applications in a system having a number of nodes each communicatively coupled to a network. The module can be configured to be fault tolerant. In one embodiment, the module uses a totally ordered transport that imposes total ordering protocols on messaging between nodes. The module can exploit the multicast ability of the network (e.g., Ethernet or other network features that enable multicast). The module includes a queue for each resource, the queue identifying the node that owns distributed lock for that resource. Each queue can be replicated across the nodes in a distributed configuration.
Owner:PROGRESS SOFTWARE
Method, system, and program for lock and transaction management
InactiveUS20070282839A1Data processing applicationsProgram synchronisationTransaction managementLock manager
Disclosed is a method, system, and program for locking management. A command is received that specifies an operation identifier. It is determined whether the command is associated with a transaction using the operation identifier. If it is determined that the command is associated with a transaction, operating at a transaction level of locking. Further disclosed is a method, system, and program for lock management. Under control of a lock manager, lock request queuing is performed, heartbeat functions are performed, and state information is maintained.
Owner:INT BUSINESS MASCH CORP
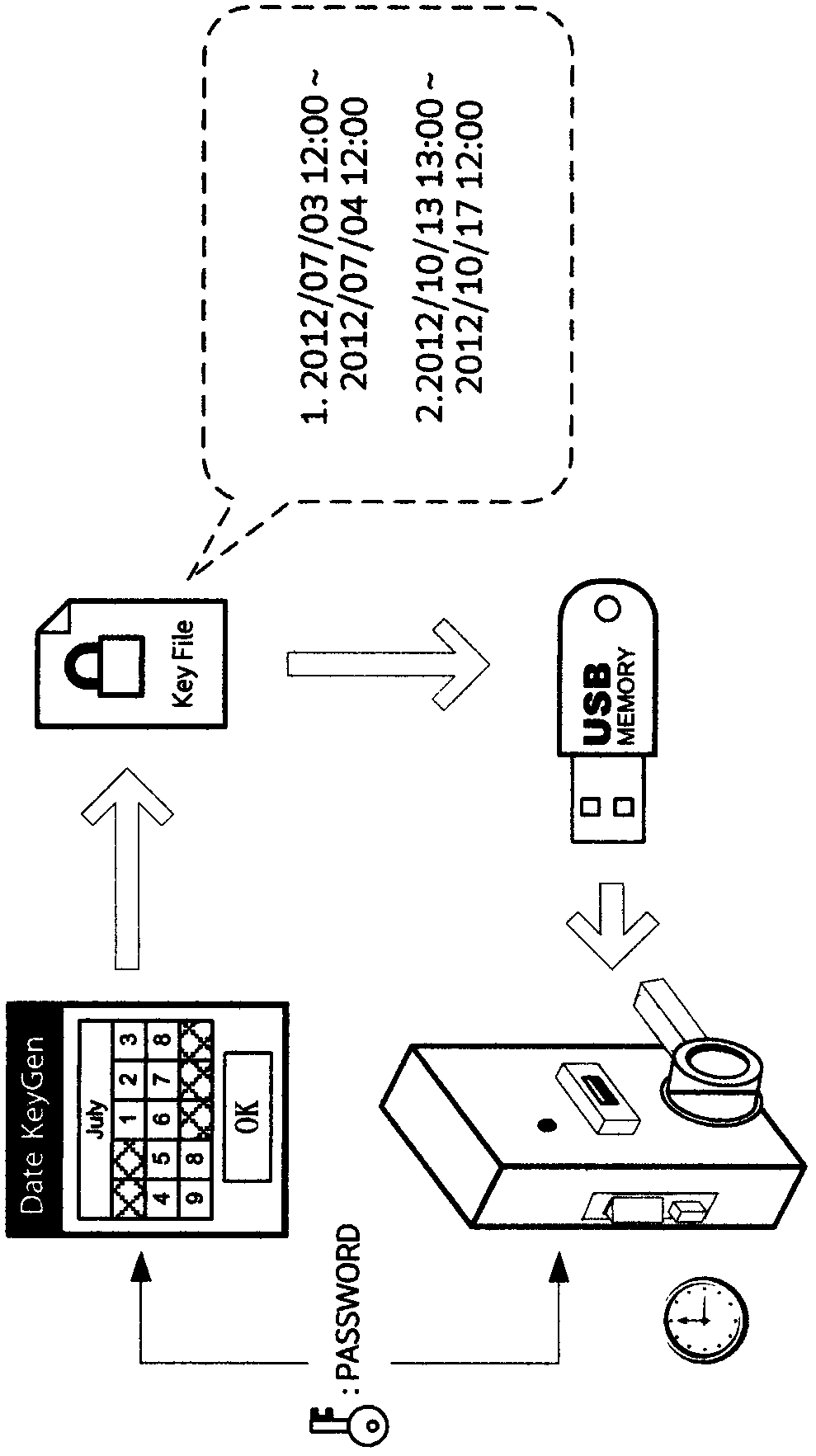
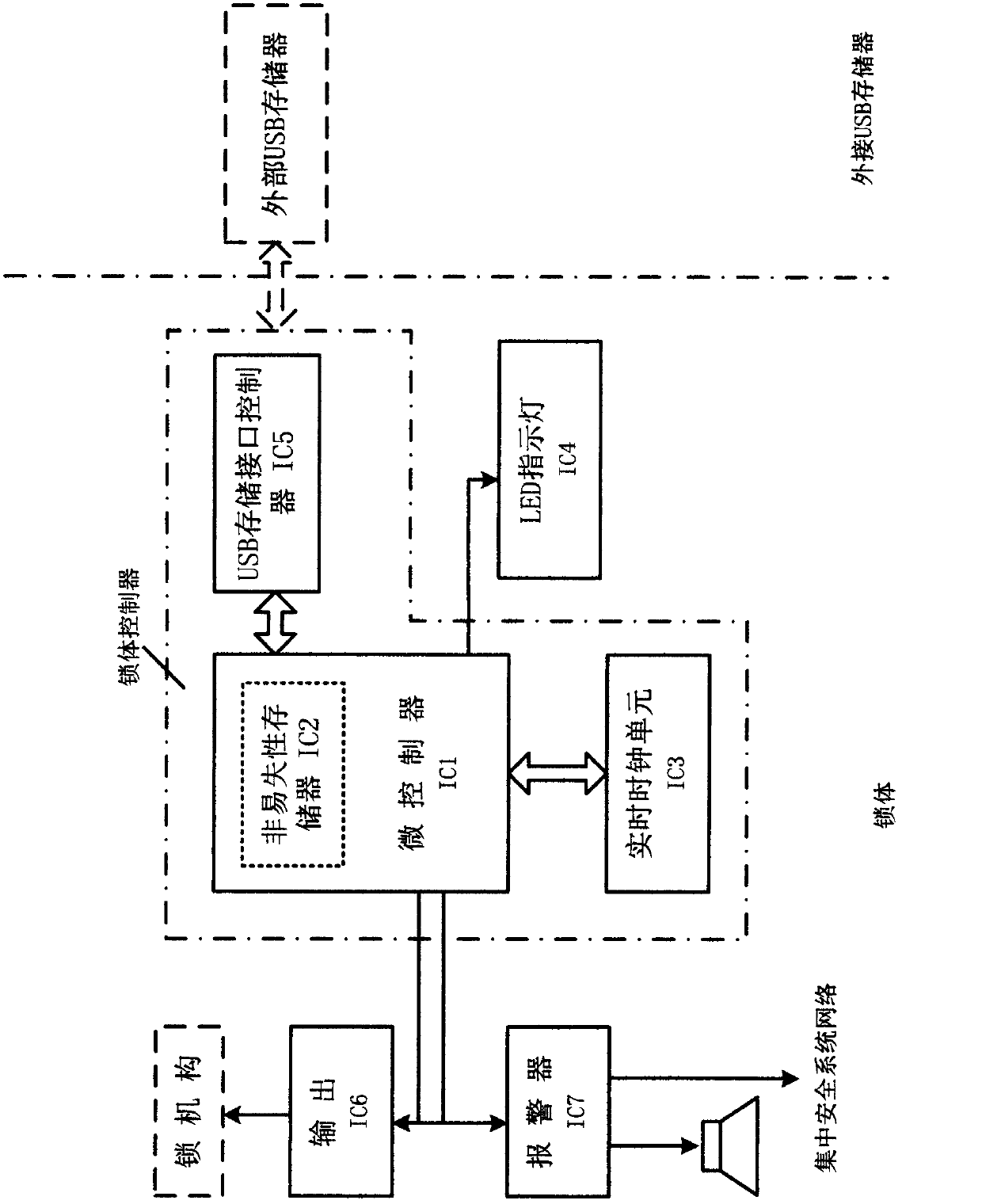
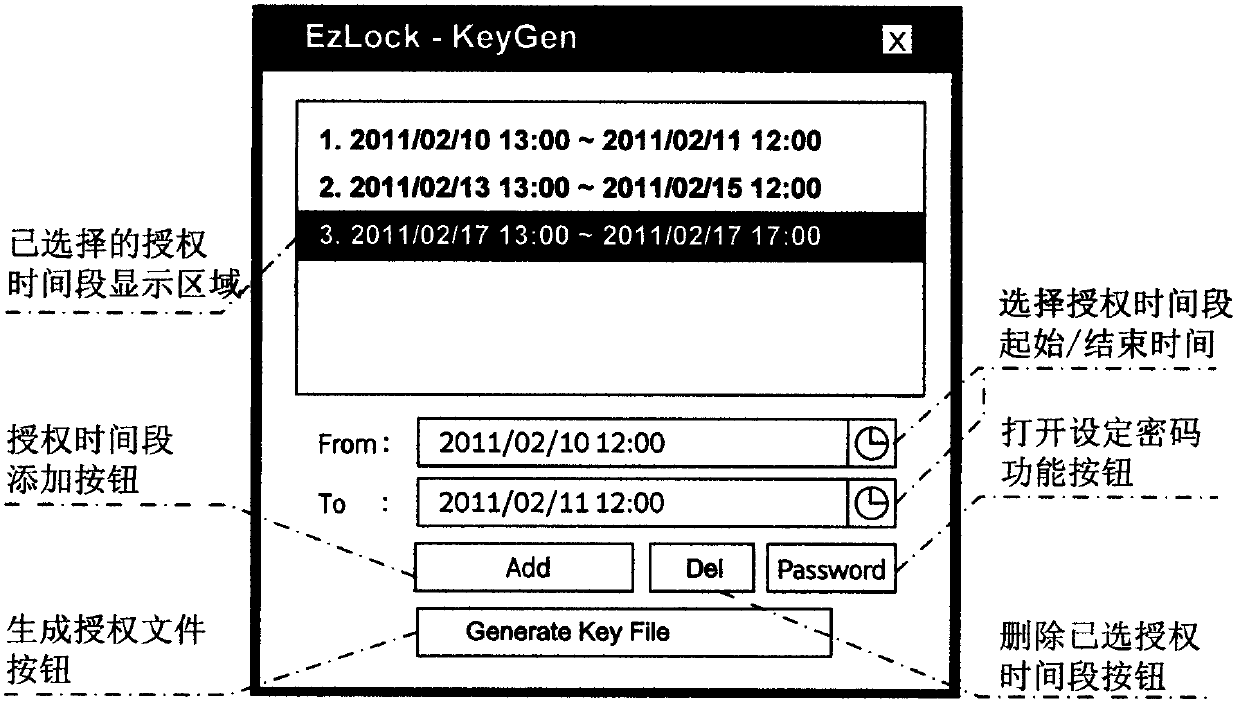
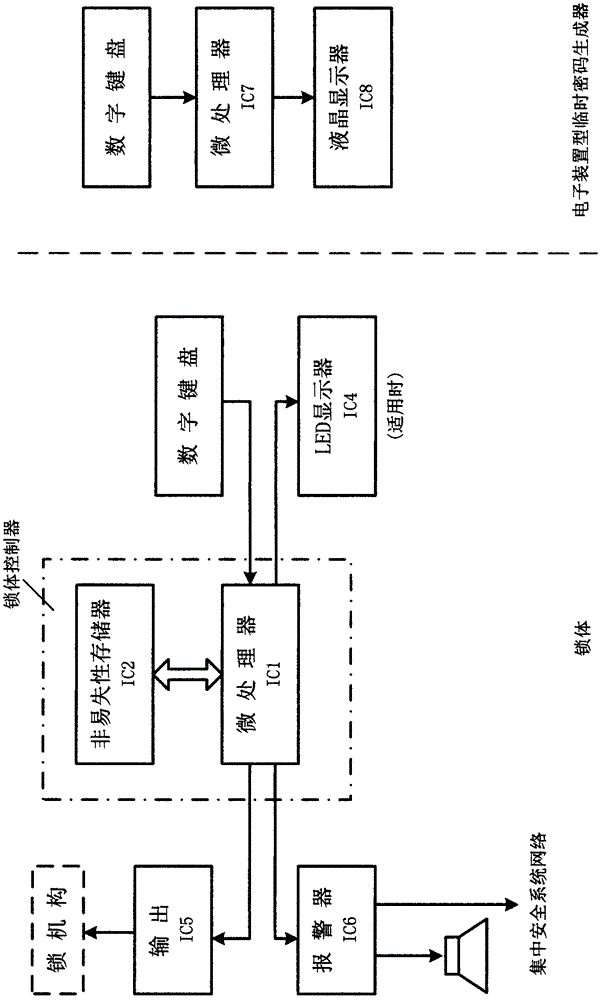
Coded lock system capable of unlocking in specific time period by using encrypted authorization data
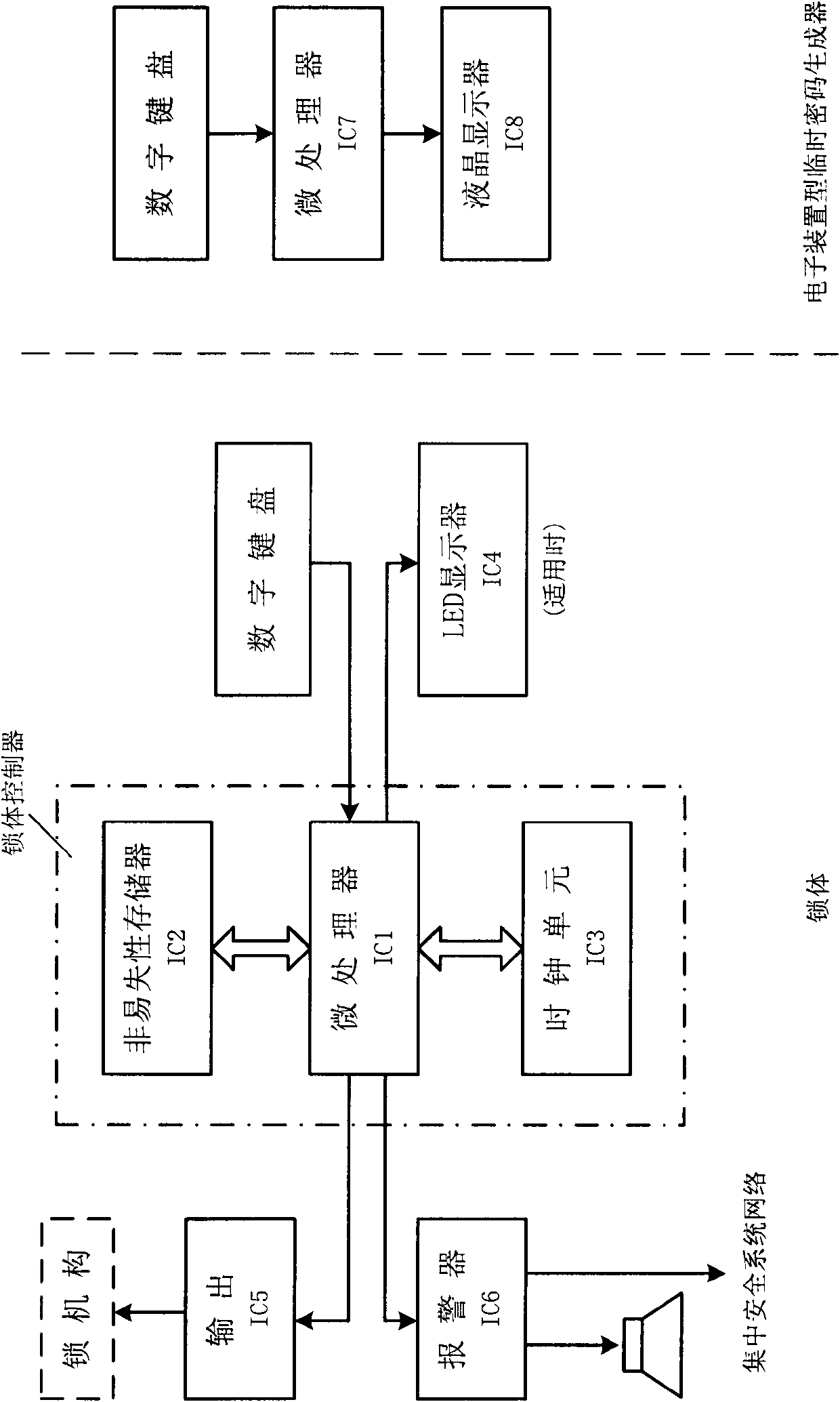
InactiveCN103700177AEasy to manageEasy accessEncryption apparatus with shift registers/memoriesIndividual entry/exit registersLock managerSpecific time
The invention provides a coded lock system capable of unlocking in the specific time period by using encrypted authorization data. A coded lock manager adopts a code P corresponding to a code F stored in a coded lock as a secret key through an encrypted authorization data generator to adopt a specific encryption algorithm (such as an asymmetrical encryption algorithm (AES) on specified authorization data in one or more time periods to generate encrypted authorization data S; a temporary user of the coded lock inputs the encrypted authorization data S into the coded lock under the specified authorization condition (such as specific date or time); a coded lock controller adopts the code F stored inside to decrypt the encrypted authorization data to acquire each authorization item (comprising time period or times); if the specified authorization condition meet the requirement of a certain authorization item (such as the operating time is in a certain authorization time period), unlocking is performed.
Owner:袁磊
Fault tolerant distributed lock management
ActiveUS7426653B2Error detection/correctionMultiprogramming arrangementsLock managerApplication software
Owner:PROGRESS SOFTWARE
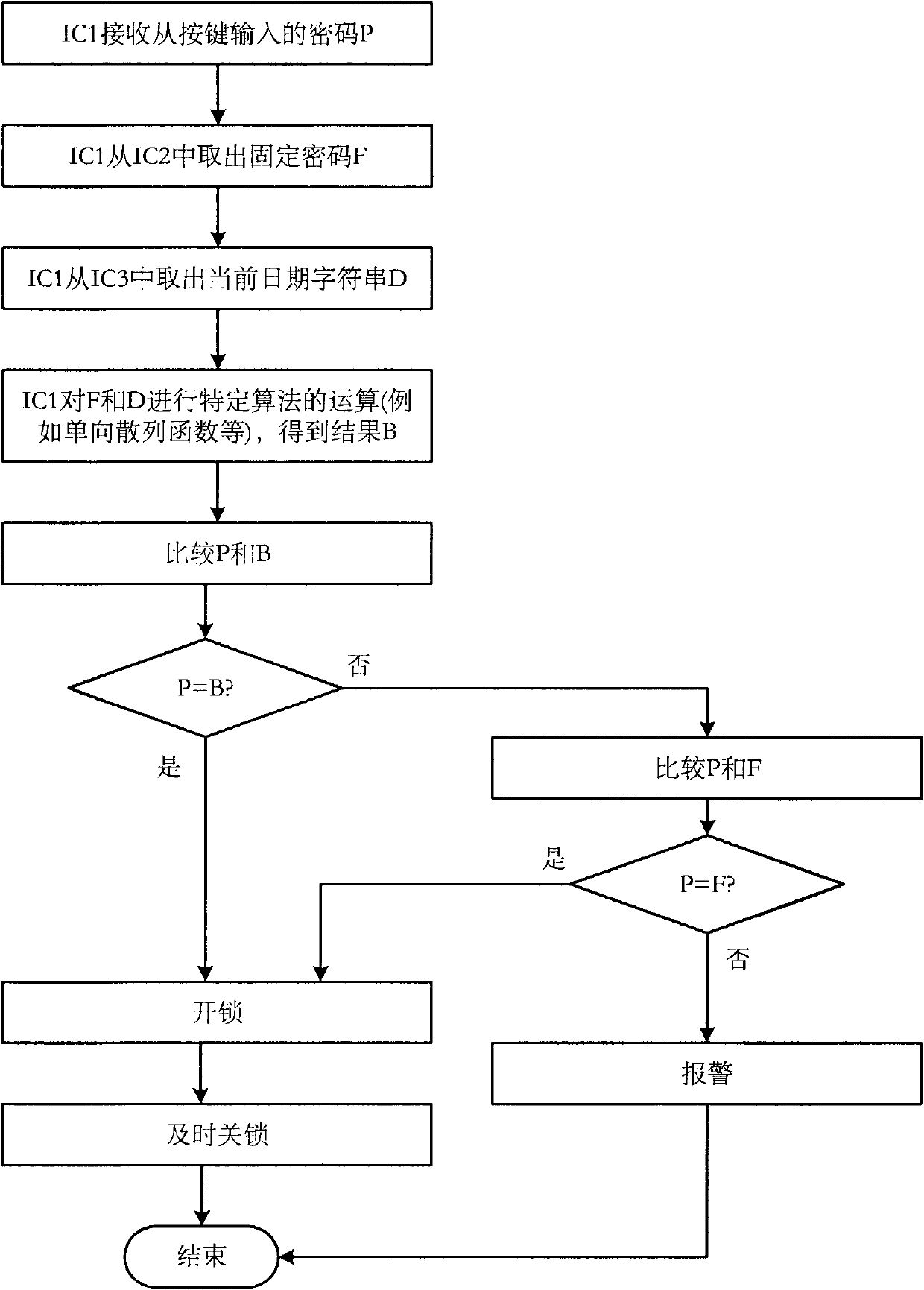
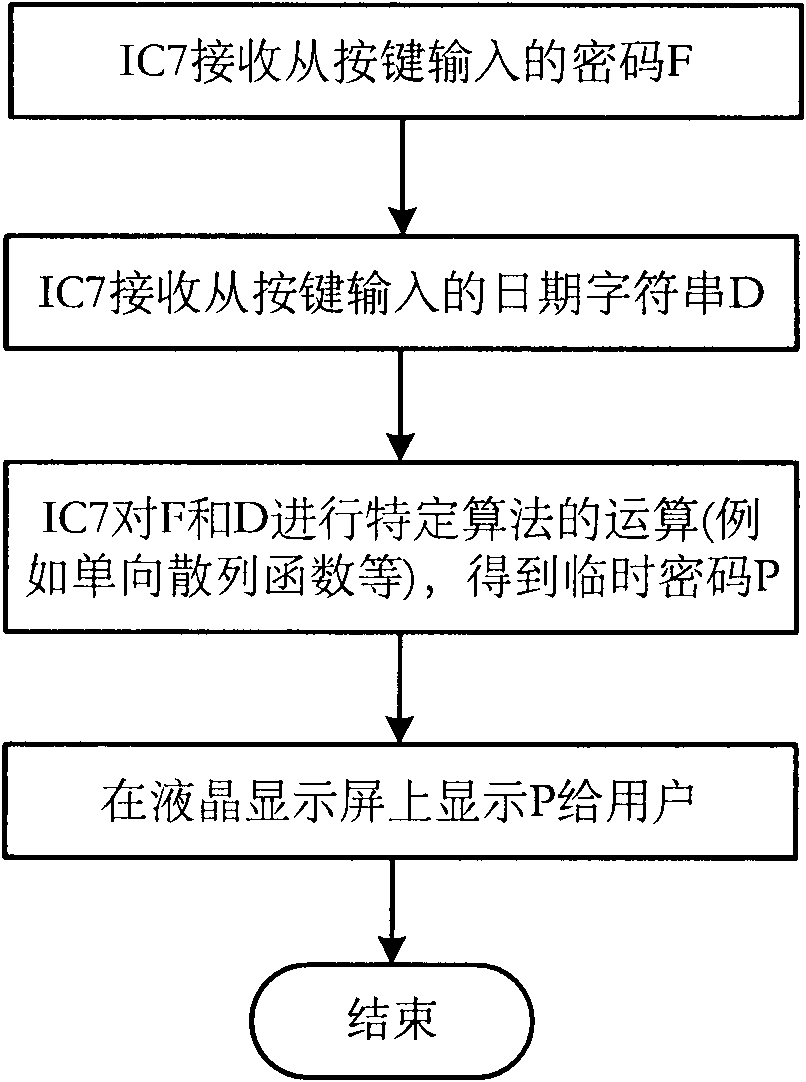
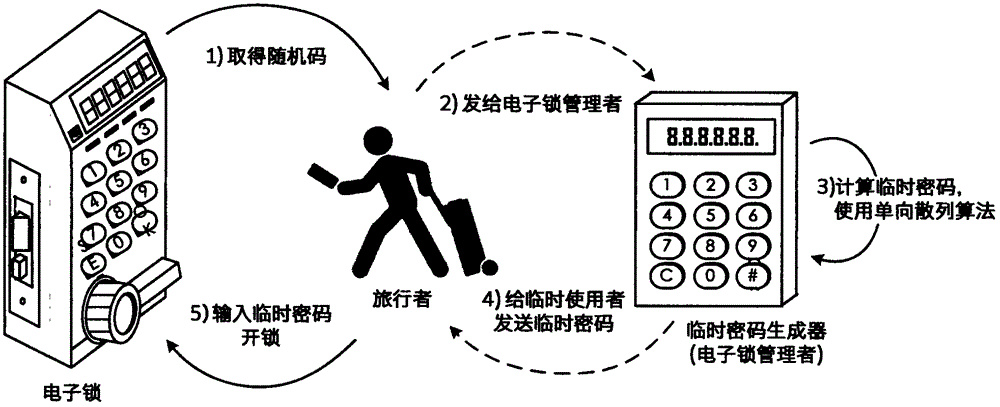
Dynamic password lock system capable of changing password with date
InactiveCN102168509AEasy to manageEasy accessRandom number generatorsMultiple keys/algorithms usageHash functionPassword
The invention provides a dynamic password lock system capable of changing a password with date (or time), which comprises a lock body and a temporary password generator. A fixed password of the password lock is stored in a non-volatile memory in the lock body; a temporary password for unlocking is calculated by a specific algorithm (such as one-way hash function and the like) according to the fixed password and the date; and with the alteration of the fixed password or the change of date, the temporary password correspondingly and automatically changes in a calculable way. Therefore, the temporary password can be calculated by a password lock manager knowing the fixed password in the password lock without touching the password lock; and after the password lock is used by a temporary user, the temporary user can unlock the password lock with the temporary password in a specific time period.
Owner:袁磊
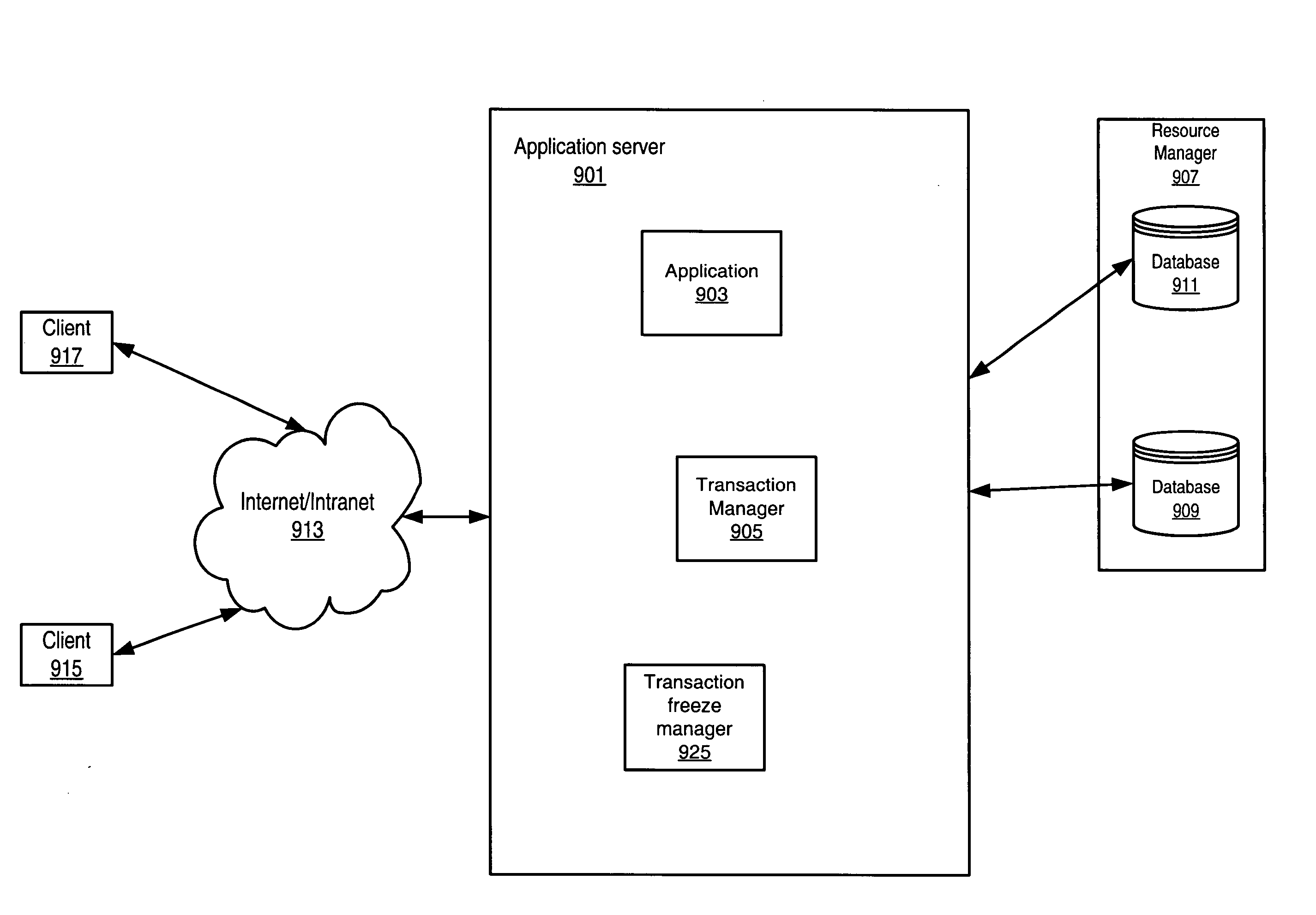
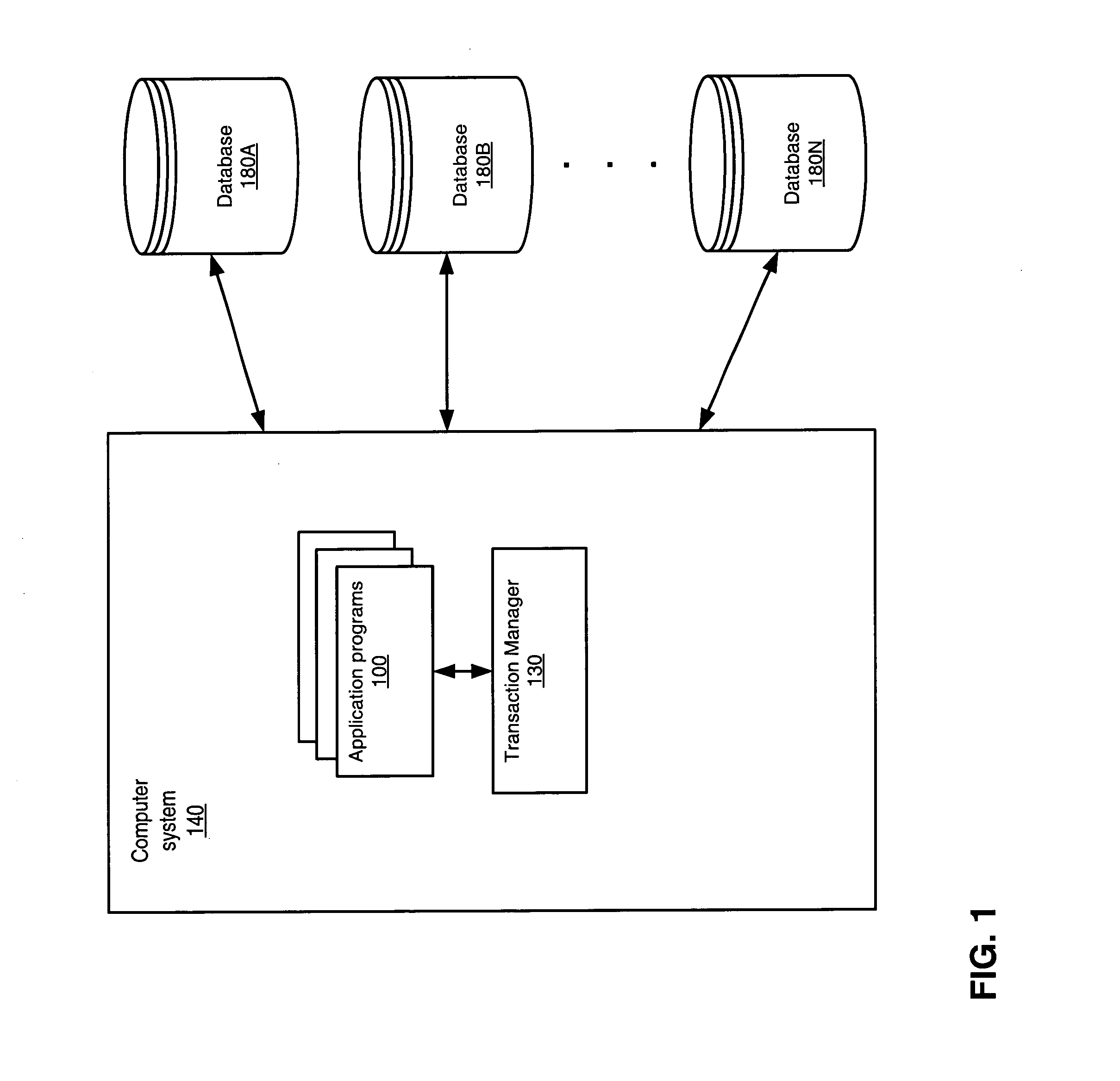
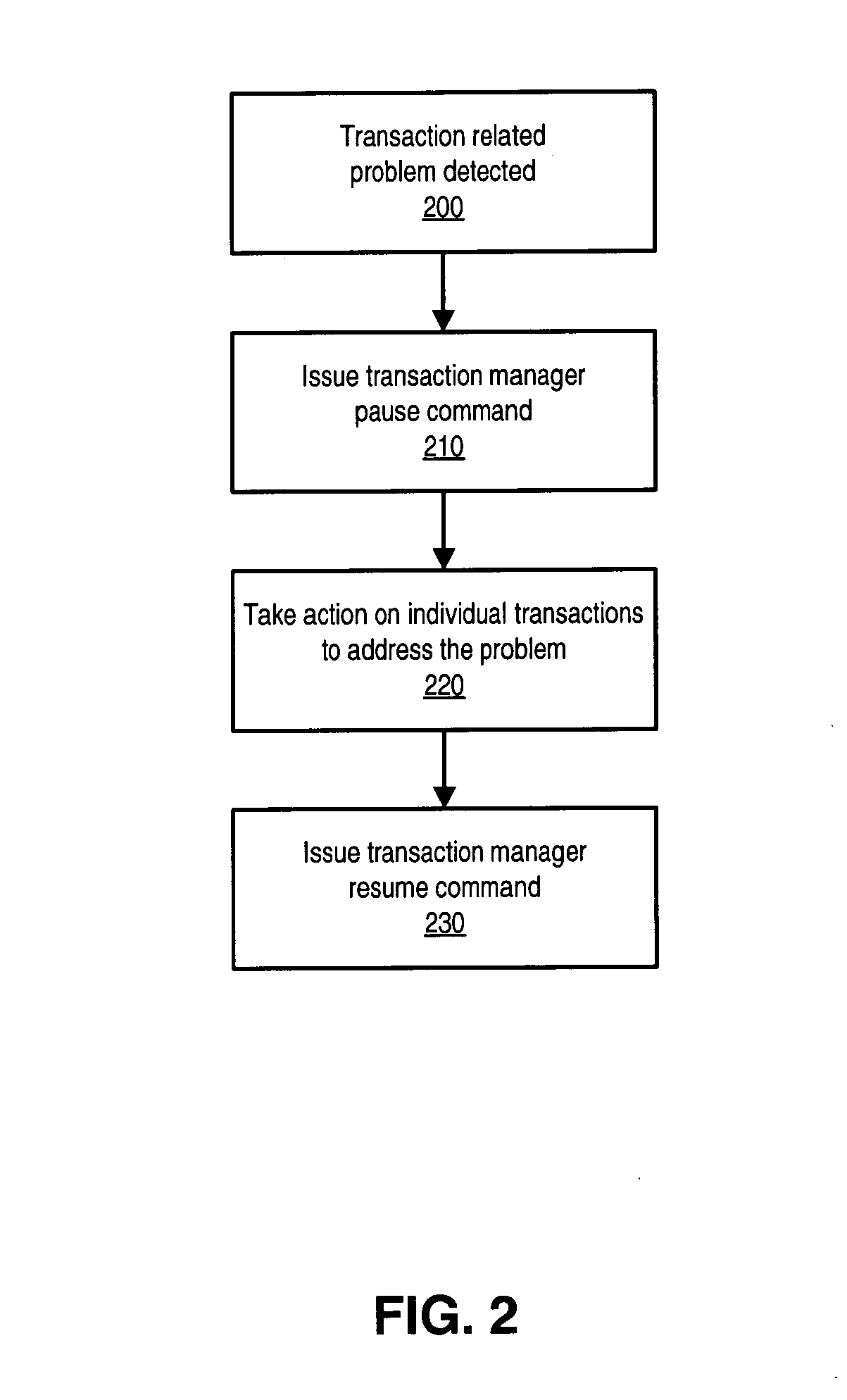
Transaction manager freezing
A transaction manager may be paused so that the transactions it manages are prevented from making transaction state changes. While the transaction manager is paused, the transactions that the transaction manager is executing may not be allowed to complete. A transaction manager may be configured to obtain permission from a transaction freeze manager in order to transition the state of a transaction. The transaction freeze manager may function as a read / write lock manager controlling locks on a transaction freeze object. In servicing a transaction state transition request, the transaction freeze manager may grant the transaction manager a read lock on the transaction freeze object. In servicing a transaction manager pause request, the transaction freeze manager may grant an administrative entity a write lock on the transaction freeze object.
Owner:ORACLE INT CORP
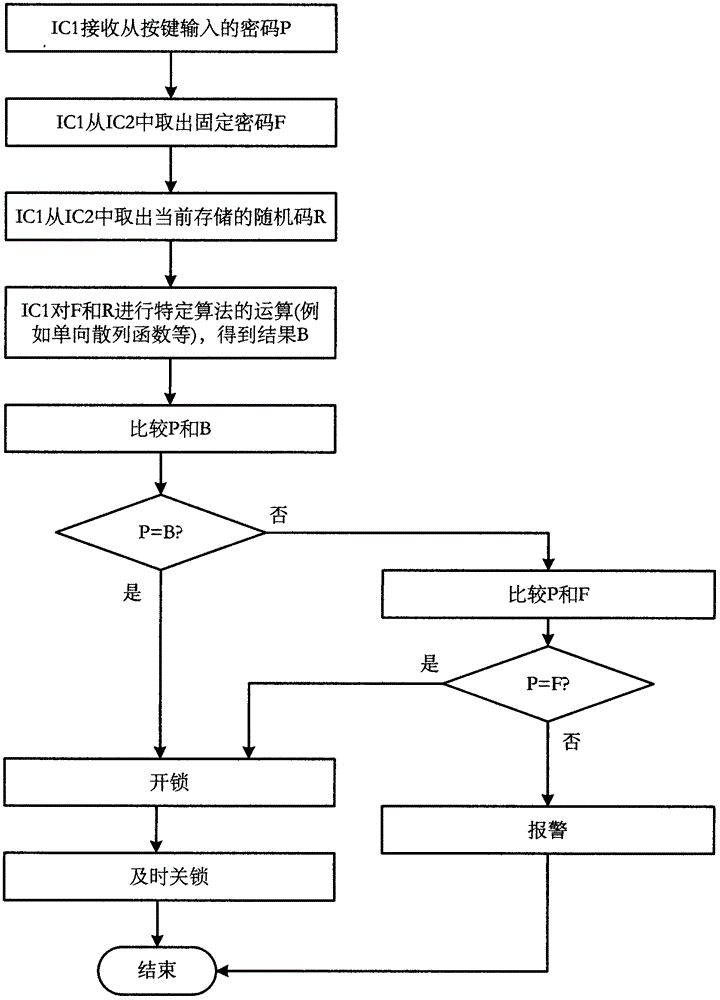
Dynamic password electronic lock system in which password changes according to random codes
The invention provides a dynamic password electronic lock system in which a password changes according to random codes. The system is composed of a lock body and a temporary password generator. A fixed password of a password lock is stored in a nonvolatile storage of the lock body, when a temporary user uses the electronic lock, the electronic lock generates the random codes R, a temporary password used for unlocking is obtained through calculation of the fixed password and the random codes according to a special algorithm (such as a one-way hash function), and automatic calculable changing is performed on the temporary password along with changes of the fixed password or differences of the random codes generates each time. Thus, the temporary password can be obtained through calculation when a password lock manager mastering the fixed password in the password lock receives the random codes, and after the system is delivered to the temporary password lock user, the temporary password lock user can perform unlocking through the temporary password in an effective period of time.
Owner:袁磊
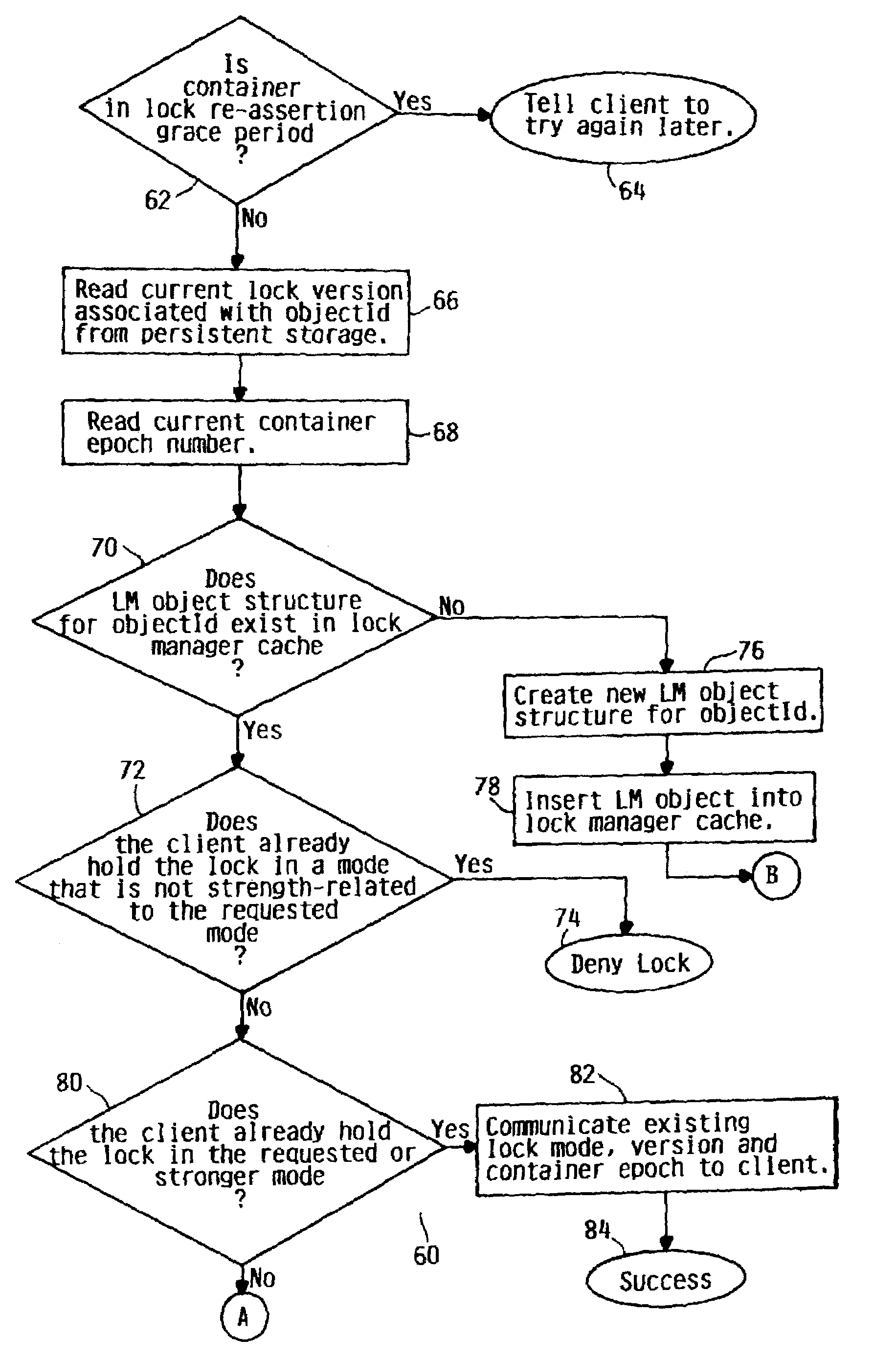
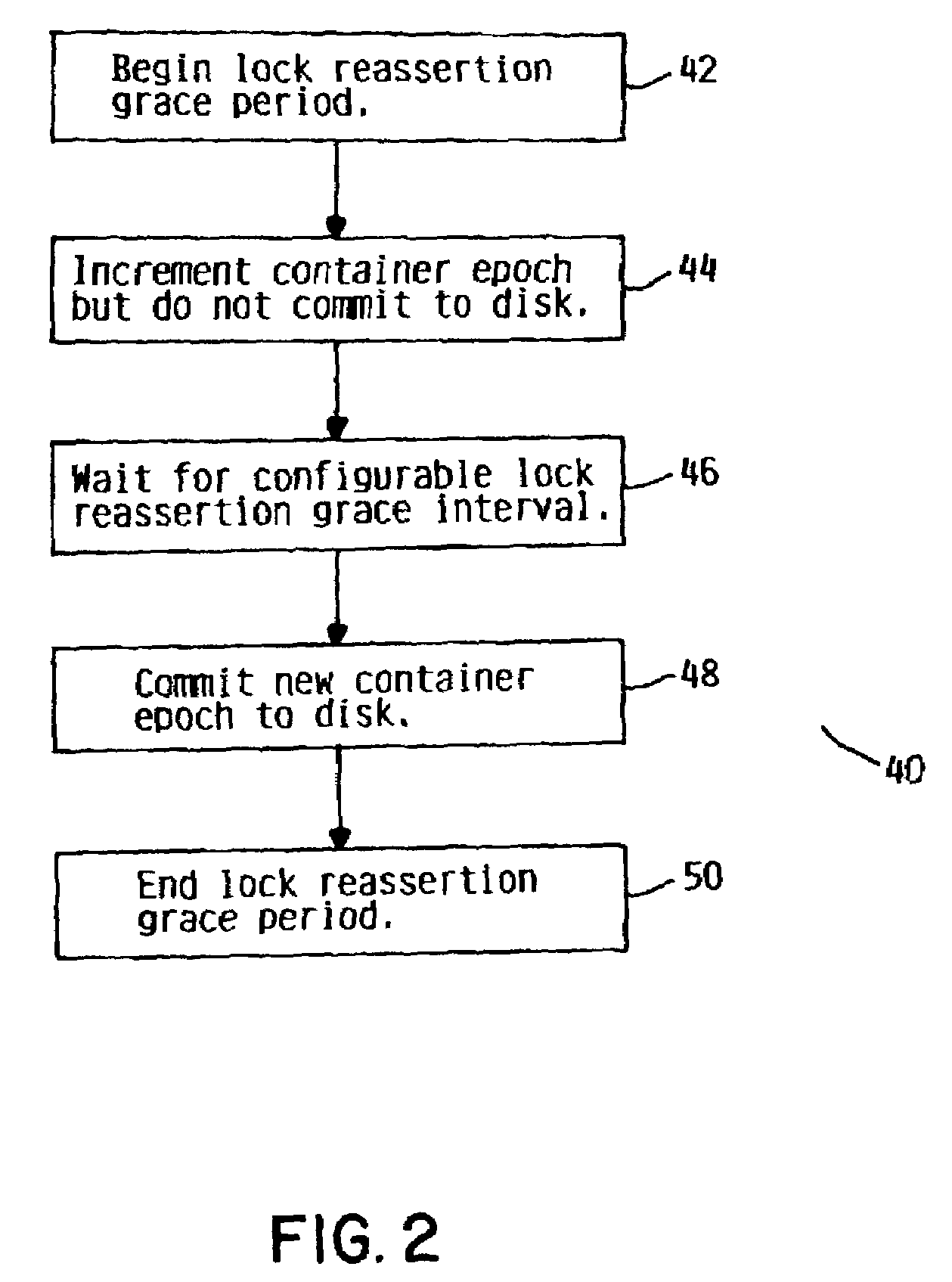
Discipline for lock reassertion in a distributed file system
InactiveUS7124131B2Data processing applicationsDigital data information retrievalDistributed File SystemLock manager
A method and system for asserting a lock in a distributed file system is provided. All distributed locks have a lease for a limited time period, wherein the lease may be renewed periodically. A lock manager data structure is provided to maintain mode compatibility of locks granted to different client nodes for the same object. The process of acquiring or reasserting a lock includes determining whether there are other valid locks in use, as well as whether a valid lock is in operation in a conflicting or compatible mode with a requested lock. A new lock lease may be granted and a lock lease which has expired may be reasserted if a conflicting lease is not present.
Owner:LINKEDIN
Distributed lock based on object memory system
InactiveCN101013381AImprove the efficiency of read locksMultiprogramming arrangementsSpecial data processing applicationsObject basedMetadata management
It's an object-based storage system to model attributes of distributed locks, a distributed storage system for storage of multi-client visit to the sharing of resources, aimed at enhancing the efficiency of Reading lock visit. The present invention include data locking and metadata management for the management of locks, running on the object-based storage system, data management lock-operation in various storage devices on the target, including data objects name space module, access patterns attribute value module installed, local Queue processing module and functional processing module; Each data lock manager responsible for data management object locking, metadata management lock-operation in various metadata servers, including metadata objects name space module, local Queue processing module and functional processing modules, each metadata management lock-lock for metadata management. The invention uses the object storage technology by expanding access pattern attribute value and improves the efficiency of Reading lock visit.
Owner:HUAZHONG UNIV OF SCI & TECH
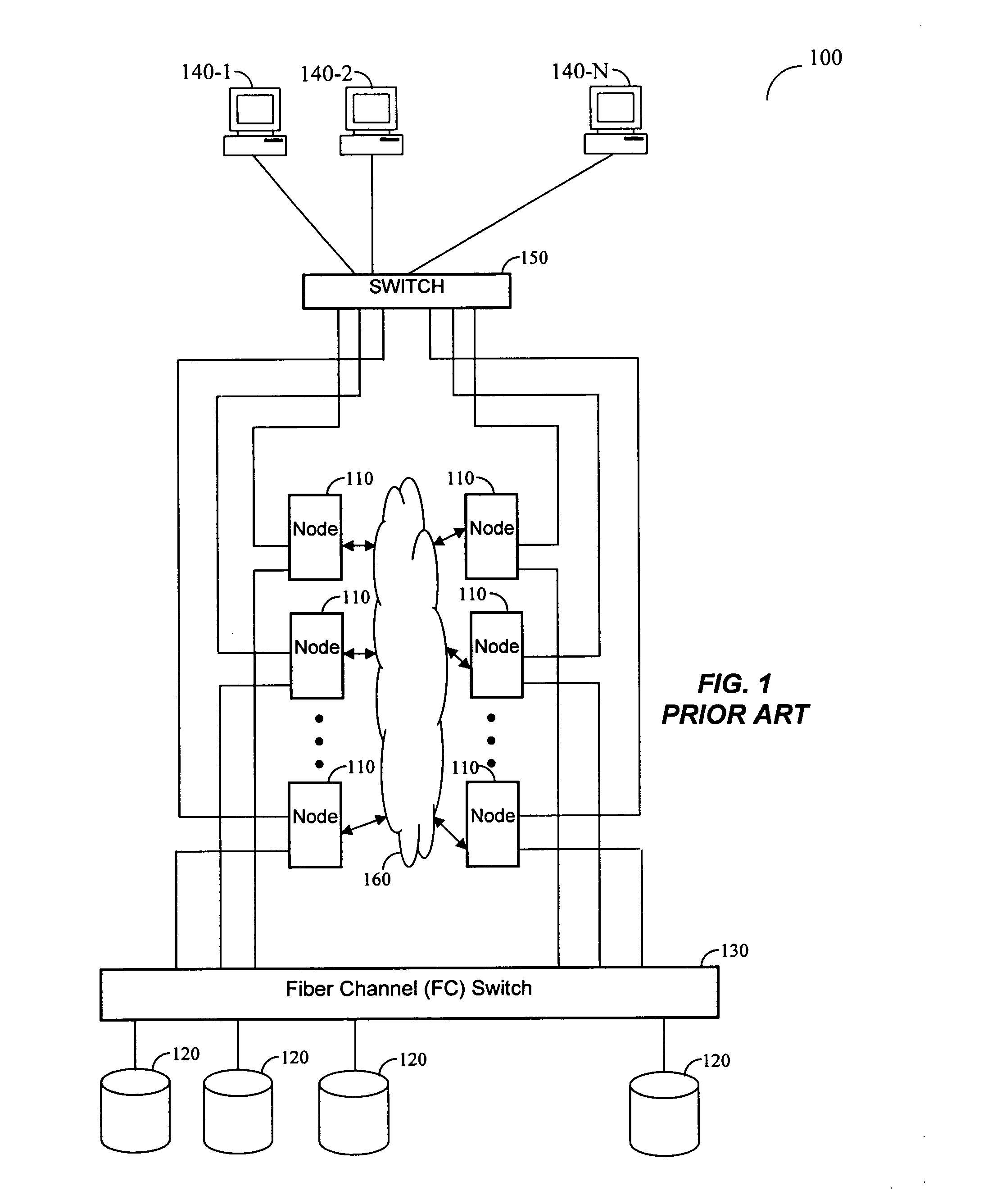
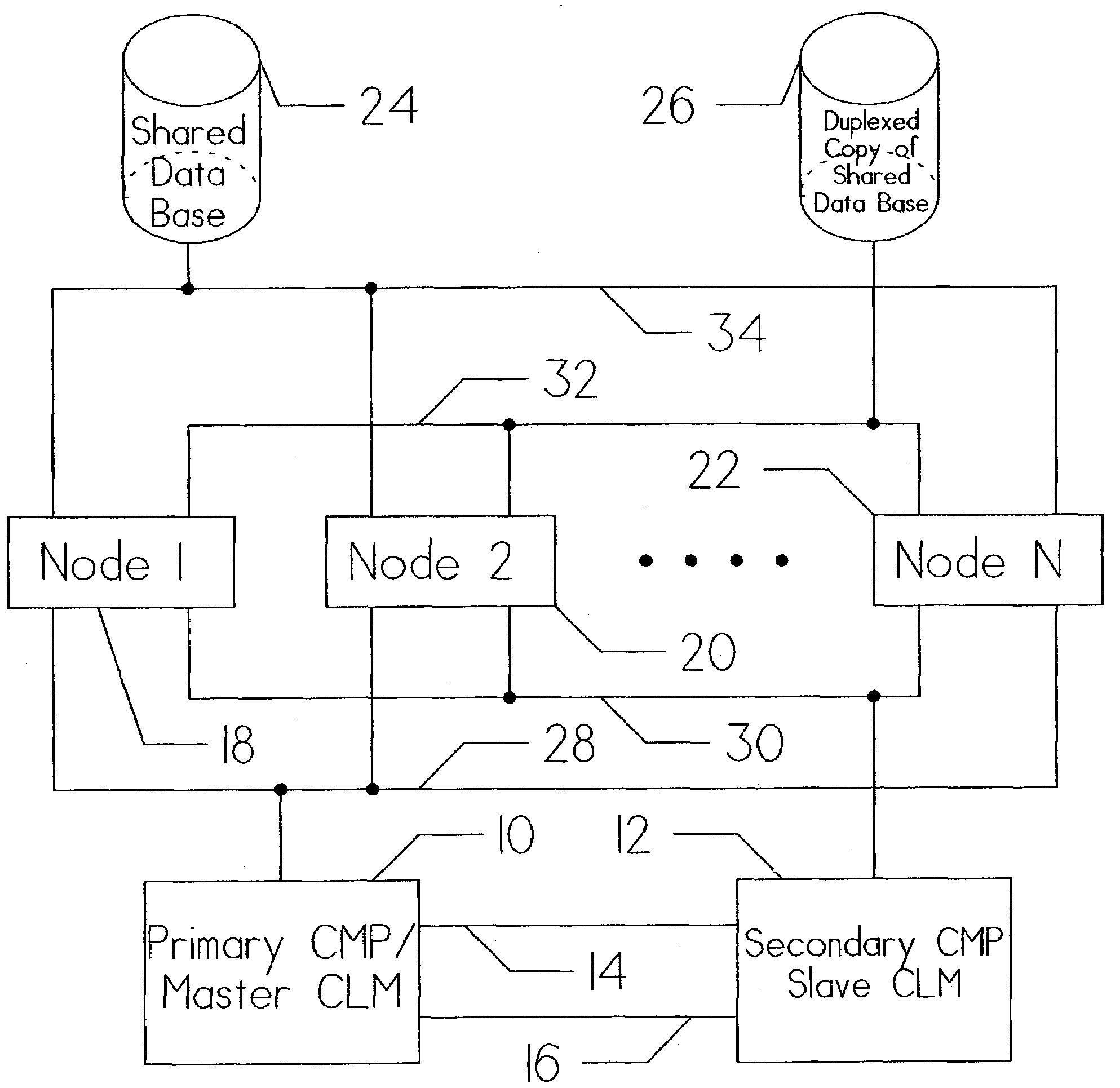
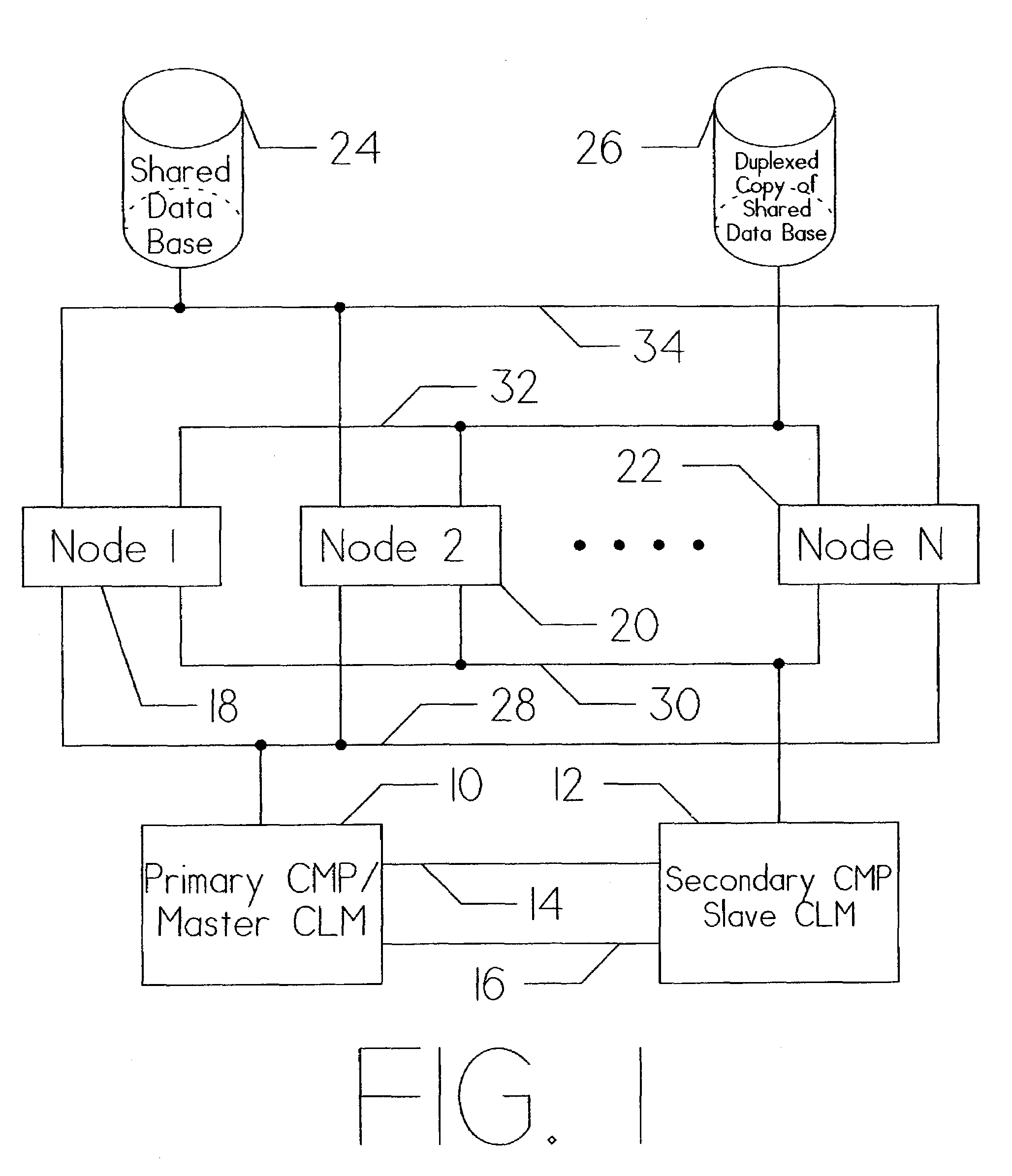
Method for shortening the resynchronization time following failure in a computer system utilizing separate servers for redundancy
ActiveUS7246255B1Efficient system recoveryMinimum computing timeDigital data information retrievalProgram synchronisationMass storageServer replication
An apparatus for and method of enhancing reliability within a cluster lock processing system having a relatively large number of commodity cluster instruction processors which are managed by a cluster lock manager. Because the commodity processors have virtually no system viability features such as memory protection, failure recovery, etc., the cluster / lock processors assume the responsibility for providing these functions. The low cost of the commodity cluster instruction processors makes the system almost linearly scalable. The cluster / locking, caching, and mass storage accessing functions are fully integrated into a single hardware platform which performs the role of the cluster / lock master. Upon failure of this hardware platform, a second redundant hardware platform converts from slave to master role. The logic for the failure detection and role swapping is placed within software, which can run as an application under a commonly available operating system. Furthermore, the recovery is completely accomplished without assistance of the Host computer(s) or ultimate user(s) coupled via the Host computer(s). Following repair of the failed server, it is restarted in an orderly fashion to resume a slave role. For the server to be completely restored, coherent memory must be copied from master to slave. Because cluster lock processing must be paused throughout the system to transfer the copy, it is important to minimize the transfer time to minimize the impact on system throughput.
Owner:UNISYS CORP
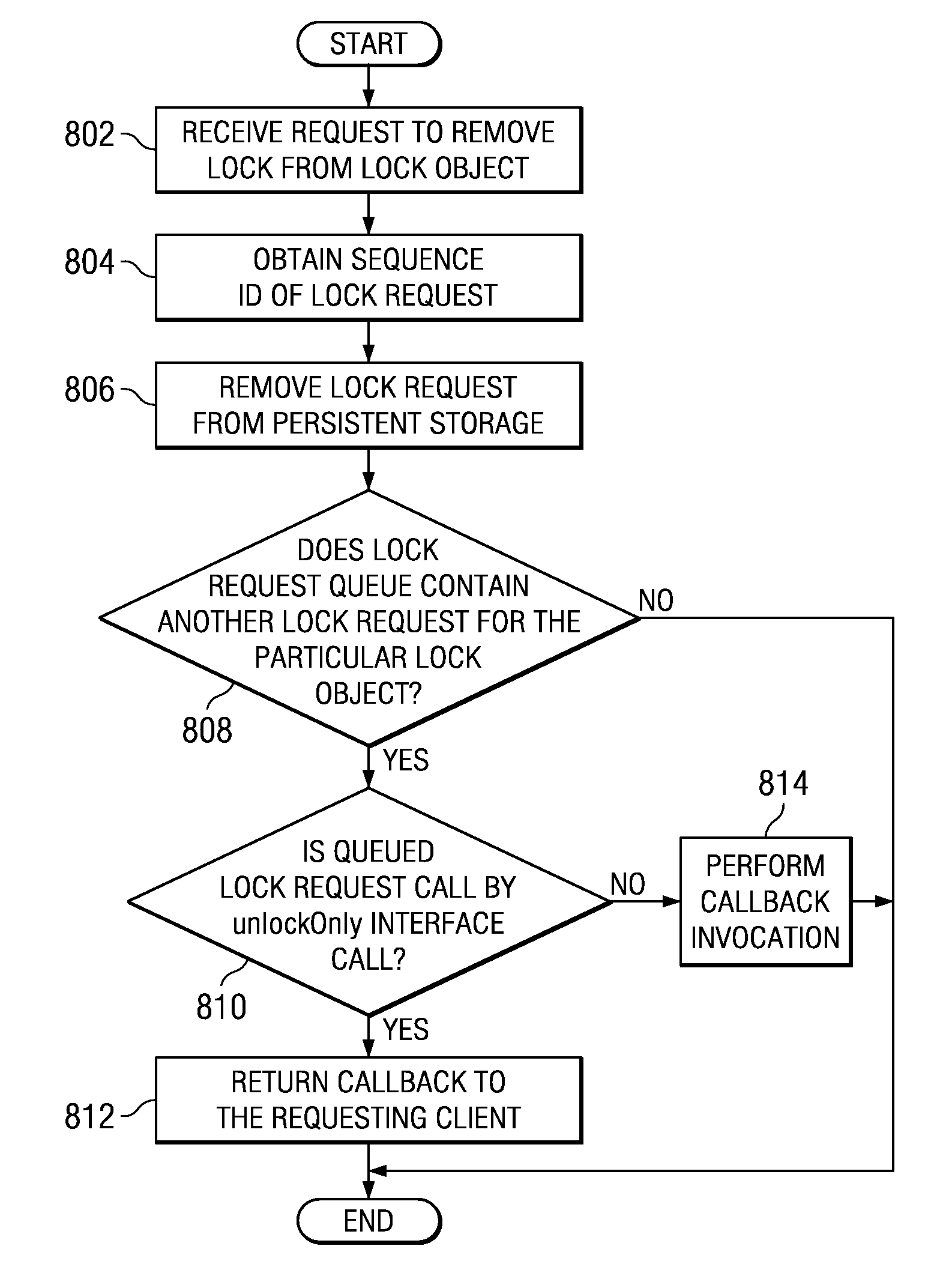
Generic locking service for business integration
InactiveUS20080082761A1Digital data information retrievalUnauthorized memory use protectionLock managerSystem failure
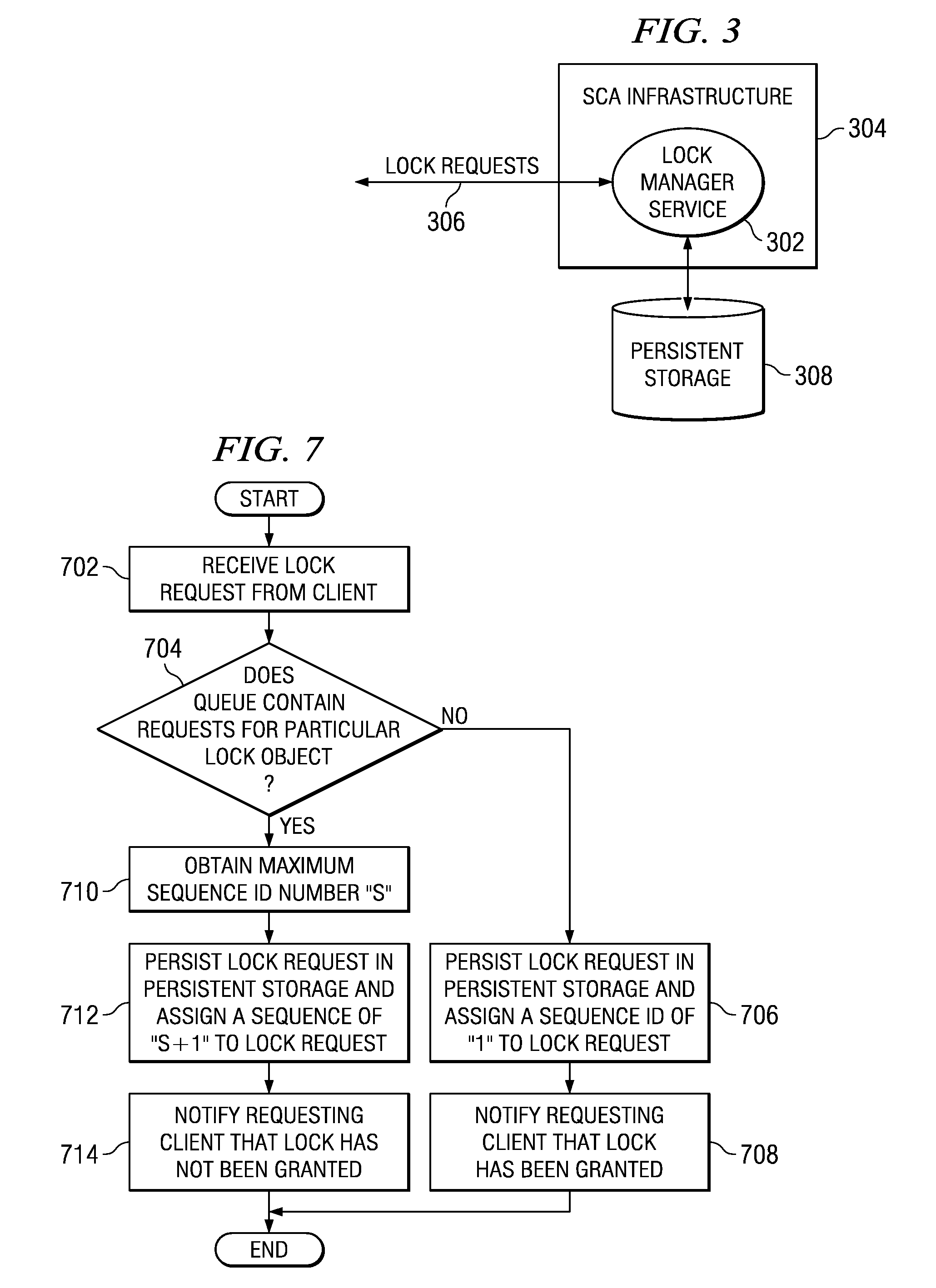
A generic lock manager service is provided which allows locks and lock requests to be recovered across system failures and restarts. When a lock request that includes a request to isolate a particular data object is received, the lock manager service examines a lock request queue to determine if the queue contains a second lock request for the data object specified in the lock request. If no second lock request is present, a sequence identifier is assigned to the lock request indicating a lock request processing order for the data object specified in the lock request, and the lock request is persisted in a persistent storage. If a second lock request is present, a maximum sequence identifier of all lock requests directed to the data object is identified. The next higher sequence identifier is assigned to the lock request and the lock request is also persisted in a persistent storage.
Owner:IBM CORP
Dynamic coded lock system for acquiring codes by virtue of table look-up
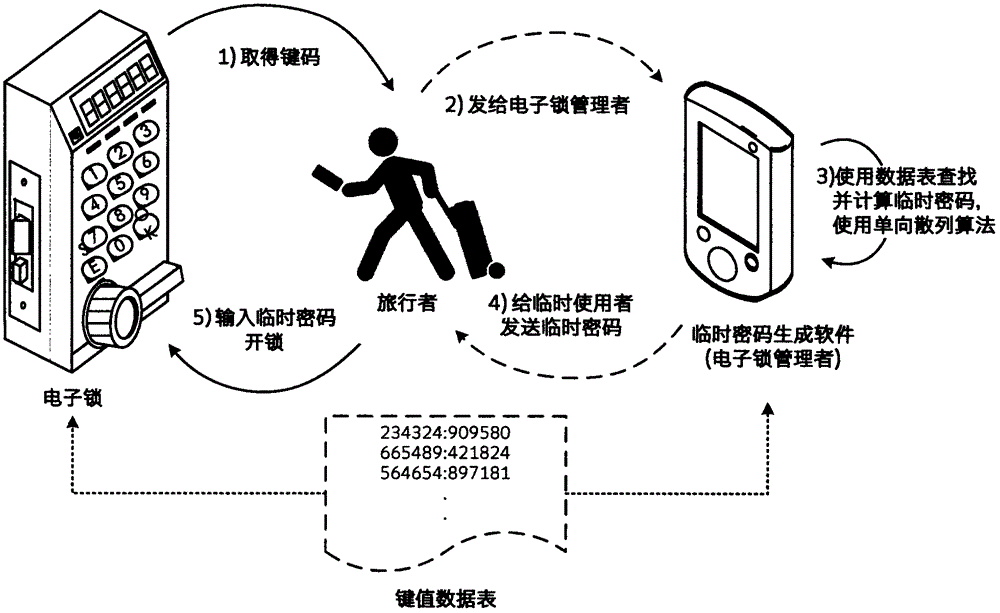
InactiveCN104537738AEasy to manageEasy to findElectric permutation locksIndividual entry/exit registersProgramming languageLock manager
The invention provides a dynamic coded lock system for acquiring codes by virtue of table look-up. The dynamic coded lock system comprises a lock body and a temporary code generator, wherein a fixed code and a key-value data table of a coded lock are stored in a nonvolatile memory in the lock body; when an electronic lock is used by a temporary user, a key code R is displayed by the electronic lock, a temporary code for unlocking the lock is obtained by finding a corresponding value code X in the data table by virtue of the key code R, besides, the fixed code can be used as a parameter to convert the value code X into the temporary code for use, and the temporary code is calculably changed along the changing of the fixed code or the difference of key codes displayed in each time. Therefore, the temporary code can be calculated by a coded lock manager knowing the fixed code and the data table in the coded lock when the key code is received, and after the temporary code is passed to the temporary coded lock user, the lock can be locked by the temporary coded lock user by virtue of the temporary code in a valid time period.
Owner:袁磊
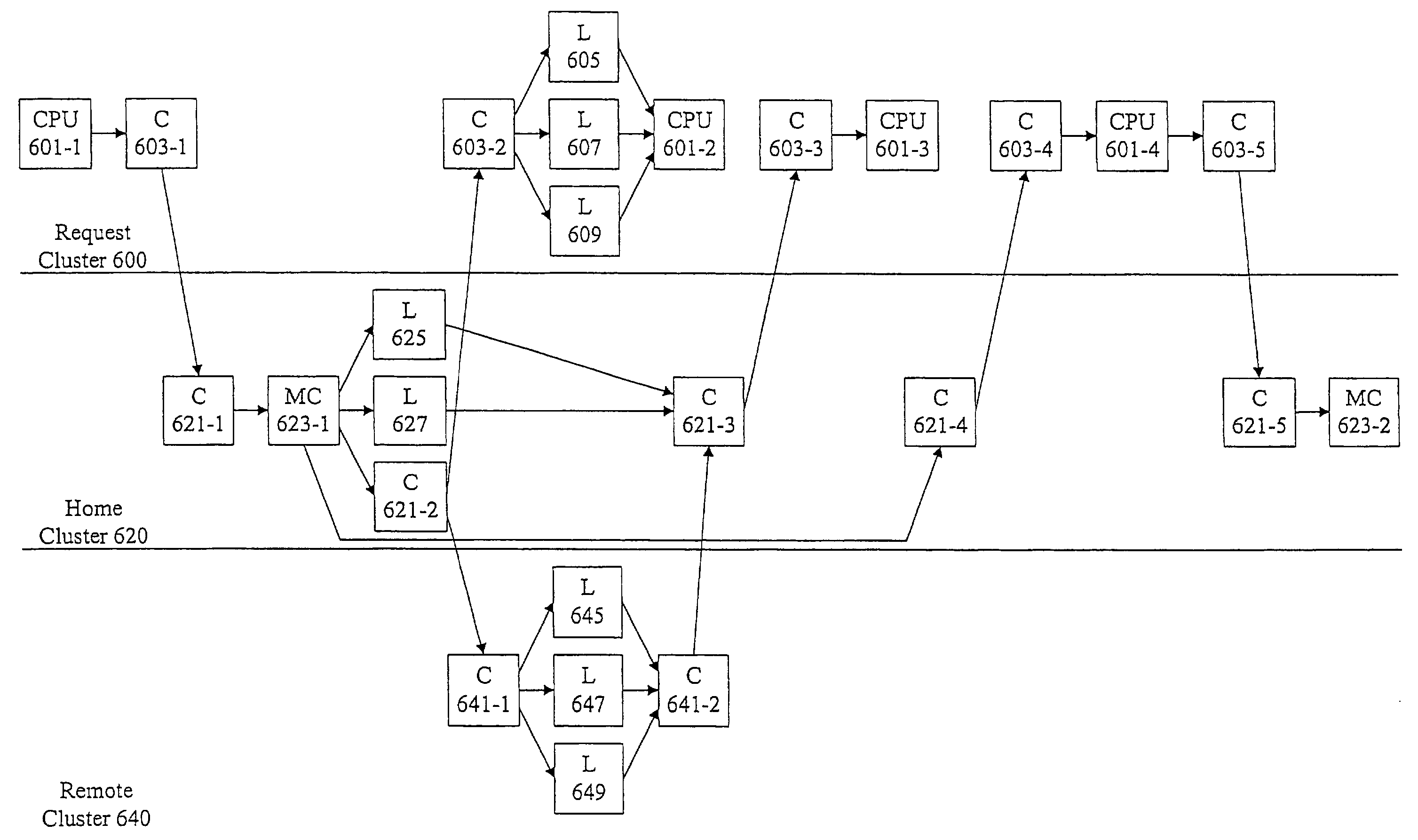
Methods and apparatus for multiple cluster locking
InactiveUS20040093469A1Memory adressing/allocation/relocationMultiprogramming arrangementsLock managerComputerized system
Methods and devices are provided for controlling lock and unlock operations within a computer system. A home cluster includes a home lock manager. The home lock manager is a master lock manager for the home cluster and for a plurality of remote clusters, the plurality of remote clusters including remote cache coherency controllers and a plurality of remote processors. Lock and unlock commands from the home lock manager are transmitted by a home cache coherency controller to the remote cache coherency controllers and forwarded to the remote processors.
Owner:SANMINA-SCI CORPORATION
Systems and methods for maintaining transactional persistence
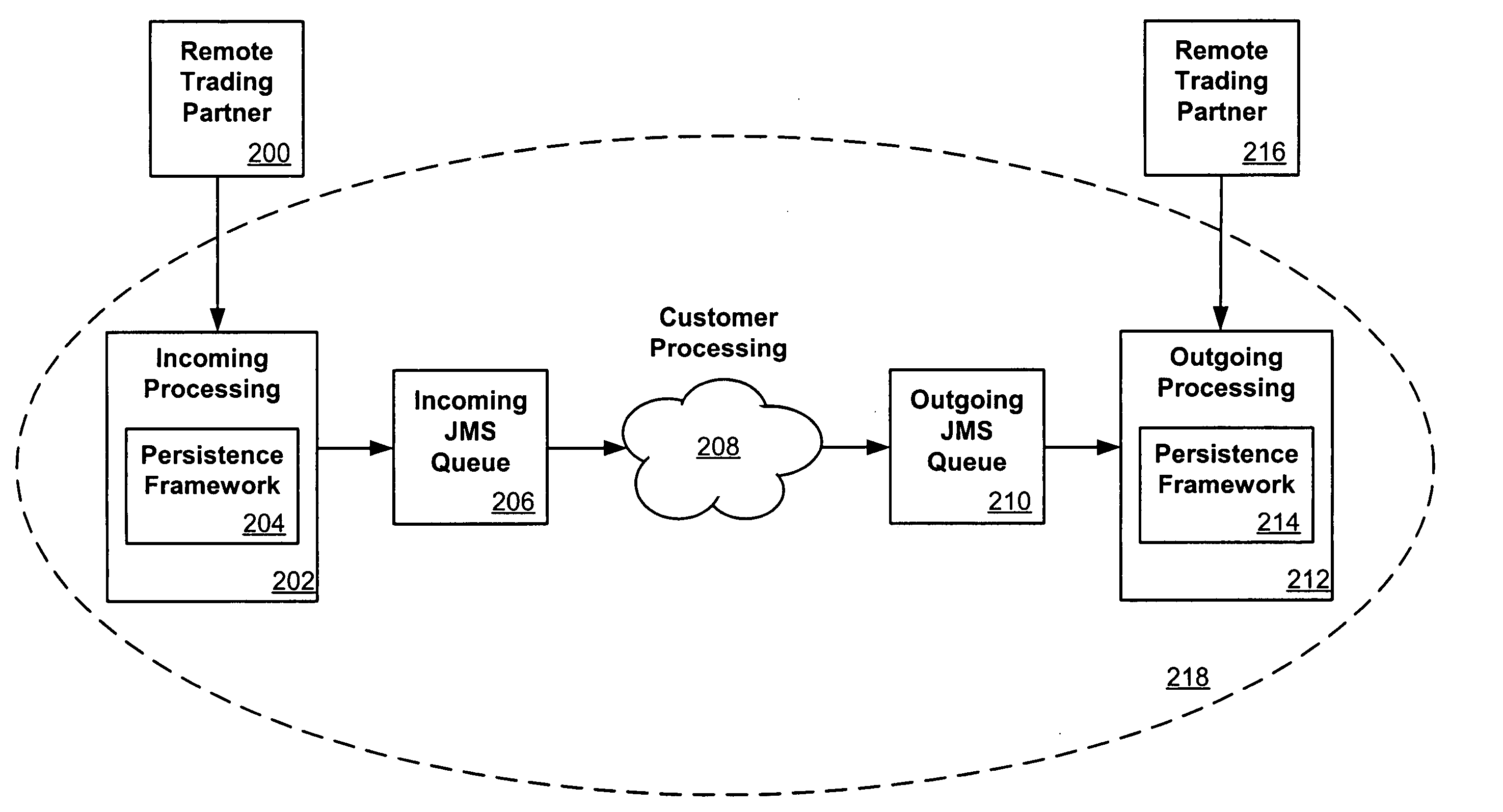
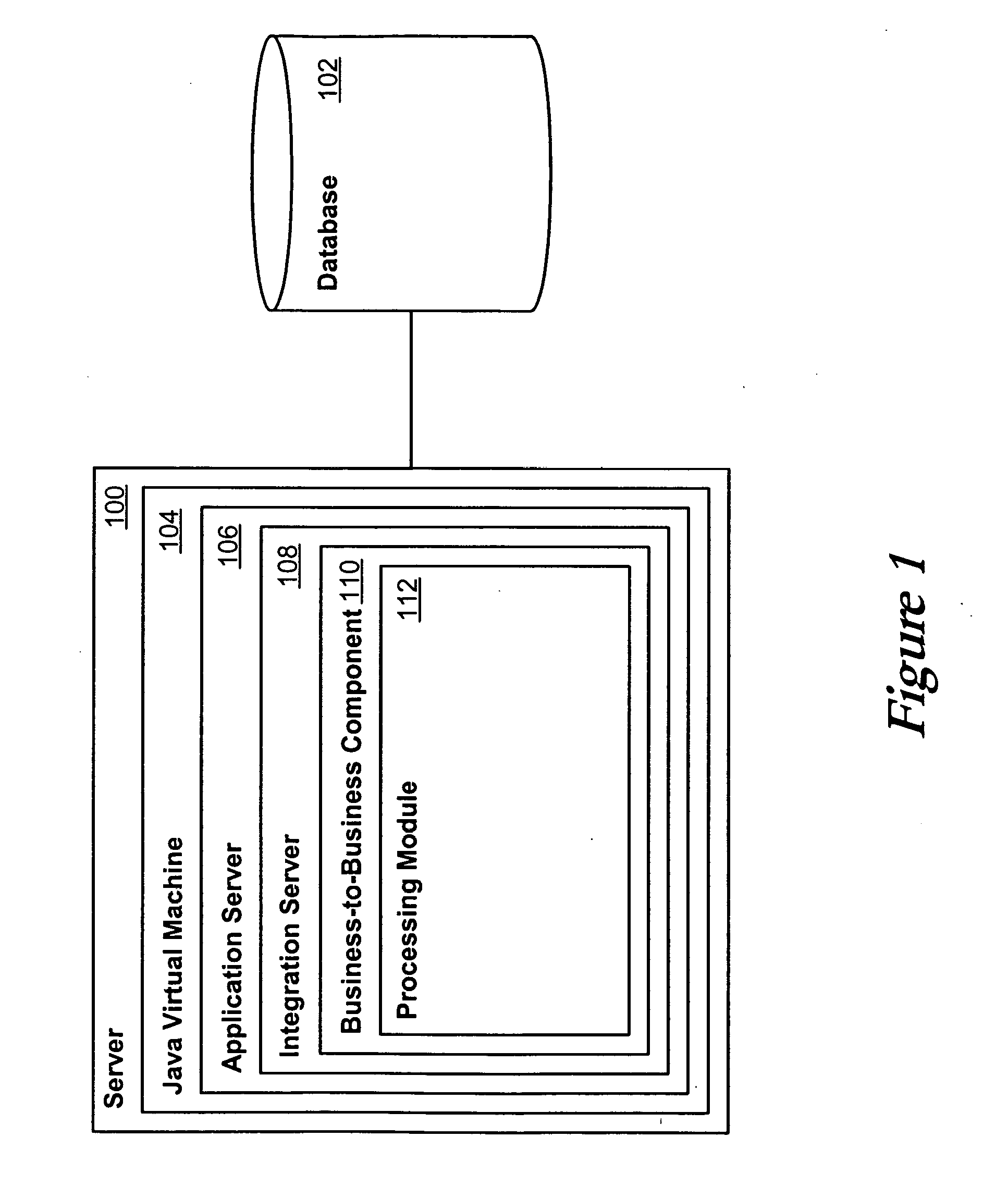
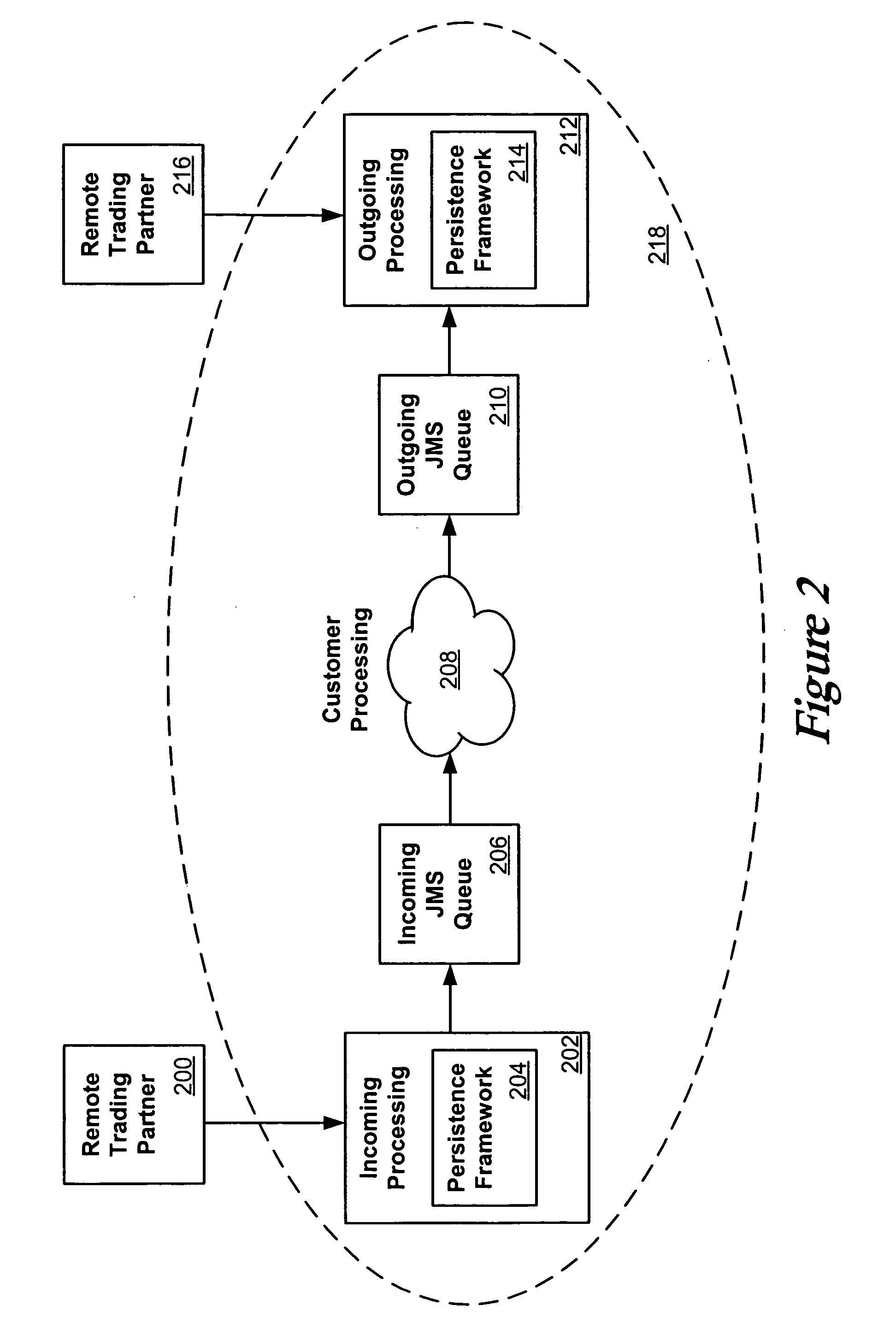
InactiveUS20050144170A1Avoid accessData processing applicationsDigital data processing detailsLock managerManagement object
Messages between trading partners can be processed persistently using a persistence framework, which can include a transaction manager, a locking manager, and a logging mechanism. A transaction manager can initiate a transaction for a request, and can enlist and modify any object or resource useful in processing the request. A locking manager can lock any of these objects, using inflated and / or individual locks, to prevent other resources or transactions from accessing the object during the transaction. A logging component can track any modifications of the object, while a transaction manager can manage state for the object. This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:ORACLE INT CORP
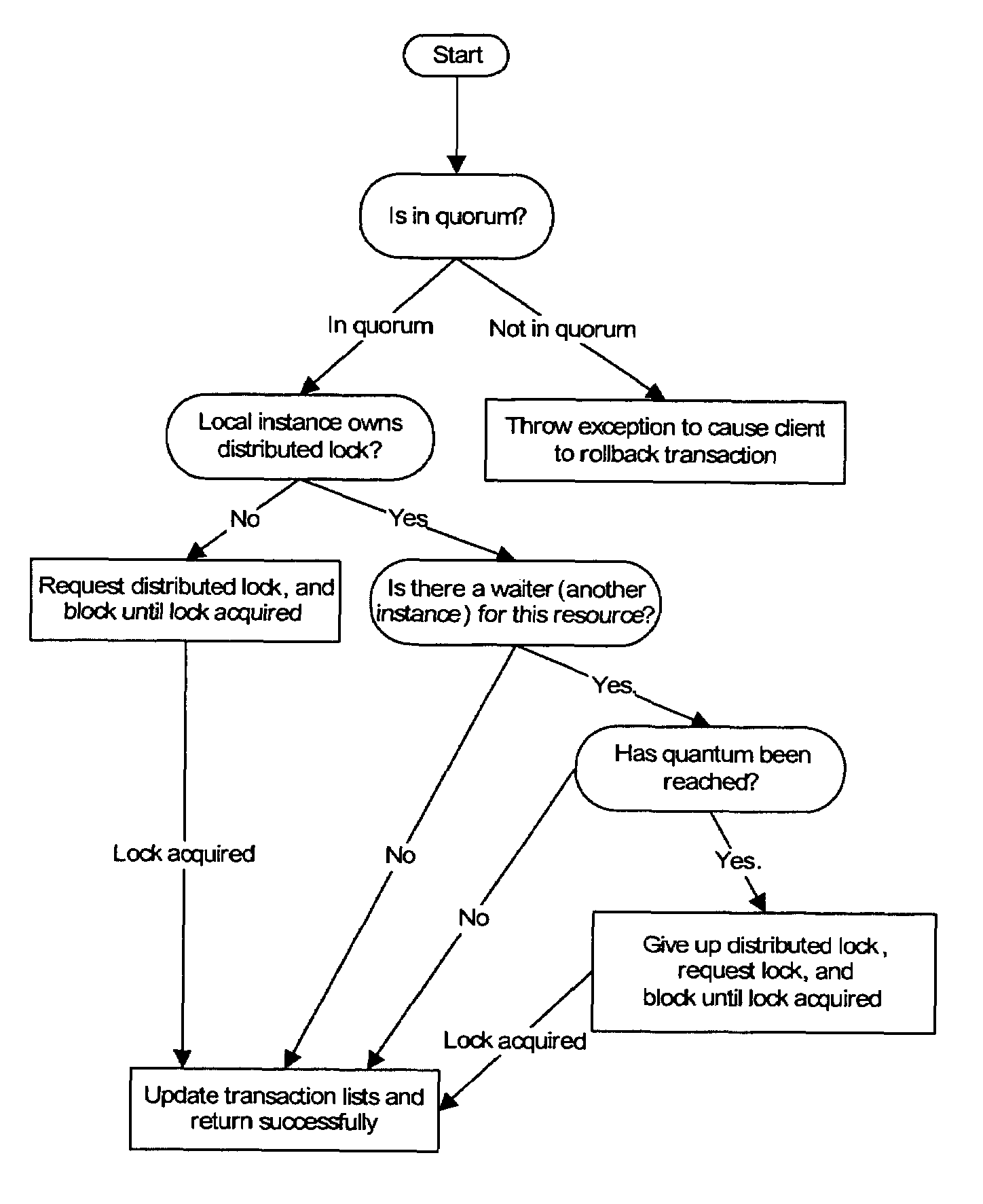
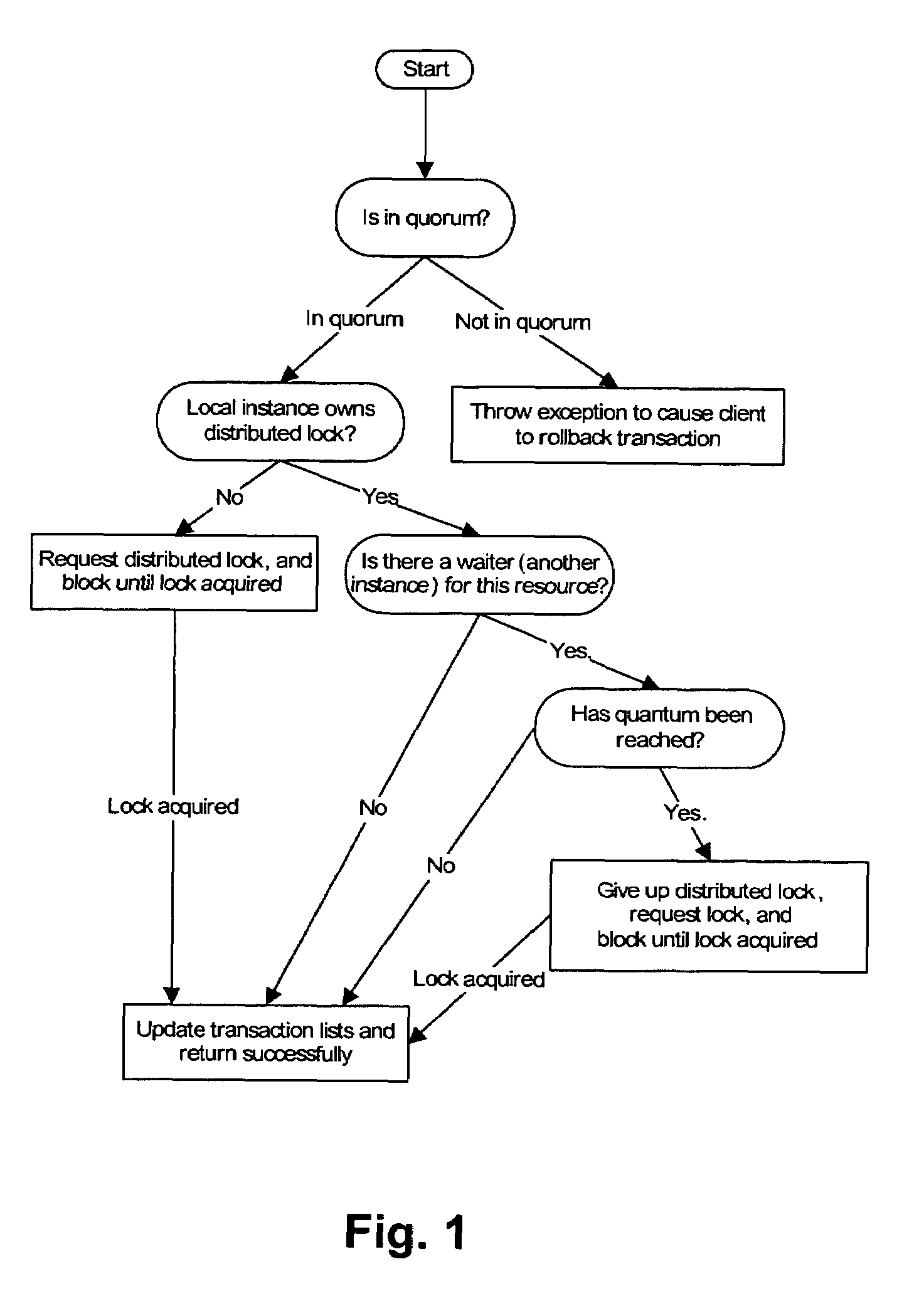
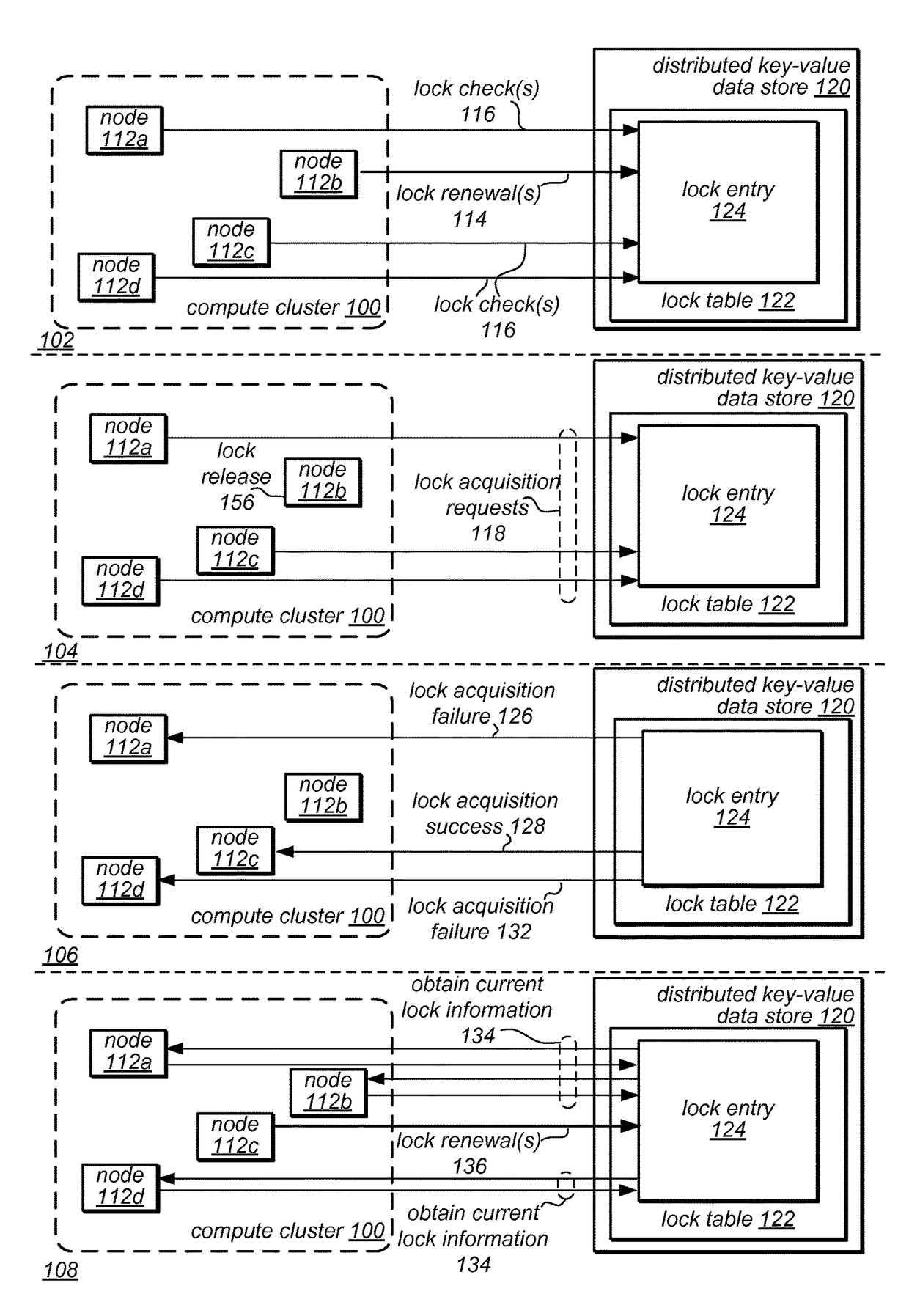
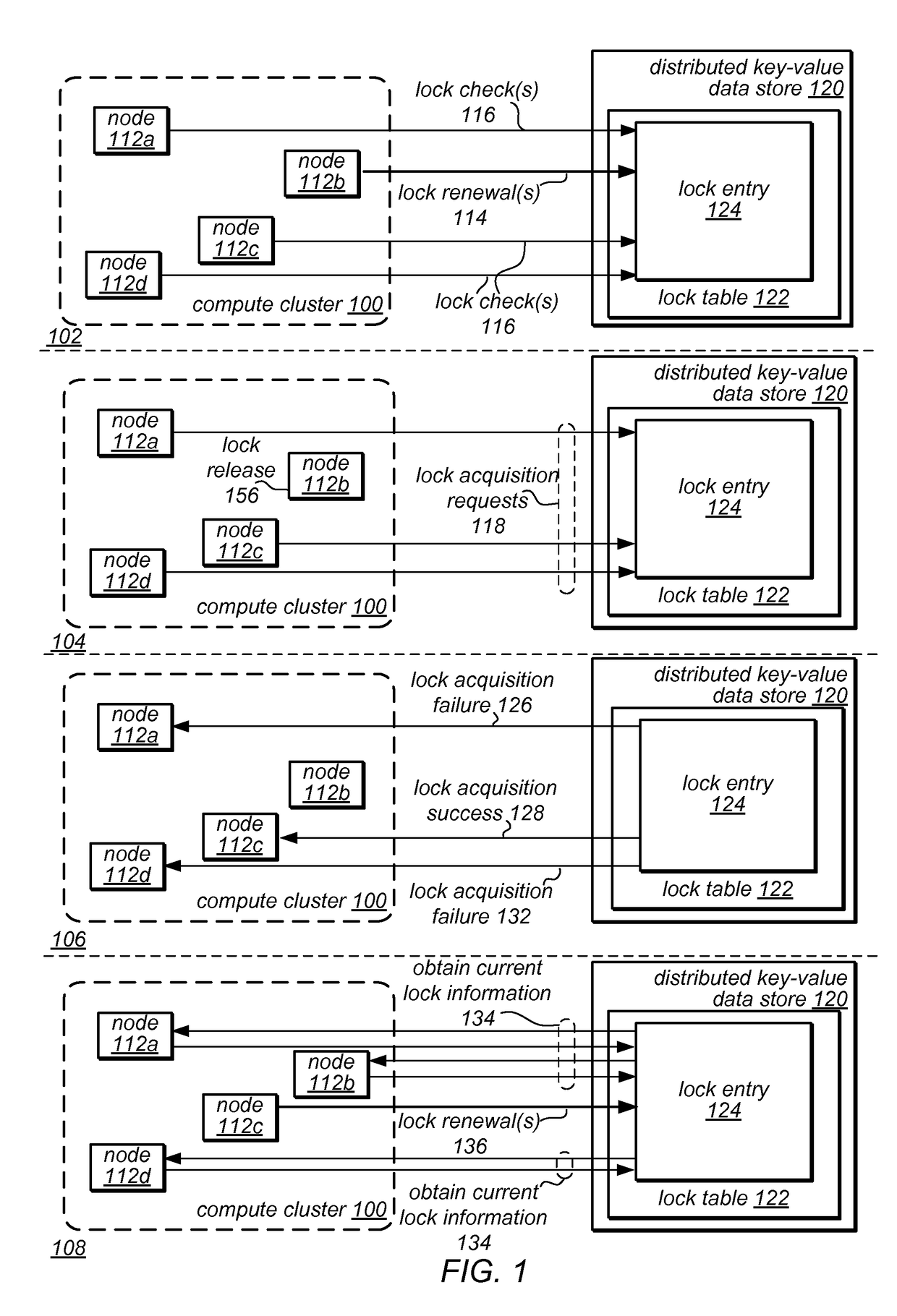
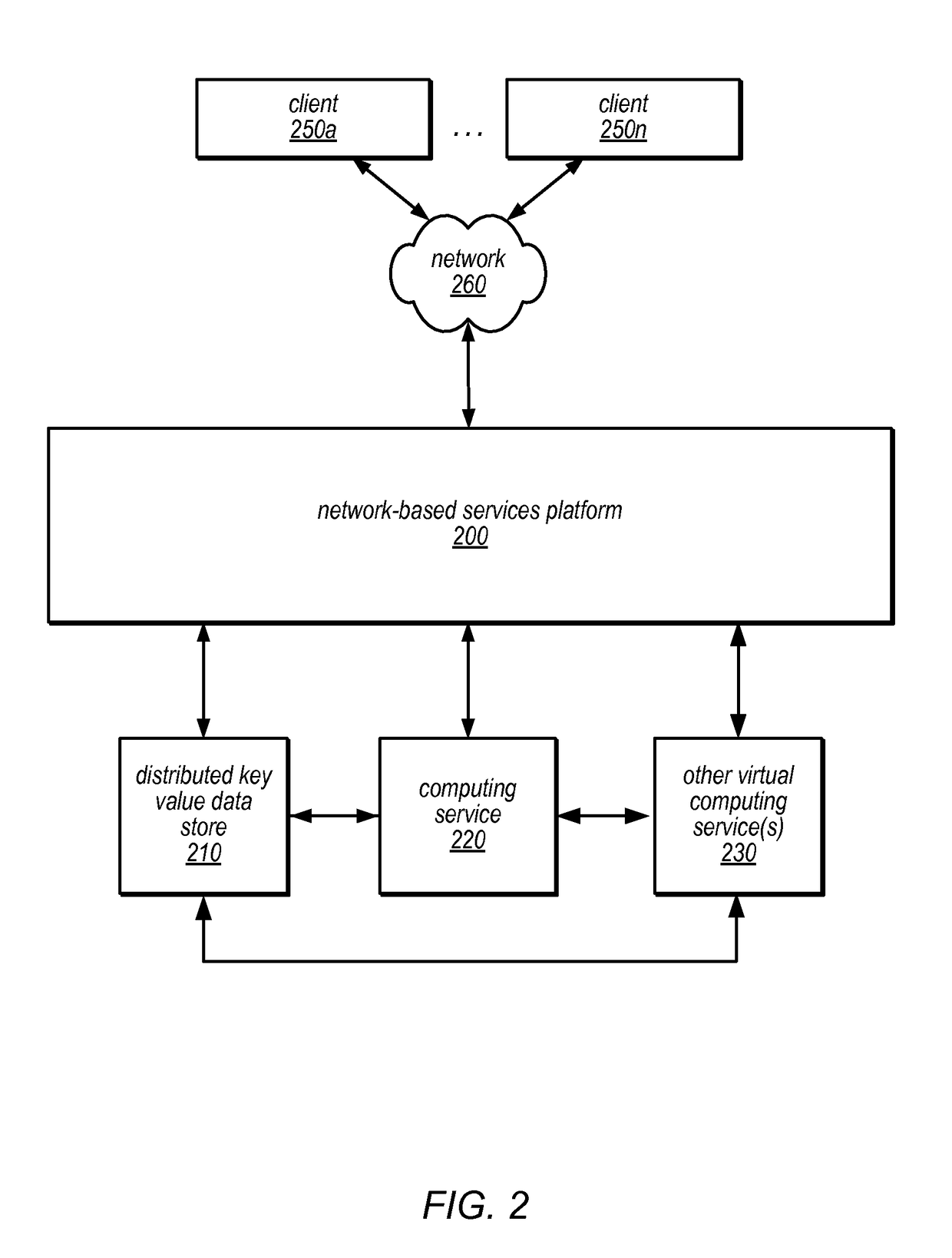
Distributed lock management using conditional updates to a distributed key value data store
A compute cluster including multiple compute nodes may implement distributed lock management using conditional updates to a distributed key value data store. It may be determined, at one or more compute nodes of a compute cluster, that particular lock is available based on a respective lock entry for the particular lock maintained in a lock manager table at a key value data store. The key value data store may be configured to perform conditional write requests for updates to data store at the key value, and may maintain data according to a distributed durability scheme. Compute nodes that determine that a lock is available may send a conditional write request to the key value data store in order to acquire the particular lock. The compute node that acquired the particular lock may be identified based on the successfully completed conditional write request to the respective lock entry.
Owner:AMAZON TECH INC
Semantic response to lock requests to reduce coherence overhead in multi-node systems
ActiveUS8086579B1Digital data information retrievalDigital data processing detailsComputer networkLock manager
Techniques are provided for lock management. The techniques are based on an enhanced lock management system that generates a semantic response in response to lock requests for a resource. The semantic response communicates both the underlying cause blocking the request, and information that may be used by the requester to obtain notification of when the underlying cause should no longer lead to denial of the lock request. The semantic response may be generated by the master of the resource, who provides the semantic response to the local lock manager of the lock requester. The semantic response may be retained by the local lock manager so that the semantic response can be provided to subsequent lock requesters, without need for interacting with another lock manager on another node.
Owner:ORACLE INT CORP
Method and Apparatus for Handling Service Requests in a Data Processing System
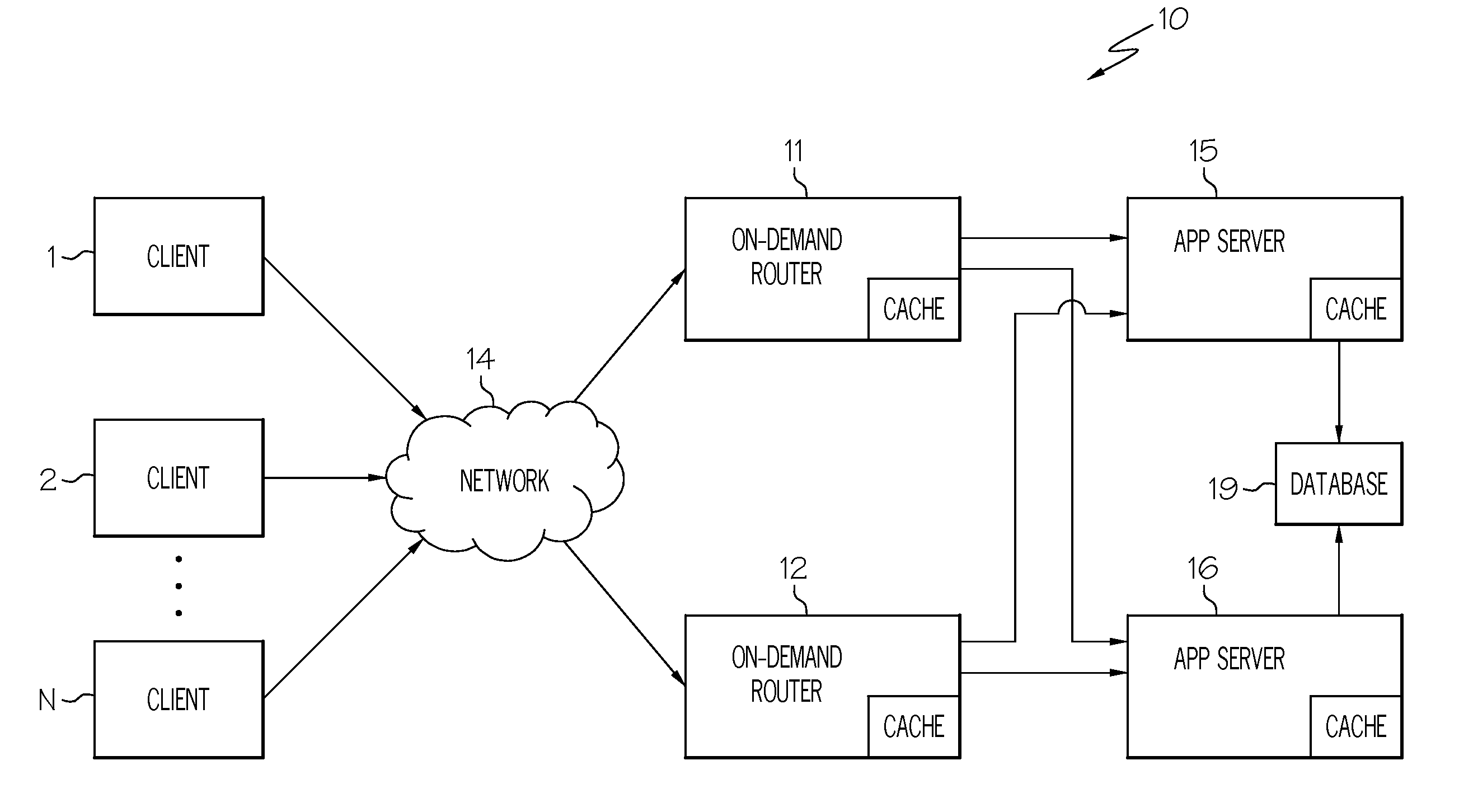
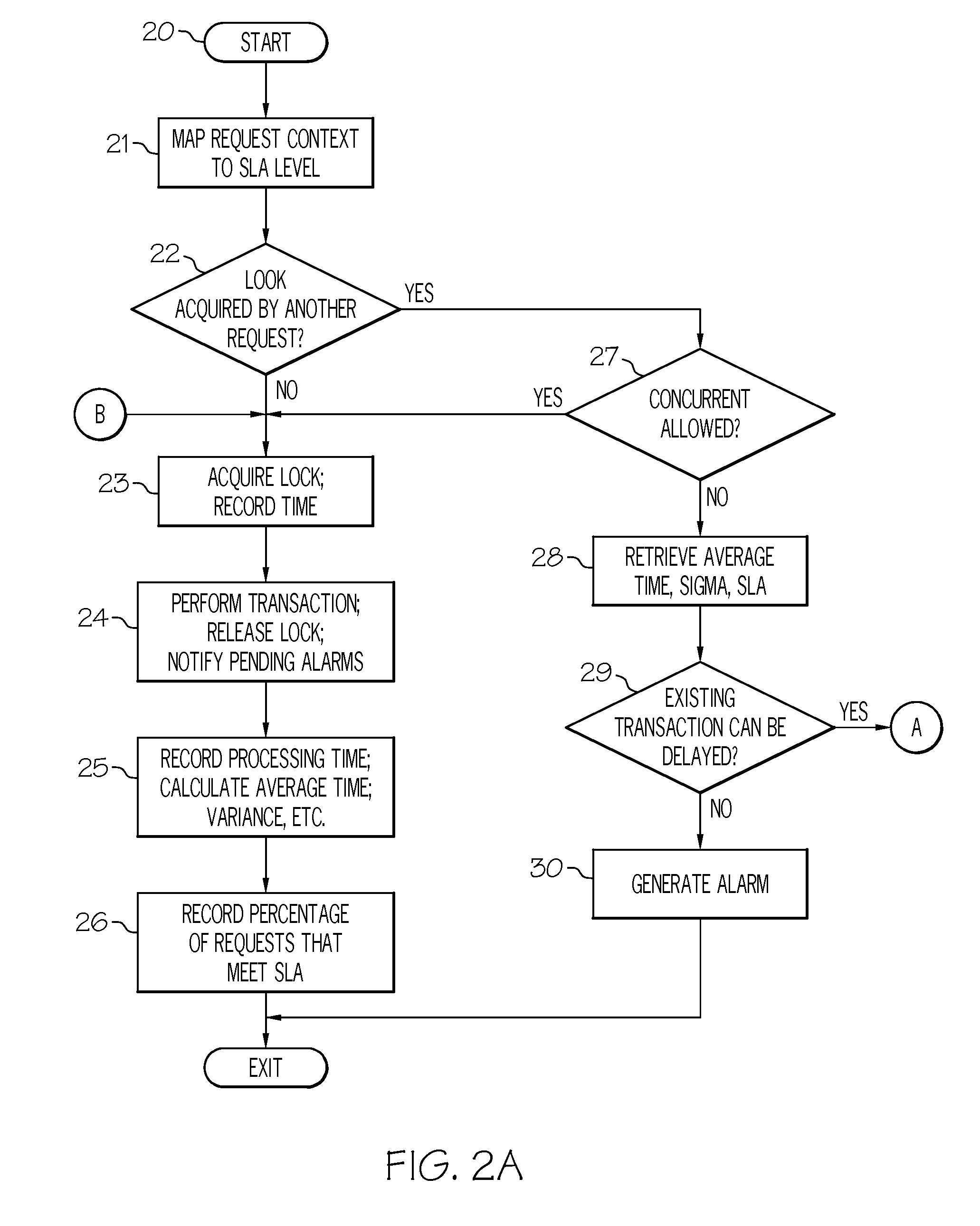
ActiveUS20080168446A1Multiple digital computer combinationsTransmissionData processing systemService-level agreement
A method for handling service requests in a data processing system is disclosed. In response to a service request, a priority of the service request is determined by mapping a context of the service request to a service level agreement (SLA). SLA-aware and timeout-conscious and preemptive and replayable lock manager is designed to account for different operational goals and different importance to satisfy various SLAs. An average processing time of the service request is then calculated based on statistical results. The service request will be allowed to process if the determined average processing time meets historical guarantee situations.
Owner:TWITTER INC
Systems and methods for maintaining transactional persistence
ActiveUS20050149526A1Data processing applicationsDigital data processing detailsLock managerManagement object
Messages between trading partners can be processed persistently using a persistence framework, which can include a transaction manager, a locking manager, and a logging mechanism. A transaction manager can initiate a transaction for a request, and can enlist and modify any object or resource useful in processing the request. A locking manager can lock any of these objects, using inflated and / or individual locks, to prevent other resources or transactions from accessing the object during the transaction. A logging component can track any modifications of the object, while a transaction manager can manage state for the object. This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:ORACLE INT CORP
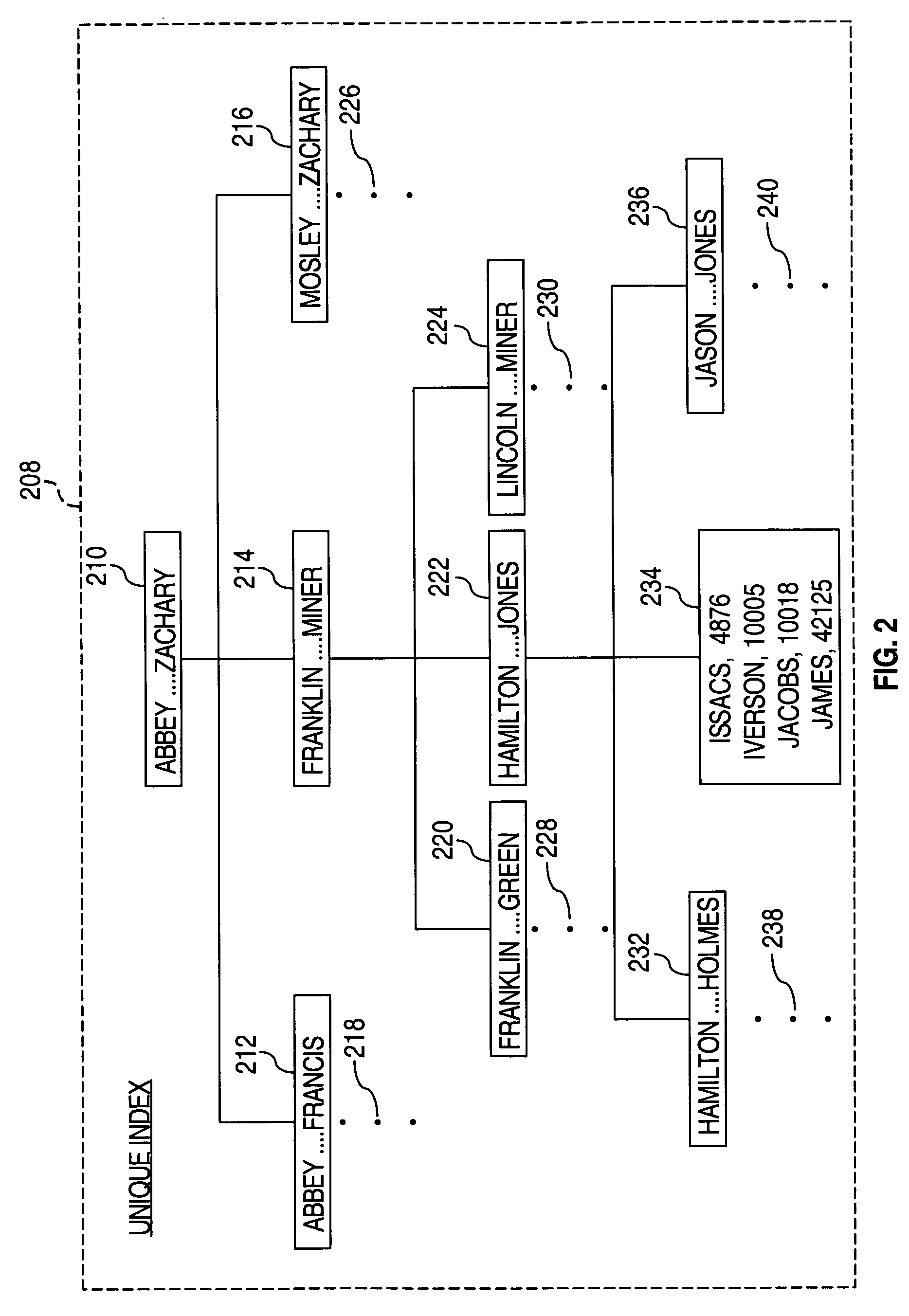
System and method for avoiding deadlock situations due to pseudo-deleted entries
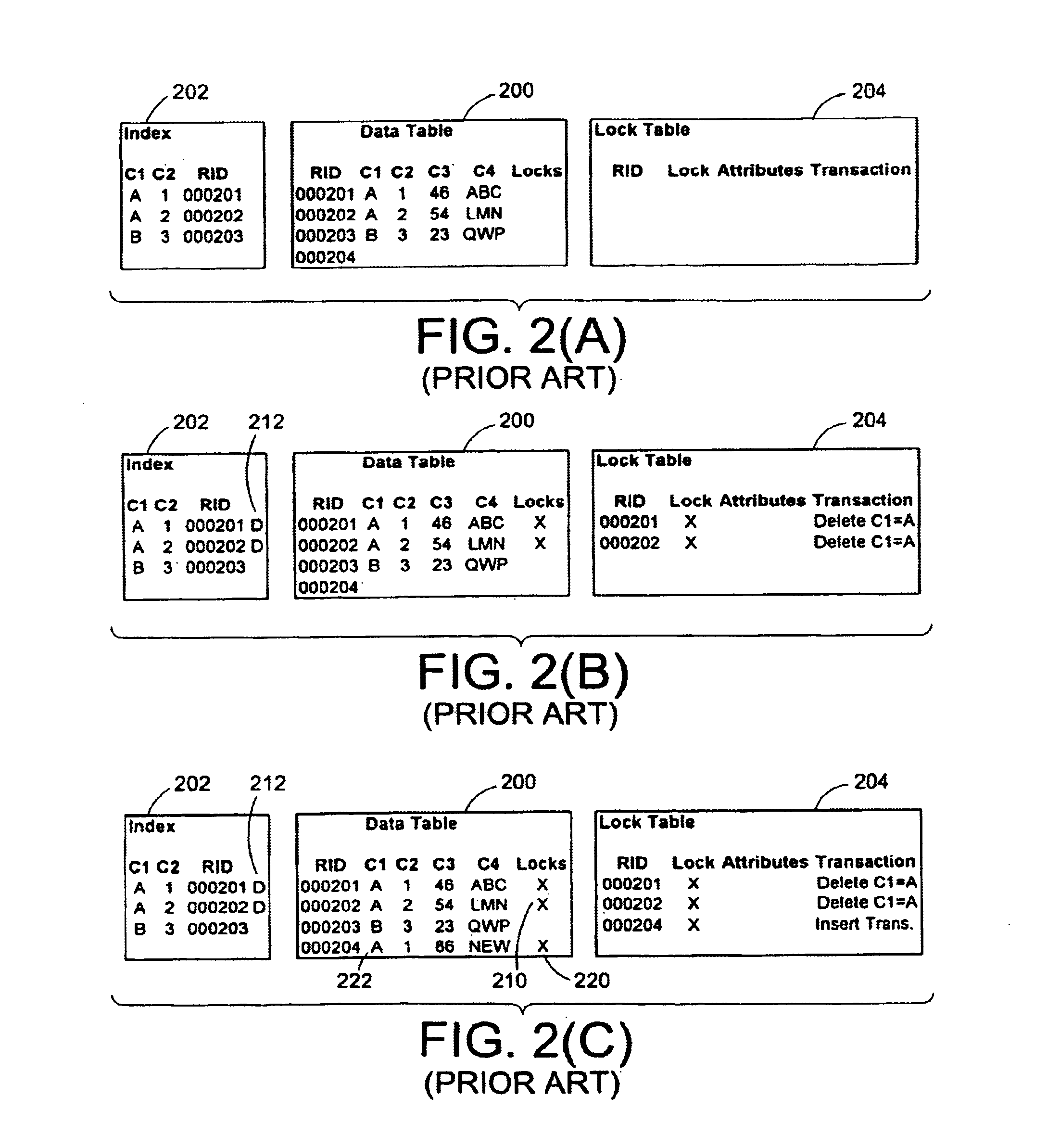
InactiveUS6944615B2Prevent deadlock situationImprove efficiencyData processing applicationsDigital data information retrievalLock managerDatabase application
In a database management system (DBMS) (60) for a database application (10) including a database (12) having a table (14, 16, 18) and a unique key index (42) having indexes (44, 46, 48) therefor, the DBMS (60) includes a data manager (64), an index manager (66), a transaction manager (62), and a lock manager (68) which restricts access to the table by assigning locks to elements thereof. In order to avoid deadlock in the database application due to the pseudo-deleted entries, the lock categories include an X-lock and a Conditional S-lock, and have lock attributes including at least a Delete attribute for the X-lock. The Conditional S-lock is compatible (granted by the lock manager) with an X-lock whose Delete attribute is NOT SET, but is not compatible (granted) with an X-lock whose Delete attribute is SET. Each index entry includes a pseudo-delete flag which is SET by the index manager (66) to indicate deletion of the indexed row. Conditional upon locating a pseudo-deleted index key corresponding to a key to be added to the index, the index manager (66) requests a Conditional S-lock on the row indexed thereby, whereby the index manager (66) verifies the Delete transaction which set the pseudo-delete flag has committed.
Owner:IBM CORP
Lock management method, lock management system, lock management system configuration method and lock management system configuration device
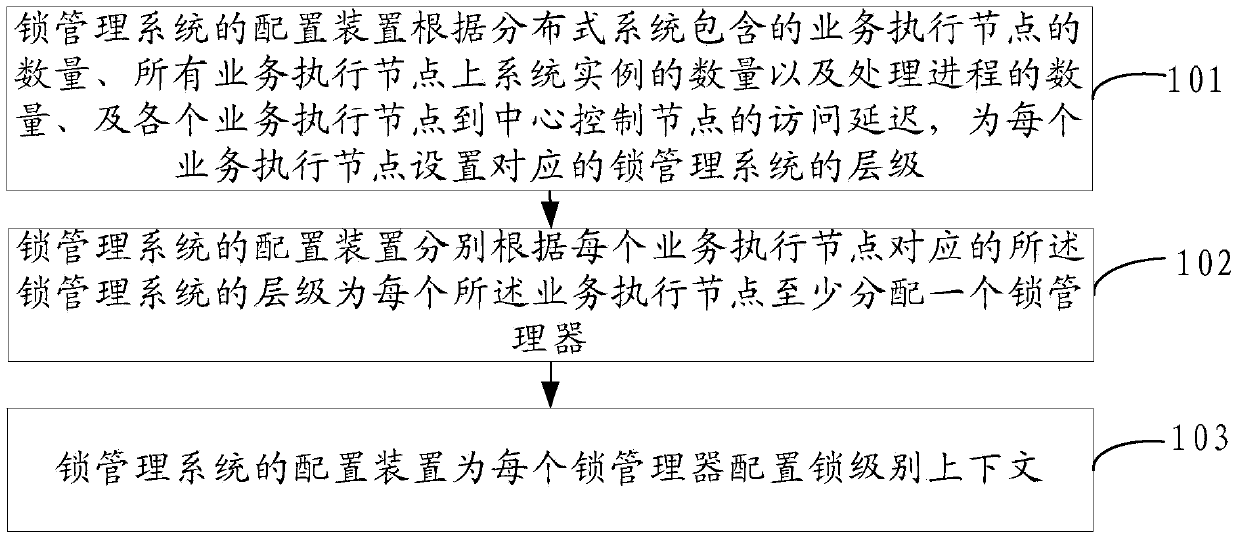
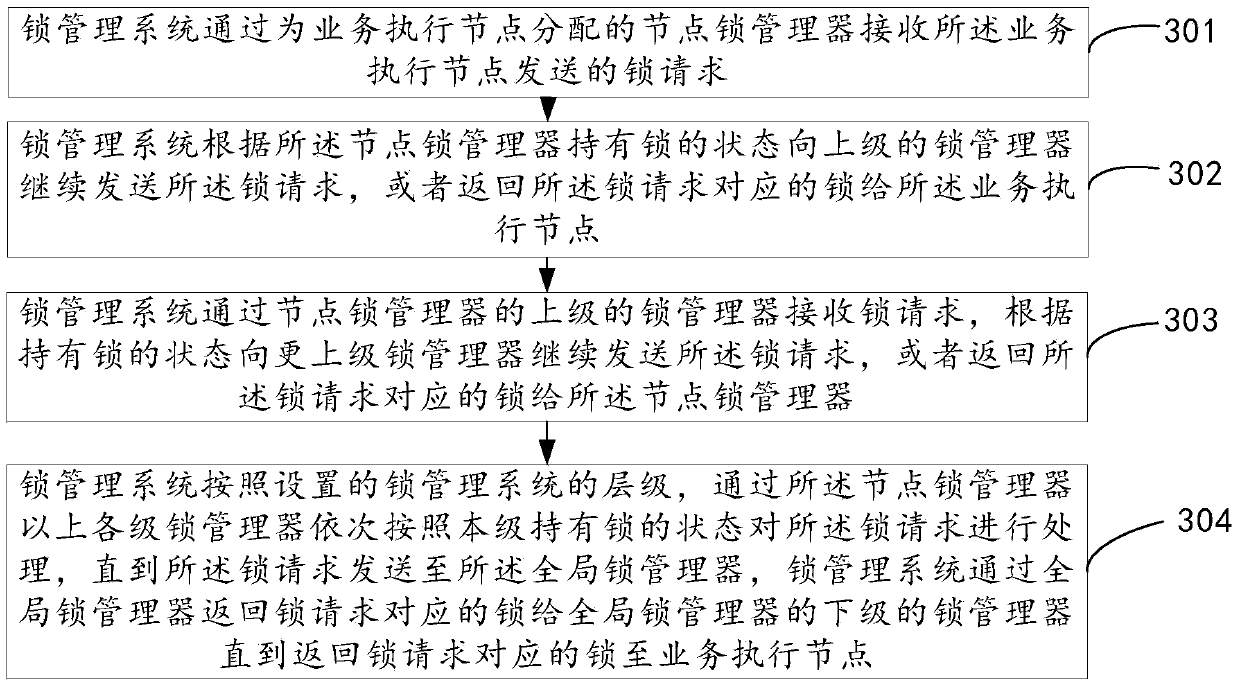
ActiveCN103744719AReduce access latencyGuaranteed uptimeResource allocationSpecial data processing applicationsLock managerManagement system
An embodiment of the invention discloses a lock management method, a lock management system, a lock management system configuration method and a lock management system configuration device, and relates to the field of computers. Lock access delay can be decreased, and the running performance of the system is improved. The specific scheme includes that a corresponding lock management system level is set for each business execution node according to the number of business execution nodes in a distributed system, the number of system cases on all the business execution nodes, the number of processes and access delay from each business execution node to a central control node of the distributed system; at least one lock manager is distributed for each business execution node according to the lock management system level corresponding to each business execution node; a lock level context is configured for each lock manager and used for determining a lock manager adjacent to each lock manager. The lock management system configuration method is used for the lock management system of the distributed system.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com