Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1180 results about "Deadlock" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
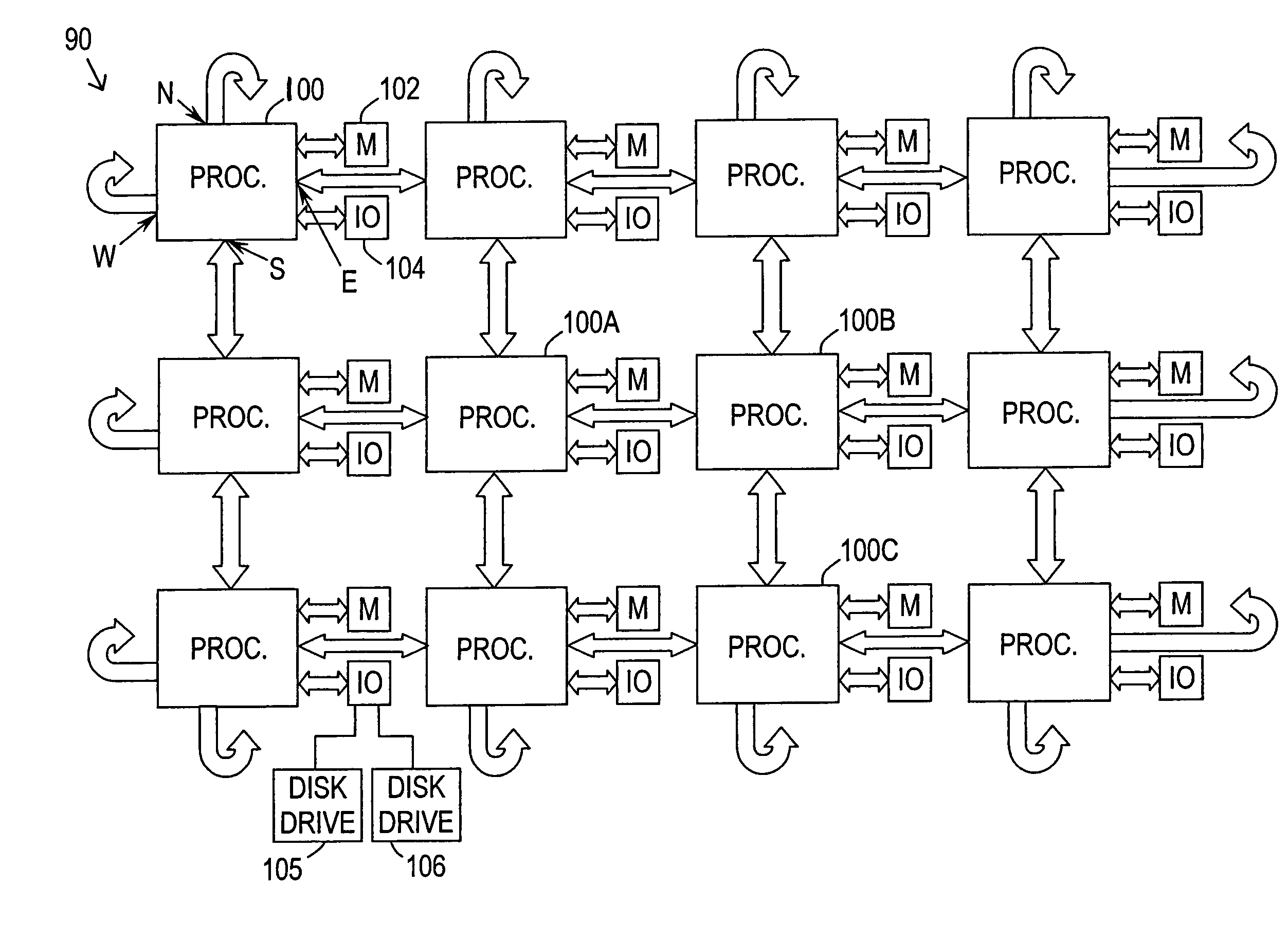
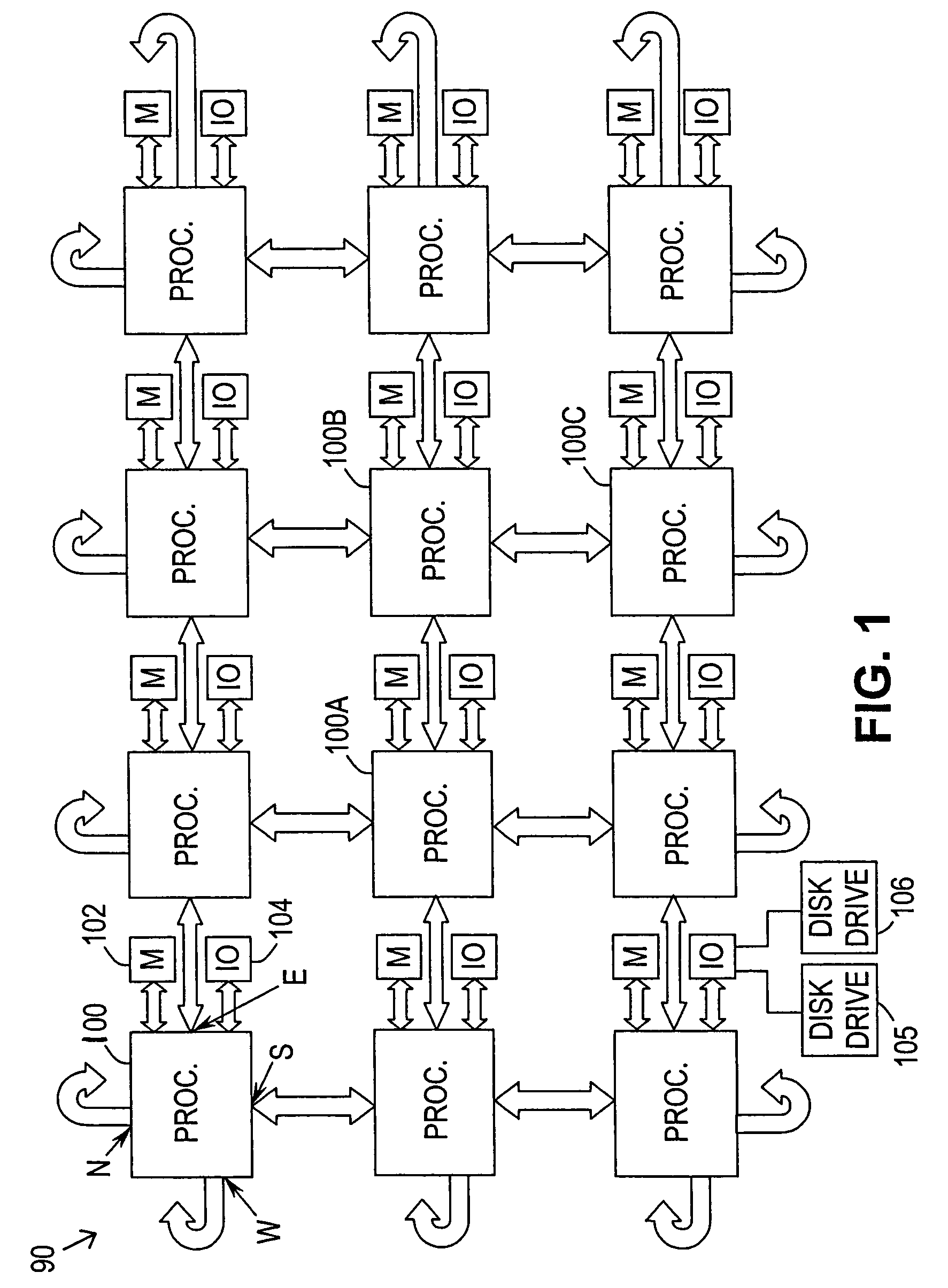
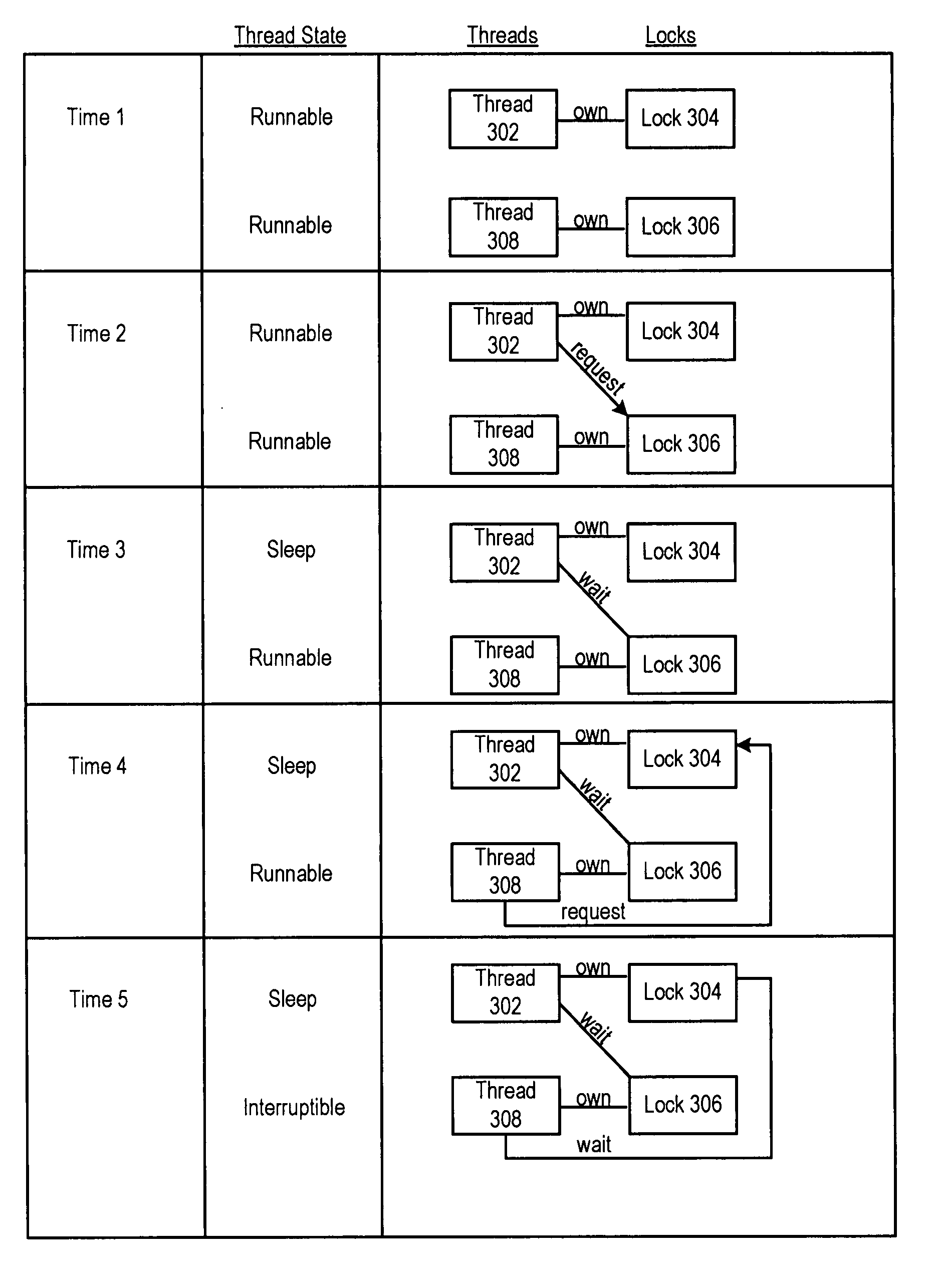
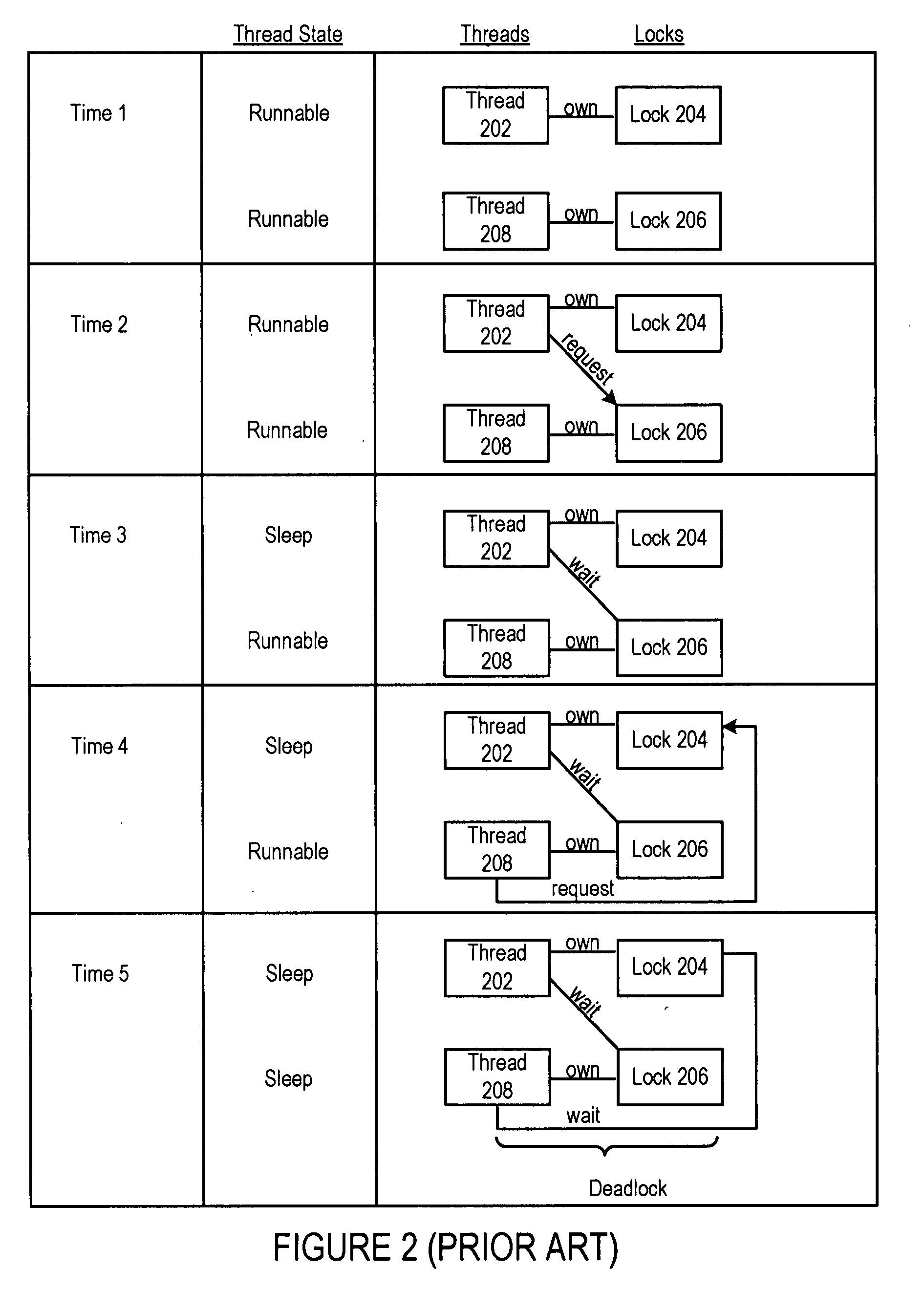
In concurrent computing, a deadlock is a state in which each member of a group is waiting for another member, including itself, to take action, such as sending a message or more commonly releasing a lock. Deadlock is a common problem in multiprocessing systems, parallel computing, and distributed systems, where software and hardware locks are used to arbitrate shared resources and implement process synchronization.
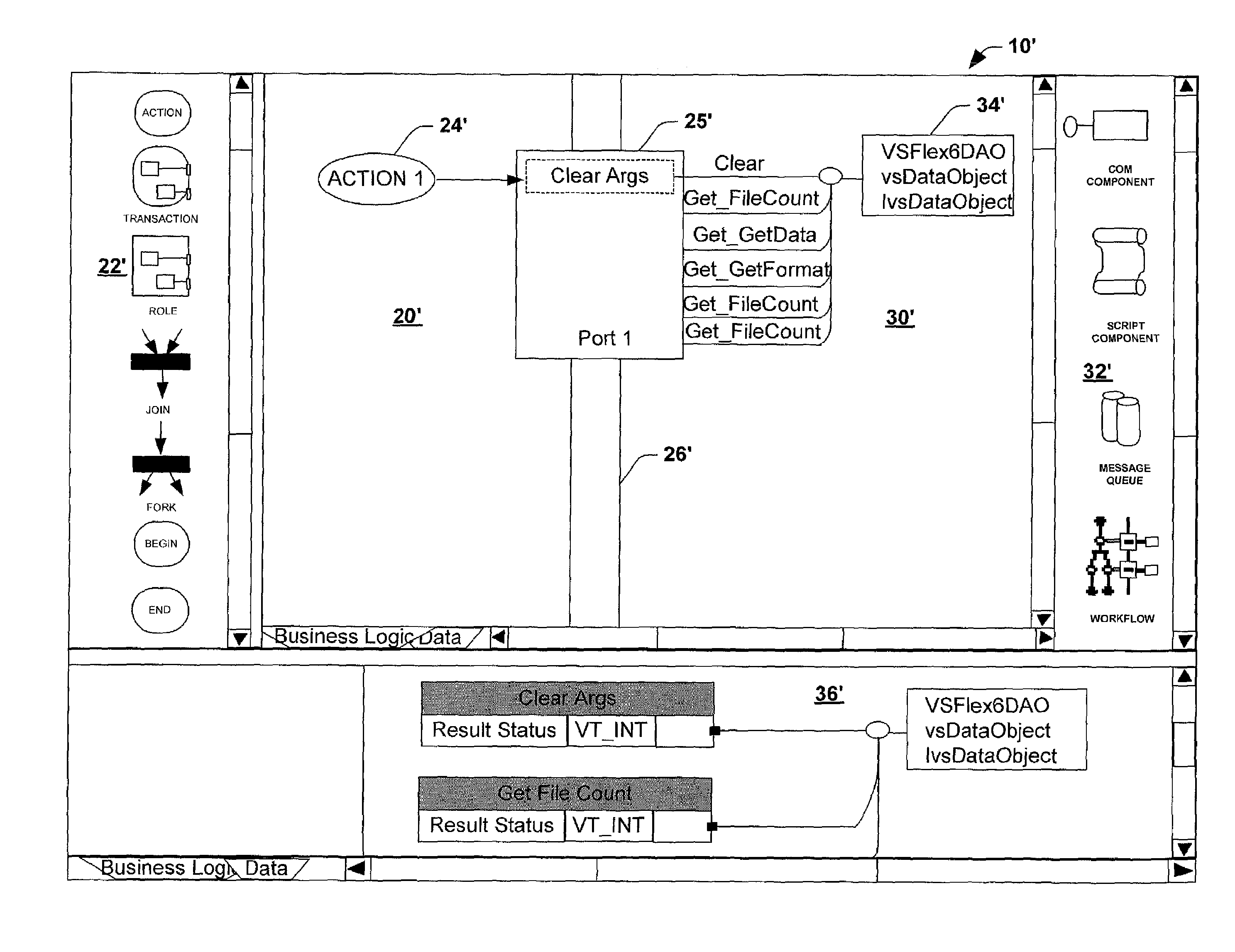
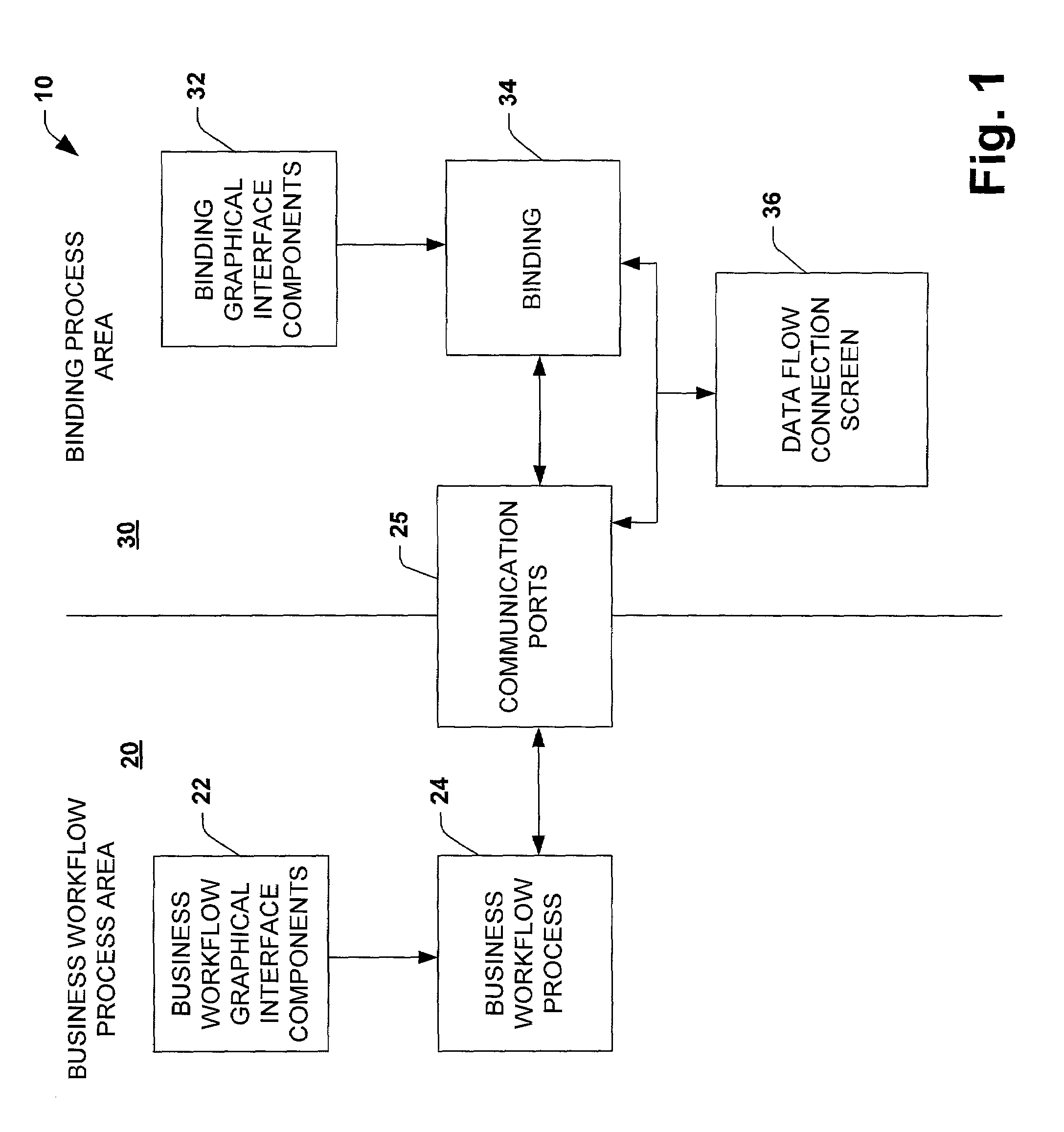
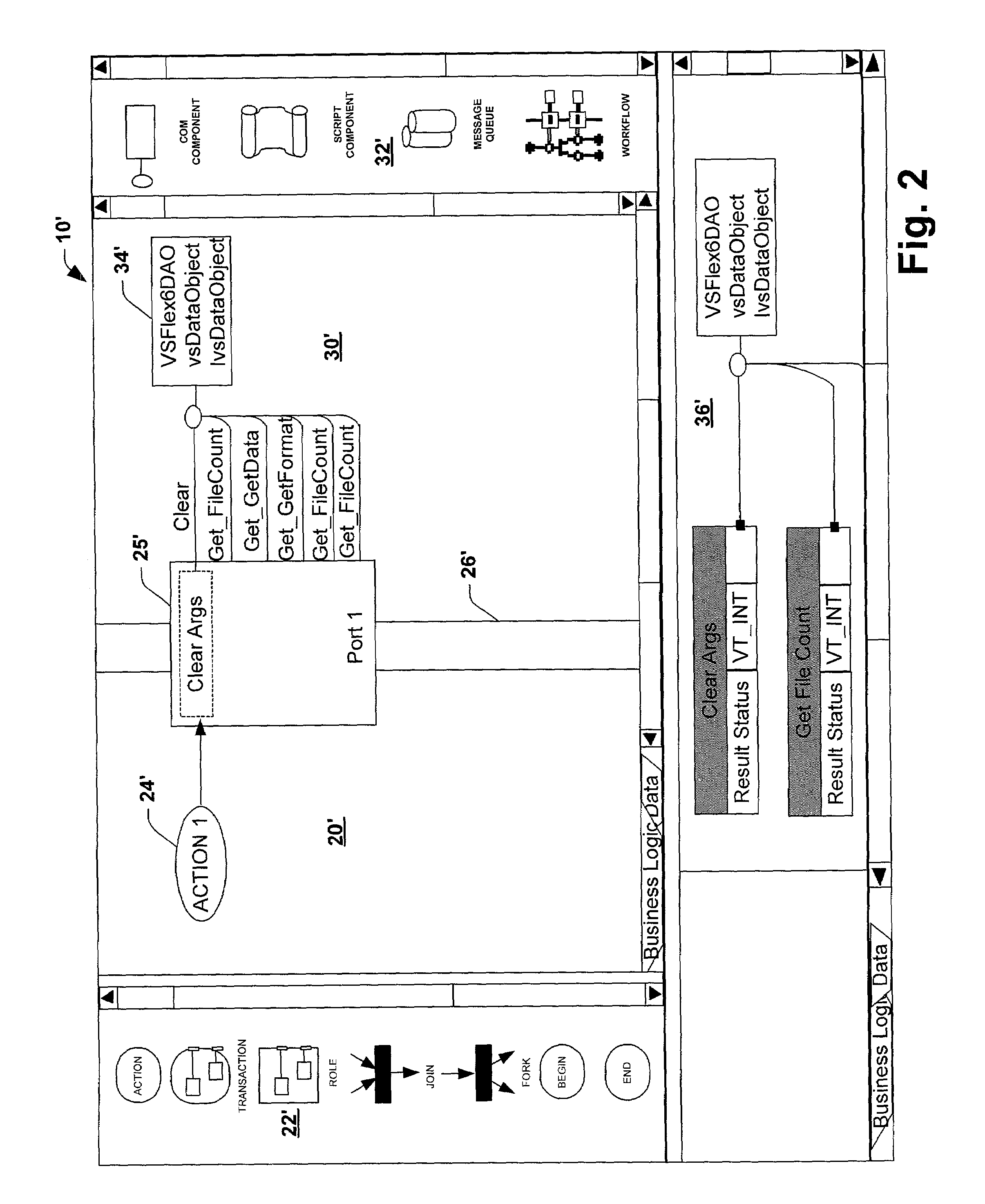
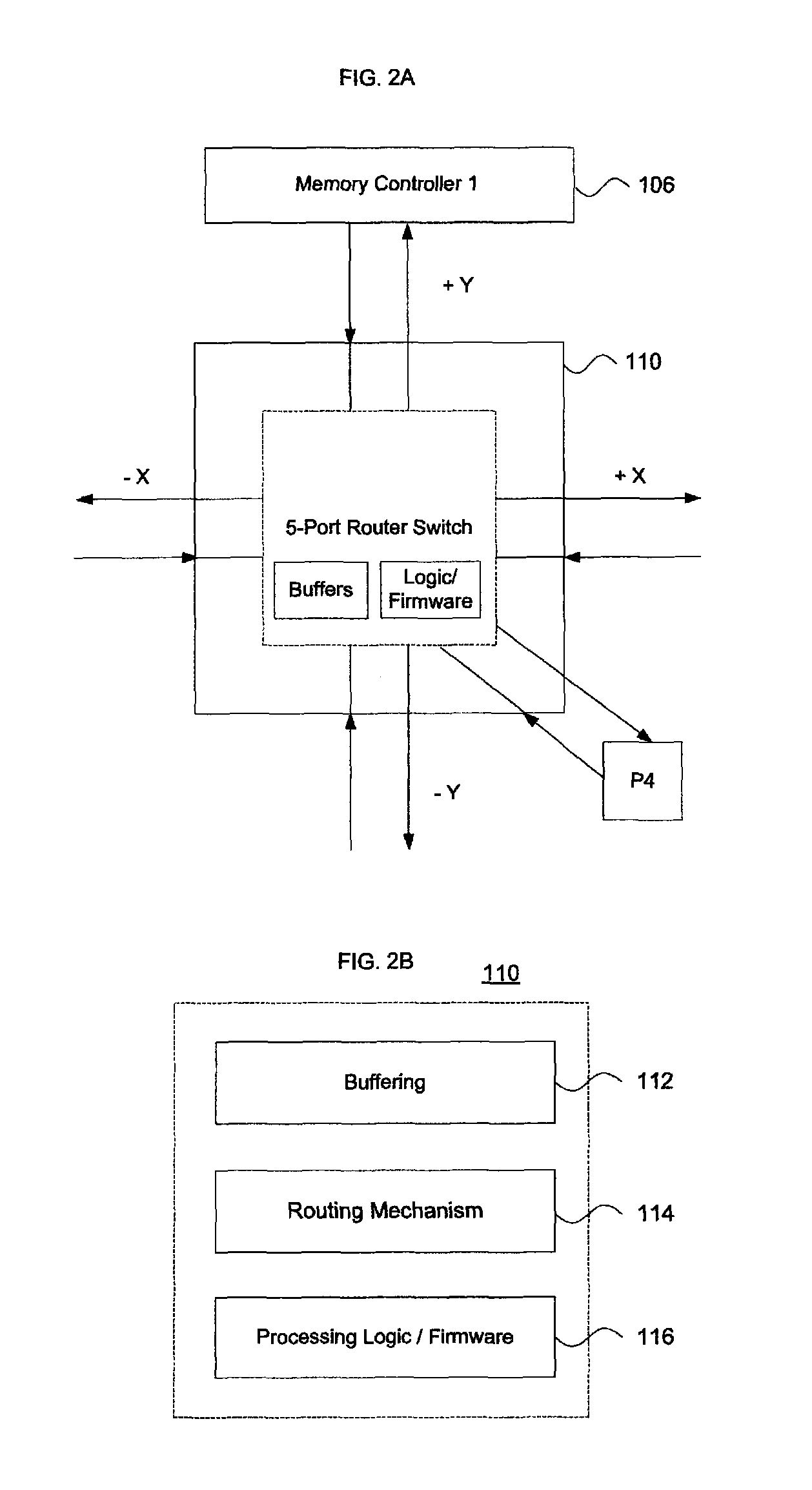
System and method utilizing a graphical user interface of a business process workflow scheduling program
InactiveUS7184967B1Promote modelOffice automationProgramme total factory controlSoftware engineeringBusiness process
A graphical user interface (GUI) scheduler program is provided for modeling business workflow processes. The GUI scheduler program includes tools to allow a user to create a schedule for business workflow processes based on a set of rules defined by the GUI scheduler program. The rules facilitate deadlock not occurring within the schedule. The program provides tools for creating and defining message flows between entities. Additionally, the program provides tools that allow a user to define a binding between the schedule and components, such as COM components, script components, message queues and other workflow schedules. The scheduler program allows a user to define actions and group actions into transactions using simple GUI scheduling tools. The schedule can then be converted to executable code in a variety of forms such as XML, C, C+ and C++. The executable code can then be converted or interpreted for running the schedule.
Owner:MICROSOFT TECH LICENSING LLC
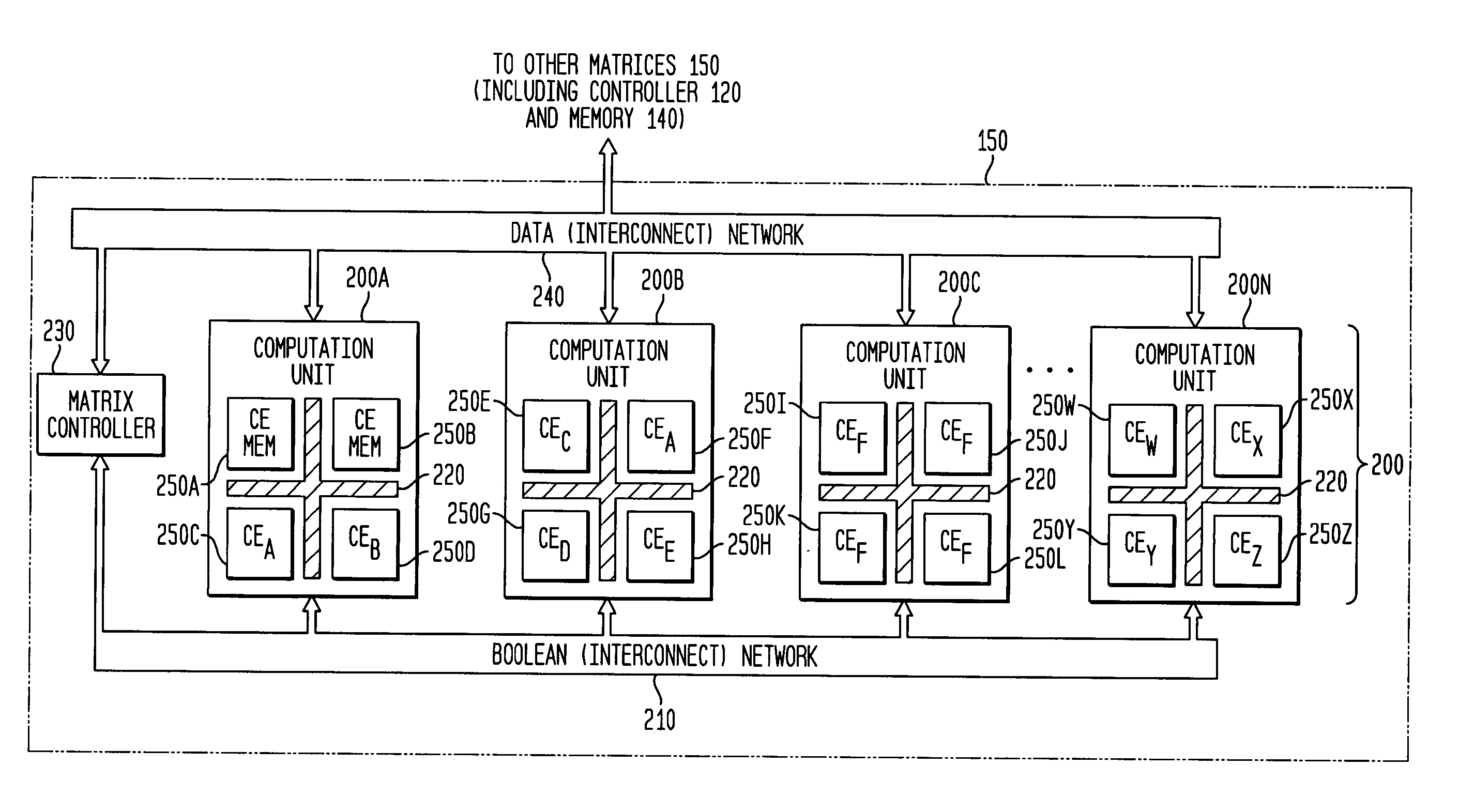
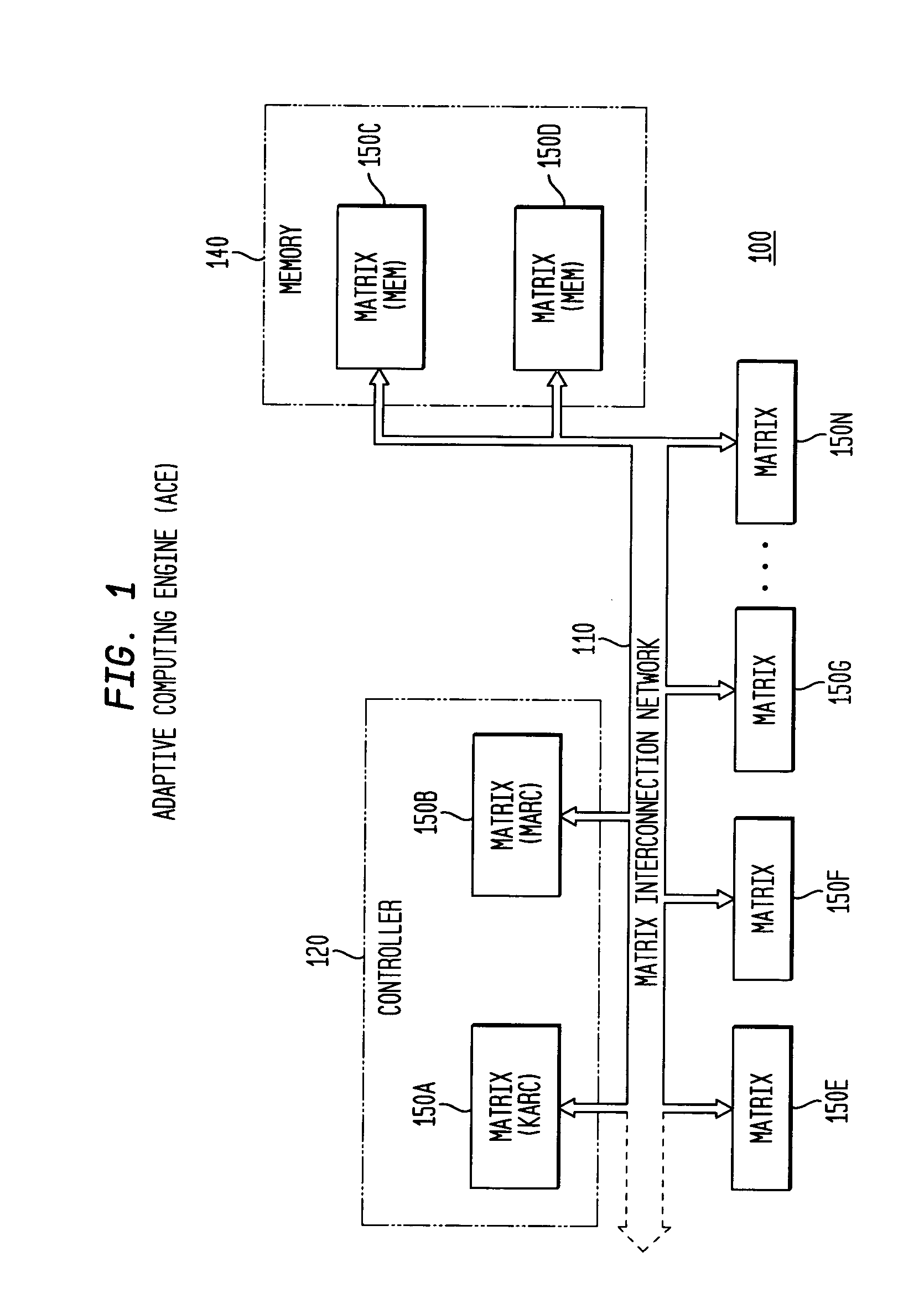
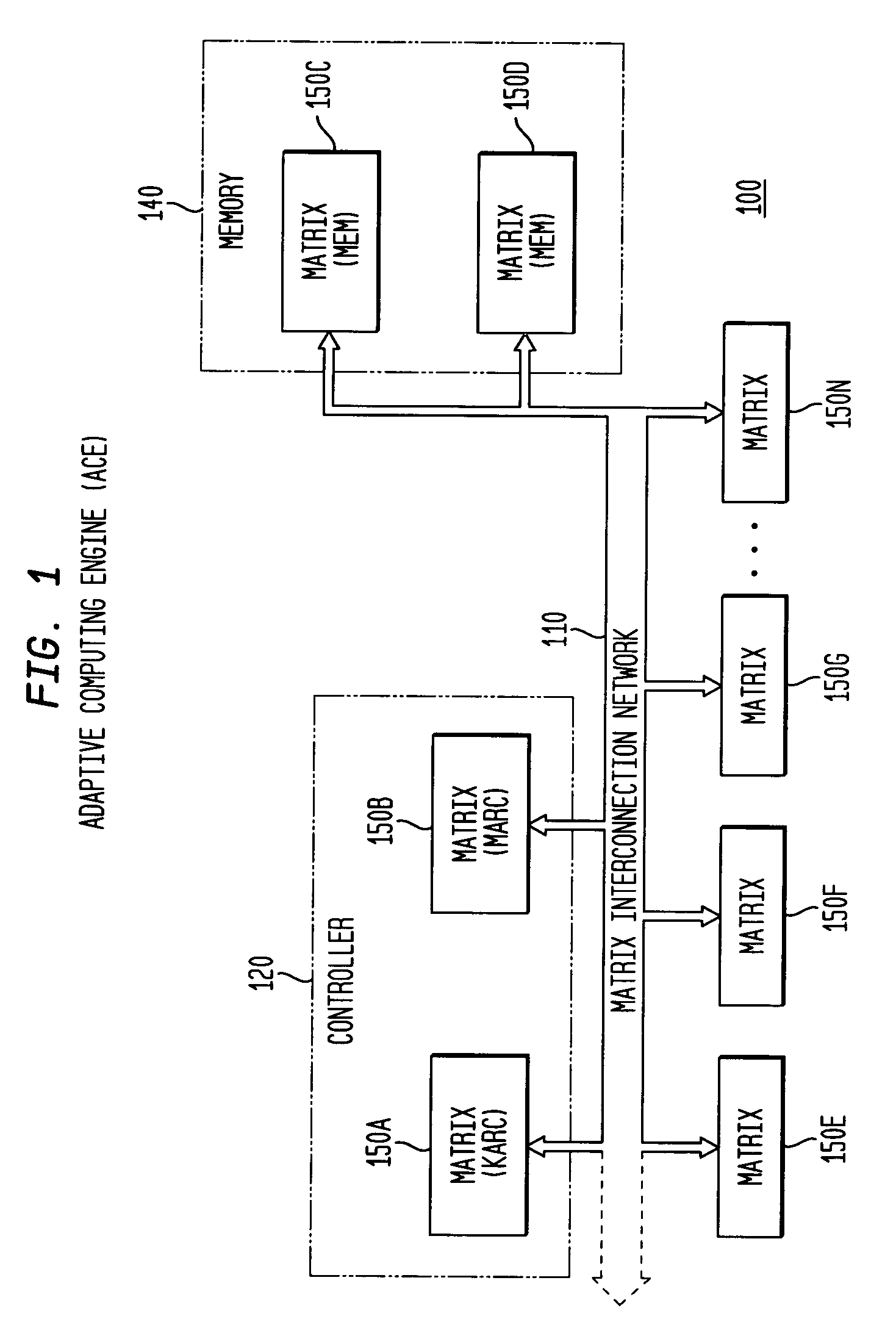
Asynchronous, independent and multiple process shared memory system in an adaptive computing architecture
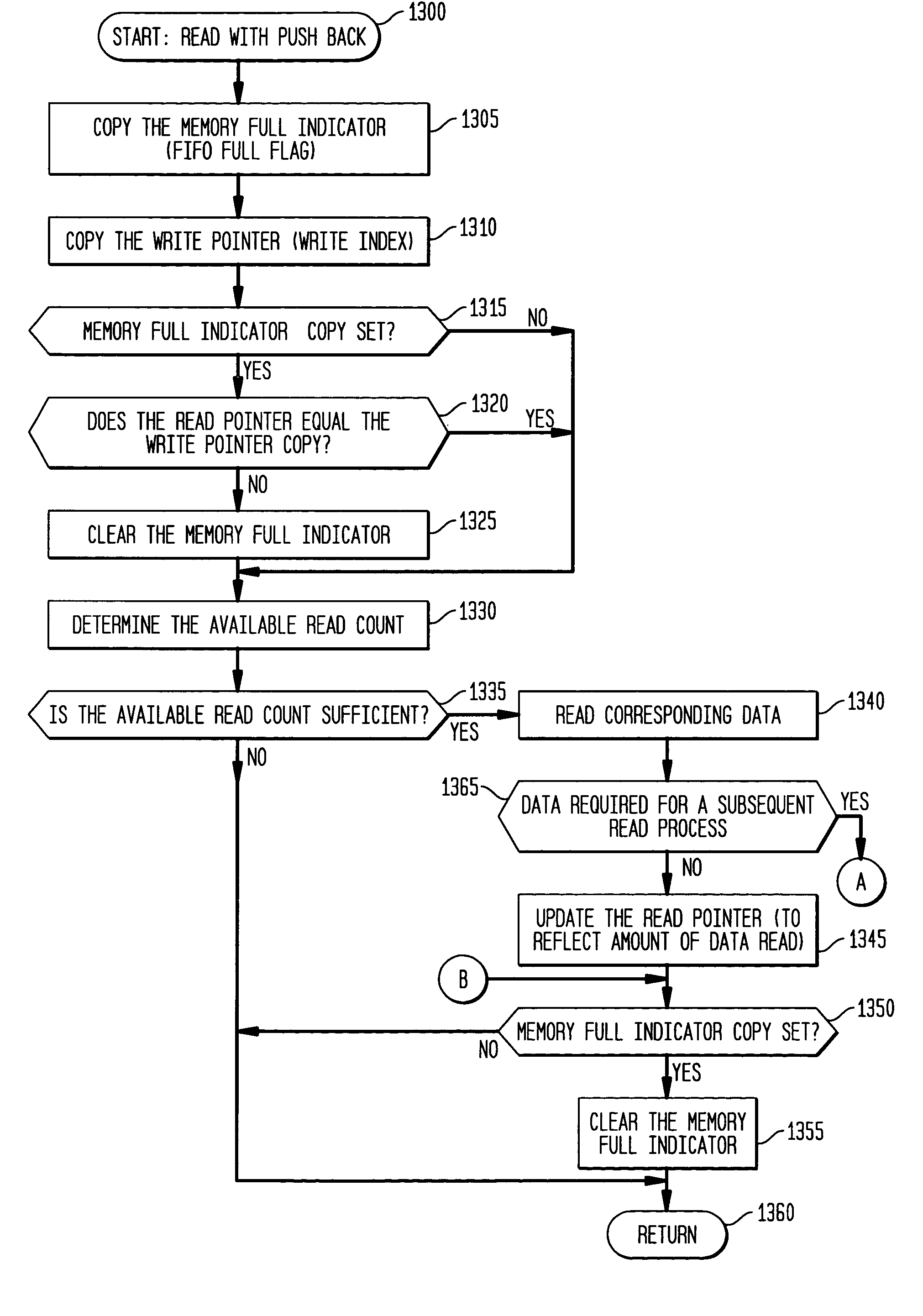
The present invention provides a system and method for implementation and use of a shared memory. The shared memory may be accessed both independently and asynchronously by one or more processes at corresponding nodes, allowing data to be streamed to multiple processes and nodes without regard to synchronization of the plurality of processes. The various nodes may be adaptive computing nodes, kernel or controller nodes, or one or more host processor nodes. The present invention maintains memory integrity, not allowing memory overruns, underruns, or deadlocks. The present invention also provides for “push back” after a memory read, for applications in which it is desirable to “unread” some elements previously read from the memory.
Owner:NVIDIA CORP
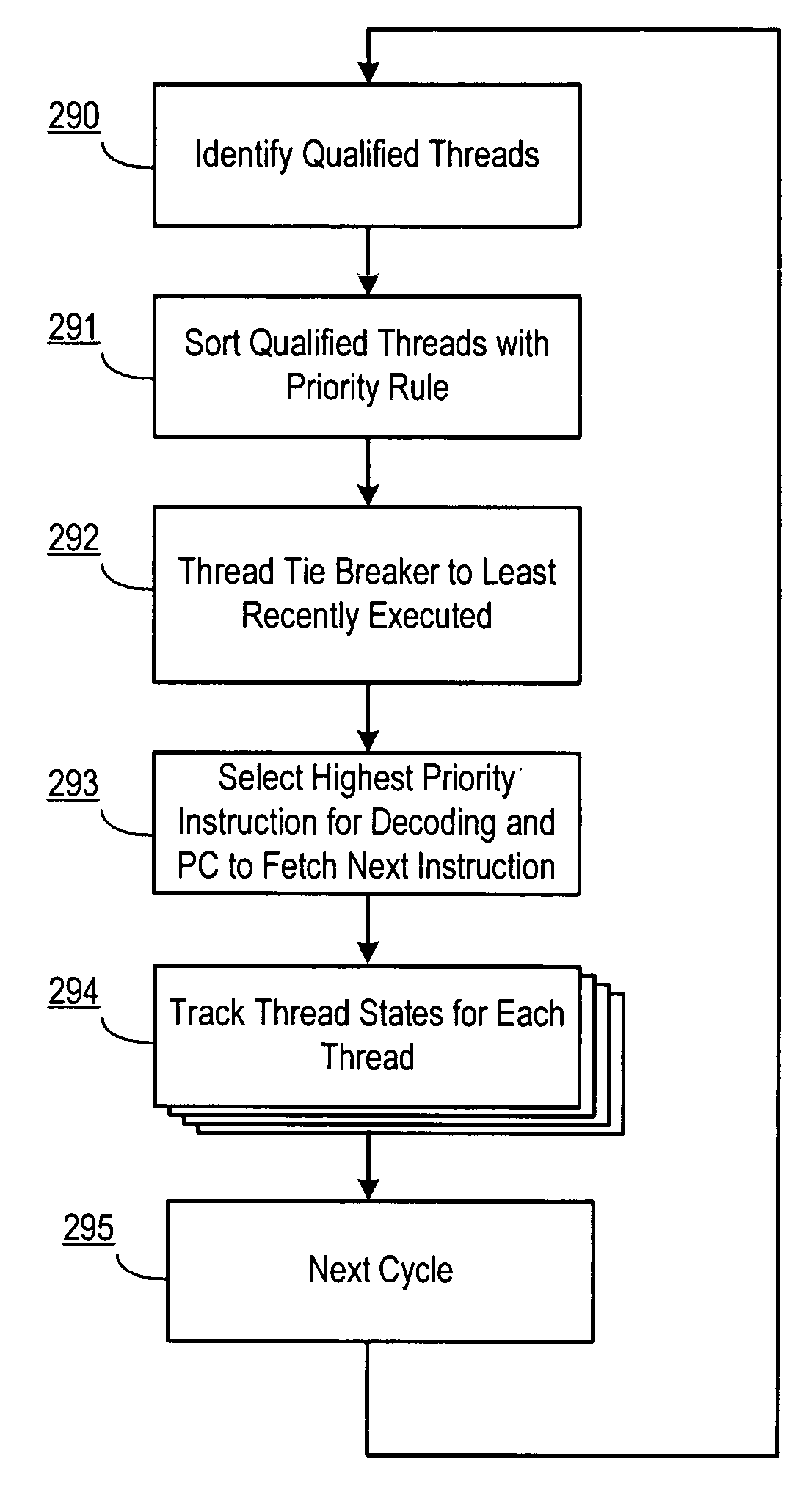
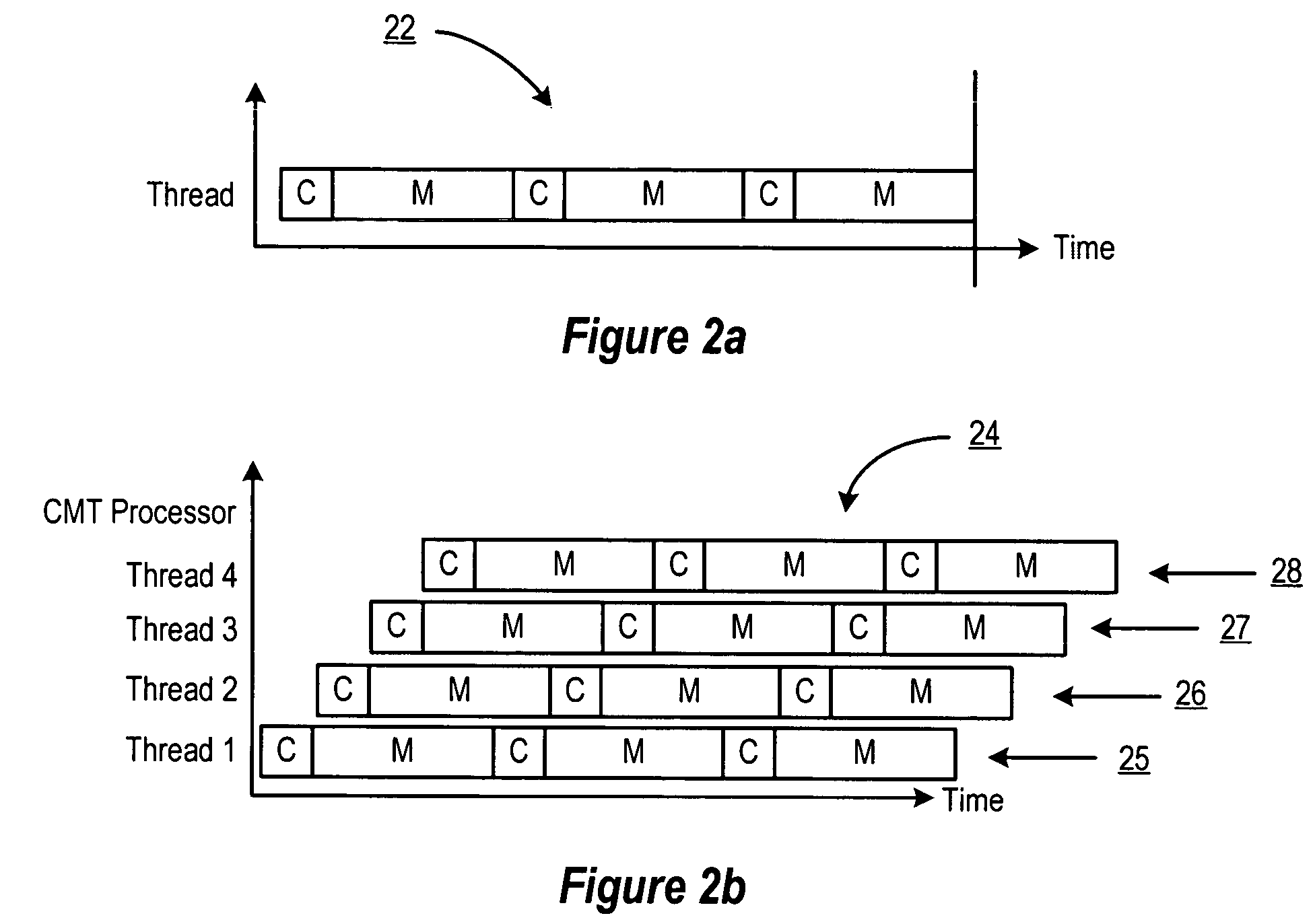
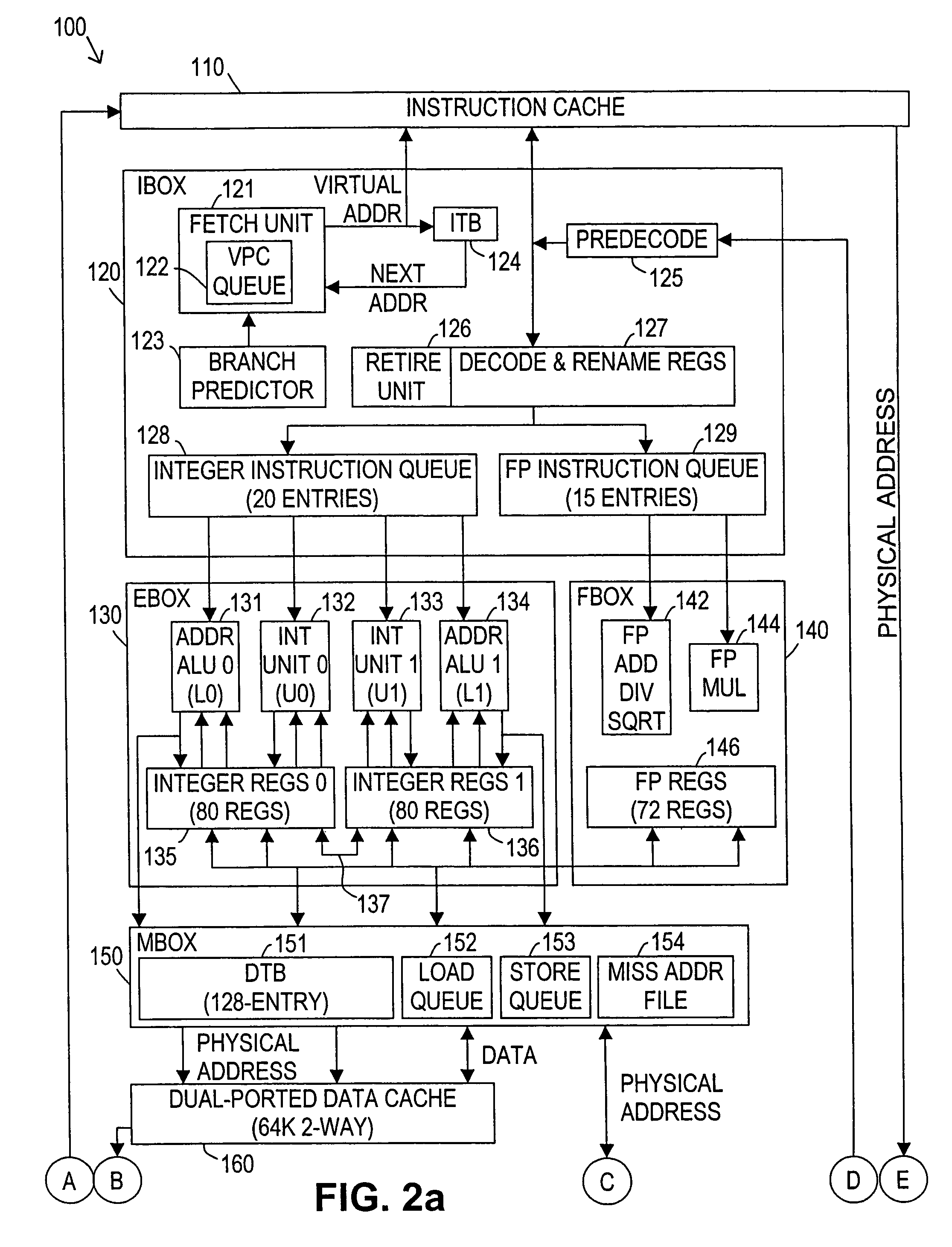
Method and apparatus for scheduling multiple threads for execution in a shared microprocessor pipeline
ActiveUS20060136915A1Efficient and fair schedulingImprove efficiencyMultiprogramming arrangementsMemory systemsParallel computingDeadlock
An apparatus and method for scheduling execution of multiple threads on a shared processor resource is described in connection with a multithreaded multiprocessor chip. Using a thread selection policy that switches between available threads every cycle to give priority to the least recently executed or scheduled threads, different threads are able to operate in a way that ensures no deadlocks or livelocks while maximizing aggregate performance and fairness between threads. Prioritization is accomplished by monitoring and sorting thread status information for each thread, including speculative states in which a thread may be speculatively scheduled, thereby improving usage of the execution pipeline by switching a thread in with a lower priority.
Owner:SUN MICROSYSTEMS INC
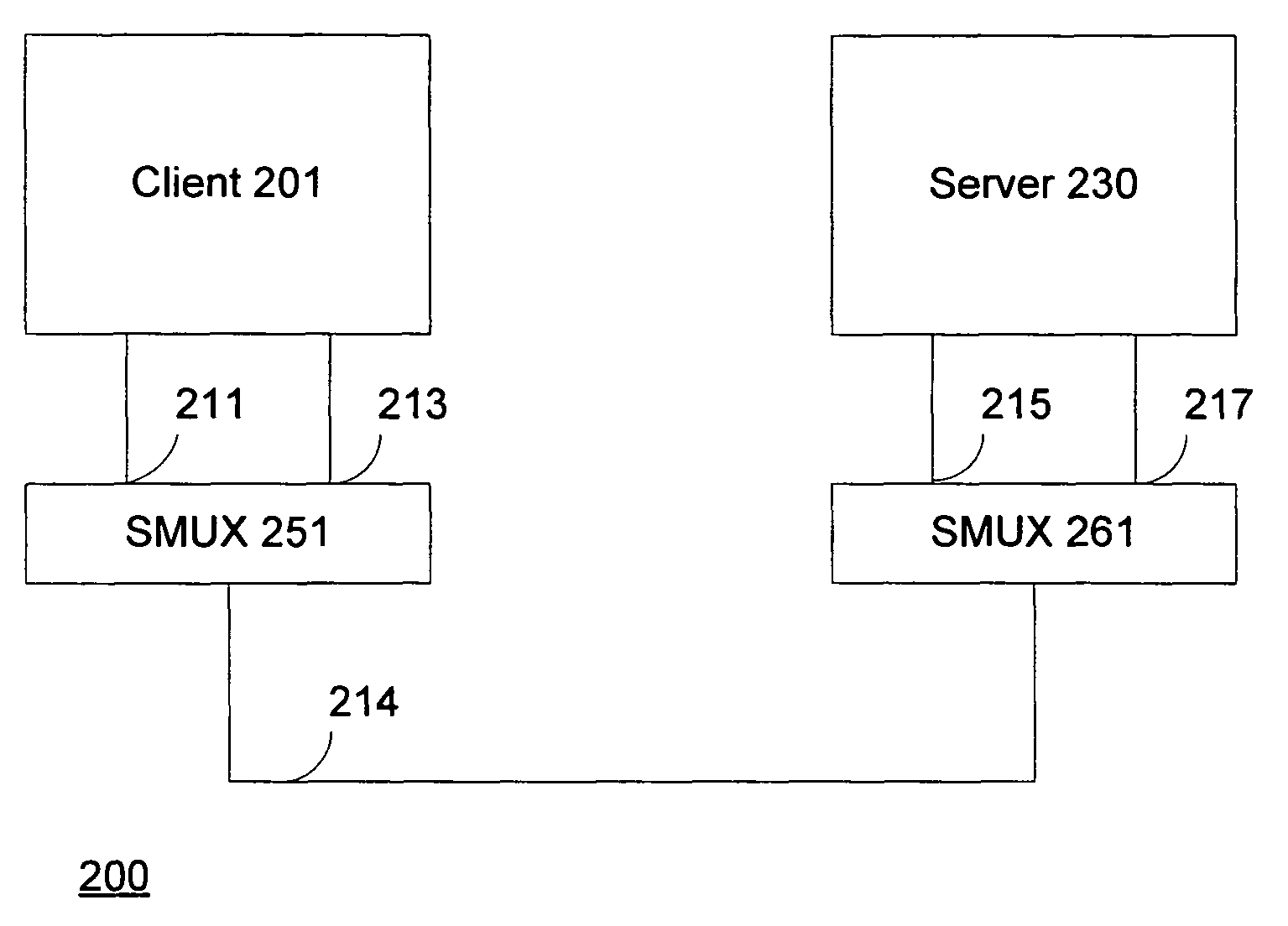
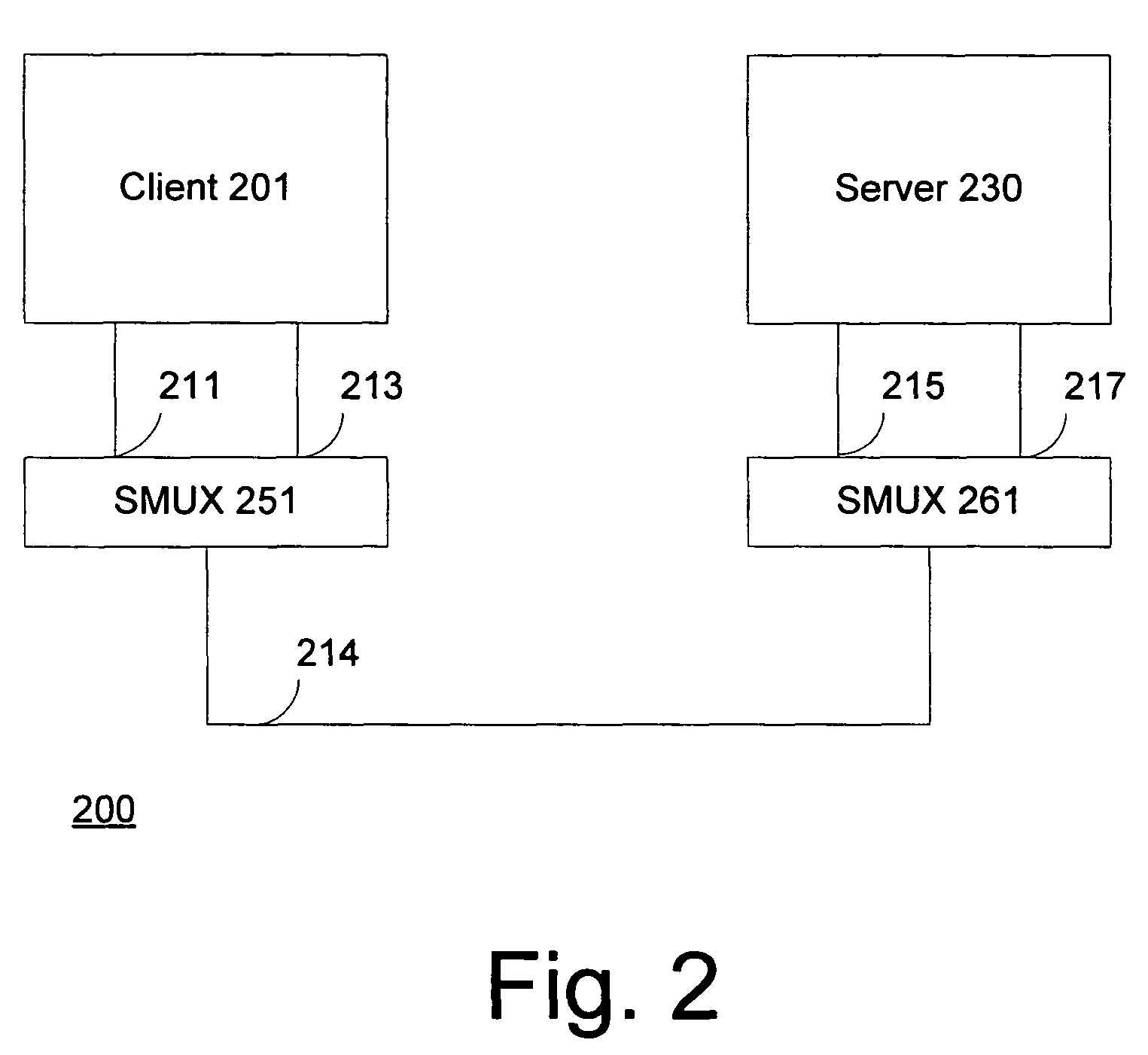
Session multiplex protocol
InactiveUS7966405B2Bandwidth is no longer wastedSave computing resourcesEnergy efficient ICTData switching by path configurationMultiplexingByte
Session multiplex protocol (“SMUX”) is a protocol layered above existing reliable transport mechanisms that can be used to create multiple sessions over a single connection. Data from several different SMUX sessions can be interleaved and message boundaries preserved. Because it sits on top of reliable transport mechanisms, it takes advantage of the underlying protocols to ensure byte-alignment, loss detection / recovery, and reliable delivery. It provides a window based flow control mechanism to ensure suitable fairness among streams of different sessions and prevent deadlocks.
Owner:MICROSOFT TECH LICENSING LLC
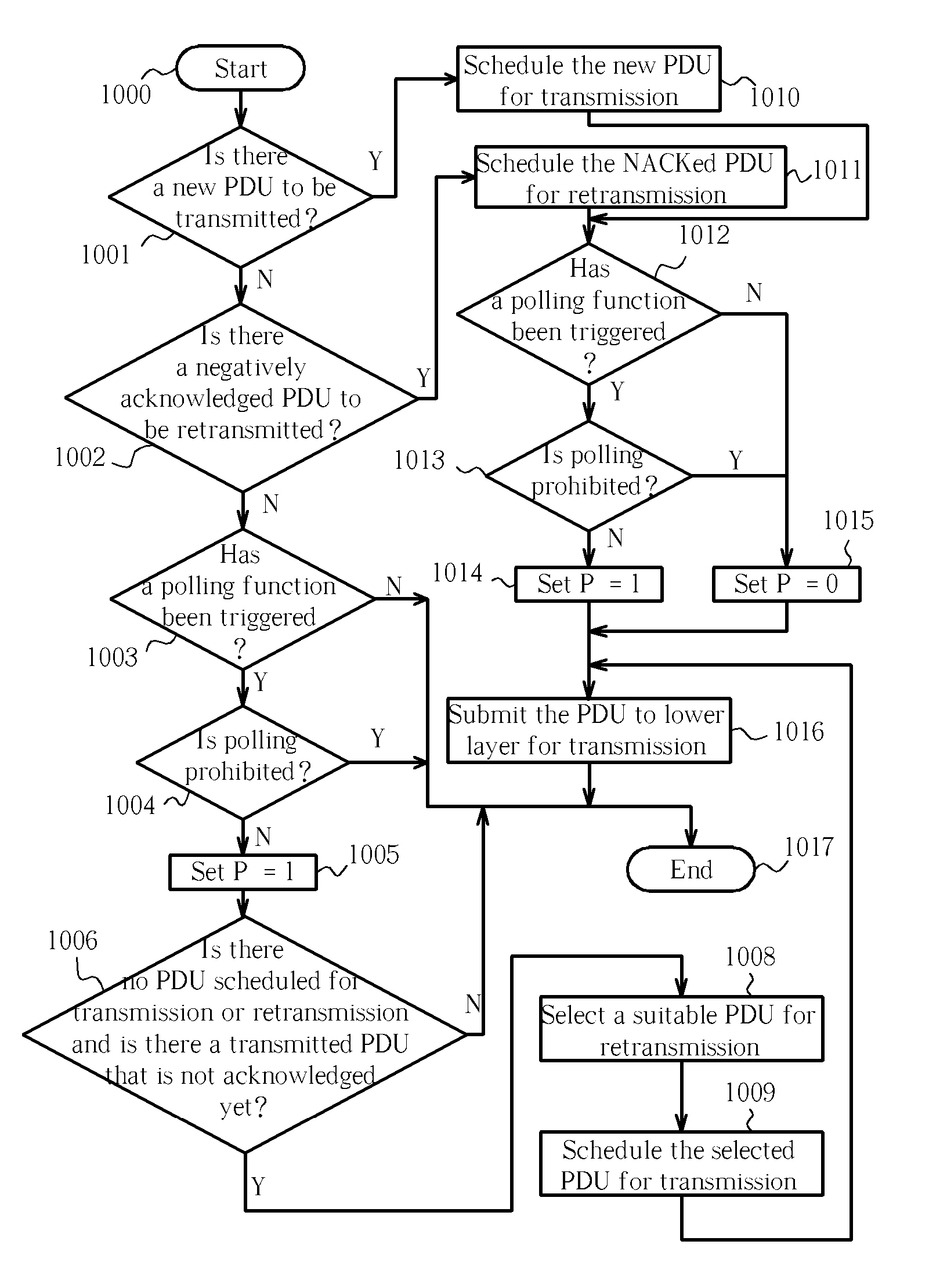
Enhanced polling method for preventing deadlock in a wireless communications system
ActiveUS20060056441A1Error prevention/detection by using return channelNetwork traffic/resource managementCommunications systemTime segment
A method of polling in a wireless communications system includes prohibiting polling within a first predetermined period and triggering a poll function while polling is prohibited. After the first predetermined period has expired the method determines that there are no protocol data units (PDUs) scheduled for transmission or re-transmission and that there is at least a transmitted PDU that is not acknowledged yet, and selects a PDU to schedule for re-transmission to fulfill the poll function.
Owner:INNOVATIVE SONIC
Method and system for deadlock detection in a distributed environment
ActiveUS20060206901A1Reduce processing timeEasy to detectUnauthorized memory use protectionMultiprogramming arrangementsDeadlockReal-time computing
A method of deadlock detection is disclosed which adjusts the detection technique based on statistics maintained for tracking the number of actual deadlocks that are detected in a distributed system, and for which types of locks are most frequently involved in deadlocks. When deadlocks occur rarely, the deadlock detection may be tuned down, for example, by reducing a threshold value which determines timeouts for waiting lock requests. When it is determined that actual deadlocks are detected frequently, the processing time for deadlock detection may be reduced, for example, by using parallel forward or backward search operations and / or by according higher priority in deadlock detection processing to locks which are more likely to involve deadlocks.
Owner:ORACLE INT CORP
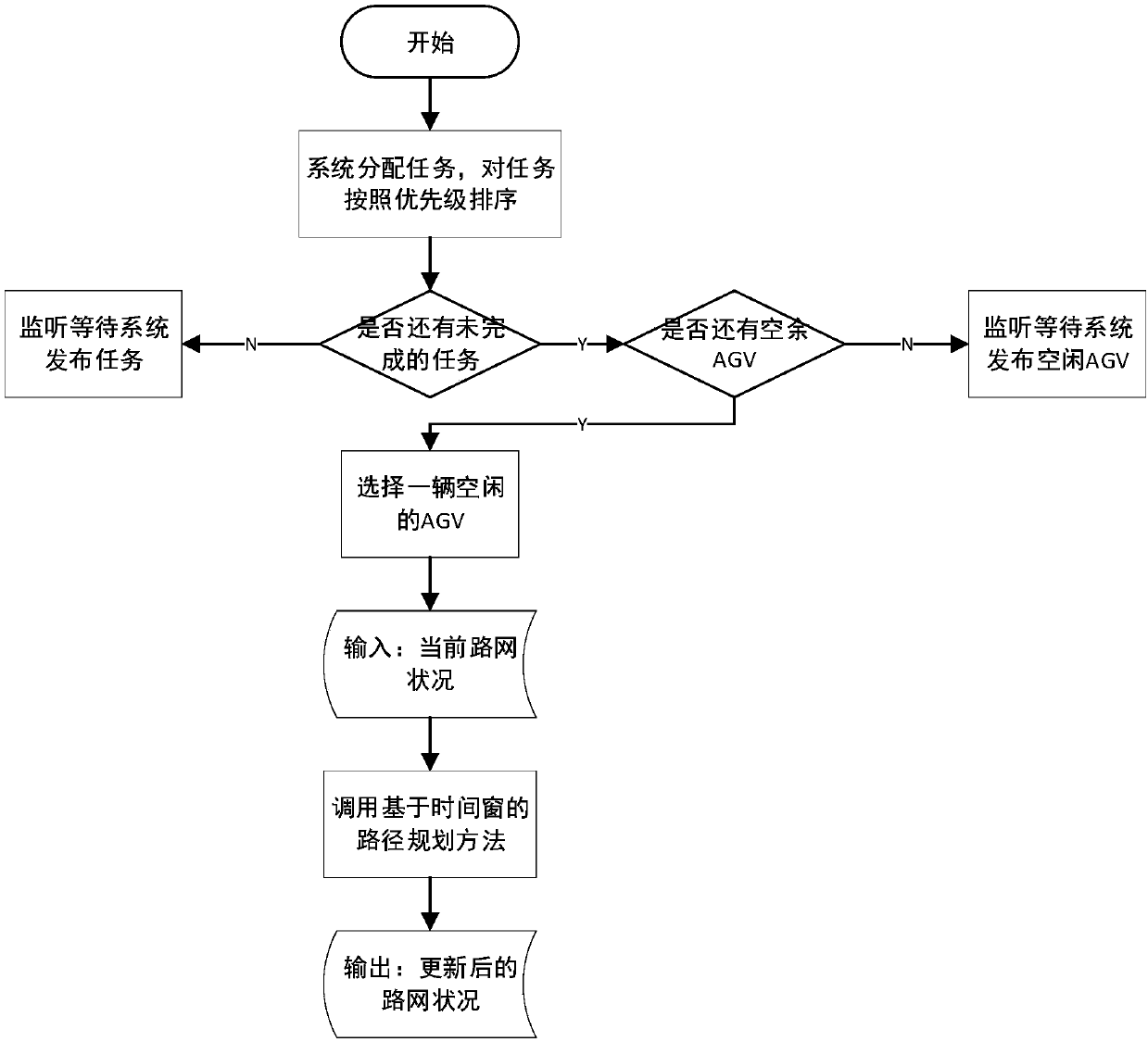
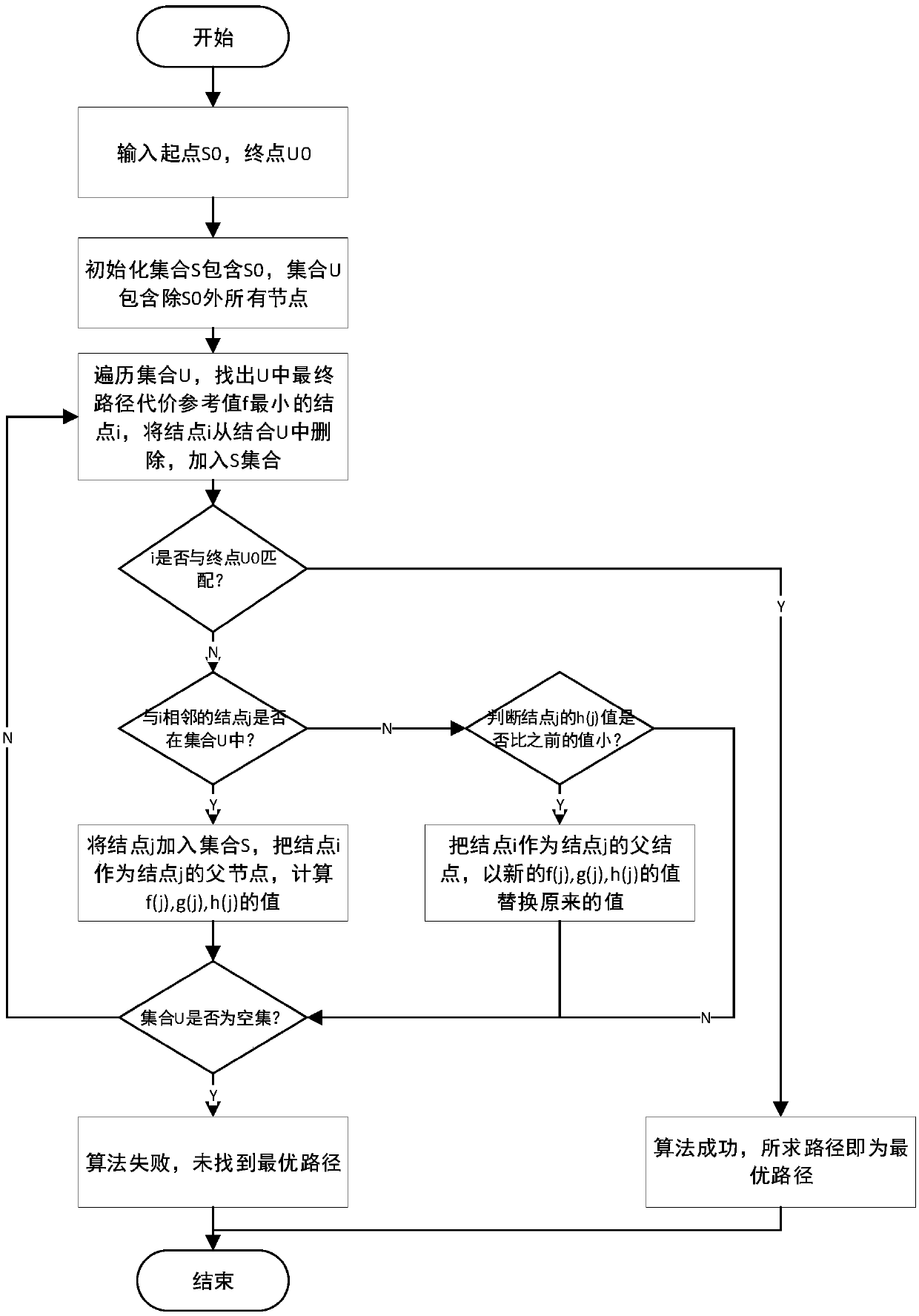
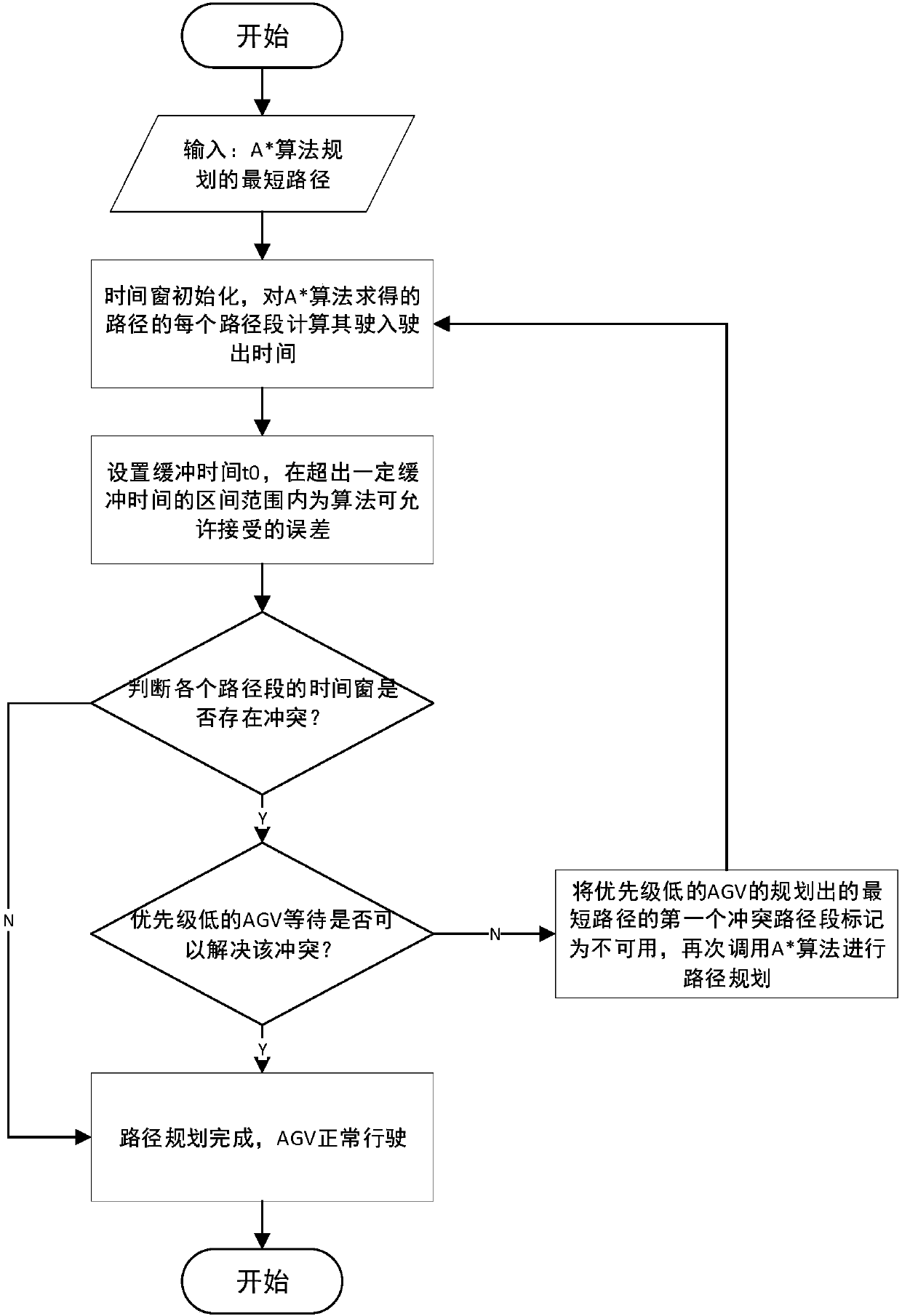
Dispatching and route-planning method for multiple AGVs used for material transportation in factory
PendingCN107727099AMake up for the shortcomings of not being able to get the optimal pathOptimal planning pathNavigational calculation instrumentsAlgorithmPlanning approach
The invention relates to a dispatching and route-planning method for multiple AGVs used for material transportation in a factory. The method comprises the following steps: (1) modeling material transportation scenes in a factory, including the travelling routes of AGVs, AGV charging points, loading and unloading points and standby zones for AGVs; (2) storing allocated tasks in a queue; (3) findingout one AGV closest to a current-task issuing site from a set of available AGVs; (4) calculating the shortest route from a current-task start point and a current-task stop point by using an A* algorithm; and (5) calling a time-window algorithm for maintenance of a time-window vector table of the shortest route obtained in the step (4). Compared with traditional A* algorithms, a heuristic functionin the A* algorithm used in the invention takes the traveling cost and turning cost of the AGVs on roads in a workshop into consideration, the time-window vector table of each route section is maintained, and whether conflicts exist in planned routes is determined by judging whether superposition exists; so the problems of collision conflicts, deadlock and the like of AGV route planning are effectively overcome.
Owner:SHANDONG UNIV
Software implementation of synchronous memory barriers
InactiveUS6996812B2Program synchronisationDigital computer detailsProcessor registerInter-processor interrupt
Selectively emulating sequential consistency in software improves efficiency in a multiprocessing computing environment. A writing CPU uses a high priority inter-processor interrupt to force each CPU in the system to execute a memory barrier. This step invalidates old data in the system. Each CPU that has executed a memory barrier instruction registers completion and sends an indicator to a memory location to indicate completion of the memory barrier instruction. Prior to updating the data, the writing CPU must check the register to ensure completion of the memory barrier execution by each CPU. The register may be in the form of an array, a bitmask, or a combining tree, or a comparable structure. This step ensures that all invalidates are removed from the system and that deadlock between two competing CPUs is avoided. Following validation that each CPU has executed the memory barrier instruction, the writing CPU may update the pointer to the data structure.
Owner:IBM CORP
Special encoding of known bad data
InactiveUS7100096B2Less likely to fall into deadlock conditionRedundant data error correctionMulti processorComputer science
A multi-processor system in which each processor receives a message from another processor in the system. The message may contain corrupted data that was corrupted during transmission from the preceding processor. Upon receiving the message, the processor detects that a portion of the message contains corrupted data. The processor then replaces the corrupted portion with a predetermined bit pattern known or otherwise programmed into all other processors in the system. The predetermined bit pattern indicates that the associated portion of data was corrupted. The processor that detects the error in the message preferably alerts the system that an error has been detected. The message now containing the predetermined bit pattern in place of the corrupted data is retransmitted to another processor. The predetermined bit pattern will indicate that an error in the message was detected by the previous processor. In response, the processor detecting the predetermined bit pattern preferably will not alert the system of the existence of an error. The same message with the predetermined bit pattern can be retransmitted to other processors which also will detect the presence of the predetermined bit pattern and in response not alert the system of the presence of an error. As such, because only the first processor to detect an error alerts the system of the error and because messages containing uncorrectable errors still are transmitted through the system, fault isolation is improved and the system is less likely to fall into a deadlock condition.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
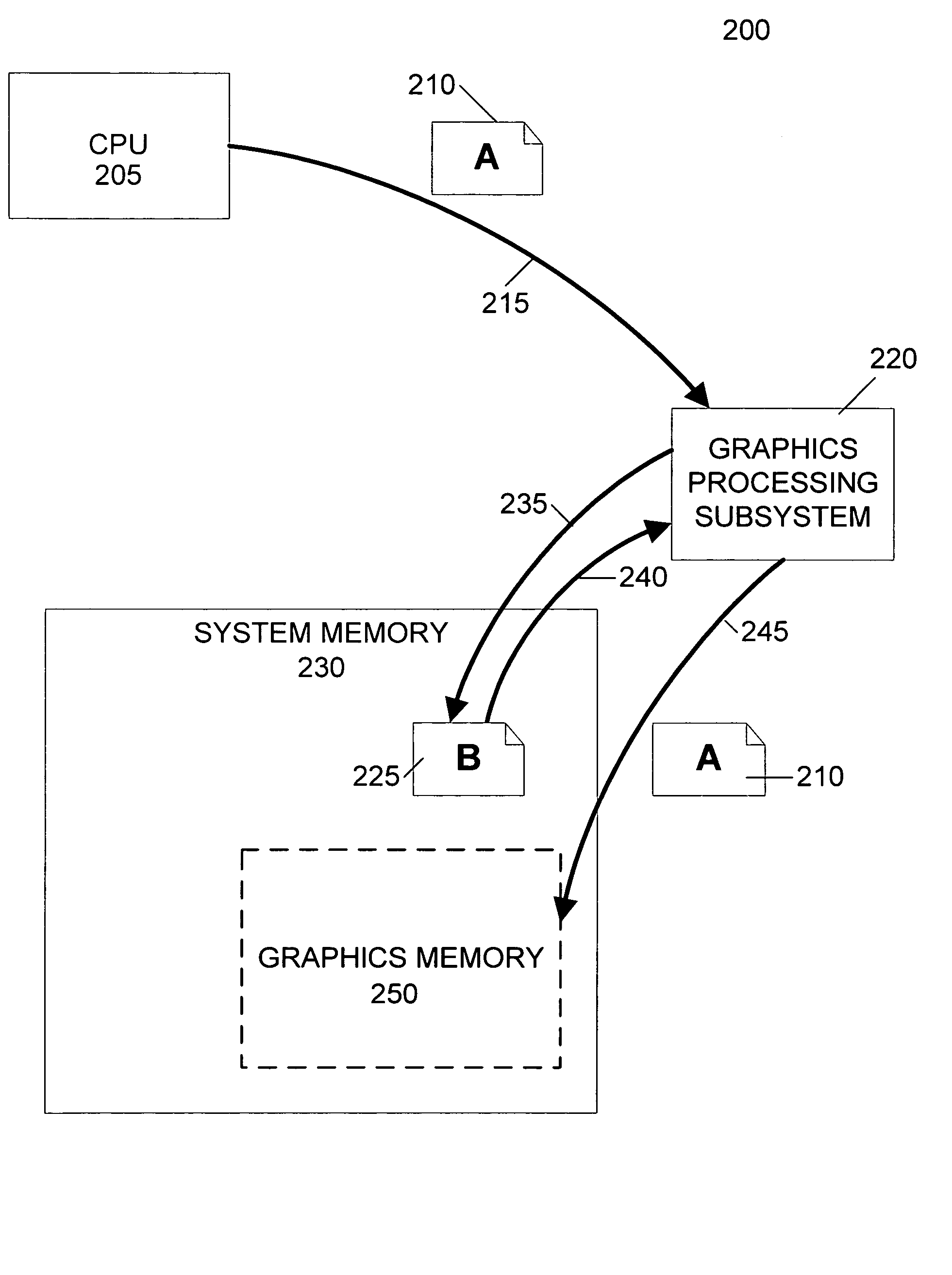
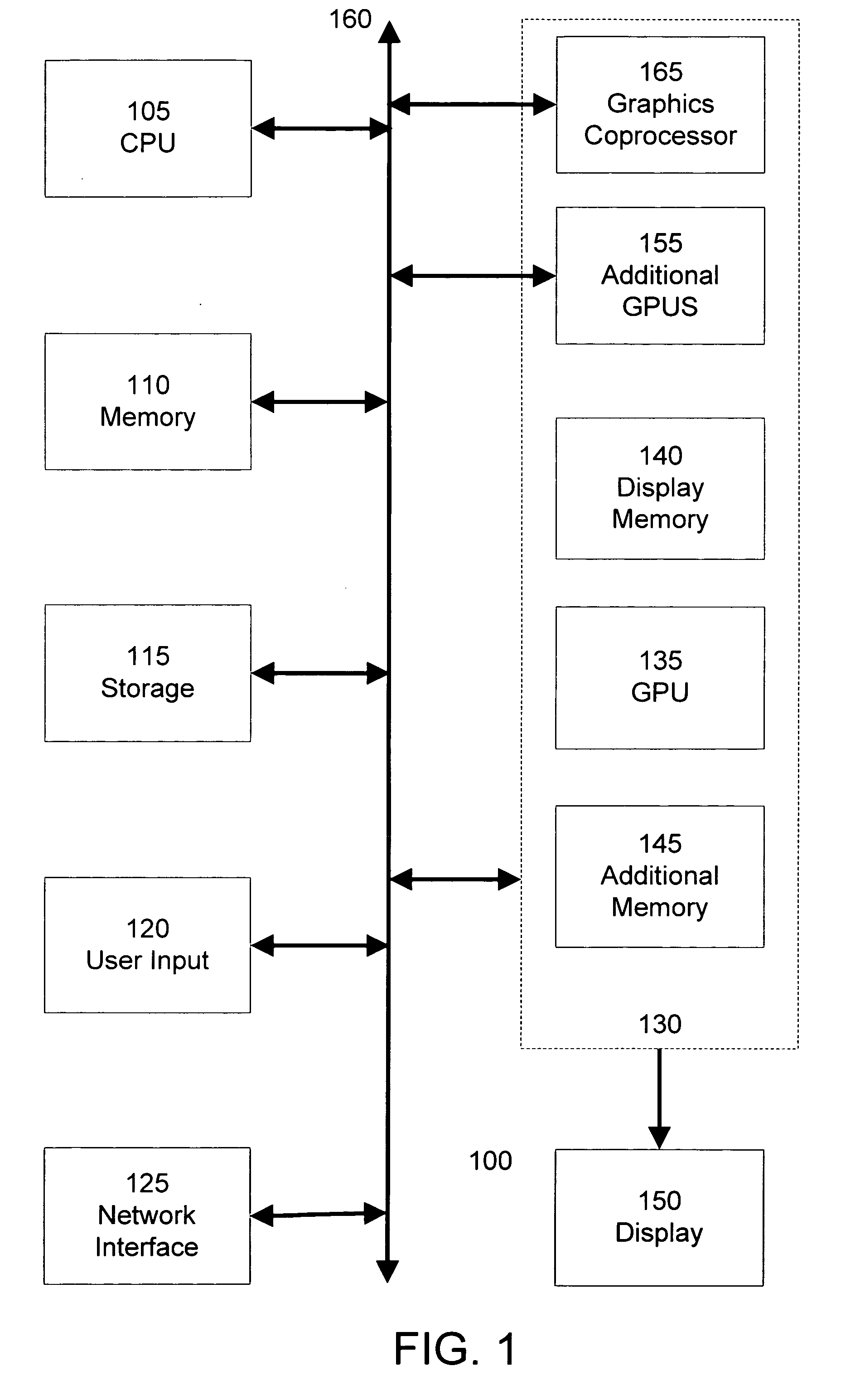
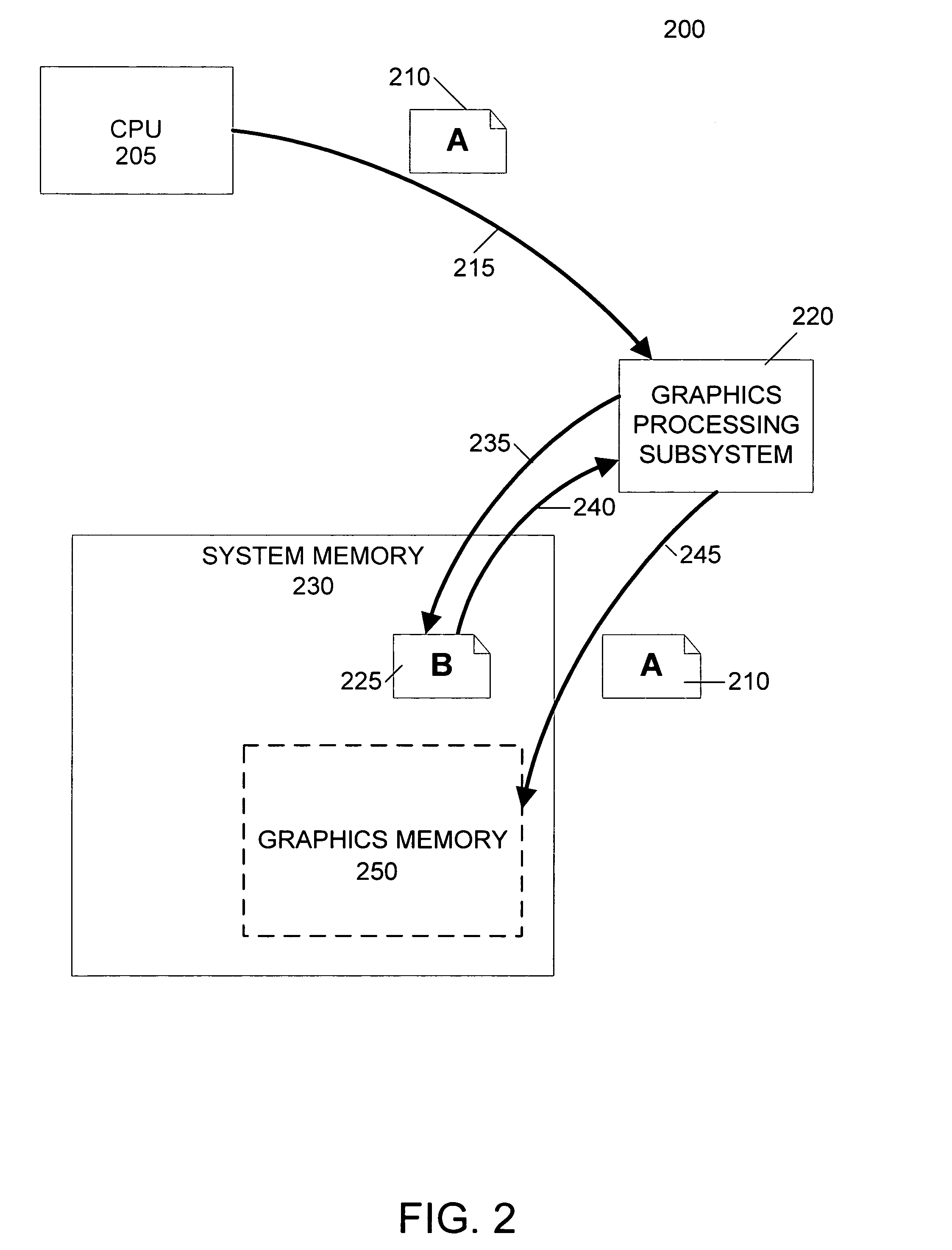
GPU rendering to system memory
InactiveUS20050237329A1Avoid deadlockHigh degree of two-dimensional localityMemory adressing/allocation/relocationCathode-ray tube indicatorsMemory addressGraphics
A graphics processing subsystem uses system memory as its graphics memory for rendering and scanout of images. To prevent deadlock of the data bus, the graphics processing subsystem may use an alternate virtual channel of the data bus to access additional data from system memory needed to complete a write operation of a first data. In communicating with the system memory, a data packet including extended byte enable information allows the graphics processing subsystem to write large quantities of data with arbitrary byte masking to system memory. To leverage the high degree of two-dimensional locality of rendered image data, the graphics processing subsystem arranges image data in a tiled format in system memory. A tile translation unit converts image data virtual addresses to corresponding system memory addresses. The graphics processing subsystem reads image data from system memory and converts it into a display signal.
Owner:NVIDIA CORP
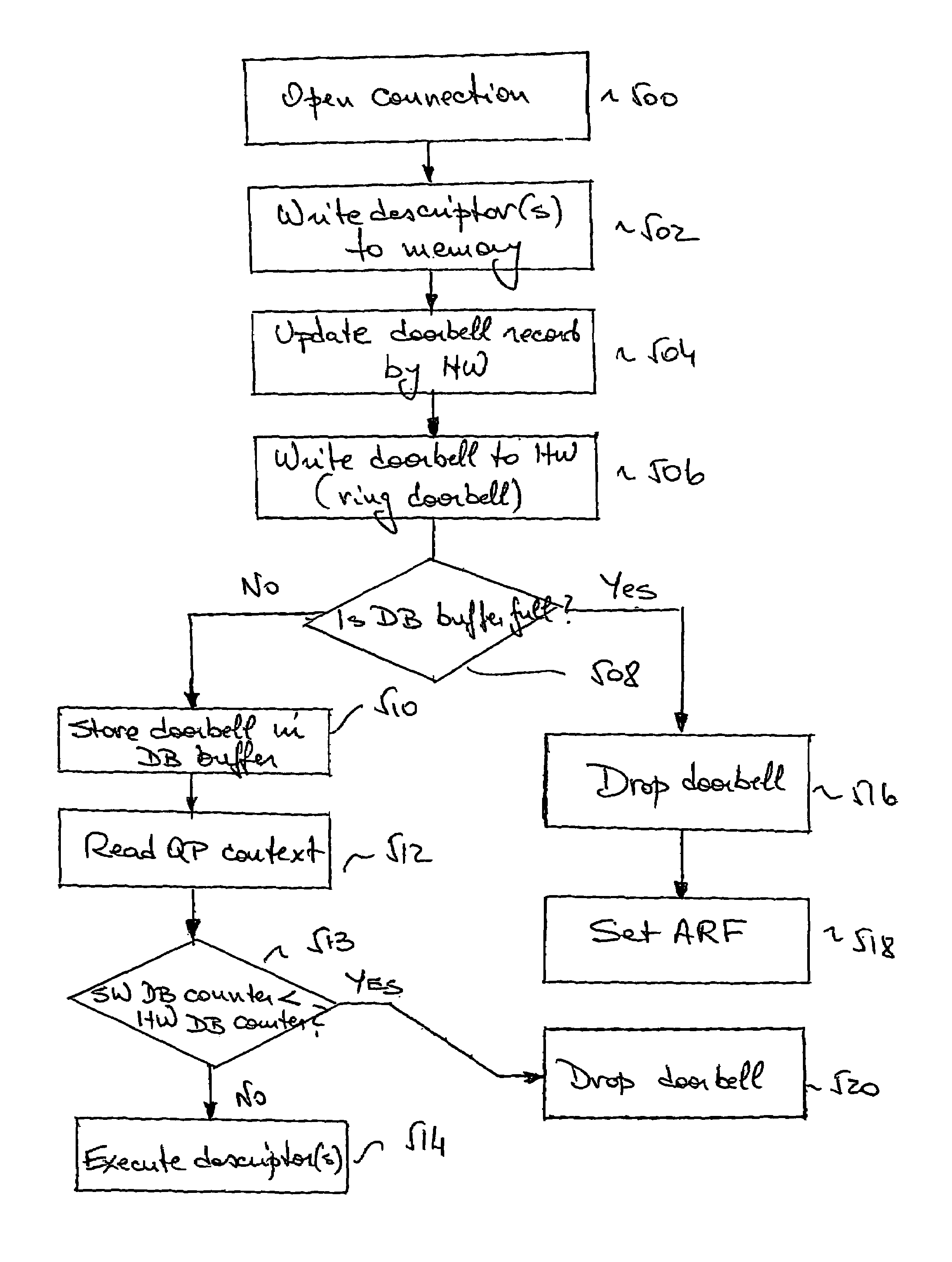
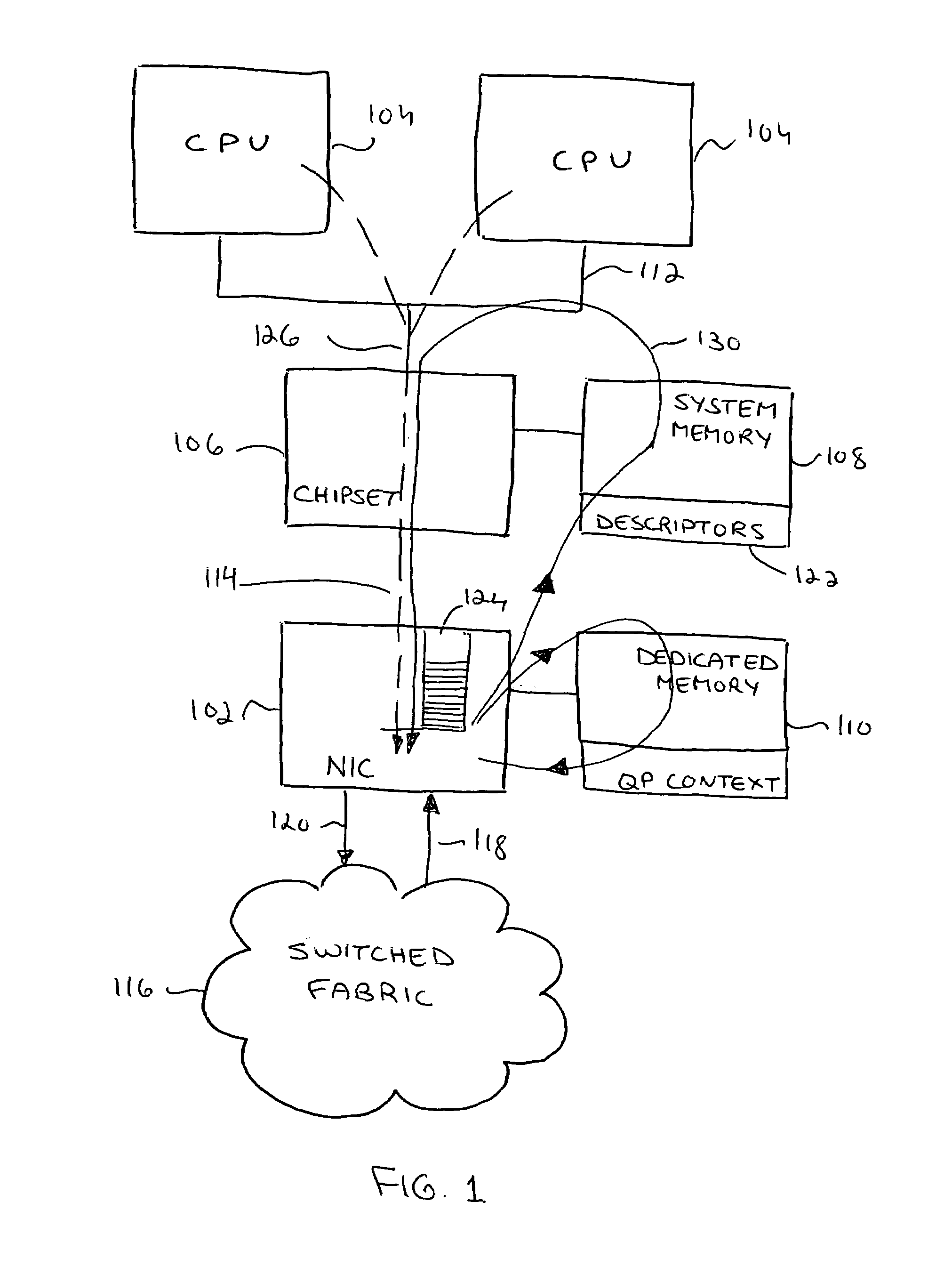
Method, system and protocol that enable unrestricted user-level access to a network interface adapter
ActiveUS7653754B2Avoid deadlockUnrestricted user-level access to the NICConveying record carriersMultiple digital computer combinationsDoorbellApplication software
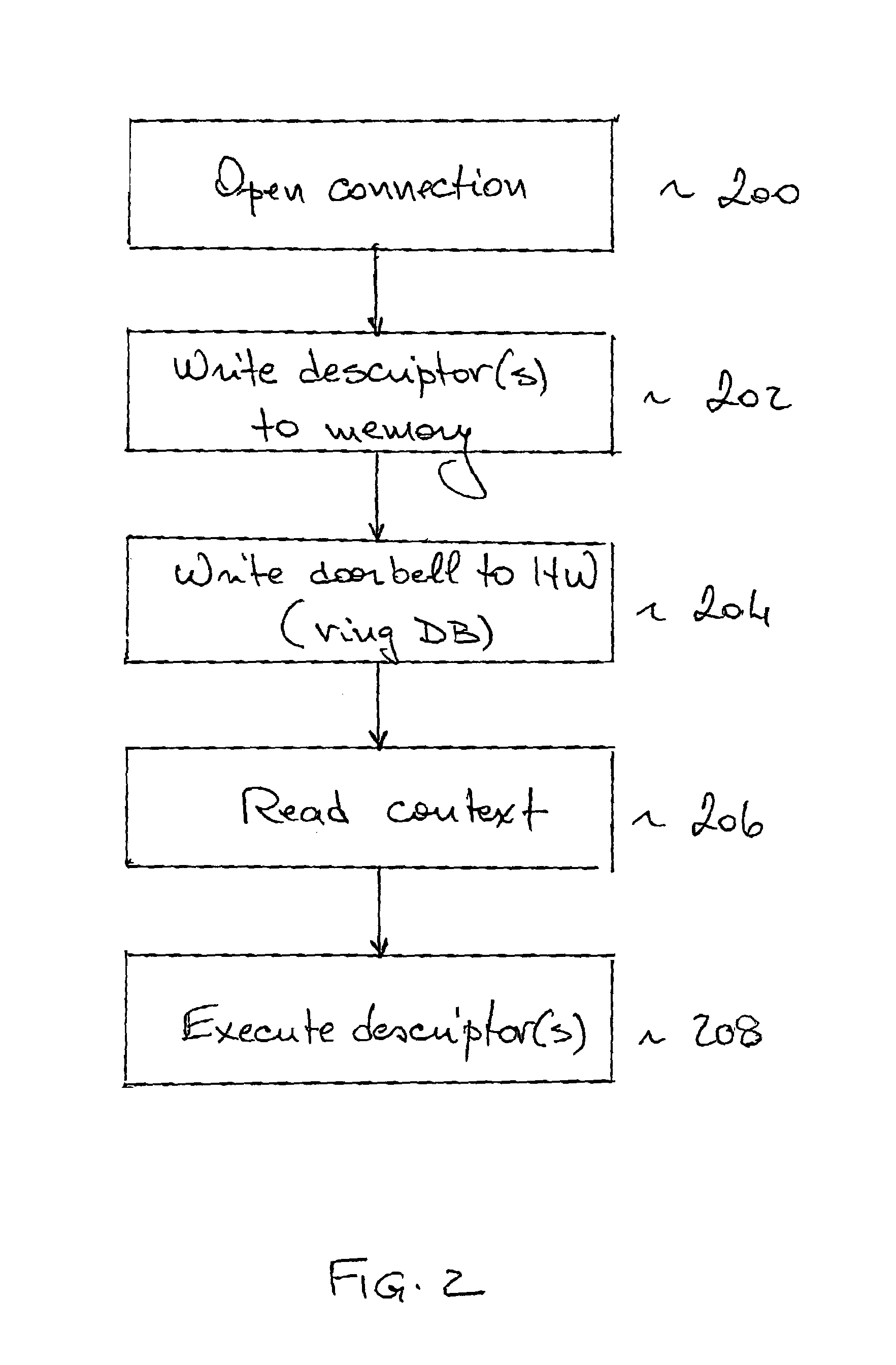
A method for preventing deadlock in communication between a host software application and a network interface card (NIC), comprises writing a doorbell associated with at least one descriptor having a descriptor context to a buffer in the NIC, dropping at least one doorbell from the buffer if the buffer is full, thereby allowing a write of a new doorbell to the buffer, and recovering each dropped doorbell for further execution of descriptors associated with this doorbell. The descriptor execution is in order of posting by the application to the NIC. A system implementing the method comprises a doorbell drop mechanism and a doorbell recovery mechanism.
Owner:MELLANOX TECHNOLOGIES LTD
Reconfigurable noc for customizing traffic and optimizing performance after noc synthesis
Systems and methods described herein are directed to solutions for Network on Chip (NoC) interconnects that supports reconfigurability to support a variety of different traffic profiles each having different sets of traffic flows after the NoC is designed and deployed in a SoC. Reconfiguration of the NoC to map and load a new traffic profile or change the currently mapped traffic profile is performed by an external optimization module which maps various transactions of a given traffic profile to the NoC and reconfigure the NoC hardware by loading the computed mapping information. As part of the mapping process, load balancing between NoC layers may be performed by automatically assigning the transactions in the traffic profile to be routed over certain NoC layers and channels, automatically determining the routes based on the bandwidth requirements of the transaction. The deadlock avoidance and isolation properties of various transactions are maintained during the mapping.
Owner:INTEL CORP
Deadlock avoidance mechanism in multi-threaded applications
InactiveUS20080209422A1Avoid deadlockResource allocationMemory systemsComputerized systemApplication software
A computer-implemented method for implementing a deadlock avoidance mechanism to prevent a plurality of threads from deadlocking in a computer system wherein a first thread of the plurality of threads request for a first resource is provided. The computer-implemented method includes employing the deadlock avoidance mechanism to intercept the request. The computer-implemented method also includes examining a status of the first resource. The computer-implemented method further includes, if the first resource is owned, identifying an owner of the first resource, analyzing the owner of the first resource to determine if the owner of the first resource is requesting a second resource, and analyzing the second resource to determine if the second resource is owned by the first thread. The computer-implemented method yet also includes, if the first thread owns the second resource, preventing deadlocking by handling a potential deadlock situation.
Owner:HEWLETT PACKARD DEV CO LP
Method and system for achieving fair command processing in storage systems that implement command-associated priority queuing
ActiveUS20080104283A1Avoid hungerEliminating and minimizing of and priority-related deadlockTransmissionInput/output processes for data processingComputer accessPriority inversion
In certain, currently available data-storage systems, incoming commands from remote host computers are subject to several levels of command-queue-depth-fairness-related throttles to ensure that all host computers accessing the data-storage systems receive a reasonable fraction of data-storage-system command-processing bandwidth to avoid starvation of one or more host computers. Recently, certain host-computer-to-data-storage-system communication protocols have been enhanced to provide for association of priorities with commands. However, these new command-associated priorities may lead to starvation of priority levels and to a risk of deadlock due to priority-level starvation and priority inversion. In various embodiments of the present invention, at least one additional level of command-queue-depth-fairness-related throttling is introduced in order to avoid starvation of one or more priority levels, thereby eliminating or minimizing the risk of priority-level starvation and priority-related deadlock.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Packet reassembly and deadlock avoidance for use in a packet switch
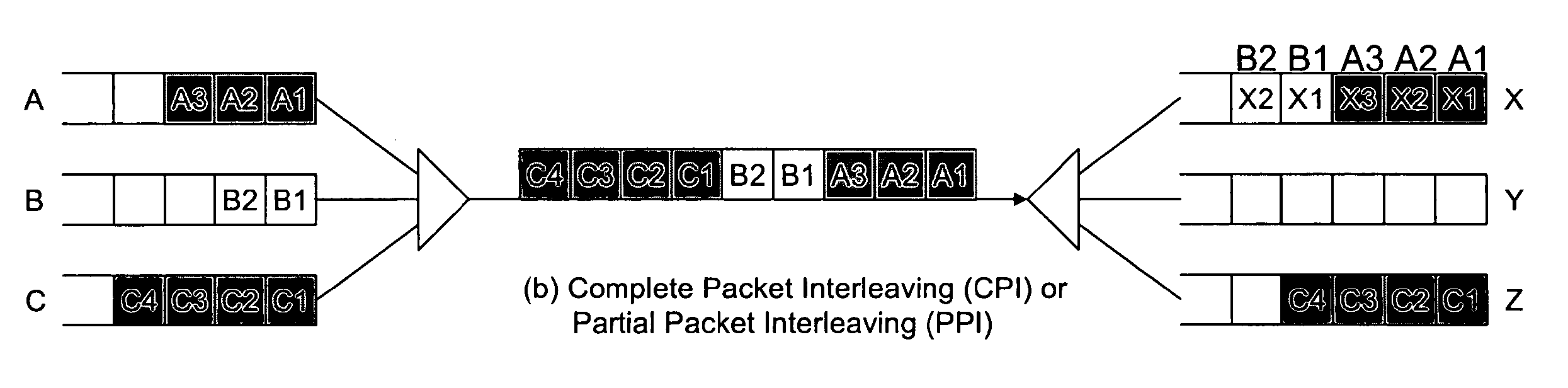
InactiveUS20050025141A1Multiplex system selection arrangementsData switching by path configurationCell spaceDeadlock
Practical packet reassembly in large, multi-plane, multi-stage switches is possible by using a scheduling technique called dynamic packet interleaving. With dynamic packet interleaving scheduling, if more than one packet is contending for the same output link in a switch module, an arbiter in the switch module gives priority to a partial packet (i.e., to a packet that has had at least one cell sent to the queue). The number of reassembly queues required to ensure reassembly is dramatically reduced (e.g., to the number of paths multiplied by the number of scheduling priorities). Deadlock may be avoided by guaranteeing (e.g., reserving) at least one cell space for all partial packets.
Owner:POLYTECHNIC INST OF NEW YORK
Reordering and flushing commands in a computer memory subsystem
InactiveUS6895482B1Avoid deadlockDetermining memory cycle performance penaltiesConcurrent instruction executionMemory systemsParallel computingMemory controller
An improved computer memory subsystem determines the most efficient memory command to execute. The physical location and any address dependency of each incoming memory command to a memory controller is ascertained and that information accompanies the command for categorization into types of command. For each type of memory command, there exists a command FIFO and associated logic in which a programmable number of the memory commands are selected for comparison with each other, with the memory command currently executing, and with the memory command previously chosen for execution. The memory command having the least memory cycle performance penalty is selected for execution unless that memory command has an address dependency. If more than one memory command of that type has the least memory cycle performance penalty, then the oldest is selected for execution. Memory commands of that type are selected for execution each subsequent cycle until a valid memory command of that type is no longer available, or until a predetermined number has been executed, or until a memory command of another type has higher priority. If an address dependency exists between memory commands of different types, then memory commands of the same type of the oldest memory command is executed to avoid deadlock.
Owner:IBM CORP
Noc interface protocol adaptive to varied host interface protocols
InactiveUS20150103822A1Hinder propertyDigital computer detailsData switching by path configurationData setTransport layer
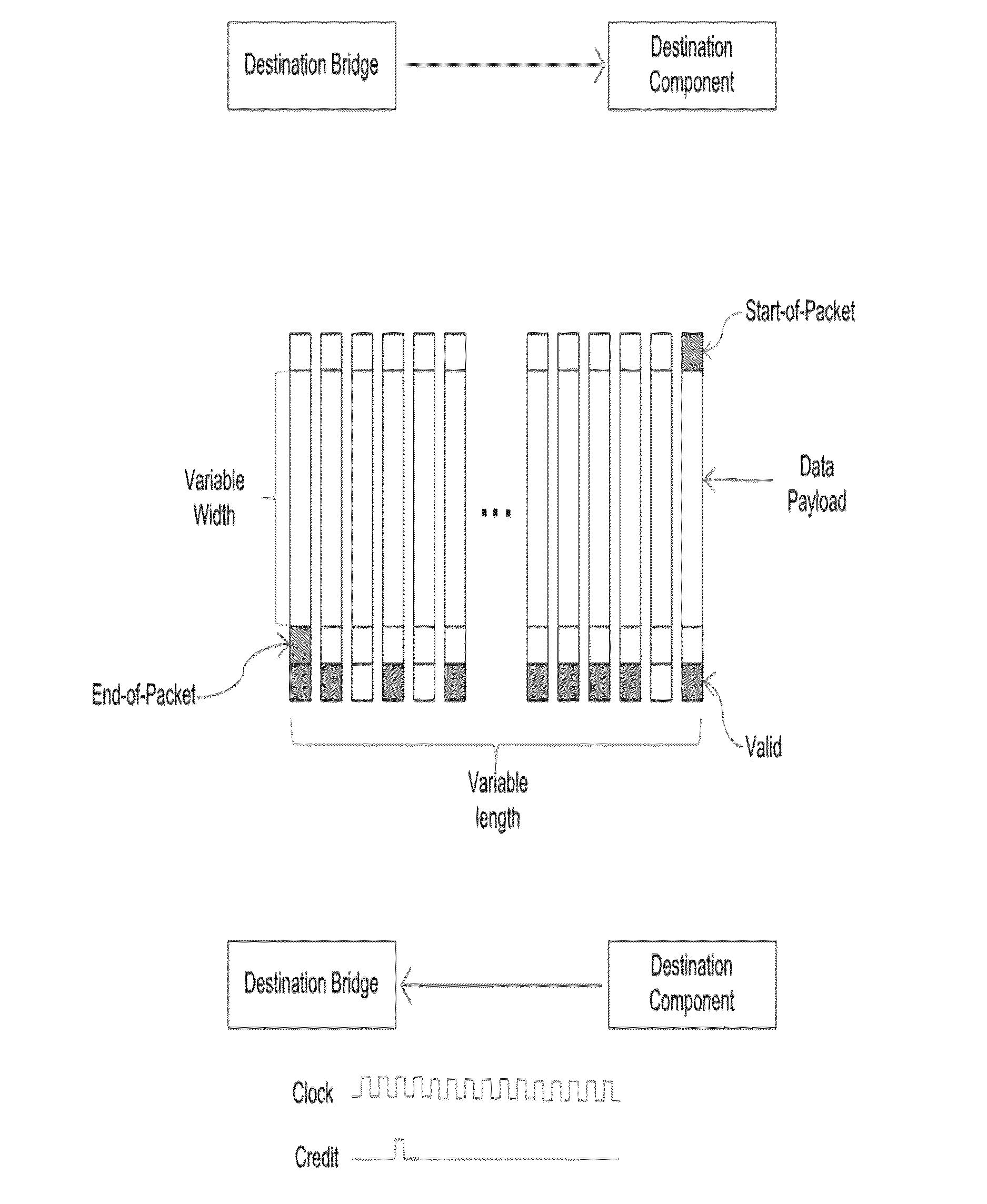
Systems and methods described herein are directed to solutions for Network on Chip (NoC) interconnects that support a variety of different component protocols each having different sets of data and / or metadata even after the NoC is designed and finalized. Example implementations include, automatically changing format of packets received from an originating SoC component by an originating bridge based on a NoC interface protocol and then transmitting the packet across the NoC interconnect to a destination bridge. The format may again be changed based on the protocol of the destination SoC component. The proposed protocol can be configured to map various transactions presented to it, be they packets belonging to the physical, data link layer, network layer or transport layer. As part of the mapping process, virtual channels for latency or deadlock avoidance may be created and may be maintained for the entire life of the packet within the NoC.
Owner:INTEL CORP
Deferred incorporation of updates for spatial indexes
ActiveUS20060074977A1Digital data information retrievalData processing applicationsDatabase indexSystem maintenance
The present invention provides techniques by which updates may be incorporated in database indexes without causing deadlocks of user transactions. In deferred-incorporate update, the updates are propagated to the index only at transaction commit time. A method of handling transactions including updates in a database management system comprises the steps of receiving an update to a database maintained by the database management system, the update operable to cause an index of the database to be modified, recording the update in a log, and receiving an indication that the transaction is to be committed and in response, incorporating the update from the log into an index of the database. The update may comprise an insert operation and / or a delete operation.
Owner:ORACLE INT CORP
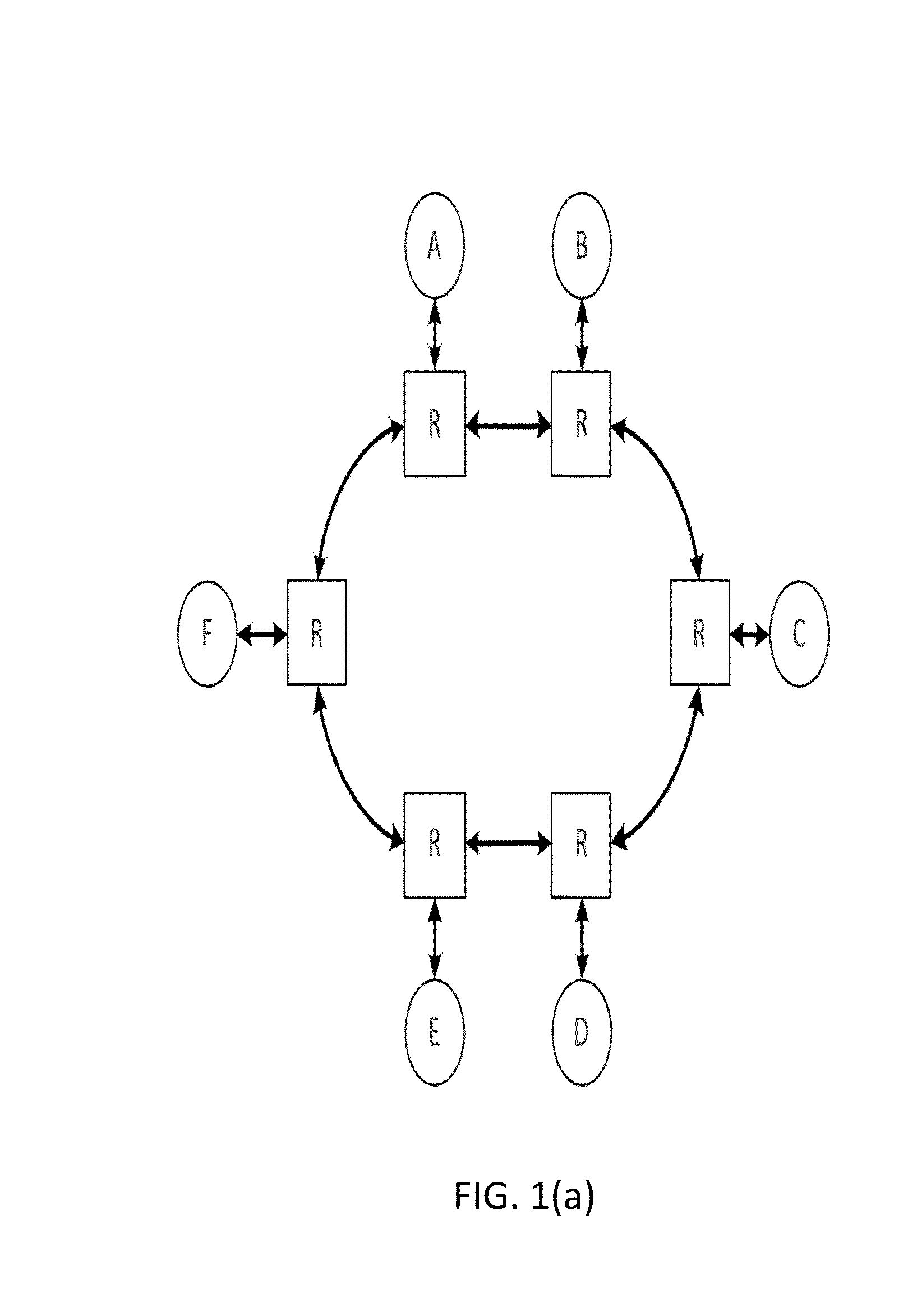
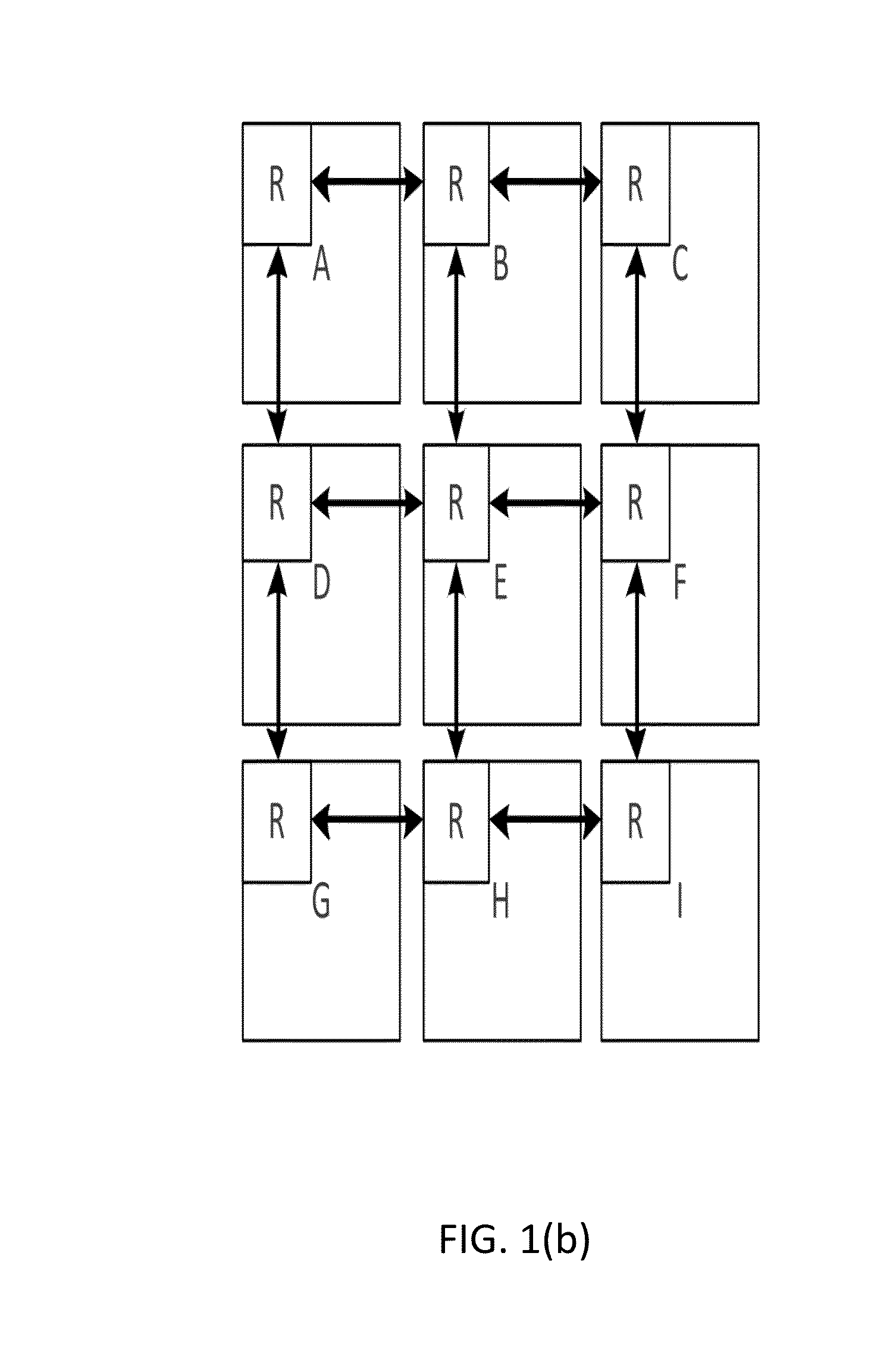
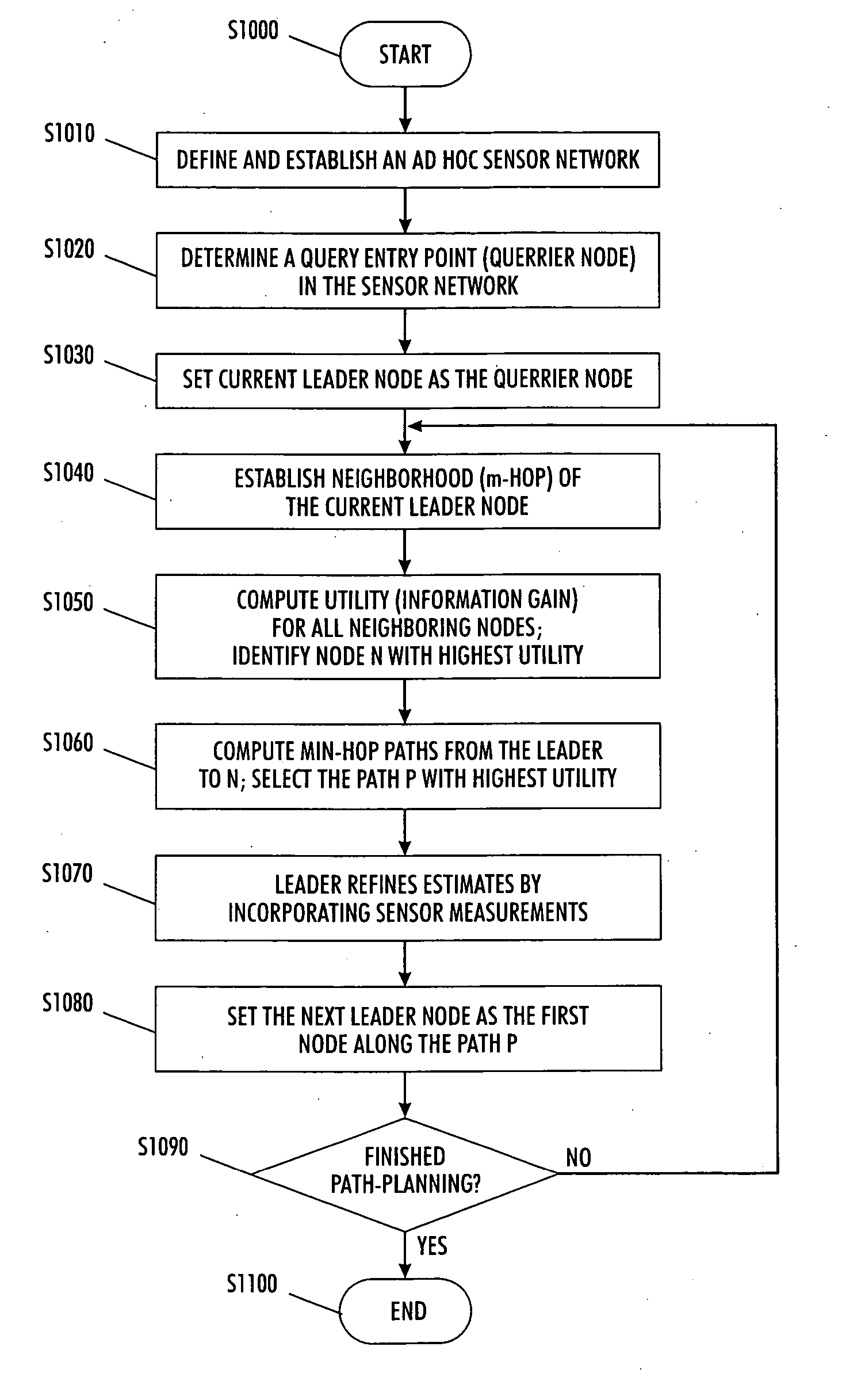
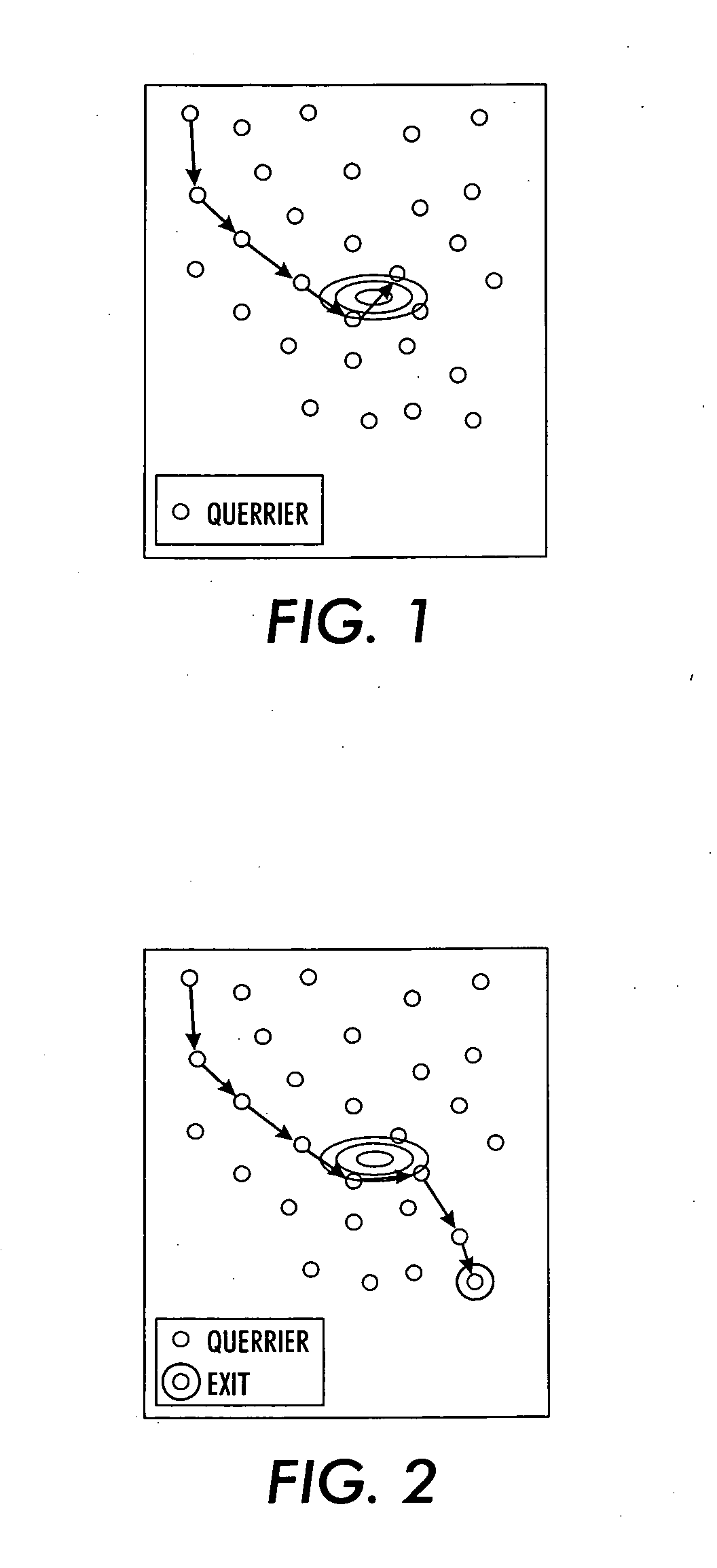
Information driven routing in ad hoc sensor networks
InactiveUS20050138200A1Improve performanceEnhanced informationError preventionTransmission systemsShort path algorithmEntry point
A sensor network routing is formulated as a joint optimization problem taking into account routing cost and information aggregation. Information gain is used explicitly to optimize the routing path. The optimization approach involves a shortest path algorithm in a modified network graph. A method is provided that routes queries from an arbitrary entry point to high activity network sensor regions using inputs from sensor nodes along the path to refine the message. The multiple step look-ahead approach provides deadlock avoidance and routing around sensor network holes. For point-to-point query routing, a method based on real-time A* (RTA*) search is provided to find a path which takes detours efficiently to maximize information aggregation. Future information expected to be gained along the path from an arbitrary node to an exit node may be estimated to allow the selection of a successor sensor node.
Owner:CISCO TECH INC
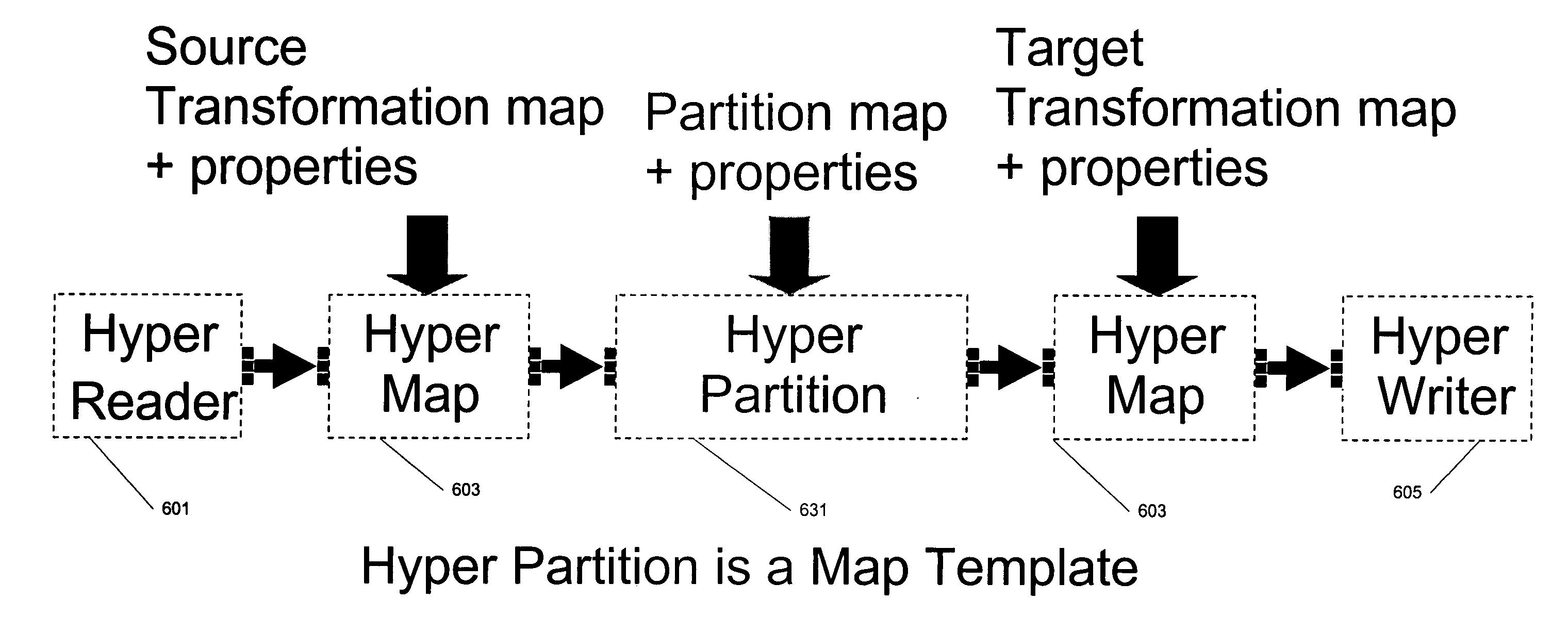
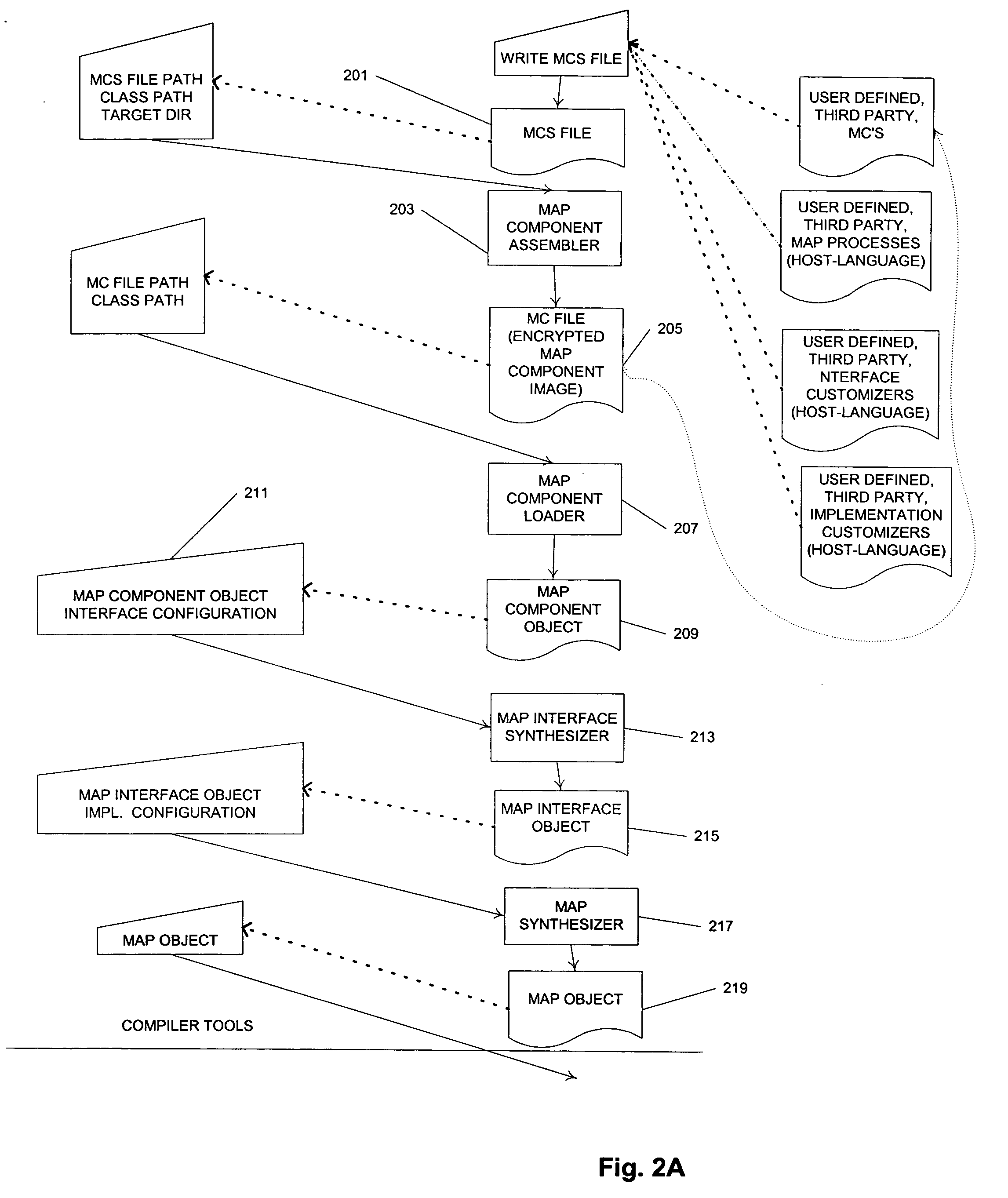
Execution environment for data transformation applications
ActiveUS20070271562A1Error preventionFrequency-division multiplex detailsExtensibilityData transformation
The execution environment provides for scalability where components will execute in parallel and exploit various patterns of parallelism. Dataflow applications are represented by reusable dataflow graphs called map components, while the executable version is called a prepared map. Using runtime properties the prepared map is executed in parallel with a thread allocated to each map process. The execution environment not only monitors threads, detects and corrects deadlocks, logs and controls program exceptions, but also data input and output ports of the map components are processed in parallel to take advantage of data partitioning schemes. Port implementation supports multi-state null value tokens to more accurately report exceptions. Data tokens are batched to minimize synchronization and transportation overhead and thread contention.
Owner:ACTIAN CORP
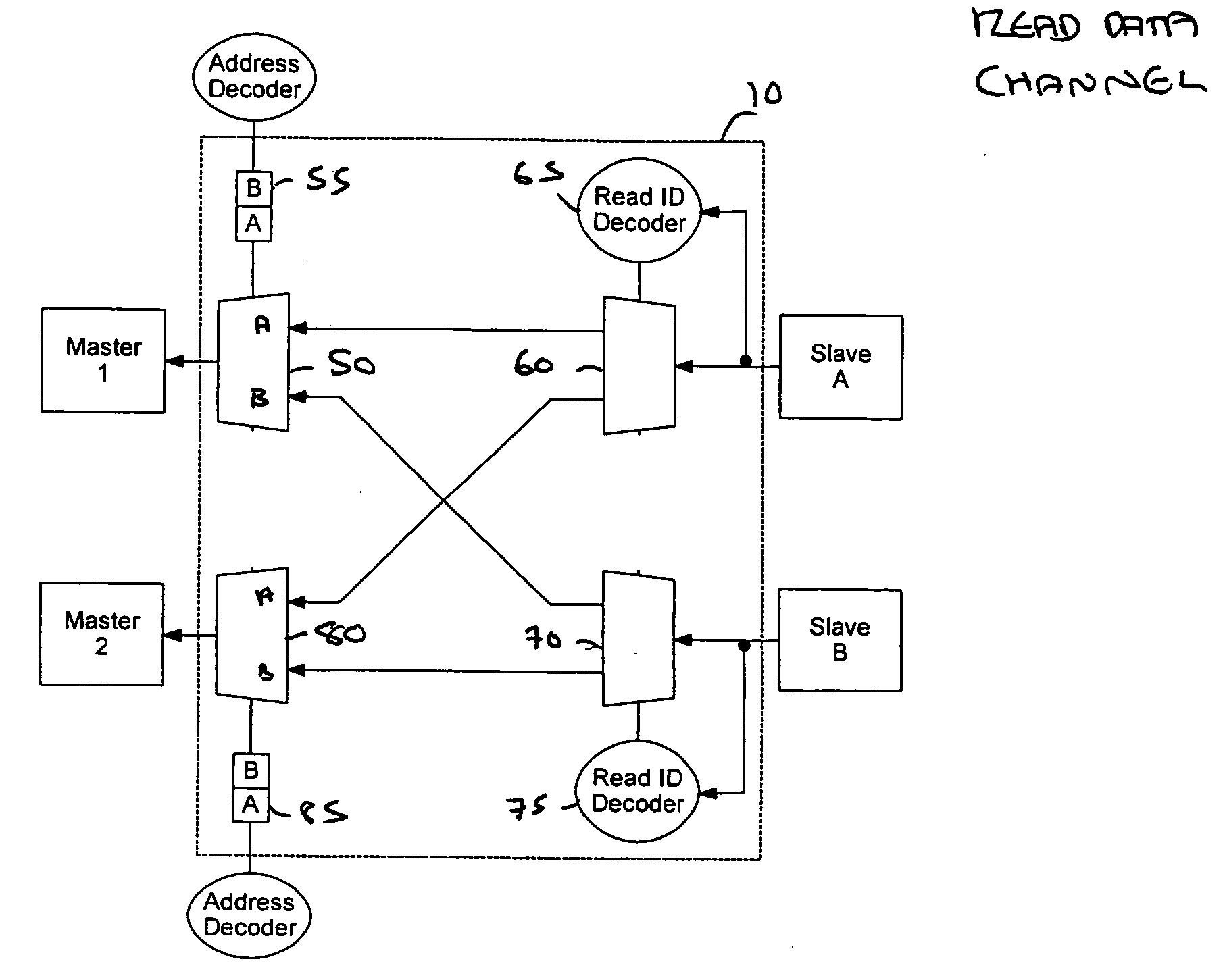
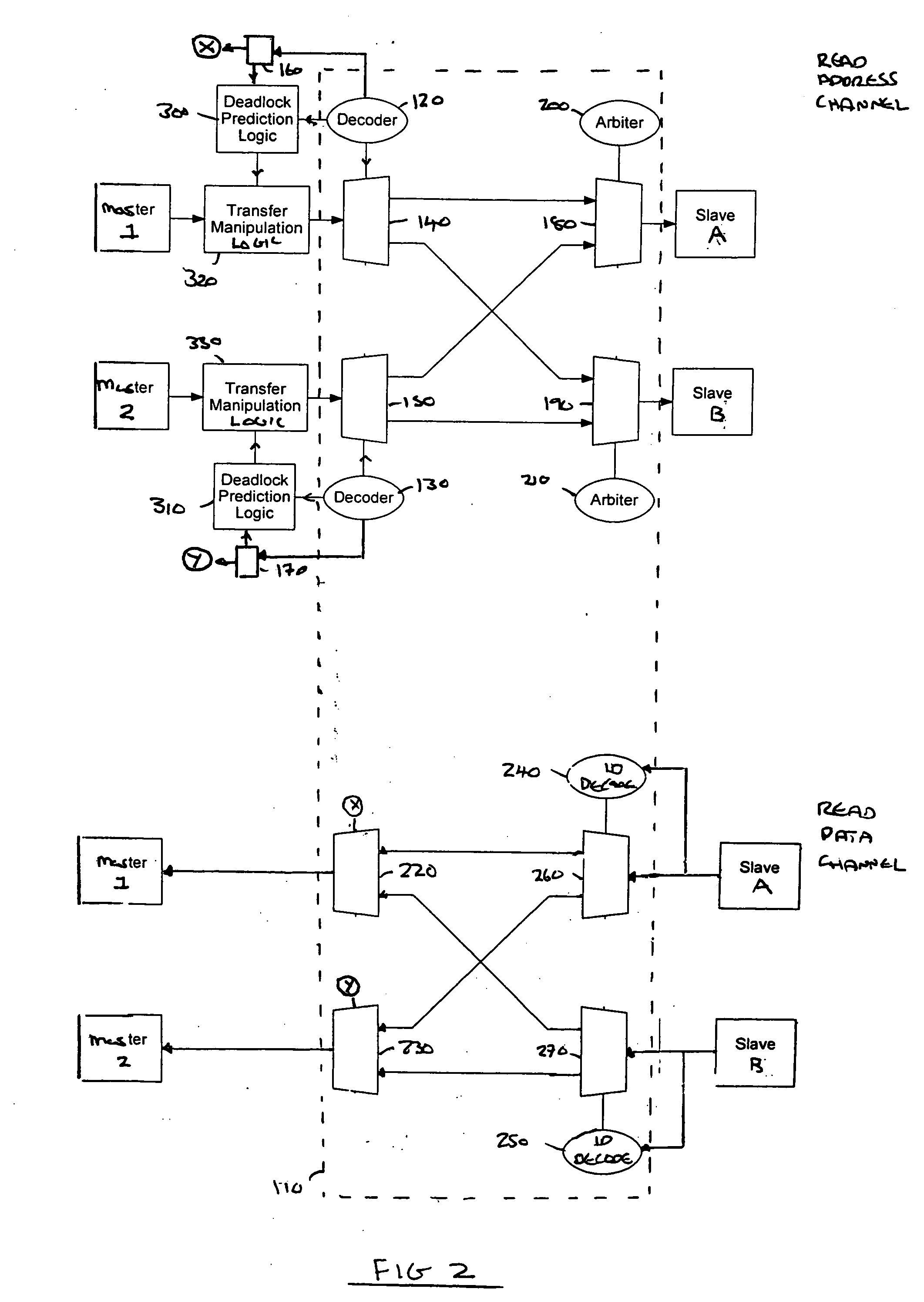
Bus deadlock avoidance
Bus logic, a data processing apparatus and a method is disclosed. The bus logic is operable to couple a plurality of master logic units with a plurality of slave logic units to enable data transfers to occur, each master logic unit being operable to perform an address transfer which, when received by a specified one of the plurality of slave logic units, causes an associated data transfer to be performed between that master logic unit and the specified one of the plurality of slave logic units, each of the plurality of slave logic units being required to complete a data transfer, once initiated, prior to performing any further data transfers, at least one of the plurality of slave logic units being operable to perform data transfers in an order which differs from that in which associated address transfers were received by that slave logic unit. The bus logic comprises interconnect logic configurable, responsive to an address transfer, to couple a master logic unit with a slave logic unit to enable a data transfer to take place. The bus logic also comprises deadlock prediction logic operable to receive information indicative of each address transfer and to determine whether propagation of that address transfer may cause the interconnect logic to be configured such that a deadlock situation can occur in which data transfers are unable to can take place between affected master logic units and slave logic units and, if so, to prevent the propagation of that address transfer. This enables the configuration of the interconnect logic to be carefully controlled such that it cannot be arranged to enable a deadlock situation to occur.
Owner:ARM LTD
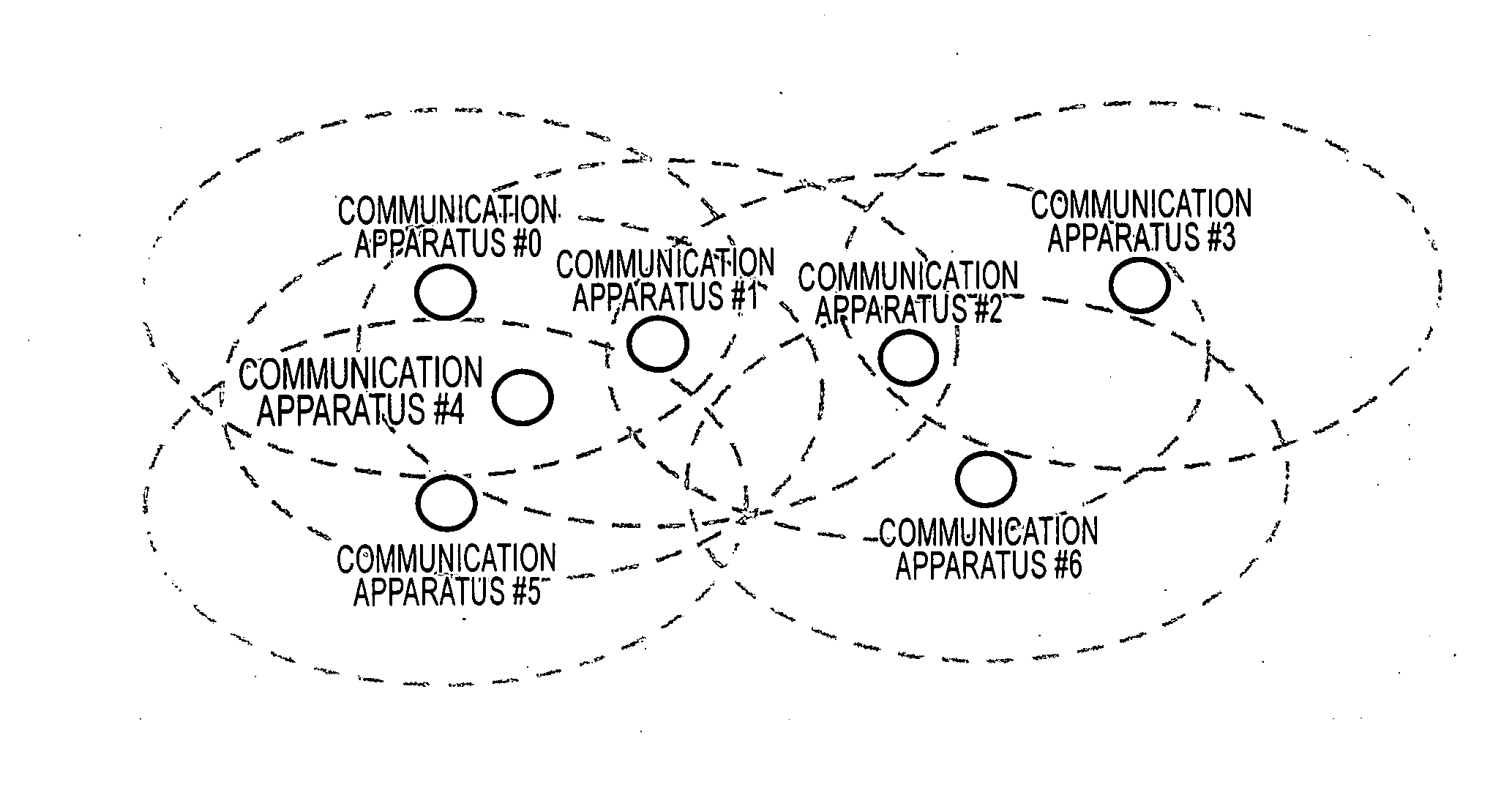
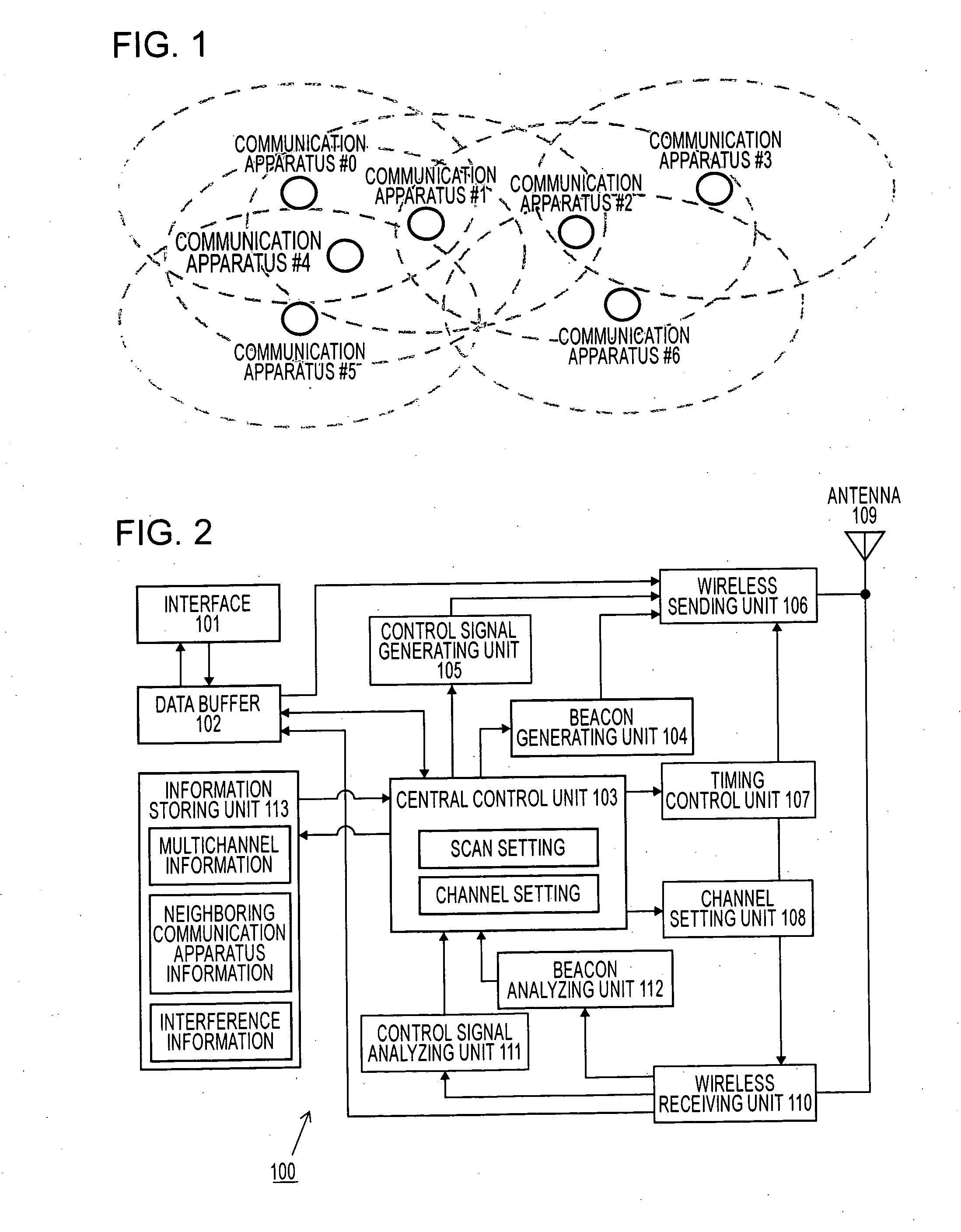
Radio communication system, radio communication device, radio communication method, and computer program
InactiveUS20060251098A1Network topologiesTime-division multiplexCommunications systemCommunication device
A deadlock state wherein each of communication stations cannot acknowledge one another's existence is avoided, and an autonomous decentralized multi-channel wireless network is formed. Communication stations select the channel which as many communication stations as possible can receive as a beacon sending channel based on the interference information of each channel specified in a beacon signal at the time of new participation or refresh. Also, in the event that there is a peripheral station which cannot receive a beacon, change in the beacon sending channel is attempted. The communication stations can receive a beacon from all peripheral station by performing beacon receiving operation over a particular channel, and can avoid the deadlock state.
Owner:SONY CORP
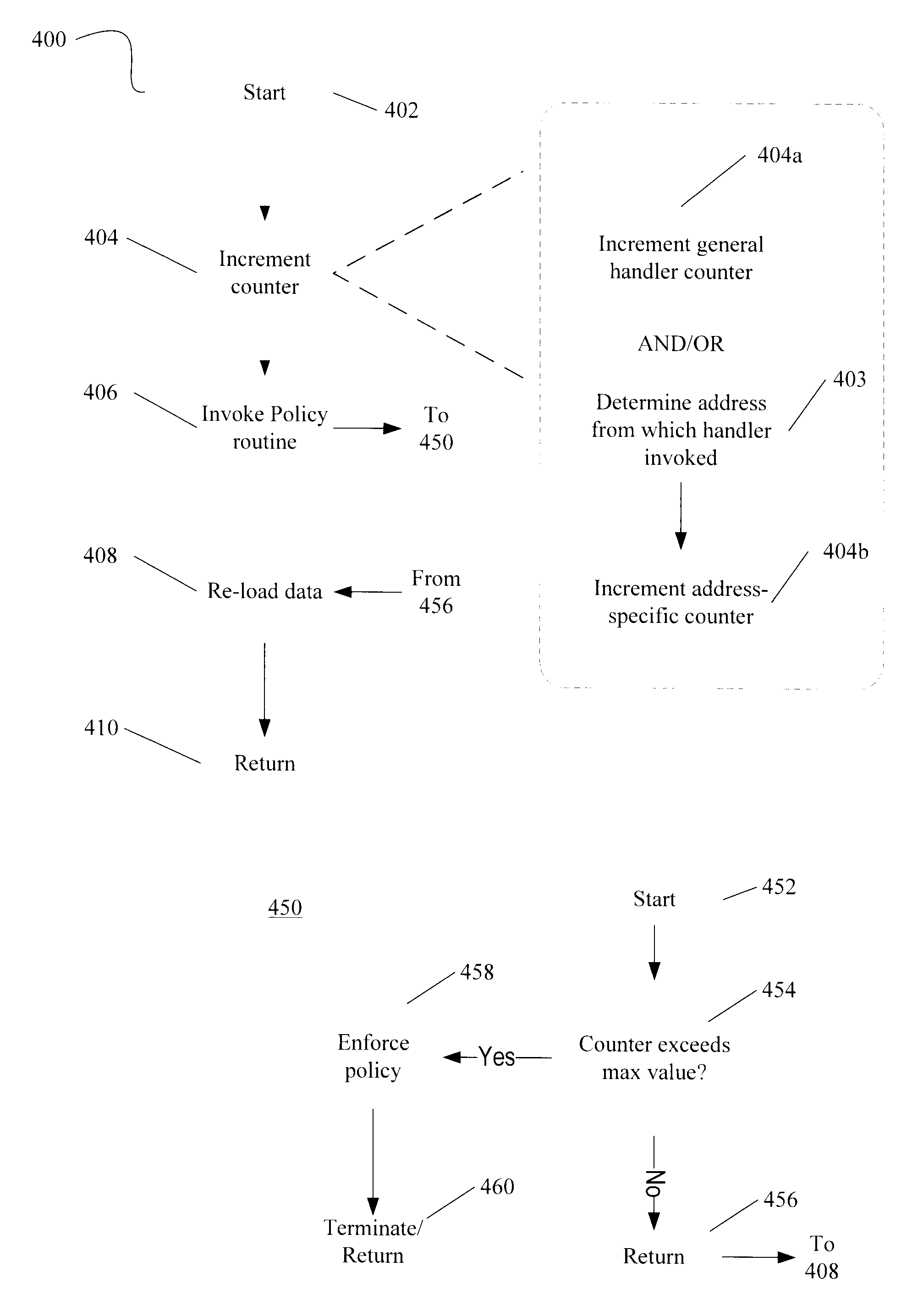
Obscuring Memory Access Patterns in Conjunction with Deadlock Detection or Avoidance
ActiveUS20090172304A1Memory architecture accessing/allocationComputer security arrangementsMonitoring featuresDeadlock
Methods, apparatus and systems for memory access obscuration are provided. A first embodiment provides memory access obscuration in conjunction with deadlock avoidance. Such embodiment utilizes processor features including an instruction to enable monitoring of specified cache lines and an instruction that sets a status bit responsive to any foreign access (e.g., write or eviction due to a read) to the specified lines. A second embodiment provides memory access obscuration in conjunction with deadlock detection. Such embodiment utilizes the monitoring feature, as well as handler registration. A user-level handler may be asynchronously invoked responsive to a foreign write to any of the specified lines. Invocation of the handler more frequently than expected indicates that a deadlock may have been encountered. In such case, a deadlock policy may be enforced. Other embodiments are also described and claimed.
Owner:INTEL CORP
Data processing method and system
ActiveCN103886079AEnhanced Concurrency ProcessingSolve bottlenecksCommerceSpecial data processing applicationsMessage queueData information
The invention discloses a data processing method and system. The data processing method comprises the first stage of data writing, wherein data information sent by a client-side is received, persistence is carried out on the data information into a database, and to-be-processed data in the data information are written into a Redis cache; the second state of data processing, wherein the to-be-processed data are obtained from the Redis cache and are processed, processed result data are sent to an information queue, the result data are obtained from the information queue, and persistence is carried out the result data into the database. As the Redis cache stores the to-be-processed data, concurrent preemption and processing of the to-be-processed data in the Redis cache are achieved, and persistence on the processed result data into the database is achieved in a serialization mode through the information queue. According to the data processing method and system, concurrency processing of the data is enhanced, good experience is brought to clients, the bottleneck problem brought to the database under the condition of high concurrency is avoided, the deadlock problem of the database is avoided, and consistency and completeness of the data are ensured.
Owner:西安京迅递供应链科技有限公司
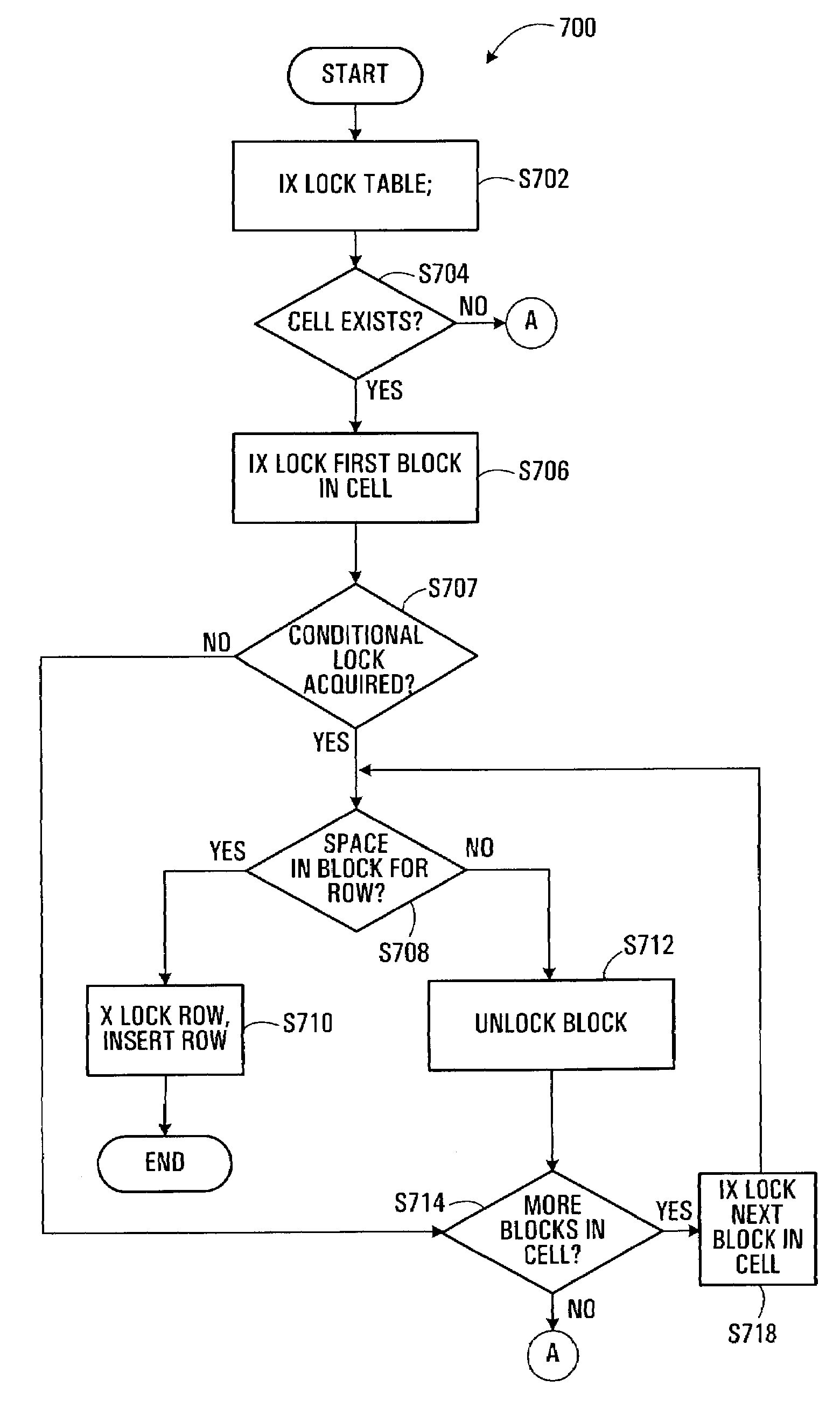
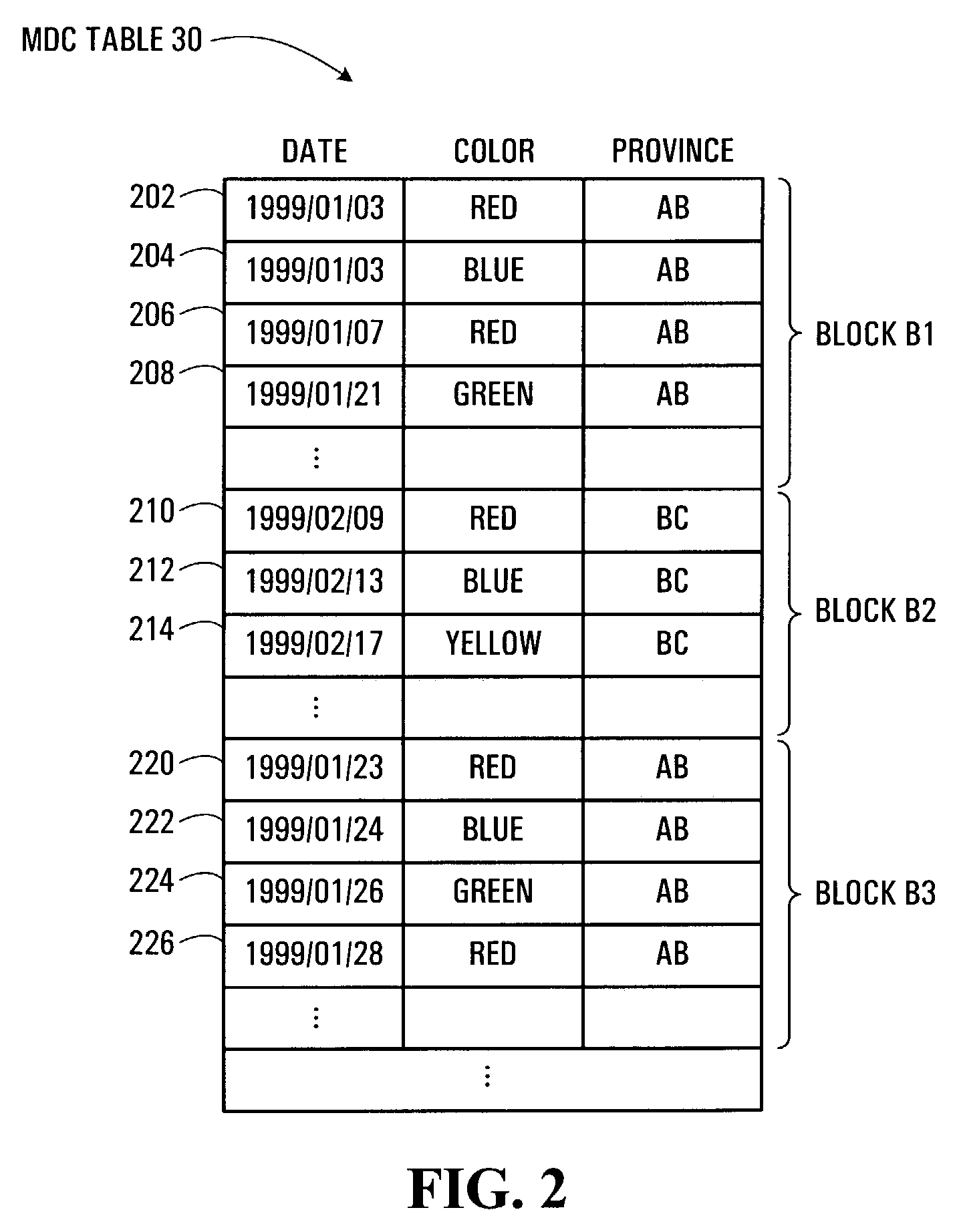
System and method for a multi-level locking hierarchy in a database with multi-dimensional clustering
InactiveUS7236974B2Avoiding undue locking overheadAvoid overheadData processing applicationsMulti-dimensional databasesGranularityRelational database
A multi-level locking hierarchy for a relational database includes a locking level applied to a multi-dimensionally clustering table, a locking level applied to blocks within the table, and a locking level applied to rows within the blocks. The hierarchy leverages the multi-dimensional clustering of the table data for efficiency and to reduce lock overhead. Data is normally locked in order of coarser to finer granularity to limit deadlock. When data of finer granularity is locked, data of coarser granularity containing the finer granularity data is also locked. Block lock durations may be employed to ensure that a block remains locked if any contained row remains locked. Block level lock attributes may facilitate detection of at least one of a concurrent scan and a row deletion within a block. Detection of the emptying of a block during a scan of the block may bar scan completion in that block.
Owner:IBM CORP
Simulation of program execution to detect problem such as deadlock
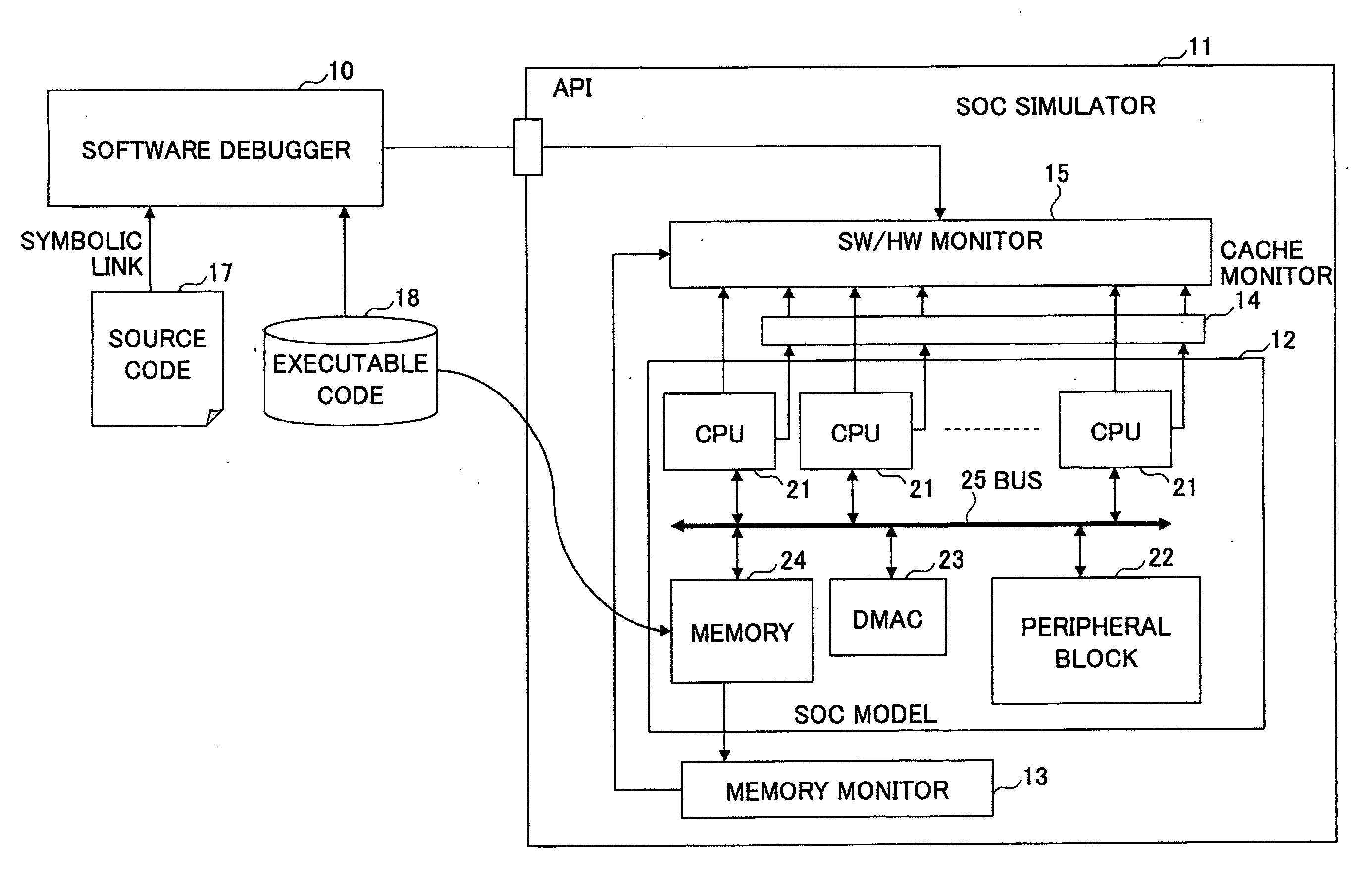
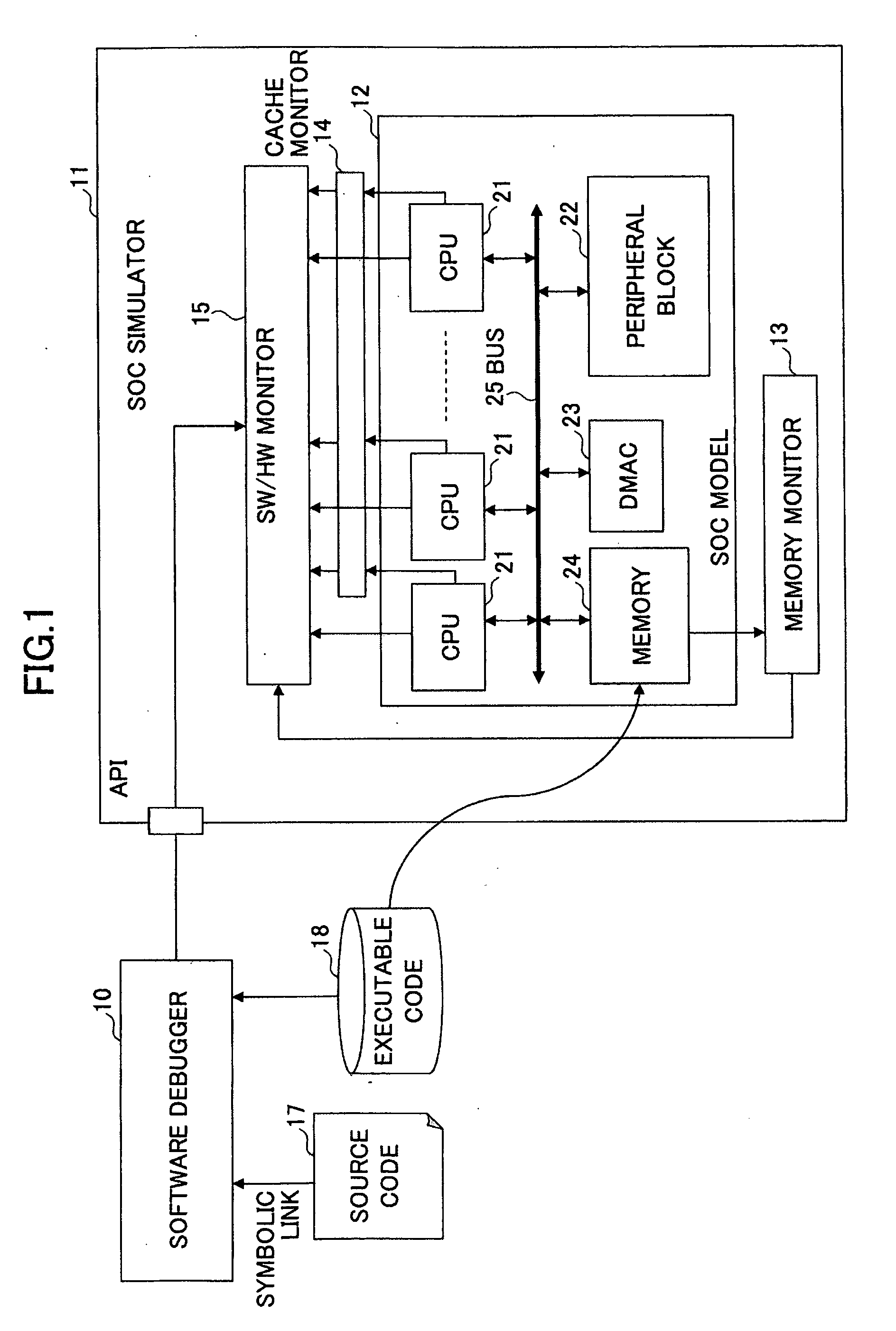
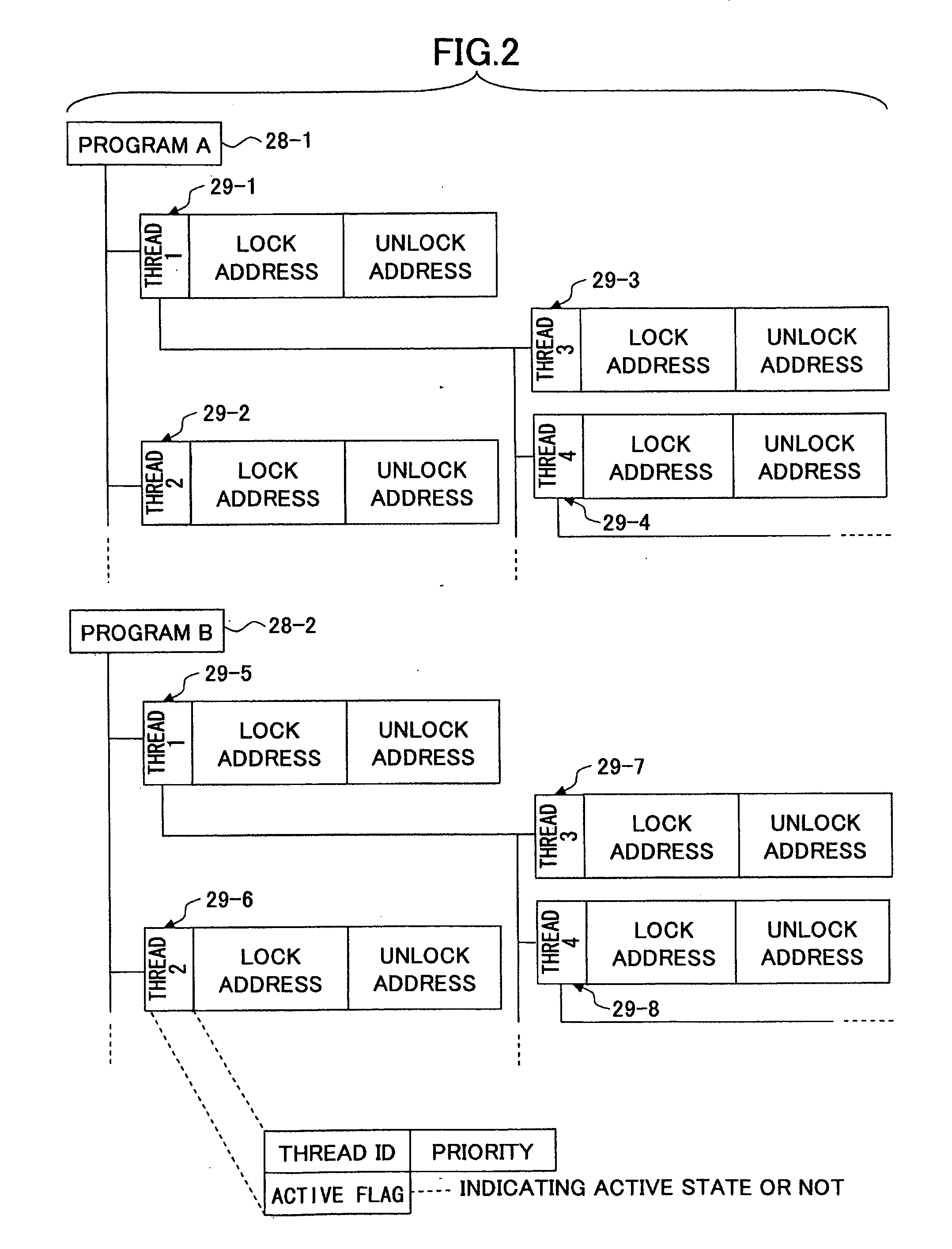
InactiveUS20090037888A1Error detection/correctionSpecific program execution arrangementsDeadlockMonitor function
A method of simulating software by use of a computer includes executing a program inclusive of a plurality of threads by a hardware model implemented as software on a software simulator, utilizing a monitor function of the simulator to collect information about accesses by monitoring accesses made by the plurality of threads with respect to resources provided in the hardware model, utilizing the monitor function to detect, from the collected information, overlapping accesses made to an identical resource area by two or more of the threads, and utilizing the monitor function to generate a message for warning of the overlapping accesses.
Owner:CYPRESS SEMICON CORP
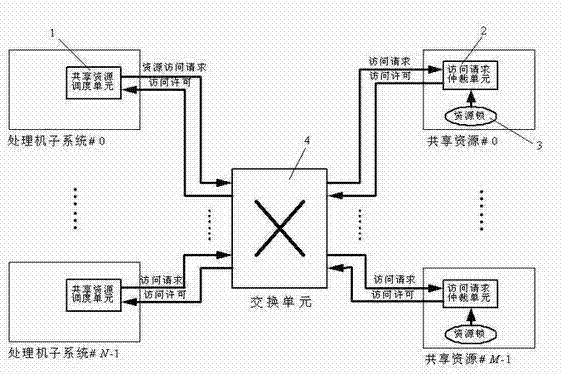
A shared resource scheduling method and system for distributed parallel processing
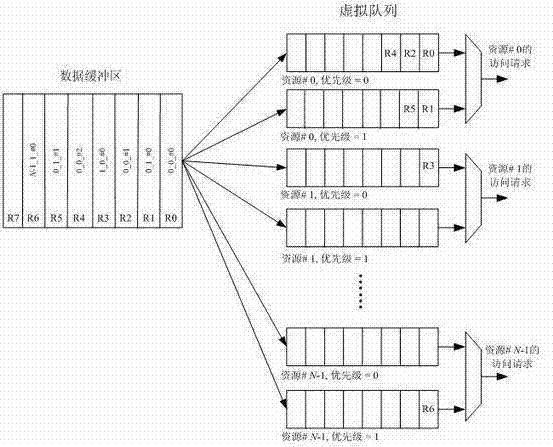
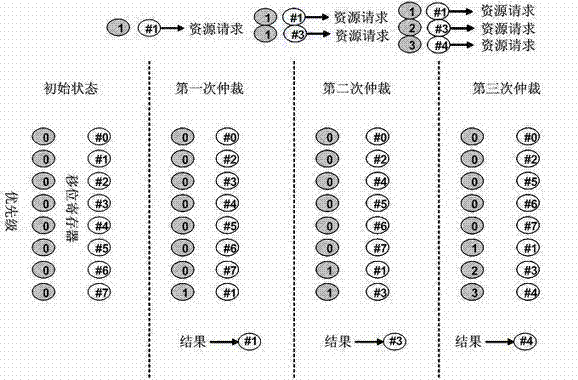
InactiveCN102298539ASolve the access contention problemAvoid deadlockProgram initiation/switchingParallel processingShared resource
The invention discloses a shared resource scheduling method and system used in distributed parallel processing. The method and system are based on a distributed operation mechanism. The shared resource scheduling units distributed in each processor subsystem are distributed in each shared Resource locks and resource request arbitration units are implemented. These distributed processing units communicate by sending messages (resource access requests / permissions) to each other through the switching unit. The shared resource scheduling unit in the processor subsystem uses virtual queue technology to manage all resource access requests in the data cache, that is, a special queue is specially opened for each accessible shared resource. Resource locks in shared resources are used to ensure the uniqueness of access to shared resources at any time. Resource locks have two states: lock occupation and lock release. The request arbitration unit in the shared resource uses a priority-based fair polling algorithm to arbitrate resource access requests from different processing nodes. The invention can effectively avoid the competition problem when each processing node accesses the shared resource, can also avoid the deadlock of the shared resource and the starvation problem of the processing node, and provides high-efficiency mutually exclusive access to the shared resource.
Owner:EAST CHINA NORMAL UNIV
Class-based deterministic packet routing
InactiveUS8306042B1Avoid deadlockMultiplex system selection arrangementsSpecial service provision for substationAnalysis dataMulti processor
Aspects of the invention pertain to deterministic packet routing systems and methods in multiprocessor computing architectures. Packets are analyzed to determine whether they are memory request packets or memory reply packets. Depending upon the packet, it is routed through nodes in the multiprocessor computer architecture in either an XY or YX path. Request and reply packets are sent in opposing routes according to a deterministic routing scheme. Multiport routers are placed at nodes in the architecture to pass the packets, using independent request and response virtual channels to avoid deadlock conditions.
Owner:GOOGLE LLC
Optimizing control method for single intersection signal in saturated traffic state
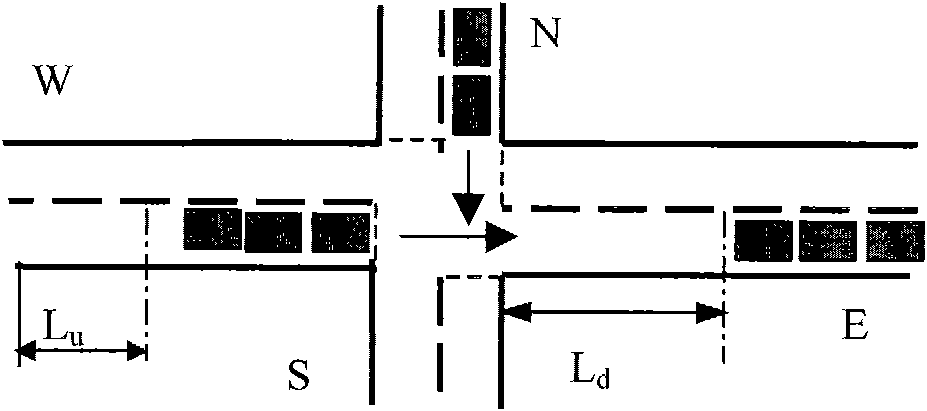
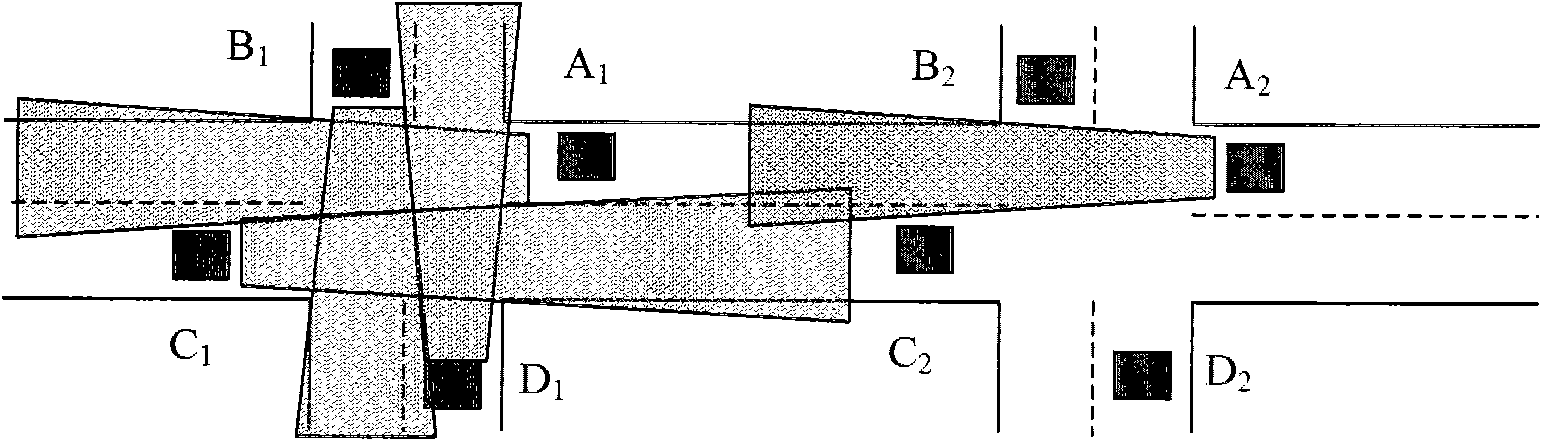
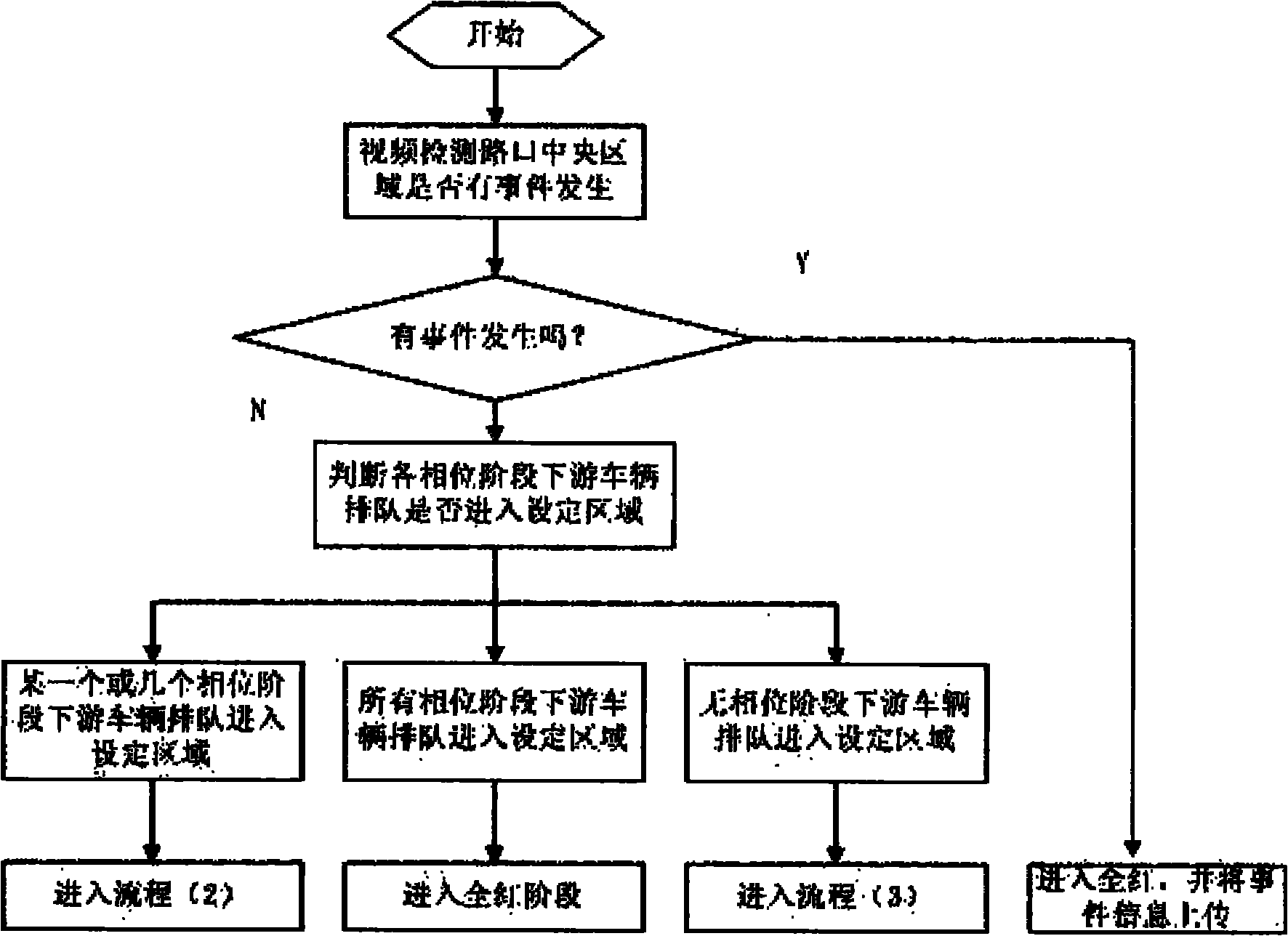
InactiveCN101968929AAvoid lossEffective distributionControlling traffic signalsTraffic capacityAir traffic control
The invention discloses an optimizing control method for a single intersection signal in a saturated traffic state, which belongs to the field of traffic detection and traffic control of urban roads. The method of the invention comprises the following steps of: detecting and recognizing intersection upstream and downstream vehicle queue setting areas and intersection central area traffic events by high-definition video and carrying out analysis processing on detected traffic data; and by a way based on the combination of the setting areas and rules, carrying out optimizing control on the traffic of the single intersection in the saturated traffic state in a plurality of aspects of intersection central area event judgment, phase downstream traffic flow queue detection and corresponding control processing, phase upstream traffic flow queue detection and corresponding control processing, and the like so that the intersection traffic in the saturated traffic state is run in order, and the traffic capacity of the intersection is improved. The method of the invention can further prevent traffic jam of the intersection in the saturated traffic state, eliminate the traffic jam as soon as possible and avoid the generation of a deadlock phenomenon of the intersection traffic, thereby remitting the problem of urban traffic jam and improving the running efficiency of urban traffic.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
Asynchronous, independent and multiple process shared memory system in an adaptive computing architecture
The present invention provides a system and method for implementation and use of a shared memory. The shared memory may be accessed both independently and asynchronously by one or more processes at corresponding nodes, allowing data to be streamed to multiple processes and nodes without regard to synchronization of the plurality of processes. The various nodes may be adaptive computing nodes, kernel or controller nodes, or one or more host processor nodes. The present invention maintains memory integrity, not allowing memory overruns, underruns, or deadlocks. The present invention also provides for “push back” after a memory read, for applications in which it is desirable to “unread” some elements previously read from the memory.
Owner:NVIDIA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com